WO2023226421A1 - Security reinforcement method and apparatus, device, and medium - Google Patents
Security reinforcement method and apparatus, device, and mediumDownload PDFInfo
- Publication number
- WO2023226421A1 WO2023226421A1PCT/CN2022/141587CN2022141587WWO2023226421A1WO 2023226421 A1WO2023226421 A1WO 2023226421A1CN 2022141587 WCN2022141587 WCN 2022141587WWO 2023226421 A1WO2023226421 A1WO 2023226421A1
- Authority
- WO
- WIPO (PCT)
- Prior art keywords
- virtual machine
- machine monitor
- security
- turned
- target
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Ceased
Links
Images
Classifications
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F9/00—Arrangements for program control, e.g. control units
- G06F9/06—Arrangements for program control, e.g. control units using stored programs, i.e. using an internal store of processing equipment to receive or retain programs
- G06F9/44—Arrangements for executing specific programs
- G06F9/445—Program loading or initiating
- G06F9/44505—Configuring for program initiating, e.g. using registry, configuration files
- G06F9/4451—User profiles; Roaming
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F11/00—Error detection; Error correction; Monitoring
- G06F11/30—Monitoring
- G06F11/3003—Monitoring arrangements specially adapted to the computing system or computing system component being monitored
- G06F11/302—Monitoring arrangements specially adapted to the computing system or computing system component being monitored where the computing system component is a software system
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F11/00—Error detection; Error correction; Monitoring
- G06F11/30—Monitoring
- G06F11/3051—Monitoring arrangements for monitoring the configuration of the computing system or of the computing system component, e.g. monitoring the presence of processing resources, peripherals, I/O links, software programs
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F9/00—Arrangements for program control, e.g. control units
- G06F9/06—Arrangements for program control, e.g. control units using stored programs, i.e. using an internal store of processing equipment to receive or retain programs
- G06F9/44—Arrangements for executing specific programs
- G06F9/455—Emulation; Interpretation; Software simulation, e.g. virtualisation or emulation of application or operating system execution engines
- G06F9/45533—Hypervisors; Virtual machine monitors
- G06F9/45558—Hypervisor-specific management and integration aspects
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F9/00—Arrangements for program control, e.g. control units
- G06F9/06—Arrangements for program control, e.g. control units using stored programs, i.e. using an internal store of processing equipment to receive or retain programs
- G06F9/44—Arrangements for executing specific programs
- G06F9/455—Emulation; Interpretation; Software simulation, e.g. virtualisation or emulation of application or operating system execution engines
- G06F9/45533—Hypervisors; Virtual machine monitors
- G06F9/45558—Hypervisor-specific management and integration aspects
- G06F2009/45587—Isolation or security of virtual machine instances
Definitions
- the present inventionrelates to the technical field of container security, and in particular to a security reinforcement method, device, equipment and medium.
- secure containersmainly prevent containers from escaping to the host (Host), thereby causing unauthorized access to the host, thereby ensuring the stability of the container environment.
- the technical solution currently used for secure containersis mainly to place the container in the guest operating system (guestOS), and guestOS runs on the virtual machine monitor (Qemu) of the host (Host), so even if the container escapes, it can only escape to the guestOS layer and cannot escape to the Host, thereby maximizing It ensures the security and stability of the Host to a certain extent, but Qemu itself, used by the secure container, has many vulnerabilities and a large attack surface. For example, Qemu only lasted for seven short months from January to August 2021. During this time, 25 common vulnerabilities and exposures (CVE) were leaked, and in the entire year of 2016, 91 CVEs were even leaked.
- CVEcommon vulnerabilities and exposures
- This applicationprovides a security hardening method, device, equipment and media to solve the problem in the prior art that if the virtual machine monitor is attacked, the host may be damaged.
- embodiments of the present applicationprovide a security hardening method, which method includes:
- the configuration file in which the target parameters are writtenis read, and the predefined parsing function in the target program is called to parse out the target parameters in the configuration file;
- the target parameterindicates that the security mechanism of the virtual machine monitor is turned on
- the target parameteris sent to the virtual machine monitor, so that the virtual machine monitor starts based on the target parameter to control its own The safety mechanism is on.
- the methodfurther includes:
- embodiments of the present applicationalso provide a security reinforcement method, which method includes:
- the target parameterindicates that the security mechanism of the virtual machine monitor is turned on, it is started based on the target parameter and controls its own security mechanism to be turned on.
- the methodalso includes:
- embodiments of the present applicationalso provide a security reinforcement device, which includes:
- a parsing moduleused to read the configuration file in which the target parameters are written if a secure container startup instruction is received, and call a predefined parsing function in the target program to parse out the target parameters in the configuration file;
- a sending moduleconfigured to send the target parameter to the virtual machine monitor if the target parameter indicates that the security mechanism of the virtual machine monitor is turned on, so that the virtual machine monitor starts based on the target parameter. , to control the opening of its own security mechanism.
- the sending moduleis also configured to send a startup instruction to the guest operating system running on the virtual machine monitor, so that the guest operating system completes startup.
- embodiments of the present applicationalso provide a security reinforcement device, which includes:
- the receiving moduleis used to receive the target parameters sent by the security container
- a control moduleconfigured to start the virtual machine monitor based on the target parameter and control its own security mechanism to open if the target parameter indicates that the security mechanism of the virtual machine monitor is turned on.
- the receiving moduleis also used to receive a query instruction whether the virtual machine security mechanism is turned on;
- the devicealso includes:
- a processing moduleused to check whether the security mechanism of the virtual machine monitor has been turned on, obtain the check result, and output the check result, wherein if the security mechanism of the virtual machine monitor has been turned on, the check
- the resultcarries the target parameters.
- embodiments of the present applicationfurther provide an electronic device.
- the electronic deviceat least includes a processor and a memory.
- the processoris configured to implement any of the above security hardening methods when executing a computer program stored in the memory. A step of.
- embodiments of the present applicationfurther provide a computer-readable storage medium that stores a computer program, and when the computer program is executed by a processor, the steps of any of the above security hardening methods are implemented.
- embodiments of the present applicationfurther provide an electronic device.
- the electronic deviceat least includes a processor and a memory.
- the processoris configured to implement any of the above security hardening methods when executing a computer program stored in the memory. A step of.
- embodiments of the present applicationfurther provide a computer-readable storage medium that stores a computer program, and when the computer program is executed by a processor, the steps of any one of the above security hardening methods are implemented.
- the configuration file with the target parameters written inis read, and the predefined parsing function in the target program is called to parse out the target parameters in the configuration file.
- the target parametersare used to indicate the virtual machine monitor's
- the security mechanismis turned on, the target parameters are sent to the virtual machine monitor, so that the virtual machine monitor starts based on the target parameters to control the opening of its own security mechanism.
- the security of the virtual machine monitorcan be reinforced by controlling the opening of the security mechanism of the virtual machine monitor, thereby reducing the exposure of the virtual machine monitor to external attacks, thereby preventing the virtual machine monitor from being attacked. The problem of being attacked and causing the host to be destroyed improves the security of the container environment.
- Figure 1is a schematic diagram of a security reinforcement process provided by an embodiment of the present application.
- Figure 2is a schematic diagram of the security hardening process of a virtual machine monitor provided by some embodiments of the present application
- Figure 3is a schematic diagram of the process of starting a guest operating system provided by some embodiments of the present application.
- Figure 4is a schematic diagram of a security reinforcement process provided by an embodiment of the present application.
- Figure 5ais a schematic diagram of a process of obtaining a configuration file provided by some embodiments of the present application.
- Figure 5bis a schematic diagram of a process for obtaining a configuration file provided by some embodiments of the present application.
- Figure 5cis a schematic diagram of a process of obtaining a configuration file provided by some embodiments of the present application.
- Figure 6is an overall framework of a virtual machine monitor provided by an embodiment of the present application before being hardened
- Figure 7is a reinforced overall framework of a virtual machine monitor provided by an embodiment of the present application.
- Figure 8is a schematic structural diagram of a safety reinforcement device provided by some embodiments of the present application.
- Figure 9is a schematic structural diagram of a safety reinforcement device provided by some embodiments of the present application.
- Figure 10is a schematic structural diagram of an electronic device provided by some embodiments of the present application.
- Figure 11is a schematic structural diagram of an electronic device provided by some embodiments of the present application.
- the configuration fileis read and the predefined parsing function is called to parse out the target parameters in the configuration file. If the target parameters are used to indicate that the security mechanism of the virtual machine monitor is turned on, the target parameters are sent. Give the virtual machine monitor so that the virtual machine monitor starts based on target parameters to control the opening of its own security mechanism.
- embodiments of the present applicationprovide a security hardening method, device, equipment and media.
- FIG. 1is a schematic diagram of a security hardening process provided by an embodiment of the present application. The process includes the following steps:
- the security hardening method provided by the embodiment of the present applicationis applied to the security container, and the security hardening method provided by the embodiment of the present application is mainly used for security hardening of the virtual monitor.
- the safe containerafter receiving the safe container start instruction, performs a start operation. Specifically, the safe container first reads a pre-saved configuration file in which the target parameters are written, in which the target parameters are written.
- the parameter configuration fileis a configuration file generated by the developer after pre-writing a program that writes the parameter assignment field, assigning the target parameter to the parameter assignment field, and then compiling the generated configuration file. Then the predefined parsing function in the target program is called to parse the target parameter in the configuration file, where the target parameter indicates whether the security mechanism of the virtual machine monitor is turned on.
- the target programis a program with parsing function that is pre-existing and saved in the security container itself.
- parsing function parsing the configuration file predefined in the calling target programis an existing technology and will not be described in detail here.
- the target parameterwhen the target parameter is on, it indicates that the security mechanism of the virtual machine monitor is turned on. When the target parameter is off, it indicates that the security mechanism of the virtual machine monitor is not turned on.
- the corresponding parameters when turned oncan be configured according to the needs.
- the target parameters and the corresponding target parameters when shutting downcan be configured in a combination of multiple specific parameters to achieve different security control levels and control ranges, which are not limited here.
- the security mechanism of the virtual machine monitorcan be turned on.
- the security containercan send the target parameter to the virtual machine monitor, so that the virtual machine monitor can be started based on the target parameter to control Open its own security mechanism to achieve security reinforcement of the virtual monitor.
- the security hardening of the virtual monitoris equivalent to introducing a security mechanism between the virtual machine monitor and the host, thereby improving the overall security of the container environment.
- the security mechanismis the Linux security mechanism (seccomp).
- the security mechanism of the virtual machine monitorcannot be turned on after the subsequent virtual monitor startup is completed.
- the security mechanism of the virtual machine monitorcan be turned on to harden the security of the virtual machine monitor, thereby reducing the exposure of the virtual machine monitor to external attacks, thereby preventing the virtual machine monitor from being attacked.
- the problem of being attacked and causing the host to be destroyedimproves the security of the container environment.
- the methodfurther includes:
- the security containersince the guest operating system runs on the virtual machine monitor, the security container sends the target parameters to the virtual machine monitor so that the virtual machine monitor starts based on the target parameters.
- the security containercan also send a startup instruction to the guest operating system running on the virtual machine monitor, so that the guest operating system is fully started.
- the security mechanism of the virtual machine monitoring systemwill not be fully turned on until the guest operating system is fully started.
- Figure 2is a schematic diagram of the security hardening process of a virtual machine monitor provided by some embodiments of the present application
- Figure 3is a schematic diagram of the process of starting a guest operating system provided by some embodiments of the present application. Figures 2 and 3 will now be described.
