WO2017063458A1 - Physical address bypass authentication method and apparatus based on software defined networking - Google Patents
Physical address bypass authentication method and apparatus based on software defined networkingDownload PDFInfo
- Publication number
- WO2017063458A1 WO2017063458A1PCT/CN2016/097682CN2016097682WWO2017063458A1WO 2017063458 A1WO2017063458 A1WO 2017063458A1CN 2016097682 WCN2016097682 WCN 2016097682WWO 2017063458 A1WO2017063458 A1WO 2017063458A1
- Authority
- WO
- WIPO (PCT)
- Prior art keywords
- software
- physical address
- packet
- defined network
- switch
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Ceased
Links
Images
Classifications
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/32—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials
Definitions
- the present inventionrelates to the field of network authentication, and in particular, to a MAB (MAC Authentication Bypass) authentication method and apparatus based on SDN (Software Defined Network).
- MABMAC Authentication Bypass
- SDNSoftware Defined Network
- FIG. 1is a schematic diagram of a conventional MAB authentication method.
- the traditional MAB authentication deviceonly supports the RADIUS (Remote Authentication Dial In User Service) mode.
- RADIUSRemote Authentication Dial In User Service
- FIG. 1when some devices that cannot install the authentication client (for example, personal computers PC1 and PC2, printers, etc.) need to use MAB authentication mode to securely access resources in the network, they pass at least one switch (for example, , switches 1 and 2) to pass data to the RADIUS server (and update server, Internet) for authentication, and each switch contains multiple Ethernet port rules (for example, Ethernet 1/0/1, Ethernet 1 /0/2, Ethernet 1/0/3, Ethernet 1/0/4, etc.).
- the MAC address of the MAB useris used as the authentication username and password, or the user name and password are used for authentication (that is, regardless of the MAB). How the user's MAC address changes, all users use the pre-configured username and password on the device for authentication).
- the main purpose of the present inventionis to provide a simpler and more flexible networking authentication method.
- the present inventionprovides a software-defined network-based physical address bypass authentication method, which is executed on a software-defined network switch and a software-defined network controller, the method comprising: reporting, by the software-defined network switch, The physical address information and the port information are provided to the software-defined network controller; the physical address bypass authentication technology is configured on the software-defined network controller; and the software-defined network switch reports the unmatched flow table message; The network controller is configured by the software to deliver the flow table according to the matched authentication result.
- the methodfurther includes: initializing an open flow channel by the software-defined network switch; and reporting, by the software-defined network switch, the physical address and port information by using a private experimenter message to the Software defined network controller.
- the methodfurther includes: after the packet enters the software definition network, querying the flow table; determining whether the packet matches the flow table, and if yes, the packet is according to the flow The table performs normal forwarding. If there is no match, the message will be sent to the software-defined network controller for processing; and the packet is further matched with the physical address bypass authentication policy. If it matches, the software The network controller sends a flow table and forwards the packet. If the packet is not matched, the packet is discarded.
- the methodfurther includes: when the software-defined network controller receives the income packet message from the software-defined network switch, extracting a source physical address of the original packet from the income-packet packet, and correspondingly a physical address and a port of the switch; and determining, by the software-defined network controller, a state of the physical address bypass authentication switch based on the software-defined network switch and port, if the state of the physical address bypass authentication switch is off, The software-defined network controller sends a flow table and forwards the packet. If the state of the physical address bypass authentication switch is on, the software-defined network controller further determines the physical address bypass authentication mode, where If the physical address bypass authentication mode is bypass, the software defines the network controller to send the flow table and forward the packet.
- the softwareis used. Define the physical address of the network switch as the username and password and perform physical address bypass verification. If the physical address bypass authentication mode is the user physical address mode, the physical address bypasses the user's physical address as the user name and password and performs physical address bypass verification. When the physical address bypass verification is passed, the software Defining a network controller to send a flow table and forwarding a message, the software defines a network switch to forward the message flow.
- both the software-defined network switch and the software-defined network controllersupport extensions of the flow table definition, wherein the matching field is the source physical address of the ingress port and the data stream, and the action field is to forward the data stream.
- the present inventionalso provides a physical address bypass authentication device based on a software defined network, the physical address bypass authentication device comprising a software defined network switch and a software defined network controller, wherein: the software defined network switch is configured as Evaluating the physical address information and the port information to the software-defined network controller; the software-defined network controller is configured to configure a physical address bypass authentication technology; the software-defined network switch is further configured to report the unmatched flow table The message; and the software defined network controller is further configured to deliver the flow table according to the matched authentication result.
- the software-defined network switchis further configured to initialize an open flow channel, and report the physical address and port information to the software-defined network controller by using a private experimenter message.
- the software-defined network switchis further configured to: after the packet enters the software-defined network, query the flow table; determine whether the packet matches the flow table, and if the packet matches, the packet Perform normal forwarding according to the flow table. If there is no match, the message will be sent to The software-defined network controller performs processing; and further matches the packet with a physical address bypass authentication policy. If the packet matches, the software-defined network controller sends a flow table and forwards the packet. If not, the packet is forwarded. Discard the message.
- the software-defined network controlleris further configured to: when the software-defined network controller receives the income packet message from the software-defined network switch, extract the original message from the income-packet message a source physical address, a physical address and a port of the corresponding switch, and a status of the physical address bypass authentication switch based on the software-defined network switch and the port, and if the status of the physical address bypass authentication switch is off, If the physical address bypass authentication mode is bypass, the software definition is performed if the physical address bypass authentication mode is bypassed. The network controller sends a flow table and forwards the packet. If the physical address bypass authentication mode is the switch physical address mode, the physical address of the software-defined network switch is used as the user name and password, and the physical address bypass verification is performed.
- the physical address bypass authentication modeis the user physical address mode
- the physical The physical address of the bypass useris used as the user name and password, and the physical address bypass verification is performed.
- the softwaredefines the network controller to send a flow table and forward the message, where the software defines The network switch forwards the packet flow.
- both the software-defined network switch and the software-defined network controllersupport extensions of the flow table definition, wherein the matching field is the source physical address of the ingress port and the data stream, and the action field is to forward the data stream.
- the software-defined network-based physical address bypass authentication method and device provided by the present inventionconcentrate all physical address bypass authentication configuration task sequences on a software-defined network controller, so the configuration work is very concentrated and the modification is convenient, and the networking is more Simple and flexible.
- Figure 1is a schematic diagram of a conventional MAB authentication method
- FIG. 2is a schematic diagram of an SDN-based MAB authentication mode according to an embodiment of the present invention.
- FIG. 3is a flowchart of an SDN-based MAB authentication method according to an embodiment of the present invention.
- FIG. 4is a flowchart of a method for reporting an SDN switch according to an embodiment of the present invention.
