USRE45087E1 - Certificate management and transfer system and method - Google Patents
Certificate management and transfer system and methodDownload PDFInfo
- Publication number
- USRE45087E1 USRE45087E1US13/964,180US201313964180AUSRE45087EUS RE45087 E1USRE45087 E1US RE45087E1US 201313964180 AUS201313964180 AUS 201313964180AUS RE45087 EUSRE45087 EUS RE45087E
- Authority
- US
- United States
- Prior art keywords
- computer system
- certs
- communication device
- cert
- wireless communication
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Expired - Fee Related
Links
Images
Classifications
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W12/00—Security arrangements; Authentication; Protecting privacy or anonymity
- H04W12/06—Authentication
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L67/00—Network arrangements or protocols for supporting network services or applications
- H04L67/01—Protocols
- H04L67/04—Protocols specially adapted for terminals or networks with limited capabilities; specially adapted for terminal portability
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06Q—INFORMATION AND COMMUNICATION TECHNOLOGY [ICT] SPECIALLY ADAPTED FOR ADMINISTRATIVE, COMMERCIAL, FINANCIAL, MANAGERIAL OR SUPERVISORY PURPOSES; SYSTEMS OR METHODS SPECIALLY ADAPTED FOR ADMINISTRATIVE, COMMERCIAL, FINANCIAL, MANAGERIAL OR SUPERVISORY PURPOSES, NOT OTHERWISE PROVIDED FOR
- G06Q10/00—Administration; Management
- G06Q10/10—Office automation; Time management
- G06Q10/107—Computer-aided management of electronic mailing [e-mailing]
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L51/00—User-to-user messaging in packet-switching networks, transmitted according to store-and-forward or real-time protocols, e.g. e-mail
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L51/00—User-to-user messaging in packet-switching networks, transmitted according to store-and-forward or real-time protocols, e.g. e-mail
- H04L51/58—Message adaptation for wireless communication
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/06—Network architectures or network communication protocols for network security for supporting key management in a packet data network
- H04L63/062—Network architectures or network communication protocols for network security for supporting key management in a packet data network for key distribution, e.g. centrally by trusted party
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/08—Network architectures or network communication protocols for network security for authentication of entities
- H04L63/0823—Network architectures or network communication protocols for network security for authentication of entities using certificates
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W12/00—Security arrangements; Authentication; Protecting privacy or anonymity
- H04W12/03—Protecting confidentiality, e.g. by encryption
- H04W12/033—Protecting confidentiality, e.g. by encryption of the user plane, e.g. user's traffic
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W12/00—Security arrangements; Authentication; Protecting privacy or anonymity
- H04W12/04—Key management, e.g. using generic bootstrapping architecture [GBA]
- H04W12/041—Key generation or derivation
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W12/00—Security arrangements; Authentication; Protecting privacy or anonymity
- H04W12/04—Key management, e.g. using generic bootstrapping architecture [GBA]
- H04W12/047—Key management, e.g. using generic bootstrapping architecture [GBA] without using a trusted network node as an anchor
- H04W12/0471—Key exchange
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W12/00—Security arrangements; Authentication; Protecting privacy or anonymity
- H04W12/10—Integrity
- H04W12/106—Packet or message integrity
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L12/00—Data switching networks
- H04L12/02—Details
- H04L12/16—Arrangements for providing special services to substations
- H04L12/18—Arrangements for providing special services to substations for broadcast or conference, e.g. multicast
- H04L12/189—Arrangements for providing special services to substations for broadcast or conference, e.g. multicast in combination with wireless systems
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/02—Network architectures or network communication protocols for network security for separating internal from external traffic, e.g. firewalls
- H04L63/0272—Virtual private networks
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/04—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks
- H04L63/0428—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks wherein the data content is protected, e.g. by encrypting or encapsulating the payload
- H04L63/0442—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks wherein the data content is protected, e.g. by encrypting or encapsulating the payload wherein the sending and receiving network entities apply asymmetric encryption, i.e. different keys for encryption and decryption
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/04—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks
- H04L63/0428—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks wherein the data content is protected, e.g. by encrypting or encapsulating the payload
- H04L63/045—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks wherein the data content is protected, e.g. by encrypting or encapsulating the payload wherein the sending and receiving network entities apply hybrid encryption, i.e. combination of symmetric and asymmetric encryption
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/10—Network architectures or network communication protocols for network security for controlling access to devices or network resources
- H04L63/101—Access control lists [ACL]
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/12—Applying verification of the received information
- H04L63/126—Applying verification of the received information the source of the received data
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W92/00—Interfaces specially adapted for wireless communication networks
- H04W92/16—Interfaces between hierarchically similar devices
- H04W92/18—Interfaces between hierarchically similar devices between terminal devices
Definitions
- This inventionrelates generally to the field of secure electronic messaging and in particular to management and transfer of Certificates between secure messaging clients.
- Certstypically includes the public key of an entity as well as identity information that is bound to the public key with one or more digital signatures.
- S/MIMESecure Multipurpose Internet Mail Extension
- public keysmay be used to encrypt data or messages.
- each messaging clientestablishes communications with a Cert source to obtain any required Certs and manages its own Certs and private keys independently of other messaging clients.
- Certsmust typically be loaded onto each messaging client from the Cert source.
- a method of Cert management and transfer between a first messaging client and a second messaging clientis provided.
- the methodmay include the steps of establishing communications between the first messaging client and the second messaging client, selecting one or more Certs stored on the first messaging client for transfer to the second messaging client, and transferring the selected Certs from the first messaging client to the second messaging client.
- a system for Cert management and transfer between a first messaging client and a second messaging clientmay comprise, at the first messaging client, a first memory comprising a first Cert store configured to store Certs, a first Cert synchronization (sync) system configured to access the first Cert store, and a first communications interface.
- the systemmay include a second memory comprising a second Cert store configured to store Certs, a second Cert sync system configured to access the second Cert store, and a second communications interface compatible with the first communications interface.
- the first Cert sync systemis may also be configured to transfer Certs stored in the first Cert store from the first messaging client to the second messaging client when a communications link is established between the first messaging client and the second messaging client via the first communications interface and the second communications interface.
- a further system, for transferring Certs between a computer system and a wireless mobile communication deviceis also provided.
- the systemmay include a serial port associated with the computer system, a mobile device cradle connected to the serial port, the mobile device cradle having an interface, and a mobile device interface associated with the wireless mobile communication device and compatible with the interface of the mobile device cradle. Certs stored at the computer system may be transferred to the wireless mobile communication device when a communications link is established between the computer system and the wireless mobile communication device by placing the wireless mobile communication device in the mobile device cradle.
- a wireless mobile communication devicemay comprise a wireless transceiver, a messaging system coupled to the wireless transceiver, a communications interface, a Cert store configured to store Certs, and a Cert sync system coupled to the Cert store and the communications interface.
- the messaging systemmay be configured to store Certs received via the wireless transceiver to the Cert store, and the Cert sync system is configured to store Certs received via the communications interface to the Cert store.
- FIG. 1is a block diagram of an exemplary messaging system.
- FIG. 2is a block diagram illustrating a secure e-mail message exchange in a messaging system.
- FIG. 3is a block diagram of a wireless mobile communication device and an associated computer system implementing a Cert management and transfer system.
- FIG. 4is a flow diagram illustrating a method of Cert management and transfer between messaging clients.
- FIG. 5is a block diagram of a wireless mobile communication device as an example of a messaging client in which systems and methods according to aspects of the present invention may be implemented.
- FIG. 6is a block diagram showing an example communication system.
- FIG. 7is a block diagram of an alternative example communication system.
- FIG. 8is a block diagram of another alternative communication system.
- a secure messageis a message that has been processed by a message sender, or possibly an intermediate system between a message sender and a message receiver, to ensure one or more of data confidentiality, data integrity and user authentication.
- Common techniques for secure messaginginclude signing a message with a digital signature and/or encrypting a message.
- a secure messagemay be a message that has been signed, encrypted, encrypted and then signed, or signed and then encrypted by a message sender, according to variants of Secure Multipurpose Internet Mail Extensions (S/MIME).
- S/MIMESecure Multipurpose Internet Mail Extensions
- a messaging clientallows a system on which it operates to receive and possibly also send messages.
- Messaging clientsmay operate on a computer system, a handheld device, or any other system or device with communications capabilities. Many messaging clients also have additional non-messaging functions.
- FIG. 1is a block diagram of an exemplary messaging system.
- the system 10includes a Wide Area Network (WAN) 12 , coupled to a computer system 14 , a wireless network gateway 16 and a corporate Local Area Network (LAN) 18 .
- the wireless network gateway 16is also connected to a wireless communication network 20 in which a wireless mobile communication device 22 (“mobile device”), is configured to operate.
- WANWide Area Network
- LANcorporate Local Area Network
- the computer system 14may be a desktop or laptop PC, which is configured to communicate to the WAN 12 , the Internet for example.
- PCssuch as computer system 14 , normally access the Internet through an Internet Service Provider (ISP), Application Service Provider (ASP) or the like.
- ISPInternet Service Provider
- ASPApplication Service Provider
- the corporate LAN 18is an example of a network-based messaging client. It is normally located behind a security firewall 24 . Within the corporate LAN 30 , a message server 26 , operating on a computer behind the firewall 24 , acts as the primary interface for the corporation to exchange messages both within the LAN 18 , and with other external messaging clients via the WAN 12 .
- Two known message servers 26include, for example, MicrosoftTMExchange Server and Lotus DominoTM. These servers are often used in conjunction with Internet mail routers that typically use UNIX-based Sendmail protocols to route and deliver mail.
- the message server 26may also provide additional functionality, such as dynamic database storage for data like calendars, todo lists, task lists, e-mail and documentation.
- the message server 26provides messaging capabilities to networked computer systems 28 coupled to the LAN 18 .
- a typical LAN 18includes multiple computer systems 28 , each of which implements a messaging client, such as Microsoft OutlookTM, Lotus NotesTM, etc.
- a messaging clientsuch as Microsoft OutlookTM, Lotus NotesTM, etc.
- messagesare received by the message server 26 , distributed to the appropriate mailboxes for user accounts addressed in the received message, and are then accessed by a user through a messaging client operating on a computer system 28 .
- the wireless gateway 16provides an interface to a wireless network 20 , through which messages may be exchanged with a mobile device 22 .
- the mobile device 22may for example be a data communication device, a voice communication device, a dual-mode communication device such as most modem cellular telephones having both data and voice communications functionality, a personal digital assistant (PDA) enabled for wireless communications, or a laptop or desktop computer system with a wireless modem.
- PDApersonal digital assistant
- the wireless gateway 16may be configured to operate with more than one wireless network 20 , in which case the wireless gateway 16 may also determine a most likely network for locating a given mobile device user and possibly track users as they roam between countries or networks.
- Any computer system with access to the WAN 12may exchange messages with the mobile device 22 through the wireless network gateway 16 .
- private wireless network gatewayssuch as wireless Virtual Private Network (VPN) routers could also be implemented to provide a private interface to a wireless network.
- VPNVirtual Private Network
- a wireless VPN implemented in the LAN 18may provide a private interface from the LAN 18 to one or more wireless mobile communication devices 22 through the wireless network 20 .
- Such a private interface to wireless mobile communication devices 22 via the wireless network gateway 16 and/or the wireless network 20may also effectively be extended to entities outside the LAN 18 by providing a message forwarding or redirection system that operates with the message server 26 .
- a message redirection systemis disclosed in U.S. Pat. No.
- incoming messages received by the message server 26 and addressed to a user of a mobile device 22are sent through the wireless network interface, either a wireless VPN router, wireless gateway 16 or other interface for example, to the wireless network 20 and to the user's mobile device 22 .
- Another alternate interface to a user's mailbox on a message server 26may be a Wireless Application Protocol (WAP) gateway.
- WAP gatewayThrough a WAP gateway, a list of messages in a user's mailbox on the message server 26 , and possibly each message or a portion of each message, may be sent to the mobile device 22 .
- a wireless network 20normally delivers messages to and from mobile devices 22 via RF transmissions between base stations and mobile devices 22 .
- the wireless network 20may for example be: (1) a data-centric wireless network, (2) a voice-centric wireless network, or (3) a dual-mode network that can support both voice and data communications over the same infrastructure.
- Recently developed networksinclude: (1) the Code Division Multiple Access (CDMA) network, (2) the Groupe Special Mobile or the Global System for Mobile Communications (GSM) and the General Packet Radio Service (GPRS), both developed by the standards committee of CEPT, and (3) third-generation (3G) networks like Enhanced Data rates for Global Evolution (EDGE) and Universal Mobile Telecommunications Systems (UMTS), which are currently under development.
- CDMACode Division Multiple Access
- GSMGlobal System for Mobile Communications
- GPRSGeneral Packet Radio Service
- 3Gthird-generation
- EDGEEnhanced Data rates for Global Evolution
- UMTSUniversal Mobile Telecommunications Systems
- GPRSis a data overlay on top of the existing GSM wireless network, which is used operating in virtually every country in Europe.
- Some older examples of data-centric networkinclude, but are not limited to: (1) the MobitexTM Radio Network (“Mobitex”), and (2) the DataTACTMRadio Network (“DataTAC”).
- MobitexMobitexTM Radio Network
- DataTACDataTACTMRadio Network
- Examples of known voice-centric data networksinclude Personal Communication Systems (PCS) networks like CDMA, GSM, and Time Division Multiple Access (TDMA) systems that have been available in North America and world-wide for several years.
- PCSPersonal Communication Systems
- TDMATime Division Multiple Access
- the mobile device 22may be a data communication device, a voice communication device, or a multiple-mode device capable of voice, data and other types of communications.
- An exemplary mobile device 22is described in further detail below.
- E-mailis sent by an e-mail sender, possibly through a message server and/or a service provider system, and typically routed through the Internet to one or more message receivers.
- E-mail messagesare normally sent in the clear and use traditional Simple Mail Transfer Protocol (SMTP), RFC822 headers and MIME body parts to define the format of the e-mail message.
- SMTPSimple Mail Transfer Protocol
- RFC822 headersand MIME body parts
- S/MIME and Pretty Good PrivacyTMare two public key secure e-mail messaging protocols that provide for both encryption, to protect data content, and signing, which both protects the integrity of a message and provides for sender authentication by a message receiver.
- Secure messagesmay also be encoded, compressed or otherwise processed in addition to being encrypted and/or signed.
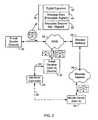
- FIG. 2is a block diagram illustrating a secure e-mail message exchange in a messaging system.
- the systemincludes an e-mail sender 30 , coupled to a WAN 32 and a wireless gateway 34 , which provides an interface between the WAN 32 and a wireless network 36 .
- a mobile device 38is adapted to operate within the wireless network 36 .
- a computer system 31associated with a mobile device 38 or a user of the mobile device 38 as described in further detail below.
- the computer system 31has a communication link 33 to an interface or connector 35 through which information may be exchanged with the mobile device 38 , as indicated by the dashed line 39 .
- the e-mail sender 30may be a PC, such as the system 14 in FIG. 1 , or it may be a network-connected computer, such as computer system 28 .
- the e-mail sender 30may also be a mobile device on which e-mail messages may be composed and sent.
- the WAN 32 , wireless gateway 34 , wireless network 36 and mobile device 38are substantially the same as similarly labelled components in FIG. 1 .
- a messageis encrypted using a one-time session key chosen by the e-mail sender 30 .
- the session keyis used to encrypt the message body and is then itself encrypted using the public key of each addressed message receiver to which the message is to be sent.
- a message encrypted in this wayincludes an encrypted message body 44 and an encrypted session key 46 .
- a message sendersuch as e-mail sender 30 must have access to the public key of each entity to which an encrypted message is to be sent.
- a secure e-mail message sender 30typically signs a message by taking a digest of the message and signing the digest using the sender's private key.
- a digestmay for example be generated by performing a check-sum, Cyclic Redundancy Check (CRC) or some other preferably non-reversible operation such as a hash on the message.
- CRCCyclic Redundancy Check
- This digestis then signed by the sender using the sender's private key.
- the private keymay be used to perform an encryption or other transformation operation on the digest to generate the digest signature.
- a digital signature including the digest and the digest signatureis then appended to the outgoing message.
- a Cert of the senderwhich includes the sender's public key and sender identity information that is bound to the public key with one or more digital signatures, and possibly any chained Certs and Certificate Revocation Lists (CRLs) associated with the sender's Cert and any chained Certs may also be attached to a secure message.
- CTLsCertificate Revocation Lists
- the secure e-mail message 40 sent by the e-mail sender 30may include the digital signature 42 , as well as the encrypted message body 44 and the encrypted session key 46 , both of which are signed.
- the sender's Cert, any chained Certs and one or more CRLsmay also be included in the message 40 .
- Certs, CRLs and digital signaturesare normally placed at the beginning of a message, and the message body is included in a file attachment.
- a secure message 40may include addressing information, such as “To:” and “From:” email addresses, and other header information.
- the secure e-mail message 40When the secure e-mail message 40 is sent from the e-mail sender 30 , it is routed through the WAN 32 to the computer system 31 , which in most cases will be either a PC associated with an e-mail address for user A or a network-connected computer workstation which accesses a mailbox on a messaging server.
- the computer system 31repackages the secure message 40 into an electronic envelope and forwards the repackaged message to the wireless gateway 34 .
- the repackaged messageis then sent through the wireless network 36 to the mobile device 38 .
- the electronic envelopeis then removed from the repackaged message to recover the original secure message 40 , which may then be processed on the mobile device 38 .
- This message repackagingmay involve such operations as compression, encryption and encoding, and will typically be performed by a software module or application operating at the computer system 31 . Where the computer system 31 accesses received e-mail on a messaging server however, the repackaging operations may be performed at the messaging server or possibly another system operating in conjunction with the messaging server. At the mobile device 38 , inverse operations are similarly performed by an unpackaging system or software module.
- the computer system 31is shown as receiving the secure message 40 , repackaging the message and then sending the repackaged message to the mobile device 38 in the illustrative example system of FIG. 2 , other implementations are also possible.
- the mobile device 38may be addressable directly, in which case the message 40 is routed to the wireless gateway 34 instead of to the computer system 31 .
- the wireless gateway 34then performs any required address translation, encoding or similar functions, if any, and sends the message through the wireless network 36 to the mobile device 38 .
- the messagemay be routed or forwarded to the mobile device 38 through other transport mechanisms than the wireless gateway 34 .
- routing to the wireless network 36may be accomplished using a wireless VPN router associated with the e-mail sender 30 , or, in the case of a message being received at a computer system 31 and then forwarded to the mobile device 38 , with the computer system 31 .
- Each receiver of a signed messagemay verify the digital signature 42 by generating a digest of the message body 44 and encrypted session key 46 , extracting the digest from the digital signature 42 , comparing the generated digest with the digest extracted from the digital signature 42 , and verifying the digest signature in the digital signature 42 .
- the digest algorithm used by a secure message receiveris the same as the algorithm used by the message sender, and may be specified for example in a message header or possibly in the digital signature 42 .
- One commonly used digest algorithmis the so-called Secure Hashing Algorithm 1 (SHA1), although other digest algorithms such as Message-Digest Algorithm 5 (MD5) may also be used.
- SHA1Secure Hashing Algorithm 1
- MD5Message-Digest Algorithm 5
- a message receiverIn order to verify the digest signature 42 , a message receiver must retrieve the sender's public key and verify the signature on the digest in the digital signature 42 by performing a reverse transformation on the digest signature. For example, if the message sender generated the digest signature by encrypting the digest using its private key, then a receiver would use the sender's public key to decrypt the digest signature to recover the original digest. If a secure message includes the sender's Cert, then the sender's public key may be extracted from the Cert. The sender's public key may instead be retrieved from a local store, for example where the public key was extracted from an earlier message from the sender and stored in a key store in the receiver's local store.
- the public keymay be retrieved from the sender's Cert if it is stored in the local store, or from a Public Key Server (PKS).
- PKSis a server that is normally associated with a Certificate Authority (CA) from which a Cert for an entity, including the entity's public key, is available.
- CACertificate Authority
- a PKSmight reside within a corporate LAN such as 18 ( FIG. 1 ), or anywhere on the WAN 32 , Internet or other network or system through which message receivers may establish communications with the PKS.
- a sender's Certmay be loaded onto a mobile device 38 from an associated computer system 31 , as described in further detail below.
- a digest algorithmis preferably a non-reversible function that produces a unique output for every unique input. Therefore, if an original message is changed or corrupted, then the digest generated by the receiver will be different from the digest extracted from the digital signature, and signature verification therefore fails. Because digest algorithms are publicly known, however, it is possible that an entity may alter a secure message, generate a new digest of the altered message, and forward the altered message to any addressed message receivers. In this case, the digest generated at the receiver on the basis of the altered message will match the new digest that was added by the entity that altered the message. The digest signature check is intended to prevent verification of a digital signature in such a situation.
- the encrypted message body 44When the digital signature 42 has been verified, or sometimes even if digital signature verification fails, the encrypted message body 44 must then be decrypted before it can be displayed or further processed by a receiving messaging client, the computer system 31 and the mobile device 38 in FIG. 2 .
- a message receiveruses its private key to decrypt the encrypted session key 46 and then uses the decrypted session key to decrypt the encrypted message body 44 and thereby recover the original message.
- An encrypted message that is addressed to more than one receiverwould include an encrypted version of the session key for each receiver that was encrypted using the public key of the receiver. Each receiver would perform the same digital signature verification operations, but would decrypt a different one of the encrypted session keys using its own private key.
- a sending messaging clientmust have access the public key of any receiver to which an encrypted message is to be sent.
- a receiving messaging clientmust be able to retrieve the sender's public key, which may be available to a messaging client through various mechanisms, in order to verify a digital signature in a signed message.
- the mobile device 38is a receiver of the secure message 40 , the mobile device 38 may be enabled for two-way communications, and may therefore require public keys for both message sending and message receiving operations.
- CertsPublic keys are commonly provided in Certs. As described above, a Cert for any particular entity typically includes the entity's public key and identification information that is bound to the public key with a digital signature. Several types of Cert currently in widespread use, including for example X.509 Certs which are typically used in S/MIME. PGP uses Certs with a slightly different format. Systems and methods according to aspects of the present invention may be used with any of these types of Cert, as well as other types of Cert, both currently known types as well as others that may be developed.
- the digital signature in a Certis generated by the issuer of the Cert, and can be checked by a message receiver substantially as described above.
