US20170235567A1 - Wireless router remote firmware upgrade - Google Patents
Wireless router remote firmware upgradeDownload PDFInfo
- Publication number
- US20170235567A1 US20170235567A1US15/383,862US201615383862AUS2017235567A1US 20170235567 A1US20170235567 A1US 20170235567A1US 201615383862 AUS201615383862 AUS 201615383862AUS 2017235567 A1US2017235567 A1US 2017235567A1
- Authority
- US
- United States
- Prior art keywords
- firmware
- wireless router
- router
- flash memory
- chunks
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Abandoned
Links
Images
Classifications
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F8/00—Arrangements for software engineering
- G06F8/60—Software deployment
- G06F8/65—Updates
- G06F8/654—Updates using techniques specially adapted for alterable solid state memories, e.g. for EEPROM or flash memories
- G06F8/665—
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/50—Monitoring users, programs or devices to maintain the integrity of platforms, e.g. of processors, firmware or operating systems
- G06F21/55—Detecting local intrusion or implementing counter-measures
- G06F21/56—Computer malware detection or handling, e.g. anti-virus arrangements
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/50—Monitoring users, programs or devices to maintain the integrity of platforms, e.g. of processors, firmware or operating systems
- G06F21/57—Certifying or maintaining trusted computer platforms, e.g. secure boots or power-downs, version controls, system software checks, secure updates or assessing vulnerabilities
- G06F21/572—Secure firmware programming, e.g. of basic input output system [BIOS]
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F3/00—Input arrangements for transferring data to be processed into a form capable of being handled by the computer; Output arrangements for transferring data from processing unit to output unit, e.g. interface arrangements
- G06F3/06—Digital input from, or digital output to, record carriers, e.g. RAID, emulated record carriers or networked record carriers
- G06F3/0601—Interfaces specially adapted for storage systems
- G06F3/0602—Interfaces specially adapted for storage systems specifically adapted to achieve a particular effect
- G06F3/0614—Improving the reliability of storage systems
- G06F3/0619—Improving the reliability of storage systems in relation to data integrity, e.g. data losses, bit errors
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F3/00—Input arrangements for transferring data to be processed into a form capable of being handled by the computer; Output arrangements for transferring data from processing unit to output unit, e.g. interface arrangements
- G06F3/06—Digital input from, or digital output to, record carriers, e.g. RAID, emulated record carriers or networked record carriers
- G06F3/0601—Interfaces specially adapted for storage systems
- G06F3/0628—Interfaces specially adapted for storage systems making use of a particular technique
- G06F3/0646—Horizontal data movement in storage systems, i.e. moving data in between storage devices or systems
- G06F3/065—Replication mechanisms
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F3/00—Input arrangements for transferring data to be processed into a form capable of being handled by the computer; Output arrangements for transferring data from processing unit to output unit, e.g. interface arrangements
- G06F3/06—Digital input from, or digital output to, record carriers, e.g. RAID, emulated record carriers or networked record carriers
- G06F3/0601—Interfaces specially adapted for storage systems
- G06F3/0628—Interfaces specially adapted for storage systems making use of a particular technique
- G06F3/0655—Vertical data movement, i.e. input-output transfer; data movement between one or more hosts and one or more storage devices
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F3/00—Input arrangements for transferring data to be processed into a form capable of being handled by the computer; Output arrangements for transferring data from processing unit to output unit, e.g. interface arrangements
- G06F3/06—Digital input from, or digital output to, record carriers, e.g. RAID, emulated record carriers or networked record carriers
- G06F3/0601—Interfaces specially adapted for storage systems
- G06F3/0668—Interfaces specially adapted for storage systems adopting a particular infrastructure
- G06F3/0671—In-line storage system
- G06F3/0673—Single storage device
- G06F3/0679—Non-volatile semiconductor memory device, e.g. flash memory, one time programmable memory [OTP]
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F9/00—Arrangements for program control, e.g. control units
- G06F9/06—Arrangements for program control, e.g. control units using stored programs, i.e. using an internal store of processing equipment to receive or retain programs
- G06F9/44—Arrangements for executing specific programs
- G06F9/4401—Bootstrapping
- G06F9/4416—Network booting; Remote initial program loading [RIPL]
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06Q—INFORMATION AND COMMUNICATION TECHNOLOGY [ICT] SPECIALLY ADAPTED FOR ADMINISTRATIVE, COMMERCIAL, FINANCIAL, MANAGERIAL OR SUPERVISORY PURPOSES; SYSTEMS OR METHODS SPECIALLY ADAPTED FOR ADMINISTRATIVE, COMMERCIAL, FINANCIAL, MANAGERIAL OR SUPERVISORY PURPOSES, NOT OTHERWISE PROVIDED FOR
- G06Q10/00—Administration; Management
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06Q—INFORMATION AND COMMUNICATION TECHNOLOGY [ICT] SPECIALLY ADAPTED FOR ADMINISTRATIVE, COMMERCIAL, FINANCIAL, MANAGERIAL OR SUPERVISORY PURPOSES; SYSTEMS OR METHODS SPECIALLY ADAPTED FOR ADMINISTRATIVE, COMMERCIAL, FINANCIAL, MANAGERIAL OR SUPERVISORY PURPOSES, NOT OTHERWISE PROVIDED FOR
- G06Q30/00—Commerce
- G06Q30/04—Billing or invoicing
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L51/00—User-to-user messaging in packet-switching networks, transmitted according to store-and-forward or real-time protocols, e.g. e-mail
- H04L51/21—Monitoring or handling of messages
- H04L51/212—Monitoring or handling of messages using filtering or selective blocking
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L67/00—Network arrangements or protocols for supporting network services or applications
- H04L67/34—Network arrangements or protocols for supporting network services or applications involving the movement of software or configuration parameters
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W12/00—Security arrangements; Authentication; Protecting privacy or anonymity
- H04W12/06—Authentication
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W12/00—Security arrangements; Authentication; Protecting privacy or anonymity
- H04W12/06—Authentication
- H04W12/069—Authentication using certificates or pre-shared keys
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L51/00—User-to-user messaging in packet-switching networks, transmitted according to store-and-forward or real-time protocols, e.g. e-mail
- H04L51/06—Message adaptation to terminal or network requirements
- H04L51/063—Content adaptation, e.g. replacement of unsuitable content
Definitions
- referencesbegins by pointing out some things that are not present in any of the references. These gaps in the references are worthy of attention, but they are merely examples of how the references could be considered. In particular, it does not follow that something X is present in the references merely because the discussion did not say that X was missing from the references.
- Shamoon [0310]recites “circuitry which remaps some of the available memory space, so that, in unsecure mode, the CPU cannot address secure memory locations.”
- Shamoon [0312]similarly recites “Some memory space may be rendered off-limits to general purpose uses, for example by remapping”.
- United States Patent Application Publication No. 2004/0083469 by Chen, et al.recites that an update method is used in an optical disk system to update firmware information stored in a firmware memory.
- Chenfurther recites that the method includes fetching program code and an update program routine from an update source, storing the program code into a first buffer, storing the update program routine into a second buffer, executing the update program routine stored in the second buffer, writing the program code stored in the first buffer into the firmware memory to update the firmware information, and changing a value of a program counter of the microprocessor such that the microprocessor executes the program code stored in the firmware memory at a predetermined location of the program code instead of executing a next instruction in the program code located after the current position of the program counter, and using the program code as updated firmware information to control the optical disk system.
- United States Patent Application Publication No. 2005/0027807 by Fengler, et al.recites that systems and methods for facilitating peripheral device firmware installation are disclosed.
- Fenglerfurther recites that in one embodiment, a system and a method pertain to transmitting a firmware availability notification, receiving a firmware download request, and transmitting a firmware file to a peripheral device for installation on the peripheral device.
- a system and a methodpertain to receiving a firmware availability notification with a peripheral device, and providing a related notification to a user, the related notification being provided by the peripheral device.
- the devicedetermines a suitable time for it to be rebooted to execute the updated software.
- the present core firmware in the deviceis copied from the partition it is in to the other partition, overwriting the auxiliary software stored there.
- the new core firmware received to update the deviceis overwritten into the first partition, the old copied core firmware being present in case of an upgrade failure, and upon a successful update of the first partition, the auxiliary software is written to the second partition, overwriting the copied old core firmware. In this manner, the position of the core firmware and auxiliary software within the partitions is preserved during normal operation of the device.
- United States Patent Application Publication No. 2008/0156178 by Georges, et al.recites that systems and methods for creating, modifying, interacting with and playing music are provided, particularly systems and methods employing a top-down process, where the user is provided with a musical composition that may be modified and interacted with and played and/or stored (for later play).
- Georgesalso recites that the system preferably is provided in a handheld form factor, and a graphical display is provided to display status information, graphical representations of musical lanes or components which preferably vary in shape as musical parameters and the like are changed for particular instruments or musical components such as a microphone input or audio samples.
- An interactive auto-composition processpreferably is utilized that employs musical rules and preferably a pseudo random number generator, which may also incorporate randomness introduced by timing of user input or the like, the user may then quickly begin creating desirable music in accordance with one or a variety of musical styles, with the user modifying the auto-composed (or previously created) musical composition, either for a real time performance and/or for storing and subsequent playback.
- musical rulespreferably a pseudo random number generator, which may also incorporate randomness introduced by timing of user input or the like
- the usermay then quickly begin creating desirable music in accordance with one or a variety of musical styles, with the user modifying the auto-composed (or previously created) musical composition, either for a real time performance and/or for storing and subsequent playback.
- the remainder of the Abstractmay be read in Georges itself.
- a methodmay include: receiving a first encrypted signal at a server of a computing network, the first encrypted signal comprising firmware encrypted by a first encryption algorithm having a first complexity level; sending a second encrypted signal over the computing network to at least one managed client in response to the first encrypted signal, the second encrypted signal comprising the firmware encrypted by a second encryption algorithm having a second complexity level, wherein said first complexity level is greater than said second complexity level; and updating existing firmware of the at least one managed client in response to receipt of the second signal at the at least one managed client.
- Herbertfurther recites that many alternatives, variations, and modifications are possible without departing from this embodiment.
- United States Patent Application Publication No. 2005/0097542 by Leerecites that a firmware update method is disclosed.
- a tagis written to a firmware storage device.
- first firmware in the firmware storage deviceis replaced by second firmware. If the replacing step is successful, the tag is deleted.
- a verification operationis executed. If the tag is not present, the second firmware is executed. If the tag is present, an abnormity processing procedure is executed. The abnormity processing procedure terminates of execution of the second firmware, reads third firmware via an interface, and replaces the second firmware with the third firmware.
- United States Patent Application Publication No. 2005/0039178 by Marolia, et al.recites that aspects of an invention may be seen in a system and method for downloading update packages into an electronic device communicatively coupled to a carrier network. Marolia further recites that the system may facilitate the update of firmware/software in the electronic device. Different protocols may be utilized for discovery and download of update packages. Also, different protocols may be utilized for provisioning and for subsequent downloading of update packages.
- United States Patent Application Publication No. 2006/0047920 by Moore, et al.recites that embodiments described therein can be used to enable one-time or few-time programmable memories to work with existing consumer electronic devices (such as those that work with flash—an erasable, non-volatile memory) without requiring a firmware upgrade, thereby providing backwards compatibility while minimizing user impact.
- Moorefurther recites that as such, these embodiments are a viable way to bridge one-time or few-time programmable memories with existing consumer electronic devices that have flash card slots.
- These embodimentsalso allow future consumer electronic devices to be designed without updating firmware to include a file system customized for a one-time or few-time programmable memory.
- United States Patent Application Publication No. 2003/0236970 by Palmer, et al.recites that in a data processing method and system a mass storage device (DASD) of a data processing system is partitioned to include a service partition. Palmer further recites that the service partition is typically located on a portion of the DASD beyond the highest address accessible to the operating system and application programs.
- the service partitionwill typically include the current versions of peripheral device firmware, any BIOS extensions, and device drivers.
- the boot codewill invoke a peripheral device call that reports the device's firmware version level to compare the firmware versions of all the peripheral devices against the archived firmware versions stored in the service partition.
- the system bootwill typically force an update of the peripheral device firmware to the level that is known to be good. Any such firmware updates are recorded in a log that is accessible to system management applications. Any revisions to firmware may be imaged into the service partition so that the revised version will be incorporated into the peripheral device itself during the next subsequent system boot.
- an information-processing apparatusincludes a nonvolatile memory device configured to store firmware.
- the information-processing apparatushas a first unit for issuing an instruction to make an operating system execute a shutdown process, and to update the firmware, stored in the nonvolatile memory device, after the operating system has completed the shutdown process.
- the information-processing apparatusalso has a second unit, responsive to the instruction to update the firmware, for updating the firmware only after the operating system has completed the shutdown process.
- United States Patent Application Publication No. 2004/0107356 by Shamoon, et al.recites that a novel method and apparatus for protection of streamed media content is disclosed.
- the apparatusincludes control means for governance of content streams or content objects, decryption means for decrypting content streams or content objects under control of the control means, and feedback means for tracking actual use of content streams or content objects.
- the control meansmay operate in accordance with rules received as part of the streamed content, or through a side-band channel.
- the rulesmay specify allowed uses of the content, including whether or not the content can be copied or transferred, and whether and under what circumstances received content may be “checked out” of one device and used in a second device.
- the rulesmay also include or specify budgets, and a requirement that audit information be collected and/or transmitted to an external server.
- the apparatusmay include a media player designed to call plugins to assist in rendering content.
- a “trust plugin”is disclosed, along with a method of using the trust plugin so that a media player designed for use with unprotected content may render protected content without the necessity of requiring any changes to the media player.
- the streamed contentmay be in a number of different formats, including MPEG-4, MP3, and the RMFF format.
- United States Patent Application Publication No. 2005/0021968 by Zimmer, et al.recites that a method for providing a secure firmware update is disclosed.
- This Zimmer applicationfurther recites that a first authentication credential is securely stored on a platform in an encrypted form using a key generated by a secure token, such as a trusted platform module (TPM).
- TPMtrusted platform module
- the authentication credentialwill identify a manufacture and the operation will be performed during manufacture of the platform.
- a configuration of the platformis “imprinted” such that an identical configuration is required to access the key used to decrypt the first authentication credential by sealing the key against the platform configuration.
- a firmware update image containing a second authentication credentialis received at the platform. If the platform configuration is the same as when the key was sealed, the key can be unsealed and used for decrypting the first authentication credential.
- a public key in the first authentication credentialcan then be used to authenticate the firmware update image via the second authentication credential.
- United States Patent Application Publication No. 2005/0289646 by Zimmer, et al.recites disclosure of a method of copying virtual firmware smart card code from a first secured memory in a system and loading the virtual firmware smart card code into a second secured memory in the system so that the code may be run on a microprocessor to provide smart card services to the system.
- some embodimentsprovide a method for upgrading a wireless router.
- a flash memory in the wireless routercontains a first version of router firmware.
- the router firmwareincludes instructions to be executed by a processor of the wireless router, and the firmware also includes data.
- the wireless routersends a request for a firmware update, the request being sent from the wireless router over a network connection toward a server.
- the wireless routerreceives over the network connection a response to the request for a firmware update, the response including at least a firmware image for a second version of router firmware which differs from the first version of router firmware by reason of containing at least one firmware change (a firmware change being a difference in firmware data and/or a difference in firmware instructions).
- the firmware imageincludes a plurality of chunks, each chunk having a size which is no greater than a predetermined chunk size.
- the wireless routerdestructively overwrites the first version of router firmware in the flash memory with the second version of router firmware.
- the destructive overwritingproceeds in a chunk-wise manner such that prior to being overwritten by all of the chunks the flash memory contains neither a complete copy of the first version nor a complete copy of the second version of the router firmware.
- the wireless routeris configured to run whatever version of router firmware is in the router's flash memory after being rebooted. The wireless router reboots, thereby making the firmware change(s) go live.
- Some embodimentsinclude writing the flash memory and then writing a kernel memory. That is, the wireless router destructively overwrites the first version of router firmware in the flash memory with the second version of router firmware, and then writes a copy of content of the second version of router firmware to a kernel memory in a volatile RAM memory in the wireless router before going live with upgraded firmware.
- Some embodimentsinclude writing both flash memory and a volatile RAM disk. That is, the wireless router destructively overwrites the first version of router firmware in the flash memory with the second version of router firmware, and also writes a copy of content of the second version of router firmware to a RAM disk in a volatile RAM memory of the router.
- the firmware image chunkshave at least one predetermined executable order, namely, an order in which the chunks are arranged in an executable copy of the firmware image.
- the step of receiving a responsive firmware imagereceives the chunks in a volatile RAM memory in the wireless router in an order which differs from the executable order, and the method includes re-ordering the chunks such that the step of destructively overwriting flash memory chunks arranges chunks in the flash memory in the executable order.
- the firmware imagehas a size and the flash memory has a storage capacity.
- the methodincludes the wireless router checking to see whether the size of the firmware image is less than a predetermined maximum firmware image size.
- the predetermined maximum firmware image sizeis at least two chunk sizes smaller than the flash memory storage capacity.
- Some embodimentsinclude the wireless router remapping a ROM memory address in the router to a RAM memory address in the router. Some include the wireless router decompressing data held within the flash memory in the router and copying the data to a RAM-based file system in the router; some include both steps.
- the wireless routerbefore going live with upgraded firmware, the wireless router overwrites at least a portion of the flash memory with user-definable configuration settings from a text file. Then after going live with upgraded firmware, the wireless router overwrites the text file with the configuration settings from the flash memory.
- the response received by the wireless routerincludes an indication that a billing status is inactive, and the method includes redirecting a web browser to a billing activation page.
- the firmware image chunkshave at least one predetermined executable order, namely, an order in which the chunks are arranged in an executable copy of the firmware image.
- the step of receiving a responsive firmware imagereceives the chunks in the wireless router in an order which differs from the executable order.
- the methodincludes re-ordering the chunks such that the step of destructively overwriting flash memory chunks arranges chunks in the flash memory in the executable order.
- the methodalso includes writing a copy of the chunks to a kernel memory in the wireless router.
- the wireless routerincludes a processor, volatile RAM memory, a network interface card, a wireless link interface, and a flash memory.
- the volatile RAM memoryis in operable communication with the processor and contains a kernel.
- the kernelincludes data and including instructions which upon execution by the processor at least partially control operation of the wireless router.
- the kernelcontains a flash memory device driver.
- the network interface cardis connectable to a TCP/IP network such as the Internet for two-way data communication of the wireless router with a remote server.
- the network interface cardis also in operable communication with the volatile RAM memory.
- the wireless link interfaceis connectable to a wireless network for two-way data communication of the wireless router with a local computer, and is also in operable communication with the volatile RAM memory.
- the flash memoryis in operable communication with the processor by use of the flash memory device driver.
- the flash memorycontains a version of wireless router firmware, which includes data, also includes and instructions which upon execution by the processor at least partially control operation of the wireless link interface.
- the wireless routeris further characterized in that upon execution of at least some of the instructions by the processor, the wireless router will do the following: send a request for a firmware update over the network interface card to the remote server, receive over the network interface a wireless router firmware image, write content of the wireless router firmware image to the flash memory, write content of the wireless router firmware image to the kernel memory after writing the content to the flash memory, and then reboot, thereby passing control to at least some of the wireless router firmware content that was written to the flash memory.
- the wireless routerdoes not necessarily send a request for a firmware update, but may instead receive the firmware update without having first requested it.
- the flash memoryhas a storage capacity
- the wireless router firmware imageincludes a plurality of chunks, each chunk having a size which is no greater than a predetermined chunk size and is less than one-eighth the flash memory storage capacity.
- the wireless routerupon execution of at least some of the instructions by the processor destructively overwrites the version of wireless router firmware in the flash memory in a chunk-wise manner with chunks of the wireless router firmware image.
- the wireless router firmware imageincludes a plurality of chunks which have at least one predetermined executable order, namely, an order in which the chunks are arranged in an executable copy of the wireless router firmware image.
- the wireless routerupon execution of at least some of the instructions by the processor receives the chunks in the RAM memory in an order which differs from the executable order, and re-orders chunks to arrange the chunks in the flash memory in the executable order.
- the remotely upgradable wireless routerincludes a ROM memory address remapped to a RAM memory address in the router.
- the wireless routeris joined with a text file containing user-defined configuration settings, and the flash memory contains a copy of the user-defined configuration settings.
- the wireless router firmware imagehas a size and the flash memory has a storage capacity.
- the wireless router firmware imageincludes a plurality of chunks. Each chunk has a size which is no greater than a predetermined chunk size and is less than one-eighth the flash memory storage capacity.
- the size of the wireless router firmware imageis at least two chunk sizes smaller than the flash memory storage capacity.
- the wireless routerupon execution of at least some of the instructions by the processor performs authentication to verify validity of the wireless router firmware image.
- the wireless link interfaceconforms with at least one 802.11 standard for wireless communications.
- the wireless routerincludes a 10/100 Mbps local area network interface card to provide a data communication connection to a local area network
- the kernelincludes instructions which upon execution by the processor at least partially control operation of the local area network interface card.
- the kernelincludes open source operating system code.
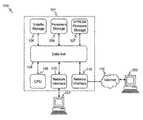
- FIG. 1depicts a schematic diagram of a system and device for processing network content
- FIG. 2Aillustrates an exemplary configuration to protect a single desktop computer
- FIG. 2Billustrates an exemplary configuration to protect a local area network (LAN), which includes multiple desktop computers;
- LANlocal area network
- FIG. 3illustrates an exemplary operating sequence of a system and device configured to process email traffic
- FIG. 4illustrates an exemplary operating sequence of a system and device configured to process various web content viewed by a user using the user's computer;
- FIGS. 5A, 5B, 6A and 6Bprovide more detailed illustration of an internal operating sequence of a system and device
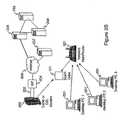
- FIGS. 7A and 7Bdepict alternative schematic diagrams of a wireless router system and device for processing network content, include one wireless router configuration with an Ethernet 10/100 Mbps local area network interface card, and one configuration without that network interface card; and
- FIG. 8is a flow chart illustrating steps of some method embodiments for remoter firmware update.
- provisional application No. 60/653,163contains 148 pages of a disclosure which was incorporated and built upon in the application that ultimately issued as U.S. Pat. No. 7,904,518.
- the present documentincorporates and builds upon both those ancestor applications. Claims of the '518 patent focus in part on filtering email message content, but the underlying applications are not limited to that topic.
- the claims presented hereare differently focused than the '518 patent claims, but an attentive reader will find common subject matter in the three applications.
- the present documentis titled “Wireless Router Remote Firmware Upgrade,” the '163 provisional discusses a Remote Flash Updater utility capable of writing firmware to flash memory, and the '518 patent Abstract states that an “appliance is provided with an automatic remote updating capability, wherein the software and data used by the appliance can be updated remotely via a network.”
