US20070028110A1 - Content extractor and analysis system - Google Patents
Content extractor and analysis systemDownload PDFInfo
- Publication number
- US20070028110A1 US20070028110A1US11/194,078US19407805AUS2007028110A1US 20070028110 A1US20070028110 A1US 20070028110A1US 19407805 AUS19407805 AUS 19407805AUS 2007028110 A1US2007028110 A1US 2007028110A1
- Authority
- US
- United States
- Prior art keywords
- file
- server
- content
- host
- files
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Granted
Links
Images
Classifications
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/32—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials
- H04L9/3247—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials involving digital signatures
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/50—Monitoring users, programs or devices to maintain the integrity of platforms, e.g. of processors, firmware or operating systems
- G06F21/55—Detecting local intrusion or implementing counter-measures
- G06F21/552—Detecting local intrusion or implementing counter-measures involving long-term monitoring or reporting
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/14—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic
- H04L63/1441—Countermeasures against malicious traffic
- H04L63/145—Countermeasures against malicious traffic the attack involving the propagation of malware through the network, e.g. viruses, trojans or worms
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/18—Network architectures or network communication protocols for network security using different networks or channels, e.g. using out of band channels
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L2209/00—Additional information or applications relating to cryptographic mechanisms or cryptographic arrangements for secret or secure communication H04L9/00
- H04L2209/60—Digital content management, e.g. content distribution
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/10—Network architectures or network communication protocols for network security for controlling access to devices or network resources
- H04L63/102—Entity profiles
Definitions
- a host agentwhich is software, sometimes used in conjunction with hardware, which operates on multiple individual computers, “hosts,” within the network.
- Host agentsgenerally work in parallel, using some of the host's resources to perform security functions in the background. By potentially having access to all significant internal functions of a host, host agents can in theory detect and stop threats on hosts before any damage is done.
- Host agent security systemsare sometimes called Endpoint Security Systems, because they operate on the “ends” of the network.
- anomaly detectionAnother enterprise endpoint technology is anomaly detection. This can be viewed as behavioral blacklisting which is determined statistically by observing behaviors over time. In addition to inheriting the shortcomings of behavioral blacklists, anomaly detection adds new error modes as both good and bad behaviors are estimated statistically, so there are certain to be estimation errors. This process often leads to unacceptably high false-alarm and missed-detection rates.
- whitelistsare lists of patterns of known good programs. If a program is not included in the list, it will not run.
- whitelistsare lists of patterns of known good programs. If a program is not included in the list, it will not run.
- whitelistsare difficult to maintain. For instance, most large enterprises deploy custom programs that are developed in-house and that can change frequently. Further, these programs may contain sensitive intellectual property and security risks which should not be exposed to a third party. It is unlikely a whitelist vendor would have access to pre-approve this software in a timely fashion.
- Other examplesare operating system and other updates. Again, there is no central clearinghouse or central authority to certify that certain programs or updates are good for all enterprises.
- the failure modes of whitelist systemsare severe, blocking access to critical, but not yet approved, applications and business functions.
- Security systems as described hereallow an administrator to detect, monitor, locate, identify, and control files installed on a large network of computers.
- the systemcan provide a defense from known and unknown viruses, worms, spyware, hackers, unapproved/unwanted software (e.g. software applications which are against business use policy) and social engineering attacks. Administrators can access detailed information and statistics on new executables, scripts, and embedded scripts as they appear and propagate to networked systems.
- the systemcan implement centralized policies that allow an administrator to approve, block, quarantine, or log file activities.
- the systemcan also collect detailed information useful for diagnosing and locating problem files or attacks.
- the systemoffers visibility, control, and protection for large computer installations.
- the system architecturepreferably includes agent software that runs on each protected host, and a server, referred to as a “server”, that provides centralized policy management, event monitoring, agent coordination and virus scanning.
- the servercan be implemented as an appliance (which generally suggests a more limited functionality device).
- a single appliancecan support many hosts, e.g. 10,000 hosts.
- a further server or appliance, sometimes referred to as a “super server,”can monitor multiple appliances.
- Agent software running on each protected host computeranalyzes file system activity and takes action based on policies configured on the servers.
- the agent softwarecalculates a hash of the file's contents to uniquely identify the file to the system.
- the agent softwareuses this hash to look up the status and policies for the file. Based on this information, the agent software might block an operation, log an event, quarantine a file, or take some other specified action(s).
- the systemalso includes many other features that can be useful in combination or individually, including the ability to extract files from archives, the ability to extract macros from files, centralized content tracking and analysis, and a “find file” function described herein.
- the systems described herecan use at least two additional states: Pending, which represents an intermediate, less-defined threat level, and Locally Approved, which is Approved for one host but not necessarily Approved for the central authority (and thus all other hosts).
- Pendingrepresents an intermediate, less-defined threat level
- Locally Approvedwhich is Approved for one host but not necessarily Approved for the central authority (and thus all other hosts).
- the latterpermits hosts to slightly diverge from the baseline.
- the Pending statepermits hosts to block or permit access to new content based on various threat levels and enterprise usage policies.
- Approved and Bannedthe division of approval into 3-4 states results in different improved capabilities for each individual state.
- software which is new and which has not been classified yetis Pending.
- Traditional binary access states for softwareare not flexible enough, and such classification systems are not as scalable.
- NameApprovepermits flexible local approval and central approval capabilities, based on where files are created on the host. In conjunction with host groups, this permits accurate flexible efficient specification of where and on which hosts new content is approved.
- the “Content Tracking” systemutilizes additional states such as Pending to monitor and analyze new content as it moves through the network.
- Current technologiesdo not permit global central visibility and tracking of every new executable file, across a large number of hosts, in real-time.
- Endpoint systemsrelying on file system scanning, like AV scanners, and host application inventorying like Tripwire, periodically and slowly crawl through large file systems looking for new or changed software. This is typically disruptive to the host, can take hours, and is normally scheduled at most once per day.
- the Content Tracking systemis more scalable and responsive. Since it is rare that new software arrives that has never been seen by any host in a large group N, and it is rarer that many hosts M have that new software appear in a short period of time, reports, response, and analysis are facilitated by this distinction.
- the “Distributed Meta-Information Query” featureaccelerates the location and identification of key file attributes in seconds, across large numbers of hosts (thousands), with centrally specified queries, centrally reported results, with little or no host disk impact.
- the inventionhere tracks file changes in memory as the files are changing, and this provides an efficient means to query hosts for file meta-information from memory. Centrally processing this information provides, for the first time, responsive global views of the movement of individual files throughout collections of host file systems.
- the “Content Extractor” featureaddresses a variety of current limitations by preserving the (nested) container relationships, and simultaneously facilitates: tracking of content, tracking of similar containers, tracking product associations, minimizing unnecessary re-analysis, minimizing file transfer bandwidth, and preserving compatibility with other analysis technologies by repackaging content as other known file types.
- the central storing and tracking of new content, and the central scheduling of analyses relative to the first appearance time of contentprovide powerful advantages in terms of security, global visibility, enterprise management system integration, and future expansion.
- FIG. 1is a block diagram showing an overview of a security system as described herein.
- FIG. 3is a flow chart illustrating a process for performing an analysis.
- FIGS. 4-5are schematics of processes performed by the system.
- FIG. 6is a chart showing an example of timed analyses.
- FIG. 7is a flow chart of steps performed during a timed analysis.
- FIG. 8is a schematic of a content extraction process.
- the kernel portion 80 of host 12has cache 82 for saving antibodies organized by file name, and a cache 84 of recent file operations and file information.
- the kernelalso has an intercept/block function 86 that receives and intercepts file operation requests, and provides these requests to a stateful filter 88 that first checks the cache of recent file operations 84 . If there is no match, it checks the triggers and actions block 90 which maintains security policies.
- This block 90is coupled to a “defcon” block 92 , which has a value that indicates a security level for the system, and policy engine 94 that governs blocks 82 , 90 , and 92 for controlling various file operations including executions, file reads, file writes, and other actions.
- the triggers and actions block 90communicates with antibody cache 82 that looks for meta-information on files based on their names. Policy engine 94 also controls actions, such as blocking, reporting, or allowing file operations, and reporting to the user.
- a centrally set parametersometimes denoted “D” or “Defcon”, that controls the policies of the hosts.
- This central policy and parametercan be applied to all hosts, or to selected groups of hosts.
- the parametercan be set manually by an operator or can be adjusted by the system without human intervention, typically in response to some event.
- the policiescan include blocking or allowing certain actions, or it can make an action pending, which makes it allowed, subject to further monitoring such as logging.
- a pending statushas multiple benefits, including taking into account latencies in the system, as well as implementing policies which do not fit the traditional binary approve/ban model. These latencies include the time before harmful code is identified, during malfunctions in the system, or times when a host is disconnected from the network.
- a central servercan specify a query of meta-information and distribute that query to all or a selected group of hosts. These hosts perform the query from a local store of meta-information and send results back to the server that can cause the server to adjust the parameter.
- the policiesreflect a tradeoff between security and usability.
- the D valuecould be changed depending on the type of connectivity, whether local (on a wired LAN), remote such as through a telephone modem or virtual private network (VPN), or completely disconnected.
- the host agentwould thus store a set of specified D values for these types of connectivity and then automatically select from the set in response to a change, for example, when a user disconnected the host from the LAN.
- different D valuescan result in decreases or increases in reporting, logging, and tracking detail.
- a certain namee.g., a top 10 list by name
- unique contentse.g., top 10 list by a hash of data
- the valuecan also be changed per server request in response to a new event perceived by the server, such as a new incoming file or a potential virus attack. In most cases, it is the administrator (a person) who initiates the change of D, following planned user operation, or on observation of certain file events. D can be automatically changed, e.g., during the process of an operation, in which case, the host/server will roll the value of D back to its original level after the operation is terminated. External triggers can change the value of D, such as SNMP.
- Another responseis for the server to automatically approve content that is on fewer than a certain threshold number of hosts, yet automatically ban access to that content when the number of hosts is exceeded.
- a policycould be used to limit the number of copies of any content or file in the network. Also, such a policy could be used to only report content that exceed the certain number of hosts.
- Serverscan maintain a policy set separately for each logical group of hosts, such as sales hosts, marketing hosts, and engineering hosts.
- Policy setscan have unique identification numbers that are similar to antibody version numbers. The difference is that, once deployed, a policy set becomes “read only” to reconcile later problems with a policy set and to undo a problem deployment. This can also be done to difference configuration and other updates, using technology similar to the Unix utilities “diff” and “patch.”
- Hostscan query the server for the current policy set ID number for their group, and if there is a mismatch, they can send the server a “GetPolicySet” query.
- the kernelcan enforce all policies without interaction with user space, except in the case of kernel antibody cache updates, D updates, and policy set updates.
- Policy setsneed only be stored in one place, and they need only be interpreted in the kernel in this implementation. Policy sets can be authenticated and stored in one secure context (the kernel), resulting in more security against tampering.
- DPolicies and actions are parameterized by D since D permits different rules to match different triggers.
- Files with certain statesmay have certain operations blocked. These states can be a combination of name and data properties. These states are determined in user space, mirrored in kernel space, and ultimately, the states are determined by the server.
- One useful policyis to block banned files, and at some D values, to block file executions of pending (new) files.
- the policiescan be provided as a set of lists of policies over a range with tradeoffs of accessibility and security.
- the servercan then provide information to cause the hosts to select one of the lists.
- Approve Report Approve NotifyNotify, New, New, Report Report Report Report New/Pending Auto Permit Permit Permit Auto Block Block Standalone Scripts Global execution, Local Execution, Write/Exec, *.vbs, *.bat, . . . Approve Report Approve Notify, Notify, New, New, Report Report Report Report New/Pending Auto Permit Permit Permit Auto Block Block Embedded Scripts Global execution, Local Execution, Write/Exec, In *.doc, *.xls, . . . Approve Report Approve Notify, Notify, New, New, Report Report Report New Web Content Auto Permit Permit Permit Permit Write Write *.html, *.asp, .
- the serverhas the system's complete set of antibodies for the system. While each host can contain a local subset of the antibodies in user cache 64 and in kernel cache 82 , the server is the authority for setting and changing to certain states. For example, the server is the authority that centrally initiates and propagates changes (to Hosts) including state transitions from Pending to Approved or Banned (those three states preferably associated with content hash), while hosts are the only authority that can set a state to locally approved.
- Each entry in database 36is persistent and preferably is easily accessible with a file data hash index.
- the databasecan optionally be indexed by other keys, such as file name, date first seen, state, analysis results, host ID, or host count, so that an administrator can easily browse the antibody database.
- the database with antibodiesis described as being in or on the server, it should be understood that this means that the database is associated with the server. It could reside physically in the same box and the server's processing functionality, or it could reside in a different box or even in a remote location. If remote, there should be suitable wired or wireless connection to obtain the data.
- tracking policiesmay be triggered, thereby setting off a chain of file and antibody analysis events.
- the hostperforms a series of steps to determine if there has been a significant modification to content that corresponds to content that has already been analyzed and for which an antibody has already been stored in a host cache. If the content antibody is not in the host cache, the server is queried to determine if the server has already analyzed the content. If the server does not have a corresponding antibody, then the content may be uploaded to the server for further analyses. Until the server can determine the state definitively, the state associated with the content is set to be pending or not yet determined. Subsequent access to pending content may be limited.
- the serverperforms analyses on the content based on a time since the content was first seen on the server. Based on the analyses or on other external determinations, the server may definitively determine changes in the state. These changes may be indicated for later retrieval by the hosts so the hosts can update their antibody caches with the changed states.
- the hostintercepts file operations ( 501 ), including execute, read, rename, or write, and provides the operation to a stateful file operation filter ( 502 ). If the file name is not in the kernel cache and there is a kernel cache miss ( 510 ) and if there has been a possible file or content modification ( 511 ), the state is invalidated.
- the filethen goes to a content extractor, which, as described in more detail below, extracts the active content of interest ( 503 ) to produce a reduced file, and provides the reduced file to a content signer ( 504 ).
- the content signerapplies a cryptographic hash, such as MD5, to the reduced file. This hash is associated with the file and the file name.
- a file operationmay be delayed/stalled while the hash and other analyses (cache miss resolution) are completed.
- the hostalso makes a local lookup based on the hash content to try to get a state ( 505 ). If the content and a state are not found, the state is sent to pending. This can mean that the file operation is allowed to proceed, although further monitoring, such as logging, could occur also. If the content is found, the name, content, container (file which contained the active content) and state are all associated together ( 507 ). If not, the host requests that the server look up the content in its memory ( 506 ). If found there, the name, content, container (file containing the active content) and state are all associated together ( 507 ).
- the stateis set to pending, and the content is uploaded to the server ( 508 ), which confirms the upload ( 509 ).
- the servercan also look to a “super server” associated with a number of the servers.
- Container relationshipsare stored and associated with files and other containers.
- Container informationis also sent to servers and hosts, as well as sent for analysis.
- a “Root Container”is a container which is not contained by another container. Containers are identified by their associated files as well as by cryptographic hashes.
- HASHFile Data/Contents
- StateThis maps Data ⁇ State.
- State (S)can contain many pieces of information, such as “approved” (white list) or “banned” (black list) or “pending” (a “grey list” such as a newly seen file that has not been fully analyzed yet).
- An advantage of this systemis the combination of name states with content states.
- the servercan specify and store multiple name bans, such as *msblast.exe.
- the serverstores name state policies as lists of regular expressions and associated meta-information. Any file drive/path/name/ext which matches the regular expression will then inherit the name meta-information. This information is updated whenever file names are changed or the name meta-information specification changes.
- Name states and policiesare propagated from the server to the hosts. For example, by adding *msblast.exe ⁇ NameBan, the server will sense the new policy/state, and will propagate that specification to the hosts. Hosts will then search their name meta-information caches for matches with *msblast.exe, and those file which match will inherit NameBan state.
- Antibodiesare stored in the databases hierarchically. There are four main storage locations for antibodies as indicated above.
- the kernelcan and does enforce policy based on the state without needing access to file contents. This is useful as the file may be encrypted in the kernel but visible in unencrypted form higher up.
- the kernelhas direct access to the name, but not to the hash.
- the kernel cachecan be weakly consistent with other caches, and ultimately the server, in that there can be long latencies (seconds, minutes, hours, days).
- a serverhas an antibody database 34 of generally every unique hash that has ever been reported by any of its hosts, and a super server (if there is one) has an antibody database of generally every unique hash which has been seen on any of its servers.
- Limiting to unique hasheslimits storage and processing, although more could be stored with further improvements in storage and processing. Also, limiting to unique hashes results in more efficient analysis and lower network traffic.
- new filespropagate from the host to the server to super server in response to “New File” or “Dirty File” events, and the newly computed antibody state propagates in reverse from super server to server to host user to host kernel in the form of antibody updates.
- the servers “own” and certify the antibodies and serversprovide authentication that the antibodies have not been altered or forged.
- Hostsmaintain their own antibodies which generally but do not necessarily correspond to those on the server. So a compromised or malfunctioning host cannot degrade a server or super server antibody collection, nor can a compromised host degrade the antibodies of other hosts.
- the antibody stateis preferably stored so that it is not associated with hash/data, but rather by name.
- Name bansare represented as a list of regular expressions and can include a wildcard (*), e.g., “*oo.exe” or “*msblast.exe”, on the server. These lists have version numbers. As hosts poll in, they check their version numbers. When a host detects a mismatch, it then sends a GetNameBans query from the server (i.e., the hosts pull the new ban data from the server). Then these regular expressions are reevaluated against the name antibodies.
- Name banis an attribute of state, and only has to be recomputed when the name ban list changes or when the file name changes. The wildcard list does not have to be compared on every file operation. So the dual nature of data antibody and name antibody is useful. Also, hundreds or thousands of name regular expressions can be simultaneously in effect without requiring thousands of regular expression match computations in the kernel for each file operation, which could be prohibitively expensive.
- an intercept/block function 86can intercept and read file access requests. It can suspend requests while obtaining policy information, block requests based on in-kernel policy, and return appropriate error codes for blocked requests.
- the function 86reads from file access requests the requesting process name, a local system time of the request, the file requested (including full path), and the action requested (e.g., read, write, or execute).
- function 86feeds all file access requests to “stateful filter” 88 , and every operation is blocked until filter 88 returns a flag indicating that the operation is either blocked or permitted.
- Filter 88intercepts file access requests from function 86 and returns an action of “block” or “permit” for most file access requests. Any file access request that cannot be associated with already-approved file access requests is forwarded to the kernel triggers and actions module 90 , which returns an action of “block” or “permit”. This action is stored by filter 88 , and is preferably returned to function 86 for any subsequent associated similar file access request.
- Cache entries whose age exceeds a certain valuemay be deleted. This allows pruning of entries which for some reason are not removed. It also allows period re-checking of a file by module 90 .
- a file write operationis caught in the kernel in a blocking shim 86 by the host agent kernel program (HK) for a file “foo.exe”.
- the file operationhere a file write operation
- the file operationis caught by an activated “dirty tracking” policy, and this sets off a “dirty” event from the host kernel program to the host agent user space program (HU). This event specifies the filename and the dirty operation.
- the kernel cache 82is not consulted for this operation, as the dirty tracking policy has that field nulled.
- HUthen performs a variety of local analysis operations in file and event processing 66 and analysis engine 68 on foo.exe.
- foo.exeis checked to see if it exists, if it is readable, and if it really is an executable. Other operations may be performed, such as the extraction of “interesting data” in filter 88 ; for example, script comments could be removed if the file were foo.bat.
- the extracted data of foo.exeis then cryptographically hashed, and this hash is used to attempt a lookup in the HU antibody cache 60 . If the name and data already exist, nothing else is done. If the name is new, but the data is known, then a new name antibody is created in the UN cache. This process is all part of what is called the “Stage 1 analysis queue.” Many files can be queued up waiting to be hashed in the Stage 1 queue on the host. The Stage 1 queue has only name antibodies and meta-information, since the data is not yet known or analyzed.
- the Stage 2 analysiswill attempt to resolve local state information from memory caches first, then from local disk-based data stores, and then from the server. If the server is connected, the Stage 2 queue will empty as the meta-information is resolved. When foo.exe is removed from this queue, the server is asked if it has seen this data hash, if that hash is not found locally. If the answer is no, then foo.exe and its hash and other meta-information is put into a Stage 3 queue for upload to the server. In addition, the server will send a default antibody state to the host, which is “pending”, if the server has not seen the hash before or if the server analysis is not yet completed sufficiently to determine other states. If the server has already computed a valid antibody and state, it returns this antibody meta-information. If the server has never seen this data for foo.exe, it is new in the sense that all machines in the server's experience have never seen this file.
- Server analysisfollows a schedule which is specified and stored on the server. This schedule is relative to the first appearance time of the file or its hash on the server. For example, if a file arrives at noon and the schedule is “Hash lookup at +0 and AV scan at +0 and AV scan at +2 hours”, then at noon, the file hash will be computed and looked up using and external hash lookup service. Then an AV scan is performed. Two hours later, at 2 pm, another AV scan of that file is performed. Another way to describe the schedule is that it is relative to “file age on the server”.
- Antibodiescan remain synchronized with a super server in a similar fashion.
- the super servercan poll servers and get antibody update lists.
- the super servercan merge them, and send out tailored updates for each server. These updates are all weakly consistent, in that they can lag by minutes or days, but there must be interlocks and safeguards to avoid “holes” in the updates.
- the kernelOn boot or other initialization of the host agent, the kernel is loaded with every valid antibody known from user space, for every known existing host file which has valid meta-information. Some antibody updates are sent into the kernel as they are received from the server or from analysis queues in user space. However, some updates are the result of kernel cache misses. If a policy is determined to be active and if the antibody state is needed and if that state is not available, the kernel will generally stall the operation for some time and send up a kernel miss event to the user space. Some events may be stalled even if the antibody is not needed right away.
- a completed FindFile requestis analogous to an email in that the server posts a request for later retrieval by specified hosts. As hosts check in, they learn if there are FindFile messages from the server waiting for them. When a host learns it has an outstanding FindFile request, it retrieves the requests using GetFindFileRequests, as shown as lines ( 1 ) in FIG. 4 . In other words, the request is preferably accomplished as a “pull” from the server. This allows a more secure implementation with no listening host sockets needed.
- the connected hostseach process their FindFile requests by accessing applicable data from their antibody caches, and post result lists to a results database shown as PostFindFileResults (lines ( 2 ) in FIG. 4 ), including some or all of the following information for each file returned:
- all host-server communicationsare accomplished by the host first connecting to the server and sending one or more network messages, and receiving server replies for the host messages, before disconnecting. Again, this has an advantage of being more secure in that no listening host sockets are needed. There is an additional advantage in that only server addressing and routes need be maintained, rather than maintaining host addressing, routes, and reducing the need for discovery of such host information.
- the super servercan also post requests to be accessed by servers in a similar fashion, or a super server could directly submit FindFile requests to the servers. Then, servers could return the merged results to the super server, which then could merge these into a larger master result. This is analogous to the relationship between servers and hosts when processing a FindFile request.
- a servercan perform analyses based on events, e.g., an analysis each time a host uploads content, or the system can perform these analyses based on time.
- new contentcan be uploaded to the server, and analyses are performed with external and/or internal analysis agents to create metadata or meta-information that is stored in a database.
- the systemcan then check for further scheduled analyses, e.g., after certain time intervals relative to a first observation of a file when new content is uploaded.
- the servers and super serverscan perform many types of further time-based analysis.
- Periodic actionsin addition to one-time timed actions, can be specified. As shown here, antivirus (AV) and anti-spyware (AS) scans can be performed at different times, and other analyses can be performed. For later time periods, this could be a comparison to others servers that may have looked at the files. Typically, the later analyses would be based on all files first seen within some time period. For example, all files first seen within a 1 hour time would get the 12 hour analysis 12 hours from the last file in the time period.
- AVantivirus
- ASanti-spyware
- the systemselects files for analysis and sends the files to perform specified analyses. Different operations can be specified for each time interval. Since the files are kept for a while on the servers, these time-activated analyses can proceed whether the original Host is still connected or not. Examples of central timed server analyses that can be performed include:
- the results of the above analysisare summarized on the server, which updates the state in the meta-information store ( 124 ), particularly the state for broadcast to the hosts.
- the servermakes recommendations as to whether a file should be approved or banned. Information is summarized so that administrators can approve or ban groups of files with one web browser action.
- the results from the analysis abovecan be used to automatically approve or ban files with certain antibodies.
- the servercan provide reports, alarms, or further information, and can alter the parametric D value for all or one or more groups of hosts.
- the serverflags the state changes for later distribution through updates ( 130 ), preferably in a manner that the hosts pull the update from the server.
- This processreduces the network traffic and footprint of the analysis stages, and it permits tracking of embedded content only and not macros associated with other files (e.g., inherited document templates). This is not true of methods that intercept macros upon their loading.
- the extractorpermits location-independent embedded macro detection and tracking.
- the repackaging of reductions as other valid file typeshas the advantage that the reductions are compatible with third party analysis systems, e.g., macros repackaged as small Word documents can be sent as email attachments to a virus scanning email gateway.
- third party analysis systemse.g., macros repackaged as small Word documents can be sent as email attachments to a virus scanning email gateway.
- Another exampleis a zip file, temp.zip, containing 5 files, only one of which is active, foo.exe.
- the reduction of temp.zipcould be a zip file foo.zip with only foo.exe in it, or the reduction could be foo.exe itself.
- the signature of foo.zip or the signature of foo.exeis preferably associated as the signature corresponding to temp.zip.
- the reductioncould again be emailed to an AS scanning email gateway.
- the user interface for the serverprovides a number of “panels,” each of which allows the configuration and management of a different aspect of the system.
- the term “user”is used to indicate an administrator who has access to the server user interface.
- the user interfacecan be accessible through a standard web browser, via an SSL encrypted connection. Authentication and access control are provided to maintain the integrity of the server and to determine the privilege level of a particular user.
- a statistics paneldisplays more detailed statistics collected by the system.
- This informationincludes the number of the following events in various time periods (e.g., last hour, last 24 hours, last week). It can include, for example, numbers of new executables seen on the network, new scripts, files with new embedded content, new web files (HTML, ASP, etc.), files that have yet to be approved, either manually or by scanning, files approved by the scanning process, files approved manually or via auto-approval, files that are failing a scan, files that are known infected that have been blocked, executables that are banned and were blocked, total events processed by the server since it was first installed, and events since last restart.
- Top10 listsinclude top ten recently discovered files ranked by count of how many hosts have at least one copy of the file, with variants of this list including count-by-unique-hash, count-by-unique-file-name, count-Banned-by-hash, count-Banned-by-name, count-recently-banned, count-recently-updated/modified, count-by-unique-group/container/root-container/product. Top10 lists are updated and exported via SNMP.
- Statistical information displayed on this panelis also available via SNMP (Simple Network Management Protocol) query to the server, allowing integration with network management systems.
- SNMPSimple Network Management Protocol
- a plots panelallows the user to plot and print graphs and charts of recent activity. This panel may be combined with the statistics panel. Plot information may also be available in XML format for display in external applications. Examples of graphs that may be plotted include activity over a recent time period (one hour by minute, one week by hour, etc.), or graphical displays of the “top ten list.”
- An antibody database panelallows the user to interact directly with the antibody database stored on the server.
- the content of the databaseis displayed and the user may choose to sort the display by different criteria or to limit the display by choosing filter patterns.
- the usermay also interact with the antibodies themselves; these operations are detailed below.
- the servermay use an ancillary informational database that includes fields that are not required in the main antibody database.
- An example of fields in this databasemight be the first file name seen or the initial file class.
- Last AnalysisThe time the file was last scanned/analyzed.
- Find ContainersLookup possible containers for the file and information for those containers.
- a file finder panelallows the user to initiate a best-effort process of finding the locations of a particular file on all the managed hosts. Since this process may be time consuming, the user will be notified before initiating a new search.
- the file findermay not be implemented in all versions of the product. FindFile progress may be reported during partial completion of the query.
- the processmay also be initiated from the antibody database panel (see section 0 ) by selecting a particular file or files, which then brings the user to the File Finder panel with the appropriate information filled in automatically.
- This processrequires all hosts that are in communication with the server to return status asynchronously, so the panel will open a new view to dynamically display the results as they are received. If the user initiates another search, the current search will be terminated. Multiple file searches may be permitted in future versions.
- a host group panelallows the hosts known by the server to be associated with a particular logical group. Full group functionality may not be available in initial versions of the interface, in which case this screen will display information about the single group supported by this server.
- the panelsupports the manipulating group membership, including:
- a file classes panelallows the viewing and editing of the file extensions that are mapped to each class.
- Some classes, as below,are defined by extension.
- Other classesare determined by analysis of content.
- Some classesare determined by both extension and analysis. These extensions are read only.
- a policy panelis the core of the configuration of the server. The user can display and edit the policies enforced on all the managed hosts, grouped by host group. This panel also displays the current global D setting for the currently selected group.
- This sectionallows the user to define the global D level for the currently selected group.
- the changeis not immediately applied, but must be selected explicitly.
- Choosing a new proposed D levelchanges the display of the policy information and actions to show those for this new level. Navigating away from the panel will not apply the changes.
- the policy listdisplays the various actions and effects of particular D levels on particular file classes (e.g. executables, scripts etc.). Policies may be enabled or disabled, but not edited. The following policies are included on the list:
- An action grid similar to the one illustrated aboveshows the user a representation of the effects of particular D levels in combination with the pre-made policies.
- the tables belowshow an example of combinations of the actions and pre-made policies at the various D levels (zero through seven).
- the notification parametersalso include a global setting that defines the image displayed at the host along with the notification message. These settings are configurable for each of the pre-made policies individually. Notification parameters are edited in the server administrative interface. Those parameters are associated with policies which are in turn assigned to host groups and propagated to hosts as policy changes.
- the serverincludes processing capability, such as a programmed microprocessor, digital signal processor (DSP), or application-specific processing and memory.
- Hostscan include personal computers or similar computers, or other processing devices, including handhelds, PDAs, or other devices on a network.