- a Certsometimes includes an expiry time or validity period from which a messaging client may determine if the Cert has expired. Verification of the validity of a Cert may also involve tracing a certification path through a Cert chain, which includes a user's Cert as well as possibly other Certs to verify that the user's Cert is authentic. A Cert may also be checked against a CRL to ensure that the Cert has not been revoked.
- the public key in the Certis assumed to be the public key of the entity for which the Cert was issued, also referred to as the subject of the Cert.
- Certsmay be available to a messaging client from several sources. When a Cert is attached to a received message, the Cert can be extracted from the message and stored by the messaging client. Otherwise, Certs can be requested and downloaded from a PKS on a LAN, the Internet or other network with which a requestor may establish communications. Alternatively, according to an aspect of the present invention, a messaging client may load Certs from other sources than a PKS. Many modem mobile devices are configured for connection to a PC. By connecting such a devices to a PC to download Certs via a physical connection such as a serial port or USB port, over-the-air transfer of Certs may be reduced.
- CertsFor entities to which a user expects to send encrypted messages, then these Certs need not be downloaded when encrypted messages are to be sent to any of these entities.
- a usermay similarly load Certs for any entities from which signed messages are expected to be received, such that digital signatures may be verified even if one of these entities does not append its Cert to a signed message.
- any Certmust be requested from a Cert source and stored on each messaging client. Certs are not normally shared between messaging clients, even when the messaging clients are associated with the same user.
- user Arequires a Cert for another entity
- user Bon both the computer system 31 and the mobile device 38
- user B's Certmust be requested and loaded twice—once for the computer system 31 and again for the mobile device 38 .
- user B's Certneed be requested and loaded on only one of the computer system 31 and the mobile device 38 .
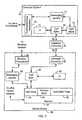
- FIG. 3is a block diagram of a mobile device and an associated computer system implementing a Cert management and transfer system.
- the computer system 31 and a mobile device 38are illustrative examples of a first messaging client and a second messaging between which Certs may be transferred.
- the first and second messaging clientscould also possibly be two mobile devices or two computer systems.
- a mobile device 38 incorporating a Cert management and transfer systemcomprises a memory 52 , a messaging system 60 , a Cert synchronization (sync) system 62 , a user interface (UI) 64 , a wireless transceiver 66 , and an interface or connector 68 .
- the memory 52preferably includes a storage area for a Cert store 54 , as well as possibly other data stores such as an address book 56 in which messaging contact information is stored, and an application data storage area 58 which stores data associated with software applications on the mobile device 38 .
- Data stores 56 and 58are illustrative examples of stores that may be implemented in a memory 52 on mobile device 38 .
- the memory 52may also be used by other device systems in addition to those shown in FIG. 3 to store other types of data.
- the memory 52is a writeable store such as a RAM into which other device components may write data.
- the Cert store 54is a storage area dedicated to storage of Certs on the mobile device 38 . Certs may be stored in the Cert store 54 in the format in which they are received, or may alternatively be parsed or otherwise translated into a storage format before being written to the store 54 .
- the messaging system 60is connected to the wireless transceiver 66 and is thus enabled for communications via a wireless network.
- the Cert sync system 62is connected to the interface/connector 68 to allow communication with the computer system 31 , through the cooperating interface/connector 35 and connections 39 and 33 .
- the UI 64may include such UI components as a keyboard or keypad, a display, or other components which may accept inputs from or provide outputs to a user of the mobile device 38 . Although shown as a single block in FIG. 3 , it should be apparent that a mobile device 38 typically includes more than one UI, and the UI 64 is therefore intended to represent one or more user interfaces.
- the computer system 31includes a physical connection 33 through which Certs may be transferred to the mobile device 38 via the interface or connector 35 . Although shown in FIG. 3 as an external component, the interface/connector 35 may alternatively be internal to the computer system 31 .
- the computer system 31includes a Cert sync system 70 , which in most implementations will be a software application.
- the Cert sync system 70interfaces with a UI 71 , which may include one or more input and output components, the connection 33 and the Cert store 72 .
- the Cert store 72could possibly be any computer storage medium, including for example a local hard disk drive or other memory unit.
- Certswhich are public information, could also be shared between computer systems within a network for example, such that the store 72 is external but accessible to the computer system 31 , for example on a network file server.
- the messaging system 70is connected to both the Cert store 72 and the communications subsystem 76 .
- a messaging client implementing a Cert management and transfer systemmay still preferably retrieve Certs in a conventional manner. This is represented in FIG. 3 by the connections between the messaging systems 60 , 74 , Cert stores 54 , 72 and a communication system, either the wireless transceiver 66 or communications subsystem 76 . Therefore, when the messaging system 60 on the mobile device 38 requires a public key for a sender of a received message or an addressee of a message to be sent, a Cert may be requested and received, from a PKS for example, through the wireless transceiver 66 . When a Cert is appended to a received message, the messaging system 60 may extract the Cert from the message and store the Cert to the Cert store 54 . The computer system 31 may perform similar operations to obtain any required Certs.
- a user of a Cert storage and transfer system as shown in FIG. 3can also preferably select and transfer Certs to a mobile device 38 from the computer system 31 , or from the mobile device 38 to the computer system 31 , via a communication link established between the interfaces or connectors 68 and 35 .
- the interfaces or connectors 68 and 35could be any of a plurality of compatible data transfer components, including for example optical data transfer interfaces such as Infrared Data Association (IrDA) ports, other short-range wireless communications interfaces, or wired interfaces such serial or Universal Serial Bus (USB) and connections.
- Known short-range wireless communications interfacesinclude, for example, “Bluetooth” modules and 802.11 modules according to the Bluetooth or 802.11 specifications, respectively. It will be apparent to those skilled in the art that Bluetooth and 802.11 denote sets of specifications, available from the Institute of Electrical and Electronics Engineers (IEEE), relating to wireless LANs and wireless personal area networks, respectively.
- references to connecting a mobile device to an associated computerincludes establishing communications between a computer system and a mobile device through either physical connections or wireless transfer schemes.
- the mobile device 38could be connected to the computer system 31 by placing the mobile device 38 in a mobile device cradle connected to a serial port on the computer system 31 , by positioning the mobile device 38 such that an optical port thereof is in a line of sight of a similar port of the computer system 31 , or by physically connecting or arranging the mobile device 38 and computer system 31 in some other manner so that data may be exchanged.
- the particular operations involved in establishing communications between a mobile device and a computer systemwill be dependent upon the types of Interfaces and/or connectors.
- the Cert sync system 70is preferably automatically started. Other operations may also be automatically executed when the mobile device 38 is connected to the computer system 31 , preferably in accordance with user-specified settings established at the computer system 31 , the mobile device 38 , or both.
- the Cert sync system 70may access the Cert store 72 to determine which Certs are stored therein.
- the Cert sync system 70then preferably generates a list of stored Certs on a UI 71 , preferably a display screen, on the computer system 31 .
- Certscould be listed for example in the order in which they are stored in the Cert store 72 , in order of frequency of use, in alphabetical order of the name of the entity for which the Cert was issued (i.e. the subject name) or any other default or user-configured order.
- Certsare preferably identified by subject name, or if contact information for the subject of a Cert is stored in an address book or similar contact information store on the computer system 31 , a Cert could alternatively be identified using a portion of the contact information such as a familiar name for example.
- a usermay then choose which of the Certs stored on the computer system 31 should be transferred to the mobile device 38 , using a mouse, keyboard or other input device that may be implemented as a UI 71 associated with the computer system 31 .
- the selected Certsare then transferred to the mobile device 38 via the connections and interfaces 33 , 35 , 39 , 68 .
- a Cert transfer operationmay for example be an add operation, to add selected Certs to the Cert store 54 on the mobile device 38 , an update operation, for example to replace an expired Cert in the Cert store 54 on the mobile device 38 with a selected Cert or to replace a less frequently used Cert with one that is or is expected to be more frequently used, or a replace all operation, in which all Certs in the Cert store on the mobile device 38 are deleted and the selected Certs are stored to the Cert store 54 .
- Other types of Cert transfersare also possible and may be selectable or configurable using the Cert sync system 70 , the Cert sync system 62 , or both.
- Certsare received by the Cert sync system 62 and processed according to the type of transfer operation selected by the user to store transferred Certs to the Cert store 54 .
- Transferred Certsmay be added to the store in addition to (add operation) or instead of (update operation) Certs already stored in the Cert store 54 or after the Certs in the Cert store 54 have been deleted (replace all operation).
- a message sender or an intermediate system through which messages are sent to the mobile device 38need not send Certs along with secure messages to the mobile device 38 .
- An intermediate systemmay also strip Certs and possibly other relatively bulky information from a received secure message before it is sent to the mobile device 38 if the Certs have already been transferred to the mobile device 38 .
- Cert store 54may have sufficient space to store only a certain number of Certs. When the Cert store 54 is full, no new Certs can be transferred from the computer system 31 to the Cert store 54 unless one or more existing Certs in the Cert store 54 are overwritten or deleted. Cert store 54 overflow could be handled by either the mobile device Cert sync system 62 , the computer system Cert sync system 70 , or both.
- the Cert sync system 62 in the mobile device 38may be configured to implement a least recently used (LRU) replacement policy in the Cert store 54 , whereby a least recently used Cert will automatically be overwritten if a new Cert is to be loaded into the mobile device 38 when the Cert store 54 is full.
- the Cert sync system 62may be configured to alert the Cert sync system 70 if the Cert store 54 is or becomes full while the mobile device 38 and computer system 31 are connected. An alert could also or instead be returned to the Cert sync system 70 when a user attempts to add a Cert to a full Cert store 54 .
- the usercould then be prompted via a UI 71 to choose whether or not a Cert in the Cert store 54 should be replaced with the Cert to be added and if so, possibly to select a Cert that should be replaced.
- a UI 71may also allow a user to abort an add operation when a Cert store 54 is full.
- the Cert sync system 70 on the computer system 31may also check each Cert in the Cert store 72 to ensure that only valid Certs are transferred to the mobile device 38 . This may involve checking one or more CRLs, an expiry time or validity period, and possibly submitting a status inquiry to an external system (not shown) for each Cert. Any Certs that have expired or are no longer valid may be deleted from the Cert store 72 and are preferably not included in the Cert list generated by the Cert sync system 70 .
- Detection of an expired or invalid Cert in the Cert store 72may also trigger either a request for a new Cert for the entity identified in the subject name or like field of the expired or invalid Cert, or a user prompt to select a further action, such as request a new Cert or simply delete the expired or invalid Cert without requesting a new one.
- Cert sync system 70If the messaging system 74 or another component in the computer system 31 periodically checks the status of all stored Certs, then a status check by the Cert sync system 70 might not be necessary every time that the mobile device is connected to the computer system 31 . In either case, a user can be assured that Certs transferred from the computer system 31 to the mobile device 38 are valid at the time of transfer. However, due primarily to the size of CRLs, processing loads associated with Cert status checking and network latency when Cert status information must be requested from an external source, Cert status checking on a mobile device 38 tends to be problematic and therefore is not commonly performed. Although valid at the time of transfer, Certs in the Cert store 54 that expire, are revoked or become invalid after the time of transfer might not always be detected on a mobile device 38 .
- Cert management systems and methodsmay alleviate this problem of expired, revoked or invalid Certs in the Cert store 54 of the mobile device 38 .
- the Cert sync systems 62 and 70can exchange Cert information between the mobile device 38 and computer system 31 .
- the Cert sync system 62similar to the Cert sync system 70 as described above, is preferably configured to access the Cert store 54 to generate at least a list of Certs stored in the Cert store 54 when the mobile device 38 is connected to the computer system 31 .
- a copy of the Certs in the Cert store 54may be passed to the Cert sync system 70 .
- the list or complete Certsmay be passed to the Cert sync system 70 either automatically or in response to a request to the Cert sync system 62 from the Cert sync system 70 .
- the Cert sync system 70uses information in the list or Certs, as well as any CRLs, expiry times or validity periods and any information from external sources if required, the Cert sync system 70 checks the status of each Cert.
- the Cert sync system 70preferably retrieves a new Cert to replace the expired Cert, from either its own Cert store 72 or an external Cert source. Alternatively, a user may be prompted (via a UI 71 or 64 ) to select whether the Cert should tie deleted from the Cert store 54 or a new Cert should be retrieved. The Cert sync system 62 then either deletes or replaces the expired, revoked or invalid Cert with a new Cert from the computer system 31 .
- Either the mobile device 38 or the computer system 31preferably maintains a record of at least the most recent Cert check for Certs on the mobile device 38 , such that the frequency of Cert checking for Certs stored on the mobile device 38 is controllable.
- this Cert check recordis accessed to determine if the Certs stored in the Cert store 54 should be checked.
- Coordinated operation of the Cert sync systems 62 and 70also provides for further Cert management functions. Since the Cert sync system 70 has access to both its own Cert store 72 and, through the Cert sync system 62 , the mobile device Cert store 54 , separate lists of Certs stored at the computer system 31 and the mobile device 38 may be generated and displayed to a user. The user can then easily determine which Certs have already been loaded onto the mobile device 38 . Alternatively, Certs that are stored in the mobile device Cert store 54 may be removed from the list of Certs that are stored in the Cert store 72 , such that only those Certs available in the Cert store 72 that are not stored in the mobile device Cert store 54 are displayed for selection and transfer to the mobile device 38 .
- a list of Certs stored in the mobile device Cert store 54is displayed to a user on the computer system 31 , the user is better able to manage the Certs in the mobile device store 54 .
- a usermay select a Cert from the device list for deletion, and can also determine how many Certs are stored on the mobile device 38 and possibly how much space is remaining in the Cert store 54 .
- Certsmay also be transferred from the mobile device 38 to the computer system 31 .
- both the computer system 31 and the mobile device 38may retrieve Certs from a variety of sources.
- the computer system 31 and the mobile device 38may receive secure messages from different senders and thus require different Certs to process the messages. Different Certs may also be required to send secure messages to different recipients.
- the mobile device 38may retrieve the Cert from another source via a wireless network for example.
- the mobile device Cert store 54contains a Cert that might not be available in the Cert store 72 of the computer system 31 .
- Such a Certmay be transferred from the mobile device 38 to the computer system 31 substantially as described above.
- the mobile device UI 64includes a display screen and one or more input devices such as a keyboard, thumbwheel and the like
- Cert management and transfer operationscould be controlled by the Cert sync system 62 .
- both the mobile device 38 and the computer system 31preferably revert to a normal operating mode.
- the Cert sync-systems 62 and 70are embodied as software applications, the applications may be closed or may instead end automatically after selected Certs have been transferred.
- the Cert sync systems 62 , 70may also be configured to start only when one or each of the sync systems is invoked by a user instead of automatically when the mobile device 38 is connected to the computer system 31 .
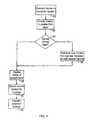
- FIG. 4is a flow diagram illustrating a method of Cert management and transfer between messaging clients.
- a mobile device and a computer systemare used as illustrative examples of a first messaging client and a second messaging client which implement a Cert management and transfer method, although as described above in conjunction with FIG. 3 , Certs may also be exchanged between mobile devices or between multiple computer systems.
- Step 80when a mobile device is connected to a computer system.
- Step 80involves establishing communications between the mobile device and the computer system, for example via a physical link such as a serial or USB connection or a wireless link such as an optical, Bluetooth, 802.11 or other short-range communication link.
- the computer systemmay check the status of any Certs stored in a Cert store on the mobile device, and possibly retrieve a new Cert for each expired, revoked or invalid Cert in the mobile device Cert store, as described above.
- Step 86may be automatic or may alternatively be dependent upon a user response to a prompt or alert generated when one or more of the Certs stored on the mobile device are found to be expired, revoked or invalid.
- a list of Certs stored in a Cert store on the computer systemis generated and displayed to the user, at step 88 .
- a list of the Certs stored at each messaging clientmay be displayed to a user. The user may then select one or more stored Certs from either of the lists at step 90 and the selected Certs are transferred from one messaging client to the other messaging client at step 92 . Steps 90 and 92 may be repeated for each selected Cert.
- a usermay select a plurality of Certs at step 90 and transfer each Cert at step 92 without requiring further action on the part of the user.
- the Cert transfer at step 92may be from the computer system to the mobile device or from the mobile device to the computer system. Cert selection and transfer steps 90 and 92 may be repeated as often as necessary to perform desired Cert transfer operations. Cert store overflow handling may be configurable, for example according to an LRU replacement policy, or in response to a further user selection to replace a stored Cert or abort the Cert transfer operation.
- Cert loading from a remote source to a computer systemis a relatively fast and simple process. Therefore, most Cert transfers at step 92 will likely be from the computer system to the mobile device be to the mobile device. However, Cert transfers between computer systems is also possible, when Certs are to be managed and/or shared between computer systems. Sharing of Certs between computer systems within a corporate LAN for example would minimize communications with external PKSs or other Cert sources for any Certs that have been retrieved from the external sources by a computer system within the LAN.
- Cert transfers at step 92may add selected Certs to a Cert store on a messaging client or replace any or all of the Certs in the Cert store on the messaging client, as described above.
- other Cert management operations than Cert transfersmay also be performed after lists of stored Certs are generated and displayed at step 88 .
- Certsmay be selected for deletion or other operations than transfer to another messaging client.
- FIG. 5is a block diagram of a wireless mobile communication device as an example of a messaging client in which the present invention may be implemented.
- the mobile device 500is preferably a two-way communication device having at least voice and data communication capabilities.
- the mobile device 500preferably has the capability to communicate with other computer systems on the Internet.
- the mobile devicemay be referred to as a data messaging device, a two-way pager, a cellular telephone with data messaging capabilities, a wireless Internet appliance, or a data communication device (with or without telephony capabilities).
- a data messaging devicea two-way pager
- a cellular telephone with data messaging capabilitiesa wireless Internet appliance
- a data communication devicewith or without telephony capabilities
- the mobile device 500includes a transceiver 511 , a microprocessor 538 , a display 522 , Flash memory 524 , RAM 526 , auxiliary input/output (I/O) devices 528 , a serial port 530 , a keyboard 532 , a speaker 534 , a microphone 536 , a short-range wireless communications sub-system 540 , and may also include other device sub-systems 542 .
- the transceiver 511preferably includes transmit and receive antennas 516 , 518 , a receiver (Rx) 512 , a transmitter (Tx) 514 , one or more local oscillators (LOs) 513 , and a digital signal processor (DSP) 520 .
- the mobile device 500preferably includes a plurality of software modules 524 A- 524 N that can be executed by the microprocessor 538 (and/or the DSP 520 ), including a voice communication module 524 A, a data communication module 524 B, and a plurality of other operational modules 524 N for carrying out a plurality of other functions.
- the mobile device 500is preferably a two-way communication device having voice and data communication capabilities.
- the mobile device 500may communicate over a voice network, such as any of the analog or digital cellular networks, and may also communicate over a data network.
- the voice and data networksare depicted FIG. 5 by the communication tower 519 .
- These voice and data networksmay be separate communication networks using separate infrastructure, such as base stations, network controllers, etc., or they may be integrated into a single wireless network. References to the network 519 should therefore be interpreted as encompassing both a single voice and data network and separate networks.
- the communication subsystem 511is used to communicate with the network 519 .
- the DSP 520is used to send and receive communication signals to and from the transmitter 514 and receiver 512 , and may also exchange control information with the transmitter 514 and receiver 512 . If the voice and data communications occur at a single frequency, or closely-spaced set of frequencies, then a single LO 513 may be used in conjunction with the transmitter 514 and receiver 512 . Alternatively, if different frequencies are utilized for voice communications versus data communications, then a plurality of LOs 513 can be used to generate a plurality of frequencies corresponding to the network 519 . Although two antennas 516 , 518 are depicted in FIG. 5 , the mobile device 500 could be used with a single antenna structure. Information, which includes both voice and data information, is communicated to and from the communication module 511 via a link between the DSP 520 and the microprocessor 538 .
- the detailed design of the communication subsystem 511such as frequency band, component selection, power level, etc., will be dependent upon the communication network 519 in which the mobile device 500 is intended to operate.
- a mobile device 500 intended to operate in a North American marketmay include a communication subsystem 511 designed to operate with the Mobitex or DataTAC mobile data communication networks and also designed to operated with any of a variety of voice communication networks, such as AMPS, TDMA, CDMA, PCS, etc., whereas a mobile device 500 intended for use in Europe may be configured to operate with the GPRS data communication network and the GSM voice communication network.
- Other types of data and voice networks, both separate and integrated,may also be utilized with the mobile device 500 .
- the access requirements for the mobile device 500may also vary.
- mobile devicesare registered on the network using a unique identification number associated with each device.
- network accessis associated with a subscriber or user of the mobile device 500 .
- a GPRS devicetypically requires a subscriber identity module (“SIM”), which is required in order to operate the mobile device 500 on a GPRS network.
- SIMsubscriber identity module
- Local or non-network communication functionsmay be operable, without the SIM, but the mobile device 500 will be unable to carry out any functions involving communications over the network 519 , other than any legally required operations, such as ‘911’ emergency calling.
- the mobile device 500may send and receive communication signals, preferably including both voice and data signals, over the network 519 .
- Signals received by the antenna 516 from the communication network 519are routed to the receiver 512 , which provides for signal amplification, frequency down conversion, filtering, channel selection, etc., and may also provide analog to digital conversion. Analog to digital conversion of the received signal allows more complex communication functions, such as digital demodulation and decoding to be performed using the DSP 520 .
- signals to be transmitted to the network 519are processed, including modulation and encoding, for example, by the DSP 520 and are then provided to the transmitter 514 for digital to analog conversion, frequency up conversion, filtering, amplification and transmission to the communication network 519 via the antenna 518 .
- a single transceiver 511is shown in FIG. 5 for both voice and data communications, it is possible that the mobile device 500 may include two distinct transceivers, a first transceiver for transmitting and receiving voice signals, and a second transceiver for transmitting and receiving data signals.
- the DSP 520may also provide for receiver and transmitter control.
- the gain levels applied to communication signals in the receiver 512 and transmitter 514may be adaptively controlled through automatic gain control algorithms implemented in the DSP 520 .
- Other transceiver control algorithmscould also be implemented in the DSP 520 in order to provide more sophisticated control of the transceiver 511 .
- the microprocessor 538preferably manages and controls the overall operation of the mobile device 500 .
- Many types of microprocessors or microcontrollerscould be used here, or, alternatively, a single DSP 520 could be used to carry out the functions of the microprocessor 538 .