- the '518 patentalso teaches that some embodiments of the appliance include functionality of a network hub or router.
- firmware change(s)means “one or more firmware changes” or equivalently “at least one firmware change”.
- overwriting a memorymeans overwriting at least a portion of the memory. That is, overwriting a memory allows overwriting the entire memory, but does not require overwriting the entire memory.
- a “chunk” of flash memoryis the smallest amount of memory that is overwritten to perform a single flash memory write.
- chunk sizeis 128 Kbytes, but different vendors may use different chunk sizes.
- a flash memory chunkis sometimes called a “block,” but care is called for because attention to context reveals that the word “block” is also used in other ways, e.g., in discussing filesystem data structures.
- a Remote Flash Updateris a utility capable of writing to flash memory, a type of non-volatile memory storage, with an image file gathered off a HTTP server.
- the RFU 701is a utility capable of writing firmware 702 to flash memory 107 or other firmware storage 108 .
- the RFUmay be implemented to run with a kernel 703 , such as an open source operating system kernel.
- the RFU 701is a Linux 2.4 kernel based user-land software running on an ARM based chipset. It is written in ANSI C programming language compiled cleanly with an ARM gcc compiler with the—Wall and ⁇ O2 compiler flags. RFU 701 development may be guided by familiarity with flash memory code source samples including source code for a flash kernel driver, and a library implementation that interfaces with the flash kernel driver. One RFU 701 uses a C library with flash I/O functionality. One RFU binary name is RFUpdater.
- the Linux 2.4 systemimplements a ROM to RAM remap 819 for file system access.
- the boot loaderdecompresses 822 data held within flash memory and copies 823 it into a RAM based file system.
- the system 101After the RFU 701 updates flash memory 107 or other firmware storage 108 with an image file, the system 101 will reboot 812 in order for the changes to be live. Secure, cross-standard and compact programming methodologies are used.
- One Updater 701 methodincludes the following steps, which are exemplary rather than the sole possible implementation of teaching herein.
- Begin updater execution.Calculate kernel 703 and ramdisk flash memory offset and size.
- Initialize POST update variables.Issue an HTTP 1.0 POST request on update.akalink.net port 80/TCP.
- Read header responsecontinue if new update is available.
- Read header responseimage file size >100 KB and ⁇ 3.5 MB.
- Authenticate 833if image file checksum is valid, continue. This is a less than 180 second cycle. Perform overlapping steps to re-program flash memory starting with kernel followed by ramdisk (a kernel-first approach 814 ): Erase next block chunk of flash, write next block chunk to flash from RAM, free up RAM block chunk. Reboot 812 system.
- a purpose of the remote flash updater 701is to write to flash memory 107 or other firmware storage 108 an image file upon invocation, the image file being gathered remotely from a HTTP site.
- Block re-ordering 817is done afterwards to validate the image checksum.
- Some embodimentsutilize already existent flash library functions to achieve the result of re-programming flash memory; they don't require re-writing a full flash implementation from scratch.
- the image filecontains the kernel image and the ramdisk image embedded as one. Therefore, byte offsets headers during the HTTP session are provided in order for the kernel image and ramdisk image to be written to the proper flash memory 107 or other firmware storage 108 area allocated for their usage.
- some embodimentsperform basic authentication 833 to verify if the image file is valid.
- the maximum size of flash memory an embodiment is utilizingis 4 MB. 256 KB of memory is reserved with another 256 KB memory of free space, therefore only 3.5 MB is allocatable to flash memory.
- the kernel imageis written to flash memory starting from 0x10000 to the size of 0x0007FFFF.
- the ramdisk imageis written to flash memory starting from 0x90000 to the size of the image.
- the flash library and flash kernel library header filesprovide information regarding flash memory offsets, instructions and function.
- An implementermay study the flash source code provided along with this document in order to write this software.
- ethloader.cis software that remotely updates flash memory by passing it a file name, kernel image or ramdisk image, with or without specifying length. It could be a good source of reference to utilize as it can broaden understanding and avoid confusion.
- the updater 701after the updater 701 is executed, it will initialize all variables regarding kernel and ramdisk memory area begin and end offsets and anything else related to that in order to know where to write what in what area, sizes of blocks, how many blocks to write, etc. It will then initialize a HTTP POST request 804 to be sent to update.akalink.net on port 80 via TCP/IP (of course, other websites will be used by other vendors).
- the socket timeoutis 5 seconds, and 15 seconds for a returned response.
- X-Update-Length2097152 ⁇ -Length of image
- X-Update-Offset668402 ⁇ -Last byte of Kernel Image from 0
- X-Update-Cksum1808e84cfcbaf71ce1073cc418ff262a ⁇ -cksum checksum
- X-Update-Itemimage ⁇ -Item requested Image file data here ⁇ -Item requested data
- the embodimentknows it is dealing with the correct item, and will proceed.
- Some embodimentswill then verify if this image file is recent by verifying if the header X-Update-Cksum is different than the Cksum cksum located in a file called “cksum” which holds the contents of the image current cksum.
- processingproceeds to see if 818 the X-Update-Length header value is less than 3.5 MB (3670016 bytes) and larger than 100 KB (102400 bytes).
- the embodimentwill read and write the image file off the HTTP server to various 128 KB RAM blocks in two different groups one for the kernel image and one for the ramdisk image, separating them based on the X-Update-Offset header value.
- the X-Update-Offset header valuerepresents the last byte of the kernel image starting from 0 byte, the rest till the last byte represents the ramdisk image.
- Some embodimentswill re-order 817 the RAM blocks in first received priority and see if 833 the cksum checksum of the total image corresponds to the value of X-Update-Cksum.
- Kernel imagegoes first (a kernel-first approach 814 ). This process is on a block level not a byte level for performance purposes.
- the procedureswill erase the next available 128 KB blocks in flash, will write to flash the next 128 KB available block chunk from RAM, and afterwards will de-allocate the RAM block chunk memory written and proceed in a cycle until the image file has been written.
- Online Upgrade Softwarewill destructively 811 upgrade the flash 107 on a chunk by chunk basis unless adequate headroom exists to maintain a redundant flash bank to hold the working software.
- a CubeUpdateris a built-in software component whose purpose is to perform software updates and check for new updates on a daily basis.
- the CubeUpdaterwill use 6 am, 12 am, 6 pm as hours during the day to attempt to perform a software update. This is used in case if the internet connectivity is down at 6 am, it will retry at different hours.
- the routerredirects 830 the browser to a billing activation page, such as a user profile web page that informs the user of billing status and invites the user to make payment or other arrangements to activate service.
- a billing activation pagesuch as a user profile web page that informs the user of billing status and invites the user to make payment or other arrangements to activate service.
- an LED status on the routeris also changed to reflect the billing status and notify the client.
- the router upgradeincludes software generally, as opposed to firmware alone.
- the upgrade softwarecan be stored on a disk local to the router, e.g., in compressed or archive format such as tar or gz format.
- the routerAfter extracting the software, setting/checking permissions, and applying the upgrade, the router continues (sometimes without rebooting) providing services to the user client.
- Some embodimentsinclude a software hierarchy, implemented in a collection of file system directories.
- .o object code for the routermay be kept in a/boot/modules directory.
- Configuration filessuch as .conf and some .txt files, may be kept in a /usr/local/ ⁇ router>/conf directory, where ⁇ router> is a name representing the router code, e.g., “hcube” or “RFU”.
- a sysconfig database configuration filemay be kept in a/usr/local/ ⁇ router>/conf directory, for example.
- User interface.html filesmay be kept in a/usr/local/ ⁇ router>/www/include/tpl/html directory, for example.
- a user interface in some embodimentsincludes pages in a web browser, through which the router receives commands (e.g., check for available updates) and notifies the user of status (e.g., billing inactive, upgrade needed, upgrade available, upgrade installed).
- Familiar mechanismsmay be used in the user interface, e.g., HTML forms and form variables, CGI files, HTML template pages, environment variables, configuration files, and so on.
- Some embodimentsperform a flash update procedure on a WEB_CONFIG_FILE to write the configuration file to flash memory storage.
- Some embodimentsupdate a text file containing configuration settings to flash memory via CGI.
- the CGI filewill be executed on a system utilizing flash memory 107 as storage, therefore this functionality is used to keep updated configuration settings in memory after a system reboot.
- the flash update functionalityis already in place, it is being used to update another file called sysconfig.
- Some embodimentscan use webconfig/flash.c function call kd_updateFlash and setDefault to provide functionality to update our custom configuration file settings to flash memory.
- the configuration file settingswill simply be a text file with variables separated by a semicolon pointing to a value separated by a new line.
- the configuration file settingsis “sample.cnf” modifiable by a define statement. Comments should be ignored.
- Some embodimentsbuild on familiar mechanisms. For some embodiments, one of skill may be interested in source provided under names such as webserver, webconfig, sysconfig.
- one embodimentincludes: at least 2 10/100 Mbps Ethernet ports, an ARM based processor of at least 10 MHz, at least 10 MB of memory which can include SDRAM, SRAM, FLASH, and also ROM, a reset button, a power supply, LEDs, and a printed circuit board or other motherboard to which the other components are soldered/attached/connected.
- the componentsare housed in a plastic case.
- a methodologyprovides an integrated plug and play solution for home networks.
- An appliancecan be used for processing of web and email traffic and can be deployed as a stand-alone appliance.
- the applianceutilizes a remote service accessed via a network.
- the systemexecutes various procedures to handle the network traffic.
- the systemis provided with an automatic remote updating capability, wherein the software and data used by the system can be updated remotely via a network.
- a methodincludes connecting a network hardware appliance to an external network within a home network configuration; including a central processing unit (CPU) on the network hardware appliance; providing a memory for storing a set of computer-readable instructions executed by the central processing unit (CPU) on the network hardware appliance; connecting the network hardware appliance to one or more user computers; installing the network hardware appliance between the external network and the user's computer; passing all network traffic between the user's computer and the external network through the network hardware appliance; generating a request to retrieve firmware; and receiving firmware.
- Some embodimentsinclude authenticating with a remote system using authentication information. Some include reading from the world wide web using HTTP protocol.
- a network hardware appliancefor use with a personal computer of a user, the personal computer being connected to a home network of the user.
- the network hardware applianceincludes a central processing unit (CPU); a first network interface connected to the personal computer of the user; a second network interface connected to an external network; and a memory storing a set of computer-readable instructions. When executed by the CPU the instructions cause the CPU to perform automatic remote firmware updates as described herein.
- the personal computer of the useris connected to an external network.
- the network hardware applianceis connected to the home network and is positioned between the personal computer of the user and the internet.
- a user request for a web resourceis intercepted.
- the systemrequests from a target web server the source code for the resource and receives the source code of the requested source from the target web server.
- an apparatusintercepts content of a web resource requested by a user.
- the requested web resourcebeing located on a target web server.
- the apparatusincludes a central processing unit (CPU), a first network interface coupled to the computer of the user, a second network interface coupled to the external network and a memory storing a set of computer-readable instructions.
- the CPUoperating under the direction of the stored instructions intercepts a user request for the web resource, requests from the target web server the source code for the resource, and receives the source code of the requested source from the target web server.
- An embodiment of the methodologyprovides an integrated plug and play solution.
- the appliancecan be used for processing of web and email traffic and can be deployed as a stand-alone appliance.
- the systememploys network level analysis and translation and executes various procedures to handle the network traffic.
- the applianceis provided with an automatic remote updating capability, wherein the software and data used by the appliance can be updated remotely via a network.
- FIG. 1depicts a schematic diagram 100 of an exemplary embodiment of a network appliance 101 for processing email communications as well as other network content.
- the appliancemay include a data bus 104 or other communication mechanism for communicating information across and among various parts of the appliance 101 , and a processor (CPU) 105 coupled with bus 104 for processing information and performing other computational and control tasks.
- the processor 105is an ARM processor with clock speed of at least 10 MHz.
- Appliance 101may also include a volatile storage 106 , such as a random access memory (RAM) or other dynamic storage device, coupled to bus 104 for storing various information as well as instructions to be executed by processor 105 .
- RAMrandom access memory
- the volatile storage 106also may be used for storing temporary variables or other intermediate information during execution of instructions by processor 105 .
- the size of the memory unit 106is at least 10 MB.
- the appliance 101may further include a read only memory (ROM or EPROM) 107 or other static storage device coupled to bus 104 for storing static information and instructions for processor 105 , such as basic input-output system (BIOS), as well as various system configuration parameters.
- ROM or EPROMread only memory
- a persistent storage device 108such as a magnetic disk, optical disk, or solid-state flash memory device is provided and coupled to bus 104 for storing information and instructions.
- the embodiment of the appliance 101 shown in FIG. 1also includes at least two communication interfaces, such as network interfaces 113 and 114 coupled to the data bus 104 .
- Communication interfaces 113 and 114provide a two-way data communication coupling to a network link 114 that is connected to the network 115 .
- network link 114may be 10/100 Mbps local area network interface cards (LAN NIC) to provide a data communication connection to a compatible LAN.
- Wireless linkssuch as well-known 802.11a, 802.11b, 802.11g and Bluetooth may also be used for network implementation.
- communication interfaces 113 and 114send and receive electrical, electromagnetic or optical signals that carry digital data streams representing various types of information.
- Network link 114typically provides data communication through one or more networks to other network resources.
- network link 114may provide a connection through network 115 to a host computer 120 , or to other network resources (not shown).
- the appliance 101can access network resources located anywhere on the Internet 115 , such as a remote network storage or web servers.
- the appliance 101may also be accessed by user computer 121 located anywhere on the corresponding local area network.
- Local network(not shown) and the Internet 115 both use electrical, electromagnetic or optical signals that carry digital data streams.
- carrier waves per seare not claimed. Whenever reference is made herein to data or instructions, it is understood that these items configure a computer-readable memory (RAM, ROM, flash, etc.), thereby transforming it to a particular article, as opposed to simply existing on paper, in a person's mind, or as a carrier wave or other transitory signal on a wire, for example. Unless expressly stated otherwise in a claim and permitted by applicable law at the relevant time, a claim does not cover a signal per se. A memory or other computer-readable storage medium is presumed to be non-transitory unless expressly stated otherwise.
- the appliance 101can send messages and receive data, including program code, through the variety of network(s) including any local area network as well as the Internet 115 by means of network links 114 and 113 .
- network(s)including any local area network as well as the Internet 115 by means of network links 114 and 113 .
- the system 101acts as a network server, it might transmit a requested code or data for an application program running on user's computer 121 client(s) and/or the host 120 through any local area network (not shown) as well as the Internet 115 .
- itmay receive code or data from other network entities.
- the system 101includes functionality of a network hub, router, modem, or other network device which has a position in the network configuration adjacent to an illustrated Spam Cube 101 position.
- some embodimentsinclude router functionality.
- Router functionalityin general is familiar. As noted, for example, in U.S. Pat. No. 6,321,267 to Donaldson, in some cases a packet-filtering router routes packets from the Internet to an SMTP proxy server via a LAN. The router operates at the network layer of the protocol reference model using the Internet Protocol version 4 (IPv4). However, with appropriate changes to the socket programming interface, router functionality also operates with other network layer protocols such as Internet Protocol version 6 (IPv6) or Novell Netware. As noted in US Patent Application Publication No. 2002/0007453 by Nemovicher, some routers switch communication traffic between a communication network and a LAN under the direction and control of a load balancer and fire wall. As noted in US Patent Application Publication No.
- IP addressesare dynamically assigned to most users by DHCP servers at the ISP or a router at the edge of the LAN on which the sender computer resides.
- a computer and/or any other appropriate system componentmay use resources such as publicly-available domain name server (DNS) data, routing data and/or the like, to investigate a server suspected of conducting fraudulent activities.
- DNSdomain name server
- the routing information in the message headermay be analyzed to determine whether the message originated from and/or was routed through a suspect domain, again enhancing the likelihood that the message is a phish.
- the received codemay be executed by processor 105 as it is received, and/or stored in persistent or volatile storage devices 108 and 106 , respectively, or other non-volatile storage for later execution.
- the appliance 101may obtain application code updates from remote network resources.
- the appliance 101may also use the network interface 114 to receive various code and data updates, which it may use in its operation. For example, such data updates may include latest virus definition files. For this purpose, the appliance may perform periodic checks to determine whether such updates are available.
- the appliance 101may also user network interfaces 114 to issue requests to remote network resources, such as remote virus scanning services and to receive the appropriate responses. Finally, the user may connect to the appliance through, for example, network interface 113 in order to perform necessary configuration of the appliance.
- one or both of the network interfaces 113 and 114may be a wireless network interface operating in accordance with a wireless networking protocol, such as Bluetooth, 802.11a, 802.11b and/or 802.11g.
- a wireless networking protocolsuch as Bluetooth, 802.11a, 802.11b and/or 802.11g.
- both interfaces 113 and 114are conventional wire-based network interfaces.
- FIG. 2Aillustrates an exemplary home network configuration, wherein the appliance 101 is configured to protect a single desktop computer 201 .
- the appliance 101is installed between the cable/DSL modem and the user's desktop computer, such that all network traffic between the user's computer 201 and the outside network 206 passes through the appliance.
- the user's computer 201is connected to one of the aforementioned two network interfaces 113 and 114 , while the other interface is coupled with the cable/DSL modem 203 .
- the modem 203is connected via connection 205 with ISP 204 , which enables the user's computer to access the internet 206 and remote servers such as servers 207 , 208 , 209 , 210 .
- the functionality of the illustrated Spam Cube 101 and of the adjacent cable or DSL modem 203is combined into a single system 101 .
- FIG. 2Billustrates an exemplary configuration of home network 300 , which includes the appliance 101 configured in a manner designed to protect a local area network (LAN), which includes multiple desktop computers 201 .
- the appliance 101is installed between the cable/DSL modem 203 and the network hub/router 301 , which provides network connectivity to the desktop computers 201 .
- the functionality and components of the illustrated Spam Cube 101is combined into a single appliance or system 101 with the functionality and components of the adjacent cable or DSL modem 203 , or with the functionality and components of the adjacent Network Hub/Router 301 , or with the functionality and components of both the modem 203 and the router 301 .
- the appliance 101can filter all network traffic reaching the computers 201 .
- the network hub 301may be wireless network-enabled. In an alternative embodiment, the network hub 301 may be integrated with the appliance 101 . The integrated hub may also be either wireless or wired.
- connection 205The other elements of the networking configuration shown in FIG. 2B , including cable/DSL modem 203 , connection 205 , and ISP 204 , are generally equivalent to the corresponding elements of FIG. 2A , described hereinabove.
- FIG. 3illustrates an exemplary operating sequence of a network appliance configured to process email traffic.
- email message 302is sent by an entity located on the external network (e.g. Internet) 206 to the user's computer 201 .
- the message 302may contain one or more attachments, which may include certain malware, such as viruses, worms or other threats.
- the appliance 101is arranged to intercept the email message 302 .
- the appliance 101Upon the interception of the message 302 by the appliance 101 , the appliance 101 performs an initial inspection of the received email message and its attachment(s) and, if necessary, submits a service request 304 to the remote antivirus scanning engine 306 .
- the aforementioned service requestmay direct the external virus scanning service to perform a virus check of any attachments to the email message 302 .
- the appliance 101may include the corresponding attachments with the request 304 .
- the appliance 101requests the anti-virus scanning of only specific attachment types. For example, during the initial inspection, the appliance 101 may determine whether the attached file is an executable and request remote scanning of the attachment based on the results of this determination.
- the remote scanning system 306After receiving the request 304 from the appliance 101 , together with the relevant attachment email files, the remote scanning system 306 performs the necessary processing of the email attachments and determines the presence of any threats therein in accordance with well-known scanning algorithms.
- the scanning systemmay utilize a plurality of alternative scanning algorithms. The exact algorithm used by the system may be selected by the user of the appliance 101 during the configuration process. The user's selection may be stored in the storage devices 106 , 107 or 108 of the appliance 101 .
- Existing scanning products which may be used by the scanning system 306include, without limitation, Norton Antivirus and McAfee Security software.
- the use of the remote scanning service 306enables the system to perform scanning operations in an on-demand manner without providing the appliance 101 with the processing power required to perform the scanning operation.
- the scanning software executing on servers 306may be easily and conveniently updated. The aforementioned two features of the system configuration enable the appliance 101 to be implemented using inexpensive hardware.
- the external scanning engine 306responds to the appliance 101 with response 305 containing information on any detected threats.
- the response 305may indicate that one or more of the attachments to the email contain viruses.
- the appliance 101neutralizes the detected threat, by, for example, removing the infected attachment, and re-writes the received email message 302 to include appropriate warning to the user.
- the aforesaid warningmay be placed either in the subject line or in the body of the message.
- the re-written email containing the warning 308is then forwarded by the appliance 101 to the user's computer 201 .
- the appliance 101performs the update of its statistics information.
- FIG. 4illustrates an exemplary operating sequence 400 of the network appliance configured to process various web content viewed by a user using user's computer.
- the depicted processis initiated when a user requests a web resource by inputting at 402 URL 401 into a web browser window on user's computer 201 .
- the browserUpon the receipt of the URL information 401 , the browser sends HTTP request 403 requesting the target web service (in the example shown in FIG. 4 , the target website is) the website of CNN news service) to provide the resource specified by the received URL.
- the request 403is intercepted by the appliance 101 , which contacts the target web server 406 on behalf of the user and sends a request 404 for the source code of the web resource specified by the user.
- the target server 406sends a reply message 405 , accompanied with the full source code of the requested resource.
- the appliance 101receives the code furnished by the web server 406 and initiates a scan of the received source code for any possible threats, including, for example, any spyware.
- the appliance 101may use a remote scan engine 408 to achieve most comprehensive threat detection.
- the appliance 101may send a request 409 to the remote network of scan engines 408 containing the entire source code of the web resource, or any portion thereof.
- the outside scan engines 408examine the content of the received source code and send reply 407 to the appliance, indicating whether any potential threats were detected.
- the appliance 101sends at 410 a warning message 411 to be displayed in the user's browser window, warning the user of the presence of any potential threats within the requested web resource.
- the useris provided with an option to either avoid viewing potentially harmful web resource or to proceed with the viewing despite the shown warning.
- FIGS. 5A, 5B, 6A and 6Bprovide more detailed illustration of the internal operating sequence of an embodiment of the appliance.
- FIG. 5Adepicts the first phase 500 of that exemplary operating sequence.
- the shown operating sequenceis executed by the CPU 105 shown in FIG. 1 .
- the appliancemay be provided with an operating system, which may be pre-loaded into one or more of the storage devices 106 , 107 and 108 of FIG. 1 .
