USRE46768E1 - System and method for identifying and assessing vulnerabilities on a mobile communications device - Google Patents
System and method for identifying and assessing vulnerabilities on a mobile communications deviceDownload PDFInfo
- Publication number
- USRE46768E1 USRE46768E1US14/109,725US201314109725AUSRE46768EUS RE46768 E1USRE46768 E1US RE46768E1US 201314109725 AUS201314109725 AUS 201314109725AUS RE46768 EUSRE46768 EUS RE46768E
- Authority
- US
- United States
- Prior art keywords
- information
- vulnerability
- communications device
- server
- mobile communications
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Active, expires
Links
Images
Classifications
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/14—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic
- H04L63/1433—Vulnerability analysis
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/50—Monitoring users, programs or devices to maintain the integrity of platforms, e.g. of processors, firmware or operating systems
- G06F21/57—Certifying or maintaining trusted computer platforms, e.g. secure boots or power-downs, version controls, system software checks, secure updates or assessing vulnerabilities
- G06F21/577—Assessing vulnerabilities and evaluating computer system security
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L12/00—Data switching networks
- H04L12/28—Data switching networks characterised by path configuration, e.g. LAN [Local Area Networks] or WAN [Wide Area Networks]
- H04L12/46—Interconnection of networks
- H04L12/4641—Virtual LANs, VLANs, e.g. virtual private networks [VPN]
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W12/00—Security arrangements; Authentication; Protecting privacy or anonymity
- H04W12/06—Authentication
- H04W12/069—Authentication using certificates or pre-shared keys
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W12/00—Security arrangements; Authentication; Protecting privacy or anonymity
- H04W12/12—Detection or prevention of fraud
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W12/00—Security arrangements; Authentication; Protecting privacy or anonymity
- H04W12/12—Detection or prevention of fraud
- H04W12/128—Anti-malware arrangements, e.g. protection against SMS fraud or mobile malware
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/02—Network architectures or network communication protocols for network security for separating internal from external traffic, e.g. firewalls
- H04L63/0272—Virtual private networks
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W84/00—Network topologies
- H04W84/02—Hierarchically pre-organised networks, e.g. paging networks, cellular networks, WLAN [Wireless Local Area Network] or WLL [Wireless Local Loop]
- H04W84/04—Large scale networks; Deep hierarchical networks
- H04W84/042—Public Land Mobile systems, e.g. cellular systems
- H04W84/045—Public Land Mobile systems, e.g. cellular systems using private Base Stations, e.g. femto Base Stations, home Node B
Definitions
- the inventionrelates generally to mobile security, and specifically, to assessing the vulnerability of a mobile communication device.
- Mobile communication devices or mobile devicessuch as cellular telephones, smartphones, wireless-enabled personal data assistants, and the like, are becoming more popular as cellular and wireless network providers are able to expand coverage and increase bandwidth.
- Mobile deviceshave evolved beyond providing simple telephone functionality and are now highly complex multifunctional devices with capabilities rivaling those of desktop or laptop computers.
- voice communicationsmany mobile devices are capable of text messaging, e-mail communications, internet access, and the ability to run full-featured application software. Mobile devices can use these capabilities to perform online transactions such as banking, stock trading, payments, and other financial activities.
- a mobile device used by an individual, a business, or a government agencycan often store confidential or private information in forms such as electronic documents, text messages, access codes, passwords, account numbers, e-mail addresses, personal communications, phone numbers, and financial information.
- mobile communication devicese.g. operating systems, hardware capabilities, software configurations
- mobile communication devicesare able to accept installation of various third-party software applications or “apps” that have been developed to extend the capabilities of the device.
- appscan alter the vulnerability state of a device, since each app may alter how and with which networks the mobile device communicates. What is therefore needed is a way to assess vulnerabilities of a mobile communication device that accounts for differences such as the operating system, the make, model, configuration, or any installed software on the mobile device. Also needed is a way for a user or administrator to view the security status of, remediate, and otherwise assess and manage the security of multiple different mobile communication devices.
- FIG. 1is an exemplary block diagram depicting an embodiment of the invention.
- FIG. 2is an exemplary flow diagram illustrating the steps of an embodiment of the invention.
- FIG. 3is an exemplary flow diagram illustrating the steps of an embodiment of the invention.
- FIG. 4is an exemplary flow diagram illustrating the steps of an embodiment of the invention.
- FIG. 5is an exemplary flow diagram illustrating the steps of an embodiment of the invention.
- FIG. 6is an exemplary flow diagram illustrating the steps of an embodiment of the invention.
- FIG. 7is an exemplary flow diagram illustrating the steps of an embodiment of the invention.
- FIG. 8is an exemplary flow diagram illustrating the steps of an embodiment of the invention.
- FIG. 9is an exemplary flow diagram illustrating the steps of an embodiment of the invention.
- FIG. 10is an exemplary flow diagram illustrating the steps of an embodiment of the invention.
- FIG. 11is an exemplary screenshot illustrating an embodiment of the invention.
- the inventionis a system and a method for identifying, assessing, and responding to vulnerabilities on or affecting a mobile communication device.
- a mobile communication devicemay transmit certain information to a server, and the server may transmit certain result information to the device that contains an assessment or identifies known or potential vulnerabilities affecting the device.
- the servermay transmit notifications about possible or actual vulnerabilities affecting a mobile communication device, which may include instructions for remediating any vulnerabilities identified as affecting the mobile communication device.
- the servermay host a management console that allows an administrator to view the security status of multiple mobile communication devices and take action to secure them if necessary.
- the inventioncan be implemented in numerous ways, including as a process, an apparatus, a system, a device, a method, a computer readable medium such as a computer readable storage medium containing computer readable instructions or computer program code, or as a computer program product comprising a computer usable medium having a computer readable program code embodied therein.
- the mobile communication device described hereinmay include any computer or computing device running an operating system for use on handheld or mobile devices, such as smartphones, PDAs, mobile phones and the like.
- a mobile communication devicemay include devices such as the Apple iPhone®, the Palm PreTM, or any device running the AndroidTM OS, Symbian OS®, Windows Mobile® OS, Palm OS® or Palm Web OSTM.
- a computer usable medium or computer readable mediummay be any medium that can contain or store the program for use by or in connection with the instruction execution system, apparatus or device.
- the computer readable storage medium or computer usable mediummay be, but is not limited to, a random access memory (RAM), read-only memory (ROM), or a persistent store, such as a mass storage device, hard drives, CDROM, DVDROM, tape, erasable programmable read-only memory (EPROM or flash memory), or any magnetic, electromagnetic, infrared, optical, or electrical system, apparatus or device for storing information.
- the computer readable storage medium or computer usable mediummay be any combination of these devices or even paper or another suitable medium upon which the program code is printed, as the program code can be electronically captured, via, for instance, optical scanning of the paper or other medium, then compiled, interpreted, or otherwise processed in a suitable manner, if necessary, and then stored in a computer memory.
- Applicationssoftware programs or computer readable instructions may be referred to as components or modules.
- Applicationsmay be hardwired or hard coded in hardware or take the form of software executing on a general purpose computer such that when the software is loaded into and/or executed by the computer, the computer becomes an apparatus for practicing the invention.
- Applicationsmay also be downloaded in whole or in part through the use of a software development kit or toolkit that enables the creation and implementation of the invention.
- these implementations, or any other form that the invention may takemay be referred to as techniques. In general, the order of the steps of disclosed processes may be altered within the scope of the invention.
- FIG. 1is a block diagram illustrating an embodiment of a system for identifying and assessing vulnerabilities on a mobile communication device.
- the systemmay include one or more mobile communication devices 101 connected on a cellular, wireless Internet or other network 121 .
- One or more servers 151may also have access to network 121 .
- the one or more servers 151may receive one or more sets of vulnerability identification information from the one or more mobile communication devices 101 , and/or may transmit one or more sets of result information to the one or more mobile communication devices 101 .
- the one or more servers 151may have access to a data storage 111 that stores information about mobile communication device vulnerabilities.
- data storage 111may be a database, data table, file system or other memory store.
- Data storage 111may be hosted on any of the one or more servers 151 , or may exist externally from the one or more servers 151 , so long as the one or more servers 151 have access to data storage 111 .
- servers 151 or data storage 111may be singular or plural, or may be physical or virtualized.
- server 151operates as an HTTP server and the device 101 operates as an HTTP client.
- mobile communication device 101 and server 151may use Transaction Layer Security (“TLS”).
- TLSTransaction Layer Security
- device 101may send one or more authentication credentials to server 151 .
- authentication credentialsmay include a username and password or any other data that identifies mobile communication device 101 to server 151 .
- Authenticationmay allow server 151 to store specific information, such as vulnerability identification information, about mobile communication device 101 , and may also provide a persistent view of the security status of mobile communication device 101 .
- data storage 111may be used to store sets of information about mobile communication device vulnerabilities (“vulnerability information”), which may be transmitted in whole or in part to one or more mobile communication devices in the form of “result information.”
- a vulnerabilitymay include an exploitable weakness on a mobile communication device that may result from the device hardware or software. Vulnerabilities may arise due to weaknesses in the device's operating system, other software or hardware flaws in the device, protocol implementation or specification flaws, misconfiguration of the device, software applications installed or stored on the device, or services provided through, to or by the device.
- Vulnerabilitiesmay arise form the features of the device, such as from the presence of Bluetooth, infrared or Internet capabilities on the device, or other communication interfaces and protocols available on the device. Vulnerabilities may arise from weaknesses in the device's interaction with, flaws in, or misconfiguration of other services and systems such as text messaging, voice mail, telephony, or other services and systems accessed through a mobile communication device.
- Information about a vulnerabilityi.e., vulnerability information
- Data storage 111may store general information about mobile communication device vulnerabilities, or may store information about vulnerabilities specific to a mobile communication device. As will be discussed further below, sets of vulnerability information corresponding to vulnerabilities that could affect or actually affect the mobile communication device may be transmitted in the form of result information, notifications, or both.
- vulnerability informationmay include the name, description, severity rating, security impact summary and remediation instructions for a vulnerability.
- Vulnerability informationmay be included in the result information server 151 transmits to mobile communication device 101 or may be stored in data storage 111 .
- Result informationmay include a list of vulnerabilities that are known to affect mobile communication device 101 , a list of potential vulnerabilities that may affect mobile communication device 101 , and a list of vulnerabilities that are known not to affect mobile communication device 101 . Each entry in a list of vulnerabilities may include some or all of the set of vulnerability information for a vulnerability.
- the result informationmay also include a binary assessment of mobile communication device 101 (e.g., good or bad, “okay” or “not okay”), a threat score, remediation instructions for known or potential vulnerabilities, or may instruct display of a graduated icon that changes depending upon state (a sad face for a vulnerable mobile communication device, to a happy face for a “safe” mobile communication device).
- Vulnerability informationmay include criteria for determining if a mobile communication device 101 is affected.
- vulnerability informationmay include information about a vulnerability such as a title, a description, a security impact summary, human or computer readable remediation instructions or a severity rating for the vulnerability.
- vulnerability identification informationincludes data that server 151 may use to determine if mobile communication device 101 is susceptible to any vulnerabilities.
- Such vulnerability identification informationmay include the operating system and version for mobile communication device 101 ; the firmware version of the mobile communication device 101 , the device model for mobile communication device 101 ; carrier information for mobile communication device 101 ; authentication information; and/or user information for the user of mobile communication device 101 .
- Vulnerability identification informationmay also include a list of files, software components, libraries and/or a list of the applications or other software installed on mobile communication device 101 , as well as other information related to these applications and software such as version and configuration information, configuration information about the mobile communication device 101 , communications interfaces and protocols in use by mobile communication device 101 (e.g., WiFi, Bluetooth, IR, SMS, MMS), cellular network information, cellular carrier information, the make and model of mobile communication device 101 , and the like.
- vulnerability information stored in data storage 111may have associated information that includes a description, a title, an overview of the security impact, remediation instructions, and criteria for affected firmware versions.
- mobile communication device 101sends vulnerability identification information to server 151 that includes the device's firmware version.
- Server 151may utilize data storage 111 to examine the vulnerability information stored therein and determine if the firmware version for mobile communication device 101 matches the firmware version criteria for any vulnerabilities. If any vulnerabilities match, server 151 may determine that mobile communication device 101 is vulnerable. Server 151 may then transmit result information to the mobile communication device 101 , as described herein and shown in the Figures. In an embodiment, server 151 only transmits result information corresponding to vulnerabilities that affect mobile communication device 101 .
- server 151transmits result information for all vulnerabilities that may affect device 101 .
- server 151transmits result information which contains all vulnerabilities that may affect device 101 and which of those vulnerabilities actually do affect device 101 .
- the firmware version criteria for being affected by a vulnerabilityincludes the version of the firmware in which the vulnerability was fixed.
- server 151may detect and transmit information for vulnerabilities regardless of the firmware version on mobile communication device 101 , thereby adding extra precautions.
- server 151may only send result information for those vulnerabilities that affect the version of firmware installed on mobile communication device 101 , thereby being more specific.
- a certain vulnerabilitymay affect a mobile communication device having firmware version 1.0, but not a mobile communication device with firmware version 2.0.
- Server 151may receive information about the firmware version of mobile communication device 101 , and if the firmware version is earlier than version 2.0, then mobile communication device 101 is determined to be susceptible to the certain vulnerability. However, if the firmware version for mobile communication device 101 is 2.0 or higher, then mobile communication device 101 may not be susceptible to the certain vulnerability.
- the determination of whether to send more or less result informationmay be a setting specified by an administrator, or may involve the application of logic depending upon the severity of the vulnerability and the risks or benefits of transmitting an overabundance of result information to mobile communication device 101 .
- the amount of result information to transmit to mobile communication device 101may also depend upon the capabilities of mobile communication device 101 or the bandwidth of the network.
- data storage 111stores vulnerability information for at least two types of mobile devices 101 .
- the two mobile device typesmay have different operating systems, firmware versions, model numbers, carrier information, authentication information, user information, configuration information, states, software applications, and the like.
- the vulnerability identification information for each of the at least two mobile deviceswill differ in some aspect.
- data storage 111may store vulnerability information for vulnerabilities that may affect both of the two device types, including vulnerabilities that may affect one device type but not the other.
- data storage 111may store vulnerability information for a variety of mobile communication devices, and will be able to provide information that will help identify, assess and remediate vulnerabilities for a variety of mobile communication devices.
- a vulnerabilitymay affect a device if the device's vulnerability identification information at least partially matches the vulnerability's criteria for affecting a device. Providing partially matching result information provides a conservative, or safer approach to detecting and identifying potential vulnerabilities, as it may provide a opportunity for further assessment and action (e.g. further analysis conducted by software on a device), rather than only providing full criteria matches.
- the partial matchincludes criteria related to a device that does not change, is unlikely to change, or is irrespective of particular software versions, firmware versions, updates, and configuration.
- criteriamay include the device's operating system, model, carrier, software applications installed, hardware capabilities, and the like.
- data storage 111may store information about a vulnerability that affects a particular range of firmware versions of the Apple iPhone® OS. This vulnerability information may include criteria that it affects the Apple iPhone® OS and criteria that it affects specific firmware ranges of various device models.
- the server 151determines that the vulnerability does affect all devices running Apple iPhone® OS that match the vulnerability information's firmware version criteria, the vulnerability may affect devices running any firmware version containing Apple iPhone® OS, and the vulnerability may not affect any devices running AndroidTM, Windows Mobile®, Symbian OS®, or other operating systems.
- the server 151determines that the vulnerability does affect all devices running Apple iPhone® OS that match the vulnerability information's firmware version criteria, the vulnerability may affect devices running any firmware version containing Apple iPhone® OS, and the vulnerability may not affect any devices running AndroidTM, Windows Mobile®, Symbian OS®, or other operating systems.
- FIGS. 2-10are exemplary flow diagrams depicting various process embodiments.
- the following figures and processesare merely exemplary, and that the invention may perform other processes without departing from the scope of this disclosure.
- the performance of the steps in the disclosed processesare not constrained by time. The time between two successive steps may differ from the time between two other successive steps. Additionally, the time to perform each step may differ each time a step is performed.
- the amount of information as described hereinis referred to as a “set of information” or a plurality of sets of information.
- a set of informationmay include at least one quanta, data point or other quantifiable amount of information, but is not designed to limit or constrain the amount of information discussed herein.
- a set of vulnerability informationmay include multiple pieces of information that relate to a given vulnerability, such as a title, a description, a threat rating, and criteria for the vulnerability to affect a device.
- a set of result informationmay include a security status for a device, and a list of vulnerabilities that the device is vulnerable to, each entry in the list comprising a set of vulnerability information.
- FIG. 2depicts and embodiment in which vulnerability information is transmitted to mobile communication device 101 .
- data storage 111stores a plurality of sets of vulnerability information related to one or more mobile communication devices 101 .
- vulnerability informationis transmitted to at least one mobile communication device 101 over network 121 .
- the transmission of vulnerability information to the at least one mobile communication device 101may be controlled by server 151 having access to data storage 111 .
- the transmitted vulnerability informationmay also be termed result information.
- FIG. 3depicts an embodiment in which result information is transmitted to mobile communication device 101 after server 151 receives vulnerability identification information from mobile communication device 101 .
- data storage 111stores a plurality of sets of vulnerability information related to one or more mobile communication devices 101 .
- server 151receives vulnerability identification information from at least one mobile communication device 101 .
- server 151correlates the received set of vulnerability identification information to at least one of the plurality of sets of vulnerability information to generate a set of result information which contains information about vulnerabilities that affect or may affect the at least one mobile communication device 101 . This may include accessing data storage 111 by server 151 .
