US9985938B2 - User control over WIFI network access - Google Patents
User control over WIFI network accessDownload PDFInfo
- Publication number
- US9985938B2 US9985938B2US15/131,889US201615131889AUS9985938B2US 9985938 B2US9985938 B2US 9985938B2US 201615131889 AUS201615131889 AUS 201615131889AUS 9985938 B2US9985938 B2US 9985938B2
- Authority
- US
- United States
- Prior art keywords
- user
- communication device
- access systems
- wifi access
- wifi
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Active
Links
- 238000004891communicationMethods0.000claimsabstractdescription141
- 238000012546transferMethods0.000claimsabstractdescription53
- 230000004044responseEffects0.000claimsabstractdescription27
- 238000000034methodMethods0.000claimsdescription15
- 238000012545processingMethods0.000claimsdescription8
- 230000007774longtermEffects0.000claimsdescription4
- 238000001514detection methodMethods0.000claims1
- 238000013475authorizationMethods0.000description47
- 230000008569processEffects0.000description4
- 230000002596correlated effectEffects0.000description2
- 238000013500data storageMethods0.000description2
- 238000000060site-specific infrared dichroism spectroscopyMethods0.000description2
- 238000012795verificationMethods0.000description2
- 238000013480data collectionMethods0.000description1
- 230000006870functionEffects0.000description1
- 238000007726management methodMethods0.000description1
- 230000007246mechanismEffects0.000description1
- 238000010295mobile communicationMethods0.000description1
- 230000006855networkingEffects0.000description1
- 230000003287optical effectEffects0.000description1
Images
Classifications
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/06—Network architectures or network communication protocols for network security for supporting key management in a packet data network
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/08—Network architectures or network communication protocols for network security for authentication of entities
- H04L63/0884—Network architectures or network communication protocols for network security for authentication of entities by delegation of authentication, e.g. a proxy authenticates an entity to be authenticated on behalf of this entity vis-à-vis an authentication entity
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/10—Network architectures or network communication protocols for network security for controlling access to devices or network resources
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/20—Network architectures or network communication protocols for network security for managing network security; network security policies in general
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W12/00—Security arrangements; Authentication; Protecting privacy or anonymity
- H04W12/04—Key management, e.g. using generic bootstrapping architecture [GBA]
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W12/00—Security arrangements; Authentication; Protecting privacy or anonymity
- H04W12/06—Authentication
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W12/00—Security arrangements; Authentication; Protecting privacy or anonymity
- H04W12/08—Access security
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/08—Network architectures or network communication protocols for network security for authentication of entities
- H04L63/083—Network architectures or network communication protocols for network security for authentication of entities using passwords
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W12/00—Security arrangements; Authentication; Protecting privacy or anonymity
- H04W12/60—Context-dependent security
- H04W12/61—Time-dependent
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W84/00—Network topologies
- H04W84/02—Hierarchically pre-organised networks, e.g. paging networks, cellular networks, WLAN [Wireless Local Area Network] or WLL [Wireless Local Loop]
- H04W84/10—Small scale networks; Flat hierarchical networks
- H04W84/12—WLAN [Wireless Local Area Networks]
Definitions
- WiFiWireless Fidelity
- a WiFi access pointbroadcasts a Service Set Identification (SSID) that is detected by user devices.
- the user devicestypically respond to the SSID with an access code that is pre-stored in the WiFi access point.
- the WiFi access pointprovides network access if the user-provided access code matches the pre-stored access code.
- the usertypically manages multiple access codes for the various WiFi access points that they use. Unfortunately, these WiFi access points are not used to provide effective and efficient user control over WiFi network access.
- wireless networksalso include user authorization systems that control network access.
- 3G networksmay have an Authentication, Authorization, and Accounting (AAA) system
- 4G networksmay have a Home Subscriber Server (HSS).
- AAAAuthentication, Authorization, and Accounting
- HSSHome Subscriber Server
- WiFi access points and these other wireless networksare not effectively used in an integrated manner to provide efficient user control over WiFi network access.
- a wireless communication devicecontrols access to a geographically-distributed Wireless Fidelity (WiFi) network.
- the wireless communication devicegraphically presents WiFi network data to receive user selections of multiple WiFi access systems, a network name, and a user password.
- the wireless communication devicereceives configuration data that associates broadcast identification signals for the WiFi access systems with the network name.
- the wireless communication devicedetects a broadcast identification signal for one of the WiFi access systems and responsively presents the network name and a password prompt to receive the user password.
- the wireless communication devicetransfers the network name and the user password to the WiFi access system, and in response, the wireless communication device exchanges user data over the WiFi access system.
- FIG. 1illustrates a communication system to provide user control over access to a WiFi network having geographically-distributed WiFi access systems.
- FIG. 2illustrates the operation of a communication system to provide user control over access to a WiFi network having geographically-distributed WiFi access systems.
- FIG. 3illustrates the operation of a communication system to provide user control over access to a WiFi network having geographically-distributed WiFi access systems by allowing user-selection of communication devices.
- FIG. 4illustrates the operation of a communication system to provide user control over access to a WiFi network having geographically-distributed WiFi access systems by transferring configuration data to a user communication device.
- FIG. 5illustrates the operation of a communication system to provide user control over access to a WiFi network having geographically-distributed WiFi access systems by using dynamic access keys.
- FIG. 6illustrates a communication device display that renders a geographic map for a user to select WiFi network access systems and specify passwords.
- FIG. 7illustrates a wireless Long Term Evolution (LTE) network to provide user control over access to a WiFi network having geographically-distributed WiFi access systems.
- LTELong Term Evolution
- FIG. 8illustrates an WiFi system to provide user control over access to a WiFi network having geographically-distributed WiFi access systems.
- FIG. 9illustrates a server system to provide user control over access to WiFi networks.
- FIG. 10illustrates wireless communication device to provide user control over access to WiFi networks.
- FIG. 1illustrates communication system 100 to provide user control over access to WiFi network 120 having geographically-distributed WiFi access systems 121 - 124 .
- Communication system 100comprises user communication devices 101 - 103 , access network 110 , WiFi network 120 , and server system 130 .
- Server system 130comprises user interface server 131 and authorization server 132 .
- User communication devices 101 - 103comprise phones, computers, media players, machine transceivers, or some other WiFi communication equipment.
- User communication devices 101 - 102 and access network 110communicate over respective access links 111 - 112 .
- User communication devices 101 - 103 and WiFi access systems 121 - 123communicate over respective WiFi links 113 - 115 .
- Access network 110 and WiFi network 120communicate with server system 130 over respective network links 116 - 117 .
- user interface server 131transfers display data to user communication device 101 over access network 110 and links 111 and 116 for presentation to a user.
- the userselects WiFi access systems 121 - 123 but not access system 124 .
- the useralso selects a single password for the user-selected WiFi access systems 121 - 123 .
