US7206847B1 - Smart card with back up - Google Patents
Smart card with back upDownload PDFInfo
- Publication number
- US7206847B1 US7206847B1US09/575,749US57574900AUS7206847B1US 7206847 B1US7206847 B1US 7206847B1US 57574900 AUS57574900 AUS 57574900AUS 7206847 B1US7206847 B1US 7206847B1
- Authority
- US
- United States
- Prior art keywords
- personal data
- data storage
- storage device
- personal
- smart card
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Expired - Fee Related
Links
Images
Classifications
- G—PHYSICS
- G07—CHECKING-DEVICES
- G07F—COIN-FREED OR LIKE APPARATUS
- G07F7/00—Mechanisms actuated by objects other than coins to free or to actuate vending, hiring, coin or paper currency dispensing or refunding apparatus
- G07F7/08—Mechanisms actuated by objects other than coins to free or to actuate vending, hiring, coin or paper currency dispensing or refunding apparatus by coded identity card or credit card or other personal identification means
- G07F7/10—Mechanisms actuated by objects other than coins to free or to actuate vending, hiring, coin or paper currency dispensing or refunding apparatus by coded identity card or credit card or other personal identification means together with a coded signal, e.g. in the form of personal identification information, like personal identification number [PIN] or biometric data
- G07F7/1016—Devices or methods for securing the PIN and other transaction-data, e.g. by encryption
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06Q—INFORMATION AND COMMUNICATION TECHNOLOGY [ICT] SPECIALLY ADAPTED FOR ADMINISTRATIVE, COMMERCIAL, FINANCIAL, MANAGERIAL OR SUPERVISORY PURPOSES; SYSTEMS OR METHODS SPECIALLY ADAPTED FOR ADMINISTRATIVE, COMMERCIAL, FINANCIAL, MANAGERIAL OR SUPERVISORY PURPOSES, NOT OTHERWISE PROVIDED FOR
- G06Q20/00—Payment architectures, schemes or protocols
- G06Q20/08—Payment architectures
- G06Q20/10—Payment architectures specially adapted for electronic funds transfer [EFT] systems; specially adapted for home banking systems
- G06Q20/102—Bill distribution or payments
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06Q—INFORMATION AND COMMUNICATION TECHNOLOGY [ICT] SPECIALLY ADAPTED FOR ADMINISTRATIVE, COMMERCIAL, FINANCIAL, MANAGERIAL OR SUPERVISORY PURPOSES; SYSTEMS OR METHODS SPECIALLY ADAPTED FOR ADMINISTRATIVE, COMMERCIAL, FINANCIAL, MANAGERIAL OR SUPERVISORY PURPOSES, NOT OTHERWISE PROVIDED FOR
- G06Q20/00—Payment architectures, schemes or protocols
- G06Q20/08—Payment architectures
- G06Q20/10—Payment architectures specially adapted for electronic funds transfer [EFT] systems; specially adapted for home banking systems
- G06Q20/105—Payment architectures specially adapted for electronic funds transfer [EFT] systems; specially adapted for home banking systems involving programming of a portable memory device, e.g. IC cards, "electronic purses"
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06Q—INFORMATION AND COMMUNICATION TECHNOLOGY [ICT] SPECIALLY ADAPTED FOR ADMINISTRATIVE, COMMERCIAL, FINANCIAL, MANAGERIAL OR SUPERVISORY PURPOSES; SYSTEMS OR METHODS SPECIALLY ADAPTED FOR ADMINISTRATIVE, COMMERCIAL, FINANCIAL, MANAGERIAL OR SUPERVISORY PURPOSES, NOT OTHERWISE PROVIDED FOR
- G06Q20/00—Payment architectures, schemes or protocols
- G06Q20/30—Payment architectures, schemes or protocols characterised by the use of specific devices or networks
- G06Q20/34—Payment architectures, schemes or protocols characterised by the use of specific devices or networks using cards, e.g. integrated circuit [IC] cards or magnetic cards
- G06Q20/341—Active cards, i.e. cards including their own processing means, e.g. including an IC or chip
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06Q—INFORMATION AND COMMUNICATION TECHNOLOGY [ICT] SPECIALLY ADAPTED FOR ADMINISTRATIVE, COMMERCIAL, FINANCIAL, MANAGERIAL OR SUPERVISORY PURPOSES; SYSTEMS OR METHODS SPECIALLY ADAPTED FOR ADMINISTRATIVE, COMMERCIAL, FINANCIAL, MANAGERIAL OR SUPERVISORY PURPOSES, NOT OTHERWISE PROVIDED FOR
- G06Q20/00—Payment architectures, schemes or protocols
- G06Q20/30—Payment architectures, schemes or protocols characterised by the use of specific devices or networks
- G06Q20/34—Payment architectures, schemes or protocols characterised by the use of specific devices or networks using cards, e.g. integrated circuit [IC] cards or magnetic cards
- G06Q20/357—Cards having a plurality of specified features
- G06Q20/3576—Multiple memory zones on card
- G—PHYSICS
- G07—CHECKING-DEVICES
- G07F—COIN-FREED OR LIKE APPARATUS
- G07F7/00—Mechanisms actuated by objects other than coins to free or to actuate vending, hiring, coin or paper currency dispensing or refunding apparatus
- G07F7/08—Mechanisms actuated by objects other than coins to free or to actuate vending, hiring, coin or paper currency dispensing or refunding apparatus by coded identity card or credit card or other personal identification means
- G07F7/0806—Details of the card
- G07F7/0813—Specific details related to card security
- G07F7/082—Features insuring the integrity of the data on or in the card
- G—PHYSICS
- G07—CHECKING-DEVICES
- G07F—COIN-FREED OR LIKE APPARATUS
- G07F7/00—Mechanisms actuated by objects other than coins to free or to actuate vending, hiring, coin or paper currency dispensing or refunding apparatus
- G07F7/08—Mechanisms actuated by objects other than coins to free or to actuate vending, hiring, coin or paper currency dispensing or refunding apparatus by coded identity card or credit card or other personal identification means
- G07F7/10—Mechanisms actuated by objects other than coins to free or to actuate vending, hiring, coin or paper currency dispensing or refunding apparatus by coded identity card or credit card or other personal identification means together with a coded signal, e.g. in the form of personal identification information, like personal identification number [PIN] or biometric data
- G07F7/1008—Active credit-cards provided with means to personalise their use, e.g. with PIN-introduction/comparison system
Definitions
- This inventionrelates to data security devices.