- result informationis transmitted to at least one mobile communication device 101 over network 121 .
- the scope or type of result information transmitted by server 151may be general information, or may be specific information about vulnerabilities that may specifically affect mobile communication device 101 .
- the result information transmitted to device 101may include all of the vulnerability information stored in data storage 111 , or may include a subset of all of the vulnerability information stored in data storage 111 .
- the option to transmit general or specific result informationmay be an option set by an administrator, may depend upon the hardware or software constraints of the mobile communication device, or may depend upon the bandwidth of the network connecting server 151 to mobile communication device 101 .
- determining which vulnerabilities specifically affect mobile communication device 101may involve correlating the vulnerability identification information provided by mobile communication device 101 to the vulnerability information available to server 151 .
- “correlating” vulnerability identification information to vulnerability informationmay involve determining whether the vulnerability described by the vulnerability information affects a device, whether it may affect a device, or whether it does not affect a device. Determinations may be made through a variety of methods, including matching vulnerability identification information with vulnerability information and determining whether identification information satisfies one or more criteria for vulnerability. Correlating may be performed by server 151 and/or data storage 111 , and may include applying logic, comparing operating systems, comparing version identifiers, checking for the presence of specific software or other data on the mobile communication device, and the like. In an embodiment, correlating may utilize an identification of the hardware or specifications of the mobile communication device. In an embodiment, correlating may also be performed by mobile device 101 .
- FIG. 4is directed to a process in which data storage 111 is updated with new vulnerability information that may be transmitted as a new or second set of result information to affected mobile communication devices 101 . As will discussed in more detail below, this process may include the transmission of one or more notifications.
- data storage 111stores a plurality of sets of vulnerability information related to one or more mobile communication devices 101 .
- server 151receives identification information for one of the one or more mobile communication devices 101 . In an embodiment, server 151 stores this identification information in data storage 111 .
- This stored informationmay be used in block 402 (discussed below) to determine if a newly received vulnerability affects devices 101 .
- the datais used to present a status or administrative interface for the device.
- storing vulnerability identification received by server 151may apply to the other processes as well. For example, any time server 151 receives vulnerability identification information, the server 151 may store the information for use in generating and transmitting user interfaces (e.g. web interfaces) or identifying whether a vulnerability affects a device 101 while the device 101 is not connected to server 151 .
- server 151performs a correlating step to identify vulnerabilities that affect or may affect the mobile communication device 101 , which may include accessing data storage 111 by server 151 .
- server 151may generate a set of result information.
- the set of result informationis transmitted to the affected mobile communication device 101 over network 121 .
- server 151 or data storage 111waits for and receives new vulnerability information.
- server 151makes a determination whether the newly received vulnerability information affects any known mobile communication device 101 having access to server 151 or data storage 111 (block 402 ).
- the determination in block 402may use the same method for determining if a vulnerability affects a device 101 as in the correlating block 302 ; however, instead of identifying which vulnerabilities affect a given device 101 , the server 151 may identify which devices 101 are affected by the newly received vulnerability.
- the server 151determines which devices are vulnerable to the newly received vulnerability by correlating vulnerability identification information for each device stored in data storage 111 to the vulnerability criteria for the newly received vulnerability.
- server 151transmits a notification of the new vulnerability or transmits information about the new vulnerability to the affected mobile communication devices 101 . If the new vulnerability information does not affect any of the mobile communication devices 101 having access to server 151 or data storage 111 , then server 151 or data storage 111 will wait until new relevant vulnerability information is received (block 401 ).
- Server 151may transmit a notification to mobile communication device 101 via a variety of mechanisms.
- a notificationmay be sent via email, text messaging, or through a client-server communication system as described in U.S. patent application Ser. No. 12/372,719, entitled, “SYSTEM AND METHOD FOR REMOTELY SECURING OR RECOVERING A MOBILE DEVICE,” and incorporated in full herein.
- a notificationmay provide information about a vulnerability, information about a potential vulnerability, the status of a mobile communication device, information about remediation instructions, or may request that the user of an affected mobile communication device perform some action to update the vulnerability information on the mobile communication device, or perform some action to remediate the mobile communication device.
- a notificationmay contain information or an instruction indicating that the mobile communication device 101 needs to connect to server 151 in order to receive new vulnerability information.
- the notificationmay be directed to software resident on the mobile communication device 101 , may include software readable remediation instructions, and may be in the form of an SMS or may be sent via a push notification service, such as that provided by Apple Computer Inc. to its iPhone® devices.
- mobile communication device 101may receive a notification with instructions that the device should be updated to protect against a new security risk.
- a specific application on the devicemay require an update, in which case the notification may also cause mobile communication device 101 to update the specific application without user intervention.
- a notificationmay be directed to the user of the mobile communication device.
- Thismay include a text message, push notification, or e-mail message containing human-readable information, or a voicemail or other verbal communication directed to the user of mobile communication device 101 .
- Notifying a mobile communication device 101allows for rapid response to new vulnerabilities, thereby greatly increasing the effectiveness of systems that would otherwise rely on a scheduled or manually-initiated check for security vulnerabilities.
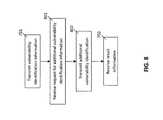
- FIG. 5illustrates an embodiment in which server 151 may require additional information about a mobile communication device 101 in order to confirm whether a vulnerability affects mobile communication device 101 .
- server 151may require additional information about a mobile communication device 101 in order to confirm whether a vulnerability affects mobile communication device 101 .
- the process illustrated in FIG. 5 and described hereinmay build upon any of the processes discussed herein, or may be performed independently of any of the other processes discussed herein.
- data storage 111stores a plurality of sets of vulnerability information related to one or more mobile communication devices 101 .
- data storage 111may be accessed by server 151 .
- server 151receives identification information for a mobile communication device 101 .
- server 151correlates the received identification information to the stored plurality of sets of vulnerability information to determine which vulnerabilities affect or may affect the mobile communication device 101 , which may include accessing data storage 111 by server 151 .
- Server 151generates a set of result information that in block 202 of FIG. 5 is transmitted to the mobile communication device 101 over network 121 .
- server 151 or data storage 111waits for and receives new vulnerability information.
- server 151assess whether there is enough information to determine which mobile communication devices may be affected by the newly received vulnerability information. If there is not enough information, then in block 502 , server 151 will request additional vulnerability identification information from one or more mobile communication devices 101 , and will then receive the additional information from the one or more mobile communication devices 101 in block 503 .
- the request in block 502may utilize notification mechanisms such as those described above or may be performed the next time the mobile communication device 101 connects to the server 151 .
- server 151may make a determination whether the newly received vulnerability information affects any of the one or more mobile communication devices 101 having access to server 151 or data storage 111 (block 402 ). If the new vulnerability information does affect any of the one or more mobile communication devices 101 having access to server 151 or data storage 111 , then in block 403 of FIG. 5 , the server 151 will transmit a notification of the new vulnerability to the affected mobile communication devices 101 , or may transmit an updated, new or second set of result information regarding the new vulnerability. If the new vulnerability information does not affect any of the mobile communication devices 101 having access to server 151 or data storage 111 , then server 151 or data storage 111 may wait until new relevant vulnerability information is received (block 401 of FIG. 5 ).
- server 151receives operating system information from a mobile communication device 101 .
- this informationis stored by server 151 in data storage 111 or other accessible storage. Later, after receiving new vulnerability information, server 151 may determine that based on the stored operating system information for mobile communication device 101 , the vulnerability could affect mobile communication device 101 . However, server 151 may require additional identification information from mobile communication device 101 in order to determine whether the device is actually affected. Server 151 may request additional configuration information from mobile communication device 101 . Server 151 will receive the requested identification information and then sends accurate vulnerability information to the device 101 .
- FIG. 6is directed to a process in which a mobile communication device 101 having access to server 151 or data storage 111 requests vulnerability information from server 151 .
- mobile communication device 101transmits a request to server 151 for vulnerability information over network 121 .
- mobile communication device 101receives vulnerability information from server 151 .
- server 151may access data storage 111 in order to gather and transmit the vulnerability information.
- mobile communication device 101correlates the received vulnerability information to its own identification information, and makes a determination whether any of the received vulnerability information is relevant to the mobile communication device 101 .
- vulnerability information processingmay thereby be performed by the mobile communication device 101 .
- both mobile communication device 101 and server 151perform processing on vulnerability information.
- the server 151may send vulnerability information to mobile communication device 101 based on the operating system of mobile communication device 101 .
- server 151may use information sent by device 101 (e.g. HTTP header information) in the request 601 or information stored in data storage 111 to determine the operating system of the device 101 .
- the mobile communication devicemay then use additional information such as the applications installed on the device, configuration information, and the versions of software libraries to perform additional processing, correlating or analysis on the received vulnerability information.
- additional informationsuch as the applications installed on the device, configuration information, and the versions of software libraries to perform additional processing, correlating or analysis on the received vulnerability information.
- FIG. 7is any exemplary flowchart of a process in which a mobile communication device 101 transmits vulnerability identification information to server 151 (block 701 ), and in response, received result information on (block 702 ).
- server 151Block 701
- received result information onblock 702
- FIG. 7 and described hereinmay be performed as part of any of the other processes described or illustrated herein, or may be performed independently of the other processes described or illustrated herein.
- FIG. 8is directed to a process in which a mobile communication device 101 transmits additional vulnerability identification information to server 151 in order to receive additional result information relevant to the mobile communication device 101 .
- mobile communication device 101transmits vulnerability identification information to server 151 .
- mobile communication device 101receives a request for additional identification information from server 151 .
- mobile communication device 101transmits additional vulnerability identification information to server 151 .
- mobile communication device 101receives correlated result information from server 151 in block 702 of FIG. 8 .
- server 151may access data storage 111 in order to provide the relevant result information for transmission to mobile communication device 101 .
- FIG. 8contemplates a situation in which a mobile communication device 101 first transmits its operating system information to a server 151 .
- Mobile communication device 101may then receive a request from server 151 for version information pertaining to software libraries installed on the device 101 .
- Mobile communication device 101may then send the requested information to server 151 and may receive result information correlated to the device's vulnerability given its specific software library version information. If the software library versions installed on mobile communication device 101 are not affected by a specific vulnerability, the result information received by mobile communication device 101 may indicate that the device 101 is not vulnerable to that vulnerability. If, however, the software library versions are affected by a specific vulnerability, then the result information received by mobile communication device 101 may indicate that mobile communication device 101 is vulnerable and may contain instructions for how to remediate the issue.
- FIG. 9illustrates a process in which vulnerabilities on a mobile communication device 101 are remediated.
- data storage 111stores a plurality of sets of vulnerability information related to one or more mobile communication devices 101 .
- server 151receives vulnerability identification information for a mobile communication device 101 .
- server 151correlates the received vulnerability identification information to vulnerability information in order to generate a set of result information about vulnerabilities affecting the mobile communication device 101 . This step may include accessing data storage 111 by server 151 .
- result informationis transmitted to the mobile communication device 101 over network 121 .
- the result informationmay include instructions for the user to remediate vulnerabilities that affect the device 101 .
- an actionmay be taken.
- server 151may notify an administrator about the vulnerable mobile communication device and that the user has not taken action in the specified period of time.
- an administratormay take manual action such as sending a personal email or otherwise notifying the user to secure the device 101 .
- server 151may automatically disable mobile communication device 101 in some fashion to prevent affecting other devices on the network 121 or to prevent further damage.
- server 151may prevent mobile communication device 101 from connecting to a specific network, email system, document repository, or other system.
- server 151may disable mobile communication device 101 such that an administrator must verify that the device is safe before it is can be used again.
- the user of mobile communication device 101may be notified by server 151 via email, text message or other means of communication that the mobile communication device is vulnerable and that corrective action was not taken within the prescribed time.
- the notificationmay serve as a reminder to help the user take action and secure the device.
- the inventiongoes beyond simply updating a mobile communication device to ensure security, or periodically scanning mobile communication devices on the network for potential vulnerabilities.
- the inventionmay provide a customized vulnerability assessment based upon the unique state and configuration of each mobile communication device on the network, and may provide notifications and remediation instructions based upon this unique state and configuration.
- a usermay receive a direct reminder after one day if his or her device is determined to be vulnerable and is not yet remediated. After two additional days, if the device is still vulnerable, an administrator may be notified and the device disallowed access to email and the organization's VPN service. Once the device is remediated, the administrator may be notified and access to email and VPN may be automatically restored.
- Other examplesare also possible without departing from this disclosure or the scope of the invention.
- server 151may wait for receipt of new vulnerability information.
- server 151may assess whether there is enough information to determine if mobile communication device 101 is affected by the newly received vulnerability information. If there is not enough information, then in block 502 of FIG. 9 , server 151 will request additional vulnerability identification information from mobile communication device 101 , and will then receive the additional vulnerability identification information from mobile communication device 101 in block 503 of FIG. 9 .
- server 151may make a determination whether the newly received vulnerability information affects mobile communication device 101 (block 402 of FIG. 9 ), thereby generating a new, updated or second set of result information. If the new vulnerability information does affect mobile communication device 101 , then in block 403 of FIG. 9 , server 151 may send a notification of the new vulnerability information to the affected mobile communication device 101 , or may send information relating to the new vulnerability to mobile communication device 101 . If the new vulnerability information does not affect mobile communication device 101 , then server 151 or data storage 111 will wait until new relevant vulnerability information is received (block 401 of FIG. 9 ).
- server 151 or data storage 111will wait until new relevant vulnerability information is received (block 401 of FIG. 9 ).
- FIG. 10is directed to a process for generating data for display, e.g. on a web interface.
- a user of the mobile communication device 101 , administrator for a group of mobile communication devices 101 , administrator for server 151 , or other partymay wish to check the security status of mobile communication devices 101 connected to the network 121 . This may be helpful for identifying which mobile communication devices are vulnerable, identifying which need manual remediation or intervention from an administrator, determining the risk posed by a new vulnerability, and performing other actions relevant to securing a group of mobile communication devices. It may also be helpful to provide a single graphical user interface that displays information on mobile communication devices having access to server 151 .
- data storage 111stores a plurality of sets of vulnerability information that may be accessed by server 151 .
- server 151receives vulnerability identification information for one or more mobile communication devices 101 connected to network 121 .
- server 151receives a request for the status of vulnerabilities for the one or more mobile communication devices 101 . This request may originate from one of the one or more mobile communication devices 101 , or from a web interface.
- server 151correlates the received set of vulnerability identification information to at least one of the plurality of sets of vulnerability information to identify vulnerabilities that affect or may affect any of the one or more mobile communication devices 101 connected to server 151 on network 121 .
- server 151transmits the status of vulnerabilities for any of the one or more mobile communication devices 101 for display on a web page or other interface.
- the statusmay include whether any of the vulnerabilities have been remediated, and if not, which mobile communication device 101 still suffers from vulnerabilities that have not been remediated.
- the actions in block 302may be performed before server 151 receives a request for vulnerability status.
- the result of the correlationmay be stored by the server 151 so that when the server receives a request for vulnerability status, the server 151 recalls the previous results.
- the storagemay be in a database, in-memory cache, or other method of storing and recalling data available to server 151 .
- the data transmitted by server 151 in block 1002 of FIG. 10may pertain to an individual mobile communication device, multiple devices, or a group of devices.
- the datamay include information about specific individual devices or aggregated information relating to multiple devices.
- the information about an individual devicemay include the device's security status (e.g. vulnerable/not vulnerable, severity of vulnerability, number of unremediated vulnerabilities), software version information, phone number, count of security events in a time period, or last time communicating with server 151 .
- Aggregated information relating to a group of devicesmay include the percentage of devices in the group that are vulnerable, the number of devices in the group that are vulnerable, the overall risk level of the group, or other information that can be combined between specific devices in the group.
- Server 151may automatically group devices using criteria such as common characteristics (e.g. operating system type, operating system version, having the presence of certain software, having a certain configuration, etc.), or common security statuses (e.g. being vulnerable, being not vulnerable, being affected by a specific vulnerability, being out of compliance, awaiting remediation, etc.).
- common characteristicse.g. operating system type, operating system version, having the presence of certain software, having a certain configuration, etc.
- common security statusese.g. being vulnerable, being not vulnerable, being affected by a specific vulnerability, being out of compliance, awaiting remediation, etc.
- the data transmitted by server 151 in block 1002 of FIG. 10may be selected by receiving searching or sorting information in the request 1001 .
- the search or sortmay reference any information stored by the server relating to specific devices. For example, a user may search for all devices with a specific piece of software installed or may sort devices based on highest severity.
- the data transmitted by server 151 in block 1002includes a prioritized list of current security issues. This list may also include recommended actions to remediate the issues and the ability to initiate such actions.
- the list of current issuesmay include iPhone® vulnerability that is severe and affects 1000 devices, an AndroidTM vulnerability that is of moderate severity and affects 1200 devices, a Windows Mobile vulnerability that is severe and affects 100 devices, and a Blackberry vulnerability that is of low severity and affects 3000 devices.
- the prioritizationtakes into account both the severity of the vulnerability and the number of devices that are part of the deployment and affected by the vulnerability.
- server 151may transmit reports based on security status information available at the server.
- the reportsmay show changes in security status over time or show a current summary.
- Some example reportsinclude the number of vulnerable of devices with respect to time, the current number of vulnerable devices with each severity level, the current number of vulnerable devices broken down by operating system type, and a list of contact information for users with the most severely vulnerable devices.
- server 151may transmit security related events that are generated both by clients and by server 151 due to automatic or administrative action.
- the eventsmay be displayed, gathered, processed, or otherwise interacted with as disclosed in U.S. patent application Ser. No. 12/255,635, entitled, “SECURITY STATUS AND INFORMATION DISPLAY SYSTEM,” which is incorporated in full herein.
