US7907935B2 - Intelligent remote device - Google Patents
Intelligent remote deviceDownload PDFInfo
- Publication number
- US7907935B2 US7907935B2US10/740,497US74049703AUS7907935B2US 7907935 B2US7907935 B2US 7907935B2US 74049703 AUS74049703 AUS 74049703AUS 7907935 B2US7907935 B2US 7907935B2
- Authority
- US
- United States
- Prior art keywords
- security token
- security
- remote device
- computer system
- intelligent remote
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Active, expires
Links
Images
Classifications
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/08—Network architectures or network communication protocols for network security for authentication of entities
- H04L63/0853—Network architectures or network communication protocols for network security for authentication of entities using an additional device, e.g. smartcard, SIM or a different communication terminal
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/30—Authentication, i.e. establishing the identity or authorisation of security principals
- G06F21/31—User authentication
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/30—Authentication, i.e. establishing the identity or authorisation of security principals
- G06F21/31—User authentication
- G06F21/34—User authentication involving the use of external additional devices, e.g. dongles or smart cards
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W12/00—Security arrangements; Authentication; Protecting privacy or anonymity
- H04W12/06—Authentication
- H04W12/069—Authentication using certificates or pre-shared keys
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W12/00—Security arrangements; Authentication; Protecting privacy or anonymity
- H04W12/08—Access security
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/16—Implementing security features at a particular protocol layer
- H04L63/166—Implementing security features at a particular protocol layer at the transport layer
Definitions
- the present inventionrelates generally to a data processing method, system and computer program product and more specifically to an intelligent remote device equipped with a security token which is used to emulate for authentication purposes, a local security token peripheral device connected to a host computer system.
- a more secure solutionis to provide a portable security device such as a security token which minimizes the number of credentials a user is required to remember and provides a much more secure mechanism to authenticate the user to a computer system.
- a portable security devicesuch as a security token which minimizes the number of credentials a user is required to remember and provides a much more secure mechanism to authenticate the user to a computer system.
- equipping each computer system with a separate security token, reader and interface softwarecan be expensive to deploy and maintain, thus presenting a daunting economic barrier to improving computer system security over the use of static user names and passwords.
- One possible solutionis to provide an alternate mechanism for authenticating to one or more computer systems which minimizes the number security tokens, readers and interface software required to be installed and maintained.
- An example of whichis shown in European patent application EP 1061482 A1 to Cuong.
- the Cuong applicationdiscloses an intelligent portable device which allows a user to authenticate to a plurality of financial service providers using a single universal security token in the form of a smart card.
- the basic goal of this applicationis to reduce the number of smart cards required to be carried by the user.
- U.S. patent application Ser. No. 09/880,795 to Audebert, et al.provides a solution which may be implemented over a public or private network using a client-server and/or a peer-to-peer authentication arrangement.
- This applicationaddresses the limitations described above but does not address security issues related to wireless telecommunications links or alternate user login mechanisms associated with accessing the user's unattended computer system.
- This applicationis to a common assignee and is not admitted as prior art to the instant application.
- a secure mechanismneeds to be established which allows a user to authenticate to his or her computer system which does not require significant changes to existing user authentication mechanisms included in computer operating systems and does not reduce the overall level of security afforded by the existing authentication mechanisms.
- the intelligent remote deviceincludes a personal data assistant (PDA), a cellular telephone having private networking capabilities, a network appliance or a personal security device such as a secure PIN pad.
- PDApersonal data assistant
- security tokenincludes hardware based security devices such as cryptographic modules, smart cards, integrated circuit chip cards, portable data carriers (PDC), personal security devices (PSD), subscriber identification modules (SIM), wireless identification modules (WIM), USB token dongles, identification tokens, secure application modules (SAM), hardware security modules (HSM), secure multi-media token (SMMC), trusted platform computing alliance chips (TPCA) and like devices.
- PDCportable data carriers
- PSDpersonal security devices
- SIMsubscriber identification modules
- WIMwireless identification modules
- USB token donglesidentification tokens
- SAMsecure application modules
- HSMMChardware security modules
- SMMCsecure multi-media token
- TPCAtrusted platform computing alliance chips
- the inventioncomprises a method for accessing a security token enabled computer system using an intelligent remote device as a communications interface for a security token.
- the methodincludes the establishment of a first communications connection between the intelligent remote device and a network gateway coupled to a network in common with a computer system.
- the network in commonincludes private wireless networking such as BlueTooth, HomeRF, and IEEE 802.11 a/b/g and its successors.
- the communications connectionutilizes existing security protocols established for the network interface devices and is essentially the connection handshake between the intelligent remote device and the network gateway. Examples of which include secure socket layer (SSL), transport layer security (TLS), private communications technology (PCT), internet protocol security (IPsec) or a secure messaging arrangement.
- SSLsecure socket layer
- TLStransport layer security
- PCTprivate communications technology
- IPsecinternet protocol security
- the secure messaging arrangementincorporates a shared symmetric key pair for cryptography purposes which is uniquely identified by a session identifier generated and assigned by the security token.
- an APDU communications pipemay be established between the computer system and the security token.
- the APDU communications pipeallows exchanging of native security token APDU commands and responses which are encapsulated in standard networking protocols such as TCP/IP.
- a critical security parameter (CSP) associated with a useris provided to the security token using the intelligent remote device as a communications interface.
- a critical security parameter as defined hereinincludes authentication data, passwords, PINs, secret and private cryptographic keys which are to be entered into or output from a cryptographic module and is intended to be synonymous with the definition of CSP included in FIPS PUB 140-2, “Security Requirements for Cryptographic Modules.”
- the provided critical security parametermay be directly entered using a user interface included with the intelligent remote device or sent from a remote location via the communications connection.
- a biometric scannermay be directly connected to the user's computer system or coupled to the network in common.
- the generally greater computing power of the user's computer systemmay be used to process a biometric sample which subsequently matched by the security token.
- the provided user's critical security parameteris then used to perform an authentication transaction, in which the user is authenticated to the computer system and the security token.
- a two factor authentication transactionmay be incorporated as well where the security token is authenticated to the computer system by exchanging authenticating information during establishment of the communications connection.
- the two factor authentication processmay be performed using dynamic one-time passwords, challenge/response or by digital certificate exchanges.
- the userUpon successful completion of the authentication transaction, the user is allowed access to at least one secure resource associated with the computer system.
- the communications connectionis initiated by sending an access request message from the intelligent remote device to the computer system.
- the access request messageprovides sufficient information to the network gateway for routing to the target computer system and includes a return network address in which the target computer system is to respond. Multiple logical connections may be established over the network with one or more computer systems to employ the intelligent remote device as a security peripheral device.
- the access request messagefurther includes information which identifies the intelligent remote device and associated security token.
- the computer systemincludes an alternate user authentication method which allows the user to remotely authenticate to the computer system over the communications connection.
- the term “method” as defined hereinis used in its broadest context which includes a function, application, routine, remotely invocable method, subroutine or applet.
- the alternate user authentication methodincludes an agent which monitors incoming network traffic directed to the computer system for an access request message. The agent invokes the alternate user authentication method which is an adjunct or replacement of a main user authentication method.
- Aural or visual feedbackis provided to the user following successful authentication. This allows the user to determine which computer system among a plurality of computer systems has been authenticated.
- the aural or visual feedbackmay be provided on either or both the intelligent remote device and the authenticated computer system.
- a trusted pathis established between the security token and the intelligent remote device.
- the trusted pathallows the intelligent remote device to be used in high security operating environments such as FIPS security levels 3 and 4 which requires that critical security parameters be entered into or output from a cryptographic module in an encrypted form to prevent interception of the critical security parameters.
- the hardware portion of the inventionincludes an intelligent remote device equipped with a security token in processing communications with a computer system over a network.
- the networkincludes a wireless private network such as BlueTooth, HomeRF, IEEE 802.11 a/b/g and successors which incorporate a secure communications protocol comprising secure socket layer (SSL), transport layer security (TLS), private communications technology (PCT), internet protocol security (IPsec) or a secure messaging arrangement.
- SSLsecure socket layer
- TLStransport layer security
- PCTprivate communications technology
- IPsecinternet protocol security
- the intelligent remote deviceincludes a personal data assistant (PDA), a cellular telephone having private networking capabilities, a network appliance or a personal security device such as a secure PIN pad.
- PDApersonal data assistant
- the intelligent remote deviceis equipped with the necessary hardware, software and firmware to emulate a security token peripheral device which is locally connected to the computer system and includes the abilities to; operatively couple the security token to the intelligent remote device, send an access request message over the network to the computer system to invoke establishment of a secure communications connection between the security token and the computer system, provide cryptographic protection of data exchanged between the intelligent remote device and the computer system, receive a critical security parameter provided by the user either directly or received through the secure communications connection, exchange information over the network using an APDU communications pipe and provide aural or visual feedback to the user upon successful completion of a two-factor authentication transaction.
- the security tokenis comprised of hardware based security devices such as cryptographic modules, smart cards, integrated circuit chip cards, portable data carriers (PDC), personal security devices (PSD), subscriber identification modules (SIM), wireless identification modules (WIM), USB token dongles, identification tokens, secure application modules (SAM), hardware security modules (HSM), secure multi-media token (SMMC), trusted platform computing alliance chips (TPCA) and like devices.
- the security tokenis provided with at least one operatively installed reference critical security parameter associated with the user and includes the abilities to; receive a critical security parameter associated with the user, perform an authentication transaction.
- the computer systemincludes at least one workstation, server, desktop, laptop, personal computer, mini computer or mainframe computer which requires user authentication prior to allowing a user to access.
- the computer system portion of the inventionis equipped with the necessary hardware, software and firmware to allow the user to remotely authenticate to the computer system over the network as if the user were local to the computer system and includes the abilities to; receive an access request sent over the network from the intelligent remote device, establish the communications connection between the computer system and the security token, execute an alternate user authentication method which allows the user to remotely authenticate to the computer system over the network using the two factor authentication transaction, exchange information over the network or communications connection using an APDU communications pipe and allow the user access to the computer system following successful completion of the two factor authentication transaction.