- this inventionrelates to a method and apparatus for securely storing data in a personal data security device commonly known as a smart card.
- Smart cardsas they are known, physically resemble the now ubiquitous credit cards but their similarities end there. These credit-card replacements are described in the literature. By way of example, they are described in an article appearing on page 47 of the February 1997 edition of the IEEE Spectrum magazine which is entitled “In Your Pocket Smartcards” by Carol Hovenga Fancher.
- smart cardsWhile smart cards physically resemble credit cards, smart cards are far more powerful in that they have one or more microcontrollers embedded in them which manage access to, and storage of, sensitive data that is actually stored in memory devices on the smart card. Data that might be stored in a smart card includes bank account numbers, personal data as well as a complete medical history, or the electronic equivalent of currency. Smart cards are widely used in Europe and are expected to eventually replace the library of cards most people carry and which include credit cards, phone cards, transit passes, frequent flyer cards, car rental cards and social security card.
- Cards on the other hand, as well as debit cards and “ATM” (automatic teller machine) cardsare mere sheets of plastic that are embossed with a series of numbers and letters that represent either the card number or an account number.
- a strip of magnetized material that is typically attached to one side of the cardis programmed (magnetized) with a limited amount of data, typically the same number that is embossed on the card.
- information programmed into the magnetic stripis read.
- a personal data storage device(a smart card) is enhanced by providing to the smart card an additional layer of security in the form of an enabling key, which when coupled to the smart card enables the processor on the smart card to access and change storage information. If the enabling key is not accessible to the smart card, the smart card remains disabled.
- the enabling keyis physically connected to a terminal of the smart card.
- a wireless radio link between the enabling key and smart cardis used.
- the smart cardis disabled if the enabling key and its own processor and data are not detected and accessed by the smart card.
- An additional level of securityis realized by physically detaching (or geographically separating) the smart card and the enabling key in which event the smart card is disabled, preventing theft. If the key-fob enabling key is lost, intelligence on the smart card provides the smart card issuer sufficient data with which the key can be replicated. If the smart card is lost by the key fob is still available, data on the fob permits the card issuer to recreate the smart card data in its entirety.
- FIG. 1depicts a simplified representation of a two-part smart card, both parts of which are required to provide smart card functionality.
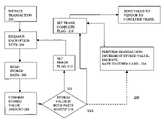
- FIG. 2depicts a simplified flow chart of the disclosed method.
- FIG. 1shows a simplified representation of a two-part personal data storage device, also known as a smart card 100 which provides increased security for sensitive user data such as credit card numbers, bank account numbers, medical history, electronic cash equivalency.
- sensitive user datasuch as credit card numbers, bank account numbers, medical history, electronic cash equivalency.
- Such data and data or information and records of similar importis referred to hereinafter as a set of user data.
- a first part of the smart card 102includes within it a processor 104 and at least one memory device, typically electrically erasable programmable read only memory 106 (EEPROM) but also possibly including read only memory (ROM) as well as random access memory (RAM), accessible via an address/data bus 108 that effectively couples together, devices that are operatively coupled to the bus 108 .
- EEPROMelectrically erasable programmable read only memory
- RAMrandom access memory
- a bi-directional data interface 110which is also coupled to the bus 108 , provides a mechanism by which the first part of the smart card 102 can communicate with external devices, such as the second part 112 of the two-part smart card 100 .
- the bi-directional data interface 110is also coupled to the processor 104 and memory 106 through the bus 108 .
- the second part 112 of the two-part smart card 100also incorporates within it a processor 116 , memory 118 and an I/O port 120 , all of which are coupled together via a separate bus 130 .
- the I/O port 120can be considered to be a second interface circuit.
- the first and second interface circuits ( 110 and 120 respectively)grant communications access to the respective first and second smart card parts ( 102 , 112 respectively).
- Electrical and mechanical coupling between the first and second ports 110 , 120 so as to achieve an electrical connection between the two smart card partsis preferably accomplished using any appropriate mechanical electrical connector device (not shown but known to those skilled in the connector art) but selected depending upon the desired physical characteristics of the smart car when the two portions are together. Alternate embodiments would include using a RF data link, an optical link or an infrared link as well.
- a broken line 119serves only to represent that all of the functionality of the second part 112 is embodied on a single piece of silicon, which in the preferred embodiment is also how the functional elements of the first part 102 are packaged.
- the first part 102 of the smart cardis considered hereinafter to be a first user data storage device in that it actually stores a first set of a users data (such as that listed above) within memory devices physically part of the device.
- the second part 112 of the smart cardis considered to be a second user data storage device in that it too stores the first set of user data within it.
- the processors 104 , 116(within the corresponding smart card parts 102 , 112 ) are coupled to the various circuits within each portion of the respective smart card parts by way of the busses 108 , 130 which carry information between the various circuits that are coupled to it.
- the processorsare able to execute the instructions stored in various memory devices 106 , 118 coupled to the busses 108 , 130 .
- the programs stored in memorygive the smart card portions intelligence.
- Various datacan be written into the first smart card part 102 via the data interface circuit 110 such as a serial or parallel computer-to-computer data link (RS-232, IEEE 488, or other equivalent data pathway) or perhaps via a wireless RF data port 109 , (but also including an optical or infrared data port as well), coupled to the processor 104 .
- the second smart card port 112data can be written into the second smart card via its own similar data port 120 or perhaps its own wireless port 124 .
- Enhanced smart card securityis achieved by denying access to the data stored in the first part of the smart card 102 , if the second part 112 is not accessible to the first part 102 (and vice versa), by either a wireless data exchange or a direct, electrical connection between the first and second parts.
- Software that controls the processor in the first part 104denies access to stored data in the first part 104 if the second part of the card 112 is considered to be missing (or inaccessible to the first part).
