WO2018145546A1 - Authentication method, device and storage medium - Google Patents
Authentication method, device and storage mediumDownload PDFInfo
- Publication number
- WO2018145546A1 WO2018145546A1PCT/CN2018/071503CN2018071503WWO2018145546A1WO 2018145546 A1WO2018145546 A1WO 2018145546A1CN 2018071503 WCN2018071503 WCN 2018071503WWO 2018145546 A1WO2018145546 A1WO 2018145546A1
- Authority
- WO
- WIPO (PCT)
- Prior art keywords
- target
- policy table
- resource
- access request
- policy
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Ceased
Links
Images
Classifications
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/10—Network architectures or network communication protocols for network security for controlling access to devices or network resources
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L67/00—Network arrangements or protocols for supporting network services or applications
- H04L67/14—Session management
- H04L67/146—Markers for unambiguous identification of a particular session, e.g. session cookie or URL-encoding
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L67/00—Network arrangements or protocols for supporting network services or applications
- H04L67/50—Network services
- H04L67/60—Scheduling or organising the servicing of application requests, e.g. requests for application data transmissions using the analysis and optimisation of the required network resources
Definitions
- the present applicationrelates to the field of information security technologies, and in particular, to an authentication method, apparatus, and storage medium.
- cloud service authentication systemusers can access cloud resources through the cloud service management platform. However, not every user has the right to access the cloud resources.
- the cloud service management platformneeds to authenticate the user who sends the resource access request, and only the user who passes the authentication can access the cloud resource.
- the embodiment of the present inventionprovides an authentication method, an apparatus, and a storage medium.
- searching data related to a resource access request from a policy table classified according to a user identifierthe search time of the resource access request related data is saved, thereby improving
- the authentication efficiency of the resource access requestavoids the waste of processing resources of the computing device caused by searching related data of the resource access request in the plurality of relation tables.
- An embodiment of the present applicationprovides an authentication method, which is applied to a computing device, including:
- Target resource access requestcarries a target user identifier, a target access resource, and a target operation mode for accessing the resource to the target;
- the target resource access requestis authenticated by using the first policy table, and the authentication result of the target resource access request is output;
- the first policy tableis a relationship table including a user identifier, an accessible resource corresponding to the user identifier, and a corresponding relationship between the operable modes of the accessible resource, where the first policy table is Classified by the user identifier, each user identifier corresponds to at least one accessible resource, and each accessible resource corresponds to at least one operable manner.
- An embodiment of the present applicationprovides an authentication apparatus, including:
- the processorexecuting the machine readable instructions to: receive a user terminal to transmit a target resource access request, where the target resource access request carries a target user identifier, a target access resource, and a target operation mode for accessing the resource to the target;
- the target resource access requestis authenticated by using the first policy table, and the authentication result of the target resource access request is output;
- the first policy tableis a relationship table including a user identifier, an accessible resource corresponding to the user identifier, and a corresponding relationship between the operable modes of the accessible resource, where the first policy table is Classified by the user identifier, each user identifier corresponds to at least one accessible resource, and each accessible resource corresponds to at least one operable manner.
- Embodiments of the present applicationalso provide a non-transitory computer readable storage medium in which machine readable instructions are stored, the machine readable instructions being executable by a processor to:
- Target resource access requestcarries a target user identifier, a target access resource, and a target operation mode for accessing the resource by the target;
- the target resource access requestis authenticated by using the first policy table, and the authentication result of the target resource access request is output;
- the first policy tableis a relationship table including a user identifier, an accessible resource corresponding to the user identifier, and a corresponding relationship between the operable modes of the accessible resource, where the first policy table is Classified by the user identifier, each user identifier corresponds to at least one accessible resource, and each accessible resource corresponds to at least one operable manner.
- FIG. 1Ais a schematic diagram of an implementation environment of an authentication method provided by an embodiment of the present application.
- FIG. 1Bis a schematic flowchart of an authentication method provided by an embodiment of the present application.
- FIG. 2is a schematic flowchart of another authentication method provided by an embodiment of the present application.
- FIG. 3is a schematic flowchart of a step 205 according to an embodiment of the present application.
- FIG. 4is a schematic structural diagram of an authentication apparatus according to an embodiment of the present application.
- FIG. 5is a schematic structural diagram of another authentication apparatus according to an embodiment of the present disclosure.
- FIG. 6is a schematic structural diagram of a first authentication unit according to an embodiment of the present disclosure.
- FIG. 7is a schematic structural diagram of a policy table updating unit according to an embodiment of the present application.
- FIG. 8is a schematic structural diagram of another authentication apparatus according to an embodiment of the present application.
- the relationship between the twois stored and managed separately.
- the relationship table between the user ID and the user group, the relationship table of the user group and the policy group, the relationship table of the policy group and the accessible resource, the policy group, and the actionable relationshipare saved. Tables, etc., can intuitively reflect the relationship between the two sets of data. However, in the authentication process, it is necessary to perform one-to-one matching from each relationship table.
- the actionable modeconfirm whether the user's operation is included. Therefore, the prior art solution needs to search multiple times from multiple relational tables to determine the authentication result, which reduces the authentication efficiency of the user access request, and wastes the processing resources of the authentication device.
- the authentication method provided by the embodiment of the present applicationmay be applied to a scenario for accessing a cloud service resource, for example, receiving a target cloud resource access request sent by a user terminal, where the target cloud resource access request carries a target user identifier, a target access cloud resource, and a target operation mode for accessing the cloud resource to the target; searching for a verification result of the target cloud resource access request in the cache table, where the cache table includes a preset time before receiving the target cloud resource access request An authentication result of the plurality of cloud resource access requests in the segment; when the authentication result of the target cloud resource access request does not exist in the cache table, the first policy table is used to check the target cloud resource access request And outputting the authentication result of the target cloud resource access request, where the first policy table is a user identifier, an accessible cloud resource corresponding to the user identifier, and the accessible cloud resource A relational table of correspondence between operable modes, since the first policy table is classified by user identifier and contains user tags And a relationship table between the accessible cloud resource corresponding
- the authentication device in the embodiment of the present applicationmay be a background device that authenticates a resource access request, and the authentication device may be a physical device that is separately set up, such as a computing device such as a server. Not limited.
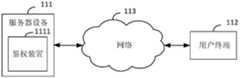
- the implementation environment of the authentication method provided by the embodiment of the present applicationmay be as shown in FIG. 1A, wherein the server device 111 is integrated with the authentication device 1111 provided by any embodiment of the present application.
- the server device 111 and the user terminal 112are connected by a network 113.
- the network 113may be a wired network or a wireless network.
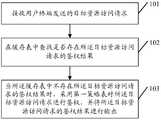
- FIG. 1Bis a schematic flowchart diagram of an authentication method according to an embodiment of the present application. As shown in FIG. 1B, the method in the embodiment of the present application may be performed by an authentication apparatus provided in any embodiment of the present application, and may include the following steps 101-103.
- Step 101Receive a target resource access request sent by a user terminal.
- the authentication devicereceives the target resource access request sent by the user terminal.
- the target resource access requestcarries a target user identifier, a target access resource, and a target operation mode for accessing the resource to the target.
- the usercan initiate a target resource access request by logging into the resource management platform.
- the target user identifieris used to mark the user who performs the target operation mode on the target access resource.
- the target access resourcemay be a file, data, or the like in the server, and the target operation mode may be a read instruction, a delete instruction, a write instruction, or the like.
- the embodiment of the present applicationdoes not limit the manner in which the target operation mode is included.
- Step 102Search, in the cache table, whether an authentication result of the target resource access request exists.
- the authentication devicesearches for a result of the authentication of the target resource access request in the cache table, where the authentication result includes the authentication pass and the authentication fail. If the authentication result is authenticated, the authentication device is configured to perform the target operation mode on the target access resource according to the target resource access request, and if the authentication result is that the authentication fails, the authentication device rejects The target resource access request.
- the cache tableincludes an authentication result of multiple resource access requests within a preset time period before receiving the target resource access request.
- the preset time periodis preset by the authentication device. For example, in a case where the resource access request is frequent, the authentication device may set a cache in the cache table to receive the target resource access request. The authentication result of all resource access requests in the hour; in the case where the resource access request is sparse, the authentication device may set all the resources in the cache table to buffer the time within the first 24 hours of receiving the target resource access request.
- the time range of the authentication result cached by the cache tableis not limited in the embodiment of the present application.
- the cache tableincludes data of a user identifier, an accessible resource, an operable manner of the accessible resource, an authentication result, and the like of each of the plurality of resource access requests.
- the target authentication result of the target resource access requestis determined by comparing the target user identifier in the target resource access request, the target access resource, and the target operation mode of the target access resource with the data in the cache table.
- Step 103When the authentication result of the target resource access request does not exist in the cache table, use the first policy table to authenticate the target resource access request, and output the authentication of the target resource access request. result.
- the authentication deviceuses the first policy table to authenticate the target resource access request, and outputs the target resource. Access the authentication result of the request.
- the first policy tableis a relationship table including a user identifier, an accessible resource corresponding to the user identifier, and a corresponding relationship between the operable modes of the accessible resource, where the first policy table is According to the user identifier, each user identifier corresponds to at least one accessible resource, and each accessible resource corresponds to at least one operable manner.
- Table 1is a policy table in a form, including a user identifier, an accessible resource, and an operable manner for the accessible resource.
- Table 1is classified according to the user identifier, so that when the target resource access request is authenticated, the accessible resource corresponding to the target user identifier and the operable mode can be quickly found from the user identifier in the first policy table, thereby improving the The efficiency of authentication of target resource access requests.
- the authentication devicewhen the authentication result of the target resource access request exists in the cache table, the authentication device outputs the authentication result found in the cache table.
- the authentication deviceprocesses the target resource access request, that is, according to the target in the target resource access request.
- the operation modeprocesses the target access resource, and after the processing is completed, the authentication device may output the processing result.
- the cache tablewhen receiving the target resource identifier that is sent by the user terminal, the target access resource, and the target operation mode of the target access resource, the cache table is used to find whether the target resource access request exists.
- the target resource access requestis authenticated by using the first policy table, and the authentication result of the target resource access request is output.
- the first policy tableis a relationship table that is classified by the user identifier and is a correspondence relationship between the user identifier, the accessible resource corresponding to the user identifier, and the operable mode of the accessible resource, so that the relationship can be in a relationship.
- the data in the table for finding the target resource access requestsaves the time for finding the related data of the target resource access request, thereby improving the authentication efficiency of the resource access request and avoiding finding the target resource access request in multiple relational tables. Waste of processing resources of computing devices caused by related data.
- FIG. 2is a schematic flowchart diagram of another authentication method according to an embodiment of the present application. As shown in FIG. 2, the method in the embodiment of the present application may be performed by the authentication apparatus provided in any embodiment of the present application, and may include the following steps 201-207.
- Step 201Receive a target resource access request sent by the user terminal.
- the authentication devicereceives the target resource access request sent by the user terminal.
- the target resource access requestcarries a target user identifier, a target access resource, and a target operation mode for accessing the resource to the target.
- the usercan initiate a target resource access request by logging into the resource management platform.
- the target user identifieris used to mark the user who performs the target operation mode on the target access resource.
- the target access resourcemay be a file, data, or the like in the server, and the target operation mode may be a read instruction, a delete instruction, a write instruction, or the like.
- the embodiment of the present applicationdoes not limit the manner in which the target operation mode is included.
- Step 202Search, in the cache table, whether an authentication result of the target resource access request exists.
- the authentication devicesearches for a result of the authentication of the target resource access request in the cache table, where the authentication result includes the authentication pass and the authentication fail. If the authentication result is authenticated, the authentication device is configured to perform the target operation mode on the target access resource according to the target resource access request, and if the authentication result is that the authentication fails, the authentication device rejects The target resource access request.
- the cache tableincludes an authentication result of multiple resource access requests within a preset time period before receiving the target resource access request.
- the preset time periodis preset by the authentication device. For example, in a case where the resource access request is frequent, the authentication device may set a cache in the cache table to receive the target resource access request. The authentication result of all resource access requests in the hour; in the case where the resource access request is sparse, the authentication device may set all the resources in the cache table to buffer the time within the first 24 hours of receiving the target resource access request.
- the time range of the authentication result cached by the cache tableis not limited in the embodiment of the present application.
- the cache tableincludes data of a user identifier, an accessible resource, an operable manner of the accessible resource, an authentication result, and the like of each of the plurality of resource access requests.
- the target authentication result of the target resource access requestis determined by comparing the target user identifier in the target resource access request, the target access resource, and the target operation mode of the target access resource with the data in the cache table.
- Step 203When the authentication result of the target resource access request exists in the cache table, the authentication device outputs the authentication result found in the cache table.
- Step 204When the authentication result of the target resource access request does not exist in the cache table, check whether the current version number of the second policy table is higher than the current version number of the first policy table.
- the authenticating devicedetects whether the current version number of the second policy table is higher than the current version number of the first policy table.
- the first policy tableis a relationship table including a user identifier, an accessible resource corresponding to the user identifier, and a corresponding relationship between the operable modes of the accessible resource, where the first policy table is According to the user identifier, each user identifier corresponds to at least one accessible resource, and each accessible resource corresponds to at least one operable manner.
- the second policy tableincludes a relationship table between a user identifier and a user group, a relationship table between the user group and the policy identifier, a mapping table of the policy identifier and the accessible resource, and a mapping between the policy identifier and the operable mode. Tables and other relational tables.
- the policy identifier in the second policy tableis used to correspond to a resource group composed of a plurality of accessible resources, or the policy identifier is used to correspond to a permission group composed of multiple operable modes.
- the current version number of the first policy table and the current version number of the second policy tablemay be represented by an update time.
- the version numbermay indicate updated data, such as changed accessible resources, changed user identification, changed operational modes, and the like.
- a changed user group identifier, a changed policy identifier, and the likemay also be included.
- the second policy tablesince the second policy table is distinguished by each policy identifier, when the user identifier or the accessible resource or the operable mode changes such as increase, decrease, etc., the second policy table may be updated first, because The second policy table includes a plurality of relation tables, and the data update can be completed by modifying one of the relationship tables, the update efficiency of the policy table can be improved, and the version number of the second policy table is updated after the second policy table is updated.
- the first policy tableis updated according to the second policy table to ensure the accuracy of the first policy table, and the version number of the first policy table is updated after the first policy table is updated.
- Step 205If the current version number of the second policy table is not higher than the current version number of the first policy table, use the first policy table to authenticate the target resource access request, and output the target. The authentication result of the resource access request.
- the authentication deviceuses the first policy table to check the target resource access request. And output an authentication result of the target resource access request.
- the first policy tableis a relationship table classified according to the user identifier, and a relationship table includes multiple data, and the target resource access request is authenticated by using the first policy table, thereby improving the authentication efficiency and avoiding the cause.
- the waste of processing resources of the computing devicecaused by finding related data of the target resource access request in the plurality of relation tables.
- step 205may include step 2051 to step 2055 .
- Step 2051Search for an accessible resource corresponding to the target user identifier and an operable manner for the accessible resource from the first policy table.
- the authentication devicesearches, from the first policy table, an accessible resource corresponding to the target user identifier and an operable manner for the accessible resource.
- Step 2052Determine whether the target access resource exists in the accessible resource.
- the authentication devicesearches for at least one accessible resource corresponding to the target user identifier to find whether the target access resource exists. If the target access resource exists in the accessible resource corresponding to the target user identifier, step 2053 is performed; if the target access resource does not exist in the accessible resource corresponding to the target user identifier, step 2055 is performed. .
- Step 2053If the target access resource exists in the accessible resource, determine whether the target operation mode exists in an operable manner of the target access resource.