- the display datarenders geographic maps that indicate WiFi access systems 121 - 124 for selection.
- the display datamay also include a data collection module to collect the password from the user.
- User communication device 101transfers user data for delivery to user interface server 131 .
- the user dataindicates the user-selected WiFi network access systems 121 - 123 , the user-selected password, and possibly other user selections and data.
- User interface server 131receives and transfers the user data to user authorization server 132 .
- Authorization server 132stores an association between the user-selected WiFi network access systems 121 - 123 and the user-selected password. Subsequently, user communication device 101 moves near WiFi access system 121 and transfers an access request to WiFi access system 121 using the user-selected password. WiFi access system 121 transfers the access request for delivery to authorization server 132 .
- Authorization server 132receives the access request for access to user-selected WiFi network access system 121 using the user-selected password. Based on the stored association between the user-selected WiFi network access system 121 and the user-selected password, authorization server 132 transfers a positive response for delivery to WiFi network access system 121 .
- WiFi network access system 121then provides WiFi access (typically to the Internet) to wireless communication device 101 over WiFi link 113 .
- User wireless communication device 102could select and use multiple WiFi access systems with a single password in a similar manner.
- wireless communication device 101is used to select the WiFi access systems and password
- communication device 102 and/or communication device 103are used to access the selected WiFi access systems with the password.
- a usermay have different passwords for different groups of access systems, devices, timeframes, and the like. If desired, the user may also use a given password for only one access system.
- a passwordcould be any sequence of letters, numbers, symbols, or other data.
- additional itemsare selected by the user responsive to the display data. These additional items may be indicated in the user data, stored in the association, and used in combination to transfer the positive response to the access request.
- the usermay specify a user name to use when accessing their selected WiFi network access systems.
- the userspecifies a communication device to use when accessing their selected WiFi network access systems.
- the userspecifies a timeframe for access to their selected WiFi network access systems.
- user interface server 131transfers configuration data for delivery to user communication device 101 and/or user communication device 102 over access network 110 .
- the configuration dataassociates broadcast identification signals for the user-selected WiFi network access systems with the user-selected password.
- User communication devices 101 - 102use the configuration data to obtain the password from the user and to transfer the access request when in range of one of the selected WiFi network access systems.
- the configuration dataincludes an access key that is correlated to the broadcast identification signals for the user-selected WiFi network access systems and with the user-selected password.
- the access keyis stored in authorization server 132 in association with the user-selected WiFi network access systems.
- User communication device 101would provide the access key in their access request when in range of one of the selected WiFi network access systems and if the password is provided by the user.
- Authorization server 132could then return a positive response based on its own stored access key.
- the configuration dataindicates a dynamically-changing network key, such as time-of-day, that is correlated to the broadcast identification signals for the user-selected WiFi network access systems and with the user-selected password.
- a dynamically-changing network keysuch as time-of-day
- user communication device 101uses the dynamically-changing network key to generate a hash value for their access request.
- authorization server 132could generate its own hash value based the dynamically-changing network key for comparison to the hash value from the access request. If the comparison indicates the relationship, then authorization server 132 returns the positive response for WiFi access. For example, if the dynamically-changing network key is time-of-day, then both hash values should correlate if calculated within the same timeframe.
- Access network 110comprises computer and communications equipment that use Wireless Fidelity (WiFi), Long Term Evolution (LTE), Global System for Mobile Communications (GSM), Evolution Data Only (EVDO), Bluetooth, DOCSYS, T1, Ethernet, Internet Protocol (IP), or some other communication protocols—including combinations thereof.
- Server system 130comprises computer equipment and software that may be implemented in a single platform or may be distributed across multiple platforms.
- Communication links 111 - 112 and 116 - 117might be wireless, optical, metallic, or some other communication media—including combinations thereof.
- Communication links 111 - 112 and 116 - 117may individually comprise multiple parallel connections that utilize different protocols and paths.
- Communication links 111 - 112 and 116 - 117may also include various intermediate networks, systems, and devices.
- FIG. 2illustrates the operation of communication system 100 to provide user control over access to WiFi network 120 .
- User interface server 131transfers display data to user communication device 101 over access network 110 , and user communication device 101 graphically presents the resulting display data to the user.
- user communication devicemight present the display data in the form of geographic maps that indicate WiFi access systems 121 - 124 for selection.
- the userselects WiFi access systems 121 - 123 .
- the useralso specifies a password for user-selected WiFi access systems 121 - 123 .
- User communication device 101transfers user data over access network 110 to user interface server 131 .
- the user dataindicates user-selected WiFi network access systems 121 - 123 , the user-selected password, and possibly other user selections and data.
- User interface server 131transfers the user data to user authorization server 132 .
- Authorization server 132stores an association between the user-selected WiFi network access systems 121 - 123 and the user-selected password—and typically other pertinent data. Various techniques to store this association are described herein.
- WiFi access system 121transmits a wireless identification signal for reception by in-range devices, such as an SSID signal, pilot signal, and the like. Subsequently, user communication device 101 detects the identification signal from WiFi access system 121 and prompts the user for a password. The user provides their selected password to user communication device 101 , and device 101 transfers an access request to WiFi access system 121 using the user-selected password. Various techniques to use the password are described herein. WiFi access system 121 transfers the access request to authorization server 132 .
- Authorization server 132processes the access request and the stored association between user-selected WiFi network access system 121 and user-selected password to determine that the request should be granted. Authorization server 132 then transfers a positive response to WiFi network access system 121 . Based on the positive response, WiFi network access system 121 provides wireless communication device 101 and the user with WiFi network access to some other data system, such as the Internet (not shown).
- FIG. 3illustrates the operation of communication system 100 to provide user control over access to WiFi network 120 by allowing user-selection of communication devices.
- User interface server 131transfers display data to user communication device 101 over access network 110 , and user communication device 101 graphically presents the resulting display data to the user.
- the userselects WiFi access systems 121 - 123 and a password.
- the useralso selects communication device 103 to access user-selected WiFi access systems 121 - 123 .
- the usermay specify communication device 103 by name, address, number, and the like.
- User interface server 131may also identify communication device 103 in the display data for selection by the user.
- User communication device 101transfers user data over access network 110 to user interface server 131 .
- the user dataindicates user-selected WiFi network access systems 121 - 123 , user-selected communication device 103 , the user-selected password, and possibly other information.
- User interface server 131transfers the user data to user authorization server 132 .
- Authorization server 132stores an association between the user-selected WiFi network access systems 121 - 123 , user-selected communication device 103 , the user-selected password, and other data. Various techniques to store this association are described herein.
- WiFi access system 123transmits its wireless identification signal.
- User communication device 103detects the identification signal from WiFi access system 123 and prompts the user for a password. The user provides their selected password to user communication device 103 , and device 103 transfers an access request to WiFi access system 123 using the user-selected password.
