USRE41186E1 - Method of encrypting information for remote access while maintaining access control - Google Patents
Method of encrypting information for remote access while maintaining access controlDownload PDFInfo
- Publication number
- USRE41186E1 USRE41186E1US10/936,829US93682904AUSRE41186EUS RE41186 E1USRE41186 E1US RE41186E1US 93682904 AUS93682904 AUS 93682904AUS RE41186 EUSRE41186 EUS RE41186E
- Authority
- US
- United States
- Prior art keywords
- decryption key
- segment
- user location
- user
- key
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Expired - Lifetime
Links
Images
Classifications
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/04—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks
- H04L63/0428—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks wherein the data content is protected, e.g. by encrypting or encapsulating the payload
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/04—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks
- H04L63/0428—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks wherein the data content is protected, e.g. by encrypting or encapsulating the payload
- H04L63/0442—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks wherein the data content is protected, e.g. by encrypting or encapsulating the payload wherein the sending and receiving network entities apply asymmetric encryption, i.e. different keys for encryption and decryption
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/06—Network architectures or network communication protocols for network security for supporting key management in a packet data network
- H04L63/062—Network architectures or network communication protocols for network security for supporting key management in a packet data network for key distribution, e.g. centrally by trusted party
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/10—Network architectures or network communication protocols for network security for controlling access to devices or network resources
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/16—Implementing security features at a particular protocol layer
- H04L63/166—Implementing security features at a particular protocol layer at the transport layer
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L2463/00—Additional details relating to network architectures or network communication protocols for network security covered by H04L63/00
- H04L2463/101—Additional details relating to network architectures or network communication protocols for network security covered by H04L63/00 applying security measures for digital rights management
Definitions
- This inventionrelates to an electronic security system for electronic objects such as documents, video and audio clips and other objects that can be transmitted via a network.
- the present inventionallows the authoring user or other controlling party to maintain access control over the electronic information.
- the object of the present inventionis to provide a system and method for encrypting electronic information so that access to the information can be controlled by the author or other controlling party.
- a further object of the present inventionis to provide an electronic encryption/decryption system and method in which a central server maintains control over the electronic encryption and decryption keys.
- a further object of the present inventionis to provide an electronic encryption/decryption system and method in which electronic encryption and decryption keys are not retained by an encrypting or decrypting party.
- a further object of the present inventionis to provide a system and method for encrypting electronic information so that access to the information can be dynamically changed from a single location without the necessity of collecting or redistributing the encrypted information.
- a further object of the present inventionis to provide an electronic encryption/decryption system and method in which access to electronic information can be permanently revoked by destroying the association of a decryption key to the electronic information.
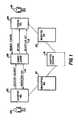
- FIG. 1is a block diagram illustrating a system configuration of an authoring tool, a viewing tool, and a remote server of the electronic encryption system.
- FIG. 2is a block diagram illustrating a detailed system configuration and functions associated with each component of the electronic encryption system.
- FIG. 1the system of the preferred embodiment can be broken down conceptually into three functional components: an authoring tool 102 , a viewing tool 104 , and a remote server 106 .
- an authoring tool 102the system of the preferred embodiment can be broken down conceptually into three functional components: an authoring tool 102 , a viewing tool 104 , and a remote server 106 .
- the embodiments described hereinare described with respect to a document in Adobe Acrobat Exchange, but other embodiments using other base software packages are possible.
- Other types of electronic information, as determined by the base software package chosen,can be encrypted using the present invention.
- the authoring tool 102allows an authoring user 108 to convert a text document 110 to unreadable form 112 using a strong encryption algorithm and an encryption key, or set of encryption keys, provided by the remote server 106 .
- the authoring tool 102also registers the electronic document or information with the remote server 106 and associates a set of access policies with the encryption key so that only selected viewing users 116 under selected circumstances may view the document in clear text.
- the document or informationmay also be broken down into segments using the authoring tool 102 , so that certain segments within a document may have different access policies. For example, a set of users may be allowed to view pages 1-5 of a 10 page document in clear text, while a subset of those users may be allowed to view all 10 pages of the document.
- the authoring tool 102also allows the authoring user 108 to block certain functions normally accessible by the viewing user 116 . For example, the authoring user 108 may deny a viewing user 116 privileges such as printing and copying of the clear text.
- the viewing tool 104allows a viewing user 116 to decrypt the document 112 an authoring user 108 has encrypted, provided the authoring user 108 has associated an access policy with the decryption key which grants access to the clear text to the viewing user 116 .
- the viewing tool 104retrieves the decryption key 118 associated with the document segment 112 from the remote server 106 , decrypts the document into clear text, renders the document segment, and destroys the decryption key and the clear text version of the document segment.
- the viewing tool 104prevents the saving of the decryption key or the clear text version of the document.
- the viewing tool 104also blocks the viewing user's machine from performing certain functions, such as printing or copying, as directed by the authoring user 108 during registration of the document 110 .
- the secure remote server 106performs several functions.
- the remote server 106generates encryption keys 114 for each document segment, maintains decryption keys 118 for registered encrypted documents 112 , authenticates requests for viewing a document segment, grants access to registered documents 112 by providing decryption keys 118 and associated access policies to authorized viewing users 116 , and maintains an encrypted secure central database which provides association between registered authoring users, registered documents, associated decryption keys, associated policies for each document, options for each user and document, and associated registered viewing users.
- the remote server 106does not store or receive the actual document, either encrypted or unencrypted.
- the authoring tool 102 and the viewing tool 104each use essentially the same suite of software tools.
- the software toolsreside on the authoring and viewing users' computers 222 , 224 , on a computer readable medium such as on the hard drive of a particular user's computer. Registration with the central remote server 206 determines which functions within the suite of software tools are available to a particular user.
- the software toolsinclude a Configuration Utility 226 , an Administrator Utility 228 , and an Application Interface 230 .
- the Application Interfaceis a “Plug-In,” which uses SDK and Plug-In Standard Interface.
- the three software toolsrun in conjunction with base viewing or playback software 232 , such as Adobe Acrobat Exchange, a web browser, a word processor, an audio or video playing application, a custom data processing, or a specialized low-level device driver, such as a hard disk driver, video driver, or audio driver.
- base software package 232will depend on the type of data stream to be encrypted/decrypted.
- the secure remote server 206is a server which is remote from an authoring or viewing user 208 , 216 .
- the server 206maintains a database 236 of encryption keys and associated decryption keys for distribution to registered or authorized users.
- the remote server 206also maintains a database which associates registered document segments, which are identified by unique segment IDs, with authoring users, user access profiles, document access policies and options, and associated encryption/decryption keys.
- the remote server 206does not actually store registered documents or segments, but instead relates identifying information about a document to the associated information.
- the remote server 206also tracks and maintains records of requests to view documents and to obtain document decryption keys 238 .
- the recordsmay be used to monitor the system for suspicious activity. For example, a single user requesting the decryption key for a document several times during a specific time period might be an indication of suspicious activity.
- the servercan then provide an alert message to a pager, e-mail or fax, thus allowing timely investigation of the activity.
- the request informationmay also be used for the purposes of non-repudiation or as a basis for billing in situations where access to the system or access to protected information is being sold.
- All communication between the remote server 206 and a user's computer 222 , 224is encrypted using Secure Socket Layer (SSL) protocols.
- SSLSecure Socket Layer
- Registration with the remote server 206 of a user or automated system wishing to use the systemis done separately from any communication for registering a document or viewing a document.
- a user wishing to register documents for viewing by other users, or viewing registered document registered by other users,must contact the server independently, possibly through a separate human Coordinator 240 or separate network link which can collect payment for the authoring, viewing, and other services, can verify the identity of the user and provide the server with user identification information and user authorization profiles.
- the servermay be a single server, a set of synchronized servers, or dual servers with a shared database.
- the Configuration Utility 226defines a local user (authoring or viewing) on the user's computer 222 , 224 .
- the Configuration Utility 226establishes the communication parameters for a local user and the remote server 206 .
- the Configuration Utility 226will query the user to define a local user profile, to include name, password and other identifying information. This local user profile must match the information provided by a user to the Coordinator 240 at the remote server 206 .
- the Configuration Utility 226is also responsible for maintaining information regarding the authentication and secure communication method used by the local user, for example, certificate, secret passphrase, smart card, etc.
- the Configuration Utility 226maintains information about the local user's secure communication method, for example, the certificate and certification authority for a certificate based secure communication system.
- the Administrator Utility 226is a network client application used by the human Coordinator 240 and other users to control access to documents selected for encryption by defining policies associated with a document.
- the Administrator Utility 228is a software program residing on the user's computer 222 , 224 .
- the Coordinator 240 or authoring user 208uses the Administrator Utility 228 to define policies related to a particular user. For example, the Coordinator 240 can use the Administrator Utility 228 to control the functions available to a particular authoring user 208 , which might depend on the fees paid by the authoring user 208 , or the Coordinator 240 can control the amount of access an authoring user 208 can allow to viewing users 216 .
- Other policies that an individual can define using the Administrator Utility 228are site policies, group policies, and default policies.
- the Administrator Utility 228allows the Coordinator 240 or authoring or viewing user 208 , 216 to determine what documents have been registered by a particular user by accessing the registered user database 236 .
- the Administrator Utility 228also allows an authoring user to permanently disable the viewing of documents by deleting the associated decryption key from the server.
- the Administrator Utility 228also allows an authoring user 208 to initially define the policies related to his documents and to change the policies after the documents have initially been registered.
- the Administrator Utility 228allows a normal authoring user 208 to create, edit, and delete time windows, network specifications and policy templates; view the list of registered documents; and view and edit the policies of documents that are registered.
- the Administrator Utility 228allows the Coordinator 240 to create, edit, and delete users and user policies; create, edit, and delete groups of users and group polices; create, edit, and delete document groups and document group policies; define and modify the Site and Default polices; create, edit, and delete document override policies; and view the activity log and set up notification policies
- the Application Interface 230 of the preferred embodimentis a standard “Plug-In” to Adobe Acrobat Exchange using SDK and Plug-In Standard Interface.
- the Plug-In 230provides a user screen interface to allow the user to access the particular functions associated with registering and viewing documents and communicating with the server.
- the Plug-In Screenmay be integral to the Adobe User Interface Window or may be a separate window.
- the Plug-In 230modifies the Adobe User Interface Window by adding functional “buttons” such as register, create policies, tag, encrypt, view and decrypt.
- the Plug-In 230allows encryption and decryption of PDF files using encryption keys from the remote server 206 .
- the Plug-In 230connects to the server 206 , authenticates the user to the server, registers documents with the server, selects policies at the server as they have been defined -by the authoring user 208 using the Administrator Utility 228 .
- the Plug-In 230blocks certain functions at the viewing user's computer 224 that are otherwise available in Adobe Acrobat Exchange. For example, if the authoring user 208 has limited access to a document so that a viewing user 216 is prohibited from printing a viewed document, the Plug-In 230 temporarily disables the print function of Adobe Acrobat Exchange. Among the functions that the Plug-In 230 can disable are print, copy, cut, paste, save, and other functions. Other functions may be disabled or limited as appropriate for the type of file viewed and the access level.
- the Application Interface 230is designed in such a way that it does not disclose either the decryption key or the clear text or unencrypted representation of the protected information content in electronic form.
- GUIGraphical User Interface
- the GUIsupports standard user interface objects such as push buttons, text input fields, lists, menus, and message boxes.
- the GUIis controlled by the mouse and keypad.
- the GUIhas multiple windows that allow real time setup of server configuration such as who may register a document, who may view a document, when a document may be viewed and on which host the document key and viewing information resides.
- a user who wishes to register or to access informationmust first register and be recognized by the server 206 , as represented by reference numeral 1042 , 1044 in FIG. 2 .
- the user 208 , 216contacts the server 206 independently, possibly through a separate human Coordinator 240 or separate network link which can collect payment for the authoring, viewing and other services; verify the identity of the user; and provide the server with user identification information and user authorization profiles.
- the suite of software toolsis provided to the user.
- the usermust have installed the base software 230 , such as Adobe Acrobat Exchange, on his computer.
- the userthen installs the Application Interface 230 provided by the Coordinator 240 , as well as the Administrator and Configuration Utilities 228 , 226 .
- the Application Interface 230upon running the Application Interface 230 , the Application Interface 230 will install the Administrator and Configuration Utilities 228 , 226 on the user's machine. There is no network activity involved in the installation of the Application Interface 230 , Administrator, or Configuration Utilities 228 , 226 .
- the Configuration Utility 226has set up identification and encryption information for the user 208 , 216 , the user authorized to do so can use the Administrator Utility 228 to create policies associated with a specific document.
- An authoring user 208 wishing to register a documentcreates policies to define who, when and how a document may be viewed or otherwise accessed.
- the authoring user 208runs the Administrator Utility 228 which has been installed on his machine 222 and instructs the Administrator Utility 228 to create policies for a document.
- the Administrator Utility 228will request the information provided during set up to the Configuration Utility 226 such as username, passphrase, and method of authentication to verify the user's identity.
- the Administrator Utility 228will also ask on which server the authoring user 208 wishes to register his document.
- the Administrator Utility 228will then establish a connection to the remote server through the Application Interface 230 .
- the remote server 206 and the authoring or viewing user's computer 222 , 224 communicating with the server 206will negotiate a standard Secure Socket Layet (SSL) encryption tunnel, as represented in FIG. 2 by reference numerals 1046 , 1056 .
- SSLSecure Socket Layet
- the user's computer 222 , 224 and the server 206negotiate a secondary session key, as represented in FIG. 2 by reference numerals 1048 , 1058 . All subsequent communications is additionally encrypted using 128-bit RC4 and this secondary session key. All communication between the users' computers 222 , 224 and the server 206 is thus doubly encrypted.
- the authoring user's computer 222provides login and authentication information to the server 206 , 1050 .
- the server 206authenticates the authoring user's 208 identity and verifies that the authoring user 208 has authority to use the system by checking a database of registered users 236 maintained on the server.
- the information provided by the authoring user 208 to the Configuration Utility 226is compared to the information provided by the user to the Coordinator 240 during the independent user registration process 1042 , 1044 .
- the database 234contains all of the access controls related to a particular user, so that if a user is only authorized to view documents, he will not be allowed to use the system to register or encrypt documents.
