US7784098B1 - Snapshot and restore technique for computer system recovery - Google Patents
Snapshot and restore technique for computer system recoveryDownload PDFInfo
- Publication number
- US7784098B1 US7784098B1US11/181,320US18132005AUS7784098B1US 7784098 B1US7784098 B1US 7784098B1US 18132005 AUS18132005 AUS 18132005AUS 7784098 B1US7784098 B1US 7784098B1
- Authority
- US
- United States
- Prior art keywords
- malware
- restore
- computer
- computer system
- point
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Active, expires
Links
Images
Classifications
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/50—Monitoring users, programs or devices to maintain the integrity of platforms, e.g. of processors, firmware or operating systems
- G06F21/55—Detecting local intrusion or implementing counter-measures
- G06F21/56—Computer malware detection or handling, e.g. anti-virus arrangements
- G06F21/568—Computer malware detection or handling, e.g. anti-virus arrangements eliminating virus, restoring damaged files
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F11/00—Error detection; Error correction; Monitoring
- G06F11/07—Responding to the occurrence of a fault, e.g. fault tolerance
- G06F11/14—Error detection or correction of the data by redundancy in operation
- G06F11/1402—Saving, restoring, recovering or retrying
- G06F11/1446—Point-in-time backing up or restoration of persistent data
- G06F11/1458—Management of the backup or restore process
- G06F11/1469—Backup restoration techniques
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F11/00—Error detection; Error correction; Monitoring
- G06F11/07—Responding to the occurrence of a fault, e.g. fault tolerance
- G06F11/14—Error detection or correction of the data by redundancy in operation
- G06F11/1402—Saving, restoring, recovering or retrying
- G06F11/1471—Saving, restoring, recovering or retrying involving logging of persistent data for recovery
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F2201/00—Indexing scheme relating to error detection, to error correction, and to monitoring
- G06F2201/84—Using snapshots, i.e. a logical point-in-time copy of the data
Definitions
- the present inventionrelates generally to addressing malicious software in computer systems. More specifically, the present invention relates to computer system recovery after malicious software is found in a computer system.
- malwaresuch as computer viruses, worms, spyware, etc.
- Malicious softwarecan delete files, slow computer performance, clog e-mail accounts, steal confidential information, cause computer crashes, allow unauthorized access and generally perform other actions that are undesirable or not expected by the user of the computer.
- FIG. 1illustrates a prior art technique for taking scheduled “snapshots” and manual “snapshots” of a computer system.
- Traditional backup/restore software applicationsallow an operating system or a user to take a snapshot of the state of a computer and its files at a particular point in time.
- a snapshottypically records changes to the computer system and its files from a previous point in time and allows a user to restore their computer system to a time when the snapshot was taken.
- Timeline 10shows a series of hourly scheduled snapshots taken automatically by the computer system and timeline 20 shows a number of manual snapshots initiated by the user.
- Scheduled snapshotsare only taken when scheduled (e.g., hourly, daily or weekly) and are not triggered by a particular event.
- timeline 10if the computer user does not become aware of the infection until after 1800 then the user might waste a lot of time trying to restore the computer at points 1800 , 1700 and 1600 , only to find that the computer is still infected. It is only when the user uses the snapshot taken at time 1400 to restore the computer is the computer finally restored to a malicious software-free state. Even if the user has taken manual snapshots as in timeline 20 , the user still is unaware of when the computer was first infected and does not know from which snapshot point to restore the computer. If the malicious software is detected days or weeks after the initial infection it can be nearly impossible to determine when the infection first occurred. A user might err on the side of caution and decide to restore the computer from a point days or weeks before the infection occurred, but then valuable system and user data might be lost.
- a techniquethat provides a prediction of the point in time when malicious software begins to infect a computer system and recommends the best point from which to restore the computer system.
- the present inventionmonitors system operations and registers an event when an operation potentially characteristic of a malware infection occurs. Events are scored and when the number and type of events reach a certain level indicative of a possible malware infection a restore point is created. Any number of restore points may be created during the course of computer system operation. Thus, restore points are created that reflect points in time when it is probable that malware has infected a computer system, rather than restore points that are created at scheduled times or manually by the user.
- the present inventionprovides a restore point suggestion to the user when the user decides it is necessary to restore the computer system to an earlier state.
- the decision on which point is the best restore pointis achieved by comparing a malware report with the restore point logs that have been created earlier.
- a restore point log that shares many of the same system changes or other effects also present in the malware reportis likely to be an indication of the beginning of a malware infection. Because there might be many restore points which appear to have the potential of being the beginning of the malware infection, it is beneficial to compare these restore points with a malware report to determine which restore point is the beginning of the malware infection. Any number of malware reports may also be compared to the restore points in question to help determine which restore point might be the beginning of a malware infection.
- a third embodiment of the inventioncombines the first to embodiments.
- the third embodimentcontemplates not only scoring system events and creating likely restore points, but also comparing a malware report (or reports) to the previously stored restore points in order to provide an intelligent recommendation to the user.
- the present inventionhas many advantages. It is suitable for malware infection recovery by providing a point in time for the beginning of a possible malware infection.
- Traditional backup/restore software applicationscannot decide which of many potential restore points is malware free; such applications work best for system error or hardware crash types of recovery because the user and application are generally aware of when the system error or hardware crash occurred.
- Such traditional applicationshave no knowledge of when malware might first have been present on a computer system.
- the inventionis also suitable for use when malware has infected a kernel mode driver. Traditional cleanup software is unable to remove malware from such drivers.
- FIG. 1illustrates a prior art technique for taking scheduled snapshots and manual snapshots of a computer system.
- FIG. 2illustrates a technique for taking a snapshot according to one embodiment of the invention.
- FIG. 3is a block diagram showing one environment for operation of the present invention.
- FIG. 4is a block diagram of the snapshot/restore system according to one embodiment of the invention.
- FIG. 5is a flow diagram describing operation of the behavior monitor module.
- FIG. 6is a flow diagram illustrating operation of the snapshot adviser module.
- FIG. 7illustrates a scoring table that associates a score with an event type.
- FIG. 8illustrates an example of a restore point log.
- FIG. 9is a flow diagram describing operation of the restore adviser module.
- FIGS. 10A-10Gillustrate an example malware report.
- FIGS. 11A and 11Billustrate a computer system 900 suitable for implementing embodiments of the present invention.
- the present inventionis applicable to all malicious software, or malware, that generally causes harm to a computer system, provides an effect that is not expected by the user, is undesirable, illegal, or otherwise causes the user to want to restore their computer system from a time prior to when it was infected by the malware.
- Malwarecan be classified based upon how is executed, how it spreads or what it does. The below descriptions are provided as guidelines for the types of malware currently existing; these classifications are not perfect in that many groups overlap. Of course, later developed software not currently known may also fall within the definition of malware.
- a Trojan horse programis a harmful piece of software that is often disguised as legitimate software. Trojan horses cannot replicate themselves, unlike viruses or worms. A Trojan horse can be deliberately attached to otherwise useful software by a programmer, or can be spread by tricking users into believing that it is useful. Some Trojan horses can spread or activate other malware, such as viruses (a dropper).
- a wabbitis a third, uncommon type of self-replicating malware. Unlike viruses, wabbits do not infect host programs or documents. And unlike worms, rabbits do not use network functionality to spread to other computers. A simple example of a wabbit is a fork bomb.
- Spywareis a piece of software that collects and sends information (such as browsing patterns or credit card numbers) about users and the results of their computer activity without explicit notification.
- Spywareusually works and spreads like Trojan horses.
- the category of spywaremay also include adware that a user deems undesirable.
- a backdooris a piece of software that allows access to the computer system by bypassing the normal authentication procedures. There are two groups of backdoors depending upon how they work and spread. The first group work much like a Trojan horse, i.e., they are manually inserted into another piece of software, executed via their host software and spread by the host software being installed. The second group work more like a worm in that they get executed as part of the boot process and are usually spread by worms carrying them as their payload.
- the term ratwarehas arisen to describe backdoor malware that turns computers into zombies for sending spam.
- RootkitsAn exploit is a piece of software that attacks a particular security vulnerability. Exploits are not necessarily malicious in intent—they are often devised by security researchers as a way of demonstrating that a vulnerability exists. They are, however, a common component of malicious programs such as network worms.
- a root kitis software inserted onto a computer system after an attacker has gained control of the system. Rootkits often include functions to hide the traces of the attack, as by deleting logged entries or by cloaking the attacker's processes. Rootkits might include backdoors, allowing the attacker to easily regain access later or to exploit software to attack other systems. Because they often hook into the operating system at the kernel level to hide their presence, rootkits can be very hard to detect.
- Key logger softwareis software that copies a computer user's keystrokes to a file which it may send to a hacker at a later time. Often the key logger software will only awaken when a computer user connects to a secure web site such as a bank. It then logs the keystrokes, which may include account numbers, PINs and passwords, before they are encrypted by the secure web site.
- a dialeris a program that replaces the telephone number in a modem's dial-up connection with a long-distance number (often out of the country) in order to run up telephone charges on pay-per-dial numbers, or dials out at night to send key logger or other information to a hacker.
- Software known as URL injection softwaremodifies a browser's behavior with respect to some or all domains. It modifies the URL submitted to the server to profit from a given scheme by the content provider of the given domain. This activity is often transparent to the user.
- FIG. 2illustrates a technique for taking an intelligent snapshot according to one embodiment of the invention.
- Timelines 10 and 20are present as in FIG. 1 and an additional timeline 30 illustrates snapshots being taken at points 40 and 50 .
- malwarehas infected the computer system at times 1420 and 1520 and the present invention operates to take a snapshot of the system at that point in time when the malware starts to infect the system.
- a snapshotis taken at point 60 when benign software within the computer system takes actions that might be interpreted as the beginning of a malware infection.
- a thresholdmay be adjusted such that snapshots are taken when malware begins to infect the computer and also when benign software takes actions that appear to be malware. Such a threshold would err on the side of caution.
- the thresholdmay be adjusted such that snapshots are only taken when it is a near certainty that malware has begun to infect the system; of course, such a threshold may miss certain types of malware.
- the thresholdis adjusted based on experience and is designed to capture all malware infections and to a lesser extent actions taken by benign software.
- the present inventionmight initiate a snapshot based upon the actions of benign software, it still initiates snapshots and creates restore points at points in time that include the beginnings of a malware infection. In other words, even though the present invention might initiate snapshots and create restore points that do not reflect a malware infection, it will also create restore points that do reflect that particular point in time when a malware infection has begun.
- the restore adviser module of the present inventionthen operates to recommend a restore point from which to restore the computer system.
- the present inventioncan then recommend performing a restore from the point in time when the malware first began to infect the computer system, unlike the prior art techniques shown in timelines 10 and 20 which cannot inform the user of when a malware infection began.
- FIG. 3is a block diagram showing one environment for operation of the present invention. Shown is a user computer 100 connected to the Internet to which is also connected a server computer 110 . Computer 100 has the potential to be infected by malware and also includes software modules embodying the present invention. Computer 100 is any suitable computing platform such as a handheld computing device, a laptop computer, a desktop computer, a server computer, etc. In one embodiment of the invention, computer 100 is an IBM-compatible desktop computer running the Microsoft operating system version XP Professional.
- Server computer 110is any suitable computer within an organization that has the capability to analyze various types of malware and to compile reports on the malware that describe its characteristics. Analysis of malware such as viruses and description of malware characteristics is known in the art; by way of example, the organization Trend Micro, Inc. has the capability to prepare such malware reports. The web site for this organization currently lists malware reports available for public inspection that describe computer viruses and other types of malware. Malware report 120 may be delivered to computer 100 via the Internet, via electronic mail, via facsimile, or via any other suitable communication means. Malware report 120 is described in greater detail below with reference to FIGS. 10A-10G .
- FIG. 4is a block diagram of the snapshot/restore system 200 according to one embodiment of the invention.
- the systemincludes the following software components.
- Behavior monitor module 210 and snapshot adviser module 220work together using operating system events and a scoring system to make a decision on when to take a system snapshot.
- Snapshot/restore application 230is any software application that can take a system snapshot and create a restore point.
- Restore adviser module 250makes an informed decision regarding which restore point is the best point from which to restore the computer system.
- Behavior monitor module 210is real-time software including two functional kernel mode drivers that monitors operating system operations.
- this moduleoperates in kernel mode (also referred to as system mode) which is one of two modes of operation of the CPU, the other being user mode.
- Kernel modeis a privileged mode of operation in which the CPU is assumed to be executing trusted software and thus can execute any instruction and reference any memory address.
- the kernel(the core of the operating system) and any applications executing in kernel mode are considered trusted software.
- Module 210monitors and intercepts operating system operations such as file and registry access, process creation and process termination, and certain system APIs such as CreateProcess( ) CreateRemoteThread( ) and VitualAlloc( ). Other operations that may be intercepted relate to network packet traffic, the kernel module list, Winsock LSP (Layer Service Provider) and COM Objects. Even e-mail events can also be intercepted in order to detect malware; such interception can be implemented by a network packet monitor.
- operating system operationssuch as file and registry access, process creation and process termination, and certain system APIs such as CreateProcess( ) CreateRemoteThread( ) and VitualAlloc( ).