- the intelligent remote device and security token enabled computer systeminclude a set of application program interfaces embodied on a computer readable medium for execution by a processor which allows the intelligent remote device to emulate a security token peripheral device locally connected to the security token enabled computer system.
- the application program interfacescomprise a first interface that exchanges information between a security token and the security token enabled computer system in a protocol native to the security token and a second interface that receives and routes a critical security parameter to the security token.
- the first set of application interface programs installed in the intelligent remote deviceprovides protocol conversion into a protocol native to the security token. In another embodiment of the invention, the first set of application interface programs installed in the intelligent remote device extracts the information from communications packets already in a protocol native to said security token.
- the programs and associated datamay be stored on transportable digital recording media such as a CD ROM, floppy disk, data tape, DVD, or removable hard disk for installation on the computer system, intelligent remote device and/or security token as one or more transportable computer program products.
- the programs and associated datacomprise executable instructions which are stored in a code format including byte code, compiled, interpreted, compliable or interpretable.
- the computer program product embodied in the tangible formis readable by a plurality of processors in processing communications and includes executable instructions stored for causing one or more of the plurality of processors to; establish a secure communications connection between a security token and a security token enabled computer system via an intelligent remote device, authenticate at least the security token to said security token enabled computer system, provide a critical security parameter associated with a user to the security token and authenticate the critical security parameter by the security token.
- FIG. 1is a generalized block diagram of a security token enabled computer system and a functionally connected security token.
- FIG. 1 Ais a generalized block diagram of a intelligent remote device.
- FIG. 1 B- 1is a detailed block diagram of the functional modules incorporated into the security token enabled computer system.
- FIG. 1 B- 2is a detailed block diagram of the functional modules incorporated into the intelligent remote device.
- FIG. 1 Cis a detailed block diagram of an initiating process which allows the intelligent remote device to emulate a local security device peripheral connected to the security token enabled computer system.
- FIG. 1 Dis a detailed block diagram of the intelligent remote device emulating a local security device peripheral connected to the security token enabled computer system.
- FIG. 2 Ais a detailed block diagram of one embodiment of a secure communications connection between the security token and the security token enabled computer system where a shared symmetric key pair are incorporated into the secure connection.
- FIG. 2 Bis a detailed block diagram of another embodiment of a secure communications connection between the security token and the security token enabled computer system where two sets of symmetric key pairs are incorporated into the secure connection.
- FIG. 2 Cis a detailed block diagram of another embodiment of a secure communications connection between the security token and the security token enabled computer system where an APDU communications pipe is incorporated into the secure connection.
- FIG. 2 Dis a detailed block diagram of another embodiment of the invention where an additional security token enabled computer system and an authentication server are securely connected to the security token.
- FIG. 3is a flow diagram illustrating the major steps associated with enabling an intelligent remote device to emulate a local security device peripheral connected to a security token enabled computer system.
- This present inventionprovides an arrangement which allows an intelligent remote device to securely emulate a local security device peripheral connected to a security token enabled computer system via a network.
- the applicationsare envisioned to be programmed in a high level language such as JavaTM, C++, C, C# or Visual BasicTM.
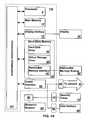
- FIG. 1a functional block diagram of the security token enabled computer system is shown which includes a central processor 5 , a main memory 10 , a display 20 electrically coupled to a display interface 15 , a secondary memory subsystem 25 electrically coupled to a hard disk drive 30 , a removable storage drive 35 electrically coupled to a removable storage unit 40 and an auxiliary removable storage interface 45 electrically coupled to an auxiliary removable storage unit 50 .
- a communications interface 55 subsystemis coupled to a network 65 via a network interface 60 .
- a security token 75is operatively coupled to the communications interface 55 via a security token interface 70 .
- User input devicesincluding a mouse and a keyboard 85 are operatively coupled to the communications interface 55 via a user interface 80 .
- an optional biometric scanneris operatively coupled to the communications interface 55 via a biometric scanner interface 90 .
- the central processor 5 , main memory 10 , display interface 15 secondary memory subsystem 25 and communications interface system 55are electrically coupled to a communications infrastructure 100 .
- the host computer system 105includes an operating system having an extensible, modifiable or replaceable logon security application, a security token application programming interface, one or more security token aware applications, one or more proprietary extensions to the logon security application, a communications agent capable of sensing an incoming access request and invoking an alternate logon method, cryptography software capable of performing symmetric and asymmetric cryptographic functions, secure messaging software and all necessary device interface and driver software.
- the security token 75includes a wireless, optical and/or electrical connection means compatible with the security token interface 70 , a processor, a cryptography co-processor, volatile and non-volatile memory electrically coupled to the processor and co-processor, a runtime operating environment, cryptography extensions available to the operating system and capable of performing symmetric and asymmetric cryptographic functions compatible with the computer system's cryptography software, a security executive application, one or more CSP protected applications including two factor authentications are functionally coupled to the security executive application and a public key infrastructure (PKI) key pair functionally coupled to the security executive application.
- PKIpublic key infrastructure
- the security token 75further includes the necessary authentication applications and cryptographic extensions to successfully perform the two factor authentication transaction with the security token enabled computer system.
- the non-volatile memoryhas operatively stored therein one or more reference CSPs which are verified by the security executive application to authenticate a user to the security token.
- the security token 75is embodied in a removable form factor, although other form factors will work as well.
- the network 65includes a wireless private network such as BlueTooth, HomeRF, IEEE 802.11 a/b/g and its successors which incorporate a secure communications protocol comprising secure socket layer (SSL), transport layer security (TLS), private communications technology protocol (PCT), internet protocol security (IPsec) or a secure messaging arrangement.
- the network 65further includes a network gateway which allows ad hoc connection to the intelligent remote device.
- the intelligent remote device 110essentially incorporates the same modular components included in the security token enabled computer described above.
- the intelligent remote deviceincludes a processor 5 ′, a main memory 10 ′, a display 20 ′ electrically coupled to a display interface 15 ′, a secondary memory subsystem 25 ′ electrically coupled to an optional hard disk drive 30 ′, a virtual storage drive 35 ′, and a removable memory interface 45 ′ electrically coupled to a removable memory module 50 ′.
- a communications interface 55 ′ subsystemis coupled to a network 65 via a network interface 60 ′, a security token 75 ′ coupled to a security token interface 70 ′ and a user input arrangement including a stylus, pen, a touch sensitive display, a miniature mouse and/or keyboard 85 ′ coupled to a user device interface 80 ′ and an optional biometric scanner 95 ′ coupled to an optional biometric scanner interface 90 ′.
- the processor 5 ′, main memory 10 ′, display interface 15 ′ secondary memory subsystem 25 ′ and communications interface system 55 ′are electrically coupled to a communications infrastructure 100 ′
- the intelligent remote device 110further includes an operating system having an extensible, modifiable or replaceable logon security application, one or more proprietary extensions to the logon security application, a security token application programming interface, for example PC/SC, one or more security token aware applications, a token emulator application capable of causing the intelligent remote device to transparently exchange security token commands and responses between the network computer system, cryptography software capable of performing symmetric and asymmetric cryptographic functions, secure messaging software and all necessary device interface and driver software.
- the security token 75 ′may be the same device normally used to access the security token enabled computer system 105 or another security token containing the necessary information to successfully complete the two factor authentication transaction.
- FIG. 1B-1a functional layer diagram of the computer system is shown.
- the various layers shownare loosely based on the Open System Interconnection model (OSI). For simplicity, certain layers are not shown and should be assumed to be present and/or incorporated into adjacent layers.
- the uppermost applications layer 115includes user and security token aware applications denoted as Token Apps 175 .
- the middleware layer 120includes security token application programming interface applications denoted as Token API 145 which allow the user and security token aware applications included in the applications layer 115 to communicate with the attached security token 75 .
- Token API 145An example of the security token application programming interface is described in the PC/SC workgroup specifications available from the organization's website www.pcscworkgroup.com.
- the operating system layer 125includes the software that controls the allocation and usage of hardware resources such as memory, central processing unit (CPU) time, disk space, and peripheral devices. Included in this layer are the logon security application(s) 150 and added extensions 155 which allows for an alternate user authentication method. A user input device 85 is shown coupled to the added extension Ext 155 .
- msgina.dlla customizable or replaceable dynamically linked library
- msgina.dlla customizable or replaceable dynamically linked library
- a brief description of how one skilled in the art would customize or replace msgina.dllis presented in “The Essentials of Replacing the Microsoft® Graphical Identification and Authentication Dynamic Link Library,” by Ben Hutz and Jack Fink both of the Microsoft Corporation, published June 2001.
- the communications layer 130is essentially a consolidation of the network and transport layers and includes an agent 160 and APDU Interface software 170 , examples of which are provided above.
- the agentis used to monitor incoming network traffic for an access request message. Detection of an access request message by the agent 160 invokes the alternate user authentication method.
- Invocation of the alternate user authentication method by detection of an access request message by the agent 160causes the resource manager 165 to toggle the security token device interface from the local token device interface 70 to the remote token device interface 180 .
- the APDU Interface softwareprovides protocol conversion between the various communications formats used by the computer system, network and security token. In an alternate embodiment of the invention, APDU protocol conversion is performed by a counterpart application installed in the intelligent remote device.
- the data link layer denoted as Device Drivers 135includes a resource manager 165 which controls access to the security token 75 and is the application responsible for selecting either the local token device driver 175 or remote token device driver 180 based on established logon policies.
- the software device driversmay be based on the PC/SC (Personal Computer/Smart Card) promulgated by the Open Card (SM) industry consortium. Additional information is available from the consortium's website at www.opencard.org.
- the final layer denoted as Physical Devices 140includes the local token device interface 70 which couples the security token 75 to the computer system 105 .