- the determining devicedetermines that the target access resource exists in the accessible resource, and further determines whether the target operation mode exists in an operable manner of the target access resource, if the operable mode If the target operation mode exists, step 2054 is performed. If the target operation mode does not exist in the operable mode, step 2055 is performed.
- step 2054if the target operation mode exists in the operability mode of the target access resource, the authentication result of the target resource access request is determined to be authenticated, and the authentication of the target resource access request is output. result.
- the authentication devicedetermines that the authentication result of the target resource access request is authentication, and outputs the target resource. Access the authentication result of the request.
- the authentication deviceprocesses the target resource access request, that is, according to the target in the target resource access request.
- the operation modeprocesses the target access resource, and after the processing is completed, the authentication device may output the processing result.
- Step 2055Determine that the authentication result of the target resource access request is that the authentication fails.
- the authentication devicedetermines that the authentication result of the target resource access request is that the authentication fails, and outputs the authentication result, so that the user understands the authentication result.
- Step 206If the current version number of the second policy table is higher than the current version number of the first policy table, use the second policy table to authenticate the target resource access request, and output the The authentication result of the target resource access request.
- the authentication deviceuses the second policy table to authenticate the target resource access request. And outputting an authentication result of the target resource access request.
- the authentication devicemay complete the authentication by searching whether the data corresponding to the target resource access request exists in the plurality of relationship tables included in the second policy table.
- Step 207If the current version number of the second policy table is higher than the current version number of the first policy table, update the first policy table according to the second policy table.
- the authentication deviceupdates the first policy table according to the second policy table. Specifically, the current version number of the first policy table is compared with the historical version information of the second policy table, and the unupdated data of the first policy table is determined. And updating, according to the unupdated data, the first policy table, and changing a current version number of the first policy table to a current version number of the second policy table.
- the second strategy tableincludes the following Table A, Table B, Table C, and Table D.
- Table BRelationship table between user groups and resource identifiers
- Table CRelationship table between resource IDs and accessible resources
- RID-1Resource identification Accessible resources RID-1 R-A, R-B RID-2 R-C RID-3 R-C; R-D
- Table DRelationship Table between Resource Identification and Operational Mode
- the first policy table corresponding to the current second policy tableis Table E.
- the authentication resultneeds to be determined through multiple relationship tables, and when the target resource access request is authenticated through the first policy table, only one relationship needs to be obtained.
- the authentication resultcan be determined in the table, which greatly reduces the time for opening the relationship table, closing the relationship table, and searching for data, which can improve the authentication efficiency and avoid the related data of finding the target resource access request in multiple relation tables.
- the waste of processing resources of the computing deviceTherefore, if the current version number of the second policy table is not higher than the current version number of the first policy table, the first policy table is used for authentication, and the current version number of the second policy table is higher than the first policy table. In the case of the current version number, the second policy table is used for authentication.
- the second policy tableintuitively reflects the relationship between the data
- the user group and the user identifier included in the second policy tablecan be directly and quickly updated.
- the relationship table, and the first policy tablealso needs to update the accessible resource and the operable mode of the newly added user identifier, so when there is new data to be updated, the second policy table is preferentially updated, so that the update efficiency is higher. And updating the version number of the second policy table after the second policy table is updated.
- the first policy tableafter updating the second policy table, may be updated according to the updated content of the second policy table.
- the method of preferentially updating the first policy tablemay be adopted, and after updating the first policy table, updating the second policy according to the updated first policy table. table.
- the first policy table and the second policy tableare updated in synchronization, which is not limited by the embodiment of the present application.
- the target resource access requestwhen receiving the target resource identifier that is sent by the user terminal, the target access resource, and the target operation mode of the target access resource, the target resource access request does not exist in the cache table. If the version number of the second policy table is not higher than the version number of the first policy table, the first policy table is used to authenticate the target resource access request, if the version number of the second policy table is higher than the first The version number of the policy table is used to authenticate the target resource access request by using the second policy table, and output the authentication result of the target resource access request.
- the first policy tableis a relationship table that is classified by the user identifier and is a correspondence relationship between the user identifier, the accessible resource corresponding to the user identifier, and the operable mode of the accessible resource, so that the first policy table can be in a relationship table.
- the data related to the target resource access requestis searched, which saves the time for finding the related data of the target resource access request, thereby improving the authentication efficiency of the resource access request and avoiding the related data of the target resource access request in multiple relational tables.
- the resulting processing resources of the computing deviceare wasted.
- the second policy tableincludes multiple relationship tables, the update can be completed relatively quickly. In the case that the second policy table stores the latest data and the first policy table is not updated, the target resource can be accessed through the second policy table. Request for authentication to ensure the accuracy of authentication.
- FIG. 4is a schematic structural diagram of an authentication apparatus according to an embodiment of the present application.
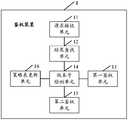
- the authentication apparatus 1 of the embodiment of the present applicationmay include: a request receiving unit 11, a result finding unit 12, and a first authentication unit 13.
- the request receiving unit 11is configured to receive a target resource access request sent by the user terminal, where the target resource access request carries a target user identifier, a target access resource, and a target operation mode for the target access resource.
- the request receiving unit 11receives a target resource access request sent by the user terminal.
- the target resource access requestcarries a target user identifier, a target access resource, and a target operation mode for accessing the resource to the target.
- the usercan initiate a target resource access request by logging into the resource management platform.
- the target user identifieris used to mark the user who performs the target operation mode on the target access resource.
- the target access resourcemay be a file, data, or the like in the server, and the target operation mode may be a read instruction, a delete instruction, a write instruction, or the like.
- the embodiment of the present applicationdoes not limit the manner in which the target operation mode is included.
- the result finding unit 12is configured to search, in the cache table, whether an authentication result of the target resource access request exists, where the cache table includes multiple resource accesses within a preset time period before receiving the target resource access request The requested authentication result.
- the result searching unit 12searches the cache table for the existence of the authentication result of the target resource access request, where the authentication result includes the authentication pass and the authentication fail. If the authentication result is authenticated, the authentication device 1 is allowed to perform a target operation mode on the target access resource according to the target resource access request, and if the authentication result is that the authentication fails, the authentication device is represented. 1 reject the target resource access request.
- the cache tableincludes an authentication result of multiple resource access requests within a preset time period before receiving the target resource access request.
- the preset time periodis preset by the authentication device 1. For example, in a case where the resource access request is frequent, the authentication device 1 may set a time in the cache table to buffer the time when the target resource access request is received. The authentication result of all the resource access requests in the previous hour; in the case where the resource access request is sparse, the authentication device 1 may set the cache within the first 24 hours of the time when the cache resource is received.
- the time range of the authentication result cached by the cache tableis not limited in the embodiment of the present application.
- the cache tableincludes data of a user identifier, an accessible resource, an operable manner of the accessible resource, an authentication result, and the like of each of the plurality of resource access requests. Determining whether there is an authentication result of the target resource access request by comparing the target user identifier in the target resource access request, the target access resource, and the target operation mode of the target access resource with the data in the cache table. .
- the first authentication unit 13is configured to: when the authentication result of the target resource access request does not exist in the cache table, use the first policy table to authenticate the target resource access request, and output the target The authentication result of the resource access request.
- the first authentication unit 13uses the first policy table to authenticate the target resource access request, and outputs the The authentication result of the target resource access request.
- the first policy tableis a relationship table including a user identifier, an accessible resource corresponding to the user identifier, and a corresponding relationship between the operable modes of the accessible resource, where the first policy table is Classified by the user identifier, each user identifier corresponds to at least one accessible resource, and each accessible resource corresponds to at least one operable manner.
- the authentication apparatus 1when the authentication result of the target resource access request exists in the cache table, the authentication apparatus 1 outputs the authentication result found in the cache table.
- the authentication apparatus 1processes the target resource access request, that is, according to the target resource access request.
- the target operation modeprocesses the target access resource, and after the processing is completed, the authentication apparatus 1 can output the processing result.
- the cache tablewhen receiving the target resource identifier that is sent by the user terminal, the target access resource, and the target operation mode of the target access resource, the cache table is used to find whether the target resource access request exists.
- the target resource access requestis authenticated by using the first policy table, and the authentication result of the target resource access request is output.
- the first policy tableis a relationship table that is classified by the user identifier and is a correspondence relationship between the user identifier, the accessible resource corresponding to the user identifier, and the operable mode of the accessible resource, so that the relationship can be in a relationship.
- the data in the table for finding the target resource access requestsaves the time for finding the related data of the target resource access request, thereby improving the authentication efficiency of the resource access request and avoiding finding the target resource access request in multiple relational tables. Waste of processing resources of computing devices caused by related data.
- FIG. 5is another schematic structural diagram of an authentication apparatus according to an embodiment of the present application.
- the authentication apparatus 1 of the embodiment of the present applicationmay include: a request receiving unit 11, a result finding unit 12, a first authentication unit 13, a version number detecting unit 14, a second authentication unit 15, and Policy table update unit 16.
- the request receiving unit 11is configured to receive a target resource access request sent by the user terminal, where the target resource access request carries a target user identifier, a target access resource, and a target operation mode for the target access resource.
- the request receiving unit 11receives a target resource access request sent by the user terminal.
- the target resource access requestcarries a target user identifier, a target access resource, and a target operation mode for accessing the resource to the target.
- the usercan initiate a target resource access request by logging into the resource management platform.
- the target user identifieris used to mark the user who performs the target operation mode on the target access resource.
- the target access resourcemay be a file, data, or the like in the server, and the target operation mode may be a read instruction, a delete instruction, a write instruction, or the like.
- the embodiment of the present applicationdoes not limit the manner in which the target operation mode is included.
- the result finding unit 12is configured to search, in the cache table, whether an authentication result of the target resource access request exists, where the cache table includes multiple resource accesses within a preset time period before receiving the target resource access request The requested authentication result.
- the result searching unit 12searches the cache table for the existence of the authentication result of the target resource access request, where the authentication result includes the authentication pass and the authentication fail, and if the authentication result is the authentication pass Indicates that the authentication device 1 allows the target operation mode to be performed on the target access resource according to the target resource access request. If the authentication result is that the authentication fails, the authentication device 1 rejects the target resource access request. .
- the cache tableincludes an authentication result of multiple resource access requests within a preset time period before receiving the target resource access request.
- the preset time periodis preset by the authentication device 1. For example, in a case where the resource access request is frequent, the authentication device 1 may set a time in the cache table to buffer the time when the target resource access request is received. The authentication result of all the resource access requests in the previous hour; in the case where the resource access request is sparse, the authentication device 1 may set the cache within the first 24 hours of the time when the cache resource is received.
- the time range of the authentication result cached by the cache tableis not limited in the embodiment of the present application.
- the cache tableincludes data of a user identifier, an accessible resource, an operable manner of the accessible resource, an authentication result, and the like of each of the plurality of resource access requests.
- the target authentication result of the target resource access requestis determined by comparing the target user identifier in the target resource access request, the target access resource, and the target operation mode of the target access resource with the data in the cache table.
- the version number detecting unit 14is configured to detect, when the authentication result of the target resource access request does not exist in the cache table, whether the current version number of the second policy table is higher than a current version number of the first policy table. .
- the version number detecting unit 14detects whether the current version number of the second policy table is higher than the current version number of the first policy table. .
- the first policy tableis a relationship table including a user identifier, an accessible resource corresponding to the user identifier, and a corresponding relationship between the operable modes of the accessible resource, where the first policy table is Classified by the user identifier, each user identifier corresponds to at least one accessible resource, and each accessible resource corresponds to at least one operable manner.
- the second policy tableincludes a relationship table between a user identifier and a user group, a relationship table between the user group and the policy identifier, a mapping table of the policy identifier and the accessible resource, and a mapping between the policy identifier and the operable mode. Tables and other relational tables.
- the policy identifier in the second policy tableis used to correspond to a resource group composed of a plurality of accessible resources, or the policy identifier is used to correspond to a permission group composed of multiple operable modes.
- the current version number of the first policy table and the current version number of the second policy tablemay be represented by an update time.
- the version numbermay indicate updated data, such as changed accessible resources, changed user identification, changed operational modes, and the like.
- a changed user group identifier, a changed policy identifier, and the likemay also be included.
- the second policy tablesince the second policy table is distinguished by each policy identifier, when the user identifier or the accessible resource or the operable mode changes such as increase, decrease, etc., the second policy table may be updated first, because The second policy table includes a plurality of relation tables, and the data update can be completed by modifying one of the relationship tables, the update efficiency of the policy table can be improved, and the version number of the second policy table is updated after the second policy table is updated.
- the first policy tableis updated according to the second policy table to ensure the accuracy of the first policy table, and after the first policy table is updated, the version number of the first policy table is updated.
- the first authentication unit 13is configured to adopt the first policy if the version number detecting unit 14 detects that the current version number of the second policy table is not higher than the current version number of the first policy table.
- the tableauthenticates the target resource access request and outputs an authentication result of the target resource access request.
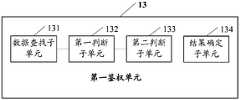
- FIG. 6is a schematic structural diagram of a first authentication unit 13 according to an embodiment of the present application.
- the first authentication unit 13includes a data search sub-unit 131 and a first The judgment sub-unit 132, the second judgment sub-unit 133, and the result determination sub-unit 134.
- the data search sub-unit 131is configured to search, from the first policy table, an accessible resource corresponding to the target user identifier and an operable manner for the accessible resource.
- the data search sub-unit 131searches the first policy table for an accessible resource corresponding to the target user identifier and an operable manner for the accessible resource.
- the first determining sub-unit 132is configured to determine whether the target access resource exists in the accessible resource.
- the first determining sub-unit 132searches for at least one accessible resource corresponding to the target user identifier to find whether the target access resource exists. If the target access resource exists in the accessible resource corresponding to the target user identifier, the second determining sub-unit 133 is executed.
- the second determining sub-unit 133is configured to determine, if the first access sub-unit 132 determines that the target access resource exists in the accessible resource, determine whether the target exists in an operable manner of the target access resource Operation method.
- the second determining sub-unit 133determines whether the operating mode of the target access resource exists.
- the target operation modeif the target operation mode exists in the operable mode, the result determination sub-unit 134 is executed.
- a result determining sub-unit 134configured to determine, when the second determining sub-unit 133 determines that the target operating mode exists in an operable manner of accessing the target resource, determining an authentication result of the target resource access request The right passes, and outputs the authentication result of the target resource access request.
- the result determining sub-unit 134determines that the authentication result of the target resource access request is an authentication pass, and outputs the The authentication result of the target resource access request.
- the authentication apparatus 1processes the target resource access request, that is, according to the target resource access request.
- the target operation modeprocesses the target access resource, and after the processing is completed, the authentication apparatus 1 can output the processing result.
- the second authentication unit 15is configured to adopt the second policy table if the version number detecting unit 14 detects that the current version number of the second policy table is higher than the current version number of the first policy table. And authenticating the target resource access request, and outputting an authentication result of the target resource access request.
- the second authentication unit 15uses the second policy table to access the target resource. The authentication is performed, and the authentication result of the target resource access request is output.
- the second authentication unit 15may perform the authentication by searching whether the data corresponding to the target resource access request exists in the plurality of relationship tables included in the second policy table.
- the policy table updating unit 16is configured to: if the version number detecting unit 14 detects that the current version number of the second policy table is higher than the current version number of the first policy table, according to the second policy table, Update the first policy table.
- FIG. 7is a schematic structural diagram of a policy table updating unit 16 according to an embodiment of the present application.
- the policy table updating unit 16includes an update data determining subunit 161 and a policy table update. Subunit 162.