- Other operations that may be interceptedrelate to network packet traffic, the kernel module list, Winsock LSP (Layer Service Provider) and COM Objects. Even e-mail events can also be intercepted in order to detect malware; such interception can be implemented by a network packet monitor.
- Winsock LSPLayer
- Module 210is implemented as two functional drivers but may also be implemented as a single driver.
- module 210includes a TMCommon module that provides the common functions for all the other kernel modules, a TMEvent management module that manages all of the hook implementation, and an activity monitor module that monitors the file, registry and process activities and reports them to user mode component.
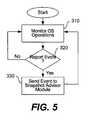
- FIG. 5is a flow diagram describing operation of the behavior monitor module.
- Step 310is a looping construct in which the module monitors all operating system operations. In particular, operations including file access, registry access, process creation and process termination are monitored and intercepted.
- Step 320decides which of these events to report to the snapshot adviser module 220 .
- all of the above operationsare reported to module 220 as they generally might be indicative of malware beginning to infect the computer system.
- certain criteriamay be used to decide which events to report and which events not to report. For example, certain registry activities are not reported; if the activities are generated by a trusted process (an operating system component, processes from a known software product) these kinds of events are not reported.
- step 330the intercepted operation is sent as an event to snapshot adviser module 220 along with any relevant data.
- process identifierFor any file event the following information is included: process identifier; file name; and the file creation flag.
- process identifierFor any registry events the following information is included: process identifier; process name; and registry data.
- process identifierFor any process event the following information is included: process identifier, process name, process's image path, and the process creation flag. If it exists, the parent process identifier is also included.
- the snapshot adviser module 220 , the snapshot/restore application 230 and the restore adviser module 250all preferably operate in user mode.
- user mode(as opposed to kernel mode) is one of two operating modes for a CPU.
- user modeis a non-privileged mode in that a process in user mode cannot access those portions of memory that have been allocated to the kernel or to other programs. In some situations, a user mode process that wants to use a service provided by the kernel can switch temporarily into kernel mode.
- Snapshot/restore application 230is any suitable custom or off-the-shelf software application that provides the ability to take a snapshot of the state of the computer system, to create restore points from which the system may be restored, and to restore the computer system from a particular restore point.
- Suitable snapshot/restore applicationsare known in the art and will typically restore such information as the registry, profiles, caches, files with certain extensions, etc. Typically, user created data is not restored (to avoid deleting user created files).
- the snapshot/restore system 200contemplates application 230 as being a separate component, thus providing the flexibility to integrate any snapshot/restore application from another party into the system. Such a separate application may be implemented as plug-in software or in other manners known in the art. Alternatively, application 230 may be a custom software application that is a separate component, or it may be integrated with other components of the system.
- the software application known as XP System Restore from Microsoft Corporationis used. XP System Restore is a feature of the Microsoft XP operating system.
- XP System RestoreWhen XP System Restore is used the present invention uses the APIs that Microsoft provides. Information on how the Microsoft API may be used is available from Microsoft Corporation and is known to those of skill in the art. Other software applications (such as snapshot adviser module 220 and restore adviser module 250 ) can provide commands to, and can receive data from, the XP System and Restore application by utilizing the Microsoft API. Of course, other snapshot/restore applications 230 may also be suitable for use with the present invention and these include backup/restore software from FalconStor Software and from Phoenix Software.
- Module 220uses a scoring system that can identify possible malware behavior and begin recording system changes at that time. For example, a score is given to each monitored system event received from the behavior monitor module and the scores are totaled while changes are being monitored. Once the total score of all monitored system events exceeds a certain threshold then this series of monitored system events will be identified as possible malware behavior and a restore point will be created.
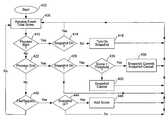
- FIG. 6is a flow diagram illustrating operation of snapshot adviser module 220 .
- a score thresholdis set that helps in determining whether a monitored set of system events might be the beginning of a malware infection.
- a score thresholdmay also be set during operation if a user so desires. For example, a threshold may be set at a total score of 10 indicating that if a total score of system events exceeds 10 then it is a suspected that the monitored system events are the beginning of a malware infection. Of course, the threshold may be set at any suitable number. A higher threshold would generate fewer suspected cases of malware, while a lower threshold would generate more suspected cases but might also include instances of benign software that merely appear to be malware.
- the thresholdit is possible for the threshold to be adjusted during operation of the system or that the threshold be adjusted depending upon certain criteria.
- the threshold settingmay be part of product configuration, the user can determine the threshold setting, or in the event of a malware outbreak the threshold setting can be adjusted.
- step 406the event along with its associated relevant data is received from the behavior monitor module and a log is kept of all events received. Also in this step a running score is kept to determine the current total score.
- FIG. 7illustrates a scoring table 450 that associates a score 456 with an event type 454 . For example, should the event indicate that a new file has been added, the running score is incremented by a value of six; a new process being added would increment the score by value of three.
- the score for a particular eventmay vary and the importance of a particular event type may be monitored or indicated by using techniques other than by keeping score. Other techniques may be used for determining if malware is present such as using CreateRemoteThread to other processes and using the SetWindowHookEx application programming interface (API).
- APIapplication programming interface
- a running scoreis kept only when a snapshot is turned on. For example, if a snapshot has been turned on then the total score will be incremented as events are received in step 406 . Keeping a running score while a snapshot is turned on is performed because it is during that period of time during which it is suspected that malware might be infecting the computer.
- steps 410 , 422 and 442check the type of event that has occurred and will turn a snapshot on, turn a snapshot off or commit a snapshot depending upon the circumstances. If the event is a process start (step 410 ) and a snapshot has already been turned on ( 414 ) then control returns to step 406 . On the other hand, if a snapshot is not already on, then in step 418 a snapshot is turned on by sending an appropriate command via an API to the snapshot/restore application 230 . In the embodiment where application 230 is XP System Restore specific commands are given as shown below:
- a snapshotis turned on at this point in time because since a new process has started it is apparent that there is activity and the computer system might begin to change. Thus, a command is given to application 230 to begin monitoring system activity and recording changes as they occur so that a restore point may be created if necessary. Application 230 thus begins to create a potential restore point. The total running score is also reset to zero when a snapshot is turned on.
- Application 230may store differential changes to the computer system in a wide variety of matters. Changes may be stored in a log format, in a table, in a database, etc. Data may be recorded using plain text, a binary representation, symbolic information, etc. In the embodiment where application 230 is XP System Restore the change information is stored in a restore point log using known techniques. An example restore point log is shown in FIG. 8 .
- step 422If the event is a process termination (step 422 ) and a snapshot is not currently on (step 426 ) then control returns to step 406 .
- a snapshotwas not turned on at the start of the process no changes have been recorded and presumably any relevant activity has already happened. This situation would happen infrequently. This situation might occur if the process starts (process parameters are initialized), is blocked by a process monitor, and then the process is terminated (cleanup of the resource occurs). In this situation the process is not actually successfully running.
- step 430the current running score is compared to the threshold number (for example, 10). If the score is not greater than the threshold then the current snapshot is canceled (by sending an appropriate command via the API to application 230 ) and control returns to step 406 .
- the threshold numberfor example, 10
- this scoreimplies that the events happening during the process are likely not to constitute malware, or that the process itself is not malware. In this situation the snapshot is canceled and no restore point is created.
- Application 230would then stop recording any differential changes to the system.
- application 230is XP System Restore specific commands are given to cancel a snapshot as shown below:
- step 438a snapshot commit is executed.
- a running score greater than the thresholdindicates that during the current snapshot there has been enough suspicious activity that the current snapshot should be stored as a restore point by application 230 .
- a commit commandis sent to application 230 which creates a restore point.
- This commandalso includes a restore point name to later identify this particular restore point.
- Application 230automatically appends the current date and time to the name provided and confirms that a restore point has been created.
- application 230is XP System Restore specific commands are given to commit a snapshot as shown below:
- the commit commandindicates to application 230 that the differential changes currently being recorded in the existing snapshot are important enough that the snapshot should be recorded as a restore point.
- Application 230will continue to record differential changes until either a commit snapshot or cancel snapshot command is received. If a restore point is created for the current snapshot (by issuing a snapshot commit command at the process end) then any future restore performed by the computer system will restore the computer to a state existing at the beginning of the process. Thus, any potential adverse effects caused by the malware during execution of process will be reversed.
- the snapshot commit commandalso functions to cancel the current snapshot in progress such that a new snapshot may be turned on immediately thereafter if necessary. Once a restore point is created, it can be analyzed later (as well as other restore points) using the restore adviser module to determine if this restore point is indeed the beginning of a malware infection.
- FIG. 8illustrates an example of a restore point log 500 .
- the restore point logincludes the information saved from the current snapshot and represents a particular restore point at a particular point in time; using information from a restore point log a user can restore a computer system to that point in time represented by the restore point.
- the restore point logincludes a snapshot of all relevant system information at a particular point in time.
- Restore point log 500is an example of a simple log that may be created after a computer system has undergone very minor changes.
- a restore point logmay become much more complicated, may contain many more entries, and may include different types of information.
- the log details section 504includes administrative details pertaining to the restore point including a restore point name, a restore type (automatic—intelligent or user—manual), a log time indicating the beginning of the snapshot and the end of the snapshot, a total score and a snapshot point.
- the snapshot pointis linked to the identifier created by snapshot/restore application ( 230 ), for example, 0x00000001, 0x00000002, etc.
- New file section 508includes a listing of any new files that have been created or “dropped” during this snapshot. This section shows that there are two new files.
- Modified file section 512includes a listing of any files that have been modified during this snapshot. Shown is a single file that has been modified.
- New Registry section 516includes a listing of any new entries into the Registry. Shown is a single new listing having a key, a value and data.
- Modified Registry section 520includes a listing of any modifications to the Registry. In this example there have been no modifications.
- Process creation section 524includes a listing of all processes created during the snapshot. Shown is a single new process that has been created.
- step 442it is determined if the event is a file access event or a registry access event. If not, then control returns to step 406 . If yes, then in step 444 it is determined if a snapshot is currently on. If yes, then in step 446 the score for that event is added to the running total and then control returns to step 406 . If a snapshot is not currently on, then control moves from step 444 to step 406 .
- the above steps in FIG. 6illustrate one example of the logic that may be used to analyze monitored system events in real time to determine if enough suspicious activity has occurred such that a restore point should be created corresponding to the beginning of that suspicious activity.
- other types of system eventsmay be considered, events may be scored differently, the threshold may be adjusted, snapshots may be turned on or off at different times and the snapshot commit command may be issued at different times.
- the above logic presented and its variationsoperate to create any number of restore points that correspond to the beginning of suspicious system activity that is likely to coincide with a malware infection.
- FIG. 9is a flow diagram describing operation of the restore adviser module 250 .
- the restore adviserreceives a malware report listing characteristics of a particular piece of malware and compares it with the user's saved restore point logs. With this analysis, the restore adviser can make an informed decision and provide a recommendation to the user regarding which restore point is the best from which to restore their computer system to achieve a malware-free state. By advising the user on which restore point to use, the present invention saves the user invaluable time and can provide assurances that the computer will be restored to a state free from malware.
- the malware reportis prepared by TrendLabs of Trend Micro, Inc. or by any other party that has the capability to analyze actions that malware takes and can prepare a report listing those actions and the characteristics of the malware.
- step 608the restore adviser module directs that any previously created restore point logs be retrieved from application 230 .
- settings or optionsare provided to allow the user to retrieve restore point logs from any previous time period such as the past 24 hours, the past week, any time previous to a certain date or time, etc.
- the usermay also specify that “the last 10 restore point logs be retrieved for comparison,” for example.
- restore point logsmay be stored external to application 230 for easier access.
- an interfaceis wrapped to query the data.
- the restore adviser modulewill retrieve all the restore point logs previously created.
- a malware reportis retrieved (or any number of malware reports are retrieved) from the entity that has prepared it by request from the restore adviser module.
- the malware reportcan be received over the Internet, by electronic mail, over a local network, or by any other suitable medium.
- malware reportsare received from Trend Micro Inc. An example malware report is discussed below.
- all malware reports availableare retrieved from the web site.
- the retrieved malware reportis compared to the restore point logs created earlier by application 230 .
- the malware reportis compared to each restore point log in turn starting with the most recent restore point log and moving backwards in time. Of course, the comparison may also be done in other orders.
- the restore point logkeeps a record of certain types of events such as any new files created, any modified files, any new entries in the registry, any modifications to the registry, any processes created and any processes terminated.
- a malware reportalso keeps track of these same types of actions (and a great deal more) that the malware performs.
- An analysisis then performed to determine if any of the entries in the restore point log are similar to the known actions of malware as indicated in the malware report. For example, new files from the restore point log are compared to new files that the malware typically creates. Also, any modified file in the restore point log is compared to the malware report to see if that particular malware also modifies the particular file. Further, new or modified registry entries from the restore point log are compared to the malware report to see if that particular malware also creates or modifies registry entries in the same fashion. In one embodiment, all of the restore point logs are compared to a single malware report first and then the logs are compared to the next malware report, etc. In an alternative embodiment, a single restore point log is compared to all of the malware reports first and then the next log is compared, etc.