- server 151allows an administrator to perform actions related to a device or group of devices. Actions that may be performed include notifying the user of the device via a push notification, text message, email, or another messaging system; disabling the device; disabling the device's access to a service, potentially using a mechanism disclosed in U.S. patent application Ser. No. 12/255,632, entitled, “SECURE MOBILE PLATFORM SYSTEM”; or those disclosed in U.S. patent application Ser. No. 12/372,719, entitled, “SYSTEM AND METHOD FOR REMOTELY SECURING OR RECOVERING A MOBILE DEVICE,” both of which are incorporated in full herein.
- server 151allows an administrator to configure how the server operates.
- One such configurationmay include custom triggers or alerts on certain events (e.g. devices not remediating in a period of time) that will result in logging and administrator notification via email, text message, or other messaging medium.
- Other examples of configuration optionsinclude: the time period the server waits before notifying an administrator of an un-remediated vulnerable device, the email address or addresses administrators should be notified at, how often to remind users of vulnerable devices that they need to take remediation actions, what method of contact server 151 should use to remind users (e.g. SMS, E-mail, push notification service), how the server interacts with e-mail or VPN services to disable access for a specific vulnerable device, and other ways of controlling the functionality disclosed herein.
- vulnerability identification informationis stored by server 151 so that, in the case of a new vulnerability, server 151 can determine whether the device is vulnerable, not vulnerable, or potentially vulnerable based on the information is has.
- the serverstores vulnerability identification information on data storage 111 . This allows an IT admin to get an instant picture of the security risk of their device deployment in the case of a new emerging vulnerability. Such rapid understanding is critical to prioritize response effort in the case of a rapidly spreading worm or severe vulnerability.
- FIG. 11is an exemplary screenshot of result information being displayed on a mobile communication device 101 .
- two vulnerabilitieshave been identified as affecting the mobile communication device.
- these vulnerabilitiesmay have been identified by server 151 after receipt of vulnerability identification information from mobile communication device 101 , as described above and illustrated in the Figures.
- the identified vulnerabilitiesmay specifically affect mobile communication device 101 because of its particular operating system version, firmware version, or software, or may be a general vulnerability that affects all similar makes and models of mobile communication device 101 .
- multiple vulnerabilitiesare shown to not affect the mobile communication device 101 .
- these vulnerabilitiesare vulnerabilities that may affect similar makes and models of mobile device but do not affect the specific device 101 .
- result information display 1101may link to another screen or to a website with more information on a vulnerability, including instructions on how to remediate the vulnerability.
- the result information display 1101may occur due to the result of the device 101 receiving result information sent by the server in response to a request from the device 101 .
- the result information display 1101may occur due to the device receiving a notification that the device 101 is vulnerable.
- other situationsmay prompt the display of result information on device 101 without departing from this disclosure.
- screen layoutsare possible, and that the screen depicted in FIG. 11 is not meant to limit the invention in any fashion.
Landscapes
- Engineering & Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- Computer Hardware Design (AREA)
- General Engineering & Computer Science (AREA)
- Signal Processing (AREA)
- Computer Networks & Wireless Communication (AREA)
- Computing Systems (AREA)
- Software Systems (AREA)
- Theoretical Computer Science (AREA)
- Physics & Mathematics (AREA)
- General Physics & Mathematics (AREA)
- Information Transfer Between Computers (AREA)
- Mobile Radio Communication Systems (AREA)
- Telephonic Communication Services (AREA)
Abstract
Description
Claims (72)
Priority Applications (4)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| US14/109,725USRE46768E1 (en) | 2009-11-18 | 2013-12-17 | System and method for identifying and assessing vulnerabilities on a mobile communications device |
| US15/898,124USRE47757E1 (en) | 2009-11-18 | 2018-02-15 | System and method for identifying and assessing vulnerabilities on a mobile communications device |
| US16/670,488USRE48669E1 (en) | 2009-11-18 | 2019-10-31 | System and method for identifying and [assessing] remediating vulnerabilities on a mobile communications device |
| US17/391,995USRE49634E1 (en) | 2009-11-18 | 2021-08-02 | System and method for determining the risk of vulnerabilities on a mobile communications device |
Applications Claiming Priority (2)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| US12/621,431US8397301B2 (en) | 2009-11-18 | 2009-11-18 | System and method for identifying and assessing vulnerabilities on a mobile communication device |
| US14/109,725USRE46768E1 (en) | 2009-11-18 | 2013-12-17 | System and method for identifying and assessing vulnerabilities on a mobile communications device |
Related Parent Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US12/621,431ReissueUS8397301B2 (en) | 2009-11-18 | 2009-11-18 | System and method for identifying and assessing vulnerabilities on a mobile communication device |
Related Child Applications (2)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US12/621,431ContinuationUS8397301B2 (en) | 2009-11-18 | 2009-11-18 | System and method for identifying and assessing vulnerabilities on a mobile communication device |
| US15/898,124ContinuationUSRE47757E1 (en) | 2009-11-18 | 2018-02-15 | System and method for identifying and assessing vulnerabilities on a mobile communications device |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| USRE46768E1true USRE46768E1 (en) | 2018-03-27 |
Family
ID=44012333
Family Applications (5)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US12/621,431CeasedUS8397301B2 (en) | 2009-11-18 | 2009-11-18 | System and method for identifying and assessing vulnerabilities on a mobile communication device |
| US14/109,725Active2031-01-18USRE46768E1 (en) | 2009-11-18 | 2013-12-17 | System and method for identifying and assessing vulnerabilities on a mobile communications device |
| US15/898,124Active2031-01-18USRE47757E1 (en) | 2009-11-18 | 2018-02-15 | System and method for identifying and assessing vulnerabilities on a mobile communications device |
| US16/670,488Active2031-01-18USRE48669E1 (en) | 2009-11-18 | 2019-10-31 | System and method for identifying and [assessing] remediating vulnerabilities on a mobile communications device |
| US17/391,995Active2031-01-18USRE49634E1 (en) | 2009-11-18 | 2021-08-02 | System and method for determining the risk of vulnerabilities on a mobile communications device |
Family Applications Before (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US12/621,431CeasedUS8397301B2 (en) | 2009-11-18 | 2009-11-18 | System and method for identifying and assessing vulnerabilities on a mobile communication device |
Family Applications After (3)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US15/898,124Active2031-01-18USRE47757E1 (en) | 2009-11-18 | 2018-02-15 | System and method for identifying and assessing vulnerabilities on a mobile communications device |
| US16/670,488Active2031-01-18USRE48669E1 (en) | 2009-11-18 | 2019-10-31 | System and method for identifying and [assessing] remediating vulnerabilities on a mobile communications device |
| US17/391,995Active2031-01-18USRE49634E1 (en) | 2009-11-18 | 2021-08-02 | System and method for determining the risk of vulnerabilities on a mobile communications device |
Country Status (1)
| Country | Link |
|---|---|
| US (5) | US8397301B2 (en) |
Cited By (3)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US11461471B2 (en)* | 2018-05-25 | 2022-10-04 | At&T Intellectual Property I, L.P. | Virtual reality for security augmentation in home and office environments |
| US20230014136A1 (en)* | 2021-07-16 | 2023-01-19 | Dell Products L.P. | Preemptive protection against malicious array access |
| US12010517B1 (en)* | 2021-05-10 | 2024-06-11 | Zimperium, Inc. | Dynamic detection for mobile device security |
Families Citing this family (132)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US7761920B2 (en)* | 2004-09-03 | 2010-07-20 | Fortinet, Inc. | Data structure for policy-based remediation selection |
| US7665119B2 (en) | 2004-09-03 | 2010-02-16 | Secure Elements, Inc. | Policy-based selection of remediation |
| US9990674B1 (en) | 2007-12-14 | 2018-06-05 | Consumerinfo.Com, Inc. | Card registry systems and methods |
| US8312033B1 (en) | 2008-06-26 | 2012-11-13 | Experian Marketing Solutions, Inc. | Systems and methods for providing an integrated identifier |
| US9367680B2 (en) | 2008-10-21 | 2016-06-14 | Lookout, Inc. | System and method for mobile communication device application advisement |
| US8347386B2 (en) | 2008-10-21 | 2013-01-01 | Lookout, Inc. | System and method for server-coupled malware prevention |
| US8051480B2 (en) | 2008-10-21 | 2011-11-01 | Lookout, Inc. | System and method for monitoring and analyzing multiple interfaces and multiple protocols |
| US8984628B2 (en) | 2008-10-21 | 2015-03-17 | Lookout, Inc. | System and method for adverse mobile application identification |
| US9235704B2 (en) | 2008-10-21 | 2016-01-12 | Lookout, Inc. | System and method for a scanning API |
| US8087067B2 (en) | 2008-10-21 | 2011-12-27 | Lookout, Inc. | Secure mobile platform system |
| US8108933B2 (en) | 2008-10-21 | 2012-01-31 | Lookout, Inc. | System and method for attack and malware prevention |
| US9781148B2 (en) | 2008-10-21 | 2017-10-03 | Lookout, Inc. | Methods and systems for sharing risk responses between collections of mobile communications devices |
| US8060936B2 (en) | 2008-10-21 | 2011-11-15 | Lookout, Inc. | Security status and information display system |
| US9043919B2 (en) | 2008-10-21 | 2015-05-26 | Lookout, Inc. | Crawling multiple markets and correlating |
| US8533844B2 (en) | 2008-10-21 | 2013-09-10 | Lookout, Inc. | System and method for security data collection and analysis |
| US8855601B2 (en) | 2009-02-17 | 2014-10-07 | Lookout, Inc. | System and method for remotely-initiated audio communication |
| US8467768B2 (en) | 2009-02-17 | 2013-06-18 | Lookout, Inc. | System and method for remotely securing or recovering a mobile device |
| US9042876B2 (en) | 2009-02-17 | 2015-05-26 | Lookout, Inc. | System and method for uploading location information based on device movement |
| US9955352B2 (en) | 2009-02-17 | 2018-04-24 | Lookout, Inc. | Methods and systems for addressing mobile communications devices that are lost or stolen but not yet reported as such |
| US8538815B2 (en) | 2009-02-17 | 2013-09-17 | Lookout, Inc. | System and method for mobile device replacement |
| US8495745B1 (en)* | 2009-11-30 | 2013-07-23 | Mcafee, Inc. | Asset risk analysis |
| US9544143B2 (en) | 2010-03-03 | 2017-01-10 | Duo Security, Inc. | System and method of notifying mobile devices to complete transactions |
| US9532222B2 (en) | 2010-03-03 | 2016-12-27 | Duo Security, Inc. | System and method of notifying mobile devices to complete transactions after additional agent verification |
| US8495747B1 (en) | 2010-03-31 | 2013-07-23 | Mcafee, Inc. | Prioritizing asset remediations |
| US8839433B2 (en)* | 2010-11-18 | 2014-09-16 | Comcast Cable Communications, Llc | Secure notification on networked devices |
| US9282085B2 (en) | 2010-12-20 | 2016-03-08 | Duo Security, Inc. | System and method for digital user authentication |
| US20120324568A1 (en)* | 2011-06-14 | 2012-12-20 | Lookout, Inc., A California Corporation | Mobile web protection |
| US8738765B2 (en) | 2011-06-14 | 2014-05-27 | Lookout, Inc. | Mobile device DNS optimization |
| US8788881B2 (en)* | 2011-08-17 | 2014-07-22 | Lookout, Inc. | System and method for mobile device push communications |
| US9467463B2 (en)* | 2011-09-02 | 2016-10-11 | Duo Security, Inc. | System and method for assessing vulnerability of a mobile device |
| US9106691B1 (en) | 2011-09-16 | 2015-08-11 | Consumerinfo.Com, Inc. | Systems and methods of identity protection and management |
| US9811667B2 (en)* | 2011-09-21 | 2017-11-07 | Mcafee, Inc. | System and method for grouping computer vulnerabilities |
| US9524388B2 (en) | 2011-10-07 | 2016-12-20 | Duo Security, Inc. | System and method for enforcing a policy for an authenticator device |
| US8763077B2 (en) | 2011-10-07 | 2014-06-24 | Duo Security, Inc. | System and method for enforcing a policy for an authenticator device |
| US8738516B1 (en) | 2011-10-13 | 2014-05-27 | Consumerinfo.Com, Inc. | Debt services candidate locator |
| US8789190B2 (en)* | 2011-12-23 | 2014-07-22 | Mcafee, Inc. | System and method for scanning for computer vulnerabilities in a network environment |
| US10198581B2 (en)* | 2012-03-07 | 2019-02-05 | Rapid7, Inc. | Controlling enterprise access by mobile devices |
| US9668137B2 (en)* | 2012-03-07 | 2017-05-30 | Rapid7, Inc. | Controlling enterprise access by mobile devices |
| US9706410B2 (en)* | 2012-03-07 | 2017-07-11 | Rapid 7, Inc. | Controlling enterprise access by mobile devices |
| US9853959B1 (en) | 2012-05-07 | 2017-12-26 | Consumerinfo.Com, Inc. | Storage and maintenance of personal data |
| US9690635B2 (en) | 2012-05-14 | 2017-06-27 | Qualcomm Incorporated | Communicating behavior information in a mobile computing device |
| US9609456B2 (en) | 2012-05-14 | 2017-03-28 | Qualcomm Incorporated | Methods, devices, and systems for communicating behavioral analysis information |
| US9202047B2 (en) | 2012-05-14 | 2015-12-01 | Qualcomm Incorporated | System, apparatus, and method for adaptive observation of mobile device behavior |
| US9324034B2 (en) | 2012-05-14 | 2016-04-26 | Qualcomm Incorporated | On-device real-time behavior analyzer |
| US9298494B2 (en) | 2012-05-14 | 2016-03-29 | Qualcomm Incorporated | Collaborative learning for efficient behavioral analysis in networked mobile device |
| US9589129B2 (en) | 2012-06-05 | 2017-03-07 | Lookout, Inc. | Determining source of side-loaded software |
| US9407443B2 (en) | 2012-06-05 | 2016-08-02 | Lookout, Inc. | Component analysis of software applications on computing devices |
| US9178897B2 (en)* | 2012-07-03 | 2015-11-03 | The Boeing Company | Methods and systems for use in identifying cyber-security threats in an aviation platform |
| US9747440B2 (en) | 2012-08-15 | 2017-08-29 | Qualcomm Incorporated | On-line behavioral analysis engine in mobile device with multiple analyzer model providers |
| US9495537B2 (en) | 2012-08-15 | 2016-11-15 | Qualcomm Incorporated | Adaptive observation of behavioral features on a mobile device |
| US9330257B2 (en) | 2012-08-15 | 2016-05-03 | Qualcomm Incorporated | Adaptive observation of behavioral features on a mobile device |
| US9319897B2 (en) | 2012-08-15 | 2016-04-19 | Qualcomm Incorporated | Secure behavior analysis over trusted execution environment |
| USD720766S1 (en)* | 2012-09-10 | 2015-01-06 | Lookout, Inc. | Mobile communication device display with graphical user interface comprising security and privacy advisor screens |
| US8655307B1 (en) | 2012-10-26 | 2014-02-18 | Lookout, Inc. | System and method for developing, updating, and using user device behavioral context models to modify user, device, and application state, settings and behavior for enhanced user security |
| US9654541B1 (en) | 2012-11-12 | 2017-05-16 | Consumerinfo.Com, Inc. | Aggregating user web browsing data |
| WO2014079039A1 (en)* | 2012-11-23 | 2014-05-30 | Telefonaktiebolaget L M Ericsson (Publ) | Network offloading |
| US9916621B1 (en) | 2012-11-30 | 2018-03-13 | Consumerinfo.Com, Inc. | Presentation of credit score factors |
| US9208215B2 (en) | 2012-12-27 | 2015-12-08 | Lookout, Inc. | User classification based on data gathered from a computing device |
| US9374369B2 (en) | 2012-12-28 | 2016-06-21 | Lookout, Inc. | Multi-factor authentication and comprehensive login system for client-server networks |
| US8855599B2 (en) | 2012-12-31 | 2014-10-07 | Lookout, Inc. | Method and apparatus for auxiliary communications with mobile communications device |