- Exemplary operating systems which may be used to control appliance 101include Linux, UNIX (example: BSD), or RTOS (example: VxWorks).
- the process illustrated in FIG. 5Ais automatically initiated when, at step 502 , the appliance 101 accepts a connection from user's computer 201 on the outbound port 110 , corresponding to TCP/IP protocol, well known to persons of skill in the art.
- the appliance 101intercepts a request generated by user's email client software to retrieve messages corresponding to user's email account from the internet service provider (ISP).
- the applianceopens a connection to the destination IP address corresponding to the email service subsystem of the ISP.
- the systemreceives authenticating information, such as username and password, corresponding to user's email account with the ISP.
- the systemuses the received authentication information to establish a session with the remote email service and, at step 506 , sends to this service a command to scan the user's mailbox for duplicate messages and, when appropriate, to delete them.
- the systemreceives the “LIST” command from the user's email client and forwards it to the email service system.
- the aforesaid list commandrequest the email service to provide the listing of all emails in the user's email account.
- the appliancereceives from the user's email client the “RETR” command, which requests the remote email subsystem to retrieve one or more email messages in the user's email account.
- the appliance 101Upon the receipt of this command from the email client, the appliance 101 forwards it to the email server, which, in response, begins a message retrieval process.
- the appliance 101Prior to retrieving a specific message, the appliance 101 first performs a check of the message size. If the size of the message is less than a predetermined threshold value, for example, 200 KB, the system retrieves the entire message, see step 510 .
- a predetermined threshold valuefor example, 200 KB
- the size of the messageexceeds the aforesaid threshold, only a block of the message is retrieved, see step 509 .
- the size of the retrieved blockis 200 KB. However, other block sizes may be used instead.
- the systemUpon the retrieval of the message, the system first checks if the sender of the message identified in the “From” field thereof matches an existing entry in the blacklist table. This table lists all senders, the email correspondence from which should be blocked. If the match in the blacklist table is found, the corresponding email message is blocked at step 521 .
- the appliancechecks whether the content of the message, as described by the “Content-Type” field of the message header, may include encrypted attachments. If the message contains only unencrypted attachments, the operation proceeds to step 514 , whereupon the system requests the remote HTTP virus scanning server to perform the scanning of the message body for viruses. If the virus is found, the system blocks the message at step 521 .
- step 513the sender of the message, which is identified in the corresponding “From” record, is compared with entries in the whitelist table.
- This tablecontains a list of sender email addresses from which email correspondence should be allowed without further inspection. If the sender address matches one of the aforesaid whitelist entries, the email message is allowed at step 520 .
- the systemchecks the recipient of the email message identified in the “To” field of the message header against entries in the parental control profile. This profile includes email addresses of recipients, which should not receive email messages. If the match is found, the email message is again blocked at step 521 . If no matching entries in the parental control profile exist, the system proceeds with step 516 , whereupon the identity fraud analysis algorithm inspects the header of the email message for possible phishing scam. If such scam is detected, the message is again blocked at step 521 .
- the message header patternis analyzed at step 517 for SPAM content. Again, if SPAM is detected, the message is blocked at step 521 . If SPAM is not detected in the header, at step 518 , the system checks whether the message header indicates presence of encrypted email message. The encrypted content is indicated, for example, by presence of “Content-Type: application/x-pkcs7-mime” record in the header of the email. If the content is not encrypted, the system inspects the body of the message for SPAM content at step 519 . If the SPAM is not detected or if the email body is encrypted, the system accepts the email at step 520 .
- the systemAfter the email is rejected at step 521 or accepted at step 520 , the system performs certain logging and user notification operations illustrated in FIG. 6A . Specifically, is the email is allowed or denied, the system collects and stores the session logging information at steps 628 and 601 , respectively. In case of a denial, the appliance at step 602 verifies whether identity fraud was detected in the email content. If this was the case, the email is tagged by placing an appropriate message, such as “[PHISH]” either in the subject line (step 603 ) or, alternatively, in the header of the email message (step 607 ), depending on the configuration parameters specified by the user. The system may further insert phishing scam alert into the body of the message at step 606 .
- an appropriate messagesuch as “[PHISH]”
- the systemthen proceeds with the determination of whether a virus was detected in the email, see step 608 . If the virus was found, the appliance again performs tagging of the email either in the subject line or in the header, depending on the user's configuration, at steps 609 - 610 and 611 - 612 , respectively. If the user's parameters call for recipient notification of virus-containing emails, the system disables the virus and re-writes the message body inserting an appropriate virus warning (steps 613 and 614 ). If the configuration requires sender notification, the appliance generates an email message to the sender of the virus-containing email, which includes a message alerting the sender of the email message of the virus (step 616 ).
- the emailis likewise tagged either in the subject or the header, at steps 618 , 620 and 621 - 622 , respectively. Finally, at step 623 , the system inserts a management control toolbar into the message body.
- the tagged email with the inserted management toolbaris forwarded to the client at step 624 .
- the clientterminates the session at step 615 with the QUIT command, which the system forwards to the remote email server.
- the systemsends the collected logging information to a remote HTTP server for storage.
- the shutdown and session terminationis performed at step 627 .
- the systemlogs detailed information on the accepted and rejected messages, as well as the detected threats. Upon the request by the user, the logged information may be displayed in a text or graphical form.
- the appliancemay be utilized in connection with any known communication protocols, including, without limitation, POP3, SMTP or HTTP.
- FIG. 8illustrates some method embodiments, in a flowchart 800 .
- zero or more illustrated steps of a methodmay be repeated. Steps in an embodiment may also be done in a different order than the top-to-bottom order that is laid out in FIG. 8 . Steps may be performed serially, in a partially overlapping manner, or fully in parallel.
- the order in which a flowchart is traversed to indicate the steps performed during a methodmay vary from one performance of the method to another performance of the method.
- the flowchart traversal ordermay also vary from one method embodiment to another method embodiment.
- Stepsmay also be omitted, combined, renamed, regrouped, or otherwise depart from the illustrated flows, provided that the method performed is operable and conforms to at least one claim. Steps described as being performed by a user may also be performed by another person, or by a machine, on behalf of a user. Another person who performs steps on behalf of a user need not have a particular user in mind.
- Some embodimentsprovide a method for upgrading a wireless router. Some include the step of containing 801 a firmware 802 version 803 , namely, a flash memory in the wireless router 101 containing a first version of router firmware, with the router firmware including instructions to be executed by a processor 105 of the wireless router, and the router firmware also including data.
- Some methodsinclude remotely requesting 804 a firmware update 805 , namely, the wireless router sending 806 a request 807 for a firmware update, with the request being sent from the wireless router over a network 115 connection toward a server 207 .
- Some methodsinclude receiving 808 a responsive firmware image 809 , namely, the wireless router receiving over the network connection a response to the request for a firmware update, with the response including at least a firmware image for a second version of router firmware which differs from the first version of router firmware by reason of containing at least one firmware change, a firmware change being a difference in firmware data and/or a difference in firmware instructions.
- the firmware imageincludes a plurality of chunks 810 , each chunk having a size which is no greater than a predetermined chunk size.
- Some methodsinclude destructively overwriting 811 flash memory chunks, namely, the wireless router destructively overwriting the first version of router firmware 802 in the flash memory with the second version of router firmware 802 .
- the destructive overwritingproceeds in a chunk-wise manner such that prior to being overwritten by all of the chunks the flash memory contains neither a complete copy of the first version nor a complete copy of the second version of the router firmware.
- the wireless router 101is configured to run whatever version of router firmware is in the router's flash memory after the router system 101 is rebooted 812 .
- Some methodsinclude going live 813 with upgraded firmware 802 , by reason of the wireless router rebooting 812 and thereby making the firmware change(s) go live.
- a wireless router upgrading methodincludes writing 814 the flash memory and then writing 814 a kernel 703 memory. That is, the wireless router destructively overwrites the first version of router firmware in the flash memory with the second version of router firmware, and then writes a copy of content of the second version of router firmware to a kernel memory in a volatile RAM memory 106 in the wireless router 101 before going live 813 with the upgraded firmware.
- Thisis a kernel-first approach described above.
- a wireless router upgrading methodincludes writing both 815 flash memory and a volatile RAM disk. That is, the wireless router destructively overwrites the first version of router firmware in the flash memory with the second version of router firmware, and also writes a copy of content of the second version of router firmware to a RAM disk in a volatile RAM memory 106 of the router 101 .
- the firmware image chunks 810have at least one predetermined executable order, namely, an order in which the chunks are arranged in an executable copy of the firmware image.
- Some router upgrading methodsinclude receiving 808 , 816 firmware chunks 810 in a volatile RAM memory in the wireless router in an order which differs from the executable order, and re-ordering 817 the chunks. For example, in some methods the step of destructively overwriting 811 flash memory chunks also arranges 817 chunks in the flash memory in the executable order.
- the firmware image 702has a size and the flash memory has a storage capacity
- the methodincludes the wireless router checking 818 to see whether the size of the firmware image is less than a predetermined maximum firmware image size.
- the predetermined maximum firmware image sizecan be at least a specified number (e.g., one, two, four, eight) of chunk sizes smaller than the flash memory storage capacity.
- the wireless routerremaps 819 a ROM memory address 820 in the router to a RAM memory address 821 in the router. This may be done, for example, to pass control to code at the remapped address.
- the wireless routerdecompresses 822 data held within the flash memory in the router and copies 823 the data to a RAM-based file system in the router. For example, the router may decompress and copy a firmware image, an operating system kernel, email filtering code, anti-virus definitions, and/or other data.
- the routeruses flash memory (in addition to or in place of a hard disk or remote store, for instance) to preserve user configuration through a reboot.
- the wireless routerBefore going live with upgraded firmware, the wireless router overwrites 824 at least a portion of the flash memory with user-definable configuration settings 825 from a text file 826 .
- the settingsmay be copied, for example, into one or more flash chunks that are not occupied by the firmware image code.
- the wireless routeroverwrites 827 the text file with the configuration settings from the flash memory.
- the response received 828includes an indication 829 that a user's billing status is inactive, and the method redirects 830 a web browser 831 to a billing activation page 832 .
- the firmware image chunks 810have at least one predetermined executable order
- the step of receiving a responsive firmware imagereceives 816 the chunks in the wireless router in an order which differs from the executable order
- the methodre-orders 817 the chunks such that the step of destructively overwriting flash memory chunks arranges chunks in the flash memory in the executable order
- the methodalso writes 815 a copy of the chunks to a kernel memory in the wireless router.
- the routerauthenticates 833 the firmware image, e.g., by using a server certificate, image checksum, decryption, and/or other familiar authentication tool or technique.
- a and “the”are inclusive of one or more of the indicated item or step.
- a reference to an itemgenerally means at least one such item is present and a reference to a step means at least one instance of the step is performed.
- Headingsare for convenience only; information on a given topic may be found outside the section whose heading indicates that topic.
Landscapes
- Engineering & Computer Science (AREA)
- Theoretical Computer Science (AREA)
- General Engineering & Computer Science (AREA)
- Physics & Mathematics (AREA)
- General Physics & Mathematics (AREA)
- Computer Security & Cryptography (AREA)
- Software Systems (AREA)
- Business, Economics & Management (AREA)
- Computer Hardware Design (AREA)
- Signal Processing (AREA)
- Computer Networks & Wireless Communication (AREA)
- Human Computer Interaction (AREA)
- Development Economics (AREA)
- Strategic Management (AREA)
- Economics (AREA)
- Marketing (AREA)
- General Business, Economics & Management (AREA)
- Accounting & Taxation (AREA)
- Finance (AREA)
- General Health & Medical Sciences (AREA)
- Human Resources & Organizations (AREA)
- Operations Research (AREA)
- Quality & Reliability (AREA)
- Tourism & Hospitality (AREA)
- Entrepreneurship & Innovation (AREA)
- Virology (AREA)
- Health & Medical Sciences (AREA)
- Stored Programmes (AREA)
- Information Transfer Between Computers (AREA)
- Data Exchanges In Wide-Area Networks (AREA)
Abstract
Description
- The present application claims priority to, and incorporates by reference, U.S. patent application Ser. No. 13/763,351 filed Feb. 8, 2013, U.S. patent application Ser. No. 13/587,394 filed Aug. 6, 2012, U.S. patent application Ser. No. 13/015,053 filed Jan. 27, 2011 which is now U.S. Pat. No. 8,326,936, and U.S. patent application Ser. No. 11/350,905 filed Feb. 8, 2006, which is now U.S. Pat. No. 7,904,518, and U.S. Provisional Patent Application Ser. No. 60/653,163 filed Feb. 15, 2005.
- To aid understanding of the technical context of the innovations claimed herein, several references are discussed below. This discussion is meant to help promote a full and accurate examination of the claims presented.
- However, there are also limits on the inferences one can properly draw from this discussion. These references were identified with the present claims in mind, and the observations made here about the references are likewise guided by the present claims. One of skill would not necessarily have combined any of these references or made such observations without the benefit of hindsight. The mere fact that two or more of the references are discussed here is not evidence of a motivation to combine those references at the time of invention without using the present claims as a blueprint.
- Moreover, the inclusion of a reference in this discussion is not a blanket acceptance of every statement made in the reference; what the references recite is not necessarily correct. Each reference must also be considered independently of this discussion to fully understand the reference's teachings, as only a brief space is allotted to any given reference here and each reference speaks for itself. The reference recitations noted here are not meant to be a full description, or even a complete overview or summary, of the teachings of any reference. Other references may also be considered worthy of attention.
- Also, a reference may use terms differently than they are used here in describing the innovations claimed, and two different references may use the same term differently. Nor is the inclusion of a reference in this discussion evidence that the reference is enabling with regard to a particular claim, or indeed, with regard to any claim that is presented here.
- The following discussion of references begins by pointing out some things that are not present in any of the references. These gaps in the references are worthy of attention, but they are merely examples of how the references could be considered. In particular, it does not follow that something X is present in the references merely because the discussion did not say that X was missing from the references.
- Bearing these guidelines in mind, the reference discussion will now proceed.
- None of these references mention an “executable order” for “chunks” of a firmware image. None recite “re-ordering” or “re-sequencing” firmware image chunks that were received in some order other than the executable order.
- With regard to destructively overwriting flash memory chunks, the only mention of “destructive” in any of these references is in Zimmer (2005/0021968) paragraph [0048] which recites a “non-destructive reset.”
- None of these references recite a “wireless router” as a device whose firmware will be upgraded. Only Georges (2008/0156178) mentions any of the “802.11” wireless communication standards, and that is not in connection with router firmware upgrades because Georges does not mention “routers” at all.
- None of these references mention “checking” to see whether the size of a firmware image is at least two chunk sizes smaller than a device's flash memory storage capacity.
- With regard to remapping a ROM memory address to a RAM memory address in the context of a firmware upgrade, only two of the references mention “remapping” an address in any context, namely, Moore, et al. (2006/0047920) and Shamoon, et al. (2004/0107356). However, Moore's Abstract directs attention at how to “enable one-time or few-time programmable memories to work with existing consumer electronic devices (such as those that work with flash—an erasable, non-volatile memory) without requiring a firmware upgrade . . . .” (emphasis added). Shamoon directs attention to remapping for security. Shamoon [0310] recites “circuitry which remaps some of the available memory space, so that, in unsecure mode, the CPU cannot address secure memory locations.” Shamoon [0312] similarly recites “Some memory space may be rendered off-limits to general purpose uses, for example by remapping”.
- With regard to writing firmware to both flash memory and a volatile RAM disk, none of these references mention a “RAM disk” or a “RAM drive”.
- United States Patent Application Publication No. 2003/0066062 by Brannock, et al. recites that a method for updating platform firmware is disclosed. Brannock further recites that this capability is facilitated by a standard software abstraction for a firmware storage device, known as Firmware Volume (FV) that is managed through a Firmware File System (FFS). The FFS enables firmware files to be created, deleted, and updated individually. The FFS also enables a plurality of firmware files to be updated atomically by managing file state information via state bits stored in a file header of each firmware file, whereby an atomic change to a single state bit simultaneously causes the FFS to use an updated set of firmware files in place of an original set of firmware files.
- United States Patent Application Publication No. 2004/0083469 by Chen, et al. recites that an update method is used in an optical disk system to update firmware information stored in a firmware memory. Chen further recites that the method includes fetching program code and an update program routine from an update source, storing the program code into a first buffer, storing the update program routine into a second buffer, executing the update program routine stored in the second buffer, writing the program code stored in the first buffer into the firmware memory to update the firmware information, and changing a value of a program counter of the microprocessor such that the microprocessor executes the program code stored in the firmware memory at a predetermined location of the program code instead of executing a next instruction in the program code located after the current position of the program counter, and using the program code as updated firmware information to control the optical disk system.
- United States Patent Application Publication No. 2005/0027807 by Fengler, et al. recites that systems and methods for facilitating peripheral device firmware installation are disclosed. Fengler further recites that in one embodiment, a system and a method pertain to transmitting a firmware availability notification, receiving a firmware download request, and transmitting a firmware file to a peripheral device for installation on the peripheral device. In another embodiment, a system and a method pertain to receiving a firmware availability notification with a peripheral device, and providing a related notification to a user, the related notification being provided by the peripheral device.
- United States Patent Application Publication No. 2005/0055595 by Frazer, et al. recites that a system for remotely updating software on at least one electronic device connected to a network is disclosed. Frazer further recites that the electronic devices have a non-volatile rewritable storage unit divided into at least two partitions, one of which will contain core firmware and the other of which will contain auxiliary software. When an update is received at the device, the updated core firmware is written to overwrite the partition in the rewritable storage unit that contained the auxiliary software. When this is completed and verified, the previous version of the core firmware stored in the storage unit is disabled from execution by the device. Next, the updated auxiliary software is written to overwrite the old version of the core firmware. When this write is complete, the device determines a suitable time for it to be rebooted to execute the updated software. In another embodiment, the present core firmware in the device is copied from the partition it is in to the other partition, overwriting the auxiliary software stored there. The new core firmware received to update the device is overwritten into the first partition, the old copied core firmware being present in case of an upgrade failure, and upon a successful update of the first partition, the auxiliary software is written to the second partition, overwriting the copied old core firmware. In this manner, the position of the core firmware and auxiliary software within the partitions is preserved during normal operation of the device.
- United States Patent Application Publication No. 2008/0156178 by Georges, et al. recites that systems and methods for creating, modifying, interacting with and playing music are provided, particularly systems and methods employing a top-down process, where the user is provided with a musical composition that may be modified and interacted with and played and/or stored (for later play). In an unusually long Abstract which is not fully reproduced here, Georges also recites that the system preferably is provided in a handheld form factor, and a graphical display is provided to display status information, graphical representations of musical lanes or components which preferably vary in shape as musical parameters and the like are changed for particular instruments or musical components such as a microphone input or audio samples. An interactive auto-composition process preferably is utilized that employs musical rules and preferably a pseudo random number generator, which may also incorporate randomness introduced by timing of user input or the like, the user may then quickly begin creating desirable music in accordance with one or a variety of musical styles, with the user modifying the auto-composed (or previously created) musical composition, either for a real time performance and/or for storing and subsequent playback. The remainder of the Abstract may be read in Georges itself.
- United States Patent Application Publication No. 2006/0143475 by Herbert, et al. recites that a method according to one embodiment may include: receiving a first encrypted signal at a server of a computing network, the first encrypted signal comprising firmware encrypted by a first encryption algorithm having a first complexity level; sending a second encrypted signal over the computing network to at least one managed client in response to the first encrypted signal, the second encrypted signal comprising the firmware encrypted by a second encryption algorithm having a second complexity level, wherein said first complexity level is greater than said second complexity level; and updating existing firmware of the at least one managed client in response to receipt of the second signal at the at least one managed client. Herbert further recites that many alternatives, variations, and modifications are possible without departing from this embodiment.
- United States Patent Application Publication No. 2005/0097542 by Lee recites that a firmware update method is disclosed. First, a tag is written to a firmware storage device. Next, first firmware in the firmware storage device is replaced by second firmware. If the replacing step is successful, the tag is deleted. Before the execution of the second firmware, a verification operation is executed. If the tag is not present, the second firmware is executed. If the tag is present, an abnormity processing procedure is executed. The abnormity processing procedure terminates of execution of the second firmware, reads third firmware via an interface, and replaces the second firmware with the third firmware.
- United States Patent Application Publication No. 2005/0039178 by Marolia, et al. recites that aspects of an invention may be seen in a system and method for downloading update packages into an electronic device communicatively coupled to a carrier network. Marolia further recites that the system may facilitate the update of firmware/software in the electronic device. Different protocols may be utilized for discovery and download of update packages. Also, different protocols may be utilized for provisioning and for subsequent downloading of update packages.
- United States Patent Application Publication No. 2002/0073304 by Marsh, et al. recites that a system and a method that uses a software application operable under a current firmware/operating system configuration to install a new firmware version without “compromising” the operating system are presented. Marsh further recites that the software application may configure a computer system to install a plurality of software fixes configured to enhance functionality under a new firmware/operating system environment after the firmware has been successfully upgraded. Such functionality enhancements may be associated with external peripherals, as well as, input/output circuit cards, processors, and the like. In addition, the software application may configure the computing device to “boot” under the new firmware/operating system environment upon subsequent system initializations. Furthermore, the software application permits the distribution of firmware upgrades via a network. The capability to install firmware remotely permits a system administrator to “push” the new firmware to a plurality of network coupled computing devices, thus avoiding manual intervention at each device.
- United States Patent Application Publication No. 2006/0047920 by Moore, et al. recites that embodiments described therein can be used to enable one-time or few-time programmable memories to work with existing consumer electronic devices (such as those that work with flash—an erasable, non-volatile memory) without requiring a firmware upgrade, thereby providing backwards compatibility while minimizing user impact. Moore further recites that as such, these embodiments are a viable way to bridge one-time or few-time programmable memories with existing consumer electronic devices that have flash card slots. These embodiments also allow future consumer electronic devices to be designed without updating firmware to include a file system customized for a one-time or few-time programmable memory.
- United States Patent Application Publication No. 2003/0236970 by Palmer, et al. recites that in a data processing method and system a mass storage device (DASD) of a data processing system is partitioned to include a service partition. Palmer further recites that the service partition is typically located on a portion of the DASD beyond the highest address accessible to the operating system and application programs. The service partition will typically include the current versions of peripheral device firmware, any BIOS extensions, and device drivers. During a system boot, the boot code will invoke a peripheral device call that reports the device's firmware version level to compare the firmware versions of all the peripheral devices against the archived firmware versions stored in the service partition. If a mismatch is detected, the system boot will typically force an update of the peripheral device firmware to the level that is known to be good. Any such firmware updates are recorded in a log that is accessible to system management applications. Any revisions to firmware may be imaged into the service partition so that the revised version will be incorporated into the peripheral device itself during the next subsequent system boot.
