US11048783B2 - Authentication method and system - Google Patents
Authentication method and systemDownload PDFInfo
- Publication number
- US11048783B2 US11048783B2US16/718,158US201916718158AUS11048783B2US 11048783 B2US11048783 B2US 11048783B2US 201916718158 AUS201916718158 AUS 201916718158AUS 11048783 B2US11048783 B2US 11048783B2
- Authority
- US
- United States
- Prior art keywords
- keypad
- image
- scrambled
- user
- identifier
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Expired - Fee Related
Links
Images
Classifications
- G—PHYSICS
- G07—CHECKING-DEVICES
- G07F—COIN-FREED OR LIKE APPARATUS
- G07F7/00—Mechanisms actuated by objects other than coins to free or to actuate vending, hiring, coin or paper currency dispensing or refunding apparatus
- G07F7/08—Mechanisms actuated by objects other than coins to free or to actuate vending, hiring, coin or paper currency dispensing or refunding apparatus by coded identity card or credit card or other personal identification means
- G07F7/10—Mechanisms actuated by objects other than coins to free or to actuate vending, hiring, coin or paper currency dispensing or refunding apparatus by coded identity card or credit card or other personal identification means together with a coded signal, e.g. in the form of personal identification information, like personal identification number [PIN] or biometric data
- G07F7/1025—Identification of user by a PIN code
- G07F7/1033—Details of the PIN pad
- G07F7/1041—PIN input keyboard gets new key allocation at each use
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F3/00—Input arrangements for transferring data to be processed into a form capable of being handled by the computer; Output arrangements for transferring data from processing unit to output unit, e.g. interface arrangements
- G06F3/01—Input arrangements or combined input and output arrangements for interaction between user and computer
- G06F3/048—Interaction techniques based on graphical user interfaces [GUI]
- G06F3/0487—Interaction techniques based on graphical user interfaces [GUI] using specific features provided by the input device, e.g. functions controlled by the rotation of a mouse with dual sensing arrangements, or of the nature of the input device, e.g. tap gestures based on pressure sensed by a digitiser
- G06F3/0489—Interaction techniques based on graphical user interfaces [GUI] using specific features provided by the input device, e.g. functions controlled by the rotation of a mouse with dual sensing arrangements, or of the nature of the input device, e.g. tap gestures based on pressure sensed by a digitiser using dedicated keyboard keys or combinations thereof
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/30—Authentication, i.e. establishing the identity or authorisation of security principals
- G06F21/31—User authentication
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/30—Authentication, i.e. establishing the identity or authorisation of security principals
- G06F21/31—User authentication
- G06F21/36—User authentication by graphic or iconic representation
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/60—Protecting data
- G06F21/62—Protecting access to data via a platform, e.g. using keys or access control rules
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06Q—INFORMATION AND COMMUNICATION TECHNOLOGY [ICT] SPECIALLY ADAPTED FOR ADMINISTRATIVE, COMMERCIAL, FINANCIAL, MANAGERIAL OR SUPERVISORY PURPOSES; SYSTEMS OR METHODS SPECIALLY ADAPTED FOR ADMINISTRATIVE, COMMERCIAL, FINANCIAL, MANAGERIAL OR SUPERVISORY PURPOSES, NOT OTHERWISE PROVIDED FOR
- G06Q20/00—Payment architectures, schemes or protocols
- G06Q20/38—Payment protocols; Details thereof
- G06Q20/40—Authorisation, e.g. identification of payer or payee, verification of customer or shop credentials; Review and approval of payers, e.g. check credit lines or negative lists
- G06Q20/401—Transaction verification
- G06Q20/4012—Verifying personal identification numbers [PIN]
- G—PHYSICS
- G07—CHECKING-DEVICES
- G07F—COIN-FREED OR LIKE APPARATUS
- G07F7/00—Mechanisms actuated by objects other than coins to free or to actuate vending, hiring, coin or paper currency dispensing or refunding apparatus
- G07F7/08—Mechanisms actuated by objects other than coins to free or to actuate vending, hiring, coin or paper currency dispensing or refunding apparatus by coded identity card or credit card or other personal identification means
- G07F7/10—Mechanisms actuated by objects other than coins to free or to actuate vending, hiring, coin or paper currency dispensing or refunding apparatus by coded identity card or credit card or other personal identification means together with a coded signal, e.g. in the form of personal identification information, like personal identification number [PIN] or biometric data
- G07F7/1025—Identification of user by a PIN code
- G07F7/1033—Details of the PIN pad
- G—PHYSICS
- G07—CHECKING-DEVICES
- G07F—COIN-FREED OR LIKE APPARATUS
- G07F7/00—Mechanisms actuated by objects other than coins to free or to actuate vending, hiring, coin or paper currency dispensing or refunding apparatus
- G07F7/08—Mechanisms actuated by objects other than coins to free or to actuate vending, hiring, coin or paper currency dispensing or refunding apparatus by coded identity card or credit card or other personal identification means
- G07F7/10—Mechanisms actuated by objects other than coins to free or to actuate vending, hiring, coin or paper currency dispensing or refunding apparatus by coded identity card or credit card or other personal identification means together with a coded signal, e.g. in the form of personal identification information, like personal identification number [PIN] or biometric data
- G07F7/1025—Identification of user by a PIN code
- G07F7/1075—PIN is checked remotely
- G—PHYSICS
- G07—CHECKING-DEVICES
- G07F—COIN-FREED OR LIKE APPARATUS
- G07F7/00—Mechanisms actuated by objects other than coins to free or to actuate vending, hiring, coin or paper currency dispensing or refunding apparatus
- G07F7/08—Mechanisms actuated by objects other than coins to free or to actuate vending, hiring, coin or paper currency dispensing or refunding apparatus by coded identity card or credit card or other personal identification means
- G07F7/10—Mechanisms actuated by objects other than coins to free or to actuate vending, hiring, coin or paper currency dispensing or refunding apparatus by coded identity card or credit card or other personal identification means together with a coded signal, e.g. in the form of personal identification information, like personal identification number [PIN] or biometric data
- G07F7/1025—Identification of user by a PIN code
- G07F7/1091—Use of an encrypted form of the PIN
Definitions
- This inventionrelates generally to the field of user authentication, and more particularly to the field of PIN-based verification.
- the inventionis suited for use in situations where a user is required to enter a code, such as a Personal Identification Number (PIN), which is validated prior to completing an operation.
- PINPersonal Identification Number
- the operationmight be any type of operation.
- Authenticationis a technique used in a variety of situations where an individual's identity and/or authorisation needs to be verified prior to being allowed to perform an act or gain access to some controlled or managed resource such as a device, building, a computer system, a financial account, a service etc.
- identifiersuch as a code or combination of symbols
- the identifieris stored in association with a particular user or group of users, and may sometimes be stored and/or used in conjunction with another pre-determined identifier such as a username, for example.
- the identifieris often selected by the user himself although sometimes it may be the resource manager or owner who determines it. The user may, in many cases, be able to change their previously selected identifier.
- the identifieris chosen when the user initially joins an organisation; for example, when he begins employment at a certain company, or registers with a provider for a certain service.
- the identifierAfter the identifier has been selected and assigned to an authorised individual, that user is required to supply the pre-determined identifier each time he requests permission to perform the controlled act or gain access to the resource or service.
- the user's inputted identifieris compared with the stored version. If the user is able to supply the correct identifier then his identity is deemed to have been verified and access is granted. If, on the other hand, the correct identifier is not supplied then access is denied.
- PICPersonal Identification Code
- PINPersonal Identification Number
- PINPersonal Identification Number
- PINPersonal Identification Number
- PINPersonal Identification Number
- PINPersonal Identification Number
- PINPersonal Identification Number
- PINPersonal Identification Number
- PINPersonal Identification Number
- PINPersonal Identification Number
- other codes of different lengths and containing different types of characters or symbolsmay be used.
- the present inventionis not intended to be limited with regard to the length of the identifier used, or the type of characters it contains. For example, it may contain numeric digits, alphabetical characters, pictures, punctuation or any other kind of symbol, or a mixture thereof.
- PIN-based verification systemstypically comprise a keypad which enables the user to enter their pre-selected PIN.
- a typical keypad layout known in the artis shown in FIG. 14 a .
- a keypadis a set of buttons or ‘keys’ arranged in a block or ‘pad’.
- the keysare set out in a grid adjacent one another to form the pad.
- the keyshave indicia (identifiers) printed, engraved, embossed or otherwise displayed on them.
- the indicia on a keytypically consists of one symbol e.g. ‘6’ but could comprise more than one symbol e.g. ‘AB’.
- the indicia on the keysare usually arranged in an ordered manner, such as a sequential series. For example, numeric digits would typically be ordered in ascending order.
- keypadmay be used interchangeably with the term ‘pinpad’.
- Keypadsare often found on alphanumeric keyboards connected to computing devices. Other devices such as calculators, push-button telephones, combination locks, and digital door locks are also known to comprise a keypad.
- Other devicessuch as calculators, push-button telephones, combination locks, and digital door locks are also known to comprise a keypad.
- keypadsintroduced into mobile devices such as mobile (cellular) telephones, tablet computers, PDAs and so on.
- Many electronic devicesnow include computer processing capabilities and a touch screen interface capable of displaying a keypad. These may be used for a variety of purposes, including allowing an authorised user to ‘unlock’ the device by entering a passcode comprising a combination of pre-selected symbols, or entering a telephone number so as to make a call.
- Card-reading terminals used in financial transactionsalso have keypads to allow the user to enter his PIN via the keypad.
- Each type of smart phonemay have a particular style of keypad associated with it as its ‘default’ keypad.
- the keysmay be arranged in a particular format or layout, or a particular font may be used for the indicia. Therefore, the user of an electronic device may become familiar with a certain ‘look and feel’ with respect to the keypad on that device.
- An example of a typical keypad generated and displayed on a widely known smart phoneis shown in FIG. 14 b .
- the default keypadis generated by the execution of a procedure call within the phone.
- a touch screencan be used to display an image of a keypad having numbered or otherwise indicated ‘hot spots’ corresponding to the physical keys of the conventional counterpart.
- the usertouches the hotspots corresponding to the keys of his choice instead of pressing a moveable key.
- Sensors placed below the surface of the screensense which area(s) have been selected by the user, thus ‘reading’ the user's input.
- ATMsautomated teller machines
- Cashpoint machinespoint of sale devices for banking cards
- financial transactionsmay be carried out by swiping the magnetic stripe on the card so as to read the card's data, or by manual entry of the card details, rather than by inserting the card into a dedicated card-reading device.
- CNP transactionsare now commonplace in today's retail environment, with many customers choosing to conduct financial operations without being at the retail location.
- PIN-based technologyprovides a relatively secure authentication solution for ‘card present’ face-to-face transactions, fraud arising from CNP transactions is rising.
- CardEase Mobile®is a mobile payment app which, in conjunction with a mobile card reader, enables a retailer to take Chip and PIN mobile card payments from a customer.
- the retailerenters the amount of the purchase into an app downloaded and installed on his mobile phone (or tablet device).
- the retailerthen gives the card reader device to the customer who swipes or inserts his credit/debit card into the reader, and enters his PIN via the keypad on the reader device.
- the readerthen connects via Bluetooth to the app on the retailer's mobile device, which then connects to the service provider via the phone's internet connection for payment authorisation. Once the payment has been approved, the customer removes his card from the reader and the retailer emails or texts a receipt to the customer.
- this known arrangementrequires the use of the card reader.
- ituses the mobile phone to play the role of the point-of-sale terminal which would usually be located within the store/shop.
- the merchant taking the paymentstill needs to be at the same location as the customer making the payment because he must hand the card reader to the customer for use with his credit or debit card.
- the systemdoes not eliminate the need for a dedicated (i.e. purpose built) card-reading device.
- the iZettle arrangementcomprises a portable card reader device for reading a smart card, a portable reader device and a payment server.
- the aim of the disclosed methodis to eliminate the unsecure keyboard in a mobile phone used for entering a PIN, and instead use a separate PIN entry device which fulfills the EMV level specification.
- the disclosed approachuses an external PIN pad provided with all the required secure chips and components and which simply communicates with the mobile phone via a Bluetooth connection.
- the iZettle disclosuredoes not solve the problem of using unsecure mobile devices for PIN entry, it simply circumvents it by using a separate PIN entry device.
- Another known arrangement(also from the applicant of WO/2012/004395 A1) comprises a device (‘dongle’) and associated software which fits into the charging port of a smart phone.
- GB 2416058 Adiscloses an approach for verifying a request for access to a server.
- a random string of charactersis generated by a ‘combination generator’ in a security server. It then uses this random string to generate ‘image data’ which is sent from the server to the user's computer.
- the keypad on the user's computeris then modified in accordance with the image data. The user then enters his PIN using the modified keypad displayed on the computer.
- Positional data relating to the user's selection within the grid of keys(e.g. first-row-first-column) is stored as a record of the user's PIN.
- the positional datais then converted by the user's machine into character data such as a string of digits to form an encoded PIN which is then sent to the server for verification.
- the encoded PINcan be ‘decoded by knowing the image data’—lines 22, 23 of page 10. Therefore, as the image data is stored on the user's computer, if the security of the user's machine is compromised (e.g. hacked into, or is infected with malware) access may be gained to the image data, therefore enabling a third party to decode the user's PIN.
- a PIN-based authentication solutionwhich would enable a user to complete a CNP transaction using a PIN to authenticate in a secure manner.
- a PIN-based authentication solutionwhich would enable a user to complete a CNP transaction using a PIN to authenticate in a secure manner.
- a computer-implemented verification methodcomprising the step of: enabling a user to input an identifier into an electronic device having:
- the imagemay be referred to as a ‘scrambled keypad image’ for ease of reference.
- the keypadis operable in that has the functionality expected of a keypad by a person skilled in the art.
- keypadto mean an electronic or mechanical grid of keys, each having at least one indicia associated with it, which, when selected by a user, causes the associated indicia to be inputted into a device or system for storage and/or processing.
- the keypadis an electronic version of a keypad. It may be thought of as a ‘virtual’ keypad in that it is a software emulation of a mechanical keypad. It provides all the functionality of a mechanical keypad, comprising labelled keys which the user can select to provide input to a computer-based system.
- the keypadmay be generated on or by the electronic device. It may be generated by a procedure call.
- the proceduremay be provided within a library supplied by the manufacturer of the device.
- the scrambled keypad imageis a representation of a keypad.
- the representationmay comprise a representation of a whole keypad or at least part of a keypad. It may depict (represent, illustrate) one or more ‘keys’.
- the imagemay be electronically formed. It may be a graphical image, an optical image, a video or some other form of visual representation. It may be formed or stored in digital format in an electronic file.
- the scrambled keypad imageis not a keypad per se because it is devoid of any functionality. It is merely a representation of a grid of keys. Touching, clicking on or otherwise selecting any ‘key’ depicted in the image does not, in and of itself, produce any effect or generate an input.
- the scrambled keypad imagemay sometimes be referred to as a ‘keypad’ ‘scrambled keypad’ or an ‘overlying keypad’ purely for ease of reference because in use it appears to function as a keypad. Areas of the image may be referred to as ‘keys’, again only for ease of reference because this is what the user appears to see and use. However, it should be remembered that this is not actually the case, and that the image is not a keypad in reality.
- the inventionmay enable the user to enter his identifier via the same device component that is used to display the scrambled keypad image (the screen).
- the screenmay serve as both the output (display) device for the scrambled keypad image and the input device via which the user's identifier may be entered.
- the keypadis displayed on one device component (e.g. screen) and the user's input is received via another device component (e.g. keyboard).
- An advantage of this featureis that it may enable the user's input from the image to be mapped to the electronic keypad which may be at least partially hidden from the user's view such that the user's input is automatically encoded upon entry by the user.
- the inputis automatically encoded in the sense that the electronic device may not need to convert, encode or in any way process the user's input.
- the keypadmay be generated by a procedure call executed on the electronic device.
- the operable, electronic keypadmay be referred to as a ‘reference’ or ‘underlying’ keypad for ease of reference.
- the user's operation of the keypad key via the imagegenerates an encoded version of the user's intended input.
- the imageis displayed within the keypad zone such that as the user touches, clicks on or otherwise identifies a location within the image, an operable keypad key at that location is activated to provide an encoded version of the user's input.
- the user's identifieris input via the image.
- the usermay select a portion of the image in order to enter the identifier.
- the image portionmay resemble or depict a keypad key.
- the usermay operate the keypad through the image.
- the imagefunctions as a mask or cover superimposed over the keypad such that when the user touches, clicks on or otherwise identifies a location within the image it operates or activates the keypad key positioned at that location within the keypad zone.
- the keypad zone and/or the imageremains in a fixed position on the screen during input of the user's identifier.
- the image of the present inventionremains in a fixed location, this provides a solution which is easier to use and requires less processing by the electronic device.
- the inventionmay be viewed as enabling a scrambled keypad image to be ‘superimposed’ over an ‘underlying’ keypad such that when the user enters his input via the overlaid scrambled keypad image it is encoded in accordance with the layout of the underlying (preferably unseen) keypad.
- the ‘underlying’ keypadmay be viewed as an object generated and residing in the device's volatile memory at run-time to provide a model of a conventional mechanical keypad.
- the inventionprovides the advantage that the user's ‘real’ identifier is never stored within the device and is not transmitted for verification. Therefore, the user's identifier cannot be derived by any potential interceptor without knowledge of the mapping between the overlaid image and underlying, functional keypad.
- the mapping between the overlaid image and underlying keypadis not stored in the electronic device, or derivable by the electronic device.
- the mapping (or correlation) between the positions of the two sets of ‘keys’may be stored on a server remote from the electronic device.
- the scrambled keypad imagemay be sent from a remotely located computer-based resource to the electronic device.
- the resourcemay be a server.
- the scrambled keypad imagemay not be generated on the electronic device.
- a version of the scrambled keypad imagemay be stored on the server.
- the versionmay be a record of the order of the symbols (“keys”) in the scrambled keypad image.
- the keypad zonemay be a defined area or portion of the screen.
- the keypad zonemay occupy the entire screen area or a portion of the screen.
- the scrambled keypad imagemay be displayed such that it covers the keypad zone completely, exactly or partially.
- the underlying keypadis at least partially hidden from view so that the user is not able to see at least some of the keys of the keypad.
- the identifiermay be a Personal Identification Code. It may be a PIN (Personal Identification Number). It may comprise any number, type or combination of symbols or indicia (as explained above). The identifier may have been pre-selected by the user prior to executing the presently claimed method. The identifier may be stored remotely from the electronic device e.g. on a server.
- the scrambled keypad image and/or keypadmay comprise numeric digits, alphabetical characters, punctuation, symbols or any other indicia, or a combination thereof. One or more symbols may be associated with each key.
- the usermay be able to select a plurality of “keys” in the scrambled keypad image to input an identifier comprising more than one symbol.
- the scrambled keypad imagemay be scrambled with respect to a reference keypad.
- the keypad imagemay depict a block or grid comprising a plurality of adjacent keys. It may be ‘scrambled’ in the sense that the symbols on the “keys” are not in sequential order and/or not in the order which one would expect, perhaps with reference to the reference keypad.
- the scramblingmay be in accordance with a random generation process, or a process that approximates to a random process.
- the reference keypadmay be the keypad operable within the keypad zone, or a default keypad associated as standard with a make, model, type of electronic device.
- the same indiciamay be present in both the underlying keypad and the scrambled keypad image but they are provided in different positions.
- the order of the keys in the reference keypadis different from that of the scrambled image.
- the scrambled keypad imagemay provide the same ‘look and feel’ as the default keypad associated with the electronic device, but with the “keys” in different relative positions.
- the respective positions of one, some or all “key(s)” in the scrambled keypad imagemay be different from the position of the same key(s) in the underlying keypad.
- the usermay operate the keys of the underlying keypad via the scrambled keypad image by interacting with the “keys” displayed on the screen.
- the user's inputmay be entered by the user touching the screen (with a finger or other device) or by selecting the desired “key(s)” using a pointing device such as a mouse or tracker ball.
- a pointing devicesuch as a mouse or tracker ball.
- Other selection methodsmay be used to similar effect, thus falling within the scope of the invention.
- the position and/or dimensions of the keypad zonemay be specified by a procedure or method call.
- the keypad zonecomprises a plurality of sub-zones or ‘hot spots’.
- the position of at least one ‘key’ in the scrambled keypad image and/or keypadmay correspond to the position of a sub-zone such that there may be a mapping between the “keys” of the scrambled keypad and the keys of the keypad and/or the plurality of sub-zones. It is desirable that the mapping is not derivable from or by the electronic device.
- the hotspotsmay underlie the keys of the scrambled keypad image.
- the (underlying) keypadmay be scrambled after each of the user's key selections. Thus, a different scrambled underlying keypad may be used for each keystroke of the user's input.
- the scrambled keypad imageis received by the electronic device from a computer-based resource (e.g. a server) located remotely from the electronic device. It may be sent to the electronic device from the server in respect to a request for an image, the request being sent from the device to the server.
- the scrambled keypad imagemay be generated by the server.
- the scrambled keypad imageis pre-generated. In one embodiment this may mean that it is generated prior to, not in response to, the request from the electronic device.
- the imagemay be generated prior to execution of the verification method.
- the encoded version of the user's inputmay be sent from the electronic device to a remote computer-based resource.
- This resourcemay be a server.
- the serverreceives the encoded version of the user's input and processes it. The processing may provide a decoded version of the user's inputted identifier.
- the user's ‘real’ identifiermay not be transmitted. Only the encoded version may be transmitted, which may be meaningless to an unauthorised party who does not know the mapping between the the “keys” in the scrambled keypad image and the keys in the underlying keypad.
- the decodingmay be performed using a stored version or form of the scrambled keypad image.
- the stored version or form of the configuration of the keysmay be a filename.
- the decoding stepmay provide a decoded version of the user's input.
- the user's ‘real’ identifiermay be generated by translating each symbol in the encoded version into its corresponding counterpart in the scrambled keypad image.
- the user's decoded inputmay be compared with a stored version of the identifier.
- the user's inputmay be deemed to be correct if the input matches the stored identifier.
- the methodfurther comprises the steps:
- the methodmay further comprise the step of:
- the methodmay further comprise the step of:
- the methodmay further comprise the step of:
- the positions of the keys in the scrambled keypad imageremain unchanged relative to one another during input of the user's identifier. This is in contrast to prior art arrangements in which the position and/or order of the keys displayed to the user may scramble or rearrange or move on the screen after each of the user's key selections and/or after each verification session.
- the symbol of at least one key in the scrambled keypad imageis at least partially obscured or obfuscated but remains readable to the user. This may have benefits in making the representation difficult to read using OCR software. This enhances the security of the system and method.
- the electronic devicemay be a mobile telephone, a PC, a tablet computer, a laptop, a PDA, a card-reading terminal or other electronic device having a screen.
- the electronic devicemay be able to support a communications protocol such as TCP/IP, either over a wireless or fixed line, although other protocols may be supported, such as Bluetooth, RS232 etc.
- the communication between the device (e.g. mobile phone) and the computer-based resource (e.g. server)may be via a fixed telecommunications line or via a mobile telecommunications/wifi etc. connection—essentially any IP-based device may be used.
- the scrambled keypad imagemay be displayed via a web browser, or an application embedded within a browser, or a standalone software application, and/or an application providing a graphical user interface to allow the user to interact with the scrambled keypad image.
- mapping correlation between the indicia positioning of the scrambled keypad image and the underlying keypadis stored remotely from the device, typically at the computer based resource remote from the device.
- the scrambled keypad imagemay be renamed and/or encrypted prior to being sent to the electronic device. This provides the benefit that 3rd parties (such as malware) are prevented or at least impeded from intercepting and decoding the identifier.
- the methodmay further comprise the step of delivering an indicator to the user to confirm that the scrambled keypad image has been provided by a legitimate source.
- the indicatormay be a ‘watermark’.
- the indicatormay be a textual message, image, video, sound, vibration or other tactile indication.
- the indicatormay have been chosen by the user.