- Various techniques to use the passwordare described herein.
- WiFi access system 123transfers the access request to authorization server 132 .
- Authorization server 132processes the access request and the stored association between user-selected WiFi network access system 123 , user-selected communication device 103 , and the user-selected password to determine that the request should be granted.
- Authorization server 132then transfers a positive response to WiFi network access system 123 .
- WiFi network access system 123provides user communication device 103 with WiFi network access to another data system, such as the Internet (not shown). Note that other items could be also selected by the user and used for authorization, such as timeframes, security formats, and the like.
- FIG. 4illustrates the operation of communication system 100 to provide user control over access to WiFi network 120 by transferring configuration data to user communication device 101 .
- User interface server 131transfers display data to user communication device 101 over access network 110 , and user communication device 101 graphically presents the resulting display data to the user.
- the userselects WiFi access systems 121 - 123 and a password.
- User communication device 101transfers user data over access network 110 to user interface server 131 .
- the user dataindicates user-selected WiFi network access systems 121 - 123 , the user-selected password, and possibly other user selections and data.
- User interface server 131transfers the user data to user authorization server 132 .
- Authorization server 132stores an association between the user-selected WiFi network access systems 121 - 123 and one or more access keys for systems 121 - 123 . The stored association may also indicate the user-selected password and other pertinent data.
- user interface server 131transfers configuration data over access network 110 to user communication device 101 .
- the configuration dataindicates identification signals (SSIDs and the like) for user-selected WiFi network access systems 121 - 123 .
- the configuration dataalso indicates the password, the access key, and perhaps other data. Note that user interface server 131 may also transfer the configuration data to other user-selected communication devices.
- User-selected WiFi access system 121transmits its wireless identification signal, and eventually, user communication device 101 detects this identification signal from WiFi access system 121 . Based on the configuration data and the ID signal, user communication device 101 prompts the user for a password. The user provides their selected password to user communication device 101 , and device 101 transfers an access request to WiFi access system 121 using the user-selected password. In this example, user communication device 101 uses the password for verification, and if the user-supplied password matches the password from the configuration data, then device 101 transfers the access key to user-selected WiFi access system 121 .
- WiFi access system 121transfers the access request including the access key to authorization server 132 .
- Authorization server 132processes the access request and the stored association between user-selected WiFi network access system 121 and user-supplied access key to determine that the request should be granted.
- Authorization server 132then transfers a positive response to WiFi network access system 121 .
- WiFi network access system 121Based on the positive response, WiFi network access system 121 provides user communication device 101 and the user with WiFi network access to some other data system, such as the Internet (not shown).
- FIG. 5illustrates the operation of communication system 100 to provide user control over access to WiFi network 120 by using dynamic access keys.
- User interface server 131transfers display data to user communication device 101 over access network 110 , and user communication device 101 graphically presents the resulting display data to the user.
- the userselects WiFi access systems 121 - 123 , a password, and user communication device 102 .
- User communication device 101transfers user data over access network 110 to user interface server 131 .
- the user dataindicates user-selected WiFi network access systems 121 - 123 , user communication device 102 , the user-selected password, and possibly other data.
- User interface server 131transfers the user data to user authorization server 132 .
- Authorization server 132stores an association between the user-selected WiFi network access systems 121 - 123 and a secret code used to generate the dynamic key. The stored association may also indicate the user-selected password and other pertinent data.
- user interface server 131transfers configuration data over access network 110 to user communication device 102 .
- the configuration dataindicates identification signals for user-selected WiFi network access systems 121 - 123 .
- the configuration dataalso indicates the password, secret code, dynamic key instructions, and perhaps other data. Note that user interface server 131 may also transfer the configuration data to other user-selected communication devices.
- User-selected WiFi access system 122transmits its wireless identification signal, and eventually, user communication device 102 detects this identification signal from WiFi access system 122 . Based on the configuration data and the ID signal, user communication device 102 prompts the user for a password. The user provides their selected password to user communication device 102 , and device 102 transfers an access request to WiFi access system 122 using the user-selected password.
- user communication device 102uses the password for verification, and if the user-supplied password matches the password from the configuration data, then device 102 generates and transfers a dynamic access key to user-selected WiFi access system 122 .
- the dynamic keyis a mathematical hash between the secret code from the configuration data and dynamically changing network data.
- the secret codecould be mathematically combined with the current time-of-day to generate the dynamic access key.
- WiFi access system 122transfers the access request including the dynamic access key to authorization server 132 .
- Authorization server 132processes the access request and the stored association (the secret code) to generate the dynamic access key in a similar manner to device 102 . If the two dynamic access keys correlate, then the access request should be granted. Note that the correlation may not require a strict match. For example, if time of day is used for the dynamic key, then two keys generated around the same time would have a detectable mathematical relationship and would correlate. Various other dynamic key techniques could be used in a similar manner.
- Authorization server 132then transfers a positive response to WiFi network access system 122 . Based on the positive response, WiFi network access system 122 provides user communication device 102 and the user with WiFi network access to some other data system, such as the Internet (not shown).
- FIG. 6illustrates communication device display 600 that renders a geographic map for a user to select WiFi network access systems 601 - 604 and specify passwords.
- the geographic mapis depicted by a simple grid on FIG. 6 . Note that navigation controls would be provided on the map, but they are not depicted for clarity.
- the userhas selected WiFi access systems 602 - 603 as indicated by the frame around systems 602 - 603 .
- Text boxesare associated with the selected WiFi access systems 602 - 603 and provide a mechanism for the user to specify passwords, user names, user devices, security settings, and the like.
- the text boxesalso provide access system information, such as SSIDs, location, and possibly other data.
- FIG. 7illustrates LTE/WiFi communication system 700 to provide user control over access to WiFi network 720 having geographically-distributed WiFi access systems 721 - 724 .
- LTE/WiFi communication system 700comprises user communication devices 701 - 703 , wireless LTE network 710 , WiFi network 720 , IP Multimedia Subsystem (IMS) 717 , and IP networks 718 .
- Wireless LTE network 710includes eNodeB 711 , serving gateway 712 , Packet Data Network (PDN) gateway 713 , Mobility Management Entity (MME) 714 , Home Subscriber Server (HSS) 715 , and Policy Charging and Rules Function (PCRF) 716 .
- PDNPacket Data Network
- MMEMobility Management Entity
- HSSHome Subscriber Server
- PCRFPolicy Charging and Rules Function
- Wireless LTE network 710also includes server system 730 that comprises user interface server 731 and authorization server 732 .
- User interface server 731 and authorization server 732operate like servers 131 - 132 described above.
- the authorization server 732is hosted by or integrated within HSS 715 .
- wireless LTE network 710operates like access network 110 described above.
- wireless LTE network 710transfers the display data, receives user-selections, transfers configuration data, and provides WiFi authorization as described above.