- the physical device layer 140further includes a software based remote token device driver 180 .
- This remote token device driver 180is included in the physical device layer 140 for simplifying the understanding of the invention only. In actuality, the remote token device driver 180 is installed in the Device Driver layer 135 .
- a network interface device 60provides the physical connection between the computer system 105 and the network 65 .
- FIG. 1B-2a functional layer diagram of the intelligent remote device 110 is shown. As described above, the various layers shown are loosely based on the Open System Interconnection model (OSI.) The intelligent remote device 110 essentially incorporates the same functional layers included in the security token enabled computer described in FIG. 1B-1 and will not be repeated here.
- a token emulator 182is shown as a middleware application 120 ′ which allows the intelligent remote device 110 to emulate a security token peripheral device locally connected to the security token enabled computer system 105 over a wireless network 65 .
- the token emulator 182includes logical interfaces that facilitates the transparent exchange of information between the security token 75 ′ and the security token enabled computer system 105 in a protocol native to the security token 75 ′ and receives and routes a critical security parameter 85 ′ entered locally to the intelligent remote device 110 or received from the wireless network 65 ′ to the security token 75 ′. While shown as a middleware application 125 ′, it will be appreciated by one skilled in the art that the token emulator 182 may also be provided as a subroutine, ActiveX control, function, remotely invocable method associated with the Token API 145 or agent 160 installed in the security token enabled computer system 105 , or a local browser applet.
- the native protocolis generally in the format of an application protocol data unit (APDU) as specified in ISO 7816-4.
- APDUapplication protocol data unit
- the token emulatorfacilitates the transparent exchange of APDU commands and responses between the security token enabled computer system 105 and the intelligent remote device 110 .
- FIGS. 2A-2DVarious communications embodiments of the invention are provided which are described in the discussions included with FIGS. 2A-2D which follows.
- FIG. 1Ca detailed block diagram illustrating the interaction of the intelligent remote device 110 with the computer system 105 is shown. Details related to security considerations for information exchanged over the network 65 is omitted in the instant discussion in order to simplify the explanation and understanding of this portion of the invention. Security considerations are included in the discussion for FIGS. 2A-2D which follows.
- a user in possession of the intelligent remote device 110selects a token aware remote authentication application 175 ′.
- the remote authentication application 175 ′causes the token emulation application 182 to execute an alternate authentication method which implements a pre-established security policy or script associated with the extension EXT 155 ′ to the logon application 150 ′.
- Invocation of the logon application 150 ′causes the remote authentication application 175 ′ to prompt the user to enter his or her critical security parameter (CSP) 188 .
- the token emulator application 182generates an access request message AR 190 which is sent over the network 65 to the computer system 105 .
- the access request messageincludes information about the intelligent remote device such as a unique identifier, information about the operatively coupled security token 75 ′ such as a unique serial number, and information about the assigned network address.
- the access request messageis used to transit a wireless access point in wireless network arrangements.
- a userenters his or her CSP 188 through a user input device 85 ′ which is routed by the logon application 150 ′ via the resource manager 165 ′ to the APDU interface 170 ′ for protocol conversion.
- the CSP 188 incorporated in APDU formatis then routed through the security token device interface 70 and into the security token 75 ′.
- the security tokenperforms an authentication transaction which authenticates the user to the security token. User authentication is performed by comparison of the entered CSP 188 to a reference CSP stored inside the security token 75 ′.
- the CSP 188may be entered from the security token enabled computer system 105 or a remote location and securely sent over the wireless connection to the security token 75 ′ via the intelligent remote device 110 .
- This alternate embodiment of the inventionis particularly suited for biometric authentication which generally requires greater processing power than may be available from the intelligent remote device.
- receipt of the access request message AR 190is detected by the agent 160 which causes invocation of the alternate user authentication method.
- invocation of the alternate user authentication methodby detection of an access request message by the agent 160 causes the resource manager 165 to toggle the security token device drivers from the local token interface device 70 to the remote token device driver 180 .
- the token API 145is concurrently invoked by the extension EXT 155 which causes the authentication transaction to be initiated.
- Control of the counterpart applications installed on the security token enabled computer system 105 and the intelligent remote devicemay be performed using remote method invocation, subroutines and callable methods.
- One skilled in the artwill appreciate that many alternate mechanisms are available in the relative art to accomplish invocation and control of the counterpart applications and modules.
- a second part of the authentication transactionis performed under the control of the token API 145 .
- the second part of the authentication transactionutilizes a pre-established security policy or script associated with the logon application 125 .
- the security policymay include challenge/response, digital certificate exchange, dynamic passwords, etc.
- Authentication datais exchanged via the APDU interface 170 and resource manager 165 using the remote security token device interface 180 and network interface 60 and exchanged over the network 65 with the intelligent remote device 110 .
- Authentication data received at the network interface 60 ′ of the intelligent remote deviceis routed by the token emulator 182 via the resource manager 165 ′ and APDU interface 170 ′ through the security token device interface 70 ′ and into the security token 75 ′.
- a secure messaging arrangementis shown where a symmetric key pair Ksys′[ID] 205 ′, Ksys[ID] 205 having a unique session identifier assigned by the security token 75 ′ is used to provide end-to-end cryptographic protection of information exchanged between the security token ST 75 ′ via the intelligent remote device IRD 110 and the computer system CS 105 over the network 65 .
- the network 65includes a network gateway NG 225 which provides an ad hoc secure connection 230 between the network gateway and the intelligent remote device ERD 110 .
- the symmetric key pair Ksys′[ID] 205 ′, Ksys[ID] 205are incorporated into a symmetric cryptography arrangement which is described in commonly assigned co-pending U.S. application Ser. No. 10/424,783, first filed on Apr. 29, 2003 entitled “Universal Secure Messaging For Cryptographic Modules,” and is herein incorporated by reference.
- FIG. 2Ban alternate secure messaging arrangement is shown where two sets of symmetric key pairs Ksys′[ID] 205 ′, Ksys[ID] 205 , Ksys′[Idx] 210 ′, Ksys[Idx] 210 , each set of key pairs having a unique session identifier assigned by the security token 75 ′ are used to provide end-to-end cryptographic protection of information exchanged between the security token ST 75 ′ via the intelligent remote device IRD 110 and the computer system CS 105 over the network 65 .
- the first symmetric key pair set Ksys′[ID] 205 ′, Ksys[ID] 205is used to provide a trusted path between the security token 75 ′ and the intelligent remote device IRD 110 .
- the trusted pathallows the intelligent remote device 110 to be used in high security operating environments such as FIPS security levels 3 and 4 which requires that critical security parameters be entered into or output from a cryptographic module in an encrypted form to prevent interception of critical security parameters.
- the second key pair set Ksys′[Idx] 210 ′, Ksys[Idx] 210provides the secure communications connection between the intelligent remote device IRD 110 and the computer system 105 .
- Other aspects of this second secure communications embodimentare likewise described in the co-pending U.S. application Ser. No. 10/424,783.
- FIG. 2Canother secure communications embodiment is shown where an APDU pipe is established between the intelligent remote device IRD 110 and the computer system CS 105 .
- a pipe server 240 applicationis installed on the computer system CS 105 .
- the pipe server application 240is used to encapsulate APDU commands into communications packets, generally TCP/IP, for transmission over the network 65 to the intelligent remote device.
- the APDU'smay be encrypted before or after encapsulation in a network communications packet.
- the pipe server application 240is also used to separate incoming APDU responses from the network communications packets, convert the resulting APDU responses into a protocol readable by other applications installed on the computer system CS 110 .
- the intelligent remote device IRD 110includes a pipe client application 245 which is used to separate incoming APDU commands from the network communications packets and route the resulting APDU commands to the security token 75 ′.
- the pipe client application 245packages APDU responses generated by the security token 75 ′ into the network communications packets for transmission over the network 65 to the computer system.
- FIG. 2Danother embodiment of the invention is shown where a first secure communications connection is established between the security token and a first computer system CS 105 using a first symmetric key pair set Ksys′[ID] 205 ′, Ksys[ID] and a second secure connection is established between the security token and a second computer system CS′ 105 ′ using a second symmetric key pair set Ksys′[Idx] 210 ′, Ksys[Idx] 210 over the network.
- This embodimentillustrates that multiple computer systems may be authenticated using the intelligent remote device IRD 110 .
- network access privilegesmay be obtained by sending an authenticating message AM 270 from the first computer system CS 105 to an authenticating server AS 250 following successful completion the two factor authentication transaction.
- Additional embodiments of the inventionallow the user to send his or her CSP in the form of a biometric sample to the security token 75 ′ via the secure communications connection.
- a biometric scanner 280is provided on the second computer system CS′ 105 ′ which is securely connected to the security token over the network 65 ′.
- the biometric scanner 280may be associated with another computer system or directly connected to the network 65 as a network appliance.
- aural 260 or visual 255 feedbackmay be provided to the user following successful completion of the two factor authentication transaction.
- the aural 260 or visual 255 feedbackmay be provided at either or both the computer systems CS 105 , CS′ 105 and/or the intelligent remote device IRD 110 .
- FIG. 3a flow chart of the major steps involved in implementing this invention is shown in FIG. 3 .
- the processis initiated 300 by a user in possession of a security token equipped intelligent remote device.
- the intelligent remote deviceestablishes an ad hoc communications connection with a security token enabled computer system 305 .
- the userexecutes a remote authentication application installed in the intelligent remote device which causes an access request message to be sent to the computer system 310 if required to transit a network gateway or access point and invokes an alternate authentication method which allows the intelligent remote device to emulate a local security device peripheral connected to the computer system.
- the useris prompted by the remote authentication application to provide his or her critical security parameter (CSP) 315 .
- the critical security parametermay be entered from the intelligent remote device, security token enabled computer system or from another computer system in processing communications with the intelligent remote device.
- An authentication transactionis then performed in which the user is authenticated to the security token using the provided CSP 320 .