| US9684870B2 (en) | 2013-01-02 | 2017-06-20 | Qualcomm Incorporated | Methods and systems of using boosted decision stumps and joint feature selection and culling algorithms for the efficient classification of mobile device behaviors |
| US9686023B2 (en) | 2013-01-02 | 2017-06-20 | Qualcomm Incorporated | Methods and systems of dynamically generating and using device-specific and device-state-specific classifier models for the efficient classification of mobile device behaviors |
| US10089582B2 (en) | 2013-01-02 | 2018-10-02 | Qualcomm Incorporated | Using normalized confidence values for classifying mobile device behaviors |
| US9424409B2 (en) | 2013-01-10 | 2016-08-23 | Lookout, Inc. | Method and system for protecting privacy and enhancing security on an electronic device |
| US9742559B2 (en) | 2013-01-22 | 2017-08-22 | Qualcomm Incorporated | Inter-module authentication for securing application execution integrity within a computing device |
| US9491187B2 (en) | 2013-02-15 | 2016-11-08 | Qualcomm Incorporated | APIs for obtaining device-specific behavior classifier models from the cloud |
| US10686819B2 (en) | 2013-02-19 | 2020-06-16 | Proofpoint, Inc. | Hierarchical risk assessment and remediation of threats in mobile networking environment |
| US9443073B2 (en) | 2013-08-08 | 2016-09-13 | Duo Security, Inc. | System and method for verifying status of an authentication device |
| US8893230B2 (en) | 2013-02-22 | 2014-11-18 | Duo Security, Inc. | System and method for proxying federated authentication protocols |
| US9338156B2 (en) | 2013-02-22 | 2016-05-10 | Duo Security, Inc. | System and method for integrating two-factor authentication in a device |
| US9607156B2 (en) | 2013-02-22 | 2017-03-28 | Duo Security, Inc. | System and method for patching a device through exploitation |
| US10699273B2 (en) | 2013-03-14 | 2020-06-30 | Lookout, Inc. | System and method for authorizing payment transaction based on device locations |
| US10102570B1 (en)* | 2013-03-14 | 2018-10-16 | Consumerinfo.Com, Inc. | Account vulnerability alerts |
| US9852416B2 (en) | 2013-03-14 | 2017-12-26 | Lookout, Inc. | System and method for authorizing a payment transaction |
| US9406085B1 (en) | 2013-03-14 | 2016-08-02 | Consumerinfo.Com, Inc. | System and methods for credit dispute processing, resolution, and reporting |
| US9519788B2 (en) | 2013-04-10 | 2016-12-13 | International Business Machines Corporation | Identifying security vulnerabilities related to inter-process communications |
| US9307412B2 (en) | 2013-04-24 | 2016-04-05 | Lookout, Inc. | Method and system for evaluating security for an interactive service operation by a mobile device |
| CA2910954C (en)* | 2013-05-06 | 2017-08-01 | Staples, Inc. | It vulnerability management system |
| US9053310B2 (en) | 2013-08-08 | 2015-06-09 | Duo Security, Inc. | System and method for verifying status of an authentication device through a biometric profile |
| US9092302B2 (en) | 2013-09-10 | 2015-07-28 | Duo Security, Inc. | System and method for determining component version compatibility across a device ecosystem |
| US9608814B2 (en) | 2013-09-10 | 2017-03-28 | Duo Security, Inc. | System and method for centralized key distribution |
| US9642008B2 (en) | 2013-10-25 | 2017-05-02 | Lookout, Inc. | System and method for creating and assigning a policy for a mobile communications device based on personal data |
| US9774448B2 (en) | 2013-10-30 | 2017-09-26 | Duo Security, Inc. | System and methods for opportunistic cryptographic key management on an electronic device |
| US9477737B1 (en) | 2013-11-20 | 2016-10-25 | Consumerinfo.Com, Inc. | Systems and user interfaces for dynamic access of multiple remote databases and synchronization of data based on user rules |
| US9125060B2 (en)* | 2013-11-22 | 2015-09-01 | At&T Mobility Ii Llc | Methods, systems, and computer program products for intercepting, in a carrier network, data destined for a mobile device to determine patterns in the data |
| US10122747B2 (en) | 2013-12-06 | 2018-11-06 | Lookout, Inc. | Response generation after distributed monitoring and evaluation of multiple devices |
| US9753796B2 (en) | 2013-12-06 | 2017-09-05 | Lookout, Inc. | Distributed monitoring, evaluation, and response for multiple devices |
| US9762590B2 (en) | 2014-04-17 | 2017-09-12 | Duo Security, Inc. | System and method for an integrity focused authentication service |
| US9195809B1 (en)* | 2014-08-14 | 2015-11-24 | Synack, Inc. | Automated vulnerability and error scanner for mobile applications |
| US9979719B2 (en) | 2015-01-06 | 2018-05-22 | Duo Security, Inc. | System and method for converting one-time passcodes to app-based authentication |
| US9641341B2 (en) | 2015-03-31 | 2017-05-02 | Duo Security, Inc. | Method for distributed trust authentication |
| US9710653B2 (en) | 2015-04-20 | 2017-07-18 | SafeBreach Ltd. | System and method for verifying malicious actions by utilizing virtualized elements |
| US9473522B1 (en) | 2015-04-20 | 2016-10-18 | SafeBreach Ltd. | System and method for securing a computer system against malicious actions by utilizing virtualized elements |
| CA2982463C (en) | 2015-05-01 | 2019-03-05 | Lookout, Inc. | Determining source of side-loaded software |
| US9930060B2 (en)* | 2015-06-01 | 2018-03-27 | Duo Security, Inc. | Method for enforcing endpoint health standards |
| US9774579B2 (en) | 2015-07-27 | 2017-09-26 | Duo Security, Inc. | Method for key rotation |
| US11032306B2 (en) | 2015-12-30 | 2021-06-08 | International Business Machines Corporation | System, method and apparatus for fully precise hybrid security verification of mobile applications |
| CN105740477B (en)* | 2016-03-18 | 2019-03-29 | 中国科学院信息工程研究所 | For the Selecting Function System method and search engine of extensive embedded device firmware |
| JP6690346B2 (en)* | 2016-03-25 | 2020-04-28 | 日本電気株式会社 | Security risk management system, server, control method, program |
| US10440053B2 (en) | 2016-05-31 | 2019-10-08 | Lookout, Inc. | Methods and systems for detecting and preventing network connection compromise |
| US10333965B2 (en) | 2016-09-12 | 2019-06-25 | Qualcomm Incorporated | Methods and systems for on-device real-time adaptive security based on external threat intelligence inputs |
| US11522901B2 (en)* | 2016-09-23 | 2022-12-06 | OPSWAT, Inc. | Computer security vulnerability assessment |
| US9749349B1 (en) | 2016-09-23 | 2017-08-29 | OPSWAT, Inc. | Computer security vulnerability assessment |
| GB201617620D0 (en)* | 2016-10-18 | 2016-11-30 | Cybernetica As | Composite digital signatures |
| CN106919844B (en)* | 2017-02-14 | 2019-08-02 | 暨南大学 | A kind of android system vulnerability of application program detection method |
| US10581802B2 (en) | 2017-03-16 | 2020-03-03 | Keysight Technologies Singapore (Sales) Pte. Ltd. | Methods, systems, and computer readable media for advertising network security capabilities |
| CN107194262A (en)* | 2017-05-19 | 2017-09-22 | 北京匡恩网络科技有限责任公司 | Method and device for scanning leak and generation vulnerability information storehouse |
| US10218697B2 (en) | 2017-06-09 | 2019-02-26 | Lookout, Inc. | Use of device risk evaluation to manage access to services |
| GB2563618B (en)* | 2017-06-20 | 2020-09-16 | Arm Ip Ltd | Electronic system vulnerability assessment |
| US10261777B2 (en) | 2017-07-25 | 2019-04-16 | Aurora Labs Ltd. | Detecting anomalies online using histograms of ECU processing activity |
| US10412113B2 (en) | 2017-12-08 | 2019-09-10 | Duo Security, Inc. | Systems and methods for intelligently configuring computer security |
| EP3776319A1 (en)* | 2018-03-25 | 2021-02-17 | British Telecommunications public limited company | Access control |
| WO2020026228A1 (en)* | 2018-08-01 | 2020-02-06 | Vdoo Connected Trust Ltd. | Firmware verification |
| US11265324B2 (en) | 2018-09-05 | 2022-03-01 | Consumerinfo.Com, Inc. | User permissions for access to secure data at third-party |
| US11030321B2 (en)* | 2018-10-02 | 2021-06-08 | International Business Machines Corporation | Processing and evaluating data based on associated device vulnerability |
| US11374958B2 (en)* | 2018-10-31 | 2022-06-28 | International Business Machines Corporation | Security protection rule prediction and enforcement |
| US11315179B1 (en) | 2018-11-16 | 2022-04-26 | Consumerinfo.Com, Inc. | Methods and apparatuses for customized card recommendations |
| US11658962B2 (en) | 2018-12-07 | 2023-05-23 | Cisco Technology, Inc. | Systems and methods of push-based verification of a transaction |
| US11238656B1 (en) | 2019-02-22 | 2022-02-01 | Consumerinfo.Com, Inc. | System and method for an augmented reality experience via an artificial intelligence bot |
| US11949711B2 (en) | 2019-07-08 | 2024-04-02 | Caci International, Inc. | Systems and methods for securing information |
| US11729222B2 (en)* | 2019-07-12 | 2023-08-15 | Palo Alto Research Center Incorporated | System and method for extracting configuration-related information for reasoning about the security and functionality of a composed internet of things system |
| US11941065B1 (en) | 2019-09-13 | 2024-03-26 | Experian Information Solutions, Inc. | Single identifier platform for storing entity data |
| US11533329B2 (en) | 2019-09-27 | 2022-12-20 | Keysight Technologies, Inc. | Methods, systems and computer readable media for threat simulation and threat mitigation recommendations |
| US11610020B2 (en)* | 2020-04-07 | 2023-03-21 | Mcafee, Llc | Securing sensitive user data stored locally by an application |
| US11363041B2 (en) | 2020-05-15 | 2022-06-14 | International Business Machines Corporation | Protecting computer assets from malicious attacks |
| US11163637B1 (en) | 2020-09-21 | 2021-11-02 | Dell Products L.P. | Determining server issues related to software versions using artificial intelligence techniques |
| US20220159028A1 (en)* | 2020-11-17 | 2022-05-19 | Bank Of America Corporation | Generating Alerts Based on Continuous Monitoring of Third Party Systems |
| US11930046B2 (en) | 2021-06-17 | 2024-03-12 | Xerox Corporation | System and method for determining vulnerability metrics for graph-based configuration security |
| US12284216B2 (en) | 2021-09-17 | 2025-04-22 | Xerox Corporation | System and method for synthesizing role-based access control assignments per a policy |
| US12223074B2 (en) | 2021-09-17 | 2025-02-11 | Xerox Corporation | System and method for securing windows discretionary access control |
| CN114143110B (en)* | 2021-12-08 | 2024-04-26 | 湖北天融信网络安全技术有限公司 | Vulnerability processing method, device and system of mimicry equipment |
| US12238132B2 (en) | 2022-04-22 | 2025-02-25 | Xerox Corporation | Method and system for facilitating a ranking score using attack volume to find optimal configurations |
Citations (171)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US3416032A (en) | 1966-03-23 | 1968-12-10 | Motorola Inc | Lamp dimming circuit |
| US4553257A (en) | 1982-04-28 | 1985-11-12 | Pioneer Electronic Corp. | Automatic sound volume control device |
| US5319776A (en) | 1990-04-19 | 1994-06-07 | Hilgraeve Corporation | In transit detection of computer virus with safeguard |
| US5574775A (en) | 1993-08-04 | 1996-11-12 | Lucent Technologies, Inc. | Universal wireless radiotelephone system |
| US6185689B1 (en) | 1998-06-24 | 2001-02-06 | Richard S. Carson & Assoc., Inc. | Method for network self security assessment |
| US6269456B1 (en) | 1997-12-31 | 2001-07-31 | Network Associates, Inc. | Method and system for providing automated updating and upgrading of antivirus applications using a computer network |
| US6272353B1 (en) | 1999-08-20 | 2001-08-07 | Siemens Information And Communication Mobile Llc. | Method and system for mobile communications |
| US6301668B1 (en) | 1998-12-29 | 2001-10-09 | Cisco Technology, Inc. | Method and system for adaptive network security using network vulnerability assessment |
| US20010044339A1 (en) | 2000-02-17 | 2001-11-22 | Angel Cordero | Multi-player computer game, system and method |
| US20020042886A1 (en) | 2000-08-31 | 2002-04-11 | Pasi Lahti | Software virus protection |
| US20020087483A1 (en) | 2000-12-29 | 2002-07-04 | Shlomi Harif | System, method and program for creating and distributing processes in a heterogeneous network |
| US20020108058A1 (en) | 2001-02-08 | 2002-08-08 | Sony Corporation And Sony Electronics Inc. | Anti-theft system for computers and other electronic devices |
| US6453345B2 (en) | 1996-11-06 | 2002-09-17 | Datadirect Networks, Inc. | Network security and surveillance system |
| US20020183060A1 (en) | 2001-05-07 | 2002-12-05 | Lg Electronics Inc. | Map message processing system and method for interworking between heterogeneous networks |
| US20020191018A1 (en) | 2001-05-31 | 2002-12-19 | International Business Machines Corporation | System and method for implementing a graphical user interface across dissimilar platforms yet retaining similar look and feel |
| US20030028803A1 (en) | 2001-05-18 | 2003-02-06 | Bunker Nelson Waldo | Network vulnerability assessment system and method |
| US6529143B2 (en) | 1998-10-23 | 2003-03-04 | Nokia Mobile Phones Ltd. | Information retrieval system |
| US20030046134A1 (en) | 2001-08-28 | 2003-03-06 | Frolick Harry A. | Web-based project management system |
| US20030079145A1 (en) | 2001-08-01 | 2003-04-24 | Networks Associates Technology, Inc. | Platform abstraction layer for a wireless malware scanning engine |
| US20030115485A1 (en) | 2001-12-14 | 2003-06-19 | Milliken Walter Clark | Hash-based systems and methods for detecting, preventing, and tracing network worms and viruses |
| US20030120951A1 (en) | 2001-12-21 | 2003-06-26 | Gartside Paul Nicholas | Generating malware definition data for mobile computing devices |
| US20030131148A1 (en) | 2002-01-10 | 2003-07-10 | David Kelley | Cross-platform software development with a software development peripheral |
| US20040022258A1 (en) | 2002-07-30 | 2004-02-05 | Docomo Communications Laboratories Usa, Inc. | System for providing access control platform service for private networks |
| US20040133624A1 (en) | 2003-01-06 | 2004-07-08 | Seung-Joon Park | Method and apparatus for performing common call processing management using common software platform |
| US20040158741A1 (en) | 2003-02-07 | 2004-08-12 | Peter Schneider | System and method for remote virus scanning in wireless networks |
| US6792543B2 (en) | 2001-08-01 | 2004-09-14 | Networks Associates Technology, Inc. | Virus scanning on thin client devices using programmable assembly language |
| US20040185900A1 (en) | 2003-03-20 | 2004-09-23 | Mcelveen William | Cell phone with digital camera and smart buttons and methods for using the phones for security monitoring |
| US20040225887A1 (en) | 2003-05-08 | 2004-11-11 | O'neil Douglas R. | Centralized authentication system |
| US20040259532A1 (en) | 2001-10-31 | 2004-12-23 | Markus Isomaki | Method for handling of messages between a terminal and a data network |
| US20050010821A1 (en) | 2003-04-29 | 2005-01-13 | Geoffrey Cooper | Policy-based vulnerability assessment |
| US20050015443A1 (en) | 2000-10-10 | 2005-01-20 | Alex Levine | Personal message delivery system |
| US20050074106A1 (en) | 2002-11-14 | 2005-04-07 | Alcatel | Call establishment method |
| US20050076246A1 (en) | 2003-10-01 | 2005-04-07 | Singhal Tara Chand | Method and apparatus for network security using a router based authentication system |
| US20050091308A1 (en) | 2003-09-29 | 2005-04-28 | Peter Bookman | Mobility device |
| US6907530B2 (en) | 2001-01-19 | 2005-06-14 | V-One Corporation | Secure internet applications with mobile code |
| US20050130627A1 (en) | 2003-11-26 | 2005-06-16 | Benoit Calmels | Authentication between a cellular phone and an access point of a short-range network |
| US20050138395A1 (en) | 2003-12-18 | 2005-06-23 | Benco David S. | Network support for mobile handset anti-virus protection |
| US20050138413A1 (en) | 2003-12-11 | 2005-06-23 | Richard Lippmann | Network security planning architecture |
| US20050154796A1 (en) | 2002-03-06 | 2005-07-14 | Forsyth John M. | Method of enabling a wireless information device to access data services |
| US20050197099A1 (en) | 2004-03-08 | 2005-09-08 | Lan-Ver Technologies Solutions Ltd. | Cellular device security apparatus and method |
| US20050227669A1 (en) | 2004-04-08 | 2005-10-13 | Ixi Mobile (R&D) Ltd. | Security key management system and method in a mobile communication network |