- restore point logsare similar to the retrieved malware report then this is an indication that the particular malware characterized by the malware report has not appeared in the computer system during the time periods represented by the restore point logs. In such a situation, control returns to step 612 where another malware report is retrieved for comparison. In this fashion, the restore adviser module can loop through all of the relevant restore points logged and the applicable malware reports to determine which particular restore point is most likely the beginning of a malware infection.
- the usermay elect an earlier restore point from which to restore, or the user may even choose a later restore point if they do not wish to lose information created after that point in time.
- the restore adviser modulewill recommend restoring from the earliest restore point that evidences a malware infection. An analysis resulting in no restore point logs matching any of the malware reports indicate that it is unlikely that malware has infected the computer and no restore is recommended.
- the technical details section of the malware reportincludes information concerning the technical nature of the malware, its installation, network propagation, its e-mailing routine, any backdoor capabilities, any password guessing techniques, any antivirus retaliation techniques, any file infection routines and other information indicating hidden behavior (such as a root kit) or API hooking.
- the technical details sectionlists which type of files the malware infects, how it propagates, the size of the malware in bytes, when initial samples were received, to which other malware it is related, the number of payloads and the actions each take including their trigger conditions. Also listed is whether the malware is compressed and using which technique, in which language it is written, which operating system events it might register (such as Windows events), whether it requires certain APIs, etc.
- the technical details sectiondescribes whether the malware drops files, and if so, the name of each file dropped and into which system folder they are dropped, and whether the dropped files are copies of the malware. This section also lists any entries the malware adds to the registry, any registry keys that the malware modifies, any registry keys that are added to help the malware install itself as a service, and any entries into WIN.INI that are added.
- the technical details sectionlists any folders into which the malware drops a copy of itself once it is active in memory, including any name it might use. It also describes whether the malware creates random file names for these copies and lists any possible extensions that these file names might use.
- the malware reportdescribes how the malware propagates itself via e-mail, if relevant. If applicable, this section describes any e-mail header characteristics such as what will be listed in the “from” line, what might be listed in the “subject” line, what a message body might be, and any lists of the attachments that the malware might attach. The report describes how the malware gathers target e-mail addresses (using registry keys, for example), and how it sends off e-mail messages.
- the malware reportlists the types of processes or the names of processes that the malware will target in order to terminate them. For example, the malware report will list processes that will be terminated because of the particular string in their name. If applicable, the malware report will also describe the file infection routines used by the malware including which files are targeted and the structure of an infected file.
- a malware reportmay also include a solution section describing how to remove the malware from the computer and a statistics section describing the distribution of the malware overtime.
- FIGS. 10A-10Gillustrate an example malware report 700 for the worm “PE_LOVGATE.L.”
- Report 700is an example of a report in that it is an abbreviated version of a full malware report available from the Trend Micro web site.
- similar type reportsmay be prepared for many other types of worms and for other malware such as viruses, spyware, etc.
- Section 705 of the malware reportprovides an overview of the worm including details such as its size 706 , related malware 707 , its payloads and trigger conditions 708 , and other details such as its language and platform 709 .
- Section 710lists the files that are dropped into the Windows system folder upon execution. The dropped executable files are copies of the malware while the dynamic link library files are its backdoor components.
- Section 715lists the registry entries added by the malware; these entries insure automatic execution of the malware at every computer start up. The last two entries in the list are added registry keys and values that allow the malware to install itself as a service.
- Section 720lists any modified registry keys.
- Section 725lists any entries added to the file “WIN.INI.”
- the malwarealso propagates itself via e-mail by replying to all my new messages received.
- Section 740shows the format of such an e-mail message.
- the attachmentis randomly selected from any of the files listed in the attachment portion. Further, the malware also propagates itself by gathering target e-mail addresses and sending an e-mail to all those addresses with itself as an attachment.
- Section 745lists the target addresses that the malware will use. The malware looks for “.ht*” files in the Windows folder and in the current folder and retrieves the target e-mail addresses from every file that it finds.
- Section 750lists any of the many subjects that might be used.
- Section 755lists any of the various message bodies that might be used, and section 760 lists any of the many attachments that might be used.
- Section 765lists characteristics of the malware related to its backdoor capabilities.
- Section 766lists the ports opened by the malware for backdoor purposes.
- Section 767lists any remote threads used by the malware to install itself in memory.
- Section 768lists any other ports open for local communication.
- Section 769lists any files to which gathered information such as IP addresses, user names and passwords, are recorded.
- Section 770lists characteristics of the malware related to its brute-force password guessing attack.
- Section 771lists the number of simultaneous threads that the malware will creates to connect to a remote machine for the guessing attack.
- Section 772lists all the passwords used by the malware for the brute force attack (the passwords have been omitted because of their sheer number).
- the malwaremay also initiate antivirus retaliation techniques.
- the malwarewill terminate any process which has any of the strings listed in section 780 in their names.
- Section 785lists characteristics of the file infection routine used by the malware to infect fixed drives as opposed to propagation via network and e-mail.
- Section 790lists any events registered by the malware.
- Section 795lists any files having APIs required by the malware.
- FIGS. 11A and 11Billustrate a computer system 900 suitable for implementing embodiments of the present invention.
- FIG. 11Ashows one possible physical form of the computer system.
- the computer systemmay have many physical forms including an integrated circuit, a printed circuit board, a small handheld device (such as a mobile telephone or PDA), a personal computer or a super computer.
- Computer system 900includes a monitor 902 , a display 904 , a housing 906 , a disk drive 908 , a keyboard 910 and a mouse 912 .
- Disk 914is a computer-readable medium used to transfer data to and from computer system 900 .
- FIG. 11Bis an example of a block diagram for computer system 900 .
- Attached to system bus 920are a wide variety of subsystems.
- Processor(s) 922also referred to as central processing units, or CPUs
- Memory 924includes random access memory (RAM) and read-only memory (ROM).
- RAMrandom access memory
- ROMread-only memory
- RAMrandom access memory
- ROMread-only memory
- Both of these types of memoriesmay include any suitable of the computer-readable media described below.
- a fixed disk 926is also coupled bi-directionally to CPU 922 ; it provides additional data storage capacity and may also include any of the computer-readable media described below.
- Fixed disk 926may be used to store programs, data and the like and is typically a secondary storage medium (such as a hard disk) that is slower than primary storage. It will be appreciated that the information retained within fixed disk 926 , may, in appropriate cases, be incorporated in standard fashion as virtual memory in memory 924 .
- Removable disk 914may take the form of any of the computer-readable media described below.
Landscapes
- Engineering & Computer Science (AREA)
- Theoretical Computer Science (AREA)
- General Engineering & Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- General Physics & Mathematics (AREA)
- Physics & Mathematics (AREA)
- Health & Medical Sciences (AREA)
- Virology (AREA)
- Computer Hardware Design (AREA)
- Quality & Reliability (AREA)
- Software Systems (AREA)
- General Health & Medical Sciences (AREA)
- Information Retrieval, Db Structures And Fs Structures Therefor (AREA)
Abstract
Description
The present invention relates generally to addressing malicious software in computer systems. More specifically, the present invention relates to computer system recovery after malicious software is found in a computer system.
Currently, it is common for malicious software such as computer viruses, worms, spyware, etc., to affect a computer such that it will not behave as expected. Malicious software can delete files, slow computer performance, clog e-mail accounts, steal confidential information, cause computer crashes, allow unauthorized access and generally perform other actions that are undesirable or not expected by the user of the computer.
Current technology allows computer users to create backups of their computer systems and of their files and to restore their computer systems and files in the event of a catastrophic failure such as a loss of power, a hard drive crash or a system operation failure. But, in these situations the computer user generally knows when the failure has occurred. Assuming that the user had performed a backup prior to the failure, it can be straightforward to restore their computer system and files to a state prior to the computer failure. Of course, those users who perform a backup more frequently will generally be able to restore their computer system to a point closer to the time of the failure. Unfortunately, these prior art techniques are not effective when dealing with infection of a computer by malicious software.
For example, intimeline 10 if the computer user does not become aware of the infection until after1800 then the user might waste a lot of time trying to restore the computer at points1800,1700 and1600, only to find that the computer is still infected. It is only when the user uses the snapshot taken at time1400 to restore the computer is the computer finally restored to a malicious software-free state. Even if the user has taken manual snapshots as intimeline 20, the user still is unaware of when the computer was first infected and does not know from which snapshot point to restore the computer. If the malicious software is detected days or weeks after the initial infection it can be nearly impossible to determine when the infection first occurred. A user might err on the side of caution and decide to restore the computer from a point days or weeks before the infection occurred, but then valuable system and user data might be lost.
Another problem arises because the computer user is unaware of when the malicious software first infected the computer system. Certain backup/restore applications store restore points and their data in protected system files. Because these system files might not be scanned by virus scanning software, it is possible that a given snapshot and its associated restore point contains malicious software. Because the user does not know at which point in time the computer became infected, he or she may inadvertently restore the computer using a snapshot that contains malicious software. Further, certain malicious software uses protected kernel mode drivers that cannot be scanned by many types of virus scanning software. In both of these situations, running virus scanning software might be ineffective and provide a false sense of security because the scanning software would be ineffective in removing the malicious software.
For the above reasons, it is desirable to have a system and technique that would address the above deficiencies in the prior art and would allow a computer system to recover properly and with minimal effort after being infected by malicious software.
To achieve the foregoing, and in accordance with the purpose of the present invention, a technique is disclosed that provides a prediction of the point in time when malicious software begins to infect a computer system and recommends the best point from which to restore the computer system.
In one embodiment the present invention monitors system operations and registers an event when an operation potentially characteristic of a malware infection occurs. Events are scored and when the number and type of events reach a certain level indicative of a possible malware infection a restore point is created. Any number of restore points may be created during the course of computer system operation. Thus, restore points are created that reflect points in time when it is probable that malware has infected a computer system, rather than restore points that are created at scheduled times or manually by the user.
In a second embodiment the present invention provides a restore point suggestion to the user when the user decides it is necessary to restore the computer system to an earlier state. The decision on which point is the best restore point is achieved by comparing a malware report with the restore point logs that have been created earlier. A restore point log that shares many of the same system changes or other effects also present in the malware report is likely to be an indication of the beginning of a malware infection. Because there might be many restore points which appear to have the potential of being the beginning of the malware infection, it is beneficial to compare these restore points with a malware report to determine which restore point is the beginning of the malware infection. Any number of malware reports may also be compared to the restore points in question to help determine which restore point might be the beginning of a malware infection.
A third embodiment of the invention combines the first to embodiments. Thus, the third embodiment contemplates not only scoring system events and creating likely restore points, but also comparing a malware report (or reports) to the previously stored restore points in order to provide an intelligent recommendation to the user.
The present invention has many advantages. It is suitable for malware infection recovery by providing a point in time for the beginning of a possible malware infection. Traditional backup/restore software applications cannot decide which of many potential restore points is malware free; such applications work best for system error or hardware crash types of recovery because the user and application are generally aware of when the system error or hardware crash occurred. Such traditional applications have no knowledge of when malware might first have been present on a computer system. The invention is also suitable for use when malware has infected a kernel mode driver. Traditional cleanup software is unable to remove malware from such drivers.
The invention, together with further advantages thereof, may best be understood by reference to the following description taken in conjunction with the accompanying drawings in which:
The present invention is applicable to all malicious software, or malware, that generally causes harm to a computer system, provides an effect that is not expected by the user, is undesirable, illegal, or otherwise causes the user to want to restore their computer system from a time prior to when it was infected by the malware. Malware can be classified based upon how is executed, how it spreads or what it does. The below descriptions are provided as guidelines for the types of malware currently existing; these classifications are not perfect in that many groups overlap. Of course, later developed software not currently known may also fall within the definition of malware.
When computer viruses first originated common targets were executable files and the boot sectors of floppy disks, later targets were documents that contain macro scripts, and more recently, many computer viruses have embedded themselves in e-mail as attachments. With executable files the virus arranges that when the host code is executed the virus code is executed as well. Normally, the host program continues to function after it is infected by the virus. Some viruses overwrite other programs with copies of themselves, thus destroying the program. Viruses often spread across computers when the software or document to which they are attached is transferred from one computer to another. Computer worms are similar to viruses but are stand-alone software and thus do not require host files or other types of host code to spread themselves. They do modify the host operating system, however, at least to the extent that they are started as part of the boot process. In order to spread, worms either exploit some vulnerability of the target host or some kind of social engineering to trick users into executing them.
A Trojan horse program is a harmful piece of software that is often disguised as legitimate software. Trojan horses cannot replicate themselves, unlike viruses or worms. A Trojan horse can be deliberately attached to otherwise useful software by a programmer, or can be spread by tricking users into believing that it is useful. Some Trojan horses can spread or activate other malware, such as viruses (a dropper). A wabbit is a third, uncommon type of self-replicating malware. Unlike viruses, wabbits do not infect host programs or documents. And unlike worms, rabbits do not use network functionality to spread to other computers. A simple example of a wabbit is a fork bomb.
Spyware is a piece of software that collects and sends information (such as browsing patterns or credit card numbers) about users and the results of their computer activity without explicit notification. Spyware usually works and spreads like Trojan horses. The category of spyware may also include adware that a user deems undesirable. A backdoor is a piece of software that allows access to the computer system by bypassing the normal authentication procedures. There are two groups of backdoors depending upon how they work and spread. The first group work much like a Trojan horse, i.e., they are manually inserted into another piece of software, executed via their host software and spread by the host software being installed. The second group work more like a worm in that they get executed as part of the boot process and are usually spread by worms carrying them as their payload. The term ratware has arisen to describe backdoor malware that turns computers into zombies for sending spam.