- access to data in the second part 112is denied if the first part of the card 104 is missing from the second part (or inaccessible).
- a transaction using the two-part smart cardpreferably proceeds according to the steps of the method 200 depicted in FIG. 2 .
- the two-part smart card userinitiates a desired transaction, which might include reading or writing a medical record or purchasing goods or services using data stored in the smart card that represents currency of the card user.
- a data handshake between the processor 104 and a terminal of a vendor or merchanttakes place via the wireless port 109 or the I/O port 110 either of which can be considered a first interface circuit.
- the first and second interface circuitsgrant conditional communications access to the data using an appropriate data exchange protocol.
- Various protocols as are known in the artcan be used.
- step 204software programmed into the first part 102 of the smart card confirms that the second part 112 is the unique mate to the first part by way of the encryption key exchange.
- a first set of user data(to be referred to as stored value) resides in both part 102 and part 112 of the two-part smart card.
- the first part of the smart card 102reads stored value from the second part after the stored value is encrypted by the processor 116 of the second part 112 in order to prevent interception of the data as it crosses the boundary between the first and second parts 102 , 112 respectively.
- step 208after receiving the encrypted stored value, which the first part 102 decrypts, the first part confirms that the value it received from the second part identically matches the value stored in the first part 102 . If as in step 210 , the value received into the first part 102 does not match the value stored in the second part, one or both parts sets an error condition flag 212 and re-attempts to confirm the identity of the second part by returning to step 204 .
- the processor 102sets a transaction complete flag in step 216 and proceeds to conclude the transaction that was started in step 202 . If the smart card user is purchasing some goods or service or performing some other transaction (as indicated by the broken line from decision block 210 ), value is transferred from the first part via the I/O port 110 or the wireless connection or link 109 to compatible data equipment of the vendor.
- step 214a financial transaction is performed (buying goods or services for example, or the stored value is incremented or decremented by a financial institution for instance), the processor in the first part 104 adjusts the stored value by the amount that was transferred, encrypts the new value and transfers the new value to the second part 112 for storage.
- the issuer of the smart cardis guaranteed that the stored value is always the same in both parts.
- the smart card issuer or agent thereofBy physically or electrically separating the two parts, it becomes impossible to access data stored in the second part 112 or in the first part 102 .
- the smart card issuer or agent thereof(having appropriate software and hardware, which is recognized by the software of the smart part parts 102 , 112 ) can recreate the data stored in the other part because both card parts carry duplicate copies of data stored in each other.
- economic loss caused by physical card losscan be reduced by keeping part of the card in the user's possession at all times.
Landscapes
- Business, Economics & Management (AREA)
- Engineering & Computer Science (AREA)
- Accounting & Taxation (AREA)
- General Physics & Mathematics (AREA)
- Physics & Mathematics (AREA)
- Finance (AREA)
- Strategic Management (AREA)
- General Business, Economics & Management (AREA)
- Theoretical Computer Science (AREA)
- Microelectronics & Electronic Packaging (AREA)
- Computer Networks & Wireless Communication (AREA)
- Computer Security & Cryptography (AREA)
- Development Economics (AREA)
- Economics (AREA)
- Storage Device Security (AREA)
Abstract
Description
Claims (17)
Priority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| US09/575,749US7206847B1 (en) | 2000-05-22 | 2000-05-22 | Smart card with back up |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| US09/575,749US7206847B1 (en) | 2000-05-22 | 2000-05-22 | Smart card with back up |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| US7206847B1true US7206847B1 (en) | 2007-04-17 |
Family
ID=37914225
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US09/575,749Expired - Fee RelatedUS7206847B1 (en) | 2000-05-22 | 2000-05-22 | Smart card with back up |
Country Status (1)
| Country | Link |
|---|---|
| US (1) | US7206847B1 (en) |
Cited By (50)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20060112283A1 (en)* | 2004-11-22 | 2006-05-25 | International Business Machines Corporation | Encrypting a credential store with a lockbox |
| US20070100754A1 (en)* | 2003-12-17 | 2007-05-03 | Brown Kerry D | Financial transaction network security |
| US20070106911A1 (en)* | 2005-11-09 | 2007-05-10 | Cisco Technology, Inc. | Method and system for redundant secure storage of sensitive data by using multiple keys |
| US20080029609A1 (en)* | 2005-02-04 | 2008-02-07 | Chun-Hsin Ho | Dual card system |
| US20090007258A1 (en)* | 2006-01-06 | 2009-01-01 | Verichk Global Technologies Inc. | Secure Access to Information Associated With a Value Item |
| US20090113546A1 (en)* | 2007-10-30 | 2009-04-30 | Samsung Electronics Co., Ltd. | Memory system for sensing attack |
| US20090159679A1 (en)* | 2007-12-20 | 2009-06-25 | Mastercard International, Inc. | Ultra Low-Power User Authentication Device for Financial Transactions |
| US20090307489A1 (en)* | 2006-01-30 | 2009-12-10 | Kyocera Corporation | Mobile Communication Equipment and Method of Controlling Same |
| US20100074445A1 (en)* | 2008-09-25 | 2010-03-25 | Nokia Corporation | Encryption/identification using array of resonators at transmitter and receiver |
