US20170063900A1 - Method And System For Monitoring Entity Activity On An Organization's Computer Network - Google Patents
Method And System For Monitoring Entity Activity On An Organization's Computer NetworkDownload PDFInfo
- Publication number
- US20170063900A1 US20170063900A1US14/928,503US201514928503AUS2017063900A1US 20170063900 A1US20170063900 A1US 20170063900A1US 201514928503 AUS201514928503 AUS 201514928503AUS 2017063900 A1US2017063900 A1US 2017063900A1
- Authority
- US
- United States
- Prior art keywords
- data
- entity
- event
- network
- model
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Abandoned
Links
Images
Classifications
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06N—COMPUTING ARRANGEMENTS BASED ON SPECIFIC COMPUTATIONAL MODELS
- G06N20/00—Machine learning
- G06N20/20—Ensemble learning
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F16/00—Information retrieval; Database structures therefor; File system structures therefor
- G06F16/20—Information retrieval; Database structures therefor; File system structures therefor of structured data, e.g. relational data
- G06F16/24—Querying
- G06F16/245—Query processing
- G06F16/2457—Query processing with adaptation to user needs
- G06F16/24578—Query processing with adaptation to user needs using ranking
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F16/00—Information retrieval; Database structures therefor; File system structures therefor
- G06F16/20—Information retrieval; Database structures therefor; File system structures therefor of structured data, e.g. relational data
- G06F16/25—Integrating or interfacing systems involving database management systems
- G06F16/254—Extract, transform and load [ETL] procedures, e.g. ETL data flows in data warehouses
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F16/00—Information retrieval; Database structures therefor; File system structures therefor
- G06F16/20—Information retrieval; Database structures therefor; File system structures therefor of structured data, e.g. relational data
- G06F16/28—Databases characterised by their database models, e.g. relational or object models
- G06F16/284—Relational databases
- G06F16/285—Clustering or classification
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F16/00—Information retrieval; Database structures therefor; File system structures therefor
- G06F16/40—Information retrieval; Database structures therefor; File system structures therefor of multimedia data, e.g. slideshows comprising image and additional audio data
- G06F16/44—Browsing; Visualisation therefor
- G06F16/444—Spatial browsing, e.g. 2D maps, 3D or virtual spaces
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F16/00—Information retrieval; Database structures therefor; File system structures therefor
- G06F16/90—Details of database functions independent of the retrieved data types
- G06F16/901—Indexing; Data structures therefor; Storage structures
- G06F16/9024—Graphs; Linked lists
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F3/00—Input arrangements for transferring data to be processed into a form capable of being handled by the computer; Output arrangements for transferring data from processing unit to output unit, e.g. interface arrangements
- G06F3/01—Input arrangements or combined input and output arrangements for interaction between user and computer
- G06F3/048—Interaction techniques based on graphical user interfaces [GUI]
- G06F3/0481—Interaction techniques based on graphical user interfaces [GUI] based on specific properties of the displayed interaction object or a metaphor-based environment, e.g. interaction with desktop elements like windows or icons, or assisted by a cursor's changing behaviour or appearance
- G06F3/0482—Interaction with lists of selectable items, e.g. menus
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F3/00—Input arrangements for transferring data to be processed into a form capable of being handled by the computer; Output arrangements for transferring data from processing unit to output unit, e.g. interface arrangements
- G06F3/01—Input arrangements or combined input and output arrangements for interaction between user and computer
- G06F3/048—Interaction techniques based on graphical user interfaces [GUI]
- G06F3/0484—Interaction techniques based on graphical user interfaces [GUI] for the control of specific functions or operations, e.g. selecting or manipulating an object, an image or a displayed text element, setting a parameter value or selecting a range
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F3/00—Input arrangements for transferring data to be processed into a form capable of being handled by the computer; Output arrangements for transferring data from processing unit to output unit, e.g. interface arrangements
- G06F3/01—Input arrangements or combined input and output arrangements for interaction between user and computer
- G06F3/048—Interaction techniques based on graphical user interfaces [GUI]
- G06F3/0484—Interaction techniques based on graphical user interfaces [GUI] for the control of specific functions or operations, e.g. selecting or manipulating an object, an image or a displayed text element, setting a parameter value or selecting a range
- G06F3/04842—Selection of displayed objects or displayed text elements
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F3/00—Input arrangements for transferring data to be processed into a form capable of being handled by the computer; Output arrangements for transferring data from processing unit to output unit, e.g. interface arrangements
- G06F3/01—Input arrangements or combined input and output arrangements for interaction between user and computer
- G06F3/048—Interaction techniques based on graphical user interfaces [GUI]
- G06F3/0484—Interaction techniques based on graphical user interfaces [GUI] for the control of specific functions or operations, e.g. selecting or manipulating an object, an image or a displayed text element, setting a parameter value or selecting a range
- G06F3/04847—Interaction techniques to control parameter settings, e.g. interaction with sliders or dials
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F40/00—Handling natural language data
- G06F40/10—Text processing
- G06F40/12—Use of codes for handling textual entities
- G06F40/134—Hyperlinking
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06N—COMPUTING ARRANGEMENTS BASED ON SPECIFIC COMPUTATIONAL MODELS
- G06N20/00—Machine learning
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06N—COMPUTING ARRANGEMENTS BASED ON SPECIFIC COMPUTATIONAL MODELS
- G06N5/00—Computing arrangements using knowledge-based models
- G06N5/02—Knowledge representation; Symbolic representation
- G06N5/022—Knowledge engineering; Knowledge acquisition
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06N—COMPUTING ARRANGEMENTS BASED ON SPECIFIC COMPUTATIONAL MODELS
- G06N5/00—Computing arrangements using knowledge-based models
- G06N5/04—Inference or reasoning models
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06N—COMPUTING ARRANGEMENTS BASED ON SPECIFIC COMPUTATIONAL MODELS
- G06N7/00—Computing arrangements based on specific mathematical models
- G06N7/01—Probabilistic graphical models, e.g. probabilistic networks
- G06N99/005—
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06V—IMAGE OR VIDEO RECOGNITION OR UNDERSTANDING
- G06V10/00—Arrangements for image or video recognition or understanding
- G06V10/20—Image preprocessing
- G06V10/22—Image preprocessing by selection of a specific region containing or referencing a pattern; Locating or processing of specific regions to guide the detection or recognition
- G06V10/225—Image preprocessing by selection of a specific region containing or referencing a pattern; Locating or processing of specific regions to guide the detection or recognition based on a marking or identifier characterising the area
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L41/00—Arrangements for maintenance, administration or management of data switching networks, e.g. of packet switching networks
- H04L41/08—Configuration management of networks or network elements
- H04L41/0893—Assignment of logical groups to network elements
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L41/00—Arrangements for maintenance, administration or management of data switching networks, e.g. of packet switching networks
- H04L41/14—Network analysis or design
- H04L41/145—Network analysis or design involving simulating, designing, planning or modelling of a network
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L41/00—Arrangements for maintenance, administration or management of data switching networks, e.g. of packet switching networks
- H04L41/22—Arrangements for maintenance, administration or management of data switching networks, e.g. of packet switching networks comprising specially adapted graphical user interfaces [GUI]
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L43/00—Arrangements for monitoring or testing data switching networks
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L43/00—Arrangements for monitoring or testing data switching networks
- H04L43/04—Processing captured monitoring data, e.g. for logfile generation
- H04L43/045—Processing captured monitoring data, e.g. for logfile generation for graphical visualisation of monitoring data
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L43/00—Arrangements for monitoring or testing data switching networks
- H04L43/06—Generation of reports
- H04L43/062—Generation of reports related to network traffic
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L43/00—Arrangements for monitoring or testing data switching networks
- H04L43/20—Arrangements for monitoring or testing data switching networks the monitoring system or the monitored elements being virtualised, abstracted or software-defined entities, e.g. SDN or NFV
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/06—Network architectures or network communication protocols for network security for supporting key management in a packet data network
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/14—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic
- H04L63/1408—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic by monitoring network traffic
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/14—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic
- H04L63/1408—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic by monitoring network traffic
- H04L63/1416—Event detection, e.g. attack signature detection
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/14—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic
- H04L63/1408—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic by monitoring network traffic
- H04L63/1425—Traffic logging, e.g. anomaly detection
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/14—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic
- H04L63/1433—Vulnerability analysis
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/14—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic
- H04L63/1441—Countermeasures against malicious traffic
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/20—Network architectures or network communication protocols for network security for managing network security; network security policies in general
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L2463/00—Additional details relating to network architectures or network communication protocols for network security covered by H04L63/00
- H04L2463/121—Timestamp
Definitions
- At least one embodiment of the present disclosurepertains to distributed data processing systems, and more particularly, to intelligence generation and activity discovery from events in a distributed data processing system.
- Activity detectionboth friendly and malicious, has long been a priority for computer network administrators.
- usersemploy devices such as desktop computers, laptop computers, tablets, smart phones, browsers, etc. to interact with others through computers and servers that are coupled to the network.
- Digital datatypically in the form of data packets, are passed along the network by interconnected network devices.
- malware activitiescan cause harm to the network's software or hardware, or its users. Malicious activities may include unauthorized access or subsequent unpermitted use of network resources and data. Network administrators seek to detect such activities, for example, by searching for patterns of behavior that are abnormal or otherwise vary from the expected use pattern of a particular entity, such as an organization or subset thereof, individual user, IP address, node or group of nodes in the network, etc.
- Security appliancesare used in known systems to provide network security.
- the appliance approachinvolves installing security appliances (which are typically servers or computers configured for providing security) at one or more locations in the network. Once installed, the appliance monitors traffic that traverses the network.
- Functions provided by the appliancemay include malware detection, intrusion detection, unauthorized access or unauthorized use of data, among others.
- security appliancescannot easily be scaled to handle temporary or permanent increases in network traffic. Increased network traffic often requires a security vendor to perform an appliance swap or an equally time-consuming appliance upgrade. Appliances also tend to have only limited network visibility because they are typically configured to monitor data traversing the link on which a respective appliance is installed only. Such an appliance will be unaware of activities occurring on other network segments monitored by other appliances and thus cannot use the additional context information pertaining to activities occurring on other network segments to detect a cleverly-designed piece of malware that may be difficult to detect from purely localized information.
- Installed software productsrather than security hardware appliances, provide another approach to security for data networks. These products, such as anti-virus or anti-malware software, typically are installed on terminal devices (e.g., desktop and laptop computers, tablets, or smart phones). Data traversing the network between the terminal device is monitored by the installed products to detect malware in either inbound or outbound data.
- installed software productsalso do not perform well in terms of scalability or network visibility. Installed products tend to be disposed locally on the terminal devices and thus also tend to have fairly localized views of the data on the network. They also tend to be installed on hardware that cannot be upgraded easily.
- FIG. 1shows a general environment in which a security platform, which is an example application of a data processing system introduced here, may be implemented.
- FIG. 2shows an example of functional layers of a security platform.
- FIG. 3shows a high-level view of an example of the processing within the security platform.
- FIG. 4shows an example of the architecture of the security platform.
- FIG. 5shows an example implementation of the real-time processing path in greater detail.
- FIG. 6shows an example representation of the process of building adaptive behavioral baselines and evaluating against such baselines to support the detection of anomalies.
- FIGS. 7A and 7Bcollectively show a table listing example types of machine data that can be found in different environments.
- FIG. 8shows an example implementation of the data intake and preparation stage of the security platform.
- FIG. 9Ashows raw event data received by the data intake and preparation stage
- FIG. 9Bshows an event-specific relationship graph based on the event shown in FIG. 9A .
- FIG. 10shows an example implementation of an identity resolution technique based on the information in the events.
- FIG. 11shows a diagram of a technique for providing a uniform access interface (“event view”) at the data intake and preparation stage for an event processing engine (e.g., at a subsequent stage) to obtain relevant information from various kinds of machine data.
- event viewa uniform access interface
- FIG. 12shows a table of example uniform access interfaces (“event views”) that can be implemented in the data intake and preparation stage.
- FIGS. 13A and 13Bcollectively show a table including example anomalies that can be identified by machine learning models and/or other types of processing entities, and various example uniform access interfaces and fields that can be used by the models/entities to receive relevant information about the events for performing further analytics.
- FIG. 14shows a sessionization technique that can be implemented at the data intake and preparation stage.
- FIG. 15is a block diagram of a machine learning-based complex event processing (CEP) engine.
- CEPcomplex event processing
- FIG. 16is a block diagram illustrating an architectural framework of a machine learning model.
- FIG. 17is a block diagram illustrating an example of the model type definition.
- FIG. 18is a block diagram illustrating an example system architecture for implementing the distributed computation system.
- FIG. 19is a flow diagram illustrating a method to execute a model preparation process thread.
- FIG. 20is a flow diagram illustrating a method to execute a model training process thread.
- FIG. 21is a flow diagram illustrating a method to execute a model deliberation process thread.
- FIG. 22shows a diagram of an example architecture of the security platform in which sharing of model state between real-time and batch processing paths can be implemented.
- FIG. 23is flow diagram illustrating at a high level, the processing hierarchy of detecting anomalies, identifying threat indicators, and identifying threats.
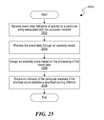
- FIG. 25is a flow diagram describing an example process for detecting anomalies.
- FIG. 26is a flow diagram describing an example process for identifying threat indicators.
- FIG. 27shows a first use case for identifying threat indicators based on entity associations with detected anomalies.
- FIG. 28shows a second use case for identifying threat indicators based on entity associations with detected anomalies.
- FIG. 29illustrates a use case for identifying threat indicators based on duration of detected anomalous behavior.
- FIG. 30illustrates a use case for identifying threat indicators based on local and global rarity analysis.
- FIG. 31Aillustrates identification of a threat indicator according to a first use case based on combining the outputs from different anomaly models.
- FIG. 31Billustrates nonidentification of a threat indicator according to the first use case based on combing the outputs from different anomaly models.
- FIG. 32Aillustrates identification of a threat indicator according to a second use case based on combining the outputs from different anomaly models.
- FIG. 32Billustrates nonidentification of a threat indicator according to the second use case based on combing the outputs from different anomaly models.
- FIG. 33illustrates a use case for identifying threat indicators by enriching the anomaly data using data from external sources.
- FIG. 34is a flow diagram describing an example process for identifying threats to network security based on threat indicators.
- FIG. 35illustrates an example process of combining and storing event-specific relationship graphs into a composite relationship graph.
- FIG. 36illustrates an example of a composite relationship graph.
- FIG. 37illustrates an example of how a composite relationship graph can be stored as separate projections.
- FIG. 38illustrates a sample process of combining event-specific relationship graphs into a composite relationship graph and detecting a security threat based on the composite relationship graph.
- FIG. 39Ais an illustrative home screen in a GUI of a system for monitoring potential computer network compromise, in accordance with various embodiments of the disclosure.
- FIG. 39Bis an illustrative screen in the GUI of FIG. 39A , depicting an expanded view of a “Views” tab selector, which enables a GUI user to select between viewing screens identifying instances of potential network compromise and viewing screens identifying entities associated with the instances of potential network compromise, in accordance with various embodiments of the disclosure.
- FIG. 40Ais an illustrative view in the GUI of FIG. 39A of a “Threats Review” screen for reviewing identified threats, in accordance with various embodiments of the disclosure.
- FIG. 40Bis an illustrative view of an expanded “Threat Types” selector for filtering the “Threats Review” screen of FIG. 40A to display only a selected type of threat, in accordance with various embodiments of the disclosure.
- FIG. 40Cis an illustrative view of an expanded “Actions” tab in the “Threats Review” screen of FIG. 40A , in accordance with various embodiments of the disclosure.
- FIG. 40Dis an illustrative view of a “Threat Relations” diagram and a “Kill Chain” diagram, which are generated upon clicking the “Details” tab in the “Threats Review” screen of FIG. 40A , in accordance with various embodiments of the disclosure.
- FIG. 40Eis an illustrative view of a “Threat Anomalies Timeline,” “Threat Anomalies Trend,” and “Threat Anomalies” listing, which are generated upon clicking the “Details” tab in the “Threats Review” screen of FIG. 40A , in accordance with various embodiments of the disclosure.
- FIG. 40Fis an illustrative view of a “Device Locations” map, which is generated upon clicking the “Details” tab in the “Threats Review” screen of FIG. 40A , in accordance with various embodiments of the disclosure.
- FIG. 40Gis an illustrative view of a text bubble generated upon hovering a cursor over a device location in the “Device Locations” map of FIG. 40F , in accordance with various embodiments of the disclosure.
- FIG. 40His an illustrative view of a text bubble generated upon hovering a cursor over a line drawn between devices in the “Device Locations” map of FIG. 40F , in accordance with various embodiments of the disclosure.
- FIG. 41is an illustrative view of a “User Facts” screen in the GUI of FIG. 39A , in accordance with various embodiments of the disclosure.
- FIG. 42is an illustrative view of an “Anomalies Table” screen in the GUI of FIG. 39A , in accordance with various embodiments of the disclosure.
- FIG. 43is an illustrative view of an “Anomaly Details” screen in the GUI of FIG. 39A , in accordance with various embodiments of the disclosure.
- FIG. 44Ais an illustrative view of an expanded “Watchlists” tab in the “Threats Review” screen of FIG. 40A , in accordance with various embodiments of the disclosure.
- FIG. 44Bis an illustrative view of an “Anomaly Details” screen in the GUI of FIG. 39A , including a “Watchlists” designation, in accordance with various embodiments of the disclosure.
- FIG. 45Ais an illustrative view of a “Threats Table” screen in the GUI of FIG. 39A , in accordance with various embodiments of the disclosure.
- FIG. 45Bis an illustrative view of a “Threats Trend” as a line chart.
- FIG. 45Cis an illustrative view of a “Threats Trend” as a column chart.
- FIG. 45Dis an illustrative view of a text bubble generated upon hovering a data point in the “Threats Trend” diagram of FIG. 45A , in accordance with various embodiments of the disclosure.
- FIG. 45Eis an illustrative view of a “Threats Details” screen in the GUI of FIG. 39A , in accordance with various embodiments of the disclosure.
- FIG. 46Ais an illustrative view of an “Anomalies Table” screen in the GUI of FIG. 39A , in accordance with various embodiments of the disclosure.
- FIG. 46Bis an illustrative view of the “Anomalies Trend” and the “Anomalies” listing in the “Anomalies Table” screen of FIG. 46A , depicting a selection of a data point in the “Anomalies Trend” diagram.
- FIG. 46Cis an illustrative view of a portion of an “Anomalies Details” screen for a selected anomaly in the GUI of FIG. 39A , including a “Users” section, “Anomaly Relations” section, and “Triggering Event” section, in accordance with various embodiments of the disclosure.
- FIG. 46Dis an illustrative view of a portion of an “Anomalies Details” screen for a selected anomaly in the GUI of FIG. 39A , including an “Anomalous Activity Sequence” diagram, in accordance with various embodiments of the disclosure.
- FIG. 46Eis an illustrative view of a portion of an “Anomalies Details” screen for a selected anomaly in the GUI of FIG. 39A , including an “User Activities Baseline” diagram, “Compare Unusual Activity with the Accounts Profile” graphic, “Additional Information” graphic, and “Anomaly Graph” diagram, in accordance with various embodiments of the disclosure.
- FIG. 46Fis an illustrative view of a portion of an “Anomalies Details” screen for an anomaly of the type “Machine Generated Beacon,” including a “Users,” “Devices,” and “Domains” sections, and an “Anomaly Relations” box.
- FIG. 47Ais an illustrative view of a “Users Table” screen in the GUI of FIG. 39A , in accordance with various embodiments of the disclosure.
- FIG. 47Bis an illustrative view of a “User Facts” screen in the GUI of FIG. 39A , in accordance with various embodiments of the disclosure.
- FIG. 47Cis another illustrative view of a “User Facts” screen in the GUI of FIG. 39A , in accordance with various embodiments of the disclosure.
- FIG. 47Dis an illustrative view of a “User Threats” screen in the GUI of FIG. 39A , in accordance with various embodiments of the disclosure.
- FIG. 47Eis an illustrative view of a “User Anomalies” screen in the GUI of FIG. 39A , in accordance with various embodiments of the disclosure.
- FIG. 47Fis an additional illustrative view of a “User Anomalies” screen in the GUI of FIG. 39A , in accordance with various embodiments of the disclosure.
- FIG. 47Gis an illustrative view of a “Watchlist” screen in the GUI of FIG. 39A , in accordance with various embodiments of the disclosure.
- FIG. 48Ais an illustrative view of a “Devices Table” screen in the GUI of FIG. 39A , in accordance with various embodiments of the disclosure.
- FIG. 48Bis an illustrative view of a “Device Facts” screen in the GUI of FIG. 39A , in accordance with various embodiments of the disclosure.
- FIG. 48Cis an illustrative view of a “Device Anomalies” screen in the GUI of FIG. 39A , in accordance with various embodiments of the disclosure.
- FIG. 49Ais an illustrative view of an “Apps Table” screen in the GUI of FIG. 39A , in accordance with various embodiments of the disclosure.
- FIG. 49Bis an illustrative view of an “App Facts” screen in the GUI of FIG. 39A , in accordance with various embodiments of the disclosure.
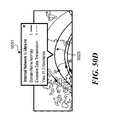
- FIG. 50Ais an illustrative view of a Geomap icon in a Threats Table view in the GUI of FIG. 39A , in accordance with various embodiments of the disclosure.
- FIG. 50Bis an illustrative view of a Geomap in the GUI of FIG. 39A , in accordance with various embodiments of the disclosure.
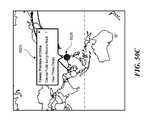
- FIG. 50Cis an illustrative view of a text bubble for a threat in a Geomap in the GUI of FIG. 39A , in accordance with various embodiments of the disclosure.
- FIG. 50Dis an illustrative view of a text bubble for anomalies in a Geomap in the GUI of FIG. 39A , in accordance with various embodiments of the disclosure.
- FIG. 51is an illustrative view of an “Analytics Dashboard” in the GUI of FIG. 39A , in accordance with various embodiments of the disclosure.
- FIG. 52shows an example of a probabilistic suffix tree based model receiving a particular sequence (e.g., during training).
- FIG. 53shows an example timeline illustrating the training of a probabilistic suffix tree based model, the establishment of a baseline prediction profile, and the activation of a particular model version.
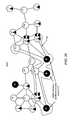
- FIG. 54Ashows an example of how a normal behavioral sequence may be represented in a probabilistic suffix tree based model.
- FIG. 54Bshows an example of how an unusual behavioral sequence may be discovered in a probabilistic suffix tree based model.
- FIG. 55Ashows an example user interface for displaying discovered anomalies.
- FIG. 55Bshows an example user interface displaying additional information about the user.
- FIG. 56shows an example user interface displaying results from comparing the marginal of the events for the anomalous window and the entire data for the user (e.g., baseline).
- FIG. 57shows an example overview of all the unusual sequence as a timeline.
- FIG. 58shows an example user interface for an administrator to interact with each timeline event.
- FIG. 59is a flowchart showing an example of an automated process for cluster identification from a graph.
- FIG. 60Ais a flowchart showing an example of an automated process for cluster identification from a bipartite graph.
- FIG. 60Bshows an example of minimizing the L1-norm values to find optimal positions for the normal nodes.
- FIG. 61Ashows an example use case corresponding to the cluster identification process for a generic graph, at a first stage of processing.
- FIG. 61Bshows an example use case corresponding to the cluster identification process for a generic graph, at a second stage of processing.
- FIG. 62illustrates an example use case corresponding to the cluster identification process for a bipartite graph.
- FIG. 63is a block diagram illustrating a machine learning model that detects lateral movement in a computer network.
- FIG. 64illustrates an example of a bipartite graph showing events of users logging into network devices.
- FIG. 65illustrates an example of a process of assigning similarity scores to network devices.
- FIG. 66Ashows an example of a bipartite graph having network devices that have many shared users and tend to have close similarity scores.
- FIG. 66Bshows an example of a bipartite graph having network devices that have multiple shared exclusive users.
- FIG. 66Cshows an example of a bipartite graph having network devices that have one shared user.
- FIG. 66Dshows an example of a bipartite graph having network devices that are associated with similar groups of users.
- FIG. 67illustrates an example of a graph data structure for detecting security threats based on a detected out-of-profile anomaly.
- FIG. 68is a high-level conceptual diagram of an example network traffic scenario for detecting anomalies indicative of malware on a computer network.
- FIG. 69is a high level flow diagram illustrating an example process for detecting an anomaly indicative of malware based on network traffic.
- FIG. 70shows two tables illustrating application of lexical analysis to a character-based entity identifier.
- FIG. 71shows an example incident response output configured for display to a user.
- FIG. 72shows an example graph of outgoing traffic from a network device.
- FIG. 73lists an example of a set of parameters that can be considered for distinguishing between machine-generated traffic and user-generated traffic.
- FIG. 74is a block diagram of an environment in which a system for detecting anomalies in machine-generated traffic can be implemented.
- FIG. 75is an example of a memory cache storing beacon types that are identified as likely to be anomalous.
- FIG. 76is a flow diagram of a process for determining whether outgoing traffic from a device is anomalous.
- FIG. 77is a flow diagram of a process for forming a group of connection requests from outgoing traffic of a device.
- FIG. 78is a flow diagram of a process for determining whether a particular group of connection requests in the outgoing traffic of a device is user-generated traffic or machine generated traffic.
- FIG. 79is a flow diagram of a process for determining whether machine-generated traffic is anomalous.
- FIG. 80is a block diagram of an environment in which a system for detecting anomalies based on rarity scores of features can be implemented.
- FIG. 81shows a table of example features and/or feature pairs to be considered for determining whether an example event is anomalous, consistent with various embodiments.
- FIG. 82shows a table listing example thresholds and/or parameters of a rarity criterion for various example events that can be used for determining whether an event is anomalous.
- FIG. 83is a flow diagram of an example process for determining an anomaly based on a rarity score for a particular value of a feature.
- FIG. 84is a flow diagram of an example process for determining a rarity score for a particular value of a feature.
- FIG. 85is a block diagram of a computing device that may be used to implement the techniques introduced here.
- references in this description to “an embodiment,” “one embodiment,” or the like,mean that the particular feature, function, structure or characteristic being described is included in at least one embodiment of the present disclosure. Occurrences of such phrases in this specification do not necessarily all refer to the same embodiment. On the other hand, the embodiments referred to also are not necessarily mutually exclusive.
- the example of a security platformis used, for illustrative purposes only, to explain various techniques that can be implemented by the data processing system.
- the techniques introduced hereare not limited in applicability to security applications, security information and event management (SIEM) applications, or to any other particular kind of application.
- SIEMsecurity information and event management
- at least some of the techniques introduced herecan be used for automated fraud detection and other purposes, based on machine data.
- the techniques introduced hereare not limited to use with security-related anomaly and threat detection; rather, the techniques can be employed with essentially any suitable behavioral analysis (e.g., fraud detection or environmental monitoring) based on machine data.
- machine datacan include performance data, diagnostic information and/or any of various other types of data indicative of performance or operation of equipment (e.g., an action such as upload, delete, or log-in) in a computing system, as described further below.
- machine dataas used herein includes timestamped event data, as discussed further below. Examples of components that may generate machine data from which events can be derived include: web servers, application servers, databases, firewalls, routers, operating systems, and software applications that execute on computer systems, mobile devices, sensors, Internet of Things (IoT) devices, etc.
- the data generated by such data sourcescan include, for example, server log files, activity log files, configuration files, messages, network packet data, performance measurements, sensor measurements, etc., which are indicative of performance or operation of a computing system in an information technology environment.
- kill chainmethodology to identify and stop the progression of malicious activities (e.g., from intrusion to lateral movement, and to exfiltration). These analysts need supporting evidence to make educated decisions in the kill chain, but traditional security products generally do not provide the support for such methodology.
- the security platformis “big data” driven and employs a number of machine learning mechanisms to perform security analytics. More specifically, the security platform introduced here can perform user behavioral analytics (UBA), or more generally user/entity behavioral analytics (UEBA), to detect the security related anomalies and threats, regardless of whether such anomalies and threats are previously known or unknown. Additionally, by presenting analytical results scored with risk ratings and supporting evidence, the security platform can enable network security administrators or analysts to respond to a detected anomaly or threat, and to take action promptly.
- UUAuser behavioral analytics
- UEBAuser/entity behavioral analytics
- the behavioral analytics techniques introduced hereenable the security platform to detect advanced, hidden and insider threats.
- the behavior analyticsleverage machine learning data processing procedures and do not require any preexisting knowledge such as known signatures or rules.
- the security platformcan also improve threat detection and targeted response by using a variety of threat indicators. Further, the security platform supplies supporting evidence within context of the kill chain to enable targeted remediation of any detected anomaly or threat.
- the security platformcan increase a security operations center's (SOC) efficiency with a number of rank-ordered lists having events in the context of a kill chain.
- the kill chaincan be linked from an anomaly or threat summary to the supporting information that is gathered over time. All generated security-related information can then be sent to a security information and event management (SIEM) application, such as the Splunk® App for Enterprise Security, to further scope, disrupt, contain and/or recover from the attack.
- SIEMsecurity information and event management
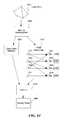
- FIG. 1shows a general environment 10 in which the security platform introduced here can be implemented.
- the environment 10may represent a networked computing environment of one or multiple companies or organizations, and can be implemented across multiple geographic regions.
- One or more elements in the environment 10are communicatively coupled to each other through a computer communications network, which can include the Internet and one or more wired or wireless networks (e.g., an Internet Protocol (IP)-based local area network (LAN), metropolitan area network (MAN) wide area network (WAN), a Wireless LAN (WLAN) network such as Wireless Fidelity (WiFi), and/or a cellular telecommunications network such as Global System for Mobile Communications (GSM) network, 3G network, or long term evolution (LTE) network).
- IPInternet Protocol
- LANlocal area network
- MANmetropolitan area network
- WANwide area network
- WiFiWireless Fidelity
- GSMGlobal System for Mobile Communications
- LTElong term evolution
- the computing devices shown in the environment 10can be, for example, a personal computer, a smart phone, a computer server, a notebook computer, or any other form of computing system or device that allows a user to access the information within the environment 10 .
- Each of the aforementioned computer systemscan include one or more distinct physical computers and/or other processing devices which, in the case of multiple devices, can be connected to each other through one or more wired and/or wireless networks.
- the security platformcan detect anomalies and threats produced by a user, a device, or an application, for example, regardless of whether the entity that causes the anomalies or threats is from outside or inside the organization's network.
- the security analytics techniques that can be adopted by the security platforminclude behavioral analytics that enable organizations of any size or skillset to detect and respond to unknown threats.
- Some specific examples that behavioral analytics can be based oninclude machine learning, behavior modeling, peer group analysis, classification, statistical models, and graph analysis. As introduced in more detail below, these analyses can utilize, for example, Markovian processing flows, inference and grouping processes, and risk scoring mechanisms to develop user and entity profiles in order to compare and contrast activities, which ultimately allow the platform to detect and expose anomalies and threats.
- the security platformcan include a graphical user interface (GUI) that can create visualizations of the detected anomalies and threats within an organization, and optionally, map the threats across an attack kill-chain in a visual way, which the security analysts in the organization can quickly and easily assimilate.
- GUIgraphical user interface
- the security platformcan be deployed at any of various locations in a network environment.
- a private networke.g., a corporate intranet
- at least part of the security platformcan be implemented at a strategic location (e.g., a router or a gateway coupled to an administrator's computer console) that can monitor and/or control the network traffic within the private intranet.
- a strategic locatione.g., a router or a gateway coupled to an administrator's computer console
- at least part of the security platformcan be implemented at, for example, the cloud-based servers.
- the security platformcan be implemented in a private network but nonetheless receive/monitor events that occur on the cloud-based servers.
- the security platformcan monitor a hybrid of both intranet and cloud-based network traffic. More details on ways to deploy the security platform and its detailed functionality are discussed below.
- the security platform introduced hereprovides a comprehensive solution to the security-related issues in a modern network environment.
- the security platform introduced hereis capable of handling large volumes of data, particularly machine data, from multiple data sources. These data sources may have different data formats and may provide data at very high data rates (e.g., gigabytes of data per second or more).
- incoming datais processed using machine learning/data science techniques to extract knowledge from large volumes of data that are structured or unstructured.
- data scienceis a continuation and expansion of the field of data mining and predictive analytics, also known as knowledge discovery and data mining (KDD).
- the security platformmay be cloud-based and may employ big data techniques to process a vast quantity of high data rate information in a highly scalable manner.
- the security platformmay be hosted in the cloud and provided as a service.
- the security platformis provided as a platform-as-a-service (PaaS).
- PaaSis a category of cloud computing services enabling customers to develop, run and manage Web applications without the complexity of building and maintaining the infrastructure typically associated with developing and launching such applications.
- PaaScan be delivered in at least two ways, namely: (i) as a public cloud service from a provider, wherein the consumer controls software deployment and configuration settings and the provider provides the networks, servers, storage devices and other services to host the consumer's application, or (ii) as software installed in private data centers or public infrastructure and managed by internal information technology (IT) departments.
- ITinformation technology
- Machine learningis employed in certain embodiments to make it unnecessary to know in advance what activity constitutes a security threat or a security threat signature. For example, a security threat may be discovered from the event data as the events occur even though that threat has not been seen before and no signature for that threat existed previously.
- security threatsare examples of a type of activity to be detected. It should be understood, however, that the security platform and techniques introduced here can be applied to detect any type of unusual or anomalous activity involving data access, data transfer, network access, and network use regardless of whether security is implicated or not.
- event datarefers to machine data related to activity on a network with respect to an entity of focus, such as one or more users, one or more network nodes, one or more network segments, one or more applications, etc.).
- incoming event data from various data sourcesis evaluated in two separate data paths: (i) a real-time processing path and (ii) a batch processing path.
- the evaluation of event data in these two data pathsoccurs concurrently.
- the real-time processing pathis configured to continuously monitor and analyze the incoming event data (e.g., in the form of an unbounded data stream) to uncover anomalies and threats.
- the evaluationis performed primarily or exclusively on event data pertaining to current events contemporaneously with the data being generated by and/or received from the data source(s).
- the real-time processing pathexcludes historical data (i.e., stored data pertaining to past events) from its evaluation.
- the real-time processing pathexcludes third-party data from the evaluation in the real-time processing path.
- eventis sometimes used synonymously with the term “event data” to mean a discrete set of machine data that represents or corresponds to a specific network activity, although “event” can also refer to the underlying activity itself, as will be apparent from context.
- an “anomaly”is a detected variation from an expected pattern of behavior on the part of an entity, which variation may or may not constitute a threat.
- An anomalyrepresents an event of possible concern, which may be actionable or warrant further investigation.
- An anomalyis an observable or detectable fact, or data representing such fact.
- An anomaly or a set of anomaliesmay be evaluated together and may result in a determination of a threat indicator or a threat.
- a threatis an interpretation of one or more anomalies and/or threat indicators. Threat indicators and threats are escalations of events of concern.
- hundreds of millions of packets of incoming event data from various data sourcesmay be analyzed to yield 100 anomalies, which may be further analyzed to yield 10 threat indicators, which may again be further analyzed to yield one or two threats.
- This manner of data scalingis one of the reasons the security platform can provide anomaly and threat detection in a real-time manner.
- historical data and third party datamay be used to create and improve the machine learning models employed to perform the evaluation; however, the amount of such historical data and/or third party data can be potentially much larger than the real-time data stream. As such, the actual evaluation of the historical data tends to be slower. Consequently, in certain embodiments, the real-time processing path does not use either or both the historical data and third party data as inputs. In other embodiments, historical and third party data may be used as inputs but the majority of the data used for evaluation in the real-time processing path still pertains to contemporaneous incoming event data. This is a consequence of the need to process the voluminous incoming event data quickly to obtain actionable threat information to prevent imminent harm.
- the anomalies and threats detected by the real-time processing pathmay be employed to automatically trigger an action, such as stopping the intrusion, shutting down network access, locking out users, preventing information theft or information transfer, shutting down software and or hardware processes, and the like.
- the discovered anomalies and threatsmay be presented to a network operator (e.g., a network security administrator or analyst) for decision.
- the decisions by the usere.g., that the anomalies and threats are correctly diagnosed, or that the discovered anomalies and threats are false positives
- batch processing pathhistorical data and third-party data are processed, optionally with the incoming real-time event data, to uncover, for example, more subtle anomalies and threats than the real-time processing path can uncover because of the real-time processing path's responsive time constraints.
- Batch processingmay occur synchronously with real-time processing or in accordance with a predefined schedule.
- Historical datarepresents past events and may include data from different instantiations of the real-time evaluators deployed in different locations in the network.
- the historical datamay span time and geography.
- only an abridged version of the incoming event datais analyzed in the real-time processing path while a more complete version is stored as historical data.
- the historical datamay, in one or more of these implementations, include event data that has more attributes than the abridged event data presented to the real-time processing path for evaluation.
- anomalies, threat indicators and threats discovered by the batch analyzermay be actionable automatically or may be presented to a human operator for decision on whether to take action.
- the action taken by the operator to validate or invalidate the conclusions reached by the batch analyzermay serve as a source of feedback to the security platform to improve its evaluation of subsequently processed data.
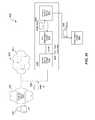
- FIG. 2illustrates a high level view of an example security platform 102 .
- a cloud computing infrastructureis shown, represented in part by a virtualization layer 104 .
- Various cloud computing operating systems or platformssuch as OpenStackTM, VMwareTM, Amazon Web ServicesTM, or Google CloudTM may be employed in virtualization layer 104 to create public clouds or private clouds.
- these cloud computing operating systems and otherspermit processing and storage to be implemented on top of a set of shared resources.
- cloud computingpermits or facilitates redundancy, fault tolerance, easy scalability, low implementation cost and freedom from geographic restrictions.
- the concept of cloud computing and the various cloud computing operating systems or infrastructuresare known.
- a software framework layer 106implements the software services executing on the virtualization layer 104 .
- software servicesinclude open-source software such as Apache HadoopTM, Apache SparkTM, and Apache StormTM.
- Apache HadoopTMis an open-source software framework for distributed storage and distributed processing of very large data sets on computer clusters built from commodity hardware.
- Apache StormTMis a distributed real-time computation engine that processes data stream record-by-record.
- Apache SparkTMis an large-scale data processing engine that collects events together for processing in batches.
- a security intelligence layer 100implements a security semantic layer 108 and a machine learning layer 110 .
- the security semantic layer 108performs the extract, transform, and load (ETL) functions that prepare the incoming event data for further processing by downstream consumers.
- ETLextract, transform, and load
- the machine learning layer 110represents one of the consumers of the data output of the security semantic layer 108 .
- event datamay be received by the security semantic layer 108 , and prepared (or “pre-processed”) to be further processed by the machine learning layer 110 .
- the application layer 114represents the layer in which application software modules may be implemented.
- the output of the machine learning layer 110includes anomalies, threat indicators, and/or threats. This output may be analyzed by the various applications such as a threat detection application 116 , a security analytics application 118 or other applications 120 .
- FIG. 3shows a high-level conceptual view of the processing within security platform 102 in FIG. 2 .
- a receive data block 202represents a logical component in which event data and other data are received from one or more data sources.
- receive data block 202includes application programming interfaces (APIs) for communicating with various data sources.
- An ETL block 204is the data preparation component in which data received from the receive data block 202 is pre-processed, for example, by adding data and/or metadata to the event data (a process interchangeably called decoration, enrichment or annotation herein), or otherwise prepared, to allow more effective consumption by downstream data consumers (e.g., machine learning models).
- the enriched event data from the ETL block 204is then provided to a real-time analyzer 210 over a real-time processing path 212 for detecting anomalies, threat indicators and threats.
- Output 214 from the real-time analyzer 210is provided for action by the human operator, in certain embodiments. It should be noted that the real-time analyzer 210 operates in real-time by analyzing event data as the event data received by the security platform 102 .
- the event data from the ETL block 204is also provided to a batch analyzer 240 over a batch processing path 242 for detecting anomalies, threat indicators and threats.
- the event datais provided to the real-time analyzer 210 in an unbounded, streaming, record-by-record manner, it is provided to the batch analyzer in the form of batches of event data (i.e., where each batch of event data contains a collection of events that arrived over the batch period).
- the batch analyzer 240processes data in batch mode instead of in real-time, in addition to the event data that the real-time analyzer 210 receives, the batch analyzer 240 can receive additional historical event data from the security platforms, prior analysis (including the analysis results, the model states, and the supporting data) from the real-time analyzer 210 (e.g., through a model management component 260 ), or prior analysis from other analyzers (real-time or batch) implemented elsewhere in the same or other networks.
- a machine learning and machine learning modelsare employed to evaluate and analyze data in certain embodiments, that is not necessarily the case in every embodiment.
- the security platformmay also adapt more appropriately or more efficiently to the environment by using a combination of other suitable forms of analysis, including rule-based analysis, algorithm-based analysis, statistical analysis, etc.
- FIG. 4illustrates an example of an overall architecture of the security platform 300 .
- Data sources 302represent various data sources that provide event data including machine data, to be analyzed for anomalies and threats.
- the event datarepresents events that take place in the network environment.
- data source 304is a source of data pertaining to logs including, for example, user log-ins and other access events. These records may be generated from operational (e.g., network routers) and security systems (e.g., firewalls or security software products).
- Data source 306is a source of data from different types of applications, including software as a service (e.g., BoxTM). Data source 306 may use different mechanisms for transmitting the event data, including a push mechanism, a pull mechanism, or a hybrid mechanism.
- Data source 306 categoryincludes human resource systems, accounting systems, customer relation databases, and the like.
- Data source 308is a source of network management or analyzer data (e.g., event data related to traffic on a node, a link, a set of nodes, or a set of links).
- the network management or analyzer datamay be obtained from various network operating systems and protocols, such as Cisco NetflowTM.
- Cisco NetflowTMThe data sources mentioned here are only examples, as other suitable data sources may also be used.
- the data sources 302provide event data to data receivers 310 , which implement various APIs and connectors to receive (or retrieve, depending on the mechanism) the event data for the security platform 300 .
- the data receivers 310may also optionally filter some of the event data. For example, to reduce the workload of the security platform, a business rule may be set to state that all query events to “www.google.com” should be filtered out as not interesting (e.g., this type of access is determined not to represent any security threat).
- Technologies employed to implement the data receiver 310may include FlumeTM and RESTTM. FlumeTM is an open-source distributed service for collecting, aggregating, and moving large amounts of log data. RESTTM is an interface for accessing large databases.
- the received datais then provided via a channel 314 to a semantic processor (or data preparation stage) 316 , which in certain embodiments performs, among other functions, ETL functions.
- the semantic processor 316may perform parsing of the incoming event data, enrichment (also called decoration or annotation) of the event data with certain information, and optionally, filtering the event data.
- the semantic processor 316 introduced hereis particularly useful when data received from the various data sources through data receiver 310 is in different formats, in which case the semantic processor 316 can prepare the data for more efficient downstream utilization (including, for example, by an event processing engine) while avoiding binding the unstructured data into any particular type of data structure.
- a parser in the semantic processor 316may parse the various fields of received event data representing an event (e.g., a record related to a log-in event).
- An identity resolution (IR) component(not shown in FIG. 4 ) may be optionally provided within the semantic processor 316 to correlate IP addresses with users, for example. This correlation permits the security platform to make certain assumptions about the relationship between an IP address and a user so that, if any event data arrives from that IP address in the future, an assumption regarding which user is associated with that IP address may be made. In some implementations, the event data pertaining to that IP address may be annotated with the identity of the user.
- Technology used to implement the data preparation functions of the semantic processor 316may include RedisTM
- An optional filter attribution block 322 in the semantic processor 316removes certain pre-defined events.
- the attribution filter 322 in the semantic processor 316may further remove events that need not be processed by the security platform.
- An example of such an eventis an internal data transfer that occurs between two IP addresses as part of a regular file backup.
- the functions of semantic processor 316are configurable by a configuration file to permit easy updating or adjusting. Examples of configurable properties of the semantic processor 316 include how to (i) parse events, (ii) correlate between users and IP address, and/or (iii) correlate between one attribute with another attribute in the event data or an external attribute.
- the configuration filecan also adjust filter parameters and other parameters in the semantic processor 316 .
- Data processed by the semantic processor 316is sent to a distribution block 320 .
- the distribution block 320can be a messaging mechanism to distribute data to one or both of the real-time processing path and the batch processing path.
- the real-time processing pathis entered via the right-facing arrow extending from the distribution block 320
- the batch processing pathis entered via arrow 388 extending downward from the distribution block 320 .
- the real-time processing pathincludes an analysis module 330 that receives data from the distribution block 320 .
- the analysis module 330analyzes the data in real-time to detect anomalies, threat indicators, and threats.
- the aforementioned StormTM platformmay be employed to implement the analysis module 330 .
- the analysis modulecould be implemented by using Apache Spark Streaming.
- topologies 332 and 334are illustrated in analysis module 330 .
- a topology in this contextis a specification of how an analysis module (e.g., module 330 ) groups and distributes work (e.g., to the different computation workers).
- a topologycan also specify how the analysis module 330 groups and distributes input data for the model-related process threads. More details on the analysis module 330 and topologies are discussed below in relevant sections.
- Different machine learning modelsmay evaluate different aspects of the pre-processed event data received from the distribution block 320 .
- the machine learning modelscan also generate security-related scores for the events.
- the results from the analysis module 330may be, for example, anomalies, threat indicators, and threats.
- a user interface (UI) system 350for review by a human operator 352 .
- UIuser interface
- a visualization map and a threat alertmay be presented to the human operator 352 for review and possible action.
- the output of the analysis module 330may also automatically trigger actions such as terminating access by a user, terminating file transfer, or any other action that may neutralize the detected threats.
- only notificationis provided from the analysis module 330 to the UI system 350 for review by the human operator 352 .
- the event data that underlies those notifications or that gives rise to the detection made by the analysis module 330are persistently stored in a database 378 .
- the human operatormay access from database 378 the event data (including raw event data and any associated information) that supports the anomalies or threat detection.
- the threat detectionis a false positive
- the human operator 352may so indicate upon being presented with the anomaly or the threat.
- the rejection of the analysis resultmay also be provided to the database 378 .
- the operator feedback information(e.g., whether an alarm is accurate or false) may be employed to update the model to improve future evaluation.
- Arrow 360represents the storing of data supporting the analysis of the anomalies and threats in the real-time path.
- the anomalies and threats as well as the event data that gives rise to detection of the anomalies and threatsmay be stored in database 378 (e.g., an SQL store) using a path represented by the arrow 360 . Additional information such as the version of the models, the identification of the models used, and the time that the detection is made, may also be stored.
- the human operator 352may review additional information in response to the notification presented by the UI system 350 .
- the data supporting the analysis of the anomalies and threatsmay be retrieved from database 378 via an access layer 364 .
- Arrow 362represents a data retrieval request via the access layer 364 to one or more of databases 370 , 372 , 374 and 378 .
- the data served up by the databaseswould be provided to the UI 350 by means of data pathway 380 .
- the access layer 364includes the APIs for accessing the various databases and the user interfaces in the UI 350 .
- block 366 Arepresents the API for accessing the HBase or HDFS (Hadoop File Service) databases.
- Block 366 Brepresents the various APIs compatible for accessing servers implementing sockets.io or node.js servers.
- SQL API 366 Crepresents the API for accessing the SQL data store 378 , which stores data pertaining to the detected threats and anomalies.
- Line 368is a conceptual line that separates the batch processing path (below line 368 ) from the real-time processing path (above line 368 ).
- the infrastructurewhich may operate in batch mode includes the SQL store 378 that stores information accessible by scripted query language (SQL), a time series database 370 that represents the database for storing time stamped data, an HBase 372 that can be an open-source, distributed, non-relational database system on which databases (e.g., the time serious database 370 ) can be implemented, and a GraphDB database 374 that stores security graphs 392 , which may be based on relationship graphs generated from events.
- the GraphDB database 374comprises a Neo4jTM graph database.
- a security graphis generally a representation of the relationships between entities in the network and any anomalies identified. For example, a security graph may map out the interactions between users, including information regarding which devices are involved, who or what is talking to whom/what, when and how interactions occur, which nodes or entities may be anomalous, and the like. The nodes of the security graph may be annotated with additional data if desired.
- a batch analysis module 382is the analysis module that processes data in batches.
- the analysis module 382may take into account the historical event data stored in databases 370 , 372 , 374 , and 378 (including “relatively” contemporary event data that is passed from distribution block 320 to the persistent layer below line 368 via network channel 388 ).
- the batch analysis module 382may employ third party data 384 . With more time allowance and more data available for analysis, the batch analysis module 382 may be able to uncover additional anomalies and threats that may not be easily detectable by the real-time analysis module 330 .
- the model management block 386includes a model store and a model registry.
- the model registrycan store model type definitions for machine learning models, and the model store can store model states for machine learning models. Additional details on the model registry and the model store are discussed below.
- Model state sharing 390may improve threat detection by various modules (e.g., two modules belonging to an international network of the same company, but one deployed in Asia and another one deployed in North America; or, one module being used in the real-time path and another in the batch path) as the model state sharing leverages knowledge learned from one module to benefit others.
- Security graphs 392may also be shared among modules, and even across different organizations. For example, activities that give rise to a detection of anomalies or a threat in one enterprise may thus be shared with other enterprises.
- Hadoop nodes 394represent the use of cloud-based big data techniques for implementing the architecture of FIG. 4 to improve scalability as well as the ability to handle a large volume of data.
- Control path 396represents the control software that may be used for monitoring and maintaining the security platform 300 .
- FIG. 5shows an example implementation of the real-time processing path in greater detail.
- the analysis module 330has been expanded as two analysis modules 330 A and 330 B to represent the anomaly detection stage and the threat detection stage, respectively.
- the analysis module 330 Ais responsible for detecting anomalies, and the output of the analysis module 330 A is provided to the analysis module 330 B for detecting threats based on the detected anomalies.
- the two stagesmay be performed by the same module utilizing different models in a staged manner.
- the output of analysis module 330 A, representing the anomalies,is provided to an anomaly writer 402 .
- the anomaly writer 402can store the anomalies (e.g., including event data representing an anomalous event and any associated information) in the database 378 .
- the same anomaliesmay also be stored in the time series database 370 and the HBase 372 .
- the anomaliesmay also be stored in the graph database 374 .
- the anomaliescan be stored in graph database 374 in the form of anomaly nodes in a graph or graphs; specifically, after an event is determined to be anomalous, an event-specific relationship graph associated with that event can be updated (e.g., by the anomaly writer 402 ) to include an additional node that represents the anomaly, as discussed further below.
- Certain embodiments of the security platformprovide the ability to aggregate, at a specified frequency (e.g., once a day), the individual event-specific relationship graphs from all the processed events in order to compose a composite relationship graph for a given enterprise or associated network.
- This aforementioned update to an individual event's relationship graphallows the composite relationship graph to include nodes representing anomalies, thereby providing more security-related information.
- the individual event-specific relationship graph and the composite relationship graphare discussed in more detail below.
- the information storedmay include the anomalies themselves and also relevant information that exists at the time of evaluation. These databases allow rapid reconstruction of the anomalies and all of their supporting data.
- the output from the analysis modules 330 B, representing threats,may be stored in the database 378 , the times series database 370 or the Hbase 372 . As in the case of anomalies, not only are the threats themselves stored, but relevant information that exists at the time of evaluation can also be stored.
- the batch analysis module 382can also operate in two stages for anomaly and threat detection in a similar fashion as discussed above with respect to the real-time analysis module 330 .
- UBAUser Behavior Analysis
- UEBAUser-Entity Behavior Analysis
- the security platform 300can detect anomalies and threats by determining behavior baselines of various entities that are part of, or that interact with, a network, such as users and devices, and then comparing activities of those entities to their behavior baselines to determine whether the activities are anomalous, or even rise to the level of threat.
- the behavior baselinescan be adaptively varied by the platform 300 as new data are received. These functions can be performed by one or more machine-learning models, for example, in the real-time path, the batch path, or both.
- FIG. 6shows an example representation of a process of building behavior baselines to support the detection of anomalies.
- a human end user 602may employ a server 606 to access a source code server 610 for his work, for example. Assume that the human user 602 occasionally accesses the data stored in servers 608 .
- the security platform 300can generate a baseline profile 612 for access activities of user 602 , based on event data indicative of network activities of user 602 .
- a human administrative user 604 other than user 602may employ the server 606 to access the data stored in the servers 608 .
- a baseline profile 614 specific for access activities of user 604can also be generated over time by the security platform 300 , based on event data indicative of network activities of user 604 .
- the security platform 300can create a behavior baseline for any type of entity (for example, a user, a group of users, a device, a group of devices, an application, and/or a group of applications).
- entityfor example, a user, a group of users, a device, a group of devices, an application, and/or a group of applications.
- the activities of server 606are monitored and a baseline profile 616 specific for the server 606 is generated over time, based on event data indicative of network activities of server 606 .
- Baseline profilescan be continuously updated (whether in real-time as event data streams in, or in batch according to a predefined schedule) in response to received event data, i.e., they can be updated dynamically and/or adaptively based on event data. If the human user 604 begins to access source code server 610 more frequently in support of his work, for example, and his accessing of source code server 610 has been judged to be legitimate by the security platform 300 or a network security administrator (i.e., the anomalies/threats detected upon behavior change have been resolved and deemed to be legitimate activities), his baseline profile 614 is updated to reflect the updated “normal” behavior for the human user 604 .
- anomalies and threatsare detected by comparing incoming event data (e.g., a series of events) against the baseline profile for an entity to which the event data relates (e.g., a user, an application, a network node or group of nodes, a software system, data files, etc.). If the variation is more than insignificant, the threshold for which may be dynamically or statically defined, an anomaly may be considered to be detected.
- the comparisonmay be based on any of various techniques, for example, time-series analysis (e.g., number of log-ins per hour), machine learning, or graphical analysis (e.g., in the case of security graphs or security graph projections).
- this detectionis performed by various machine learning models.
- security platformincluding, for example, the data intake and preparation engine, event processing engine, configurations for real-time implementations, configurations for batch implementation, machine learning models and different applications, various kinds of anomaly and threat detections, and graphic user interfaces for presenting security-related issues.
- FIGS. 7A and 7Bcollectively show a table 700 listing example types of machine data that can be generated in different environments and the meaning of these data.
- machine datacan include performance data, diagnostic information and/or any of various other types of data indicative of performance or operation of equipment (e.g., an action such as upload, delete, or log-in) in a computing system.
- Such datacan be analyzed to diagnose equipment performance problems, monitor user actions and interactions, and to derive other insights like user behavior baseline, anomalies and threats.
- machine datamay contain a record (e.g., a log) of an event that takes place in the network environment, such as an activity of a customer, a user, an transaction, an application, a server, a network or a mobile device.
- a recorde.g., a log
- machine datacan be more than mere logs—it can include configurations, data from APIs, message queues, change events, the output of diagnostic commands, call detail records, sensor data from industrial systems, and so forth.
- an eventmay refer to the actual event or activity that takes place in the network, or for the simplicity of the discussion, it may refer to the machine data (or “event data”) that records, corresponds to, or otherwise represents the event.
- event dataor “event data”
- extract dataor “event data”
- extract-transform-load (ETL) stagethe data intake and preparation stage disclosed here is not limited to traditional ETL techniques.
- the data intake and preparation stageincludes an ETL engine/pipeline, but also includes/performs other functions beyond or different from a traditional ETL stage, as henceforth described herein. Consequently, the term “data pre-processing” is used interchangeably with “data preparation,” and is intended to include any combination of data extraction, transformation, annotation/supplementation, and/or other additional techniques introduced here.
- stageas in the data intake and preparation stage, may also be referred to as “engine.”
- Events occurring in a computer networkmay belong to different event categories (e.g., a firewall event, a threat information, a login event) and may be generated by different machines (e.g., a CiscoTM router, a HadoopTM Distributed File System (HDFS) server, or a cloud-based server such as Amazon Web ServicesTM (AWS) CloudTrailTM). Therefore, machine data can come in many different formats, at least some of which may not be predictable.
- Traditional monitoring and analysis toolsare not designed for the variety, velocity, volume or variability of such a data environment.
- different kinds of event data typescan contain different information. Generally, the higher the communication layer (in terms of the well-known open system interconnection (OSI) model) to which an event belongs, the richer the information that event contains.
- OSIopen system interconnection
- a network packet logmay only include information on which machine communicates with which other machine(s); in contrast, an application log may have the richest information, thereby having a higher value. Particularly, in an application log, not only is it possible to obtain information on which machine is communicating with which other machine(s), but it is also possible to ascertain what kind of information these machines are sharing.
- session layer datamay be used to identify (e.g., via techniques disclosed here) which user is attempting to log in with what credential and using which particular session, and therefore would be more valuable than lower-level network layer data.
- a typical computer networkhas significantly more lower-level layer data than higher-level layer data. Therefore, as the variety, velocity, and volume of the data in the environment greatly increase, traditional monitoring and analysis systems either simply ignore a large portion of the data, or they quickly become overloaded by the data, thereby losing accuracy and responsiveness.
- the security platform introduced hereincludes various aspects that are specifically tailored to this data environment, including techniques for obtaining different kinds of data, preparing data, and processing data, by using different stages, to enable quick diagnosis of service problems, detection of sophisticated security threats, understanding of the health and performance of remote equipment, and demonstration of compliance.
- FIG. 8shows an example implementation of a data intake and preparation stage 800 of the security platform.
- the data intake and preparation stage (or engine) 800can be an implementation of ETL stage 204 in FIG. 3 and/or semantic processor 316 in FIG. 5 .
- the data intake and preparation stage 800can include a number of components that perform a variety of functions disclosed herein.
- the data intake and preparation stage of the security platformincludes a number of data connectors 802 , a format detector 804 , a number of parsers 806 , a field mapper 808 , a relationship graph generator 810 , an identity resolution module 812 , a number of decorators 814 , and event view adder 816 .
- componentse.g., sets of instructions
- these componentsneed not be implemented as separate software programs, procedures or modules, and thus various subsets of these components may be combined or otherwise rearranged in various embodiments.
- the components shown in FIG. 8are only one example of the data intake and preparation stage components that can be used by the security platform; the data intake and preparation stage could have more or fewer components than shown, or a different configuration of components.
- the various components shown in FIG. 8can be implemented by using hardware, software, firmware or a combination thereof, including one or more signal processing and/or application specific integrated circuits.
- the components in the stage 800are shown arranged in a way that facilitates the discussion herein; therefore, any perceivable sequence in the stage 800 is merely an example and can be rearranged. Any step in the stage 800 may be performed out-of-sequence and/or in parallel to the extent that such rearrangement does not violate the logic dependency of the steps.
- One or more steps described for the stage 800may be optional, depending on the deployed environment.
- the data output from the data intake and preparation stage 800can also be referred to herein as “decorated events” or “event feature sets.”
- a decorated eventincludes the raw machine data associated with an event, plus any decoration, enrichment, information, or any other suitable intelligence that is generated based upon or extracted from the event during the data intake and preparation stage.
- the data intake and preparation enginemay be implemented separately from the rest of the stages in the security platform, for example, on a standalone server or on dedicated nodes in a distributed computer cluster.
- Various data connectors 802can be employed by the security platform (e.g., at the data intake stage) to support various data sources.
- Embodiments of the data connectors 802can provide support for accessing/receiving indexed data, unindexed data (e.g., data directly from a machine at which an event occurs), data from a third-party provider (e.g., threat feeds such as NorseTM, or messages from AWSTM CloudTrailTM), or data from a distributed file system (e.g., HDFSTM).
- the data connectors 802enable the security platform to obtain machine data from various different data sources.
- Some example categories of such data sourcesinclude:
- Identity/Authenticatione.g., active directory/domain controller, single sign-on (SSO), human resource management system (HRMS), virtual private network (VPN), domain name system (DNS), or dynamic host configuration protocol (DHCP);
- SSOsingle sign-on
- HRMShuman resource management system
- VPNvirtual private network
- DNSdomain name system
- DHCPdynamic host configuration protocol
- Activitye.g., web gateway, proxy server, firewall, NetflowTM, data loss prevention (DLP) server, file server, or file host activity logs;
- DLPdata loss prevention
- Security Productse.g., endpoint security, intrusion prevention system, intrusion detection system, or antivirus;
- SaaSSoftware as a Service
- Mobilee.g., AWSTM CloudTrailTM, SaaS applications such as BoxTM or DropboxTM, or directly from mobile devices; and
- External Threat Feedse.g., NorceTM, TreatStreamTM, Financial Services Information Sharing and Analysis Center (FS-ISAC)TM, or third-party blacklisted IP/domains.
- FS-ISACFinancial Services Information Sharing and Analysis Center
- external threat feedsmay directly feed to the security platform, or indirectly through one or more security products that may be coexisting in the environment within which the security platform is deployed.
- heterogeneous eventrefers to the notion that incoming events may have different characteristics, such as different data formats, different levels of information, and so forth. Heterogeneous events can be a result of the events originating from different machines, different types of machines (e.g., a firewall versus a DHCP server), being in a different data format, or a combination thereof.
- the data connectors 802can implement various techniques to obtain machine data from the data sources. Depending on the data source, the data connectors 802 can adopt a pull mechanism, a push mechanism, or a hybrid mechanism. For those data sources (e.g., a query-based system, such as Splunk®) that use a pull mechanism, the data connectors 802 actively collect the data by issuing suitable instructions to the data sources to grab data from those data sources into the security platform. For those data sources (e.g., ArcSigntTM) that use a push mechanism, the data connectors 802 can identify an input (e.g., a port) for the data sources to push the data into the system.
- an inpute.g., a port
- the data connectors 802can also interact with a data source (e.g., BoxTM) that adopts a hybrid mechanism.
- a data sourcee.g., BoxTM
- the data connectors 802can receive from the data source a notification of a new event, acknowledges the notification, and at a suitable time communicate with the data source to receive the event.
- the queriescan be specifically tailored for real-time (e.g., in terms of seconds or less) performance. For example, some queries limit the amount of the anticipated data by limiting the query to a certain type of data, such as authentication data or firewall related data, which tends to be more relevant to security-related issues. Additionally or alternatively, some queries may place a time constraint on the time at which an event takes place.
- the data connectors 802can obtain data from a distributed file system such as HDFSTM. Because such a system may include a large amount of data (e.g., terabytes of data or more), it is preferable to reduce data movement so as to conserve network resources. Therefore, some embodiments of the data connectors 802 can generate a number of data processing jobs, send the jobs to a job processing cluster that is coupled to the distributed file system, and receive the results from the job processing cluster. For example, the data connectors 802 can generate MapReduceTM jobs, and issue those jobs to a job processing cluster (e.g., YARNTM) that is coupled to the distributed file system. The output of the job processing cluster is received back into the security platform for further analysis, but in that case, no or very little raw machine data is moved across the network. The data is left in the distributed file system. In some examples, the generated jobs are user behavior analysis related.
- the format detector 804can be used to detect the data format of the input data. For example, the format detector 804 can perform pattern matching for all known formats to determine the most likely format of a particular event data. In some instances, the format detector 804 can embed regular expression rules and/or statistical rules in performing the format detection. Some examples of the format detector 804 employ a number of heuristics that can use a hierarchical way to perform pattern matching on complex data format, such as an event that may have been generated and/or processed by multiple intermediate machines.
- the format detector 804is configured to recursively perform data format pattern matching by stripping away a format that has been identified (e.g., by stripping away a known event header, like a Syslog header) in order to detect a format within a format.
- the format detector 804can determine what data format the input data may be at run time.
- the formats of the machine dataare known in advance (e.g., an administrator would know what kind of firewall is deployed in the environment). Therefore, as long as the data source and the data format are specified, the data intake and preparation stage can map the data according to known data formats of a particular event source, without the need of performing data format detection.
- the security platformcan prompt (e.g., through a user interface) the administrator to specify the data format or the type of machine(s) the environment includes, and can automatically configure, for example, the parsers 806 in the data intake and preparation stage for such machines.
- the security platformprovides a way to easily supporting new data format.
- the administratorcan create a new configuration file (e.g., a configuration “snippet”) to customize the data intake and preparation stage for the environment.
- the configuration filecan identify, in the received data representing an event, which field represents a token that may correspond to a timestamp, an entity, an action, an IP address, an event identifier (ID), a process ID, a type of the event, a type of machine that generates the event, and so forth.
- IDevent identifier
- the security platformallows an administrator to leverage an existing tokenizer/parser by changing the configuration file, or to choose to implement a new, customized parser or tokenizer.
- the administratorcan also identify, for example, field mappings, decorators, parameters for identity resolution (IR), and/or other parameters of the data intake and preparation stage.
- the configuration snippetcan be monitored and executed by the data intake and preparation engine on the fly to allow the an administrator to change how various components in the data intake and preparation engine functions without the need to recompile codes and/or restart the security platform.
- the parsers 806parse the event data according to a predetermined data format.
- the data formatcan be specified in, for example, the configuration file.
- the data formatcan be used for several functions.
- the data formatcan enable the parser to tokenize the event data into tokens, which may be keys, values, or more commonly, key-value pairs. Examples of supported data format include event data output from an active-directory event, a proxy event, an authentication event, a firewall event, an event from a web gateway, a virtual private network (VPN) connection event, an intrusion detection system event, a network traffic analyzer event, or an event generated from a malware engine.
- VPNvirtual private network
- Each parsercan implement a set of steps.
- the initial stepscan including using regular expression to perform extraction or stripping. For example, if the data is a system log (syslog), then a syslog regular expression can be first used to strip away the packet of syslog (i.e., the outer shell of syslog) to reveal the event message inside. Then, the parser can tokenize the event data into a number of tokens for further processing.
- syslog regular expressioncan be first used to strip away the packet of syslog (i.e., the outer shell of syslog) to reveal the event message inside. Then, the parser can tokenize the event data into a number of tokens for further processing.
- the field mapper 808can map the extracted tokens to one or more corresponding fields with predetermined meanings.
- the data formatcan assist the field mapper 808 to identify and extract entities from the tokens, and more specifically, the data format can specify which of the extracted tokens represent entities.
- the field mapper 808can perform entity extraction in accordance with those embodiments that can identify which tokens represent entities.
- An entitycan include, for example, a user, a device, an application, a session, a uniform resource locator (URL), or a threat.
- the data formatcan also specify which tokens represent actions that have taken place in the event.
- an actioncan be performed by one entity with respect to another entity; examples of an action include use, visit, connect to, log in, log out, and so forth.
- the filed mapper 808can map a value extracted to a key to create a key-value pair, based on the predetermined data format.
- the entity extraction performed by the field mapper 804enables the security platform to gain potential insight on the environment in which the security platform is operating, for example, who the users are, how many users there may be in the system, how many applications that are actually being used by the users, or how many devices there are in the environment.
- FIGS. 9A and 9Bshow an example event relationship discovery and recordation technique, which can be implemented in the data intake and preparation stage. To facilitate description, FIGS. 9A and 9B are explained below with reference to FIG. 8 .
- the relationship discovery and recordation techniquecan be performed by, for example, the relationship graph generator 810 .
- the relationship graph generator 810is operable to identify a number of relationships between the entities, and to explicitly record these relationships between the entities.
- Some implementations of the relationship graph generator 810generate a single relationship graph for each event; such an event-specific relationship graph may also be called a “mini-graph.” Further, some implementations incorporate the generated relationship graph into the event data that represents the event, in the form of a data structure representing the relationship graph.
- a graph in the context of this descriptionincludes a number of nodes and edges.
- Each node in the relationship graphrepresents one of the entities involved in the event, and each edge represents a relationship between two of the entities.
- any eventinvolves at least two entities with some relationship between them (e.g., a device and a user who accesses the device) and therefore can be represented as an event-specific relationship graph.
- the graph generator 810can identify a relationship between entities involved in an event based on the actions that are performed by one entity with respect to another entity. For example, the graph generator 810 can identify a relationship based on comparing the action with a table of identifiable relationships. Such a table of identifiable relationship may be customizable and provides the flexibility to the administrator to tailor the system to his data sources (described above).
- Possible relationshipscan include, for example, “connects to,” “uses,” “runs on,” “visits,” “uploads,” “downloads,” “successfully logs onto,” “restarts,” “shuts down,” “unsuccessfully attempts to log onto,” “attacks,” and “infects.”
- the identified relationship between the entitiescan be indicative of the action, meaning that the identifiable relationship can include the action and also any suitable inference that can be made from the action. For example, an event that records a GET command (which is an action) may indicate that the user is using a machine with a certain IP address to visit a certain website, which has another IP address.
- identifiable relationshipscan be directly correlated to the size of the graph, which may impact the security platform's responsiveness and performance.
- identifiable relationshipscan include a relationship between entities of the same type (e.g., two users) or entities of different types (e.g., user and device).
- a portion of the configuration filecan specify, for the relationship graph generator 810 , that an edge is to be created from an entity “srcUser” to another entity “sourceIP,” with a relationship that corresponds to an event category to which the event belongs, such as “uses.”
- FIG. 9Aillustrates raw event data 900 received by the data intake and preparation stage.
- the raw event data 900representing an event that occurs, are log data generated by a web gateway server.
- the web gatewayis located where network traffic in and out the environment goes through, and therefore can log the data transfer and web communication from a system inside the environment.
- the particular event as represented by the event data 900indicates that, at a particular point of time identified by the timestamp, the user “psibbal” uses the IP address “10.33.240.240” to communicate with an external IP address “74.125.239.107,” and transfers 106 bytes of data.
- the status code of that eventis “200,” and the event is a TCP event where the HTTP status is “GET.”
- the event data 900also includes a significant amount of additional information.
- the graph generator 810can readily identify that the event represented in the FIG. 9A involves a number of entities, such as the user “psibbal,” the source IP “10.33.240.240,” the destination IP “74.125.239.107,” and an URL “sample.site.com.”
- the graph generator 810also identifies that an action “GET” is involved in the event. Accordingly, the graph generator 810 can compare the action to the table of identifiable actions, identify one or more relationships between the entities, and create an event-specific relationship graph 902 based on the event. As shown in FIG. 9B , the relationship graph 902 includes the entities that are involved in the events.
- the relationship graph 902also includes edges that link the nodes representing entities.
- the identified relationships between the entitiesare the edges in the graph 902 .
- the relationship graph 902can be stored in known data structures (e.g., an array) suitable for representing graphs that have nodes and edges.
- the components introduced heremay be tailored or customized to the environment in which the platform is deployed.
- the network administratorwishes to receive data in a new data format, he can edit the configuration file to create rules (e.g., in the form of functions or macros) for the particular data format including, for example, identifying how to tokenize the data, identifying which data are the entities in the particular format, and/or identifying the logic on how to establish a relationship.
- the data input and preparation stagethen can automatically adjust to understand the new data format, identify identities and relationships in event data in the new format, and create event relationship graphs therefrom.
- the graph generator 810attaches the relationship graph 902 to the associated event data 900 .
- the graph 902may be recorded as an additional field of the event data 900 .
- the relationship graph 902can be stored and/or transferred individually (i.e., separate from the event data 900 ) to subsequent nodes in the security platform.
- the event data 900 including the relationship graph 902can be sent to a distributed messaging system, which may be implemented based on Apache KafkaTM.
- the messaging systemcan in turn send the event data 900 to an event processing engine (e.g., a machine learning model execution and analytics engine, such as the complex event processing engine introduced here and described further below) for further processing.
- an event processing enginee.g., a machine learning model execution and analytics engine, such as the complex event processing engine introduced here and described further below
- the event processing engineis operable to use machine learning models to perform analytics based on the events and, in some instances, in conjunction with their associated relationship graphs, to security-oriented anomalies and threats in the environment.
- the messaging systemcan also accumulate or aggregate, over a predetermined period of time (e.g., one day), all the relationship graphs that are generated from the events as the events come into the security platform.
- a predetermined period of timee.g., one day
- certain types of behavioral anomalies and threatscan become more readily identifiable when multiple events are compared together, and sometimes such comparison may even be the only way to identify the anomalies and/or threats.
- a beaconing anomalyhappens when there is a device in the network that communicates with a device outside the network in an unexpected and (mostly) periodic fashion, and that anomaly would become more identifiable when relationship graphs associated with all the device's related beacons are combined into a composite relationship graph.
- the relationship graphsfor all events, or at least for multiple events, can be combined into a larger, composite relationship graph.
- a computer program or a servercan be coupled to the messaging system to perform this process of combining individual relationship graphs into a composite relationship graph, which can also be called an enterprise security graph.
- the composite relationship graph or enterprise security graphcan be stored, for example, as multiple files, one file for each of multiple predetermined time periods. The time period depends on the environment (e.g., the network traffic) and the administrator.
- the composite relationship graphis stored (or “mined” in data mining context) per day; however, the graph mining time period can be a week, a month, and so forth.
- event-specific relationship graphsare merged into the composite relationship graph on an ongoing basis, such that the composite relationship graph continuously grows over time.
- the nodes and edges of the composite graphare written to time namespaces partitioned graph files. Then, each smaller segment can be merged with a master partition (e.g., per day). The merge can combine similar nodes and edges into the same record, and in some embodiments, can increase the weight of the merged entity nodes. Note that the exact order of the events' arrival becomes less important, because even if the events arrive in an order that is not the same as how they actually took place, as long as the events have timestamps, they can be partitioned into the correct bucket and merged with the correct master partition. Some implementations provide that the composite graphs can be created on multiple nodes in a parallelized fashion.
- this composite relationship graphcan include all identified relationships among all identified entities involved in the events that take place over the predetermined period of time. As the number of events received by the security platform increases, so does the size of this composite relationship graph. Therefore, even though a relation graph from a single event may not carry much meaning from a security detection and decision standpoint, when there are enough events and all the relationship graphs from those events are combined into a composite relationship graph, the composite relationship graph can provide a good indication of the behavior of many entities, and the quality/accuracy of this indication increases over time as the composite relationship graph grows.
- the subsequent processing stagescan use models to perform analytics on the composite relationship graph or on any particular portion (i.e., “projection”, discussed further below) of the composite relationship graph.
- the composite relationship graphis persistently stored using a distributed file system such as HDFSTM.
- each such event's relationship graphcan be further updated with any information (e.g., anomalies) that is discovered by downstream processes in the security platform. For example, if an event is found to be an anomalous, then the relationship graph associated with that anomalous event can be updated to include this information. In one example, the individual relationship graph of that anomalous event is revised to include an anomaly node (along appropriate edges), so that when the composite relationship graph is created, it can be used to determine what other entities might be involved or affected by this anomaly.
- anomaliese.g., anomalies
- the composite graphenables the security platform to perform analytics on entity behaviors, which can be a sequence of activities, a certain volume of activities, or can be custom defined by the administrator (e.g., through a machine learning model).
- entity behaviorscan be a sequence of activities, a certain volume of activities, or can be custom defined by the administrator (e.g., through a machine learning model).
- the relationship graph generator 810can enable the analytics engines introduced here (e.g., the complex processing engine) to employ various machine learning models, which may focus on different portions or aspects of the discovered relationships between all the events in the environment, in order to detect anomalies or threats.
- FIG. 10shows an example identity resolution technique based on the information in the events, which can be implemented in the data intake and preparation stage described above. To facilitate description, FIG. 10 is explained below with reference to FIG. 8 .
- Identity resolutioncan be performed by, for example, the identity resolution module 812 . Specifically, after the entities are identified in the tokens, the identity resolution module 812 is operable to perform an identity resolution, which enables keeping track of which user logged into which particular computer system or device across the network.
- one traditional techniquemay be a simple lookup, such as where the administrator maintains a resource attribution file that records a particular IP address belongs to a particular person.
- a resource attribution filethat records a particular IP address belongs to a particular person.
- such a fileis often hard to keep accurate and easily becomes obsolete, especially when the amount of the devices in the environment is very large, as is often the case in today's environment.
- the security platform introduced herecan perform identity resolution based on the facts.
- the identity resolution module 812can gain the knowledge by observing the system environment (e.g., based on authentication logs), thereby building the intelligence to make an educated identity resolution determination. That is, the identity resolution module 812 is able to develop user identity intelligence specific and relevant to the system's environment without any explicit user identity information.
- the identity resolution module 812can utilize a machine learning model to generate and track a probability of association between a user and a machine identifier. Specifically, after the entities in event data that represents an event are extracted (e.g., by the field mapper 808 ), the identity resolution module 812 can identify whether the event data includes a user identifier and/or a machine identifier, and can create or update the probability of association accordingly. As is discussed in more detail in other sections of this disclosure, the model initiated by the identity resolution module 812 can, in some embodiments, obtain the information it needs, e.g., obtaining machine identifiers in an event, through one or more interfaces.
- a machine identifieris an identifier that can be associated with a machine, a device, or a computing system; for example, a machine identifier can be a media access control (MAC) address, or an Internet Protocol (IP) address. Different machine identifiers can be generated by the same machine.
- a user identifieris an identifier that can be associated with a user; for example, a user identifier can be a user login identifier (ID), a username, or an electronic mail address.
- IDuser login identifier
- some embodiments of the identity resolution module 812can resolve a user identity of a particular user by, for example, querying a database using a user identifier as a key.
- the databasewhich may be a human resource management system (HRMS), can have records indicating a number of user identifiers that are registered to the user identity.
- HRMShuman resource management system
- a user identifiermay be directly treated as a user for simpler implementation, even though such implementation may not be an ideal one because behaviors of the same user may not be detected because the user has used different user identifiers.
- a machine learning modelcan have different phases, for example, a training phase (after initiation and before ready) and an active phase (after ready and before expiration).
- a training phase of a machine learning modelif an event that is received involves both a user and a machine identifier (e.g., if the event data representing the event has both a user identifier and a machine identifier), then machine learning model that is employed by the identity resolution module 812 can use this event to create or update the probability of association between the user and the machine identifier.
- an authentication evente.g., when a user logs into a particular machine
- a usere.g., identified by a user identifier such as a username
- a machine identifiersuch as a username
- the modellearns that the user is now associated with the machine identifier, at least for a period of time until the user logs out or times out from the particular machine.
- the identity resolution module 812creates a probabilistic graph to record a probability of association for each user it is currently tracking.
- the probabilistic graphcan include peripheral nodes, a center node, and edges.
- An example of such probabilistic graph 1000is shown in FIG. 10 .
- nodes 1004 , 1006 , 1008 , and 1010are the peripheral nodes representing the machine identifiers.
- Node 1002is the center node representing the user. Edges between each peripheral node and the center node represent the probability of association between the particular machine identifier and the user.
- the machine learning models used for identification resolutionare user specific.
- the machine learning models used in the identity resolutionare generally simpler than those models that would be used for anomaly and threat detection.
- the models that are used in the identity resolution and/or device resolutionare time-sequenced probabilistic graphs, in which the probability changes over time.
- the models that are used to generate and track the probability of association between each user and possible machine identifiersare time-dependent, meaning that a result from the models has a time-based dependence on current and past inputs.
- the time dependenceis useful to capture the scenario where a device is first assigned or given to a particular user, and is subsequently reassigned to a different user, which happens often in a large organization.
- the identity resolution module 812can initiate, for a given user, different versions of the machine learning model at different point of time, and each version may have a valid life time. As events related to the given user arrive, versions of a machine learning model are initiated, trained, activated, (optionally) continually updated, and finally expired.
- the modelscan be trained and, in some implementations, continually updated after their activation, by relevant events when the events are received.
- An example of a relevant eventis an authentication event, which inherently involves a user (e.g., which may be represented by a user identifier) and a number of machine identifiers (e.g., an IP address or a MAC address).
- other criteria for an event to be considered relevant for model training and/or updating purposesmay include, for example, when a new event includes a particular machine identifier, a particular user identifier, and/or the recency of the new event.
- some modelsmay assign a different weight to the new event based on what type of event it is. For example, given that the new event is an authentication event, some models assign more weight to a physical login type of authentication event than to any other type of authentication event (e.g., a remote login).
- the machine learning modelcan be considered trained and ready when one or more criteria are met.
- a version of the modelcan be considered trained when a certain number of events have gone through that version of the model.
- a version of the modelcan be considered trained when a certain time period has passed after the version of the model is initiated.
- a version of the modelis considered trained when a certain number of criteria are met (e.g., when the model becomes sufficiently similar to another model). Additional details of machine learning models that can be employed (including training, readiness, activation, and expiration) by various engines and components in the security platform are discussed in other sections of this disclosure.
- the identity resolution module 812After a version of a model is sufficiently trained (e.g., when the probability of association exceeds a confidence threshold, which depends on the model's definition and can be tuned by the administrator for the environment), the identity resolution module 812 then can activate the version of the model. Thereafter, when a new event arrives, if the new event meets certain criteria for the identity resolution, the identity resolution module 812 can create a user association record (e.g., in memory) indicative that the new event is associated with a particular user.
- the criteria for the identity resolutioncan include, for example, when the new event includes a machine identifier (regardless of whether it also includes a user identifier), and/or when the new event is received during a time period which the version is active. It is observed that the identity resolution technique is especially useful to help identify an event that includes only a machine identifier but no user identifier.
- the identity resolution module 812can annotate the new event to explicitly connect the new event to the particular user. For example, the identity resolution module 812 can add, as a field, the particular user's name to the new event in its associated event data. Alternatively, the identity resolution module 812 can annotate the new event by adding a user identifier that belongs to the particular user. In addition, the identity resolution module 812 can send the user association record to a cache server that is implemented based on RedisTM.
- the security platformhas the ability to attribute an event that happens on a device to a user, and to detect behavioral anomalies and threats based on that attribution.
- the security platformcan achieve this without the need of maintaining an explicit look-up file and irrespective of what the data source is (i.e., regardless of whether a data source for an event includes a user identifier or not).
- an embodiment of the data intake and preparation stagecan also implement a device resolution module to create an association between one machine identifier and another.
- the device resolution modulecan track the possibility of association between a first machine identifier and a second machine identifier. Thereafter, when a new event is received, if the event includes the first machine identifier but not the second, the device resolution module can create a machine association record indicative that the new event having the first machine identifier is associated with the second machine identifier.
- the machine identifiercan be translated into a more user-friendly machine name, such as “Tony's Laptop.”
- the device resolution techniquecan be particularly useful in an environment that includes a dynamic host configuration protocol (DHCP) service, and therefore a computer in the environment does not have a static IP address. Because the same computer can potentially get a different IP address each time it starts in such environment, naively attributing a behavior to a particular IP address may lead to incorrect analysis.
- the device resolutioncan create a mapping between, for example, a MAC address and an IP address, which can remain valid for a period of time.
- One example of events where the relationship between a MAC address and an IP address can be foundis the DHCP logs.
- identity resolutionsuch machine identifier mapping can be dynamically updated as the time goes by and more events are received.
- the device resolution modulecan derive a new mapping, meaning that the same IP address can become associated with a different, updated MAC address. Note that, for the particular case of DHCP services, it is generally easier to estimate when a particular version of a device resolution model should expire, because a DHCP service setting typically includes explicit lease expiration provisions.
- the data intake and preparation stagecan also include additional event decorators 814 . Similar to how a format detector 804 may be customized or how a new format detector may be added, the event decorators 814 can be in the form of software code (e.g., in JavaTM) written by a third-party (e.g., the administrator) or can be added/configured through the configuration snippet. In some embodiments, the event decorators 814 can include a geographical decorator, which can be configured to decorate the received events (e.g., by adding a field in the event data that represents the events) so all events with an IP address receive an additional field about their respective IP's geographical location.
- a geographical decoratorcan be configured to decorate the received events (e.g., by adding a field in the event data that represents the events) so all events with an IP address receive an additional field about their respective IP's geographical location.
- the event decorators 814can include a server identifier, which can explicitly annotate an event when the event is from a server.
- the server identifiercan implement a look-up technique in order to identify that a machine is being used as a server, or it can implement heuristics and make a determination based on how many users have logged into it within a predetermined time period.
- Other examples of the event decorators 814can include a Whois Lookup, Whitelisting, and so forth.
- FIG. 11shows a diagram of a technique for providing uniform access interfaces (also called “event views”) to event data at the data intake and preparation stage for an event processing engine (e.g., at a subsequent stage) to obtain relevant information from various kinds of machine data.
- uniform access interfacesalso called “event views”
- FIG. 11is explained below with reference to FIG. 8 .
- the data intake and decoration stage introduced herecan provide an uniform access interface for select information contained in the events.
- the uniform access interfaces described hereserve to decouple the main intelligence of the security platform (e.g., the analytic models running therein) from the multiple, potentially heterogeneous data source inputs (which may be heterogeneous in nature (i.e., of different data types, formats, etc.)), and to create a homogeneous way of access information contained in the events that are originated from these various input systems.
- bindingis a process in which unstructured data is processed and transformed into structured data.
- any information in the original, unstructured databecomes lost if not captured in the structured data.
- the data intake and preparation stage introduced heregenerally implements the notion of a “late binding” schema, which means that the binding is only made when an operation (e.g., a query) is made against the data.
- an “early binding” schemagenerally means that data is transformed into structured data (i.e., become bonded to data structures) at an early stage, typically at data intake.
- an early binding schemacan provide homogeneous ways to access the data (because the data becomes structured after intake), using an early binding schema may risk losing potentially important information, information that may later become particularly important when it comes to determining unknown anomalies and threats.
- unstructured data in various data formatpresents a technical problem to a systematic way to process these data, especially in an application (e.g., security platform) where both time and accuracy are of the essence, because there is no convenient way to access the data using an uniform manner (i.e., using the same way to access select information in events that are in various data formats).
- the data intake and preparation stage introduced heredoes not put the event data into any kind of fixed structure; thus, even after the application of the various preparation or pre-processing techniques introduced here, the event data are still generally in the original form (more importantly, retaining all the raw event data) after the data intake and preparation stage.
- the event viewenables the security platform to both implement late binding and have a homogeneous way to access the unstructured event data.
- an access interfacecan be implemented as a class (in object-oriented programming terms, e.g., a JavaTM class).
- An event viewincludes a name (e.g., view identifier) for subscription purposes.
- An event viewcan include a number of fields to access certain attributes of an event; for example, the fields can be used by a machine learning model to identify which subset of the event data (e.g., serverIP, sourceIP, sourcePort, etc.) is the information that the model wants to receive.
- the event viewcan also include a number of methods (in object-oriented programming terms) and logic associated with the methods to access information generated based on attributes of an event; for example, a method can be used by a machine learning model to obtain a randomness of a URL in an event (e.g., getRandomnessOfURL( )), in which the logic associated with the method can include performing algorithmic operations to compute the URL against a predetermined set of URLs.
- a methodcan be used by a machine learning model to obtain a randomness of a URL in an event (e.g., getRandomnessOfURL( )), in which the logic associated with the method can include performing algorithmic operations to compute the URL against a predetermined set of URLs.
- an event viewcan include an input for controlling actions or operations that the logic associated with a method performs.
- any programming-related term of art used hereinmay, but does not necessarily, have the same meaning as how the term may be used in a traditional programming sense; therefore, any term of art used herein is to be construed in the context of the present disclosure.
- the event viewse.g., the object-oriented classes
- the model execution librarywhich may be a part of an event processing engine such as the CEP engine
- the event viewcan be loaded by, for example, a known JavaTM class loader.
- the data intake and decoration stageincludes an event view adder 816 that can provide the event views by adding one or more view identifiers to the event data.
- a view identifiercan be added, for example, as a field in the event data.
- the view identifiersallow a downstream entity (e.g., a complex event processing (CEP) engine) to receive the select information through the event views identified by the view identifiers.
- CEPcomplex event processing
- the information in the model registrydiscussed herein in other sections
- each machine learning modelcan designate one or more view identifiers to indicate the event views that are of interest to the model, to identify the events of interest and to receive select information about those events.
- the security platformprovides a mechanism for the machine learning models to subscribe (e.g., using the model registry) to a group of event views in order to receive select information about the events of interest as each event of interest arrives.
- the view identifiersare added to event data by the event view adder 816 on a per-event basis.
- the view identifierscan be added by the event view adder 816 to an event at any suitable moment during the data intake and preparation stage after the data connector 802 retrieves or receives the event.
- the event view adder 816can selectively add the view identifiers based on the event data, and more precisely, based on an event category to which the event belongs.
- the event view adder 816can also determine the event category based on the type of machine that generated the event. For example, a firewall event can be an event category.
- Other example event categoriesinclude authentication, network, entity acquisition, and so forth. Shown in FIG. 13 is a table 1300 including example event views available for event annotation in the data intake and preparation stage.
- a firewall event exampleis illustrated in FIG. 11 .
- the event view adder 816When a Cisco RSATM event (event data) 1100 arrives, the event view adder 816 first determines that the machine that generated the event is a Cisco RSATM type (which may be defined in the configuration snippet by the administrator). Based on the machine type, the event view adder 816 determines (e.g., by performing a lookup of the event code in the event against a list of Cisco RSATM event codes) that the event belongs to a firewall event. Then, based on the configuration, the event view adder 816 automatically adds to the event 1100 two view identifiers, namely Network and Firewall.
- the determination of which view identifiers should be addedmay be adjusted by the administrator (e.g., via the configuration file) based on the knowledge of the devices in the environment, such that the added view identifiers (and the corresponding event views) correctly reflect or correspond to the event category.
- a downstream entitye.g., the CEP engine
- the machine learning model 1104can subscribe to the event views in, for example, the model registry (e.g., by specifying corresponding view identifiers).
- the subscriptioncauses or allows the automatic routing of the select information to the machine learning model 1104 .
- the information accessible via the event viewscan include: information generated by logic included in the interface (e.g., through the methods in the interfaces), and/or a predefined subset of a complete set of the event data (e.g., through the fields).
- FIG. 12shows a table 1200 of example uniform access interfaces (“event views”) that can be implemented in the data intake and preparation stage.
- FIGS. 13A and 13Bcollectively show a table 1300 that includes example anomalies that can be identified by machine learning models, as well as various event views and fields that can be used by the models to receive relevant information about the events for performing further analytics.
- FIG. 14shows a technique for session correlation, also called “sessionization,” that can be implemented in conjunction with other introduced techniques (e.g., identity resolution) in the data intake and preparation stage.
- the data intake and preparation stagecan further include a session tracker and a session resolver (not illustrated in FIG. 8 for simplicity).
- sessionizationcan be created by using the same or similar data structure as that used for correlating users with devices in identity resolution.
- the event data associated with events from the sessionshould be explicitly marked (e.g., as a field in the event data).
- all data events resolved to the user within the time window of an active sessionare associated with the session.
- the data intake and preparation enginecan also mark certain events for session correlation, for example, events that may indicate a remote network login such as using a remote desktop protocol (RDP) or a secure shell (SSH) protocol to log into another device.
- RDPremote desktop protocol
- SSHsecure shell
- session lineageThis correlation is referred to herein as session lineage.
- an active directory (AD) sessionis first started on the machine with the IP address of 10.245.0.6 by user “zzsmssvcl” at time 10:13 PM.
- this userthen started an SSH session to log into a new system as “root.”
- These two sessions, along with any anomalies detected during these two sessions,should all be attributed to the user “zzsmssvcl.”
- These two sessionsare said to have session lineage, and can be correlated with each other using the sessionization technique introduced here.
- Every session that is trackedbe assigned with a session identifier (“sessionId”) and a correlation identifier (“correlationId”).
- the session identifieris used to identify the same session, and the correlation identifier is used to find other sessions that can possibly be in the same lineage.
- the session trackeris used to track the user sessions based on login/logout events, for example, from active directory (AD), virtual private network (VPN), and secure shell (SSH) logs.
- the session trackercan create and maintain session states in a sessions database.
- the session trackercan also link sessions based on session linking events (e.g. an AD Event with code 5156 , which may correspond to a remote-desktop connection from machine-A to machine-B).
- the session resolverqueries the session database using user, device and event time information from data event. Then, if there is any closely matching active session found in the session database (e.g., which can be determined based on the event's time), then a corresponding session identifier (e.g., “sessionId”) can be assigned to the data event.
- sessionIda session identifier
- session trackingmay vary depending on what existing techniques (such as those introduced here) are implemented in the data intake and preparation stage. Introduced here is a specific implementation where session correlation is performed after entity extraction, device resolution and identity resolution, and event view assignment. Therefore, instead of using specific attributes of data events from various data formats, the components that are logically located after event view assignment, which include the session tracker, can conveniently operate over sets of normalized attributes (e.g., from calling a specific event view for obtaining select information, introduced above). With the specific information based on the attributes on the event, the session tracker can inspect the event data to determine whether the event represented by the event data belongs to any session of interest (e.g., AD, VPN, and SSH). If affirmative, then the session tracker starts to track the event.
- any session of intereste.g., AD, VPN, and SSH
- a new eventarrives, and an event type is set as “SessionStart” (e.g., by using an “association” event view), then that signifies that a new session is created.
- the session trackerthen starts a tracking process by storing the new event in the session database.
- the sessionis stored with information about start time, user identifier (e.g., user account), device identifier (e.g., IP address), and sessionID (or perhaps a hash of the sessionID).
- a derived property attribute “LinkContext”can also be generated from the event view, and the stored session also has its LinkContext stored along with session information.
- An example of a LinkContext of a sessionmay be an IP address along with the user account used.
- a process threadstarts to automatically look for any preexisting session in the session database that can be linked with the information provided by the new session. Whether to link two sessions is determined based on comparing three items: “from-session-link-context”, “to-session-link-context”, and “Link-Event time.”
- An example of the “from-session-link-context”is the combination of the IP address of and the user account used on a source machine from which the session is established.
- An example of the “to-session-link-context”is the combination of the IP address of and the user account used on a target machine to which the session is established.
- the “Link-Event time”is the time that the new session is recorded.
- Two existing sessionsshould be linked or correlated if the newly added session (1) matches a link event time range, (2a) has a match in one of its from-session-link-context or to-session-link-context with those of one existing session, and (2b) has at least a partial match in one of its from-session-link-context or to-session-link-context with those of another existing session.
- this sessionization techniquewould be where a user uses user account A to log into a first machine of a first IP address, thereby creating a first session. Then, from the first machine, the same user uses user account B to log into a second machine of a second IP address, thereby creating a second session.
- the two existing sessions that are visible in the environmentare that the first machine of the first IP address is logged in by user account A, and that the second machine of the second IP address is logged in by user account B. Without sessionization, the two sessions would not be linked or correlated to each other.
- RDPremote desktop protocol
- This RDP eventcan be used by the sessionization technique introduced here to discover that these two seemingly unrelated sessions are actually initiated by the same user and should be correlated. This is because, using the aforementioned mechanisms and assuming the RDP event's time is within the valid range, the RDP event would have a match with the first session in its “from-session-link-context”, and have a match with the second session in its “to-session-link-context.”
- additional linkingcan be done by an offline session scanner process, which can run at a configured interval (e.g., every 15 minutes).
- a configured intervale.g., every 15 minutes.
- identity resolutionis performed, then the user account may be further transformed into a user identity to more accurately track the user for sessionization.
- the sessionization processmay receive an event indicating that a session may have been timed out.
- a new session entrycan be created in the session database with a state “Timed Out.” For example, an already timed out session may be identified if the sum of a session start time and an expiration duration is less than the current system time.
- a user log-out eventis received, a corresponding session is marked as “User Ended” in the session database.
- session ending eventsdo not contain any specific context (e.g., lack a context that may be used as the LinkContext, and therefore unable to be used for matching purposes in the session database).
- a certain type of AD eventmay contain only the from and to IP address of connection, but not the user account information.
- identity resolution (IR) lookupcan help identify that existing session if the IR takes place before processing the session end event.
- all eventspass through the session assignment logic (e.g., the session tracker and the session resolver) in the data intake and preparation stage.
- the session assignment logicBased on session-lookup context (e.g., using event views) in an event, the session assignment logic tries to identify if there is any open session at time T of the event. This can be achieved by locating those sessions with the time T included between their start time and end time.
- Such identified sessioncan be associated with the event, and if such event triggers an anomaly (e.g., in downstream processing), then the anomalous event can be annotated or otherwise associated with the sessionId of the identified session.
- Such anomalies with the associated session(s)can be displayed in the user interface for review. Further, if a session identified for an event has other sessions linked to the session, then the current user on the event is replaced with the user of the root (source) session.
- one aspect of the sessionization techniqueincludes offline session linking. Specifically, if user login/logout events or events that indicate possible connection between two sessions are out of order, then session linking may be missed in real-time.
- a session linking processcan run at a configurable intervals (e.g., configured in the configuration file). This process looks for any pending sessions that can be linked in the session database, and links the appropriate sessions together. Also, when this session linking process is executed, if any of the linked sessions is already associated with an anomaly, then the anomaly will also include the root session's sessionID.
- Certain embodiments introduced hereinclude a machine learning-(ML-) based complex event processing (CEP) engine that provides a mechanism to process data from multiple sources in a target computer network to derive anomaly-related or threat-related conclusions in real-time so that an appropriate response can be formulated prior to escalation.
- a CEP engineis a processing entity that tracks and reliably analyzes and processes unbounded streams of electronic records to derive a conclusion therefrom.
- An “unbounded stream” in this contextis an open-ended sequence of data that is continuously received by the CEP engine.
- An unbounded streamis not part of a data container with a fixed file size; instead, it is a data sequence whose endpoint is not presently known by the receiving device or system.
- a CEP enginecan be useful to provide real-time analysis of machine data to identify anomalies.
- the ML-based CEP engine described hereinenables real-time detection of and response to computer security problems.
- the input data of the ML-based CEP engineincludes event feature sets, where each event feature set corresponds to an observable event in the target computer network.
- a conventional CEP enginerelies on user-specified rules to process an incoming event to identity a real-time conclusion. User-specified rules benefit from its computational simplicity that makes real-time computation plausible.
- conventional CEP enginesrely on people to identify known event patterns corresponding to known conclusions. Accordingly, conventional CEP engines are unable to derive conclusions based on patterns or behaviors that are not previously known to authors of the user-specified rules.
- Conventional CEP enginesdo not consider historical events. The added complexity (e.g., memory consumption and processing power requirement) associated with the inclusion of the historical events would likely overtax an otherwise resource-limited computer system that supports a conventional CEP engine.
- Certain embodiments introduced hereinclude an ML-based CEP engine that utilizes distributed training and deliberation of one or more machine learning models.
- “Deliberation” of a machine learning model or a version of a machine learning modelinvolves processing data through a model state of the machine learning model or version of the machine learning model.
- deliberationcan include scoring input data according to a model deliberation process logic as configured by the model state.
- the ML-based CEP engineprocesses event feature sets through the ML models to generate conclusions (e.g., security-related anomalies, security-related threat indicators, security-related threats, or any combination thereof) in real-time.
- “Real-time” computingor “reactive computing”, describes computer systems subject to a processing responsiveness restriction (e.g., in a service level objective (SLO) in a service level agreement (SLA)).
- SLOservice level objective
- SLAservice level agreement
- conclusionsare reached substantially immediately following the receipt of input data such that the conclusions can be used to respond the observed environment.
- the ML-based CEP enginecontinuously receives new incoming event feature sets and reacts to each new incoming event feature set by processing it through at least one machine learning model. Because of real-time processing, the ML-based CEP engine can begin to process a time slice of the unbounded stream prior to when a subsequent time slice from the unbounded stream becomes available.
- the ML-based CEP engineis implemented as, or within, analysis module 330 in FIG. 8 and couples to a data intake and preparation stage (data intake and preparation stage 800 of FIG. 8 ) that receives raw event data from a target-side computer system (e.g., multiple data sources from the target-side computer system).
- the target-side computer systemis operated in a target computer network, which the ML-based CEP engine monitors for computer security issues.
- the target-side computer systemcollects machine data from the target computer network as the raw event data.
- the data intake and preparation stagecreates an event feature set from raw event data pertaining to a single machine-observed event or a sequence of machine-observed events.
- the event feature setcan include at least a subset of the raw event data; metadata associated with the raw event data; transformed, summarized, and/or normalized representation of portions of the raw event data; derived attributes from portions of the raw event data; labels for portions of the raw event data; or any combination thereof.
- the data intake and preparation stagecan process, in real-time, the raw event data as it is received.
- the data intake and preparation stage and the ML-based CEP enginecan store its inputs and outputs in non-persistent memory (e.g., volatile memory), such that all I/O operations of the ML-based CEP engine and the data intake and preparation stage operate on the non-persistent memory.
- non-persistent memorycan help reduce the time lag of the ML-based CEP engine to satisfy the processing responsiveness restriction.
- the inputs and outputsare stored in solid-state memory (e.g., one or more Flash drives), which is typically faster than hard disks and other non-solid-state data storage devices.
- the ML-based CEP enginetrains and retrains (e.g., updates) the machine learning models in real-time and applies (e.g., during the model deliberation phase) the machine learning models in real-time. Parallelization of training and deliberation enables the ML-based CEP engine to utilize machine learning models without preventing or hindering the formation of real-time conclusions.
- the ML-based CEP enginecan be implemented on a distributed computation system (e.g., a distributed computation cluster) optimized for real-time processing.
- a distributed computation systemsuch as Apache StormTM, can implement task parallelism instead of data parallelism.
- Stormis an open source distributed real-time computation system.
- the distributed computation systemcan be implemented with data parallelism, such as Apache SparkTM or Apache Spark Streaming.
- Sparkis an open source cluster computing framework.
- the distributed computation systemcan be coupled to other distributed components, such as a cluster-based cache (e.g., Redis), a distributed file system (e.g., HDFS), a distributed resource management system, or any combination thereof.
- the ML-based CEP enginecan implement additional services to facilitate the distributed training and deliberation of machine learning models, such as a distributed messaging platform and a central service for distributed synchronization and centralized naming and configuration services.
- the ML-based CEP engine disclosed hereinis advantageous in comparison to conventional CEP engines at least because of its ability to recognize unknown patterns and to incorporate historical data without overburdening the distributed computation system by use of machine learning models. Because the ML-based CEP engine can utilize unsupervised machine learning models, it can identify entity behaviors and event patterns that are not previously known to security experts. In some embodiments, the ML-based CEP engine can also utilize supervised, semi-supervised, and deep machine learning models.
- the ML-based CEP engineis further capable of condensing and summarizing historical knowledge by observing streams of events to train the machine learning models. This enables the ML-based CEP engine to include a form of historical comparison as part of its analysis without consuming too much data storage capacity.
- the ML-based CEP enginecan train a decision tree based on the historical events. In this case, the trained decision tree is superior to a user-specified rule because it can make predictions based on historical sequence of events.
- the ML-based CEP enginecan train a state machine. Not only is the state machine trained based on a historical sequences of events, but it is also applied based on a historical sequence of events.
- the ML-based CEP enginecan track a number of “states” for the entity.
- These run-time statesrepresent the history of the entity without having to track every historical event involving the entity.
- the machine learning modelsenable the ML-based CEP engine to perform many types of analysis, from various event data sources in various contextual settings, and with various resolutions and granularity levels.
- a machine learning model in the ML-based CEP enginecan perform entity-specific behavioral analysis, time series analysis of event sequences, graph correlation analysis of entity activities, peer group analysis of entities, or any combination thereof.
- the data sources of the raw event datacan include network equipment, application service servers, messaging servers, end-user devices, or other computing device capable of recording machine data.
- the contextual settingscan involve scenarios such as specific networking scenarios, user login scenarios, file access scenarios, application execution scenarios, or any combination thereof.
- an anomaly detected by the machine learning models in the ML-based CEP enginecan correspond to an event, a sequence of events, an entity, a group of entities, or any combination thereof.
- the outputs of the machine learning modelscan be an anomaly, a threat indicator, or a threat.
- the ML-based CEP enginecan present these outputs through one or more output devices, such as a display or a speaker.
- entity-specific behavioral analysisexamples include hierarchical temporal memory processes that employ modified probabilistic suffix trees (PST), collaborative filtering, content-based recommendation analysis, statistical matches in whitelists and blacklists using text models, entropy/randomness/n-gram analysis for uniform resource locators (e.g., URLs), other network resource locators and domains (AGDs), rare categorical feature/association analysis, identity resolution models for entities, land speed violation/geo location analysis, or any combination thereof.
- PSTprobabilistic suffix trees
- collaborative filteringe.g., collaborative filtering
- content-based recommendation analysise.g., text models
- statistical matches in whitelists and blacklists using text modelse.g., a uniform resource locators (e.g., URLs), other network resource locators and domains (AGDs)
- rare categorical feature/association analysise.g., identity resolution models for entities, land speed violation/geo location analysis, or any combination thereof.
- time series analysis of event sequencesinclude Bayesian time-series statistical foundation for discrete time-series data (based on variable-memory Markov models and context-tree weighting), dynamic thresholding analysis with periodicity patterns at several scales, change-point detection via maximum-a-posteriori-probability (MAP) modeling, cross-correlation and causality analysis via variable-memory modeling and estimation of directed mutual information, outlier analysis, or any combination thereof.
- MAPmaximum-a-posteriori-probability
- Examples of graph-based analysis of entity activitiesinclude command and control detection analysis, beaconing detector, device, IP, domain and user reputation analysis, lateral movement detector, dynamic fingerprinting for users/devices, or any combination thereof.
- Examples of peer group analysis of entitiesinclude grouping of entities based on similarity and page rank, social-neighborhood graph-based clustering, online distributed clustering, clustering for bipartite and generic graphs, or any combination thereof.
- FIG. 15is a block diagram of an ML-based CEP engine 1500 , in accordance with various embodiments.
- the ML-based CEP engine 1500receives an unbounded stream 1502 of event feature sets as its input.
- the ML-based CEP engine 1500receives the unbounded stream 1502 from the data intake and preparation stage 800 of FIG. 8 .
- Each event feature setcorresponds to a machine-observed event.
- the ML-based CEP engine 1500can train machine learning models using the unbounded stream 1502 .
- the ML-based CEP engine 1500can also compute security-related conclusions (e.g., an anomaly, a threat indicator, or a threat as described in this disclosure) by processing at least a subset of the event feature sets (e.g., from the unbounded stream 1502 ) through the machine learning models.
- security-related conclusionse.g., an anomaly, a threat indicator, or a threat as described in this disclosure
- the ML-based CEP engine 1500includes a cache component 1512 , a distributed filesystem 1514 , a messaging platform 1518 , and a distributed computation system 1520 .
- the ML-based CEP engine 1500can include other data access systems.
- the data access systemsinclude a relational database (e.g., a structured query language (SQL) database), a non-relational database (e.g., HBase), a time series database, a graph database, or any combination thereof.
- the ML-based CEP engine 1500can include other resource management systems (e.g., a distributed coordination system, such as ZooKeeper).
- the cache component 1512can be non-persistent memory (e.g., volatile memory).
- the cache component 1512can be a distributed cache, such as a cluster-based cache or a peer-to-peer cache.
- the cache component 1512is implemented in REDIS, an open source key-value cache.
- the distributed filesystem 1514stores data on a cluster of computing machines to provide high aggregate bandwidth across the cluster.
- the distributed filesystem 1514includes at least a name node and a plurality of data nodes. Each data node serves blocks of data over a network using a file access protocol (e.g., block protocol or file-based protocol) specific to the distributed filesystem 1514 .
- a file access protocole.g., block protocol or file-based protocol
- the distributed filesystem 1514is implemented according to the Hadoop distributed file system (HDFS).
- HDFSHadoop distributed file system
- the distributed filesystem 1514stores a model registry 1530 , a model store 1532 , and a model execution code base 1534 .
- the model execution code base 1534is part of the model registry 1530 .
- the model registry 1530stores model type definitions.
- a model type definitioncan configure whether a distributed computation system is responsible for a model type and can configure a model training workflow (i.e., a workflow of how to train machine learning models of a model type) and a model deliberation workflow (i.e., a workflow of how to apply machine learning models of a model type) of the model type.
- the model store 1532stores model states that represent machine learning models or versions of the machine learning models.
- a model stateis a collection of numeric parameters in a data structure.
- a model training process threadproduces and updates a model state.
- a model deliberation process threadis configured by a model state to process event feature sets into security-related conclusions.
- the model execution code base 1534stores process logics for running model-related process threads. In some embodiments, the model execution code base 1534 also stores process logics associated with event views.
- the content of the distributed file system 1514can be shared with another distributed computation system (e.g., a batch data processing engine discussed in various parts of this disclosure).
- another distributed computation systeme.g., a batch data processing engine discussed in various parts of this disclosure.
- a model state stored in the model store 1532 representing a machine learning model or a version of a machine learning modelcan be shared with the other distributed computation system.
- one or more model types in the model registry 1530 and the model execution code base 1534can be shared with the other distributed computation system.
- the cache component 1512stores an event feature store 1540 and a security-related conclusion store 1542 .
- the cache component 1512can cache (e.g., the most recently used or most recently received event feature sets) from the unbounded stream 1502 in the event feature store 1540 .
- the cache component 1512can cache the security-related conclusions (e.g., the most recently produced or the most recently used) in the security-related conclusion store 1542 .
- the ML-based CEP engine 1500can compute the security-related conclusions by processing the event feature sets through the machine learning models.
- the cache component 1512stores copies or references to entries in the model store 1532 .
- the cache component 1512stores copies or references to entries in the model registry 1530 .
- the cache component 1512stores copies or references to at least a portion of the model execution code base 1534 .
- the messaging platform 1518provides a computer application service to facilitate communication amongst the various system components of the ML-based CEP engine 1500 and between external systems (e.g., the data intake and preparation stage) and the ML-based CEP engine 1500 .
- the messaging platform 1518can be Apache Kafka, an open-source message broker utilizing a publish-subscribe messaging protocol.
- the messaging platform 1518can deliver (e.g., via self-triggered interrupt messages or message queues) the event feature sets from the unbounded stream 1502 to model-related process threads (e.g., one or more of model training process threads, model deliberation process threads, and model preparation process threads) running in the distributed computation system 1520 .
- the messaging platform 1518can also send data within the cache component 1512 or the distributed filesystem 1514 to the model-related process threads and between any two of the model-related process threads.
- the distributed computation system 1520is a real-time data processing engine.
- the distributed computation system 1520can be implemented on the same computer cluster as the distributed filesystem 1514 .
- an ML-based batch processing engineruns in parallel to the ML-based CEP engine.
- the ML-based batch processing enginecan implement a distributed computation system configured as a batch processing engine (e.g., using a data parallelism architecture).
- the system architecture of the ML-based batch processing enginecan be identical to the ML-based CEP engine 1500 , except for the distributed computing platform engine running on the distributed computation system, and the ML-based batch processing engine's inputs including batch data containers of event feature sets (instead of an unbounded stream of incoming event feature sets).
- the distributed computation system 1520can be a distributed computation cluster.
- the distributed computation system 1520coordinates the use of multiple computing nodes 1522 (e.g., physical computing machines or virtualized computing machines) to execute the model-related process threads.
- the distributed computation system 1520can parallelize the execution of the model-related process threads.
- the distributed computation system 1520can implement a distributed resource manager (e.g., Apache Hadoop YARN) and a real-time distributed computation engine (e.g., Storm or Spark Streaming) to coordinate its computing nodes 1522 and the model-related process threads running thereon.
- the real-time distributed computation enginecan be implemented based on a task parallel architecture. In an alternative embodiment, the real-time distributed computation engine can be implemented based on a data-parallel architecture.
- Each computing node 1522can implement one or more computation workers (or simply “workers”) 1526 .
- a computation workeris a logical construct of a sandboxed operating environment for process threads to run on.
- a computation workercan be considered a “processing node” of the computing cluster of the distributed computation system 1520 .
- at least one of the computing nodes 1522implements a cluster manager 1528 to supervise the computation workers 1526 .
- Each of the computation workers 1526can execute one or more model-related process threads.
- a computation worker 1526only executes one type of model-related process thread, where process threads of that type share the same input data.
- FIG. 16is a block diagram illustrating an architectural framework of a machine learning model, in accordance with various embodiments.
- a machine learning model 1600corresponds to a model type 1602 .
- the ML-based CEP engine 1500can implement multiple machine learning models of the same model type.
- a model typecan define a workflow for entity-specific models to be trained and applied.
- the ML-based CEP engine 1500trains as many models of the model type as there are known entities.
- the model type 1602is defined by a model type definition 1700 stored in the model registry 1530 .
- FIG. 17is a block diagram illustrating an example of the model type definition 1700 .
- the model type definition 1700includes various configurations of how a machine learning model is to be trained or applied.
- the model type definition 1700includes a code reference 1702 to a model execution code 1610 in the model execution code base 1534 .
- the model type definition 1700includes a model type identifier 1704 , a model type name 1706 , a processing mode specifier 1708 for the model training workflow, a processing mode specifier 1710 for the model deliberation workflow, a model input type configuration 1712 (e.g., one or more subscriptions to one or more event views as described in this disclosure), a model type topology 1714 , or any combination thereof.
- a processing mode specifierspecifies a processing mode, such as a real-time processing mode or a batch processing mode.
- the model input type configuration 1712specifies what event views (e.g., described in this disclosure) that the model type 1602 subscribes to.
- the event feature sets from the unbounded stream 1502can be labeled with event view labels corresponding to the event views.
- the ML-based CEP engine 1500can select the event feature sets received from the unbounded stream 1502 based on event view labels of the event feature sets (e.g., selecting only the event feature sets based on the event view labels corresponding to the event view subscriptions in the model input type configuration 1712 ).
- the ML-based CEP engine 1500can call and execute an access interface associated with an event view subscription to organize the selected event feature sets and provide format/bind at least a subset of features within the selected event feature sets to a preferred data structure for a model-related process thread.
- the ML-based CEP engine 1500can provide (e.g., stream via a data pipeline) the selected and formatted event feature sets to a model-related process thread of the model type 1602 .
- the model type topology 1714specifies how the ML-based CEP engine 1500 groups and distributes model-specific process threads to, for example, the different computation workers 1526 in the distributed computation system 1520 .
- the model type topology 1714also specifies how the ML-based CEP engine 1500 groups and distribute the input data for the model-specific process threads of the same model type 1602 .
- the ML-based CEP engine 1500groups and divides the input data for the model-specific process threads into mutually exclusive partitions.
- the ML-based CEP engine 1500groups the input data for the model-specific process threads into groups that have at least some overlap.
- the model type topology 1714can specify an entity type (e.g., a type associated with users, devices, systems, applications, process threads, network resource locators, or any combination thereof).
- entity typee.g., a type associated with users, devices, systems, applications, process threads, network resource locators, or any combination thereof.
- the ML-based CEP engine 1500groups the selected event feature sets by user groups. For example, the ML-based CEP engine 1500 can divide all known user entities into user groups, and divide the selected event feature sets by the user group or groups to which each event feature set corresponds. Consequently, the distributed computation system 1520 can assign a computation worker 1526 to process event feature sets corresponding to each group/partition.
- One or more model states stored in the model store 1532represent the machine learning model 1600 . If the ML-based CEP engine 1500 trains and applies a single version of the machine learning model 1600 , then a single model state represents the machine learning model 1600 . In embodiments where the ML-based CEP engine 1500 trains multiple versions of the machine learning model 1600 , each model version 1604 corresponds to a different model state stored in the model store 1532 . In such embodiments, a group of model states corresponds to different model versions representing different training stages of the machine learning model 1600 . In this case, the group of model versions is part of the same machine learning model 1600 because these model states are all trained for a specific entity or a specific purpose.
- a machine learning modelcan be a label used to refer to the group of model states that are specifically trained by event feature sets corresponding to a single user and applied to event feature sets corresponding to that single user.
- Each model state of each model versioncan correspond to a different sequence of event feature sets used to train the model state (herein the different sequences of event feature sets correspond to different “training stages”).
- a machine learning modelcan be a label used to refer to the group of model states that are specifically trained by a specific type of anomalies and applied to that type of anomalies.
- a model stateis the output of a model training process thread 1606 .
- the ML-based CEP engine 1500instantiates a model deliberation process thread 1608 based on the model state.
- the model training process thread 1606 and the model deliberation process thread 1608can be referred to as “model-specific process threads.”
- the ML-based CEP engine 1500can instantiate the model-specific process threads in the distributed computation system 1520 .
- “instantiating” a modelrefers to instantiating the model deliberation process thread 1608 for a particular version of a machine learning model.
- processing” input data “through” a modelrefers to processing the input data by the model deliberation process thread 1608 corresponding to the model.
- the model execution code 1610includes model program logic 1612 that describes data structures associated with model-related process threads and logic of the model-related process threads.
- the model program logic 1612references model training process logic 1616 and model deliberation process logic 1618 .
- the model training process logic 1616defines how the model training process thread 1606 is to transform input data (e.g., one or more event feature sets) into a model state or an update to the model state.
- the model stateis representative of a machine learning model or at least a version of a machine learning model (when there are multiple versions). As more input data is provided to the model training thread, the model training thread can update the model state.
- the model deliberation process logic 1618defines how input data (e.g., one or more event feature sets) to a model deliberation process thread, configured by a model state, is to be transformed into security-related conclusions.
- the model execution code 1610also includes a model program template 1622 , a model training program template 1626 , and a model deliberation program template 1628 .
- These program templatescontain process logics that are shared amongst all types of machine learning models.
- These program templatesalso impose restrictions such that an author of the model program logic 1612 , the model training process logic 1616 , and the model deliberation process logic 1618 creates consistent process logics that can function in the ML-based CEP engine 1500 .
- the model program template 1622can impose a restriction that any model program logic, such as the model program logic 1612 , has to reference at least a model training process logic and a model deliberation process logic.
- the architectural framework described in FIG. 16enables real-time registration of a new model type.
- Real-time registrationenables a network security administrator to deploy updates to the ML-based CEP engine 1500 or an ML-based batch processing engine without having to shut down the engines or any model-related process threads running thereon.
- the program templates and the workflow configurations using the model type definition 1700provide a formal way to train and apply machine learning models.
- the use of the distributed filesystem 1514facilitates persistence of model states while the model-related process threads are running in a distributed manner.
- the ability to label the model version 1604 to a model state in the model store 1532enables the ML-based CEP engine 1500 to maintain lineage between training data sets for a machine learning model and the model states produced therefrom.
- the versioning of the machine learning modelsenables simultaneous training of different machine learning models using the same data to produce model states corresponding to different windows of training data sets.
- the simultaneous training of the machine learning modelsfurther enables the ML-based CEP engine 1500 to “expire” model versions that have been trained with outdated data.
- FIG. 18is a block diagram illustrating a system architecture for implementing the distributed computation system 1520 , in accordance with various embodiments.
- the distributed computation system 1520implements a cluster resource manager 1802 (e.g., YARN).
- the cluster resource manager 1802can function as an operating system for running data processing platform engines.
- the cluster resource manager 1802can implement a distributed computing platform engine 1804 (e.g., a real-time distributed computation platform, such as Storm or Spark Streaming).
- the processes running on the distributed computing platform engine 1804can access various data access systems in a data access layer 1806 .
- the data access layer 1806can provide access to a relational database, a graph database, a non-relational database, a time series database, the cache component 1512 , the distributed filesystem 1514 , or any combination thereof.
- the distributed computing platform engine 1804can implement a model execution engine 1808 .
- the model execution engine 1808can then initialize one or more model-related process threads 1810 (e.g., a model preparation thread, one or more model training threads and/or model deliberation threads) managed by the distributed computing platform engine 1804 .
- Each model-related process thread 1810is a sequence of program instructions related to training, deliberation, or preparation of a machine learning model.
- Each model-related process thread 1810can be managed independently by the distributed computing platform engine 1804 .
- method 1900illustrates a potential workflow of a model preparation thread
- method 2000illustrates a potential workflow of a model training thread
- method 2100illustrates a potential workflow of a model deliberation thread.
- the data access layer 1806can enable the model-related process threads 1810 to access model type definitions in the model registry 1530 , model states in the model store 1532 , and event feature sets in the cache component 1512 .
- FIG. 19is a flow diagram illustrating a method 1900 to execute a model preparation process thread, in accordance with various embodiments.
- the model execution engine 1808reads the model registry 1530 to determine which model types are assigned to the ML-based CEP engine 1500 (e.g., as opposed to an ML-based batch processing engine).
- the model execution engine 1808executes the model preparation process thread. This process similarly applies to the model execution engine of the ML-based batch processing engine.
- the model execution engine 1808 running on the distributed computation system 1520extracts the parameters of each model type definition to configure the workflows of that model type.
- the model execution engine 1808can instantiate a model preparation process thread in the ML-based CEP engine 1500 for each model type that has either the processing mode specifier for training 1708 or the processing mode specifier 1710 designating the real-time processing mode.
- Each model preparation process threadcan initiate multiple model-specific process threads corresponding to its model type. Accordingly, the ML-based CEP engine 1500 can be concurrently training and/or deliberating multiple machine learning models of different model types.
- the model preparation process threadselects a subset of event feature sets in the cache component 1512 for the model type.
- the model preparation process threadcan select the subset from the most recent event feature sets (e.g., a real-time time slice) that are yet to be processed by the model execution engine 1808 or any other model preparation process threads. For example, the model preparation process thread selects and filters the event feature sets based on event view labels in the event feature sets.
- the model preparation process threadcan request the subset from the messaging platform 1518 .
- the model preparation process threadcan select the subset that has event view labels corresponding to event view subscriptions in the model type associated with the model preparation process thread.
- the model input type configuration 1712 of the model typespecifies the event view subscriptions.
- the model preparation process threadcan format the selected subset into a model-type-specific format.
- a binding process specified by one or more access interfaces (described above in this disclosure) respectively associated with the event view subscriptionscan configure the model-type-specific format.
- the formattingincludes removing some feature fields from the selected subset.
- the model preparation process threadcan assign (e.g., partition) the formatted subset of event feature sets into data groups (also referred to as “data partitions”) according to the model type topology 1714 of the model type.
- the model typecan correspond to an entity type (e.g., users, devices, systems, resource locators, applications, process threads, or anomalies) or a purpose type (e.g., for global beaconing detection).
- a global purpose-specific model typecan have a single model training process thread and/or a single model deliberation process thread.
- the model preparation process threadcan determine the number of known entities of the entity type.
- the model preparation process threadcan partition the event feature sets in the formatted subset into a number of data groups corresponding to the number of available computation workers for the model type. Each data group corresponds to the number of entities equal to the total number of known entities divided by the number of data groups.
- the model type topology 1714may specify a user level topology.
- the model preparation process threadcan request the total number of users from the target-side computer system. Based on the total number of available computation workers in the distributed computation system 1520 , the model execution engine 1808 can evenly assign computation workers to each model type. Then, the model preparation process thread can assign a number of data groups based on the available computation workers for its model type. Each available computation worker can be assigned a data group. For example, there can be five available computation workers and 20 known users. In this example, the model preparation process thread can assign a data group corresponding to 4 users to each computation worker. Event feature sets corresponding to these 4 users would be part of the data group.
- the model preparation process threadcan perform a consistent hash on the formatted subset of event-based features.
- the data group assignmentcan be based on the consistent hash, such as distributed hash tables (DHTs).
- Consistent hashingis a kind of hashing such that when a hash table is resized and consistent hashing is used, only K/n keys need to be remapped on average, where K is the number of keys, and n is the number of slots. In contrast, in most traditional hash tables, a change in the number of array slots causes nearly all keys to be remapped.
- the consistent hashing conceptapplies to DHTs. DHTs use consistent hashing to partition a keyspace among a distributed set of nodes (e.g., the computation worker corresponding to the data group), and additionally provide an overlay network that connects nodes such that the node responsible for any key can be efficiently located.
- the model preparation process threadsorts each data group of the formatted subset (e.g., by timestamps of the formatted event feature sets). This step is executed if the order of the formatted event feature sets is part of model training or model deliberation. For example, time sequence prediction models, such as probabilistic suffix trees (PSTs), are trained based on an ordered sequence of event features.
- PSTsprobabilistic suffix trees
- the data intake and preparation stagemay not have received raw event data in temporal order from the target-side computer system.
- the target computer networkmay not have recorded the raw event data in temporal order.
- step 1910can ensure, via sorting, that groups of the formatted subsets are in order.
- the model preparation process threadinstantiates one or more model-specific process threads to at least a subset of the computation workers 1526 according to the model type topology 1714 .
- each computation workerruns only model-specific process threads of one model type.
- each computationruns only model-specific process threads of one model type and either only model training process threads (e.g., corresponding to a model training workflow) or only model deliberation process threads (e.g., corresponding to a model deliberation workflow).
- the model preparation process threadcan schedule one or more model training process threads to run on the subset of computation workers 1526 .
- the model preparation process threadcan schedule one or more model deliberation process threads to run on the subset of computation workers 1526 .
- the model preparation process threadcan schedule one or more model training process threads to run on a subset of computation workers in a batch processing cluster.
- the model preparation process threadcan schedule one or more model deliberation process threads to run on a subset of computation workers in the batch processing cluster.
- the model preparation process threadcan determine, based on the model type topology 1714 , how many model training process threads of the model type to instantiate for the model training workflow and/or how many model deliberation process threads for the model deliberation workflow.
- the model type topology 1714can correspond to an entity type (e.g., users, devices, applications, process threads, network resource locators, systems, anomalies, etc.) and/or a purpose-type.
- the number of model-specific process threadse.g., training or deliberation
- the model preparation process threadcan identify the known entities and instantiate a model-specific process thread corresponding respectively to the known entities.
- the model preparation process threadcan query the target-side computer system in the target computer network for the identities and/or the total number of the known entities.
- the target-side computer systemprovides this information on its own and this information is saved in the cache component 1512 or the distributed filesystem 1514 .
- the model preparation process threadgenerates group-specific data streams to the computation workers of each model-specific process thread instantiated in step 1912 .
- the group-specific data streamscorrespond to the assigned data groups in step 1908 .
- the model preparation process threadcan configure the messaging platform 1518 to send appropriate event feature sets in the data group through the group-specific data streams.
- the model preparation process threadcan execute steps 1912 and 1914 concurrently.
- the ML-based CEP engine 1500determines the assignments of the group-specific data streams and the model-specific process threads to the computation workers 1526 based on the model type topology 1714 . These assignments can be referred to as topology-based assignments.
- the topology-based assignmentscan be used to optimize model-specific process threads regardless of whether the ML-based CEP engine 1500 or an ML-based batch processing engine is used as an execution platform.
- the model type topologyis decoupled from the execution platform unlike traditional methodologies.
- the topology-based assignmentsmaintain a directed acyclical graph (DAG) structure that allows for dynamic execution of model-specific process threads and management of the input data dependencies of these model-specific process threads.
- DAGdirected acyclical graph
- the DAG approachenables model-specific process threads to freely move, start, or stop amongst the computation workers 1526 based on the performance of the machine learning models.
- the DAG approachfurther enhances security, scalability (e.g., the ability to employ services for caching, the load-balancing, replication, or concentration of data streams), and modularity (e.g., updates to any particular model-specific process thread only affect a limited portion of the computation workers 1526 ).
- the DAG approachenables process replication, data redistribution, proxy processes or groups of proxy processes, integration of subsystems, and/or redundant connections to be added in the distributed computation system 1520 .
- FIG. 20is a flow diagram illustrating a method 2000 to execute a model training process thread, in accordance with various embodiments.
- a computation workerexecutes the model training process thread.
- the computation workerexecute multiple model training process threads associated with a single model type.
- the computation workerexecutes multiple model-specific process threads associated with a single model type.
- the computation workerexecutes multiple model-specific process threads associated with different model types. If a model state corresponding to the model training process thread is not already in the model store 1532 , at step 2002 , the model training process thread processes a time slice of event feature sets, from the group-specific data stream described in step 1914 of FIG.
- the model training process threadcan save the model state in the model store 1532 (e.g., in the distributed filesystem 1514 or the cache component 1512 ).
- the model training process threadcontinuously retrains the model state as the group-specific data stream provides additional event feature sets.
- the model training process logic 1616describes a single-pass training process logic. That is, the model training operates without recursion or iteration over the same input data.
- the model training process logic 1616involves an incremental training process. For example, the model training process thread isolates a portion of the model state affected by the time slice of event feature sets and re-trains only the portion of the model state. Model types with incremental property enable the ML-based CEP engine 1500 to execute in real-time because of reduction in resource consumption during model training.
- the model training process threadcalls a model readiness logic in the model training process logic 1616 to determine when the model state has sufficient training.
- the model readiness logiccan include measuring how many event feature sets have been used to train the model state; measuring how long the model state has been in training in real-time; whether the model state is converging (i.e., not changing within a threshold percentage despite additional training); or any combination thereof. Different model types can have different model readiness logics.
- the model training process threadmarks the model state for deployment.
- FIG. 21is a flow diagram illustrating a method 2100 to execute a model deliberation process thread, in accordance with various embodiments.
- a computation workerexecutes the model deliberation process thread.
- the computation workerexecute multiple model training process threads associated with a single model type.
- the computation workerexecute multiple model-specific process threads associated with a single model type.
- the computation workerexecute multiple model-specific process threads associated with different model types.
- the model deliberation process threadprocesses the most recent time slice from the group-specific data stream to compute a score associated with the most recent time slice.
- the most recent time slicecan correspond to an event or a sequence of event observed at the target computer network.
- the group-specific data stream used by the model deliberation process threadis also used by a corresponding model training process thread for the same entity. That is, the model training process thread can train a model state of an entity-specific machine learning model by processing a previous time slice of the group-specific data stream.
- the model execution engine 1808can initiate the model deliberation process thread based on the model state while the model training process thread continues to create new versions (e.g., new model states).
- the model deliberation process threadcan reconfigure to an updated model state without pausing or restarting.
- the model deliberation process threadgenerates a security-related conclusion based on the score.
- the security-related conclusioncan identify the event or the sequence of events corresponding to the time slice as a security-related anomaly, threat indicator or threat.
- the model deliberation processcompares the score against a constant threshold and makes the security-related conclusion based on the comparison.
- the model deliberation processcompares the score against a dynamically updated baseline (e.g., statistical baseline) and makes the security-related conclusion based on the comparison.
- the model deliberation process threadaggregates the security-related conclusion into the security-related conclusion store 1542 .
- the aggregation of the security-related conclusionscan be used in an analytic platform of the ML-based CEP engine 1500 .
- the security-related conclusion store 1542is backed up to the distributed file system 1514 .
- the model deliberation process threadpublishes the security-related conclusion to the messaging platform 1518 , such that another model deliberation process thread or model training process thread can utilize the security-related conclusion.
- the model deliberation process threadcan generate a user interface element to solicit an action command to activate a threat response.
- the user interface elementtriggers the action command for sending a message to the target-side computer system to demand termination of a problematic application, blocking of specific network traffic, or removal of a user account.
- the model deliberation process threadcan generate a user interface element to accept feedback from a user to confirm or reject the security-related conclusion.
- the model execution engine 1808can provide the feedback to a model training process thread to update the model state used to configure the model deliberation process thread.
- the model deliberation process threadcan check, at step 2114 , its own performance health. For example, the model deliberation process thread can compare the computed score or the generated security-related conclusion against that of other model deliberation process threads to determine if there are significant deviations or biases. The model deliberation process thread can also check to see if there is an unusual bias in its production of security-related conclusions. For example, if more than a threshold percentage of its security-related conclusions correspond to anomalies or threats, then the model deliberation process thread sets its own health status to failure. Based on the conclusion in step 2114 , the model deliberation process thread can decommission itself at step 2116 . In some embodiments, a separate process thread can perform steps 2114 and 2116 by externally monitoring the health status of the model deliberation process thread.
- the method 2100enables dynamic deployment of a model state.
- the machine learning model associated with the model deliberation process threadcan have multiple versions.
- Step 2102can initially be configured by a model state corresponding to an active version of the machine learning model.
- a model training process threadcan train another version (e.g., another model state) of the machine learning model in parallel.
- this other versionis ready for active deployment (e.g., has sufficient training)
- the model deliberation processcan “live swap” in the other version as the active version (e.g., to compute the score for subsequent time slices from the group-specific data stream). Live swapping involves re-configuring the model deliberation process thread with the other model state without terminating the model deliberation process thread.
- the security platformincludes two event processing engines in different paths—a real-time path and a batch path.
- the event processing engine in the real-time pathoperates in a real-time mode to process unbounded, streaming data that enters the security platform.
- the event processing engine in the batch pathoperates in a batch mode to process batches of stored, historical event data.
- an event processing engine implemented on the batch pathbe able to (1) interact with the distributed data cluster that stores the data, instead of moving or copying the data into the platform; and (2) utilize various programming models that are optimized for processing and generating large data sets in a parallel, distributed manner on a computer cluster.
- One example of such a programming modelis MapReduceTM.
- one of the data connectors that can be used by the security platform 300 introduced hereis a specialized connector (e.g., the HDFSTM connector) that can issue instructions (e.g., a query), operations, or otherwise interact with the non-relational database that stores the data (e.g., HDFSTM).
- the HDFS connectorcan to retrieve the stored event data in the order that the event takes place.
- the machine learning models utilized by the batch event processing enginecan be “reducible,” in order to be compatible with parallel, distributed types of operations (e.g., MapReduceTM operations).
- a reducible modelis a model that can be mapped into multiple copies for processing data. Each copy of the model only processes (e.g., for training and/or scoring) a particular subset of a larger set of data. Then, all the information generated by the copies of the model can be reduced back to the model, achieving the same result as if a single copy of the model has processed the entire data set. That is, a reducible model can process data in a parallel manner. Note that, depending on the model, some models may be reducible in their training phase but not their scoring phase, some models may be reducible in their scoring phase but not their training phase, and some models may be reducible in both training and scoring phases.
- the batch event processing engine introduced herecan cooperate with the HDFSTM connector to access data stored in the HDFSTM.