| US6959184B1 (en) | 1999-06-30 | 2005-10-25 | Lucent Technologies Inc. | Method for determining the security status of transmissions in a telecommunications network |
| US20050237970A1 (en) | 2000-09-14 | 2005-10-27 | Kabushiki Kaisha Toshiba | Packet transfer scheme using mobile terminal and router for preventing attacks using global address |
| WO2005101789A1 (en) | 2004-04-14 | 2005-10-27 | Gurunath Samir Kalekar | A system for real-time network based vulnerability assessment of a host/device |
| US20050254654A1 (en) | 2004-04-19 | 2005-11-17 | The Boeing Company | Security state vector for mobile network platform |
| US20050278777A1 (en) | 2004-06-14 | 2005-12-15 | Hackerproof Security, Inc. | Method and system for enforcing secure network connection |
| US20050282533A1 (en) | 2004-03-22 | 2005-12-22 | Vadim Draluk | Method and apparatus for dynamic extension of device management tree data model on a mobile |
| US20060026283A1 (en) | 2004-07-30 | 2006-02-02 | Trueba Luis Ruben Z | System and method for updating software on a computer |
| US7020895B2 (en) | 1999-12-24 | 2006-03-28 | F-Secure Oyj | Remote computer virus scanning |
| US7023383B2 (en) | 1999-01-08 | 2006-04-04 | Trueposition, Inc. | Multiple pass location processor |
| US20060073820A1 (en) | 2002-10-10 | 2006-04-06 | Craswell Ronald J | Method and apparatus for remote control and updating of wireless mobile devices |
| US20060080680A1 (en) | 2004-10-12 | 2006-04-13 | Majid Anwar | Platform independent dynamic linking |
| US20060095454A1 (en) | 2004-10-29 | 2006-05-04 | Texas Instruments Incorporated | System and method for secure collaborative terminal identity authentication between a wireless communication device and a wireless operator |
| US20060101518A1 (en)* | 2004-11-05 | 2006-05-11 | Schumaker Troy T | Method to generate a quantitative measurement of computer security vulnerabilities |
| US20060130145A1 (en) | 2004-11-20 | 2006-06-15 | Choi Byeong C | System and method for analyzing malicious code protocol and generating harmful traffic |
| US7069589B2 (en) | 2000-07-14 | 2006-06-27 | Computer Associates Think, Inc.. | Detection of a class of viral code |
| US20060150238A1 (en) | 2005-01-04 | 2006-07-06 | Symbol Technologies, Inc. | Method and apparatus of adaptive network policy management for wireless mobile computers |
| US20060150256A1 (en) | 2004-12-03 | 2006-07-06 | Whitecell Software Inc. A Delaware Corporation | Secure system for allowing the execution of authorized computer program code |
| US20060179485A1 (en) | 2005-02-09 | 2006-08-10 | Gary Longsine | Intrusion handling system and method for a packet network with dynamic network address utilization |
| US20060218482A1 (en) | 2002-04-19 | 2006-09-28 | Droplet Technology, Inc. | Mobile imaging application, device architecture, service platform architecture and services |
| US20060224742A1 (en) | 2005-02-28 | 2006-10-05 | Trust Digital | Mobile data security system and methods |
| US7123933B2 (en) | 2001-05-31 | 2006-10-17 | Orative Corporation | System and method for remote application management of a wireless device |
| WO2006110181A2 (en) | 2004-10-29 | 2006-10-19 | Skyhook Wireless, Inc. | Location beacon database and server, method of building location beacon database, and location based service using same |
| US7127455B2 (en) | 2002-11-12 | 2006-10-24 | Hewlett-Packard Development Company, L.P. | Taxonomy for mobile e-services |
| US20060253584A1 (en) | 2005-05-03 | 2006-11-09 | Dixon Christopher J | Reputation of an entity associated with a content item |
| US20060253205A1 (en) | 2005-05-09 | 2006-11-09 | Michael Gardiner | Method and apparatus for tabular process control |
| US7143441B2 (en)* | 2001-05-08 | 2006-11-28 | Aramira Corporation | Wireless device mobile application security system |
| US20060272011A1 (en) | 2000-06-30 | 2006-11-30 | Internet Security Systems, Inc. | Method and apparatus for network assessment and authentication |
| US20060277408A1 (en) | 2005-06-03 | 2006-12-07 | Bhat Sathyanarayana P | System and method for monitoring and maintaining a wireless device |
| US20060294582A1 (en) | 2005-06-28 | 2006-12-28 | Symbol Technologies, Inc. | Mobility policy manager for mobile computing devices |
| US20070005327A1 (en) | 2000-01-24 | 2007-01-04 | Radioscape Limited | Digital wireless basestation |
| US20070011319A1 (en) | 2002-01-15 | 2007-01-11 | Mcclure Stuart C | System and method for network vulnerability detection and reporting |
| US20070015519A1 (en) | 2005-07-12 | 2007-01-18 | Qwest Communications International Inc. | User defined location based notification for a mobile communications device systems and methods |
| US20070016953A1 (en) | 2005-06-30 | 2007-01-18 | Prevx Limited | Methods and apparatus for dealing with malware |
| US20070016955A1 (en) | 2004-09-24 | 2007-01-18 | Ygor Goldberg | Practical threat analysis |
| US20070028304A1 (en) | 2005-07-29 | 2007-02-01 | Bit 9, Inc. | Centralized timed analysis in a network security system |
| US20070028303A1 (en) | 2005-07-29 | 2007-02-01 | Bit 9, Inc. | Content tracking in a network security system |
| US20070028095A1 (en) | 2005-07-28 | 2007-02-01 | Allen David L | Security certificate management |
| US7178166B1 (en) | 2000-09-19 | 2007-02-13 | Internet Security Systems, Inc. | Vulnerability assessment and authentication of a computer by a local scanner |
| US20070050471A1 (en) | 2005-08-31 | 2007-03-01 | Microsoft Corporation | Portable Remoting Component With A Scaleable Feature Set |
| GB2430588A (en) | 2005-09-20 | 2007-03-28 | Alireza Mousavi Khalkhali | Multiple protocol platform for mobile applications |
| US20070086476A1 (en) | 2001-07-20 | 2007-04-19 | Smartmatic, Corp. | Method for smart device network application infrastructure (SDNA) |
| US20070088948A1 (en)* | 2005-10-15 | 2007-04-19 | Huawei Technologies Co., Ltd | Method for implementing security update of mobile station and a correlative reacting system |
| US7210168B2 (en) | 2001-10-15 | 2007-04-24 | Mcafee, Inc. | Updating malware definition data for mobile data processing devices |
| US7228566B2 (en) | 2001-07-10 | 2007-06-05 | Core Sdi, Incorporated | Automated computer system security compromise |
| US7236598B2 (en) | 2000-05-23 | 2007-06-26 | Invicta Networks, Inc. | Systems and methods for communication protection |
| US7237264B1 (en) | 2001-06-04 | 2007-06-26 | Internet Security Systems, Inc. | System and method for preventing network misuse |
| US20070154014A1 (en) | 2005-12-30 | 2007-07-05 | Selim Aissi | Using a trusted-platform-based shared-secret derivation and WWAN infrastructure-based enrollment to establish a secure local channel |
| WO2007081356A2 (en) | 2005-02-22 | 2007-07-19 | Skyhook Wireless, Inc. | Continuous data optimization in positioning system |
| US20070174472A1 (en) | 2006-01-20 | 2007-07-26 | Verimatrix, Inc. | Network security system and method |
| US20070186282A1 (en) | 2006-02-06 | 2007-08-09 | Microsoft Corporation | Techniques for identifying and managing potentially harmful web traffic |
| US7266810B2 (en) | 2002-04-09 | 2007-09-04 | Hewlett-Packard Development Company, Lp. | Runtime profiling of platform-independent software applications |
| US20070214504A1 (en) | 2004-03-30 | 2007-09-13 | Paolo Milani Comparetti | Method And System For Network Intrusion Detection, Related Network And Computer Program Product |
| US20070240221A1 (en) | 2006-04-06 | 2007-10-11 | George Tuvell | Non-Signature Malware Detection System and Method for Mobile Platforms |
| US20070250627A1 (en) | 2006-04-21 | 2007-10-25 | May Robert A | Method, apparatus, signals and medium for enforcing compliance with a policy on a client computer |
| US20070248047A1 (en) | 2006-01-31 | 2007-10-25 | Peter Shorty | Home electrical device control within a wireless mesh network |
| US7290276B2 (en) | 2003-02-06 | 2007-10-30 | Lenovo Singapore Pte. Ltd. | Information processing apparatus for secure information recovery |
| US7308712B2 (en) | 2001-12-31 | 2007-12-11 | Mcafee, Inc. | Automated computer vulnerability resolution system |
| US7308256B2 (en) | 2002-02-28 | 2007-12-11 | Ntt Docomo, Inc. | Mobile communication terminal, information processing apparatus, relay server apparatus, information processing system, and information processing method |
| US20070293263A1 (en) | 2006-06-14 | 2007-12-20 | Hossein Eslambolchi | Method and apparatus for providing multi-system cellular communications |
| US20070297610A1 (en) | 2006-06-23 | 2007-12-27 | Microsoft Corporation | Data protection for a mobile device |
| WO2008007111A1 (en) | 2006-07-14 | 2008-01-17 | Vodaphone Group Plc | Telecommunications device security |
| US7325249B2 (en) | 2001-04-30 | 2008-01-29 | Aol Llc | Identifying unwanted electronic messages |
| US20080028470A1 (en) | 2006-07-25 | 2008-01-31 | Mark Remington | Systems and Methods for Vulnerability Detection and Scoring with Threat Assessment |
| US20080046557A1 (en) | 2005-03-23 | 2008-02-21 | Cheng Joseph C | Method and system for designing, implementing, and managing client applications on mobile devices |
| US20080047007A1 (en) | 2006-08-18 | 2008-02-21 | Microsoft Corporation | Network security page |
| US20080065507A1 (en) | 2006-09-12 | 2008-03-13 | James Morrison | Interactive digital media services |
| US20080070495A1 (en) | 2006-08-18 | 2008-03-20 | Michael Stricklen | Mobile device management |
| US20080072329A1 (en) | 2006-09-14 | 2008-03-20 | Interdigital Technology Corporation | Method and system for enhancing flow of behavior metrics and evaluation of security of a node |
| US7356835B2 (en) | 2003-08-26 | 2008-04-08 | Mitel Networks Corporation | Security monitor for PDA attached telephone |
| US20080086776A1 (en) | 2006-10-06 | 2008-04-10 | George Tuvell | System and method of malware sample collection on mobile networks |
| US20080086773A1 (en) | 2006-10-06 | 2008-04-10 | George Tuvell | System and method of reporting and visualizing malware on mobile networks |
| US20080109871A1 (en) | 2006-09-13 | 2008-05-08 | Richard Jacobs | Policy management |
| WO2008057737A2 (en) | 2006-11-07 | 2008-05-15 | Skyhook Wireless, Inc. | System and method for estimating positioning error within a wlan-based positioning system |
| US7376969B1 (en) | 2002-12-02 | 2008-05-20 | Arcsight, Inc. | Real time monitoring and analysis of events from multiple network security devices |
| US20080127179A1 (en) | 2006-09-25 | 2008-05-29 | Barrie Jon Moss | System and apparatus for deployment of application and content to different platforms |
| US20080127171A1 (en) | 2006-09-15 | 2008-05-29 | Altiris, Inc. | Method and System for Creating and Executing Generic Software Packages |
| US20080127336A1 (en) | 2006-09-19 | 2008-05-29 | Microsoft Corporation | Automated malware signature generation |
| US20080127334A1 (en) | 2006-09-14 | 2008-05-29 | Computer Associates Think, Inc. | System and method for using rules to protect against malware |
| US20080132218A1 (en) | 2006-11-30 | 2008-06-05 | Yuval Samson | Method and Apparatus for Starting Applications |
| US20080134281A1 (en) | 2006-11-30 | 2008-06-05 | Mcafee, Inc. | Method and system for enhanced wireless network security |
| US7386297B2 (en) | 2002-12-28 | 2008-06-10 | Curitel Communications, Inc. | Mobile communication system and mobile terminal having function of inactivating mobile communication viruses, and method thereof |
| US20080140767A1 (en) | 2006-06-14 | 2008-06-12 | Prasad Rao | Divitas description protocol and methods therefor |
| US20080148381A1 (en) | 2006-10-30 | 2008-06-19 | Jeffrey Aaron | Methods, systems, and computer program products for automatically configuring firewalls |
| US7392043B2 (en) | 2003-04-17 | 2008-06-24 | Ntt Docomo, Inc. | API system, method and computer program product for accessing content/security analysis functionality in a mobile communication framework |
| US7392543B2 (en) | 2003-06-30 | 2008-06-24 | Symantec Corporation | Signature extraction system and method |
| US7397424B2 (en) | 2005-02-03 | 2008-07-08 | Mexens Intellectual Property Holding, Llc | System and method for enabling continuous geographic location estimation for wireless computing devices |
| US7397434B2 (en) | 2005-09-16 | 2008-07-08 | Samsung Electro-Mechanics Co., Ltd. | Built-in antenna module of wireless communication terminal |
| US20080172746A1 (en) | 2007-01-17 | 2008-07-17 | Lotter Robert A | Mobile communication device monitoring systems and methods |
| US20080178294A1 (en) | 2006-11-27 | 2008-07-24 | Guoning Hu | Wireless intrusion prevention system and method |
| US20080181116A1 (en) | 2007-01-17 | 2008-07-31 | Richard Thomas Kavanaugh | Quality of service application programming interface over socket |
| US20080196104A1 (en) | 2007-02-09 | 2008-08-14 | George Tuvell | Off-line mms malware scanning system and method |
| US7415270B2 (en) | 2002-02-15 | 2008-08-19 | Telefonaktiebolaget L M Ericsson (Publ) | Middleware services layer for platform system for mobile terminals |
| US20080200160A1 (en) | 2006-09-28 | 2008-08-21 | Dudley Fitzpatrick | Apparatuses, Methods and Systems for Ambiguous Code-Triggered Information Querying and Serving on Mobile Devices |
| US20080209557A1 (en) | 2007-02-28 | 2008-08-28 | Microsoft Corporation | Spyware detection mechanism |
| US20080208950A1 (en) | 2004-08-19 | 2008-08-28 | Sk Telecom Co., Ltd. | Method and Apparatus for Integrating and Managing Information of Mobile Terminal |
| US20080235801A1 (en) | 2007-03-20 | 2008-09-25 | Microsoft Corporation | Combining assessment models and client targeting to identify network security vulnerabilities |
| US20080276111A1 (en) | 2004-09-03 | 2008-11-06 | Jacoby Grant A | Detecting Software Attacks By Monitoring Electric Power Consumption Patterns |
| US20080293396A1 (en) | 2007-05-23 | 2008-11-27 | Robert John Barnes | Integrating Mobile Device Based Communication Session Recordings |
| US7467206B2 (en) | 2002-12-23 | 2008-12-16 | Microsoft Corporation | Reputation system for web services |
| US20080318562A1 (en) | 2007-03-02 | 2008-12-25 | Aegis Mobility, Inc. | System and methods for monitoring the context associated with a mobile communication device |
| US7471954B2 (en) | 2006-02-24 | 2008-12-30 | Skyhook Wireless, Inc. | Methods and systems for estimating a user position in a WLAN positioning system based on user assigned access point locations |
| US7472422B1 (en) | 2003-09-10 | 2008-12-30 | Symantec Corporation | Security management system including feedback and control |
| US7502620B2 (en) | 2005-03-04 | 2009-03-10 | Shyhook Wireless, Inc. | Encoding and compression of a location beacon database |
| US7515578B2 (en) | 2006-05-08 | 2009-04-07 | Skyhook Wireless, Inc. | Estimation of position using WLAN access point radio propagation characteristics in a WLAN positioning system |
| US7525541B2 (en) | 2004-04-05 | 2009-04-28 | Actuality Systems, Inc. | Data processing for three-dimensional displays |
| US7551579B2 (en) | 2006-05-08 | 2009-06-23 | Skyhook Wireless, Inc. | Calculation of quality of wlan access point characterization for use in a wlan positioning system |
| US7551929B2 (en) | 2006-05-08 | 2009-06-23 | Skyhook Wireless, Inc. | Estimation of speed and direction of travel in a WLAN positioning system using multiple position estimations |
| US20090199298A1 (en) | 2007-06-26 | 2009-08-06 | Miliefsky Gary S | Enterprise security management for network equipment |
| US20090205047A1 (en)* | 2008-02-08 | 2009-08-13 | Guy Podjarny | Method and Apparatus for Security Assessment of a Computing Platform |
| US20090248623A1 (en) | 2007-05-09 | 2009-10-01 | The Go Daddy Group, Inc. | Accessing digital identity related reputation data |
| US20090293125A1 (en) | 2008-05-21 | 2009-11-26 | Symantec Corporation | Centralized Scanner Database With Qptimal Definition Distribution Using Network Queries |
| US20100064341A1 (en) | 2006-03-27 | 2010-03-11 | Carlo Aldera | System for Enforcing Security Policies on Mobile Communications Devices |
| US7685132B2 (en) | 2006-03-15 | 2010-03-23 | Mog, Inc | Automatic meta-data sharing of existing media through social networking |
| US7696923B2 (en) | 2005-02-03 | 2010-04-13 | Mexens Intellectual Property Holding Llc | System and method for determining geographic location of wireless computing devices |
| US20100100963A1 (en) | 2008-10-21 | 2010-04-22 | Flexilis, Inc. | System and method for attack and malware prevention |
| US20100100939A1 (en) | 2008-10-21 | 2010-04-22 | Flexilis, Inc. | Secure mobile platform system |