- Low-level communication functionsincluding at least data and voice communications, are performed through the DSP 520 in the transceiver 511 .
- Other, high-level communication applicationssuch as a voice communication application 524 A, and a data communication application 524 B may be stored in the Flash memory 524 for execution by the microprocessor 538 .
- the voice communication module 524 Amay provide a high-level user interface operable to transmit and receive voice calls between the mobile device 500 and a plurality of other voice devices via the network 519 .
- the data communication module 524 Bmay provide a high-level user interface operable for sending and receiving data, such as e-mail messages, files, organizer information, short text messages, etc., between the mobile device 500 and a plurality of other data devices via the network 519 .
- a secure messaging software applicationincorporating software modules corresponding to the messaging system 60 and Cert sync system 62 in FIG. 3 for example, may operate in conjunction with the data communication module 524 B in order to implement the techniques described above.
- the microprocessor 538also interacts with other device subsystems, such as the display 522 , Flash memory 524 , random access memory (RAM) 526 , auxiliary input/output (I/O) subsystems 528 , serial port 530 , keyboard 532 , speaker 534 , microphone 536 , a short-range communications subsystem 540 and any other device subsystems generally designated as 542 .
- the modules 524 A-Nare executed by the microprocessor 538 and may provide a high-level interface between a user of the mobile device and the mobile device.
- This interfacetypically includes a graphical component provided through the display 522 , and an input/output component provided through the auxiliary I/O 528 , keyboard 532 , speaker 534 , or microphone 536 .
- Such interfacesare designated generally as UI 64 in FIG. 3 .
- Some of the subsystems shown in FIG. 5perform communication-related functions, whereas other subsystems may provide “resident” or on-device functions.
- some subsystemssuch as keyboard 532 and display 522 may be used for both communication-related functions, such as entering a text message for transmission over a data communication network, and device-resident functions such as a calculator or task list or other PDA type functions.
- Operating system software used by the microprocessor 538is preferably stored in a persistent store such as Flash memory 524 .
- the Flash memory 524may also include a file system for storing data.
- a storage areais also preferably provided in the Flash memory 524 to store Certs, address book entries and possibly other information required for messaging, shown as data stores 54 , 56 and 58 in FIG. 3 .
- the operating system, specific device applications or modules, or parts thereof,may be temporarily loaded into a volatile store, such as RAM 526 for faster operation.
- received communication signalsmay also be temporarily stored to RAM 526 , before permanently writing them to a file system located in the persistent store 524 .
- An exemplary application module 524 N that may be loaded onto the mobile device 500is a personal information manager (PIM) application providing PDA functionality, such as calendar events, appointments, and task items.
- PIMpersonal information manager
- This module 524 Nmay also interact with the voice communication module 524 A for managing phone calls, voice mails, etc., and may also interact with the data communication module 524 B for managing e-mail communications and other data transmissions.
- all of the functionality of the voice communication module 524 A and the data communication module 524 Bmay be integrated into the PIM module.
- the Flash memory 524preferably provides a file system to facilitate storage of PIM data items on the device.
- the PIM applicationpreferably includes the ability to send and receive data items, either by itself, or in conjunction with the voice and data communication modules 524 A, 524 B, via the wireless network 519 .
- the PIM data itemsare preferably seamlessly integrated, synchronized and updated, via the wireless network 519 , with a corresponding set of data items stored or associated with a host computer system, thereby creating a mirrored system for data items associated with a particular user.
- the mobile device 500may also be manually synchronized with a host system by placing the mobile device 500 in an interface cradle, which couples the serial port 530 of the mobile device 500 to the serial port of the host system.
- the serial port 530may also be used to enable a user to set preferences through an external device or software application, to download other application modules 524 N for installation, and to manage Certs on a device as described above.
- This wired download pathmay further be used to load an encryption key onto the device, which is a more secure method than exchanging encryption information via the wireless network 519 .
- Additional application modules 524 Nmay be loaded onto the mobile device 500 through the network 519 , through an auxiliary I/O subsystem 528 , through the serial port 530 , through the short-range communications subsystem 540 , or through any other suitable subsystem 542 , and installed by a user in the Flash memory 524 or RAM 526 .
- Such flexibility in application installationincreases the functionality of the mobile device 500 and may provide enhanced on-device functions, communication-related functions, or both.
- secure communication applicationsmay enable electronic commerce functions and other such financial transactions to be performed using the mobile device 500 .
- a received signalsuch as a text message or a web page download
- the transceiver 511When the mobile device 500 is operating in a data communication mode, a received signal, such as a text message or a web page download, will be processed by the transceiver 511 and provided to the microprocessor 538 , which will preferably further process the received signal for output to the display 522 , or, alternatively, to an auxiliary I/O device 528 .
- a Cert received by the transceiver 511in response to a request to a PKS or attached to a secure message for example, will be processed as described above to add the Cert to a Cert store in the Flash memory 524 if it has not already been stored, and to extract and store contact information in a new address book entry in the Flash memory 524 if necessary.
- a user of mobile device 500may also compose data items, such as email messages, using the keyboard 532 , which is preferably a complete alphanumeric keyboard laid out in the QWERTY style, although other styles of complete alphanumeric keyboards such as the known DVORAK style may also be used.
- User input to the mobile device 500is further enhanced with a plurality of auxiliary I/O devices 528 , which may include a thumbwheel input device, a touchpad, a variety of switches, a rocker input switch, etc.
- the composed data items input by the usermay then be transmitted over the communication network 519 via the transceiver 511 .
- the overall operation of the mobile device 500is substantially similar to the data mode, except that received signals are preferably output to the speaker 534 and voice signals for transmission are generated by a microphone 536 .
- the secure messaging techniques described abovemight not necessarily be applied to voice communications.
- Alternative voice or audio I/O subsystemssuch as a voice message recording subsystem, may also be implemented on the mobile device 500 .
- voice or audio signal outputis preferably accomplished primarily through the speaker 534
- the display 522may also be used to provide an indication of the identity of a calling party, the duration of a voice call, or other voice call related information.
- the microprocessor 538in conjunction with the voice communication module 524 A and the operating system software, may detect the caller identification information of an incoming voice call and display it on the display 522 .
- a short-range communications subsystem 540may also be included in the mobile device 500 .
- the subsystem 540may include an infrared device and associated circuits and components, or a Bluetooth or 802.11 short-range wireless communication module to provide for communication with similarly-enabled systems and devices.
- Cert management and transfer operations as described abovemay be enabled on the mobile device 500 via the serial port 530 or other short-range communications subsystem 540 . More than one such interface may be used, depending upon the type of messaging client with which mobile device Cert management and/or transfer operations will be performed.
- the serial port 530may be used, whereas for mobile device to mobile device operations, another short-range communications subsystem 540 could be used.
- Cert management and transfermay also be useful in other types of communication systems.
- FIG. 6is a block diagram showing an example communication system.
- a computer system 602there is shown a computer system 602 , a WAN 604 , corporate LAN 606 behind a security firewall 608 , wireless infrastructure 610 , wireless networks 612 and 614 , and mobile devices 616 and 618 .
- the corporate LAN 606includes a message server 620 , a wireless connector system 628 , a data store 617 including at least a plurality of mailboxes 619 , a desktop computer system 622 having a communication link directly to a mobile device such as through physical connection 624 to an interface or connector 626 , and a wireless VPN router 632 . Operation of the system in FIG. 6 will be described below with reference to the messages 33 , 34 and 36 .
- the computer system 602may, for example, be a laptop, desktop or palmtop computer system configured for connection to the WAN 604 .
- a computer systemmay connect to the WAN 604 via an ISP or ASP.
- the computer system 602may be a network-connected computer system that accesses the WAN 604 through a LAN or other network.
- Many modem mobile devicesare enabled for connection to a WAN through various infrastructure and gateway arrangements, so that the computer system 602 may also be a mobile device.
- the corporate LAN 606is an illustrative example of a central, server-based messaging system that has been enabled for wireless communications.
- the corporate LAN 606may be referred to as a “host system”, in that it hosts both a data store 617 with mailboxes 619 for messages, as well as possibly further data stores (not shown) for other data items, that may be sent to or received from mobile devices 616 and 618 , and the wireless connector system 628 , the wireless VPN router 632 , or possibly other components enabling communications between the corporate LAN 606 and one or more mobile devices 616 and 618 .
- a host systemmay be one or more computers at, with or in association with which a wireless connector system is operating.
- the corporate LAN 606is one preferred embodiment of a host system, in which the host system is a server computer running within a corporate network environment operating behind and protected by at least one security communications firewall 608 .
- Other possible central host systemsinclude ISP, ASP and other service provider or mail systems.
- the desktop computer system 624 and interface/connector 626may be located outside such host systems, wireless communication operations may be similar to those described below.
- the corporate LAN 606implements the wireless connector system 628 as an associated wireless communications enabling component, which will normally be a software program, a software application, or a software component built to work with at least one or more message server.
- the wireless connector system 628is used to send user-selected information to, and to receive information from, one or more mobile devices 616 and 618 , via one or more wireless networks 612 and 614 .
- the wireless connector system 628may be a separate component of a messaging system, as shown in FIG. 6 , or may instead be partially or entirely incorporated into other communication system components.
- the message server 620may incorporate a software program, application, or component implementing the wireless connector system 628 , portions thereof, or some or all of its functionality.
- the message server 620running on a computer behind the firewall 608 , acts as the main interface for the corporation to exchange messages, including for example e-mail, calendaring data, voice mail, electronic documents, and other personal information management (PIM) data with the WAN 604 , which will typically be the Internet.
- PIMpersonal information management
- a message serveris often used in conjunction with Internet mail routers to route and deliver messages.
- the particular intermediate operations and computerswill be dependent upon the specific type of message delivery mechanisms and networks via which messages are exchanged, and therefore have not been shown in FIG. 6 .
- the functionality of the message server 20may extend beyond message sending and receiving, providing such features as dynamic database storage for data like calendars, todo lists, task lists, e-mail and documentation, as described above.
- Message servers such as 620normally maintain a plurality of mailboxes 619 in one or more data stores such as 617 for each user having an account on the server.
- the data store 817includes mailboxes 619 for a number of (“n”) user accounts. Messages received by the message server 620 that Identify a user, a user account, a mailbox, or possibly another address associated with a user, account or mailbox 619 as a message recipient will typically be stored in the corresponding mailbox 619 . If a message is addressed to multiple recipients or a distribution list, then copies of the same message may be stored to more than one mailbox 619 .
- the message server 620may store a single copy of such a message in a data store accessible to all of the users having an account on the message server, and store a pointer or other identifier in each recipient's mailbox 619 .
- each usermay then access his or her mailbox 619 and its contents using a messaging client such as Microsoft Outlook or Lotus Notes, which normally operates on a PC, such as the desktop computer system 622 , connected in the LAN 606 .
- a messaging clientsuch as Microsoft Outlook or Lotus Notes, which normally operates on a PC, such as the desktop computer system 622 , connected in the LAN 606 .
- desktop computer system 622is shown in FIG. 6 , those skilled in the art will appreciate that a LAN will typically contain many desktop, notebook and laptop computer systems.
- Each messaging clientnormally accesses a mailbox 619 through the message server 620 , although in some systems, a messaging client may enable direct access to the data store 617 and a mailbox 619 stored thereon by the desktop computer system 622 . Messages may also be downloaded from the data store 617 to a local data store (not shown) on the desktop computer system 622 .
- the wireless connector system 628operates in conjunction with the message server 620 .
- the wireless connector system 628may reside on the same computer system as the message server 620 , or may instead be implemented on a different computer system.
- Software implementing the wireless connector system 628may also be partially or entirely integrated with the message server 620 .
- the wireless connector system 628 and the message server 620are preferably designed to cooperate and interact to allow the pushing of information to mobile devices 616 , 618 .
- the wireless connector system 628is preferably configured to send information that is stored in one or more data stores associated with the corporate LAN 606 to one or more mobile devices 616 , 618 , through the corporate firewall 608 and via the WAN 604 and one of the wireless networks 612 , 614 .
- a user that has an account and associated mailbox 619 in the data store 617may also have a mobile device, such as 616 .
- messages received by the message server 620 that identify a user, account or mailbox 619are stored to a corresponding mailbox 619 by the message server 620 .
- messages received by the message server 620 and stored to the user's mailbox 619are preferably detected by the wireless connector system 628 and sent to the user's mobile device 616 .
- This type of functionalityrepresents a “push” message sending technique.
- the wireless connector system 628may instead employ a “pull” technique, in which items stored in a mailbox 619 are sent to a mobile device 616 , 618 responsive to a request or access operation made using the mobile device, or some combination of both techniques.
- a wireless connector 628thereby enables a messaging system including a message server 620 to be extended so that each user's mobile device 616 , 618 has access to stored messages of the message server 620 .
- a more detailed description of push-based messagingmay be found in U.S. Pat. No. 6,219,694, referenced above, and in the following co-pending and commonly-owned U.S. patent applications, all of which are related to the '694 patent: U.S. patent application Ser. No. 09/401,868, Ser. No. 09/545,963, Ser. No. 09/528,495; Ser. No. 09/545,962, and Ser. No.
- FIG. 6there are several paths for exchanging information with a mobile device 616 , 618 from the corporate LAN 606 .
- One possible information transfer pathis through the physical connection 624 such as a serial port, using an interface or connector 626 .
- This pathmay be useful for example for bulk information, such as Certs and CRLs as described above, or updates often performed at initialization of a mobile device 616 , 618 or periodically when a user of a mobile device 616 , 618 is working at a computer system in the LAN 606 , such as the computer system 622 .
- the physical connection 624may also be used to transfer other information from a desktop computer system 622 to a mobile device 616 , 618 , including private keys such as private encryption or signature keys associated with the desktop computer system 622 .
- Private key exchange using a physical connection 624 and connector or interface 626allows a user's desktop computer system 622 and mobile device 616 or 618 to share at least one identity for accessing all encrypted and/or signed mail.
- the user's desktop computer system 622 and mobile device 616 or 618can thereby also be used to manage and transfer private keys, so that either the host system 622 or mobile device 616 or 618 can process secure messages addressed to the user's mailbox or account on the message server 620 .
- a physical pathhas also been used to transfer messages from mailboxes 619 associated with a message server 620 to mobile devices 616 and 618 .
- Another method for data exchange with a mobile device 616 , 618is over-the-air, through the wireless connector system 628 and using wireless networks 612 , 614 .
- thiscould involve a Wireless VPN router 632 , if available in the network 606 , or, alternatively, a traditional WAN connection to wireless infrastructure 610 that provides an interface to one or more wireless networks 612 , 614 .
- the Wireless VPN router 632provides for creation of a VPN connection directly through a specific wireless network 612 to a wireless device 616 .
- Such a Wireless VPN router 632may be used in conjunction with a static addressing scheme.
- the wireless network 612is an Internet Protocol (IP) based wireless network
- IPInternet Protocol
- IPV6IP Version 6
- a primary advantage of using a wireless VPN router 632is that it could be an off-the-shelf VPN component which would not require wireless infrastructure 610 .
- a VPN connectionmay use a Transmission Control Protocol over IP (TCP/IP) or User Datagram Protocol over IP (UDP/IP) connection to deliver messages directly to and from a mobile device 616 .
- TCP/IPTransmission Control Protocol over IP
- UDP/IPUser Datagram Protocol over IP
- wireless infrastructure 610is preferably used.
- One example of a wireless infrastructure 610is the gateway 16 in FIG. 1 .
- the wireless infrastructure 610may also determine a most likely wireless network for locating a given user, and track users as they roam between countries or networks.
- wireless networkssuch as 612 and 614 , messages are normally delivered to and from mobile devices 616 , 618 via RF transmissions between base stations (not shown) and the mobile devices 616 , 618 .
- a plurality of connections to wireless networks 612 and 614may be provided, including, for example, Integrated Services Digital Network (ISDN), Frame Relay or T1 connections using the TCP/IP protocol used throughout the Internet.
- ISDNIntegrated Services Digital Network
- the wireless networks 612 and 614could represent distinct, unique and unrelated networks, or they could represent the same network in different countries, and may be any of the different types of networks described above in conjunction with the wireless network 20 in FIG. 1 .
- more than one over-the-air information exchange mechanismmay be provided in the corporate LAN 606 .
- mobile devices 616 , 618 associated with users having mailboxes 619 associated with user accounts on the message server 620are configured to operate on different wireless networks 612 and 614 . If the wireless network 612 supports IPv6 addressing, then the wireless VPN router 632 may be used by the wireless connector system 628 to exchange data with any mobile device 616 operating within the wireless network 612 .
- the wireless network 614may be a different type of wireless network, however, such as the Mobitex network, in which case information may instead be exchanged with a mobile device 18 operating within the wireless network 614 by the wireless connector system 628 via a connection to the WAN 604 and the wireless infrastructure 610 .
- e-mail message 633sent from the computer system 602 and addressed to at least one recipient having both an account and mailbox 619 or like data store associated with the message server 620 and a mobile device 616 or 618 .
- the e-mail message 633is intended for illustrative purposes only.
- the exchange of other types of information between the corporate LAN 606is preferably also enabled by the wireless connector system 628 .
- the e-mail message 633sent from the computer system 602 via the WAN 604 , may be fully in the clear, or signed with a digital signature and/or encrypted, depending upon the particular messaging scheme used. For example, if the computer system 602 is enabled for secure messaging using S/MIME, then the e-mail message 633 may be signed, encrypted, or both, and processed as described above.
- E-mail messages such as 633normally use traditional Simple Mail Transfer Protocol (SMTP), RFC822 headers and Multipurpose Internet Mail Extensions (MIME) body parts to define the format of the e-mail message. These techniques are all well known to one in the art.
- the e-mail message 633arrives at the message server 620 , which determines into which mailboxes 619 the e-mail message 633 should be stored.
- a messagesuch as the e-mail message 633 may include a user name, a user account, a mailbox identifier, or other type of identifier that may be mapped to a particular account or associated mailbox 619 by the message server 620 .
- recipientsare typically identified using e-mail addresses corresponding to a user account and thus a mailbox 619 .
- the wireless connector system 628sends or mirrors, via a wireless network 612 or 614 , certain user-selected data items or parts of data items from the corporate LAN 606 to the user's mobile device 616 or 618 , preferably, upon detecting that one or more triggering events has occurred.
- a triggering eventincludes, but is not limited to, one or more of the following: screen saver activation at a user's networked computer system 622 , disconnection of the user's mobile device 616 or 618 from the interface 626 , or receipt of a command sent from a mobile device 616 or 618 to the host system to start sending one or more messages stored at the host system.
- the wireless connector system 628may detect triggering events associated with the message server 620 , such as receipt of a command, or with one or more networked computer systems 622 , including the screen saver and disconnection events described above.
- triggering events associated with the message server 620such as receipt of a command, or with one or more networked computer systems 622 , including the screen saver and disconnection events described above.
- data items selected by the userare preferably sent to the user's mobile device.
- the e-mail message 633assuming that a triggering event has been detected, the arrival of the message 633 at the message server 620 is detected by the wireless connector system 628 .
- the wireless connector system 628may register for advise syncs provided by the Microsoft Messaging Application Programming Interface (MAPI) to thereby receive notifications when a new message is stored to a mailbox 619 .
- MMIMicrosoft Messaging Application Programming Interface
- the wireless connector system 628When a data item such as the e-mail message 633 is to be sent to a mobile device 616 or 618 , the wireless connector system 628 preferably repackages the data item in a manner that is transparent to the mobile device, so that information sent to and received by the mobile device appears similar to the information as stored on and accessible at the host system, LAN 606 in FIG. 6 .
- One preferred repackaging methodincludes wrapping received messages to be sent via a wireless network 612 , 614 in an electronic envelope that corresponds to the wireless network address of the mobile device 616 , 618 to which the message is to be sent.
- other repackaging methodscould be used, such as special-purpose TCP/IP wrapping techniques.
- Such repackagingpreferably also results in e-mail messages sent from a mobile device 616 or 618 appearing to come from a corresponding host system account or mailbox 619 even though they are composed and sent from a mobile device.
- a user of a mobile device 616 or 618may thereby effectively share a single e-mail address between a host system account or mailbox 619 and the mobile device.
- Repackaging of the e-mail message 633is indicated at 634 and 636 .
- Repackaging techniquesmay be similar for any available transfer paths or may be dependent upon the particular transfer path, either the wireless infrastructure 610 or the wireless VPN router 632 .
- the e-mail message 633is preferably compressed and encrypted, either before or after being repackaged at 634 , to thereby effectively provide for secure transfer to the mobile device 618 . Compression reduces the bandwidth required to send the message, whereas encryption ensures confidentiality of any messages or other information sent to mobile devices 616 and 618 .
- messages transferred via a VPN router 632might only be compressed and not encrypted, since a VPN connection established by the VPN router 632 is inherently secure.
- Messagesare thereby securely sent, via either encryption at the wireless connector system 628 , which may be considered a non-standard VPN tunnel or a VPN-like connection for example, or the VPN router 632 , to mobile devices 616 and 618 . Accessing messages using a mobile device 616 or 618 is thus no less secure than accessing mailboxes at the LAN 606 using the desktop computer system 622 .
- a repackaged message 634 or 636arrives at a mobile device 616 or 618 , via the wireless infrastructure 610 , or via the wireless VPN router 632 , the mobile device 616 or 618 removes the outer electronic envelope from the repackaged message 634 or 636 , and performs any required decompression and decryption operations.
- the original message 633is a secure message
- further processingmay also be performed by the mobile device 616 , 618 .
- Messages sent from a mobile device 616 or 618 and addressed to one or more recipientsare preferably similarly repackaged, and possibly compressed and encrypted, and sent to a host system such as the LAN 606 . The host system may then remove the electronic envelope from the repackaged message, decrypt and decompress the message if desired, and route the message to the addressed recipients.
- Another goal of using an outer envelopeis to maintain at least some of the addressing information in the original e-mail message 633 .
- the outer envelope used to route information to mobile devices 616 , 618is addressed using a network address of one or more mobile devices, the outer envelope preferably encapsulates the entire original e-mail message 633 , including at least one address field, possibly in compressed and/or encrypted form. This allows original “To”, “From” and “CC” addresses of the e-mail message 633 to be displayed when the outer envelope is removed and the message is displayed on a mobile device 616 or 618 .
- the repackagingalso allows reply messages to be delivered to addressed recipients, with the “From” field reflecting an address of the mobile device user's account or mailbox on the host system, when the outer envelope of a repackaged outgoing message sent from a mobile device is removed by the wireless connector system 628 .