- the platformcan include (e.g., in the batch path) a job controller and a directory catalog.
- the job controllercan function as the batch event processing engine's manager and works with the connector.
- the job controllercan cause the connector to run a query against the HDFS database, and select a set of the returning event data to be processed by the batch event processing engine.
- the querycan, for example, specify a time range, and/or specify that the result should be ordered by event time.
- certain kinds of log filesare preferably to be processed before others, and the HDFS connector can select to retrieve those log files that need to be processed first.
- data of events that have richer informationcan be retrieved first in order to increase the accuracy of the overall security analysis.
- those log files with device informatione.g., DHCP
- log files which associate user data with devicese.g., AD or VPN
- the query that is sent by the connectorcan specify that the retrieved files (e.g., representing events) should be ordered by their formats (e.g., DHCP, then AD/VPN, then others).
- the job controllerlaunches a job for the batch event processing engine (e.g., in SparkTM) with the retrieved files, tracks the analysis progress, and marks the events as analysis completed or analysis failed.
- the job controllercan perform other tasks, such as exporting the result of identity resolution (e.g., into RedisTM), exporting the time-series data (e.g., into OpenTSDBTM), or pushing the anomalies raised by the batch event processing engine into a messaging system (e.g., KafkaTM).
- the job controllercan start the aforementioned file retrieval process based on a time schedule.
- the file retrieval processcan be set to run every hour, every N hours, every N days, and so forth.
- the job controllerAfter the connector retrieves the files, the batch of files is passed to the job controller, which in turn initiates the batch event processing engine to analyze the files.
- the directory catalogis a database (e.g., coupled to the HDFS) that enables the job controller (working with the connector) to determine which files to parse and the order in which the files get parsed.
- the followingis a specific example of how a specialized connector (e.g., the HDFS connector) introduced here can interact with a distributed database storage system (e.g., HDFSTM) to retrieve files.
- the connectorcan determine a time for the first event in a file in the HDFS.
- the filerecords a number of events.
- the time for the first eventcan be used by the job controller to determine whether it should retrieve this file and process it for anomaly/threat detection.
- the connectorWhen the connector (e.g., HDFS connector) is activated to retrieve files of a particular time range (e.g., each file representing a number of events that take place within the particular time range), the connector first refers to a table in the database (“directoryCatalog”) to check if there is any row in the table (e.g., indicating a file) that still needs to process (e.g., which may be a leftover from a previous run). The connector also stores the last time it was run in the database (“lastRunTime”).
- directoryCataloge.g., indicating a file
- the connectorcrawls the currently specified directory (that corresponds to the particular time range), to see if there is any file to process.
- the connectorretrieves a modification time (“mtime”) of the file, and discards the file if the file is earlier than the lastRunTime. Otherwise, the connector parses the file to get the time of the first event from the file.
- the connectorcan parse the file with a parser that corresponds to the file's data format, and extract only the time from the event. In this manner, the connector can continue to process a few select events in the file and determine if the events are recorded in the file in an ascending order (or in any order).
- the connectordetermines that the events are recorded in an ascending order (within a tolerance of a few seconds), then the connector can stop parsing and return the time of the first event. Conversely, if the events are stored in a descending order, the connector then seeks toward (e.g., to a few kilobytes short of) the end of the file and retrieves the time of the first event from there. In the case that the connector determines that the events are recorded in an unsorted manner, the connector parses the entire file and returns the lowest time found as the event time of the first event recorded in the file. Then, the connector adds an entry in the database with the filename, time of the first event and other status (e.g., retrieved).
- the batch event processing enginecan perform analysis based on information that is not available in the real-time path.
- An example of such informationis the composite relationship graph (which is described in greater detail in a section below). Accordingly, the batch event processing engine can process a projection (portion) of the composite graph in utilizing some of the machine learning models.
- the batch event processing enginecan first locate the composite relationship graph that is associated with the historic event data. Then, based on the requirement of a particular machine learning model, the batch event processing engine can obtain a projection of the composite relationship graph.
- the composite relationship graphcan include information from the data intake and preparation stage (e.g., per-event relationship graph) and information generated by the real-time event processing engine processing the unbounded stream of event data (e.g., detected anomalies, which can be added to the per-event relationship graph of the anomalous event).
- a projection of the composite relationship graphincludes a graph of users associated with machines, to facilitate tracking (by the particular machine learning model) of user lateral movement.
- the projectionincludes a graph that associates entities identified as having security-related issues to facilitate correlating (by the particular machine learning model) user anomalies so as to identify sophisticated threats.
- the projectionincludes a graph of website visitation activities of users to facilitate identification (by the particular machine learning model) of commonly accessed websites by potentially security-compromised users. More details on the models that can utilize projections of the composite relationship graph are discussed below with respect to anomaly and threat models.
- one of the features of the security platform introduced hereis the capability to share information between different analytics entities (including, for example, an event processing engine such as the CEP engine). Information or knowledge sharing in this manner can be especially useful in detecting unknown security-related anomalies and threats.
- the security platformcan include at least two event processing engines—one event processing engine operating in a real-time mode to process unbounded, streaming data that enters the security platform, and the other event processing engine operating in a batch mode to process batches of historical event data.
- a security platform deployed in an environmente.g., an organization or an enterprise
- the security platform's architectureis configured so that the model store (which stores one or more groups of model states, each group corresponding to versions of an entity-specific or purpose-specific machine learning model) that is used in the security platform can be shared.
- the phrase “sharing a model state”means more than one engine sharing the same version of a model. This notion should be distinguished from the notion of “sharing a model type,” which implies that more than one engine can share the model registry (which stores the model type) in the security platform.
- Sharing a model typecan enable two engines to use or produce machine learning models that have the same model execution logic (e.g., training logic and/or deliberation logic) for different purposes.
- the general notion of “sharing a model”can be referring to either or both of these notions, whichever is made apparent by the context.
- this configurationenables the real-time event processing engine and the batch event processing engine to share a model state of a particular machine learning model. Then, for example, a first engine can first use a particular machine learning model to process a first set of data to produce a score for detecting a network security-related issue, and in doing so, the particular model is trained by the first engine with the first set of data, thereby creating a model state reflecting a version of such model. Thereafter, a second engine uses the same particular machine learning model to process a second set of data for producing a score for detecting a network security-related issue.
- the second enginecan use the version of the model that has been trained by the first engine to process the second set of data, thereby leveraging the knowledge gained by the first engine to discover a security-related issue in the second set of data.
- this model state sharingis non-blocking, meaning that a model state can be read and/or updated by any engine at any time.
- FIG. 22shows of an example architecture 2200 of the security platform, in which the model state sharing technique introduced here may be implemented.
- the security platformcan be implemented by using various components in a big data oriented software framework, such as HadoopTM.
- the frameworkenables the components in the platform to be able to communicate with each other.
- the example security platformincludes a real-time event processing engine implemented on a first processing system of the platform.
- this first processing systemis implemented using Apache StormTM.
- the first processing systemcould be implemented by using Apache Spark Streaming.
- the real-time event processing engineis configured to process an unbounded stream of event data to detect a plurality of network security-related issues.
- the real-time event processing enginecan utilize various machine learning models to perform anomaly and threat detection. In doing so, the real-time event processing engine trains the machine learning models, and in some embodiments, establishes behavioral baselines for various specific entities.
- the example security platformincludes a batch event processing engine on a second processing system of the platform.
- this first processing systemis implemented using Apache SparkTM.
- the batch event processing engineis configured to process a batch of historic event data to detect a plurality of network security-related issues.
- the real-time event processing enginecan also utilize machine learning models, establish behavioral baselines, and so forth.
- the security platformcan be configured to enable sharing of model states between the real-time processing engine and the batch processing engine for network security anomaly and threat detection.
- a particular machine learning modelcan be configured to process a time slice of data to produce a score for detecting a network security-related issue, and with model state sharing, the size of the time slice can be controlled by whichever event processing engine currently utilizes the particular machine learning model. For example, if the real-time processing engine is utilizing the model, then the time slice can be set by the real-time processing engine to real-time (e.g., event-by-event as the data streams into the platform).
- the time slicecan be set by the batch processing engine to whichever time period length is suitable for grouping the historic events (i.e., events that are already stored as opposed to being currently streamed) into batches for processing.
- the shared model statecan form a positive intelligence feedback loop between the two engines. From the batch event processing engine's perspective, this loop enables the batch event processing engine to use knowledge gained by the real-time event processing engine to discover a security-related issue in the historic event data that is undetectable by the batch event processing engine without the knowledge. More specifically, the shared model state enables the batch event processing engine to use new knowledge gained by the real-time event processing engine from processing the unbounded stream of event data, to inspect the historic event data to discover a security-related issue that would be undetectable by the batch event processing engine without that new knowledge. The new knowledge is knowledge gained after the last time the batch event processing engine performs historic event data inspection using the particular machine learning model, and therefore it is valuable because the batch event processing engine would not have this new knowledge but for the model state sharing.
- the batch event processing enginecan update the shared model state of the particular machine learning model to incorporate the new knowledge. In this way, by using the shared model state, the real-time event processing engine can perform an inspection of newly streamed event data based on this new knowledge gained by the batch event processing engine.
- the behavioral baseline establishment technique described abovecan also be integrated with the model state sharing technique here. That is, in addition or as an alternative to sharing model states, a behavioral baseline established by one engine (e.g., the real-time event processing engine) by using a particular machine learning model can be shared along with the model state with another engine (e.g., the batch event processing engine). With both the model state and the behavioral baseline established, one engine can take fuller advantage of the knowledge gained by another engine.
- a particular machine learning modelis trained by the real-time event processing engine, and a behavioral baseline is established for a specific entity, also by the real-time event processing engine.
- the batch event processing enginecan locate, in the batch of historic event data, data representing a plurality of events that are associated with the specific entity. Then, the batch event processing engine can perform a behavioral analysis of the entity to detect a behavioral anomaly using the same version of machine learning model that has been trained by the real-time event processing engine to compute a degree of behavioral deviation, as compared to the behavioral baseline specific to the entity.
- the behavioral anomaly analysisis not limited in application to comparing a specific entity with its past behavioral baseline; it can also include comparing a specific entity's behavior against the behavior of other similar entities. In other words, other similar entities' behaviors can be used for establishing a behavioral baseline for a specific entity. Therefore, the combination of the behavioral baseline establishment technique and the model state sharing technique can be particularly useful to detect a specific entity's anomalous behavior when historical data of that specific entity is not available (e.g., a new employee joins the enterprise).
- the mechanism of sharing the model statealso enables, at least indirectly, updating a machine learning model based on the user feedback when the security platform receives such user feedback regarding a determination of a detected security-related issue. For example, such an update can be performed by one of the engines to the model state, and through the shared model state, the effect of that feedback can be propagated into the other engine's anomaly and threat detection processes.
- the security platform 300detects anomalies in event data, and further detects threats based on detected anomalies.
- the security platformalso defines and detects an additional type of indicator of potential security breach, called threat indicators.
- Threat indicatorsare an intermediary level of potential security breach indicator defined within a hierarchy of security breach indicators that includes anomalies at the bottom level, threat indicators as an intermediate level, and threats at the top level.
- FIG. 23is flow diagram illustrating at a high level, a processing hierarchy 2300 of detecting anomalies, identifying threat indicators, and identifying threats with the security platform 300 . Reducing false positives in identifying security threats to the network is one goal of the security platform.
- flow diagramdescribes an overall process 2300 by which large amounts of incoming event data 2302 are processed to detect anomalies.
- the resulting anomaly data 2304comprising a plurality of anomalies across a computer network is then further processed to identify threat indicators.
- This identification of threat indicatorscan be conceptualized as an intermediate step between detecting anomalies and identifying security threats to a computer network.
- the threat indicator data 2306comprising a plurality of threat indicators identified across a computer network is further processed to identify a security threat or threats.
- an anomalyrepresents a detected variation from an expected pattern of behavior on the part of an entity, which variation may or may not constitute a threat.
- An anomalyrepresents an event of possible concern and possibly may be actionable or warrant further investigation.
- a detected anomaly in the activity on a computer networkis often associated with one or more entities of the computer network, such as one or more physical computing devices, virtual computing devices, users, software modules, accounts, identifiers, and/or addresses.
- An anomaly or a set of anomaliesmay be evaluated (e.g. scored) together, which evaluation may result in a determination of a threat indicator or a threat.
- Threat indicatorsrepresent an escalation of events of concern and are evaluated to identify if a threat to the security of the network exists.
- hundreds of millions of packets of incoming event data from various data sourcesmay be processed to yield 100 anomalies, which may be further processed to yield 10 threat indicators, which may again be further processed to yield one or two threats.
- FIG. 24is flow diagram illustrating in more detail an example process 2400 for detecting anomalies, identifying threat indicators, and identifying threats to network security.
- the processbegins by detecting anomalies in activity on a computer network, based on received event data.
- incoming event data 2302is processed through a plurality of anomaly models 1 through N, which may be machine learning models as discussed above, and which at step 2404 may output anomaly data 2304 indicative of a plurality of anomalies 1 through M.
- an anomalyis not necessarily detected for a given set of event data 2302 .
- no anomalyis detected.
- the processcontinues with generating anomaly data 2304 indicative of the anomalies in response to the detection.
- the anomaly data 2304generally refers to the entire set or a subset of the detected anomalies across the computer network.
- the processing of event data 2302 according to the plurality of models at step 2402leads to the outputting of anomalies (or associated data) 1 through M at step 2404 .
- the anomaly data 2304includes only the event data 2302 associated with detected anomalies. In other words, the anomaly processing can be viewed as a filtering process to pass on only event data associated with anomalous activity.
- the anomaly data 2404includes data in addition to the underlying event data 2302 .
- the anomaly data associated with a particular entitymay include the underlying event data associated with the anomalous activity, annotated information about that entity (e.g. a user ID or account associated with a device), timing data associated with the anomalous activity (e.g. when the anomaly occurred, when a similar anomaly last occurred, or periodicity of this type of anomaly showing up for the particular entity), etc.
- the anomaly data 2304is stored in a data structure in the form of an anomaly graph.
- the anomaly graphincludes a plurality of vertices (nodes) representing entities associated with the computer network and a plurality of edges, each of the plurality of edges representing an anomaly linking two of the plurality of vertices (nodes).
- the processcontinues with identifying threat indicators by processing the anomaly data.
- the anomaly data 2304(or at least a subset of anomaly data 2304 ) is processed through a plurality of threat indicator models 1 through Y, which at step 2410 may output threat indicator data 2306 including a plurality of threat indicators.
- the processing of event data 2302 at step 2402 to produce anomaly data 2304occurs on a per entity basis, while the processing of anomaly data 2304 at step 2408 can occur across the computer network whose security is being monitored, or at least a subgroup of the computer network.
- each anomaly 1 through Mis detected as anomalous for a particular entity given event data associated with the given entity.
- the plurality of threat indicator models 1 through Yare evaluating the plurality of anomalies 1 through M that occur across the computer network being monitored, not just for a particular entity. As shown in FIG. 24 , a threat indicator is not necessarily identified based on a given set of anomaly data 2304 . For example, as shown at step 2412 , when the anomaly data 2304 is processed according to threat indicator model Y, no threat indicator is identified.
- the processcontinues with generating threat indicator data 2306 indicative of the threat indicators in response to the identifying the threat indicators.
- the threat indicator data 2306generally refers to the entire set or a subset of the identified threat indicators across the computer network being monitored.
- the processing of anomaly data 2304 according to the plurality of threat indicator models at step 2408leads to the outputting of threat indicators (or associated data) 1 through X at step 2410 .
- the threat indicator data 2306simply includes only the event data 2302 associated with identified threat indicators. In other words, the threat indicator processing can be viewed as a further filtering of the event data 2302 to pass on only event data 2302 associated with threat indicators.
- the threat indicator data 2306includes data beyond the underlying event data 2302 .
- the threat indicator data 2306may include the underlying event data associated with the anomalous activity, annotated information about the entities (e.g. users, devices, etc.) associated with the threat indicator, timing data associated with the threat indicator (e.g. when the threat indicator was raised, when a similar threat indicator last occurred, periodicity of this type of threat indicator, etc.).
- the threat indicator data 2306is stored in a data structure in the form of a threat indicator graph.
- the threat indicator graphmay include a plurality of vertices (nodes) representing entities associated with the computer network and a plurality of edges, each of the plurality of edges representing a threat indicator linking two of the plurality of vertices (nodes).
- the threat indicator data 2306is instead stored in a relational database or a key-store database.
- the threat indicator data 2306is incorporated into a network security graph, which may be the composite relationship graph discussed above.
- the network security graphcan include a plurality of vertices (nodes) representing entities associated with the computer network and a plurality of edges linking two or more of the plurality of vertices (nodes). Each edge in such a graph represents an association between the entities represented by the vertices (nodes). Accordingly, anomalies defined in the anomaly data 2304 , and/or threat indicators defined in the threat indicator data 2306 , can be incorporated into the graph as vertices (nodes), each linked to one or more of the entities by one or more edges.
- a threat indicatoris identified and is associated with a user 1 using a device 1 operating on a computer network.
- the user and deviceare each defined as a node with an edge linking them to represent the association (i.e. user 1 uses device 1 ).
- An anomaly or a threat indicatoris then incorporated as a third node into the simplified graph with edges linking to both the node representing user 1 and the node representing device 1 .
- step 2414The process continues with at step 2414 with identifying threats to the security of the computer network by processing the threat indicator data 2306 .
- FIG. 25is a flow diagram describing an example process 2500 for detecting anomalies.
- Process 2500begins at step 2502 with receiving event data 2302 indicative of activity by a particular entity associated with a computer network.
- event data 2302is received by a security platform from a plurality of entities associated with the computer network via an ETL pipeline.
- an anomaly modelincludes at least model processing logic defining a process for assigning an anomaly score to the event data 2302 and a model state defining a set of parameters for applying the model processing logic.
- a plurality of anomaly models instancesmay be instantiated for each entity associated with the computer network.
- Each model instancemay be of a particular model type configured to detect a particular category of anomalies based on incoming event data.
- a computer on computer networkis associated with various anomaly models, with one of the anomaly models configured to detect an anomaly indicative of a machine generated beacon communication to an entity outside the computer network.
- the security platformincludes anomaly models configured to detect a number of different kinds of anomalous activity, such as lateral movement, blacklisted entities, malware communications, rare events, and beacon activity. Each of these anomaly models would include unique processing logic and parameters for applying the processing logic. Similarly, each model instance (i.e. for a particular entity) may include unique processing logic and parameters for applying the processing logic.
- processing of event data 2302is performed in real-time as the event data is received. In such an embodiment, real-time processing may be performed by a processing engine optimized for high rate or real-time processing, such as Apache Storm or Apache Spark Streaming.
- Process 2500continues at step 2506 with assigning an anomaly score based on the processing of the event data 2302 through the anomaly model.
- Calculation of the anomaly scoreis done by the processing logic contained within the anomaly model and represents a quantification of a degree to which the processed event data is associated with anomalous activity on the network.
- the anomaly scoreis a value in a specified range.
- the resulting anomaly scoremay be a value between 0 and 10, with 0 being the least anomalous and 10 being the most anomalous.
- Process 2500continues at step 2508 with outputting an indicator of a particular anomaly if the anomaly score satisfies a specified criterion (e.g., exceeds a threshold).
- a specified criterione.g., exceeds a threshold.
- the specified criterionmay be set such that an anomaly is detected if the anomaly score is 6 or above, for example.
- the specified criterionneed not be static, however.
- the criterion(e.g., threshold) is dynamic and changes based on situational factors.
- the situational factorsmay include volume of event data, presence or absence of pre-conditional events, user configurations, and volume of detected anomalies.
- FIG. 26is a flow diagram describing an example process 2600 for identifying threat indicators.
- Process 2600begins at step 2602 with processing the anomaly data 2304 through a threat indicator model, which like the anomaly models may also be a machine learning model.
- a threat indicator modelincludes model processing logic defining a process for assigning a threat indicator score based on processing the anomaly data 2304 and a model state defining a set of parameters for applying the model processing logic.
- model processing logicdefining a process for assigning a threat indicator score based on processing the anomaly data 2304 and a model state defining a set of parameters for applying the model processing logic.
- Specific use cases for identifying threat indicators based on detected anomaliesare discussed in more detail herein. In each described use case the steps to identifying a threat indicator may be incorporated into the processing logic.
- processing of the anomaly data 2304may include aggregating anomaly data across the computer network, correlating different anomalies within the anomaly data, and/or enhancing the anomaly data through enrichment using external data sources.
- processing of anomaly data 2304is performed in real-time as the event data is received and anomalies are generated.
- real-time processingmay be performed by a processing engine optimized for high rate or real-time processing, for example, Apache Storm or Apache Spark Streaming.
- processing of anomaly data 2304is instead or additionally performed in batch mode.
- batch mode processingmay be performed by a processing engine optimized high volumes of data, such as Apache Spark on a Hadoop distributed computing cluster.
- Process 2600continues at step 2604 with assigning a threat indicator score based on processing the anomaly data 2304 .
- calculation of the threat indicator scoreis based on the processing logic contained within the threat indicator model and represents a quantification of a degree to which the processed anomaly data is associated with activity that may be a threat to the security of the network.
- a threat indicatorcan be conceptualized as an escalation or intermediate step between detection of an anomaly and identification of a threat to network security.
- the threat indicator scoreis a value in a specified range.
- the resulting threat indicator scoremay be a value between 0 and 10, with 0 being the least threating and 10 being the most threatening.
- Process 2600continues at step 2606 with identifying a threat indicator if the threat indicator score satisfies a specified criterion (e.g., a threshold).
- a specified criterione.g., a threshold
- the specified criterionmay be set such that a threat indicator is identified if the threat indicator score is 6 or above, for example.
- the specified criterionneed not be static, however.
- the criterion(e.g., threshold) is dynamic and changes based on situational factors.
- the situational factorsmay include volume of event data, presence or absence of pre-conditional events, user configurations, and volume of detected anomalies.
- a detected anomalyis typically associated with one or more entities associated with a computer network. For example, if an anomaly is detected that is suggestive of beacon activity (discussed further below), that beacon activity is typically from one or more devices operating within the network being monitored. Each of those devices may be associated with one or more users.
- the threat indicator modelssuch as those described previously with respect to FIG. 26 , are configured to analyze the relationships between entities on the computer network and the detected anomalies making up the set of anomaly data 2304 across the computer network.
- FIG. 27illustrates a use case for identifying threat indicators based on entity associations with detected anomalies.
- the use case illustrated in FIG. 27is identifying a threat indicator if, based on processing the anomaly data, it is determined that a high number of entities are associated with a particular anomaly or a particular category of anomaly.
- anomaly data 2304A shown in FIG. 27 , a number of detected anomalies 1 though M are included in anomaly data 2304 , which is surrounded by the larger dotted line box. Associated with these detected anomalies are various entities including devices 1 though S and users 1 through R. In this example, anomaly 1 is shown to be associated with at least seven unique entities, including users 1 through R, and devices 1 through S. Anomalies 2 , 3 , and M, however, are each associated with just one entity, user 3 , device, 1 , and user R (respectively). This use case assumes that a correlation among anomalies and entities that establishes relatively high interrelationship is more suspicious than individual occurrences of anomalous activity.
- anomaly 1surrounded by the smaller dotted line box, may be identified as a threat indicator based on the processing of anomaly data 2304 . It is important to note here that this type of system wide view of anomalous activity is not possible at the anomaly detection level, according to some embodiments, because the anomaly model instances are set up to process event data on a per-entity basis. In other words, an anomaly model is only concerned with what is occurring at a particular entity, while a threat indicator model is concerned with what is occurring across the entire computer system.
- Anomaly 1is shown in FIG. 27 as a single anomaly for clarity purposes, however it may also represent a cluster of anomalies that are somehow related to one another.
- anomaly 1may represent a set of anomalies of a particular category of anomaly. For example, a threat indicator may be identified if a high number of entities within a computer network are associated with beacon activity. That beacon activity may be associated with hundreds or thousands of detected anomalies across the network.
- anomaly 1as shown in FIG. 27 , may represent a cluster of anomalies of not just the same category, but substantially matching on a lower level as well. For example, beacon activity broadly describes a wide range of behavior.
- beacon communications known to be associated with malware command and control communicationsmay exhibit similar characteristics. These characteristics may be described in profile or footprint associated with a particular anomaly. This profile or footprint is based on the underlying event data 2302 that gave rise to the anomaly. For example, while individually unique, a set of anomalies based on beacon communications may exhibit patterns related to destination entities, periodicity of communications, etc. Accordingly, anomaly 1 , as shown in FIG. 27 may represent a plurality of individual anomalies that, although unique, all have substantially matching profiles or footprints.
- the use case described in FIG. 27involves a process that begins with determining a measure (e.g., a count) of entities of the computer network associated with a particular anomaly, a particular category of anomaly, or a set of anomalies with substantially matching profiles or footprints. In some embodiments, this determination is based on an absolute number tracked from when monitoring of the computer network commenced. In other embodiments, this determination may be over a pre-determined and/or dynamic time period.
- a measuree.g., a count
- the processcontinues with identifying a threat indicator if the measure of entities associated with the particular anomaly, particular category of anomaly, or a set of anomalies with substantially matching profiles or footprints, satisfies a specified criterion.
- the specified criterionmay simply be a threshold number of entities associated with an anomaly. For example, identifying a threat indicator if 20 entities are associated with a beacon related anomaly. This threshold value need not be static however. The threshold value may depend on the type of anomaly detected, the types of entities associated (e.g. mission critical systems vs. non-critical systems), the temporal clustering of entities associated with the anomaly, etc.
- a threat indicator modelas described with respect to FIG.
- a threat indicator scorecan be assigned based on the processing of the anomaly data with a threat indicator being identified if the threat indicator score satisfies a specified criterion. For example, the 20 entities associated with a particular anomaly may lead to assigning an threat indicator score of 6 on a scale of 1 to 10. Accordingly a threat indicator is identified because the assigned threat indicator score is at least 6.
- FIG. 28illustrates a second use case for identifying threat indicators based on entity associations with detected anomalies.
- the use case illustrated in FIG. 28is identifying a threat indicator if, based on processing the anomaly data, it is determined that a high number of anomalies are associated with a particular entity.
- a number of detected anomalies 1 though Mare included in anomaly data 2304 , which is surrounded by the larger dotted line box.
- various entitiesincluding devices 1 though S and users 1 through R.
- user 1is shown to be associated with at least four anomalies 1 though M (as indicated by the first of two smaller dotted line boxes)
- device 1is shown to be associated with least four anomalies 1 though M (as indicated by the second of two smaller dotted line boxes).
- this use caseassumes that a correlation among anomalies and entities that establishes relatively high interrelationship is more suspicious than individual occurrences of anomalous activity.
- an entitysuch as a user or device
- an entitythat is associated with a high number of detected anomalies may be more indicative of threating activity.
- two threat indicatorsare identified based on the anomaly data 2304 shown in FIG. 28 , one threat indicator based on the anomalies associated with user 1 and one threat indicator based on the anomalies associated with device 1 .
- each anomaly 1 through M shown in FIG. 28is shown as a single anomaly for clarity purposes.
- each anomaly shown in FIG. 28may also represent a cluster of anomalies that are somehow related to one another.
- anomaly 1may represent a single instance of an anomaly, multiple anomalies of the same category, or multiple anomalies with substantially matching profiles or footprints.
- the use case described in FIG. 28involves a process that begins with determining a measure (e.g. a count) of anomalies associated with a particular entity of the computer network. In some embodiments, this determination is based on an absolute number tracked from when monitoring of the computer network commenced. In other embodiments, this determination may be over a pre-determined and/or dynamic time period.
- a measuree.g. a count
- this determinationis based on an absolute number tracked from when monitoring of the computer network commenced. In other embodiments, this determination may be over a pre-determined and/or dynamic time period.
- the processcontinues with identifying a threat indicator if the measure of anomalies associated with the particular entity satisfies a specified criterion.
- the specified criterionmay simply be a threshold number of anomalies associated with a particular entity. For example, identifying a threat indicator if 20 beacon anomalies are associated with particular user device on the network. This threshold value need not be static, however. The threshold value may depend on the type of anomaly detected, the types of entity associated with the anomalies (e.g. mission critical systems vs. non-critical systems), the temporal clustering of anomalies associated with a particular entity, etc.
- a threat indicator scorecan be assigned based on the processing of the anomaly data 2304 with a threat indicator being identified if the threat indicator score satisfies a specified criterion. For example, the 20 anomalies associated with a particular entity may lead to assigning an threat indicator score of 6 on a scale of 1 to 10. Accordingly a threat indicator is identified because the assigned threat indicator score is at least 6.
- FIG. 29illustrates a use case for identifying threat indicators based on duration of detected anomalous behavior.
- Anomaliesmay be detected over a period of time, for example, as shown in FIG. 29 , anomalies 1 through M are detected at time periods t 1 through tm.
- This use caseassumes that a temporal correlation among detected anomalies is indicative of suspicious activity. For example, a high number of anomalies occurring in a short time period may be indicative of a concentrated threat to the security of the network.
- the use case described in FIG. 29involves a process that begins with monitoring a duration of a particular anomaly over a time period.
- anomalies 1 through M shown in FIG. 29are shown as discrete events, in some cases an anomaly may have duration with a starting time and an end time.
- the processcontinues with identifying a threat indicator if the monitored duration of the anomaly satisfies a specified criterion.
- the use case described in FIG. 29involves a process that begins with determining a number of anomalies that have substantially matching profiles or footprints (e.g. as described in the previous use case) over a time period. These substantially matching anomalies may indicate a pattern of anomalous activity that has duration. The process continues with identifying a threat indicator if the number of anomalies with substantially matching profiles satisfy a specified criterion.
- FIG. 30illustrates a use case for identifying threat indicators based on local and global rarity analysis.
- anomaliesare detected based on a rarity analysis.
- a rarity analysisi.e. is determined to be rare
- This anomaly detection based on rarity analysisis local rarity analysis, because it looks at the rarity of the event in the context of a particular entity.
- the anomalies detected based on local rarity analysisare analyzed across the computer network according to a global rarity analysis.
- the number of similar anomaliesis important indicator of their severity. For example, a machine generated beacon anomaly may be interpreted as malicious if occurring in only a small number of systems (intruders of malware infections typically affect only a small number of systems, sophisticated attackers will infect a single device).
- event data 2302is processed through a number of local rarity analysis models 1 through U that are associated with entities 1 through V.
- the detected anomalies 1 through Mare then analyzed according to a global rarity analysis model to identify a threat indicator.
- the use case described in FIG. 30involves a process that begins with performing a global rarity analysis across the anomaly data 2304 (or a subset of the anomaly data 2304 ) over a time period, with the anomaly data 2304 based on anomalies detected using local rarity analysis.
- the processcontinues with identifying a threat indicator if a pattern in the detected anomalies satisfies a global rarity criterion.
- a global rarity modelis a model that applies the same processing logic as a local rarity model, except that it is applied to the set of anomalies across the network being monitored instead of the event data pertaining to a single entity.
- FIGS. 31A-31Billustrate a use case for identifying threat indicators based on combining the outputs (i.e. detected anomalies) from different anomaly models.
- different types of anomaliesare detected based a different models.
- a threat indicatoris identified by processing the anomaly data 2304 according to a threat indicator model if anomalies 1 and 2 are present. For example, two types of beacon activity may be considered to be more suspicious when observed in combination. However, as shown in FIG. 31B , if anomaly 2 is not detected (and therefore not part of anomaly data 2304 ), the threat indicator is not identified based on processing according to the threat indicator model.
- the use case described in FIGS. 31A-31Binvolves combining anomaly data associated with different types of anomalies, assigning a threat indicator score based on the result of the combining, and identifying a threat indicator if the threat indicator score satisfies a specified criterion.
- FIGS. 32A-32Billustrate a second use case for identifying threat indicators based on combining the outputs (i.e. detected anomalies) from different anomaly models.
- a threat indicatoris identified by processing the output from an anomaly model of a first type with a an anomaly model of a second type. Recall the previous example of a beacon anomaly processed according to a rarity analysis to determine if the beacon is rare for a given environment. That example involves processing event data 2302 according to a beacon detection model to detect a beacon anomaly and then processing the detected beacon anomaly according to a rarity analysis model to detect a rarity anomaly. In some embodiments, if the second anomaly is detected, a threat indicator is identified.
- anomaly 1is detected based on processing of event data 2302 through anomaly model 1 .
- Anomaly 1is then input into anomaly model 2 for processing.
- the output anomaly 1is processed along with other event data 2302 through anomaly model 2 .
- a second anomaly 2is detected based on processing anomaly 1 (and, and in some embodiments, event data 2302 ) through anomaly model 2 .
- FIG. 32Bshows the same process as in FIG. 32A except that a threat indicator is not identified because anomaly 1 was not detected.
- the same processmay have yielded anomaly 1 , but not anomaly 2 .
- a beacon anomalyis detected, but a rarity anomaly associated with that beacon is not detected because the beacon is common to a particular environment. Accordingly a threat indicator is not identified.
- the use case described in FIGS. 32A-32Binvolves a process of detecting a first type of anomaly based on processing event 2302 data by a first type of anomaly model.
- the processcontinues with inputting the first type of anomaly into a second type of anomaly model.
- the processconcludes with identifying a threat indicator if a second type of anomaly model is detected based on processing the first type of anomaly by the second type of anomaly model.
- FIGS. 31A-32Bdepict simple combinations of two anomalies, however, the concept can easily be applied to more complex combinations of multiple anomaly outputs.
- FIG. 33illustrates a use case for identifying threat indicators by enriching the anomaly data using data from external sources.
- a detected anomalymay provide more insight if combined with other data that indicates a malicious nature. For example, consider the detection of an anomalous connection to particular domain xyz.com outside the computer network. The detected anomaly indicates that the domain may be associated with malicious activity, however, beyond the fact that it may appear machine generated or rare, additional information may be required to confirm that suspicion. It is therefore possible to access additional external public information (e.g. a WHOIS lookup) that will provide additional information about the domain, for example, who registered the domain name and how long ago. A website registered very recently in a country deemed to be “high risk” is likely to be viewed as more suspicious. By incorporating the external information the, a confidence level that a particular anomaly is associated with malicious activity can be increased, and in some cases a threat indicator identified.
- additional external public informatione.g. a WHOIS lookup
- event data 2302is processed through an anomaly model resulting in detection of an anomaly at step 3304 .
- Additional information from an external data sourceis obtained (e.g., by a push or pull modality) at step 3306 during a process of data enrichment resulting in annotated anomaly data at step 3308 .
- This annotated anomaly datais processed according to threat indicator model and a threat indicator is identified if a specified criterion is satisfied.
- pulling this external information at step 3306e.g. via a WHOIS lookup
- is computationally expensiveso it makes sense to annotate the anomaly data 2304 instead of the higher volume event data 2302 if the enrichment process is occurring in real-time or near real-time.
- the use case described in FIG. 33involves a process that begins with identifying a particular entity associated with the anomaly data. This identification may be based on the underlying event data used to generate the anomaly. As in the last example, an anomaly may be associated with a domain xyz.com. The process continues with comparing the particular entity against data stored in an database of known security risks. For example, an external publicly available database may include a list of domains known to be associated with malicious beacon activity. The process continues with identifying a threat indicator if the particular entity substantially matches a known security risk contained in the external database.
- the use case described in FIG. 33involves a process that begins with identifying an anomaly associated with a connection to a domain considered to be unfamiliar. The process continues with determining whether the domain considered to be unfamiliar matches a domain known to be a security risk, for example, by using information from an external data source. The process continues with identifying a threat indicator if the domain considered to be unfamiliar substantially matches a domain known to be a security risk.
- FIG. 34is a flow diagram depicting an example process 3400 for identifying threats to the security of a computer network based on threat indicators.
- the process of identifying threats based on correlation of anomaliesis described in more detail elsewhere in this specification. The same concept applies here, except that the threat is identified based on correlating the threat indicator data 2306 including a plurality of identified threat indicators instead of the anomaly data 2404 .
- Process 3400begins at step 3402 with correlating the threat indicator data 2306 , or at least a subset of the threat indicator data 2306 .
- Process 3400continues at step 3404 with identifying a set of candidate security threats based on the correlation.
- Types of correlationare described elsewhere in this specification but can include network-wide correlation for malware threats, connected component correlation for kill chain type threats, per-entity analysis for kill chain type threats, and per-burst analysis for insider threats.
- Process 3400continues at step 3406 with comparing the subset of the threat indicator data against pre-configured patterns or pre-set rules associated with each candidate threat. For example, an insider threat may be associated with known patterns identified by security experts and therefore be associated with pre-set rules.
- Process 3400continues at step 3408 with generating a pattern matching score based on a result of the comparing.
- the pattern matching scoreis a value in a set range.
- the resulting pattern matching scoremay be a value between 0 and 10 with 0 being the least likely to be a threat and 10 being the most likely to be a threat.
- Process 3400concludes at step 3410 with identifying a security threat if the pattern matching score satisfies a specified criterion.
- the specified criterionmay be set such that an threat is identified if the pattern matching score is 6 or above.
- the specified criterionneed not be static, however.
- the criterionis dynamic and changes based on situational factors. Situational factors may include volume of event data, presence or absence of pre-conditional events, user configurations, volume of detected anomalies, and involvement of mission critical systems.
- the security platform 300can combine the individual event-specific relationship graphs from all processed events into a composite relationship graph that summarizes all significant (from a security standpoint) network activity for an entire enterprise or network.
- the composite relationship graphcan include nodes representing the various entities associated with the network as well as nodes representing the detected anomalies. Subsets, or “projections,” of the composite relationship graph can then be used by various different threat models to detect security threats, as will now be further described.
- FIGS. 35 through 38relate to a method for storing and analyzing a security data structure (e.g., a graph including nodes and edges) for identifying security threats in a computer network.
- the nodesrepresent entities in or associated with the computer network, such as users, devices, applications, and anomalies.
- the edgeswhich connect nodes, represent the relationships between the entities.
- An ETL processgenerates event-specific graph data structures (also referred to as “mini-graphs” or “relationship graphs”) corresponding to events that have occurred in the computer network.
- the method introduced heredetects anomalies based on the mini-graphs, and combines the anomalies with the mini-graphs to generate the composite relationship graph, which may also be called an “enterprise security graph” to the extent it may relate to a network of a particular enterprise (e.g., a corporation, educational institution, government agency, etc.).
- the composite relationship graphincludes nodes that represent the anomalies and edges that represent relationships between anomalies and other entities involved in the events.
- the methodcondenses network activities that are of the same type and associated with the same user into a single entry of combined network activity.
- the methodfurther assigns these combined network activities into different projections of the composite relationship graph, depending on the type of activity.
- Each projectionrepresents a subset of the composite relationship graph that relates to a certain type or types of user action or other category (e.g., login, web visit, file access, anomaly, etc.).
- the projectioncan be stored in a cluster (e.g., a Hadoop cluster) and further broken down into multiple files based on the timestamps. Relevant files can be stored in proximity in the cluster for data access efficiency.
- the methodfurther identifies security threats by correlating the anomalies across the composite relationship graph. For example, the method can use a neighborhood computation algorithm to identify a group of related anomalies in the composite relationship graph that represent a security threat. Alternatively, the method can identify an insider who poses a security threat based on a group of anomalies being close to each other in time and their confidence metrics.
- FIG. 35illustrates an example process of combining and storing relationship graphs into a composite relationship graph.
- the processreceives event data from various data sources.
- the event datacan be, e.g., timestamped machine data.
- the processuses parsers 3510 to conduct an ETL procedure to generate information about the entities in the computer network and the relationships between the entities.
- the processorganizes the information about the entities and the relationships for each event into a mini-graph.
- Each of the mini-graphs 3522 , 3524 and 3526includes nodes and one or more edges each interconnecting a pair of the nodes.
- the nodesrepresent the entities involved in the particular event.
- the edgesrepresent the relationships between the entities in the event.
- An analytics engine 3530can process these mini-graphs 3522 , 3524 and 3526 (e.g., using various machine learning models) to detect anomalies.
- a separate machine learning model called aggregator 3540combines the mini-graphs and detected anomalies into the composite relationship graph.
- the composite relationship graphincludes nodes that represent the entities, as well as nodes that represent the detected anomalies.
- the composite relationship graphis created first in volatile memory of one or more computing devices, and then saved to non-volatile storage.
- a graph library component 3550handles the storage of the composite relationship graph in a non-volatile storage facility called graph database 3560 .
- the nodesalso referred to as vertices
- edges and associated metadata of the composite relationship graphare stored in one or more data files.
- the nodes and edges of the composite relationshipcan be partitioned based on the timestamps (from the event data) of the corresponding network activities.
- Each data filecan be designated for storing nodes and edges for a particular time period.
- a graph merger component 3570runs a background job to merge new segments into the composite relationship graph at a predetermined periodicity. As the system continuously receives new event data and generates new mini-graphs and new anomalies based on the new event data, the graph merger component 3570 merges these newly created mini-graphs and associated detected anomalies into the composite relationship graph.
- FIG. 36illustrates an example of a composite relationship graph.
- the illustrated composite relationship graph 3600includes a number of nodes U 1 through U 11 that represent users (also referred to as “user nodes”) and a number of nodes IP 1 through IP 7 that represent network devices (also referred to as “device nodes”).
- the composite relationship graph 3600further includes a number of nodes I 1 through I 4 that represent anomalies (also referred to as “anomaly nodes”). For example, anomaly node I 1 suggests that a user represented by node U 5 has engaged in certain suspicious activity with, or in relation to, the device represented by node IP 3 .
- anomaly nodes I 1 , I 2 and I 4connected to the same device node IP 3 . These anomaly nodes may be indicative of a security threat involving the device IP 3 .
- the anomaly nodes I 1 , I 2 and I 4also connect to the user nodes U 4 , U 5 and U 7 and device node IP 5 . This may indicate that users U 4 , U 5 and U 7 are suspicious, meaning these users can potentially be malicious users who engage in or will engage in activities detrimental to the security of the computer network. For example, users U 4 , U 5 and U 7 may be invaders who have breached network devices with malicious intentions.
- a decision enginee.g., including a machine learning model
- a security threatrepresented by a group of nodes in question, including, in the illustrated example, anomaly nodes II, 12 and 14 , user nodes U 4 , U 5 and U 7 , and device nodes IP 3 and IP 5 .
- the composite relationship graphcan include a number of projections that correspond to different categories of computer network activities. Each projection is a subset of the composite relationship graph and includes edges representing computer network activities of a particular category.
- the graph library component 3550can write the content of the different projections into separate data files.
- the graph library component 3550can write the different projections into other types of data containers, such as logical unit numbers (LUNs).
- LUNslogical unit numbers
- FIG. 37illustrates an example of how a composite relationship graph can be stored as separate projections.
- the graph library component 3550examines the edge's type to determine the projection to which the edge belongs.
- the different projections in the illustrated exampleinclude a login projection 3710 , a website-visit projection 3720 and an anomaly projection 3730 .
- the composite relationship graphcan include other types of projections, such as a projection for activities of users accessing files stored in the devices in the computer network.
- the graph library component 3550determines that a particular edge corresponds to an activity of a user logging into a device, the graph library component 3550 assigns the particular edge to that particular login projection. For example, if the graph library component 3550 determines that a particular edge corresponds to an activity of a user visiting a website, the graph library component 3550 assigns the particular edge to the website-visit projection 3720 . If the graph library component 3550 determines that a particular edge relates to an anomaly (e.g., the edge connecting to an anomaly node), the graph library component 3550 assigns the particular edge to the anomaly projection 3730 .
- an anomalye.g., the edge connecting to an anomaly node
- the graph library component 3550can further break down the projections into a plurality of files. Each of the files stores network activities that have occurred in a particular time period. For example, as shown in FIG. 37 , the projection is broken down into a sequence of files, each of which stores network activities that have occurred in one particular day. In some alternative embodiments, the graph library component 3550 can further break down the projection into finer granularity. For example, the projection may be broken down into a sequence of directories corresponding to days. Each directory may then include files corresponding to each hour of the day.
- the graph library component 3550can dynamically adjust the granularity. For example, in one embodiment, for network activities that occurred during the last two months, the graph library component 3550 may break down the projection data into files corresponding to each hour of the last two months; whereas, for network activities that occurred prior to the last two months, the graph library component 3550 breaks down the projection data into files corresponding two months the graph library component 3550 may break down the projection data into files corresponding to each week or each month. As time goes by, some network activities stored in a daily granularity become older than two months. Thus, the graph library component 3550 continuously combines files storing these network activities into files corresponding to the weekly or monthly granularity.
- FIG. 38illustrates an example process of combining event-specific relationship graphs into a composite relationship graph and detecting a security threat based on the composite relationship graph.
- the processreceives event data representing a plurality of events on a computer network.
- the event dataare indicative of a plurality of entities and at least one anomaly involved in the events.
- the entitiescan include various types of entities involved in the computer network.
- the entitiescan include, e.g., devices in the computer network, users of the devices in the computer network, websites, applications and/or data files stored in the devices in the computer network.
- the processacquires an event-specific relationship graph (e.g., a mini-graph), for example, from the data intake and preparation stage via the distributed messaging platform.
- the event-specific relationship graphis indicative of entities involved in the associated event and one or more relationships between the entities involved in the event.
- the event-specific relationship graphincludes a number of nodes and at least one edge interconnecting nodes. The nodes represent the entities involved in the event. Each edge represents an interaction between a pair of the entities.
- the processacquires anomaly data indicative of various security-related anomalies detected from the event data.
- the computer systemcan further store the event data associated with the anomaly in long-term (non-volatile) storage.
- the security platform 300can generate a visualization of the event data associated with the anomaly when the platform receives an instruction to visualize details of the anomaly.
- the processcondenses the computer network activities in the event-specific relationship graph into combined computer network activities. For each event, the process identifies one or more computer network activities of a particular type based on the event-specific relationship graph. The identified computer network activities are associated with the same entity and occur during a predefined time period. The process then combines the computer network activities of the particular type into a data entry representing the combined computer network activity and counts the computer network activities that occur during the predefined time period.
- the processstores the data entry representing the combined computer network activity and the count in non-volatile storage, such as a data file designated for the particular type and the time period.
- the stored data entry for the combined computer network activityincludes information about an activity type, an originating entity, a target entity, the number of times the computer network activities occur in the time period, a start time, an end time, an average gap period between the computer network activities that occur in the time period, or a standard deviation of gap periods between the computer network activities that occur in the time period.
- the processcombines the event-specific relationship graphs for the received events with the anomaly data into a composite relationship graph.
- the composite relationship graphincludes nodes that represent the entities involved in the events and nodes that represent the anomalies detected based on the event data.
- the entities involved in the eventsinclude at least two types of entities, such as users and devices.
- the composite relationship graphfurther includes edges that represent the relationships between the entities involved in the events and the anomalies.
- the composite relationship graphcan include a plurality of projections.
- Each of the projectionsis a subset of the composite relationship graph that includes edges representing a plurality of computer network activities of a particular category.
- the particular category of network activitiescorresponds to users logging into devices in the computer network, users visiting websites, users accessing files stored devices in the computer network, or users conducting anomaly activities.
- one of the projectionsis the anomaly projection 3730 , which is a subset of the composite relationship graph that includes edges representing anomalous activities conducted by users.
- Each projectioncan be stored in a cluster of storage device and distributed amongst data containers (e.g., files) based on timestamps of the associated event data.
- the computer systemcan further identify events that have timestamps satisfying a specific closeness criterion (e.g., the timestamps having differences less than a threshold value), and store the edge data of these identified computer network activities in proximity to each other in the long-term non-volatile storage. In this way, the read efficiency for the computer network activities can be improved.
- the computer systemcan determine an association between the combined computer network activity of the particular type and a particular projection of the composite relationship graph. Then the combined computer network activity is stored into a file designated for the associated projection.
- the computer systemtransfers the data structures representing the edges of the composite relationship graphs from memory of the computer system to persistent (long-term) storage at a predetermined periodicity. For example, if the computer system detects that a time period since a last time of transferring the data structures representing the edges of the composite relationship graphs from memory of the computer system to a persistent storage exceeds a threshold value, the computer system transfers the data structures currently in memory to the persistent storage.
- the computer systemcan further have a memory storage size limit. Once the size of the data structures representing the edges of the composite relationship graphs stored in the memory exceeds the memory storage size limit, the computer system transfers the data structures currently in the memory of the computer system to the persistent storage.
- the processreceives, at a specified periodicity from one or more machine learning models, requests for data of a projection of the composite relationship graph and corresponding to a time range.
- the requested datacan include combined computer network activities including information about computer network activities from multiple events. Since the requests from the machine learning models are for data from a common projection range and corresponding to a common time range, at step 3870 , the process combines the data within the common projection range and the common time range into a single input data structure as an input for the machine learning models.
- Some machine learning modelreceives a portion (e.g., projection) of the composite relationship graph as inputs and identify security threats and/or anomalies based thereon.
- the one or more machine learning modelscan be executed in a batch mode.
- the processdetects a security threat by processing at least a portion (e.g., one or more projections) of the composite relationship graph with a decision engine.
- the decisioncan be, e.g., a machine learning model or an analytics engine running a machine learning model.
- the processfirst converts at least a portion of the composite relationship graph (e.g., the anomaly projection) into an anomaly relationship graph.
- the anomaly relationship graphincludes anomaly nodes that represent anomalies and entity nodes that represent entities in the computer network.
- the computer systeminputs the anomaly relationship graph into the decision engine.
- the decision enginecan then identify a security threat by analyzing the anomalies in any of various different ways.
- a machine learning modelidentifies a set of anomaly nodes interconnecting entities nodes that form a neighborhood cluster in the anomaly relation graph. Another possible way is that the machine learning model identifies a subset of the anomaly relationship graph including anomaly nodes and entity nodes that have no relationships with other nodes outside of the subset in the anomaly relationship graph. Yet another possible way is that the machine learning model identifies a set of anomaly nodes directly connecting a particular entity node in the anomaly relationship graph.
- the machine learning modelcan further identify a group of anomaly nodes within the identified plurality of anomaly nodes, wherein the group of anomaly nodes have timestamps that satisfy a specific closeness criterion. For example, the timestamps may have an average time gap less than a threshold value.
- the processconfirms that the anomalies form a security threat by applying a security rule to the anomalies based on assigned categories of the anomalies.
- the computer systemcan assign the anomalies into categories of, e.g., internal anomaly, malware anomaly, incoming anomaly and exfiltration anomaly.
- An administrator of the computer networkcan specify the rules based on his/her knowledge of typical security threats that occur in the computer network.
- the identified set of anomaly nodesrepresent a set of related anomalies.
- the processcan present the security threat including the set of anomalies to an administrator of the computer network or any party that handles security issues of the computer network.
- Any of the steps in the process illustrated in FIG. 38can be performed by processing logic of a machine learning model. Further, any of the steps can be performed in real-time as the event data are received, or in a batch mode based on the event data retrieved from persistent storage.
- GUIGraphical User Interface
- the present disclosurerelates to methods and systems for organizing and presenting information concerning potential network compromise to one or more users tasked with monitoring the network and thwarting attacks, stolen data, and other harm.
- Embodiments of the present disclosureinclude an innovative graphical user interface that is visually communicative, highly integrated, adaptable, and user interactive.
- GUIgraphical user interface
- the security platform described hereinmay include a GUI generator module that gathers the generated anomaly data, threat data, and other data, and that based on such gathered data, generates display data.
- the GUI generator modulesends the generated display data to one or more physical display devices, to cause those display devices to display the GUI features described herein.
- the GUI modulealso receives user inputs and modifies the display data based on those inputs to provide an interactive display.
- GUIgraphs, timelines, maps, charts, lists and other visualization features are generated to illustrate trends, recent activity, and relationships between different data.
- the GUIcan provide views that are automatically configured via default settings, or the GUI can enable a user to customize a view, for example, to filter out data points that are less critical, distracting, or unnecessary, to zoom in and out, or re-format the view (e.g., from a line chart to a bar chart).
- the GUIcan include links in the data to generate different views that provide additional detail about information of interest.
- the GUIalso can enable the user to set watchlists to track information while navigating the various views. Watchlists can be used, for example, to remind the user that certain data already has been reviewed and considered by the user. Once a user reviews sufficient information to draw a conclusion about a threat, the GUI also enables a user to “take action,” for example, by re-designating the identified threat as “Not a Threat,” or by emailing threat data or exporting it to another data mining platform.
- the GUIprovides these capabilities and many more to facilitate effective network security monitoring via simple user inputs (such as point-and-click actions), with little or no typing and without requiring the user to engage in laborious set-up or programming.
- the GUI introduced heregenerates views pertaining to threats and anomalies identified from event data generated from network activities.
- network activitiesmay include log-ins, email traffic, internet browsing, or file transfers on a network operated by a corporation, university, household, or other organization (referred to collectively as an “organization”).
- Event datacomprises timestamped machine data related to network activity by various entities, including users, devices, and applications.
- “Users”may be employees or others who are associated with an organization. Users might have unlimited rights or privileges to access an organization's network, or they might be authorized to have only limited network access. When user identification information is included in event data, it may appear as a “username” or “User ID” (or “User ID/Password” combination). Typically, users are registered with an account on an organization's network. Whenever a user logs into the organization's network or server(s), from any location and using any device, event data is created that can be tracked for potential instances of network compromise.
- “Devices”may be machines that access the network.
- a devicemight be an IP address associated with a client computer (laptop, desktop, tablet, smartphone, etc.), server, and/or any other machine capable of accessing the organization's network.
- a devicemay be operated by a user who is registered with the network, or it may be operated by someone else who can access the network, either in an authorized or unauthorized capacity.
- many organizationsallow guests to access their networks or allow network traffic by visitors to the organization's website.
- Emails and other file transfers from users to others outside the organization, such as clients, customers, etc.involve communications with devices that are external to the organization's network.
- a network serverWhen a device accesses the network, a network server generates logs and other machine data that identify the device, for example, by IP address. Machine data that includes device information is additional event data that also can be tracked for potential instances of network compromise.
- Application informationidentifies a program that is executed on a network's servers or on a computer in communication.
- an applicationmight be run by a user without proper authorization, or by an intruder outside the organization.
- the applicationmay be malware, or it might be authorized software that has become infected with a virus.
- Machine data that includes information about application activityis yet another example of event data that can be tracked for potential instances of network compromise.
- the event datais analyzed, via various machine learning techniques as disclosed herein, to identify anomalies from expected or authorized network activity or behavior.
- An “anomaly” in the context of this descriptionis a detected fact, i.e., it is objective information, whereas a “threat” (discussed further below) is an interpretation or conclusion that is based on one or more detected anomalies.
- Anomaliescan be classified into various types. As examples, anomalies can be alarms, blacklisted applications/domains/IP addresses, domain name anomalies, excessive uploads or downloads, website attacks, land speed violations, machine generated beacons, login errors, multiple outgoing connections, unusual activity time/sequence/file access/network activity, etc. Anomalies typically occur at a particular date and time and involve one or more participants, which can include both users and devices.
- the event datais analyzed to identify threats.
- Threatsare interpretations or conclusions based on, and therefore associated with, one or more anomalies.
- Threatscan be categorized or grouped into various types, both external and internal to the organization. Examples of threats include data exfiltration (by compromised account, by malware, or by a suspicious user or device), public-facing website attack, suspicious behavior by an insider, and breach of a rule (such as a blacklist, file transfers).
- a threatcan be associated with one or more participants, including users, devices, and applications.
- a threatneed not have a specific event date, because it might be ongoing, in which case it can have a start date and a date of last update. Each threat is based on at least one anomaly.
- a graphical user interface for a user in accordance with the present disclosurealso organizes, tracks, and presents information concerning these entities and instances of potential network compromise. Since information pertaining to different entities and instances may be interrelated, the graphical user interface, in accordance with various embodiments of the present disclosure, provides various views for causing display of this information. The graphical user interface also includes links in these views to cross-reference the information. These capabilities facilitate a user's ability to understand the connections and relationships between different entities and/or instances to better understand security risks and causes of a problem.
- the graphical user interfaceprovides several different ways for a user to access information pertaining to a particular device that seems suspicious.
- the usermay search for the device directly through a “device view.”
- the usermay notice the device when reviewing a threat, and then click on a link for the device from within a threat view.
- the usermight become aware of the device when reviewing information about an anomaly, and click on a link for the device from an anomaly view.
- the usermight notice the device when navigating a “user view,” and clock on the link from within the user view.
- the user reviews information about the suspicious devicethe user can use a “watchlist” to “mark” the device (e.g., as suspicious). Once the device is put in the watchlist, that tracking information can stay with the device and obtained upon access device information from any view.
- FIG. 39Aprovides an example high level, “home screen” view 3900 generated by display data for display in a graphical user interface (“GUI”). This may be the first screen viewed after log-in.
- Toolbar 3901also may be included in all views generated for display in the GUI.
- the toolbarincludes a “Views” tab 3902 , “Analytics” tab 3903 , “Config” tab 3904 , and GUI user name tab 3905 for log-in.
- a GUI usercan toggle the GUI between a “Threats” view 3906 , “Anomalies” view 3907 , “Users” view 3908 , “Devices” view 3909 , and “Applications” view 3910 .
- the “Threats” view 3906provides a listing of all active threats and the “Anomalies” view 3907 provides a listing of all anomalies.
- the “Users” view 3908 , “Devices” view 3909 , and “Applications” view 3910provide separate listings for each type of entity (namely, users, devices, and applications, respectively) that is associated with an anomaly or threat.
- the home screen view 3900also may include a summary status bar 3911 indicating, for example, the number of threats, anomalies, total users, total devices, total apps, and total sessions on the network being monitored.
- the summary status barcan enable the GUI user to see, at a glance, the volume of information that can be reviewed and evaluated.
- the home screen view 3900can additionally include summary charts and illustrations, such as, as shown in FIG. 39A , a “Threats by Threat Type” box 3912 , a “Latest Threats” box 3913 , and an “Events Trend” graphic 3914 .
- the “Threats by Threat Type” box 3912compares by number each different type of threat that has been identified.
- the listing in the “Latest Threats” box 3913identifies the most recent threats by date.
- the “Events Trend” graphic 3914is a timeline showing the volume of events along a timeline.
- the example home screen view 3900also prompts a user, via status bar 3911 , to begin a “Threat Review” or view an “Analytics Dashboard.” Upon clicking, via the graphical user interface, on the “Start Threat Review” button 3915 , a “Threats Review” view 4000 is provided, as described with reference to FIG. 40A .
- an example “Threats Review” view 4000enables a user to separately click through each active threat that has been identified from the event data.
- a count and toggle 4001enables the user to step through each identified threat.
- the view 4000can include a filter section 4020 that enables the user to selectively filter out threat results according to time, severity, or type. For example, as shown in FIG. 40B , the default provides views of “All Threat Types” 4021 but a user can change this to just review pages for “External,” “Insider,” or “Rule-Based” threats.
- the filter section 4020also provides an option to “Select Threat Types,” which enables the user to select the specific types of threats to be included in the Threat Review.
- the filter section 4020also enables the user to filter out threats based on their scores by clicking the “Scores” tab 4022 . (For example, if the user is only interested in evaluating high risk threats, the user might filter out any threats with a score less than 5).
- the usercan also click on the “Time” tab 4023 to filter out threats based on a date range. For example, if the user is only interested in evaluating very recent threats, the user can choose to filter out any threats earlier than the past 24
- each “Threat Review” view 4000can identify a particular threat by its type and provides a summary description 4002 along with a threat score 4003 .
- the threat scoredetermined based on machine learning from the event data, provides an indication of the severity of the risk for network compromise associated with the threat.
- the “Threats Review” view 4000can additionally include a status chart 4004 that provides a Timeline, list of Anomalies, list of Users, list of Devices, list of Apps, and a suggestion of “What Next.”
- the Timelineidentifies the date that the threat began, the last update concerning the threat, and the duration of time that the threat has been active.
- the list of Anomaliesidentifies each type of anomaly that is associated with the threat and how many anomalies of each type.
- the list of Anomaliesalso provides a score for each type of anomaly, which indicates the severity associated with each type of anomaly.
- the list of Usersidentifies each user associated with the threat and provides a score for each user.
- the list of Devices and list of Appsidentify each device (by IP address) and App (by file name/type), respectively, along with a score.
- a linkis included such that, if the link is clicked, the user is taken to a separate view for that selected entity. For example, if the link associated with “Mark Pittman” 4005 is clicked, a “Users Facts” page 300 within the Threats Review is generated, as can be seen from FIG. 41 .
- Threats Review view 4000additionally prompts the user to take “Actions” 4010 , view additional “Details” 4011 , or set up a “Watchlist” 4021 .
- the usercan select from several options, as shown in FIG. 40C . If the user determines that the threat is not a concern, the user can select “Not a Threat” 4011 . By making this selection, the user instructs the network security system to delete the threat page from the Threats View and to no longer identify it as a threat. As a consequence, the total number of threats will decrease (as will be depicted in the status bar 3911 in FIG. 39A ).
- Another option in the “Actions” tab 4010is the “Email Threat” selection 4012 , which enables the user to email the threat to a designated email address. Yet another option is the “Export” selection 4013 , which enables the user to export data associated with the threat to another data mining platform.
- the Threats Review view 4000also includes a “Details” tab 4011 .
- the Threats Review viewis augmented with several additional charts and graphics, as shown in FIGS. 40D, 40E, and 40F , as will be described next.
- FIG. 40Dillustrates a “Threat Relations” flow 4040 , which depicts the relationship between users, devices, and applications that are associated with the threat. Dotted lines connect one or more entities that are participants together in one or more anomalies associated with the threat. For example, in this flow, device “10.116.240.105” is connected via a dotted line with “10.1.21.153,” which runs application “ms-ds-smb” and is associated with “Fred Samuels” and “Mark Pittman.” The dotted is color-coded to indicate that it is “minor” in nature.
- display dataWhen a user “hovers” the cursor over (or highlights) the name of a user, device, or application (or an arrow pointing to the user, device, or application), display data generates a bubble in the GUI view that provides a high-level summary of information about that entity. For example, hovering over “Mark Pittman” causes bubble 4043 to appear, which indicates that “Mark Pittman” is associated with three anomalies: two “Land Speed Violations” (color-coded to indicate that these are considered “major”) and one “Unusual Activity Time.”
- the bubble 4043additionally prompts the user to click a “View All 3 Anomalies” link. As shown in FIG. 42 , clicking on this link causes the GUI to generate an Anomalies Table view 4200 that lists and provides high-level information about the three anomalies.
- the usercan click on an entity to select to receive a view concerning that entity. For example, if the user clicks on “Mark Pittman,” the GUI generates a “User Facts” view 4100 for Mark Pittman, as shown in FIG. 41 .
- FIG. 40Dillustrates a “Kill Chain View” 4050 associated with the threat.
- the Kill Chain viewillustrates three stages of the threat: “Intrusion” 4051 , “Expansion” 4052 , and “Exfiltration” 4053 .
- the GUIincludes a summary of the anomaly or anomalies in that stage. For example, two Land Speed Violation anomalies 4054 occurred during the “Intrusion” stage.
- the GUIindicates that one of these violations 4056 was from Pittsburgh, in the US, to Beijing, in China.
- the GUIindicates the number of times that land speed violation occurred (once) and provides a color-code to indicate the severity of that violation as it relates to the threat.
- the GUIcan include a link for each anomaly in stages 4051 , 4052 , and 4053 of Kill Chain 4050 in FIG. 40D .
- a link for each anomaly in stages 4051 , 4052 , and 4053 of Kill Chain 4050 in FIG. 40DFor example, by clicking on “Land Speed Violation from Pittsburgh, US, to Beijing, China” 4056 , the user navigates to Anomaly Details view 4300 for this selected anomaly, as shown in FIG. 43 .
- the two anomalies associated with the Exfiltration stage 4053are both “Excessive Data Transmission” 4055 . These are color-coded in red to provide an indication of their high level of severity.
- the Kill Chain viewadditionally can include a timeline 4057 that illustrates the timing of each phase.
- the Intrusion phase 4051is associated with 3 anomalies, beginning on Nov. 15, 2014.
- the Expansion phase 4052is associated with 8 anomalies, beginning on Nov. 21, 2014, and concluding on Nov. 23, 2014.
- the Exfiltration stage 4053is associated with 2 anomalies, beginning on Dec. 1, 2014, and concluding (or their last update occurred) on Dec. 3, 2014.
- clicking on the “Details” tab 4011 in the Threats Review view 4000also can generate illustrations of a Threat Anomalies Timeline 4060 , Threat Anomalies Trend 4070 , and Threat Anomalies listing 4080 and Device Locations 4090 , in FIGS. 40E and 40F .
- Threat Anomalies Timeline 4060provides a timeline of each anomaly, sorted by anomaly type.
- the timelineshows a circle corresponding to each occurrence, which is color-coded to indicate its severity. If there is more than one anomaly of the same type on the same date, the circle is made larger.
- a bubbleis generated that provides the date of the anomaly or anomalies and prompts the user to select more detailed information (not shown).
- the GUIUpon clicking on a bubble, the GUI generates an associated Anomalies Table view 4200 , in the format shown in FIG. 42 .
- FIG. 40Eadditionally includes Threat Anomalies Trend 4070 .
- Threat Anomalies Trend 4070This provides a line graph indicating the number of anomalies during periods of time. With this illustration, a GUI user can quickly discern whether a large number of anomalies occurred on a particular date or time period, and whether there is a trend of increasing or decreasing anomalies. By hovering over a point on the line, the GUI generates a bubble indicating the date and number of anomalies on that date. Similar to the Threat Anomalies Timeline 4060 , upon clicking on a bubble, the GUI generates an associated Anomalies Table view 4200 , in the format shown in FIG. 42 .
- the “Details” version of the Threats Review view 4000also includes a Threat Anomalies listing 4080 .
- each entryis associated with an “Anomaly Type” 4082 , one or more “Participants” 4083 , a “Summary” 4084 , an “Event Date” 4095 , and a “Score” 4086 .
- “Land Speed Violation” 4087the first listed anomaly type, is associated with three “Participants,” user “Mark Pittman” and devices “1.94.32.234” and “66.39.90.214.”
- the listingsummaries that the anomaly is “From Pittsburgh, US to Beijing, CN,” and indicates that the anomaly occurred on “Nov. 15, 2014.”
- the score associated with the anomalyis “5”. By clicking on “Land Speed Violation,” the GUI navigates to Anomaly Details view 4300 as shown in FIG. 43 .
- the listing of Anomalies 4080provides a summary indicating each type of anomaly associated with the threat and the number of anomalies per type. The default for the listing is to display all anomalies as indicated by the “All Anomalies” tab 4081 , but a GUI user can opt to view only anomalies of a selected type.
- the detailed version of the Threats Review page 4000also includes a Devices Location map 4090 .
- This mapprovides a visual indication of the location of the devices associated with the threat.
- Deviceis represented on the map by a circle, color-coded to indicate the score, or severity of risk associated with the device or location. If there are multiple devices at a single location (or vicinity), it is represented by a larger circle.
- FIG. 40Fthere are four locations represented, one in China, two in California, and one in Pittsburgh, Pa.
- the GUIBy hovering over a circle, such as 4092 , the GUI generates a bubble, as shown in FIG.
- GUI 40Gthat provides more detailed location information (in this case, “Beijing—China”), the device name/IP address (“1.94.32.234”), and a link to “View Device Details.” If the GUI user clicks on the link, the GUI navigates to the User Facts view 4100 of FIG. 41 .
- Devices Location map 4009also includes color-coded lines that connect the devices.
- line 4093connects the devices represented by circle 4091 to the device represented by circle 4092 .
- the linescorrespond to the one or more anomalies for which the connected devices are participants.
- the GUIby hovering over line 4093 , the GUI generates a bubble 4095 that identifies each anomaly represented by that line and a color-code indicating the score for that anomaly.
- the bubble 4095additionally includes a link for the GUI user to view all associated anomalies (e.g., “View All 2 Anomalies”). Upon clicking on the link to view all anomalies, the GUI navigates to the associated Anomalies Table 4200 , in the format shown in FIG. 42 .
- the GUI introduced hereenables a user to access the same views and information via several possible navigational paths.
- link 4056 in the Kill Chain view in FIG. 40Dlink 4087 in the Threat Anomalies listing in FIG. 40D
- link 4201 in the Anomalies Table in FIG. 42each navigate to the “Land Speed Violation” Anomaly Details view 4300 in FIG. 43 .
- there are several pathsvia the charts, diagrams, listings, and maps shown in FIGS. 40E, 40F, 40G, and 40H , to access User Facts 4100 in FIG. 41 and Anomalies Table 4200 in FIG. 42 .
- Threats Review page 4000additionally includes “Watchlist” tab 4012 , which enables the GUI user to track the threat.
- the GUIUpon clicking on tab 4412 , as shown in FIG. 44A , the GUI provides a bubble 4400 prompting the user to tag the threat with “Threat Watchlist,” “False Positive,” “Important,” “Reviewed,” “Save for Later,” or to define a new category for tagging (via the “New Threat Watchlist” selection).
- the tagremains associated with the threat until the GUI user changes the watchlist. For example, by designating the threat as “Reviewed” 4410 , as shown in FIG. 44A , the GUI associates the threat as “Reviewed” in subsequent reviews of the threat, as shown at 4411 in FIG. 44B .
- the GUIIn addition to providing threat, anomaly, and entity information in various views via the “Threat Review,” the GUI also enables users to directly navigate to desired views containing the same information via the Views tab 3902 as shown in FIG. 39B .
- the Views tab 3902can be accessed from any view in the GUI. As shown in FIG. 39B , the Views tab 3902 enables a user to toggle between a Threats view 3906 , Anomalies view 3907 , Users view 3908 , Devices view 3909 , and Applications view 3910 .
- FIG. 45Aprovides an example view that the GUI generates when a GUI user selects the Threats view 3906 in FIG. 39B .
- the Threats Table view 4500provides a Threats Trend timeline 4510 and a Threats listing 4520 .
- the Threats Trend 4510illustrates the number of threats over a period of time. This can be provided as a line chart, as shown in FIG. 45A . As alternatives, the same information can be re-formatted as a column chart, as shown in FIG. 45B , or as a breakdown column chart as shown in FIG. 45C .
- the GUI usercan use the cursor to hover over displayed data to receive more specific information. For example, referring to FIG. 45A , hovering over the data on the line at 4511 causes a text bubble 4512 to appear, indicating a specific date (or time) and the number of threats at that point, as shown in FIG. 45D .
- the Threats listing 4520lists all active threats.
- the Threats listingprovides, for each entry, the Threat Type 4530 , Participants 4531 , Event Date 4532 , Last Update 4533 , and Score 4534 .
- a summary section 4535identifies the number of threats of each type and provides an option to just display the threats of a certain specified type.
- the Threats listing 4520changes to display only the subset of threats that are associated with the selected date on the timeline.
- the GUIthen navigates to the Threat Details page 4540 , as shown in FIG. 45E .
- This pageprovides the same information (including the same charts, graphs, etc.) provided in the Threats Review page 4000 when the “Details” tab 4011 is selected. In the same manner as shown in FIGS.
- the Threats Detail page 4540also provides the same summary chart, Threats Relations graphic, Kill Chain view, Threat Anomalies Timeline, Threat Anomalies Trend, Threat Anomalies listing, and Device Locations map. And as in FIG. 2 , the Threats Detail page 4540 also enables the GUI user to create a Watchlist or to take Action.
- GUI usercan navigate to the User Facts view 4100 in FIG. 41 or the Anomaly Details 500 in FIG. 43 in largely the same manner.
- a GUI usercan click on the link for any participant (user, device, or application) and then receive the User Facts view 4100 .
- a GUI usercan select any anomaly associated with a phase in the Kill Chain (namely, intrusion, expansion, and exfiltration, and view the Users Table or equivalent information concerning other entities.
- FIG. 46Aprovides an example view that the GUI generates when a GUI user selects the Anomalies view 3907 in FIG. 39B .
- the Anomalies table 4600provides an Anomalies Trend timeline 4610 and an Anomalies listing 4620 .
- the Anomalies Trend 4610illustrates the number of anomalies over a period of time. This can be provided as a line chart, as shown in FIG. 46A . As alternatives, the same information can be re-formatted as a column chart, or as a breakdown column chart (not shown), analogous to the Threat Trend as shown in FIGS. 45A-45C .
- the GUI usercan use the cursor to hover over displayed data to receive more specific information. For example, referring to FIG. 46A , hovering over the data on the line at 4611 causes a text bubble to appear, indicating a specific date (or time) and the number of anomalies at that point (not shown).
- the Anomalies listing 4620lists all active anomalies.
- the Anomalies listingprovides, for each entry, the Anomaly Type 4630 , Participants 4631 , Summary 4632 , Event Date 4633 , and Score 4634 .
- the viewidentifies the number of anomalies of each type and provides an option to just display the anomalies of a certain specified type.
- the Anomalies listing 4620changes, as indicated at 4641 , to display only the subset of anomalies that are associated with the selected date on the timeline, as shown at 4642 .
- the GUI usercan click on an entry in the Anomaly listing 4620 . Each entry is a link. Upon clicking, the GUI navigates to an Anomaly Details view 4650 that corresponds with the selected entry in the Anomaly listing.
- An example of an Anomaly Details view 4650is shown in FIGS. 46C-46E .
- the Anomaly Details view 4650provides specific information, charts and graphics about the selected anomaly, along with additional links to the entities that participated in the anomaly.
- the Anomaly Details page 4650can include a summary section 4651 identifying the anomaly by type (e.g., “Unusual AD Activity Sequence”), event date (e.g., “Jan. 2, 2014 10:10 PM”) a short description (e.g., “An unusual event appeared for this account Login . . . ”), and a score (e.g., “5”).
- typee.g., “Unusual AD Activity Sequence”
- event datee.g., “Jan. 2, 2014 10:10 PM”
- a short descriptione.g., “An unusual event appeared for this account Login . . . ”
- a scoree.g., “5”.
- the Anomaly Details view 4650includes a box identifying the “Users” 4652 (e.g., “Clint Dempsey”) along with the user's associated score (e.g., “4”). “Users” can include all personnel in the organization who caused the anomaly, were victims, or otherwise participated in some network activity that triggered the identification of the anomaly.
- the Anomaly Details view 4650additionally includes an “Anomaly Relations” box 4653 .
- This boxillustrates the connection, or “relationship” between different entities (users, devices, and applications) that participated in the anomaly. Since, in the example Anomaly Details page 4650 , there is only listed User, the “Anomaly Relations” graphic is left blank.
- FIG. 46Fprovides a second example of an Anomaly Details view, this time for a “Machine Generated Beacon” that occurred on Jul. 27, 2014 at 4:36 PM, as shown at 4655 .
- This anomalyis associated with 4 entities: User “ggawrych” 4656 , Internal Device “10.104.31.18” and External Device “46.214.107.142” 4657 , and Domain “46.214.107.142” 4658 .
- Anomaly Relations box 4659illustrates the relationship between these entities. As can be seen, User “ggawrych” uses Internal Device “10.104.31.18” to access domain “46.214.142” operating on External Device “46.214.107.142.”
- the detailed viewadditionally includes a “Triggering Event” box 4654 .
- This boxprovides the event data that triggered identification of the anomaly.
- FIG. 46Dillustrates an “Anomalous Activity Sequence” box 4660 in the Anomaly Details view 4650 .
- Anomaly Details view 4650Given that the type of anomaly in Anomaly Details view 4650 is an “Unusual AD Activity Sequence,” this graphic illustrates the string of activities that triggered the anomaly. It is worth noting that this graphic would not apply for other types of anomalies, such as the “Machine Generated Beacon” 4655 of FIG. 46F . Accordingly, each Anomalies Detailed View provides different boxes and graphics to illustrate parameters that correspond to the type of anomaly in the view.
- FIG. 46Eprovides additional boxes that may be associated with the “Unusual AD Activity Sequence,” in Anomaly Details view 4650 .
- the Anomaly Details view 4650may include a box for “Additional Information” 4663 and an “Anomaly Graph” box 4664 illustrating the relationship between the user and the anomaly.
- the “Anomalies” view in FIGS. 46A-46Fincludes a multitude of links by which the GUI user can navigate to additional pages. For example, in FIG. 46A , upon selection of one of the “Participants” in the Anomalies listing 4620 , if the “Participant” is a user, the GUI will generate a “User Facts” view corresponding to the user, similar to that in FIG. 41 . If the “Participant” is a device or application, then the GUI will instead generate a “Device Facts” or “Application Facts” view (not shown).
- the user, device or applicationcan be selected in the Anomaly Details view, such as in FIG. 46C or FIG. 46F , to generates the “User Facts,” “Device Facts,” or “Application Facts” views.
- the GUI usercan configure the “Watchlist” from the Anomaly Details view, in a similar manner as for the Threat Details view.
- the “Users Table”provides a list of each user that is associated with a threat or anomaly.
- the listingcan include the user name 4701 , the Department in which the user works in the organization, if known from the event data or other data, the number of associated anomalies 4703 , the number of associated threats 4704 , the date and/or time of the most recent update 4705 , and the score associated with that user 4706 .
- the GUInavigates to the Users Facts view 4710 for that selected user, as shown in FIG. 47B .
- the User Facts viewcan include a summary section 4717 providing, for example, the number of threats 4711 , the number of anomalies 4712 , the number of total sessions 4713 , the number of anomalous sessions 4714 , and the number of events 4715 .
- the viewcan additionally include a “User Score Trend” box 4716 , which illustrates the change, if any, in the score associated with the user over a period of time.
- the Users Table view 4707can additionally include a user profile box 4720 indicating, for example, the user's HR (human resources) status, Department in the organization (e.g., “Sales”), email address, login ID, Phone number, Address, and AD groups.
- the profile boxmay also include information concerning Similar Users, Top Devices, and Top Apps.
- the Users Table viewmay also include a User Events Trend box 4721 , which depicts how many events that the user participated in over a time period. A sudden increase in the number of events can be useful in evaluating potential network compromise.
- the Users Table viewcan provide a User Events Classes box 4722 , which shows the number of each class of events for which the user was a participant.
- each number in the summary section 4717can provide a link to other views.
- the “User Threats” view 4730can include a summary section, including, for example, the number and type of each associated threat 4731 , the number and type of each associated anomaly 4732 , the number of devices operated by the user that have been associated with anomalies 4733 , and the domains involved in the anomalies that the user accessed 4734 .
- the summary viewadditionally can include an associated score for each threat, each anomaly, and each device.
- Each device identified in 4733can provide a link to a “Device Facts” view that corresponds to that selected device, as further described below.
- each domain identified in 4734can provide a link to a “Domain Facts” view that corresponds to that selected domain, as also further described below.
- the “User Threats” view 4730also may include a “User Threats Timeline” box 4735 that visually depicts when the user became associated with each type of threat identified in 4731 and the duration of that threat.
- the data on the timelinecan be color-coded according to the score of the threat. Hovering (or highlighting) the data on the timeline causes the GUI to generate a text bubble that summarizes the identity and timing of the threat.
- the “User Threats” view 4730also may include a “User Threats” listing 4736 , which, for each threat associated with the user, identifies the threat type, all participants, the last update, and the score.
- a “User Threats” listing 4736which, for each threat associated with the user, identifies the threat type, all participants, the last update, and the score.
- there is a single entry in the listingbecause there is one threat associated with the user.
- the GUI usernavigates to the “Threats Details” view corresponding to that threat, similar to “Threats Details” view 4540 of FIG. 45E .
- the GUIby clocking on the number of anomalies (e.g., “2”) 4713 , the GUI generates a “User Anomalies” view 4740 as shown in FIG. 47E .
- the “User Anomalies” view 4740can include the same summary of information section provided in the “User Threats” view 4730 .
- the “User Anomalies” view 4740additionally can include a “User Relations” box 4741 , which illustrates the connections between the user (“Rick Browne”), the Internal device that he operates (“10.104.105.166”), and the external device (“46.214.107.142”) and domain (“mpdhgokh.ddns.net”) that he communicated with when the anomaly was triggered.
- a “User Relations” box 4741which illustrates the connections between the user (“Rick Browne”), the Internal device that he operates (“10.104.105.166”), and the external device (“46.214.107.142”) and domain (“mpdhgokh.ddns.net”) that he communicated with when the anomaly was triggered.
- the “User Anomalies” view 4740additionally can include a “User Anomalies Timeline” box 4742 .
- the timelinedepicts each anomaly that is associated with the user as a circle and indicates the date that the anomaly occurred. In this example, it can be seen that two anomalies, “Exploit Chain” and “Machine Generated Beacon,” both occurred on Jul. 28, 2014.
- View 4740also may include a “User Anomalies Trend” box 4743 , indicating how many anomalies occur on each date. As shown in FIG.
- the “User Anomalies” view 4740also can include a “User Anomalies” box 4744 that lists each anomaly and for each, it identifies each participant, a summary of the anomaly, the event date, and the score.
- a GUI usercan click on the listing to navigate to an “Anomaly Details” view, similar to that shown in FIGS. 46C and 46F .
- the GUI usercan also click on a device or domain identified in the “Participants” column shown in FIG. 47F to navigate to a ““Device Facts” view that corresponds to that selected device, as further described below.
- each domain identified in 4744can provide a link to a “Domain Facts” view that corresponds to that selected domain, as also further described below.
- the “User Threats” view 4730 and “User Anomalies” view 4740each may include a “Watchlist,” the functionality was explained previously with reference to FIG. 44A .
- a “Watchlist” for a user 4745is shown in FIG. 47G .
- the GUI usernavigates to a “Devices Table” view 4800 as illustrated in FIG. 48A .
- the “Devices Table”provides a list of each device that is associated with a threat or anomaly.
- the listingcan include the IP Address 4801 , the Scope (e.g., “External” or “Internal”) 4802 , the number of associated anomalies 4803 , the number of associated threats 4804 , the date and/or time of the most recent update 4805 , and the score associated with that user 4806 .
- the GUInavigates to the “Devices Facts” view 4810 for that selected device, as shown in FIG. 48B .
- the “Devices Facts” viewcan include a summary section and other information, such as a “Device Score Trend” box 4811 , which indicates the date that the device was assigned a score and whether that score has changed over time.
- the viewcan additionally include a “Device Score Trend” box 4811 , which illustrates the change, if any, in the score associated with the user over a period of time.
- the “Device Facts” view 4810may include a “Top Users” box 4812 , which indicates whether there are one or more primary users for the device, and a “Top Apps” box 4813 , indicating whether, from the event data, it can be discerned whether there are any known applications running on the device.
- a “Watchlist” tab 4814is provided.
- FIG. 48Bby clicking on the Anomalies (“1”) 4816 in the summary view, the user navigates to a “Device Anomalies” view 4815 in FIG. 48C , analogous to the “User Anomalies” view 4740 in FIG. 47E .
- the Users Table view 4709can additionally include a user profile box 4720 indicating, for example, the user's HR (human resources) status, Department in the organization (e.g., “Sales”), email address, login ID, Phone number, Address, and AD groups.
- the profile boxmay also include information concerning Similar Users, Top Devices, and Top Apps.
- the Users Table viewmay also include a User Events Trend box 4721 , which depicts how many events that the user participated in over a time period. A sudden increase in the number of events can be useful in evaluating potential network compromise.
- the Users Table viewcan provide a User Events Classes box 4722 , which shows the number of each class of events for which the user was a participant.
- the GUI usernavigates to an “Applications Table” view 4900 as illustrated in FIG. 49A .
- the “Applications Table”provides a list of each application that is associated with a threat or anomaly.
- the listingcan include the application name, the number of associated anomalies, the number of associated threats, the date and/or time of the most recent update, and the score associated with the application.
- the GUInavigates to the “App Facts” view 4910 for that selected application as shown in FIG. 49B .
- the “App Facts” viewcan include a summary section and other information, such as an “App Score Trend,” “App Activities Baseline,” and “App Graph,” which are analogous to graphs and charts described previously with reference to the “User Facts” and “Device Facts” views.
- a “Watchlist” tabis provided.
- the GUI as introduced hereadditionally includes a selector from the “Threats Table” that, upon selection, generates the display of a geographical representation of the identified threats.
- the GUIby selecting the globe icon 5010 , the GUI generates a “Threats Geo Map” 5020 , as shown in FIG. 50B .
- the Threats Geo Mapdepicts, on a globe, each identified threat as a circle on the map at the threat's location.
- threat 5023is located in Asia, in or near Thailand, and there is at least two threats 5022 on the East coast of the United States.
- Each circle designating a threatis color-coded according to the score associated with the threat.
- threat 5023may be a yellow color, indicating that the threat is minor (see the reference table at 5026 ), whereas threat 5028 (in China) may be orange, indicating that the threat is major.
- the threats depicted on the Geo Mapalso may be of different sizes, indicating that number of threats at a particular location. For example, threat 5023 is a small circle, whereas threat 5024 is a larger circle.
- a text bubbleBy hovering over a threat, such as a threat at 5022 , a text bubble will appear, indicating the location and number of threats at that location. Clicking on a threat modifies the text bubble to provide an indication of the type of threat and a link to “View Threat Details.” Upon clicking on this link, the GUI user navigates to the associated “Threat Details” view, such as the “Threat Details” view 4540 of FIG. 45E .
- Another icon 5029is depicted where the internal network is located. Lines are then shown connecting the internal network location 5029 , as a hub, to each threat location. The lines include arrows, indicating that the threat is radiating from the internal network hub to other geographical locations.
- Line 5025is an example of a line connecting the internal hub to a threat.
- a text bubbleappears that identifies the one or more anomalies that are associated with the threat.
- the text bubbleidentifies each type of anomaly by type, the number of anomalies of each type, and a color-coding indicating the severity of each anomaly.
- the text bubblealso provides a link by which the user can click to “View All 2 Anomalies.” Upon clicking on this link, the GUI user navigates to the “Anomalies Table” view, such as the “Anomalies Table” view 4600 as shown in FIG. 46A .
- the GUIupon selecting the “Analytics” tab 3903 , the GUI generates an “Analytics Dashboard” 5100 as shown in FIG. 51 .
- This dashboardpresents several charts and other graphics similar to those shown in other figures shown above, including “Threats By Threat Type,” “Anomalies by Anomalies Type,” “Latest Threats,” and “Latest Anomalies.”
- the security platformcan achieve this through any of various machine learning models.
- a number of these machine learning modelscan be adapted to perform security-related analysis, including behavioral analysis for specific entities (e.g., a user, a machine, a group of user or machines).
- machine learning modelscan establish behavioral baselines for various different entities of various different types (e.g., users, devices, etc.) and can detect behavioral deviations from such baselines as potentially indicative of malicious activities.
- the security platformprovides a structure for the network administrators or security analysts to easily design, configure, and/or modify the models in order to suit their own purposes and the deployed environment.
- the PST based data processing procedurecan utilize a “windowed” version of a probabilistic suffix tree to detect an unusual sequence (e.g., event sequence).
- a sequencecan by any timely ordered sequence of arbitrary symbols.
- these symbolscan denote particular types of security events including, for example, Connection-Fail, Password-Rest, or File-Access.
- each symbol discussed hereinis an event feature set as discussed in this disclosure.
- a symbolcan correspond to at least a machine-observed event.
- the PST based data processing procedure described hereis generally applicable to any type of sequence, not limited to those that are disclosed herein.
- Event-Typesare used as an example of the symbols.
- Event-Type symbols discussed heremay be denoted with single characters (e.g., x, y, z) and/or integers (e.g., 0, 1), which will be made clear by the context.
- the PST based data processing proceduremay be referred to herein as the PST-based machine learning model or, simply, the PST model.
- the PST modelis to be used in a way that, given an observation window with a number of previous symbols, the PST model can predict what the next symbol may be, to identify whether a target window is anomalous (e.g., by having an anomaly count beyond a baseline).
- the PST modelneeds to receive training so that it can more accurately anticipate or predict the next symbol.
- the PST modelcan be trained by a certain set of historical symbols. This set of historical symbols (i.e., the amount of training) denotes whether the PST model is considered ready (i.e., the prediction can be considered enough trustworthy).
- the amount of trainingcan be controlled based on any of various training principles including, for example, by a fixed time, by a fixed number of symbols, or by other suitable methods including automatic training.
- the fixed time type of trainingcan include training the PST model by using all previous symbols that took place within a certain time window (e.g., one week).
- the fixed symbol number type of trainingcan include training the PST model by using a select number of previous symbols (e.g., 5,000 events).
- An example of an automatic trainingcan include training the PST model by using past symbols until the PST model meets a certain criterion, such as convergence.
- a vector comprised of computed scores from the in-training PST modelcan be built and compared to other versions of the PST model to determine if the model state of the in-training PST model is ready (e.g., is converging or has converged by a certain degree).
- the observation windowis to be kept at a relatively small size (e.g., around four to five symbols) in order to keep computational complexity at a reasonable degree. According to some embodiments, a maximum value of five symbols is used for such observation window.
- sequence generation process of the PST modelcan be modeled as a variable length Markov chain, which may be similar to a formation of finite state automaton.
- the “memory capacity” of the PST modelcan be controlled by the maximum length of historic symbols, which is the probabilistic suffix tree's depth, and is the length of the Markov chain.
- a PST modelAfter a PST model is trained, it can be used to more reliably predict the next symbol. Specifically, given a history of a number of symbols (e.g., five symbols), a trained PST model can generate the entire probability distribution for all “next” symbols for the entire set of possible symbols seen for a particular entity.
- the probability of a particular next symbol given a particular sequence of historical symbolis denoted as “P(next
- aabcd)0.1, P(b
- aabcd)0.8, P(c
- aabcd)0.1, and P(d
- aabcd)0, it means that, given the history “aabcd,” the probability of the next symbol in the sequence being “a” is 10%, “b” is 80%, “c” is 10%, and it is highly unlikely to see “d” as the next symbol.
- next symbol in the sequenceis “a”, “b”, or “c,” these symbols may be deemed acceptable or normal because they are acceptably predicted (e.g., because they all have probabilities that meet or exceed a certain threshold, for example, 10%).
- an unusual symbole.g., representing an event
- a thresholdfor example, 0.1% or 0.01%.
- the thresholdcan be selected and/or adjusted by the administrator according to the environment.
- FIG. 52An example of a PST model having been trained by a particular sequence [100111] is shown in FIG. 52 . In the PST model shown in FIG. 52 , the PST's depth is 3.
- various embodiments of the PST modelcan be configured to first establish a baseline prediction profile (or simply “baseline”) for a specific entity after the PST model is trained. Specifically, a profiling window of successive prediction can be used to build the baseline prediction profile (e.g., for a specific entity, to learn that how many unusual events per window for the specific entity is consider normal).
- the results of the PST model's next symbol predictions within a profiling windowcan be recorded.
- the profiling windowhas a fixed length.
- a profiling windowcan be denoted as “W,” and the length of a profiling window can be denoted as
- An example timeline 5300is shown in FIG. 53 , illustrating the training of a probabilistic suffix tree based model, the establishment of a baseline prediction profile, and the activation of a particular model version.
- the properties of a profiling windowcan be easily changed or tweaked. Different variations of the profiling window can also be used by a PST model to suit different purposes.
- to establish the baseline prediction profile using the profiling window techniqueis to learn what a usual R is for a particular user.
- the predictions (of the occurrence of unusual events) inside each profiling window during a certain time lengthare collected, by sliding a profiling window through the certain time length.
- This time lengthis denoted as the baseline prediction profiling phase on FIG. 53 .
- a histogramcan be made to record all the ratios that are observed.
- This histogramessentially records the usual R for a particular user.
- the collecting of the predictions from each profiling windowcan be repeatedly performed for a period of time (i.e., “sliding through” the period of time). This period of time may be N times the length of the profiling window (i.e., N ⁇
- the R for each profiling windowis tracked and stored in a histogram.
- This learned histogramcan be denoted as “H.”
- the PST modelcan produce a P(R
- H)is the probability of seeing a window with a ratio R, given the history of previous Rs. In this manner, a baseline prediction profile for a specific entity can be built.
- the PST modelcan be activated to detect anomalies for the specific entity. This can also be referred to as the scoring phase.
- an anomalye.g., an abnormal behavior of a specific entity as exhibited by a sequence of events
- one implementationis to first make record of the rare sequence for the particular entity.
- a target windowcan be used by the PST model to identify the rare sequence.
- the PST modelcan be used to generate predictions and calculate the ratio R for a given target window in order to score the target window. For better prediction accuracy, the size of the target window can be set to the same size as the profiling window.
- the PST modelAfter generating an R for a target window, the PST model then refers to the histogram to find the probability of encountering such window with at least an R of this level. If this probability (i.e., P(R
- a certain thresholde.g., ⁇ 0.5%
- an anomalous window expansion techniquecan be used to more fully capture the anomalous activity.
- a window collection processis initiated.
- the purpose of the anomalous window expansion techniqueis to expand the window of unusual activity with the attempt to include as many related unusual actions of the entity inside a single window as possible.
- One example of the techniqueallows the original target window (e.g., which is of a fixed length, such as
- the expanded windowcan be denoted as “E,” where
- the PST modelcan fix the start point of that target window and start increasing the window's size (e.g., by one window) each time it is determined that the next target window also has an R score that is below or equal to the R that triggered the anomalous window expansion process (or until the maximum expansion size is reached).
- the collection process of the anomalous windowcan stop.
- the aforementioned collected anomalous windowcan be compared with a database of rare windows.
- a database of rare windowsalso referred to here as rare window cache
- rare window cachecan be maintained to keep record of rare windows that the system have seen in the past.
- This databasecan be referenced to check if there has been any “similar” rare window in the past, and if so, how many.
- the rationale for this rare window cache techniqueis the observation that a rare window that has been observed many times in the past tends to be less “anomalous” than a rare window of activity that does not appear to be similar to anything that has been observed before. This technique can be useful in some instances, for example, to discover whether a shared account (e.g., root) may be stolen.
- the PST modelis capable of comparing two sequences with each other. There are many known methods to compare sequences and determine similarity.
- PST-SIMThe PST implementation of cosine similarity (PST-SIM) is the cosine similarity between two vectors representing the two sequences. Each vector is comprised of the probabilities learned by training an isolated PST for each sequences (more details on building a vector for a sequence are discussed below). This PST-SIM metric can be useful to capture the similarity between the frequent subsequences of the two sequences.
- some embodimentsemploy a combination of two metrics.
- the PST-SIMputs emphasis on a bigger, overall picture of the symbol distribution and evaluates how similar the distributions are.
- the JAC-SIMis more sensitive to the presence or absence of symbols between two sequences. In other words, the more new symbols there is in one sequence as compared to the other, the more different the JAC-SIM result becomes. Conversely, if only a few symbols are missing, and the remaining common symbols appear in the same or similar manner in both sequences, then the PST-SIM result typically is not very affected by the few missing symbols.
- a PSTe.g., in a PST model, shown in FIG. 52
- a PSTcontains the conditional and marginal probabilities of all the symbols used in the training. Therefore, one way to compare two PSTs is to vectorize the two PSTs, and compare their corresponding probabilities (both marginal and conditional) one by one. After vectorizing the PSTs, resulting in two probability vectors, a suitable vector similarity metric (e.g., Euclidian distance, or cosine similarity) can be used to compare the two PSTs.
- a suitable vector similarity metrice.g., Euclidian distance, or cosine similarity
- the rare window cacheFor each rare sequence, only this PST summary of the rare sequence (i.e., vectorized PST) is kept in the rare window cache. Because the PST summary of the sequence includes all the probability information, the PST summary can be treated as a rare window signature.
- the PST summary, representing a rare sequencecan be used to compare with another sequence, for example, by using a combination of the PST-SIM and the JAC-SIM.
- the rare window cachekeeps a record of how many times the rare window has been observed and, in some embodiments, for how many distinct days.
- the PST modelcan check the rare window cache to determine whether the new rare window has appeared before, and if affirmative, for how many times and over how many different days. This information can be useful for deciding if the new rare window is worth raising an alarm or not.
- FIG. 54Ashows an example of how a normal behavioral sequence may be represented in a probabilistic suffix tree based model
- FIG. 54Bshows an example of how an unusual behavioral sequence may be discovered in a probabilistic suffix tree based model.
- the PST modelcan be very powerful to distinguish abnormal behaviors from normal behaviors, even in an complex network environment with many users collaborating.
- FIG. 55A through FIG. 58show example graphical user interface (GUI) display screens of how an unusual behavioral sequence discovered can be presented to an administrator for actions and/or feedbacks.
- GUIgraphical user interface
- the resultcan be presented to a user via a user interface, such as a GUI.
- the user interfacecan include textual description, such as which user has an unusual window, what kind of unusual sequence it is (e.g., Active Directory), how many events are in the window, how long the window has lasted, and so on.
- additional information about the usercan be presented in the user interface, such as information about the training of the model for the user.
- results from comparing the marginal of the events for the anomalous window and the entire data for the usere.g., baseline
- results from comparing the marginal of the events for the anomalous window and the entire data for the usere.g., baseline
- the entire data for the usere.g., baseline
- all the “unusual” PST predictions that contributed to the high Rcan be shown to the administrator, and in some embodiments, can be shown as a timeline of unusual sequences. Illustrated in FIG. 57 is an overview of all the unusual sequence, shown as a timeline. Then, the administrator can interact with (e.g., click on) each timeline event and expand on the unusual sequence of events that lead to the low PST prediction, such as shown in FIG. 58 .
- the PST modelcan enable the security platform to discover behavioral anomalies by determining whether a given sequence of events as associated with an entity deviates from an generally anticipated behavioral baseline, even though each event individually may well be considered not malicious. Also, the security platform provides intuitive ways for the administrator to receive alert and to understand relevant information in order to make an educated decision.
- node clustersor “clusters”
- a graphsuch as in the above-mentioned composite relationship graph or a projection of it. Doing so may be advantageous for various reasons, such as detecting similarities between users or devices and/or detecting deviations in an entity's activity from a behavioral baseline. For example, identification of node clusters can facilitate detection of lateral movement by user (e.g., a user accessing a device that he does not normally access) or detection of an account takeover situation.
- the systemmay initially determine that a particular entity is a member of a particular node cluster, or that the entity normally interacts with an entity that is a member of the node cluster.
- a clustermay represent a group of users who all tend to access the same set of devices on the network, for example.
- a decision enginemay detect that the particular user in that group has engaged in activity that represents a divergence from the identified cluster, such as a user in the cluster accessing a device that is not among those normally accessed by users in his cluster.
- the decision enginecan determine that the user's activity represents an anomaly, or perhaps even a threat.
- the techniquecan be implemented by one or more of the above-mentioned machine learning models, for example, and can be implemented in the real-time path, the batch path, or both.
- an automated cluster identification processcomputes L1-norm values for the nodes in a graph to assign positions to the nodes on a one-dimensional (1D) grid.
- the processthen identifies one or more node clusters in the graph based on the assigned positions of the nodes on the 1D grid. More specifically, the process creates node groups by iteratively relocating nodes on the 1D grid to positions where the L1-norm for each node is minimum. After finding optimal positions for the nodes on the 1D grid in this manner, each group of nodes located at the same position on the 1D grid (if any) represents a cluster.
- FIG. 59is a flowchart showing an example of the above-mentioned process.
- the initial input to the processis any graph, an example of which is shown as graph 6101 in FIG. 61A .
- the process of FIG. 59may be performed while a graph is being constructed. It is assumed that edge weights are represented by integers, not floating point numbers, and that multiple associations between nodes are collapsed into the weight of a single edge after proper boosting/weighting.
- the processinitially traverses the graph node by node and maps the nodes onto a one-dimensional (1D) grid.
- the graphmay be traversed in any order.
- a breadth first search (BFS) ordermay be convenient.
- An example of a 1D grid resulting from traversing graph 6101 in BFS orderis shown as grid 6102 in FIG. 61A .
- the numeral inside each node (circle)indicates the order in which the node has been “touched” during a BFS traversal and, hence, its position in the 1D grid 6102 . Therefore, to facilitate description, the nodes of graph 6101 are referred to by their positions in the 1D grid 6102 , e.g., Node 1 , Node 2 , etc., corresponding respectively to positions 1 , 2 , etc.
- the process at step S 902creates groups of nodes that have the same position on the 1D grid, by iteratively minimizing the L1-norm of each node to find its “optimal” position on the 1D grid.
- a “norm” in this contextis a function that assigns a strictly positive length or size to each vector in a vector space (except the zero vector, which is assigned a length of zero).
- an L1-normat least in the context of this description, is the sum of the individual distances (absolute) along the 1D grid between each candidate position for a node under consideration and each other candidate position for the node under consideration.
- the candidate positionsare the positions of all nodes directly connected to the node under consideration in the graph.
- the “optimal” position for a node under considerationis the position of that node, in the 1D grid, where the node's L1-norm is minimum.
- the processwill initially attempt to determine the optimal position for Node 1 . To do so, the process computes the L1-norm for Node 1 in each of its candidate positions. Node 1 is directly connected to Nodes 2 , 5 and 6 in the graph 6101 (i.e., the nodes that occupy positions 2 , 5 and 6 and the 1D grid). Therefore, the candidate positions for Node 1 are the positions occupied by Nodes 2 , 5 and 6 on grid 6102 .
- 10.
- L1-Norm 1,5
- 4.
- the L1-norm of Node 1is minimum at position 5 on grid 6102 in the example of FIGS. 61A and 61B . Therefore, the position of Node 5 is deemed to be the optimal position of Node 1 in the initial iteration, so Node 1 is moved to the position of Node 5 , as shown in FIG. 61B . Note that a node's optimal position can change in subsequent iterations, however, as the node and/or other nodes may be relocated along the 1D grid.
- one or more nodesmay occupy the same position on the 1D grid; such nodes are considered to constitute a node group, which may be a cluster.
- the processlooks for any node(s) in each node group that have a stronger connection to nodes outside their group; such nodes should be removed from their current group (i.e., relocated along the 1D grid).
- step S 903the process detects the actual clusters in each group based on the internal-to-external edge ratios of the nodes.
- a nodecan have one or more “internal” edges and one or more “external” edges.
- An internal edgeis any edge that connects the node to another node within the same node group (created in step S 902 ), whereas an external edge is any edge that connects a node to another node outside its node group.
- step S 904removes that node from its current node group by shifting the node one position to the left or right along the 1D grid (the direction does not matter).
- Each node relocated in this manneris called a “floater.”
- the processproceeds to 5907 , in which the process iterates through all of the floater nodes and merges them with the existing cluster(s). If there are no floaters at step S 905 , the process proceeds to step S 906 , in which it outputs the identified clusters (e.g., to another machine learning model, a decision engine, a user interface, etc.).
- FIG. 61Balso shows, at the bottom, the positions of all of the nodes after three iterations. It can be seen that three clusters have been identified: Nodes 1 through 6 ; Nodes 7 through 11 ; and Nodes 12 through 14 .
- this processis also incremental, which means if a single node or multiple nodes are added to the graph, it is not necessary to remap the entire (modified) graph onto the 1D grid; instead each newly added node of the graph can be inserted directly into the 1D grid by minimizing its L1-norm as described above.
- a bipartite graphis a graph whose nodes can be divided into two disjoint sets, called normal nodes and pseudo-nodes (i.e., normal nodes and pseudo-nodes are each independent sets), such that every edge connects a normal node to a pseudo-node.
- a bipartite graphmay be created in which the normal nodes represent users and the pseudo-nodes represent devices accessed by those users. Such a graph can be used, for example, to facilitate detection of lateral movement by users.
- FIGS. 60A and 60BAn example of such an implementation for bipartite graphs is illustrated in FIGS. 60A and 60B , with a corresponding example of a use case illustrated in FIG. 62 .
- the processinitially traverses the bipartite graph and maps only the normal nodes onto a 1D grid.
- the graphmay be traversed in any order, such as BFS order.
- the processcreate groups of nodes that occupy the same position in 1-D grid, by minimizing the L1-norm of each normal node to find its optimal position in the 1-D grid.
- the normal nodesare Nodes 1 through 7 (i.e., the left column of graph 6201 ) whose positions are the positions on the 1D grid, while the pseudo-nodes are Nodes 8 through 10 (the right column of graph 6201 ).
- the process of minimizing L1-norms for a bipartite graphis described further below.
- the processdetermines at step 6003 whether any normal nodes were moved during step 6002 . If any normal nodes were moved during step 6002 , the process loops back to step 6002 for another iteration. Otherwise, the process outputs the identified cluster(s) (e.g., to another machine learning model, a decision engine, a user interface, etc.), where a cluster is a group of nodes that occupy the same position on the 1D grid.
- the processoutputs the identified cluster(s) (e.g., to another machine learning model, a decision engine, a user interface, etc.), where a cluster is a group of nodes that occupy the same position on the 1D grid.
- FIG. 60Bshows in greater detail the step 6002 of FIG. 60A , i.e., the step of minimizing the L1-norm values to find optimal positions for the normal nodes.
- the processselects a normal node of the graph (the “node under consideration”).
- the processidentifies all of the pseudo-nodes to which the selected normal node is directly connected, at step 6012 .
- normal Node 1is connected only to pseudo-Node 8 .
- the processthen, at step 6013 , identifies the minimum and maximum of positions, on the 1D grid, of all normal nodes to which the identified pseudo-node(s) is/are connected.
- step 6013if (normal) Node 1 were the selected node, then the minimum and maximum positions would be 1 and 2, respectively, since Node 1 is connected only to pseudo-Node 8 , which is also connected to normal Node 2 . If Node 6 were the selected node, then the minimum and maximum positions would be 3 and 7, respectively, since Node 6 is connected to pseudo-Node 9 , which is also connected to normal Nodes 3 and 4 , and to pseudo-Node 10 , which is also connected to normal Nodes 5 and 7 .
- the processnext determines at step 6014 the “optimal” position for the normal node, as the position on the 1D grid that corresponds most closely to the midpoint between the minimum and maximum positions determined in step 6013 (rounding up if the exact midpoint falls between two positions on the grid).
- the processmoves the selected normal node to the position determined in step 6014 , with the effect being to minimize the selected node's L1-norm. This process repeats for each normal node until all of the normal nodes have been processed in this manner, and then returns to the process of FIG. 60A , proceeding then to step 6003 in FIG. 60A as described above.
- the processidentifies two clusters from the example graph 6201 , namely, Nodes 1 and 2 as one cluster, and Nodes 3 through 7 as another cluster.
- the process of FIGS. 60A and 60Bis also incremental, such that the addition of a new node or nodes to the graph does not require remapping the entire graph onto the 1D grid; rather the new node(s) can be added directly to the 2D grid as described above.
- FIGS. 63 through 67relate to a method for identifying a security threat based on detecting suspicious lateral movement of a user.
- Lateral movementrefers to a user using a device or devices that he or she does not normally use, which may be (but is not necessarily) indicative of a security threat.
- Lateral movementmay indicate the possibility that the credential of a user has been stolen, or the user's device has been controlled by a malicious software.
- a wrongdoermay steal a user's credential and use the stolen credential to access a device that the user typically does not access.
- An analyzere.g., the real-time analyzer 210 or the batch analyzer 240 in FIG. 3
- An analyzermay recognize such an event as an anomaly.
- the analyzerdetects that the anomaly (directly or through other anomalies) leads to a result that the wrongdoer (disguised as a legitimate user) gains access to a device designated as a critical resource, the analyzer can recognize a security threat represented by a set of the relevant anomalies.
- the lateral movement detection method introduced hereassigns similarity scores to devices in a computer network based on the relationships between users and the devices.
- the relationshipscan include information regarding certain users logging into devices.
- the similarity scoressuggest the similarities between the devices in terms of associated users.
- the methodfurther generates or identifies classification metadata of the user and the device, based on event data about the login event, to further explain the relevance of the user and the device in a security context.
- the methoddetects an anomaly based on the classification metadata and similarity scores when a user interacts with a device having a similarity score that is significantly different from the similarity scores of devices with which the user usually interacts. Based on the detected anomaly, the method may further determine a security threat based on the relationship information by identifying, in a relationship graph, a relationship path from a user through anomalies to a critical resource.
- the method described herecan be implemented by a machine learning model.
- processing logic of a machine learning modecan generate the classification metadata, or assign usage similarity scores, or both, as further described below.
- the processes of generating the classification metadata and/or assigning usage similarity scoresare performed in real-time as the event data are received. In other embodiments, either or both of these processes are performed in batch mode based on event data stored in a non-volatile storage facility.
- FIG. 63is a block diagram illustrating a machine learning model that detects lateral movement in a computer network.
- the computer networkincludes entities, such as devices and network devices.
- the machine learning model 6300analyzes event data 6310 .
- the event data 6310can be, e.g., timestamped machine data.
- the event data 6310include information regarding the computer network activities of the users and network devices.
- the event data 6310includes a projection of the security graph.
- the particular projection of the security graphalso referred to as “login projection” or “login graph” records the information that relates to login events in which the users log into the network devices in the computer network.
- the machine learning model 6300Based on the event data 6310 (e.g., the login graph), the machine learning model 6300 generates classification metadata 6320 for each of the network devices and for each of the users.
- the classification metadata 6320helps explain the relevance in a network security context of each of the users and each of the network devices.
- the classification metadata 6320 for a particular usercan include metadata indicative that the user is a regular user, an administrative user, or an automated (machine-implemented) user, for example.
- the classification metadata 6320 for a particular network devicecan include metadata indicative that the particular network device is a workstation, a server or a printer, for example.
- the machine learning model 6300does not need additional metadata that explicitly annotates the types of the user and network devices.
- the machine learning model 6300can automatically recognize the types of the users and network devices, based on the event data representing the network activities involving the users and network devices.
- the machine learning model 6300further identifies usage relationships 6330 between the users and the network devices based on the event data 6310 .
- the event data 6310includes a login graph having information that relates to the login events
- the machine learning model 6300can identify the usage relationships 6330 as login events indicative of the users logging into the network devices.
- the usage relationship 6330can be presented as a graph having nodes and edges interconnecting the nodes, as illustrated in FIG. 63 .
- the nodesrepresent network entities such as users and network devices, and the edges represent the login events that the users log into the network devices.
- the usage relationships 6330 between the users and the network devicescan be captured in a bipartite graph including a first set of nodes representing users (nodes 6341 , 6342 , 6343 and 6344 ) and a second set of nodes representing network devices (nodes 6351 , 6352 , 6353 and 6354 ).
- the first and second setsare disjoint sets. Every edge in the bipartite graph connects a user node in the first set to a device node in the second set.
- the relationships 6330 between the user nodes and the device nodesalso represent a time series of events in which the users have interacted (e.g., logged in) with the network devices.
- the machine learning model 6300assigns usage similarity scores 6360 (also referred to as “similarity scores”) to the network devices represented by the device nodes.
- the usage similarity scores 6360indicate which of the devices have been used by the same or similar group of users. The details of the process of assigning usage similarity scores 6360 are illustrated in FIG. 65 .
- the similarity scoresare assigned such that any given set of network devices that are accessed by the same or similar group of users are assigned similarity scores that are closer in value to each other than the similarity scores of any other set of network devices that are not accessed by the same or similar group of users.
- a group of network devices that have similar groups of login userstend to have similarity scores that are closer in value to each other than similarity scores of network devices that do not have similar groups of login users.
- FIG. 64illustrates an example of a bipartite graph showing events of users logging into network devices.
- the bipartite graph 6400includes a group of user nodes 6411 , 6412 , 6413 and 6414 , and a group of device nodes 6421 , 6422 , 6423 and 6424 .
- the edges between the user nodes and device nodesrepresent the login activities.
- the reference numerals in FIG. 64are used interchangeably to refer to the nodes and the users or network devices represented by those nodes.
- devices 6421 , 6422 and 6423are associated with a similar groups of users, i.e., users 6411 , 6412 and 6413 .
- the machine learning model 6300determines the similarity score of the particular device 6424 (i.e., 0.06 for device 6424 ) fails to satisfy a specific closeness criterion relative to similarity scores of network devices with which the particular user usually interacts (i.e., 0.30 for device 6422 and 0.33 for device 6423 ).
- the closeness criterioncan be of various different types in different embodiments.
- the machine learning device 6300may determine that the difference between the similarity score of the particular network device 6424 and an average of the similarity scores for network devices 6422 and 6423 is 0.255, which exceeds a threshold of 0.2. The machine learning model 6300 then detects an anomaly because the difference of similarity scores exceeds the threshold value.
- the machine learning model 6300can further calculate an anomaly score for the particular user and decide whether anomaly is detected based on the anomaly score.
- the anomaly scoreindicates a likelihood that the anomaly relates to a security threat.
- the anomaly scorecan be calculated based on, for example, the difference between a similarity score of the particular network device and a statistical measure (e.g., an average) of similarity scores of other devices with which the user has interacted.
- the machine learning model 6300detects the anomaly if the model determines that the anomaly score exceeds a threshold value for anomaly scores.
- the similarity score of the network device 6424is 0.06
- the average similarity score of network devices 6422 and 6423is 0.315.
- the difference between the similarity scoresis 0.255.
- the machine learning modelcalculates the anomaly score as, e.g., 0.355, by summing the similarity score difference of 0.255 and an extra weight of 0.1 in recognition that the network device 6424 is a server of high importance. Because the anomaly score of 0.355 exceeds a threshold of 0.3, the machine learning model 6300 detects an anomaly.
- the machine learning model 6300can detect an anomaly based on an access profile of a particular user.
- the access profile of the particular userincludes network devices with which the particular user interacts and that have similarity scores that satisfy a specific closeness criterion. For example, the differences of the similarity scores of network devices 6422 and 6423 within the access profile of user 6412 is 0.03 and is less than a threshold value of 0.1.
- the access profile of the particular user 6412can further include, e.g., information of events indicative that the particular user succeeded logging in to a network device, failed logging in to a network device, succeeded validating credential of a network device, failed validating credential of a network device, succeeded accessing a network object stored on a network device, or failed in accessing a network object stored on a network device.
- the machine learning model 6300calculates the anomaly score for the particular user based on a difference between the similarity score of the particular network device 6424 and the average of similarity scores of network devices 6422 and 6423 in the access profile of the particular user 6412 .
- the machine learning model 6300detects the anomaly if the similarity score difference indicates that the particular user 6412 has interacted with the particular network device 6424 outside of the access profile of the particular user 6412 .
- the machine learning model 6300can assign similarity scores to the network devices in various ways.
- FIG. 65illustrates an example of a process of assigning similarity scores to network devices.
- the machine learning model 6300receives a bipartite graph.
- the bipartite graphincludes a group of nodes U 1 -U 6 representing users (also referred to as “user nodes”) and another group of nodes D 1 -D 6 representing network devices (also referred to as “device nodes”).
- the bipartite graphfurther includes edges interconnecting the nodes. The edges represent the relationships between the users and the network devices.
- the machine learning model 6300selects a device node D 4 and assigns an initial weight value of 1 to the selected device node D 4 .
- the machine learning model 6300can, e.g., select the device node in a random manner.
- the initial weight valuecan also have a value different from 1.
- the machine learning model 6300keeps a percentage (15%) of the initial weight value of 1 at the device node D 4 , and equally distributes a remainder of the initial weight value 1 from the device node D 4 along the edges of D 4 to nodes U 2 , U 3 and U 6 . In some embodiments, the machine learning model decides the percentage of 15% before starting the similarity score assignment process.
- the value distribution processcan be viewed as a Markov chain process.
- the similarity score assignment processcan use a percentage other than 15%.
- the machine learning model 6300For each node, the machine learning model 6300 repeats the process of distributing along edges until the weight values at the network devices D 1 -D 6 converge.
- the step D in FIG. 65shows the next step in the iterative process.
- the machine learning model 6300continues the iterative process until the weight values at the network devices D 1 -D 6 converge. At each step of the iterative process, for each node, the machine learning model 6300 keeps 15% of the weight value at the node and then equally distributes the remainder of the weight values along the edges to other nodes.
- the convergence criterioncan be any criterion indicative of this type of convergence. For example, the machine learning model 6300 can determine that the iterative process reaches a convergence when the change of weight values between two consecutive steps at each node is less than a threshold value.
- Step Z of FIG. 65shows the status of a final step with converged weight values when the iterative process reaches a convergence.
- the converged weight values at the devices D 1 -D 6are similarity scores assigned to these devices.
- the machine learning model 6300uses the similarity scores to determine whether multiple network devices are similar in terms of associated users that interact with the devices.
- FIGS. 66A through 66Dillustrates examples of bipartite graphs that the machine learning model 6300 uses to determine whether network devices are similar in terms of interacting users.
- the network devices 6610 and 6611have many shared users ( 6615 , 6616 , 6618 and 6619 ) and therefore tend to have similarity scores close to each other.
- the network devices 6620 and 6621have multiple shared exclusive users ( 6628 and 6629 ).
- Exclusive usersare users that interact with the network devices 6620 and 6621 only.
- the network devices 6620 and 6621thus tend to have similarity scores close to each other.
- the network devices 6630 and 6631only have a single shared user 6637 .
- the network devices 6630 and 6631thus tend to have similarity scores that have a large difference.
- the network devices 6641 , 6642 and 6643are associated with similar groups of users, including users 6651 , 6652 , 6653 and 6654 .
- the network devices 6644 , 6645 and 6646are associated with similar groups of users, including 6654 , 6655 and 6656 . If the user 6654 is removed from the bipartite group, the devices can be separated into two groups N 1 ( 6641 , 6642 and 6643 ) and N 2 ( 6644 , 6645 and 6646 ) without interactions between the two groups, based on the user interactions.
- User 6654is the only user that has connected to devices of both groups N 1 and N 2 .
- the group N 1 of devices 6641 , 6642 and 6643have similarity scores close to each other.
- the group N 2 of devices 6644 , 6645 and 6646have similarity scores close to each other. Assuming that user 6654 typically interacts with device 6645 from group N 2 , the access profile of user 6654 includes the group N 2 of devices 6644 , 6645 and 6646 .
- the interaction between the user 6654 and device 6642 from group N 1then triggers an out-of-group access anomaly, because the similarity score of device 6642 is significantly different from the similarity scores of devices 6644 , 6645 and 6646 within the access profile of user 6654 .
- the detected out-of-group anomalyis an indication of a suspicious lateral movement of a particular user in the network.
- the machine learning model 6300can further decide whether the anomaly 6370 leads to a security threat 6380 , as illustrated in FIG. 63 .
- FIG. 67illustrates an example of a data structure for detecting security threats based on the detected out-of-profile anomaly.
- the machine learning module 6300retrieves a graph data structure 6700 that records anomalies in the network and the relationships between the anomalies and the users and network devices.
- the graph data structureincludes nodes interconnected by edges.
- the nodesrepresent anomalies and entities such as users and network devices; while the edges represent relationships between the entities and anomalies.
- FIG. 67shows that the retrieved graph data structure 6700 includes user nodes U 6701 , U 6705 , U 6709 and U 6711 and device nodes D 6703 , D 6707 , D 6708 and D 6710 .
- the retrieved graph data structure 6700further includes anomaly nodes A 6702 , A 6704 and A 6706 .
- the anomaly node A 6702represent an out-of-profile anomaly.
- the user represented by user node U 6701has accessed the device represented by device node D 6703 with which the user does not usually interact.
- the retrieved graph data structure 6700is different from the login graph that the machine learning module 6300 uses to detect the out-of-profile anomaly.
- the login graphonly records information that relates to the login events of the users.
- the retrieved graph data structure 6700can include relationships beyond the login events and can include anomalies of other types besides out-of-profile anomalies.
- the retrieved graph data structure 6700includes anomaly node A 6706 representing a blacklist anomaly.
- the blacklist anomalyindicates that the user U 6705 has accessed the network device D 6707 from a blacklisted IP address.
- the retrieved graph data structure 6700further includes anomaly node A 6704 representing a beaconing anomaly.
- the beaconing anomalyindicates that the device represented by device node D 6703 sends suspicious beaconing messages periodically to a user device associated with the user represented by user node U 6705 .
- the machine learning model 6300identifies, in the retrieved graph data structure 6700 , a relationship path 6720 that suggests a security threat.
- the relationship path 6720starts with user node U 6701 and anomaly node A 6702 that represents the out-of-profile anomaly.
- the relationship path 6720ends with the anomaly node A 6706 and device node D 6707 that represents a device designated as a critical resource.
- the device designated as a critical resourcecan be, e.g., a domain controller server that responds to security authentication requests within the computer network.
- the relationship path 6720includes user nodes and device nodes interlinked by anomaly nodes A 6702 , A 6704 and A 6706 .
- the relationship path 6720starts from user U 6701 through anomaly nodes A 6702 , A 6704 and A 6706 to the device D 6707 designated as a critical resource of the computer network.
- the machine learning model 6300identifies a security threat based on the relationship path 6720 .
- the security threatis represented by the anomaly nodes A 6702 , A 6704 and A 6706 along the relationship path 6720 . These anomaly nodes suggest that the security threat is imposed by a series of anomalies.
- the security threatcan indicate that an unauthorized user (invader) has misappropriated a credential of the particular legitimate user to enter the network through device D 6703 and breached one or more network devices (D 6703 , D 6707 ) along the relationship path to access the critical resource on device D 6707 .
- the security platformWhen a security threat has been detected, the security platform then reports the threat to an administrator of the network (e.g., via the GUI features described above) and/or writes the security threat into a threat log for later review by an administrator.
- malwareis generally understood to be unauthorized software operating on or associated with entities (e.g. devices) within a computer network.
- the detection of malware based on analysis of network trafficrests on the assumption that malware in certain instances leaves an observable footprint in the traffic.
- malware operating as part of a malicious command and control infrastructuremay periodically transmit a beacon signal to another entity seeking command instructions.
- malwaremay be inferred based on detecting any of a set anomalous activity, such as communications to machine-generated domains, machine-generated communications (e.g., beacons), and communications to blacklisted entities (e.g. users, domains, addresses, etc.).
- a set anomalous activitysuch as communications to machine-generated domains, machine-generated communications (e.g., beacons), and communications to blacklisted entities (e.g. users, domains, addresses, etc.).
- anomaly detectionoccurs in real-time or near real-time as the event data is received, instead of relying on historical log data to perform batch processing.
- An example processing engine suitable for high rate data processing in real-timeis Apache Storm. In other embodiments the processing engine could be implemented by using Apache Spark Streaming.
- FIG. 68is a high-level conceptual diagram of an example network traffic scenario that illustrates the above principle.
- FIG. 68shows a computer network 6810 enclosed by the dotted line.
- computer network 6810Within computer network 6810 are a number of associated internal entities 6820 including, for example users and devices.
- entitiesinclude physical computing devices, virtual computing devices, users, software modules, accounts, identifiers, and addresses. The identification of a particular entity or set of entities associated with a particular set of event data can be resolved through a process described elsewhere in this specification.
- a machine generated log entry associated with an eventmay contain information associating that event with one or more of a an IP address, a unique identification (UID), uniform resource locator (URL), and user ID.
- each of these identifiersmay be considered a discrete entity associated with the computer network or two or more identifiers maybe associated with the same entity.
- a static IP address, MAC address, and UIDmay all be associated with a physical computing device entity.
- multiple user account IDsmay be associated with a single physical user (i.e. a person) of the computer network.
- Operating outside of computer network 6810is an external entity 6840 that may be associated with a malicious actor. Communications may occur between different internal entities 6820 , and between internal 6820 and external entities 6840 , as shown. In some embodiments, an analysis of these communications based on received event data, leads to the detection of anomalies 6880 indicating the presence of malware 6860 within the computer network 6810 .
- FIG. 69is a high level diagram illustrating an example process 6900 for detecting an anomaly indicative of malware based on network traffic.
- the process 6900begins with receiving event data 6901 .
- Event data 6901is generally understood to include any data related to activity on the computer network.
- the event data 6901preferably includes timestamped machine data such as domain name system (DNS) generated log data, firewall generated log data, or proxy generated log data.
- DNSdomain name system
- the event data 6901is associated with a communication between an internal entity within a computer network and an external entity outside the computer network.
- the event data 6901is also associated with communications between internal entities within a computer network.
- event data 6901is received from a data intake and preparation stage, which may include an ETL pipeline.
- the process of receiving event data 6901includes adaptively filtering the event data according to a dynamic whitelist at process 6902 .
- Thisis in contrast with static filtering, for example according to a static whitelist, to filter out communications to entities known to be benign.
- adaptive filteringcan be applied to filter out event data associated with more common or more popular network traffic given a particular context.
- popularity metricsare defined based on an analysis of network traffic across the entire network or across a particular subgroup within the network. For example, while domain xyz.com may not be known to be benign, an analysis of the network traffic can uncover that a high percentage of users on the network regularly connect to xyz.com.
- xyz.comis benign and that it is not worth the processing effort to analyze the domain for malware associations.
- this process of adaptively filtering the received event datais not necessary to the overall anomaly detection process, however it can streamline computational processing, which aids in detecting anomalies in real-time or near real-time. The filtering also helps to reduce the number of false positives.
- Process 6900continues with generating a plurality of feature scores by processing the filtered event data 6903 or unfiltered event data 6901 (collectively referred to herein as event data 6901 ) as shown at feature score generation 6920 , and generating an entity profile associated with at an entity (internal or external) that includes a plurality of generated feature scores as shown at entity profile generation 6904 .
- feature score generation 6920includes generation of a plurality of feature scores, each of the plurality of feature scores generated by a different one of various different analyses of the event data.
- feature score generationcan include timing analysis 6906 , lexical analysis 6908 , communications statistics 6910 , sequencing analysis 6912 , entity associations analysis 6914 , referrals analysis 6916 , and various other types of analysis 6918 .
- one or more feature scores for a particular entityare generated based on each above-mentioned category of analysis.
- timing analysiscould yield two or more feature scores, including at least a feature score based on a periodicity of communications associated with a particular entity and a feature score based on variance in interval periods between communications associated with a particular entity.
- Feature scoresare described in more detail below, however, note that the listed categories of analysis are only examples, and no particular category is necessary.
- An embodimentmay include more or fewer categories resulting in more or fewer feature scores.
- entity profile generation 6904includes a process of forensic data enrichment 6922 through global evidence collection 6926 .
- data regarding a particular entitymay be gathered from sources internal (e.g. a system blacklist) or external (e.g. a WHOIS lookup) to the computer network. Additional data gathered through evidenced collection 6926 and applied via enrichment 6922 may impact feature score generation and anomaly detection based on the underlying feature scores.
- a feature scorecan represent a quantified evaluation of the risk associated with a particular entity based on a particular analysis. Accordingly, the models used to generate feature scores may depend on additional available (e.g.
- enrichment 6922data associated with an entity. For example, processing equivalent sets of event data 6901 using the same analysis (e.g. periodicity of communications) may yield different feature scores for mission critical systems than for non-critical systems. As with the adaptive filtering 6902 , Global evidence collection 6926 and forensic enrichment 6922 are not required.
- entity profile generation 6904includes a process for score normalization 6924 .
- Score normalization 6924involves normalizing the plurality of feature scores for later processing at the anomaly score generation stage, as described elsewhere herein.
- Process 6900continues with generating an anomaly score based on the entity profile including the plurality of feature scores included in the entity profile, for example as shown at anomaly score generation 6928 . Generating an anomaly score is described in more detail elsewhere herein.
- Process 6900concludes with detecting an anomaly if the generated anomaly score satisfies a specified criterion, for example as shown at anomaly detection 6930 .
- the detected anomalyis indicative of malware within a computer network. Anomaly detection is also described in more detail elsewhere herein.
- each feature scoreis generated based on one various different analyses of the event data.
- Feature scoresare calculated on a per-entity basis and can be understood broadly as a quantified evaluation of a level of risk associated with the entity or a likelihood that the entity is associated with malware.
- feature scoresare calculated or assigned by processing the event data through a model to generate a numerical value.
- the modelincludes model processing logic defining a process for assigning a feature score based on processing the event data X 102 and a model state defining a set of parameters for applying the model processing logic.
- the models used to generate feature scoresare the same as the anomaly models used to generate anomaly scores.
- the models used to generate feature scoresare machine-learning (both supervised and unsupervised) models.
- a supervised machine learning modelmay use training examples developed by network security experts to more effectively generate feature scores based on received data.
- each feature scoreis a numerical value in a range.
- processing event data according to a feature score modelmay yield a value between 0 and 10 with 0 being the least anomalous (or risky) and 10 being the most anomalous (or risky).
- feature scoresare calculated on a per-entity basis. Therefore a plurality of feature scores is generated for a particular entity.
- the combined set of feature values associated with particular entitymake up the entity profile.
- the table belowlists feature scores f 1 though f n for an example external domain, xyz.com.
- an entity profile for a particular entitymight include tens or even hundreds of feature scores.
- the different analyses used to generate the feature scorescan include, for example, lexical analysis (e.g. sequencing of characters in a domain name associated with an entity, analysis of the timing of communications associated with an entity (e.g. periodicity of communications and/or variance of interval times between communications), analysis of the sequencing of communications associated with the entity (e.g. to detect exploit chains, analysis of data transmission statistics associated with the entity (e.g. ratio of bytes in to bytes out), and analysis of referral strings associated with the entity.
- lexical analysise.g. sequencing of characters in a domain name associated with an entity
- analysis of the timing of communications associated with an entitye.g. periodicity of communications and/or variance of interval times between communications
- analysis of the sequencing of communications associated with the entitye.g. to detect exploit chains
- analysis of data transmission statistics associated with the entitye.g. ratio of bytes in to bytes out
- referral stringse.g. referral strings associated with the entity.
- generating the feature scoresincludes analyzing a sequencing of characters in an entity identifier (e.g., a domain name) associated with an entity (internal or external) and assigning a feature score based on the analysis, wherein the feature score is indicative of the level of confidence that the entity identifier is machine-generated.
- entity identifiere.g., a domain name
- assigning a feature score based on the analysiswherein the feature score is indicative of the level of confidence that the entity identifier is machine-generated.
- applying a lexical analysisto a character-based entity identifier to assign a feature score indicative of whether the identifier is machine generated or not.
- This analysis and feature scoringassumes, based on industry expertise, that a machine-generated identifier is more likely to be associated with malicious activity (e.g. malware) given the context.
- malware running within a computer networkmay periodically transmit a beacon message (“beacon”) to an external entity (e.g. a domain) seeking command and control instructions.
- an external entitye.g. a domain
- malwaremay be configured to communicate with external entities through continuously changing machine-generated domain names.
- FIG. 70shows two tables 7002 and 7004 of domain names with associated probabilities based on n-gram analysis. As shown in FIG.
- table 7002includes domain names with lower probabilities relative to the domain names of table 7004 .
- the probabilities sequence of characters in the domain names in table 7002 occurring in natural human languageare lower relative to the probabilities of the sequencing of characters in the domain names in table 7004 .
- generating the plurality of feature scoresincludes analyzing the timing of communications associated with the entity (internal or external) over a time period and assigning a feature score based on the analysis, wherein the feature score is indicative of a level of confidence that the communications are machine-generated.
- the timing of communicationse.g. periodicity and/or variance of interval times
- communications with high periodicityare less likely to be human generated and more likely to be machine generated, for example a beacon communication.
- generating the plurality of feature scoresincludes analyzing a sequencing of communications associated with an entity (internal or external) over a time period and assigning a feature score based on the analysis, wherein the feature score is indicative of a level of confidence that the communications are associated with an exploit chain.
- An Exploitis a piece of software, a chunk of data, or a sequence of commands that takes advantage of a bug or vulnerability in order to cause unintended or unanticipated behavior to occur on computer software, hardware, or something electronic (usually computerized). Such behavior frequently includes things like gaining control of a computer system, allowing privilege escalation, or a denial-of-service attack.
- An exploit chaintypically involves patterns in the sequencing of communications.
- generating the plurality of feature scoresincludes analyzing the data transmission statistics associated with an entity (internal or external) over a time period and assigning a feature score based on the analysis, wherein the feature score is indicative of a level of confidence that the external entity is associated with a command and control infrastructure external to the computer network. For example, the ratio of bytes in to bytes out in a particular communication or set of communications may provide insight into the purpose of the communication. A higher volume of data going out to an external entity than is coming in may indicate the exfiltration data by malware within the network in response to commands from the external entity.
- the anomaly score associated with a particular entityis based on the entity profile (including the underlying feature scores) of the particular entity.
- the anomaly scoremay be conceptualized as combination of all of the feature scores for a particular entity.
- anomaly scores calculated or assigned by processing event data through an anomaly model to generate a numerical valueis calculated or assigned by processing the plurality of feature scores through an anomaly model.
- the anomaly modelincludes model processing logic defining a process for assigning a feature score based on the plurality of feature scores and a model state defining a set of parameters for applying the model processing logic.
- the models used to generate the anomaly scoresare machine-learning (both supervised and unsupervised) models. For example, a supervised machine learning model may use training examples developed by network security experts to more effectively generate an anomaly score based on the plurality of feature scores.
- generating the anomaly scoremay include an ensemble learning process in which multiple different types of machine learning models are applied to processed the plurality of feature scores.
- the anomaly scoreis a numerical value in a set range. For example, processing the plurality of feature scores according to an anomaly model may yield a value between 0 and 10 with 0 being the least anomalous (or risky) and 10 being the most anomalous (or risky).
- generating the anomaly scoremay simply involve a calculating a weighted linear combination of feature scores.
- the anomaly scoremay simply be represented as:
- w iis a weighting factor applied to each feature score f i and wherein the anomaly score is simply the summation of each of the plurality of feature scores with the weighting factor.