- the scrambled keypad imageis erased from the electronic device following the user's input, or following a specified period of time.
- a new (i.e. different) scrambled keypad imagemay be sent to the device if the user makes a mistake when inputting the identifier.
- PICCPersonal Identification Code
- a computer-implemented method for verifying a pre-stored Personal Identification Codecomprising the steps:
- a computer-implemented method for verifying a pre-stored Personal Identification Codecomprising the steps:
- a computer-implemented verification methodcomprising the step of:
- the benefits of the inventioninclude:
- FIGS. 1 to 4illustrate some examples of the various types of keypads that can be generated in accordance with the invention.
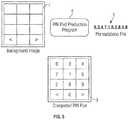
- FIG. 5illustrates the production of a scrambled keypad representation according to an exemplary embodiment of the invention.
- FIG. 6illustrates the Registration process in accordance with the invention.
- FIG. 7illustrates an exemplary custom keypad database created for the registered device.
- FIG. 8shows an illustrative transaction process in accordance with the invention
- FIGS. 9 and 10illustrate an overview of an example secure transaction application process in accordance with an embodiment of the invention.
- FIG. 11shows an illustrative ‘standard’ keypad in accordance with an embodiment the invention.
- FIGS. 12 a , 12 b and 12 cshow examples of scrambled keypad images which are suitable for being superimposed over the standard keypad of FIG. 11 .
- FIG. 13shows a scrambled keypad images being superimposed on top of the standard (reference) keypad of a device.
- FIG. 14 ashows a standard numeric key pad as known in the prior art.
- FIG. 14 bshows a numeric keypad on a mobile phone as known in the prior art.
- FIG. 15 ashows a pre-generated keypad image prior to the application of a watermark.
- FIG. 15 bshows the keypad image of FIG. 15 a with the watermark provided in the bottom left corner of the keypad zone.
- FIG. 15 cshows the keypad image of FIG. 15 b but with the watermark in a different position (bottom left).
- FIG. 15 dshows the keypad image of 15 a with a photographic image used as a watermark in the background.
- FIG. 16 a to FIG. 16 eshow different scrambled keypad images generated from 4 different numeric sequences.
- FIG. 17shows a scrambled keypad image having a combination of alphabetical and numeric keys.
- FIG. 18shows three partial images which, when shown repeatedly in rapid succession, form an apparently static, recognisable image.
- FIG. 19shows an example of how the invention may be implemented within a financial transaction processing system.
- FIGS. 20A-20Eshow an example of the generation of an encrypted PIN based on a user's PIN.
- an exemplary embodimentis now described in relation to use with a mobile phone.
- the inventionmay be used to perform PIN verification on a variety of different types of device, assuming that the device has some processing capabilities and a screen for the display of a keypad.
- the exemplary embodimentalso relates to use in respect of financial transactions.
- One application for which the invention is suitedis that of on-line banking.
- the skilled addresseewill readily understand that the invention may be employed in other settings and for non-financial purposes. It is not limited to business or commercial applications.
- the inventioncan be used in any situation where verification of an individual's identity is required before allowing that individual to have access to some controlled resource.
- That controlled resourcemay be any type of resource. It may be funds sitting in a financial account. Equally, it could be a building, a computer system, a patient's medical records, a service and so on. For example, it may be used for the verification of a passcode on a door lock to establish authentication prior to allowing entry to a building.
- the inventiondoes not constitute a means for performing a transaction per se. It is a verification tool useful for authenticating the identity of an individual who has requested access to a controlled resource. It does not dictate how that access is performed after authorisation is established, neither does it dictate how any other operation or possible transaction is conducted following successful verification.
- the exemplary embodiment described belowessentially operates by creating an image of a scrambled version of a keypad (which may alternatively be called a ‘PIN pad’).
- the scrambled keypad imageis sent for presentation or display on the target electronic device 1 for the user to view.
- the target deviceis a mobile phone 1 , as shown in FIG. 6 .
- the scrambled keypad imageis arranged to resemble the standard, default keypad for the device.
- Each brand and/or model of devicetypically has its own style of default keypad which might be different in layout, symbols, size, colour etc. from the default keypads associated with other devices.
- the default keypadis usually generated and displayed on the mobile phone by a procedure call, which specifies the format of the keypad for that device and where it is to be displayed on the screen.
- the default keypadis a grid which occupies a specific area on the screen i.e. it is displayed at a specified location. It is a pre-defined area or portion (referred to herein as a ‘keypad zone’) within the phone's screen.
- the keypad zoneis divided up into sub-zones wherein each sub-zone represents a key in the default key pad. Another way of saying this is to say that each sub-zone is associated with a particular symbol. The symbol for each key is displayed for the user to see on the screen within the location of its respective sub-zone. Therefore, if the user selects (e.g. touches or clicks on) an area designated to a particular sub-zone, the symbol for that associated key is recorded.
- the keypadserves as a virtual version of a mechanical keypad, generated electronically by software, detecting the location of the user's input within a defined screen area and using that to generate the input data rather than using physically pressable keys.
- each subzoneis essentially a ‘hotspot’ on the screen, and a plurality of hotspots are combined adjacent one another to form a keypad.
- the default keypad 2 of the phoneis arranged as a 3 ⁇ 4 grid of keys, each key 4 having a symbol associated with it. In this case, the symbols include numeric digits.
- Each key 4is a ‘hotspot’ area of the screen, each hotspot being associated with a symbol in the virtual keypad.
- FIG. 11An example of a well-known style of default keypad 2 used with smart phones is shown in FIG. 11 .
- the default keypad 2is generated on the target device 1 itself—it is not sent to the device 1 from the remotely located server.
- This standard keypad 2is then ‘overlaid’ with the scrambled keypad image 3 which is sent to the phone and is displayed on the screen at the keypad zone.
- This superimpositionis achieved by displaying the image of the scrambled keypad within the keypad display zone such that the positions of the scrambled ‘keys’ correspond to the positions of the hotspots in the default keypad.
- the alignment of the two keypadsis such that only the scrambled keypad image is seen by the user and the underlying, operable keypad is hidden, at least partially but preferably entirely, by the image. Therefore, as far as the user is concerned, there is only one keypad, which looks exactly like the keypad the user expects, except with the keys in different positions relative to one another.
- the default keypad for the mobile phoneis the ‘norm’ against which the scrambled keypad is referenced, it may be referred to as a ‘reference keypad’.
- FIGS. 12 a , 12 b and 12 cshow examples of keypad images 3 which are suitable for overlay on top of the standard keypad 2 of FIG. 11 .
- the scrambled keypadis sent to the phone as an image. Alternatively, it could be sent as a video file, to be discussed in more detail further below.
- This picture, video or image 3may be referred to as a ‘representation’ because in one sense it represents a physical (depressible) keypad.
- the scrambled keypad image 3has been pre-generated (i.e. prior to the initialisation of the verification process). It is randomly selected from a set of pre-generated scrambled keypad representations and then sent over a telecommunications network to the handset (i.e. mobile phone) 1 .
- the scrambled keypad image of FIG. 3is a representation of the default keypad layout 2 .
- the difference between the default keypad 2 and the scrambled keypad image 3is that the respective keys 4 are ordered differently. In other words, the same digits are present in each keypad but at least two are in different positions within the keypad grid.
- This keypad representation 3has been generated to have exactly the same dimensions as the default keypad so that it can perfectly superimpose it.
- the mobile phone usercustomer views only one seamless keypad.
- the useris unaware that there is an underlying keypad 2 which has been generated in the background, behind the one that he sees and uses for entering his input.
- the imageis sent to the user's device together with one or more instructions to invoke or call the necessary procedure for generating the underlying keypad.
- the randomly-selected, scrambled keypad image 3is effectively overlaid onto the phone's default keypad 2 so that when the user enters his PIN, a different result is generated within the device other than that which the user intended to enter, or at least thought he was entering. This is achieved as a result of the relationship (mapping) between the differently positioned keys 4 in the two keypads 2 , 3 .
- the usertouches the screen at a particular location to enter a digit shown in the overlying scrambled keypad image 3 , but this is interpreted as being the digit in the underlying keypad 2 at that sub-zone.
- As the user enters a subsequent inputits corresponding, underlying symbol is concatenated to the previous input to construct a complete PIN.
- an encoded version of the user's PINis produced based upon the position of the hidden keys 4 which the user selects via the scrambled keypad representation 3 . If the user makes a mistake, a new (different) keypad representation 3 is sent to the device 1 .
- the PIN that the user thinks he is enteringis not the PIN recorded by the software residing on the user's phone.
- the user's ‘real’ PINis never stored on the insecure phone 1 , and is not transmitted over any (insecure) network. Only the encoded version is stored, transmitted.
- the encoded version of the PINmay be encrypted prior to transmission to further enhance security.
- any interceptorwould be unable to decode, guess or re-translate the real PIN without knowing how the positions of the keys in each keypad map to one another.
- the decoding processis handled by a component of the invention which ‘knows’ the layout of the keys in both keypads and is, therefore, able to map the encoded digits back to their original counterparts, thus arriving back at the user's intended input.
- This deciphered PINcan then be compared against the user's previously stored PIN for verification purposes.
- the scrambled keypad image 3is encrypted before it is sent to the phone 1 .
- the phone 1Upon arrival at the phone 1 it is loaded into a secure or protected portion of memory on the device 1 (or at least as protected as it can be).
- all of the usual security featuresare used by the invention as if the customer's real PIN has been entered (rather than a translated version). This provides another layer of security and protection.
- the ‘PIN Pad Production Program’ 6is responsible for generating all of the scrambled keypad images 3 used throughout the system. An overview of this aspect of the invention is shown in FIG. 5 .
- PIN pad (image) generationscrambled key pad images that would have one or more keys positionally corresponding to the standard keypad are discarded.
- the PIN pad productionis therefore preferably not purely random, but is subjected to a selection process to select/discard according to a specific criteria.
- the PIN pad (image) generationtakes place in a secure environment, typically complaint with payment card industry data security standard.
- the output resolution and file typemust be initially set up before use on a particular target device 1 (in this case the type of mobile phone). This ensures that outputted images are generated to the optimum resolution for that device e.g. 256 ⁇ 184.
- a master ‘Background Image’ 7is then selected which matches the resolution as set above, and a ‘Permutations File’ 5 selected containing all the required permutations of digits (keys) for the final keypad images.
- this file 5must be a comma separated text file with each permutation on a new line.
- each permutationcould be separated by a # or *.
- the ‘Permutations File’ 5is then merged with the ‘Background Image’ 7 using the user's selection of Font Type, Size and Colour to produce the completed keypad image 3 .
- the completed keypad image 3is then optimized and reduced in size to be as small as possible for optimum transmission speed.
- the background image 7may be manipulated.
- the colour of the background and/or the default font type, size and colourcan be altered so that an unlimited database of keypads may be generated for every type of screen and device.
- advertisements, educational messages or other contentmay be incorporated in the presented imagery.
- These keypad imagesmay employ special fonts or colours to enable any specific regional characters e.g. Arabic to be used, and also to ensure that the images cannot be read by unauthorised Optical Character Recognition programs (thus enhancing security).
- Each keypad image that is producedis also given a unique filename and a master index is created for all keypad images that have been generated.
- a scrambled keypad imageis sent to the device, a copy of the filename of that image is temporarily stored. This filename contains the order of the keys within the keypad image. This enables the mapping between the scrambled keypad image and the reference keypad to be recorded.
- the scrambled keypad image 3is renamed before it is encrypted and sent to the remote device 1 ; this prevents malware or other unauthorised parties from possibly intercepting and decoding the PIN.
- FIGS. 1 to 4illustrate some examples of the various appearances that the scrambled keypad images 3 can be provided with in accordance with the invention.
- FIG. 2shows a scrambled keypad image 3 having a background of autumn leaves. This can be used by the retailer for seasonal variations or can be used for advertising purposes.
- FIG. 3shows a black and white only image distorted so that it cannot be read by OCR software. The skilled addressee will be aware that such images require high resolution screens to display correctly.
- FIG. 4shows a monochrome keypad image that has been modified for the Arabic alphabet.
- the skilled addresseewill appreciate that this regional difference in the characters can also be combined with the other imagery techniques methods illustrated in FIGS. 2 and 3 .
- a video overlaymay be used instead of a static image to further decrease the potential that OCR software could be used to read the keypad. This feature could also be used for advertising purposes.
- the scrambled keypad imageis presented to the user in a plain format (ie non special fonts are used and the background is ‘normal’) but the file itself is a small video file which, when played, tricks the eye into thinking that the image is solid and static. In reality no single frame contains enough information for it to be reverse engineered back into understandable, useable content.
- the systemcan be achieved in as little as 3 frames, each played quickly and in succession so as to appear static.
- An exampleis given in FIG. 18 .
- the static word ‘Licentia’is displayed but the individual images are unreadable by an OCR package.
- FIG. 6This aspect of the invention is illustrated in FIG. 6 .
- a device 1must be registered before it can be used with the system of the present invention and a small application 8 downloaded to the target device 1 . If the device being used is a mobile phone 1 then the update process can occur ‘Over The Air’ automatically; if the device is a fixed terminal then the software 8 may be downloaded over a fixed line, although it may alternatively be built into the device at the time of manufacture and simply updated if required.
- a custom database (or index) 13 of keypad imagesis created from the Master Database 11 .
- the Master Databaseconsists of keypad images that have been generated specifically for the user's registered model of device to ensure optimal display.
- This database (or Index) 11is then randomized 12 to ensure that no two devices have the same order of scrambled keypad images i.e. keypad ref ‘AXF015689.gif’ may be in location 65894 for one device but in position 125948 on another. Again, this enhances security.
- user registrationmay not be a requirement. This may be the case where the software is integrated into a 3 rd party application. In such embodiments, the required registration method may have been put in place by the third party.
- FIG. 8This aspect of the invention is illustrated in FIG. 8 .
- An authenticationcan be initiated by several methods depending on the manner in which the system has been integrated with 3 rd party applications.
- the serverwhich may be referred to as the ‘computer-based resource’
- the incoming device 1is identified and authenticated and, if successful, the next keypad image from the device's ‘Index’ 13 is encrypted and transmitted to the device 1 .
- the keypad imagesare sent sequentially as per the devices ‘index 2 ’ as shown in item 13 of FIG. 7 (in order from top to bottom) and are not reused.
- FIG. 9Secure Terminal Application This aspect of the invention is illustrated in FIG. 9 and FIG. 10 .
- the ‘Secure Terminal Application’is the program that resides on the target device/phone 1 or the fixed terminal and is responsible for the secure input and transmission of the user's inputted PIN back to the server.
- a keypad 2is created on the device in a 3 ⁇ 4 grid. Each hotspot is assigned a numerical character. The application then ‘overlays’ this reference keypad 2 with the randomised keypad representation 3 that has been pre-generated and sent down to the handset 1 . This scrambled keypad representation 3 has been generated to exactly the same dimensions as the keypad 2 underneath and perfectly overlays it, as described above.
- the central server(‘computer-based resource’) receives the incoming encoded and encrypted PIN from the handset 1 it must be converted back into the original user PIN.
- the ‘Decryption Engine’which is held on a separate secure server solely for this purpose.
- the unique filename for the keypad image that was sent to the device 1is temporarily stored.
- This filenamecontains the order of the keys within the keypad i.e. for the keypad image shown in FIG. 9 the filename would be ‘0347152986’. This enables the mapping between the scrambled keypad image and the reference keypad to be recorded. For security purposes, the scrambled keypad image 3 is renamed before it is encrypted and sent to the remote device 1 .
- the messageis firstly decrypted using the shared key used for the handset/device (this may be Triple DES or Public Private Key, or whatever is deemed appropriate during development according to the handset).
- the shared key used for the handset/devicethis may be Triple DES or Public Private Key, or whatever is deemed appropriate during development according to the handset.
- the encoded PIN that was generated by the user inputmust be decrypted.
- the filename of the keypad image that was sentis copied into a temporary array and then for each number that was generated by the user input the number in the corresponding array position is substituted, thus revealing the actual PIN number.
- the handsetgenerated and transmitted an encrypted PIN of 0476.
- This PIN number 6725is then encrypted using standard banking encryption and passed to the Acquirer or banking partner for processing. It should be noted that this is only further encrypted and passed to the acquirer in embodiments relating to a financial transaction.
- the datamay or may not be further encrypted depending upon the nature and requires of the specific application.
- the arrayis then securely erased to ensure security, along with any other temporary data.
- 12 smaller key picturesmay be provided.
- the phone or other devicemay be arranged to to select a random number and rearrange the individual pictures into a 3 ⁇ 4 array (and thus making up a virtual keypad on demand).
- Such embodimentspresent potential security loopholes and may provide several access points for malware to obtain the user's PIN (as the handset/device would have to transmit the random number and thus the order of the PIN pad back to the server). Therefore, such an embodiment is suitable for applications where required security levels are somewhat relaxed.
- the devicecould be a personal computer, or a laptop, or a tablet computer.
- the embodimentwould function essentially as described above except that as general purpose computing devices, such as PCs, do not typically comprise a standard procedure call for generating a keypad as mobile phones do, the keypad zone and hotspots are specified by a purpose-built software component executing on the device.
- the softwarespecifies the portion of the screen which makes up the keypad zone, and the locations of the sub-zones (keys) and their associated symbols within the keypad zone.
- the scrambled keypad imageis displayed at that location to provide the superimposition technique described above.
- the underlying keypadis generated using the same (or substantially the same) procedure call used by the smart phone implementation.
- a terminalcould be provided which resembles the known card-reading terminals used in retail environments.
- the terminalmay comprise a touch screen and comprise internal components replicating those of a mobile telephone.
- the terminalcan receive and send data as a phone can, and the terminal can function is accordance with the invention as described above in with reference to the target device being a mobile phone.
- the inventioncan be configured for use with a variety of computing-related devices to equal effect.
- the inventioncan be configured to include various features which further enhance the security of the user's data.
- Such a featuremay be implemented in a variety of ways. For example, when a retailer registers to use the system they choose and store a secret indicator (word, phrase, number, name, image etc.) that only they and the trusted party knows. Then, when a transaction is required the following process is performed:
- the merchantWhen the PIN entry screen is displayed the merchant must physically check that the pre-selected secret word etc that they registered is displayed on the screen before handing the terminal to the customer for their PIN entry. This is essentially the same principle which is employed in ssl technology wherein one looks for the small yellow lock icon as confirmation of the site's legitimacy.
- FIG. 15 ashows a pre-generated pin pad picture that is blank. The system creates a new pin pad picture to include the user's secret word ‘jellybean’ which is then encrypted and sent to the device. This is shown in FIG. 15 b.
- the usermay also choose where to have the watermark displayed e.g. right, left, centre, top etc.
- a keypad image having the watermark in the bottom left corneris shown in FIG. 15 c .
- a text colour or font style, or sizemay also be chosen.
- the watermarkdoes not have to be in textual form.
- the usermay upload a photograph or other file (for example, a family photo or a photo of the shop etc.) so that this picture is displayed in the background. This is illustrated in FIG. 15 d.
- This watermarking featureis suitable for employment with all embodiments of the invention, irrespective of the context in which the invention is used or the nature of the device used to display the keypad (e.g. online through a browser, via a terminal arranged for use with the invention, or a mobile phone etc.)
- the inventionmay employ one or more techniques for making it more difficult for an unauthorised party to figure out, discern or calculate the mapping between the displayed keypad image (i.e. the one that the user uses to enter his PIN) and the underlying keypad.
- One possible approach to overcoming thiscould be to create more than one underlying keypad. For example, a virtual keypad could be generated for each key press. An example is given below.
- FIG. 16 ashows a scrambled keypad image
- FIG. 16 bshows an ‘underlying’ keypad. If the user's PIN is 1111 then the encoded PIN sent back to the server would be 9999. This provides a potential hacker with a starting point for an attempt at calculating or guessing the user's PIN.
- the top pin pad as per FIG. 16 ais sent to the target device as an image, in accordance with the description set out above. Then, 4 numeric sequences are sent for the creation of the underlying keypad e.g. 3156790482, 0746189352, 0347156289, 2581673904. This produces the keypads shown in FIGS. 16 b to 16 e.
- the code 9857is produced and sent back to the server for decryption.
- the serverknows which scrambled keypad image was sent, and which sequences of digits, the resulting encoded PIN appears to be much more random and is therefore much harder to decipher by an interceptor.
- the decryption process at the server endremains as set out above.
- the use of randomly generated strings of characters in the bottom keypadreduces the need to ‘filter’ the underlying keypads (as described above) to remove potentially unsuitable keypads which might provide an attacker with a possible starting point for an attack.
- FIG. 19illustrates one manner in which the invention may be implemented into a transaction system.
- FIG. 19includes the following system components, or modules.
- Device appan app that runs on a terminal or mobile phone to manage user interaction and technical process flow including initiating a payment transaction, interacting with card reader, requesting an oPinPad (i.e. scrambled keypad image), encrypting the entered oPin and sending the transaction online for authorization.
- oPinPadi.e. scrambled keypad image
- OPinPad Management Modulea stand-alone application module that runs in a central secure data center on a dedicated server. It holds a database of all oPinPad TIF images and manages distribution of the oPinPad TIFs on demand.
- Auth Clienta stand-alone application module that runs in a central secure data center, possibly on the same server as the oPinPad Management Module (or, in some embodiments on its own dedicated server). It receives the message from the Device and prepares it to be sent to the Payments Switch for Authorisation.
- HPSAM Appliancea stand-alone application module that runs in central secure data centre on a dedicated server.
- the servermay be security hardened.
- the deviceinitiates a payment transaction and captures the Amount (from the user interface) and Card Details (from the Card Reader). Sensitive data from the Card Reader is encrypted before getting to the App.
- the Appgoes online and requests an oPinPad from the server. If possible the oPinPad would be requested at the same time as the card details are retrieved from the Card Reader.
- the oPinPad Management Moduleretrieves an oPinPad (i.e. scrambled keypad image) from a database and assigns it with a Tag.
- the oPinPad TIF and the Tag (unique id)are sent back to the device.
- the oPinPad Arrayis sent to the HPSAM along with the Tag (unique id).
- the Device Appdisplays the oPinPad TIF (scrambled keypad) image on the device and gathers the oPin as described above; the oPin is immediately encrypted using a field encryption method (such as DUKPT).
- the whole authorization messageis then sent to the Auth Client for payments authorization (this message includes the Amount, the encrypted card details and the encrypted oPin).
- the Auth Clientgathers the transaction details and passes it on to the Payments Switch.
- the Payments Switchintercepts the transaction during standard routing processing so that the oPin can be replaced with the Real Pin. This is done by sending the oPin with the Tag to the HPSAM.
- the HPSAMretrieves the oPinPad Array and uses it to map the oPin to the Real Pin.
- the Real Pinis immediately encrypted using 3DES and a ZMK which is aligned with the Payments Switch.
- the Real Pinis sent back to the Payments Switch as a PinBlock and is added to the transaction to make an industry standard Online Pin payments authorization message (such as, for instance, an ATM message).
- the Real Pin blockis translated using an industry standard HSM such that the encrypted Pin can be handled by the receiving institution (Acquirer, Processor, Issuer).
Landscapes
- Engineering & Computer Science (AREA)
- General Physics & Mathematics (AREA)
- Physics & Mathematics (AREA)
- Theoretical Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- General Engineering & Computer Science (AREA)
- Computer Hardware Design (AREA)
- Software Systems (AREA)
- General Health & Medical Sciences (AREA)
- Bioethics (AREA)
- Health & Medical Sciences (AREA)
- Business, Economics & Management (AREA)
- Accounting & Taxation (AREA)
- Human Computer Interaction (AREA)
- Strategic Management (AREA)
- General Business, Economics & Management (AREA)
- Finance (AREA)
- Input From Keyboards Or The Like (AREA)
- Telephone Function (AREA)
- User Interface Of Digital Computer (AREA)
- Cash Registers Or Receiving Machines (AREA)
- Microelectronics & Electronic Packaging (AREA)
- Computer Networks & Wireless Communication (AREA)
Abstract
Description
- ‘A more practical solution would be if a credit card payment could be conducted using a well-known, non-bulky and commonly used device such as a mobile phone. However, an ordinary mobile phone does not have a built-in card reader where you could swipe your credit card, and even if that particular problem could be overcome, there is still and issue regarding the level of security a mobile phone provides. It is well known that for instance a spy program could infiltrate the mobile phone and hijack credit card information and identification information, such as the PIN code entered into the mobile phone via the phone's keyboard when conducting a credit card payment, without the user even knowing it. In light of the above, a standard mobile phone is generally not considered to be a secure device, and thus not suitable for making credit card payments with. Thus, finding a way to make secure credit card payments with a mobile phone is highly sought after’.