- configuration.tomlRead the configuration file (configuration.toml), and call the predefined parsing function in the target program to parse out the target parameters (seccompsandbox parameters) in the configuration file, then send the target parameters to the virtual machine monitor to enable virtual machine monitoring
- the serverstarts based on this target parameter to control the opening of its own security mechanism, as shown in Figure 2.
- guestOSguest operating system
- FIG. 4is a schematic diagram of a security hardening process provided by an embodiment of the present application. The process includes the following steps:
- S401Receive the target parameters sent by the security container.
- the security hardening method provided by the embodiment of this applicationis applied to the virtual machine monitor.
- the security containerin order to protect the host from being destroyed, the security container will send the obtained target parameters to the virtual machine monitor.
- the target parametersmay be parameters that indicate that the security mechanism of the virtual machine monitor is turned on, or may be parameters that indicate that the security mechanism of the virtual machine monitor is turned on. For parameters where the security mechanism of the virtual machine monitor is not turned on, the virtual machine monitor will receive the target parameters sent by the security container.
- the security mechanism of the virtual machine monitorwhen the target parameter is set to on in advance, the security mechanism of the virtual machine monitor is turned on, and when the target parameter is set to off in advance, the security mechanism of the virtual machine monitor is not turned on. Specifically, it can be based on It is required to configure the corresponding target parameters when it is turned on and the corresponding target parameters when it is turned off. It also supports the configuration of multiple specific parameter combinations to achieve different security control levels and control ranges. There are no restrictions here.
- the virtual machine monitoris started based on the target parameter, and then the security mechanism of the virtual machine monitor is controlled to be turned on, so as to realize security hardening of the virtual machine monitor.
- the methodfurther includes:
- the result information of whether the security mechanism of the virtual machine monitor is turned onmay be output.
- a query instructioncan be sent to the virtual machine monitor, and the virtual machine monitor can receive a query instruction of whether the security mechanism of the virtual machine is turned on. , check whether the security mechanism of the virtual machine is turned on, obtain the corresponding check result, and output the check result.
- the check resultcan be output in text or voice.
- the text "The virtual machine monitor has turned on the security mechanism”can be output, or the text "The virtual machine monitor has been turned on” can be output.
- "Safety Mechanism” voicecan be output.
- the check resultcan also carry the result of the target parameter, for example, if When the security mechanism of the virtual machine monitor has been turned on, the corresponding target parameter is on. After querying that the security mechanism of the virtual machine monitor has been turned on, "the status of the virtual machine monitor is on" and so on can be output.
- developersIn order to achieve security hardening, developers first pre-write a program that writes the parameter assignment field. After assigning the target parameter to the parameter assignment field, it compiles and generates a configuration file with the target parameter written in it. Subsequently, the secure container starts after receiving the secure container After the instruction, the configuration file is read, and the predefined parsing function in the target program is called to parse out the target parameters in the configuration file. If the target parameter indicates that the security mechanism of the virtual machine monitor is turned on, the target parameter is sent to Virtual machine monitor. After receiving the target parameter, the virtual machine monitor starts based on the target parameter to control the opening of its own security mechanism.
- Figures 5a-5care schematic diagrams of a process of obtaining a configuration file provided by some embodiments of the present application; Figures 5a-5c will now be described.
- the first step to obtain the configuration fileis: the developer modifies the Makefile of the Kata Runtime part and adds a compilation macro.
- the compilation macrocan be DEFSECCOMPSANDBOXPARAM.
- the compilation macrois used to control whether to turn on the security mechanism of the virtual machine monitor. , among which, this security mechanism is equivalent to reducing the attack surface of the virtual machine monitor on the host by reducing certain types of system calls that are not allowed.
- the virtual machine monitoris not allowed to use abandoned system calls
- the virtual machine monitoris not allowed to increase the priority to use all setuid/gid system calls
- qemuis not allowed spawn new threads and processes and disallow the hypervisor from using process affinity and setting scheduler priorities, etc.
- the program corresponding to the newly added compilation macrocan be:
- the modified Makefilecan be passed into the Kata Runtime compilation system (kata Building System), see Figure 5a.
- the second step to obtain the configuration fileis to modify the configuration file configuration-qemu.toml.in of kata runtime for the underlying virtual machine monitor qemu, and add the parameter seccompsandbox (target parameter) as follows:
- the compilation systemwhen compiling kata runtime, the compilation system will automatically parse the definition of DEFSECCOMPSANDBOXPARAM macro in the first step, and then pass it to the seccompsandbox parameter (target parameter) of configuration-qemu.toml.in to facilitate subsequent Kata runtime initialization It is parsed at the time, and then the configuration-qemu.toml.in is passed to the compilation system of Kata Runtime together with the modified Makefile in the first step, see Figure 5b.
- target parametertarget parameter
- the third step to obtain the configuration fileis to modify the hypervisor struct of katautils config.go and add the SeccompSandbox string ⁇ toml:"seccompsandbox" ⁇ field.
- the new SeccompSandbox string ⁇ toml:"seccompsandbox” ⁇ fieldis used for Receive the seccompsandbox parameter content in the configuration-qemu.toml.in configuration file to facilitate subsequent internal processing.
- the fourth step to obtain the configuration fileis to modify the newQemuHypervisorConfig function implementation of katautils config.go.
- the fourth step to obtain the configuration fileis to modify the newQemuHypervisorConfig function implementation of katautils config.go.
- When generating the vc.HypervisorConfig structureadd a new field SeccompSandbox:h.SeccompSandbox.
- the fifth step to obtain the configuration fileis to modify the govmm code and add a new field SeccompSandbox string to its data structure Config struct, which is used to receive the internal storage after parsing the configuration-qemu.toml.in configuration file.
- the sixth step to obtain the configuration fileis to modify the code implementation of govmm and add a new function appendSeccompSandbox() so that it can parse the seccompsandbox parameter of the toml configuration file.
- appendSeccompSandbox()is used to ensure that subsequent target programs can parse the configuration of configuration-qemu.toml.in. If the configuration-qemu.toml.in file is configured with the seccompsandbox parameter, this function will convert the parameter content into the startup command line parameters of the underlying virtual machine monitor of the Kata secure container, that is, make the virtual machine monitor based on the seccompsandbox parameters to start to control the opening of its own security mechanism.
- the seventh step to obtain the configuration fileis to modify the LaunchQemu code to call appendSeccompSandbox() implemented in the third step:
- the LaunchQemu codeis routed as follows:
- Figure 6is an overall framework of a virtual machine monitor provided by an embodiment of the present application before being hardened.
- Figure 7is an overall framework of a virtual machine monitor provided by an embodiment of the present application after being hardened. Now, with reference to Figures 6 and 7 Be explained.
- the guest operating systemmay be compromised. See Attack 1. However, it is difficult to attack the host from the guestOS, that is, attack 2 generally does not occur. Condition. However, the attacker can attack the host from another angle, that is, attack from the virtual machine monitor (Qemu) side, see Attack 3, causing the host to be destroyed, see Figure 6.
- the virtual machine monitorimplements security hardening, that is to say, after the virtual machine monitor turns on the security mechanism, when the security container (container) is attacked, the guest operating system (guestOS) may be breached. See Attack 1.
- a secure containercontainer
- attack 2it is difficult to attack the host from the guestOS, that is, attack 2 generally does not occur.
- attack 3the host will not be damaged, that is, attack 3 will not occur.
- Figure 8is a schematic structural diagram of a security reinforcement device provided by some embodiments of the present application.
- the deviceincludes:
- the parsing module 801is used to read the configuration file in which the target parameters are written if the secure container startup instruction is received, and call the predefined parsing function in the target program to parse out the target parameters in the configuration file;
- Sending module 802configured to send the target parameter to the virtual machine monitor if the target parameter indicates that the security mechanism of the virtual machine monitor is turned on, so that the virtual machine monitor performs operations based on the target parameter. Start to control the opening of its own security mechanism.
- the sending module 802is also configured to send a startup instruction to the guest operating system running on the virtual machine monitor, so that the guest operating system completes startup.
- Figure 9is a schematic structural diagram of a security reinforcement device provided by some embodiments of the present application.
- the deviceincludes:
- the receiving module 901is used to receive the target parameters sent by the security container;
- the control module 902is configured to start the virtual machine monitor based on the target parameter and control its own security mechanism to open if the target parameter indicates that the security mechanism of the virtual machine monitor is turned on.
- the receiving module 901is also used to receive a query instruction whether the virtual machine security mechanism is turned on;
- the devicealso includes:
- the processing module 903is used to check whether the security mechanism of the virtual machine monitor has been turned on, obtain the check result, and output the check result, wherein if the security mechanism of the virtual machine monitor has been turned on, the The inspection results carry the target parameters.
- some embodiments of the present applicationalso provide an electronic device, as shown in Figure 10, including: a processor 1001, a communication interface 1002, a memory 1003 and a communication bus 1004, where the processor 1001 , the communication interface 1002 and the memory 1003 complete communication with each other through the communication bus 1004.
- the memory 1003stores a computer program. When the program is executed by the processor 1001, the processor 1001 performs the following steps:
- the configuration file in which the target parameters are writtenis read, and the predefined parsing function in the target program is called to parse out the target parameters in the configuration file;
- the target parameterindicates that the security mechanism of the virtual machine monitor is turned on
- the target parameteris sent to the virtual machine monitor, so that the virtual machine monitor starts based on the target parameter to control its own The safety mechanism is on.
- processor 1001is also configured to send a startup instruction to the guest operating system running on the virtual machine monitor, so that the guest operating system completes startup.
- the communication bus mentioned in the above-mentioned servercan be the Peripheral Component Interconnect (PCI) bus or the Extended Industry Standard Architecture (EISA) bus, etc.
- PCIPeripheral Component Interconnect
- EISAExtended Industry Standard Architecture
- the communication buscan be divided into address bus, data bus, control bus, etc. For ease of presentation, only one thick line is used in the figure, but it does not mean that there is only one bus or one type of bus.
- the communication interface 1002is used for communication between the above-mentioned electronic device and other devices.
- the memorymay include random access memory (Random Access Memory, RAM) or non-volatile memory (Non-Volatile Memory, NVM), such as at least one disk memory.
- RAMRandom Access Memory
- NVMNon-Volatile Memory
- the memorymay also be at least one storage device located remotely from the aforementioned processor.
- the above-mentioned processorcan be a general-purpose processor, including a central processing unit, a network processor (Network Processor, NP), etc.; it can also be a digital instruction processor (Digital Signal Processing, DSP), an application-specific integrated circuit, a field programmable gate array, or Other programmable logic devices, discrete gate or transistor logic devices, discrete hardware components, etc.
- NPNetwork Processor
- DSPDigital Signal Processing
- some embodiments of the present applicationalso provide an electronic device, as shown in Figure 11, including: a processor 1101, a communication interface 1102, a memory 1103 and a communication bus 1104, where the processor 1101 , the communication interface 1102 and the memory 1103 complete communication with each other through the communication bus 1104.
- the memory 1103stores a computer program.
- the processor 1101executes the following steps:
- the target parameterindicates that the security mechanism of the virtual machine monitor is turned on, it is started based on the target parameter and controls its own security mechanism to be turned on.
- processor 1101is also configured to receive a query instruction whether the virtual machine security mechanism is turned on;
- the communication bus mentioned in the above-mentioned servercan be the Peripheral Component Interconnect (PCI) bus or the Extended Industry Standard Architecture (EISA) bus, etc.