- the weighting factor, w i applied to any given feature score in the anomaly scoring processmay depend on a number of factors, including the type of entity to which the feature score is applied, the volume of data used to calculate the feature score, user configuration preferences, or the type of analysis used to generate the feature score.
- the plurality of feature scoresmay be processed according to one or more machine learning models to generate an anomaly score indicative of the probability or likelihood that malware is present in the computer network given the set of feature scores for a particular entity.
- Some machine-learning models appropriate for this applicationinclude naive Bayes and logistic regression.
- ensemble learning techniquescan be applied to process the plurality of feature scores according to a plurality of models (including machine-learning models) to achieve better predictive performance in the anomaly scoring and reduce false positives.
- An example model suitable for ensemble learningis Random Forest.
- the processmay involve, processing an entity profile according to a plurality of machine-learning models, assigning a plurality of intermediate anomaly scores, each of the plurality of intermediate anomaly scores based on processing of the entity profile according to one of the plurality of machine-learning models, processing the plurality of intermediate anomaly scores according to an ensemble-learning model, and assigning the anomaly score based on processing the plurality of intermediate anomaly scores.
- Machine learning modelsare typically more effective if provided large volumes of data to process and learn from. Accordingly, in some embodiments, the type of model applied to generate an anomaly score depends on the volume of data used to generate the feature scores. For example, some events are associated with no more than a single log line of event data, while others are associated with hundreds of lines of log lines of event data. Accordingly, in some embodiments, a process for generating an anomaly score involves first determining a volume of event data used to generate the entity profile or any one of the plurality of feature scores. Next the entity profile is processed according to one or more of a plurality of anomaly models depending on the determined volume of event data. For example, in an embodiment, the entity profile is processed through a first anomaly model (e.g.
- an ensemble learning modelif the volume of event data is at or above a threshold volume or the entity profile is processed through a second anomaly model (e.g. weighted linear combination) if the volume of event data is below the threshold volume.
- An anomaly scoreis then assigned based on the processing.
- the thresholds described abovecan be static or dynamic.
- a dynamic thresholdmay adaptively change based on a number of factors, such as the overall volume of event data being generated on the computer network, the type of entity to which the anomaly score is applied, user configuration preferences, and the types of analysis used to generate the feature scores.
- a plurality of threshold valuesestablish a number of regimes under which the entity profile is processed. For example, the detected volume of data may fall under one of three regimes, low volume, medium volume, and high volume. Depending on the regime, the profile entity is processed according to a different anomaly model.
- the entity profilecan, in some cases, include additional data beyond the plurality of feature scores.
- entity profile generationincludes a process of forensic data enrichment through global evidence collection. In such a process, data regarding a particular entity is gathered from sources internal (e.g. a system blacklist) or external (e.g. a WHOIS lookup) to the computer network. In some embodiments, this data enrichment process aids the process of generating an anomaly score to reduce false positives.
- the parameters used to apply the processing logiccan depend on information about the entity and/or environment not otherwise indicated in the plurality of feature scores. For example, an mission critical computing system associated with a given set of feature scores is viewed differently than a non-critical computing system associated with the exact same set of feature scores.
- external datacan be applied validate an anomaly detection.
- the process of generating the anomaly scoreincludes comparing an entity identifier associated with an entity (internal or external) with entries in an external data source external to the computer network (e.g. a WHOIS lookup) and assigning an anomaly score indicating a confidence level that the entity identifier matches a particular entry in the external data source based on the comparing.
- an anomaly indicating malware in the computer networkis detected if the anomaly score satisfies a specified criterion.
- a specified criterionmay be set such that an anomaly is detected if the anomaly score is 6 or above.
- the specified criterionneed not be static, however.
- the criterionis dynamic and changes based on situational factors. Situational factors may include volume of event data, presence or absence of pre-conditional events, user configurations, and volume of event data.
- FIG. 71shows an example incident response output 7100 based on entity profiles configured for display to a user.
- the incident response output 7100is represented in simplified form for clarity as a table including a plurality of entity identifiers 7102 with associated feature scores 7104 a - 7104 d and a recommended response 7106 based on the plurality of feature scores.
- the particular arrangement of informationshould not be construed as limiting.
- the entity identifieris a domain name
- the entity identifier associated with the entitycan be any identifier, such as a domain name, a uniform resource locater (URL), uniform resource identifier (URI), an Internet Protocol (IP) address, a unique identifier (UID), a device identification, or a user identification.
- the plurality of feature scores 7104 a - 7104 dare displayed as classifications, i.e. no risk, moderate risk, and high risk, instead of numerical values. These classifications can be based on the underlying numerical feature scores.
- the numerical feature score values(e.g. 0 to 10) are displayed to the user via the incident response output.
- the analyst recommendation 7106provides information guiding the user to take action based on the raised anomaly associated with entity 7102 .
- entity 7102For example, the domain “www.evil.com” has a communication feature score indicative of a high risk to network security due to ongoing unblocked communications.
- the recommendation 7106accordingly lists this as a critical priority due to the ongoing and unblocked nature of the communications.
- the analyst recommendation 7106is provided by a human security analyst based on an assessment of the feature scores associated with the entity.
- the analyst recommendationis automatically generated by the system based on the feature scores and or the anomaly score, for example through the use of established network security rules.
- Detected anomalies indicative of malware on the computer networkcan be stored in an anomaly graph data structure that includes a plurality of nodes representing entities associated with the computer network, and a plurality of edges representing an anomaly linking two of the plurality of nodes. Further, the anomaly data can be incorporated into a system wide network security graph.
- a network security graphincludes a plurality of nodes representing entities associated with the computer network and a plurality of edges, each of the plurality of edges linking two of the plurality of nodes and representing an association between the entities represented by the nodes. In such a graph the detected anomalies can be incorporated as a node linked to one or more entities by an edge.
- Malwareis malicious software (e.g., virus, Trojan horse, or the like) installed on a computer or other device without the knowledge or permission of the owner of the device for an improper purpose, such as to steal private data or as a prank.
- malicious softwaree.g., virus, Trojan horse, or the like
- IPInternet Protocol
- monitoring the IP pairs of outgoing trafficcan be resource intensive, especially if the outgoing traffic of the computer is voluminous.
- the problemis only compounded as the number of computers in a network, e.g., computers in an organization's network, increases. Monitoring the computers in real-time can also be challenging considering the number of IP pairs can be in significantly large numbers.
- Malware programstend to communicate with their command and control (C&C) entity (e.g., a website) to receive new instructions and they tend to contact the C&C entity periodically.
- C&Ccommand and control
- machine-generated trafficsuch as traffic generated by malware
- user-generated trafficsuch as traffic generated from a user browsing a webpage or accessing other resources on the Internet.
- Most techniquesfail to recognize the distinction between the machine-generated traffic and the user-generated traffic that can help in detecting malware efficiently.
- the outgoing trafficcan include user-generated traffic, which can include connection requests generated from a user associated with the device, such as when the user accesses a website, checks email and downloads applications.
- the outgoing trafficcan also include legitimate (not malware related) machine-generated traffic, which is generated by the device or an application executing on the device without intervention from the user, such as updates to applications, messages for synchronizing time of the device, device-to-device communication within another device in a distributed computing system of which the device is a part, a heartbeat signal generated by an application on the device, which can be a signal that is generated at regular intervals to indicate that the application is working as expected.
- the machine-generated trafficcan also include traffic generated by some applications, such as a malware, that can be malicious in nature.
- Some of the machine-generated trafficcan be in the form of a beacon, which is a signal that is transmitted periodically or in a manner that satisfies a particular criterion for periodicity/regularity.
- the malware beacon detection technique introduced heredistinguishes between user-generated traffic and machine-generated traffic and, if the traffic is machine-generated, determine whether the machine-generated traffic is benign or suspicious (e.g., anomalous).
- the techniquecan use various methods to filter out benign machine-generated traffic. For example, the technique can use different heuristics and whitelists to determine whether the traffic is benign. The technique can further analyze the anomalies to determine whether they are a threat and raise an alarm if they are one.
- the techniquedetermine if the outgoing traffic is user-generated traffic based on a number of parameters, such as number of connection requests originating from the device in a predefined period, periodicity of the connections, number of web objects requested by the device, number of destinations contacted by the device, number of times a destination is contacted and number of ports of the destinations contacted.
- the malware beacon detection technique introduced herecan operate in real-time, e.g., as and when the traffic is generated from the computer device.
- the techniquecan perform the above described method using real-time infrastructure, e.g., real-time analyzer 210 of FIG. 2 and/or analysis module 330 of FIG. 3 described above. Additionally or alternatively, the technique can operate in a batch processing mode by using the batch processing infrastructure, e.g., batch analyzer 240 and/or batch analysis module 382 .
- the above described methodcan be performed by a model, such as a machine learning model.
- the modelcan output the result of the detection as a yes or no (or the equivalent), or as a score based on which the machine-generated traffic can be determined as an anomalous or not.
- the modelcan be implemented in real-time infrastructure and/or batch processing infrastructure.
- FIG. 72shows an example graph 7200 of outgoing traffic of a device.
- the example graph 7200depicts traffic generated from a device over a period, e.g., seventeen seconds.
- the example graph 7200depicts the traffic as a number of connection requests originating from the device.
- the outgoing trafficcan include two categories of traffic: user-generated traffic and machine-generated traffic.
- the first outgoing traffic 7205 and the second outgoing traffic 7215which represent traffic generated from user activity, e.g., from a web browsing activity, are categorized as user-generated traffic.
- the third outgoing traffic 7210 and the fourth outgoing traffic 7220which represent traffic generated due to various machine-related activities that are performed without the intervention of a user of the device, are categorized as machine-generated traffic.
- machine-generated trafficcan include a beacon to an external server, which determines whether there is any update available for an application installed at the device; a message from the device to a server for synchronizing time of the device; or malware that is communicating with a C&C entity.
- the userwhen the user performs an activity, e.g., browses a webpage, the user generates a large volume of connection requests.
- an activitye.g., browses a webpage
- the userWhen the user does not interact with the computer, there can be a silent period, e.g., a period with minimal activity or no activity.
- the techniquecan detect these silent periods and analyze the traffic generated during that time. For example, if malware contacts its C&C entity during the silent periods, the technique can detect such machine-generated traffic as anomalous.
- the first outgoing traffic 7205which can represent traffic corresponding to a user accessing a webpage
- a significantly high number of connection requestse.g., reaching almost fifty, have been generated within a span of four seconds.
- a websitecan host content stored at different locations, e.g., at different servers.
- a webpage of the websitecan host a number of images, advertisements, etc. that are stored at different servers.
- the devicecan generate a number of connection requests that are sent to different servers for obtaining different portions of the webpage, e.g., images, cascading stylesheets (CSS).
- the trafficdecreases and the number of connections decrease to zero. That is, the number of connections increases and/or decreases rapidly.
- the number of requestsare comparatively low, e.g., do not exceed ten at any instance. That is, for a predefined period, the number of requests is typically lower than the number of requests compared to user-generated traffic.
- the connection requests in the second outgoing traffic 7210is more periodic than the connection requests in the first outgoing traffic 7205 . For example, the connection requests appear every two seconds in the second outgoing traffic 7210 .
- a user-generated activitycan include a significantly higher number of connection requests than machine-generated traffic for a predefined period. It can also be observed that the connection requests in the user-generated traffic increase and/or decrease at a rate higher than a specified threshold, i.e., connection requests are generated aperiodically or irregularly. In the machine-generated traffic, the connection requests are generated in a more periodic manner than the user-generated traffic.
- FIG. 73lists an example of a set of parameters that can be considered for distinguishing between machine-generated traffic and user-generated traffic, consistent with various embodiments.
- the techniquecan distinguish between machine-generated traffic and user-generated traffic as a function of one or more of the set of parameters 7300 .
- the set of parameters 7300can include a number of connection requests generated at a device in a predefined period, periodicity of the connection requests, e.g., a period or frequency between the connections, number of different destinations contacted, e.g., a diversity of the Internet Protocol (IP) addresses, a number of web objects downloaded to the device, a number of ports at which the destinations are contacted and a Uniform Resource Identifier (URI) of the destinations.
- IPInternet Protocol
- Some of the set of parameters 7300can be part of the outgoing traffic data and therefore, can be readily available for use by the technique. However, some of the set of parameters 7300 are determined by the technique, e.g., based on the parameters available in the outgoing traffic data. Additional details with respect to distinguishing between user-generated traffic and machine-generated traffic are described at least with reference to FIGS. 74 and 75 .
- FIG. 74is a block diagram of an environment 7400 in which a system 7425 for detecting anomalies in machine-generated traffic can be implemented, consistent with various embodiments.
- the system 7425is implemented as part of the threat detection platform 300 of FIG. 3 .
- the system 7425can be implemented as part of the real-time infrastructure 330 or batch processing infrastructure 382 .
- the system 7425is implemented as part of the real-time infrastructure 330 .
- at least a portion of the system 7425is implemented as part of a model in the real-time infrastructure 330 or batch processing infrastructure 382 .
- the environment 7400includes a computer device 7405 whose outgoing traffic is monitored for detection of anomalies and/or threats.
- the device 7405can be part of a distributed computing system having a number of devices.
- the device 7405can be one of many devices in a computer network 7465 of an organization.
- the network 7465can be a local area network (LAN), a wide area network (WAN), etc.
- the outgoing traffic from device 7405can include outgoing traffic that is internal to the network 7465 (“internal traffic”), e.g., communications with devices in the network 7465 , and outgoing traffic that is external to the network 7465 (“external traffic”), e.g., communications with servers 7415 in the network 7410 such as Internet.
- the network 7410is external to the network 7465 .
- the system 7425monitors the outgoing traffic of the device 7405 , e.g., using outgoing traffic log 7450 , and detects any existence of anomalies and/or threats.
- the system 7425is configured to monitor a portion of the outgoing traffic from the device 7405 , e.g., external traffic.
- the outgoing traffic log 7450can be obtained from a proxy, gateway or a firewall of the network 7465 in which case the outgoing traffic log 7450 may not include internal traffic information.
- the monitoringmay not be restricted to external traffic and the system 7425 can be used to monitor both external and internal traffic.
- the outgoing trafficcan be any class of traffic, e.g., web traffic or IP traffic.
- the web trafficcan include Hyper-Text Transfer Protocol (HTTP) message, which can be associated with parameters such as a destination IP address, a URI of the destination, a port number, a type of web request—GET or POST, etc.
- HTTPHyper-Text Transfer Protocol
- the IP trafficcan be associated with parameters such as a destination IP address and a port number.
- the outgoing traffic log 7450can be processed by one or more components prior to being input to the system 7425 .
- the semantic processor 316can process the outgoing traffic information to remove, add or modify at least some of the information and generate the outgoing traffic log 7450 in a condition that is suitable for further processing by the system 7425 efficiently.
- the semantic processor 316can remove internal traffic, e.g., data transfers that occur between two internal devices as part of file backup, which is less likely or unlikely to be an anomaly, from the outgoing traffic information.
- the traffic classification module 7430analyzes the outgoing traffic log 7450 and detects if the outgoing traffic is machine-generated traffic 7445 . If the outgoing traffic is machine-generated traffic 7445 , the traffic classification module 7430 passes the outgoing traffic to the anomaly detection module 7435 , which determines if the machine-generated traffic 7445 is benign traffic or an anomaly 7455 . If the machine-generated traffic 7445 is an anomaly 7455 , the anomaly detection module 7435 passes the anomaly 7455 to a threat analysis module 7460 . The threat analysis module 7460 determines if the anomaly 7455 is a threat and generates a notification, e.g., an alarm, if it is one.
- a threat analysis module 7460determines if the anomaly 7455 is a threat and generates a notification, e.g., an alarm, if it is one.
- the traffic classification module 7430analyzes the connection requests in the outgoing traffic log 7450 to form a group of connection requests and determines if the group is user-generated traffic or machine-generated traffic.
- the group of connection requestsis either machine-generated traffic or user-generated traffic and cannot be both.
- two different groupscan be of different classes of traffic.
- the traffic classification module 7430can form the group based on various criteria.
- the traffic classification module 7430can form a group by grouping the connection requests in the outgoing traffic log 7450 that are closer to each other in time.
- the traffic classification module 7430groups the connection requests that are generated within “20” seconds from the time a first connection request of the outgoing traffic log 7450 is generated into the same group.
- the outgoing traffic log 7450is received in real-time and the traffic classification module 7430 can start forming the group as and when the first connection request is generated at the device 7405 .
- the traffic classification module 7450determines whether the group of connection requests is user-generated traffic or machine-generated traffic.
- the user-generated trafficas described above, can be a result of an activity performed by a user 7420 associated with the device 7405 , e.g., accessing a webpage in the Internet using the device 7405 .
- the machine-generated trafficas described above, can be generated by the device 7405 or an application executing on the device 7405 without intervention from the user 7420 , such as updates to applications, messages for synchronizing time of the device, a heartbeat signal from an application or beacons from a malware.
- the traffic classification module 7450determines whether the group of connection requests is user-generated traffic or machine-generated traffic based on a set of parameters, e.g., set of parameters 7300 of FIG. 73 . For example, the traffic classification module 7450 determines whether the group is user-generated traffic or machine-generated traffic as a function of one or more of a number of different destination IP addresses in the group, that is, a number of destinations contacted by the device 7405 ; a number of web objects downloaded by the group; a number of destination ports in the group; or a periodicity of the connection requests in the group.
- the traffic classification module 7430determines whether a periodicity of the connections in the group satisfy a periodicity criterion.
- the periodicity of the connection requestsis determined as a function of the timing between the connection requests in the group.
- the periodicitycan be an average of the periods between each of the connection requests in the group.
- the traffic classification module 7430determines that the group is likely to be machine-generated traffic if the periodicity of the connection requests satisfies a periodicity criterion, e.g., exceeds a specified threshold; otherwise determines the group as likely to be user-generated traffic.
- a user activitysuch as accessing a webpage can generate a high number of requests to different destinations within a predefined period, download a significant number of web objects, e.g., images, cascading stylesheets (CSS), and/or contact different destinations at different ports.
- web objectse.g., images, cascading stylesheets (CSS)
- CSScascading stylesheets
- the traffic classification module 7450determines that the group is likely to be user-generated traffic if a diversity of the destination IP addresses in the group (i.e., the number of destinations contacted) exceeds a specified threshold. In some embodiments, the traffic classification module 7450 determines that the group is likely to be user-generated traffic if the number of web objects downloaded exceeds a specified threshold. In some embodiments, the traffic classification module 7450 determines that the group is likely to be user-generated traffic if the number of ports in the group exceeds a specified threshold.
- the traffic classification module 7430can be configured to consider one or more of the above parameters for determining whether the outgoing traffic is user-generated traffic. If the traffic classification module 7430 determines that the outgoing traffic is likely to be user-generated traffic, the group may not be analyzed further to detect an anomaly.
- the system 7425can check if the group includes connection requests to any whitelisted destinations.
- a whitelistcan be a list of destinations that are considered to be safe to be accessed by the devices in the network 7465 .
- a usersuch as an administrator of the network 7465 can generate the whitelist.
- the whitelistcan also be created and/or modified automatically, e.g., by one or more models executing in the real-time infrastructure 330 or the batch processing infrastructure 382 . If the group includes connections requests to the whitelisted destinations the group may not be analyzed any further for detecting an anomaly.
- the system 7425determines if the group includes whitelisted destinations prior to determining whether the group is user-generated traffic so that if the group includes whitelisted destinations the system 7425 does not have to analyze the group any further, thereby saving computing resources.
- the analysis of whether the group includes whitelisted destinationscan be performed by the traffic analysis module 7425 or other modules, e.g., semantic processor 316 .
- the anomaly detection module 7435further analyzes the machine-generated traffic 7445 to determine whether it is likely to be an anomaly. As described above, some of the machine-generated traffic 7445 can be benign and some anomalous, e.g., malicious. The anomaly detection module 7435 analyzes the group further to determine if the machine-generated traffic 7445 includes benign traffic or anomalous traffic. The anomaly detection module 7435 extracts beacon data 7470 from the machine-generated traffic 7445 .
- the beacon data 7470can include parameters such as destination IP address(es) of the connection requests in the group, destination port(s), and if the connection request is a HTTP request, the beacon data 7470 can also include a type of the connection request, e.g., a GET or POST, and URI of the destination.
- the anomaly detection module 7435compares the beacon data 7470 with any of the known group types (also referred to as “beacon types”) that are identified as likely to be anomalous to determine whether the machine-generated traffic is anomalous. Additional details of determining whether the machine-generated traffic is anomalous are described at least with reference to FIG. 75 .
- the traffic classification module 7430can determine that the group is likely to be machine-generated traffic 7445 if the group is not whitelisted, satisfies periodicity criterion and not user-generated traffic. Further, the machine-generated traffic that is not identified as benign traffic is recognized as anomalous.
- FIG. 75shows an example 7500 of a memory cache storing beacon types that are identified as likely to be anomalous, consistent with various embodiments.
- a beacon typeincludes a group or a number of similar groups that are identified as likely to be anomalous.
- the anomaly detection module 7435can store the beacon type in a memory cache 7440 associated with the system 7425 .
- a beacon type 7505can store beacon parameters 7510 such as destination IP address(es) of connection requests in a group, destination port(s), the type of connection request, e.g., HTTP GET or POST, a URI of the destination.
- the anomaly detection module 7440stores the beacon parameters 7510 of a group as a vector 7520 and a timestamp, which indicates the time at which the group occurred in the outgoing traffic, in an array 7515 of the beacon type 7505 . If multiple groups are stored in the beacon type 7505 , then the beacon type 7505 can include multiple vectors, e.g., one for each corresponding group, and a timestamp entry for each of the groups in the array 7515 .
- the anomaly detection module 7435compares the beacon data 7470 with the beacon types in the memory cache 7440 to determine if the beacon data 7445 matches with any of the beacon types in the memory cache 7440 . If the beacon data 7445 matches with any of the beacon types, e.g., beacon type C, the anomaly detection module 7435 adds the beacon data 7445 to the beacon type C. The anomaly detection module 7435 determines if the group represents an anomaly as a function of a frequency of the occurrence of the groups in the beacon type C.
- some of the machine-generated traffic 7445can be benign and some anomalous, e.g., malicious.
- the anomaly detection module 7435analyzes the group further to determine if the machine-generated traffic 7445 includes benign traffic or anomalous traffic.
- malwaresends a beacon to its C&C regularly and in high frequency. That is, a gap or timing between the beacons is typically lesser than a specified threshold. Long gaps between the connection requests, e.g., timing exceeding the specified threshold, can usually be attributed to benign traffic, such as an application on a device checking with a server in the Internet for software updates, which can also send beacons regularly. However, the beacons for such software updates can be less frequent than the beacons of malware.
- the first occurrence of a group of beacon type Cis at time t, the second occurrence at time (t+x), the third occurrence at time (t+x+y), the fourth occurrence at time (t+x+y+z) and so on.
- the anomaly detection module 7435determines the number of occurrences of the groups and timing between the occurrences of the group.
- the anomaly detection module 7435determines the group to which the beacon data 7470 corresponds and the other groups of the beacon type with which the beacon data 7470 matches as anomalous.
- a groupis recurring but not strictly periodic, e.g., the average timing (average (x, y, z)) does not satisfy the specified timing threshold, the anomaly detection module 7435 determines if the groups occurred at least a second threshold number of times in which the second threshold number is greater than the first threshold number. If the groups occurred at least a second threshold number of times, the anomaly detection module 7435 determines the groups as anomalous. If neither of the periodicity thresholds is satisfied, the group is determined as likely to be benign traffic.
- the anomaly detection module 7435determines the groups to be anomalous, the anomaly detection module 7435 indicates those groups as an anomaly 7455 to the threat analysis module 7460 , which can further analyze the anomaly 7455 to determine if it is a threat and raise an alarm, e.g., generate a notification, if it is one.
- the anomaly 7455can include various information, e.g., information from the beacon data 7470 and/or information from the beacon type with which the beacon data 7470 matched.
- the anomaly detection module 7435can also include additional data in the anomaly 7455 which can be used by the threat analysis module 7460 in determining if the anomaly 7455 is a threat.
- the set of parameters that may be considered to determine a matchcan include at least one of destination IP address(es) of the connection requests, destination port(s), and if the connection request is a HTTP request, a type of the connection request, e.g., a GET or POST, and a URI of the destination.
- a particular group matches with a beacon typethen the particular group and the groups stored in the beacon type can be considered to be similar groups.
- Various criteriacan be defined to determine whether a group matches with a beacon type. For example, the beacon data 7470 is considered to match with a beacon type in the memory cache if all of the set of parameters of the beacon data matches with that of the beacon type.
- the beacon data 7470is considered to match with the beacon type if at least one of the set of parameters of the beacon data matches with that of the beacon type. In another example, the beacon data 7470 is considered to match with the beacon type if at least a portion of one of the set of parameters, e.g., a portion of the destination IP address, of the beacon data matches with that of the beacon type.
- FIG. 76is a flow diagram of a process 7600 for determining whether outgoing traffic from a device is an anomalous traffic, consistent with various embodiments.
- the process 7600is implemented in the environment 7400 and using the system 7425 .
- the process 7600can be performed as part of a model in the real-time infrastructure 330 or batch infrastructure 382 .
- the traffic classification module 7430receives information regarding outgoing traffic of a device.
- the traffic classification module 7430receives outgoing traffic log 7450 , which contains information regarding outgoing connection requests from device 7405 .
- a connection requestis a request for connecting to a particular computer/server in network 7465 and/or network 7410 .
- the outgoing trafficcan be web traffic, e.g., HTTP traffic, or IP traffic. Further, in some embodiments, the outgoing traffic does not include internal traffic, e.g., traffic between devices within the network 7465 .
- the traffic classification module 7430analyzes the outgoing traffic to form a group of connection requests.
- the connection requests in the outgoing trafficcan be grouped based on various criteria.
- the connection requestsare grouped based on a time at which the connection requests were generated at the device. For example, connection requests that are closer in time to each other within a predefined period are grouped together. Additional details with respect to forming the group are described at least with reference to FIG. 77 .
- the traffic classification module 7430determines if the group contains connection requests to one or more destinations that are identified as acceptable destinations.
- the system 7425can have access to a list of acceptable destinations, e.g., a whitelist.
- the destination information in the whitelistcan include one or more of IP address of a destination, a URI of the destination or port of the destination.
- connection requestsare to whitelisted destinations, then the group is not monitored any further and the process 7600 returns.
- the traffic classification module 7430analyzes the group to determine whether the group is user-generated traffic or machine-generated traffic. Examples of user-generated traffic can include traffic generated as a result of user activity, such as the user accessing a website, checking email and downloading applications.
- Examples of machine-generated trafficcan include traffic generated by the device or an application executing on the device without intervention from the user, such as updates to applications, messages for synchronizing time of the device, device-to-device communication between devices in a distributed computing system, benign beacons, e.g., heartbeat signals generated by an application on the device, or beacons generated by malware.
- traffic generated by the device or an application executing on the devicewithout intervention from the user, such as updates to applications, messages for synchronizing time of the device, device-to-device communication between devices in a distributed computing system, benign beacons, e.g., heartbeat signals generated by an application on the device, or beacons generated by malware.
- the traffic classification modulemakes the determination of whether the group is user-generated traffic or machine-generated traffic based on a set of parameters described at least with reference to FIG. 73 . If the traffic classification module 7430 determines the group as user-generated traffic, then the group is not monitored any further and the process 7600 returns.
- the anomaly detection module 7435determines whether the group represents anomalous traffic. In some embodiments, the anomaly detection module 7435 makes the determination as a function of a frequency of occurrence of the group in the outgoing traffic, or as a frequency of occurrence of groups determined to be similar to the group. Additional details with respect to determining whether the machine-generated is anomalous are described at least with reference to FIG. 78 .
- FIG. 77is a flow diagram of a process 7700 for forming a group of connection requests from outgoing traffic of a device, consistent with various embodiments.
- the process 7700may be implemented as part of block 7610 of process 7600 .
- the traffic classification module 7430monitors the outgoing traffic log 7450 to identify a first connection request from the device 7405 .
- the traffic classification moduleforms a group and adds the first connection request to the group.
- the traffic classification module 7430also records the time at which the first connection request was generated.
- the traffic classification module 7430continues to monitor the outgoing traffic log 7450 for subsequent connection requests from the device 7405 .
- the traffic classification module 7430detects a subsequent connection request in the outgoing traffic log 7450 .
- the traffic classification module 7430determines if the subsequent connection request satisfies a grouping criterion.
- the grouping criterioncan be based on a period between the time at which the first connection is generated and that of the subsequent connection request.
- the traffic classification modulecan determine whether the subsequent request is received within a predefined period from the time the first connection request was received, e.g., within twenty seconds from the first connection request.
- the traffic classification module 7430adds the subsequent connection request to the group, and the process continues monitoring for subsequent requests. On the other hand, if the subsequent connection request does not satisfy the grouping criterion, the process 7700 returns.
- FIG. 78is a flow diagram of a process 7800 for determining whether a particular group of connection requests in the outgoing traffic of a device is user-generated traffic or machine generated traffic, consistent with various embodiments.
- the process 7800may be implemented as part of block 7620 of process 7600 .
- the traffic classification module 7430analyzes the connection requests to obtain a set of parameters for determining whether the particular group is user-generated traffic or machine-generated traffic.
- the set of parameterscan include one or more of IP addresses of destinations of the connection requests in the particular group, (b) a number of web objects downloaded by the connection requests in the particular group, (c) a number of ports of the destinations, or (d) periodicity of the connection requests.
- the traffic classification module 7430determines if the set of parameters satisfies the user-generated activity criteria. For example, the traffic classification module 7430 determines that the group is user-generated traffic if the number of different IP addresses of the destinations, that is, a diversity of the IP addresses, exceeds a first specified threshold. In another example, the traffic classification module 7430 determines that the group is user-generated traffic if the number of web objects downloaded by the particular group exceeds a second specified threshold. In another example, the traffic classification module 7430 determines that the group is user-generated traffic if the number of ports exceeds a third specified threshold.
- the periodicity of the connection requestsis determined as a function of the timing between the connection requests in the particular group.
- the periodicitycan be an average of the periods between each of the connection requests in the group.
- the traffic classification module 7430determines that the particular group is likely to be machine-generated traffic if the periodicity of the connection requests satisfies a periodicity criterion, e.g., exceeds a specified threshold; otherwise determines the particular group as likely to be user-generated traffic.
- the user-generated activity criteriacan be configured in various ways. In some embodiments, all of the set of parameters have to satisfy the criteria for determining that the group is user-generated activity. In some embodiments, one or more of the set of parameters have to satisfy the criteria for determining that the group is user-generated activity.
- the traffic classification module 7430determines that the particular group is user-generated activity; the traffic classification module 7430 stops analyzing the particular group further and the process 7800 returns. On the other hand, if the set of parameters does not satisfy the user-generated activity criteria, at block 7815 , the traffic classification module determines that the particular group is machine-generated traffic.
- FIG. 79is a flow diagram of a process 7900 for determining whether machine-generated traffic is anomalous, consistent with various embodiments.
- the process 7900may be implemented as part of block 7625 of process 7600 .
- the system 7425analyzes a particular group of connection requests that is identified as machine-generated traffic, e.g., in process 7800 , to determine whether the machine-generated traffic is benign or anomalous.
- the anomaly detection module 7435compares the particular group with one or more beacon types, e.g., beacon types in memory cache 7440 , that are identified as likely to be anomalous to determine if the particular group is similar to any of the beacon types. In some embodiments, the comparison is performed as described at least with reference to FIG. 75 .
- the anomaly detection module 7435adds the particular group to the beacon type “C.” If the particular group is not similar to any of the beacon types, at block 7925 , the anomaly detection module determines that the particular group is likely to be benign traffic and the process 7900 returns.
- the anomaly detection module 7435determines if the groups in the beacon type satisfy a periodicity criterion.
- a periodicity of the groupsis determined as a function of the frequency at which the groups in the beacon type occurred in the outgoing traffic.
- the periodicitycan be an average of the periods between each of the groups in the beacon type.
- the groupmay have to occur at least “X” times and periodically.
- the groupmay have to occur at least “Y” times, where “Y”>“X” because a periodic behavior is a stronger indication of machine activity. Therefore, if a group is simply recurring, but not periodically enough, the group may have to occur more times before the anomaly detection module 7435 can determine it as anomalous.
- the groupscan be considered to be periodic, if an average timing between the occurrences of the groups in the beacon type satisfies a specified timing threshold.
- the periodicity criterioncan state that if the groups in the beacon type are periodic, then groups have to occur a first threshold number of times else the groups have to occur a second threshold number of times for the groups in the beacon type to be considered as anomalous. Further, the periodicity criterion can require that the second threshold number to be greater than the first threshold number.
- the anomaly detection module 7435determines that the groups in the beacon type are anomalous. If the groups in the beacon type do not satisfy the periodicity criterion, at block 7925 , the anomaly detection module 7435 determines that the groups in the beacon type are likely to be benign traffic, and the process 7900 returns.
- Described hereinis a technique for determining rarity of features of data traffic (“traffic”) in a computer network. Determination of rarity can be used to detect anomalies represented in event data. The technique computes a rarity score for each of various values of a feature of event data, where each rarity score indicates how rare the occurrence of the corresponding particular value is relative to occurrences of other values of that feature, and then determines if network activity or an event in which that particular value of the feature occurs is anomalous, based on the rarity score.
- Examples of features regarding which a rarity score can be computed in this mannerinclude, for example: a field, attribute, and/or property of the data traffic on and/or an entity associated with the computer network, e.g., a username of a user, a source zone of the network from which the traffic is originating, a destination zone of the network to which the traffic is destined, the port identifier of a port through which data is transmitted, a name of an application that transmits and/or receives the data, and an identification (ID) of a device, such as an Internet Protocol (IP) address, that transmits and/or receives the data.
- IPInternet Protocol
- the featurecan be of high cardinality, i.e., can have one of a finite number of values.
- a feature such as a portcan have multiple values, e.g., 20, 22, 23, 25, 80, which are associated with specific network protocols.
- a particular value of a featuremay occur more commonly, e.g., more number of times, than another value of the feature.
- port 80which corresponds to Hyper Text Transfer Protocol (HTTP)
- HTTPHyper Text Transfer Protocol
- the rarity determination techniquedetermines the rarity of a particular value of a feature (such as one of the features mentioned above) as a function of the probability of occurrence of that particular value relative to the probability of occurrence of other values of the feature. In some embodiments, the technique considers the values that are as likely or less likely to occur than that particular value to determine the probability (also referred to as “relative probability”) of occurrence of the particular value. After determining the probability of the particular value relative to the other values, the technique may compute a confidence interval of that probability to obtain the rarity score. In some embodiments, the rarity score is a value between 0 and 1. The technique can use known methods, such as the delta method, for computing the confidence interval.
- the techniquecan identify an activity or event in which the particular value occurred as anomalous.
- the rarity scoresatisfies the rarity criterion if the rarity score is below a specified score threshold and the number of times that the particular value has been identified as corresponding to an anomaly is less than a specified count threshold.
- datacan be transmitted from one or more source devices to one or more destination devices.
- the datacan be transmitted from a portion of the network identified as “Zone A” to a portion of the network identified as “Zone B,” from “Zone C” to “Zone B,” “Zone D to “Zone B,” and/or “Zone A to “Zone D.”
- the techniquecan determine how rare it is to observe a source zone being “Zone A” when the destination zone is “Zone B.” Based on the rarity score of the feature pair, the technique can determine whether an event of which the feature pair is a part corresponds to an anomaly.
- FIG. 80is a block diagram of an environment 8000 in which a system 8025 for detecting anomalies based on rarity scores of features can be implemented.
- the system 8025is implemented as part of the security platform 300 of FIG. 3 .
- the system 8025can be implemented as part of the real-time infrastructure 330 or batch processing infrastructure 382 . Further, in some embodiments, at least a portion of the system 8025 is implemented as part of a machine learning model in the real-time infrastructure 330 or batch processing infrastructure 382 .
- the environment 8000includes a computer device (“device”) 8005 whose data traffic is monitored for detection of anomalies and/or threats.
- the device 8005can be part of a distributed computing system having a number of devices.
- the device 8005can be one of many devices in a computer network 8065 of an organization.
- the network 8065can be a local area network (LAN), a wide area network (WAN), etc.
- LANlocal area network
- WANwide area network
- the trafficcan include data transmitted by or received at the computer device 8005 .
- the traffic from device 8005can include traffic that is internal to the network 8065 (“internal traffic”), e.g., communications with devices in the network 8065 , and traffic that is external to the network 8065 (“external traffic”), e.g., communications with servers 8015 in the network 8010 such as Internet.
- the network 8010is external to the network 8065 .
- at least a portion of the trafficis generated due to activity of a user 8020 associated with the computer device 8005 .
- the system 8025monitors the traffic of the device 8005 , e.g., using traffic log 8050 , and detects any existence of anomalies and/or threats.
- the traffic log 8050includes event data including multiple events representative of traffic into and/or out of the network 8065 .
- the traffic log 8050can be generated based on data obtained from a proxy, a gateway or a firewall associated with the network 8065 .
- the trafficcan be any class of data traffic, e.g., web traffic or IP traffic.
- the web trafficcan include an HTTP message, which can have parameters such as a destination IP address, a URI of the destination, a port number, a type of web request—GET or POST, etc.
- the IP trafficcan have parameters such as a destination IP address and a port number.
- a machine learning model that implements the rarity analysis technique described herecan subscribe to one or more event views (described above), via the model registry. Through such event view(s), the model can access the appropriate features of the event data that includes or represents traffic log 8050 , to enable the model to perform the rarity analysis.
- the semantic processor 316( FIG. 3 ) can process the event data to remove, add or modify at least some of the information and generate the traffic log 8050 in a condition that is suitable for further processing by the system 8025 efficiently. For example, the semantic processor 316 can remove traffic that is between two devices which are identified as acceptable end points for message transmission, as such traffic is less likely or unlikely to be an anomaly.
- Any event in the traffic log 8050can include one or more features.
- the system 8025may analyze some or all of the features in the event.
- the feature tracking module 8030analyzes the traffic log 8050 to identify only the features that are needed for determining whether a particular event is anomalous.
- a usere.g., an administrator associated with the network 8065 , can provide the list of features to be tracked for determining whether an event is anomalous. The list of features to be tracked may be provided in the definition of an event view.
- the feature tracking module 8030identifies the relevant features (i.e., features of interest) and the values of each relevant feature occurring in the traffic log 8050 and stores a count of the occurrences of each value of each relevant feature.
- a featuresuch as the “port” field can occur multiple times in the traffic log 8050 some occurrences of which can have the same value, e.g., same port number, and other occurrences of which can have other values.
- a first number of events in the traffic log 8050can include port identifier of 80 and a second number of events can have different port identifiers, such as 20 , 22 , 23 . Accordingly, the feature tracking module 8030 stores a count of the occurrences of values of a feature.
- the feature tracking module 8030stores a count of the occurrences of values of other features.
- the feature tracking module 8030can store the count in a data structure that is convenient for easy and efficient storage and retrieval of the count data.
- the data structurecan be stored in a storage system associated with the system 8025 , e.g., persistence layer 368 of FIG. 3 .
- the feature tracking module 8030also tracks occurrences of a set of features in an event, e.g., a feature pair. As described above, the technique can also determine how rare it is to observe a first feature at a particular value when the second feature is observed at a first value. For example, the technique can determine, in data transmission between two entities, how rare it is to observe a source zone as “Zone A” when the destination zone is “Zone B”. The feature tracking module 8030 can identify occurrences of such feature pairs and store a count of the occurrence of such feature pairs. The feature tracking module 8030 can store the count in a second data structure that is convenient and efficient for easy storage and retrieval of the count data of the feature pairs. The second data structure can be stored in a storage system associated with the system 8025 , e.g., persistence layer 368 of FIG. 3 .
- the rarity determination module 8035determines a rarity score of each particular value of each relevant feature, where the score is indicative of how rare it is to observe that particular value of the feature relative to other values of the feature. To do so, the rarity determination module 8035 first determines a probability of occurrence of the particular value as a function of probabilities of other values of the feature that are as likely or less likely to occur than the particular value. The probability of each of the possible values can be determined from the total observed number of occurrences of each value in the event data in relation to the total number of occurrences of all values for that feature. The rarity determination module 8035 can obtain count data 8045 of the feature, which includes counts of the numbers of occurrences of various values of the feature, from the feature tracking module 8030 or associated storage system.
- the rarity determination module 8035After determining the probability of the particular value relative to the other values of the feature as described above, the rarity determination module 8035 computes a confidence interval of the probability to obtain a rarity score 8070 .
- the rarity determination module 8035can compute the confidence interval at an upper bound value, such as 95th percentile. In some embodiments, the rarity score is a value between 0 and 1.
- the rarity determination module 8035can use any of various known methods, e.g., delta method, to compute the confidence interval. In some embodiments, computing the confidence interval is accomplished by using the delta method, which ensures that the rarity score 8070 is between 0 and 1.
- the rarity determination module 8035identifies the set of values of the feature whose numbers of occurrences in the traffic log 8050 are less than or equal to the number of occurrences of the particular value in question. For the particular value, the rarity determination module 8035 determines the sum of the number of occurrences of that set of values and the particular value, which is denoted as “k”. The rarity determination module 8035 determines the total number of occurrences of the feature, which is denoted as “n”. The rarity determination module 8035 determines the rarity score 8070 of the particular value of the feature as a function of (k, n), e.g., as a confidence interval of the binomial (k, n).
- the followingis an example describing determining the rarity score for a geographic (“geo”)-location feature, e.g., a location from where a connection request to the network 8065 is originating, where each value of the feature is a two-letter country identifier.
- geo-location featuree.g., a location from where a connection request to the network 8065 is originating, where each value of the feature is a two-letter country identifier.
- the feature tracking module 8030has tracked the following numbers of occurrences of various values (country identifiers) for the geo-location feature: “US: 100, UK: 30, IN: 20, RU: 3, CN: 2, JP: 1.”
- the events with value [US] for the geo location featurehas occurred “100” times.
- the rarity determination module 8035can compute the rarity of seeing the value [RU] as the sum of the probabilities of seeing (RU, CN, JP), where [CN] and [JP] in this example are values of the geo-location that have appeared as many or fewer times than [RU].
- the sum of probabilities of (RU, CN, JP), which can indicate the relative probability of [RU]is used to determine the rarity score.
- kdenotes the sum of occurrences of the particular value [RU] and occurrences of the values that have appeared as many or fewer times than [RU], and
- ndenotes the total number of occurrences of the feature geo-location.
- the rarity determination module 8035can compute the rarity score as a 95% confidence interval.
- the rarity score of [RU]indicates how rare it is to observe the value [RU] relative to other values for the geo-location feature.
- the rarity determination module 8035can also determine the rarity score 8070 for feature pairs.
- the rarity determination module 8035can obtain the count data 8045 for the feature pair, determine the respective counts and then determine the rarity score 8070 for the feature pair.
- the rarity determination module 8035can determine a rarity score for observing a connection request for a given application, such as a virtual private network (VPN), from a geo location such as [RU].
- the rarity determination module 8035identifies a set of locations whose number of occurrences in the traffic log 8050 for the VPN connection request is less than or equal to the number of occurrences of the [RU] location.
- the rarity determination module 8035determines a sum of the number of occurrences of the set of locations and the location [RU], which is denoted as “k”. The rarity determination module 8035 determines a total number of occurrences of the feature pair with the application as VPN connection request, which is denoted as “n”. The rarity determination module 8035 determines the rarity score 8070 of the particular value of the feature as a function of (k, n), e.g., as 95% confidence interval for the binomial (k, n).
- the rarity determination module 8035can determine the rarity score 8070 for a particular value of the feature, and/or for a feature pair.
- the anomaly detection module 8040determines whether an activity in which the particular value of the feature occurred is anomalous based on whether a rarity score criterion (e.g., one or more thresholds) is satisfied by the rarity score of the particular value.
- the rarity criterioncan be a tuple of (score threshold, anomaly count threshold).
- the score thresholdspecifies a threshold for the rarity score and the anomaly count threshold specifies a threshold for the number of times a particular value can be identified as an anomaly 8055 .
- the anomaly detection module 8040can determine that a particular value of the feature corresponds to an anomaly 8055 if the rarity score 8070 of that particular value is below the score threshold and the number of times that the particular value has been identified as an anomaly 8055 is below the anomaly count threshold.
- the anomaly detection module 8040may not identify the particular value as anomaly. In some embodiments, if the particular value has occurred enough times, e.g., exceeds the anomaly count threshold, in a specified time interval, the anomaly detection module 8040 may determine that the particular value is no longer considered an anomaly and may, therefore, dynamically adjust the rarity criterion, e.g., the score threshold and/or the anomaly count threshold, to minimize and/or stop identifying the particular value as corresponding to an anomaly.
- the rarity criterione.g., the score threshold and/or the anomaly count threshold
- the anomaly detection module 8040can similarly determine whether an activity in which a particular feature pair occurred is anomalous based on whether the particular feature pair satisfies a rarity criterion.
- an event in the traffic log 8050can include a number of associated features.
- the anomaly detection module 8040may in some cases have to determine whether one or more of the features and/or feature pairs in an event is anomalous to determine whether the event is anomalous.
- FIG. 81shows a table 8100 of example features and/or feature pairs to be considered for determining whether an example event is anomalous.
- the example eventcan be a “cloudtrail” event 8105 , which is an event representative of application programming interface (API) calls for a web service.
- the cloudtrail event 8105can include features such as: Event Class, which can be indicative of a class of the event; User Agent, which can be indicative of a name of the application; Device, which can be an identification of a device (e.g., IP address) contacting the web service, and User, which can be an identification of the user associated with the device (e.g., username of the user).
- the table 8100indicates the features and the feature pairs that have to be analyzed to determine whether the event corresponds to an anomaly 8055 .
- the table 8100indicates that the features, Event Class and User Agent, and the feature pairs, (Event Class::Device), (Event Class::User), (User Agent::Device), and (User Agent::User) may have to be analyzed to determine whether the cloudtrail event 8105 is an anomaly 8055 . That is, the anomaly detection module 8040 determines that the cloudtrail event 8105 corresponds to an anomaly if the above listed features and the feature pairs satisfy the rarity criterion.
- the rarity criterion for determining whether an event is anomalouscan include additional parameters, such as a minimum number of features and/or feature pairs in the event to be anomalous, a list of features and/or feature pairs in the event to be anomalous.
- FIG. 82shows a table 8200 listing examples of thresholds and/or parameters of a rarity criterion, for various example events, that can be used for determining whether an event is anomalous.
- the thresholds in the table 8200include a score threshold, a feature count threshold (which specifies the minimum number of features and/or feature pairs to be anomalous) and an anomaly count threshold.
- the parameters in the table 8200can include rare features and/or rare feature pairs, which indicate the features and/or feature pairs, respectively, that have to be determined as anomalous to determine that the event itself is anomalous.
- the ignore featureindicates the features that when found to be anomalous, results in ignoring the event, that is, the event is not to be identified as an anomaly.
- a score thresholdis set to “0.001,” a feature count threshold is set to “1” and the anomaly count threshold is set to “50.”
- the rare features and rare feature pairsis set to null value.
- the ignore featureis set to null value.
- one or more of the above thresholdsare configurable, e.g., by a user, such as an administrator of the network 8065 , or by the system 8025 .
- the system 8025may dynamically adjust the score threshold to a lower value if a significant number of occurrences of the particular value is identified as an anomaly, e.g., in a predefined period.
- one or more of the above parametersare also configurable, e.g., by the user.
- the anomaly detection module 8040determines that a particular value of a feature, a feature pair and/or an event is an anomaly 8055 if the particular value, the feature pair and/or the event satisfies the rarity criterion.
- the anomaly detection module 8040determines the particular value, feature pair and/or event to be anomalous
- the anomaly detection module 8040indicates the particular value, feature pair and/or event as an anomaly 8055 to a threat analysis module 8060 .
- the threat analysis module 8060can further analyze the anomaly 8055 to determine if it is a threat and raise an alarm, e.g., generate a notification, if it is one.
- the anomaly 8055can include various information, e.g., rarity score 8070 and/or information regarding various rarity criterion parameters, which can be used by the threat analysis module 8060 in determining if the anomaly 8055 is a threat.
- FIG. 83is a flow diagram of a process 8300 for determining an anomaly based on a rarity score for a particular value of a feature, consistent with various embodiments.
- the process 8400can be implemented in the environment 8000 and using the system 8025 .
- the process 8300can be performed as part of a model in the real-time infrastructure 330 or batch infrastructure 382 .
- the feature tracking module 8030identifies the occurrence of a feature and one or more values of the feature in the traffic of a network, such as network 8065 .
- the geo locationcan be a feature and the various possible geo locations such as [US], [UK], [IN] or [RU] can be values of the feature.
- the process 8300can facilitate determining whether the occurrence of a particular value of the feature is anomalous.
- the feature tracking module 8030identifies a set of values of the feature whose probability of occurrence does not exceed a probability of occurrence of the particular value. That is, the feature tracking module 8030 identifies the set of values that are as likely or less likely to occur in the traffic than the particular value of the feature.
- the rarity determination module 8035determines a rarity score for the particular value as a function of the probabilities of the occurrence of the set of values, in the manner described above.
- the rarity scorecan indicate a probability of occurrence of the particular value relative to the set of values, i.e., how rare is the occurrence of the particular value relative to the set of values.
- the anomaly detection module 8040determines whether the rarity score for the particular value of the feature satisfies a rarity criterion. If the anomaly detection module 8040 determines that the rarity score satisfies the rarity criterion, at block 8325 , the anomaly detection module 8040 determines that an activity in the computer network associated with the particular value of the feature is anomalous. If the rarity score does not satisfy the rarity criterion, the process 8300 returns.
- the anomaly detection module 8040determines whether the one or more thresholds of and/or parameters of the rarity criterion are satisfied. For example, the anomaly detection module 8040 can determine a particular value of the feature as an anomaly if the rarity score for the particular value is below a score threshold and a number of times the particular value has been identified as an anomaly is below an anomaly count threshold of the rarity criterion.
- the process 8300can also be used to determine whether an observed event of the traffic, which can include multiple features, is an anomaly based on a rarity score of the one or more features and/or feature pairs.
- the anomaly detection module 8040can determine whether the event is anomalous by determining whether one or more parameters such as a rarity score of the one or more features of the event, a minimum number of features in the event that need to be anomalous, or a list of features that need to be anomalous satisfy the rarity criterion.
- FIG. 84is a flow diagram of a process 8400 for determining a rarity score for a particular value of a feature, consistent with various embodiments.
- the process 8400can be implemented in the environment 8000 and using the system 8025 .
- the process 8400can also be performed as part of a model in the real-time infrastructure 330 or batch infrastructure 382 .
- the process 8400can be performed as part of blocks 8310 and 8315 of process 8300 .
- the feature tracking module 8030identifies, from the traffic log 8050 , a set of values of the feature that has occurred as many or fewer times than the particular value in the traffic.
- the rarity determination module 8035determines the rarity score for the particular value by computing a confidence interval for the parameters (k, n).
- the rarity scoreis computed as an upper bound confidence interval, e.g., 95% confidence interval, of the parameters.
- the confidence interval method employed for computing the rarity scorecan be selected such that the rarity score is computed to a value between 0 and 1.
- the rarity determination module 8035employs a delta method for computing the confidence interval.
- the rarity score for [RU]indicates how rare it is to observe an occurrence of the geo location as [RU] relative to other locations.
- a security platform such as described abovecan be implemented using one or more conventional physical processing devices.
- FIG. 85is a block diagram showing an example of such a processing device, e.g., a computer system 8500 . Multiple instances of such a computer system may be used to implement the security platform in a given embodiment.
- computer system 8500includes one or more processor(s) 8510 , memory 8520 , one or more input/output (I/O) devices 8530 , a network adapter 8540 , and a storage adapter 8550 , all interconnected by an interconnect 8560 .
- Memory 8520includes storage locations that are addressable by processor(s) 8510 and adapters 8540 and 8550 for storing software program code and data structures associated with the techniques introduced here.
- Memory 8520may include multiple physically distinct memory devices, which may be all of the same type or of different types (e.g., volatile memory such as SRAM or DRAM, non-volatile memory such as flash, etc.).
- Processor(s) 8510 and adapters 8540 and 8550may, in turn, include processing elements and/or logic circuitry configured to execute the software code and manipulate the data structures. It will be apparent to those skilled in the art that other processing and memory implementations, including various machine-readable storage media, may be used for storing and executing program instructions pertaining to the techniques introduced here.
- Network adapter 8540includes one or more ports to couple computer system 8500 with one or more other devices over one or more point-to-point links, local area networks (LANs), wide area networks (WANs), the global Internet, virtual private networks (VPNs) implemented over a public network, or the like.
- Network adapter 8540can include the mechanical components and electrical circuitry needed to connect storage server 8500 to a network.
- One or more systemscan communicate with other systems over the network by exchanging packets or frames of data according to pre-defined protocols, such as TCP/IP.
- Storage adapter 8550interfaces with an operating system running on processor(s) 8510 to access information on attached storage devices.
- the informationmay be stored on any type of attached array of writable storage media, such as hard disk drives, magnetic tape, optical disk, flash memory, solid-state drives, RAM, MEMs and/or any other similar media adapted to store information.
- Storage adapter 8550includes a plurality of ports having I/O interface circuitry that couples with disks or other storage related devices over an I/O interconnect arrangement.
- Embodiments of the techniques introduced hereinclude various steps and operations, which have been described above. A variety of these steps and operations may be performed by hardware components or may be embodied in machine-executable instructions, which may be used to cause one or more general-purpose or special-purpose processors programmed with the instructions to perform the steps. Alternatively, the steps may be performed by a combination of hardware, software, and/or firmware.
- Embodiments of the techniques introduced heremay be implemented, at least in part, by a computer program product which may include a non-transitory machine-readable medium having stored thereon instructions that may be used to program/configure a computer or other electronic device to perform some or all of the operations described above.
- the machine-readable mediummay include, for example, magnetic hard disk drives, compact disc read-only memories (CD-ROMs), magneto-optical disks, floppy disks, ROMs, RAMs, various forms of erasable programmable read-only memories (EPROMs), magnetic or optical cards, flash memory, or other type of machine-readable medium suitable for storing electronic instructions.
- embodiments of the present inventionmay also be downloaded as a computer program product, wherein the program may be transferred from a remote computer to a requesting computer by way of data signals embodied in a carrier wave or other propagation medium via a communication link.
Landscapes
- Engineering & Computer Science (AREA)
- Theoretical Computer Science (AREA)
- General Engineering & Computer Science (AREA)
- Physics & Mathematics (AREA)
- General Physics & Mathematics (AREA)
- Computer Security & Cryptography (AREA)
- Signal Processing (AREA)
- Computer Networks & Wireless Communication (AREA)
- Data Mining & Analysis (AREA)
- Computing Systems (AREA)
- Databases & Information Systems (AREA)
- Software Systems (AREA)
- Computer Hardware Design (AREA)
- Artificial Intelligence (AREA)
- Mathematical Physics (AREA)
- Evolutionary Computation (AREA)
- Human Computer Interaction (AREA)
- Computational Linguistics (AREA)
- Medical Informatics (AREA)
- Computer Vision & Pattern Recognition (AREA)
- Multimedia (AREA)
- Computational Mathematics (AREA)
- Pure & Applied Mathematics (AREA)
- Probability & Statistics with Applications (AREA)
- Mathematical Optimization (AREA)
- Mathematical Analysis (AREA)
- Algebra (AREA)
- Audiology, Speech & Language Pathology (AREA)
- General Health & Medical Sciences (AREA)
- Health & Medical Sciences (AREA)
- Debugging And Monitoring (AREA)
- Environmental & Geological Engineering (AREA)
- Data Exchanges In Wide-Area Networks (AREA)
- Computer And Data Communications (AREA)
Abstract
Description
- This application claims the benefit of U.S. provisional patent application No. 62/212,541 filed on Aug. 31, 2015, and titled “Network Security System,” which is incorporated by reference herein in its entirety.
- A portion of the disclosure of this patent document contains material which is subject to copyright protection. The copyright owner has no objection to the facsimile reproduction by anyone of the patent document or the patent disclosure, as it appears in the Patent and Trademark Office patent file or records, but otherwise reserves all copyright rights whatsoever.
- At least one embodiment of the present disclosure pertains to distributed data processing systems, and more particularly, to intelligence generation and activity discovery from events in a distributed data processing system.
- Activity detection, both friendly and malicious, has long been a priority for computer network administrators. In known public and private computer networks, users employ devices such as desktop computers, laptop computers, tablets, smart phones, browsers, etc. to interact with others through computers and servers that are coupled to the network. Digital data, typically in the form of data packets, are passed along the network by interconnected network devices.
- Unfortunately, however, malicious activities can cause harm to the network's software or hardware, or its users. Malicious activities may include unauthorized access or subsequent unpermitted use of network resources and data. Network administrators seek to detect such activities, for example, by searching for patterns of behavior that are abnormal or otherwise vary from the expected use pattern of a particular entity, such as an organization or subset thereof, individual user, IP address, node or group of nodes in the network, etc.
- Security appliances are used in known systems to provide network security. The appliance approach involves installing security appliances (which are typically servers or computers configured for providing security) at one or more locations in the network. Once installed, the appliance monitors traffic that traverses the network. Functions provided by the appliance may include malware detection, intrusion detection, unauthorized access or unauthorized use of data, among others. Unfortunately, security appliances cannot easily be scaled to handle temporary or permanent increases in network traffic. Increased network traffic often requires a security vendor to perform an appliance swap or an equally time-consuming appliance upgrade. Appliances also tend to have only limited network visibility because they are typically configured to monitor data traversing the link on which a respective appliance is installed only. Such an appliance will be unaware of activities occurring on other network segments monitored by other appliances and thus cannot use the additional context information pertaining to activities occurring on other network segments to detect a cleverly-designed piece of malware that may be difficult to detect from purely localized information.
- Installed software products, rather than security hardware appliances, provide another approach to security for data networks. These products, such as anti-virus or anti-malware software, typically are installed on terminal devices (e.g., desktop and laptop computers, tablets, or smart phones). Data traversing the network between the terminal device is monitored by the installed products to detect malware in either inbound or outbound data. Unfortunately, installed software products also do not perform well in terms of scalability or network visibility. Installed products tend to be disposed locally on the terminal devices and thus also tend to have fairly localized views of the data on the network. They also tend to be installed on hardware that cannot be upgraded easily.
- Certain embodiments of the present disclosure are illustrated, by way of example, in the figures of the accompanying drawings, in which like references indicate similar elements.
FIG. 1 shows a general environment in which a security platform, which is an example application of a data processing system introduced here, may be implemented.FIG. 2 shows an example of functional layers of a security platform.FIG. 3 shows a high-level view of an example of the processing within the security platform.FIG. 4 shows an example of the architecture of the security platform.FIG. 5 shows an example implementation of the real-time processing path in greater detail.FIG. 6 shows an example representation of the process of building adaptive behavioral baselines and evaluating against such baselines to support the detection of anomalies.FIGS. 7A and 7B collectively show a table listing example types of machine data that can be found in different environments.FIG. 8 shows an example implementation of the data intake and preparation stage of the security platform.FIG. 9A shows raw event data received by the data intake and preparation stageFIG. 9B shows an event-specific relationship graph based on the event shown inFIG. 9A .FIG. 10 shows an example implementation of an identity resolution technique based on the information in the events.FIG. 11 shows a diagram of a technique for providing a uniform access interface (“event view”) at the data intake and preparation stage for an event processing engine (e.g., at a subsequent stage) to obtain relevant information from various kinds of machine data.FIG. 12 shows a table of example uniform access interfaces (“event views”) that can be implemented in the data intake and preparation stage.FIGS. 13A and 13B collectively show a table including example anomalies that can be identified by machine learning models and/or other types of processing entities, and various example uniform access interfaces and fields that can be used by the models/entities to receive relevant information about the events for performing further analytics.FIG. 14 shows a sessionization technique that can be implemented at the data intake and preparation stage.FIG. 15 is a block diagram of a machine learning-based complex event processing (CEP) engine.FIG. 16 is a block diagram illustrating an architectural framework of a machine learning model.FIG. 17 is a block diagram illustrating an example of the model type definition.FIG. 18 is a block diagram illustrating an example system architecture for implementing the distributed computation system.FIG. 19 is a flow diagram illustrating a method to execute a model preparation process thread.FIG. 20 is a flow diagram illustrating a method to execute a model training process thread.FIG. 21 is a flow diagram illustrating a method to execute a model deliberation process thread.FIG. 22 shows a diagram of an example architecture of the security platform in which sharing of model state between real-time and batch processing paths can be implemented.FIG. 23 is flow diagram illustrating at a high level, the processing hierarchy of detecting anomalies, identifying threat indicators, and identifying threats.FIG. 24 is flow diagram illustrating in more detail an example process for detecting anomalies, identifying threat indicators, and identifying threats to network security.FIG. 25 is a flow diagram describing an example process for detecting anomalies.FIG. 26 is a flow diagram describing an example process for identifying threat indicators.FIG. 27 shows a first use case for identifying threat indicators based on entity associations with detected anomalies.FIG. 28 shows a second use case for identifying threat indicators based on entity associations with detected anomalies.FIG. 29 illustrates a use case for identifying threat indicators based on duration of detected anomalous behavior.FIG. 30 illustrates a use case for identifying threat indicators based on local and global rarity analysis.FIG. 31A illustrates identification of a threat indicator according to a first use case based on combining the outputs from different anomaly models.FIG. 31B illustrates nonidentification of a threat indicator according to the first use case based on combing the outputs from different anomaly models.FIG. 32A illustrates identification of a threat indicator according to a second use case based on combining the outputs from different anomaly models.FIG. 32B illustrates nonidentification of a threat indicator according to the second use case based on combing the outputs from different anomaly models.FIG. 33 illustrates a use case for identifying threat indicators by enriching the anomaly data using data from external sources.FIG. 34 is a flow diagram describing an example process for identifying threats to network security based on threat indicators.FIG. 35 illustrates an example process of combining and storing event-specific relationship graphs into a composite relationship graph.FIG. 36 illustrates an example of a composite relationship graph.FIG. 37 illustrates an example of how a composite relationship graph can be stored as separate projections.FIG. 38 illustrates a sample process of combining event-specific relationship graphs into a composite relationship graph and detecting a security threat based on the composite relationship graph.FIG. 39A is an illustrative home screen in a GUI of a system for monitoring potential computer network compromise, in accordance with various embodiments of the disclosure.FIG. 39B is an illustrative screen in the GUI ofFIG. 39A , depicting an expanded view of a “Views” tab selector, which enables a GUI user to select between viewing screens identifying instances of potential network compromise and viewing screens identifying entities associated with the instances of potential network compromise, in accordance with various embodiments of the disclosure.FIG. 40A is an illustrative view in the GUI ofFIG. 39A of a “Threats Review” screen for reviewing identified threats, in accordance with various embodiments of the disclosure.FIG. 40B is an illustrative view of an expanded “Threat Types” selector for filtering the “Threats Review” screen ofFIG. 40A to display only a selected type of threat, in accordance with various embodiments of the disclosure.FIG. 40C is an illustrative view of an expanded “Actions” tab in the “Threats Review” screen ofFIG. 40A , in accordance with various embodiments of the disclosure.FIG. 40D is an illustrative view of a “Threat Relations” diagram and a “Kill Chain” diagram, which are generated upon clicking the “Details” tab in the “Threats Review” screen ofFIG. 40A , in accordance with various embodiments of the disclosure.FIG. 40E is an illustrative view of a “Threat Anomalies Timeline,” “Threat Anomalies Trend,” and “Threat Anomalies” listing, which are generated upon clicking the “Details” tab in the “Threats Review” screen ofFIG. 40A , in accordance with various embodiments of the disclosure.FIG. 40F is an illustrative view of a “Device Locations” map, which is generated upon clicking the “Details” tab in the “Threats Review” screen ofFIG. 40A , in accordance with various embodiments of the disclosure.FIG. 40G is an illustrative view of a text bubble generated upon hovering a cursor over a device location in the “Device Locations” map ofFIG. 40F , in accordance with various embodiments of the disclosure.FIG. 40H is an illustrative view of a text bubble generated upon hovering a cursor over a line drawn between devices in the “Device Locations” map ofFIG. 40F , in accordance with various embodiments of the disclosure.FIG. 41 is an illustrative view of a “User Facts” screen in the GUI ofFIG. 39A , in accordance with various embodiments of the disclosure.FIG. 42 is an illustrative view of an “Anomalies Table” screen in the GUI ofFIG. 39A , in accordance with various embodiments of the disclosure.FIG. 43 is an illustrative view of an “Anomaly Details” screen in the GUI ofFIG. 39A , in accordance with various embodiments of the disclosure.FIG. 44A is an illustrative view of an expanded “Watchlists” tab in the “Threats Review” screen ofFIG. 40A , in accordance with various embodiments of the disclosure.FIG. 44B is an illustrative view of an “Anomaly Details” screen in the GUI ofFIG. 39A , including a “Watchlists” designation, in accordance with various embodiments of the disclosure.FIG. 45A is an illustrative view of a “Threats Table” screen in the GUI ofFIG. 39A , in accordance with various embodiments of the disclosure.FIG. 45B is an illustrative view of a “Threats Trend” as a line chart.FIG. 45C is an illustrative view of a “Threats Trend” as a column chart.FIG. 45D is an illustrative view of a text bubble generated upon hovering a data point in the “Threats Trend” diagram ofFIG. 45A , in accordance with various embodiments of the disclosure.FIG. 45E is an illustrative view of a “Threats Details” screen in the GUI ofFIG. 39A , in accordance with various embodiments of the disclosure.FIG. 46A is an illustrative view of an “Anomalies Table” screen in the GUI ofFIG. 39A , in accordance with various embodiments of the disclosure.FIG. 46B is an illustrative view of the “Anomalies Trend” and the “Anomalies” listing in the “Anomalies Table” screen ofFIG. 46A , depicting a selection of a data point in the “Anomalies Trend” diagram.FIG. 46C is an illustrative view of a portion of an “Anomalies Details” screen for a selected anomaly in the GUI ofFIG. 39A , including a “Users” section, “Anomaly Relations” section, and “Triggering Event” section, in accordance with various embodiments of the disclosure.FIG. 46D is an illustrative view of a portion of an “Anomalies Details” screen for a selected anomaly in the GUI ofFIG. 39A , including an “Anomalous Activity Sequence” diagram, in accordance with various embodiments of the disclosure.FIG. 46E is an illustrative view of a portion of an “Anomalies Details” screen for a selected anomaly in the GUI ofFIG. 39A , including an “User Activities Baseline” diagram, “Compare Unusual Activity with the Accounts Profile” graphic, “Additional Information” graphic, and “Anomaly Graph” diagram, in accordance with various embodiments of the disclosure.FIG. 46F is an illustrative view of a portion of an “Anomalies Details” screen for an anomaly of the type “Machine Generated Beacon,” including a “Users,” “Devices,” and “Domains” sections, and an “Anomaly Relations” box.FIG. 47A is an illustrative view of a “Users Table” screen in the GUI ofFIG. 39A , in accordance with various embodiments of the disclosure.FIG. 47B is an illustrative view of a “User Facts” screen in the GUI ofFIG. 39A , in accordance with various embodiments of the disclosure.FIG. 47C is another illustrative view of a “User Facts” screen in the GUI ofFIG. 39A , in accordance with various embodiments of the disclosure.FIG. 47D is an illustrative view of a “User Threats” screen in the GUI ofFIG. 39A , in accordance with various embodiments of the disclosure.FIG. 47E is an illustrative view of a “User Anomalies” screen in the GUI ofFIG. 39A , in accordance with various embodiments of the disclosure.FIG. 47F is an additional illustrative view of a “User Anomalies” screen in the GUI ofFIG. 39A , in accordance with various embodiments of the disclosure.FIG. 47G is an illustrative view of a “Watchlist” screen in the GUI ofFIG. 39A , in accordance with various embodiments of the disclosure.FIG. 48A is an illustrative view of a “Devices Table” screen in the GUI ofFIG. 39A , in accordance with various embodiments of the disclosure.FIG. 48B is an illustrative view of a “Device Facts” screen in the GUI ofFIG. 39A , in accordance with various embodiments of the disclosure.FIG. 48C is an illustrative view of a “Device Anomalies” screen in the GUI ofFIG. 39A , in accordance with various embodiments of the disclosure.FIG. 49A is an illustrative view of an “Apps Table” screen in the GUI ofFIG. 39A , in accordance with various embodiments of the disclosure.FIG. 49B is an illustrative view of an “App Facts” screen in the GUI ofFIG. 39A , in accordance with various embodiments of the disclosure.FIG. 50A is an illustrative view of a Geomap icon in a Threats Table view in the GUI ofFIG. 39A , in accordance with various embodiments of the disclosure.FIG. 50B is an illustrative view of a Geomap in the GUI ofFIG. 39A , in accordance with various embodiments of the disclosure.FIG. 50C is an illustrative view of a text bubble for a threat in a Geomap in the GUI ofFIG. 39A , in accordance with various embodiments of the disclosure.FIG. 50D is an illustrative view of a text bubble for anomalies in a Geomap in the GUI ofFIG. 39A , in accordance with various embodiments of the disclosure.FIG. 51 is an illustrative view of an “Analytics Dashboard” in the GUI ofFIG. 39A , in accordance with various embodiments of the disclosure.FIG. 52 shows an example of a probabilistic suffix tree based model receiving a particular sequence (e.g., during training).FIG. 53 shows an example timeline illustrating the training of a probabilistic suffix tree based model, the establishment of a baseline prediction profile, and the activation of a particular model version.FIG. 54A shows an example of how a normal behavioral sequence may be represented in a probabilistic suffix tree based model.FIG. 54B shows an example of how an unusual behavioral sequence may be discovered in a probabilistic suffix tree based model.FIG. 55A shows an example user interface for displaying discovered anomalies.FIG. 55B shows an example user interface displaying additional information about the user.FIG. 56 shows an example user interface displaying results from comparing the marginal of the events for the anomalous window and the entire data for the user (e.g., baseline).FIG. 57 shows an example overview of all the unusual sequence as a timeline.FIG. 58 shows an example user interface for an administrator to interact with each timeline event.FIG. 59 is a flowchart showing an example of an automated process for cluster identification from a graph.FIG. 60A is a flowchart showing an example of an automated process for cluster identification from a bipartite graph.FIG. 60B shows an example of minimizing the L1-norm values to find optimal positions for the normal nodes.FIG. 61A shows an example use case corresponding to the cluster identification process for a generic graph, at a first stage of processing.FIG. 61B shows an example use case corresponding to the cluster identification process for a generic graph, at a second stage of processing.FIG. 62 illustrates an example use case corresponding to the cluster identification process for a bipartite graph.FIG. 63 is a block diagram illustrating a machine learning model that detects lateral movement in a computer network.FIG. 64 illustrates an example of a bipartite graph showing events of users logging into network devices.FIG. 65 illustrates an example of a process of assigning similarity scores to network devices.FIG. 66A shows an example of a bipartite graph having network devices that have many shared users and tend to have close similarity scores.FIG. 66B shows an example of a bipartite graph having network devices that have multiple shared exclusive users.FIG. 66C shows an example of a bipartite graph having network devices that have one shared user.FIG. 66D shows an example of a bipartite graph having network devices that are associated with similar groups of users.FIG. 67 illustrates an example of a graph data structure for detecting security threats based on a detected out-of-profile anomaly.FIG. 68 is a high-level conceptual diagram of an example network traffic scenario for detecting anomalies indicative of malware on a computer network.FIG. 69 is a high level flow diagram illustrating an example process for detecting an anomaly indicative of malware based on network traffic.FIG. 70 shows two tables illustrating application of lexical analysis to a character-based entity identifier.FIG. 71 shows an example incident response output configured for display to a user.FIG. 72 shows an example graph of outgoing traffic from a network device.FIG. 73 lists an example of a set of parameters that can be considered for distinguishing between machine-generated traffic and user-generated traffic.FIG. 74 is a block diagram of an environment in which a system for detecting anomalies in machine-generated traffic can be implemented.FIG. 75 is an example of a memory cache storing beacon types that are identified as likely to be anomalous.FIG. 76 is a flow diagram of a process for determining whether outgoing traffic from a device is anomalous.FIG. 77 is a flow diagram of a process for forming a group of connection requests from outgoing traffic of a device.FIG. 78 is a flow diagram of a process for determining whether a particular group of connection requests in the outgoing traffic of a device is user-generated traffic or machine generated traffic.FIG. 79 is a flow diagram of a process for determining whether machine-generated traffic is anomalous.FIG. 80 is a block diagram of an environment in which a system for detecting anomalies based on rarity scores of features can be implemented.FIG. 81 shows a table of example features and/or feature pairs to be considered for determining whether an example event is anomalous, consistent with various embodiments.FIG. 82 shows a table listing example thresholds and/or parameters of a rarity criterion for various example events that can be used for determining whether an event is anomalous.FIG. 83 is a flow diagram of an example process for determining an anomaly based on a rarity score for a particular value of a feature.FIG. 84 is a flow diagram of an example process for determining a rarity score for a particular value of a feature.FIG. 85 is a block diagram of a computing device that may be used to implement the techniques introduced here.- References in this description to “an embodiment,” “one embodiment,” or the like, mean that the particular feature, function, structure or characteristic being described is included in at least one embodiment of the present disclosure. Occurrences of such phrases in this specification do not necessarily all refer to the same embodiment. On the other hand, the embodiments referred to also are not necessarily mutually exclusive.
- In the following description, the example of a security platform is used, for illustrative purposes only, to explain various techniques that can be implemented by the data processing system. Note, however, that the techniques introduced here are not limited in applicability to security applications, security information and event management (SIEM) applications, or to any other particular kind of application. For example, at least some of the techniques introduced here can be used for automated fraud detection and other purposes, based on machine data. Additionally, the techniques introduced here are not limited to use with security-related anomaly and threat detection; rather, the techniques can be employed with essentially any suitable behavioral analysis (e.g., fraud detection or environmental monitoring) based on machine data. In general, “machine data” can include performance data, diagnostic information and/or any of various other types of data indicative of performance or operation of equipment (e.g., an action such as upload, delete, or log-in) in a computing system, as described further below. In general, “machine data” as used herein includes timestamped event data, as discussed further below. Examples of components that may generate machine data from which events can be derived include: web servers, application servers, databases, firewalls, routers, operating systems, and software applications that execute on computer systems, mobile devices, sensors, Internet of Things (IoT) devices, etc. The data generated by such data sources can include, for example, server log files, activity log files, configuration files, messages, network packet data, performance measurements, sensor measurements, etc., which are indicative of performance or operation of a computing system in an information technology environment.
- In today's enterprises, attacks by users with trusted access often go undetected by existing security approaches. Indeed, traditional security products often suffer from several major drawbacks, including the inability to detect unknown threats and insider threats, and the inability to scale and process huge amount of data. Whether access is obtained by using compromised accounts/systems or by leveraging existing privileges to conduct malicious activities, nowadays attackers often do not need to employ additional malware. The patterns of these malicious activities vary dynamically, and attackers can almost always find ways to evade traditional security technologies, such as rules-driven malware detection, malicious file signature comparison, and sandboxing. Also, as the amount of the data increases, using human analysis to perform threat detection becomes increasingly expensive and time prohibitive and such human analysis does not allow the threat to be responded to in a timely and effective manner. Further, security analysts such as network administrators often use a “kill chain” methodology to identify and stop the progression of malicious activities (e.g., from intrusion to lateral movement, and to exfiltration). These analysts need supporting evidence to make educated decisions in the kill chain, but traditional security products generally do not provide the support for such methodology.
- Introduced here, therefore, is a data processing and analytics system (and, as a particular example, a security platform) that employs a variety of techniques and mechanisms for anomalous activity detection in a networked environment in ways that are more insightful and scalable than the conventional techniques. As is described in more detail below, the security platform is “big data” driven and employs a number of machine learning mechanisms to perform security analytics. More specifically, the security platform introduced here can perform user behavioral analytics (UBA), or more generally user/entity behavioral analytics (UEBA), to detect the security related anomalies and threats, regardless of whether such anomalies and threats are previously known or unknown. Additionally, by presenting analytical results scored with risk ratings and supporting evidence, the security platform can enable network security administrators or analysts to respond to a detected anomaly or threat, and to take action promptly. The behavioral analytics techniques introduced here enable the security platform to detect advanced, hidden and insider threats. As one aspect of this disclosure, the behavior analytics leverage machine learning data processing procedures and do not require any preexisting knowledge such as known signatures or rules. The security platform can also improve threat detection and targeted response by using a variety of threat indicators. Further, the security platform supplies supporting evidence within context of the kill chain to enable targeted remediation of any detected anomaly or threat.
- Moreover, as introduced here, the security platform can increase a security operations center's (SOC) efficiency with a number of rank-ordered lists having events in the context of a kill chain. In some examples, the kill chain can be linked from an anomaly or threat summary to the supporting information that is gathered over time. All generated security-related information can then be sent to a security information and event management (SIEM) application, such as the Splunk® App for Enterprise Security, to further scope, disrupt, contain and/or recover from the attack.
FIG. 1 shows ageneral environment 10 in which the security platform introduced here can be implemented. Theenvironment 10 may represent a networked computing environment of one or multiple companies or organizations, and can be implemented across multiple geographic regions. One or more elements in theenvironment 10 are communicatively coupled to each other through a computer communications network, which can include the Internet and one or more wired or wireless networks (e.g., an Internet Protocol (IP)-based local area network (LAN), metropolitan area network (MAN) wide area network (WAN), a Wireless LAN (WLAN) network such as Wireless Fidelity (WiFi), and/or a cellular telecommunications network such as Global System for Mobile Communications (GSM) network, 3G network, or long term evolution (LTE) network). The computing devices shown in theenvironment 10 can be, for example, a personal computer, a smart phone, a computer server, a notebook computer, or any other form of computing system or device that allows a user to access the information within theenvironment 10. Each of the aforementioned computer systems can include one or more distinct physical computers and/or other processing devices which, in the case of multiple devices, can be connected to each other through one or more wired and/or wireless networks.- The security platform can detect anomalies and threats produced by a user, a device, or an application, for example, regardless of whether the entity that causes the anomalies or threats is from outside or inside the organization's network. The security analytics techniques that can be adopted by the security platform include behavioral analytics that enable organizations of any size or skillset to detect and respond to unknown threats. Some specific examples that behavioral analytics can be based on include machine learning, behavior modeling, peer group analysis, classification, statistical models, and graph analysis. As introduced in more detail below, these analyses can utilize, for example, Markovian processing flows, inference and grouping processes, and risk scoring mechanisms to develop user and entity profiles in order to compare and contrast activities, which ultimately allow the platform to detect and expose anomalies and threats. Also, as mentioned above, the security platform can include a graphical user interface (GUI) that can create visualizations of the detected anomalies and threats within an organization, and optionally, map the threats across an attack kill-chain in a visual way, which the security analysts in the organization can quickly and easily assimilate.
- The security platform can be deployed at any of various locations in a network environment. In the case of a private network (e.g., a corporate intranet), at least part of the security platform can be implemented at a strategic location (e.g., a router or a gateway coupled to an administrator's computer console) that can monitor and/or control the network traffic within the private intranet. In the case of cloud-based application where an organization may rely on Internet-based computer servers for data storage and data processing, at least part of the security platform can be implemented at, for example, the cloud-based servers. Additionally or alternatively, the security platform can be implemented in a private network but nonetheless receive/monitor events that occur on the cloud-based servers. In some embodiments, the security platform can monitor a hybrid of both intranet and cloud-based network traffic. More details on ways to deploy the security platform and its detailed functionality are discussed below.
- By addressing the entire lifecycle of known and unknown advanced security threats, and by providing a platform to detect, respond to, and automate actions, the security platform introduced here provides a comprehensive solution to the security-related issues in a modern network environment.
- The security platform introduced here is capable of handling large volumes of data, particularly machine data, from multiple data sources. These data sources may have different data formats and may provide data at very high data rates (e.g., gigabytes of data per second or more). In some embodiments, incoming data is processed using machine learning/data science techniques to extract knowledge from large volumes of data that are structured or unstructured. In a general sense, data science is a continuation and expansion of the field of data mining and predictive analytics, also known as knowledge discovery and data mining (KDD).
- The security platform may be cloud-based and may employ big data techniques to process a vast quantity of high data rate information in a highly scalable manner. In certain embodiments, the security platform may be hosted in the cloud and provided as a service. In certain embodiments, the security platform is provided as a platform-as-a-service (PaaS). PaaS is a category of cloud computing services enabling customers to develop, run and manage Web applications without the complexity of building and maintaining the infrastructure typically associated with developing and launching such applications. PaaS can be delivered in at least two ways, namely: (i) as a public cloud service from a provider, wherein the consumer controls software deployment and configuration settings and the provider provides the networks, servers, storage devices and other services to host the consumer's application, or (ii) as software installed in private data centers or public infrastructure and managed by internal information technology (IT) departments.
- Machine learning is employed in certain embodiments to make it unnecessary to know in advance what activity constitutes a security threat or a security threat signature. For example, a security threat may be discovered from the event data as the events occur even though that threat has not been seen before and no signature for that threat existed previously.
- In various embodiments discussed herein, security threats are examples of a type of activity to be detected. It should be understood, however, that the security platform and techniques introduced here can be applied to detect any type of unusual or anomalous activity involving data access, data transfer, network access, and network use regardless of whether security is implicated or not.
- In this description the term “event data” refers to machine data related to activity on a network with respect to an entity of focus, such as one or more users, one or more network nodes, one or more network segments, one or more applications, etc.). In certain embodiments, incoming event data from various data sources is evaluated in two separate data paths: (i) a real-time processing path and (ii) a batch processing path. Preferably, the evaluation of event data in these two data paths occurs concurrently. The real-time processing path is configured to continuously monitor and analyze the incoming event data (e.g., in the form of an unbounded data stream) to uncover anomalies and threats. To operate in real-time, the evaluation is performed primarily or exclusively on event data pertaining to current events contemporaneously with the data being generated by and/or received from the data source(s). In certain embodiments, the real-time processing path excludes historical data (i.e., stored data pertaining to past events) from its evaluation. Alternatively in an embodiment, the real-time processing path excludes third-party data from the evaluation in the real-time processing path. These example types of data that are excluded from the real-time path can be evaluated in the batch processing path.
- In this description the term “event” is sometimes used synonymously with the term “event data” to mean a discrete set of machine data that represents or corresponds to a specific network activity, although “event” can also refer to the underlying activity itself, as will be apparent from context.
- Also in this description, an “anomaly” is a detected variation from an expected pattern of behavior on the part of an entity, which variation may or may not constitute a threat. An anomaly represents an event of possible concern, which may be actionable or warrant further investigation. An anomaly is an observable or detectable fact, or data representing such fact. An anomaly or a set of anomalies may be evaluated together and may result in a determination of a threat indicator or a threat. A threat is an interpretation of one or more anomalies and/or threat indicators. Threat indicators and threats are escalations of events of concern. As an example of scale, hundreds of millions of packets of incoming event data from various data sources may be analyzed to yield 100 anomalies, which may be further analyzed to yield 10 threat indicators, which may again be further analyzed to yield one or two threats. This manner of data scaling is one of the reasons the security platform can provide anomaly and threat detection in a real-time manner.
- In the context of machine-learning evaluation, historical data and third party data may be used to create and improve the machine learning models employed to perform the evaluation; however, the amount of such historical data and/or third party data can be potentially much larger than the real-time data stream. As such, the actual evaluation of the historical data tends to be slower. Consequently, in certain embodiments, the real-time processing path does not use either or both the historical data and third party data as inputs. In other embodiments, historical and third party data may be used as inputs but the majority of the data used for evaluation in the real-time processing path still pertains to contemporaneous incoming event data. This is a consequence of the need to process the voluminous incoming event data quickly to obtain actionable threat information to prevent imminent harm.
- The anomalies and threats detected by the real-time processing path may be employed to automatically trigger an action, such as stopping the intrusion, shutting down network access, locking out users, preventing information theft or information transfer, shutting down software and or hardware processes, and the like. In certain embodiments, the discovered anomalies and threats may be presented to a network operator (e.g., a network security administrator or analyst) for decision. As an alternative or in addition to automatically taking action based on the discovered anomalies and threats, the decisions by the user (e.g., that the anomalies and threats are correctly diagnosed, or that the discovered anomalies and threats are false positives) can then be provided as feedback data in order to update and improve the models.
- In the batch processing path, historical data and third-party data are processed, optionally with the incoming real-time event data, to uncover, for example, more subtle anomalies and threats than the real-time processing path can uncover because of the real-time processing path's responsive time constraints. Batch processing may occur synchronously with real-time processing or in accordance with a predefined schedule.
- Historical data represents past events and may include data from different instantiations of the real-time evaluators deployed in different locations in the network. The historical data may span time and geography. In some implementations, only an abridged version of the incoming event data is analyzed in the real-time processing path while a more complete version is stored as historical data. Thus, the historical data may, in one or more of these implementations, include event data that has more attributes than the abridged event data presented to the real-time processing path for evaluation.
- As in the real-time data path, anomalies, threat indicators and threats discovered by the batch analyzer may be actionable automatically or may be presented to a human operator for decision on whether to take action. The action taken by the operator to validate or invalidate the conclusions reached by the batch analyzer may serve as a source of feedback to the security platform to improve its evaluation of subsequently processed data.
FIG. 2 illustrates a high level view of anexample security platform 102. InFIG. 2 , a cloud computing infrastructure is shown, represented in part by avirtualization layer 104. Various cloud computing operating systems or platforms, such as OpenStack™, VMware™, Amazon Web Services™, or Google Cloud™ may be employed invirtualization layer 104 to create public clouds or private clouds. Generally speaking, these cloud computing operating systems and others permit processing and storage to be implemented on top of a set of shared resources. Among its many advantages, cloud computing permits or facilitates redundancy, fault tolerance, easy scalability, low implementation cost and freedom from geographic restrictions. The concept of cloud computing and the various cloud computing operating systems or infrastructures are known.- Above the
virtualization layer 104, asoftware framework layer 106 implements the software services executing on thevirtualization layer 104. Examples of such software services include open-source software such as Apache Hadoop™, Apache Spark™, and Apache Storm™. Apache Hadoop™ is an open-source software framework for distributed storage and distributed processing of very large data sets on computer clusters built from commodity hardware. Apache Storm™ is a distributed real-time computation engine that processes data stream record-by-record. Apache Spark™ is an large-scale data processing engine that collects events together for processing in batches. These are only examples of software that may be employed to implement thesoftware framework layer 106. - A
security intelligence layer 100 implements a securitysemantic layer 108 and amachine learning layer 110. The securitysemantic layer 108 performs the extract, transform, and load (ETL) functions that prepare the incoming event data for further processing by downstream consumers. Note that the term ETL here is used in an illustrative sense to facilitate understanding, as the ETL stage described herein may include functionality in addition to or different from traditional ETL techniques. Themachine learning layer 110 represents one of the consumers of the data output of the securitysemantic layer 108. In an example, event data may be received by the securitysemantic layer 108, and prepared (or “pre-processed”) to be further processed by themachine learning layer 110. - Above the
security intelligence layer 100 is anapplication layer 114. Theapplication layer 114 represents the layer in which application software modules may be implemented. In an example, the output of themachine learning layer 110 includes anomalies, threat indicators, and/or threats. This output may be analyzed by the various applications such as athreat detection application 116, asecurity analytics application 118 orother applications 120. These layers, modules and their operation will be discussed in greater detail below. FIG. 3 shows a high-level conceptual view of the processing withinsecurity platform 102 inFIG. 2 . A receivedata block 202 represents a logical component in which event data and other data are received from one or more data sources. In an example, receive data block202 includes application programming interfaces (APIs) for communicating with various data sources. AnETL block 204 is the data preparation component in which data received from the receivedata block 202 is pre-processed, for example, by adding data and/or metadata to the event data (a process interchangeably called decoration, enrichment or annotation herein), or otherwise prepared, to allow more effective consumption by downstream data consumers (e.g., machine learning models).- The enriched event data from the
ETL block 204 is then provided to a real-time analyzer 210 over a real-time processing path 212 for detecting anomalies, threat indicators and threats.Output 214 from the real-time analyzer 210 is provided for action by the human operator, in certain embodiments. It should be noted that the real-time analyzer 210 operates in real-time by analyzing event data as the event data received by thesecurity platform 102. - The event data from the
ETL block 204 is also provided to abatch analyzer 240 over a batch processing path242 for detecting anomalies, threat indicators and threats. However, while the event data is provided to the real-time analyzer 210 in an unbounded, streaming, record-by-record manner, it is provided to the batch analyzer in the form of batches of event data (i.e., where each batch of event data contains a collection of events that arrived over the batch period). Because thebatch analyzer 240 processes data in batch mode instead of in real-time, in addition to the event data that the real-time analyzer 210 receives, thebatch analyzer 240 can receive additional historical event data from the security platforms, prior analysis (including the analysis results, the model states, and the supporting data) from the real-time analyzer210 (e.g., through a model management component260), or prior analysis from other analyzers (real-time or batch) implemented elsewhere in the same or other networks. - A machine learning and machine learning models are employed to evaluate and analyze data in certain embodiments, that is not necessarily the case in every embodiment. In some cases, the security platform may also adapt more appropriately or more efficiently to the environment by using a combination of other suitable forms of analysis, including rule-based analysis, algorithm-based analysis, statistical analysis, etc.
FIG. 4 illustrates an example of an overall architecture of thesecurity platform 300.Data sources 302 represent various data sources that provide event data including machine data, to be analyzed for anomalies and threats. The event data represents events that take place in the network environment. For example,data source 304 is a source of data pertaining to logs including, for example, user log-ins and other access events. These records may be generated from operational (e.g., network routers) and security systems (e.g., firewalls or security software products).Data source 306 is a source of data from different types of applications, including software as a service (e.g., Box™).Data source 306 may use different mechanisms for transmitting the event data, including a push mechanism, a pull mechanism, or a hybrid mechanism. Other data sources which may fall into thedata source 306 category include human resource systems, accounting systems, customer relation databases, and the like.Data source 308 is a source of network management or analyzer data (e.g., event data related to traffic on a node, a link, a set of nodes, or a set of links). The network management or analyzer data may be obtained from various network operating systems and protocols, such as Cisco Netflow™. The data sources mentioned here are only examples, as other suitable data sources may also be used.- The
data sources 302 provide event data todata receivers 310, which implement various APIs and connectors to receive (or retrieve, depending on the mechanism) the event data for thesecurity platform 300. Thedata receivers 310 may also optionally filter some of the event data. For example, to reduce the workload of the security platform, a business rule may be set to state that all query events to “www.google.com” should be filtered out as not interesting (e.g., this type of access is determined not to represent any security threat). Technologies employed to implement thedata receiver 310 may include Flume™ and REST™. Flume™ is an open-source distributed service for collecting, aggregating, and moving large amounts of log data. REST™ is an interface for accessing large databases. - The received data is then provided via a
channel 314 to a semantic processor (or data preparation stage)316, which in certain embodiments performs, among other functions, ETL functions. In particular, thesemantic processor 316 may perform parsing of the incoming event data, enrichment (also called decoration or annotation) of the event data with certain information, and optionally, filtering the event data. Thesemantic processor 316 introduced here is particularly useful when data received from the various data sources throughdata receiver 310 is in different formats, in which case thesemantic processor 316 can prepare the data for more efficient downstream utilization (including, for example, by an event processing engine) while avoiding binding the unstructured data into any particular type of data structure. - A parser in the
semantic processor 316 may parse the various fields of received event data representing an event (e.g., a record related to a log-in event). An identity resolution (IR) component (not shown inFIG. 4 ) may be optionally provided within thesemantic processor 316 to correlate IP addresses with users, for example. This correlation permits the security platform to make certain assumptions about the relationship between an IP address and a user so that, if any event data arrives from that IP address in the future, an assumption regarding which user is associated with that IP address may be made. In some implementations, the event data pertaining to that IP address may be annotated with the identity of the user. Technology used to implement the data preparation functions of thesemantic processor 316 may include Redis™ - An optional
filter attribution block 322 in thesemantic processor 316 removes certain pre-defined events. Theattribution filter 322 in thesemantic processor 316 may further remove events that need not be processed by the security platform. An example of such an event is an internal data transfer that occurs between two IP addresses as part of a regular file backup. In some embodiments, the functions ofsemantic processor 316 are configurable by a configuration file to permit easy updating or adjusting. Examples of configurable properties of thesemantic processor 316 include how to (i) parse events, (ii) correlate between users and IP address, and/or (iii) correlate between one attribute with another attribute in the event data or an external attribute. The configuration file can also adjust filter parameters and other parameters in thesemantic processor 316. - Data processed by the
semantic processor 316 is sent to adistribution block 320. Thedistribution block 320 can be a messaging mechanism to distribute data to one or both of the real-time processing path and the batch processing path. The real-time processing path is entered via the right-facing arrow extending from thedistribution block 320, whereas the batch processing path is entered viaarrow 388 extending downward from thedistribution block 320. - The real-time processing path includes an
analysis module 330 that receives data from thedistribution block 320. Theanalysis module 330 analyzes the data in real-time to detect anomalies, threat indicators, and threats. In certain embodiments, the aforementioned Storm™ platform may be employed to implement theanalysis module 330. In other embodiments, the analysis module could be implemented by using Apache Spark Streaming. - In
FIG. 4 , at least twotopologies analysis module 330. Generally, a topology in this context is a specification of how an analysis module (e.g., module330) groups and distributes work (e.g., to the different computation workers). A topology can also specify how theanalysis module 330 groups and distributes input data for the model-related process threads. More details on theanalysis module 330 and topologies are discussed below in relevant sections. Different machine learning models may evaluate different aspects of the pre-processed event data received from thedistribution block 320. The machine learning models can also generate security-related scores for the events. The results from theanalysis module 330 may be, for example, anomalies, threat indicators, and threats. - These anomalies, threat indicators and threats may be provided to a user interface (UI)
system 350 for review by ahuman operator 352. As an example, a visualization map and a threat alert may be presented to thehuman operator 352 for review and possible action. The output of theanalysis module 330 may also automatically trigger actions such as terminating access by a user, terminating file transfer, or any other action that may neutralize the detected threats. In certain embodiments, only notification is provided from theanalysis module 330 to theUI system 350 for review by thehuman operator 352. The event data that underlies those notifications or that gives rise to the detection made by theanalysis module 330 are persistently stored in adatabase 378. If the human operator decides to investigate a particular notification, he or she may access fromdatabase 378 the event data (including raw event data and any associated information) that supports the anomalies or threat detection. On the other hand, if the threat detection is a false positive, thehuman operator 352 may so indicate upon being presented with the anomaly or the threat. The rejection of the analysis result may also be provided to thedatabase 378. The operator feedback information (e.g., whether an alarm is accurate or false) may be employed to update the model to improve future evaluation. Arrow 360 represents the storing of data supporting the analysis of the anomalies and threats in the real-time path. For example, the anomalies and threats as well as the event data that gives rise to detection of the anomalies and threats may be stored in database378 (e.g., an SQL store) using a path represented by thearrow 360. Additional information such as the version of the models, the identification of the models used, and the time that the detection is made, may also be stored.- The
human operator 352 may review additional information in response to the notification presented by theUI system 350. The data supporting the analysis of the anomalies and threats may be retrieved fromdatabase 378 via an access layer364.Arrow 362 represents a data retrieval request via the access layer364 to one or more ofdatabases UI 350 by means ofdata pathway 380. The access layer364 includes the APIs for accessing the various databases and the user interfaces in theUI 350. For example, block366A represents the API for accessing the HBase or HDFS (Hadoop File Service) databases.Block 366B represents the various APIs compatible for accessing servers implementing sockets.io or node.js servers.SQL API 366C represents the API for accessing theSQL data store 378, which stores data pertaining to the detected threats and anomalies. Line 368 is a conceptual line that separates the batch processing path (below line368) from the real-time processing path (above line368). The infrastructure which may operate in batch mode includes theSQL store 378 that stores information accessible by scripted query language (SQL), atime series database 370 that represents the database for storing time stamped data, anHBase 372 that can be an open-source, distributed, non-relational database system on which databases (e.g., the time serious database370) can be implemented, and aGraphDB database 374 that storessecurity graphs 392, which may be based on relationship graphs generated from events. In some embodiments, theGraphDB database 374 comprises a Neo4j™ graph database.- A security graph, as described further below, is generally a representation of the relationships between entities in the network and any anomalies identified. For example, a security graph may map out the interactions between users, including information regarding which devices are involved, who or what is talking to whom/what, when and how interactions occur, which nodes or entities may be anomalous, and the like. The nodes of the security graph may be annotated with additional data if desired.
- A
batch analysis module 382 is the analysis module that processes data in batches. Theanalysis module 382 may take into account the historical event data stored indatabases distribution block 320 to the persistent layer belowline 368 via network channel388). In one example, thebatch analysis module 382 may employthird party data 384. With more time allowance and more data available for analysis, thebatch analysis module 382 may be able to uncover additional anomalies and threats that may not be easily detectable by the real-time analysis module 330. Themodel management block 386 includes a model store and a model registry. The model registry can store model type definitions for machine learning models, and the model store can store model states for machine learning models. Additional details on the model registry and the model store are discussed below. - In certain embodiments, the models that are employed for evaluation by one analysis module may be shared with another module. Model state sharing390 may improve threat detection by various modules (e.g., two modules belonging to an international network of the same company, but one deployed in Asia and another one deployed in North America; or, one module being used in the real-time path and another in the batch path) as the model state sharing leverages knowledge learned from one module to benefit others.
Security graphs 392 may also be shared among modules, and even across different organizations. For example, activities that give rise to a detection of anomalies or a threat in one enterprise may thus be shared with other enterprises.Hadoop nodes 394 represent the use of cloud-based big data techniques for implementing the architecture ofFIG. 4 to improve scalability as well as the ability to handle a large volume of data.Control path 396 represents the control software that may be used for monitoring and maintaining thesecurity platform 300. FIG. 5 shows an example implementation of the real-time processing path in greater detail. With reference to bothFIGS. 4 and 5 , theanalysis module 330 has been expanded as twoanalysis modules analysis module 330A is responsible for detecting anomalies, and the output of theanalysis module 330A is provided to theanalysis module 330B for detecting threats based on the detected anomalies. In practice, the two stages may be performed by the same module utilizing different models in a staged manner.- The output of
analysis module 330A, representing the anomalies, is provided to ananomaly writer 402. Theanomaly writer 402 can store the anomalies (e.g., including event data representing an anomalous event and any associated information) in thedatabase 378. The same anomalies may also be stored in thetime series database 370 and theHBase 372. The anomalies may also be stored in thegraph database 374. In some embodiments, the anomalies can be stored ingraph database 374 in the form of anomaly nodes in a graph or graphs; specifically, after an event is determined to be anomalous, an event-specific relationship graph associated with that event can be updated (e.g., by the anomaly writer402) to include an additional node that represents the anomaly, as discussed further below. Certain embodiments of the security platform provide the ability to aggregate, at a specified frequency (e.g., once a day), the individual event-specific relationship graphs from all the processed events in order to compose a composite relationship graph for a given enterprise or associated network. This aforementioned update to an individual event's relationship graph allows the composite relationship graph to include nodes representing anomalies, thereby providing more security-related information. The individual event-specific relationship graph and the composite relationship graph are discussed in more detail below. The information stored may include the anomalies themselves and also relevant information that exists at the time of evaluation. These databases allow rapid reconstruction of the anomalies and all of their supporting data. - The output from the
analysis modules 330B, representing threats, may be stored in thedatabase 378, thetimes series database 370 or theHbase 372. As in the case of anomalies, not only are the threats themselves stored, but relevant information that exists at the time of evaluation can also be stored. - The
batch analysis module 382 can also operate in two stages for anomaly and threat detection in a similar fashion as discussed above with respect to the real-time analysis module 330. - The
security platform 300 can detect anomalies and threats by determining behavior baselines of various entities that are part of, or that interact with, a network, such as users and devices, and then comparing activities of those entities to their behavior baselines to determine whether the activities are anomalous, or even rise to the level of threat. The behavior baselines can be adaptively varied by theplatform 300 as new data are received. These functions can be performed by one or more machine-learning models, for example, in the real-time path, the batch path, or both. FIG. 6 shows an example representation of a process of building behavior baselines to support the detection of anomalies. Ahuman end user 602 may employ aserver 606 to access asource code server 610 for his work, for example. Assume that thehuman user 602 occasionally accesses the data stored inservers 608. In a manner described in more detail below, thesecurity platform 300 can generate abaseline profile 612 for access activities ofuser 602, based on event data indicative of network activities ofuser 602. Likewise, a humanadministrative user 604 other thanuser 602 may employ theserver 606 to access the data stored in theservers 608. Abaseline profile 614 specific for access activities ofuser 604 can also be generated over time by thesecurity platform 300, based on event data indicative of network activities ofuser 604.- The
security platform 300 can create a behavior baseline for any type of entity (for example, a user, a group of users, a device, a group of devices, an application, and/or a group of applications). In the example ofFIG. 6 , the activities ofserver 606 are monitored and abaseline profile 616 specific for theserver 606 is generated over time, based on event data indicative of network activities ofserver 606. - Baseline profiles can be continuously updated (whether in real-time as event data streams in, or in batch according to a predefined schedule) in response to received event data, i.e., they can be updated dynamically and/or adaptively based on event data. If the
human user 604 begins to accesssource code server 610 more frequently in support of his work, for example, and his accessing ofsource code server 610 has been judged to be legitimate by thesecurity platform 300 or a network security administrator (i.e., the anomalies/threats detected upon behavior change have been resolved and deemed to be legitimate activities), hisbaseline profile 614 is updated to reflect the updated “normal” behavior for thehuman user 604. - In certain embodiments, anomalies and threats are detected by comparing incoming event data (e.g., a series of events) against the baseline profile for an entity to which the event data relates (e.g., a user, an application, a network node or group of nodes, a software system, data files, etc.). If the variation is more than insignificant, the threshold for which may be dynamically or statically defined, an anomaly may be considered to be detected. The comparison may be based on any of various techniques, for example, time-series analysis (e.g., number of log-ins per hour), machine learning, or graphical analysis (e.g., in the case of security graphs or security graph projections). Preferably, this detection is performed by various machine learning models.
- Additional details are discussed below regarding various components of the security platform including, for example, the data intake and preparation engine, event processing engine, configurations for real-time implementations, configurations for batch implementation, machine learning models and different applications, various kinds of anomaly and threat detections, and graphic user interfaces for presenting security-related issues.
FIGS. 7A and 7B collectively show a table700 listing example types of machine data that can be generated in different environments and the meaning of these data. During operation, various components within a computing environment often generate significant volumes of machine-generated data (i.e., “machine data”). In general, machine data can include performance data, diagnostic information and/or any of various other types of data indicative of performance or operation of equipment (e.g., an action such as upload, delete, or log-in) in a computing system. Such data can be analyzed to diagnose equipment performance problems, monitor user actions and interactions, and to derive other insights like user behavior baseline, anomalies and threats.- As shown in the table700, machine data may contain a record (e.g., a log) of an event that takes place in the network environment, such as an activity of a customer, a user, an transaction, an application, a server, a network or a mobile device. However, in many instances, machine data can be more than mere logs—it can include configurations, data from APIs, message queues, change events, the output of diagnostic commands, call detail records, sensor data from industrial systems, and so forth.
- As used herein, “an event” may refer to the actual event or activity that takes place in the network, or for the simplicity of the discussion, it may refer to the machine data (or “event data”) that records, corresponds to, or otherwise represents the event. The term's meaning is made apparent by the context of the discussion and the two meanings of the term may be used in an interchangeable manner in some scenarios. For example, “extracting a token from an event” will be understood as extracting a token from the event data that represents the event. Also, note that the data intake and preparation stage described herein may be as alternatively called the extract-transform-load (ETL) stage; however, the data intake and preparation stage disclosed here is not limited to traditional ETL techniques. In some implementations, the data intake and preparation stage includes an ETL engine/pipeline, but also includes/performs other functions beyond or different from a traditional ETL stage, as henceforth described herein. Consequently, the term “data pre-processing” is used interchangeably with “data preparation,” and is intended to include any combination of data extraction, transformation, annotation/supplementation, and/or other additional techniques introduced here. The term “stage,” as in the data intake and preparation stage, may also be referred to as “engine.”
- Events occurring in a computer network may belong to different event categories (e.g., a firewall event, a threat information, a login event) and may be generated by different machines (e.g., a Cisco™ router, a Hadoop™ Distributed File System (HDFS) server, or a cloud-based server such as Amazon Web Services™ (AWS) CloudTrail™). Therefore, machine data can come in many different formats, at least some of which may not be predictable. Traditional monitoring and analysis tools are not designed for the variety, velocity, volume or variability of such a data environment. Furthermore, different kinds of event data types can contain different information. Generally, the higher the communication layer (in terms of the well-known open system interconnection (OSI) model) to which an event belongs, the richer the information that event contains. For example, a network packet log may only include information on which machine communicates with which other machine(s); in contrast, an application log may have the richest information, thereby having a higher value. Particularly, in an application log, not only is it possible to obtain information on which machine is communicating with which other machine(s), but it is also possible to ascertain what kind of information these machines are sharing. For another example, session layer data may be used to identify (e.g., via techniques disclosed here) which user is attempting to log in with what credential and using which particular session, and therefore would be more valuable than lower-level network layer data. However, a typical computer network has significantly more lower-level layer data than higher-level layer data. Therefore, as the variety, velocity, and volume of the data in the environment greatly increase, traditional monitoring and analysis systems either simply ignore a large portion of the data, or they quickly become overloaded by the data, thereby losing accuracy and responsiveness.
- Accordingly, the security platform introduced here includes various aspects that are specifically tailored to this data environment, including techniques for obtaining different kinds of data, preparing data, and processing data, by using different stages, to enable quick diagnosis of service problems, detection of sophisticated security threats, understanding of the health and performance of remote equipment, and demonstration of compliance.
FIG. 8 shows an example implementation of a data intake andpreparation stage 800 of the security platform. The data intake and preparation stage (or engine)800 can be an implementation ofETL stage 204 inFIG. 3 and/orsemantic processor 316 inFIG. 5 . The data intake andpreparation stage 800 can include a number of components that perform a variety of functions disclosed herein. In the example ofstage 800, the data intake and preparation stage of the security platform includes a number ofdata connectors 802, aformat detector 804, a number ofparsers 806, afield mapper 808, arelationship graph generator 810, anidentity resolution module 812, a number ofdecorators 814, andevent view adder 816. These components (e.g., sets of instructions) need not be implemented as separate software programs, procedures or modules, and thus various subsets of these components may be combined or otherwise rearranged in various embodiments. Also, the components shown inFIG. 8 are only one example of the data intake and preparation stage components that can be used by the security platform; the data intake and preparation stage could have more or fewer components than shown, or a different configuration of components.- The various components shown in
FIG. 8 can be implemented by using hardware, software, firmware or a combination thereof, including one or more signal processing and/or application specific integrated circuits. The components in thestage 800 are shown arranged in a way that facilitates the discussion herein; therefore, any perceivable sequence in thestage 800 is merely an example and can be rearranged. Any step in thestage 800 may be performed out-of-sequence and/or in parallel to the extent that such rearrangement does not violate the logic dependency of the steps. One or more steps described for thestage 800 may be optional, depending on the deployed environment. The data output from the data intake andpreparation stage 800 can also be referred to herein as “decorated events” or “event feature sets.” A decorated event includes the raw machine data associated with an event, plus any decoration, enrichment, information, or any other suitable intelligence that is generated based upon or extracted from the event during the data intake and preparation stage. In some embodiments, because of the computationally intensive processes that the data intake and preparation stage may perform, the data intake and preparation engine may be implemented separately from the rest of the stages in the security platform, for example, on a standalone server or on dedicated nodes in a distributed computer cluster. Various data connectors 802 can be employed by the security platform (e.g., at the data intake stage) to support various data sources. Embodiments of thedata connectors 802 can provide support for accessing/receiving indexed data, unindexed data (e.g., data directly from a machine at which an event occurs), data from a third-party provider (e.g., threat feeds such as Norse™, or messages from AWS™ CloudTrail™), or data from a distributed file system (e.g., HDFS™). Hence, thedata connectors 802 enable the security platform to obtain machine data from various different data sources. Some example categories of such data sources include:- (1) Identity/Authentication: e.g., active directory/domain controller, single sign-on (SSO), human resource management system (HRMS), virtual private network (VPN), domain name system (DNS), or dynamic host configuration protocol (DHCP);
- (2) Activity: e.g., web gateway, proxy server, firewall, Netflow™, data loss prevention (DLP) server, file server, or file host activity logs;
- (3) Security Products: e.g., endpoint security, intrusion prevention system, intrusion detection system, or antivirus;
- (4) Software as a Service (SaaS) or Mobile: e.g., AWS™ CloudTrail™, SaaS applications such as Box™ or Dropbox™, or directly from mobile devices; and
- (5) External Threat Feeds: e.g., Norce™, TreatStream™, Financial Services Information Sharing and Analysis Center (FS-ISAC)™, or third-party blacklisted IP/domains.
- Depending on the embodiment, external threat feeds may directly feed to the security platform, or indirectly through one or more security products that may be coexisting in the environment within which the security platform is deployed. As used herein, the term “heterogeneous event” refers to the notion that incoming events may have different characteristics, such as different data formats, different levels of information, and so forth. Heterogeneous events can be a result of the events originating from different machines, different types of machines (e.g., a firewall versus a DHCP server), being in a different data format, or a combination thereof.
- The
data connectors 802 can implement various techniques to obtain machine data from the data sources. Depending on the data source, thedata connectors 802 can adopt a pull mechanism, a push mechanism, or a hybrid mechanism. For those data sources (e.g., a query-based system, such as Splunk®) that use a pull mechanism, thedata connectors 802 actively collect the data by issuing suitable instructions to the data sources to grab data from those data sources into the security platform. For those data sources (e.g., ArcSignt™) that use a push mechanism, thedata connectors 802 can identify an input (e.g., a port) for the data sources to push the data into the system. Thedata connectors 802 can also interact with a data source (e.g., Box™) that adopts a hybrid mechanism. In one embodiment of thedata connectors 802 for such hybrid mechanism, thedata connectors 802 can receive from the data source a notification of a new event, acknowledges the notification, and at a suitable time communicate with the data source to receive the event. - For those
data connectors 802 that may issue queries, the queries can be specifically tailored for real-time (e.g., in terms of seconds or less) performance. For example, some queries limit the amount of the anticipated data by limiting the query to a certain type of data, such as authentication data or firewall related data, which tends to be more relevant to security-related issues. Additionally or alternatively, some queries may place a time constraint on the time at which an event takes place. - Moreover, in some examples, the
data connectors 802 can obtain data from a distributed file system such as HDFS™. Because such a system may include a large amount of data (e.g., terabytes of data or more), it is preferable to reduce data movement so as to conserve network resources. Therefore, some embodiments of thedata connectors 802 can generate a number of data processing jobs, send the jobs to a job processing cluster that is coupled to the distributed file system, and receive the results from the job processing cluster. For example, thedata connectors 802 can generate MapReduce™ jobs, and issue those jobs to a job processing cluster (e.g., YARN™) that is coupled to the distributed file system. The output of the job processing cluster is received back into the security platform for further analysis, but in that case, no or very little raw machine data is moved across the network. The data is left in the distributed file system. In some examples, the generated jobs are user behavior analysis related. - Optionally, after the
data connectors 802 obtain/receive the data, if the data format of the data is unknown (e.g., the administrator has not specified how to parse the data), then theformat detector 804 can be used to detect the data format of the input data. For example, theformat detector 804 can perform pattern matching for all known formats to determine the most likely format of a particular event data. In some instances, theformat detector 804 can embed regular expression rules and/or statistical rules in performing the format detection. Some examples of theformat detector 804 employ a number of heuristics that can use a hierarchical way to perform pattern matching on complex data format, such as an event that may have been generated and/or processed by multiple intermediate machines. In one example, theformat detector 804 is configured to recursively perform data format pattern matching by stripping away a format that has been identified (e.g., by stripping away a known event header, like a Syslog header) in order to detect a format within a format. - However, using the
format detector 804 to determine what data format the input data may be at run time may be a time- and resource-consuming process. At least in the cybersecurity space, it is typical that the formats of the machine data are known in advance (e.g., an administrator would know what kind of firewall is deployed in the environment). Therefore, as long as the data source and the data format are specified, the data intake and preparation stage can map the data according to known data formats of a particular event source, without the need of performing data format detection. In certain embodiments, the security platform can prompt (e.g., through a user interface) the administrator to specify the data format or the type of machine(s) the environment includes, and can automatically configure, for example, theparsers 806 in the data intake and preparation stage for such machines. - Further, the security platform provides a way to easily supporting new data format. Some embodiments provide that the administrator can create a new configuration file (e.g., a configuration “snippet”) to customize the data intake and preparation stage for the environment. For example, for a particular data source, the configuration file can identify, in the received data representing an event, which field represents a token that may correspond to a timestamp, an entity, an action, an IP address, an event identifier (ID), a process ID, a type of the event, a type of machine that generates the event, and so forth. In other examples (e.g., if a new data format is binary), then the security platform allows an administrator to leverage an existing tokenizer/parser by changing the configuration file, or to choose to implement a new, customized parser or tokenizer.
- In a number of implementations, through the configuration file (e.g., snippet), the administrator can also identify, for example, field mappings, decorators, parameters for identity resolution (IR), and/or other parameters of the data intake and preparation stage. The configuration snippet can be monitored and executed by the data intake and preparation engine on the fly to allow the an administrator to change how various components in the data intake and preparation engine functions without the need to recompile codes and/or restart the security platform.
- After receiving the event data by the
data connectors 802, theparsers 806 parse the event data according to a predetermined data format. The data format can be specified in, for example, the configuration file. The data format can be used for several functions. The data format can enable the parser to tokenize the event data into tokens, which may be keys, values, or more commonly, key-value pairs. Examples of supported data format include event data output from an active-directory event, a proxy event, an authentication event, a firewall event, an event from a web gateway, a virtual private network (VPN) connection event, an intrusion detection system event, a network traffic analyzer event, or an event generated from a malware engine. - Each parser can implement a set of steps. Depending on what type of data the data intake and preparation stage is currently processing, in some embodiments, the initial steps can including using regular expression to perform extraction or stripping. For example, if the data is a system log (syslog), then a syslog regular expression can be first used to strip away the packet of syslog (i.e., the outer shell of syslog) to reveal the event message inside. Then, the parser can tokenize the event data into a number of tokens for further processing.
- The
field mapper 808 can map the extracted tokens to one or more corresponding fields with predetermined meanings. For example, the data format can assist thefield mapper 808 to identify and extract entities from the tokens, and more specifically, the data format can specify which of the extracted tokens represent entities. In other words, thefield mapper 808 can perform entity extraction in accordance with those embodiments that can identify which tokens represent entities. An entity can include, for example, a user, a device, an application, a session, a uniform resource locator (URL), or a threat. Additionally, the data format can also specify which tokens represent actions that have taken place in the event. Although not necessarily, an action can be performed by one entity with respect to another entity; examples of an action include use, visit, connect to, log in, log out, and so forth. In yet another example, the filedmapper 808 can map a value extracted to a key to create a key-value pair, based on the predetermined data format. - The entity extraction performed by the
field mapper 804 enables the security platform to gain potential insight on the environment in which the security platform is operating, for example, who the users are, how many users there may be in the system, how many applications that are actually being used by the users, or how many devices there are in the environment. - A. Event Relationship Discovery/Mini-Graphs
FIGS. 9A and 9B show an example event relationship discovery and recordation technique, which can be implemented in the data intake and preparation stage. To facilitate description,FIGS. 9A and 9B are explained below with reference toFIG. 8 . The relationship discovery and recordation technique can be performed by, for example, therelationship graph generator 810. Specifically, after the entities are identified in the tokens, therelationship graph generator 810 is operable to identify a number of relationships between the entities, and to explicitly record these relationships between the entities. Some implementations of therelationship graph generator 810 generate a single relationship graph for each event; such an event-specific relationship graph may also be called a “mini-graph.” Further, some implementations incorporate the generated relationship graph into the event data that represents the event, in the form of a data structure representing the relationship graph. A graph in the context of this description includes a number of nodes and edges. Each node in the relationship graph represents one of the entities involved in the event, and each edge represents a relationship between two of the entities. In general, any event involves at least two entities with some relationship between them (e.g., a device and a user who accesses the device) and therefore can be represented as an event-specific relationship graph.- In some implementations, the
graph generator 810 can identify a relationship between entities involved in an event based on the actions that are performed by one entity with respect to another entity. For example, thegraph generator 810 can identify a relationship based on comparing the action with a table of identifiable relationships. Such a table of identifiable relationship may be customizable and provides the flexibility to the administrator to tailor the system to his data sources (described above). Possible relationships can include, for example, “connects to,” “uses,” “runs on,” “visits,” “uploads,” “downloads,” “successfully logs onto,” “restarts,” “shuts down,” “unsuccessfully attempts to log onto,” “attacks,” and “infects.” Also, the identified relationship between the entities can be indicative of the action, meaning that the identifiable relationship can include the action and also any suitable inference that can be made from the action. For example, an event that records a GET command (which is an action) may indicate that the user is using a machine with a certain IP address to visit a certain website, which has another IP address. In practice, however, the number of identifiable relationships can be directly correlated to the size of the graph, which may impact the security platform's responsiveness and performance. Also, identifiable relationships can include a relationship between entities of the same type (e.g., two users) or entities of different types (e.g., user and device). - In some embodiments, specific details on how to construct the edges and the identifiable relationships are recorded in the configuration file (e.g., snippet). For example, a portion of the configuration file can specify, for the
relationship graph generator 810, that an edge is to be created from an entity “srcUser” to another entity “sourceIP,” with a relationship that corresponds to an event category to which the event belongs, such as “uses.” FIG. 9A illustratesraw event data 900 received by the data intake and preparation stage. Theraw event data 900, representing an event that occurs, are log data generated by a web gateway server. The web gateway is located where network traffic in and out the environment goes through, and therefore can log the data transfer and web communication from a system inside the environment. The particular event as represented by theevent data 900 indicates that, at a particular point of time identified by the timestamp, the user “psibbal” uses the IP address “10.33.240.240” to communicate with an external IP address “74.125.239.107,” and transfers 106 bytes of data. The status code of that event is “200,” and the event is a TCP event where the HTTP status is “GET.” As illustrated, theevent data 900 also includes a significant amount of additional information.- Using the aforementioned techniques (e.g., the
parsers 806, and the field mapper808), thegraph generator 810 can readily identify that the event represented in theFIG. 9A involves a number of entities, such as the user “psibbal,” the source IP “10.33.240.240,” the destination IP “74.125.239.107,” and an URL “sample.site.com.” Thegraph generator 810 also identifies that an action “GET” is involved in the event. Accordingly, thegraph generator 810 can compare the action to the table of identifiable actions, identify one or more relationships between the entities, and create an event-specific relationship graph 902 based on the event. As shown inFIG. 9B , therelationship graph 902 includes the entities that are involved in the events. Each entity is represented by a different node. Therelationship graph 902 also includes edges that link the nodes representing entities. The identified relationships between the entities are the edges in thegraph 902. Therelationship graph 902 can be stored in known data structures (e.g., an array) suitable for representing graphs that have nodes and edges. - Note, however, that the components introduced here (e.g., the graph generator810) may be tailored or customized to the environment in which the platform is deployed. As described above, if the network administrator wishes to receive data in a new data format, he can edit the configuration file to create rules (e.g., in the form of functions or macros) for the particular data format including, for example, identifying how to tokenize the data, identifying which data are the entities in the particular format, and/or identifying the logic on how to establish a relationship. The data input and preparation stage then can automatically adjust to understand the new data format, identify identities and relationships in event data in the new format, and create event relationship graphs therefrom.
- Then, in some embodiments, the
graph generator 810 attaches therelationship graph 902 to the associatedevent data 900. For example, thegraph 902 may be recorded as an additional field of theevent data 900. In alternative embodiments, therelationship graph 902 can be stored and/or transferred individually (i.e., separate from the event data900) to subsequent nodes in the security platform. After additional processes (e.g., identity resolution, sessionization, and/or other decorations) in the data intake and preparation stage, theevent data 900 including therelationship graph 902 can be sent to a distributed messaging system, which may be implemented based on Apache Kafka™. The messaging system can in turn send theevent data 900 to an event processing engine (e.g., a machine learning model execution and analytics engine, such as the complex event processing engine introduced here and described further below) for further processing. As described further below, the event processing engine is operable to use machine learning models to perform analytics based on the events and, in some instances, in conjunction with their associated relationship graphs, to security-oriented anomalies and threats in the environment. - The messaging system (e.g., Apache Kafka™) can also accumulate or aggregate, over a predetermined period of time (e.g., one day), all the relationship graphs that are generated from the events as the events come into the security platform. Particularly, note that certain types of behavioral anomalies and threats can become more readily identifiable when multiple events are compared together, and sometimes such comparison may even be the only way to identify the anomalies and/or threats. For example, a beaconing anomaly happens when there is a device in the network that communicates with a device outside the network in an unexpected and (mostly) periodic fashion, and that anomaly would become more identifiable when relationship graphs associated with all the device's related beacons are combined into a composite relationship graph. As such, at the messaging system, the relationship graphs (mini-graphs) for all events, or at least for multiple events, can be combined into a larger, composite relationship graph. For example, a computer program or a server can be coupled to the messaging system to perform this process of combining individual relationship graphs into a composite relationship graph, which can also be called an enterprise security graph. The composite relationship graph or enterprise security graph can be stored, for example, as multiple files, one file for each of multiple predetermined time periods. The time period depends on the environment (e.g., the network traffic) and the administrator. In some implementations, the composite relationship graph is stored (or “mined” in data mining context) per day; however, the graph mining time period can be a week, a month, and so forth.
- In some embodiments, event-specific relationship graphs are merged into the composite relationship graph on an ongoing basis, such that the composite relationship graph continuously grows over time. However, in such embodiments it may also be desirable to remove (“age out”) data deemed to be too old, from the composite relationship graph, periodically or from time to time.
- In some embodiments, the nodes and edges of the composite graph are written to time namespaces partitioned graph files. Then, each smaller segment can be merged with a master partition (e.g., per day). The merge can combine similar nodes and edges into the same record, and in some embodiments, can increase the weight of the merged entity nodes. Note that the exact order of the events' arrival becomes less important, because even if the events arrive in an order that is not the same as how they actually took place, as long as the events have timestamps, they can be partitioned into the correct bucket and merged with the correct master partition. Some implementations provide that the composite graphs can be created on multiple nodes in a parallelized fashion.
- In this manner, this composite relationship graph can include all identified relationships among all identified entities involved in the events that take place over the predetermined period of time. As the number of events received by the security platform increases, so does the size of this composite relationship graph. Therefore, even though a relation graph from a single event may not carry much meaning from a security detection and decision standpoint, when there are enough events and all the relationship graphs from those events are combined into a composite relationship graph, the composite relationship graph can provide a good indication of the behavior of many entities, and the quality/accuracy of this indication increases over time as the composite relationship graph grows. Then, the subsequent processing stages (e.g., the complex processing engine) can use models to perform analytics on the composite relationship graph or on any particular portion (i.e., “projection”, discussed further below) of the composite relationship graph. In some embodiments, the composite relationship graph is persistently stored using a distributed file system such as HDFS™.
- In some embodiments, when various individual events' relationship graphs (along with their associated decorated events) are stored in the messaging system but have not yet been combined to create the composite relationship graph, each such event's relationship graph can be further updated with any information (e.g., anomalies) that is discovered by downstream processes in the security platform. For example, if an event is found to be an anomalous, then the relationship graph associated with that anomalous event can be updated to include this information. In one example, the individual relationship graph of that anomalous event is revised to include an anomaly node (along appropriate edges), so that when the composite relationship graph is created, it can be used to determine what other entities might be involved or affected by this anomaly.
- At least in some embodiments, the composite graph enables the security platform to perform analytics on entity behaviors, which can be a sequence of activities, a certain volume of activities, or can be custom defined by the administrator (e.g., through a machine learning model). By having an explicit recordation of relationships among the events, the
relationship graph generator 810 can enable the analytics engines introduced here (e.g., the complex processing engine) to employ various machine learning models, which may focus on different portions or aspects of the discovered relationships between all the events in the environment, in order to detect anomalies or threats. - B. Identity Resolution (IR) and Device Resolution (DR)
FIG. 10 shows an example identity resolution technique based on the information in the events, which can be implemented in the data intake and preparation stage described above. To facilitate description,FIG. 10 is explained below with reference toFIG. 8 . Identity resolution can be performed by, for example, theidentity resolution module 812. Specifically, after the entities are identified in the tokens, theidentity resolution module 812 is operable to perform an identity resolution, which enables keeping track of which user logged into which particular computer system or device across the network.- In the context of computer security and especially unknown threat detection, information about a user's behavior can be very important. However, as previously discussed, not all events/activities/logs include user information. Consider a typical firewall event as an example. Except for a few advanced firewall products, many typical firewalls do not know and do not record the user's identity in an event. Therefore, many times even when a particular communication is determined to be malicious, traditional security products are unable to attribute the malicious behavior to a particular user. Thus, when logs or device-level events do not capture the user information, the
identity resolution module 812 in the data intake and preparation stage can attribute those events (and behaviors) to the right user. - In addition, traditional solutions for identity resolution adopt techniques that are too simplistic and lack responsiveness to any changes to the environment. For example, one traditional technique may be a simple lookup, such as where the administrator maintains a resource attribution file that records a particular IP address belongs to a particular person. However, such a file is often hard to keep accurate and easily becomes obsolete, especially when the amount of the devices in the environment is very large, as is often the case in today's environment.
- Accordingly, the security platform introduced here can perform identity resolution based on the facts. The
identity resolution module 812 can gain the knowledge by observing the system environment (e.g., based on authentication logs), thereby building the intelligence to make an educated identity resolution determination. That is, theidentity resolution module 812 is able to develop user identity intelligence specific and relevant to the system's environment without any explicit user identity information. - To facilitate this fact-based identity resolution functionality in the security platform, the
identity resolution module 812 can utilize a machine learning model to generate and track a probability of association between a user and a machine identifier. Specifically, after the entities in event data that represents an event are extracted (e.g., by the field mapper808), theidentity resolution module 812 can identify whether the event data includes a user identifier and/or a machine identifier, and can create or update the probability of association accordingly. As is discussed in more detail in other sections of this disclosure, the model initiated by theidentity resolution module 812 can, in some embodiments, obtain the information it needs, e.g., obtaining machine identifiers in an event, through one or more interfaces. A machine identifier is an identifier that can be associated with a machine, a device, or a computing system; for example, a machine identifier can be a media access control (MAC) address, or an Internet Protocol (IP) address. Different machine identifiers can be generated by the same machine. A user identifier is an identifier that can be associated with a user; for example, a user identifier can be a user login identifier (ID), a username, or an electronic mail address. Although not illustrated inFIG. 8 , some embodiments of theidentity resolution module 812 can resolve a user identity of a particular user by, for example, querying a database using a user identifier as a key. The database, which may be a human resource management system (HRMS), can have records indicating a number of user identifiers that are registered to the user identity. Note that, in some alternative embodiments, a user identifier may be directly treated as a user for simpler implementation, even though such implementation may not be an ideal one because behaviors of the same user may not be detected because the user has used different user identifiers. - More specifically, a machine learning model can have different phases, for example, a training phase (after initiation and before ready) and an active phase (after ready and before expiration). In a training phase of a machine learning model, if an event that is received involves both a user and a machine identifier (e.g., if the event data representing the event has both a user identifier and a machine identifier), then machine learning model that is employed by the
identity resolution module 812 can use this event to create or update the probability of association between the user and the machine identifier. For example, when an authentication event is received (e.g., when a user logs into a particular machine) and involves a user (e.g., identified by a user identifier such as a username) and a machine identifier, the model learns that the user is now associated with the machine identifier, at least for a period of time until the user logs out or times out from the particular machine. - As more events are received, the model can become increasingly better trained about the probability of association between the user and the machine identifiers. In some embodiments, the
identity resolution module 812 creates a probabilistic graph to record a probability of association for each user it is currently tracking. The probabilistic graph can include peripheral nodes, a center node, and edges. An example of suchprobabilistic graph 1000 is shown inFIG. 10 . Ingraph 1000,nodes Node 1002 is the center node representing the user. Edges between each peripheral node and the center node represent the probability of association between the particular machine identifier and the user. According to some embodiments, the machine learning models used for identification resolution are user specific. It is also noted that the machine learning models used in the identity resolution (and device resolution, introduced below) are generally simpler than those models that would be used for anomaly and threat detection. In many embodiments, the models that are used in the identity resolution and/or device resolution are time-sequenced probabilistic graphs, in which the probability changes over time. - According to a number of embodiments, the models that are used to generate and track the probability of association between each user and possible machine identifiers are time-dependent, meaning that a result from the models has a time-based dependence on current and past inputs. The time dependence is useful to capture the scenario where a device is first assigned or given to a particular user, and is subsequently reassigned to a different user, which happens often in a large organization. To achieve this, in some embodiments, the
identity resolution module 812 can initiate, for a given user, different versions of the machine learning model at different point of time, and each version may have a valid life time. As events related to the given user arrive, versions of a machine learning model are initiated, trained, activated, (optionally) continually updated, and finally expired. - The models can be trained and, in some implementations, continually updated after their activation, by relevant events when the events are received. An example of a relevant event is an authentication event, which inherently involves a user (e.g., which may be represented by a user identifier) and a number of machine identifiers (e.g., an IP address or a MAC address). Depending on the model, other criteria for an event to be considered relevant for model training and/or updating purposes may include, for example, when a new event includes a particular machine identifier, a particular user identifier, and/or the recency of the new event. Moreover, some models may assign a different weight to the new event based on what type of event it is. For example, given that the new event is an authentication event, some models assign more weight to a physical login type of authentication event than to any other type of authentication event (e.g., a remote login).
- Depending on the particular deployment, the machine learning model can be considered trained and ready when one or more criteria are met. In one example, a version of the model can be considered trained when a certain number of events have gone through that version of the model. In another example, a version of the model can be considered trained when a certain time period has passed after the version of the model is initiated. Additionally or alternatively, a version of the model is considered trained when a certain number of criteria are met (e.g., when the model becomes sufficiently similar to another model). Additional details of machine learning models that can be employed (including training, readiness, activation, and expiration) by various engines and components in the security platform are discussed in other sections of this disclosure.
- After a version of a model is sufficiently trained (e.g., when the probability of association exceeds a confidence threshold, which depends on the model's definition and can be tuned by the administrator for the environment), the
identity resolution module 812 then can activate the version of the model. Thereafter, when a new event arrives, if the new event meets certain criteria for the identity resolution, theidentity resolution module 812 can create a user association record (e.g., in memory) indicative that the new event is associated with a particular user. The criteria for the identity resolution can include, for example, when the new event includes a machine identifier (regardless of whether it also includes a user identifier), and/or when the new event is received during a time period which the version is active. It is observed that the identity resolution technique is especially useful to help identify an event that includes only a machine identifier but no user identifier. - Based on this user association record, the
identity resolution module 812 can annotate the new event to explicitly connect the new event to the particular user. For example, theidentity resolution module 812 can add, as a field, the particular user's name to the new event in its associated event data. Alternatively, theidentity resolution module 812 can annotate the new event by adding a user identifier that belongs to the particular user. In addition, theidentity resolution module 812 can send the user association record to a cache server that is implemented based on Redis™. - With the fact-based identity resolution techniques disclosed herein, the security platform has the ability to attribute an event that happens on a device to a user, and to detect behavioral anomalies and threats based on that attribution. The security platform can achieve this without the need of maintaining an explicit look-up file and irrespective of what the data source is (i.e., regardless of whether a data source for an event includes a user identifier or not).
- Although not illustrated in
FIG. 8 , an embodiment of the data intake and preparation stage can also implement a device resolution module to create an association between one machine identifier and another. In a manner similar to how theidentity resolution module 812 tracks the possibility of association between a user and a machine identifier, the device resolution module can track the possibility of association between a first machine identifier and a second machine identifier. Thereafter, when a new event is received, if the event includes the first machine identifier but not the second, the device resolution module can create a machine association record indicative that the new event having the first machine identifier is associated with the second machine identifier. Optionally, the machine identifier can be translated into a more user-friendly machine name, such as “Tony's Laptop.” - The device resolution technique can be particularly useful in an environment that includes a dynamic host configuration protocol (DHCP) service, and therefore a computer in the environment does not have a static IP address. Because the same computer can potentially get a different IP address each time it starts in such environment, naively attributing a behavior to a particular IP address may lead to incorrect analysis. In manners similar to the identity resolution, the device resolution can create a mapping between, for example, a MAC address and an IP address, which can remain valid for a period of time. One example of events where the relationship between a MAC address and an IP address can be found is the DHCP logs. Like identity resolution, such machine identifier mapping can be dynamically updated as the time goes by and more events are received. Whenever the environment changes, the device resolution module can derive a new mapping, meaning that the same IP address can become associated with a different, updated MAC address. Note that, for the particular case of DHCP services, it is generally easier to estimate when a particular version of a device resolution model should expire, because a DHCP service setting typically includes explicit lease expiration provisions.