Landscapes
- Engineering & Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- Theoretical Computer Science (AREA)
- Signal Processing (AREA)
- Computer Hardware Design (AREA)
- General Engineering & Computer Science (AREA)
- Computer Networks & Wireless Communication (AREA)
- Software Systems (AREA)
- Physics & Mathematics (AREA)
- General Physics & Mathematics (AREA)
- Computing Systems (AREA)
- Small-Scale Networks (AREA)
- Mobile Radio Communication Systems (AREA)
- Computer And Data Communications (AREA)
- Telephonic Communication Services (AREA)
Abstract
Description
Claims (52)
Priority Applications (6)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| US10/740,497US7907935B2 (en) | 2003-12-22 | 2003-12-22 | Intelligent remote device |
| EP14167129.7AEP2770693B1 (en) | 2003-12-22 | 2004-12-22 | Remote device for emulating a local security device |
| ES04293088.3TES2481396T3 (en) | 2003-12-22 | 2004-12-22 | Remote device to emulate a local security device |
| EP04293088.3AEP1549018B1 (en) | 2003-12-22 | 2004-12-22 | Remote device for emulating a local security device |
| US12/931,351US8200195B2 (en) | 2003-12-22 | 2011-01-28 | Intelligent remote device |
| US13/472,752US20130019100A1 (en) | 2003-12-22 | 2012-05-16 | Intelligent remote device |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| US10/740,497US7907935B2 (en) | 2003-12-22 | 2003-12-22 | Intelligent remote device |
Related Child Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US12/931,351ContinuationUS8200195B2 (en) | 2003-12-22 | 2011-01-28 | Intelligent remote device |
Publications (2)
| Publication Number | Publication Date |
|---|---|
| US20050136964A1 US20050136964A1 (en) | 2005-06-23 |
| US7907935B2true US7907935B2 (en) | 2011-03-15 |
Family
ID=34552795
Family Applications (3)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US10/740,497Active2026-09-30US7907935B2 (en) | 2003-12-22 | 2003-12-22 | Intelligent remote device |
| US12/931,351Expired - LifetimeUS8200195B2 (en) | 2003-12-22 | 2011-01-28 | Intelligent remote device |
| US13/472,752AbandonedUS20130019100A1 (en) | 2003-12-22 | 2012-05-16 | Intelligent remote device |
Family Applications After (2)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US12/931,351Expired - LifetimeUS8200195B2 (en) | 2003-12-22 | 2011-01-28 | Intelligent remote device |
| US13/472,752AbandonedUS20130019100A1 (en) | 2003-12-22 | 2012-05-16 | Intelligent remote device |
Country Status (3)
| Country | Link |
|---|---|
| US (3) | US7907935B2 (en) |
| EP (2) | EP1549018B1 (en) |
| ES (1) | ES2481396T3 (en) |
Cited By (16)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20040143730A1 (en)* | 2001-06-15 | 2004-07-22 | Wu Wen | Universal secure messaging for remote security tokens |
| US20080089521A1 (en)* | 2003-04-29 | 2008-04-17 | Eric Le Saint | Universal secure messaging for cryptographic modules |
| US20110058516A1 (en)* | 2009-09-09 | 2011-03-10 | T-Mobile Usa, Inc. | Accessory Based Data Distribution |
| US20110175748A1 (en)* | 2010-01-19 | 2011-07-21 | T-Mobile Usa, Inc. | Element Mapping to Control Illumination of a Device Shell |
| USH2270H1 (en)* | 2009-07-09 | 2012-06-05 | Actividentity, Inc. | Open protocol for authentication and key establishment with privacy |
| US8595810B1 (en)* | 2013-01-13 | 2013-11-26 | Mourad Ben Ayed | Method for automatically updating application access security |
| US20140101212A1 (en)* | 2012-10-05 | 2014-04-10 | Gary Robin Maze | Document management systems and methods |
| US20140113589A1 (en)* | 2012-10-18 | 2014-04-24 | Futurewei Technologies, Inc. | Seamless Telephone Login |
| US20140359301A1 (en)* | 2003-04-29 | 2014-12-04 | Assa Abloy Ab | Uniform modular framework for a host computer system |
| US9215075B1 (en) | 2013-03-15 | 2015-12-15 | Poltorak Technologies Llc | System and method for secure relayed communications from an implantable medical device |
| US20160253525A1 (en)* | 2013-10-29 | 2016-09-01 | Feitian Technologies Co., Ltd. | Implementation method for driving of software and hardware supporting opensc |
| US20200374284A1 (en)* | 2019-05-20 | 2020-11-26 | Citrix Systems, Inc. | Virtual delivery appliance and system with remote authentication and related methods |
| US10936191B1 (en) | 2018-12-05 | 2021-03-02 | Pure Storage, Inc. | Access control for a computing system |
| US11436461B2 (en) | 2005-02-22 | 2022-09-06 | Kepler Computing Inc. | Mobile phone with magnetic card emulation |
| US11632360B1 (en) | 2018-07-24 | 2023-04-18 | Pure Storage, Inc. | Remote access to a storage device |
| US11997197B1 (en)* | 2023-06-29 | 2024-05-28 | Cyberark Software Ltd. | Push architecture for secure provision of secrets |
Families Citing this family (42)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| JP2005085266A (en)* | 2003-09-04 | 2005-03-31 | Stmicroelectronics Sa | Access control of microprocessor peripheral device |
| US8055907B2 (en)* | 2003-10-24 | 2011-11-08 | Microsoft Corporation | Programming interface for a computer platform |
| US7477913B2 (en)* | 2005-04-04 | 2009-01-13 | Research In Motion Limited | Determining a target transmit power of a wireless transmission according to security requirements |
| US20060230423A1 (en)* | 2005-04-11 | 2006-10-12 | Doug Burgett | System and method for providing calibration/verification services at a CATV service organization site on a prepaid basis |
| DE102005032311A1 (en)* | 2005-07-11 | 2007-01-25 | Giesecke & Devrient Gmbh | Method for the subsequent implementation of a SIM functionality in a security module |
| US7627124B2 (en)* | 2005-09-22 | 2009-12-01 | Konica Minolta Technology U.S.A., Inc. | Wireless communication authentication process and system |
| EP1791315A1 (en)* | 2005-11-23 | 2007-05-30 | Research In Motion Limited | System and method to provide mobile VPN connectivity |
| US7882557B2 (en) | 2005-11-23 | 2011-02-01 | Research In Motion Limited | System and method to provide built-in and mobile VPN connectivity |
| US20070198244A1 (en)* | 2006-01-31 | 2007-08-23 | King James M | Emulation of a device protocol |
| US9137012B2 (en)* | 2006-02-03 | 2015-09-15 | Emc Corporation | Wireless authentication methods and apparatus |
| WO2007092429A2 (en)* | 2006-02-06 | 2007-08-16 | Id Rank Security, Inc. | Secure system and method for providing same |
| US7747540B2 (en)* | 2006-02-24 | 2010-06-29 | Microsoft Corporation | Account linking with privacy keys |
| WO2008064261A2 (en)* | 2006-11-21 | 2008-05-29 | Telos Corporation | Method and system for remote security token extension |
| US7991158B2 (en)* | 2006-12-13 | 2011-08-02 | Tyfone, Inc. | Secure messaging |
| US20080244208A1 (en)* | 2007-03-30 | 2008-10-02 | Narendra Siva G | Memory card hidden command protocol |
| US20080301433A1 (en)* | 2007-05-30 | 2008-12-04 | Atmel Corporation | Secure Communications |
| US9741027B2 (en)* | 2007-12-14 | 2017-08-22 | Tyfone, Inc. | Memory card based contactless devices |
| US20090197573A1 (en)* | 2008-02-06 | 2009-08-06 | Broadcom Corporation | Secure use of a handheld computing unit |
| US12147863B2 (en) | 2008-08-08 | 2024-11-19 | Icashe, Inc. | Method and apparatus for transmitting data via NFC for mobile applications including mobile payments and ticketing |
| US7961101B2 (en) | 2008-08-08 | 2011-06-14 | Tyfone, Inc. | Small RFID card with integrated inductive element |
| US8451122B2 (en) | 2008-08-08 | 2013-05-28 | Tyfone, Inc. | Smartcard performance enhancement circuits and systems |
| TWI420398B (en)* | 2009-02-24 | 2013-12-21 | Tyfone Inc | Contactless device with miniaturized antenna |
| US9596989B2 (en) | 2009-03-12 | 2017-03-21 | Raytheon Company | Networked symbiotic edge user infrastructure |
| US8855550B2 (en) | 2011-01-14 | 2014-10-07 | Covidien Lp | Wireless relay module having emergency call functionality |
| US8903308B2 (en) | 2011-01-14 | 2014-12-02 | Covidien Lp | System and method for patient identification in a remote monitoring system |
| US8897198B2 (en) | 2011-01-14 | 2014-11-25 | Covidien Lp | Medical device wireless network architectures |
| US9495511B2 (en) | 2011-03-01 | 2016-11-15 | Covidien Lp | Remote monitoring systems and methods for medical devices |
| US9020419B2 (en) | 2011-01-14 | 2015-04-28 | Covidien, LP | Wireless relay module for remote monitoring systems having power and medical device proximity monitoring functionality |
| US9294281B2 (en) | 2012-02-10 | 2016-03-22 | Microsoft Technology Licensing, Llc | Utilization of a protected module to prevent offline dictionary attacks |
| CN104620245A (en) | 2012-09-13 | 2015-05-13 | 柯惠有限合伙公司 | Docking station for enteral feeding pump |
| US9479489B2 (en)* | 2013-03-05 | 2016-10-25 | Comcast Cable Communications, Llc | Systems and methods for providing services |
| US9270649B1 (en)* | 2013-03-11 | 2016-02-23 | Emc Corporation | Secure software authenticator data transfer between processing devices |
| US9426154B2 (en) | 2013-03-14 | 2016-08-23 | Amazon Technologies, Inc. | Providing devices as a service |
| USD746441S1 (en) | 2013-09-13 | 2015-12-29 | Covidien Lp | Pump |