- could be implemented on a portable electronic device such as a mobile phone, tablet computing device, laptop, PDA etc, or on a desktop computer or fixed device;
- would enable PIN-based authentication to be performed on any suitably arranged device having some computing capabilities;
- would require the user to enter his PIN using the same digits as his stored PIN and in the same order (rather than requiring the user to enter an ‘encoded’ or somehow disguised/translated version of his PIN);
- would be easy and intuitive to use;
- would not require the user's machine to have access to the user's ‘real’ PIN, or any knowledge of how to calculate it
- would not need to execute any conversion or encoding algorithm (which carries with it a time and processing overhead, and can be used to discern the user's PIN).
- i) a screen; and
- ii) a keypad operable within a keypad zone of the screen;
by operating at least one key of the keypad via an image of at least part of a scrambled keypad which is displayed at least partially within the keypad zone.
- generating a plurality of scrambled keypad images;
- selecting one scrambled keypad image from the plurality; and
- sending a copy of the selected scrambled keypad image to the electronic device.
- removing at least one scrambled keypad image from the plurality prior to performing the selection.
- removing the selected scrambled keypad image from the plurality after sending the copy to the electronic device.
- removing from the plurality any scrambled keypad image which has at least one key in the same position as the same key in a reference keypad.
- generating a representation of a keypad wherein the position of at least one indicia in the representation is different from the position of the respective indicia in the keypad;
- sending the representation to a remote device for presentation to a user to enable the user to input a PIC using the representation;
- receiving an encoded version of the inputted PIC from the remote device;
- decoding the encoded version to provide a decoded version of the inputted PIC
- comparing the decoded version of the inputted PIC with the pre-stored PIC
- receiving a representation of a keypad from a remotely located computer-based resource, wherein the position of at least one indicia in the representation is different from the position of the respective indicia in the keypad;
- presenting the representation to a user to enable the user to input a PIC using the representation;
- generating an encoded version of the inputted PIC;
- sending the encoded version of the inputted PIC to the computer-based resource for decoding such that the decoded version of the inputted PIC can be compared with the pre-stored PIC.
- using a computer-based resource to generate a representation of a keypad wherein the position of at least one indicia in the representation is different from the position of the respective indicia in the keypad;
- sending the representation to a remote device;
- presenting the representation to a user via the remote device to enable the user to input a PIC using the representation;
- sending an encoded version of the inputted PIC from the remote device to the computer-based resource;
- using the computer-based resource to decode the encoded version to provide a decoded version of the inputted PIC and compare it with the pre-stored PIC
- enabling a user to input an identifier by selecting at least one key via a scrambled keypad presented to the user within a keypad zone of a screen associated with an electronic device.
- a reduction in the likelihood of fraud arising from CNP transactions;
- a significant reduction in the cost associated with such fraud;
- a shift in liability from the card issuer to the user in respect of fraudulent card usage;
- the convenience for the user of secure CNP transactions.
- 1. Logo onto
registration service 9 via a web-based interface (e.g. web site)10 - 2. Enter their personal details i.e. Name, Address, Postcode (ZIP), Phone Make Model, Email address, Mobile Phone Number
- The nature and type of data required may be stipulated by the system operator and vary from country to country depending on the application with which the system is being used. Furthermore, registration data may already be held by the operator as the customer may be an existing client and therefore only the application may need to be pushed to the device.
- 3. A link is then sent to the
mobile handset 1 for the user to follow or theapplication 8 is simply ‘pushed’ down to the handset.- When run for the first time, the
application 8 sets up thedevice 1 and downloads any additional data which may be required, such as encryption keys etc. A custom keypad image database is also created on the server for the registered device (as shown inFIG. 7 ).
- When run for the first time, the
- 1. Logo onto
- 1. Logo onto
registration service 9 via a web-basedinterface 10 - 2. Enter their personal details i.e. Name, Address, Postcode (ZIP), Phone Make Model, Email address
- As above for the mobile phone, the required data would be dictated by the system operator.
- 3. The device then connects to the server either via a fixed line or wireless and if required updates the internal application. Any additional data that is required, such as encryption keys etc., is downloaded. A custom keypad image database is also created on the server for the registered device (see
FIG. 7 )
- 1. Logo onto
- a. Manufacture card swipe or chip reading devices that are attached to the mobile device, or
- b. Push financial information and subsequent payment request down to the handset i.e. toll road applications; or
- c. Provide websites which require secure PIN entry to gain access to information when used in applications such as online banking access.
- 1. the consumer's card is read
- 2. The transaction amount is entered
- 3. the pin entry screen is displayed on the terminal
- Device: Payment Terminal or Mobile Phone where payment transaction is taking place
- oPin: “Obfuscated PIN”—the encoded PIN which is generated by the keys of the underlying Device keypad; this is not the actual cardholder's PIN
- Real Pin: The real PIN associated with the consumer's card that would be ‘swapped’ for the oPin before being verified by the card issuer
- oPinPad: Obfuscated Pin Pad (i.e. the scrambled keypad image)—the TIF image which is presented to the card holder to enter their PIN and having ‘keys’ in scrambled positions relative to the underlying Device keypad
- oPinPad Array: Array to be used for mapping the oPin with the Real Pin, as described above
- HPSAM: Hosted Payment Security Access Module
- HSM: Hardware Security Module
- Card Reader: The terminal/mobile device which contains or is connected to a Card Reader which retrieves payment card details from the consumer
- Tag: Unique identification number assigned to the oPinPad to assist with later processing
- ZMK: Zone Master Key.
| 0 | The device initiates a payment transaction and captures the Amount |
| (from the user interface) and Card Details (from the Card Reader). | |
| Sensitive data from the Card Reader is encrypted before getting to the | |
| App. The App goes online and requests an oPinPad from the server. If | |
| possible the oPinPad would be requested at the same time as the card | |
| details are retrieved from the Card Reader. | |
| 1 | The oPinPad Management Module retrieves an oPinPad (i.e. |
| scrambled keypad image) from a database and assigns it with a Tag. | |
| The oPinPad TIF and the Tag (unique id) are sent back to the device. | |
| 2 | The oPinPad Array is sent to the HPSAM along with the Tag |
| (unique id). All traces of the Tag/Array combination are deleted | |
| from the oPin Management Module (in particular from memory). | |
| 3 | The Device App displays the oPinPad TIF (scrambled keypad) image |
| on the device and gathers the oPin as described above; the oPin is | |
| immediately encrypted using a field encryption method (such as | |
| DUKPT). The whole authorization message is then sent to the | |
| Auth Client for payments authorization (this message includes | |
| the Amount, the encrypted card details and the encrypted oPin). | |
| 4 | The Auth Client gathers the transaction details and passes it on to the |
| Payments Switch. | |
| 5 | The Payments Switch intercepts the transaction during standard |
| routing processing so that the oPin can be replaced with the Real Pin. | |
| This is done by sending the oPin with the Tag to the HPSAM. | |
| 6 | Using the Tag, the HPSAM retrieves the oPinPad Array and uses it to |
| map the oPin to the Real Pin. The Real Pin is immediately encrypted | |
| using 3DES and a ZMK which is aligned with the Payments Switch. | |
| 7 | The Real Pin is sent back to the Payments Switch as a PinBlock and |
| is added to the transaction to make an industry standard Online Pin | |
| payments authorization message (such as, for instance, an ATM | |
| message). | |
| 8 | The Real Pin block is translated using an industry standard HSM |
| such that the encrypted Pin can be handled by the receiving | |
| institution (Acquirer, Processor, Issuer). | |
Claims (34)
Priority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| US16/718,158US11048783B2 (en) | 2012-07-20 | 2019-12-17 | Authentication method and system |
Applications Claiming Priority (11)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| GB201212878AGB201212878D0 (en) | 2012-07-20 | 2012-07-20 | Authentication method and system |
| GB1212878 | 2012-07-20 | ||
| GB1212878.1 | 2012-07-20 | ||
| GB1306053 | 2013-04-04 | ||
| GB1306053.8 | 2013-04-04 | ||
| GB201306053AGB201306053D0 (en) | 2012-07-20 | 2013-04-04 | Authentication Method and System |
| PCT/GB2013/051913WO2014013252A2 (en) | 2012-07-20 | 2013-07-17 | Authentication method and system |
| US201514416054A | 2015-01-20 | 2015-01-20 | |
| US15/094,383US10366215B2 (en) | 2012-07-20 | 2016-04-08 | Authentication method and system |
| US15/197,086US10565359B2 (en) | 2012-07-20 | 2016-06-29 | Authentication method and system |
| US16/718,158US11048783B2 (en) | 2012-07-20 | 2019-12-17 | Authentication method and system |
Related Parent Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US15/197,086ContinuationUS10565359B2 (en) | 2012-07-20 | 2016-06-29 | Authentication method and system |
Publications (2)
| Publication Number | Publication Date |
|---|---|
| US20200201960A1 US20200201960A1 (en) | 2020-06-25 |
| US11048783B2true US11048783B2 (en) | 2021-06-29 |
Family
ID=46881666
Family Applications (7)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US14/416,054Expired - Fee RelatedUS9552465B2 (en) | 2012-07-20 | 2013-07-17 | Authentication method and system |
| US15/094,383ActiveUS10366215B2 (en) | 2012-07-20 | 2016-04-08 | Authentication method and system |
| US15/197,086Expired - Fee RelatedUS10565359B2 (en) | 2012-07-20 | 2016-06-29 | Authentication method and system |
| US16/718,158Expired - Fee RelatedUS11048783B2 (en) | 2012-07-20 | 2019-12-17 | Authentication method and system |
| US16/730,017Expired - Fee RelatedUS11048784B2 (en) | 2012-07-20 | 2019-12-30 | Authentication method and system |
| US16/776,195Active2033-08-09US11194892B2 (en) | 2012-07-20 | 2020-01-29 | Authentication method and system |
| US17/537,257AbandonedUS20220156350A1 (en) | 2012-07-20 | 2021-11-29 | Authentication method and system |
Family Applications Before (3)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US14/416,054Expired - Fee RelatedUS9552465B2 (en) | 2012-07-20 | 2013-07-17 | Authentication method and system |
| US15/094,383ActiveUS10366215B2 (en) | 2012-07-20 | 2016-04-08 | Authentication method and system |
| US15/197,086Expired - Fee RelatedUS10565359B2 (en) | 2012-07-20 | 2016-06-29 | Authentication method and system |
Family Applications After (3)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US16/730,017Expired - Fee RelatedUS11048784B2 (en) | 2012-07-20 | 2019-12-30 | Authentication method and system |
| US16/776,195Active2033-08-09US11194892B2 (en) | 2012-07-20 | 2020-01-29 | Authentication method and system |
| US17/537,257AbandonedUS20220156350A1 (en) | 2012-07-20 | 2021-11-29 | Authentication method and system |
Country Status (18)
| Country | Link |
|---|---|
| US (7) | US9552465B2 (en) |
| EP (3) | EP3489918A1 (en) |
| JP (2) | JP6364408B2 (en) |
| KR (1) | KR101916173B1 (en) |
| CN (3) | CN104584086B (en) |
| AU (4) | AU2013291755B2 (en) |
| BR (1) | BR112015000980B1 (en) |
| CA (1) | CA2878728A1 (en) |
| GB (5) | GB201212878D0 (en) |
| IL (2) | IL236779A (en) |
| MX (2) | MX354996B (en) |
| MY (1) | MY171482A (en) |
| NZ (2) | NZ744304A (en) |
| RU (2) | RU2639674C2 (en) |
| SG (2) | SG11201500411YA (en) |
| TW (1) | TWI628555B (en) |
| WO (1) | WO2014013252A2 (en) |
| ZA (1) | ZA201409529B (en) |
Families Citing this family (50)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US9846866B2 (en)* | 2007-02-22 | 2017-12-19 | First Data Corporation | Processing of financial transactions using debit networks |
| GB201212878D0 (en) | 2012-07-20 | 2012-09-05 | Pike Justin | Authentication method and system |
| US10373149B1 (en) | 2012-11-12 | 2019-08-06 | Square, Inc. | Secure data entry using a card reader with minimal display and input capabilities having a display |
| IN2013CH01162A (en)* | 2013-03-18 | 2015-08-14 | Ncr Corp | |
| JP5796725B2 (en)* | 2013-03-22 | 2015-10-21 | カシオ計算機株式会社 | Authentication processing apparatus, authentication processing method, and program |
| KR101492054B1 (en)* | 2013-11-08 | 2015-02-10 | 한국정보통신주식회사 | Card reader, terminal and method for processing payment information thereof |
| US9613353B1 (en) | 2013-12-26 | 2017-04-04 | Square, Inc. | Passcode entry through motion sensing |
| JP6326247B2 (en)* | 2014-02-27 | 2018-05-16 | 沖電気工業株式会社 | Information processing apparatus, information processing system, information processing method, and program |
| CN103905590B (en)* | 2014-04-22 | 2018-03-06 | 锤子科技(北京)有限公司 | Mobile device and its dial panel |
| KR101514706B1 (en) | 2014-06-26 | 2015-04-23 | 주식회사 하렉스인포텍 | Method of user authentication using a variable keypad and biometrics and, the system thereof |
| US9483653B2 (en)* | 2014-10-29 | 2016-11-01 | Square, Inc. | Secure display element |
| US9430635B2 (en) | 2014-10-29 | 2016-08-30 | Square, Inc. | Secure display element |
| US10673622B2 (en) | 2014-11-14 | 2020-06-02 | Square, Inc. | Cryptographic shader in display hardware |
| JP6481487B2 (en)* | 2015-04-30 | 2019-03-13 | 富士通コネクテッドテクノロジーズ株式会社 | Information processing apparatus, input control program, and input control method |
| US10015364B2 (en)* | 2015-05-11 | 2018-07-03 | Pictureworks Pte Ltd | System and method for previewing digital content |
| GB201520741D0 (en)* | 2015-05-27 | 2016-01-06 | Mypinpad Ltd And Licentia Group Ltd | Authentication methods and systems |
| CN104850770A (en)* | 2015-06-05 | 2015-08-19 | 深圳市智诺微智能电子科技有限公司 | Gesture password input virtual keyboard and application method |
| KR101691173B1 (en)* | 2015-06-18 | 2016-12-30 | 한국정보통신주식회사 | A portable terminal, a method for processing transaction information using it |
| KR101691172B1 (en)* | 2015-06-18 | 2016-12-30 | 한국정보통신주식회사 | A portable terminal, a method for processing information using it |
| KR101691171B1 (en)* | 2015-06-18 | 2016-12-30 | 한국정보통신주식회사 | A portable terminal, a method for processing card information using it |
| KR101691170B1 (en)* | 2015-06-18 | 2016-12-30 | 한국정보통신주식회사 | A portable terminal, a method for processing card information using it |
| CN106485848B (en)* | 2015-08-31 | 2020-05-01 | 崔胜辛 | Key input system and method using disposable keyboard |
| KR101710998B1 (en)* | 2015-09-23 | 2017-03-02 | 주식회사 하렉스인포텍 | Method of user authentication using a variable keypad and, the system thereof |
| US9619802B1 (en)* | 2015-12-09 | 2017-04-11 | Square, Inc. | Interception of touch pad events for handling in a secure environment |
| AU2016380914B2 (en)* | 2015-12-28 | 2021-01-07 | Mobeewave Systems Ulc | System for and method of authenticating a user on a device |
| JP6786272B2 (en)* | 2016-06-24 | 2020-11-18 | キヤノン株式会社 | Image processing device, its control method, and computer program |
| EP3291504B1 (en)* | 2016-08-30 | 2020-03-11 | Wacom Co., Ltd. | Authentication and secure transmission of data between signature devices and host computers using transport layer security |
| FR3058814B1 (en)* | 2016-11-15 | 2019-10-25 | Ingenico Group | METHOD FOR PROCESSING TRANSACTIONAL DATA, COMMUNICATION TERMINAL, CARD READER AND CORRESPONDING PROGRAM. |
| FR3060171B1 (en)* | 2016-12-09 | 2019-08-02 | Ingenico Group | METHOD OF SECURING DATA ENTRY, COMMUNICATION TERMINAL AND CORRESPONDING PROGRAM. |
| RU2634179C1 (en) | 2016-12-12 | 2017-10-24 | Акционерное общество "Лаборатория Касперского" | Method and system for trusted information breakthrough to user |
| TWI621029B (en)* | 2017-05-02 | 2018-04-11 | Ctbc Bank Co Ltd | Personal identity authentication method and system using graphic lock |
| KR101981992B1 (en)* | 2017-11-14 | 2019-05-24 | 로움아이티 주식회사 | Method and apparatus for user authenticating using virtual keypad |
| US10869194B2 (en) | 2017-12-22 | 2020-12-15 | Dish Network L.L.C. | Devices, systems, and processes for authenticating devices |
| EP3518130A1 (en) | 2018-01-30 | 2019-07-31 | OneVisage SA | Method and system for 3d graphical authentication on electronic devices |
| US10893041B2 (en)* | 2018-10-10 | 2021-01-12 | International Business Machines Corporation | Single use passcode authentication |
| US11010467B2 (en)* | 2018-10-30 | 2021-05-18 | Blue Popcon Co.Ltd | Multifactor-based password authentication |
| CN109934025A (en)* | 2018-12-26 | 2019-06-25 | 电子科技大学 | An automatic login method for bank security controls |
| TR201905756A2 (en)* | 2019-04-18 | 2019-05-21 | Kartek Kart Ve Bilisim Teknolojileri Ticaret Anonim Sirketi | Software security system and method for PIN entry, storage and transmission to software-based POS (SoftPOS). |
| US11556628B2 (en) | 2019-04-30 | 2023-01-17 | International Business Machines Corporation | Multidimensional attribute authentication |
| KR102266470B1 (en)* | 2019-06-11 | 2021-06-17 | 주식회사 이니라인 | System and method for outputting character securely, and a recording medium having computer readable program for executing the method |
| CN110730162B (en)* | 2019-09-16 | 2022-03-18 | 北京齐尔布莱特科技有限公司 | Page verification method, mobile terminal and readable storage medium |
| US11127410B2 (en)* | 2019-11-12 | 2021-09-21 | Wen-Ta Chiu | Voice decoding device and method thereof |
| GB201916441D0 (en) | 2019-11-12 | 2019-12-25 | Mypinpad Ltd | Computer-implemented system and method |
| US11558375B1 (en)* | 2019-12-16 | 2023-01-17 | Trend Micro Incorporated | Password protection with independent virtual keyboard |
| WO2021183073A1 (en)* | 2020-03-12 | 2021-09-16 | Kartek Kart Ve Bi̇li̇şi̇m Teknoloji̇leri̇ Ti̇caret Anoni̇m Şi̇rketi̇ | A secure payment system with emv card transaction flow and pin confirmation without sharing card information of the mobile phone, computer or tablet of the cardholder and a method thereof |
| EP3979102A1 (en)* | 2020-09-30 | 2022-04-06 | Rubean AG | Electronic device for performing an authentication operation |
| WO2022172068A1 (en)* | 2021-02-10 | 2022-08-18 | Polu Vishwanath Reddy | System and method for user access control for accessing an authenticated entity |
| US11580210B2 (en)* | 2021-02-18 | 2023-02-14 | International Business Machines Corporation | Password authentication |
| US12141316B2 (en) | 2021-10-11 | 2024-11-12 | International Business Machines Corporation | Obfuscation of sensitive information through non-visual feedback |
| CN116049779A (en)* | 2022-12-05 | 2023-05-02 | 中国建设银行股份有限公司上海市分行 | Method, device, computing device and storage medium for password authentication |
Citations (409)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| GB271884A (en) | 1926-05-25 | 1928-06-28 | Ig Farbenindustrie Ag | Manufacture of ª‡-anthraquinonyl ketones |
| US2819067A (en) | 1955-12-22 | 1958-01-07 | Burroughs Corp | Check shingling machine |
| US3176324A (en) | 1963-01-11 | 1965-04-06 | American Metal Prod | Spring construction |
| US3201732A (en) | 1959-09-25 | 1965-08-17 | Westinghouse Electric Corp | Wound magnetic core having turns which are given a predetermined set in radius before winding |
| US3255323A (en) | 1964-05-21 | 1966-06-07 | Edward C Austin | Automotive maintenance signalling device |
| US3270720A (en) | 1963-03-09 | 1966-09-06 | Daimler Benz Ag | Rotary piston internal combustion engine |
| US3347103A (en) | 1964-11-27 | 1967-10-17 | Bendix Corp | Velocity sensor |
| US3364601A (en) | 1966-01-19 | 1968-01-23 | Albert H. Korenek | Apparatus for excavating plants for transplanting |
| US3375428A (en) | 1964-02-04 | 1968-03-26 | Lorain Prod Corp | Regulated rectifier circuit |
| US3392846A (en) | 1964-10-01 | 1968-07-16 | American Air Filter Co | Unit filter assembly |
| US3413071A (en) | 1963-07-18 | 1968-11-26 | Davis Chester | Hexamethyltriaminophenylfluorene printing composition and manifolding sheet therewith |
| US3621242A (en) | 1969-12-31 | 1971-11-16 | Bendix Corp | Dynamic field time-of-flight mass spectrometer |
| US3762876A (en) | 1971-10-07 | 1973-10-02 | Honeywell Inc | Driven vane anemometers |
| US3965066A (en) | 1974-03-15 | 1976-06-22 | General Electric Company | Combustor-turbine nozzle interconnection |
| FR2622322A1 (en) | 1987-10-21 | 1989-04-28 | Weck Arnaud De | Encrypted keyboard system |
| EP0432409A1 (en) | 1989-12-05 | 1991-06-19 | Theodor Kromer GmbH & Co.KG Spezialfabrik für Sicherheitsschlösser | Data input keyboard for coded locks or the like |
| DE4129202A1 (en) | 1991-09-03 | 1993-03-04 | Hauni Elektronik Gmbh | Protection circuit for personal identification number key=pad - uses number of keys to enter PIN value, with indicated values varying in pseudo-random manner |
| US5193152A (en) | 1989-11-03 | 1993-03-09 | Racal-Datacom, Inc. | Network management system with group naming |
| US5209102A (en) | 1992-01-31 | 1993-05-11 | American Air Liquide | Method of introducing and controlling compressed gases for impurity analysis |