- C. Additional Event Decoration
- The data intake and preparation stage can also include
additional event decorators 814. Similar to how aformat detector 804 may be customized or how a new format detector may be added, theevent decorators 814 can be in the form of software code (e.g., in Java™) written by a third-party (e.g., the administrator) or can be added/configured through the configuration snippet. In some embodiments, theevent decorators 814 can include a geographical decorator, which can be configured to decorate the received events (e.g., by adding a field in the event data that represents the events) so all events with an IP address receive an additional field about their respective IP's geographical location. In another embodiment, theevent decorators 814 can include a server identifier, which can explicitly annotate an event when the event is from a server. The server identifier can implement a look-up technique in order to identify that a machine is being used as a server, or it can implement heuristics and make a determination based on how many users have logged into it within a predetermined time period. Other examples of theevent decorators 814 can include a Whois Lookup, Whitelisting, and so forth. - D. Event Views
FIG. 11 shows a diagram of a technique for providing uniform access interfaces (also called “event views”) to event data at the data intake and preparation stage for an event processing engine (e.g., at a subsequent stage) to obtain relevant information from various kinds of machine data. To facilitate description,FIG. 11 is explained below with reference toFIG. 8 .- The large variety of different types event data would make it difficult for traditional data analysis platforms to perform automated, real-time analysis. Therefore, the data intake and decoration stage introduced here can provide an uniform access interface for select information contained in the events. The uniform access interfaces described here serve to decouple the main intelligence of the security platform (e.g., the analytic models running therein) from the multiple, potentially heterogeneous data source inputs (which may be heterogeneous in nature (i.e., of different data types, formats, etc.)), and to create a homogeneous way of access information contained in the events that are originated from these various input systems.
- In particular, binding is a process in which unstructured data is processed and transformed into structured data. However, during binding, any information in the original, unstructured data becomes lost if not captured in the structured data. Accordingly, the data intake and preparation stage introduced here generally implements the notion of a “late binding” schema, which means that the binding is only made when an operation (e.g., a query) is made against the data. In contrast, an “early binding” schema generally means that data is transformed into structured data (i.e., become bonded to data structures) at an early stage, typically at data intake. Even though an early binding schema can provide homogeneous ways to access the data (because the data becomes structured after intake), using an early binding schema may risk losing potentially important information, information that may later become particularly important when it comes to determining unknown anomalies and threats. On the other hand, unstructured data in various data format presents a technical problem to a systematic way to process these data, especially in an application (e.g., security platform) where both time and accuracy are of the essence, because there is no convenient way to access the data using an uniform manner (i.e., using the same way to access select information in events that are in various data formats).
- In other words, the data intake and preparation stage introduced here does not put the event data into any kind of fixed structure; thus, even after the application of the various preparation or pre-processing techniques introduced here, the event data are still generally in the original form (more importantly, retaining all the raw event data) after the data intake and preparation stage. In the manner introduced here, the event view enables the security platform to both implement late binding and have a homogeneous way to access the unstructured event data.
- According to some examples, an access interface, also called an “event view”, can be implemented as a class (in object-oriented programming terms, e.g., a Java™ class). An event view includes a name (e.g., view identifier) for subscription purposes. An event view can include a number of fields to access certain attributes of an event; for example, the fields can be used by a machine learning model to identify which subset of the event data (e.g., serverIP, sourceIP, sourcePort, etc.) is the information that the model wants to receive. The event view can also include a number of methods (in object-oriented programming terms) and logic associated with the methods to access information generated based on attributes of an event; for example, a method can be used by a machine learning model to obtain a randomness of a URL in an event (e.g., getRandomnessOfURL( )), in which the logic associated with the method can include performing algorithmic operations to compute the URL against a predetermined set of URLs.
- Regarding the late binding aspect, the binding is made only when a field in the event view is referenced or a method in the event view is called. Optionally, an event view can include an input for controlling actions or operations that the logic associated with a method performs. Note that any programming-related term of art used herein may, but does not necessarily, have the same meaning as how the term may be used in a traditional programming sense; therefore, any term of art used herein is to be construed in the context of the present disclosure. In a number of implementations, the event views (e.g., the object-oriented classes) can be stored in a library. When an event view is called (e.g., by the model execution library, which may be a part of an event processing engine such as the CEP engine), the event view can be loaded by, for example, a known Java™ class loader.
- In various embodiments, the data intake and decoration stage includes an
event view adder 816 that can provide the event views by adding one or more view identifiers to the event data. A view identifier can be added, for example, as a field in the event data. The view identifiers allow a downstream entity (e.g., a complex event processing (CEP) engine) to receive the select information through the event views identified by the view identifiers. For example, the information in the model registry (discussed herein in other sections) for each machine learning model can designate one or more view identifiers to indicate the event views that are of interest to the model, to identify the events of interest and to receive select information about those events. In other words, the security platform provides a mechanism for the machine learning models to subscribe (e.g., using the model registry) to a group of event views in order to receive select information about the events of interest as each event of interest arrives. In a number of embodiments, the view identifiers are added to event data by theevent view adder 816 on a per-event basis. - More specifically, the view identifiers can be added by the
event view adder 816 to an event at any suitable moment during the data intake and preparation stage after thedata connector 802 retrieves or receives the event. Theevent view adder 816 can selectively add the view identifiers based on the event data, and more precisely, based on an event category to which the event belongs. Theevent view adder 816 can also determine the event category based on the type of machine that generated the event. For example, a firewall event can be an event category. Other example event categories include authentication, network, entity acquisition, and so forth. Shown inFIG. 13 is a table1300 including example event views available for event annotation in the data intake and preparation stage. - A firewall event example is illustrated in
FIG. 11 . When a Cisco RSA™ event (event data)1100 arrives, theevent view adder 816 first determines that the machine that generated the event is a Cisco RSA™ type (which may be defined in the configuration snippet by the administrator). Based on the machine type, theevent view adder 816 determines (e.g., by performing a lookup of the event code in the event against a list of Cisco RSA™ event codes) that the event belongs to a firewall event. Then, based on the configuration, theevent view adder 816 automatically adds to theevent 1100 two view identifiers, namely Network and Firewall. Note that the determination of which view identifiers should be added may be adjusted by the administrator (e.g., via the configuration file) based on the knowledge of the devices in the environment, such that the added view identifiers (and the corresponding event views) correctly reflect or correspond to the event category. - Thereafter, a downstream entity (e.g., the CEP engine) can run analytics on events using information about the plurality of events, for example, by using a
machine learning model 1104. Themachine learning model 1104 can subscribe to the event views in, for example, the model registry (e.g., by specifying corresponding view identifiers). In various embodiments, the subscription causes or allows the automatic routing of the select information to themachine learning model 1104. As previously described, the information accessible via the event views can include: information generated by logic included in the interface (e.g., through the methods in the interfaces), and/or a predefined subset of a complete set of the event data (e.g., through the fields). FIG. 12 shows a table1200 of example uniform access interfaces (“event views”) that can be implemented in the data intake and preparation stage.FIGS. 13A and 13B collectively show a table1300 that includes example anomalies that can be identified by machine learning models, as well as various event views and fields that can be used by the models to receive relevant information about the events for performing further analytics.- E. Sessionization
FIG. 14 shows a technique for session correlation, also called “sessionization,” that can be implemented in conjunction with other introduced techniques (e.g., identity resolution) in the data intake and preparation stage. In addition to what is discussed above with respect to identity resolution and device resolution, the data intake and preparation stage can further include a session tracker and a session resolver (not illustrated inFIG. 8 for simplicity).- Generally, sessionization can be created by using the same or similar data structure as that used for correlating users with devices in identity resolution. When the beginning or end of a session is detected, the event data associated with events from the session should be explicitly marked (e.g., as a field in the event data). Then, with the identity resolution and the device resolution techniques, all data events resolved to the user within the time window of an active session are associated with the session. The data intake and preparation engine can also mark certain events for session correlation, for example, events that may indicate a remote network login such as using a remote desktop protocol (RDP) or a secure shell (SSH) protocol to log into another device. Further, because a network login to a target device also creates a new session, the current session should be correlated with the new session. This correlation is referred to herein as session lineage. As shown in
FIG. 14 , an active directory (AD) session is first started on the machine with the IP address of 10.245.0.6 by user “zzsmssvcl” at time 10:13 PM. However, this user then started an SSH session to log into a new system as “root.” These two sessions, along with any anomalies detected during these two sessions, should all be attributed to the user “zzsmssvcl.” These two sessions are said to have session lineage, and can be correlated with each other using the sessionization technique introduced here. - More specifically, every session that is tracked be assigned with a session identifier (“sessionId”) and a correlation identifier (“correlationId”). The session identifier is used to identify the same session, and the correlation identifier is used to find other sessions that can possibly be in the same lineage. The session tracker is used to track the user sessions based on login/logout events, for example, from active directory (AD), virtual private network (VPN), and secure shell (SSH) logs. In some examples, the session tracker can create and maintain session states in a sessions database. The session tracker can also link sessions based on session linking events (e.g. an AD Event with code5156, which may correspond to a remote-desktop connection from machine-A to machine-B). The session resolver queries the session database using user, device and event time information from data event. Then, if there is any closely matching active session found in the session database (e.g., which can be determined based on the event's time), then a corresponding session identifier (e.g., “sessionId”) can be assigned to the data event.
- Details on how to perform the session tracking may vary depending on what existing techniques (such as those introduced here) are implemented in the data intake and preparation stage. Introduced here is a specific implementation where session correlation is performed after entity extraction, device resolution and identity resolution, and event view assignment. Therefore, instead of using specific attributes of data events from various data formats, the components that are logically located after event view assignment, which include the session tracker, can conveniently operate over sets of normalized attributes (e.g., from calling a specific event view for obtaining select information, introduced above). With the specific information based on the attributes on the event, the session tracker can inspect the event data to determine whether the event represented by the event data belongs to any session of interest (e.g., AD, VPN, and SSH). If affirmative, then the session tracker starts to track the event.
- For example, if a new event arrives, and an event type is set as “SessionStart” (e.g., by using an “association” event view), then that signifies that a new session is created. (For simplicity of discussion, assume that this session is a session of interest.) The session tracker then starts a tracking process by storing the new event in the session database. The session is stored with information about start time, user identifier (e.g., user account), device identifier (e.g., IP address), and sessionID (or perhaps a hash of the sessionID). According to the present embodiments, a derived property attribute “LinkContext” can also be generated from the event view, and the stored session also has its LinkContext stored along with session information. An example of a LinkContext of a session may be an IP address along with the user account used.
- With the new session created in the session database, a process thread starts to automatically look for any preexisting session in the session database that can be linked with the information provided by the new session. Whether to link two sessions is determined based on comparing three items: “from-session-link-context”, “to-session-link-context”, and “Link-Event time.” An example of the “from-session-link-context” is the combination of the IP address of and the user account used on a source machine from which the session is established. An example of the “to-session-link-context” is the combination of the IP address of and the user account used on a target machine to which the session is established. The “Link-Event time” is the time that the new session is recorded. Two existing sessions should be linked or correlated if the newly added session (1) matches a link event time range, (2a) has a match in one of its from-session-link-context or to-session-link-context with those of one existing session, and (2b) has at least a partial match in one of its from-session-link-context or to-session-link-context with those of another existing session.
- Similar to what is shown in
FIG. 14 , a practical example of this sessionization technique would be where a user uses user account A to log into a first machine of a first IP address, thereby creating a first session. Then, from the first machine, the same user uses user account B to log into a second machine of a second IP address, thereby creating a second session. The two existing sessions that are visible in the environment are that the first machine of the first IP address is logged in by user account A, and that the second machine of the second IP address is logged in by user account B. Without sessionization, the two sessions would not be linked or correlated to each other. Now, if the user actually uses remote desktop protocol (RDP) to login from the first machine to the second machine, then an RDP event is received. This RDP event can be used by the sessionization technique introduced here to discover that these two seemingly unrelated sessions are actually initiated by the same user and should be correlated. This is because, using the aforementioned mechanisms and assuming the RDP event's time is within the valid range, the RDP event would have a match with the first session in its “from-session-link-context”, and have a match with the second session in its “to-session-link-context.” - If a matching link is not found, then additional linking can be done by an offline session scanner process, which can run at a configured interval (e.g., every 15 minutes). The offline session linking is discussed further below. Note that, if identity resolution is performed, then the user account may be further transformed into a user identity to more accurately track the user for sessionization.
- In some situations, the sessionization process may receive an event indicating that a session may have been timed out. In such case, a new session entry can be created in the session database with a state “Timed Out.” For example, an already timed out session may be identified if the sum of a session start time and an expiration duration is less than the current system time. When a user log-out event is received, a corresponding session is marked as “User Ended” in the session database.
- Note that, in certain types of events, session ending events do not contain any specific context (e.g., lack a context that may be used as the LinkContext, and therefore unable to be used for matching purposes in the session database). For example, a certain type of AD event may contain only the from and to IP address of connection, but not the user account information. In such case, identity resolution (IR) lookup can help identify that existing session if the IR takes place before processing the session end event.
- In some embodiments, for effective session linking and user assignment, all events pass through the session assignment logic (e.g., the session tracker and the session resolver) in the data intake and preparation stage. Based on session-lookup context (e.g., using event views) in an event, the session assignment logic tries to identify if there is any open session at time T of the event. This can be achieved by locating those sessions with the time T included between their start time and end time. Such identified session can be associated with the event, and if such event triggers an anomaly (e.g., in downstream processing), then the anomalous event can be annotated or otherwise associated with the sessionId of the identified session. Such anomalies with the associated session(s) can be displayed in the user interface for review. Further, if a session identified for an event has other sessions linked to the session, then the current user on the event is replaced with the user of the root (source) session.
- Additionally, one aspect of the sessionization technique includes offline session linking. Specifically, if user login/logout events or events that indicate possible connection between two sessions are out of order, then session linking may be missed in real-time. To resolve this out of order data problem, a session linking process can run at a configurable intervals (e.g., configured in the configuration file). This process looks for any pending sessions that can be linked in the session database, and links the appropriate sessions together. Also, when this session linking process is executed, if any of the linked sessions is already associated with an anomaly, then the anomaly will also include the root session's sessionID.
- Certain embodiments introduced here include a machine learning-(ML-) based complex event processing (CEP) engine that provides a mechanism to process data from multiple sources in a target computer network to derive anomaly-related or threat-related conclusions in real-time so that an appropriate response can be formulated prior to escalation. A CEP engine is a processing entity that tracks and reliably analyzes and processes unbounded streams of electronic records to derive a conclusion therefrom. An “unbounded stream” in this context is an open-ended sequence of data that is continuously received by the CEP engine. An unbounded stream is not part of a data container with a fixed file size; instead, it is a data sequence whose endpoint is not presently known by the receiving device or system. In a computer security context, a CEP engine can be useful to provide real-time analysis of machine data to identify anomalies.
- The ML-based CEP engine described herein enables real-time detection of and response to computer security problems. For example, the input data of the ML-based CEP engine includes event feature sets, where each event feature set corresponds to an observable event in the target computer network.
- A conventional CEP engine relies on user-specified rules to process an incoming event to identity a real-time conclusion. User-specified rules benefit from its computational simplicity that makes real-time computation plausible. However, conventional CEP engines rely on people to identify known event patterns corresponding to known conclusions. Accordingly, conventional CEP engines are unable to derive conclusions based on patterns or behaviors that are not previously known to authors of the user-specified rules. Conventional CEP engines do not consider historical events. The added complexity (e.g., memory consumption and processing power requirement) associated with the inclusion of the historical events would likely overtax an otherwise resource-limited computer system that supports a conventional CEP engine.
- Certain embodiments introduced here include an ML-based CEP engine that utilizes distributed training and deliberation of one or more machine learning models. “Deliberation” of a machine learning model or a version of a machine learning model involves processing data through a model state of the machine learning model or version of the machine learning model. For example, deliberation can include scoring input data according to a model deliberation process logic as configured by the model state. The ML-based CEP engine processes event feature sets through the ML models to generate conclusions (e.g., security-related anomalies, security-related threat indicators, security-related threats, or any combination thereof) in real-time. “Real-time” computing, or “reactive computing”, describes computer systems subject to a processing responsiveness restriction (e.g., in a service level objective (SLO) in a service level agreement (SLA)). In real-time processing, conclusions are reached substantially immediately following the receipt of input data such that the conclusions can be used to respond the observed environment. The ML-based CEP engine continuously receives new incoming event feature sets and reacts to each new incoming event feature set by processing it through at least one machine learning model. Because of real-time processing, the ML-based CEP engine can begin to process a time slice of the unbounded stream prior to when a subsequent time slice from the unbounded stream becomes available.
- In some embodiments, the ML-based CEP engine is implemented as, or within,
analysis module 330 inFIG. 8 and couples to a data intake and preparation stage (data intake andpreparation stage 800 ofFIG. 8 ) that receives raw event data from a target-side computer system (e.g., multiple data sources from the target-side computer system). The target-side computer system is operated in a target computer network, which the ML-based CEP engine monitors for computer security issues. The target-side computer system collects machine data from the target computer network as the raw event data. The data intake and preparation stage creates an event feature set from raw event data pertaining to a single machine-observed event or a sequence of machine-observed events. The event feature set can include at least a subset of the raw event data; metadata associated with the raw event data; transformed, summarized, and/or normalized representation of portions of the raw event data; derived attributes from portions of the raw event data; labels for portions of the raw event data; or any combination thereof. To facilitate real-time processing in the ML-based CEP engine, the data intake and preparation stage can process, in real-time, the raw event data as it is received. The data intake and preparation stage and the ML-based CEP engine can store its inputs and outputs in non-persistent memory (e.g., volatile memory), such that all I/O operations of the ML-based CEP engine and the data intake and preparation stage operate on the non-persistent memory. Operations in non-persistent memory can help reduce the time lag of the ML-based CEP engine to satisfy the processing responsiveness restriction. In some embodiments, instead of the non-persistent memory, the inputs and outputs are stored in solid-state memory (e.g., one or more Flash drives), which is typically faster than hard disks and other non-solid-state data storage devices. - The ML-based CEP engine trains and retrains (e.g., updates) the machine learning models in real-time and applies (e.g., during the model deliberation phase) the machine learning models in real-time. Parallelization of training and deliberation enables the ML-based CEP engine to utilize machine learning models without preventing or hindering the formation of real-time conclusions. The ML-based CEP engine can be implemented on a distributed computation system (e.g., a distributed computation cluster) optimized for real-time processing. For example, a distributed computation system, such as Apache Storm™, can implement task parallelism instead of data parallelism. Storm is an open source distributed real-time computation system. In other embodiments, the distributed computation system can be implemented with data parallelism, such as Apache Spark™ or Apache Spark Streaming. Spark is an open source cluster computing framework. The distributed computation system can be coupled to other distributed components, such as a cluster-based cache (e.g., Redis), a distributed file system (e.g., HDFS), a distributed resource management system, or any combination thereof. The ML-based CEP engine can implement additional services to facilitate the distributed training and deliberation of machine learning models, such as a distributed messaging platform and a central service for distributed synchronization and centralized naming and configuration services.
- The ML-based CEP engine disclosed herein is advantageous in comparison to conventional CEP engines at least because of its ability to recognize unknown patterns and to incorporate historical data without overburdening the distributed computation system by use of machine learning models. Because the ML-based CEP engine can utilize unsupervised machine learning models, it can identify entity behaviors and event patterns that are not previously known to security experts. In some embodiments, the ML-based CEP engine can also utilize supervised, semi-supervised, and deep machine learning models.
- The ML-based CEP engine is further capable of condensing and summarizing historical knowledge by observing streams of events to train the machine learning models. This enables the ML-based CEP engine to include a form of historical comparison as part of its analysis without consuming too much data storage capacity. For example, the ML-based CEP engine can train a decision tree based on the historical events. In this case, the trained decision tree is superior to a user-specified rule because it can make predictions based on historical sequence of events. In another example, the ML-based CEP engine can train a state machine. Not only is the state machine trained based on a historical sequences of events, but it is also applied based on a historical sequence of events. For example, when the ML-based CEP engine processes event feature sets corresponding to an entity through the state machine, the ML-based CEP engine can track a number of “states” for the entity. These run-time states (different from a “model state” as used in this disclosure) represent the history of the entity without having to track every historical event involving the entity.
- The machine learning models enable the ML-based CEP engine to perform many types of analysis, from various event data sources in various contextual settings, and with various resolutions and granularity levels. For example, a machine learning model in the ML-based CEP engine can perform entity-specific behavioral analysis, time series analysis of event sequences, graph correlation analysis of entity activities, peer group analysis of entities, or any combination thereof. For example, the data sources of the raw event data can include network equipment, application service servers, messaging servers, end-user devices, or other computing device capable of recording machine data. The contextual settings can involve scenarios such as specific networking scenarios, user login scenarios, file access scenarios, application execution scenarios, or any combination thereof. For example, an anomaly detected by the machine learning models in the ML-based CEP engine can correspond to an event, a sequence of events, an entity, a group of entities, or any combination thereof. The outputs of the machine learning models can be an anomaly, a threat indicator, or a threat. The ML-based CEP engine can present these outputs through one or more output devices, such as a display or a speaker.
- Examples of entity-specific behavioral analysis include hierarchical temporal memory processes that employ modified probabilistic suffix trees (PST), collaborative filtering, content-based recommendation analysis, statistical matches in whitelists and blacklists using text models, entropy/randomness/n-gram analysis for uniform resource locators (e.g., URLs), other network resource locators and domains (AGDs), rare categorical feature/association analysis, identity resolution models for entities, land speed violation/geo location analysis, or any combination thereof. Examples of time series analysis of event sequences include Bayesian time-series statistical foundation for discrete time-series data (based on variable-memory Markov models and context-tree weighting), dynamic thresholding analysis with periodicity patterns at several scales, change-point detection via maximum-a-posteriori-probability (MAP) modeling, cross-correlation and causality analysis via variable-memory modeling and estimation of directed mutual information, outlier analysis, or any combination thereof.
- Examples of graph-based analysis of entity activities include command and control detection analysis, beaconing detector, device, IP, domain and user reputation analysis, lateral movement detector, dynamic fingerprinting for users/devices, or any combination thereof. Examples of peer group analysis of entities include grouping of entities based on similarity and page rank, social-neighborhood graph-based clustering, online distributed clustering, clustering for bipartite and generic graphs, or any combination thereof.
FIG. 15 is a block diagram of an ML-basedCEP engine 1500, in accordance with various embodiments. The ML-basedCEP engine 1500 receives anunbounded stream 1502 of event feature sets as its input. For example, the ML-basedCEP engine 1500 receives theunbounded stream 1502 from the data intake andpreparation stage 800 ofFIG. 8 . Each event feature set corresponds to a machine-observed event. The ML-basedCEP engine 1500 can train machine learning models using theunbounded stream 1502. The ML-basedCEP engine 1500 can also compute security-related conclusions (e.g., an anomaly, a threat indicator, or a threat as described in this disclosure) by processing at least a subset of the event feature sets (e.g., from the unbounded stream1502) through the machine learning models.- The ML-based
CEP engine 1500 includes acache component 1512, a distributedfilesystem 1514, amessaging platform 1518, and a distributedcomputation system 1520. The ML-basedCEP engine 1500 can include other data access systems. For example, the data access systems include a relational database (e.g., a structured query language (SQL) database), a non-relational database (e.g., HBase), a time series database, a graph database, or any combination thereof. The ML-basedCEP engine 1500 can include other resource management systems (e.g., a distributed coordination system, such as ZooKeeper). Thecache component 1512 can be non-persistent memory (e.g., volatile memory). Thecache component 1512 can be a distributed cache, such as a cluster-based cache or a peer-to-peer cache. For example, thecache component 1512 is implemented in REDIS, an open source key-value cache. - The distributed
filesystem 1514 stores data on a cluster of computing machines to provide high aggregate bandwidth across the cluster. The distributedfilesystem 1514 includes at least a name node and a plurality of data nodes. Each data node serves blocks of data over a network using a file access protocol (e.g., block protocol or file-based protocol) specific to the distributedfilesystem 1514. For example, the distributedfilesystem 1514 is implemented according to the Hadoop distributed file system (HDFS). - The distributed
filesystem 1514 stores amodel registry 1530, amodel store 1532, and a modelexecution code base 1534. In some embodiments, the modelexecution code base 1534 is part of themodel registry 1530. Themodel registry 1530 stores model type definitions. A model type definition can configure whether a distributed computation system is responsible for a model type and can configure a model training workflow (i.e., a workflow of how to train machine learning models of a model type) and a model deliberation workflow (i.e., a workflow of how to apply machine learning models of a model type) of the model type. Themodel store 1532 stores model states that represent machine learning models or versions of the machine learning models. A model state, described further below, is a collection of numeric parameters in a data structure. A model training process thread produces and updates a model state. A model deliberation process thread is configured by a model state to process event feature sets into security-related conclusions. The modelexecution code base 1534 stores process logics for running model-related process threads. In some embodiments, the modelexecution code base 1534 also stores process logics associated with event views. - In some embodiments, the content of the distributed
file system 1514 can be shared with another distributed computation system (e.g., a batch data processing engine discussed in various parts of this disclosure). For example, a model state stored in themodel store 1532 representing a machine learning model or a version of a machine learning model can be shared with the other distributed computation system. For another example, one or more model types in themodel registry 1530 and the modelexecution code base 1534 can be shared with the other distributed computation system. - The
cache component 1512 stores anevent feature store 1540 and a security-relatedconclusion store 1542. Thecache component 1512 can cache (e.g., the most recently used or most recently received event feature sets) from theunbounded stream 1502 in theevent feature store 1540. Thecache component 1512 can cache the security-related conclusions (e.g., the most recently produced or the most recently used) in the security-relatedconclusion store 1542. The ML-basedCEP engine 1500 can compute the security-related conclusions by processing the event feature sets through the machine learning models. In some embodiments, thecache component 1512 stores copies or references to entries in themodel store 1532. In some embodiments, thecache component 1512 stores copies or references to entries in themodel registry 1530. In some embodiments, thecache component 1512 stores copies or references to at least a portion of the modelexecution code base 1534. - The
messaging platform 1518 provides a computer application service to facilitate communication amongst the various system components of the ML-basedCEP engine 1500 and between external systems (e.g., the data intake and preparation stage) and the ML-basedCEP engine 1500. For example, themessaging platform 1518 can be Apache Kafka, an open-source message broker utilizing a publish-subscribe messaging protocol. For example, themessaging platform 1518 can deliver (e.g., via self-triggered interrupt messages or message queues) the event feature sets from theunbounded stream 1502 to model-related process threads (e.g., one or more of model training process threads, model deliberation process threads, and model preparation process threads) running in the distributedcomputation system 1520. Themessaging platform 1518 can also send data within thecache component 1512 or the distributedfilesystem 1514 to the model-related process threads and between any two of the model-related process threads. - For the ML-based
CEP engine 1500, the distributedcomputation system 1520 is a real-time data processing engine. The distributedcomputation system 1520 can be implemented on the same computer cluster as the distributedfilesystem 1514. In some embodiments, an ML-based batch processing engine runs in parallel to the ML-based CEP engine. In those embodiments, the ML-based batch processing engine can implement a distributed computation system configured as a batch processing engine (e.g., using a data parallelism architecture). The system architecture of the ML-based batch processing engine can be identical to the ML-basedCEP engine 1500, except for the distributed computing platform engine running on the distributed computation system, and the ML-based batch processing engine's inputs including batch data containers of event feature sets (instead of an unbounded stream of incoming event feature sets). - The distributed
computation system 1520 can be a distributed computation cluster. The distributedcomputation system 1520 coordinates the use of multiple computing nodes1522 (e.g., physical computing machines or virtualized computing machines) to execute the model-related process threads. The distributedcomputation system 1520 can parallelize the execution of the model-related process threads. The distributedcomputation system 1520 can implement a distributed resource manager (e.g., Apache Hadoop YARN) and a real-time distributed computation engine (e.g., Storm or Spark Streaming) to coordinate itscomputing nodes 1522 and the model-related process threads running thereon. The real-time distributed computation engine can be implemented based on a task parallel architecture. In an alternative embodiment, the real-time distributed computation engine can be implemented based on a data-parallel architecture. - Each
computing node 1522 can implement one or more computation workers (or simply “workers”)1526. A computation worker is a logical construct of a sandboxed operating environment for process threads to run on. A computation worker can be considered a “processing node” of the computing cluster of the distributedcomputation system 1520. In some implementations, at least one of thecomputing nodes 1522 implements a cluster manager1528 to supervise thecomputation workers 1526. Each of thecomputation workers 1526 can execute one or more model-related process threads. In some implementations, acomputation worker 1526 only executes one type of model-related process thread, where process threads of that type share the same input data. FIG. 16 is a block diagram illustrating an architectural framework of a machine learning model, in accordance with various embodiments. Amachine learning model 1600 corresponds to amodel type 1602. The ML-basedCEP engine 1500 can implement multiple machine learning models of the same model type. For example, a model type can define a workflow for entity-specific models to be trained and applied. In this example, the ML-basedCEP engine 1500 trains as many models of the model type as there are known entities. Themodel type 1602 is defined by amodel type definition 1700 stored in themodel registry 1530.FIG. 17 is a block diagram illustrating an example of themodel type definition 1700. Themodel type definition 1700 includes various configurations of how a machine learning model is to be trained or applied. Themodel type definition 1700 includes acode reference 1702 to amodel execution code 1610 in the modelexecution code base 1534. Themodel type definition 1700 includes amodel type identifier 1704, amodel type name 1706, aprocessing mode specifier 1708 for the model training workflow, aprocessing mode specifier 1710 for the model deliberation workflow, a model input type configuration1712 (e.g., one or more subscriptions to one or more event views as described in this disclosure), amodel type topology 1714, or any combination thereof. A processing mode specifier specifies a processing mode, such as a real-time processing mode or a batch processing mode.- The model input type configuration1712 specifies what event views (e.g., described in this disclosure) that the
model type 1602 subscribes to. The event feature sets from theunbounded stream 1502 can be labeled with event view labels corresponding to the event views. The ML-basedCEP engine 1500 can select the event feature sets received from theunbounded stream 1502 based on event view labels of the event feature sets (e.g., selecting only the event feature sets based on the event view labels corresponding to the event view subscriptions in the model input type configuration1712). The ML-basedCEP engine 1500 can call and execute an access interface associated with an event view subscription to organize the selected event feature sets and provide format/bind at least a subset of features within the selected event feature sets to a preferred data structure for a model-related process thread. The ML-basedCEP engine 1500 can provide (e.g., stream via a data pipeline) the selected and formatted event feature sets to a model-related process thread of themodel type 1602. - The
model type topology 1714 specifies how the ML-basedCEP engine 1500 groups and distributes model-specific process threads to, for example, thedifferent computation workers 1526 in the distributedcomputation system 1520. Themodel type topology 1714 also specifies how the ML-basedCEP engine 1500 groups and distribute the input data for the model-specific process threads of thesame model type 1602. In some embodiments, the ML-basedCEP engine 1500 groups and divides the input data for the model-specific process threads into mutually exclusive partitions. In other embodiments, the ML-basedCEP engine 1500 groups the input data for the model-specific process threads into groups that have at least some overlap. For example, themodel type topology 1714 can specify an entity type (e.g., a type associated with users, devices, systems, applications, process threads, network resource locators, or any combination thereof). In one specific example, if themodel type topology 1714 specifies users as the entity type, the ML-basedCEP engine 1500 groups the selected event feature sets by user groups. For example, the ML-basedCEP engine 1500 can divide all known user entities into user groups, and divide the selected event feature sets by the user group or groups to which each event feature set corresponds. Consequently, the distributedcomputation system 1520 can assign acomputation worker 1526 to process event feature sets corresponding to each group/partition. - One or more model states stored in the
model store 1532 represent themachine learning model 1600. If the ML-basedCEP engine 1500 trains and applies a single version of themachine learning model 1600, then a single model state represents themachine learning model 1600. In embodiments where the ML-basedCEP engine 1500 trains multiple versions of themachine learning model 1600, eachmodel version 1604 corresponds to a different model state stored in themodel store 1532. In such embodiments, a group of model states corresponds to different model versions representing different training stages of themachine learning model 1600. In this case, the group of model versions is part of the samemachine learning model 1600 because these model states are all trained for a specific entity or a specific purpose. For example, a machine learning model can be a label used to refer to the group of model states that are specifically trained by event feature sets corresponding to a single user and applied to event feature sets corresponding to that single user. Each model state of each model version can correspond to a different sequence of event feature sets used to train the model state (herein the different sequences of event feature sets correspond to different “training stages”). For another example, a machine learning model can be a label used to refer to the group of model states that are specifically trained by a specific type of anomalies and applied to that type of anomalies. - A model state is the output of a model
training process thread 1606. The ML-basedCEP engine 1500 instantiates a modeldeliberation process thread 1608 based on the model state. The modeltraining process thread 1606 and the modeldeliberation process thread 1608 can be referred to as “model-specific process threads.” The ML-basedCEP engine 1500 can instantiate the model-specific process threads in the distributedcomputation system 1520. For simplicity, in parts of this disclosure, “instantiating” a model refers to instantiating the modeldeliberation process thread 1608 for a particular version of a machine learning model. Also for simplicity, in parts of this disclosure, “processing” input data “through” a model refers to processing the input data by the modeldeliberation process thread 1608 corresponding to the model. - The
model execution code 1610 includesmodel program logic 1612 that describes data structures associated with model-related process threads and logic of the model-related process threads. Themodel program logic 1612 references modeltraining process logic 1616 and model deliberation process logic1618. The modeltraining process logic 1616 defines how the modeltraining process thread 1606 is to transform input data (e.g., one or more event feature sets) into a model state or an update to the model state. The model state is representative of a machine learning model or at least a version of a machine learning model (when there are multiple versions). As more input data is provided to the model training thread, the model training thread can update the model state. The model deliberation process logic1618 defines how input data (e.g., one or more event feature sets) to a model deliberation process thread, configured by a model state, is to be transformed into security-related conclusions. - The
model execution code 1610 also includes amodel program template 1622, a modeltraining program template 1626, and a modeldeliberation program template 1628. These program templates contain process logics that are shared amongst all types of machine learning models. These program templates also impose restrictions such that an author of themodel program logic 1612, the modeltraining process logic 1616, and the model deliberation process logic1618 creates consistent process logics that can function in the ML-basedCEP engine 1500. For example, themodel program template 1622 can impose a restriction that any model program logic, such as themodel program logic 1612, has to reference at least a model training process logic and a model deliberation process logic. - The architectural framework described in
FIG. 16 enables real-time registration of a new model type. Real-time registration enables a network security administrator to deploy updates to the ML-basedCEP engine 1500 or an ML-based batch processing engine without having to shut down the engines or any model-related process threads running thereon. The program templates and the workflow configurations using themodel type definition 1700 provide a formal way to train and apply machine learning models. The use of the distributedfilesystem 1514 facilitates persistence of model states while the model-related process threads are running in a distributed manner. - The ability to label the
model version 1604 to a model state in themodel store 1532 enables the ML-basedCEP engine 1500 to maintain lineage between training data sets for a machine learning model and the model states produced therefrom. The versioning of the machine learning models enables simultaneous training of different machine learning models using the same data to produce model states corresponding to different windows of training data sets. The simultaneous training of the machine learning models further enables the ML-basedCEP engine 1500 to “expire” model versions that have been trained with outdated data. FIG. 18 is a block diagram illustrating a system architecture for implementing the distributedcomputation system 1520, in accordance with various embodiments. The distributedcomputation system 1520 implements a cluster resource manager1802 (e.g., YARN). The cluster resource manager1802 can function as an operating system for running data processing platform engines. For example, the cluster resource manager1802 can implement a distributed computing platform engine1804 (e.g., a real-time distributed computation platform, such as Storm or Spark Streaming). The processes running on the distributedcomputing platform engine 1804 can access various data access systems in adata access layer 1806. For example, thedata access layer 1806 can provide access to a relational database, a graph database, a non-relational database, a time series database, thecache component 1512, the distributedfilesystem 1514, or any combination thereof.- The distributed
computing platform engine 1804 can implement amodel execution engine 1808. Themodel execution engine 1808 can then initialize one or more model-related process threads1810 (e.g., a model preparation thread, one or more model training threads and/or model deliberation threads) managed by the distributedcomputing platform engine 1804. Each model-relatedprocess thread 1810 is a sequence of program instructions related to training, deliberation, or preparation of a machine learning model. Each model-relatedprocess thread 1810 can be managed independently by the distributedcomputing platform engine 1804. For example,method 1900 illustrates a potential workflow of a model preparation thread;method 2000 illustrates a potential workflow of a model training thread, andmethod 2100 illustrates a potential workflow of a model deliberation thread. Thedata access layer 1806 can enable the model-relatedprocess threads 1810 to access model type definitions in themodel registry 1530, model states in themodel store 1532, and event feature sets in thecache component 1512. FIG. 19 is a flow diagram illustrating amethod 1900 to execute a model preparation process thread, in accordance with various embodiments. Themodel execution engine 1808 reads themodel registry 1530 to determine which model types are assigned to the ML-based CEP engine1500 (e.g., as opposed to an ML-based batch processing engine). Themodel execution engine 1808 executes the model preparation process thread. This process similarly applies to the model execution engine of the ML-based batch processing engine. Themodel execution engine 1808 running on the distributedcomputation system 1520 extracts the parameters of each model type definition to configure the workflows of that model type. Themodel execution engine 1808 can instantiate a model preparation process thread in the ML-basedCEP engine 1500 for each model type that has either the processing mode specifier fortraining 1708 or theprocessing mode specifier 1710 designating the real-time processing mode. Each model preparation process thread can initiate multiple model-specific process threads corresponding to its model type. Accordingly, the ML-basedCEP engine 1500 can be concurrently training and/or deliberating multiple machine learning models of different model types.- At
step 1902, the model preparation process thread selects a subset of event feature sets in thecache component 1512 for the model type. The model preparation process thread can select the subset from the most recent event feature sets (e.g., a real-time time slice) that are yet to be processed by themodel execution engine 1808 or any other model preparation process threads. For example, the model preparation process thread selects and filters the event feature sets based on event view labels in the event feature sets. In some embodiments, the model preparation process thread can request the subset from themessaging platform 1518. The model preparation process thread can select the subset that has event view labels corresponding to event view subscriptions in the model type associated with the model preparation process thread. The model input type configuration1712 of the model type specifies the event view subscriptions. Atstep 1904, the model preparation process thread can format the selected subset into a model-type-specific format. A binding process specified by one or more access interfaces (described above in this disclosure) respectively associated with the event view subscriptions can configure the model-type-specific format. In some embodiments, the formatting includes removing some feature fields from the selected subset. - At
step 1908, the model preparation process thread can assign (e.g., partition) the formatted subset of event feature sets into data groups (also referred to as “data partitions”) according to themodel type topology 1714 of the model type. The model type can correspond to an entity type (e.g., users, devices, systems, resource locators, applications, process threads, or anomalies) or a purpose type (e.g., for global beaconing detection). A global purpose-specific model type can have a single model training process thread and/or a single model deliberation process thread. For example, the model preparation process thread can determine the number of known entities of the entity type. The model preparation process thread can partition the event feature sets in the formatted subset into a number of data groups corresponding to the number of available computation workers for the model type. Each data group corresponds to the number of entities equal to the total number of known entities divided by the number of data groups. - For example, the
model type topology 1714 may specify a user level topology. The model preparation process thread can request the total number of users from the target-side computer system. Based on the total number of available computation workers in the distributedcomputation system 1520, themodel execution engine 1808 can evenly assign computation workers to each model type. Then, the model preparation process thread can assign a number of data groups based on the available computation workers for its model type. Each available computation worker can be assigned a data group. For example, there can be five available computation workers and 20 known users. In this example, the model preparation process thread can assign a data group corresponding to 4 users to each computation worker. Event feature sets corresponding to these 4 users would be part of the data group. - In some embodiments, the model preparation process thread can perform a consistent hash on the formatted subset of event-based features. The data group assignment can be based on the consistent hash, such as distributed hash tables (DHTs). Consistent hashing is a kind of hashing such that when a hash table is resized and consistent hashing is used, only K/n keys need to be remapped on average, where K is the number of keys, and n is the number of slots. In contrast, in most traditional hash tables, a change in the number of array slots causes nearly all keys to be remapped. The consistent hashing concept applies to DHTs. DHTs use consistent hashing to partition a keyspace among a distributed set of nodes (e.g., the computation worker corresponding to the data group), and additionally provide an overlay network that connects nodes such that the node responsible for any key can be efficiently located.
- Optionally, at
step 1910, the model preparation process thread sorts each data group of the formatted subset (e.g., by timestamps of the formatted event feature sets). This step is executed if the order of the formatted event feature sets is part of model training or model deliberation. For example, time sequence prediction models, such as probabilistic suffix trees (PSTs), are trained based on an ordered sequence of event features. The data intake and preparation stage may not have received raw event data in temporal order from the target-side computer system. The target computer network may not have recorded the raw event data in temporal order. In these cases,step 1910 can ensure, via sorting, that groups of the formatted subsets are in order. - At
step 1912, the model preparation process thread instantiates one or more model-specific process threads to at least a subset of thecomputation workers 1526 according to themodel type topology 1714. In some embodiments, each computation worker runs only model-specific process threads of one model type. In some embodiments, each computation runs only model-specific process threads of one model type and either only model training process threads (e.g., corresponding to a model training workflow) or only model deliberation process threads (e.g., corresponding to a model deliberation workflow). In the ML-basedCEP engine 1500, when theprocessing mode specifier 1708 corresponds to a real-time processing mode, the model preparation process thread can schedule one or more model training process threads to run on the subset ofcomputation workers 1526. Also in the ML-basedCEP engine 1500, when theprocessing mode specifier 1710 corresponds to a real-time processing mode, the model preparation process thread can schedule one or more model deliberation process threads to run on the subset ofcomputation workers 1526. In the ML-based batch processing engine, when theprocessing mode specifier 1708 corresponds to a batch processing mode, the model preparation process thread can schedule one or more model training process threads to run on a subset of computation workers in a batch processing cluster. Also in the ML-based batch processing engine, when theprocessing mode specifier 1710 corresponds to a batch processing mode, the model preparation process thread can schedule one or more model deliberation process threads to run on a subset of computation workers in the batch processing cluster. - The model preparation process thread can determine, based on the
model type topology 1714, how many model training process threads of the model type to instantiate for the model training workflow and/or how many model deliberation process threads for the model deliberation workflow. For example, themodel type topology 1714 can correspond to an entity type (e.g., users, devices, applications, process threads, network resource locators, systems, anomalies, etc.) and/or a purpose-type. The number of model-specific process threads (e.g., training or deliberation) can match the number of known entities of the entity type. The model preparation process thread can identify the known entities and instantiate a model-specific process thread corresponding respectively to the known entities. The model preparation process thread can query the target-side computer system in the target computer network for the identities and/or the total number of the known entities. In some embodiments, the target-side computer system provides this information on its own and this information is saved in thecache component 1512 or the distributedfilesystem 1514. - At
step 1914, the model preparation process thread generates group-specific data streams to the computation workers of each model-specific process thread instantiated instep 1912. The group-specific data streams correspond to the assigned data groups instep 1908. The model preparation process thread can configure themessaging platform 1518 to send appropriate event feature sets in the data group through the group-specific data streams. The model preparation process thread can executesteps - Topology
- In several embodiments, the ML-based
CEP engine 1500 determines the assignments of the group-specific data streams and the model-specific process threads to thecomputation workers 1526 based on themodel type topology 1714. These assignments can be referred to as topology-based assignments. The topology-based assignments can be used to optimize model-specific process threads regardless of whether the ML-basedCEP engine 1500 or an ML-based batch processing engine is used as an execution platform. Here, the model type topology is decoupled from the execution platform unlike traditional methodologies. The topology-based assignments maintain a directed acyclical graph (DAG) structure that allows for dynamic execution of model-specific process threads and management of the input data dependencies of these model-specific process threads. For example, the DAG approach enables model-specific process threads to freely move, start, or stop amongst thecomputation workers 1526 based on the performance of the machine learning models. The DAG approach further enhances security, scalability (e.g., the ability to employ services for caching, the load-balancing, replication, or concentration of data streams), and modularity (e.g., updates to any particular model-specific process thread only affect a limited portion of the computation workers1526). The DAG approach enables process replication, data redistribution, proxy processes or groups of proxy processes, integration of subsystems, and/or redundant connections to be added in the distributedcomputation system 1520. FIG. 20 is a flow diagram illustrating amethod 2000 to execute a model training process thread, in accordance with various embodiments. A computation worker executes the model training process thread. In some embodiments, the computation worker execute multiple model training process threads associated with a single model type. In some embodiments, the computation worker executes multiple model-specific process threads associated with a single model type. In some embodiments, the computation worker executes multiple model-specific process threads associated with different model types. If a model state corresponding to the model training process thread is not already in themodel store 1532, atstep 2002, the model training process thread processes a time slice of event feature sets, from the group-specific data stream described instep 1914 ofFIG. 19 , to produce a model state in themodel store 1532 according to the modeltraining process logic 1616. The time slice can correspond to an event or a sequence of events observed at the target computer network. The time slice can be the most recent event feature set or sequence of event feature sets. The model training process thread can save the model state in the model store1532 (e.g., in the distributedfilesystem 1514 or the cache component1512).- At
step 2004, the model training process thread continuously retrains the model state as the group-specific data stream provides additional event feature sets. In several embodiments, the modeltraining process logic 1616 describes a single-pass training process logic. That is, the model training operates without recursion or iteration over the same input data. In some embodiments, the modeltraining process logic 1616 involves an incremental training process. For example, the model training process thread isolates a portion of the model state affected by the time slice of event feature sets and re-trains only the portion of the model state. Model types with incremental property enable the ML-basedCEP engine 1500 to execute in real-time because of reduction in resource consumption during model training. - At
step 2006, the model training process thread calls a model readiness logic in the modeltraining process logic 1616 to determine when the model state has sufficient training. The model readiness logic can include measuring how many event feature sets have been used to train the model state; measuring how long the model state has been in training in real-time; whether the model state is converging (i.e., not changing within a threshold percentage despite additional training); or any combination thereof. Different model types can have different model readiness logics. Atstep 2008, when the model readiness logic determines that the model state has sufficient training, the model training process thread marks the model state for deployment. FIG. 21 is a flow diagram illustrating amethod 2100 to execute a model deliberation process thread, in accordance with various embodiments. A computation worker executes the model deliberation process thread. In some embodiments, the computation worker execute multiple model training process threads associated with a single model type. In some embodiments, the computation worker execute multiple model-specific process threads associated with a single model type. In some embodiments, the computation worker execute multiple model-specific process threads associated with different model types. Atstep 2102, the model deliberation process thread processes the most recent time slice from the group-specific data stream to compute a score associated with the most recent time slice. The most recent time slice can correspond to an event or a sequence of event observed at the target computer network. In some embodiments, the group-specific data stream used by the model deliberation process thread is also used by a corresponding model training process thread for the same entity. That is, the model training process thread can train a model state of an entity-specific machine learning model by processing a previous time slice of the group-specific data stream. Themodel execution engine 1808 can initiate the model deliberation process thread based on the model state while the model training process thread continues to create new versions (e.g., new model states). In some embodiments, the model deliberation process thread can reconfigure to an updated model state without pausing or restarting.- At
step 2104, the model deliberation process thread generates a security-related conclusion based on the score. The security-related conclusion can identify the event or the sequence of events corresponding to the time slice as a security-related anomaly, threat indicator or threat. In one example, the model deliberation process compares the score against a constant threshold and makes the security-related conclusion based on the comparison. In another example, the model deliberation process compares the score against a dynamically updated baseline (e.g., statistical baseline) and makes the security-related conclusion based on the comparison. - At
step 2106, the model deliberation process thread aggregates the security-related conclusion into the security-relatedconclusion store 1542. The aggregation of the security-related conclusions can be used in an analytic platform of the ML-basedCEP engine 1500. In some embodiments, the security-relatedconclusion store 1542 is backed up to the distributedfile system 1514. Optionally, atstep 2108, the model deliberation process thread publishes the security-related conclusion to themessaging platform 1518, such that another model deliberation process thread or model training process thread can utilize the security-related conclusion. - When the security-related conclusion indicates that a potential security breach (e.g., a threat or a threat indicator) has occurred, at step2110, the model deliberation process thread can generate a user interface element to solicit an action command to activate a threat response. In one example, the user interface element triggers the action command for sending a message to the target-side computer system to demand termination of a problematic application, blocking of specific network traffic, or removal of a user account. In some embodiments, at step2112, the model deliberation process thread can generate a user interface element to accept feedback from a user to confirm or reject the security-related conclusion. The
model execution engine 1808 can provide the feedback to a model training process thread to update the model state used to configure the model deliberation process thread. - The model deliberation process thread can check, at
step 2114, its own performance health. For example, the model deliberation process thread can compare the computed score or the generated security-related conclusion against that of other model deliberation process threads to determine if there are significant deviations or biases. The model deliberation process thread can also check to see if there is an unusual bias in its production of security-related conclusions. For example, if more than a threshold percentage of its security-related conclusions correspond to anomalies or threats, then the model deliberation process thread sets its own health status to failure. Based on the conclusion instep 2114, the model deliberation process thread can decommission itself atstep 2116. In some embodiments, a separate process thread can performsteps - The
method 2100 enables dynamic deployment of a model state. For example, the machine learning model associated with the model deliberation process thread can have multiple versions.Step 2102 can initially be configured by a model state corresponding to an active version of the machine learning model. However, while the active version is used to configure the model deliberation process thread, a model training process thread can train another version (e.g., another model state) of the machine learning model in parallel. When this other version is ready for active deployment (e.g., has sufficient training), the model deliberation process can “live swap” in the other version as the active version (e.g., to compute the score for subsequent time slices from the group-specific data stream). Live swapping involves re-configuring the model deliberation process thread with the other model state without terminating the model deliberation process thread. - In some embodiments, the security platform includes two event processing engines in different paths—a real-time path and a batch path. The event processing engine in the real-time path operates in a real-time mode to process unbounded, streaming data that enters the security platform. The event processing engine in the batch path operates in a batch mode to process batches of stored, historical event data. Because the batch event processing engine tends to have more time to process data but also tends to handle a larger amount of data (e.g., stored in HDFS™), it is desirable for an event processing engine implemented on the batch path be able to (1) interact with the distributed data cluster that stores the data, instead of moving or copying the data into the platform; and (2) utilize various programming models that are optimized for processing and generating large data sets in a parallel, distributed manner on a computer cluster. One example of such a programming model is MapReduce™.
- Therefore, in one aspect, one of the data connectors that can be used by the
security platform 300 introduced here is a specialized connector (e.g., the HDFS™ connector) that can issue instructions (e.g., a query), operations, or otherwise interact with the non-relational database that stores the data (e.g., HDFS™). In some embodiments, because the downstream processing may be dependent on the order of the events (e.g., for building a behavioral baseline for a user or a device), the HDFS connector can to retrieve the stored event data in the order that the event takes place. - In another aspect, the machine learning models utilized by the batch event processing engine can be “reducible,” in order to be compatible with parallel, distributed types of operations (e.g., MapReduce™ operations). As used herein, a reducible model is a model that can be mapped into multiple copies for processing data. Each copy of the model only processes (e.g., for training and/or scoring) a particular subset of a larger set of data. Then, all the information generated by the copies of the model can be reduced back to the model, achieving the same result as if a single copy of the model has processed the entire data set. That is, a reducible model can process data in a parallel manner. Note that, depending on the model, some models may be reducible in their training phase but not their scoring phase, some models may be reducible in their scoring phase but not their training phase, and some models may be reducible in both training and scoring phases.
- Generally, the batch event processing engine introduced here can cooperate with the HDFS™ connector to access data stored in the HDFS™. To achieve this functionality, in some embodiments, the platform can include (e.g., in the batch path) a job controller and a directory catalog. The job controller can function as the batch event processing engine's manager and works with the connector. For example, the job controller can cause the connector to run a query against the HDFS database, and select a set of the returning event data to be processed by the batch event processing engine. The query can, for example, specify a time range, and/or specify that the result should be ordered by event time.
- In addition, in some embodiments, certain kinds of log files are preferably to be processed before others, and the HDFS connector can select to retrieve those log files that need to be processed first. Typically, data of events that have richer information can be retrieved first in order to increase the accuracy of the overall security analysis. For example, to enable identity resolution, device resolution, and session tracking, those log files with device information (e.g., DHCP) are preferably processed first, followed by log files which associate user data with devices (e.g., AD or VPN), followed by all other files. Additionally or alternatively, the query that is sent by the connector can specify that the retrieved files (e.g., representing events) should be ordered by their formats (e.g., DHCP, then AD/VPN, then others).
- In response to the retrieved data, the job controller then launches a job for the batch event processing engine (e.g., in Spark™) with the retrieved files, tracks the analysis progress, and marks the events as analysis completed or analysis failed. Once the analysis is completed, then the job controller can perform other tasks, such as exporting the result of identity resolution (e.g., into Redis™), exporting the time-series data (e.g., into OpenTSDB™), or pushing the anomalies raised by the batch event processing engine into a messaging system (e.g., Kafka™).
- The job controller can start the aforementioned file retrieval process based on a time schedule. For example, the file retrieval process can be set to run every hour, every N hours, every N days, and so forth. After the connector retrieves the files, the batch of files is passed to the job controller, which in turn initiates the batch event processing engine to analyze the files.
- The directory catalog is a database (e.g., coupled to the HDFS) that enables the job controller (working with the connector) to determine which files to parse and the order in which the files get parsed. The following is a specific example of how a specialized connector (e.g., the HDFS connector) introduced here can interact with a distributed database storage system (e.g., HDFS™) to retrieve files. In this example, the connector can determine a time for the first event in a file in the HDFS. The file records a number of events. The time for the first event can be used by the job controller to determine whether it should retrieve this file and process it for anomaly/threat detection.
- When the connector (e.g., HDFS connector) is activated to retrieve files of a particular time range (e.g., each file representing a number of events that take place within the particular time range), the connector first refers to a table in the database (“directoryCatalog”) to check if there is any row in the table (e.g., indicating a file) that still needs to process (e.g., which may be a leftover from a previous run). The connector also stores the last time it was run in the database (“lastRunTime”).
- If the connector does not find any files in the directoryCatalog, then the connector crawls the currently specified directory (that corresponds to the particular time range), to see if there is any file to process. When the connector encounters a file, the connector retrieves a modification time (“mtime”) of the file, and discards the file if the file is earlier than the lastRunTime. Otherwise, the connector parses the file to get the time of the first event from the file. In one example, the connector can parse the file with a parser that corresponds to the file's data format, and extract only the time from the event. In this manner, the connector can continue to process a few select events in the file and determine if the events are recorded in the file in an ascending order (or in any order).
- Thereafter, if the connector determines that the events are recorded in an ascending order (within a tolerance of a few seconds), then the connector can stop parsing and return the time of the first event. Conversely, if the events are stored in a descending order, the connector then seeks toward (e.g., to a few kilobytes short of) the end of the file and retrieves the time of the first event from there. In the case that the connector determines that the events are recorded in an unsorted manner, the connector parses the entire file and returns the lowest time found as the event time of the first event recorded in the file. Then, the connector adds an entry in the database with the filename, time of the first event and other status (e.g., retrieved).
- The batch event processing engine can perform analysis based on information that is not available in the real-time path. An example of such information is the composite relationship graph (which is described in greater detail in a section below). Accordingly, the batch event processing engine can process a projection (portion) of the composite graph in utilizing some of the machine learning models.
- In some embodiments, the batch event processing engine can first locate the composite relationship graph that is associated with the historic event data. Then, based on the requirement of a particular machine learning model, the batch event processing engine can obtain a projection of the composite relationship graph. The composite relationship graph can include information from the data intake and preparation stage (e.g., per-event relationship graph) and information generated by the real-time event processing engine processing the unbounded stream of event data (e.g., detected anomalies, which can be added to the per-event relationship graph of the anomalous event).
- In some examples, a projection of the composite relationship graph includes a graph of users associated with machines, to facilitate tracking (by the particular machine learning model) of user lateral movement. In some examples, the projection includes a graph that associates entities identified as having security-related issues to facilitate correlating (by the particular machine learning model) user anomalies so as to identify sophisticated threats. In some examples, the projection includes a graph of website visitation activities of users to facilitate identification (by the particular machine learning model) of commonly accessed websites by potentially security-compromised users. More details on the models that can utilize projections of the composite relationship graph are discussed below with respect to anomaly and threat models.
- As discussed above, one of the features of the security platform introduced here is the capability to share information between different analytics entities (including, for example, an event processing engine such as the CEP engine). Information or knowledge sharing in this manner can be especially useful in detecting unknown security-related anomalies and threats.
- Among other reasons, the big-data based, highly modularized characteristics of the security platform architecture introduced here present many opportunities for different components to benefit from intelligence sharing. For example, in certain implementations, as mentioned above, the security platform can include at least two event processing engines—one event processing engine operating in a real-time mode to process unbounded, streaming data that enters the security platform, and the other event processing engine operating in a batch mode to process batches of historical event data. In another example, a security platform deployed in an environment (e.g., an organization or an enterprise) may communicate with another security platform deployed in a different environment. All these event processing engines, because of their different operating modes, different data input, and/or different deployed environment, can potentially benefit from the knowledge gained by each another.
- Thus, with the aforementioned discussion regarding the CEP engine's functionalities in mind, introduced here is a particular way to configure the security platform to further enhance anomaly and threat detection. Specifically, the security platform's architecture is configured so that the model store (which stores one or more groups of model states, each group corresponding to versions of an entity-specific or purpose-specific machine learning model) that is used in the security platform can be shared. As used herein, the phrase “sharing a model state” means more than one engine sharing the same version of a model. This notion should be distinguished from the notion of “sharing a model type,” which implies that more than one engine can share the model registry (which stores the model type) in the security platform. Sharing a model type can enable two engines to use or produce machine learning models that have the same model execution logic (e.g., training logic and/or deliberation logic) for different purposes. The general notion of “sharing a model” can be referring to either or both of these notions, whichever is made apparent by the context.
- By allowing different engines to access the model store in the security platform, this configuration enables the real-time event processing engine and the batch event processing engine to share a model state of a particular machine learning model. Then, for example, a first engine can first use a particular machine learning model to process a first set of data to produce a score for detecting a network security-related issue, and in doing so, the particular model is trained by the first engine with the first set of data, thereby creating a model state reflecting a version of such model. Thereafter, a second engine uses the same particular machine learning model to process a second set of data for producing a score for detecting a network security-related issue. With the model state sharing, the second engine can use the version of the model that has been trained by the first engine to process the second set of data, thereby leveraging the knowledge gained by the first engine to discover a security-related issue in the second set of data. Note that, in certain embodiments, this model state sharing is non-blocking, meaning that a model state can be read and/or updated by any engine at any time.
FIG. 22 shows of anexample architecture 2200 of the security platform, in which the model state sharing technique introduced here may be implemented. As shown, the security platform can be implemented by using various components in a big data oriented software framework, such as Hadoop™. The framework enables the components in the platform to be able to communicate with each other. As shown inFIG. 22 , the example security platform includes a real-time event processing engine implemented on a first processing system of the platform. In the illustrated example, this first processing system is implemented using Apache Storm™. In other embodiments, the first processing system could be implemented by using Apache Spark Streaming. The real-time event processing engine is configured to process an unbounded stream of event data to detect a plurality of network security-related issues. In a manner described above, the real-time event processing engine can utilize various machine learning models to perform anomaly and threat detection. In doing so, the real-time event processing engine trains the machine learning models, and in some embodiments, establishes behavioral baselines for various specific entities.- Similar to the real-time event processing engine, the example security platform includes a batch event processing engine on a second processing system of the platform. In the illustrated example, this first processing system is implemented using Apache Spark™. The batch event processing engine is configured to process a batch of historic event data to detect a plurality of network security-related issues. Like the real-time event processing engine, the real-time event processing engine can also utilize machine learning models, establish behavioral baselines, and so forth.
- In accordance with some embodiments, the security platform can be configured to enable sharing of model states between the real-time processing engine and the batch processing engine for network security anomaly and threat detection. As described above with respect to the CEP engine and the machine learning models, a particular machine learning model can be configured to process a time slice of data to produce a score for detecting a network security-related issue, and with model state sharing, the size of the time slice can be controlled by whichever event processing engine currently utilizes the particular machine learning model. For example, if the real-time processing engine is utilizing the model, then the time slice can be set by the real-time processing engine to real-time (e.g., event-by-event as the data streams into the platform). Similarly, if the batch processing engine is utilizing the model, the time slice can be set by the batch processing engine to whichever time period length is suitable for grouping the historic events (i.e., events that are already stored as opposed to being currently streamed) into batches for processing.
- In this way, the shared model state can form a positive intelligence feedback loop between the two engines. From the batch event processing engine's perspective, this loop enables the batch event processing engine to use knowledge gained by the real-time event processing engine to discover a security-related issue in the historic event data that is undetectable by the batch event processing engine without the knowledge. More specifically, the shared model state enables the batch event processing engine to use new knowledge gained by the real-time event processing engine from processing the unbounded stream of event data, to inspect the historic event data to discover a security-related issue that would be undetectable by the batch event processing engine without that new knowledge. The new knowledge is knowledge gained after the last time the batch event processing engine performs historic event data inspection using the particular machine learning model, and therefore it is valuable because the batch event processing engine would not have this new knowledge but for the model state sharing.
- Further, after the batch event processing engine performs an analysis on the historic event data to detect a security-related issue, the analysis may result in acquisition of new knowledge of event data. For the benefit of the real-time event processing engine, the batch event processing engine can update the shared model state of the particular machine learning model to incorporate the new knowledge. In this way, by using the shared model state, the real-time event processing engine can perform an inspection of newly streamed event data based on this new knowledge gained by the batch event processing engine.
- The behavioral baseline establishment technique described above (see discussion of UBA/UEBA) can also be integrated with the model state sharing technique here. That is, in addition or as an alternative to sharing model states, a behavioral baseline established by one engine (e.g., the real-time event processing engine) by using a particular machine learning model can be shared along with the model state with another engine (e.g., the batch event processing engine). With both the model state and the behavioral baseline established, one engine can take fuller advantage of the knowledge gained by another engine. In one example, a particular machine learning model is trained by the real-time event processing engine, and a behavioral baseline is established for a specific entity, also by the real-time event processing engine. Utilizing the techniques introduced here, the batch event processing engine can locate, in the batch of historic event data, data representing a plurality of events that are associated with the specific entity. Then, the batch event processing engine can perform a behavioral analysis of the entity to detect a behavioral anomaly using the same version of machine learning model that has been trained by the real-time event processing engine to compute a degree of behavioral deviation, as compared to the behavioral baseline specific to the entity.
- Note that the behavioral anomaly analysis is not limited in application to comparing a specific entity with its past behavioral baseline; it can also include comparing a specific entity's behavior against the behavior of other similar entities. In other words, other similar entities' behaviors can be used for establishing a behavioral baseline for a specific entity. Therefore, the combination of the behavioral baseline establishment technique and the model state sharing technique can be particularly useful to detect a specific entity's anomalous behavior when historical data of that specific entity is not available (e.g., a new employee joins the enterprise).
- In addition, the mechanism of sharing the model state also enables, at least indirectly, updating a machine learning model based on the user feedback when the security platform receives such user feedback regarding a determination of a detected security-related issue. For example, such an update can be performed by one of the engines to the model state, and through the shared model state, the effect of that feedback can be propagated into the other engine's anomaly and threat detection processes.
- As mentioned above, the
security platform 300 detects anomalies in event data, and further detects threats based on detected anomalies. In some embodiments, the security platform also defines and detects an additional type of indicator of potential security breach, called threat indicators. Threat indicators are an intermediary level of potential security breach indicator defined within a hierarchy of security breach indicators that includes anomalies at the bottom level, threat indicators as an intermediate level, and threats at the top level. FIG. 23 is flow diagram illustrating at a high level, aprocessing hierarchy 2300 of detecting anomalies, identifying threat indicators, and identifying threats with thesecurity platform 300. Reducing false positives in identifying security threats to the network is one goal of the security platform. To this end, flow diagram describes anoverall process 2300 by which large amounts ofincoming event data 2302 are processed to detect anomalies. The resultinganomaly data 2304 comprising a plurality of anomalies across a computer network is then further processed to identify threat indicators. This identification of threat indicators can be conceptualized as an intermediate step between detecting anomalies and identifying security threats to a computer network. As shown, thethreat indicator data 2306 comprising a plurality of threat indicators identified across a computer network is further processed to identify a security threat or threats.- As discussed above, an anomaly represents a detected variation from an expected pattern of behavior on the part of an entity, which variation may or may not constitute a threat. An anomaly represents an event of possible concern and possibly may be actionable or warrant further investigation. A detected anomaly in the activity on a computer network is often associated with one or more entities of the computer network, such as one or more physical computing devices, virtual computing devices, users, software modules, accounts, identifiers, and/or addresses. An anomaly or a set of anomalies may be evaluated (e.g. scored) together, which evaluation may result in a determination of a threat indicator or a threat. Threat indicators represent an escalation of events of concern and are evaluated to identify if a threat to the security of the network exists. As an example of scale, hundreds of millions of packets of incoming event data from various data sources may be processed to yield 100 anomalies, which may be further processed to yield 10 threat indicators, which may again be further processed to yield one or two threats.
FIG. 24 is flow diagram illustrating in more detail anexample process 2400 for detecting anomalies, identifying threat indicators, and identifying threats to network security. The process begins by detecting anomalies in activity on a computer network, based on received event data. As shown inFIG. 24 atstep 2402,incoming event data 2302 is processed through a plurality ofanomaly models 1 through N, which may be machine learning models as discussed above, and which atstep 2404 mayoutput anomaly data 2304 indicative of a plurality ofanomalies 1 through M. As shown inFIG. 24 , an anomaly is not necessarily detected for a given set ofevent data 2302. For example, as shown atstep 2406, when theevent data 2302 is processed by anomaly model N, no anomaly is detected.- The process continues with generating
anomaly data 2304 indicative of the anomalies in response to the detection. Theanomaly data 2304, as used herein, generally refers to the entire set or a subset of the detected anomalies across the computer network. For example, as represented inFIG. 24 , the processing ofevent data 2302 according to the plurality of models atstep 2402 leads to the outputting of anomalies (or associated data)1 through M atstep 2404. In some embodiments, theanomaly data 2304 includes only theevent data 2302 associated with detected anomalies. In other words, the anomaly processing can be viewed as a filtering process to pass on only event data associated with anomalous activity. In other embodiments and as explained elsewhere in this specification, theanomaly data 2404 includes data in addition to theunderlying event data 2302. For example, the anomaly data associated with a particular entity may include the underlying event data associated with the anomalous activity, annotated information about that entity (e.g. a user ID or account associated with a device), timing data associated with the anomalous activity (e.g. when the anomaly occurred, when a similar anomaly last occurred, or periodicity of this type of anomaly showing up for the particular entity), etc. In some embodiments, theanomaly data 2304 is stored in a data structure in the form of an anomaly graph. In such embodiments, the anomaly graph includes a plurality of vertices (nodes) representing entities associated with the computer network and a plurality of edges, each of the plurality of edges representing an anomaly linking two of the plurality of vertices (nodes). - The process continues with identifying threat indicators by processing the anomaly data. As shown in
FIG. 24 , atstep 2408 the anomaly data2304 (or at least a subset of anomaly data2304) is processed through a plurality ofthreat indicator models 1 through Y, which atstep 2410 may outputthreat indicator data 2306 including a plurality of threat indicators. In an embodiment, the processing ofevent data 2302 atstep 2402 to produceanomaly data 2304 occurs on a per entity basis, while the processing ofanomaly data 2304 atstep 2408 can occur across the computer network whose security is being monitored, or at least a subgroup of the computer network. In other words, eachanomaly 1 through M is detected as anomalous for a particular entity given event data associated with the given entity. While useful, this evaluation is performed without reference to other activity on the computer network. Atstep 2408, however, the plurality ofthreat indicator models 1 through Y are evaluating the plurality ofanomalies 1 through M that occur across the computer network being monitored, not just for a particular entity. As shown inFIG. 24 , a threat indicator is not necessarily identified based on a given set ofanomaly data 2304. For example, as shown atstep 2412, when theanomaly data 2304 is processed according to threat indicator model Y, no threat indicator is identified. - The process continues with generating
threat indicator data 2306 indicative of the threat indicators in response to the identifying the threat indicators. Again, as with theanomaly data 2304, thethreat indicator data 2306, as used herein, generally refers to the entire set or a subset of the identified threat indicators across the computer network being monitored. For example, as represented inFIG. 24 , the processing ofanomaly data 2304 according to the plurality of threat indicator models atstep 2408 leads to the outputting of threat indicators (or associated data)1 through X atstep 2410. In some embodiments, thethreat indicator data 2306 simply includes only theevent data 2302 associated with identified threat indicators. In other words, the threat indicator processing can be viewed as a further filtering of theevent data 2302 to pass ononly event data 2302 associated with threat indicators. In other embodiments and as explained elsewhere in this specification, thethreat indicator data 2306 includes data beyond theunderlying event data 2302. For example, thethreat indicator data 2306 may include the underlying event data associated with the anomalous activity, annotated information about the entities (e.g. users, devices, etc.) associated with the threat indicator, timing data associated with the threat indicator (e.g. when the threat indicator was raised, when a similar threat indicator last occurred, periodicity of this type of threat indicator, etc.). In some embodiments thethreat indicator data 2306 is stored in a data structure in the form of a threat indicator graph. In such embodiments, the threat indicator graph may include a plurality of vertices (nodes) representing entities associated with the computer network and a plurality of edges, each of the plurality of edges representing a threat indicator linking two of the plurality of vertices (nodes). In other embodiments, thethreat indicator data 2306 is instead stored in a relational database or a key-store database. - In some embodiments, the
threat indicator data 2306 is incorporated into a network security graph, which may be the composite relationship graph discussed above. The network security graph can include a plurality of vertices (nodes) representing entities associated with the computer network and a plurality of edges linking two or more of the plurality of vertices (nodes). Each edge in such a graph represents an association between the entities represented by the vertices (nodes). Accordingly, anomalies defined in theanomaly data 2304, and/or threat indicators defined in thethreat indicator data 2306, can be incorporated into the graph as vertices (nodes), each linked to one or more of the entities by one or more edges. For example consider an example in which a threat indicator is identified and is associated with auser 1 using adevice 1 operating on a computer network. In a highly simplified network security graph, the user and device are each defined as a node with an edge linking them to represent the association (i.e.user 1 uses device1). An anomaly or a threat indicator is then incorporated as a third node into the simplified graph with edges linking to both thenode representing user 1 and thenode representing device 1. - The process continues with at
step 2414 with identifying threats to the security of the computer network by processing thethreat indicator data 2306. - A. Detecting Anomalies
FIG. 25 is a flow diagram describing anexample process 2500 for detecting anomalies.Process 2500 begins atstep 2502 with receivingevent data 2302 indicative of activity by a particular entity associated with a computer network. As described in more detail herein, in some embodiments,event data 2302 is received by a security platform from a plurality of entities associated with the computer network via an ETL pipeline.Process 2500 continues atstep 2504 with processing theevent data 2302 through an anomaly model. According to an embodiment, an anomaly model includes at least model processing logic defining a process for assigning an anomaly score to theevent data 2302 and a model state defining a set of parameters for applying the model processing logic. A plurality of anomaly models instances may be instantiated for each entity associated with the computer network. Each model instance may be of a particular model type configured to detect a particular category of anomalies based on incoming event data. For example, in an embodiment, a computer on computer network is associated with various anomaly models, with one of the anomaly models configured to detect an anomaly indicative of a machine generated beacon communication to an entity outside the computer network. According to some embodiments, the security platform includes anomaly models configured to detect a number of different kinds of anomalous activity, such as lateral movement, blacklisted entities, malware communications, rare events, and beacon activity. Each of these anomaly models would include unique processing logic and parameters for applying the processing logic. Similarly, each model instance (i.e. for a particular entity) may include unique processing logic and parameters for applying the processing logic. In some embodiments, processing ofevent data 2302 is performed in real-time as the event data is received. In such an embodiment, real-time processing may be performed by a processing engine optimized for high rate or real-time processing, such as Apache Storm or Apache Spark Streaming.Process 2500 continues atstep 2506 with assigning an anomaly score based on the processing of theevent data 2302 through the anomaly model. Calculation of the anomaly score is done by the processing logic contained within the anomaly model and represents a quantification of a degree to which the processed event data is associated with anomalous activity on the network. In some embodiments, the anomaly score is a value in a specified range. For example, the resulting anomaly score may be a value between 0 and 10, with 0 being the least anomalous and 10 being the most anomalous.Process 2500 continues atstep 2508 with outputting an indicator of a particular anomaly if the anomaly score satisfies a specified criterion (e.g., exceeds a threshold). Continuing with the given example, the specified criterion may be set such that an anomaly is detected if the anomaly score is 6 or above, for example. The specified criterion need not be static, however. In some embodiments, the criterion (e.g., threshold) is dynamic and changes based on situational factors. The situational factors may include volume of event data, presence or absence of pre-conditional events, user configurations, and volume of detected anomalies.- B. Identifying Threat Indicators—Generally
FIG. 26 is a flow diagram describing anexample process 2600 for identifying threat indicators.Process 2600 begins atstep 2602 with processing theanomaly data 2304 through a threat indicator model, which like the anomaly models may also be a machine learning model. As with the previously described anomaly models, according to some embodiments, a threat indicator model includes model processing logic defining a process for assigning a threat indicator score based on processing theanomaly data 2304 and a model state defining a set of parameters for applying the model processing logic. Specific use cases for identifying threat indicators based on detected anomalies are discussed in more detail herein. In each described use case the steps to identifying a threat indicator may be incorporated into the processing logic. In some embodiments, processing of theanomaly data 2304 may include aggregating anomaly data across the computer network, correlating different anomalies within the anomaly data, and/or enhancing the anomaly data through enrichment using external data sources. In some embodiments, processing ofanomaly data 2304 is performed in real-time as the event data is received and anomalies are generated. In such an embodiment, real-time processing may be performed by a processing engine optimized for high rate or real-time processing, for example, Apache Storm or Apache Spark Streaming. In some embodiments, processing ofanomaly data 2304 is instead or additionally performed in batch mode. In such an embodiment, batch mode processing may be performed by a processing engine optimized high volumes of data, such as Apache Spark on a Hadoop distributed computing cluster.Process 2600 continues atstep 2604 with assigning a threat indicator score based on processing theanomaly data 2304. As with the anomaly models, in some embodiments, calculation of the threat indicator score is based on the processing logic contained within the threat indicator model and represents a quantification of a degree to which the processed anomaly data is associated with activity that may be a threat to the security of the network. As previously described, a threat indicator can be conceptualized as an escalation or intermediate step between detection of an anomaly and identification of a threat to network security. In some embodiments, the threat indicator score is a value in a specified range. For example, the resulting threat indicator score may be a value between 0 and 10, with 0 being the least threating and 10 being the most threatening.Process 2600 continues atstep 2606 with identifying a threat indicator if the threat indicator score satisfies a specified criterion (e.g., a threshold). Continuing with the given example, the specified criterion may be set such that a threat indicator is identified if the threat indicator score is 6 or above, for example. The specified criterion need not be static, however. In some embodiments, the criterion (e.g., threshold) is dynamic and changes based on situational factors. The situational factors may include volume of event data, presence or absence of pre-conditional events, user configurations, and volume of detected anomalies.- C. Identifying Threat Indicators—Entity Associations
- As described previously, a detected anomaly is typically associated with one or more entities associated with a computer network. For example, if an anomaly is detected that is suggestive of beacon activity (discussed further below), that beacon activity is typically from one or more devices operating within the network being monitored. Each of those devices may be associated with one or more users. In this particular use case, the threat indicator models, such as those described previously with respect to
FIG. 26 , are configured to analyze the relationships between entities on the computer network and the detected anomalies making up the set ofanomaly data 2304 across the computer network. FIG. 27 illustrates a use case for identifying threat indicators based on entity associations with detected anomalies. The use case illustrated inFIG. 27 is identifying a threat indicator if, based on processing the anomaly data, it is determined that a high number of entities are associated with a particular anomaly or a particular category of anomaly.- A shown in
FIG. 27 , a number of detectedanomalies 1 though M are included inanomaly data 2304, which is surrounded by the larger dotted line box. Associated with these detected anomalies are variousentities including devices 1 though S andusers 1 through R. In this example,anomaly 1 is shown to be associated with at least seven unique entities, includingusers 1 through R, anddevices 1 throughS. Anomalies user 3, device,1, and user R (respectively). This use case assumes that a correlation among anomalies and entities that establishes relatively high interrelationship is more suspicious than individual occurrences of anomalous activity. In other words, if a detected anomaly is associated with a high number of entities (e.g. users and/or devices) on a computer network, that anomaly may be more indicative of threating activity. Accordingly,anomaly 1, surrounded by the smaller dotted line box, may be identified as a threat indicator based on the processing ofanomaly data 2304. It is important to note here that this type of system wide view of anomalous activity is not possible at the anomaly detection level, according to some embodiments, because the anomaly model instances are set up to process event data on a per-entity basis. In other words, an anomaly model is only concerned with what is occurring at a particular entity, while a threat indicator model is concerned with what is occurring across the entire computer system. Anomaly 1 is shown inFIG. 27 as a single anomaly for clarity purposes, however it may also represent a cluster of anomalies that are somehow related to one another. In one embodiment,anomaly 1, as shown inFIG. 27 , may represent a set of anomalies of a particular category of anomaly. For example, a threat indicator may be identified if a high number of entities within a computer network are associated with beacon activity. That beacon activity may be associated with hundreds or thousands of detected anomalies across the network. In another embodiment,anomaly 1, as shown inFIG. 27 , may represent a cluster of anomalies of not just the same category, but substantially matching on a lower level as well. For example, beacon activity broadly describes a wide range of behavior. However, analysis at a lower level can uncover similarities among certain types of beaconing. For example, beacon communications known to be associated with malware command and control communications may exhibit similar characteristics. These characteristics may be described in profile or footprint associated with a particular anomaly. This profile or footprint is based on theunderlying event data 2302 that gave rise to the anomaly. For example, while individually unique, a set of anomalies based on beacon communications may exhibit patterns related to destination entities, periodicity of communications, etc. Accordingly,anomaly 1, as shown inFIG. 27 may represent a plurality of individual anomalies that, although unique, all have substantially matching profiles or footprints.- In some embodiments, the use case described in
FIG. 27 involves a process that begins with determining a measure (e.g., a count) of entities of the computer network associated with a particular anomaly, a particular category of anomaly, or a set of anomalies with substantially matching profiles or footprints. In some embodiments, this determination is based on an absolute number tracked from when monitoring of the computer network commenced. In other embodiments, this determination may be over a pre-determined and/or dynamic time period. - The process continues with identifying a threat indicator if the measure of entities associated with the particular anomaly, particular category of anomaly, or a set of anomalies with substantially matching profiles or footprints, satisfies a specified criterion. The specified criterion may simply be a threshold number of entities associated with an anomaly. For example, identifying a threat indicator if 20 entities are associated with a beacon related anomaly. This threshold value need not be static however. The threshold value may depend on the type of anomaly detected, the types of entities associated (e.g. mission critical systems vs. non-critical systems), the temporal clustering of entities associated with the anomaly, etc. In the context of a threat indicator model as described with respect to
FIG. 26 , a threat indicator score can be assigned based on the processing of the anomaly data with a threat indicator being identified if the threat indicator score satisfies a specified criterion. For example, the 20 entities associated with a particular anomaly may lead to assigning an threat indicator score of 6 on a scale of 1 to 10. Accordingly a threat indicator is identified because the assigned threat indicator score is at least 6. FIG. 28 illustrates a second use case for identifying threat indicators based on entity associations with detected anomalies. The use case illustrated inFIG. 28 is identifying a threat indicator if, based on processing the anomaly data, it is determined that a high number of anomalies are associated with a particular entity.- As shown in
FIG. 28 , a number of detectedanomalies 1 though M are included inanomaly data 2304, which is surrounded by the larger dotted line box. Associated with these detected anomalies are variousentities including devices 1 though S andusers 1 through R. Here,user 1 is shown to be associated with at least fouranomalies 1 though M (as indicated by the first of two smaller dotted line boxes), anddevice 1 is shown to be associated with least fouranomalies 1 though M (as indicated by the second of two smaller dotted line boxes). As with the use case described with respect toFIG. 27 , this use case assumes that a correlation among anomalies and entities that establishes relatively high interrelationship is more suspicious than individual occurrences of anomalous activity. In other words, an entity (such as a user or device) that is associated with a high number of detected anomalies may be more indicative of threating activity. Accordingly, two threat indicators are identified based on theanomaly data 2304 shown inFIG. 28 , one threat indicator based on the anomalies associated withuser 1 and one threat indicator based on the anomalies associated withdevice 1. - As described with respect to
FIG. 27 , eachanomaly 1 through M shown inFIG. 28 is shown as a single anomaly for clarity purposes. However, each anomaly shown inFIG. 28 may also represent a cluster of anomalies that are somehow related to one another. For example,anomaly 1 may represent a single instance of an anomaly, multiple anomalies of the same category, or multiple anomalies with substantially matching profiles or footprints. - In some embodiments, the use case described in
FIG. 28 involves a process that begins with determining a measure (e.g. a count) of anomalies associated with a particular entity of the computer network. In some embodiments, this determination is based on an absolute number tracked from when monitoring of the computer network commenced. In other embodiments, this determination may be over a pre-determined and/or dynamic time period. - The process continues with identifying a threat indicator if the measure of anomalies associated with the particular entity satisfies a specified criterion.
- In an embodiment, the specified criterion may simply be a threshold number of anomalies associated with a particular entity. For example, identifying a threat indicator if 20 beacon anomalies are associated with particular user device on the network. This threshold value need not be static, however. The threshold value may depend on the type of anomaly detected, the types of entity associated with the anomalies (e.g. mission critical systems vs. non-critical systems), the temporal clustering of anomalies associated with a particular entity, etc. In the context of a threat indicator model as described with respect to
FIG. 26 , a threat indicator score can be assigned based on the processing of theanomaly data 2304 with a threat indicator being identified if the threat indicator score satisfies a specified criterion. For example, the 20 anomalies associated with a particular entity may lead to assigning an threat indicator score of 6 on a scale of 1 to 10. Accordingly a threat indicator is identified because the assigned threat indicator score is at least 6. - D. Identifying Threat Indicators—Anomaly Duration
FIG. 29 illustrates a use case for identifying threat indicators based on duration of detected anomalous behavior. Anomalies may be detected over a period of time, for example, as shown inFIG. 29 ,anomalies 1 through M are detected at time periods t1 through tm. This use case assumes that a temporal correlation among detected anomalies is indicative of suspicious activity. For example, a high number of anomalies occurring in a short time period may be indicative of a concentrated threat to the security of the network.- In some embodiments, the use case described in
FIG. 29 involves a process that begins with monitoring a duration of a particular anomaly over a time period. Althoughanomalies 1 through M shown inFIG. 29 are shown as discrete events, in some cases an anomaly may have duration with a starting time and an end time. The process continues with identifying a threat indicator if the monitored duration of the anomaly satisfies a specified criterion. - In some embodiments, the use case described in
FIG. 29 involves a process that begins with determining a number of anomalies that have substantially matching profiles or footprints (e.g. as described in the previous use case) over a time period. These substantially matching anomalies may indicate a pattern of anomalous activity that has duration. The process continues with identifying a threat indicator if the number of anomalies with substantially matching profiles satisfy a specified criterion. - E. Identifying Threat Indicators—Local Vs. Global Rarity Analysis
FIG. 30 illustrates a use case for identifying threat indicators based on local and global rarity analysis. As described elsewhere in this specification, in some embodiments, anomalies are detected based on a rarity analysis. In other words, if an event satisfies a rarity analysis (i.e. is determined to be rare), it is detected as an anomaly. This anomaly detection based on rarity analysis is local rarity analysis, because it looks at the rarity of the event in the context of a particular entity. In this use case the anomalies detected based on local rarity analysis are analyzed across the computer network according to a global rarity analysis. In some cases the number of similar anomalies is important indicator of their severity. For example, a machine generated beacon anomaly may be interpreted as malicious if occurring in only a small number of systems (intruders of malware infections typically affect only a small number of systems, sophisticated attackers will infect a single device).- As shown in
FIG. 30 ,event data 2302 is processed through a number of localrarity analysis models 1 through U that are associated withentities 1 through V. The detectedanomalies 1 through M are then analyzed according to a global rarity analysis model to identify a threat indicator. In some embodiments, the use case described inFIG. 30 involves a process that begins with performing a global rarity analysis across the anomaly data2304 (or a subset of the anomaly data2304) over a time period, with theanomaly data 2304 based on anomalies detected using local rarity analysis. The process continues with identifying a threat indicator if a pattern in the detected anomalies satisfies a global rarity criterion. In some embodiments a global rarity model is a model that applies the same processing logic as a local rarity model, except that it is applied to the set of anomalies across the network being monitored instead of the event data pertaining to a single entity. - Detection of anomalies by using rarity analysis is discussed in greater detail in a section below.
- F. Identifying Threat Indicators—Combining Anomalies
FIGS. 31A-31B illustrate a use case for identifying threat indicators based on combining the outputs (i.e. detected anomalies) from different anomaly models. As described elsewhere in this specification, in some embodiments, different types of anomalies are detected based a different models. In such cases, it may be beneficial to correlate the anomalies detected using different model types. For example, a machine generated beacon anomaly (detected by a beacon detection model) provides more insight if the destination of the beacon is rare for the environment (detected with a rarity analysis model).- As shown in
FIG. 31A , a threat indicator is identified by processing theanomaly data 2304 according to a threat indicator model ifanomalies FIG. 31B , ifanomaly 2 is not detected (and therefore not part of anomaly data2304), the threat indicator is not identified based on processing according to the threat indicator model. - In some embodiments, the use case described in
FIGS. 31A-31B involves combining anomaly data associated with different types of anomalies, assigning a threat indicator score based on the result of the combining, and identifying a threat indicator if the threat indicator score satisfies a specified criterion. FIGS. 32A-32B illustrate a second use case for identifying threat indicators based on combining the outputs (i.e. detected anomalies) from different anomaly models. In some embodiments, a threat indicator is identified by processing the output from an anomaly model of a first type with a an anomaly model of a second type. Recall the previous example of a beacon anomaly processed according to a rarity analysis to determine if the beacon is rare for a given environment. That example involves processingevent data 2302 according to a beacon detection model to detect a beacon anomaly and then processing the detected beacon anomaly according to a rarity analysis model to detect a rarity anomaly. In some embodiments, if the second anomaly is detected, a threat indicator is identified.- As shown in
FIG. 32A ,anomaly 1 is detected based on processing ofevent data 2302 throughanomaly model 1.Anomaly 1 is then input intoanomaly model 2 for processing. In some embodiments, theoutput anomaly 1 is processed along withother event data 2302 throughanomaly model 2. Asecond anomaly 2 is detected based on processing anomaly1 (and, and in some embodiments, event data2302) throughanomaly model 2.FIG. 32B shows the same process as inFIG. 32A except that a threat indicator is not identified becauseanomaly 1 was not detected. Although not shown, the same process may have yieldedanomaly 1, but notanomaly 2. For example, a beacon anomaly is detected, but a rarity anomaly associated with that beacon is not detected because the beacon is common to a particular environment. Accordingly a threat indicator is not identified. - In some embodiments, the use case described in
FIGS. 32A-32B involves a process of detecting a first type of anomaly based onprocessing event 2302 data by a first type of anomaly model. The process continues with inputting the first type of anomaly into a second type of anomaly model. The process concludes with identifying a threat indicator if a second type of anomaly model is detected based on processing the first type of anomaly by the second type of anomaly model. - The processes described in
FIGS. 31A-32B depict simple combinations of two anomalies, however, the concept can easily be applied to more complex combinations of multiple anomaly outputs. - G. Identifying Threat Indicators—Enrichment of Anomaly Data
FIG. 33 illustrates a use case for identifying threat indicators by enriching the anomaly data using data from external sources. A detected anomaly may provide more insight if combined with other data that indicates a malicious nature. For example, consider the detection of an anomalous connection to particular domain xyz.com outside the computer network. The detected anomaly indicates that the domain may be associated with malicious activity, however, beyond the fact that it may appear machine generated or rare, additional information may be required to confirm that suspicion. It is therefore possible to access additional external public information (e.g. a WHOIS lookup) that will provide additional information about the domain, for example, who registered the domain name and how long ago. A website registered very recently in a country deemed to be “high risk” is likely to be viewed as more suspicious. By incorporating the external information the, a confidence level that a particular anomaly is associated with malicious activity can be increased, and in some cases a threat indicator identified.- As shown in
FIG. 33 , atstep 3302event data 2302 is processed through an anomaly model resulting in detection of an anomaly atstep 3304. Additional information from an external data source is obtained (e.g., by a push or pull modality) atstep 3306 during a process of data enrichment resulting in annotated anomaly data atstep 3308. This annotated anomaly data is processed according to threat indicator model and a threat indicator is identified if a specified criterion is satisfied. In some embodiments, pulling this external information at step3306 (e.g. via a WHOIS lookup) is computationally expensive so it makes sense to annotate theanomaly data 2304 instead of the highervolume event data 2302 if the enrichment process is occurring in real-time or near real-time. - In some embodiments, the use case described in
FIG. 33 involves a process that begins with identifying a particular entity associated with the anomaly data. This identification may be based on the underlying event data used to generate the anomaly. As in the last example, an anomaly may be associated with a domain xyz.com. The process continues with comparing the particular entity against data stored in an database of known security risks. For example, an external publicly available database may include a list of domains known to be associated with malicious beacon activity. The process continues with identifying a threat indicator if the particular entity substantially matches a known security risk contained in the external database. - In some embodiments, the use case described in
FIG. 33 involves a process that begins with identifying an anomaly associated with a connection to a domain considered to be unfamiliar. The process continues with determining whether the domain considered to be unfamiliar matches a domain known to be a security risk, for example, by using information from an external data source. The process continues with identifying a threat indicator if the domain considered to be unfamiliar substantially matches a domain known to be a security risk. - H. Identifying Threats
FIG. 34 is a flow diagram depicting anexample process 3400 for identifying threats to the security of a computer network based on threat indicators. The process of identifying threats based on correlation of anomalies is described in more detail elsewhere in this specification. The same concept applies here, except that the threat is identified based on correlating thethreat indicator data 2306 including a plurality of identified threat indicators instead of theanomaly data 2404.Process 3400 begins atstep 3402 with correlating thethreat indicator data 2306, or at least a subset of thethreat indicator data 2306.Process 3400 continues atstep 3404 with identifying a set of candidate security threats based on the correlation. Types of correlation are described elsewhere in this specification but can include network-wide correlation for malware threats, connected component correlation for kill chain type threats, per-entity analysis for kill chain type threats, and per-burst analysis for insider threats.Process 3400 continues at step3406 with comparing the subset of the threat indicator data against pre-configured patterns or pre-set rules associated with each candidate threat. For example, an insider threat may be associated with known patterns identified by security experts and therefore be associated with pre-set rules.Process 3400 continues atstep 3408 with generating a pattern matching score based on a result of the comparing. In some embodiments, the pattern matching score is a value in a set range. For example, the resulting pattern matching score may be a value between 0 and 10 with 0 being the least likely to be a threat and 10 being the most likely to be a threat.Process 3400 concludes atstep 3410 with identifying a security threat if the pattern matching score satisfies a specified criterion. Continuing with the given example, the specified criterion may be set such that an threat is identified if the pattern matching score is 6 or above. The specified criterion need not be static, however. In some embodiments, the criterion is dynamic and changes based on situational factors. Situational factors may include volume of event data, presence or absence of pre-conditional events, user configurations, volume of detected anomalies, and involvement of mission critical systems.- As described above, the
security platform 300 can combine the individual event-specific relationship graphs from all processed events into a composite relationship graph that summarizes all significant (from a security standpoint) network activity for an entire enterprise or network. The composite relationship graph can include nodes representing the various entities associated with the network as well as nodes representing the detected anomalies. Subsets, or “projections,” of the composite relationship graph can then be used by various different threat models to detect security threats, as will now be further described. FIGS. 35 through 38 relate to a method for storing and analyzing a security data structure (e.g., a graph including nodes and edges) for identifying security threats in a computer network. The nodes represent entities in or associated with the computer network, such as users, devices, applications, and anomalies. The edges, which connect nodes, represent the relationships between the entities. An ETL process generates event-specific graph data structures (also referred to as “mini-graphs” or “relationship graphs”) corresponding to events that have occurred in the computer network. The method introduced here detects anomalies based on the mini-graphs, and combines the anomalies with the mini-graphs to generate the composite relationship graph, which may also be called an “enterprise security graph” to the extent it may relate to a network of a particular enterprise (e.g., a corporation, educational institution, government agency, etc.). The composite relationship graph includes nodes that represent the anomalies and edges that represent relationships between anomalies and other entities involved in the events.- During the above-mentioned combining, the method condenses network activities that are of the same type and associated with the same user into a single entry of combined network activity. The method further assigns these combined network activities into different projections of the composite relationship graph, depending on the type of activity. Each projection represents a subset of the composite relationship graph that relates to a certain type or types of user action or other category (e.g., login, web visit, file access, anomaly, etc.). The projection can be stored in a cluster (e.g., a Hadoop cluster) and further broken down into multiple files based on the timestamps. Relevant files can be stored in proximity in the cluster for data access efficiency.
- The method further identifies security threats by correlating the anomalies across the composite relationship graph. For example, the method can use a neighborhood computation algorithm to identify a group of related anomalies in the composite relationship graph that represent a security threat. Alternatively, the method can identify an insider who poses a security threat based on a group of anomalies being close to each other in time and their confidence metrics.
FIG. 35 illustrates an example process of combining and storing relationship graphs into a composite relationship graph. The process receives event data from various data sources. The event data can be, e.g., timestamped machine data. The process usesparsers 3510 to conduct an ETL procedure to generate information about the entities in the computer network and the relationships between the entities.- The process organizes the information about the entities and the relationships for each event into a mini-graph. Each of the mini-graphs3522,3524 and3526 includes nodes and one or more edges each interconnecting a pair of the nodes. The nodes represent the entities involved in the particular event. The edges represent the relationships between the entities in the event. An
analytics engine 3530 can process these mini-graphs3522,3524 and3526 (e.g., using various machine learning models) to detect anomalies. - A separate machine learning model called
aggregator 3540 combines the mini-graphs and detected anomalies into the composite relationship graph. The composite relationship graph includes nodes that represent the entities, as well as nodes that represent the detected anomalies. In some embodiments, the composite relationship graph is created first in volatile memory of one or more computing devices, and then saved to non-volatile storage. - A
graph library component 3550 handles the storage of the composite relationship graph in a non-volatile storage facility calledgraph database 3560. In thegraph database 3560, the nodes (also referred to as vertices), edges and associated metadata of the composite relationship graph are stored in one or more data files. The nodes and edges of the composite relationship can be partitioned based on the timestamps (from the event data) of the corresponding network activities. Each data file can be designated for storing nodes and edges for a particular time period. - In addition, a
graph merger component 3570 runs a background job to merge new segments into the composite relationship graph at a predetermined periodicity. As the system continuously receives new event data and generates new mini-graphs and new anomalies based on the new event data, thegraph merger component 3570 merges these newly created mini-graphs and associated detected anomalies into the composite relationship graph. FIG. 36 illustrates an example of a composite relationship graph. The illustratedcomposite relationship graph 3600 includes a number of nodes U1 through U11 that represent users (also referred to as “user nodes”) and a number of nodes IP1 through IP7 that represent network devices (also referred to as “device nodes”). Thecomposite relationship graph 3600 further includes a number of nodes I1 through I4 that represent anomalies (also referred to as “anomaly nodes”). For example, anomaly node I1 suggests that a user represented by node U5 has engaged in certain suspicious activity with, or in relation to, the device represented by node IP3.- In
graph 3600 there are three anomaly nodes I1, I2 and I4 connected to the same device node IP3. These anomaly nodes may be indicative of a security threat involving the device IP3. The anomaly nodes I1, I2 and I4 also connect to the user nodes U4, U5 and U7 and device node IP5. This may indicate that users U4, U5 and U7 are suspicious, meaning these users can potentially be malicious users who engage in or will engage in activities detrimental to the security of the computer network. For example, users U4, U5 and U7 may be invaders who have breached network devices with malicious intentions. Thus, a decision engine (e.g., including a machine learning model) can identify a security threat represented by a group of nodes in question, including, in the illustrated example, anomaly nodes II,12 and14, user nodes U4, U5 and U7, and device nodes IP3 and IP5. - The composite relationship graph can include a number of projections that correspond to different categories of computer network activities. Each projection is a subset of the composite relationship graph and includes edges representing computer network activities of a particular category. When the
graph library component 3550 writes the composite relationship graph into non-volatile storage (as shown inFIG. 35 ), thegraph library component 3550 can write the content of the different projections into separate data files. Alternatively, thegraph library component 3550 can write the different projections into other types of data containers, such as logical unit numbers (LUNs). FIG. 37 illustrates an example of how a composite relationship graph can be stored as separate projections. For each edge (relationship) in the composite relationship graph, thegraph library component 3550 examines the edge's type to determine the projection to which the edge belongs. The different projections in the illustrated example include alogin projection 3710, a website-visit projection 3720 and ananomaly projection 3730. In some alternative embodiments, the composite relationship graph can include other types of projections, such as a projection for activities of users accessing files stored in the devices in the computer network.- If the
graph library component 3550 determines that a particular edge corresponds to an activity of a user logging into a device, thegraph library component 3550 assigns the particular edge to that particular login projection. For example, if thegraph library component 3550 determines that a particular edge corresponds to an activity of a user visiting a website, thegraph library component 3550 assigns the particular edge to the website-visit projection 3720. If thegraph library component 3550 determines that a particular edge relates to an anomaly (e.g., the edge connecting to an anomaly node), thegraph library component 3550 assigns the particular edge to theanomaly projection 3730. - The
graph library component 3550 can further break down the projections into a plurality of files. Each of the files stores network activities that have occurred in a particular time period. For example, as shown inFIG. 37 , the projection is broken down into a sequence of files, each of which stores network activities that have occurred in one particular day. In some alternative embodiments, thegraph library component 3550 can further break down the projection into finer granularity. For example, the projection may be broken down into a sequence of directories corresponding to days. Each directory may then include files corresponding to each hour of the day. - In some embodiments, the
graph library component 3550 can dynamically adjust the granularity. For example, in one embodiment, for network activities that occurred during the last two months, thegraph library component 3550 may break down the projection data into files corresponding to each hour of the last two months; whereas, for network activities that occurred prior to the last two months, thegraph library component 3550 breaks down the projection data into files corresponding two months thegraph library component 3550 may break down the projection data into files corresponding to each week or each month. As time goes by, some network activities stored in a daily granularity become older than two months. Thus, thegraph library component 3550 continuously combines files storing these network activities into files corresponding to the weekly or monthly granularity. FIG. 38 illustrates an example process of combining event-specific relationship graphs into a composite relationship graph and detecting a security threat based on the composite relationship graph. Atstep 3810, the process receives event data representing a plurality of events on a computer network. The event data are indicative of a plurality of entities and at least one anomaly involved in the events. The entities can include various types of entities involved in the computer network. For example, the entities can include, e.g., devices in the computer network, users of the devices in the computer network, websites, applications and/or data files stored in the devices in the computer network.- At
step 3820, for each event, the process acquires an event-specific relationship graph (e.g., a mini-graph), for example, from the data intake and preparation stage via the distributed messaging platform. The event-specific relationship graph is indicative of entities involved in the associated event and one or more relationships between the entities involved in the event. The event-specific relationship graph includes a number of nodes and at least one edge interconnecting nodes. The nodes represent the entities involved in the event. Each edge represents an interaction between a pair of the entities. - At
step 3830, the process acquires anomaly data indicative of various security-related anomalies detected from the event data. For each anomaly detected from the event data, the computer system can further store the event data associated with the anomaly in long-term (non-volatile) storage. In that way, thesecurity platform 300 can generate a visualization of the event data associated with the anomaly when the platform receives an instruction to visualize details of the anomaly. - At
step 3840, the process condenses the computer network activities in the event-specific relationship graph into combined computer network activities. For each event, the process identifies one or more computer network activities of a particular type based on the event-specific relationship graph. The identified computer network activities are associated with the same entity and occur during a predefined time period. The process then combines the computer network activities of the particular type into a data entry representing the combined computer network activity and counts the computer network activities that occur during the predefined time period. - The process stores the data entry representing the combined computer network activity and the count in non-volatile storage, such as a data file designated for the particular type and the time period. In some embodiments, the stored data entry for the combined computer network activity includes information about an activity type, an originating entity, a target entity, the number of times the computer network activities occur in the time period, a start time, an end time, an average gap period between the computer network activities that occur in the time period, or a standard deviation of gap periods between the computer network activities that occur in the time period.
- At
step 3850, the process combines the event-specific relationship graphs for the received events with the anomaly data into a composite relationship graph. The composite relationship graph includes nodes that represent the entities involved in the events and nodes that represent the anomalies detected based on the event data. The entities involved in the events include at least two types of entities, such as users and devices. The composite relationship graph further includes edges that represent the relationships between the entities involved in the events and the anomalies. - As shown in
FIG. 37 , the composite relationship graph can include a plurality of projections. Each of the projections is a subset of the composite relationship graph that includes edges representing a plurality of computer network activities of a particular category. In some embodiments, the particular category of network activities corresponds to users logging into devices in the computer network, users visiting websites, users accessing files stored devices in the computer network, or users conducting anomaly activities. - As illustrated in
FIG. 37 , one of the projections is theanomaly projection 3730, which is a subset of the composite relationship graph that includes edges representing anomalous activities conducted by users. Each projection can be stored in a cluster of storage device and distributed amongst data containers (e.g., files) based on timestamps of the associated event data. The computer system can further identify events that have timestamps satisfying a specific closeness criterion (e.g., the timestamps having differences less than a threshold value), and store the edge data of these identified computer network activities in proximity to each other in the long-term non-volatile storage. In this way, the read efficiency for the computer network activities can be improved. - For each combined computer network activity, the computer system can determine an association between the combined computer network activity of the particular type and a particular projection of the composite relationship graph. Then the combined computer network activity is stored into a file designated for the associated projection.
- In one embodiment, the computer system transfers the data structures representing the edges of the composite relationship graphs from memory of the computer system to persistent (long-term) storage at a predetermined periodicity. For example, if the computer system detects that a time period since a last time of transferring the data structures representing the edges of the composite relationship graphs from memory of the computer system to a persistent storage exceeds a threshold value, the computer system transfers the data structures currently in memory to the persistent storage. The computer system can further have a memory storage size limit. Once the size of the data structures representing the edges of the composite relationship graphs stored in the memory exceeds the memory storage size limit, the computer system transfers the data structures currently in the memory of the computer system to the persistent storage.
- Referring again to
FIG. 38 , atstep 3860, the process receives, at a specified periodicity from one or more machine learning models, requests for data of a projection of the composite relationship graph and corresponding to a time range. The requested data can include combined computer network activities including information about computer network activities from multiple events. Since the requests from the machine learning models are for data from a common projection range and corresponding to a common time range, atstep 3870, the process combines the data within the common projection range and the common time range into a single input data structure as an input for the machine learning models. - In some embodiments, there are different types of machine learning models. Some machine learning model receives a portion (e.g., projection) of the composite relationship graph as inputs and identify security threats and/or anomalies based thereon. The one or more machine learning models can be executed in a batch mode.
- At
step 3870, the process detects a security threat by processing at least a portion (e.g., one or more projections) of the composite relationship graph with a decision engine. The decision can be, e.g., a machine learning model or an analytics engine running a machine learning model. During the detection, the process first converts at least a portion of the composite relationship graph (e.g., the anomaly projection) into an anomaly relationship graph. The anomaly relationship graph includes anomaly nodes that represent anomalies and entity nodes that represent entities in the computer network. The computer system inputs the anomaly relationship graph into the decision engine. The decision engine can then identify a security threat by analyzing the anomalies in any of various different ways. - One possible way is that a machine learning model identifies a set of anomaly nodes interconnecting entities nodes that form a neighborhood cluster in the anomaly relation graph. Another possible way is that the machine learning model identifies a subset of the anomaly relationship graph including anomaly nodes and entity nodes that have no relationships with other nodes outside of the subset in the anomaly relationship graph. Yet another possible way is that the machine learning model identifies a set of anomaly nodes directly connecting a particular entity node in the anomaly relationship graph. The machine learning model can further identify a group of anomaly nodes within the identified plurality of anomaly nodes, wherein the group of anomaly nodes have timestamps that satisfy a specific closeness criterion. For example, the timestamps may have an average time gap less than a threshold value.
- At
step 3880, as an optional step, the process confirms that the anomalies form a security threat by applying a security rule to the anomalies based on assigned categories of the anomalies. The computer system can assign the anomalies into categories of, e.g., internal anomaly, malware anomaly, incoming anomaly and exfiltration anomaly. An administrator of the computer network can specify the rules based on his/her knowledge of typical security threats that occur in the computer network. - The identified set of anomaly nodes represent a set of related anomalies. The process can present the security threat including the set of anomalies to an administrator of the computer network or any party that handles security issues of the computer network.
- Any of the steps in the process illustrated in
FIG. 38 can be performed by processing logic of a machine learning model. Further, any of the steps can be performed in real-time as the event data are received, or in a batch mode based on the event data retrieved from persistent storage. - In addition to, and in conjunction with, methods and systems for analyzing network activities to detect, identify, and track threats and anomalies on a computer network, the present disclosure relates to methods and systems for organizing and presenting information concerning potential network compromise to one or more users tasked with monitoring the network and thwarting attacks, stolen data, and other harm. Embodiments of the present disclosure include an innovative graphical user interface that is visually communicative, highly integrated, adaptable, and user interactive.
- As described below with reference to
FIGS. 39 through 51 , the graphical user interface (“GUI”) introduced here enables a user to configure displays according to the user's particular tasks and priorities. The security platform described herein may include a GUI generator module that gathers the generated anomaly data, threat data, and other data, and that based on such gathered data, generates display data. The GUI generator module sends the generated display data to one or more physical display devices, to cause those display devices to display the GUI features described herein. The GUI module also receives user inputs and modifies the display data based on those inputs to provide an interactive display. - In the described GUI, graphs, timelines, maps, charts, lists and other visualization features are generated to illustrate trends, recent activity, and relationships between different data. The GUI can provide views that are automatically configured via default settings, or the GUI can enable a user to customize a view, for example, to filter out data points that are less critical, distracting, or unnecessary, to zoom in and out, or re-format the view (e.g., from a line chart to a bar chart). To easily navigate between different views, and to better understand the relationships between different data associated with a security-related threat or anomaly, the GUI can include links in the data to generate different views that provide additional detail about information of interest.
- The GUI also can enable the user to set watchlists to track information while navigating the various views. Watchlists can be used, for example, to remind the user that certain data already has been reviewed and considered by the user. Once a user reviews sufficient information to draw a conclusion about a threat, the GUI also enables a user to “take action,” for example, by re-designating the identified threat as “Not a Threat,” or by emailing threat data or exporting it to another data mining platform. The GUI provides these capabilities and many more to facilitate effective network security monitoring via simple user inputs (such as point-and-click actions), with little or no typing and without requiring the user to engage in laborious set-up or programming.
- The GUI introduced here generates views pertaining to threats and anomalies identified from event data generated from network activities. As examples, network activities may include log-ins, email traffic, internet browsing, or file transfers on a network operated by a corporation, university, household, or other organization (referred to collectively as an “organization”). Event data comprises timestamped machine data related to network activity by various entities, including users, devices, and applications.
- “Users” may be employees or others who are associated with an organization. Users might have unlimited rights or privileges to access an organization's network, or they might be authorized to have only limited network access. When user identification information is included in event data, it may appear as a “username” or “User ID” (or “User ID/Password” combination). Typically, users are registered with an account on an organization's network. Whenever a user logs into the organization's network or server(s), from any location and using any device, event data is created that can be tracked for potential instances of network compromise.
- “Devices” may be machines that access the network. For example, a device might be an IP address associated with a client computer (laptop, desktop, tablet, smartphone, etc.), server, and/or any other machine capable of accessing the organization's network. A device may be operated by a user who is registered with the network, or it may be operated by someone else who can access the network, either in an authorized or unauthorized capacity. For example, many organizations allow guests to access their networks or allow network traffic by visitors to the organization's website. Emails and other file transfers from users to others outside the organization, such as clients, customers, etc., involve communications with devices that are external to the organization's network. When a device accesses the network, a network server generates logs and other machine data that identify the device, for example, by IP address. Machine data that includes device information is additional event data that also can be tracked for potential instances of network compromise.
- “Application information” identifies a program that is executed on a network's servers or on a computer in communication. For example, an application might be run by a user without proper authorization, or by an intruder outside the organization. The application may be malware, or it might be authorized software that has become infected with a virus. Machine data that includes information about application activity is yet another example of event data that can be tracked for potential instances of network compromise.
- In one aspect of the techniques introduced here, the event data is analyzed, via various machine learning techniques as disclosed herein, to identify anomalies from expected or authorized network activity or behavior. An “anomaly” in the context of this description is a detected fact, i.e., it is objective information, whereas a “threat” (discussed further below) is an interpretation or conclusion that is based on one or more detected anomalies. Anomalies can be classified into various types. As examples, anomalies can be alarms, blacklisted applications/domains/IP addresses, domain name anomalies, excessive uploads or downloads, website attacks, land speed violations, machine generated beacons, login errors, multiple outgoing connections, unusual activity time/sequence/file access/network activity, etc. Anomalies typically occur at a particular date and time and involve one or more participants, which can include both users and devices.
- In another, related aspect of the disclosure, the event data is analyzed to identify threats. Threats are interpretations or conclusions based on, and therefore associated with, one or more anomalies. Threats can be categorized or grouped into various types, both external and internal to the organization. Examples of threats include data exfiltration (by compromised account, by malware, or by a suspicious user or device), public-facing website attack, suspicious behavior by an insider, and breach of a rule (such as a blacklist, file transfers). Like an anomaly, a threat can be associated with one or more participants, including users, devices, and applications. A threat need not have a specific event date, because it might be ongoing, in which case it can have a start date and a date of last update. Each threat is based on at least one anomaly.
- Because network security monitoring can involve tracking network activity by users, devices, and applications (referred to collectively as “entities”) to identify and track anomalies and threats (referred to collectively as “instance of potential network compromise,” or “instances”), a graphical user interface for a user in accordance with the present disclosure also organizes, tracks, and presents information concerning these entities and instances of potential network compromise. Since information pertaining to different entities and instances may be interrelated, the graphical user interface, in accordance with various embodiments of the present disclosure, provides various views for causing display of this information. The graphical user interface also includes links in these views to cross-reference the information. These capabilities facilitate a user's ability to understand the connections and relationships between different entities and/or instances to better understand security risks and causes of a problem.
- For example, the graphical user interface provides several different ways for a user to access information pertaining to a particular device that seems suspicious. The user may search for the device directly through a “device view.” Alternatively, the user may notice the device when reviewing a threat, and then click on a link for the device from within a threat view. Instead, the user might become aware of the device when reviewing information about an anomaly, and click on a link for the device from an anomaly view. As yet another alternative, the user might notice the device when navigating a “user view,” and clock on the link from within the user view. Once the user reviews information about the suspicious device, the user can use a “watchlist” to “mark” the device (e.g., as suspicious). Once the device is put in the watchlist, that tracking information can stay with the device and obtained upon access device information from any view.
- In accordance with various aspects of the present disclosure,
FIG. 39A provides an example high level, “home screen”view 3900 generated by display data for display in a graphical user interface (“GUI”). This may be the first screen viewed after log-in.Toolbar 3901 also may be included in all views generated for display in the GUI. In this example, the toolbar includes a “Views”tab 3902, “Analytics”tab 3903, “Config”tab 3904, and GUIuser name tab 3905 for log-in. - By clicking on the “Views”
tab 3902, as shown inFIG. 39B , a GUI user can toggle the GUI between a “Threats”view 3906, “Anomalies”view 3907, “Users” view3908, “Devices”view 3909, and “Applications”view 3910. As described in further detail below, the “Threats”view 3906 provides a listing of all active threats and the “Anomalies”view 3907 provides a listing of all anomalies. The “Users” view3908, “Devices”view 3909, and “Applications”view 3910 provide separate listings for each type of entity (namely, users, devices, and applications, respectively) that is associated with an anomaly or threat. - Returning to
FIG. 39A , thehome screen view 3900 also may include asummary status bar 3911 indicating, for example, the number of threats, anomalies, total users, total devices, total apps, and total sessions on the network being monitored. The summary status bar can enable the GUI user to see, at a glance, the volume of information that can be reviewed and evaluated. - The
home screen view 3900 can additionally include summary charts and illustrations, such as, as shown inFIG. 39A , a “Threats by Threat Type”box 3912, a “Latest Threats”box 3913, and an “Events Trend” graphic3914. The “Threats by Threat Type”box 3912 compares by number each different type of threat that has been identified. The listing in the “Latest Threats”box 3913 identifies the most recent threats by date. The “Events Trend” graphic3914 is a timeline showing the volume of events along a timeline. - The example
home screen view 3900 also prompts a user, viastatus bar 3911, to begin a “Threat Review” or view an “Analytics Dashboard.” Upon clicking, via the graphical user interface, on the “Start Threat Review”button 3915, a “Threats Review”view 4000 is provided, as described with reference toFIG. 40A . - As shown in
FIG. 40A , an example “Threats Review”view 4000 enables a user to separately click through each active threat that has been identified from the event data. In the upper-right of the view, a count andtoggle 4001 enables the user to step through each identified threat. - The
view 4000 can include afilter section 4020 that enables the user to selectively filter out threat results according to time, severity, or type. For example, as shown inFIG. 40B , the default provides views of “All Threat Types”4021 but a user can change this to just review pages for “External,” “Insider,” or “Rule-Based” threats. Thefilter section 4020 also provides an option to “Select Threat Types,” which enables the user to select the specific types of threats to be included in the Threat Review. Thefilter section 4020 also enables the user to filter out threats based on their scores by clicking the “Scores”tab 4022. (For example, if the user is only interested in evaluating high risk threats, the user might filter out any threats with a score less than 5). The user can also click on the “Time”tab 4023 to filter out threats based on a date range. For example, if the user is only interested in evaluating very recent threats, the user can choose to filter out any threats earlier than the past 24 hours. - Returning to
FIG. 40A , each “Threat Review”view 4000 can identify a particular threat by its type and provides asummary description 4002 along with athreat score 4003. The threat score, determined based on machine learning from the event data, provides an indication of the severity of the risk for network compromise associated with the threat. - The “Threats Review”
view 4000 can additionally include astatus chart 4004 that provides a Timeline, list of Anomalies, list of Users, list of Devices, list of Apps, and a suggestion of “What Next.” The Timeline identifies the date that the threat began, the last update concerning the threat, and the duration of time that the threat has been active. The list of Anomalies identifies each type of anomaly that is associated with the threat and how many anomalies of each type. The list of Anomalies also provides a score for each type of anomaly, which indicates the severity associated with each type of anomaly. The list of Users identifies each user associated with the threat and provides a score for each user. Similarly, the list of Devices and list of Apps identify each device (by IP address) and App (by file name/type), respectively, along with a score. - For each entity (e.g., user, device, and app), a link is included such that, if the link is clicked, the user is taken to a separate view for that selected entity. For example, if the link associated with “Mark Pittman”4005 is clicked, a “Users Facts”
page 300 within the Threats Review is generated, as can be seen fromFIG. 41 . - Returning again to
FIG. 40A ,Threats Review view 4000 additionally prompts the user to take “Actions”4010, view additional “Details”4011, or set up a “Watchlist”4021. By clicking on the “Actions”tab 4010, the user can select from several options, as shown inFIG. 40C . If the user determines that the threat is not a concern, the user can select “Not a Threat”4011. By making this selection, the user instructs the network security system to delete the threat page from the Threats View and to no longer identify it as a threat. As a consequence, the total number of threats will decrease (as will be depicted in thestatus bar 3911 inFIG. 39A ). Another option in the “Actions”tab 4010 is the “Email Threat”selection 4012, which enables the user to email the threat to a designated email address. Yet another option is the “Export”selection 4013, which enables the user to export data associated with the threat to another data mining platform. - As shown in
FIG. 40A , theThreats Review view 4000 also includes a “Details”tab 4011. When the user selects this tab, in the example provided in this figure, the Threats Review view is augmented with several additional charts and graphics, as shown inFIGS. 40D, 40E, and 40F , as will be described next. FIG. 40D illustrates a “Threat Relations”flow 4040, which depicts the relationship between users, devices, and applications that are associated with the threat. Dotted lines connect one or more entities that are participants together in one or more anomalies associated with the threat. For example, in this flow, device “10.116.240.105” is connected via a dotted line with “10.1.21.153,” which runs application “ms-ds-smb” and is associated with “Fred Samuels” and “Mark Pittman.” The dotted is color-coded to indicate that it is “minor” in nature.- When a user “hovers” the cursor over (or highlights) the name of a user, device, or application (or an arrow pointing to the user, device, or application), display data generates a bubble in the GUI view that provides a high-level summary of information about that entity. For example, hovering over “Mark Pittman” causes
bubble 4043 to appear, which indicates that “Mark Pittman” is associated with three anomalies: two “Land Speed Violations” (color-coded to indicate that these are considered “major”) and one “Unusual Activity Time.” - In this example, the
bubble 4043 additionally prompts the user to click a “View All 3 Anomalies” link. As shown inFIG. 42 , clicking on this link causes the GUI to generate anAnomalies Table view 4200 that lists and provides high-level information about the three anomalies. - Instead of, or in addition to, hovering the cursor over an entity, the user can click on an entity to select to receive a view concerning that entity. For example, if the user clicks on “Mark Pittman,” the GUI generates a “User Facts”
view 4100 for Mark Pittman, as shown inFIG. 41 . FIG. 40D illustrates a “Kill Chain View”4050 associated with the threat. The Kill Chain view illustrates three stages of the threat: “Intrusion”4051, “Expansion”4052, and “Exfiltration”4053. For each stage, the GUI includes a summary of the anomaly or anomalies in that stage. For example, two LandSpeed Violation anomalies 4054 occurred during the “Intrusion” stage. The GUI indicates that one of theseviolations 4056 was from Pittsburgh, in the US, to Beijing, in China. The GUI indicates the number of times that land speed violation occurred (once) and provides a color-code to indicate the severity of that violation as it relates to the threat.- The GUI can include a link for each anomaly in
stages Kill Chain 4050 inFIG. 40D . For example, by clicking on “Land Speed Violation from Pittsburgh, US, to Beijing, China”4056, the user navigates to Anomaly Details view4300 for this selected anomaly, as shown inFIG. 43 . In the example view provided inFIG. 40D , the two anomalies associated with theExfiltration stage 4053 are both “Excessive Data Transmission”4055. These are color-coded in red to provide an indication of their high level of severity. - The Kill Chain view additionally can include a
timeline 4057 that illustrates the timing of each phase. In this example inFIG. 40D , theIntrusion phase 4051 is associated with 3 anomalies, beginning on Nov. 15, 2014. TheExpansion phase 4052 is associated with 8 anomalies, beginning on Nov. 21, 2014, and concluding on Nov. 23, 2014. TheExfiltration stage 4053 is associated with 2 anomalies, beginning on Dec. 1, 2014, and concluding (or their last update occurred) on Dec. 3, 2014. - Returning to
FIG. 40A , clicking on the “Details”tab 4011 in theThreats Review view 4000 also can generate illustrations of aThreat Anomalies Timeline 4060,Threat Anomalies Trend 4070, and Threat Anomalies listing4080 andDevice Locations 4090, inFIGS. 40E and 40F . - Referring to
FIG. 40E ,Threat Anomalies Timeline 4060 provides a timeline of each anomaly, sorted by anomaly type. In this example, there are four anomaly types: “Excessive Data Transmission,” “Land Speed Violation,” “Unusual Network Activity,” and “Unusual Activity Time.” The timeline shows a circle corresponding to each occurrence, which is color-coded to indicate its severity. If there is more than one anomaly of the same type on the same date, the circle is made larger. By hovering over a circle, a bubble is generated that provides the date of the anomaly or anomalies and prompts the user to select more detailed information (not shown). Upon clicking on a bubble, the GUI generates an associatedAnomalies Table view 4200, in the format shown inFIG. 42 . FIG. 40E additionally includesThreat Anomalies Trend 4070. This provides a line graph indicating the number of anomalies during periods of time. With this illustration, a GUI user can quickly discern whether a large number of anomalies occurred on a particular date or time period, and whether there is a trend of increasing or decreasing anomalies. By hovering over a point on the line, the GUI generates a bubble indicating the date and number of anomalies on that date. Similar to theThreat Anomalies Timeline 4060, upon clicking on a bubble, the GUI generates an associatedAnomalies Table view 4200, in the format shown inFIG. 42 .- The “Details” version of the
Threats Review view 4000 also includes a Threat Anomalies listing4080. In the listing, each entry is associated with an “Anomaly Type”4082, one or more “Participants”4083, a “Summary”4084, an “Event Date”4095, and a “Score”4086. For example, “Land Speed Violation”4087, the first listed anomaly type, is associated with three “Participants,” user “Mark Pittman” and devices “1.94.32.234” and “66.39.90.214.” The listing summaries that the anomaly is “From Pittsburgh, US to Beijing, CN,” and indicates that the anomaly occurred on “Nov. 15, 2014.” The score associated with the anomaly is “5”. By clicking on “Land Speed Violation,” the GUI navigates to Anomaly Details view4300 as shown inFIG. 43 . - The listing of
Anomalies 4080 provides a summary indicating each type of anomaly associated with the threat and the number of anomalies per type. The default for the listing is to display all anomalies as indicated by the “All Anomalies”tab 4081, but a GUI user can opt to view only anomalies of a selected type. - Referring to
FIG. 40F , the detailed version of theThreats Review page 4000 also includes aDevices Location map 4090. This map provides a visual indication of the location of the devices associated with the threat. Device is represented on the map by a circle, color-coded to indicate the score, or severity of risk associated with the device or location. If there are multiple devices at a single location (or vicinity), it is represented by a larger circle. InFIG. 40F , there are four locations represented, one in China, two in California, and one in Pittsburgh, Pa. By hovering over a circle, such as4092, the GUI generates a bubble, as shown inFIG. 40G , that provides more detailed location information (in this case, “Beijing—China”), the device name/IP address (“1.94.32.234”), and a link to “View Device Details.” If the GUI user clicks on the link, the GUI navigates to the User Facts view4100 ofFIG. 41 . - Devices Location map4009 also includes color-coded lines that connect the devices. For example,
line 4093 connects the devices represented bycircle 4091 to the device represented bycircle 4092. The lines correspond to the one or more anomalies for which the connected devices are participants. As shown inFIG. 40H , by hovering overline 4093, the GUI generates abubble 4095 that identifies each anomaly represented by that line and a color-code indicating the score for that anomaly. Thebubble 4095 additionally includes a link for the GUI user to view all associated anomalies (e.g., “View All 2 Anomalies”). Upon clicking on the link to view all anomalies, the GUI navigates to the associated Anomalies Table4200, in the format shown inFIG. 42 . - As can be seen, the GUI introduced here enables a user to access the same views and information via several possible navigational paths. For example, link4056 in the Kill Chain view in
FIG. 40D , link4087 in the Threat Anomalies listing inFIG. 40D , and link4201 in the Anomalies Table inFIG. 42 each navigate to the “Land Speed Violation” Anomaly Details view4300 inFIG. 43 . Similarly, there are several paths (via the charts, diagrams, listings, and maps shown inFIGS. 40E, 40F, 40G, and 40H , to accessUser Facts 4100 inFIG. 41 and Anomalies Table4200 inFIG. 42 . - As shown in
FIG. 40A ,Threats Review page 4000 additionally includes “Watchlist”tab 4012, which enables the GUI user to track the threat. Upon clicking on tab4412, as shown inFIG. 44A , the GUI provides abubble 4400 prompting the user to tag the threat with “Threat Watchlist,” “False Positive,” “Important,” “Reviewed,” “Save for Later,” or to define a new category for tagging (via the “New Threat Watchlist” selection). The tag remains associated with the threat until the GUI user changes the watchlist. For example, by designating the threat as “Reviewed”4410, as shown inFIG. 44A , the GUI associates the threat as “Reviewed” in subsequent reviews of the threat, as shown at4411 inFIG. 44B . - In addition to providing threat, anomaly, and entity information in various views via the “Threat Review,” the GUI also enables users to directly navigate to desired views containing the same information via the
Views tab 3902 as shown inFIG. 39B . TheViews tab 3902 can be accessed from any view in the GUI. As shown inFIG. 39B , theViews tab 3902 enables a user to toggle between aThreats view 3906, Anomalies view3907, Users view3908, Devices view3909, and Applications view3910. FIG. 45A provides an example view that the GUI generates when a GUI user selects the Threats view3906 inFIG. 39B . TheThreats Table view 4500 provides aThreats Trend timeline 4510 and aThreats listing 4520. TheThreats Trend 4510 illustrates the number of threats over a period of time. This can be provided as a line chart, as shown inFIG. 45A . As alternatives, the same information can be re-formatted as a column chart, as shown inFIG. 45B , or as a breakdown column chart as shown inFIG. 45C .- While viewing the Threats Trend3906 (in any format), the GUI user can use the cursor to hover over displayed data to receive more specific information. For example, referring to
FIG. 45A , hovering over the data on the line at4511 causes atext bubble 4512 to appear, indicating a specific date (or time) and the number of threats at that point, as shown inFIG. 45D . - Referring back to
FIG. 45A , the Threats listing4520 lists all active threats. The Threats listing provides, for each entry, theThreat Type 4530,Participants 4531,Event Date 4532,Last Update 4533, andScore 4534. Asummary section 4535 identifies the number of threats of each type and provides an option to just display the threats of a certain specified type. - In
FIG. 45D , if the GUI user clicks on thetext bubble 4512, the Threats listing4520 changes to display only the subset of threats that are associated with the selected date on the timeline. To receive specific information about a threat in the subset of threats, the GUI user clicks on a link in the Threats listing4520. The GUI then navigates to theThreat Details page 4540, as shown inFIG. 45E . This page provides the same information (including the same charts, graphs, etc.) provided in theThreats Review page 4000 when the “Details”tab 4011 is selected. In the same manner as shown inFIGS. 40A-40E and as described above with reference to those figures, theThreats Detail page 4540 also provides the same summary chart, Threats Relations graphic, Kill Chain view, Threat Anomalies Timeline, Threat Anomalies Trend, Threat Anomalies listing, and Device Locations map. And as inFIG. 2 , theThreats Detail page 4540 also enables the GUI user to create a Watchlist or to take Action. - Finally, while viewing Threats Table4500, the GUI user can navigate to the User Facts view4100 in
FIG. 41 or theAnomaly Details 500 inFIG. 43 in largely the same manner. For example, from within the Threats listing4520 onFIG. 45A , a GUI user can click on the link for any participant (user, device, or application) and then receive the User Facts view4100. As another example, from the Kill Chain view inFIG. 45E , a GUI user can select any anomaly associated with a phase in the Kill Chain (namely, intrusion, expansion, and exfiltration, and view the Users Table or equivalent information concerning other entities. FIG. 46A provides an example view that the GUI generates when a GUI user selects the Anomalies view3907 inFIG. 39B . The Anomalies table4600 provides anAnomalies Trend timeline 4610 and anAnomalies listing 4620. TheAnomalies Trend 4610 illustrates the number of anomalies over a period of time. This can be provided as a line chart, as shown inFIG. 46A . As alternatives, the same information can be re-formatted as a column chart, or as a breakdown column chart (not shown), analogous to the Threat Trend as shown inFIGS. 45A-45C .- While viewing the Anomalies Trend4610 (in any format), the GUI user can use the cursor to hover over displayed data to receive more specific information. For example, referring to
FIG. 46A , hovering over the data on the line at4611 causes a text bubble to appear, indicating a specific date (or time) and the number of anomalies at that point (not shown). - In the
Anomalies Table view 4600, the Anomalies listing4620 lists all active anomalies. The Anomalies listing provides, for each entry, theAnomaly Type 4630,Participants 4631,Summary 4632,Event Date 4633, andScore 4634. To the left of the listing, the view identifies the number of anomalies of each type and provides an option to just display the anomalies of a certain specified type. - As shown in
FIG. 46B , if the GUI user clicks on the graph of the Anomalies Trend at4611, the Anomalies listing4620 changes, as indicated at4641, to display only the subset of anomalies that are associated with the selected date on the timeline, as shown at4642. - To receive specific information about an anomaly, the GUI user can click on an entry in the
Anomaly listing 4620. Each entry is a link. Upon clicking, the GUI navigates to an Anomaly Details view4650 that corresponds with the selected entry in the Anomaly listing. An example of an Anomaly Details view4650 is shown inFIGS. 46C-46E . The Anomaly Details view4650 provides specific information, charts and graphics about the selected anomaly, along with additional links to the entities that participated in the anomaly. - As can be seen in
FIG. 46C , the Anomaly Detailspage 4650 can include asummary section 4651 identifying the anomaly by type (e.g., “Unusual AD Activity Sequence”), event date (e.g., “Jan. 2, 2014 10:10 PM”) a short description (e.g., “An unusual event appeared for this account Login . . . ”), and a score (e.g., “5”). - For the anomaly corresponding to the Anomaly Details view4650 (“Unusual AD Activity Sequence”), a single user is the only entity that is associated with the anomaly. The Anomaly Details view4650 includes a box identifying the “Users”4652 (e.g., “Clint Dempsey”) along with the user's associated score (e.g., “4”). “Users” can include all personnel in the organization who caused the anomaly, were victims, or otherwise participated in some network activity that triggered the identification of the anomaly.