| CN103647770A (en)* | 2013-12-10 | 2014-03-19 | 上海众人网络安全技术有限公司 | Subaudio electronic cipherer and dynamic password generation method thereof |
| JP2015118400A (en)* | 2013-12-16 | 2015-06-25 | キヤノン株式会社 | Information processing device, control method thereof, and program |
| US9742752B1 (en)* | 2014-06-20 | 2017-08-22 | Ca, Inc. | Data backup and self-service data restoration |
| US10565396B2 (en) | 2016-03-30 | 2020-02-18 | Zoll Medical Corporation | Patient data hub |
| US20190130082A1 (en)* | 2017-10-26 | 2019-05-02 | Motorola Mobility Llc | Authentication Methods and Devices for Allowing Access to Private Data |
| JP7052616B2 (en)* | 2018-07-25 | 2022-04-12 | 大日本印刷株式会社 | Communication devices, data transmission methods, and programs |
| US20230209341A1 (en)* | 2021-11-04 | 2023-06-29 | Waters Technologies Ireland Limited | Methods, mediums, and systems for accessing analytical chemistry systems |
| US20250233751A1 (en)* | 2024-01-11 | 2025-07-17 | Schneider Electric USA, Inc. | Temporary Enablement of Functionality of a Secure Device |
Citations (55)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US4945468A (en) | 1988-02-01 | 1990-07-31 | International Business Machines Corporation | Trusted path mechanism for virtual terminal environments |
| US4993068A (en) | 1989-11-27 | 1991-02-12 | Motorola, Inc. | Unforgeable personal identification system |
| FR2695364A1 (en) | 1992-09-04 | 1994-03-11 | Renault | Electronic anti-theft system for motor vehicle. |
| US5491752A (en) | 1993-03-18 | 1996-02-13 | Digital Equipment Corporation, Patent Law Group | System for increasing the difficulty of password guessing attacks in a distributed authentication scheme employing authentication tokens |
| EP0733971A2 (en) | 1995-03-22 | 1996-09-25 | Sun Microsystems, Inc. | Method and apparatus for managing connections for communication among objects in a distributed object system |
| EP0737907A2 (en) | 1992-04-17 | 1996-10-16 | Secure Computing Corporation | Cryptographic data security in a secured computer system |
| US5577121A (en) | 1994-06-09 | 1996-11-19 | Electronic Payment Services, Inc. | Transaction system for integrated circuit cards |
| FR2738436A1 (en) | 1995-03-06 | 1997-03-07 | Novella Carmelo | Access control system using electronic key |
| US5655148A (en) | 1994-05-27 | 1997-08-05 | Microsoft Corporation | Method for automatically configuring devices including a network adapter without manual intervention and without prior configuration information |
| US5802176A (en) | 1996-03-22 | 1998-09-01 | Activcard | System for controlling access to a function, using a plurality of dynamic encryption variables |
| US5841868A (en) | 1993-09-21 | 1998-11-24 | Helbig, Sr.; Walter Allen | Trusted computer system |
| DE19724901A1 (en) | 1997-06-12 | 1998-12-17 | Siemens Nixdorf Inf Syst | Mobile radio telephone and those with a coupled computer for Internet or network applications and method for operating such a combination of devices |
| US5878142A (en) | 1994-07-12 | 1999-03-02 | Information Resource Engineering, Inc. | Pocket encrypting and authenticating communications device |
| US5887065A (en) | 1996-03-22 | 1999-03-23 | Activcard | System and method for user authentication having clock synchronization |
| EP0913979A2 (en) | 1997-10-30 | 1999-05-06 | Robert Bosch Gmbh | Mobile telephone and method for operating the same |
| US5937068A (en) | 1996-03-22 | 1999-08-10 | Activcard | System and method for user authentication employing dynamic encryption variables |
| EP0949595A2 (en) | 1998-03-30 | 1999-10-13 | Citicorp Development Center, Inc. | Method and system for managing applications for a multi-function smartcard |
| EP0957651A2 (en) | 1998-05-12 | 1999-11-17 | Sectra Communications AB | Mobile telephone with cypher card |
| US6005942A (en) | 1997-03-24 | 1999-12-21 | Visa International Service Association | System and method for a multi-application smart card which can facilitate a post-issuance download of an application onto the smart card |
| US6016476A (en) | 1997-08-11 | 2000-01-18 | International Business Machines Corporation | Portable information and transaction processing system and method utilizing biometric authorization and digital certificate security |
| US6038551A (en) | 1996-03-11 | 2000-03-14 | Microsoft Corporation | System and method for configuring and managing resources on a multi-purpose integrated circuit card using a personal computer |
| US6076075A (en) | 1995-09-25 | 2000-06-13 | Cardis Enterprise International N.V. | Retail unit and a payment unit for serving a customer on a purchase and method for executing the same |
| US6108789A (en) | 1998-05-05 | 2000-08-22 | Liberate Technologies | Mechanism for users with internet service provider smart cards to roam among geographically disparate authorized network computer client devices without mediation of a central authority |
| WO2000049820A1 (en) | 1999-02-18 | 2000-08-24 | Schlumberger Systemes | Identification module and method in first and second telecommunication networks |
| EP1061482A1 (en) | 1999-06-18 | 2000-12-20 | Citicorp Development Center, Inc. | Method, system, and apparatus for transmitting, receiving, and displaying information |
| US6169804B1 (en) | 1996-11-21 | 2001-01-02 | Pitney Bowes Inc. | Method for verifying the expected postage security device and its status |
| US6175922B1 (en) | 1996-12-04 | 2001-01-16 | Esign, Inc. | Electronic transaction systems and methods therefor |
| US6178504B1 (en) | 1998-03-12 | 2001-01-23 | Cheyenne Property Trust C/O Data Securities International, Inc. | Host system elements for an international cryptography framework |
| WO2001017310A1 (en) | 1999-08-31 | 2001-03-08 | Telefonaktiebolaget L M Ericsson (Publ) | Gsm security for packet data networks |
| EP1128335A2 (en) | 2000-02-28 | 2001-08-29 | Klaus Döbel | Access control device |
| EP1132800A2 (en) | 2000-03-08 | 2001-09-12 | Rainbow Technologies Inc. | Non-wire contact device application for cryptographic module interfaces |
| US6308317B1 (en) | 1996-10-25 | 2001-10-23 | Schlumberger Technologies, Inc. | Using a high level programming language with a microcontroller |
| WO2001098876A2 (en) | 2000-06-21 | 2001-12-27 | Microsoft Corporation | Filtering a permission set using permission requests associated with a code assembly |
| US20020002684A1 (en) | 1998-05-01 | 2002-01-03 | Barbara L. Fox | Intelligent trust management method and system |
| US20020040936A1 (en) | 1998-10-27 | 2002-04-11 | David C. Wentker | Delegated management of smart card applications |
| US6385729B1 (en)* | 1998-05-26 | 2002-05-07 | Sun Microsystems, Inc. | Secure token device access to services provided by an internet service provider (ISP) |
| US6397328B1 (en) | 1996-11-21 | 2002-05-28 | Pitney Bowes Inc. | Method for verifying the expected postage security device and an authorized host system |
| US20020095587A1 (en) | 2001-01-17 | 2002-07-18 | International Business Machines Corporation | Smart card with integrated biometric sensor |
| US20020162021A1 (en)* | 2001-04-30 | 2002-10-31 | Audebert Yves Louis Gabriel | Method and system for establishing a remote connection to a personal security device |
| WO2002089444A1 (en) | 2001-04-30 | 2002-11-07 | Activcard Ireland, Limited | Method and system for authenticating a personal security device vis-a-vis at least one remote computer system |
| WO2002091316A1 (en) | 2001-04-30 | 2002-11-14 | Activcard Ireland, Limited | Method and system for remote activation and management of personal security devices |
| US20020169975A1 (en) | 2001-05-10 | 2002-11-14 | Gordon Good | Security policy management for network devices |
| US20020194499A1 (en)* | 2001-06-15 | 2002-12-19 | Audebert Yves Louis Gabriel | Method, system and apparatus for a portable transaction device |
| EP1271436A2 (en) | 2001-06-25 | 2003-01-02 | NTT DoCoMo, Inc. | A mobile terminal authentication method and a mobile terminal therefor |
| US6547150B1 (en) | 1999-05-11 | 2003-04-15 | Microsoft Corporation | Smart card application development system and method |
| US20030119482A1 (en)* | 2000-05-26 | 2003-06-26 | Pierre Girard | Making secure data exchanges between controllers |
| US20030154375A1 (en) | 2002-02-08 | 2003-08-14 | Weimin Yang | Universal crypto-adaptor system for supporting multiple APIs and multiple smart cards |
| US6609199B1 (en) | 1998-10-26 | 2003-08-19 | Microsoft Corporation | Method and apparatus for authenticating an open system application to a portable IC device |
| US6657956B1 (en) | 1996-03-07 | 2003-12-02 | Bull Cp8 | Method enabling secure access by a station to at least one server, and device using same |
| US6694436B1 (en) | 1998-05-22 | 2004-02-17 | Activcard | Terminal and system for performing secure electronic transactions |
| US6738901B1 (en) | 1999-12-15 | 2004-05-18 | 3M Innovative Properties Company | Smart card controlled internet access |
| US6748532B1 (en) | 1999-10-29 | 2004-06-08 | Sun Microsystems, Inc. | Universal smart card access system |
| US6788956B2 (en) | 1999-12-06 | 2004-09-07 | Alcatel | Terminal to execute a terminal application |