- PCIPeripheral Component Interconnect
- EISAExtended Industry Standard Architecture
- the communication buscan be divided into address bus, data bus, control bus, etc. For ease of presentation, only one thick line is used in the figure, but it does not mean that there is only one bus or one type of bus.
- the communication interface 1102is used for communication between the above-mentioned electronic device and other devices.
- the memorymay include random access memory (Random Access Memory, RAM) or non-volatile memory (Non-Volatile Memory, NVM), such as at least one disk memory.
- RAMRandom Access Memory
- NVMNon-Volatile Memory
- the memorymay also be at least one storage device located remotely from the aforementioned processor.
- the above-mentioned processorcan be a general-purpose processor, including a central processing unit, a network processor (Network Processor, NP), etc.; it can also be a digital instruction processor (Digital Signal Processing, DSP), an application-specific integrated circuit, a field programmable gate array, or Other programmable logic devices, discrete gate or transistor logic devices, discrete hardware components, etc.
- NPNetwork Processor
- DSPDigital Signal Processing
- some embodiments of the present applicationalso provide a computer-readable storage medium.
- the computer-readable storage mediumstores a computer program that can be executed by an electronic device. When the program is in the When running on an electronic device, the following steps are implemented when the electronic device is executed:
- the configuration file in which the target parameters are writtenis read, and the predefined parsing function in the target program is called to parse out the target parameters in the configuration file;
- the target parameterindicates that the security mechanism of the virtual machine monitor is turned on
- the target parameteris sent to the virtual machine monitor, so that the virtual machine monitor starts based on the target parameter to control its own The safety mechanism is on.
- the methodfurther includes:
- some embodiments of the present applicationalso provide a computer-readable storage medium.
- the computer-readable storage mediumstores a computer program that can be executed by an electronic device. When the program is in the When running on an electronic device, the following steps are implemented when the electronic device is executed:
- the target parameterindicates that the security mechanism of the virtual machine monitor is turned on, it is started based on the target parameter and controls its own security mechanism to be turned on.
- the methodalso includes:
- the security of the virtual machine monitorcan be reinforced by controlling the opening of the security mechanism of the virtual machine monitor, thereby reducing the exposure of the virtual machine monitor to external attacks, thereby preventing the virtual machine monitor from being attacked.
- the problem of being attacked and causing the host to be destroyedimproves the security of the container environment.
- embodiments of the present applicationmay be provided as methods, systems, or computer program products. Accordingly, the present application may take the form of an entirely hardware embodiment, an entirely software embodiment, or an embodiment that combines software and hardware aspects. Furthermore, the present application may take the form of a computer program product embodied on one or more computer-usable storage media (including, but not limited to, disk storage, CD-ROM, optical storage, etc.) having computer-usable program code embodied therein.
- computer-usable storage mediaincluding, but not limited to, disk storage, CD-ROM, optical storage, etc.
- These computer program instructionsmay also be stored in a computer-readable memory that causes a computer or other programmable data processing apparatus to operate in a particular manner, such that the instructions stored in the computer-readable memory produce an article of manufacture including the instruction means, the instructions
- the deviceimplements the functions specified in a process or processes of the flowchart and/or a block or blocks of the block diagram.
- These computer program instructionsmay also be loaded onto a computer or other programmable data processing device, causing a series of operating steps to be performed on the computer or other programmable device to produce computer-implemented processing, thereby executing on the computer or other programmable device.
- Instructionsprovide steps for implementing the functions specified in a process or processes of a flowchart diagram and/or a block or blocks of a block diagram.
Landscapes
- Engineering & Computer Science (AREA)
- Theoretical Computer Science (AREA)
- Software Systems (AREA)
- Physics & Mathematics (AREA)
- General Engineering & Computer Science (AREA)
- General Physics & Mathematics (AREA)
- Computing Systems (AREA)
- Quality & Reliability (AREA)
- Mathematical Physics (AREA)
- Stored Programmes (AREA)
Abstract
Description
Translated fromChinese本发明涉及容器安全技术领域,尤其涉及一种安全加固方法、装置、设备及介质。The present invention relates to the technical field of container security, and in particular to a security reinforcement method, device, equipment and medium.
随着越来越多的企业开始上云,业务普遍开始云化,云安全问题已经成为了企业业务防护工作的重中之重,然而云和容器之间有着本质的联系,且云安全离不开容器安全,当然,也不可能脱离容器安全而单独去定义云安全,因此,为了保证容器安全性,业界提出了安全容器的概念,并在短时间内实践并落地了各种安全容器解决方案。As more and more enterprises begin to move to the cloud, and their businesses generally begin to become cloud-based, cloud security issues have become the top priority of enterprise business protection work. However, there is an essential connection between the cloud and containers, and cloud security is inseparable. Of course, it is impossible to define cloud security separately from container security. Therefore, in order to ensure container security, the industry has proposed the concept of secure containers, and has implemented and implemented various secure container solutions in a short period of time. .
其中,安全容器,主要是防止容器逃逸到主机(Host)上,从而造成对主机的越权访问,进而保证容器环境的稳定性,安全容器目前使用的技术方案主要是把容器放在客户机操作系统(guestOS)上运行,且guestOS是运行在主机(Host)的虚拟机监控器(Qemu)上的,所以即使容器发生逃逸,也只能逃逸到guestOS这一层,不能逃逸到Host上,从而最大程度的保证了Host的安全性和稳固性,但安全容器使用的Qemu本身存在漏洞较多,被攻击面较大的问题,比如,Qemu仅仅在2021年一月至八月短短七个月的时间里,就被纰漏出了25个公共漏洞和暴露(Common Vulnerabilities&Exposure,CVE),在2016年一整年的时间里,甚至纰漏出了91个CVE。Among them, secure containers mainly prevent containers from escaping to the host (Host), thereby causing unauthorized access to the host, thereby ensuring the stability of the container environment. The technical solution currently used for secure containers is mainly to place the container in the guest operating system (guestOS), and guestOS runs on the virtual machine monitor (Qemu) of the host (Host), so even if the container escapes, it can only escape to the guestOS layer and cannot escape to the Host, thereby maximizing It ensures the security and stability of the Host to a certain extent, but Qemu itself, used by the secure container, has many vulnerabilities and a large attack surface. For example, Qemu only lasted for seven short months from January to August 2021. During this time, 25 common vulnerabilities and exposures (CVE) were leaked, and in the entire year of 2016, 91 CVEs were even leaked.
若Qemu被攻击,则可能导致host被破坏,因此对于host得保护度还是不高,容器环境的安全性也不高。If Qemu is attacked, it may cause the host to be destroyed. Therefore, the degree of protection for the host is still not high, and the security of the container environment is not high.
本申请提供了一种安全加固方法、装置、设备及介质,用以解决现有技术中若虚拟机监控器被攻击,则有可能导致主机被破坏的问题。This application provides a security hardening method, device, equipment and media to solve the problem in the prior art that if the virtual machine monitor is attacked, the host may be damaged.
第一方面,本申请实施例提供了一种安全加固方法,所述方法包括:In a first aspect, embodiments of the present application provide a security hardening method, which method includes:
若接收到安全容器启动指令,则读取写入了目标参数的配置文件,并调用目标程序中预先定义的解析函数解析出所述配置文件中的所述目标参数;If the secure container startup instruction is received, the configuration file in which the target parameters are written is read, and the predefined parsing function in the target program is called to parse out the target parameters in the configuration file;
若所述目标参数指示虚拟机监控器的安全机制打开,则将所述目标参数发送给所述虚拟机监控器,以使所述虚拟机监控器基于所述目标参数进行启动,来控制自身的安全机制打开。If the target parameter indicates that the security mechanism of the virtual machine monitor is turned on, the target parameter is sent to the virtual machine monitor, so that the virtual machine monitor starts based on the target parameter to control its own The safety mechanism is on.
进一步地,所述将所述目标参数发送给虚拟机监控器之后,所述方法还包括:Further, after sending the target parameters to the virtual machine monitor, the method further includes:
向运行在所述虚拟机监控器上的客户机操作系统发送启动指令,以使所述客户机操作系 统完成启动。Send a startup instruction to the guest operating system running on the virtual machine monitor, so that the guest operating system completes startup.
第二方面,本申请实施例还提供了一种安全加固方法,所述方法包括:In a second aspect, embodiments of the present application also provide a security reinforcement method, which method includes:
接收安全容器发送的目标参数;Receive the target parameters sent by the security container;
若所述目标参数指示虚拟机监控器的安全机制打开,则基于所述目标参数进行启动,控制自身的安全机制打开。If the target parameter indicates that the security mechanism of the virtual machine monitor is turned on, it is started based on the target parameter and controls its own security mechanism to be turned on.
进一步地,所述方法还包括:Further, the method also includes:
接收虚拟机安全机制是否打开的查询指令;Receive the query instruction whether the virtual machine security mechanism is turned on;
查验所述虚拟机监控器是否已经打开了安全机制,获得查验结果,并将所述查验结果输出,其中,若所述虚拟机监控器的安全机制已经打开,则所述查验结果中携带所述目标参数。Check whether the security mechanism of the virtual machine monitor has been turned on, obtain the check result, and output the check result. Wherein, if the security mechanism of the virtual machine monitor has been turned on, the check result carries the target parameters.
第三方面,本申请实施例还提供了一种安全加固装置,所述装置包括:In a third aspect, embodiments of the present application also provide a security reinforcement device, which includes:
解析模块,用于若接收到安全容器启动指令,则读取写入了目标参数的配置文件,并调用目标程序中预先定义的解析函数解析出所述配置文件中的所述目标参数;A parsing module, used to read the configuration file in which the target parameters are written if a secure container startup instruction is received, and call a predefined parsing function in the target program to parse out the target parameters in the configuration file;
发送模块,用于若所述目标参数指示虚拟机监控器的安全机制打开,则将所述目标参数发送给所述虚拟机监控器,以使所述虚拟机监控器基于所述目标参数进行启动,来控制自身的安全机制打开。A sending module, configured to send the target parameter to the virtual machine monitor if the target parameter indicates that the security mechanism of the virtual machine monitor is turned on, so that the virtual machine monitor starts based on the target parameter. , to control the opening of its own security mechanism.
进一步地,所述发送模块,还用于向运行在所述虚拟机监控器上的客户机操作系统发送启动指令,以使所述客户机操作系统完成启动。Further, the sending module is also configured to send a startup instruction to the guest operating system running on the virtual machine monitor, so that the guest operating system completes startup.
第四方面,本申请实施例还提供了一种安全加固装置,所述装置包括:In a fourth aspect, embodiments of the present application also provide a security reinforcement device, which includes:
接收模块,用于接收安全容器发送的目标参数;The receiving module is used to receive the target parameters sent by the security container;
控制模块,用于若所述目标参数指示虚拟机监控器的安全机制打开,则基于所述目标参数进行启动,控制自身的安全机制打开。A control module configured to start the virtual machine monitor based on the target parameter and control its own security mechanism to open if the target parameter indicates that the security mechanism of the virtual machine monitor is turned on.
进一步地,所述接收模块,还用于接收虚拟机安全机制是否打开的查询指令;Further, the receiving module is also used to receive a query instruction whether the virtual machine security mechanism is turned on;
所述装置还包括:The device also includes:
处理模块,用于查验所述虚拟机监控器是否已经打开了安全机制,获得查验结果,并将所述查验结果输出,其中,若所述虚拟机监控器的安全机制已经打开,则所述查验结果中携带所述目标参数。A processing module, used to check whether the security mechanism of the virtual machine monitor has been turned on, obtain the check result, and output the check result, wherein if the security mechanism of the virtual machine monitor has been turned on, the check The result carries the target parameters.