An exploit is a piece of software that attacks a particular security vulnerability. Exploits are not necessarily malicious in intent—they are often devised by security researchers as a way of demonstrating that a vulnerability exists. They are, however, a common component of malicious programs such as network worms. A root kit is software inserted onto a computer system after an attacker has gained control of the system. Rootkits often include functions to hide the traces of the attack, as by deleting logged entries or by cloaking the attacker's processes. Rootkits might include backdoors, allowing the attacker to easily regain access later or to exploit software to attack other systems. Because they often hook into the operating system at the kernel level to hide their presence, rootkits can be very hard to detect.
Key logger software is software that copies a computer user's keystrokes to a file which it may send to a hacker at a later time. Often the key logger software will only awaken when a computer user connects to a secure web site such as a bank. It then logs the keystrokes, which may include account numbers, PINs and passwords, before they are encrypted by the secure web site. A dialer is a program that replaces the telephone number in a modem's dial-up connection with a long-distance number (often out of the country) in order to run up telephone charges on pay-per-dial numbers, or dials out at night to send key logger or other information to a hacker. Software known as URL injection software modifies a browser's behavior with respect to some or all domains. It modifies the URL submitted to the server to profit from a given scheme by the content provider of the given domain. This activity is often transparent to the user.
Even though the present invention might initiate a snapshot based upon the actions of benign software, it still initiates snapshots and creates restore points at points in time that include the beginnings of a malware infection. In other words, even though the present invention might initiate snapshots and create restore points that do not reflect a malware infection, it will also create restore points that do reflect that particular point in time when a malware infection has begun. As will be described in greater detail below, the restore adviser module of the present invention then operates to recommend a restore point from which to restore the computer system. Advantageously, the present invention can then recommend performing a restore from the point in time when the malware first began to infect the computer system, unlike the prior art techniques shown intimelines
Other system operations that might be indicative of execution of malware may also be monitored and intercepted. These system operations are reported as an event to a user mode component (snapshot adviser module220) when the monitored system operation occurs.Module 210 is implemented as two functional drivers but may also be implemented as a single driver. In one specific embodiment,module 210 includes a TMCommon module that provides the common functions for all the other kernel modules, a TMEvent management module that manages all of the hook implementation, and an activity monitor module that monitors the file, registry and process activities and reports them to user mode component.
If the operation is not to be reported then control returns to step310 were monitoring continues. Otherwise, instep 330 the intercepted operation is sent as an event tosnapshot adviser module 220 along with any relevant data. For example, for any file event the following information is included: process identifier; file name; and the file creation flag. For any registry events the following information is included: process identifier; process name; and registry data. For any process event the following information is included: process identifier, process name, process's image path, and the process creation flag. If it exists, the parent process identifier is also included. Once the event and its associated data has been sent tosnapshot adviser module 220 control returns to step310.
Thesnapshot adviser module 220, the snapshot/restoreapplication 230 and the restoreadviser module 250 all preferably operate in user mode. As mentioned above, user mode (as opposed to kernel mode) is one of two operating modes for a CPU. As is known in the art, user mode is a non-privileged mode in that a process in user mode cannot access those portions of memory that have been allocated to the kernel or to other programs. In some situations, a user mode process that wants to use a service provided by the kernel can switch temporarily into kernel mode. Snapshot/restoreapplication 230 is any suitable custom or off-the-shelf software application that provides the ability to take a snapshot of the state of the computer system, to create restore points from which the system may be restored, and to restore the computer system from a particular restore point. In some situations,application 230 may also include the capability to back up user and system files. Asuitable application 230 enables a user, system administrator or other to restore a computer to a previous state in the event of a problem without losing data files.Application 230 can create restore points at a scheduled time or times each day, can automatically create restore points at the time of significant system events such as application or driver installation, or can create restore points manually at the direction of a user.
Suitable snapshot/restore applications are known in the art and will typically restore such information as the registry, profiles, caches, files with certain extensions, etc. Typically, user created data is not restored (to avoid deleting user created files). The snapshot/restoresystem 200 contemplatesapplication 230 as being a separate component, thus providing the flexibility to integrate any snapshot/restore application from another party into the system. Such a separate application may be implemented as plug-in software or in other manners known in the art. Alternatively,application 230 may be a custom software application that is a separate component, or it may be integrated with other components of the system. In one embodiment of the invention, the software application known as XP System Restore from Microsoft Corporation is used. XP System Restore is a feature of the Microsoft XP operating system. When XP System Restore is used the present invention uses the APIs that Microsoft provides. Information on how the Microsoft API may be used is available from Microsoft Corporation and is known to those of skill in the art. Other software applications (such assnapshot adviser module 220 and restore adviser module250) can provide commands to, and can receive data from, the XP System and Restore application by utilizing the Microsoft API. Of course, other snapshot/restoreapplications 230 may also be suitable for use with the present invention and these include backup/restore software from FalconStor Software and from Phoenix Software.
Returning now to a discussion of the components ofsystem 200, considersnapshot adviser module 220.Module 220 uses a scoring system that can identify possible malware behavior and begin recording system changes at that time. For example, a score is given to each monitored system event received from the behavior monitor module and the scores are totaled while changes are being monitored. Once the total score of all monitored system events exceeds a certain threshold then this series of monitored system events will be identified as possible malware behavior and a restore point will be created.
Instep 406 the event along with its associated relevant data is received from the behavior monitor module and a log is kept of all events received. Also in this step a running score is kept to determine the current total score.FIG. 7 illustrates a scoring table450 that associates ascore 456 with anevent type 454. For example, should the event indicate that a new file has been added, the running score is incremented by a value of six; a new process being added would increment the score by value of three. Of course, the score for a particular event may vary and the importance of a particular event type may be monitored or indicated by using techniques other than by keeping score. Other techniques may be used for determining if malware is present such as using CreateRemoteThread to other processes and using the SetWindowHookEx application programming interface (API).
In one embodiment of the present invention, a running score is kept only when a snapshot is turned on. For example, if a snapshot has been turned on then the total score will be incremented as events are received instep 406. Keeping a running score while a snapshot is turned on is performed because it is during that period of time during which it is suspected that malware might be infecting the computer.
Next, steps410,422 and442 check the type of event that has occurred and will turn a snapshot on, turn a snapshot off or commit a snapshot depending upon the circumstances. If the event is a process start (step410) and a snapshot has already been turned on (414) then control returns to step406. On the other hand, if a snapshot is not already on, then in step418 a snapshot is turned on by sending an appropriate command via an API to the snapshot/restoreapplication 230. In the embodiment whereapplication 230 is XP System Restore specific commands are given as shown below:
Set pRestorePtSpec.dwEventType=BEGIN_SYSTEM_CHANGE
SRSetRestorePoint(PRESTOREPOINTINFO, pRestorePtSpec, PSTATEMGRSTATUS pSmgrStatus)
A snapshot is turned on at this point in time because since a new process has started it is apparent that there is activity and the computer system might begin to change. Thus, a command is given toapplication 230 to begin monitoring system activity and recording changes as they occur so that a restore point may be created if necessary.Application 230 thus begins to create a potential restore point. The total running score is also reset to zero when a snapshot is turned on.Application 230 may store differential changes to the computer system in a wide variety of matters. Changes may be stored in a log format, in a table, in a database, etc. Data may be recorded using plain text, a binary representation, symbolic information, etc. In the embodiment whereapplication 230 is XP System Restore the change information is stored in a restore point log using known techniques. An example restore point log is shown inFIG. 8 .
If the event is a process termination (step422) and a snapshot is not currently on (step426) then control returns to step406. In this situation, because a snapshot was not turned on at the start of the process no changes have been recorded and presumably any relevant activity has already happened. This situation would happen infrequently. This situation might occur if the process starts (process parameters are initialized), is blocked by a process monitor, and then the process is terminated (cleanup of the resource occurs). In this situation the process is not actually successfully running.
On the other hand, if a snapshot has been turned on, then instep 430 the current running score is compared to the threshold number (for example, 10). If the score is not greater than the threshold then the current snapshot is canceled (by sending an appropriate command via the API to application230) and control returns to step406. In other words, if the process has ended while a snapshot is on but the nature of the monitored events is such that their total score is not greater than the threshold, then this score implies that the events happening during the process are likely not to constitute malware, or that the process itself is not malware. In this situation the snapshot is canceled and no restore point is created.Application 230 would then stop recording any differential changes to the system. In the embodiment whereapplication 230 is XP System Restore specific commands are given to cancel a snapshot as shown below:
Set pRestorePtSpec.dwEventType=END_SYSTEM_CHANGE
Set pRestorePtSpec.dwRestorePtType=CANCELLED_OPERATION
SRSetRestorePoint(PRESTOREPOINTINFO, pRestorePtSpec, PSTATEMGRSTATUS pSmgrStatus)
But, if the running score is greater than the threshold (step430), then in step438 a snapshot commit is executed. A running score greater than the threshold indicates that during the current snapshot there has been enough suspicious activity that the current snapshot should be stored as a restore point byapplication 230. Accordingly, in step438 a commit command is sent toapplication 230 which creates a restore point. This command also includes a restore point name to later identify this particular restore point.Application 230 automatically appends the current date and time to the name provided and confirms that a restore point has been created. In the embodiment whereapplication 230 is XP System Restore specific commands are given to commit a snapshot as shown below:
Set pRestorePtSpec.dwEventType=END_SYSTEM_CHANGE
SRSetRestorePoint(PRESTOREPOINTINFO, pRestorePtSpec, PSTATEMGRSTATUS pSmgrStatus)
The commit command indicates toapplication 230 that the differential changes currently being recorded in the existing snapshot are important enough that the snapshot should be recorded as a restore point.Application 230 will continue to record differential changes until either a commit snapshot or cancel snapshot command is received. If a restore point is created for the current snapshot (by issuing a snapshot commit command at the process end) then any future restore performed by the computer system will restore the computer to a state existing at the beginning of the process. Thus, any potential adverse effects caused by the malware during execution of process will be reversed. The snapshot commit command also functions to cancel the current snapshot in progress such that a new snapshot may be turned on immediately thereafter if necessary. Once a restore point is created, it can be analyzed later (as well as other restore points) using the restore adviser module to determine if this restore point is indeed the beginning of a malware infection.
Restore point log500 is an example of a simple log that may be created after a computer system has undergone very minor changes. Of course, a restore point log may become much more complicated, may contain many more entries, and may include different types of information. The log detailssection 504 includes administrative details pertaining to the restore point including a restore point name, a restore type (automatic—intelligent or user—manual), a log time indicating the beginning of the snapshot and the end of the snapshot, a total score and a snapshot point. The snapshot point is linked to the identifier created by snapshot/restore application (230), for example, 0x00000001, 0x00000002, etc.
Instep 442 it is determined if the event is a file access event or a registry access event. If not, then control returns to step406. If yes, then instep 444 it is determined if a snapshot is currently on. If yes, then instep 446 the score for that event is added to the running total and then control returns to step406. If a snapshot is not currently on, then control moves fromstep 444 to step406.
The above steps inFIG. 6 illustrate one example of the logic that may be used to analyze monitored system events in real time to determine if enough suspicious activity has occurred such that a restore point should be created corresponding to the beginning of that suspicious activity. Of course, other types of system events may be considered, events may be scored differently, the threshold may be adjusted, snapshots may be turned on or off at different times and the snapshot commit command may be issued at different times. Advantageously, the above logic presented and its variations operate to create any number of restore points that correspond to the beginning of suspicious system activity that is likely to coincide with a malware infection.
In step604 a user or administrator of the computer system in question makes a determination or realizes that malware has infected the computer system or is present on the computer system, and desires to take action to remove the malware. The user then takes action to initiate operation of the restore adviser module of the present invention. Because the present invention has previously been in operation on the computer system monitoring system operations and creating restore points, the restore adviser module can now analyze those previously created restore points to determine which one to recommend.
Instep 608 the restore adviser module directs that any previously created restore point logs be retrieved fromapplication 230. In various embodiments settings or options are provided to allow the user to retrieve restore point logs from any previous time period such as the past 24 hours, the past week, any time previous to a certain date or time, etc. The user may also specify that “the last 10 restore point logs be retrieved for comparison,” for example.
In the embodiment in whichapplication 230 is Microsoft XP System Restore the restore point logs may be stored external toapplication 230 for easier access. To retrieve the logs from storage in one embodiment an interface is wrapped to query the data. By default, the restore adviser module will retrieve all the restore point logs previously created.
In step612 a malware report is retrieved (or any number of malware reports are retrieved) from the entity that has prepared it by request from the restore adviser module. The malware report can be received over the Internet, by electronic mail, over a local network, or by any other suitable medium. In a preferred embodiment, malware reports are received from Trend Micro Inc. An example malware report is discussed below. In one specific embodiment, all malware reports available are retrieved from the web site.