| US7024689B2 (en) | 2002-12-13 | 2006-04-04 | Intuit, Inc. | Granting access rights to unattended software |
| US7152230B2 (en) | 2000-11-09 | 2006-12-19 | Hitachi, Ltd. | Storage media storing data related to smart card, smart card system and smart card application loading method |
Family Cites Families (3)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US6230002B1 (en)* | 1997-11-19 | 2001-05-08 | Telefonaktiebolaget L M Ericsson (Publ) | Method, and associated apparatus, for selectively permitting access by a mobile terminal to a packet data network |
| US6797599B2 (en)* | 2001-08-31 | 2004-09-28 | Texas Instruments Incorporated | Gate structure and method |
| US7506161B2 (en)* | 2003-09-02 | 2009-03-17 | Authernative, Inc. | Communication session encryption and authentication system |
- 2003
- 2003-12-22USUS10/740,497patent/US7907935B2/enactiveActive
- 2004
- 2004-12-22EPEP04293088.3Apatent/EP1549018B1/ennot_activeExpired - Lifetime
- 2004-12-22ESES04293088.3Tpatent/ES2481396T3/ennot_activeExpired - Lifetime
- 2004-12-22EPEP14167129.7Apatent/EP2770693B1/ennot_activeExpired - Lifetime
- 2011
- 2011-01-28USUS12/931,351patent/US8200195B2/ennot_activeExpired - Lifetime
- 2012
- 2012-05-16USUS13/472,752patent/US20130019100A1/ennot_activeAbandoned
Patent Citations (57)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US4945468A (en) | 1988-02-01 | 1990-07-31 | International Business Machines Corporation | Trusted path mechanism for virtual terminal environments |
| US4993068A (en) | 1989-11-27 | 1991-02-12 | Motorola, Inc. | Unforgeable personal identification system |
| EP0737907A2 (en) | 1992-04-17 | 1996-10-16 | Secure Computing Corporation | Cryptographic data security in a secured computer system |
| FR2695364A1 (en) | 1992-09-04 | 1994-03-11 | Renault | Electronic anti-theft system for motor vehicle. |
| US5491752A (en) | 1993-03-18 | 1996-02-13 | Digital Equipment Corporation, Patent Law Group | System for increasing the difficulty of password guessing attacks in a distributed authentication scheme employing authentication tokens |
| US5841868A (en) | 1993-09-21 | 1998-11-24 | Helbig, Sr.; Walter Allen | Trusted computer system |
| US5655148A (en) | 1994-05-27 | 1997-08-05 | Microsoft Corporation | Method for automatically configuring devices including a network adapter without manual intervention and without prior configuration information |
| US5577121A (en) | 1994-06-09 | 1996-11-19 | Electronic Payment Services, Inc. | Transaction system for integrated circuit cards |
| US5878142A (en) | 1994-07-12 | 1999-03-02 | Information Resource Engineering, Inc. | Pocket encrypting and authenticating communications device |
| FR2738436A1 (en) | 1995-03-06 | 1997-03-07 | Novella Carmelo | Access control system using electronic key |
| EP0733971A2 (en) | 1995-03-22 | 1996-09-25 | Sun Microsystems, Inc. | Method and apparatus for managing connections for communication among objects in a distributed object system |
| US6076075A (en) | 1995-09-25 | 2000-06-13 | Cardis Enterprise International N.V. | Retail unit and a payment unit for serving a customer on a purchase and method for executing the same |
| US6657956B1 (en) | 1996-03-07 | 2003-12-02 | Bull Cp8 | Method enabling secure access by a station to at least one server, and device using same |
| US6038551A (en) | 1996-03-11 | 2000-03-14 | Microsoft Corporation | System and method for configuring and managing resources on a multi-purpose integrated circuit card using a personal computer |
| US5887065A (en) | 1996-03-22 | 1999-03-23 | Activcard | System and method for user authentication having clock synchronization |
| US5937068A (en) | 1996-03-22 | 1999-08-10 | Activcard | System and method for user authentication employing dynamic encryption variables |
| US5802176A (en) | 1996-03-22 | 1998-09-01 | Activcard | System for controlling access to a function, using a plurality of dynamic encryption variables |
| US6308317B1 (en) | 1996-10-25 | 2001-10-23 | Schlumberger Technologies, Inc. | Using a high level programming language with a microcontroller |
| US6397328B1 (en) | 1996-11-21 | 2002-05-28 | Pitney Bowes Inc. | Method for verifying the expected postage security device and an authorized host system |
| US6169804B1 (en) | 1996-11-21 | 2001-01-02 | Pitney Bowes Inc. | Method for verifying the expected postage security device and its status |
| US6175922B1 (en) | 1996-12-04 | 2001-01-16 | Esign, Inc. | Electronic transaction systems and methods therefor |
| US6005942A (en) | 1997-03-24 | 1999-12-21 | Visa International Service Association | System and method for a multi-application smart card which can facilitate a post-issuance download of an application onto the smart card |
| US6233683B1 (en) | 1997-03-24 | 2001-05-15 | Visa International Service Association | System and method for a multi-application smart card which can facilitate a post-issuance download of an application onto the smart card |
| WO1998057510A2 (en) | 1997-06-12 | 1998-12-17 | Siemens Nixdorf Informationssysteme Ag | Telecommunication and/or remote control device with a chip card unit, same device with a coupled computer for internet or network applications |
| DE19724901A1 (en) | 1997-06-12 | 1998-12-17 | Siemens Nixdorf Inf Syst | Mobile radio telephone and those with a coupled computer for Internet or network applications and method for operating such a combination of devices |
| US6016476A (en) | 1997-08-11 | 2000-01-18 | International Business Machines Corporation | Portable information and transaction processing system and method utilizing biometric authorization and digital certificate security |
| EP0913979A2 (en) | 1997-10-30 | 1999-05-06 | Robert Bosch Gmbh | Mobile telephone and method for operating the same |
| US6178504B1 (en) | 1998-03-12 | 2001-01-23 | Cheyenne Property Trust C/O Data Securities International, Inc. | Host system elements for an international cryptography framework |
| EP0949595A2 (en) | 1998-03-30 | 1999-10-13 | Citicorp Development Center, Inc. | Method and system for managing applications for a multi-function smartcard |
| US20020002684A1 (en) | 1998-05-01 | 2002-01-03 | Barbara L. Fox | Intelligent trust management method and system |
| US6108789A (en) | 1998-05-05 | 2000-08-22 | Liberate Technologies | Mechanism for users with internet service provider smart cards to roam among geographically disparate authorized network computer client devices without mediation of a central authority |
| EP0957651A2 (en) | 1998-05-12 | 1999-11-17 | Sectra Communications AB | Mobile telephone with cypher card |
| US6694436B1 (en) | 1998-05-22 | 2004-02-17 | Activcard | Terminal and system for performing secure electronic transactions |
| US6385729B1 (en)* | 1998-05-26 | 2002-05-07 | Sun Microsystems, Inc. | Secure token device access to services provided by an internet service provider (ISP) |
| US6609199B1 (en) | 1998-10-26 | 2003-08-19 | Microsoft Corporation | Method and apparatus for authenticating an open system application to a portable IC device |
| US20020040936A1 (en) | 1998-10-27 | 2002-04-11 | David C. Wentker | Delegated management of smart card applications |
| WO2000049820A1 (en) | 1999-02-18 | 2000-08-24 | Schlumberger Systemes | Identification module and method in first and second telecommunication networks |
| US6547150B1 (en) | 1999-05-11 | 2003-04-15 | Microsoft Corporation | Smart card application development system and method |
| EP1061482A1 (en) | 1999-06-18 | 2000-12-20 | Citicorp Development Center, Inc. | Method, system, and apparatus for transmitting, receiving, and displaying information |
| WO2001017310A1 (en) | 1999-08-31 | 2001-03-08 | Telefonaktiebolaget L M Ericsson (Publ) | Gsm security for packet data networks |
| US6748532B1 (en) | 1999-10-29 | 2004-06-08 | Sun Microsystems, Inc. | Universal smart card access system |
| US6788956B2 (en) | 1999-12-06 | 2004-09-07 | Alcatel | Terminal to execute a terminal application |
| US6738901B1 (en) | 1999-12-15 | 2004-05-18 | 3M Innovative Properties Company | Smart card controlled internet access |
| EP1128335A2 (en) | 2000-02-28 | 2001-08-29 | Klaus Döbel | Access control device |
| EP1132800A2 (en) | 2000-03-08 | 2001-09-12 | Rainbow Technologies Inc. | Non-wire contact device application for cryptographic module interfaces |
| US20030119482A1 (en)* | 2000-05-26 | 2003-06-26 | Pierre Girard | Making secure data exchanges between controllers |
| WO2001098876A2 (en) | 2000-06-21 | 2001-12-27 | Microsoft Corporation | Filtering a permission set using permission requests associated with a code assembly |
| US7152230B2 (en) | 2000-11-09 | 2006-12-19 | Hitachi, Ltd. | Storage media storing data related to smart card, smart card system and smart card application loading method |
| US20020095587A1 (en) | 2001-01-17 | 2002-07-18 | International Business Machines Corporation | Smart card with integrated biometric sensor |
| US20020162021A1 (en)* | 2001-04-30 | 2002-10-31 | Audebert Yves Louis Gabriel | Method and system for establishing a remote connection to a personal security device |