第五方面,本申请实施例还提供了一种电子设备,所述电子设备至少包括处理器和存储器,所述处理器用于执行存储器中存储的计算机程序时实现如上述任一所述安全加固方法的步骤。In a fifth aspect, embodiments of the present application further provide an electronic device. The electronic device at least includes a processor and a memory. The processor is configured to implement any of the above security hardening methods when executing a computer program stored in the memory. A step of.
第六方面,本申请实施例还提供了一种计算机可读存储介质,其存储有计算机程序,所述计算机程序被处理器执行时实现如上述任一所述安全加固方法的步骤。In a sixth aspect, embodiments of the present application further provide a computer-readable storage medium that stores a computer program, and when the computer program is executed by a processor, the steps of any of the above security hardening methods are implemented.
第七方面,本申请实施例还提供了一种电子设备,所述电子设备至少包括处理器和存储器,所述处理器用于执行存储器中存储的计算机程序时实现如上述任一所述安全加固方法的步骤。In a seventh aspect, embodiments of the present application further provide an electronic device. The electronic device at least includes a processor and a memory. The processor is configured to implement any of the above security hardening methods when executing a computer program stored in the memory. A step of.
第八方面,本申请实施例还提供了一种计算机可读存储介质,其存储有计算机程序,所述计算机程序被处理器执行时实现如上述任一所述安全加固方法的步骤。In an eighth aspect, embodiments of the present application further provide a computer-readable storage medium that stores a computer program, and when the computer program is executed by a processor, the steps of any one of the above security hardening methods are implemented.
若接收到安全容器启动指令,则读取写入了目标参数的配置文件,并调用目标程序中预先定义的解析函数解析出配置文件中的目标参数,若目标参数用于指示虚拟机监控器的安全机制打开,则将目标参数发送给虚拟机监控器,以使虚拟机监控器基于目标参数进行启动,来控制自身的安全机制打开。由于在本申请实施例中,可以通过控制虚拟机监控器的安全机制打开的方式,来对虚拟机监控器进行安全加固,减少虚拟机监控器对外的被攻击暴露面,从而避免虚拟机监控器被攻击,导致主机被破坏的问题,提高了容器环境的安全性。If the secure container startup command is received, the configuration file with the target parameters written in is read, and the predefined parsing function in the target program is called to parse out the target parameters in the configuration file. If the target parameters are used to indicate the virtual machine monitor's If the security mechanism is turned on, the target parameters are sent to the virtual machine monitor, so that the virtual machine monitor starts based on the target parameters to control the opening of its own security mechanism. In this embodiment of the present application, the security of the virtual machine monitor can be reinforced by controlling the opening of the security mechanism of the virtual machine monitor, thereby reducing the exposure of the virtual machine monitor to external attacks, thereby preventing the virtual machine monitor from being attacked. The problem of being attacked and causing the host to be destroyed improves the security of the container environment.
为了更清楚地说明本申请实施例中的技术方案,下面将对实施例描述中所需要使用的附图作简要介绍,显而易见地,下面描述中的附图仅仅是本申请的一些实施例,对于本领域的普通技术人员来讲,在不付出创造性劳动性的前提下,还可以根据这些附图获得其他的附图。In order to more clearly illustrate the technical solutions in the embodiments of the present application, a brief introduction will be given below to the drawings needed to be used in the description of the embodiments. Obviously, the drawings in the following description are only some embodiments of the present application. Those of ordinary skill in the art can also obtain other drawings based on these drawings without exerting any creative effort.
图1为本申请实施例提供的一种安全加固的过程示意图;Figure 1 is a schematic diagram of a security reinforcement process provided by an embodiment of the present application;
图2为本申请一些实施例提供的一种虚拟机监控器的安全加固过程示意图;Figure 2 is a schematic diagram of the security hardening process of a virtual machine monitor provided by some embodiments of the present application;
图3为本申请一些实施例提供的一种客户机操作系统启动的过程示意图;Figure 3 is a schematic diagram of the process of starting a guest operating system provided by some embodiments of the present application;
图4为本申请实施例提供的一种安全加固的过程示意图;Figure 4 is a schematic diagram of a security reinforcement process provided by an embodiment of the present application;
图5a为本申请一些实施例提供的一种获得配置文件的过程示意图;Figure 5a is a schematic diagram of a process of obtaining a configuration file provided by some embodiments of the present application;
图5b为本申请一些实施例提供的一种获得配置文件的过程示意图;Figure 5b is a schematic diagram of a process for obtaining a configuration file provided by some embodiments of the present application;
图5c为本申请一些实施例提供的一种获得配置文件的过程示意图;Figure 5c is a schematic diagram of a process of obtaining a configuration file provided by some embodiments of the present application;
图6为本申请实施例提供的一种虚拟机监控器未加固前的整体框架;Figure 6 is an overall framework of a virtual machine monitor provided by an embodiment of the present application before being hardened;
图7为本申请实施例提供的一种虚拟机监控器加固后的整体框架;Figure 7 is a reinforced overall framework of a virtual machine monitor provided by an embodiment of the present application;
图8为本申请一些实施例提供的一种安全加固装置结构示意图;Figure 8 is a schematic structural diagram of a safety reinforcement device provided by some embodiments of the present application;
图9为本申请一些实施例提供的一种安全加固装置结构示意图;Figure 9 is a schematic structural diagram of a safety reinforcement device provided by some embodiments of the present application;
图10为本申请一些实施例提供的一种电子设备的结构示意图;Figure 10 is a schematic structural diagram of an electronic device provided by some embodiments of the present application;
图11为本申请一些实施例提供的一种电子设备的结构示意图。Figure 11 is a schematic structural diagram of an electronic device provided by some embodiments of the present application.
为了使本申请的目的、技术方案和优点更加清楚,下面将结合附图对本申请作进一步地详细描述,显然,所描述的实施例仅仅是本申请一部分实施例,而不是全部的实施例。基于本申请中的实施例,本领域普通技术人员在没有做出创造性劳动前提下所获得的所有其它实施例,都属于本申请保护的范围。In order to make the purpose, technical solutions and advantages of the present application clearer, the present application will be described in further detail below in conjunction with the accompanying drawings. Obviously, the described embodiments are only some of the embodiments of the present application, not all of them. Based on the embodiments in this application, all other embodiments obtained by those of ordinary skill in the art without creative efforts fall within the scope of protection of this application.
若接收到安全容器启动指令,则读取配置文件,并调用预先定义的解析函数解析出配置文件中的目标参数,若目标参数用于指示虚拟机监控器的安全机制打开,则将目标参数发送给虚拟机监控器,以使虚拟机监控器基于目标参数进行启动,来控制自身的安全机制打开。If a secure container startup command is received, the configuration file is read and the predefined parsing function is called to parse out the target parameters in the configuration file. If the target parameters are used to indicate that the security mechanism of the virtual machine monitor is turned on, the target parameters are sent. Give the virtual machine monitor so that the virtual machine monitor starts based on target parameters to control the opening of its own security mechanism.
为了避免虚拟机监控器受到攻击时,主机被破坏,本申请实施例提供了一种安全加固方法、装置、设备及介质。In order to prevent the host from being destroyed when the virtual machine monitor is attacked, embodiments of the present application provide a security hardening method, device, equipment and media.
图1为本申请实施例提供的一种安全加固的过程示意图,该过程包括以下步骤:Figure 1 is a schematic diagram of a security hardening process provided by an embodiment of the present application. The process includes the following steps:
S101:若接收到安全容器启动指令,则读取写入了目标参数的配置文件,并调用目标程序中预先定义的解析函数解析出所述配置文件中的所述目标参数。S101: If a secure container startup instruction is received, read the configuration file in which the target parameters are written, and call a predefined parsing function in the target program to parse out the target parameters in the configuration file.
本申请实施例提供的安全加固方法应用于安全容器,且本申请实施例提供的安全加固方法主要用于对虚拟监控器进行安全加固。The security hardening method provided by the embodiment of the present application is applied to the security container, and the security hardening method provided by the embodiment of the present application is mainly used for security hardening of the virtual monitor.
在本申请实施例中,安全容器在接收到安全容器启动指令后,则进行启动操作,具体的,安全容器先读取预先保存的写入了目标参数的配置文件,其中,该写入了目标参数的配置文件为开发人员预先编写了写入了参数赋值字段的程序后,将目标参数赋值给该参数赋值字段后编译生成的配置文件。然后调用目标程序中预先定义的解析函数解析该配置文件中的目标参数,其中,该目标参数指示虚拟机监控器的安全机制是否打开。其中,该目标程序为安全容器本身预先存在和保存的具有解析功能的程序。In the embodiment of the present application, after receiving the safe container start instruction, the safe container performs a start operation. Specifically, the safe container first reads a pre-saved configuration file in which the target parameters are written, in which the target parameters are written. The parameter configuration file is a configuration file generated by the developer after pre-writing a program that writes the parameter assignment field, assigning the target parameter to the parameter assignment field, and then compiling the generated configuration file. Then the predefined parsing function in the target program is called to parse the target parameter in the configuration file, where the target parameter indicates whether the security mechanism of the virtual machine monitor is turned on. Among them, the target program is a program with parsing function that is pre-existing and saved in the security container itself.
其中,该调用目标程序中预先定义的解析函数解析配置文件为现有技术,在此不做赘述。Among them, the parsing function parsing the configuration file predefined in the calling target program is an existing technology and will not be described in detail here.
具体的,可以预先设置目标参数为on时,指示虚拟机监控器的安全机制打开,目标参数为off时,指示虚拟机监控器的安全机制不打开,具体的,可以根据需求配置打开时对应的目标参数以及关闭时对应的目标参数,同时支持多个具体参数组合的方式来进行配置,以此来达到不同的安全控制级别和控制范围,在此不做限制。Specifically, when the target parameter is on, it indicates that the security mechanism of the virtual machine monitor is turned on. When the target parameter is off, it indicates that the security mechanism of the virtual machine monitor is not turned on. Specifically, the corresponding parameters when turned on can be configured according to the needs. The target parameters and the corresponding target parameters when shutting down can be configured in a combination of multiple specific parameters to achieve different security control levels and control ranges, which are not limited here.
S102:若所述目标参数指示虚拟机监控器的安全机制打开,则将所述目标参数发送给所述虚拟机监控器,以使所述虚拟机监控器基于所述目标参数进行启动,来控制自身的安全机 制打开。S102: If the target parameter indicates that the security mechanism of the virtual machine monitor is turned on, send the target parameter to the virtual machine monitor, so that the virtual machine monitor starts based on the target parameter to control Its own safety mechanism is turned on.
为了避免虚拟机监控器被攻击时,导致主机也被破坏,在本申请实施例中,可以将虚拟机监控器的安全机制打开。In order to prevent the host from being damaged when the virtual machine monitor is attacked, in this embodiment of the present application, the security mechanism of the virtual machine monitor can be turned on.