| US20100154032A1 (en) | 2008-12-12 | 2010-06-17 | International Business Machines Corporation | System and Method for Classification of Unwanted or Malicious Software Through the Identification of Encrypted Data Communication |
| US7768963B2 (en) | 2006-07-07 | 2010-08-03 | Skyhook Wireless, Inc. | System and method of improving sampling of WLAN packet information to improve estimates of Doppler frequency of a WLAN positioning device |
| US7774637B1 (en) | 2007-09-05 | 2010-08-10 | Mu Dynamics, Inc. | Meta-instrumentation for security analysis |
| US7809353B2 (en) | 2006-05-18 | 2010-10-05 | Research In Motion Limited | Automatic security action invocation for mobile communications device |
| US7835754B2 (en) | 2006-05-08 | 2010-11-16 | Skyhook Wireless, Inc. | Estimation of speed and direction of travel in a WLAN positioning system |
| US20100313270A1 (en) | 2009-06-05 | 2010-12-09 | The Regents Of The University Of Michigan | System and method for detecting energy consumption anomalies and mobile malware variants |
| US7856373B2 (en) | 2006-09-14 | 2010-12-21 | Shah Ullah | Targeting content to network-enabled devices based upon stored profiles |
| US20100332593A1 (en) | 2009-06-29 | 2010-12-30 | Igor Barash | Systems and methods for operating an anti-malware network on a cloud computing platform |
| US7907966B1 (en) | 2005-07-19 | 2011-03-15 | Aol Inc. | System and method for cross-platform applications on a wireless phone |
| US7999742B2 (en) | 2008-06-06 | 2011-08-16 | Skyhook Wireless, Inc. | System and method for using a satellite positioning system to filter WLAN access points in a hybrid positioning system |
| US8014788B2 (en) | 2006-05-08 | 2011-09-06 | Skyhook Wireless, Inc. | Estimation of speed of travel using the dynamic signal strength variation of multiple WLAN access points |
| US8127358B1 (en) | 2007-05-30 | 2012-02-28 | Trend Micro Incorporated | Thin client for computer security applications |
| US8126456B2 (en) | 2007-01-17 | 2012-02-28 | Eagency, Inc. | Mobile communication device monitoring systems and methods |
| US20120137369A1 (en)* | 2010-11-29 | 2012-05-31 | Infosec Co., Ltd. | Mobile terminal with security functionality and method of implementing the same |
Family Cites Families (21)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US6938174B2 (en) | 2000-10-06 | 2005-08-30 | International Business Machines Corporation | Method and system with adaptive data transfer policy based on a power state of a computing device |
| DE10121549A1 (en)* | 2001-05-03 | 2002-11-14 | Infineon Technologies Ag | Device on GaAs and manufacturing process |
| US7325252B2 (en)* | 2001-05-18 | 2008-01-29 | Achilles Guard Inc. | Network security testing |
| US7020457B2 (en) | 2001-05-31 | 2006-03-28 | Orative Corporation | System and method for proxy-enabling a wireless device to an existing IP-based service |
| US7096006B2 (en) | 2003-03-24 | 2006-08-22 | Inventec Appliances Corp. | Method of playing instant game on wireless network terminal device |
| US7386883B2 (en)* | 2003-07-22 | 2008-06-10 | International Business Machines Corporation | Systems, methods and computer program products for administration of computer security threat countermeasures to a computer system |
| US7346922B2 (en)* | 2003-07-25 | 2008-03-18 | Netclarity, Inc. | Proactive network security system to protect against hackers |
| US7370345B2 (en)* | 2004-03-02 | 2008-05-06 | Lenovo Singapore Pte. Ltd | Domain controlling systems, methods and computer program products for administration of computer security threat countermeasures to a domain of target computer systems |
| JP4268074B2 (en) | 2004-03-05 | 2009-05-27 | 株式会社東海理化電機製作所 | connector |
| US8458793B2 (en)* | 2004-07-13 | 2013-06-04 | International Business Machines Corporation | Methods, computer program products and data structures for intrusion detection, intrusion response and vulnerability remediation across target computer systems |
| US8082506B1 (en)* | 2004-08-12 | 2011-12-20 | Verizon Corporate Services Group Inc. | Geographical vulnerability mitigation response mapping system |
| US20060101517A1 (en)* | 2004-10-28 | 2006-05-11 | Banzhof Carl E | Inventory management-based computer vulnerability resolution system |
| US20060095961A1 (en)* | 2004-10-29 | 2006-05-04 | Priya Govindarajan | Auto-triage of potentially vulnerable network machines |
| US8438643B2 (en)* | 2005-09-22 | 2013-05-07 | Alcatel Lucent | Information system service-level security risk analysis |
| EP1932385B1 (en) | 2005-10-04 | 2013-05-01 | Telefonaktiebolaget L M Ericsson (publ) | Access control in radio access network having pico base stations |
| US7774837B2 (en) | 2006-06-14 | 2010-08-10 | Cipheroptics, Inc. | Securing network traffic by distributing policies in a hierarchy over secure tunnels |
| CN100464992C (en) | 2006-07-11 | 2009-03-04 | 黄建新 | Stamp material and production method thereof |
| KR100817799B1 (en)* | 2006-10-13 | 2008-03-31 | 한국정보보호진흥원 | System and method for integrated network vulnerability analysis using multiple vulnerability checking tools |
| GB2459629A (en)* | 2007-02-16 | 2009-11-04 | Veracode Inc | Assessment and analysis of software security flaws |
| US20100281248A1 (en)* | 2007-02-16 | 2010-11-04 | Lockhart Malcolm W | Assessment and analysis of software security flaws |
| US8881272B2 (en)* | 2009-03-20 | 2014-11-04 | Achilles Guard, Inc. | System and method for selecting and applying filters for intrusion protection system within a vulnerability management system |
- 2009
- 2009-11-18USUS12/621,431patent/US8397301B2/ennot_activeCeased
- 2013
- 2013-12-17USUS14/109,725patent/USRE46768E1/enactiveActive
- 2018
- 2018-02-15USUS15/898,124patent/USRE47757E1/enactiveActive
- 2019
- 2019-10-31USUS16/670,488patent/USRE48669E1/enactiveActive
- 2021
- 2021-08-02USUS17/391,995patent/USRE49634E1/enactiveActive
Patent Citations (198)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US3416032A (en) | 1966-03-23 | 1968-12-10 | Motorola Inc | Lamp dimming circuit |
| US4553257A (en) | 1982-04-28 | 1985-11-12 | Pioneer Electronic Corp. | Automatic sound volume control device |
| US5319776A (en) | 1990-04-19 | 1994-06-07 | Hilgraeve Corporation | In transit detection of computer virus with safeguard |
| US5574775A (en) | 1993-08-04 | 1996-11-12 | Lucent Technologies, Inc. | Universal wireless radiotelephone system |
| US6453345B2 (en) | 1996-11-06 | 2002-09-17 | Datadirect Networks, Inc. | Network security and surveillance system |
| US6269456B1 (en) | 1997-12-31 | 2001-07-31 | Network Associates, Inc. | Method and system for providing automated updating and upgrading of antivirus applications using a computer network |
| US6185689B1 (en) | 1998-06-24 | 2001-02-06 | Richard S. Carson & Assoc., Inc. | Method for network self security assessment |
| US6529143B2 (en) | 1998-10-23 | 2003-03-04 | Nokia Mobile Phones Ltd. | Information retrieval system |
| US6301668B1 (en) | 1998-12-29 | 2001-10-09 | Cisco Technology, Inc. | Method and system for adaptive network security using network vulnerability assessment |
| US7023383B2 (en) | 1999-01-08 | 2006-04-04 | Trueposition, Inc. | Multiple pass location processor |
| US6959184B1 (en) | 1999-06-30 | 2005-10-25 | Lucent Technologies Inc. | Method for determining the security status of transmissions in a telecommunications network |
| US6272353B1 (en) | 1999-08-20 | 2001-08-07 | Siemens Information And Communication Mobile Llc. | Method and system for mobile communications |
| US7020895B2 (en) | 1999-12-24 | 2006-03-28 | F-Secure Oyj | Remote computer virus scanning |
| US20070005327A1 (en) | 2000-01-24 | 2007-01-04 | Radioscape Limited | Digital wireless basestation |
| US20010044339A1 (en) | 2000-02-17 | 2001-11-22 | Angel Cordero | Multi-player computer game, system and method |
| US7236598B2 (en) | 2000-05-23 | 2007-06-26 | Invicta Networks, Inc. | Systems and methods for communication protection |
| US7634800B2 (en) | 2000-06-30 | 2009-12-15 | International Business Machines Corporation | Method and apparatus for network assessment and authentication |
| US20060272011A1 (en) | 2000-06-30 | 2006-11-30 | Internet Security Systems, Inc. | Method and apparatus for network assessment and authentication |
| US7069589B2 (en) | 2000-07-14 | 2006-06-27 | Computer Associates Think, Inc.. | Detection of a class of viral code |
| US20070220608A1 (en) | 2000-08-31 | 2007-09-20 | F-Secure Oyj | Software virus protection |
| US20020042886A1 (en) | 2000-08-31 | 2002-04-11 | Pasi Lahti | Software virus protection |
| US20050237970A1 (en) | 2000-09-14 | 2005-10-27 | Kabushiki Kaisha Toshiba | Packet transfer scheme using mobile terminal and router for preventing attacks using global address |
| US7178166B1 (en) | 2000-09-19 | 2007-02-13 | Internet Security Systems, Inc. | Vulnerability assessment and authentication of a computer by a local scanner |
| US20050015443A1 (en) | 2000-10-10 | 2005-01-20 | Alex Levine | Personal message delivery system |
| US20020087483A1 (en) | 2000-12-29 | 2002-07-04 | Shlomi Harif | System, method and program for creating and distributing processes in a heterogeneous network |
| US6907530B2 (en) | 2001-01-19 | 2005-06-14 | V-One Corporation | Secure internet applications with mobile code |
| US20020108058A1 (en) | 2001-02-08 | 2002-08-08 | Sony Corporation And Sony Electronics Inc. | Anti-theft system for computers and other electronic devices |
| US7325249B2 (en) | 2001-04-30 | 2008-01-29 | Aol Llc | Identifying unwanted electronic messages |
| US20020183060A1 (en) | 2001-05-07 | 2002-12-05 | Lg Electronics Inc. | Map message processing system and method for interworking between heterogeneous networks |
| US7143441B2 (en)* | 2001-05-08 | 2006-11-28 | Aramira Corporation | Wireless device mobile application security system |
| US20030028803A1 (en) | 2001-05-18 | 2003-02-06 | Bunker Nelson Waldo | Network vulnerability assessment system and method |
| US7123933B2 (en) | 2001-05-31 | 2006-10-17 | Orative Corporation | System and method for remote application management of a wireless device |
| US20020191018A1 (en) | 2001-05-31 | 2002-12-19 | International Business Machines Corporation | System and method for implementing a graphical user interface across dissimilar platforms yet retaining similar look and feel |
| US7237264B1 (en) | 2001-06-04 | 2007-06-26 | Internet Security Systems, Inc. | System and method for preventing network misuse |
| US7228566B2 (en) | 2001-07-10 | 2007-06-05 | Core Sdi, Incorporated | Automated computer system security compromise |
| US20070086476A1 (en) | 2001-07-20 | 2007-04-19 | Smartmatic, Corp. | Method for smart device network application infrastructure (SDNA) |
| US20040025042A1 (en) | 2001-08-01 | 2004-02-05 | Networks Associates Technology, Inc. | Malware scanning user interface for wireless devices |
| US6792543B2 (en) | 2001-08-01 | 2004-09-14 | Networks Associates Technology, Inc. | Virus scanning on thin client devices using programmable assembly language |
| US7171690B2 (en) | 2001-08-01 | 2007-01-30 | Mcafee, Inc. | Wireless malware scanning back-end system and method |
| US7861303B2 (en) | 2001-08-01 | 2010-12-28 | Mcafee, Inc. | Malware scanning wireless service agent system and method |
| US20030079145A1 (en) | 2001-08-01 | 2003-04-24 | Networks Associates Technology, Inc. | Platform abstraction layer for a wireless malware scanning engine |
| US7096368B2 (en) | 2001-08-01 | 2006-08-22 | Mcafee, Inc. | Platform abstraction layer for a wireless malware scanning engine |
| US20030046134A1 (en) | 2001-08-28 | 2003-03-06 | Frolick Harry A. | Web-based project management system |
| US7210168B2 (en) | 2001-10-15 | 2007-04-24 | Mcafee, Inc. | Updating malware definition data for mobile data processing devices |
| US20040259532A1 (en) | 2001-10-31 | 2004-12-23 | Markus Isomaki | Method for handling of messages between a terminal and a data network |
| US20030115485A1 (en) | 2001-12-14 | 2003-06-19 | Milliken Walter Clark | Hash-based systems and methods for detecting, preventing, and tracing network worms and viruses |
| US20030120951A1 (en) | 2001-12-21 | 2003-06-26 | Gartside Paul Nicholas | Generating malware definition data for mobile computing devices |
| US7401359B2 (en) | 2001-12-21 | 2008-07-15 | Mcafee, Inc. | Generating malware definition data for mobile computing devices |
| US7308712B2 (en) | 2001-12-31 | 2007-12-11 | Mcafee, Inc. | Automated computer vulnerability resolution system |
| US20030131148A1 (en) | 2002-01-10 | 2003-07-10 | David Kelley | Cross-platform software development with a software development peripheral |
| US20060075388A1 (en) | 2002-01-10 | 2006-04-06 | Microsoft Corporation | Cross-platform software development with and software development peripheral |
| US20050125779A1 (en) | 2002-01-10 | 2005-06-09 | Microsoft Corporation | Cross-platform software development with a software development peripheral |
| US20070011319A1 (en) | 2002-01-15 | 2007-01-11 | Mcclure Stuart C | System and method for network vulnerability detection and reporting |
| US7415270B2 (en) | 2002-02-15 | 2008-08-19 | Telefonaktiebolaget L M Ericsson (Publ) | Middleware services layer for platform system for mobile terminals |
| US7308256B2 (en) | 2002-02-28 | 2007-12-11 | Ntt Docomo, Inc. | Mobile communication terminal, information processing apparatus, relay server apparatus, information processing system, and information processing method |
| US20050154796A1 (en) | 2002-03-06 | 2005-07-14 | Forsyth John M. | Method of enabling a wireless information device to access data services |
| US7266810B2 (en) | 2002-04-09 | 2007-09-04 | Hewlett-Packard Development Company, Lp. | Runtime profiling of platform-independent software applications |
| US20060218482A1 (en) | 2002-04-19 | 2006-09-28 | Droplet Technology, Inc. | Mobile imaging application, device architecture, service platform architecture and services |
| US20040022258A1 (en) | 2002-07-30 | 2004-02-05 | Docomo Communications Laboratories Usa, Inc. | System for providing access control platform service for private networks |
| US20060073820A1 (en) | 2002-10-10 | 2006-04-06 | Craswell Ronald J | Method and apparatus for remote control and updating of wireless mobile devices |
| US7127455B2 (en) | 2002-11-12 | 2006-10-24 | Hewlett-Packard Development Company, L.P. | Taxonomy for mobile e-services |
| US20050074106A1 (en) | 2002-11-14 | 2005-04-07 | Alcatel | Call establishment method |
| US7376969B1 (en) | 2002-12-02 | 2008-05-20 | Arcsight, Inc. | Real time monitoring and analysis of events from multiple network security devices |
| US7467206B2 (en) | 2002-12-23 | 2008-12-16 | Microsoft Corporation | Reputation system for web services |
| US7386297B2 (en) | 2002-12-28 | 2008-06-10 | Curitel Communications, Inc. | Mobile communication system and mobile terminal having function of inactivating mobile communication viruses, and method thereof |
| US20040133624A1 (en) | 2003-01-06 | 2004-07-08 | Seung-Joon Park | Method and apparatus for performing common call processing management using common software platform |
| US7290276B2 (en) | 2003-02-06 | 2007-10-30 | Lenovo Singapore Pte. Ltd. | Information processing apparatus for secure information recovery |
| US20040158741A1 (en) | 2003-02-07 | 2004-08-12 | Peter Schneider | System and method for remote virus scanning in wireless networks |
| US20040185900A1 (en) | 2003-03-20 | 2004-09-23 | Mcelveen William | Cell phone with digital camera and smart buttons and methods for using the phones for security monitoring |
| US7392043B2 (en) | 2003-04-17 | 2008-06-24 | Ntt Docomo, Inc. | API system, method and computer program product for accessing content/security analysis functionality in a mobile communication framework |
| US20050010821A1 (en) | 2003-04-29 | 2005-01-13 | Geoffrey Cooper | Policy-based vulnerability assessment |
| US20040225887A1 (en) | 2003-05-08 | 2004-11-11 | O'neil Douglas R. | Centralized authentication system |
| US7392543B2 (en) | 2003-06-30 | 2008-06-24 | Symantec Corporation | Signature extraction system and method |
| US7356835B2 (en) | 2003-08-26 | 2008-04-08 | Mitel Networks Corporation | Security monitor for PDA attached telephone |
| US7472422B1 (en) | 2003-09-10 | 2008-12-30 | Symantec Corporation | Security management system including feedback and control |
| US20050091308A1 (en) | 2003-09-29 | 2005-04-28 | Peter Bookman | Mobility device |
| US20050076246A1 (en) | 2003-10-01 | 2005-04-07 | Singhal Tara Chand | Method and apparatus for network security using a router based authentication system |