- In this example, the Anomaly Details view4650 additionally includes an “Anomaly Relations”
box 4653. This box illustrates the connection, or “relationship” between different entities (users, devices, and applications) that participated in the anomaly. Since, in the exampleAnomaly Details page 4650, there is only listed User, the “Anomaly Relations” graphic is left blank. FIG. 46F provides a second example of an Anomaly Details view, this time for a “Machine Generated Beacon” that occurred on Jul. 27, 2014 at 4:36 PM, as shown at4655. This anomaly is associated with 4 entities: User “ggawrych”4656, Internal Device “10.104.31.18” and External Device “46.214.107.142”4657, and Domain “46.214.107.142”4658.Anomaly Relations box 4659 illustrates the relationship between these entities. As can be seen, User “ggawrych” uses Internal Device “10.104.31.18” to access domain “46.214.142” operating on External Device “46.214.107.142.”- Returning to the Anomaly Details view4650 in
FIG. 46C , the detailed view additionally includes a “Triggering Event”box 4654. This box provides the event data that triggered identification of the anomaly. FIG. 46D illustrates an “Anomalous Activity Sequence”box 4660 in the Anomaly Details view4650. Given that the type of anomaly in Anomaly Details view4650 is an “Unusual AD Activity Sequence,” this graphic illustrates the string of activities that triggered the anomaly. It is worth noting that this graphic would not apply for other types of anomalies, such as the “Machine Generated Beacon”4655 ofFIG. 46F . Accordingly, each Anomalies Detailed View provides different boxes and graphics to illustrate parameters that correspond to the type of anomaly in the view.FIG. 46E provides additional boxes that may be associated with the “Unusual AD Activity Sequence,” in Anomaly Details view4650. This includes “User Activities Baseline”box 4661, which illustrates the typical activities for the user that do not trigger an anomaly and the “Compare Unusual Activity with the Account's Profile” box4662. Finally, the Anomaly Details view4650 may include a box for “Additional Information”4663 and an “Anomaly Graph”box 4664 illustrating the relationship between the user and the anomaly.- Similar to the “Threats” view in
FIGS. 45A-45E , the “Anomalies” view inFIGS. 46A-46F includes a multitude of links by which the GUI user can navigate to additional pages. For example, inFIG. 46A , upon selection of one of the “Participants” in the Anomalies listing4620, if the “Participant” is a user, the GUI will generate a “User Facts” view corresponding to the user, similar to that inFIG. 41 . If the “Participant” is a device or application, then the GUI will instead generate a “Device Facts” or “Application Facts” view (not shown). In the same manner, the user, device or application can be selected in the Anomaly Details view, such as inFIG. 46C orFIG. 46F , to generates the “User Facts,” “Device Facts,” or “Application Facts” views. Also, the GUI user can configure the “Watchlist” from the Anomaly Details view, in a similar manner as for the Threat Details view. - Returning to
FIG. 39B , by selecting the “Users” toggle in the “Views”tab 3902, the GUI user navigates to a “Users Table”view 4700 as illustrated inFIG. 47A . The “Users Table” provides a list of each user that is associated with a threat or anomaly. The listing can include theuser name 4701, the Department in which the user works in the organization, if known from the event data or other data, the number of associatedanomalies 4703, the number of associatedthreats 4704, the date and/or time of the mostrecent update 4705, and the score associated with thatuser 4706. - By clicking on an entry in the Users Table view, such as “Rick Browne”4707, the GUI navigates to the Users Facts view4710 for that selected user, as shown in
FIG. 47B . The User Facts view can include asummary section 4717 providing, for example, the number ofthreats 4711, the number ofanomalies 4712, the number oftotal sessions 4713, the number of anomalous sessions4714, and the number ofevents 4715. The view can additionally include a “User Score Trend”box 4716, which illustrates the change, if any, in the score associated with the user over a period of time. - The Users Table view4707 can additionally include a
user profile box 4720 indicating, for example, the user's HR (human resources) status, Department in the organization (e.g., “Sales”), email address, login ID, Phone number, Address, and AD groups. The profile box may also include information concerning Similar Users, Top Devices, and Top Apps. As also shown inFIG. 47C , the Users Table view may also include a UserEvents Trend box 4721, which depicts how many events that the user participated in over a time period. A sudden increase in the number of events can be useful in evaluating potential network compromise. As yet another example, the Users Table view can provide a UserEvents Classes box 4722, which shows the number of each class of events for which the user was a participant. - Referring back to
FIG. 47B , each number in thesummary section 4717 can provide a link to other views. For example, by clicking on the number of threats (“1”)4711, the GUI generates a “User Threats”view 4730 as shown inFIG. 47D . The “User Threats”view 4730 can include a summary section, including, for example, the number and type of each associatedthreat 4731, the number and type of each associatedanomaly 4732, the number of devices operated by the user that have been associated withanomalies 4733, and the domains involved in the anomalies that the user accessed4734. The summary view additionally can include an associated score for each threat, each anomaly, and each device. Each device identified in4733 can provide a link to a “Device Facts” view that corresponds to that selected device, as further described below. Likewise, each domain identified in4734 can provide a link to a “Domain Facts” view that corresponds to that selected domain, as also further described below. - The “User Threats”
view 4730 also may include a “User Threats Timeline”box 4735 that visually depicts when the user became associated with each type of threat identified in4731 and the duration of that threat. The data on the timeline can be color-coded according to the score of the threat. Hovering (or highlighting) the data on the timeline causes the GUI to generate a text bubble that summarizes the identity and timing of the threat. - Finally, the “User Threats”
view 4730 also may include a “User Threats” listing4736, which, for each threat associated with the user, identifies the threat type, all participants, the last update, and the score. In the example shown inFIG. 47D , there is a single entry in the listing because there is one threat associated with the user. By clicking on an entry in the listing, the GUI user navigates to the “Threats Details” view corresponding to that threat, similar to “Threats Details”view 4540 ofFIG. 45E . - Referring back to
FIG. 47B , by clocking on the number of anomalies (e.g., “2”)4713, the GUI generates a “User Anomalies”view 4740 as shown inFIG. 47E . The “User Anomalies”view 4740 can include the same summary of information section provided in the “User Threats”view 4730. The “User Anomalies”view 4740 additionally can include a “User Relations”box 4741, which illustrates the connections between the user (“Rick Browne”), the Internal device that he operates (“10.104.105.166”), and the external device (“46.214.107.142”) and domain (“mpdhgokh.ddns.net”) that he communicated with when the anomaly was triggered. - The “User Anomalies”
view 4740 additionally can include a “User Anomalies Timeline”box 4742. The timeline depicts each anomaly that is associated with the user as a circle and indicates the date that the anomaly occurred. In this example, it can be seen that two anomalies, “Exploit Chain” and “Machine Generated Beacon,” both occurred on Jul. 28, 2014.View 4740 also may include a “User Anomalies Trend”box 4743, indicating how many anomalies occur on each date. As shown inFIG. 47F , the “User Anomalies”view 4740 also can include a “User Anomalies”box 4744 that lists each anomaly and for each, it identifies each participant, a summary of the anomaly, the event date, and the score. A GUI user can click on the listing to navigate to an “Anomaly Details” view, similar to that shown inFIGS. 46C and 46F . The GUI user can also click on a device or domain identified in the “Participants” column shown inFIG. 47F to navigate to a ““Device Facts” view that corresponds to that selected device, as further described below. Likewise, each domain identified in4744 can provide a link to a “Domain Facts” view that corresponds to that selected domain, as also further described below. - Finally, the “User Threats”
view 4730 and “User Anomalies”view 4740 each may include a “Watchlist,” the functionality was explained previously with reference toFIG. 44A . A “Watchlist” for auser 4745 is shown inFIG. 47G . - Returning again to
FIG. 1B , by selecting the “Devices” toggle in the “Views”tab 3902, the GUI user navigates to a “Devices Table”view 4800 as illustrated inFIG. 48A . Analogous to the “Users Table”4700 described above with reference toFIG. 47A , the “Devices Table” provides a list of each device that is associated with a threat or anomaly. The listing can include theIP Address 4801, the Scope (e.g., “External” or “Internal”)4802, the number of associatedanomalies 4803, the number of associatedthreats 4804, the date and/or time of the mostrecent update 4805, and the score associated with thatuser 4806. - By clicking on an entry in the “Devices Table” view, such as “207.46,1.127”4807, the GUI navigates to the “Devices Facts”
view 4810 for that selected device, as shown inFIG. 48B . The “Devices Facts” view can include a summary section and other information, such as a “Device Score Trend”box 4811, which indicates the date that the device was assigned a score and whether that score has changed over time. The view can additionally include a “Device Score Trend”box 4811, which illustrates the change, if any, in the score associated with the user over a period of time. As other examples, the “Device Facts”view 4810 may include a “Top Users”box 4812, which indicates whether there are one or more primary users for the device, and a “Top Apps”box 4813, indicating whether, from the event data, it can be discerned whether there are any known applications running on the device. As with the “User Facts” table, a “Watchlist”tab 4814 is provided. - In the example of
FIG. 48B , by clicking on the Anomalies (“1”)4816 in the summary view, the user navigates to a “Device Anomalies”view 4815 inFIG. 48C , analogous to the “User Anomalies”view 4740 inFIG. 47E . In this example, there are no threats associated with the device. If, however, there is an associated threat, then upon clicking on the “Threats” number in thesummary view 4810, the user will navigate to a “Device Threats” view, analogous to the “User Threats” view described previously. - The Users Table view4709 can additionally include a
user profile box 4720 indicating, for example, the user's HR (human resources) status, Department in the organization (e.g., “Sales”), email address, login ID, Phone number, Address, and AD groups. The profile box may also include information concerning Similar Users, Top Devices, and Top Apps. As also shown inFIG. 9C , the Users Table view may also include a UserEvents Trend box 4721, which depicts how many events that the user participated in over a time period. A sudden increase in the number of events can be useful in evaluating potential network compromise. As yet another example, the Users Table view can provide a UserEvents Classes box 4722, which shows the number of each class of events for which the user was a participant. - Returning once again to
FIG. 39B , by selecting the “Applications”toggle 3910 in the “Views”tab 3902, the GUI user navigates to an “Applications Table”view 4900 as illustrated inFIG. 49A . Analogous to the “Users Table” and “Devices Table” described above, the “Applications Table” provides a list of each application that is associated with a threat or anomaly. The listing can include the application name, the number of associated anomalies, the number of associated threats, the date and/or time of the most recent update, and the score associated with the application. - By clicking on an entry in the “Apps Table” view, such as “ssh,” the GUI navigates to the “App Facts”
view 4910 for that selected application as shown inFIG. 49B . The “App Facts” view can include a summary section and other information, such as an “App Score Trend,” “App Activities Baseline,” and “App Graph,” which are analogous to graphs and charts described previously with reference to the “User Facts” and “Device Facts” views. As with the “User Facts” and “Device Facts” table, a “Watchlist” tab is provided. - Returning to the “Threats Table”
view 4500 inFIG. 45A , the GUI as introduced here additionally includes a selector from the “Threats Table” that, upon selection, generates the display of a geographical representation of the identified threats. Referring toFIG. 50A , by selecting theglobe icon 5010, the GUI generates a “Threats Geo Map”5020, as shown inFIG. 50B . The Threats Geo Map depicts, on a globe, each identified threat as a circle on the map at the threat's location. For example,threat 5023 is located in Asia, in or near Thailand, and there is at least twothreats 5022 on the East coast of the United States. Each circle designating a threat is color-coded according to the score associated with the threat. For example,threat 5023 may be a yellow color, indicating that the threat is minor (see the reference table at5026), whereas threat5028 (in China) may be orange, indicating that the threat is major. - The threats depicted on the Geo Map also may be of different sizes, indicating that number of threats at a particular location. For example,
threat 5023 is a small circle, whereasthreat 5024 is a larger circle. - By hovering over a threat, such as a threat at5022, a text bubble will appear, indicating the location and number of threats at that location. Clicking on a threat modifies the text bubble to provide an indication of the type of threat and a link to “View Threat Details.” Upon clicking on this link, the GUI user navigates to the associated “Threat Details” view, such as the “Threat Details”
view 4540 ofFIG. 45E . - Another
icon 5029 is depicted where the internal network is located. Lines are then shown connecting theinternal network location 5029, as a hub, to each threat location. The lines include arrows, indicating that the threat is radiating from the internal network hub to other geographical locations. Line 5025 is an example of a line connecting the internal hub to a threat. Upon clicking on the line, as shown inFIG. 50D , a text bubble appears that identifies the one or more anomalies that are associated with the threat. The text bubble identifies each type of anomaly by type, the number of anomalies of each type, and a color-coding indicating the severity of each anomaly. In the example ofFIG. 50D , the text bubble also provides a link by which the user can click to “View All 2 Anomalies.” Upon clicking on this link, the GUI user navigates to the “Anomalies Table” view, such as the “Anomalies Table”view 4600 as shown inFIG. 46A .- Returning to
FIG. 39A , upon selecting the “Analytics”tab 3903, the GUI generates an “Analytics Dashboard”5100 as shown inFIG. 51 . This dashboard presents several charts and other graphics similar to those shown in other figures shown above, including “Threats By Threat Type,” “Anomalies by Anomalies Type,” “Latest Threats,” and “Latest Anomalies.” - As discussed above, one of the many features of the security platform introduced here is the capability of detecting unknown anomalies and threats. The security platform can achieve this through any of various machine learning models. Specifically, a number of these machine learning models can be adapted to perform security-related analysis, including behavioral analysis for specific entities (e.g., a user, a machine, a group of user or machines). Using the techniques discussed herein, machine learning models can establish behavioral baselines for various different entities of various different types (e.g., users, devices, etc.) and can detect behavioral deviations from such baselines as potentially indicative of malicious activities. In addition, the security platform provides a structure for the network administrators or security analysts to easily design, configure, and/or modify the models in order to suit their own purposes and the deployed environment.
- Many traditional techniques only focus on detecting security breaches on a per event basis (e.g., inspecting each event according to rules or signature comparison to determine whether any single event is malicious), and these traditional techniques would not be able to detect any security-related issue if each of the events considered individually appears to be normal. To address this problem, a number of example models (e.g., an event sequence prediction model, which may be customized for detecting abnormal entity behaviors) utilized by the security platform are configured to discover behavioral anomalies by determining whether a given sequence of events as associated with an entity deviates from an anticipated behavioral baseline, even though each event individually may well be considered not malicious or anomalous. For this purpose, in various implementations of these models, a probabilistic suffix tree (PST) based data processing procedure can be employed.
- The PST based data processing procedure can utilize a “windowed” version of a probabilistic suffix tree to detect an unusual sequence (e.g., event sequence). As used herein, a sequence can by any timely ordered sequence of arbitrary symbols. In practical implementations, these symbols can denote particular types of security events including, for example, Connection-Fail, Password-Rest, or File-Access. In several embodiments, each symbol discussed herein is an event feature set as discussed in this disclosure. A symbol can correspond to at least a machine-observed event. However, note that the PST based data processing procedure described here is generally applicable to any type of sequence, not limited to those that are disclosed herein. To facilitate discussion, in the following context, Event-Types are used as an example of the symbols. Further, for simplicity, the Event-Type symbols discussed here may be denoted with single characters (e.g., x, y, z) and/or integers (e.g., 0, 1), which will be made clear by the context. Also, the PST based data processing procedure may be referred to herein as the PST-based machine learning model or, simply, the PST model.
- More specifically, the PST model is to be used in a way that, given an observation window with a number of previous symbols, the PST model can predict what the next symbol may be, to identify whether a target window is anomalous (e.g., by having an anomaly count beyond a baseline). Before the PST model is ready to do so, the PST model needs to receive training so that it can more accurately anticipate or predict the next symbol. For example, the PST model can be trained by a certain set of historical symbols. This set of historical symbols (i.e., the amount of training) denotes whether the PST model is considered ready (i.e., the prediction can be considered enough trustworthy). The amount of training can be controlled based on any of various training principles including, for example, by a fixed time, by a fixed number of symbols, or by other suitable methods including automatic training. The fixed time type of training can include training the PST model by using all previous symbols that took place within a certain time window (e.g., one week). The fixed symbol number type of training can include training the PST model by using a select number of previous symbols (e.g., 5,000 events). An example of an automatic training can include training the PST model by using past symbols until the PST model meets a certain criterion, such as convergence. For example, in some embodiments, similar to how the PST model can score (discussed in more detail below), a vector comprised of computed scores from the in-training PST model can be built and compared to other versions of the PST model to determine if the model state of the in-training PST model is ready (e.g., is converging or has converged by a certain degree). Note that, in some applications, the observation window is to be kept at a relatively small size (e.g., around four to five symbols) in order to keep computational complexity at a reasonable degree. According to some embodiments, a maximum value of five symbols is used for such observation window. This approach to sequence analysis utilizes the property of the PST that can “memorize history.” The sequence generation process of the PST model can be modeled as a variable length Markov chain, which may be similar to a formation of finite state automaton. The “memory capacity” of the PST model can be controlled by the maximum length of historic symbols, which is the probabilistic suffix tree's depth, and is the length of the Markov chain.
- After a PST model is trained, it can be used to more reliably predict the next symbol. Specifically, given a history of a number of symbols (e.g., five symbols), a trained PST model can generate the entire probability distribution for all “next” symbols for the entire set of possible symbols seen for a particular entity. For simplicity, the probability of a particular next symbol given a particular sequence of historical symbol is denoted as “P(next|history),” which is also referred to herein as “predictions.” For example, if a PST model generates that P(a|aabcd)=0.1, P(b|aabcd)=0.8, P(c|aabcd)=0.1, and P(d|aabcd)=0, it means that, given the history “aabcd,” the probability of the next symbol in the sequence being “a” is 10%, “b” is 80%, “c” is 10%, and it is highly unlikely to see “d” as the next symbol. In this way, if the actual next symbol in the sequence is “a”, “b”, or “c,” these symbols may be deemed acceptable or normal because they are acceptably predicted (e.g., because they all have probabilities that meet or exceed a certain threshold, for example, 10%).
- However, if the actual next symbol that appears is a “d,” then because the prediction of the probability of “d” appearing is very low, this event/symbol is considered unusual, or rare. Thereafter, in some embodiments, such rare event can trigger an alert to the administrator for further analysis. As used herein, an unusual symbol (e.g., representing an event) is the actual occurrence of a symbol when the PST model predicts the probability of such symbol's occurrence is less than a threshold, for example, 0.1% or 0.01%. The threshold can be selected and/or adjusted by the administrator according to the environment. An example of a PST model having been trained by a particular sequence [100111] is shown in
FIG. 52 . In the PST model shown inFIG. 52 , the PST's depth is 3. - In addition, because different types of entities may have different characteristics in their behaviors, to further enhance the accuracy of behavioral anomaly detection for a specific entity (e.g., a user), various embodiments of the PST model can be configured to first establish a baseline prediction profile (or simply “baseline”) for a specific entity after the PST model is trained. Specifically, a profiling window of successive prediction can be used to build the baseline prediction profile (e.g., for a specific entity, to learn that how many unusual events per window for the specific entity is consider normal).
- In some implementations, when the PST model is ready (i.e., has been sufficiently trained), the results of the PST model's next symbol predictions within a profiling window can be recorded. Some embodiments provide that the profiling window has a fixed length. With this additional layer of baseline prediction profile, the PST model can become more robust against the potential noise from the presence of a few unusual events, thereby less likely to trigger a false alarm. In other words, if it is actually normal for a certain type of entity (e.g., an administrative user) to have a certain number of unusual symbol predictions within a profiling window, then the PST model can learn this by the baseline prediction profile, reducing the probability that the PST model triggers a false alarm in those normal and common cases. For simplicity, a profiling window can be denoted as “W,” and the length of a profiling window can be denoted as |W|. An
example timeline 5300 is shown inFIG. 53 , illustrating the training of a probabilistic suffix tree based model, the establishment of a baseline prediction profile, and the activation of a particular model version. - In certain embodiments, the properties of a profiling window can be easily changed or tweaked. Different variations of the profiling window can also be used by a PST model to suit different purposes. In a number of implementations, a profiling window can be evaluated based on a count on the ratio, R, of the number of predictions that are below a threshold (e.g., 0.01%) inside the profiling window to the length of the window. This R can also be referred to as the rarity score. For example, if inside a given profiling window of
length 10, there are 4 predictions that are below 0.01%, then the ratio R of unusual events in that profiling window is 4/10 (or R=0.4). In some implementations, to establish the baseline prediction profile using the profiling window technique is to learn what a usual R is for a particular user. - In order to do so, in some embodiments, after the PST model becomes ready, the predictions (of the occurrence of unusual events) inside each profiling window during a certain time length are collected, by sliding a profiling window through the certain time length. This time length is denoted as the baseline prediction profiling phase on
FIG. 53 . Then, a histogram can be made to record all the ratios that are observed. This histogram essentially records the usual R for a particular user. Specifically, the collecting of the predictions from each profiling window can be repeatedly performed for a period of time (i.e., “sliding through” the period of time). This period of time may be N times the length of the profiling window (i.e., N×|W|). In some examples, N is 10. During the baseline prediction profile establishment (shown inFIG. 53 ), for a period of time after the PST model becomes ready, the R for each profiling window is tracked and stored in a histogram. This learned histogram can be denoted as “H.” With this histogram built for the specific entity, for any new R, the PST model can produce a P(R|H). The P(R|H) is the probability of seeing a window with a ratio R, given the history of previous Rs. In this manner, a baseline prediction profile for a specific entity can be built. - After the histogram is built, the PST model can be activated to detect anomalies for the specific entity. This can also be referred to as the scoring phase. To detect an anomaly (e.g., an abnormal behavior of a specific entity as exhibited by a sequence of events), one implementation is to first make record of the rare sequence for the particular entity. Specifically, after the PST model is activated, a target window can be used by the PST model to identify the rare sequence. Similar to the scoring process for the profiling window during the baseline prediction profiling phase, the PST model can be used to generate predictions and calculate the ratio R for a given target window in order to score the target window. For better prediction accuracy, the size of the target window can be set to the same size as the profiling window. After generating an R for a target window, the PST model then refers to the histogram to find the probability of encountering such window with at least an R of this level. If this probability (i.e., P(R|H)) is lower than a certain threshold (e.g., <0.5%), then the PST model determines that this particular target window is anomalous (i.e., for having a rare sequence for the particular entity), and that this anomalous window needs to be recorded (e.g., in a database of rare windows, described below) and/or flagged as anomalous.
- Furthermore, in a number of implementations, an anomalous window expansion technique can be used to more fully capture the anomalous activity. In some of these implementations, when a target window has an R that has low enough probability, a window collection process is initiated. The purpose of the anomalous window expansion technique is to expand the window of unusual activity with the attempt to include as many related unusual actions of the entity inside a single window as possible. One example of the technique allows the original target window (e.g., which is of a fixed length, such as |W|) to be expanded up to a certain size when such target window is found to be anomalous. Note that, however, the longer the window can expand, the larger the required memory is to accommodate such expansion. The expanded window can be denoted as “E,” where |E| is equal to or greater than |W|.
- In at least one example, to achieve this suspicion window expansion, upon the detection of an unusual R in a target window, the PST model can fix the start point of that target window and start increasing the window's size (e.g., by one window) each time it is determined that the next target window also has an R score that is below or equal to the R that triggered the anomalous window expansion process (or until the maximum expansion size is reached). When a next window with a normal R appears, the collection process of the anomalous window can stop.
- Then, in certain embodiments, the aforementioned collected anomalous window can be compared with a database of rare windows. Specifically, in these embodiments, a database of rare windows (also referred to here as rare window cache) can be maintained to keep record of rare windows that the system have seen in the past. Each time there is a new rare window, this database can be referenced to check if there has been any “similar” rare window in the past, and if so, how many. The rationale for this rare window cache technique is the observation that a rare window that has been observed many times in the past tends to be less “anomalous” than a rare window of activity that does not appear to be similar to anything that has been observed before. This technique can be useful in some instances, for example, to discover whether a shared account (e.g., root) may be stolen.
- Specifically, for a given sequence, in order to determine whether the system have seen any similar sequence before, the PST model is capable of comparing two sequences with each other. There are many known methods to compare sequences and determine similarity.
- Nonetheless, disclosed here is a particular way that can be used to compare the similarity, namely, by using a combination of two metrics, the cosine similarity and the Jaccard similarity.
- PST-SIM: The PST implementation of cosine similarity (PST-SIM) is the cosine similarity between two vectors representing the two sequences. Each vector is comprised of the probabilities learned by training an isolated PST for each sequences (more details on building a vector for a sequence are discussed below). This PST-SIM metric can be useful to capture the similarity between the frequent subsequences of the two sequences.
- JAC-SIM: The PST implementation of the Jaccard similarity (also known as the Jaccard index) is the Jaccard similarity between the symbols in the two sequences. It can be defined as JAC-SIM(A, B)=|A intersection B|/|A union B|. This JAC-SIM metric gives more weight to the presence of few different symbols, and it does not take into consideration the symbols' appearance frequencies or their order.
- Because it is observed that these two metrics have different goals, some embodiments employ a combination of two metrics. In particular, the PST-SIM puts emphasis on a bigger, overall picture of the symbol distribution and evaluates how similar the distributions are. On the other hand, the JAC-SIM is more sensitive to the presence or absence of symbols between two sequences. In other words, the more new symbols there is in one sequence as compared to the other, the more different the JAC-SIM result becomes. Conversely, if only a few symbols are missing, and the remaining common symbols appear in the same or similar manner in both sequences, then the PST-SIM result typically is not very affected by the few missing symbols. In some embodiments, the similarity between two sequences is calculated by Sim(S1, S2)=0.5×PST-SIM(S1, S2)+0.5×JAC-SIM(S1, S2).
- In some occasions, such as those described above (e.g., to see whether a PST trainee has started to converge to another PST, or to perform the PST-SIM comparison), two PSTs need to be compared. A PST (e.g., in a PST model, shown in
FIG. 52 ) contains the conditional and marginal probabilities of all the symbols used in the training. Therefore, one way to compare two PSTs is to vectorize the two PSTs, and compare their corresponding probabilities (both marginal and conditional) one by one. After vectorizing the PSTs, resulting in two probability vectors, a suitable vector similarity metric (e.g., Euclidian distance, or cosine similarity) can be used to compare the two PSTs. - Consider an example with three possible symbols, {x,y,z}, and a PST of depth2 (meaning that the PST model at most looks at two historical symbols to predict the next one). Further, in this example, assume that the marginal probabilities are P(x)=0.8, P(y)=0.15, and P(z)=0.05, and the conditional probabilities are P(x|xx)=0.7, P(y|xx)=0.3, P(z|y)=1.0, and so forth. Then, for two sequences A and B, Table 1 is an example of two probability vectors of the PSTs for the two sequences.
TABLE 1 P(x) P(y) P(z) P(x|xx) P(y|xx) P(z|y) . . . PST-A 0.8 0.15 0.05 0.7 0.3 1 . . . PST-B 0.6 0.4 0 1 0.4 0.8 . . . - Note that, in some embodiments, for each rare sequence, only this PST summary of the rare sequence (i.e., vectorized PST) is kept in the rare window cache. Because the PST summary of the sequence includes all the probability information, the PST summary can be treated as a rare window signature. The PST summary, representing a rare sequence, can be used to compare with another sequence, for example, by using a combination of the PST-SIM and the JAC-SIM. In addition, for each rare window, the rare window cache keeps a record of how many times the rare window has been observed and, in some embodiments, for how many distinct days. In this way, when a new rare window is observed, the PST model can check the rare window cache to determine whether the new rare window has appeared before, and if affirmative, for how many times and over how many different days. This information can be useful for deciding if the new rare window is worth raising an alarm or not.
- With all the above in mind,
FIG. 54A shows an example of how a normal behavioral sequence may be represented in a probabilistic suffix tree based model, andFIG. 54B shows an example of how an unusual behavioral sequence may be discovered in a probabilistic suffix tree based model. As can been seen from these two figures, the PST model can be very powerful to distinguish abnormal behaviors from normal behaviors, even in an complex network environment with many users collaborating. FIG. 55A throughFIG. 58 show example graphical user interface (GUI) display screens of how an unusual behavioral sequence discovered can be presented to an administrator for actions and/or feedbacks. When an anomaly is discovered, the result can be presented to a user via a user interface, such as a GUI. As illustrated inFIG. 55A , the user interface can include textual description, such as which user has an unusual window, what kind of unusual sequence it is (e.g., Active Directory), how many events are in the window, how long the window has lasted, and so on. As illustrated inFIG. 55B , additional information about the user can be presented in the user interface, such as information about the training of the model for the user. Further, as illustrated inFIG. 56 , results from comparing the marginal of the events for the anomalous window and the entire data for the user (e.g., baseline) can be automatically shown (e.g., in diagrams).- Further, as an option, all the “unusual” PST predictions that contributed to the high R can be shown to the administrator, and in some embodiments, can be shown as a timeline of unusual sequences. Illustrated in
FIG. 57 is an overview of all the unusual sequence, shown as a timeline. Then, the administrator can interact with (e.g., click on) each timeline event and expand on the unusual sequence of events that lead to the low PST prediction, such as shown inFIG. 58 . - In the above described manner, the PST model can enable the security platform to discover behavioral anomalies by determining whether a given sequence of events as associated with an entity deviates from an generally anticipated behavioral baseline, even though each event individually may well be considered not malicious. Also, the security platform provides intuitive ways for the administrator to receive alert and to understand relevant information in order to make an educated decision.
- In a network security context it may be advantageous to identify clusters of nodes (“node clusters” or “clusters”) in a graph, such as in the above-mentioned composite relationship graph or a projection of it. Doing so may be advantageous for various reasons, such as detecting similarities between users or devices and/or detecting deviations in an entity's activity from a behavioral baseline. For example, identification of node clusters can facilitate detection of lateral movement by user (e.g., a user accessing a device that he does not normally access) or detection of an account takeover situation.
- For example, the system may initially determine that a particular entity is a member of a particular node cluster, or that the entity normally interacts with an entity that is a member of the node cluster. A cluster may represent a group of users who all tend to access the same set of devices on the network, for example. Subsequently a decision engine may detect that the particular user in that group has engaged in activity that represents a divergence from the identified cluster, such as a user in the cluster accessing a device that is not among those normally accessed by users in his cluster. In response to detecting this divergence, the decision engine can determine that the user's activity represents an anomaly, or perhaps even a threat.
- What follows is a description of efficient, highly scalable, and parallelizable technique for identifying node clusters in a graph. The technique can be implemented by one or more of the above-mentioned machine learning models, for example, and can be implemented in the real-time path, the batch path, or both.
- Briefly stated, in the cluster identification technique introduced here, an automated cluster identification process (e.g., from logic of a machine learning model) computes L1-norm values for the nodes in a graph to assign positions to the nodes on a one-dimensional (1D) grid. The process then identifies one or more node clusters in the graph based on the assigned positions of the nodes on the 1D grid. More specifically, the process creates node groups by iteratively relocating nodes on the 1D grid to positions where the L1-norm for each node is minimum. After finding optimal positions for the nodes on the 1D grid in this manner, each group of nodes located at the same position on the 1D grid (if any) represents a cluster.
- The technique is now further described with reference to
FIGS. 59 through 62 .FIG. 59 is a flowchart showing an example of the above-mentioned process. The initial input to the process is any graph, an example of which is shown asgraph 6101 inFIG. 61A . In other embodiments, the process ofFIG. 59 may be performed while a graph is being constructed. It is assumed that edge weights are represented by integers, not floating point numbers, and that multiple associations between nodes are collapsed into the weight of a single edge after proper boosting/weighting. - At step S901 in
FIG. 59 , the process initially traverses the graph node by node and maps the nodes onto a one-dimensional (1D) grid. The graph may be traversed in any order. For example, a breadth first search (BFS) order may be convenient. An example of a 1D grid resulting from traversinggraph 6101 in BFS order is shown asgrid 6102 inFIG. 61A . InFIG. 61A , the numeral inside each node (circle) indicates the order in which the node has been “touched” during a BFS traversal and, hence, its position in the1D grid 6102. Therefore, to facilitate description, the nodes ofgraph 6101 are referred to by their positions in the1D grid 6102, e.g.,Node 1,Node 2, etc., corresponding respectively topositions - After mapping the nodes to the 1D grid, the process at step S902 creates groups of nodes that have the same position on the 1D grid, by iteratively minimizing the L1-norm of each node to find its “optimal” position on the 1D grid. A “norm” in this context is a function that assigns a strictly positive length or size to each vector in a vector space (except the zero vector, which is assigned a length of zero). an L1-norm, at least in the context of this description, is the sum of the individual distances (absolute) along the 1D grid between each candidate position for a node under consideration and each other candidate position for the node under consideration. The candidate positions are the positions of all nodes directly connected to the node under consideration in the graph. The “optimal” position for a node under consideration is the position of that node, in the 1D grid, where the node's L1-norm is minimum.
- Referring to the example of
FIGS. 61A and 61B , therefore, after mapping all the nodes to the1D grid 6102, the process will initially attempt to determine the optimal position forNode 1. To do so, the process computes the L1-norm forNode 1 in each of its candidate positions.Node 1 is directly connected toNodes positions Node 1 are the positions occupied byNodes grid 6102. Therefore, the process computes the L1-norm forNode 1 each of those candidate positions, and chooses the position at which the L1-norm is smallest as the optimal position forNode 1. IfNode 1 were maintained at its initial position on the 1D grid, its L1-norm would be computed as the sum of the absolute distances, along the 1D grid, betweenposition 1 andpositions Node 1 atposition 1 is L1-Norm1,1=|1−2|+|1−5|+1−6|=10. In contrast, ifNode 1 were to be moved to the position ofNode 5 on the 1D grid, the L1-norm ofNode 1 atposition 5 would be computed as L1-Norm1,5=|5−2|+|5−5|+5−6|=4. - As can be easily verified, the L1-norm of
Node 1 is minimum atposition 5 ongrid 6102 in the example ofFIGS. 61A and 61B . Therefore, the position ofNode 5 is deemed to be the optimal position ofNode 1 in the initial iteration, soNode 1 is moved to the position ofNode 5, as shown inFIG. 61B . Note that a node's optimal position can change in subsequent iterations, however, as the node and/or other nodes may be relocated along the 1D grid. - After processing all of the nodes of the graph in this manner in step S902, one or more nodes may occupy the same position on the 1D grid; such nodes are considered to constitute a node group, which may be a cluster. However, before concluding that a node group is in fact a cluster, the process looks for any node(s) in each node group that have a stronger connection to nodes outside their group; such nodes should be removed from their current group (i.e., relocated along the 1D grid).
- Referring back to
FIG. 59 , therefore, in step S903 the process detects the actual clusters in each group based on the internal-to-external edge ratios of the nodes. In this context, a node can have one or more “internal” edges and one or more “external” edges. An internal edge is any edge that connects the node to another node within the same node group (created in step S902), whereas an external edge is any edge that connects a node to another node outside its node group. If any node has external edges whose summed weight exceeds the summed weight of all of its internal edges (i.e., its internal/external edge ratio is less than one), then at step S904 removes that node from its current node group by shifting the node one position to the left or right along the 1D grid (the direction does not matter). Each node relocated in this manner is called a “floater.” Hence, if at step S905 there are any floaters, the process proceeds to5907, in which the process iterates through all of the floater nodes and merges them with the existing cluster(s). If there are no floaters at step S905, the process proceeds to step S906, in which it outputs the identified clusters (e.g., to another machine learning model, a decision engine, a user interface, etc.). FIG. 61B also shows, at the bottom, the positions of all of the nodes after three iterations. It can be seen that three clusters have been identified:Nodes 1 through6;Nodes 7 through11; andNodes 12 through14.- In addition to being efficient, highly scalable and parallelizable, this process is also incremental, which means if a single node or multiple nodes are added to the graph, it is not necessary to remap the entire (modified) graph onto the 1D grid; instead each newly added node of the graph can be inserted directly into the 1D grid by minimizing its L1-norm as described above.
- The above-described cluster identification technique can be used to identify clusters in essentially any kind of graph. A special case of such a graph, however, is a bipartite graph. A bipartite graph is a graph whose nodes can be divided into two disjoint sets, called normal nodes and pseudo-nodes (i.e., normal nodes and pseudo-nodes are each independent sets), such that every edge connects a normal node to a pseudo-node. For example, a bipartite graph may be created in which the normal nodes represent users and the pseudo-nodes represent devices accessed by those users. Such a graph can be used, for example, to facilitate detection of lateral movement by users. An implementation of the above-described technique can be applied to detect clusters in a bipartite graph, as discussed further in a section below. An example of such an implementation for bipartite graphs is illustrated in
FIGS. 60A and 60B , with a corresponding example of a use case illustrated inFIG. 62 . - Referring first to
FIG. 60A , atstep 6001 the process initially traverses the bipartite graph and maps only the normal nodes onto a 1D grid. The graph may be traversed in any order, such as BFS order. Next, atstep 6002 the process create groups of nodes that occupy the same position in 1-D grid, by minimizing the L1-norm of each normal node to find its optimal position in the 1-D grid. Referring toFIG. 62 , the normal nodes areNodes 1 through7 (i.e., the left column of graph6201) whose positions are the positions on the 1D grid, while the pseudo-nodes areNodes 8 through10 (the right column of graph6201). The process of minimizing L1-norms for a bipartite graph is described further below. - The process then determines at
step 6003 whether any normal nodes were moved duringstep 6002. If any normal nodes were moved duringstep 6002, the process loops back to step6002 for another iteration. Otherwise, the process outputs the identified cluster(s) (e.g., to another machine learning model, a decision engine, a user interface, etc.), where a cluster is a group of nodes that occupy the same position on the 1D grid. FIG. 60B shows in greater detail thestep 6002 ofFIG. 60A , i.e., the step of minimizing the L1-norm values to find optimal positions for the normal nodes. Initially, atstep 6011 the process selects a normal node of the graph (the “node under consideration”). The process then identifies all of the pseudo-nodes to which the selected normal node is directly connected, atstep 6012. For example, ingraph 6201 ofFIG. 62 ,normal Node 1 is connected only topseudo-Node 8. The process then, atstep 6013, identifies the minimum and maximum of positions, on the 1D grid, of all normal nodes to which the identified pseudo-node(s) is/are connected.- For example, in
step 6013, if (normal)Node 1 were the selected node, then the minimum and maximum positions would be 1 and 2, respectively, sinceNode 1 is connected only topseudo-Node 8, which is also connected tonormal Node 2. IfNode 6 were the selected node, then the minimum and maximum positions would be 3 and 7, respectively, sinceNode 6 is connected topseudo-Node 9, which is also connected tonormal Nodes pseudo-Node 10, which is also connected tonormal Nodes - The process next determines at
step 6014 the “optimal” position for the normal node, as the position on the 1D grid that corresponds most closely to the midpoint between the minimum and maximum positions determined in step6013 (rounding up if the exact midpoint falls between two positions on the grid). Atstep 6015 the process moves the selected normal node to the position determined instep 6014, with the effect being to minimize the selected node's L1-norm. This process repeats for each normal node until all of the normal nodes have been processed in this manner, and then returns to the process ofFIG. 60A , proceeding then to step6003 inFIG. 60A as described above. - As shown in
FIG. 62 , the process identifies two clusters from theexample graph 6201, namely,Nodes Nodes 3 through7 as another cluster. The process ofFIGS. 60A and 60B is also incremental, such that the addition of a new node or nodes to the graph does not require remapping the entire graph onto the 1D grid; rather the new node(s) can be added directly to the 2D grid as described above. FIGS. 63 through 67 relate to a method for identifying a security threat based on detecting suspicious lateral movement of a user. Lateral movement refers to a user using a device or devices that he or she does not normally use, which may be (but is not necessarily) indicative of a security threat.- Lateral movement may indicate the possibility that the credential of a user has been stolen, or the user's device has been controlled by a malicious software. For example, a wrongdoer may steal a user's credential and use the stolen credential to access a device that the user typically does not access. An analyzer (e.g., the real-
time analyzer 210 or thebatch analyzer 240 inFIG. 3 ) may recognize such an event as an anomaly. Furthermore, if the analyzer detects that the anomaly (directly or through other anomalies) leads to a result that the wrongdoer (disguised as a legitimate user) gains access to a device designated as a critical resource, the analyzer can recognize a security threat represented by a set of the relevant anomalies. - The lateral movement detection method introduced here assigns similarity scores to devices in a computer network based on the relationships between users and the devices. For example, the relationships can include information regarding certain users logging into devices. The similarity scores suggest the similarities between the devices in terms of associated users. The method further generates or identifies classification metadata of the user and the device, based on event data about the login event, to further explain the relevance of the user and the device in a security context. The method then detects an anomaly based on the classification metadata and similarity scores when a user interacts with a device having a similarity score that is significantly different from the similarity scores of devices with which the user usually interacts. Based on the detected anomaly, the method may further determine a security threat based on the relationship information by identifying, in a relationship graph, a relationship path from a user through anomalies to a critical resource.
- In some embodiments, the method described here can be implemented by a machine learning model. For example, processing logic of a machine learning mode can generate the classification metadata, or assign usage similarity scores, or both, as further described below.
- In some embodiments, the processes of generating the classification metadata and/or assigning usage similarity scores are performed in real-time as the event data are received. In other embodiments, either or both of these processes are performed in batch mode based on event data stored in a non-volatile storage facility.
FIG. 63 is a block diagram illustrating a machine learning model that detects lateral movement in a computer network. The computer network includes entities, such as devices and network devices. Themachine learning model 6300 analyzesevent data 6310. Theevent data 6310 can be, e.g., timestamped machine data. Theevent data 6310 include information regarding the computer network activities of the users and network devices. In one embodiment, theevent data 6310 includes a projection of the security graph. The particular projection of the security graph (also referred to as “login projection” or “login graph”) records the information that relates to login events in which the users log into the network devices in the computer network.- Based on the event data6310 (e.g., the login graph), the
machine learning model 6300 generatesclassification metadata 6320 for each of the network devices and for each of the users. Theclassification metadata 6320 helps explain the relevance in a network security context of each of the users and each of the network devices. For example, theclassification metadata 6320 for a particular user can include metadata indicative that the user is a regular user, an administrative user, or an automated (machine-implemented) user, for example. Similarly theclassification metadata 6320 for a particular network device can include metadata indicative that the particular network device is a workstation, a server or a printer, for example. - Because the
classification metadata 6320 are generated based on theevent data 6310, themachine learning model 6300 does not need additional metadata that explicitly annotates the types of the user and network devices. Themachine learning model 6300 can automatically recognize the types of the users and network devices, based on the event data representing the network activities involving the users and network devices. - The
machine learning model 6300 further identifies usage relationships6330 between the users and the network devices based on theevent data 6310. For example, if theevent data 6310 includes a login graph having information that relates to the login events, themachine learning model 6300 can identify the usage relationships6330 as login events indicative of the users logging into the network devices. In some embodiments, the usage relationship6330 can be presented as a graph having nodes and edges interconnecting the nodes, as illustrated inFIG. 63 . The nodes represent network entities such as users and network devices, and the edges represent the login events that the users log into the network devices. - As shown in
FIG. 63 , the usage relationships6330 between the users and the network devices can be captured in a bipartite graph including a first set of nodes representing users (nodes nodes - Based on the usage relationships6330, the
machine learning model 6300 assigns usage similarity scores6360 (also referred to as “similarity scores”) to the network devices represented by the device nodes. Theusage similarity scores 6360 indicate which of the devices have been used by the same or similar group of users. The details of the process of assigningusage similarity scores 6360 are illustrated inFIG. 65 . - The similarity scores are assigned such that any given set of network devices that are accessed by the same or similar group of users are assigned similarity scores that are closer in value to each other than the similarity scores of any other set of network devices that are not accessed by the same or similar group of users. In other words, a group of network devices that have similar groups of login users tend to have similarity scores that are closer in value to each other than similarity scores of network devices that do not have similar groups of login users.
FIG. 64 illustrates an example of a bipartite graph showing events of users logging into network devices. The bipartite graph6400 includes a group ofuser nodes device nodes FIG. 64 are used interchangeably to refer to the nodes and the users or network devices represented by those nodes.- As shown in
FIG. 64 , twousers device 6421. Twousers device 6422. Twousers 412 and6413 have logged into thedevice 6423. Therefore,devices users - In contrast, before
user 6412 logs intodevice 6424, wherein the dashed line represents that particular login activity, onlyuser 6414 has logged intodevice 6424. The group of user(s) that has/have logged intodevice 6424 is substantially different from the groups of users that have logged intodevices devices Devices device 6424 has a similarity score of 0.06, which is significantly different from the similarity scores ofdevices - Once the
user 6412 logs into device6424 (as represented by the dashed line inFIG. 64 ), themachine learning model 6300 determines the similarity score of the particular device6424 (i.e., 0.06 for device6424) fails to satisfy a specific closeness criterion relative to similarity scores of network devices with which the particular user usually interacts (i.e., 0.30 fordevice 6422 and 0.33 for device6423). The closeness criterion can be of various different types in different embodiments. For example, themachine learning device 6300 may determine that the difference between the similarity score of theparticular network device 6424 and an average of the similarity scores fornetwork devices machine learning model 6300 then detects an anomaly because the difference of similarity scores exceeds the threshold value. - In an alternative embodiment, the
machine learning model 6300 can further calculate an anomaly score for the particular user and decide whether anomaly is detected based on the anomaly score. The anomaly score indicates a likelihood that the anomaly relates to a security threat. The anomaly score can be calculated based on, for example, the difference between a similarity score of the particular network device and a statistical measure (e.g., an average) of similarity scores of other devices with which the user has interacted. Themachine learning model 6300 then detects the anomaly if the model determines that the anomaly score exceeds a threshold value for anomaly scores. - For example, the similarity score of the
network device 6424 is 0.06, and the average similarity score ofnetwork devices network device 6424 is a server of high importance. Because the anomaly score of 0.355 exceeds a threshold of 0.3, themachine learning model 6300 detects an anomaly. - Alternatively, the
machine learning model 6300 can detect an anomaly based on an access profile of a particular user. The access profile of the particular user includes network devices with which the particular user interacts and that have similarity scores that satisfy a specific closeness criterion. For example, the differences of the similarity scores ofnetwork devices user 6412 is 0.03 and is less than a threshold value of 0.1. In some embodiments, the access profile of theparticular user 6412 can further include, e.g., information of events indicative that the particular user succeeded logging in to a network device, failed logging in to a network device, succeeded validating credential of a network device, failed validating credential of a network device, succeeded accessing a network object stored on a network device, or failed in accessing a network object stored on a network device. - When the
user 6412 interacts with aparticular network device 6424, themachine learning model 6300 calculates the anomaly score for the particular user based on a difference between the similarity score of theparticular network device 6424 and the average of similarity scores ofnetwork devices particular user 6412. Themachine learning model 6300 detects the anomaly if the similarity score difference indicates that theparticular user 6412 has interacted with theparticular network device 6424 outside of the access profile of theparticular user 6412. - The
machine learning model 6300 can assign similarity scores to the network devices in various ways.FIG. 65 illustrates an example of a process of assigning similarity scores to network devices. At step A inFIG. 65 , themachine learning model 6300 receives a bipartite graph. The bipartite graph includes a group of nodes U1-U6 representing users (also referred to as “user nodes”) and another group of nodes D1-D6 representing network devices (also referred to as “device nodes”). The bipartite graph further includes edges interconnecting the nodes. The edges represent the relationships between the users and the network devices. Themachine learning model 6300 selects a device node D4 and assigns an initial weight value of 1 to the selected device node D4. In some embodiments, themachine learning model 6300 can, e.g., select the device node in a random manner. The initial weight value can also have a value different from 1. - At step B in
FIG. 65 , themachine learning model 6300 keeps a percentage (15%) of the initial weight value of 1 at the device node D4, and equally distributes a remainder of theinitial weight value 1 from the device node D4 along the edges of D4 to nodes U2, U3 and U6. In some embodiments, the machine learning model decides the percentage of 15% before starting the similarity score assignment process. - The value distribution process can be viewed as a Markov chain process. At each step, the value distributor(s) have a probability of 15% (hence the percentage is also referred to as “probability percentage”) to remain at the same node as in the previous step; the value distributor(s) have a probability of (100%−15%=85%) to follow an edge of the node to move to another node. In some other embodiments, the similarity score assignment process can use a percentage other than 15%.
- As show in step C of
FIG. 65 after the distribution, themachine learning model 6300 keeps a weight value of 0.15 (=1*15%) at the device node D4. Themachine learning model 6300 equally distributes a remainder of the initial weight value (0.85=1*0.85%) to user nodes U2, U3 and U6. Each node of user nodes U2, U3 and U6 receives a weight value of 0.283 (=0.85/3). - For each node, the
machine learning model 6300 repeats the process of distributing along edges until the weight values at the network devices D1-D6 converge. The step D inFIG. 65 shows the next step in the iterative process. For device node D4, themachine learning model 6300 keeps a weight value of 0.023 (=0.15*15%) at device node D4, and distributes 0.042 (=(0.15*85%)/3) to each of user nodes U2, U3 and U6. For user node U2, themachine learning model 6300 keeps a weight value of 0.042 (=0.283*15%) at user node U2, and distributes 0.120 (=(0.283*85%)/2) to each of device nodes D1 and D4. - Similarly, for user node U3, the
machine learning model 6300 keeps a weight value of 0.042 (=0.283*15%) at user node U3, and distributes 0.241 (=(0.283*85%)/1) to device D4. For user node U6, themachine learning model 6300 keeps a weight value of 0.042 (=0.283*15%) at user node U6, and distributes 0.120 (=(0.283*85%)/2) to each of device nodes D4 and D6. - The
machine learning model 6300 continues the iterative process until the weight values at the network devices D1-D6 converge. At each step of the iterative process, for each node, themachine learning model 6300 keeps 15% of the weight value at the node and then equally distributes the remainder of the weight values along the edges to other nodes. The convergence criterion can be any criterion indicative of this type of convergence. For example, themachine learning model 6300 can determine that the iterative process reaches a convergence when the change of weight values between two consecutive steps at each node is less than a threshold value. - Step Z of
FIG. 65 shows the status of a final step with converged weight values when the iterative process reaches a convergence. The converged weight values at the devices D1-D6 are similarity scores assigned to these devices. Themachine learning model 6300 uses the similarity scores to determine whether multiple network devices are similar in terms of associated users that interact with the devices. FIGS. 66A through 66D illustrates examples of bipartite graphs that themachine learning model 6300 uses to determine whether network devices are similar in terms of interacting users. InFIG. 66A , thenetwork devices - In
FIG. 66B , thenetwork devices network devices network devices FIG. 66C , thenetwork devices user 6637. Thenetwork devices - In
FIG. 66D , thenetwork devices network devices - User6654 is the only user that has connected to devices of both groups N1 and N2. The group N1 of
devices devices device 6645 from group N2, the access profile of user6654 includes the group N2 ofdevices device 6642 from group N1 then triggers an out-of-group access anomaly, because the similarity score ofdevice 6642 is significantly different from the similarity scores ofdevices - The detected out-of-group anomaly is an indication of a suspicious lateral movement of a particular user in the network. Based on the anomaly, the
machine learning model 6300 can further decide whether theanomaly 6370 leads to asecurity threat 6380, as illustrated inFIG. 63 .FIG. 67 illustrates an example of a data structure for detecting security threats based on the detected out-of-profile anomaly. - The
machine learning module 6300 retrieves agraph data structure 6700 that records anomalies in the network and the relationships between the anomalies and the users and network devices. The graph data structure includes nodes interconnected by edges. The nodes represent anomalies and entities such as users and network devices; while the edges represent relationships between the entities and anomalies. - For example,
FIG. 67 shows that the retrievedgraph data structure 6700 includes user nodes U6701, U6705, U6709 and U6711 and device nodes D6703, D6707, D6708 and D6710. The retrievedgraph data structure 6700 further includes anomaly nodes A6702, A6704 and A6706. Among the anomaly nodes, the anomaly node A6702 represent an out-of-profile anomaly. In other words, the user represented by user node U6701 has accessed the device represented by device node D6703 with which the user does not usually interact. - The retrieved
graph data structure 6700 is different from the login graph that themachine learning module 6300 uses to detect the out-of-profile anomaly. The login graph only records information that relates to the login events of the users. In contrast, the retrievedgraph data structure 6700 can include relationships beyond the login events and can include anomalies of other types besides out-of-profile anomalies. For example, the retrievedgraph data structure 6700 includes anomaly node A6706 representing a blacklist anomaly. The blacklist anomaly indicates that the user U6705 has accessed the network device D6707 from a blacklisted IP address. - The retrieved
graph data structure 6700 further includes anomaly node A6704 representing a beaconing anomaly. The beaconing anomaly indicates that the device represented by device node D6703 sends suspicious beaconing messages periodically to a user device associated with the user represented by user node U6705. - The
machine learning model 6300 identifies, in the retrievedgraph data structure 6700, arelationship path 6720 that suggests a security threat. Therelationship path 6720 starts with user node U6701 and anomaly node A6702 that represents the out-of-profile anomaly. Therelationship path 6720 ends with the anomaly node A6706 and device node D6707 that represents a device designated as a critical resource. For example, the device designated as a critical resource can be, e.g., a domain controller server that responds to security authentication requests within the computer network. - The
relationship path 6720 includes user nodes and device nodes interlinked by anomaly nodes A6702, A6704 and A6706. In other words, therelationship path 6720 starts from user U6701 through anomaly nodes A6702, A6704 and A6706 to the device D6707 designated as a critical resource of the computer network. - The
machine learning model 6300 identifies a security threat based on therelationship path 6720. The security threat is represented by the anomaly nodes A6702, A6704 and A6706 along therelationship path 6720. These anomaly nodes suggest that the security threat is imposed by a series of anomalies. For example, in one embodiment, the security threat can indicate that an unauthorized user (invader) has misappropriated a credential of the particular legitimate user to enter the network through device D6703 and breached one or more network devices (D6703, D6707) along the relationship path to access the critical resource on device D6707. - When a security threat has been detected, the security platform then reports the threat to an administrator of the network (e.g., via the GUI features described above) and/or writes the security threat into a threat log for later review by an administrator.
- Techniques will now be disclosed for detecting anomalies indicative of the presence of malware within a computer network based on an analysis of network traffic, including communications between entities (both internal and external) associated with the network. Malware is generally understood to be unauthorized software operating on or associated with entities (e.g. devices) within a computer network. In some embodiments, the detection of malware based on analysis of network traffic rests on the assumption that malware in certain instances leaves an observable footprint in the traffic. For example, malware operating as part of a malicious command and control infrastructure may periodically transmit a beacon signal to another entity seeking command instructions. As described in other sections of this specification, the presence of malware may be inferred based on detecting any of a set anomalous activity, such as communications to machine-generated domains, machine-generated communications (e.g., beacons), and communications to blacklisted entities (e.g. users, domains, addresses, etc.).
- While any individual inference may have value, reducing false positives in identifying security threats to the network is desirable. To that end, embodiments are described here that analyze a range of anomalous behavior to detect an anomaly indicative of the presence of malware. In some embodiments anomaly detection occurs in real-time or near real-time as the event data is received, instead of relying on historical log data to perform batch processing. An example processing engine suitable for high rate data processing in real-time is Apache Storm. In other embodiments the processing engine could be implemented by using Apache Spark Streaming.
FIG. 68 is a high-level conceptual diagram of an example network traffic scenario that illustrates the above principle.FIG. 68 shows acomputer network 6810 enclosed by the dotted line. Withincomputer network 6810 are a number of associatedinternal entities 6820 including, for example users and devices. As used herein, an entity should be broadly understood to include any sort of element or component operating within or otherwise associated with a computer network. For example, entities include physical computing devices, virtual computing devices, users, software modules, accounts, identifiers, and addresses. The identification of a particular entity or set of entities associated with a particular set of event data can be resolved through a process described elsewhere in this specification. As an illustrative example, a machine generated log entry associated with an event may contain information associating that event with one or more of a an IP address, a unique identification (UID), uniform resource locator (URL), and user ID. In such an example each of these identifiers may be considered a discrete entity associated with the computer network or two or more identifiers maybe associated with the same entity. For example, a static IP address, MAC address, and UID may all be associated with a physical computing device entity. Similarly multiple user account IDs may be associated with a single physical user (i.e. a person) of the computer network.- Operating outside of
computer network 6810 is anexternal entity 6840 that may be associated with a malicious actor. Communications may occur between differentinternal entities 6820, and between internal6820 andexternal entities 6840, as shown. In some embodiments, an analysis of these communications based on received event data, leads to the detection ofanomalies 6880 indicating the presence ofmalware 6860 within thecomputer network 6810. - A. Malware Communications Detection—Process
FIG. 69 is a high level diagram illustrating anexample process 6900 for detecting an anomaly indicative of malware based on network traffic. Theprocess 6900 begins with receivingevent data 6901.Event data 6901 is generally understood to include any data related to activity on the computer network. Here, because network data traffic activity is a primary focus, theevent data 6901 preferably includes timestamped machine data such as domain name system (DNS) generated log data, firewall generated log data, or proxy generated log data. In some embodiments, theevent data 6901 is associated with a communication between an internal entity within a computer network and an external entity outside the computer network. In some embodiments, theevent data 6901 is also associated with communications between internal entities within a computer network. As described in more detail elsewhere in this specification, in some embodiments,event data 6901 is received from a data intake and preparation stage, which may include an ETL pipeline.- In some embodiments, the process of receiving
event data 6901 includes adaptively filtering the event data according to a dynamic whitelist atprocess 6902. This is in contrast with static filtering, for example according to a static whitelist, to filter out communications to entities known to be benign. Here, adaptive filtering can be applied to filter out event data associated with more common or more popular network traffic given a particular context. In some embodiments, popularity metrics are defined based on an analysis of network traffic across the entire network or across a particular subgroup within the network. For example, while domain xyz.com may not be known to be benign, an analysis of the network traffic can uncover that a high percentage of users on the network regularly connect to xyz.com. Accordingly, it can be inferred that xyz.com is benign and that it is not worth the processing effort to analyze the domain for malware associations. Note that this process of adaptively filtering the received event data is not necessary to the overall anomaly detection process, however it can streamline computational processing, which aids in detecting anomalies in real-time or near real-time. The filtering also helps to reduce the number of false positives. Process 6900 continues with generating a plurality of feature scores by processing the filteredevent data 6903 or unfiltered event data6901 (collectively referred to herein as event data6901) as shown atfeature score generation 6920, and generating an entity profile associated with at an entity (internal or external) that includes a plurality of generated feature scores as shown atentity profile generation 6904. As shown inFIG. 69 ,feature score generation 6920 includes generation of a plurality of feature scores, each of the plurality of feature scores generated by a different one of various different analyses of the event data. For example, feature score generation can includetiming analysis 6906,lexical analysis 6908,communications statistics 6910,sequencing analysis 6912,entity associations analysis 6914,referrals analysis 6916, and various other types ofanalysis 6918.- In an embodiment, one or more feature scores for a particular entity are generated based on each above-mentioned category of analysis. For example, timing analysis could yield two or more feature scores, including at least a feature score based on a periodicity of communications associated with a particular entity and a feature score based on variance in interval periods between communications associated with a particular entity. Feature scores are described in more detail below, however, note that the listed categories of analysis are only examples, and no particular category is necessary. An embodiment may include more or fewer categories resulting in more or fewer feature scores.
- As shown in
FIG. 69 , in some embodiments,entity profile generation 6904 includes a process offorensic data enrichment 6922 throughglobal evidence collection 6926. For example, data regarding a particular entity may be gathered from sources internal (e.g. a system blacklist) or external (e.g. a WHOIS lookup) to the computer network. Additional data gathered through evidencedcollection 6926 and applied viaenrichment 6922 may impact feature score generation and anomaly detection based on the underlying feature scores. As with anomaly scores, a feature score can represent a quantified evaluation of the risk associated with a particular entity based on a particular analysis. Accordingly, the models used to generate feature scores may depend on additional available (e.g. through enrichment6922) data associated with an entity. For example, processing equivalent sets ofevent data 6901 using the same analysis (e.g. periodicity of communications) may yield different feature scores for mission critical systems than for non-critical systems. As with theadaptive filtering 6902,Global evidence collection 6926 andforensic enrichment 6922 are not required. - As shown in
FIG. 69 , in some embodiments,entity profile generation 6904 includes a process forscore normalization 6924.Score normalization 6924 involves normalizing the plurality of feature scores for later processing at the anomaly score generation stage, as described elsewhere herein. Process 6900 continues with generating an anomaly score based on the entity profile including the plurality of feature scores included in the entity profile, for example as shown atanomaly score generation 6928. Generating an anomaly score is described in more detail elsewhere herein.Process 6900 concludes with detecting an anomaly if the generated anomaly score satisfies a specified criterion, for example as shown atanomaly detection 6930. Here the detected anomaly is indicative of malware within a computer network. Anomaly detection is also described in more detail elsewhere herein.- B. Generating Feature Scores and the Entity Profile
- As previously described, each feature score is generated based on one various different analyses of the event data. Feature scores are calculated on a per-entity basis and can be understood broadly as a quantified evaluation of a level of risk associated with the entity or a likelihood that the entity is associated with malware. In some embodiments feature scores are calculated or assigned by processing the event data through a model to generate a numerical value. In some embodiments the model includes model processing logic defining a process for assigning a feature score based on processing the event data X102 and a model state defining a set of parameters for applying the model processing logic. For example, in some embodiments, the models used to generate feature scores are the same as the anomaly models used to generate anomaly scores. In some embodiments, the models used to generate feature scores are machine-learning (both supervised and unsupervised) models. For example, a supervised machine learning model may use training examples developed by network security experts to more effectively generate feature scores based on received data. In some embodiments, each feature score is a numerical value in a range. For example, processing event data according to a feature score model may yield a value between 0 and 10 with 0 being the least anomalous (or risky) and 10 being the most anomalous (or risky).
- As mentioned, feature scores are calculated on a per-entity basis. Therefore a plurality of feature scores is generated for a particular entity. The combined set of feature values associated with particular entity make up the entity profile. For example, the table below lists feature scores f1though fnfor an example external domain, xyz.com.
Timing Comms. Lexical Other analysis analysis analysis analysis Entity f1 f2 f3 fn xyz.com 5.2 4.0 3.2 7.8 - The above example is simplified for clarity. In use, an entity profile for a particular entity might include tens or even hundreds of feature scores. In some embodiments, the feature scores associated with a particular entity are represented as a feature vector, f={f1f2f3. . . fn}. For example, the entity profile for domain xyz.com can be represented as feature vector, f={5.2 4.0 3.2 . . . 7.8}.
- As previously discussed, the different analyses used to generate the feature scores can include, for example, lexical analysis (e.g. sequencing of characters in a domain name associated with an entity, analysis of the timing of communications associated with an entity (e.g. periodicity of communications and/or variance of interval times between communications), analysis of the sequencing of communications associated with the entity (e.g. to detect exploit chains, analysis of data transmission statistics associated with the entity (e.g. ratio of bytes in to bytes out), and analysis of referral strings associated with the entity.
- In some embodiments, generating the feature scores includes analyzing a sequencing of characters in an entity identifier (e.g., a domain name) associated with an entity (internal or external) and assigning a feature score based on the analysis, wherein the feature score is indicative of the level of confidence that the entity identifier is machine-generated. In other words, applying a lexical analysis to a character-based entity identifier to assign a feature score indicative of whether the identifier is machine generated or not. This analysis and feature scoring assumes, based on industry expertise, that a machine-generated identifier is more likely to be associated with malicious activity (e.g. malware) given the context. For example, malware running within a computer network may periodically transmit a beacon message (“beacon”) to an external entity (e.g. a domain) seeking command and control instructions. As network security has advanced so has malware. It is no longer effective for malware to transmit beacons to a static domain because that domain can be quickly identified and blacklisted by existing network security solutions. Instead, the malware may be configured to communicate with external entities through continuously changing machine-generated domain names.
- One characteristic that can reveal the machine-generated nature of a character-based identifier is a high degree of entropy or randomness in the sequencing of characters. One way to analyze the entropy or randomness in the characters is through an n-gram analysis. In some embodiments, a machine learning model for n-gram analysis can be trained using a large body of lexical information for domain names in any number of languages. Based on this training, a list of n-gram probabilities are developed. In other words, a model based on n-gram analysis can provide the chance of observing a specific sequence of characters.
FIG. 70 shows two tables7002 and7004 of domain names with associated probabilities based on n-gram analysis. As shown inFIG. 70 , table7002 includes domain names with lower probabilities relative to the domain names of table7004. In other words, the probabilities sequence of characters in the domain names in table7002 occurring in natural human language are lower relative to the probabilities of the sequencing of characters in the domain names in table7004. This clear to a human observer just by looking at the domain names, but the n-gram probabilities provide important insight to a computer-based model tasked with feature scoring. - In some embodiments, generating the plurality of feature scores includes analyzing the timing of communications associated with the entity (internal or external) over a time period and assigning a feature score based on the analysis, wherein the feature score is indicative of a level of confidence that the communications are machine-generated. This is similar to the ideas introduced in the discussion of beacon detection in this Specification. Generally, the timing of communications (e.g. periodicity and/or variance of interval times) can provide insight into the nature of the communications. For example, based on industry expertise, communications with high periodicity are less likely to be human generated and more likely to be machine generated, for example a beacon communication.
- In some embodiments, generating the plurality of feature scores includes analyzing a sequencing of communications associated with an entity (internal or external) over a time period and assigning a feature score based on the analysis, wherein the feature score is indicative of a level of confidence that the communications are associated with an exploit chain. An Exploit is a piece of software, a chunk of data, or a sequence of commands that takes advantage of a bug or vulnerability in order to cause unintended or unanticipated behavior to occur on computer software, hardware, or something electronic (usually computerized). Such behavior frequently includes things like gaining control of a computer system, allowing privilege escalation, or a denial-of-service attack. An exploit chain typically involves patterns in the sequencing of communications.
- In some embodiments, generating the plurality of feature scores includes analyzing the data transmission statistics associated with an entity (internal or external) over a time period and assigning a feature score based on the analysis, wherein the feature score is indicative of a level of confidence that the external entity is associated with a command and control infrastructure external to the computer network. For example, the ratio of bytes in to bytes out in a particular communication or set of communications may provide insight into the purpose of the communication. A higher volume of data going out to an external entity than is coming in may indicate the exfiltration data by malware within the network in response to commands from the external entity.
- C. Generating an Anomaly Score
- The anomaly score associated with a particular entity is based on the entity profile (including the underlying feature scores) of the particular entity. The anomaly score may be conceptualized as combination of all of the feature scores for a particular entity.
- As has been described in this Specification, in some cases anomaly scores calculated or assigned by processing event data through an anomaly model to generate a numerical value. Here, the anomaly score is calculated or assigned by processing the plurality of feature scores through an anomaly model. In some embodiments the anomaly model includes model processing logic defining a process for assigning a feature score based on the plurality of feature scores and a model state defining a set of parameters for applying the model processing logic. In some embodiments, the models used to generate the anomaly scores are machine-learning (both supervised and unsupervised) models. For example, a supervised machine learning model may use training examples developed by network security experts to more effectively generate an anomaly score based on the plurality of feature scores. In some embodiments, generating the anomaly score may include an ensemble learning process in which multiple different types of machine learning models are applied to processed the plurality of feature scores. In some embodiments, the anomaly score is a numerical value in a set range. For example, processing the plurality of feature scores according to an anomaly model may yield a value between 0 and 10 with 0 being the least anomalous (or risky) and 10 being the most anomalous (or risky).
- In some embodiments, generating the anomaly score may simply involve a calculating a weighted linear combination of feature scores. Recall that an entity profile including a plurality of feature scores may be represented as a feature vector, f={f1f2f3. . . fn}). In such an embodiment, the anomaly score may simply be represented as:
- Wherein wiis a weighting factor applied to each feature score fiand wherein the anomaly score is simply the summation of each of the plurality of feature scores with the weighting factor.
- The weighting factor, wiapplied to any given feature score in the anomaly scoring process may depend on a number of factors, including the type of entity to which the feature score is applied, the volume of data used to calculate the feature score, user configuration preferences, or the type of analysis used to generate the feature score.
- As mentioned, in other embodiments, the plurality of feature scores may be processed according to one or more machine learning models to generate an anomaly score indicative of the probability or likelihood that malware is present in the computer network given the set of feature scores for a particular entity. Some machine-learning models appropriate for this application include naive Bayes and logistic regression.
- In some embodiments ensemble learning techniques can be applied to process the plurality of feature scores according to a plurality of models (including machine-learning models) to achieve better predictive performance in the anomaly scoring and reduce false positives. An example model suitable for ensemble learning is Random Forest. In such an embodiment, the process may involve, processing an entity profile according to a plurality of machine-learning models, assigning a plurality of intermediate anomaly scores, each of the plurality of intermediate anomaly scores based on processing of the entity profile according to one of the plurality of machine-learning models, processing the plurality of intermediate anomaly scores according to an ensemble-learning model, and assigning the anomaly score based on processing the plurality of intermediate anomaly scores.
- Machine learning models are typically more effective if provided large volumes of data to process and learn from. Accordingly, in some embodiments, the type of model applied to generate an anomaly score depends on the volume of data used to generate the feature scores. For example, some events are associated with no more than a single log line of event data, while others are associated with hundreds of lines of log lines of event data. Accordingly, in some embodiments, a process for generating an anomaly score involves first determining a volume of event data used to generate the entity profile or any one of the plurality of feature scores. Next the entity profile is processed according to one or more of a plurality of anomaly models depending on the determined volume of event data. For example, in an embodiment, the entity profile is processed through a first anomaly model (e.g. an ensemble learning model) if the volume of event data is at or above a threshold volume or the entity profile is processed through a second anomaly model (e.g. weighted linear combination) if the volume of event data is below the threshold volume. An anomaly score is then assigned based on the processing. The thresholds described above can be static or dynamic. A dynamic threshold may adaptively change based on a number of factors, such as the overall volume of event data being generated on the computer network, the type of entity to which the anomaly score is applied, user configuration preferences, and the types of analysis used to generate the feature scores. In some embodiments a plurality of threshold values establish a number of regimes under which the entity profile is processed. For example, the detected volume of data may fall under one of three regimes, low volume, medium volume, and high volume. Depending on the regime, the profile entity is processed according to a different anomaly model.
- The entity profile can, in some cases, include additional data beyond the plurality of feature scores. For example, in some embodiments, entity profile generation includes a process of forensic data enrichment through global evidence collection. In such a process, data regarding a particular entity is gathered from sources internal (e.g. a system blacklist) or external (e.g. a WHOIS lookup) to the computer network. In some embodiments, this data enrichment process aids the process of generating an anomaly score to reduce false positives. The parameters used to apply the processing logic can depend on information about the entity and/or environment not otherwise indicated in the plurality of feature scores. For example, an mission critical computing system associated with a given set of feature scores is viewed differently than a non-critical computing system associated with the exact same set of feature scores. Similarly, external data can be applied validate an anomaly detection. Here the process of generating the anomaly score includes comparing an entity identifier associated with an entity (internal or external) with entries in an external data source external to the computer network (e.g. a WHOIS lookup) and assigning an anomaly score indicating a confidence level that the entity identifier matches a particular entry in the external data source based on the comparing.
- D. Anomaly Detection and Notification
- Once the anomaly score is generated, an anomaly indicating malware in the computer network is detected if the anomaly score satisfies a specified criterion. Consider the previously discussed example range of values from 0 to 10 for anomaly scores. In this example, the specified criterion may be set such that an anomaly is detected if the anomaly score is 6 or above. The specified criterion need not be static, however. In some embodiments, the criterion is dynamic and changes based on situational factors. Situational factors may include volume of event data, presence or absence of pre-conditional events, user configurations, and volume of event data.
- If an anomaly indicating malware in the computer network is detected, and indication of that anomaly can be outputted for display to a user via a user interface of a computing device.
FIG. 71 shows an exampleincident response output 7100 based on entity profiles configured for display to a user. Theincident response output 7100 is represented in simplified form for clarity as a table including a plurality ofentity identifiers 7102 with associated feature scores7104a-7104dand arecommended response 7106 based on the plurality of feature scores. The particular arrangement of information should not be construed as limiting. In this example, the entity identifier is a domain name, however, the entity identifier associated with the entity can be any identifier, such as a domain name, a uniform resource locater (URL), uniform resource identifier (URI), an Internet Protocol (IP) address, a unique identifier (UID), a device identification, or a user identification. As shown inFIG. 71 , the plurality of feature scores7104a-7104dare displayed as classifications, i.e. no risk, moderate risk, and high risk, instead of numerical values. These classifications can be based on the underlying numerical feature scores. In some embodiments, the numerical feature score values (e.g. 0 to 10) are displayed to the user via the incident response output. Theanalyst recommendation 7106 provides information guiding the user to take action based on the raised anomaly associated withentity 7102. For example, the domain “www.evil.com” has a communication feature score indicative of a high risk to network security due to ongoing unblocked communications. Therecommendation 7106, accordingly lists this as a critical priority due to the ongoing and unblocked nature of the communications. In some embodiments, theanalyst recommendation 7106 is provided by a human security analyst based on an assessment of the feature scores associated with the entity. In some embodiments, the analyst recommendation is automatically generated by the system based on the feature scores and or the anomaly score, for example through the use of established network security rules. - Detected anomalies indicative of malware on the computer network can be stored in an anomaly graph data structure that includes a plurality of nodes representing entities associated with the computer network, and a plurality of edges representing an anomaly linking two of the plurality of nodes. Further, the anomaly data can be incorporated into a system wide network security graph. A network security graph includes a plurality of nodes representing entities associated with the computer network and a plurality of edges, each of the plurality of edges linking two of the plurality of nodes and representing an association between the entities represented by the nodes. In such a graph the detected anomalies can be incorporated as a node linked to one or more entities by an edge.
- Malware is malicious software (e.g., virus, Trojan horse, or the like) installed on a computer or other device without the knowledge or permission of the owner of the device for an improper purpose, such as to steal private data or as a prank.
- Various techniques have used to detect and defend malware. Many of these techniques monitor the Internet Protocol (IP) pairs in outgoing traffic from a computer to determine whether the outgoing traffic is indicative of malware. Each IP pair includes an IP address of the computer from which the traffic originates and IP address of the traffic's destination. The techniques can detect malwares by examining whether any of the IP addresses are blacklisted, occurring frequently, etc. These techniques have drawbacks, however.
- For example, monitoring the IP pairs of outgoing traffic can be resource intensive, especially if the outgoing traffic of the computer is voluminous. Further, the problem is only compounded as the number of computers in a network, e.g., computers in an organization's network, increases. Monitoring the computers in real-time can also be challenging considering the number of IP pairs can be in significantly large numbers.
- Malware programs tend to communicate with their command and control (C&C) entity (e.g., a website) to receive new instructions and they tend to contact the C&C entity periodically. Typically, machine-generated traffic, such as traffic generated by malware, tends to have a distinct pattern from user-generated traffic, such as traffic generated from a user browsing a webpage or accessing other resources on the Internet. Most techniques fail to recognize the distinction between the machine-generated traffic and the user-generated traffic that can help in detecting malware efficiently.
- Described herein is a technique for detecting machine-generated traffic in outgoing traffic of a computer device (“device”) and determining whether the machine-generated traffic represents an anomaly. The outgoing traffic can include user-generated traffic, which can include connection requests generated from a user associated with the device, such as when the user accesses a website, checks email and downloads applications. The outgoing traffic can also include legitimate (not malware related) machine-generated traffic, which is generated by the device or an application executing on the device without intervention from the user, such as updates to applications, messages for synchronizing time of the device, device-to-device communication within another device in a distributed computing system of which the device is a part, a heartbeat signal generated by an application on the device, which can be a signal that is generated at regular intervals to indicate that the application is working as expected. The machine-generated traffic can also include traffic generated by some applications, such as a malware, that can be malicious in nature. Some of the machine-generated traffic can be in the form of a beacon, which is a signal that is transmitted periodically or in a manner that satisfies a particular criterion for periodicity/regularity.
- The malware beacon detection technique introduced here distinguishes between user-generated traffic and machine-generated traffic and, if the traffic is machine-generated, determine whether the machine-generated traffic is benign or suspicious (e.g., anomalous). The technique can use various methods to filter out benign machine-generated traffic. For example, the technique can use different heuristics and whitelists to determine whether the traffic is benign. The technique can further analyze the anomalies to determine whether they are a threat and raise an alarm if they are one.
- The technique determine if the outgoing traffic is user-generated traffic based on a number of parameters, such as number of connection requests originating from the device in a predefined period, periodicity of the connections, number of web objects requested by the device, number of destinations contacted by the device, number of times a destination is contacted and number of ports of the destinations contacted.
- The malware beacon detection technique introduced here can operate in real-time, e.g., as and when the traffic is generated from the computer device. The technique can perform the above described method using real-time infrastructure, e.g., real-
time analyzer 210 ofFIG. 2 and/oranalysis module 330 ofFIG. 3 described above. Additionally or alternatively, the technique can operate in a batch processing mode by using the batch processing infrastructure, e.g.,batch analyzer 240 and/orbatch analysis module 382. - Further, the above described method can be performed by a model, such as a machine learning model. The model can output the result of the detection as a yes or no (or the equivalent), or as a score based on which the machine-generated traffic can be determined as an anomalous or not. The model can be implemented in real-time infrastructure and/or batch processing infrastructure.
- Turning now to the figures,
FIG. 72 shows anexample graph 7200 of outgoing traffic of a device. Theexample graph 7200 depicts traffic generated from a device over a period, e.g., seventeen seconds. Theexample graph 7200 depicts the traffic as a number of connection requests originating from the device. The outgoing traffic can include two categories of traffic: user-generated traffic and machine-generated traffic. For example, the first outgoing traffic7205 and the secondoutgoing traffic 7215 which represent traffic generated from user activity, e.g., from a web browsing activity, are categorized as user-generated traffic. On the other hand, the thirdoutgoing traffic 7210 and the fourthoutgoing traffic 7220, which represent traffic generated due to various machine-related activities that are performed without the intervention of a user of the device, are categorized as machine-generated traffic. Examples of such machine-generated traffic can include a beacon to an external server, which determines whether there is any update available for an application installed at the device; a message from the device to a server for synchronizing time of the device; or malware that is communicating with a C&C entity. - In the
example graph 7200, when the user performs an activity, e.g., browses a webpage, the user generates a large volume of connection requests. When the user does not interact with the computer, there can be a silent period, e.g., a period with minimal activity or no activity. The technique can detect these silent periods and analyze the traffic generated during that time. For example, if malware contacts its C&C entity during the silent periods, the technique can detect such machine-generated traffic as anomalous. - In the first outgoing traffic7205, which can represent traffic corresponding to a user accessing a webpage, a significantly high number of connection requests, e.g., reaching almost fifty, have been generated within a span of four seconds. A website can host content stored at different locations, e.g., at different servers. For example, a webpage of the website can host a number of images, advertisements, etc. that are stored at different servers. When a user accesses the webpage, the device can generate a number of connection requests that are sent to different servers for obtaining different portions of the webpage, e.g., images, cascading stylesheets (CSS). As the content of webpage is retrieved from their respective locations, the traffic decreases and the number of connections decrease to zero. That is, the number of connections increases and/or decreases rapidly.
- In the second
outgoing traffic 7210, which represents machine-generated traffic, the number of requests are comparatively low, e.g., do not exceed ten at any instance. That is, for a predefined period, the number of requests is typically lower than the number of requests compared to user-generated traffic. Also, the connection requests in the secondoutgoing traffic 7210 is more periodic than the connection requests in the first outgoing traffic7205. For example, the connection requests appear every two seconds in the secondoutgoing traffic 7210. - From the
example graph 7200, it can be observed that a user-generated activity can include a significantly higher number of connection requests than machine-generated traffic for a predefined period. It can also be observed that the connection requests in the user-generated traffic increase and/or decrease at a rate higher than a specified threshold, i.e., connection requests are generated aperiodically or irregularly. In the machine-generated traffic, the connection requests are generated in a more periodic manner than the user-generated traffic. FIG. 73 lists an example of a set of parameters that can be considered for distinguishing between machine-generated traffic and user-generated traffic, consistent with various embodiments. The technique can distinguish between machine-generated traffic and user-generated traffic as a function of one or more of the set ofparameters 7300. The set ofparameters 7300 can include a number of connection requests generated at a device in a predefined period, periodicity of the connection requests, e.g., a period or frequency between the connections, number of different destinations contacted, e.g., a diversity of the Internet Protocol (IP) addresses, a number of web objects downloaded to the device, a number of ports at which the destinations are contacted and a Uniform Resource Identifier (URI) of the destinations. Some of the set ofparameters 7300 can be part of the outgoing traffic data and therefore, can be readily available for use by the technique. However, some of the set ofparameters 7300 are determined by the technique, e.g., based on the parameters available in the outgoing traffic data. Additional details with respect to distinguishing between user-generated traffic and machine-generated traffic are described at least with reference toFIGS. 74 and 75 .FIG. 74 is a block diagram of anenvironment 7400 in which asystem 7425 for detecting anomalies in machine-generated traffic can be implemented, consistent with various embodiments. In some embodiments, thesystem 7425 is implemented as part of thethreat detection platform 300 ofFIG. 3 . Thesystem 7425 can be implemented as part of the real-time infrastructure 330 orbatch processing infrastructure 382. In some embodiments, thesystem 7425 is implemented as part of the real-time infrastructure 330. Further, in some embodiments, at least a portion of thesystem 7425 is implemented as part of a model in the real-time infrastructure 330 orbatch processing infrastructure 382. Theenvironment 7400 includes a computer device7405 whose outgoing traffic is monitored for detection of anomalies and/or threats. The device7405 can be part of a distributed computing system having a number of devices. For example, the device7405 can be one of many devices in acomputer network 7465 of an organization. Thenetwork 7465 can be a local area network (LAN), a wide area network (WAN), etc.- The outgoing traffic from device7405 can include outgoing traffic that is internal to the network7465 (“internal traffic”), e.g., communications with devices in the
network 7465, and outgoing traffic that is external to the network7465 (“external traffic”), e.g., communications withservers 7415 in thenetwork 7410 such as Internet. Thenetwork 7410 is external to thenetwork 7465. Thesystem 7425 monitors the outgoing traffic of the device7405, e.g., usingoutgoing traffic log 7450, and detects any existence of anomalies and/or threats. - In some embodiments, the
system 7425 is configured to monitor a portion of the outgoing traffic from the device7405, e.g., external traffic. Theoutgoing traffic log 7450 can be obtained from a proxy, gateway or a firewall of thenetwork 7465 in which case theoutgoing traffic log 7450 may not include internal traffic information. However, the monitoring may not be restricted to external traffic and thesystem 7425 can be used to monitor both external and internal traffic. - The outgoing traffic can be any class of traffic, e.g., web traffic or IP traffic. The web traffic can include Hyper-Text Transfer Protocol (HTTP) message, which can be associated with parameters such as a destination IP address, a URI of the destination, a port number, a type of web request—GET or POST, etc. The IP traffic can be associated with parameters such as a destination IP address and a port number.
- The
outgoing traffic log 7450 can be processed by one or more components prior to being input to thesystem 7425. For example, after adata receiver 310 obtains information regarding the outgoing traffic of the device7405 from one of thesources 302, thesemantic processor 316 can process the outgoing traffic information to remove, add or modify at least some of the information and generate theoutgoing traffic log 7450 in a condition that is suitable for further processing by thesystem 7425 efficiently. For example, thesemantic processor 316 can remove internal traffic, e.g., data transfers that occur between two internal devices as part of file backup, which is less likely or unlikely to be an anomaly, from the outgoing traffic information. - The
traffic classification module 7430 analyzes theoutgoing traffic log 7450 and detects if the outgoing traffic is machine-generatedtraffic 7445. If the outgoing traffic is machine-generatedtraffic 7445, thetraffic classification module 7430 passes the outgoing traffic to theanomaly detection module 7435, which determines if the machine-generatedtraffic 7445 is benign traffic or ananomaly 7455. If the machine-generatedtraffic 7445 is ananomaly 7455, theanomaly detection module 7435 passes theanomaly 7455 to athreat analysis module 7460. Thethreat analysis module 7460 determines if theanomaly 7455 is a threat and generates a notification, e.g., an alarm, if it is one. - Referring back to the detection of machine-generated
traffic 7445, thetraffic classification module 7430 analyzes the connection requests in theoutgoing traffic log 7450 to form a group of connection requests and determines if the group is user-generated traffic or machine-generated traffic. In some embodiments, the group of connection requests is either machine-generated traffic or user-generated traffic and cannot be both. However, two different groups can be of different classes of traffic. Thetraffic classification module 7430 can form the group based on various criteria. Thetraffic classification module 7430 can form a group by grouping the connection requests in theoutgoing traffic log 7450 that are closer to each other in time. For example, thetraffic classification module 7430 groups the connection requests that are generated within “20” seconds from the time a first connection request of theoutgoing traffic log 7450 is generated into the same group. In some embodiments, theoutgoing traffic log 7450 is received in real-time and thetraffic classification module 7430 can start forming the group as and when the first connection request is generated at the device7405. - The
traffic classification module 7450 determines whether the group of connection requests is user-generated traffic or machine-generated traffic. The user-generated traffic, as described above, can be a result of an activity performed by auser 7420 associated with the device7405, e.g., accessing a webpage in the Internet using the device7405. The machine-generated traffic, as described above, can be generated by the device7405 or an application executing on the device7405 without intervention from theuser 7420, such as updates to applications, messages for synchronizing time of the device, a heartbeat signal from an application or beacons from a malware. - The
traffic classification module 7450 determines whether the group of connection requests is user-generated traffic or machine-generated traffic based on a set of parameters, e.g., set ofparameters 7300 ofFIG. 73 . For example, thetraffic classification module 7450 determines whether the group is user-generated traffic or machine-generated traffic as a function of one or more of a number of different destination IP addresses in the group, that is, a number of destinations contacted by the device7405; a number of web objects downloaded by the group; a number of destination ports in the group; or a periodicity of the connection requests in the group. - The
traffic classification module 7430 determines whether a periodicity of the connections in the group satisfy a periodicity criterion. In some embodiments, the periodicity of the connection requests is determined as a function of the timing between the connection requests in the group. For example, the periodicity can be an average of the periods between each of the connection requests in the group. Thetraffic classification module 7430 determines that the group is likely to be machine-generated traffic if the periodicity of the connection requests satisfies a periodicity criterion, e.g., exceeds a specified threshold; otherwise determines the group as likely to be user-generated traffic. - As described above at least with reference to
FIG. 72 , a user activity such as accessing a webpage can generate a high number of requests to different destinations within a predefined period, download a significant number of web objects, e.g., images, cascading stylesheets (CSS), and/or contact different destinations at different ports. - In some embodiments, the
traffic classification module 7450 determines that the group is likely to be user-generated traffic if a diversity of the destination IP addresses in the group (i.e., the number of destinations contacted) exceeds a specified threshold. In some embodiments, thetraffic classification module 7450 determines that the group is likely to be user-generated traffic if the number of web objects downloaded exceeds a specified threshold. In some embodiments, thetraffic classification module 7450 determines that the group is likely to be user-generated traffic if the number of ports in the group exceeds a specified threshold. Thetraffic classification module 7430 can be configured to consider one or more of the above parameters for determining whether the outgoing traffic is user-generated traffic. If thetraffic classification module 7430 determines that the outgoing traffic is likely to be user-generated traffic, the group may not be analyzed further to detect an anomaly. - The
system 7425 can check if the group includes connection requests to any whitelisted destinations. A whitelist can be a list of destinations that are considered to be safe to be accessed by the devices in thenetwork 7465. A user such as an administrator of thenetwork 7465 can generate the whitelist. The whitelist can also be created and/or modified automatically, e.g., by one or more models executing in the real-time infrastructure 330 or thebatch processing infrastructure 382. If the group includes connections requests to the whitelisted destinations the group may not be analyzed any further for detecting an anomaly. - In some embodiments, the
system 7425 determines if the group includes whitelisted destinations prior to determining whether the group is user-generated traffic so that if the group includes whitelisted destinations thesystem 7425 does not have to analyze the group any further, thereby saving computing resources. The analysis of whether the group includes whitelisted destinations can be performed by thetraffic analysis module 7425 or other modules, e.g.,semantic processor 316. - The
anomaly detection module 7435 further analyzes the machine-generatedtraffic 7445 to determine whether it is likely to be an anomaly. As described above, some of the machine-generatedtraffic 7445 can be benign and some anomalous, e.g., malicious. Theanomaly detection module 7435 analyzes the group further to determine if the machine-generatedtraffic 7445 includes benign traffic or anomalous traffic. Theanomaly detection module 7435extracts beacon data 7470 from the machine-generatedtraffic 7445. Thebeacon data 7470 can include parameters such as destination IP address(es) of the connection requests in the group, destination port(s), and if the connection request is a HTTP request, thebeacon data 7470 can also include a type of the connection request, e.g., a GET or POST, and URI of the destination. Theanomaly detection module 7435 compares thebeacon data 7470 with any of the known group types (also referred to as “beacon types”) that are identified as likely to be anomalous to determine whether the machine-generated traffic is anomalous. Additional details of determining whether the machine-generated traffic is anomalous are described at least with reference toFIG. 75 . - The
traffic classification module 7430 can determine that the group is likely to be machine-generatedtraffic 7445 if the group is not whitelisted, satisfies periodicity criterion and not user-generated traffic. Further, the machine-generated traffic that is not identified as benign traffic is recognized as anomalous. FIG. 75 shows an example7500 of a memory cache storing beacon types that are identified as likely to be anomalous, consistent with various embodiments. In some embodiments, a beacon type includes a group or a number of similar groups that are identified as likely to be anomalous. Theanomaly detection module 7435 can store the beacon type in amemory cache 7440 associated with thesystem 7425. Abeacon type 7505 can storebeacon parameters 7510 such as destination IP address(es) of connection requests in a group, destination port(s), the type of connection request, e.g., HTTP GET or POST, a URI of the destination. Theanomaly detection module 7440 stores thebeacon parameters 7510 of a group as avector 7520 and a timestamp, which indicates the time at which the group occurred in the outgoing traffic, in anarray 7515 of thebeacon type 7505. If multiple groups are stored in thebeacon type 7505, then thebeacon type 7505 can include multiple vectors, e.g., one for each corresponding group, and a timestamp entry for each of the groups in thearray 7515.- In determining whether the group to which the
beacon data 7470 corresponds is anomalous, theanomaly detection module 7435 compares thebeacon data 7470 with the beacon types in thememory cache 7440 to determine if thebeacon data 7445 matches with any of the beacon types in thememory cache 7440. If thebeacon data 7445 matches with any of the beacon types, e.g., beacon type C, theanomaly detection module 7435 adds thebeacon data 7445 to the beacon type C. Theanomaly detection module 7435 determines if the group represents an anomaly as a function of a frequency of the occurrence of the groups in the beacon type C. - As described above, some of the machine-generated
traffic 7445 can be benign and some anomalous, e.g., malicious. Theanomaly detection module 7435 analyzes the group further to determine if the machine-generatedtraffic 7445 includes benign traffic or anomalous traffic. Typically, malware sends a beacon to its C&C regularly and in high frequency. That is, a gap or timing between the beacons is typically lesser than a specified threshold. Long gaps between the connection requests, e.g., timing exceeding the specified threshold, can usually be attributed to benign traffic, such as an application on a device checking with a server in the Internet for software updates, which can also send beacons regularly. However, the beacons for such software updates can be less frequent than the beacons of malware. - In the example7500, the first occurrence of a group of beacon type C, is at time t, the second occurrence at time (t+x), the third occurrence at time (t+x+y), the fourth occurrence at time (t+x+y+z) and so on. The
anomaly detection module 7435 determines the number of occurrences of the groups and timing between the occurrences of the group. If the frequency of the groups satisfy a periodicity criterion, e.g., if an average timing (average (x, y, z)) between the occurrences of the groups satisfies a specified timing threshold, and the groups occur at least a first threshold number of times, theanomaly detection module 7435 determines the group to which thebeacon data 7470 corresponds and the other groups of the beacon type with which thebeacon data 7470 matches as anomalous. When a group is recurring but not strictly periodic, e.g., the average timing (average (x, y, z)) does not satisfy the specified timing threshold, theanomaly detection module 7435 determines if the groups occurred at least a second threshold number of times in which the second threshold number is greater than the first threshold number. If the groups occurred at least a second threshold number of times, theanomaly detection module 7435 determines the groups as anomalous. If neither of the periodicity thresholds is satisfied, the group is determined as likely to be benign traffic. - After the
anomaly detection module 7435 determines the groups to be anomalous, theanomaly detection module 7435 indicates those groups as ananomaly 7455 to thethreat analysis module 7460, which can further analyze theanomaly 7455 to determine if it is a threat and raise an alarm, e.g., generate a notification, if it is one. Theanomaly 7455 can include various information, e.g., information from thebeacon data 7470 and/or information from the beacon type with which thebeacon data 7470 matched. Theanomaly detection module 7435 can also include additional data in theanomaly 7455 which can be used by thethreat analysis module 7460 in determining if theanomaly 7455 is a threat. - Referring back to determining a matching beacon type in the
memory cache 7440, the set of parameters that may be considered to determine a match can include at least one of destination IP address(es) of the connection requests, destination port(s), and if the connection request is a HTTP request, a type of the connection request, e.g., a GET or POST, and a URI of the destination. If a particular group matches with a beacon type, then the particular group and the groups stored in the beacon type can be considered to be similar groups. Various criteria can be defined to determine whether a group matches with a beacon type. For example, thebeacon data 7470 is considered to match with a beacon type in the memory cache if all of the set of parameters of the beacon data matches with that of the beacon type. In another example, thebeacon data 7470 is considered to match with the beacon type if at least one of the set of parameters of the beacon data matches with that of the beacon type. In another example, thebeacon data 7470 is considered to match with the beacon type if at least a portion of one of the set of parameters, e.g., a portion of the destination IP address, of the beacon data matches with that of the beacon type. FIG. 76 is a flow diagram of aprocess 7600 for determining whether outgoing traffic from a device is an anomalous traffic, consistent with various embodiments. In some embodiments, theprocess 7600 is implemented in theenvironment 7400 and using thesystem 7425. Theprocess 7600 can be performed as part of a model in the real-time infrastructure 330 orbatch infrastructure 382. Atblock 7605, thetraffic classification module 7430 receives information regarding outgoing traffic of a device. For example, thetraffic classification module 7430 receives outgoingtraffic log 7450, which contains information regarding outgoing connection requests from device7405. A connection request is a request for connecting to a particular computer/server innetwork 7465 and/ornetwork 7410. The outgoing traffic can be web traffic, e.g., HTTP traffic, or IP traffic. Further, in some embodiments, the outgoing traffic does not include internal traffic, e.g., traffic between devices within thenetwork 7465.- At
block 7610, thetraffic classification module 7430 analyzes the outgoing traffic to form a group of connection requests. The connection requests in the outgoing traffic can be grouped based on various criteria. In some embodiments, the connection requests are grouped based on a time at which the connection requests were generated at the device. For example, connection requests that are closer in time to each other within a predefined period are grouped together. Additional details with respect to forming the group are described at least with reference toFIG. 77 . - At
determination block 7615, thetraffic classification module 7430 determines if the group contains connection requests to one or more destinations that are identified as acceptable destinations. Thesystem 7425 can have access to a list of acceptable destinations, e.g., a whitelist. The destination information in the whitelist can include one or more of IP address of a destination, a URI of the destination or port of the destination. - If the connection requests are to whitelisted destinations, then the group is not monitored any further and the
process 7600 returns. On the other hand, if the connection requests are to destinations that are not whitelisted, at determination block7620, thetraffic classification module 7430 analyzes the group to determine whether the group is user-generated traffic or machine-generated traffic. Examples of user-generated traffic can include traffic generated as a result of user activity, such as the user accessing a website, checking email and downloading applications. Examples of machine-generated traffic can include traffic generated by the device or an application executing on the device without intervention from the user, such as updates to applications, messages for synchronizing time of the device, device-to-device communication between devices in a distributed computing system, benign beacons, e.g., heartbeat signals generated by an application on the device, or beacons generated by malware. - In some embodiments, the traffic classification module makes the determination of whether the group is user-generated traffic or machine-generated traffic based on a set of parameters described at least with reference to
FIG. 73 . If thetraffic classification module 7430 determines the group as user-generated traffic, then the group is not monitored any further and theprocess 7600 returns. - On the other hand, if the
traffic classification module 7430 determines the group as machine-generated traffic, atblock 7625, theanomaly detection module 7435 determines whether the group represents anomalous traffic. In some embodiments, theanomaly detection module 7435 makes the determination as a function of a frequency of occurrence of the group in the outgoing traffic, or as a frequency of occurrence of groups determined to be similar to the group. Additional details with respect to determining whether the machine-generated is anomalous are described at least with reference toFIG. 78 . FIG. 77 is a flow diagram of aprocess 7700 for forming a group of connection requests from outgoing traffic of a device, consistent with various embodiments. Theprocess 7700 may be implemented as part ofblock 7610 ofprocess 7600. Atblock 7705, thetraffic classification module 7430 monitors theoutgoing traffic log 7450 to identify a first connection request from the device7405. Upon identification of a first connection request, atblock 7710, the traffic classification module forms a group and adds the first connection request to the group. Thetraffic classification module 7430 also records the time at which the first connection request was generated.- The
traffic classification module 7430 continues to monitor theoutgoing traffic log 7450 for subsequent connection requests from the device7405. Atblock 7715, thetraffic classification module 7430 detects a subsequent connection request in theoutgoing traffic log 7450. Atdetermination block 7720, thetraffic classification module 7430 determines if the subsequent connection request satisfies a grouping criterion. The grouping criterion can be based on a period between the time at which the first connection is generated and that of the subsequent connection request. The traffic classification module can determine whether the subsequent request is received within a predefined period from the time the first connection request was received, e.g., within twenty seconds from the first connection request. - If the subsequent connection request satisfies the grouping criterion, at
block 7725, thetraffic classification module 7430 adds the subsequent connection request to the group, and the process continues monitoring for subsequent requests. On the other hand, if the subsequent connection request does not satisfy the grouping criterion, theprocess 7700 returns. FIG. 78 is a flow diagram of aprocess 7800 for determining whether a particular group of connection requests in the outgoing traffic of a device is user-generated traffic or machine generated traffic, consistent with various embodiments. In some embodiments, theprocess 7800 may be implemented as part of block7620 ofprocess 7600. Atblock 7805, thetraffic classification module 7430 analyzes the connection requests to obtain a set of parameters for determining whether the particular group is user-generated traffic or machine-generated traffic. As described inFIG. 73 , the set of parameters can include one or more of IP addresses of destinations of the connection requests in the particular group, (b) a number of web objects downloaded by the connection requests in the particular group, (c) a number of ports of the destinations, or (d) periodicity of the connection requests.- At
determination block 7810, thetraffic classification module 7430 determines if the set of parameters satisfies the user-generated activity criteria. For example, thetraffic classification module 7430 determines that the group is user-generated traffic if the number of different IP addresses of the destinations, that is, a diversity of the IP addresses, exceeds a first specified threshold. In another example, thetraffic classification module 7430 determines that the group is user-generated traffic if the number of web objects downloaded by the particular group exceeds a second specified threshold. In another example, thetraffic classification module 7430 determines that the group is user-generated traffic if the number of ports exceeds a third specified threshold. - In some embodiments, the periodicity of the connection requests is determined as a function of the timing between the connection requests in the particular group. For example, the periodicity can be an average of the periods between each of the connection requests in the group. In some embodiments, the
traffic classification module 7430 determines that the particular group is likely to be machine-generated traffic if the periodicity of the connection requests satisfies a periodicity criterion, e.g., exceeds a specified threshold; otherwise determines the particular group as likely to be user-generated traffic. - The user-generated activity criteria can be configured in various ways. In some embodiments, all of the set of parameters have to satisfy the criteria for determining that the group is user-generated activity. In some embodiments, one or more of the set of parameters have to satisfy the criteria for determining that the group is user-generated activity.
- If the set of parameters satisfies the user-generated activity criteria, at
block 7820, thetraffic classification module 7430 determines that the particular group is user-generated activity; thetraffic classification module 7430 stops analyzing the particular group further and theprocess 7800 returns. On the other hand, if the set of parameters does not satisfy the user-generated activity criteria, atblock 7815, the traffic classification module determines that the particular group is machine-generated traffic. FIG. 79 is a flow diagram of aprocess 7900 for determining whether machine-generated traffic is anomalous, consistent with various embodiments. Theprocess 7900 may be implemented as part ofblock 7625 ofprocess 7600. Thesystem 7425 analyzes a particular group of connection requests that is identified as machine-generated traffic, e.g., inprocess 7800, to determine whether the machine-generated traffic is benign or anomalous. Atdetermination block 7905, theanomaly detection module 7435 compares the particular group with one or more beacon types, e.g., beacon types inmemory cache 7440, that are identified as likely to be anomalous to determine if the particular group is similar to any of the beacon types. In some embodiments, the comparison is performed as described at least with reference toFIG. 75 .- If the particular group is similar to any of the beacon types, e.g., beacon type “C”, at
block 7910, theanomaly detection module 7435 adds the particular group to the beacon type “C.” If the particular group is not similar to any of the beacon types, atblock 7925, the anomaly detection module determines that the particular group is likely to be benign traffic and theprocess 7900 returns. - At
determination block 7915, theanomaly detection module 7435 determines if the groups in the beacon type satisfy a periodicity criterion. In some embodiments, a periodicity of the groups is determined as a function of the frequency at which the groups in the beacon type occurred in the outgoing traffic. For example, the periodicity can be an average of the periods between each of the groups in the beacon type. - In some embodiments, to determine the group as anomalous, the group may have to occur at least “X” times and periodically. When a group is recurring but not strictly periodic, the group may have to occur at least “Y” times, where “Y”>“X” because a periodic behavior is a stronger indication of machine activity. Therefore, if a group is simply recurring, but not periodically enough, the group may have to occur more times before the
anomaly detection module 7435 can determine it as anomalous. The groups can be considered to be periodic, if an average timing between the occurrences of the groups in the beacon type satisfies a specified timing threshold. - Accordingly, the periodicity criterion can state that if the groups in the beacon type are periodic, then groups have to occur a first threshold number of times else the groups have to occur a second threshold number of times for the groups in the beacon type to be considered as anomalous. Further, the periodicity criterion can require that the second threshold number to be greater than the first threshold number.
- Referring back to
determination block 7915, if the groups in the beacon type satisfy the periodicity criterion, atblock 7920, theanomaly detection module 7435 determines that the groups in the beacon type are anomalous. If the groups in the beacon type do not satisfy the periodicity criterion, atblock 7925, theanomaly detection module 7435 determines that the groups in the beacon type are likely to be benign traffic, and theprocess 7900 returns. - Described herein is a technique for determining rarity of features of data traffic (“traffic”) in a computer network. Determination of rarity can be used to detect anomalies represented in event data. The technique computes a rarity score for each of various values of a feature of event data, where each rarity score indicates how rare the occurrence of the corresponding particular value is relative to occurrences of other values of that feature, and then determines if network activity or an event in which that particular value of the feature occurs is anomalous, based on the rarity score.
- Examples of features regarding which a rarity score can be computed in this manner include, for example: a field, attribute, and/or property of the data traffic on and/or an entity associated with the computer network, e.g., a username of a user, a source zone of the network from which the traffic is originating, a destination zone of the network to which the traffic is destined, the port identifier of a port through which data is transmitted, a name of an application that transmits and/or receives the data, and an identification (ID) of a device, such as an Internet Protocol (IP) address, that transmits and/or receives the data. The feature can be of high cardinality, i.e., can have one of a finite number of values. For example, a feature such as a port can have multiple values, e.g., 20, 22, 23, 25, 80, which are associated with specific network protocols. In the data traffic, a particular value of a feature may occur more commonly, e.g., more number of times, than another value of the feature. For example, in a computer network where most traffic into and/or out of the network is web traffic,
port 80, which corresponds to Hyper Text Transfer Protocol (HTTP), may occur more commonly than other ports, e.g.,port 23. - In some embodiments, the rarity determination technique determines the rarity of a particular value of a feature (such as one of the features mentioned above) as a function of the probability of occurrence of that particular value relative to the probability of occurrence of other values of the feature. In some embodiments, the technique considers the values that are as likely or less likely to occur than that particular value to determine the probability (also referred to as “relative probability”) of occurrence of the particular value. After determining the probability of the particular value relative to the other values, the technique may compute a confidence interval of that probability to obtain the rarity score. In some embodiments, the rarity score is a value between 0 and 1. The technique can use known methods, such as the delta method, for computing the confidence interval.
- If the rarity score for the particular value satisfies a rarity criterion, the technique can identify an activity or event in which the particular value occurred as anomalous. In some embodiments, the rarity score satisfies the rarity criterion if the rarity score is below a specified score threshold and the number of times that the particular value has been identified as corresponding to an anomaly is less than a specified count threshold.
- The technique can also determine the rarity score for more than one feature, e.g., a feature pair, which indicates how rare it is to observe a first feature at a particular value when the second feature is observed at a first value. That is, the rarity score of a feature pair (X, Y) indicates how rare it is to observe “X=a” when “Y=p” and/or how rare it is to observe “Y=p” when “X=a.” Consider an example in which data can be transmitted from one or more source devices to one or more destination devices. The data can be transmitted from a portion of the network identified as “Zone A” to a portion of the network identified as “Zone B,” from “Zone C” to “Zone B,” “Zone D to “Zone B,” and/or “Zone A to “Zone D.” The technique can determine how rare it is to observe a source zone being “Zone A” when the destination zone is “Zone B.” Based on the rarity score of the feature pair, the technique can determine whether an event of which the feature pair is a part corresponds to an anomaly.
- Turning now to the figures,
FIG. 80 is a block diagram of anenvironment 8000 in which asystem 8025 for detecting anomalies based on rarity scores of features can be implemented. In some embodiments, thesystem 8025 is implemented as part of thesecurity platform 300 ofFIG. 3 . Thesystem 8025 can be implemented as part of the real-time infrastructure 330 orbatch processing infrastructure 382. Further, in some embodiments, at least a portion of thesystem 8025 is implemented as part of a machine learning model in the real-time infrastructure 330 orbatch processing infrastructure 382. Theenvironment 8000 includes a computer device (“device”)8005 whose data traffic is monitored for detection of anomalies and/or threats. Thedevice 8005 can be part of a distributed computing system having a number of devices. For example, thedevice 8005 can be one of many devices in acomputer network 8065 of an organization. Thenetwork 8065 can be a local area network (LAN), a wide area network (WAN), etc. - The traffic can include data transmitted by or received at the
computer device 8005. The traffic fromdevice 8005 can include traffic that is internal to the network8065 (“internal traffic”), e.g., communications with devices in thenetwork 8065, and traffic that is external to the network8065 (“external traffic”), e.g., communications withservers 8015 in thenetwork 8010 such as Internet. Thenetwork 8010 is external to thenetwork 8065. In some embodiments, at least a portion of the traffic is generated due to activity of auser 8020 associated with thecomputer device 8005. Thesystem 8025 monitors the traffic of thedevice 8005, e.g., usingtraffic log 8050, and detects any existence of anomalies and/or threats. Thetraffic log 8050 includes event data including multiple events representative of traffic into and/or out of thenetwork 8065. Thetraffic log 8050 can be generated based on data obtained from a proxy, a gateway or a firewall associated with thenetwork 8065. - The traffic can be any class of data traffic, e.g., web traffic or IP traffic. The web traffic can include an HTTP message, which can have parameters such as a destination IP address, a URI of the destination, a port number, a type of web request—GET or POST, etc. The IP traffic can have parameters such as a destination IP address and a port number.
- A machine learning model that implements the rarity analysis technique described here can subscribe to one or more event views (described above), via the model registry. Through such event view(s), the model can access the appropriate features of the event data that includes or represents
traffic log 8050, to enable the model to perform the rarity analysis. The semantic processor316 (FIG. 3 ) can process the event data to remove, add or modify at least some of the information and generate thetraffic log 8050 in a condition that is suitable for further processing by thesystem 8025 efficiently. For example, thesemantic processor 316 can remove traffic that is between two devices which are identified as acceptable end points for message transmission, as such traffic is less likely or unlikely to be an anomaly. - Any event in the
traffic log 8050 can include one or more features. To determine whether or not an event is anomalous, thesystem 8025 may analyze some or all of the features in the event. In some embodiments, thefeature tracking module 8030 analyzes thetraffic log 8050 to identify only the features that are needed for determining whether a particular event is anomalous. In some embodiments, a user, e.g., an administrator associated with thenetwork 8065, can provide the list of features to be tracked for determining whether an event is anomalous. The list of features to be tracked may be provided in the definition of an event view. - The
feature tracking module 8030 identifies the relevant features (i.e., features of interest) and the values of each relevant feature occurring in thetraffic log 8050 and stores a count of the occurrences of each value of each relevant feature. For example, a feature such as the “port” field can occur multiple times in thetraffic log 8050 some occurrences of which can have the same value, e.g., same port number, and other occurrences of which can have other values. For example, a first number of events in thetraffic log 8050 can include port identifier of80 and a second number of events can have different port identifiers, such as20,22,23. Accordingly, thefeature tracking module 8030 stores a count of the occurrences of values of a feature. Similarly, thefeature tracking module 8030 stores a count of the occurrences of values of other features. Thefeature tracking module 8030 can store the count in a data structure that is convenient for easy and efficient storage and retrieval of the count data. The data structure can be stored in a storage system associated with thesystem 8025, e.g.,persistence layer 368 ofFIG. 3 . - In some embodiments, the
feature tracking module 8030 also tracks occurrences of a set of features in an event, e.g., a feature pair. As described above, the technique can also determine how rare it is to observe a first feature at a particular value when the second feature is observed at a first value. For example, the technique can determine, in data transmission between two entities, how rare it is to observe a source zone as “Zone A” when the destination zone is “Zone B”. Thefeature tracking module 8030 can identify occurrences of such feature pairs and store a count of the occurrence of such feature pairs. Thefeature tracking module 8030 can store the count in a second data structure that is convenient and efficient for easy storage and retrieval of the count data of the feature pairs. The second data structure can be stored in a storage system associated with thesystem 8025, e.g.,persistence layer 368 ofFIG. 3 . - The
rarity determination module 8035 determines a rarity score of each particular value of each relevant feature, where the score is indicative of how rare it is to observe that particular value of the feature relative to other values of the feature. To do so, therarity determination module 8035 first determines a probability of occurrence of the particular value as a function of probabilities of other values of the feature that are as likely or less likely to occur than the particular value. The probability of each of the possible values can be determined from the total observed number of occurrences of each value in the event data in relation to the total number of occurrences of all values for that feature. Therarity determination module 8035 can obtaincount data 8045 of the feature, which includes counts of the numbers of occurrences of various values of the feature, from thefeature tracking module 8030 or associated storage system. - After determining the probability of the particular value relative to the other values of the feature as described above, the
rarity determination module 8035 computes a confidence interval of the probability to obtain ararity score 8070. Therarity determination module 8035 can compute the confidence interval at an upper bound value, such as 95th percentile. In some embodiments, the rarity score is a value between 0 and 1. Therarity determination module 8035 can use any of various known methods, e.g., delta method, to compute the confidence interval. In some embodiments, computing the confidence interval is accomplished by using the delta method, which ensures that therarity score 8070 is between 0 and 1. - As noted above, as one step in the rarity score computation, the
rarity determination module 8035 identifies the set of values of the feature whose numbers of occurrences in thetraffic log 8050 are less than or equal to the number of occurrences of the particular value in question. For the particular value, therarity determination module 8035 determines the sum of the number of occurrences of that set of values and the particular value, which is denoted as “k”. Therarity determination module 8035 determines the total number of occurrences of the feature, which is denoted as “n”. Therarity determination module 8035 determines therarity score 8070 of the particular value of the feature as a function of (k, n), e.g., as a confidence interval of the binomial (k, n). - The following is an example describing determining the rarity score for a geographic (“geo”)-location feature, e.g., a location from where a connection request to the
network 8065 is originating, where each value of the feature is a two-letter country identifier. Consider that thefeature tracking module 8030 has tracked the following numbers of occurrences of various values (country identifiers) for the geo-location feature: “US: 100, UK: 30, IN: 20, RU: 3, CN: 2, JP: 1.” For example, the events with value [US] for the geo location feature has occurred “100” times. Therarity determination module 8035 can compute the rarity of seeing the value [RU] as the sum of the probabilities of seeing (RU, CN, JP), where [CN] and [JP] in this example are values of the geo-location that have appeared as many or fewer times than [RU]. The sum of probabilities of (RU, CN, JP), which can indicate the relative probability of [RU], is used to determine the rarity score. Therarity determination module 8035 can determine the rarity score as a confidence interval for the binomial (k=6 and n=156), where - k denotes the sum of occurrences of the particular value [RU] and occurrences of the values that have appeared as many or fewer times than [RU], and
- n denotes the total number of occurrences of the feature geo-location.
- The
rarity determination module 8035 can compute the rarity score as a 95% confidence interval. The rarity score of [RU] indicates how rare it is to observe the value [RU] relative to other values for the geo-location feature. - Similarly, the
rarity determination module 8035 can also determine therarity score 8070 for feature pairs. Therarity determination module 8035 can obtain thecount data 8045 for the feature pair, determine the respective counts and then determine therarity score 8070 for the feature pair. For example, therarity determination module 8035 can determine a rarity score for observing a connection request for a given application, such as a virtual private network (VPN), from a geo location such as [RU]. Therarity determination module 8035 identifies a set of locations whose number of occurrences in thetraffic log 8050 for the VPN connection request is less than or equal to the number of occurrences of the [RU] location. Therarity determination module 8035 determines a sum of the number of occurrences of the set of locations and the location [RU], which is denoted as “k”. Therarity determination module 8035 determines a total number of occurrences of the feature pair with the application as VPN connection request, which is denoted as “n”. Therarity determination module 8035 determines therarity score 8070 of the particular value of the feature as a function of (k, n), e.g., as 95% confidence interval for the binomial (k, n). - Accordingly, the
rarity determination module 8035 can determine therarity score 8070 for a particular value of the feature, and/or for a feature pair. - The
anomaly detection module 8040 determines whether an activity in which the particular value of the feature occurred is anomalous based on whether a rarity score criterion (e.g., one or more thresholds) is satisfied by the rarity score of the particular value. The rarity criterion can be a tuple of (score threshold, anomaly count threshold). The score threshold specifies a threshold for the rarity score and the anomaly count threshold specifies a threshold for the number of times a particular value can be identified as ananomaly 8055. In some embodiments, theanomaly detection module 8040 can determine that a particular value of the feature corresponds to ananomaly 8055 if therarity score 8070 of that particular value is below the score threshold and the number of times that the particular value has been identified as ananomaly 8055 is below the anomaly count threshold. - If the number of times the particular value has been identified as an
anomaly 8055 exceeds the anomaly count threshold, theanomaly detection module 8040 may not identify the particular value as anomaly. In some embodiments, if the particular value has occurred enough times, e.g., exceeds the anomaly count threshold, in a specified time interval, theanomaly detection module 8040 may determine that the particular value is no longer considered an anomaly and may, therefore, dynamically adjust the rarity criterion, e.g., the score threshold and/or the anomaly count threshold, to minimize and/or stop identifying the particular value as corresponding to an anomaly. - The
anomaly detection module 8040 can similarly determine whether an activity in which a particular feature pair occurred is anomalous based on whether the particular feature pair satisfies a rarity criterion. - As described above, in some embodiments, an event in the
traffic log 8050 can include a number of associated features. Theanomaly detection module 8040 may in some cases have to determine whether one or more of the features and/or feature pairs in an event is anomalous to determine whether the event is anomalous. FIG. 81 shows a table8100 of example features and/or feature pairs to be considered for determining whether an example event is anomalous. The example event can be a “cloudtrail”event 8105, which is an event representative of application programming interface (API) calls for a web service. Thecloudtrail event 8105 can include features such as: Event Class, which can be indicative of a class of the event; User Agent, which can be indicative of a name of the application; Device, which can be an identification of a device (e.g., IP address) contacting the web service, and User, which can be an identification of the user associated with the device (e.g., username of the user). The table8100 indicates the features and the feature pairs that have to be analyzed to determine whether the event corresponds to ananomaly 8055.- For example, the table8100 indicates that the features, Event Class and User Agent, and the feature pairs, (Event Class::Device), (Event Class::User), (User Agent::Device), and (User Agent::User) may have to be analyzed to determine whether the
cloudtrail event 8105 is ananomaly 8055. That is, theanomaly detection module 8040 determines that thecloudtrail event 8105 corresponds to an anomaly if the above listed features and the feature pairs satisfy the rarity criterion. - In some embodiments, the rarity criterion for determining whether an event is anomalous can include additional parameters, such as a minimum number of features and/or feature pairs in the event to be anomalous, a list of features and/or feature pairs in the event to be anomalous.
FIG. 82 shows a table8200 listing examples of thresholds and/or parameters of a rarity criterion, for various example events, that can be used for determining whether an event is anomalous. The thresholds in the table8200 include a score threshold, a feature count threshold (which specifies the minimum number of features and/or feature pairs to be anomalous) and an anomaly count threshold. The parameters in the table8200 can include rare features and/or rare feature pairs, which indicate the features and/or feature pairs, respectively, that have to be determined as anomalous to determine that the event itself is anomalous. The ignore feature indicates the features that when found to be anomalous, results in ignoring the event, that is, the event is not to be identified as an anomaly.- For example, for an event such as transmitting data to/from an application via a port, a score threshold is set to “0.001,” a feature count threshold is set to “1” and the anomaly count threshold is set to “50.” The rare features and rare feature pairs is set to null value. The ignore feature is set to null value.
- It should be noted that one or more of the above thresholds are configurable, e.g., by a user, such as an administrator of the
network 8065, or by thesystem 8025. For example, thesystem 8025 may dynamically adjust the score threshold to a lower value if a significant number of occurrences of the particular value is identified as an anomaly, e.g., in a predefined period. Further, one or more of the above parameters are also configurable, e.g., by the user. - The
anomaly detection module 8040 determines that a particular value of a feature, a feature pair and/or an event is ananomaly 8055 if the particular value, the feature pair and/or the event satisfies the rarity criterion. - After the
anomaly detection module 8040 determines the particular value, feature pair and/or event to be anomalous, theanomaly detection module 8040 indicates the particular value, feature pair and/or event as ananomaly 8055 to athreat analysis module 8060. Thethreat analysis module 8060 can further analyze theanomaly 8055 to determine if it is a threat and raise an alarm, e.g., generate a notification, if it is one. Theanomaly 8055 can include various information, e.g.,rarity score 8070 and/or information regarding various rarity criterion parameters, which can be used by thethreat analysis module 8060 in determining if theanomaly 8055 is a threat. FIG. 83 is a flow diagram of aprocess 8300 for determining an anomaly based on a rarity score for a particular value of a feature, consistent with various embodiments. Theprocess 8400 can be implemented in theenvironment 8000 and using thesystem 8025. Theprocess 8300 can be performed as part of a model in the real-time infrastructure 330 orbatch infrastructure 382. Atblock 8305, thefeature tracking module 8030 identifies the occurrence of a feature and one or more values of the feature in the traffic of a network, such asnetwork 8065. For example, for an event data in the traffic log8059 representing a VPN connection request to anetwork 8065 from a user in a specific geo location, the geo location can be a feature and the various possible geo locations such as [US], [UK], [IN] or [RU] can be values of the feature. Theprocess 8300 can facilitate determining whether the occurrence of a particular value of the feature is anomalous.- At
block 8310, thefeature tracking module 8030 identifies a set of values of the feature whose probability of occurrence does not exceed a probability of occurrence of the particular value. That is, thefeature tracking module 8030 identifies the set of values that are as likely or less likely to occur in the traffic than the particular value of the feature. - At
block 8315, therarity determination module 8035 determines a rarity score for the particular value as a function of the probabilities of the occurrence of the set of values, in the manner described above. The rarity score can indicate a probability of occurrence of the particular value relative to the set of values, i.e., how rare is the occurrence of the particular value relative to the set of values. - At
determination block 8320, theanomaly detection module 8040 determines whether the rarity score for the particular value of the feature satisfies a rarity criterion. If theanomaly detection module 8040 determines that the rarity score satisfies the rarity criterion, atblock 8325, theanomaly detection module 8040 determines that an activity in the computer network associated with the particular value of the feature is anomalous. If the rarity score does not satisfy the rarity criterion, theprocess 8300 returns. - In determining whether the rarity score satisfies the rarity criterion, the
anomaly detection module 8040 determines whether the one or more thresholds of and/or parameters of the rarity criterion are satisfied. For example, theanomaly detection module 8040 can determine a particular value of the feature as an anomaly if the rarity score for the particular value is below a score threshold and a number of times the particular value has been identified as an anomaly is below an anomaly count threshold of the rarity criterion. - Further, the
process 8300 can also be used to determine whether an observed event of the traffic, which can include multiple features, is an anomaly based on a rarity score of the one or more features and/or feature pairs. Theanomaly detection module 8040 can determine whether the event is anomalous by determining whether one or more parameters such as a rarity score of the one or more features of the event, a minimum number of features in the event that need to be anomalous, or a list of features that need to be anomalous satisfy the rarity criterion. FIG. 84 is a flow diagram of aprocess 8400 for determining a rarity score for a particular value of a feature, consistent with various embodiments. Theprocess 8400 can be implemented in theenvironment 8000 and using thesystem 8025. Theprocess 8400 can also be performed as part of a model in the real-time infrastructure 330 orbatch infrastructure 382. In some embodiments, theprocess 8400 can be performed as part ofblocks process 8300. Atblock 8405, thefeature tracking module 8030 identifies, from thetraffic log 8050, a set of values of the feature that has occurred as many or fewer times than the particular value in the traffic. Consider that thefeature tracking module 8030 has tracked the following occurrences of various values for a geo location feature: “US: 100, UK: 30, IN: 20, RU: 3, CN: 2, JP: 1.” To determine a rarity score for the location “Russia,” i.e., for value [RU], thefeature tracking module 8030 determines the set of locations that have occurred as many or fewer times than [RU], which are “China,” i.e., [CN] and “Japan,” i.e., [JP]. Thefeature tracking module 8030 determines the sum of occurrences of the particular value [RU] and the set of values, [CN] and [JP], as (k=6).- At
block 8410, thefeature tracking module 8030 determines a total number of occurrences of the feature. Continuing with the above example, thefeature tracking module 8030 determines the total number of occurrences of the geo location feature, which includes occurrences of all values of the feature, as (n=156). - At
block 8415, therarity determination module 8035 determines the rarity score for the particular value by computing a confidence interval for the parameters (k, n). In some embodiments, the rarity score is computed as an upper bound confidence interval, e.g., 95% confidence interval, of the parameters. The confidence interval method employed for computing the rarity score can be selected such that the rarity score is computed to a value between 0 and 1. In some embodiments, therarity determination module 8035 employs a delta method for computing the confidence interval. - Continuing with the above example, the
rarity determination module 8035 can determine the rarity score for [RU] as 95% th confidence interval of parameters (k=6 and n=156). The rarity score for [RU] indicates how rare it is to observe an occurrence of the geo location as [RU] relative to other locations. - Reference in this specification to “one embodiment” or “an embodiment” means that a particular feature, structure, or characteristic described in connection with the embodiment is included in at least one embodiment of the disclosure. The appearances of the phrase “in one embodiment” in various places in the specification are not necessarily all referring to the same embodiment, nor are separate or alternative embodiments mutually exclusive of other embodiments. Moreover, various features are described which may be exhibited by some embodiments and not by others. Similarly, various requirements are described which may be requirements for some embodiments but not for other embodiments.
- A security platform such as described above (e.g., security platform300) can be implemented using one or more conventional physical processing devices.
FIG. 85 is a block diagram showing an example of such a processing device, e.g., acomputer system 8500. Multiple instances of such a computer system may be used to implement the security platform in a given embodiment. - In an illustrative embodiment,
computer system 8500 includes one or more processor(s)8510,memory 8520, one or more input/output (I/O)devices 8530, anetwork adapter 8540, and astorage adapter 8550, all interconnected by aninterconnect 8560.Memory 8520 includes storage locations that are addressable by processor(s)8510 andadapters Memory 8520 may include multiple physically distinct memory devices, which may be all of the same type or of different types (e.g., volatile memory such as SRAM or DRAM, non-volatile memory such as flash, etc.). Processor(s)8510 andadapters Network adapter 8540 includes one or more ports to couplecomputer system 8500 with one or more other devices over one or more point-to-point links, local area networks (LANs), wide area networks (WANs), the global Internet, virtual private networks (VPNs) implemented over a public network, or the like.Network adapter 8540 can include the mechanical components and electrical circuitry needed to connectstorage server 8500 to a network. One or more systems can communicate with other systems over the network by exchanging packets or frames of data according to pre-defined protocols, such as TCP/IP.Storage adapter 8550 interfaces with an operating system running on processor(s)8510 to access information on attached storage devices. The information may be stored on any type of attached array of writable storage media, such as hard disk drives, magnetic tape, optical disk, flash memory, solid-state drives, RAM, MEMs and/or any other similar media adapted to store information.Storage adapter 8550 includes a plurality of ports having I/O interface circuitry that couples with disks or other storage related devices over an I/O interconnect arrangement.- Embodiments of the techniques introduced here include various steps and operations, which have been described above. A variety of these steps and operations may be performed by hardware components or may be embodied in machine-executable instructions, which may be used to cause one or more general-purpose or special-purpose processors programmed with the instructions to perform the steps. Alternatively, the steps may be performed by a combination of hardware, software, and/or firmware.
- Embodiments of the techniques introduced here may be implemented, at least in part, by a computer program product which may include a non-transitory machine-readable medium having stored thereon instructions that may be used to program/configure a computer or other electronic device to perform some or all of the operations described above. The machine-readable medium may include, for example, magnetic hard disk drives, compact disc read-only memories (CD-ROMs), magneto-optical disks, floppy disks, ROMs, RAMs, various forms of erasable programmable read-only memories (EPROMs), magnetic or optical cards, flash memory, or other type of machine-readable medium suitable for storing electronic instructions. Moreover, embodiments of the present invention may also be downloaded as a computer program product, wherein the program may be transferred from a remote computer to a requesting computer by way of data signals embodied in a carrier wave or other propagation medium via a communication link.