Instep 616 the retrieved malware report is compared to the restore point logs created earlier byapplication 230. In one embodiment of invention, the malware report is compared to each restore point log in turn starting with the most recent restore point log and moving backwards in time. Of course, the comparison may also be done in other orders. As shown inFIG. 8 , the restore point log keeps a record of certain types of events such as any new files created, any modified files, any new entries in the registry, any modifications to the registry, any processes created and any processes terminated. In a similar fashion, a malware report also keeps track of these same types of actions (and a great deal more) that the malware performs.
An analysis is then performed to determine if any of the entries in the restore point log are similar to the known actions of malware as indicated in the malware report. For example, new files from the restore point log are compared to new files that the malware typically creates. Also, any modified file in the restore point log is compared to the malware report to see if that particular malware also modifies the particular file. Further, new or modified registry entries from the restore point log are compared to the malware report to see if that particular malware also creates or modifies registry entries in the same fashion. In one embodiment, all of the restore point logs are compared to a single malware report first and then the logs are compared to the next malware report, etc. In an alternative embodiment, a single restore point log is compared to all of the malware reports first and then the next log is compared, etc.
A restore point log is compared to a malware report by event category. For example, the event of a dropped file is compared between the restore point log and the malware report. If any transformations are required they are performed before the comparison. For example, we transform “% windows %\explorer.exe” in a malware report to “c:\windows\explorer.exe” to be compatible with the client machine's restore point log.
If it is determined that none of the restore point logs are similar to the retrieved malware report then this is an indication that the particular malware characterized by the malware report has not appeared in the computer system during the time periods represented by the restore point logs. In such a situation, control returns to step612 where another malware report is retrieved for comparison. In this fashion, the restore adviser module can loop through all of the relevant restore points logged and the applicable malware reports to determine which particular restore point is most likely the beginning of a malware infection.
The restore adviser determines that a restore point log is similar to a particular malware report using any of a wide variety of criteria. For example, if a malware report lists three occurrences of files being dropped in a particular folder, and a restore point log lists a total of ten events that include the same three files being dropped in the same folder as indicated by the malware report, then it can be determined that the malware has infected the computer during the time period indicated by the restore point log. Other criteria may also be used to determine that a restore point log is similar to a malware report. For example, consider a restore point log that includes the following information:
KEY: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CunentVersion\Run
VALUE: CallSpyware
DATA: C: \Windows\spyware.exe
Now consider a malware report that includes:
KEY: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
VALUE: CallAdware
DATA: % Windows %\spyware.exe
Although the value is different in the restore point log it points to the same file location, so we treat this entry as being the same item.
Once the analysis has determined that malware has infected the computer system at a particular restore point, the restore adviser module recommends that the user perform a restore from that restore point or from an earlier restore point. In other words, should the events recorded in a restore point log indicate that malware is present, restoring the computer system using that restore point will restore the state of the computer to a point in time just prior to when the malware infection began. The restore adviser module will thus recommend that this restore point be used; the computer will be restored to a malware-free state that is as late in time as possible.
Alternatively, the user may elect an earlier restore point from which to restore, or the user may even choose a later restore point if they do not wish to lose information created after that point in time. In addition, in a situation where the above analysis indicates that malware is present at multiple restore points, the restore adviser module will recommend restoring from the earliest restore point that evidences a malware infection. An analysis resulting in no restore point logs matching any of the malware reports indicate that it is unlikely that malware has infected the computer and no restore is recommended.
A malware report may contain any of a variety of information that describes the characteristics of malware, actions that it takes, identifying features, solutions for its removal, statistics regarding its spread, etc. In one embodiment of the invention, a malware report is a text document including sections that provide an overview of the malware, technical details, its solution and statistics. A malware report may also be embodied in other forms and include other information such as the antivirus software detection result log.
An overview section of the malware report lists the name of the malware, its type, whether it is operating in the wild, whether it is destructive, the language it uses, the platform on which it operates and whether it is encrypted or not. A brief description of the malware is given including where it drops files and their names, how it might propagate itself via e-mail, whether it has backdoor capabilities, etc. A much fuller detailed description of the malware is provided in the technical details section of the malware report.
The technical details section of the malware report includes information concerning the technical nature of the malware, its installation, network propagation, its e-mailing routine, any backdoor capabilities, any password guessing techniques, any antivirus retaliation techniques, any file infection routines and other information indicating hidden behavior (such as a root kit) or API hooking.
The technical details section lists which type of files the malware infects, how it propagates, the size of the malware in bytes, when initial samples were received, to which other malware it is related, the number of payloads and the actions each take including their trigger conditions. Also listed is whether the malware is compressed and using which technique, in which language it is written, which operating system events it might register (such as Windows events), whether it requires certain APIs, etc.
Regarding its installation, the technical details section describes whether the malware drops files, and if so, the name of each file dropped and into which system folder they are dropped, and whether the dropped files are copies of the malware. This section also lists any entries the malware adds to the registry, any registry keys that the malware modifies, any registry keys that are added to help the malware install itself as a service, and any entries into WIN.INI that are added.
Regarding network propagation, the technical details section lists any folders into which the malware drops a copy of itself once it is active in memory, including any name it might use. It also describes whether the malware creates random file names for these copies and lists any possible extensions that these file names might use. Regarding its mailing routine, the malware report describes how the malware propagates itself via e-mail, if relevant. If applicable, this section describes any e-mail header characteristics such as what will be listed in the “from” line, what might be listed in the “subject” line, what a message body might be, and any lists of the attachments that the malware might attach. The report describes how the malware gathers target e-mail addresses (using registry keys, for example), and how it sends off e-mail messages.
Any backdoor capabilities of the malware is also described including which dropped files it uses, which ports it opens, and whether or not it sends off an e-mail message to a remote location. A full description of these capabilities is also provided. Any password guessing attack is also provided if applicable, including a brute force guessing attack in which the malware report lists how the attack progresses and the passwords that are used. This section also describes what actions the malware takes if the attack is successful such as how the malware searches for possible user names and passwords and where this information is saved.
If the malware uses an antivirus retaliation technique the malware report lists the types of processes or the names of processes that the malware will target in order to terminate them. For example, the malware report will list processes that will be terminated because of the particular string in their name. If applicable, the malware report will also describe the file infection routines used by the malware including which files are targeted and the structure of an infected file.
A malware report may also include a solution section describing how to remove the malware from the computer and a statistics section describing the distribution of the malware overtime.
The malware also propagates itself via e-mail by replying to all my new messages received.Section 740 shows the format of such an e-mail message. The attachment is randomly selected from any of the files listed in the attachment portion. Further, the malware also propagates itself by gathering target e-mail addresses and sending an e-mail to all those addresses with itself as an attachment.Section 745 lists the target addresses that the malware will use. The malware looks for “.ht*” files in the Windows folder and in the current folder and retrieves the target e-mail addresses from every file that it finds.Section 750 lists any of the many subjects that might be used.Section 755 lists any of the various message bodies that might be used, andsection 760 lists any of the many attachments that might be used.
The malware may also initiate antivirus retaliation techniques. The malware will terminate any process which has any of the strings listed insection 780 in their names.Section 785 lists characteristics of the file infection routine used by the malware to infect fixed drives as opposed to propagation via network and e-mail.Section 790 lists any events registered by the malware.Section 795 lists any files having APIs required by the malware.
In addition, embodiments of the present invention further relate to computer storage products with a computer-readable medium that have computer code thereon for performing various computer-implemented operations. The media and computer code may be those specially designed and constructed for the purposes of the present invention, or they may be of the kind well known and available to those having skill in the computer software arts. Examples of computer-readable media include, but are not limited to: magnetic media such as hard disks, floppy disks, and magnetic tape; optical media such as CD-ROMs and holographic devices; magneto-optical media such as floptical disks; and hardware devices that are specially configured to store and execute program code, such as application-specific integrated circuits (ASICs), programmable logic devices (PLDs) and ROM and RAM devices. Examples of computer code include machine code, such as produced by a compiler, and files containing higher level code that are executed by a computer using an interpreter.
Although the foregoing invention has been described in some detail for purposes of clarity of understanding, it will be apparent that certain changes and modifications may be practiced within the scope of the appended claims. Therefore, the described embodiments should be taken as illustrative and not restrictive, and the invention should not be limited to the details given herein but should be defined by the following claims and their full scope of equivalents.
Claims (33)
1. A method of creating a restore point for a computer system, said method comprising:
monitoring operating system operations of said computer system using a module of said computer system;
opening a restore point log at the start of a computer process and logging operating system changes in said log after said restore point log is opened;
assigning a score to each of said operations being monitored, said score reflecting the extent to which each of said operations is suspected of being caused by malware;
keeping a running total of said scores for said operations being monitored;
making a determination that said running total is greater than a threshold value; and
creating a restore point for said computer system using said operating system changes that have been logged in said restore point log, wherein said restore point represents a point in time before the beginning of possible malware activity in said computer system.
2. A method as recited inclaim 1 wherein said creating a restore point makes use of an application programming interface (API) to communicate with a software application.
3. A method as recited inclaim 1 wherein said monitoring operating system operations occurs in a module of the kernel of said computer system.
4. A method as recited inclaim 1 further comprising:
recommending said restore point from which to restore said computer system.
5. A method as recited inclaim 1 wherein said malware is a computer virus, a computer worm or a computer Trojan horse.
6. A method as recited inclaim 1 further comprising:
creating said restore point at a point in time before said operating system changes occur.
7. A method as recited inclaim 1 wherein said steps of assigning, keeping and making occur while said operating system operations are being monitored.
8. A method as recited inclaim 1 further comprising:
making said determination at the end of said computer process.
9. A method of creating a restore point for a computer system, said method comprising:
monitoring operating system operations of said computer system using a kernel mode module of said computer system;
turning on a snapshot utility of said computer system at the start of a computer process and beginning to log operating system changes in a restore point log after said snapshot utility is turned on;
assigning a score to each of said operations being monitored, said score reflecting the extent to which each of said operations is suspected of being caused by malware;
keeping a running total of said scores for said operations being monitored;
making a determination that said running total is greater than a threshold value; and
issuing a snapshot commit command and creating a restore point for said computer system using said operating system changes that have been logged in said restore point log, wherein said restore point represents a point in time before the beginning of possible malware activity in said computer system.
10. A method as recited inclaim 9 wherein said creating a restore point makes use of an application programming interface (API) to communicate with a software application.
11. A method as recited inclaim 9 further comprising:
recommending said restore point from which to restore said computer system.
12. A method as recited inclaim 9 wherein said malware is a computer virus, a computer worm or a computer Trojan horse.
13. A method as recited inclaim 9 further comprising:
creating said restore point at a point in time before said operating system changes occur.
14. A method as recited inclaim 9 wherein said steps of assigning, keeping and making occur while said operating system operations are being monitored.
15. A method as recited inclaim 9 further comprising:
making said determination at the end of said computer process.
16. A method of recommending a restore point for a computer system, said method comprising:
retrieving a plurality of restore point logs previously created for said computer system using a module of said computer system;
retrieving a malware report that describes characteristics of a particular piece of malware;
comparing said malware report to said restore point logs;
determining that said malware report is similar to one of said restore point logs; and
making a recommendation that said computer system be restored from a point in time represented by said one of said restore point logs, said point in time being prior to a malware infection.
17. A method as recited inclaim 16 wherein said comparing compares said malware report to one of said restore point logs category-by-category.
18. A method as recited inclaim 16 wherein said malware is a computer virus, a computer worm or a computer Trojan horse.
19. A method as recited inclaim 16 wherein each of said restore point logs includes information indicating malware activities within said computer system.
20. A method of recommending a restore point for a computer system, said method comprising:
determining that said computer system should be restored to a previous point in time using a module of said computer system;
retrieving a plurality of restore point logs previously created for said computer system, said restore point logs including changes to said computer system;
retrieving a malware report that describes changes made by said malware to computer systems in which it is present;
comparing said changes in said malware report to said changes in said restore point logs;
determining that said malware report is similar to one of said restore point logs; and
making a recommendation that said computer system be restored from a point in time represented by said one of said restore point logs, said point in time being prior to a malware infection.
21. A method as recited inclaim 20 wherein said comparing compares said malware report to one of said restore point logs category-by-category.
22. A method as recited inclaim 20 wherein said malware is a computer virus, a computer worm or a computer Trojan horse.
23. A method of recovering from malware present in a computer system, said method comprising:
monitoring operating system operations of said computer system using a module of said computer system;
logging operating system changes in a log from a particular point in time;
ranking each of said operating system operations from said particular point in time, said rankings reflecting the extent to which each of said operations is suspected of being caused by malware;
making a determination that a value of said rankings has crossed a threshold value and creating a restore point for said computer system that includes said logged operating system changes;
comparing a malware report to said log, said malware report describing characteristics of a particular piece of malware;
determining that said malware report is similar to said log; and
restoring said computer system using said restore point.
24. A method as recited inclaim 23 wherein said creating a restore point makes use of an application programming interface (API) to communicate with a software application.
25. A method as recited inclaim 23 wherein said monitoring operating system operations occurs in a module of the kernel of said computer system.
26. A method as recited inclaim 23 further comprising:
recommending said restore point from which to restore said computer system.
27. A method as recited inclaim 23 wherein said malware is a computer virus, a computer worm or a computer Trojan horse.
28. A method as recited inclaim 23 wherein said comparing compares said malware report to said restore point log category-by-category.