- the Administrator Utility 228allows the authoring use 208 to create policies applicable to a particular viewing user 216 , a group of viewing users, or a default policy for all other users.
- the policiesare then communicated to the server 206 , 1051 .
- Policiesdefine who may view a document, when, and under what conditions. Policies are created by combining a set of constraints including allowable or denied users and groups, time ranges, and Internet Protocol (IP) addresses. Access to a document by a viewing user 216 is determined by combining the user policy, document policy, as well as possibly the group policy and document group policy.
- the overridetakes precedence over the regular document policy defined by the authoring user.
- Policiesinclude limiting who may view a document or portion of a document and the time frame during which a user may view the document.
- the Administrator Utility 228also allows the authoring user 208 to create options. Options specify what functions of the base software 232 are temporarily disabled so that the viewing user 216 is prohibited from accessing them while viewing the document. An option can also enforce a watermark on printing. For example, the authoring user 208 can prohibit a particular viewing user 216 from printing, saving, or copying a particular document or portion of a document. These Options are defined by the authoring user 208 using the Administrator Utility 228 , but the options are enforced by the Application Interface 230 .
- An authoring user 208 wishing to encrypt a documentwill open the document on his computer 222 .
- the Application Interface 230must also be loaded before the document or information can be encrypted.
- the Plug-In 230adds menu items to the menu bar in Adobe Acrobat Exchange such as “tag” and “encrypt” “Tag” allows the authoring user 208 to select segments of the document to be encrypted.
- the authoring user 208can assign different policies to different tagged segments of a single document, i.e., policies are associated with segments. A segment may consist of any subset of the entire document or the entire document. Once the document has been segmented or “tagged,” the authoring user selects “encrypt” from the menu bar.
- the Plug-In 230will force a log in to the remote server 206 through the Administrator Utility 228 .
- a log-in screenis provided and the authoring user 208 must log-in to the server 206 .
- the server 206authenticates the authoring user 208 and verifies that the authoring user 208 is authorized to register documents.
- the Plug-In 230assigns a unique segment ID for each tagged segment after the authoring user has tagged all segments and has instructed the Plug-In 230 to go ahead with the encryption.
- the PlugIn 230transmits the segment IDs to the server 206 .
- the server 206generates a random encryption key for each segment ID and communicates the encryption key to the authoring user's computer 222 , 1054 .
- the server 206stores the segment ID, the key associated with the particular segment ID, and the policy associated with a particular segment ID in the central database 234 , and then transmits the key to the Plug-In 230 at the authoring user's computer 222 .
- the Plug-In 230 at the authoring user's computer 222encrypts the segment, immediately destroys or removes the key from the authoring user's machine 222 , and then deletes the clear text for the segment from the Plug-In 230 .
- key lifetimeis very short on the authoring user's machine.
- the encryption keyis never stored on the authoring user's machine where it is accessible, such as the hard disk. The key can even be obfuscated while in the memory of the authoring user's machine.
- the duration of the key's existencedepends on the speed of the computer which actually performs the encryption, since the key is destroyed immediately after the encryption.
- 128-bit RC4is used for document and segment encryption.
- the Plug-In 230produces a hash of the entire document and sends the hash to the server as document identification, 1055 .
- the server 206stores the hash with the keys associated with the document. Thus, the document is never transmitted to the server 206 , only the segment IDs and hash.
- a pop-up windowasks the authoring user 208 where he wishes to store the encrypted document.
- the encrypted documentoverwrites the clear text document on the authoring user's machine 222 .
- a user wishing to view a documentmust have installed the Configuration Utility 226 , Administrator Utility 228 , and the Application Interface 230 on his computer 224 .
- the viewing user 216must be independently registered with the Coordinator 240 as a user.
- the viewing user 216must also have installed the base software application 232 for viewing the document, such as Adobe Acrobat Exchange.
- the viewing user 216must enter the Configuration Utility 226 and provide user set up information.
- the Configuration Utility 226will request the user to provide information defining both the viewing user 216 and the viewing user's computer 224 . If the viewing user 216 is a new user, the viewing user 216 will select a button on the Configuration Utility's interface window indicating that a new user profile needs to be provided. The Configuration Utility 226 will provide a query screen to the user and the user will input identification information, such as a user name. The identification information will be checked against the information provided to the server 206 or Coordinator 240 during the independent user registration process.
- the Application Interface 230will check to see if the user is logged onto the remote server 206 . If the viewing user 216 has not logged onto the remote server, the Application Interface 230 provides a pop-up window so that the user can log in to the server. An SSL tunnel and session key are negotiated, 1056 , 1058 .
- the viewing user's computer 224provides login and authentication information to the server 206 , 1060 .
- the Application Interface 230requests access to the document or information 1062 by asking the server 206 for the decryption key for the first segment of the document or information to be accessed.
- the server 206uses the segment ID to check the database to find the policies associated with the segment and thus to determine whether the viewing user 216 is authorized to access this segment or the document as a whole.
- the viewing user 216is not authorized to access the segment, the viewing user 216 is so informed. If the user 216 is authorized to access the segment, the server 206 sends the decryption key and options for that segment to the Application Interface 230 at the viewing user's computer 224 and the Application Interface 230 decrypts the segment using the decryption key. After decrypting the segment, the Application Interface 230 immediately discards/destroys the key, renders the decrypted segment to the screen, and then destroys the decrypted version of the segment. When the viewing user moves to a different segment, the process is repeated.
- the Application Interface 230enforces the options which were assigned by the authoring user 230 to the segment viewed by the viewing user 216 . For example, if the authoring user 208 assigned that the viewing user 216 cannot print the clear text document or segment, then the Plug-In 230 disables the print function of Adobe Acrobat Exchange while the clear text document or segment is available to the viewing user 216 . Other functions which can be controlled or disabled by the Plug-In 230 are save, copy, paste, and print with watermark. For other base software packages such as audio 230 , the functions controlled by the Application Interface 230 could be play, copy, and save unencrypted. Thus, using the options, the viewing user 216 has no ability to permanently acquire the clear text document or data.
- the secure central database 234resides on the remote server 206 . It may be a distributed or shared database residing on multiple remote servers 206 . In the preferred embodiment the database 234 is maintained in Berkley DB software. All records maintained in the central database 234 are encrypted and the database is password protected. The Coordinator 240 controls the database 234 and has access to the database 234 using the password.
- the database 234provides a structure for associating segment IDs with an associated decryption key, policies for accessing that segment, and options for accessing that segment.
- the authoring user 208may change a policy associated with a segment ID through the Administrator Utility 228 on his computer. The change in policy is communicated to the remote server 206 and the database 234 is updated accordingly.
- the update policy functionallows an authoring user 208 to revoke access to a segment or document by a user or group of users.
- the authoring user 208can destroy the decryption key or the association of a decryption key to a segment or document on the database 234 using the Administrator Utility 228 . By destroying the decryption key or the association of the decryption key with a Segment or Document, the authoring user 208 destroys the ability to decrypt the information, effectively shredding all copies of the information.
Landscapes
- Engineering & Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- Computer Hardware Design (AREA)
- Computing Systems (AREA)
- General Engineering & Computer Science (AREA)
- Computer Networks & Wireless Communication (AREA)
- Signal Processing (AREA)
- Storage Device Security (AREA)
Abstract
Description
Claims (11)
Priority Applications (2)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| US10/936,829USRE41186E1 (en) | 1999-05-28 | 2004-09-09 | Method of encrypting information for remote access while maintaining access control |
| US11/129,746USRE44364E1 (en) | 1999-05-28 | 2005-05-16 | Method of encrypting information for remote access while maintaining access control |
Applications Claiming Priority (4)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| US09/321,839US6289450B1 (en) | 1999-05-28 | 1999-05-28 | Information security architecture for encrypting documents for remote access while maintaining access control |
| US09/906,811US6339825B2 (en) | 1999-05-28 | 2001-07-18 | Method of encrypting information for remote access while maintaining access control |
| US09/985,096US6449721B1 (en) | 1999-05-28 | 2001-11-01 | Method of encrypting information for remote access while maintaining access control |
| US10/936,829USRE41186E1 (en) | 1999-05-28 | 2004-09-09 | Method of encrypting information for remote access while maintaining access control |
Related Parent Applications (2)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US09/906,811DivisionUS6339825B2 (en) | 1999-05-28 | 2001-07-18 | Method of encrypting information for remote access while maintaining access control |
| US09/985,096ReissueUS6449721B1 (en) | 1999-05-28 | 2001-11-01 | Method of encrypting information for remote access while maintaining access control |
Related Child Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US09/985,096ContinuationUS6449721B1 (en) | 1999-05-28 | 2001-11-01 | Method of encrypting information for remote access while maintaining access control |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| USRE41186E1true USRE41186E1 (en) | 2010-03-30 |
Family
ID=23252254
Family Applications (5)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US09/321,839Expired - LifetimeUS6289450B1 (en) | 1999-05-28 | 1999-05-28 | Information security architecture for encrypting documents for remote access while maintaining access control |
| US09/906,811Expired - LifetimeUS6339825B2 (en) | 1999-05-28 | 2001-07-18 | Method of encrypting information for remote access while maintaining access control |
| US09/985,096CeasedUS6449721B1 (en) | 1999-05-28 | 2001-11-01 | Method of encrypting information for remote access while maintaining access control |
| US10/936,829Expired - LifetimeUSRE41186E1 (en) | 1999-05-28 | 2004-09-09 | Method of encrypting information for remote access while maintaining access control |
| US11/129,746Expired - LifetimeUSRE44364E1 (en) | 1999-05-28 | 2005-05-16 | Method of encrypting information for remote access while maintaining access control |
Family Applications Before (3)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US09/321,839Expired - LifetimeUS6289450B1 (en) | 1999-05-28 | 1999-05-28 | Information security architecture for encrypting documents for remote access while maintaining access control |
| US09/906,811Expired - LifetimeUS6339825B2 (en) | 1999-05-28 | 2001-07-18 | Method of encrypting information for remote access while maintaining access control |
| US09/985,096CeasedUS6449721B1 (en) | 1999-05-28 | 2001-11-01 | Method of encrypting information for remote access while maintaining access control |
Family Applications After (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US11/129,746Expired - LifetimeUSRE44364E1 (en) | 1999-05-28 | 2005-05-16 | Method of encrypting information for remote access while maintaining access control |
Country Status (3)
| Country | Link |
|---|---|
| US (5) | US6289450B1 (en) |
| AU (1) | AU5280400A (en) |
| WO (1) | WO2000074299A1 (en) |