| WO1993011551A1 (en) | 1991-12-06 | 1993-06-10 | Maurras Jean Francois | Rendum reset keypad |
| US5219794A (en) | 1991-03-14 | 1993-06-15 | Hitachi, Ltd. | Semiconductor integrated circuit device and method of fabricating same |
| US5234389A (en) | 1992-03-23 | 1993-08-10 | Ford Motor Company | Releasable overrunning coupling power transmission mechanism acting in cooperation with a friction brake |
| US5257486A (en) | 1991-04-23 | 1993-11-02 | Adhesives Technology Corporation 1987 | Nozzle for injecting a sealant into a crack |
| US5363449A (en) | 1993-03-11 | 1994-11-08 | Tandem Computers Incorporated | Personal identification encryptor and method |
| EP0662665A2 (en) | 1994-01-05 | 1995-07-12 | Transaction Technology, Inc. | Wireless banking terminal using cellular telephone communication |
| US5434702A (en) | 1992-03-04 | 1995-07-18 | Northern Telecom Limited | Optical repeaters |
| US5504808A (en) | 1994-06-01 | 1996-04-02 | Hamrick, Jr.; James N. | Secured disposable debit card calling system and method |
| US5549194A (en) | 1993-12-16 | 1996-08-27 | Joh. Winklhofer & Sohne | Accumulating conveyor chain |
| WO1997005578A1 (en) | 1995-07-28 | 1997-02-13 | Mytec Technologies Inc. | Method and apparatus for securely handling a personal identification number or cryptographic key using biometric techniques |
| US5715078A (en) | 1994-03-24 | 1998-02-03 | Kabushiki Kaisha Toshiba | Optical exposure unit and image forming unit used in optical exposure unit |
| US5754652A (en) | 1994-12-14 | 1998-05-19 | Lucent Technologies Inc. | Method and apparatus for secure pin entry |
| EP0870222A2 (en) | 1995-08-21 | 1998-10-14 | Cornel Sirbu | Conditional access method and device |
| DE19803339A1 (en) | 1998-01-29 | 1999-08-05 | Deutsche Telekom Ag | Access authorization verification method for banking machine or computer system |
| US5949348A (en) | 1992-08-17 | 1999-09-07 | Ncr Corporation | Method and apparatus for variable keyboard display |
| US5990586A (en) | 1997-06-23 | 1999-11-23 | Seitz Corporation | Multi-actuator having position controller |
| JP2000099801A (en) | 1998-09-24 | 2000-04-07 | Oki Electric Ind Co Ltd | PIN input device |
| WO2000025474A1 (en) | 1998-10-26 | 2000-05-04 | Bradley Madison Company Doing Business As Evolv Adaptive Technology | Cryptographic protocol for financial transactions |
| JP2000165378A (en) | 1998-11-26 | 2000-06-16 | Kodo Ido Tsushin Security Gijutsu Kenkyusho:Kk | Fingerprint authentication device |
| US6193152B1 (en) | 1997-05-09 | 2001-02-27 | Receiptcity.Com, Inc. | Modular signature and data-capture system and point of transaction payment and reward system |
| US6209102B1 (en) | 1999-02-12 | 2001-03-27 | Arcot Systems, Inc. | Method and apparatus for secure entry of access codes in a computer environment |
| US6219794B1 (en) | 1997-04-21 | 2001-04-17 | Mytec Technologies, Inc. | Method for secure key management using a biometric |
| US6234389B1 (en) | 1998-04-29 | 2001-05-22 | @Pos.Com, Inc. | PCMCIA-based point of sale transaction system |
| WO2001046922A2 (en) | 1999-12-20 | 2001-06-28 | Online Resources Corp. | Method and apparatus for securely conducting financial transactions over an insecure network |
| US6257486B1 (en) | 1998-11-23 | 2001-07-10 | Cardis Research & Development Ltd. | Smart card pin system, card, and reader |
| EP1161060A1 (en) | 1999-12-10 | 2001-12-05 | NTT DoCoMo, Inc. | Mobile communication terminal and card information reader |
| FR2810067A3 (en) | 2000-04-10 | 2001-12-14 | Lundar Electric Ind Co Ltd | Hinge for oven door has cut outs in door flanges fitting onto stubs on oven casing and retained by pins |
| FR2812423A1 (en) | 2000-07-26 | 2002-02-01 | Yohan Amsellem | Card payment for an Internet transaction, uses code table prepared when card is manufactured with server interrogation of user who must return correct entries from the code table |
| US20020016918A1 (en) | 2000-05-12 | 2002-02-07 | David Tucker | Information security method and system |
| US20020023215A1 (en) | 1996-12-04 | 2002-02-21 | Wang Ynjiun P. | Electronic transaction systems and methods therefor |
| US20020029342A1 (en) | 2000-09-07 | 2002-03-07 | Keech Winston Donald | Systems and methods for identity verification for secure transactions |
| US20020046185A1 (en) | 2000-08-30 | 2002-04-18 | Jean-Marc Villart | System and method conducting POS transactions |
| US20020082962A1 (en) | 2000-07-27 | 2002-06-27 | Farris Robert G. | Value transfer system for unbanked customers |
| FR2819067A1 (en) | 2000-12-29 | 2002-07-05 | Yakoubi Boualem | Method for controlling access to a secure system, such as an automatic teller machine, using a keyboard for PIN entry, where the values of the keys displayed on a touch screen are changed in a random manner to prevent fraud |
| DE10100188A1 (en) | 2001-01-04 | 2002-07-18 | Rohde & Schwarz | System for encoding PIN code encodes code using biometric signal and stores it; stored encoded PIN code can only be read out of memory and decoded by using same biometric signal |
| US6434702B1 (en) | 1998-12-08 | 2002-08-13 | International Business Machines Corporation | Automatic rotation of digit location in devices used in passwords |
| US20020123972A1 (en) | 2001-02-02 | 2002-09-05 | Hodgson Robert B. | Apparatus for and method of secure ATM debit card and credit card payment transactions via the internet |
| US20020129250A1 (en) | 2001-02-27 | 2002-09-12 | Akira Kimura | Authentication system and method, identification information inputting method and apparatus ands portable terminal |
| WO2002071177A2 (en) | 2001-03-03 | 2002-09-12 | Moneyhive.Com Pte Ltd | Method and system for substantially secure electronic transactions |
| US20020188872A1 (en) | 2001-06-06 | 2002-12-12 | Willeby Tandy G. | Secure key entry using a graphical user inerface |
| US20030004877A1 (en) | 2001-06-27 | 2003-01-02 | Fujitsu Limited | Transaction terminal apparatus |
| US20030002667A1 (en) | 2001-06-29 | 2003-01-02 | Dominique Gougeon | Flexible prompt table arrangement for a PIN entery device |
| US6549194B1 (en) | 1999-10-01 | 2003-04-15 | Hewlett-Packard Development Company, L.P. | Method for secure pin entry on touch screen display |
| US20030120612A1 (en) | 2000-06-13 | 2003-06-26 | Kabushiki Kaisha Eighting | Method of electronic settlement with a mobile terminal |
| US20030120936A1 (en) | 2001-08-01 | 2003-06-26 | Eft Datalink | Encryption of financial information |
| US20030132918A1 (en) | 2002-01-11 | 2003-07-17 | Fitch Timothy R. | Ergonomically designed multifunctional transaction terminal |
| WO2003058947A2 (en) | 2001-12-26 | 2003-07-17 | Vivotech, Inc. | Adaptor for magnetic stripe card reader |
| US6630928B1 (en) | 1999-10-01 | 2003-10-07 | Hewlett-Packard Development Company, L.P. | Method and apparatus for touch screen data entry |
| GB2387702A (en) | 2002-04-17 | 2003-10-22 | Cellectivity Ltd | Method of access control using PIN codes |
| GB2388229A (en) | 2002-05-04 | 2003-11-05 | Robert Macalonan | Keypad for generating code with scrambled displayed key sequence |
| US20030212327A1 (en) | 2000-11-24 | 2003-11-13 | U-Systems Inc. | Adjunctive ultrasound processing and display for breast cancer screening |
| JP2003346098A (en) | 2002-05-24 | 2003-12-05 | Fuji Xerox Co Ltd | Personal identification system and method and terminal device for personal identification |
| US20030229597A1 (en) | 2002-06-05 | 2003-12-11 | Sun Microsystems, Inc., A Delaware Corporation | Apparatus for private personal identification number management |
| US20030229598A1 (en) | 2002-06-05 | 2003-12-11 | Sun Microsystems, Inc., A Delaware Corporation | Method and apparatus for protecting against side channel attacks against personal identification numbers |
| US20030229791A1 (en) | 2002-06-05 | 2003-12-11 | Sun Microsystems, Inc. A Delaware Corporation | Method for private personal identification number management |
| GB2389693A (en) | 2002-06-10 | 2003-12-17 | Consignia Plc | Payment systems |
| US6671405B1 (en) | 1999-12-14 | 2003-12-30 | Eastman Kodak Company | Method for automatic assessment of emphasis and appeal in consumer images |
| US20040010690A1 (en) | 2000-11-11 | 2004-01-15 | Eon-Cheol Shin | Method and system for inputting secret information |
| US20040039933A1 (en) | 2002-08-26 | 2004-02-26 | Cricket Technologies | Document data profiler apparatus, system, method, and electronically stored computer program product |
| US20040044739A1 (en) | 2002-09-04 | 2004-03-04 | Robert Ziegler | System and methods for processing PIN-authenticated transactions |
| US6715078B1 (en) | 2000-03-28 | 2004-03-30 | Ncr Corporation | Methods and apparatus for secure personal identification number and data encryption |
| JP2004102460A (en) | 2002-09-06 | 2004-04-02 | Hitachi Software Eng Co Ltd | Personal authentication method and program therefor |
| US20040073809A1 (en) | 2002-10-10 | 2004-04-15 | Wing Keong Bernard Ignatius Ng | System and method for securing a user verification on a network using cursor control |
| US20040122768A1 (en) | 2002-12-19 | 2004-06-24 | International Business Machines Corporation | Electronic wallet for wireless computing device |
| US20040122771A1 (en) | 2002-12-19 | 2004-06-24 | International Business Machines Corporation | Automated teller machine for use with computing devices |
| DE10306352A1 (en) | 2003-02-15 | 2004-09-02 | Fuchsenberger, Walter, Dipl.-Ing. (FH) | Code number input device for PIN or password in cash machine or access control system, randomly assigns symbols of keypad to individual keys, and resets after input process |
| US20040182921A1 (en) | 2000-05-09 | 2004-09-23 | Dickson Timothy E. | Card reader module with account encryption |
| GB2402649A (en) | 2003-06-11 | 2004-12-15 | Mathew Jonathan Dawson | Personal identification code entry device |
| US20050010786A1 (en) | 2001-03-30 | 2005-01-13 | Michener John R. | Trusted authorization device |
| US20050012715A1 (en) | 2003-06-12 | 2005-01-20 | Peter Charles Shann Hubird Ford | Method, system, and software for interactive communication and analysis |
| US20050036611A1 (en) | 2003-03-31 | 2005-02-17 | Visa U.S.A., Inc. | Method and system for secure authentication |
| US20050043997A1 (en) | 2003-08-18 | 2005-02-24 | Sahota Jagdeep Singh | Method and system for generating a dynamic verification value |
| US20050075973A1 (en) | 2000-08-22 | 2005-04-07 | Siamack Yousofi | Validation of transactions |
| JP2005107678A (en) | 2003-09-29 | 2005-04-21 | Nec Corp | Device, method and program for password authentication |
| US20050127158A1 (en) | 2003-12-15 | 2005-06-16 | Figueras Ilka H. | Control card check |
| US20050127156A1 (en) | 2003-12-15 | 2005-06-16 | Samsung Electronics Co., Ltd. | Portable handset having a radio frequency indentification(RFID) function and method using the same |
| US20050144449A1 (en) | 2003-12-30 | 2005-06-30 | Entrust Limited | Method and apparatus for providing mutual authentication between a sending unit and a recipient |
| US20050140832A1 (en) | 2003-12-31 | 2005-06-30 | Ron Goldman | Laser projection display |
| US20050146447A1 (en) | 2004-01-05 | 2005-07-07 | Samsung Electronics Co., Ltd. | Terminal having keyboard with keys variable in arrangement, and method of rearranging keys of keyboard |
| US20050177522A1 (en) | 2004-02-05 | 2005-08-11 | Sun Microsystems, Inc. | Method and system for accepting a pass code |
| US20050193208A1 (en) | 2004-02-26 | 2005-09-01 | Charrette Edmond E.Iii | User authentication |
| US20050212763A1 (en) | 2004-03-26 | 2005-09-29 | Cannon Kabushiki Kaisha | Information processing apparatus and method |
| WO2005104428A2 (en) | 2004-04-23 | 2005-11-03 | Virtual Fonlink, Inc. | Enhanced system and method for wireless transactions |
| EP1599786A2 (en) | 2003-02-25 | 2005-11-30 | Banco Ita S.A. | Virtual keyboard |
| EP1600847A1 (en) | 2004-05-17 | 2005-11-30 | Ahmed Merrouk | Universal device for secure input of confidential data |
| US20060003706A1 (en) | 2004-06-30 | 2006-01-05 | Welland David R | Ratiometric transmit path architecture for communication systems |
| EP1615181A1 (en) | 2004-07-09 | 2006-01-11 | Tricerion Ltd | A method of secure data communication |
| US6990586B1 (en) | 2000-06-02 | 2006-01-24 | International Business Machines Corp. | Secure data transmission from unsecured input environments |
| US20060018467A1 (en) | 2004-07-20 | 2006-01-26 | Scribocel, Inc. | Device for authentication and identification for computerized and networked systems |
| WO2006010058A2 (en) | 2004-07-07 | 2006-01-26 | Bharosa Inc. | Online data encryption and decryption |
| US20060017691A1 (en) | 2004-07-23 | 2006-01-26 | Juan Manuel Cruz-Hernandez | System and method for controlling audio output associated with haptic effects |
| US20060026440A1 (en) | 2002-05-31 | 2006-02-02 | Jean-Paul Sauvebois | Method for securing an on-line transaction |
| US20060032705A1 (en) | 2004-08-16 | 2006-02-16 | Isham William R | Lightweight composite ladder rail having supplemental reinforcement in regions subject to greater structural stress |
| US7003316B1 (en) | 2002-02-22 | 2006-02-21 | Virtual Fonlink, Inc. | System and method for wireless transactions |
| US7010806B2 (en) | 2001-05-18 | 2006-03-07 | Sun Microsystems, Inc. | Dynamic downloading of keyboard keycode data to a networked client |
| US20060053301A1 (en) | 2002-12-23 | 2006-03-09 | Hwa-Shik Shin | Device and method for inputting password using random keypad |
| US7047222B1 (en) | 1997-08-06 | 2006-05-16 | International Business Machines Corporation | Secure encryption of data packets for transmission over unsecured networks |
| US20060136334A1 (en) | 2004-11-29 | 2006-06-22 | Atkinson Steven P | Electronic system for provision of banking services |
| US20060133597A1 (en) | 2004-12-08 | 2006-06-22 | Song Seung M | System for protecting personal information of a customer when receiving on-line services from a service provider |
| WO2006064241A2 (en) | 2004-12-16 | 2006-06-22 | Mark Dwight Bedworth | User validation using images |
| US20060146169A1 (en) | 2005-01-03 | 2006-07-06 | Yosef Segman | Electronic viewing device |
| US20060149845A1 (en) | 2004-12-30 | 2006-07-06 | Xinnia Technology, Llc | Managed quality of service for users and applications over shared networks |
| US20060155619A1 (en) | 2002-09-27 | 2006-07-13 | Rhiando Maxwell E | Identification system |
| US7091845B2 (en) | 2003-09-05 | 2006-08-15 | Hirsch Electronics Corporation | Data entry systems with biometric devices for security access control |
| US7092915B2 (en) | 2002-01-07 | 2006-08-15 | International Business Machines Corporation | PDA password management tool |
| US20060182715A1 (en) | 2002-09-27 | 2006-08-17 | Alfred Sandrock | Therapies for chronic inflammatory demyelinating polyneuropathy using interferon-ss |
| JP2006243938A (en) | 2005-03-01 | 2006-09-14 | Oki Electric Ind Co Ltd | Password input device |
| WO2006095203A1 (en) | 2005-03-07 | 2006-09-14 | Tricerion Ltd | A method of secure data communication |
| US20060206919A1 (en) | 2005-03-10 | 2006-09-14 | Axalto Sa | System and method of secure login on insecure systems |
| US20060221059A1 (en) | 2005-04-01 | 2006-10-05 | Samsung Electronics Co., Ltd. | Portable terminal having display buttons and method of inputting functions using display buttons |
| US20060224523A1 (en) | 2005-03-31 | 2006-10-05 | Elvitigala Rajith T | Dynamic keypad |
| US20060247533A1 (en) | 2005-04-27 | 2006-11-02 | Sony Corporation | Pseudorandom number generation apparatus, pseudorandom number generation method and program |
| GB2427059A (en) | 2005-06-06 | 2006-12-13 | Bristol Office Machines | Portable transaction processing device |
| US20070005500A1 (en) | 2005-06-20 | 2007-01-04 | Microsoft Corporation | Secure online transactions using a captcha image as a watermark |
| EP1742450A2 (en) | 2005-07-05 | 2007-01-10 | Sony Ericsson Mobile Communications Japan, Inc. | Method and mobile terminal device with biometric encrypted personal identification number |
| US20070014415A1 (en) | 2005-06-16 | 2007-01-18 | Harrison Keith A | Quantum key distribution method and apparatus |
| US20070073937A1 (en)* | 2005-09-15 | 2007-03-29 | Eugene Feinberg | Content-Aware Digital Media Storage Device and Methods of Using the Same |
| US20070089164A1 (en) | 2005-10-18 | 2007-04-19 | Gao Jie J | System and method of alternative key pad layout for enhanced security |
| US20070101150A1 (en) | 2005-11-02 | 2007-05-03 | Konica Minolta Business Technologies, Inc. | Information processing apparatus |
| US20070110224A1 (en) | 2005-11-14 | 2007-05-17 | Accenture Global Services Gmbh | Data masking application |
| WO2007056746A2 (en) | 2005-11-08 | 2007-05-18 | Ultra-Scan Corporation | System and method for providing security |
| US7243237B2 (en) | 2003-05-02 | 2007-07-10 | Microsoft Corporation | Secure communication with a keyboard or related device |
| US20070182715A1 (en) | 2006-02-03 | 2007-08-09 | Research In Motion Limited | Configurable handheld electronic device |
| US20070209014A1 (en) | 2006-01-11 | 2007-09-06 | Youssef Youmtoub | Method and apparatus for secure data input |
| US20070213090A1 (en) | 2006-03-07 | 2007-09-13 | Sony Ericsson Mobile Communications Ab | Programmable keypad |
| EP1840778A1 (en) | 2006-03-29 | 2007-10-03 | Laurent Busser | Single-use identification device |
| US7305565B1 (en) | 2000-05-31 | 2007-12-04 | Symbol Technologies, Inc. | Secure, encrypting pin pad |
| CN101082948A (en) | 2007-07-05 | 2007-12-05 | 上海麦柯信息技术有限公司 | Portable anti-peeping safety keyboard and method of use thereof |
| US20070282756A1 (en) | 2006-06-02 | 2007-12-06 | First Data Corporation | Pin creation system and method |
| US20070279391A1 (en) | 2006-06-06 | 2007-12-06 | Marttila Charles A | Keypad with virtual image |
| GB2438886A (en) | 2006-06-10 | 2007-12-12 | Gina Maria Eldon | Random personal identification number input screen |
| WO2007143740A2 (en) | 2006-06-08 | 2007-12-13 | Mastercard International Incorporated | All-in-one proximity payment device with local authentication |
| US20080014818A1 (en) | 2006-07-12 | 2008-01-17 | Marc Privitera | Post conversion nonwovens processing |
| US20080011098A1 (en) | 2006-06-29 | 2008-01-17 | Krohne Ag | A heated pipe connecting device for installation of a flow meter |
| CN101126967A (en) | 2007-09-11 | 2008-02-20 | 卢心东 | Password input unit |
| CN201035502Y (en) | 2006-12-28 | 2008-03-12 | 上海麦柯信息技术有限公司 | Safety accidental dynamic soft keyboard |
| US20080110981A1 (en)* | 2006-11-13 | 2008-05-15 | Gilbarco Inc. | Projected user input device for a fuel dispenser and related applications |
| US20080148186A1 (en) | 2006-12-18 | 2008-06-19 | Krishnamurthy Sandeep Raman | Secure data entry device and method |
| US7395506B2 (en) | 2004-05-10 | 2008-07-01 | Microsoft Corporation | Spy-resistant keyboard |
| US20080165035A1 (en) | 2007-01-10 | 2008-07-10 | Bhella Kenneth S | Method and System for Customizing Keyboard Map Variants |
| US20080168546A1 (en) | 2007-01-10 | 2008-07-10 | John Almeida | Randomized images collection method enabling a user means for entering data from an insecure client-computing device to a server-computing device |
| US20080184036A1 (en) | 2007-01-31 | 2008-07-31 | Microsoft Corporation | Password authentication via a one-time keyboard map |
| US20080209223A1 (en) | 2007-02-27 | 2008-08-28 | Ebay Inc. | Transactional visual challenge image for user verification |
| CN201111222Y (en) | 2007-06-08 | 2008-09-03 | 北京工业大学 | Smart Security Keyboard |
| JP2008204409A (en) | 2007-02-23 | 2008-09-04 | Oki Electric Ind Co Ltd | Password input display device and method |
| US20080251969A1 (en) | 2007-02-16 | 2008-10-16 | Isham William R | Bladder Molding Systems and Methods For Fabricating Composite Articles |
| US20080280652A1 (en) | 2007-05-08 | 2008-11-13 | Firefly Mobile, Inc. | Reconfigurable keypad method in handset device operable with plural subsystems |
| US20080289035A1 (en) | 2007-05-18 | 2008-11-20 | International Business Machines Corporation | Method and system for preventing password theft through unauthorized keylogging |
| US20080306995A1 (en) | 2007-06-05 | 2008-12-11 | Newell Catherine D | Automatic story creation using semantic classifiers for images and associated meta data |
| US20080319902A1 (en) | 2005-11-18 | 2008-12-25 | Mark Mervyn Chazan | Method and Apparatus for Facilitating a Secure Transaction |
| WO2009000223A2 (en) | 2007-06-27 | 2008-12-31 | Universität Tübingen | Device and method for tap-proof and manipulation-proof encoding of online accounts |
| WO2009009788A1 (en) | 2007-07-12 | 2009-01-15 | Jobmann Brian C | Identity authentication and secured access systems, components, and methods |
| WO2009012326A1 (en) | 2007-07-16 | 2009-01-22 | Qualcomm Incorporated | Methods and systems personalizing and branding mobile device keypads |
| US20090033522A1 (en) | 2007-07-30 | 2009-02-05 | Palm, Inc. | Electronic Device with Reconfigurable Keypad |
| US20090044282A1 (en) | 2007-08-09 | 2009-02-12 | Technology Properties Limited | System and Method for Generating and Displaying a Keyboard Comprising a Random Layout of Keys |
| US20090067627A1 (en) | 2005-11-04 | 2009-03-12 | Christian Hogl | Method and System for Transmitting Data From a First Data Processing Device to a Second Data Processing Device |
| US20090066660A1 (en) | 2007-09-06 | 2009-03-12 | Ure Michael J | Interface with and communication between mobile electronic devices |
| US20090077383A1 (en) | 2007-08-06 | 2009-03-19 | De Monseignat Bernard | System and method for authentication, data transfer, and protection against phishing |
| US20090106827A1 (en) | 2007-10-22 | 2009-04-23 | International Business Machines Corporation | System and method for user password protection |
| FR2923034A1 (en) | 2007-10-26 | 2009-05-01 | Ingenico Sa | Payment terminal e.g. computer, for e.g. automatic fuel vending machine, has memory storing program for modifying keyboard configuration data before inputting information and controlling displaying of configuration after modifying data |
| GB2454459A (en) | 2007-11-06 | 2009-05-13 | Andrew Small | Personal identification code entry device |