- FIG. 5is a schematic diagram of a private experimenter message according to an embodiment of the present invention.
- FIG. 6is a schematic diagram of a processing flow of an SDN switch according to an embodiment of the present disclosure.
- FIG. 7is a schematic diagram of a packet format with SDN switch information according to an embodiment of the present invention.
- FIG. 8is a schematic diagram of a processing flow of an SDN controller according to an embodiment of the present invention.
- FIG. 2is a schematic diagram of an SDN-based MAB authentication mode according to an embodiment of the present invention.
- the SDN-based MAB authentication modeis a network access authentication mode based on the MAB user access port and MAC address.
- the MAB userdoes not need to install any authentication client.
- the SDN controllerAfter receiving the packet sent by the MAB, the SDN controller initiates authentication according to the MAC address of the MAB user.
- the SDN controllerstores the authentication information corresponding to the MAC address of the MAB user, and releases the matching port and the source MAC packet when the authentication succeeds.
- the MAB useris not required to manually enter the authentication username and password.
- the way the SDN controller selects the authentication username and passwordcan use the MAC address of the MAB user as the authenticated username and password.
- the SDN controllercan also authenticate using a fixed username and password. That is, regardless of how the MAC address of the MAB user changes, all users authenticate using the MAC address of the pre-configured switch on the access switch as the username and password.
- the SDN-based MAB authentication methodmay include a source host (for example, host A), at least one switch (for example, switches S0-S3), an SDN controller, and a destination host (for example, host B). ).
- the SDN-based MAB authentication mode shown in FIG. 2is controlled by the SDN controller and implements the MAB authentication process, and the switches S0-S3 and the SDN controller jointly form an SDN network.
- the source hosteg, host A
- issues the original message P1(as shown in step 1).
- the packet P1first passes through the switch S1 in the SDN network.
- the switch S1can try to match the original packet P1 with the flow table.
- the packet P1is rooted. Normal forwarding is performed according to the flow table (for example, forwarded to switch S3 and host B).
- the switch S1if the switch S1 matches the original packet P1 and the result of the flow table does not match, the switch S1 inserts the SDN switch information, and encapsulates the original packet P1 into a packet format of the packet (Packet_In) and sends it to the SDN. Controller (as shown in step 2).
- the SDN controllerreceives the Packet_In packet from the switch S1, and extracts the source MAC address of the original packet P1, the MAC address and port of the corresponding switch from the Packet_In packet, wherein the MAC address of the SDN switch can be used as an identifier of the SDN switch.
- the SDN controllerperforms corresponding authentication based on the SDN switch and the port (as shown in step 3).
- the authentication processincludes: determining the status of the MAB authentication switch (for example, opening or closing) and/or determining the MAB authentication mode.
- the SDN controllerselectively sends the flow table (as shown in step 4) and forwards the message to the switch S3 and the host B (as shown in step 5).
- the location of host Achanges, and the connected port also changes from switch S1 to switch S0. It is assumed that the authentication mode of the SDN controller is based on the MAC address of the switch S1, and the source MAC address is X.
- the original message (MAC: X)can be successfully forwarded to the host B after the switch S1 accesses the SDN network. After the location of host A changes, the packet (MAC:X) cannot be successfully forwarded to host B after it is connected to the SDN network from switch S0.
- the authentication process of the MABis controlled and implemented by the SDN controller, and the original message P1 is successfully forwarded from the source host (e.g., host A) to the destination host (e.g., host B).
- the SDN controllerconfigures the MAB authentication information according to the requirements of the user, and all the configuration task sequences of the MAB authentication information are centralized on the SDN controller. Therefore, the configuration work is centralized and the modification is convenient, so that the networking is more convenient and flexible.
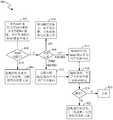
- FIG. 3is a flowchart of an SDN-based MAB authentication method 300 according to an embodiment of the present invention. As shown in FIG. 3, the SDN-based MAB authentication method 300 includes the following steps:
- Step 302The SDN switch reports its own MAC information and port information to the SDN controller.
- Step 304Configure the MAB authentication technology on the SDN controller.
- Step 306The SDN switch reports the packet that does not match the flow table.
- Step 308The SDN controller sends the flow table according to the authentication result in step 306. If the packet authentication succeeds, the SDN controller sends a flow table according to the authentication result. If the packet authentication fails, the SDN controller discards the packet directly.
- FIG. 4is a flowchart of an SDN switch reporting method 400 according to an embodiment of the present invention.
- the SDN switchinitializes an OpenFlow channel.
- the SDN switchreports its own MAC address and port information to the SDN controller through a private experimenter (Experimenter) message, that is, the MAC address of the SDN switch can be used as an identifier of the SDN switch.
- FIG. 5is a schematic diagram of a private Experimenter message according to an embodiment of the present invention.
- an Experimenter value of 255requires an application to the Open Network Foundation (ONF) organization.
- a Experimenter type value of 1indicates that it is from the SDN switch direction to the SDN controller.
- the reported port numbersupports up to 128 ports.
- FIG. 6is a schematic diagram of a process flow 600 of an SDN switch according to an embodiment of the present invention. As shown in FIG. 6, the process flow 600 of the SDN switch includes the following steps:
- Step 602The packet enters the SDN network, and the flow table is first queried.
- Step 604Determine whether the message matches the flow table. If the flow table is matched, the process proceeds to step 606, and the message is forwarded according to the flow table. If the flow table is not matched, the process proceeds to step 608, and the message is sent to the SDN controller for processing.
- Step 610Further matching the packet with the MAB authentication policy. If the MAB authentication policy is matched, the process proceeds to step 612. The SDN controller sends a flow table and forwards the message. If the MAB authentication policy is not matched, the process proceeds to step 614 to discard the message.
- FIG. 7is a schematic diagram of a packet format with SDN switch information according to an embodiment of the present invention.
- the MAB authentication policycan be as shown in Table 1:
- FIG. 8is a schematic diagram of a process flow 800 of an SDN controller according to an embodiment of the present invention. As shown in FIG. 8, the process flow 800 of the SDN controller includes the following steps:
- Step 802The SDN controller receives the Packet_In packet from the SDN switch, and extracts the source MAC address of the original packet, the MAC address and port of the corresponding switch from the Packet_In packet.
- the MAC address of the SDN switchcan be used as an identifier for the SDN switch.
- Step 804The SDN controller determines the state (for example, on or off) of the MAB authentication switch based on the SDN switch and the port. If the state of the MAB authentication switch is off, then step 806 is entered. If the state of the MAB authentication switch is on, then step 808 is entered.
- Step 806The SDN controller sends a flow table and forwards the packet, and the SDN switch forwards the packet flow.