| US20100287083A1 (en)* | 2007-12-28 | 2010-11-11 | Mastercard International, Inc. | Detecting modifications to financial terminals |
| US20100293384A1 (en)* | 2009-05-12 | 2010-11-18 | Miodrag Potkonjak | Digital Signatures |
| US20100293612A1 (en)* | 2009-05-12 | 2010-11-18 | Miodrag Potkonjak | Secure Authentication |
| US20100322418A1 (en)* | 2009-06-17 | 2010-12-23 | Miodrag Potkonjak | Hardware Based Cryptography |
| US20110184994A1 (en)* | 2010-01-22 | 2011-07-28 | Arjun Prakash Kumar | Network and method for data input, storage and retrieval |
| WO2011157708A1 (en) | 2010-06-14 | 2011-12-22 | Fraunhofer-Gesellschaft zur Förderung der angewandten Forschung e.V. | Methods and systems for securely handling datasets in computer systems |
| US20120005732A1 (en)* | 2009-03-13 | 2012-01-05 | Fujitsu Limited | Person authentication system and person authentication method |
| US8117449B2 (en) | 2007-12-27 | 2012-02-14 | Mastercard International, Inc. | Method to detect man-in-the-middle (MITM) or relay attacks |
| US20120089520A1 (en)* | 2008-06-06 | 2012-04-12 | Ebay Inc. | Trusted service manager (tsm) architectures and methods |
| TWI382742B (en)* | 2007-05-18 | 2013-01-11 | Taisys Technologies Co Ltd | Dual card system |
| US8527415B2 (en) | 2007-12-27 | 2013-09-03 | Mastercard International, Inc. | Techniques for conducting financial transactions using mobile communication devices |
| US8571937B2 (en) | 2010-10-20 | 2013-10-29 | Playspan Inc. | Dynamic payment optimization apparatuses, methods and systems |
| US8577803B2 (en) | 2011-06-03 | 2013-11-05 | Visa International Service Association | Virtual wallet card selection apparatuses, methods and systems |
| US9117225B2 (en) | 2011-09-16 | 2015-08-25 | Visa International Service Association | Apparatuses, methods and systems for transforming user infrastructure requests inputs to infrastructure design product and infrastructure allocation outputs |
| US9355393B2 (en) | 2011-08-18 | 2016-05-31 | Visa International Service Association | Multi-directional wallet connector apparatuses, methods and systems |
| US9646291B2 (en) | 2011-05-11 | 2017-05-09 | Visa International Service Association | Electronic receipt manager apparatuses, methods and systems |
| US9652765B2 (en) | 2008-08-26 | 2017-05-16 | Visa International Service Association | System and method for implementing financial assistance programs |
| US9710807B2 (en) | 2011-08-18 | 2017-07-18 | Visa International Service Association | Third-party value added wallet features and interfaces apparatuses, methods and systems |
| US9773212B2 (en) | 2011-02-28 | 2017-09-26 | Visa International Service Association | Secure anonymous transaction apparatuses, methods and systems |
| US9830328B2 (en) | 2012-02-02 | 2017-11-28 | Visa International Service Association | Multi-source, multi-dimensional, cross-entry, multimedia merchant analytics database platform apparatuses, methods and systems |
| US9953378B2 (en) | 2012-04-27 | 2018-04-24 | Visa International Service Association | Social checkout widget generation and integration apparatuses, methods and systems |
| US9953334B2 (en) | 2011-02-10 | 2018-04-24 | Visa International Service Association | Electronic coupon issuance and redemption apparatuses, methods and systems |
| US9996838B2 (en) | 2011-03-04 | 2018-06-12 | Visa International Service Association | Cloud service facilitator apparatuses, methods and systems |
| US10096022B2 (en) | 2011-12-13 | 2018-10-09 | Visa International Service Association | Dynamic widget generator apparatuses, methods and systems |
| US10121129B2 (en) | 2011-07-05 | 2018-11-06 | Visa International Service Association | Electronic wallet checkout platform apparatuses, methods and systems |
| US10154084B2 (en) | 2011-07-05 | 2018-12-11 | Visa International Service Association | Hybrid applications utilizing distributed models and views apparatuses, methods and systems |
| US10204327B2 (en) | 2011-02-05 | 2019-02-12 | Visa International Service Association | Merchant-consumer bridging platform apparatuses, methods and systems |
| US10223691B2 (en) | 2011-02-22 | 2019-03-05 | Visa International Service Association | Universal electronic payment apparatuses, methods and systems |
| US10223710B2 (en) | 2013-01-04 | 2019-03-05 | Visa International Service Association | Wearable intelligent vision device apparatuses, methods and systems |
| US10223730B2 (en) | 2011-09-23 | 2019-03-05 | Visa International Service Association | E-wallet store injection search apparatuses, methods and systems |
| US10242358B2 (en) | 2011-08-18 | 2019-03-26 | Visa International Service Association | Remote decoupled application persistent state apparatuses, methods and systems |
| US10262148B2 (en) | 2012-01-09 | 2019-04-16 | Visa International Service Association | Secure dynamic page content and layouts apparatuses, methods and systems |
| US10318941B2 (en) | 2011-12-13 | 2019-06-11 | Visa International Service Association | Payment platform interface widget generation apparatuses, methods and systems |
| US10438176B2 (en) | 2011-07-17 | 2019-10-08 | Visa International Service Association | Multiple merchant payment processor platform apparatuses, methods and systems |
| US10586227B2 (en) | 2011-02-16 | 2020-03-10 | Visa International Service Association | Snap mobile payment apparatuses, methods and systems |
| US10825001B2 (en) | 2011-08-18 | 2020-11-03 | Visa International Service Association | Multi-directional wallet connector apparatuses, methods and systems |
| US11216468B2 (en) | 2015-02-08 | 2022-01-04 | Visa International Service Association | Converged merchant processing apparatuses, methods and systems |
| US11288661B2 (en) | 2011-02-16 | 2022-03-29 | Visa International Service Association | Snap mobile payment apparatuses, methods and systems |
| US11308227B2 (en) | 2012-01-09 | 2022-04-19 | Visa International Service Association | Secure dynamic page content and layouts apparatuses, methods and systems |
| US11354723B2 (en) | 2011-09-23 | 2022-06-07 | Visa International Service Association | Smart shopping cart with E-wallet store injection search |