- the “From” fieldreflecting an address of the mobile device user's account or mailbox on the host system, when the outer envelope of a repackaged outgoing message sent from a mobile device is removed by the wireless connector system 628 .
- Using the user's account or mailbox address from the mobile device 616 or 618allows a message sent from a mobile device to appear as though the message originated from the user's mailbox 619 or account at the host system rather than the mobile device.
- FIG. 7is a block diagram of an alternative exemplary communication system, in which wireless communications are enabled by a component associated with an operator of a wireless network.
- the systemincludes a computer system 702 , WAN 704 , a corporate LAN 707 located behind a security firewall 708 , network operator infrastructure 740 , a wireless network 711 , and mobile devices 713 and 715 .
- the computer system 702 , WAN 704 , security firewall 708 , message server 720 , data store 717 , mailboxes 719 , and VPN router 735are substantially the same as the similarly-labelled components in FIG. 6 .
- the VPN router 735communicates with the network operator infrastructure 740 , it need not necessarily be a wireless VPN router in the system of FIG. 7 .
- the network operator infrastructure 740enables wireless information exchange between the LAN 707 and mobile devices 713 , 715 , respectively associated with the computer systems 742 and 752 and configured to operate within the wireless network 711 .
- a plurality of desktop computer systems 742 , 752are shown, each having a physical connection 746 , 756 to an interface or connector 748 , 758 .
- a wireless connector system 744 , 754is operating on or in conjunction with each computer system 742 , 752 .
- the wireless connector systems 744 , 754may be similar to the wireless connector system 628 described above, in that they enable data items, such as e-mail messages and other items that are stored in mailboxes 719 , and possibly data items stored in a local or network data store, to be sent from the LAN 707 to one or more mobile devices 713 , 715 .
- the network operator infrastructure 740provides an interface between the mobile devices 713 , 715 and the LAN 707 .
- operation of the system shown in FIG. 7will be described below in the context of an e-mail message 733 as an illustrative example of a data item that may be sent to a mobile device 713 , 715 .
- the message server 720When an e-mail message 733 , addressed to one or more recipients having an account on the message server 720 , is received by the message server 720 , the message, or possibly a pointer to a single copy of the message stored in a central mailbox or data store, is stored into the mailbox 719 of each such recipient. Once the e-mail message 733 or pointer has been stored to a mailbox 719 , it may preferably be accessed using a mobile device 713 or 715 . In the example shown in FIG. 7 , the e-mail message 733 has been addressed to the mailboxes 719 associated with both desktop computer systems 742 and 752 and thus both mobile devices 713 and 715 .
- communication network protocols commonly used in wired networks such as the LAN 707 and/or the WAN 704are not suitable or compatible with wireless network communication protocols used within wireless networks such as 711 .
- communication bandwidth, protocol overhead and network latency, which are primary concerns in wireless network communicationsare less significant in wired networks, which typically have much higher capacity and speed than wireless networks. Therefore, mobile devices 713 and 715 cannot normally access the data store 717 directly.
- the network operator infrastructure 740provides a bridge between the wireless network 711 and the LAN 707 .
- the network operator infrastructure 740enables a mobile device 713 , 715 to establish a connection to the LAN 707 through the WAN 704 , and may, for example, be operated by an operator of the wireless network 711 or a service provider that provides wireless communication service for mobile devices 713 and 715 .
- a mobile device 713 , 715may establish a communication session with the network operator infrastructure 740 using a wireless network compatible communication scheme, preferably a secure scheme such as Wireless Transport Layer Security (WTLS) when information should remain confidential, and a wireless web browser such as a Wireless Application Protocol (WAP) browser.
- WTLSWireless Transport Layer Security
- WAPWireless Application Protocol
- a usermay then request (through manual selection or pre-selected defaults in the software residing in the mobile device) any or all information, or just new information for example, stored in a mailbox 719 in the data store 717 at the LAN 707 .
- the network operator infrastructure 740then establishes a connection or session with a wireless connector system 744 , 754 , using Secure Hypertext Transfer Protocol (HTTPS) for example, if no session has already been established.
- HTTPSSecure Hypertext Transfer Protocol
- a session between the network operator infrastructure 740 and a wireless connector system 744 , 754may be made via a typical WAN connection or through the VPN router 735 if available.
- the network operator infrastructure 740 and the wireless connector systems 744 , 754may be configured so that a communication connection remains open once established.
- requests originating from mobile device A 713 and B 715would be sent to the wireless connector systems 744 and 754 , respectively.
- a wireless connector system 744 , 754retrieves requested information from a data store.
- the wireless connector system 744 , 754retrieves the e-mail message 733 from the appropriate mailbox 719 , typically through a messaging client operating in conjunction with the computer system 742 , 752 , which may access a mailbox 719 either via the message server 720 or directly.
- a wireless connector system 744 , 754may be configured to access mailboxes 719 itself, directly or through the message server 720 .
- both network data stores similar to the data store 717 and local data stores associated with each computer system 742 , 752may be accessible to a wireless connector system 744 , 754 , and thus to a mobile device 713 , 715 .
- the e-mail message 733may be sent to the network operator infrastructure 740 as shown at 760 and 762 , which then sends a copy of the e-mail message to each mobile device 713 and 715 , as indicated at 764 and 766 .
- Informationmay be transferred between the wireless connector systems 744 , 754 and the network operator infrastructure 740 via either a connection to the WAN 704 or the VPN router 735 .
- translation operationsmay be performed by the network operator infrastructure 740 .
- Repackaging techniquesmay also be used between the wireless connector systems 744 , 754 and the network operator infrastructure 740 , and between each mobile device 713 , 715 and the network operator infrastructure 740 .
- Messages or other information to be sent from a mobile device 713 , 715may be processed in a similar manner, with such information first being transferred from a mobile device 713 , 715 to the network operator infrastructure 740 .
- the network operator infrastructure 740may then send the information to a wireless connector system 744 , 754 for storage in a mailbox 719 and delivery to any addressed recipients by the message server 720 for example, or may alternatively deliver the information to the addressed recipients.
- the above description of the system in FIG. 7relates to pull-based operations.
- the wireless connector systems 744 , 754 and the network operator infrastructuremay instead be configured to push data items to mobile devices 713 and 715 .
- a combined push/pull systemis also possible. For example, a notification of a new message or a list of data items currently stored in a data store at the LAN 707 could be pushed to a mobile device 713 , 715 , which may then be used to request messages or data items from the LAN 707 via the network operator infrastructure 740 .
- each wireless networkmay have an associated wireless network infrastructure component similar to 740 .
- wireless connector systems 744 , 754may preferably be configured to operate in conjunction with more than one computer system 742 , 752 , or to access a data store or mailbox 719 associated with more than one computer system.
- the wireless connector system 744may be granted access to the mailboxes 719 associated with both the computer system 742 and the computer system 752 . Requests for data items from either mobile device A 713 or B 715 may then be processed by the wireless connector system 744 .
- This configurationmay be useful to enable wireless communications between the LAN 707 and the mobile devices 713 and 715 without requiring a desktop computer system 742 , 752 to be running for each mobile device user.
- a wireless connector systemmay instead be implemented in conjunction with the message server 720 to enable wireless communications.
- FIG. 8is a block diagram of another alternative communication system.
- the systemincludes a computer system 802 , WAN 804 , a corporate LAN 809 located behind a security firewall 808 , an access gateway 880 , data store 882 , wireless networks 884 and 886 , and mobile devices 888 and 890 .
- the LAN 809 , the computer system 802 , WAN 804 , security firewall 808 , message server 820 , data store 817 , mailboxes 819 , desktop computer system 822 , physical connection 824 , interface or connector 826 and VPN router 835are substantially the same as the corresponding components described above.
- the access gateway 880 and data store 882provide mobile devices 88 and 90 with access to data items stored at the LAN 809 .
- a wireless connector system 878operates on or in conjunction with the message server 820 , although a wireless connector system may instead operate on or in conjunction with one or more desktop computer systems in the LAN 809 .
- the wireless connector system 878provides for transfer of data items stored at the LAN 809 to one or more mobile devices 888 , 890 .
- These data itemspreferably include e-mail messages stored in mailboxes 819 in the data store 817 , as well as possibly other items stored in the data store 817 or another network data store or a local data store of a computer system such as 822 .
- an e-mail message 833 addressed to one or more recipients having an account on the message server 820 and received by the message server 820may be stored into the mailbox 819 of each such recipient.
- the external data store 882preferably has a similar structure to, and remains synchronized with, the data store 817 .
- PIM information or data stored at data store 882preferably is independently modifiable to the PIM information or data stored at the host system.
- the independently modifiable information at the external data store 882may maintain synchronization of a plurality of data stores associated with a user (i.e., data on a mobile device, data on a personal computer at home, data at the corporate LAN, etc.).
- This synchronizationmay be accomplished, for example, through updates sent to the data store 882 by the wireless connector system 878 at certain time intervals, each time an entry in the data store 817 is added or changed, at certain times of day, or when initiated at the LAN 809 , by the message server 820 or a computer system 822 , at the data store 882 , or possibly by a mobile device 888 , 890 through the access gateway 880 .
- an update sent to the data store 882 some time after the e-mail message 833 is receivedmay indicate that the message 833 has been stored in a certain mailbox 819 in the store 817 , and a copy of the e-mail message will be stored to a corresponding storage area in the data store 882 .
- the e-mail message 833has been stored in the mailboxes 819 corresponding to the mobile devices 888 and 890 for example, one or more copies of the e-mail message, indicated at 892 and 894 in FIG. 8 , will be sent to and stored in corresponding storage areas or mailboxes in the data store 882 .
- updates or copies of stored information in the data store 817may be sent to the data store 882 via a connection to the WAN 804 or the VPN router 835 .
- the wireless connector system 878may post updates or stored information to a resource in the data store 882 via an HTTP post request.
- a secure protocolsuch as HTTPS or Secure Sockets Layer (SSL) may be used.
- SSLSecure Sockets Layer
- This copy of the data itemcould then be stored either in more than one corresponding location in the data store 882 , or a single copy may be stored in the data store 882 , with a pointer or other identifier of the stored data item being stored in each corresponding location in the data store 882 .
- the access gateway 880is effectively an access platform, in that it provides mobile devices 888 and 890 with access to the data store 882 .
- the data store 882may be configured as a resource accessible on the WAN 804
- the access gateway 880may be an ISP system or WAP gateway through which mobile devices 888 and 890 may connect to the WAN 804 .
- a WAP browser or other browser compatible with the wireless networks 884 and 886may then be used to access the data store 882 , which is synchronized with the data store 817 , and download stored data items either automatically or responsive to a request from a mobile device 888 , 890 .
- copies of the e-mail message 833may be sent to the mobile devices 888 and 890 .
- a data store (not shown) on each mobile device 888 , 890may thereby be synchronized with a portion, such as a mailbox 819 , of a data store 817 on a corporate LAN 809 . Changes to a mobile device data store may similarly be reflected in the data stores 882 and 817 .
- a wireless mobile communication deviceis shown in FIGS. 3-5 and described as one of the messaging clients, the invention is also applicable to other messaging clients, including those operating on desktop and laptop computer systems, networked computer workstations and other types of messaging clients between which Cert management and transfer, to allow sharing of Certs for example, is desired.
- Cert-related informationmay be managed and transferred between messaging clients substantially as described above.
- CRLs, public keys and private keyscould similarly be managed and/or transferred.
Landscapes
- Engineering & Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- Computer Networks & Wireless Communication (AREA)
- Signal Processing (AREA)
- Business, Economics & Management (AREA)
- Computer Hardware Design (AREA)
- Human Resources & Organizations (AREA)
- Strategic Management (AREA)
- Computing Systems (AREA)
- General Engineering & Computer Science (AREA)
- Entrepreneurship & Innovation (AREA)
- Economics (AREA)
- Data Mining & Analysis (AREA)
- Marketing (AREA)
- Operations Research (AREA)
- Quality & Reliability (AREA)
- Tourism & Hospitality (AREA)
- Physics & Mathematics (AREA)
- General Business, Economics & Management (AREA)
- General Physics & Mathematics (AREA)
- Theoretical Computer Science (AREA)
- Information Transfer Between Computers (AREA)
- Mobile Radio Communication Systems (AREA)
- Computer And Data Communications (AREA)
Abstract
Description
Claims (30)
Priority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| US13/964,180USRE45087E1 (en) | 2001-06-12 | 2013-08-12 | Certificate management and transfer system and method |
Applications Claiming Priority (5)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| US29768101P | 2001-06-12 | 2001-06-12 | |
| US36553302P | 2002-03-20 | 2002-03-20 | |
| PCT/CA2002/000868WO2002101580A1 (en) | 2001-06-12 | 2002-06-12 | Certificate management and transfer system and method |
| US12/480,841US8015400B2 (en) | 2001-06-12 | 2009-06-09 | Certificate management and transfer system and method |
| US13/964,180USRE45087E1 (en) | 2001-06-12 | 2013-08-12 | Certificate management and transfer system and method |
Related Parent Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US12/480,841ReissueUS8015400B2 (en) | 2001-06-12 | 2009-06-09 | Certificate management and transfer system and method |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| USRE45087E1true USRE45087E1 (en) | 2014-08-19 |
Family
ID=26970262
Family Applications (4)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US10/480,615Expired - LifetimeUS7546453B2 (en) | 2001-06-12 | 2002-06-12 | Certificate management and transfer system and method |
| US12/480,841CeasedUS8015400B2 (en) | 2001-06-12 | 2009-06-09 | Certificate management and transfer system and method |
| US13/223,999Expired - LifetimeUS8539226B2 (en) | 2001-06-12 | 2011-09-01 | Certificate management and transfer system and method |
| US13/964,180Expired - Fee RelatedUSRE45087E1 (en) | 2001-06-12 | 2013-08-12 | Certificate management and transfer system and method |
Family Applications Before (3)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US10/480,615Expired - LifetimeUS7546453B2 (en) | 2001-06-12 | 2002-06-12 | Certificate management and transfer system and method |
| US12/480,841CeasedUS8015400B2 (en) | 2001-06-12 | 2009-06-09 | Certificate management and transfer system and method |
| US13/223,999Expired - LifetimeUS8539226B2 (en) | 2001-06-12 | 2011-09-01 | Certificate management and transfer system and method |
Country Status (8)
| Country | Link |
|---|---|
| US (4) | US7546453B2 (en) |
| EP (1) | EP1399853A1 (en) |
| JP (2) | JP2004532590A (en) |
| KR (1) | KR20040015272A (en) |
| CN (1) | CN100410927C (en) |
| CA (2) | CA2717229A1 (en) |
| IL (2) | IL159342A0 (en) |
| WO (1) | WO2002101580A1 (en) |
Cited By (1)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US9837044B2 (en) | 2015-03-18 | 2017-12-05 | Samsung Electronics Co., Ltd. | Electronic device and method of updating screen of display panel thereof |
Families Citing this family (87)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| DE60115072T3 (en) | 2000-09-21 | 2010-04-01 | Research In Motion Ltd., Waterloo | SYSTEM AND METHOD FOR SUBMITING A SOFTWARE CODE |
| CA2717229A1 (en) | 2001-06-12 | 2002-12-19 | Research In Motion Limited | Certificate management and transfer system and method |
| US7254712B2 (en)* | 2001-06-12 | 2007-08-07 | Research In Motion Limited | System and method for compressing secure e-mail for exchange with a mobile data communication device |
| WO2002102009A2 (en) | 2001-06-12 | 2002-12-19 | Research In Motion Limited | Method for processing encoded messages for exchange with a mobile data communication device |
| US9628269B2 (en) | 2001-07-10 | 2017-04-18 | Blackberry Limited | System and method for secure message key caching in a mobile communication device |
| EP1417814B1 (en)* | 2001-08-06 | 2008-10-29 | Research In Motion Limited | System and method for processing encoded messages |
| JP3687599B2 (en)* | 2001-12-06 | 2005-08-24 | ソニー株式会社 | COMMUNICATION DEVICE AND METHOD, RECORDING MEDIUM, AND PROGRAM |
| JP3988451B2 (en)* | 2001-12-06 | 2007-10-10 | ソニー株式会社 | COMMUNICATION DEVICE AND METHOD, RECORDING MEDIUM, AND PROGRAM |
| US20030154408A1 (en)* | 2002-02-13 | 2003-08-14 | Yanong Zhu | Method and apparatus for secured unified public communication network based on IP and common channel signaling |
| AU2003213910A1 (en) | 2002-03-20 | 2003-09-29 | Research In Motion Limited | Certificate information storage system and method |
| US20040203646A1 (en)* | 2002-07-18 | 2004-10-14 | Rudd Michael L. | System and method for a mobile expert device |
| US20040078601A1 (en)* | 2002-08-02 | 2004-04-22 | Chris Tengwall | System and method for operating a wireless device network |
| US8230363B2 (en)* | 2002-08-06 | 2012-07-24 | Goldman, Sachs & Co. | Management of corporate entities |
| EP2501161B1 (en)* | 2002-11-11 | 2014-03-26 | Nokia Corp. | Location dependent messaging |
| US8965980B2 (en)* | 2003-03-27 | 2015-02-24 | Siebel Systems, Inc. | Universal support for multiple external messaging systems |
| US7844254B2 (en)* | 2003-06-12 | 2010-11-30 | Sri International | Method and apparatus for collaboration and media access using mobile communications devices |
| US7493393B2 (en)* | 2003-06-23 | 2009-02-17 | Nokia Corporation | Apparatus and method for security management in wireless IP networks |
| US8255804B2 (en)* | 2003-09-22 | 2012-08-28 | Broadcom Corporation | Resource controlled user interface resource management |
| US8271880B2 (en)* | 2003-09-22 | 2012-09-18 | Broadcom Corporation | Central system based user interface resource management |
| EP1544761A1 (en)* | 2003-12-17 | 2005-06-22 | Axel Dr. Glanz | Method and apparatus for the generation and transmission of a graphical image of an electronically generated document |
| US8572388B2 (en)* | 2004-03-10 | 2013-10-29 | Elynx, Ltd. | Electronic document management system |
| US20050210273A1 (en)* | 2004-03-17 | 2005-09-22 | Elynx, Ltd. | Secure electronic message system |
| US8050653B2 (en) | 2004-03-22 | 2011-11-01 | Research In Motion Limited | System and method for viewing message attachments |
| EP1580953B1 (en)* | 2004-03-22 | 2011-02-09 | Research In Motion Limited | System and method for viewing message attachments |
| US7430663B2 (en)* | 2004-08-09 | 2008-09-30 | Research In Motion Limited | System and method for enabling bulk retrieval of certificates |
| US9094429B2 (en) | 2004-08-10 | 2015-07-28 | Blackberry Limited | Server verification of secure electronic messages |
| US7631183B2 (en) | 2004-09-01 | 2009-12-08 | Research In Motion Limited | System and method for retrieving related certificates |
| US7549043B2 (en) | 2004-09-01 | 2009-06-16 | Research In Motion Limited | Providing certificate matching in a system and method for searching and retrieving certificates |