- the update data determining subunit 161is configured to compare the first policy table if the version number detecting unit 14 detects that the current version number of the second policy table is higher than the current version number of the first policy table.
- the current version number and the historical version information of the second policy tabledetermine the unupdated data of the first policy table.
- the policy table update sub-unit 162is configured to update the first policy table according to the unupdated data, and change a current version number of the first policy table to a current version number of the second policy table. .
- the target resource access requestwhen receiving the target resource identifier that is sent by the user terminal, the target access resource, and the target operation mode of the target access resource, the target resource access request does not exist in the cache table. If the version number of the second policy table is not higher than the version number of the first policy table, the first policy table is used to authenticate the target resource access request, if the version number of the second policy table is higher than the first The version number of the policy table is used to authenticate the target resource access request by using the second policy table, and output the authentication result of the target resource access request.
- the first policy tableis a relationship table that is classified by the user identifier and is a correspondence relationship between the user identifier, the accessible resource corresponding to the user identifier, and the operable mode of the accessible resource, so that the first policy table can be in a relationship table.
- the data related to the target resource access requestis searched, which saves the time for finding the related data of the target resource access request, thereby improving the authentication efficiency of the resource access request and avoiding the related data of the target resource access request in multiple relational tables.
- the resulting processing resources of the computing deviceare wasted.
- the second policy tableincludes multiple relationship tables, the update can be completed relatively quickly. In the case that the second policy table stores the latest data and the first policy table is not updated, the target resource can be accessed through the second policy table. Request for authentication to ensure the accuracy of authentication.
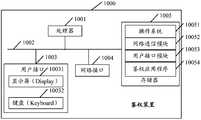
- FIG. 8is a schematic structural diagram of another authentication apparatus according to an embodiment of the present application.
- the authentication apparatus 1000may include at least one processor 1001, such as a CPU (Central Processing Unit), at least one network interface 1004, a memory 1005, and at least one communication bus 1002.
- the network interface 1004can optionally include a standard wired interface, a wireless interface (such as a WI-FI interface).
- the memory 1005may be a high speed RAM memory or a non-volatile memory such as at least one disk memory. According to an embodiment of the present application, the memory 1005 may also be at least one storage device located away from the processor 1001. Among them, the communication bus 1002 is used to implement connection communication between these components.
- the authentication device 1000includes a user interface 1003, wherein the user interface 1003 may include a display 10031 and a keyboard 10032.
- the user interface 1003may include a display 10031 and a keyboard 10032.
- an operating system 10051, a network communication module 10052, a user interface module 10053, and machine readable instructions, such as an authentication application 10054,may be included in the memory 1005 as a computer storage medium.
- the user interface 1003is mainly used to receive a user-initiated target resource access request and the like; and the processor 1001 can be used to invoke an authentication application stored in the memory 1005, and specifically execute the following: operating:
- Target resource access requestcarries a target user identifier, a target access resource, and a target operation mode for accessing the resource by the target;
- the target resource access requestis authenticated by using the first policy table, and the authentication result of the target resource access request is output;
- the first policy tableis a relationship table including a user identifier, an accessible resource corresponding to the user identifier, and a corresponding relationship between the operable modes of the accessible resource, where the first policy table is Classified by the user identifier, each user identifier corresponds to at least one accessible resource, and each accessible resource corresponds to at least one operable manner.
- the processor 1001performs the following operations before performing the authentication on the target resource access request by using the first policy table, and outputting the authentication result of the target resource access request:
- the target resource access requestis authenticated by using the first policy table, and the target resource is output Access the authentication result of the request;
- the second policy tableincludes a plurality of relationship tables, where the relationship table includes a relationship between the user identifier and the user group, a relationship table between the user group and the policy identifier, a mapping table of the policy identifier and the accessible resource, and a policy.
- a mapping table of identification and actionable methodsis included in the relationship table.
- the processor 1001further performs the following operations:
- the target resource access requestis authenticated by using the second policy table, and the target resource access is output The requested authentication result.
- the processor 1001further performs the following operations:
- the processor 1001performs updating the first policy table according to the second policy table, and specifically performs the following operations:
- the processor 1001performs the authentication of the target resource access request by using the first policy table, and outputs the authentication result of the target resource access request, and specifically performs the following operations:
- the target access resourceexists in the accessible resource, determining whether the target operation mode exists in an operable manner of accessing the resource to the target;
- the authentication result of the target resource access requestis determined to be authenticated, and the authentication result of the target resource access request is output.
- the cache tablewhen receiving the target resource identifier that is sent by the user terminal, the target access resource, and the target operation mode of the target access resource, the cache table is used to find whether the target resource access request exists.
- the target resource access requestis authenticated by using the first policy table, and the authentication result of the target resource access request is output.
- the first policy tableis a relationship table that is classified by the user identifier and is a correspondence relationship between the user identifier, the accessible resource corresponding to the user identifier, and the operable mode of the accessible resource, so that the relationship can be in a relationship.
- the data in the table for finding the target resource access requestsaves the time for finding the related data of the target resource access request, thereby improving the authentication efficiency of the resource access request and avoiding finding the target resource access request in multiple relational tables. Waste of processing resources of computing devices caused by related data.
- the module or unit in the embodiment of the present applicationmay be implemented by a general-purpose integrated circuit, such as a CPU, or by an ASIC (Application Specific Integrated Circuit).
- a general-purpose integrated circuitsuch as a CPU
- ASICApplication Specific Integrated Circuit
- the modules or units in the terminal device in this embodiment of the present applicationmay be combined, divided, and deleted according to actual needs.
- the storage mediummay be a magnetic disk, an optical disk, a read-only memory (ROM), or a random access memory (RAM).
Landscapes
- Engineering & Computer Science (AREA)
- Computer Networks & Wireless Communication (AREA)
- Signal Processing (AREA)
- Computer Hardware Design (AREA)
- Computer Security & Cryptography (AREA)
- Computing Systems (AREA)
- General Engineering & Computer Science (AREA)
- Storage Device Security (AREA)
Abstract
Description
Translated fromChinese本申请要求于2017年2月7日提交中国专利局、申请号为201710067325.5,发明名称为“一种鉴权方法及装置”的中国专利申请的优先权,其全部内容通过引用结合在本申请中。The present application claims priority to Chinese Patent Application No. JP-A No. No. No. No. No. No. No. No. No. No. No. No. .
本申请涉及信息安全技术领域,尤其涉及一种鉴权方法、装置及存储介质。The present application relates to the field of information security technologies, and in particular, to an authentication method, apparatus, and storage medium.
发明背景Background of the invention
在云服务的鉴权体系中,用户可以通过云服务管理平台访问云资源。然而,并非每个用户都具备访问云资源的资格,云服务管理平台需要对发送资源访问请求的用户进行鉴权,只有鉴权通过的用户才可以访问云资源。In the cloud service authentication system, users can access cloud resources through the cloud service management platform. However, not every user has the right to access the cloud resources. The cloud service management platform needs to authenticate the user who sends the resource access request, and only the user who passes the authentication can access the cloud resource.
在鉴权过程中需要对用户所访问的资源和对所访问资源的操作方式分别进行鉴定。In the authentication process, it is necessary to separately identify the resources accessed by the user and the operation modes of the accessed resources.
发明内容Summary of the invention
本申请实施例提供一种鉴权方法、装置及存储介质,通过从一个按照用户标识分类的策略表中查找到与资源访问请求相关的数据,节省了资源访问请求相关数据的查找时间,进而提高了对资源访问请求的鉴权效率,避免因在多个关系表中查找资源访问请求的相关数据而造成的计算设备的处理资源的浪费。The embodiment of the present invention provides an authentication method, an apparatus, and a storage medium. By searching data related to a resource access request from a policy table classified according to a user identifier, the search time of the resource access request related data is saved, thereby improving The authentication efficiency of the resource access request avoids the waste of processing resources of the computing device caused by searching related data of the resource access request in the plurality of relation tables.
本申请实施例提供了一种鉴权方法,应用于一计算设备,包括:An embodiment of the present application provides an authentication method, which is applied to a computing device, including:
接收用户终端发送的目标资源访问请求,所述目标资源访问请求携 带目标用户标识、目标访问资源和对所述目标访问资源的目标操作方式;Receiving a target resource access request sent by the user terminal, where the target resource access request carries a target user identifier, a target access resource, and a target operation mode for accessing the resource to the target;
在缓存表中查找是否存在所述目标资源访问请求的鉴权结果,所述缓存表包含接收到所述目标资源访问请求之前的预设时间段内的多个资源访问请求的鉴权结果;Querying, in the cache table, whether an authentication result of the target resource access request exists, where the cache table includes an authentication result of multiple resource access requests within a preset time period before receiving the target resource access request;
当所述缓存表中不存在所述目标资源访问请求的鉴权结果时,采用第一策略表对所述目标资源访问请求进行鉴权,并输出所述目标资源访问请求的鉴权结果;When the authentication result of the target resource access request does not exist in the cache table, the target resource access request is authenticated by using the first policy table, and the authentication result of the target resource access request is output;
其中,所述第一策略表为包含用户标识、所述用户标识对应的可访问资源、对所述可访问资源的可操作方式之间的对应关系的一个关系表,所述第一策略表是以用户标识进行分类的,每个用户标识对应至少一个可访问资源,以及每个可访问资源对应至少一个可操作方式。The first policy table is a relationship table including a user identifier, an accessible resource corresponding to the user identifier, and a corresponding relationship between the operable modes of the accessible resource, where the first policy table is Classified by the user identifier, each user identifier corresponds to at least one accessible resource, and each accessible resource corresponds to at least one operable manner.
本申请实施例提供了一种鉴权装置,包括:An embodiment of the present application provides an authentication apparatus, including:
处理器以及与所述处理器相连接的存储器,所述存储器中存储有可由所述处理器执行的机器可读指令;所述处理器执行所述机器可读指令完成以下操作:接收用户终端发送的目标资源访问请求,所述目标资源访问请求携带目标用户标识、目标访问资源和对所述目标访问资源的目标操作方式;a processor and a memory coupled to the processor, the memory having machine readable instructions executable by the processor; the processor executing the machine readable instructions to: receive a user terminal to transmit a target resource access request, where the target resource access request carries a target user identifier, a target access resource, and a target operation mode for accessing the resource to the target;
在缓存表中查找是否存在所述目标资源访问请求的鉴权结果,所述缓存表包含接收到所述目标资源访问请求之前的预设时间段内的多个资源访问请求的鉴权结果;Querying, in the cache table, whether an authentication result of the target resource access request exists, where the cache table includes an authentication result of multiple resource access requests within a preset time period before receiving the target resource access request;
当所述缓存表中不存在所述目标资源访问请求的鉴权结果时,采用第一策略表对所述目标资源访问请求进行鉴权,并输出所述目标资源访问请求的鉴权结果;When the authentication result of the target resource access request does not exist in the cache table, the target resource access request is authenticated by using the first policy table, and the authentication result of the target resource access request is output;
其中,所述第一策略表为包含用户标识、所述用户标识对应的可访问资源、对所述可访问资源的可操作方式之间的对应关系的一个关系表,所述第一策略表是以用户标识进行分类的,每个用户标识对应至少一个可访问资源,以及每个可访问资源对应至少一个可操作方式。The first policy table is a relationship table including a user identifier, an accessible resource corresponding to the user identifier, and a corresponding relationship between the operable modes of the accessible resource, where the first policy table is Classified by the user identifier, each user identifier corresponds to at least one accessible resource, and each accessible resource corresponds to at least one operable manner.
本申请实施例还提供了一种非易失性计算机可读存储介质,所述存 储介质中存储有机器可读指令,所述机器可读指令可以由处理器执行以完成以下操作:Embodiments of the present application also provide a non-transitory computer readable storage medium in which machine readable instructions are stored, the machine readable instructions being executable by a processor to:
接收用户终端发送的目标资源访问请求,所述目标资源访问请求携带目标用户标识、目标访问资源和对所述目标访问资源的目标操作方式;Receiving a target resource access request sent by the user terminal, where the target resource access request carries a target user identifier, a target access resource, and a target operation mode for accessing the resource by the target;
在缓存表中查找是否存在所述目标资源访问请求的鉴权结果,所述缓存表包含接收到所述目标资源访问请求之前的预设时间段内的多个资源访问请求的鉴权结果;Querying, in the cache table, whether an authentication result of the target resource access request exists, where the cache table includes an authentication result of multiple resource access requests within a preset time period before receiving the target resource access request;
当所述缓存表中不存在所述目标资源访问请求的鉴权结果时,采用第一策略表对所述目标资源访问请求进行鉴权,并输出所述目标资源访问请求的鉴权结果;When the authentication result of the target resource access request does not exist in the cache table, the target resource access request is authenticated by using the first policy table, and the authentication result of the target resource access request is output;
其中,所述第一策略表为包含用户标识、所述用户标识对应的可访问资源、对所述可访问资源的可操作方式之间的对应关系的一个关系表,所述第一策略表是以用户标识进行分类的,每个用户标识对应至少一个可访问资源,以及每个可访问资源对应至少一个可操作方式。The first policy table is a relationship table including a user identifier, an accessible resource corresponding to the user identifier, and a corresponding relationship between the operable modes of the accessible resource, where the first policy table is Classified by the user identifier, each user identifier corresponds to at least one accessible resource, and each accessible resource corresponds to at least one operable manner.
附图简要说明BRIEF DESCRIPTION OF THE DRAWINGS
为了更清楚地说明本申请实施例的技术方案,下面将对实施例描述中所需要使用的附图作简单地介绍,显而易见地,下面描述中的附图仅仅是本申请的一些实施例,对于本领域普通技术人员来讲,在不付出创造性劳动的前提下,还可以根据这些附图获得其他的附图。In order to more clearly illustrate the technical solutions of the embodiments of the present application, the drawings used in the description of the embodiments will be briefly described below. It is obvious that the drawings in the following description are only some embodiments of the present application, Those skilled in the art can also obtain other drawings based on these drawings without paying any creative work.
图1A是本申请实施例提供的鉴权方法的实施环境示意图;1A is a schematic diagram of an implementation environment of an authentication method provided by an embodiment of the present application;
图1B是本申请实施例提供的一种鉴权方法的流程示意图;1B is a schematic flowchart of an authentication method provided by an embodiment of the present application;
图2是本申请实施例提供的另一种鉴权方法的流程示意图;2 is a schematic flowchart of another authentication method provided by an embodiment of the present application;
图3是本申请实施例提供的一种步骤205的流程示意图;FIG. 3 is a schematic flowchart of a
图4是本申请实施例提供的一种鉴权装置的结构示意图;4 is a schematic structural diagram of an authentication apparatus according to an embodiment of the present application;
图5是本申请实施例提供的另一种鉴权装置的结构示意图;FIG. 5 is a schematic structural diagram of another authentication apparatus according to an embodiment of the present disclosure;
图6是本申请实施例提供的一种第一鉴权单元的结构示意图;FIG. 6 is a schematic structural diagram of a first authentication unit according to an embodiment of the present disclosure;
图7是本申请实施例提供的一种策略表更新单元的结构示意图;FIG. 7 is a schematic structural diagram of a policy table updating unit according to an embodiment of the present application;
图8是本申请实施例提供的另一种鉴权装置的结构示意图。FIG. 8 is a schematic structural diagram of another authentication apparatus according to an embodiment of the present application.