| US20050130627A1 (en) | 2003-11-26 | 2005-06-16 | Benoit Calmels | Authentication between a cellular phone and an access point of a short-range network |
| US20050138413A1 (en) | 2003-12-11 | 2005-06-23 | Richard Lippmann | Network security planning architecture |
| US20050138395A1 (en) | 2003-12-18 | 2005-06-23 | Benco David S. | Network support for mobile handset anti-virus protection |
| US20050197099A1 (en) | 2004-03-08 | 2005-09-08 | Lan-Ver Technologies Solutions Ltd. | Cellular device security apparatus and method |
| US20050282533A1 (en) | 2004-03-22 | 2005-12-22 | Vadim Draluk | Method and apparatus for dynamic extension of device management tree data model on a mobile |
| US20070214504A1 (en) | 2004-03-30 | 2007-09-13 | Paolo Milani Comparetti | Method And System For Network Intrusion Detection, Related Network And Computer Program Product |
| US7525541B2 (en) | 2004-04-05 | 2009-04-28 | Actuality Systems, Inc. | Data processing for three-dimensional displays |
| US20050227669A1 (en) | 2004-04-08 | 2005-10-13 | Ixi Mobile (R&D) Ltd. | Security key management system and method in a mobile communication network |
| WO2005101789A1 (en) | 2004-04-14 | 2005-10-27 | Gurunath Samir Kalekar | A system for real-time network based vulnerability assessment of a host/device |
| US20050254654A1 (en) | 2004-04-19 | 2005-11-17 | The Boeing Company | Security state vector for mobile network platform |
| US20050278777A1 (en) | 2004-06-14 | 2005-12-15 | Hackerproof Security, Inc. | Method and system for enforcing secure network connection |
| US20060026283A1 (en) | 2004-07-30 | 2006-02-02 | Trueba Luis Ruben Z | System and method for updating software on a computer |
| US20080208950A1 (en) | 2004-08-19 | 2008-08-28 | Sk Telecom Co., Ltd. | Method and Apparatus for Integrating and Managing Information of Mobile Terminal |
| US20080276111A1 (en) | 2004-09-03 | 2008-11-06 | Jacoby Grant A | Detecting Software Attacks By Monitoring Electric Power Consumption Patterns |
| US20070016955A1 (en) | 2004-09-24 | 2007-01-18 | Ygor Goldberg | Practical threat analysis |
| US20060080680A1 (en) | 2004-10-12 | 2006-04-13 | Majid Anwar | Platform independent dynamic linking |
| US7414988B2 (en) | 2004-10-29 | 2008-08-19 | Skyhook Wireless, Inc. | Server for updating location beacon database |
| US7305245B2 (en) | 2004-10-29 | 2007-12-04 | Skyhook Wireless, Inc. | Location-based services that choose location algorithms based on number of detected access points within range of user device |
| US8031657B2 (en) | 2004-10-29 | 2011-10-04 | Skyhook Wireless, Inc. | Server for updating location beacon database |
| US7818017B2 (en) | 2004-10-29 | 2010-10-19 | Skyhook Wireless, Inc. | Location-based services that choose location algorithms based on number of detected wireless signal stations within range of user device |
| US20060095454A1 (en) | 2004-10-29 | 2006-05-04 | Texas Instruments Incorporated | System and method for secure collaborative terminal identity authentication between a wireless communication device and a wireless operator |
| WO2006110181A2 (en) | 2004-10-29 | 2006-10-19 | Skyhook Wireless, Inc. | Location beacon database and server, method of building location beacon database, and location based service using same |
| US7769396B2 (en) | 2004-10-29 | 2010-08-03 | Skyhook Wireless, Inc. | Location-based services that choose location algorithms based on number of detected access points within range of user device |
| US7403762B2 (en) | 2004-10-29 | 2008-07-22 | Skyhook Wireless, Inc. | Method and system for building a location beacon database |
| US7433694B2 (en) | 2004-10-29 | 2008-10-07 | Skyhook Wireless, Inc. | Location beacon database |
| US20060101518A1 (en)* | 2004-11-05 | 2006-05-11 | Schumaker Troy T | Method to generate a quantitative measurement of computer security vulnerabilities |
| US20060130145A1 (en) | 2004-11-20 | 2006-06-15 | Choi Byeong C | System and method for analyzing malicious code protocol and generating harmful traffic |
| US20060150256A1 (en) | 2004-12-03 | 2006-07-06 | Whitecell Software Inc. A Delaware Corporation | Secure system for allowing the execution of authorized computer program code |
| US20060150238A1 (en) | 2005-01-04 | 2006-07-06 | Symbol Technologies, Inc. | Method and apparatus of adaptive network policy management for wireless mobile computers |
| US7397424B2 (en) | 2005-02-03 | 2008-07-08 | Mexens Intellectual Property Holding, Llc | System and method for enabling continuous geographic location estimation for wireless computing devices |
| US7696923B2 (en) | 2005-02-03 | 2010-04-13 | Mexens Intellectual Property Holding Llc | System and method for determining geographic location of wireless computing devices |
| US20060179485A1 (en) | 2005-02-09 | 2006-08-10 | Gary Longsine | Intrusion handling system and method for a packet network with dynamic network address utilization |
| US7474897B2 (en) | 2005-02-22 | 2009-01-06 | Skyhook Wireless, Inc. | Continuous data optimization by filtering and positioning systems |
| WO2007081356A2 (en) | 2005-02-22 | 2007-07-19 | Skyhook Wireless, Inc. | Continuous data optimization in positioning system |
| US7493127B2 (en) | 2005-02-22 | 2009-02-17 | Skyhook Wireless, Inc. | Continuous data optimization of new access points in positioning systems |
| US20060224742A1 (en) | 2005-02-28 | 2006-10-05 | Trust Digital | Mobile data security system and methods |
| US7502620B2 (en) | 2005-03-04 | 2009-03-10 | Shyhook Wireless, Inc. | Encoding and compression of a location beacon database |
| US20080046557A1 (en) | 2005-03-23 | 2008-02-21 | Cheng Joseph C | Method and system for designing, implementing, and managing client applications on mobile devices |
| US20060253584A1 (en) | 2005-05-03 | 2006-11-09 | Dixon Christopher J | Reputation of an entity associated with a content item |
| US20060253205A1 (en) | 2005-05-09 | 2006-11-09 | Michael Gardiner | Method and apparatus for tabular process control |
| US20060277408A1 (en) | 2005-06-03 | 2006-12-07 | Bhat Sathyanarayana P | System and method for monitoring and maintaining a wireless device |
| US20060294582A1 (en) | 2005-06-28 | 2006-12-28 | Symbol Technologies, Inc. | Mobility policy manager for mobile computing devices |
| US20070016953A1 (en) | 2005-06-30 | 2007-01-18 | Prevx Limited | Methods and apparatus for dealing with malware |
| US20070015519A1 (en) | 2005-07-12 | 2007-01-18 | Qwest Communications International Inc. | User defined location based notification for a mobile communications device systems and methods |
| US7907966B1 (en) | 2005-07-19 | 2011-03-15 | Aol Inc. | System and method for cross-platform applications on a wireless phone |
| US20070028095A1 (en) | 2005-07-28 | 2007-02-01 | Allen David L | Security certificate management |
| US20070028303A1 (en) | 2005-07-29 | 2007-02-01 | Bit 9, Inc. | Content tracking in a network security system |
| US20070028304A1 (en) | 2005-07-29 | 2007-02-01 | Bit 9, Inc. | Centralized timed analysis in a network security system |
| US20070050471A1 (en) | 2005-08-31 | 2007-03-01 | Microsoft Corporation | Portable Remoting Component With A Scaleable Feature Set |
| US7397434B2 (en) | 2005-09-16 | 2008-07-08 | Samsung Electro-Mechanics Co., Ltd. | Built-in antenna module of wireless communication terminal |
| GB2430588A (en) | 2005-09-20 | 2007-03-28 | Alireza Mousavi Khalkhali | Multiple protocol platform for mobile applications |
| US20070088948A1 (en)* | 2005-10-15 | 2007-04-19 | Huawei Technologies Co., Ltd | Method for implementing security update of mobile station and a correlative reacting system |
| US20070154014A1 (en) | 2005-12-30 | 2007-07-05 | Selim Aissi | Using a trusted-platform-based shared-secret derivation and WWAN infrastructure-based enrollment to establish a secure local channel |
| US20070174472A1 (en) | 2006-01-20 | 2007-07-26 | Verimatrix, Inc. | Network security system and method |
| US20070248047A1 (en) | 2006-01-31 | 2007-10-25 | Peter Shorty | Home electrical device control within a wireless mesh network |
| US20070186282A1 (en) | 2006-02-06 | 2007-08-09 | Microsoft Corporation | Techniques for identifying and managing potentially harmful web traffic |
| US7471954B2 (en) | 2006-02-24 | 2008-12-30 | Skyhook Wireless, Inc. | Methods and systems for estimating a user position in a WLAN positioning system based on user assigned access point locations |
| US7685132B2 (en) | 2006-03-15 | 2010-03-23 | Mog, Inc | Automatic meta-data sharing of existing media through social networking |
| US20100064341A1 (en) | 2006-03-27 | 2010-03-11 | Carlo Aldera | System for Enforcing Security Policies on Mobile Communications Devices |
| US20070240218A1 (en) | 2006-04-06 | 2007-10-11 | George Tuvell | Malware Detection System and Method for Mobile Platforms |
| US20070240221A1 (en) | 2006-04-06 | 2007-10-11 | George Tuvell | Non-Signature Malware Detection System and Method for Mobile Platforms |
| US20070240222A1 (en) | 2006-04-06 | 2007-10-11 | George Tuvell | System and Method for Managing Malware Protection on Mobile Devices |
| US20070250627A1 (en) | 2006-04-21 | 2007-10-25 | May Robert A | Method, apparatus, signals and medium for enforcing compliance with a policy on a client computer |
| US7551579B2 (en) | 2006-05-08 | 2009-06-23 | Skyhook Wireless, Inc. | Calculation of quality of wlan access point characterization for use in a wlan positioning system |
| US7515578B2 (en) | 2006-05-08 | 2009-04-07 | Skyhook Wireless, Inc. | Estimation of position using WLAN access point radio propagation characteristics in a WLAN positioning system |
| US8090386B2 (en) | 2006-05-08 | 2012-01-03 | Skyhook Wireless, Inc. | Estimation of speed and direction of travel in a WLAN positioning system |
| US7551929B2 (en) | 2006-05-08 | 2009-06-23 | Skyhook Wireless, Inc. | Estimation of speed and direction of travel in a WLAN positioning system using multiple position estimations |
| US8014788B2 (en) | 2006-05-08 | 2011-09-06 | Skyhook Wireless, Inc. | Estimation of speed of travel using the dynamic signal strength variation of multiple WLAN access points |
| US7916661B2 (en) | 2006-05-08 | 2011-03-29 | Skyhook Wireless, Inc. | Estimation of position using WLAN access point radio propagation characteristics in a WLAN positioning system |
| US7835754B2 (en) | 2006-05-08 | 2010-11-16 | Skyhook Wireless, Inc. | Estimation of speed and direction of travel in a WLAN positioning system |
| US7809353B2 (en) | 2006-05-18 | 2010-10-05 | Research In Motion Limited | Automatic security action invocation for mobile communications device |
| US20080140767A1 (en) | 2006-06-14 | 2008-06-12 | Prasad Rao | Divitas description protocol and methods therefor |
| US20070293263A1 (en) | 2006-06-14 | 2007-12-20 | Hossein Eslambolchi | Method and apparatus for providing multi-system cellular communications |
| US20070297610A1 (en) | 2006-06-23 | 2007-12-27 | Microsoft Corporation | Data protection for a mobile device |
| US7768963B2 (en) | 2006-07-07 | 2010-08-03 | Skyhook Wireless, Inc. | System and method of improving sampling of WLAN packet information to improve estimates of Doppler frequency of a WLAN positioning device |
| WO2008007111A1 (en) | 2006-07-14 | 2008-01-17 | Vodaphone Group Plc | Telecommunications device security |
| US20080028470A1 (en) | 2006-07-25 | 2008-01-31 | Mark Remington | Systems and Methods for Vulnerability Detection and Scoring with Threat Assessment |
| US20080047007A1 (en) | 2006-08-18 | 2008-02-21 | Microsoft Corporation | Network security page |
| US20080070495A1 (en) | 2006-08-18 | 2008-03-20 | Michael Stricklen | Mobile device management |
| US20080065507A1 (en) | 2006-09-12 | 2008-03-13 | James Morrison | Interactive digital media services |
| US20080109871A1 (en) | 2006-09-13 | 2008-05-08 | Richard Jacobs | Policy management |
| US20080127334A1 (en) | 2006-09-14 | 2008-05-29 | Computer Associates Think, Inc. | System and method for using rules to protect against malware |
| US20080072329A1 (en) | 2006-09-14 | 2008-03-20 | Interdigital Technology Corporation | Method and system for enhancing flow of behavior metrics and evaluation of security of a node |
| US7856373B2 (en) | 2006-09-14 | 2010-12-21 | Shah Ullah | Targeting content to network-enabled devices based upon stored profiles |
| US20080127171A1 (en) | 2006-09-15 | 2008-05-29 | Altiris, Inc. | Method and System for Creating and Executing Generic Software Packages |
| US20080127336A1 (en) | 2006-09-19 | 2008-05-29 | Microsoft Corporation | Automated malware signature generation |
| US20080127179A1 (en) | 2006-09-25 | 2008-05-29 | Barrie Jon Moss | System and apparatus for deployment of application and content to different platforms |
| US20080200160A1 (en) | 2006-09-28 | 2008-08-21 | Dudley Fitzpatrick | Apparatuses, Methods and Systems for Ambiguous Code-Triggered Information Querying and Serving on Mobile Devices |
| US20080086776A1 (en) | 2006-10-06 | 2008-04-10 | George Tuvell | System and method of malware sample collection on mobile networks |
| US20080086773A1 (en) | 2006-10-06 | 2008-04-10 | George Tuvell | System and method of reporting and visualizing malware on mobile networks |
| US20080148381A1 (en) | 2006-10-30 | 2008-06-19 | Jeffrey Aaron | Methods, systems, and computer program products for automatically configuring firewalls |
| WO2008057737A2 (en) | 2006-11-07 | 2008-05-15 | Skyhook Wireless, Inc. | System and method for estimating positioning error within a wlan-based positioning system |
| US8019357B2 (en) | 2006-11-07 | 2011-09-13 | Skyhook Wireless, Inc. | System and method for estimating positioning error within a WLAN-based positioning system |
| US7856234B2 (en) | 2006-11-07 | 2010-12-21 | Skyhook Wireless, Inc. | System and method for estimating positioning error within a WLAN-based positioning system |
| US20080178294A1 (en) | 2006-11-27 | 2008-07-24 | Guoning Hu | Wireless intrusion prevention system and method |
| US20080134281A1 (en) | 2006-11-30 | 2008-06-05 | Mcafee, Inc. | Method and system for enhanced wireless network security |
| US20080132218A1 (en) | 2006-11-30 | 2008-06-05 | Yuval Samson | Method and Apparatus for Starting Applications |
| US8126456B2 (en) | 2007-01-17 | 2012-02-28 | Eagency, Inc. | Mobile communication device monitoring systems and methods |
| US20080172746A1 (en) | 2007-01-17 | 2008-07-17 | Lotter Robert A | Mobile communication device monitoring systems and methods |
| US20080181116A1 (en) | 2007-01-17 | 2008-07-31 | Richard Thomas Kavanaugh | Quality of service application programming interface over socket |
| US20080196104A1 (en) | 2007-02-09 | 2008-08-14 | George Tuvell | Off-line mms malware scanning system and method |
| US20080209557A1 (en) | 2007-02-28 | 2008-08-28 | Microsoft Corporation | Spyware detection mechanism |
| US20080318562A1 (en) | 2007-03-02 | 2008-12-25 | Aegis Mobility, Inc. | System and methods for monitoring the context associated with a mobile communication device |
| US20080235801A1 (en) | 2007-03-20 | 2008-09-25 | Microsoft Corporation | Combining assessment models and client targeting to identify network security vulnerabilities |
| US20090248623A1 (en) | 2007-05-09 | 2009-10-01 | The Go Daddy Group, Inc. | Accessing digital identity related reputation data |
| US20080293396A1 (en) | 2007-05-23 | 2008-11-27 | Robert John Barnes | Integrating Mobile Device Based Communication Session Recordings |
| US8127358B1 (en) | 2007-05-30 | 2012-02-28 | Trend Micro Incorporated | Thin client for computer security applications |
| US20090199298A1 (en) | 2007-06-26 | 2009-08-06 | Miliefsky Gary S | Enterprise security management for network equipment |
| US7774637B1 (en) | 2007-09-05 | 2010-08-10 | Mu Dynamics, Inc. | Meta-instrumentation for security analysis |
| US20090205047A1 (en)* | 2008-02-08 | 2009-08-13 | Guy Podjarny | Method and Apparatus for Security Assessment of a Computing Platform |
| US20090293125A1 (en) | 2008-05-21 | 2009-11-26 | Symantec Corporation | Centralized Scanner Database With Qptimal Definition Distribution Using Network Queries |
| US7999742B2 (en) | 2008-06-06 | 2011-08-16 | Skyhook Wireless, Inc. | System and method for using a satellite positioning system to filter WLAN access points in a hybrid positioning system |
| US8089398B2 (en) | 2008-06-06 | 2012-01-03 | Skyhook Wireless, Inc. | Methods and systems for stationary user detection in a hybrid positioning system |
| US8089399B2 (en) | 2008-06-06 | 2012-01-03 | Skyhook Wireless, Inc. | System and method for refining a WLAN-PS estimated location using satellite measurements in a hybrid positioning system |