| US7640428B2 (en)* | 2004-09-02 | 2009-12-29 | Research In Motion Limited | System and method for searching and retrieving certificates |
| US9282455B2 (en) | 2004-10-01 | 2016-03-08 | Intel Corporation | System and method for user certificate initiation, distribution, and provisioning in converged WLAN-WWAN interworking networks |
| US7643818B2 (en) | 2004-11-22 | 2010-01-05 | Seven Networks, Inc. | E-mail messaging to/from a mobile terminal |
| US20060217108A1 (en)* | 2005-03-25 | 2006-09-28 | Nec Corporation | Network authentication apparatus, network authentication method, network authentication system, and network authentication program |
| JP4920915B2 (en)* | 2005-06-27 | 2012-04-18 | キヤノン株式会社 | Information processing apparatus, control method for information processing apparatus, and control program |
| JP4148246B2 (en) | 2005-06-30 | 2008-09-10 | ブラザー工業株式会社 | Communication system, certificate update apparatus, certificate update program, communication apparatus, and alternative update program |
| US20070191000A1 (en)* | 2005-09-01 | 2007-08-16 | Veni Salvatore Iii | Pagers over a wireless network |
| US8340289B2 (en) | 2005-09-29 | 2012-12-25 | Research In Motion Limited | System and method for providing an indication of randomness quality of random number data generated by a random data service |
| US7797545B2 (en)* | 2005-09-29 | 2010-09-14 | Research In Motion Limited | System and method for registering entities for code signing services |
| EP1803249B1 (en) | 2005-10-14 | 2010-04-07 | Research In Motion Limited | System and method for protecting master encryption keys |
| US7814161B2 (en) | 2006-06-23 | 2010-10-12 | Research In Motion Limited | System and method for handling electronic mail mismatches |
| KR100908242B1 (en)* | 2006-11-23 | 2009-07-20 | 한국전자통신연구원 | Certificate transmission server and system for transmitting certificate stored in fixed terminal to mobile terminal and method thereof |
| KR100715359B1 (en)* | 2006-12-19 | 2007-05-09 | 한국버추얼페이먼트 주식회사 | Mobile payment verification system and method |
| US8707421B2 (en)* | 2007-06-29 | 2014-04-22 | Siemens Industry, Inc. | System and method for a web based teleservice for updating machine software |
| US7949355B2 (en)* | 2007-09-04 | 2011-05-24 | Research In Motion Limited | System and method for processing attachments to messages sent to a mobile device |
| US8254582B2 (en) | 2007-09-24 | 2012-08-28 | Research In Motion Limited | System and method for controlling message attachment handling functions on a mobile device |
| US20090113543A1 (en)* | 2007-10-25 | 2009-04-30 | Research In Motion Limited | Authentication certificate management for access to a wireless communication device |
| US8073959B2 (en)* | 2008-03-28 | 2011-12-06 | Microsoft Corporation | Automatically detecting whether a computer is connected to a public or private network |
| US8321662B2 (en) | 2008-05-08 | 2012-11-27 | International Business Machines Corporation | Certificate renewal using secure handshake |
| US8862874B2 (en)* | 2008-05-09 | 2014-10-14 | International Business Machines Corporation | Certificate distribution using secure handshake |
| US8005991B2 (en)* | 2008-08-15 | 2011-08-23 | Dell Products, Lp | Virtual machine image management system and methods thereof |
| CN101404575B (en)* | 2008-11-06 | 2011-09-28 | 阿里巴巴集团控股有限公司 | Method and system for updating indorsement algorithm |
| US8484462B2 (en)* | 2008-11-07 | 2013-07-09 | Lockheed Martin Corporation | System and method for establishing a self-realizing expandable communications network |
| US8560851B1 (en)* | 2009-05-15 | 2013-10-15 | Sprint Communications Company L.P. | Managing digital certificates |
| US9680819B2 (en)* | 2009-12-23 | 2017-06-13 | Symantec Corporation | Method and system for co-termination of digital certificates |
| JP5521542B2 (en)* | 2009-12-25 | 2014-06-18 | ブラザー工業株式会社 | Information processing device |
| US9197630B2 (en)* | 2010-03-08 | 2015-11-24 | Microsoft Technology Licensing, Llc | Automated certificate management |
| US8621220B2 (en)* | 2010-03-11 | 2013-12-31 | Ebay Inc. | Systems and methods for identity encapsulated cryptography |
| KR101119874B1 (en)* | 2010-05-17 | 2012-02-22 | 삼성에스디에스 주식회사 | System and method for share certificate with a devices |
| US20110302215A1 (en)* | 2010-06-04 | 2011-12-08 | Research In Motion Limited | Assembly, and associated method, for controlling disposition of enterprise data at a wireless device |
| US8984271B2 (en) | 2010-06-07 | 2015-03-17 | Protected Mobility, Llc | User interface systems and methods for input and display of secure and insecure message oriented communications |
| US9172680B2 (en) | 2010-06-07 | 2015-10-27 | Protected Mobility, Llc | Systems and methods for enabling secure messaging, command, and control of remote devices, communicated via a short message service or other message oriented communications mediums |
| US9143324B2 (en) | 2010-06-07 | 2015-09-22 | Protected Mobility, Llc | Secure messaging |
| US9602277B2 (en)* | 2010-06-07 | 2017-03-21 | Protected Mobilty, Llc | User interface systems and methods for secure message oriented communications |
| US8924706B2 (en) | 2010-11-05 | 2014-12-30 | Protected Mobility, Llc | Systems and methods using one time pads during the exchange of cryptographic material |
| CN102567769B (en)* | 2010-12-31 | 2015-04-01 | 上海格尔软件股份有限公司 | USBKEY with certificate selection |
| CN102307349B (en)* | 2011-08-16 | 2015-04-01 | 宇龙计算机通信科技(深圳)有限公司 | Access method of wireless network, terminal and server |
| US8984273B2 (en) | 2011-12-16 | 2015-03-17 | Protected Mobility, Llc | Method to provide secure multimedia messaging between peer systems |
| US9160719B2 (en) | 2012-07-20 | 2015-10-13 | Protected Mobility, Llc | Hiding ciphertext using a linguistics algorithm with dictionaries |
| WO2014030199A1 (en)* | 2012-08-20 | 2014-02-27 | 富士通株式会社 | Seamless application push system and method for same |
| US8830206B2 (en) | 2012-10-05 | 2014-09-09 | Dell Products, Lp | Systems and methods for locking image orientation |
| CN103001965B (en)* | 2012-12-10 | 2016-01-27 | 北京星网锐捷网络技术有限公司 | Server certificate update method and server |
| US9215075B1 (en) | 2013-03-15 | 2015-12-15 | Poltorak Technologies Llc | System and method for secure relayed communications from an implantable medical device |
| CN104065558A (en)* | 2013-03-20 | 2014-09-24 | 东方斯泰克信息技术研究院(北京)有限公司 | Sending and accepting methods and sending and accepting devices for email |
| US9763067B2 (en) | 2013-05-28 | 2017-09-12 | Protected Mobility, Llc | Methods and apparatus for long-short wave, low-high frequency radio secure message service |
| US9453976B2 (en)* | 2014-09-30 | 2016-09-27 | Apple Inc. | Optical connector |
| US10887370B2 (en)* | 2014-12-18 | 2021-01-05 | Trading Technologies International, Inc. | Visual representation of a user interface |
| WO2017015752A1 (en)* | 2015-07-24 | 2017-02-02 | Radio Ip Software Inc. | Mobile communication system and pre-authentication filters |
| KR102381371B1 (en)* | 2015-12-10 | 2022-03-31 | 삼성전자주식회사 | System and method for providing information by using near field communication |
| US9705859B2 (en)* | 2015-12-11 | 2017-07-11 | Amazon Technologies, Inc. | Key exchange through partially trusted third party |
| US10412098B2 (en) | 2015-12-11 | 2019-09-10 | Amazon Technologies, Inc. | Signed envelope encryption |
| US10715502B2 (en)* | 2015-12-31 | 2020-07-14 | Verisign, Inc. | Systems and methods for automating client-side synchronization of public keys of external contacts |
| CN105516207B (en)* | 2016-01-28 | 2018-08-14 | 浪潮电子信息产业股份有限公司 | Certificate management method in remote authentication |
| US9887975B1 (en)* | 2016-08-03 | 2018-02-06 | KryptCo, Inc. | Systems and methods for delegated cryptography |
| US10187377B2 (en)* | 2017-02-08 | 2019-01-22 | A10 Networks, Inc. | Caching network generated security certificates |
| US10616242B2 (en)* | 2017-10-10 | 2020-04-07 | Blackberry Limited | Forward and backward NIAP migration of certificate stores |
| CN113132108B (en)* | 2019-12-31 | 2022-02-25 | 华为技术有限公司 | Method and device for revoking and verifying digital certificate |
| CN111277581A (en)* | 2020-01-15 | 2020-06-12 | 江苏满运软件科技有限公司 | Certificate early warning management method and device, electronic equipment and storage medium |
| CN113542081B (en)* | 2021-09-16 | 2021-12-24 | 深圳市万睿智能科技有限公司 | Safe intelligent household control method and system |
Citations (158)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US4028500A (en) | 1973-05-15 | 1977-06-07 | Martin Marietta Corporation | Mobile unit supervisory control sequencer and method |
| WO1994012938A1 (en) | 1992-12-02 | 1994-06-09 | Compaq Computer Corporation | Handheld computer with automatic data synchronization with host computer |
| JPH06276221A (en) | 1993-03-17 | 1994-09-30 | Toshiba Corp | Electronic mail system containing top secret mail function |
| WO1994019238A3 (en) | 1993-02-24 | 1994-12-08 | Altair Corp | Control system for aircraft |
| US5410602A (en) | 1993-09-27 | 1995-04-25 | Motorola, Inc. | Method for key management of point-to-point communications |
| JPH07162407A (en) | 1993-12-03 | 1995-06-23 | Fujitsu Ltd | User support device for encrypted communication in network system |
| US5457748A (en) | 1992-11-30 | 1995-10-10 | Motorola, Inc. | Method and apparatus for improved security within encrypted communication devices |
| JPH08251221A (en) | 1995-03-13 | 1996-09-27 | Nippon Telegr & Teleph Corp <Ntt> | Message handling method |
| EP0500245B1 (en) | 1991-02-08 | 1996-11-06 | Kabushiki Kaisha Toshiba | Cipher communication system for transaction data |
| WO1996036934A1 (en) | 1995-05-17 | 1996-11-21 | Smart Touch, L.L.C. | Tokenless identification system for authorization of electronic transactions and electronic transmissions |
| JPH0946330A (en) | 1995-07-28 | 1997-02-14 | Toshiba Corp | E-mail encryption device and e-mail transfer device |
| US5623546A (en) | 1995-06-23 | 1997-04-22 | Motorola, Inc. | Encryption method and system for portable data |
| EP0500222B1 (en) | 1991-02-14 | 1997-10-22 | Hewlett-Packard Company | Method for reconciling entries in a plurality of lists |
| WO1997041661A3 (en) | 1996-04-29 | 1997-12-11 | Motorola Inc | Use of an encryption server for encrypting messages |
| US5710922A (en) | 1993-06-02 | 1998-01-20 | Apple Computer, Inc. | Method for synchronizing and archiving information between computer systems |
| JPH1022992A (en) | 1996-07-05 | 1998-01-23 | Hitachi Inf Syst Ltd | Message broadcast communication method and storage medium |
| US5727202A (en) | 1995-10-18 | 1998-03-10 | Palm Computing, Inc. | Method and apparatus for synchronizing information on two different computer systems |
| JPH10107832A (en) | 1996-09-25 | 1998-04-24 | Hitachi Software Eng Co Ltd | Cipher multi-address mail system |
| US5778068A (en) | 1995-02-13 | 1998-07-07 | Eta Technologies Corporation | Personal access management system |
| US5778346A (en) | 1992-01-21 | 1998-07-07 | Starfish Software, Inc. | System and methods for appointment reconcilation |
| WO1998034374A1 (en) | 1997-01-31 | 1998-08-06 | Motorola Inc. | Encryption and decryption method and apparatus |
| US5812671A (en) | 1996-07-17 | 1998-09-22 | Xante Corporation | Cryptographic communication system |
| WO1999005814A2 (en) | 1997-07-24 | 1999-02-04 | Worldtalk Corporation | E-mail firewall with stored key encryption/decryption |
| US5870030A (en) | 1996-04-04 | 1999-02-09 | Motorola, Inc. | Advertiser pays information and messaging system and apparatus |
| WO1999006900A3 (en) | 1997-07-30 | 1999-04-08 | Visto Corp | System and method for globally and securely accessing unified information in a computer network |
| WO1999017564A1 (en) | 1997-09-29 | 1999-04-08 | Motorola Inc. | Method and apparatus for providing subscriber identification protection to a receiver |
| WO1999027678A3 (en) | 1997-11-26 | 1999-08-12 | Nokia Telecommunications Oy | Security of data connections |
| US5956707A (en) | 1997-02-13 | 1999-09-21 | Chu; Wesley W. | Database system with query relaxation using type abstraction hierarchy (TAH) as query condition relaxation structure |
| JPH11272581A (en) | 1998-03-25 | 1999-10-08 | Toshiba Corp | Mail transmission method and system and recording medium on which the method is programmed and recorded |
| JPH11272582A (en) | 1998-03-25 | 1999-10-08 | Sony Corp | Electronic mail providing device and electronic mail providing method |
| US5991399A (en) | 1997-12-18 | 1999-11-23 | Intel Corporation | Method for securely distributing a conditional use private key to a trusted entity on a remote system |
| US6000000A (en) | 1995-10-13 | 1999-12-07 | 3Com Corporation | Extendible method and apparatus for synchronizing multiple files on two different computer systems |
| WO1999064946A1 (en) | 1998-06-12 | 1999-12-16 | Microsoft Corporation | Method and system for secure running of untrusted content |
| JP2000010477A (en) | 1998-06-22 | 2000-01-14 | Mitsubishi Electric Corp | Certificate collection information generation device, certificate verification device, and public key cryptographic operation system |
| JP2000049766A (en) | 1998-07-27 | 2000-02-18 | Hitachi Ltd | Key management server system |
| EP0942568A3 (en) | 1998-02-17 | 2000-04-12 | Phone.Com Inc. | Centralized certificate management system for two-way interactive communication devices in data networks |
| WO1999063709A3 (en) | 1998-05-29 | 2000-04-13 | Research In Motion Ltd | System and method for pushing information from a host system to a mobile data communication device |
| US6061448A (en) | 1997-04-01 | 2000-05-09 | Tumbleweed Communications Corp. | Method and system for dynamic server document encryption |
| WO2000031931A1 (en) | 1998-11-24 | 2000-06-02 | Telefonaktiebolaget Lm Ericsson (Publ) | Method and system for securing data objects |
| US6073237A (en) | 1997-11-06 | 2000-06-06 | Cybercash, Inc. | Tamper resistant method and apparatus |
| US6081601A (en) | 1998-01-08 | 2000-06-27 | Nokia Telecommunications Oy | Method of implementing connection security in a wireless network |
| US6085323A (en) | 1996-04-15 | 2000-07-04 | Kabushiki Kaisha Toshiba | Information processing system having function of securely protecting confidential information |
| US6084969A (en) | 1997-12-31 | 2000-07-04 | V-One Corporation | Key encryption system and method, pager unit, and pager proxy for a two-way alphanumeric pager network |
| US6108788A (en) | 1997-12-08 | 2000-08-22 | Entrust Technologies Limited | Certificate management system and method for a communication security system |
| US6119228A (en) | 1997-08-22 | 2000-09-12 | Compaq Computer Corporation | Method for securely communicating remote control commands in a computer network |
| US6125369A (en) | 1997-10-02 | 2000-09-26 | Microsoft Corporation | Continuous object sychronization between object stores on different computers |
| WO2000069114A1 (en) | 1999-05-10 | 2000-11-16 | Telefonaktiebolaget Lm Ericsson (Publ) | Indirect public-key encryption |
| WO2000072506A1 (en) | 1999-05-21 | 2000-11-30 | International Business Machines Corporation | Method and apparatus for initializing secure communications among, and for exclusively pairing wireless devices |
| WO2001001644A1 (en) | 1999-06-29 | 2001-01-04 | Samsung Electronics Co., Ltd. | Apparatus for securing user's information in a mobile communication system connected to the internet and method thereof |
| WO2001016933A1 (en) | 1999-08-30 | 2001-03-08 | Fujitsu Limited | Device for data reproduction |
| US6209098B1 (en) | 1996-10-25 | 2001-03-27 | Intel Corporation | Circuit and method for ensuring interconnect security with a multi-chip integrated circuit package |
| WO2001024434A1 (en) | 1999-09-30 | 2001-04-05 | B.M.N. Technology | System for providing messages |
| JP2001103571A (en) | 1999-10-01 | 2001-04-13 | Mitsubishi Electric Corp | Mobile communication service providing system |
| US6229894B1 (en) | 1997-07-14 | 2001-05-08 | Entrust Technologies, Ltd. | Method and apparatus for access to user-specific encryption information |
| US6230186B1 (en) | 1998-04-28 | 2001-05-08 | Rhoda Yaker | Private electronic message system |
| US6231985B1 (en) | 1999-05-18 | 2001-05-15 | Ashland Inc. | Heat and radio frequency-curable two-pack soy protein-based polyurethane adhesive compositions |
| JP2001147849A (en) | 1999-11-19 | 2001-05-29 | Toshiba Corp | Communication method and electronic device for data synchronization processing |
| JP2001197055A (en) | 2000-01-07 | 2001-07-19 | Nippon Steel Corp | Authentication proxy device, authentication proxy method, authentication proxy service system, and computer-readable recording medium |
| US6266775B1 (en) | 1997-08-25 | 2001-07-24 | Nec Corporation | Method and apparatus for displaying information and information recording medium having information displaying means |
| US6266420B1 (en) | 1998-10-08 | 2001-07-24 | Entrust Technologies Limited | Method and apparatus for secure group communications |
| WO2001063386A1 (en) | 2000-02-23 | 2001-08-30 | Kim Leeper | A system and method for authenticating electronic documents |
| US6301658B1 (en) | 1998-09-09 | 2001-10-09 | Secure Computing Corporation | Method and system for authenticating digital certificates issued by an authentication hierarchy |
| US6314190B1 (en) | 1997-06-06 | 2001-11-06 | Networks Associates Technology, Inc. | Cryptographic system with methods for user-controlled message recovery |
| US20010046307A1 (en) | 1998-04-30 | 2001-11-29 | Hewlett-Packard Company | Method and apparatus for digital watermarking of images |
| US20010050990A1 (en) | 1997-02-19 | 2001-12-13 | Frank Wells Sudia | Method for initiating a stream-oriented encrypted communication |
| US20020007453A1 (en) | 2000-05-23 | 2002-01-17 | Nemovicher C. Kerry | Secured electronic mail system and method |
| US6348972B1 (en) | 1995-06-01 | 2002-02-19 | Tokyo Shibaura Electric Co | Network print system for allowing a printer or printers to select a host |
| WO2001041353A3 (en) | 1999-11-30 | 2002-02-21 | Sun Microsystems Inc | Method and apparatus for sending encrypted electronic mail through a distribution list exploder |
| US20020032861A1 (en) | 2000-07-14 | 2002-03-14 | Nec Corporation | System and method for executing and assuring security of electronic mail for users, and storage medium storing program to cause computer to implement same method |
| WO2001078491A3 (en) | 2000-04-14 | 2002-03-14 | Postx Corp | Systems and methods for encrypting/decrypting data using a broker agent |
| US20020035685A1 (en) | 2000-09-11 | 2002-03-21 | Masahiro Ono | Client-server system with security function intermediary |
| US20020035687A1 (en) | 2000-06-07 | 2002-03-21 | Kristofer Skantze | Method and device for secure wireless transmission of information |
| US20020038420A1 (en) | 2000-04-13 | 2002-03-28 | Collins Timothy S. | Method for efficient public key based certification for mobile and desktop environments |
| GB2328125B (en) | 1997-08-08 | 2002-04-10 | Ericsson Telefon Ab L M | Network control system |
| US20020053023A1 (en) | 2000-08-17 | 2002-05-02 | Patterson Andrew John | Certification validation system |
| US20020051544A1 (en) | 1993-12-03 | 2002-05-02 | Fujitsu Limited | User support system for cryptographic communication in network systems |
| WO2001071608A3 (en) | 2000-03-17 | 2002-05-02 | Mark Nair | System, method and apparatus for controlling the dissemination of digital works |
| US20020053032A1 (en) | 2000-09-14 | 2002-05-02 | Dowling William Race | System and method for secure data transmission |
| US6389455B1 (en) | 1998-09-22 | 2002-05-14 | Richard C. Fuisz | Method and apparatus for bouncing electronic messages |
| US20020059375A1 (en) | 1999-04-08 | 2002-05-16 | Alvin Pivowar | System and method for sharing data among a plurality of personal digital assistants |
| US20020059383A1 (en) | 2000-06-19 | 2002-05-16 | Takeo Katsuda | Apparatus, portable terminal unit, and system for controlling E-mail, and its method, computer-readable recording medium and program product for processing E-mail |
| US20020080752A1 (en) | 2000-12-22 | 2002-06-27 | Fredrik Johansson | Route optimization technique for mobile IP |
| US20020099766A1 (en) | 2001-01-24 | 2002-07-25 | Tuli Raja Singh | Portable high speed internet access device with encryption |
| US6463463B1 (en) | 1998-05-29 | 2002-10-08 | Research In Motion Limited | System and method for pushing calendar event messages from a host system to a mobile data communication device |
| US20020147905A1 (en) | 2001-04-05 | 2002-10-10 | Sun Microsystems, Inc. | System and method for shortening certificate chains |
| JP2002535884A (en) | 1999-01-14 | 2002-10-22 | タンブルウィード コミュニケーションズ コーポレイション | Distribution of web-based secure email messages |
| US20020165967A1 (en) | 2001-05-02 | 2002-11-07 | Morgan Paul A. | Global personalization engine |
| US20020169954A1 (en) | 1998-11-03 | 2002-11-14 | Bandini Jean-Christophe Denis | Method and system for e-mail message transmission |
| US20020173295A1 (en) | 2001-05-15 | 2002-11-21 | Petri Nykanen | Context sensitive web services |
| US20020176067A1 (en) | 2001-05-23 | 2002-11-28 | Canesta, Inc. | Method and system to enhance dynamic range conversion useable with CMOS three-dimensional imaging |
| WO2002101580A1 (en) | 2001-06-12 | 2002-12-19 | Research In Motion Limited | Certificate management and transfer system and method |
| US20030002671A1 (en) | 2001-06-11 | 2003-01-02 | Eastman Kodak Company | Delivery of electronic content over a network using a hybrid optical disk for authentication |