下面将结合本申请实施例中的附图,对本申请实施例中的技术方案进行清楚、完整地描述,显然,所描述的实施例仅仅是本申请一部分实施例,而不是全部的实施例。基于本申请中的实施例,本领域普通技术人员在没有付出创造性劳动前提下所获得的所有其他实施例,都属于本申请保护的范围。The technical solutions in the embodiments of the present application are clearly and completely described in the following with reference to the drawings in the embodiments of the present application. It is obvious that the described embodiments are only a part of the embodiments of the present application, and not all of the embodiments. All other embodiments obtained by a person of ordinary skill in the art based on the embodiments of the present application without departing from the inventive scope are the scope of the present application.
需要说明的是,在本申请实施例中使用的术语是仅仅出于描述特定实施例的目的,而非旨在限制本申请。在本申请实施例和所附权利要求书中所使用的单数形式的“一种”、“所述”和“该”也旨在包括多数形式,除非上下文清楚地表示其他含义。还应当理解,本申请实施例中使用的术语“和/或”是指并包含一个或多个相关联的列出项目的任何或所有可能组合。另外,本申请的说明书和权利要求书及上述附图中的术语“第一”、“第二”、“第三”和“第四”等是用于区别不同对象,而不是用于描述特定顺序。此外,术语“包括”和“具有”以及它们任何变形,意图在于覆盖不排他的包含。例如包含了一系列步骤或单元的过程、方法、系统、产品或设备没有限定于已列出的步骤或单元,而是可选地还包括没有列出的步骤或单元,或可选地还包括对于这些过程、方法、产品或设备固有的其它步骤或单元。It should be noted that the terminology used in the embodiments of the present application is for the purpose of describing the specific embodiments, and is not intended to limit the application. The singular forms "a", "the", and "the" It should also be understood that the term "and/or" used in the embodiments of the present application refers to and encompasses any and all possible combinations of one or more associated listed items. In addition, the terms "first", "second", "third", and "fourth" and the like in the specification and claims of the present application and the above drawings are used to distinguish different objects, and are not used to describe specific order. Furthermore, the terms "comprises" and "comprising" and "comprising" are intended to cover a non-exclusive inclusion. For example, a process, method, system, product, or device that comprises a series of steps or units is not limited to the listed steps or units, but optionally also includes steps or units not listed, or alternatively Other steps or units inherent to these processes, methods, products or equipment.
在传统的云服务的鉴权过程中,在对用户所访问的资源以及对所访问资源的操作方式进行鉴定时,对于用户标识、用户组、用户标识对应的可访问资源、可操作方式等之间的关系是分别存储和管理的,例如,保存了用户标识和用户组的关系表、用户组和策略组的关系表,策略组和可访问资源的关系表、策略组和可操作方式的关系表等,这样能够直观的体现出两组数据之间的关系。但是在鉴权过程中,需要从各个关系表中进行一一匹配,例如要先查看用户标识和用户组的关系表以确定用 户所在的组,然后查找用户组和策略组的关系表以确定与用户组相关的策略,再查找策略组和可访问资源的关系表以从策略对应的可访问资源中查找是否包含用户请求的资源;还需要查找策略组和可操作方式的关系表以从策略对应的可操作方式中确认是否包含用户的操作。因此,现有技术方案需要从多个关系表中多次查找才可以确定鉴权结果,降低了对用户访问请求的鉴权效率,浪费了鉴权设备的处理资源。In the authentication process of the traditional cloud service, when the user accesses the resource and the operation mode of the accessed resource, the user identifier, the user group, the accessible resource corresponding to the user identifier, the operable mode, etc. The relationship between the two is stored and managed separately. For example, the relationship table between the user ID and the user group, the relationship table of the user group and the policy group, the relationship table of the policy group and the accessible resource, the policy group, and the actionable relationship are saved. Tables, etc., can intuitively reflect the relationship between the two sets of data. However, in the authentication process, it is necessary to perform one-to-one matching from each relationship table. For example, first check the relationship between the user ID and the user group to determine the group in which the user is located, and then look up the relationship table between the user group and the policy group to determine A policy related to the user group, and then look up the relationship table of the policy group and the accessible resource to find out whether the resource requested by the user is included in the accessible resource corresponding to the policy; and also need to find a relationship table between the policy group and the operable mode to correspond to the policy. In the actionable mode, confirm whether the user's operation is included. Therefore, the prior art solution needs to search multiple times from multiple relational tables to determine the authentication result, which reduces the authentication efficiency of the user access request, and wastes the processing resources of the authentication device.
本申请实施例提供的鉴权方法可以应用于访问云服务资源的场景中,例如,接收用户终端发送的目标云资源访问请求,所述目标云资源访问请求携带目标用户标识、目标访问云资源和对所述目标访问云资源的目标操作方式;在缓存表中查找是否存在所述目标云资源访问请求的鉴权结果,所述缓存表包含接收到所述目标云资源访问请求之前的预设时间段内的多个云资源访问请求的鉴权结果;当所述缓存表中不存在所述目标云资源访问请求的鉴权结果时,采用第一策略表对所述目标云资源访问请求进行鉴权,并将所述目标云资源访问请求的鉴权结果进行输出;其中,所述第一策略表为包含用户标识、所述用户标识对应的可访问云资源、对所述可访问云资源的可操作方式之间的对应关系的一个关系表,由于第一策略表是以用户标识分类的且为包含用户标识、所述用户标识对应的可访问云资源、对可访问云资源的可操作方式之间的对应关系的一个关系表,这样能够在一个关系表中查找目标云资源访问请求的相关数据,节省了查找目标云资源访问请求的相关数据的时间,进而提高了对云资源访问请求的鉴权效率,避免因在多个关系表中查找目标云资源访问请求的相关数据而造成的计算设备的处理资源的浪费。所述的处理资源包括但不限于:中央处理器消耗、存储器消耗、带宽传输消耗等。The authentication method provided by the embodiment of the present application may be applied to a scenario for accessing a cloud service resource, for example, receiving a target cloud resource access request sent by a user terminal, where the target cloud resource access request carries a target user identifier, a target access cloud resource, and a target operation mode for accessing the cloud resource to the target; searching for a verification result of the target cloud resource access request in the cache table, where the cache table includes a preset time before receiving the target cloud resource access request An authentication result of the plurality of cloud resource access requests in the segment; when the authentication result of the target cloud resource access request does not exist in the cache table, the first policy table is used to check the target cloud resource access request And outputting the authentication result of the target cloud resource access request, where the first policy table is a user identifier, an accessible cloud resource corresponding to the user identifier, and the accessible cloud resource A relational table of correspondence between operable modes, since the first policy table is classified by user identifier and contains user tags And a relationship table between the accessible cloud resource corresponding to the user identifier and the operable relationship between the accessible cloud resource, so that the related data of the target cloud resource access request can be searched in a relational table, thereby saving The time for finding the related data of the target cloud resource access request, thereby improving the authentication efficiency of the cloud resource access request, and avoiding the processing resource of the computing device caused by searching the related data of the target cloud resource access request in the plurality of relation tables. Waste. The processing resources include, but are not limited to, central processor consumption, memory consumption, bandwidth transmission consumption, and the like.
本申请实施例涉及的鉴权装置可以是对资源访问请求进行鉴权等的后台设备,所述鉴权装置可以为单独设立的一台物理机,如服务器等计算设备,本发明实施例对此不做限定。The authentication device in the embodiment of the present application may be a background device that authenticates a resource access request, and the authentication device may be a physical device that is separately set up, such as a computing device such as a server. Not limited.
本申请实施例提供的鉴权方法的实施环境可如图1A所示,其中, 服务器设备111集成有本申请任一实施例提供的鉴权装置1111。该服务器设备111与用户终端112之间通过网络113连接,所述网络113可以是有线网络,也可以是无线网络。The implementation environment of the authentication method provided by the embodiment of the present application may be as shown in FIG. 1A, wherein the
请参见图1B,为本申请实施例提供的一种鉴权方法的流程示意图。如图1B所示,本申请实施例的所述方法可由本申请任一实施例提供的鉴权装置执行,可以包括以下步骤101-步骤103。FIG. 1B is a schematic flowchart diagram of an authentication method according to an embodiment of the present application. As shown in FIG. 1B, the method in the embodiment of the present application may be performed by an authentication apparatus provided in any embodiment of the present application, and may include the following steps 101-103.
步骤101,接收用户终端发送的目标资源访问请求。Step 101: Receive a target resource access request sent by a user terminal.
具体的,鉴权装置接收用户终端发送的目标资源访问请求。其中,所述目标资源访问请求携带有目标用户标识、目标访问资源和对所述目标访问资源的目标操作方式。Specifically, the authentication device receives the target resource access request sent by the user terminal. The target resource access request carries a target user identifier, a target access resource, and a target operation mode for accessing the resource to the target.
举例来说,用户可以通过登陆资源管理平台发起目标资源访问请求。其中,目标用户标识是用于标记对目标访问资源执行目标操作方式的用户的。例如,所述目标访问资源可以为所述服务器中的某一个文件、数据等等,所述目标操作方式可以为读取指令(read)、删除指令(delete)、写入指令(write)等等,本申请实施例对目标操作方式所包含的方式不做限定。For example, the user can initiate a target resource access request by logging into the resource management platform. The target user identifier is used to mark the user who performs the target operation mode on the target access resource. For example, the target access resource may be a file, data, or the like in the server, and the target operation mode may be a read instruction, a delete instruction, a write instruction, or the like. The embodiment of the present application does not limit the manner in which the target operation mode is included.
步骤102,在缓存表中查找是否存在所述目标资源访问请求的鉴权结果。Step 102: Search, in the cache table, whether an authentication result of the target resource access request exists.
具体的,所述鉴权装置在缓存表中查找是否存在所述目标资源访问请求的鉴权结果,其中,鉴权结果包括鉴权通过和鉴权不通过。若鉴权结果为鉴权通过,表示所述鉴权装置允许按照所述目标资源访问请求对目标访问资源执行目标操作方式,若鉴权结果为鉴权不通过,则表示所述鉴权装置拒绝所述目标资源访问请求。Specifically, the authentication device searches for a result of the authentication of the target resource access request in the cache table, where the authentication result includes the authentication pass and the authentication fail. If the authentication result is authenticated, the authentication device is configured to perform the target operation mode on the target access resource according to the target resource access request, and if the authentication result is that the authentication fails, the authentication device rejects The target resource access request.
根据本申请一实施例,所述缓存表包含接收到所述目标资源访问请求之前的预设时间段内的多个资源访问请求的鉴权结果。预设时间段是所述鉴权装置预先设定的,例如,对于资源访问请求较为频繁的情况,所述鉴权装置可以设定在缓存表中缓存接收到目标资源访问请求的时 刻的前一小时内的全部资源访问请求的鉴权结果;对于资源访问请求较为稀疏的情况,所述鉴权装置可以设定在缓存表中缓存接收到目标资源访问请求的时刻的前24小时内的全部资源访问请求的鉴权结果,本申请实施例对缓存表所缓存的鉴权结果的时间范围不做限定。According to an embodiment of the present application, the cache table includes an authentication result of multiple resource access requests within a preset time period before receiving the target resource access request. The preset time period is preset by the authentication device. For example, in a case where the resource access request is frequent, the authentication device may set a cache in the cache table to receive the target resource access request. The authentication result of all resource access requests in the hour; in the case where the resource access request is sparse, the authentication device may set all the resources in the cache table to buffer the time within the first 24 hours of receiving the target resource access request. The time range of the authentication result cached by the cache table is not limited in the embodiment of the present application.
根据本申请一实施例,所述缓存表包含多个资源访问请求中每个资源访问请求的用户标识、可访问资源、对所述可访问资源的可操作方式、鉴权结果等等数据。通过将目标资源访问请求中的目标用户标识、目标访问资源和对所述目标访问资源的目标操作方式与缓存表中的数据一一比对,进而确定该目标资源访问请求的鉴权结果。According to an embodiment of the present application, the cache table includes data of a user identifier, an accessible resource, an operable manner of the accessible resource, an authentication result, and the like of each of the plurality of resource access requests. The target authentication result of the target resource access request is determined by comparing the target user identifier in the target resource access request, the target access resource, and the target operation mode of the target access resource with the data in the cache table.
步骤103,当所述缓存表中不存在所述目标资源访问请求的鉴权结果时,采用第一策略表对所述目标资源访问请求进行鉴权,并输出所述目标资源访问请求的鉴权结果。Step 103: When the authentication result of the target resource access request does not exist in the cache table, use the first policy table to authenticate the target resource access request, and output the authentication of the target resource access request. result.
具体的,当所述缓存表中不存在所述目标资源访问请求的鉴权结果时,所述鉴权装置采用第一策略表对所述目标资源访问请求进行鉴权,并输出所述目标资源访问请求的鉴权结果。其中,所述第一策略表为包含用户标识、所述用户标识对应的可访问资源、对所述可访问资源的可操作方式之间的对应关系的一个关系表,所述第一策略表是根据用户标识进行分类的,每个用户标识对应至少一个可访问资源,每个可访问资源对应至少一个可操作方式。Specifically, when the authentication result of the target resource access request does not exist in the cache table, the authentication device uses the first policy table to authenticate the target resource access request, and outputs the target resource. Access the authentication result of the request. The first policy table is a relationship table including a user identifier, an accessible resource corresponding to the user identifier, and a corresponding relationship between the operable modes of the accessible resource, where the first policy table is According to the user identifier, each user identifier corresponds to at least one accessible resource, and each accessible resource corresponds to at least one operable manner.
表1:第一策略表Table 1: First Strategy Table
例如,请参见上表,为一种形式下的策略表,包含用户标识、可访问资源、对所述可访问资源的可操作方式。表1按照用户标识进行分类,这样在对目标资源访问请求进行鉴权时,能够快速地从第一策略表中的用户标识中查找到目标用户标识对应的可访问资源以及可操作方式,进而提高了对目标资源访问请求的鉴权效率。For example, refer to the above table, which is a policy table in a form, including a user identifier, an accessible resource, and an operable manner for the accessible resource. Table 1 is classified according to the user identifier, so that when the target resource access request is authenticated, the accessible resource corresponding to the target user identifier and the operable mode can be quickly found from the user identifier in the first policy table, thereby improving the The efficiency of authentication of target resource access requests.
进一步的,当所述缓存表中存在所述目标资源访问请求的鉴权结果时,所述鉴权装置将在所述缓存表中查找到的鉴权结果进行输出。Further, when the authentication result of the target resource access request exists in the cache table, the authentication device outputs the authentication result found in the cache table.
根据本申请一实施例,若所述目标资源访问请求的鉴权结果为鉴权通过,则所述鉴权装置对所述目标资源访问请求进行处理,即按照所述目标资源访问请求中的目标操作方式对目标访问资源进行处理,在处理完成之后,所述鉴权装置可以将处理结果进行输出。According to an embodiment of the present application, if the authentication result of the target resource access request is authenticated, the authentication device processes the target resource access request, that is, according to the target in the target resource access request. The operation mode processes the target access resource, and after the processing is completed, the authentication device may output the processing result.
在本申请实施例中,当接收到用户终端发送的携带目标用户标识、目标访问资源和对目标访问资源的目标操作方式的目标资源访问请求时,在缓存表中查找是否存在目标资源访问请求的鉴权结果,当缓存表中不存在目标资源访问请求的鉴权结果时,采用第一策略表对目标资源访问请求进行鉴权,并将目标资源访问请求的鉴权结果进行输出。由于第一策略表是以用户标识分类的且为包含用户标识、所述用户标识对应的可访问资源、对可访问资源的可操作方式之间的对应关系的一个关系表,这样能够在一个关系表中查找目标资源访问请求的相关数据,节省了查找目标资源访问请求的相关数据的时间,进而提高了对资源访问请求的鉴权效率,避免因在多个关系表中查找目标资源访问请求的相关数据而造成的计算设备的处理资源的浪费。In the embodiment of the present application, when receiving the target resource identifier that is sent by the user terminal, the target access resource, and the target operation mode of the target access resource, the cache table is used to find whether the target resource access request exists. As a result of the authentication, when the authentication result of the target resource access request does not exist in the cache table, the target resource access request is authenticated by using the first policy table, and the authentication result of the target resource access request is output. The first policy table is a relationship table that is classified by the user identifier and is a correspondence relationship between the user identifier, the accessible resource corresponding to the user identifier, and the operable mode of the accessible resource, so that the relationship can be in a relationship. The data in the table for finding the target resource access request saves the time for finding the related data of the target resource access request, thereby improving the authentication efficiency of the resource access request and avoiding finding the target resource access request in multiple relational tables. Waste of processing resources of computing devices caused by related data.