Landscapes
- Engineering & Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- Computer Hardware Design (AREA)
- General Engineering & Computer Science (AREA)
- Signal Processing (AREA)
- Computer Networks & Wireless Communication (AREA)
- Computing Systems (AREA)
- Software Systems (AREA)
- Theoretical Computer Science (AREA)
- Physics & Mathematics (AREA)
- Virology (AREA)
- General Health & Medical Sciences (AREA)
- Health & Medical Sciences (AREA)
- General Physics & Mathematics (AREA)
- Computer And Data Communications (AREA)
- Storage Device Security (AREA)
Abstract
Description
- Large enterprises have large information technology (IT) security budgets and layered IT security systems, yet network compromises, damage from viruses and worms, and spyware problems are common. Current IT security technologies are expensive to maintain and do not provide protection against many new or unknown threats, while new threats are distributed, detected, and reported at increasing rates.
- Security solutions which are located at the network perimeter, such as firewalls, have visibility limited to network traffic which passes directly through them. Entry vectors such as email viruses, web browser exploits, wireless access, VPN's, instant messaging, and file-sharing create an increasingly porous perimeter which bypasses these technologies. It is hard to define a perimeter in a modern network which provides sufficient control and visibility. Many attacks only generate network traffic after they have compromised a machine or network. For instance, by the time a virus starts emailing from a machine within a network, that machine is already compromised. To stop attacks before they execute, it is generally necessary to protect files, not just network traffic.
- Visibility and protection can be provided by a host agent, which is software, sometimes used in conjunction with hardware, which operates on multiple individual computers, “hosts,” within the network. Host agents generally work in parallel, using some of the host's resources to perform security functions in the background. By potentially having access to all significant internal functions of a host, host agents can in theory detect and stop threats on hosts before any damage is done. Host agent security systems are sometimes called Endpoint Security Systems, because they operate on the “ends” of the network.
- Current enterprise endpoint security systems often attempt to detect and block attacks with known bit patterns, such as anti-virus (AV) scanning and anti-spyware (AS) scanning. Pattern scanning uses blacklists of patterns which are pre-identified as bad. Similarly, some security systems use detected known behavioral profiles, which can be described as a blacklist of bad behavioral patterns. In both cases, blacklists are perpetually out of date, unable to respond to attacks which are new or unknown. Blacklists are also ineffective against attacks such as new viruses which can spread faster than the ability to derive, test, and distribute blacklist updates. With dozens of new viruses discovered each week, blacklists of all kinds become increasingly ineffective. Behavior patterns are complex to develop and test, and as a result they have high false-alarm rates; that is, they erroneously conclude a behavior is bad when in fact it is benign. As new attacks evolve, behaviors change, leading to errors of missed detection instead. By waiting until an attack, like a virus, exhibits a bad behavior, the affected machine may be already compromised. In summary, blacklists attempt to track what is already known to be wrong, while what is wrong is constantly changing.
- Another enterprise endpoint technology is anomaly detection. This can be viewed as behavioral blacklisting which is determined statistically by observing behaviors over time. In addition to inheriting the shortcomings of behavioral blacklists, anomaly detection adds new error modes as both good and bad behaviors are estimated statistically, so there are certain to be estimation errors. This process often leads to unacceptably high false-alarm and missed-detection rates.
- Another class of endpoint security systems limits execution to only programs which are on whitelists, which are lists of patterns of known good programs. If a program is not included in the list, it will not run. Such a system is not flexible enough for a typical modern enterprise, and the resulting whitelists are difficult to maintain. For instance, most large enterprises deploy custom programs that are developed in-house and that can change frequently. Further, these programs may contain sensitive intellectual property and security risks which should not be exposed to a third party. It is unlikely a whitelist vendor would have access to pre-approve this software in a timely fashion. Other examples are operating system and other updates. Again, there is no central clearinghouse or central authority to certify that certain programs or updates are good for all enterprises. The failure modes of whitelist systems are severe, blocking access to critical, but not yet approved, applications and business functions.
- As a result, systems which centrally classify file content access into only one or two states, Approved and Banned, will have issues with race (timing) conditions. A large amount of software does not clearly fit into either category, and there is no central authority which will be universally trusted for all software within an enterprise. Even when this is not a factor, it can take time to classify the intermediate software. In the case of a new virus, it can take 6-48 hours or more to classify a new virus as bad, and by then the outbreak can be a pandemic. So even with strong network connectivity from the host to the central approval authority, it can take longer than a few minutes to detect and analyze new software. To transparently add this content-based authorization to an operating system in the background, the delays must typically be less than one minute, or else the file system can time out, and false access-blocking errors occur.
- Security systems as described here allow an administrator to detect, monitor, locate, identify, and control files installed on a large network of computers. The system can provide a defense from known and unknown viruses, worms, spyware, hackers, unapproved/unwanted software (e.g. software applications which are against business use policy) and social engineering attacks. Administrators can access detailed information and statistics on new executables, scripts, and embedded scripts as they appear and propagate to networked systems. The system can implement centralized policies that allow an administrator to approve, block, quarantine, or log file activities. The system can also collect detailed information useful for diagnosing and locating problem files or attacks. The system offers visibility, control, and protection for large computer installations.
- The system architecture preferably includes agent software that runs on each protected host, and a server, referred to as a “server”, that provides centralized policy management, event monitoring, agent coordination and virus scanning. The server can be implemented as an appliance (which generally suggests a more limited functionality device). A single appliance can support many hosts, e.g. 10,000 hosts. A further server or appliance, sometimes referred to as a “super server,” can monitor multiple appliances.
- Agent software running on each protected host computer analyzes file system activity and takes action based on policies configured on the servers. In one implementation, when a host attempts to open or write a file, the agent software calculates a hash of the file's contents to uniquely identify the file to the system. The agent software uses this hash to look up the status and policies for the file. Based on this information, the agent software might block an operation, log an event, quarantine a file, or take some other specified action(s).
- The system also includes many other features that can be useful in combination or individually, including the ability to extract files from archives, the ability to extract macros from files, centralized content tracking and analysis, and a “find file” function described herein.
- The systems described here can use at least two additional states: Pending, which represents an intermediate, less-defined threat level, and Locally Approved, which is Approved for one host but not necessarily Approved for the central authority (and thus all other hosts). The latter permits hosts to slightly diverge from the baseline. The Pending state permits hosts to block or permit access to new content based on various threat levels and enterprise usage policies. Although using common binary approval terminology, Approved and Banned, the division of approval into 3-4 states results in different improved capabilities for each individual state. Generally, software which is new and which has not been classified yet is Pending. Traditional binary access states for software (ban/approve) are not flexible enough, and such classification systems are not as scalable.
- The designation of software as new/Pending is useful. Most enterprises have a “no new executable” policy in some form, such as “employees are not permitted to download and run unapproved software from the Internet.” And yet, enterprises cannot detect new software as it propagates, until it is too late, do not know when their policies are being violated, and have no means to effectively enforce their policies. By tracking new programs as Pending while they are being modified/written to the file system, a host agent can detect and report new content, in real-time, as it enters the network from almost any means, whether email, instant messenger, download, USB key, mobile laptop, etc. By identifying programs as Pending, some simple, scalable, effective policies are possible, such as: “Permit, but warn when hosts run new executables” or “No new unapproved programs can be installed or run by this group of hosts” or “Warn when the same new unapproved program appears on more than N hosts within 24 hours”. Thus, new programs can be safely located, tracked, and analyzed while being blocked. Other approved business software will continue to run. New approved software can be installed and run, such as AV updates or security patches. This approach is a proactive response, protecting against unknown possibly malicious software while permitting productivity, and gaining analysis time while not requiring any time-critical blacklist or whitelist updates.
- Existing file whitelist and blacklist systems tend to be global in nature, since maintaining many separate lists centrally, one for each host, is difficult. As described here, hosts can maintain their own lists, which may diverge from the central lists. In particular, this can be the case with Local Approve and Pending states, and it is often true with name-based states, such as NameBan and NameApprove. Since “name” is generally a local property, these states can diverge from the centrally controlled states. For example, if a file “foo” has a certain hash=x and a central server state Pending, on a host the file could be Local Approved or Name-Banned or Name-Approved, the latter two depending on the local name of the file on the host. The systems described here permit efficient management and policy implementation of thousands of name properties simultaneously applied to every file on every host. NameApprove permits flexible local approval and central approval capabilities, based on where files are created on the host. In conjunction with host groups, this permits accurate flexible efficient specification of where and on which hosts new content is approved.
- Even with this new flexible policy system, enterprises usually need to enforce different policies for different roles and situations. For instance, IT administrators and internal software developers may need to carefully run new software, while other employees require only a small standard suite of relatively static applications. This situation could change quickly when under attack. For instance, if a virus is detected on more than N hosts, it may make sense to expand the scope of the “no new executable” policy. This flexibility and incremental response is an advantage of a “Parametric Content Control” system described here, compared to rigid systems that cannot adapt to varying policies within and enterprise and over different conditions. “Parametric Content Control” permits a flexible lockdown mode which can be centrally managed and quickly varied based on network and host conditions. And this permits incremental file content and/or file name-based restrictions and approvals.
- Unlike other endpoint security technologies which process host user credentials, process identifiers, data source (URL), directory structures, and operating system security descriptors, the systems described here do not need to utilize these factors as part of host policy. On a host, these factors can be unreliable and can be vulnerable to compromise, and they can hinder scalability. These factors result in less scalable policies, as fine-grained policies can interact across a variety of hosts in complex ways. Even if the operating system is compromised, and an attack gains admin privileges and all associated security descriptors, a “no new executable” policy as described here will provide substantial protection.
- The “Content Tracking” system utilizes additional states such as Pending to monitor and analyze new content as it moves through the network. Current technologies do not permit global central visibility and tracking of every new executable file, across a large number of hosts, in real-time. Endpoint systems relying on file system scanning, like AV scanners, and host application inventorying like Tripwire, periodically and slowly crawl through large file systems looking for new or changed software. This is typically disruptive to the host, can take hours, and is normally scheduled at most once per day. By focusing on what is new, and storing that information in memory, the Content Tracking system is more scalable and responsive. Since it is rare that new software arrives that has never been seen by any host in a large group N, and it is rarer that many hosts M have that new software appear in a short period of time, reports, response, and analysis are facilitated by this distinction.
- Once new software is detected, it can be useful to locate and identify it in a timely fashion. If some new software turns out to be a new attack and is spreading, it is desirable to respond very quickly. Again, current technologies can locate single new files on single hosts on a network, on a timescale of several minutes to hours. Even on a single host, finding a very new file by name or content can take 15-60 minutes, and it will negatively impact the disk performance of the host while the query is being processed. Over the past 20 years, hard disks have gotten much larger in byte storage capacity but have not increased proportionately in speed. The “Distributed Meta-Information Query” feature accelerates the location and identification of key file attributes in seconds, across large numbers of hosts (thousands), with centrally specified queries, centrally reported results, with little or no host disk impact. Unlike traditional tracking technologies which track all files, including those which have not changed, the invention here tracks file changes in memory as the files are changing, and this provides an efficient means to query hosts for file meta-information from memory. Centrally processing this information provides, for the first time, responsive global views of the movement of individual files throughout collections of host file systems. Finally, as a security service, it is important that the hosts connect to, post to, and query from the central server. This is an important part of the invention in that it permits hosts to be separated from servers by one or more firewalls or NAT devices, and the difficult problem of securing an additional host network socket in accept/listen mode is avoided.
- Current endpoint host agent systems that use content analysis have issues with updating host agents. For example, for AV scanners to be most effective, they should be updated within hours or minutes of an update being made available. Any hosts with AV which lags are at risk, and many AV systems are improperly configured, resulting in update lag. Because they do not efficiently track file changes, AV scanners typically take a relatively long time to respond to new content written to a file system. Also, current host content analysis technologies needlessly re-analyze files without taking security factors into account. For instance, it is more important to analyze new content more often, the newer it is. If a file has been completely unchanged in the network for 2 years, it likely does not need to be scanned every ten minutes. However, if a new file is spreading through a network starting ten minutes ago, then scanning the new file often the first two days can make sense. There is generally less and less new information about new malicious executable files as time progresses. The “Centralized Timed Analysis” feature addresses these issues. Only one analysis agent needs to be updated, the central one, and all hosts immediately benefit. There is less chance a host configuration can interfere with content analysis updates. By tracking only new files and by scheduling analysis based on age (time) exposed to the network, new bad content can be located and identified efficiently and more quickly. Finally, many endpoint content analysis technologies, like AV, are tightly integrated with the operating system. As a result, it can be difficult to put several content inspection agents from different vendors on one host. Diversification of analysis technologies improves detection and classification accuracy. Again, the invention solves this problem by using a central server to dispatch analyses to different servers, if necessary.
- Executable content (exe files) and embedded macros (macros embedded within Microsoft Office documents) tend to propagate in clusters or groups. A word processing document might contain 10 macros, and be over 30 MB in size, yet the macros only occupy a fraction of that space. A large installation package can be hundreds of MB in size, and yet the executable portions of its internal archives typically occupy a small portion of total size. Viruses often travel through email as archive attachments, such as zip files, to avoid detection. Inside these archives, the virus payload may be small. For all of these cases, larger “container” files can obscure the propagation of possibly unwanted new code. The “Content Extractor” feature addresses a variety of current limitations by preserving the (nested) container relationships, and simultaneously facilitates: tracking of content, tracking of similar containers, tracking product associations, minimizing unnecessary re-analysis, minimizing file transfer bandwidth, and preserving compatibility with other analysis technologies by repackaging content as other known file types. The central storing and tracking of new content, and the central scheduling of analyses relative to the first appearance time of content, provide powerful advantages in terms of security, global visibility, enterprise management system integration, and future expansion.
- While the systems described here have been distinguished from other systems, such distinctions are not meant to disclaim coverage of the claims to these systems. The systems and features described here can be provided as a group or separately, and in many cases, can be integrated into prior and known systems, including those identified above.
- Other features and advantages will become apparent from the following drawings, detailed description, and claims.
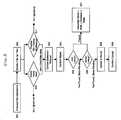
FIG. 1 is a block diagram showing an overview of a security system as described herein.FIG. 2 is a much more detailed block diagram showing components of the system inFIG. 1 .FIG. 3 is a flow chart illustrating a process for performing an analysis.FIGS. 4-5 are schematics of processes performed by the system.FIG. 6 is a chart showing an example of timed analyses.FIG. 7 is a flow chart of steps performed during a timed analysis.FIG. 8 is a schematic of a content extraction process.- Referring to
FIG. 1 , a system, also referred to as a digital antibody system (DAS)10, allows an administrator to monitor, understand, and control files installed on a large network of computers, and can provide a defense from known and unknown viruses, worms, spyware, hackers, and social engineering attacks, as well as unapproved software (e.g., file sharing software not for business use). The system includes one or more servers, one of which is shown here as server14 (appliance). This server provides centralized policy management, event monitoring, agent coordination, and content analysis (e.g., spyware and virus scanning). A single server can supportmany hosts 12, e.g., hundreds or thousands of hosts. The server also maintains a database of metadata relating to analyses, such as scan histories and approval states, with respect to files and programs. This metadata is referred to as an “antibody” for each of the files and programs. - Each protected
host 12 has ahost agent 16, preferably implemented as software. It analyzes file system activity and takes action based on policies configured on a server. These policies, described in more detail below, identify whether to block, log, allow, or quarantine actions such as file accesses and execution of executables. Eachhost agent 16 has a local “antibody”store 16, which is a cache of meta-information relating to files, and aparametric policy engine 20 for implementing policies fromserver 14. Server 14 has a number of functions and interfaces. The interfaces include host communications interface22 for communication with the hosts, a web-based graphical user interface (GUI) for communicating with web browseradministrative consoles 26, a reportinginterface 26 for serving as an interface toenterprise management systems 28, and aremote analysis interface 30 for communicating with content analysis services32 (e.g., virus and spyware scanners).Server 14 also includes ananalysis block 34 and amaster antibody store 36 that communicates with antibody analysis services38 and that stores a master list of antibodies for the associated hosts. Services38 can include an off-site certification authority with additional information associated with the antibodies, e.g., classification of an antibody as a member of a certain product package such as Microsoft Office.FIG. 2 shows an expanded view of the system and its components including theserver 14,host 12 with user and kernel portions, and other network andweb services 40. As shown here, the server includes a new file processing and file pools block42, which includes copies of recent files which have appeared on the network, a scheduled analysis engine44 for identifying files and hashes which are to be analyzed, a content signer46 for creating a cryptographic hash of contents using algorithms such as MD5 and SHA-1,master antibody store 36,configuration management 50, and logging and reporting52. The server interacts with network andweb services 40 including analyses54, AV (or other content) scanner56, andmanagement services 57.- The user portion60 of
host 12 has anantibody cache 64 for holding updates fromdatabase 34 by both name and data, file andevent processing 66, ananalysis engine 68, a content extractor70 for extracting content of interest and associating groups of individual content in a package, a content signer72 for creating a cryptographic hash of the contents, server meta-information (MI) state resolver74 for checkingantibody cache 64 for the antibody and checking the server for the antibody, and filestate resolver 76 for checking the progress of content uploads to the server and checking the server for certification of the upload. - The kernel portion80 of
host 12 hascache 82 for saving antibodies organized by file name, and acache 84 of recent file operations and file information. The kernel also has an intercept/block function86 that receives and intercepts file operation requests, and provides these requests to astateful filter 88 that first checks the cache ofrecent file operations 84. If there is no match, it checks the triggers and actions block90 which maintains security policies. Thisblock 90 is coupled to a “defcon” block92, which has a value that indicates a security level for the system, andpolicy engine 94 that governsblocks antibody cache 82 that looks for meta-information on files based on their names.Policy engine 94 also controls actions, such as blocking, reporting, or allowing file operations, and reporting to the user. - The system includes numerous methods and aspects for using this security system, many of which can be used alone or in combination with others. These methods and aspects are described in more detail below.
- One aspect is the use of a centralized scan to check documents or executables and to maintain a hash indicating whether that data has previously been checked. The hash values can be stored in a database and also cached in local hosts.
- Another aspect is in the use of a centrally set parameter, sometimes denoted “D” or “Defcon”, that controls the policies of the hosts. This central policy and parameter can be applied to all hosts, or to selected groups of hosts. The parameter can be set manually by an operator or can be adjusted by the system without human intervention, typically in response to some event. The policies can include blocking or allowing certain actions, or it can make an action pending, which makes it allowed, subject to further monitoring such as logging. A pending status has multiple benefits, including taking into account latencies in the system, as well as implementing policies which do not fit the traditional binary approve/ban model. These latencies include the time before harmful code is identified, during malfunctions in the system, or times when a host is disconnected from the network.
- In still another aspect, a central server can specify a query of meta-information and distribute that query to all or a selected group of hosts. These hosts perform the query from a local store of meta-information and send results back to the server that can cause the server to adjust the parameter.
- In yet another aspect, the system includes a method for protecting against spreading macro viruses that can be embedded within other documents. This functionality can be used with Visual Basic macros, but the methods could apply to any other macro language other than Visual Basic.
- In another aspect, all copies of new files are kept in a special directory in a server42. Further analysis can be performed based on timers, and could be performed days after the file is first seen. After some period of time from the first appearance of a file, such as 30 days, the file can be rescanned for viruses, spy ware, or other problems, and can the system can take action depending on the results. For example, an analysis which indicates a virus is contained in a file would then cause the
corresponding Antibody Database 36 entry for this file to include a Banned state. This change, along with other Antibody Database changes, will be propagated to the Hosts. - Centrally Set Parameter and Parametric Content Policy
- The security in the system is based on policies that are defined in each server and propagated to all the associated hosts or groups of hosts, through push and/or pull techniques. These policies relate to what can be done with executables and files, such as reading, executing, and writing, what to do when they are created or altered by hosts, how scans are run, how logging is done, and many other functions, and for each policy (e.g., what operations can be done with a newly seen executable) there can be a number of policy options (such as ban, allow, or allow and log). The policies can be based on the content (data) in a file or the name of the file, or a combination. The content can be defined by a signature, such as one or more cryptographic hashes. A non-exclusive list of sample policies includes:
- 1. Block/log execution of new executables and detached scripts (e.g., *.exe or *.bat)
- 2. Block/log reading/execution of new embedded content (e.g., macros in *.doc)
- 3. Block/log installation/modification of Web content (alteration of content in *.html or *.cgi files)
- 4. Permit updates for policies such as (3) above
- 5. Auto approve files that pass two virus scans (e.g., set the corresponding file state to Approved)
- 6. Block/log installation/execution of files specifically banned by administrator
- 7. Quarantine/delete/log infected files by data
- 8. Quarantine/log infected files by name
- 9. Block/log execution of new files in an administratively defined “class”; e.g., an administrator might want to block screen savers *.scr, but not the entire class of executables *.exe, *.dll, *.sys, etc. . .
- 10. Log when specified files are copied to removable media
- 11. Block/log execution of new executables, scripts, and embedded content, except in a certain directory i.e., allow a user to create new scripts or executable in a special directory but protect the rest of the file system
- 12. Different policies for hosts when offline, remotely connected or locally connected
- 13. List hosts/paths that contain a specific file by data or by name
- 14. List hosts with blocked executables, scripts, and embedded scripts
- 15. List hosts/paths with infected or banned files
- 16. Auto-approve files from defined update services, e.g., if from trusted sources
- 17. Block/log execution of files specifically banned by administrator for specific host groups (i.e., there is more then one group)
- 18. Completely deactivate the host system for performance reasons and testing.
- 19. Auto-approve a file after a period of time (user configurable)
- 20. Allow a new file to be installed/executed up to x times (user configurable). Block any more installations and/or executions until approved.
- 21. Locally Approve new files as they are written
- 22. Centrally Approve new files as they are written
- The server can maintain one or more policies for each host group, and each policy is variably enforced according to a parameter that is centrally set and that indicates options for the policies. These policies and options can be logically organized as a two-dimensional array, where the parameter in effect moves along one dimension to select the policy options for various policies. This parameter is referred to here as a D value. All hosts can have one value for D, or logical subgroups of hosts have their own value of D; e.g., hosts in the sales department could be assigned D=1 and hosts in the marketing department could simultaneously be assigned D=2. In one implementation, hosts check (poll) the server to see if the value of D has changed. As each host discovers that D has changed, they each begin to “move” to the new value of D. This movement can be done in steps. These polls can be provided as network messages from the hosts to the server. The D value controls policy actions. For a given policy (e.g. “No New Executables” or “No New Scripts”), D=2 blocks policy violating actions (in this case, the execution of a “new executable”), D=4 warns (silent alarm to server) but permits, and D=6 permits and does not warn at all. Regardless of whether D=2, 4, or 6, the hosts preferably continue to notice and record new executables as they are written. While the examples here use a numeric value for D, D can have a “value” that is expressed in letters, words, or any combination of letters and numerals.
- The D value also controls policy activation. For a given policy (e.g. “No New Executables” or “No New Scripts”), D=1 enables a “write protection” policy, so new executables can not be written at all, while D=8 completely disables all policies, and the D=2, 4, and 6 cases can be as set out above. In this case, D=8 can even disable the policy of noticing when new executables are written to the file system.
- While the value of D can be set centrally in a server, it is implemented locally on a host. It can be set by an administrator through a graphical user interface (GUI) on an administrative console by using a browser connected to a server, or via Simple Network Management Protocol (SNMP). The D values are considered “target” values; hosts attempt to move as close as they can to this value, which may take seconds or minutes. In some cases, a host can diverge locally from the target value as specified by the server. A command-line program can be invoked on the host, or the user can be prompted for certain values of D, and the target value of D can be overridden. This feature can be useful, for example, in cases where an individual's machine needs to have the security disabled (D=8) and there is no network connectivity with the server. Certain actions can automatically change the value of D on a host, such as detection of an update from an authorized program (e.g., antivirus update).
- The policies reflect a tradeoff between security and usability. In the examples above, D=8 is maximally useful, and minimally secure—no policies are activated, and the host agents are effectively disabled from blocking and tracking. As D moves toward maximal security (D=1), more and more restrictive policies are activated, and the actions performed when the policies are violated become more and more severe. Ordered states are desirable in that they are easier to visualize and test (generally, one can just test the endpoints need be tested, such as D=1 and D=8). With ordered states the numbers of files and users become successively more accessible or more restrictive as the value is increased or decreased. These ordered states naturally reflect tradeoffs between security and usability.
- As D is changed on a live system, race conditions can occur. The basic problem is that an installation of multiple files could become “half-blocked” or “half-installed” if a value of D were to be changed from 8→1 while installing a program. As a result, certain D transitions can trigger file antibody state reanalysis and file antibody bulk state transformations.
- Local D changes can sometimes be caused by local policy triggers. Normally, D is set centrally on the server. But sometimes, a local host policy is triggered, which then causes the local host D value to change. This is useful, for example, to complete an install on a locked system (D=2). Continuing this example, installing printer drivers at D=2 could otherwise result in problems, because some of the unpacked new install files need to execute to complete the installation. Further, different host machines may need to unpack and execute different programs to complete the installation (e.g., Windows 2000 and Windows XP). In this case, execution of a certain antibody file type, an approved program “printer setup.exe”, will move that host's local D from 2→3, which is a slightly weaker state that automatically locally approves only these new installation files and their progeny.
- The D value could be changed depending on the type of connectivity, whether local (on a wired LAN), remote such as through a telephone modem or virtual private network (VPN), or completely disconnected. The host agent would thus store a set of specified D values for these types of connectivity and then automatically select from the set in response to a change, for example, when a user disconnected the host from the LAN. Also, different D values can result in decreases or increases in reporting, logging, and tracking detail.
- Policies can also be set from a central server, referred to sometimes as a “super server,” which can control many servers/servers. Assuming each server controlled 2,000 hosts, and there were 1000 super-servers, it is unlikely that a super server command to set D=1 would be proper for all 2,000,000 hosts. Instead, the super server could command all servers and hosts to have as strong a D as locally permitted. So some servers, and their connected hosts, would go to their limit of, e.g., D=2. Other servers might go to D=1, but then perhaps some of their host groups would be limited to D=4, so those hosts would go as strong, but no stronger, than D=4. The same limiting is true for the other end of the spectrum. If the super server commands D=8, some servers and hosts might only go to D=6 instead. Since D is an ordered state, these constraints are simple integer ranges (maximums and minimums).
- The value of D can change based on the detection of some event, such as spreading files. If too many copies of a new file are propagating among a server's hosts, the server can optionally increase D to stop the spread (e.g., go to D=2). This event can be specified as too many of a certain name (e.g., a top 10 list by name) or too many by unique contents (e.g., top 10 list by a hash of data).
- The value can also be changed per server request in response to a new event perceived by the server, such as a new incoming file or a potential virus attack. In most cases, it is the administrator (a person) who initiates the change of D, following planned user operation, or on observation of certain file events. D can be automatically changed, e.g., during the process of an operation, in which case, the host/server will roll the value of D back to its original level after the operation is terminated. External triggers can change the value of D, such as SNMP.
- Another response is for the server to automatically approve content that is on fewer than a certain threshold number of hosts, yet automatically ban access to that content when the number of hosts is exceeded. Such a policy could be used to limit the number of copies of any content or file in the network. Also, such a policy could be used to only report content that exceed the certain number of hosts.
- Servers can maintain a policy set separately for each logical group of hosts, such as sales hosts, marketing hosts, and engineering hosts. Policy sets can have unique identification numbers that are similar to antibody version numbers. The difference is that, once deployed, a policy set becomes “read only” to reconcile later problems with a policy set and to undo a problem deployment. This can also be done to difference configuration and other updates, using technology similar to the Unix utilities “diff” and “patch.” Hosts can query the server for the current policy set ID number for their group, and if there is a mismatch, they can send the server a “GetPolicySet” query.
- A policy set can include multiple policies, such as a “New Executables” policy and a “New Script” policy. Each policy can be in active (on), inactive (off), or in test mode (where blocks are permitted but a “would have blocked” message is sent to the server). Each policy can have multiple rules, each rule with a basic “trigger and action” model. Triggers are patterns which are tested. If the pattern matches, the resulting actions are performed. For example, “blocking execution of new executables at D=2” could be specified as follows:
- Trigger=(D=2 & FileOp=Execute & State=Pending & FileExtensionClass=ExecutableClass) where ExecutableClass=(*.exe|*.sys|*.dll| . . . )
- Action=(Block & Report & Notify(P)) where “Block” stops the operation, “Report” sends notification to the server, and “Notify” alerts the user with parameter set P.
- With this structure, the kernel can enforce all policies without interaction with user space, except in the case of kernel antibody cache updates, D updates, and policy set updates. Policy sets need only be stored in one place, and they need only be interpreted in the kernel in this implementation. Policy sets can be authenticated and stored in one secure context (the kernel), resulting in more security against tampering.
- Policies and actions are parameterized by D since D permits different rules to match different triggers. Files with certain states may have certain operations blocked. These states can be a combination of name and data properties. These states are determined in user space, mirrored in kernel space, and ultimately, the states are determined by the server. One useful policy is to block banned files, and at some D values, to block file executions of pending (new) files.
- The policies can be provided as a set of lists of policies over a range with tradeoffs of accessibility and security. The server can then provide information to cause the hosts to select one of the lists. By having the lists present at the hosts and allowing the hosts to update policies using the “pull” approach, the hosts can conveniently update security policies under control of the server.
- The following table shows an example of how the D value can affect various policies in a master policy set, where the rows are policies in the master set, the columns are actions, and the cells have numeric ranges of D for indicating the actions. The actions specified in the table and other details are summarized below:
D Value vs Policy Name D = 10 D = 8 D = 6 D = 4 D = 3 D = 1 Global Protection Tracking Silent Local D = 2 Write Approval Disabled Only Alarm Approval Lockdown Protect New/Pending Auto Permit Permit Permit Auto Block Block Executables Global execution, Local Execution, Write/Exec, *.exe, *.sys, . . . Approve Report Approve Notify, Notify, New, New, Report Report Report Report New/Pending Auto Permit Permit Permit Auto Block Block Standalone Scripts Global execution, Local Execution, Write/Exec, *.vbs, *.bat, . . . Approve Report Approve Notify, Notify, New, New, Report Report Report Report New/Pending Auto Permit Permit Permit Auto Block Block Embedded Scripts Global execution, Local Execution, Write/Exec, In *.doc, *.xls, . . . Approve Report Approve Notify, Notify, New, New, Report Report Report Report New Web Content Auto Permit Permit Permit Permit Write Write *.html, *.asp, . . . Global Writes, Writes, Protect, Protect, Approve Report Report Report Report New, Report Approved Permit Permit Permit Permit Permit Permit Permit (hash and/or name) Exes/Scripts/Embed Banned/Unapproved Permit Permit Block Block Block Block Block (by hash) Execution, Execution, Execution, Execution, Execution, Exes/Scripts/Embed Notify, Notify, Notify, Notify, Notify, Report Report Report Report Report Banned/Unapproved Permit Permit Block Block Block Block Block (by name) Execution, Execution, Execution, Execution, Execution, Exes/Scripts/Embed Notify, Notify, Notify, Notify, Notify, Report Report Report Report Report Content change and Track, Permit Track, Track, Track, Track, Track, Content creation Report Report Report Report Report Report tracking - (1) Permit: Permit the operation, otherwise silent
- (2) Block: Block the operation, otherwise silent
- (3) Track: Track the operation and resulting content (if content is Pending or Banned), otherwise silent. Approved content is generally not tracked.