- United States Patent Application Publication No. 2004/0015941 by Sekine recites that an information-processing apparatus includes a nonvolatile memory device configured to store firmware. Sekine further recites that the information-processing apparatus has a first unit for issuing an instruction to make an operating system execute a shutdown process, and to update the firmware, stored in the nonvolatile memory device, after the operating system has completed the shutdown process. The information-processing apparatus also has a second unit, responsive to the instruction to update the firmware, for updating the firmware only after the operating system has completed the shutdown process.
- United States Patent Application Publication No. 2004/0107356 by Shamoon, et al. recites that a novel method and apparatus for protection of streamed media content is disclosed. Shamoon further recites that in one aspect, the apparatus includes control means for governance of content streams or content objects, decryption means for decrypting content streams or content objects under control of the control means, and feedback means for tracking actual use of content streams or content objects. The control means may operate in accordance with rules received as part of the streamed content, or through a side-band channel. The rules may specify allowed uses of the content, including whether or not the content can be copied or transferred, and whether and under what circumstances received content may be “checked out” of one device and used in a second device. The rules may also include or specify budgets, and a requirement that audit information be collected and/or transmitted to an external server. In a different aspect, the apparatus may include a media player designed to call plugins to assist in rendering content. A “trust plugin” is disclosed, along with a method of using the trust plugin so that a media player designed for use with unprotected content may render protected content without the necessity of requiring any changes to the media player. In one aspect, the streamed content may be in a number of different formats, including MPEG-4, MP3, and the RMFF format.
- United States Patent Application Publication No. 2005/0021968 by Zimmer, et al. recites that a method for providing a secure firmware update is disclosed. This Zimmer application further recites that a first authentication credential is securely stored on a platform in an encrypted form using a key generated by a secure token, such as a trusted platform module (TPM). Typically, the authentication credential will identify a manufacture and the operation will be performed during manufacture of the platform. A configuration of the platform is “imprinted” such that an identical configuration is required to access the key used to decrypt the first authentication credential by sealing the key against the platform configuration. During a subsequent firmware update process, a firmware update image containing a second authentication credential is received at the platform. If the platform configuration is the same as when the key was sealed, the key can be unsealed and used for decrypting the first authentication credential. A public key in the first authentication credential can then be used to authenticate the firmware update image via the second authentication credential.
- United States Patent Application Publication No. 2005/0289646 by Zimmer, et al. recites disclosure of a method of copying virtual firmware smart card code from a first secured memory in a system and loading the virtual firmware smart card code into a second secured memory in the system so that the code may be run on a microprocessor to provide smart card services to the system.
- Various systems/devices and methods for remotely updating router firmware are described herein. For example, some embodiments provide a method for upgrading a wireless router. A flash memory in the wireless router contains a first version of router firmware. The router firmware includes instructions to be executed by a processor of the wireless router, and the firmware also includes data. The wireless router sends a request for a firmware update, the request being sent from the wireless router over a network connection toward a server. The wireless router receives over the network connection a response to the request for a firmware update, the response including at least a firmware image for a second version of router firmware which differs from the first version of router firmware by reason of containing at least one firmware change (a firmware change being a difference in firmware data and/or a difference in firmware instructions). The firmware image includes a plurality of chunks, each chunk having a size which is no greater than a predetermined chunk size. The wireless router destructively overwrites the first version of router firmware in the flash memory with the second version of router firmware. The destructive overwriting proceeds in a chunk-wise manner such that prior to being overwritten by all of the chunks the flash memory contains neither a complete copy of the first version nor a complete copy of the second version of the router firmware. The wireless router is configured to run whatever version of router firmware is in the router's flash memory after being rebooted. The wireless router reboots, thereby making the firmware change(s) go live.
- Some embodiments include writing the flash memory and then writing a kernel memory. That is, the wireless router destructively overwrites the first version of router firmware in the flash memory with the second version of router firmware, and then writes a copy of content of the second version of router firmware to a kernel memory in a volatile RAM memory in the wireless router before going live with upgraded firmware.
- Some embodiments include writing both flash memory and a volatile RAM disk. That is, the wireless router destructively overwrites the first version of router firmware in the flash memory with the second version of router firmware, and also writes a copy of content of the second version of router firmware to a RAM disk in a volatile RAM memory of the router.
- In some embodiments, the firmware image chunks have at least one predetermined executable order, namely, an order in which the chunks are arranged in an executable copy of the firmware image. The step of receiving a responsive firmware image receives the chunks in a volatile RAM memory in the wireless router in an order which differs from the executable order, and the method includes re-ordering the chunks such that the step of destructively overwriting flash memory chunks arranges chunks in the flash memory in the executable order.
- In some embodiments, the firmware image has a size and the flash memory has a storage capacity. The method includes the wireless router checking to see whether the size of the firmware image is less than a predetermined maximum firmware image size. The predetermined maximum firmware image size is at least two chunk sizes smaller than the flash memory storage capacity.
- Some embodiments include the wireless router remapping a ROM memory address in the router to a RAM memory address in the router. Some include the wireless router decompressing data held within the flash memory in the router and copying the data to a RAM-based file system in the router; some include both steps.
- In some embodiments, before going live with upgraded firmware, the wireless router overwrites at least a portion of the flash memory with user-definable configuration settings from a text file. Then after going live with upgraded firmware, the wireless router overwrites the text file with the configuration settings from the flash memory.
- In some embodiments, the response received by the wireless router includes an indication that a billing status is inactive, and the method includes redirecting a web browser to a billing activation page.
- In some embodiments, the firmware image chunks have at least one predetermined executable order, namely, an order in which the chunks are arranged in an executable copy of the firmware image. The step of receiving a responsive firmware image receives the chunks in the wireless router in an order which differs from the executable order. The method includes re-ordering the chunks such that the step of destructively overwriting flash memory chunks arranges chunks in the flash memory in the executable order. The method also includes writing a copy of the chunks to a kernel memory in the wireless router.
- Some embodiments described herein provide a remotely upgradable wireless router. The wireless router includes a processor, volatile RAM memory, a network interface card, a wireless link interface, and a flash memory. The volatile RAM memory is in operable communication with the processor and contains a kernel. The kernel includes data and including instructions which upon execution by the processor at least partially control operation of the wireless router. In particular, the kernel contains a flash memory device driver. The network interface card is connectable to a TCP/IP network such as the Internet for two-way data communication of the wireless router with a remote server. The network interface card is also in operable communication with the volatile RAM memory. The wireless link interface is connectable to a wireless network for two-way data communication of the wireless router with a local computer, and is also in operable communication with the volatile RAM memory. The flash memory is in operable communication with the processor by use of the flash memory device driver. The flash memory contains a version of wireless router firmware, which includes data, also includes and instructions which upon execution by the processor at least partially control operation of the wireless link interface.
- In some embodiments, the wireless router is further characterized in that upon execution of at least some of the instructions by the processor, the wireless router will do the following: send a request for a firmware update over the network interface card to the remote server, receive over the network interface a wireless router firmware image, write content of the wireless router firmware image to the flash memory, write content of the wireless router firmware image to the kernel memory after writing the content to the flash memory, and then reboot, thereby passing control to at least some of the wireless router firmware content that was written to the flash memory. In some embodiments, the wireless router does not necessarily send a request for a firmware update, but may instead receive the firmware update without having first requested it.
- In some embodiments, the flash memory has a storage capacity, and the wireless router firmware image includes a plurality of chunks, each chunk having a size which is no greater than a predetermined chunk size and is less than one-eighth the flash memory storage capacity. The wireless router upon execution of at least some of the instructions by the processor destructively overwrites the version of wireless router firmware in the flash memory in a chunk-wise manner with chunks of the wireless router firmware image.
- In some embodiments, the wireless router firmware image includes a plurality of chunks which have at least one predetermined executable order, namely, an order in which the chunks are arranged in an executable copy of the wireless router firmware image. The wireless router upon execution of at least some of the instructions by the processor receives the chunks in the RAM memory in an order which differs from the executable order, and re-orders chunks to arrange the chunks in the flash memory in the executable order.
- In some embodiments, the remotely upgradable wireless router includes a ROM memory address remapped to a RAM memory address in the router. In some, the wireless router is joined with a text file containing user-defined configuration settings, and the flash memory contains a copy of the user-defined configuration settings.
- In some embodiments, the wireless router firmware image has a size and the flash memory has a storage capacity. The wireless router firmware image includes a plurality of chunks. Each chunk has a size which is no greater than a predetermined chunk size and is less than one-eighth the flash memory storage capacity. The size of the wireless router firmware image is at least two chunk sizes smaller than the flash memory storage capacity.
- In some embodiments, the wireless router upon execution of at least some of the instructions by the processor performs authentication to verify validity of the wireless router firmware image.
- In some embodiments, the wireless link interface conforms with at least one 802.11 standard for wireless communications. In some, the wireless router includes a 10/100 Mbps local area network interface card to provide a data communication connection to a local area network, and the kernel includes instructions which upon execution by the processor at least partially control operation of the local area network interface card. In some embodiments, the kernel includes open source operating system code.
- The examples given are merely illustrative. This Summary is not intended to identify key features or essential features of the claimed subject matter, nor is it intended to be used to limit the scope of the claimed subject matter. Rather, this Summary is provided to introduce—in a simplified form—some concepts that are further described below in the Detailed Description. The innovation is defined with claims, and to the extent this Summary conflicts with the claims, the claims should prevail.
- A more particular description will be given with reference to the attached drawings. These drawings only illustrate selected aspects and thus do not fully determine coverage or scope.
FIG. 1 depicts a schematic diagram of a system and device for processing network content;FIG. 2A illustrates an exemplary configuration to protect a single desktop computer;FIG. 2B illustrates an exemplary configuration to protect a local area network (LAN), which includes multiple desktop computers;FIG. 3 illustrates an exemplary operating sequence of a system and device configured to process email traffic;FIG. 4 illustrates an exemplary operating sequence of a system and device configured to process various web content viewed by a user using the user's computer;FIGS. 5A, 5B, 6A and 6B provide more detailed illustration of an internal operating sequence of a system and device;FIGS. 7A and 7B depict alternative schematic diagrams of a wireless router system and device for processing network content, include one wireless router configuration with an Ethernet 10/100 Mbps local area network interface card, and one configuration without that network interface card; andFIG. 8 is a flow chart illustrating steps of some method embodiments for remoter firmware update.- Observations on Focus
- It is not unusual for a child application to set forth claims which have a different focus than the claims of a parent application. In the present situation, provisional application No. 60/653,163 contains 148 pages of a disclosure which was incorporated and built upon in the application that ultimately issued as U.S. Pat. No. 7,904,518. The present document incorporates and builds upon both those ancestor applications. Claims of the '518 patent focus in part on filtering email message content, but the underlying applications are not limited to that topic. The claims presented here are differently focused than the '518 patent claims, but an attentive reader will find common subject matter in the three applications. For example, the present document is titled “Wireless Router Remote Firmware Upgrade,” the '163 provisional discusses a Remote Flash Updater utility capable of writing firmware to flash memory, and the '518 patent Abstract states that an “appliance is provided with an automatic remote updating capability, wherein the software and data used by the appliance can be updated remotely via a network.” The '518 patent also teaches that some embodiments of the appliance include functionality of a network hub or router.
- Observations on Meaning and Scope
- Reference will now be made to exemplary embodiments such as those illustrated in the drawings, and specific language will be used herein to describe the same. But alterations and further modifications of the features illustrated herein, and additional applications of the principles illustrated herein, which would occur to one skilled in the relevant art(s) and having possession of this disclosure, should be considered within the scope of the claims.
- The meaning of terms is clarified in this disclosure, so the claims should be read with careful attention to these clarifications. Specific examples are given, but those of skill in the relevant art(s) will understand that other examples may also fall within the meaning of the terms used, and within the scope of one or more claims. Terms do not necessarily have the same meaning here that they have in general usage, in the usage of a particular industry, in a given reference document discussing others' work, or in a particular dictionary or set of dictionaries. Reference numerals may be used with various phrasings, to help show the breadth of a term. Omission of a reference numeral from a given piece of text does not necessarily mean that the content of a Figure is not being discussed by the text. The inventors assert and exercise the right to their own lexicography. Terms may be defined, either explicitly or implicitly, here in the Detailed Description and/or elsewhere in the application file.
- Reference will be made to the accompanying drawings. The drawings show by way of illustration, and not by way of limitation, specific embodiments and implementations consistent with principles and possibilities presented herein. The mere fact that the same reference number is used in two places in the figures and/or the text does not imply that the referenced item is identical in every respect in each instance. For example,
appliance 101 shown inFIG. 1 is not necessarily identical in every respect withappliance 101 shown inFIG. 2A , or withappliance 101 shown inFIG. 2B , and so on. The various implementations are described in sufficient detail to enable those skilled in the art to practice the invention and it is to be understood that other implementations may be utilized and that structural changes and/or substitutions of various elements may be made without departing from the scope and spirit of the claimed invention. The description is, therefore, not to be construed in a limited sense. Additionally, various embodiments described may be implemented in the form of a software running on a general purpose computer, in the form of a specialized hardware, or combination of software and hardware, except as otherwise required by the claim being considered. - Throughout this document, use of the optional plural “(s)” means that one or more of the indicated feature is present. For example, the term “firmware change(s)” means “one or more firmware changes” or equivalently “at least one firmware change”.
- As used herein, “overwriting” a memory means overwriting at least a portion of the memory. That is, overwriting a memory allows overwriting the entire memory, but does not require overwriting the entire memory.
- As used herein, “updating” and “upgrading” are used interchangeably.
- As used herein, a “chunk” of flash memory is the smallest amount of memory that is overwritten to perform a single flash memory write. In a typical flash memory, chunk size is 128 Kbytes, but different vendors may use different chunk sizes. A flash memory chunk is sometimes called a “block,” but care is called for because attention to context reveals that the word “block” is also used in other ways, e.g., in discussing filesystem data structures.
- Remote Flash Updater
- In some embodiments, a Remote Flash Updater (RFU) is a utility capable of writing to flash memory, a type of non-volatile memory storage, with an image file gathered off a HTTP server. With reference to
FIGS. 7A, 7B, and 8 , for example, in some embodiments theRFU 701 is a utility capable of writingfirmware 702 toflash memory 107 orother firmware storage 108. The RFU may be implemented to run with akernel 703, such as an open source operating system kernel. - In one embodiment, the
RFU 701 is a Linux 2.4 kernel based user-land software running on an ARM based chipset. It is written in ANSI C programming language compiled cleanly with an ARM gcc compiler with the—Wall and −O2 compiler flags.RFU 701 development may be guided by familiarity with flash memory code source samples including source code for a flash kernel driver, and a library implementation that interfaces with the flash kernel driver. OneRFU 701 uses a C library with flash I/O functionality. One RFU binary name is RFUpdater. - In one embodiment, the Linux 2.4 system implements a ROM to RAM remap819 for file system access. Upon boot, the boot loader decompresses822 data held within flash memory and copies823 it into a RAM based file system.
- After the
RFU 701 updatesflash memory 107 orother firmware storage 108 with an image file, thesystem 101 will reboot812 in order for the changes to be live. Secure, cross-standard and compact programming methodologies are used. - One
Updater 701 method includes the following steps, which are exemplary rather than the sole possible implementation of teaching herein. Begin updater execution. Calculatekernel 703 and ramdisk flash memory offset and size. Initialize POST update variables. Issue an HTTP 1.0 POST request on update.akalink.net port 80/TCP. Read header response, continue if new update is available. Read header response, image file size >100 KB and <3.5 MB. Calculate kernel and ramdisk flash memory offsets from image file. Write815 image file to 128 KB blocks of RAM (write kernel and ramdisk separately). Re-order817 RAM blocks in received order.Authenticate 833—if image file checksum is valid, continue. This is a less than 180 second cycle. Perform overlapping steps to re-program flash memory starting with kernel followed by ramdisk (a kernel-first approach814): Erase next block chunk of flash, write next block chunk to flash from RAM, free up RAM block chunk. Reboot812 system. - In some embodiments, a purpose of the
remote flash updater 701 is to write toflash memory 107 orother firmware storage 108 an image file upon invocation, the image file being gathered remotely from a HTTP site. - During a process of downloading the image file off the HTTP server, some embodiments require the image file to be chunked down in 128 KB memory blocks since the
system 101 won't be able to allocate 3.5 MB of memory in a single allocation. This option is dynamic for tuning purposes. Block re-ordering817 is done afterwards to validate the image checksum. - Some embodiments utilize already existent flash library functions to achieve the result of re-programming flash memory; they don't require re-writing a full flash implementation from scratch.
- In some embodiments, the image file contains the kernel image and the ramdisk image embedded as one. Therefore, byte offsets headers during the HTTP session are provided in order for the kernel image and ramdisk image to be written to the
proper flash memory 107 orother firmware storage 108 area allocated for their usage. - During the process of receiving808 the
image 809 file off the HTTP server and writing the image file to flash memory, some embodiments performbasic authentication 833 to verify if the image file is valid. - In some embodiments, the maximum size of flash memory an embodiment is utilizing is 4 MB. 256 KB of memory is reserved with another 256 KB memory of free space, therefore only 3.5 MB is allocatable to flash memory.
- In some embodiments, the kernel image is written to flash memory starting from 0x10000 to the size of 0x0007FFFF. The ramdisk image is written to flash memory starting from 0x90000 to the size of the image.
- In some embodiments, the flash library and flash kernel library header files provide information regarding flash memory offsets, instructions and function. An implementer may study the flash source code provided along with this document in order to write this software. Along with the source code, ethloader.c is software that remotely updates flash memory by passing it a file name, kernel image or ramdisk image, with or without specifying length. It could be a good source of reference to utilize as it can broaden understanding and avoid confusion.
- In some embodiments, after the
updater 701 is executed, it will initialize all variables regarding kernel and ramdisk memory area begin and end offsets and anything else related to that in order to know where to write what in what area, sizes of blocks, how many blocks to write, etc. It will then initialize aHTTP POST request 804 to be sent to update.akalink.net on port 80 via TCP/IP (of course, other websites will be used by other vendors). The socket timeout is 5 seconds, and 15 seconds for a returned response. - An example of a POST request:
- action=update
name=hcube
item=image - An example of a POST response:
- X-Update-Length: 2097152<-Length of image
X-Update-Offset: 668402<-Last byte of Kernel Image from 0
X-Update-Cksum: 1808e84cfcbaf71ce1073cc418ff262a<-cksum checksum
X-Update-Item: image<-Item requested
Image file data here<-Item requested data - If the X-Update-Item header value is “image” in such embodiments, the embodiment knows it is dealing with the correct item, and will proceed.
- Some embodiments will then verify if this image file is recent by verifying if the header X-Update-Cksum is different than the Cksum cksum located in a file called “cksum” which holds the contents of the image current cksum.
- If so, processing proceeds to see if818 the X-Update-Length header value is less than 3.5 MB (3670016 bytes) and larger than 100 KB (102400 bytes).
- If so the embodiment will read and write the image file off the HTTP server to various 128 KB RAM blocks in two different groups one for the kernel image and one for the ramdisk image, separating them based on the X-Update-Offset header value.
- Before the Offset starting from 0 is the kernel image, and after the offset is the ramdisk image. The X-Update-Offset header value represents the last byte of the kernel image starting from 0 byte, the rest till the last byte represents the ramdisk image.
- Some embodiments will re-order817 the RAM blocks in first received priority and see if833 the cksum checksum of the total image corresponds to the value of X-Update-Cksum.
- Some embodiments will begin to re-program flash memory, and will proceed to start writing the kernel byte offset range rather than the ramdisk offset range afterwards. Kernel image goes first (a kernel-first approach814). This process is on a block level not a byte level for performance purposes.
- In some embodiments, the procedures will erase the next available 128 KB blocks in flash, will write to flash the next 128 KB available block chunk from RAM, and afterwards will de-allocate the RAM block chunk memory written and proceed in a cycle until the image file has been written.
- Once the embodiment has completed writing the image file to flash memory, it will reboot812 the system in order for the image file changes to go live.
- In some embodiments, Online Upgrade Software will destructively811 upgrade the
flash 107 on a chunk by chunk basis unless adequate headroom exists to maintain a redundant flash bank to hold the working software. - In some embodiments, a CubeUpdater is a built-in software component whose purpose is to perform software updates and check for new updates on a daily basis. The CubeUpdater will use 6 am, 12 am, 6 pm as hours during the day to attempt to perform a software update. This is used in case if the internet connectivity is down at 6 am, it will retry at different hours.
- When it comes time to perform the software update, it will connect to update.spamcube.com on port 80 and issue a HTTP POST with the following variables: mac=>00:20:ed:25:34:37. Other websites and addresses will, of course, be used in other implementations.
- It will return the following answer if there is an error:
- 0: Invalid client identification
2: No updates available
3: Billing information is inactive - If the client billing is not active, the next time the client browses a site, the router redirects830 the browser to a billing activation page, such as a user profile web page that informs the user of billing status and invites the user to make payment or other arrangements to activate service. In some embodiments, an LED status on the router is also changed to reflect the billing status and notify the client.
- In some embodiments, the router upgrade includes software generally, as opposed to firmware alone. The upgrade software can be stored on a disk local to the router, e.g., in compressed or archive format such as tar or gz format.
- After extracting the software, setting/checking permissions, and applying the upgrade, the router continues (sometimes without rebooting) providing services to the user client.
- Some embodiments include a software hierarchy, implemented in a collection of file system directories. In a Linux system or other UNIX-style system, for example, .o object code for the router may be kept in a/boot/modules directory. Configuration files such as .conf and some .txt files, may be kept in a /usr/local/<router>/conf directory, where <router> is a name representing the router code, e.g., “hcube” or “RFU”. A sysconfig database configuration file may be kept in a/usr/local/<router>/conf directory, for example. User interface.html files may be kept in a/usr/local/<router>/www/include/tpl/html directory, for example.
- A user interface in some embodiments includes pages in a web browser, through which the router receives commands (e.g., check for available updates) and notifies the user of status (e.g., billing inactive, upgrade needed, upgrade available, upgrade installed). Familiar mechanisms may be used in the user interface, e.g., HTML forms and form variables, CGI files, HTML template pages, environment variables, configuration files, and so on. Some embodiments perform a flash update procedure on a WEB_CONFIG_FILE to write the configuration file to flash memory storage.
- Some embodiments update a text file containing configuration settings to flash memory via CGI. The CGI file will be executed on a system utilizing
flash memory 107 as storage, therefore this functionality is used to keep updated configuration settings in memory after a system reboot. In some embodiments, the flash update functionality is already in place, it is being used to update another file called sysconfig. Some embodiments can use webconfig/flash.c function call kd_updateFlash and setDefault to provide functionality to update our custom configuration file settings to flash memory. - In some embodiments, the configuration file settings will simply be a text file with variables separated by a semicolon pointing to a value separated by a new line. The configuration file settings is “sample.cnf” modifiable by a define statement. Comments should be ignored.