| US11595820B2 (en) | 2011-09-02 | 2023-02-28 | Paypal, Inc. | Secure elements broker (SEB) for application communication channel selector optimization |
Citations (14)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US5311595A (en)* | 1989-06-07 | 1994-05-10 | Kommunedata I/S | Method of transferring data, between computer systems using electronic cards |
| US5434395A (en)* | 1990-03-05 | 1995-07-18 | Jean-Rene Storck | Method and device for effecting a transaction between a first and at least one second data carrier and carrier used for this purpose |
| US5497418A (en)* | 1992-10-09 | 1996-03-05 | Nagra Plus S.A. | Data processing system having a set of memory cards |
| US5763862A (en)* | 1996-06-24 | 1998-06-09 | Motorola, Inc. | Dual card smart card reader |
| US5787101A (en)* | 1994-06-15 | 1998-07-28 | Thomson Consumer Electronics, Inc. | Smart card message transfer without microprocessor intervention |
| US5923759A (en)* | 1995-04-20 | 1999-07-13 | Lee; Philip S. | System for securely exchanging data with smart cards |
| US5978840A (en)* | 1996-09-26 | 1999-11-02 | Verifone, Inc. | System, method and article of manufacture for a payment gateway system architecture for processing encrypted payment transactions utilizing a multichannel, extensible, flexible architecture |
| US5979773A (en)* | 1994-12-02 | 1999-11-09 | American Card Technology, Inc. | Dual smart card access control electronic data storage and retrieval system and methods |
| US6003134A (en)* | 1997-01-13 | 1999-12-14 | Kuo; Chih-Cheng | Secure open smart card architecture |
| US6003014A (en)* | 1997-08-22 | 1999-12-14 | Visa International Service Association | Method and apparatus for acquiring access using a smart card |
| US6289324B1 (en)* | 1998-02-04 | 2001-09-11 | Citicorp Development Center, Inc. | System for performing financial transactions using a smart card |
| US6324525B1 (en)* | 1996-06-17 | 2001-11-27 | Hewlett-Packard Company | Settlement of aggregated electronic transactions over a network |
| US6351813B1 (en)* | 1996-02-09 | 2002-02-26 | Digital Privacy, Inc. | Access control/crypto system |
| US6581162B1 (en)* | 1996-12-31 | 2003-06-17 | Compaq Information Technologies Group, L.P. | Method for securely creating, storing and using encryption keys in a computer system |
- 2000
- 2000-05-22USUS09/575,749patent/US7206847B1/ennot_activeExpired - Fee Related
Patent Citations (14)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US5311595A (en)* | 1989-06-07 | 1994-05-10 | Kommunedata I/S | Method of transferring data, between computer systems using electronic cards |
| US5434395A (en)* | 1990-03-05 | 1995-07-18 | Jean-Rene Storck | Method and device for effecting a transaction between a first and at least one second data carrier and carrier used for this purpose |
| US5497418A (en)* | 1992-10-09 | 1996-03-05 | Nagra Plus S.A. | Data processing system having a set of memory cards |
| US5787101A (en)* | 1994-06-15 | 1998-07-28 | Thomson Consumer Electronics, Inc. | Smart card message transfer without microprocessor intervention |
| US5979773A (en)* | 1994-12-02 | 1999-11-09 | American Card Technology, Inc. | Dual smart card access control electronic data storage and retrieval system and methods |
| US5923759A (en)* | 1995-04-20 | 1999-07-13 | Lee; Philip S. | System for securely exchanging data with smart cards |
| US6351813B1 (en)* | 1996-02-09 | 2002-02-26 | Digital Privacy, Inc. | Access control/crypto system |
| US6324525B1 (en)* | 1996-06-17 | 2001-11-27 | Hewlett-Packard Company | Settlement of aggregated electronic transactions over a network |
| US5763862A (en)* | 1996-06-24 | 1998-06-09 | Motorola, Inc. | Dual card smart card reader |
| US5978840A (en)* | 1996-09-26 | 1999-11-02 | Verifone, Inc. | System, method and article of manufacture for a payment gateway system architecture for processing encrypted payment transactions utilizing a multichannel, extensible, flexible architecture |
| US6581162B1 (en)* | 1996-12-31 | 2003-06-17 | Compaq Information Technologies Group, L.P. | Method for securely creating, storing and using encryption keys in a computer system |
| US6003134A (en)* | 1997-01-13 | 1999-12-14 | Kuo; Chih-Cheng | Secure open smart card architecture |
| US6003014A (en)* | 1997-08-22 | 1999-12-14 | Visa International Service Association | Method and apparatus for acquiring access using a smart card |
| US6289324B1 (en)* | 1998-02-04 | 2001-09-11 | Citicorp Development Center, Inc. | System for performing financial transactions using a smart card |
Non-Patent Citations (2)
| Title |
|---|
| Baldwin et al., "Locking the e-safe", RSA Data Security, IEEE Spectrum, Feb. 1997. |
| Fancher, C., "In Your Pocket Smartcards", IEEE Spectrum, Feb. 1997, pp. 47. |
Cited By (100)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20070100754A1 (en)* | 2003-12-17 | 2007-05-03 | Brown Kerry D | Financial transaction network security |
| US8195959B2 (en)* | 2004-11-22 | 2012-06-05 | International Business Machines Corporation | Encrypting a credential store with a lockbox |
| US20060112283A1 (en)* | 2004-11-22 | 2006-05-25 | International Business Machines Corporation | Encrypting a credential store with a lockbox |
| US7866564B2 (en)* | 2005-02-04 | 2011-01-11 | Chun-Hsin Ho | Dual card system |
| US20080029609A1 (en)* | 2005-02-04 | 2008-02-07 | Chun-Hsin Ho | Dual card system |
| US7747861B2 (en)* | 2005-11-09 | 2010-06-29 | Cisco Technology, Inc. | Method and system for redundant secure storage of sensitive data by using multiple keys |
| US20070106911A1 (en)* | 2005-11-09 | 2007-05-10 | Cisco Technology, Inc. | Method and system for redundant secure storage of sensitive data by using multiple keys |
| US9397837B2 (en)* | 2006-01-06 | 2016-07-19 | Sicpa Holding Sa | Secure access to information associated with a value item |
| US20090007258A1 (en)* | 2006-01-06 | 2009-01-01 | Verichk Global Technologies Inc. | Secure Access to Information Associated With a Value Item |