| WO2002091316A1 (en) | 2001-04-30 | 2002-11-14 | Activcard Ireland, Limited | Method and system for remote activation and management of personal security devices |
| WO2002089444A1 (en) | 2001-04-30 | 2002-11-07 | Activcard Ireland, Limited | Method and system for authenticating a personal security device vis-a-vis at least one remote computer system |
| US20020169975A1 (en) | 2001-05-10 | 2002-11-14 | Gordon Good | Security policy management for network devices |
| US20020194499A1 (en)* | 2001-06-15 | 2002-12-19 | Audebert Yves Louis Gabriel | Method, system and apparatus for a portable transaction device |
| EP1271436A2 (en) | 2001-06-25 | 2003-01-02 | NTT DoCoMo, Inc. | A mobile terminal authentication method and a mobile terminal therefor |
| US20030154375A1 (en) | 2002-02-08 | 2003-08-14 | Weimin Yang | Universal crypto-adaptor system for supporting multiple APIs and multiple smart cards |
| US7024689B2 (en) | 2002-12-13 | 2006-04-04 | Intuit, Inc. | Granting access rights to unattended software |
Non-Patent Citations (56)
| Title |
|---|
| "Background for the Government Interoperability Specification," Jun. 2002, 2 pages total. |
| "Ensure Technologies: How Xyloc Works," http://www.ensuretech.com/products/technology/technology.html, Dec. 10, 2003, 4 pages total. |
| "Global Platform Card Specification v2.0.1", [Online] XP002362776, www.globalplafform.org/specifications/archived/card-tech-201.zip, Apr. 7, 2000, 180 pages. |
| "Government Smart Card, Smart Card Standards and the Government Smart Card Interoperability Specification (GSC-IS)," Apr. 24, 2002, pp. 1-15. |
| "Interoperability Specification for ICCs and Personal Computer Systems," Part 1, "Introduction and Architecture Overview," PC/SC workgroup, Revision 1.0, Dec. 1997, 21 pages total. |
| "Interoperability Specification for ICCs and Personal Computer Systems," Part 2, "Interface Requirements for Compatible IC Cards and Readers," PC/SC workgroup, Revision 1.0, Dec. 1997, 22 pages total. |
| "Interoperability Specification for ICCs and Personal Computer Systems," Part 3, "Requirements for PC-connected Interface Devices," PC/SC workgroup, Revision 1.0, Dec. 1997, 23 pages total. |
| "Interoperability Specification for ICCs and Personal Computer Systems," Part 4, "IFD Design Considerations and Reference Design Information," PC/SC workgroup, Revision 1.0, Dec. 1997, 22 pages total. |
| "Interoperability Specification for ICCs and Personal Computer Systems," Part 5, "ICC Resource Manager Definition," PC/SC workgroup, Revision 1.0, Dec. 1997, 24 pages total. |
| "Interoperability Specification for ICCs and Personal Computer Systems," Part 6, "ICC Searvice Provider Interface Definition," PC/SC workgroup, Revision 1.0, Dec. 1997, 41 pages total. |
| "Interoperability Specification for ICCs and Personal Computer Systems," Part 7, "Application Domain and Developer Design Considerations," PC/SC workgroup, Revision 1.0, Dec. 1997, 17 pages total. |
| "Interoperability Specification for ICCs and Personal Computer Systems," Part 8, "Recommendations for ICC Security and Privacy Devices," PC/SC workgroup, Revision 1.0, Dec. 1997, 42 pages total. |
| "Java Card(TM) 2.2 Application Programming Interface," Sun Microsystems, Inc., Palo Alto, CA, Revision 1.1, Sep. 2002, pp. i-195. |
| "Java Card™ 2.2 Application Programming Interface," Sun Microsystems, Inc., Palo Alto, CA, Revision 1.1, Sep. 2002, pp. i-195. |
| "M.U.S.C.L.E, Movement for the Use of Smart Cards in a Linux Environment," http://www.linuxnet.com/apps.html, Dec. 10, 2003, 1 page total. |
| "M.U.S.C.L.E, Movement for the Use of Smart Cards in a Linux Environment," http://www.linuxnet.com/index.html, Dec. 10, 2003, 1 page total. |
| "M.U.S.C.L.E, Movement for the Use of Smart Cards in a Linux Environment," http://www.linuxnet.com/software.html, Dec. 10, 2003, 1 page total. |
| "Microsoft Windows 2000 Server, Smart Cards," Microsoft Corporation, 1999, 16 pages total. |
| "Microsoft Windows 2000 Server, The Essential of Replacing the Microsoft Graphical Identification and Authentication Dynamic Link Library," Hutx et al., Microsoft Corporation, Jun. 2001, 34 pages total. |
| "OpenCard and PC/SC-Two New Industry Initiatives for Smart Cards," Seliger F., 13 pages total. |
| "OpenCard Framework 1.2-Programmer's Guide," IBM, 4th Edition, Dec. 1999, 93 pages total. |
| "OpenCard Framework-General Information Web Document," IBM, 2nd Edition, Oct. 1998, 24 pages total. |
| "PC/SC Workgroup Specification Overview," http://www.pcscworkgroup.com/specifications/SpecificationsOverview.html, Dec. 10, 2003, 2 pages total. |
| "PPP EAP TLS Authentication Protocol," Network Working Group, Request for 2716, Adoba, et al., Oct. 1999, 23 pages total. |
| "PPP Extensible Authentication Protocol (EAP)," Network Working Group, Request for comments 2284, Blunk, et al., Mar. 1998, 15 pages total. |
| "Strong Authentication Using a Mobile Phone as a Security Token," Connectotel, Ltd., 1999-2001. |
| "Understanding the Layers of Wireless LAN Security & Management," AirDefense, 2003, 6 pages total. |
| A. Amegah, et al., "An Access Controller for Java Card", Gemplus, Security Technology Department, Jun. 20-21, 2001, pp. 1-8. |
| Abrams, et al., "New Thinking About Information Technology Security," Computers & Security, Elsevier Science Publishers, Amsterdam, vol. 14, No. 1, XP004001979, pp. 69-81, 1995. |
| D. Perovich, et al., "A Simple Methodology for Secure Object Sharing," pp. 1-7, Oct. 2000. |
| Dermot McGrath "Even With Its Drawbacks, Bluetooth Could Be One Protocol That Lives Up to Its Hype," Microtimes Magazine, Mar. 26, 2001. |
| Deutche Telecom AG: "Das TeleSec LineCrypt L Fur Sichere Netzwerkverbindungen," Linecrypt L Benutzeerhandbuch, XP-002207127, pp. 5-38, Apr. 14, 2000. |
| Deutche Telecom AG: "Das TeleSec LineCrypt L Fur Sichere Netzwerkverbindungen," Linecrypt L Benutzerhandbuch, XP002207127, pp. 5-39, Apr. 14, 2000. |
| Dray, Jim, "The Government Smart Card Interoperability Specification," CardTech/SecurTech, Apr. 2002, 12 pages total. |
| European Search Report dated Apr. 12, 2005. |
| European Search Report dated Apr. 7, 2005. |
| European Search Report dated Jan. 12, 2005. |
| European Search Report dated Jun. 9, 2004. |
| European Search Report dated May 27, 2005. |
| FIPS Pub 140-2, "Security Requirements For Cryptographic Modules," Information Technology Laboratory, National Institute of Standards and Technology, May 25, 2001, pp. i-55. |
| Hassler, et al., "Opencard Framework Application Development Using Java to Buljd Platform-Independent Smartcards," , Dr. Dobb's Journal, M& T Publication, Redwood City, CA, vol. 309, XP001001494, pp. 70, 72, 74-76, Feb. 2000. |
| Java Card(TM) 2.2 Runtime Environment (JCRE) Specification,: Sun Microsystems, Inc., Palo Alto, CA, Jun. 2002, pp. i-274. |
| Java Card™ 2.2 Runtime Environment (JCRE) Specification,: Sun Microsystems, Inc., Palo Alto, CA, Jun. 2002, pp. i-274. |
| Mary Behr, et al., "Choose Your Weapon," PC Magazine, Apr. 24, 2001. |
| Menezes, A. J. et al., "Handbook of Applied Cryptography,", CRC Press Series on Discrete Mathematics and Its Applications, Boca Raton, FL, CRC Press, SP002283799, pp. 489-508. |
| Office Action dated Aug. 2, 2006 in U.S. Appl. No. 10/424,783. |
| Office Action dated Feb. 5, 2007 in U.S. Appl. No. 10/402,960. |
| Office Action dated Oct. 5, 2006 in U.S. Appl. No. 10/425,028. |
| P. Girard, et al., "Java Card or How to Cope with the New Security Issues Raised by Open Cards?," Gemplus Research Lab, Technical Report SM-99-02, Jun. 1999, 12 pages total. |
| R. C. Ferreira: "The Smart Card: A high security tool in EDP", Philips Telecommunication Review, Philips Telecommunicatie Industrie N.V. Hilversum, NL, vol. 47, No. 3, Sep. 1, 1989, pp. 1-19. XP000072642. |
| S. Motre: "Formal Model and Implementation of the Java Card Dynamic Security Policy", Technical Report SM-99-09, XP002267048, Jul. 1999, 13 pages. |
| Shanley, "Plug and Play System Architecture," Mindshare Inc., Addision Wesley, XP002313206, 7 pages total, 1995. |
| Shanley, "Plug and Play System Architecture," Mindshare Inc.,Plug and Play System Architecture, System Architecture Series, XP002042679, pp. 14-15, 43-50, 1995. |
| Sun Microsystems: "Java Card 2.1.1 Runtime Environment (JCRE) Specification", Internet Citation, XP002167364, ftp.java.sun.com/pub/javacard/adjfklad-211/java-card-kit-2-1-1-doc.zip, May 18, 2000, pp. i-x and 1-62. |
| T. Schwarzhoff, et al., "Government Smart Card Interoperability Specification," National Institute of Standards and Technology, Technology Administration U.S. Department of Commerce, Version 2.1, Interagency Report 6887-2003 Edition, Jul. 16, 2003, 230 pages total. |
| Zao, et al., "Domain Based Internet Security Policy Management," Proceedings Darpa Information Survivability Conference and Exposition, XP002276485, pp. 41-53 Dec. 31, 1999. |
Cited By (38)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US8209753B2 (en)* | 2001-06-15 | 2012-06-26 | Activcard, Inc. | Universal secure messaging for remote security tokens |