- the usermay operate one of communication devices 701 - 703 to access user interface server 731 and select WiFi access systems 721 - 722 and 724 , a user name, a password, user devices 701 - 703 , timeframes, and the like.
- WiFi access systems 721 - 722 and 724select WiFi access systems 721 - 722 and 724 , a user name, a password, user devices 701 - 703 , timeframes, and the like.
- the user devicewill interact with the proximate WiFi access system as described above.
- the proximate WiFi access systemwill transfer access requests to authorization server 732 in HSS 715 —typically through various proxies and interfaces.
- Authorization server 732 in HSS 715transfers positive responses as described above.
- FIG. 8illustrates WiFi communication system 800 to provide user control over access to WiFi network 820 having geographically-distributed WiFi access systems 821 - 824 .
- WiFi communication system 800comprises user communication devices 801 - 803 , IP access network 810 , IP networks 818 , and server system 830 .
- Server system 830resides in the core of a nationwide wireless communication network.
- Server system 830comprises user interface server 831 and authorization server 832 .
- User interface server 831 and authorization server 832and operate like servers 131 - 132 described above.
- server system 830transfers the display data, receives user-selections, transfers configuration data, and provides WiFi authorization as described above.
- the usermay operate one of communication devices 801 - 803 to access user interface server 831 and select WiFi access systems 821 - 822 and 824 , a user name, a password, user devices 801 - 803 , timeframes, and the like.
- WiFi access systems 821 - 822 and 824select WiFi access systems 821 - 822 and 824 , a user name, a password, user devices 801 - 803 , timeframes, and the like.
- the user devicewill interact with the proximate WiFi access system as described above.
- the proximate WiFi access systemwill transfer access requests to authorization server 832 .
- Authorization server 832transfers positive responses as described above.
- portions of the server systems described hereincould be integrated into the authorization systems of other networks.
- the AAA system in a 2G or 3G networkcould host the user interface server and/or the authorization servers described herein.
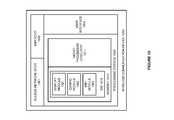
- FIG. 9illustrates server system 900 to provide user control over access to WiFi networks.
- Server system 900is an example of the server system 130 , although system 130 may use alternative configurations and operations.
- Server system 900comprises communication transceivers 901 and processing system 903 .
- Processing system 903comprises micro-processing circuitry 911 and memory 912 .
- Memory 912stores software 913 .
- Server system 900may be integrated into a single platform or may be distributed across multiple diverse computer and communication systems. Some conventional aspects of server system 900 are omitted for clarity, such as power supplies, enclosures, and the like.
- Communication transceivers 901comprise communication components, such as ports, circuitry, memory, software, and the like. Communication transceivers 901 typically utilize Ethernet, Internet, or some other networking protocol—including combinations thereof.
- Micro-processor circuitry 911comprises circuit boards that hold integrated circuitry and associated electronics.
- Memory 912comprises non-transitory, computer-readable, data storage media, such as flash drives, disc drives, and the like.
- Software 913comprises computer-readable instructions that control the operation of micro-processor circuitry 911 when executed.
- Software 913includes modules 921 - 923 and may also include operating systems, applications, utilities, databases, and the like.
- Micro-processor circuitry 911 and memory 912may be integrated into a single computer system or may be distributed across multiple computer systems.
- user module 921When executed by circuitry 911 , user module 921 directs circuitry 911 to interact with user devices to enable the user to select access systems, passwords, and the like. User module 921 also directs circuitry 911 to transfer configuration data in some examples.
- database module 922When executed by circuitry 911 , directs circuitry 911 to stores the associations as described above.
- authorization module 923When executed by circuitry 911 , authorization module 923 directs circuitry 911 to provide positive or negative responses to WiFi access requests based on the stored associations.
- FIG. 10illustrates wireless communication device 1000 to provide user control over access to WiFi networks.
- Wireless communication device 1000is an example of user communication devices 101 - 103 , although devices 101 - 103 may use alternative configurations and operations.
- Wireless communication device 1000comprises access network transceiver 1001 , network transceiver 1002 , processing system 1003 , and user interface 1004 .
- Processing system 1003comprises micro-processing circuitry 1011 and memory 1012 .
- Memory 1012stores software 1013 .
- Some conventional aspects of wireless communication device 1000are omitted for clarity, such as power supplies, enclosures, and the like.
- Wireless communication device 1000may be integrated into other systems or devices.
- Access network transceiver 1001 and WiFi transceiver 1002each comprise communication components, such as circuitry, memory, software, antennas, amplifiers, filters, modulators, signal processors, and the like.
- the radio communicationsinclude multiple transceiver sub-systems for near-field, local network, and wide-area network data communications.
- Access network transceiver 1001exchanges user data and configuration data as described above.
- WiFi network transceiver 1002detects WiFi identification signals, transfers WiFi access requests, and provides WiFi network access.
- User interface 1004includes components to interact with a human operator, such as a touch display, speaker, microphone, camera, buttons, and switches.
- User interface 1004displays maps, text boxes, user prompts and the like.
- a touch display in user interface 1004receives the user instructions that trigger the actions described herein.
- Micro-processor circuitry 1011comprises one or more circuit boards that hold integrated circuit chips and associated electronics.
- Memory 1012comprises non-transitory data storage media, such as flash drives, disc drives, and the like.
- Software 1013comprises computer-readable instructions that control the operation of micro-processor circuitry 1011 when executed.
- Software 1013includes modules 1021 - 1023 and may also include additional operating systems, applications, utilities, databases, and the like.
- display module 1021directs circuitry 1011 to display maps, text boxes, and the like to receive user selections.
- configuration module 1022direct circuitry 1011 to receive and store configuration data as described herein.
- WiFi module 1023directs circuitry 1011 to prompt for passwords and transfer access requests as described herein.