Claims (30)
Priority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| US14/928,503US20170063900A1 (en) | 2015-08-31 | 2015-10-30 | Method And System For Monitoring Entity Activity On An Organization's Computer Network |
Applications Claiming Priority (2)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| US201562212541P | 2015-08-31 | 2015-08-31 | |
| US14/928,503US20170063900A1 (en) | 2015-08-31 | 2015-10-30 | Method And System For Monitoring Entity Activity On An Organization's Computer Network |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| US20170063900A1true US20170063900A1 (en) | 2017-03-02 |
Family
ID=57400072
Family Applications (51)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US14/841,634Active2035-11-18US9699205B2 (en) | 2015-08-31 | 2015-08-31 | Network security system |
| US14/929,132Active2036-06-03US10063570B2 (en) | 2015-08-31 | 2015-10-30 | Probabilistic suffix trees for network security analysis |
| US14/929,224ActiveUS9591010B1 (en) | 2015-08-31 | 2015-10-30 | Dual-path distributed architecture for network security analysis |
| US14/928,563ActiveUS9609011B2 (en) | 2015-08-31 | 2015-10-30 | Interface having selectable, interactive views for evaluating potential network compromise |
| US14/929,037Active2036-04-03US10419450B2 (en) | 2015-08-31 | 2015-10-30 | Detection of anomalies, threat indicators, and threats to network security |
| US14/929,203ActiveUS9596254B1 (en) | 2015-08-31 | 2015-10-30 | Event mini-graphs in data intake stage of machine data processing platform |
| US14/928,985Active2036-03-14US9838410B2 (en) | 2015-08-31 | 2015-10-30 | Identity resolution in data intake stage of machine data processing platform |
| US14/929,196Active2036-06-11US10015177B2 (en) | 2015-08-31 | 2015-10-30 | Lateral movement detection for network security analysis |
| US14/929,204Active2036-06-26US10038707B2 (en) | 2015-08-31 | 2015-10-30 | Rarity analysis in network security anomaly/threat detection |
| US14/929,187Active2038-07-28US10904270B2 (en) | 2015-08-31 | 2015-10-30 | Enterprise security graph |
| US14/929,042ActiveUS9667641B2 (en) | 2015-08-31 | 2015-10-30 | Complex event processing of computer network data |
| US14/928,471Active2036-02-07US10469508B2 (en) | 2015-08-31 | 2015-10-30 | Interactive threat geo-map for monitoring computer network security |
| US14/929,168ActiveUS9516053B1 (en) | 2015-08-31 | 2015-10-30 | Network security threat detection by user/user-entity behavioral analysis |
| US14/929,047AbandonedUS20170063907A1 (en) | 2015-08-31 | 2015-10-30 | Multi-Stage Network Security Threat Detection |
| US14/928,451Active2036-07-20US10154047B2 (en) | 2015-08-31 | 2015-10-30 | Method and system for generating a kill chain for monitoring computer network security |
| US14/929,035ActiveUS10110617B2 (en) | 2015-08-31 | 2015-10-30 | Modular model workflow in a distributed computation system |
| US14/929,141Active2036-05-24US10158652B2 (en) | 2015-08-31 | 2015-10-30 | Sharing model state between real-time and batch paths in network security anomaly detection |
| US14/929,183Active2036-01-30US10389738B2 (en) | 2015-08-31 | 2015-10-30 | Malware communications detection |
| US14/928,503AbandonedUS20170063900A1 (en) | 2015-08-31 | 2015-10-30 | Method And System For Monitoring Entity Activity On An Organization's Computer Network |
| US14/928,421Active2036-05-28US10193901B2 (en) | 2015-08-31 | 2015-10-30 | Interface providing an interactive timeline for evaluating instances of potential network compromise |
| US14/928,918ActiveUS10243970B2 (en) | 2015-08-31 | 2015-10-30 | Event views in data intake stage of machine data processing platform |
| US14/929,184Active2035-12-28US10069849B2 (en) | 2015-08-31 | 2015-10-30 | Machine-generated traffic detection (beaconing) |
| US14/929,182Active2036-08-24US10003605B2 (en) | 2015-08-31 | 2015-10-30 | Detection of clustering in graphs in network security analysis |
| US14/928,535Active2035-11-21US10212174B2 (en) | 2015-08-31 | 2015-10-30 | Method and system for reviewing identified threats for performing computer security monitoring |
| US15/335,250ActiveUS9609009B2 (en) | 2015-08-31 | 2016-10-26 | Network security threat detection by user/user-entity behavioral analysis |
| US15/413,336ActiveUS10135848B2 (en) | 2015-08-31 | 2017-01-23 | Network security threat detection using shared variable behavior baseline |
| US15/415,747ActiveUS9813435B2 (en) | 2015-08-31 | 2017-01-25 | Network security analysis using real-time and batch detection engines |
| US15/418,546ActiveUS10116670B2 (en) | 2015-08-31 | 2017-01-27 | Event specific relationship graph generation and application in a machine data processing platform |
| US15/490,849ActiveUS10148677B2 (en) | 2015-08-31 | 2017-04-18 | Model training and deployment in complex event processing of computer network data |
| US15/616,889ActiveUS9900332B2 (en) | 2015-08-31 | 2017-06-07 | Network security system with real-time and batch paths |
| US15/800,000Active2036-03-23US10581881B2 (en) | 2015-08-31 | 2017-10-31 | Model workflow control in a distributed computation system |
| US15/800,010ActiveUS10291635B2 (en) | 2015-08-31 | 2017-10-31 | Identity resolution in data intake of a distributed data processing system |
| US15/860,049ActiveUS10419462B2 (en) | 2015-08-31 | 2018-01-02 | Event information access interface in data intake stage of a distributed data processing system |
| US15/926,961ActiveUS10419463B2 (en) | 2015-08-31 | 2018-03-20 | Event specific entity relationship discovery in data intake stage of a distributed data processing system |
| US15/995,073ActiveUS10476898B2 (en) | 2015-08-31 | 2018-05-31 | Lateral movement detection for network security analysis |
| US16/016,472Active2036-12-26US11470096B2 (en) | 2015-08-31 | 2018-06-22 | Network security anomaly and threat detection using rarity scoring |
| US16/041,637ActiveUS10560468B2 (en) | 2015-08-31 | 2018-07-20 | Window-based rarity determination using probabilistic suffix trees for network security analysis |
| US16/050,368ActiveUS10587633B2 (en) | 2015-08-31 | 2018-07-31 | Anomaly detection based on connection requests in network traffic |
| US16/182,469ActiveUS10419465B2 (en) | 2015-08-31 | 2018-11-06 | Data retrieval in security anomaly detection platform with shared model state between real-time and batch paths |
| US16/215,350ActiveUS10778703B2 (en) | 2015-08-31 | 2018-12-10 | Method and system for generating an interactive kill chain view for training a machine learning model for identifying threats |
| US16/259,999ActiveUS10666668B2 (en) | 2015-08-31 | 2019-01-28 | Interface providing an interactive trendline for a detected threat to facilitate evaluation for false positives |
| US16/264,514ActiveUS10986106B2 (en) | 2015-08-31 | 2019-01-31 | Method and system for generating an entities view with risk-level scoring for performing computer security monitoring |
| US16/503,181Active2036-10-25US11258807B2 (en) | 2015-08-31 | 2019-07-03 | Anomaly detection based on communication between entities over a network |
| US16/516,471Active2036-08-07US11411966B2 (en) | 2015-08-31 | 2019-07-19 | Processing anomaly data to identify threats to network security |
| US16/532,312Active2036-02-01US11146574B2 (en) | 2015-08-31 | 2019-08-05 | Annotation of event data to include access interface identifiers for use by downstream entities in a distributed data processing system |
| US16/547,235ActiveUS10911468B2 (en) | 2015-08-31 | 2019-08-21 | Sharing of machine learning model state between batch and real-time processing paths for detection of network security issues |
| US16/568,106ActiveUS10798113B2 (en) | 2015-08-31 | 2019-09-11 | Interactive geographic representation of network security threats |
| US16/581,094ActiveUS10911470B2 (en) | 2015-08-31 | 2019-09-24 | Detecting anomalies in a computer network based on usage similarity scores |
| US17/125,130Active2036-04-02US11575693B1 (en) | 2015-08-31 | 2020-12-17 | Composite relationship graph for network security |
| US17/676,022Active2036-01-24US12438891B1 (en) | 2015-08-31 | 2022-02-18 | Anomaly detection based on ensemble machine learning model |
| US17/845,383ActiveUS11824646B1 (en) | 2015-08-31 | 2022-06-21 | Processing anomaly data to identify network security threats by use of rarity analysis |
Family Applications Before (18)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US14/841,634Active2035-11-18US9699205B2 (en) | 2015-08-31 | 2015-08-31 | Network security system |
| US14/929,132Active2036-06-03US10063570B2 (en) | 2015-08-31 | 2015-10-30 | Probabilistic suffix trees for network security analysis |
| US14/929,224ActiveUS9591010B1 (en) | 2015-08-31 | 2015-10-30 | Dual-path distributed architecture for network security analysis |
| US14/928,563ActiveUS9609011B2 (en) | 2015-08-31 | 2015-10-30 | Interface having selectable, interactive views for evaluating potential network compromise |
| US14/929,037Active2036-04-03US10419450B2 (en) | 2015-08-31 | 2015-10-30 | Detection of anomalies, threat indicators, and threats to network security |
| US14/929,203ActiveUS9596254B1 (en) | 2015-08-31 | 2015-10-30 | Event mini-graphs in data intake stage of machine data processing platform |
| US14/928,985Active2036-03-14US9838410B2 (en) | 2015-08-31 | 2015-10-30 | Identity resolution in data intake stage of machine data processing platform |
| US14/929,196Active2036-06-11US10015177B2 (en) | 2015-08-31 | 2015-10-30 | Lateral movement detection for network security analysis |
| US14/929,204Active2036-06-26US10038707B2 (en) | 2015-08-31 | 2015-10-30 | Rarity analysis in network security anomaly/threat detection |
| US14/929,187Active2038-07-28US10904270B2 (en) | 2015-08-31 | 2015-10-30 | Enterprise security graph |
| US14/929,042ActiveUS9667641B2 (en) | 2015-08-31 | 2015-10-30 | Complex event processing of computer network data |
| US14/928,471Active2036-02-07US10469508B2 (en) | 2015-08-31 | 2015-10-30 | Interactive threat geo-map for monitoring computer network security |
| US14/929,168ActiveUS9516053B1 (en) | 2015-08-31 | 2015-10-30 | Network security threat detection by user/user-entity behavioral analysis |
| US14/929,047AbandonedUS20170063907A1 (en) | 2015-08-31 | 2015-10-30 | Multi-Stage Network Security Threat Detection |
| US14/928,451Active2036-07-20US10154047B2 (en) | 2015-08-31 | 2015-10-30 | Method and system for generating a kill chain for monitoring computer network security |
| US14/929,035ActiveUS10110617B2 (en) | 2015-08-31 | 2015-10-30 | Modular model workflow in a distributed computation system |
| US14/929,141Active2036-05-24US10158652B2 (en) | 2015-08-31 | 2015-10-30 | Sharing model state between real-time and batch paths in network security anomaly detection |
| US14/929,183Active2036-01-30US10389738B2 (en) | 2015-08-31 | 2015-10-30 | Malware communications detection |
Family Applications After (32)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US14/928,421Active2036-05-28US10193901B2 (en) | 2015-08-31 | 2015-10-30 | Interface providing an interactive timeline for evaluating instances of potential network compromise |
| US14/928,918ActiveUS10243970B2 (en) | 2015-08-31 | 2015-10-30 | Event views in data intake stage of machine data processing platform |
| US14/929,184Active2035-12-28US10069849B2 (en) | 2015-08-31 | 2015-10-30 | Machine-generated traffic detection (beaconing) |
| US14/929,182Active2036-08-24US10003605B2 (en) | 2015-08-31 | 2015-10-30 | Detection of clustering in graphs in network security analysis |
| US14/928,535Active2035-11-21US10212174B2 (en) | 2015-08-31 | 2015-10-30 | Method and system for reviewing identified threats for performing computer security monitoring |
| US15/335,250ActiveUS9609009B2 (en) | 2015-08-31 | 2016-10-26 | Network security threat detection by user/user-entity behavioral analysis |
| US15/413,336ActiveUS10135848B2 (en) | 2015-08-31 | 2017-01-23 | Network security threat detection using shared variable behavior baseline |
| US15/415,747ActiveUS9813435B2 (en) | 2015-08-31 | 2017-01-25 | Network security analysis using real-time and batch detection engines |
| US15/418,546ActiveUS10116670B2 (en) | 2015-08-31 | 2017-01-27 | Event specific relationship graph generation and application in a machine data processing platform |
| US15/490,849ActiveUS10148677B2 (en) | 2015-08-31 | 2017-04-18 | Model training and deployment in complex event processing of computer network data |
| US15/616,889ActiveUS9900332B2 (en) | 2015-08-31 | 2017-06-07 | Network security system with real-time and batch paths |
| US15/800,000Active2036-03-23US10581881B2 (en) | 2015-08-31 | 2017-10-31 | Model workflow control in a distributed computation system |
| US15/800,010ActiveUS10291635B2 (en) | 2015-08-31 | 2017-10-31 | Identity resolution in data intake of a distributed data processing system |
| US15/860,049ActiveUS10419462B2 (en) | 2015-08-31 | 2018-01-02 | Event information access interface in data intake stage of a distributed data processing system |
| US15/926,961ActiveUS10419463B2 (en) | 2015-08-31 | 2018-03-20 | Event specific entity relationship discovery in data intake stage of a distributed data processing system |
| US15/995,073ActiveUS10476898B2 (en) | 2015-08-31 | 2018-05-31 | Lateral movement detection for network security analysis |
| US16/016,472Active2036-12-26US11470096B2 (en) | 2015-08-31 | 2018-06-22 | Network security anomaly and threat detection using rarity scoring |
| US16/041,637ActiveUS10560468B2 (en) | 2015-08-31 | 2018-07-20 | Window-based rarity determination using probabilistic suffix trees for network security analysis |
| US16/050,368ActiveUS10587633B2 (en) | 2015-08-31 | 2018-07-31 | Anomaly detection based on connection requests in network traffic |
| US16/182,469ActiveUS10419465B2 (en) | 2015-08-31 | 2018-11-06 | Data retrieval in security anomaly detection platform with shared model state between real-time and batch paths |
| US16/215,350ActiveUS10778703B2 (en) | 2015-08-31 | 2018-12-10 | Method and system for generating an interactive kill chain view for training a machine learning model for identifying threats |
| US16/259,999ActiveUS10666668B2 (en) | 2015-08-31 | 2019-01-28 | Interface providing an interactive trendline for a detected threat to facilitate evaluation for false positives |
| US16/264,514ActiveUS10986106B2 (en) | 2015-08-31 | 2019-01-31 | Method and system for generating an entities view with risk-level scoring for performing computer security monitoring |
| US16/503,181Active2036-10-25US11258807B2 (en) | 2015-08-31 | 2019-07-03 | Anomaly detection based on communication between entities over a network |
| US16/516,471Active2036-08-07US11411966B2 (en) | 2015-08-31 | 2019-07-19 | Processing anomaly data to identify threats to network security |
| US16/532,312Active2036-02-01US11146574B2 (en) | 2015-08-31 | 2019-08-05 | Annotation of event data to include access interface identifiers for use by downstream entities in a distributed data processing system |
| US16/547,235ActiveUS10911468B2 (en) | 2015-08-31 | 2019-08-21 | Sharing of machine learning model state between batch and real-time processing paths for detection of network security issues |
| US16/568,106ActiveUS10798113B2 (en) | 2015-08-31 | 2019-09-11 | Interactive geographic representation of network security threats |
| US16/581,094ActiveUS10911470B2 (en) | 2015-08-31 | 2019-09-24 | Detecting anomalies in a computer network based on usage similarity scores |
| US17/125,130Active2036-04-02US11575693B1 (en) | 2015-08-31 | 2020-12-17 | Composite relationship graph for network security |
| US17/676,022Active2036-01-24US12438891B1 (en) | 2015-08-31 | 2022-02-18 | Anomaly detection based on ensemble machine learning model |
| US17/845,383ActiveUS11824646B1 (en) | 2015-08-31 | 2022-06-21 | Processing anomaly data to identify network security threats by use of rarity analysis |
Country Status (1)
| Country | Link |
|---|---|
| US (51) | US9699205B2 (en) |
Cited By (26)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN107623862A (en)* | 2017-09-21 | 2018-01-23 | 广州华多网络科技有限公司 | multimedia information push control method, device and server |
| WO2019067513A1 (en)* | 2017-09-26 | 2019-04-04 | Jpmorgan Chase Bank, N.A. | Cyber security enhanced monitoring |
| US20190244146A1 (en)* | 2018-01-18 | 2019-08-08 | D&B Business Information Solutions | Elastic distribution queuing of mass data for the use in director driven company assessment |
| US10404635B2 (en) | 2017-03-21 | 2019-09-03 | Bank Of America Corporation | Optimizing data replication across multiple data centers |
| US10469508B2 (en) | 2015-08-31 | 2019-11-05 | Splunk Inc. | Interactive threat geo-map for monitoring computer network security |
| US10541881B2 (en)* | 2017-12-14 | 2020-01-21 | Disney Enterprises, Inc. | Automated network supervision including detecting an anonymously administered node, identifying the administrator of the anonymously administered node, and registering the administrator and the anonymously administered node |
| CN110832529A (en)* | 2017-05-18 | 2020-02-21 | 比利时联合金融集团 | Determining risks associated with real estate and reconstruction |
| US10616231B2 (en) | 2017-03-21 | 2020-04-07 | Cyber 2.0 (2015) LTD | Preventing unauthorized outgoing communications |
| US10686741B2 (en) | 2017-06-29 | 2020-06-16 | Salesforce.Com, Inc. | Method and system for real-time blocking of content from an organization activity timeline |
| US10721263B2 (en)* | 2014-12-29 | 2020-07-21 | Palantir Technologies Inc. | Systems for network risk assessment including processing of user access rights associated with a network of devices |
| US10719811B2 (en)* | 2017-06-29 | 2020-07-21 | Salesforce.Com, Inc. | Method and system for retroactive removal of content from an organization activity timeline |
| US11005727B2 (en)* | 2019-07-25 | 2021-05-11 | Vmware, Inc. | Visual overlays for network insights |
| CN112995104A (en)* | 2019-12-16 | 2021-06-18 | 海信集团有限公司 | Communication equipment and network security prediction method |
| WO2021127778A1 (en)* | 2019-12-23 | 2021-07-01 | Myplanet Internet Solutions Ltd | Method and system for recognizing user intent and updating a graphical user interface |
| US11153091B2 (en) | 2016-03-30 | 2021-10-19 | British Telecommunications Public Limited Company | Untrusted code distribution |
| US11271824B2 (en) | 2019-07-25 | 2022-03-08 | Vmware, Inc. | Visual overlays for network insights |
| US20220100721A1 (en)* | 2016-01-07 | 2022-03-31 | Amazon Technologies, Inc. | Outlier detection for streaming data |
| US11341237B2 (en)* | 2017-03-30 | 2022-05-24 | British Telecommunications Public Limited Company | Anomaly detection for computer systems |
| US11526603B2 (en)* | 2020-03-30 | 2022-12-13 | Microsoft Technology Licensing, Llc | Model for identifying the most relevant person(s) for an event associated with a resource |
| US20220407893A1 (en)* | 2021-06-18 | 2022-12-22 | Capital One Services, Llc | Systems and methods for network security |
| EP4083823A3 (en)* | 2021-08-16 | 2023-02-01 | Beijing Baidu Netcom Science Technology Co., Ltd. | Method and apparatus for determining risk level of instance on cloud server and electronic device |
| US20230033647A1 (en)* | 2021-07-30 | 2023-02-02 | Microsoft Technology Licensing, Llc | Method and system for evaluating peer groups for comparative anomaly |
| US11586751B2 (en) | 2017-03-30 | 2023-02-21 | British Telecommunications Public Limited Company | Hierarchical temporal memory for access control |
| US11640609B1 (en) | 2019-12-13 | 2023-05-02 | Wells Fargo Bank, N.A. | Network based features for financial crime detection |
| US11711391B2 (en) | 2020-10-16 | 2023-07-25 | Visa International Service Association | System, method, and computer program product for user network activity anomaly detection |
| WO2024154049A1 (en)* | 2023-01-17 | 2024-07-25 | VMware LLC | Automated enterprise information technology alerting system |
Families Citing this family (2165)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US8732004B1 (en) | 2004-09-22 | 2014-05-20 | Experian Information Solutions, Inc. | Automated analysis of data to generate prospect notifications based on trigger events |
| US8510596B1 (en) | 2006-02-09 | 2013-08-13 | Virsec Systems, Inc. | System and methods for run time detection and correction of memory corruption |
| US9690820B1 (en) | 2007-09-27 | 2017-06-27 | Experian Information Solutions, Inc. | Database system for triggering event notifications based on updates to database records |
| US10275569B2 (en)* | 2007-10-15 | 2019-04-30 | 22andMe, Inc. | Family inheritance |
| US9990674B1 (en) | 2007-12-14 | 2018-06-05 | Consumerinfo.Com, Inc. | Card registry systems and methods |
| US8312033B1 (en) | 2008-06-26 | 2012-11-13 | Experian Marketing Solutions, Inc. | Systems and methods for providing an integrated identifier |
| US20100131513A1 (en) | 2008-10-23 | 2010-05-27 | Lundberg Steven W | Patent mapping |
| US20100174638A1 (en) | 2009-01-06 | 2010-07-08 | ConsumerInfo.com | Report existence monitoring |
| US10805331B2 (en) | 2010-09-24 | 2020-10-13 | BitSight Technologies, Inc. | Information technology security assessment system |
| US20130086093A1 (en)* | 2011-10-03 | 2013-04-04 | Steven W. Lundberg | System and method for competitive prior art analytics and mapping |
| US8738516B1 (en) | 2011-10-13 | 2014-05-27 | Consumerinfo.Com, Inc. | Debt services candidate locator |
| US11416325B2 (en) | 2012-03-13 | 2022-08-16 | Servicenow, Inc. | Machine-learning and deep-learning techniques for predictive ticketing in information technology systems |
| US10740692B2 (en) | 2017-10-17 | 2020-08-11 | Servicenow, Inc. | Machine-learning and deep-learning techniques for predictive ticketing in information technology systems |
| US10600002B2 (en) | 2016-08-04 | 2020-03-24 | Loom Systems LTD. | Machine learning techniques for providing enriched root causes based on machine-generated data |
| US9460131B2 (en)* | 2012-05-04 | 2016-10-04 | International Business Machines Corporation | Data stream quality management for analytic environments |
| US9411327B2 (en) | 2012-08-27 | 2016-08-09 | Johnson Controls Technology Company | Systems and methods for classifying data in building automation systems |
| US11080718B2 (en)* | 2012-09-28 | 2021-08-03 | Rex Wiig | System and method of a requirement, active compliance and resource management for cyber security application |
| US20190394243A1 (en)* | 2012-09-28 | 2019-12-26 | Rex Wiig | System and method of a requirement, active compliance and resource management for cyber security application |
| US9654541B1 (en) | 2012-11-12 | 2017-05-16 | Consumerinfo.Com, Inc. | Aggregating user web browsing data |
| US9686305B2 (en) | 2012-11-20 | 2017-06-20 | Securboration, Inc. | Cyber-semantic account management system |
| US9916621B1 (en) | 2012-11-30 | 2018-03-13 | Consumerinfo.Com, Inc. | Presentation of credit score factors |
| US9208051B2 (en)* | 2012-12-26 | 2015-12-08 | Bmc Software, Inc. | Automatic creation of graph time layer of model of computer network objects and relationships |
| GB2526501A (en) | 2013-03-01 | 2015-11-25 | Redowl Analytics Inc | Modeling social behavior |
| US20140250052A1 (en) | 2013-03-01 | 2014-09-04 | RedOwl Analytics, Inc. | Analyzing social behavior |
| US10102570B1 (en) | 2013-03-14 | 2018-10-16 | Consumerinfo.Com, Inc. | Account vulnerability alerts |
| US9406085B1 (en) | 2013-03-14 | 2016-08-02 | Consumerinfo.Com, Inc. | System and methods for credit dispute processing, resolution, and reporting |
| US9594545B2 (en)* | 2013-06-05 | 2017-03-14 | Splunk Inc. | System for displaying notification dependencies between component instances |
| US10061626B2 (en) | 2013-06-05 | 2018-08-28 | Splunk Inc. | Application framework providing a registry for mapping names to component instances |
| US8756614B2 (en) | 2013-06-05 | 2014-06-17 | Splunk Inc. | Central registry for binding features using dynamic pointers |
| US9632858B2 (en) | 2013-07-28 | 2017-04-25 | OpsClarity Inc. | Organizing network performance metrics into historical anomaly dependency data |
| US9811665B1 (en) | 2013-07-30 | 2017-11-07 | Palo Alto Networks, Inc. | Static and dynamic security analysis of apps for mobile devices |
| US10019575B1 (en) | 2013-07-30 | 2018-07-10 | Palo Alto Networks, Inc. | Evaluating malware in a virtual machine using copy-on-write |
| US9438615B2 (en) | 2013-09-09 | 2016-09-06 | BitSight Technologies, Inc. | Security risk management |
| WO2015038944A1 (en) | 2013-09-12 | 2015-03-19 | Virsec Systems, Inc. | Automated runtime detection of malware |
| EP3049916B1 (en)* | 2013-09-24 | 2021-12-22 | Telefonaktiebolaget LM Ericsson (publ) | Simplified creation of an application in a selected stream processing platform |
| US10033693B2 (en) | 2013-10-01 | 2018-07-24 | Nicira, Inc. | Distributed identity-based firewalls |
| US11393035B2 (en) | 2013-10-22 | 2022-07-19 | Fiduciary Benchmarks Insights, Llc | System and method for evaluating a service provider of a retirement Plan |
| US9692789B2 (en) | 2013-12-13 | 2017-06-27 | Oracle International Corporation | Techniques for cloud security monitoring and threat intelligence |
| WO2015113156A1 (en) | 2014-01-30 | 2015-08-06 | Marketwired L.P. | Systems and methods for continuous active data security |
| US11405410B2 (en) | 2014-02-24 | 2022-08-02 | Cyphort Inc. | System and method for detecting lateral movement and data exfiltration |
| US10326778B2 (en) | 2014-02-24 | 2019-06-18 | Cyphort Inc. | System and method for detecting lateral movement and data exfiltration |
| US10095866B2 (en)* | 2014-02-24 | 2018-10-09 | Cyphort Inc. | System and method for threat risk scoring of security threats |
| US11017330B2 (en) | 2014-05-20 | 2021-05-25 | Elasticsearch B.V. | Method and system for analysing data |
| CN106687981B (en) | 2014-06-24 | 2020-09-01 | 弗塞克系统公司 | System and method for automated detection of input and output verification and resource management vulnerabilities |
| US10140827B2 (en) | 2014-07-07 | 2018-11-27 | Google Llc | Method and system for processing motion event notifications |
| US9170707B1 (en) | 2014-09-30 | 2015-10-27 | Google Inc. | Method and system for generating a smart time-lapse video clip |
| US9501915B1 (en) | 2014-07-07 | 2016-11-22 | Google Inc. | Systems and methods for analyzing a video stream |
| US9489516B1 (en) | 2014-07-14 | 2016-11-08 | Palo Alto Networks, Inc. | Detection of malware using an instrumented virtual machine environment |
| US9118714B1 (en)* | 2014-07-23 | 2015-08-25 | Lookingglass Cyber Solutions, Inc. | Apparatuses, methods and systems for a cyber threat visualization and editing user interface |
| GB2529150B (en) | 2014-08-04 | 2022-03-30 | Darktrace Ltd | Cyber security |
| US10164995B1 (en)* | 2014-08-14 | 2018-12-25 | Pivotal Software, Inc. | Determining malware infection risk |
| USD762659S1 (en)* | 2014-09-02 | 2016-08-02 | Apple Inc. | Display screen or portion thereof with graphical user interface |
| USD810768S1 (en)* | 2014-09-18 | 2018-02-20 | Aetna Inc. | Display screen with graphical user interface |
| USD840422S1 (en) | 2014-09-18 | 2019-02-12 | Aetna Inc. | Display screen with graphical user interface |
| USD839289S1 (en) | 2014-09-18 | 2019-01-29 | Aetna Inc. | Display screen with graphical user interface |
| USD863328S1 (en) | 2014-09-18 | 2019-10-15 | Aetna Inc. | Display screen with graphical user interface |
| US9798883B1 (en)* | 2014-10-06 | 2017-10-24 | Exabeam, Inc. | System, method, and computer program product for detecting and assessing security risks in a network |
| USD782495S1 (en)* | 2014-10-07 | 2017-03-28 | Google Inc. | Display screen or portion thereof with graphical user interface |
| US10915543B2 (en) | 2014-11-03 | 2021-02-09 | SavantX, Inc. | Systems and methods for enterprise data search and analysis |
| US10360229B2 (en) | 2014-11-03 | 2019-07-23 | SavantX, Inc. | Systems and methods for enterprise data search and analysis |
| US10216938B2 (en) | 2014-12-05 | 2019-02-26 | T-Mobile Usa, Inc. | Recombinant threat modeling |
| US10574675B2 (en) | 2014-12-05 | 2020-02-25 | T-Mobile Usa, Inc. | Similarity search for discovering multiple vector attacks |
| US9805193B1 (en) | 2014-12-18 | 2017-10-31 | Palo Alto Networks, Inc. | Collecting algorithmically generated domains |
| US10460391B2 (en)* | 2014-12-19 | 2019-10-29 | Mx Technologies, Inc. | Historical transaction-based account monitoring |
| US11855768B2 (en) | 2014-12-29 | 2023-12-26 | Guidewire Software, Inc. | Disaster scenario based inferential analysis using feedback for extracting and combining cyber risk information |
| US9891940B2 (en) | 2014-12-29 | 2018-02-13 | Nicira, Inc. | Introspection method and apparatus for network access filtering |
| US11863590B2 (en) | 2014-12-29 | 2024-01-02 | Guidewire Software, Inc. | Inferential analysis using feedback for extracting and combining cyber risk information |
| US9774604B2 (en) | 2015-01-16 | 2017-09-26 | Zingbox, Ltd. | Private cloud control |
| US11924018B2 (en)* | 2015-01-27 | 2024-03-05 | Dell Products L.P. | System for decomposing events and unstructured data |
| USD817980S1 (en)* | 2015-02-03 | 2018-05-15 | Api Healthcare Corporation | Display screen or portion thereof with graphical user interface |
| US10298608B2 (en)* | 2015-02-11 | 2019-05-21 | Honeywell International Inc. | Apparatus and method for tying cyber-security risk analysis to common risk methodologies and risk levels |
| US10891383B2 (en) | 2015-02-11 | 2021-01-12 | British Telecommunications Public Limited Company | Validating computer resource usage |
| US10026097B2 (en)* | 2015-02-18 | 2018-07-17 | Oath (Americas) Inc. | Systems and methods for inferring matches and logging-in of online users across devices |
| US10242062B2 (en)* | 2015-02-20 | 2019-03-26 | Threatstop, Inc. | Normalization and extraction of log data |
| US10427048B1 (en) | 2015-03-27 | 2019-10-01 | Electronic Arts Inc. | Secure anti-cheat system |
| US20160279878A1 (en)* | 2015-03-27 | 2016-09-29 | John AMBIELLI | Rapid synthetic material prototyping process |
| US10404748B2 (en) | 2015-03-31 | 2019-09-03 | Guidewire Software, Inc. | Cyber risk analysis and remediation using network monitored sensors and methods of use |
| US10509684B2 (en) | 2015-04-06 | 2019-12-17 | EMC IP Holding Company LLC | Blockchain integration for scalable distributed computations |
| US10791063B1 (en) | 2015-04-06 | 2020-09-29 | EMC IP Holding Company LLC | Scalable edge computing using devices with limited resources |
| US10505863B1 (en)* | 2015-04-06 | 2019-12-10 | EMC IP Holding Company LLC | Multi-framework distributed computation |
| US10860622B1 (en) | 2015-04-06 | 2020-12-08 | EMC IP Holding Company LLC | Scalable recursive computation for pattern identification across distributed data processing nodes |
| US10528875B1 (en) | 2015-04-06 | 2020-01-07 | EMC IP Holding Company LLC | Methods and apparatus implementing data model for disease monitoring, characterization and investigation |
| US10277668B1 (en) | 2015-04-06 | 2019-04-30 | EMC IP Holding Company LLC | Beacon-based distributed data processing platform |
| US10511659B1 (en)* | 2015-04-06 | 2019-12-17 | EMC IP Holding Company LLC | Global benchmarking and statistical analysis at scale |
| US10812341B1 (en) | 2015-04-06 | 2020-10-20 | EMC IP Holding Company LLC | Scalable recursive computation across distributed data processing nodes |
| US10366111B1 (en)* | 2015-04-06 | 2019-07-30 | EMC IP Holding Company LLC | Scalable distributed computations utilizing multiple distinct computational frameworks |
| US10425350B1 (en) | 2015-04-06 | 2019-09-24 | EMC IP Holding Company LLC | Distributed catalog service for data processing platform |
| US10496926B2 (en) | 2015-04-06 | 2019-12-03 | EMC IP Holding Company LLC | Analytics platform for scalable distributed computations |
| US10541938B1 (en) | 2015-04-06 | 2020-01-21 | EMC IP Holding Company LLC | Integration of distributed data processing platform with one or more distinct supporting platforms |
| US10348810B1 (en)* | 2015-04-06 | 2019-07-09 | EMC IP Holding Company LLC | Scalable distributed computations utilizing multiple distinct clouds |
| US10515097B2 (en)* | 2015-04-06 | 2019-12-24 | EMC IP Holding Company LLC | Analytics platform for scalable distributed computations |
| US10706970B1 (en) | 2015-04-06 | 2020-07-07 | EMC IP Holding Company LLC | Distributed data analytics |
| US10404787B1 (en)* | 2015-04-06 | 2019-09-03 | EMC IP Holding Company LLC | Scalable distributed data streaming computations across multiple data processing clusters |
| US10776404B2 (en)* | 2015-04-06 | 2020-09-15 | EMC IP Holding Company LLC | Scalable distributed computations utilizing multiple distinct computational frameworks |
| US10541936B1 (en)* | 2015-04-06 | 2020-01-21 | EMC IP Holding Company LLC | Method and system for distributed analysis |
| US10212178B2 (en) | 2015-04-07 | 2019-02-19 | Zingbox, Ltd. | Packet analysis based IoT management |
| US9654485B1 (en)* | 2015-04-13 | 2017-05-16 | Fireeye, Inc. | Analytics-based security monitoring system and method |
| US10476753B2 (en)* | 2015-04-16 | 2019-11-12 | Nec Corporation | Behavior-based host modeling |
| CN106155298B (en)* | 2015-04-21 | 2019-11-08 | 阿里巴巴集团控股有限公司 | The acquisition method and device of man-machine recognition methods and device, behavioural characteristic data |
| US10320813B1 (en)* | 2015-04-30 | 2019-06-11 | Amazon Technologies, Inc. | Threat detection and mitigation in a virtualized computing environment |
| WO2016183391A1 (en)* | 2015-05-12 | 2016-11-17 | New York University | System, method and computer-accessible medium for making a prediction from market data |
| US10701037B2 (en) | 2015-05-27 | 2020-06-30 | Ping Identity Corporation | Scalable proxy clusters |
| US9361011B1 (en) | 2015-06-14 | 2016-06-07 | Google Inc. | Methods and systems for presenting multiple live video feeds in a user interface |
| WO2016205286A1 (en)* | 2015-06-18 | 2016-12-22 | Aware, Inc. | Automatic entity resolution with rules detection and generation system |
| US10303697B1 (en)* | 2015-06-25 | 2019-05-28 | National Technology & Engineering Solutions Of Sandia, Llc | Temporal data system |
| US10356068B2 (en) | 2015-07-14 | 2019-07-16 | Avocado Systems Inc. | Security key generator module for security sensitive applications |
| WO2017021154A1 (en) | 2015-07-31 | 2017-02-09 | British Telecommunications Public Limited Company | Access control |
| US10853750B2 (en) | 2015-07-31 | 2020-12-01 | British Telecommunications Public Limited Company | Controlled resource provisioning in distributed computing environments |
| WO2017021153A1 (en) | 2015-07-31 | 2017-02-09 | British Telecommunications Public Limited Company | Expendable access control |
| US20170032300A1 (en)* | 2015-07-31 | 2017-02-02 | International Business Machines Corporation | Dynamic selection of resources on which an action is performed |
| US10354070B2 (en) | 2015-08-22 | 2019-07-16 | Avocado Systems Inc. | Thread level access control to socket descriptors and end-to-end thread level policies for thread protection |
| US9943111B2 (en)* | 2015-08-31 | 2018-04-17 | Lunatech, Llc | Methods and systems for vapor cooling |
| WO2017041067A2 (en) | 2015-09-03 | 2017-03-09 | Synthro Inc. | Systems and techniques for aggregation, display, and sharing of data |
| SG10201507051WA (en)* | 2015-09-03 | 2017-04-27 | Certis Cisco Security Pte Ltd | System and method for high frequency heuristic data acquisition and analytics of information security events |
| US9794158B2 (en)* | 2015-09-08 | 2017-10-17 | Uber Technologies, Inc. | System event analyzer and outlier visualization |
| US10284453B2 (en) | 2015-09-08 | 2019-05-07 | Uber Technologies, Inc. | System event analyzer and outlier visualization |
| US10643141B2 (en)* | 2015-09-09 | 2020-05-05 | Oath Inc. | User action prediction |
| US10140287B2 (en)* | 2015-09-09 | 2018-11-27 | International Business Machines Corporation | Scalable and accurate mining of control flow from execution logs across distributed systems |
| JP6048555B1 (en)* | 2015-09-10 | 2016-12-21 | 日本電気株式会社 | Classification information creation device, classification information creation method, classification information creation program, search device, search method, and search program |
| US20170076323A1 (en)* | 2015-09-11 | 2017-03-16 | Adobe Systems Incorporated | Matching devices with entities using real-time data and batch-processed data |
| US10462116B1 (en)* | 2015-09-15 | 2019-10-29 | Amazon Technologies, Inc. | Detection of data exfiltration |
| US10326789B1 (en)* | 2015-09-25 | 2019-06-18 | Amazon Technologies, Inc. | Web Bot detection and human differentiation |
| US9967265B1 (en)* | 2015-09-29 | 2018-05-08 | EMC IP Holding Company LLC | Detecting malicious online activities using event stream processing over a graph database |
| JP6558188B2 (en)* | 2015-09-30 | 2019-08-14 | 富士通株式会社 | Distributed processing system, learning model creation method, data processing method, learning model creation program, and data processing program |
| US9838409B2 (en)* | 2015-10-08 | 2017-12-05 | Cisco Technology, Inc. | Cold start mechanism to prevent compromise of automatic anomaly detection systems |
| US10228996B2 (en)* | 2015-10-08 | 2019-03-12 | Lightbend, Inc. | Context-aware rule engine for anomaly detection |
| US10586169B2 (en)* | 2015-10-16 | 2020-03-10 | Microsoft Technology Licensing, Llc | Common feature protocol for collaborative machine learning |
| US10389742B2 (en)* | 2015-10-21 | 2019-08-20 | Vmware, Inc. | Security feature extraction for a network |
| US10534326B2 (en) | 2015-10-21 | 2020-01-14 | Johnson Controls Technology Company | Building automation system with integrated building information model |
| US10454889B2 (en)* | 2015-10-26 | 2019-10-22 | Oath Inc. | Automatic anomaly detection framework for grid resources |
| US12041091B2 (en) | 2015-10-28 | 2024-07-16 | Qomplx Llc | System and methods for automated internet- scale web application vulnerability scanning and enhanced security profiling |
| US11757920B2 (en) | 2015-10-28 | 2023-09-12 | Qomplx, Inc. | User and entity behavioral analysis with network topology enhancements |
| US11757849B2 (en) | 2015-10-28 | 2023-09-12 | Qomplx, Inc. | Detecting and mitigating forged authentication object attacks in multi-cloud environments |
| US12206708B2 (en) | 2015-10-28 | 2025-01-21 | Qomplx Llc | Correlating network event anomalies using active and passive external reconnaissance to identify attack information |
| US11968235B2 (en) | 2015-10-28 | 2024-04-23 | Qomplx Llc | System and method for cybersecurity analysis and protection using distributed systems |
| US12058177B2 (en) | 2015-10-28 | 2024-08-06 | Qomplx Llc | Cybersecurity risk analysis and anomaly detection using active and passive external reconnaissance |
| US12058178B2 (en) | 2015-10-28 | 2024-08-06 | Qomplx Llc | Privilege assurance of enterprise computer network environments using logon session tracking and logging |
| US11055601B2 (en) | 2015-10-28 | 2021-07-06 | Qomplx, Inc. | System and methods for creation of learning agents in simulated environments |
| US11635994B2 (en) | 2015-10-28 | 2023-04-25 | Qomplx, Inc. | System and method for optimizing and load balancing of applications using distributed computer clusters |
| US12184697B2 (en) | 2015-10-28 | 2024-12-31 | Qomplx Llc | AI-driven defensive cybersecurity strategy analysis and recommendation system |
| US9936737B2 (en)* | 2015-10-28 | 2018-04-10 | Lunatech, Llc | Methods and systems for a dual function vapor device |
| US10673887B2 (en)* | 2015-10-28 | 2020-06-02 | Qomplx, Inc. | System and method for cybersecurity analysis and score generation for insurance purposes |
| US11055630B2 (en) | 2015-10-28 | 2021-07-06 | Qomplx, Inc. | Multitemporal data analysis |
| US10594714B2 (en)* | 2015-10-28 | 2020-03-17 | Qomplx, Inc. | User and entity behavioral analysis using an advanced cyber decision platform |
| US12113831B2 (en)* | 2015-10-28 | 2024-10-08 | Qomplx Llc | Privilege assurance of enterprise computer network environments using lateral movement detection and prevention |
| US12335310B2 (en) | 2015-10-28 | 2025-06-17 | Qomplx Llc | System and method for collaborative cybersecurity defensive strategy analysis utilizing virtual network spaces |
| US11055451B2 (en) | 2015-10-28 | 2021-07-06 | Qomplx, Inc. | System and methods for multi-language abstract model creation for digital environment simulations |
| US12107895B2 (en) | 2015-10-28 | 2024-10-01 | Qomplx Llc | Privilege assurance of enterprise computer network environments using attack path detection and prediction |
| US12204921B2 (en) | 2015-10-28 | 2025-01-21 | Qomplx Llc | System and methods for creation and use of meta-models in simulated environments |
| US11025674B2 (en)* | 2015-10-28 | 2021-06-01 | Qomplx, Inc. | Cybersecurity profiling and rating using active and passive external reconnaissance |
| US12438851B2 (en) | 2015-10-28 | 2025-10-07 | Qomplx Llc | Detecting and mitigating forged authentication object attacks in multi-cloud environments with attestation |
| US11323484B2 (en)* | 2015-10-28 | 2022-05-03 | Qomplx, Inc. | Privilege assurance of enterprise computer network environments |
| US20220014555A1 (en) | 2015-10-28 | 2022-01-13 | Qomplx, Inc. | Distributed automated planning and execution platform for designing and running complex processes |
| US10681074B2 (en) | 2015-10-28 | 2020-06-09 | Qomplx, Inc. | System and method for comprehensive data loss prevention and compliance management |
| US11570209B2 (en) | 2015-10-28 | 2023-01-31 | Qomplx, Inc. | Detecting and mitigating attacks using forged authentication objects within a domain |
| US20230362142A1 (en)* | 2015-10-28 | 2023-11-09 | Qomplx, Inc. | Network action classification and analysis using widely distributed and selectively attributed sensor nodes and cloud-based processing |
| US11637866B2 (en) | 2015-10-28 | 2023-04-25 | Qomplx, Inc. | System and method for the secure evaluation of cyber detection products |
| US12236172B2 (en) | 2015-10-28 | 2025-02-25 | Qomplx Llc | System and method for creating domain specific languages for digital environment simulations |
| US11089045B2 (en) | 2015-10-28 | 2021-08-10 | Qomplx, Inc. | User and entity behavioral analysis with network topology enhancements |
| US11179639B1 (en) | 2015-10-30 | 2021-11-23 | Electronic Arts Inc. | Fraud detection system |
| US10324746B2 (en) | 2015-11-03 | 2019-06-18 | Nicira, Inc. | Extended context delivery for context-based authorization |
| US10043026B1 (en)* | 2015-11-09 | 2018-08-07 | 8X8, Inc. | Restricted replication for protection of replicated databases |
| US9876809B2 (en)* | 2015-11-10 | 2018-01-23 | Sap Se | Standard metadata model for analyzing events with fraud, attack, or any other malicious background |
| US10685043B2 (en)* | 2015-11-10 | 2020-06-16 | International Business Machines Corporation | Event analysis in network management event streams |
| US9943116B2 (en)* | 2015-11-17 | 2018-04-17 | Lunatech, Llc | Electronic vapor device warning system |
| US9936738B2 (en)* | 2015-11-17 | 2018-04-10 | Lunatech, Llc | Methods and systems for smooth vapor delivery |
| US11410230B1 (en) | 2015-11-17 | 2022-08-09 | Consumerinfo.Com, Inc. | Realtime access and control of secure regulated data |
| WO2017087612A1 (en)* | 2015-11-17 | 2017-05-26 | John Cameron | Portable wireless electronic vapor device |
| US10375095B1 (en)* | 2015-11-20 | 2019-08-06 | Triad National Security, Llc | Modeling behavior in a network using event logs |
| US10594710B2 (en)* | 2015-11-20 | 2020-03-17 | Webroot Inc. | Statistical analysis of network behavior using event vectors to identify behavioral anomalies using a composite score |
| US10200387B2 (en)* | 2015-11-30 | 2019-02-05 | International Business Machines Corporation | User state tracking and anomaly detection in software-as-a-service environments |
| WO2017095374A1 (en)* | 2015-11-30 | 2017-06-08 | Hewlett Packard Enterprise Development Lp | Alignment and deduplication of time-series datasets |
| WO2017094820A1 (en)* | 2015-12-02 | 2017-06-08 | 日本電気株式会社 | Assistance device, assistance method, and recording medium |
| JP6672751B2 (en)* | 2015-12-03 | 2020-03-25 | 富士通株式会社 | Packet collection method, packet collection program, and packet collection device |
| US11144939B2 (en)* | 2015-12-04 | 2021-10-12 | Adobe, Inc. | Cross-device consumer identification and device type determination |
| US11457809B1 (en)* | 2015-12-08 | 2022-10-04 | Verily Life Sciences Llc | NFC beacons for bidirectional communication between an electrochemical sensor and a reader device |
| WO2017100664A1 (en)* | 2015-12-09 | 2017-06-15 | Unify Square, Inc. | Automated detection and analysis of call conditions in communication system |
| US10148674B2 (en)* | 2015-12-11 | 2018-12-04 | Dell Products, Lp | Method for semi-supervised learning approach to add context to malicious events |
| AU2016367922B2 (en)* | 2015-12-11 | 2019-08-08 | Servicenow, Inc. | Computer network threat assessment |
| US10200380B2 (en)* | 2015-12-16 | 2019-02-05 | At&T Intellectual Property I, L.P. | System for providing layered security |
| US9967275B1 (en)* | 2015-12-17 | 2018-05-08 | EMC IP Holding Company LLC | Efficient detection of network anomalies |
| US11010702B1 (en)* | 2015-12-17 | 2021-05-18 | Wells Fargo Bank, N.A. | Model management system |
| US10334017B2 (en)* | 2015-12-18 | 2019-06-25 | Accenture Global Solutions Limited | Tracking a status of a file transfer using feedback files corresponding to file transfer events |
| US9800607B2 (en)* | 2015-12-21 | 2017-10-24 | Bank Of America Corporation | System for determining effectiveness and allocation of information security technologies |
| WO2017111927A1 (en)* | 2015-12-21 | 2017-06-29 | Hewlett Packard Enterprise Development Lp | Identifying malicious activity using data complexity anomalies |
| GB2545895B (en)* | 2015-12-21 | 2020-01-01 | F Secure Corp | A method and apparatus for detecting exploits |
| US10776506B2 (en) | 2015-12-28 | 2020-09-15 | Salesforce.Com, Inc. | Self-monitoring time series database system that enforces usage policies |
| US10949426B2 (en)* | 2015-12-28 | 2021-03-16 | Salesforce.Com, Inc. | Annotating time series data points with alert information |
| EP3188010A1 (en) | 2015-12-29 | 2017-07-05 | Tata Consultancy Services Limited | System and method for creating an integrated digital platform |
| US10656861B1 (en) | 2015-12-29 | 2020-05-19 | EMC IP Holding Company LLC | Scalable distributed in-memory computation |
| US10050998B1 (en)* | 2015-12-30 | 2018-08-14 | Fireeye, Inc. | Malicious message analysis system |
| US20190089595A1 (en)* | 2017-09-18 | 2019-03-21 | Cyber 2.0 (2015) LTD | Automatic security configuration |
| WO2017120579A1 (en)* | 2016-01-10 | 2017-07-13 | Presenso, Ltd. | System and method for validating unsupervised machine learning models |
| USD857721S1 (en)* | 2016-01-12 | 2019-08-27 | Google Llc | Display screen with graphical user interface for presenting user activity timeline in a colloquial style |
| JP6827266B2 (en)* | 2016-01-15 | 2021-02-10 | 富士通株式会社 | Detection program, detection method and detection device |
| JP6679943B2 (en)* | 2016-01-15 | 2020-04-15 | 富士通株式会社 | Detection program, detection method, and detection device |
| US10152596B2 (en)* | 2016-01-19 | 2018-12-11 | International Business Machines Corporation | Detecting anomalous events through runtime verification of software execution using a behavioral model |
| US10742667B1 (en) | 2016-01-20 | 2020-08-11 | Cyarx Technologies Ltd. | System and method for dynamical modeling multi-dimensional security event data into a graph representation |
| US10262133B1 (en)* | 2016-01-20 | 2019-04-16 | Cyarx Technologies Ltd. | System and method for contextually analyzing potential cyber security threats |
| US12196437B2 (en) | 2016-01-22 | 2025-01-14 | Tyco Fire & Security Gmbh | Systems and methods for monitoring and controlling an energy plant |
| US11947785B2 (en) | 2016-01-22 | 2024-04-02 | Johnson Controls Technology Company | Building system with a building graph |
| US11268732B2 (en) | 2016-01-22 | 2022-03-08 | Johnson Controls Technology Company | Building energy management system with energy analytics |
| US20190005533A1 (en)* | 2016-01-25 | 2019-01-03 | Quaero | Signal Matching for Entity Resolution |
| US10775751B2 (en)* | 2016-01-29 | 2020-09-15 | Cisco Technology, Inc. | Automatic generation of regular expression based on log line data |
| US10169434B1 (en) | 2016-01-31 | 2019-01-01 | Splunk Inc. | Tokenized HTTP event collector |
| US10534791B1 (en)* | 2016-01-31 | 2020-01-14 | Splunk Inc. | Analysis of tokenized HTTP event collector |
| US10642896B2 (en) | 2016-02-05 | 2020-05-05 | Sas Institute Inc. | Handling of data sets during execution of task routines of multiple languages |
| US10650046B2 (en)* | 2016-02-05 | 2020-05-12 | Sas Institute Inc. | Many task computing with distributed file system |
| US10795935B2 (en) | 2016-02-05 | 2020-10-06 | Sas Institute Inc. | Automated generation of job flow definitions |
| US10650045B2 (en) | 2016-02-05 | 2020-05-12 | Sas Institute Inc. | Staged training of neural networks for improved time series prediction performance |
| GB2547202B (en) | 2016-02-09 | 2022-04-20 | Darktrace Ltd | An anomaly alert system for cyber threat detection |
| GB2547201B (en)* | 2016-02-09 | 2022-08-31 | Darktrace Holdings Ltd | Cyber security |
| US10055199B2 (en)* | 2016-02-10 | 2018-08-21 | NodeSource, Inc. | Transparent node runtime and management layer |
| US11356484B2 (en)* | 2016-02-12 | 2022-06-07 | Micro Focus Llc | Strength of associations among data records in a security information sharing platform |
| WO2017138957A1 (en)* | 2016-02-12 | 2017-08-17 | Entit Software Llc | Visualization of associations among data records in a security information sharing platform |
| US11182720B2 (en)* | 2016-02-16 | 2021-11-23 | BitSight Technologies, Inc. | Relationships among technology assets and services and the entities responsible for them |
| GB201603304D0 (en)* | 2016-02-25 | 2016-04-13 | Darktrace Ltd | Cyber security |
| GB2567335B (en)* | 2016-02-25 | 2019-12-04 | Sas Inst Inc | Cybersecurity system |
| US10354066B2 (en) | 2016-02-26 | 2019-07-16 | Cylance Inc. | Retention and accessibility of data characterizing events on an endpoint computer |
| US10536478B2 (en)* | 2016-02-26 | 2020-01-14 | Oracle International Corporation | Techniques for discovering and managing security of applications |
| US10200389B2 (en) | 2016-02-29 | 2019-02-05 | Palo Alto Networks, Inc. | Malware analysis platform for threat intelligence made actionable |
| US10230749B1 (en) | 2016-02-29 | 2019-03-12 | Palo Alto Networks, Inc. | Automatically grouping malware based on artifacts |
| US10200390B2 (en) | 2016-02-29 | 2019-02-05 | Palo Alto Networks, Inc. | Automatically determining whether malware samples are similar |
| US10389809B2 (en)* | 2016-02-29 | 2019-08-20 | Netapp, Inc. | Systems and methods for resource management in a networked environment |
| US10333948B2 (en)* | 2016-02-29 | 2019-06-25 | Palo Alto Networks, Inc. | Alerting and tagging using a malware analysis platform for threat intelligence made actionable |
| US11140167B1 (en) | 2016-03-01 | 2021-10-05 | Exabeam, Inc. | System, method, and computer program for automatically classifying user accounts in a computer network using keys from an identity management system |
| US10013869B2 (en)* | 2016-03-03 | 2018-07-03 | Intel Corporation | Effective handling of distress signals in an internet of things environment |
| US10936617B1 (en)* | 2016-03-11 | 2021-03-02 | Veritas Technologies Llc | Systems and methods for updating email analytics databases |
| US10459827B1 (en)* | 2016-03-22 | 2019-10-29 | Electronic Arts Inc. | Machine-learning based anomaly detection for heterogenous data sources |
| JP1572638S (en)* | 2016-03-24 | 2017-03-27 | ||
| US10003607B1 (en)* | 2016-03-24 | 2018-06-19 | EMC IP Holding Company LLC | Automated detection of session-based access anomalies in a computer network through processing of session data |
| US10764321B2 (en)* | 2016-03-24 | 2020-09-01 | Lenovo Enterprise Solutions (Singapore) Pte. Ltd | Identifying and remediating at-risk resources in a computing environment |
| US10341369B2 (en)* | 2016-03-29 | 2019-07-02 | Ncr Corporation | Security system monitoring techniques by mapping received security score with newly identified security score |
| US10313382B2 (en)* | 2016-03-29 | 2019-06-04 | The Mitre Corporation | System and method for visualizing and analyzing cyber-attacks using a graph model |
| US10129276B1 (en)* | 2016-03-29 | 2018-11-13 | EMC IP Holding Company LLC | Methods and apparatus for identifying suspicious domains using common user clustering |
| US11023248B2 (en) | 2016-03-30 | 2021-06-01 | British Telecommunications Public Limited Company | Assured application services |
| EP3437291B1 (en) | 2016-03-30 | 2022-06-01 | British Telecommunications public limited company | Network traffic threat identification |
| EP3437007B1 (en) | 2016-03-30 | 2021-04-28 | British Telecommunications public limited company | Cryptocurrencies malware based detection |
| WO2017167544A1 (en) | 2016-03-30 | 2017-10-05 | British Telecommunications Public Limited Company | Detecting computer security threats |
| US11768004B2 (en) | 2016-03-31 | 2023-09-26 | Johnson Controls Tyco IP Holdings LLP | HVAC device registration in a distributed building management system |
| US11537791B1 (en) | 2016-04-05 | 2022-12-27 | Intellective Ai, Inc. | Unusual score generators for a neuro-linguistic behavorial recognition system |
| US10657434B2 (en)* | 2016-04-05 | 2020-05-19 | Intellective Ai, Inc. | Anomaly score adjustment across anomaly generators |
| US12432233B1 (en)* | 2016-04-06 | 2025-09-30 | Intellective Ai, Inc. | Adaptive anomaly context description |
| SG11201606387QA (en)* | 2016-04-11 | 2017-11-29 | Certis Cisco Security Pte Ltd | System and method for threat incidents corroboration in discrete temporal reference using 3d abstract modelling |
| US10291483B2 (en)* | 2016-04-19 | 2019-05-14 | Nec Corporation | Entity embedding-based anomaly detection for heterogeneous categorical events |
| US11176480B2 (en)* | 2016-04-21 | 2021-11-16 | Oracle International Corporation | System and method for partitioning models in a database |
| US10079721B2 (en)* | 2016-04-22 | 2018-09-18 | Netsights360 | Integrated digital network management platform |
| KR101695278B1 (en)* | 2016-04-26 | 2017-01-23 | (주)시큐레이어 | Method for detecting real-time event and server using the same |
| US10135859B2 (en)* | 2016-05-03 | 2018-11-20 | Cisco Technology, Inc. | Automated security enclave generation |
| US10417451B2 (en) | 2017-09-27 | 2019-09-17 | Johnson Controls Technology Company | Building system with smart entity personal identifying information (PII) masking |
| US11774920B2 (en) | 2016-05-04 | 2023-10-03 | Johnson Controls Technology Company | Building system with user presentation composition based on building context |
| US10505756B2 (en) | 2017-02-10 | 2019-12-10 | Johnson Controls Technology Company | Building management system with space graphs |
| EP3455776B1 (en)* | 2016-05-10 | 2021-11-10 | Firstpoint Mobile Guard Ltd. | System for securing communication and information of mobile devices through a controlled cellular communication network |
| US10320821B2 (en) | 2016-05-10 | 2019-06-11 | Allstate Insurance Company | Digital safety and account discovery |
| US10419455B2 (en)* | 2016-05-10 | 2019-09-17 | Allstate Insurance Company | Cyber-security presence monitoring and assessment |
| US9906541B2 (en) | 2016-05-10 | 2018-02-27 | Allstate Insurance Company | Digital safety and account discovery |
| EP3455775B1 (en)* | 2016-05-11 | 2022-05-18 | British Telecommunications public limited company | Software container profiling |
| EP3455774B1 (en)* | 2016-05-11 | 2020-12-16 | British Telecommunications Public Limited Company | Software container access control |
| US10810088B1 (en)* | 2016-05-13 | 2020-10-20 | NortonLifeLock Inc. | System and method of dynamic backup policy generation |
| US10341391B1 (en)* | 2016-05-16 | 2019-07-02 | EMC IP Holding Company LLC | Network session based user behavior pattern analysis and associated anomaly detection and verification |
| TWI599905B (en)* | 2016-05-23 | 2017-09-21 | 緯創資通股份有限公司 | Protecting method and system for malicious code, and monitor apparatus |
| USD826962S1 (en)* | 2016-05-24 | 2018-08-28 | Xerox Corporation | Display screen with graphical user interface for a printing machine |
| US10681059B2 (en)* | 2016-05-25 | 2020-06-09 | CyberOwl Limited | Relating to the monitoring of network security |
| US10506237B1 (en) | 2016-05-27 | 2019-12-10 | Google Llc | Methods and devices for dynamic adaptation of encoding bitrate for video streaming |
| US10958667B1 (en) | 2016-06-03 | 2021-03-23 | Mcafee Llc | Determining computing system incidents using node graphs |
| EP3469777B1 (en)* | 2016-06-08 | 2022-08-03 | Cylance Inc. | Deployment of machine learning models for discernment of threats |
| EP3255581A1 (en)* | 2016-06-10 | 2017-12-13 | General Electric Company | Digital pattern prognostics |
| CA3027728A1 (en)* | 2016-06-16 | 2017-12-21 | Virsec Systems, Inc. | Systems and methods for remediating memory corruption in a computer application |
| US10372910B2 (en)* | 2016-06-20 | 2019-08-06 | Jask Labs Inc. | Method for predicting and characterizing cyber attacks |
| US10084802B1 (en) | 2016-06-21 | 2018-09-25 | Palantir Technologies Inc. | Supervisory control and data acquisition |
| US10412099B2 (en)* | 2016-06-22 | 2019-09-10 | Paypal, Inc. | System security configurations based on assets associated with activities |
| US10230744B1 (en)* | 2016-06-24 | 2019-03-12 | EMC IP Holding Company LLC | Detecting periodic behavior in a communication session using clustering |
| US10075468B2 (en)* | 2016-06-24 | 2018-09-11 | Fortinet, Inc. | Denial-of-service (DoS) mitigation approach based on connection characteristics |
| US20180005127A1 (en)* | 2016-06-29 | 2018-01-04 | Alcatel-Lucent Usa Inc. | Predicting problem events from machine data |
| GB2572471B (en)* | 2016-06-30 | 2020-10-21 | Sophos Ltd | Detecting lateral movement by malicious applications |
| WO2018004600A1 (en) | 2016-06-30 | 2018-01-04 | Sophos Limited | Proactive network security using a health heartbeat |
| US10972482B2 (en)* | 2016-07-05 | 2021-04-06 | Webroot Inc. | Automatic inline detection based on static data |
| US10380429B2 (en) | 2016-07-11 | 2019-08-13 | Google Llc | Methods and systems for person detection in a video feed |
| US9948664B2 (en)* | 2016-07-11 | 2018-04-17 | Petabi, Inc. | Method and system for correlation and management of distributed and heterogeneous events |
| US9729416B1 (en) | 2016-07-11 | 2017-08-08 | Extrahop Networks, Inc. | Anomaly detection using device relationship graphs |
| US10957171B2 (en) | 2016-07-11 | 2021-03-23 | Google Llc | Methods and systems for providing event alerts |
| US10367704B2 (en)* | 2016-07-12 | 2019-07-30 | At&T Intellectual Property I, L.P. | Enterprise server behavior profiling |
| US10241847B2 (en) | 2016-07-19 | 2019-03-26 | 2236008 Ontario Inc. | Anomaly detection using sequences of system calls |
| US10536476B2 (en)* | 2016-07-21 | 2020-01-14 | Sap Se | Realtime triggering framework |
| US10938844B2 (en)* | 2016-07-22 | 2021-03-02 | At&T Intellectual Property I, L.P. | Providing security through characterizing mobile traffic by domain names |
| US10846389B2 (en)* | 2016-07-22 | 2020-11-24 | Aetna Inc. | Incorporating risk-based decision in standard authentication and authorization systems |
| US10565837B1 (en) | 2016-07-23 | 2020-02-18 | David Michael Hesford | Security monitoring system and methods |
| WO2018022424A1 (en)* | 2016-07-23 | 2018-02-01 | Hesford David Michael | Security monitoring system and methods |
| US10410508B2 (en) | 2016-07-23 | 2019-09-10 | David Michael Hesford | Methods and apparatus for security monitoring |
| US10764077B2 (en)* | 2016-07-26 | 2020-09-01 | RAM Laboratories, Inc. | Crowd-sourced event identification that maintains source privacy |
| US11227208B2 (en) | 2016-07-29 | 2022-01-18 | Splunk Inc. | Automated data-generation for event-based system |
| US10552728B2 (en) | 2016-07-29 | 2020-02-04 | Splunk Inc. | Automated anomaly detection for event-based system |
| US11314799B2 (en) | 2016-07-29 | 2022-04-26 | Splunk Inc. | Event-based data intake and query system employing non-text machine data |
| US10956481B2 (en) | 2016-07-29 | 2021-03-23 | Splunk Inc. | Event-based correlation of non-text machine data |
| CN106302661B (en)* | 2016-08-02 | 2019-08-13 | 网宿科技股份有限公司 | P2P data accelerated method, device and system |
| US20180039905A1 (en)* | 2016-08-03 | 2018-02-08 | International Business Machines Corporation | Large scale distributed training of data analytics models |
| US10719408B2 (en) | 2016-08-03 | 2020-07-21 | Microsoft Technology Licensing, Llc | Retain locally deleted content at storage service |
| US10789119B2 (en) | 2016-08-04 | 2020-09-29 | Servicenow, Inc. | Determining root-cause of failures based on machine-generated textual data |
| US10193913B2 (en)* | 2016-08-04 | 2019-01-29 | Cisco Technology, Inc. | Joint anomaly detection across IOT devices |
| US10963634B2 (en)* | 2016-08-04 | 2021-03-30 | Servicenow, Inc. | Cross-platform classification of machine-generated textual data |
| US10614042B2 (en)* | 2016-08-08 | 2020-04-07 | Microsoft Technology Licensing, Llc | Detection of bulk operations associated with remotely stored content |
| US10305746B2 (en) | 2016-08-09 | 2019-05-28 | Conviva Inc. | Network insights |
| US10460320B1 (en) | 2016-08-10 | 2019-10-29 | Electronic Arts Inc. | Fraud detection in heterogeneous information networks |
| US10320829B1 (en)* | 2016-08-11 | 2019-06-11 | Balbix, Inc. | Comprehensive modeling and mitigation of security risk vulnerabilities in an enterprise network |
| US10601854B2 (en)* | 2016-08-12 | 2020-03-24 | Tata Consultancy Services Limited | Comprehensive risk assessment in a heterogeneous dynamic network |
| US10313365B2 (en)* | 2016-08-15 | 2019-06-04 | International Business Machines Corporation | Cognitive offense analysis using enriched graphs |
| US10542015B2 (en)* | 2016-08-15 | 2020-01-21 | International Business Machines Corporation | Cognitive offense analysis using contextual data and knowledge graphs |
| US11074514B2 (en) | 2016-08-18 | 2021-07-27 | International Business Machines Corporation | Confidence intervals for anomalies in computer log data |
| US10616210B2 (en) | 2016-08-19 | 2020-04-07 | Microsoft Technology Licensing, Llc | Protection feature for data stored at storage service |
| US10437840B1 (en) | 2016-08-19 | 2019-10-08 | Palantir Technologies Inc. | Focused probabilistic entity resolution from multiple data sources |
| US10560536B2 (en)* | 2016-08-24 | 2020-02-11 | International Business Machines Corporation | Simplifying user interactions with decision tree dialog managers |
| JP6786960B2 (en)* | 2016-08-26 | 2020-11-18 | 富士通株式会社 | Cyber attack analysis support program, cyber attack analysis support method and cyber attack analysis support device |
| US10938837B2 (en) | 2016-08-30 | 2021-03-02 | Nicira, Inc. | Isolated network stack to manage security for virtual machines |
| CA3035277C (en) | 2016-09-02 | 2024-05-14 | FutureVault Inc. | Real-time document filtering systems and methods |
| USD916120S1 (en)* | 2016-09-03 | 2021-04-13 | Synthro Inc. | Display screen or portion thereof with graphical user interface |
| USD898067S1 (en) | 2016-09-03 | 2020-10-06 | Synthro Inc. | Display screen or portion thereof with animated graphical user interface |
| USD875126S1 (en) | 2016-09-03 | 2020-02-11 | Synthro Inc. | Display screen or portion thereof with animated graphical user interface |
| EP3291120B1 (en)* | 2016-09-06 | 2021-04-21 | Accenture Global Solutions Limited | Graph database analysis for network anomaly detection systems |
| US10476896B2 (en)* | 2016-09-13 | 2019-11-12 | Accenture Global Solutions Limited | Malicious threat detection through time series graph analysis |
| US10601778B2 (en)* | 2016-09-15 | 2020-03-24 | Arbor Networks, Inc. | Visualization of traffic flowing through a host |
| US10567415B2 (en)* | 2016-09-15 | 2020-02-18 | Arbor Networks, Inc. | Visualization of network threat monitoring |
| US10530809B1 (en)* | 2016-09-15 | 2020-01-07 | Symantec Corporation | Systems and methods for remediating computer stability issues |
| US10135853B2 (en)* | 2016-09-20 | 2018-11-20 | Northrop Grumman Systems Corporation | Multi-tier aggregation for complex event correlation in streams |
| US10200259B1 (en)* | 2016-09-21 | 2019-02-05 | Symantec Corporation | Systems and methods for detecting obscure cyclic application-layer message sequences in transport-layer message sequences |
| US20180082190A1 (en)* | 2016-09-21 | 2018-03-22 | Scianta Analytics, LLC | System for dispatching cognitive computing across multiple workers |
| US10936969B2 (en)* | 2016-09-26 | 2021-03-02 | Shabaz Basheer Patel | Method and system for an end-to-end artificial intelligence workflow |
| US10673880B1 (en)* | 2016-09-26 | 2020-06-02 | Splunk Inc. | Anomaly detection to identify security threats |
| US10409629B1 (en)* | 2016-09-26 | 2019-09-10 | EMC IP Holding Company LLC | Automated host data protection configuration |
| US11093476B1 (en)* | 2016-09-26 | 2021-08-17 | Splunk Inc. | HTTP events with custom fields |
| US10542071B1 (en)* | 2016-09-27 | 2020-01-21 | Amazon Technologies, Inc. | Event driven health checks for non-HTTP applications |
| AU2017335762B2 (en) | 2016-09-27 | 2022-03-17 | Bigfoot Biomedical, Inc. | Medicine injection and disease management systems, devices, and methods |
| USD838278S1 (en)* | 2016-09-29 | 2019-01-15 | United Services Automobile Association (Usaa) | Display screen or portion thereof with a payday forecast graphical user interface |
| US10534910B1 (en)* | 2016-10-04 | 2020-01-14 | Hewlett-Packard Development Company, L.P. | Using threat model to monitor host execution |
| US10534925B2 (en)* | 2016-10-05 | 2020-01-14 | Microsoft Technology Licensing, Llc | Detection of compromised devices via user states |
| US10855706B2 (en)* | 2016-10-11 | 2020-12-01 | Battelle Memorial Institute | System and methods for automated detection, reasoning and recommendations for resilient cyber systems |
| US10542017B1 (en)* | 2016-10-13 | 2020-01-21 | Symantec Corporation | Systems and methods for personalizing security incident reports |
| US10592689B2 (en) | 2016-10-20 | 2020-03-17 | Microsoft Technology Licensing, Llc | Selective container use for device usage sessions |
| US10122743B2 (en) | 2016-10-24 | 2018-11-06 | Senrio Inc. | Methods and systems for detecting anomalous behavior of network-connected embedded devices |
| US10509541B2 (en)* | 2016-10-25 | 2019-12-17 | Servicenow, Inc. | System and method for generating geographical maps for initiating discovery of a computer network |
| US10681012B2 (en)* | 2016-10-26 | 2020-06-09 | Ping Identity Corporation | Methods and systems for deep learning based API traffic security |
| US10158654B2 (en)* | 2016-10-31 | 2018-12-18 | Acentium Inc. | Systems and methods for computer environment situational awareness |
| US10284589B2 (en) | 2016-10-31 | 2019-05-07 | Acentium Inc. | Methods and systems for ranking, filtering and patching detected vulnerabilities in a networked system |
| US10412110B2 (en) | 2016-10-31 | 2019-09-10 | Acentium, Inc. | Systems and methods for multi-tier cache visual system and visual modes |
| US11824880B2 (en)* | 2016-10-31 | 2023-11-21 | Armis Security Ltd. | Detection of vulnerable wireless networks |
| US10511620B2 (en) | 2016-10-31 | 2019-12-17 | Armis Security Ltd. | Detection of vulnerable devices in wireless networks |
| JP6793524B2 (en)* | 2016-11-01 | 2020-12-02 | 株式会社日立製作所 | Log analysis system and its method |
| USD820855S1 (en)* | 2016-11-02 | 2018-06-19 | Google Llc | Computer display screen with graphical user interface for navigation |
| US10339308B1 (en) | 2016-11-10 | 2019-07-02 | Symantec Corporation | Systems and methods for remediating computer reliability issues |
| US10382352B2 (en)* | 2016-11-15 | 2019-08-13 | Vmware Inc. | Distributed resource scheduling based on network utilization |
| US10635509B2 (en)* | 2016-11-17 | 2020-04-28 | Sung Jin Cho | System and method for creating and managing an interactive network of applications |
| US10462170B1 (en)* | 2016-11-21 | 2019-10-29 | Alert Logic, Inc. | Systems and methods for log and snort synchronized threat detection |
| US10769549B2 (en)* | 2016-11-21 | 2020-09-08 | Google Llc | Management and evaluation of machine-learned models based on locally logged data |
| US10380348B2 (en) | 2016-11-21 | 2019-08-13 | ZingBox, Inc. | IoT device risk assessment |
| US9906401B1 (en) | 2016-11-22 | 2018-02-27 | Gigamon Inc. | Network visibility appliances for cloud computing architectures |
| US10657158B2 (en)* | 2016-11-23 | 2020-05-19 | Google Llc | Template-based structured document classification and extraction |
| US10841337B2 (en) | 2016-11-28 | 2020-11-17 | Secureworks Corp. | Computer implemented system and method, and computer program product for reversibly remediating a security risk |
| US10904275B2 (en)* | 2016-11-30 | 2021-01-26 | Cisco Technology, Inc. | Leveraging synthetic traffic data samples for flow classifier training |
| TWI617939B (en)* | 2016-12-01 | 2018-03-11 | 財團法人資訊工業策進會 | Attacking node detection apparatus, method, and computer program product thereof |
| US10348758B1 (en)* | 2016-12-02 | 2019-07-09 | Symantec Corporation | Systems and methods for providing interfaces for visualizing threats within networked control systems |
| TWI610196B (en) | 2016-12-05 | 2018-01-01 | 財團法人資訊工業策進會 | Network attack pattern determination apparatus, determination method, and computer program product thereof |
| US10303533B1 (en)* | 2016-12-06 | 2019-05-28 | Amazon Technologies, Inc. | Real-time log analysis service for integrating external event data with log data for use in root cause analysis |
| WO2018106612A1 (en) | 2016-12-06 | 2018-06-14 | Nicira, Inc. | Performing context-rich attribute-based services on a host |
| US10771487B2 (en)* | 2016-12-12 | 2020-09-08 | Gryphon Online Safety Inc. | Method for protecting IoT devices from intrusions by performing statistical analysis |
| TR201618313A2 (en)* | 2016-12-12 | 2018-06-21 | Turkcell Technology Research And Development Co | A SYSTEM FOR DETERMINING whether MOBILE SUBSCRIBERS ARE LINE HOLDERS |
| EP3500161A4 (en) | 2016-12-12 | 2020-01-08 | Bigfoot Biomedical, Inc. | ALARMS AND WARNINGS FOR MEDICINE DELIVERY DEVICES AND RELATED SYSTEMS AND METHODS |
| US20180173853A1 (en)* | 2016-12-15 | 2018-06-21 | International Business Machines Corporation | Cognitive adaptations for well-being management |
| US11146578B2 (en) | 2016-12-16 | 2021-10-12 | Patternex, Inc. | Method and system for employing graph analysis for detecting malicious activity in time evolving networks |
| US10601915B2 (en)* | 2016-12-20 | 2020-03-24 | Striim, Inc. | Data stream processor with both in memory and persisted messaging |
| US11310247B2 (en)* | 2016-12-21 | 2022-04-19 | Micro Focus Llc | Abnormal behavior detection of enterprise entities using time-series data |
| US10728262B1 (en) | 2016-12-21 | 2020-07-28 | Palantir Technologies Inc. | Context-aware network-based malicious activity warning systems |
| US10142357B1 (en)* | 2016-12-21 | 2018-11-27 | Symantec Corporation | Systems and methods for preventing malicious network connections using correlation-based anomaly detection |
| US10565377B1 (en)* | 2016-12-21 | 2020-02-18 | Palo Alto Networks, Inc. | Context-based analysis of applications |
| US11032246B2 (en) | 2016-12-22 | 2021-06-08 | Nicira, Inc. | Context based firewall services for data message flows for multiple concurrent users on one machine |
| US10805332B2 (en)* | 2017-07-25 | 2020-10-13 | Nicira, Inc. | Context engine model |
| US10581960B2 (en) | 2016-12-22 | 2020-03-03 | Nicira, Inc. | Performing context-rich attribute-based load balancing on a host |
| US10803173B2 (en) | 2016-12-22 | 2020-10-13 | Nicira, Inc. | Performing context-rich attribute-based process control services on a host |
| US10812451B2 (en) | 2016-12-22 | 2020-10-20 | Nicira, Inc. | Performing appID based firewall services on a host |
| US10503536B2 (en) | 2016-12-22 | 2019-12-10 | Nicira, Inc. | Collecting and storing threat level indicators for service rule processing |
| US10389743B1 (en)* | 2016-12-22 | 2019-08-20 | Symantec Corporation | Tracking of software executables that come from untrusted locations |
| US10721262B2 (en)* | 2016-12-28 | 2020-07-21 | Palantir Technologies Inc. | Resource-centric network cyber attack warning system |
| CN108255862B (en)* | 2016-12-29 | 2019-09-17 | 北京国双科技有限公司 | A kind of search method and device of judgement document |
| US11315045B2 (en)* | 2016-12-29 | 2022-04-26 | Intel Corporation | Entropy-based weighting in random forest models |
| US10412111B2 (en)* | 2016-12-30 | 2019-09-10 | eSentire, Inc. | System and method for determining network security threats |
| EP3343422B1 (en)* | 2016-12-30 | 2021-04-28 | Capital One Services, LLC | Systems and methods for detecting resources responsible for events |
| US10552609B2 (en)* | 2016-12-30 | 2020-02-04 | Intel Corporation | Malicious object detection in a runtime environment |
| US11004010B2 (en)* | 2016-12-30 | 2021-05-11 | eSentire, Inc. | Processing real-time processing requests using machine learning models |
| US10374968B1 (en) | 2016-12-30 | 2019-08-06 | EMC IP Holding Company LLC | Data-driven automation mechanism for analytics workload distribution |
| US10805324B2 (en)* | 2017-01-03 | 2020-10-13 | General Electric Company | Cluster-based decision boundaries for threat detection in industrial asset control system |
| KR101780933B1 (en)* | 2017-01-05 | 2017-09-26 | 한국인터넷진흥원 | Method for visualization of relationships between incident resources and apparatus for detrmining event level of monitoring result |
| CN108280346B (en)* | 2017-01-05 | 2022-05-31 | 腾讯科技(深圳)有限公司 | Application protection monitoring method, device and system |
| US10684033B2 (en) | 2017-01-06 | 2020-06-16 | Johnson Controls Technology Company | HVAC system with automated device pairing |
| KR101764674B1 (en)* | 2017-01-06 | 2017-08-03 | 한국인터넷진흥원 | Method for generating graph database of incident resources and apparatus thereof |
| US10491615B2 (en)* | 2017-01-09 | 2019-11-26 | Sap Se | User classification by local to global sequence alignment techniques for anomaly-based intrusion detection |
| US10699012B2 (en) | 2017-01-11 | 2020-06-30 | Cylance Inc. | Endpoint detection and response utilizing machine learning |
| CN108337156B (en) | 2017-01-20 | 2020-12-18 | 阿里巴巴集团控股有限公司 | Information pushing method and device |
| US10855783B2 (en)* | 2017-01-23 | 2020-12-01 | Adobe Inc. | Communication notification trigger modeling preview |
| US10395016B2 (en)* | 2017-01-24 | 2019-08-27 | International Business Machines Corporation | Communication pattern recognition |
| US10785247B2 (en)* | 2017-01-24 | 2020-09-22 | Cisco Technology, Inc. | Service usage model for traffic analysis |
| US10367837B2 (en) | 2017-01-25 | 2019-07-30 | International Business Machines Corporation | Optimizing security analyses in SaaS environments |
| US10547642B2 (en) | 2017-01-27 | 2020-01-28 | T-Mobile Usa, Inc. | Security via adaptive threat modeling |
| US10237294B1 (en)* | 2017-01-30 | 2019-03-19 | Splunk Inc. | Fingerprinting entities based on activity in an information technology environment |
| US10205735B2 (en) | 2017-01-30 | 2019-02-12 | Splunk Inc. | Graph-based network security threat detection across time and entities |
| US10999308B2 (en) | 2017-01-30 | 2021-05-04 | Xm Cyber Ltd. | Setting-up penetration testing campaigns |
| WO2018138608A2 (en)* | 2017-01-30 | 2018-08-02 | XM Ltd. | Penetration testing of a networked system |
| US10574679B2 (en)* | 2017-02-01 | 2020-02-25 | Cisco Technology, Inc. | Identifying a security threat to a web-based resource |
| US11625437B2 (en) | 2017-02-02 | 2023-04-11 | Kensho Technologies, Llc | Graphical user interface for displaying search engine results |
| US10726071B2 (en)* | 2017-02-02 | 2020-07-28 | Kensho Technologies, Llc | Content search engine |
| US10909097B2 (en)* | 2017-02-05 | 2021-02-02 | Veritas Technologies Llc | Method and system for dependency analysis of workloads for orchestration |
| USD898059S1 (en) | 2017-02-06 | 2020-10-06 | Sas Institute Inc. | Display screen or portion thereof with graphical user interface |
| US11900287B2 (en) | 2017-05-25 | 2024-02-13 | Johnson Controls Tyco IP Holdings LLP | Model predictive maintenance system with budgetary constraints |
| US10992693B2 (en) | 2017-02-09 | 2021-04-27 | Microsoft Technology Licensing, Llc | Near real-time detection of suspicious outbound traffic |
| US11360447B2 (en) | 2017-02-10 | 2022-06-14 | Johnson Controls Technology Company | Building smart entity system with agent based communication and control |
| US11764991B2 (en) | 2017-02-10 | 2023-09-19 | Johnson Controls Technology Company | Building management system with identity management |
| US10854194B2 (en) | 2017-02-10 | 2020-12-01 | Johnson Controls Technology Company | Building system with digital twin based data ingestion and processing |
| US10154067B2 (en) | 2017-02-10 | 2018-12-11 | Edgewise Networks, Inc. | Network application security policy enforcement |
| US11280509B2 (en) | 2017-07-17 | 2022-03-22 | Johnson Controls Technology Company | Systems and methods for agent based building simulation for optimal control |
| US10439985B2 (en) | 2017-02-15 | 2019-10-08 | Edgewise Networks, Inc. | Network application security policy generation |
| US11307538B2 (en) | 2017-02-10 | 2022-04-19 | Johnson Controls Technology Company | Web services platform with cloud-eased feedback control |
| US10417245B2 (en) | 2017-02-10 | 2019-09-17 | Johnson Controls Technology Company | Building management system with eventseries processing |
| US10452043B2 (en) | 2017-02-10 | 2019-10-22 | Johnson Controls Technology Company | Building management system with nested stream generation |
| US11994833B2 (en) | 2017-02-10 | 2024-05-28 | Johnson Controls Technology Company | Building smart entity system with agent based data ingestion and entity creation using time series data |
| US12184444B2 (en) | 2017-02-10 | 2024-12-31 | Johnson Controls Technology Company | Space graph based dynamic control for buildings |
| US10515098B2 (en) | 2017-02-10 | 2019-12-24 | Johnson Controls Technology Company | Building management smart entity creation and maintenance using time series data |
| US10491616B2 (en) | 2017-02-13 | 2019-11-26 | Microsoft Technology Licensing, Llc | Multi-signal analysis for compromised scope identification |
| US10887325B1 (en) | 2017-02-13 | 2021-01-05 | Exabeam, Inc. | Behavior analytics system for determining the cybersecurity risk associated with first-time, user-to-entity access alerts |
| US10735468B1 (en)* | 2017-02-14 | 2020-08-04 | Ca, Inc. | Systems and methods for evaluating security services |
| US10320818B2 (en)* | 2017-02-14 | 2019-06-11 | Symantec Corporation | Systems and methods for detecting malicious computing events |
| US11552985B2 (en)* | 2017-02-17 | 2023-01-10 | Nec Corporation | Method for predicting events using a joint representation of different feature types |
| US11481644B2 (en)* | 2017-02-17 | 2022-10-25 | Nike, Inc. | Event prediction |
| US11218497B2 (en)* | 2017-02-20 | 2022-01-04 | Micro Focus Llc | Reporting behavior anomalies |
| CN106933622A (en)* | 2017-02-21 | 2017-07-07 | 清华大学 | The Hadoop dispositions methods of model-driven in cloud environment |
| US10616251B2 (en)* | 2017-02-23 | 2020-04-07 | Cisco Technology, Inc. | Anomaly selection using distance metric-based diversity and relevance |
| US11777963B2 (en) | 2017-02-24 | 2023-10-03 | LogRhythm Inc. | Analytics for processing information system data |
| US11062230B2 (en)* | 2017-02-28 | 2021-07-13 | International Business Machines Corporation | Detecting data anomalies |
| WO2018160605A1 (en)* | 2017-02-28 | 2018-09-07 | SavantX, Inc. | System and method for analysis and navigation of data |
| US11328128B2 (en) | 2017-02-28 | 2022-05-10 | SavantX, Inc. | System and method for analysis and navigation of data |
| EP3570504B1 (en)* | 2017-03-09 | 2020-12-23 | Nippon Telegraph and Telephone Corporation | Attack countermeasure determination device, attack countermeasure determination method, and attack countermeasure determination program |
| CN106790292A (en)* | 2017-03-13 | 2017-05-31 | 摩贝(上海)生物科技有限公司 | The web application layer attacks detection and defence method of Behavior-based control characteristic matching and analysis |
| US10560364B1 (en)* | 2017-03-15 | 2020-02-11 | Pivotal Software, Inc. | Detecting network anomalies using node scoring |
| EP3376441B1 (en)* | 2017-03-15 | 2021-07-14 | Siemens Aktiengesellschaft | A method for execution of a machine learning model on memory restricted industrial device |
| US10581802B2 (en) | 2017-03-16 | 2020-03-03 | Keysight Technologies Singapore (Sales) Pte. Ltd. | Methods, systems, and computer readable media for advertising network security capabilities |
| US11334802B2 (en) | 2017-03-21 | 2022-05-17 | Choral Systems, Llc | Data analysis and visualization using structured data tables and nodal networks |
| US11657028B2 (en) | 2017-03-21 | 2023-05-23 | Choral Systems, Llc | Data analysis and visualization using structured data tables and nodal networks |
| US11630815B2 (en)* | 2017-03-21 | 2023-04-18 | Choral Systems, Llc | Data analysis and visualization using structured data tables and nodal networks |
| US11328213B2 (en) | 2017-03-21 | 2022-05-10 | Choral Systems, Llc | Data analysis and visualization using structured data tables and nodal networks |
| US10476673B2 (en) | 2017-03-22 | 2019-11-12 | Extrahop Networks, Inc. | Managing session secrets for continuous packet capture systems |
| US11042144B2 (en) | 2017-03-24 | 2021-06-22 | Johnson Controls Technology Company | Building management system with dynamic channel communication |
| CN108259449B (en)* | 2017-03-27 | 2020-03-06 | 新华三技术有限公司 | Method and system for defending against APT (android packet) attack |
| US10637737B2 (en) | 2017-03-28 | 2020-04-28 | Ca Technologies, Inc. | Managing alarms from distributed applications |
| US10841321B1 (en)* | 2017-03-28 | 2020-11-17 | Veritas Technologies Llc | Systems and methods for detecting suspicious users on networks |
| EP3382591B1 (en) | 2017-03-30 | 2020-03-25 | British Telecommunications public limited company | Hierarchical temporal memory for expendable access control |
| US10313344B2 (en) | 2017-03-30 | 2019-06-04 | Bank Of America Corporation | Internal footprint repository |
| CN108665297B (en)* | 2017-03-31 | 2021-01-26 | 北京京东尚科信息技术有限公司 | Method and device for detecting abnormal access behavior, electronic equipment and storage medium |
| US11416751B2 (en)* | 2017-03-31 | 2022-08-16 | H2O.Ai Inc. | Time-based ensemble machine learning model |
| US10580225B2 (en)* | 2017-03-31 | 2020-03-03 | Toyota Motor Engineering & Manufacturing North America, Inc. | Privacy-aware signal monitoring systems and methods |
| US10440037B2 (en)* | 2017-03-31 | 2019-10-08 | Mcafee, Llc | Identifying malware-suspect end points through entropy changes in consolidated logs |
| US11372744B1 (en)* | 2017-03-31 | 2022-06-28 | Headspin, Inc. | System for identifying issues during testing of applications |
| US10791367B1 (en) | 2017-03-31 | 2020-09-29 | Conviva Inc. | Correlating playback information of video segments |
| US11010342B2 (en) | 2017-04-03 | 2021-05-18 | Splunk Inc. | Network activity identification and characterization based on characteristic active directory (AD) event segments |
| US10834103B2 (en)* | 2017-04-03 | 2020-11-10 | Juniper Networks, Inc. | Tracking and mitigation of an infected host device |
| US11263275B1 (en)* | 2017-04-03 | 2022-03-01 | Massachusetts Mutual Life Insurance Company | Systems, devices, and methods for parallelized data structure processing |
| US11500826B2 (en)* | 2017-04-04 | 2022-11-15 | Hcl Technologies Limited | System for translating data, extracted from disparate datasources, based on a defined metadata and schema |
| US10841338B1 (en) | 2017-04-05 | 2020-11-17 | Exabeam, Inc. | Dynamic rule risk score determination in a cybersecurity monitoring system |
| US10817608B2 (en) | 2017-04-07 | 2020-10-27 | Zscaler, Inc. | System and method for malware detection on a per packet basis |
| US10819749B2 (en) | 2017-04-21 | 2020-10-27 | Netskope, Inc. | Reducing error in security enforcement by a network security system (NSS) |
| US11327737B2 (en) | 2017-04-21 | 2022-05-10 | Johnson Controls Tyco IP Holdings LLP | Building management system with cloud management of gateway configurations |
| US10652280B2 (en)* | 2017-04-24 | 2020-05-12 | Unisys Corporation | User interface features for enterprise security management |
| CN107040422B (en)* | 2017-04-25 | 2020-05-05 | 浙江工业大学 | A visualization method of network big data based on materialized cache |
| US10447713B2 (en) | 2017-04-26 | 2019-10-15 | At&T Intellectual Property I, L.P. | Internet traffic classification via time-frequency analysis |
| US11621969B2 (en) | 2017-04-26 | 2023-04-04 | Elasticsearch B.V. | Clustering and outlier detection in anomaly and causation detection for computing environments |
| CN111066015B (en) | 2017-04-26 | 2024-02-23 | 西兰克公司 | Endpoint detection and response system event feature data transmission |
| US11783046B2 (en)* | 2017-04-26 | 2023-10-10 | Elasticsearch B.V. | Anomaly and causation detection in computing environments |
| US20180314821A1 (en)* | 2017-04-26 | 2018-11-01 | Microsoft Technology Licensing, Llc | Transferring Containers |
| US10986110B2 (en) | 2017-04-26 | 2021-04-20 | Elasticsearch B.V. | Anomaly and causation detection in computing environments using counterfactual processing |
| US10439884B1 (en) | 2017-04-27 | 2019-10-08 | Dflabs S.P.A. | Cybersecurity incident response and security operation system employing playbook generation through custom machine learning |
| US10838950B2 (en)* | 2017-04-29 | 2020-11-17 | Cisco Technology, Inc. | Dynamic review cadence for intellectual capital |
| US10462169B2 (en) | 2017-04-29 | 2019-10-29 | Splunk Inc. | Lateral movement detection through graph-based candidate selection |
| US10536505B2 (en)* | 2017-04-30 | 2020-01-14 | Cisco Technology, Inc. | Intelligent data transmission by network device agent |
| US9864956B1 (en) | 2017-05-01 | 2018-01-09 | SparkCognition, Inc. | Generation and use of trained file classifiers for malware detection |
| US10637715B1 (en) | 2017-05-02 | 2020-04-28 | Conviva Inc. | Fault isolation in over-the-top content (OTT) broadband networks |
| US10489720B2 (en)* | 2017-05-02 | 2019-11-26 | Secureworks Corp. | System and method for vendor agnostic automatic supplementary intelligence propagation |
| WO2018206405A1 (en) | 2017-05-08 | 2018-11-15 | British Telecommunications Public Limited Company | Interoperation of machine learning algorithms |
| EP3622448A1 (en) | 2017-05-08 | 2020-03-18 | British Telecommunications Public Limited Company | Adaptation of machine learning algorithms |
| US11698818B2 (en) | 2017-05-08 | 2023-07-11 | British Telecommunications Public Limited Company | Load balancing of machine learning algorithms |
| WO2018206408A1 (en) | 2017-05-08 | 2018-11-15 | British Telecommunications Public Limited Company | Management of interoperating machine leaning algorithms |
| US11386343B2 (en) | 2017-05-09 | 2022-07-12 | Elasticsearch B.V. | Real time detection of cyber threats using behavioral analytics |
| US10178117B2 (en)* | 2017-05-09 | 2019-01-08 | Oath Inc. | Systems and methods for network traffic analysis |
| US10788229B2 (en) | 2017-05-10 | 2020-09-29 | Johnson Controls Technology Company | Building management system with a distributed blockchain database |
| CN107122489B (en)* | 2017-05-11 | 2021-03-09 | 苏州浪潮智能科技有限公司 | Data comparison method and device |
| JP6869100B2 (en)* | 2017-05-12 | 2021-05-12 | 株式会社Pfu | Information processing device, fraudulent activity classification method and fraudulent activity classification program |
| USD861712S1 (en)* | 2017-05-12 | 2019-10-01 | Adp, Llc | Display screen with an animated graphical user interface |
| USD861711S1 (en)* | 2017-05-12 | 2019-10-01 | Adp, Llc | Display screen with an animated graphical user interface |
| US11108788B1 (en)* | 2017-05-15 | 2021-08-31 | RiskIQ, Inc. | Techniques for managing projects and monitoring network-based assets |
| US11888859B2 (en) | 2017-05-15 | 2024-01-30 | Forcepoint Llc | Associating a security risk persona with a phase of a cyber kill chain |
| US11632382B2 (en)* | 2017-05-15 | 2023-04-18 | Forcepoint Llc | Anomaly detection using endpoint counters |
| US10943019B2 (en) | 2017-05-15 | 2021-03-09 | Forcepoint, LLC | Adaptive trust profile endpoint |
| JP6839360B2 (en)* | 2017-05-15 | 2021-03-10 | 富士通株式会社 | Display program, display method and display device |
| US10862927B2 (en) | 2017-05-15 | 2020-12-08 | Forcepoint, LLC | Dividing events into sessions during adaptive trust profile operations |
| US10129269B1 (en) | 2017-05-15 | 2018-11-13 | Forcepoint, LLC | Managing blockchain access to user profile information |
| US10917423B2 (en) | 2017-05-15 | 2021-02-09 | Forcepoint, LLC | Intelligently differentiating between different types of states and attributes when using an adaptive trust profile |
| US9882918B1 (en) | 2017-05-15 | 2018-01-30 | Forcepoint, LLC | User behavior profile in a blockchain |
| US10447718B2 (en) | 2017-05-15 | 2019-10-15 | Forcepoint Llc | User profile definition and management |
| US10999297B2 (en) | 2017-05-15 | 2021-05-04 | Forcepoint, LLC | Using expected behavior of an entity when prepopulating an adaptive trust profile |
| US10999296B2 (en) | 2017-05-15 | 2021-05-04 | Forcepoint, LLC | Generating adaptive trust profiles using information derived from similarly situated organizations |
| US11949700B2 (en) | 2017-05-15 | 2024-04-02 | Forcepoint Llc | Using content stored in an entity behavior catalog in combination with an entity risk score |
| US10878102B2 (en) | 2017-05-16 | 2020-12-29 | Micro Focus Llc | Risk scores for entities |
| US11074280B2 (en)* | 2017-05-18 | 2021-07-27 | Aiqudo, Inc | Cluster based search and recommendation method to rapidly on-board commands in personal assistants |
| US20180336437A1 (en)* | 2017-05-19 | 2018-11-22 | Nec Laboratories America, Inc. | Streaming graph display system with anomaly detection |
| US11005864B2 (en) | 2017-05-19 | 2021-05-11 | Salesforce.Com, Inc. | Feature-agnostic behavior profile based anomaly detection |
| USD861713S1 (en) | 2017-05-22 | 2019-10-01 | Reveal Usa, Inc. | Display screen with a graphical user interface |
| US20180343184A1 (en)* | 2017-05-25 | 2018-11-29 | Ehrlich Wesen & Dauer, LLC. | Platform for Multi-Function Network Resource Analysis |
| JP7184797B2 (en) | 2017-05-25 | 2022-12-06 | ジョンソン コントロールズ テクノロジー カンパニー | Model predictive maintenance system for building equipment |
| US10904278B2 (en)* | 2017-05-26 | 2021-01-26 | Alien Vault, Inc. | Detection system for network security threats |
| US10410086B2 (en) | 2017-05-30 | 2019-09-10 | Google Llc | Systems and methods of person recognition in video streams |
| US11783010B2 (en) | 2017-05-30 | 2023-10-10 | Google Llc | Systems and methods of person recognition in video streams |
| WO2018222852A1 (en)* | 2017-05-31 | 2018-12-06 | Shiftleft Inc. | System and method for application security profiling |
| US11044533B1 (en)* | 2017-06-02 | 2021-06-22 | Conviva Inc. | Automatic diagnostics alerts |
| US10878103B2 (en) | 2017-06-05 | 2020-12-29 | Karamba Security Ltd. | In-memory protection for controller security |
| USD898060S1 (en) | 2017-06-05 | 2020-10-06 | Sas Institute Inc. | Display screen or portion thereof with graphical user interface |
| US10204219B2 (en) | 2017-06-05 | 2019-02-12 | Karamba Security | In-memory protection for controller security |
| US11022947B2 (en) | 2017-06-07 | 2021-06-01 | Johnson Controls Technology Company | Building energy optimization system with economic load demand response (ELDR) optimization and ELDR user interfaces |
| CN107229976A (en)* | 2017-06-08 | 2017-10-03 | 郑州云海信息技术有限公司 | A kind of distributed machines learning system based on spark |
| US10467083B2 (en)* | 2017-06-08 | 2019-11-05 | International Business Machines Corporation | Event relationship analysis in fault management |
| US10313379B1 (en)* | 2017-06-09 | 2019-06-04 | Symantec Corporation | Systems and methods for making security-related predictions |
| US10902533B2 (en) | 2017-06-12 | 2021-01-26 | Microsoft Technology Licensing, Llc | Dynamic event processing |
| US10417039B2 (en)* | 2017-06-12 | 2019-09-17 | Microsoft Technology Licensing, Llc | Event processing using a scorable tree |
| US10505954B2 (en) | 2017-06-14 | 2019-12-10 | Microsoft Technology Licensing, Llc | Detecting malicious lateral movement across a computer network |
| US10681061B2 (en) | 2017-06-14 | 2020-06-09 | International Business Machines Corporation | Feedback-based prioritized cognitive analysis |
| US11888883B2 (en) | 2017-06-14 | 2024-01-30 | International Business Machines Corporation | Threat disposition analysis and modeling using supervised machine learning |
| WO2018232147A1 (en) | 2017-06-15 | 2018-12-20 | Johnson Controls Technology Company | Building management system with artificial intelligence for unified agent based control of building subsystems |
| US10506367B2 (en) | 2017-06-16 | 2019-12-10 | Best Network Systems Inc. | IOT messaging communications systems and methods |
| US10489019B2 (en)* | 2017-06-16 | 2019-11-26 | Florida Power & Light Company | Identifying and presenting related electrical power distribution system events |
| US11416119B2 (en)* | 2017-06-16 | 2022-08-16 | Florida Power & Light Company | Locating a power line event downstream from a power line branch point |
| US10887323B2 (en) | 2017-06-19 | 2021-01-05 | International Business Machines Corporation | Detecting malicious beaconing communities using lockstep detection and co-occurrence graph |
| GB201709812D0 (en) | 2017-06-20 | 2017-08-02 | Ibm | Identification of software components based on filtering of corresponding events |
| US10341373B2 (en)* | 2017-06-21 | 2019-07-02 | Symantec Corporation | Automatically detecting insider threats using user collaboration patterns |
| US10425380B2 (en) | 2017-06-22 | 2019-09-24 | BitSight Technologies, Inc. | Methods for mapping IP addresses and domains to organizations using user activity data |
| US11874845B2 (en)* | 2017-06-28 | 2024-01-16 | Fortinet, Inc. | Centralized state database storing state information |
| US10530794B2 (en) | 2017-06-30 | 2020-01-07 | Sap Se | Pattern creation in enterprise threat detection |
| US10305923B2 (en) | 2017-06-30 | 2019-05-28 | SparkCognition, Inc. | Server-supported malware detection and protection |
| US10616252B2 (en) | 2017-06-30 | 2020-04-07 | SparkCognition, Inc. | Automated detection of malware using trained neural network-based file classifiers and machine learning |
| CN107465696A (en)* | 2017-07-03 | 2017-12-12 | 南京骏腾信息技术有限公司 | Security risk intellectuality management-control method based on SaaS cloud service patterns |
| US10606990B2 (en) | 2017-07-06 | 2020-03-31 | Ebay Inc. | Machine learning system for computing asset access |
| EP3651083B1 (en)* | 2017-07-07 | 2025-03-26 | Sony Group Corporation | System, processing device, information processing method, and program |
| US11238164B2 (en)* | 2017-07-10 | 2022-02-01 | Burstiq, Inc. | Secure adaptive data storage platform |
| US12184781B2 (en) | 2017-07-10 | 2024-12-31 | Burstiq, Inc. | Systems and methods for accessing digital assets in a blockchain using owner consent contracts |
| US11810185B2 (en)* | 2017-07-12 | 2023-11-07 | Visa International Service Association | Systems and methods for generating behavior profiles for new entities |
| US20190019213A1 (en)* | 2017-07-12 | 2019-01-17 | Cerebri AI Inc. | Predicting the effectiveness of a marketing campaign prior to deployment |
| US20190018545A1 (en)* | 2017-07-13 | 2019-01-17 | International Business Machines Corporation | System and method for rapid financial app prototyping |
| USD832286S1 (en)* | 2017-07-13 | 2018-10-30 | Henry G. Ilyasov | Display screen or portion thereof with graphical user interface |
| US11018949B2 (en)* | 2017-07-14 | 2021-05-25 | Accenture Global Solutions Limited | System for generating an architecture diagram |
| US10419460B2 (en)* | 2017-07-21 | 2019-09-17 | Oath, Inc. | Method and system for detecting abnormal online user activity |
| US11422516B2 (en) | 2017-07-21 | 2022-08-23 | Johnson Controls Tyco IP Holdings LLP | Building management system with dynamic rules with sub-rule reuse and equation driven smart diagnostics |
| CN107154950B (en)* | 2017-07-24 | 2021-05-04 | 深信服科技股份有限公司 | Method and system for detecting log stream abnormity |
| US10318729B2 (en) | 2017-07-26 | 2019-06-11 | Forcepoint, LLC | Privacy protection during insider threat monitoring |
| US12387270B2 (en)* | 2017-07-26 | 2025-08-12 | Guidewire Software, Inc. | Synthetic diversity analysis with actionable feedback methodologies |
| US10648692B2 (en) | 2017-07-27 | 2020-05-12 | Johnson Controls Technology Company | Building management system with multi-dimensional analysis of building energy and equipment performance |
| US10217071B2 (en) | 2017-07-28 | 2019-02-26 | SecurityScorecard, Inc. | Reducing cybersecurity risk level of a portfolio of companies using a cybersecurity risk multiplier |
| US10614401B2 (en)* | 2017-07-28 | 2020-04-07 | SecurityScorecard, Inc. | Reducing cybersecurity risk level of portfolio of companies using a cybersecurity risk multiplier |
| US10735273B2 (en)* | 2017-07-31 | 2020-08-04 | Accenture Global Solutions Limited | Using machine learning to make network management decisions |
| US10891338B1 (en)* | 2017-07-31 | 2021-01-12 | Palantir Technologies Inc. | Systems and methods for providing information |
| US11611574B2 (en)* | 2017-08-02 | 2023-03-21 | Code42 Software, Inc. | User behavior analytics for insider threat detection |
| US11068593B2 (en)* | 2017-08-03 | 2021-07-20 | B. G. Negev Technologies And Applications Ltd., At Ben-Gurion University | Using LSTM encoder-decoder algorithm for detecting anomalous ADS-B messages |
| WO2019028341A1 (en)* | 2017-08-03 | 2019-02-07 | T-Mobile Usa, Inc. | Similarity search for discovering multiple vector attacks |
| US11093607B1 (en) | 2017-08-04 | 2021-08-17 | Chronicle Llc | Efficient processing of computer security data |
| CN107528832B (en)* | 2017-08-04 | 2020-07-07 | 北京中晟信达科技有限公司 | Baseline construction and unknown abnormal behavior detection method for system logs |
| US11048718B2 (en)* | 2017-08-10 | 2021-06-29 | International Business Machines Corporation | Methods and systems for feature engineering |
| CN107479990B (en)* | 2017-08-11 | 2020-12-18 | 恒丰银行股份有限公司 | Distributed software service system |
| IL253987B (en)* | 2017-08-14 | 2019-05-30 | Cyberbit Ltd | Cyber threat detection system and method |
| US10530805B1 (en)* | 2017-08-16 | 2020-01-07 | Symantec Corporation | Systems and methods for detecting security incidents |
| CN107454089A (en)* | 2017-08-16 | 2017-12-08 | 北京科技大学 | A kind of network safety situation diagnostic method based on multinode relevance |
| CN107622309B (en)* | 2017-08-18 | 2021-01-08 | 长安大学 | Road congestion detection method based on VANETs and improved D-S evidence theory |
| CN107302547B (en)* | 2017-08-21 | 2021-07-02 | 深信服科技股份有限公司 | Web service anomaly detection method and device |
| US10841329B2 (en)* | 2017-08-23 | 2020-11-17 | International Business Machines Corporation | Cognitive security for workflows |
| US10581945B2 (en) | 2017-08-28 | 2020-03-03 | Banjo, Inc. | Detecting an event from signal data |
| US20190251138A1 (en)* | 2018-02-09 | 2019-08-15 | Banjo, Inc. | Detecting events from features derived from multiple ingested signals |
| US10432648B1 (en) | 2017-08-28 | 2019-10-01 | Palo Alto Networks, Inc. | Automated malware family signature generation |
| US10313413B2 (en) | 2017-08-28 | 2019-06-04 | Banjo, Inc. | Detecting events from ingested communication signals |
| US11025693B2 (en) | 2017-08-28 | 2021-06-01 | Banjo, Inc. | Event detection from signal data removing private information |
| US10063434B1 (en) | 2017-08-29 | 2018-08-28 | Extrahop Networks, Inc. | Classifying applications or activities based on network behavior |
| US10984099B2 (en) | 2017-08-29 | 2021-04-20 | Micro Focus Llc | Unauthorized authentication events |
| US10599857B2 (en) | 2017-08-29 | 2020-03-24 | Micro Focus Llc | Extracting features for authentication events |
| US11397413B2 (en) | 2017-08-29 | 2022-07-26 | Micro Focus Llc | Training models based on balanced training data sets |
| US10592666B2 (en) | 2017-08-31 | 2020-03-17 | Micro Focus Llc | Detecting anomalous entities |
| US11449561B1 (en)* | 2017-08-31 | 2022-09-20 | What'scommon, Inc. | System and method for event-based searching on social media |
| US10586051B2 (en) | 2017-08-31 | 2020-03-10 | International Business Machines Corporation | Automatic transformation of security event detection rules |
| US11192325B2 (en)* | 2017-08-31 | 2021-12-07 | Daio Paper Corporation | Hygienic thin-leaf paper |
| CN107508817B (en)* | 2017-09-04 | 2020-05-05 | 北京经纬信安科技有限公司 | Network security defense equipment for endogenous threat of enterprises and institutions |
| USD833460S1 (en)* | 2017-09-06 | 2018-11-13 | Box, Inc. | Display screen or portion thereof with graphical user interface for display of content upload |
| USD833459S1 (en)* | 2017-09-06 | 2018-11-13 | Box, Inc. | Display screen or portion thereof with graphical user interface for display of content approval |
| USD833458S1 (en)* | 2017-09-06 | 2018-11-13 | Box, Inc. | Display screen or portion thereof with graphical user interface for display of content feedback |
| USD833472S1 (en)* | 2017-09-06 | 2018-11-13 | Box, Inc. | Display screen or portion thereof with graphical user interface for display of profile page |
| US20190081963A1 (en)* | 2017-09-08 | 2019-03-14 | Sophos Limited | Realtime event detection |
| CN107644267B (en)* | 2017-09-11 | 2020-04-24 | 河南科技大学 | Greenhouse control decision fusion method based on D-S evidence theory |
| US10430584B2 (en)* | 2017-09-11 | 2019-10-01 | Bank Of America Corporation | Multiplexed—proactive resiliency system |
| US10447721B2 (en) | 2017-09-13 | 2019-10-15 | Xm Cyber Ltd. | Systems and methods for using multiple lateral movement strategies in penetration testing |
| US10904276B2 (en)* | 2017-09-14 | 2021-01-26 | Nokia Technologies Oy | Systems and methods for anomaly detection |
| US11134227B2 (en) | 2017-09-20 | 2021-09-28 | Google Llc | Systems and methods of presenting appropriate actions for responding to a visitor to a smart home environment |
| US10664688B2 (en) | 2017-09-20 | 2020-05-26 | Google Llc | Systems and methods of detecting and responding to a visitor to a smart home environment |
| US20190141068A1 (en)* | 2017-09-21 | 2019-05-09 | Camp Mobile Corporation | Online service abuser detection |
| US10944766B2 (en)* | 2017-09-22 | 2021-03-09 | Microsoft Technology Licensing, Llc | Configurable cyber-attack trackers |
| CN111095257A (en)* | 2017-09-25 | 2020-05-01 | 索尼公司 | Authentication device, information processing method, and program |
| US10887369B2 (en)* | 2017-09-25 | 2021-01-05 | Splunk Inc. | Customizable load balancing in a user behavior analytics deployment |
| US10771486B2 (en) | 2017-09-25 | 2020-09-08 | Splunk Inc. | Systems and methods for detecting network security threat event patterns |
| US11120012B2 (en) | 2017-09-27 | 2021-09-14 | Johnson Controls Tyco IP Holdings LLP | Web services platform with integration and interface of smart entities with enterprise applications |
| US10559180B2 (en) | 2017-09-27 | 2020-02-11 | Johnson Controls Technology Company | Building risk analysis system with dynamic modification of asset-threat weights |
| US11314788B2 (en) | 2017-09-27 | 2022-04-26 | Johnson Controls Tyco IP Holdings LLP | Smart entity management for building management systems |
| US10962945B2 (en) | 2017-09-27 | 2021-03-30 | Johnson Controls Technology Company | Building management system with integration of data into smart entities |
| US12339825B2 (en) | 2017-09-27 | 2025-06-24 | Tyco Fire & Security Gmbh | Building risk analysis system with risk cards |
| US11070568B2 (en) | 2017-09-27 | 2021-07-20 | Palo Alto Networks, Inc. | IoT device management visualization |
| US11258683B2 (en)* | 2017-09-27 | 2022-02-22 | Johnson Controls Tyco IP Holdings LLP | Web services platform with nested stream generation |
| US10791128B2 (en)* | 2017-09-28 | 2020-09-29 | Microsoft Technology Licensing, Llc | Intrusion detection |
| US10885393B1 (en)* | 2017-09-28 | 2021-01-05 | Architecture Technology Corporation | Scalable incident-response and forensics toolkit |
| US10686816B1 (en)* | 2017-09-28 | 2020-06-16 | NortonLifeLock Inc. | Insider threat detection under user-resource bi-partite graphs |
| US10951639B2 (en)* | 2017-09-28 | 2021-03-16 | Yokogawa Electric Corporation | Systems, methods and computer program products for anomaly detection |
| US10679129B2 (en)* | 2017-09-28 | 2020-06-09 | D5Ai Llc | Stochastic categorical autoencoder network |
| US11637844B2 (en) | 2017-09-28 | 2023-04-25 | Oracle International Corporation | Cloud-based threat detection |
| US10599839B2 (en) | 2017-09-29 | 2020-03-24 | Hewlett Packard Enterprise Development Lp | Security investigations using a card system framework |
| US10949535B2 (en)* | 2017-09-29 | 2021-03-16 | Microsoft Technology Licensing, Llc | Security model training and threshold selection |
| US10812498B2 (en)* | 2017-09-29 | 2020-10-20 | Hewlett Packard Enterprise Development Lp | Playbook-based security investigations using a card system framework |
| CN107807956A (en)* | 2017-09-30 | 2018-03-16 | 平安科技(深圳)有限公司 | Electronic installation, data processing method and computer-readable recording medium |
| US10735457B2 (en)* | 2017-10-03 | 2020-08-04 | Microsoft Technology Licensing, Llc | Intrusion investigation |
| US11037080B2 (en)* | 2017-10-05 | 2021-06-15 | Aconex Limited | Operational process anomaly detection |
| US10637879B2 (en) | 2017-10-06 | 2020-04-28 | Carbonite, Inc. | Systems and methods for detection and mitigation of malicious encryption |
| US10956574B2 (en) | 2017-10-07 | 2021-03-23 | Shiftleft Inc. | System and method for securing applications through an application-aware runtime agent |
| CN107861985A (en)* | 2017-10-12 | 2018-03-30 | 中国煤炭地质总局九勘探队 | A kind of batch processing method for extracting multiple sub-folders similarly hereinafter class file |
| US10867036B2 (en) | 2017-10-12 | 2020-12-15 | Cisco Technology, Inc. | Multiple pairwise feature histograms for representing network traffic |
| US20190114362A1 (en)* | 2017-10-12 | 2019-04-18 | Facebook, Inc. | Searching Online Social Networks Using Entity-based Embeddings |
| CN107704594B (en)* | 2017-10-13 | 2021-02-09 | 东南大学 | Real-time processing method for log data of power system based on spark streaming |
| JP7120708B2 (en)* | 2017-10-13 | 2022-08-17 | ホアウェイ・テクノロジーズ・カンパニー・リミテッド | System and method for cloud device collaborative real-time user usage and performance anomaly detection |
| EP3471007B1 (en) | 2017-10-13 | 2022-02-23 | Ping Identity Corporation | Methods and apparatus for analyzing sequences of application programming interface traffic to identify potential malicious actions |
| US10650128B2 (en)* | 2017-10-18 | 2020-05-12 | Mastercard International Incorporated | Methods and systems for automatically configuring user authentication rules |
| US11012462B2 (en)* | 2017-10-20 | 2021-05-18 | International Business Machines Corporation | Security management for data systems |
| US10904271B2 (en)* | 2017-10-20 | 2021-01-26 | Cisco Technology, Inc. | Active prioritization of investigation targets in network security |
| US10915625B2 (en)* | 2017-10-24 | 2021-02-09 | Nec Corporation | Graph model for alert interpretation in enterprise security system |
| US10785318B2 (en)* | 2017-10-25 | 2020-09-22 | Adobe Inc. | Classification of website sessions using one-class labeling techniques |
| US9967292B1 (en) | 2017-10-25 | 2018-05-08 | Extrahop Networks, Inc. | Inline secret sharing |
| US10719365B2 (en) | 2017-10-27 | 2020-07-21 | International Business Machines Corporation | Cognitive learning workflow execution |
| US11082296B2 (en) | 2017-10-27 | 2021-08-03 | Palo Alto Networks, Inc. | IoT device grouping and labeling |
| US10552779B2 (en) | 2017-10-27 | 2020-02-04 | International Business Machines Corporation | Cognitive learning workflow execution |
| US10719795B2 (en) | 2017-10-27 | 2020-07-21 | International Business Machines Corporation | Cognitive learning workflow execution |
| US10713084B2 (en) | 2017-10-27 | 2020-07-14 | International Business Machines Corporation | Cognitive learning workflow execution |
| US11134098B1 (en) | 2017-10-30 | 2021-09-28 | EMC IP Holding Company LLC | Container life cycle management with session dilution time |
| US10951651B1 (en)* | 2017-10-30 | 2021-03-16 | EMC IP Holding Company LLC | Container life cycle management with retention rate adjustment based on detected anomalies |
| USD916718S1 (en)* | 2017-10-30 | 2021-04-20 | Siemens Healthcare Gmbh | Display screen or portion thereof with a graphical user interface |
| US10791144B1 (en) | 2017-10-30 | 2020-09-29 | EMC IP Holding Company LLC | Container life cycle management with honeypot service |
| US10803178B2 (en)* | 2017-10-31 | 2020-10-13 | Forcepoint Llc | Genericized data model to perform a security analytics operation |
| CN107861804A (en)* | 2017-10-31 | 2018-03-30 | 用友金融信息技术股份有限公司 | Big data computational methods, computing system, computer equipment and readable storage medium storing program for executing |
| US10735470B2 (en) | 2017-11-06 | 2020-08-04 | Secureworks Corp. | Systems and methods for sharing, distributing, or accessing security data and/or security applications, models, or analytics |
| US11489851B2 (en)* | 2017-11-06 | 2022-11-01 | Cyber Defence Qcd Corporation | Methods and systems for monitoring cyber-events |
| CN107886243A (en)* | 2017-11-10 | 2018-04-06 | 阿里巴巴集团控股有限公司 | Risk identification model construction and Risk Identification Method, device and equipment |
| EP3707883B1 (en) | 2017-11-10 | 2023-08-30 | Zscaler, Inc. | Automated load balancer discovery |
| US10042879B1 (en) | 2017-11-13 | 2018-08-07 | Lendingclub Corporation | Techniques for dynamically enriching and propagating a correlation context |
| US11354301B2 (en) | 2017-11-13 | 2022-06-07 | LendingClub Bank, National Association | Multi-system operation audit log |
| US11816586B2 (en)* | 2017-11-13 | 2023-11-14 | International Business Machines Corporation | Event identification through machine learning |
| US10778651B2 (en) | 2017-11-15 | 2020-09-15 | Nicira, Inc. | Performing context-rich attribute-based encryption on a host |
| US10809682B2 (en) | 2017-11-15 | 2020-10-20 | Johnson Controls Technology Company | Building management system with optimized processing of building system data |
| US11281169B2 (en) | 2017-11-15 | 2022-03-22 | Johnson Controls Tyco IP Holdings LLP | Building management system with point virtualization for online meters |
| EP3711279A1 (en) | 2017-11-15 | 2020-09-23 | XM Cyber Ltd. | Selectively choosing between actual-attack and simulation/evaluation for validating a vulnerability of a network node during execution of a penetration testing campaign |
| US11973784B1 (en) | 2017-11-27 | 2024-04-30 | Lacework, Inc. | Natural language interface for an anomaly detection framework |
| US12058160B1 (en) | 2017-11-22 | 2024-08-06 | Lacework, Inc. | Generating computer code for remediating detected events |
| US11785104B2 (en) | 2017-11-27 | 2023-10-10 | Lacework, Inc. | Learning from similar cloud deployments |
| US11127235B2 (en) | 2017-11-22 | 2021-09-21 | Johnson Controls Tyco IP Holdings LLP | Building campus with integrated smart environment |
| US20190166024A1 (en)* | 2017-11-24 | 2019-05-30 | Institute For Information Industry | Network anomaly analysis apparatus, method, and non-transitory computer readable storage medium thereof |
| US12368745B1 (en) | 2017-11-27 | 2025-07-22 | Fortinet, Inc. | Using natural language queries to conduct an investigation of a monitored system |
| US12130878B1 (en) | 2017-11-27 | 2024-10-29 | Fortinet, Inc. | Deduplication of monitored communications data in a cloud environment |
| US20220232024A1 (en) | 2017-11-27 | 2022-07-21 | Lacework, Inc. | Detecting deviations from typical user behavior |
| US20220232025A1 (en) | 2017-11-27 | 2022-07-21 | Lacework, Inc. | Detecting anomalous behavior of a device |
| US12355787B1 (en) | 2017-11-27 | 2025-07-08 | Fortinet, Inc. | Interdependence of agentless and agent-based operations by way of a data platform |
| US12335286B1 (en) | 2017-11-27 | 2025-06-17 | Fortinet, Inc. | Compute environment security monitoring using data collected from a sub-kernel space |
| US12405849B1 (en) | 2017-11-27 | 2025-09-02 | Fortinet, Inc. | Transitive identity usage tracking by a data platform |
| US12355793B1 (en) | 2017-11-27 | 2025-07-08 | Fortinet, Inc. | Guided interactions with a natural language interface |
| US12284197B1 (en) | 2017-11-27 | 2025-04-22 | Fortinet, Inc. | Reducing amounts of data ingested into a data warehouse |
| US11818156B1 (en) | 2017-11-27 | 2023-11-14 | Lacework, Inc. | Data lake-enabled security platform |
| US12375573B1 (en) | 2017-11-27 | 2025-07-29 | Fortinet, Inc. | Container event monitoring using kernel space communication |
| US20190164092A1 (en)* | 2017-11-27 | 2019-05-30 | International Business Machines Corporation | Determining risk assessment based on assigned protocol values |
| US12034754B2 (en) | 2017-11-27 | 2024-07-09 | Lacework, Inc. | Using static analysis for vulnerability detection |
| US11741238B2 (en) | 2017-11-27 | 2023-08-29 | Lacework, Inc. | Dynamically generating monitoring tools for software applications |
| US12407702B1 (en) | 2017-11-27 | 2025-09-02 | Fortinet, Inc. | Gathering and presenting information related to common vulnerabilities and exposures |
| US12309185B1 (en) | 2017-11-27 | 2025-05-20 | Fortinet, Inc. | Architecture for a generative artificial intelligence (AI)-enabled assistant |
| US11792284B1 (en) | 2017-11-27 | 2023-10-17 | Lacework, Inc. | Using data transformations for monitoring a cloud compute environment |
| US12355626B1 (en) | 2017-11-27 | 2025-07-08 | Fortinet, Inc. | Tracking infrastructure as code (IaC) asset lifecycles |
| US12341797B1 (en) | 2017-11-27 | 2025-06-24 | Fortinet, Inc. | Composite events indicative of multifaceted security threats within a compute environment |
| US12425430B1 (en) | 2017-11-27 | 2025-09-23 | Fortinet, Inc. | Runtime workload data-based modification of permissions for an entity |
| US11770398B1 (en) | 2017-11-27 | 2023-09-26 | Lacework, Inc. | Guided anomaly detection framework |
| US12368746B1 (en) | 2017-11-27 | 2025-07-22 | Fortinet, Inc. | Modular agentless scanning of cloud workloads |
| US12401669B1 (en) | 2017-11-27 | 2025-08-26 | Fortinet, Inc. | Container vulnerability management by a data platform |
| US12126643B1 (en) | 2017-11-27 | 2024-10-22 | Fortinet, Inc. | Leveraging generative artificial intelligence (‘AI’) for securing a monitored deployment |
| US12335348B1 (en) | 2017-11-27 | 2025-06-17 | Fortinet, Inc. | Optimizing data warehouse utilization by a data ingestion pipeline |
| US12418555B1 (en) | 2017-11-27 | 2025-09-16 | Fortinet Inc. | Guiding query creation for a generative artificial intelligence (AI)-enabled assistant |
| US20220224707A1 (en) | 2017-11-27 | 2022-07-14 | Lacework, Inc. | Establishing a location profile for a user device |
| US12267345B1 (en) | 2017-11-27 | 2025-04-01 | Fortinet, Inc. | Using user feedback for attack path analysis in an anomaly detection framework |
| US12425428B1 (en) | 2017-11-27 | 2025-09-23 | Fortinet, Inc. | Activity monitoring of a cloud compute environment based on container orchestration data |
| US12418552B1 (en) | 2017-11-27 | 2025-09-16 | Fortinet, Inc. | Virtual data streams in a data streaming platform |
| US12363148B1 (en) | 2017-11-27 | 2025-07-15 | Fortinet, Inc. | Operational adjustment for an agent collecting data from a cloud compute environment monitored by a data platform |
| US12323449B1 (en) | 2017-11-27 | 2025-06-03 | Fortinet, Inc. | Code analysis feedback loop for code created using generative artificial intelligence (‘AI’) |
| US11979422B1 (en) | 2017-11-27 | 2024-05-07 | Lacework, Inc. | Elastic privileges in a secure access service edge |
| US11894984B2 (en) | 2017-11-27 | 2024-02-06 | Lacework, Inc. | Configuring cloud deployments based on learnings obtained by monitoring other cloud deployments |
| US12095794B1 (en) | 2017-11-27 | 2024-09-17 | Lacework, Inc. | Universal cloud data ingestion for stream processing |
| US12309236B1 (en) | 2017-11-27 | 2025-05-20 | Fortinet, Inc. | Analyzing log data from multiple sources across computing environments |
| US10614071B1 (en)* | 2017-11-27 | 2020-04-07 | Lacework Inc. | Extensible query interface for dynamic data compositions and filter applications |
| US11765249B2 (en) | 2017-11-27 | 2023-09-19 | Lacework, Inc. | Facilitating developer efficiency and application quality |
| US12381901B1 (en) | 2017-11-27 | 2025-08-05 | Fortinet, Inc. | Unified storage for event streams in an anomaly detection framework |
| US12095796B1 (en) | 2017-11-27 | 2024-09-17 | Lacework, Inc. | Instruction-level threat assessment |
| US12261866B1 (en) | 2017-11-27 | 2025-03-25 | Fortinet, Inc. | Time series anomaly detection |
| US11849000B2 (en) | 2017-11-27 | 2023-12-19 | Lacework, Inc. | Using real-time monitoring to inform static analysis |
| US12407701B1 (en) | 2017-11-27 | 2025-09-02 | Fortinet, Inc. | Community-based generation of policies for a data platform |
| US12348545B1 (en) | 2017-11-27 | 2025-07-01 | Fortinet, Inc. | Customizable generative artificial intelligence (‘AI’) assistant |
| US12309182B1 (en) | 2017-11-27 | 2025-05-20 | Fortinet, Inc. | Customer onboarding and integration with anomaly detection systems |
| US12021888B1 (en) | 2017-11-27 | 2024-06-25 | Lacework, Inc. | Cloud infrastructure entitlement management by a data platform |
| US10491485B2 (en) | 2017-11-30 | 2019-11-26 | At&T Intellectual Property I, L.P. | Expansive network control design system |
| US10616260B2 (en) | 2017-11-30 | 2020-04-07 | Bank Of America Corporation | System for information security threat assessment |
| US10635822B2 (en)* | 2017-11-30 | 2020-04-28 | Bank Of America Corporation | Data integration system for triggering analysis of connection oscillations |
| US10826929B2 (en) | 2017-12-01 | 2020-11-03 | Bank Of America Corporation | Exterior data deployment system using hash generation and confirmation triggering |
| CN107995293A (en)* | 2017-12-04 | 2018-05-04 | 南京海道普数据技术有限公司 | Big data all-in-one machine and application system based on Internet of Things information |
| US10209974B1 (en) | 2017-12-04 | 2019-02-19 | Banjo, Inc | Automated model management methods |
| US10817545B2 (en)* | 2017-12-04 | 2020-10-27 | Accenture Global Solutions Limited | Cognitive decision system for security and log analysis using associative memory mapping in graph database |
| US11074362B2 (en) | 2017-12-04 | 2021-07-27 | ShiftLeft, Inc. | System and method for code-based protection of sensitive data |
| US10979302B2 (en) | 2017-12-04 | 2021-04-13 | Cisco Technology, Inc. | Meta behavioral analytics for a network or system |
| US10819730B2 (en)* | 2017-12-05 | 2020-10-27 | International Business Machines Corporation | Automatic user session profiling system for detecting malicious intent |
| US20190173735A1 (en)* | 2017-12-06 | 2019-06-06 | Chronicle Llc | Network user identification using traffic analysis |
| US11250348B1 (en)* | 2017-12-06 | 2022-02-15 | Amdocs Development Limited | System, method, and computer program for automatically determining customer issues and resolving issues using graphical user interface (GUI) based interactions with a chatbot |
| US20190180216A1 (en)* | 2017-12-07 | 2019-06-13 | International Business Machines Corporation | Cognitive task assignment for computer security operations |
| US10735272B1 (en)* | 2017-12-08 | 2020-08-04 | Logichub, Inc. | Graphical user interface for security intelligence automation platform using flows |
| US10785239B2 (en)* | 2017-12-08 | 2020-09-22 | Mcafee, Llc | Learning maliciousness in cybersecurity graphs |
| US10666666B1 (en) | 2017-12-08 | 2020-05-26 | Logichub, Inc. | Security intelligence automation platform using flows |
| US11632391B2 (en)* | 2017-12-08 | 2023-04-18 | Radware Ltd. | System and method for out of path DDoS attack detection |
| US10834118B2 (en)* | 2017-12-11 | 2020-11-10 | International Business Machines Corporation | Ambiguity resolution system and method for security information retrieval |
| USD856367S1 (en)* | 2017-12-11 | 2019-08-13 | Citrix Systems, Inc. | Display screen or portion thereof with transitional graphical user interface |
| US20210166106A1 (en)* | 2017-12-12 | 2021-06-03 | The Regents Of The University Of California | Residual binary neural network |
| US10433140B2 (en)* | 2017-12-12 | 2019-10-01 | Best Network Systems Inc. | IOT devices based messaging systems and methods |
| US10756992B2 (en) | 2017-12-13 | 2020-08-25 | Micro Focus Llc | Display of network activity data |
| US10432539B2 (en) | 2017-12-13 | 2019-10-01 | Micro Focus Llc | Network traffic data summarization |
| US11663067B2 (en) | 2017-12-15 | 2023-05-30 | International Business Machines Corporation | Computerized high-speed anomaly detection |
| US10681064B2 (en)* | 2017-12-19 | 2020-06-09 | Sap Se | Analysis of complex relationships among information technology security-relevant entities using a network graph |
| US10986111B2 (en) | 2017-12-19 | 2021-04-20 | Sap Se | Displaying a series of events along a time axis in enterprise threat detection |
| US11606387B2 (en)* | 2017-12-21 | 2023-03-14 | Radware Ltd. | Techniques for reducing the time to mitigate of DDoS attacks |
| US11074272B1 (en) | 2017-12-21 | 2021-07-27 | Seeq Corporation | System and method for managing streaming calculations |
| US11423143B1 (en) | 2017-12-21 | 2022-08-23 | Exabeam, Inc. | Anomaly detection based on processes executed within a network |
| US11321464B2 (en) | 2017-12-22 | 2022-05-03 | Wipro Limited | Method and system for generating cognitive security intelligence for detecting and preventing malwares |
| US11271955B2 (en) | 2017-12-28 | 2022-03-08 | Fireeye Security Holdings Us Llc | Platform and method for retroactive reclassification employing a cybersecurity-based global data store |
| US10867055B2 (en)* | 2017-12-28 | 2020-12-15 | Corlina, Inc. | System and method for monitoring the trustworthiness of a networked system |
| US11240275B1 (en)* | 2017-12-28 | 2022-02-01 | Fireeye Security Holdings Us Llc | Platform and method for performing cybersecurity analyses employing an intelligence hub with a modular architecture |
| US11855971B2 (en)* | 2018-01-11 | 2023-12-26 | Visa International Service Association | Offline authorization of interactions and controlled tasks |
| US11049033B2 (en)* | 2018-01-12 | 2021-06-29 | Cisco Technology, Inc. | Deriving highly interpretable cognitive patterns for network assurance |
| US10812510B2 (en)* | 2018-01-12 | 2020-10-20 | The Boeing Company | Anticipatory cyber defense |
| US20190220762A1 (en)* | 2018-01-12 | 2019-07-18 | Gamalon, Inc. | Probabilistic modeling system and method |
| US10673882B2 (en)* | 2018-01-15 | 2020-06-02 | International Business Machines Corporation | Network flow control of internet of things (IoT) devices |
| US11010233B1 (en) | 2018-01-18 | 2021-05-18 | Pure Storage, Inc | Hardware-based system monitoring |
| US10970395B1 (en) | 2018-01-18 | 2021-04-06 | Pure Storage, Inc | Security threat monitoring for a storage system |
| US10841322B2 (en) | 2018-01-18 | 2020-11-17 | General Electric Company | Decision system and method for separating faults from attacks |
| US11588846B2 (en)* | 2018-01-22 | 2023-02-21 | Nec Corporation | Network control device and network control method |
| WO2019142345A1 (en)* | 2018-01-22 | 2019-07-25 | 日本電気株式会社 | Security information processing device, information processing method, and recording medium |
| US11831658B2 (en) | 2018-01-22 | 2023-11-28 | Nuix Limited | Endpoint security architecture with programmable logic engine |
| US11368474B2 (en) | 2018-01-23 | 2022-06-21 | Rapid7, Inc. | Detecting anomalous internet behavior |
| US10757123B2 (en) | 2018-01-25 | 2020-08-25 | Bank Of America Corporation | Dynamic record identification and analysis computer system with event monitoring components |
| US10547518B2 (en) | 2018-01-26 | 2020-01-28 | Cisco Technology, Inc. | Detecting transient vs. perpetual network behavioral patterns using machine learning |
| US10673728B2 (en)* | 2018-01-26 | 2020-06-02 | Cisco Technology, Inc. | Dynamic selection of models for hybrid network assurance architectures |
| US10862773B2 (en) | 2018-01-26 | 2020-12-08 | Nicira, Inc. | Performing services on data messages associated with endpoint machines |
| US10802893B2 (en) | 2018-01-26 | 2020-10-13 | Nicira, Inc. | Performing process control services on endpoint machines |
| US11443230B2 (en)* | 2018-01-26 | 2022-09-13 | Cisco Technology, Inc. | Intrusion detection model for an internet-of-things operations environment |
| US10607021B2 (en) | 2018-01-26 | 2020-03-31 | Bank Of America Corporation | Monitoring usage of an application to identify characteristics and trigger security control |
| US10771313B2 (en)* | 2018-01-29 | 2020-09-08 | Cisco Technology, Inc. | Using random forests to generate rules for causation analysis of network anomalies |
| GB2578268B (en) | 2018-01-29 | 2021-12-29 | Ge Aviat Systems Ltd | Configurable network switch for industrial control systems including deterministic networks |
| US11509636B2 (en) | 2018-01-30 | 2022-11-22 | Corlina, Inc. | User and device onboarding |
| US10812500B2 (en)* | 2018-01-30 | 2020-10-20 | The United States Of America As Represented By The Secretary Of The Air Force | Method of cyberthreat detection by learning first-order rules on large-scale social media |
| US10936717B1 (en)* | 2018-01-30 | 2021-03-02 | EMC IP Holding Company LLC | Monitoring containers running on container host devices for detection of anomalies in current container behavior |
| US10741176B2 (en) | 2018-01-31 | 2020-08-11 | International Business Machines Corporation | Customizing responses to users in automated dialogue systems |
| US10430447B2 (en) | 2018-01-31 | 2019-10-01 | International Business Machines Corporation | Predicting intent of a user from anomalous profile data |
| US11163722B2 (en)* | 2018-01-31 | 2021-11-02 | Salesforce.Com, Inc. | Methods and apparatus for analyzing a live stream of log entries to detect patterns |
| US20190236249A1 (en)* | 2018-01-31 | 2019-08-01 | Citrix Systems, Inc. | Systems and methods for authenticating device users through behavioral analysis |
| US10956075B2 (en) | 2018-02-02 | 2021-03-23 | Bank Of America Corporation | Blockchain architecture for optimizing system performance and data storage |
| US11176101B2 (en) | 2018-02-05 | 2021-11-16 | Bank Of America Corporation | System and method for decentralized regulation and hierarchical control of blockchain architecture |
| US10389574B1 (en) | 2018-02-07 | 2019-08-20 | Extrahop Networks, Inc. | Ranking alerts based on network monitoring |
| US10264003B1 (en) | 2018-02-07 | 2019-04-16 | Extrahop Networks, Inc. | Adaptive network monitoring with tuneable elastic granularity |
| US10038611B1 (en) | 2018-02-08 | 2018-07-31 | Extrahop Networks, Inc. | Personalization of alerts based on network monitoring |
| US10585724B2 (en) | 2018-04-13 | 2020-03-10 | Banjo, Inc. | Notifying entities of relevant events |