- For example, “SysIPAddress: 192.168.200.1\n” would be a configuration line.
- Some embodiments build on familiar mechanisms. For some embodiments, one of skill may be interested in source provided under names such as webserver, webconfig, sysconfig.
- By way of example, and not limitation, one embodiment includes: at least 2 10/100 Mbps Ethernet ports, an ARM based processor of at least 10 MHz, at least 10 MB of memory which can include SDRAM, SRAM, FLASH, and also ROM, a reset button, a power supply, LEDs, and a printed circuit board or other motherboard to which the other components are soldered/attached/connected. The components are housed in a plastic case. But with regard to hardware, one of skill will understand that methods described herein can be used for a wide variety of hardware combinations, including variations in memory capacity, processor architecture and speed, interface capabilities, and other characteristics of computing/networking hardware.
- It is to be understood that both the foregoing and the following descriptions are exemplary and explanatory only and are not intended to limit the claimed invention or application thereof in any manner whatsoever.
- Automatic Remote (Networked) Updating Capability
- Additional aspects related to the invention will be set forth in part in the description which follows, and in part will be obvious from the description, or may be learned by practice of the invention. Aspects of the invention may be realized and attained by means of the elements and combinations of various elements and aspects particularly pointed out in the following detailed description and the appended claims.
- In some embodiments, a methodology provides an integrated plug and play solution for home networks. An appliance can be used for processing of web and email traffic and can be deployed as a stand-alone appliance. In one implementation, the appliance utilizes a remote service accessed via a network. The system executes various procedures to handle the network traffic. In one embodiment, the system is provided with an automatic remote updating capability, wherein the software and data used by the system can be updated remotely via a network.
- In some embodiments, a method includes connecting a network hardware appliance to an external network within a home network configuration; including a central processing unit (CPU) on the network hardware appliance; providing a memory for storing a set of computer-readable instructions executed by the central processing unit (CPU) on the network hardware appliance; connecting the network hardware appliance to one or more user computers; installing the network hardware appliance between the external network and the user's computer; passing all network traffic between the user's computer and the external network through the network hardware appliance; generating a request to retrieve firmware; and receiving firmware. Some embodiments include authenticating with a remote system using authentication information. Some include reading from the world wide web using HTTP protocol.
- Some embodiments relate to an appliance for processing email and web traffic. In some embodiments, for example, a network hardware appliance is provided for use with a personal computer of a user, the personal computer being connected to a home network of the user. The network hardware appliance includes a central processing unit (CPU); a first network interface connected to the personal computer of the user; a second network interface connected to an external network; and a memory storing a set of computer-readable instructions. When executed by the CPU the instructions cause the CPU to perform automatic remote firmware updates as described herein.
- In some embodiments, the personal computer of the user is connected to an external network. The network hardware appliance is connected to the home network and is positioned between the personal computer of the user and the internet.
- In some embodiments, a user request for a web resource is intercepted. The system requests from a target web server the source code for the resource and receives the source code of the requested source from the target web server. In some embodiments, an apparatus intercepts content of a web resource requested by a user. The requested web resource being located on a target web server. The apparatus includes a central processing unit (CPU), a first network interface coupled to the computer of the user, a second network interface coupled to the external network and a memory storing a set of computer-readable instructions. The CPU operating under the direction of the stored instructions intercepts a user request for the web resource, requests from the target web server the source code for the resource, and receives the source code of the requested source from the target web server.
- An embodiment of the methodology provides an integrated plug and play solution. The appliance can be used for processing of web and email traffic and can be deployed as a stand-alone appliance. In an embodiment, the system employs network level analysis and translation and executes various procedures to handle the network traffic. In one embodiment, the appliance is provided with an automatic remote updating capability, wherein the software and data used by the appliance can be updated remotely via a network.
FIG. 1 depicts a schematic diagram100 of an exemplary embodiment of anetwork appliance 101 for processing email communications as well as other network content. With reference toFIG. 1 , the appliance may include adata bus 104 or other communication mechanism for communicating information across and among various parts of theappliance 101, and a processor (CPU)105 coupled withbus 104 for processing information and performing other computational and control tasks. In one embodiment theprocessor 105 is an ARM processor with clock speed of at least 10 MHz.Appliance 101 may also include avolatile storage 106, such as a random access memory (RAM) or other dynamic storage device, coupled tobus 104 for storing various information as well as instructions to be executed byprocessor 105. Thevolatile storage 106 also may be used for storing temporary variables or other intermediate information during execution of instructions byprocessor 105. In one embodiment, the size of thememory unit 106 is at least 10 MB. Theappliance 101 may further include a read only memory (ROM or EPROM)107 or other static storage device coupled tobus 104 for storing static information and instructions forprocessor 105, such as basic input-output system (BIOS), as well as various system configuration parameters. Apersistent storage device 108, such as a magnetic disk, optical disk, or solid-state flash memory device is provided and coupled tobus 104 for storing information and instructions.- The embodiment of the
appliance 101 shown inFIG. 1 also includes at least two communication interfaces, such as network interfaces113 and114 coupled to thedata bus 104. Communication interfaces113 and114 provide a two-way data communication coupling to anetwork link 114 that is connected to thenetwork 115. For example, communication interfaces113 and114 may be 10/100 Mbps local area network interface cards (LAN NIC) to provide a data communication connection to a compatible LAN. Wireless links, such as well-known 802.11a, 802.11b, 802.11g and Bluetooth may also be used for network implementation. In any such implementation, communication interfaces113 and114 send and receive electrical, electromagnetic or optical signals that carry digital data streams representing various types of information. - Network link114 typically provides data communication through one or more networks to other network resources. For example,
network link 114 may provide a connection throughnetwork 115 to ahost computer 120, or to other network resources (not shown). Thus, theappliance 101 can access network resources located anywhere on theInternet 115, such as a remote network storage or web servers. On the other hand, theappliance 101 may also be accessed byuser computer 121 located anywhere on the corresponding local area network. - Local network (not shown) and the
Internet 115 both use electrical, electromagnetic or optical signals that carry digital data streams. The signals sent through the various networks and the signals onnetwork links appliance 101, are exemplary forms of carrier waves transporting the information. - However, carrier waves per se are not claimed. Whenever reference is made herein to data or instructions, it is understood that these items configure a computer-readable memory (RAM, ROM, flash, etc.), thereby transforming it to a particular article, as opposed to simply existing on paper, in a person's mind, or as a carrier wave or other transitory signal on a wire, for example. Unless expressly stated otherwise in a claim and permitted by applicable law at the relevant time, a claim does not cover a signal per se. A memory or other computer-readable storage medium is presumed to be non-transitory unless expressly stated otherwise.
- The
appliance 101 can send messages and receive data, including program code, through the variety of network(s) including any local area network as well as theInternet 115 by means ofnetwork links system 101 acts as a network server, it might transmit a requested code or data for an application program running on user'scomputer 121 client(s) and/or thehost 120 through any local area network (not shown) as well as theInternet 115. Similarly, it may receive code or data from other network entities. Likewise, in some embodiments thesystem 101 includes functionality of a network hub, router, modem, or other network device which has a position in the network configuration adjacent to an illustratedSpam Cube 101 position. - In particular, some embodiments include router functionality. Router functionality in general is familiar. As noted, for example, in U.S. Pat. No. 6,321,267 to Donaldson, in some cases a packet-filtering router routes packets from the Internet to an SMTP proxy server via a LAN. The router operates at the network layer of the protocol reference model using the Internet Protocol version 4 (IPv4). However, with appropriate changes to the socket programming interface, router functionality also operates with other network layer protocols such as Internet Protocol version 6 (IPv6) or Novell Netware. As noted in US Patent Application Publication No. 2002/0007453 by Nemovicher, some routers switch communication traffic between a communication network and a LAN under the direction and control of a load balancer and fire wall. As noted in US Patent Application Publication No. 2006/0053293 by Zager et al., in some cases IP addresses are dynamically assigned to most users by DHCP servers at the ISP or a router at the edge of the LAN on which the sender computer resides. As noted in US Patent Application Publication No. 2006/0068755 by Shraim et al., a computer and/or any other appropriate system component may use resources such as publicly-available domain name server (DNS) data, routing data and/or the like, to investigate a server suspected of conducting fraudulent activities. As another example, the routing information in the message header may be analyzed to determine whether the message originated from and/or was routed through a suspect domain, again enhancing the likelihood that the message is a phish.
- With continued attention to
FIG. 1 , the received code may be executed byprocessor 105 as it is received, and/or stored in persistent orvolatile storage devices appliance 101 may obtain application code updates from remote network resources. - The
appliance 101 may also use thenetwork interface 114 to receive various code and data updates, which it may use in its operation. For example, such data updates may include latest virus definition files. For this purpose, the appliance may perform periodic checks to determine whether such updates are available. Theappliance 101 may also user network interfaces114 to issue requests to remote network resources, such as remote virus scanning services and to receive the appropriate responses. Finally, the user may connect to the appliance through, for example,network interface 113 in order to perform necessary configuration of the appliance. - In one embodiment, one or both of the network interfaces113 and114 may be a wireless network interface operating in accordance with a wireless networking protocol, such as Bluetooth, 802.11a, 802.11b and/or 802.11g. In another embodiment both
interfaces FIG. 2A illustrates an exemplary home network configuration, wherein theappliance 101 is configured to protect asingle desktop computer 201. In this exemplary configuration, theappliance 101 is installed between the cable/DSL modem and the user's desktop computer, such that all network traffic between the user'scomputer 201 and theoutside network 206 passes through the appliance. To this end, the user'scomputer 201 is connected to one of the aforementioned twonetwork interfaces DSL modem 203. Themodem 203, in turn is connected viaconnection 205 withISP 204, which enables the user's computer to access theinternet 206 and remote servers such asservers Spam Cube 101 and of the adjacent cable orDSL modem 203 is combined into asingle system 101.FIG. 2B illustrates an exemplary configuration ofhome network 300, which includes theappliance 101 configured in a manner designed to protect a local area network (LAN), which includesmultiple desktop computers 201. In this configuration, theappliance 101 is installed between the cable/DSL modem 203 and the network hub/router 301, which provides network connectivity to thedesktop computers 201.- In alternative embodiments, the functionality and components of the illustrated
Spam Cube 101 is combined into a single appliance orsystem 101 with the functionality and components of the adjacent cable orDSL modem 203, or with the functionality and components of the adjacent Network Hub/Router 301, or with the functionality and components of both themodem 203 and therouter 301. In such configurations, theappliance 101 can filter all network traffic reaching thecomputers 201. - The
network hub 301 may be wireless network-enabled. In an alternative embodiment, thenetwork hub 301 may be integrated with theappliance 101. The integrated hub may also be either wireless or wired. - The other elements of the networking configuration shown in
FIG. 2B , including cable/DSL modem 203,connection 205, andISP 204, are generally equivalent to the corresponding elements ofFIG. 2A , described hereinabove. FIG. 3 illustrates an exemplary operating sequence of a network appliance configured to process email traffic. In accordance with the illustrated sequence,email message 302 is sent by an entity located on the external network (e.g. Internet)206 to the user'scomputer 201. Themessage 302 may contain one or more attachments, which may include certain malware, such as viruses, worms or other threats. In order to facilitate protection of the user's personal computer from the threats contained in theemail 302, theappliance 101, is arranged to intercept theemail message 302. Upon the interception of themessage 302 by theappliance 101, theappliance 101 performs an initial inspection of the received email message and its attachment(s) and, if necessary, submits a service request304 to the remoteantivirus scanning engine 306. The aforementioned service request may direct the external virus scanning service to perform a virus check of any attachments to theemail message 302. In order to enable the requested scanning, theappliance 101 may include the corresponding attachments with the request304. In one embodiment, theappliance 101 requests the anti-virus scanning of only specific attachment types. For example, during the initial inspection, theappliance 101 may determine whether the attached file is an executable and request remote scanning of the attachment based on the results of this determination.- After receiving the request304 from the
appliance 101, together with the relevant attachment email files, theremote scanning system 306 performs the necessary processing of the email attachments and determines the presence of any threats therein in accordance with well-known scanning algorithms. The scanning system may utilize a plurality of alternative scanning algorithms. The exact algorithm used by the system may be selected by the user of theappliance 101 during the configuration process. The user's selection may be stored in thestorage devices appliance 101. Existing scanning products which may be used by thescanning system 306 include, without limitation, Norton Antivirus and McAfee Security software. The use of theremote scanning service 306 enables the system to perform scanning operations in an on-demand manner without providing theappliance 101 with the processing power required to perform the scanning operation. In addition, the scanning software executing onservers 306 may be easily and conveniently updated. The aforementioned two features of the system configuration enable theappliance 101 to be implemented using inexpensive hardware. - After the completion of the scanning process, the
external scanning engine 306 responds to theappliance 101 with response305 containing information on any detected threats. For example, the response305 may indicate that one or more of the attachments to the email contain viruses. Upon receipt of the response, theappliance 101 neutralizes the detected threat, by, for example, removing the infected attachment, and re-writes the receivedemail message 302 to include appropriate warning to the user. The aforesaid warning may be placed either in the subject line or in the body of the message. The re-written email containing thewarning 308 is then forwarded by theappliance 101 to the user'scomputer 201. Finally, theappliance 101 performs the update of its statistics information. FIG. 4 illustrates anexemplary operating sequence 400 of the network appliance configured to process various web content viewed by a user using user's computer. The depicted process is initiated when a user requests a web resource by inputting at402URL 401 into a web browser window on user'scomputer 201. Upon the receipt of theURL information 401, the browser sendsHTTP request 403 requesting the target web service (in the example shown inFIG. 4 , the target website is) the website of CNN news service) to provide the resource specified by the received URL. Therequest 403 is intercepted by theappliance 101, which contacts thetarget web server 406 on behalf of the user and sends arequest 404 for the source code of the web resource specified by the user. In response to the received request, thetarget server 406 sends areply message 405, accompanied with the full source code of the requested resource. Theappliance 101 receives the code furnished by theweb server 406 and initiates a scan of the received source code for any possible threats, including, for example, any spyware.- During the scan process, the
appliance 101 may use aremote scan engine 408 to achieve most comprehensive threat detection. To this end, theappliance 101 may send arequest 409 to the remote network ofscan engines 408 containing the entire source code of the web resource, or any portion thereof. Theoutside scan engines 408 examine the content of the received source code and sendreply 407 to the appliance, indicating whether any potential threats were detected. Upon the receipt of thereply 407, theappliance 101 sends at410 awarning message 411 to be displayed in the user's browser window, warning the user of the presence of any potential threats within the requested web resource. In one embodiment, after the appropriate warning is displayed to the user, the user is provided with an option to either avoid viewing potentially harmful web resource or to proceed with the viewing despite the shown warning. FIGS. 5A, 5B, 6A and 6B provide more detailed illustration of the internal operating sequence of an embodiment of the appliance. Specifically,FIG. 5A depicts thefirst phase 500 of that exemplary operating sequence. The shown operating sequence is executed by theCPU 105 shown inFIG. 1 . In order to enable the appliance to execute the described procedures, the appliance may be provided with an operating system, which may be pre-loaded into one or more of thestorage devices FIG. 1 . Exemplary operating systems which may be used to controlappliance 101 include Linux, UNIX (example: BSD), or RTOS (example: VxWorks).- The process illustrated in
FIG. 5A is automatically initiated when, atstep 502, theappliance 101 accepts a connection from user'scomputer 201 on theoutbound port 110, corresponding to TCP/IP protocol, well known to persons of skill in the art. Through the established connection, atstep 503, theappliance 101 intercepts a request generated by user's email client software to retrieve messages corresponding to user's email account from the internet service provider (ISP). Atstep 504, the appliance opens a connection to the destination IP address corresponding to the email service subsystem of the ISP. Atstep 505, the system receives authenticating information, such as username and password, corresponding to user's email account with the ISP. The system uses the received authentication information to establish a session with the remote email service and, atstep 506, sends to this service a command to scan the user's mailbox for duplicate messages and, when appropriate, to delete them. Atstep 507, the system receives the “LIST” command from the user's email client and forwards it to the email service system. The aforesaid list command request the email service to provide the listing of all emails in the user's email account. - The continuation of the
first phase 500 of the process shown inFIG. 5A is illustrated inFIG. 5B . At step508, the appliance receives from the user's email client the “RETR” command, which requests the remote email subsystem to retrieve one or more email messages in the user's email account. Upon the receipt of this command from the email client, theappliance 101 forwards it to the email server, which, in response, begins a message retrieval process. Prior to retrieving a specific message, theappliance 101 first performs a check of the message size. If the size of the message is less than a predetermined threshold value, for example, 200 KB, the system retrieves the entire message, seestep 510. On the other hand, if the size of the message exceeds the aforesaid threshold, only a block of the message is retrieved, see step509. In one embodiment of the system, the size of the retrieved block is 200 KB. However, other block sizes may be used instead. - Upon the retrieval of the message, the system first checks if the sender of the message identified in the “From” field thereof matches an existing entry in the blacklist table. This table lists all senders, the email correspondence from which should be blocked. If the match in the blacklist table is found, the corresponding email message is blocked at step521. At step512, the appliance checks whether the content of the message, as described by the “Content-Type” field of the message header, may include encrypted attachments. If the message contains only unencrypted attachments, the operation proceeds to step514, whereupon the system requests the remote HTTP virus scanning server to perform the scanning of the message body for viruses. If the virus is found, the system blocks the message at step521. If, no virus is found or if the message may contain encrypted attachments, the operation of the system proceeds to step513, whereupon the sender of the message, which is identified in the corresponding “From” record, is compared with entries in the whitelist table. This table contains a list of sender email addresses from which email correspondence should be allowed without further inspection. If the sender address matches one of the aforesaid whitelist entries, the email message is allowed at
step 520. - On the other hand, if the message sender email address does not match any entries in the whitelist, the system checks the recipient of the email message identified in the “To” field of the message header against entries in the parental control profile. This profile includes email addresses of recipients, which should not receive email messages. If the match is found, the email message is again blocked at step521. If no matching entries in the parental control profile exist, the system proceeds with
step 516, whereupon the identity fraud analysis algorithm inspects the header of the email message for possible phishing scam. If such scam is detected, the message is again blocked at step521. - Upon passing of the phishing scam inspection, the message header pattern is analyzed at
step 517 for SPAM content. Again, if SPAM is detected, the message is blocked at step521. If SPAM is not detected in the header, at step518, the system checks whether the message header indicates presence of encrypted email message. The encrypted content is indicated, for example, by presence of “Content-Type: application/x-pkcs7-mime” record in the header of the email. If the content is not encrypted, the system inspects the body of the message for SPAM content at step519. If the SPAM is not detected or if the email body is encrypted, the system accepts the email atstep 520. - After the email is rejected at step521 or accepted at
step 520, the system performs certain logging and user notification operations illustrated inFIG. 6A . Specifically, is the email is allowed or denied, the system collects and stores the session logging information at steps628 and601, respectively. In case of a denial, the appliance atstep 602 verifies whether identity fraud was detected in the email content. If this was the case, the email is tagged by placing an appropriate message, such as “[PHISH]” either in the subject line (step603) or, alternatively, in the header of the email message (step607), depending on the configuration parameters specified by the user. The system may further insert phishing scam alert into the body of the message atstep 606. - The system then proceeds with the determination of whether a virus was detected in the email, see step608. If the virus was found, the appliance again performs tagging of the email either in the subject line or in the header, depending on the user's configuration, at steps609-610 and611-612, respectively. If the user's parameters call for recipient notification of virus-containing emails, the system disables the virus and re-writes the message body inserting an appropriate virus warning (
steps 613 and614). If the configuration requires sender notification, the appliance generates an email message to the sender of the virus-containing email, which includes a message alerting the sender of the email message of the virus (step616). - If SPAM was detected in the email message, the email is likewise tagged either in the subject or the header, at
steps step 623, the system inserts a management control toolbar into the message body. - The continuation of the described operating process is illustrated in
FIG. 6B . With reference to this figure, the tagged email with the inserted management toolbar is forwarded to the client atstep 624. The client terminates the session atstep 615 with the QUIT command, which the system forwards to the remote email server. Finally, atstep 626, the system sends the collected logging information to a remote HTTP server for storage. The shutdown and session termination is performed atstep 627. The system logs detailed information on the accepted and rejected messages, as well as the detected threats. Upon the request by the user, the logged information may be displayed in a text or graphical form. - It should be noted that the present invention is not limited to any specific email or web communication protocols. The appliance may be utilized in connection with any known communication protocols, including, without limitation, POP3, SMTP or HTTP.
- Finally, it should be understood that processes and techniques described herein are not inherently related to any particular apparatus and may be implemented by any suitable combination of components. Further, various types of general purpose devices may be used in accordance with the teachings described herein. It may also prove advantageous to construct specialized apparatus to perform the method steps described herein. The present invention has been described in relation to particular examples, which are intended in all respects to be illustrative rather than restrictive. Those skilled in the art will appreciate that many different combinations of hardware, software, and firmware will be suitable for practicing the present invention. For example, the described software may be implemented in a wide variety of programming or scripting languages, such as Assembler, C/C++, perl, shell, PHP, ASP.NET, Java, Ruby, AJAX, Rails etc.
- Moreover, other implementations of the invention will be apparent to those skilled in the art from consideration of the specification and practice of the invention disclosed herein. Various aspects and/or components of the described embodiments may be used singly or in any combination in the computerized content filtering system. It is intended that the specification and examples be considered as exemplary only, with a true scope and spirit of the invention being indicated by the following claims.