请参见图2,为本申请实施例提供的另一种鉴权方法的流程示意图。如图2所示,本申请实施例的所述方法可由本申请任一实施例提供的鉴权装置执行,可以包括以下步骤201-步骤207。FIG. 2 is a schematic flowchart diagram of another authentication method according to an embodiment of the present application. As shown in FIG. 2, the method in the embodiment of the present application may be performed by the authentication apparatus provided in any embodiment of the present application, and may include the following steps 201-207.
步骤201,接收用户终端发送的目标资源访问请求。Step 201: Receive a target resource access request sent by the user terminal.
具体的,鉴权装置接收用户终端发送的目标资源访问请求。其中,所述目标资源访问请求携带目标用户标识、目标访问资源和对所述目标访问资源的目标操作方式。Specifically, the authentication device receives the target resource access request sent by the user terminal. The target resource access request carries a target user identifier, a target access resource, and a target operation mode for accessing the resource to the target.
举例来说,用户可以通过登陆资源管理平台发起目标资源访问请求。其中,目标用户标识是用于标记对目标访问资源执行目标操作方式的用户的。例如,所述目标访问资源可以为所述服务器中的某一个文件、数据等等,所述目标操作方式可以为读取指令(read)、删除指令(delete)、写入指令(write)等等,本申请实施例对目标操作方式所包含的方式不做限定。For example, the user can initiate a target resource access request by logging into the resource management platform. The target user identifier is used to mark the user who performs the target operation mode on the target access resource. For example, the target access resource may be a file, data, or the like in the server, and the target operation mode may be a read instruction, a delete instruction, a write instruction, or the like. The embodiment of the present application does not limit the manner in which the target operation mode is included.
步骤202,在缓存表中查找是否存在所述目标资源访问请求的鉴权结果。Step 202: Search, in the cache table, whether an authentication result of the target resource access request exists.
具体的,所述鉴权装置在缓存表中查找是否存在所述目标资源访问请求的鉴权结果,其中,鉴权结果包括鉴权通过和鉴权不通过。若鉴权结果为鉴权通过,表示所述鉴权装置允许按照所述目标资源访问请求对目标访问资源执行目标操作方式,若鉴权结果为鉴权不通过,则表示所述鉴权装置拒绝所述目标资源访问请求。Specifically, the authentication device searches for a result of the authentication of the target resource access request in the cache table, where the authentication result includes the authentication pass and the authentication fail. If the authentication result is authenticated, the authentication device is configured to perform the target operation mode on the target access resource according to the target resource access request, and if the authentication result is that the authentication fails, the authentication device rejects The target resource access request.
根据本申请一实施例,所述缓存表包含接收到所述目标资源访问请求之前的预设时间段内的多个资源访问请求的鉴权结果。预设时间段是所述鉴权装置预先设定的,例如,对于资源访问请求较为频繁的情况,所述鉴权装置可以设定在缓存表中缓存接收到目标资源访问请求的时刻的前一小时内的全部资源访问请求的鉴权结果;对于资源访问请求较为稀疏的情况,所述鉴权装置可以设定在缓存表中缓存接收到目标资源访问请求的时刻的前24小时内的全部资源访问请求的鉴权结果,本申请实施例对缓存表所缓存的鉴权结果的时间范围不做限定。According to an embodiment of the present application, the cache table includes an authentication result of multiple resource access requests within a preset time period before receiving the target resource access request. The preset time period is preset by the authentication device. For example, in a case where the resource access request is frequent, the authentication device may set a cache in the cache table to receive the target resource access request. The authentication result of all resource access requests in the hour; in the case where the resource access request is sparse, the authentication device may set all the resources in the cache table to buffer the time within the first 24 hours of receiving the target resource access request. The time range of the authentication result cached by the cache table is not limited in the embodiment of the present application.
根据本申请一实施例,所述缓存表包含多个资源访问请求中每个资源访问请求的用户标识、可访问资源、对所述可访问资源的可操作方式、鉴权结果等等数据。通过将目标资源访问请求中的目标用户标识、目标 访问资源和对所述目标访问资源的目标操作方式与缓存表中的数据一一比对,进而确定该目标资源访问请求的鉴权结果。According to an embodiment of the present application, the cache table includes data of a user identifier, an accessible resource, an operable manner of the accessible resource, an authentication result, and the like of each of the plurality of resource access requests. The target authentication result of the target resource access request is determined by comparing the target user identifier in the target resource access request, the target access resource, and the target operation mode of the target access resource with the data in the cache table.
步骤203,当所述缓存表中存在所述目标资源访问请求的鉴权结果时,所述鉴权装置将在所述缓存表中查找到的鉴权结果进行输出。Step 203: When the authentication result of the target resource access request exists in the cache table, the authentication device outputs the authentication result found in the cache table.
步骤204,当所述缓存表中不存在所述目标资源访问请求的鉴权结果时,检测第二策略表的当前版本号是否高于所述第一策略表的当前版本号。Step 204: When the authentication result of the target resource access request does not exist in the cache table, check whether the current version number of the second policy table is higher than the current version number of the first policy table.
具体的,当缓存表中不存在所述目标资源访问请求的鉴权结果时,所述鉴权装置检测第二策略表的当前版本号是否高于所述第一策略表的当前版本号。Specifically, when the authentication result of the target resource access request does not exist in the cache table, the authenticating device detects whether the current version number of the second policy table is higher than the current version number of the first policy table.
其中,所述第一策略表为包含用户标识、所述用户标识对应的可访问资源、对所述可访问资源的可操作方式之间的对应关系的一个关系表,所述第一策略表是根据用户标识进行分类的,每个用户标识对应至少一个可访问资源,以及每个可访问资源对应至少一个可操作方式。The first policy table is a relationship table including a user identifier, an accessible resource corresponding to the user identifier, and a corresponding relationship between the operable modes of the accessible resource, where the first policy table is According to the user identifier, each user identifier corresponds to at least one accessible resource, and each accessible resource corresponds to at least one operable manner.
根据本申请一实施例,所述第二策略表包含用户标识和用户组的关系表、用户组和策略标识的关系表、策略标识和可访问资源的映射表以及策略标识和可操作方式的映射表等多个关系表。第二策略表中的策略标识用于对应由多个可访问资源组成的资源组,或者,所述策略标识用于对应由多个可操作方式组成的权限组。According to an embodiment of the present application, the second policy table includes a relationship table between a user identifier and a user group, a relationship table between the user group and the policy identifier, a mapping table of the policy identifier and the accessible resource, and a mapping between the policy identifier and the operable mode. Tables and other relational tables. The policy identifier in the second policy table is used to correspond to a resource group composed of a plurality of accessible resources, or the policy identifier is used to correspond to a permission group composed of multiple operable modes.
根据本申请一实施例,第一策略表的当前版本号和第二策略表的当前版本号可以通过更新时间表示。版本号可以指示所更新的数据,例如,变化的可访问资源、变化的用户标识、变化的可操作方式等等。对于第二策略表而言,还可以包括变化的用户组标识、变化的策略标识等等。According to an embodiment of the present application, the current version number of the first policy table and the current version number of the second policy table may be represented by an update time. The version number may indicate updated data, such as changed accessible resources, changed user identification, changed operational modes, and the like. For the second policy table, a changed user group identifier, a changed policy identifier, and the like may also be included.
根据本申请一实施例,由于第二策略表是通过各个策略标识进行区分的,当用户标识或可访问资源或可操作方式发生诸如增加、减少等变化时,可以先更新第二策略表,由于第二策略表包含了多个关系表,通过修改其中一个关系表就可完成数据的更新,能够提高策略表的更新效率,并在第二策略表更新之后,更新第二策略表的版本号。在第二策略 表更新之后,再根据第二策略表更新第一策略表,以保证第一策略表的准确性,并在第一策略表更新之后,更新第一策略表的版本号。According to an embodiment of the present application, since the second policy table is distinguished by each policy identifier, when the user identifier or the accessible resource or the operable mode changes such as increase, decrease, etc., the second policy table may be updated first, because The second policy table includes a plurality of relation tables, and the data update can be completed by modifying one of the relationship tables, the update efficiency of the policy table can be improved, and the version number of the second policy table is updated after the second policy table is updated. After the second policy table is updated, the first policy table is updated according to the second policy table to ensure the accuracy of the first policy table, and the version number of the first policy table is updated after the first policy table is updated.
步骤205,若第二策略表的当前版本号不高于所述第一策略表的当前版本号,则采用所述第一策略表对所述目标资源访问请求进行鉴权,并输出所述目标资源访问请求的鉴权结果。Step 205: If the current version number of the second policy table is not higher than the current version number of the first policy table, use the first policy table to authenticate the target resource access request, and output the target. The authentication result of the resource access request.
具体的,若所述第二策略表的当前版本号不高于所述第一策略表的当前版本号,则所述鉴权装置采用所述第一策略表对所述目标资源访问请求进行鉴权,并输出所述目标资源访问请求的鉴权结果。由于第一策略表为按照用户标识分类的一个关系表,且一个关系表中包含了多个数据,通过第一策略表对所述目标资源访问请求进行鉴权,能够提高鉴权效率,避免因在多个关系表中查找目标资源访问请求的相关数据而造成的计算设备的处理资源的浪费。Specifically, if the current version number of the second policy table is not higher than the current version number of the first policy table, the authentication device uses the first policy table to check the target resource access request. And output an authentication result of the target resource access request. The first policy table is a relationship table classified according to the user identifier, and a relationship table includes multiple data, and the target resource access request is authenticated by using the first policy table, thereby improving the authentication efficiency and avoiding the cause. The waste of processing resources of the computing device caused by finding related data of the target resource access request in the plurality of relation tables.
请一并参见图3,为本申请实施例提供的步骤205的流程示意图,如图3所示,步骤205可以包括步骤2051至步骤2055。Please refer to FIG. 3 , which is a schematic flowchart of
步骤2051,从所述第一策略表中查找与所述目标用户标识对应的可访问资源和对所述可访问资源的可操作方式。Step 2051: Search for an accessible resource corresponding to the target user identifier and an operable manner for the accessible resource from the first policy table.
具体的,所述鉴权装置从所述第一策略表中查找与所述目标用户标识对应的可访问资源和对所述可访问资源的可操作方式。Specifically, the authentication device searches, from the first policy table, an accessible resource corresponding to the target user identifier and an operable manner for the accessible resource.
步骤2052,判断所述可访问资源中是否存在所述目标访问资源。Step 2052: Determine whether the target access resource exists in the accessible resource.
具体的,所述鉴权装置在与所述目标用户标识对应的至少一个可访问资源中查找是否存在所述目标访问资源。若所述与目标用户标识对应的可访问资源中存在所述目标访问资源,则执行步骤2053;若所述与目标用户标识对应的可访问资源中不存在所述目标访问资源,则执行步骤2055。Specifically, the authentication device searches for at least one accessible resource corresponding to the target user identifier to find whether the target access resource exists. If the target access resource exists in the accessible resource corresponding to the target user identifier,
步骤2053,若所述可访问资源中存在所述目标访问资源,则判断对所述目标访问资源的可操作方式中是否存在所述目标操作方式。Step 2053: If the target access resource exists in the accessible resource, determine whether the target operation mode exists in an operable manner of the target access resource.
具体的,所述鉴权装置判断所述可访问资源中存在所述目标访问资源,则进一步判断对所述目标访问资源的可操作方式中是否存在所述目 标操作方式,若所述可操作方式中存在所述目标操作方式,则执行步骤2054,若所述可操作方式中不存在所述目标操作方式,则执行步骤2055。Specifically, the determining device determines that the target access resource exists in the accessible resource, and further determines whether the target operation mode exists in an operable manner of the target access resource, if the operable mode If the target operation mode exists, step 2054 is performed. If the target operation mode does not exist in the operable mode,
步骤2054,若对所述目标访问资源的可操作方式中存在所述目标操作方式,则确定所述目标资源访问请求的鉴权结果为鉴权通过,并输出所述目标资源访问请求的鉴权结果。In step 2054, if the target operation mode exists in the operability mode of the target access resource, the authentication result of the target resource access request is determined to be authenticated, and the authentication of the target resource access request is output. result.
具体的,若对所述目标访问资源的可操作方式中存在所述目标操作方式,则所述鉴权装置确定所述目标资源访问请求的鉴权结果为鉴权通过,并输出所述目标资源访问请求的鉴权结果。Specifically, if the target operation mode exists in an operative mode for accessing the resource, the authentication device determines that the authentication result of the target resource access request is authentication, and outputs the target resource. Access the authentication result of the request.
根据本申请一实施例,若所述目标资源访问请求的鉴权结果为鉴权通过,则所述鉴权装置对所述目标资源访问请求进行处理,即按照所述目标资源访问请求中的目标操作方式对目标访问资源进行处理,在处理完成之后,所述鉴权装置可以将处理结果进行输出。According to an embodiment of the present application, if the authentication result of the target resource access request is authenticated, the authentication device processes the target resource access request, that is, according to the target in the target resource access request. The operation mode processes the target access resource, and after the processing is completed, the authentication device may output the processing result.
步骤2055,确定所述目标资源访问请求的鉴权结果为鉴权不通过。Step 2055: Determine that the authentication result of the target resource access request is that the authentication fails.
具体的,若所述与目标用户标识对应的可访问资源中不存在所述目标访问资源,或者,若所述对所述目标访问资源的可操作方式中不存在所述目标操作方式,则所述鉴权装置确定所述目标资源访问请求的鉴权结果为鉴权不通过,并将鉴权结果进行输出,以使用户了解鉴权结果。Specifically, if the target access resource does not exist in the accessible resource corresponding to the target user identifier, or if the target operation mode does not exist in the operable mode of the target access resource, The authentication device determines that the authentication result of the target resource access request is that the authentication fails, and outputs the authentication result, so that the user understands the authentication result.
步骤206,若所述第二策略表的当前版本号高于所述第一策略表的当前版本号,则采用所述第二策略表对所述目标资源访问请求进行鉴权,并输出所述目标资源访问请求的鉴权结果。Step 206: If the current version number of the second policy table is higher than the current version number of the first policy table, use the second policy table to authenticate the target resource access request, and output the The authentication result of the target resource access request.
具体的,若所述第二策略表的当前版本号高于所述第一策略表的当前版本号,则所述鉴权装置采用所述第二策略表对所述目标资源访问请求进行鉴权,并输出所述目标资源访问请求的鉴权结果。Specifically, if the current version number of the second policy table is higher than the current version number of the first policy table, the authentication device uses the second policy table to authenticate the target resource access request. And outputting an authentication result of the target resource access request.
根据本申请一实施例,所述鉴权装置可以通过从所述第二策略表包含的多个关系表中查找是否存在所述目标资源访问请求对应的数据,以完成鉴权。According to an embodiment of the present application, the authentication device may complete the authentication by searching whether the data corresponding to the target resource access request exists in the plurality of relationship tables included in the second policy table.