- Step 808The SDN controller further determines the MAB authentication mode. As shown in Table 1, there are three types of MAB authentication: the first is BYPASS, the second is the MAC address of the MAB user as the username and password, and the third is pre-configured on the SDN switch. The MAC address is used as the username and password.
- step 810the SDN controller sends the flow table and forwards the packet, and the SDN switch forwards the packet flow.
- step 812use the MAC address of the SDN switch as the username and password.
- step 814use the MAC address of the MAB user as the username and password.
- Steps 812 and 814both go to the next steps 816 and 818: MAB verification of the MAC address, username and password. If the MAB verification fails, the process proceeds to step 820 to discard the message. If MAB If the verification is successful, the process proceeds to step 822: the SDN controller sends a flow table and forwards the message, and the SDN switch forwards the message flow.
- the SDN-based MAB authentication apparatusincludes an SDN controller and an SDN switch for implementing the SDN-based MAB authentication method as described in FIGS. 2-8. For the sake of brevity, it will not be repeated here.
- the SDN-based MAB authentication method and deviceconcentrate all MAB authentication configuration task sequences on the SDN controller, so the configuration work is very centralized and the modification is convenient, and the networking is simpler and more flexible.
- the SDN-based MAB authentication method and deviceexpands the flow table and supports SDN-based access management technology.
Landscapes
- Engineering & Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- Computer Networks & Wireless Communication (AREA)
- Signal Processing (AREA)
- Data Exchanges In Wide-Area Networks (AREA)
- Small-Scale Networks (AREA)
Abstract
Description
Translated fromChinese本申请要求2015年10月13日提交的申请号为:201510659060.9、发明名称为“基于软件定义网络的物理地址旁路认证方法及装置”的中国专利申请的优先权,其全部内容合并在此。The present application claims the priority of the Chinese Patent Application No. 2015.
本发明涉及网络认证领域,尤其涉及一种基于SDN(软件定义网络,Software Defined Network)的MAB(物理地址旁路认证,MAC Authentication Bypass)认证方法及装置。The present invention relates to the field of network authentication, and in particular, to a MAB (MAC Authentication Bypass) authentication method and apparatus based on SDN (Software Defined Network).
在实际网络中存在一些无法安装认证客户端的设备,例如打印机、PDA设备等。由于这些设备无法安装认证客户端,无法进行802.1x认证,因此它们需要使用MAB认证来安全访问网络中的资源。There are some devices in the actual network where the authentication client cannot be installed, such as printers, PDA devices, and so on. Because these devices cannot install authentication clients and cannot perform 802.1x authentication, they need to use MAB authentication to securely access resources on the network.
图1为传统的MAB认证方式的示意图。传统的MAB认证设备只支持RADIUS(远程用户服务拨号认证,Remote Authentication Dial In User Service)方式。具体地,如图1所示,当一些无法安装认证客户端的设备(例如,个人计算机PC1和PC2、打印机等)需要使用MAB认证方式来安全访问网络中的资源时,它们通过至少一个交换机(例如,交换机1和2)来传递数据到RADIUS服务器(以及更新服务器、因特网)来进行认证,并且其中每个交换机中包含多个以太网端口规则(例如,以太网1/0/1、以太网1/0/2、以太网1/0/3、以太网1/0/4等)。在传统的MAB认证方式中,使用MAB用户的MAC地址作为认证的用户名和密码,或使用固定的用户名和密码进行认证(即,无论MAB用户的MAC地址如何变化,所有用户均使用在设备上预先配置的用户名和密码进行认证)。Figure 1 is a schematic diagram of a conventional MAB authentication method. The traditional MAB authentication device only supports the RADIUS (Remote Authentication Dial In User Service) mode. Specifically, as shown in FIG. 1, when some devices that cannot install the authentication client (for example, personal computers PC1 and PC2, printers, etc.) need to use MAB authentication mode to securely access resources in the network, they pass at least one switch (for example, , switches 1 and 2) to pass data to the RADIUS server (and update server, Internet) for authentication, and each switch contains multiple Ethernet port rules (for example, Ethernet 1/0/1, Ethernet 1 /0/2, Ethernet 1/0/3, Ethernet 1/0/4, etc.). In the traditional MAB authentication mode, the MAC address of the MAB user is used as the authentication username and password, or the user name and password are used for authentication (that is, regardless of the MAB).How the user's MAC address changes, all users use the pre-configured username and password on the device for authentication).
然而,这种传统方式是分布式的、缺乏控制器的集中控制,MAB认证的配置任务需要基于每个交换机(例如,交换机1和2)。如果构建的网络非常庞大(例如,交换机数量过多),配置工作将会非常复杂并且容易出错(例如,需应用不同的以太网端口规则)。其次,传统的MAB认证需要RADIUS服务器,整个组网复杂,缺乏灵活性。However, this traditional approach is distributed, lacking centralized control of the controller, and the configuration tasks for MAB authentication need to be based on each switch (eg, switches 1 and 2). If the network being built is very large (for example, the number of switches is too large), the configuration work will be very complicated and error-prone (for example, different Ethernet port rules need to be applied). Secondly, the traditional MAB authentication requires a RADIUS server, and the entire networking is complicated and lacks flexibility.
因此,需要一种改进的MAB认证方式及装置来提供更简单、灵活的组网认证方式。Therefore, there is a need for an improved MAB authentication method and apparatus to provide a simpler and more flexible networking authentication method.
发明内容Summary of the invention
本发明的主要目的在于提供更简单、灵活的组网认证方式。The main purpose of the present invention is to provide a simpler and more flexible networking authentication method.
为实现上述目的,本发明提供一种基于软件定义网络的物理地址旁路认证方法,在软件定义网络交换机和软件定义网络控制器上执行,所述方法包括:由所述软件定义网络交换机上报自己的物理地址信息和端口信息给所述软件定义网络控制器;在所述软件定义网络控制器上配置物理地址旁路认证技术;由所述软件定义网络交换机上报未匹配流表的报文;以及由所述软件定义网络控制器根据所述匹配的认证结果来下发流表。To achieve the above object, the present invention provides a software-defined network-based physical address bypass authentication method, which is executed on a software-defined network switch and a software-defined network controller, the method comprising: reporting, by the software-defined network switch, The physical address information and the port information are provided to the software-defined network controller; the physical address bypass authentication technology is configured on the software-defined network controller; and the software-defined network switch reports the unmatched flow table message; The network controller is configured by the software to deliver the flow table according to the matched authentication result.
进一步地,所述方法还包括:由所述软件定义网络交换机初始化开放流通道;以及由所述软件定义网络交换机通过私有的实验者报文来上报所述自己的物理地址和端口信息给所述软件定义网络控制器。Further, the method further includes: initializing an open flow channel by the software-defined network switch; and reporting, by the software-defined network switch, the physical address and port information by using a private experimenter message to the Software defined network controller.