- (4) Report: Send a notification to the server
- (5) Notify: Indicate to the host endpoint user why the operation was blocked/interrupted
- (6) Auto Local Approve: New host files and/or new content with local host state=Pending are locally set to host state=Approved or state=LocallyApproved only on the local host as the files/content are created/modified.
- (7) Auto Global Approve: New host files and/or new content with local state=Pending are globally set to server state=Approved on the server as the files/content are created/modified.
Antibody Introduction, File Meta-Information
- Referring particularly to
FIG. 2 , for actions that are allowed, the server in the system includes anantibody database 36 that is used primarily to keep track of file scan histories and the approval states for each of the files. An antibody is a block of data about a file (i.e., metadata or meta-information) that can include some or all of the following fields: - Time First Seen. When the file or hash was first seen by the hosts and reported to the server.
- File ID. A unique identifier for the file, including one or more hashes of content such as MD5, SHA-1, and OMAC.
- File Type. The file class (e.g. executable, script, office document, archive, etc.). This is derived from the file name as it was first seen (see below) and also from analysis of file contents.
- Status/State. The current file status, including Approved, Pending, or Banned.
- Method. The way in which the server learned about the file (automatically, manually, etc.).
- Filename. The name of the file, as first seen and reported to the server. This may not be the file's current name, but is just the name of the first instance seen on the network.
- File Path. The path of the file, as first seen and reported to the server.
- Host file name/path/extension when first seen/reported
- Host file name/path/extension when last seen/reported
- Host IP address file first seen/reported
- First Seen Host. The name of the host on which the file or hash was first seen and reported.
- Analysis Results. The result of the latest scans or other analyses.
- First Analysis. The time of the first scan/analysis of the file.
- Last Analysis. The time the file was last scanned/analyzed.
- Last Updated. The time the file state was last modified.
- Parent Containers. Links to other files which have been associated with the file.
- Parent Container Attributes. File name, first seen time, first seen host, file path, product classifications, and state of one associated container file.
- Root Containers. Links to other files which have been associated with the file. A root container is one which is not contained in another container.
- Root Container Attributes. File name, first seen time, first seen host, file path, product classifications, and state of one associated root container file.
- Reference parent file containers, if known. These are used to maintain containing associations such as: “file of this hash=y was observed inside an archive file of hash=x”.
- File content type (determined by content analysis) such as executable, script file, embedded macro
- The server has the system's complete set of antibodies for the system. While each host can contain a local subset of the antibodies in
user cache 64 and inkernel cache 82, the server is the authority for setting and changing to certain states. For example, the server is the authority that centrally initiates and propagates changes (to Hosts) including state transitions from Pending to Approved or Banned (those three states preferably associated with content hash), while hosts are the only authority that can set a state to locally approved. Each entry indatabase 36 is persistent and preferably is easily accessible with a file data hash index. The database can optionally be indexed by other keys, such as file name, date first seen, state, analysis results, host ID, or host count, so that an administrator can easily browse the antibody database. - While the database with antibodies is described as being in or on the server, it should be understood that this means that the database is associated with the server. It could reside physically in the same box and the server's processing functionality, or it could reside in a different box or even in a remote location. If remote, there should be suitable wired or wireless connection to obtain the data.
- Antibody (AB) Tracking Introduction
- As new files are created or existing files are modified, tracking policies may be triggered, thereby setting off a chain of file and antibody analysis events. First, the host performs a series of steps to determine if there has been a significant modification to content that corresponds to content that has already been analyzed and for which an antibody has already been stored in a host cache. If the content antibody is not in the host cache, the server is queried to determine if the server has already analyzed the content. If the server does not have a corresponding antibody, then the content may be uploaded to the server for further analyses. Until the server can determine the state definitively, the state associated with the content is set to be pending or not yet determined. Subsequent access to pending content may be limited. The server performs analyses on the content based on a time since the content was first seen on the server. Based on the analyses or on other external determinations, the server may definitively determine changes in the state. These changes may be indicated for later retrieval by the hosts so the hosts can update their antibody caches with the changed states.
- Host Antibody Tracking
- Referring to
FIG. 3 , the host intercepts file operations (501), including execute, read, rename, or write, and provides the operation to a stateful file operation filter (502). If the file name is not in the kernel cache and there is a kernel cache miss (510) and if there has been a possible file or content modification (511), the state is invalidated. The file then goes to a content extractor, which, as described in more detail below, extracts the active content of interest (503) to produce a reduced file, and provides the reduced file to a content signer (504). The content signer applies a cryptographic hash, such as MD5, to the reduced file. This hash is associated with the file and the file name. A file operation may be delayed/stalled while the hash and other analyses (cache miss resolution) are completed. - The host also makes a local lookup based on the hash content to try to get a state (505). If the content and a state are not found, the state is sent to pending. This can mean that the file operation is allowed to proceed, although further monitoring, such as logging, could occur also. If the content is found, the name, content, container (file which contained the active content) and state are all associated together (507). If not, the host requests that the server look up the content in its memory (506). If found there, the name, content, container (file containing the active content) and state are all associated together (507). If the content and state are not found, the state is set to pending, and the content is uploaded to the server (508), which confirms the upload (509). The server can also look to a “super server” associated with a number of the servers. Container relationships are stored and associated with files and other containers. Container information is also sent to servers and hosts, as well as sent for analysis. A “Root Container” is a container which is not contained by another container. Containers are identified by their associated files as well as by cryptographic hashes.
- Generally, antibody states are assigned to a hash or signature of the “active” parts of file contents or of entire file contents. So generally, HASH(File Data/Contents)→State. This maps Data→State. State (S) can contain many pieces of information, such as “approved” (white list) or “banned” (black list) or “pending” (a “grey list” such as a newly seen file that has not been fully analyzed yet).
- An advantage of this system is the combination of name states with content states. For instance, the server can specify and store multiple name bans, such as *msblast.exe. The server stores name state policies as lists of regular expressions and associated meta-information. Any file drive/path/name/ext which matches the regular expression will then inherit the name meta-information. This information is updated whenever file names are changed or the name meta-information specification changes. Name states and policies are propagated from the server to the hosts. For example, by adding *msblast.exe→NameBan, the server will sense the new policy/state, and will propagate that specification to the hosts. Hosts will then search their name meta-information caches for matches with *msblast.exe, and those file which match will inherit NameBan state. Host file state is a superposition of name and data states: for example, if temp_msblast.exe had content state=Pending, its combined state is Banned since NameBan has precedence over Pending. Name approval states are handled in a similar fashion.
- Antibodies are stored in the databases hierarchically. There are four main storage locations for antibodies as indicated above. In a host agent, a
kernel antibody cache 82 maps file NAME→antibody STATE. For example, NAME=c:\windows\bar.exe→STATE=approved. In shorthand, this mapping is N→S. The kernel can and does enforce policy based on the state without needing access to file contents. This is useful as the file may be encrypted in the kernel but visible in unencrypted form higher up. The kernel has direct access to the name, but not to the hash. The kernel cache can be weakly consistent with other caches, and ultimately the server, in that there can be long latencies (seconds, minutes, hours, days). - The host agent has a user antibody name cache (UN) and a user antibody data cache (UD)60. The UN maps the file name to a hash of the file contents (Data), i.e., UN maps N→Data. And similarly, the UD maps data to state Data→S. Generally, the mapping of N→Data is many-to-one, and UN mirrors the structure of the local file system. The mapping of Data→S is generally one-to-one, as hash collisions are rare with strong hashes that are preferably used, such as MD5. The UN and UD caches are also weakly consistent with the server, but both UN and UD are strongly consistent with the local host file system, as is the kernel cache. UN and UD can be combined as follows: N→Data→S=N→S.
- A server has an
antibody database 34 of generally every unique hash that has ever been reported by any of its hosts, and a super server (if there is one) has an antibody database of generally every unique hash which has been seen on any of its servers. Limiting to unique hashes limits storage and processing, although more could be stored with further improvements in storage and processing. Also, limiting to unique hashes results in more efficient analysis and lower network traffic. - Generally, new files propagate from the host to the server to super server in response to “New File” or “Dirty File” events, and the newly computed antibody state propagates in reverse from super server to server to host user to host kernel in the form of antibody updates. In this way, antibodies are centrally controlled, managed, and verified. The servers “own” and certify the antibodies and servers provide authentication that the antibodies have not been altered or forged. Hosts maintain their own antibodies which generally but do not necessarily correspond to those on the server. So a compromised or malfunctioning host cannot degrade a server or super server antibody collection, nor can a compromised host degrade the antibodies of other hosts.
- On the host, the antibody state is preferably stored so that it is not associated with hash/data, but rather by name. The kernel parses, interprets, and enforces policy, and the state of a file is looked up by name. It is understood that the preferred implementation enforces policy in the kernel, but other implementations can enforce policy in user space. When looking up state, in either user space or kernel, it is actually a mixture which determines the resulting state. For instance, if the data antibody for foo.exe is pending, but the name antibody was banned based on its name, then the GetABState(foo.exe) returns a result of “banned by name”. There is a separate policy to block executions of files with antibody State=NameBan. The actions for that policy are parameterized by the value of D as above. One difference is that policies which block “Banned by Name” are active at lower D security settings. For instance at D=4, “pending” files will execute (with silent alarm) but banned files will not execute.
- Name bans are represented as a list of regular expressions and can include a wildcard (*), e.g., “*oo.exe” or “*msblast.exe”, on the server. These lists have version numbers. As hosts poll in, they check their version numbers. When a host detects a mismatch, it then sends a GetNameBans query from the server (i.e., the hosts pull the new ban data from the server). Then these regular expressions are reevaluated against the name antibodies. Name ban is an attribute of state, and only has to be recomputed when the name ban list changes or when the file name changes. The wildcard list does not have to be compared on every file operation. So the dual nature of data antibody and name antibody is useful. Also, hundreds or thousands of name regular expressions can be simultaneously in effect without requiring thousands of regular expression match computations in the kernel for each file operation, which could be prohibitively expensive.
- File Content Tracking
- Referring back to
FIG. 2 , an intercept/block function86 can intercept and read file access requests. It can suspend requests while obtaining policy information, block requests based on in-kernel policy, and return appropriate error codes for blocked requests. The function86 reads from file access requests the requesting process name, a local system time of the request, the file requested (including full path), and the action requested (e.g., read, write, or execute). In one embodiment, function86 feeds all file access requests to “stateful filter”88, and every operation is blocked untilfilter 88 returns a flag indicating that the operation is either blocked or permitted. Filter 88 intercepts file access requests from function86 and returns an action of “block” or “permit” for most file access requests. Any file access request that cannot be associated with already-approved file access requests is forwarded to the kernel triggers andactions module 90, which returns an action of “block” or “permit”. This action is stored byfilter 88, and is preferably returned to function86 for any subsequent associated similar file access request.Filter 88 maintainscache 84 of already-open files (indexed by a kernel-wide unique identifier; e.g., kernel file handle in Windows NT). Each cache entry contains a file identifier (kernel file handle) and block or permit permissions for a read, write, or execute.- If multiple processes access the same file, each will have its own cache entry. If a given process attempts a new file access, the stateful filter will experience a cache miss for that file, which will cause it to submit the file access request to the triggers and actions module. The flag for the requested operation (read, write, or execute) should be set to “permit” if
module 90 allows it. Otherwise, it should be set to “block”. If a process which has only obtained one kind of permission (e.g., read) then tries another kind of access (e.g., write),module 90 will again be contacted. - Cache entries whose age exceeds a certain value (e.g., 60 seconds) may be deleted. This allows pruning of entries which for some reason are not removed. It also allows period re-checking of a file by
module 90. - In this example, a file write operation is caught in the kernel in a blocking shim86 by the host agent kernel program (HK) for a file “foo.exe”. At a value of D=4, the file operation, here a file write operation, is caught by an activated “dirty tracking” policy, and this sets off a “dirty” event from the host kernel program to the host agent user space program (HU). This event specifies the filename and the dirty operation. The
kernel cache 82 is not consulted for this operation, as the dirty tracking policy has that field nulled. - HU then performs a variety of local analysis operations in file and
event processing 66 andanalysis engine 68 on foo.exe. First, foo.exe is checked to see if it exists, if it is readable, and if it really is an executable. Other operations may be performed, such as the extraction of “interesting data” infilter 88; for example, script comments could be removed if the file were foo.bat. The extracted data of foo.exe is then cryptographically hashed, and this hash is used to attempt a lookup in the HU antibody cache60. If the name and data already exist, nothing else is done. If the name is new, but the data is known, then a new name antibody is created in the UN cache. This process is all part of what is called the “Stage 1 analysis queue.” Many files can be queued up waiting to be hashed in theStage 1 queue on the host. TheStage 1 queue has only name antibodies and meta-information, since the data is not yet known or analyzed. - If the host has seen this file data and hash, then the corresponding known meta-information for that hash is associated with the host file meta-information for that file, retrived from UD local memory or local disk stores, in that order. If the host has not seen this data, the UD cache “misses.” The hash is put into a
Stage 2 analysis queue. In reality, there are data antibodies, that is, states which logically track data, such as “Approved”, “Banned”, or “Pending,” and there are also Name antibodies, e.g., “Banned by Name”. For example, if the server bans “*oo.exe”, then the name antibody for foo.exe will indicate “NameBan” and name-banning policies can block based on that. So even though the caches may know that foo.exe is already banned (by name), the dirty tracking resolution still continues. This distinction of the name and data antibodies is local in scope to the individual hosts, but it does become important for the FindFile function (described below) and for policy enforcement. The data antibody is thus put into theStage 2 queue. - The
Stage 2 analysis will attempt to resolve local state information from memory caches first, then from local disk-based data stores, and then from the server. If the server is connected, theStage 2 queue will empty as the meta-information is resolved. When foo.exe is removed from this queue, the server is asked if it has seen this data hash, if that hash is not found locally. If the answer is no, then foo.exe and its hash and other meta-information is put into aStage 3 queue for upload to the server. In addition, the server will send a default antibody state to the host, which is “pending”, if the server has not seen the hash before or if the server analysis is not yet completed sufficiently to determine other states. If the server has already computed a valid antibody and state, it returns this antibody meta-information. If the server has never seen this data for foo.exe, it is new in the sense that all machines in the server's experience have never seen this file. - When foo.exe is removed from the
Stage 3 queue, it is uploaded to the server using encrypted one-way transfer. That is, using FTPS (secure file transfer protocol) and a write-only server directory, files can be uploaded to the server but not downloaded. When the upload is successfully completed, the host informs the server that foo.exe was transferred. This transfer is referred to by hash, so as to minimize information leakage and for additional security. - When the server learns that foo.exe is uploaded, it starts by analyzing the file through several stages as the host does. A new antibody is created in this case, with the server using its synchronized verified clock to timestamp its first appearance. Also, the extraction and hash is performed, and those results supersede the host's.
- Server analysis follows a schedule which is specified and stored on the server. This schedule is relative to the first appearance time of the file or its hash on the server. For example, if a file arrives at noon and the schedule is “Hash lookup at +0 and AV scan at +0 and AV scan at +2 hours”, then at noon, the file hash will be computed and looked up using and external hash lookup service. Then an AV scan is performed. Two hours later, at 2 pm, another AV scan of that file is performed. Another way to describe the schedule is that it is relative to “file age on the server”.
- When an antibody changes state on the server, an incrementing counter value is written to the antibody. This counter is used to select just the range of antibodies which have changed since any particular host or super server checked in. For example, if a previous antibody change was glorp.bat transitioning from Pending→Approved and the global antibody version counter was277, the server antibody corresponding to the hash of glorp.bat would get a version number277 and the counter would be278. So the version number corresponding to antibody foo.exe is278 and the counter is279.
- When hosts periodically poll, they provide their last antibody version number, and the server will send all antibodies which have changed since the last poll. Preferably, the server sends the current number, and when the host realizes the mismatch, it asks the server for an antibody update, and the list of data antibodies is returned. These then are merged into the host antibodies, and changes are also sent down into the kernel too. Although the host may get and store some antibodies for data which it has never seen, generally only those antibodies which correspond to existing host files are merged. The others are usually discarded. The server caches the last few minutes of updates, to minimize the effect of custom-tailoring all the updates to each host. Again, since hosts typically get more antibodies than they need, and because new antibodies are rare, this traffic is limited. Antibody updates are small, as are most of the other messages.
- Antibodies can remain synchronized with a super server in a similar fashion. Here, the super server can poll servers and get antibody update lists. The super server can merge them, and send out tailored updates for each server. These updates are all weakly consistent, in that they can lag by minutes or days, but there must be interlocks and safeguards to avoid “holes” in the updates.
- There are other aspects and features related to merging of antibodies. For example, some servers may not accept certain antibody updates from the super server. Also, hosts will not permit certain local states to change to certain server specified states.
- One issue is with the initial states of the cache and initial policies. The server cache can be preloaded with known good and bad hash antibodies, or it can be empty, and all is well. However, hosts must occasionally “Trickle Charge”. For example, when a host first connects to a certain server, this fact is detected, and the host will perform a trickle charge where every single interesting file on the host file systems is inserted into the
Stage 1 queue. A special value of D is engaged during this process to ensure that the indeterminate cache will not cause problems. Antibodies generally all start with state “pending”, and they slowly synchronize with the server. Also, all host antibodies and queue information and related globals are persisted periodically and over reboots. - Kernel Cache Consistency
- On boot or other initialization of the host agent, the kernel is loaded with every valid antibody known from user space, for every known existing host file which has valid meta-information. Some antibody updates are sent into the kernel as they are received from the server or from analysis queues in user space. However, some updates are the result of kernel cache misses. If a policy is determined to be active and if the antibody state is needed and if that state is not available, the kernel will generally stall the operation for some time and send up a kernel miss event to the user space. Some events may be stalled even if the antibody is not needed right away. This is the case when a policy permits the host user to override a restrictive state (Pending) by interacting with a user interface (message box popup), for example, clicking yes to override a blocked Pending operation and to cause subsequent restricted operations to succeed without blocking for some time.
- In one example, an installation program unpacks a new program called inst.exe and then renames and executes it. The kernel will avoid temporary inconsistency by delaying the rename, and delaying the execution, while the analysis is performed. The resulting antibody is sent down asynchronously from user space, and then the pending operations unblock and the policy is evaluated with the required state information, as soon as the asynchronous update is completed.
- The kernel cache contains antibodies for almost all files in the file system upon initialization. Operations that could leave holes in the kernel cache or other inconsistencies, even for brief times, are delayed and interlocked so that consistency is maintained. The user space caches are optimized to resolve kernel misses with very low latencies. Whereas the kernel and user space caches are quite insensitive to server-side latencies, the kernel cache is sensitive to interlocks and proper persistence.
- FindFile
- Because the UN and UD caches are preferably optimized for low latency lookups, these caches can be used as part of a distributed antibody query from the server, referred to here as the “FindFile” function, to produce a view of what files are on what hosts. A FindFile request can be specified by an administrator by submitting a web browser form via a web interface on a server or super server. For example, the following qualifiers can be jointly specified:
- (1) a regular expression pattern specification for file name,
- (2) a regular expression pattern specification for file path,
- (3) a hash of contents of interest of a file,
- (4) a hash or other ID of a container which is associated with a file,
- (5) a time range of when a file or the hash of the file was first seen by the host,
- (6) name of the host,
- (7) IP address of the host,
- (8) type of the file,
- (9) one or more host file states associated with the file from a set of at least three states: approved, banned, pending analysis. For example, a set AllBanned=(NameBan, BanByHash).
- (10) whether certain file operations have been performed by the host on the file, and
- (11) a host group.
- Referring to
FIG. 4 , a completed FindFile request is analogous to an email in that the server posts a request for later retrieval by specified hosts. As hosts check in, they learn if there are FindFile messages from the server waiting for them. When a host learns it has an outstanding FindFile request, it retrieves the requests using GetFindFileRequests, as shown as lines (1) inFIG. 4 . In other words, the request is preferably accomplished as a “pull” from the server. This allows a more secure implementation with no listening host sockets needed. - The connected hosts each process their FindFile requests by accessing applicable data from their antibody caches, and post result lists to a results database shown as PostFindFileResults (lines (2) in
FIG. 4 ), including some or all of the following information for each file returned: - (1) a file name,
- (2) a file path,
- (3) a hash of contents of interest of a file,
- (4) a time when a file or the hash of the file was first seen by the host,
- (5) name of the host,
- (6) IP address of the host,
- (7) type of the file,
- (8) container information for the file,
- (9) one or more host file states associated with the file from a set of at least three states: approved, banned, pending analysis,
- (10) whether certain file operations have been performed by the host on the file, and
- (11) a host group.
- In one implementation, all host-server communications (not just FindFile) are accomplished by the host first connecting to the server and sending one or more network messages, and receiving server replies for the host messages, before disconnecting. Again, this has an advantage of being more secure in that no listening host sockets are needed. There is an additional advantage in that only server addressing and routes need be maintained, rather than maintaining host addressing, routes, and reducing the need for discovery of such host information.
- The server merges and builds up a master list of the FindFile result lists from the hosts. This union of these lists is the complete FindFile request response, and it builds up over time, usually completing in less than one minute. Since the local host processing only accesses the antibody caches, and not the host file system, these queries can be fast. The dual name and data antibody association system and caches permit this. The server then exports the results to the administrator, e.g., through a web interface. Also, certain FindFile results can affect and trigger SNMP, syslog, alarms, and other notification systems.
- The super server can also post requests to be accessed by servers in a similar fashion, or a super server could directly submit FindFile requests to the servers. Then, servers could return the merged results to the super server, which then could merge these into a larger master result. This is analogous to the relationship between servers and hosts when processing a FindFile request.
- Timer-Triggered Central Analyses
- Referring to
FIG. 5 , a server can perform analyses based on events, e.g., an analysis each time a host uploads content, or the system can perform these analyses based on time. As indicated above, new content can be uploaded to the server, and analyses are performed with external and/or internal analysis agents to create metadata or meta-information that is stored in a database. The system can then check for further scheduled analyses, e.g., after certain time intervals relative to a first observation of a file when new content is uploaded. The servers and super servers can perform many types of further time-based analysis. - Referring to
FIG. 6 , as a file is first seen and its antibody is added to a server database, the effect is as if a timer is started for each file. So, for example, the time intervals could be (t=0=immediate, t=12 hours later, t=2 days later, and t=30 days later after the first sighting or report to the server), and could be based on the server's clock. Periodic actions, in addition to one-time timed actions, can be specified. As shown here, antivirus (AV) and anti-spyware (AS) scans can be performed at different times, and other analyses can be performed. For later time periods, this could be a comparison to others servers that may have looked at the files. Typically, the later analyses would be based on all files first seen within some time period. For example, all files first seen within a 1 hour time would get the 12hour analysis 12 hours from the last file in the time period. - Referring to
FIG. 7 , the system selects files for analysis and sends the files to perform specified analyses. Different operations can be specified for each time interval. Since the files are kept for a while on the servers, these time-activated analyses can proceed whether the original Host is still connected or not. Examples of central timed server analyses that can be performed include: - (1) Compute alternate hashes (e.g., using MD5 or SHA1 algorithms), verify the reported hashes, and store all of the hashes.
- (2) Authenticate and sign content with server credentials or other third party credentials.
- (3) Lookup hashes against known bad databases (black list) either locally or via query of another server
- (4) Lookup hashes against known good databases (white list) either locally or via query of another server
- (5) Lookup hashes against known product classification databases to identify the product (and other information) which corresponds to the file hash
- (6) Send files for virus scanning (e.g., by FTP or SMTP as MIME attachments for example) or perform locally
- (7) Send files for spyware scanning as in (4) or perform locally
- (8) Send files for site-specific custom analysis as in (4) or perform locally
- (9) Export files to a special restricted-network-access subdirectory on a network file server (e.g., authenticated samba or FTPS)
- (10) Send SNMP traps that new files need analysis and specify their locations
- (11) Send Syslog or email messages that new files need analysis and specify their locations
- (12) Check certain directories to see if another system has approved or disapproved of the file
- (13) Perform custom analyses on the server
- (14) Automatically perform a second analysis conditioned on the result of a first analysis
- (15) Receive authenticated network messages containing analysis results from external analysis systems
- The results of the above analysis are summarized on the server, which updates the state in the meta-information store (124), particularly the state for broadcast to the hosts. The server makes recommendations as to whether a file should be approved or banned. Information is summarized so that administrators can approve or ban groups of files with one web browser action. Optionally, the results from the analysis above can be used to automatically approve or ban files with certain antibodies. The server can provide reports, alarms, or further information, and can alter the parametric D value for all or one or more groups of hosts. The server flags the state changes for later distribution through updates (130), preferably in a manner that the hosts pull the update from the server.
- Antibody Analysis/Approval Services
- Since the system focuses on new files, outsourced file analysis services can be made practical and useful. These services can be automated (e.g., with SOAP/Web Services calls) or manual (follow authenticated links to the servers of a service provider). These services, which can be performed locally or off site using remote servers, can include:
- (1) Entering a hash manually or follow a pre-computed web link to get query results of known good and bad database lookups. Entities, such as companies, may want to maintain global white lists or global black lists. The latter will not work for hashes because they are too numerous. The former will not work because different companies have different policies which qualify “good” programs. These services handle white/black/gray lists and voting as indicated below.
- (2) Find antibodies related to a particular antibody (e.g., groups of files associated with the same application or similar applications)
- (3) Identify vendor and application associated with the hash
- (4) Find out how many companies and computers have that file and for how long. These companies would not be identified be name, only counted. The service provider would gather this information confidentially as part of this service. The service provider creates the double-blind database of the results and the service.
- (5) Find out how many companies have banned or approved the file, and which files they have approved along with it. Again, these are all blind and done by hash, from the perspective of the end-user. The service provider does not need to gather or store file names or file data, just the meta information in the form of the antibody. In fact, file names, and certainly files themselves should be considered proprietary information.
- (6) Automated server-side approval based on the results of the above queries as well as based on server-side analysis too.
Content Extractor (CE)
- Content usually forms groups or packages of content. Examples of this include executable programs and viruses inside of zip files or macros inside Microsoft Office documents (e.g., Word, Excel, and Powerpoint files) or files inside installation packages, such as Microsoft .msi files. Referring to
FIG. 8 , a file is received and the content extractor looks for embedded content types, e.g., macros inside an Office document. Preferably only such “active” types of content are extracted. - After detecting a possible file modification (600) or unknown state, the extractor takes the extracted portion(s) and converts them into a valid content file type, e.g., a Word (.doc) file with no text or figures, to repackage them. This process is illustrated as steps600-605. The resulting repackaged file is generally much smaller than the original file (the “container”) and is referred to as a “reduction.” A hash of the reduction is computed (603), and the reduction hashes are associated with the container hash (604). Containers can be nested and those has associations are tracked as well. Later, if the content needs to be uploaded, only the reductions are uploaded. Optionally, the container file and its meta-information can be uploaded based on the result of the analysis of the extraction. Root containers and their meta-information may be uploaded based on the result of the analysis of the extraction. For example, a file setup.exe contains a file main.cab which in turn contains a file install.exe. Relative to install.exe, main.cab is the parent container for install.exe, and setup.exe is the root container for install.exe as well as the parent container for main.cab. All of these associations are stored, preferably saved as relationships among the hashes of the individual files.
- This process reduces the network traffic and footprint of the analysis stages, and it permits tracking of embedded content only and not macros associated with other files (e.g., inherited document templates). This is not true of methods that intercept macros upon their loading. The extractor permits location-independent embedded macro detection and tracking.
- The repackaging of reductions as other valid file types has the advantage that the reductions are compatible with third party analysis systems, e.g., macros repackaged as small Word documents can be sent as email attachments to a virus scanning email gateway. Another example is a zip file, temp.zip, containing 5 files, only one of which is active, foo.exe. The reduction of temp.zip could be a zip file foo.zip with only foo.exe in it, or the reduction could be foo.exe itself. The signature of foo.zip or the signature of foo.exe is preferably associated as the signature corresponding to temp.zip. The reduction could again be emailed to an AS scanning email gateway. Some containers are devoid of active content, and as such may not be tracked. There are efficiency advantages in tracking reductions, but there are also advantages to detecting and analyzing only new content. In this way, more accurate statistics, alarms, and analysis can be produced. The automatic and specific early detection of unclassified content, such as Pending state files, permits powerful policies and content management.
- Server User Interface
- The user interface for the server provides a number of “panels,” each of which allows the configuration and management of a different aspect of the system. In this section the term “user” is used to indicate an administrator who has access to the server user interface. The user interface can be accessible through a standard web browser, via an SSL encrypted connection. Authentication and access control are provided to maintain the integrity of the server and to determine the privilege level of a particular user.
- When the user first accesses the system, the user is authenticated and assigned a privilege level based on this authentication. This privilege level determines whether the user is allowed unlimited access or read-only access; finer granularity of access can also be provided. User actions are tracked and logged by username and time. Certificates installed on the server can be used to control and encrypt both access to the user interface and also to provide signatures for and possible encryption of information returned to the hosts. These certificates may be installed and updated in a maintenance panel. All input to the interface should be properly validated to ensure that the server is supplying correct information to the hosts in their configuration.
- A network status interface provides an overview of the running system, including: recent events and associated information, including unique file identifier, event time stamp, event type, event priority, file type and name, and host system, identified by both name and unique identifier. The interface also provides summary information on the state of the system during certain time periods (e.g., last hour, last day). More detailed information is available in a statistics panel. Information displayed here includes numbers of new executables detected, new scripts detected, files with new embedded content, unapproved files, and infected files.