步骤207,若所述第二策略表的当前版本号高于所述第一策略表的当前版本号,则根据所述第二策略表,更新所述第一策略表。Step 207: If the current version number of the second policy table is higher than the current version number of the first policy table, update the first policy table according to the second policy table.
具体的,当所述第二策略表的当前版本号高于所述第一策略表的当前版本号时,所述鉴权装置根据所述第二策略表,更新所述第一策略表。具体地,将所述第一策略表的当前版本号与所述第二策略表的历史版本信息进行对比,确定所述第一策略表的未更新数据。按照所述未更新数据,对所述第一策略表进行更新,并将所述第一策略表的当前版本号变更为所述第二策略表的当前版本号。Specifically, when the current version number of the second policy table is higher than the current version number of the first policy table, the authentication device updates the first policy table according to the second policy table. Specifically, the current version number of the first policy table is compared with the historical version information of the second policy table, and the unupdated data of the first policy table is determined. And updating, according to the unupdated data, the first policy table, and changing a current version number of the first policy table to a current version number of the second policy table.
举例来说,对于一用户标识而言,可能对应于两个或者两个以上的用户组,不同用户组对应不同的资源标识,不同资源标识对应的可访问资源不同或者可操作方式不同,例如:第二策略表包括以下表A、表B、表C、表D。For example, for a user identifier, it may correspond to two or more user groups, and different user groups correspond to different resource identifiers. Different resource identifiers may have different accessible resources or different operable modes, for example: The second strategy table includes the following Table A, Table B, Table C, and Table D.
表A:用户组和用户标识的关系表Table A: Relationship between user groups and user IDs
表B:用户组和资源标识的关系表Table B: Relationship table between user groups and resource identifiers
表C:资源标识和可访问资源的关系表Table C: Relationship table between resource IDs and accessible resources
表D:资源标识和可操作方式的关系表Table D: Relationship Table between Resource Identification and Operational Mode
而与当前的第二策略表对应的第一策略表为表E。The first policy table corresponding to the current second policy table is Table E.
表E:第一策略表Table E: First Strategy Table
可以看出,通过第二策略表对目标资源访问请求进行鉴权时,需要通过多个关系表来确定鉴权结果,而通过第一策略表对目标资源访问请求进行鉴权时,仅需要从一个关系表中就可以确定鉴权结果,大量了减少了打开关系表、关闭关系表、查找数据的时间,能够提高鉴权效率,避免因在多个关系表中查找目标资源访问请求的相关数据而造成的计算设备的处理资源的浪费。因此,在第二策略表的当前版本号不高于第一策略表的当前版本号的情况下,采用第一策略表进行鉴权,在第二策略表的当前版本号高于第一策略表的当前版本号的情况下,采用第二策略表进行鉴权。It can be seen that when the target resource access request is authenticated by the second policy table, the authentication result needs to be determined through multiple relationship tables, and when the target resource access request is authenticated through the first policy table, only one relationship needs to be obtained. The authentication result can be determined in the table, which greatly reduces the time for opening the relationship table, closing the relationship table, and searching for data, which can improve the authentication efficiency and avoid the related data of finding the target resource access request in multiple relation tables. The waste of processing resources of the computing device. Therefore, if the current version number of the second policy table is not higher than the current version number of the first policy table, the first policy table is used for authentication, and the current version number of the second policy table is higher than the first policy table. In the case of the current version number, the second policy table is used for authentication.
根据本申请一实施例,由于第二策略表直观的体现了各个数据之间 的关系,当用户组新增用户标识时,可以直接且快速地更新第二策略表所包含的用户组和用户标识的关系表,而对于第一策略表还需要更新新增用户标识的可访问资源和可操作方式,因此在有新的数据需要更新时,优先更新第二策略表,使得更新效率更高协,并在第二策略表更新后更新第二策略表的版本号。According to an embodiment of the present application, since the second policy table intuitively reflects the relationship between the data, when the user group adds the user identifier, the user group and the user identifier included in the second policy table can be directly and quickly updated. The relationship table, and the first policy table also needs to update the accessible resource and the operable mode of the newly added user identifier, so when there is new data to be updated, the second policy table is preferentially updated, so that the update efficiency is higher. And updating the version number of the second policy table after the second policy table is updated.
根据本申请一实施例,在更新第二策略表之后,可以根据第二策略表的更新内容更新第一策略表。According to an embodiment of the present application, after updating the second policy table, the first policy table may be updated according to the updated content of the second policy table.
根据本申请一实施例,当接收到策略表的变更请求时,还可以采用优先更新第一策略表的方式,在更新第一策略表之后,再根据更新之后的第一策略表更新第二策略表。或者,当接收到策略表的变更请求时,同步更新第一策略表和第二策略表,本申请实施例对此不做限定。According to an embodiment of the present application, when the change request of the policy table is received, the method of preferentially updating the first policy table may be adopted, and after updating the first policy table, updating the second policy according to the updated first policy table. table. Or, when the change request of the policy table is received, the first policy table and the second policy table are updated in synchronization, which is not limited by the embodiment of the present application.
在本申请实施例中,当接收到用户终端发送的携带目标用户标识、目标访问资源和对目标访问资源的目标操作方式的目标资源访问请求时,当缓存表中不存在目标资源访问请求的鉴权结果时,若第二策略表的版本号不高于第一策略表的版本号,则采用第一策略表对目标资源访问请求进行鉴权,若第二策略表的版本号高于第一策略表的版本号,则采用第二策略表对目标资源访问请求进行鉴权,并将目标资源访问请求的鉴权结果进行输出。由于第一策略表是以用户标识分类的且为包含用户标识、用户标识对应的可访问资源、对可访问资源的可操作方式之间的对应关系的一个关系表,这样能够在一个关系表中查找目标资源访问请求的相关数据,节省了查找目标资源访问请求的相关数据的时间,进而提高了对资源访问请求的鉴权效率,避免因在多个关系表中查找目标资源访问请求的相关数据而造成的计算设备的处理资源的浪费。另外,由于第二策略表包含多个关系表,能够较快的完成更新,在第二策略表保存有最新数据且第一策略表未更新的情况下,可以通过第二策略表对目标资源访问请求进行鉴权,保证了鉴权的准确性。In the embodiment of the present application, when receiving the target resource identifier that is sent by the user terminal, the target access resource, and the target operation mode of the target access resource, the target resource access request does not exist in the cache table. If the version number of the second policy table is not higher than the version number of the first policy table, the first policy table is used to authenticate the target resource access request, if the version number of the second policy table is higher than the first The version number of the policy table is used to authenticate the target resource access request by using the second policy table, and output the authentication result of the target resource access request. The first policy table is a relationship table that is classified by the user identifier and is a correspondence relationship between the user identifier, the accessible resource corresponding to the user identifier, and the operable mode of the accessible resource, so that the first policy table can be in a relationship table. The data related to the target resource access request is searched, which saves the time for finding the related data of the target resource access request, thereby improving the authentication efficiency of the resource access request and avoiding the related data of the target resource access request in multiple relational tables. The resulting processing resources of the computing device are wasted. In addition, since the second policy table includes multiple relationship tables, the update can be completed relatively quickly. In the case that the second policy table stores the latest data and the first policy table is not updated, the target resource can be accessed through the second policy table. Request for authentication to ensure the accuracy of authentication.
请参见图4,为本申请实施例提供的一种鉴权装置的结构示意图。 如图4所示,本申请实施例的所述鉴权装置1可以包括:请求接收单元11、结果查找单元12和第一鉴权单元13。FIG. 4 is a schematic structural diagram of an authentication apparatus according to an embodiment of the present application. As shown in FIG. 4, the
请求接收单元11,用于接收用户终端发送的目标资源访问请求,所述目标资源访问请求携带目标用户标识、目标访问资源和对所述目标访问资源的目标操作方式。The
具体的,所述请求接收单元11接收用户终端发送的目标资源访问请求。其中,所述目标资源访问请求携带目标用户标识、目标访问资源和对所述目标访问资源的目标操作方式。Specifically, the
举例来说,用户可以通过登陆资源管理平台发起目标资源访问请求。其中,目标用户标识是用于标记对目标访问资源执行目标操作方式的用户的。例如,所述目标访问资源可以为所述服务器中的某一个文件、数据等等,所述目标操作方式可以为读取指令(read)、删除指令(delete)、写入指令(write)等等,本申请实施例对目标操作方式所包含的方式不做限定。For example, the user can initiate a target resource access request by logging into the resource management platform. The target user identifier is used to mark the user who performs the target operation mode on the target access resource. For example, the target access resource may be a file, data, or the like in the server, and the target operation mode may be a read instruction, a delete instruction, a write instruction, or the like. The embodiment of the present application does not limit the manner in which the target operation mode is included.
结果查找单元12,用于在缓存表中查找是否存在所述目标资源访问请求的鉴权结果,所述缓存表包含接收到所述目标资源访问请求之前的预设时间段内的多个资源访问请求的鉴权结果。The
具体的,所述结果查找单元12在缓存表中查找是否存在所述目标资源访问请求的鉴权结果,其中,鉴权结果包括鉴权通过和鉴权不通过。若鉴权结果为鉴权通过,表示所述鉴权装置1允许按照所述目标资源访问请求对目标访问资源执行目标操作方式,若鉴权结果为鉴权不通过,则表示所述鉴权装置1拒绝所述目标资源访问请求。Specifically, the
根据本申请一实施例,所述缓存表包含接收到所述目标资源访问请求之前的预设时间段内的多个资源访问请求的鉴权结果。预设时间段是所述鉴权装置1预先设定的,例如,对于资源访问请求较为频繁的情况,所述鉴权装置1可以设定在缓存表中缓存接收到目标资源访问请求的时刻的前一小时内的全部资源访问请求的鉴权结果;对于资源访问请求较为稀疏的情况,所述鉴权装置1可以设定在缓存表中缓存接收到目标资 源访问请求的时刻的前24小时内的全部资源访问请求的鉴权结果,本申请实施例对缓存表所缓存的鉴权结果的时间范围不做限定。According to an embodiment of the present application, the cache table includes an authentication result of multiple resource access requests within a preset time period before receiving the target resource access request. The preset time period is preset by the
根据本申请一实施例,所述缓存表包含多个资源访问请求中每个资源访问请求的用户标识、可访问资源、对所述可访问资源的可操作方式、鉴权结果等等数据。通过将目标资源访问请求中的目标用户标识、目标访问资源和对所述目标访问资源的目标操作方式与缓存表中的数据一一比对,进而确定是否存在该目标资源访问请求的鉴权结果。According to an embodiment of the present application, the cache table includes data of a user identifier, an accessible resource, an operable manner of the accessible resource, an authentication result, and the like of each of the plurality of resource access requests. Determining whether there is an authentication result of the target resource access request by comparing the target user identifier in the target resource access request, the target access resource, and the target operation mode of the target access resource with the data in the cache table. .
第一鉴权单元13,用于当所述缓存表中不存在所述目标资源访问请求的鉴权结果时,采用第一策略表对所述目标资源访问请求进行鉴权,并输出所述目标资源访问请求的鉴权结果。The
具体的,当所述缓存表中不存在所述目标资源访问请求的鉴权结果时,所述第一鉴权单元13采用第一策略表对所述目标资源访问请求进行鉴权,并输出所述目标资源访问请求的鉴权结果。其中,所述第一策略表为包含用户标识、所述用户标识对应的可访问资源、对所述可访问资源的可操作方式之间的对应关系的一个关系表,所述第一策略表是以用户标识进行分类的,每个用户标识对应至少一个可访问资源,以及每个可访问资源对应至少一个可操作方式。Specifically, when the authentication result of the target resource access request does not exist in the cache table, the
根据本申请一实施例,当所述缓存表中存在所述目标资源访问请求的鉴权结果时,所述鉴权装置1将在所述缓存表中查找到的鉴权结果进行输出。According to an embodiment of the present application, when the authentication result of the target resource access request exists in the cache table, the
根据本申请一实施例,若所述目标资源访问请求的鉴权结果为鉴权通过,则所述鉴权装置1对所述目标资源访问请求进行处理,即按照所述目标资源访问请求中的目标操作方式对目标访问资源进行处理,在处理完成之后,所述鉴权装置1可以将处理结果进行输出。According to an embodiment of the present application, if the authentication result of the target resource access request is authenticated, the
在本申请实施例中,当接收到用户终端发送的携带目标用户标识、目标访问资源和对目标访问资源的目标操作方式的目标资源访问请求时,在缓存表中查找是否存在目标资源访问请求的鉴权结果,当缓存表中不存在目标资源访问请求的鉴权结果时,采用第一策略表对目标资源 访问请求进行鉴权,并将目标资源访问请求的鉴权结果进行输出。由于第一策略表是以用户标识分类的且为包含用户标识、所述用户标识对应的可访问资源、对可访问资源的可操作方式之间的对应关系的一个关系表,这样能够在一个关系表中查找目标资源访问请求的相关数据,节省了查找目标资源访问请求的相关数据的时间,进而提高了对资源访问请求的鉴权效率,避免因在多个关系表中查找目标资源访问请求的相关数据而造成的计算设备的处理资源的浪费。In the embodiment of the present application, when receiving the target resource identifier that is sent by the user terminal, the target access resource, and the target operation mode of the target access resource, the cache table is used to find whether the target resource access request exists. As a result of the authentication, when the authentication result of the target resource access request does not exist in the cache table, the target resource access request is authenticated by using the first policy table, and the authentication result of the target resource access request is output. The first policy table is a relationship table that is classified by the user identifier and is a correspondence relationship between the user identifier, the accessible resource corresponding to the user identifier, and the operable mode of the accessible resource, so that the relationship can be in a relationship. The data in the table for finding the target resource access request saves the time for finding the related data of the target resource access request, thereby improving the authentication efficiency of the resource access request and avoiding finding the target resource access request in multiple relational tables. Waste of processing resources of computing devices caused by related data.
请参见图5,为本申请实施例提供的一种鉴权装置的另一结构示意图。如图5所示,本申请实施例的所述鉴权装置1可以包括:请求接收单元11、结果查找单元12、第一鉴权单元13、版本号检测单元14、第二鉴权单元15和策略表更新单元16。FIG. 5 is another schematic structural diagram of an authentication apparatus according to an embodiment of the present application. As shown in FIG. 5, the
请求接收单元11,用于接收用户终端发送的目标资源访问请求,所述目标资源访问请求携带目标用户标识、目标访问资源和对所述目标访问资源的目标操作方式。The
具体的,所述请求接收单元11接收用户终端发送的目标资源访问请求。其中,所述目标资源访问请求携带目标用户标识、目标访问资源和对所述目标访问资源的目标操作方式。Specifically, the
举例来说,用户可以通过登陆资源管理平台发起目标资源访问请求。其中,目标用户标识是用于标记对目标访问资源执行目标操作方式的用户的。例如,所述目标访问资源可以为所述服务器中的某一个文件、数据等等,所述目标操作方式可以为读取指令(read)、删除指令(delete)、写入指令(write)等等,本申请实施例对目标操作方式所包含的方式不做限定。For example, the user can initiate a target resource access request by logging into the resource management platform. The target user identifier is used to mark the user who performs the target operation mode on the target access resource. For example, the target access resource may be a file, data, or the like in the server, and the target operation mode may be a read instruction, a delete instruction, a write instruction, or the like. The embodiment of the present application does not limit the manner in which the target operation mode is included.