进一步地,所述方法还包括:在所述报文进入软件定义网络之后,查询所述流表;判断所述报文是否匹配所述流表,如果匹配,则所述报文根据所述流表进行正常转发,如果不匹配,则所述报文将被送往所述软件定义网络控制器进行处理;以及进一步匹配所述报文与物理地址旁路认证策略,如果匹配,则所述软件定义网络控制器下发流表并转发报文,如果不匹配,则丢弃所述报文。Further, the method further includes: after the packet enters the software definition network, querying the flow table; determining whether the packet matches the flow table, and if yes, the packet is according to the flow The table performs normal forwarding. If there is no match, the message will be sent to the software-defined network controller for processing; and the packet is further matched with the physical address bypass authentication policy. If it matches, the software The network controller sends a flow table and forwards the packet. If the packet is not matched, the packet is discarded.
进一步地,所述方法还包括:当所述软件定义网络控制器从所述软件定义网络交换机接收到收入封包报文时,从所述收入封包报文中提取原始报文的源物理地址、对应交换机的物理地址和端口;以及由所述软件定义网络控制器基于所述软件定义网络交换机和端口来判断物理地址旁路认证开关的状态,如果所述物理地址旁路认证开关的状态为关闭,则所述软件定义网络控制器下发流表并转发报文,如果所述物理地址旁路认证开关的状态为打开,则由所述软件定义网络控制器进一步判断物理地址旁路认证方式,其中如果所述物理地址旁路认证方式为旁路,则所述软件定义网络控制器下发流表并转发报文,如果所述物理地址旁路认证方式为交换机物理地址方式,则将所述软件定义网络交换机的物理地址作为用户名和密码并进行物理地址旁路验证,如果所述物理地址旁路认证方式为用户物理地址方式,则将所述物理地址旁路用户的物理地址作为用户名和密码并进行物理地址旁路验证,当所述物理地址旁路验证通过时,所述软件定义网络控制器下发流表并转发报文,所述软件定义网络交换机转发所述报文流。Further, the method further includes: when the software-defined network controller receives the income packet message from the software-defined network switch, extracting a source physical address of the original packet from the income-packet packet, and correspondingly a physical address and a port of the switch; and determining, by the software-defined network controller, a state of the physical address bypass authentication switch based on the software-defined network switch and port, if the state of the physical address bypass authentication switch is off, The software-defined network controller sends a flow table and forwards the packet. If the state of the physical address bypass authentication switch is on, the software-defined network controller further determines the physical address bypass authentication mode, where If the physical address bypass authentication mode is bypass, the software defines the network controller to send the flow table and forward the packet. If the physical address bypass authentication mode is the physical address mode of the switch, the software is used. Define the physical address of the network switch as the username and password and perform physical address bypass verification. If the physical address bypass authentication mode is the user physical address mode, the physical address bypasses the user's physical address as the user name and password and performs physical address bypass verification. When the physical address bypass verification is passed, the software Defining a network controller to send a flow table and forwarding a message, the software defines a network switch to forward the message flow.
进一步地,所述软件定义网络交换机和所述软件定义网络控制器都支持流表定义的扩展,其中匹配字段为入端口和数据流的源物理地址,动作字段为转发所述数据流。Further, both the software-defined network switch and the software-defined network controller support extensions of the flow table definition, wherein the matching field is the source physical address of the ingress port and the data stream, and the action field is to forward the data stream.
本发明还提供一种基于软件定义网络的物理地址旁路认证装置,所述物理地址旁路认证装置包括软件定义网络交换机和软件定义网络控制器,其特征在于:所述软件定义网络交换机配置为上报自己的物理地址信息和端口信息给所述软件定义网络控制器;所述软件定义网络控制器配置为配置物理地址旁路认证技术;所述软件定义网络交换机还配置为上报未匹配流表的报文;以及所述软件定义网络控制器还配置为根据所述匹配的认证结果来下发流表。The present invention also provides a physical address bypass authentication device based on a software defined network, the physical address bypass authentication device comprising a software defined network switch and a software defined network controller, wherein: the software defined network switch is configured as Evaluating the physical address information and the port information to the software-defined network controller; the software-defined network controller is configured to configure a physical address bypass authentication technology; the software-defined network switch is further configured to report the unmatched flow table The message; and the software defined network controller is further configured to deliver the flow table according to the matched authentication result.
进一步地,所述软件定义网络交换机还配置为初始化开放流通道,并且通过私有的实验者报文来上报所述自己的物理地址和端口信息给所述软件定义网络控制器。Further, the software-defined network switch is further configured to initialize an open flow channel, and report the physical address and port information to the software-defined network controller by using a private experimenter message.
进一步地,所述软件定义网络交换机还配置为:在所述报文进入软件定义网络之后,查询所述流表;判断所述报文是否匹配所述流表,如果匹配,则所述报文根据所述流表进行正常转发,如果不匹配,则所述报文将被送往所述软件定义网络控制器进行处理;以及进一步匹配所述报文与物理地址旁路认证策略,如果匹配,则所述软件定义网络控制器下发流表并转发报文,如果不匹配,则丢弃所述报文。Further, the software-defined network switch is further configured to: after the packet enters the software-defined network, query the flow table; determine whether the packet matches the flow table, and if the packet matches, the packet Perform normal forwarding according to the flow table. If there is no match, the message will be sent toThe software-defined network controller performs processing; and further matches the packet with a physical address bypass authentication policy. If the packet matches, the software-defined network controller sends a flow table and forwards the packet. If not, the packet is forwarded. Discard the message.
进一步地,所述软件定义网络控制器还配置为:当所述软件定义网络控制器从所述软件定义网络交换机接收到收入封包报文时,从所述收入封包报文中提取原始报文的源物理地址、对应交换机的物理地址和端口;以及基于所述软件定义网络交换机和端口来判断物理地址旁路认证开关的状态,如果所述物理地址旁路认证开关的状态为关闭,则下发流表并转发报文,如果所述物理地址旁路认证开关的状态为打开,则进一步判断物理地址旁路认证方式,其中如果所述物理地址旁路认证方式为旁路,则所述软件定义网络控制器下发流表并转发报文,如果所述物理地址旁路认证方式为交换机物理地址方式,则将所述软件定义网络交换机的物理地址作为用户名和密码并进行物理地址旁路验证,如果所述物理地址旁路认证方式为用户物理地址方式,则将所述物理地址旁路用户的物理地址作为用户名和密码并进行物理地址旁路验证,当所述物理地址旁路验证通过时,所述软件定义网络控制器下发流表并转发报文,所述软件定义网络交换机转发所述报文流。Further, the software-defined network controller is further configured to: when the software-defined network controller receives the income packet message from the software-defined network switch, extract the original message from the income-packet message a source physical address, a physical address and a port of the corresponding switch, and a status of the physical address bypass authentication switch based on the software-defined network switch and the port, and if the status of the physical address bypass authentication switch is off, If the physical address bypass authentication mode is bypass, the software definition is performed if the physical address bypass authentication mode is bypassed. The network controller sends a flow table and forwards the packet. If the physical address bypass authentication mode is the switch physical address mode, the physical address of the software-defined network switch is used as the user name and password, and the physical address bypass verification is performed. If the physical address bypass authentication mode is the user physical address mode, the physical The physical address of the bypass user is used as the user name and password, and the physical address bypass verification is performed. When the physical address bypass verification is passed, the software defines the network controller to send a flow table and forward the message, where the software defines The network switch forwards the packet flow.