- Methods
FIG. 8 illustrates some method embodiments, in aflowchart 800. In a given embodiment zero or more illustrated steps of a method may be repeated. Steps in an embodiment may also be done in a different order than the top-to-bottom order that is laid out inFIG. 8 . Steps may be performed serially, in a partially overlapping manner, or fully in parallel. The order in which a flowchart is traversed to indicate the steps performed during a method may vary from one performance of the method to another performance of the method. The flowchart traversal order may also vary from one method embodiment to another method embodiment. Steps may also be omitted, combined, renamed, regrouped, or otherwise depart from the illustrated flows, provided that the method performed is operable and conforms to at least one claim. Steps described as being performed by a user may also be performed by another person, or by a machine, on behalf of a user. Another person who performs steps on behalf of a user need not have a particular user in mind.- Some embodiments provide a method for upgrading a wireless router. Some include the step of containing801 a
firmware 802version 803, namely, a flash memory in thewireless router 101 containing a first version of router firmware, with the router firmware including instructions to be executed by aprocessor 105 of the wireless router, and the router firmware also including data. - Some methods include remotely requesting804 a
firmware update 805, namely, the wireless router sending806 arequest 807 for a firmware update, with the request being sent from the wireless router over anetwork 115 connection toward aserver 207. - Some methods include receiving808 a
responsive firmware image 809, namely, the wireless router receiving over the network connection a response to the request for a firmware update, with the response including at least a firmware image for a second version of router firmware which differs from the first version of router firmware by reason of containing at least one firmware change, a firmware change being a difference in firmware data and/or a difference in firmware instructions. The firmware image includes a plurality of chunks810, each chunk having a size which is no greater than a predetermined chunk size. - Some methods include destructively overwriting811 flash memory chunks, namely, the wireless router destructively overwriting the first version of
router firmware 802 in the flash memory with the second version ofrouter firmware 802. In some, the destructive overwriting proceeds in a chunk-wise manner such that prior to being overwritten by all of the chunks the flash memory contains neither a complete copy of the first version nor a complete copy of the second version of the router firmware. In some embodiments, thewireless router 101 is configured to run whatever version of router firmware is in the router's flash memory after therouter system 101 is rebooted812. - Some methods include going live813 with upgraded
firmware 802, by reason of the wireless router rebooting812 and thereby making the firmware change(s) go live. - In some embodiments, a wireless router upgrading method includes writing814 the flash memory and then writing814 a
kernel 703 memory. That is, the wireless router destructively overwrites the first version of router firmware in the flash memory with the second version of router firmware, and then writes a copy of content of the second version of router firmware to a kernel memory in avolatile RAM memory 106 in thewireless router 101 before going live813 with the upgraded firmware. This is a kernel-first approach described above. - In some embodiments, a wireless router upgrading method includes writing both815 flash memory and a volatile RAM disk. That is, the wireless router destructively overwrites the first version of router firmware in the flash memory with the second version of router firmware, and also writes a copy of content of the second version of router firmware to a RAM disk in a
volatile RAM memory 106 of therouter 101. - In some embodiments, the firmware image chunks810 have at least one predetermined executable order, namely, an order in which the chunks are arranged in an executable copy of the firmware image. Some router upgrading methods include receiving808,816 firmware chunks810 in a volatile RAM memory in the wireless router in an order which differs from the executable order, and re-ordering817 the chunks. For example, in some methods the step of destructively overwriting811 flash memory chunks also arranges817 chunks in the flash memory in the executable order.
- In some embodiments, the
firmware image 702 has a size and the flash memory has a storage capacity, and the method includes the wireless router checking818 to see whether the size of the firmware image is less than a predetermined maximum firmware image size. For example, the predetermined maximum firmware image size can be at least a specified number (e.g., one, two, four, eight) of chunk sizes smaller than the flash memory storage capacity. - In some embodiments, the wireless router remaps819 a ROM memory address820 in the router to a RAM memory address821 in the router. This may be done, for example, to pass control to code at the remapped address. In some methods, the wireless router decompresses822 data held within the flash memory in the router and copies823 the data to a RAM-based file system in the router. For example, the router may decompress and copy a firmware image, an operating system kernel, email filtering code, anti-virus definitions, and/or other data.
- In some embodiments, the router uses flash memory (in addition to or in place of a hard disk or remote store, for instance) to preserve user configuration through a reboot. Before going live with upgraded firmware, the wireless router overwrites824 at least a portion of the flash memory with user-definable configuration settings825 from a text file826. The settings may be copied, for example, into one or more flash chunks that are not occupied by the firmware image code. After going live with upgraded firmware, the wireless router overwrites827 the text file with the configuration settings from the flash memory.
- In some embodiments, the response received828 includes an indication829 that a user's billing status is inactive, and the method redirects830 a
web browser 831 to abilling activation page 832. - In some embodiments, the firmware image chunks810 have at least one predetermined executable order, the step of receiving a responsive firmware image receives816 the chunks in the wireless router in an order which differs from the executable order, and the method re-orders817 the chunks such that the step of destructively overwriting flash memory chunks arranges chunks in the flash memory in the executable order, and the method also writes815 a copy of the chunks to a kernel memory in the wireless router.
- In some embodiments, the router authenticates833 the firmware image, e.g., by using a server certificate, image checksum, decryption, and/or other familiar authentication tool or technique.
- Although particular embodiments are expressly illustrated and described herein as methods or as devices, it will be appreciated that discussion of one type of embodiment also generally extends to other embodiment types. For instance, the descriptions of methods in connection with
FIG. 8 also help describe the operation of devices/systems like those discussed in connection withFIGS. 1, 2A, 2B, 3, 4, 7A, and 7B . It does not follow that limitations from one embodiment are necessarily read into another. - Not every item shown in the Figures or discussed in the text need be present in every embodiment. Although some possibilities are illustrated here in text and drawings by specific examples, embodiments may depart from these examples. For instance, specific features of an example may be omitted, renamed, grouped differently, repeated, or be a mix of features appearing in two or more of the examples. Thus, email filtering is omitted from some embodiments of
appliance 101. Functionality shown at one location may also be provided at a different location in some embodiments. Thus, someappliances 101 have a mix of wireless hub functionality as well as remote update functionality. - Reference has been made to the figures throughout by reference numerals. Any apparent inconsistencies in the phrasing associated with a given reference numeral, in the figures or in the text, should be understood as simply broadening the scope of what is referenced by that numeral.
- As used herein, terms such as “a” and “the” are inclusive of one or more of the indicated item or step. In particular, in the claims a reference to an item generally means at least one such item is present and a reference to a step means at least one instance of the step is performed.
- Headings are for convenience only; information on a given topic may be found outside the section whose heading indicates that topic.
- All claims as filed are part of the specification.
- While exemplary embodiments have been shown in the drawings and described above, it will be apparent to those of ordinary skill in the art that numerous modifications can be made without departing from the principles and concepts set forth in the claims. Although the subject matter is described in language specific to structural features and/or methodological acts, it is to be understood that the subject matter defined in the appended claims is not necessarily limited to the specific features or acts described above the claims. It is not necessary for every means or aspect identified in a given definition or example to be present or to be utilized in every embodiment. Rather, the specific features and acts described are disclosed as examples for consideration when implementing the claims.
- All changes which come within the meaning and range of equivalency of the claims are to be embraced within their scope to the full extent permitted by law.
Claims (20)
Priority Applications (6)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| US15/383,862US20170235567A1 (en) | 2005-02-15 | 2016-12-19 | Wireless router remote firmware upgrade |
| US15/950,451US20180232226A1 (en) | 2005-02-15 | 2018-04-11 | Wireless router remote firmware upgrade |
| US16/283,125US20190250905A1 (en) | 2005-02-15 | 2019-02-22 | Wireless router remote firmware upgrade |
| US16/752,505US20200159521A1 (en) | 2005-02-15 | 2020-01-24 | Wireless router remote firmware upgrade |
| US17/215,764US20210216304A1 (en) | 2005-02-15 | 2021-03-29 | Wireless router remote firmware upgrade |
| US18/090,111US20230140329A1 (en) | 2005-02-15 | 2022-12-28 | Wireless router remote firmware upgrade |
Applications Claiming Priority (6)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| US65316305P | 2005-02-15 | 2005-02-15 | |
| US11/350,905US7904518B2 (en) | 2005-02-15 | 2006-02-08 | Apparatus and method for analyzing and filtering email and for providing web related services |
| US13/015,053US8326936B2 (en) | 2005-02-15 | 2011-01-27 | Apparatus and method for analyzing and filtering email and for providing web related services |
| US13/587,394US8402109B2 (en) | 2005-02-15 | 2012-08-16 | Wireless router remote firmware upgrade |
| US13/763,351US9558353B2 (en) | 2005-02-15 | 2013-02-08 | Wireless router remote firmware upgrade |
| US15/383,862US20170235567A1 (en) | 2005-02-15 | 2016-12-19 | Wireless router remote firmware upgrade |
Related Parent Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US13/763,351ContinuationUS9558353B2 (en) | 2005-02-15 | 2013-02-08 | Wireless router remote firmware upgrade |
Related Child Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US15/950,451ContinuationUS20180232226A1 (en) | 2005-02-15 | 2018-04-11 | Wireless router remote firmware upgrade |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| US20170235567A1true US20170235567A1 (en) | 2017-08-17 |
Family
ID=36816910
Family Applications (9)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US11/350,905Expired - Fee RelatedUS7904518B2 (en) | 2005-02-15 | 2006-02-08 | Apparatus and method for analyzing and filtering email and for providing web related services |
| US13/015,053Expired - Fee RelatedUS8326936B2 (en) | 2005-02-15 | 2011-01-27 | Apparatus and method for analyzing and filtering email and for providing web related services |
| US13/763,351Expired - Fee RelatedUS9558353B2 (en) | 2005-02-15 | 2013-02-08 | Wireless router remote firmware upgrade |
| US15/383,862AbandonedUS20170235567A1 (en) | 2005-02-15 | 2016-12-19 | Wireless router remote firmware upgrade |
| US15/950,451AbandonedUS20180232226A1 (en) | 2005-02-15 | 2018-04-11 | Wireless router remote firmware upgrade |
| US16/283,125AbandonedUS20190250905A1 (en) | 2005-02-15 | 2019-02-22 | Wireless router remote firmware upgrade |
| US16/752,505AbandonedUS20200159521A1 (en) | 2005-02-15 | 2020-01-24 | Wireless router remote firmware upgrade |
| US17/215,764AbandonedUS20210216304A1 (en) | 2005-02-15 | 2021-03-29 | Wireless router remote firmware upgrade |
| US18/090,111AbandonedUS20230140329A1 (en) | 2005-02-15 | 2022-12-28 | Wireless router remote firmware upgrade |
Family Applications Before (3)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US11/350,905Expired - Fee RelatedUS7904518B2 (en) | 2005-02-15 | 2006-02-08 | Apparatus and method for analyzing and filtering email and for providing web related services |
| US13/015,053Expired - Fee RelatedUS8326936B2 (en) | 2005-02-15 | 2011-01-27 | Apparatus and method for analyzing and filtering email and for providing web related services |
| US13/763,351Expired - Fee RelatedUS9558353B2 (en) | 2005-02-15 | 2013-02-08 | Wireless router remote firmware upgrade |
Family Applications After (5)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US15/950,451AbandonedUS20180232226A1 (en) | 2005-02-15 | 2018-04-11 | Wireless router remote firmware upgrade |
| US16/283,125AbandonedUS20190250905A1 (en) | 2005-02-15 | 2019-02-22 | Wireless router remote firmware upgrade |
| US16/752,505AbandonedUS20200159521A1 (en) | 2005-02-15 | 2020-01-24 | Wireless router remote firmware upgrade |
| US17/215,764AbandonedUS20210216304A1 (en) | 2005-02-15 | 2021-03-29 | Wireless router remote firmware upgrade |
| US18/090,111AbandonedUS20230140329A1 (en) | 2005-02-15 | 2022-12-28 | Wireless router remote firmware upgrade |
Country Status (1)
| Country | Link |
|---|---|
| US (9) | US7904518B2 (en) |
Cited By (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20170277529A1 (en)* | 2016-03-24 | 2017-09-28 | Nec Corporation | Firmware distribution system, distribution apparatus, firmware distribution method and program recording medium |
| CN108540344A (en)* | 2018-03-29 | 2018-09-14 | 四川斐讯信息技术有限公司 | A kind of router upgrade test method and system |
| CN109669708A (en)* | 2018-11-02 | 2019-04-23 | 金卡智能集团股份有限公司 | Remote upgrade method for modularization internet-of-things terminal equipment |
| EP4365732A1 (en)* | 2022-11-07 | 2024-05-08 | Samsung Electronics Co., Ltd. | Efficient firmware download operation in storage devices |
Families Citing this family (274)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US8578480B2 (en)* | 2002-03-08 | 2013-11-05 | Mcafee, Inc. | Systems and methods for identifying potentially malicious messages |
| US20060015942A1 (en) | 2002-03-08 | 2006-01-19 | Ciphertrust, Inc. | Systems and methods for classification of messaging entities |
| US8561167B2 (en) | 2002-03-08 | 2013-10-15 | Mcafee, Inc. | Web reputation scoring |
| US20050223074A1 (en)* | 2004-03-31 | 2005-10-06 | Morris Robert P | System and method for providing user selectable electronic message action choices and processing |
| US8375444B2 (en) | 2006-04-20 | 2013-02-12 | Fireeye, Inc. | Dynamic signature creation and enforcement |
| US8561177B1 (en) | 2004-04-01 | 2013-10-15 | Fireeye, Inc. | Systems and methods for detecting communication channels of bots |
| US8566946B1 (en) | 2006-04-20 | 2013-10-22 | Fireeye, Inc. | Malware containment on connection |
| US8006305B2 (en)* | 2004-06-14 | 2011-08-23 | Fireeye, Inc. | Computer worm defense system and method |
| US8539582B1 (en) | 2004-04-01 | 2013-09-17 | Fireeye, Inc. | Malware containment and security analysis on connection |
| US7587537B1 (en) | 2007-11-30 | 2009-09-08 | Altera Corporation | Serializer-deserializer circuits formed from input-output circuit registers |
| US8898788B1 (en) | 2004-04-01 | 2014-11-25 | Fireeye, Inc. | Systems and methods for malware attack prevention |
| US8204984B1 (en) | 2004-04-01 | 2012-06-19 | Fireeye, Inc. | Systems and methods for detecting encrypted bot command and control communication channels |
| US8171553B2 (en) | 2004-04-01 | 2012-05-01 | Fireeye, Inc. | Heuristic based capture with replay to virtual machine |
| US9106694B2 (en) | 2004-04-01 | 2015-08-11 | Fireeye, Inc. | Electronic message analysis for malware detection |
| US8793787B2 (en) | 2004-04-01 | 2014-07-29 | Fireeye, Inc. | Detecting malicious network content using virtual environment components |
| US8528086B1 (en) | 2004-04-01 | 2013-09-03 | Fireeye, Inc. | System and method of detecting computer worms |
| US8881282B1 (en) | 2004-04-01 | 2014-11-04 | Fireeye, Inc. | Systems and methods for malware attack detection and identification |
| US8584239B2 (en)* | 2004-04-01 | 2013-11-12 | Fireeye, Inc. | Virtual machine with dynamic data flow analysis |
| US8549638B2 (en) | 2004-06-14 | 2013-10-01 | Fireeye, Inc. | System and method of containing computer worms |
| US9027135B1 (en) | 2004-04-01 | 2015-05-05 | Fireeye, Inc. | Prospective client identification using malware attack detection |
| US8635690B2 (en) | 2004-11-05 | 2014-01-21 | Mcafee, Inc. | Reputation based message processing |
| US8769663B2 (en)* | 2005-08-24 | 2014-07-01 | Fortinet, Inc. | Systems and methods for detecting undesirable network traffic content |
| US7958557B2 (en)* | 2006-05-17 | 2011-06-07 | Computer Associates Think, Inc. | Determining a source of malicious computer element in a computer network |
| US20080016572A1 (en)* | 2006-07-12 | 2008-01-17 | Microsoft Corporation | Malicious software detection via memory analysis |
| US8095967B2 (en) | 2006-07-27 | 2012-01-10 | White Sky, Inc. | Secure web site authentication using web site characteristics, secure user credentials and private browser |
| KR100859664B1 (en)* | 2006-11-13 | 2008-09-23 | 삼성에스디에스 주식회사 | How to determine if your email is virus infected |
| US8577968B2 (en)* | 2006-11-14 | 2013-11-05 | Mcafee, Inc. | Method and system for handling unwanted email messages |
| US7779156B2 (en)* | 2007-01-24 | 2010-08-17 | Mcafee, Inc. | Reputation based load balancing |
| US8763114B2 (en) | 2007-01-24 | 2014-06-24 | Mcafee, Inc. | Detecting image spam |
| US8214497B2 (en) | 2007-01-24 | 2012-07-03 | Mcafee, Inc. | Multi-dimensional reputation scoring |
| US8719364B2 (en)* | 2007-03-30 | 2014-05-06 | Canon Denshi Kabushiki Kaisha | System, method and program for network management using saved history information |
| US9394756B2 (en) | 2007-04-02 | 2016-07-19 | Halliburton Energy Services, Inc. | Timeline from slumber to collection of RFID tags in a well environment |
| US9394785B2 (en) | 2007-04-02 | 2016-07-19 | Halliburton Energy Services, Inc. | Methods and apparatus for evaluating downhole conditions through RFID sensing |
| US9394784B2 (en) | 2007-04-02 | 2016-07-19 | Halliburton Energy Services, Inc. | Algorithm for zonal fault detection in a well environment |
| US8166535B2 (en)* | 2007-10-10 | 2012-04-24 | Microsoft Corporation | Universal media firewall |
| US8185930B2 (en) | 2007-11-06 | 2012-05-22 | Mcafee, Inc. | Adjusting filter or classification control settings |
| US8589503B2 (en) | 2008-04-04 | 2013-11-19 | Mcafee, Inc. | Prioritizing network traffic |
| JP5396779B2 (en)* | 2008-09-03 | 2014-01-22 | ヤマハ株式会社 | Relay device and program |
| US8850571B2 (en) | 2008-11-03 | 2014-09-30 | Fireeye, Inc. | Systems and methods for detecting malicious network content |
| US8997219B2 (en) | 2008-11-03 | 2015-03-31 | Fireeye, Inc. | Systems and methods for detecting malicious PDF network content |
| US20100180027A1 (en)* | 2009-01-10 | 2010-07-15 | Barracuda Networks, Inc | Controlling transmission of unauthorized unobservable content in email using policy |
| US8621614B2 (en)* | 2009-05-26 | 2013-12-31 | Microsoft Corporation | Managing potentially phishing messages in a non-web mail client context |
| US8078691B2 (en)* | 2009-08-26 | 2011-12-13 | Microsoft Corporation | Web page load time prediction and simulation |
| US9565207B1 (en) | 2009-09-04 | 2017-02-07 | Amazon Technologies, Inc. | Firmware updates from an external channel |
| US10177934B1 (en)* | 2009-09-04 | 2019-01-08 | Amazon Technologies, Inc. | Firmware updates inaccessible to guests |
| US8887144B1 (en) | 2009-09-04 | 2014-11-11 | Amazon Technologies, Inc. | Firmware updates during limited time period |
| US8214653B1 (en) | 2009-09-04 | 2012-07-03 | Amazon Technologies, Inc. | Secured firmware updates |
| US8601170B1 (en) | 2009-09-08 | 2013-12-03 | Amazon Technologies, Inc. | Managing firmware update attempts |
| US8971538B1 (en) | 2009-09-08 | 2015-03-03 | Amazon Technologies, Inc. | Firmware validation from an external channel |
| US8300641B1 (en) | 2009-09-09 | 2012-10-30 | Amazon Technologies, Inc. | Leveraging physical network interface functionality for packet processing |
| US8959611B1 (en) | 2009-09-09 | 2015-02-17 | Amazon Technologies, Inc. | Secure packet management for bare metal access |
| US8381264B1 (en) | 2009-09-10 | 2013-02-19 | Amazon Technologies, Inc. | Managing hardware reboot and reset in shared environments |
| US8832829B2 (en) | 2009-09-30 | 2014-09-09 | Fireeye, Inc. | Network-based binary file extraction and analysis for malware detection |
| US9264342B2 (en)* | 2009-12-24 | 2016-02-16 | Samsung Electronics Co., Ltd. | Terminal device based on content name, and method for routing based on content name |