| WO2003007570A1 (en) | 2001-07-10 | 2003-01-23 | Research In Motion Limited | System and method for secure message key caching in a mobile communication device |
| WO2002101605A3 (en) | 2001-06-12 | 2003-03-06 | Research In Motion Ltd | System and method for compressing secure e-mail for exchange with a mobile data communication device |
| US6531985B1 (en) | 2000-08-14 | 2003-03-11 | 3Com Corporation | Integrated laptop antenna using two or more antennas |
| WO2002102009A3 (en) | 2001-06-12 | 2003-04-10 | Research In Motion Ltd | Method for processing encoded messages for exchange with a mobile data communication device |
| US20030074555A1 (en) | 2001-10-17 | 2003-04-17 | Fahn Paul Neil | URL-based certificate in a PKI |
| US6564320B1 (en) | 1998-06-30 | 2003-05-13 | Verisign, Inc. | Local hosting of digital certificate services |
| WO2003015367A3 (en) | 2001-08-06 | 2003-05-30 | Research In Motion Ltd | System and method for processing encoded messages |
| WO2003009561A3 (en) | 2001-07-16 | 2003-05-30 | Research In Motion Ltd | A system and method for supporting multiple certificate authorities on a mobile communication device |
| US20030126085A1 (en) | 2001-12-27 | 2003-07-03 | Slamdunk Networks, Inc. | Dynamic authentication of electronic messages using a reference to a certificate |
| KR20030059303A (en) | 2000-12-07 | 2003-07-07 | 톰슨 라이센싱 소시에떼 아노님 | Method of secure transmission of digital data from a source to a receiver |
| US20030172122A1 (en) | 2002-03-06 | 2003-09-11 | Little Herbert A. | System and method for providing secure message signature status and trust status indication |
| WO2003075530A1 (en) | 2002-03-01 | 2003-09-12 | Research In Motion Limited | System and method for providing secure message signature status and trust status indication |
| WO2003079628A1 (en) | 2002-03-20 | 2003-09-25 | Research In Motion Limited | Certificate information storage system and method |
| US20030198350A1 (en) | 2002-04-18 | 2003-10-23 | International Business Machines Corporation | Method, system and program product for managing a size of a key management block during content distribution |
| US20030212888A1 (en) | 1998-08-26 | 2003-11-13 | Wildish Michael Andrew | System and method of looking up and validating a digital certificate in one pass |
| US6661927B1 (en) | 2000-07-27 | 2003-12-09 | Motorola, Inc. | System and method for efficiently encoding an image by prioritizing groups of spatially correlated coefficients based on an activity measure |
| WO2003079627A3 (en) | 2002-03-20 | 2003-12-18 | Research In Motion Ltd | System and method for supporting multiple certificate status providers on a mobile communication device |
| JP2004048139A (en) | 2002-07-09 | 2004-02-12 | Nikon Corp | Image transmission system, image relay device, and electronic image equipment |
| EP0841770B1 (en) | 1996-11-06 | 2004-02-18 | Nokia Corporation | Method for sending a secure message in a telecommunications system |
| US6697942B1 (en) | 1999-02-04 | 2004-02-24 | Earthlink, Inc. | Method for remotely managing a remote device using an electronic mail message |
| US6725262B1 (en) | 2000-04-27 | 2004-04-20 | Microsoft Corporation | Methods and systems for synchronizing multiple computing devices |
| US20040093493A1 (en) | 1995-01-17 | 2004-05-13 | Bisbee Stephen F. | System and method for electronic transmission, storage and retrieval of authenticated documents |
| WO2003005636A8 (en) | 2001-07-04 | 2004-05-13 | Ericsson Telefon Ab L M | Secure header information for multi-content e-mail |
| US6745024B1 (en) | 2000-01-10 | 2004-06-01 | Qualcomm Incorporated | System and method for preparing and sending an electronic mail communication using a wireless communications device |
| US20040133775A1 (en) | 2003-01-07 | 2004-07-08 | Callas Jonathan D. | System and method for secure electronic communication in a partially keyless environment |
| US20040133520A1 (en) | 2003-01-07 | 2004-07-08 | Callas Jonathan D. | System and method for secure and transparent electronic communication |
| US6779115B1 (en) | 2000-02-18 | 2004-08-17 | Digital5, Inc. | Portable device using a smart card to receive and decrypt digital data |
| US6819766B1 (en) | 1999-03-30 | 2004-11-16 | International Business Machines Corporation | Method and system for managing keys for encrypted data |
| US6829357B1 (en) | 1999-12-14 | 2004-12-07 | Trw Inc. | Communication system having a transmitter and a receiver that engage in reduced size encrypted data communication |
| US20050005097A1 (en) | 2003-06-12 | 2005-01-06 | Minolta Co., Ltd. | Communication system and method in public key infrastructure |
| US20050039100A1 (en) | 2003-08-14 | 2005-02-17 | International Business Machines Corporation | Method and system for automatic error recovery in an electronic mail system |
| US20050114671A1 (en) | 2002-03-20 | 2005-05-26 | Research In Motion Ltd. | System and method for transmitting and utilizing attachments |
| US6904521B1 (en) | 2001-02-16 | 2005-06-07 | Networks Associates Technology, Inc. | Non-repudiation of e-mail messages |
| US6918038B1 (en) | 1996-08-13 | 2005-07-12 | Angel Secure Networks, Inc. | System and method for installing an auditable secure network |
| US6925568B1 (en) | 1998-01-16 | 2005-08-02 | Sonera Oyj | Method and system for the processing of messages in a telecommunication system |
| US6931532B1 (en) | 1999-10-21 | 2005-08-16 | International Business Machines Corporation | Selective data encryption using style sheet processing |
| US20050188219A1 (en) | 2003-12-26 | 2005-08-25 | Orange France | Method and a system for communication between a terminal and at least one communication equipment |
| US20050203855A1 (en) | 2000-11-08 | 2005-09-15 | Orchestria Limited | Information management system |
| US20050210289A1 (en) | 2004-03-22 | 2005-09-22 | Brown Michael K | System and method for viewing message attachments |
| US20050222991A1 (en) | 2004-02-04 | 2005-10-06 | Kazuyuki Ikenoya | Information providing apparatus, information providing method, information providing program, and recording medium |
| US20050246763A1 (en) | 2004-03-25 | 2005-11-03 | National University Of Ireland | Secure digital content reproduction using biometrically derived hybrid encryption techniques |
| US6983367B2 (en) | 2000-03-14 | 2006-01-03 | Sony Corporation | Information providing apparatus and method, information processing apparatus and method, and program storage medium |
| US20060015722A1 (en) | 2004-07-16 | 2006-01-19 | Geotrust | Security systems and services to provide identity and uniform resource identifier verification |
| US6993137B2 (en) | 2000-06-16 | 2006-01-31 | Entriq, Inc. | Method and system to securely distribute content via a network |
| US6996720B1 (en) | 1999-12-17 | 2006-02-07 | Microsoft Corporation | System and method for accessing protected content in a rights-management architecture |
| CA2476914A1 (en) | 2004-08-09 | 2006-02-09 | Research In Motion Limited | System and method for certificate searching and retrieval |
| US20060036849A1 (en) | 2004-08-09 | 2006-02-16 | Research In Motion Limited | System and method for certificate searching and retrieval |
| US20060036848A1 (en) | 2004-08-09 | 2006-02-16 | Research In Motion Limited | System and method for enabling bulk retrieval of certificates |
| US20060036865A1 (en) | 2004-08-10 | 2006-02-16 | Research In Motion Limited | Server verification of secure electronic messages |
| US7003667B1 (en) | 1999-10-04 | 2006-02-21 | Canon Kabushiki Kaisha | Targeted secure printing |
| US20060059332A1 (en) | 2004-09-02 | 2006-03-16 | Research In Motion Limited | System and method for searching and retrieving certificates |
| US7020708B2 (en) | 1999-05-14 | 2006-03-28 | Cingular Wireless Ii, Llc | Aircraft data services |
| US7032240B1 (en) | 1999-12-07 | 2006-04-18 | Pace Anti-Piracy, Inc. | Portable authorization device for authorizing use of protected information and associated method |
| US7113927B1 (en) | 1998-10-09 | 2006-09-26 | Victor Company Of Japan, Limited | Data distribution system, data distribution method, portable terminal with data receiving capability, portable terminal with data transmitting/receiving capability, recording medium onto which data content is recorded, encoding apparatus, and decoding apparatus |
| US7127604B2 (en) | 2002-07-09 | 2006-10-24 | Texas Instruments Incorporated | Changing a codec or MAC size without affecting the encryption key in PacketCable communication |
| US7171552B1 (en) | 1999-11-29 | 2007-01-30 | Cisco Technology, Inc. | Encrypting information in a communications network |
| US20070083749A1 (en) | 2005-10-12 | 2007-04-12 | The Boeing Company | Systems and methods for automated exchange of electronic mail encryption certificates |
| US20070118874A1 (en) | 2005-11-18 | 2007-05-24 | Research In Motion Limited | System and method for handling electronic messages |
| US20070123307A1 (en) | 2005-11-30 | 2007-05-31 | Research In Motion Limited | Display of secure messages on a mobile communication device |
| US7228418B1 (en) | 1999-04-08 | 2007-06-05 | France Telecom | Authentication and signature method for messages using reduced size of binary units of information content and corresponding systems |
| EP1806683A1 (en) | 2005-11-30 | 2007-07-11 | Research In Motion Limited | Display of secure messages on a mobile communication device |
| US20070165844A1 (en) | 2005-10-14 | 2007-07-19 | Research In Motion Limited | System and method for protecting master encryption keys |
| US7299502B2 (en) | 2001-02-14 | 2007-11-20 | Hewlett-Packard Development Company, L.P. | System and method for providing customized secure access to shared documents |
| US7529374B2 (en) | 2002-02-02 | 2009-05-05 | F-Secure Oyj | Method and apparatus for encrypting data |
| EP1580953B1 (en) | 2004-03-22 | 2011-02-09 | Research In Motion Limited | System and method for viewing message attachments |
| US7953971B2 (en) | 2005-10-27 | 2011-05-31 | Research In Motion Limited | Synchronizing certificates between a device and server |
Family Cites Families (6)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| JPH0322259A (en)* | 1989-03-22 | 1991-01-30 | Seiko Epson Corp | Small-sized data display and reproducing device |
| DE10350063A1 (en) | 2003-10-27 | 2005-05-25 | Rohde & Schwarz Gmbh & Co. Kg | Radio interference levels measuring method e.g. for RF circuits, involves measuring level of signal and in each case with limit value compared and during excess of limit value by measuring level, respective measuring frequency is marked |
| JP4428272B2 (en) | 2005-03-28 | 2010-03-10 | セイコーエプソン株式会社 | Display driver and electronic device |
| JP4666498B2 (en) | 2005-12-16 | 2011-04-06 | 大豊建設株式会社 | Earth pressure shield |
| JP5192752B2 (en) | 2007-08-15 | 2013-05-08 | 古河電気工業株式会社 | Method for producing silica nanoparticles using reverse micelle dispersion, silica nanoparticles obtained by the method, and labeling reagent using the same |
| JP5137783B2 (en) | 2008-10-31 | 2013-02-06 | 三菱電機株式会社 | Hash generation device, verification device, hash generation program, and hash generation method |
- 2002
- 2002-06-12CACA2717229Apatent/CA2717229A1/ennot_activeAbandoned
- 2002-06-12JPJP2003504272Apatent/JP2004532590A/enactivePending
- 2002-06-12WOPCT/CA2002/000868patent/WO2002101580A1/enactiveApplication Filing
- 2002-06-12KRKR10-2003-7016487Apatent/KR20040015272A/ennot_activeCeased
- 2002-06-12EPEP02737687Apatent/EP1399853A1/ennot_activeCeased
- 2002-06-12ILIL15934202Apatent/IL159342A0/enactiveIP Right Grant
- 2002-06-12CNCNB028153820Apatent/CN100410927C/ennot_activeExpired - Lifetime
- 2002-06-12CACA2450584Apatent/CA2450584C/ennot_activeExpired - Lifetime
- 2002-06-12USUS10/480,615patent/US7546453B2/ennot_activeExpired - Lifetime
- 2003
- 2003-12-11ILIL159342Apatent/IL159342A/enunknown
- 2007
- 2007-03-09JPJP2007061073Apatent/JP2007221806A/enactivePending
- 2009
- 2009-06-09USUS12/480,841patent/US8015400B2/ennot_activeCeased
- 2011
- 2011-09-01USUS13/223,999patent/US8539226B2/ennot_activeExpired - Lifetime
- 2013
- 2013-08-12USUS13/964,180patent/USRE45087E1/ennot_activeExpired - Fee Related
Patent Citations (187)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US4028500A (en) | 1973-05-15 | 1977-06-07 | Martin Marietta Corporation | Mobile unit supervisory control sequencer and method |
| EP0500245B1 (en) | 1991-02-08 | 1996-11-06 | Kabushiki Kaisha Toshiba | Cipher communication system for transaction data |
| EP0500222B1 (en) | 1991-02-14 | 1997-10-22 | Hewlett-Packard Company | Method for reconciling entries in a plurality of lists |
| US5778346A (en) | 1992-01-21 | 1998-07-07 | Starfish Software, Inc. | System and methods for appointment reconcilation |
| US5457748A (en) | 1992-11-30 | 1995-10-10 | Motorola, Inc. | Method and apparatus for improved security within encrypted communication devices |
| WO1994012938A1 (en) | 1992-12-02 | 1994-06-09 | Compaq Computer Corporation | Handheld computer with automatic data synchronization with host computer |
| JPH07509333A (en) | 1992-12-02 | 1995-10-12 | コンパック・コンピュータ・コーポレイション | Handheld computer with automatic data synchronization with host computer |
| US5666530A (en) | 1992-12-02 | 1997-09-09 | Compaq Computer Corporation | System for automatic synchronization of common file between portable computer and host computer via communication channel selected from a plurality of usable channels there between |
| US20010011308A1 (en) | 1992-12-02 | 2001-08-02 | Ted H. Clark | Handheld computer synchronized with a host computer |
| WO1994019238A3 (en) | 1993-02-24 | 1994-12-08 | Altair Corp | Control system for aircraft |
| JPH06276221A (en) | 1993-03-17 | 1994-09-30 | Toshiba Corp | Electronic mail system containing top secret mail function |
| US5710922A (en) | 1993-06-02 | 1998-01-20 | Apple Computer, Inc. | Method for synchronizing and archiving information between computer systems |
| US5410602A (en) | 1993-09-27 | 1995-04-25 | Motorola, Inc. | Method for key management of point-to-point communications |
| US20020051544A1 (en) | 1993-12-03 | 2002-05-02 | Fujitsu Limited | User support system for cryptographic communication in network systems |
| JPH07162407A (en) | 1993-12-03 | 1995-06-23 | Fujitsu Ltd | User support device for encrypted communication in network system |
| US20040093493A1 (en) | 1995-01-17 | 2004-05-13 | Bisbee Stephen F. | System and method for electronic transmission, storage and retrieval of authenticated documents |
| US5778068A (en) | 1995-02-13 | 1998-07-07 | Eta Technologies Corporation | Personal access management system |
| JPH08251221A (en) | 1995-03-13 | 1996-09-27 | Nippon Telegr & Teleph Corp <Ntt> | Message handling method |
| WO1996036934A1 (en) | 1995-05-17 | 1996-11-21 | Smart Touch, L.L.C. | Tokenless identification system for authorization of electronic transactions and electronic transmissions |
| US6348972B1 (en) | 1995-06-01 | 2002-02-19 | Tokyo Shibaura Electric Co | Network print system for allowing a printer or printers to select a host |
| US5623546A (en) | 1995-06-23 | 1997-04-22 | Motorola, Inc. | Encryption method and system for portable data |
| JPH0946330A (en) | 1995-07-28 | 1997-02-14 | Toshiba Corp | E-mail encryption device and e-mail transfer device |
| US6289105B1 (en) | 1995-07-28 | 2001-09-11 | Kabushiki Kaisha Toshiba | Method and apparatus for encrypting and transferring electronic mails |
| US6000000A (en) | 1995-10-13 | 1999-12-07 | 3Com Corporation | Extendible method and apparatus for synchronizing multiple files on two different computer systems |
| US5727202A (en) | 1995-10-18 | 1998-03-10 | Palm Computing, Inc. | Method and apparatus for synchronizing information on two different computer systems |
| US6313732B1 (en) | 1996-04-04 | 2001-11-06 | Motorola, Inc. | Advertiser pays information and messaging system, apparatus and method |
| US5870030A (en) | 1996-04-04 | 1999-02-09 | Motorola, Inc. | Advertiser pays information and messaging system and apparatus |
| US6085323A (en) | 1996-04-15 | 2000-07-04 | Kabushiki Kaisha Toshiba | Information processing system having function of securely protecting confidential information |
| WO1997041661A3 (en) | 1996-04-29 | 1997-12-11 | Motorola Inc | Use of an encryption server for encrypting messages |
| JPH1022992A (en) | 1996-07-05 | 1998-01-23 | Hitachi Inf Syst Ltd | Message broadcast communication method and storage medium |
| US5812671A (en) | 1996-07-17 | 1998-09-22 | Xante Corporation | Cryptographic communication system |
| US6918038B1 (en) | 1996-08-13 | 2005-07-12 | Angel Secure Networks, Inc. | System and method for installing an auditable secure network |
| JPH10107832A (en) | 1996-09-25 | 1998-04-24 | Hitachi Software Eng Co Ltd | Cipher multi-address mail system |
| US6209098B1 (en) | 1996-10-25 | 2001-03-27 | Intel Corporation | Circuit and method for ensuring interconnect security with a multi-chip integrated circuit package |
| EP0841770B1 (en) | 1996-11-06 | 2004-02-18 | Nokia Corporation | Method for sending a secure message in a telecommunications system |
| WO1998034374A1 (en) | 1997-01-31 | 1998-08-06 | Motorola Inc. | Encryption and decryption method and apparatus |
| US5956707A (en) | 1997-02-13 | 1999-09-21 | Chu; Wesley W. | Database system with query relaxation using type abstraction hierarchy (TAH) as query condition relaxation structure |
| US20010050990A1 (en) | 1997-02-19 | 2001-12-13 | Frank Wells Sudia | Method for initiating a stream-oriented encrypted communication |
| US6061448A (en) | 1997-04-01 | 2000-05-09 | Tumbleweed Communications Corp. | Method and system for dynamic server document encryption |
| US6314190B1 (en) | 1997-06-06 | 2001-11-06 | Networks Associates Technology, Inc. | Cryptographic system with methods for user-controlled message recovery |
| US6229894B1 (en) | 1997-07-14 | 2001-05-08 | Entrust Technologies, Ltd. | Method and apparatus for access to user-specific encryption information |
| WO1999005814A2 (en) | 1997-07-24 | 1999-02-04 | Worldtalk Corporation | E-mail firewall with stored key encryption/decryption |
| WO1999006900A3 (en) | 1997-07-30 | 1999-04-08 | Visto Corp | System and method for globally and securely accessing unified information in a computer network |
| GB2328125B (en) | 1997-08-08 | 2002-04-10 | Ericsson Telefon Ab L M | Network control system |
| US6119228A (en) | 1997-08-22 | 2000-09-12 | Compaq Computer Corporation | Method for securely communicating remote control commands in a computer network |
| US6266775B1 (en) | 1997-08-25 | 2001-07-24 | Nec Corporation | Method and apparatus for displaying information and information recording medium having information displaying means |
| WO1999017564A1 (en) | 1997-09-29 | 1999-04-08 | Motorola Inc. | Method and apparatus for providing subscriber identification protection to a receiver |
| US6125369A (en) | 1997-10-02 | 2000-09-26 | Microsoft Corporation | Continuous object sychronization between object stores on different computers |
| US6073237A (en) | 1997-11-06 | 2000-06-06 | Cybercash, Inc. | Tamper resistant method and apparatus |
| WO1999027678A3 (en) | 1997-11-26 | 1999-08-12 | Nokia Telecommunications Oy | Security of data connections |
| US6108788A (en) | 1997-12-08 | 2000-08-22 | Entrust Technologies Limited | Certificate management system and method for a communication security system |
| US5991399A (en) | 1997-12-18 | 1999-11-23 | Intel Corporation | Method for securely distributing a conditional use private key to a trusted entity on a remote system |
| US6084969A (en) | 1997-12-31 | 2000-07-04 | V-One Corporation | Key encryption system and method, pager unit, and pager proxy for a two-way alphanumeric pager network |
| US6081601A (en) | 1998-01-08 | 2000-06-27 | Nokia Telecommunications Oy | Method of implementing connection security in a wireless network |
| US6925568B1 (en) | 1998-01-16 | 2005-08-02 | Sonera Oyj | Method and system for the processing of messages in a telecommunication system |
| EP0942568A3 (en) | 1998-02-17 | 2000-04-12 | Phone.Com Inc. | Centralized certificate management system for two-way interactive communication devices in data networks |
| JPH11272581A (en) | 1998-03-25 | 1999-10-08 | Toshiba Corp | Mail transmission method and system and recording medium on which the method is programmed and recorded |
| JPH11272582A (en) | 1998-03-25 | 1999-10-08 | Sony Corp | Electronic mail providing device and electronic mail providing method |
| US6230186B1 (en) | 1998-04-28 | 2001-05-08 | Rhoda Yaker | Private electronic message system |
| US20010046307A1 (en) | 1998-04-30 | 2001-11-29 | Hewlett-Packard Company | Method and apparatus for digital watermarking of images |
| WO1999063709A3 (en) | 1998-05-29 | 2000-04-13 | Research In Motion Ltd | System and method for pushing information from a host system to a mobile data communication device |
| US6463463B1 (en) | 1998-05-29 | 2002-10-08 | Research In Motion Limited | System and method for pushing calendar event messages from a host system to a mobile data communication device |
| EP1096725B1 (en) | 1998-05-29 | 2009-03-11 | Research In Motion Limited | System and method for pushing information from a host system to a mobile data communication device |
| US6219694B1 (en) | 1998-05-29 | 2001-04-17 | Research In Motion Limited | System and method for pushing information from a host system to a mobile data communication device having a shared electronic address |
| EP1096727B1 (en) | 1998-05-29 | 2006-03-22 | Research In Motion Limited | System and method for pushing information from a host system to a mobile data communication device |
| WO1999064946A1 (en) | 1998-06-12 | 1999-12-16 | Microsoft Corporation | Method and system for secure running of untrusted content |