进一步地,所述软件定义网络交换机和所述软件定义网络控制器都支持流表定义的扩展,其中匹配字段为入端口和数据流的源物理地址,动作字段为转发所述数据流。Further, both the software-defined network switch and the software-defined network controller support extensions of the flow table definition, wherein the matching field is the source physical address of the ingress port and the data stream, and the action field is to forward the data stream.
本发明所提供的基于软件定义网络的物理地址旁路认证方法及装置将所有物理地址旁路认证配置任务序列都集中在软件定义网络控制器上,因此配置工作非常集中并且修改方便,组网更加简单、灵活。The software-defined network-based physical address bypass authentication method and device provided by the present invention concentrate all physical address bypass authentication configuration task sequences on a software-defined network controller, so the configuration work is very concentrated and the modification is convenient, and the networking is more Simple and flexible.
图1为传统的MAB认证方式的示意图;Figure 1 is a schematic diagram of a conventional MAB authentication method;
图2为本发明实施例提供的一种基于SDN的MAB认证方式的示意图;2 is a schematic diagram of an SDN-based MAB authentication mode according to an embodiment of the present invention;
图3为本发明实施例提供的一种基于SDN的MAB认证方法的流程图;FIG. 3 is a flowchart of an SDN-based MAB authentication method according to an embodiment of the present invention;
图4为本发明实施例提供的一种SDN交换机上报方法的流程图;4 is a flowchart of a method for reporting an SDN switch according to an embodiment of the present invention;
图5为本发明实施例提供的一种私有实验者报文的示意图;FIG. 5 is a schematic diagram of a private experimenter message according to an embodiment of the present invention;
图6为本发明实施例提供的一种SDN交换机的处理流程的示意图;FIG. 6 is a schematic diagram of a processing flow of an SDN switch according to an embodiment of the present disclosure;
图7为本发明实施例提供的一种带有SDN交换机信息的报文格式的示意图;以及FIG. 7 is a schematic diagram of a packet format with SDN switch information according to an embodiment of the present invention;
图8为本发明实施例提供的一种SDN控制器的处理流程的示意图。FIG. 8 is a schematic diagram of a processing flow of an SDN controller according to an embodiment of the present invention.
本发明的实现、功能特点及优点将结合实施例,参照附图作进一步说明。The implementation, functional features, and advantages of the present invention will be further described in conjunction with the accompanying drawings.
以下结合说明书附图对本发明的优选实施例进行说明,应当理解,此处所描述的优选实施例仅用于说明和解释本发明,并不用于限定本发明,并且在不冲突的情况下,本发明中的实施例及实施例中的特征可以相互组合。The preferred embodiments of the present invention are described in conjunction with the accompanying drawings, and the preferred embodiments described herein are intended to illustrate and explain the invention, and not to limit the invention, and The embodiments and the features in the embodiments can be combined with each other.
不同于现有技术,图2为本发明实施例提供的一种基于SDN的MAB认证方式的示意图。如图2所示,基于SDN的MAB认证方式是一种基于MAB用户接入端口和MAC地址的网络接入认证方式。MAB用户不需要安装任何认证客户端,在SDN控制器收到MAB发出的报文之后,根据MAB用户的MAC地址发起认证。在SDN控制器中存储有MAB用户的MAC地址所对应的认证信息,当认证通过时放行匹配端口和源MAC的报文。在整个认证过程中,不需要MAB用户手动输入认证用户名和密码。Different from the prior art, FIG. 2 is a schematic diagram of an SDN-based MAB authentication mode according to an embodiment of the present invention. As shown in Figure 2, the SDN-based MAB authentication mode is a network access authentication mode based on the MAB user access port and MAC address. The MAB user does not need to install any authentication client. After receiving the packet sent by the MAB, the SDN controller initiates authentication according to the MAC address of the MAB user. The SDN controller stores the authentication information corresponding to the MAC address of the MAB user, and releases the matching port and the source MAC packet when the authentication succeeds. During the entire authentication process, the MAB user is not required to manually enter the authentication username and password.
SDN控制器对于认证用户名和密码选择的方式可使用MAB用户的MAC地址作为认证的用户名和密码。在另一实施例中,SDN控制器也可使用固定的用户名和密码进行认证。即,无论MAB用户的MAC地址如何变化,所有用户均使用在接入交换机上预先配置的交换机的MAC地址作为用户名和密码进行认证。The way the SDN controller selects the authentication username and password can use the MAC address of the MAB user as the authenticated username and password. In another embodiment, the SDN controller can also authenticate using a fixed username and password. That is, regardless of how the MAC address of the MAB user changes, all users authenticate using the MAC address of the pre-configured switch on the access switch as the username and password.