29. A method of recovering from malware present in a computer system, said method comprising:
monitoring operating system operations of said computer system using a module of said computer system;
turning on a snapshot utility of said computer system and beginning to log operating system changes at a particular point in time in a log;
ranking each of said operating system operations from said particular point in time, said rankings reflecting the extent to which each of said operations is suspected of being caused by malware;
making a determination that a value of said rankings has crossed a threshold value;
issuing a snapshot commit command and creating a restore point for said computer system using said operating system changes that have been logged in said log;
retrieving a malware report that describes characteristics of said malware;
comparing said malware report with said log; and
making a recommendation that said computer system be restored from a point in time represented by said log.
30. A method as recited inclaim 29 wherein said creating a restore point makes use of an application programming interface (API) to communicate with a software application.
31. A method as recited inclaim 29 wherein said monitoring operating system operations occurs in a module of the kernel of said computer system.
32. A method as recited inclaim 29 wherein said malware is a computer virus, a computer worm or a computer Trojan horse.
33. A method as recited inclaim 29 wherein said comparing compares said malware report to said restore point log category-by-category.
Priority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| US11/181,320US7784098B1 (en) | 2005-07-14 | 2005-07-14 | Snapshot and restore technique for computer system recovery |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| US11/181,320US7784098B1 (en) | 2005-07-14 | 2005-07-14 | Snapshot and restore technique for computer system recovery |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| US7784098B1true US7784098B1 (en) | 2010-08-24 |
Family
ID=42583481
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US11/181,320Active2029-05-17US7784098B1 (en) | 2005-07-14 | 2005-07-14 | Snapshot and restore technique for computer system recovery |
Country Status (1)
| Country | Link |
|---|---|
| US (1) | US7784098B1 (en) |
Cited By (55)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20080016564A1 (en)* | 2005-08-16 | 2008-01-17 | Emc Corporation | Information protection method and system |
| US20080047013A1 (en)* | 2005-08-16 | 2008-02-21 | Emc Corporation | Method and system for detecting malware |
| US20080276299A1 (en)* | 2007-04-02 | 2008-11-06 | Samsung Electronics Co., Ltd. | Wireless terminal apparatus and method of protecting system resources |
| US20090038012A1 (en)* | 2007-08-03 | 2009-02-05 | Lenovo (Beijing) Limited | Method and system for deleting or isolating computer viruses |
| US20100115334A1 (en)* | 2008-11-05 | 2010-05-06 | Mark Allen Malleck | Lightweight application-level runtime state save-and-restore utility |
| US7934262B1 (en)* | 2007-12-26 | 2011-04-26 | Emc (Benelux) B.V., S.A.R.L. | Methods and apparatus for virus detection using journal data |
| US20110099632A1 (en)* | 2005-07-15 | 2011-04-28 | Microsoft Corporation | Detecting user-mode rootkits |
| US20110197279A1 (en)* | 2009-05-29 | 2011-08-11 | Hitachi, Ltd. | Management methods of storage system and file system |
| US20110296237A1 (en)* | 2010-05-26 | 2011-12-01 | International Business Machines Corporation | Selecting a data restore point with an optimal recovery time and recovery point |
| US20120143826A1 (en)* | 2007-12-19 | 2012-06-07 | Microsoft Corporation | Creating and utilizing network restore points |
| US20120158661A1 (en)* | 2010-12-15 | 2012-06-21 | Microsoft Corporation | Context-specific rollback |
| US20120297488A1 (en)* | 2011-05-16 | 2012-11-22 | Microsoft Corporation | Discovering Malicious Input Files and Performing Automatic and Distributed Remediation |
| US20120322439A1 (en)* | 2010-06-14 | 2012-12-20 | Future Dial Inc. | System and Method for Enhanced Diagnostics on Mobile Communication Devices |
| US8352522B1 (en)* | 2010-09-01 | 2013-01-08 | Trend Micro Incorporated | Detection of file modifications performed by malicious codes |
| US8392539B1 (en)* | 2008-03-19 | 2013-03-05 | Trend Micro, Inc. | Operating system banking and portability |
| US8418251B1 (en)* | 2009-04-27 | 2013-04-09 | Symantec Corporation | Detecting malware using cost characteristics |
| CN103065091A (en)* | 2011-12-22 | 2013-04-24 | 微软公司 | Extension of system restoration by using malware detection |
| US20130160131A1 (en)* | 2011-12-20 | 2013-06-20 | Matias Madou | Application security testing |
| WO2013087603A1 (en)* | 2011-12-14 | 2013-06-20 | F-Secure Corporation | Disinfection of a file system |
| US8683576B1 (en)* | 2009-09-30 | 2014-03-25 | Symantec Corporation | Systems and methods for detecting a process to establish a backdoor connection with a computing device |
| US20140122859A1 (en)* | 2012-11-01 | 2014-05-01 | International Business Machines Corporation | Configuring configuration settings using a user context |
| WO2014209825A1 (en)* | 2013-06-25 | 2014-12-31 | Microsoft Corporation | Reverse replication to rollback corrupted files |
| US8949187B1 (en)* | 2008-05-30 | 2015-02-03 | Symantec Corporation | Systems and methods for creating and managing backups based on health information |
| US8996916B2 (en) | 2011-08-16 | 2015-03-31 | Future Dial, Inc. | System and method for identifying problems via a monitoring application that repetitively records multiple separate consecutive files listing launched or installed applications |
| US9323924B1 (en)* | 2014-05-09 | 2016-04-26 | Symantec Corporation | Systems and methods for establishing reputations of files |
| US9378096B1 (en)* | 2012-06-30 | 2016-06-28 | Emc Corporation | System and method for cache management |
| EP2972772A4 (en)* | 2013-03-15 | 2016-11-16 | Amazon Tech Inc | INSTANT COPIES IN PLACE |
| US9734337B1 (en)* | 2017-01-24 | 2017-08-15 | Malwarebytes Inc. | Behavior-based ransomware detection |
| US9773026B1 (en)* | 2012-12-20 | 2017-09-26 | EMC IP Holding Company LLC | Calculation of system utilization |
| US20180167403A1 (en)* | 2016-12-12 | 2018-06-14 | Ut Battelle, Llc | Malware analysis and recovery |
| US10043026B1 (en)* | 2015-11-09 | 2018-08-07 | 8X8, Inc. | Restricted replication for protection of replicated databases |
| US10326599B2 (en) | 2016-05-09 | 2019-06-18 | Hewlett Packard Enterprise Development Lp | Recovery agents and recovery plans over networks |
| WO2019190936A1 (en)* | 2018-03-30 | 2019-10-03 | Microsoft Technology Licensing, Llc | Selection of restore point based on detection of malware attack |
| US20190306179A1 (en)* | 2018-03-30 | 2019-10-03 | Microsoft Technology Licensing, Llc | Service identification of ransomware impacted files |
| US10440039B1 (en) | 2015-11-09 | 2019-10-08 | 8X8, Inc. | Delayed replication for protection of replicated databases |
| US10769278B2 (en) | 2018-03-30 | 2020-09-08 | Microsoft Technology Licensing, Llc | Service identification of ransomware impact at account level |
| US10885196B2 (en) | 2016-04-29 | 2021-01-05 | Hewlett Packard Enterprise Development Lp | Executing protected code |
| US10896085B2 (en) | 2018-05-08 | 2021-01-19 | Hewlett-Packard Development Company, L.P. | Mitigating actions |
| US11010470B2 (en)* | 2017-12-15 | 2021-05-18 | Microsoft Technology Licensing, Llc | Anti-virus file system cache for operating system remediation |
| US11153373B2 (en) | 2019-05-03 | 2021-10-19 | EMC IP Holding Company LLC | Method and system for performance-driven load shifting |
| US20220058103A1 (en)* | 2020-08-19 | 2022-02-24 | Unitedhealth Group Incorporated | Dynamic post-change computing-system evaluation |
| CN114116322A (en)* | 2022-01-27 | 2022-03-01 | 深圳市科力锐科技有限公司 | Data recovery method, device, equipment and storage medium |
| US11275834B1 (en)* | 2017-01-12 | 2022-03-15 | Richard Offer | System for analyzing backups for threats and irregularities |
| US11308207B2 (en) | 2018-03-30 | 2022-04-19 | Microsoft Technology Licensing, Llc | User verification of malware impacted files |
| US11809559B2 (en) | 2018-08-03 | 2023-11-07 | Hewlett-Packard Development Company, L.P. | Intrusion resilient applications |
| US20230388340A1 (en)* | 2022-05-31 | 2023-11-30 | WithSecure Corporation | Arrangement and method of threat detection in a computer or computer network |
| US12131294B2 (en) | 2012-06-21 | 2024-10-29 | Open Text Corporation | Activity stream based interaction |
| US12149623B2 (en) | 2018-02-23 | 2024-11-19 | Open Text Inc. | Security privilege escalation exploit detection and mitigation |
| US12164466B2 (en) | 2010-03-29 | 2024-12-10 | Open Text Inc. | Log file management |
| US12197383B2 (en) | 2015-06-30 | 2025-01-14 | Open Text Corporation | Method and system for using dynamic content types |
| US12235960B2 (en) | 2019-03-27 | 2025-02-25 | Open Text Inc. | Behavioral threat detection definition and compilation |
| US12261822B2 (en) | 2014-06-22 | 2025-03-25 | Open Text Inc. | Network threat prediction and blocking |
| US12282549B2 (en) | 2005-06-30 | 2025-04-22 | Open Text Inc. | Methods and apparatus for malware threat research |
| US12412413B2 (en) | 2015-05-08 | 2025-09-09 | Open Text Corporation | Image box filtering for optical character recognition |
| US12437068B2 (en) | 2015-05-12 | 2025-10-07 | Open Text Inc. | Automatic threat detection of executable files based on static data analysis |
Citations (35)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US5381545A (en)* | 1991-06-04 | 1995-01-10 | International Business Machines Corporation | Data backup and recovery in a data processing system |
| US6067410A (en)* | 1996-02-09 | 2000-05-23 | Symantec Corporation | Emulation repair system |
| US6128630A (en)* | 1997-12-18 | 2000-10-03 | International Business Machines Corporation | Journal space release for log-structured storage systems |
| US6161130A (en) | 1998-06-23 | 2000-12-12 | Microsoft Corporation | Technique which utilizes a probabilistic classifier to detect "junk" e-mail by automatically updating a training and re-training the classifier based on the updated training set |
| US20020178374A1 (en)* | 2001-05-25 | 2002-11-28 | International Business Machines Corporation | Method and apparatus for repairing damage to a computer system using a system rollback mechanism |
| US20030023733A1 (en)* | 2001-07-26 | 2003-01-30 | International Business Machines Corporation | Apparatus and method for using a network processor to guard against a "denial-of-service" attack on a server or server cluster |
| US20030187853A1 (en)* | 2002-01-24 | 2003-10-02 | Hensley Roy Austin | Distributed data storage system and method |
| US20030191782A1 (en)* | 2002-04-09 | 2003-10-09 | International Business Machines Corporation | Data recovery system |
| US20030208500A1 (en)* | 2002-02-15 | 2003-11-06 | Daynes Laurent P. | Multi-level undo of main-memory and volatile resources |
| US20040034813A1 (en)* | 2002-02-22 | 2004-02-19 | Francois-Xavier Chaboud | Validation device |
| US20040111557A1 (en)* | 2002-12-04 | 2004-06-10 | Yoji Nakatani | Updated data write method using journal log |
| US20040199827A1 (en) | 2003-04-01 | 2004-10-07 | Muttik Igor Garrievich | Malware detection uswing external core characteristics |
| US20050060528A1 (en)* | 2003-09-17 | 2005-03-17 | Samsung Electronics Co., Ltd. | Booting and boot code update method and system thereof |
| US20050060699A1 (en)* | 2003-09-17 | 2005-03-17 | Samsung Electronics Co., Ltd. | Method and system for updating software |
| US6877109B2 (en)* | 2001-11-19 | 2005-04-05 | Lsi Logic Corporation | Method for the acceleration and simplification of file system logging techniques using storage device snapshots |
| US20050216759A1 (en) | 2004-03-29 | 2005-09-29 | Rothman Michael A | Virus scanning of input/output traffic of a computer system |
| US6973577B1 (en) | 2000-05-26 | 2005-12-06 | Mcafee, Inc. | System and method for dynamically detecting computer viruses through associative behavioral analysis of runtime state |
| US20060041942A1 (en) | 2004-06-24 | 2006-02-23 | Mcafee, Inc. | System, method and computer program product for preventing spyware/malware from installing a registry |