Cited By (6)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20080107271A1 (en)* | 2006-11-03 | 2008-05-08 | Verizon Services Organization Inc. | Systems and Methods for Document Control Using Public Key Encryption |
| US8170213B1 (en)* | 2007-12-27 | 2012-05-01 | Emc Corporation | Methodology for coordinating centralized key management and encryption keys cached through proxied elements |
| US8555342B1 (en) | 2009-12-23 | 2013-10-08 | Emc Corporation | Providing secure access to a set of credentials within a data security mechanism of a data storage system |
| US20180268169A1 (en)* | 2011-11-14 | 2018-09-20 | Esw Holdings, Inc. | Security Systems and Methods for Encoding and Decoding Digital Content |
| US10607029B2 (en) | 2011-11-14 | 2020-03-31 | Esw Holdings, Inc. | Security systems and methods for encoding and decoding content |
| US11244074B2 (en)* | 2011-11-14 | 2022-02-08 | Esw Holdings, Inc. | Security systems and methods for social networking |
Families Citing this family (308)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US7912856B2 (en)* | 1998-06-29 | 2011-03-22 | Sonicwall, Inc. | Adaptive encryption |
| US7821926B2 (en) | 1997-03-10 | 2010-10-26 | Sonicwall, Inc. | Generalized policy server |
| US6408336B1 (en) | 1997-03-10 | 2002-06-18 | David S. Schneider | Distributed administration of access to information |
| US8914410B2 (en) | 1999-02-16 | 2014-12-16 | Sonicwall, Inc. | Query interface to policy server |
| FI107859B (en)* | 1998-03-23 | 2001-10-15 | Nokia Networks Oy | Ordering services in a mobile communication system |
| US6289450B1 (en) | 1999-05-28 | 2001-09-11 | Authentica, Inc. | Information security architecture for encrypting documents for remote access while maintaining access control |
| US20030103079A1 (en)* | 1999-06-14 | 2003-06-05 | Lycos, Inc., A Virginia Corporation | Media resource manager/player |
| US6742176B1 (en)* | 1999-06-14 | 2004-05-25 | Lycos, Inc. | Secure flexible plugin software architecture |
| US6449598B1 (en)* | 1999-09-02 | 2002-09-10 | Xware Compliance, Inc. | Health care policy on-line maintenance dissemination and compliance testing system |
| JP4359974B2 (en)* | 1999-09-29 | 2009-11-11 | 富士ゼロックス株式会社 | Access authority delegation method |
| US7536561B2 (en)* | 1999-10-15 | 2009-05-19 | Ebrary, Inc. | Method and apparatus for improved information transactions |
| US8311946B1 (en)* | 1999-10-15 | 2012-11-13 | Ebrary | Method and apparatus for improved information transactions |
| SE9904094D0 (en)* | 1999-11-12 | 1999-11-12 | Protegrity Research & Dev | Method for reencryption of a database |
| US6868405B1 (en)* | 1999-11-29 | 2005-03-15 | Microsoft Corporation | Copy detection for digitally-formatted works |
| JP2003528398A (en)* | 2000-03-21 | 2003-09-24 | リットマスター,テッド・アール | System and process for delivering information to a communication network |
| US7266681B1 (en)* | 2000-04-07 | 2007-09-04 | Intertrust Technologies Corp. | Network communications security agent |
| US6816906B1 (en)* | 2000-05-08 | 2004-11-09 | International Business Machines Corporation | Mechanism for building access control structures for authoring systems |
| US7231418B2 (en)* | 2000-05-24 | 2007-06-12 | Canon Kabushiki Kaisha | Information providing method, information providing system, terminal apparatus, and storage medium storing information providing program |
| JP2001338205A (en) | 2000-05-24 | 2001-12-07 | Canon Inc | Information management system, information management device and control method thereof, computer readable memory |
| AU2001285161A1 (en)* | 2000-08-21 | 2002-03-04 | United States Postal Services | Delivery point validation system |
| JP2004509398A (en)* | 2000-09-14 | 2004-03-25 | プロビックス・インコーポレイテッド | System for establishing an audit trail for the protection of objects distributed over a network |
| EP1323258A1 (en)* | 2000-09-14 | 2003-07-02 | Probix, Inc. | System for protecting objects distributed over a network |
| JP2002101087A (en)* | 2000-09-21 | 2002-04-05 | Hitachi Ltd | Information storage system and information transfer system and storage medium used for them |
| US6925497B1 (en)* | 2000-09-26 | 2005-08-02 | Microsoft Corporation | Systems and methods for controlling the number of clients that access a server |
| US7444587B1 (en)* | 2000-09-29 | 2008-10-28 | Microsoft Corporation | Selection services component for an extensible editor |
| US7036078B1 (en)* | 2000-09-29 | 2006-04-25 | Microsoft Corporation | Highlight rendering services component for an extensible editor |
| US7069507B1 (en)* | 2000-09-29 | 2006-06-27 | Microsoft Corporation | Event routing model for an extensible editor |
| US20030058274A1 (en)* | 2000-11-17 | 2003-03-27 | Jake Hill | Interface device |
| US20020071560A1 (en)* | 2000-12-12 | 2002-06-13 | Kurn David Michael | Computer system having an autonomous process for centralized cryptographic key administration |
| US6978376B2 (en)* | 2000-12-15 | 2005-12-20 | Authentica, Inc. | Information security architecture for encrypting documents for remote access while maintaining access control |
| US6965683B2 (en)* | 2000-12-21 | 2005-11-15 | Digimarc Corporation | Routing networks for use with watermark systems |
| US7496767B2 (en)* | 2001-01-19 | 2009-02-24 | Xerox Corporation | Secure content objects |
| US20020199118A1 (en)* | 2001-02-02 | 2002-12-26 | Medinservice.Com, Inc. | Internet training course system and methods |
| US7424747B2 (en)* | 2001-04-24 | 2008-09-09 | Microsoft Corporation | Method and system for detecting pirated content |
| US7003662B2 (en)* | 2001-05-24 | 2006-02-21 | International Business Machines Corporation | System and method for dynamically determining CRL locations and access methods |
| US20020178240A1 (en)* | 2001-05-24 | 2002-11-28 | International Business Machines Corporation | System and method for selectively confirming digital certificates in a virtual private network |
| US20020178366A1 (en)* | 2001-05-24 | 2002-11-28 | Amiran Ofir | Method for performing on behalf of a registered user an operation on data stored on a publicly accessible data access server |
| US6938155B2 (en)* | 2001-05-24 | 2005-08-30 | International Business Machines Corporation | System and method for multiple virtual private network authentication schemes |
| US7562146B2 (en)* | 2003-10-10 | 2009-07-14 | Citrix Systems, Inc. | Encapsulating protocol for session persistence and reliability |
| US20050198379A1 (en)* | 2001-06-13 | 2005-09-08 | Citrix Systems, Inc. | Automatically reconnecting a client across reliable and persistent communication sessions |
| US7100200B2 (en) | 2001-06-13 | 2006-08-29 | Citrix Systems, Inc. | Method and apparatus for transmitting authentication credentials of a user across communication sessions |
| US20030061567A1 (en)* | 2001-09-05 | 2003-03-27 | International Business Machines Corporation | Apparatus and method for protecting entries in a form using access rights information |
| US7171562B2 (en)* | 2001-09-05 | 2007-01-30 | International Business Machines Corporation | Apparatus and method for providing a user interface based on access rights information |
| US20030051039A1 (en)* | 2001-09-05 | 2003-03-13 | International Business Machines Corporation | Apparatus and method for awarding a user for accessing content based on access rights information |
| US20030177248A1 (en)* | 2001-09-05 | 2003-09-18 | International Business Machines Corporation | Apparatus and method for providing access rights information on computer accessible content |
| US20030046578A1 (en)* | 2001-09-05 | 2003-03-06 | International Business Machines Incorporation | Apparatus and method for providing access rights information in metadata of a file |
| US20030051172A1 (en)* | 2001-09-13 | 2003-03-13 | Lordemann David A. | Method and system for protecting digital objects distributed over a network |
| CA2358980A1 (en)* | 2001-10-12 | 2003-04-12 | Karthika Technologies Inc. | Distributed security architecture for storage area networks (san) |
| US7725490B2 (en)* | 2001-11-16 | 2010-05-25 | Crucian Global Services, Inc. | Collaborative file access management system |
| US7487233B2 (en)* | 2001-12-05 | 2009-02-03 | Canon Kabushiki Kaisha | Device access based on centralized authentication |
| US8001052B2 (en)* | 2001-12-10 | 2011-08-16 | Dunkeld Bryan C | System and method for unique digital asset identification and transaction management |
| US7631184B2 (en) | 2002-05-14 | 2009-12-08 | Nicholas Ryan | System and method for imposing security on copies of secured items |
| US8065713B1 (en) | 2001-12-12 | 2011-11-22 | Klimenty Vainstein | System and method for providing multi-location access management to secured items |
| US7178033B1 (en) | 2001-12-12 | 2007-02-13 | Pss Systems, Inc. | Method and apparatus for securing digital assets |
| US7921288B1 (en) | 2001-12-12 | 2011-04-05 | Hildebrand Hal S | System and method for providing different levels of key security for controlling access to secured items |
| US7478418B2 (en) | 2001-12-12 | 2009-01-13 | Guardian Data Storage, Llc | Guaranteed delivery of changes to security policies in a distributed system |
| US7921284B1 (en) | 2001-12-12 | 2011-04-05 | Gary Mark Kinghorn | Method and system for protecting electronic data in enterprise environment |
| US7921450B1 (en) | 2001-12-12 | 2011-04-05 | Klimenty Vainstein | Security system using indirect key generation from access rules and methods therefor |
| US10033700B2 (en) | 2001-12-12 | 2018-07-24 | Intellectual Ventures I Llc | Dynamic evaluation of access rights |
| US7565683B1 (en) | 2001-12-12 | 2009-07-21 | Weiqing Huang | Method and system for implementing changes to security policies in a distributed security system |
| USRE41546E1 (en) | 2001-12-12 | 2010-08-17 | Klimenty Vainstein | Method and system for managing security tiers |
| US7681034B1 (en) | 2001-12-12 | 2010-03-16 | Chang-Ping Lee | Method and apparatus for securing electronic data |
| US7380120B1 (en) | 2001-12-12 | 2008-05-27 | Guardian Data Storage, Llc | Secured data format for access control |
| US7783765B2 (en) | 2001-12-12 | 2010-08-24 | Hildebrand Hal S | System and method for providing distributed access control to secured documents |
| US8006280B1 (en)* | 2001-12-12 | 2011-08-23 | Hildebrand Hal S | Security system for generating keys from access rules in a decentralized manner and methods therefor |
| US7930756B1 (en)* | 2001-12-12 | 2011-04-19 | Crocker Steven Toye | Multi-level cryptographic transformations for securing digital assets |
| US7562232B2 (en) | 2001-12-12 | 2009-07-14 | Patrick Zuili | System and method for providing manageability to security information for secured items |
| US7260555B2 (en) | 2001-12-12 | 2007-08-21 | Guardian Data Storage, Llc | Method and architecture for providing pervasive security to digital assets |
| US10360545B2 (en) | 2001-12-12 | 2019-07-23 | Guardian Data Storage, Llc | Method and apparatus for accessing secured electronic data off-line |
| US7950066B1 (en) | 2001-12-21 | 2011-05-24 | Guardian Data Storage, Llc | Method and system for restricting use of a clipboard application |
| US8176334B2 (en) | 2002-09-30 | 2012-05-08 | Guardian Data Storage, Llc | Document security system that permits external users to gain access to secured files |
| US8245306B2 (en)* | 2002-02-15 | 2012-08-14 | Galo Gimenez | Digital rights management printing system |
| AU2003219823A1 (en)* | 2002-02-20 | 2003-09-09 | Bitpipe, Inc. | Electronic document tracking |
| US7984157B2 (en)* | 2002-02-26 | 2011-07-19 | Citrix Systems, Inc. | Persistent and reliable session securely traversing network components using an encapsulating protocol |
| US7661129B2 (en)* | 2002-02-26 | 2010-02-09 | Citrix Systems, Inc. | Secure traversal of network components |
| WO2003081440A1 (en)* | 2002-03-21 | 2003-10-02 | Snapp Robert F | Method and system for storing and retrieving data using hash-accessed multiple data stores |
| US7664731B2 (en) | 2002-03-21 | 2010-02-16 | United States Postal Service | Method and system for storing and retrieving data using hash-accessed multiple data stores |
| US8688461B1 (en)* | 2002-03-29 | 2014-04-01 | Fannie Mae | Electronic registry for authenticating transferable records |
| JP4265145B2 (en)* | 2002-04-08 | 2009-05-20 | 株式会社日立製作所 | Access control method and system |
| US7614077B2 (en)* | 2002-04-10 | 2009-11-03 | International Business Machines Corporation | Persistent access control of protected content |
| US7748045B2 (en)* | 2004-03-30 | 2010-06-29 | Michael Frederick Kenrich | Method and system for providing cryptographic document retention with off-line access |
| US8613102B2 (en)* | 2004-03-30 | 2013-12-17 | Intellectual Ventures I Llc | Method and system for providing document retention using cryptography |
| US7089424B1 (en)* | 2002-05-10 | 2006-08-08 | 3Com Corporation | Peripheral device for protecting data stored on host device and method and system using the same |
| FR2840708A1 (en)* | 2002-06-07 | 2003-12-12 | Netfinances Services | System for secure data exchange in a computer network managing transfer of goods and financial counterflows between separate computerized sites, includes verification and creation of a certificate based on user identification |
| FR2841070B1 (en)* | 2002-06-17 | 2005-02-04 | Cryptolog | INTERFACE METHOD AND DEVICE FOR PROTECTED EXCHANGING ONLINE CONTENT DATA |