具体地,如图2所示,基于SDN的MAB认证方式可包括源主机(例如,主机A)、至少一个交换机(例如,交换机S0-S3)、SDN控制器,以及目的主机(例如,主机B)。不同于图1中传统的MAB认证方式,图2所示的基于SDN的MAB认证方式是由SDN控制器来控制并实现MAB的认证过程,并且交换机S0-S3以及SDN控制器共同形成SDN网络。在一个示例中,源主机(例如,主机A)发出原始报文P1(如步骤1所示)。该报文P1首先经过SDN网络中的交换机S1,此时交换机S1可尝试匹配原始报文P1与流表,假设匹配,则报文P1根据流表进行正常转发(例如,转发给交换机S3和主机B)。在图2的示例中,交换机S1匹配原始报文P1与流表的结果为不匹配,则交换机S1插入SDN交换机信息,将原始报文P1封装成收入封包(Packet_In)的报文格式送往SDN控制器(如步骤2所示)。SDN控制器从交换机S1接收到Packet_In报文,从Packet_In报文中提取原始报文P1的源MAC地址、对应交换机的MAC地址和端口,其中SDN交换机的MAC地址可以作为SDN交换机的标识符。SDN控制器基于SDN交换机和端口来进行相应认证(如步骤3所示),认证过程包括:判断MAB认证开关的状态(例如,打开或关闭)和/或判断MAB认证方式。MAB认证方式分为三种:第一种是旁路(BYPASS),第二种是将MAB用户的MAC地址作为用户名和密码,第三种是将SDN交换机上预先配置的MAC地址作为用户名和密码。根据上述认证结果,SDN控制器选择性地下发流表(如步骤4所示)并转发报文到交换机S3和主机B(如步骤5所示)。Specifically, as shown in FIG. 2, the SDN-based MAB authentication method may include a source host (for example, host A), at least one switch (for example, switches S0-S3), an SDN controller, and a destination host (for example, host B). ). Different from the traditional MAB authentication mode in FIG. 1, the SDN-based MAB authentication mode shown in FIG. 2 is controlled by the SDN controller and implements the MAB authentication process, and the switches S0-S3 and the SDN controller jointly form an SDN network. In one example, the source host (eg, host A) issues the original message P1 (as shown in step 1). The packet P1 first passes through the switch S1 in the SDN network. At this time, the switch S1 can try to match the original packet P1 with the flow table. If the match is matched, the packet P1 is rooted.Normal forwarding is performed according to the flow table (for example, forwarded to switch S3 and host B). In the example of FIG. 2, if the switch S1 matches the original packet P1 and the result of the flow table does not match, the switch S1 inserts the SDN switch information, and encapsulates the original packet P1 into a packet format of the packet (Packet_In) and sends it to the SDN. Controller (as shown in step 2). The SDN controller receives the Packet_In packet from the switch S1, and extracts the source MAC address of the original packet P1, the MAC address and port of the corresponding switch from the Packet_In packet, wherein the MAC address of the SDN switch can be used as an identifier of the SDN switch. The SDN controller performs corresponding authentication based on the SDN switch and the port (as shown in step 3). The authentication process includes: determining the status of the MAB authentication switch (for example, opening or closing) and/or determining the MAB authentication mode. There are three types of MAB authentication: the first is BYPASS, the second is the MAC address of the MAB user as the username and password, and the third is the pre-configured MAC address on the SDN switch as the username and password. . According to the above authentication result, the SDN controller selectively sends the flow table (as shown in step 4) and forwards the message to the switch S3 and the host B (as shown in step 5).
在如图2中虚线所示的另一示例中,主机A的位置发生改变,并且所连接端口也从交换机S1变成交换机S0。假设SDN控制器的认证方式为基于交换机S1的MAC地址,源MAC地址为X。原本报文(MAC:X)从交换机S1接入SDN网络后能够被成功转发到主机B。在主机A的位置发生改变之后,报文(MAC:X)从交换机S0接入SDN网络后则无法成功转发到主机B。In another example, as shown by the dashed line in FIG. 2, the location of host A changes, and the connected port also changes from switch S1 to switch S0. It is assumed that the authentication mode of the SDN controller is based on the MAC address of the switch S1, and the source MAC address is X. The original message (MAC: X) can be successfully forwarded to the host B after the switch S1 accesses the SDN network. After the location of host A changes, the packet (MAC:X) cannot be successfully forwarded to host B after it is connected to the SDN network from switch S0.
以此方式,由SDN控制器来控制并实现MAB的认证过程,并将原始报文P1成功地从源主机(例如,主机A)转发到目的主机(例如,主机B)。SDN控制器根据用户需求来配置MAB的认证信息,并且所有MAB认证信息的配置任务序列都集中在SDN控制器上完成的,因此配置工作集中且修改方便,从而组网更加方便、灵活。In this manner, the authentication process of the MAB is controlled and implemented by the SDN controller, and the original message P1 is successfully forwarded from the source host (e.g., host A) to the destination host (e.g., host B). The SDN controller configures the MAB authentication information according to the requirements of the user, and all the configuration task sequences of the MAB authentication information are centralized on the SDN controller. Therefore, the configuration work is centralized and the modification is convenient, so that the networking is more convenient and flexible.
图2中的SDN交换机和SDN控制器的具体工作原理将在以下图3-图8中作进一步阐述。The specific operation of the SDN switch and SDN controller in Figure 2 will be further illustrated in Figures 3-8 below.
图3为本发明实施例提供的一种基于SDN的MAB认证方法300的流程图。如图3所示,基于SDN的MAB认证方法300包括以下步骤:FIG. 3 is a flowchart of an SDN-based
步骤302:SDN交换机上报自己的MAC信息和端口信息给SDN控制器。Step 302: The SDN switch reports its own MAC information and port information to the SDN controller.
步骤304:在SDN控制器上配置MAB认证技术。Step 304: Configure the MAB authentication technology on the SDN controller.
步骤306:SDN交换机上报未匹配流表的报文。Step 306: The SDN switch reports the packet that does not match the flow table.
步骤308:SDN控制器根据步骤306中的认证结果来下发流表。如果报文认证通过,则SDN控制器根据认证结果下发流表。如果报文认证未通过,则SDN控制器直接丢弃报文。Step 308: The SDN controller sends the flow table according to the authentication result in step 306. If the packet authentication succeeds, the SDN controller sends a flow table according to the authentication result. If the packet authentication fails, the SDN controller discards the packet directly.
由图3中描述可知,在进行基于SDN的MAB认证方法300之前,SDN交换机与SDN控制器必须先建立通道,其具体操作为图4所示。图4为本发明实施例提供的一种SDN交换机上报方法400的流程图。在步骤402中,SDN交换机初始化开放流(OpenFlow)通道。在步骤404中,SDN交换机通过私有的实验者(Experimenter)报文来上报自己的MAC地址和端口信息给SDN控制器,即SDN交换机的MAC地址可以作为SDN交换机的标识符。图5为本发明实施例提供的一种私有Experimenter报文的示意图。如图5所示,Experimenter值为255需要向开放式网络基金会(ONF)组织申请。Experimenter类型值为1表明是从SDN交换机方向到SDN控制器。上报的端口号最大支持128个。It can be seen from FIG. 3 that before the SDN-based
图6为本发明实施例提供的一种SDN交换机的处理流程600的示意图。如图6所示,SDN交换机的处理流程600包括以下步骤:FIG. 6 is a schematic diagram of a
步骤602:报文进入到SDN网络,首先查询流表。Step 602: The packet enters the SDN network, and the flow table is first queried.
步骤604:判断报文是否匹配流表。若匹配流表,则进入步骤606,报文根据流表进行正常转发;若不匹配流表,则进入步骤608,报文将被送往SDN控制器进行处理。Step 604: Determine whether the message matches the flow table. If the flow table is matched, the process proceeds to step 606, and the message is forwarded according to the flow table. If the flow table is not matched, the process proceeds to step 608, and the message is sent to the SDN controller for processing.