| US20090183098A1 (en) | 2008-01-14 | 2009-07-16 | Dell Products, Lp | Configurable Keyboard |
| US20090193210A1 (en) | 2008-01-29 | 2009-07-30 | Hewett Jeffrey R | System for Automatic Legal Discovery Management and Data Collection |
| GB2457733A (en) | 2008-02-25 | 2009-08-26 | Mobank Ltd | Securing inputting of sensitive information |
| US20090213132A1 (en) | 2008-02-25 | 2009-08-27 | Kargman James B | Secure computer screen entry system and method |
| JP2009199581A (en) | 2008-01-21 | 2009-09-03 | Nec Corp | Personal identification number input device, method, and program, and cellular phone |
| US20090235199A1 (en) | 2008-03-12 | 2009-09-17 | International Business Machines Corporation | Integrated masking for viewing of data |
| US20090254986A1 (en) | 2008-04-08 | 2009-10-08 | Peter William Harris | Method and apparatus for processing and displaying secure and non-secure data |
| JP2009237774A (en) | 2008-03-26 | 2009-10-15 | Advanced Media Inc | Authentication server, service providing server, authentication method, communication terminal, and log-in method |
| DE102008050609A1 (en) | 2008-04-09 | 2009-10-22 | Kevin Wessel | Actuating device for keypad of automated teller machine, has encoding device arranged between input keypad and actuating unit for another keypad, where encoding device comprises hydraulic and/or pneumatic unit |
| WO2009130985A1 (en) | 2008-04-23 | 2009-10-29 | コニカミノルタホールディングス株式会社 | Information input system |
| US20090270078A1 (en) | 2006-05-30 | 2009-10-29 | Gi-Seon Nam | Method for configurating keypad of terminal and the terminal and system including the terminal and the keypad capable of reconfiguration |
| US20090277968A1 (en) | 2006-09-07 | 2009-11-12 | Matthew Walker | Visual code transaction verification |
| KR20090130455A (en) | 2008-06-16 | 2009-12-24 | 성균관대학교산학협력단 | How to change graphic keypad, key layout of graphic keypad, password authentication using graphic keypad |
| EP2141647A1 (en) | 2008-06-30 | 2010-01-06 | Accullink LLC | Systems and methods for secure pin-based transactions via a host based pin pad |
| CN100583113C (en) | 2003-09-19 | 2010-01-20 | 谢道裕 | Magic square digital antifake method and its antifake system |
| US20100036783A1 (en) | 2008-08-06 | 2010-02-11 | Rodriguez Ralph A | Method of and apparatus for combining artificial intelligence (AI) concepts with event-driven security architectures and ideas |
| US20100049768A1 (en) | 2006-07-20 | 2010-02-25 | Robert James C | Automatic management of digital archives, in particular of audio and/or video files |
| US20100098300A1 (en) | 2005-08-05 | 2010-04-22 | Tilman Otto | Method and system for biometric identification or verification |
| US20100109920A1 (en) | 2008-11-05 | 2010-05-06 | Michael Dennis Spradling | Security - input key shuffle |
| DE102008056605A1 (en) | 2008-11-10 | 2010-05-12 | Borchert, Bernd, Dr. | Method for manipulation-secure transmission of e.g. password, from client to server via computer network, for online-banking, involves reconstructing code word, and declining execution of transaction by server |
| US20100117792A1 (en) | 2008-11-13 | 2010-05-13 | Patrick Faith | Device including authentication glyph |
| US20100121737A1 (en) | 2007-01-12 | 2010-05-13 | Kenji Yoshida | Personal identification number code input method using dot pattern, personal identification number code input method, and internet shopping settlement system |
| US20100125509A1 (en) | 2008-11-14 | 2010-05-20 | Kranzley Arthur D | Methods and systems for secure mobile device initiated payments using generated image data |
| US20100138666A1 (en) | 2008-12-01 | 2010-06-03 | Neil Patrick Adams | Simplified multi-factor authentication |
| US7735121B2 (en) | 2003-01-07 | 2010-06-08 | Masih Madani | Virtual pad |
| JP2010126913A (en) | 2008-11-25 | 2010-06-10 | Alpha Corp | Electronic lock device and locker equipment |
| US20100149100A1 (en) | 2008-12-15 | 2010-06-17 | Sony Ericsson Mobile Communications Ab | Electronic Devices, Systems, Methods and Computer Program Products for Detecting a User Input Device Having an Optical Marker Thereon |
| US20100153270A1 (en) | 2006-11-27 | 2010-06-17 | Broca Communications Limited | Authentication of message recipients |
| US20100175016A1 (en) | 2009-01-06 | 2010-07-08 | Wei Cheng Tian | Security key inputting system for touch screen device |
| US20100174653A1 (en) | 2009-01-07 | 2010-07-08 | Tian Weicheng | Secure method and device of financial transaction |
| US20100180336A1 (en) | 2009-01-13 | 2010-07-15 | Nolan Jones | System and Method for Authenticating a User Using a Graphical Password |
| US20100182244A1 (en) | 2007-02-28 | 2010-07-22 | Ntt Docomo, Inc. | Information processing device and program |
| US20100186076A1 (en) | 2006-03-31 | 2010-07-22 | Axalto Sa | Method and system of providing security services using a secure device |
| US20100215270A1 (en) | 2009-02-26 | 2010-08-26 | Pradheesh Manohar | System and Methods for Automatically Accessing a Web Site on Behalf of a Client |
| DE102009022845A1 (en) | 2008-08-15 | 2010-09-02 | Günzel, Andrea | Method for input of personal identification number keyboard for input of personal identification number, involves defining number allocation to individual push buttons or pressure zones with each input of chip or magnetic card in associated |
| US20100223663A1 (en) | 2006-04-21 | 2010-09-02 | Mitsubishi Electric Corporation | Authenticating server device, terminal device, authenticating system and authenticating method |
| US20100242104A1 (en) | 2009-03-23 | 2010-09-23 | Wankmueller John R | Methods and systems for secure authentication |
| US20100259561A1 (en) | 2009-04-10 | 2010-10-14 | Qualcomm Incorporated | Virtual keypad generator with learning capabilities |
| US20100287097A1 (en) | 2009-05-08 | 2010-11-11 | Bank Of America Corporation | Conducting Commercial Transactions with a Mobile Device |
| US20100287382A1 (en) | 2009-05-07 | 2010-11-11 | John Charles Gyorffy | Two-factor graphical password for text password and encryption key generation |
| WO2010131218A1 (en) | 2009-05-15 | 2010-11-18 | Setcom (Pty) Ltd | Security system and method |
| WO2010134808A1 (en) | 2009-05-20 | 2010-11-25 | Bell Identification B.V. | Method of securing entry of an alphanumeric code on a computer system, interaction and dedicated driver entity therefor. |
| US20100306283A1 (en) | 2009-01-28 | 2010-12-02 | Digitiliti, Inc. | Information object creation for a distributed computing system |
| DE102009023925A1 (en) | 2009-06-04 | 2010-12-09 | Jan Fricke | Sensible data i.e. personal identification number, inputting device for e.g. automated teller machine, has display comprising number pad, and vision protection filter permitting vision of user on umber pad only from angle of vision |
| US20100323617A1 (en) | 2008-03-25 | 2010-12-23 | Logomotion, S.R.O. | Method, connection and data carrier to perform repeated operations on the key-board of mobile communication device |
| US20110004769A1 (en) | 2009-07-03 | 2011-01-06 | Yoo-Jae Won | Password input system using an alphanumeric matrix and password input method using the same |
| US20110020414A1 (en) | 2009-07-27 | 2011-01-27 | Audrey Kunin | Moisturizing retinol composition |
| US20110018033A1 (en) | 2008-03-26 | 2011-01-27 | Sumitomo Chemical Company, Limited | Semiconductor wafer, semiconductor device, and method of manufacturing a semiconductor device |
| US20110055084A1 (en) | 2009-08-31 | 2011-03-03 | Saheednanda Singh | Techniques for remote controlled physical transactions with dynamic key generation and authentication |
| US20110090097A1 (en) | 2009-10-20 | 2011-04-21 | Beshke Thomas C | Keyless entry with visual rolling code display |
| US20110109567A1 (en) | 2009-11-09 | 2011-05-12 | Kim Hyun-Kook | Mobile terminal and displaying device thereof |
| US20110144586A1 (en) | 2009-07-30 | 2011-06-16 | Tandem Diabetes Care, Inc. | Infusion pump system with disposable cartridge having pressure venting and pressure feedback |
| US20110185319A1 (en) | 2010-01-28 | 2011-07-28 | Giovanni Carapelli | Virtual pin pad for fuel payment systems |
| US20110180336A1 (en) | 2008-09-30 | 2011-07-28 | Toyota Jidosha Kabushiki Kaisha | Vehicle motor driving system |
| US20110185313A1 (en) | 2010-01-26 | 2011-07-28 | Idan Harpaz | Method and system for customizing a user-interface of an end-user device |
| US7992007B2 (en) | 2002-02-05 | 2011-08-02 | Cardinalcommerce Corporation | Dynamic pin pad for credit/debit/ other electronic transactions |
| WO2011093998A1 (en) | 2010-01-27 | 2011-08-04 | Rem Holdings 3, Llc | Card reader device and method of use |
| US20110191591A1 (en) | 2008-07-08 | 2011-08-04 | Li Cheng | Transmitting Information Using Virtual Input Layout |
| US20110199387A1 (en) | 2009-11-24 | 2011-08-18 | John David Newton | Activating Features on an Imaging Device Based on Manipulations |
| US20110204140A1 (en) | 2009-11-24 | 2011-08-25 | Hart Annmarie D | System and method for conducting secure pin debit transactions |
| EP2365469A1 (en) | 2010-03-10 | 2011-09-14 | Telecash Spólka z Ograniczona Odpowiedzialnoscia | Method for performing payment transaction using personal mobile device and arrangement for personal mobile device |
| US20110246369A1 (en) | 2010-03-30 | 2011-10-06 | De Oliveira Marcelo Gomes | Event access with data field encryption for validation and access control |
| US20110281630A1 (en) | 2009-01-30 | 2011-11-17 | Omarco Networks Solutions Limited | Multifunction authentication systems |
| DE102010022368A1 (en) | 2010-06-01 | 2011-12-01 | Frank Knopf | Touch-screen control panel for e.g. automated teller machine, has number arrangement that ranges between specific values, where arrangement is not rigid and changes each time before operating system configuration |
| WO2011155915A1 (en) | 2010-06-10 | 2011-12-15 | Woronec John S | Method and apparatus for securely activating a credit card for a limited period of time |
| FR2961330A1 (en) | 2010-06-14 | 2011-12-16 | Jean Claude Pailles | Method for securing electronic transaction between user of e.g. personal computer and goods or service merchant during purchasing of train tickets, involves assuring coherence between constitutive elements of contract and signed message |
| US20110313871A1 (en) | 2010-05-18 | 2011-12-22 | Laura Greenwood | Apparatus, system, and method for facilitating a payment |
| US20110310019A1 (en) | 2010-06-16 | 2011-12-22 | International Business Machines Corporation | Reconfiguration of virtual keyboard |
| EP2400426A1 (en) | 2009-01-30 | 2011-12-28 | Research In Motion Limited | System and method for access control in a portable electronic device |
| US20110321138A1 (en) | 2010-06-28 | 2011-12-29 | International Business Machines Corporation | Mask Based Challenge Response Test |
| WO2012004395A1 (en) | 2010-07-09 | 2012-01-12 | Izettle Hardware Ab | Stand-alone secure pin entry device for enabling emv card transactions with separate card reader |
| WO2012009334A1 (en) | 2010-07-13 | 2012-01-19 | Kopin Corporation | Personal secure terminal with virtual keypad |
| US8117458B2 (en) | 2006-05-24 | 2012-02-14 | Vidoop Llc | Methods and systems for graphical image authentication |
| US20120042365A1 (en) | 2010-08-11 | 2012-02-16 | Emc Corporation | Disposable browser for commercial banking |
| CN202150070U (en) | 2010-12-14 | 2012-02-22 | 深圳市中成汇实业有限公司 | Personal on-line transaction terminal |
| US20120079273A1 (en) | 2010-09-28 | 2012-03-29 | Mu Hua Investments Limited | Biometric Key |
| US20120095867A1 (en) | 2010-10-13 | 2012-04-19 | Mckelvey Jim | Integrated read head device |
| US20120096277A1 (en) | 2009-04-20 | 2012-04-19 | Alter Core, S.L. | System and method for personal authentication using a mobile device |
| US20120098750A1 (en) | 2010-10-22 | 2012-04-26 | Southern Methodist University | Method for subject classification using a pattern recognition input device |
| US8176324B1 (en) | 2009-07-02 | 2012-05-08 | Exelis Inc. | Method and system for a secure virtual keyboard |
| EP2458491A2 (en) | 2010-11-29 | 2012-05-30 | Wincor Nixdorf International GmbH | Device for reading magnetic strips and/or chip cards with touch-screen for PIN entry |
| WO2012077098A1 (en) | 2010-12-06 | 2012-06-14 | Deutsche Telekom Ag | A method for authentication and verification of user identity |
| US8201732B1 (en) | 2010-04-12 | 2012-06-19 | Diebold Self-Service Systems Division Of Diebold, Incorporated | Banking system controlled responsive to data bearing records |
| EP2466515A1 (en) | 2010-12-16 | 2012-06-20 | Research In Motion Limited | Multi-layer orientation-changing password |
| EP2466514A1 (en) | 2010-12-16 | 2012-06-20 | Research In Motion Limited | Multi-layer multi-point or randomized passwords |
| EP2466517A1 (en) | 2010-12-16 | 2012-06-20 | Research In Motion Limited | Simple algebraic and multi-layered passwords |
| EP2466520A1 (en) | 2010-12-16 | 2012-06-20 | Research In Motion Limited | Multi-layer multi-point or pathway-based passwords |
| EP2466512A1 (en) | 2010-12-16 | 2012-06-20 | Research In Motion Limited | Pressure sensitive multi-layer passwords |
| EP2466516A1 (en) | 2010-12-16 | 2012-06-20 | Research In Motion Limited | Adjusting the position of an endpoint reference for increasing security during device log-on |
| EP2466513A1 (en) | 2010-12-16 | 2012-06-20 | Research In Motion Limited | Visual or touchscreen password entry |
| EP2466519A1 (en) | 2010-12-16 | 2012-06-20 | Research In Motion Limited | Password entry using moving images |
| EP2466521A1 (en) | 2010-12-16 | 2012-06-20 | Research In Motion Limited | Obscuring visual login |
| EP2466518A1 (en) | 2010-12-16 | 2012-06-20 | Research In Motion Limited | Password entry using 3D image with spatial alignment |
| US20120158672A1 (en) | 2010-12-16 | 2012-06-21 | Microsoft Corporation | Extensible Pipeline for Data Deduplication |
| US20120159593A1 (en) | 2010-12-16 | 2012-06-21 | Research In Motion Limited | Multi-layer orientation-changing password |
| US20120159160A1 (en) | 2010-12-21 | 2012-06-21 | Poisner David I | High security display of private data |
| US20120159582A1 (en) | 2010-12-16 | 2012-06-21 | Research In Motion Limited | Obscuring visual login |
| US20120159616A1 (en) | 2010-12-16 | 2012-06-21 | Research In Motion Limited | Pressure sensitive multi-layer passwords |
| US20120159592A1 (en) | 2010-12-16 | 2012-06-21 | Research In Motion Limited | Multi-layered color-sensitive passwords |
| US20120159614A1 (en) | 2010-12-16 | 2012-06-21 | Research In Motion Limited | Simple algebraic and multi-layer passwords |
| US20120159609A1 (en) | 2010-12-16 | 2012-06-21 | Research In Motion Limited | Password entry using moving images |
| US20120159613A1 (en) | 2010-12-16 | 2012-06-21 | Jason Tyler Griffin | Multi-layer multi-point or randomized passwords |
| US20120159594A1 (en) | 2010-12-16 | 2012-06-21 | Research In Motion Limited | Adjusting the position of an endpoint reference for increasing security during device log-on |
| US20120159583A1 (en) | 2010-12-16 | 2012-06-21 | Research In Motion Limited | Visual or touchscreen password entry |
| FR2969342A1 (en) | 2010-12-21 | 2012-06-22 | Oberthur Technologies | Method for entering confidential code to device e.g. computer, to authenticate user, involves selecting character based on time of detection switching of input button, and forming ring for entering each letter in confidential code |
| US20120162086A1 (en) | 2010-12-27 | 2012-06-28 | Samsung Electronics Co., Ltd. | Character input method and apparatus of terminal |
| JP2012138011A (en) | 2010-12-27 | 2012-07-19 | Ns Solutions Corp | Information processing system, information processing method and program |
| US20120185398A1 (en) | 2009-09-17 | 2012-07-19 | Meir Weis | Mobile payment system with two-point authentication |
| EP2487620A1 (en) | 2010-12-16 | 2012-08-15 | Research In Motion Limited | Multi-layered color-sensitive passwords |
| US8255323B1 (en) | 2009-01-09 | 2012-08-28 | Apple Inc. | Motion based payment confirmation |
| US20120222100A1 (en) | 2011-02-24 | 2012-08-30 | International Business Machines Corporation | Advanced captcha using integrated images |
| US20120222102A1 (en) | 2011-02-24 | 2012-08-30 | Empire Technology Development Llc | Authentication using mobile devices |
| US8270720B1 (en) | 2006-02-21 | 2012-09-18 | Gruntworx, Llc | Method and system for secure data entry |
| US20120249295A1 (en) | 2011-03-30 | 2012-10-04 | Acer Incorporated | User interface, touch-controlled device and method for authenticating a user of a touch-controlled device |
| WO2012131420A1 (en) | 2011-03-31 | 2012-10-04 | Infosys Limited | System and method for utilizing a dynamic virtual keyboard |
| US20120253971A1 (en) | 2011-03-28 | 2012-10-04 | Ebay Inc. | Simplified orders using words or phrases |
| US20120256723A1 (en) | 2011-04-08 | 2012-10-11 | Avaya Inc. | Random location authentication |
| JP2012194648A (en) | 2011-03-15 | 2012-10-11 | Nec Personal Computers Ltd | Authentication server, authentication system and authentication method of server |
| US20120260326A1 (en) | 2011-04-05 | 2012-10-11 | Sap Ag | Image maps for credential-based security |
| EP2512090A1 (en) | 2011-04-14 | 2012-10-17 | Telefónica Germany GmbH & Co. OHG | Method for authenticating a subscriber |
| US8297173B1 (en) | 2007-01-10 | 2012-10-30 | Wilcox Industries Corp. | Modular weapon video display system |
| WO2012146587A1 (en) | 2011-04-27 | 2012-11-01 | Vance Burkill | Improvements in or relating to password generation and recall |
| EP2523137A1 (en) | 2011-05-09 | 2012-11-14 | Research In Motion Limited | Touchscreen password entry |
| US20120291120A1 (en) | 2011-05-09 | 2012-11-15 | Research In Motion Limited | Touchscreen password entry |
| US20120305648A1 (en) | 2011-06-03 | 2012-12-06 | Liquid Payment Solutions Pte Ltd | Hybrid Mobile Phone/Pin Entry Device, System, Method and Article |
| US20120311723A1 (en) | 2011-05-06 | 2012-12-06 | Google Inc. | Physical Confirmation For Network-Provided Content |
| US20120313858A1 (en) | 2011-06-10 | 2012-12-13 | Samsung Electronics Co., Ltd. | Method and apparatus for providing character input interface |
| US20120323788A1 (en) | 2002-02-05 | 2012-12-20 | Cardinalcommerce Corporation | Dynamic pin pad for credit/debit/other electronic transactions |
| US20130019320A1 (en) | 2011-07-13 | 2013-01-17 | Salesforce. Com, Inc. | Mechanism for facilitating management of data in an on-demand services environment |
| US20130018800A1 (en) | 2011-07-15 | 2013-01-17 | Rangaraju Devaraju | Secure Authorization of a Financial Transaction |
| WO2013013192A2 (en) | 2011-07-20 | 2013-01-24 | Visa International Service Association | Cryptographic expansion device and related protocols |
| US20130021233A1 (en) | 2011-07-21 | 2013-01-24 | Frederick Umminger | Apparatus, system, and method for providing feedback sensations of temperature and hardness-softness to a controller |
| US20130020389A1 (en) | 2011-07-18 | 2013-01-24 | Barnett Timothy W | Systems and methods for authenticating near field communcation financial transactions |
| US20130023240A1 (en) | 2011-05-17 | 2013-01-24 | Avish Jacob Weiner | System and method for transaction security responsive to a signed authentication |
| US8364601B2 (en) | 2008-12-31 | 2013-01-29 | Intel Corporation | Methods and systems to directly render an image and correlate corresponding user input in a secure memory domain |
| US20130026513A1 (en) | 2011-07-25 | 2013-01-31 | Deeder Aurongzeb | Oled assembly and luminaire with removable diffuser |
| US20130029824A1 (en) | 2011-07-27 | 2013-01-31 | Flexicell Inc. | Tier cap forming apparatus |
| US8375428B2 (en) | 2009-07-03 | 2013-02-12 | Korea Internet & Security Agency | Password input system using alphanumeric matrices and password input method using the same |
| WO2013021233A1 (en) | 2011-08-05 | 2013-02-14 | Mt Bilgi Teknolojileri Dis Tic, A.S. | Multi-communication featured, touch-operated or keyboard cash register with contact and non-contact credit card reader |
| US20130042318A1 (en) | 2010-04-29 | 2013-02-14 | Rakesh Thatha | Authentication System and Method Using Arrays |
| US20130047237A1 (en) | 2010-04-26 | 2013-02-21 | Kyu Choul Ahn | Password security input system using shift value of password key and password security input method thereof |
| US20130050088A1 (en) | 2011-08-29 | 2013-02-28 | Ncr Corporation | User interface |
| US20130060739A1 (en) | 2011-09-01 | 2013-03-07 | Microsoft Corporation | Optimization of a Partially Deduplicated File |
| US20130078951A1 (en) | 2011-09-23 | 2013-03-28 | Jaeseung MUN | Mobile terminal and method of providing security thereto |
| US8413071B2 (en) | 2009-09-15 | 2013-04-02 | Samsung Electronics Co., Ltd. | Image processing apparatus and method |
| US20130086382A1 (en) | 2011-10-04 | 2013-04-04 | Timothy W. Barnett | Systems and methods for securely transferring personal identifiers |
| US20130091583A1 (en) | 2010-06-15 | 2013-04-11 | Thomson Licensing | Method and device for secured entry of personal data |
| US20130106690A1 (en) | 2011-11-01 | 2013-05-02 | Pepsico, Inc. | Dispensing System and User Interface |
| US20130117573A1 (en) | 2011-11-03 | 2013-05-09 | Proxama Limited | Method for verifying a password |
| US8453207B1 (en)* | 2012-07-11 | 2013-05-28 | Daon Holdings Limited | Methods and systems for improving the security of secret authentication data during authentication transactions |
| US8453027B2 (en) | 2009-09-17 | 2013-05-28 | Microsoft Corporation | Similarity detection for error reports |
| US20130148044A1 (en) | 2011-12-13 | 2013-06-13 | Japan Display West, Inc. | Liquid crystal display device and electronic apparatus |
| US20130154937A1 (en) | 2011-12-20 | 2013-06-20 | Electronics And Telecommunications Research Institute | Apparatus and method for providing customized keyboard user interface |
| US20130154981A1 (en) | 2011-12-20 | 2013-06-20 | Samsung Electronics Co., Ltd. | Method and apparatus for providing a shortcut number in a user device |
| US20130159196A1 (en) | 2011-12-20 | 2013-06-20 | Ebay, Inc. | Secure PIN Verification for Mobile Payment Systems |
| US20130198459A1 (en) | 2012-01-27 | 2013-08-01 | Fusion-Io, Inc. | Systems and methods for a de-duplication cache |