| US20030237005A1 (en)* | 2002-06-21 | 2003-12-25 | Yuval Bar-Or | Method and system for protecting digital objects distributed over a network by electronic mail |
| US7159119B2 (en)* | 2002-09-06 | 2007-01-02 | United States Postal Service | Method and system for efficiently retrieving secured data by securely pre-processing provided access information |
| US7512810B1 (en) | 2002-09-11 | 2009-03-31 | Guardian Data Storage Llc | Method and system for protecting encrypted files transmitted over a network |
| US20040125402A1 (en)* | 2002-09-13 | 2004-07-01 | Yoichi Kanai | Document printing program, document protecting program, document protecting system, document printing apparatus for printing out a document based on security policy |
| JP2004164604A (en)* | 2002-10-11 | 2004-06-10 | Ricoh Co Ltd | Electronic file management device and program, and file access control method |
| TWI303764B (en)* | 2002-10-25 | 2008-12-01 | Digital information protecting method and system | |
| US7836310B1 (en) | 2002-11-01 | 2010-11-16 | Yevgeniy Gutnik | Security system that uses indirect password-based encryption |
| US7188245B2 (en)* | 2002-12-09 | 2007-03-06 | Kabushiki Kaisha Toshiba | Contents transmission/reception scheme with function for limiting recipients |
| US7367060B2 (en) | 2002-12-11 | 2008-04-29 | Ravi Someshwar | Methods and apparatus for secure document printing |
| US7577838B1 (en) | 2002-12-20 | 2009-08-18 | Alain Rossmann | Hybrid systems for securing digital assets |
| US7890990B1 (en) | 2002-12-20 | 2011-02-15 | Klimenty Vainstein | Security system with staging capabilities |
| US20040128259A1 (en)* | 2002-12-31 | 2004-07-01 | Blakeley Douglas Burnette | Method for ensuring privacy in electronic transactions with session key blocks |
| US7509569B2 (en)* | 2003-03-31 | 2009-03-24 | Ricoh Co., Ltd. | Action stickers for nested collections |
| US7703002B2 (en)* | 2003-03-31 | 2010-04-20 | Ricoh Company, Ltd. | Method and apparatus for composing multimedia documents |
| US7536638B2 (en)* | 2003-03-31 | 2009-05-19 | Ricoh Co., Ltd. | Action stickers for identifying and processing stored documents |
| US7739583B2 (en) | 2003-03-31 | 2010-06-15 | Ricoh Company, Ltd. | Multimedia document sharing method and apparatus |
| US20070050696A1 (en)* | 2003-03-31 | 2007-03-01 | Piersol Kurt W | Physical key for accessing a securely stored digital document |
| US7757162B2 (en)* | 2003-03-31 | 2010-07-13 | Ricoh Co. Ltd. | Document collection manipulation |
| US10275723B2 (en)* | 2005-09-14 | 2019-04-30 | Oracle International Corporation | Policy enforcement via attestations |
| US10063523B2 (en)* | 2005-09-14 | 2018-08-28 | Oracle International Corporation | Crafted identities |
| US9781154B1 (en) | 2003-04-01 | 2017-10-03 | Oracle International Corporation | Systems and methods for supporting information security and sub-system operational protocol conformance |
| US7493499B1 (en) | 2003-05-22 | 2009-02-17 | Copyright Clearance Center, Inc. | Method and apparatus for secure delivery and rights management of digital content |
| WO2004107130A2 (en)* | 2003-05-28 | 2004-12-09 | Caymas Systems, Inc. | Multilayer access control security system |
| US8707034B1 (en) | 2003-05-30 | 2014-04-22 | Intellectual Ventures I Llc | Method and system for using remote headers to secure electronic files |
| EP1629382A4 (en)* | 2003-06-02 | 2011-12-21 | Liquid Machines Inc | Managing data objects in dynamic, distributed and collaborative contexts |
| US20050021980A1 (en)* | 2003-06-23 | 2005-01-27 | Yoichi Kanai | Access control decision system, access control enforcing system, and security policy |
| US7730543B1 (en) | 2003-06-30 | 2010-06-01 | Satyajit Nath | Method and system for enabling users of a group shared across multiple file security systems to access secured files |
| US8468330B1 (en) | 2003-06-30 | 2013-06-18 | Oracle International Corporation | Methods, systems, and data structures for loading and authenticating a module |
| US7324648B1 (en) | 2003-07-08 | 2008-01-29 | Copyright Clearance Center, Inc. | Method and apparatus for secure key delivery for decrypting bulk digital content files at an unsecure site |
| US7373330B1 (en) | 2003-07-08 | 2008-05-13 | Copyright Clearance Center, Inc. | Method and apparatus for tracking and controlling e-mail forwarding of encrypted documents |
| US8006307B1 (en) | 2003-07-09 | 2011-08-23 | Imophaze Research Co., L.L.C. | Method and apparatus for distributing secure digital content that can be indexed by third party search engines |
| US7299500B1 (en)* | 2003-07-17 | 2007-11-20 | Copyright Clearance Center, Inc. | Method and apparatus for secure delivery and rights management of digital content at an unsecure site |
| US7555558B1 (en) | 2003-08-15 | 2009-06-30 | Michael Frederick Kenrich | Method and system for fault-tolerant transfer of files across a network |
| US7380209B2 (en)* | 2003-09-02 | 2008-05-27 | International Business Machines Corporation | Managing electronic documents utilizing a digital seal |
| US7434048B1 (en) | 2003-09-09 | 2008-10-07 | Adobe Systems Incorporated | Controlling access to electronic documents |
| US20050069138A1 (en)* | 2003-09-25 | 2005-03-31 | Sun Microsystems, Inc., A Delaware Corporation | Application program obfuscation |
| US7363620B2 (en)* | 2003-09-25 | 2008-04-22 | Sun Microsystems, Inc. | Non-linear execution of application program instructions for application program obfuscation |
| US7424620B2 (en)* | 2003-09-25 | 2008-09-09 | Sun Microsystems, Inc. | Interleaved data and instruction streams for application program obfuscation |
| US7389273B2 (en) | 2003-09-25 | 2008-06-17 | Scott Andrew Irwin | System and method for federated rights management |
| US8220058B2 (en)* | 2003-09-25 | 2012-07-10 | Oracle America, Inc. | Rendering and encryption engine for application program obfuscation |
| US7415618B2 (en)* | 2003-09-25 | 2008-08-19 | Sun Microsystems, Inc. | Permutation of opcode values for application program obfuscation |
| US7353499B2 (en)* | 2003-09-25 | 2008-04-01 | Sun Microsystems, Inc. | Multiple instruction dispatch tables for application program obfuscation |
| US8127366B2 (en) | 2003-09-30 | 2012-02-28 | Guardian Data Storage, Llc | Method and apparatus for transitioning between states of security policies used to secure electronic documents |
| US7703140B2 (en) | 2003-09-30 | 2010-04-20 | Guardian Data Storage, Llc | Method and system for securing digital assets using process-driven security policies |
| US20050086531A1 (en)* | 2003-10-20 | 2005-04-21 | Pss Systems, Inc. | Method and system for proxy approval of security changes for a file security system |
| US7346769B2 (en)* | 2003-10-23 | 2008-03-18 | International Business Machines Corporation | Method for selective encryption within documents |
| US7930757B2 (en)* | 2003-10-31 | 2011-04-19 | Adobe Systems Incorporated | Offline access in a document control system |
| US8108672B1 (en) | 2003-10-31 | 2012-01-31 | Adobe Systems Incorporated | Transparent authentication process integration |
| US20050108387A1 (en)* | 2003-10-31 | 2005-05-19 | Bingjun Li | System and apparatus for a network management system using presence and instant message techniques |
| US8627489B2 (en)* | 2003-10-31 | 2014-01-07 | Adobe Systems Incorporated | Distributed document version control |
| US7978716B2 (en) | 2003-11-24 | 2011-07-12 | Citrix Systems, Inc. | Systems and methods for providing a VPN solution |
| JP4070708B2 (en)* | 2003-11-14 | 2008-04-02 | 株式会社リコー | Security ensuring support program, server device for executing the program, and storage medium storing the program |
| JP4704010B2 (en)* | 2003-11-14 | 2011-06-15 | 株式会社リコー | Image forming apparatus, image forming system, security management apparatus, and security management method |
| JP2005151459A (en)* | 2003-11-19 | 2005-06-09 | Canon Inc | Image processing system and image data processing method thereof |
| DE60321009D1 (en)* | 2003-11-19 | 2008-06-26 | Sony Deutschland Gmbh | Copy protected digital data |
| US20050114672A1 (en)* | 2003-11-20 | 2005-05-26 | Encryptx Corporation | Data rights management of digital information in a portable software permission wrapper |
| JP4217146B2 (en)* | 2003-11-21 | 2009-01-28 | 株式会社リコー | Scanner device, viewer device, image protection method, |
| US20050138371A1 (en)* | 2003-12-19 | 2005-06-23 | Pss Systems, Inc. | Method and system for distribution of notifications in file security systems |
| US7702909B2 (en)* | 2003-12-22 | 2010-04-20 | Klimenty Vainstein | Method and system for validating timestamps |
| EP1551146B1 (en)* | 2004-01-05 | 2011-08-24 | Ricoh Company, Ltd. | Document security management for repeatedly reproduced hardcopy and electronic documents |
| US8583739B2 (en) | 2004-03-02 | 2013-11-12 | International Business Machines Corporation | Facilitating the sending of mail from a restricted communications network |
| JP2005284985A (en)* | 2004-03-30 | 2005-10-13 | Ricoh Co Ltd | Network-compatible device, maintenance method for maintaining network-compatible device, program, medium on which program is recorded, and maintenance system |
| US7426713B2 (en)* | 2004-03-31 | 2008-09-16 | International Business Machines Corporation | Controlling a GUI display for a plug-in |
| US9003548B2 (en)* | 2004-04-13 | 2015-04-07 | Nl Systems, Llc | Method and system for digital rights management of documents |
| US7484107B2 (en)* | 2004-04-15 | 2009-01-27 | International Business Machines Corporation | Method for selective encryption within documents |
| US7870386B2 (en)* | 2004-04-29 | 2011-01-11 | International Business Machines Corporation | Method for permanent decryption of selected sections of an encrypted document |
| WO2005119960A2 (en)* | 2004-06-01 | 2005-12-15 | Ben-Gurion University Of The Negev Research And Development Authority | Structure preserving database encryption method and system |
| US20050289639A1 (en)* | 2004-06-23 | 2005-12-29 | Leung Wai K | System and method of securing the management of documentation |
| US7757074B2 (en) | 2004-06-30 | 2010-07-13 | Citrix Application Networking, Llc | System and method for establishing a virtual private network |
| US8739274B2 (en) | 2004-06-30 | 2014-05-27 | Citrix Systems, Inc. | Method and device for performing integrated caching in a data communication network |
| US8495305B2 (en) | 2004-06-30 | 2013-07-23 | Citrix Systems, Inc. | Method and device for performing caching of dynamically generated objects in a data communication network |
| US7707427B1 (en) | 2004-07-19 | 2010-04-27 | Michael Frederick Kenrich | Multi-level file digests |
| US7609721B2 (en) | 2004-07-23 | 2009-10-27 | Citrix Systems, Inc. | Systems and methods for adjusting the maximum transmission unit for encrypted communications |
| US8363650B2 (en) | 2004-07-23 | 2013-01-29 | Citrix Systems, Inc. | Method and systems for routing packets from a gateway to an endpoint |
| WO2006015182A2 (en) | 2004-07-29 | 2006-02-09 | Infoassure, Inc. | Object access level |
| US7458102B2 (en)* | 2004-08-17 | 2008-11-25 | Emc Corporation | Information security architecture for remote access control using non-bidirectional protocols |
| JP2007026412A (en)* | 2004-08-25 | 2007-02-01 | Ricoh Co Ltd | Maintenance intermediary device, maintenance method for maintenance target device, maintenance program, recording medium on which maintenance program is recorded, and maintenance system |
| US20060048224A1 (en)* | 2004-08-30 | 2006-03-02 | Encryptx Corporation | Method and apparatus for automatically detecting sensitive information, applying policies based on a structured taxonomy and dynamically enforcing and reporting on the protection of sensitive data through a software permission wrapper |
| US7707642B1 (en) | 2004-08-31 | 2010-04-27 | Adobe Systems Incorporated | Document access auditing |
| US8099660B1 (en) | 2004-09-30 | 2012-01-17 | Google Inc. | Tool for managing online content |
| US20060101028A1 (en)* | 2004-10-21 | 2006-05-11 | Banks Lanette E | Method and apparatus for efficient electronic document management |
| US20060117016A1 (en)* | 2004-10-21 | 2006-06-01 | International Business Machines Corporation | Method and apparatus for efficient electronic document management |
| EP1653349B1 (en)* | 2004-10-27 | 2008-07-09 | Sap Ag | Method and system for generating a transport track through a software system landscape |
| EP1653317A1 (en)* | 2004-10-27 | 2006-05-03 | Sap Ag | Method and system for setting change options of software systems |
| DE602004006630T2 (en) | 2004-10-27 | 2008-01-17 | Sap Ag | Method for carrying out a software service in a system landscape |
| EP1653345B1 (en)* | 2004-10-27 | 2008-07-23 | Sap Ag | Method and computer system for effecting software maintenance in a software system landscape |
| EP1653348A1 (en)* | 2004-10-27 | 2006-05-03 | Sap Ag | Method for tracking transport requests and computer system with trackable transport requests |
| EP1653351B1 (en)* | 2004-10-27 | 2008-06-25 | Sap Ag | Method and computer system for effecting changes in a software system landscape |
| ATE410729T1 (en) | 2004-10-27 | 2008-10-15 | Sap Ag | COMPUTER SYSTEM AND METHOD FOR EFFECTING AN INTRODUCTORY SOFTWARE SERVICE IN A PRODUCTIVE SYSTEM OF A SOFTWARE SYSTEM LANDSCAPE |