步骤610:进一步匹配报文与MAB认证策略。若匹配MAB认证策略,则进入步骤612,SDN控制器下发流表并转发报文;若不匹配MAB认证策略,则进入步骤614,丢弃报文。Step 610: Further matching the packet with the MAB authentication policy. If the MAB authentication policy is matched, the process proceeds to step 612. The SDN controller sends a flow table and forwards the message. If the MAB authentication policy is not matched, the process proceeds to step 614 to discard the message.
具体地,对于步骤608,如果原始报文不匹配流表,则需被SDN交换机插入SDN交换机信息,封装成Packet_In的报文格式送往SDN控制器。图7为本发明实施例提供的一种带有SDN交换机信息的报文格式的示意图。Specifically, for
具体地,对于步骤610,可参考以下表1和图8作进一步理解。MAB认证策略可如表1所示:Specifically, for step 610, further understanding can be made with reference to Table 1 below and FIG. 8. The MAB authentication policy can be as shown in Table 1:
表1Table 1
图8为本发明实施例提供的一种SDN控制器的处理流程800的示意图。如图8所示,SDN控制器的处理流程800包括以下步骤:FIG. 8 is a schematic diagram of a
步骤802:SDN控制器从SDN交换机接收到Packet_In报文,从Packet_In报文中提取原始报文的源MAC地址、对应交换机的MAC地址和端口。如上所述,SDN交换机的MAC地址可以作为SDN交换机的标识符。Step 802: The SDN controller receives the Packet_In packet from the SDN switch, and extracts the source MAC address of the original packet, the MAC address and port of the corresponding switch from the Packet_In packet. As mentioned above, the MAC address of the SDN switch can be used as an identifier for the SDN switch.
步骤804:SDN控制器基于SDN交换机和端口来判断MAB认证开关的状态(例如,打开或关闭)。如果MAB认证开关的状态为关闭,则进入步骤806。如果MAB认证开关的状态为打开,则进入步骤808。Step 804: The SDN controller determines the state (for example, on or off) of the MAB authentication switch based on the SDN switch and the port. If the state of the MAB authentication switch is off, then step 806 is entered. If the state of the MAB authentication switch is on, then step 808 is entered.
步骤806:SDN控制器下发流表并转发报文,SDN交换机将转发此报文流。Step 806: The SDN controller sends a flow table and forwards the packet, and the SDN switch forwards the packet flow.
步骤808:SDN控制器进一步判断MAB认证方式。如表1所述,MAB认证方式分为三种:第一种是旁路(BYPASS),第二种是将MAB用户的MAC地址作为用户名和密码,第三种是将SDN交换机上预先配置的MAC地址作为用户名和密码。Step 808: The SDN controller further determines the MAB authentication mode. As shown in Table 1, there are three types of MAB authentication: the first is BYPASS, the second is the MAC address of the MAB user as the username and password, and the third is pre-configured on the SDN switch. The MAC address is used as the username and password.
如果MAB认证方式是旁路方式,则转到步骤810:SDN控制器下发流表并转发报文,SDN交换机将转发此报文流。If the MAB authentication mode is the bypass mode, go to step 810: the SDN controller sends the flow table and forwards the packet, and the SDN switch forwards the packet flow.
如果MAB认证方式是交换机MAC地址方式,则转到步骤812:将SDN交换机的MAC地址作为用户名和密码。If the MAB authentication mode is the switch MAC address mode, go to step 812: use the MAC address of the SDN switch as the username and password.
如果MAB认证方式是用户MAC地址方式,则转到步骤814:将MAB用户的MAC地址作为用户名和密码。If the MAB authentication mode is the user MAC address mode, go to step 814: use the MAC address of the MAB user as the username and password.
步骤812和814都转到下一步骤816和818:将MAC地址、用户名和密码进行MAB验证。如果MAB验证不通过,则进入步骤820,丢弃报文。如果MAB验证通过,则进入步骤822:SDN控制器下发流表并转发报文,SDN交换机将转发此报文流。
以上SDN控制器和SDN交换机都支持流表的扩充,其流表定义的扩展如以下表2所示:Both the above SDN controller and SDN switch support the expansion of the flow table, and the extension of the flow table definition is as shown in Table 2 below:
表2Table 2
本领域技术人员应容易从图2-图8的基于SDN的MAB认证方法来实现基于SDN的MAB认证装置。该基于SDN的MAB认证装置包含SDN控制器和SDN交换机,用于实施如图2-图8描述的基于SDN的MAB认证方法。为简洁起见,此处不另赘述。Those skilled in the art should readily implement the SDN-based MAB authentication device from the SDN-based MAB authentication method of FIGS. 2-8. The SDN-based MAB authentication apparatus includes an SDN controller and an SDN switch for implementing the SDN-based MAB authentication method as described in FIGS. 2-8. For the sake of brevity, it will not be repeated here.
有利地,基于SDN的MAB认证方法及装置将所有MAB认证配置任务序列都集中在SDN控制器上,因此配置工作非常集中并且修改方便,组网更加简单、灵活。此外,基于SDN的MAB认证方法及装置扩充了流表,支持基于SDN的访问管理技术。Advantageously, the SDN-based MAB authentication method and device concentrate all MAB authentication configuration task sequences on the SDN controller, so the configuration work is very centralized and the modification is convenient, and the networking is simpler and more flexible. In addition, the SDN-based MAB authentication method and device expands the flow table and supports SDN-based access management technology.
以上仅为本发明的优选实施例,并非因此限制本发明的专利范围,凡是利用本发明说明书及附图内容所作的等效结构或等效流程变换,或直接或间接运用在其它相关的技术领域,均同理包括在本发明的专利保护范围内。The above are only the preferred embodiments of the present invention, and are not intended to limit the scope of the present invention, and the equivalent structure or equivalent process transformations made by the description of the present invention and the drawings are directly or indirectly applied to other related technical fields. The same is included in the scope of patent protection of the present invention.