Landscapes
- Engineering & Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- Computer Networks & Wireless Communication (AREA)
- Signal Processing (AREA)
- Computer Hardware Design (AREA)
- Computing Systems (AREA)
- General Engineering & Computer Science (AREA)
- Mobile Radio Communication Systems (AREA)
Abstract
Description
Claims (10)
Priority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| US15/131,889US9985938B2 (en) | 2012-07-19 | 2016-04-18 | User control over WIFI network access |
Applications Claiming Priority (2)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| US13/552,749US9344452B2 (en) | 2012-07-19 | 2012-07-19 | User control over WiFi network access |
| US15/131,889US9985938B2 (en) | 2012-07-19 | 2016-04-18 | User control over WIFI network access |
Related Parent Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US13/552,749ContinuationUS9344452B2 (en) | 2012-07-19 | 2012-07-19 | User control over WiFi network access |
Publications (2)
| Publication Number | Publication Date |
|---|---|
| US20160234179A1 US20160234179A1 (en) | 2016-08-11 |
| US9985938B2true US9985938B2 (en) | 2018-05-29 |
Family
ID=48875786
Family Applications (2)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US13/552,749ActiveUS9344452B2 (en) | 2012-07-19 | 2012-07-19 | User control over WiFi network access |
| US15/131,889ActiveUS9985938B2 (en) | 2012-07-19 | 2016-04-18 | User control over WIFI network access |
Family Applications Before (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US13/552,749ActiveUS9344452B2 (en) | 2012-07-19 | 2012-07-19 | User control over WiFi network access |
Country Status (4)
| Country | Link |
|---|---|
| US (2) | US9344452B2 (en) |
| EP (1) | EP2875663B1 (en) |
| CA (1) | CA2879117C (en) |
| WO (1) | WO2014014880A1 (en) |
Families Citing this family (24)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US8984277B2 (en)* | 2012-09-28 | 2015-03-17 | Cisco Technology, Inc. | Reduced authentication times in constrained computer networks |
| US9763098B2 (en) | 2013-01-11 | 2017-09-12 | Apple Inc. | Bypassing security authentication scheme on a lost device to return the device to the owner |
| CN104519020B (en) | 2013-09-29 | 2017-10-13 | 阿里巴巴集团控股有限公司 | Manage method, server and the system of wireless network login password sharing function |
| US8943569B1 (en) | 2013-10-01 | 2015-01-27 | Myth Innovations, Inc. | Wireless server access control system and method |
| US9686692B2 (en) | 2014-03-20 | 2017-06-20 | Microsoft Technology Licesning, LLC | Wi-Fi tile transfer |
| CN105282862B (en) | 2014-06-17 | 2020-07-31 | 南京中兴软件有限责任公司 | Wireless network access point connection method and terminal |
| US20160261576A1 (en)* | 2015-03-05 | 2016-09-08 | M-Files Oy | Method, an apparatus, a computer program product and a server for secure access to an information management system |
| US20160328120A1 (en)* | 2015-05-04 | 2016-11-10 | Rivada Networks, Llc | Methods and System for Dynamic Spectrum Arbitrage with a Graphic Administration Application |
| US9756505B1 (en)* | 2015-06-08 | 2017-09-05 | Symantec Corporation | Systems and methods for utilizing authentication requests for on-demand provisioning of access-point accounts |
| US9628992B2 (en) | 2015-07-31 | 2017-04-18 | Wyfi, Inc. | WiFi access management system and methods of operation thereof |
| US9922225B2 (en)* | 2015-09-16 | 2018-03-20 | CloudMondo, Inc. | Cloud-based authentication of user devices for onboarding to a Wi-Fi network |
| US10064058B2 (en)* | 2015-12-08 | 2018-08-28 | Cisco Technology, Inc. | Node selection using a combination of subscription entitlement and nodal characteristics |
| JP2018029220A (en)* | 2016-08-15 | 2018-02-22 | 富士ゼロックス株式会社 | Wireless network device, image formation apparatus, wireless network system and program |
| WO2018125703A1 (en)* | 2016-12-27 | 2018-07-05 | Bandwidthx Inc. | Environment signatures |
| US10194382B2 (en) | 2016-12-27 | 2019-01-29 | Bandwidthx Inc. | Auto-discovery of amenities |
| WO2018125704A1 (en) | 2016-12-27 | 2018-07-05 | Bandwidthx Inc. | Radio management based on user intervention |
| CN108282736B (en)* | 2016-12-30 | 2020-11-10 | 腾讯科技(深圳)有限公司 | Networking method and device of intelligent terminal |
| CN108696868B (en)* | 2017-03-01 | 2020-06-19 | 西安西电捷通无线网络通信股份有限公司 | Processing method and device of credential information for network connection |
| US10820361B2 (en) | 2017-05-02 | 2020-10-27 | Samsung Electronics Co., Ltd. | Method and system for application-controlled multiple Wi-Fi connections |
| US11689925B2 (en) | 2017-09-29 | 2023-06-27 | Plume Design, Inc. | Controlled guest access to Wi-Fi networks |
| US11496902B2 (en) | 2017-09-29 | 2022-11-08 | Plume Design, Inc. | Access to Wi-Fi networks via two-step and two-party control |
| KR102414927B1 (en)* | 2018-03-21 | 2022-06-30 | 삼성전자 주식회사 | Method and apparatus for authenticating a device using wireless local area network service |
| CN111726807A (en)* | 2020-04-22 | 2020-09-29 | 深圳市伟文无线通讯技术有限公司 | Device and method for realizing network access of embedded WIFI module through voice interaction |
| US11930548B2 (en) | 2021-06-23 | 2024-03-12 | Microsoft Technology Licensing, Llc | Establishing multiple infrastructure connections to multiple access points via a single wireless network interface controller |
Citations (40)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| WO2001041401A2 (en) | 1999-12-03 | 2001-06-07 | At & T Corp. | System and method for encoding user information in domain names |
| US6614774B1 (en) | 1998-12-04 | 2003-09-02 | Lucent Technologies Inc. | Method and system for providing wireless mobile server and peer-to-peer services with dynamic DNS update |
| WO2004014024A2 (en) | 2002-08-02 | 2004-02-12 | Wavelink Corporation | Managed roaming for wlans |
| US20040052238A1 (en) | 2002-08-30 | 2004-03-18 | 3Com Corporation | Method and system of transferring session speed and state information between access and home networks |
| US20040215717A1 (en) | 2002-11-06 | 2004-10-28 | Nils Seifert | Method for prefetching of structured data between a client device and a server device |