- A statistics panel displays more detailed statistics collected by the system. This information includes the number of the following events in various time periods (e.g., last hour, last 24 hours, last week). It can include, for example, numbers of new executables seen on the network, new scripts, files with new embedded content, new web files (HTML, ASP, etc.), files that have yet to be approved, either manually or by scanning, files approved by the scanning process, files approved manually or via auto-approval, files that are failing a scan, files that are known infected that have been blocked, executables that are banned and were blocked, total events processed by the server since it was first installed, and events since last restart.
- Along with the statistics for each category, the user can view “top ten lists” of an item, highlighting the most frequently seen instances of each across all hosts managed by the server. Examples of Top10 lists include top ten recently discovered files ranked by count of how many hosts have at least one copy of the file, with variants of this list including count-by-unique-hash, count-by-unique-file-name, count-Banned-by-hash, count-Banned-by-name, count-recently-banned, count-recently-updated/modified, count-by-unique-group/container/root-container/product. Top10 lists are updated and exported via SNMP. A configuration panel can be used to configure alarms and automatic responses based on Top10 counts and other updated variables. Alarms include log reports, SNMP traps, syslog messages, email notifications, and other network messages. Responses include banning files, approving files, changing parameter D for one or more host groups, changing policy for one or more host groups, changing the host group assignment of one or more hosts, and analyzing files.
- The statistics panel also includes overall information about the system, including: the total number of hosts served by this server, broken down by active and inactive (an inactive host is one that has not recently contacted the server); the total number of antibodies in the server database; and uptime, i.e., how long the system has been up since the last reboot.
- Statistical information displayed on this panel is also available via SNMP (Simple Network Management Protocol) query to the server, allowing integration with network management systems.
- A plots panel allows the user to plot and print graphs and charts of recent activity. This panel may be combined with the statistics panel. Plot information may also be available in XML format for display in external applications. Examples of graphs that may be plotted include activity over a recent time period (one hour by minute, one week by hour, etc.), or graphical displays of the “top ten list.”
- There may be some limitations on the variety of plots available, due to constraints on the statistical information retained by the server. Where the administrator is using an SNMP management system, it too may be able to provide statistical plots in a format that is already in use within the organization.
- An antibody database panel allows the user to interact directly with the antibody database stored on the server. The content of the database is displayed and the user may choose to sort the display by different criteria or to limit the display by choosing filter patterns. The user may also interact with the antibodies themselves; these operations are detailed below.
- The server may use an ancillary informational database that includes fields that are not required in the main antibody database. An example of fields in this database might be the first file name seen or the initial file class.
- For each file, the following information is displayed on this panel:
- Time First Seen. When the file or hash was first seen by the hosts and reported to the server.
- File ID. A unique identifier for the file, including one or more hashes of content such as MD5, SHA-1, and OMAC.
- File Type. The file class (e.g. executable, script, office document, archive, etc.). This is derived from the file name as it was first seen (see below) and also from analysis of file contents.
- Status/State. The current file status, including Approved, Pending, Banned.
- Method. The way in which the server learned about the file (automatically, manually, etc.).
- Filename. The name of the file, as first seen and reported to the server. This may not be the file's current name, but is just the name of the first instance seen on the network.
- File Path. The path of the file, as first seen and reported to the server.
- First Seen Host. The name of the host on which the file or hash was first seen and reported.
- Analysis Results. The result of the latest scans or other analyses.
- First Analysis. The time of the first scan/analysis of the file.
- Last Analysis. The time the file was last scanned/analyzed.
- Last Updated. The time the file state was last modified.
- Parent Containers. Links to other files which have been associated with the file.
- Parent Container Attributes. File name, first seen time, first seen host, file path, product classifications, and state of one associated container file.
- Root Containers. Links to other files which have been associated with the file. A root container is one which is not contained in another container.
- Root Container Attributes. File name, first seen time, first seen host, file path, product classifications, and state of one associated root container file.
The following operations can be performed on a file selected from the list: - File Detail. This provides additional information on the file from the antibody database, including the interface user who approved or banned the file, where the file was first seen and any comments added by users.
- Approve. Explicitly approve the currently selected files. This option should provide the user adequate warning, since it will approve the files across all hosts.
- Unapprove. Explicitly unapprove files that are already approved, preferably transitioning state to Pending.
- Ban. Explicitly ban a file. This causes the file to be banned on all hosts.
- Analyze/Virus Scan. Force the scheduling of an analysis/scan for the selected files.
- Delete. Remove information on this file. This will cause the server to treat the file as new the next time it is seen.
- Find Files on Hosts. This operation links to the file finder, providing the selected file names as input.
- Find Containers. Lookup possible containers for the file and information for those containers.
- Find Root Containers. Lookup possible root containers for the file and information for those containers.
- Find Web-Service Information. Query various other network servers to find additional information about the file and/or its containers/products.
- A file finder panel allows the user to initiate a best-effort process of finding the locations of a particular file on all the managed hosts. Since this process may be time consuming, the user will be notified before initiating a new search. The file finder may not be implemented in all versions of the product. FindFile progress may be reported during partial completion of the query.
- The process may also be initiated from the antibody database panel (see section0) by selecting a particular file or files, which then brings the user to the File Finder panel with the appropriate information filled in automatically.
- This process requires all hosts that are in communication with the server to return status asynchronously, so the panel will open a new view to dynamically display the results as they are received. If the user initiates another search, the current search will be terminated. Multiple file searches may be permitted in future versions.
- A host group panel allows the hosts known by the server to be associated with a particular logical group. Full group functionality may not be available in initial versions of the interface, in which case this screen will display information about the single group supported by this server.
- The panel supports the manipulating group membership, including:
- Addition of new groups.
- Removal of existing groups. When a group is removed, the hosts are not removed from the server's database, but are reassigned to a default group.
- Moving hosts from one group to another.
- The following information is displayed on this panel about each host:
- Host. The host's DNS name.
- Unique ID. The host's unique identifier.
- IP Address. The last known IP address of this host.
- Status. The online status of the host.
- Last Seen. The last time that the host checked in with the server.
- Operating system. The operating system version of the host.
- Version. The version of the operating system on the host.
- A file classes panel allows the viewing and editing of the file extensions that are mapped to each class. Some classes, as below, are defined by extension. Other classes are determined by analysis of content. Some classes are determined by both extension and analysis. These extensions are read only.
- Some pre-defined extension classes are:
- Executables. Extensions including exe, com, dll, pif, scr, drv, and ocx.
- Scripts. Extensions including vbs, bat and cmd.
- Embedded Macro Content. Extensions including doc, dot, xls, xla, xlt, xlw, ppt, pps and pot.
- Web Content. Extensions including htm, html, asp, and cgi.
- A policy panel is the core of the configuration of the server. The user can display and edit the policies enforced on all the managed hosts, grouped by host group. This panel also displays the current global D setting for the currently selected group.
- This section allows the user to define the global D level for the currently selected group. When a new D level is chosen, the change is not immediately applied, but must be selected explicitly. Choosing a new proposed D level changes the display of the policy information and actions to show those for this new level. Navigating away from the panel will not apply the changes.
- The policy list displays the various actions and effects of particular D levels on particular file classes (e.g. executables, scripts etc.). Policies may be enabled or disabled, but not edited. The following policies are included on the list:
- New Executables
- New Standalone Scripts
- New Embedded Scripts
- New Web Content
- Unapproved Files
- Ignore Update Agent (automatically approves new content from certain update sources/processes/locations)
- Virus/Spyware Infested Files
- Whenever a policy is disabled, tracking of files of that class still continues, but no action is taken by the host systems affected.
- For each policy, an action grid is displayed. The grid indicates which policy settings apply at the currently selected D level.
- Action
- Block Execution. Will execution of this file class be blocked?
- Block Write. Will writing to files of this file class be blocked? This setting is only used for web content and unapproved files. It is used for tightly controlled systems only and not for normal operation.
- Quarantine. Will files of this class be quarantined? Files may be quarantined by blocking reading, rather than moving to a separate directory. In the case of virus infected files, these may be written, but later deleted, but this functionality may also not be implemented initially.
- Log. Will access to files of this class be logged?
- Approval
- Implicit Approve. Will files be implicitly approved at this D level? An implicit approval changes the approved state of the file after appropriate scans and waiting time.
- Explicit Approve. Will files be explicitly approved at this D level?
- An action grid similar to the one illustrated above shows the user a representation of the effects of particular D levels in combination with the pre-made policies. The tables below show an example of combinations of the actions and pre-made policies at the various D levels (zero through seven).
- Notifier Parameters
- When content access is blocked, the host user is notified. For each policy on the list, and for each host group, the following settings are available:
- Message displayed. The text displayed on the user interaction dialog. Multiple messages are listed in a list box.
- Button text. The text displayed on the single button on the user interaction dialog.
- Timeout. How long the dialog will be displayed to the user. A timeout of zero indicates until accepted by the user, and the dialog remains displayed indefinitely.
- Optionally, for certain values of D, a button to override content restrictions for a period of time.
- URL link with more information on the policy
- The notification parameters also include a global setting that defines the image displayed at the host along with the notification message. These settings are configurable for each of the pre-made policies individually. Notification parameters are edited in the server administrative interface. Those parameters are associated with policies which are in turn assigned to host groups and propagated to hosts as policy changes.
- Scan Age Parameters
- This section allows the user to configure the time between when a file is first seen and is approved (auto approval scan), the time that the second (approval) scan is conducted and the time that a third (repeat) scan occurs. More scans and times can be specified as in
FIG. 7 . - Maintenance
- The Maintenance section allows the user to configure global settings for the server itself.
- System Configuration. Settings related to the server's interaction with the local network and host systems.
- IP address and subnet masks. Subnet masks permit classification of hosts into Remote and Local types. Remote hosts have more restricted communications to conserve bandwidth. Host groups may have different policy set and D parameter settings, which are specified for each connection type Remote, Local, or Disconnected. Remote hosts will generate less network traffic, for example, fewer server reports. And remote hosts preferably report hashes of new content to the server, but not upload the content.
- IP routing information.
- Passwords. Set or reset passwords for access to the server interface.
- Certificates. Install certificates from removable media (and optionally the network). These are used by the hosts to verify the identity of the server and also for the SSL interface to the server.
- SNMP. Set a list of SNMP servers to receive traps and be allowed to query the server's configuration.
- SNMP trap selection. Select which event type causes which traps and to which SNMP service the trap will be sent (and also priority critical, high, medium, low, informational, etc. . . ).
- Syslog. Set a list of servers to receive logging information via syslog for various event types and priorities.
- NTP time synchronization server. Set a list of servers for time synchronization. Time on the server is taken from its internal clock at boot time and then synchronized with this external NTP time source. Host deviations from server time will be tracked by the server.
- System Status (Server)
- Uptime. Display the time since the last system reboot.
- Software version. Display the version information for the server software.
- Disk space. Display local disk and storage statistics for the server.
- Virus/Spyware Signature Updates
- Last Signature Update. The time of the last signature update.
- Update service configuration. Configure the update service for the installed anti-virus software, including download locations and schedules.
- Update Scanner. Update the virus scanner software.
- Update Signatures. Force an update of the virus signatures.
- Server Software Update
- Current Version. Displays the current server software version.
- Reboot. Reboot the server using the currently installed image.
- Load new image. Load a new software image to the server from removable media or the network (e.g., via FTP).
- Revert to previous version. Revert to the previously used software image.
- External Service Configuration.
- Network address, service type, and approval authority for content scanning systems.
- Network address, service type, and approval authority for meta-information sharing services.
- External file server addresses, protocols, logins, and directories for external content transfers and user-defined analyses.
- External content notification services configuration for SNMP, syslog, email, and SOAP notification of new content.
- Backup. Backs and restores the configuration to removable media (and also to the network).
- Save configuration and database. Save the configuration and antibody database (e.g., via XML)
- Load configuration and database. Load the configuration and antibody database (e.g., in XML).
- System Configuration. Settings related to the server's interaction with the local network and host systems.
- The server includes processing capability, such as a programmed microprocessor, digital signal processor (DSP), or application-specific processing and memory. Hosts can include personal computers or similar computers, or other processing devices, including handhelds, PDAs, or other devices on a network.
- Having described embodiments of inventions herein, it should be apparent that modifications can be made without departing from the scope of the inventions as claimed.
Claims (27)
Priority Applications (9)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| US11/194,078US8984636B2 (en) | 2005-07-29 | 2005-07-29 | Content extractor and analysis system |
| CN200680034493.4ACN101569129B (en) | 2005-07-29 | 2006-07-27 | Network security system and method |
| EP06788969.1AEP1920338B1 (en) | 2005-07-29 | 2006-07-27 | Network security systems and methods |
| CA2617204ACA2617204C (en) | 2005-07-29 | 2006-07-27 | Network security systems and methods |
| CN201410112822.9ACN103984891A (en) | 2005-07-29 | 2006-07-27 | Network security systems and methods |
| JP2008524253AJP2009507271A (en) | 2005-07-29 | 2006-07-27 | Network security system and method |
| PCT/US2006/029714WO2007016478A2 (en) | 2005-07-29 | 2006-07-27 | Network security systems and methods |
| BRPI0616018-2ABRPI0616018A2 (en) | 2005-07-29 | 2006-07-27 | security systems and methods for computer networks |
| JP2012046805AJP5809084B2 (en) | 2005-07-29 | 2012-03-02 | Network security system and method |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| US11/194,078US8984636B2 (en) | 2005-07-29 | 2005-07-29 | Content extractor and analysis system |
Publications (2)
| Publication Number | Publication Date |
|---|---|
| US20070028110A1true US20070028110A1 (en) | 2007-02-01 |
| US8984636B2 US8984636B2 (en) | 2015-03-17 |
Family
ID=37695749
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US11/194,078Active2029-04-03US8984636B2 (en) | 2005-07-29 | 2005-07-29 | Content extractor and analysis system |
Country Status (1)
| Country | Link |
|---|---|
| US (1) | US8984636B2 (en) |
Cited By (61)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20070112814A1 (en)* | 2005-11-12 | 2007-05-17 | Cheshire Stuart D | Methods and systems for providing improved security when using a uniform resource locator (URL) or other address or identifier |
| US20080034434A1 (en)* | 2006-08-03 | 2008-02-07 | Rolf Repasi | Obtaining network origins of potential software threats |
| US20080250100A1 (en)* | 2007-04-03 | 2008-10-09 | Sony Corporation | Information processing apparatus, information processing method and computer program |
| US20080271147A1 (en)* | 2007-04-30 | 2008-10-30 | Microsoft Corporation | Pattern matching for spyware detection |
| US20090012813A1 (en)* | 2007-07-06 | 2009-01-08 | Mckesson Financial Holdings Limited | Systems and methods for managing medical information |
| US20090077428A1 (en)* | 2007-09-14 | 2009-03-19 | Softkvm Llc | Software Method And System For Controlling And Observing Computer Networking Devices |
| US20090172768A1 (en)* | 2007-12-28 | 2009-07-02 | Huifeng Le | Methods and apparatus for operating embedded information technology applications with a service operating system |
| CN101539772A (en)* | 2008-01-25 | 2009-09-23 | 洛克威尔自动控制技术股份有限公司 | Product lifecycle management method and apparatus |
| US20100083380A1 (en)* | 2008-09-29 | 2010-04-01 | Harris Mark D | Network stream scanning facility |
| US20100161608A1 (en)* | 2008-12-18 | 2010-06-24 | Sumooh Inc. | Methods and apparatus for content-aware data de-duplication |
| US7840958B1 (en)* | 2006-02-17 | 2010-11-23 | Trend Micro, Inc. | Preventing spyware installation |
| CN101286986B (en)* | 2008-05-15 | 2011-09-14 | 成都市华为赛门铁克科技有限公司 | Active defense method, device and system |
| US20110225141A1 (en)* | 2010-03-12 | 2011-09-15 | Copiun, Inc. | Distributed Catalog, Data Store, and Indexing |
| US20110231374A1 (en)* | 2010-03-16 | 2011-09-22 | Copiun, Inc. | Highly Scalable and Distributed Data De-Duplication |
| US20120066762A1 (en)* | 2010-09-13 | 2012-03-15 | Rade Todorovic | System and method of whitelisting parent virtual images |
| US8161548B1 (en) | 2005-08-15 | 2012-04-17 | Trend Micro, Inc. | Malware detection using pattern classification |
| US20120150897A1 (en)* | 2010-12-08 | 2012-06-14 | International Business Machines Corporation | Calculating State of Cryptographic Objects and Generating Search Filter for Querying Cryptographic Objects |
| US20120198553A1 (en)* | 2009-09-14 | 2012-08-02 | Junko Suginaka | Secure auditing system and secure auditing method |
| US20140040403A1 (en)* | 2006-02-09 | 2014-02-06 | John Sargent | System, method and computer program product for gathering information relating to electronic content utilizing a dns server |
| US8706745B1 (en)* | 2008-05-30 | 2014-04-22 | Symantec Corporation | Systems and methods for determining a file set |
| US8819655B1 (en)* | 2007-09-17 | 2014-08-26 | Symantec Corporation | Systems and methods for computer program update protection |
| US9043920B2 (en) | 2012-06-27 | 2015-05-26 | Tenable Network Security, Inc. | System and method for identifying exploitable weak points in a network |
| US9059956B2 (en) | 2003-01-31 | 2015-06-16 | Good Technology Corporation | Asynchronous real-time retrieval of data |
| US20150180888A1 (en)* | 2007-06-05 | 2015-06-25 | Harish Balasubramanian | System, Method and Computer Program Product for Making a Scan Decision During Communication of Data Over a Network |
| US9088606B2 (en) | 2012-07-05 | 2015-07-21 | Tenable Network Security, Inc. | System and method for strategic anti-malware monitoring |
| US9305159B2 (en) | 2004-12-03 | 2016-04-05 | Fortinet, Inc. | Secure system for allowing the execution of authorized computer program code |
| US20160119375A1 (en)* | 2013-06-04 | 2016-04-28 | Beijing Qihoo Technology Company Limited | Cloud security-based file processing method and apparatus |
| US20160226901A1 (en)* | 2015-01-30 | 2016-08-04 | Securonix, Inc. | Anomaly Detection Using Adaptive Behavioral Profiles |
| US9467464B2 (en) | 2013-03-15 | 2016-10-11 | Tenable Network Security, Inc. | System and method for correlating log data to discover network vulnerabilities and assets |
| CN106096397A (en)* | 2016-05-26 | 2016-11-09 | 倪茂志 | A kind of prevention method extorting software and system |
| US9602539B1 (en)* | 2012-09-28 | 2017-03-21 | Palo Alto Networks, Inc. | Externally defined objects in security policy |
| US9621405B2 (en) | 2010-08-24 | 2017-04-11 | Good Technology Holdings Limited | Constant access gateway and de-duplicated data cache server |
| US9628513B2 (en) | 2007-04-30 | 2017-04-18 | Mcafee, Inc. | Electronic message manager system, method, and computer program product for scanning an electronic message for unwanted content and associated unwanted sites |
| US9680848B2 (en)* | 2014-12-03 | 2017-06-13 | Korea Internet & Security Agency | Apparatus, system and method for detecting and preventing malicious scripts using code pattern-based static analysis and API flow-based dynamic analysis |
| US20170351870A1 (en)* | 2016-06-03 | 2017-12-07 | Honeywell International Inc. | Apparatus and method for device whitelisting and blacklisting to override protections for allowed media at nodes of a protected system |
| US9846706B1 (en)* | 2012-12-28 | 2017-12-19 | EMC IP Holding Company LLC | Managing mounting of file systems |
| CN107948123A (en)* | 2016-10-12 | 2018-04-20 | 阿里巴巴集团控股有限公司 | Document transmission method and device |
| CN108804925A (en)* | 2015-05-27 | 2018-11-13 | 安恒通(北京)科技有限公司 | method and system for detecting malicious code |
| US10152518B2 (en)* | 2014-10-30 | 2018-12-11 | The Johns Hopkins University | Apparatus and method for efficient identification of code similarity |
| US10225323B2 (en)* | 2012-09-07 | 2019-03-05 | Oracle International Corporation | System and method for providing java cloud services for use with a cloud computing environment |
| US20190121959A1 (en)* | 2017-08-01 | 2019-04-25 | PC Pitstop, Inc | System, Method, and Apparatus for Computer Security |
| US10419504B1 (en)* | 2009-04-10 | 2019-09-17 | Open Invention Network Llc | System and method for streaming application isolation |
| US10476936B1 (en) | 2018-12-13 | 2019-11-12 | Software Ag | Plugin-based file transfer systems and/or methods |
| US10496812B2 (en) | 2013-09-06 | 2019-12-03 | Michael Guidry | Systems and methods for security in computer systems |
| US10592942B1 (en) | 2009-04-10 | 2020-03-17 | Open Invention Network Llc | System and method for usage billing of hosted applications |
| US10606634B1 (en) | 2009-04-10 | 2020-03-31 | Open Invention Network Llc | System and method for application isolation |
| US10693917B1 (en) | 2009-04-10 | 2020-06-23 | Open Invention Network Llc | System and method for on-line and off-line streaming application isolation |
| US10873588B2 (en) | 2017-08-01 | 2020-12-22 | Pc Matic, Inc. | System, method, and apparatus for computer security |
| US20210026951A1 (en)* | 2017-08-01 | 2021-01-28 | PC Matic, Inc | System, Method, and Apparatus for Computer Security |
| US20210034767A1 (en)* | 2019-08-01 | 2021-02-04 | Palantir Technologies Inc. | Systems and methods for conducting data extraction using dedicated data extraction devices |
| US11237802B1 (en) | 2020-07-20 | 2022-02-01 | Bank Of America Corporation | Architecture diagram analysis tool for software development |
| US11314560B1 (en) | 2009-04-10 | 2022-04-26 | Open Invention Network Llc | System and method for hierarchical interception with isolated environments |
| US11323482B2 (en)* | 2019-12-31 | 2022-05-03 | Mcafee, Llc | Methods, systems, and media for protecting computer systems from user-created objects |
| CN114679410A (en)* | 2020-12-24 | 2022-06-28 | 网神信息技术(北京)股份有限公司 | Method, device, electronic device and storage medium for reducing external network resource occupation |
| US11425170B2 (en) | 2018-10-11 | 2022-08-23 | Honeywell International Inc. | System and method for deploying and configuring cyber-security protection solution using portable storage device |
| US20220382892A1 (en)* | 2021-05-27 | 2022-12-01 | Microsoft Technology Licensing, Llc | Centralized access control for cloud relational database management system resources |
| US11538078B1 (en) | 2009-04-10 | 2022-12-27 | International Business Machines Corporation | System and method for usage billing of hosted applications |
| CN117707608A (en)* | 2024-02-04 | 2024-03-15 | 深圳市分秒网络科技有限公司 | Methods and systems for automating configuration file parameters |
| US20240241980A1 (en)* | 2021-05-27 | 2024-07-18 | Microsoft Technology Licensing, Llc | Centralized access control for cloud relational database management system resources |
| US12216785B2 (en)* | 2022-09-21 | 2025-02-04 | Acronis International Gmbh | Systems and methods for generating file systems of data sources incompatible with anti-virus scanners |
| US12229261B1 (en)* | 2024-05-03 | 2025-02-18 | Halcyon Tech, Inc. | Antiransomware file analysis and scoring |
Families Citing this family (6)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US10122753B2 (en)* | 2014-04-28 | 2018-11-06 | Sophos Limited | Using reputation to avoid false malware detections |
| US9917851B2 (en) | 2014-04-28 | 2018-03-13 | Sophos Limited | Intrusion detection using a heartbeat |
| GB201915196D0 (en) | 2014-12-18 | 2019-12-04 | Sophos Ltd | A method and system for network access control based on traffic monitoring and vulnerability detection using process related information |
| CN107248951B (en)* | 2017-08-10 | 2018-12-04 | 北京明朝万达科技股份有限公司 | A kind of post-processing system, method and device |
| CN107743306B (en)* | 2017-11-20 | 2021-08-24 | 上海动联信息技术股份有限公司 | Intelligent POS machine WIFI setting method based on multi-password control and intelligent POS machine |
| RU2739865C2 (en)* | 2018-12-28 | 2020-12-29 | Акционерное общество "Лаборатория Касперского" | System and method of detecting a malicious file |
Citations (99)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US4809160A (en)* | 1985-10-28 | 1989-02-28 | Hewlett-Packard Company | Privilege level checking instruction for implementing a secure hierarchical computer system |
| US4908861A (en)* | 1987-08-28 | 1990-03-13 | International Business Machines Corporation | Data authentication using modification detection codes based on a public one way encryption function |
| US5278901A (en)* | 1992-04-30 | 1994-01-11 | International Business Machines Corporation | Pattern-oriented intrusion-detection system and method |
| US5283830A (en)* | 1991-12-17 | 1994-02-01 | International Computers Limited | Security mechanism for a computer system |
| US5485575A (en)* | 1994-11-21 | 1996-01-16 | International Business Machines Corporation | Automatic analysis of a computer virus structure and means of attachment to its hosts |
| US5495533A (en)* | 1994-04-29 | 1996-02-27 | International Business Machines Corporation | Personal key archive |
| US5495571A (en)* | 1992-09-30 | 1996-02-27 | Microsoft Corporation | Method and system for performing parametric testing of a functional programming interface |
| US5502815A (en)* | 1992-03-30 | 1996-03-26 | Cozza; Paul D. | Method and apparatus for increasing the speed at which computer viruses are detected |
| US5613107A (en)* | 1992-12-22 | 1997-03-18 | Bull, S.A. | Method and apparatus for managing file versions in an information processing system based on a predetermined amount of storage media |