具体的,若该目标参数是指示虚拟机监控器的安全机制打开的,则安全容器可以将该目标参数发送给虚拟机监控器,以使虚拟机监控器可以基于该目标参数进行启动,来控制自身的安全机制打开,进而来实现对虚拟监控器的安全加固。其中,该虚拟监控器的安全加固就相当于在虚拟机监控器和主机之间引入安全机制,从而使容器环境的整体安全性得到提升。在本申请中,该安全机制为Linux的安全机制(seccomp)。Specifically, if the target parameter indicates that the security mechanism of the virtual machine monitor is turned on, the security container can send the target parameter to the virtual machine monitor, so that the virtual machine monitor can be started based on the target parameter to control Open its own security mechanism to achieve security reinforcement of the virtual monitor. Among them, the security hardening of the virtual monitor is equivalent to introducing a security mechanism between the virtual machine monitor and the host, thereby improving the overall security of the container environment. In this application, the security mechanism is the Linux security mechanism (seccomp).
若该目标参数不是指示虚拟机监控器的安全机制打开的,则后续虚拟监控器启动完成之后,也不能将虚拟机监控器的安全机制打开。If the target parameter does not indicate that the security mechanism of the virtual machine monitor is turned on, the security mechanism of the virtual machine monitor cannot be turned on after the subsequent virtual monitor startup is completed.
由于在本申请实施例中,可以通过使得虚拟机监控器的安全机制打开的方式,来对虚拟机监控器进行安全加固,减少虚拟机监控器对外的被攻击暴露面,从而避免虚拟机监控器被攻击,导致主机被破坏的问题,提高了容器环境的安全性。In this embodiment of the present application, the security mechanism of the virtual machine monitor can be turned on to harden the security of the virtual machine monitor, thereby reducing the exposure of the virtual machine monitor to external attacks, thereby preventing the virtual machine monitor from being attacked. The problem of being attacked and causing the host to be destroyed improves the security of the container environment.
为了使得虚拟机监控器的安全机制完全打开,在上述实施例的基础上,在本申请实施例中,所述将所述目标参数发送给虚拟机监控器之后,所述方法还包括:In order to fully open the security mechanism of the virtual machine monitor, based on the above embodiments, in this embodiment of the present application, after sending the target parameters to the virtual machine monitor, the method further includes:
向运行在所述虚拟机监控器上的客户机操作系统发送启动指令,以使所述客户机操作系统完成启动。Send a startup instruction to the guest operating system running on the virtual machine monitor, so that the guest operating system completes startup.
在本申请实施例中,由于客户机操作系统是运行在虚拟机监控器上的,因此,安全容器在将目标参数发送给虚拟机监控器,以使该虚拟机监控器基于该目标参数进行启动,来控制自身的安全机制打开之后,在本申请实施例中,安全容器还可以向运行在虚拟机监控器上的客户机操作系统发送启动指令,以使得该客户机操作系统完全启动,当该客户机操作系统完全启动之后,该虚拟机监控系统的安全机制才会完全打开。In this embodiment of the present application, since the guest operating system runs on the virtual machine monitor, the security container sends the target parameters to the virtual machine monitor so that the virtual machine monitor starts based on the target parameters. , to control its own security mechanism, in the embodiment of the present application, the security container can also send a startup instruction to the guest operating system running on the virtual machine monitor, so that the guest operating system is fully started. When the The security mechanism of the virtual machine monitoring system will not be fully turned on until the guest operating system is fully started.
图2为本申请一些实施例提供的一种虚拟机监控器的安全加固过程示意图;图3为本申请一些实施例提供的一种客户机操作系统启动的过程示意图。现针对图2和图3进行说明。Figure 2 is a schematic diagram of the security hardening process of a virtual machine monitor provided by some embodiments of the present application; Figure 3 is a schematic diagram of the process of starting a guest operating system provided by some embodiments of the present application. Figures 2 and 3 will now be described.
读取配置文件(configuration.toml),并调用目标程序中预先定义的解析函数解析出配置文件中的目标参数(seccompsandbox参数),则将该目标参数发送给虚拟机监控器,以使虚拟机监控器基于该目标参数进行启动,来控制自身的安全机制打开,如图2所示。Read the configuration file (configuration.toml), and call the predefined parsing function in the target program to parse out the target parameters (seccompsandbox parameters) in the configuration file, then send the target parameters to the virtual machine monitor to enable virtual machine monitoring The server starts based on this target parameter to control the opening of its own security mechanism, as shown in Figure 2.
虚拟机监控器的安全机制打开之后,紧接着客户机操作系统(guestOS)会随之启动,进而完后曾虚拟机监控器的安全加固,如图3所示。After the security mechanism of the virtual machine monitor is turned on, the guest operating system (guestOS) will be started, and then the security of the virtual machine monitor is hardened, as shown in Figure 3.
图4为本申请实施例提供的一种安全加固的过程示意图,该过程包括以下步骤:Figure 4 is a schematic diagram of a security hardening process provided by an embodiment of the present application. The process includes the following steps:
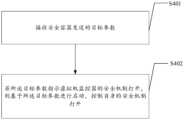
S401:接收安全容器发送的目标参数。S401: Receive the target parameters sent by the security container.
本申请实施例提供的安全加固方法应用于虚拟机监控器。The security hardening method provided by the embodiment of this application is applied to the virtual machine monitor.
在本申请实施例中,为了保护主机不被破坏,安全容器会向虚拟机监控器发送获取到的目标参数,该目标参数可以是指示虚拟机监控器的安全机制打开的参数,也可以是指示虚拟机监控器的安全机制不打开的参数,虚拟机监控器将会接收到安全容器发送的目标参数。In the embodiment of this application, in order to protect the host from being destroyed, the security container will send the obtained target parameters to the virtual machine monitor. The target parameters may be parameters that indicate that the security mechanism of the virtual machine monitor is turned on, or may be parameters that indicate that the security mechanism of the virtual machine monitor is turned on. For parameters where the security mechanism of the virtual machine monitor is not turned on, the virtual machine monitor will receive the target parameters sent by the security container.
在本申请实施例中,可以预先设置目标参数为on时,指示虚拟机监控器的安全机制打开,预先设置目标参数为off时,指示虚拟机监控器的安全机制不打开,具体的,可以根据需求配置打开时对应的目标参数以及关闭时对应的目标参数,同时支持多个具体参数组合的方式来进行配置,以此来达到不同的安全控制级别和控制范围,在此不做限制。In the embodiment of the present application, when the target parameter is set to on in advance, the security mechanism of the virtual machine monitor is turned on, and when the target parameter is set to off in advance, the security mechanism of the virtual machine monitor is not turned on. Specifically, it can be based on It is required to configure the corresponding target parameters when it is turned on and the corresponding target parameters when it is turned off. It also supports the configuration of multiple specific parameter combinations to achieve different security control levels and control ranges. There are no restrictions here.
S402:若所述目标参数指示虚拟机监控器的安全机制打开,则基于所述目标参数进行启动,控制自身的安全机制打开。S402: If the target parameter indicates that the security mechanism of the virtual machine monitor is turned on, start it based on the target parameter and control its own security mechanism to turn on.
若目标参数指示虚拟机监控器的安全机制打开,则虚拟机监控器基于该目标参数进行启动,进而控制该虚拟机监控器的安全机制打开,以实现虚拟机监控器的安全加固。If the target parameter indicates that the security mechanism of the virtual machine monitor is turned on, the virtual machine monitor is started based on the target parameter, and then the security mechanism of the virtual machine monitor is controlled to be turned on, so as to realize security hardening of the virtual machine monitor.
为了便于用户确定虚拟机监控器的安全机制是否打开,在上述各实施例的基础上,在本申请实施例中,所述方法还包括:In order to facilitate the user to determine whether the security mechanism of the virtual machine monitor is turned on, based on the above embodiments, in the embodiment of the present application, the method further includes:
接收虚拟机安全机制是否打开的查询指令;Receive the query instruction whether the virtual machine security mechanism is turned on;
查验所述虚拟机监控器是否已经打开了安全机制,获得查验结果,并将所述查验结果输出,其中,若所述虚拟机监控器的安全机制已经打开,则所述查验结果中携带所述目标参数。Check whether the security mechanism of the virtual machine monitor has been turned on, obtain the check result, and output the check result. Wherein, if the security mechanism of the virtual machine monitor has been turned on, the check result carries the target parameters.
在本申请实施例中,为了便于用户确定虚拟机监控器的安全机制是否打开,可以将该虚拟机监控器的安全机制是否打开的结果信息输出。In this embodiment of the present application, in order to facilitate the user to determine whether the security mechanism of the virtual machine monitor is turned on, the result information of whether the security mechanism of the virtual machine monitor is turned on may be output.
具体的,为了确定虚拟机监控器的安全机制是否打开,在本申请实施例中,可以向虚拟机监控器发送查询指令,虚拟机监控器可以在接收到虚拟机安全机制是否打开的查询指令时,对虚拟机的安全机制是否打开进行查验,并获得对应的查验结果,并将该查验结果输出。Specifically, in order to determine whether the security mechanism of the virtual machine monitor is turned on, in the embodiment of the present application, a query instruction can be sent to the virtual machine monitor, and the virtual machine monitor can receive a query instruction of whether the security mechanism of the virtual machine is turned on. , check whether the security mechanism of the virtual machine is turned on, obtain the corresponding check result, and output the check result.
具体的,可以将该查验结果通过文字的方式输出,还可以通过语音的方式输出,比如,可以输出“虚拟机监控器已经打开了安全机制”的文字,或者输出“虚拟机监控器已经打开了安全机制”的语音。Specifically, the check result can be output in text or voice. For example, the text "The virtual machine monitor has turned on the security mechanism" can be output, or the text "The virtual machine monitor has been turned on" can be output. "Safety Mechanism" voice.
在本申请实施例中,由于预先针对虚拟机监控器的安全机制是否已经打开设置了对应的目标参数,因此,在本申请实施例中,该查验结果还可以携带目标参数的结果,比如,若虚 拟机监控的安全机制已经打开时对应的目标参数为on,则在查询出虚拟机监控器的安全机制已经打开后,可以输出“虚拟机监控器的状态为on”等等。In the embodiment of the present application, since the corresponding target parameters are set in advance regarding whether the security mechanism of the virtual machine monitor has been turned on, in the embodiment of the present application, the check result can also carry the result of the target parameter, for example, if When the security mechanism of the virtual machine monitor has been turned on, the corresponding target parameter is on. After querying that the security mechanism of the virtual machine monitor has been turned on, "the status of the virtual machine monitor is on" and so on can be output.
为了便于描述,后续以一个具体的实施例进行说明:For the convenience of description, a specific embodiment will be used to illustrate:
为了实现安全加固,首先开发人员预先编写了写入了参数赋值字段的程序,将目标参数赋值给该参数赋值字段后编译生成写入了目标参数的配置文件,后续安全容器在接收到安全容器启动指令之后,则读取配置文件,并调用目标程序中预先定义的解析函数解析出该配置文件中的目标参数,若该目标参数指示虚拟机监控器的安全机制打开,则将该目标参数发送给虚拟机监控器,虚拟机监控器在接收到该目标参数之后,基于该目标参数进行启动,来控制自身的安全机制打开。In order to achieve security hardening, developers first pre-write a program that writes the parameter assignment field. After assigning the target parameter to the parameter assignment field, it compiles and generates a configuration file with the target parameter written in it. Subsequently, the secure container starts after receiving the secure container After the instruction, the configuration file is read, and the predefined parsing function in the target program is called to parse out the target parameters in the configuration file. If the target parameter indicates that the security mechanism of the virtual machine monitor is turned on, the target parameter is sent to Virtual machine monitor. After receiving the target parameter, the virtual machine monitor starts based on the target parameter to control the opening of its own security mechanism.
图5a-图5c图为本申请一些实施例提供的一种获得配置文件的过程示意图;现针对图5a-图5c进行说明。Figures 5a-5c are schematic diagrams of a process of obtaining a configuration file provided by some embodiments of the present application; Figures 5a-5c will now be described.