| US20040230446A1 (en) | 2003-05-13 | 2004-11-18 | Samsung Electronics Co., Ltd. | Method and system of automatically registering domain name |
| US20050050180A1 (en) | 2003-04-03 | 2005-03-03 | Samsung Electronics Co., Ltd. | Method of automatically determining device's nickname, and method of solving redundant nicknames for devices in network and network system thereof |
| US20050054343A1 (en) | 2003-09-05 | 2005-03-10 | Nokia Corporation | Providing address information for reaching a wireless terminal |
| US20050143065A1 (en) | 2002-11-26 | 2005-06-30 | Pathan Arnavkumar M. | Inter subnet roaming system and method |
| US6944167B1 (en) | 2000-10-24 | 2005-09-13 | Sprint Communications Company L.P. | Method and apparatus for dynamic allocation of private address space based upon domain name service queries |
| EP1633083A1 (en) | 2003-06-06 | 2006-03-08 | Huawei Technologies Co., Ltd. | A method of user access authorization in the wlan |
| US20060098610A1 (en)* | 2004-11-05 | 2006-05-11 | Krister Sundberg | Method for providing a mobile station with seamless coverage in a 2G/3G communication network and a WLAN |
| US20070081496A1 (en) | 2005-06-10 | 2007-04-12 | Ralf Karge | Method and system for the localization of a mobile WLAN client |
| US20070091861A1 (en)* | 2005-10-11 | 2007-04-26 | Parag Gupta | Technique for managing wireless networks |
| US7224673B1 (en) | 2002-05-24 | 2007-05-29 | Cisco Technology, Inc. | Mobile IP registration message compression |
| US7313631B1 (en) | 1999-09-06 | 2007-12-25 | University Of Bristol | DNS updating in communication network |
| US20080037498A1 (en) | 2006-08-10 | 2008-02-14 | Motorola, Inc. | Optimized tunneling methods in a network |
| US7447182B2 (en) | 2001-04-06 | 2008-11-04 | Nortel Networks Limited | Discovering an address of a name server |
| US20090003297A1 (en) | 2007-06-27 | 2009-01-01 | Futurewei Technologies, Inc. | METHOD AND APPARATUS FOR DYNAMIC LMA ASSIGNMENT IN PROXY MOBILE IPv6 PROTOCOL |
| US20090059874A1 (en)* | 2005-04-20 | 2009-03-05 | Connect Spot Ltd. | Wireless access systems |
| US7510113B2 (en) | 2001-06-07 | 2009-03-31 | Fujitsu Limited | Billing system, and device constituting same |
| US7545762B1 (en) | 2002-08-20 | 2009-06-09 | Sprint Spectrum L.P. | Method and system for network presence notification |
| US20090198808A1 (en) | 2008-01-31 | 2009-08-06 | Lucent Technologies Inc. | Method and apparatus for providing virtual wi-fi access |
| US20090199281A1 (en)* | 2008-01-31 | 2009-08-06 | Lucent Technologies Inc. | Method and apparatus for virtual wi-fi service with authentication and accounting control |
| US7636569B2 (en) | 2002-06-28 | 2009-12-22 | Nokia Corporation | Method of registering home address of a mobile node with a home agent |
| US20100002668A1 (en) | 2003-01-14 | 2010-01-07 | Panasonic Corporation | Service in wlan inter-working, address management system, and method |
| US7668174B1 (en) | 2002-10-17 | 2010-02-23 | Cisco Technology, Inc. | Methods and apparatus for home address management at home agent for NAI based mobile nodes |
| US20100100928A1 (en) | 2008-10-22 | 2010-04-22 | Gasparini Louis A | Secure network computing |
| US7707310B2 (en) | 2002-11-20 | 2010-04-27 | Cisco Technology, Inc. | Mobile IP registration supporting port identification |
| EP2200223A1 (en) | 2007-09-12 | 2010-06-23 | Panasonic Corporation | Wireless terminal device, wireless connection method, and program |
| US20100322123A1 (en) | 2006-08-18 | 2010-12-23 | Wifi Rail, Inc. | System and method of authenticating mobile devices |
| US7958544B2 (en) | 2006-07-21 | 2011-06-07 | Google Inc. | Device authentication |
| US7962122B2 (en) | 2003-05-23 | 2011-06-14 | Telefonaktiebolaget Lm Ericsson (Publ) | Secure traffic redirection in a mobile communication system |
| US8059643B1 (en) | 2009-05-11 | 2011-11-15 | Sprint Communications Company L.P. | IPv4 and IPv6 single session on a home agent |
| US20130089001A1 (en) | 2011-10-05 | 2013-04-11 | Siddhartha Dattagupta | Associating wi-fi stations with an access point in a multi-access point infrastructure network |
| US8457594B2 (en) | 2006-08-25 | 2013-06-04 | Qwest Communications International Inc. | Protection against unauthorized wireless access points |
| US20130152168A1 (en)* | 2011-12-09 | 2013-06-13 | Verizon Patent And Licensing, Inc. | Wireless connection method and device |
| US20130163442A1 (en) | 2011-12-21 | 2013-06-27 | Kik Interactive, Inc. | Methods and apparatus for initializing a network connection for an output device |
| US20130283358A1 (en) | 2012-04-24 | 2013-10-24 | Arun Manroa | Convenient wifi network access using unique identifier value |
| US8614976B1 (en) | 2010-03-29 | 2013-12-24 | Sprint Spectrum L.P. | Method and system for registering a nickname associated with a mobile node |
Family Cites Families (1)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| JP2004266568A (en) | 2003-02-28 | 2004-09-24 | Nec Corp | Name resolution server and packet transfer device |
- 2012
- 2012-07-19USUS13/552,749patent/US9344452B2/enactiveActive
- 2013
- 2013-07-16EPEP13742116.0Apatent/EP2875663B1/enactiveActive
- 2013-07-16WOPCT/US2013/050635patent/WO2014014880A1/enactiveApplication Filing
- 2013-07-16CACA2879117Apatent/CA2879117C/enactiveActive
- 2016
- 2016-04-18USUS15/131,889patent/US9985938B2/enactiveActive
Patent Citations (42)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US6614774B1 (en) | 1998-12-04 | 2003-09-02 | Lucent Technologies Inc. | Method and system for providing wireless mobile server and peer-to-peer services with dynamic DNS update |
| US7313631B1 (en) | 1999-09-06 | 2007-12-25 | University Of Bristol | DNS updating in communication network |
| WO2001041401A2 (en) | 1999-12-03 | 2001-06-07 | At & T Corp. | System and method for encoding user information in domain names |
| US6944167B1 (en) | 2000-10-24 | 2005-09-13 | Sprint Communications Company L.P. | Method and apparatus for dynamic allocation of private address space based upon domain name service queries |
| US7447182B2 (en) | 2001-04-06 | 2008-11-04 | Nortel Networks Limited | Discovering an address of a name server |