| US7995758B1 (en) | 2004-11-30 | 2011-08-09 | Adobe Systems Incorporated | Family of encryption keys |
| US20070168292A1 (en)* | 2004-12-21 | 2007-07-19 | Fabrice Jogand-Coulomb | Memory system with versatile content control |
| US8601283B2 (en)* | 2004-12-21 | 2013-12-03 | Sandisk Technologies Inc. | Method for versatile content control with partitioning |
| US8504849B2 (en)* | 2004-12-21 | 2013-08-06 | Sandisk Technologies Inc. | Method for versatile content control |
| TW200636554A (en)* | 2004-12-21 | 2006-10-16 | Sandisk Corp | Memory ststem with versatile content control |
| US8051052B2 (en)* | 2004-12-21 | 2011-11-01 | Sandisk Technologies Inc. | Method for creating control structure for versatile content control |
| US8954595B2 (en) | 2004-12-30 | 2015-02-10 | Citrix Systems, Inc. | Systems and methods for providing client-side accelerated access to remote applications via TCP buffering |
| US8706877B2 (en) | 2004-12-30 | 2014-04-22 | Citrix Systems, Inc. | Systems and methods for providing client-side dynamic redirection to bypass an intermediary |
| US8549149B2 (en) | 2004-12-30 | 2013-10-01 | Citrix Systems, Inc. | Systems and methods for providing client-side accelerated access to remote applications via TCP multiplexing |
| US8700695B2 (en) | 2004-12-30 | 2014-04-15 | Citrix Systems, Inc. | Systems and methods for providing client-side accelerated access to remote applications via TCP pooling |
| US7810089B2 (en) | 2004-12-30 | 2010-10-05 | Citrix Systems, Inc. | Systems and methods for automatic installation and execution of a client-side acceleration program |
| US8255456B2 (en) | 2005-12-30 | 2012-08-28 | Citrix Systems, Inc. | System and method for performing flash caching of dynamically generated objects in a data communication network |
| US7840564B2 (en) | 2005-02-16 | 2010-11-23 | Ebrary | System and method for automatic anthology creation using document aspects |
| WO2006109307A2 (en)* | 2005-04-13 | 2006-10-19 | Discretix Technologies Ltd. | Method, device, and system of selectively accessing data |
| US7661146B2 (en)* | 2005-07-01 | 2010-02-09 | Privamed, Inc. | Method and system for providing a secure multi-user portable database |
| US7433869B2 (en) | 2005-07-01 | 2008-10-07 | Ebrary, Inc. | Method and apparatus for document clustering and document sketching |
| US7748031B2 (en) | 2005-07-08 | 2010-06-29 | Sandisk Corporation | Mass storage device with automated credentials loading |
| US8832047B2 (en) | 2005-07-27 | 2014-09-09 | Adobe Systems Incorporated | Distributed document version control |
| US9282081B2 (en) | 2005-07-28 | 2016-03-08 | Vaporstream Incorporated | Reduced traceability electronic message system and method |
| US7610345B2 (en) | 2005-07-28 | 2009-10-27 | Vaporstream Incorporated | Reduced traceability electronic message system and method |
| EP1924944A4 (en)* | 2005-09-12 | 2012-11-07 | Sand Box Technologies Inc | System and method for controlling distribution of electronic information |
| US8090945B2 (en)* | 2005-09-16 | 2012-01-03 | Tara Chand Singhal | Systems and methods for multi-factor remote user authentication |
| US8239682B2 (en) | 2005-09-28 | 2012-08-07 | Nl Systems, Llc | Method and system for digital rights management of documents |
| US8250151B2 (en)* | 2005-10-12 | 2012-08-21 | Bloomberg Finance L.P. | System and method for providing secure data transmission |
| US20070130289A1 (en)* | 2005-12-07 | 2007-06-07 | Christopher Defazio | Remote access |
| US8456653B2 (en)* | 2005-12-12 | 2013-06-04 | Canon Kabushiki Kaisha | Data processing apparatus for producing print job data whose authority is managed by external server, and image processing apparatus for printing a print job whose authority is managed by external server |
| TWI307593B (en)* | 2005-12-14 | 2009-03-11 | Chung Shan Inst Of Science | System and method of protecting digital data |
| US8526666B1 (en) | 2005-12-15 | 2013-09-03 | Emc Corporation | Method and system for rendering watermarked content using a watermark window |
| US8321947B2 (en)* | 2005-12-15 | 2012-11-27 | Emc Corporation | Method and system for dynamically generating a watermarked document during a printing or display operation |
| US8312552B1 (en) | 2005-12-15 | 2012-11-13 | Emc Corporation | Method and system for rendering watermarked content |
| US7987494B1 (en)* | 2005-12-19 | 2011-07-26 | Adobe Systems Incorporated | Method and apparatus providing end to end protection for a document |
| US10380568B1 (en)* | 2005-12-20 | 2019-08-13 | Emc Corporation | Accessing rights-managed content from constrained connectivity devices |
| US20070143423A1 (en)* | 2005-12-21 | 2007-06-21 | Oliver Kieselbach | Method and system for allowing a session initiating user to select one or more privacy settings to be applied to an instant messaging session from among multiple possible privacy controls |
| US8244745B2 (en)* | 2005-12-29 | 2012-08-14 | Nextlabs, Inc. | Analyzing usage information of an information management system |
| US8150816B2 (en)* | 2005-12-29 | 2012-04-03 | Nextlabs, Inc. | Techniques of optimizing policies in an information management system |
| US8301839B2 (en) | 2005-12-30 | 2012-10-30 | Citrix Systems, Inc. | System and method for performing granular invalidation of cached dynamically generated objects in a data communication network |
| US7921184B2 (en) | 2005-12-30 | 2011-04-05 | Citrix Systems, Inc. | System and method for performing flash crowd caching of dynamically generated objects in a data communication network |
| EP1999883A4 (en)* | 2006-03-14 | 2013-03-06 | Divx Llc | Federated digital rights management scheme including trusted systems |
| US7552320B2 (en)* | 2006-03-31 | 2009-06-23 | Lenovo (Singapore) Pte. Ltd. | Arrangement for initiating a re-imaging process for a computer system |
| US20070239998A1 (en)* | 2006-04-11 | 2007-10-11 | Medox Exchange, Inc. | Dynamic binding of access and usage rights to computer-based resources |
| US20070261116A1 (en)* | 2006-04-13 | 2007-11-08 | Verisign, Inc. | Method and apparatus to provide a user profile for use with a secure content service |
| US9288052B2 (en)* | 2006-04-13 | 2016-03-15 | Moreover Acquisition Corporation | Method and apparatus to provide an authoring tool to create content for a secure content service |
| US20070245230A1 (en)* | 2006-04-14 | 2007-10-18 | Cherkasov Aleksey G | Method, system, and computer-readable medium to uniformly render document annotations across multiple computer platforms |
| US8171523B2 (en)* | 2006-04-29 | 2012-05-01 | Lenovo (Singapore) Pte. Ltd. | Embedded email receiver authentication |
| US20070283446A1 (en)* | 2006-06-05 | 2007-12-06 | Kabushiki Kaisha Toshiba | System and method for secure handling of scanned documents |
| US7975143B2 (en)* | 2006-06-12 | 2011-07-05 | International Business Machines Corporation | Method, system, and program product for generating and validating digital signatures |
| US8572751B2 (en)* | 2006-06-12 | 2013-10-29 | International Business Machines Corporation | Method, system, and program product for preventing unauthorized changes to an electronic document |
| US7995568B2 (en)* | 2006-06-12 | 2011-08-09 | International Business Machines Corporation | Capturing user interface switch states |
| US8855296B2 (en) | 2006-06-28 | 2014-10-07 | Voltage Security, Inc. | Data processing systems with format-preserving encryption and decryption engines |
| US8639939B2 (en)* | 2006-07-07 | 2014-01-28 | Sandisk Technologies Inc. | Control method using identity objects |
| US8245031B2 (en)* | 2006-07-07 | 2012-08-14 | Sandisk Technologies Inc. | Content control method using certificate revocation lists |
| US20100138652A1 (en)* | 2006-07-07 | 2010-06-03 | Rotem Sela | Content control method using certificate revocation lists |
| US8266711B2 (en)* | 2006-07-07 | 2012-09-11 | Sandisk Technologies Inc. | Method for controlling information supplied from memory device |
| US8140843B2 (en)* | 2006-07-07 | 2012-03-20 | Sandisk Technologies Inc. | Content control method using certificate chains |
| US8613103B2 (en)* | 2006-07-07 | 2013-12-17 | Sandisk Technologies Inc. | Content control method using versatile control structure |
| US8776166B1 (en)* | 2006-07-17 | 2014-07-08 | Juniper Networks, Inc. | Plug-in based policy evaluation |
| US20080043274A1 (en)* | 2006-08-16 | 2008-02-21 | Lida Wang | Secure printing system with privilege table referenced across different domains |
| US20080077704A1 (en)* | 2006-09-24 | 2008-03-27 | Void Communications, Inc. | Variable Electronic Communication Ping Time System and Method |
| US8958562B2 (en) | 2007-01-16 | 2015-02-17 | Voltage Security, Inc. | Format-preserving cryptographic systems |
| US20080201440A1 (en)* | 2007-02-15 | 2008-08-21 | Void Communications, Inc. | Electronic Messaging Recordlessness Warning and Routing System and Method |
| KR100867130B1 (en)* | 2007-02-23 | 2008-11-06 | (주)코리아센터닷컴 | System and method of transmitting/receiving security data |
| WO2008103000A1 (en)* | 2007-02-23 | 2008-08-28 | Koreacenter Co., Ltd | System and method of transmitting/receiving security data |
| US8402278B2 (en)* | 2007-04-13 | 2013-03-19 | Ca, Inc. | Method and system for protecting data |
| KR100932847B1 (en)* | 2007-06-26 | 2009-12-21 | 엔에이치엔(주) | Copy protection methods and systems |
| US8010779B2 (en) | 2007-09-19 | 2011-08-30 | Novell Inc. | Techniques for secure network searching |
| US20090100060A1 (en)* | 2007-10-11 | 2009-04-16 | Noam Livnat | Device, system, and method of file-utilization management |
| US8997161B2 (en) | 2008-01-02 | 2015-03-31 | Sonic Ip, Inc. | Application enhancement tracks |
| JP5356409B2 (en)* | 2008-01-21 | 2013-12-04 | テレフオンアクチーボラゲット エル エム エリクソン(パブル) | Abstraction functions in mobile handsets |
| US8838554B2 (en)* | 2008-02-19 | 2014-09-16 | Bank Of America Corporation | Systems and methods for providing content aware document analysis and modification |
| US11488134B2 (en) | 2008-05-02 | 2022-11-01 | Micro Focus Llc | Format-preserving cryptographic systems |
| US8099599B2 (en)* | 2008-08-29 | 2012-01-17 | Microsoft Corporation | Controlling access to data streams |
| US20100088364A1 (en)* | 2008-10-08 | 2010-04-08 | International Business Machines Corporation | Social networking architecture in which profile data hosting is provided by the profile owner |
| US20100127022A1 (en)* | 2008-11-21 | 2010-05-27 | Symyx Technologies, Inc. | Dispensing valve |
| US9104618B2 (en)* | 2008-12-18 | 2015-08-11 | Sandisk Technologies Inc. | Managing access to an address range in a storage device |
| JP4897782B2 (en)* | 2008-12-27 | 2012-03-14 | キヤノンマーケティングジャパン株式会社 | Document management system, document management method, and program thereof |
| AU2010203605B2 (en) | 2009-01-07 | 2015-05-14 | Divx, Llc | Singular, collective and automated creation of a media guide for online content |
| US9031876B2 (en)* | 2009-06-19 | 2015-05-12 | Hewlett-Packard Development Company, L.P. | Managing keys for encrypted shared documents |
| US9542408B2 (en) | 2010-08-27 | 2017-01-10 | Pneuron Corp. | Method and process for enabling distributing cache data sources for query processing and distributed disk caching of large data and analysis requests |
| SG178589A1 (en)* | 2009-08-28 | 2012-04-27 | Pneuron Corp | System and method using neural networks for real-time business intelligence and automation control |
| US9311465B2 (en)* | 2009-09-21 | 2016-04-12 | James McNulty | Secure information storage and retrieval apparatus and method |
| US8781122B2 (en) | 2009-12-04 | 2014-07-15 | Sonic Ip, Inc. | Elementary bitstream cryptographic material transport systems and methods |
| WO2011082489A1 (en)* | 2010-01-06 | 2011-07-14 | Vitrium Systems Inc. | Method and system of providing a viewing experience with respect to a document having read-only content |
| GB201000288D0 (en)* | 2010-01-11 | 2010-02-24 | Scentrics Information Security | System and method of enforcing a computer policy |
| US9104659B2 (en)* | 2010-01-20 | 2015-08-11 | Bank Of America Corporation | Systems and methods for providing content aware document analysis and modification |
| US8539165B2 (en) | 2010-09-29 | 2013-09-17 | International Business Machines Corporation | Methods for managing ownership of redundant data and systems thereof |
| US8612682B2 (en) | 2010-09-29 | 2013-12-17 | International Business Machines Corporation | Methods for managing ownership of redundant data and systems thereof |
| US20120078931A1 (en) | 2010-09-29 | 2012-03-29 | International Business Machines Corporation | Methods for managing ownership of redundant data and systems thereof |
| US8539154B2 (en) | 2010-09-29 | 2013-09-17 | International Business Machines Corporation | Methods for managing ownership of redundant data and systems thereof |
| US8645636B2 (en) | 2010-09-29 | 2014-02-04 | International Business Machines Corporation | Methods for managing ownership of redundant data and systems thereof |
| US9247312B2 (en) | 2011-01-05 | 2016-01-26 | Sonic Ip, Inc. | Systems and methods for encoding source media in matroska container files for adaptive bitrate streaming using hypertext transfer protocol |
| US20120179904A1 (en)* | 2011-01-11 | 2012-07-12 | Safenet, Inc. | Remote Pre-Boot Authentication |
| US9378379B1 (en) | 2011-01-19 | 2016-06-28 | Bank Of America Corporation | Method and apparatus for the protection of information in a device upon separation from a network |