| US5613002A (en)* | 1994-11-21 | 1997-03-18 | International Business Machines Corporation | Generic disinfection of programs infected with a computer virus |
| US5708709A (en)* | 1995-12-08 | 1998-01-13 | Sun Microsystems, Inc. | System and method for managing try-and-buy usage of application programs |
| US5708780A (en)* | 1995-06-07 | 1998-01-13 | Open Market, Inc. | Internet server access control and monitoring systems |
| US5859966A (en)* | 1995-10-10 | 1999-01-12 | Data General Corporation | Security system for computer systems |
| US6018747A (en)* | 1997-11-26 | 2000-01-25 | International Business Machines Corporation | Method for generating and reconstructing in-place delta files |
| US6021510A (en)* | 1997-11-24 | 2000-02-01 | Symantec Corporation | Antivirus accelerator |
| US6021491A (en)* | 1996-11-27 | 2000-02-01 | Sun Microsystems, Inc. | Digital signatures for data streams and data archives |
| US6023723A (en)* | 1997-12-22 | 2000-02-08 | Accepted Marketing, Inc. | Method and system for filtering unwanted junk e-mail utilizing a plurality of filtering mechanisms |
| US6023586A (en)* | 1998-02-10 | 2000-02-08 | Novell, Inc. | Integrity verifying and correcting software |
| US6026502A (en)* | 1997-01-27 | 2000-02-15 | Wakayama; Hironori | Method and mechanism for preventing from invading of computer virus and/or hacker |
| US6026402A (en)* | 1998-01-07 | 2000-02-15 | Hewlett-Packard Company | Process restriction within file system hierarchies |
| US6026205A (en)* | 1997-01-21 | 2000-02-15 | Molecular Optoelectronics Corporation | Compound optical waveguide and filter applications thereof |
| US6029256A (en)* | 1997-12-31 | 2000-02-22 | Network Associates, Inc. | Method and system for allowing computer programs easy access to features of a virus scanning engine |
| US6029175A (en)* | 1995-10-26 | 2000-02-22 | Teknowledge Corporation | Automatic retrieval of changed files by a network software agent |
| US6173284B1 (en)* | 1997-05-20 | 2001-01-09 | University Of Charlotte City Of Charlotte | Systems, methods and computer program products for automatically monitoring police records for a crime profile |
| US6178508B1 (en)* | 1995-12-28 | 2001-01-23 | International Business Machines Corp. | System for controlling access to encrypted data files by a plurality of users |
| US6195587B1 (en)* | 1993-10-29 | 2001-02-27 | Sophos Plc | Validity checking |
| US20020002684A1 (en)* | 1998-05-01 | 2002-01-03 | Barbara L. Fox | Intelligent trust management method and system |
| US6338149B1 (en)* | 1998-07-31 | 2002-01-08 | Westinghouse Electric Company Llc | Change monitoring system for a computer system |
| US6338141B1 (en)* | 1998-09-30 | 2002-01-08 | Cybersoft, Inc. | Method and apparatus for computer virus detection, analysis, and removal in real time |
| US20020004908A1 (en)* | 2000-07-05 | 2002-01-10 | Nicholas Paul Andrew Galea | Electronic mail message anti-virus system and method |
| US20020004874A1 (en)* | 2000-05-01 | 2002-01-10 | Hideyuki Agata | Apparatus and method for processing information, and program and medium used therefor |
| US20020004902A1 (en)* | 2000-07-07 | 2002-01-10 | Eng-Whatt Toh | Secure and reliable document delivery |
| US20020005105A1 (en)* | 2000-05-09 | 2002-01-17 | Mcpherson Mathew | Arrangement of a sound hole and construction of a sound board in an acoustic guitar |
| US20020005017A1 (en)* | 2000-03-31 | 2002-01-17 | Jsr Corporation | Aqueous dispersion for chemical mechanical polishing |
| US20020019932A1 (en)* | 1999-06-10 | 2002-02-14 | Eng-Whatt Toh | Cryptographically secure network |
| US6349311B1 (en)* | 1999-02-01 | 2002-02-19 | Symantec Corporation | Storage of reverse delta updates |
| US6351776B1 (en)* | 1999-11-04 | 2002-02-26 | Xdrive, Inc. | Shared internet storage resource, user interface system, and method |
| US20020026576A1 (en)* | 2000-08-18 | 2002-02-28 | Hewlett-Packard Company | Apparatus and method for establishing trust |
| US20030004922A1 (en)* | 2001-06-27 | 2003-01-02 | Ontrack Data International, Inc. | System and method for data management |
| US6505237B2 (en)* | 1998-07-24 | 2003-01-07 | Siemens Information & Communication Networks, Inc. | Method and system for management of message attachments |
| US6505300B2 (en)* | 1998-06-12 | 2003-01-07 | Microsoft Corporation | Method and system for secure running of untrusted content |
| US20030018903A1 (en)* | 2001-03-19 | 2003-01-23 | Greca Damon G. Della | Method of containing spread of computer viruses |
| US20030015973A1 (en)* | 2001-07-18 | 2003-01-23 | Kevin Ovens | Solid state traffic light with predictive failure analysis |
| US6513122B1 (en)* | 2001-06-29 | 2003-01-28 | Networks Associates Technology, Inc. | Secure gateway for analyzing textual content to identify a harmful impact on computer systems with known vulnerabilities |
| US6513111B2 (en)* | 1998-02-09 | 2003-01-28 | Reuters, Ltd | Method of controlling software applications specific to a group of users |
| US6513039B1 (en)* | 1999-06-24 | 2003-01-28 | International Business Machines Corporation | Profile inferencing through automated access control list analysis heuristics |
| US20030023866A1 (en)* | 2001-07-26 | 2003-01-30 | Hinchliffe Alex James | Centrally managed malware scanning |
| US20030023857A1 (en)* | 2001-07-26 | 2003-01-30 | Hinchliffe Alexander James | Malware infection suppression |
| US20030023560A1 (en)* | 2001-07-27 | 2003-01-30 | Fujitsu Limited | Design asset information search system |
| US20030023864A1 (en)* | 2001-07-25 | 2003-01-30 | Igor Muttik | On-access malware scanning |
| US20030023867A1 (en)* | 2001-07-25 | 2003-01-30 | Thibadeau Robert H. | Methods and systems for promoting security in a computer system employing attached storage devices |
| US6516395B1 (en)* | 1997-11-20 | 2003-02-04 | Advanced Micro Devices, Inc. | System and method for controlling access to a privilege-partitioned address space with a fixed set of attributes |
| US20030028785A1 (en)* | 2001-08-01 | 2003-02-06 | Pak Michael Chin-Hwan | System and method for executing computer virus definitions containing general purpose programming language extensions |
| US20030033308A1 (en)* | 2001-08-03 | 2003-02-13 | Patel Sujal M. | System and methods for providing a distributed file system utilizing metadata to track information about data stored throughout the system |
| US20030033303A1 (en)* | 2001-08-07 | 2003-02-13 | Brian Collins | System and method for restricting access to secured data |
| US20040003279A1 (en)* | 2002-06-28 | 2004-01-01 | Beilinson Craig Adam | User controls for a computer |
| US20040003274A1 (en)* | 2002-06-28 | 2004-01-01 | Strom Clifford P. | Protecting content on medium from unfettered distribution |
| US6675205B2 (en)* | 1999-10-14 | 2004-01-06 | Arcessa, Inc. | Peer-to-peer automated anonymous asynchronous file sharing |
| US6678741B1 (en)* | 1999-04-09 | 2004-01-13 | Sun Microsystems, Inc. | Method and apparatus for synchronizing firmware |
| US20040010602A1 (en)* | 2002-07-10 | 2004-01-15 | Van Vleck Paul F. | System and method for managing access to digital content via digital rights policies |
| US6681227B1 (en)* | 1997-11-19 | 2004-01-20 | Ns Solutions Corporation | Database system and a method of data retrieval from the system |
| US6681344B1 (en)* | 2000-09-14 | 2004-01-20 | Microsoft Corporation | System and method for automatically diagnosing a computer problem |
| US6681387B1 (en)* | 1999-12-01 | 2004-01-20 | Board Of Trustees Of The University Of Illinois | Method and apparatus for instruction execution hot spot detection and monitoring in a data processing unit |
| US6684210B1 (en)* | 1998-04-06 | 2004-01-27 | Matsushita Electric Industrial Co., Ltd. | File managing system, file management apparatus, file management method, and program storage medium |
| US20040019878A1 (en)* | 2002-07-23 | 2004-01-29 | Sreekrishna Kotnur | Software tool to detect and restore damaged or lost software components |
| US20040025043A1 (en)* | 2002-05-22 | 2004-02-05 | Microsoft Corporation | System and method for identifying potential security risks in controls |
| US20040031028A1 (en)* | 2002-08-06 | 2004-02-12 | Aardwork Software Limited | Updating of software |
| US20040030913A1 (en)* | 2002-08-08 | 2004-02-12 | Trend Micro Incorporated | System and method for computer protection against malicious electronic mails by analyzing, profiling and trapping the same |
| US6694336B1 (en)* | 2000-01-25 | 2004-02-17 | Fusionone, Inc. | Data transfer and synchronization system |
| US6694457B2 (en)* | 2001-03-06 | 2004-02-17 | Hewlett-Packard Development Company, L.P. | System and method for monitoring execution of privileged instructions |
| US6694328B1 (en)* | 2000-01-13 | 2004-02-17 | International Business Machines Corporation | Method for creating queries on version objects |
| US20040034794A1 (en)* | 2000-05-28 | 2004-02-19 | Yaron Mayer | System and method for comprehensive general generic protection for computers against malicious programs that may steal information and/or cause damages |
| US20040034638A1 (en)* | 2002-07-18 | 2004-02-19 | International Business Machines Corporation | Method for analyzing and characterizing the usage pattern of a device |
| US6697810B2 (en)* | 2001-04-19 | 2004-02-24 | Vigilance, Inc. | Security system for event monitoring, detection and notification system |
| US6697950B1 (en)* | 1999-12-22 | 2004-02-24 | Networks Associates Technology, Inc. | Method and apparatus for detecting a macro computer virus using static analysis |
| US20040039921A1 (en)* | 2000-10-17 | 2004-02-26 | Shyne-Song Chuang | Method and system for detecting rogue software |
| US20040039924A1 (en)* | 2001-04-09 | 2004-02-26 | Baldwin Robert W. | System and method for security of computing devices |
| US20040039932A1 (en)* | 2002-08-23 | 2004-02-26 | Gidon Elazar | Apparatus, system and method for securing digital documents in a digital appliance |
| US6839721B2 (en)* | 2001-01-12 | 2005-01-04 | Hewlett-Packard Development Company, L.P. | Integration of a database into file management software for protecting, tracking, and retrieving data |
| US20050005161A1 (en)* | 2003-07-04 | 2005-01-06 | Adrian Baldwin | Services and secure processing environments |
| US20050004873A1 (en)* | 2003-02-03 | 2005-01-06 | Robin Pou | Distribution and rights management of digital content |
| US20050004954A1 (en)* | 2003-07-01 | 2005-01-06 | Hand Held Products, Inc. | Systems and methods for expedited data transfer in a communication system using hash segmentation |
| US20050005168A1 (en)* | 2003-03-11 | 2005-01-06 | Richard Dick | Verified personal information database |
| US20050010806A1 (en)* | 2003-04-18 | 2005-01-13 | Ounce Labs, Inc. | Method and system for detecting privilege escalation vulnerabilities in source code |
| US20050010804A1 (en)* | 2002-12-19 | 2005-01-13 | Bruening Derek L. | Secure execution of a computer program using a code cache |
| US20050015592A1 (en)* | 2003-07-15 | 2005-01-20 | Jeou-Kai Lin | System and method for application and user-based class of security |
| US20050015675A1 (en)* | 2003-07-03 | 2005-01-20 | Kolawa Adam K. | Method and system for automatic error prevention for computer software |
| US20050015591A1 (en)* | 2003-06-12 | 2005-01-20 | International Business Machines Corporation | Multi-level multi-user web services security system and method |
| US20050015760A1 (en)* | 2003-07-16 | 2005-01-20 | Oleg Ivanov | Automatic detection and patching of vulnerable files |
| US20050022018A1 (en)* | 2003-06-30 | 2005-01-27 | Symantec Corporation | Signature extraction system and method |
| US20050022016A1 (en)* | 2002-12-12 | 2005-01-27 | Alexander Shipp | Method of and system for heuristically detecting viruses in executable code |
| US20050022004A1 (en)* | 2001-04-24 | 2005-01-27 | Microsoft Corporation | Robust recognizer of perceptually similar content |
| US20050021994A1 (en)* | 2003-07-21 | 2005-01-27 | Barton Christopher Andrew | Pre-approval of computer files during a malware detection |
| US20050028002A1 (en)* | 2003-07-29 | 2005-02-03 | Mihai Christodorescu | Method and apparatus to detect malicious software |
| US20050033976A1 (en)* | 2003-08-04 | 2005-02-10 | Sbc Knowledge Ventures, L.P. | Host intrusion detection and isolation |
| US20050033975A1 (en)* | 2001-08-17 | 2005-02-10 | Pasi Lahti | Preventing virus infection in a computer system |
| US20050033978A1 (en)* | 2003-08-08 | 2005-02-10 | Hyser Chris D. | Method and system for securing a computer system |
| US20050033980A1 (en)* | 2003-08-07 | 2005-02-10 | Willman Bryan Mark | Projection of trustworthiness from a trusted environment to an untrusted environment |
| US7483993B2 (en)* | 2001-04-06 | 2009-01-27 | Symantec Corporation | Temporal access control for computer virus prevention |
Family Cites Families (534)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US5175852A (en) | 1987-02-13 | 1992-12-29 | International Business Machines Corporation | Distributed file access structure lock |
| US5201043A (en) | 1989-04-05 | 1993-04-06 | Intel Corporation | System using both a supervisor level control bit and a user level control bit to enable/disable memory reference alignment checking |
| US5144659A (en) | 1989-04-19 | 1992-09-01 | Richard P. Jones | Computer file protection system |
| JPH0388052A (en) | 1989-08-31 | 1991-04-12 | Toshiba Corp | Security processing method |
| US5050212A (en) | 1990-06-20 | 1991-09-17 | Apple Computer, Inc. | Method and apparatus for verifying the integrity of a file stored separately from a computer |
| US5893117A (en) | 1990-08-17 | 1999-04-06 | Texas Instruments Incorporated | Time-stamped database transaction and version management system |
| US5579509A (en) | 1991-02-08 | 1996-11-26 | International Business Machines Corporation | Apparatus and method for verifying compatibility of system components |
| ATE124552T1 (en) | 1991-04-01 | 1995-07-15 | Cray Research Inc | CATCHING A PRIVILEGED COMMAND WORD TO CONTROL AN OPERATING SYSTEM. |
| US5408642A (en) | 1991-05-24 | 1995-04-18 | Symantec Corporation | Method for recovery of a computer program infected by a computer virus |
| US5355474A (en) | 1991-09-27 | 1994-10-11 | Thuraisngham Bhavani M | System for multilevel secure database management using a knowledge base with release-based and other security constraints for query, response and update modification |
| US5694590A (en) | 1991-09-27 | 1997-12-02 | The Mitre Corporation | Apparatus and method for the detection of security violations in multilevel secure databases |
| IL99747A (en) | 1991-10-15 | 1994-12-29 | News Datacom Ltd | File-secure computer system |
| WO1993013477A1 (en) | 1991-12-23 | 1993-07-08 | Onyx Technologies (Usa) Inc. | Computer protection device |
| DK170490B1 (en) | 1992-04-28 | 1995-09-18 | Multi Inform As | Data Processing Plant |
| GB9205774D0 (en) | 1992-03-17 | 1992-04-29 | Int Computers Ltd | Computer security system |
| US5649095A (en) | 1992-03-30 | 1997-07-15 | Cozza; Paul D. | Method and apparatus for detecting computer viruses through the use of a scan information cache |
| US5473769A (en) | 1992-03-30 | 1995-12-05 | Cozza; Paul D. | Method and apparatus for increasing the speed of the detecting of computer viruses |
| US5528490A (en) | 1992-04-10 | 1996-06-18 | Charles E. Hill & Associates, Inc. | Electronic catalog system and method |
| US5421006A (en) | 1992-05-07 | 1995-05-30 | Compaq Computer Corp. | Method and apparatus for assessing integrity of computer system software |
| WO1993025024A1 (en) | 1992-05-26 | 1993-12-09 | Cyberlock Data Intelligence, Inc. | Computer virus monitoring system |
| US5241594A (en) | 1992-06-02 | 1993-08-31 | Hughes Aircraft Company | One-time logon means and methods for distributed computing systems |
| US5428795A (en) | 1992-07-31 | 1995-06-27 | International Business Machines Corporation | Method of and apparatus for providing automatic security control of distributions within a data processing system |
| US5339261A (en) | 1992-10-22 | 1994-08-16 | Base 10 Systems, Inc. | System for operating application software in a safety critical environment |
| US5327563A (en) | 1992-11-13 | 1994-07-05 | Hewlett-Packard | Method for locking software files to a specific storage device |
| US5359730A (en) | 1992-12-04 | 1994-10-25 | International Business Machines Corporation | Method of operating a data processing system having a dynamic software update facility |
| JP2501771B2 (en) | 1993-01-19 | 1996-05-29 | インターナショナル・ビジネス・マシーンズ・コーポレイション | Method and apparatus for obtaining multiple valid signatures of an unwanted software entity |
| US5440723A (en) | 1993-01-19 | 1995-08-08 | International Business Machines Corporation | Automatic immune system for computers and computer networks |
| US5448668A (en) | 1993-07-08 | 1995-09-05 | Perelson; Alan S. | Method of detecting changes to a collection of digital signals |
| US5444850A (en) | 1993-08-04 | 1995-08-22 | Trend Micro Devices Incorporated | Method and apparatus for controlling network and workstation access prior to workstation boot |
| US5615373A (en) | 1993-08-26 | 1997-03-25 | International Business Machines Corporation | Data lock management in a distributed file server system determines variable lock lifetime in response to request to access data object |
| US5664098A (en) | 1993-09-28 | 1997-09-02 | Bull Hn Information Systems Inc. | Dual decor capability for a host system which runs emulated application programs to enable direct access to host facilities for executing emulated system operations |
| US5566326A (en) | 1993-09-28 | 1996-10-15 | Bull Hn Information Systems Inc. | Copy file mechanism for transferring files between a host system and an emulated file system |
| US5675771A (en) | 1993-09-28 | 1997-10-07 | Bull Hn Information Systems Inc. | Mechanism for enabling emulation system users to directly invoke a number of host system facilities for executing host procedures either synchronously or asynchronously in a secure manner through automatically created shell mechanisms |
| US5983012A (en) | 1993-09-28 | 1999-11-09 | Bull Hn Information Systems Inc. | Executing programs of a first system on a second system |
| US5572711A (en) | 1993-09-28 | 1996-11-05 | Bull Hn Information Systems Inc. | Mechanism for linking together the files of emulated and host system for access by emulated system users |
| US5475826A (en) | 1993-11-19 | 1995-12-12 | Fischer; Addison M. | Method for protecting a volatile file using a single hash |
| US5584023A (en) | 1993-12-27 | 1996-12-10 | Hsu; Mike S. C. | Computer system including a transparent and secure file transform mechanism |
| US5689700A (en) | 1993-12-29 | 1997-11-18 | Microsoft Corporation | Unification of directory service with file system services |
| US6119151A (en)* | 1994-03-07 | 2000-09-12 | International Business Machines Corp. | System and method for efficient cache management in a distributed file system |
| US6760840B1 (en) | 1994-03-15 | 2004-07-06 | Kabushiki Kaisha Toshiba | File editing system and shared file editing system with file content secrecy, file version management, and asynchronous editing |
| DE69529635T2 (en) | 1994-03-15 | 2003-10-23 | Toshiba Kawasaki Kk | Share a file system with secret file content, version management and asynchronous editing |
| US6732358B1 (en) | 1994-03-24 | 2004-05-04 | Ncr Corporation | Automatic updating of computer software |
| US5572590A (en) | 1994-04-12 | 1996-11-05 | International Business Machines Corporation | Discrimination of malicious changes to digital information using multiple signatures |
| US5802275A (en) | 1994-06-22 | 1998-09-01 | Lucent Technologies Inc. | Isolation of non-secure software from secure software to limit virus infection |
| US5778222A (en) | 1994-06-27 | 1998-07-07 | International Business Machines Corporation | Method and system for managing access to objects |
| US5530757A (en) | 1994-06-28 | 1996-06-25 | International Business Machines Corporation | Distributed fingerprints for information integrity verification |
| EP0696003B1 (en) | 1994-08-05 | 2001-02-28 | Canon Kabushiki Kaisha | A method and an apparatus for document processing |
| DE69427347T2 (en) | 1994-08-15 | 2001-10-31 | International Business Machines Corp., Armonk | Process and system for improved access control based on the roles in distributed and centralized computer systems |
| US5701463A (en) | 1994-09-09 | 1997-12-23 | Cheyenne Advanced Technology Limited | Method of replacing the identity of a file with another as part of a file open request in a computer system |
| US5537540A (en) | 1994-09-30 | 1996-07-16 | Compaq Computer Corporation | Transparent, secure computer virus detection method and apparatus |
| US5586301A (en) | 1994-11-09 | 1996-12-17 | Ybm Technologies, Inc. | Personal computer hard disk protection system |
| US5657470A (en) | 1994-11-09 | 1997-08-12 | Ybm Technologies, Inc. | Personal computer hard disk protection system |
| JPH08263438A (en) | 1994-11-23 | 1996-10-11 | Xerox Corp | Distribution and use control system of digital work and access control method to digital work |
| SE517910C2 (en) | 1994-11-29 | 2002-07-30 | Telia Ab | Computer network with access control |
| JP2912840B2 (en) | 1994-12-07 | 1999-06-28 | 富士通株式会社 | File management system |
| US5956715A (en) | 1994-12-13 | 1999-09-21 | Microsoft Corporation | Method and system for controlling user access to a resource in a networked computing environment |
| US5699507A (en) | 1995-01-17 | 1997-12-16 | Lucent Technologies Inc. | Method of identifying similarities in code segments |
| US5644710A (en) | 1995-02-13 | 1997-07-01 | Eta Technologies Corporation | Personal access management system |
| US5689564A (en) | 1995-02-13 | 1997-11-18 | Eta Technologies Corporation | Personal access management system |
| US5727061A (en) | 1995-02-13 | 1998-03-10 | Eta Technologies Corporation | Personal access management systems |
| US6255943B1 (en) | 1995-03-29 | 2001-07-03 | Cabletron Systems, Inc. | Method and apparatus for distributed object filtering |
| US5958056A (en) | 1995-05-26 | 1999-09-28 | Intel Corporation | Method and apparatus for selecting operating voltages in a backplane bus |
| JP4162099B2 (en) | 1995-06-02 | 2008-10-08 | 富士通株式会社 | Device having function to cope with virus infection and storage device thereof |
| EP0830611A4 (en) | 1995-06-02 | 2007-05-09 | Cisco Systems Inc | Remote monitoring of computer programs |
| US5678041A (en) | 1995-06-06 | 1997-10-14 | At&T | System and method for restricting user access rights on the internet based on rating information stored in a relational database |
| US5819275A (en) | 1995-06-07 | 1998-10-06 | Trusted Information Systems, Inc. | System and method for superimposing attributes on hierarchically organized file systems |
| GB2301912A (en) | 1995-06-09 | 1996-12-18 | Ibm | Security for computer system resources |
| US5799141A (en) | 1995-06-09 | 1998-08-25 | Qualix Group, Inc. | Real-time data protection system and method |
| US5826269A (en) | 1995-06-21 | 1998-10-20 | Microsoft Corporation | Electronic mail interface for a network server |
| EP0752652B1 (en) | 1995-07-03 | 1998-12-16 | Sun Microsystems, Inc. | System and method for implementing a hierarchical policy for computer system administration |
| US5799315A (en) | 1995-07-07 | 1998-08-25 | Sun Microsystems, Inc. | Method and apparatus for event-tagging data files automatically correlated with a time of occurence in a computer system |
| JPH0934765A (en) | 1995-07-20 | 1997-02-07 | Fuji Xerox Co Ltd | File managing device |
| US6061795A (en) | 1995-07-31 | 2000-05-09 | Pinnacle Technology Inc. | Network desktop management security system and method |
| US5757915A (en) | 1995-08-25 | 1998-05-26 | Intel Corporation | Parameterized hash functions for access control |
| US5634053A (en) | 1995-08-29 | 1997-05-27 | Hughes Aircraft Company | Federated information management (FIM) system and method for providing data site filtering and translation for heterogeneous databases |
| JP4014662B2 (en) | 1995-09-18 | 2007-11-28 | ファナック株式会社 | Robot teaching operation panel |
| US5701458A (en) | 1995-09-20 | 1997-12-23 | International Business Machines Corporation | System and method for managing arbitrary subsets of access control lists in a computer network |
| US5623600A (en) | 1995-09-26 | 1997-04-22 | Trend Micro, Incorporated | Virus detection and removal apparatus for computer networks |
| US5826013A (en) | 1995-09-28 | 1998-10-20 | Symantec Corporation | Polymorphic virus detection module |
| US5854916A (en) | 1995-09-28 | 1998-12-29 | Symantec Corporation | State-based cache for antivirus software |
| US5696822A (en) | 1995-09-28 | 1997-12-09 | Symantec Corporation | Polymorphic virus detection module |
| US6366933B1 (en)* | 1995-10-27 | 2002-04-02 | At&T Corp. | Method and apparatus for tracking and viewing changes on the web |
| US5974568A (en) | 1995-11-17 | 1999-10-26 | Mci Communications Corporation | Hierarchical error reporting system |
| US5692047A (en) | 1995-12-08 | 1997-11-25 | Sun Microsystems, Inc. | System and method for executing verifiable programs with facility for using non-verifiable programs from trusted sources |
| US5974455A (en) | 1995-12-13 | 1999-10-26 | Digital Equipment Corporation | System for adding new entry to web page table upon receiving web page including link to another web page not having corresponding entry in web page table |
| AU1206097A (en) | 1995-12-28 | 1997-07-28 | Eyal Dotan | Method for protecting executable software programs against infection by software viruses |
| US5966715A (en) | 1995-12-29 | 1999-10-12 | Csg Systems, Inc. | Application and database security and integrity system and method |
| JPH09233068A (en) | 1996-02-23 | 1997-09-05 | Digital Vision Lab:Kk | Electronic verification system |
| US5737523A (en) | 1996-03-04 | 1998-04-07 | Sun Microsystems, Inc. | Methods and apparatus for providing dynamic network file system client authentication |
| GB9605338D0 (en) | 1996-03-13 | 1996-05-15 | Arendee Ltd | Improvements in or relating to computer systems |
| US5822517A (en) | 1996-04-15 | 1998-10-13 | Dotan; Eyal | Method for detecting infection of software programs by memory resident software viruses |
| US6138238A (en) | 1997-12-11 | 2000-10-24 | Sun Microsystems, Inc. | Stack-based access control using code and executor identifiers |
| US20030056103A1 (en) | 2000-12-18 | 2003-03-20 | Levy Kenneth L. | Audio/video commerce application architectural framework |
| US5978484A (en) | 1996-04-25 | 1999-11-02 | Microsoft Corporation | System and method for safety distributing executable objects |
| US5974309A (en) | 1996-05-03 | 1999-10-26 | Telefonaktiebolaget L M Ericsson (Publ) | Method and apparatus for facilitating law enforcement agency monitoring of cellular telephone calls |
| US5815654A (en) | 1996-05-20 | 1998-09-29 | Chrysler Corporation | Method for determining software reliability |
| DE19625196A1 (en) | 1996-06-24 | 1998-01-02 | Godi Meyer Gizella | Data archiving system |
| US5987123A (en) | 1996-07-03 | 1999-11-16 | Sun Microsystems, Incorporated | Secure file system |
| JPH1027123A (en) | 1996-07-11 | 1998-01-27 | Toshiba Corp | Computer software copy protection |
| US5692124A (en) | 1996-08-30 | 1997-11-25 | Itt Industries, Inc. | Support of limited write downs through trustworthy predictions in multilevel security of computer network communications |
| US5832208A (en)* | 1996-09-05 | 1998-11-03 | Cheyenne Software International Sales Corp. | Anti-virus agent for use with databases and mail servers |
| US5845067A (en) | 1996-09-09 | 1998-12-01 | Porter; Jack Edward | Method and apparatus for document management utilizing a messaging system |
| US5983350A (en) | 1996-09-18 | 1999-11-09 | Secure Computing Corporation | Secure firewall supporting different levels of authentication based on address or encryption status |
| US5951698A (en) | 1996-10-02 | 1999-09-14 | Trend Micro, Incorporated | System, apparatus and method for the detection and removal of viruses in macros |
| US5884325A (en) | 1996-10-09 | 1999-03-16 | Oracle Corporation | System for synchronizing shared data between computers |
| US5832529A (en) | 1996-10-11 | 1998-11-03 | Sun Microsystems, Inc. | Methods, apparatus, and product for distributed garbage collection |
| US5930792A (en) | 1996-11-07 | 1999-07-27 | Intervoice Limited Partnership | Monitoring and directing flow of HTML documents for security and access |
| US6802028B1 (en) | 1996-11-11 | 2004-10-05 | Powerquest Corporation | Computer virus detection and removal |
| US6044381A (en) | 1997-09-11 | 2000-03-28 | Puma Technology, Inc. | Using distributed history files in synchronizing databases |
| US5878417A (en) | 1996-11-20 | 1999-03-02 | International Business Machines Corporation | Method and apparatus for network security in browser based interfaces |
| US5958051A (en) | 1996-11-27 | 1999-09-28 | Sun Microsystems, Inc. | Implementing digital signatures for data streams and data archives |
| US6006228A (en) | 1996-12-11 | 1999-12-21 | Ncr Corporation | Assigning security levels to particular documents on a document by document basis in a database |
| DK2997A (en) | 1997-01-09 | 1997-01-14 | Hans Jessen | Procedure for preventing unauthorized use of computer program |
| US6317742B1 (en) | 1997-01-09 | 2001-11-13 | Sun Microsystems, Inc. | Method and apparatus for controlling software access to system resources |
| US5898836A (en) | 1997-01-14 | 1999-04-27 | Netmind Services, Inc. | Change-detection tool indicating degree and location of change of internet documents by comparison of cyclic-redundancy-check(CRC) signatures |
| WO1998032073A1 (en) | 1997-01-17 | 1998-07-23 | International Business Machines Corporation | Protecting resources in a distributed computer system |
| US5956481A (en) | 1997-02-06 | 1999-09-21 | Microsoft Corporation | Method and apparatus for protecting data files on a computer from virus infection |
| JPH10232878A (en) | 1997-02-19 | 1998-09-02 | Hitachi Ltd | Document management method and apparatus |
| US5848418A (en) | 1997-02-19 | 1998-12-08 | Watchsoft, Inc. | Electronic file analyzer and selector |
| US5930801A (en) | 1997-03-07 | 1999-07-27 | Xerox Corporation | Shared-data environment in which each file has independent security properties |