| US7510113B2 (en) | 2001-06-07 | 2009-03-31 | Fujitsu Limited | Billing system, and device constituting same |
| US7224673B1 (en) | 2002-05-24 | 2007-05-29 | Cisco Technology, Inc. | Mobile IP registration message compression |
| US7636569B2 (en) | 2002-06-28 | 2009-12-22 | Nokia Corporation | Method of registering home address of a mobile node with a home agent |
| WO2004014024A2 (en) | 2002-08-02 | 2004-02-12 | Wavelink Corporation | Managed roaming for wlans |
| US7545762B1 (en) | 2002-08-20 | 2009-06-09 | Sprint Spectrum L.P. | Method and system for network presence notification |
| US20040052238A1 (en) | 2002-08-30 | 2004-03-18 | 3Com Corporation | Method and system of transferring session speed and state information between access and home networks |
| US7218609B2 (en) | 2002-08-30 | 2007-05-15 | Utstarcom, Inc. | Method and system of transferring session speed and state information between access and home networks |
| US7668174B1 (en) | 2002-10-17 | 2010-02-23 | Cisco Technology, Inc. | Methods and apparatus for home address management at home agent for NAI based mobile nodes |
| US20040215717A1 (en) | 2002-11-06 | 2004-10-28 | Nils Seifert | Method for prefetching of structured data between a client device and a server device |
| US7707310B2 (en) | 2002-11-20 | 2010-04-27 | Cisco Technology, Inc. | Mobile IP registration supporting port identification |
| US20050143065A1 (en) | 2002-11-26 | 2005-06-30 | Pathan Arnavkumar M. | Inter subnet roaming system and method |
| US20100002668A1 (en) | 2003-01-14 | 2010-01-07 | Panasonic Corporation | Service in wlan inter-working, address management system, and method |
| US20050050180A1 (en) | 2003-04-03 | 2005-03-03 | Samsung Electronics Co., Ltd. | Method of automatically determining device's nickname, and method of solving redundant nicknames for devices in network and network system thereof |
| US20040230446A1 (en) | 2003-05-13 | 2004-11-18 | Samsung Electronics Co., Ltd. | Method and system of automatically registering domain name |
| US7962122B2 (en) | 2003-05-23 | 2011-06-14 | Telefonaktiebolaget Lm Ericsson (Publ) | Secure traffic redirection in a mobile communication system |
| EP1633083A1 (en) | 2003-06-06 | 2006-03-08 | Huawei Technologies Co., Ltd. | A method of user access authorization in the wlan |
| US20050054343A1 (en) | 2003-09-05 | 2005-03-10 | Nokia Corporation | Providing address information for reaching a wireless terminal |
| US20060098610A1 (en)* | 2004-11-05 | 2006-05-11 | Krister Sundberg | Method for providing a mobile station with seamless coverage in a 2G/3G communication network and a WLAN |
| US20090059874A1 (en)* | 2005-04-20 | 2009-03-05 | Connect Spot Ltd. | Wireless access systems |
| US20070081496A1 (en) | 2005-06-10 | 2007-04-12 | Ralf Karge | Method and system for the localization of a mobile WLAN client |
| US20070091861A1 (en)* | 2005-10-11 | 2007-04-26 | Parag Gupta | Technique for managing wireless networks |
| US7958544B2 (en) | 2006-07-21 | 2011-06-07 | Google Inc. | Device authentication |
| US8068499B2 (en) | 2006-08-10 | 2011-11-29 | Motorola Solutions, Inc. | Optimized tunneling methods in a network |
| US20080037498A1 (en) | 2006-08-10 | 2008-02-14 | Motorola, Inc. | Optimized tunneling methods in a network |
| US20100322123A1 (en) | 2006-08-18 | 2010-12-23 | Wifi Rail, Inc. | System and method of authenticating mobile devices |
| US8457594B2 (en) | 2006-08-25 | 2013-06-04 | Qwest Communications International Inc. | Protection against unauthorized wireless access points |
| US20090003297A1 (en) | 2007-06-27 | 2009-01-01 | Futurewei Technologies, Inc. | METHOD AND APPARATUS FOR DYNAMIC LMA ASSIGNMENT IN PROXY MOBILE IPv6 PROTOCOL |
| EP2200223A1 (en) | 2007-09-12 | 2010-06-23 | Panasonic Corporation | Wireless terminal device, wireless connection method, and program |
| US20090198808A1 (en) | 2008-01-31 | 2009-08-06 | Lucent Technologies Inc. | Method and apparatus for providing virtual wi-fi access |
| US20090199281A1 (en)* | 2008-01-31 | 2009-08-06 | Lucent Technologies Inc. | Method and apparatus for virtual wi-fi service with authentication and accounting control |
| US20100100928A1 (en) | 2008-10-22 | 2010-04-22 | Gasparini Louis A | Secure network computing |
| US8059643B1 (en) | 2009-05-11 | 2011-11-15 | Sprint Communications Company L.P. | IPv4 and IPv6 single session on a home agent |
| US8614976B1 (en) | 2010-03-29 | 2013-12-24 | Sprint Spectrum L.P. | Method and system for registering a nickname associated with a mobile node |
| US20130089001A1 (en) | 2011-10-05 | 2013-04-11 | Siddhartha Dattagupta | Associating wi-fi stations with an access point in a multi-access point infrastructure network |
| US20130152168A1 (en)* | 2011-12-09 | 2013-06-13 | Verizon Patent And Licensing, Inc. | Wireless connection method and device |
| US20130163442A1 (en) | 2011-12-21 | 2013-06-27 | Kik Interactive, Inc. | Methods and apparatus for initializing a network connection for an output device |
| US20130283358A1 (en) | 2012-04-24 | 2013-10-24 | Arun Manroa | Convenient wifi network access using unique identifier value |
Non-Patent Citations (9)
| Title |
|---|
| 3rd Generation Partnership Project 2, "cdma2000 Wireless IP Network Standard: Simple IP and Mobile IP Access Services," 3GPP2 X.S0011-002-C, Version 1.0.0, Aug. 2003. |
| Aboba, et al., "The Network Access Identifier," Network Working Group, Request for Comments: 4282, Dec. 2005. |
| Johnson, et al., "Mobility Support in 1Pv6," Network Working Group, Request for Comments: 3775, Jun. 2004. |
| Junbiao Zhang, et al.; "Virtual Operator based AAA in Wireless LAN Hot Spots with Ad-hoc Networking Support;" Mobile Computing and Communications Review; Jul. 1, 2002; pp. 10-21; vol. 6, No. 3; New York, NY. |
| Perkins, "IP Mobility Support for 1Pv4," Network Working Group, Request for Comments: 3344, Aug. 2002. |
| Rigney, et al., "Remote Authentication Dial in User Service (RADIUS)," Network Working Group, Request for Comments: 2865, Jun. 2000. |
| U.S. Appl. No. 11/500,706, filed Aug. 8, 2006. |
| Vixie, et al., "Dynamic Updates in the Domain Name System (DNS Update)," Network Working Group, Request for Comments: 2136, Apr. 1997. |