结果查找单元12,用于在缓存表中查找是否存在所述目标资源访问请求的鉴权结果,所述缓存表包含接收到所述目标资源访问请求之前的预设时间段内的多个资源访问请求的鉴权结果。The
具体的,所述结果查找单元12在缓存表中查找是否存在所述目标 资源访问请求的鉴权结果,其中,鉴权结果包括鉴权通过和鉴权不通过,若鉴权结果为鉴权通过,表示所述鉴权装置1允许按照所述目标资源访问请求对目标访问资源执行目标操作方式,若鉴权结果为鉴权不通过,则表示所述鉴权装置1拒绝所述目标资源访问请求。Specifically, the
根据本申请一实施例,所述缓存表包含接收到所述目标资源访问请求之前的预设时间段内的多个资源访问请求的鉴权结果。预设时间段是所述鉴权装置1预先设定的,例如,对于资源访问请求较为频繁的情况,所述鉴权装置1可以设定在缓存表中缓存接收到目标资源访问请求的时刻的前一小时内的全部资源访问请求的鉴权结果;对于资源访问请求较为稀疏的情况,所述鉴权装置1可以设定在缓存表中缓存接收到目标资源访问请求的时刻的前24小时内的全部资源访问请求的鉴权结果,本申请实施例对缓存表所缓存的鉴权结果的时间范围不做限定。According to an embodiment of the present application, the cache table includes an authentication result of multiple resource access requests within a preset time period before receiving the target resource access request. The preset time period is preset by the
根据本申请一实施例,所述缓存表包含多个资源访问请求中每个资源访问请求的用户标识、可访问资源、对所述可访问资源的可操作方式、鉴权结果等等数据。通过将目标资源访问请求中的目标用户标识、目标访问资源和对所述目标访问资源的目标操作方式与缓存表中的数据一一比对,进而确定该目标资源访问请求的鉴权结果。According to an embodiment of the present application, the cache table includes data of a user identifier, an accessible resource, an operable manner of the accessible resource, an authentication result, and the like of each of the plurality of resource access requests. The target authentication result of the target resource access request is determined by comparing the target user identifier in the target resource access request, the target access resource, and the target operation mode of the target access resource with the data in the cache table.
版本号检测单元14,用于当所述缓存表中不存在所述目标资源访问请求的鉴权结果时,检测第二策略表的当前版本号是否高于所述第一策略表的当前版本号。The version
具体的,若缓存表中不存在所述目标资源访问请求的鉴权结果时,所述版本号检测单元14检测第二策略表的当前版本号是否高于所述第一策略表的当前版本号。Specifically, if the authentication result of the target resource access request does not exist in the cache table, the version
其中,所述第一策略表为包含用户标识、所述用户标识对应的可访问资源、对所述可访问资源的可操作方式之间的对应关系的一个关系表,所述第一策略表是以用户标识进行分类的,每个用户标识对应至少一个可访问资源,以及每个可访问资源对应至少一个可操作方式。The first policy table is a relationship table including a user identifier, an accessible resource corresponding to the user identifier, and a corresponding relationship between the operable modes of the accessible resource, where the first policy table is Classified by the user identifier, each user identifier corresponds to at least one accessible resource, and each accessible resource corresponds to at least one operable manner.
根据本申请一实施例,所述第二策略表包含用户标识和用户组的关 系表、用户组和策略标识的关系表、策略标识和可访问资源的映射表以及策略标识和可操作方式的映射表等多个关系表。第二策略表中的策略标识用于对应由多个可访问资源组成的资源组,或者,所述策略标识用于对应由多个可操作方式组成的权限组。According to an embodiment of the present application, the second policy table includes a relationship table between a user identifier and a user group, a relationship table between the user group and the policy identifier, a mapping table of the policy identifier and the accessible resource, and a mapping between the policy identifier and the operable mode. Tables and other relational tables. The policy identifier in the second policy table is used to correspond to a resource group composed of a plurality of accessible resources, or the policy identifier is used to correspond to a permission group composed of multiple operable modes.
根据本申请一实施例,第一策略表的当前版本号和第二策略表的当前版本号可以通过更新时间表示。版本号可以指示所更新的数据,例如,变化的可访问资源、变化的用户标识、变化的可操作方式等等。对于第二策略表而言,还可以包括变化的用户组标识、变化的策略标识等等。According to an embodiment of the present application, the current version number of the first policy table and the current version number of the second policy table may be represented by an update time. The version number may indicate updated data, such as changed accessible resources, changed user identification, changed operational modes, and the like. For the second policy table, a changed user group identifier, a changed policy identifier, and the like may also be included.
根据本申请一实施例,由于第二策略表是通过各个策略标识进行区分的,当用户标识或可访问资源或可操作方式发生诸如增加、减少等变化时,可以先更新第二策略表,由于第二策略表包含了多个关系表,通过修改其中一个关系表就可完成数据的更新,能够提高策略表的更新效率,并在第二策略表更新之后,更新第二策略表的版本号。在第二策略表更新之后,再根据第二策略表更新第一策略表,以保证第一策略表的准确性,并在第一策略表更新之后,更新第一策略表的版本号。According to an embodiment of the present application, since the second policy table is distinguished by each policy identifier, when the user identifier or the accessible resource or the operable mode changes such as increase, decrease, etc., the second policy table may be updated first, because The second policy table includes a plurality of relation tables, and the data update can be completed by modifying one of the relationship tables, the update efficiency of the policy table can be improved, and the version number of the second policy table is updated after the second policy table is updated. After the second policy table is updated, the first policy table is updated according to the second policy table to ensure the accuracy of the first policy table, and after the first policy table is updated, the version number of the first policy table is updated.
第一鉴权单元13,用于若所述版本号检测单元14检测到所述第二策略表的当前版本号不高于所述第一策略表的当前版本号,则采用所述第一策略表对所述目标资源访问请求进行鉴权,并输出所述目标资源访问请求的鉴权结果。The
具体的,请一并参见图6,为本申请实施例提供的第一鉴权单元13的结构示意图,如图6所示,所述第一鉴权单元13包括数据查找子单元131、第一判断子单元132、第二判断子单元133和结果确定子单元134。Specifically, please refer to FIG. 6 , which is a schematic structural diagram of a
数据查找子单元131,用于从所述第一策略表中查找与所述目标用户标识对应的可访问资源和对所述可访问资源的可操作方式。The data search
具体的,所述数据查找子单元131从所述第一策略表中查找与所述目标用户标识对应的可访问资源和对所述可访问资源的可操作方式。Specifically, the data search sub-unit 131 searches the first policy table for an accessible resource corresponding to the target user identifier and an operable manner for the accessible resource.
第一判断子单元132,用于判断所述可访问资源中是否存在所述目 标访问资源。The first determining
具体的,所述第一判断子单元132在与所述目标用户标识对应的至少一个可访问资源中查找是否存在所述目标访问资源。若所述与目标用户标识对应的可访问资源中存在所述目标访问资源,则执行第二判断子单元133。Specifically, the first determining sub-unit 132 searches for at least one accessible resource corresponding to the target user identifier to find whether the target access resource exists. If the target access resource exists in the accessible resource corresponding to the target user identifier, the second determining
第二判断子单元133,用于若所述第一判断子单元132判断所述可访问资源中存在所述目标访问资源,则判断对所述目标访问资源的可操作方式中是否存在所述目标操作方式。The second determining
具体的,若所述第一判断子单元132判断所述可访问资源中存在所述目标访问资源,所述第二判断子单元133判断对所述目标访问资源的可操作方式中是否存在所述目标操作方式,若所述可操作方式中存在所述目标操作方式,则执行结果确定子单元134。Specifically, if the first determining
结果确定子单元134,用于若所述第二判断子单元133判断对所述目标访问资源的可操作方式中存在所述目标操作方式,则确定所述目标资源访问请求的鉴权结果为鉴权通过,并输出所述目标资源访问请求的鉴权结果。a result determining sub-unit 134, configured to determine, when the second determining
具体的,若对所述目标访问资源的可操作方式中存在所述目标操作方式,则所述结果确定子单元134确定所述目标资源访问请求的鉴权结果为鉴权通过,并输出所述目标资源访问请求的鉴权结果。Specifically, if the target operation mode exists in an operable mode for accessing the resource, the result determining sub-unit 134 determines that the authentication result of the target resource access request is an authentication pass, and outputs the The authentication result of the target resource access request.
根据本申请一实施例,若所述目标资源访问请求的鉴权结果为鉴权通过,则所述鉴权装置1对所述目标资源访问请求进行处理,即按照所述目标资源访问请求中的目标操作方式对目标访问资源进行处理,在处理完成之后,所述鉴权装置1可以将处理结果进行输出。According to an embodiment of the present application, if the authentication result of the target resource access request is authenticated, the
第二鉴权单元15,用于若所述版本号检测单元14检测到所述第二策略表的当前版本号高于所述第一策略表的当前版本号,则采用所述第二策略表对所述目标资源访问请求进行鉴权,并输出所述目标资源访问请求的鉴权结果。The
具体的,若所述第二策略表的当前版本号高于所述第一策略表的当 前版本号,则所述第二鉴权单元15采用所述第二策略表对所述目标资源访问请求进行鉴权,并输出所述目标资源访问请求的鉴权结果。所述第二鉴权单元15可以通过从所述第二策略表包含的多个关系表中查找是否存在所述目标资源访问请求对应的数据,以完成鉴权。Specifically, if the current version number of the second policy table is higher than the current version number of the first policy table, the
策略表更新单元16,用于若所述版本号检测单元14检测到所述第二策略表的当前版本号高于所述第一策略表的当前版本号,则根据所述第二策略表,更新所述第一策略表。The policy
具体的,请一并参见图7,为本申请实施例提供的策略表更新单元16的结构示意图,如图7所示,所述策略表更新单元16包括更新数据确定子单元161和策略表更新子单元162。Specifically, please refer to FIG. 7 , which is a schematic structural diagram of a policy
更新数据确定子单元161,用于若所述版本号检测单元14检测到所述第二策略表的当前版本号高于所述第一策略表的当前版本号,比较所述第一策略表的当前版本号与所述第二策略表的历史版本信息,确定所述第一策略表的未更新数据。The update
策略表更新子单元162,用于按照所述未更新数据,对所述第一策略表进行更新,并将所述第一策略表的当前版本号变更为所述第二策略表的当前版本号。The policy table update sub-unit 162 is configured to update the first policy table according to the unupdated data, and change a current version number of the first policy table to a current version number of the second policy table. .
在本申请实施例中,当接收到用户终端发送的携带目标用户标识、目标访问资源和对目标访问资源的目标操作方式的目标资源访问请求时,当缓存表中不存在目标资源访问请求的鉴权结果时,若第二策略表的版本号不高于第一策略表的版本号,则采用第一策略表对目标资源访问请求进行鉴权,若第二策略表的版本号高于第一策略表的版本号,则采用第二策略表对目标资源访问请求进行鉴权,并将目标资源访问请求的鉴权结果进行输出。由于第一策略表是以用户标识分类的且为包含用户标识、用户标识对应的可访问资源、对可访问资源的可操作方式之间的对应关系的一个关系表,这样能够在一个关系表中查找目标资源访问请求的相关数据,节省了查找目标资源访问请求的相关数据的时间,进而提高了对资源访问请求的鉴权效率,避免因在多个关系表中查找目标 资源访问请求的相关数据而造成的计算设备的处理资源的浪费。另外,由于第二策略表包含多个关系表,能够较快的完成更新,在第二策略表保存有最新数据且第一策略表未更新的情况下,可以通过第二策略表对目标资源访问请求进行鉴权,保证了鉴权的准确性。In the embodiment of the present application, when receiving the target resource identifier that is sent by the user terminal, the target access resource, and the target operation mode of the target access resource, the target resource access request does not exist in the cache table. If the version number of the second policy table is not higher than the version number of the first policy table, the first policy table is used to authenticate the target resource access request, if the version number of the second policy table is higher than the first The version number of the policy table is used to authenticate the target resource access request by using the second policy table, and output the authentication result of the target resource access request. The first policy table is a relationship table that is classified by the user identifier and is a correspondence relationship between the user identifier, the accessible resource corresponding to the user identifier, and the operable mode of the accessible resource, so that the first policy table can be in a relationship table. The data related to the target resource access request is searched, which saves the time for finding the related data of the target resource access request, thereby improving the authentication efficiency of the resource access request and avoiding the related data of the target resource access request in multiple relational tables. The resulting processing resources of the computing device are wasted. In addition, since the second policy table includes multiple relationship tables, the update can be completed relatively quickly. In the case that the second policy table stores the latest data and the first policy table is not updated, the target resource can be accessed through the second policy table. Request for authentication to ensure the accuracy of authentication.
请参见图8,为本申请实施例提供的另一种鉴权装置的结构示意图。如图8所示,所述鉴权装置1000可以包括:至少一个处理器1001,例如CPU(Central Processing Unit,中央处理器),至少一个网络接口1004,存储器1005,至少一个通信总线1002。网络接口1004可选的可以包括标准的有线接口、无线接口(如WI-FI接口)。存储器1005可以是高速RAM存储器,也可以是非不稳定的存储器(non-volatile memory),例如至少一个磁盘存储器。根据本申请一实施例,存储器1005还可以是至少一个位于远离前述处理器1001的存储装置。其中,通信总线1002用于实现这些组件之间的连接通信。FIG. 8 is a schematic structural diagram of another authentication apparatus according to an embodiment of the present application. As shown in FIG. 8, the
根据本申请一实施例,所述鉴权装置1000包括用户接口1003,其中,用户接口1003可以包括显示屏(Display)10031、键盘(Keyboard)10032。如图8所示,作为一种计算机存储介质的存储器1005中可以包括操作系统10051、网络通信模块10052、用户接口模块10053以及机器可读指令,如鉴权应用程序10054。According to an embodiment of the present application, the
在图8所示的鉴权装置1000中,用户接口1003主要用于接收用户发起的目标资源访问请求等;而处理器1001可以用于调用存储器1005中存储的鉴权应用程序,并具体执行以下操作:In the
接收用户终端发送的目标资源访问请求,所述目标资源访问请求携带目标用户标识、目标访问资源和对所述目标访问资源的目标操作方式;Receiving a target resource access request sent by the user terminal, where the target resource access request carries a target user identifier, a target access resource, and a target operation mode for accessing the resource by the target;
在缓存表中查找是否存在所述目标资源访问请求的鉴权结果,所述缓存表包含接收到所述目标资源访问请求之前的预设时间段内的多个资源访问请求的鉴权结果;Querying, in the cache table, whether an authentication result of the target resource access request exists, where the cache table includes an authentication result of multiple resource access requests within a preset time period before receiving the target resource access request;
当所述缓存表中不存在所述目标资源访问请求的鉴权结果时,采用 第一策略表对所述目标资源访问请求进行鉴权,并输出所述目标资源访问请求的鉴权结果;When the authentication result of the target resource access request does not exist in the cache table, the target resource access request is authenticated by using the first policy table, and the authentication result of the target resource access request is output;
其中,所述第一策略表为包含用户标识、所述用户标识对应的可访问资源、对所述可访问资源的可操作方式之间的对应关系的一个关系表,所述第一策略表是以用户标识进行分类的,每个用户标识对应至少一个可访问资源,以及每个可访问资源对应至少一个可操作方式。The first policy table is a relationship table including a user identifier, an accessible resource corresponding to the user identifier, and a corresponding relationship between the operable modes of the accessible resource, where the first policy table is Classified by the user identifier, each user identifier corresponds to at least one accessible resource, and each accessible resource corresponds to at least one operable manner.