| US5897637A (en) | 1997-03-07 | 1999-04-27 | Apple Computer, Inc. | System and method for rapidly identifying the existence and location of an item in a file |
| WO1998047259A2 (en) | 1997-03-10 | 1998-10-22 | Fielder Guy L | File encryption method and system |
| US6263444B1 (en) | 1997-03-11 | 2001-07-17 | National Aerospace Laboratory Of Science & Technology Agency | Network unauthorized access analysis method, network unauthorized access analysis apparatus utilizing the method, and computer-readable recording medium having network unauthorized access analysis program recorded thereon |
| US5907848A (en) | 1997-03-14 | 1999-05-25 | Lakeview Technology, Inc. | Method and system for defining transactions from a database log |
| US5960170A (en) | 1997-03-18 | 1999-09-28 | Trend Micro, Inc. | Event triggered iterative virus detection |
| US6122631A (en) | 1997-03-28 | 2000-09-19 | International Business Machines Corporation | Dynamic server-managed access control for a distributed file system |
| US5937160A (en) | 1997-05-01 | 1999-08-10 | Reedy Creek Technologies, Inc. | Systems, methods and computer program products for updating hypertext documents via electronic mail |
| WO1998050843A1 (en) | 1997-05-02 | 1998-11-12 | Network Associates, Inc. | Process-level data security system |
| EP0980545B1 (en) | 1997-05-08 | 2001-09-26 | Pinnacle Technology, Inc. | Network desktop management security system and method |
| US6161145A (en) | 1997-05-08 | 2000-12-12 | International Business Machines Corporation | Updating server-related data at a client |
| US6123737A (en) | 1997-05-21 | 2000-09-26 | Symantec Corporation | Push deployment of software packages using notification transports |
| US5948104A (en) | 1997-05-23 | 1999-09-07 | Neuromedical Systems, Inc. | System and method for automated anti-viral file update |
| US6434607B1 (en) | 1997-06-19 | 2002-08-13 | International Business Machines Corporation | Web server providing role-based multi-level security |
| US6061686A (en) | 1997-06-26 | 2000-05-09 | Digital Equipment Corporation | Updating a copy of a remote document stored in a local computer system |
| EP0895149B1 (en) | 1997-07-31 | 2003-09-17 | Siemens Aktiengesellschaft | Computer system for protecting a file and a method for protecting a file |
| US6282701B1 (en) | 1997-07-31 | 2001-08-28 | Mutek Solutions, Ltd. | System and method for monitoring and analyzing the execution of computer programs |
| US5919257A (en) | 1997-08-08 | 1999-07-06 | Novell, Inc. | Networked workstation intrusion detection system |
| US6006329A (en) | 1997-08-11 | 1999-12-21 | Symantec Corporation | Detection of computer viruses spanning multiple data streams |
| US6249805B1 (en) | 1997-08-12 | 2001-06-19 | Micron Electronics, Inc. | Method and system for filtering unauthorized electronic mail messages |
| US5978917A (en) | 1997-08-14 | 1999-11-02 | Symantec Corporation | Detection and elimination of macro viruses |
| US6275938B1 (en) | 1997-08-28 | 2001-08-14 | Microsoft Corporation | Security enhancement for untrusted executable code |
| US6044469A (en) | 1997-08-29 | 2000-03-28 | Preview Software | Software publisher or distributor configurable software security mechanism |
| US6226652B1 (en) | 1997-09-05 | 2001-05-01 | International Business Machines Corp. | Method and system for automatically detecting collision and selecting updated versions of a set of files |
| JP3437065B2 (en) | 1997-09-05 | 2003-08-18 | 富士通株式会社 | Virus removal method, information processing device, and computer-readable recording medium on which virus removal program is recorded |
| IL126148A (en) | 1997-09-09 | 2004-02-19 | Sanctum Ltd | Method and system for maintaining restricted operating environments for application programs or operating systems |
| US5983348A (en) | 1997-09-10 | 1999-11-09 | Trend Micro Incorporated | Computer network malicious code scanner |
| US6154775A (en) | 1997-09-12 | 2000-11-28 | Lucent Technologies Inc. | Methods and apparatus for a computer network firewall with dynamic rule processing with the ability to dynamically alter the operations of rules |
| US5909689A (en) | 1997-09-18 | 1999-06-01 | Sony Corporation | Automatic update of file versions for files shared by several computers which record in respective file directories temporal information for indicating when the files have been created |
| US6192108B1 (en) | 1997-09-19 | 2001-02-20 | Mci Communications Corporation | Performing automated testing using automatically generated logs |
| US6357008B1 (en) | 1997-09-23 | 2002-03-12 | Symantec Corporation | Dynamic heuristic method for detecting computer viruses using decryption exploration and evaluation phases |
| US5991856A (en) | 1997-09-30 | 1999-11-23 | Network Associates, Inc. | System and method for computer operating system protection |
| US5924096A (en) | 1997-10-15 | 1999-07-13 | Novell, Inc. | Distributed database using indexed into tags to tracks events according to type, update cache, create virtual update log on demand |
| EP0911827B1 (en) | 1997-10-21 | 2011-11-30 | Sony Corporation | Recording and/or reproduction apparatus, file management method and providing medium |
| US6081894A (en) | 1997-10-22 | 2000-06-27 | Rvt Technologies, Inc. | Method and apparatus for isolating an encrypted computer system upon detection of viruses and similar data |
| US6128774A (en) | 1997-10-28 | 2000-10-03 | Necula; George C. | Safe to execute verification of software |
| US5991772A (en) | 1997-10-31 | 1999-11-23 | Oracle Corporation | Method and apparatus for restoring a portion of a database |
| US6073128A (en) | 1997-10-31 | 2000-06-06 | Oracle Corporation | Method and apparatus for identifying files used to restore a file |
| US7092914B1 (en) | 1997-11-06 | 2006-08-15 | Intertrust Technologies Corporation | Methods for matching, selecting, narrowcasting, and/or classifying based on rights management and/or other information |
| US6119165A (en) | 1997-11-17 | 2000-09-12 | Trend Micro, Inc. | Controlled distribution of application programs in a computer network |
| US6397329B1 (en) | 1997-11-21 | 2002-05-28 | Telcordia Technologies, Inc. | Method for efficiently revoking digital identities |
| US6108799A (en) | 1997-11-21 | 2000-08-22 | International Business Machines Corporation | Automated sample creation of polymorphic and non-polymorphic marcro viruses |
| US6094731A (en) | 1997-11-24 | 2000-07-25 | Symantec Corporation | Antivirus accelerator for computer networks |
| US6208986B1 (en) | 1997-12-15 | 2001-03-27 | International Business Machines Corporation | Web interface and method for accessing and displaying directory information |
| US6035423A (en) | 1997-12-31 | 2000-03-07 | Network Associates, Inc. | Method and system for providing automated updating and upgrading of antivirus applications using a computer network |
| US5999932A (en) | 1998-01-13 | 1999-12-07 | Bright Light Technologies, Inc. | System and method for filtering unsolicited electronic mail messages using data matching and heuristic processing |
| US6122738A (en) | 1998-01-22 | 2000-09-19 | Symantec Corporation | Computer file integrity verification |
| US6141771A (en) | 1998-02-06 | 2000-10-31 | International Business Machines Corporation | Method and system for providing a trusted machine state |
| US5987610A (en) | 1998-02-12 | 1999-11-16 | Ameritech Corporation | Computer virus screening methods and systems |
| US6205482B1 (en) | 1998-02-19 | 2001-03-20 | Ameritech Corporation | System and method for executing a request from a client application |
| US6457130B2 (en) | 1998-03-03 | 2002-09-24 | Network Appliance, Inc. | File access control in a multi-protocol file server |
| US20010044901A1 (en) | 1998-03-24 | 2001-11-22 | Symantec Corporation | Bubble-protected system for automatic decryption of file data on a per-use basis and automatic re-encryption |
| US6052531A (en) | 1998-03-25 | 2000-04-18 | Symantec Corporation | Multi-tiered incremental software updating |
| JPH11282779A (en) | 1998-03-27 | 1999-10-15 | Matsushita Electric Ind Co Ltd | File distribution system |
| US6263342B1 (en) | 1998-04-01 | 2001-07-17 | International Business Machines Corp. | Federated searching of heterogeneous datastores using a federated datastore object |
| US6272488B1 (en) | 1998-04-01 | 2001-08-07 | International Business Machines Corporation | Managing results of federated searches across heterogeneous datastores with a federated collection object |
| US6098079A (en) | 1998-04-02 | 2000-08-01 | Mitsubishi Electric Information Technology Center America, Inc. (Ita) | File version reconciliation using hash codes |
| US6230316B1 (en) | 1998-04-17 | 2001-05-08 | Symantec Corporation | Patching rebased and realigned executable files |
| GB2336696B (en) | 1998-04-24 | 2002-12-18 | Dialog Corp Plc The | Analysing data files |
| US6154751A (en) | 1998-05-14 | 2000-11-28 | International Business Machines Corporation | Method for executing a user-requested CGI program in a new authentication context while protecting operation of a default web server program |
| US6792540B1 (en) | 1998-05-28 | 2004-09-14 | Oracle International Corporation | Data replication security |
| US6134447A (en) | 1998-05-29 | 2000-10-17 | Ericsson Inc. | System and method for monitoring and barring location applications |
| US6279111B1 (en) | 1998-06-12 | 2001-08-21 | Microsoft Corporation | Security model using restricted tokens |
| US6308274B1 (en) | 1998-06-12 | 2001-10-23 | Microsoft Corporation | Least privilege via restricted tokens |
| US6256393B1 (en) | 1998-06-23 | 2001-07-03 | General Instrument Corporation | Authorization and access control of software object residing in set-top terminals |
| US6638314B1 (en) | 1998-06-26 | 2003-10-28 | Microsoft Corporation | Method of web crawling utilizing crawl numbers |
| DE19838605A1 (en) | 1998-08-25 | 2000-03-02 | Siemens Ag | Method and device for forming a detection variable that enables detection of digital signing of an electronic file, and method and device for detection that an electronic file has been digitally signed |
| US6115709A (en) | 1998-09-18 | 2000-09-05 | Tacit Knowledge Systems, Inc. | Method and system for constructing a knowledge profile of a user having unrestricted and restricted access portions according to respective levels of confidence of content of the portions |
| US6397381B1 (en) | 1998-09-21 | 2002-05-28 | Microsoft Corporation | System and method for repairing a damaged application program |
| US6237144B1 (en) | 1998-09-21 | 2001-05-22 | Microsoft Corporation | Use of relational databases for software installation |
| US6401210B1 (en) | 1998-09-23 | 2002-06-04 | Intel Corporation | Method of managing computer virus infected files |
| US6711583B2 (en) | 1998-09-30 | 2004-03-23 | International Business Machines Corporation | System and method for detecting and repairing document-infecting viruses using dynamic heuristics |
| US6301670B1 (en) | 1998-10-06 | 2001-10-09 | Ricoh Corporation | Method and apparatus for erasing data when a problem is identified |
| US6205558B1 (en) | 1998-10-07 | 2001-03-20 | Symantec Corporation | Recovery of file systems after modification failure |
| US6230288B1 (en) | 1998-10-29 | 2001-05-08 | Network Associates, Inc. | Method of treating whitespace during virus detection |
| US6598090B2 (en) | 1998-11-03 | 2003-07-22 | International Business Machines Corporation | Centralized control of software for administration of a distributed computing environment |
| US6378069B1 (en) | 1998-11-04 | 2002-04-23 | Nortel Networks Limited | Apparatus and methods for providing software updates to devices in a communication network |
| US6334150B1 (en) | 1998-11-30 | 2001-12-25 | International Business Machines Corporation | Data processing system and method for remotely disabling a client computer system |
| US6263388B1 (en) | 1998-11-30 | 2001-07-17 | International Business Machines Corporation | Data processing system and method for remotely disabling network activity in a client computer system |
| US6163859A (en) | 1998-12-02 | 2000-12-19 | Support.Com, Inc. | Software vault |
| US6370648B1 (en) | 1998-12-08 | 2002-04-09 | Visa International Service Association | Computer network intrusion detection |
| CA2292041A1 (en) | 1998-12-22 | 2000-06-22 | Scott Alan Thomson | Software program protection mechanism |
| US6311187B1 (en) | 1998-12-29 | 2001-10-30 | Sun Microsystems, Inc. | Propogating updates efficiently in hierarchically structured data under a push model |
| US20030191957A1 (en) | 1999-02-19 | 2003-10-09 | Ari Hypponen | Distributed computer virus detection and scanning |
| EP1159799B1 (en) | 1999-02-26 | 2006-07-26 | Bitwise Designs, Inc. | Digital file management and imaging system and method including secure file marking |
| US6735766B1 (en) | 1999-03-03 | 2004-05-11 | Microsoft Corporation | Method and computer-readable medium for installing an upgrade to an application program |
| WO2000054385A1 (en) | 1999-03-10 | 2000-09-14 | Preview Systems, Inc. | User transparent software malfunction detection and reporting |
| US6725377B1 (en) | 1999-03-12 | 2004-04-20 | Networks Associates Technology, Inc. | Method and system for updating anti-intrusion software |
| US6829708B1 (en) | 1999-03-27 | 2004-12-07 | Microsoft Corporation | Specifying security for an element by assigning a scaled value representative of the relative security thereof |
| US6816596B1 (en) | 2000-01-14 | 2004-11-09 | Microsoft Corporation | Encrypting a digital object based on a key ID selected therefor |
| CA2365245C (en) | 1999-03-31 | 2008-12-09 | British Telecommunications Public Limited Company | Server computer for guaranteeing files integrity |
| EP1069745A1 (en) | 1999-07-13 | 2001-01-17 | BRITISH TELECOMMUNICATIONS public limited company | Server computer providing integrity of files stored in it |
| US6775779B1 (en) | 1999-04-06 | 2004-08-10 | Microsoft Corporation | Hierarchical trusted code for content protection in computers |
| JP3056732B1 (en) | 1999-04-09 | 2000-06-26 | コナミ株式会社 | Computer system, computer program execution method, and computer program recording medium |
| WO2000064095A1 (en) | 1999-04-15 | 2000-10-26 | Motorola Inc. | Electronic document protection system |
| US6721795B1 (en) | 1999-04-26 | 2004-04-13 | America Online, Inc. | Data transfer server |
| WO2000067130A1 (en) | 1999-04-30 | 2000-11-09 | Fujitsu Limited | File managing system |
| US6434615B1 (en) | 1999-04-30 | 2002-08-13 | Compaq Information Technologies Group, L.P. | Method and apparatus for remote computer management using HTML in a web browser application and an internet server extension on an internet server API-compliant web server |
| JP4212717B2 (en) | 1999-04-30 | 2009-01-21 | 富士通株式会社 | File processing unit processing method |
| US6654746B1 (en) | 1999-05-03 | 2003-11-25 | Symantec Corporation | Methods and apparatuses for single-connection file synchronization workgroup file update |
| US6574657B1 (en) | 1999-05-03 | 2003-06-03 | Symantec Corporation | Methods and apparatuses for file synchronization and updating using a signature list |
| US6681331B1 (en) | 1999-05-11 | 2004-01-20 | Cylant, Inc. | Dynamic software system intrusion detection |
| WO2000072200A1 (en) | 1999-05-21 | 2000-11-30 | Infraworks Corporation | Method and apparatus for securing files |
| GB2350449A (en) | 1999-05-27 | 2000-11-29 | Ibm | Detecting replication of a computer virus using a counter virus |
| US6618810B1 (en) | 1999-05-27 | 2003-09-09 | Dell Usa, L.P. | Bios based method to disable and re-enable computers |
| US20020101998A1 (en) | 1999-06-10 | 2002-08-01 | Chee-Hong Wong | Fast escrow delivery |
| US6594671B1 (en) | 1999-06-14 | 2003-07-15 | International Business Machines Corporation | Separating privileged functions from non-privileged functions in a server instance |
| TW462025B (en) | 1999-06-23 | 2001-11-01 | Micro Star Int Co Ltd | BIOS virus protection method |
| NL1012435C2 (en) | 1999-06-25 | 2000-12-28 | Koninkl Kpn Nv | System for secure storage and management in a TTP server. |
| US6643648B1 (en) | 1999-06-30 | 2003-11-04 | Raf Technology, Inc. | Secure, limited-access database system and method |
| JP2003503795A (en) | 1999-06-30 | 2003-01-28 | マイクロソフト コーポレイション | Method and system for reporting and resolving support incidents |
| EP1076336A3 (en) | 1999-07-12 | 2002-01-16 | DCS Desarrollos Tecnologicos S.A. | Method and device for storing, selecting and playing digital audio in magnetic memory and electronic security system against unauthorized copies |
| AU6222900A (en) | 1999-07-20 | 2001-02-05 | Getlivemusic.Com | Systems for digital watermarking and distribution of recorded content |
| US6779117B1 (en) | 1999-07-23 | 2004-08-17 | Cybersoft, Inc. | Authentication program for a computer operating system |
| AU779120B2 (en) | 1999-08-02 | 2005-01-06 | Harris Interactive, Inc. | System for protecting information over the internet |
| US20020009622A1 (en) | 1999-08-03 | 2002-01-24 | Goodson David M. | Sprayable phosphate cementitious coatings and a method and apparatus for the production thereof |
| GB2354347B (en) | 1999-08-04 | 2003-09-03 | Internat Federation Of The Pho | Reproduction control system |
| US6493744B1 (en) | 1999-08-16 | 2002-12-10 | International Business Machines Corporation | Automatic rating and filtering of data files for objectionable content |
| US6959382B1 (en) | 1999-08-16 | 2005-10-25 | Accela, Inc. | Digital signature service |
| US6647400B1 (en) | 1999-08-30 | 2003-11-11 | Symantec Corporation | System and method for analyzing filesystems to detect intrusions |
| US6826697B1 (en) | 1999-08-30 | 2004-11-30 | Symantec Corporation | System and method for detecting buffer overflow attacks |
| US6301666B1 (en) | 1999-08-31 | 2001-10-09 | Everdream, Inc. | Method and apparatus for remotely enabling a preinstalled and previously disabled application on a computer system |
| US6976165B1 (en) | 1999-09-07 | 2005-12-13 | Emc Corporation | System and method for secure storage, transfer and retrieval of content addressable information |
| US6792416B2 (en) | 1999-09-21 | 2004-09-14 | International Business Machines Corporation | Managing results of federated searches across heterogeneous datastores with a federated result set cursor object |
| US8914361B2 (en) | 1999-09-22 | 2014-12-16 | Google Inc. | Methods and systems for determining a meaning of a document to match the document to content |
| US6618727B1 (en) | 1999-09-22 | 2003-09-09 | Infoglide Corporation | System and method for performing similarity searching |
| US6324537B1 (en) | 1999-09-30 | 2001-11-27 | M-Systems Flash Disk Pioneers Ltd. | Device, system and method for data access control |
| US7043553B2 (en) | 1999-10-07 | 2006-05-09 | Cisco Technology, Inc. | Method and apparatus for securing information access |
| US6594780B1 (en) | 1999-10-19 | 2003-07-15 | Inasoft, Inc. | Operating system and data protection |
| US6430561B1 (en) | 1999-10-29 | 2002-08-06 | International Business Machines Corporation | Security policy for protection of files on a storage device |
| US6453347B1 (en) | 1999-10-29 | 2002-09-17 | Mcafee.Com, Inc. | Active marketing based on client computer configurations |
| US6631480B2 (en) | 1999-11-10 | 2003-10-07 | Symantec Corporation | Methods and systems for protecting data from potential corruption by a crashed computer program |
| US6738775B2 (en) | 1999-11-30 | 2004-05-18 | Base One International Corp. | Database communication system and method for communicating with a database |
| US6728886B1 (en) | 1999-12-01 | 2004-04-27 | Trend Micro Incorporated | Distributed virus scanning arrangements and methods therefor |
| US6550061B1 (en) | 1999-12-02 | 2003-04-15 | Dell Usa, L.P. | System and method for modifying configuration files in a secured operating system |
| US6742023B1 (en) | 2000-04-28 | 2004-05-25 | Roxio, Inc. | Use-sensitive distribution of data files between users |
| JP3546787B2 (en)* | 1999-12-16 | 2004-07-28 | インターナショナル・ビジネス・マシーンズ・コーポレーション | Access control system, access control method, and storage medium |
| ES2304929T3 (en) | 1999-12-21 | 2008-11-01 | Contentguard Holdings, Inc. | METHOD TO TRANSFER THE RIGHTS TO DECODE MONTHLY. |
| WO2001048582A2 (en) | 1999-12-24 | 2001-07-05 | Ravenpack Ag | Method and device for presenting data to a user |
| GB2353372B (en) | 1999-12-24 | 2001-08-22 | F Secure Oyj | Remote computer virus scanning |
| WO2001048634A2 (en) | 1999-12-27 | 2001-07-05 | Texar Software Corp. | Virtual resource attribute directory |
| US6654888B1 (en) | 1999-12-31 | 2003-11-25 | International Business Machines Corporation | Installing and controlling trial software |
| EP1315067B1 (en) | 2000-01-06 | 2006-07-26 | International Business Machines Corporation | Method and system for using a virus free file certificate |
| US6735700B1 (en) | 2000-01-11 | 2004-05-11 | Network Associates Technology, Inc. | Fast virus scanning using session stamping |
| US6763466B1 (en) | 2000-01-11 | 2004-07-13 | Networks Associates Technology, Inc. | Fast virus scanning |
| US6772340B1 (en) | 2000-01-14 | 2004-08-03 | Microsoft Corporation | Digital rights management system operating on computing device and having black box tied to computing device |
| US6785818B1 (en) | 2000-01-14 | 2004-08-31 | Symantec Corporation | Thwarting malicious registry mapping modifications and map-loaded module masquerade attacks |
| WO2001053909A2 (en) | 2000-01-18 | 2001-07-26 | Telcordia Technologies, Inc. | Method and systems for data security |
| US6721767B2 (en) | 2000-01-31 | 2004-04-13 | Commvault Systems, Inc. | Application specific rollback in a computer system |
| US7293175B2 (en) | 2000-06-29 | 2007-11-06 | Lockheed Martin Corporation | Automatic information sanitizer |
| US6704730B2 (en) | 2000-02-18 | 2004-03-09 | Avamar Technologies, Inc. | Hash file system and method for use in a commonality factoring system |
| US6560776B1 (en) | 2000-02-18 | 2003-05-06 | Avaya Technology Corp. | Software installation verification tool |
| US6594665B1 (en) | 2000-02-18 | 2003-07-15 | Intel Corporation | Storing hashed values of data in media to allow faster searches and comparison of data |
| US20010032188A1 (en) | 2000-02-25 | 2001-10-18 | Yoshiyuki Miyabe | Information distribution system |
| IL151455A0 (en) | 2000-03-03 | 2003-04-10 | Sanctum Ltd | System for determining web application vulnerabilities |
| CA2299946A1 (en) | 2000-03-03 | 2001-09-03 | Destiny Software Productions Inc. | Digital media distribution method and system |
| US6775780B1 (en) | 2000-03-16 | 2004-08-10 | Networks Associates Technology, Inc. | Detecting malicious software by analyzing patterns of system calls generated during emulation |
| AU2001250952A1 (en) | 2000-03-22 | 2001-10-03 | Interwoven, Inc. | Method and apparatus for storing changes to file attributes without having to store an additional copy of the file contents |
| US6842861B1 (en) | 2000-03-24 | 2005-01-11 | Networks Associates Technology, Inc. | Method and system for detecting viruses on handheld computers |
| WO2001073533A1 (en) | 2000-03-28 | 2001-10-04 | The Wingard Company | System and method for safeguarding electronic files and digital information in a network environment |
| US6658406B1 (en) | 2000-03-29 | 2003-12-02 | Microsoft Corporation | Method for selecting terms from vocabularies in a category-based system |
| US6856993B1 (en) | 2000-03-30 | 2005-02-15 | Microsoft Corporation | Transactional file system |
| US6748534B1 (en) | 2000-03-31 | 2004-06-08 | Networks Associates, Inc. | System and method for partitioned distributed scanning of a large dataset for viruses and other malware |
| US6826609B1 (en) | 2000-03-31 | 2004-11-30 | Tumbleweed Communications Corp. | Policy enforcement in a secure data file delivery system |
| US6823398B1 (en) | 2000-03-31 | 2004-11-23 | Dphi Acquisitions, Inc. | File system management embedded in a storage device |
| US6820082B1 (en) | 2000-04-03 | 2004-11-16 | Allegis Corporation | Rule based database security system and method |
| KR20010096814A (en) | 2000-04-14 | 2001-11-08 | 홍기융 | Digital Signature Certificate Based Security Kernel Method for File System Protection |
| WO2001082033A1 (en) | 2000-04-19 | 2001-11-01 | Syntion Ag | Method for detecting the utilization of a computer program in a billable manner |
| US6640317B1 (en) | 2000-04-20 | 2003-10-28 | International Business Machines Corporation | Mechanism for automated generic application damage detection and repair in strongly encapsulated application |
| US6754718B1 (en) | 2000-05-10 | 2004-06-22 | Emc Corporation | Pushing attribute information to storage devices for network topology access |
| US20010042204A1 (en) | 2000-05-11 | 2001-11-15 | David Blaker | Hash-ordered databases and methods, systems and computer program products for use of a hash-ordered database |
| DE60128290T2 (en) | 2000-05-11 | 2007-08-30 | Matsushita Electric Industrial Co., Ltd., Kadoma | Device for file management |
| US20020062258A1 (en) | 2000-05-18 | 2002-05-23 | Bailey Steven C. | Computer-implemented procurement of items using parametric searching |
| MXPA02011760A (en) | 2000-05-31 | 2003-04-10 | Matsushita Electric Ind Co Ltd | Information recording medium, information recording method, information recording apparatus, information reproducing method, and information reproducing apparatus. |
| US6640287B2 (en) | 2000-06-10 | 2003-10-28 | Hewlett-Packard Development Company, L.P. | Scalable multiprocessor system and cache coherence method incorporating invalid-to-dirty requests |
| US6711572B2 (en) | 2000-06-14 | 2004-03-23 | Xosoft Inc. | File system for distributing content in a data network and related methods |
| US6785721B1 (en)* | 2000-06-19 | 2004-08-31 | International Business Machines Corporation | System and method for providing a distributable runtime that deploys web applications and services from a workflow, enterprise, and mail-enabled web application server and platform |
| US7669238B2 (en) | 2000-06-21 | 2010-02-23 | Microsoft Corporation | Evidence-based application security |
| GB2364404B (en) | 2000-07-01 | 2002-10-02 | Marconi Comm Ltd | Method of detecting malicious code |
| US7251728B2 (en) | 2000-07-07 | 2007-07-31 | Message Secure Corporation | Secure and reliable document delivery using routing lists |
| US6470329B1 (en) | 2000-07-11 | 2002-10-22 | Sun Microsystems, Inc. | One-way hash functions for distributed data synchronization |
| US7210040B2 (en) | 2000-07-14 | 2007-04-24 | Computer Associates Think, Inc. | Detection of suspicious privileged access to restricted computer resources |
| US7350204B2 (en) | 2000-07-24 | 2008-03-25 | Microsoft Corporation | Policies for secure software execution |
| US6711557B1 (en) | 2000-08-14 | 2004-03-23 | Adobe Systems Incorporated | Client-based background update monitoring |
| US6732125B1 (en) | 2000-09-08 | 2004-05-04 | Storage Technology Corporation | Self archiving log structured volume with intrinsic data protection |
| US6785732B1 (en) | 2000-09-11 | 2004-08-31 | International Business Machines Corporation | Web server apparatus and method for virus checking |
| JP2004509398A (en) | 2000-09-14 | 2004-03-25 | プロビックス・インコーポレイテッド | System for establishing an audit trail for the protection of objects distributed over a network |
| US6802012B1 (en) | 2000-10-03 | 2004-10-05 | Networks Associates Technology, Inc. | Scanning computer files for unwanted properties |
| US6757830B1 (en) | 2000-10-03 | 2004-06-29 | Networks Associates Technology, Inc. | Detecting unwanted properties in received email messages |
| GB0024919D0 (en) | 2000-10-11 | 2000-11-22 | Sealedmedia Ltd | Method of further securing an operating system |
| US20020048372A1 (en) | 2000-10-19 | 2002-04-25 | Eng-Whatt Toh | Universal signature object for digital data |
| US6970939B2 (en) | 2000-10-26 | 2005-11-29 | Intel Corporation | Method and apparatus for large payload distribution in a network |
| EP1202148A1 (en) | 2000-10-31 | 2002-05-02 | Hewlett-Packard Company, A Delaware Corporation | Virus check on altered data |
| EP1330890B1 (en) | 2000-11-03 | 2008-06-25 | Digital Authentication Technologies Inc. | Electronic file protection using location |
| US7343324B2 (en) | 2000-11-03 | 2008-03-11 | Contentguard Holdings Inc. | Method, system, and computer readable medium for automatically publishing content |
| US6715106B1 (en) | 2000-11-10 | 2004-03-30 | Dell Products L.P. | Bios corruption detection system and method |
| US7322047B2 (en) | 2000-11-13 | 2008-01-22 | Digital Doors, Inc. | Data security system and method associated with data mining |
| EP1350167A4 (en) | 2000-11-16 | 2007-10-24 | Dlj Long Term Invest Corp | System and method for application-level security |
| US7660902B2 (en) | 2000-11-20 | 2010-02-09 | Rsa Security, Inc. | Dynamic file access control and management |
| JP2004515166A (en) | 2000-11-28 | 2004-05-20 | スイベル テクノロジーズ リミテッド | Secure file transfer method and system |
| US7003551B2 (en) | 2000-11-30 | 2006-02-21 | Bellsouth Intellectual Property Corp. | Method and apparatus for minimizing storage of common attachment files in an e-mail communications server |
| EP1340170A1 (en) | 2000-12-08 | 2003-09-03 | IPC Gmbh | Method and system for supplying information via a communication network |
| US7150045B2 (en) | 2000-12-14 | 2006-12-12 | Widevine Technologies, Inc. | Method and apparatus for protection of electronic media |
| US6708174B1 (en) | 2000-12-20 | 2004-03-16 | I2 Technologies, Inc. | System and method for retrieving information according to improved matching criteria |
| US7296070B2 (en) | 2000-12-22 | 2007-11-13 | Tier-3 Pty. Ltd. | Integrated monitoring system |
| US6985586B2 (en) | 2000-12-22 | 2006-01-10 | Nagracard S.A. | Distributed information and storage system |
| US7058667B2 (en) | 2000-12-27 | 2006-06-06 | Microsoft Corporation | Method and system for creating and maintaining version-specific properties in a file |
| US20020087876A1 (en) | 2000-12-28 | 2002-07-04 | Larose Gordon Edward | Adaptive software installation process supporting multiple layers of security-related attributes |
| GB2371125A (en) | 2001-01-13 | 2002-07-17 | Secr Defence | Computer protection system |
| US6684224B2 (en) | 2001-01-16 | 2004-01-27 | Chipdata, Inc. | Remote database update method and apparatus |