| US20090307489A1 (en)* | 2006-01-30 | 2009-12-10 | Kyocera Corporation | Mobile Communication Equipment and Method of Controlling Same |
| TWI382742B (en)* | 2007-05-18 | 2013-01-11 | Taisys Technologies Co Ltd | Dual card system |
| US20090113546A1 (en)* | 2007-10-30 | 2009-04-30 | Samsung Electronics Co., Ltd. | Memory system for sensing attack |
| US20090159679A1 (en)* | 2007-12-20 | 2009-06-25 | Mastercard International, Inc. | Ultra Low-Power User Authentication Device for Financial Transactions |
| US8117449B2 (en) | 2007-12-27 | 2012-02-14 | Mastercard International, Inc. | Method to detect man-in-the-middle (MITM) or relay attacks |
| US8527415B2 (en) | 2007-12-27 | 2013-09-03 | Mastercard International, Inc. | Techniques for conducting financial transactions using mobile communication devices |
| US20100287083A1 (en)* | 2007-12-28 | 2010-11-11 | Mastercard International, Inc. | Detecting modifications to financial terminals |
| US8417643B2 (en)* | 2008-06-06 | 2013-04-09 | Ebay Inc. | Trusted service manager (TSM) architectures and methods |
| US20180218358A1 (en)* | 2008-06-06 | 2018-08-02 | Paypal, Inc. | Trusted service manager (tsm) architectures and methods |
| US11521194B2 (en)* | 2008-06-06 | 2022-12-06 | Paypal, Inc. | Trusted service manager (TSM) architectures and methods |
| US20120089520A1 (en)* | 2008-06-06 | 2012-04-12 | Ebay Inc. | Trusted service manager (tsm) architectures and methods |
| US9852418B2 (en)* | 2008-06-06 | 2017-12-26 | Paypal, Inc. | Trusted service manager (TSM) architectures and methods |
| US9652765B2 (en) | 2008-08-26 | 2017-05-16 | Visa International Service Association | System and method for implementing financial assistance programs |
| US9742555B2 (en)* | 2008-09-25 | 2017-08-22 | Nokia Technologies Oy | Encryption/identification using array of resonators at transmitter and receiver |
| US20100074445A1 (en)* | 2008-09-25 | 2010-03-25 | Nokia Corporation | Encryption/identification using array of resonators at transmitter and receiver |
| US20120005732A1 (en)* | 2009-03-13 | 2012-01-05 | Fujitsu Limited | Person authentication system and person authentication method |
| US9032476B2 (en)* | 2009-05-12 | 2015-05-12 | Empire Technology Development Llc | Secure authentication |
| US8850281B2 (en) | 2009-05-12 | 2014-09-30 | Empire Technology Development Llc | Digital signatures |
| US20100293384A1 (en)* | 2009-05-12 | 2010-11-18 | Miodrag Potkonjak | Digital Signatures |
| US20100293612A1 (en)* | 2009-05-12 | 2010-11-18 | Miodrag Potkonjak | Secure Authentication |
| US8379856B2 (en) | 2009-06-17 | 2013-02-19 | Empire Technology Development Llc | Hardware based cryptography |
| US20100322418A1 (en)* | 2009-06-17 | 2010-12-23 | Miodrag Potkonjak | Hardware Based Cryptography |
| US8469279B2 (en) | 2010-01-22 | 2013-06-25 | Spqkumar Inc. | Network and method for data input, storage and retrieval |
| US20110184994A1 (en)* | 2010-01-22 | 2011-07-28 | Arjun Prakash Kumar | Network and method for data input, storage and retrieval |
| DE102011077513A1 (en) | 2010-06-14 | 2012-08-23 | Fraunhofer-Gesellschaft zur Förderung der angewandten Forschung e.V. | Method for the secure processing of data |
| DE102011077512A1 (en) | 2010-06-14 | 2012-03-01 | Fraunhofer-Gesellschaft zur Förderung der angewandten Forschung e.V. | Method for the secure processing of data stored in an electronic safe |
| WO2011157708A1 (en) | 2010-06-14 | 2011-12-22 | Fraunhofer-Gesellschaft zur Förderung der angewandten Forschung e.V. | Methods and systems for securely handling datasets in computer systems |
| US8571937B2 (en) | 2010-10-20 | 2013-10-29 | Playspan Inc. | Dynamic payment optimization apparatuses, methods and systems |
| US10500481B2 (en) | 2010-10-20 | 2019-12-10 | Playspan Inc. | Dynamic payment optimization apparatuses, methods and systems |
| US9757644B2 (en) | 2010-10-20 | 2017-09-12 | Playspin Inc. | Dynamic payment optimization apparatuses, methods and systems |
| US10688385B2 (en) | 2010-10-20 | 2020-06-23 | Playspan Inc. | In-application universal storefront apparatuses, methods and systems |
| US11311797B2 (en) | 2010-10-20 | 2022-04-26 | Playspan Inc. | Dynamic payment optimization apparatuses, methods and systems |
| US11093919B2 (en) | 2011-02-05 | 2021-08-17 | Visa International Service Association | Merchant-consumer bridging platform apparatuses, methods and systems |
| US10204327B2 (en) | 2011-02-05 | 2019-02-12 | Visa International Service Association | Merchant-consumer bridging platform apparatuses, methods and systems |
| US10621605B2 (en) | 2011-02-10 | 2020-04-14 | Visa International Service Association | Electronic coupon issuance and redemption apparatuses, methods and systems |
| US9953334B2 (en) | 2011-02-10 | 2018-04-24 | Visa International Service Association | Electronic coupon issuance and redemption apparatuses, methods and systems |
| US10586227B2 (en) | 2011-02-16 | 2020-03-10 | Visa International Service Association | Snap mobile payment apparatuses, methods and systems |
| US11288661B2 (en) | 2011-02-16 | 2022-03-29 | Visa International Service Association | Snap mobile payment apparatuses, methods and systems |
| US10223691B2 (en) | 2011-02-22 | 2019-03-05 | Visa International Service Association | Universal electronic payment apparatuses, methods and systems |
| US11023886B2 (en) | 2011-02-22 | 2021-06-01 | Visa International Service Association | Universal electronic payment apparatuses, methods and systems |
| US11250352B2 (en) | 2011-02-28 | 2022-02-15 | Visa International Service Association | Secure anonymous transaction apparatuses, methods and systems |
| US10482398B2 (en) | 2011-02-28 | 2019-11-19 | Visa International Service Association | Secure anonymous transaction apparatuses, methods and systems |
| US9773212B2 (en) | 2011-02-28 | 2017-09-26 | Visa International Service Association | Secure anonymous transaction apparatuses, methods and systems |