| US8054219B2 (en) | 2008-06-06 | 2011-11-08 | Skyhook Wireless, Inc. | Systems and methods for determining position using a WLAN-PS estimated position as an initial position in a hybrid positioning system |
| US20100100939A1 (en) | 2008-10-21 | 2010-04-22 | Flexilis, Inc. | Secure mobile platform system |
| US20100100963A1 (en) | 2008-10-21 | 2010-04-22 | Flexilis, Inc. | System and method for attack and malware prevention |
| US20100154032A1 (en) | 2008-12-12 | 2010-06-17 | International Business Machines Corporation | System and Method for Classification of Unwanted or Malicious Software Through the Identification of Encrypted Data Communication |
| US20100313270A1 (en) | 2009-06-05 | 2010-12-09 | The Regents Of The University Of Michigan | System and method for detecting energy consumption anomalies and mobile malware variants |
| US20100332593A1 (en) | 2009-06-29 | 2010-12-30 | Igor Barash | Systems and methods for operating an anti-malware network on a cloud computing platform |
| US20120137369A1 (en)* | 2010-11-29 | 2012-05-31 | Infosec Co., Ltd. | Mobile terminal with security functionality and method of implementing the same |
Non-Patent Citations (83)
| Title |
|---|
| "Android Cloud to Device Messaging Framework," Google Code Labs, available at <http://code.google.com/android/c2dm/>, retrieved Sep. 14, 2011, 9 pages. |
| "Berry Locator", 2007, Mobireport LLC, 1 page. |
| "BlackBerry Push Service Overview," Dec. 16, 2009, available at <http://us.blackberry.com/developers/platform/pushapi.jsp#tab_tab_resources>, retrieved Sep. 14, 2011, 21 pages. |
| "eSoft unveils SiteFilter 3.0 for OEMs," Infosecurity, Mar. 23, 2010, available at <http://www.infosecurity-magazine.com/view/8273/esoft-unveils-sitefilter-30-for-oems/>, retrieved Mar. 30, 2012, 2 pages. |
| "Firefox", Wikipedia, Jul. 20, 2011, available at <http://en.wikipedia.org/wiki/firefox> Retrieved Aug. 10, 2011, 37 Pages. |
| "F-Secure Mobile Security for S60 Users Guide", F-Secure Corporation 2009, pp. 1-34. |
| "Get the Physical Location of Wireless Router From its MAC Address (BSSID)," Coderrr, Sep. 10, 2008, available at <http://coderrr.wordpress.com/2008/09/10/get-the-physical-location-of-wireless-router-from-its-mac-address-bssid/>, retrieved Mar. 30, 2012, 13 pages. |
| "Hooking-Wikipedia, the Free Encyclopedia," Internet Archive Wayback Machine, Apr. 13, 2010, available at <http://web.archive.org/web/20100415154752/http://en.wikipedia.org/wiki/Hooking>, retrieved Mar. 30, 2012, 6 pages. |
| "Java Virtual Machine", Wikipedia, Aug. 7, 2011, Available at <http://en.wikipedia.org/wiki/Java_Virtual_Machine> Retrieved Aug. 10, 2011, 7 pages. |
| "Kaspersky Mobile Security", Kaspersky Lab 1997-2007, 1 page. |
| "Kaspersky Mobile Security", Kaspersky Lab 2008, available at <http://www.kaspersky.com/kaspersky_mobile_security> Retrieved Sep. 11, 2008, 2 Pages. |
| "Norton Smartphone Security",Symantec, 2007, Available at <http://www.symantec.com/norton/smartphone-security> Retrieved Oct. 21, 2008, 2 pages. |
| "PhoneBak PDA Phone Anti-theft software for your PDA phone", 2007, Bak2u Pte Ltd (Singapore) pp. 1-4. |
| "PhoneBak: Mobile Phone Theft Recovery Software", 2007, Westin Tech. |
| "Pidgin the Universal Chat Client," Pidign, available at <http://www.pidgin.im/>, retrieved Sep. 14, 2011, 14 pages. |
| "Symantec Endpoint Protection", Symantec, 2008, Available at <http://www.symantec.com/business/products/family.jsp?familyid=endpointsecurity>, 6 pages. |
| "Symantec Mobile Security Suite for Windows Mobile", Symantec, 2008 Available at <http://www.symantec.com/business/products/sysreq.jsp?pcid=2241&pvid=mobile_security_suite_1>, 5 pages. |
| "TippingPoint Security Management System (SMS)", TippingPoint, Available at <http://www.tippingpoint.com/products_sms.html>, 2 pages. |
| "Twilio Cloud Communications Web Service API for Building Voice and SMS Applications," Twilio available at <http://www.twilio.com>, retrieved Sep. 14, 2011, 12 pages. |
| "Understanding Direct Push," Microsoft, Feb. 18, 2009, available at <http://technet.microsoft.com/en-us/library/aa997252(v=exchg.80).aspx>, retrieved Mar. 30, 2012, 3 pages. |
| "Urban Airship: Powering Modern Mobile," available at <http://urbanairship.com/products/>, retrieved Sep. 16, 2011, 14 pages. |
| "zVeloDB URL Database," zVelo, available at <https://zvelo.com/technology/zvelodb-url-database>, retrieved Mar. 30, 2012, 2 pages. |
| "Hooking—Wikipedia, the Free Encyclopedia," Internet Archive Wayback Machine, Apr. 13, 2010, available at <http://web.archive.org/web/20100415154752/http://en.wikipedia.org/wiki/Hooking>, retrieved Mar. 30, 2012, 6 pages. |
| Amazon.com: Mining the Web Discovering Knowledge from Hypertext Data (9781558607545): Soumen Chakrabarti: Books, Amazon available at <http://www.amazon.com/exec/obidos/Asin/1558607544/>, retrieved Jun. 7, 2012, pp. 1-7. |
| Clickatell, available at <http://www.clickatell.com>, retrieved Sep. 14, 2011, 11 pages. |
| Diligenti, M., et al., Focused Crawling Using Context Graphs:, Proceedings of the 26th VLDB Conference, Cairo, Egypt, 2000, pp. 1-8. |
| Dolcourt, Jessica; Dashwire: Manage Your Cell Phone on the Web, News Blog, with Jessica Dolocourt, Oct. 29, 2007, 5:00am PDT <http://news.cnet.com/8301-10784_3-9805657-7.html> retrieved Jun. 15, 2009; pp. 1-3. |
| Fette, Ian "Understanding Phishing and Malware Protection in Google Chrome," The Chromium Blog, Nov. 14, 2008, available at <http://blog.chromium.org/2008/11/understanding-phishing-and-malware.htm>, retrieved May 17, 2011, 6 pages. |
| Fisher, Oliver "Malware? We Don't Need No Stinking Malware!," Google, Oct. 24, 2008, available at <http://googlewebmastercentral.blogspot.com/2008/10/malware-we-dont-need-no-stinking.html>, retrieved Mar. 30, 2012, 11 pages. |
| Grafio "Stay Secure", Opera Software, Sep. 29, 2008, Available at <http://widgets.opera.com/widget/4495> Retrieved Oct. 21, 2008, 4 pages. |
| Jeffries, Charles P. "Webroot AntiVirus 2010 With Spy Sweeper Review," Notebook Review, Jun. 22, 2010, available at <http:// http://www.notebookreview.com/default.asp?newsID=5700&review=Webroot+AntiVirus+2010+With+Spy+Sweeper+Review>, retrieved May 18, 2011, 3 pages. |
| Keane, Justin K. "Using the Google Safe Browsing API from PHP," Mad Irish, Aug. 7, 2009, available at <http://www.madirish.net/node/245>, retrieved Mar. 30, 2012, 5 pages. |
| Kincaid, Jason "Urban Airship Brings Easy Push Notifications To Android," TechCrunch, Aug. 10, 2010, available at <http://techcrunch.com/2010/08/10/urban-airship-brings-easy-push-notifications-to-android/>, retrieved Jun. 16, 2011, 5 pages. |
| McAfee, Internet Archive, Way Back Machine, available at <http://web.archive.org/web/20080517102505/www.mcafeesecure.com/us/technology-intro.jsp>, retrieved Feb. 23, 2011, 2 pages. |
| MobileWipe web page, pp. 1-4. |
| Mytton, David "How to Build an Apple Push Notification Provider Server (Tutorial)," Server Density, Jul. 10, 2009, available at <http://blog.serverdensity.com/2009/07/10/how-to-build-an-apple-push-notification-provider-server-tutorial/>, retrieved Apr. 2, 2012, 33 pages. |
| PagerDuty, available at <http://www.pagerduty.com>, retrieved Sep. 14, 2011, 23 pages. |
| PCT International Search Report and Written Opinion of the International Searching Authority for PCT/US2009/061370; dated Dec. 14, 2009; pp. 1-12. |
| PCT International Search Report and Written Opinion of the International Searching Authority for PCT/US2009/061372; dated Mar. 24, 2010; pp. 1-16. |
| PCT International Search Report and Written Opinion of the International Searching Authority for PCT/US2011/049182; dated Dec. 23, 2011; pp. 1-11. |
| Pogue, David "Simplifying the Lives of Web Users," The New York Times, Aug. 18, 2010, available at <http://www.nytimes.com/2010/08/19/technology/personaltech/19pogue.html>, retrieved May 17, 2011, 5 pages. |
| Prey, available at <http://preyproject.com/>, retrieved Jan. 10, 2012, 4 pages. |
| Qualys, "Executive Dashbard," Internet Archive, Way Back Machine, available at <http://web.archive.org/web/20080507161417/ www.qualys.com/products/screens/?screen=Executive + Dashboard>, retrieved Feb. 23, 2011, 1 page. |
| Qualys, "Executive Dashbard," Internet Archive, Way Back Machine, available at <http://web.archive.org/web/20080507161417/www.qualys.com/products/screens/?screen=Executive + Dashboard>, retireved Feb. 23, 2011, 1 page. |
| Qualys, "Vulnerability Management," Internet Archive, Way Back Machine, available at <http://web.archive.org/web/20080611095201/www.qualys.com/solutions/vulnerability_management> Retrieved Feb. 24, 2011, 1 page. |
| Real world Computing, Jun. 16, 2008 (PC Pro), pp. 1-2. |
| Reardon, Marguerite "Mobile Phones That Track Your Buddies," Cnet, Nov. 14, 2006, available at <http://news.cnet.com/Mobile-phones-that-track-your-buddies/2100-1039_3-6135209.html>, retrieved Mar. 30, 2012, 4 pages. |
| Richardson, Alexis "Introduction to RabbitMQ," Google UK, Sep. 25, 2008, available at <http://www.rabbitmq.com/resources/google-tech-talk-final/alexis-google-rabbitmq-talk.pdf>, retrieved Mar. 30, 2012, 33 pages. |
| Simone, "Playing with ActiveMQ," Mostly Useless, Dec. 27, 2007, available at <http://www.mostly-useless.com/blog/2007/12/27/playing-with-activemq/>, retrieved Mar. 30, 2012, 6 pages. |
| Summerson, Cameron "5 Android Antivirus Apps Compared, Find Out Which Ones Are Worth Having!," Android Headlines, Mar. 8, 2011, available at <http://androidheadlines.com/2011/03/5-android-antivirus-apps-comapred-find-out-which-ones-are-worth-having.html>, retrieved Mar. 30, 2012, 9 pages. |
| Teh, Joe, "Norton 360 Version 3.0 Review," Mar. 9, 2009, available at <http://techielobang.com/blog/2009/03/09/norton-360-version-30-review/> retrieved Feb. 23, 2011, 12 pages. |
| Ten, Joe, "Norton 360 Version 3.0 Review," Mar. 9, 2009, available at <http://techielobang.com/blog/2009/03/09/norton-360-version-30-review/> retrieved Feb. 23, 2011, 12 pages. |
| Trillian, available at <http://www.trillian.im/>, retrieved Sep. 14, 2011, 24 pages. |
| U.S. Appl. No. 11/397,521. |
| U.S. Appl. No. 12/255,614. (including Office Action dated Apr. 14, 2011.). |
| U.S. Appl. No. 12/255,614. Prosecution history available via USPTO (including Office Action dated Apr. 14, 2011). |
| U.S. Appl. No. 12/255,621. (including Office Action dated Apr. 13, 2011.). |
| U.S. Appl. No. 12/255,621. Prosecution history available via USPTO (including Office Action dated Apr. 13, 2011). |
| U.S. Appl. No. 12/255,626. (including Office Action dated Feb. 1, 2011.). |
| U.S. Appl. No. 12/255,626. Prosecution history available via USPTO (including Office Action dated Feb. 1, 2011). |
| U.S. Appl. No. 12/255,632. (including office action dated Apr. 13, 2011). |
| U.S. Appl. No. 12/255,635. (including Office Action dated Mar. 24, 2011.). |
| U.S. Appl. No. 12/372,719. |
| U.S. Appl. No. 12/621,431. |
| U.S. Appl. No. 12/868,669. |
| U.S. Appl. No. 12/868,672. |
| U.S. Appl. No. 12/868,676. |
| U.S. Appl. No. 12/876,018. |
| U.S. Appl. No. 13/033,025. |
| U.S. Appl. No. 13/160,382. |
| U.S. Appl. No. 13/160,447. |
| U.S. Appl. No. 13/162,477. |
| U.S. Appl. No. 13/212,055. |
| U.S. Appl. No. 13/267,731. |
| U.S. Appl. No. 13/284,248. |
| U.S. Appl. No. 13/313,937. |
| U.S. Appl. No. 13/314,032. |
| U.S. Appl. No. 13/333,654. |
| U.S. Appl. No. 13/335,779. |
| U.S. Appl. No. 13/410,979. |
| Virus Total, VT Community, www.virustotal.com/index.html; Dated Dec. 16, 2011; 44 Pages. |
| Windows Update, Internet Archive, Way Back Machine, available at <http://web.archive.org/web/200710221913017/http://en.wikipedia.org/wiki/Windows_Update> retrieved Feb. 23, 2011, 3 pages. |
| Windows Update, Internet Archive, Way Back Machine, available at <http://web.archive.org/web/20071022193017/http://en.wikipedia.org/wiki/Windows_Update> retrieved Feb. 23, 2011, 3 pages. |
Cited By (5)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US11461471B2 (en)* | 2018-05-25 | 2022-10-04 | At&T Intellectual Property I, L.P. | Virtual reality for security augmentation in home and office environments |
| US12010517B1 (en)* | 2021-05-10 | 2024-06-11 | Zimperium, Inc. | Dynamic detection for mobile device security |
| US12375923B1 (en) | 2021-05-10 | 2025-07-29 | Zimperium, Inc. | Dynamic detection for mobile device security |
| US20230014136A1 (en)* | 2021-07-16 | 2023-01-19 | Dell Products L.P. | Preemptive protection against malicious array access |
| US11841940B2 (en)* | 2021-07-16 | 2023-12-12 | Dell Products L.P. | Preemptive protection against malicious array access |
Also Published As
| Publication number | Publication date |
|---|---|
| US20110119765A1 (en) | 2011-05-19 |
| USRE48669E1 (en) | 2021-08-03 |
| USRE49634E1 (en) | 2023-08-29 |
| USRE47757E1 (en) | 2019-12-03 |
| US8397301B2 (en) | 2013-03-12 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| USRE49634E1 (en) | System and method for determining the risk of vulnerabilities on a mobile communications device | |
| US9055090B2 (en) | Network based device security and controls | |
| US9407640B2 (en) | Assessing a security state of a mobile communications device to determine access to specific tasks | |
| US8984628B2 (en) | System and method for adverse mobile application identification | |
| US9294500B2 (en) | System and method for creating and applying categorization-based policy to secure a mobile communications device from access to certain data objects | |
| EP2609538B1 (en) | System and method for server-coupled malware prevention | |
| US9740852B2 (en) | System and method for assessing an application to be installed on a mobile communications device | |
| US20140380478A1 (en) | User centric fraud detection | |
| US20180219914A1 (en) | Security via adaptive threat modeling | |
| US9973513B2 (en) | Method and apparatus for communication number update | |
| US12341778B2 (en) | Di chip, smartphone, system, and operating method | |
| EP2661852A1 (en) | Limiting virulence of malicious messages using a proxy server | |
| WO2020000753A1 (en) | Device security monitoring method and apparatus | |
| US12346436B2 (en) | DI chip, communication device, system, and operating method | |
| US20240104200A1 (en) | Systems and methods for identity and access risk reduction informed by risk signaling and device posture | |
| Bhuiyan | Yet Another Symbian Vulnerability Update | |
| HK1185174A (en) | System and method for server-coupled malware prevention |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| AS | Assignment | Owner name:SILICON VALLEY BANK, CALIFORNIA Free format text:SECURITY INTEREST;ASSIGNOR:LOOKOUT, INC.;REEL/FRAME:048208/0947 Effective date:20181026 | |
| AS | Assignment | Owner name:OBSIDIAN AGENCY SERVICES, INC., CALIFORNIA Free format text:SECURITY INTEREST;ASSIGNOR:LOOKOUT, INC.;REEL/FRAME:049408/0861 Effective date:20190606 | |
| MAFP | Maintenance fee payment | Free format text:PAYMENT OF MAINTENANCE FEE, 8TH YR, SMALL ENTITY (ORIGINAL EVENT CODE: M2552); ENTITY STATUS OF PATENT OWNER: SMALL ENTITY Year of fee payment:8 | |
| AS | Assignment | Owner name:LOOKOUT INC., UNITED STATES Free format text:RELEASE BY SECURED PARTY;ASSIGNOR:OBSIDIAN AGENCY SERVICES, INC.;REEL/FRAME:054716/0923 Effective date:20201119 | |
| FEPP | Fee payment procedure | Free format text:ENTITY STATUS SET TO UNDISCOUNTED (ORIGINAL EVENT CODE: BIG.); ENTITY STATUS OF PATENT OWNER: LARGE ENTITY | |
| AS | Assignment | Owner name:LOOKOUT, INC., CALIFORNIA Free format text:RELEASE BY SECURED PARTY;ASSIGNOR:SILICON VALLEY BANK (THE "BANK");REEL/FRAME:059909/0668 Effective date:20220506 Owner name:ALTER DOMUS (US) LLC, ILLINOIS Free format text:SECURITY INTEREST;ASSIGNOR:LOOKOUT, INC.;REEL/FRAME:059909/0764 Effective date:20220506 | |
| AS | Assignment | Owner name:LOOKOUT, INC., CALIFORNIA Free format text:RELEASE OF PATENT SECURITY INTEREST AT REEL 59909 AND FRAME 0764;ASSIGNOR:ALTER DOMUS (US) LLC, AS ADMINISTRATIVE AGENT;REEL/FRAME:063844/0638 Effective date:20230602 | |
| FEPP | Fee payment procedure | Free format text:ENTITY STATUS SET TO SMALL (ORIGINAL EVENT CODE: SMAL); ENTITY STATUS OF PATENT OWNER: SMALL ENTITY | |
| AS | Assignment | Owner name:MIDCAP FINANCIAL TRUST, MARYLAND Free format text:SECURITY INTEREST;ASSIGNOR:LOOKOUT, INC.;REEL/FRAME:068538/0177 Effective date:20240612 | |
| MAFP | Maintenance fee payment | Free format text:PAYMENT OF MAINTENANCE FEE, 12TH YR, SMALL ENTITY (ORIGINAL EVENT CODE: M2553); ENTITY STATUS OF PATENT OWNER: SMALL ENTITY Year of fee payment:12 |