| US7386513B2 (en) | 2001-01-17 | 2008-06-10 | Contentguard Holdings, Inc. | Networked services licensing system and method |
| EP1225513A1 (en) | 2001-01-19 | 2002-07-24 | Eyal Dotan | Method for protecting computer programs and data from hostile code |
| US7057993B2 (en) | 2001-01-29 | 2006-06-06 | Eastman Kodak Company | Copy protection using multiple security levels on a programmable CD-ROM |
| US7406529B2 (en) | 2001-02-09 | 2008-07-29 | Yahoo! Inc. | System and method for detecting and verifying digitized content over a computer network |
| US20020111911A1 (en) | 2001-02-13 | 2002-08-15 | Kennedy Kelli Hodge | Document distribution system and method with consolidated document services management |
| US7213146B2 (en) | 2001-02-20 | 2007-05-01 | Hewlett-Packard Development Company, L.P. | System and method for establishing security profiles of computers |
| US7272724B2 (en) | 2001-02-20 | 2007-09-18 | Mcafee, Inc. | User alerts in an anti computer virus system |
| GB2372595A (en) | 2001-02-23 | 2002-08-28 | Hewlett Packard Co | Method of and apparatus for ascertaining the status of a data processing environment. |
| US6829355B2 (en) | 2001-03-05 | 2004-12-07 | The United States Of America As Represented By The National Security Agency | Device for and method of one-way cryptographic hashing |
| US7404212B2 (en) | 2001-03-06 | 2008-07-22 | Cybersoft, Inc. | Apparatus and methods for intercepting, examining and controlling code, data and files and their transfer |
| US7373643B2 (en)* | 2001-03-06 | 2008-05-13 | Cybersoft, Inc. | Apparatus, methods and articles of manufacture for data transmission |
| US7647402B2 (en) | 2001-03-08 | 2010-01-12 | International Business Machines Corporation | Protecting contents of computer data files from suspected intruders by renaming and hiding data files subjected to intrusion |
| AU2002252287A1 (en) | 2001-03-12 | 2002-09-24 | Smart Mediary Systems, Llc | Many-to-many mediated commercial electronic publishing |
| US7284271B2 (en) | 2001-03-14 | 2007-10-16 | Microsoft Corporation | Authorizing a requesting entity to operate upon data structures |
| US7302584B2 (en) | 2001-03-16 | 2007-11-27 | Mcafee, Inc. | Mechanisms for banning computer programs from use |
| EP1372063A4 (en) | 2001-03-19 | 2008-03-19 | Sony Corp | Software updating system, software updating method, and software updating program |
| US20020144130A1 (en) | 2001-03-29 | 2002-10-03 | Koninklijke Philips Electronics N.V. | Apparatus and methods for detecting illicit content that has been imported into a secure domain |
| US7114184B2 (en) | 2001-03-30 | 2006-09-26 | Computer Associates Think, Inc. | System and method for restoring computer systems damaged by a malicious computer program |
| IL142487A0 (en) | 2001-04-05 | 2003-09-17 | Hexalock Ltd | Method and system for protecting data |
| JP3946965B2 (en) | 2001-04-09 | 2007-07-18 | ソニー株式会社 | Recording apparatus, recording method, recording medium, and program for recording information protecting intangible property rights |
| US6966000B2 (en) | 2001-04-13 | 2005-11-15 | Ge Medical Technology Services, Inc. | Method and system to remotely grant limited access to software options resident on a device |
| US7502939B2 (en) | 2001-04-19 | 2009-03-10 | Cybersoft, Inc. | Software virus detection methods and apparatus |
| US7043634B2 (en) | 2001-05-15 | 2006-05-09 | Mcafee, Inc. | Detecting malicious alteration of stored computer files |
| US7188368B2 (en) | 2001-05-25 | 2007-03-06 | Lenovo (Singapore) Pte. Ltd. | Method and apparatus for repairing damage to a computer system using a system rollback mechanism |
| US6643653B1 (en) | 2001-06-01 | 2003-11-04 | Oracle International Corporation | Method and apparatus for identifying a data sequence related to a given data sequence |
| DE60203711T2 (en) | 2001-06-12 | 2006-03-02 | International Business Machines Corp. | METHOD FOR AUTHENTICATING MULTIPLE FILES ASSOCIATED WITH A TEXT DOCUMENT |
| US7213148B2 (en) | 2001-06-13 | 2007-05-01 | Corrent Corporation | Apparatus and method for a hash processing system using integrated message digest and secure hash architectures |
| US7249255B2 (en) | 2001-06-13 | 2007-07-24 | Corrent Corporation | Apparatus and method for a hash processing system using multiple hash storage areas |
| US20020194490A1 (en) | 2001-06-18 | 2002-12-19 | Avner Halperin | System and method of virus containment in computer networks |
| US7203966B2 (en) | 2001-06-27 | 2007-04-10 | Microsoft Corporation | Enforcement architecture and method for digital rights management system for roaming a license to a plurality of user devices |
| FI118358B (en) | 2001-06-29 | 2007-10-15 | Sanako Oy | A method for controlling the use of digital media content |
| KR100762276B1 (en) | 2001-07-17 | 2007-10-01 | 샤프 가부시키가이샤 | Apparatus and method for generating forgery detection data of encrypted data in process |
| US7487544B2 (en) | 2001-07-30 | 2009-02-03 | The Trustees Of Columbia University In The City Of New York | System and methods for detection of new malicious executables |
| US7146524B2 (en) | 2001-08-03 | 2006-12-05 | Isilon Systems, Inc. | Systems and methods for providing a distributed file system incorporating a virtual hot spare |
| AU2002323431A1 (en) | 2001-08-27 | 2003-03-10 | Dataplay, Inc. | A secure access method and system |
| US6662198B2 (en)* | 2001-08-30 | 2003-12-09 | Zoteca Inc. | Method and system for asynchronous transmission, backup, distribution of data and file sharing |
| US6826601B2 (en) | 2001-09-06 | 2004-11-30 | Bea Systems, Inc. | Exactly one cache framework |
| US7234167B2 (en) | 2001-09-06 | 2007-06-19 | Mcafee, Inc. | Automatic builder of detection and cleaning routines for computer viruses |
| US7260725B2 (en) | 2001-09-14 | 2007-08-21 | Computer Associates Think, Inc. | Virus detection system |
| US7266844B2 (en) | 2001-09-27 | 2007-09-04 | Mcafee, Inc. | Heuristic detection of polymorphic computer viruses based on redundancy in viral code |
| US20030074578A1 (en) | 2001-10-16 | 2003-04-17 | Richard Ford | Computer virus containment |
| US6654751B1 (en) | 2001-10-18 | 2003-11-25 | Networks Associates Technology, Inc. | Method and apparatus for a virus information patrol |
| FR2841409B1 (en) | 2001-10-19 | 2004-07-30 | Marc Viot | DATA PROTECTION METHOD AND DEVICE |
| WO2003036505A1 (en) | 2001-10-24 | 2003-05-01 | Bea Systems, Inc. | System and method for delegated administration |
| US7444393B2 (en) | 2001-10-30 | 2008-10-28 | Keicy K. Chung | Read-only storage device having network interface, a system including the device, and a method of distributing files over a network |
| US20030159060A1 (en) | 2001-10-31 | 2003-08-21 | Gales George S. | System and method of defining the security condition of a computer system |
| US8387111B2 (en) | 2001-11-01 | 2013-02-26 | International Business Machines Corporation | Type independent permission based access control |
| US20030084325A1 (en) | 2001-11-01 | 2003-05-01 | International Business Machines Corporation | Method and apparatus for implementing permission based access control through permission type inheritance |
| US7603440B1 (en)* | 2001-11-09 | 2009-10-13 | Persystent Technology Corporation | System and method for management of end user computing devices |
| US6816985B2 (en) | 2001-11-13 | 2004-11-09 | Sun Microsystems, Inc. | Method and apparatus for detecting corrupt software code |
| US7243230B2 (en) | 2001-11-16 | 2007-07-10 | Microsoft Corporation | Transferring application secrets in a trusted operating system environment |
| JP2003150424A (en) | 2001-11-16 | 2003-05-23 | Fujitsu Ltd | File system, control method, and program |
| US7840488B2 (en) | 2001-11-20 | 2010-11-23 | Contentguard Holdings, Inc. | System and method for granting access to an item or permission to use an item based on configurable conditions |
| JP2003223363A (en) | 2001-11-21 | 2003-08-08 | Ricoh Co Ltd | Document processing device |
| US20030101234A1 (en) | 2001-11-28 | 2003-05-29 | International Business Machines Corporation | System and method for indicating whether a document is cached |
| US20030101381A1 (en) | 2001-11-29 | 2003-05-29 | Nikolay Mateev | System and method for virus checking software |
| JP3914757B2 (en) | 2001-11-30 | 2007-05-16 | デュアキシズ株式会社 | Apparatus, method and system for virus inspection |
| US7234164B2 (en) | 2001-11-30 | 2007-06-19 | Computer Associates Think, Inc. | Method and system for blocking execution of malicious code |
| US20030105973A1 (en) | 2001-12-04 | 2003-06-05 | Trend Micro Incorporated | Virus epidemic outbreak command system and method using early warning monitors in a network environment |
| US7062553B2 (en) | 2001-12-04 | 2006-06-13 | Trend Micro, Inc. | Virus epidemic damage control system and method for network environment |
| US7631184B2 (en) | 2002-05-14 | 2009-12-08 | Nicholas Ryan | System and method for imposing security on copies of secured items |
| US20030110169A1 (en) | 2001-12-12 | 2003-06-12 | Secretseal Inc. | System and method for providing manageability to security information for secured items |
| US7783765B2 (en) | 2001-12-12 | 2010-08-24 | Hildebrand Hal S | System and method for providing distributed access control to secured documents |
| US10033700B2 (en) | 2001-12-12 | 2018-07-24 | Intellectual Ventures I Llc | Dynamic evaluation of access rights |
| US7260555B2 (en) | 2001-12-12 | 2007-08-21 | Guardian Data Storage, Llc | Method and architecture for providing pervasive security to digital assets |
| US7058975B2 (en) | 2001-12-14 | 2006-06-06 | Mcafee, Inc. | Method and system for delayed write scanning for detecting computer malwares |
| DE10162291A1 (en) | 2001-12-19 | 2003-07-03 | Philips Intellectual Property | Method for preventing unauthorized execution of a computer program, especially for preventing unauthorized execution of a ROM based self-test of a smart card, by incorporation of an internal signature within the self-test routine |
| WO2003054724A2 (en) | 2001-12-20 | 2003-07-03 | Douglas Monahan | File identification system and method |
| US7398389B2 (en) | 2001-12-20 | 2008-07-08 | Coretrace Corporation | Kernel-based network security infrastructure |
| GB0130805D0 (en) | 2001-12-22 | 2002-02-06 | Koninkl Philips Electronics Nv | Dealing with a computer virus which self-propagates by e-mail |
| US7114185B2 (en) | 2001-12-26 | 2006-09-26 | Mcafee, Inc. | Identifying malware containing computer files using embedded text |
| US7415726B2 (en) | 2001-12-28 | 2008-08-19 | Mcafee, Inc. | Controlling access to suspicious files |
| TWI286701B (en) | 2002-01-09 | 2007-09-11 | Via Tech Inc | Process for avoiding system infection of software viruses |
| US7168008B2 (en) | 2002-01-18 | 2007-01-23 | Mobitv, Inc. | Method and system for isolating and protecting software components |
| US7363506B2 (en) | 2002-01-30 | 2008-04-22 | Cybersoft, Inc. | Software virus detection methods, apparatus and articles of manufacture |
| US7249379B2 (en) | 2002-02-01 | 2007-07-24 | Systems Advisory Group Enterprises, Inc. | Method and apparatus for implementing process-based security in a computer system |
| US20030154394A1 (en) | 2002-02-13 | 2003-08-14 | Levin Lawrence R. | Computer virus control |
| JP4088082B2 (en) | 2002-02-15 | 2008-05-21 | 株式会社東芝 | Apparatus and program for preventing infection by unknown computer virus |
| US20030158872A1 (en) | 2002-02-19 | 2003-08-21 | Media Vu, Llc | Method and system for checking content before dissemination |
| AU2003219823A1 (en) | 2002-02-20 | 2003-09-09 | Bitpipe, Inc. | Electronic document tracking |
| US7631196B2 (en) | 2002-02-25 | 2009-12-08 | Intel Corporation | Method and apparatus for loading a trustable operating system |
| US7096498B2 (en) | 2002-03-08 | 2006-08-22 | Cipher Trust, Inc. | Systems and methods for message threat management |
| EP1488330B1 (en) | 2002-03-15 | 2014-05-07 | Shinkuro, Inc. | Method for forming groups |
| JP4078454B2 (en) | 2002-03-22 | 2008-04-23 | 株式会社日立製作所 | Digital signature management method, digital signature processing apparatus, program, and recording medium |
| US20030178381A1 (en) | 2002-03-22 | 2003-09-25 | Linda Liang | Collapsible article holder |
| US20030182561A1 (en) | 2002-03-25 | 2003-09-25 | International Business Machines Corporation | Tamper detection mechanism for a personal computer and a method of use thereof |
| EP1349033B1 (en) | 2002-03-26 | 2004-03-31 | Soteres GmbH | A method of protecting the integrity of a computer program |
| US20030187848A1 (en) | 2002-04-02 | 2003-10-02 | Hovhannes Ghukasyan | Method and apparatus for restricting access to a database according to user permissions |
| WO2003085532A1 (en) | 2002-04-02 | 2003-10-16 | Corporation For National Research Initiatives | Authenticating and using digital objects |
| US20030192041A1 (en) | 2002-04-03 | 2003-10-09 | Mentze Duane E. | software distribution system and method |
| AU2003227314A1 (en) | 2002-04-03 | 2003-10-13 | Invisicom, Inc. | Protection of data by hiding the data |
| JP2004005008A (en) | 2002-04-04 | 2004-01-08 | Scinet Corp | Protection method for contents of writing in electronic publication distribution |
| US7543333B2 (en) | 2002-04-08 | 2009-06-02 | Microsoft Corporation | Enhanced computer intrusion detection methods and systems |
| ATE426858T1 (en) | 2002-04-13 | 2009-04-15 | Computer Ass Think Inc | SYSTEM AND METHOD FOR DETECTING MALICIOUS CODE |
| US6782477B2 (en) | 2002-04-16 | 2004-08-24 | Song Computer Entertainment America Inc. | Method and system for using tamperproof hardware to provide copy protection and online security |
| US6715085B2 (en) | 2002-04-18 | 2004-03-30 | International Business Machines Corporation | Initializing, maintaining, updating and recovering secure operation within an integrated system employing a data access control function |
| DE10217862A1 (en) | 2002-04-22 | 2003-11-13 | Fraunhofer Ges Forschung | Method for labeling a virtual goods and device for providing a label for a virtual goods |
| US6976023B2 (en) | 2002-04-23 | 2005-12-13 | International Business Machines Corporation | System and method for managing application specific privileges in a content management system |
| US6782349B2 (en) | 2002-05-03 | 2004-08-24 | International Business Machines Corporation | Method and system for updating a root of trust measurement function in a personal computer |
| EP2110975A1 (en) | 2002-05-06 | 2009-10-21 | Bentley Systems, Incorporated | Method and system for digital signatures |
| US20040111632A1 (en) | 2002-05-06 | 2004-06-10 | Avner Halperin | System and method of virus containment in computer networks |
| US8327446B2 (en) | 2002-05-06 | 2012-12-04 | Trend Micro Inc. | Antivirus stand-alone network or internet appliance and methods therefor |
| WO2003100556A2 (en) | 2002-05-20 | 2003-12-04 | Smarte Solutions, Inc. | Cd media anti-piracy generation and management system and process |
| US7409717B1 (en) | 2002-05-23 | 2008-08-05 | Symantec Corporation | Metamorphic computer virus detection |
| GB0212315D0 (en) | 2002-05-28 | 2002-07-10 | Symbian Ltd | Secure mobile wireless device with protected file systems |
| US7065759B2 (en) | 2002-06-18 | 2006-06-20 | Hewlett-Packard Development Company, L.P. | System and method for assigning basic blocks to computer control flow paths |
| US20030236995A1 (en) | 2002-06-21 | 2003-12-25 | Fretwell Lyman Jefferson | Method and apparatus for facilitating detection of network intrusion |
| US20060031381A1 (en) | 2002-07-24 | 2006-02-09 | Koninklijke Philips Electrices N.V. | Method and device for regulating file sharing |
| NL1021300C2 (en) | 2002-08-19 | 2004-03-01 | Tno | Computer network security. |
| US20040044628A1 (en) | 2002-08-27 | 2004-03-04 | Microsoft Corporation | Method and system for enforcing online identity consent polices |
| US7748039B2 (en) | 2002-08-30 | 2010-06-29 | Symantec Corporation | Method and apparatus for detecting malicious code in an information handling system |
| US7832011B2 (en) | 2002-08-30 | 2010-11-09 | Symantec Corporation | Method and apparatus for detecting malicious code in an information handling system |
| US7401221B2 (en) | 2002-09-04 | 2008-07-15 | Microsoft Corporation | Advanced stream format (ASF) data stream header object protection |
| US7225461B2 (en) | 2002-09-04 | 2007-05-29 | Hitachi, Ltd. | Method for updating security information, client, server and management computer therefor |
| US20040054893A1 (en) | 2002-09-18 | 2004-03-18 | Anthony Ellis | Method and system for a file encryption and monitoring system |
| US20040073607A1 (en) | 2002-09-25 | 2004-04-15 | Su Chi Chung | Multimedia messaging system and method |
| US7334219B2 (en) | 2002-09-30 | 2008-02-19 | Ensco, Inc. | Method and system for object level software testing |
| US7188369B2 (en) | 2002-10-03 | 2007-03-06 | Trend Micro, Inc. | System and method having an antivirus virtual scanning processor with plug-in functionalities |
| US20040068559A1 (en) | 2002-10-04 | 2004-04-08 | Shaw Terry D. | Method for detection of unauthorized computer system usage |
| US7337471B2 (en) | 2002-10-07 | 2008-02-26 | Symantec Corporation | Selective detection of malicious computer code |
| US7469419B2 (en) | 2002-10-07 | 2008-12-23 | Symantec Corporation | Detection of malicious computer code |
| US20040073789A1 (en) | 2002-10-15 | 2004-04-15 | Powers John Stephenson | Method for collaborative software licensing of electronically distributed computer programs |
| JP4400059B2 (en) | 2002-10-17 | 2010-01-20 | 株式会社日立製作所 | Policy setting support tool |
| US20040078580A1 (en) | 2002-10-18 | 2004-04-22 | Trend Micro Incorporated | Antivirus network system and method for handling electronic mails infected by computer viruses |
| US20040128169A1 (en) | 2002-10-18 | 2004-07-01 | Lusen William D. | Multiple organization data access monitoring and management system |
| US7039833B2 (en) | 2002-10-21 | 2006-05-02 | I2 Technologies Us, Inc. | Stack trace generated code compared with database to find error resolution information |
| JP2004151195A (en) | 2002-10-29 | 2004-05-27 | Sony Corp | Device and method for communication, program, storage medium, and terminal device |
| US7278019B2 (en) | 2002-11-04 | 2007-10-02 | Hewlett-Packard Development Company, L.P. | Method of hindering the propagation of a computer virus |
| US7984435B2 (en) | 2002-11-13 | 2011-07-19 | Hewlett-Packard Development Company, L.P. | Update system employing reference software to reduce number of update packages |
| WO2004044756A1 (en) | 2002-11-14 | 2004-05-27 | Mobidata Group Pty Limited | System and method relating to remotely accessible securely stored data files |
| US7484219B2 (en) | 2002-11-21 | 2009-01-27 | Microsoft Corporation | Synchronizing centralized data store from distributed independent data stores using fixed application programming interfaces |
| US6786076B2 (en) | 2002-11-25 | 2004-09-07 | Reliable Instruments Llc | Thin film gas sensor |
| US7440571B2 (en) | 2002-12-03 | 2008-10-21 | Nagravision S.A. | Method for securing software updates |
| US7020804B2 (en) | 2002-12-03 | 2006-03-28 | Lockheed Martin Corporation | Test data generation system for evaluating data cleansing applications |
| US8024781B2 (en) | 2002-12-04 | 2011-09-20 | Microsoft Corporation | Signing-in to software applications having secured features |
| US7428751B2 (en) | 2002-12-05 | 2008-09-23 | Microsoft Corporation | Secure recovery in a serverless distributed file system |
| US20040111414A1 (en) | 2002-12-06 | 2004-06-10 | International Business Machines Corporation | System and method for selective execution of statements with surrogate authority |
| US7024689B2 (en) | 2002-12-13 | 2006-04-04 | Intuit, Inc. | Granting access rights to unattended software |
| US7120635B2 (en) | 2002-12-16 | 2006-10-10 | International Business Machines Corporation | Event-based database access execution |
| US7373664B2 (en) | 2002-12-16 | 2008-05-13 | Symantec Corporation | Proactive protection against e-mail worms and spam |
| US7631353B2 (en) | 2002-12-17 | 2009-12-08 | Symantec Corporation | Blocking replication of e-mail worms |
| US7418730B2 (en) | 2002-12-17 | 2008-08-26 | International Business Machines Corporation | Automatic client responses to worm or hacker attacks |
| US20040123117A1 (en) | 2002-12-18 | 2004-06-24 | Symantec Corporation | Validation for behavior-blocking system |
| US7594111B2 (en) | 2002-12-19 | 2009-09-22 | Massachusetts Institute Of Technology | Secure execution of a computer program |
| EP1573478A2 (en) | 2002-12-19 | 2005-09-14 | International Business Machines Corporation | A method for distributing software licenses using xml documents |
| US7305564B2 (en) | 2002-12-19 | 2007-12-04 | International Business Machines Corporation | System and method to proactively detect software tampering |
| US7013483B2 (en) | 2003-01-03 | 2006-03-14 | Aladdin Knowledge Systems Ltd. | Method for emulating an executable code in order to detect maliciousness |
| US7533148B2 (en) | 2003-01-09 | 2009-05-12 | Microsoft Corporation | Framework to enable integration of anti-spam technologies |
| US7200598B2 (en) | 2003-01-16 | 2007-04-03 | Hewlett-Packard Development Company, L.P. | System and method for efficiently replicating a file among a plurality of recipients having improved scalability |
| US20040143749A1 (en) | 2003-01-16 | 2004-07-22 | Platformlogic, Inc. | Behavior-based host-based intrusion prevention system |
| US7174334B2 (en) | 2003-01-16 | 2007-02-06 | Hewlett-Packard Development Company, L.P. | System and method for efficiently replicating a file among a plurality of recipients |
| US20040153644A1 (en) | 2003-02-05 | 2004-08-05 | Mccorkendale Bruce | Preventing execution of potentially malicious software |
| US7228563B2 (en) | 2003-02-06 | 2007-06-05 | Symantec Corporation | Shell code blocking system and method |
| US7293290B2 (en) | 2003-02-06 | 2007-11-06 | Symantec Corporation | Dynamic detection of computer worms |
| US20040158730A1 (en) | 2003-02-11 | 2004-08-12 | International Business Machines Corporation | Running anti-virus software on a network attached storage device |
| US20040162781A1 (en) | 2003-02-14 | 2004-08-19 | Kennsco, Inc. | Monitoring and alert systems and methods |
| WO2004072834A1 (en) | 2003-02-14 | 2004-08-26 | Whale Communications Ltd. | System and method for providing conditional access to server-based applications from remote access devices |
| US7565551B2 (en) | 2003-02-19 | 2009-07-21 | Microsoft Corporation | Enhancing software integrity through installation and verification |
| EP2182465B1 (en) | 2003-02-21 | 2013-05-01 | Research In Motion Limited | System and method of multiple-level control of electronic devices |
| US20040168005A1 (en) | 2003-02-21 | 2004-08-26 | Sun Microsystems, Inc. | Methods for interrupting a program and for obtaining program execution acquisition |
| JP2004258777A (en) | 2003-02-24 | 2004-09-16 | Fujitsu Ltd | Security management device, security management system, security management method, security management program |
| US7478096B2 (en) | 2003-02-26 | 2009-01-13 | Burnside Acquisition, Llc | History preservation in a computer storage system |
| JP4077336B2 (en) | 2003-02-26 | 2008-04-16 | 富士通株式会社 | Anomaly detection method, anomaly detection program, server, computer |
| US7555749B2 (en) | 2003-03-10 | 2009-06-30 | Microsoft Corporation | Software updating system and method |
| WO2004081758A2 (en) | 2003-03-12 | 2004-09-23 | Digex, Inc. | System and method for maintaining installed software compliance with build standards |
| FR2852413B1 (en) | 2003-03-12 | 2005-05-20 | SECURE, INVIOLABLE AND INFALSIFIABLE DEVICE FOR THE STORAGE OF AUTHENTICATED AND DATED DATA WITH LEGAL OR LEGAL VALUE | |
| KR20040080844A (en) | 2003-03-14 | 2004-09-20 | 주식회사 안철수연구소 | Method to detect malicious scripts using static analysis |
| KR100509650B1 (en) | 2003-03-14 | 2005-08-23 | 주식회사 안철수연구소 | Method to detect malicious scripts using code insertion technique |
| US7185015B2 (en) | 2003-03-14 | 2007-02-27 | Websense, Inc. | System and method of monitoring and controlling application files |
| KR100503386B1 (en) | 2003-03-14 | 2005-07-26 | 주식회사 안철수연구소 | Method to detect malicious code patterns with due regard to control and data flow |
| US7584467B2 (en) | 2003-03-17 | 2009-09-01 | Microsoft Corporation | Software updating system and method |
| US7546638B2 (en) | 2003-03-18 | 2009-06-09 | Symantec Corporation | Automated identification and clean-up of malicious computer code |
| JP3835421B2 (en) | 2003-03-28 | 2006-10-18 | コニカミノルタビジネステクノロジーズ株式会社 | Control program and control device |
| JP3945438B2 (en) | 2003-03-28 | 2007-07-18 | コニカミノルタビジネステクノロジーズ株式会社 | Control program and control device |
| GB2403820A (en) | 2003-03-28 | 2005-01-12 | Hewlett Packard Development Co | Security policy in trusted computing systems |
| US7353535B2 (en) | 2003-03-31 | 2008-04-01 | Microsoft Corporation | Flexible, selectable, and fine-grained network trust policies |
| US8171551B2 (en) | 2003-04-01 | 2012-05-01 | Mcafee, Inc. | Malware detection using external call characteristics |
| FR2853742B1 (en) | 2003-04-08 | 2005-07-08 | Regie Autonome Transports | CENTRALIZED INFORMATION BACKUP SYSTEM |
| US20040205419A1 (en) | 2003-04-10 | 2004-10-14 | Trend Micro Incorporated | Multilevel virus outbreak alert based on collaborative behavior |
| US7788724B2 (en) | 2003-04-10 | 2010-08-31 | Symantec Corporation | System and method for detecting malicious applications |
| GB2400463B (en) | 2003-04-11 | 2005-05-25 | Nextenders | Data processing apparatus and method for distributing and authenticating electronic documents |
| US7254811B2 (en) | 2003-04-17 | 2007-08-07 | Ntt Docomo, Inc. | Update system and method for updating a scanning subsystem in a mobile communication framework |
| WO2004095176A2 (en) | 2003-04-18 | 2004-11-04 | Ounce Labs, Inc. | Detecting vulnerabilities in source code |
| US7587422B2 (en) | 2003-04-24 | 2009-09-08 | Neopath Networks, Inc. | Transparent file replication using namespace replication |
| US20040215656A1 (en) | 2003-04-25 | 2004-10-28 | Marcus Dill | Automated data mining runs |
| US7139781B2 (en) | 2003-04-29 | 2006-11-21 | International Business Machines Corporation | Managing filesystem versions |
| US7461395B2 (en) | 2003-05-06 | 2008-12-02 | Oracle International Corporation | Distributed capability-based authorization architecture using roles |
| US7322029B2 (en) | 2003-05-08 | 2008-01-22 | American Megatrends, Inc. | Method and system for recovering program code in a computer system |
| US20040225877A1 (en) | 2003-05-09 | 2004-11-11 | Zezhen Huang | Method and system for protecting computer system from malicious software operation |
| EP1634136A1 (en) | 2003-05-13 | 2006-03-15 | International Business Machines Corporation | System for real-time healing of vital computer files |
| US7386617B2 (en) | 2003-05-15 | 2008-06-10 | International Business Machines Corporation | Method, system and program product for managing multiple network application versions |
| US7917751B2 (en) | 2003-05-22 | 2011-03-29 | International Business Machines Corporation | Distributed filesystem network security extension |
| US20040250086A1 (en) | 2003-05-23 | 2004-12-09 | Harris Corporation | Method and system for protecting against software misuse and malicious code |
| US7257835B2 (en) | 2003-05-28 | 2007-08-14 | Microsoft Corporation | Securely authorizing the performance of actions |
| US7231667B2 (en) | 2003-05-29 | 2007-06-12 | Computer Associates Think, Inc. | System and method for computer virus detection utilizing heuristic analysis |
| US7730033B2 (en) | 2003-06-13 | 2010-06-01 | Microsoft Corporation | Mechanism for exposing shadow copies in a networked environment |
| MXPA06000102A (en) | 2003-06-23 | 2006-06-27 | Sony Pictures Entertainment | Fingerprinting of data. |
| US20050005105A1 (en) | 2003-06-24 | 2005-01-06 | Brown Larry Cecil | Remote access control feature for limiting access to configuration file components |
| US7567991B2 (en) | 2003-06-25 | 2009-07-28 | Emc Corporation | Replication of snapshot using a file system copy differential |
| JP4150854B2 (en) | 2003-06-27 | 2008-09-17 | 日本電気株式会社 | Access system and client for shared disk device on storage area network |
| US7155484B2 (en) | 2003-06-30 | 2006-12-26 | Bellsouth Intellectual Property Corporation | Filtering email messages corresponding to undesirable geographical regions |
| US20040267837A1 (en) | 2003-06-30 | 2004-12-30 | Nokia Inc. | System and method for updating network appliances using urgent update notifications |
| US7596807B2 (en) | 2003-07-03 | 2009-09-29 | Arbor Networks, Inc. | Method and system for reducing scope of self-propagating attack code in network |
| US20040172551A1 (en) | 2003-12-09 | 2004-09-02 | Michael Connor | First response computer virus blocking. |
| US7555777B2 (en) | 2004-01-13 | 2009-06-30 | International Business Machines Corporation | Preventing attacks in a data processing system |
- 2005
- 2005-07-29USUS11/194,078patent/US8984636B2/enactiveActive
Patent Citations (99)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US4809160A (en)* | 1985-10-28 | 1989-02-28 | Hewlett-Packard Company | Privilege level checking instruction for implementing a secure hierarchical computer system |
| US4908861A (en)* | 1987-08-28 | 1990-03-13 | International Business Machines Corporation | Data authentication using modification detection codes based on a public one way encryption function |
| US5283830A (en)* | 1991-12-17 | 1994-02-01 | International Computers Limited | Security mechanism for a computer system |
| US5502815A (en)* | 1992-03-30 | 1996-03-26 | Cozza; Paul D. | Method and apparatus for increasing the speed at which computer viruses are detected |
| US5278901A (en)* | 1992-04-30 | 1994-01-11 | International Business Machines Corporation | Pattern-oriented intrusion-detection system and method |
| US5495571A (en)* | 1992-09-30 | 1996-02-27 | Microsoft Corporation | Method and system for performing parametric testing of a functional programming interface |
| US5613107A (en)* | 1992-12-22 | 1997-03-18 | Bull, S.A. | Method and apparatus for managing file versions in an information processing system based on a predetermined amount of storage media |