| US8611544B1 (en)* | 2011-01-25 | 2013-12-17 | Adobe Systems Incorporated | Systems and methods for controlling electronic document use |
| US9137014B2 (en) | 2011-01-25 | 2015-09-15 | Adobe Systems Incorporated | Systems and methods for controlling electronic document use |
| EP2695050A4 (en) | 2011-04-07 | 2016-03-23 | Pneuron Corp | Legacy application migration to real time, parallel performance cloud |
| US9467708B2 (en) | 2011-08-30 | 2016-10-11 | Sonic Ip, Inc. | Selection of resolutions for seamless resolution switching of multimedia content |
| US8964977B2 (en) | 2011-09-01 | 2015-02-24 | Sonic Ip, Inc. | Systems and methods for saving encoded media streamed using adaptive bitrate streaming |
| US8909922B2 (en) | 2011-09-01 | 2014-12-09 | Sonic Ip, Inc. | Systems and methods for playing back alternative streams of protected content protected using common cryptographic information |
| US10630559B2 (en) | 2011-09-27 | 2020-04-21 | UST Global (Singapore) Pte. Ltd. | Virtual machine (VM) realm integration and management |
| CA2855828C (en)* | 2011-11-14 | 2021-02-16 | Wave Systems Corp. | Security systems and methods for encoding and decoding digital content |
| US10824698B2 (en) | 2011-11-29 | 2020-11-03 | Cardlogix | Multimode smart card system with embedded USB connectivity |
| US11132672B2 (en)* | 2011-11-29 | 2021-09-28 | Cardlogix | Layered security for age verification and transaction authorization |
| WO2013090555A1 (en) | 2011-12-13 | 2013-06-20 | Pneuron Corp. | Pneuron distributed analytics |
| CN104662870B (en)* | 2012-09-10 | 2019-02-05 | 云深系统有限公司 | data security management system |
| US9313510B2 (en) | 2012-12-31 | 2016-04-12 | Sonic Ip, Inc. | Use of objective quality measures of streamed content to reduce streaming bandwidth |
| US9191457B2 (en) | 2012-12-31 | 2015-11-17 | Sonic Ip, Inc. | Systems, methods, and media for controlling delivery of content |
| US11354623B2 (en) | 2013-02-15 | 2022-06-07 | Dav Acquisition Corp. | Remotely diagnosing conditions and providing prescriptions using a multi-access health care provider portal |
| US9959385B2 (en)* | 2013-02-15 | 2018-05-01 | Davincian Healthcare, Inc. | Messaging within a multi-access health care provider portal |
| US9906785B2 (en) | 2013-03-15 | 2018-02-27 | Sonic Ip, Inc. | Systems, methods, and media for transcoding video data according to encoding parameters indicated by received metadata |
| US10397292B2 (en) | 2013-03-15 | 2019-08-27 | Divx, Llc | Systems, methods, and media for delivery of content |
| US9058495B2 (en) | 2013-05-16 | 2015-06-16 | Airwatch Llc | Rights management services integration with mobile device management |
| US9094737B2 (en) | 2013-05-30 | 2015-07-28 | Sonic Ip, Inc. | Network video streaming with trick play based on separate trick play files |
| US9247317B2 (en) | 2013-05-30 | 2016-01-26 | Sonic Ip, Inc. | Content streaming with client device trick play index |
| US9967305B2 (en) | 2013-06-28 | 2018-05-08 | Divx, Llc | Systems, methods, and media for streaming media content |
| US9866878B2 (en) | 2014-04-05 | 2018-01-09 | Sonic Ip, Inc. | Systems and methods for encoding and playing back video at different frame rates using enhancement layers |
| US9129095B1 (en)* | 2014-12-19 | 2015-09-08 | Tresorit, Kft | Client-side encryption with DRM |
| GB2535183B (en) | 2015-02-11 | 2017-02-15 | Livedrive Internet Ltd | Methods and systems for virtual file storage and encryption |
| US10853502B1 (en) | 2015-03-04 | 2020-12-01 | Micro Focus Llc | Systems and methods for reducing computational difficulty of cryptographic operations |
| US9954832B2 (en) | 2015-04-24 | 2018-04-24 | Encryptics, Llc | System and method for enhanced data protection |
| GB201508872D0 (en)* | 2015-05-22 | 2015-07-01 | Exate Technology Ltd | Encryption and decryption system |
| US10083315B2 (en)* | 2015-06-29 | 2018-09-25 | Microsoft Technology Licensing, Llc | Privacy enhanced personal search index |
| US9674202B1 (en) | 2015-12-29 | 2017-06-06 | Imperva, Inc. | Techniques for preventing large-scale data breaches utilizing differentiated protection layers |
| US9674201B1 (en) | 2015-12-29 | 2017-06-06 | Imperva, Inc. | Unobtrusive protection for large-scale data breaches utilizing user-specific data object access budgets |
| US9596079B1 (en) | 2016-04-14 | 2017-03-14 | Wickr Inc. | Secure telecommunications |
| WO2017189984A1 (en)* | 2016-04-28 | 2017-11-02 | Gilkey Quentin | Audio watermarking system and processes |
| CN109496414B (en)* | 2016-07-28 | 2022-05-24 | 皇家飞利浦有限公司 | Identifying a network node to which data is to be copied |
| US10498795B2 (en) | 2017-02-17 | 2019-12-03 | Divx, Llc | Systems and methods for adaptive switching between multiple content delivery networks during adaptive bitrate streaming |
| US10749674B2 (en) | 2017-09-29 | 2020-08-18 | Micro Focus Llc | Format preserving encryption utilizing a key version |
| US11101999B2 (en) | 2017-11-08 | 2021-08-24 | Amazon Technologies, Inc. | Two-way handshake for key establishment for secure communications |
| US10778432B2 (en) | 2017-11-08 | 2020-09-15 | Wickr Inc. | End-to-end encryption during a secure communication session |
| US10855440B1 (en) | 2017-11-08 | 2020-12-01 | Wickr Inc. | Generating new encryption keys during a secure communication session |
| US10541814B2 (en) | 2017-11-08 | 2020-01-21 | Wickr Inc. | End-to-end encryption during a secure communication session |
| US11537724B2 (en)* | 2019-03-26 | 2022-12-27 | International Business Machines Corporation | Generating data migration plan for in-place encryption of data |
| EP4322470B1 (en) | 2022-08-08 | 2025-03-12 | Ostrean IT Technologies s.r.o. | Data encryption system and method |
Citations (47)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US4605820A (en)* | 1983-11-10 | 1986-08-12 | Visa U.S.A. Inc. | Key management system for on-line communication |
| US4803108A (en) | 1987-05-01 | 1989-02-07 | Essex Specialty Products, Inc. | Honeycomb reinforcing sheet for the reinforcement of panels and method of reinforcing panels |
| US4937863A (en)* | 1988-03-07 | 1990-06-26 | Digital Equipment Corporation | Software licensing management system |
| US5058164A (en)* | 1990-05-03 | 1991-10-15 | National Semiconductor Corp. | Encryption of streams of addressed information to be used for program code protection |
| US5098124A (en) | 1990-09-06 | 1992-03-24 | Automotive Technologies International Inc. | Padding to reduce injuries in automobile accidents |
| US5263157A (en)* | 1990-02-15 | 1993-11-16 | International Business Machines Corporation | Method and system for providing user access control within a distributed data processing system by the exchange of access control profiles |
| US5349893A (en) | 1992-02-20 | 1994-09-27 | Dunn Eric S | Impact absorbing armor |
| US5356177A (en) | 1993-06-25 | 1994-10-18 | Davidson Textron Inc. | Side impact protection apparatus |
| US5410602A (en)* | 1993-09-27 | 1995-04-25 | Motorola, Inc. | Method for key management of point-to-point communications |
| US5410598A (en)* | 1986-10-14 | 1995-04-25 | Electronic Publishing Resources, Inc. | Database usage metering and protection system and method |
| US5432849A (en)* | 1990-08-22 | 1995-07-11 | International Business Machines Corporation | Secure cryptographic operations using control vectors generated inside a cryptographic facility |
| US5438508A (en)* | 1991-06-28 | 1995-08-01 | Digital Equipment Corporation | License document interchange format for license management system |
| US5440631A (en)* | 1992-04-24 | 1995-08-08 | Fijitsu Limited | Information distribution system wherein storage medium storing ciphered information is distributed |
| US5509070A (en)* | 1992-12-15 | 1996-04-16 | Softlock Services Inc. | Method for encouraging purchase of executable and non-executable software |
| US5586186A (en)* | 1994-07-15 | 1996-12-17 | Microsoft Corporation | Method and system for controlling unauthorized access to information distributed to users |
| US5604801A (en)* | 1995-02-03 | 1997-02-18 | International Business Machines Corporation | Public key data communications system under control of a portable security device |
| US5629980A (en)* | 1994-11-23 | 1997-05-13 | Xerox Corporation | System for controlling the distribution and use of digital works |
| US5673316A (en)* | 1996-03-29 | 1997-09-30 | International Business Machines Corporation | Creation and distribution of cryptographic envelope |
| US5689560A (en)* | 1994-04-25 | 1997-11-18 | International Business Machines Corporation | Method and apparatus for enabling trial period use of software products: method and apparatus for allowing a try-and-buy user interaction |
| US5708709A (en)* | 1995-12-08 | 1998-01-13 | Sun Microsystems, Inc. | System and method for managing try-and-buy usage of application programs |
| US5727065A (en)* | 1994-11-14 | 1998-03-10 | Hughes Electronics | Deferred billing, broadcast, electronic document distribution system and method |
| US5754646A (en)* | 1995-07-19 | 1998-05-19 | Cable Television Laboratories, Inc. | Method for protecting publicly distributed software |
| US5765152A (en)* | 1995-10-13 | 1998-06-09 | Trustees Of Dartmouth College | System and method for managing copyrighted electronic media |
| US5796825A (en)* | 1996-01-16 | 1998-08-18 | Symantec Corporation | System for automatic decryption of file data on a per-use basis and automatic re-encryption within context of multi-threaded operating system under which applications run in real-time |
| US5809145A (en)* | 1996-06-28 | 1998-09-15 | Paradata Systems Inc. | System for distributing digital information |
| US5818936A (en)* | 1996-03-15 | 1998-10-06 | Novell, Inc. | System and method for automically authenticating a user in a distributed network system |
| US5822524A (en) | 1995-07-21 | 1998-10-13 | Infovalue Computing, Inc. | System for just-in-time retrieval of multimedia files over computer networks by transmitting data packets at transmission rate determined by frame size |
| US5883955A (en)* | 1995-06-07 | 1999-03-16 | Digital River, Inc. | On-line try before you buy software distribution system |
| US5892900A (en)* | 1996-08-30 | 1999-04-06 | Intertrust Technologies Corp. | Systems and methods for secure transaction management and electronic rights protection |
| US5933498A (en)* | 1996-01-11 | 1999-08-03 | Mrj, Inc. | System for controlling access and distribution of digital property |
| US5956034A (en)* | 1996-08-13 | 1999-09-21 | Softbook Press, Inc. | Method and apparatus for viewing electronic reading materials |
| US5978475A (en)* | 1997-07-18 | 1999-11-02 | Counterpane Internet Security, Inc. | Event auditing system |
| US5997077A (en) | 1997-08-23 | 1999-12-07 | Volkswagen Ag | Deformable structure for protection of vehicle occupants |
| US6002772A (en)* | 1995-09-29 | 1999-12-14 | Mitsubishi Corporation | Data management system |
| US6064736A (en) | 1997-09-15 | 2000-05-16 | International Business Machines Corporation | Systems, methods and computer program products that use an encrypted session for additional password verification |
| US6182220B1 (en) | 1998-03-30 | 2001-01-30 | International Business Machines Corporation | System and method for building and exchanging encrypted passwords between a client and server |
| US6245408B1 (en) | 1999-05-19 | 2001-06-12 | Hexcel Corporation | Honeycomb core with controlled crush properties |
| US6289450B1 (en)* | 1999-05-28 | 2001-09-11 | Authentica, Inc. | Information security architecture for encrypting documents for remote access while maintaining access control |
| US6308256B1 (en) | 1999-08-18 | 2001-10-23 | Sun Microsystems, Inc. | Secure execution of program instructions provided by network interactions with processor |
| US20010055396A1 (en) | 2000-02-24 | 2001-12-27 | David Jevans | Mechanism for efficient private bulk messaging |
| US6401204B1 (en)* | 1996-06-05 | 2002-06-04 | Siemens Aktiengesellschaft | Process for cryptographic code management between a first computer unit and a second computer unit |
| US6499106B1 (en) | 1999-01-15 | 2002-12-24 | Sony Corporation | Method and apparatus for secure distribution of information recorded of fixed media |
| US6547280B1 (en) | 1998-11-21 | 2003-04-15 | Cellbond Limited | Energy-absorbing structures |
| US6658566B1 (en)* | 1997-03-13 | 2003-12-02 | Bull Cp8 | Process for storage and use of sensitive information in a security module and the associated security module |
| US6682128B2 (en) | 1998-02-04 | 2004-01-27 | Oakwood Energy Management, Inc. | Composite energy absorber |
| US6711553B1 (en) | 2000-02-25 | 2004-03-23 | Kent Ridge Digital Labs | Method and apparatus for digital content copy protection |
| US6732106B2 (en) | 2000-12-08 | 2004-05-04 | Matsushita Electric Industrial Co., Ltd. | Digital data distribution system |
Family Cites Families (3)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US5544161A (en)* | 1995-03-28 | 1996-08-06 | Bell Atlantic Network Services, Inc. | ATM packet demultiplexer for use in full service network having distributed architecture |
| US5689565A (en)* | 1995-06-29 | 1997-11-18 | Microsoft Corporation | Cryptography system and method for providing cryptographic services for a computer application |