Claims (10)
Translated fromChineseApplications Claiming Priority (2)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN201510659060.9ACN105162608A (en) | 2015-10-13 | 2015-10-13 | Physical address bypass authentication method and device based on software-defined network |
| CN201510659060.9 | 2015-10-13 |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| WO2017063458A1true WO2017063458A1 (en) | 2017-04-20 |
Family
ID=54803372
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| PCT/CN2016/097682CeasedWO2017063458A1 (en) | 2015-10-13 | 2016-08-31 | Physical address bypass authentication method and apparatus based on software defined networking |
Country Status (2)
| Country | Link |
|---|---|
| CN (1) | CN105162608A (en) |
| WO (1) | WO2017063458A1 (en) |
Cited By (1)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| TWI668987B (en)* | 2018-04-26 | 2019-08-11 | 中華電信股份有限公司 | System of host protection based on moving target defense and method thereof |
Families Citing this family (10)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN105162608A (en)* | 2015-10-13 | 2015-12-16 | 上海斐讯数据通信技术有限公司 | Physical address bypass authentication method and device based on software-defined network |
| CN105791113B (en)* | 2016-02-25 | 2019-11-29 | 上海斐讯数据通信技术有限公司 | A kind of multilink delay equalization method and system based on SDN |
| CN105591754B (en)* | 2016-02-26 | 2018-09-28 | 上海斐讯数据通信技术有限公司 | A kind of verification head verification method and system based on SDN |
| CN105681102A (en)* | 2016-03-01 | 2016-06-15 | 上海斐讯数据通信技术有限公司 | Behavioral strategy method and system based on SDN |
| CN105933225B (en)* | 2016-04-20 | 2020-04-10 | 上海斐讯数据通信技术有限公司 | Strategy routing method and system based on SDN |
| CN106100996A (en)* | 2016-05-30 | 2016-11-09 | 上海斐讯数据通信技术有限公司 | Switch based on software defined network, controller and the system of inspection |
| CN106059933A (en)* | 2016-05-30 | 2016-10-26 | 杭州华三通信技术有限公司 | Method and device for maintaining software defined network (SDN) |
| CN108055254B (en)* | 2017-12-07 | 2021-01-15 | 锐捷网络股份有限公司 | Method and device for non-perception authentication |
| CN113612787B (en)* | 2021-08-10 | 2023-05-30 | 浪潮思科网络科技有限公司 | Terminal authentication method |
| CN115412319B (en)* | 2022-08-19 | 2024-03-26 | 浪潮思科网络科技有限公司 | Network authority control method, device and medium based on strategy following |
Citations (5)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN103595712A (en)* | 2013-11-06 | 2014-02-19 | 福建星网锐捷网络有限公司 | Method, device and system for Web authentication |
| CN104022953A (en)* | 2013-02-28 | 2014-09-03 | 杭州华三通信技术有限公司 | Message forwarding method and device based on Open Flow |
| US20150026794A1 (en)* | 2013-07-18 | 2015-01-22 | Palo Alto Networks, Inc. | Packet classification for network routing |
| CN104618360A (en)* | 2015-01-22 | 2015-05-13 | 盛科网络(苏州)有限公司 | Bypass authentication method and system based on 802.1X protocol |
| CN105162608A (en)* | 2015-10-13 | 2015-12-16 | 上海斐讯数据通信技术有限公司 | Physical address bypass authentication method and device based on software-defined network |
Family Cites Families (5)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN101702687B (en)* | 2009-11-27 | 2011-12-14 | 北京傲天动联技术有限公司 | Method for utilizing device with exchange board structure as broadband access server |
| CN103442358B (en)* | 2013-08-30 | 2017-01-18 | 杭州华三通信技术有限公司 | Method for local forwarding concentrated authentication and control device |
| CN104901825B (en)* | 2014-03-05 | 2019-02-19 | 新华三技术有限公司 | A kind of method and apparatus for realizing zero configuration starting |
| CN104113839A (en)* | 2014-07-14 | 2014-10-22 | 蓝盾信息安全技术有限公司 | Mobile data safety protection system and method based on SDN |
| CN104506511A (en)* | 2014-12-15 | 2015-04-08 | 蓝盾信息安全技术股份有限公司 | Moving target defense system and moving target defense method for SDN (self-defending network) |
- 2015
- 2015-10-13CNCN201510659060.9Apatent/CN105162608A/enactivePending
- 2016
- 2016-08-31WOPCT/CN2016/097682patent/WO2017063458A1/ennot_activeCeased
Patent Citations (5)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN104022953A (en)* | 2013-02-28 | 2014-09-03 | 杭州华三通信技术有限公司 | Message forwarding method and device based on Open Flow |
| US20150026794A1 (en)* | 2013-07-18 | 2015-01-22 | Palo Alto Networks, Inc. | Packet classification for network routing |
| CN103595712A (en)* | 2013-11-06 | 2014-02-19 | 福建星网锐捷网络有限公司 | Method, device and system for Web authentication |
| CN104618360A (en)* | 2015-01-22 | 2015-05-13 | 盛科网络(苏州)有限公司 | Bypass authentication method and system based on 802.1X protocol |
| CN105162608A (en)* | 2015-10-13 | 2015-12-16 | 上海斐讯数据通信技术有限公司 | Physical address bypass authentication method and device based on software-defined network |
Cited By (1)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| TWI668987B (en)* | 2018-04-26 | 2019-08-11 | 中華電信股份有限公司 | System of host protection based on moving target defense and method thereof |
Also Published As
| Publication number | Publication date |
|---|---|
| CN105162608A (en) | 2015-12-16 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| WO2017063458A1 (en) | Physical address bypass authentication method and apparatus based on software defined networking | |
| US9654395B2 (en) | SDN-based service chaining system | |
| US9876704B2 (en) | Packet tracing in a software-defined networking environment | |
| US9178910B2 (en) | Communication system, control apparatus, policy management apparatus, communication method, and program | |
| EP3522460B1 (en) | Flow table processing method and apparatus | |
| US20160301603A1 (en) | Integrated routing method based on software-defined network and system thereof | |
| US9516061B2 (en) | Smart virtual private network | |
| CN107404470A (en) | Connection control method and device | |
| US9432260B2 (en) | Automated configuration for network devices | |
| CN106453409B (en) | Message processing method and access device | |
| US11528270B2 (en) | Network authorization in web-based or single sign-on authentication environments | |
| KR101855742B1 (en) | Method and apparatus for destination based packet forwarding control in software defined networking | |
| US9912592B2 (en) | Troubleshooting openflow networks | |
| CN104767696A (en) | Method and device for controlling user access in SDN-based access network | |
| US20160352637A1 (en) | Client-based port filter table | |
| KR101746105B1 (en) | Openflow switch capable of service chaining | |
| CN108076459B (en) | Network access control method, related equipment and system | |
| CN103534999B (en) | Method and device for message forwarding | |
| WO2017063578A1 (en) | Data packet processing method and apparatus | |
| CN112737850B (en) | Mutually exclusive access method and device | |
| JP6275180B2 (en) | SETTING INFORMATION GENERATION DEVICE, NETWORK CONTROL DEVICE, METHOD, AND PROGRAM | |
| JP2015530763A (en) | Access control system, access control method and program | |
| Behringer et al. | Autonomic networking-from theory to practice | |
| KR101739097B1 (en) | Service chaining method in openflow switch | |
| KR101739100B1 (en) | Method of controlling openflow switch capable of service chaining and controller thereof |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| 121 | Ep: the epo has been informed by wipo that ep was designated in this application | Ref document number:16854840 Country of ref document:EP Kind code of ref document:A1 | |
| NENP | Non-entry into the national phase | Ref country code:DE | |
| 122 | Ep: pct application non-entry in european phase | Ref document number:16854840 Country of ref document:EP Kind code of ref document:A1 |