获得配置文件的第一个步骤为:开发人员修改Kata Runtime部分的Makefile,新增一个编译宏,该编译宏可以为DEFSECCOMPSANDBOXPARAM,具体的,该编译宏用于控制是否打开虚拟机监控器的安全机制,其中,该安全机制也就是相当于通过减少某类系统调用不被允许的方式,来减小虚拟机监控器对主机攻击面。在本申请实施例中,可以不允许以下类的系统调用:不允许虚拟机监控器使用废弃的系统调用、不允许虚拟机监控器提升优先级来使用所有的setuid/gid系统调用、不允许qemu spawn新的线程和进程以及不允许虚拟机监控器使用进程亲和性和设置调度器优先级等等。The first step to obtain the configuration file is: the developer modifies the Makefile of the Kata Runtime part and adds a compilation macro. The compilation macro can be DEFSECCOMPSANDBOXPARAM. Specifically, the compilation macro is used to control whether to turn on the security mechanism of the virtual machine monitor. , among which, this security mechanism is equivalent to reducing the attack surface of the virtual machine monitor on the host by reducing certain types of system calls that are not allowed. In the embodiment of this application, the following types of system calls may not be allowed: the virtual machine monitor is not allowed to use abandoned system calls, the virtual machine monitor is not allowed to increase the priority to use all setuid/gid system calls, and qemu is not allowed spawn new threads and processes and disallow the hypervisor from using process affinity and setting scheduler priorities, etc.
具体的,新增编译宏对应的程序可以为:Specifically, the program corresponding to the newly added compilation macro can be:
DEFSECCOMPSANDBOXPARAM:=on,obsolete=deny,elevateprivileges=deny,spawn=deny,resourcecontrol=denyDEFSECCOMPSANDBOXPARAM:=on,obsolete=deny,elevateprivileges=deny,spawn=deny,resourcecontrol=deny
其中,obsolete=deny:表示不允许虚拟机监控器使用废弃的系统调用;elevateprivileges=deny:表示不允许虚拟机监控器提升优先级来使用所有的setuid/gid系统调用;spawn=deny:表示不允许qemu spawn新的线程和进程;resourcecontrol=deny:表示不允许虚拟机监控器使用进程亲和性和设置调度器优先级。Among them, obsolete=deny: means that the virtual machine monitor is not allowed to use abandoned system calls; elevateprivileges=deny: means that the virtual machine monitor is not allowed to increase the priority to use all setuid/gid system calls; spawn=deny: means that it is not allowed qemu spawn new threads and processes; resourcecontrol=deny: Indicates that the virtual machine monitor is not allowed to use process affinity and set scheduler priority.
在将Makefile修改完成后,可将修改后的Makefile传入Kata Runtime的编译系统(kata Building System),参见图5a。After the Makefile is modified, the modified Makefile can be passed into the Kata Runtime compilation system (kata Building System), see Figure 5a.
获得配置文件的第二个步骤为:修改kata runtime对底层虚拟机监控器qemu的配置文件configuration-qemu.toml.in,新增参数seccompsandbox(目标参数),如下:The second step to obtain the configuration file is to modify the configuration file configuration-qemu.toml.in of kata runtime for the underlying virtual machine monitor qemu, and add the parameter seccompsandbox (target parameter) as follows:
seccompsandbox="@DEFSECCOMPSANDBOXPARAM@"seccompsandbox="@DEFSECCOMPSANDBOXPARAM@"
具体的,在对kata runtime编译时,编译系统会自动解析第一个步骤中的 DEFSECCOMPSANDBOXPARAM宏的定义,然后传递给configuration-qemu.toml.in的seccompsandbox参数(目标参数),以便于后续Kata runtime初始化时对其进行解析,然后将该configuration-qemu.toml.in与第一个步骤中修改后的Makefile文件一起传入到Kata Runtime的编译系统,见图5b。Specifically, when compiling kata runtime, the compilation system will automatically parse the definition of DEFSECCOMPSANDBOXPARAM macro in the first step, and then pass it to the seccompsandbox parameter (target parameter) of configuration-qemu.toml.in to facilitate subsequent Kata runtime initialization It is parsed at the time, and then the configuration-qemu.toml.in is passed to the compilation system of Kata Runtime together with the modified Makefile in the first step, see Figure 5b.
获得配置文件的第三个步骤为:修改katautils config.go的结构体hypervisor struct,新增SeccompSandbox string`toml:"seccompsandbox"`字段,该新增的SeccompSandbox string`toml:"seccompsandbox"`字段用于接收configuration-qemu.toml.in配置文件里的seccompsandbox参数内容,便于后续对其进行内部处理。The third step to obtain the configuration file is to modify the hypervisor struct of katautils config.go and add the SeccompSandbox string `toml:"seccompsandbox"` field. The new SeccompSandbox string `toml:"seccompsandbox"` field is used for Receive the seccompsandbox parameter content in the configuration-qemu.toml.in configuration file to facilitate subsequent internal processing.
具体的,对应的程序为:Specifically, the corresponding procedures are:
获得配置文件的第四个步骤为:修改katautils config.go的newQemuHypervisorConfig函数实现,在生成vc.HypervisorConfig结构体的时候,新增字段SeccompSandbox:h.SeccompSandbox。The fourth step to obtain the configuration file is to modify the newQemuHypervisorConfig function implementation of katautils config.go. When generating the vc.HypervisorConfig structure, add a new field SeccompSandbox:h.SeccompSandbox.
newQemuHypervisorConfig被调用的代码路径如下:The code path where newQemuHypervisorConfig is called is as follows:
loadRuntimeConfigloadRuntimeConfig
LoadConfigurationLoadConfiguration
updateRuntimeConfigupdateRuntimeConfig
updateRuntimeConfigHypervisorupdateRuntimeConfigHypervisor
newQemuHypervisorConfignewQemuHypervisorConfig
获得配置文件的第五个步骤为:修改govmm的代码,对其数据结构Config struct新增字段SeccompSandbox string,用于接收解析configuration-qemu.toml.in配置文件以后的内部存储。The fifth step to obtain the configuration file is to modify the govmm code and add a new field SeccompSandbox string to its data structure Config struct, which is used to receive the internal storage after parsing the configuration-qemu.toml.in configuration file.
具体的,对应的程序为:Specifically, the corresponding procedures are:
获得配置文件的第六个步骤为:修改govmm的代码实现,新增函数appendSeccompSandbox(),使之能解析toml配置文件的seccompsandbox参数The sixth step to obtain the configuration file is to modify the code implementation of govmm and add a new function appendSeccompSandbox() so that it can parse the seccompsandbox parameter of the toml configuration file.
具体的,对应的程序为:Specifically, the corresponding procedures are:
其中,appendSeccompSandbox()用于保证后续目标程序可以解析configuration-qemu.toml.in的配置。如果configuration-qemu.toml.in文件配置了seccompsandbox参数,则此函数会把参数内容转换成Kata安全容器的底层虚拟机监控器的启动命令行参数,也就是说,使得虚拟机监控器基于该seccompsandbox参数进行启动,来控制自身的安全机制打开。Among them, appendSeccompSandbox() is used to ensure that subsequent target programs can parse the configuration of configuration-qemu.toml.in. If the configuration-qemu.toml.in file is configured with the seccompsandbox parameter, this function will convert the parameter content into the startup command line parameters of the underlying virtual machine monitor of the Kata secure container, that is, make the virtual machine monitor based on the seccompsandbox parameters to start to control the opening of its own security mechanism.
获得配置文件的第七个步骤为:修改LaunchQemu代码,使之调用第三个步骤里实现的appendSeccompSandbox():The seventh step to obtain the configuration file is to modify the LaunchQemu code to call appendSeccompSandbox() implemented in the third step:
具体的,对应的程序为:Specifically, the corresponding procedures are:
LaunchQemu代码被路径如下:The LaunchQemu code is routed as follows:
createSandboxFromConfigcreateSandboxFromConfig
startVMstartVM
startSandboxstartSandbox
LaunchQemuLaunchQemu
config.appendSandboxOn()config.appendSandboxOn()
在完成步骤一到步骤七的过程以后,用标准方法重新编译Kata Runtime模块。After completing steps one through seven, recompile the Kata Runtime module using standard methods.
具体的,编译步骤如下:Specifically, the compilation steps are as follows:
cd$GOPATH/src/github.com/kata-containers/kata-containers/src/runtimecd$GOPATH/src/github.com/kata-containers/kata-containers/src/runtime
make cleanmake clean
MakeMake
编译完成后,会得到Kata二进制文件containerd-shim-kata-v2和配置文本文件configuration.toml(写入了目标参数的配置文件),见图5c。After compilation is completed, you will get the Kata binary file containerd-shim-kata-v2 and the configuration text file configuration.toml (the configuration file with the target parameters written in it), see Figure 5c.
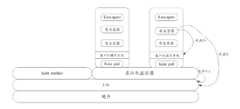
图6为本申请实施例提供的一种虚拟机监控器未加固前的整体框架,图7为本申请实施例提供的一种虚拟机监控器加固后的整体框架,现针对图6和图7进行说明。Figure 6 is an overall framework of a virtual machine monitor provided by an embodiment of the present application before being hardened. Figure 7 is an overall framework of a virtual machine monitor provided by an embodiment of the present application after being hardened. Now, with reference to Figures 6 and 7 Be explained.
虚拟机监控器未加固前,当安全容器(container)被攻击时,客户机操作系统(guestOS)有可能被攻破,参见攻击1,却难以从guestOS攻击到主机,即一般不会出现攻击2的情况。但是攻击者可以从另一个角度来攻击主机,即从虚拟机监控器(Qemu)侧进行攻击,参见攻击3,造成主机被破坏,参见图6。Before the virtual machine monitor is hardened, when the security container (container) is attacked, the guest operating system (guestOS) may be compromised. See Attack 1. However, it is difficult to attack the host from the guestOS, that is, attack 2 generally does not occur. Condition. However, the attacker can attack the host from another angle, that is, attack from the virtual machine monitor (Qemu) side, see Attack 3, causing the host to be destroyed, see Figure 6.
虚拟机监控器实现安全加固后,也就是说,虚拟机监控器打开了安全机制之后,当安全容器(container)被攻击时,客户机操作系统(guestOS)有可能被攻破,参见攻击1,当安全容器(container)被攻击时,难以从guestOS攻击到主机,即一般不会出现攻击2的情况。且攻击者从虚拟机监控器Qemu侧进行攻击,也不会造成主机被破坏,即也不会出现攻击3的情况。After the virtual machine monitor implements security hardening, that is to say, after the virtual machine monitor turns on the security mechanism, when the security container (container) is attacked, the guest operating system (guestOS) may be breached. See Attack 1. When When a secure container (container) is attacked, it is difficult to attack the host from the guestOS, that is, attack 2 generally does not occur. And if the attacker attacks from the Qemu side of the virtual machine monitor, the host will not be damaged, that is, attack 3 will not occur.