| US20130207902A1 (en) | 2012-02-10 | 2013-08-15 | Hand Held Products, Inc. | Apparatus having random ordered keypad |
| US20130232549A1 (en) | 2010-11-02 | 2013-09-05 | Michael Ian Hawkes | Method and apparatus for securing network communications |
| WO2013148044A1 (en) | 2012-03-26 | 2013-10-03 | Symbol Technologies, Inc. | Mobile computer with integrated near field communication antenna |
| US20130265136A1 (en) | 2012-04-05 | 2013-10-10 | Bank Of America | Dynamic keypad and fingerprinting sequence authentication |
| US20130298246A1 (en) | 2012-05-07 | 2013-11-07 | International Business Machines Corporation | Obfuscating entry of sensitive information |
| US20130301830A1 (en) | 2012-05-08 | 2013-11-14 | Hagai Bar-El | Device, system, and method of secure entry and handling of passwords |
| US8621242B2 (en) | 2004-06-11 | 2013-12-31 | Arm Limited | Display of a verification image to confirm security |
| US20140002558A1 (en) | 2012-06-29 | 2014-01-02 | Xerox Corporation | Method and apparatus for determining a degree of cure in an ultraviolet printing system |
| US20140013252A1 (en) | 2012-07-06 | 2014-01-09 | Sap Ag | Organizer for Managing Employee Time and Attendance |
| WO2014013252A2 (en) | 2012-07-20 | 2014-01-23 | Licentia Group Limited | Authentication method and system |
| US20140025580A1 (en) | 2008-02-20 | 2014-01-23 | Steven V. Bacastow | Method and System for Securing Payment Transactions |
| US20140096201A1 (en) | 2011-12-15 | 2014-04-03 | Arupratan Gupta | Systems and methods for secured entry of user authentication data |
| US20140162598A1 (en) | 2010-11-17 | 2014-06-12 | Antony-Euclid C. Villa-Real | Customer-controlled instant-response anti-fraud/anti-identity theft devices (with true- personal identity verification), method and systems for secured global applications in personal/business e-banking, e-commerce, e-medical/health insurance checker, e-education/research/invention, e-disaster advisor, e-immigration, e-airport/aircraft security, e-military/e-law enforcement, with or without NFC component and system, with cellular/satellite phone/internet/multi-media functions |
| US20140168083A1 (en) | 2012-07-18 | 2014-06-19 | Sap Ag | Virtual touchscreen keyboards |
| US20140173492A1 (en) | 2012-12-14 | 2014-06-19 | Samsung Electronics Co., Ltd. | Method and apparatus for virtual keypad control |
| US8762876B2 (en) | 2012-06-21 | 2014-06-24 | Google Inc. | Secure data entry via a virtual keyboard |
| US20140195429A1 (en) | 2013-01-08 | 2014-07-10 | Cirque Corporation | Method for protecting cardholder data in a mobile device that performs secure payment transactions and which enables the mobile device to function as a secure payment terminal |
| US20140201831A1 (en) | 2011-11-10 | 2014-07-17 | Soongsil University Research Consortium Techno-Park | Method and apparatus for authenticating password of user terminal |
| WO2014111689A1 (en) | 2013-01-18 | 2014-07-24 | Licentia Group Limited | Authentication device & related methods |
| WO2014132193A2 (en) | 2013-02-26 | 2014-09-04 | Visa International Service Association | Systems, methods and devices for performing passcode authentication |
| EP2775421A1 (en) | 2013-03-05 | 2014-09-10 | Wincor Nixdorf International GmbH | Trusted terminal platform |
| US20140283022A1 (en) | 2012-07-11 | 2014-09-18 | Jason Chris BELONCIK | Methods and sysems for improving the security of secret authentication data during authentication transactions |
| US20140310531A1 (en) | 2013-04-15 | 2014-10-16 | International Business Machines Corporation | Method and system for securing the entry of data to a device |
| US20140324708A1 (en) | 2012-06-12 | 2014-10-30 | Square, Inc. | Raw sensor input encryption for passcode entry security |
| US20140324698A1 (en) | 2012-02-29 | 2014-10-30 | Mobeewave, Inc. | Method, device, add-on and secure element for conducting a secured financial transaction on a device |
| US8965066B1 (en) | 2013-09-16 | 2015-02-24 | Eye Verify LLC | Biometric template security and key generation |
| US20150095241A1 (en) | 2013-09-30 | 2015-04-02 | Square, Inc. | Scrambling passcode entry interface |
| WO2015055973A1 (en) | 2013-10-16 | 2015-04-23 | Mads Landrok | Trusted user interface and touchscreen |
| US20150116225A1 (en) | 2012-07-05 | 2015-04-30 | Tencent Technology (Shenzhen) Company Limited | Character Input Method And Apparatus |
| WO2015063474A1 (en) | 2013-10-29 | 2015-05-07 | Cryptomathic Ltd | Secure mobile user interface and mobile device case |
| KR101520803B1 (en) | 2014-12-01 | 2015-05-15 | 금오공과대학교 산학협력단 | Apparatus and method for inputting personal identification number with enhanced security |
| US20150154598A1 (en) | 2013-12-02 | 2015-06-04 | At&T Intellectual Property I, L.P. | Secure Interaction with Input Devices |
| US9082253B1 (en) | 2005-12-20 | 2015-07-14 | Diebold Self-Service Systems Division Of Diebold, Incorporated | Banking system controlled responsive to data bearing records |
| US20150261968A1 (en) | 2014-03-12 | 2015-09-17 | Ebay Inc. | Visualizing random characters for keyboard-less devices |
| US20150332038A1 (en) | 2014-05-17 | 2015-11-19 | Adriana Lyons | Secure entry of secrets |
| US20150350163A1 (en) | 2014-06-02 | 2015-12-03 | Blackberry Limited | System and method for initiating protected instant messaging conversations |
| US20150347774A1 (en) | 2014-05-30 | 2015-12-03 | Apple Inc. | Restricted resource classes of an operating system |
| US20150379288A1 (en) | 2014-06-25 | 2015-12-31 | International Business Machines Corporation | Secure access to running client application features from a browser application |
| US9235967B1 (en) | 2005-12-20 | 2016-01-12 | Diebold Self-Service Systems Division Of Diebold, Incorporated | Banking system controlled responsive to data bearing records |
| US20160034718A1 (en) | 2013-10-02 | 2016-02-04 | Criptext, Inc. | Method and apparatus for communicating private messages with partially obscured content to limit or prevent unauthorized use of data to impede privacy violations |
| US20160042190A1 (en) | 2014-08-11 | 2016-02-11 | International Business Machines Corporation | Providing access control of applications on computing device by establishing screen passcodes that allow access to designated screens with designated applications |
| US20160065546A1 (en) | 2014-08-27 | 2016-03-03 | Microsoft Technology Licensing, Llc | Sharing content with permission control using near field communication |
| US20160063230A1 (en) | 2014-08-29 | 2016-03-03 | Dropbox, Inc. | Fingerprint gestures |
| WO2016048236A1 (en) | 2014-09-23 | 2016-03-31 | Singapore Management University | Leakage resilient password system and method |
| WO2016046458A1 (en) | 2014-09-22 | 2016-03-31 | Prove & Run | Smartphone or tablet having a secure display |
| US20160125193A1 (en) | 2014-10-29 | 2016-05-05 | Square, Inc. | Secure Display Element |
| US20160154980A1 (en) | 2013-07-12 | 2016-06-02 | ADUCID s.r.o | Method of secret information entering into electronic digital devices |
| US20160246955A1 (en) | 2015-02-24 | 2016-08-25 | Image Match Design Inc. | Fingerprint encoding method and system, and fingerprint authenticating method and system |
| US20160253508A1 (en) | 2015-02-26 | 2016-09-01 | Kairos Social Solutions, Inc. | Device, System, and Method of Preventing Unauthorized Recording of Visual Content Displayed on an Electronic Device |
| CN105956857A (en) | 2016-05-06 | 2016-09-21 | 上海动联信息技术股份有限公司 | System and method for generating security virtual password keyboard |
| US20160283013A1 (en) | 2015-03-25 | 2016-09-29 | Sony Mobile Communications Inc. | Device display control for protecting sensitive data |
| CN106022172A (en) | 2016-05-24 | 2016-10-12 | 中国银行股份有限公司 | Password input method and system protecting password keyboard button input operation |
| US20160314468A1 (en) | 2013-12-26 | 2016-10-27 | Ned M. Smith | Secure transactions using a personal device |
| US20160320965A1 (en) | 2005-04-22 | 2016-11-03 | Neopad Inc. | Creation method for characters/words and the information and communication service method thereby |
| US20160337857A1 (en) | 2014-01-10 | 2016-11-17 | Telsy Elettronica E Telecomunicazioni Spa | Secure voice and data method and system |
| WO2016189325A1 (en) | 2015-05-27 | 2016-12-01 | Licentia Group Limited | Authentication methods and systems |
| US20170006140A1 (en) | 2015-07-01 | 2017-01-05 | Lg Electronics Inc. | Method of transmitting and receiving data using new layer in wireless communication system |
| US9576411B2 (en) | 2013-10-18 | 2017-02-21 | Electronics And Telecommunications Research Institute | Apparatus and method for providing security keypad through shift of keypad |
| US20170061408A1 (en) | 2015-08-31 | 2017-03-02 | Seungshin CHOI | Security key input system and method using one-time keypad |
| US20170061138A1 (en) | 1998-07-16 | 2017-03-02 | NoisyCloud, Inc. | System and method for secure data transmission and storage |
| WO2017065576A1 (en) | 2015-10-14 | 2017-04-20 | 주식회사 하렉스인포텍 | User authentication method and system, which use variable keypad |
| EP3163926A1 (en) | 2014-06-26 | 2017-05-03 | Harexinfotech Inc. | User authentication method and system using variable keypad and biometric identification |
| US20170140354A1 (en) | 2005-12-20 | 2017-05-18 | Diebold Nixdorf, Incorporated | Tactile touch screen |
| EP3176722A1 (en) | 2015-05-28 | 2017-06-07 | Smart Electronic Industrial (Dong Guan) Co., Ltd. | Password setting method and equipment therefor |
| US20170192670A1 (en) | 2008-09-19 | 2017-07-06 | Google Inc. | Quick Gesture Input |
| US20170235926A1 (en) | 2012-01-26 | 2017-08-17 | Blackberry Limited | Methods and devices for distributing content to an electronic device |
| US20170270764A1 (en) | 2014-05-09 | 2017-09-21 | Smiths Heimann Gmbh | The method and device for monitoring the attentiveness of an operating person |
| WO2017190561A1 (en) | 2016-05-06 | 2017-11-09 | 平安科技(深圳)有限公司 | Method for realizing password inputting by means of virtual keyboard, terminal, server, system and storage medium |
| US20180032831A1 (en) | 2009-07-31 | 2018-02-01 | Samsung Electronics Co., Ltd. | Character recognition and character input apparatus using touch screen and method thereof |
| KR20180056116A (en) | 2016-11-18 | 2018-05-28 | 조선대학교산학협력단 | Method and apparatus for authentication using circulation secure keypad and overlapping image |
| EP3355512A1 (en) | 2015-09-23 | 2018-08-01 | Harex Infotech Inc. | Method and system for authenticating identity using variable keypad |
| US10108796B2 (en) | 2012-12-12 | 2018-10-23 | BBPOS Limited | System and method for PIN entry on mobile devices |
| US20180374392A1 (en) | 2015-12-28 | 2018-12-27 | Mobeewave, Inc. | System for and method of authenticating a user on a device |
Family Cites Families (27)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| NL9100234A (en) | 1991-02-11 | 1992-09-01 | Philips Nv | CODING CIRCUIT FOR TRANSFORMING CODING OF AN IMAGE SIGNAL AND DECODING CIRCUIT FOR DECODING THEREOF. |
| US5638501A (en)* | 1993-05-10 | 1997-06-10 | Apple Computer, Inc. | Method and apparatus for displaying an overlay image |
| US5475756A (en)* | 1994-02-17 | 1995-12-12 | At&T Corp. | Method of authenticating a terminal in a transaction execution system |
| US5802199A (en)* | 1994-11-28 | 1998-09-01 | Smarttouch, Llc | Use sensitive identification system |
| AU727387B2 (en)* | 1996-08-28 | 2000-12-14 | Via, Inc. | Touch screen systems and methods |
| JP2001117873A (en)* | 1999-10-19 | 2001-04-27 | Hitachi Ltd | Terminal identification method |
| BR0109210A (en) | 2000-03-13 | 2002-12-17 | Pittway Corp | Integrated security and communication system with secure communication connection |
| US7086085B1 (en)* | 2000-04-11 | 2006-08-01 | Bruce E Brown | Variable trust levels for authentication |
| JP2004514161A (en)* | 2000-11-11 | 2004-05-13 | スリーウィンドットコム カンパニー リミティッド | Secret information input method and device |
| US20150135206A1 (en)* | 2002-05-10 | 2015-05-14 | Convergent Media Solutions Llc | Method and apparatus for browsing using alternative linkbases |
| BRPI0401255A (en)* | 2004-03-16 | 2005-11-01 | Chang Das Estrelas Wilches | Dynamic coding interface authentication system and method |
| US7515135B2 (en)* | 2004-06-15 | 2009-04-07 | Research In Motion Limited | Virtual keypad for touchscreen display |
| KR100594443B1 (en) | 2004-06-17 | 2006-06-30 | 엘지전자 주식회사 | How to enter a secure password |
| US7596701B2 (en)* | 2004-07-07 | 2009-09-29 | Oracle International Corporation | Online data encryption and decryption |
| US20070007393A1 (en)* | 2004-08-04 | 2007-01-11 | Interstellar Technologies Corporation | Method for propulsion |
| AU2007268223B2 (en)* | 2006-05-24 | 2010-10-07 | Vidoop, L.L.C. | Graphical image authentication and security system |
| US8834408B2 (en)* | 2006-11-06 | 2014-09-16 | Aardvark Medical, Inc. | Irrigation and aspiration devices and methods |
| ITRM20070260A1 (en)* | 2007-05-09 | 2008-11-10 | Menstecnica S R L | PORTABLE AND INDEPENDENT SYSTEM FOR THE MEMORY STORAGE AND DISPLACEMENT OF PASSWORD AND PIN |
| US8532498B2 (en)* | 2008-02-08 | 2013-09-10 | Celight | Secure orthogonal frequency multiplexed optical communications |
| KR101412586B1 (en)* | 2008-07-01 | 2014-07-02 | 엘지전자 주식회사 | Method for input of mobile terminal |
| US20110029971A1 (en)* | 2009-07-30 | 2011-02-03 | Fujitsu Limited | Information processing apparatus, image processing method and computer program |
| CN102262760A (en)* | 2010-05-28 | 2011-11-30 | 杨筑平 | Transaction security method, acceptance device and submission software |
| CN102486678B (en)* | 2010-12-01 | 2015-01-28 | 福建星网视易信息系统有限公司 | Electronic device and keyboard device thereof and keyboard input method |
| US9195321B2 (en)* | 2011-03-17 | 2015-11-24 | Intellitact Llc | Input device user interface enhancements |
| US20140341109A1 (en)* | 2011-06-02 | 2014-11-20 | Interdigital Patent Holdings, Inc. | Methods, Apparatus and Systems for Managing Converged Gateway Communications |
| EP2716115A1 (en)* | 2011-06-02 | 2014-04-09 | Interdigital Patent Holdings, Inc. | Methods, apparatus and systems for inter-converged gateway (icgw) communications |
| JP5568077B2 (en)* | 2011-12-28 | 2014-08-06 | 楽天株式会社 | Information processing apparatus, information processing method, information processing program, and recording medium on which information processing program is recorded |
- 2012
- 2012-07-20GBGB201212878Apatent/GB201212878D0/ennot_activeCeased
- 2013
- 2013-04-04GBGB201306053Apatent/GB201306053D0/ennot_activeCeased
- 2013-07-17CACA2878728Apatent/CA2878728A1/ennot_activeAbandoned
- 2013-07-17EPEP19151229.2Apatent/EP3489918A1/ennot_activeCeased
- 2013-07-17USUS14/416,054patent/US9552465B2/ennot_activeExpired - Fee Related
- 2013-07-17JPJP2015522167Apatent/JP6364408B2/ennot_activeExpired - Fee Related
- 2013-07-17RURU2015103804Apatent/RU2639674C2/enactive
- 2013-07-17KRKR1020157004266Apatent/KR101916173B1/ennot_activeExpired - Fee Related
- 2013-07-17SGSG11201500411YApatent/SG11201500411YA/enunknown
- 2013-07-17MXMX2015000757Apatent/MX354996B/enactiveIP Right Grant
- 2013-07-17NZNZ744304Apatent/NZ744304A/ennot_activeIP Right Cessation
- 2013-07-17MXMX2017015124Apatent/MX372767B/enunknown
- 2013-07-17WOPCT/GB2013/051913patent/WO2014013252A2/enactiveApplication Filing
- 2013-07-17GBGB1502190.0Apatent/GB2520207B8/enactiveActive
- 2013-07-17RURU2017141959Apatent/RU2759365C1/enactive
- 2013-07-17BRBR112015000980-8Apatent/BR112015000980B1/ennot_activeIP Right Cessation
- 2013-07-17EPEP13744777.7Apatent/EP2875496B1/enactiveActive
- 2013-07-17CNCN201380038373.1Apatent/CN104584086B/ennot_activeExpired - Fee Related
- 2013-07-17NZNZ739581Apatent/NZ739581A/ennot_activeIP Right Cessation
- 2013-07-17SGSG10201701975WApatent/SG10201701975WA/enunknown
- 2013-07-17AUAU2013291755Apatent/AU2013291755B2/ennot_activeCeased
- 2013-07-17GBGB1500219.9Apatent/GB2517879B/ennot_activeExpired - Fee Related
- 2013-07-17MYMYPI2015000114Apatent/MY171482A/enunknown
- 2013-07-17EPEP21168370.1Apatent/EP3929888A1/ennot_activeWithdrawn
- 2013-07-17GBGB1906165.4Apatent/GB2571019B/ennot_activeExpired - Fee Related
- 2013-07-17CNCN202110878983.9Apatent/CN113393612A/enactivePending
- 2013-07-17CNCN201710958821.XApatent/CN107742362B/ennot_activeExpired - Fee Related
- 2013-07-18TWTW102125757Apatent/TWI628555B/ennot_activeIP Right Cessation
- 2014
- 2014-12-23ZAZA2014/09529Apatent/ZA201409529B/enunknown
- 2015
- 2015-01-18ILIL236779Apatent/IL236779A/enactiveIP Right Grant
- 2016
- 2016-04-08USUS15/094,383patent/US10366215B2/enactiveActive
- 2016-06-29USUS15/197,086patent/US10565359B2/ennot_activeExpired - Fee Related
- 2016-07-12JPJP2016137756Apatent/JP2016197443A/enactivePending
- 2016-09-07AUAU2016101576Apatent/AU2016101576B4/ennot_activeExpired
- 2016-09-07AUAU2016225848Apatent/AU2016225848B2/ennot_activeCeased
- 2016-09-07AUAU2016101577Apatent/AU2016101577B4/ennot_activeExpired
- 2017
- 2017-08-27ILIL254163Apatent/IL254163B/enactiveIP Right Grant
- 2019
- 2019-12-17USUS16/718,158patent/US11048783B2/ennot_activeExpired - Fee Related
- 2019-12-30USUS16/730,017patent/US11048784B2/ennot_activeExpired - Fee Related
- 2020
- 2020-01-29USUS16/776,195patent/US11194892B2/enactiveActive
- 2021
- 2021-11-29USUS17/537,257patent/US20220156350A1/ennot_activeAbandoned
Patent Citations (441)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| GB271884A (en) | 1926-05-25 | 1928-06-28 | Ig Farbenindustrie Ag | Manufacture of ª‡-anthraquinonyl ketones |
| US2819067A (en) | 1955-12-22 | 1958-01-07 | Burroughs Corp | Check shingling machine |
| US3201732A (en) | 1959-09-25 | 1965-08-17 | Westinghouse Electric Corp | Wound magnetic core having turns which are given a predetermined set in radius before winding |
| US3176324A (en) | 1963-01-11 | 1965-04-06 | American Metal Prod | Spring construction |
| US3270720A (en) | 1963-03-09 | 1966-09-06 | Daimler Benz Ag | Rotary piston internal combustion engine |
| US3413071A (en) | 1963-07-18 | 1968-11-26 | Davis Chester | Hexamethyltriaminophenylfluorene printing composition and manifolding sheet therewith |
| US3375428A (en) | 1964-02-04 | 1968-03-26 | Lorain Prod Corp | Regulated rectifier circuit |
| US3255323A (en) | 1964-05-21 | 1966-06-07 | Edward C Austin | Automotive maintenance signalling device |
| US3392846A (en) | 1964-10-01 | 1968-07-16 | American Air Filter Co | Unit filter assembly |
| US3347103A (en) | 1964-11-27 | 1967-10-17 | Bendix Corp | Velocity sensor |
| US3364601A (en) | 1966-01-19 | 1968-01-23 | Albert H. Korenek | Apparatus for excavating plants for transplanting |
| US3621242A (en) | 1969-12-31 | 1971-11-16 | Bendix Corp | Dynamic field time-of-flight mass spectrometer |
| US3762876A (en) | 1971-10-07 | 1973-10-02 | Honeywell Inc | Driven vane anemometers |
| US3965066A (en) | 1974-03-15 | 1976-06-22 | General Electric Company | Combustor-turbine nozzle interconnection |
| FR2622322A1 (en) | 1987-10-21 | 1989-04-28 | Weck Arnaud De | Encrypted keyboard system |
| US5193152A (en) | 1989-11-03 | 1993-03-09 | Racal-Datacom, Inc. | Network management system with group naming |
| EP0432409A1 (en) | 1989-12-05 | 1991-06-19 | Theodor Kromer GmbH & Co.KG Spezialfabrik für Sicherheitsschlösser | Data input keyboard for coded locks or the like |
| US5219794A (en) | 1991-03-14 | 1993-06-15 | Hitachi, Ltd. | Semiconductor integrated circuit device and method of fabricating same |
| US5257486A (en) | 1991-04-23 | 1993-11-02 | Adhesives Technology Corporation 1987 | Nozzle for injecting a sealant into a crack |
| DE4129202A1 (en) | 1991-09-03 | 1993-03-04 | Hauni Elektronik Gmbh | Protection circuit for personal identification number key=pad - uses number of keys to enter PIN value, with indicated values varying in pseudo-random manner |
| WO1993011551A1 (en) | 1991-12-06 | 1993-06-10 | Maurras Jean Francois | Rendum reset keypad |
| US5209102A (en) | 1992-01-31 | 1993-05-11 | American Air Liquide | Method of introducing and controlling compressed gases for impurity analysis |
| US5434702A (en) | 1992-03-04 | 1995-07-18 | Northern Telecom Limited | Optical repeaters |
| US5234389A (en) | 1992-03-23 | 1993-08-10 | Ford Motor Company | Releasable overrunning coupling power transmission mechanism acting in cooperation with a friction brake |
| US5949348A (en) | 1992-08-17 | 1999-09-07 | Ncr Corporation | Method and apparatus for variable keyboard display |
| US5363449A (en) | 1993-03-11 | 1994-11-08 | Tandem Computers Incorporated | Personal identification encryptor and method |
| US5549194A (en) | 1993-12-16 | 1996-08-27 | Joh. Winklhofer & Sohne | Accumulating conveyor chain |
| EP0662665A2 (en) | 1994-01-05 | 1995-07-12 | Transaction Technology, Inc. | Wireless banking terminal using cellular telephone communication |
| US5715078A (en) | 1994-03-24 | 1998-02-03 | Kabushiki Kaisha Toshiba | Optical exposure unit and image forming unit used in optical exposure unit |
| US5504808A (en) | 1994-06-01 | 1996-04-02 | Hamrick, Jr.; James N. | Secured disposable debit card calling system and method |
| US5754652A (en) | 1994-12-14 | 1998-05-19 | Lucent Technologies Inc. | Method and apparatus for secure pin entry |
| WO1997005578A1 (en) | 1995-07-28 | 1997-02-13 | Mytec Technologies Inc. | Method and apparatus for securely handling a personal identification number or cryptographic key using biometric techniques |
| EP0870222A2 (en) | 1995-08-21 | 1998-10-14 | Cornel Sirbu | Conditional access method and device |
| US20020023215A1 (en) | 1996-12-04 | 2002-02-21 | Wang Ynjiun P. | Electronic transaction systems and methods therefor |
| US6219794B1 (en) | 1997-04-21 | 2001-04-17 | Mytec Technologies, Inc. | Method for secure key management using a biometric |
| US6193152B1 (en) | 1997-05-09 | 2001-02-27 | Receiptcity.Com, Inc. | Modular signature and data-capture system and point of transaction payment and reward system |
| US5990586A (en) | 1997-06-23 | 1999-11-23 | Seitz Corporation | Multi-actuator having position controller |
| US7047222B1 (en) | 1997-08-06 | 2006-05-16 | International Business Machines Corporation | Secure encryption of data packets for transmission over unsecured networks |