| Williamson, et al., "Referral Whois (RWhois) Protocol V1.5," Network Working Group, Request for Comments: 2167, Jun. 1997. |
Also Published As
| Publication number | Publication date |
|---|---|
| WO2014014880A1 (en) | 2014-01-23 |
| CA2879117C (en) | 2017-04-11 |
| US20160234179A1 (en) | 2016-08-11 |
| US20140026192A1 (en) | 2014-01-23 |
| CA2879117A1 (en) | 2014-01-23 |
| US9344452B2 (en) | 2016-05-17 |
| EP2875663A1 (en) | 2015-05-27 |
| EP2875663B1 (en) | 2018-01-10 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| US9985938B2 (en) | User control over WIFI network access | |
| US11973746B2 (en) | Connecting IMSI-less devices to the EPC | |
| EP3016419B1 (en) | Method of changing profile using identification module and electronic device implementing same | |
| US10887745B2 (en) | Method and device for sharing file between different terminals | |
| US9121921B2 (en) | Location information collection method and system for dual SIM mobile terminals | |
| US9936390B2 (en) | Method and apparatus of triggering applications in a wireless environment | |
| EP3668204B1 (en) | Network registration method of internet of things device, and device therefor | |
| US9130919B2 (en) | Hosted IMS instance with authentication framework for network-based applications | |
| CN103685176B (en) | Terminal equipment, equipment management server and connection establishment method | |
| US20200169867A1 (en) | Interception method, core network device and base station | |
| US9047470B2 (en) | Secure provisioning of commercial off-the-shelf (COTS) devices | |
| WO2012063558A1 (en) | User verification device and user verification method | |
| US10292187B2 (en) | Wireless communication apparatus, server, payment apparatus, wireless communication method, and program | |
| KR102025363B1 (en) | Portable Terminal | |
| US9560047B1 (en) | Multi-device authorization to access wireless network communications based on shared event times | |
| CN106357492A (en) | Network access method and device for household appliance and household appliance | |
| JP5819017B1 (en) | Communication system and connection method | |
| CN105451304B (en) | A kind of information processing method and router |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| AS | Assignment | Owner name:SPRINT COMMUNICATIONS COMPANY L.P., KANSAS Free format text:ASSIGNMENT OF ASSIGNORS INTEREST;ASSIGNORS:GATEWOOD, JOHN M.;SCHNITZER, LEE ALAN;WOODRUM, SHARON L.;AND OTHERS;REEL/FRAME:038309/0138 Effective date:20120718 | |
| AS | Assignment | Owner name:DEUTSCHE BANK TRUST COMPANY AMERICAS, NEW YORK Free format text:GRANT OF FIRST PRIORITY AND JUNIOR PRIORITY SECURITY INTEREST IN PATENT RIGHTS;ASSIGNOR:SPRINT COMMUNICATIONS COMPANY L.P.;REEL/FRAME:041895/0210 Effective date:20170203 | |
| STCF | Information on status: patent grant | Free format text:PATENTED CASE | |
| AS | Assignment | Owner name:SPRINT COMMUNICATIONS COMPANY L.P., KANSAS Free format text:TERMINATION AND RELEASE OF FIRST PRIORITY AND JUNIOR PRIORITY SECURITY INTEREST IN PATENT RIGHTS;ASSIGNOR:DEUTSCHE BANK TRUST COMPANY AMERICAS;REEL/FRAME:052969/0475 Effective date:20200401 Owner name:DEUTSCHE BANK TRUST COMPANY AMERICAS, NEW YORK Free format text:SECURITY AGREEMENT;ASSIGNORS:T-MOBILE USA, INC.;ISBV LLC;T-MOBILE CENTRAL LLC;AND OTHERS;REEL/FRAME:053182/0001 Effective date:20200401 | |
| AS | Assignment | Owner name:T-MOBILE INNOVATIONS LLC, KANSAS Free format text:ASSIGNMENT OF ASSIGNORS INTEREST;ASSIGNOR:SPRINT COMMUNICATIONS COMPANY L.P.;REEL/FRAME:055604/0001 Effective date:20210303 | |
| MAFP | Maintenance fee payment | Free format text:PAYMENT OF MAINTENANCE FEE, 4TH YEAR, LARGE ENTITY (ORIGINAL EVENT CODE: M1551); ENTITY STATUS OF PATENT OWNER: LARGE ENTITY Year of fee payment:4 | |
| AS | Assignment | Owner name:SPRINT SPECTRUM LLC, KANSAS Free format text:RELEASE BY SECURED PARTY;ASSIGNOR:DEUTSCHE BANK TRUST COMPANY AMERICAS;REEL/FRAME:062595/0001 Effective date:20220822 Owner name:SPRINT INTERNATIONAL INCORPORATED, KANSAS Free format text:RELEASE BY SECURED PARTY;ASSIGNOR:DEUTSCHE BANK TRUST COMPANY AMERICAS;REEL/FRAME:062595/0001 Effective date:20220822 Owner name:SPRINT COMMUNICATIONS COMPANY L.P., KANSAS Free format text:RELEASE BY SECURED PARTY;ASSIGNOR:DEUTSCHE BANK TRUST COMPANY AMERICAS;REEL/FRAME:062595/0001 Effective date:20220822 Owner name:SPRINTCOM LLC, KANSAS Free format text:RELEASE BY SECURED PARTY;ASSIGNOR:DEUTSCHE BANK TRUST COMPANY AMERICAS;REEL/FRAME:062595/0001 Effective date:20220822 Owner name:CLEARWIRE IP HOLDINGS LLC, KANSAS Free format text:RELEASE BY SECURED PARTY;ASSIGNOR:DEUTSCHE BANK TRUST COMPANY AMERICAS;REEL/FRAME:062595/0001 Effective date:20220822 Owner name:CLEARWIRE COMMUNICATIONS LLC, KANSAS Free format text:RELEASE BY SECURED PARTY;ASSIGNOR:DEUTSCHE BANK TRUST COMPANY AMERICAS;REEL/FRAME:062595/0001 Effective date:20220822 Owner name:BOOST WORLDWIDE, LLC, KANSAS Free format text:RELEASE BY SECURED PARTY;ASSIGNOR:DEUTSCHE BANK TRUST COMPANY AMERICAS;REEL/FRAME:062595/0001 Effective date:20220822 Owner name:ASSURANCE WIRELESS USA, L.P., KANSAS Free format text:RELEASE BY SECURED PARTY;ASSIGNOR:DEUTSCHE BANK TRUST COMPANY AMERICAS;REEL/FRAME:062595/0001 Effective date:20220822 Owner name:T-MOBILE USA, INC., WASHINGTON Free format text:RELEASE BY SECURED PARTY;ASSIGNOR:DEUTSCHE BANK TRUST COMPANY AMERICAS;REEL/FRAME:062595/0001 Effective date:20220822 Owner name:T-MOBILE CENTRAL LLC, WASHINGTON Free format text:RELEASE BY SECURED PARTY;ASSIGNOR:DEUTSCHE BANK TRUST COMPANY AMERICAS;REEL/FRAME:062595/0001 Effective date:20220822 Owner name:PUSHSPRING, LLC, WASHINGTON Free format text:RELEASE BY SECURED PARTY;ASSIGNOR:DEUTSCHE BANK TRUST COMPANY AMERICAS;REEL/FRAME:062595/0001 Effective date:20220822 Owner name:LAYER3 TV, LLC, WASHINGTON Free format text:RELEASE BY SECURED PARTY;ASSIGNOR:DEUTSCHE BANK TRUST COMPANY AMERICAS;REEL/FRAME:062595/0001 Effective date:20220822 Owner name:IBSV LLC, WASHINGTON Free format text:RELEASE BY SECURED PARTY;ASSIGNOR:DEUTSCHE BANK TRUST COMPANY AMERICAS;REEL/FRAME:062595/0001 Effective date:20220822 |