图8为本申请一些实施例提供的一种安全加固装置结构示意图,该装置包括:Figure 8 is a schematic structural diagram of a security reinforcement device provided by some embodiments of the present application. The device includes:
解析模块801,用于若接收到安全容器启动指令,则读取写入了目标参数的配置文件,并调用目标程序中预先定义的解析函数解析出所述配置文件中的所述目标参数;The
发送模块802,用于若所述目标参数指示虚拟机监控器的安全机制打开,则将所述目标参数发送给所述虚拟机监控器,以使所述虚拟机监控器基于所述目标参数进行启动,来控制自身的安全机制打开。Sending
在一种可能的实施方式中,所述发送模块802,还用于向运行在所述虚拟机监控器上的客户机操作系统发送启动指令,以使所述客户机操作系统完成启动。In a possible implementation, the sending
图9为本申请一些实施例提供的一种安全加固装置结构示意图,该装置包括:Figure 9 is a schematic structural diagram of a security reinforcement device provided by some embodiments of the present application. The device includes:
接收模块901,用于接收安全容器发送的目标参数;The receiving
控制模块902,用于若所述目标参数指示虚拟机监控器的安全机制打开,则基于所述目标参数进行启动,控制自身的安全机制打开。The
在一种可能的实施方式中,所述接收模块901,还用于接收虚拟机安全机制是否打开的查询指令;In a possible implementation, the receiving
所述装置还包括:The device also includes:
处理模块903,用于查验所述虚拟机监控器是否已经打开了安全机制,获得查验结果, 并将所述查验结果输出,其中,若所述虚拟机监控器的安全机制已经打开,则所述查验结果中携带所述目标参数。The
在上述各实施例的基础上,本申请一些实施例还提供了一种电子设备,如图10所示,包括:处理器1001、通信接口1002、存储器1003和通信总线1004,其中,处理器1001,通信接口1002,存储器1003通过通信总线1004完成相互间的通信。Based on the above embodiments, some embodiments of the present application also provide an electronic device, as shown in Figure 10, including: a
所述存储器1003中存储有计算机程序,当所述程序被所述处理器1001执行时,使得所述处理器1001执行如下步骤:The
若接收到安全容器启动指令,则读取写入了目标参数的配置文件,并调用目标程序中预先定义的解析函数解析出所述配置文件中的所述目标参数;If the secure container startup instruction is received, the configuration file in which the target parameters are written is read, and the predefined parsing function in the target program is called to parse out the target parameters in the configuration file;
若所述目标参数指示虚拟机监控器的安全机制打开,则将所述目标参数发送给所述虚拟机监控器,以使所述虚拟机监控器基于所述目标参数进行启动,来控制自身的安全机制打开。If the target parameter indicates that the security mechanism of the virtual machine monitor is turned on, the target parameter is sent to the virtual machine monitor, so that the virtual machine monitor starts based on the target parameter to control its own The safety mechanism is on.
进一步地,所述处理器1001,还用于向运行在所述虚拟机监控器上的客户机操作系统发送启动指令,以使所述客户机操作系统完成启动。Further, the
上述服务器提到的通信总线可以是外设部件互连标准(Peripheral Component Interconnect,PCI)总线或扩展工业标准结构(Extended Industry Standard Architecture,EISA)总线等。该通信总线可以分为地址总线、数据总线、控制总线等。为便于表示,图中仅用一条粗线表示,但并不表示仅有一根总线或一种类型的总线。The communication bus mentioned in the above-mentioned server can be the Peripheral Component Interconnect (PCI) bus or the Extended Industry Standard Architecture (EISA) bus, etc. The communication bus can be divided into address bus, data bus, control bus, etc. For ease of presentation, only one thick line is used in the figure, but it does not mean that there is only one bus or one type of bus.
通信接口1002用于上述电子设备与其他设备之间的通信。The
存储器可以包括随机存取存储器(Random Access Memory,RAM),也可以包括非易失性存储器(Non-Volatile Memory,NVM),例如至少一个磁盘存储器。可选地,存储器还可以是至少一个位于远离前述处理器的存储装置。The memory may include random access memory (Random Access Memory, RAM) or non-volatile memory (Non-Volatile Memory, NVM), such as at least one disk memory. Optionally, the memory may also be at least one storage device located remotely from the aforementioned processor.
上述处理器可以是通用处理器,包括中央处理器、网络处理器(Network Processor,NP)等;还可以是数字指令处理器(Digital Signal Processing,DSP)、专用集成电路、现场可编程门阵列或者其他可编程逻辑器件、分立门或者晶体管逻辑器件、分立硬件组件等。The above-mentioned processor can be a general-purpose processor, including a central processing unit, a network processor (Network Processor, NP), etc.; it can also be a digital instruction processor (Digital Signal Processing, DSP), an application-specific integrated circuit, a field programmable gate array, or Other programmable logic devices, discrete gate or transistor logic devices, discrete hardware components, etc.
在上述各实施例的基础上,本申请一些实施例还提供了一种电子设备,如图11所示,包括:处理器1101、通信接口1102、存储器1103和通信总线1104,其中,处理器1101,通信接口1102,存储器1103通过通信总线1104完成相互间的通信。Based on the above embodiments, some embodiments of the present application also provide an electronic device, as shown in Figure 11, including: a
所述存储器1103中存储有计算机程序,当所述程序被所述处理器1101执行时,使得所述处理器1101执行如下步骤:The
接收安全容器发送的目标参数;Receive the target parameters sent by the security container;
若所述目标参数指示虚拟机监控器的安全机制打开,则基于所述目标参数进行启动,控制自身的安全机制打开。If the target parameter indicates that the security mechanism of the virtual machine monitor is turned on, it is started based on the target parameter and controls its own security mechanism to be turned on.
进一步地,所述处理器1101,还用于接收虚拟机安全机制是否打开的查询指令;Further, the
查验所述虚拟机监控器是否已经打开了安全机制,获得查验结果,并将所述查验结果输出,其中,若所述虚拟机监控器的安全机制已经打开,则所述查验结果中携带所述目标参数。Check whether the security mechanism of the virtual machine monitor has been turned on, obtain the check result, and output the check result. Wherein, if the security mechanism of the virtual machine monitor has been turned on, the check result carries the target parameters.
上述服务器提到的通信总线可以是外设部件互连标准(Peripheral Component Interconnect,PCI)总线或扩展工业标准结构(Extended Industry Standard Architecture,EISA)总线等。该通信总线可以分为地址总线、数据总线、控制总线等。为便于表示,图中仅用一条粗线表示,但并不表示仅有一根总线或一种类型的总线。The communication bus mentioned in the above-mentioned server can be the Peripheral Component Interconnect (PCI) bus or the Extended Industry Standard Architecture (EISA) bus, etc. The communication bus can be divided into address bus, data bus, control bus, etc. For ease of presentation, only one thick line is used in the figure, but it does not mean that there is only one bus or one type of bus.
通信接口1102用于上述电子设备与其他设备之间的通信。The
存储器可以包括随机存取存储器(Random Access Memory,RAM),也可以包括非易失性存储器(Non-Volatile Memory,NVM),例如至少一个磁盘存储器。可选地,存储器还可以是至少一个位于远离前述处理器的存储装置。The memory may include random access memory (Random Access Memory, RAM) or non-volatile memory (Non-Volatile Memory, NVM), such as at least one disk memory. Optionally, the memory may also be at least one storage device located remotely from the aforementioned processor.
上述处理器可以是通用处理器,包括中央处理器、网络处理器(Network Processor,NP)等;还可以是数字指令处理器(Digital Signal Processing,DSP)、专用集成电路、现场可编程门阵列或者其他可编程逻辑器件、分立门或者晶体管逻辑器件、分立硬件组件等。The above-mentioned processor can be a general-purpose processor, including a central processing unit, a network processor (Network Processor, NP), etc.; it can also be a digital instruction processor (Digital Signal Processing, DSP), an application-specific integrated circuit, a field programmable gate array, or Other programmable logic devices, discrete gate or transistor logic devices, discrete hardware components, etc.
在上述各实施例的基础上,本申请一些实施例还提供了一种计算机可读存储介质,所述计算机可读存储介质内存储有可由电子设备执行的计算机程序,当所述程序在所述电子设备上运行时,使得所述电子设备执行时实现如下步骤:On the basis of the above embodiments, some embodiments of the present application also provide a computer-readable storage medium. The computer-readable storage medium stores a computer program that can be executed by an electronic device. When the program is in the When running on an electronic device, the following steps are implemented when the electronic device is executed:
若接收到安全容器启动指令,则读取写入了目标参数的配置文件,并调用目标程序中预先定义的解析函数解析出所述配置文件中的所述目标参数;If the secure container startup instruction is received, the configuration file in which the target parameters are written is read, and the predefined parsing function in the target program is called to parse out the target parameters in the configuration file;
若所述目标参数指示虚拟机监控器的安全机制打开,则将所述目标参数发送给所述虚拟机监控器,以使所述虚拟机监控器基于所述目标参数进行启动,来控制自身的安全机制打开。If the target parameter indicates that the security mechanism of the virtual machine monitor is turned on, the target parameter is sent to the virtual machine monitor, so that the virtual machine monitor starts based on the target parameter to control its own The safety mechanism is on.
进一步地,所述将所述目标参数发送给虚拟机监控器之后,所述方法还包括:Further, after sending the target parameters to the virtual machine monitor, the method further includes:
向运行在所述虚拟机监控器上的客户机操作系统发送启动指令,以使所述客户机操作系统完成启动。Send a startup instruction to the guest operating system running on the virtual machine monitor, so that the guest operating system completes startup.
在上述各实施例的基础上,本申请一些实施例还提供了一种计算机可读存储介质,所述 计算机可读存储介质内存储有可由电子设备执行的计算机程序,当所述程序在所述电子设备上运行时,使得所述电子设备执行时实现如下步骤:On the basis of the above embodiments, some embodiments of the present application also provide a computer-readable storage medium. The computer-readable storage medium stores a computer program that can be executed by an electronic device. When the program is in the When running on an electronic device, the following steps are implemented when the electronic device is executed:
接收安全容器发送的目标参数;Receive the target parameters sent by the security container;
若所述目标参数指示虚拟机监控器的安全机制打开,则基于所述目标参数进行启动,控制自身的安全机制打开。If the target parameter indicates that the security mechanism of the virtual machine monitor is turned on, it is started based on the target parameter and controls its own security mechanism to be turned on.
进一步地,所述方法还包括:Further, the method also includes:
接收虚拟机安全机制是否打开的查询指令;Receive the query instruction whether the virtual machine security mechanism is turned on;
查验所述虚拟机监控器是否已经打开了安全机制,获得查验结果,并将所述查验结果输出,其中,若所述虚拟机监控器的安全机制已经打开,则所述查验结果中携带所述目标参数。Check whether the security mechanism of the virtual machine monitor has been turned on, obtain the check result, and output the check result. Wherein, if the security mechanism of the virtual machine monitor has been turned on, the check result carries the target parameters.
由于在本申请实施例中,可以通过控制虚拟机监控器的安全机制打开的方式,来对虚拟机监控器进行安全加固,减少虚拟机监控器对外的被攻击暴露面,从而避免虚拟机监控器被攻击,导致主机被破坏的问题,提高了容器环境的安全性。In this embodiment of the present application, the security of the virtual machine monitor can be reinforced by controlling the opening of the security mechanism of the virtual machine monitor, thereby reducing the exposure of the virtual machine monitor to external attacks, thereby preventing the virtual machine monitor from being attacked. The problem of being attacked and causing the host to be destroyed improves the security of the container environment.