| US9268813B2 (en)* | 2009-12-24 | 2016-02-23 | Samsung Electronics Co., Ltd. | Terminal device based on content name, and method for routing based on content name |
| US8621638B2 (en) | 2010-05-14 | 2013-12-31 | Mcafee, Inc. | Systems and methods for classification of messaging entities |
| US9465935B2 (en) | 2010-06-11 | 2016-10-11 | D2L Corporation | Systems, methods, and apparatus for securing user documents |
| CN102098235B (en)* | 2011-01-18 | 2013-08-07 | 南京邮电大学 | Fishing mail inspection method based on text characteristic analysis |
| US9634896B2 (en)* | 2011-02-17 | 2017-04-25 | Circle Media Inc. | Plug-and-play network filter |
| US9419928B2 (en) | 2011-03-11 | 2016-08-16 | James Robert Miner | Systems and methods for message collection |
| US8819156B2 (en) | 2011-03-11 | 2014-08-26 | James Robert Miner | Systems and methods for message collection |
| US9285966B2 (en)* | 2011-07-18 | 2016-03-15 | Verizon Patent And Licensing Inc. | Message notification system |
| US8484741B1 (en)* | 2012-01-27 | 2013-07-09 | Chapman Technology Group, Inc. | Software service to facilitate organizational testing of employees to determine their potential susceptibility to phishing scams |
| US9519782B2 (en) | 2012-02-24 | 2016-12-13 | Fireeye, Inc. | Detecting malicious network content |
| CN102663291B (en)* | 2012-03-23 | 2015-02-25 | 北京奇虎科技有限公司 | Mail information prompt method and device |
| US11245672B2 (en) | 2012-06-18 | 2022-02-08 | Microsoft Technologly Licensing, LLC | System and method to access content of encrypted data items in unsupported digital environments |
| US9189225B2 (en) | 2012-10-16 | 2015-11-17 | Imprivata, Inc. | Secure, non-disruptive firmware updating |
| US10572665B2 (en) | 2012-12-28 | 2020-02-25 | Fireeye, Inc. | System and method to create a number of breakpoints in a virtual machine via virtual machine trapping events |
| US9053326B2 (en) | 2013-02-08 | 2015-06-09 | PhishMe, Inc. | Simulated phishing attack with sequential messages |
| US8966637B2 (en) | 2013-02-08 | 2015-02-24 | PhishMe, Inc. | Performance benchmarking for simulated phishing attacks |
| US9356948B2 (en) | 2013-02-08 | 2016-05-31 | PhishMe, Inc. | Collaborative phishing attack detection |
| US9398038B2 (en) | 2013-02-08 | 2016-07-19 | PhishMe, Inc. | Collaborative phishing attack detection |
| US9253207B2 (en) | 2013-02-08 | 2016-02-02 | PhishMe, Inc. | Collaborative phishing attack detection |
| US9009823B1 (en) | 2013-02-23 | 2015-04-14 | Fireeye, Inc. | Framework for efficient security coverage of mobile software applications installed on mobile devices |
| US9367681B1 (en) | 2013-02-23 | 2016-06-14 | Fireeye, Inc. | Framework for efficient security coverage of mobile software applications using symbolic execution to reach regions of interest within an application |
| US9159035B1 (en) | 2013-02-23 | 2015-10-13 | Fireeye, Inc. | Framework for computer application analysis of sensitive information tracking |
| US9824209B1 (en) | 2013-02-23 | 2017-11-21 | Fireeye, Inc. | Framework for efficient security coverage of mobile software applications that is usable to harden in the field code |
| US9176843B1 (en) | 2013-02-23 | 2015-11-03 | Fireeye, Inc. | Framework for efficient security coverage of mobile software applications |
| US9195829B1 (en) | 2013-02-23 | 2015-11-24 | Fireeye, Inc. | User interface with real-time visual playback along with synchronous textual analysis log display and event/time index for anomalous behavior detection in applications |
| US8990944B1 (en) | 2013-02-23 | 2015-03-24 | Fireeye, Inc. | Systems and methods for automatically detecting backdoors |
| US9009822B1 (en) | 2013-02-23 | 2015-04-14 | Fireeye, Inc. | Framework for multi-phase analysis of mobile applications |
| US9104867B1 (en) | 2013-03-13 | 2015-08-11 | Fireeye, Inc. | Malicious content analysis using simulated user interaction without user involvement |
| US9626509B1 (en) | 2013-03-13 | 2017-04-18 | Fireeye, Inc. | Malicious content analysis with multi-version application support within single operating environment |
| US9565202B1 (en) | 2013-03-13 | 2017-02-07 | Fireeye, Inc. | System and method for detecting exfiltration content |
| US9355247B1 (en) | 2013-03-13 | 2016-05-31 | Fireeye, Inc. | File extraction from memory dump for malicious content analysis |
| US9430646B1 (en) | 2013-03-14 | 2016-08-30 | Fireeye, Inc. | Distributed systems and methods for automatically detecting unknown bots and botnets |
| US9311479B1 (en) | 2013-03-14 | 2016-04-12 | Fireeye, Inc. | Correlation and consolidation of analytic data for holistic view of a malware attack |
| US9251343B1 (en) | 2013-03-15 | 2016-02-02 | Fireeye, Inc. | Detecting bootkits resident on compromised computers |
| US9413781B2 (en) | 2013-03-15 | 2016-08-09 | Fireeye, Inc. | System and method employing structured intelligence to verify and contain threats at endpoints |
| US10713358B2 (en) | 2013-03-15 | 2020-07-14 | Fireeye, Inc. | System and method to extract and utilize disassembly features to classify software intent |
| US9495180B2 (en) | 2013-05-10 | 2016-11-15 | Fireeye, Inc. | Optimized resource allocation for virtual machines within a malware content detection system |
| US9635039B1 (en) | 2013-05-13 | 2017-04-25 | Fireeye, Inc. | Classifying sets of malicious indicators for detecting command and control communications associated with malware |
| US9843624B1 (en)* | 2013-06-13 | 2017-12-12 | Pouya Taaghol | Distributed software defined networking |
| US10133863B2 (en) | 2013-06-24 | 2018-11-20 | Fireeye, Inc. | Zero-day discovery system |
| US9536091B2 (en) | 2013-06-24 | 2017-01-03 | Fireeye, Inc. | System and method for detecting time-bomb malware |
| US9300686B2 (en) | 2013-06-28 | 2016-03-29 | Fireeye, Inc. | System and method for detecting malicious links in electronic messages |
| US9888016B1 (en) | 2013-06-28 | 2018-02-06 | Fireeye, Inc. | System and method for detecting phishing using password prediction |
| US9552368B1 (en)* | 2013-07-02 | 2017-01-24 | Google Inc. | Electronic mail attachments garden |
| US9559996B1 (en) | 2013-07-02 | 2017-01-31 | Google Inc. | Systems and methods for integrating cloud storage and network service |
| WO2016059846A1 (en)* | 2014-10-14 | 2016-04-21 | デジタルア-ツ株式会社 | Information processing device and program |
| JP5606599B1 (en)* | 2013-07-29 | 2014-10-15 | デジタルア−ツ株式会社 | Information processing apparatus, program, and information processing method |
| US9294501B2 (en) | 2013-09-30 | 2016-03-22 | Fireeye, Inc. | Fuzzy hash of behavioral results |
| US9736179B2 (en) | 2013-09-30 | 2017-08-15 | Fireeye, Inc. | System, apparatus and method for using malware analysis results to drive adaptive instrumentation of virtual machines to improve exploit detection |
| US9628507B2 (en) | 2013-09-30 | 2017-04-18 | Fireeye, Inc. | Advanced persistent threat (APT) detection center |
| US10089461B1 (en) | 2013-09-30 | 2018-10-02 | Fireeye, Inc. | Page replacement code injection |
| US10192052B1 (en) | 2013-09-30 | 2019-01-29 | Fireeye, Inc. | System, apparatus and method for classifying a file as malicious using static scanning |
| US10515214B1 (en) | 2013-09-30 | 2019-12-24 | Fireeye, Inc. | System and method for classifying malware within content created during analysis of a specimen |
| US9171160B2 (en) | 2013-09-30 | 2015-10-27 | Fireeye, Inc. | Dynamically adaptive framework and method for classifying malware using intelligent static, emulation, and dynamic analyses |
| US9690936B1 (en) | 2013-09-30 | 2017-06-27 | Fireeye, Inc. | Multistage system and method for analyzing obfuscated content for malware |
| US9921978B1 (en) | 2013-11-08 | 2018-03-20 | Fireeye, Inc. | System and method for enhanced security of storage devices |
| US9189627B1 (en) | 2013-11-21 | 2015-11-17 | Fireeye, Inc. | System, apparatus and method for conducting on-the-fly decryption of encrypted objects for malware detection |
| US9756074B2 (en) | 2013-12-26 | 2017-09-05 | Fireeye, Inc. | System and method for IPS and VM-based detection of suspicious objects |
| US9747446B1 (en) | 2013-12-26 | 2017-08-29 | Fireeye, Inc. | System and method for run-time object classification |
| US9740857B2 (en) | 2014-01-16 | 2017-08-22 | Fireeye, Inc. | Threat-aware microvisor |
| US9262629B2 (en) | 2014-01-21 | 2016-02-16 | PhishMe, Inc. | Methods and systems for preventing malicious use of phishing simulation records |
| US9262635B2 (en) | 2014-02-05 | 2016-02-16 | Fireeye, Inc. | Detection efficacy of virtual machine-based analysis with application specific events |
| US10140381B2 (en) | 2014-03-11 | 2018-11-27 | Cisco Technology, Inc. | HTML device tags to control operational features of devices in an internet of things |
| US9633131B2 (en)* | 2014-03-11 | 2017-04-25 | Cisco Technology, Inc. | HTML network service tags used with web browsers for controlling network elements |
| US9241010B1 (en) | 2014-03-20 | 2016-01-19 | Fireeye, Inc. | System and method for network behavior detection |
| US10242185B1 (en) | 2014-03-21 | 2019-03-26 | Fireeye, Inc. | Dynamic guest image creation and rollback |
| US9591015B1 (en) | 2014-03-28 | 2017-03-07 | Fireeye, Inc. | System and method for offloading packet processing and static analysis operations |
| US9223972B1 (en) | 2014-03-31 | 2015-12-29 | Fireeye, Inc. | Dynamically remote tuning of a malware content detection system |
| US9432389B1 (en) | 2014-03-31 | 2016-08-30 | Fireeye, Inc. | System, apparatus and method for detecting a malicious attack based on static analysis of a multi-flow object |
| US9438623B1 (en) | 2014-06-06 | 2016-09-06 | Fireeye, Inc. | Computer exploit detection using heap spray pattern matching |
| US9594912B1 (en) | 2014-06-06 | 2017-03-14 | Fireeye, Inc. | Return-oriented programming detection |
| US9973531B1 (en) | 2014-06-06 | 2018-05-15 | Fireeye, Inc. | Shellcode detection |
| US9723498B2 (en)* | 2014-06-18 | 2017-08-01 | Google Inc. | Automatically updating an access point |
| US10084813B2 (en) | 2014-06-24 | 2018-09-25 | Fireeye, Inc. | Intrusion prevention and remedy system |
| US9398028B1 (en) | 2014-06-26 | 2016-07-19 | Fireeye, Inc. | System, device and method for detecting a malicious attack based on communcations between remotely hosted virtual machines and malicious web servers |
| US10805340B1 (en) | 2014-06-26 | 2020-10-13 | Fireeye, Inc. | Infection vector and malware tracking with an interactive user display |
| US10002252B2 (en) | 2014-07-01 | 2018-06-19 | Fireeye, Inc. | Verification of trusted threat-aware microvisor |
| US20160027516A1 (en)* | 2014-07-24 | 2016-01-28 | Elster Solutions, Llc | Efficient modification of data in non-volatile memory |
| US10032027B2 (en)* | 2014-07-29 | 2018-07-24 | Digital Arts Inc. | Information processing apparatus and program for executing an electronic data in an execution environment |
| US9363280B1 (en) | 2014-08-22 | 2016-06-07 | Fireeye, Inc. | System and method of detecting delivery of malware using cross-customer data |
| US8964596B1 (en)* | 2014-08-29 | 2015-02-24 | Level 3 Communications, Llc | Network service aware routers, and applications thereof |
| US9634894B2 (en)* | 2014-08-29 | 2017-04-25 | Level 3 Communications, Llc | Network service aware routers, and applications thereof |
| US9571465B1 (en) | 2014-09-18 | 2017-02-14 | Amazon Technologies, Inc. | Security verification by message interception and modification |
| US10671726B1 (en) | 2014-09-22 | 2020-06-02 | Fireeye Inc. | System and method for malware analysis using thread-level event monitoring |
| US10027689B1 (en) | 2014-09-29 | 2018-07-17 | Fireeye, Inc. | Interactive infection visualization for improved exploit detection and signature generation for malware and malware families |
| US9773112B1 (en) | 2014-09-29 | 2017-09-26 | Fireeye, Inc. | Exploit detection of malware and malware families |
| US10331428B1 (en)* | 2014-09-30 | 2019-06-25 | EMC IP Holding Company LLC | Automated firmware update management on huge big-data clusters |
| US9798377B2 (en) | 2014-10-08 | 2017-10-24 | Apple Inc. | Methods and apparatus for recovering errors with an inter-processor communication link between independently operable processors |
| IL235423A0 (en)* | 2014-10-30 | 2015-01-29 | Ironscales Ltd | Method and system for mitigating spear-phishing attacks |
| WO2016072790A1 (en)* | 2014-11-07 | 2016-05-12 | 박현수 | Protective system, device, and method for protecting electronic communication device |
| US9942182B2 (en) | 2014-11-17 | 2018-04-10 | At&T Intellectual Property I, L.P. | System and method for cloud based IP mobile messaging spam detection and defense |
| US9690933B1 (en) | 2014-12-22 | 2017-06-27 | Fireeye, Inc. | Framework for classifying an object as malicious with machine learning for deploying updated predictive models |
| US10075455B2 (en) | 2014-12-26 | 2018-09-11 | Fireeye, Inc. | Zero-day rotating guest image profile |
| US9934376B1 (en) | 2014-12-29 | 2018-04-03 | Fireeye, Inc. | Malware detection appliance architecture |
| US9838417B1 (en) | 2014-12-30 | 2017-12-05 | Fireeye, Inc. | Intelligent context aware user interaction for malware detection |
| JP2016148967A (en)* | 2015-02-12 | 2016-08-18 | 富士通株式会社 | Information processing apparatus, information processing method, and program |
| US10148693B2 (en) | 2015-03-25 | 2018-12-04 | Fireeye, Inc. | Exploit detection system |
| US9690606B1 (en) | 2015-03-25 | 2017-06-27 | Fireeye, Inc. | Selective system call monitoring |
| US9438613B1 (en) | 2015-03-30 | 2016-09-06 | Fireeye, Inc. | Dynamic content activation for automated analysis of embedded objects |
| US10474813B1 (en) | 2015-03-31 | 2019-11-12 | Fireeye, Inc. | Code injection technique for remediation at an endpoint of a network |
| US10417031B2 (en) | 2015-03-31 | 2019-09-17 | Fireeye, Inc. | Selective virtualization for security threat detection |
| US9483644B1 (en) | 2015-03-31 | 2016-11-01 | Fireeye, Inc. | Methods for detecting file altering malware in VM based analysis |
| US9906539B2 (en) | 2015-04-10 | 2018-02-27 | PhishMe, Inc. | Suspicious message processing and incident response |
| US9654485B1 (en) | 2015-04-13 | 2017-05-16 | Fireeye, Inc. | Analytics-based security monitoring system and method |
| US9594904B1 (en) | 2015-04-23 | 2017-03-14 | Fireeye, Inc. | Detecting malware based on reflection |
| US10042794B2 (en) | 2015-06-12 | 2018-08-07 | Apple Inc. | Methods and apparatus for synchronizing uplink and downlink transactions on an inter-device communication link |
| US9882934B2 (en)* | 2015-06-29 | 2018-01-30 | Synopsys, Inc. | Simple trusted transfer to internet of things devices |
| US11113086B1 (en) | 2015-06-30 | 2021-09-07 | Fireeye, Inc. | Virtual system and method for securing external network connectivity |
| US10642753B1 (en) | 2015-06-30 | 2020-05-05 | Fireeye, Inc. | System and method for protecting a software component running in virtual machine using a virtualization layer |
| US10454950B1 (en) | 2015-06-30 | 2019-10-22 | Fireeye, Inc. | Centralized aggregation technique for detecting lateral movement of stealthy cyber-attacks |
| US10726127B1 (en) | 2015-06-30 | 2020-07-28 | Fireeye, Inc. | System and method for protecting a software component running in a virtual machine through virtual interrupts by the virtualization layer |
| US10715542B1 (en) | 2015-08-14 | 2020-07-14 | Fireeye, Inc. | Mobile application risk analysis |
| US10176321B2 (en) | 2015-09-22 | 2019-01-08 | Fireeye, Inc. | Leveraging behavior-based rules for malware family classification |
| US10394572B2 (en)* | 2015-09-24 | 2019-08-27 | Guangdong Oppo Mobile Telecommunications Corp. Ltd. | Power adapter and method for upgrading the power adapter |
| US10033747B1 (en) | 2015-09-29 | 2018-07-24 | Fireeye, Inc. | System and method for detecting interpreter-based exploit attacks |
| US10210329B1 (en) | 2015-09-30 | 2019-02-19 | Fireeye, Inc. | Method to detect application execution hijacking using memory protection |
| US10706149B1 (en) | 2015-09-30 | 2020-07-07 | Fireeye, Inc. | Detecting delayed activation malware using a primary controller and plural time controllers |
| US9825976B1 (en) | 2015-09-30 | 2017-11-21 | Fireeye, Inc. | Detection and classification of exploit kits |
| US9825989B1 (en) | 2015-09-30 | 2017-11-21 | Fireeye, Inc. | Cyber attack early warning system |
| US10601865B1 (en) | 2015-09-30 | 2020-03-24 | Fireeye, Inc. | Detection of credential spearphishing attacks using email analysis |
| US10817606B1 (en) | 2015-09-30 | 2020-10-27 | Fireeye, Inc. | Detecting delayed activation malware using a run-time monitoring agent and time-dilation logic |
| EP3160167A1 (en)* | 2015-10-20 | 2017-04-26 | Gemalto SA | Method for updating a package |
| US10284575B2 (en) | 2015-11-10 | 2019-05-07 | Fireeye, Inc. | Launcher for setting analysis environment variations for malware detection |
| US10447728B1 (en) | 2015-12-10 | 2019-10-15 | Fireeye, Inc. | Technique for protecting guest processes using a layered virtualization architecture |
| US10846117B1 (en) | 2015-12-10 | 2020-11-24 | Fireeye, Inc. | Technique for establishing secure communication between host and guest processes of a virtualization architecture |
| US10108446B1 (en) | 2015-12-11 | 2018-10-23 | Fireeye, Inc. | Late load technique for deploying a virtualization layer underneath a running operating system |
| DE102015016616A1 (en)* | 2015-12-22 | 2017-06-22 | Giesecke & Devrient Gmbh | Device and method for connecting a production device to a network |
| US10050998B1 (en) | 2015-12-30 | 2018-08-14 | Fireeye, Inc. | Malicious message analysis system |
| US10621338B1 (en) | 2015-12-30 | 2020-04-14 | Fireeye, Inc. | Method to detect forgery and exploits using last branch recording registers |
| US10565378B1 (en) | 2015-12-30 | 2020-02-18 | Fireeye, Inc. | Exploit of privilege detection framework |
| US10133866B1 (en) | 2015-12-30 | 2018-11-20 | Fireeye, Inc. | System and method for triggering analysis of an object for malware in response to modification of that object |
| US9824216B1 (en) | 2015-12-31 | 2017-11-21 | Fireeye, Inc. | Susceptible environment detection system |
| US11552986B1 (en) | 2015-12-31 | 2023-01-10 | Fireeye Security Holdings Us Llc | Cyber-security framework for application of virtual features |
| US10581874B1 (en) | 2015-12-31 | 2020-03-03 | Fireeye, Inc. | Malware detection system with contextual analysis |
| US10191852B2 (en) | 2016-02-29 | 2019-01-29 | Apple Inc. | Methods and apparatus for locking at least a portion of a shared memory resource |
| US10785255B1 (en) | 2016-03-25 | 2020-09-22 | Fireeye, Inc. | Cluster configuration within a scalable malware detection system |
| US10671721B1 (en) | 2016-03-25 | 2020-06-02 | Fireeye, Inc. | Timeout management services |
| US10601863B1 (en) | 2016-03-25 | 2020-03-24 | Fireeye, Inc. | System and method for managing sensor enrollment |
| US10616266B1 (en) | 2016-03-25 | 2020-04-07 | Fireeye, Inc. | Distributed malware detection system and submission workflow thereof |
| US10826933B1 (en) | 2016-03-31 | 2020-11-03 | Fireeye, Inc. | Technique for verifying exploit/malware at malware detection appliance through correlation with endpoints |
| US10893059B1 (en) | 2016-03-31 | 2021-01-12 | Fireeye, Inc. | Verification and enhancement using detection systems located at the network periphery and endpoint devices |
| US10198364B2 (en) | 2016-03-31 | 2019-02-05 | Apple Inc. | Memory access protection apparatus and methods for memory mapped access between independently operable processors |
| US10333950B2 (en) | 2016-05-01 | 2019-06-25 | International Business Machines Corporation | Defending against malicious electronic messages |
| US10169585B1 (en) | 2016-06-22 | 2019-01-01 | Fireeye, Inc. | System and methods for advanced malware detection through placement of transition events |
| US10462173B1 (en) | 2016-06-30 | 2019-10-29 | Fireeye, Inc. | Malware detection verification and enhancement by coordinating endpoint and malware detection systems |
| US10592678B1 (en) | 2016-09-09 | 2020-03-17 | Fireeye, Inc. | Secure communications between peers using a verified virtual trusted platform module |
| US10491627B1 (en) | 2016-09-29 | 2019-11-26 | Fireeye, Inc. | Advanced malware detection using similarity analysis |
| JP6753257B2 (en)* | 2016-10-04 | 2020-09-09 | 富士通株式会社 | Information processing device, information processing system, information processing device control method and information processing device control program |
| US10795991B1 (en) | 2016-11-08 | 2020-10-06 | Fireeye, Inc. | Enterprise search |
| US10775871B2 (en) | 2016-11-10 | 2020-09-15 | Apple Inc. | Methods and apparatus for providing individualized power control for peripheral sub-systems |
| US10591976B2 (en) | 2016-11-10 | 2020-03-17 | Apple Inc. | Methods and apparatus for providing peripheral sub-system stability |
| US10587647B1 (en) | 2016-11-22 | 2020-03-10 | Fireeye, Inc. | Technique for malware detection capability comparison of network security devices |
| US10581879B1 (en) | 2016-12-22 | 2020-03-03 | Fireeye, Inc. | Enhanced malware detection for generated objects |
| US10552610B1 (en) | 2016-12-22 | 2020-02-04 | Fireeye, Inc. | Adaptive virtual machine snapshot update framework for malware behavioral analysis |
| US10523609B1 (en) | 2016-12-27 | 2019-12-31 | Fireeye, Inc. | Multi-vector malware detection and analysis |
| US10757058B2 (en)* | 2017-02-17 | 2020-08-25 | International Business Machines Corporation | Outgoing communication scam prevention |
| US10810510B2 (en) | 2017-02-17 | 2020-10-20 | International Business Machines Corporation | Conversation and context aware fraud and abuse prevention agent |
| US10102868B2 (en) | 2017-02-17 | 2018-10-16 | International Business Machines Corporation | Bot-based honeypot poison resilient data collection |
| CN108574588B (en)* | 2017-03-10 | 2023-09-15 | 中兴通讯股份有限公司 | Client, server and differentiated upgrading method |
| US10904286B1 (en) | 2017-03-24 | 2021-01-26 | Fireeye, Inc. | Detection of phishing attacks using similarity analysis |