| US20060047931A1 (en)* | 2004-08-27 | 2006-03-02 | Nobuyuki Saika | Method and program for creating a snapshot, and storage system |
| US7039830B2 (en)* | 2000-12-14 | 2006-05-02 | Far Stone Technology Corporation | Backup/recovery system and methods for protecting a computer system |
| US20060137010A1 (en)* | 2004-12-21 | 2006-06-22 | Microsoft Corporation | Method and system for a self-healing device |
| US20060136720A1 (en)* | 2004-12-21 | 2006-06-22 | Microsoft Corporation | Computer security management, such as in a virtual machine or hardened operating system |
| US20060136771A1 (en)* | 2004-12-06 | 2006-06-22 | Hitachi, Ltd. | Storage system and snapshot data preparation method in storage system |
| US20060173935A1 (en)* | 2005-02-03 | 2006-08-03 | Arif Merchant | Method of restoring data |
| US7103913B2 (en) | 2002-05-08 | 2006-09-05 | International Business Machines Corporation | Method and apparatus for determination of the non-replicative behavior of a malicious program |
| US20060236049A1 (en)* | 2005-04-13 | 2006-10-19 | Hitachi, Ltd. | Remote copy system and remote copy method |
| US20070006304A1 (en)* | 2005-06-30 | 2007-01-04 | Microsoft Corporation | Optimizing malware recovery |
| US7188369B2 (en) | 2002-10-03 | 2007-03-06 | Trend Micro, Inc. | System and method having an antivirus virtual scanning processor with plug-in functionalities |
| US20070088970A1 (en)* | 2003-04-10 | 2007-04-19 | Lenovo (Singapore) Pte.Ltd | Recovery from failures within data processing systems |
| US7376970B2 (en) | 2004-02-20 | 2008-05-20 | Microsoft Corporation | System and method for proactive computer virus protection |
| US7409791B2 (en) | 2003-12-02 | 2008-08-12 | Grip Pod Systems, L.L.C. | Vertical fore grip with bipod |
| US7565382B1 (en)* | 2003-08-14 | 2009-07-21 | Symantec Corporation | Safely rolling back a computer image |
| US7581136B2 (en)* | 2006-05-19 | 2009-08-25 | Hitachi, Ltd. | Method and apparatus for data recovery |
| US7587760B1 (en)* | 2004-07-26 | 2009-09-08 | Cisco Technology, Inc. | System and methods for preventing denial of service attacks |
| US7636946B2 (en)* | 2005-08-31 | 2009-12-22 | Microsoft Corporation | Unwanted file modification and transactions |
- 2005
- 2005-07-14USUS11/181,320patent/US7784098B1/enactiveActive
Patent Citations (42)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US5381545A (en)* | 1991-06-04 | 1995-01-10 | International Business Machines Corporation | Data backup and recovery in a data processing system |
| US6067410A (en)* | 1996-02-09 | 2000-05-23 | Symantec Corporation | Emulation repair system |
| US6128630A (en)* | 1997-12-18 | 2000-10-03 | International Business Machines Corporation | Journal space release for log-structured storage systems |
| US6161130A (en) | 1998-06-23 | 2000-12-12 | Microsoft Corporation | Technique which utilizes a probabilistic classifier to detect "junk" e-mail by automatically updating a training and re-training the classifier based on the updated training set |
| US6973577B1 (en) | 2000-05-26 | 2005-12-06 | Mcafee, Inc. | System and method for dynamically detecting computer viruses through associative behavioral analysis of runtime state |
| US7039830B2 (en)* | 2000-12-14 | 2006-05-02 | Far Stone Technology Corporation | Backup/recovery system and methods for protecting a computer system |
| US20020178374A1 (en)* | 2001-05-25 | 2002-11-28 | International Business Machines Corporation | Method and apparatus for repairing damage to a computer system using a system rollback mechanism |
| US7188368B2 (en)* | 2001-05-25 | 2007-03-06 | Lenovo (Singapore) Pte. Ltd. | Method and apparatus for repairing damage to a computer system using a system rollback mechanism |
| US7047303B2 (en)* | 2001-07-26 | 2006-05-16 | International Business Machines Corporation | Apparatus and method for using a network processor to guard against a “denial-of-service” attack on a server or server cluster |
| US20030023733A1 (en)* | 2001-07-26 | 2003-01-30 | International Business Machines Corporation | Apparatus and method for using a network processor to guard against a "denial-of-service" attack on a server or server cluster |
| US6877109B2 (en)* | 2001-11-19 | 2005-04-05 | Lsi Logic Corporation | Method for the acceleration and simplification of file system logging techniques using storage device snapshots |
| US20030187853A1 (en)* | 2002-01-24 | 2003-10-02 | Hensley Roy Austin | Distributed data storage system and method |
| US20030208500A1 (en)* | 2002-02-15 | 2003-11-06 | Daynes Laurent P. | Multi-level undo of main-memory and volatile resources |
| US7234076B2 (en)* | 2002-02-15 | 2007-06-19 | Sun Microsystems, Inc. | Multi-level undo of main-memory and volatile resources |
| US20040034813A1 (en)* | 2002-02-22 | 2004-02-19 | Francois-Xavier Chaboud | Validation device |
| US20030191782A1 (en)* | 2002-04-09 | 2003-10-09 | International Business Machines Corporation | Data recovery system |
| US6993537B2 (en)* | 2002-04-09 | 2006-01-31 | Lenovo (Singapore) Pte. Ltd. | Data recovery system |
| US7103913B2 (en) | 2002-05-08 | 2006-09-05 | International Business Machines Corporation | Method and apparatus for determination of the non-replicative behavior of a malicious program |
| US7188369B2 (en) | 2002-10-03 | 2007-03-06 | Trend Micro, Inc. | System and method having an antivirus virtual scanning processor with plug-in functionalities |
| US20040111557A1 (en)* | 2002-12-04 | 2004-06-10 | Yoji Nakatani | Updated data write method using journal log |
| US20040199827A1 (en) | 2003-04-01 | 2004-10-07 | Muttik Igor Garrievich | Malware detection uswing external core characteristics |
| US20070088970A1 (en)* | 2003-04-10 | 2007-04-19 | Lenovo (Singapore) Pte.Ltd | Recovery from failures within data processing systems |
| US7565382B1 (en)* | 2003-08-14 | 2009-07-21 | Symantec Corporation | Safely rolling back a computer image |
| US7664923B2 (en)* | 2003-09-17 | 2010-02-16 | Samsung Electronics Co., Ltd | Method and system for updating software |
| US20050060699A1 (en)* | 2003-09-17 | 2005-03-17 | Samsung Electronics Co., Ltd. | Method and system for updating software |
| US20050060528A1 (en)* | 2003-09-17 | 2005-03-17 | Samsung Electronics Co., Ltd. | Booting and boot code update method and system thereof |
| US7409791B2 (en) | 2003-12-02 | 2008-08-12 | Grip Pod Systems, L.L.C. | Vertical fore grip with bipod |
| US7376970B2 (en) | 2004-02-20 | 2008-05-20 | Microsoft Corporation | System and method for proactive computer virus protection |
| US20050216759A1 (en) | 2004-03-29 | 2005-09-29 | Rothman Michael A | Virus scanning of input/output traffic of a computer system |
| US20060041942A1 (en) | 2004-06-24 | 2006-02-23 | Mcafee, Inc. | System, method and computer program product for preventing spyware/malware from installing a registry |
| US7587760B1 (en)* | 2004-07-26 | 2009-09-08 | Cisco Technology, Inc. | System and methods for preventing denial of service attacks |
| US7181583B2 (en)* | 2004-08-27 | 2007-02-20 | Hitachi, Ltd. | Method and program for creating a snapshot, and storage system |
| US20060047931A1 (en)* | 2004-08-27 | 2006-03-02 | Nobuyuki Saika | Method and program for creating a snapshot, and storage system |
| US20060136771A1 (en)* | 2004-12-06 | 2006-06-22 | Hitachi, Ltd. | Storage system and snapshot data preparation method in storage system |
| US7409719B2 (en)* | 2004-12-21 | 2008-08-05 | Microsoft Corporation | Computer security management, such as in a virtual machine or hardened operating system |
| US20060136720A1 (en)* | 2004-12-21 | 2006-06-22 | Microsoft Corporation | Computer security management, such as in a virtual machine or hardened operating system |
| US20060137010A1 (en)* | 2004-12-21 | 2006-06-22 | Microsoft Corporation | Method and system for a self-healing device |
| US20060173935A1 (en)* | 2005-02-03 | 2006-08-03 | Arif Merchant | Method of restoring data |
| US20060236049A1 (en)* | 2005-04-13 | 2006-10-19 | Hitachi, Ltd. | Remote copy system and remote copy method |
| US20070006304A1 (en)* | 2005-06-30 | 2007-01-04 | Microsoft Corporation | Optimizing malware recovery |
| US7636946B2 (en)* | 2005-08-31 | 2009-12-22 | Microsoft Corporation | Unwanted file modification and transactions |
| US7581136B2 (en)* | 2006-05-19 | 2009-08-25 | Hitachi, Ltd. | Method and apparatus for data recovery |
Non-Patent Citations (4)
| Title |
|---|
| Office Action dated Apr. 2, 2009 in U.S. Appl. No. 11/204,567. |
| Office Action dated Jan. 16, 2009 in U.S. Appl. No. 11/247,349. |
| Office Action dated Jun. 15, 2009 in U.S. Appl. No. 11/247,349. |
| Office Action dated Jun. 3, 2009 in U.S. Appl. No. 11/356,600. |
Cited By (99)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US12282549B2 (en) | 2005-06-30 | 2025-04-22 | Open Text Inc. | Methods and apparatus for malware threat research |
| US8661541B2 (en)* | 2005-07-15 | 2014-02-25 | Microsoft Corporation | Detecting user-mode rootkits |
| US20110099632A1 (en)* | 2005-07-15 | 2011-04-28 | Microsoft Corporation | Detecting user-mode rootkits |
| US20080047013A1 (en)* | 2005-08-16 | 2008-02-21 | Emc Corporation | Method and system for detecting malware |
| US8468604B2 (en) | 2005-08-16 | 2013-06-18 | Emc Corporation | Method and system for detecting malware |
| US8255998B2 (en)* | 2005-08-16 | 2012-08-28 | Emc Corporation | Information protection method and system |
| US20080016564A1 (en)* | 2005-08-16 | 2008-01-17 | Emc Corporation | Information protection method and system |
| US20080276299A1 (en)* | 2007-04-02 | 2008-11-06 | Samsung Electronics Co., Ltd. | Wireless terminal apparatus and method of protecting system resources |
| US20090038012A1 (en)* | 2007-08-03 | 2009-02-05 | Lenovo (Beijing) Limited | Method and system for deleting or isolating computer viruses |
| US8365285B2 (en)* | 2007-08-03 | 2013-01-29 | Lenovo (Beijing) Limited | Method and system for deleting or isolating computer viruses |
| US20120143826A1 (en)* | 2007-12-19 | 2012-06-07 | Microsoft Corporation | Creating and utilizing network restore points |
| US8612391B2 (en)* | 2007-12-19 | 2013-12-17 | Microsoft Corporation | Creating and utilizing network restore points |
| US7934262B1 (en)* | 2007-12-26 | 2011-04-26 | Emc (Benelux) B.V., S.A.R.L. | Methods and apparatus for virus detection using journal data |
| US8392539B1 (en)* | 2008-03-19 | 2013-03-05 | Trend Micro, Inc. | Operating system banking and portability |
| US8949187B1 (en)* | 2008-05-30 | 2015-02-03 | Symantec Corporation | Systems and methods for creating and managing backups based on health information |
| US8291261B2 (en)* | 2008-11-05 | 2012-10-16 | Vulcan Technologies Llc | Lightweight application-level runtime state save-and-restore utility |
| US20100115334A1 (en)* | 2008-11-05 | 2010-05-06 | Mark Allen Malleck | Lightweight application-level runtime state save-and-restore utility |
| US8418251B1 (en)* | 2009-04-27 | 2013-04-09 | Symantec Corporation | Detecting malware using cost characteristics |
| US20110197279A1 (en)* | 2009-05-29 | 2011-08-11 | Hitachi, Ltd. | Management methods of storage system and file system |
| US8683576B1 (en)* | 2009-09-30 | 2014-03-25 | Symantec Corporation | Systems and methods for detecting a process to establish a backdoor connection with a computing device |
| US12164466B2 (en) | 2010-03-29 | 2024-12-10 | Open Text Inc. | Log file management |
| US12210479B2 (en) | 2010-03-29 | 2025-01-28 | Open Text Inc. | Log file management |
| US8452735B2 (en)* | 2010-05-26 | 2013-05-28 | International Business Machines Corporation | Selecting a data restore point with an optimal recovery time and recovery point |
| US20110296237A1 (en)* | 2010-05-26 | 2011-12-01 | International Business Machines Corporation | Selecting a data restore point with an optimal recovery time and recovery point |
| US20120322439A1 (en)* | 2010-06-14 | 2012-12-20 | Future Dial Inc. | System and Method for Enhanced Diagnostics on Mobile Communication Devices |
| US9585033B2 (en) | 2010-06-14 | 2017-02-28 | Future Dial, Inc. | System and method for enhanced diagnostics on mobile communication devices |
| US8855627B2 (en)* | 2010-06-14 | 2014-10-07 | Future Dial, Inc. | System and method for enhanced diagnostics on mobile communication devices |
| US8352522B1 (en)* | 2010-09-01 | 2013-01-08 | Trend Micro Incorporated | Detection of file modifications performed by malicious codes |