| US6134660A (en)* | 1997-06-30 | 2000-10-17 | Telcordia Technologies, Inc. | Method for revoking computer backup files using cryptographic techniques |
- 1999
- 1999-05-28USUS09/321,839patent/US6289450B1/ennot_activeExpired - Lifetime
- 2000
- 2000-05-23AUAU52804/00Apatent/AU5280400A/ennot_activeAbandoned
- 2000-05-23WOPCT/US2000/013996patent/WO2000074299A1/enactiveApplication Filing
- 2001
- 2001-07-18USUS09/906,811patent/US6339825B2/ennot_activeExpired - Lifetime
- 2001-11-01USUS09/985,096patent/US6449721B1/ennot_activeCeased
- 2004
- 2004-09-09USUS10/936,829patent/USRE41186E1/ennot_activeExpired - Lifetime
- 2005
- 2005-05-16USUS11/129,746patent/USRE44364E1/ennot_activeExpired - Lifetime
Patent Citations (49)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US4605820A (en)* | 1983-11-10 | 1986-08-12 | Visa U.S.A. Inc. | Key management system for on-line communication |
| US5410598A (en)* | 1986-10-14 | 1995-04-25 | Electronic Publishing Resources, Inc. | Database usage metering and protection system and method |
| US4803108A (en) | 1987-05-01 | 1989-02-07 | Essex Specialty Products, Inc. | Honeycomb reinforcing sheet for the reinforcement of panels and method of reinforcing panels |
| US4937863A (en)* | 1988-03-07 | 1990-06-26 | Digital Equipment Corporation | Software licensing management system |
| US5263157A (en)* | 1990-02-15 | 1993-11-16 | International Business Machines Corporation | Method and system for providing user access control within a distributed data processing system by the exchange of access control profiles |
| US5058164A (en)* | 1990-05-03 | 1991-10-15 | National Semiconductor Corp. | Encryption of streams of addressed information to be used for program code protection |
| US5432849A (en)* | 1990-08-22 | 1995-07-11 | International Business Machines Corporation | Secure cryptographic operations using control vectors generated inside a cryptographic facility |
| US5098124A (en) | 1990-09-06 | 1992-03-24 | Automotive Technologies International Inc. | Padding to reduce injuries in automobile accidents |
| US5438508A (en)* | 1991-06-28 | 1995-08-01 | Digital Equipment Corporation | License document interchange format for license management system |
| US5349893A (en) | 1992-02-20 | 1994-09-27 | Dunn Eric S | Impact absorbing armor |
| US5440631A (en)* | 1992-04-24 | 1995-08-08 | Fijitsu Limited | Information distribution system wherein storage medium storing ciphered information is distributed |
| US5509070A (en)* | 1992-12-15 | 1996-04-16 | Softlock Services Inc. | Method for encouraging purchase of executable and non-executable software |
| US5356177A (en) | 1993-06-25 | 1994-10-18 | Davidson Textron Inc. | Side impact protection apparatus |
| US5410602A (en)* | 1993-09-27 | 1995-04-25 | Motorola, Inc. | Method for key management of point-to-point communications |
| US5689560A (en)* | 1994-04-25 | 1997-11-18 | International Business Machines Corporation | Method and apparatus for enabling trial period use of software products: method and apparatus for allowing a try-and-buy user interaction |
| US5586186A (en)* | 1994-07-15 | 1996-12-17 | Microsoft Corporation | Method and system for controlling unauthorized access to information distributed to users |
| US5727065A (en)* | 1994-11-14 | 1998-03-10 | Hughes Electronics | Deferred billing, broadcast, electronic document distribution system and method |
| US5629980A (en)* | 1994-11-23 | 1997-05-13 | Xerox Corporation | System for controlling the distribution and use of digital works |
| US5604801A (en)* | 1995-02-03 | 1997-02-18 | International Business Machines Corporation | Public key data communications system under control of a portable security device |
| US5883955A (en)* | 1995-06-07 | 1999-03-16 | Digital River, Inc. | On-line try before you buy software distribution system |
| US5754646A (en)* | 1995-07-19 | 1998-05-19 | Cable Television Laboratories, Inc. | Method for protecting publicly distributed software |
| US5822524A (en) | 1995-07-21 | 1998-10-13 | Infovalue Computing, Inc. | System for just-in-time retrieval of multimedia files over computer networks by transmitting data packets at transmission rate determined by frame size |
| US6002772A (en)* | 1995-09-29 | 1999-12-14 | Mitsubishi Corporation | Data management system |
| US5765152A (en)* | 1995-10-13 | 1998-06-09 | Trustees Of Dartmouth College | System and method for managing copyrighted electronic media |
| US5708709A (en)* | 1995-12-08 | 1998-01-13 | Sun Microsystems, Inc. | System and method for managing try-and-buy usage of application programs |
| US5933498A (en)* | 1996-01-11 | 1999-08-03 | Mrj, Inc. | System for controlling access and distribution of digital property |
| US5796825A (en)* | 1996-01-16 | 1998-08-18 | Symantec Corporation | System for automatic decryption of file data on a per-use basis and automatic re-encryption within context of multi-threaded operating system under which applications run in real-time |
| US5818936A (en)* | 1996-03-15 | 1998-10-06 | Novell, Inc. | System and method for automically authenticating a user in a distributed network system |
| US5673316A (en)* | 1996-03-29 | 1997-09-30 | International Business Machines Corporation | Creation and distribution of cryptographic envelope |
| US6401204B1 (en)* | 1996-06-05 | 2002-06-04 | Siemens Aktiengesellschaft | Process for cryptographic code management between a first computer unit and a second computer unit |
| US5809145A (en)* | 1996-06-28 | 1998-09-15 | Paradata Systems Inc. | System for distributing digital information |
| US5956034A (en)* | 1996-08-13 | 1999-09-21 | Softbook Press, Inc. | Method and apparatus for viewing electronic reading materials |
| US5892900A (en)* | 1996-08-30 | 1999-04-06 | Intertrust Technologies Corp. | Systems and methods for secure transaction management and electronic rights protection |
| US6658566B1 (en)* | 1997-03-13 | 2003-12-02 | Bull Cp8 | Process for storage and use of sensitive information in a security module and the associated security module |
| US5978475A (en)* | 1997-07-18 | 1999-11-02 | Counterpane Internet Security, Inc. | Event auditing system |
| US5997077A (en) | 1997-08-23 | 1999-12-07 | Volkswagen Ag | Deformable structure for protection of vehicle occupants |
| US6064736A (en) | 1997-09-15 | 2000-05-16 | International Business Machines Corporation | Systems, methods and computer program products that use an encrypted session for additional password verification |
| US6682128B2 (en) | 1998-02-04 | 2004-01-27 | Oakwood Energy Management, Inc. | Composite energy absorber |
| US6182220B1 (en) | 1998-03-30 | 2001-01-30 | International Business Machines Corporation | System and method for building and exchanging encrypted passwords between a client and server |
| US6547280B1 (en) | 1998-11-21 | 2003-04-15 | Cellbond Limited | Energy-absorbing structures |
| US6499106B1 (en) | 1999-01-15 | 2002-12-24 | Sony Corporation | Method and apparatus for secure distribution of information recorded of fixed media |
| US6245408B1 (en) | 1999-05-19 | 2001-06-12 | Hexcel Corporation | Honeycomb core with controlled crush properties |
| US6339825B2 (en)* | 1999-05-28 | 2002-01-15 | Authentica, Inc. | Method of encrypting information for remote access while maintaining access control |
| US6449721B1 (en)* | 1999-05-28 | 2002-09-10 | Authentica Security Technologies, Inc. | Method of encrypting information for remote access while maintaining access control |
| US6289450B1 (en)* | 1999-05-28 | 2001-09-11 | Authentica, Inc. | Information security architecture for encrypting documents for remote access while maintaining access control |
| US6308256B1 (en) | 1999-08-18 | 2001-10-23 | Sun Microsystems, Inc. | Secure execution of program instructions provided by network interactions with processor |
| US20010055396A1 (en) | 2000-02-24 | 2001-12-27 | David Jevans | Mechanism for efficient private bulk messaging |
| US6711553B1 (en) | 2000-02-25 | 2004-03-23 | Kent Ridge Digital Labs | Method and apparatus for digital content copy protection |
| US6732106B2 (en) | 2000-12-08 | 2004-05-04 | Matsushita Electric Industrial Co., Ltd. | Digital data distribution system |
Cited By (17)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20080107271A1 (en)* | 2006-11-03 | 2008-05-08 | Verizon Services Organization Inc. | Systems and Methods for Document Control Using Public Key Encryption |
| US7916870B2 (en)* | 2006-11-03 | 2011-03-29 | Verizon Patent And Licensing Inc. | Systems and methods for document control using public key encryption |
| US20110167266A1 (en)* | 2006-11-03 | 2011-07-07 | Verizon Patent And Licensing, Inc. | Systems and methods for document control using public key encryption |
| US8681994B2 (en)* | 2006-11-03 | 2014-03-25 | Verizon Patent And Licensing Inc. | Systems and methods for document control using public key encryption |
| US8170213B1 (en)* | 2007-12-27 | 2012-05-01 | Emc Corporation | Methodology for coordinating centralized key management and encryption keys cached through proxied elements |
| US8555342B1 (en) | 2009-12-23 | 2013-10-08 | Emc Corporation | Providing secure access to a set of credentials within a data security mechanism of a data storage system |
| US10607029B2 (en) | 2011-11-14 | 2020-03-31 | Esw Holdings, Inc. | Security systems and methods for encoding and decoding content |
| US10552636B2 (en)* | 2011-11-14 | 2020-02-04 | Esw Holdings, Inc. | Security systems and methods for encoding and decoding digital content |
| US20180268169A1 (en)* | 2011-11-14 | 2018-09-20 | Esw Holdings, Inc. | Security Systems and Methods for Encoding and Decoding Digital Content |
| US20210383025A1 (en)* | 2011-11-14 | 2021-12-09 | Esw Holdings, Inc. | Security Systems and Methods for Encoding and Decoding Content |
| US11244074B2 (en)* | 2011-11-14 | 2022-02-08 | Esw Holdings, Inc. | Security systems and methods for social networking |
| US20220121780A1 (en)* | 2011-11-14 | 2022-04-21 | Esw Holdings, Inc. | Security Systems and Methods for Social Networking |
| US11741264B2 (en)* | 2011-11-14 | 2023-08-29 | Esw Holdings, Inc. | Security systems and methods for social networking |
| US11775686B2 (en)* | 2011-11-14 | 2023-10-03 | Esw Holdings, Inc. | Security systems and methods for encoding and decoding content |
| US20230385452A1 (en)* | 2011-11-14 | 2023-11-30 | Esw Holdings, Inc. | Security Systems and Methods for Encoding and Decoding Content |
| US20240020418A1 (en)* | 2011-11-14 | 2024-01-18 | Esw Holdings, Inc. | Security Systems and Methods for Social Networking |
| US12333052B2 (en)* | 2011-11-14 | 2025-06-17 | Esw Holdings, Inc. | Security systems and methods for social networking |
Also Published As
| Publication number | Publication date |
|---|---|
| US6339825B2 (en) | 2002-01-15 |
| USRE44364E1 (en) | 2013-07-09 |
| AU5280400A (en) | 2000-12-18 |
| WO2000074299A1 (en) | 2000-12-07 |
| US20020029340A1 (en) | 2002-03-07 |
| US6449721B1 (en) | 2002-09-10 |
| US6289450B1 (en) | 2001-09-11 |
| US20010052074A1 (en) | 2001-12-13 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| USRE41186E1 (en) | Method of encrypting information for remote access while maintaining access control | |
| US6978376B2 (en) | Information security architecture for encrypting documents for remote access while maintaining access control | |
| US7458102B2 (en) | Information security architecture for remote access control using non-bidirectional protocols | |
| US7921450B1 (en) | Security system using indirect key generation from access rules and methods therefor | |
| US8006280B1 (en) | Security system for generating keys from access rules in a decentralized manner and methods therefor | |
| US9286484B2 (en) | Method and system for providing document retention using cryptography | |
| US10229279B2 (en) | Methods and systems for providing access control to secured data | |
| US8341406B2 (en) | System and method for providing different levels of key security for controlling access to secured items | |
| EP1320011B1 (en) | Method and architecture for providing pervasive security to digital assets | |
| US7748045B2 (en) | Method and system for providing cryptographic document retention with off-line access | |
| US10360545B2 (en) | Method and apparatus for accessing secured electronic data off-line | |
| KR100423797B1 (en) | Method of protecting digital information and system thereof | |
| EP1320012B1 (en) | System and method for providing distributed access control to secured items | |
| US20020046350A1 (en) | Method and system for establishing an audit trail to protect objects distributed over a network | |
| US20030051172A1 (en) | Method and system for protecting digital objects distributed over a network | |
| EP1323258A1 (en) | System for protecting objects distributed over a network | |
| US20030237005A1 (en) | Method and system for protecting digital objects distributed over a network by electronic mail | |
| JP3877388B2 (en) | Information provision system |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| AS | Assignment | Owner name:EMC CORPORATION, CALIFORNIA Free format text:ASSIGNMENT OF ASSIGNORS INTEREST;ASSIGNOR:AUTHENTICA, INC.;REEL/FRAME:017821/0737 Effective date:20060227 Owner name:EMC CORPORATION,CALIFORNIA Free format text:ASSIGNMENT OF ASSIGNORS INTEREST;ASSIGNOR:AUTHENTICA, INC.;REEL/FRAME:017821/0737 Effective date:20060227 | |