在本申请一个实施例中,所述处理器1001执行采用第一策略表对所述目标资源访问请求进行鉴权,并输出所述目标资源访问请求的鉴权结果之前,还执行以下操作:In an embodiment of the present application, the
检测第二策略表的当前版本号是否高于所述第一策略表的当前版本号;Detecting whether a current version number of the second policy table is higher than a current version number of the first policy table;
若所述第二策略表的当前版本号不高于所述第一策略表的当前版本号,则采用所述第一策略表对所述目标资源访问请求进行鉴权,并输出所述目标资源访问请求的鉴权结果;If the current version number of the second policy table is not higher than the current version number of the first policy table, the target resource access request is authenticated by using the first policy table, and the target resource is output Access the authentication result of the request;
其中,所述第二策略表包含多个关系表,所述多个关系表包括用户标识和用户组的关系表、用户组和策略标识的关系表、策略标识和可访问资源的映射表以及策略标识和可操作方式的映射表。The second policy table includes a plurality of relationship tables, where the relationship table includes a relationship between the user identifier and the user group, a relationship table between the user group and the policy identifier, a mapping table of the policy identifier and the accessible resource, and a policy. A mapping table of identification and actionable methods.
在本申请一个实施例中,所述处理器1001还执行以下操作:In an embodiment of the present application, the
若所述第二策略表的当前版本号高于所述第一策略表的当前版本号,则采用所述第二策略表对所述目标资源访问请求进行鉴权,并输出所述目标资源访问请求的鉴权结果。And if the current version number of the second policy table is higher than the current version number of the first policy table, the target resource access request is authenticated by using the second policy table, and the target resource access is output The requested authentication result.
在本申请一个实施例中,所述处理器1001还执行以下操作:In an embodiment of the present application, the
若所述第二策略表的当前版本号高于所述第一策略表的当前版本号,则根据所述第二策略表,更新所述第一策略表。And if the current version number of the second policy table is higher than a current version number of the first policy table, updating the first policy table according to the second policy table.
在本申请一个实施例中,所述处理器1001执行根据所述第二策略表,更新所述第一策略表,具体执行以下操作:In an embodiment of the present application, the
比较所述第一策略表的当前版本号与所述第二策略表的历史版本信息,确定所述第一策略表的未更新数据;Comparing a current version number of the first policy table with historical version information of the second policy table to determine unupdated data of the first policy table;
按照所述未更新数据,对所述第一策略表进行更新,并将所述第一策略表的当前版本号变更为所述第二策略表的当前版本号。And updating, according to the unupdated data, the first policy table, and changing a current version number of the first policy table to a current version number of the second policy table.
在本申请一个实施例中,所述处理器1001执行采用第一策略表对所述目标资源访问请求进行鉴权,并输出所述目标资源访问请求的鉴权结果,具体执行以下操作:In an embodiment of the present application, the
从所述第一策略表中查找与所述目标用户标识对应的可访问资源和对所述可访问资源的可操作方式;Finding, by the first policy table, an accessible resource corresponding to the target user identifier and an operable manner for the accessible resource;
判断所述可访问资源中是否存在所述目标访问资源;Determining whether the target access resource exists in the accessible resource;
若所述可访问资源中存在所述目标访问资源,则判断对所述目标访问资源的可操作方式中是否存在所述目标操作方式;If the target access resource exists in the accessible resource, determining whether the target operation mode exists in an operable manner of accessing the resource to the target;
若对所述目标访问资源的可操作方式中存在所述目标操作方式,则确定所述目标资源访问请求的鉴权结果为鉴权通过,并输出所述目标资源访问请求的鉴权结果。If the target operation mode exists in the operable mode of accessing the resource, the authentication result of the target resource access request is determined to be authenticated, and the authentication result of the target resource access request is output.
需要说明的是,本申请实施例所描述的处理器1001调用存储器1005中存储的鉴权应用程序所执行的步骤可根据上述图1B-至图3所示方法实施例中的方法具体实现,此处不再赘述。It should be noted that the steps performed by the
在本申请实施例中,当接收到用户终端发送的携带目标用户标识、目标访问资源和对目标访问资源的目标操作方式的目标资源访问请求时,在缓存表中查找是否存在目标资源访问请求的鉴权结果,当缓存表中不存在目标资源访问请求的鉴权结果时,采用第一策略表对目标资源访问请求进行鉴权,并将目标资源访问请求的鉴权结果进行输出。由于第一策略表是以用户标识分类的且为包含用户标识、所述用户标识对应的可访问资源、对可访问资源的可操作方式之间的对应关系的一个关系表,这样能够在一个关系表中查找目标资源访问请求的相关数据,节省了查找目标资源访问请求的相关数据的时间,进而提高了对资源访问请求的鉴权效率,避免因在多个关系表中查找目标资源访问请求的相关数据而造成的计算设备的处理资源的浪费。In the embodiment of the present application, when receiving the target resource identifier that is sent by the user terminal, the target access resource, and the target operation mode of the target access resource, the cache table is used to find whether the target resource access request exists. As a result of the authentication, when the authentication result of the target resource access request does not exist in the cache table, the target resource access request is authenticated by using the first policy table, and the authentication result of the target resource access request is output. The first policy table is a relationship table that is classified by the user identifier and is a correspondence relationship between the user identifier, the accessible resource corresponding to the user identifier, and the operable mode of the accessible resource, so that the relationship can be in a relationship. The data in the table for finding the target resource access request saves the time for finding the related data of the target resource access request, thereby improving the authentication efficiency of the resource access request and avoiding finding the target resource access request in multiple relational tables. Waste of processing resources of computing devices caused by related data.
本申请实施例中所述模块或单元,可以通过通用集成电路,例如 CPU,或通过ASIC(Application Specific Integrated Circuit,专用集成电路)来实现。The module or unit in the embodiment of the present application may be implemented by a general-purpose integrated circuit, such as a CPU, or by an ASIC (Application Specific Integrated Circuit).
本申请实施例方法中的步骤可以根据实际需要进行顺序上的调整、合并和删减。The steps in the method of the embodiment of the present application may be sequentially adjusted, merged, and deleted according to actual needs.
本申请实施例终端设备中的模块或单元可以根据实际需要进行合并、划分和删减。The modules or units in the terminal device in this embodiment of the present application may be combined, divided, and deleted according to actual needs.
本领域普通技术人员可以理解实现上述实施例方法中的全部或部分流程,是可以通过计算机程序来指令相关的硬件来完成,所述的程序可存储于一计算机可读取存储介质中,该程序在执行时,可实现如上述各方法的实施例的流程。其中,所述的存储介质可为磁碟、光盘、只读存储记忆体(Read-Only Memory,ROM)或随机存储记忆体(Random Access Memory,RAM)等。One of ordinary skill in the art can understand that all or part of the process of implementing the foregoing embodiments can be completed by a computer program to instruct related hardware, and the program can be stored in a computer readable storage medium. When executed, the flow of an embodiment of the methods as described above can be implemented. The storage medium may be a magnetic disk, an optical disk, a read-only memory (ROM), or a random access memory (RAM).
以上所揭露的仅为本申请较佳实施例而已,当然不能以此来限定本申请之权利范围,因此依本申请权利要求所作的等同变化,仍属本申请实施例所涵盖的范围。The above is only the preferred embodiment of the present application, and the scope of the application is not limited thereto. Therefore, the equivalent changes made in the claims of the present application are still within the scope of the embodiments of the present application.
Claims (18)
Translated fromChineseApplications Claiming Priority (2)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN201710067325.5ACN106790262B (en) | 2017-02-07 | 2017-02-07 | Authentication method and device |
| CN201710067325.5 | 2017-02-07 |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| WO2018145546A1true WO2018145546A1 (en) | 2018-08-16 |
Family
ID=58956278
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| PCT/CN2018/071503CeasedWO2018145546A1 (en) | 2017-02-07 | 2018-01-05 | Authentication method, device and storage medium |
Country Status (2)
| Country | Link |
|---|---|
| CN (1) | CN106790262B (en) |
| WO (1) | WO2018145546A1 (en) |
Cited By (1)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN112752300A (en)* | 2020-12-29 | 2021-05-04 | 锐捷网络股份有限公司 | Method and device for realizing local distribution |
Families Citing this family (8)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN106790262B (en)* | 2017-02-07 | 2022-02-11 | 腾讯科技(深圳)有限公司 | Authentication method and device |
| CN107172057A (en)* | 2017-06-01 | 2017-09-15 | 浙江数链科技有限公司 | Authentication implementing method and device |
| CN109495432B (en)* | 2017-09-13 | 2021-05-25 | 腾讯科技(深圳)有限公司 | An authentication method and server for an anonymous account |
| CN110197075B (en)* | 2018-04-11 | 2023-03-17 | 腾讯科技(深圳)有限公司 | Resource access method, device, computing equipment and storage medium |
| CN110224974B (en)* | 2019-04-26 | 2022-08-30 | 平安科技(深圳)有限公司 | Interface authentication method based on third party access and related equipment |
| CN112651001B (en)* | 2020-12-30 | 2025-02-11 | 中国平安财产保险股份有限公司 | Access request authentication method, device, equipment and readable storage medium |
| CN112995165B (en)* | 2021-02-10 | 2023-04-14 | 北京金山云网络技术有限公司 | Resource access authentication method and device, storage medium and electronic equipment |
| CN115278672B (en)* | 2022-07-28 | 2024-12-27 | 中国电信股份有限公司 | Authentication method, device, electronic device and medium |
Citations (7)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20070160198A1 (en)* | 2005-11-18 | 2007-07-12 | Security First Corporation | Secure data parser method and system |
| WO2009094890A1 (en)* | 2008-01-29 | 2009-08-06 | Huawei Technologies Co., Ltd. | A service scheduling method and the system, apparatus for scheduling services |
| CN103067911A (en)* | 2012-12-17 | 2013-04-24 | 中国联合网络通信集团有限公司 | Method and equipment used for controlling hardware module |
| CN103888409A (en)* | 2012-12-19 | 2014-06-25 | 中国电信股份有限公司 | Distributed unified authentication method and system |
| CN104484617A (en)* | 2014-12-05 | 2015-04-01 | 中国航空工业集团公司第六三一研究所 | Database access control method on basis of multi-strategy integration |
| CN105357190A (en)* | 2015-10-26 | 2016-02-24 | 网宿科技股份有限公司 | Method and system for performing authentication on access request |
| CN106790262A (en)* | 2017-02-07 | 2017-05-31 | 腾讯科技(深圳)有限公司 | A kind of method for authenticating and device |
Family Cites Families (8)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US6715082B1 (en)* | 1999-01-14 | 2004-03-30 | Cisco Technology, Inc. | Security server token caching |
| US7120691B2 (en)* | 2002-03-15 | 2006-10-10 | International Business Machines Corporation | Secured and access controlled peer-to-peer resource sharing method and apparatus |
| CN102523490A (en)* | 2011-12-02 | 2012-06-27 | 深圳市同洲视讯传媒有限公司 | Authentication method, authentication device and authentication system of ordered products |
| CN104363211A (en)* | 2014-10-31 | 2015-02-18 | 北京思特奇信息技术股份有限公司 | Method and system for managing authority |
| CN105306448A (en)* | 2015-09-22 | 2016-02-03 | 深圳前海华视移动互联有限公司 | Method for accessing extranet data, car-mounted multimedia terminal and kernel Netfilter module of car-mounted multimedia terminal |
| CN105245554B (en)* | 2015-11-24 | 2018-04-10 | 无锡江南计算技术研究所 | A kind of dynamic attribute access control method under cloud environment |
| CN105978774B (en)* | 2016-07-14 | 2019-06-07 | 杭州迪普科技股份有限公司 | A kind of method and apparatus of access authentication |
| CN106254528B (en)* | 2016-09-14 | 2019-12-06 | 北京佰才邦技术有限公司 | Resource downloading method and caching device |
- 2017
- 2017-02-07CNCN201710067325.5Apatent/CN106790262B/enactiveActive
- 2018
- 2018-01-05WOPCT/CN2018/071503patent/WO2018145546A1/ennot_activeCeased
Patent Citations (7)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20070160198A1 (en)* | 2005-11-18 | 2007-07-12 | Security First Corporation | Secure data parser method and system |
| WO2009094890A1 (en)* | 2008-01-29 | 2009-08-06 | Huawei Technologies Co., Ltd. | A service scheduling method and the system, apparatus for scheduling services |
| CN103067911A (en)* | 2012-12-17 | 2013-04-24 | 中国联合网络通信集团有限公司 | Method and equipment used for controlling hardware module |
| CN103888409A (en)* | 2012-12-19 | 2014-06-25 | 中国电信股份有限公司 | Distributed unified authentication method and system |
| CN104484617A (en)* | 2014-12-05 | 2015-04-01 | 中国航空工业集团公司第六三一研究所 | Database access control method on basis of multi-strategy integration |
| CN105357190A (en)* | 2015-10-26 | 2016-02-24 | 网宿科技股份有限公司 | Method and system for performing authentication on access request |
| CN106790262A (en)* | 2017-02-07 | 2017-05-31 | 腾讯科技(深圳)有限公司 | A kind of method for authenticating and device |
Cited By (2)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN112752300A (en)* | 2020-12-29 | 2021-05-04 | 锐捷网络股份有限公司 | Method and device for realizing local distribution |
| CN112752300B (en)* | 2020-12-29 | 2022-09-20 | 锐捷网络股份有限公司 | Method and device for realizing local distribution |
Also Published As
| Publication number | Publication date |
|---|---|
| CN106790262A (en) | 2017-05-31 |
| CN106790262B (en) | 2022-02-11 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| WO2018145546A1 (en) | Authentication method, device and storage medium | |
| US10757106B2 (en) | Resource access control method and device | |
| US20190384956A1 (en) | Device fingerprinting, tracking, and management | |
| US10229208B2 (en) | Optimization of query execution | |
| JP6435398B2 (en) | Method and system for facilitating terminal identifiers | |
| US20140101117A1 (en) | Methods and systems for managing records in an on-demand system | |
| WO2018149292A1 (en) | Object clustering method and apparatus | |
| CN106886429B (en) | A method and server for loading driver | |
| WO2015197008A1 (en) | Biometric authentication method and terminal | |
| CN103995674B (en) | Access request processing method, device and equipment | |
| CN103488791A (en) | Data access method and system and data warehouse | |
| US20200104850A1 (en) | Trust platform | |
| CN110197075B (en) | Resource access method, device, computing equipment and storage medium | |
| BR112014018207B1 (en) | METHOD IMPLEMENTED BY A ROUTER AND DEVICE TO ACQUIRE RESOURCE INFORMATION | |
| WO2017059717A1 (en) | Identification method and system for user information in social network | |
| US20170257382A1 (en) | Maintaining dynamic configuration information of a multi-host off-cluster service on a cluster | |
| US12019730B2 (en) | Systems and methods for identifying computing devices | |
| US20170309298A1 (en) | Digital fingerprint indexing | |
| WO2022143758A1 (en) | Data desensitization method and apparatus, and storage system | |
| US10394816B2 (en) | Detecting product lines within product search queries | |
| WO2021051569A1 (en) | Data isolation method and apparatus, computer device and storage medium | |
| WO2019052328A1 (en) | Authentication method for anonymous account, and server | |
| US20210144123A1 (en) | Serialization of firewall rules with user, device, and application correlation | |
| CN108268769A (en) | The method and system of data access entitlement are performed to user | |
| CN110457905A (en) | Sample virus detection method, device, computer equipment and storage medium |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| 121 | Ep: the epo has been informed by wipo that ep was designated in this application | Ref document number:18751940 Country of ref document:EP Kind code of ref document:A1 | |
| NENP | Non-entry into the national phase | Ref country code:DE | |
| 122 | Ep: pct application non-entry in european phase | Ref document number:18751940 Country of ref document:EP Kind code of ref document:A1 |