| US10970184B2 (en) | 2018-02-09 | 2021-04-06 | Banjo, Inc. | Event detection removing private information |
| US10270794B1 (en) | 2018-02-09 | 2019-04-23 | Extrahop Networks, Inc. | Detection of denial of service attacks |
| CN108229590B (en)* | 2018-02-13 | 2020-05-15 | 阿里巴巴集团控股有限公司 | Method and device for acquiring multi-label user portrait |
| US11609984B2 (en)* | 2018-02-14 | 2023-03-21 | Digital Guardian Llc | Systems and methods for determining a likelihood of an existence of malware on an executable |
| US10884805B2 (en)* | 2018-02-15 | 2021-01-05 | Amazon Technologies, Inc. | Dynamically configurable operation information collection |
| US11522887B2 (en) | 2018-02-20 | 2022-12-06 | Darktrace Holdings Limited | Artificial intelligence controller orchestrating network components for a cyber threat defense |
| US11477222B2 (en) | 2018-02-20 | 2022-10-18 | Darktrace Holdings Limited | Cyber threat defense system protecting email networks with machine learning models using a range of metadata from observed email communications |
| US11463457B2 (en)* | 2018-02-20 | 2022-10-04 | Darktrace Holdings Limited | Artificial intelligence (AI) based cyber threat analyst to support a cyber security appliance |
| US11924238B2 (en) | 2018-02-20 | 2024-03-05 | Darktrace Holdings Limited | Cyber threat defense system, components, and a method for using artificial intelligence models trained on a normal pattern of life for systems with unusual data sources |
| US12063243B2 (en) | 2018-02-20 | 2024-08-13 | Darktrace Holdings Limited | Autonomous email report generator |
| US11985142B2 (en) | 2020-02-28 | 2024-05-14 | Darktrace Holdings Limited | Method and system for determining and acting on a structured document cyber threat risk |
| US11962552B2 (en) | 2018-02-20 | 2024-04-16 | Darktrace Holdings Limited | Endpoint agent extension of a machine learning cyber defense system for email |
| US11277421B2 (en)* | 2018-02-20 | 2022-03-15 | Citrix Systems, Inc. | Systems and methods for detecting and thwarting attacks on an IT environment |
| US10931687B2 (en)* | 2018-02-20 | 2021-02-23 | General Electric Company | Cyber-attack detection, localization, and neutralization for unmanned aerial vehicles |
| JP6795533B2 (en)* | 2018-02-27 | 2020-12-02 | 日本電信電話株式会社 | Traffic anomaly detection device, traffic anomaly detection method, and traffic anomaly detection program |
| JP7013940B2 (en)* | 2018-02-27 | 2022-02-01 | 日本電信電話株式会社 | Classification device and classification method |
| KR102031592B1 (en)* | 2018-02-27 | 2019-10-14 | 아주대학교산학협력단 | Method and apparatus for detecting the malware |
| US11238414B2 (en)* | 2018-02-28 | 2022-02-01 | Dropbox, Inc. | Generating digital associations between documents and digital calendar events based on content connections |
| EP3759633A1 (en)* | 2018-02-28 | 2021-01-06 | Cyber Defence Qcd Corporation | Methods and systems for cyber-monitoring and visually depicting cyber-activities |
| US10776462B2 (en)* | 2018-03-01 | 2020-09-15 | Bank Of America Corporation | Dynamic hierarchical learning engine matrix |
| USD841043S1 (en)* | 2018-03-02 | 2019-02-19 | Xerox Corporation | Display screen with graphical user interface for a printing machine |
| US10678569B2 (en) | 2018-03-05 | 2020-06-09 | Disney Enterprises, Inc. | Enhanced virtual desktop infrastructures |
| USD889477S1 (en) | 2018-03-06 | 2020-07-07 | Google Llc | Display screen or a portion thereof with an animated graphical interface |
| JP6977625B2 (en)* | 2018-03-07 | 2021-12-08 | 富士通株式会社 | Evaluation program, evaluation method and evaluation device |
| WO2019172813A1 (en)* | 2018-03-08 | 2019-09-12 | Telefonaktiebolaget Lm Ericsson (Publ) | Managing communication in a wireless communications network |
| CN108595473A (en)* | 2018-03-09 | 2018-09-28 | 广州市优普计算机有限公司 | A kind of big data application platform based on cloud computing |
| CN111819530B (en)* | 2018-03-09 | 2024-08-06 | 三星电子株式会社 | Electronic device and on-device method for enhancing user experience in electronic device |
| US11455641B1 (en)* | 2018-03-11 | 2022-09-27 | Secureauth Corporation | System and method to identify user and device behavior abnormalities to continuously measure transaction risk |
| US10257219B1 (en) | 2018-03-12 | 2019-04-09 | BitSight Technologies, Inc. | Correlated risk in cybersecurity |
| US11954713B2 (en) | 2018-03-13 | 2024-04-09 | Johnson Controls Tyco IP Holdings LLP | Variable refrigerant flow system with electricity consumption apportionment |
| CN108429753A (en)* | 2018-03-16 | 2018-08-21 | 重庆邮电大学 | A Fast Feature Matching Method for DDoS Intrusion Detection in Industrial Networks |
| US10958649B2 (en)* | 2018-03-21 | 2021-03-23 | Akamai Technologies, Inc. | Systems and methods for internet-wide monitoring and protection of user credentials |
| US12261870B2 (en) | 2018-03-23 | 2025-03-25 | Juniper Networks, Inc. | Tracking host threats in a network and enforcing threat policy actions for the host threats |
| US10887327B2 (en)* | 2018-03-23 | 2021-01-05 | Juniper Networks, Inc. | Enforcing threat policy actions based on network addresses of host threats |
| US10862912B2 (en) | 2018-03-23 | 2020-12-08 | Juniper Networks, Inc. | Tracking host threats in a network and enforcing threat policy actions for the host threats |
| US10958681B2 (en)* | 2018-03-23 | 2021-03-23 | Cisco Technology, Inc. | Network security indicator of compromise based on human control classifications |
| US10992519B2 (en) | 2018-03-26 | 2021-04-27 | Alien Vault, Inc. | Storage system for network information |
| CN108683517B (en)* | 2018-03-26 | 2021-03-23 | 国网冀北电力有限公司信息通信分公司 | A network fault detection system for operation and maintenance robots based on machine learning |
| US11205128B2 (en)* | 2018-03-28 | 2021-12-21 | Microsoft Technology Licensing, Llc | Inferred profiles on online social networking systems using network graphs |
| US11108787B1 (en)* | 2018-03-29 | 2021-08-31 | NortonLifeLock Inc. | Securing a network device by forecasting an attack event using a recurrent neural network |
| US11188917B2 (en)* | 2018-03-29 | 2021-11-30 | Paypal, Inc. | Systems and methods for compressing behavior data using semi-parametric or non-parametric models |
| ES2935141T3 (en)* | 2018-03-30 | 2023-03-01 | V2Com S A | System and method for the management and allocation of resources in a self-optimizing network of heterogeneous processing nodes |
| US10887326B2 (en)* | 2018-03-30 | 2021-01-05 | Microsoft Technology Licensing, Llc | Distributed system for adaptive protection against web-service- targeted vulnerability scanners |
| US11176488B2 (en)* | 2018-03-30 | 2021-11-16 | EMC IP Holding Company LLC | Online anomaly detection using pairwise agreement in heterogeneous model ensemble |
| USD928199S1 (en)* | 2018-04-02 | 2021-08-17 | Bigfoot Biomedical, Inc. | Medication delivery device with icons |
| US10972431B2 (en) | 2018-04-04 | 2021-04-06 | Sophos Limited | Device management based on groups of network adapters |
| US11140195B2 (en) | 2018-04-04 | 2021-10-05 | Sophos Limited | Secure endpoint in a heterogenous enterprise network |
| US11616758B2 (en) | 2018-04-04 | 2023-03-28 | Sophos Limited | Network device for securing endpoints in a heterogeneous enterprise network |
| US11271950B2 (en) | 2018-04-04 | 2022-03-08 | Sophos Limited | Securing endpoints in a heterogenous enterprise network |
| US10440044B1 (en) | 2018-04-08 | 2019-10-08 | Xm Cyber Ltd. | Identifying communicating network nodes in the same local network |
| US11416863B2 (en) | 2018-04-11 | 2022-08-16 | Wells Fargo Bank, N.A. | System and methods for assessing risk of fraud in an electronic transaction |
| US10812520B2 (en) | 2018-04-17 | 2020-10-20 | BitSight Technologies, Inc. | Systems and methods for external detection of misconfigured systems |
| US11314787B2 (en) | 2018-04-18 | 2022-04-26 | Forcepoint, LLC | Temporal resolution of an entity |
| US10749882B2 (en)* | 2018-04-19 | 2020-08-18 | Raytheon Bbn Technologies Corp. | Network security system and methods for encoding network connectivity for activity classification |
| US11676220B2 (en) | 2018-04-20 | 2023-06-13 | Meta Platforms, Inc. | Processing multimodal user input for assistant systems |
| US11715042B1 (en)* | 2018-04-20 | 2023-08-01 | Meta Platforms Technologies, Llc | Interpretability of deep reinforcement learning models in assistant systems |
| US11704370B2 (en) | 2018-04-20 | 2023-07-18 | Microsoft Technology Licensing, Llc | Framework for managing features across environments |
| US11010179B2 (en) | 2018-04-20 | 2021-05-18 | Facebook, Inc. | Aggregating semantic information for improved understanding of users |
| US11307880B2 (en) | 2018-04-20 | 2022-04-19 | Meta Platforms, Inc. | Assisting users with personalized and contextual communication content |
| US11514354B2 (en)* | 2018-04-20 | 2022-11-29 | Accenture Global Solutions Limited | Artificial intelligence based performance prediction system |
| US11886473B2 (en) | 2018-04-20 | 2024-01-30 | Meta Platforms, Inc. | Intent identification for agent matching by assistant systems |
| US11122064B2 (en) | 2018-04-23 | 2021-09-14 | Micro Focus Llc | Unauthorized authentication event detection |
| FR3080692B1 (en)* | 2018-04-25 | 2021-07-30 | Univ Grenoble Alpes | CYBER-PHYSICAL PROCESS SECURITY SYSTEM |
| CN108595655B (en)* | 2018-04-27 | 2022-04-01 | 福建师范大学 | Abnormal user detection method based on session feature similarity fuzzy clustering |
| US10650559B2 (en) | 2018-04-30 | 2020-05-12 | Robert Bosch Gmbh | Methods and systems for simplified graphical depictions of bipartite graphs |
| US10931674B2 (en)* | 2018-04-30 | 2021-02-23 | Paypal, Inc. | Detecting whether to implement one or more security measures on a shared resource |
| US12406280B2 (en)* | 2018-04-30 | 2025-09-02 | Affle (India) Limited | Method and system for hardware and software based user identification for advertisement fraud detection |
| CA3041875A1 (en) | 2018-05-01 | 2019-11-01 | Royal Bank Of Canada | System and method for reducing false positive security events |
| US20190340614A1 (en)* | 2018-05-04 | 2019-11-07 | International Business Machines Corporation | Cognitive methodology for sequence of events patterns in fraud detection using petri-net models |
| US11223649B2 (en)* | 2018-05-06 | 2022-01-11 | Nec Corporation | User-added-value-based ransomware detection and prevention |
| USD859450S1 (en) | 2018-05-07 | 2019-09-10 | Google Llc | Display screen or portion thereof with an animated graphical interface |
| USD894951S1 (en)* | 2018-05-07 | 2020-09-01 | Google Llc | Display screen or portion thereof with an animated graphical interface |
| USD858555S1 (en) | 2018-05-07 | 2019-09-03 | Google Llc | Display screen or portion thereof with an animated graphical interface |
| USD894952S1 (en) | 2018-05-07 | 2020-09-01 | Google Llc | Display screen or portion thereof with an animated graphical interface |
| USD858556S1 (en) | 2018-05-07 | 2019-09-03 | Google Llc | Display screen or portion thereof with an animated graphical interface |
| US10965562B2 (en)* | 2018-05-07 | 2021-03-30 | Cisco Technology, Inc. | Dynamically adjusting prediction ranges in a network assurance system |
| US11544374B2 (en)* | 2018-05-07 | 2023-01-03 | Micro Focus Llc | Machine learning-based security threat investigation guidance |
| US11238366B2 (en)* | 2018-05-10 | 2022-02-01 | International Business Machines Corporation | Adaptive object modeling and differential data ingestion for machine learning |
| US11055411B2 (en)* | 2018-05-10 | 2021-07-06 | Acronis International Gmbh | System and method for protection against ransomware attacks |
| US10530662B2 (en)* | 2018-05-11 | 2020-01-07 | Cisco Technology, Inc. | Machine learning method to validate run-time rules and detect software/hardware consistency errors for network elements |
| US10972491B1 (en)* | 2018-05-11 | 2021-04-06 | Amazon Technologies, Inc. | Anomaly detection with missing values and forecasting data streams |
| US10673883B2 (en)* | 2018-05-14 | 2020-06-02 | Cisco Technology, Inc. | Time synchronization attack detection in a deterministic network |
| US11431741B1 (en) | 2018-05-16 | 2022-08-30 | Exabeam, Inc. | Detecting unmanaged and unauthorized assets in an information technology network with a recurrent neural network that identifies anomalously-named assets |
| IT201800005412A1 (en)* | 2018-05-16 | 2019-11-16 | System and method for the creation and verification of behavioral baselines. | |
| US10116679B1 (en) | 2018-05-18 | 2018-10-30 | Extrahop Networks, Inc. | Privilege inference and monitoring based on network behavior |
| EP3794509A4 (en)* | 2018-05-18 | 2022-04-06 | Deep Labs, Inc. | SYSTEMS AND METHODS FOR GENERATION OF HASH TREES AND USE OF NEURAL NETWORKS TO PROCESS SAME |
| US11347867B2 (en) | 2018-05-18 | 2022-05-31 | Ns Holdings Llc | Methods and apparatuses to evaluate cyber security risk by establishing a probability of a cyber-attack being successful |
| US11921861B2 (en) | 2018-05-21 | 2024-03-05 | International Business Machines Corporation | Providing the status of model extraction in the presence of colluding users |
| WO2019226715A1 (en) | 2018-05-21 | 2019-11-28 | Promptlink Communications, Inc. | Techniques for assessing a customer premises equipment device |
| US11064013B2 (en)* | 2018-05-22 | 2021-07-13 | Netskope, Inc. | Data loss prevention using category-directed parsers |
| USD892151S1 (en)* | 2018-05-25 | 2020-08-04 | Nanthealth, Inc. | Display screen or portion thereof with graphical user interface |
| USD891451S1 (en)* | 2018-05-25 | 2020-07-28 | Nanthealth, Inc. | Display screen or portion thereof with graphical user interface |
| CN110545251A (en)* | 2018-05-29 | 2019-12-06 | 国际关系学院 | evidence chain construction method for Trojan attack scene |
| US11012448B2 (en) | 2018-05-30 | 2021-05-18 | Bank Of America Corporation | Dynamic cyber event analysis and control |
| US11336506B1 (en) | 2018-05-31 | 2022-05-17 | Conviva Inc. | Automatic diagnostics alerts for streaming content encoded by multiple entities |
| US12019742B1 (en)* | 2018-06-01 | 2024-06-25 | Amazon Technologies, Inc. | Automated threat modeling using application relationships |
| US20190370688A1 (en)* | 2018-06-01 | 2019-12-05 | Jumio Corporation | Machine learning for isolated data sets |
| US10536344B2 (en) | 2018-06-04 | 2020-01-14 | Cisco Technology, Inc. | Privacy-aware model generation for hybrid machine learning systems |
| US10972484B1 (en) | 2018-06-04 | 2021-04-06 | Target Brands, Inc. | Enriching malware information for use with network security analysis and malware detection |
| US11134090B1 (en) | 2018-06-04 | 2021-09-28 | Target Brands, Inc. | Network security analysis and malware detection using multiple types of malware information |
| US10735442B1 (en)* | 2018-06-04 | 2020-08-04 | Target Brands, Inc. | Network security analysis and malware detection using multiple types of malware information |
| US10965703B2 (en) | 2018-06-06 | 2021-03-30 | Reliaquest Holdings, Llc | Threat mitigation system and method |
| US11709946B2 (en) | 2018-06-06 | 2023-07-25 | Reliaquest Holdings, Llc | Threat mitigation system and method |
| US10795752B2 (en)* | 2018-06-07 | 2020-10-06 | Accenture Global Solutions Limited | Data validation |
| US11392435B2 (en) | 2018-06-07 | 2022-07-19 | Hewlett-Packard Development Company, L.P. | Evaluation of a performance parameter of a monitoring service |
| US10846268B2 (en) | 2018-06-08 | 2020-11-24 | Saphyre, Inc. and Gabino M. Roche Jr. | Technologies for file sharing |
| USD873289S1 (en)* | 2018-06-08 | 2020-01-21 | Saphyre, Inc. | Display screen or portion thereof with graphical user interface |
| US11303632B1 (en)* | 2018-06-08 | 2022-04-12 | Wells Fargo Bank, N.A. | Two-way authentication system and method |
| CN108874982A (en)* | 2018-06-11 | 2018-11-23 | 华南理工大学 | A method of based on the offline real-time processing data of Spark big data frame |
| CN108900478B (en)* | 2018-06-11 | 2021-06-11 | 创新先进技术有限公司 | Detection method and device for transaction attack and safety protection equipment |
| US11539749B2 (en) | 2018-06-12 | 2022-12-27 | Netskope, Inc. | Systems and methods for alert prioritization using security events graph |
| US11165803B2 (en)* | 2018-06-12 | 2021-11-02 | Netskope, Inc. | Systems and methods to show detailed structure in a security events graph |
| CN108667672A (en)* | 2018-06-13 | 2018-10-16 | 四川斐讯信息技术有限公司 | A kind of automatic adaptation method and router of LAN interface and wan interface |
| US10936826B2 (en) | 2018-06-14 | 2021-03-02 | International Business Machines Corporation | Proactive data breach prevention in remote translation environments |
| US11132697B2 (en) | 2018-06-15 | 2021-09-28 | Wells Fargo Bank, N.A. | Risk detection of false customer information |
| JP7098000B2 (en) | 2018-06-18 | 2022-07-08 | パロ アルト ネットワークス,インコーポレイテッド | Pattern matching based detection in IoT security |
| US11119630B1 (en) | 2018-06-19 | 2021-09-14 | Palantir Technologies Inc. | Artificial intelligence assisted evaluations and user interface for same |
| US11019083B2 (en)* | 2018-06-20 | 2021-05-25 | Cisco Technology, Inc. | System for coordinating distributed website analysis |
| US11438357B2 (en) | 2018-06-22 | 2022-09-06 | Senseon Tech Ltd | Endpoint network sensor and related cybersecurity infrastructure |
| GB2602254B (en) | 2020-12-15 | 2023-04-05 | Senseon Tech Ltd | Network traffic monitoring |
| US11171982B2 (en)* | 2018-06-22 | 2021-11-09 | International Business Machines Corporation | Optimizing ingestion of structured security information into graph databases for security analytics |
| GB201810294D0 (en)* | 2018-06-22 | 2018-08-08 | Senseon Tech Ltd | Cybe defence system |
| CN110634381A (en)* | 2018-06-25 | 2019-12-31 | 百度在线网络技术(北京)有限公司 | Method and device for determining labeling style |
| US11991061B2 (en)* | 2018-06-25 | 2024-05-21 | British Telecommunications Public Limited Company | Processing local area network diagnostic data |
| US11196649B2 (en) | 2018-06-25 | 2021-12-07 | British Telecommunications Public Limited Company | Processing local area network diagnostic data |
| US10951638B2 (en) | 2018-06-27 | 2021-03-16 | International Business Machines Corporation | Security of server hosting remote application |
| JP6984551B2 (en)* | 2018-06-27 | 2021-12-22 | 日本電信電話株式会社 | Anomaly detection device and anomaly detection method |
| US12052218B2 (en)* | 2018-06-28 | 2024-07-30 | Visa International Service Association | Systems and methods to secure API platforms |
| CN109033194B (en)* | 2018-06-28 | 2019-11-08 | 北京百度网讯科技有限公司 | Event display method and device |
| US10956573B2 (en) | 2018-06-29 | 2021-03-23 | Palo Alto Networks, Inc. | Dynamic analysis techniques for applications |
| GB2575098B (en)* | 2018-06-29 | 2020-07-29 | F Secure Corp | Method for threat control in a computer network security system |
| WO2020006562A1 (en)* | 2018-06-29 | 2020-01-02 | Rocus Group, Llc | Integrated security and threat prevention and detection device |
| US11010474B2 (en) | 2018-06-29 | 2021-05-18 | Palo Alto Networks, Inc. | Dynamic analysis techniques for applications |
| US11075951B1 (en)* | 2018-06-29 | 2021-07-27 | NortonLifeLock Inc. | Query learning for automated incident investigation and remediation |
| US11562064B2 (en) | 2018-06-29 | 2023-01-24 | Netiq Corporation | Machine learning-based security alert escalation guidance |
| US11238368B2 (en) | 2018-07-02 | 2022-02-01 | Paypal, Inc. | Machine learning and security classification of user accounts |
| US11063967B2 (en)* | 2018-07-03 | 2021-07-13 | The Boeing Company | Network threat indicator extraction and response |
| JP7235503B2 (en)* | 2018-07-03 | 2023-03-08 | 韓國電子通信研究院 | Cross-domain workflow control system and method based on hierarchical engine framework |
| CN108921728B (en)* | 2018-07-03 | 2020-11-13 | 北京科东电力控制系统有限责任公司 | Distributed real-time library system based on power grid dispatching system |
| WO2020014181A1 (en)* | 2018-07-09 | 2020-01-16 | Siemens Aktiengesellschaft | Knowledge graph for real time industrial control system security event monitoring and management |
| US10579932B1 (en)* | 2018-07-10 | 2020-03-03 | Uptake Technologies, Inc. | Computer system and method for creating and deploying an anomaly detection model based on streaming data |
| US11016939B2 (en)* | 2018-07-11 | 2021-05-25 | EMC IP Holding Company, LLC | Architecture for scalable metadata microservices orchestration |
| US10949428B2 (en) | 2018-07-12 | 2021-03-16 | Forcepoint, LLC | Constructing event distributions via a streaming scoring operation |
| US11755584B2 (en) | 2018-07-12 | 2023-09-12 | Forcepoint Llc | Constructing distributions of interrelated event features |
| US11810012B2 (en) | 2018-07-12 | 2023-11-07 | Forcepoint Llc | Identifying event distributions using interrelated events |
| US11436512B2 (en)* | 2018-07-12 | 2022-09-06 | Forcepoint, LLC | Generating extracted features from an event |
| WO2020016906A1 (en)* | 2018-07-16 | 2020-01-23 | Sriram Govindan | Method and system for intrusion detection in an enterprise |
| CN108965055B (en)* | 2018-07-17 | 2021-07-13 | 成都信息工程大学 | A network traffic anomaly detection method based on historical time point method |
| US11025638B2 (en) | 2018-07-19 | 2021-06-01 | Forcepoint, LLC | System and method providing security friction for atypical resource access requests |
| US11228614B1 (en)* | 2018-07-24 | 2022-01-18 | Amazon Technologies, Inc. | Automated management of security operations centers |
| US10601677B2 (en)* | 2018-07-25 | 2020-03-24 | Inforich Electronics Corp. | Device and method for a dynamic virtual private network and computer readable recording medium |
| CN109086605A (en)* | 2018-07-26 | 2018-12-25 | 佛山市甜慕链客科技有限公司 | A kind of distributed data processing method |
| GB201812171D0 (en) | 2018-07-26 | 2018-09-12 | Senseon Tech Ltd | Cyber defence system |
| CN109255069A (en)* | 2018-07-31 | 2019-01-22 | 阿里巴巴集团控股有限公司 | A kind of discrete text content risks recognition methods and system |
| US11194906B2 (en)* | 2018-07-31 | 2021-12-07 | Nec Corporation | Automated threat alert triage via data provenance |
| US11271939B2 (en)* | 2018-07-31 | 2022-03-08 | Splunk Inc. | Facilitating detection of suspicious access to resources |
| US20210226999A1 (en)* | 2018-08-07 | 2021-07-22 | Triad National Security, Llc | Modeling anomalousness of new subgraphs observed locally in a dynamic graph based on subgraph attributes and a community model |
| US11184373B2 (en)* | 2018-08-09 | 2021-11-23 | Mcafee, Llc | Cryptojacking detection |
| US10411978B1 (en) | 2018-08-09 | 2019-09-10 | Extrahop Networks, Inc. | Correlating causes and effects associated with network activity |
| US11290479B2 (en) | 2018-08-11 | 2022-03-29 | Rapid7, Inc. | Determining insights in an electronic environment |
| US11526799B2 (en)* | 2018-08-15 | 2022-12-13 | Salesforce, Inc. | Identification and application of hyperparameters for machine learning |
| US11601442B2 (en) | 2018-08-17 | 2023-03-07 | The Research Foundation For The State University Of New York | System and method associated with expedient detection and reconstruction of cyber events in a compact scenario representation using provenance tags and customizable policy |
| US11297082B2 (en)* | 2018-08-17 | 2022-04-05 | Nec Corporation | Protocol-independent anomaly detection |
| CN110019372B (en)* | 2018-08-21 | 2023-04-11 | 平安科技(深圳)有限公司 | Data monitoring method, device, server and storage medium |
| US11003767B2 (en) | 2018-08-21 | 2021-05-11 | Beijing Didi Infinity Technology And Development Co., Ltd. | Multi-layer data model for security analytics |
| US10594718B1 (en)* | 2018-08-21 | 2020-03-17 | Extrahop Networks, Inc. | Managing incident response operations based on monitored network activity |
| TWI726749B (en)* | 2018-08-22 | 2021-05-01 | 新加坡商賽博創新新加坡股份有限公司 | Method for diagnosing whether network system is breached by hackers and related method for generating multiple associated data frames |
| US11500655B2 (en) | 2018-08-22 | 2022-11-15 | Microstrategy Incorporated | Inline and contextual delivery of database content |
| US10944791B2 (en)* | 2018-08-27 | 2021-03-09 | Microsoft Technology Licensing, Llc | Increasing security of network resources utilizing virtual honeypots |
| CN109165325B (en)* | 2018-08-27 | 2021-08-17 | 北京百度网讯科技有限公司 | Method, apparatus, device, and computer-readable storage medium for slicing graph data |
| CN112640380B (en) | 2018-08-27 | 2022-08-19 | 华为云计算技术有限公司 | Apparatus and method for anomaly detection of an input stream of events |
| US11146467B2 (en)* | 2018-08-30 | 2021-10-12 | Streamworx.Ai Inc. | Systems, methods and computer program products for scalable, low-latency processing of streaming data |
| US11645093B2 (en) | 2018-08-30 | 2023-05-09 | Express Scripts Strategic Development, Inc. | Systems and methods for user interface adaptation for per-user metrics |
| US10896048B1 (en) | 2018-08-30 | 2021-01-19 | Express Scripts Strategie Development, Inc. | Systems and methods for user interface adaptation for per-user metrics |
| GB2614426B (en)* | 2018-08-31 | 2023-10-11 | Sophos Ltd | Enterprise network threat detection |
| US10846651B2 (en) | 2018-08-31 | 2020-11-24 | Kinaxis Inc. | Analysis and correction of supply chain design through machine learning |
| US11552962B2 (en)* | 2018-08-31 | 2023-01-10 | Sophos Limited | Computer assisted identification of intermediate level threats |
| US10832196B2 (en) | 2018-08-31 | 2020-11-10 | Kinaxis Inc. | Analysis and correction of supply chain design through machine learning |
| US10757093B1 (en) | 2018-08-31 | 2020-08-25 | Splunk Inc. | Identification of runtime credential requirements |
| US11811799B2 (en) | 2018-08-31 | 2023-11-07 | Forcepoint Llc | Identifying security risks using distributions of characteristic features extracted from a plurality of events |
| US10853478B1 (en)* | 2018-08-31 | 2020-12-01 | Splunk Inc. | Encrypted storage and provision of authentication information for use when responding to an information technology incident |
| CN109255237B (en)* | 2018-08-31 | 2020-10-09 | 新华三大数据技术有限公司 | Security event correlation analysis method and device |
| JP7156869B2 (en)* | 2018-09-03 | 2022-10-19 | パナソニックホールディングス株式会社 | Log output device, log output method and log output system |
| US10834214B2 (en)* | 2018-09-04 | 2020-11-10 | At&T Intellectual Property I, L.P. | Separating intended and non-intended browsing traffic in browsing history |
| EP3847571A4 (en) | 2018-09-04 | 2022-06-01 | Palo Alto Networks, Inc. | LEARN AN IOT APPLICATION |
| US11265324B2 (en) | 2018-09-05 | 2022-03-01 | Consumerinfo.Com, Inc. | User permissions for access to secure data at third-party |
| US11030311B1 (en)* | 2018-09-07 | 2021-06-08 | Ca, Inc. | Detecting and protecting against computing breaches based on lateral movement of a computer file within an enterprise |
| US10382473B1 (en) | 2018-09-12 | 2019-08-13 | Xm Cyber Ltd. | Systems and methods for determining optimal remediation recommendations in penetration testing |
| US11113173B2 (en)* | 2018-09-13 | 2021-09-07 | Rovi Guides, Inc. | Systems and methods for detecting, analyzing, and evaluating interaction paths |
| US11017088B2 (en)* | 2018-09-17 | 2021-05-25 | Microsofttechnology Licensing, Llc | Crowdsourced, self-learning security system through smart feedback loops |
| CN109242633B (en)* | 2018-09-20 | 2022-04-08 | 创新先进技术有限公司 | Commodity pushing method and device based on bipartite graph network |
| US11003568B2 (en) | 2018-09-22 | 2021-05-11 | Manhattan Engineering Incorporated | Error recovery |
| US10531305B1 (en)* | 2018-09-27 | 2020-01-07 | Palo Alto Networks, Inc. | Service-based security per subscription and/or equipment identifiers in mobile networks |
| US10462653B1 (en) | 2018-09-27 | 2019-10-29 | Palo Alto Networks, Inc. | Service-based security per data network name in mobile networks |
| EP3857853B1 (en)* | 2018-09-27 | 2023-11-01 | OPSWAT Inc. | System and methods for automated computer security policy generation and anomaly detection |
| US10574670B1 (en) | 2018-09-27 | 2020-02-25 | Palo Alto Networks, Inc. | Multi-access distributed edge security in mobile networks |
| US10477390B1 (en)* | 2018-09-27 | 2019-11-12 | Palo Alto Networks, Inc. | Service-based security per user location in mobile networks |
| US10944796B2 (en) | 2018-09-27 | 2021-03-09 | Palo Alto Networks, Inc. | Network slice-based security in mobile networks |
| US11475053B1 (en) | 2018-09-28 | 2022-10-18 | Splunk Inc. | Providing completion recommendations for a partial natural language request received by a natural language processing system |
| US11017764B1 (en)* | 2018-09-28 | 2021-05-25 | Splunk Inc. | Predicting follow-on requests to a natural language request received by a natural language processing system |
| US11762869B1 (en) | 2018-09-28 | 2023-09-19 | Splunk Inc. | Generating journey flow visualization with node placement based on shortest distance to journey start |
| US11144185B1 (en) | 2018-09-28 | 2021-10-12 | Splunk Inc. | Generating and providing concurrent journey visualizations associated with different journey definitions |
| US11334832B2 (en)* | 2018-10-03 | 2022-05-17 | Verint Americas Inc. | Risk assessment using Poisson Shelves |
| US11469969B2 (en)* | 2018-10-04 | 2022-10-11 | Hewlett Packard Enterprise Development Lp | Intelligent lifecycle management of analytic functions for an IoT intelligent edge with a hypergraph-based approach |
| USD899437S1 (en) | 2018-10-05 | 2020-10-20 | Vmware, Inc. | Display screen, or portion thereof, having a graphical user interface |
| US11086914B2 (en)* | 2018-10-08 | 2021-08-10 | International Business Machines Corporation | Archiving of topmost ranked answers of a cognitive search |
| US10728307B2 (en)* | 2018-10-08 | 2020-07-28 | Sonrai Security Inc. | Cloud intelligence data model and framework |
| EP3848806A4 (en)* | 2018-10-11 | 2021-11-03 | Nippon Telegraph And Telephone Corporation | INFORMATION PROCESSING DEVICE, PROTOCOL ANALYSIS PROCEDURE AND PROGRAM FOR IT |
| US11354320B2 (en)* | 2018-10-11 | 2022-06-07 | International Business Machines Corporation | Determining causes of events in data |
| CN119782027A (en) | 2018-10-15 | 2025-04-08 | 帕洛阿尔托网络公司 | Multi-dimensional periodic detection of IoT device behavior |
| US12288222B2 (en) | 2018-10-15 | 2025-04-29 | Affle (India) Limited | Method and system for application installation and detection of fraud in advertisement |
| US11200323B2 (en) | 2018-10-17 | 2021-12-14 | BitSight Technologies, Inc. | Systems and methods for forecasting cybersecurity ratings based on event-rate scenarios |
| CN109375912B (en)* | 2018-10-18 | 2021-09-21 | 腾讯科技(北京)有限公司 | Model serialization method, device and storage medium |
| US11258827B2 (en) | 2018-10-19 | 2022-02-22 | Oracle International Corporation | Autonomous monitoring of applications in a cloud environment |
| US11392894B2 (en)* | 2018-10-19 | 2022-07-19 | Oracle International Corporation | Systems and methods for intelligent field matching and anomaly detection |
| CN109410109B (en)* | 2018-10-19 | 2020-10-16 | 智器云南京信息科技有限公司 | Big data based accompanying event analysis method and system |
| US11568179B2 (en)* | 2018-10-19 | 2023-01-31 | Oracle International Corporation | Selecting an algorithm for analyzing a data set based on the distribution of the data set |
| US11573962B2 (en) | 2018-10-19 | 2023-02-07 | Oracle International Corporation | Dynamic performance tuning based on implied data characteristics |
| US10805343B2 (en)* | 2018-10-22 | 2020-10-13 | Booz Allen Hamilton Inc. | Network security using artificial intelligence and high speed computing |
| US11025659B2 (en) | 2018-10-23 | 2021-06-01 | Forcepoint, LLC | Security system using pseudonyms to anonymously identify entities and corresponding security risk related behaviors |
| US10977265B2 (en)* | 2018-10-23 | 2021-04-13 | Drumwave Inc. | Path-based population visualization |
| CN109344906B (en)* | 2018-10-24 | 2024-08-27 | 中国平安人寿保险股份有限公司 | User risk classification method, device, medium and equipment based on machine learning |
| US11269995B2 (en) | 2018-10-25 | 2022-03-08 | Micro Focus Llc | Chain of events representing an issue based on an enriched representation |
| US11354325B2 (en) | 2018-10-25 | 2022-06-07 | Bank Of America Corporation | Methods and apparatus for a multi-graph search and merge engine |
| US10521583B1 (en) | 2018-10-25 | 2019-12-31 | BitSight Technologies, Inc. | Systems and methods for remote detection of software through browser webinjects |
| US11258817B2 (en)* | 2018-10-26 | 2022-02-22 | Tenable, Inc. | Rule-based assignment of criticality scores to assets and generation of a criticality rules table |
| US11711398B2 (en) | 2018-10-26 | 2023-07-25 | Netography, Inc. | Distributed network security service |
| US20200136923A1 (en) | 2018-10-28 | 2020-04-30 | Netz Forecasts Ltd. | Systems and methods for prediction of anomalies |
| US11126612B2 (en)* | 2018-10-29 | 2021-09-21 | EMC IP Holding Company LLC | Identifying anomalies in user internet of things activity profile using analytic engine |
| US12174963B1 (en) | 2018-10-29 | 2024-12-24 | Amazon Technologies, Inc. | Automated selection of secure design patterns |
| TWI704782B (en)* | 2018-10-29 | 2020-09-11 | 財團法人電信技術中心 | Method and system for backbone network flow anomaly detection |
| TWI710922B (en)* | 2018-10-29 | 2020-11-21 | 安碁資訊股份有限公司 | System and method of training behavior labeling model |
| US11488727B2 (en)* | 2018-10-30 | 2022-11-01 | LogicMatter, Inc. | Immutable system of records for IoT/control systems for compliance |
| US11016648B2 (en)* | 2018-10-30 | 2021-05-25 | Johnson Controls Technology Company | Systems and methods for entity visualization and management with an entity node editor |
| US11388040B2 (en) | 2018-10-31 | 2022-07-12 | EXFO Solutions SAS | Automatic root cause diagnosis in networks |
| US12113768B2 (en)* | 2018-10-31 | 2024-10-08 | Hewlett Packard Enterprise Development Lp | Using intent to access in discovery protocols in a network for analytics |
| US11055162B2 (en)* | 2018-10-31 | 2021-07-06 | Salesforce.Com, Inc. | Database system performance degradation detection |
| US11171980B2 (en) | 2018-11-02 | 2021-11-09 | Forcepoint Llc | Contagion risk detection, analysis and protection |
| US10469521B1 (en) | 2018-11-04 | 2019-11-05 | Xm Cyber Ltd. | Using information about exportable data in penetration testing |
| US10924481B2 (en) | 2018-11-06 | 2021-02-16 | Bank Of America Corporation | Processing system for providing console access to a cyber range virtual environment |
| US10958670B2 (en) | 2018-11-06 | 2021-03-23 | Bank Of America Corporation | Processing system for providing console access to a cyber range virtual environment |
| US11012463B2 (en)* | 2018-11-07 | 2021-05-18 | International Business Machines Corporation | Predicting condition of a host for cybersecurity applications |
| USD899440S1 (en)* | 2018-11-09 | 2020-10-20 | Life Technologies Corporation | Display screen or portion thereof with graphical user interface |
| CN109672663B (en)* | 2018-11-09 | 2022-03-25 | 杭州安恒信息技术股份有限公司 | A closed-loop network security supervision method and system for security threat events |
| US11481665B2 (en) | 2018-11-09 | 2022-10-25 | Hewlett Packard Enterprise Development Lp | Systems and methods for determining machine learning training approaches based on identified impacts of one or more types of concept drift |
| US11514172B2 (en) | 2018-11-15 | 2022-11-29 | Grabango Co. | System and method for information flow analysis of application code |
| DE112018008071B4 (en)* | 2018-11-16 | 2023-08-31 | Mitsubishi Electric Corporation | ATTACK DETECTION DEVICE, ATTACK DETECTION METHOD AND ATTACK DETECTION PROGRAM |
| US11315179B1 (en) | 2018-11-16 | 2022-04-26 | Consumerinfo.Com, Inc. | Methods and apparatuses for customized card recommendations |
| US10630726B1 (en) | 2018-11-18 | 2020-04-21 | Bank Of America Corporation | Cybersecurity threat detection and mitigation system |
| US11927925B2 (en) | 2018-11-19 | 2024-03-12 | Johnson Controls Tyco IP Holdings LLP | Building system with a time correlated reliability data stream |
| US11232204B2 (en)* | 2018-11-20 | 2022-01-25 | Sap Se | Threat detection using artifact change analysis |
| US11269911B1 (en)* | 2018-11-23 | 2022-03-08 | Amazon Technologies, Inc. | Using specified performance attributes to configure machine learning pipeline stages for an ETL job |
| US11562225B2 (en)* | 2018-11-26 | 2023-01-24 | International Business Machines Corporation | Automatic monitoring and adjustment of machine learning model training |
| US10681056B1 (en) | 2018-11-27 | 2020-06-09 | Sailpoint Technologies, Inc. | System and method for outlier and anomaly detection in identity management artificial intelligence systems using cluster based analysis of network identity graphs |
| US10341430B1 (en) | 2018-11-27 | 2019-07-02 | Sailpoint Technologies, Inc. | System and method for peer group detection, visualization and analysis in identity management artificial intelligence systems using cluster based analysis of network identity graphs |
| US11023576B2 (en)* | 2018-11-28 | 2021-06-01 | International Business Machines Corporation | Detecting malicious activity on a computer system |
| US10776231B2 (en)* | 2018-11-29 | 2020-09-15 | International Business Machines Corporation | Adaptive window based anomaly detection |
| US10824676B2 (en) | 2018-11-29 | 2020-11-03 | Bank Of America Corporation | Hybrid graph and relational database architecture |
| EP3660716B1 (en) | 2018-11-30 | 2020-12-23 | Ovh | Service infrastructure and methods of predicting and detecting potential anomalies at the service infrastructure |
| US11025666B1 (en)* | 2018-12-03 | 2021-06-01 | NortonLifeLock Inc. | Systems and methods for preventing decentralized malware attacks |
| US10803182B2 (en) | 2018-12-03 | 2020-10-13 | Bank Of America Corporation | Threat intelligence forest for distributed software libraries |
| CN109600365A (en)* | 2018-12-04 | 2019-04-09 | 沈阳安信合科技有限公司 | Gene similitude intrusion detection method based on electric power networks IEC specification |
| US11176230B2 (en) | 2018-12-05 | 2021-11-16 | Bank Of America Corporation | Processing authentication requests to secured information systems based on user behavior profiles |
| US11113370B2 (en) | 2018-12-05 | 2021-09-07 | Bank Of America Corporation | Processing authentication requests to secured information systems using machine-learned user-account behavior profiles |
| CN109542011B (en)* | 2018-12-05 | 2021-10-22 | 国网江西省电力有限公司信息通信分公司 | A Standardized Acquisition System of Multi-source Heterogeneous Monitoring Data |
| US11036838B2 (en) | 2018-12-05 | 2021-06-15 | Bank Of America Corporation | Processing authentication requests to secured information systems using machine-learned user-account behavior profiles |
| US11048793B2 (en) | 2018-12-05 | 2021-06-29 | Bank Of America Corporation | Dynamically generating activity prompts to build and refine machine learning authentication models |
| US11159510B2 (en) | 2018-12-05 | 2021-10-26 | Bank Of America Corporation | Utilizing federated user identifiers to enable secure information sharing |
| US11120109B2 (en) | 2018-12-05 | 2021-09-14 | Bank Of America Corporation | Processing authentication requests to secured information systems based on machine-learned event profiles |
| JP7211052B2 (en)* | 2018-12-06 | 2023-01-24 | 富士通株式会社 | AUTOMATIC GENERATION METHOD OF STREAM PROCESSING PIPELINE, DATA STREAM PROCESSING PROGRAM AND DATA STREAM PROCESSING SYSTEM |
| CN109361699A (en)* | 2018-12-06 | 2019-02-19 | 四川长虹电器股份有限公司 | Anomalous traffic detection method based on Spark Streaming |
| CN109450700B (en)* | 2018-12-07 | 2022-04-12 | 中国联合网络通信集团有限公司 | Visual service detection method and device |
| US12114185B2 (en) | 2018-12-11 | 2024-10-08 | Teleonaktiebolaget LM Ericsson (publ) | Method and system to predict network performance of a fixed wireless network |
| US11568133B2 (en)* | 2018-12-11 | 2023-01-31 | Intuit Inc. | Method and apparatus for detecting anomalies in mission critical environments |
| US11645293B2 (en) | 2018-12-11 | 2023-05-09 | EXFO Solutions SAS | Anomaly detection in big data time series analysis |
| US11451571B2 (en) | 2018-12-12 | 2022-09-20 | Palo Alto Networks, Inc. | IoT device risk assessment and scoring |
| WO2020122902A1 (en) | 2018-12-12 | 2020-06-18 | Hewlett-Packard Development Company, L.P. | Updates of machine learning models based on confidential data |
| US10574687B1 (en) | 2018-12-13 | 2020-02-25 | Xm Cyber Ltd. | Systems and methods for dynamic removal of agents from nodes of penetration testing systems |
| US11743153B2 (en)* | 2018-12-14 | 2023-08-29 | Newsouth Innovations Pty Limited | Apparatus and process for monitoring network behaviour of Internet-of-things (IoT) devices |
| US11122084B1 (en) | 2018-12-17 | 2021-09-14 | Wells Fargo Bank, N.A. | Automatic monitoring and modeling |
| US10958677B2 (en)* | 2018-12-18 | 2021-03-23 | At&T Intellectual Property I, L.P. | Risk identification for unlabeled threats in network traffic |
| US11032312B2 (en) | 2018-12-19 | 2021-06-08 | Abnormal Security Corporation | Programmatic discovery, retrieval, and analysis of communications to identify abnormal communication activity |
| US11050793B2 (en) | 2018-12-19 | 2021-06-29 | Abnormal Security Corporation | Retrospective learning of communication patterns by machine learning models for discovering abnormal behavior |
| CN109635948A (en)* | 2018-12-19 | 2019-04-16 | 北京达佳互联信息技术有限公司 | On-line training method, apparatus, system and computer readable storage medium |
| US11824870B2 (en) | 2018-12-19 | 2023-11-21 | Abnormal Security Corporation | Threat detection platforms for detecting, characterizing, and remediating email-based threats in real time |
| US11087179B2 (en) | 2018-12-19 | 2021-08-10 | Netskope, Inc. | Multi-label classification of text documents |
| US11431738B2 (en) | 2018-12-19 | 2022-08-30 | Abnormal Security Corporation | Multistage analysis of emails to identify security threats |
| WO2020129031A1 (en)* | 2018-12-21 | 2020-06-25 | Element Ai Inc. | Method and system for generating investigation cases in the context of cybersecurity |
| US11140179B1 (en)* | 2018-12-26 | 2021-10-05 | Musarubra Us Llc | Cybersecurity investigation tools utilizing information graphs |
| US11301496B2 (en)* | 2018-12-26 | 2022-04-12 | Imperva, Inc. | Using access logs for network entities type classification |
| CN111381567B (en)* | 2018-12-27 | 2021-11-05 | 北京安控科技股份有限公司 | Safety detection system and method for industrial control system |
| US11223638B2 (en) | 2018-12-27 | 2022-01-11 | Rapid7, Inc. | Stable network user account classifier |
| CN111385747B (en)* | 2018-12-27 | 2023-05-16 | 物流及供应链多元技术研发中心有限公司 | Systems and methods for attack detection in wireless beacon systems |
| US11330016B2 (en)* | 2018-12-28 | 2022-05-10 | Imperva, Inc. | Generating collection rules based on security rules |
| RU2739866C2 (en)* | 2018-12-28 | 2020-12-29 | Акционерное общество "Лаборатория Касперского" | Method for detecting compatible means for systems with anomalies |
| US11487879B2 (en)* | 2018-12-28 | 2022-11-01 | Tenable, Inc. | Threat score prediction model |
| KR102165494B1 (en)* | 2018-12-28 | 2020-10-14 | 네이버 주식회사 | Method, apparatus and computer program for detecting abusing activity in online service |
| RU2739865C2 (en)* | 2018-12-28 | 2020-12-29 | Акционерное общество "Лаборатория Касперского" | System and method of detecting a malicious file |
| US11146581B2 (en)* | 2018-12-31 | 2021-10-12 | Radware Ltd. | Techniques for defending cloud platforms against cyber-attacks |
| US11159945B2 (en)* | 2018-12-31 | 2021-10-26 | T-Mobile Usa, Inc. | Protecting a telecommunications network using network components as blockchain nodes |
| US10438001B1 (en)* | 2018-12-31 | 2019-10-08 | Arceo Labs Inc. | Identification, prediction, and assessment of cyber security risk |
| US11329982B2 (en) | 2018-12-31 | 2022-05-10 | T-Mobile Usa, Inc. | Managing internet of things devices using blockchain operations |
| EP4369229A3 (en)* | 2018-12-31 | 2024-09-25 | INTEL Corporation | Securing systems employing artificial intelligence |
| US11689573B2 (en) | 2018-12-31 | 2023-06-27 | Palo Alto Networks, Inc. | Multi-layered policy management |
| US11039317B2 (en) | 2018-12-31 | 2021-06-15 | T-Mobile Usa, Inc. | Using a blockchain to determine trustworthiness of messages within a telecommunications network for a smart city |
| US11601787B2 (en) | 2018-12-31 | 2023-03-07 | T-Mobile Usa, Inc. | Using a blockchain to determine trustworthiness of messages between vehicles over a telecommunications network |
| US10936659B2 (en) | 2019-01-02 | 2021-03-02 | International Business Machines Corporation | Parallel graph events processing |
| US11496475B2 (en) | 2019-01-04 | 2022-11-08 | Ping Identity Corporation | Methods and systems for data traffic based adaptive security |
| US20200218940A1 (en)* | 2019-01-08 | 2020-07-09 | International Business Machines Corporation | Creating and managing machine learning models in a shared network environment |
| US12367443B2 (en) | 2019-01-14 | 2025-07-22 | Tyco Fire & Security Gmbh | System and method for showing key performance indicators |
| US11159360B2 (en)* | 2019-01-15 | 2021-10-26 | Cisco Technology, Inc. | Dynamic statistics correlation for computing resources in a multi-tenant environment |
| US11334665B2 (en)* | 2019-01-17 | 2022-05-17 | Jpmorgan Chase Bank, N.A. | Systems and methods for automated detection and analysis of security threats |
| US11769117B2 (en) | 2019-01-18 | 2023-09-26 | Johnson Controls Tyco IP Holdings LLP | Building automation system with fault analysis and component procurement |
| US10977112B2 (en) | 2019-01-22 | 2021-04-13 | International Business Machines Corporation | Performance anomaly detection |
| US11487873B2 (en)* | 2019-01-22 | 2022-11-01 | EMC IP Holding Company LLC | Risk score generation utilizing monitored behavior and predicted impact of compromise |
| US10986121B2 (en) | 2019-01-24 | 2021-04-20 | Darktrace Limited | Multivariate network structure anomaly detector |
| US11480934B2 (en)* | 2019-01-24 | 2022-10-25 | Uptake Technologies, Inc. | Computer system and method for creating an event prediction model |
| US11374948B2 (en) | 2019-01-25 | 2022-06-28 | Target Brands, Inc. | Computer security system with network traffic analysis |
| USD916865S1 (en)* | 2019-01-25 | 2021-04-20 | Aristocrat Technologies Australia Pty Limited | Display screen or portion thereof with transitional graphical user interface |
| US11038910B1 (en)* | 2019-01-25 | 2021-06-15 | Trend Micro Incorporated | Cybersecurity for a smart home |
| US10788798B2 (en) | 2019-01-28 | 2020-09-29 | Johnson Controls Technology Company | Building management system with hybrid edge-cloud processing |
| US11113650B2 (en)* | 2019-01-30 | 2021-09-07 | EMC IP Holding Company LLC | Automated generation of adaptive policies from organizational data for detection of risk-related events |
| US11763154B1 (en) | 2019-01-30 | 2023-09-19 | Amazon Technologies, Inc. | Machine learning services with pre-trained models |
| US11425149B2 (en) | 2019-01-31 | 2022-08-23 | Rapid7, Inc. | Multi-baseline unsupervised security-incident and network behavioral anomaly detection in cloud-based compute environments |
| US12010127B1 (en)* | 2019-01-31 | 2024-06-11 | Rapid7 Israel Technologies Limited | Cyberattack detection using probabilistic graphical models |
| CN109829543B (en)* | 2019-01-31 | 2020-05-26 | 中国科学院空间应用工程与技术中心 | Space effective load data flow online anomaly detection method based on ensemble learning |
| US10997192B2 (en) | 2019-01-31 | 2021-05-04 | Splunk Inc. | Data source correlation user interface |
| US11297142B2 (en)* | 2019-01-31 | 2022-04-05 | Nec Corporation | Temporal discrete event analytics system |
| US12008222B1 (en)* | 2019-01-31 | 2024-06-11 | Rapid7 Israel Technologies Limited | Unsupervised detection of security incidents in a cloud environment |
| US11405413B2 (en) | 2019-02-01 | 2022-08-02 | Microsoft Technology Licensing, Llc | Anomaly lookup for cyber security hunting |
| US20200252281A1 (en)* | 2019-02-05 | 2020-08-06 | Microstrategy Incorporated | System performance using semantic graph data |
| US11829417B2 (en) | 2019-02-05 | 2023-11-28 | Microstrategy Incorporated | Context-based customization using semantic graph data |
| US11625426B2 (en) | 2019-02-05 | 2023-04-11 | Microstrategy Incorporated | Incorporating opinion information with semantic graph data |
| WO2020161532A1 (en) | 2019-02-06 | 2020-08-13 | Xm Cyber Ltd. | Taking privilege escalation into account in penetration testing campaigns |
| US12375502B2 (en)* | 2019-02-08 | 2025-07-29 | Fortinet, Inc. | Providing secure data-replication between a master node and tenant nodes of a multi-tenancy architecture |
| US10592544B1 (en) | 2019-02-12 | 2020-03-17 | Live Objects, Inc. | Generation of process models in domains with unstructured data |
| US10819797B2 (en) | 2019-02-12 | 2020-10-27 | Citrix Systems, Inc. | Computing system providing SaaS application integration with internet of things (IoT) sensors through automated application program interface (API) generation and related methods |
| US10607042B1 (en) | 2019-02-12 | 2020-03-31 | Live Objects, Inc. | Dynamically trained models of named entity recognition over unstructured data |
| CN109828751A (en)* | 2019-02-15 | 2019-05-31 | 福州大学 | Integrated machine learning algorithm library and unified programming framework |
| US11637738B2 (en) | 2019-02-18 | 2023-04-25 | Sap Se | Logical networking and affinity determination of IoT devices using partitioned virtual space |
| US11330048B2 (en)* | 2019-02-18 | 2022-05-10 | Sap Se | Affinity determination and logical networking of IoT devices |
| US11238656B1 (en) | 2019-02-22 | 2022-02-01 | Consumerinfo.Com, Inc. | System and method for an augmented reality experience via an artificial intelligence bot |
| US10768908B1 (en)* | 2019-02-25 | 2020-09-08 | Microsoft Technology Licensing, Llc | Workflow engine tool |
| CN109902176B (en)* | 2019-02-26 | 2021-07-13 | 北京微步在线科技有限公司 | A data association extension method and non-transitory computer instruction storage medium |
| US10523682B1 (en) | 2019-02-26 | 2019-12-31 | Sailpoint Technologies, Inc. | System and method for intelligent agents for decision support in network identity graph based identity management artificial intelligence systems |
| US10447727B1 (en)* | 2019-02-27 | 2019-10-15 | Cyberark Software Ltd. | Predicting and addressing harmful or sensitive network activity |
| IN201911007700A (en) | 2019-02-27 | 2019-03-22 | ||
| US11057410B1 (en) | 2019-02-27 | 2021-07-06 | Rapid7, Inc. | Data exfiltration detector |
| US11283827B2 (en) | 2019-02-28 | 2022-03-22 | Xm Cyber Ltd. | Lateral movement strategy during penetration testing of a networked system |
| US10554665B1 (en) | 2019-02-28 | 2020-02-04 | Sailpoint Technologies, Inc. | System and method for role mining in identity management artificial intelligence systems using cluster based analysis of network identity graphs |
| US11063897B2 (en)* | 2019-03-01 | 2021-07-13 | Cdw Llc | Method and system for analyzing electronic communications and customer information to recognize and mitigate message-based attacks |
| US11968240B2 (en)* | 2019-03-04 | 2024-04-23 | Cisco Technology, Inc. | Network posture based suggestion of applications and services |
| US11106789B2 (en)* | 2019-03-05 | 2021-08-31 | Microsoft Technology Licensing, Llc | Dynamic cybersecurity detection of sequence anomalies |
| USD904429S1 (en)* | 2019-03-07 | 2020-12-08 | Fujifilm Sonosite, Inc. | Display screen or portion thereof with an animated graphical user interface |
| CN110008100B (en)* | 2019-03-08 | 2023-03-14 | 创新先进技术有限公司 | Method and device for detecting abnormal access volume of web page |
| WO2020186009A1 (en)* | 2019-03-12 | 2020-09-17 | Ellucian Company L.P. | Systems and methods for aiding higher education administration using machine learning models |
| US11531908B2 (en) | 2019-03-12 | 2022-12-20 | Ebay Inc. | Enhancement of machine learning-based anomaly detection using knowledge graphs |
| EP3938898A4 (en)* | 2019-03-13 | 2023-03-29 | Cognizant Technology Solutions U.S. Corporation | System and method for implementing modular universal reparameterization for deep multi-task learning across diverse domains |
| US11228485B2 (en) | 2019-03-14 | 2022-01-18 | Cisco Technology, Inc. | Dynamic action dashlet for real-time systems operation management |
| CN109933620A (en)* | 2019-03-18 | 2019-06-25 | 上海大学 | Spark-based thermal power big data mining method |
| US10931706B2 (en)* | 2019-03-20 | 2021-02-23 | Booz Allen Hamilton Inc. | System and method for detecting and identifying a cyber-attack on a network |
| US11336617B2 (en) | 2019-03-21 | 2022-05-17 | Cisco Technology, Inc. | Graphical representation of security threats in a network |
| RU2747474C2 (en)* | 2019-03-29 | 2021-05-05 | Акционерное общество "Лаборатория Касперского" | Method for asynchronous selection of compatible products |
| US10922218B2 (en)* | 2019-03-25 | 2021-02-16 | Aurora Labs Ltd. | Identifying software interdependencies using line-of-code behavior and relation models |
| WO2020198520A1 (en) | 2019-03-27 | 2020-10-01 | Cognizant Technology Solutions U.S. Corporation | Process and system including an optimization engine with evolutionary surrogate-assisted prescriptions |
| US11171978B2 (en) | 2019-03-27 | 2021-11-09 | Microsoft Technology Licensing, Llc. | Dynamic monitoring, detection of emerging computer events |
| AU2020204346B2 (en)* | 2019-03-28 | 2021-09-30 | Palo Alto Networks, Inc. | Multi-access distributed edge security in mobile networks |
| US11265336B2 (en)* | 2019-03-28 | 2022-03-01 | Red Hat, Inc. | Detecting anomalies in networks |
| US11363036B2 (en)* | 2019-03-28 | 2022-06-14 | Microsoft Technology Licensing, Llc | Detecting a missing security alert using a machine learning model |
| FR3094600B1 (en)* | 2019-03-29 | 2022-05-06 | Orange | Method for extracting at least one communication pattern in a communication network |
| US11212298B2 (en)* | 2019-04-04 | 2021-12-28 | Microsoft Technology Licensing, Llc | Automated onboarding of detections for security operations center monitoring |
| WO2020206204A1 (en)* | 2019-04-05 | 2020-10-08 | Choral Systems, Llc | Data analysis and visualization using structured data tables and nodal networks |
| US11475368B2 (en) | 2019-04-05 | 2022-10-18 | Zscaler, Inc. | Machine learning model abstraction layer for runtime efficiency |
| US11770311B2 (en)* | 2019-04-05 | 2023-09-26 | Palo Alto Networks, Inc. | Automatic and dynamic performance benchmarking and scoring of applications based on crowdsourced traffic data |
| US11082434B2 (en) | 2019-04-06 | 2021-08-03 | International Business Machines Corporation | Inferring temporal relationships for cybersecurity events |
| WO2020210362A1 (en)* | 2019-04-08 | 2020-10-15 | Ares Technologies, Inc. | Systems, devices, and methods for machine learning using a distributed framework |
| US11681831B2 (en) | 2019-04-10 | 2023-06-20 | International Business Machines Corporation | Threat detection using hardware physical properties and operating system metrics with AI data mining |
| US11330005B2 (en)* | 2019-04-15 | 2022-05-10 | Vectra Ai, Inc. | Privileged account breach detections based on behavioral access patterns |
| US11334666B2 (en) | 2019-04-15 | 2022-05-17 | Qualys Inc. | Attack kill chain generation and utilization for threat analysis |
| US11343263B2 (en)* | 2019-04-15 | 2022-05-24 | Qualys, Inc. | Asset remediation trend map generation and utilization for threat mitigation |
| US11277425B2 (en)* | 2019-04-16 | 2022-03-15 | International Business Machines Corporation | Anomaly and mode inference from time series data |
| US12019739B2 (en)* | 2019-04-17 | 2024-06-25 | International Business Machines Corporation | User behavior risk analytic system with multiple time intervals and shared data extraction |
| US11431734B2 (en) | 2019-04-18 | 2022-08-30 | Kyndryl, Inc. | Adaptive rule generation for security event correlation |
| US10853496B2 (en) | 2019-04-26 | 2020-12-01 | Forcepoint, LLC | Adaptive trust profile behavioral fingerprint |
| US10754638B1 (en) | 2019-04-29 | 2020-08-25 | Splunk Inc. | Enabling agile functionality updates using multi-component application |
| WO2020222734A1 (en) | 2019-04-29 | 2020-11-05 | Hewlett-Packard Development Company, L.P. | Digital assistant to collect user information |
| US11206265B2 (en)* | 2019-04-30 | 2021-12-21 | Infoblox Inc. | Smart whitelisting for DNS security |
| US11580442B2 (en)* | 2019-04-30 | 2023-02-14 | Cylance Inc. | Machine learning model score obfuscation using time-based score oscillations |
| US11461441B2 (en)* | 2019-05-02 | 2022-10-04 | EMC IP Holding Company LLC | Machine learning-based anomaly detection for human presence verification |
| US11558408B2 (en)* | 2019-05-03 | 2023-01-17 | EMC IP Holding Company LLC | Anomaly detection based on evaluation of user behavior using multi-context machine learning |
| US10757117B1 (en) | 2019-05-03 | 2020-08-25 | Greynoise Intelligence Inc. | Contextual analyses of network traffic |
| CN110221988B (en)* | 2019-05-05 | 2021-04-30 | 福建天泉教育科技有限公司 | Cache optimization method and system for third-party data |
| USD921000S1 (en) | 2019-05-06 | 2021-06-01 | Google Llc | Display screen or portion thereof with an animated graphical user interface |
| USD921002S1 (en) | 2019-05-06 | 2021-06-01 | Google Llc | Display screen with animated graphical interface |
| USD921647S1 (en) | 2019-05-06 | 2021-06-08 | Google Llc | Display screen or portion thereof with an animated graphical user interface |
| USD921001S1 (en) | 2019-05-06 | 2021-06-01 | Google Llc | Display screen or portion thereof with an animated graphical user interface |
| US11100167B2 (en)* | 2019-05-06 | 2021-08-24 | Advanced New Technologies Co., Ltd. | Obtaining dynamic embedding vectors of nodes in relationship graphs |
| CN110851852B (en)* | 2019-05-07 | 2023-03-07 | 中山大学 | Data access control policy generation method based on mobile social network |
| US11206281B2 (en) | 2019-05-08 | 2021-12-21 | Xm Cyber Ltd. | Validating the use of user credentials in a penetration testing campaign |
| US10764315B1 (en)* | 2019-05-08 | 2020-09-01 | Capital One Services, Llc | Virtual private cloud flow log event fingerprinting and aggregation |
| EP3748562A1 (en)* | 2019-05-08 | 2020-12-09 | EXFO Solutions SAS | Timeline visualization & investigation systems and methods for time lasting events |
| US11397805B2 (en)* | 2019-05-09 | 2022-07-26 | Microsoft Technology Licensing, Llc | Lateral movement path detector |
| US11082454B1 (en) | 2019-05-10 | 2021-08-03 | Bank Of America Corporation | Dynamically filtering and analyzing internal communications in an enterprise computing environment |
| US20200364586A1 (en)* | 2019-05-13 | 2020-11-19 | Feedzai - Consultadoria e Inovação Tecnólogica, S.A. | Explanation reporting based on differentiation between items in different data groups |
| CN110187912B (en)* | 2019-05-16 | 2022-03-29 | 华为技术有限公司 | Node selection method and device |
| US11386208B1 (en)* | 2019-05-16 | 2022-07-12 | Ca, Inc. | Systems and methods for malware detection using localized machine learning |
| CN110213353A (en)* | 2019-05-19 | 2019-09-06 | 复旦大学 | A kind of distributed data node cooperates method |
| CN110287215A (en)* | 2019-05-20 | 2019-09-27 | 湖南大学 | Real-time Finding Method of Large-Scale Area Targets Based on Hilbert Curve |
| US11362902B2 (en) | 2019-05-20 | 2022-06-14 | Microsoft Technology Licensing, Llc | Techniques for correlating service events in computer network diagnostics |
| US11196613B2 (en)* | 2019-05-20 | 2021-12-07 | Microsoft Technology Licensing, Llc | Techniques for correlating service events in computer network diagnostics |
| US11876798B2 (en)* | 2019-05-20 | 2024-01-16 | Citrix Systems, Inc. | Virtual delivery appliance and system with remote authentication and related methods |
| US12235969B2 (en) | 2019-05-20 | 2025-02-25 | Securin Inc. | System and method for calculating and understanding aggregation risk and systemic risk across a population of organizations with respect to cybersecurity for purposes of damage coverage, consequence management, and disaster avoidance |
| US11252182B2 (en)* | 2019-05-20 | 2022-02-15 | Cloudflare, Inc. | Identifying malicious client network applications based on network request characteristics |
| US11924232B2 (en)* | 2019-05-21 | 2024-03-05 | Schneider Electric USA, Inc. | Establishing and maintaining secure device communication |
| AU2020278769A1 (en)* | 2019-05-22 | 2022-01-27 | Computed Futures, Lcc | Systems and methods for detecting and mitigating cyber security threats |
| US10802807B1 (en) | 2019-05-23 | 2020-10-13 | Xilinx, Inc. | Control and reconfiguration of data flow graphs on heterogeneous computing platform |
| US11182400B2 (en) | 2019-05-23 | 2021-11-23 | International Business Machines Corporation | Anomaly comparison across multiple assets and time-scales |
| WO2020243116A1 (en)* | 2019-05-26 | 2020-12-03 | Vilynx, Inc. | Self-learning knowledge graph |
| US11587101B2 (en)* | 2019-05-28 | 2023-02-21 | DeepRisk.ai, LLC | Platform for detecting abnormal entities and activities using machine learning algorithms |
| US10965702B2 (en) | 2019-05-28 | 2021-03-30 | Extrahop Networks, Inc. | Detecting injection attacks using passive network monitoring |
| US11909517B2 (en)* | 2019-05-29 | 2024-02-20 | CEO Vision, Inc | Systems and methods for secure, low bandwidth replicated virtual worlds for shared space computing |
| US11736508B2 (en)* | 2019-05-29 | 2023-08-22 | Johnson Controls Tyco IP Holdings LLP | System and method for managing the security health of a network device |
| US11516228B2 (en)* | 2019-05-29 | 2022-11-29 | Kyndryl, Inc. | System and method for SIEM rule sorting and conditional execution |
| US11263104B2 (en) | 2019-05-30 | 2022-03-01 | Micro Focus Llc | Mapping between raw anomaly scores and transformed anomaly scores |
| US20220229716A1 (en)* | 2019-05-30 | 2022-07-21 | Nec Corporation | Evaluation device, system, control method, and program |
| US11244043B2 (en) | 2019-05-30 | 2022-02-08 | Micro Focus Llc | Aggregating anomaly scores from anomaly detectors |
| CN112016927B (en)* | 2019-05-31 | 2023-10-27 | 慧安金科(北京)科技有限公司 | Method, apparatus and computer readable storage medium for detecting abnormal data |
| CN110362995B (en)* | 2019-05-31 | 2022-12-02 | 电子科技大学成都学院 | Malicious software detection and analysis system based on reverse direction and machine learning |
| US11620477B2 (en) | 2019-06-03 | 2023-04-04 | Cerebri AI Inc. | Decoupled scalable data engineering architecture |
| US11368550B2 (en) | 2019-06-03 | 2022-06-21 | Raytheon Company | Systems and methods for entity aware allocation of electronic resources |
| US11625366B1 (en) | 2019-06-04 | 2023-04-11 | Exabeam, Inc. | System, method, and computer program for automatic parser creation |
| USD926810S1 (en) | 2019-06-05 | 2021-08-03 | Reliaquest Holdings, Llc | Display screen or portion thereof with a graphical user interface |
| USD926809S1 (en) | 2019-06-05 | 2021-08-03 | Reliaquest Holdings, Llc | Display screen or portion thereof with a graphical user interface |
| USD926811S1 (en) | 2019-06-06 | 2021-08-03 | Reliaquest Holdings, Llc | Display screen or portion thereof with a graphical user interface |
| US10623423B1 (en)* | 2019-06-06 | 2020-04-14 | Sift Science, Inc. | Systems and methods for intelligently implementing a machine learning-based digital threat mitigation service |
| USD926200S1 (en) | 2019-06-06 | 2021-07-27 | Reliaquest Holdings, Llc | Display screen or portion thereof with a graphical user interface |
| USD926782S1 (en) | 2019-06-06 | 2021-08-03 | Reliaquest Holdings, Llc | Display screen or portion thereof with a graphical user interface |
| US11403389B2 (en)* | 2019-06-07 | 2022-08-02 | Acronis International Gmbh | System and method of detecting unauthorized access to computing resources for cryptomining |
| WO2020251866A1 (en)* | 2019-06-08 | 2020-12-17 | Trustarc Inc | Risk management of processes utilizing personal data |
| US20220237268A1 (en)* | 2019-06-11 | 2022-07-28 | Sony Group Corporation | Information processing method, information processing device, and program |
| US12120142B2 (en)* | 2019-06-11 | 2024-10-15 | Nec Corporation | Analysis apparatus, analysis system, analysis method, and non-transitory computer readable medium storing program |
| US10635273B1 (en)* | 2019-06-13 | 2020-04-28 | Lyft, Inc. | Rapidly generating help access point user interface flows |
| US11323463B2 (en)* | 2019-06-14 | 2022-05-03 | Datadog, Inc. | Generating data structures representing relationships among entities of a high-scale network infrastructure |
| US11314517B2 (en) | 2019-06-14 | 2022-04-26 | Here Global B.V. | Method and apparatus for updating pipeline operations for data processing |
| CN110288465A (en)* | 2019-06-19 | 2019-09-27 | 北京明略软件系统有限公司 | Object determines method and device, storage medium, electronic device |
| US11258806B1 (en)* | 2019-06-24 | 2022-02-22 | Mandiant, Inc. | System and method for automatically associating cybersecurity intelligence to cyberthreat actors |
| US11620389B2 (en) | 2019-06-24 | 2023-04-04 | University Of Maryland Baltimore County | Method and system for reducing false positives in static source code analysis reports using machine learning and classification techniques |
| US12001548B2 (en)* | 2019-06-25 | 2024-06-04 | Paypal, Inc. | Threat detection using machine learning query analysis |
| US11388184B2 (en) | 2019-06-26 | 2022-07-12 | Saudi Arabian Oil Company | Network security system and method for preemptively identifying or remediating security vulnerabilities |
| TWI744909B (en)* | 2019-06-28 | 2021-11-01 | 日商住友重機械工業股份有限公司 | A prediction system for predicting the operating state of the target device, its prediction, its prediction program, and a display device for grasping the operating state of the target device |
| US11003501B2 (en)* | 2019-07-03 | 2021-05-11 | Advanced New Technologies Co., Ltd. | Loading models on nodes having multiple model service frameworks |
| US10637883B1 (en) | 2019-07-04 | 2020-04-28 | Xm Cyber Ltd. | Systems and methods for determining optimal remediation recommendations in penetration testing |
| RU2716029C1 (en)* | 2019-07-04 | 2020-03-05 | Общество с ограниченной ответственностью «Инлексис» (ООО «Инлексис») | System for monitoring quality and processes based on machine learning |
| US11983609B2 (en) | 2019-07-10 | 2024-05-14 | Sony Interactive Entertainment LLC | Dual machine learning pipelines for transforming data and optimizing data transformation |
| DE102019210227A1 (en)* | 2019-07-10 | 2021-01-14 | Robert Bosch Gmbh | Device and method for anomaly detection in a communication network |
| US11138163B2 (en) | 2019-07-11 | 2021-10-05 | EXFO Solutions SAS | Automatic root cause diagnosis in networks based on hypothesis testing |
| US10972572B2 (en) | 2019-07-12 | 2021-04-06 | Zycada Networks | Programmable delivery network |
| US11729222B2 (en)* | 2019-07-12 | 2023-08-15 | Palo Alto Research Center Incorporated | System and method for extracting configuration-related information for reasoning about the security and functionality of a composed internet of things system |
| US11561959B2 (en) | 2019-07-15 | 2023-01-24 | Huawei Cloud Computing Technologies Co., Ltd. | Method and system for automatic anomaly detection in data |
| US11250322B2 (en)* | 2019-07-15 | 2022-02-15 | Sony Interactive Entertainment LLC | Self-healing machine learning system for transformed data |
| WO2021010999A1 (en)* | 2019-07-17 | 2021-01-21 | Nagrastar, Llc | Systems and methods for piracy detection and prevention |
| US10726136B1 (en) | 2019-07-17 | 2020-07-28 | BitSight Technologies, Inc. | Systems and methods for generating security improvement plans for entities |
| US11245600B2 (en)* | 2019-07-18 | 2022-02-08 | Citrix Systems, Inc. | System and method for processing network data |
| US10474506B1 (en) | 2019-07-18 | 2019-11-12 | Capital One Services, Llc | Finite state machine driven workflows |
| US11258825B1 (en)* | 2019-07-18 | 2022-02-22 | Trend Micro Incorporated | Computer network monitoring with event prediction |
| EP3767553A1 (en)* | 2019-07-18 | 2021-01-20 | Thomson Licensing | Method and device for detecting anomalies, corresponding computer program product and non-transitory computer-readable carrier medium |
| CN112242984B (en)* | 2019-07-19 | 2023-05-30 | 伊姆西Ip控股有限责任公司 | Method, electronic device and computer program product for detecting abnormal network request |
| US11367009B2 (en) | 2019-07-22 | 2022-06-21 | Chronicle Llc | Parsing unlabeled computer security data logs |
| CN110417005B (en)* | 2019-07-23 | 2020-09-25 | 清华大学 | A Transient Stability Severe Fault Screening Method Combining Deep Learning and Simulation Computing |
| US12316648B1 (en)* | 2019-07-23 | 2025-05-27 | Rapid7, Inc. | Data value classifier |
| KR102819125B1 (en)* | 2019-07-24 | 2025-06-11 | 성균관대학교산학협력단 | I2nsf consumer-facing interface yang data model |
| JP7235967B2 (en)* | 2019-07-24 | 2023-03-09 | 富士通株式会社 | Network analysis program, network analysis device and network analysis method |
| US10574683B1 (en)* | 2019-07-25 | 2020-02-25 | Confluera, Inc. | Methods and system for detecting behavioral indicators of compromise in infrastructure |
| US10630703B1 (en) | 2019-07-25 | 2020-04-21 | Confluera, Inc. | Methods and system for identifying relationships among infrastructure security-related events |
| CN110351299B (en)* | 2019-07-25 | 2022-04-22 | 新华三信息安全技术有限公司 | Network connection detection method and device |
| US10630716B1 (en) | 2019-07-25 | 2020-04-21 | Confluera, Inc. | Methods and system for tracking security risks over infrastructure |
| US10630715B1 (en) | 2019-07-25 | 2020-04-21 | Confluera, Inc. | Methods and system for characterizing infrastructure security-related events |
| US10630704B1 (en) | 2019-07-25 | 2020-04-21 | Confluera, Inc. | Methods and systems for identifying infrastructure attack progressions |
| US11196614B2 (en) | 2019-07-26 | 2021-12-07 | Cisco Technology, Inc. | Network issue tracking and resolution system |
| WO2021021737A1 (en)* | 2019-07-26 | 2021-02-04 | Reliaquest Holdings, Llc | Threat mitigation system and method |
| US20210027167A1 (en)* | 2019-07-26 | 2021-01-28 | Cisco Technology, Inc. | Model structure extraction for analyzing unstructured text data |
| WO2021018440A1 (en) | 2019-07-26 | 2021-02-04 | Sony Corporation | METHODS FOR DETECTING A CYBERATTACK ON AN ELECTRONIC DEVICE, METHOD FOR OBTAINING A SUPERVISED RANDOM FOREST MODEL FOR DETECTING A DDoS ATTACK OR A BRUTE FORCE ATTACK, AND ELECTRONIC DEVICE CONFIGURED TO DETECT A CYBERATTACK ON ITSELF |
| US11475357B2 (en) | 2019-07-29 | 2022-10-18 | Apmplitude, Inc. | Machine learning system to predict causal treatment effects of actions performed on websites or applications |
| US11165814B2 (en) | 2019-07-29 | 2021-11-02 | Extrahop Networks, Inc. | Modifying triage information based on network monitoring |
| US11271957B2 (en) | 2019-07-30 | 2022-03-08 | International Business Machines Corporation | Contextual anomaly detection across assets |
| US10880326B1 (en) | 2019-08-01 | 2020-12-29 | Xm Cyber Ltd. | Systems and methods for determining an opportunity for node poisoning in a penetration testing campaign, based on actual network traffic |
| US11516237B2 (en) | 2019-08-02 | 2022-11-29 | Crowdstrike, Inc. | Visualization and control of remotely monitored hosts |
| US11582246B2 (en)* | 2019-08-02 | 2023-02-14 | Crowd Strike, Inc. | Advanced incident scoring |
| US11588832B2 (en) | 2019-08-02 | 2023-02-21 | Crowdstrike, Inc. | Malicious incident visualization |
| US11631014B2 (en)* | 2019-08-02 | 2023-04-18 | Capital One Services, Llc | Computer-based systems configured for detecting, classifying, and visualizing events in large-scale, multivariate and multidimensional datasets and methods of use thereof |
| US11792210B2 (en) | 2019-08-02 | 2023-10-17 | Crowdstrike, Inc. | Mapping unbounded incident scores to a fixed range |
| US10742530B1 (en) | 2019-08-05 | 2020-08-11 | Extrahop Networks, Inc. | Correlating network traffic that crosses opaque endpoints |
| US11388072B2 (en) | 2019-08-05 | 2022-07-12 | Extrahop Networks, Inc. | Correlating network traffic that crosses opaque endpoints |
| US11449607B2 (en) | 2019-08-07 | 2022-09-20 | Rubrik, Inc. | Anomaly and ransomware detection |
| US12143407B2 (en)* | 2019-08-07 | 2024-11-12 | Rubrik, Inc. | Anomaly and ransomware detection |
| US11522889B2 (en) | 2019-08-07 | 2022-12-06 | Rubrik, Inc. | Anomaly and ransomware detection |
| US11290473B2 (en) | 2019-08-08 | 2022-03-29 | Microsoft Technology Licensing, Llc | Automatic generation of detection alerts |
| US11036488B2 (en)* | 2019-08-12 | 2021-06-15 | International Business Machines Corporation | System and method for optimal hierarchical upgrade time prediction |
| US11496492B2 (en)* | 2019-08-14 | 2022-11-08 | Hewlett Packard Enterprise Development Lp | Managing false positives in a network anomaly detection system |
| CN110351307B (en)* | 2019-08-14 | 2022-01-28 | 杭州安恒信息技术股份有限公司 | Abnormal user detection method and system based on ensemble learning |
| GB201911760D0 (en)* | 2019-08-16 | 2019-10-02 | Eigen Tech Ltd | Training and applying structured data extraction models |
| CN110493817B (en)* | 2019-08-22 | 2023-01-06 | 广州大学 | Data flow monitoring method and device, medium and equipment based on representative object |
| US11086948B2 (en) | 2019-08-22 | 2021-08-10 | Yandex Europe Ag | Method and system for determining abnormal crowd-sourced label |
| US11710137B2 (en) | 2019-08-23 | 2023-07-25 | Yandex Europe Ag | Method and system for identifying electronic devices of genuine customers of organizations |
| US11956265B2 (en) | 2019-08-23 | 2024-04-09 | BitSight Technologies, Inc. | Systems and methods for inferring entity relationships via network communications of users or user devices |
| EP3786823A1 (en) | 2019-08-29 | 2021-03-03 | Darktrace Limited | An endpoint agent extension of a machine learning cyber defense system for email |
| US12034767B2 (en) | 2019-08-29 | 2024-07-09 | Darktrace Holdings Limited | Artificial intelligence adversary red team |
| US11736498B1 (en)* | 2019-08-29 | 2023-08-22 | Trend Micro Incorporated | Stateful detection of cyberattacks |
| US12132706B2 (en)* | 2019-08-30 | 2024-10-29 | Ahp-Tech Inc. | Data collection system for effectively processing big data |
| CN110572382B (en)* | 2019-09-02 | 2021-05-18 | 西安电子科技大学 | Malicious flow detection method based on SMOTE algorithm and ensemble learning |
| USD982021S1 (en)* | 2019-09-03 | 2023-03-28 | Silvus Technologies, Inc. | Display screen or portion thereof with a graphical user interface |
| USD954086S1 (en)* | 2019-09-03 | 2022-06-07 | Rubrik, Inc. | Display screen or portion thereof with graphical user interface |
| US11593639B1 (en)* | 2019-09-03 | 2023-02-28 | Amazon Technologies, Inc. | Scoring events using noise-contrastive estimation for anomaly detection |
| US10742677B1 (en) | 2019-09-04 | 2020-08-11 | Extrahop Networks, Inc. | Automatic determination of user roles and asset types based on network monitoring |
| US10992696B2 (en) | 2019-09-04 | 2021-04-27 | Morgan Stanley Services Group Inc. | Enterprise-level security method and system |
| RU2757007C2 (en) | 2019-09-05 | 2021-10-08 | Общество С Ограниченной Ответственностью «Яндекс» | Method and system for detecting malicious actions of certain type |
| US11108802B2 (en)* | 2019-09-05 | 2021-08-31 | Yandex Europe Ag | Method of and system for identifying abnormal site visits |
| US11334559B2 (en) | 2019-09-09 | 2022-05-17 | Yandex Europe Ag | Method of and system for identifying abnormal rating activity |
| US11836583B2 (en)* | 2019-09-09 | 2023-12-05 | Huawei Cloud Computing Technologies Co., Ltd. | Method, apparatus and system for secure vertical federated learning |
| CA3150278A1 (en)* | 2019-09-09 | 2021-03-18 | Brian P. Murphy | Threat mitigation system and method |
| US11128645B2 (en) | 2019-09-09 | 2021-09-21 | Yandex Europe Ag | Method and system for detecting fraudulent access to web resource |
| US11281561B2 (en)* | 2019-09-09 | 2022-03-22 | Red Hat, Inc. | Determining user behavior with a user interface using user interface log records |
| WO2021050061A1 (en)* | 2019-09-11 | 2021-03-18 | Visa International Service Association | Method, system, and computer program product for managing model updates |
| TWI717831B (en) | 2019-09-11 | 2021-02-01 | 財團法人資訊工業策進會 | Attack path detection method, attack path detection system and non-transitory computer-readable medium |
| US11196765B2 (en) | 2019-09-13 | 2021-12-07 | Palo Alto Networks, Inc. | Simulating user interactions for malware analysis |
| US11941065B1 (en) | 2019-09-13 | 2024-03-26 | Experian Information Solutions, Inc. | Single identifier platform for storing entity data |
| US11223642B2 (en) | 2019-09-14 | 2022-01-11 | International Business Machines Corporation | Assessing technical risk in information technology service management using visual pattern recognition |
| CN110781258B (en)* | 2019-09-16 | 2021-07-09 | 北京三快在线科技有限公司 | Packet query method and device, electronic equipment and readable storage medium |
| US12314385B1 (en)* | 2019-09-18 | 2025-05-27 | Rapid7, Inc. | Automated generation of anomaly scenarios for testing machine learned anomaly detection models |
| US12182670B1 (en)* | 2019-09-18 | 2024-12-31 | Rapid7, Inc. | Automated dimensionality reduction for machine learning anomaly detection pipeline |
| US11853853B1 (en) | 2019-09-18 | 2023-12-26 | Rapid7, Inc. | Providing human-interpretable explanation for model-detected anomalies |
| US12088600B1 (en) | 2019-09-18 | 2024-09-10 | Rapid7, Inc. | Machine learning system for detecting anomalies in hunt data |
| CN112533234B (en)* | 2019-09-19 | 2023-04-07 | 中国移动通信集团重庆有限公司 | 5G carrier bandwidth configuration method and device based on machine learning |
| US11188320B2 (en)* | 2019-09-20 | 2021-11-30 | International Business Machines Corporation | Systems and methods for updating detection models and maintaining data privacy |
| US11216268B2 (en)* | 2019-09-20 | 2022-01-04 | International Business Machines Corporation | Systems and methods for updating detection models and maintaining data privacy |
| US11888886B1 (en)* | 2019-09-20 | 2024-01-30 | Cowbell Cyber, Inc. | Cyber security risk assessment and cyber security insurance platform |
| US11157776B2 (en)* | 2019-09-20 | 2021-10-26 | International Business Machines Corporation | Systems and methods for maintaining data privacy in a shared detection model system |
| US11080352B2 (en) | 2019-09-20 | 2021-08-03 | International Business Machines Corporation | Systems and methods for maintaining data privacy in a shared detection model system |
| DE112020003693T5 (en)* | 2019-09-20 | 2022-04-21 | International Business Machines Corporation | UPDATE COLLECTION MODELS AND COMPLY WITH PRIVACY |
| WO2021053647A1 (en)* | 2019-09-21 | 2021-03-25 | Cashshield Pte. Ltd. | Detection of use of malicious tools on mobile devices |
| GB2587355B (en)* | 2019-09-24 | 2022-11-16 | Withsecure Corp | Method of data-efficient threat detection in a computer network |
| US10848382B1 (en) | 2019-09-26 | 2020-11-24 | BitSight Technologies, Inc. | Systems and methods for network asset discovery and association thereof with entities |
| US11368479B2 (en) | 2019-09-27 | 2022-06-21 | Musarubra Us Llc | Methods and apparatus to identify and report cloud-based security vulnerabilities |
| US11533329B2 (en)* | 2019-09-27 | 2022-12-20 | Keysight Technologies, Inc. | Methods, systems and computer readable media for threat simulation and threat mitigation recommendations |
| CN110677413B (en)* | 2019-09-29 | 2021-07-30 | 南京大学 | Method and device for security verification of attacked smart home Internet of Things system |
| US11032244B2 (en) | 2019-09-30 | 2021-06-08 | BitSight Technologies, Inc. | Systems and methods for determining asset importance in security risk management |
| US11637862B1 (en)* | 2019-09-30 | 2023-04-25 | Mandiant, Inc. | System and method for surfacing cyber-security threats with a self-learning recommendation engine |
| GB201914344D0 (en) | 2019-10-04 | 2019-11-20 | Palantir Technologies Inc | System event detection system and method |
| US11275643B2 (en) | 2019-10-09 | 2022-03-15 | Microsoft Technology Licensing, Llc | Dynamic configuration of anomaly detection |
| JP7032366B2 (en)* | 2019-10-09 | 2022-03-08 | 株式会社日立製作所 | Operations support system and method |
| US11533323B2 (en) | 2019-10-10 | 2022-12-20 | Target Brands, Inc. | Computer security system for ingesting and analyzing network traffic |
| US11144935B2 (en) | 2019-10-18 | 2021-10-12 | Capital One Services, Llc | Technique to aggregate merchant level information for use in a supervised learning model to detect recurring trends in consumer transactions |
| US11151125B1 (en) | 2019-10-18 | 2021-10-19 | Splunk Inc. | Efficient updating of journey instances detected within unstructured event data |
| US11599549B2 (en) | 2019-10-18 | 2023-03-07 | Splunk Inc. | Sampling-based preview mode for a data intake and query system |
| US11216751B2 (en) | 2019-10-18 | 2022-01-04 | Capital One Services, Llc | Incremental time window procedure for selecting training samples for a supervised learning algorithm |
| US11188397B2 (en)* | 2019-10-18 | 2021-11-30 | Splunk Inc. | Mobile application for an information technology (IT) and security operations application |
| US11620157B2 (en) | 2019-10-18 | 2023-04-04 | Splunk Inc. | Data ingestion pipeline anomaly detection |
| CN110753049B (en)* | 2019-10-21 | 2021-04-13 | 清华大学 | Safety situation sensing system based on industrial control network flow |
| US11736503B2 (en)* | 2019-10-22 | 2023-08-22 | Salesforce, Inc. | Detection of anomalous lateral movement in a computer network |
| GB201915265D0 (en) | 2019-10-22 | 2019-12-04 | Senseon Tech Ltd | Anomaly detection |
| US12095639B2 (en) | 2019-10-23 | 2024-09-17 | Aryaka Networks, Inc. | Method, device and system for improving performance of point anomaly based data pattern change detection associated with network entity features in a cloud-based application acceleration as a service environment |
| US12088473B2 (en) | 2019-10-23 | 2024-09-10 | Aryaka Networks, Inc. | Method, device and system for enhancing predictive classification of anomalous events in a cloud-based application acceleration as a service environment |
| CN110753064B (en)* | 2019-10-28 | 2021-05-07 | 中国科学技术大学 | Security Detection System Fusion of Machine Learning and Rule Matching |
| US11165815B2 (en)* | 2019-10-28 | 2021-11-02 | Capital One Services, Llc | Systems and methods for cyber security alert triage |
| US20230325255A1 (en)* | 2019-10-30 | 2023-10-12 | Scenera, Inc. | Curation of custom workflows using multiple cameras, with ai trained from the workflow |
| EP3817316A1 (en)* | 2019-10-30 | 2021-05-05 | Vocalink Limited | Detection of security threats in a network environment |
| US11599643B2 (en) | 2019-10-30 | 2023-03-07 | Rubrik, Inc. | Facilitating analysis of software vulnerabilities |
| US11663340B2 (en)* | 2019-10-30 | 2023-05-30 | Rubrik, Inc. | Managing software vulnerabilities |
| US20230305903A1 (en)* | 2019-10-30 | 2023-09-28 | Scenera, Inc. | Curation of custom workflows using multiple cameras, with ai to provide awareness of situations |
| US11593491B2 (en) | 2019-10-30 | 2023-02-28 | Rubrik, Inc. | Identifying a software vulnerability |
| TWI779245B (en)* | 2019-10-31 | 2022-10-01 | 安碁資訊股份有限公司 | Abnormal traffic detection method and abnormal traffic detection device |
| US11468385B2 (en) | 2019-11-01 | 2022-10-11 | Mastercard International Incorporated | Systems and methods for evaluating data security of a target system |
| US11507786B2 (en) | 2019-11-04 | 2022-11-22 | FinancialForce.com, Inc. | Dynamic generation of client-specific feature maps |
| US11853450B2 (en)* | 2019-11-05 | 2023-12-26 | Saudi Arabian Oil Company | Detection of web application anomalies using machine learning |
| US11005878B1 (en) | 2019-11-07 | 2021-05-11 | Xm Cyber Ltd. | Cooperation between reconnaissance agents in penetration testing campaigns |
| CN110909380B (en)* | 2019-11-11 | 2021-10-19 | 西安交通大学 | A kind of abnormal file access behavior monitoring method and device |
| US11410082B2 (en)* | 2019-11-12 | 2022-08-09 | International Business Machines Corporation | Data loss machine learning model update |
| US11640465B2 (en)* | 2019-11-13 | 2023-05-02 | Vmware, Inc. | Methods and systems for troubleshooting applications using streaming anomaly detection |
| WO2021100087A1 (en)* | 2019-11-18 | 2021-05-27 | 日本電信電話株式会社 | Data processing system, high-speed response processing device, and program |
| US11526422B2 (en) | 2019-11-18 | 2022-12-13 | Bmc Software, Inc. | System and method for troubleshooting abnormal behavior of an application |
| CN112907308B (en)* | 2019-11-19 | 2024-05-24 | 京东科技控股股份有限公司 | Data detection method and device, and computer readable storage medium |
| US12058135B2 (en)* | 2019-11-20 | 2024-08-06 | Royal Bank Of Canada | System and method for unauthorized activity detection |
| US11500788B2 (en) | 2019-11-22 | 2022-11-15 | Pure Storage, Inc. | Logical address based authorization of operations with respect to a storage system |
| US12204657B2 (en) | 2019-11-22 | 2025-01-21 | Pure Storage, Inc. | Similar block detection-based detection of a ransomware attack |
| US11520907B1 (en) | 2019-11-22 | 2022-12-06 | Pure Storage, Inc. | Storage system snapshot retention based on encrypted data |
| US11687418B2 (en) | 2019-11-22 | 2023-06-27 | Pure Storage, Inc. | Automatic generation of recovery plans specific to individual storage elements |
| US11720692B2 (en) | 2019-11-22 | 2023-08-08 | Pure Storage, Inc. | Hardware token based management of recovery datasets for a storage system |
| US11657155B2 (en) | 2019-11-22 | 2023-05-23 | Pure Storage, Inc | Snapshot delta metric based determination of a possible ransomware attack against data maintained by a storage system |
| US12248566B2 (en) | 2019-11-22 | 2025-03-11 | Pure Storage, Inc. | Snapshot deletion pattern-based determination of ransomware attack against data maintained by a storage system |
| US12153670B2 (en) | 2019-11-22 | 2024-11-26 | Pure Storage, Inc. | Host-driven threat detection-based protection of storage elements within a storage system |
| US11615185B2 (en) | 2019-11-22 | 2023-03-28 | Pure Storage, Inc. | Multi-layer security threat detection for a storage system |
| US12067118B2 (en) | 2019-11-22 | 2024-08-20 | Pure Storage, Inc. | Detection of writing to a non-header portion of a file as an indicator of a possible ransomware attack against a storage system |
| US11625481B2 (en) | 2019-11-22 | 2023-04-11 | Pure Storage, Inc. | Selective throttling of operations potentially related to a security threat to a storage system |
| US12050689B2 (en) | 2019-11-22 | 2024-07-30 | Pure Storage, Inc. | Host anomaly-based generation of snapshots |
| US12079502B2 (en) | 2019-11-22 | 2024-09-03 | Pure Storage, Inc. | Storage element attribute-based determination of a data protection policy for use within a storage system |
| US11675898B2 (en) | 2019-11-22 | 2023-06-13 | Pure Storage, Inc. | Recovery dataset management for security threat monitoring |
| US11651075B2 (en) | 2019-11-22 | 2023-05-16 | Pure Storage, Inc. | Extensible attack monitoring by a storage system |
| US12079356B2 (en) | 2019-11-22 | 2024-09-03 | Pure Storage, Inc. | Measurement interval anomaly detection-based generation of snapshots |
| US11941116B2 (en) | 2019-11-22 | 2024-03-26 | Pure Storage, Inc. | Ransomware-based data protection parameter modification |
| US11755751B2 (en) | 2019-11-22 | 2023-09-12 | Pure Storage, Inc. | Modify access restrictions in response to a possible attack against data stored by a storage system |
| US11645162B2 (en) | 2019-11-22 | 2023-05-09 | Pure Storage, Inc. | Recovery point determination for data restoration in a storage system |
| US12050683B2 (en) | 2019-11-22 | 2024-07-30 | Pure Storage, Inc. | Selective control of a data synchronization setting of a storage system based on a possible ransomware attack against the storage system |
| CN111314278A (en)* | 2019-11-22 | 2020-06-19 | 南京聚铭网络科技有限公司 | Safety detection method based on Ethernet IP industrial control protocol |
| US12079333B2 (en) | 2019-11-22 | 2024-09-03 | Pure Storage, Inc. | Independent security threat detection and remediation by storage systems in a synchronous replication arrangement |
| US12411962B2 (en) | 2019-11-22 | 2025-09-09 | Pure Storage, Inc. | Managed run-time environment-based detection of a ransomware attack |
| US11720714B2 (en) | 2019-11-22 | 2023-08-08 | Pure Storage, Inc. | Inter-I/O relationship based detection of a security threat to a storage system |
| US11341236B2 (en) | 2019-11-22 | 2022-05-24 | Pure Storage, Inc. | Traffic-based detection of a security threat to a storage system |
| KR102134653B1 (en)* | 2019-11-25 | 2020-07-16 | 한국인터넷진흥원 | Apparatus for rule optimization to improve detection accuracy for exploit attacks and method thereof |
| US11455554B2 (en) | 2019-11-25 | 2022-09-27 | International Business Machines Corporation | Trustworthiness of artificial intelligence models in presence of anomalous data |
| US10990885B1 (en) | 2019-11-26 | 2021-04-27 | Capital One Services, Llc | Determining variable attribution between instances of discrete series models |
| US11586487B2 (en)* | 2019-12-04 | 2023-02-21 | Kyndryl, Inc. | Rest application programming interface route modeling |
| CN111125728A (en)* | 2019-12-04 | 2020-05-08 | 深圳昂楷科技有限公司 | Method and device for treating database security problems and treatment equipment |
| US11893795B2 (en) | 2019-12-09 | 2024-02-06 | Google Llc | Interacting with visitors of a connected home environment |
| US11818145B2 (en)* | 2019-12-09 | 2023-11-14 | International Business Machines Corporation | Characterizing user behavior in a computer system by automated learning of intention embedded in a system-generated event graph |
| US11409516B2 (en)* | 2019-12-10 | 2022-08-09 | Cisco Technology, Inc. | Predicting the impact of network software upgrades on machine learning model performance |
| US11588839B2 (en)* | 2019-12-10 | 2023-02-21 | Fortinet, Inc. | Leveraging user-behavior analytics for improved security event classification |
| US20210182269A1 (en)* | 2019-12-11 | 2021-06-17 | Bank Of America Corporation | System for reinforcing resource integrity based on event impact analysis |
| US11611576B2 (en)* | 2019-12-11 | 2023-03-21 | GE Precision Healthcare LLC | Methods and systems for securing an imaging system |
| US12063223B1 (en)* | 2019-12-11 | 2024-08-13 | Amazon Technologies, Inc. | Security event analysis and remediation system |
| US20210182387A1 (en)* | 2019-12-12 | 2021-06-17 | International Business Machines Corporation | Automated semantic modeling of system events |
| US12387118B1 (en)* | 2019-12-12 | 2025-08-12 | Rapid7, Inc. | Predictive modeling to identify anomalous log data |
| CN111050205B (en)* | 2019-12-13 | 2022-03-25 | 广州酷狗计算机科技有限公司 | Video clip acquisition method, device, equipment and storage medium |
| US11522877B2 (en) | 2019-12-16 | 2022-12-06 | Secureworks Corp. | Systems and methods for identifying malicious actors or activities |
| WO2021126167A1 (en)* | 2019-12-17 | 2021-06-24 | Visa International Service Association | System, method, and computer program product for authenticating a device based on an application profile |
| US11645603B1 (en)* | 2019-12-17 | 2023-05-09 | Wells Fargo Bank, N.A. | Computer system for automatic alert assessment |
| US11165823B2 (en) | 2019-12-17 | 2021-11-02 | Extrahop Networks, Inc. | Automated preemptive polymorphic deception |
| CN111193617B (en)* | 2019-12-17 | 2022-10-18 | 中移(杭州)信息技术有限公司 | Webpage tampering identification method and device, electronic equipment and storage medium |
| CN111339398A (en)* | 2019-12-19 | 2020-06-26 | 杭州安恒信息技术股份有限公司 | Diversified big data information analysis system and analysis method thereof |
| US11418526B2 (en) | 2019-12-20 | 2022-08-16 | Microsoft Technology Licensing, Llc | Detecting anomalous network activity |
| US12197299B2 (en) | 2019-12-20 | 2025-01-14 | Tyco Fire & Security Gmbh | Building system with ledger based software gateways |
| US11188571B1 (en) | 2019-12-23 | 2021-11-30 | Lacework Inc. | Pod communication graph |
| US11256759B1 (en) | 2019-12-23 | 2022-02-22 | Lacework Inc. | Hierarchical graph analysis |
| US11201955B1 (en) | 2019-12-23 | 2021-12-14 | Lacework Inc. | Agent networking in a containerized environment |
| US10873592B1 (en) | 2019-12-23 | 2020-12-22 | Lacework Inc. | Kubernetes launch graph |
| RU2752241C2 (en) | 2019-12-25 | 2021-07-23 | Общество С Ограниченной Ответственностью «Яндекс» | Method and system for identifying malicious activity of predetermined type in local network |
| US11818146B2 (en)* | 2019-12-27 | 2023-11-14 | Forescout Technologies, Inc. | Framework for investigating events |
| US11393232B2 (en)* | 2019-12-27 | 2022-07-19 | LendingClub Bank, National Association | Extracting values from images of documents |
| US12057959B2 (en)* | 2019-12-31 | 2024-08-06 | Mcafee, Llc | Device identification |
| USD905728S1 (en) | 2019-12-31 | 2020-12-22 | Saphyre, Inc. | Display screen or portion thereof with graphical user interface |
| US11769066B2 (en) | 2021-11-17 | 2023-09-26 | Johnson Controls Tyco IP Holdings LLP | Building data platform with digital twin triggers and actions |
| US11562068B2 (en)* | 2019-12-31 | 2023-01-24 | Fortinet, Inc. | Performing threat detection by synergistically combining results of static file analysis and behavior analysis |
| US12021650B2 (en) | 2019-12-31 | 2024-06-25 | Tyco Fire & Security Gmbh | Building data platform with event subscriptions |
| US12231255B2 (en) | 2019-12-31 | 2025-02-18 | Tyco Fire & Security Gmbh | Building data platform with graph projections |
| US11734441B2 (en)* | 2019-12-31 | 2023-08-22 | Digital Guardian Llc | Systems and methods for tracing data across file-related operations |
| US11894944B2 (en) | 2019-12-31 | 2024-02-06 | Johnson Controls Tyco IP Holdings LLP | Building data platform with an enrichment loop |
| CN111177433B (en)* | 2019-12-31 | 2021-07-20 | 北京百度网讯科技有限公司 | Method and apparatus for parallel processing of information |
| US20210200713A1 (en) | 2019-12-31 | 2021-07-01 | Johnson Controls Technology Company | Systems and methods for generating a data structure from multiple bim files |
| US11477228B2 (en)* | 2020-01-03 | 2022-10-18 | Saudi Arabian Oil Company | Method and system for blockchain accreditation mechanism based on cybersecurity risk |
| US11070584B1 (en)* | 2020-01-06 | 2021-07-20 | General Electric Company | Graceful neutralization of industrial assett attack using cruise control |
| CN111277564B (en)* | 2020-01-08 | 2022-06-28 | 山东浪潮科学研究院有限公司 | Enterprise network anomaly detection method and system based on dynamic storage network |
| US11438373B2 (en) | 2020-01-09 | 2022-09-06 | Cymulate Ltd. | Monitoring for security threats from lateral movements |
| US11012861B1 (en) | 2020-01-09 | 2021-05-18 | Allstate Insurance Company | Fraud-detection based on geolocation data |
| US11403084B2 (en) | 2020-01-10 | 2022-08-02 | Jpmorgan Chase Bank, N.A. | System and method for implementing an orchestration engine |
| US11425150B1 (en)* | 2020-01-10 | 2022-08-23 | Bank Of America Corporation | Lateral movement visualization for intrusion detection and remediation |
| US11539718B2 (en) | 2020-01-10 | 2022-12-27 | Vmware, Inc. | Efficiently performing intrusion detection |
| US11803536B2 (en)* | 2020-01-10 | 2023-10-31 | Amplitude, Inc. | Real time system for ingestion, aggregation, and identity association of data from user actions performed on websites or applications |
| US11063842B1 (en)* | 2020-01-10 | 2021-07-13 | Cisco Technology, Inc. | Forecasting network KPIs |
| US11620483B2 (en)* | 2020-01-17 | 2023-04-04 | Salesforce, Inc. | Discovering suspicious person profiles |
| US11570197B2 (en) | 2020-01-22 | 2023-01-31 | Forcepoint Llc | Human-centric risk modeling framework |
| US20210226969A1 (en) | 2020-01-22 | 2021-07-22 | Forcepoint, LLC | Determining an Abstraction Level for Contents of an Entity Behavior Catalog |
| US11567965B2 (en)* | 2020-01-23 | 2023-01-31 | Microstrategy Incorporated | Enhanced preparation and integration of data sets |
| WO2021154720A1 (en)* | 2020-01-27 | 2021-08-05 | Acentium Inc | Systems and methods for intelligent segmentation and rendering of computer environment data |
| US11575700B2 (en) | 2020-01-27 | 2023-02-07 | Xm Cyber Ltd. | Systems and methods for displaying an attack vector available to an attacker of a networked system |
| US11856022B2 (en) | 2020-01-27 | 2023-12-26 | Netskope, Inc. | Metadata-based detection and prevention of phishing attacks |
| US12192276B1 (en)* | 2020-01-29 | 2025-01-07 | Amazon Technologies, Inc. | Delivery of log records to stateless clients |
| US11556568B2 (en)* | 2020-01-29 | 2023-01-17 | Optum Services (Ireland) Limited | Apparatuses, methods, and computer program products for data perspective generation and visualization |
| US10791140B1 (en) | 2020-01-29 | 2020-09-29 | BitSight Technologies, Inc. | Systems and methods for assessing cybersecurity state of entities based on computer network characterization |
| WO2021154460A1 (en)* | 2020-01-30 | 2021-08-05 | Qomplx, Inc. | Cybersecurity profiling and rating using active and passive external reconnaissance |
| US11399039B2 (en)* | 2020-01-30 | 2022-07-26 | Microsoft Technology Licensing, Llc | Automatic detection of illicit lateral movement |
| US10893067B1 (en) | 2020-01-31 | 2021-01-12 | BitSight Technologies, Inc. | Systems and methods for rapidly generating security ratings |
| US11630901B2 (en) | 2020-02-03 | 2023-04-18 | Forcepoint Llc | External trigger induced behavioral analyses |
| US11520876B2 (en)* | 2020-02-03 | 2022-12-06 | Dell Products L.P. | Efficiently authenticating an application during I/O request handling |
| US11856013B2 (en)* | 2020-02-04 | 2023-12-26 | The George Washington University | Method and system for detecting lateral movement in enterprise computer networks |
| US12100280B2 (en) | 2020-02-04 | 2024-09-24 | Tyco Fire & Security Gmbh | Systems and methods for software defined fire detection and risk assessment |
| US11250015B2 (en) | 2020-02-07 | 2022-02-15 | Coupang Corp. | Systems and methods for low-latency aggregated-data provision |
| US11941096B2 (en)* | 2020-02-11 | 2024-03-26 | TruU, Inc. | Risk assessment framework for identity verification system |
| RU2740027C1 (en)* | 2020-02-12 | 2020-12-30 | Варити Менеджмент Сервисез Лимитед | Method and system for preventing malicious automated attacks |
| US11522766B2 (en) | 2020-02-12 | 2022-12-06 | EXFO Solutions SAS | Method and system for determining root-cause diagnosis of events occurring during the operation of a communication network |
| US11416504B2 (en) | 2020-02-12 | 2022-08-16 | EXFO Solutions SAS | Detection, characterization, and prediction of real-time events occurring approximately periodically |
| USD969166S1 (en)* | 2020-02-14 | 2022-11-08 | GE Precision Healthcare LLC | Display screen with icon |
| US11757918B2 (en)* | 2020-02-18 | 2023-09-12 | Noblis, Inc. | Capability based insider threat detection |
| CN111324509B (en)* | 2020-02-18 | 2023-07-11 | 广东小天才科技有限公司 | A method and device for identifying addiction to applications |
| US11405778B2 (en) | 2020-02-20 | 2022-08-02 | International Business Machines Corporation | User confidentiality protection system |
| US11636202B2 (en) | 2020-02-21 | 2023-04-25 | Cylance Inc. | Projected vector overflow penalty as mitigation for machine learning model string stuffing |
| US11470042B2 (en) | 2020-02-21 | 2022-10-11 | Abnormal Security Corporation | Discovering email account compromise through assessments of digital activities |
| RU2722692C1 (en) | 2020-02-21 | 2020-06-03 | Общество с ограниченной ответственностью «Группа АйБи ТДС» | Method and system for detecting malicious files in a non-isolated medium |
| US11997125B2 (en)* | 2020-02-24 | 2024-05-28 | Strikeready Inc. | Automated actions in a security platform |
| US12216791B2 (en) | 2020-02-24 | 2025-02-04 | Forcepoint Llc | Re-identifying pseudonymized or de-identified data utilizing distributed ledger technology |
| US11816596B2 (en) | 2020-02-25 | 2023-11-14 | Apps Consultants Inc. | Process discovery and optimization using time-series databases, graph-analytics, and machine learning |
| US11620481B2 (en)* | 2020-02-26 | 2023-04-04 | International Business Machines Corporation | Dynamic machine learning model selection |
| RU2749252C1 (en)* | 2020-02-26 | 2021-06-07 | Акционерное общество "Лаборатория Касперского" | Method of determining anomaly sources in a cyber-physical system |
| US10764298B1 (en) | 2020-02-26 | 2020-09-01 | BitSight Technologies, Inc. | Systems and methods for improving a security profile of an entity based on peer security profiles |
| US11080109B1 (en) | 2020-02-27 | 2021-08-03 | Forcepoint Llc | Dynamically reweighting distributions of event observations |
| US11665180B2 (en)* | 2020-02-28 | 2023-05-30 | International Business Machines Corporation | Artificially intelligent security incident and event management |
| EP4111343A1 (en) | 2020-02-28 | 2023-01-04 | Darktrace Holdings Limited | An artificial intelligence adversary red team |
| US20210273961A1 (en) | 2020-02-28 | 2021-09-02 | Darktrace Limited | Apparatus and method for a cyber-threat defense system |
| US11477234B2 (en) | 2020-02-28 | 2022-10-18 | Abnormal Security Corporation | Federated database for establishing and tracking risk of interactions with third parties |
| CN111431865B (en)* | 2020-02-28 | 2022-01-04 | 四川亿览态势科技有限公司 | Network deep threat detection method |
| WO2021178423A1 (en) | 2020-03-02 | 2021-09-10 | Abnormal Security Corporation | Multichannel threat detection for protecting against account compromise |
| US11836265B2 (en) | 2020-03-02 | 2023-12-05 | Forcepoint Llc | Type-dependent event deduplication |
| US11252189B2 (en) | 2020-03-02 | 2022-02-15 | Abnormal Security Corporation | Abuse mailbox for facilitating discovery, investigation, and analysis of email-based threats |
| US11429697B2 (en) | 2020-03-02 | 2022-08-30 | Forcepoint, LLC | Eventually consistent entity resolution |
| US11222134B2 (en) | 2020-03-04 | 2022-01-11 | Sotero, Inc. | System and methods for data encryption and application-agnostic querying of encrypted data |
| TWI715457B (en)* | 2020-03-04 | 2021-01-01 | 國立中正大學 | Unsupervised malicious flow detection system and method |
| USD951270S1 (en) | 2020-03-06 | 2022-05-10 | Saphyre, Inc. | Display screen or portion thereof with graphical user interface |
| JP2021140585A (en)* | 2020-03-06 | 2021-09-16 | 株式会社日立システムズ | Management assist device, management assist system, pogram, and management assist method |
| CN111510340B (en)* | 2020-03-10 | 2021-12-28 | 北京三快在线科技有限公司 | Access request detection method and device, electronic equipment and readable storage medium |
| RU2738344C1 (en) | 2020-03-10 | 2020-12-11 | Общество с ограниченной ответственностью «Группа АйБи ТДС» | Method and system for searching for similar malware based on results of their dynamic analysis |
| US11461677B2 (en) | 2020-03-10 | 2022-10-04 | Sailpoint Technologies, Inc. | Systems and methods for data correlation and artifact matching in identity management artificial intelligence systems |
| US11451576B2 (en) | 2020-03-12 | 2022-09-20 | Abnormal Security Corporation | Investigation of threats using queryable records of behavior |
| US11836251B2 (en)* | 2020-03-12 | 2023-12-05 | Dell Products L.P. | Malware detection using a machine learning model |
| US11443168B2 (en)* | 2020-03-13 | 2022-09-13 | EMC IP Holding Company LLC | Log analysis system employing long short-term memory recurrent neural net works |
| US12086261B2 (en) | 2020-03-13 | 2024-09-10 | International Business Machines Corporation | Displaying cyber threat data in a narrative-like format |
| US11503047B2 (en)* | 2020-03-13 | 2022-11-15 | International Business Machines Corporation | Relationship-based conversion of cyber threat data into a narrative-like format |
| US11567756B2 (en)* | 2020-03-16 | 2023-01-31 | Microsoft Technology Licensing, Llc | Causality determination of upgrade regressions via comparisons of telemetry data |
| US12248311B2 (en) | 2020-03-17 | 2025-03-11 | Tyco Fire & Security Gmbh | System and method for determining and predicting vulnerability of building management systems |
| US20210294713A1 (en)* | 2020-03-20 | 2021-09-23 | 5thColumn LLC | Generation of an identification evaluation regarding a system aspect of a system |
| US11379720B2 (en)* | 2020-03-20 | 2022-07-05 | Avid Technology, Inc. | Adaptive deep learning for efficient media content creation and manipulation |
| US11294804B2 (en) | 2020-03-23 | 2022-04-05 | International Business Machines Corporation | Test case failure with root cause isolation |
| JP7639273B2 (en)* | 2020-03-23 | 2025-03-05 | 富士フイルムビジネスイノベーション株式会社 | Information processing device and information processing program |
| US11563755B2 (en)* | 2020-03-24 | 2023-01-24 | Fortinet, Inc. | Machine-learning based approach for dynamically generating incident-specific playbooks for a security orchestration, automation and response (SOAR) platform |
| IT202000006265A1 (en) | 2020-03-25 | 2021-09-25 | Cleafy Spa | Method for monitoring and protecting access to an online service |
| IT202000006343A1 (en) | 2020-03-25 | 2021-09-25 | Cleafy Spa | Method for monitoring and protecting access to an online service |
| IT202000006340A1 (en)* | 2020-03-25 | 2021-09-25 | Cleafy Spa | Method for monitoring and protecting access to an online service |
| US11604871B2 (en)* | 2020-03-27 | 2023-03-14 | Cylance Inc. | Projected vector modification as mitigation for machine learning model string stuffing |
| US11080032B1 (en) | 2020-03-31 | 2021-08-03 | Forcepoint Llc | Containerized infrastructure for deployment of microservices |
| US11461346B2 (en)* | 2020-03-31 | 2022-10-04 | At&T Intellectual Property I, L.P. | Managing temporal views of data |
| AU2020439978B2 (en) | 2020-04-01 | 2023-07-06 | Google Llc | Enabling media features provided on a first screen device to be presented on a second screen device |
| US11410178B2 (en) | 2020-04-01 | 2022-08-09 | Mastercard International Incorporated | Systems and methods for message tracking using real-time normalized scoring |
| US11715106B2 (en) | 2020-04-01 | 2023-08-01 | Mastercard International Incorporated | Systems and methods for real-time institution analysis based on message traffic |
| US11582256B2 (en) | 2020-04-06 | 2023-02-14 | Xm Cyber Ltd. | Determining multiple ways for compromising a network node in a penetration testing campaign |
| US11537386B2 (en) | 2020-04-06 | 2022-12-27 | Johnson Controls Tyco IP Holdings LLP | Building system with dynamic configuration of network resources for 5G networks |
| US11481413B2 (en)* | 2020-04-07 | 2022-10-25 | Saudi Arabian Oil Company | Systems and methods for evaluating petroleum data for automated processes |
| US12099934B2 (en)* | 2020-04-07 | 2024-09-24 | Cognizant Technology Solutions U.S. Corporation | Framework for interactive exploration, evaluation, and improvement of AI-generated solutions |
| US11442990B2 (en) | 2020-04-08 | 2022-09-13 | Liveramp, Inc. | Asserted relationship data structure |
| US11486230B2 (en) | 2020-04-09 | 2022-11-01 | Saudi Arabian Oil Company | Allocating resources for implementing a well-planning process |
| US11693140B2 (en) | 2020-04-09 | 2023-07-04 | Saudi Arabian Oil Company | Identifying hydrocarbon reserves of a subterranean region using a reservoir earth model that models characteristics of the region |
| US11815650B2 (en) | 2020-04-09 | 2023-11-14 | Saudi Arabian Oil Company | Optimization of well-planning process for identifying hydrocarbon reserves using an integrated multi-dimensional geological model |
| US11914719B1 (en) | 2020-04-15 | 2024-02-27 | Wells Fargo Bank, N.A. | Systems and methods for cyberthreat-risk education and awareness |
| US11568136B2 (en) | 2020-04-15 | 2023-01-31 | Forcepoint Llc | Automatically constructing lexicons from unlabeled datasets |
| US11443242B2 (en) | 2020-04-21 | 2022-09-13 | International Business Machines Corporation | Iterative training of a machine learning model |
| CN111460005B (en)* | 2020-04-22 | 2021-08-13 | 北京工业大学 | An Outlier Detection Method for Time Series Data Based on JSD |
| US11451550B2 (en) | 2020-04-23 | 2022-09-20 | Bank Of America Corporation | System for automated electronic data exfiltration path identification, prioritization, and remediation |
| EP4139801A4 (en) | 2020-04-23 | 2024-08-14 | Abnormal Security Corporation | Detection and prevention of external fraud |
| US11349863B2 (en)* | 2020-04-27 | 2022-05-31 | WootCloud Inc. | Assessing computer network risk |
| EP4091084B1 (en)* | 2020-04-28 | 2025-07-09 | Absolute Software Corporation | Endpoint security using an action prediction model |
| US12039276B2 (en)* | 2020-04-29 | 2024-07-16 | Cisco Technology, Inc. | Anomaly classification with attendant word enrichment |
| US11269876B1 (en) | 2020-04-30 | 2022-03-08 | Splunk Inc. | Supporting graph data structure transformations in graphs generated from a query to event data |
| EP4143711A1 (en)* | 2020-04-30 | 2023-03-08 | British Telecommunications public limited company | Network anomaly identification |
| CN113748658B (en)* | 2020-04-30 | 2024-01-23 | 新华三技术有限公司 | Equipment protection method and equipment |
| US11516206B2 (en) | 2020-05-01 | 2022-11-29 | Forcepoint Llc | Cybersecurity system having digital certificate reputation system |
| US12130908B2 (en) | 2020-05-01 | 2024-10-29 | Forcepoint Llc | Progressive trigger data and detection model |
| US20210342430A1 (en)* | 2020-05-01 | 2021-11-04 | Capital One Services, Llc | Identity verification using task-based behavioral biometrics |
| US11989676B2 (en)* | 2020-05-04 | 2024-05-21 | Certinia Inc. | Risk management data channel interleaved with enterprise data to facilitate assessment responsive to a risk event |
| US12184683B2 (en)* | 2020-05-05 | 2024-12-31 | The United States Of America As Represented By The Secretary Of The Army | Cybersecurity resilience by integrating adversary and defender actions, deep learning, and graph thinking |
| US11544390B2 (en) | 2020-05-05 | 2023-01-03 | Forcepoint Llc | Method, system, and apparatus for probabilistic identification of encrypted files |
| USD921679S1 (en)* | 2020-05-06 | 2021-06-08 | Fiduciary Benchmarks Insights, Llc | Display screen or portion thereof with graphical user interface |
| USD921678S1 (en)* | 2020-05-06 | 2021-06-08 | Fiduciary Benchmarks Insights, Llc | Display screen or portion thereof with graphical user interface |
| USD921686S1 (en)* | 2020-05-06 | 2021-06-08 | Fiduciary Benchmarks Insights, Llc | Display screen or portion thereof with graphical user interface |
| USD921673S1 (en) | 2020-05-06 | 2021-06-08 | Fiduciary Benchmarks Insights, Llc | Display screen or portion thereof with graphical user interface |
| USD921681S1 (en)* | 2020-05-06 | 2021-06-08 | Fiduciary Benchmarks Insights, Llc | Display screen or portion thereof with graphical user interface |
| USD921687S1 (en) | 2020-05-06 | 2021-06-08 | Fiduciary Benchmarks Insights, Llc | Display screen or portion thereof with graphical user interface |
| USD921685S1 (en) | 2020-05-06 | 2021-06-08 | Fiduciary Benchmarks Insights, Llc | Display screen or portion thereof with graphical user interface |
| USD921028S1 (en) | 2020-05-06 | 2021-06-01 | Fiduciary Benchmarks Insights, Llc | Display screen or portion thereof with graphical user interface |
| USD921676S1 (en) | 2020-05-06 | 2021-06-08 | Fiduciary Benchmarks Insights, Llc | Display screen or portion thereof with graphical user interface |
| US20210352099A1 (en)* | 2020-05-06 | 2021-11-11 | Samos Cyber Inc. | System for automatically discovering, enriching and remediating entities interacting in a computer network |
| USD921677S1 (en) | 2020-05-06 | 2021-06-08 | Fiduciary Benchmarks Insights, Llc | Display screen or portion thereof with graphical user interface |
| USD921684S1 (en)* | 2020-05-06 | 2021-06-08 | Fiduciary Benchmarks Insights, Llc | Display screen or portion thereof with graphical user interface |
| USD921680S1 (en)* | 2020-05-06 | 2021-06-08 | Fiduciary Benchmarks Insights, Llc | Display screen or portion thereof with graphical user interface |
| USD921682S1 (en)* | 2020-05-06 | 2021-06-08 | Fiduciary Benchmarks Insights, Llc | Display screen or portion thereof with graphical user interface |
| US11388179B2 (en)* | 2020-05-06 | 2022-07-12 | Wells Fargo Bank, N.A. | Centralized threat intelligence |
| USD921683S1 (en)* | 2020-05-06 | 2021-06-08 | Fiduciary Benchmarks Insights, Llc | Display screen or portion thereof with graphical user interface |
| USD921675S1 (en)* | 2020-05-06 | 2021-06-08 | Fiduciary Benchmarks Insights, Llc | Display screen or portion thereof with graphical user interface |
| USD921674S1 (en) | 2020-05-06 | 2021-06-08 | Fiduciary Benchmarks Insights, Llc | Display screen or portion thereof with graphical user interface |
| US11074512B1 (en) | 2020-05-07 | 2021-07-27 | Dflabs S.P.A. | Cybersecurity incident response and security operation system employing playbook generation and parent matching through custom machine learning |
| US12438916B2 (en) | 2020-05-13 | 2025-10-07 | Qomplx Llc | Intelligent automated planning system for large-scale operations |
| CN112291533A (en)* | 2020-05-14 | 2021-01-29 | 陈洋洋 | Security monitoring method and system based on Internet of things and artificial intelligence |
| US11973773B2 (en)* | 2020-05-15 | 2024-04-30 | Arbor Networks, Inc. | Detecting and mitigating zero-day attacks |
| US11381640B2 (en) | 2020-05-15 | 2022-07-05 | Cisco Technology, Inc. | Detection of isolated changes in network metrics using smart-peering |
| WO2021236663A1 (en)* | 2020-05-18 | 2021-11-25 | Darktrace, Inc. | Cyber security for instant messaging across platforms |
| WO2021233524A1 (en)* | 2020-05-18 | 2021-11-25 | Telefonaktiebolaget Lm Ericsson (Publ) | Network monitoring |
| US11895158B2 (en) | 2020-05-19 | 2024-02-06 | Forcepoint Llc | Cybersecurity system having security policy visualization |
| US11947542B2 (en)* | 2020-05-22 | 2024-04-02 | Yahoo Assets Llc | Certifying events in a streaming pipeline |
| CN111355619B (en)* | 2020-05-26 | 2020-08-14 | 成都信息工程大学 | A cross-chain collaboration method for multi-core mesh collaboration relationship |
| US11023585B1 (en) | 2020-05-27 | 2021-06-01 | BitSight Technologies, Inc. | Systems and methods for managing cybersecurity alerts |
| PL3916556T3 (en)* | 2020-05-29 | 2023-07-10 | Ovh | Method and system for detecting anomalies in a data pipeline |
| US11483342B2 (en) | 2020-05-29 | 2022-10-25 | Saudi Arabian Oil Company | Utilizing web application firewall and machine learning to detect command and control |
| US20210373914A1 (en)* | 2020-05-29 | 2021-12-02 | Intuit Inc. | Batch to stream processing in a feature management platform |
| US12302451B2 (en) | 2020-06-01 | 2025-05-13 | Palo Alto Networks, Inc. | IoT security policy on a firewall |
| US11115799B1 (en) | 2020-06-01 | 2021-09-07 | Palo Alto Networks, Inc. | IoT device discovery and identification |
| US20240211784A1 (en)* | 2020-06-05 | 2024-06-27 | State Farm Mutual Automobile Insurance Company | Systems and methods for processing using directed acyclic graphs |
| US11874809B2 (en) | 2020-06-08 | 2024-01-16 | Johnson Controls Tyco IP Holdings LLP | Building system with naming schema encoding entity type and entity relationships |
| CN111679953B (en)* | 2020-06-09 | 2022-04-12 | 平安科技(深圳)有限公司 | Fault node identification method, device, equipment and medium based on artificial intelligence |
| US10862928B1 (en)* | 2020-06-12 | 2020-12-08 | Sailpoint Technologies, Inc. | System and method for role validation in identity management artificial intelligence systems using analysis of network identity graphs |
| US11775841B2 (en) | 2020-06-15 | 2023-10-03 | Cognizant Technology Solutions U.S. Corporation | Process and system including explainable prescriptions through surrogate-assisted evolution |
| US11956253B1 (en) | 2020-06-15 | 2024-04-09 | Exabeam, Inc. | Ranking cybersecurity alerts from multiple sources using machine learning |
| US20210392146A1 (en)* | 2020-06-16 | 2021-12-16 | Zscaler, Inc. | Machine Learning-based user and entity behavior analysis for network security |
| US10887337B1 (en) | 2020-06-17 | 2021-01-05 | Confluera, Inc. | Detecting and trail-continuation for attacks through remote desktop protocol lateral movement |
| US20210397903A1 (en)* | 2020-06-18 | 2021-12-23 | Zoho Corporation Private Limited | Machine learning powered user and entity behavior analysis |
| KR102199704B1 (en)* | 2020-06-26 | 2021-01-08 | 주식회사 이스트시큐리티 | An apparatus for selecting a representative token from the detection names of multiple vaccines, a method therefor, and a computer recordable medium storing program to perform the method |
| US11770377B1 (en)* | 2020-06-29 | 2023-09-26 | Cyral Inc. | Non-in line data monitoring and security services |
| US11989627B1 (en)* | 2020-06-29 | 2024-05-21 | Amazon Technologies, Inc. | Automated machine learning pipeline generation |
| US11816461B2 (en) | 2020-06-30 | 2023-11-14 | Paypal, Inc. | Computer model management system |
| US11556636B2 (en) | 2020-06-30 | 2023-01-17 | Microsoft Technology Licensing, Llc | Malicious enterprise behavior detection tool |
| US12141280B2 (en)* | 2020-06-30 | 2024-11-12 | Microsoft Technology Licensing, Llc | Deep learning-based analysis of signals for threat detection |
| US11588830B1 (en) | 2020-06-30 | 2023-02-21 | Sequoia Benefits and Insurance Services, LLC | Using machine learning to detect malicious upload activity |
| US20220006783A1 (en)* | 2020-07-02 | 2022-01-06 | Accenture Global Solutions Limited | Privacy preserving cooperative firewall rule optimizer |
| CN111538642B (en)* | 2020-07-02 | 2020-10-02 | 杭州海康威视数字技术股份有限公司 | Abnormal behavior detection method and device, electronic equipment and storage medium |
| WO2022006421A1 (en)* | 2020-07-02 | 2022-01-06 | Pindrop Security, Inc. | Fraud importance system |
| US11622273B2 (en) | 2020-07-06 | 2023-04-04 | T-Mobile Usa, Inc. | Security system for directing 5G network traffic |
| US11822435B2 (en)* | 2020-07-06 | 2023-11-21 | Bank Of America Corporation | Consolidated data restoration framework |
| US11516670B2 (en)* | 2020-07-06 | 2022-11-29 | T-Mobile Usa, Inc. | Security system for vulnerability-risk-threat (VRT) detection |
| US11743729B2 (en) | 2020-07-06 | 2023-08-29 | T-Mobile Usa, Inc. | Security system for managing 5G network traffic |
| US11770713B2 (en)* | 2020-07-06 | 2023-09-26 | T-Mobile Usa, Inc. | Distributed security system for vulnerability-risk-threat (VRT) detection |
| US11800361B2 (en)* | 2020-07-06 | 2023-10-24 | T-Mobile Usa, Inc. | Security system with 5G network traffic incubation |
| US12424335B2 (en) | 2020-07-08 | 2025-09-23 | Cognizant Technology Solutions U.S. Corporation | AI based optimized decision making for epidemiological modeling |
| CN111914255B (en)* | 2020-07-14 | 2024-03-22 | 北京人人云图信息技术有限公司 | Semi-automatic anti-climbing system based on behavior characteristics |
| US11715046B2 (en) | 2020-07-14 | 2023-08-01 | Micro Focus Llc | Enhancing data-analytic visualizations with machine learning |
| US20220019909A1 (en)* | 2020-07-14 | 2022-01-20 | Adobe Inc. | Intent-based command recommendation generation in an analytics system |
| CN111818069B (en)* | 2020-07-14 | 2022-07-15 | 绿盟科技集团股份有限公司 | Method, device, medium and computer equipment for presenting security event processing flow |
| US11966820B2 (en)* | 2020-07-15 | 2024-04-23 | Accenture Global Solutions Limited | Utilizing machine learning models with a centralized repository of log data to predict events and generate alerts and recommendations |
| US11770387B1 (en)* | 2020-07-17 | 2023-09-26 | Rapid7, Inc. | Graph-based detection of lateral movement in computer networks |
| US11601449B2 (en) | 2020-07-21 | 2023-03-07 | Absolute Software Corporation | Event evaluation pipeline for alert engine |
| US11595282B2 (en)* | 2020-07-21 | 2023-02-28 | Google Llc | Network anomaly detection |
| US11146472B1 (en)* | 2020-07-21 | 2021-10-12 | Bank Of America Corporation | Artificial intelligence-based lateral movement identification tool |
| US20220027331A1 (en)* | 2020-07-23 | 2022-01-27 | International Business Machines Corporation | Cross-Environment Event Correlation Using Domain-Space Exploration and Machine Learning Techniques |
| US11455235B2 (en)* | 2020-07-24 | 2022-09-27 | Paypal, Inc. | Online query execution using a big data framework |
| CN112087420B (en)* | 2020-07-24 | 2022-06-14 | 西安电子科技大学 | Network killing chain detection method, prediction method and system |
| US12278729B2 (en)* | 2020-07-24 | 2025-04-15 | Skyhigh Security Llc | Systems, methods, and media for monitoring cloud configuration settings |
| US11652833B2 (en) | 2020-07-24 | 2023-05-16 | Microsoft Technology Licensing, Llc | Detection of anomalous count of new entities |
| US11108728B1 (en) | 2020-07-24 | 2021-08-31 | Vmware, Inc. | Fast distribution of port identifiers for rule processing |
| US12120141B2 (en)* | 2020-07-28 | 2024-10-15 | Hewlett-Packard Development Company, L.P. | Security scores |
| US12205022B2 (en) | 2020-07-31 | 2025-01-21 | Splunk Inc. | Data field extraction by a data intake and query system |
| US11663176B2 (en) | 2020-07-31 | 2023-05-30 | Splunk Inc. | Data field extraction model training for a data intake and query system |
| US11741131B1 (en)* | 2020-07-31 | 2023-08-29 | Splunk Inc. | Fragmented upload and re-stitching of journey instances detected within event data |
| US11704490B2 (en) | 2020-07-31 | 2023-07-18 | Splunk Inc. | Log sourcetype inference model training for a data intake and query system |
| WO2022031523A1 (en)* | 2020-08-03 | 2022-02-10 | Kount Inc. | Techniques for identity data characterization for data protection |
| RU2747476C1 (en)* | 2020-08-04 | 2021-05-05 | Публичное Акционерное Общество "Сбербанк России" (Пао Сбербанк) | Intelligent risk and vulnerability management system for infrastructure elements |
| US11539735B2 (en)* | 2020-08-05 | 2022-12-27 | Cisco Technology, Inc. | Systems and methods for application placement in a network based on host security posture |
| CN112019521B (en)* | 2020-08-07 | 2023-04-07 | 杭州安恒信息技术股份有限公司 | Asset scoring method and device, computer equipment and storage medium |
| CA3191440A1 (en)* | 2020-08-10 | 2022-02-17 | Liveramp, Inc. | Machine for analysis of entity resolution data graphs using peer data structures |
| US11716343B2 (en) | 2020-08-11 | 2023-08-01 | Cisco Technology, Inc. | Secure neighborhoods assessment in enterprise networks |
| US20220051111A1 (en)* | 2020-08-17 | 2022-02-17 | Accenture Global Solutions Limited | Knowledge graph enhancement by prioritizing cardinal nodes |
| CN112134723A (en)* | 2020-08-21 | 2020-12-25 | 杭州数梦工场科技有限公司 | Network anomaly monitoring method and device, computer equipment and storage medium |
| US12033037B2 (en) | 2020-08-24 | 2024-07-09 | International Business Machines Corporation | Open feature library management |
| US11651096B2 (en) | 2020-08-24 | 2023-05-16 | Burstiq, Inc. | Systems and methods for accessing digital assets in a blockchain using global consent contracts |
| US11483351B2 (en) | 2020-08-26 | 2022-10-25 | Cisco Technology, Inc. | Securing network resources from known threats |
| CA3191077A1 (en)* | 2020-08-27 | 2022-03-03 | Liveramp, Inc. | Evolutionary analysis of an identity graph data structure |
| US12050686B2 (en)* | 2020-08-27 | 2024-07-30 | Royal Bank Of Canada | System and method for anomalous database access monitoring |
| US11907676B1 (en)* | 2020-08-28 | 2024-02-20 | Amazon Technologies, Inc. | Processing orchestration for systems including distributed components |
| US11704387B2 (en) | 2020-08-28 | 2023-07-18 | Forcepoint Llc | Method and system for fuzzy matching and alias matching for streaming data sets |
| US11329998B1 (en) | 2020-08-31 | 2022-05-10 | Secureauth Corporation | Identification (ID) proofing and risk engine integration system and method |
| US11588834B2 (en)* | 2020-09-03 | 2023-02-21 | Secureworks Corp. | Systems and methods for identifying attack patterns or suspicious activity in client networks |
| CN114257565B (en)* | 2020-09-10 | 2023-09-05 | 中国移动通信集团广东有限公司 | Method, system and server for mining potential threat domain names |
| US11514161B2 (en) | 2020-09-11 | 2022-11-29 | Mcafee, Llc | Method and apparatus for detecting malware via analysis of a screen capture |
| US20220083661A1 (en)* | 2020-09-11 | 2022-03-17 | Zscaler, Inc. | Utilizing Machine Learning to detect malicious Office documents |
| US11803641B2 (en) | 2020-09-11 | 2023-10-31 | Zscaler, Inc. | Utilizing Machine Learning to detect malicious executable files efficiently and effectively |
| US11647034B2 (en)* | 2020-09-12 | 2023-05-09 | Microsoft Technology Licensing, Llc | Service access data enrichment for cybersecurity |
| US12132753B2 (en) | 2020-09-15 | 2024-10-29 | Bank Of America Corporation | Enhanced network security based on inter-application data flow diagrams |
| CN112153221B (en)* | 2020-09-16 | 2021-06-29 | 北京邮电大学 | A Communication Behavior Recognition Method Based on Social Network Graph Computing |
| US10938828B1 (en) | 2020-09-17 | 2021-03-02 | Sailpoint Technologies, Inc. | System and method for predictive platforms in identity management artificial intelligence systems using analysis of network identity graphs |
| US11693837B2 (en)* | 2020-09-18 | 2023-07-04 | Databricks, Inc. | Model ML registry and model serving |
| US11503055B2 (en) | 2020-09-21 | 2022-11-15 | International Business Machines Corporation | Identifying siem event types |
| WO2022066910A1 (en) | 2020-09-23 | 2022-03-31 | Extrahop Networks, Inc. | Monitoring encrypted network traffic |
| US12301590B2 (en)* | 2020-09-23 | 2025-05-13 | Open Text Holdings, Inc. | Endpoint security systems and methods with telemetry filters for event log monitoring |
| US11463466B2 (en) | 2020-09-23 | 2022-10-04 | Extrahop Networks, Inc. | Monitoring encrypted network traffic |
| KR20220040695A (en)* | 2020-09-24 | 2022-03-31 | 삼성전자주식회사 | Electronic apparatus and the method thereof |
| US11546368B2 (en)* | 2020-09-28 | 2023-01-03 | T-Mobile Usa, Inc. | Network security system including a multi-dimensional domain name system to protect against cybersecurity threats |
| US12210619B2 (en)* | 2020-09-28 | 2025-01-28 | Robert Bosch Gmbh | Method and system for breaking backdoored classifiers through adversarial examples |
| US20220100857A1 (en)* | 2020-09-28 | 2022-03-31 | Elasticsearch B.V. | Systems and Methods of Anomalous Pattern Discovery and Mitigation |
| US11496522B2 (en) | 2020-09-28 | 2022-11-08 | T-Mobile Usa, Inc. | Digital on-demand coupons for security service of communications system |
| US12063226B1 (en) | 2020-09-29 | 2024-08-13 | Exabeam, Inc. | Graph-based multi-staged attack detection in the context of an attack framework |
| US11397773B2 (en) | 2020-09-30 | 2022-07-26 | Johnson Controls Tyco IP Holdings LLP | Building management system with semantic model integration |
| US11954154B2 (en) | 2020-09-30 | 2024-04-09 | Johnson Controls Tyco IP Holdings LLP | Building management system with semantic model integration |
| TWI737506B (en)* | 2020-09-30 | 2021-08-21 | 中華電信股份有限公司 | SYSTEM AND METHOD FOR IPv6 TRAFFIC DETECTION AND DEFENSE BASED ON SOFTWARE-DEFINED NETWORK |
| US20220101336A1 (en)* | 2020-09-30 | 2022-03-31 | EMC IP Holding Company LLC | Compliant and auditable data handling in a data confidence fabric |
| US12346381B2 (en) | 2020-09-30 | 2025-07-01 | Tyco Fire & Security Gmbh | Building management system with semantic model integration |