本领域内的技术人员应明白,本申请的实施例可提供为方法、系统、或计算机程序产品。因此,本申请可采用完全硬件实施例、完全软件实施例、或结合软件和硬件方面的实施例的形式。而且,本申请可采用在一个或多个其中包含有计算机可用程序代码的计算机可用存储介质(包括但不限于磁盘存储器、CD-ROM、光学存储器等)上实施的计算机程序产品的形式。Those skilled in the art will understand that embodiments of the present application may be provided as methods, systems, or computer program products. Accordingly, the present application may take the form of an entirely hardware embodiment, an entirely software embodiment, or an embodiment that combines software and hardware aspects. Furthermore, the present application may take the form of a computer program product embodied on one or more computer-usable storage media (including, but not limited to, disk storage, CD-ROM, optical storage, etc.) having computer-usable program code embodied therein.
本申请是参照根据本申请的方法、设备(系统)、和计算机程序产品的流程图和/或方框图来描述的。应理解可由计算机程序指令实现流程图和/或方框图中的每一流程和/或方框、以及流程图和/或方框图中的流程和/或方框的结合。可提供这些计算机程序指令到通用计算机、专用计算机、嵌入式处理机或其他可编程数据处理设备的处理器以产生一个机器,使得通过计算机或其他可编程数据处理设备的处理器执行的指令产生用于实现在流程图一个流程或多个流程和/或方框图一个方框或多个方框中指定的功能的装置。The present application is described with reference to flowchart illustrations and/or block diagrams of methods, apparatus (systems), and computer program products according to the present application. It will be understood that each process and/or block in the flowchart illustrations and/or block diagrams, and combinations of processes and/or blocks in the flowchart illustrations and/or block diagrams, can be implemented by computer program instructions. These computer program instructions may be provided to a processor of a general purpose computer, special purpose computer, embedded processor, or other programmable data processing device to produce a machine, such that the instructions executed by the processor of the computer or other programmable data processing device produce a use A device for realizing the functions specified in one process or multiple processes of the flowchart and/or one block or multiple blocks of the block diagram.
这些计算机程序指令也可存储在能引导计算机或其他可编程数据处理设备以特定方式工作的计算机可读存储器中,使得存储在该计算机可读存储器中的指令产生包括指令装置的制造品,该指令装置实现在流程图一个流程或多个流程和/或方框图一个方框或多个方框中指定的功能。These computer program instructions may also be stored in a computer-readable memory that causes a computer or other programmable data processing apparatus to operate in a particular manner, such that the instructions stored in the computer-readable memory produce an article of manufacture including the instruction means, the instructions The device implements the functions specified in a process or processes of the flowchart and/or a block or blocks of the block diagram.
这些计算机程序指令也可装载到计算机或其他可编程数据处理设备上,使得在计算机或其他可编程设备上执行一系列操作步骤以产生计算机实现的处理,从而在计算机或其他可编 程设备上执行的指令提供用于实现在流程图一个流程或多个流程和/或方框图一个方框或多个方框中指定的功能的步骤。These computer program instructions may also be loaded onto a computer or other programmable data processing device, causing a series of operating steps to be performed on the computer or other programmable device to produce computer-implemented processing, thereby executing on the computer or other programmable device. Instructions provide steps for implementing the functions specified in a process or processes of a flowchart diagram and/or a block or blocks of a block diagram.
显然,本领域的技术人员可以对本申请进行各种改动和变型而不脱离本申请的精神和范围。这样,倘若本申请的这些修改和变型属于本申请权利要求及其等同技术的范围之内,则本申请也意图包含这些改动和变型在内。Obviously, those skilled in the art can make various changes and modifications to the present application without departing from the spirit and scope of the present application. In this way, if these modifications and variations of the present application fall within the scope of the claims of the present application and equivalent technologies, the present application is also intended to include these modifications and variations.
Claims (10)
Translated fromChineseApplications Claiming Priority (2)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202210591394.7 | 2022-05-27 | ||
| CN202210591394.7ACN115033302B (en) | 2022-05-27 | 2022-05-27 | A security reinforcement method, device, equipment and medium |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| WO2023226421A1true WO2023226421A1 (en) | 2023-11-30 |
Family
ID=83121786
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| PCT/CN2022/141587CeasedWO2023226421A1 (en) | 2022-05-27 | 2022-12-23 | Security reinforcement method and apparatus, device, and medium |
Country Status (2)
| Country | Link |
|---|---|
| CN (1) | CN115033302B (en) |
| WO (1) | WO2023226421A1 (en) |
Families Citing this family (1)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN115033302B (en)* | 2022-05-27 | 2024-11-26 | 天翼云科技有限公司 | A security reinforcement method, device, equipment and medium |
Citations (5)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN110059453A (en)* | 2019-03-13 | 2019-07-26 | 中国科学院计算技术研究所 | A kind of container virtualization safety reinforced device and method |
| US20200026859A1 (en)* | 2018-07-20 | 2020-01-23 | George Mason University | Methods and systems for system call reduction |
| US20200285733A1 (en)* | 2019-03-08 | 2020-09-10 | Electronics And Telecommunications Research Institute | System and method for generating security profile of container instance |
| CN114035886A (en)* | 2021-09-28 | 2022-02-11 | 中国科学院信息工程研究所 | Container security reinforcement system and method for kernel data |
| CN115033302A (en)* | 2022-05-27 | 2022-09-09 | 天翼云科技有限公司 | A security reinforcement method, device, equipment and medium |
Family Cites Families (13)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN103345604A (en)* | 2013-07-16 | 2013-10-09 | 湘潭大学 | Sandbox system based on light-weight virtual machine monitor and method for monitoring OS with sandbox system |
| CN103902885B (en)* | 2014-03-04 | 2017-11-17 | 重庆邮电大学 | Towards multi-security level(MSL) virtual desktop system secure virtual machine shielding system and method |
| CN106529284B (en)* | 2016-11-02 | 2020-04-28 | 深圳前海生生科技有限公司 | Virtual machine monitor security reinforcement method based on security chip |
| CN109358949A (en)* | 2018-10-18 | 2019-02-19 | 郑州云海信息技术有限公司 | A virtual machine system security controlled device |
| CN109858288B (en)* | 2018-12-26 | 2021-04-13 | 中国科学院信息工程研究所 | Method and device for realizing safety isolation of virtual machine |
| CN110008001B (en)* | 2019-03-29 | 2021-01-05 | 网御安全技术(深圳)有限公司 | Security reinforcement method and system for virtual machine monitor and hardware security monitoring card |
| CN111190692A (en)* | 2019-12-26 | 2020-05-22 | 山东乾云启创信息科技股份有限公司 | Monitoring method and system based on Roc processor and readable medium |
| CN110825499B (en)* | 2020-01-13 | 2020-06-19 | 中软信息系统工程有限公司 | Method and device for realizing security isolation based on unified container cloud platform |
| CN111400702B (en)* | 2020-03-24 | 2023-06-27 | 上海瓶钵信息科技有限公司 | Virtualized operating system kernel protection method |
| CN113448682B (en)* | 2020-03-27 | 2024-04-19 | 支付宝(杭州)信息技术有限公司 | Virtual machine monitor loading method and device and electronic equipment |
| CN114253655B (en)* | 2020-09-24 | 2025-07-29 | 电科云(北京)科技有限公司 | MIPS64 instruction set-based security container isolation method and device |
| CN112364343B (en)* | 2020-11-16 | 2022-05-06 | 支付宝(杭州)信息技术有限公司 | Method and device for protecting secrets of virtual machine monitor and electronic equipment |
| CN112650554A (en)* | 2020-12-21 | 2021-04-13 | 浪潮云信息技术股份公司 | Method for realizing strong isolation of container |
- 2022
- 2022-05-27CNCN202210591394.7Apatent/CN115033302B/enactiveActive
- 2022-12-23WOPCT/CN2022/141587patent/WO2023226421A1/ennot_activeCeased
Patent Citations (5)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20200026859A1 (en)* | 2018-07-20 | 2020-01-23 | George Mason University | Methods and systems for system call reduction |
| US20200285733A1 (en)* | 2019-03-08 | 2020-09-10 | Electronics And Telecommunications Research Institute | System and method for generating security profile of container instance |
| CN110059453A (en)* | 2019-03-13 | 2019-07-26 | 中国科学院计算技术研究所 | A kind of container virtualization safety reinforced device and method |
| CN114035886A (en)* | 2021-09-28 | 2022-02-11 | 中国科学院信息工程研究所 | Container security reinforcement system and method for kernel data |
| CN115033302A (en)* | 2022-05-27 | 2022-09-09 | 天翼云科技有限公司 | A security reinforcement method, device, equipment and medium |
Non-Patent Citations (2)
| Title |
|---|
| ANONYMOUS: "Using Seccomp to Restrict System Calls to Containers", KUBERNETES V1.19 [STABLE], 24 February 2022 (2022-02-24), XP093112574, Retrieved from the Internet <URL:https://kubernetes.io/zh-cn/docs/tutorials/security/seccomp/> [retrieved on 20231215]* |
| YE CHEN, XIN FAN: "Docker Container Security Application Restrictions Seccomp", THBLOG, 21 June 2021 (2021-06-21), XP093112580, Retrieved from the Internet <URL:https://www.tnblog.net/hb/article/details/6154> [retrieved on 20231215]* |
Also Published As
| Publication number | Publication date |
|---|---|
| CN115033302B (en) | 2024-11-26 |
| CN115033302A (en) | 2022-09-09 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| US10489187B2 (en) | Systems and methods for auditing a virtual machine | |
| JP6248153B2 (en) | Activate trust level | |
| US8099574B2 (en) | Providing protected access to critical memory regions | |
| US9811663B2 (en) | Generic unpacking of applications for malware detection | |
| TWI533204B (en) | Method and system for application execution in a restricted application execution environment, and computer-readable storage medium for recording related instructions thereon | |
| US10545851B2 (en) | Breakpoint insertion into kernel pages | |
| JP7228751B2 (en) | Method and apparatus for authority management, computer equipment and storage medium | |
| US20080047023A1 (en) | User space virtualization system | |
| CN1585927A (en) | A method for providing system integrity and legacy environment emulation | |
| JP2010511227A (en) | Compile executable code into unreliable address space | |
| JP2007249933A (en) | Managing access to content in data processing equipment | |
| EP3701411B1 (en) | Software packages policies management in a securela booted enclave | |
| WO2019128075A1 (en) | Application management method for terminal, application server and terminal | |
| WO2023226421A1 (en) | Security reinforcement method and apparatus, device, and medium | |
| US11354407B2 (en) | Techniques for library behavior verification | |
| WO2021118730A1 (en) | Overlap customer planned activity to migrate a virtual machine | |
| CN116522413A (en) | Method of operation, processor, electronic device and storage medium of a computer system | |
| US20240362049A1 (en) | Using virtual machine privilege levels to control write access to kernel memory in a virtual machine | |
| US20250245343A1 (en) | Vulnerability mitigation using a runtime agent | |
| Iseal | Understanding UEFI Capsule Update Mechanisms | |
| WO2024217281A1 (en) | Data processing method and apparatus, and computer-readable storage medium | |
| CN114579254A (en) | System calling method and device of microkernel virtualization operating system | |
| CN118821207A (en) | Driver file installation script generation method, device, computer equipment and medium | |
| CN117272377A (en) | Authorization data processing method, device and electronic equipment | |
| CN120693613A (en) | Methods for embedding applications in real-time environments |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| 121 | Ep: the epo has been informed by wipo that ep was designated in this application | Ref document number:22943606 Country of ref document:EP Kind code of ref document:A1 | |
| NENP | Non-entry into the national phase | Ref country code:DE | |
| 122 | Ep: pct application non-entry in european phase | Ref document number:22943606 Country of ref document:EP Kind code of ref document:A1 |