| DE19803339A1 (en) | 1998-01-29 | 1999-08-05 | Deutsche Telekom Ag | Access authorization verification method for banking machine or computer system |
| US6234389B1 (en) | 1998-04-29 | 2001-05-22 | @Pos.Com, Inc. | PCMCIA-based point of sale transaction system |
| US20170061138A1 (en) | 1998-07-16 | 2017-03-02 | NoisyCloud, Inc. | System and method for secure data transmission and storage |
| JP2000099801A (en) | 1998-09-24 | 2000-04-07 | Oki Electric Ind Co Ltd | PIN input device |
| WO2000025474A1 (en) | 1998-10-26 | 2000-05-04 | Bradley Madison Company Doing Business As Evolv Adaptive Technology | Cryptographic protocol for financial transactions |
| US6257486B1 (en) | 1998-11-23 | 2001-07-10 | Cardis Research & Development Ltd. | Smart card pin system, card, and reader |
| JP2000165378A (en) | 1998-11-26 | 2000-06-16 | Kodo Ido Tsushin Security Gijutsu Kenkyusho:Kk | Fingerprint authentication device |
| US6434702B1 (en) | 1998-12-08 | 2002-08-13 | International Business Machines Corporation | Automatic rotation of digit location in devices used in passwords |
| US6209102B1 (en) | 1999-02-12 | 2001-03-27 | Arcot Systems, Inc. | Method and apparatus for secure entry of access codes in a computer environment |
| US6630928B1 (en) | 1999-10-01 | 2003-10-07 | Hewlett-Packard Development Company, L.P. | Method and apparatus for touch screen data entry |
| US6549194B1 (en) | 1999-10-01 | 2003-04-15 | Hewlett-Packard Development Company, L.P. | Method for secure pin entry on touch screen display |
| EP1161060A1 (en) | 1999-12-10 | 2001-12-05 | NTT DoCoMo, Inc. | Mobile communication terminal and card information reader |
| US6671405B1 (en) | 1999-12-14 | 2003-12-30 | Eastman Kodak Company | Method for automatic assessment of emphasis and appeal in consumer images |
| WO2001046922A2 (en) | 1999-12-20 | 2001-06-28 | Online Resources Corp. | Method and apparatus for securely conducting financial transactions over an insecure network |
| US6715078B1 (en) | 2000-03-28 | 2004-03-30 | Ncr Corporation | Methods and apparatus for secure personal identification number and data encryption |
| FR2810067A3 (en) | 2000-04-10 | 2001-12-14 | Lundar Electric Ind Co Ltd | Hinge for oven door has cut outs in door flanges fitting onto stubs on oven casing and retained by pins |
| US20040182921A1 (en) | 2000-05-09 | 2004-09-23 | Dickson Timothy E. | Card reader module with account encryption |
| US20020016918A1 (en) | 2000-05-12 | 2002-02-07 | David Tucker | Information security method and system |
| US7305565B1 (en) | 2000-05-31 | 2007-12-04 | Symbol Technologies, Inc. | Secure, encrypting pin pad |
| US6990586B1 (en) | 2000-06-02 | 2006-01-24 | International Business Machines Corp. | Secure data transmission from unsecured input environments |
| US20030120612A1 (en) | 2000-06-13 | 2003-06-26 | Kabushiki Kaisha Eighting | Method of electronic settlement with a mobile terminal |
| FR2812423A1 (en) | 2000-07-26 | 2002-02-01 | Yohan Amsellem | Card payment for an Internet transaction, uses code table prepared when card is manufactured with server interrogation of user who must return correct entries from the code table |
| US20020082962A1 (en) | 2000-07-27 | 2002-06-27 | Farris Robert G. | Value transfer system for unbanked customers |
| US20050075973A1 (en) | 2000-08-22 | 2005-04-07 | Siamack Yousofi | Validation of transactions |
| US20020046185A1 (en) | 2000-08-30 | 2002-04-18 | Jean-Marc Villart | System and method conducting POS transactions |
| US20020029342A1 (en) | 2000-09-07 | 2002-03-07 | Keech Winston Donald | Systems and methods for identity verification for secure transactions |
| US20040010690A1 (en) | 2000-11-11 | 2004-01-15 | Eon-Cheol Shin | Method and system for inputting secret information |
| US20030212327A1 (en) | 2000-11-24 | 2003-11-13 | U-Systems Inc. | Adjunctive ultrasound processing and display for breast cancer screening |
| FR2819067A1 (en) | 2000-12-29 | 2002-07-05 | Yakoubi Boualem | Method for controlling access to a secure system, such as an automatic teller machine, using a keyboard for PIN entry, where the values of the keys displayed on a touch screen are changed in a random manner to prevent fraud |
| DE10100188A1 (en) | 2001-01-04 | 2002-07-18 | Rohde & Schwarz | System for encoding PIN code encodes code using biometric signal and stores it; stored encoded PIN code can only be read out of memory and decoded by using same biometric signal |
| US20020123972A1 (en) | 2001-02-02 | 2002-09-05 | Hodgson Robert B. | Apparatus for and method of secure ATM debit card and credit card payment transactions via the internet |
| US20020129250A1 (en) | 2001-02-27 | 2002-09-12 | Akira Kimura | Authentication system and method, identification information inputting method and apparatus ands portable terminal |
| WO2002071177A2 (en) | 2001-03-03 | 2002-09-12 | Moneyhive.Com Pte Ltd | Method and system for substantially secure electronic transactions |
| US20050010786A1 (en) | 2001-03-30 | 2005-01-13 | Michener John R. | Trusted authorization device |
| US7010806B2 (en) | 2001-05-18 | 2006-03-07 | Sun Microsystems, Inc. | Dynamic downloading of keyboard keycode data to a networked client |
| US20020188872A1 (en) | 2001-06-06 | 2002-12-12 | Willeby Tandy G. | Secure key entry using a graphical user inerface |
| US20030004877A1 (en) | 2001-06-27 | 2003-01-02 | Fujitsu Limited | Transaction terminal apparatus |
| US20030002667A1 (en) | 2001-06-29 | 2003-01-02 | Dominique Gougeon | Flexible prompt table arrangement for a PIN entery device |
| US20030120936A1 (en) | 2001-08-01 | 2003-06-26 | Eft Datalink | Encryption of financial information |
| WO2003058947A2 (en) | 2001-12-26 | 2003-07-17 | Vivotech, Inc. | Adaptor for magnetic stripe card reader |
| US7092915B2 (en) | 2002-01-07 | 2006-08-15 | International Business Machines Corporation | PDA password management tool |
| US20030132918A1 (en) | 2002-01-11 | 2003-07-17 | Fitch Timothy R. | Ergonomically designed multifunctional transaction terminal |
| US7992007B2 (en) | 2002-02-05 | 2011-08-02 | Cardinalcommerce Corporation | Dynamic pin pad for credit/debit/ other electronic transactions |
| US20120323788A1 (en) | 2002-02-05 | 2012-12-20 | Cardinalcommerce Corporation | Dynamic pin pad for credit/debit/other electronic transactions |
| US7003316B1 (en) | 2002-02-22 | 2006-02-21 | Virtual Fonlink, Inc. | System and method for wireless transactions |
| GB2387702A (en) | 2002-04-17 | 2003-10-22 | Cellectivity Ltd | Method of access control using PIN codes |
| GB2388229A (en) | 2002-05-04 | 2003-11-05 | Robert Macalonan | Keypad for generating code with scrambled displayed key sequence |
| JP2003346098A (en) | 2002-05-24 | 2003-12-05 | Fuji Xerox Co Ltd | Personal identification system and method and terminal device for personal identification |
| US20060026440A1 (en) | 2002-05-31 | 2006-02-02 | Jean-Paul Sauvebois | Method for securing an on-line transaction |
| US20030229597A1 (en) | 2002-06-05 | 2003-12-11 | Sun Microsystems, Inc., A Delaware Corporation | Apparatus for private personal identification number management |
| US20030229598A1 (en) | 2002-06-05 | 2003-12-11 | Sun Microsystems, Inc., A Delaware Corporation | Method and apparatus for protecting against side channel attacks against personal identification numbers |
| US20030229791A1 (en) | 2002-06-05 | 2003-12-11 | Sun Microsystems, Inc. A Delaware Corporation | Method for private personal identification number management |
| GB2389693A (en) | 2002-06-10 | 2003-12-17 | Consignia Plc | Payment systems |
| US20040039933A1 (en) | 2002-08-26 | 2004-02-26 | Cricket Technologies | Document data profiler apparatus, system, method, and electronically stored computer program product |
| US20040044739A1 (en) | 2002-09-04 | 2004-03-04 | Robert Ziegler | System and methods for processing PIN-authenticated transactions |
| JP2004102460A (en) | 2002-09-06 | 2004-04-02 | Hitachi Software Eng Co Ltd | Personal authentication method and program therefor |
| US20060182715A1 (en) | 2002-09-27 | 2006-08-17 | Alfred Sandrock | Therapies for chronic inflammatory demyelinating polyneuropathy using interferon-ss |
| US20060155619A1 (en) | 2002-09-27 | 2006-07-13 | Rhiando Maxwell E | Identification system |
| US20040073809A1 (en) | 2002-10-10 | 2004-04-15 | Wing Keong Bernard Ignatius Ng | System and method for securing a user verification on a network using cursor control |
| US20040122768A1 (en) | 2002-12-19 | 2004-06-24 | International Business Machines Corporation | Electronic wallet for wireless computing device |
| US20040122771A1 (en) | 2002-12-19 | 2004-06-24 | International Business Machines Corporation | Automated teller machine for use with computing devices |
| US7698563B2 (en) | 2002-12-23 | 2010-04-13 | Hwa-Shik Shin | Device and method for inputting password using random keypad |
| US20060053301A1 (en) | 2002-12-23 | 2006-03-09 | Hwa-Shik Shin | Device and method for inputting password using random keypad |
| US7735121B2 (en) | 2003-01-07 | 2010-06-08 | Masih Madani | Virtual pad |
| DE10306352A1 (en) | 2003-02-15 | 2004-09-02 | Fuchsenberger, Walter, Dipl.-Ing. (FH) | Code number input device for PIN or password in cash machine or access control system, randomly assigns symbols of keypad to individual keys, and resets after input process |
| EP1599786A2 (en) | 2003-02-25 | 2005-11-30 | Banco Ita S.A. | Virtual keyboard |
| US20050036611A1 (en) | 2003-03-31 | 2005-02-17 | Visa U.S.A., Inc. | Method and system for secure authentication |
| US7243237B2 (en) | 2003-05-02 | 2007-07-10 | Microsoft Corporation | Secure communication with a keyboard or related device |
| GB2402649A (en) | 2003-06-11 | 2004-12-15 | Mathew Jonathan Dawson | Personal identification code entry device |
| US20050012715A1 (en) | 2003-06-12 | 2005-01-20 | Peter Charles Shann Hubird Ford | Method, system, and software for interactive communication and analysis |
| US20050043997A1 (en) | 2003-08-18 | 2005-02-24 | Sahota Jagdeep Singh | Method and system for generating a dynamic verification value |
| US7091845B2 (en) | 2003-09-05 | 2006-08-15 | Hirsch Electronics Corporation | Data entry systems with biometric devices for security access control |
| CN100583113C (en) | 2003-09-19 | 2010-01-20 | 谢道裕 | Magic square digital antifake method and its antifake system |
| JP2005107678A (en) | 2003-09-29 | 2005-04-21 | Nec Corp | Device, method and program for password authentication |
| US20050127158A1 (en) | 2003-12-15 | 2005-06-16 | Figueras Ilka H. | Control card check |
| US20050127156A1 (en) | 2003-12-15 | 2005-06-16 | Samsung Electronics Co., Ltd. | Portable handset having a radio frequency indentification(RFID) function and method using the same |
| US20050144449A1 (en) | 2003-12-30 | 2005-06-30 | Entrust Limited | Method and apparatus for providing mutual authentication between a sending unit and a recipient |
| US20050140832A1 (en) | 2003-12-31 | 2005-06-30 | Ron Goldman | Laser projection display |
| US20050146447A1 (en) | 2004-01-05 | 2005-07-07 | Samsung Electronics Co., Ltd. | Terminal having keyboard with keys variable in arrangement, and method of rearranging keys of keyboard |
| US20050177522A1 (en) | 2004-02-05 | 2005-08-11 | Sun Microsystems, Inc. | Method and system for accepting a pass code |
| US20050193208A1 (en) | 2004-02-26 | 2005-09-01 | Charrette Edmond E.Iii | User authentication |
| US20050212763A1 (en) | 2004-03-26 | 2005-09-29 | Cannon Kabushiki Kaisha | Information processing apparatus and method |
| WO2005104428A2 (en) | 2004-04-23 | 2005-11-03 | Virtual Fonlink, Inc. | Enhanced system and method for wireless transactions |
| US7395506B2 (en) | 2004-05-10 | 2008-07-01 | Microsoft Corporation | Spy-resistant keyboard |
| EP1600847A1 (en) | 2004-05-17 | 2005-11-30 | Ahmed Merrouk | Universal device for secure input of confidential data |
| US8621242B2 (en) | 2004-06-11 | 2013-12-31 | Arm Limited | Display of a verification image to confirm security |
| US20060003706A1 (en) | 2004-06-30 | 2006-01-05 | Welland David R | Ratiometric transmit path architecture for communication systems |
| JP2008506198A (en) | 2004-07-07 | 2008-02-28 | バローザ インコーポレイテッド | Online data encryption and decryption |
| US20060104446A1 (en) | 2004-07-07 | 2006-05-18 | Varghese Thomas E | Online data encryption and decryption |
| WO2006010058A2 (en) | 2004-07-07 | 2006-01-26 | Bharosa Inc. | Online data encryption and decryption |
| GB2416058A (en) | 2004-07-09 | 2006-01-11 | Tricerion Ltd | Secure data communication between a client terminal and remote server |
| US20060037067A1 (en) | 2004-07-09 | 2006-02-16 | Tricerion Ltd. | Method of secure data communication |
| EP1615181A1 (en) | 2004-07-09 | 2006-01-11 | Tricerion Ltd | A method of secure data communication |
| US20060018467A1 (en) | 2004-07-20 | 2006-01-26 | Scribocel, Inc. | Device for authentication and identification for computerized and networked systems |
| US20060017691A1 (en) | 2004-07-23 | 2006-01-26 | Juan Manuel Cruz-Hernandez | System and method for controlling audio output associated with haptic effects |
| US20060032705A1 (en) | 2004-08-16 | 2006-02-16 | Isham William R | Lightweight composite ladder rail having supplemental reinforcement in regions subject to greater structural stress |
| US20060136334A1 (en) | 2004-11-29 | 2006-06-22 | Atkinson Steven P | Electronic system for provision of banking services |
| US20060133597A1 (en) | 2004-12-08 | 2006-06-22 | Song Seung M | System for protecting personal information of a customer when receiving on-line services from a service provider |
| US20090328197A1 (en) | 2004-12-16 | 2009-12-31 | Mark Dwight Newell | User validation using images |
| WO2006064241A2 (en) | 2004-12-16 | 2006-06-22 | Mark Dwight Bedworth | User validation using images |
| US20060149845A1 (en) | 2004-12-30 | 2006-07-06 | Xinnia Technology, Llc | Managed quality of service for users and applications over shared networks |
| US20060146169A1 (en) | 2005-01-03 | 2006-07-06 | Yosef Segman | Electronic viewing device |
| JP2006243938A (en) | 2005-03-01 | 2006-09-14 | Oki Electric Ind Co Ltd | Password input device |
| WO2006095203A1 (en) | 2005-03-07 | 2006-09-14 | Tricerion Ltd | A method of secure data communication |
| JP2008537210A (en) | 2005-03-07 | 2008-09-11 | トリセリオン リミテッド | Secured data communication method |
| US20060206919A1 (en) | 2005-03-10 | 2006-09-14 | Axalto Sa | System and method of secure login on insecure systems |
| US20060224523A1 (en) | 2005-03-31 | 2006-10-05 | Elvitigala Rajith T | Dynamic keypad |
| US20060221059A1 (en) | 2005-04-01 | 2006-10-05 | Samsung Electronics Co., Ltd. | Portable terminal having display buttons and method of inputting functions using display buttons |
| US20160320965A1 (en) | 2005-04-22 | 2016-11-03 | Neopad Inc. | Creation method for characters/words and the information and communication service method thereby |
| US20060247533A1 (en) | 2005-04-27 | 2006-11-02 | Sony Corporation | Pseudorandom number generation apparatus, pseudorandom number generation method and program |
| GB2427059A (en) | 2005-06-06 | 2006-12-13 | Bristol Office Machines | Portable transaction processing device |
| US20070014415A1 (en) | 2005-06-16 | 2007-01-18 | Harrison Keith A | Quantum key distribution method and apparatus |
| US20070005500A1 (en) | 2005-06-20 | 2007-01-04 | Microsoft Corporation | Secure online transactions using a captcha image as a watermark |
| EP1742450A2 (en) | 2005-07-05 | 2007-01-10 | Sony Ericsson Mobile Communications Japan, Inc. | Method and mobile terminal device with biometric encrypted personal identification number |
| US20100098300A1 (en) | 2005-08-05 | 2010-04-22 | Tilman Otto | Method and system for biometric identification or verification |
| US20070073937A1 (en)* | 2005-09-15 | 2007-03-29 | Eugene Feinberg | Content-Aware Digital Media Storage Device and Methods of Using the Same |
| US20070089164A1 (en) | 2005-10-18 | 2007-04-19 | Gao Jie J | System and method of alternative key pad layout for enhanced security |
| US20080172735A1 (en) | 2005-10-18 | 2008-07-17 | Jie Jenie Gao | Alternative Key Pad Layout for Enhanced Security |
| US20070101150A1 (en) | 2005-11-02 | 2007-05-03 | Konica Minolta Business Technologies, Inc. | Information processing apparatus |
| US20090067627A1 (en) | 2005-11-04 | 2009-03-12 | Christian Hogl | Method and System for Transmitting Data From a First Data Processing Device to a Second Data Processing Device |
| WO2007056746A2 (en) | 2005-11-08 | 2007-05-18 | Ultra-Scan Corporation | System and method for providing security |
| US20070110224A1 (en) | 2005-11-14 | 2007-05-17 | Accenture Global Services Gmbh | Data masking application |
| US20080319902A1 (en) | 2005-11-18 | 2008-12-25 | Mark Mervyn Chazan | Method and Apparatus for Facilitating a Secure Transaction |
| US9235967B1 (en) | 2005-12-20 | 2016-01-12 | Diebold Self-Service Systems Division Of Diebold, Incorporated | Banking system controlled responsive to data bearing records |
| US20170140354A1 (en) | 2005-12-20 | 2017-05-18 | Diebold Nixdorf, Incorporated | Tactile touch screen |
| US9082253B1 (en) | 2005-12-20 | 2015-07-14 | Diebold Self-Service Systems Division Of Diebold, Incorporated | Banking system controlled responsive to data bearing records |
| US20070209014A1 (en) | 2006-01-11 | 2007-09-06 | Youssef Youmtoub | Method and apparatus for secure data input |
| US20070182715A1 (en) | 2006-02-03 | 2007-08-09 | Research In Motion Limited | Configurable handheld electronic device |
| US8270720B1 (en) | 2006-02-21 | 2012-09-18 | Gruntworx, Llc | Method and system for secure data entry |
| US20070213090A1 (en) | 2006-03-07 | 2007-09-13 | Sony Ericsson Mobile Communications Ab | Programmable keypad |
| EP1840778A1 (en) | 2006-03-29 | 2007-10-03 | Laurent Busser | Single-use identification device |
| US20100186076A1 (en) | 2006-03-31 | 2010-07-22 | Axalto Sa | Method and system of providing security services using a secure device |
| US20100223663A1 (en) | 2006-04-21 | 2010-09-02 | Mitsubishi Electric Corporation | Authenticating server device, terminal device, authenticating system and authenticating method |
| US8117458B2 (en) | 2006-05-24 | 2012-02-14 | Vidoop Llc | Methods and systems for graphical image authentication |
| US20090270078A1 (en) | 2006-05-30 | 2009-10-29 | Gi-Seon Nam | Method for configurating keypad of terminal and the terminal and system including the terminal and the keypad capable of reconfiguration |
| US20070282756A1 (en) | 2006-06-02 | 2007-12-06 | First Data Corporation | Pin creation system and method |
| US20070279391A1 (en) | 2006-06-06 | 2007-12-06 | Marttila Charles A | Keypad with virtual image |
| WO2007143740A2 (en) | 2006-06-08 | 2007-12-13 | Mastercard International Incorporated | All-in-one proximity payment device with local authentication |
| GB2438886A (en) | 2006-06-10 | 2007-12-12 | Gina Maria Eldon | Random personal identification number input screen |
| US20080011098A1 (en) | 2006-06-29 | 2008-01-17 | Krohne Ag | A heated pipe connecting device for installation of a flow meter |
| US20080014818A1 (en) | 2006-07-12 | 2008-01-17 | Marc Privitera | Post conversion nonwovens processing |
| US20100049768A1 (en) | 2006-07-20 | 2010-02-25 | Robert James C | Automatic management of digital archives, in particular of audio and/or video files |
| US20090277968A1 (en) | 2006-09-07 | 2009-11-12 | Matthew Walker | Visual code transaction verification |
| US20080110981A1 (en)* | 2006-11-13 | 2008-05-15 | Gilbarco Inc. | Projected user input device for a fuel dispenser and related applications |
| US20100153270A1 (en) | 2006-11-27 | 2010-06-17 | Broca Communications Limited | Authentication of message recipients |
| US20080148186A1 (en) | 2006-12-18 | 2008-06-19 | Krishnamurthy Sandeep Raman | Secure data entry device and method |
| CN201035502Y (en) | 2006-12-28 | 2008-03-12 | 上海麦柯信息技术有限公司 | Safety accidental dynamic soft keyboard |
| US20080168546A1 (en) | 2007-01-10 | 2008-07-10 | John Almeida | Randomized images collection method enabling a user means for entering data from an insecure client-computing device to a server-computing device |
| US20080165035A1 (en) | 2007-01-10 | 2008-07-10 | Bhella Kenneth S | Method and System for Customizing Keyboard Map Variants |
| US8297173B1 (en) | 2007-01-10 | 2012-10-30 | Wilcox Industries Corp. | Modular weapon video display system |
| US20100121737A1 (en) | 2007-01-12 | 2010-05-13 | Kenji Yoshida | Personal identification number code input method using dot pattern, personal identification number code input method, and internet shopping settlement system |
| US20080184036A1 (en) | 2007-01-31 | 2008-07-31 | Microsoft Corporation | Password authentication via a one-time keyboard map |
| US20080251969A1 (en) | 2007-02-16 | 2008-10-16 | Isham William R | Bladder Molding Systems and Methods For Fabricating Composite Articles |
| JP2008204409A (en) | 2007-02-23 | 2008-09-04 | Oki Electric Ind Co Ltd | Password input display device and method |
| US20080209223A1 (en) | 2007-02-27 | 2008-08-28 | Ebay Inc. | Transactional visual challenge image for user verification |
| US20100182244A1 (en) | 2007-02-28 | 2010-07-22 | Ntt Docomo, Inc. | Information processing device and program |
| US20080280652A1 (en) | 2007-05-08 | 2008-11-13 | Firefly Mobile, Inc. | Reconfigurable keypad method in handset device operable with plural subsystems |
| US20080289035A1 (en) | 2007-05-18 | 2008-11-20 | International Business Machines Corporation | Method and system for preventing password theft through unauthorized keylogging |
| US20080306995A1 (en) | 2007-06-05 | 2008-12-11 | Newell Catherine D | Automatic story creation using semantic classifiers for images and associated meta data |
| CN201111222Y (en) | 2007-06-08 | 2008-09-03 | 北京工业大学 | Smart Security Keyboard |
| WO2009000223A2 (en) | 2007-06-27 | 2008-12-31 | Universität Tübingen | Device and method for tap-proof and manipulation-proof encoding of online accounts |
| CN101082948A (en) | 2007-07-05 | 2007-12-05 | 上海麦柯信息技术有限公司 | Portable anti-peeping safety keyboard and method of use thereof |