| JP2000010477A (en) | 1998-06-22 | 2000-01-14 | Mitsubishi Electric Corp | Certificate collection information generation device, certificate verification device, and public key cryptographic operation system |
| US6564320B1 (en) | 1998-06-30 | 2003-05-13 | Verisign, Inc. | Local hosting of digital certificate services |
| JP2000049766A (en) | 1998-07-27 | 2000-02-18 | Hitachi Ltd | Key management server system |
| US20030212888A1 (en) | 1998-08-26 | 2003-11-13 | Wildish Michael Andrew | System and method of looking up and validating a digital certificate in one pass |
| US6301658B1 (en) | 1998-09-09 | 2001-10-09 | Secure Computing Corporation | Method and system for authenticating digital certificates issued by an authentication hierarchy |
| US6389455B1 (en) | 1998-09-22 | 2002-05-14 | Richard C. Fuisz | Method and apparatus for bouncing electronic messages |
| US6266420B1 (en) | 1998-10-08 | 2001-07-24 | Entrust Technologies Limited | Method and apparatus for secure group communications |
| US7113927B1 (en) | 1998-10-09 | 2006-09-26 | Victor Company Of Japan, Limited | Data distribution system, data distribution method, portable terminal with data receiving capability, portable terminal with data transmitting/receiving capability, recording medium onto which data content is recorded, encoding apparatus, and decoding apparatus |
| US20020169954A1 (en) | 1998-11-03 | 2002-11-14 | Bandini Jean-Christophe Denis | Method and system for e-mail message transmission |
| WO2000031931A1 (en) | 1998-11-24 | 2000-06-02 | Telefonaktiebolaget Lm Ericsson (Publ) | Method and system for securing data objects |
| JP2002535884A (en) | 1999-01-14 | 2002-10-22 | タンブルウィード コミュニケーションズ コーポレイション | Distribution of web-based secure email messages |
| US6697942B1 (en) | 1999-02-04 | 2004-02-24 | Earthlink, Inc. | Method for remotely managing a remote device using an electronic mail message |
| US6819766B1 (en) | 1999-03-30 | 2004-11-16 | International Business Machines Corporation | Method and system for managing keys for encrypted data |
| US20020059375A1 (en) | 1999-04-08 | 2002-05-16 | Alvin Pivowar | System and method for sharing data among a plurality of personal digital assistants |
| US7228418B1 (en) | 1999-04-08 | 2007-06-05 | France Telecom | Authentication and signature method for messages using reduced size of binary units of information content and corresponding systems |
| WO2000069114A1 (en) | 1999-05-10 | 2000-11-16 | Telefonaktiebolaget Lm Ericsson (Publ) | Indirect public-key encryption |
| US7020708B2 (en) | 1999-05-14 | 2006-03-28 | Cingular Wireless Ii, Llc | Aircraft data services |
| US6231985B1 (en) | 1999-05-18 | 2001-05-15 | Ashland Inc. | Heat and radio frequency-curable two-pack soy protein-based polyurethane adhesive compositions |
| CA2371329C (en) | 1999-05-21 | 2005-12-06 | International Business Machines Corporation | Method and apparatus for initializing secure communications among, and for exclusively pairing wireless devices |
| WO2000072506A1 (en) | 1999-05-21 | 2000-11-30 | International Business Machines Corporation | Method and apparatus for initializing secure communications among, and for exclusively pairing wireless devices |
| WO2001001644A1 (en) | 1999-06-29 | 2001-01-04 | Samsung Electronics Co., Ltd. | Apparatus for securing user's information in a mobile communication system connected to the internet and method thereof |
| WO2001016933A1 (en) | 1999-08-30 | 2001-03-08 | Fujitsu Limited | Device for data reproduction |
| WO2001024434A1 (en) | 1999-09-30 | 2001-04-05 | B.M.N. Technology | System for providing messages |
| JP2001103571A (en) | 1999-10-01 | 2001-04-13 | Mitsubishi Electric Corp | Mobile communication service providing system |
| US7003667B1 (en) | 1999-10-04 | 2006-02-21 | Canon Kabushiki Kaisha | Targeted secure printing |
| US6931532B1 (en) | 1999-10-21 | 2005-08-16 | International Business Machines Corporation | Selective data encryption using style sheet processing |
| JP2001147849A (en) | 1999-11-19 | 2001-05-29 | Toshiba Corp | Communication method and electronic device for data synchronization processing |
| US6732144B1 (en) | 1999-11-19 | 2004-05-04 | Kabushiki Kaisha Toshiba | Communication method for data synchronization processing and electronic device therefor |
| US7171552B1 (en) | 1999-11-29 | 2007-01-30 | Cisco Technology, Inc. | Encrypting information in a communications network |
| WO2001041353A3 (en) | 1999-11-30 | 2002-02-21 | Sun Microsystems Inc | Method and apparatus for sending encrypted electronic mail through a distribution list exploder |
| US7032240B1 (en) | 1999-12-07 | 2006-04-18 | Pace Anti-Piracy, Inc. | Portable authorization device for authorizing use of protected information and associated method |
| US6829357B1 (en) | 1999-12-14 | 2004-12-07 | Trw Inc. | Communication system having a transmitter and a receiver that engage in reduced size encrypted data communication |
| US6996720B1 (en) | 1999-12-17 | 2006-02-07 | Microsoft Corporation | System and method for accessing protected content in a rights-management architecture |
| JP2001197055A (en) | 2000-01-07 | 2001-07-19 | Nippon Steel Corp | Authentication proxy device, authentication proxy method, authentication proxy service system, and computer-readable recording medium |
| US6745024B1 (en) | 2000-01-10 | 2004-06-01 | Qualcomm Incorporated | System and method for preparing and sending an electronic mail communication using a wireless communications device |
| US6779115B1 (en) | 2000-02-18 | 2004-08-17 | Digital5, Inc. | Portable device using a smart card to receive and decrypt digital data |
| WO2001063386A1 (en) | 2000-02-23 | 2001-08-30 | Kim Leeper | A system and method for authenticating electronic documents |
| US6983367B2 (en) | 2000-03-14 | 2006-01-03 | Sony Corporation | Information providing apparatus and method, information processing apparatus and method, and program storage medium |
| WO2001071608A3 (en) | 2000-03-17 | 2002-05-02 | Mark Nair | System, method and apparatus for controlling the dissemination of digital works |
| US20020038420A1 (en) | 2000-04-13 | 2002-03-28 | Collins Timothy S. | Method for efficient public key based certification for mobile and desktop environments |
| WO2001078491A3 (en) | 2000-04-14 | 2002-03-14 | Postx Corp | Systems and methods for encrypting/decrypting data using a broker agent |
| US6725262B1 (en) | 2000-04-27 | 2004-04-20 | Microsoft Corporation | Methods and systems for synchronizing multiple computing devices |
| US20020007453A1 (en) | 2000-05-23 | 2002-01-17 | Nemovicher C. Kerry | Secured electronic mail system and method |
| US20020035687A1 (en) | 2000-06-07 | 2002-03-21 | Kristofer Skantze | Method and device for secure wireless transmission of information |
| US6993137B2 (en) | 2000-06-16 | 2006-01-31 | Entriq, Inc. | Method and system to securely distribute content via a network |
| US20020059383A1 (en) | 2000-06-19 | 2002-05-16 | Takeo Katsuda | Apparatus, portable terminal unit, and system for controlling E-mail, and its method, computer-readable recording medium and program product for processing E-mail |
| US20020032861A1 (en) | 2000-07-14 | 2002-03-14 | Nec Corporation | System and method for executing and assuring security of electronic mail for users, and storage medium storing program to cause computer to implement same method |
| US6661927B1 (en) | 2000-07-27 | 2003-12-09 | Motorola, Inc. | System and method for efficiently encoding an image by prioritizing groups of spatially correlated coefficients based on an activity measure |
| US6531985B1 (en) | 2000-08-14 | 2003-03-11 | 3Com Corporation | Integrated laptop antenna using two or more antennas |
| US20020053023A1 (en) | 2000-08-17 | 2002-05-02 | Patterson Andrew John | Certification validation system |
| US20020035685A1 (en) | 2000-09-11 | 2002-03-21 | Masahiro Ono | Client-server system with security function intermediary |
| US20020053032A1 (en) | 2000-09-14 | 2002-05-02 | Dowling William Race | System and method for secure data transmission |
| US20050203855A1 (en) | 2000-11-08 | 2005-09-15 | Orchestria Limited | Information management system |
| US20040083364A1 (en) | 2000-12-07 | 2004-04-29 | Jean-Pierre Andreaux | Method of secure transmission of digital data from a source to a receiver |
| KR20030059303A (en) | 2000-12-07 | 2003-07-07 | 톰슨 라이센싱 소시에떼 아노님 | Method of secure transmission of digital data from a source to a receiver |
| US20020080752A1 (en) | 2000-12-22 | 2002-06-27 | Fredrik Johansson | Route optimization technique for mobile IP |
| US20020099766A1 (en) | 2001-01-24 | 2002-07-25 | Tuli Raja Singh | Portable high speed internet access device with encryption |
| US7299502B2 (en) | 2001-02-14 | 2007-11-20 | Hewlett-Packard Development Company, L.P. | System and method for providing customized secure access to shared documents |
| US6904521B1 (en) | 2001-02-16 | 2005-06-07 | Networks Associates Technology, Inc. | Non-repudiation of e-mail messages |
| US20020147905A1 (en) | 2001-04-05 | 2002-10-10 | Sun Microsystems, Inc. | System and method for shortening certificate chains |
| US20020165967A1 (en) | 2001-05-02 | 2002-11-07 | Morgan Paul A. | Global personalization engine |
| US20020173295A1 (en) | 2001-05-15 | 2002-11-21 | Petri Nykanen | Context sensitive web services |
| US20020176067A1 (en) | 2001-05-23 | 2002-11-28 | Canesta, Inc. | Method and system to enhance dynamic range conversion useable with CMOS three-dimensional imaging |
| US20030002671A1 (en) | 2001-06-11 | 2003-01-02 | Eastman Kodak Company | Delivery of electronic content over a network using a hybrid optical disk for authentication |
| WO2002102009A3 (en) | 2001-06-12 | 2003-04-10 | Research In Motion Ltd | Method for processing encoded messages for exchange with a mobile data communication device |
| US20100115264A1 (en) | 2001-06-12 | 2010-05-06 | Research In Motion Limited | System and Method for Processing Encoded Messages for Exchange with a Mobile Data Communication Device |
| US20080016359A1 (en) | 2001-06-12 | 2008-01-17 | Godfrey James A | System and method for compressing secure e-mail for exchange with a mobile data communication device |
| WO2002101605A3 (en) | 2001-06-12 | 2003-03-06 | Research In Motion Ltd | System and method for compressing secure e-mail for exchange with a mobile data communication device |
| US7546453B2 (en) | 2001-06-12 | 2009-06-09 | Research In Motion Limited | Certificate management and transfer system and method |
| US20090292916A1 (en) | 2001-06-12 | 2009-11-26 | Little Herbert A | Certificate Management and Transfer System and Method |
| US7827406B2 (en) | 2001-06-12 | 2010-11-02 | Research In Motion Limited | System and method for processing encoded messages for exchange with a mobile data communication device |
| US7653815B2 (en) | 2001-06-12 | 2010-01-26 | Research In Motion Limited | System and method for processing encoded messages for exchange with a mobile data communication device |
| US7657736B2 (en) | 2001-06-12 | 2010-02-02 | Research In Motion Limited | System and method for compressing secure e-mail for exchange with a mobile data communication device |
| US20100124333A1 (en) | 2001-06-12 | 2010-05-20 | Research In Motion Limited | System and Method for Processing Encoded Messages for Exchange with a Mobile Data Communication Device |
| US20050163320A1 (en) | 2001-06-12 | 2005-07-28 | Brown Michael S. | System and method for processing encoded messages for exchange with a mobile data communication device |
| US7254712B2 (en) | 2001-06-12 | 2007-08-07 | Research In Motion Limited | System and method for compressing secure e-mail for exchange with a mobile data communication device |
| US20040196978A1 (en) | 2001-06-12 | 2004-10-07 | Godfrey James A. | System and method for processing encoded messages for exchange with a mobile data communication device |
| US20100122089A1 (en) | 2001-06-12 | 2010-05-13 | Research In Motion Limited | System and method for compressing secure e-mail for exchange with a mobile data communication device |
| WO2002101580A1 (en) | 2001-06-12 | 2002-12-19 | Research In Motion Limited | Certificate management and transfer system and method |
| US8015400B2 (en) | 2001-06-12 | 2011-09-06 | Research In Motion Limited | Certificate management and transfer system and method |
| US20040171369A1 (en) | 2001-06-12 | 2004-09-02 | Little Herbert A. | Certificate management and transfer system and method |
| WO2003005636A8 (en) | 2001-07-04 | 2004-05-13 | Ericsson Telefon Ab L M | Secure header information for multi-content e-mail |
| WO2003007570A1 (en) | 2001-07-10 | 2003-01-23 | Research In Motion Limited | System and method for secure message key caching in a mobile communication device |
| US20040205248A1 (en) | 2001-07-10 | 2004-10-14 | Herbert A Little | System and method for secure message key caching in a mobile communication device |
| WO2003009561A3 (en) | 2001-07-16 | 2003-05-30 | Research In Motion Ltd | A system and method for supporting multiple certificate authorities on a mobile communication device |
| WO2003015367A3 (en) | 2001-08-06 | 2003-05-30 | Research In Motion Ltd | System and method for processing encoded messages |
| US20040202327A1 (en) | 2001-08-06 | 2004-10-14 | Little Herbert A. | System and method for processing encoded messages |
| US20030074555A1 (en) | 2001-10-17 | 2003-04-17 | Fahn Paul Neil | URL-based certificate in a PKI |
| US20030126085A1 (en) | 2001-12-27 | 2003-07-03 | Slamdunk Networks, Inc. | Dynamic authentication of electronic messages using a reference to a certificate |
| US7529374B2 (en) | 2002-02-02 | 2009-05-05 | F-Secure Oyj | Method and apparatus for encrypting data |
| WO2003075530A1 (en) | 2002-03-01 | 2003-09-12 | Research In Motion Limited | System and method for providing secure message signature status and trust status indication |
| US20030172122A1 (en) | 2002-03-06 | 2003-09-11 | Little Herbert A. | System and method for providing secure message signature status and trust status indication |
| WO2003079627A3 (en) | 2002-03-20 | 2003-12-18 | Research In Motion Ltd | System and method for supporting multiple certificate status providers on a mobile communication device |
| US20050114671A1 (en) | 2002-03-20 | 2005-05-26 | Research In Motion Ltd. | System and method for transmitting and utilizing attachments |
| WO2003079628A1 (en) | 2002-03-20 | 2003-09-25 | Research In Motion Limited | Certificate information storage system and method |
| US20050148323A1 (en) | 2002-03-20 | 2005-07-07 | Research In Motion Limited | System and method for supporting multiple certificate status providers on a mobile communication device |
| US20050149442A1 (en) | 2002-03-20 | 2005-07-07 | Research In Motion Limited | Certificate information storage system and method |
| US20030198350A1 (en) | 2002-04-18 | 2003-10-23 | International Business Machines Corporation | Method, system and program product for managing a size of a key management block during content distribution |
| JP2004048139A (en) | 2002-07-09 | 2004-02-12 | Nikon Corp | Image transmission system, image relay device, and electronic image equipment |
| US7127604B2 (en) | 2002-07-09 | 2006-10-24 | Texas Instruments Incorporated | Changing a codec or MAC size without affecting the encryption key in PacketCable communication |
| US20040133775A1 (en) | 2003-01-07 | 2004-07-08 | Callas Jonathan D. | System and method for secure electronic communication in a partially keyless environment |
| US20040133520A1 (en) | 2003-01-07 | 2004-07-08 | Callas Jonathan D. | System and method for secure and transparent electronic communication |
| US20050005097A1 (en) | 2003-06-12 | 2005-01-06 | Minolta Co., Ltd. | Communication system and method in public key infrastructure |
| US20050039100A1 (en) | 2003-08-14 | 2005-02-17 | International Business Machines Corporation | Method and system for automatic error recovery in an electronic mail system |
| US20050188219A1 (en) | 2003-12-26 | 2005-08-25 | Orange France | Method and a system for communication between a terminal and at least one communication equipment |
| US20050222991A1 (en) | 2004-02-04 | 2005-10-06 | Kazuyuki Ikenoya | Information providing apparatus, information providing method, information providing program, and recording medium |
| US20050210289A1 (en) | 2004-03-22 | 2005-09-22 | Brown Michael K | System and method for viewing message attachments |
| EP1580953B1 (en) | 2004-03-22 | 2011-02-09 | Research In Motion Limited | System and method for viewing message attachments |
| US20050246763A1 (en) | 2004-03-25 | 2005-11-03 | National University Of Ireland | Secure digital content reproduction using biometrically derived hybrid encryption techniques |
| US20060015722A1 (en) | 2004-07-16 | 2006-01-19 | Geotrust | Security systems and services to provide identity and uniform resource identifier verification |
| US20060036848A1 (en) | 2004-08-09 | 2006-02-16 | Research In Motion Limited | System and method for enabling bulk retrieval of certificates |
| CA2476914A1 (en) | 2004-08-09 | 2006-02-09 | Research In Motion Limited | System and method for certificate searching and retrieval |
| US20060036849A1 (en) | 2004-08-09 | 2006-02-16 | Research In Motion Limited | System and method for certificate searching and retrieval |
| US20060036865A1 (en) | 2004-08-10 | 2006-02-16 | Research In Motion Limited | Server verification of secure electronic messages |
| US20060059332A1 (en) | 2004-09-02 | 2006-03-16 | Research In Motion Limited | System and method for searching and retrieving certificates |
| US20070083749A1 (en) | 2005-10-12 | 2007-04-12 | The Boeing Company | Systems and methods for automated exchange of electronic mail encryption certificates |
| US20070165844A1 (en) | 2005-10-14 | 2007-07-19 | Research In Motion Limited | System and method for protecting master encryption keys |
| US7953971B2 (en) | 2005-10-27 | 2011-05-31 | Research In Motion Limited | Synchronizing certificates between a device and server |
| US20070118874A1 (en) | 2005-11-18 | 2007-05-24 | Research In Motion Limited | System and method for handling electronic messages |
| US20070123307A1 (en) | 2005-11-30 | 2007-05-31 | Research In Motion Limited | Display of secure messages on a mobile communication device |
| EP1806683A1 (en) | 2005-11-30 | 2007-07-11 | Research In Motion Limited | Display of secure messages on a mobile communication device |
Non-Patent Citations (159)
| Title |
|---|
| Advisory Action from USPTO dated Apr. 11, 2008 for U.S. Appl. No. 10/480,615. |
| Australian Examiner's Report issued on Oct. 12, 2006 for Australian patent application No. 2005204223. |
| Berson T et al.: "Cryptography as a network serivce" 8th Annual Symposium on Network and Distributed System Security. (NDSS' 01) Internet Soc Reston, VA, USA, Feb. 7, 2001-Feb. 9, 2001 pp. 1-12, XP002551706. |
| Blom et al. "Conversational IP Multimedia Security", 4th International Workshop on Mobile and Wireless Communications Network, Sep. 9-11, 2002, pp. 147-151. |
| Brief Communication, in connection with Application No. 02737687.0-2201, dated Aug. 20, 2010. |
| Brown I., et al.: "A Proxy Approach to E-Mail Security", Software Practice & Experience, John Wiley & Sons Ltd. Chichester, GB, vol. 29, No. 12, Oct. 1999, pp. 1049-1060, XP00852351. |
| Brown M., et al.: "PGP in Constrained Wireless Devices", Proceedings of the 9th Usenix Security Symposium, Denver, CO, Aug. 14-17, 2000, XP002210575. |
| Butrico M. et al.: "Enterprise data access from mobile computers: an end-to-end story" Research Issues in Data Engineering, 2000. Ride 2000. Proceedings. Tenth International Workshop on San Diego, CA, USA Feb. 28-29, 2000, Los Alamitos, CA, USA, IEEE Comput. Soc. US, Feb. 28, 2000, pp. 9-16, XP010377083. |
| Certificate of Grant of Patent, dated Dec. 30, 2005, Singapore Application No. 200307398.8. |
| Chadwick, D.W., et al., "Modifying LDAP to Support X.509-based PKIs", In Seventeenth Annual IFIP WG 11.3 Working Conference on Database and Applications Security at Estes Park, Colorado, Aug. 2003. |
| Chinese First Office Action (English translation). Application No. 200510095984.7. Dated: Nov. 21, 2008. |
| Chinese Office Action, issued Mar. 9, 2007, for Chinese Patent Application No. 02817741.X, along with an English translation thereof. |
| Cole R., et al: "An Architecture for a Mobile OSI Mail Access System", IEEE Journal on Selected Areas in Communications, IEEE Inc., New York, US, vol. 7, No. 2, Feb. 1989, pp. 249-256, XP000904914. |
| Co-pending U.S. Appl. No. 10/483,282 entitled "System and method for secure message key caching in a mobile communication device", claims 1-49 stand rejected. |
| Co-pending U.S. Appl. No. 10/486,406 entitled "System and Method for Processing Encoded Messages", claims 1-34, 36-47 and 49-62 have been allowed (RCE has been filed). |
| Co-pending U.S. Appl. No. 12/686,046 entitled "System and Method for Processing Encoded Messages for Exchange with a Mobile Data Communication Device". |
| Co-pending U.S. Appl. No. 12/691,204 entitled "System and Method for Compressing Secure E-Mail for Exchange With a Mobile Data Communication Device". |
| Co-pending U.S. Appl. No. 12/693,021 entitled "System and Method for Processing Encoded Messages for Exahange with a Mobile Data Communication Device". |
| Crocker S. et al. "MIME Object Security Services: rfc1848.text". IETF Standard, Internet Engineering Task Force, IETF, CH, Oct. 1995, XP015007633. |
| Crocker S. et al.: "MIME Object Security Services; rfc1848.text". IETF Standard, Internet Engineering Task Force, IETF, CH, Oct. 1995, XP015007633. |
| Decision from Intellectual Property Tribunal, Korean Application No. 2003-7016487, dated Oct. 31, 2007. |
| Decision from Patent Court, Korean Application No. 2003-7016487, dated Nov. 21, 2008. |