| US20040143730A1 (en)* | 2001-06-15 | 2004-07-22 | Wu Wen | Universal secure messaging for remote security tokens |
| US20140359301A1 (en)* | 2003-04-29 | 2014-12-04 | Assa Abloy Ab | Uniform modular framework for a host computer system |
| US20080089521A1 (en)* | 2003-04-29 | 2008-04-17 | Eric Le Saint | Universal secure messaging for cryptographic modules |
| US9576111B2 (en)* | 2003-04-29 | 2017-02-21 | Assa Abloy Ab | Uniform modular framework for a host computer system |
| US10554393B2 (en) | 2003-04-29 | 2020-02-04 | Assa Abloy Ab | Universal secure messaging for cryptographic modules |
| US8306228B2 (en) | 2003-04-29 | 2012-11-06 | Activcard Ireland, Limited | Universal secure messaging for cryptographic modules |
| US11436461B2 (en) | 2005-02-22 | 2022-09-06 | Kepler Computing Inc. | Mobile phone with magnetic card emulation |
| US11720777B2 (en) | 2005-02-22 | 2023-08-08 | Icashe, Inc. | Mobile phone with magnetic card emulation |
| US12223378B2 (en) | 2005-02-22 | 2025-02-11 | Icashe, Inc. | Electronic transaction mechanism |
| US20120144193A1 (en)* | 2009-07-09 | 2012-06-07 | Le Saint Eric F | Open protocol for authentication and key establishment with privacy |
| USH2270H1 (en)* | 2009-07-09 | 2012-06-05 | Actividentity, Inc. | Open protocol for authentication and key establishment with privacy |
| US8832815B2 (en)* | 2009-09-09 | 2014-09-09 | T-Mobile Usa, Inc. | Accessory based data distribution |
| US20110058516A1 (en)* | 2009-09-09 | 2011-03-10 | T-Mobile Usa, Inc. | Accessory Based Data Distribution |
| US9429989B2 (en) | 2010-01-19 | 2016-08-30 | T-Mobile Usa, Inc. | Interactive electronic device shell |
| US8860581B2 (en) | 2010-01-19 | 2014-10-14 | T-Mobile Usa, Inc. | Element mapping to control illumination of a device shell |
| US20110175748A1 (en)* | 2010-01-19 | 2011-07-21 | T-Mobile Usa, Inc. | Element Mapping to Control Illumination of a Device Shell |
| US8933813B2 (en) | 2010-01-19 | 2015-01-13 | T-Mobile Usa, Inc. | Interactive electronic device shell |
| US20110175747A1 (en)* | 2010-01-19 | 2011-07-21 | T-Mobile Usa, Inc. | Interactive Electronic Device Shell |
| US20140101212A1 (en)* | 2012-10-05 | 2014-04-10 | Gary Robin Maze | Document management systems and methods |
| US8924443B2 (en)* | 2012-10-05 | 2014-12-30 | Gary Robin Maze | Document management systems and methods |
| US9094822B2 (en)* | 2012-10-18 | 2015-07-28 | Futurewei Technologies, Inc. | Seamless telephone login |
| US20140113589A1 (en)* | 2012-10-18 | 2014-04-24 | Futurewei Technologies, Inc. | Seamless Telephone Login |
| US8595810B1 (en)* | 2013-01-13 | 2013-11-26 | Mourad Ben Ayed | Method for automatically updating application access security |
| US9215075B1 (en) | 2013-03-15 | 2015-12-15 | Poltorak Technologies Llc | System and method for secure relayed communications from an implantable medical device |
| US11930126B2 (en) | 2013-03-15 | 2024-03-12 | Piltorak Technologies LLC | System and method for secure relayed communications from an implantable medical device |
| US10841104B2 (en) | 2013-03-15 | 2020-11-17 | Poltorak Technologies Llc | System and method for secure relayed communications from an implantable medical device |
| US12225141B2 (en) | 2013-03-15 | 2025-02-11 | Poltorak Technologies Llc | System and method for secure relayed communications from an implantable medical device |
| US11588650B2 (en) | 2013-03-15 | 2023-02-21 | Poltorak Technologies Llc | System and method for secure relayed communications from an implantable medical device |
| US10305695B1 (en) | 2013-03-15 | 2019-05-28 | Poltorak Technologies Llc | System and method for secure relayed communications from an implantable medical device |
| US9942051B1 (en) | 2013-03-15 | 2018-04-10 | Poltorak Technologies Llc | System and method for secure relayed communications from an implantable medical device |
| US20160253525A1 (en)* | 2013-10-29 | 2016-09-01 | Feitian Technologies Co., Ltd. | Implementation method for driving of software and hardware supporting opensc |
| US10133882B2 (en)* | 2013-10-29 | 2018-11-20 | Feitian Technologies Co., Ltd. | Implementation method for driving of software and hardware supporting OpenSC |
| US11632360B1 (en) | 2018-07-24 | 2023-04-18 | Pure Storage, Inc. | Remote access to a storage device |
| US10936191B1 (en) | 2018-12-05 | 2021-03-02 | Pure Storage, Inc. | Access control for a computing system |
| US11876798B2 (en)* | 2019-05-20 | 2024-01-16 | Citrix Systems, Inc. | Virtual delivery appliance and system with remote authentication and related methods |
| US20200374284A1 (en)* | 2019-05-20 | 2020-11-26 | Citrix Systems, Inc. | Virtual delivery appliance and system with remote authentication and related methods |
| US11997197B1 (en)* | 2023-06-29 | 2024-05-28 | Cyberark Software Ltd. | Push architecture for secure provision of secrets |
Also Published As
| Publication number | Publication date |
|---|---|
| US20110252466A1 (en) | 2011-10-13 |
| EP1549018B1 (en) | 2014-05-21 |
| US20130019100A1 (en) | 2013-01-17 |
| EP2770693A1 (en) | 2014-08-27 |
| US20050136964A1 (en) | 2005-06-23 |
| ES2481396T3 (en) | 2014-07-30 |
| EP1549018A1 (en) | 2005-06-29 |
| EP2770693B1 (en) | 2019-08-14 |
| US8200195B2 (en) | 2012-06-12 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| US7907935B2 (en) | Intelligent remote device | |
| Ghosh et al. | Software security and privacy risks in mobile e-commerce | |
| AU2007267836B2 (en) | Policy driven, credential delegation for single sign on and secure access to network resources | |
| KR100783208B1 (en) | System and method using security of secure communication channel to secure non-secure communication channel | |
| US8209753B2 (en) | Universal secure messaging for remote security tokens | |
| EP1384369B1 (en) | Method and system for establishing a communications pipe between a personal security device and a remote computer system | |
| EP2332089B1 (en) | Authorization of server operations | |
| US9092635B2 (en) | Method and system of providing security services using a secure device | |
| US9521119B2 (en) | Extensible access control architecture | |
| US20040107360A1 (en) | System and Methodology for Policy Enforcement | |
| US20230126673A1 (en) | Secondary Device Authentication Proxied From Authenticated Primary Device | |
| US20100197293A1 (en) | Remote computer access authentication using a mobile device | |
| KR101656458B1 (en) | Authentication method and system for user confirmation and user authentication | |
| CN104737177A (en) | Methods used to provide security services | |
| WO2011141579A2 (en) | System and method for providing security for cloud computing resources using portable security devices | |
| Lu | Network smart card review and analysis | |
| KR101639794B1 (en) | Authentication method and system for user confirmation and user authentication | |
| Armando et al. | Trusted host-based card emulation | |
| Catuogno et al. | Smartk: Smart cards in operating systems at kernel level | |
| CN112513905B (en) | Method and system for implementing virtual smart card services | |
| Urien et al. | A new cooperative architecture for sharing services managed by secure elements controlled by android phones with IP objects | |
| Stirparo et al. | Secure Bluetooth for Trusted m-Commerce | |
| KR100867002B1 (en) | Smart card for providing convergence authentication in heterogeneous wireless networks and wireless device having the same | |
| Baglietto et al. | Application level smart card support through networked mobile devices | |
| Uddin et al. | USB Key as an active device of Security System |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| AS | Assignment | Owner name:ACTIVCARD IRELAND, LIMITED, IRELAND Free format text:ASSIGNMENT OF ASSIGNORS INTEREST;ASSIGNORS:LE SAINT, ERIC F.;FEDRONIC, DOMINIQUE LOUIS JOSEPH;REEL/FRAME:014838/0531 Effective date:20031014 | |
| STCF | Information on status: patent grant | Free format text:PATENTED CASE | |
| AS | Assignment | Owner name:ACTIVCARD IRELAND, LIMITED, IRELAND Free format text:ASSIGNMENT OF ASSIGNORS INTEREST;ASSIGNOR:ACTIVIDENTITY, INC.;REEL/FRAME:029444/0562 Effective date:20120726 | |
| AS | Assignment | Owner name:ACTIVIDENTITY, INC., CALIFORNIA Free format text:CORRECTIVE ASSIGNMENT TO CORRECT THE ASSIGNOR AND ASSIGNEE NAMES PREVIOUSLY RECORDED ON REEL 029444 FRAME 0562. ASSIGNOR(S) HEREBY CONFIRMS THE ASSIGNMENT OF ASSIGNORS INTEREST;ASSIGNOR:ACTIVCARD IRELAND LIMITED;REEL/FRAME:029565/0770 Effective date:20120726 | |
| AS | Assignment | Owner name:ASSA ABLOY AB, SWEDEN Free format text:ASSIGNMENT OF ASSIGNORS INTEREST;ASSIGNOR:ACTIVIDENTITY, INC.;REEL/FRAME:032404/0466 Effective date:20131217 | |
| FPAY | Fee payment | Year of fee payment:4 | |
| MAFP | Maintenance fee payment | Free format text:PAYMENT OF MAINTENANCE FEE, 8TH YEAR, LARGE ENTITY (ORIGINAL EVENT CODE: M1552); ENTITY STATUS OF PATENT OWNER: LARGE ENTITY Year of fee payment:8 | |
| MAFP | Maintenance fee payment | Free format text:PAYMENT OF MAINTENANCE FEE, 12TH YEAR, LARGE ENTITY (ORIGINAL EVENT CODE: M1553); ENTITY STATUS OF PATENT OWNER: LARGE ENTITY Year of fee payment:12 |