| US9996838B2 (en) | 2011-03-04 | 2018-06-12 | Visa International Service Association | Cloud service facilitator apparatuses, methods and systems |
| US11263640B2 (en) | 2011-03-04 | 2022-03-01 | Visa International Service Association | Cloud service facilitator apparatuses, methods and systems |
| US11263601B2 (en) | 2011-05-11 | 2022-03-01 | Visa International Service Association | Electronic receipt manager apparatuses, methods and systems |
| US11853977B2 (en) | 2011-05-11 | 2023-12-26 | Visa International Service Association | Electronic receipt manager apparatuses, methods and systems |
| US9646291B2 (en) | 2011-05-11 | 2017-05-09 | Visa International Service Association | Electronic receipt manager apparatuses, methods and systems |
| US10489756B2 (en) | 2011-05-11 | 2019-11-26 | Visa International Service Association | Electronic receipt manager apparatuses, methods and systems |
| US8577803B2 (en) | 2011-06-03 | 2013-11-05 | Visa International Service Association | Virtual wallet card selection apparatuses, methods and systems |
| US10154084B2 (en) | 2011-07-05 | 2018-12-11 | Visa International Service Association | Hybrid applications utilizing distributed models and views apparatuses, methods and systems |
| US11900359B2 (en) | 2011-07-05 | 2024-02-13 | Visa International Service Association | Electronic wallet checkout platform apparatuses, methods and systems |
| US10419529B2 (en) | 2011-07-05 | 2019-09-17 | Visa International Service Association | Hybrid applications utilizing distributed models and views apparatuses, methods and systems |
| US10121129B2 (en) | 2011-07-05 | 2018-11-06 | Visa International Service Association | Electronic wallet checkout platform apparatuses, methods and systems |
| US11010753B2 (en) | 2011-07-05 | 2021-05-18 | Visa International Service Association | Electronic wallet checkout platform apparatuses, methods and systems |
| US10803449B2 (en) | 2011-07-05 | 2020-10-13 | Visa International Service Association | Electronic wallet checkout platform apparatuses, methods and systems |
| US10438176B2 (en) | 2011-07-17 | 2019-10-08 | Visa International Service Association | Multiple merchant payment processor platform apparatuses, methods and systems |
| US11397931B2 (en) | 2011-08-18 | 2022-07-26 | Visa International Service Association | Multi-directional wallet connector apparatuses, methods and systems |
| US11037138B2 (en) | 2011-08-18 | 2021-06-15 | Visa International Service Association | Third-party value added wallet features and interfaces apparatuses, methods, and systems |
| US9355393B2 (en) | 2011-08-18 | 2016-05-31 | Visa International Service Association | Multi-directional wallet connector apparatuses, methods and systems |
| US9959531B2 (en) | 2011-08-18 | 2018-05-01 | Visa International Service Association | Multi-directional wallet connector apparatuses, methods and systems |
| US10242358B2 (en) | 2011-08-18 | 2019-03-26 | Visa International Service Association | Remote decoupled application persistent state apparatuses, methods and systems |
| US10354240B2 (en) | 2011-08-18 | 2019-07-16 | Visa International Service Association | Multi-directional wallet connector apparatuses, methods and systems |
| US10825001B2 (en) | 2011-08-18 | 2020-11-03 | Visa International Service Association | Multi-directional wallet connector apparatuses, methods and systems |
| US11803825B2 (en) | 2011-08-18 | 2023-10-31 | Visa International Service Association | Multi-directional wallet connector apparatuses, methods and systems |
| US11763294B2 (en) | 2011-08-18 | 2023-09-19 | Visa International Service Association | Remote decoupled application persistent state apparatuses, methods and systems |
| US11010756B2 (en) | 2011-08-18 | 2021-05-18 | Visa International Service Association | Remote decoupled application persistent state apparatuses, methods and systems |
| US9710807B2 (en) | 2011-08-18 | 2017-07-18 | Visa International Service Association | Third-party value added wallet features and interfaces apparatuses, methods and systems |
| US12277537B2 (en) | 2011-08-18 | 2025-04-15 | Visa International Service Association | Multi-directional wallet connector apparatuses, methods and systems |
| US12022290B2 (en) | 2011-09-02 | 2024-06-25 | Paypal, Inc. | Secure elements broker (SEB) for application communication channel selector optimization |
| US11595820B2 (en) | 2011-09-02 | 2023-02-28 | Paypal, Inc. | Secure elements broker (SEB) for application communication channel selector optimization |
| US9117225B2 (en) | 2011-09-16 | 2015-08-25 | Visa International Service Association | Apparatuses, methods and systems for transforming user infrastructure requests inputs to infrastructure design product and infrastructure allocation outputs |
| US11354723B2 (en) | 2011-09-23 | 2022-06-07 | Visa International Service Association | Smart shopping cart with E-wallet store injection search |
| US10223730B2 (en) | 2011-09-23 | 2019-03-05 | Visa International Service Association | E-wallet store injection search apparatuses, methods and systems |
| US10096022B2 (en) | 2011-12-13 | 2018-10-09 | Visa International Service Association | Dynamic widget generator apparatuses, methods and systems |
| US10846670B2 (en) | 2011-12-13 | 2020-11-24 | Visa International Service Association | Payment platform interface widget generation apparatuses, methods and systems |
| US10318941B2 (en) | 2011-12-13 | 2019-06-11 | Visa International Service Association | Payment platform interface widget generation apparatuses, methods and systems |
| US10685379B2 (en) | 2012-01-05 | 2020-06-16 | Visa International Service Association | Wearable intelligent vision device apparatuses, methods and systems |
| US10262148B2 (en) | 2012-01-09 | 2019-04-16 | Visa International Service Association | Secure dynamic page content and layouts apparatuses, methods and systems |
| US11308227B2 (en) | 2012-01-09 | 2022-04-19 | Visa International Service Association | Secure dynamic page content and layouts apparatuses, methods and systems |