| US9378369B1 (en)* | 2010-09-01 | 2016-06-28 | Trend Micro Incorporated | Detection of file modifications performed by malicious codes |
| US20120158661A1 (en)* | 2010-12-15 | 2012-06-21 | Microsoft Corporation | Context-specific rollback |
| US20120297488A1 (en)* | 2011-05-16 | 2012-11-22 | Microsoft Corporation | Discovering Malicious Input Files and Performing Automatic and Distributed Remediation |
| US9436826B2 (en)* | 2011-05-16 | 2016-09-06 | Microsoft Technology Licensing, Llc | Discovering malicious input files and performing automatic and distributed remediation |
| US10467080B2 (en) | 2011-08-16 | 2019-11-05 | Future Dial, Inc. | Systems and methods to reprogram mobile devices |
| US11815991B2 (en) | 2011-08-16 | 2023-11-14 | Future Dial, Inc. | Systems and methods to reprogram mobile devices including a cross-matrix controller to port connection |
| US8996916B2 (en) | 2011-08-16 | 2015-03-31 | Future Dial, Inc. | System and method for identifying problems via a monitoring application that repetitively records multiple separate consecutive files listing launched or installed applications |
| US10503579B2 (en) | 2011-08-16 | 2019-12-10 | Future Dial, Inc. | System and method for identifying operational disruptions in mobile computing devices |
| US10572328B2 (en) | 2011-08-16 | 2020-02-25 | Future Dial, Inc. | Systems and methods to reprogram mobile devices |
| US11099923B2 (en) | 2011-08-16 | 2021-08-24 | Future Dial, Inc. | Systems and methods to reprogram mobile devices |
| US11169867B2 (en) | 2011-08-16 | 2021-11-09 | Future Dial, Inc. | System and method for identifying operational disruptions in mobile computing devices via a monitoring application that repetitively records multiple separate consecutive files listing launched or installed applications |
| US12339734B2 (en) | 2011-08-16 | 2025-06-24 | Future Dial, Inc. | Systems and methods to reprogram mobile devices based on identity information queried using a low-functionality driver |
| US11507450B2 (en) | 2011-08-16 | 2022-11-22 | Future Dial, Inc. | Systems and methods to reprogram mobile devices via a cross-matrix controller to port connection |
| US9661490B2 (en) | 2011-08-16 | 2017-05-23 | Future Dial, Inc. | System and method for identifying operational disruptions in mobile computing devices |
| WO2013087603A1 (en)* | 2011-12-14 | 2013-06-20 | F-Secure Corporation | Disinfection of a file system |
| US10701097B2 (en)* | 2011-12-20 | 2020-06-30 | Micro Focus Llc | Application security testing |
| US20130160131A1 (en)* | 2011-12-20 | 2013-06-20 | Matias Madou | Application security testing |
| US20130167235A1 (en)* | 2011-12-22 | 2013-06-27 | Microsoft Corproation | Augmenting system restore with malware detection |
| EP2795525A4 (en)* | 2011-12-22 | 2015-08-12 | Microsoft Technology Licensing Llc | INCREASING SYSTEM RESTORATION BY DETECTING MALWARE SOFTWARE |
| WO2013096140A1 (en) | 2011-12-22 | 2013-06-27 | Microsoft Corporation | Augmenting system restore with malware detection |
| CN103065091B (en)* | 2011-12-22 | 2016-03-09 | 微软技术许可有限责任公司 | Reduce with malware detection expanding system |
| US9613209B2 (en)* | 2011-12-22 | 2017-04-04 | Microsoft Technology Licensing, Llc. | Augmenting system restore with malware detection |
| CN103065091A (en)* | 2011-12-22 | 2013-04-24 | 微软公司 | Extension of system restoration by using malware detection |
| US12131294B2 (en) | 2012-06-21 | 2024-10-29 | Open Text Corporation | Activity stream based interaction |
| US10324843B1 (en) | 2012-06-30 | 2019-06-18 | EMC IP Holding Company LLC | System and method for cache management |
| US9378096B1 (en)* | 2012-06-30 | 2016-06-28 | Emc Corporation | System and method for cache management |
| US20140122859A1 (en)* | 2012-11-01 | 2014-05-01 | International Business Machines Corporation | Configuring configuration settings using a user context |
| US9501648B2 (en)* | 2012-11-01 | 2016-11-22 | International Business Machines Corporation | Configuring configuration settings using a user context |
| US20140122853A1 (en)* | 2012-11-01 | 2014-05-01 | International Business Machines Corporation | Configuring configuration settings using a user context |
| US9928368B2 (en)* | 2012-11-01 | 2018-03-27 | International Business Machines Corporation | Configuring configuration settings using a user context |
| US9754110B2 (en)* | 2012-11-01 | 2017-09-05 | International Business Machines Corporation | Configuring configuration settings using a user context |
| US9773026B1 (en)* | 2012-12-20 | 2017-09-26 | EMC IP Holding Company LLC | Calculation of system utilization |
| EP2972772A4 (en)* | 2013-03-15 | 2016-11-16 | Amazon Tech Inc | INSTANT COPIES IN PLACE |
| US10180951B2 (en) | 2013-03-15 | 2019-01-15 | Amazon Technologies, Inc. | Place snapshots |
| CN105518694A (en)* | 2013-06-25 | 2016-04-20 | 微软技术许可有限责任公司 | Reverse copy to restore damaged files |
| US10204113B2 (en) | 2013-06-25 | 2019-02-12 | Microsoft Technology Licensing, Llc | Reverse replication to rollback corrupted files |
| WO2014209825A1 (en)* | 2013-06-25 | 2014-12-31 | Microsoft Corporation | Reverse replication to rollback corrupted files |
| US9323924B1 (en)* | 2014-05-09 | 2016-04-26 | Symantec Corporation | Systems and methods for establishing reputations of files |
| US12261822B2 (en) | 2014-06-22 | 2025-03-25 | Open Text Inc. | Network threat prediction and blocking |
| US12301539B2 (en) | 2014-06-22 | 2025-05-13 | Open Text Inc. | Network threat prediction and blocking |
| US12412413B2 (en) | 2015-05-08 | 2025-09-09 | Open Text Corporation | Image box filtering for optical character recognition |
| US12437068B2 (en) | 2015-05-12 | 2025-10-07 | Open Text Inc. | Automatic threat detection of executable files based on static data analysis |
| US12197383B2 (en) | 2015-06-30 | 2025-01-14 | Open Text Corporation | Method and system for using dynamic content types |
| US10043026B1 (en)* | 2015-11-09 | 2018-08-07 | 8X8, Inc. | Restricted replication for protection of replicated databases |
| US11120132B1 (en)* | 2015-11-09 | 2021-09-14 | 8X8, Inc. | Restricted replication for protection of replicated databases |
| US11153335B1 (en) | 2015-11-09 | 2021-10-19 | 8X8, Inc. | Delayed replication for protection of replicated databases |
| US10440039B1 (en) | 2015-11-09 | 2019-10-08 | 8X8, Inc. | Delayed replication for protection of replicated databases |
| US10885196B2 (en) | 2016-04-29 | 2021-01-05 | Hewlett Packard Enterprise Development Lp | Executing protected code |
| US10326599B2 (en) | 2016-05-09 | 2019-06-18 | Hewlett Packard Enterprise Development Lp | Recovery agents and recovery plans over networks |
| US20180167403A1 (en)* | 2016-12-12 | 2018-06-14 | Ut Battelle, Llc | Malware analysis and recovery |
| US10931685B2 (en)* | 2016-12-12 | 2021-02-23 | Ut-Battelle, Llc | Malware analysis and recovery |
| US11275834B1 (en)* | 2017-01-12 | 2022-03-15 | Richard Offer | System for analyzing backups for threats and irregularities |
| US9734337B1 (en)* | 2017-01-24 | 2017-08-15 | Malwarebytes Inc. | Behavior-based ransomware detection |
| US10032025B1 (en) | 2017-01-24 | 2018-07-24 | Malwarebytes Inc. | Behavior-based ransomware detection |
| US11010470B2 (en)* | 2017-12-15 | 2021-05-18 | Microsoft Technology Licensing, Llc | Anti-virus file system cache for operating system remediation |
| US12149623B2 (en) | 2018-02-23 | 2024-11-19 | Open Text Inc. | Security privilege escalation exploit detection and mitigation |
| US10963564B2 (en) | 2018-03-30 | 2021-03-30 | Microsoft Technology Licensing, Llc | Selection of restore point based on detection of malware attack |
| US10917416B2 (en)* | 2018-03-30 | 2021-02-09 | Microsoft Technology Licensing, Llc | Service identification of ransomware impacted files |
| US20190306179A1 (en)* | 2018-03-30 | 2019-10-03 | Microsoft Technology Licensing, Llc | Service identification of ransomware impacted files |
| WO2019190936A1 (en)* | 2018-03-30 | 2019-10-03 | Microsoft Technology Licensing, Llc | Selection of restore point based on detection of malware attack |
| US11308207B2 (en) | 2018-03-30 | 2022-04-19 | Microsoft Technology Licensing, Llc | User verification of malware impacted files |
| US10769278B2 (en) | 2018-03-30 | 2020-09-08 | Microsoft Technology Licensing, Llc | Service identification of ransomware impact at account level |
| US10896085B2 (en) | 2018-05-08 | 2021-01-19 | Hewlett-Packard Development Company, L.P. | Mitigating actions |
| US11809559B2 (en) | 2018-08-03 | 2023-11-07 | Hewlett-Packard Development Company, L.P. | Intrusion resilient applications |
| US12235960B2 (en) | 2019-03-27 | 2025-02-25 | Open Text Inc. | Behavioral threat detection definition and compilation |
| US11153373B2 (en) | 2019-05-03 | 2021-10-19 | EMC IP Holding Company LLC | Method and system for performance-driven load shifting |
| US11720470B2 (en)* | 2020-08-19 | 2023-08-08 | Unitedhealth Group Incorporated | Dynamic post-change computing-system evaluation |
| US20220058103A1 (en)* | 2020-08-19 | 2022-02-24 | Unitedhealth Group Incorporated | Dynamic post-change computing-system evaluation |
| CN114116322B (en)* | 2022-01-27 | 2022-05-24 | 深圳市科力锐科技有限公司 | Data recovery method, device, equipment and storage medium |
| CN114116322A (en)* | 2022-01-27 | 2022-03-01 | 深圳市科力锐科技有限公司 | Data recovery method, device, equipment and storage medium |
| US20230388340A1 (en)* | 2022-05-31 | 2023-11-30 | WithSecure Corporation | Arrangement and method of threat detection in a computer or computer network |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| US7784098B1 (en) | Snapshot and restore technique for computer system recovery | |
| Kharraz et al. | Redemption: Real-time protection against ransomware at end-hosts | |
| US7779472B1 (en) | Application behavior based malware detection | |
| US9317686B1 (en) | File backup to combat ransomware | |
| US10291634B2 (en) | System and method for determining summary events of an attack | |
| US8381298B2 (en) | Malware detention for suspected malware | |
| US8171552B1 (en) | Simultaneous execution of multiple anti-virus programs | |
| US7934261B1 (en) | On-demand cleanup system | |
| US11232201B2 (en) | Cloud based just in time memory analysis for malware detection | |
| US8590045B2 (en) | Malware detection by application monitoring | |
| US7607171B1 (en) | Virus detection by executing e-mail code in a virtual machine | |
| US7716743B2 (en) | Privacy friendly malware quarantines | |
| US8195953B1 (en) | Computer program with built-in malware protection | |
| US7840958B1 (en) | Preventing spyware installation | |
| US7729690B1 (en) | Backup and restore of user data for mobile telephone | |
| US20110047618A1 (en) | Method, System, and Computer Program Product for Malware Detection, Analysis, and Response | |
| US20080301051A1 (en) | Internet fraud prevention | |
| US12001555B1 (en) | System, method, and apparatus for preventing ransomware | |
| US8918874B2 (en) | Malware scanning | |
| WO2007035575A2 (en) | Method and apparatus for removing harmful software | |
| US20190095285A1 (en) | Backup and recovery of data files using hard links | |
| US11113391B2 (en) | Method and computer system for preventing malicious software from attacking files of the computer system and corresponding non-transitory computer readable storage medium | |
| Alzahrani et al. | Ransomware in windows and android platforms | |
| Strunk et al. | Intrusion detection, diagnosis, and recovery with self-securing storage | |
| CN116204880A (en) | Computer virus defense system |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| AS | Assignment | Owner name:TREND MICRO, INC., JAPAN Free format text:ASSIGNMENT OF ASSIGNORS INTEREST;ASSIGNORS:FAN, PAUL;LIN, JASON;WANG, PUMBAA;REEL/FRAME:016646/0913 Effective date:20050818 | |
| STCF | Information on status: patent grant | Free format text:PATENTED CASE | |
| FPAY | Fee payment | Year of fee payment:4 | |
| MAFP | Maintenance fee payment | Free format text:PAYMENT OF MAINTENANCE FEE, 8TH YEAR, LARGE ENTITY (ORIGINAL EVENT CODE: M1552) Year of fee payment:8 | |
| MAFP | Maintenance fee payment | Free format text:PAYMENT OF MAINTENANCE FEE, 12TH YEAR, LARGE ENTITY (ORIGINAL EVENT CODE: M1553); ENTITY STATUS OF PATENT OWNER: LARGE ENTITY Year of fee payment:12 | |
| AS | Assignment | Owner name:TREND MICRO INCORPORATED, TEXAS Free format text:ASSIGNMENT OF ASSIGNORS INTEREST;ASSIGNOR:TREND MICRO INCORPORATED;REEL/FRAME:061686/0342 Effective date:20221010 |