| US10554507B1 (en) | 2017-03-30 | 2020-02-04 | Fireeye, Inc. | Multi-level control for enhanced resource and object evaluation management of malware detection system |
| US10902119B1 (en) | 2017-03-30 | 2021-01-26 | Fireeye, Inc. | Data extraction system for malware analysis |
| US10791138B1 (en) | 2017-03-30 | 2020-09-29 | Fireeye, Inc. | Subscription-based malware detection |
| US10798112B2 (en) | 2017-03-30 | 2020-10-06 | Fireeye, Inc. | Attribute-controlled malware detection |
| US10412736B2 (en)* | 2017-05-08 | 2019-09-10 | T-Mobile Usa, Inc. | Internet of things (IoT) device firewalling |
| US10455416B2 (en) | 2017-05-26 | 2019-10-22 | Honeywell International Inc. | Systems and methods for providing a secured password and authentication mechanism for programming and updating software or firmware |
| US10503904B1 (en) | 2017-06-29 | 2019-12-10 | Fireeye, Inc. | Ransomware detection and mitigation |
| US10855700B1 (en) | 2017-06-29 | 2020-12-01 | Fireeye, Inc. | Post-intrusion detection of cyber-attacks during lateral movement within networks |
| US10601848B1 (en) | 2017-06-29 | 2020-03-24 | Fireeye, Inc. | Cyber-security system and method for weak indicator detection and correlation to generate strong indicators |
| US10893068B1 (en) | 2017-06-30 | 2021-01-12 | Fireeye, Inc. | Ransomware file modification prevention technique |
| US10346226B2 (en) | 2017-08-07 | 2019-07-09 | Time Warner Cable Enterprises Llc | Methods and apparatus for transmitting time sensitive data over a tunneled bus interface |
| US10747872B1 (en) | 2017-09-27 | 2020-08-18 | Fireeye, Inc. | System and method for preventing malware evasion |
| US10805346B2 (en) | 2017-10-01 | 2020-10-13 | Fireeye, Inc. | Phishing attack detection |
| US11108809B2 (en) | 2017-10-27 | 2021-08-31 | Fireeye, Inc. | System and method for analyzing binary code for malware classification using artificial neural network techniques |
| CN111433773B (en)* | 2017-11-30 | 2023-04-11 | Abb瑞士股份有限公司 | Updating gateways in substations |
| EP3729766A1 (en) | 2017-12-24 | 2020-10-28 | Arilou Information Security Technologies Ltd. | System and method for tunnel-based malware detection |
| US11271955B2 (en) | 2017-12-28 | 2022-03-08 | Fireeye Security Holdings Us Llc | Platform and method for retroactive reclassification employing a cybersecurity-based global data store |
| US11240275B1 (en) | 2017-12-28 | 2022-02-01 | Fireeye Security Holdings Us Llc | Platform and method for performing cybersecurity analyses employing an intelligence hub with a modular architecture |
| US11005860B1 (en) | 2017-12-28 | 2021-05-11 | Fireeye, Inc. | Method and system for efficient cybersecurity analysis of endpoint events |
| US10331612B1 (en) | 2018-01-09 | 2019-06-25 | Apple Inc. | Methods and apparatus for reduced-latency data transmission with an inter-processor communication link between independently operable processors |
| US10826931B1 (en) | 2018-03-29 | 2020-11-03 | Fireeye, Inc. | System and method for predicting and mitigating cybersecurity system misconfigurations |
| US11558401B1 (en) | 2018-03-30 | 2023-01-17 | Fireeye Security Holdings Us Llc | Multi-vector malware detection data sharing system for improved detection |
| US11003773B1 (en) | 2018-03-30 | 2021-05-11 | Fireeye, Inc. | System and method for automatically generating malware detection rule recommendations |
| US10956477B1 (en) | 2018-03-30 | 2021-03-23 | Fireeye, Inc. | System and method for detecting malicious scripts through natural language processing modeling |
| US10838739B2 (en) | 2018-04-19 | 2020-11-17 | Circle Media Labs Inc. | Network-connected computing devices and methods for executing operating programs in RAM memory |
| US10430352B1 (en) | 2018-05-18 | 2019-10-01 | Apple Inc. | Methods and apparatus for reduced overhead data transfer with a shared ring buffer |
| US11314859B1 (en) | 2018-06-27 | 2022-04-26 | FireEye Security Holdings, Inc. | Cyber-security system and method for detecting escalation of privileges within an access token |
| US11075930B1 (en) | 2018-06-27 | 2021-07-27 | Fireeye, Inc. | System and method for detecting repetitive cybersecurity attacks constituting an email campaign |
| US11228491B1 (en) | 2018-06-28 | 2022-01-18 | Fireeye Security Holdings Us Llc | System and method for distributed cluster configuration monitoring and management |
| US11316900B1 (en) | 2018-06-29 | 2022-04-26 | FireEye Security Holdings Inc. | System and method for automatically prioritizing rules for cyber-threat detection and mitigation |
| US10585699B2 (en) | 2018-07-30 | 2020-03-10 | Apple Inc. | Methods and apparatus for verifying completion of groups of data transactions between processors |
| TWI678904B (en)* | 2018-08-27 | 2019-12-01 | 宏碁股份有限公司 | E-mail checking method and email checking system |
| US11151248B1 (en)* | 2018-09-11 | 2021-10-19 | NuRD LLC | Increasing zero-day malware detection throughput on files attached to emails |
| US11182473B1 (en) | 2018-09-13 | 2021-11-23 | Fireeye Security Holdings Us Llc | System and method for mitigating cyberattacks against processor operability by a guest process |
| US11763004B1 (en) | 2018-09-27 | 2023-09-19 | Fireeye Security Holdings Us Llc | System and method for bootkit detection |
| CN109409032A (en)* | 2018-10-24 | 2019-03-01 | 山东超越数控电子股份有限公司 | A kind of system kernel analysis method of Safety-Critical System |
| CN111104149A (en)* | 2018-10-25 | 2020-05-05 | 华为技术有限公司 | A firmware upgrade method, device and terminal |
| CN109558357B (en)* | 2018-10-31 | 2020-10-30 | 许继集团有限公司 | A method for collecting and controlling signals and main CPU plug-in and sub-plug-in |
| US11277495B2 (en)* | 2018-12-10 | 2022-03-15 | Electronics And Telecommunications Research Institute | System and method for providing microservice-based device control interface |
| US11368475B1 (en) | 2018-12-21 | 2022-06-21 | Fireeye Security Holdings Us Llc | System and method for scanning remote services to locate stored objects with malware |
| US12074887B1 (en) | 2018-12-21 | 2024-08-27 | Musarubra Us Llc | System and method for selectively processing content after identification and removal of malicious content |
| CN109933353B (en)* | 2019-03-22 | 2022-04-12 | 陕西建工安装集团(河南)有限公司 | Embedded Web-based controller firmware upgrading method |
| US11258806B1 (en) | 2019-06-24 | 2022-02-22 | Mandiant, Inc. | System and method for automatically associating cybersecurity intelligence to cyberthreat actors |
| US11556640B1 (en) | 2019-06-27 | 2023-01-17 | Mandiant, Inc. | Systems and methods for automated cybersecurity analysis of extracted binary string sets |
| US11392700B1 (en) | 2019-06-28 | 2022-07-19 | Fireeye Security Holdings Us Llc | System and method for supporting cross-platform data verification |
| CN110460462A (en)* | 2019-07-24 | 2019-11-15 | 中国移动通信集团黑龙江有限公司 | Dual network router control system and dual network router |
| US11295020B2 (en) | 2019-08-05 | 2022-04-05 | Bank Of America Corporation | System for integrated natural language processing and event analysis for threat detection in computing systems |
| US11886585B1 (en) | 2019-09-27 | 2024-01-30 | Musarubra Us Llc | System and method for identifying and mitigating cyberattacks through malicious position-independent code execution |
| US11637862B1 (en) | 2019-09-30 | 2023-04-25 | Mandiant, Inc. | System and method for surfacing cyber-security threats with a self-learning recommendation engine |
| US12032948B2 (en)* | 2020-01-24 | 2024-07-09 | Insyde Software Corp. | System and method for runtime capsule firmware update with low-latency software SMIs |
| US11625186B2 (en)* | 2020-07-16 | 2023-04-11 | Blancco Technology Group IP Oy | Data erasure of network devices |
| US11379212B2 (en)* | 2020-08-31 | 2022-07-05 | Microsoft Technology Licensing, Llc | Systems and methods for disaggregating system firmware configuration data into a management subsystem for seamless updates |
| US11888895B2 (en)* | 2020-09-02 | 2024-01-30 | Proofpoint, Inc. | Using neural networks to process forensics and generate threat intelligence information |
| CN115576576A (en)* | 2021-06-21 | 2023-01-06 | 广州视源电子科技股份有限公司 | Firmware upgrade method, server and terminal equipment |
| CN113391836B (en)* | 2021-07-14 | 2022-11-18 | 威海新北洋技术服务有限公司 | Firmware program upgrading method and device and electronic equipment |
| US12124841B2 (en)* | 2021-11-11 | 2024-10-22 | Carrier Corporation | Live firmware and configuration updates of multi-node alarm systems |
| CN114513368B (en)* | 2022-03-29 | 2023-10-27 | 广州长嘉电子有限公司 | Online software upgrading method, device and system for intelligent sound box |
| US12079619B2 (en) | 2022-07-27 | 2024-09-03 | T-Mobile Usa, Inc. | Firmware-over-the-air (FOTA) update for wireless devices in an internet of things (IoT) network |
| CN116339776B (en)* | 2023-03-13 | 2025-09-26 | 福建星云电子股份有限公司 | A charging pile upgrade method that dynamically adapts to program size |
| TWI878036B (en)* | 2024-02-29 | 2025-03-21 | 大陸商星宸科技股份有限公司 | Method for upgrading program and program upgrading device |
Citations (2)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20130347103A1 (en)* | 2012-06-21 | 2013-12-26 | Mark Veteikis | Packet capture for error tracking |
| US20130346814A1 (en)* | 2012-06-21 | 2013-12-26 | Timothy Zadigian | Jtag-based programming and debug |
Family Cites Families (45)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US7809138B2 (en) | 1999-03-16 | 2010-10-05 | Intertrust Technologies Corporation | Methods and apparatus for persistent control and protection of content |
| US6854007B1 (en)* | 1998-09-17 | 2005-02-08 | Micron Technology, Inc. | Method and system for enhancing reliability of communication with electronic messages |
| US6321267B1 (en) | 1999-11-23 | 2001-11-20 | Escom Corporation | Method and apparatus for filtering junk email |
| US6701440B1 (en)* | 2000-01-06 | 2004-03-02 | Networks Associates Technology, Inc. | Method and system for protecting a computer using a remote e-mail scanning device |
| US20020007453A1 (en)* | 2000-05-23 | 2002-01-17 | Nemovicher C. Kerry | Secured electronic mail system and method |
| US6785732B1 (en)* | 2000-09-11 | 2004-08-31 | International Business Machines Corporation | Web server apparatus and method for virus checking |
| US7055148B2 (en) | 2000-12-07 | 2006-05-30 | Hewlett-Packard Development Company, L.P. | System and method for updating firmware |
| US7069334B2 (en) | 2000-12-27 | 2006-06-27 | Intel Corporation | Image restoration and reconfiguration support for crashed devices |
| JP2002244874A (en) | 2001-02-15 | 2002-08-30 | Toshiba Corp | Information processing apparatus and firmware update method |
| US6941466B2 (en)* | 2001-02-22 | 2005-09-06 | International Business Machines Corporation | Method and apparatus for providing automatic e-mail filtering based on message semantics, sender's e-mail ID, and user's identity |
| CA2357382A1 (en) | 2001-09-17 | 2003-03-17 | Soma Networks, Inc. | Software update method, apparatus and system |
| US7299463B2 (en) | 2001-09-28 | 2007-11-20 | Intel Corporation | Method for atomically updating a plurality of files |
| US7243347B2 (en) | 2002-06-21 | 2007-07-10 | International Business Machines Corporation | Method and system for maintaining firmware versions in a data processing system |
| US20040083469A1 (en) | 2002-10-23 | 2004-04-29 | Ping-Sheng Chen | Method for updating firmware of optical disk system |
| US7928310B2 (en) | 2002-11-12 | 2011-04-19 | MediaLab Solutions Inc. | Systems and methods for portable audio synthesis |
| US20060168006A1 (en)* | 2003-03-24 | 2006-07-27 | Mr. Marvin Shannon | System and method for the classification of electronic communication |
| US20050021968A1 (en) | 2003-06-25 | 2005-01-27 | Zimmer Vincent J. | Method for performing a trusted firmware/bios update |
| EP1639435A4 (en) | 2003-06-27 | 2009-12-30 | Hewlett Packard Development Co | System and method for downloading update packages into a mobile handset in a carrier network |
| US7027463B2 (en) | 2003-07-11 | 2006-04-11 | Sonolink Communications Systems, Llc | System and method for multi-tiered rule filtering |
| US20050021637A1 (en)* | 2003-07-22 | 2005-01-27 | Red Hat, Inc. | Electronic mail control system |
| US20050027807A1 (en) | 2003-07-30 | 2005-02-03 | Lynda Fengler | Systems and methods for facilitating peripheral device firmware installation |
| US6986049B2 (en)* | 2003-08-26 | 2006-01-10 | Yahoo! Inc. | Method and system for authenticating a message sender using domain keys |
| TWI256587B (en) | 2003-10-31 | 2006-06-11 | Asustek Comp Inc | Firmware upgrading method and system executing same |
| US20050198173A1 (en) | 2004-01-02 | 2005-09-08 | Evans Alexander W. | System and method for controlling receipt of electronic messages |
| US20050198160A1 (en) | 2004-03-03 | 2005-09-08 | Marvin Shannon | System and Method for Finding and Using Styles in Electronic Communications |
| US7870608B2 (en) | 2004-05-02 | 2011-01-11 | Markmonitor, Inc. | Early detection and monitoring of online fraud |
| US7529802B2 (en)* | 2004-06-16 | 2009-05-05 | International Business Machines Corporation | Method for performing multiple hierarchically tests to verify identity of sender of an email message and assigning the highest confidence value |
| US20060004896A1 (en)* | 2004-06-16 | 2006-01-05 | International Business Machines Corporation | Managing unwanted/unsolicited e-mail protection using sender identity |
| US20050283519A1 (en) | 2004-06-17 | 2005-12-22 | Commtouch Software, Ltd. | Methods and systems for combating spam |
| US7364087B2 (en) | 2004-06-24 | 2008-04-29 | Intel Corporation | Virtual firmware smart card |
| US7694135B2 (en)* | 2004-07-16 | 2010-04-06 | Geotrust, Inc. | Security systems and services to provide identity and uniform resource identifier verification |
| US7398348B2 (en) | 2004-08-24 | 2008-07-08 | Sandisk 3D Llc | Method and apparatus for using a one-time or few-time programmable memory with a host device designed for erasable/rewritable memory |
| US20060047766A1 (en)* | 2004-08-30 | 2006-03-02 | Squareanswer, Inc. | Controlling transmission of email |
| US20060069732A1 (en) | 2004-09-07 | 2006-03-30 | Marvin Shannon | Systems and Methods to Rank Electronic Messages and Detect Spammer Probe Accounts |
| US7422115B2 (en)* | 2004-09-07 | 2008-09-09 | Iconix, Inc. | Techniques for to defeat phishing |
| US7413085B2 (en)* | 2004-09-07 | 2008-08-19 | Iconix, Inc. | Techniques for displaying emails listed in an email inbox |
| US7376870B2 (en) | 2004-09-30 | 2008-05-20 | Intel Corporation | Self-monitoring and updating of firmware over a network |
| US7770003B2 (en) | 2004-12-29 | 2010-08-03 | Intel Corporation | Updating firmware securely over a network |
| CA2600344A1 (en)* | 2005-03-02 | 2006-09-08 | Markmonitor Inc. | Distribution of trust data |
| JP4669348B2 (en)* | 2005-05-11 | 2011-04-13 | 株式会社エヌ・ティ・ティ・ドコモ | Spam mail discrimination device and spam mail discrimination method |
| US7926108B2 (en)* | 2005-11-23 | 2011-04-12 | Trend Micro Incorporated | SMTP network security processing in a transparent relay in a computer network |
| US20060184635A1 (en)* | 2006-05-18 | 2006-08-17 | The Go Daddy Group, Inc. | Electronic mail method using email tickler |
| US20070271342A1 (en)* | 2006-05-19 | 2007-11-22 | Sbc Knowledge Ventures, L.P. | Methods and systems to deliver electronic mail using payments |
| US20070274230A1 (en) | 2006-05-23 | 2007-11-29 | Werber Ryan A | System and method for modifying router firmware |
| US7797421B1 (en)* | 2006-12-15 | 2010-09-14 | Amazon Technologies, Inc. | Method and system for determining and notifying users of undesirable network content |
- 2006
- 2006-02-08USUS11/350,905patent/US7904518B2/ennot_activeExpired - Fee Related
- 2011
- 2011-01-27USUS13/015,053patent/US8326936B2/ennot_activeExpired - Fee Related
- 2013
- 2013-02-08USUS13/763,351patent/US9558353B2/ennot_activeExpired - Fee Related
- 2016
- 2016-12-19USUS15/383,862patent/US20170235567A1/ennot_activeAbandoned
- 2018
- 2018-04-11USUS15/950,451patent/US20180232226A1/ennot_activeAbandoned
- 2019
- 2019-02-22USUS16/283,125patent/US20190250905A1/ennot_activeAbandoned
- 2020
- 2020-01-24USUS16/752,505patent/US20200159521A1/ennot_activeAbandoned
- 2021
- 2021-03-29USUS17/215,764patent/US20210216304A1/ennot_activeAbandoned
- 2022
- 2022-12-28USUS18/090,111patent/US20230140329A1/ennot_activeAbandoned
Patent Citations (2)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20130347103A1 (en)* | 2012-06-21 | 2013-12-26 | Mark Veteikis | Packet capture for error tracking |
| US20130346814A1 (en)* | 2012-06-21 | 2013-12-26 | Timothy Zadigian | Jtag-based programming and debug |
Cited By (6)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20170277529A1 (en)* | 2016-03-24 | 2017-09-28 | Nec Corporation | Firmware distribution system, distribution apparatus, firmware distribution method and program recording medium |
| US10528338B2 (en)* | 2016-03-24 | 2020-01-07 | Nec Corporation | Firmware distribution system, distribution apparatus, firmware distribution method and program recording medium |
| CN108540344A (en)* | 2018-03-29 | 2018-09-14 | 四川斐讯信息技术有限公司 | A kind of router upgrade test method and system |
| CN109669708A (en)* | 2018-11-02 | 2019-04-23 | 金卡智能集团股份有限公司 | Remote upgrade method for modularization internet-of-things terminal equipment |
| EP4365732A1 (en)* | 2022-11-07 | 2024-05-08 | Samsung Electronics Co., Ltd. | Efficient firmware download operation in storage devices |
| US12353865B2 (en) | 2022-11-07 | 2025-07-08 | Samsung Electronics Co., Ltd. | Efficient firmware download operation in storage devices |
Also Published As
| Publication number | Publication date |
|---|---|
| US20140052976A1 (en) | 2014-02-20 |
| US20200159521A1 (en) | 2020-05-21 |
| US8326936B2 (en) | 2012-12-04 |
| US20210216304A1 (en) | 2021-07-15 |
| US20180232226A1 (en) | 2018-08-16 |
| US9558353B2 (en) | 2017-01-31 |
| US20230140329A1 (en) | 2023-05-04 |
| US7904518B2 (en) | 2011-03-08 |
| US20060184632A1 (en) | 2006-08-17 |
| US20190250905A1 (en) | 2019-08-15 |
| US20110119343A1 (en) | 2011-05-19 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| US20230140329A1 (en) | Wireless router remote firmware upgrade | |
| US8402109B2 (en) | Wireless router remote firmware upgrade | |
| JP5396051B2 (en) | Method and system for creating and updating a database of authorized files and trusted domains | |
| Parampalli et al. | A practical mimicry attack against powerful system-call monitors | |
| US9038174B2 (en) | Resisting the spread of unwanted code and data | |
| JP5970141B2 (en) | Method, boot loader, user trusted device, and system for executing software modules on a computer | |
| Rogers | Nessus network auditing | |
| Saini | Squid Proxy Server 3.1: beginner's guide | |
| US20110289556A1 (en) | Method and Apparatus for Serving Content Elements of a Markup Language Document Protected Against Cross-Site Scripting Attack | |
| CN111030963B (en) | Document tracking method, gateway equipment and server | |
| JP2011525003A (en) | Secure application streaming | |
| Apvrille | Symbian worm Yxes: Towards mobile botnets? | |
| WO2019184664A1 (en) | Method, apparatus, and system for detecting malicious file | |
| JP3630087B2 (en) | Automatic data processor | |
| Liu et al. | Security analysis of vendor customized code in firmware of embedded device | |
| Olegård | Security & Forensic Analysis of an Internet of Things Smart Home Ecosystem | |
| Borg et al. | IoT Pentesting: Obtaining the firmware of a smart lock | |
| Avaznejad | Disk encryption on Talos operating system | |
| De Decker | A comparative study on the security of network-connected devices | |
| Bärschneider | Forensic investigation artifacts on BSD | |
| Porter | Detecting Malicious Behavior in OpenWrt with QEMU Tracing | |
| für die Master-Prüfung et al. | Exploiting Network Printers | |
| Baker | Installing and Configuring Services | |
| KR101124634B1 (en) | integrated management system of network based on embedded operating gateway | |
| Edgecombe | Detection of SSL-related security vulnerabilities in Android applications Computer Science Tripos, Part II Pembroke College |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| AS | Assignment | Owner name:GYTHEION NETWORKS LLC, DELAWARE Free format text:ASSIGNMENT OF ASSIGNORS INTEREST;ASSIGNOR:OGILVIE, JOHN;REEL/FRAME:042620/0357 Effective date:20170528 | |
| AS | Assignment | Owner name:GYTHEION NETWORKS LLC, NEW YORK Free format text:ASSIGNMENT OF ASSIGNORS INTEREST;ASSIGNORS:MARINO, JOSEPH P;FORTIN, JONATHAN;REEL/FRAME:043027/0208 Effective date:20120814 | |
| STCB | Information on status: application discontinuation | Free format text:ABANDONED -- FAILURE TO RESPOND TO AN OFFICE ACTION | |
| AS | Assignment | Owner name:MARINO, JOSEPH P, NEW YORK Free format text:ASSIGNMENT OF ASSIGNORS INTEREST;ASSIGNOR:GYTHEION NETWORKS LLC;REEL/FRAME:045882/0175 Effective date:20180428 | |
| AS | Assignment | Owner name:MARINO, JOSEPH P, NEW YORK Free format text:CORRECTIVE ASSIGNMENT TO CORRECT THE INCORRECT APPL. NO. 12/074,717 PREVIOUSLY RECORDED AT REEL: 045882 FRAME: 0175. ASSIGNOR(S) HEREBY CONFIRMS THE ASSIGNMENT;ASSIGNOR:GYTHEION NETWORKS LLC;REEL/FRAME:046356/0658 Effective date:20180428 | |
| AS | Assignment | Owner name:GYTHEION NETWORKS LLC, WYOMING Free format text:ASSIGNMENT OF ASSIGNORS INTEREST;ASSIGNOR:MARINO, JOSEPH P;REEL/FRAME:046372/0821 Effective date:20180612 | |
| AS | Assignment | Owner name:BLACKBIRD TECH LLC, MASSACHUSETTS Free format text:ASSIGNMENT OF ASSIGNORS INTEREST;ASSIGNOR:GYTHEION NETWORKS LLC;REEL/FRAME:046712/0767 Effective date:20180820 | |
| AS | Assignment | Owner name:GYTHEION NETWORKS, LLC, WYOMING Free format text:ASSIGNMENT OF ASSIGNORS INTEREST;ASSIGNOR:BLACKBIRD TECH LLC;REEL/FRAME:068890/0921 Effective date:20241003 | |
| AS | Assignment | Owner name:GYTHEION NETWORKS, LLC, WYOMING Free format text:CORRECTIVE ASSIGNMENT TO CORRECT THE CONVEYING PARTY DATA PREVIOUSLY RECORDED ON REEL 68890 FRAME 921. ASSIGNOR(S) HEREBY CONFIRMS THE ASSIGNMENT;ASSIGNOR:SARTORI, ELISA;REEL/FRAME:069333/0659 Effective date:20241003 |