| Decision to refuse a European Patent application, in connection with Application No. 02737687.0-2201, dated Sep. 7, 2010. |
| Deroest J.: "Ubiquitous Mobile Computing" Sunexpert Magazine, 'Online! Jul. 1998, pp. 54-56, SP002213003 Retrieved from the Internet: 'retrieved on Sep. 10, 2002. |
| Deroest J.: "Ubiquitous Mobile Computing" Sunexpert Magazine, 'Online! Jul. 1998, pp. 54-56, SP002213003 Retrieved from the Internet: <URL:http://swexpert.com/C8/SE.C8.JUL.98.pdf> 'retrieved on Sep. 10, 2002. |
| Dusse et al., "S/MIME Version 2 Message Specification," The Internet Society, Mar. 1998, pp. 1-37. |
| Dusse et al.: "S/MIME Version 2 Certificate Handling," Database IETF RFC Online IETF: RFC 2312, Mar. 1998, pp. 1-20 (Chapter 2.1, Chapter 4.1), XP002220385. |
| Encrypt Pre-shared Keys in Cisco IOS Router Configuration Example, Document 1D 46420 Cisco Systems, Internet Address: htto:/lwww.cisco.com/en/US/tech/tk5S3/tk3721technologies-configuration-example09186a00801f2336.shtml. |
| Encrypt Pre-shared Keys in Cisco IOS Router Configuration Example. Document 1D 46420 Cisco Systems, Internet Address: htto:/lwww.cisco.com/en/US/tech/tk5S3/tk3721technologies—configuration—example09186a00801f2336.shtml. |
| EPO Communication Pursuant to Article 96(2) EPC, in connection with Application No. 02737687.0-2201, dated Apr. 21, 2004. |
| EPO Communication Pursuant to Article 96(2) EPC, in connection with Application No. 02737687.0-2201, dated Oct. 15, 2007. |
| EPO Communication Pursuant to Article 96(2) EPC, in connection with Application No. 02737687.0-2201, dated Sep. 19, 2006. |
| EPO Communication Pursuant to Article 96(2) EPC, in connection with Application No. 02737687.0-2201, dated Setpember 19, 2006. |
| EPO Communication Pursuant to Article 96(2) EPC, issued by the European Patent Office on Dec. 6, 2006 in connection with application No. 04104240.9. |
| Eskicioglu et al. "A Key Transport Protocol Based on Secret Sharing Applications to Information Security", IEEE Transactions on Consumer Electronics, vol. 46, No. 4, Nov. 2002, pp. 816-824. |
| European Examination Report dated Apr. 20, 2009, European Patent Application No. 05826460.7. |
| European Examination Report, Application No. 05826460.7, Apr. 4, 2008. |
| European Search Report of Application No. EP 05022525.9-2146 dated Jan. 24, 2006—4 pgs. |
| European Supplementary Search Report, Application No. 05826460.7, Feb. 14, 2008. |
| Exhibit B-4 cited by KIPO, Patent Court Case No. 2008 HUH 620. Office Action from USPTO dated May 14, 2007 for U.S. Appl. No. 10/480,615. |
| Fesearch in Motion Limited, Blackberry Security White Paper Release 4.0 2005 Internet Address: http://blackberry.comlknowledgecenterpubliclivelink.exe?func=ll&objld=S2S044&objAction=browse&sort=name. |
| Final office Action dated Mar. 7, 2013, U.S. Appl. No. 13/223,999. |
| Final Office Action for Japanese Application No. 2007-61073, dated Mar. 3, 2011. |
| Final Office Action from USPTO dated Nov. 25, 2008 for U.S. Appl. No. 10/480,615. |
| Final Office Action, Japanese Application No. 2003-504272, dated Dec. 7, 2006 (mailed Dec. 11, 2006). |
| Final Office Action, Korean Application No. 2003-7016487, dated May 26, 2006. |
| First Examination Report, Indian Application No. 2173/DELNP/2003, dated Apr. 27, 2004. |
| First Office Action, Chinese Application No. 02815382.0, Feb. 24, 2006. |
| Fourth Office Action, Chinese Application No. 02815382.0, dated Jun. 29, 2007. |
| Fumy et al. Principles of Key Management, IEEE Journal on Selected Areas in Communications, VDI, 11, No. 5, Jun. 1999, pp. 785-793. |
| Gong et al.: "Multicast Security and its Extension to a Mobile Environment," SRI International, Computer Science Laboratory, J.C. Baltzer AG, Science Publishers, Wireless Networks I (1995) pp. 281-295. |
| Hämetvaara, Vesa. "Modifying LDAP to Support X.509-based PKIs", In Seventeenth Annual IFIP WG 11.3 Working Conference on Database and Applications Security at Estes Park, Colorado, Aug. 2003. |
| Harris A.: "Content Privacy and Content Security Working Together", Internet Article. Content Technologies White Paper, Online! Sep. 1999, XP002223158, pp. 8-9. |
| Harris, "Content privacy and content security working together," Internet Article, Content Technologies White Paper, pp. 1-10 (Sep. 1999). |
| Hiroyuki Sawano, Create a Secure Electronic Mail Environment with S/MIME!, @IT Security & Trust, May 30, 2001, URL. http://www.atmarkit.co.jp/fsecurity/special/04smime/smime01.html. |
| Hoffman: "Enhanced Services for S/MIME," Database IETF RFC Online IETF;RFC 2634, Jun. 1999, pp. 1-58 (Chapter 3, pp. 24-32), XP002220386. |
| Housley, R. et al. "Internet X.509 Public Key Infrastructure Certificate and CRL Profile (RFC 2459)", Jan. 1999. |
| Indian Examination Letter. Application No. 2290/DEL/2005, Dated: Apr. 13, 2007. |
| Inquiry issued by the Japanese Patent Office on Mar. 13, 2009 for Japanese Patent Application No. 2003-504272. |
| International Preliminary Examination Report for PCT/CA02/00868 dated Jul. 3, 2003. |
| International Preliminary Examination Report for PCT/CA92/00868 dated Jul. 3, 2003. |
| International Search Report for PCT/CA02/00868 mailed Oct. 2, 2002. |
| International Search Report of Application No. PCT/CA02/00889, date of mailing Dec. 23, 2002, 10 pages. |
| International Search Report of Application No. PCT/CA02/00890, date of mailing Dec. 23, 2002-12 pgs. |
| Intimation of Grant, Indian Application No. 2173/DELNP/2003 dated Mar. 27, 2008 (copy not located). |
| Intimation of Grant, Indian Application No. 2173/DELNP/2003 dated Mar. 27, 2008. |
| ITU-T, "Information technology-Open systems interconnection-The Directory: Public-key and attribute certificate frameworks", Mar. 2000. |
| Japanese Office Action dated Jun. 17, 2009, Japanese Application No. 2006-293228. |
| Jin Jing et al.: "Client-server computing in mobile environments" ACM Computing Surveys, Jun. 1999, ACM, USA, vol. 31, No. 2, pp. 117-157, XP002212945. |
| Jin Jing et al.: "Client-server computing in mobile environments" ACM Computing Surveys, Jun. 1999, ACM, USA, vol. 31. No. 2, pp. 117-157, XP002212945. |
| Katsuro Inaya, et al., "Use Windows CE Now", ASCII, Oct. 1, 1999, vol. 23, No. 10, pp. 266-285. |
| Kiely, Don, Sal Server 2005 Secures Your Data Like Never Before, Sep. 29, 2005. Internet Address: http://www.devx.comlcodemaglArticle/29351?trk=DXESS-DB. |
| Korean Decision for Final Rejection (English translation). Application No. 10-2005-0081103. Dated: Apr. 12, 2007. |
| Korean Examination Report (English translation). Application No. 10-2007-7011342. Dated: Jul. 15, 2008. |
| Kotzanikoloau et al. "Hybrid Key Establishment for Multiphase Self-Organized Sensor Networks", 6'' IEEE International Symposium on a World of Wireless Mobile and Multimedia Networks, Jun. 13-16, 2005, pp. 581-587. |
| Kotzanikoloau et al. "Hybrid Key Establishment for Multiphase Self-Organized Sensor Networks", 6″ IEEE International Symposium on a World of Wireless Mobile and Multimedia Networks, Jun. 13-16, 2005, pp. 581-587. |
| Lai, M.K.E., et al.: "A Mobile Subscriber Proxy Preserving Writer-to-Reader Message Security", Military Communications Conference, 1996, Milcom '96, Conference Proceedings, IEEE McLean, VA, USA Oct. 21-24, 1996, New York, NY, USA, IEEE, US, Oct. 21, 1996, pp. 461-467, XP010203896 (XP00090914). |
| Levien: "Protecting Internet E-Mail From Prying Eyes," Data Communications, McGraw Hill, New York, US, vol. 25, No. 6 (May 1, 1996), pp. 117-118, 120, 122, XP 000587586. |
| Levien: "Protecting Internet E-Mail From Prying Eyes," Data Communications, McGraw Hill, New York, US, vol. 25, No. 6, May 1, 1996), pp. 117-118, 120, 122, XP000587586. |
| Mambo M. et al.: "Proxy Signatures: Delegation of the Power to Sign Messages" IEICE Transactions on Fundamentals of Electronics, Communications and Computer Sciences, IECE Tokyo, JP, vol. E79-A, No. 9, Sep. 1, 1996, pp. 1338-1353, XP000679624. |
| Mambo M., et al., "Proxy Signatures: Delegation of the Power to Sign Messages" IEICE Transactions on Fundamentals of Electronics, Communications and Computer Sciences, IEICE Tokyo, JP, vol. E79-A, No. 9, Sep. 1, 1996, pp. 1338-1353, XP000679624. |
| Minutes of the oral proceedings before the Examining Division, in connection with Application No. 02737687.0-2201, dated Sep. 7, 2010. |
| Myers, M. et al. "Certificate Management Messages over CMS (RFC 2797)", Apr. 2000. |
| Myers, M. et al., X.509 Internet Public Key Infrastructure Online Certificate Status Protocol-OCSP, RFC2560 (Jun. 1999). |
| Nakajima et al.: "Adaptive continuous media applications in mobile computing environments" Multimedia Computing Systems '97. Proceedings., IEEE International Conference on Ottawa, Ont., Canada Jun. 3-6, 1997, Los Alamitos, CA, USA, IEEE Comput. Soc. US, Jun. 3, 1997, pp. 152-160, XP010239184. |
| Notice of Abandonment dated Aug. 7, 2012, Canadian Patent Application No. 2,717,229. |
| Notice of Allowance (Notification for the Grant of Invention), Chinese Application No. 02815382.0, dated May 16, 2008. |
| Notice of Allowance dated May 21, 2013, U.S. Appl. No. 13/223,999. |
| Notice of Allowance from USPTO dated Feb. 6, 2009 for U.S. Appl. No. 10/480,615. |
| Notice of Allowance, Canadian Application No. 2450584, dated Apr. 16, 2010. |
| Notice of Reason for Rejection for Japanese Application No. 2003-504272, dated May 12, 2006 (mailed May 16, 2006). |
| Notice of Reason for Rejection issued by the Japanese Patent Office on Feb. 16, 2009 for Japanese Patent Application No. 2005-253511. |
| Notice of Reason for Rejection issued by the Japanese Patent Office on Jan. 5, 2010 for Japanese Patent Application No. 2005-253511. |
| Notice of Reason for Rejection issued by the Japanese Patent Office on May 12, 2006 for Japanese Patent Application No. 2003-504272. |
| Office Action dated Aug. 28, 2012, U.S. Appl. No. 13/223,999. |
| Office Action for Japanese Application No. 2003-504272, dated Mar. 2009. |
| Office Action for Japanese Application No. 2003-504272, dated May 28, 2010. |
| Office Action for Japanese Application No. 2007-61073, dated May 28, 2010. |
| Office Action from CIPO issued on Feb. 2, 2011, Canadian Application No. 2,717,229. |
| Office Action from USPTO (Interview Summary) dated Sep. 4, 2008 for U.S. Appl. No. 10/480,615. |
| Office Action from USPTO dated Jan. 22, 2008 for U.S. Appl. No. 10/480,615. |
| Office Action from USPTO dated Jun. 9, 2008 for U.S. Appl. No. 10/480,615. |
| Office Action issued by the Canadian Intellectual Property Office on Jul. 13, 2009 for Canadian Patent Appl. No. 2,517,211. |
| Office Action issued by the USPTO on Apr. 15, 2009 for U.S. Appl. No. 11/259,372. |
| Office Action issued by the USPTO on Apr. 27, 2009 for U.S. Appl. No. 11/291,178. |
| Office Action issued by the USPTO on Jan. 13, 2009 for U.S. Appl. No. 10/914,634. |
| Office Action issued by the USPTO on Jul. 15, 2008 for U.S. Appl. No. 10/931,983. |
| Office Action issued by the USPTO on Jun. 23, 2010 for U.S. Appl. No. 10/486,406. |
| Office Action issued by the USPTO on Nov. 13, 2007 for U.S. Appl. No. 10/931,983. |
| Office Action issued by the USPTO On Oct. 29, 2009 for U.S. Appl. No. 11/259,372. |
| Office Action, Canadian Application No. 2450584, dated Feb. 3, 2009. |
| Office Action, Canadian Application No. 2450584, dated Mar. 14, 2006. |
| Office Action, Korean Application No. 2003-7016487, dated Nov. 1, 2005. |
| Official Action (Inquiry), Japanese Application No. 2003-504272 dated Mar. 13, 2009. |
| PCT International Search Report and Written Opinion of the International Searching Authority, Int'ernational App. No. PCT/CA2005/D01956, Jul. 29, 2006. |
| Policht, Martin, Sal Server 2005 Security-Part 3 Encryption, Database Journal Internet Address: http//www.databasejournal.com/features/mssql/article.php/34S3931. |
| Policht, Martin, Sal Server 2005 Security—Part 3 Encryption, Database Journal Internet Address: http://www.databasejournal.com/features/mssql/article.php/34S3931. |
| Ramsdell, D. et al. "Secure/Multi-purpose Internet Mail Extensions (S/MIME) Version 3.1 Certificate Handling (RFC 3850)", Jul. 2004. |
| Refusal of Amendment for Reconsideration Issued and Final Rejection Maintained, Korean Application No. 2003-7016487, dated Oct. 10, 2006. |
| Rejection of Appeal, Japanese Application No. 2003-504272, dated Dec. 7, 2009. |
| Report of Pre-Appeal Examination, Japanese Application No. 2003-504272, dated Jul. 20, 2007. |
| Request for Continued Examination (RCE) Transmittal dated Apr. 22, 2008 for U.S. Appl. No. 10/480,615. |
| Research in Motion Limited, Blackberry Security White Paper Release 4.0. 2005 Internet Address: http://blackberry.comlknowledgecenterpublicllivelink.exe?func=ll&objld=S2S044&objAction=browse&sort=name. |
| Research in Motion Limited, BlackBerry Security with the S/MIME Support Package, version 1.5, Dec. 17, 2003. |
| Research in Motion Limited, Blackberry Security with theS/MIME Support Package, version 1.5, Dec. 17, 2003. |
| Response Brief to Patent Court, Korean Application No. 2003-7016487, dated Apr. 19, 2008. |
| Response dated May 2, 2013, U.S. Appl. No. 13/223,999. |
| Response dated Nov. 28, 2012, U.S. Appl. No. 13/223,999. |
| Response to Office Action from USPTO dated Mar. 24, 2008 for U.S. Appl. No. 10/480,615. |
| Response to Office Action from USPTO dated Nov. 14, 2007 for U.S. Appl. No. 10/480,615. |
| Response to Office Action from USPTO dated Sep. 9, 2008 for U.S. Appl. No. 10/480,615. |
| Response to Office from USPTO dated Jan. 26, 2009 for U.S. Appl. No. 10/480,615. |
| Response to Official Communication of Apr. 21, 2004, in connection with Application No. 02737687.0-2201, dated Sep. 1, 2004. |
| Response to Official Communication of Oct. 15, 2007, in connection with Application No. 02737687.0-2201, dated Apr. 24, 2008. |
| Response to Official Communication of Sep. 19, 2006, in connection with Application No. 02737687.0-2201, dated Jan. 26, 2007. |
| Russell S: "Fast checking of individual certificate revocation on small systems" Computer Security Applications Conference, 1999. (ACSAC '99). Proceedings. 15th Annual Phoenix, AZ, USA Dec. 6-10, 1999, Los Alamitos, CA, USA, IEEE Comput. Soc. US. Dec. 6, 1999, pp. 249-255, XP010368617. |
| Russell S: "Fast checking of individual certificate revocation on small systems" Computer Security Applications Conference, 1999. (ACSAC '99). Proceedings. 15TH Annual Phoenix, AZ, USA Dec. 6-10, 1999, Los Alamitos, CA, USA, IEEE Comput. Soc. US, Dec. 6, 1999, pp. 249-255, XP010368617. |
| Sawano Hiroyuki, "Create a secure electronic mail environment with S/MIME", @IT Security & Trust, May 30, 2001, URL: http://www.atmarkit.co.jp/fsecurity/special/04smime/smime01.html. |
| Schumacher: "AutoPGP FAQ, Version 1," Internet Newsgroup 'Online! (Apr. 19, 1994), XP002230742. |
| Second Office Action, Chinese Application No. 02815382.0, dated Aug. 25, 2006. |
| Singapore Examination Report. Application No. 200505340-0. Dated: Sep. 19, 2006. |
| Stale Schumacher: "AutoPGP FAQ, Version 1," Internet Newsgroup, 'Online (Apr. 19, 1994), XP002230742. |
| Stallings, W.: "S/MIME: E-Mail Gets Secure". Byte, McGraw-Hill Inc., St. Peterborough, US, vol. 23, No. 7, Jul. 1998, pp. 41-42, XO000774260. |
| Subramanyam V., et al.: "Security in mobile systems", Reliable Distributed Systems, 1998 Proceedings. 17th IEEE Symposium on W. Lafayette, IN, USA, Oct. 20-23, 1998, Los Alamitos, CA, USA IEEE Comput. Soc., US. Oct. 20, 1998, pp. 407-412, XP010319125. |
| Summons to Attend Oral Proceedings Pursuant to Rule 115(1) EPC, in connection with Application No. 02737687.0-2201, dated May 18, 2010. |
| Syverson: "Limitations on Design Principles for Public Key Protocols," Security and Privacy, 1996, Proceedings, 1996 IEEE Symposium on Oakland, CA, USA, May 6-8, 1996, Los Alamitos, CA, USA, IEEE Comput. Soc., US, May 6, 1996, pp. 62-72, XP010164926. |
| Third Office Action, Chinese Application No. 02815382.0, dated Jan. 26, 2007. |
| Torvinen V.: "Wireless PKI: Fundamentals", Internet Article, Radicchio White Paper, 'Online! 2000, XP002223159, pp. 1-15. |
| Torvinen V.: "Wireless PKI: Fundamentals", Internet Article, Radicchio White Paper, 'Online! 2000, XP002223159, pp. 12-13. |
| U.S. Appl. No. 10/480,615 entitled "Certificate Management and Transfer System and Method", issued as U.S. Patent No. 7,546,453 (Prosecution Documents). |
| U.S. Appl. No. 12/480,841 entitled "Certificate Management and Transfer System and Method", issued as U.S. Patent No. 8,015,400 (Prosecution Documents). |
| Wasley D.L. et al.: "Improving Digital Credential Management in Browsers" Internet Article. HEPKI-TAG Recommendation, 'Online! Jul. 21, 2000, XP02213004 Retrieved from the Internet: 'retrieved on Sep. 10, 2002. |
| Wasley D.L. et al.: "Improving Digital Credential Management in Browsers" Internet Article. HEPKI-TAG Recommendation, 'Online! Jul. 21, 2000, XP02213004 Retrieved from the Internet: <URL:http://middleware.internet2.edu/hepk i-tag/HEPKI-TAG-Certs-Browser-03.pdf> 'retrieved on Sep. 10, 2002. |
| Written Opinion issued on Dec. 23, 2005 by the Australian Patent Office for Singapore patent application No. 200505624-7. |
| Written Opinion issued on Jan. 21, 2003 by European Patent Office for PCT/CA02/00868. |
| Written Opinion issued on Mar. 24, 2003 by European Patent Office for PCT/CA02/00868. |
| Written submission in response to Summons, dated Jul. 26, 2010, European Application No. 02737687.0. |
| Zollner J: "Gateway to overcome incompatibilities of security mechanisms" Reliable Distributed Systems, 1999. Proceedings of the 19TH IEEE Sympo Sium on Lausanne, Switzerland Oct. 19-22, 1999, Los Alamitos, CAL, USA, IEEE Comput. Soc, US Oct. 19, 1999, pp. 372-377, XP010357040 ISBN: 978-0-7695-0290-8 *the whole document*. |
| Zollner J: "Gateways to Overcome Incompatibilities of Security Mechanisms" Reliable Distributed Systems, 1999. Proceedings of the 19TH IEEE Symposium on Lausanne, Switzerland Oct. 19-22, 1999, Los Alamitos, Cal., USA, IEEE Comput. Soc, US Oct. 19, 1999, pp. 372-377. |
Cited By (1)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US9837044B2 (en) | 2015-03-18 | 2017-12-05 | Samsung Electronics Co., Ltd. | Electronic device and method of updating screen of display panel thereof |
Also Published As
| Publication number | Publication date |
|---|---|
| US8015400B2 (en) | 2011-09-06 |
| JP2007221806A (en) | 2007-08-30 |
| JP2004532590A (en) | 2004-10-21 |
| US20040171369A1 (en) | 2004-09-02 |
| CN100410927C (en) | 2008-08-13 |
| IL159342A (en) | 2008-08-07 |
| IL159342A0 (en) | 2004-06-01 |
| KR20040015272A (en) | 2004-02-18 |
| WO2002101580A1 (en) | 2002-12-19 |
| CA2717229A1 (en) | 2002-12-19 |
| US8539226B2 (en) | 2013-09-17 |
| CA2450584C (en) | 2011-01-04 |
| US20090292916A1 (en) | 2009-11-26 |
| CA2450584A1 (en) | 2002-12-19 |
| EP1399853A1 (en) | 2004-03-24 |
| US20120060026A1 (en) | 2012-03-08 |
| US7546453B2 (en) | 2009-06-09 |
| CN1539111A (en) | 2004-10-20 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| USRE45087E1 (en) | Certificate management and transfer system and method | |
| US9807082B2 (en) | Certificate information storage system and method | |
| US7865720B2 (en) | System and method for supporting multiple certificate status providers on a mobile communication device | |
| US9628269B2 (en) | System and method for secure message key caching in a mobile communication device | |
| US8966246B2 (en) | System and method for checking digital certificate status | |
| US8423763B2 (en) | System and method for supporting multiple certificate status providers on a mobile communication device | |
| EP1417814B1 (en) | System and method for processing encoded messages | |
| HK1071644B (en) | Certificate information storage system and method | |
| HK1071647B (en) | System and method for supporting multiple certificate status providers on a mobile communication device |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| AS | Assignment | Owner name:RESEARCH IN MOTION LIMITED, ONTARIO Free format text:ASSIGNMENT OF ASSIGNORS INTEREST;ASSIGNORS:LITTLE, HERBERT A.;ADAMS, NEIL P.;TAPUSKA, DAVID F.;SIGNING DATES FROM 20041123 TO 20041124;REEL/FRAME:030989/0841 Owner name:RESEARCH IN MOTION LIMITED, ONTARIO Free format text:ASSIGNMENT OF ASSIGNORS INTEREST;ASSIGNORS:BROWN, MICHAEL S.;KIRKUP, MICHAEL G.;GODFREY, JAMES A.;SIGNING DATES FROM 20050421 TO 20050428;REEL/FRAME:030989/0922 | |
| AS | Assignment | Owner name:BLACKBERRY LIMITED, ONTARIO Free format text:CHANGE OF NAME;ASSIGNOR:RESEARCH IN MOTION LIMITED;REEL/FRAME:033134/0228 Effective date:20130709 | |
| FPAY | Fee payment | Year of fee payment:4 | |
| MAFP | Maintenance fee payment | Free format text:PAYMENT OF MAINTENANCE FEE, 8TH YEAR, LARGE ENTITY (ORIGINAL EVENT CODE: M1552); ENTITY STATUS OF PATENT OWNER: LARGE ENTITY Year of fee payment:8 | |
| FEPP | Fee payment procedure | Free format text:MAINTENANCE FEE REMINDER MAILED (ORIGINAL EVENT CODE: REM.); ENTITY STATUS OF PATENT OWNER: LARGE ENTITY | |
| AS | Assignment | Owner name:MALIKIE INNOVATIONS LIMITED, IRELAND Free format text:NUNC PRO TUNC ASSIGNMENT;ASSIGNOR:OT PATENT ESCROW, LLC;REEL/FRAME:064015/0001 Effective date:20230511 Owner name:OT PATENT ESCROW, LLC, ILLINOIS Free format text:ASSIGNMENT OF ASSIGNORS INTEREST;ASSIGNOR:BLACKBERRY LIMITED;REEL/FRAME:064007/0061 Effective date:20230320 | |
| AS | Assignment | Owner name:MALIKIE INNOVATIONS LIMITED, IRELAND Free format text:NUNC PRO TUNC ASSIGNMENT;ASSIGNOR:BLACKBERRY LIMITED;REEL/FRAME:064066/0001 Effective date:20230511 | |
| LAPS | Lapse for failure to pay maintenance fees | Free format text:PATENT EXPIRED FOR FAILURE TO PAY MAINTENANCE FEES (ORIGINAL EVENT CODE: EXP.); ENTITY STATUS OF PATENT OWNER: LARGE ENTITY |