| FEPP | Fee payment procedure | Free format text:PAYOR NUMBER ASSIGNED (ORIGINAL EVENT CODE: ASPN); ENTITY STATUS OF PATENT OWNER: LARGE ENTITY | |
| AS | Assignment | Owner name:THE BANK OF NEW YORK MELLON TRUST COMPANY, N.A., AS NOTES COLLATERAL AGENT, TEXAS Free format text:SECURITY AGREEMENT;ASSIGNORS:ASAP SOFTWARE EXPRESS, INC.;AVENTAIL LLC;CREDANT TECHNOLOGIES, INC.;AND OTHERS;REEL/FRAME:040136/0001 Effective date:20160907 Owner name:CREDIT SUISSE AG, CAYMAN ISLANDS BRANCH, AS COLLATERAL AGENT, NORTH CAROLINA Free format text:SECURITY AGREEMENT;ASSIGNORS:ASAP SOFTWARE EXPRESS, INC.;AVENTAIL LLC;CREDANT TECHNOLOGIES, INC.;AND OTHERS;REEL/FRAME:040134/0001 Effective date:20160907 Owner name:CREDIT SUISSE AG, CAYMAN ISLANDS BRANCH, AS COLLAT Free format text:SECURITY AGREEMENT;ASSIGNORS:ASAP SOFTWARE EXPRESS, INC.;AVENTAIL LLC;CREDANT TECHNOLOGIES, INC.;AND OTHERS;REEL/FRAME:040134/0001 Effective date:20160907 Owner name:THE BANK OF NEW YORK MELLON TRUST COMPANY, N.A., A Free format text:SECURITY AGREEMENT;ASSIGNORS:ASAP SOFTWARE EXPRESS, INC.;AVENTAIL LLC;CREDANT TECHNOLOGIES, INC.;AND OTHERS;REEL/FRAME:040136/0001 Effective date:20160907 | |
| AS | Assignment | Owner name:AUTHENTICA SECURITY TECHNOLOGIES, INC., MASSACHUSE Free format text:ASSIGNMENT OF ASSIGNORS INTEREST;ASSIGNORS:PENSAK, DAVID A;CRISTY, JOHN J;SINGLES, STEVEN J;REEL/FRAME:039863/0152 Effective date:19990712 Owner name:AUTHENTICA, INC., MASSACHUSETTS Free format text:CHANGE OF NAME;ASSIGNOR:AUTHENTICA SECURITY TECHNOLOGIES, INC.;REEL/FRAME:040164/0911 Effective date:19990721 | |
| AS | Assignment | Owner name:AUTHENTICA, INC., MASSACHUSETTS Free format text:CHANGE OF NAME;ASSIGNOR:AUTHENTICA SECURITY TECHNOLOGIES, INC.;REEL/FRAME:040337/0393 Effective date:19990729 | |
| AS | Assignment | Owner name:THE BANK OF NEW YORK MELLON TRUST COMPANY, N.A., T Free format text:SECURITY AGREEMENT;ASSIGNORS:CREDANT TECHNOLOGIES, INC.;DELL INTERNATIONAL L.L.C.;DELL MARKETING L.P.;AND OTHERS;REEL/FRAME:049452/0223 Effective date:20190320 Owner name:THE BANK OF NEW YORK MELLON TRUST COMPANY, N.A., TEXAS Free format text:SECURITY AGREEMENT;ASSIGNORS:CREDANT TECHNOLOGIES, INC.;DELL INTERNATIONAL L.L.C.;DELL MARKETING L.P.;AND OTHERS;REEL/FRAME:049452/0223 Effective date:20190320 | |
| AS | Assignment | Owner name:THE BANK OF NEW YORK MELLON TRUST COMPANY, N.A., TEXAS Free format text:SECURITY AGREEMENT;ASSIGNORS:CREDANT TECHNOLOGIES INC.;DELL INTERNATIONAL L.L.C.;DELL MARKETING L.P.;AND OTHERS;REEL/FRAME:053546/0001 Effective date:20200409 | |
| AS | Assignment | Owner name:WYSE TECHNOLOGY L.L.C., CALIFORNIA Free format text:RELEASE BY SECURED PARTY;ASSIGNOR:CREDIT SUISSE AG, CAYMAN ISLANDS BRANCH;REEL/FRAME:058216/0001 Effective date:20211101 Owner name:SCALEIO LLC, MASSACHUSETTS Free format text:RELEASE BY SECURED PARTY;ASSIGNOR:CREDIT SUISSE AG, CAYMAN ISLANDS BRANCH;REEL/FRAME:058216/0001 Effective date:20211101 Owner name:MOZY, INC., WASHINGTON Free format text:RELEASE BY SECURED PARTY;ASSIGNOR:CREDIT SUISSE AG, CAYMAN ISLANDS BRANCH;REEL/FRAME:058216/0001 Effective date:20211101 Owner name:MAGINATICS LLC, CALIFORNIA Free format text:RELEASE BY SECURED PARTY;ASSIGNOR:CREDIT SUISSE AG, CAYMAN ISLANDS BRANCH;REEL/FRAME:058216/0001 Effective date:20211101 Owner name:FORCE10 NETWORKS, INC., CALIFORNIA Free format text:RELEASE BY SECURED PARTY;ASSIGNOR:CREDIT SUISSE AG, CAYMAN ISLANDS BRANCH;REEL/FRAME:058216/0001 Effective date:20211101 Owner name:EMC IP HOLDING COMPANY LLC, TEXAS Free format text:RELEASE BY SECURED PARTY;ASSIGNOR:CREDIT SUISSE AG, CAYMAN ISLANDS BRANCH;REEL/FRAME:058216/0001 Effective date:20211101 Owner name:EMC CORPORATION, MASSACHUSETTS Free format text:RELEASE BY SECURED PARTY;ASSIGNOR:CREDIT SUISSE AG, CAYMAN ISLANDS BRANCH;REEL/FRAME:058216/0001 Effective date:20211101 Owner name:DELL SYSTEMS CORPORATION, TEXAS Free format text:RELEASE BY SECURED PARTY;ASSIGNOR:CREDIT SUISSE AG, CAYMAN ISLANDS BRANCH;REEL/FRAME:058216/0001 Effective date:20211101 Owner name:DELL SOFTWARE INC., CALIFORNIA Free format text:RELEASE BY SECURED PARTY;ASSIGNOR:CREDIT SUISSE AG, CAYMAN ISLANDS BRANCH;REEL/FRAME:058216/0001 Effective date:20211101 Owner name:DELL PRODUCTS L.P., TEXAS Free format text:RELEASE BY SECURED PARTY;ASSIGNOR:CREDIT SUISSE AG, CAYMAN ISLANDS BRANCH;REEL/FRAME:058216/0001 Effective date:20211101 Owner name:DELL MARKETING L.P., TEXAS Free format text:RELEASE BY SECURED PARTY;ASSIGNOR:CREDIT SUISSE AG, CAYMAN ISLANDS BRANCH;REEL/FRAME:058216/0001 Effective date:20211101 Owner name:DELL INTERNATIONAL, L.L.C., TEXAS Free format text:RELEASE BY SECURED PARTY;ASSIGNOR:CREDIT SUISSE AG, CAYMAN ISLANDS BRANCH;REEL/FRAME:058216/0001 Effective date:20211101 Owner name:DELL USA L.P., TEXAS Free format text:RELEASE BY SECURED PARTY;ASSIGNOR:CREDIT SUISSE AG, CAYMAN ISLANDS BRANCH;REEL/FRAME:058216/0001 Effective date:20211101 Owner name:CREDANT TECHNOLOGIES, INC., TEXAS Free format text:RELEASE BY SECURED PARTY;ASSIGNOR:CREDIT SUISSE AG, CAYMAN ISLANDS BRANCH;REEL/FRAME:058216/0001 Effective date:20211101 Owner name:AVENTAIL LLC, CALIFORNIA Free format text:RELEASE BY SECURED PARTY;ASSIGNOR:CREDIT SUISSE AG, CAYMAN ISLANDS BRANCH;REEL/FRAME:058216/0001 Effective date:20211101 Owner name:ASAP SOFTWARE EXPRESS, INC., ILLINOIS Free format text:RELEASE BY SECURED PARTY;ASSIGNOR:CREDIT SUISSE AG, CAYMAN ISLANDS BRANCH;REEL/FRAME:058216/0001 Effective date:20211101 | |
| AS | Assignment | Owner name:SCALEIO LLC, MASSACHUSETTS Free format text:RELEASE OF SECURITY INTEREST IN PATENTS PREVIOUSLY RECORDED AT REEL/FRAME (040136/0001);ASSIGNOR:THE BANK OF NEW YORK MELLON TRUST COMPANY, N.A., AS NOTES COLLATERAL AGENT;REEL/FRAME:061324/0001 Effective date:20220329 Owner name:EMC IP HOLDING COMPANY LLC (ON BEHALF OF ITSELF AND AS SUCCESSOR-IN-INTEREST TO MOZY, INC.), TEXAS Free format text:RELEASE OF SECURITY INTEREST IN PATENTS PREVIOUSLY RECORDED AT REEL/FRAME (040136/0001);ASSIGNOR:THE BANK OF NEW YORK MELLON TRUST COMPANY, N.A., AS NOTES COLLATERAL AGENT;REEL/FRAME:061324/0001 Effective date:20220329 Owner name:EMC CORPORATION (ON BEHALF OF ITSELF AND AS SUCCESSOR-IN-INTEREST TO MAGINATICS LLC), MASSACHUSETTS Free format text:RELEASE OF SECURITY INTEREST IN PATENTS PREVIOUSLY RECORDED AT REEL/FRAME (040136/0001);ASSIGNOR:THE BANK OF NEW YORK MELLON TRUST COMPANY, N.A., AS NOTES COLLATERAL AGENT;REEL/FRAME:061324/0001 Effective date:20220329 Owner name:DELL MARKETING CORPORATION (SUCCESSOR-IN-INTEREST TO FORCE10 NETWORKS, INC. AND WYSE TECHNOLOGY L.L.C.), TEXAS Free format text:RELEASE OF SECURITY INTEREST IN PATENTS PREVIOUSLY RECORDED AT REEL/FRAME (040136/0001);ASSIGNOR:THE BANK OF NEW YORK MELLON TRUST COMPANY, N.A., AS NOTES COLLATERAL AGENT;REEL/FRAME:061324/0001 Effective date:20220329 Owner name:DELL PRODUCTS L.P., TEXAS Free format text:RELEASE OF SECURITY INTEREST IN PATENTS PREVIOUSLY RECORDED AT REEL/FRAME (040136/0001);ASSIGNOR:THE BANK OF NEW YORK MELLON TRUST COMPANY, N.A., AS NOTES COLLATERAL AGENT;REEL/FRAME:061324/0001 Effective date:20220329 Owner name:DELL INTERNATIONAL L.L.C., TEXAS Free format text:RELEASE OF SECURITY INTEREST IN PATENTS PREVIOUSLY RECORDED AT REEL/FRAME (040136/0001);ASSIGNOR:THE BANK OF NEW YORK MELLON TRUST COMPANY, N.A., AS NOTES COLLATERAL AGENT;REEL/FRAME:061324/0001 Effective date:20220329 Owner name:DELL USA L.P., TEXAS Free format text:RELEASE OF SECURITY INTEREST IN PATENTS PREVIOUSLY RECORDED AT REEL/FRAME (040136/0001);ASSIGNOR:THE BANK OF NEW YORK MELLON TRUST COMPANY, N.A., AS NOTES COLLATERAL AGENT;REEL/FRAME:061324/0001 Effective date:20220329 Owner name:DELL MARKETING L.P. (ON BEHALF OF ITSELF AND AS SUCCESSOR-IN-INTEREST TO CREDANT TECHNOLOGIES, INC.), TEXAS Free format text:RELEASE OF SECURITY INTEREST IN PATENTS PREVIOUSLY RECORDED AT REEL/FRAME (040136/0001);ASSIGNOR:THE BANK OF NEW YORK MELLON TRUST COMPANY, N.A., AS NOTES COLLATERAL AGENT;REEL/FRAME:061324/0001 Effective date:20220329 Owner name:DELL MARKETING CORPORATION (SUCCESSOR-IN-INTEREST TO ASAP SOFTWARE EXPRESS, INC.), TEXAS Free format text:RELEASE OF SECURITY INTEREST IN PATENTS PREVIOUSLY RECORDED AT REEL/FRAME (040136/0001);ASSIGNOR:THE BANK OF NEW YORK MELLON TRUST COMPANY, N.A., AS NOTES COLLATERAL AGENT;REEL/FRAME:061324/0001 Effective date:20220329 | |
| AS | Assignment | Owner name:SCALEIO LLC, MASSACHUSETTS Free format text:RELEASE OF SECURITY INTEREST IN PATENTS PREVIOUSLY RECORDED AT REEL/FRAME (045455/0001);ASSIGNOR:THE BANK OF NEW YORK MELLON TRUST COMPANY, N.A., AS NOTES COLLATERAL AGENT;REEL/FRAME:061753/0001 Effective date:20220329 Owner name:EMC IP HOLDING COMPANY LLC (ON BEHALF OF ITSELF AND AS SUCCESSOR-IN-INTEREST TO MOZY, INC.), TEXAS Free format text:RELEASE OF SECURITY INTEREST IN PATENTS PREVIOUSLY RECORDED AT REEL/FRAME (045455/0001);ASSIGNOR:THE BANK OF NEW YORK MELLON TRUST COMPANY, N.A., AS NOTES COLLATERAL AGENT;REEL/FRAME:061753/0001 Effective date:20220329 Owner name:EMC CORPORATION (ON BEHALF OF ITSELF AND AS SUCCESSOR-IN-INTEREST TO MAGINATICS LLC), MASSACHUSETTS Free format text:RELEASE OF SECURITY INTEREST IN PATENTS PREVIOUSLY RECORDED AT REEL/FRAME (045455/0001);ASSIGNOR:THE BANK OF NEW YORK MELLON TRUST COMPANY, N.A., AS NOTES COLLATERAL AGENT;REEL/FRAME:061753/0001 Effective date:20220329 Owner name:DELL MARKETING CORPORATION (SUCCESSOR-IN-INTEREST TO FORCE10 NETWORKS, INC. AND WYSE TECHNOLOGY L.L.C.), TEXAS Free format text:RELEASE OF SECURITY INTEREST IN PATENTS PREVIOUSLY RECORDED AT REEL/FRAME (045455/0001);ASSIGNOR:THE BANK OF NEW YORK MELLON TRUST COMPANY, N.A., AS NOTES COLLATERAL AGENT;REEL/FRAME:061753/0001 Effective date:20220329 Owner name:DELL PRODUCTS L.P., TEXAS Free format text:RELEASE OF SECURITY INTEREST IN PATENTS PREVIOUSLY RECORDED AT REEL/FRAME (045455/0001);ASSIGNOR:THE BANK OF NEW YORK MELLON TRUST COMPANY, N.A., AS NOTES COLLATERAL AGENT;REEL/FRAME:061753/0001 Effective date:20220329 Owner name:DELL INTERNATIONAL L.L.C., TEXAS Free format text:RELEASE OF SECURITY INTEREST IN PATENTS PREVIOUSLY RECORDED AT REEL/FRAME (045455/0001);ASSIGNOR:THE BANK OF NEW YORK MELLON TRUST COMPANY, N.A., AS NOTES COLLATERAL AGENT;REEL/FRAME:061753/0001 Effective date:20220329 Owner name:DELL USA L.P., TEXAS Free format text:RELEASE OF SECURITY INTEREST IN PATENTS PREVIOUSLY RECORDED AT REEL/FRAME (045455/0001);ASSIGNOR:THE BANK OF NEW YORK MELLON TRUST COMPANY, N.A., AS NOTES COLLATERAL AGENT;REEL/FRAME:061753/0001 Effective date:20220329 Owner name:DELL MARKETING L.P. (ON BEHALF OF ITSELF AND AS SUCCESSOR-IN-INTEREST TO CREDANT TECHNOLOGIES, INC.), TEXAS Free format text:RELEASE OF SECURITY INTEREST IN PATENTS PREVIOUSLY RECORDED AT REEL/FRAME (045455/0001);ASSIGNOR:THE BANK OF NEW YORK MELLON TRUST COMPANY, N.A., AS NOTES COLLATERAL AGENT;REEL/FRAME:061753/0001 Effective date:20220329 Owner name:DELL MARKETING CORPORATION (SUCCESSOR-IN-INTEREST TO ASAP SOFTWARE EXPRESS, INC.), TEXAS Free format text:RELEASE OF SECURITY INTEREST IN PATENTS PREVIOUSLY RECORDED AT REEL/FRAME (045455/0001);ASSIGNOR:THE BANK OF NEW YORK MELLON TRUST COMPANY, N.A., AS NOTES COLLATERAL AGENT;REEL/FRAME:061753/0001 Effective date:20220329 | |
| AS | Assignment | Owner name:DELL MARKETING L.P. (ON BEHALF OF ITSELF AND AS SUCCESSOR-IN-INTEREST TO CREDANT TECHNOLOGIES, INC.), TEXAS Free format text:RELEASE OF SECURITY INTEREST IN PATENTS PREVIOUSLY RECORDED AT REEL/FRAME (053546/0001);ASSIGNOR:THE BANK OF NEW YORK MELLON TRUST COMPANY, N.A., AS NOTES COLLATERAL AGENT;REEL/FRAME:071642/0001 Effective date:20220329 Owner name:DELL INTERNATIONAL L.L.C., TEXAS Free format text:RELEASE OF SECURITY INTEREST IN PATENTS PREVIOUSLY RECORDED AT REEL/FRAME (053546/0001);ASSIGNOR:THE BANK OF NEW YORK MELLON TRUST COMPANY, N.A., AS NOTES COLLATERAL AGENT;REEL/FRAME:071642/0001 Effective date:20220329 Owner name:DELL PRODUCTS L.P., TEXAS Free format text:RELEASE OF SECURITY INTEREST IN PATENTS PREVIOUSLY RECORDED AT REEL/FRAME (053546/0001);ASSIGNOR:THE BANK OF NEW YORK MELLON TRUST COMPANY, N.A., AS NOTES COLLATERAL AGENT;REEL/FRAME:071642/0001 Effective date:20220329 Owner name:DELL USA L.P., TEXAS Free format text:RELEASE OF SECURITY INTEREST IN PATENTS PREVIOUSLY RECORDED AT REEL/FRAME (053546/0001);ASSIGNOR:THE BANK OF NEW YORK MELLON TRUST COMPANY, N.A., AS NOTES COLLATERAL AGENT;REEL/FRAME:071642/0001 Effective date:20220329 Owner name:EMC CORPORATION, MASSACHUSETTS Free format text:RELEASE OF SECURITY INTEREST IN PATENTS PREVIOUSLY RECORDED AT REEL/FRAME (053546/0001);ASSIGNOR:THE BANK OF NEW YORK MELLON TRUST COMPANY, N.A., AS NOTES COLLATERAL AGENT;REEL/FRAME:071642/0001 Effective date:20220329 Owner name:DELL MARKETING CORPORATION (SUCCESSOR-IN-INTEREST TO FORCE10 NETWORKS, INC. AND WYSE TECHNOLOGY L.L.C.), TEXAS Free format text:RELEASE OF SECURITY INTEREST IN PATENTS PREVIOUSLY RECORDED AT REEL/FRAME (053546/0001);ASSIGNOR:THE BANK OF NEW YORK MELLON TRUST COMPANY, N.A., AS NOTES COLLATERAL AGENT;REEL/FRAME:071642/0001 Effective date:20220329 Owner name:EMC IP HOLDING COMPANY LLC, TEXAS Free format text:RELEASE OF SECURITY INTEREST IN PATENTS PREVIOUSLY RECORDED AT REEL/FRAME (053546/0001);ASSIGNOR:THE BANK OF NEW YORK MELLON TRUST COMPANY, N.A., AS NOTES COLLATERAL AGENT;REEL/FRAME:071642/0001 Effective date:20220329 |