| US11935077B2 (en)* | 2020-10-04 | 2024-03-19 | Vunet Systems Private Limited | Operational predictive scoring of components and services of an information technology system |
| EP3982280A1 (en)* | 2020-10-06 | 2022-04-13 | Atos IT Services UK Limited | Method and system to remediate a security issue |
| US20220116782A1 (en)* | 2020-10-08 | 2022-04-14 | Qatar Foundation For Education, Science And Community Development | Compromised mobile device detection system and method |
| US11606694B2 (en) | 2020-10-08 | 2023-03-14 | Surendra Goel | System that provides cybersecurity in a home or office by interacting with internet of things devices and other devices |
| US12271447B2 (en) | 2020-10-09 | 2025-04-08 | Y.E. Hub Armenia LLC | Methods and servers for determining metric-specific thresholds to be used with a plurality of nested metrics for binary classification of a digital object |
| CN112115192B (en)* | 2020-10-09 | 2021-07-02 | 北京东方通软件有限公司 | Efficient flow arrangement method and system for ETL system |
| US11720595B2 (en)* | 2020-10-16 | 2023-08-08 | Salesforce, Inc. | Generating a query using training observations |
| USD946046S1 (en)* | 2020-10-19 | 2022-03-15 | Splunk Inc. | Display screen or portion thereof having an animated graphical user interface for dynamically formatting a presentation of information |
| US20220121981A1 (en)* | 2020-10-19 | 2022-04-21 | Oracle International Corporation | Cognitive Error Recommendation Based on Log Data |
| CN111970309B (en)* | 2020-10-20 | 2021-02-02 | 南京理工大学 | Intrusion detection method and system based on Spark Internet of Vehicles combined deep learning |
| US11528242B2 (en) | 2020-10-23 | 2022-12-13 | Abnormal Security Corporation | Discovering graymail through real-time analysis of incoming email |
| US12248435B2 (en) | 2021-03-31 | 2025-03-11 | Nutanix, Inc. | File analytics systems and methods |
| CN112000703B (en)* | 2020-10-27 | 2021-02-05 | 港胜技术服务(深圳)有限公司 | Data warehousing processing method and device, computer equipment and storage medium |
| US11190589B1 (en) | 2020-10-27 | 2021-11-30 | Forcepoint, LLC | System and method for efficient fingerprinting in cloud multitenant data loss prevention |
| US11727318B2 (en) | 2020-10-30 | 2023-08-15 | International Business Machines Corporation | Meeting room selection based on internet of things privacy level |
| US12231496B2 (en) | 2020-10-30 | 2025-02-18 | Tyco Fire & Security Gmbh | Building management system with dynamic building model enhanced by digital twins |
| US11334626B1 (en) | 2020-11-02 | 2022-05-17 | Bank Of America Corporation | Hybrid graph and relational database architecture |
| CN112380683B (en)* | 2020-11-05 | 2023-01-31 | 贵州电网有限责任公司 | Handling decision method based on fault evolution path |
| US11546475B2 (en) | 2020-11-06 | 2023-01-03 | Micro Focus Llc | System and method for dynamic driven context management |
| US11502894B2 (en) | 2020-11-10 | 2022-11-15 | Accenture Global Solutions Limited | Predicting performance of a network order fulfillment system |
| US11940770B2 (en) | 2020-11-11 | 2024-03-26 | Mapped Inc. | Automated data integration pipeline with storage and enrichment |
| US20220159029A1 (en)* | 2020-11-13 | 2022-05-19 | Cyberark Software Ltd. | Detection of security risks based on secretless connection data |
| CN112118272B (en)* | 2020-11-18 | 2021-01-15 | 中国人民解放军国防科技大学 | Network Attack and Defense Deduction Platform Based on Simulation Experiment Design |
| US11818147B2 (en)* | 2020-11-23 | 2023-11-14 | Fair Isaac Corporation | Overly optimistic data patterns and learned adversarial latent features |
| US11196775B1 (en) | 2020-11-23 | 2021-12-07 | Sailpoint Technologies, Inc. | System and method for predictive modeling for entitlement diffusion and role evolution in identity management artificial intelligence systems using network identity graphs |
| CN112526905B (en)* | 2020-11-27 | 2022-09-27 | 杭州萤石软件有限公司 | Processing method and system for index abnormity |
| CN112565227B (en)* | 2020-11-27 | 2023-05-19 | 深圳前海微众银行股份有限公司 | Abnormal task detection method and device |
| US12033048B1 (en)* | 2020-11-30 | 2024-07-09 | Amazon Technologies, Inc. | Anomaly detection using feedback |
| US12405933B2 (en)* | 2020-11-30 | 2025-09-02 | Getac Technology Corporation | Content management system for trained machine learning models |
| US11271865B1 (en)* | 2020-12-02 | 2022-03-08 | Microsoft Technology Licensing, Llc | Resource popularity assessment and utilization |
| FR3117228A1 (en)* | 2020-12-03 | 2022-06-10 | Thales | Digital data plotting process |
| US12197585B2 (en)* | 2020-12-07 | 2025-01-14 | International Business Machines Corporation | Machine learning based vulnerable target identification in ransomware attack |
| US11687648B2 (en) | 2020-12-10 | 2023-06-27 | Abnormal Security Corporation | Deriving and surfacing insights regarding security threats |
| US11122073B1 (en) | 2020-12-11 | 2021-09-14 | BitSight Technologies, Inc. | Systems and methods for cybersecurity risk mitigation and management |
| WO2022120840A1 (en)* | 2020-12-11 | 2022-06-16 | Beijing Didi Infinity Technology And Development Co., Ltd. | Systems and methods for improving security |
| US11947519B2 (en) | 2020-12-14 | 2024-04-02 | International Business Machines Corporation | Assigning an anomaly level to a non-instrumented object |
| US12021885B2 (en)* | 2020-12-14 | 2024-06-25 | International Business Machines Corporation | Aggregating results from multiple anomaly detection engines |
| US11775654B2 (en) | 2020-12-14 | 2023-10-03 | International Business Machines Corporation | Anomaly detection with impact assessment |
| US20220191211A1 (en)* | 2020-12-15 | 2022-06-16 | ClearVector, Inc. | Computer-implemented methods, systems comprising computer-readable media, and electronic devices for resource preservation and intervention within a network computing environment |
| US11811804B1 (en)* | 2020-12-15 | 2023-11-07 | Red Hat, Inc. | System and method for detecting process anomalies in a distributed computation system utilizing containers |
| US11848948B2 (en)* | 2020-12-18 | 2023-12-19 | Vmware, Inc. | Correlation-based security threat analysis |
| US12061453B2 (en) | 2020-12-18 | 2024-08-13 | Tyco Fire & Security Gmbh | Building management system performance index |
| US20250069011A1 (en)* | 2020-12-22 | 2025-02-27 | Pointillist, Inc. | Escalation management and journey mining |
| IL279697A (en)* | 2020-12-23 | 2022-07-01 | B G Negev Technologies And Applications Ltd At Ben Gurion Univ | System and method for detecting suspicious websites in information streams from proxy servers |
| US11681511B2 (en)* | 2020-12-24 | 2023-06-20 | Sway AI Inc. | Systems and methods for building and deploying machine learning applications |
| US20220207043A1 (en)* | 2020-12-28 | 2022-06-30 | Vmware, Inc. | Entity data services for virtualized computing and data systems |
| CN112738088B (en)* | 2020-12-28 | 2023-03-21 | 上海观安信息技术股份有限公司 | Behavior sequence anomaly detection method and system based on unsupervised algorithm |
| US12069072B2 (en) | 2020-12-29 | 2024-08-20 | IronNet Cybersecurity, Inc. | Systems and methods for detecting malicious network traffic using multi-domain machine learning |
| EP4272474A4 (en)* | 2020-12-30 | 2024-02-21 | Telefonaktiebolaget LM Ericsson (publ) | Method and network node for detecting anomalous access behaviours |
| CN113723734B (en) | 2020-12-30 | 2025-05-23 | 京东城市(北京)数字科技有限公司 | Abnormality monitoring method and device for time sequence data, electronic equipment and storage medium |
| US11606378B1 (en) | 2020-12-30 | 2023-03-14 | Rapid7, Inc. | Lateral movement detection using a mixture of online anomaly scoring models |
| US11941599B2 (en)* | 2020-12-31 | 2024-03-26 | Capital One Services, Llc | Machine-learning based electronic activity accuracy verification and detection of anomalous attributes and methods thereof |
| GB2602628B (en) | 2020-12-31 | 2023-03-29 | British Telecomm | Identifying Computer Systems for Malware Infection Mitigation |
| CN114697068B (en)* | 2020-12-31 | 2025-01-10 | 华为技术有限公司 | A method and related device for identifying malicious traffic |
| CN113515672B (en)* | 2020-12-31 | 2025-05-16 | 腾讯科技(深圳)有限公司 | Data processing method, device, computer readable medium and electronic device |
| CN112667907B (en)* | 2021-01-04 | 2023-10-17 | 深圳市华通易点信息技术有限公司 | Multi-platform information delivery and data statistics system and method |
| US11604642B2 (en) | 2021-01-04 | 2023-03-14 | Bank Of America Corporation | System for computer program code issue detection and resolution using an automated progressive code quality engine |
| US11943235B2 (en) | 2021-01-04 | 2024-03-26 | Saudi Arabian Oil Company | Detecting suspicious user logins in private networks using machine learning |
| US11663164B2 (en)* | 2021-01-05 | 2023-05-30 | EMC IP Holding Company LLC | Performing file-based time series management |
| AU2022205946A1 (en)* | 2021-01-06 | 2023-08-17 | ARETE SECURITY INC. dba DRUVSTAR | Systems, devices, and methods for observing and/or securing data access to a computer network |
| WO2022150513A1 (en)* | 2021-01-06 | 2022-07-14 | ARETE SECURITY INC. dba DRUVSTAR | Systems, devices, and methods for observing and/or securing data access to a computer network |
| US12086038B2 (en)* | 2021-01-06 | 2024-09-10 | Kyndryl, Inc. | Unsupervised log data anomaly detection |
| US11792211B2 (en) | 2021-01-07 | 2023-10-17 | Bank Of America Corporation | System for detecting and remediating computing system breaches using computing network traffic monitoring |
| WO2022150653A1 (en)* | 2021-01-08 | 2022-07-14 | Darktrace, Inc. | Artificial intelligence based analyst as an evaluator |
| EP4275122A4 (en) | 2021-01-08 | 2024-10-09 | Darktrace Holdings Limited | USER AGENT INFERENCE AND ACTIVE ENDPOINT FINGERPRINTING FOR ENCRYPTED CONNECTIONS |
| US11652828B1 (en)* | 2021-01-11 | 2023-05-16 | Wells Fargo Bank, N.A. | Systems and methods for automated anomalous behavior detection and risk-scoring individuals |
| US11678148B2 (en) | 2021-01-15 | 2023-06-13 | Oshkosh Corporation | Equipment visual status indicator system and method |
| EP4266200B1 (en)* | 2021-01-20 | 2025-10-01 | NTT, Inc. | Generating device, generating method, and generating program |
| US12218961B2 (en)* | 2021-01-21 | 2025-02-04 | Noname Gate Ltd. | Techniques for securing computing interfaces |
| US20220237509A1 (en)* | 2021-01-26 | 2022-07-28 | Oracle International Corporation | Machine learning traceback-enabled decision rationales as models for explainability |
| US12153669B2 (en)* | 2021-01-26 | 2024-11-26 | EMC IP Holding Company LLC | Cyber immunity system as a biological self-recognition model on operating systems |
| US20220237482A1 (en)* | 2021-01-27 | 2022-07-28 | Intuit Inc. | Feature randomization for securing machine learning models |
| US11765129B2 (en) | 2021-01-28 | 2023-09-19 | Okta, Inc. | Automated creation of trusted network perimeter |
| US12050693B2 (en)* | 2021-01-29 | 2024-07-30 | Varmour Networks, Inc. | System and method for attributing user behavior from multiple technical telemetry sources |
| US11687438B1 (en) | 2021-01-29 | 2023-06-27 | Splunk Inc. | Adaptive thresholding of data streamed to a data processing pipeline |
| US12034731B2 (en)* | 2021-01-29 | 2024-07-09 | Paypal, Inc. | Evaluating access requests using assigned common actor identifiers |
| US12250235B2 (en)* | 2021-01-29 | 2025-03-11 | Rubrik, Inc. | Scalable automated training framework |
| US20220245240A1 (en)* | 2021-02-01 | 2022-08-04 | Apiiro Ltd. | System, method, and process for identifying and protecting against advanced attacks based on code, binary and contributors behavior |
| CN112785320B (en)* | 2021-02-01 | 2023-09-19 | 北京互金新融科技有限公司 | Credit risk determination method and device, storage medium and electronic equipment |
| US12183081B2 (en)* | 2021-02-01 | 2024-12-31 | The Government of the United States of America, as represented by the Secretary of Homeland Security | Scanners to characterize and distinguish anomalies based on multiple mode scans |
| US12052134B2 (en) | 2021-02-02 | 2024-07-30 | Exfo Inc. | Identification of clusters of elements causing network performance degradation or outage |
| WO2022169892A1 (en)* | 2021-02-02 | 2022-08-11 | Quantum Metric Inc. | Detecting, diagnosing, and alerting anomalies in network applications |
| SE545760C2 (en)* | 2021-02-04 | 2024-01-02 | Eqt Ab | Method and system for performing a digital process |
| US12235617B2 (en) | 2021-02-08 | 2025-02-25 | Tyco Fire & Security Gmbh | Site command and control tool with dynamic model viewer |
| WO2022169461A1 (en)* | 2021-02-08 | 2022-08-11 | Hewlett-Packard Development Company, L.P. | Malware scans |
| US12224985B2 (en)* | 2021-02-12 | 2025-02-11 | International Business Machines Corporation | Edge data correctness and correctness spread determination |
| WO2022174034A1 (en)* | 2021-02-12 | 2022-08-18 | Chevron U.S.A. Inc. | Machine learning workflow to predict sanding events |
| US12381786B2 (en)* | 2021-02-14 | 2025-08-05 | Cytex, Inc. | System and method for monitoring data disclosures |
| US11528294B2 (en)* | 2021-02-18 | 2022-12-13 | SecureworksCorp. | Systems and methods for automated threat detection |
| US11295241B1 (en) | 2021-02-19 | 2022-04-05 | Sailpoint Technologies, Inc. | System and method for incremental training of machine learning models in artificial intelligence systems, including incremental training using analysis of network identity graphs |
| JP7616901B2 (en)* | 2021-02-19 | 2025-01-17 | 日立Astemo株式会社 | Electronic Control System |
| US11941020B2 (en) | 2021-02-26 | 2024-03-26 | Micro Focus Llc | Displaying query results using machine learning model-determined query results visualizations |
| US11409629B1 (en)* | 2021-03-05 | 2022-08-09 | Sift Science, Inc. | Systems and methods for optimizing a machine learning-informed automated decisioning workflow in a machine learning task-oriented digital threat mitigation platform |
| US12143412B2 (en)* | 2021-03-08 | 2024-11-12 | Tenable, Inc. | Automatic generation of vulnerability metrics using machine learning |
| US11683246B2 (en) | 2021-03-09 | 2023-06-20 | Ayla Networks, Inc. | Edge-based intelligence for anomaly detection |
| US20220292006A1 (en)* | 2021-03-09 | 2022-09-15 | Vunet Systems Private Limited | System for Automatically Generating Insights by Analysing Telemetric Data |
| US11550907B2 (en)* | 2021-03-11 | 2023-01-10 | Expel, Inc. | Systems and methods for intelligent cyber security threat detection and intelligent verification-informed handling of cyber security events through automated verification workflows |
| US12093720B2 (en) | 2021-03-15 | 2024-09-17 | International Business Machines Corporation | Software container prestart configuration with kubectl prestart runtime commands |
| CN113067808B (en)* | 2021-03-15 | 2022-07-05 | 上海哔哩哔哩科技有限公司 | Data processing method, live broadcast method, authentication server and live broadcast data server |
| US11943200B2 (en) | 2021-03-16 | 2024-03-26 | Saudi Arabian Oil Company | Systems and methods for detecting anomalous virtual private network sessions using machine learning |
| IT202100006383A1 (en)* | 2021-03-17 | 2022-09-17 | Cleafy Spa | METHOD OF MONITORING AND SECURING ACCESS TO AN ONLINE SERVICE |
| WO2022197964A1 (en) | 2021-03-17 | 2022-09-22 | Johnson Controls Tyco IP Holdings LLP | Systems and methods for determining equipment energy waste |
| CN113064932B (en)* | 2021-03-18 | 2023-01-24 | 中国石油大学(华东) | A Network Situation Assessment Method Based on Data Mining |
| US11816210B2 (en)* | 2021-03-22 | 2023-11-14 | Adobe Inc. | Risk-based alerting for computer security |
| US11526617B2 (en) | 2021-03-24 | 2022-12-13 | Bank Of America Corporation | Information security system for identifying security threats in deployed software package |
| US11363049B1 (en) | 2021-03-25 | 2022-06-14 | Bank Of America Corporation | Information security system and method for anomaly detection in data transmission |
| CN112698926B (en)* | 2021-03-25 | 2021-07-02 | 成都新希望金融信息有限公司 | Data processing method, device, equipment, storage medium and system |
| US11709935B2 (en) | 2021-03-26 | 2023-07-25 | International Business Machines Corporation | Detecting potentially malicious code in data through data profiling with an information analyzer |
| US11558412B1 (en) | 2021-03-29 | 2023-01-17 | Splunk Inc. | Interactive security visualization of network entity data |
| US11947572B2 (en)* | 2021-03-29 | 2024-04-02 | Group IB TDS, Ltd | Method and system for clustering executable files |
| US11805141B2 (en) | 2021-03-30 | 2023-10-31 | International Business Machines Corporation | Predicting security response impact |
| US11936513B2 (en) | 2021-03-30 | 2024-03-19 | Acronis International Gmbh | System and method for anomaly detection in a computer network |
| US20220318332A1 (en)* | 2021-03-30 | 2022-10-06 | Traceable Inc. | Intelligent naming of application program interfaces |
| US12248434B2 (en) | 2021-03-31 | 2025-03-11 | Nutanix, Inc. | File analytics systems including examples providing metrics adjusted for application operation |
| US12079347B2 (en) | 2021-03-31 | 2024-09-03 | BitSight Technologies, Inc. | Systems and methods for assessing cybersecurity risk in a work from home environment |
| US12242455B2 (en) | 2021-03-31 | 2025-03-04 | Nutanix, Inc. | File analytics systems and methods including receiving and processing file system event data in order |
| WO2022208303A1 (en)* | 2021-03-31 | 2022-10-06 | Jio Platforms Limited | Systems and methods for identifying spatial clusters of users having poor experience in a heterogeneous network |
| US12367108B2 (en) | 2021-03-31 | 2025-07-22 | Nutanix, Inc. | File analytics systems and methods including retrieving metadata from file system snapshots |
| US20240168923A1 (en)* | 2021-03-31 | 2024-05-23 | Nutanix, Inc. | File analytics systems and methods |
| US11811786B1 (en)* | 2021-04-02 | 2023-11-07 | Wiz, Inc. | Lateral movement analysis using certificate private keys |
| US11799874B1 (en)* | 2021-04-02 | 2023-10-24 | Wiz, Inc. | System and method for detecting lateral movement using SSH private keys |
| US11811787B1 (en)* | 2021-04-02 | 2023-11-07 | Wiz, Inc. | System and method for detecting lateral movement using cloud access keys |
| US11895134B2 (en) | 2021-04-12 | 2024-02-06 | Sap Se | Securing applications through similarity-based risk assessment |
| CN113094525B (en)* | 2021-04-12 | 2024-07-02 | 中铁工程设计咨询集团有限公司 | Monorail turnout fault on-line diagnosis method, device, equipment and readable storage medium |
| US12437063B2 (en)* | 2021-04-12 | 2025-10-07 | Ge Vernova Infrastructure Technology Llc | Unified multi-agent system for abnormality detection and isolation |
| US11916940B2 (en)* | 2021-04-12 | 2024-02-27 | Ge Infrastructure Technology Llc | Attack detection and localization with adaptive thresholding |
| US12160433B1 (en)* | 2021-04-15 | 2024-12-03 | Amazon Technologies, Inc. | Device-to-account anomaly detection |
| US12355797B2 (en) | 2021-04-20 | 2025-07-08 | Rapid7, Inc. | System for collecting computer network entity information employing abstract models |
| CN113138875B (en)* | 2021-04-22 | 2022-12-06 | 深圳感臻智能股份有限公司 | Fault detection method, terminal and computer storage medium |
| US12032538B2 (en)* | 2021-04-23 | 2024-07-09 | Capital One Services, Llc | Anomaly detection in a split timeseries dataset |
| US11789915B2 (en)* | 2021-04-23 | 2023-10-17 | Capital One Services, Llc | Automatic model selection for a time series |
| US11856014B2 (en)* | 2021-04-23 | 2023-12-26 | Capital One Services, Llc | Anomaly detection in computing computing system events |
| TWI778597B (en)* | 2021-04-23 | 2022-09-21 | 新加坡商鴻運科股份有限公司 | Deployment method of remote desktop gateways, computer device, and storage medium |
| CN115242637B (en) | 2021-04-23 | 2023-10-17 | 深圳富联富桂精密工业有限公司 | Remote desktop gateway allocation method, computer device and storage medium |
| CN112862111B (en)* | 2021-04-26 | 2021-08-24 | 之江实验室 | Method and device for accelerating gradient convergence of distributed machine learning |
| US20220353279A1 (en)* | 2021-04-29 | 2022-11-03 | KnowBe4, Inc. | Systems and methods for determination of indicators of malicious elements within messages |
| US11599523B2 (en) | 2021-04-30 | 2023-03-07 | Bank Of America Corporation | System for computing system configuration file state identification using decentralized multidimensional snapshots |
| US11843626B2 (en)* | 2021-04-30 | 2023-12-12 | Microsoft Technology Licensing, Llc | Connected component-based collaborative filtering in recommendation intrusion detection systems |
| US12026274B2 (en)* | 2021-04-30 | 2024-07-02 | Capital One Services, Llc | Computer-based systems configured for managing permission messages in a database and methods of use thereof |
| US11307952B1 (en) | 2021-04-30 | 2022-04-19 | Bank Of America Corporation | System for computing system configuration file state mirroring on peer computing devices |
| US20220350686A1 (en)* | 2021-04-30 | 2022-11-03 | Imperva, Inc. | Application programming interface (api) and site discovery via request similarity |
| US12309660B2 (en) | 2021-05-06 | 2025-05-20 | Universal City Studios Llc | Systems and methods for layered data reporting in an attraction |
| US11973779B2 (en) | 2021-05-11 | 2024-04-30 | Bank Of America Corporation | Detecting data exfiltration and compromised user accounts in a computing network |
| US12166780B2 (en) | 2021-05-11 | 2024-12-10 | Bank Of America Corporation | Detecting data exfiltration and compromised user accounts in a computing network |
| CN113411303B (en)* | 2021-05-12 | 2022-06-03 | 桂林电子科技大学 | Construction Method of Evaluation Index System Based on Hierarchical Clustering and Analytic Hierarchy Process |
| US20220366316A1 (en)* | 2021-05-12 | 2022-11-17 | Capital One Services, Llc | Ensemble machine learning for anomaly detection |
| US11875185B2 (en) | 2021-05-19 | 2024-01-16 | International Business Machines Corporation | Determining a validity of an event emitter based on a rule |
| WO2022246131A1 (en)* | 2021-05-20 | 2022-11-24 | Netskope, Inc. | Scoring confidence in user compliance with an organization's security policies |
| US11481709B1 (en) | 2021-05-20 | 2022-10-25 | Netskope, Inc. | Calibrating user confidence in compliance with an organization's security policies |
| US12061628B1 (en)* | 2021-05-21 | 2024-08-13 | Riverbed Technology, LLC | Computing a digital experience index |
| KR20220157565A (en)* | 2021-05-21 | 2022-11-29 | 삼성에스디에스 주식회사 | Apparatus and method for detecting web scanning attack |
| JPWO2022249816A1 (en)* | 2021-05-26 | 2022-12-01 | ||
| CN113489677B (en)* | 2021-05-27 | 2022-06-07 | 贵州电网有限责任公司 | Zero rule attack detection method and device based on semantic context |
| CN113190415B (en)* | 2021-05-27 | 2025-01-07 | 北京京东拓先科技有限公司 | Internet hospital system monitoring method, equipment, storage medium and program product |
| US11716340B2 (en) | 2021-05-28 | 2023-08-01 | Microsoft Technology Licensing, Llc | Threat detection using cloud resource management logs |
| US12235812B2 (en)* | 2021-05-29 | 2025-02-25 | Jpmorgan Chase Bank, N.A. | Method and system for recursive data refinement and republishing |
| US11924019B2 (en)* | 2021-05-31 | 2024-03-05 | Jio Platforms Limited | Alarm management module for internet-of-things (IoT) network |
| US20220383141A1 (en)* | 2021-06-01 | 2022-12-01 | Saferide Technologies Ltd. | System and method for feature selection recommendation |
| US11902308B2 (en)* | 2021-06-03 | 2024-02-13 | At&T Intellectual Property I, L.P. | Detecting threat pathways using sequence graphs |
| US11831661B2 (en) | 2021-06-03 | 2023-11-28 | Abnormal Security Corporation | Multi-tiered approach to payload detection for incoming communications |
| CN117441321A (en)* | 2021-06-07 | 2024-01-23 | 日本电信电话株式会社 | Detection device, detection method and detection procedure |
| US12166516B2 (en) | 2021-06-08 | 2024-12-10 | Silvus Technologies, Inc. | Adaptive wideband interference cancellation for MIMO networks |
| EP4341840A4 (en)* | 2021-06-11 | 2024-06-19 | Telefonaktiebolaget LM Ericsson (publ) | Method and device relating to decision-making threshold |
| US11748231B2 (en)* | 2021-06-15 | 2023-09-05 | International Business Machines Corporation | Machine logic for performing anomaly detection |
| US20220407864A1 (en)* | 2021-06-17 | 2022-12-22 | Onapsis Inc. | System and method for scalable multi-application user access and segregation of duties review |
| US11930046B2 (en) | 2021-06-17 | 2024-03-12 | Xerox Corporation | System and method for determining vulnerability metrics for graph-based configuration security |
| US11349861B1 (en) | 2021-06-18 | 2022-05-31 | Extrahop Networks, Inc. | Identifying network entities based on beaconing activity |
| US11899723B2 (en) | 2021-06-22 | 2024-02-13 | Johnson Controls Tyco IP Holdings LLP | Building data platform with context based twin function processing |
| KR102585591B1 (en)* | 2021-06-23 | 2023-10-10 | 한국과학기술원 | Slo-aware artificial intelligence inference scheduler for heterogeneous processors in edge platforms |
| US11856015B2 (en)* | 2021-06-24 | 2023-12-26 | Microsoft Technology Licensing, Llc | Anomalous action security assessor |
| US11294723B1 (en) | 2021-06-25 | 2022-04-05 | Sedai Inc. | Autonomous application management for distributed computing systems |
| US12159205B2 (en)* | 2021-06-28 | 2024-12-03 | Bank Of America Corporation | Machine learning model scenario-based training system |
| US11816080B2 (en) | 2021-06-29 | 2023-11-14 | International Business Machines Corporation | Severity computation of anomalies in information technology operations |
| WO2023275599A1 (en)* | 2021-07-01 | 2023-01-05 | Telefonaktiebolaget Lm Ericsson (Publ) | Training a machine learning model to identify a relationship between data items |
| US12353563B2 (en) | 2021-07-01 | 2025-07-08 | BitSight Technologies, Inc. | Systems and methods for accelerating cybersecurity assessments |
| WO2023283423A1 (en) | 2021-07-09 | 2023-01-12 | Sotero, Inc. | Autonomous machine learning methods for detecting and thwarting malicious database access |
| TWI751090B (en)* | 2021-07-13 | 2021-12-21 | 中華電信股份有限公司 | Dynamic detection system, method and computer-readable medium for networked device |
| US12177233B2 (en)* | 2021-07-20 | 2024-12-24 | CyCarrier Technology Co., Ltd. | Information security incident diagnosis system for assisting in intrusion detection and related computer program |
| US11914709B2 (en)* | 2021-07-20 | 2024-02-27 | Bank Of America Corporation | Hybrid machine learning and knowledge graph approach for estimating and mitigating the spread of malicious software |
| US20240378515A1 (en)* | 2021-07-21 | 2024-11-14 | Nippon Telegraph And Telephone Corporation | Generation apparatus, generation method, data structure of model data, data structure of relation data and generation program |
| US11645252B2 (en) | 2021-07-23 | 2023-05-09 | Bank Of America Corporation | System and method for efficiently validating time-series data using a hash-based representation of the data |
| US11640389B2 (en) | 2021-07-23 | 2023-05-02 | Bank Of America Corporation | Hash-based identification of data corruption issues in time-series data |
| US12093357B2 (en) | 2021-07-29 | 2024-09-17 | Bank Of America Corporation | Biometric authentication based on behavioral analysis |
| US11227055B1 (en) | 2021-07-30 | 2022-01-18 | Sailpoint Technologies, Inc. | System and method for automated access request recommendations |
| US11888760B2 (en) | 2021-07-30 | 2024-01-30 | Cisco Technology, Inc. | Identifying unmanaged cloud resources with endpoint and network logs |
| US11949570B2 (en) | 2021-07-30 | 2024-04-02 | Keysight Technologies, Inc. | Methods, systems, and computer readable media for utilizing machine learning to automatically configure filters at a network packet broker |
| US11930000B2 (en) | 2021-08-02 | 2024-03-12 | Cisco Technology, Inc. | Detection of anomalous authentications |
| US20230042661A1 (en)* | 2021-08-03 | 2023-02-09 | Orev Secure Networks LLC | First Detection of Potential Harmful Activities |
| US12047379B2 (en) | 2021-08-04 | 2024-07-23 | International Business Machines Corporation | Data access control management computer system for event driven dynamic security |
| US12135789B2 (en) | 2021-08-04 | 2024-11-05 | Secureworks Corp. | Systems and methods of attack type and likelihood prediction |
| US11949701B2 (en)* | 2021-08-04 | 2024-04-02 | Microsoft Technology Licensing, Llc | Network access anomaly detection via graph embedding |
| US12250236B2 (en)* | 2021-08-10 | 2025-03-11 | Level 3 Communications, Llc | Collecting endpoint data and network data to detect an anomaly |
| US12041075B2 (en)* | 2021-08-11 | 2024-07-16 | Capital One Services, Llc | Detecting malicious activity associated with resetting authentication information |
| US11861476B2 (en)* | 2021-08-18 | 2024-01-02 | International Business Machines Corporation | Secure ensemble training and inference using heterogeneous private machine learning models |
| US11513772B1 (en) | 2021-08-22 | 2022-11-29 | Dataplate Ltd. | System and method of providing an interactive development platform in a distributed computing environment |
| KR20230029040A (en)* | 2021-08-23 | 2023-03-03 | 삼성에스디에스 주식회사 | Apparatus and method for scheming model for detecting secure shell communication |
| US11966922B2 (en) | 2021-08-24 | 2024-04-23 | Bank Of America Corporation | Electronic system for scanning and mapping entity portals to distribution processing systems |
| US11397808B1 (en) | 2021-09-02 | 2022-07-26 | Confluera, Inc. | Attack detection based on graph edge context |
| CN113705714B (en)* | 2021-09-03 | 2024-06-11 | 上海观安信息技术股份有限公司 | Abnormal behavior detection method and device for power distribution Internet of things equipment based on behavior sequence |
| WO2023034419A1 (en)* | 2021-09-03 | 2023-03-09 | Lacework, Inc. | Detecting anomalous behavior of a device |
| WO2023034444A1 (en)* | 2021-09-03 | 2023-03-09 | Lacework, Inc. | Generating user-specific polygraphs for network activity |
| EP4396703A4 (en)* | 2021-09-03 | 2025-06-25 | Open Text Holdings, Inc. | Systems and methods for asset-based event prioritization for remote endpoint security |
| CN113722740B (en)* | 2021-09-06 | 2023-07-28 | 全知科技(杭州)有限责任公司 | Method for detecting risk of horizontal unauthorized access to sensitive data based on interface portrait |
| US12406261B2 (en)* | 2021-09-13 | 2025-09-02 | Early Warning Services, Llc | Unsupervised clustering feature engineering |
| US12223074B2 (en) | 2021-09-17 | 2025-02-11 | Xerox Corporation | System and method for securing windows discretionary access control |
| US12284216B2 (en) | 2021-09-17 | 2025-04-22 | Xerox Corporation | System and method for synthesizing role-based access control assignments per a policy |
| US12355763B2 (en) | 2021-09-17 | 2025-07-08 | Capital One Services, Llc | Methods and systems for identifying unauthorized logins |
| US12425437B2 (en) | 2021-09-17 | 2025-09-23 | BitSight Technologies, Inc. | Systems and methods for precomputation of digital asset inventories |
| US20230094856A1 (en)* | 2021-09-20 | 2023-03-30 | Normalyze, Inc. | Compact cloud access network based on role-to-resource detection with resource state change tracking and provenance |
| US11611573B1 (en) | 2021-09-20 | 2023-03-21 | Normalyze, Inc. | In-cloud and constant time scanners |
| WO2023046402A1 (en)* | 2021-09-21 | 2023-03-30 | British Telecommunications Public Limited Company | Graph-based condition identification |
| US12250246B2 (en)* | 2021-09-23 | 2025-03-11 | International Business Machines Corporation | Perform edge processing by selecting edge devices based on security levels |
| US11296967B1 (en) | 2021-09-23 | 2022-04-05 | Extrahop Networks, Inc. | Combining passive network analysis and active probing |
| US11996985B2 (en)* | 2021-09-24 | 2024-05-28 | The Boston Consulting Group, Inc. | Broadband data analytics engine in a data analytics system |
| US12088609B1 (en)* | 2021-09-29 | 2024-09-10 | Amazon Technologies, Inc. | Investigative playbooks for cloud security events |
| US12088633B2 (en)* | 2021-09-30 | 2024-09-10 | Hewlett Packard Enterprise Development Lp | Dynamic intrusion detection and prevention in computer networks |
| US12034751B2 (en) | 2021-10-01 | 2024-07-09 | Secureworks Corp. | Systems and methods for detecting malicious hands-on-keyboard activity via machine learning |
| US20230105021A1 (en)* | 2021-10-05 | 2023-04-06 | Edgio, Inc. | Systems and Methods for Adaptive Network Security Based on Unsupervised Behavioral Modeling |
| CN114118400B (en)* | 2021-10-11 | 2023-01-03 | 中国科学院自动化研究所 | Concentration network-based cluster countermeasure method and device |
| US12348525B2 (en) | 2021-10-13 | 2025-07-01 | Zscaler, Inc. | Generating zero-trust policy for application access using machine learning |
| US11893125B2 (en)* | 2021-10-14 | 2024-02-06 | Cohesity, Inc. | Providing a graphical representation of anomalous events |
| US12333018B2 (en)* | 2021-10-15 | 2025-06-17 | Capital One Services, Llc | Security vulnerability communication and remediation with machine learning |
| CA3233841A1 (en)* | 2021-10-15 | 2024-04-03 | Sean Scott | Security intelligence platform architecture and functionality |
| WO2023069121A1 (en)* | 2021-10-18 | 2023-04-27 | Jpmorgan Chase Bank, N.A. | System and method for auto-mining of resources, building dependency registry and notifying impacted services |
| US20230123421A1 (en)* | 2021-10-18 | 2023-04-20 | International Business Machines Corporation | Capturing Ordinal Historical Dependence in Graphical Event Models with Tree Representations |
| TWI815202B (en)* | 2021-10-25 | 2023-09-11 | 財團法人工業技術研究院 | Method and apparatus for determining efficiency influencing factors |
| US11985154B2 (en)* | 2021-10-26 | 2024-05-14 | Cisco Technology, Inc. | Comprehensible threat detection |
| US11552975B1 (en) | 2021-10-26 | 2023-01-10 | Palo Alto Networks, Inc. | IoT device identification with packet flow behavior machine learning model |
| US11503038B1 (en) | 2021-10-27 | 2022-11-15 | Netskope, Inc. | Policy enforcement and visibility for IaaS and SaaS open APIs |
| US20230137553A1 (en)* | 2021-10-28 | 2023-05-04 | Intuit Inc. | Gradient based anomaly detection system for time series features |
| US20240264977A1 (en)* | 2021-10-29 | 2024-08-08 | Featurespace Limited | Storing and searching for data in data stores |
| US20230135660A1 (en)* | 2021-11-01 | 2023-05-04 | Darktrace Holding Limited | Educational Tool for Business and Enterprise Risk Management |
| US11907194B2 (en) | 2021-11-03 | 2024-02-20 | Capital One Services, Llc | Systems and methods for executing and hashing modeling flows |
| US20230140623A1 (en)* | 2021-11-04 | 2023-05-04 | Mastercard International Incorporated | Method and system for tamper-resistant event sourcing using a distributed ledger |
| US20230134191A1 (en)* | 2021-11-04 | 2023-05-04 | State Farm Mutual Automobile Insurance Company | Systems and methods for insurance application processing |
| US20230147451A1 (en)* | 2021-11-08 | 2023-05-11 | Intelepeer | Methods and systems for generating a virtual graph of multi channel communications |
| KR102433830B1 (en)* | 2021-11-10 | 2022-08-18 | 한국인터넷진흥원 | System and method for security threats anomaly detection based on artificial intelligence |
| US11528279B1 (en) | 2021-11-12 | 2022-12-13 | Netskope, Inc. | Automatic user directory synchronization and troubleshooting |
| US12289332B2 (en) | 2021-11-15 | 2025-04-29 | Cfd Research Corporation | Cybersecurity systems and methods for protecting, detecting, and remediating critical application security attacks |
| US11796974B2 (en) | 2021-11-16 | 2023-10-24 | Johnson Controls Tyco IP Holdings LLP | Building data platform with schema extensibility for properties and tags of a digital twin |
| US11966470B2 (en)* | 2021-11-16 | 2024-04-23 | International Business Machines Corporation | Detecting and preventing distributed data exfiltration attacks |
| US12399467B2 (en) | 2021-11-17 | 2025-08-26 | Tyco Fire & Security Gmbh | Building management systems and methods for tuning fault detection thresholds |
| US11934966B2 (en) | 2021-11-17 | 2024-03-19 | Johnson Controls Tyco IP Holdings LLP | Building data platform with digital twin inferences |
| US20230156031A1 (en)* | 2021-11-18 | 2023-05-18 | Honeywell International Inc. | Real-time visualizations of cyber-risk data for asset-based hierarchies |
| US12192076B2 (en) | 2021-11-18 | 2025-01-07 | Zscaler, Inc. | Network traffic identification using machine learning |
| US20230164156A1 (en)* | 2021-11-19 | 2023-05-25 | IronNet Cybersecurity, Inc. | Detection of abnormal events |
| US11936682B2 (en)* | 2021-11-23 | 2024-03-19 | Microsoft Technology Licensing, Llc | Deep learning to detect abusive sequences of user activity in online network |
| US11991197B2 (en) | 2021-11-23 | 2024-05-21 | Microsoft Technology Licensing, Llc | Deep learning using activity graph to detect abusive user activity in online networks |
| US12177665B2 (en) | 2021-11-23 | 2024-12-24 | Bank Of America Corporation | System for processing mobile resource transfers using secure tokens on a distributed register |
| US11704311B2 (en) | 2021-11-24 | 2023-07-18 | Johnson Controls Tyco IP Holdings LLP | Building data platform with a distributed digital twin |
| US11907368B1 (en)* | 2021-11-24 | 2024-02-20 | Trend Micro Incorporated | Graph-based anomaly detection for cybersecurity |
| US12013673B2 (en) | 2021-11-29 | 2024-06-18 | Tyco Fire & Security Gmbh | Building control system using reinforcement learning |
| US12412003B2 (en) | 2021-11-29 | 2025-09-09 | Tyco Fire & Security Gmbh | Building data platform with digital twin based predictive recommendation visualization |
| US11714930B2 (en) | 2021-11-29 | 2023-08-01 | Johnson Controls Tyco IP Holdings LLP | Building data platform with digital twin based inferences and predictions for a graphical building model |
| DE102021131272A1 (en)* | 2021-11-29 | 2023-06-01 | Consumer Marketing Borell GmbH | Method for controlling a user's access to a network, network and computer program |
| US12032706B2 (en) | 2021-11-30 | 2024-07-09 | Kyndryl, Inc. | Application security scoring |
| US12333657B2 (en) | 2021-12-01 | 2025-06-17 | Tyco Fire & Security Gmbh | Building data platform with augmented reality based digital twins |
| CN114139158B (en)* | 2021-12-03 | 2025-04-04 | 南京航空航天大学 | On-chip network hardware Trojan detection platform based on machine learning |
| US11671516B1 (en)* | 2021-12-09 | 2023-06-06 | Sap Se | Importation of analytics cloud content into custom location in destination tenant |
| CN116260601A (en)* | 2021-12-10 | 2023-06-13 | 奇安信科技集团股份有限公司 | Network threat monitoring method and device, storage medium, terminal |
| US20230188440A1 (en)* | 2021-12-14 | 2023-06-15 | EXFO Solutions SAS | Automatic classification of correlated anomalies from a network through interpretable clustering |
| US20230230000A1 (en)* | 2021-12-17 | 2023-07-20 | Blackthorn Ip, Llc | Systems and methods for linking data entries in database systems |
| US12184692B2 (en)* | 2021-12-21 | 2024-12-31 | Oracle International Corporation | Invalid traffic detection using explainable unsupervised graph ML |
| US11874933B2 (en) | 2021-12-29 | 2024-01-16 | Qualys, Inc. | Security event modeling and threat detection using behavioral, analytical, and threat intelligence attributes |
| CN114357449B (en)* | 2021-12-31 | 2025-01-03 | 中国电信股份有限公司 | Abnormal process detection method and device, electronic device and storage medium |
| US11936545B1 (en)* | 2022-01-11 | 2024-03-19 | Splunk Inc. | Systems and methods for detecting beaconing communications in aggregated traffic data |
| US12267299B2 (en)* | 2022-01-12 | 2025-04-01 | Bank Of America Corporation | Preemptive threat detection for an information system |
| US12093676B2 (en)* | 2022-01-14 | 2024-09-17 | Dell Products L.P. | Intelligent management of software deployment based on code change |
| US11893267B2 (en)* | 2022-01-14 | 2024-02-06 | Bank Of America Corporation | Data flow control and routing using machine learning |
| US12238127B1 (en)* | 2022-01-18 | 2025-02-25 | Rapid7, Inc. | Anomalous data transfer detection |
| US12050522B2 (en)* | 2022-01-18 | 2024-07-30 | Oracle International Corporation | Graph machine learning for case similarity |
| CN114513536B (en)* | 2022-01-18 | 2023-12-08 | 成都网域探行科技有限公司 | Internet of things safety management analysis method |
| US20230231859A1 (en)* | 2022-01-18 | 2023-07-20 | Microsoft Technology Licensing, Llc | Output of baseline behaviors corresponding to features of anomalous events |
| US12301600B2 (en) | 2022-01-18 | 2025-05-13 | Palo Alto Networks, Inc. | IoT device identification by machine learning with time series behavioral and statistical features |
| US12137124B2 (en)* | 2022-01-20 | 2024-11-05 | Dell Products L.P. | Detecting physical anomalies of a computing environment using machine learning techniques |
| US12143393B2 (en)* | 2022-01-24 | 2024-11-12 | VMware LLC | Modifying network relationships using a heterogenous network flows graph |
| US11513927B1 (en)* | 2022-01-25 | 2022-11-29 | Dell Products L.P. | Method and system for performing testing operations for information handling systems |
| US12341788B2 (en)* | 2022-01-25 | 2025-06-24 | Target Brands, Inc. | Network security systems for identifying attempts to subvert security walls |
| US12166774B2 (en) | 2022-01-25 | 2024-12-10 | Target Brands, Inc. | Network security systems for attributing network events to users |
| US11656926B1 (en) | 2022-01-26 | 2023-05-23 | Bank Of America Corporation | Systems and methods for automatically applying configuration changes to computing clusters |
| US12079329B2 (en)* | 2022-01-26 | 2024-09-03 | Dell Products L.P. | Structured data flow identification for proactive issue detection |
| US11714698B1 (en) | 2022-01-28 | 2023-08-01 | Splunk Inc. | System and method for machine-learning based alert prioritization |
| US12282564B2 (en) | 2022-01-31 | 2025-04-22 | BitSight Technologies, Inc. | Systems and methods for assessment of cyber resilience |
| US12111933B2 (en) | 2022-02-07 | 2024-10-08 | Bank Of America Corporation | System and method for dynamically updating existing threat models based on newly identified active threats |
| US11892940B2 (en) | 2022-02-09 | 2024-02-06 | Bank Of America Corporation | Network integrated diagnostic system and predictive analysis tool for mitigating service impacts on application services |
| KR102447280B1 (en) | 2022-02-09 | 2022-09-27 | 주식회사 샌즈랩 | Apparatus for processing cyber threat information, method for processing cyber threat information, and medium for storing a program processing cyber threat information |
| US12411486B2 (en) | 2022-02-11 | 2025-09-09 | International Business Machines Corporation | Asset health identification from multi-modality data analysis |
| US12170016B2 (en)* | 2022-02-15 | 2024-12-17 | Tyco Fire & Security Gmbh | Systems and methods for detecting security events in an environment |
| AU2023220143B2 (en)* | 2022-02-21 | 2025-09-04 | Cranium Ai, Inc. | System and method for implementing an artificial intelligence security platform |
| CN114219374B (en)* | 2022-02-21 | 2022-05-06 | 济南法诺商贸有限公司 | Big data analysis decision system and method based on block chain |
| CN114546979B (en)* | 2022-02-21 | 2024-07-16 | 马上消费金融股份有限公司 | Distributed storage system, and management method, device and equipment thereof |
| US12407705B1 (en) | 2022-02-22 | 2025-09-02 | Everything Set Inc. | Prediction of network vulnerability of a user's network-connected smart device using crowdsourced vulnerability profiles |
| US12301608B1 (en) | 2022-02-22 | 2025-05-13 | Everything Set Inc. | Identification of one or more services for a user's network-connected smart device using a smart device fingerprint of the network-connected smart device |
| US12081518B1 (en) | 2022-02-22 | 2024-09-03 | Everything Set Inc. | Selective inspection of network traffic associated with a plurality of network-connected smart devices using man-in-the-middle (MITM) gateway |
| US12149543B1 (en) | 2022-02-22 | 2024-11-19 | Everything Set Inc. | Crowdsourced Bayesian packet analysis for detecting anomalies in network packet header data associated with a user's smart device |
| US11902176B2 (en) | 2022-02-24 | 2024-02-13 | Bank Of America Corporation | System for detecting multi-dimensional linkage and layering of resource transfers using a distributed server network |
| US12105582B2 (en) | 2022-02-24 | 2024-10-01 | Bank Of America Corporation | System for code base sharing during computing application failure using a distributed register network |
| US12061465B2 (en) | 2022-02-25 | 2024-08-13 | Bank Of America Corporation | Automatic system anomaly detection |
| US12007832B2 (en) | 2022-02-25 | 2024-06-11 | Bank Of America Corporation | Restoring a system by load switching to an alternative cloud instance and self healing |
| US12231448B2 (en)* | 2022-02-25 | 2025-02-18 | Microsoft Technology Licensing, Llc | Using graph enrichment to detect a potentially malicious access attempt |
| US20230275908A1 (en)* | 2022-02-28 | 2023-08-31 | Microsoft Technology Licensing, Llc | Thumbprinting security incidents via graph embeddings |
| US11954693B2 (en)* | 2022-03-03 | 2024-04-09 | Lenovo Global Technology (United States) Inc. | Dynamic test suite creation using event communications from customers |
| US11843530B2 (en)* | 2022-03-08 | 2023-12-12 | Amdocs Development Limited | System, method, and computer program for unobtrusive propagation of solutions for detected incidents in computer applications |
| US12413608B2 (en)* | 2022-03-10 | 2025-09-09 | C3.Ai, Inc. | Enterprise cybersecurity AI platform |
| US11968218B2 (en)* | 2022-03-16 | 2024-04-23 | Impart Security Inc. | Systems and methods for contextually securing remote function calls |
| CN116801292A (en)* | 2022-03-18 | 2023-09-22 | 华为技术有限公司 | A method and device for handling abnormal events |
| US20230306432A1 (en)* | 2022-03-23 | 2023-09-28 | Capital One Services, Llc | Transmitting notifications based on machine learning model outputs |
| WO2023183387A1 (en)* | 2022-03-23 | 2023-09-28 | Visa International Service Association | System, method, and computer program product for dynamic peer group analysis of systematic changes in large scale data |
| US12432244B2 (en)* | 2022-03-24 | 2025-09-30 | At&T Intellectual Property I, L.P. | Home gateway monitoring for vulnerable home internet of things devices |
| US12316666B2 (en)* | 2022-03-25 | 2025-05-27 | Cisco Technology, Inc. | Systems and methods for deriving application security signals from application performance data |
| US11843606B2 (en) | 2022-03-30 | 2023-12-12 | Extrahop Networks, Inc. | Detecting abnormal data access based on data similarity |
| US12204870B2 (en) | 2022-03-31 | 2025-01-21 | Sophos Limited | Natural language analysis of a command line using a machine learning model to generate a natural language description of the command line |
| US20230317279A1 (en)* | 2022-03-31 | 2023-10-05 | Quantiphi Inc | Method and system for medical diagnosis using graph embeddings |
| US12130923B2 (en) | 2022-03-31 | 2024-10-29 | Sophos Limited | Methods and apparatus for augmenting training data using large language models |
| US11962621B2 (en)* | 2022-03-31 | 2024-04-16 | Sophos Limited | Applying network access control configurations with a network switch based on device health |
| US12265526B2 (en) | 2022-03-31 | 2025-04-01 | Sophos Limited | Methods and apparatus for natural language interface for constructing complex database queries |
| US20230315844A1 (en)* | 2022-04-01 | 2023-10-05 | Cisco Technology, Inc. | Systems and methods for generating attack tactic probabilities for historical text documents |
| US12229294B2 (en)* | 2022-04-01 | 2025-02-18 | Blackberry Limited | Event data processing |
| US12231511B2 (en)* | 2022-04-01 | 2025-02-18 | Blackberry Limited | Event data processing |
| WO2023192680A1 (en)* | 2022-04-01 | 2023-10-05 | Reliaquest Holdings, Llc | Threat mitigation system and method |
| US12192066B2 (en)* | 2022-04-04 | 2025-01-07 | Forescout Technologies, Inc. | Decision optimization mechanism for device classification |
| US11588843B1 (en) | 2022-04-08 | 2023-02-21 | Morgan Stanley Services Group Inc. | Multi-level log analysis to detect software use anomalies |
| US12124572B2 (en)* | 2022-04-08 | 2024-10-22 | Microsoft Technology Licensing, Llc | Anomalous activity detection in container images |
| US20230325690A1 (en)* | 2022-04-12 | 2023-10-12 | Optum, Inc. | Predictive data analysis operations using a hierarchical intervention recommendation machine learning framework |
| CN114745183B (en)* | 2022-04-14 | 2023-10-27 | 浙江网商银行股份有限公司 | Alarm method and device |
| US12333250B2 (en) | 2022-04-18 | 2025-06-17 | Bank Of America Corporation | System for machine-learning based identification and filtering of electronic network communication |
| US12346487B2 (en) | 2022-04-18 | 2025-07-01 | Armis Security Ltd. | System and method for detecting cybersecurity vulnerabilities via device attribute resolution |
| US12021878B2 (en)* | 2022-04-19 | 2024-06-25 | Bank Of America Corporation | Unauthorized activity detection based on spatially aware devices |
| US12238132B2 (en) | 2022-04-22 | 2025-02-25 | Xerox Corporation | Method and system for facilitating a ranking score using attack volume to find optimal configurations |
| US12301615B2 (en)* | 2022-04-24 | 2025-05-13 | Microsoft Technology Licensing, Llc | Organization-level ransomware incrimination |
| US20240211436A1 (en)* | 2022-04-24 | 2024-06-27 | Morgan Stanley Services Group Inc. | Distributed query execution and aggregation with custom code execution |
| EP4270227B1 (en)* | 2022-04-28 | 2024-11-06 | Siemens Aktiengesellschaft | Method and system for anomaly detection in a network |
| US12271385B2 (en)* | 2022-04-29 | 2025-04-08 | Microsoft Technology Licensing, Llc | Observation stream engine in a security management system |
| US12204337B2 (en) | 2022-05-04 | 2025-01-21 | International Business Machines Corporation | Multidirectional movement of materials |
| US12372955B2 (en) | 2022-05-05 | 2025-07-29 | Tyco Fire & Security Gmbh | Building data platform with digital twin functionality indicators |
| WO2023215892A1 (en) | 2022-05-06 | 2023-11-09 | Mapped Inc. | Ensemble learning for extracting semantics of data in building systems |
| US12088603B2 (en)* | 2022-05-09 | 2024-09-10 | Bank Of America Corporation | Multi-computer system for comprehensive threat detection and mitigation |
| US12088604B2 (en) | 2022-05-10 | 2024-09-10 | Bank Of America Corporation | Security system for dynamic detection of attempted security breaches using artificial intelligence, machine learning, and a mixed reality graphical interface |
| US11917000B2 (en)* | 2022-05-12 | 2024-02-27 | Bank Of America Corporation | Message queue routing system |
| WO2023217393A1 (en)* | 2022-05-13 | 2023-11-16 | Abb Schweiz Ag | Industrial automation system and method |
| US11782877B1 (en)* | 2022-05-17 | 2023-10-10 | Bank Of America Corporation | Search technique for noisy logs and resulting user interfaces displaying log entries in ranked order of importance |
| US12105799B2 (en) | 2022-05-31 | 2024-10-01 | As0001, Inc. | Systems and methods for security intelligence exchange |
| US12189787B2 (en) | 2022-05-31 | 2025-01-07 | As0001, Inc. | Systems and methods for protection modeling |
| US12236491B2 (en) | 2022-05-31 | 2025-02-25 | As0001, Inc. | Systems and methods for synchronizing and protecting data |
| US12333612B2 (en) | 2022-05-31 | 2025-06-17 | As0001, Inc. | Systems and methods for dynamic valuation of protection products |
| US12177242B2 (en) | 2022-05-31 | 2024-12-24 | As0001, Inc. | Systems and methods for dynamic valuation of protection products |
| US12047400B2 (en)* | 2022-05-31 | 2024-07-23 | As0001, Inc. | Adaptive security architecture based on state of posture |
| USD1029872S1 (en)* | 2022-05-31 | 2024-06-04 | Raptor Technologies LLC | Display panel with animated graphical user interface |
| US20240340301A1 (en) | 2022-05-31 | 2024-10-10 | As0001, Inc. | Adaptive security architecture based on state of posture |
| US12244703B2 (en) | 2022-05-31 | 2025-03-04 | As0001, Inc. | Systems and methods for configuration locking |
| US12216786B2 (en) | 2022-05-31 | 2025-02-04 | As0001, Inc. | Systems and methods for posture-based modeling |
| US20230394136A1 (en)* | 2022-06-01 | 2023-12-07 | Armis Security Ltd. | System and method for device attribute identification based on queries of interest |
| US20230401288A1 (en)* | 2022-06-10 | 2023-12-14 | Opswat Inc. | Managing machine learning models |
| US12244561B2 (en)* | 2022-06-14 | 2025-03-04 | Bank Of America Corporation | Preventing data loss using enhanced analysis of the URLs and URIs in webpage requests |
| US12223056B1 (en)* | 2022-06-14 | 2025-02-11 | Amazon Technologies, Inc. | Graph-based detection of abusive computational nodes |
| CN117616400A (en) | 2022-06-22 | 2024-02-27 | 瞻博网络公司 | Anomaly detection of network devices using intent-based analytics |
| US12015623B2 (en) | 2022-06-24 | 2024-06-18 | Secureworks Corp. | Systems and methods for consensus driven threat intelligence |
| US20230421587A1 (en)* | 2022-06-24 | 2023-12-28 | Crowdstrike, Inc. | Distributed Digital Security System for Predicting Malicious Behavior |
| US11704173B1 (en)* | 2022-06-30 | 2023-07-18 | Intuit Inc. | Streaming machine learning platform |
| US20240012920A1 (en)* | 2022-07-05 | 2024-01-11 | Bank Of America Corporation | System and method for controlling access security protocols in a database management system |
| US12223278B2 (en) | 2022-07-08 | 2025-02-11 | Sap Se | Automatic data card generation |
| US12380243B2 (en) | 2022-07-11 | 2025-08-05 | Sap Se | Image segmentation for anonymization for image processing |
| US20240020409A1 (en)* | 2022-07-12 | 2024-01-18 | Capital One Services, Llc | Predicting and adding metadata to a dataset |
| US12061600B2 (en) | 2022-07-14 | 2024-08-13 | International Business Machines Corporation | API management for batch processing |
| US20240022585A1 (en)* | 2022-07-15 | 2024-01-18 | HiddenLayer Inc. | Detecting and responding to malicious acts directed towards machine learning model |
| US12353311B2 (en)* | 2022-07-20 | 2025-07-08 | Zscaler, Inc. | Dynamic applicative session grouping |
| US20240028646A1 (en)* | 2022-07-21 | 2024-01-25 | Sap Se | Textual similarity model for graph-based metadata |
| US20240037103A1 (en)* | 2022-07-26 | 2024-02-01 | AVAST Software s.r.o. | Computing threat detection rule systems and methods |
| US12072961B2 (en)* | 2022-07-29 | 2024-08-27 | Bank Of America Corporation | Systems and methods for password spraying identification and prevention using hash signature segmentation and behavior clustering analysis |
| US12430907B2 (en) | 2022-08-02 | 2025-09-30 | Motorola Solutions, Inc. | Device, system, and method for implementing role-based machine learning models |
| US20240045693A1 (en)* | 2022-08-02 | 2024-02-08 | Bank Of America Corporation | System and method for automated command access approval across a network of servers |
| US12326801B2 (en) | 2022-08-03 | 2025-06-10 | Bank Of America Corporation | System and method for generating non-fungible token-based test suites from design diagrams |
| US20240054124A1 (en)* | 2022-08-15 | 2024-02-15 | At&T Intellectual Property I, L.P. | Machine learning-based database integrity verification |
| US12393709B2 (en)* | 2022-08-23 | 2025-08-19 | Target Brands, Inc. | Methods and systems for model management |
| US12118084B2 (en)* | 2022-08-25 | 2024-10-15 | Capital One Services, Llc | Automatic selection of data for target monitoring |
| US11893400B1 (en) | 2022-08-26 | 2024-02-06 | Bank Of America Corporation | System and method for automated adjustment of software application function integrations of graphical user interface |
| US12294600B2 (en)* | 2022-08-30 | 2025-05-06 | International Business Machines Corporation | Real time behavioral alert processing in computing environments |
| US12339817B2 (en)* | 2022-08-30 | 2025-06-24 | Charter Communications Operating, Llc | Methods and systems for identifying and correcting anomalies in a data environment |
| US12107742B2 (en) | 2022-08-31 | 2024-10-01 | Hughes Network Systems, Llc | Machine learning to enhance satellite terminal performance |
| CN115632809B (en)* | 2022-09-01 | 2024-07-12 | 国网福建省电力有限公司 | Wind control platform system for intelligently identifying abnormal events based on big data |
| US12265640B2 (en) | 2022-09-02 | 2025-04-01 | Bank Of America Corporation | System and method for controlling resources using parallel computing devices |
| US12013823B2 (en) | 2022-09-08 | 2024-06-18 | Tyco Fire & Security Gmbh | Gateway system that maps points into a graph schema |
| US12061633B2 (en) | 2022-09-08 | 2024-08-13 | Tyco Fire & Security Gmbh | Building system that maps points into a graph schema |
| US20240086538A1 (en)* | 2022-09-09 | 2024-03-14 | Sandfly Security Limited | Computer investigation method and system for investigating authentication in remote host computers |
| US12386951B2 (en)* | 2022-09-09 | 2025-08-12 | Micro Focus Llc | Using thread patterns to identify anomalous behavior |
| WO2024059676A1 (en) | 2022-09-14 | 2024-03-21 | Sotero, Inc. | Autonomous machine learning methods for detecting and thwarting ransomware attacks |
| US11947450B1 (en) | 2022-09-16 | 2024-04-02 | Bank Of America Corporation | Detecting and mitigating application security threats based on quantitative analysis |
| US12401672B2 (en)* | 2022-09-16 | 2025-08-26 | Nvidia Corporation | Finding anomalous patterns |
| US12099601B2 (en) | 2022-09-16 | 2024-09-24 | Bank Of America Corporation | Detecting and mitigating application security threats based on threat change patterns |
| US11893037B1 (en) | 2022-09-24 | 2024-02-06 | Bank Of America Corporation | Dynamic code generation utility with configurable connections and variables |
| USD1041488S1 (en) | 2022-09-29 | 2024-09-10 | Fiduciary Benchmarks Insights, Llc | Display screen or portion thereof with graphical user interface |
| USD1048086S1 (en) | 2022-09-29 | 2024-10-22 | Fiduciary Benchmarks Insights, Llc | Display screen or portion thereof with graphical user interface |
| USD1042520S1 (en) | 2022-09-29 | 2024-09-17 | Fiduciary Benchmarks Insights, Llc | Display screen or portion thereof with graphical user interface |
| USD1041487S1 (en) | 2022-09-29 | 2024-09-10 | Fiduciary Benchmarks Insights, Llc | Display screen or portion thereof with graphical user interface |
| USD1041497S1 (en) | 2022-09-29 | 2024-09-10 | Fiduciary Benchmarks Insights, Llc | Display screen or portion thereof with graphical user interface |
| USD1041496S1 (en) | 2022-09-29 | 2024-09-10 | Fiduciary Benchmarks Insights, Llc | Display screen or portion thereof with graphical user interface |
| USD1043722S1 (en) | 2022-09-29 | 2024-09-24 | Fiduciary Benchmarks Insights, Llc | Display screen or portion thereof with graphical user interface |
| USD1041498S1 (en) | 2022-09-29 | 2024-09-10 | Fiduciary Benchmarks Insights, Llc | Display screen or portion thereof with graphical user interface |
| USD1042521S1 (en) | 2022-09-29 | 2024-09-17 | Fiduciary Benchmarks Insights, Llc | Display screen or portion thereof with graphical user interface |
| USD1041489S1 (en) | 2022-09-29 | 2024-09-10 | Fiduciary Benchmarks Insights, Llc | Display screen or portion thereof with graphical user interface |
| USD1041491S1 (en) | 2022-09-29 | 2024-09-10 | Fiduciary Benchmarks Insights, Llc | Display screen or portion thereof with graphical user interface |
| USD1041490S1 (en) | 2022-09-29 | 2024-09-10 | Fiduciary Benchmarks Insights, Llc | Display screen or portion thereof with graphical user interface |
| USD1042501S1 (en) | 2022-09-29 | 2024-09-17 | Fiduciary Benchmarks Insights, Llc | Display screen or portion thereof with graphical user interface |
| USD1043723S1 (en) | 2022-09-29 | 2024-09-24 | Fiduciary Benchmarks Insights, Llc | Display screen or portion thereof with graphical user interface |
| US20240111719A1 (en)* | 2022-09-30 | 2024-04-04 | Scinapsis Analytics Inc., dba BenchSci | Exposing risk types of biomedical information |
| US12284207B2 (en)* | 2022-10-07 | 2025-04-22 | Cyborg Security, Inc. | System for generating information security management packages through malware tracing, logging, and analysis |
| US11743298B1 (en) | 2022-10-13 | 2023-08-29 | Netskope, Inc. | Machine learning-based risk determination and recommendations for web access |
| US12081385B2 (en) | 2022-10-14 | 2024-09-03 | International Business Machines Corporation | Topology-homogeneity for enriching event patterns in artificial intelligence operations |
| US12316660B2 (en)* | 2022-10-18 | 2025-05-27 | Bank Of America Corporation | Systems, methods, and apparatuses for tracking network traffic data and identifying rogue access patterns in an electronic network |
| US12287803B2 (en)* | 2022-10-21 | 2025-04-29 | Twilio Inc. | Techniques for generating customer profiles in a data warehouse |
| US12314393B2 (en)* | 2022-10-31 | 2025-05-27 | Hewlett Packard Enterprise Development Lp | Detection of ransomware attack using entropy values |
| US12111825B2 (en)* | 2022-11-10 | 2024-10-08 | Bank Of America Corporation | Event-driven batch processing system with granular operational access |
| US11792214B1 (en) | 2022-11-18 | 2023-10-17 | Arctic Wolf Networks, Inc. | Methods and apparatus for monitoring network events for intrusion detection |
| US12225024B2 (en) | 2022-11-18 | 2025-02-11 | Arctic Wolf Networks, Inc. | Methods and apparatus for monitoring network events for intrusion detection |
| US12375363B2 (en) | 2022-11-22 | 2025-07-29 | Bank Of America Corporation | System and method for reconstructing time aware data activity across multiple software applications |
| US20240187432A1 (en)* | 2022-12-01 | 2024-06-06 | Bank Of America Corporation | Systems, methods, and apparatuses for determining resource misappropriation based on distribution frequency in an electronic network |
| US12099429B2 (en) | 2022-12-02 | 2024-09-24 | Bank Of America Corporation | Systems, methods, and apparatuses for identifying, logging and reporting application events in an electronic network |
| US12174025B2 (en)* | 2022-12-02 | 2024-12-24 | Fujitsu Limited | Route generation for vehicle routing problem and variants thereof |
| KR102832399B1 (en)* | 2022-12-14 | 2025-07-11 | 한국전자통신연구원 | Method and apparatus for visualizing medical device network and security attack |
| US12238185B2 (en)* | 2022-12-14 | 2025-02-25 | Microsoft Technology Licensing, Llc | Generating service-to-service dependency map from DNS and authentication logs |
| US12393785B2 (en) | 2022-12-15 | 2025-08-19 | Capital One Services, Llc | Systems and methods for label generation for real-time processed and batch-processed streams for machine learning training |
| WO2024130180A2 (en)* | 2022-12-15 | 2024-06-20 | Capital One Services, Llc | Systems and methods for real-time and batch-processed data stream label generation, unlabelled data handling, label selection, and label versioning in machine learning model training |
| US20240223578A1 (en)* | 2022-12-29 | 2024-07-04 | Trustwave Holdings Inc | Automated incident response tracking and enhanced framework for cyber threat analysis |
| US12436865B2 (en) | 2023-01-03 | 2025-10-07 | Bank Of America Corporation | Natural language processing engine for automated detection of source code discrepancies |
| US12401563B2 (en) | 2023-01-08 | 2025-08-26 | Keysight Technologies, Inc. | Methods, systems, and computer readable media for detecting network service anomalies |
| US12277485B2 (en)* | 2023-01-26 | 2025-04-15 | Intuit Inc. | Efficient real time serving of ensemble models |
| US12341676B2 (en)* | 2023-01-26 | 2025-06-24 | Rakuten Symphony, Inc. | Network monitoring and management profile generation interface, apparatus and method |
| US12010003B1 (en) | 2023-01-26 | 2024-06-11 | Bank Of America Corporation | Systems and methods for deploying automated diagnostic engines for identification of network controls status |
| US12088463B1 (en) | 2023-01-27 | 2024-09-10 | Wells Fargo Bank, N.A. | Automated configuration of software applications |
| GB2625390B (en)* | 2023-01-30 | 2025-01-29 | Lloyds Banking Group Plc | Methods and systems for indicating the possibility of a cyber-attack on a computer network |
| US12363099B2 (en) | 2023-02-06 | 2025-07-15 | Bank Of America Corporation | Securing user interfaces of a computing cluster |
| EP4415312A1 (en) | 2023-02-07 | 2024-08-14 | Fibabanka Anonim Sirketi | A secure blockchain-based architecture for enabling collective intelligence in distributed iot networks |
| US12052206B1 (en)* | 2023-02-16 | 2024-07-30 | Practical Creativity LLC | Systems and methods for improving interactions with artificial intelligence models |
| US12314380B2 (en) | 2023-02-23 | 2025-05-27 | HiddenLayer, Inc. | Scanning and detecting threats in machine learning models |
| WO2024181960A1 (en)* | 2023-02-27 | 2024-09-06 | Rakuten Symphony, Inc. | Kafka header based schema management in encoding and decoding performance management (pm)/fault management (fm) data |
| US20250200179A1 (en)* | 2023-03-10 | 2025-06-19 | Louisiana Tech Research Corporation; of Louisiana Tech University Foundation, Inc. | Open source software behavioral visibility and threat intelligence |
| US12417309B1 (en)* | 2023-03-13 | 2025-09-16 | Blue Yonder Group, Inc. | Securing sensitive and personal data through cognitive actions |
| US12367127B2 (en) | 2023-04-18 | 2025-07-22 | Bank Of America Corporation | Dynamic response generation based on an anomaly associated with a software application |
| US12438898B2 (en)* | 2023-04-20 | 2025-10-07 | Charles Schwab & Co., Inc | Method, apparatus, system, and non-transitory computer readable medium for detecting anomalous user access behaviors |
| US12425438B1 (en)* | 2023-04-21 | 2025-09-23 | Hitrust Services Corp. | Threat activity statistical analysis driven adaptation of a control specification |
| WO2024226745A1 (en)* | 2023-04-25 | 2024-10-31 | Netography, Inc. | Generating enhanced descriptions of detected network events for efficient human interpretation and response |
| US11743281B1 (en)* | 2023-04-25 | 2023-08-29 | Citibank, N.A. | Microservices anomaly detection |
| US12418509B2 (en) | 2023-05-03 | 2025-09-16 | Bank Of America Corporation | System and method for updating a firewall security configuration in a decentralized network |
| US12028207B1 (en) | 2023-05-03 | 2024-07-02 | Bank Of America Corporation | System and method for dynamically aggregating multiple firewall security configurations in a decentralized network |
| CN116232770B (en)* | 2023-05-08 | 2023-07-21 | 中国石油大学(华东) | An enterprise network security protection system and method based on SDN controller |
| US12155526B1 (en)* | 2023-05-12 | 2024-11-26 | Cisco Technology, Inc. | Deploying network anomaly detection systems based on endpoint criticality |
| US12095607B1 (en) | 2023-05-22 | 2024-09-17 | Bank Of America Corporation | System for enhanced anomaly recognition in network topologies using interactive visualization |
| US11956117B1 (en) | 2023-05-22 | 2024-04-09 | Google Llc | Network monitoring and healing based on a behavior model |
| US12363176B2 (en) | 2023-05-23 | 2025-07-15 | Bank Of America Corporation | System and method for data protection in a distributed network via reconstruction and analysis of data segments |
| US20240394377A1 (en)* | 2023-05-26 | 2024-11-28 | Palo Alto Networks, Inc. | Data security risk posture |
| US20240404258A1 (en)* | 2023-05-30 | 2024-12-05 | Acer Incorporated | Automatic efficient small model selection for monocular depth estimation |
| IL303363A (en)* | 2023-05-31 | 2024-12-01 | B G Negev Tech And Applications Ltd | A method for detecting improper use of authorization in a serverless cloud environment |
| US20240411871A1 (en)* | 2023-06-09 | 2024-12-12 | Brex Inc. | System alert modeling based on hypergraph alert clusters |
| US12348646B2 (en) | 2023-06-12 | 2025-07-01 | Wiz, Inc. | Techniques for validating a virtual workload signature from a software repository |
| WO2024259174A1 (en)* | 2023-06-13 | 2024-12-19 | Iot365 Llc | Cybersecurity platform including traffic sensor |
| US12399984B1 (en) | 2023-06-13 | 2025-08-26 | Exabeam, Inc. | System, method, and computer program for predictive autoscaling for faster searches of event logs in a cybersecurity system |
| CN116633664B (en)* | 2023-06-20 | 2023-11-03 | 广东网安科技有限公司 | Evaluation system for network security monitoring |
| US20240427916A1 (en)* | 2023-06-20 | 2024-12-26 | Bank Of America Corporation | Machine learning-based system for dynamic variable determination and labeling |
| US20240430279A1 (en)* | 2023-06-23 | 2024-12-26 | Palo Alto Networks, Inc. | Multi-perspective user and entity behavior analytics for software-as-a-service applications |
| US20240430181A1 (en)* | 2023-06-23 | 2024-12-26 | Qualtrics, Llc | Detecting and validating anomalies from ongoing data collection |
| US12204495B1 (en)* | 2023-06-30 | 2025-01-21 | International Business Machines Corporation | Utilizing structured logs of declarative computing environments |
| WO2025014463A1 (en)* | 2023-07-07 | 2025-01-16 | Visa International Service Association | Method, system, and computer program product for classifying network activity based on classification-specific data patterns |
| CN119311534A (en)* | 2023-07-12 | 2025-01-14 | 戴尔产品有限公司 | Intelligent log collection optimization mechanism based on scoring |
| US12242639B2 (en)* | 2023-07-17 | 2025-03-04 | Bank Of America Corporation | Tunable AI system and models associated therewith based on security clearance level |
| US20250036755A1 (en)* | 2023-07-25 | 2025-01-30 | International Business Machines Corporation | Visualizing unauthorized access tactics used to access machines located on industrial floor |
| GB202311799D0 (en)* | 2023-08-01 | 2023-09-13 | Senseon Tech Ltd | Processing cybersecurity telemetry data |
| US20250055877A1 (en)* | 2023-08-07 | 2025-02-13 | Bank Of America Corporation | Monitoring and preventing spoofing, tampering, and denial of service attacks on cloud containers |
| CN116800543A (en)* | 2023-08-16 | 2023-09-22 | 北京升鑫网络科技有限公司 | Detection method and device of scanner, electronic equipment and readable storage medium |
| US12328232B2 (en) | 2023-08-16 | 2025-06-10 | Bank Of America Corporation | System for automated self-discoverable generation of networked computing application flows |
| US12425309B2 (en)* | 2023-08-24 | 2025-09-23 | Bank Of America Corporation | Intelligent monitoring platform using graph neural networks with a cybersecurity mesh and associated cybersecurity applications |
| USD1076952S1 (en)* | 2023-09-12 | 2025-05-27 | Salesforce, Inc. | Display screen or portion thereof with graphical user interface |
| US20250097268A1 (en)* | 2023-09-14 | 2025-03-20 | Microsoft Technology Licensing, Llc | Unified security graph |
| CN116915515B (en)* | 2023-09-14 | 2023-11-10 | 北京东方森太科技发展有限公司 | Access security control method and system for industrial control network |
| US12423092B2 (en) | 2023-09-18 | 2025-09-23 | Bank Of America Corporation | System and method for classifying software code based on functionality and criticality |
| US12436759B2 (en) | 2023-09-18 | 2025-10-07 | Bank Of America Corporation | System and method for dynamic switching between an old version and a new version of a software code |
| US20250103879A1 (en)* | 2023-09-27 | 2025-03-27 | Paypal, Inc. | Near real-time vector index building and serving solution |
| US12418558B1 (en)* | 2023-09-29 | 2025-09-16 | Amazon Technologies, Inc. | Detection of malicious domains |
| US12008138B1 (en) | 2023-09-29 | 2024-06-11 | Lightbeam.ai, Inc. | Method for maintaining privacy and security of data |
| US12407682B2 (en) | 2023-10-03 | 2025-09-02 | Bank Of America Corporation | System, device, and method for performing secured operations |
| WO2025080884A1 (en)* | 2023-10-10 | 2025-04-17 | Reynold Vogel Inc. | Methods and systems of scrutinizing questions, answers, and answer hints based on customizable criteria |
| WO2025079096A1 (en)* | 2023-10-10 | 2025-04-17 | Jio Platforms Limited | Method and system of detection of one or more anomalies in a network |
| US20250126134A1 (en)* | 2023-10-13 | 2025-04-17 | Dell Products L.P. | Secure edge computing network management |
| US20250126143A1 (en)* | 2023-10-17 | 2025-04-17 | Dell Products L.P. | Anomaly detection at scale |
| US20250159011A1 (en)* | 2023-11-12 | 2025-05-15 | Computed Future, Inc | Systems and methods for detecting and mitigating cyber security threats |
| US20250156207A1 (en)* | 2023-11-14 | 2025-05-15 | Microsoft Technology Licensing, Llc | Detecting anomalous behavior in a cloud computing environment |
| US12155700B1 (en)* | 2023-11-21 | 2024-11-26 | Intelligent Communication Assistant, Inc. | Systems and method for optimizing personal communications through objective alignment |
| CN117421718B (en)* | 2023-12-18 | 2024-02-20 | 南京创能百泰自动化科技有限公司 | Data platform information security monitoring management system |
| US20250209158A1 (en)* | 2023-12-22 | 2025-06-26 | Atlassian Pty Ltd. | Enhanced access threat detection for collaborative software application frameworks |
| US12222938B1 (en) | 2023-12-22 | 2025-02-11 | Capital One Services, Llc | Systems and methods for query optimization |
| US12438868B2 (en) | 2024-01-02 | 2025-10-07 | Bank Of America Corporation | Pre-access automated login to computing devices, applications and web sites/services based on machine-learning determined user access patterns |
| US20250233869A1 (en)* | 2024-01-11 | 2025-07-17 | Cisco Technology, Inc. | Hierarchical event representation in extended detection and response systems |
| US20250238878A1 (en)* | 2024-01-22 | 2025-07-24 | True Analytics, Llc. | Issue identification systems, processes and methods |
| US12401618B1 (en)* | 2024-02-23 | 2025-08-26 | Freename Ag | Internet infrastructure system and method |
| US20250272215A1 (en)* | 2024-02-26 | 2025-08-28 | Bank Of America Corporation | Autocorrecting Batch Processing System |
| CN118227361B (en)* | 2024-03-11 | 2025-02-11 | 北京邮电大学 | An unsupervised log anomaly detection method that does not rely on log parsers |
| FI131655B1 (en)* | 2024-03-14 | 2025-08-26 | Elisa Oyj | Identification of UEs involved in a security threat |
| US12248883B1 (en) | 2024-03-14 | 2025-03-11 | HiddenLayer, Inc. | Generative artificial intelligence model prompt injection classifier |
| US20250307383A1 (en)* | 2024-04-02 | 2025-10-02 | SimpliSafe, Inc. | Assigning records of events detected by a security system to monitoring agents |
| CN118413352B (en)* | 2024-04-08 | 2024-09-27 | 南京聚铭网络科技有限公司 | Threat detection method and device in virtual detection environment |
| US12166778B1 (en)* | 2024-06-07 | 2024-12-10 | Wiz, Inc. | Techniques for incident response and static analysis representation in computing environments |
| US12229265B1 (en) | 2024-08-01 | 2025-02-18 | HiddenLayer, Inc. | Generative AI model protection using sidecars |
| US12293277B1 (en) | 2024-08-01 | 2025-05-06 | HiddenLayer, Inc. | Multimodal generative AI model protection using sequential sidecars |
| CN118710224B (en)* | 2024-08-28 | 2025-01-17 | 深圳市拜特科技股份有限公司 | Enterprise platform safety management method and system based on artificial intelligence |
| US12301622B1 (en)* | 2024-09-09 | 2025-05-13 | Morgan Stanley Services Group Inc. | System for cybersecurity campaign artifact discovery and tasking |
| US12273373B1 (en) | 2024-10-11 | 2025-04-08 | Wiz, Inc. | System and method for software service cybersecurity remediation |
| US12361096B1 (en)* | 2024-10-14 | 2025-07-15 | Provenir, Inc. | Intelligent data integration system |
| CN119299194B (en)* | 2024-10-17 | 2025-04-11 | 山东唯选康科技创新有限公司 | A network security protection method for cloud service system |
| US12406084B1 (en) | 2024-11-27 | 2025-09-02 | Alpha Deal Llc | Providing access to composite AI-generated data |
| US12361220B1 (en) | 2024-11-27 | 2025-07-15 | Alpha Deal Llc | Customized integrated entity analysis using an artificial intelligence (AI) model |
| US12388850B1 (en) | 2024-12-16 | 2025-08-12 | Wiz, Inc. | Cybersecurity root cause analysis using computing resource name correlation |
| US12328331B1 (en) | 2025-02-04 | 2025-06-10 | HiddenLayer, Inc. | Detection of privacy attacks on machine learning models |
Citations (5)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20070239495A1 (en)* | 2006-04-11 | 2007-10-11 | Bank Of America Corporation | Application Risk and Control Assessment Tool |
| US8181264B2 (en)* | 2007-02-07 | 2012-05-15 | Apple Inc. | Method and apparatus for deferred security analysis |
| US8201257B1 (en)* | 2004-03-31 | 2012-06-12 | Mcafee, Inc. | System and method of managing network security risks |
| US20130041796A1 (en)* | 2011-08-08 | 2013-02-14 | Bank Of America Corporation | Application governance process and tool |
| US20130198119A1 (en)* | 2012-01-09 | 2013-08-01 | DecisionQ Corporation | Application of machine learned bayesian networks to detection of anomalies in complex systems |
Family Cites Families (264)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US6400285B1 (en) | 1992-10-08 | 2002-06-04 | Henry Gifford | Ergonomic keyboard |
| US6453345B2 (en) | 1996-11-06 | 2002-09-17 | Datadirect Networks, Inc. | Network security and surveillance system |
| US6321338B1 (en) | 1998-11-09 | 2001-11-20 | Sri International | Network surveillance |
| DE60002290T2 (en)* | 2000-01-31 | 2004-04-08 | Miriad Technologies | Method of detecting anomalies in a signal |
| EP1182822B1 (en) | 2000-02-21 | 2013-02-13 | Kabushiki Kaisha Toshiba | Network Management Equipment |
| US7159237B2 (en) | 2000-03-16 | 2007-01-02 | Counterpane Internet Security, Inc. | Method and system for dynamic network intrusion monitoring, detection and response |
| US6507852B1 (en) | 2000-04-17 | 2003-01-14 | Ncr Corporation | Location-independent service for monitoring and alerting on an event log |
| US7089428B2 (en) | 2000-04-28 | 2006-08-08 | Internet Security Systems, Inc. | Method and system for managing computer security information |
| GB2362231B (en)* | 2000-05-08 | 2002-08-14 | 3Com Corp | Storage of data relating to events in a network |
| US20020093527A1 (en)* | 2000-06-16 | 2002-07-18 | Sherlock Kieran G. | User interface for a security policy system and method |
| US20020049623A1 (en) | 2000-07-20 | 2002-04-25 | Martin June Dianne | System and method for implementing an image-based document handling and delivery system |
| US7917393B2 (en) | 2000-09-01 | 2011-03-29 | Sri International, Inc. | Probabilistic alert correlation |
| US20070192863A1 (en)* | 2005-07-01 | 2007-08-16 | Harsh Kapoor | Systems and methods for processing data flows |
| US7929562B2 (en) | 2000-11-08 | 2011-04-19 | Genesis Telecommunications Laboratories, Inc. | Method and apparatus for optimizing response time to events in queue |
| US6400265B1 (en) | 2001-04-24 | 2002-06-04 | Microstrategy, Inc. | System and method for monitoring security systems by using video images |
| US20030145075A1 (en) | 2002-01-29 | 2003-07-31 | Weaver David John | Diagnostics and network provisioning tool for bi-directional communication devices |
| US7093292B1 (en) | 2002-02-08 | 2006-08-15 | Mcafee, Inc. | System, method and computer program product for monitoring hacker activities |
| KR100468232B1 (en) | 2002-02-19 | 2005-01-26 | 한국전자통신연구원 | Network-based Attack Tracing System and Method Using Distributed Agent and Manager Systems |
| ATE374493T1 (en)* | 2002-03-29 | 2007-10-15 | Global Dataguard Inc | ADAPTIVE BEHAVIORAL INTRUSION DETECTION |
| AU2003267109A1 (en) | 2002-09-13 | 2004-04-30 | Natural Selection, Inc. | Intelligently interactive profiling system and method |
| US7716737B2 (en) | 2002-11-04 | 2010-05-11 | Riverbed Technology, Inc. | Connection based detection of scanning attacks |
| US8090809B2 (en)* | 2002-11-04 | 2012-01-03 | Riverbed Technology, Inc. | Role grouping |
| US8504879B2 (en)* | 2002-11-04 | 2013-08-06 | Riverbed Technology, Inc. | Connection based anomaly detection |
| US7774839B2 (en)* | 2002-11-04 | 2010-08-10 | Riverbed Technology, Inc. | Feedback mechanism to minimize false assertions of a network intrusion |
| US7686214B1 (en)* | 2003-05-12 | 2010-03-30 | Id Analytics, Inc. | System and method for identity-based fraud detection using a plurality of historical identity records |
| US9100431B2 (en) | 2003-07-01 | 2015-08-04 | Securityprofiling, Llc | Computer program product and apparatus for multi-path remediation |
| US7463590B2 (en) | 2003-07-25 | 2008-12-09 | Reflex Security, Inc. | System and method for threat detection and response |
| US7089250B2 (en)* | 2003-10-08 | 2006-08-08 | International Business Machines Corporation | Method and system for associating events |
| US20050114706A1 (en) | 2003-11-26 | 2005-05-26 | Destefano Jason Michael | System and method for the collection and transmission of log data over a wide area network |
| KR100609170B1 (en) | 2004-02-13 | 2006-08-02 | 엘지엔시스(주) | Network Security System and Its Operation Method |
| US7464263B2 (en)* | 2004-03-25 | 2008-12-09 | International Business Machines Corporation | Method, system and program product for associating event categorization and routing with security authorization roles |
| US7555523B1 (en) | 2004-05-06 | 2009-06-30 | Symantec Corporation | Spam discrimination by generalized Ngram analysis of small header fields |
| US20060020866A1 (en) | 2004-06-15 | 2006-01-26 | K5 Systems Inc. | System and method for monitoring performance of network infrastructure and applications by automatically identifying system variables or components constructed from such variables that dominate variance of performance |
| US8631493B2 (en)* | 2004-08-12 | 2014-01-14 | Verizon Patent And Licensing Inc. | Geographical intrusion mapping system using telecommunication billing and inventory systems |
| US8418246B2 (en) | 2004-08-12 | 2013-04-09 | Verizon Patent And Licensing Inc. | Geographical threat response prioritization mapping system and methods of use |
| US8572734B2 (en)* | 2004-08-12 | 2013-10-29 | Verizon Patent And Licensing Inc. | Geographical intrusion response prioritization mapping through authentication and flight data correlation |
| US20060242694A1 (en) | 2004-11-08 | 2006-10-26 | Jeffrey Gold | Mitigation and mitigation management of attacks in networked systems |
| US7979889B2 (en) | 2005-01-07 | 2011-07-12 | Cisco Technology, Inc. | Methods and apparatus providing security to computer systems and networks |
| US8250654B1 (en) | 2005-01-27 | 2012-08-21 | Science Applications International Corporation | Systems and methods for implementing and scoring computer network defense exercises |
| US7593013B2 (en) | 2005-03-11 | 2009-09-22 | University Of Utah Research Foundation | Systems and methods for displaying and querying heterogeneous sets of data |
| US20060248096A1 (en)* | 2005-04-28 | 2006-11-02 | Adam Unternehmensberatung Gmbh | Early detection and warning systems and methods |
| US20070073519A1 (en)* | 2005-05-31 | 2007-03-29 | Long Kurt J | System and Method of Fraud and Misuse Detection Using Event Logs |
| US7490355B2 (en) | 2005-06-16 | 2009-02-10 | Chung Shan Institute Of Science And Technology | Method of detecting network worms |
| US7814548B2 (en) | 2005-09-13 | 2010-10-12 | Honeywell International Inc. | Instance based learning framework for effective behavior profiling and anomaly intrusion detection |
| US7624448B2 (en) | 2006-03-04 | 2009-11-24 | 21St Century Technologies, Inc. | Intelligent intrusion detection system utilizing enhanced graph-matching of network activity with context data |
| US7788720B2 (en) | 2006-05-16 | 2010-08-31 | Cisco Technology, Inc. | Techniques for providing security protection in wireless networks by switching modes |
| US8132260B1 (en)* | 2006-06-12 | 2012-03-06 | Redseal Systems, Inc. | Methods and apparatus for prioritization of remediation techniques for network security risks |
| US8127000B2 (en) | 2006-06-30 | 2012-02-28 | Tealeaf Technology, Inc. | Method and apparatus for monitoring and synchronizing user interface events with network data |
| US7583187B1 (en)* | 2006-07-11 | 2009-09-01 | Mcafee, Inc. | System, method and computer program product for automatically summarizing security events |
| US20080034424A1 (en) | 2006-07-20 | 2008-02-07 | Kevin Overcash | System and method of preventing web applications threats |
| US7934253B2 (en) | 2006-07-20 | 2011-04-26 | Trustwave Holdings, Inc. | System and method of securing web applications across an enterprise |
| US8931055B2 (en)* | 2006-08-31 | 2015-01-06 | Accenture Global Services Gmbh | Enterprise entitlement framework |
| US7904456B2 (en)* | 2006-09-01 | 2011-03-08 | Robert John Hennan | Security monitoring tool for computer network |
| WO2008043110A2 (en) | 2006-10-06 | 2008-04-10 | Smobile Systems, Inc. | System and method of malware sample collection on mobile networks |
| US8108550B2 (en) | 2006-10-25 | 2012-01-31 | Hewlett-Packard Development Company, L.P. | Real-time identification of an asset model and categorization of an asset to assist in computer network security |
| JP2008146586A (en) | 2006-12-13 | 2008-06-26 | Fujitsu Ltd | Annotation management program, annotation management apparatus, and annotation management method |
| US7926026B2 (en) | 2006-12-20 | 2011-04-12 | Sap Ag | Graphical analysis to detect process object anomalies |
| US8095979B2 (en) | 2007-01-26 | 2012-01-10 | Microsoft Corporation | Analysis of event information to perform contextual audit |
| US7818338B2 (en) | 2007-01-26 | 2010-10-19 | International Business Machines Corporation | Problem determination service |
| US8205244B2 (en) | 2007-02-27 | 2012-06-19 | Airdefense, Inc. | Systems and methods for generating, managing, and displaying alarms for wireless network monitoring |
| EP2150050B1 (en) | 2007-04-20 | 2014-07-30 | Nippon Hoso Kyokai | Scramble key management unit, scramble key management information transmitting unit, method for scramble key output management, scramble key management program, license information management unit, license management information transmitting unit, method for license information output management, and license information man |
| US20080307525A1 (en) | 2007-06-05 | 2008-12-11 | Computer Associates Think, Inc. | System and method for evaluating security events in the context of an organizational structure |
| WO2008156782A2 (en) | 2007-06-19 | 2008-12-24 | Sand Holdings, Llc | Devices and methods for automatic reset of monitored network network equipment |
| US8099787B2 (en)* | 2007-08-15 | 2012-01-17 | Bank Of America Corporation | Knowledge-based and collaborative system for security assessment of web applications |
| US7991726B2 (en)* | 2007-11-30 | 2011-08-02 | Bank Of America Corporation | Intrusion detection system alerts mechanism |
| US8307344B2 (en) | 2008-02-08 | 2012-11-06 | Texas Instruments Incorporated | Sliding granularity time stamping |
| WO2012061813A1 (en)* | 2010-11-05 | 2012-05-10 | Georgetown University | Event detection, workflow analysis, and reporting system and method |
| US7996374B1 (en) | 2008-03-28 | 2011-08-09 | Symantec Corporation | Method and apparatus for automatically correlating related incidents of policy violations |
| US20090254970A1 (en) | 2008-04-04 | 2009-10-08 | Avaya Inc. | Multi-tier security event correlation and mitigation |
| US8472328B2 (en)* | 2008-07-31 | 2013-06-25 | Riverbed Technology, Inc. | Impact scoring and reducing false positives |
| US8677480B2 (en)* | 2008-09-03 | 2014-03-18 | Cisco Technology, Inc. | Anomaly information distribution with threshold |
| US9258217B2 (en) | 2008-12-16 | 2016-02-09 | At&T Intellectual Property I, L.P. | Systems and methods for rule-based anomaly detection on IP network flow |
| US10057285B2 (en) | 2009-01-30 | 2018-08-21 | Oracle International Corporation | System and method for auditing governance, risk, and compliance using a pluggable correlation architecture |
| US9208453B2 (en) | 2009-02-13 | 2015-12-08 | Paypal, Inc. | Targeted multi-dimension data extraction for real-time analysis |
| US20100208064A1 (en) | 2009-02-19 | 2010-08-19 | Panasonic Corporation | System and method for managing video storage on a video surveillance system |
| US20100223213A1 (en) | 2009-02-27 | 2010-09-02 | Optillel Solutions, Inc. | System and method for parallelization of machine learning computing code |
| US8239847B2 (en) | 2009-03-18 | 2012-08-07 | Microsoft Corporation | General distributed reduction for data parallel computing |
| US8856783B2 (en) | 2010-10-12 | 2014-10-07 | Citrix Systems, Inc. | Allocating virtual machines according to user-specific virtual machine metrics |
| WO2011014169A1 (en)* | 2009-07-30 | 2011-02-03 | Hewlett-Packard Development Company, L.P. | Constructing a bayesian network based on received events associated with network entities |
| US8789173B2 (en)* | 2009-09-03 | 2014-07-22 | Juniper Networks, Inc. | Protecting against distributed network flood attacks |
| US20120137367A1 (en) | 2009-11-06 | 2012-05-31 | Cataphora, Inc. | Continuous anomaly detection based on behavior modeling and heterogeneous information analysis |
| WO2011063269A1 (en) | 2009-11-20 | 2011-05-26 | Alert Enterprise, Inc. | Method and apparatus for risk visualization and remediation |
| US20110231361A1 (en) | 2009-12-31 | 2011-09-22 | Fiberlink Communications Corporation | Consolidated security application dashboard |
| US8448221B2 (en) | 2010-03-12 | 2013-05-21 | Mcafee, Inc. | System, method, and computer program product for displaying network events in terms of objects managed by a security appliance and/or a routing device |
| US8555343B2 (en) | 2010-03-23 | 2013-10-08 | Verizon Patent And Licensing Inc. | Managing resource allocations based on traffic patterns |
| JP5190084B2 (en) | 2010-03-30 | 2013-04-24 | 株式会社日立製作所 | Virtual machine migration method and system |
| US8438638B2 (en) | 2010-04-08 | 2013-05-07 | At&T Intellectual Property I, L.P. | Bot-network detection based on simple mail transfer protocol (SMTP) characteristics of e-mail senders within IP address aggregates |
| US8779921B1 (en)* | 2010-05-14 | 2014-07-15 | Solio Security, Inc. | Adaptive security network, sensor node and method for detecting anomalous events in a security network |
| US9202049B1 (en) | 2010-06-21 | 2015-12-01 | Pulse Secure, Llc | Detecting malware on mobile devices |
| US9384112B2 (en)* | 2010-07-01 | 2016-07-05 | Logrhythm, Inc. | Log collection, structuring and processing |
| US9092736B2 (en) | 2010-07-07 | 2015-07-28 | Qualcomm Incorporated | Communication and synapse training method and hardware for biologically inspired networks |
| US20120180126A1 (en)* | 2010-07-13 | 2012-07-12 | Lei Liu | Probable Computing Attack Detector |
| US8938800B2 (en) | 2010-07-28 | 2015-01-20 | Mcafee, Inc. | System and method for network level protection against malicious software |
| US8918430B2 (en) | 2010-08-27 | 2014-12-23 | SCR Technologies, Inc. | Sequential chain registry for event awareness |
| US20120054136A1 (en) | 2010-08-31 | 2012-03-01 | Connectiva Systems, Inc | System And Method For An Auto-Configurable Architecture For Managing Business Operations Favoring Optimizing Hardware Resources |
| US9032513B2 (en) | 2010-09-01 | 2015-05-12 | Apixio, Inc. | Systems and methods for event stream platforms which enable applications |
| US9015843B2 (en)* | 2010-12-03 | 2015-04-21 | Microsoft Corporation | Predictive malware threat mitigation |
| US8682814B2 (en) | 2010-12-14 | 2014-03-25 | Symantec Corporation | User interface and workflow for performing machine learning |
| US8613086B2 (en) | 2011-01-31 | 2013-12-17 | Bank Of America Corporation | Ping and scan of computer systems |
| US8504673B2 (en) | 2011-03-31 | 2013-08-06 | Verisign, Inc. | Traffic like NXDomains |
| WO2012139127A1 (en) | 2011-04-08 | 2012-10-11 | Wombat Security Technologies, Inc. | Context-aware training systems, apparatuses, and methods |
| US8949668B2 (en) | 2011-05-23 | 2015-02-03 | The Boeing Company | Methods and systems for use in identifying abnormal behavior in a control system including independent comparisons to user policies and an event correlation model |
| US8555388B1 (en) | 2011-05-24 | 2013-10-08 | Palo Alto Networks, Inc. | Heuristic botnet detection |
| US8528088B2 (en)* | 2011-05-26 | 2013-09-03 | At&T Intellectual Property I, L.P. | Modeling and outlier detection in threat management system data |
| WO2012166581A2 (en) | 2011-05-27 | 2012-12-06 | Ctc Tech Corp. | Creation, use and training of computer-based discovery avatars |
| US9118702B2 (en)* | 2011-05-31 | 2015-08-25 | Bce Inc. | System and method for generating and refining cyber threat intelligence data |
| EP2737404A4 (en)* | 2011-07-26 | 2015-04-29 | Light Cyber Ltd | METHOD FOR DETECTING ABNORMAL ACTIONS IN A COMPUTER NETWORK |
| US8776241B2 (en) | 2011-08-29 | 2014-07-08 | Kaspersky Lab Zao | Automatic analysis of security related incidents in computer networks |
| US10031646B2 (en) | 2011-09-07 | 2018-07-24 | Mcafee, Llc | Computer system security dashboard |
| ES2755780T3 (en) | 2011-09-16 | 2020-04-23 | Veracode Inc | Automated behavior and static analysis using an instrumented sandbox and machine learning classification for mobile security |
| US9729549B2 (en) | 2011-09-24 | 2017-08-08 | Elwha Llc | Behavioral fingerprinting with adaptive development |
| US20130191887A1 (en)* | 2011-10-13 | 2013-07-25 | Marc E. Davis | Social network based trust verification Schema |
| US8555077B2 (en) | 2011-11-23 | 2013-10-08 | Elwha Llc | Determining device identity using a behavioral fingerprint |
| US8881289B2 (en)* | 2011-10-18 | 2014-11-04 | Mcafee, Inc. | User behavioral risk assessment |
| US8839349B2 (en) | 2011-10-18 | 2014-09-16 | Mcafee, Inc. | Integrating security policy and event management |
| US9031382B1 (en) | 2011-10-20 | 2015-05-12 | Coincident.Tv, Inc. | Code execution in complex audiovisual experiences |
| US9686293B2 (en) | 2011-11-03 | 2017-06-20 | Cyphort Inc. | Systems and methods for malware detection and mitigation |
| US9235396B2 (en) | 2011-12-13 | 2016-01-12 | Microsoft Technology Licensing, Llc | Optimizing data partitioning for data-parallel computing |
| US9276948B2 (en)* | 2011-12-29 | 2016-03-01 | 21Ct, Inc. | Method and apparatus for identifying a threatening network |
| US8973147B2 (en)* | 2011-12-29 | 2015-03-03 | Mcafee, Inc. | Geo-mapping system security events |
| US9832211B2 (en) | 2012-03-19 | 2017-11-28 | Qualcomm, Incorporated | Computing device to detect malware |
| US20150047026A1 (en) | 2012-03-22 | 2015-02-12 | Los Alamos National Security, Llc | Anomaly detection to identify coordinated group attacks in computer networks |
| US8990948B2 (en)* | 2012-05-01 | 2015-03-24 | Taasera, Inc. | Systems and methods for orchestrating runtime operational integrity |
| US20120266209A1 (en) | 2012-06-11 | 2012-10-18 | David Jeffrey Gooding | Method of Secure Electric Power Grid Operations Using Common Cyber Security Services |
| US9258321B2 (en)* | 2012-08-23 | 2016-02-09 | Raytheon Foreground Security, Inc. | Automated internet threat detection and mitigation system and associated methods |
| US20140067800A1 (en) | 2012-08-31 | 2014-03-06 | Amit Sharma | Systems and methods for analyzing and predicting automotive data |
| US8788525B2 (en) | 2012-09-07 | 2014-07-22 | Splunk Inc. | Data model for machine data for semantic search |
| US9292688B2 (en) | 2012-09-26 | 2016-03-22 | Northrop Grumman Systems Corporation | System and method for automated machine-learning, zero-day malware detection |
| US20140101761A1 (en)* | 2012-10-09 | 2014-04-10 | James Harlacher | Systems and methods for capturing, replaying, or analyzing time-series data |
| US8949358B2 (en)* | 2012-10-25 | 2015-02-03 | Palo Alto Research Center Incorporated | Method and system for building an entity profile from email address and name information |
| US9027127B1 (en) | 2012-12-04 | 2015-05-05 | Google Inc. | Methods for detecting machine-generated attacks based on the IP address size |
| US20140304407A1 (en)* | 2012-12-21 | 2014-10-09 | Boundary, Inc. | Visualizing Ephemeral Traffic |
| JP5751496B2 (en) | 2012-12-27 | 2015-07-22 | 横河電機株式会社 | Event analysis apparatus and computer program |
| US20140279770A1 (en)* | 2013-03-15 | 2014-09-18 | REMTCS Inc. | Artificial neural network interface and methods of training the same for various use cases |
| US20140222997A1 (en)* | 2013-02-05 | 2014-08-07 | Cisco Technology, Inc. | Hidden markov model based architecture to monitor network node activities and predict relevant periods |
| US9418241B2 (en) | 2013-02-15 | 2016-08-16 | Infosys Limited | Unified platform for big data processing |
| US10686819B2 (en)* | 2013-02-19 | 2020-06-16 | Proofpoint, Inc. | Hierarchical risk assessment and remediation of threats in mobile networking environment |
| WO2014142792A1 (en) | 2013-03-11 | 2014-09-18 | Mcafee, Inc. | Using learned flow reputation as a heuristic to control deep packet inspection under load |
| US20140266984A1 (en) | 2013-03-14 | 2014-09-18 | Amit Sharma | Systems and methods for input/output of automotive data with attendant devices |
| US9674212B2 (en) | 2013-03-15 | 2017-06-06 | Zerofox, Inc. | Social network data removal |
| US9104982B2 (en) | 2013-03-15 | 2015-08-11 | Google Inc. | Prevention of invalid selections based on machine learning of user-specific latency |
| US9324119B2 (en)* | 2013-03-15 | 2016-04-26 | Alert Enterprise | Identity and asset risk score intelligence and threat mitigation |
| US9160758B2 (en)* | 2013-03-15 | 2015-10-13 | Stephen SOHN | Method and system for protective distribution system (PDS) and infrastructure protection and management |
| US8973141B2 (en)* | 2013-03-15 | 2015-03-03 | Click Security, Inc. | Universal actor correlator |
| CN105324786A (en)* | 2013-04-11 | 2016-02-10 | 布兰德席德有限公司 | Device, system and method for protecting brand names and domain names |
| US8972992B2 (en) | 2013-04-30 | 2015-03-03 | Splunk Inc. | Proactive monitoring tree with state distribution ring |
| US9270694B2 (en)* | 2013-05-21 | 2016-02-23 | Rapid7, Llc | Systems and methods for assessing security for a network of assets and providing recommendations |
| US9747554B2 (en) | 2013-05-24 | 2017-08-29 | Qualcomm Incorporated | Learning device with continuous configuration capability |
| US9558346B1 (en)* | 2013-05-28 | 2017-01-31 | EMC IP Holding Company LLC | Information processing systems with security-related feedback |
| US9183387B1 (en) | 2013-06-05 | 2015-11-10 | Google Inc. | Systems and methods for detecting online attacks |
| US9491186B2 (en) | 2013-06-19 | 2016-11-08 | Verizon Patent And Licensing Inc. | Method and apparatus for providing hierarchical pattern recognition of communication network data |
| US9202052B1 (en) | 2013-06-21 | 2015-12-01 | Emc Corporation | Dynamic graph anomaly detection framework and scalable system architecture |
| KR20150004169A (en)* | 2013-07-02 | 2015-01-12 | 삼성전자주식회사 | Power supply device, micro server having the same and method for power supplying |
| US9582490B2 (en) | 2013-07-12 | 2017-02-28 | Microsoft Technolog Licensing, LLC | Active labeling for computer-human interactive learning |
| CA2918589A1 (en)* | 2013-07-18 | 2015-01-22 | Level 3 Communications, Llc | Systems and methods for generating customer solutions |
| US9215240B2 (en) | 2013-07-25 | 2015-12-15 | Splunk Inc. | Investigative and dynamic detection of potential security-threat indicators from events in big data |
| US8826434B2 (en) | 2013-07-25 | 2014-09-02 | Splunk Inc. | Security threat detection based on indications in big data of access to newly registered domains |
| US9306962B1 (en) | 2013-07-25 | 2016-04-05 | Niddel Corp | Systems and methods for classifying malicious network events |
| US8978036B2 (en) | 2013-07-29 | 2015-03-10 | Splunk Inc. | Dynamic scheduling of tasks for collecting and processing data from external sources |
| US8752178B2 (en) | 2013-07-31 | 2014-06-10 | Splunk Inc. | Blacklisting and whitelisting of security-related events |
| US10574548B2 (en) | 2013-07-31 | 2020-02-25 | Splunk Inc. | Key indicators view |
| US8966074B1 (en) | 2013-09-13 | 2015-02-24 | Network Kinetix, LLC | System and method for real-time analysis of network traffic |
| JP5891213B2 (en)* | 2013-09-18 | 2016-03-22 | ヤフー株式会社 | A posteriori probability calculation device, posterior probability calculation method, and program |
| US9852041B2 (en)* | 2013-09-27 | 2017-12-26 | Microsoft Technology Licensing, Llc | Systems and methods for categorizing exceptions and logs |
| EP3053074A4 (en) | 2013-09-30 | 2017-04-05 | Hewlett-Packard Enterprise Development LP | Hierarchical threat intelligence |
| US9367809B2 (en) | 2013-10-11 | 2016-06-14 | Accenture Global Services Limited | Contextual graph matching based anomaly detection |
| US9712548B2 (en) | 2013-10-27 | 2017-07-18 | Cyber-Ark Software Ltd. | Privileged analytics system |
| US9392007B2 (en) | 2013-11-04 | 2016-07-12 | Crypteia Networks S.A. | System and method for identifying infected networks and systems from unknown attacks |
| US9288220B2 (en) | 2013-11-07 | 2016-03-15 | Cyberpoint International Llc | Methods and systems for malware detection |
| US9231962B1 (en) | 2013-11-12 | 2016-01-05 | Emc Corporation | Identifying suspicious user logins in enterprise networks |
| US10223530B2 (en) | 2013-11-13 | 2019-03-05 | Proofpoint, Inc. | System and method of protecting client computers |
| US9503465B2 (en)* | 2013-11-14 | 2016-11-22 | At&T Intellectual Property I, L.P. | Methods and apparatus to identify malicious activity in a network |
| US10063654B2 (en) | 2013-12-13 | 2018-08-28 | Oracle International Corporation | Systems and methods for contextual and cross application threat detection and prediction in cloud applications |
| US9692789B2 (en) | 2013-12-13 | 2017-06-27 | Oracle International Corporation | Techniques for cloud security monitoring and threat intelligence |
| US20150172096A1 (en)* | 2013-12-17 | 2015-06-18 | Microsoft Corporation | System alert correlation via deltas |
| US10367827B2 (en) | 2013-12-19 | 2019-07-30 | Splunk Inc. | Using network locations obtained from multiple threat lists to evaluate network data or machine data |
| US9830450B2 (en) | 2013-12-23 | 2017-11-28 | Interset Software, Inc. | Method and system for analyzing risk |
| US9363282B1 (en) | 2014-01-28 | 2016-06-07 | Infoblox Inc. | Platforms for implementing an analytics framework for DNS security |
| US9910860B2 (en) | 2014-02-06 | 2018-03-06 | International Business Machines Corporation | Split elimination in MapReduce systems |
| US10009358B1 (en) | 2014-02-11 | 2018-06-26 | DataVisor Inc. | Graph based framework for detecting malicious or compromised accounts |
| US20150235154A1 (en) | 2014-02-19 | 2015-08-20 | Clemens UTSCHIG | Computerized method and system and method to provide business process & case modeling and execution of business processes and activities |
| US9009827B1 (en) | 2014-02-20 | 2015-04-14 | Palantir Technologies Inc. | Security sharing system |
| US20150256413A1 (en)* | 2014-03-06 | 2015-09-10 | Sideband Networks Inc. | Network system with live topology mechanism and method of operation thereof |
| US9630324B2 (en)* | 2014-03-28 | 2017-04-25 | SKUR, Inc. | Enhanced system and method for control of robotic devices |
| WO2015168203A1 (en)* | 2014-04-29 | 2015-11-05 | PEGRight, Inc. | Characterizing user behavior via intelligent identity analytics |
| US9356950B2 (en) | 2014-05-07 | 2016-05-31 | Attivo Networks Inc. | Evaluating URLS for malicious content |
| US9462008B2 (en) | 2014-05-16 | 2016-10-04 | Cisco Technology, Inc. | Identifying threats based on hierarchical classification |
| US9503467B2 (en) | 2014-05-22 | 2016-11-22 | Accenture Global Services Limited | Network anomaly detection |
| US8881281B1 (en) | 2014-05-29 | 2014-11-04 | Singularity Networks, Inc. | Application and network abuse detection with adaptive mitigation utilizing multi-modal intelligence data |
| US10409665B2 (en) | 2014-06-09 | 2019-09-10 | Northrup Grumman Systems Corporation | System and method for real-time detection of anomalies in database usage |
| US10212176B2 (en) | 2014-06-23 | 2019-02-19 | Hewlett Packard Enterprise Development Lp | Entity group behavior profiling |
| US10469514B2 (en) | 2014-06-23 | 2019-11-05 | Hewlett Packard Enterprise Development Lp | Collaborative and adaptive threat intelligence for computer security |
| US20150379083A1 (en) | 2014-06-25 | 2015-12-31 | Microsoft Corporation | Custom query execution engine |
| US9712645B2 (en)* | 2014-06-26 | 2017-07-18 | Oracle International Corporation | Embedded event processing |
| US10540606B2 (en)* | 2014-06-30 | 2020-01-21 | Amazon Technologies, Inc. | Consistent filtering of machine learning data |
| US10318882B2 (en) | 2014-09-11 | 2019-06-11 | Amazon Technologies, Inc. | Optimized training of linear machine learning models |
| US9672474B2 (en) | 2014-06-30 | 2017-06-06 | Amazon Technologies, Inc. | Concurrent binning of machine learning data |
| US10452992B2 (en)* | 2014-06-30 | 2019-10-22 | Amazon Technologies, Inc. | Interactive interfaces for machine learning model evaluations |
| WO2016001998A1 (en) | 2014-06-30 | 2016-01-07 | 楽天株式会社 | Similarity calculation system, similarity calculation method, and program |
| US10963810B2 (en) | 2014-06-30 | 2021-03-30 | Amazon Technologies, Inc. | Efficient duplicate detection for machine learning data sets |
| US9021260B1 (en) | 2014-07-03 | 2015-04-28 | Palantir Technologies Inc. | Malware data item analysis |
| US9485263B2 (en)* | 2014-07-16 | 2016-11-01 | Microsoft Technology Licensing, Llc | Volatility-based classifier for security solutions |
| US9635050B2 (en)* | 2014-07-23 | 2017-04-25 | Cisco Technology, Inc. | Distributed supervised architecture for traffic segregation under attack |
| US9118714B1 (en) | 2014-07-23 | 2015-08-25 | Lookingglass Cyber Solutions, Inc. | Apparatuses, methods and systems for a cyber threat visualization and editing user interface |
| AU2015294618A1 (en)* | 2014-07-25 | 2017-02-02 | Gregory Aharonian | Use of coca leaf or Valerian root to reduce bitterness in foods containing unsweetened cocoa |
| US9166999B1 (en) | 2014-07-25 | 2015-10-20 | Fmr Llc | Security risk aggregation, analysis, and adaptive control |
| US10176236B2 (en) | 2014-07-29 | 2019-01-08 | Microsoft Technology Licensing, Llc | Systems and methods for a distributed query execution engine |
| US20160057159A1 (en) | 2014-08-22 | 2016-02-25 | Syracuse University | Semantics-aware android malware classification |
| US9756062B2 (en)* | 2014-08-27 | 2017-09-05 | General Electric Company | Collaborative infrastructure supporting cyber-security analytics in industrial networks |
| US20160065594A1 (en) | 2014-08-29 | 2016-03-03 | Verizon Patent And Licensing Inc. | Intrusion detection platform |
| US20160098573A1 (en)* | 2014-10-03 | 2016-04-07 | Zettaset, Inc. | Securing a Distributed File System |
| US20160103433A1 (en)* | 2014-10-08 | 2016-04-14 | General Electric Company | System and method to provide an intelligent pipeline management graphical user interface map display |
| EP3215943B1 (en) | 2014-11-03 | 2021-04-21 | Vectra AI, Inc. | A system for implementing threat detection using threat and risk assessment of asset-actor interactions |
| US20160132787A1 (en) | 2014-11-11 | 2016-05-12 | Massachusetts Institute Of Technology | Distributed, multi-model, self-learning platform for machine learning |
| US9569776B2 (en) | 2014-11-12 | 2017-02-14 | BenedorTSE LLC | Secure authorizations using independent communications and different one-time-use encryption keys for each party to a transaction |
| US10061632B2 (en)* | 2014-11-24 | 2018-08-28 | Anodot Ltd. | System and method for transforming observed metrics into detected and scored anomalies |
| US20160162582A1 (en) | 2014-12-09 | 2016-06-09 | Moodwire, Inc. | Method and system for conducting an opinion search engine and a display thereof |
| US10884891B2 (en) | 2014-12-11 | 2021-01-05 | Micro Focus Llc | Interactive detection of system anomalies |
| US9584536B2 (en) | 2014-12-12 | 2017-02-28 | Fortinet, Inc. | Presentation of threat history associated with network activity |
| US10805337B2 (en)* | 2014-12-19 | 2020-10-13 | The Boeing Company | Policy-based network security |
| US9367872B1 (en)* | 2014-12-22 | 2016-06-14 | Palantir Technologies Inc. | Systems and user interfaces for dynamic and interactive investigation of bad actor behavior based on automatic clustering of related data in various data structures |
| US20160219066A1 (en) | 2015-01-26 | 2016-07-28 | Cisco Technology, Inc. | Event correlation in a network merging local graph models from distributed nodes |
| US20160226893A1 (en)* | 2015-01-30 | 2016-08-04 | Wipro Limited | Methods for optimizing an automated determination in real-time of a risk rating of cyber-attack and devices thereof |
| US9928369B2 (en) | 2015-02-09 | 2018-03-27 | Cisco Technologies, Inc. | Information technology vulnerability assessment |
| US20160241574A1 (en)* | 2015-02-16 | 2016-08-18 | Taasera, Inc. | Systems and methods for determining trustworthiness of the signaling and data exchange between network systems |
| EP3262815B1 (en) | 2015-02-24 | 2020-10-14 | Cisco Technology, Inc. | System and method for securing an enterprise computing environment |
| US9819689B2 (en) | 2015-03-13 | 2017-11-14 | Microsoft Technology Licensing, Llc | Large scale malicious process detection |
| US20160269378A1 (en)* | 2015-03-14 | 2016-09-15 | Gewei Ye | First Artificial Intelligence Methods and Systems for Asset Trendspotting (PNN), Cyber Security (DeepCyber), and Portable Big Data Cloud (MCPS) |
| US9930065B2 (en)* | 2015-03-25 | 2018-03-27 | University Of Georgia Research Foundation, Inc. | Measuring, categorizing, and/or mitigating malware distribution paths |
| US9794229B2 (en) | 2015-04-03 | 2017-10-17 | Infoblox Inc. | Behavior analysis based DNS tunneling detection and classification framework for network security |
| WO2016163903A1 (en) | 2015-04-08 | 2016-10-13 | Siemens Aktiengesellschaft | Method and apparatus for automated generation of a data processing topology |
| US9712554B2 (en)* | 2015-04-09 | 2017-07-18 | Accenture Global Services Limited | Event correlation across heterogeneous operations |
| US10289973B2 (en) | 2015-04-10 | 2019-05-14 | Telefonaktiebolaget Lm Ericsson (Publ) | System and method for analytics-driven SLA management and insight generation in clouds |
| US10305917B2 (en) | 2015-04-16 | 2019-05-28 | Nec Corporation | Graph-based intrusion detection using process traces |
| US9836598B2 (en) | 2015-04-20 | 2017-12-05 | Splunk Inc. | User activity monitoring |
| US10410135B2 (en) | 2015-05-21 | 2019-09-10 | Software Ag Usa, Inc. | Systems and/or methods for dynamic anomaly detection in machine sensor data |
| US20160358099A1 (en) | 2015-06-04 | 2016-12-08 | The Boeing Company | Advanced analytical infrastructure for machine learning |
| US10142353B2 (en)* | 2015-06-05 | 2018-11-27 | Cisco Technology, Inc. | System for monitoring and managing datacenters |
| US10395181B2 (en) | 2015-06-05 | 2019-08-27 | Facebook, Inc. | Machine learning system flow processing |
| US9407652B1 (en) | 2015-06-26 | 2016-08-02 | Palantir Technologies Inc. | Network anomaly detection |
| US9756067B2 (en)* | 2015-08-10 | 2017-09-05 | Accenture Global Services Limited | Network security |
| US9699205B2 (en) | 2015-08-31 | 2017-07-04 | Splunk Inc. | Network security system |
| US10594714B2 (en)* | 2015-10-28 | 2020-03-17 | Qomplx, Inc. | User and entity behavioral analysis using an advanced cyber decision platform |
| US10248910B2 (en)* | 2015-10-28 | 2019-04-02 | Fractal Industries, Inc. | Detection mitigation and remediation of cyberattacks employing an advanced cyber-decision platform |
| US9817971B2 (en)* | 2015-10-29 | 2017-11-14 | International Business Machines Corporation | Using call stack snapshots to detect anomalous computer behavior |
| US20170192782A1 (en) | 2015-12-30 | 2017-07-06 | Robert Valentine | Systems, Apparatuses, and Methods for Aggregate Gather and Stride |
| GB2547202B (en)* | 2016-02-09 | 2022-04-20 | Darktrace Ltd | An anomaly alert system for cyber threat detection |
| US10764321B2 (en)* | 2016-03-24 | 2020-09-01 | Lenovo Enterprise Solutions (Singapore) Pte. Ltd | Identifying and remediating at-risk resources in a computing environment |
| US10476752B2 (en)* | 2016-04-04 | 2019-11-12 | Nec Corporation | Blue print graphs for fusing of heterogeneous alerts |
| US20170295193A1 (en) | 2016-04-06 | 2017-10-12 | Omni Ai, Inc. | Adaptive anomaly context description |
| US10305921B2 (en) | 2016-04-28 | 2019-05-28 | International Business Machines Corporation | Network security apparatus and method of detecting malicious behavior in computer networks via cost-sensitive and connectivity constrained classification |
| US10205734B2 (en) | 2016-05-09 | 2019-02-12 | Accenture Global Solutions Limited | Network sampling based path decomposition and anomaly detection |
| US10015182B1 (en) | 2016-06-30 | 2018-07-03 | Symantec Corporation | Systems and methods for protecting computing resources |
| US10771345B1 (en) | 2016-12-28 | 2020-09-08 | Amazon Technologies, Inc. | Network monitoring service |
| US10523691B2 (en) | 2017-01-06 | 2019-12-31 | Cisco Technology, Inc. | Graph prioritization for improving precision of threat propagation algorithms |
| US10237294B1 (en) | 2017-01-30 | 2019-03-19 | Splunk Inc. | Fingerprinting entities based on activity in an information technology environment |
| US10205735B2 (en) | 2017-01-30 | 2019-02-12 | Splunk Inc. | Graph-based network security threat detection across time and entities |
| EP3376446A1 (en)* | 2017-03-18 | 2018-09-19 | Tata Consultancy Services Limited | Method and system for anomaly detection, missing data imputation and consumption prediction in energy data |
| US10511585B1 (en)* | 2017-04-27 | 2019-12-17 | EMC IP Holding Company LLC | Smoothing of discretized values using a transition matrix |
| US9860257B1 (en)* | 2017-06-12 | 2018-01-02 | Cisco Technology, Inc. | Anomaly detection and threat prediction through combined power and network analytics |
| US11169514B2 (en)* | 2018-08-27 | 2021-11-09 | Nec Corporation | Unsupervised anomaly detection, diagnosis, and correction in multivariate time series data |
| US11711391B2 (en) | 2020-10-16 | 2023-07-25 | Visa International Service Association | System, method, and computer program product for user network activity anomaly detection |
| US11949701B2 (en) | 2021-08-04 | 2024-04-02 | Microsoft Technology Licensing, Llc | Network access anomaly detection via graph embedding |
| US11777786B2 (en)* | 2021-10-25 | 2023-10-03 | Rakuten Mobile, Inc. | Method, device and computer program product for anomaly detection and root cause analysis |
- 2015
- 2015-08-31USUS14/841,634patent/US9699205B2/enactiveActive
- 2015-10-30USUS14/929,132patent/US10063570B2/enactiveActive
- 2015-10-30USUS14/929,224patent/US9591010B1/enactiveActive
- 2015-10-30USUS14/928,563patent/US9609011B2/enactiveActive
- 2015-10-30USUS14/929,037patent/US10419450B2/enactiveActive
- 2015-10-30USUS14/929,203patent/US9596254B1/enactiveActive
- 2015-10-30USUS14/928,985patent/US9838410B2/enactiveActive
- 2015-10-30USUS14/929,196patent/US10015177B2/enactiveActive
- 2015-10-30USUS14/929,204patent/US10038707B2/enactiveActive
- 2015-10-30USUS14/929,187patent/US10904270B2/enactiveActive
- 2015-10-30USUS14/929,042patent/US9667641B2/enactiveActive
- 2015-10-30USUS14/928,471patent/US10469508B2/enactiveActive
- 2015-10-30USUS14/929,168patent/US9516053B1/enactiveActive
- 2015-10-30USUS14/929,047patent/US20170063907A1/ennot_activeAbandoned
- 2015-10-30USUS14/928,451patent/US10154047B2/enactiveActive
- 2015-10-30USUS14/929,035patent/US10110617B2/enactiveActive
- 2015-10-30USUS14/929,141patent/US10158652B2/enactiveActive
- 2015-10-30USUS14/929,183patent/US10389738B2/enactiveActive
- 2015-10-30USUS14/928,503patent/US20170063900A1/ennot_activeAbandoned
- 2015-10-30USUS14/928,421patent/US10193901B2/enactiveActive
- 2015-10-30USUS14/928,918patent/US10243970B2/enactiveActive
- 2015-10-30USUS14/929,184patent/US10069849B2/enactiveActive
- 2015-10-30USUS14/929,182patent/US10003605B2/enactiveActive
- 2015-10-30USUS14/928,535patent/US10212174B2/enactiveActive
- 2016
- 2016-10-26USUS15/335,250patent/US9609009B2/enactiveActive
- 2017
- 2017-01-23USUS15/413,336patent/US10135848B2/enactiveActive
- 2017-01-25USUS15/415,747patent/US9813435B2/enactiveActive
- 2017-01-27USUS15/418,546patent/US10116670B2/enactiveActive
- 2017-04-18USUS15/490,849patent/US10148677B2/enactiveActive
- 2017-06-07USUS15/616,889patent/US9900332B2/enactiveActive
- 2017-10-31USUS15/800,000patent/US10581881B2/enactiveActive
- 2017-10-31USUS15/800,010patent/US10291635B2/enactiveActive
- 2018
- 2018-01-02USUS15/860,049patent/US10419462B2/enactiveActive
- 2018-03-20USUS15/926,961patent/US10419463B2/enactiveActive
- 2018-05-31USUS15/995,073patent/US10476898B2/enactiveActive
- 2018-06-22USUS16/016,472patent/US11470096B2/enactiveActive
- 2018-07-20USUS16/041,637patent/US10560468B2/enactiveActive
- 2018-07-31USUS16/050,368patent/US10587633B2/enactiveActive
- 2018-11-06USUS16/182,469patent/US10419465B2/enactiveActive
- 2018-12-10USUS16/215,350patent/US10778703B2/enactiveActive
- 2019
- 2019-01-28USUS16/259,999patent/US10666668B2/enactiveActive
- 2019-01-31USUS16/264,514patent/US10986106B2/enactiveActive
- 2019-07-03USUS16/503,181patent/US11258807B2/enactiveActive
- 2019-07-19USUS16/516,471patent/US11411966B2/enactiveActive
- 2019-08-05USUS16/532,312patent/US11146574B2/enactiveActive
- 2019-08-21USUS16/547,235patent/US10911468B2/enactiveActive
- 2019-09-11USUS16/568,106patent/US10798113B2/enactiveActive
- 2019-09-24USUS16/581,094patent/US10911470B2/enactiveActive
- 2020
- 2020-12-17USUS17/125,130patent/US11575693B1/enactiveActive
- 2022
- 2022-02-18USUS17/676,022patent/US12438891B1/enactiveActive
- 2022-06-21USUS17/845,383patent/US11824646B1/enactiveActive
Patent Citations (5)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US8201257B1 (en)* | 2004-03-31 | 2012-06-12 | Mcafee, Inc. | System and method of managing network security risks |
| US20070239495A1 (en)* | 2006-04-11 | 2007-10-11 | Bank Of America Corporation | Application Risk and Control Assessment Tool |
| US8181264B2 (en)* | 2007-02-07 | 2012-05-15 | Apple Inc. | Method and apparatus for deferred security analysis |
| US20130041796A1 (en)* | 2011-08-08 | 2013-02-14 | Bank Of America Corporation | Application governance process and tool |
| US20130198119A1 (en)* | 2012-01-09 | 2013-08-01 | DecisionQ Corporation | Application of machine learned bayesian networks to detection of anomalies in complex systems |
Cited By (46)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US10721263B2 (en)* | 2014-12-29 | 2020-07-21 | Palantir Technologies Inc. | Systems for network risk assessment including processing of user access rights associated with a network of devices |
| US12250243B2 (en) | 2014-12-29 | 2025-03-11 | Palantir Technologies Inc. | Systems for network risk assessment including processing of user access rights associated with a network of devices |
| US10666668B2 (en) | 2015-08-31 | 2020-05-26 | Splunk Inc. | Interface providing an interactive trendline for a detected threat to facilitate evaluation for false positives |
| US10798113B2 (en) | 2015-08-31 | 2020-10-06 | Splunk Inc. | Interactive geographic representation of network security threats |
| US10469508B2 (en) | 2015-08-31 | 2019-11-05 | Splunk Inc. | Interactive threat geo-map for monitoring computer network security |
| US10986106B2 (en) | 2015-08-31 | 2021-04-20 | Splunk Inc. | Method and system for generating an entities view with risk-level scoring for performing computer security monitoring |
| US10778703B2 (en) | 2015-08-31 | 2020-09-15 | Splunk Inc. | Method and system for generating an interactive kill chain view for training a machine learning model for identifying threats |
| US20220100721A1 (en)* | 2016-01-07 | 2022-03-31 | Amazon Technologies, Inc. | Outlier detection for streaming data |
| US12174807B2 (en)* | 2016-01-07 | 2024-12-24 | Amazon Technologies, Inc. | Outlier detection for streaming data |
| US11153091B2 (en) | 2016-03-30 | 2021-10-19 | British Telecommunications Public Limited Company | Untrusted code distribution |
| US10404635B2 (en) | 2017-03-21 | 2019-09-03 | Bank Of America Corporation | Optimizing data replication across multiple data centers |
| US10616231B2 (en) | 2017-03-21 | 2020-04-07 | Cyber 2.0 (2015) LTD | Preventing unauthorized outgoing communications |
| US11586751B2 (en) | 2017-03-30 | 2023-02-21 | British Telecommunications Public Limited Company | Hierarchical temporal memory for access control |
| US11341237B2 (en)* | 2017-03-30 | 2022-05-24 | British Telecommunications Public Limited Company | Anomaly detection for computer systems |
| CN110832529A (en)* | 2017-05-18 | 2020-02-21 | 比利时联合金融集团 | Determining risks associated with real estate and reconstruction |
| US10719811B2 (en)* | 2017-06-29 | 2020-07-21 | Salesforce.Com, Inc. | Method and system for retroactive removal of content from an organization activity timeline |
| US10686741B2 (en) | 2017-06-29 | 2020-06-16 | Salesforce.Com, Inc. | Method and system for real-time blocking of content from an organization activity timeline |
| CN107623862A (en)* | 2017-09-21 | 2018-01-23 | 广州华多网络科技有限公司 | multimedia information push control method, device and server |
| US20210377291A1 (en)* | 2017-09-26 | 2021-12-02 | Jpmorgan Chase Bank, N.A. | Cyber security enhanced monitoring |
| CN111542811A (en)* | 2017-09-26 | 2020-08-14 | 摩根大通国家银行 | Monitoring for enhanced network security |
| US11122066B2 (en)* | 2017-09-26 | 2021-09-14 | Jpmorgan Chase Bank, N.A. | Cyber security enhanced monitoring |
| EP3688589A4 (en)* | 2017-09-26 | 2021-06-23 | JPMorgan Chase Bank, N.A. | Cyber security enhanced monitoring |
| WO2019067513A1 (en)* | 2017-09-26 | 2019-04-04 | Jpmorgan Chase Bank, N.A. | Cyber security enhanced monitoring |
| US11722505B2 (en)* | 2017-09-26 | 2023-08-08 | Jpmorgan Chase Bank, N.A. | Cyber security enhanced monitoring |
| US10541881B2 (en)* | 2017-12-14 | 2020-01-21 | Disney Enterprises, Inc. | Automated network supervision including detecting an anonymously administered node, identifying the administrator of the anonymously administered node, and registering the administrator and the anonymously administered node |
| US20190244146A1 (en)* | 2018-01-18 | 2019-08-08 | D&B Business Information Solutions | Elastic distribution queuing of mass data for the use in director driven company assessment |
| US11271824B2 (en) | 2019-07-25 | 2022-03-08 | Vmware, Inc. | Visual overlays for network insights |
| US11522770B2 (en) | 2019-07-25 | 2022-12-06 | Vmware, Inc. | Visual overlays for network insights |
| US11005727B2 (en)* | 2019-07-25 | 2021-05-11 | Vmware, Inc. | Visual overlays for network insights |
| US12229782B2 (en) | 2019-12-13 | 2025-02-18 | Wells Fargo Bank, N.A. | Network based features for financial crime detection |
| US11640609B1 (en) | 2019-12-13 | 2023-05-02 | Wells Fargo Bank, N.A. | Network based features for financial crime detection |
| CN112995104A (en)* | 2019-12-16 | 2021-06-18 | 海信集团有限公司 | Communication equipment and network security prediction method |
| WO2021127778A1 (en)* | 2019-12-23 | 2021-07-01 | Myplanet Internet Solutions Ltd | Method and system for recognizing user intent and updating a graphical user interface |
| US12067408B2 (en) | 2019-12-23 | 2024-08-20 | Myplanet Internet Solutions Ltd. | Method and system for recognizing user intent and updating a graphical user interface |
| US11526603B2 (en)* | 2020-03-30 | 2022-12-13 | Microsoft Technology Licensing, Llc | Model for identifying the most relevant person(s) for an event associated with a resource |
| US12074893B2 (en) | 2020-10-16 | 2024-08-27 | Visa International Service Association | System, method, and computer program product for user network activity anomaly detection |
| US11711391B2 (en) | 2020-10-16 | 2023-07-25 | Visa International Service Association | System, method, and computer program product for user network activity anomaly detection |
| US11831688B2 (en)* | 2021-06-18 | 2023-11-28 | Capital One Services, Llc | Systems and methods for network security |
| US20240179189A1 (en)* | 2021-06-18 | 2024-05-30 | Capital One Services, Llc | Systems and methods for network security |
| US20220407893A1 (en)* | 2021-06-18 | 2022-12-22 | Capital One Services, Llc | Systems and methods for network security |
| US12301632B2 (en)* | 2021-06-18 | 2025-05-13 | Capital One Services, Llc | Systems and methods for network security |
| US11601325B2 (en)* | 2021-07-30 | 2023-03-07 | Microsoft Technology Licensing, Llc | Method and system for evaluating peer groups for comparative anomaly |
| US20230033647A1 (en)* | 2021-07-30 | 2023-02-02 | Microsoft Technology Licensing, Llc | Method and system for evaluating peer groups for comparative anomaly |
| EP4083823A3 (en)* | 2021-08-16 | 2023-02-01 | Beijing Baidu Netcom Science Technology Co., Ltd. | Method and apparatus for determining risk level of instance on cloud server and electronic device |
| US12368740B2 (en) | 2021-08-16 | 2025-07-22 | Beijing Baidu Netcom Science Technology Co., Ltd. | Method for determining risk level of instance on cloud server, and electronic device |
| WO2024154049A1 (en)* | 2023-01-17 | 2024-07-25 | VMware LLC | Automated enterprise information technology alerting system |
Also Published As
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| US10911468B2 (en) | Sharing of machine learning model state between batch and real-time processing paths for detection of network security issues |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| AS | Assignment | Owner name:SPLUNK INC., CALIFORNIA Free format text:ASSIGNMENT OF ASSIGNORS INTEREST;ASSIGNORS:MUDDU, SUDHAKAR;TRYFONAS, CHRISTOS;REEL/FRAME:037141/0221 Effective date:20151029 | |
| STCV | Information on status: appeal procedure | Free format text:APPEAL BRIEF (OR SUPPLEMENTAL BRIEF) ENTERED AND FORWARDED TO EXAMINER | |
| STPP | Information on status: patent application and granting procedure in general | Free format text:TC RETURN OF APPEAL | |
| STCV | Information on status: appeal procedure | Free format text:EXAMINER'S ANSWER TO APPEAL BRIEF MAILED | |
| STCV | Information on status: appeal procedure | Free format text:ON APPEAL -- AWAITING DECISION BY THE BOARD OF APPEALS | |
| STCV | Information on status: appeal procedure | Free format text:BOARD OF APPEALS DECISION RENDERED | |
| STPP | Information on status: patent application and granting procedure in general | Free format text:DOCKETED NEW CASE - READY FOR EXAMINATION | |
| STPP | Information on status: patent application and granting procedure in general | Free format text:NON FINAL ACTION MAILED | |
| STPP | Information on status: patent application and granting procedure in general | Free format text:RESPONSE TO NON-FINAL OFFICE ACTION ENTERED AND FORWARDED TO EXAMINER | |
| STPP | Information on status: patent application and granting procedure in general | Free format text:FINAL REJECTION MAILED | |
| STCB | Information on status: application discontinuation | Free format text:ABANDONED -- FAILURE TO RESPOND TO AN OFFICE ACTION | |
| AS | Assignment | Owner name:SPLUNK LLC, CALIFORNIA Free format text:CHANGE OF NAME;ASSIGNOR:SPLUNK INC.;REEL/FRAME:069825/0558 Effective date:20240923 | |
| AS | Assignment | Owner name:SPLUNK LLC, CALIFORNIA Free format text:CHANGE OF NAME;ASSIGNOR:SPLUNK INC.;REEL/FRAME:072170/0599 Effective date:20240923 Owner name:CISCO TECHNOLOGY, INC., CALIFORNIA Free format text:ASSIGNMENT OF ASSIGNORS INTEREST;ASSIGNOR:SPLUNK LLC;REEL/FRAME:072173/0058 Effective date:20250722 |