| US11074218B2 (en) | 2012-02-02 | 2021-07-27 | Visa International Service Association | Multi-source, multi-dimensional, cross-entity, multimedia merchant analytics database platform apparatuses, methods and systems |
| US9830328B2 (en) | 2012-02-02 | 2017-11-28 | Visa International Service Association | Multi-source, multi-dimensional, cross-entry, multimedia merchant analytics database platform apparatuses, methods and systems |
| US10013423B2 (en) | 2012-02-02 | 2018-07-03 | Visa International Service Association | Multi-source, multi-dimensional, cross-entity, multimedia analytical model sharing database platform apparatuses, methods and systems |
| US11036681B2 (en) | 2012-02-02 | 2021-06-15 | Visa International Service Association | Multi-source, multi-dimensional, cross-entity, multimedia analytical model sharing database platform apparatuses, methods and systems |
| US10983960B2 (en) | 2012-02-02 | 2021-04-20 | Visa International Service Association | Multi-source, multi-dimensional, cross-entity, multimedia centralized personal information database platform apparatuses, methods and systems |
| US10262001B2 (en) | 2012-02-02 | 2019-04-16 | Visa International Service Association | Multi-source, multi-dimensional, cross-entity, multimedia merchant analytics database platform apparatuses, methods and systems |
| US10430381B2 (en) | 2012-02-02 | 2019-10-01 | Visa International Service Association | Multi-source, multi-dimensional, cross-entity, multimedia centralized personal information database platform apparatuses, methods and systems |
| US9953378B2 (en) | 2012-04-27 | 2018-04-24 | Visa International Service Association | Social checkout widget generation and integration apparatuses, methods and systems |
| US10223710B2 (en) | 2013-01-04 | 2019-03-05 | Visa International Service Association | Wearable intelligent vision device apparatuses, methods and systems |
| US11216468B2 (en) | 2015-02-08 | 2022-01-04 | Visa International Service Association | Converged merchant processing apparatuses, methods and systems |
| US11941008B2 (en) | 2015-02-08 | 2024-03-26 | Visa International Service Association | Converged merchant processing apparatuses, methods and systems |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| US7206847B1 (en) | Smart card with back up | |
| CN1344396B (en) | Portable electronic payment and authorization device and method thereof | |
| US7870998B2 (en) | Private information exchange in smart card commerce | |
| EP0981807B1 (en) | Integrated circuit card with application history list | |
| Fancher | In your pocket: smartcards | |
| US6983882B2 (en) | Personal biometric authentication and authorization device | |
| US6594759B1 (en) | Authorization firmware for conducting transactions with an electronic transaction system and methods therefor | |
| US5898783A (en) | System and method for employing a telecommunications network to remotely disable a SIM or smartcard | |
| CN101329786B (en) | Method and system for acquiring bank card magnetic track information or payment application for mobile terminal | |
| AU2022205660B2 (en) | Devices, systems, and methods for public/private key authentication | |
| TW498284B (en) | Card memory apparatus | |
| KR20140061474A (en) | Improved device and method for smart card assisted digital content purchase and storage | |
| JP2002507297A (en) | Payment methods and systems | |
| EP1053536A1 (en) | System and method for controlling access to computer code in an ic card | |
| JP2003123032A (en) | IC card terminal and personal authentication method | |
| JPH09265254A (en) | Mutual authentication system for information storage media | |
| AU740143B2 (en) | Process to manange data in a chip card | |
| JP2000507380A (en) | Safety module | |
| JP3693709B2 (en) | Information writing / reading method for portable information recording medium | |
| AU723525B2 (en) | A method for certifying a running total in a reader | |
| KR20240019899A (en) | Private asset systems for protecting of digital and physical assets | |
| KR20240019900A (en) | Cold wallet activation system through physical combining of material object and cold wallet | |
| Elhennawy et al. | Smart Cards Structure and Applications: Emerging and Evolution | |
| JPS62280965A (en) | Protection system for information in ic card | |
| Guthery et al. | PART I—SMART CARD BACKGROUND AND BASICS CHAPTER 1—SMART CARD PROGRAMMING |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| AS | Assignment | Owner name:MOTOROLA, INC., CORPORATE OFFICES, ILLINOIS Free format text:ASSIGNMENT OF ASSIGNORS INTEREST;ASSIGNORS:ALBERTH, WILLIAM P. JR.;KOTZIN, MICHAEL;REEL/FRAME:010831/0312;SIGNING DATES FROM 20000512 TO 20000518 | |
| STCF | Information on status: patent grant | Free format text:PATENTED CASE | |
| FPAY | Fee payment | Year of fee payment:4 | |
| AS | Assignment | Owner name:MOTOROLA MOBILITY, INC, ILLINOIS Free format text:ASSIGNMENT OF ASSIGNORS INTEREST;ASSIGNOR:MOTOROLA, INC;REEL/FRAME:025673/0558 Effective date:20100731 | |
| AS | Assignment | Owner name:MOTOROLA MOBILITY LLC, ILLINOIS Free format text:CHANGE OF NAME;ASSIGNOR:MOTOROLA MOBILITY, INC.;REEL/FRAME:029216/0282 Effective date:20120622 | |
| FPAY | Fee payment | Year of fee payment:8 | |
| AS | Assignment | Owner name:GOOGLE TECHNOLOGY HOLDINGS LLC, CALIFORNIA Free format text:ASSIGNMENT OF ASSIGNORS INTEREST;ASSIGNOR:MOTOROLA MOBILITY LLC;REEL/FRAME:034430/0001 Effective date:20141028 | |
| FEPP | Fee payment procedure | Free format text:MAINTENANCE FEE REMINDER MAILED (ORIGINAL EVENT CODE: REM.); ENTITY STATUS OF PATENT OWNER: LARGE ENTITY | |
| LAPS | Lapse for failure to pay maintenance fees | Free format text:PATENT EXPIRED FOR FAILURE TO PAY MAINTENANCE FEES (ORIGINAL EVENT CODE: EXP.); ENTITY STATUS OF PATENT OWNER: LARGE ENTITY | |
| STCH | Information on status: patent discontinuation | Free format text:PATENT EXPIRED DUE TO NONPAYMENT OF MAINTENANCE FEES UNDER 37 CFR 1.362 | |
| FP | Lapsed due to failure to pay maintenance fee | Effective date:20190417 |