| US6195587B1 (en)* | 1993-10-29 | 2001-02-27 | Sophos Plc | Validity checking |
| US5495533A (en)* | 1994-04-29 | 1996-02-27 | International Business Machines Corporation | Personal key archive |
| US5613002A (en)* | 1994-11-21 | 1997-03-18 | International Business Machines Corporation | Generic disinfection of programs infected with a computer virus |
| US5485575A (en)* | 1994-11-21 | 1996-01-16 | International Business Machines Corporation | Automatic analysis of a computer virus structure and means of attachment to its hosts |
| US5708780A (en)* | 1995-06-07 | 1998-01-13 | Open Market, Inc. | Internet server access control and monitoring systems |
| US5859966A (en)* | 1995-10-10 | 1999-01-12 | Data General Corporation | Security system for computer systems |
| US6029175A (en)* | 1995-10-26 | 2000-02-22 | Teknowledge Corporation | Automatic retrieval of changed files by a network software agent |
| US5708709A (en)* | 1995-12-08 | 1998-01-13 | Sun Microsystems, Inc. | System and method for managing try-and-buy usage of application programs |
| US6178508B1 (en)* | 1995-12-28 | 2001-01-23 | International Business Machines Corp. | System for controlling access to encrypted data files by a plurality of users |
| US6021491A (en)* | 1996-11-27 | 2000-02-01 | Sun Microsystems, Inc. | Digital signatures for data streams and data archives |
| US6026205A (en)* | 1997-01-21 | 2000-02-15 | Molecular Optoelectronics Corporation | Compound optical waveguide and filter applications thereof |
| US6026502A (en)* | 1997-01-27 | 2000-02-15 | Wakayama; Hironori | Method and mechanism for preventing from invading of computer virus and/or hacker |
| US6173284B1 (en)* | 1997-05-20 | 2001-01-09 | University Of Charlotte City Of Charlotte | Systems, methods and computer program products for automatically monitoring police records for a crime profile |
| US6681227B1 (en)* | 1997-11-19 | 2004-01-20 | Ns Solutions Corporation | Database system and a method of data retrieval from the system |
| US6516395B1 (en)* | 1997-11-20 | 2003-02-04 | Advanced Micro Devices, Inc. | System and method for controlling access to a privilege-partitioned address space with a fixed set of attributes |
| US6021510A (en)* | 1997-11-24 | 2000-02-01 | Symantec Corporation | Antivirus accelerator |
| US6018747A (en)* | 1997-11-26 | 2000-01-25 | International Business Machines Corporation | Method for generating and reconstructing in-place delta files |
| US6023723A (en)* | 1997-12-22 | 2000-02-08 | Accepted Marketing, Inc. | Method and system for filtering unwanted junk e-mail utilizing a plurality of filtering mechanisms |
| US6029256A (en)* | 1997-12-31 | 2000-02-22 | Network Associates, Inc. | Method and system for allowing computer programs easy access to features of a virus scanning engine |
| US6026402A (en)* | 1998-01-07 | 2000-02-15 | Hewlett-Packard Company | Process restriction within file system hierarchies |
| US6513111B2 (en)* | 1998-02-09 | 2003-01-28 | Reuters, Ltd | Method of controlling software applications specific to a group of users |
| US6023586A (en)* | 1998-02-10 | 2000-02-08 | Novell, Inc. | Integrity verifying and correcting software |
| US6684210B1 (en)* | 1998-04-06 | 2004-01-27 | Matsushita Electric Industrial Co., Ltd. | File managing system, file management apparatus, file management method, and program storage medium |
| US20020002684A1 (en)* | 1998-05-01 | 2002-01-03 | Barbara L. Fox | Intelligent trust management method and system |
| US6505300B2 (en)* | 1998-06-12 | 2003-01-07 | Microsoft Corporation | Method and system for secure running of untrusted content |
| US6505237B2 (en)* | 1998-07-24 | 2003-01-07 | Siemens Information & Communication Networks, Inc. | Method and system for management of message attachments |
| US6338149B1 (en)* | 1998-07-31 | 2002-01-08 | Westinghouse Electric Company Llc | Change monitoring system for a computer system |
| US6338141B1 (en)* | 1998-09-30 | 2002-01-08 | Cybersoft, Inc. | Method and apparatus for computer virus detection, analysis, and removal in real time |
| US6349311B1 (en)* | 1999-02-01 | 2002-02-19 | Symantec Corporation | Storage of reverse delta updates |
| US6678741B1 (en)* | 1999-04-09 | 2004-01-13 | Sun Microsystems, Inc. | Method and apparatus for synchronizing firmware |
| US20020019932A1 (en)* | 1999-06-10 | 2002-02-14 | Eng-Whatt Toh | Cryptographically secure network |
| US6513039B1 (en)* | 1999-06-24 | 2003-01-28 | International Business Machines Corporation | Profile inferencing through automated access control list analysis heuristics |
| US6675205B2 (en)* | 1999-10-14 | 2004-01-06 | Arcessa, Inc. | Peer-to-peer automated anonymous asynchronous file sharing |
| US6351776B1 (en)* | 1999-11-04 | 2002-02-26 | Xdrive, Inc. | Shared internet storage resource, user interface system, and method |
| US6681387B1 (en)* | 1999-12-01 | 2004-01-20 | Board Of Trustees Of The University Of Illinois | Method and apparatus for instruction execution hot spot detection and monitoring in a data processing unit |
| US6697950B1 (en)* | 1999-12-22 | 2004-02-24 | Networks Associates Technology, Inc. | Method and apparatus for detecting a macro computer virus using static analysis |
| US6694328B1 (en)* | 2000-01-13 | 2004-02-17 | International Business Machines Corporation | Method for creating queries on version objects |
| US6694336B1 (en)* | 2000-01-25 | 2004-02-17 | Fusionone, Inc. | Data transfer and synchronization system |
| US20020005017A1 (en)* | 2000-03-31 | 2002-01-17 | Jsr Corporation | Aqueous dispersion for chemical mechanical polishing |
| US20020004874A1 (en)* | 2000-05-01 | 2002-01-10 | Hideyuki Agata | Apparatus and method for processing information, and program and medium used therefor |
| US20020005105A1 (en)* | 2000-05-09 | 2002-01-17 | Mcpherson Mathew | Arrangement of a sound hole and construction of a sound board in an acoustic guitar |
| US20040034794A1 (en)* | 2000-05-28 | 2004-02-19 | Yaron Mayer | System and method for comprehensive general generic protection for computers against malicious programs that may steal information and/or cause damages |
| US20020004908A1 (en)* | 2000-07-05 | 2002-01-10 | Nicholas Paul Andrew Galea | Electronic mail message anti-virus system and method |
| US20020004902A1 (en)* | 2000-07-07 | 2002-01-10 | Eng-Whatt Toh | Secure and reliable document delivery |
| US20020026576A1 (en)* | 2000-08-18 | 2002-02-28 | Hewlett-Packard Company | Apparatus and method for establishing trust |
| US6681344B1 (en)* | 2000-09-14 | 2004-01-20 | Microsoft Corporation | System and method for automatically diagnosing a computer problem |
| US20040039921A1 (en)* | 2000-10-17 | 2004-02-26 | Shyne-Song Chuang | Method and system for detecting rogue software |
| US6839721B2 (en)* | 2001-01-12 | 2005-01-04 | Hewlett-Packard Development Company, L.P. | Integration of a database into file management software for protecting, tracking, and retrieving data |
| US6694457B2 (en)* | 2001-03-06 | 2004-02-17 | Hewlett-Packard Development Company, L.P. | System and method for monitoring execution of privileged instructions |
| US20030018903A1 (en)* | 2001-03-19 | 2003-01-23 | Greca Damon G. Della | Method of containing spread of computer viruses |
| US7483993B2 (en)* | 2001-04-06 | 2009-01-27 | Symantec Corporation | Temporal access control for computer virus prevention |
| US20040039924A1 (en)* | 2001-04-09 | 2004-02-26 | Baldwin Robert W. | System and method for security of computing devices |
| US6697810B2 (en)* | 2001-04-19 | 2004-02-24 | Vigilance, Inc. | Security system for event monitoring, detection and notification system |
| US20050022004A1 (en)* | 2001-04-24 | 2005-01-27 | Microsoft Corporation | Robust recognizer of perceptually similar content |
| US20030004922A1 (en)* | 2001-06-27 | 2003-01-02 | Ontrack Data International, Inc. | System and method for data management |
| US6513122B1 (en)* | 2001-06-29 | 2003-01-28 | Networks Associates Technology, Inc. | Secure gateway for analyzing textual content to identify a harmful impact on computer systems with known vulnerabilities |
| US20030015973A1 (en)* | 2001-07-18 | 2003-01-23 | Kevin Ovens | Solid state traffic light with predictive failure analysis |
| US20030023867A1 (en)* | 2001-07-25 | 2003-01-30 | Thibadeau Robert H. | Methods and systems for promoting security in a computer system employing attached storage devices |
| US20030023864A1 (en)* | 2001-07-25 | 2003-01-30 | Igor Muttik | On-access malware scanning |
| US20030023866A1 (en)* | 2001-07-26 | 2003-01-30 | Hinchliffe Alex James | Centrally managed malware scanning |
| US20030023857A1 (en)* | 2001-07-26 | 2003-01-30 | Hinchliffe Alexander James | Malware infection suppression |
| US20030023560A1 (en)* | 2001-07-27 | 2003-01-30 | Fujitsu Limited | Design asset information search system |
| US20030028785A1 (en)* | 2001-08-01 | 2003-02-06 | Pak Michael Chin-Hwan | System and method for executing computer virus definitions containing general purpose programming language extensions |
| US20030033308A1 (en)* | 2001-08-03 | 2003-02-13 | Patel Sujal M. | System and methods for providing a distributed file system utilizing metadata to track information about data stored throughout the system |
| US20030033303A1 (en)* | 2001-08-07 | 2003-02-13 | Brian Collins | System and method for restricting access to secured data |
| US20050033975A1 (en)* | 2001-08-17 | 2005-02-10 | Pasi Lahti | Preventing virus infection in a computer system |
| US20040025043A1 (en)* | 2002-05-22 | 2004-02-05 | Microsoft Corporation | System and method for identifying potential security risks in controls |
| US20040003279A1 (en)* | 2002-06-28 | 2004-01-01 | Beilinson Craig Adam | User controls for a computer |
| US20040003274A1 (en)* | 2002-06-28 | 2004-01-01 | Strom Clifford P. | Protecting content on medium from unfettered distribution |
| US20040010602A1 (en)* | 2002-07-10 | 2004-01-15 | Van Vleck Paul F. | System and method for managing access to digital content via digital rights policies |
| US20040034638A1 (en)* | 2002-07-18 | 2004-02-19 | International Business Machines Corporation | Method for analyzing and characterizing the usage pattern of a device |
| US20040019878A1 (en)* | 2002-07-23 | 2004-01-29 | Sreekrishna Kotnur | Software tool to detect and restore damaged or lost software components |
| US20040031028A1 (en)* | 2002-08-06 | 2004-02-12 | Aardwork Software Limited | Updating of software |
| US20040030913A1 (en)* | 2002-08-08 | 2004-02-12 | Trend Micro Incorporated | System and method for computer protection against malicious electronic mails by analyzing, profiling and trapping the same |
| US20040039932A1 (en)* | 2002-08-23 | 2004-02-26 | Gidon Elazar | Apparatus, system and method for securing digital documents in a digital appliance |
| US20050022016A1 (en)* | 2002-12-12 | 2005-01-27 | Alexander Shipp | Method of and system for heuristically detecting viruses in executable code |
| US20050010804A1 (en)* | 2002-12-19 | 2005-01-13 | Bruening Derek L. | Secure execution of a computer program using a code cache |
| US20050004873A1 (en)* | 2003-02-03 | 2005-01-06 | Robin Pou | Distribution and rights management of digital content |
| US20050005168A1 (en)* | 2003-03-11 | 2005-01-06 | Richard Dick | Verified personal information database |
| US20050010806A1 (en)* | 2003-04-18 | 2005-01-13 | Ounce Labs, Inc. | Method and system for detecting privilege escalation vulnerabilities in source code |
| US20050015591A1 (en)* | 2003-06-12 | 2005-01-20 | International Business Machines Corporation | Multi-level multi-user web services security system and method |
| US20050022018A1 (en)* | 2003-06-30 | 2005-01-27 | Symantec Corporation | Signature extraction system and method |
| US20050004954A1 (en)* | 2003-07-01 | 2005-01-06 | Hand Held Products, Inc. | Systems and methods for expedited data transfer in a communication system using hash segmentation |
| US20050015675A1 (en)* | 2003-07-03 | 2005-01-20 | Kolawa Adam K. | Method and system for automatic error prevention for computer software |
| US20050005161A1 (en)* | 2003-07-04 | 2005-01-06 | Adrian Baldwin | Services and secure processing environments |
| US20050015592A1 (en)* | 2003-07-15 | 2005-01-20 | Jeou-Kai Lin | System and method for application and user-based class of security |
| US20050015760A1 (en)* | 2003-07-16 | 2005-01-20 | Oleg Ivanov | Automatic detection and patching of vulnerable files |
| US20050021994A1 (en)* | 2003-07-21 | 2005-01-27 | Barton Christopher Andrew | Pre-approval of computer files during a malware detection |
| US20050028002A1 (en)* | 2003-07-29 | 2005-02-03 | Mihai Christodorescu | Method and apparatus to detect malicious software |
| US20050033976A1 (en)* | 2003-08-04 | 2005-02-10 | Sbc Knowledge Ventures, L.P. | Host intrusion detection and isolation |
| US20050033980A1 (en)* | 2003-08-07 | 2005-02-10 | Willman Bryan Mark | Projection of trustworthiness from a trusted environment to an untrusted environment |
| US20050033978A1 (en)* | 2003-08-08 | 2005-02-10 | Hyser Chris D. | Method and system for securing a computer system |
Cited By (99)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US9059956B2 (en) | 2003-01-31 | 2015-06-16 | Good Technology Corporation | Asynchronous real-time retrieval of data |
| US9665708B2 (en) | 2004-12-03 | 2017-05-30 | Fortinet, Inc. | Secure system for allowing the execution of authorized computer program code |
| US9842203B2 (en) | 2004-12-03 | 2017-12-12 | Fortinet, Inc. | Secure system for allowing the execution of authorized computer program code |
| US9305159B2 (en) | 2004-12-03 | 2016-04-05 | Fortinet, Inc. | Secure system for allowing the execution of authorized computer program code |
| US8161548B1 (en) | 2005-08-15 | 2012-04-17 | Trend Micro, Inc. | Malware detection using pattern classification |
| US7930289B2 (en) | 2005-11-12 | 2011-04-19 | Apple Inc. | Methods and systems for providing improved security when using a uniform resource locator (URL) or other address or identifier |
| US20070112814A1 (en)* | 2005-11-12 | 2007-05-17 | Cheshire Stuart D | Methods and systems for providing improved security when using a uniform resource locator (URL) or other address or identifier |
| US20070112774A1 (en)* | 2005-11-12 | 2007-05-17 | Cheshire Stuart D | Methods and systems for providing improved security when using a uniform resource locator (URL) or other address or identifier |
| US20140040403A1 (en)* | 2006-02-09 | 2014-02-06 | John Sargent | System, method and computer program product for gathering information relating to electronic content utilizing a dns server |
| US9246860B2 (en)* | 2006-02-09 | 2016-01-26 | Mcafee, Inc. | System, method and computer program product for gathering information relating to electronic content utilizing a DNS server |
| US7840958B1 (en)* | 2006-02-17 | 2010-11-23 | Trend Micro, Inc. | Preventing spyware installation |
| US7971257B2 (en)* | 2006-08-03 | 2011-06-28 | Symantec Corporation | Obtaining network origins of potential software threats |
| US20080034434A1 (en)* | 2006-08-03 | 2008-02-07 | Rolf Repasi | Obtaining network origins of potential software threats |
| US20080250100A1 (en)* | 2007-04-03 | 2008-10-09 | Sony Corporation | Information processing apparatus, information processing method and computer program |
| US7991832B2 (en)* | 2007-04-03 | 2011-08-02 | Sony Corporation | Information processing apparatus, information processing method and computer program |
| US7854002B2 (en) | 2007-04-30 | 2010-12-14 | Microsoft Corporation | Pattern matching for spyware detection |
| US9628513B2 (en) | 2007-04-30 | 2017-04-18 | Mcafee, Inc. | Electronic message manager system, method, and computer program product for scanning an electronic message for unwanted content and associated unwanted sites |
| US20080271147A1 (en)* | 2007-04-30 | 2008-10-30 | Microsoft Corporation | Pattern matching for spyware detection |
| US20150180888A1 (en)* | 2007-06-05 | 2015-06-25 | Harish Balasubramanian | System, Method and Computer Program Product for Making a Scan Decision During Communication of Data Over a Network |
| US8589181B2 (en) | 2007-07-06 | 2013-11-19 | Mckesson Financial Holdings | Systems and methods for managing medical information |
| US20090012813A1 (en)* | 2007-07-06 | 2009-01-08 | Mckesson Financial Holdings Limited | Systems and methods for managing medical information |
| US8670999B2 (en) | 2007-07-06 | 2014-03-11 | Mckesson Financial Holdings | Systems and methods for managing medical information |
| US20090077218A1 (en)* | 2007-09-14 | 2009-03-19 | Softkvm Llc | Software Method And System For Controlling And Observing Computer Networking Devices |
| US20090077428A1 (en)* | 2007-09-14 | 2009-03-19 | Softkvm Llc | Software Method And System For Controlling And Observing Computer Networking Devices |
| US8819655B1 (en)* | 2007-09-17 | 2014-08-26 | Symantec Corporation | Systems and methods for computer program update protection |
| US20090172768A1 (en)* | 2007-12-28 | 2009-07-02 | Huifeng Le | Methods and apparatus for operating embedded information technology applications with a service operating system |
| CN101539772A (en)* | 2008-01-25 | 2009-09-23 | 洛克威尔自动控制技术股份有限公司 | Product lifecycle management method and apparatus |
| CN101286986B (en)* | 2008-05-15 | 2011-09-14 | 成都市华为赛门铁克科技有限公司 | Active defense method, device and system |
| US8706745B1 (en)* | 2008-05-30 | 2014-04-22 | Symantec Corporation | Systems and methods for determining a file set |
| US8607347B2 (en)* | 2008-09-29 | 2013-12-10 | Sophos Limited | Network stream scanning facility |
| US20100083380A1 (en)* | 2008-09-29 | 2010-04-01 | Harris Mark D | Network stream scanning facility |
| US20100161608A1 (en)* | 2008-12-18 | 2010-06-24 | Sumooh Inc. | Methods and apparatus for content-aware data de-duplication |
| US7925683B2 (en) | 2008-12-18 | 2011-04-12 | Copiun, Inc. | Methods and apparatus for content-aware data de-duplication |
| US20100161685A1 (en)* | 2008-12-18 | 2010-06-24 | Sumooh Inc. | Methods and apparatus for content-aware data partitioning |
| US8589455B2 (en) | 2008-12-18 | 2013-11-19 | Copiun, Inc. | Methods and apparatus for content-aware data partitioning |
| US10693917B1 (en) | 2009-04-10 | 2020-06-23 | Open Invention Network Llc | System and method for on-line and off-line streaming application isolation |
| US11616821B1 (en)* | 2009-04-10 | 2023-03-28 | International Business Machines Corporation | System and method for streaming application isolation |
| US10606634B1 (en) | 2009-04-10 | 2020-03-31 | Open Invention Network Llc | System and method for application isolation |
| US10592942B1 (en) | 2009-04-10 | 2020-03-17 | Open Invention Network Llc | System and method for usage billing of hosted applications |
| US11314560B1 (en) | 2009-04-10 | 2022-04-26 | Open Invention Network Llc | System and method for hierarchical interception with isolated environments |
| US10419504B1 (en)* | 2009-04-10 | 2019-09-17 | Open Invention Network Llc | System and method for streaming application isolation |
| US11538078B1 (en) | 2009-04-10 | 2022-12-27 | International Business Machines Corporation | System and method for usage billing of hosted applications |
| US20120198553A1 (en)* | 2009-09-14 | 2012-08-02 | Junko Suginaka | Secure auditing system and secure auditing method |
| US9110915B2 (en) | 2009-12-18 | 2015-08-18 | Copiun, Inc. | Highly scalable and distributed data de-duplication |
| US9135264B2 (en) | 2010-03-12 | 2015-09-15 | Copiun, Inc. | Distributed catalog, data store, and indexing |
| US20110225141A1 (en)* | 2010-03-12 | 2011-09-15 | Copiun, Inc. | Distributed Catalog, Data Store, and Indexing |
| US20110231374A1 (en)* | 2010-03-16 | 2011-09-22 | Copiun, Inc. | Highly Scalable and Distributed Data De-Duplication |
| US8452739B2 (en) | 2010-03-16 | 2013-05-28 | Copiun, Inc. | Highly scalable and distributed data de-duplication |
| US9621405B2 (en) | 2010-08-24 | 2017-04-11 | Good Technology Holdings Limited | Constant access gateway and de-duplicated data cache server |
| US20120066762A1 (en)* | 2010-09-13 | 2012-03-15 | Rade Todorovic | System and method of whitelisting parent virtual images |
| US8407804B2 (en)* | 2010-09-13 | 2013-03-26 | Sophos Plc | System and method of whitelisting parent virtual images |
| US20120150897A1 (en)* | 2010-12-08 | 2012-06-14 | International Business Machines Corporation | Calculating State of Cryptographic Objects and Generating Search Filter for Querying Cryptographic Objects |
| US8788545B2 (en)* | 2010-12-08 | 2014-07-22 | International Business Machines Corporation | Calculating state of cryptographic objects and generating search filter for querying cryptographic objects |
| US9298767B1 (en) | 2010-12-08 | 2016-03-29 | International Business Machines Corporation | Calculating state of cryptographic objects and generating search filter for querying cryptographic objects |
| US9043920B2 (en) | 2012-06-27 | 2015-05-26 | Tenable Network Security, Inc. | System and method for identifying exploitable weak points in a network |
| US9860265B2 (en) | 2012-06-27 | 2018-01-02 | Tenable Network Security, Inc. | System and method for identifying exploitable weak points in a network |
| US10171490B2 (en) | 2012-07-05 | 2019-01-01 | Tenable, Inc. | System and method for strategic anti-malware monitoring |
| US9088606B2 (en) | 2012-07-05 | 2015-07-21 | Tenable Network Security, Inc. | System and method for strategic anti-malware monitoring |
| US10826975B2 (en)* | 2012-09-07 | 2020-11-03 | Oracle International Corporation | System and method for providing java cloud services for use with a cloud computing environment |
| US10225323B2 (en)* | 2012-09-07 | 2019-03-05 | Oracle International Corporation | System and method for providing java cloud services for use with a cloud computing environment |
| US20190166189A1 (en)* | 2012-09-07 | 2019-05-30 | Oracle International Corporation | System and method for providing java cloud services for use with a cloud computing environment |
| US9602539B1 (en)* | 2012-09-28 | 2017-03-21 | Palo Alto Networks, Inc. | Externally defined objects in security policy |
| US10404750B2 (en)* | 2012-09-28 | 2019-09-03 | Palo Alto Networks, Inc. | Externally defined objects in security policy |
| US20170195369A1 (en)* | 2012-09-28 | 2017-07-06 | Palo Alto Networks, Inc. | Externally defined objects in security policy |
| US9846706B1 (en)* | 2012-12-28 | 2017-12-19 | EMC IP Holding Company LLC | Managing mounting of file systems |
| US9467464B2 (en) | 2013-03-15 | 2016-10-11 | Tenable Network Security, Inc. | System and method for correlating log data to discover network vulnerabilities and assets |
| US20160119375A1 (en)* | 2013-06-04 | 2016-04-28 | Beijing Qihoo Technology Company Limited | Cloud security-based file processing method and apparatus |
| US9948670B2 (en)* | 2013-06-04 | 2018-04-17 | Beijing Qihoo Technology Company Limited | Cloud security-based file processing by generating feedback message based on signature information and file features |
| US10496812B2 (en) | 2013-09-06 | 2019-12-03 | Michael Guidry | Systems and methods for security in computer systems |
| US10152518B2 (en)* | 2014-10-30 | 2018-12-11 | The Johns Hopkins University | Apparatus and method for efficient identification of code similarity |
| US9680848B2 (en)* | 2014-12-03 | 2017-06-13 | Korea Internet & Security Agency | Apparatus, system and method for detecting and preventing malicious scripts using code pattern-based static analysis and API flow-based dynamic analysis |
| US9544321B2 (en)* | 2015-01-30 | 2017-01-10 | Securonix, Inc. | Anomaly detection using adaptive behavioral profiles |
| TWI595375B (en)* | 2015-01-30 | 2017-08-11 | 瑟古爾歐尼克斯股份有限公司 | Anomaly detection using adaptive behavioral profiles |
| US20160226901A1 (en)* | 2015-01-30 | 2016-08-04 | Securonix, Inc. | Anomaly Detection Using Adaptive Behavioral Profiles |
| CN108804925A (en)* | 2015-05-27 | 2018-11-13 | 安恒通(北京)科技有限公司 | method and system for detecting malicious code |
| CN106096397A (en)* | 2016-05-26 | 2016-11-09 | 倪茂志 | A kind of prevention method extorting software and system |
| US20170351870A1 (en)* | 2016-06-03 | 2017-12-07 | Honeywell International Inc. | Apparatus and method for device whitelisting and blacklisting to override protections for allowed media at nodes of a protected system |
| US10402577B2 (en)* | 2016-06-03 | 2019-09-03 | Honeywell International Inc. | Apparatus and method for device whitelisting and blacklisting to override protections for allowed media at nodes of a protected system |
| CN107948123A (en)* | 2016-10-12 | 2018-04-20 | 阿里巴巴集团控股有限公司 | Document transmission method and device |
| US11375001B2 (en) | 2016-10-12 | 2022-06-28 | Alibaba Group Holding Limited | File transmission method and apparatus |
| US20190121959A1 (en)* | 2017-08-01 | 2019-04-25 | PC Pitstop, Inc | System, Method, and Apparatus for Computer Security |
| US20210026951A1 (en)* | 2017-08-01 | 2021-01-28 | PC Matic, Inc | System, Method, and Apparatus for Computer Security |
| US11487868B2 (en)* | 2017-08-01 | 2022-11-01 | Pc Matic, Inc. | System, method, and apparatus for computer security |
| US10873588B2 (en) | 2017-08-01 | 2020-12-22 | Pc Matic, Inc. | System, method, and apparatus for computer security |
| US10783239B2 (en)* | 2017-08-01 | 2020-09-22 | Pc Matic, Inc. | System, method, and apparatus for computer security |
| US11425170B2 (en) | 2018-10-11 | 2022-08-23 | Honeywell International Inc. | System and method for deploying and configuring cyber-security protection solution using portable storage device |
| US10476936B1 (en) | 2018-12-13 | 2019-11-12 | Software Ag | Plugin-based file transfer systems and/or methods |
| US12061709B2 (en)* | 2019-08-01 | 2024-08-13 | Palantir Technologies Inc. | Systems and methods for conducting data extraction using dedicated data extraction devices |
| US20210034767A1 (en)* | 2019-08-01 | 2021-02-04 | Palantir Technologies Inc. | Systems and methods for conducting data extraction using dedicated data extraction devices |
| US11323482B2 (en)* | 2019-12-31 | 2022-05-03 | Mcafee, Llc | Methods, systems, and media for protecting computer systems from user-created objects |
| US11237802B1 (en) | 2020-07-20 | 2022-02-01 | Bank Of America Corporation | Architecture diagram analysis tool for software development |
| CN114679410A (en)* | 2020-12-24 | 2022-06-28 | 网神信息技术(北京)股份有限公司 | Method, device, electronic device and storage medium for reducing external network resource occupation |
| US20220382892A1 (en)* | 2021-05-27 | 2022-12-01 | Microsoft Technology Licensing, Llc | Centralized access control for cloud relational database management system resources |
| US11934548B2 (en)* | 2021-05-27 | 2024-03-19 | Microsoft Technology Licensing, Llc | Centralized access control for cloud relational database management system resources |
| US20240241980A1 (en)* | 2021-05-27 | 2024-07-18 | Microsoft Technology Licensing, Llc | Centralized access control for cloud relational database management system resources |
| US12259992B2 (en)* | 2021-05-27 | 2025-03-25 | Microsoft Technology Licensing, Llc | Centralized access control for cloud relational database management system resources |
| US12216785B2 (en)* | 2022-09-21 | 2025-02-04 | Acronis International Gmbh | Systems and methods for generating file systems of data sources incompatible with anti-virus scanners |
| CN117707608A (en)* | 2024-02-04 | 2024-03-15 | 深圳市分秒网络科技有限公司 | Methods and systems for automating configuration file parameters |
| US12229261B1 (en)* | 2024-05-03 | 2025-02-18 | Halcyon Tech, Inc. | Antiransomware file analysis and scoring |
Also Published As
| Publication number | Publication date |
|---|---|
| US8984636B2 (en) | 2015-03-17 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| US8984636B2 (en) | Content extractor and analysis system | |
| US8782800B2 (en) | Parametric content control in a network security system | |
| US7895651B2 (en) | Content tracking in a network security system | |
| US8272058B2 (en) | Centralized timed analysis in a network security system | |
| CA2617204C (en) | Network security systems and methods | |
| US20070028302A1 (en) | Distributed meta-information query in a network | |
| US12314396B2 (en) | Systems and methods for providing security services during power management mode | |
| US12294595B2 (en) | Computer investigation method and system | |
| US20090271863A1 (en) | Identifying unauthorized privilege escalations | |
| US20140165130A1 (en) | Application-specific re-adjustment of computer security settings | |
| US20110087899A1 (en) | Firewall plus storage apparatus, method and system | |
| US12292966B2 (en) | Systems and methods for folder and file sequestration | |
| US20240086538A1 (en) | Computer investigation method and system for investigating authentication in remote host computers |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| AS | Assignment | Owner name:BIT 9, INC., MASSACHUSETTS Free format text:ASSIGNMENT OF ASSIGNORS INTEREST;ASSIGNOR:BRENNAN, TODD F.;REEL/FRAME:017004/0061 Effective date:20051012 | |
| STCF | Information on status: patent grant | Free format text:PATENTED CASE | |
| MAFP | Maintenance fee payment | Free format text:PAYMENT OF MAINTENANCE FEE, 4TH YR, SMALL ENTITY (ORIGINAL EVENT CODE: M2551); ENTITY STATUS OF PATENT OWNER: SMALL ENTITY Year of fee payment:4 | |
| AS | Assignment | Owner name:CARBON BLACK, INC., MASSACHUSETTS Free format text:CHANGE OF NAME;ASSIGNOR:BIT9, INC.;REEL/FRAME:050123/0127 Effective date:20160127 Owner name:BIT9, INC., MASSACHUSETTS Free format text:CHANGE OF NAME;ASSIGNOR:BIT 9, INC.;REEL/FRAME:050123/0109 Effective date:20050425 | |
| FEPP | Fee payment procedure | Free format text:ENTITY STATUS SET TO UNDISCOUNTED (ORIGINAL EVENT CODE: BIG.); ENTITY STATUS OF PATENT OWNER: LARGE ENTITY | |
| MAFP | Maintenance fee payment | Free format text:PAYMENT OF MAINTENANCE FEE, 8TH YEAR, LARGE ENTITY (ORIGINAL EVENT CODE: M1552); ENTITY STATUS OF PATENT OWNER: LARGE ENTITY Year of fee payment:8 | |
| AS | Assignment | Owner name:VMWARE LLC, CALIFORNIA Free format text:MERGER;ASSIGNOR:CARBON BLACK, LLC;REEL/FRAME:070019/0171 Effective date:20240820 Owner name:CARBON BLACK, LLC, CALIFORNIA Free format text:CHANGE OF NAME;ASSIGNOR:CARBON BLACK, INC.;REEL/FRAME:070023/0225 Effective date:20200122 |