| WO2009009788A1 (en) | 2007-07-12 | 2009-01-15 | Jobmann Brian C | Identity authentication and secured access systems, components, and methods |
| JP2010533925A (en) | 2007-07-16 | 2010-10-28 | クゥアルコム・インコーポレイテッド | Method and system for personalizing and branding a mobile device keypad |
| WO2009012326A1 (en) | 2007-07-16 | 2009-01-22 | Qualcomm Incorporated | Methods and systems personalizing and branding mobile device keypads |
| US20090033522A1 (en) | 2007-07-30 | 2009-02-05 | Palm, Inc. | Electronic Device with Reconfigurable Keypad |
| US20090077383A1 (en) | 2007-08-06 | 2009-03-19 | De Monseignat Bernard | System and method for authentication, data transfer, and protection against phishing |
| US20090044282A1 (en) | 2007-08-09 | 2009-02-12 | Technology Properties Limited | System and Method for Generating and Displaying a Keyboard Comprising a Random Layout of Keys |
| US20090066660A1 (en) | 2007-09-06 | 2009-03-12 | Ure Michael J | Interface with and communication between mobile electronic devices |
| CN101126967A (en) | 2007-09-11 | 2008-02-20 | 卢心东 | Password input unit |
| US20090106827A1 (en) | 2007-10-22 | 2009-04-23 | International Business Machines Corporation | System and method for user password protection |
| FR2923034A1 (en) | 2007-10-26 | 2009-05-01 | Ingenico Sa | Payment terminal e.g. computer, for e.g. automatic fuel vending machine, has memory storing program for modifying keyboard configuration data before inputting information and controlling displaying of configuration after modifying data |
| GB2454459A (en) | 2007-11-06 | 2009-05-13 | Andrew Small | Personal identification code entry device |
| US20090183098A1 (en) | 2008-01-14 | 2009-07-16 | Dell Products, Lp | Configurable Keyboard |
| JP2009199581A (en) | 2008-01-21 | 2009-09-03 | Nec Corp | Personal identification number input device, method, and program, and cellular phone |
| US20090193210A1 (en) | 2008-01-29 | 2009-07-30 | Hewett Jeffrey R | System for Automatic Legal Discovery Management and Data Collection |
| US20140025580A1 (en) | 2008-02-20 | 2014-01-23 | Steven V. Bacastow | Method and System for Securing Payment Transactions |
| GB2457733A (en) | 2008-02-25 | 2009-08-26 | Mobank Ltd | Securing inputting of sensitive information |
| US20110191856A1 (en) | 2008-02-25 | 2011-08-04 | Dominic John Keen | Receiving input data |
| US20090213132A1 (en) | 2008-02-25 | 2009-08-27 | Kargman James B | Secure computer screen entry system and method |
| US20090235199A1 (en) | 2008-03-12 | 2009-09-17 | International Business Machines Corporation | Integrated masking for viewing of data |
| US20100323617A1 (en) | 2008-03-25 | 2010-12-23 | Logomotion, S.R.O. | Method, connection and data carrier to perform repeated operations on the key-board of mobile communication device |
| US20110018033A1 (en) | 2008-03-26 | 2011-01-27 | Sumitomo Chemical Company, Limited | Semiconductor wafer, semiconductor device, and method of manufacturing a semiconductor device |
| JP2009237774A (en) | 2008-03-26 | 2009-10-15 | Advanced Media Inc | Authentication server, service providing server, authentication method, communication terminal, and log-in method |
| US20090254986A1 (en) | 2008-04-08 | 2009-10-08 | Peter William Harris | Method and apparatus for processing and displaying secure and non-secure data |
| DE102008050609A1 (en) | 2008-04-09 | 2009-10-22 | Kevin Wessel | Actuating device for keypad of automated teller machine, has encoding device arranged between input keypad and actuating unit for another keypad, where encoding device comprises hydraulic and/or pneumatic unit |
| WO2009130985A1 (en) | 2008-04-23 | 2009-10-29 | コニカミノルタホールディングス株式会社 | Information input system |
| KR20090130455A (en) | 2008-06-16 | 2009-12-24 | 성균관대학교산학협력단 | How to change graphic keypad, key layout of graphic keypad, password authentication using graphic keypad |
| EP2141647A1 (en) | 2008-06-30 | 2010-01-06 | Accullink LLC | Systems and methods for secure pin-based transactions via a host based pin pad |
| US20110191591A1 (en) | 2008-07-08 | 2011-08-04 | Li Cheng | Transmitting Information Using Virtual Input Layout |
| US20100036783A1 (en) | 2008-08-06 | 2010-02-11 | Rodriguez Ralph A | Method of and apparatus for combining artificial intelligence (AI) concepts with event-driven security architectures and ideas |
| DE102009022845A1 (en) | 2008-08-15 | 2010-09-02 | Günzel, Andrea | Method for input of personal identification number keyboard for input of personal identification number, involves defining number allocation to individual push buttons or pressure zones with each input of chip or magnetic card in associated |
| US20170192670A1 (en) | 2008-09-19 | 2017-07-06 | Google Inc. | Quick Gesture Input |
| US20110180336A1 (en) | 2008-09-30 | 2011-07-28 | Toyota Jidosha Kabushiki Kaisha | Vehicle motor driving system |
| US20100109920A1 (en) | 2008-11-05 | 2010-05-06 | Michael Dennis Spradling | Security - input key shuffle |
| DE102008056605A1 (en) | 2008-11-10 | 2010-05-12 | Borchert, Bernd, Dr. | Method for manipulation-secure transmission of e.g. password, from client to server via computer network, for online-banking, involves reconstructing code word, and declining execution of transaction by server |
| US20100117792A1 (en) | 2008-11-13 | 2010-05-13 | Patrick Faith | Device including authentication glyph |
| US20100125509A1 (en) | 2008-11-14 | 2010-05-20 | Kranzley Arthur D | Methods and systems for secure mobile device initiated payments using generated image data |
| JP2010126913A (en) | 2008-11-25 | 2010-06-10 | Alpha Corp | Electronic lock device and locker equipment |
| US20100138666A1 (en) | 2008-12-01 | 2010-06-03 | Neil Patrick Adams | Simplified multi-factor authentication |
| US20100149100A1 (en) | 2008-12-15 | 2010-06-17 | Sony Ericsson Mobile Communications Ab | Electronic Devices, Systems, Methods and Computer Program Products for Detecting a User Input Device Having an Optical Marker Thereon |
| US8364601B2 (en) | 2008-12-31 | 2013-01-29 | Intel Corporation | Methods and systems to directly render an image and correlate corresponding user input in a secure memory domain |
| US20100175016A1 (en) | 2009-01-06 | 2010-07-08 | Wei Cheng Tian | Security key inputting system for touch screen device |
| US20100174653A1 (en) | 2009-01-07 | 2010-07-08 | Tian Weicheng | Secure method and device of financial transaction |
| US8255323B1 (en) | 2009-01-09 | 2012-08-28 | Apple Inc. | Motion based payment confirmation |
| US8347103B2 (en) | 2009-01-13 | 2013-01-01 | Nic, Inc. | System and method for authenticating a user using a graphical password |
| US20100180336A1 (en) | 2009-01-13 | 2010-07-15 | Nolan Jones | System and Method for Authenticating a User Using a Graphical Password |
| US20100306283A1 (en) | 2009-01-28 | 2010-12-02 | Digitiliti, Inc. | Information object creation for a distributed computing system |
| EP2400426A1 (en) | 2009-01-30 | 2011-12-28 | Research In Motion Limited | System and method for access control in a portable electronic device |
| US20110281630A1 (en) | 2009-01-30 | 2011-11-17 | Omarco Networks Solutions Limited | Multifunction authentication systems |
| US20100215270A1 (en) | 2009-02-26 | 2010-08-26 | Pradheesh Manohar | System and Methods for Automatically Accessing a Web Site on Behalf of a Client |
| US20100242104A1 (en) | 2009-03-23 | 2010-09-23 | Wankmueller John R | Methods and systems for secure authentication |
| US20100259561A1 (en) | 2009-04-10 | 2010-10-14 | Qualcomm Incorporated | Virtual keypad generator with learning capabilities |
| US20120096277A1 (en) | 2009-04-20 | 2012-04-19 | Alter Core, S.L. | System and method for personal authentication using a mobile device |
| US20100287382A1 (en) | 2009-05-07 | 2010-11-11 | John Charles Gyorffy | Two-factor graphical password for text password and encryption key generation |
| US20100287097A1 (en) | 2009-05-08 | 2010-11-11 | Bank Of America Corporation | Conducting Commercial Transactions with a Mobile Device |
| US20120047564A1 (en) | 2009-05-15 | 2012-02-23 | Setcom (Pty) Ltd. | Security system and method |
| WO2010131218A1 (en) | 2009-05-15 | 2010-11-18 | Setcom (Pty) Ltd | Security system and method |
| WO2010134808A1 (en) | 2009-05-20 | 2010-11-25 | Bell Identification B.V. | Method of securing entry of an alphanumeric code on a computer system, interaction and dedicated driver entity therefor. |
| DE102009023925A1 (en) | 2009-06-04 | 2010-12-09 | Jan Fricke | Sensible data i.e. personal identification number, inputting device for e.g. automated teller machine, has display comprising number pad, and vision protection filter permitting vision of user on umber pad only from angle of vision |
| US8176324B1 (en) | 2009-07-02 | 2012-05-08 | Exelis Inc. | Method and system for a secure virtual keyboard |
| US8375428B2 (en) | 2009-07-03 | 2013-02-12 | Korea Internet & Security Agency | Password input system using alphanumeric matrices and password input method using the same |
| US20110004769A1 (en) | 2009-07-03 | 2011-01-06 | Yoo-Jae Won | Password input system using an alphanumeric matrix and password input method using the same |
| US20110020414A1 (en) | 2009-07-27 | 2011-01-27 | Audrey Kunin | Moisturizing retinol composition |
| US20110144586A1 (en) | 2009-07-30 | 2011-06-16 | Tandem Diabetes Care, Inc. | Infusion pump system with disposable cartridge having pressure venting and pressure feedback |
| US20180032831A1 (en) | 2009-07-31 | 2018-02-01 | Samsung Electronics Co., Ltd. | Character recognition and character input apparatus using touch screen and method thereof |
| US20110055084A1 (en) | 2009-08-31 | 2011-03-03 | Saheednanda Singh | Techniques for remote controlled physical transactions with dynamic key generation and authentication |
| US8413071B2 (en) | 2009-09-15 | 2013-04-02 | Samsung Electronics Co., Ltd. | Image processing apparatus and method |
| US20120185398A1 (en) | 2009-09-17 | 2012-07-19 | Meir Weis | Mobile payment system with two-point authentication |
| US8453027B2 (en) | 2009-09-17 | 2013-05-28 | Microsoft Corporation | Similarity detection for error reports |
| US20110090097A1 (en) | 2009-10-20 | 2011-04-21 | Beshke Thomas C | Keyless entry with visual rolling code display |
| US20110109567A1 (en) | 2009-11-09 | 2011-05-12 | Kim Hyun-Kook | Mobile terminal and displaying device thereof |
| US20110204140A1 (en) | 2009-11-24 | 2011-08-25 | Hart Annmarie D | System and method for conducting secure pin debit transactions |
| US20110199387A1 (en) | 2009-11-24 | 2011-08-18 | John David Newton | Activating Features on an Imaging Device Based on Manipulations |
| US20110185313A1 (en) | 2010-01-26 | 2011-07-28 | Idan Harpaz | Method and system for customizing a user-interface of an end-user device |
| WO2011093998A1 (en) | 2010-01-27 | 2011-08-04 | Rem Holdings 3, Llc | Card reader device and method of use |
| US20110185319A1 (en) | 2010-01-28 | 2011-07-28 | Giovanni Carapelli | Virtual pin pad for fuel payment systems |
| US8392846B2 (en) | 2010-01-28 | 2013-03-05 | Gilbarco, S.R.L. | Virtual pin pad for fuel payment systems |
| EP2365469A1 (en) | 2010-03-10 | 2011-09-14 | Telecash Spólka z Ograniczona Odpowiedzialnoscia | Method for performing payment transaction using personal mobile device and arrangement for personal mobile device |
| US20110246369A1 (en) | 2010-03-30 | 2011-10-06 | De Oliveira Marcelo Gomes | Event access with data field encryption for validation and access control |
| US8201732B1 (en) | 2010-04-12 | 2012-06-19 | Diebold Self-Service Systems Division Of Diebold, Incorporated | Banking system controlled responsive to data bearing records |
| US20130047237A1 (en) | 2010-04-26 | 2013-02-21 | Kyu Choul Ahn | Password security input system using shift value of password key and password security input method thereof |
| US20130042318A1 (en) | 2010-04-29 | 2013-02-14 | Rakesh Thatha | Authentication System and Method Using Arrays |
| US20110313871A1 (en) | 2010-05-18 | 2011-12-22 | Laura Greenwood | Apparatus, system, and method for facilitating a payment |
| DE102010022368A1 (en) | 2010-06-01 | 2011-12-01 | Frank Knopf | Touch-screen control panel for e.g. automated teller machine, has number arrangement that ranges between specific values, where arrangement is not rigid and changes each time before operating system configuration |
| WO2011155915A1 (en) | 2010-06-10 | 2011-12-15 | Woronec John S | Method and apparatus for securely activating a credit card for a limited period of time |
| FR2961330A1 (en) | 2010-06-14 | 2011-12-16 | Jean Claude Pailles | Method for securing electronic transaction between user of e.g. personal computer and goods or service merchant during purchasing of train tickets, involves assuring coherence between constitutive elements of contract and signed message |
| US20130091583A1 (en) | 2010-06-15 | 2013-04-11 | Thomson Licensing | Method and device for secured entry of personal data |
| US20110310019A1 (en) | 2010-06-16 | 2011-12-22 | International Business Machines Corporation | Reconfiguration of virtual keyboard |
| US20110321138A1 (en) | 2010-06-28 | 2011-12-29 | International Business Machines Corporation | Mask Based Challenge Response Test |
| WO2012004395A1 (en) | 2010-07-09 | 2012-01-12 | Izettle Hardware Ab | Stand-alone secure pin entry device for enabling emv card transactions with separate card reader |
| WO2012009334A1 (en) | 2010-07-13 | 2012-01-19 | Kopin Corporation | Personal secure terminal with virtual keypad |
| US20120042365A1 (en) | 2010-08-11 | 2012-02-16 | Emc Corporation | Disposable browser for commercial banking |
| US20120079273A1 (en) | 2010-09-28 | 2012-03-29 | Mu Hua Investments Limited | Biometric Key |
| US20120095867A1 (en) | 2010-10-13 | 2012-04-19 | Mckelvey Jim | Integrated read head device |
| US20120098750A1 (en) | 2010-10-22 | 2012-04-26 | Southern Methodist University | Method for subject classification using a pattern recognition input device |
| US20130232549A1 (en) | 2010-11-02 | 2013-09-05 | Michael Ian Hawkes | Method and apparatus for securing network communications |
| US20140162598A1 (en) | 2010-11-17 | 2014-06-12 | Antony-Euclid C. Villa-Real | Customer-controlled instant-response anti-fraud/anti-identity theft devices (with true- personal identity verification), method and systems for secured global applications in personal/business e-banking, e-commerce, e-medical/health insurance checker, e-education/research/invention, e-disaster advisor, e-immigration, e-airport/aircraft security, e-military/e-law enforcement, with or without NFC component and system, with cellular/satellite phone/internet/multi-media functions |
| US20120132705A1 (en) | 2010-11-29 | 2012-05-31 | Wincor Nixdorf International Gmbh | Device for reading magnetic stripe and/or chip cards with a touch screen for pin entry |
| EP2458491A2 (en) | 2010-11-29 | 2012-05-30 | Wincor Nixdorf International GmbH | Device for reading magnetic strips and/or chip cards with touch-screen for PIN entry |
| WO2012077098A1 (en) | 2010-12-06 | 2012-06-14 | Deutsche Telekom Ag | A method for authentication and verification of user identity |
| CN202150070U (en) | 2010-12-14 | 2012-02-22 | 深圳市中成汇实业有限公司 | Personal on-line transaction terminal |
| US20120159592A1 (en) | 2010-12-16 | 2012-06-21 | Research In Motion Limited | Multi-layered color-sensitive passwords |
| EP2466519A1 (en) | 2010-12-16 | 2012-06-20 | Research In Motion Limited | Password entry using moving images |
| US20120159614A1 (en) | 2010-12-16 | 2012-06-21 | Research In Motion Limited | Simple algebraic and multi-layer passwords |
| EP2487620A1 (en) | 2010-12-16 | 2012-08-15 | Research In Motion Limited | Multi-layered color-sensitive passwords |
| US20120159582A1 (en) | 2010-12-16 | 2012-06-21 | Research In Motion Limited | Obscuring visual login |
| EP2466517A1 (en) | 2010-12-16 | 2012-06-20 | Research In Motion Limited | Simple algebraic and multi-layered passwords |
| EP2466520A1 (en) | 2010-12-16 | 2012-06-20 | Research In Motion Limited | Multi-layer multi-point or pathway-based passwords |
| EP2466512A1 (en) | 2010-12-16 | 2012-06-20 | Research In Motion Limited | Pressure sensitive multi-layer passwords |
| US20120159583A1 (en) | 2010-12-16 | 2012-06-21 | Research In Motion Limited | Visual or touchscreen password entry |
| US20120159594A1 (en) | 2010-12-16 | 2012-06-21 | Research In Motion Limited | Adjusting the position of an endpoint reference for increasing security during device log-on |
| US20120159613A1 (en) | 2010-12-16 | 2012-06-21 | Jason Tyler Griffin | Multi-layer multi-point or randomized passwords |
| US20120159609A1 (en) | 2010-12-16 | 2012-06-21 | Research In Motion Limited | Password entry using moving images |
| EP2466516A1 (en) | 2010-12-16 | 2012-06-20 | Research In Motion Limited | Adjusting the position of an endpoint reference for increasing security during device log-on |
| EP2466515A1 (en) | 2010-12-16 | 2012-06-20 | Research In Motion Limited | Multi-layer orientation-changing password |
| US20120159593A1 (en) | 2010-12-16 | 2012-06-21 | Research In Motion Limited | Multi-layer orientation-changing password |
| US20120158672A1 (en) | 2010-12-16 | 2012-06-21 | Microsoft Corporation | Extensible Pipeline for Data Deduplication |
| EP2466518A1 (en) | 2010-12-16 | 2012-06-20 | Research In Motion Limited | Password entry using 3D image with spatial alignment |
| EP2466514A1 (en) | 2010-12-16 | 2012-06-20 | Research In Motion Limited | Multi-layer multi-point or randomized passwords |
| EP2466521A1 (en) | 2010-12-16 | 2012-06-20 | Research In Motion Limited | Obscuring visual login |
| US20120159616A1 (en) | 2010-12-16 | 2012-06-21 | Research In Motion Limited | Pressure sensitive multi-layer passwords |
| EP2466513A1 (en) | 2010-12-16 | 2012-06-20 | Research In Motion Limited | Visual or touchscreen password entry |
| US20120159160A1 (en) | 2010-12-21 | 2012-06-21 | Poisner David I | High security display of private data |
| FR2969342A1 (en) | 2010-12-21 | 2012-06-22 | Oberthur Technologies | Method for entering confidential code to device e.g. computer, to authenticate user, involves selecting character based on time of detection switching of input button, and forming ring for entering each letter in confidential code |
| US20120162086A1 (en) | 2010-12-27 | 2012-06-28 | Samsung Electronics Co., Ltd. | Character input method and apparatus of terminal |
| JP2012138011A (en) | 2010-12-27 | 2012-07-19 | Ns Solutions Corp | Information processing system, information processing method and program |
| US20120222100A1 (en) | 2011-02-24 | 2012-08-30 | International Business Machines Corporation | Advanced captcha using integrated images |
| US20120222102A1 (en) | 2011-02-24 | 2012-08-30 | Empire Technology Development Llc | Authentication using mobile devices |
| JP2012194648A (en) | 2011-03-15 | 2012-10-11 | Nec Personal Computers Ltd | Authentication server, authentication system and authentication method of server |
| US20120253971A1 (en) | 2011-03-28 | 2012-10-04 | Ebay Inc. | Simplified orders using words or phrases |
| US20120249295A1 (en) | 2011-03-30 | 2012-10-04 | Acer Incorporated | User interface, touch-controlled device and method for authenticating a user of a touch-controlled device |
| WO2012131420A1 (en) | 2011-03-31 | 2012-10-04 | Infosys Limited | System and method for utilizing a dynamic virtual keyboard |
| US20120260326A1 (en) | 2011-04-05 | 2012-10-11 | Sap Ag | Image maps for credential-based security |
| US20120256723A1 (en) | 2011-04-08 | 2012-10-11 | Avaya Inc. | Random location authentication |
| EP2512090A1 (en) | 2011-04-14 | 2012-10-17 | Telefónica Germany GmbH & Co. OHG | Method for authenticating a subscriber |
| WO2012146587A1 (en) | 2011-04-27 | 2012-11-01 | Vance Burkill | Improvements in or relating to password generation and recall |
| US20120311723A1 (en) | 2011-05-06 | 2012-12-06 | Google Inc. | Physical Confirmation For Network-Provided Content |
| US20120291120A1 (en) | 2011-05-09 | 2012-11-15 | Research In Motion Limited | Touchscreen password entry |
| EP2523137A1 (en) | 2011-05-09 | 2012-11-14 | Research In Motion Limited | Touchscreen password entry |
| US20130023240A1 (en) | 2011-05-17 | 2013-01-24 | Avish Jacob Weiner | System and method for transaction security responsive to a signed authentication |
| US20120305648A1 (en) | 2011-06-03 | 2012-12-06 | Liquid Payment Solutions Pte Ltd | Hybrid Mobile Phone/Pin Entry Device, System, Method and Article |
| US20120313858A1 (en) | 2011-06-10 | 2012-12-13 | Samsung Electronics Co., Ltd. | Method and apparatus for providing character input interface |
| US20130019320A1 (en) | 2011-07-13 | 2013-01-17 | Salesforce. Com, Inc. | Mechanism for facilitating management of data in an on-demand services environment |
| US20130018800A1 (en) | 2011-07-15 | 2013-01-17 | Rangaraju Devaraju | Secure Authorization of a Financial Transaction |
| US20130020389A1 (en) | 2011-07-18 | 2013-01-24 | Barnett Timothy W | Systems and methods for authenticating near field communcation financial transactions |
| WO2013013192A2 (en) | 2011-07-20 | 2013-01-24 | Visa International Service Association | Cryptographic expansion device and related protocols |
| US20130021233A1 (en) | 2011-07-21 | 2013-01-24 | Frederick Umminger | Apparatus, system, and method for providing feedback sensations of temperature and hardness-softness to a controller |
| US20130026513A1 (en) | 2011-07-25 | 2013-01-31 | Deeder Aurongzeb | Oled assembly and luminaire with removable diffuser |
| US20130029824A1 (en) | 2011-07-27 | 2013-01-31 | Flexicell Inc. | Tier cap forming apparatus |
| WO2013021233A1 (en) | 2011-08-05 | 2013-02-14 | Mt Bilgi Teknolojileri Dis Tic, A.S. | Multi-communication featured, touch-operated or keyboard cash register with contact and non-contact credit card reader |
| US20130050088A1 (en) | 2011-08-29 | 2013-02-28 | Ncr Corporation | User interface |
| US20130060739A1 (en) | 2011-09-01 | 2013-03-07 | Microsoft Corporation | Optimization of a Partially Deduplicated File |
| US20130078951A1 (en) | 2011-09-23 | 2013-03-28 | Jaeseung MUN | Mobile terminal and method of providing security thereto |
| US20130086382A1 (en) | 2011-10-04 | 2013-04-04 | Timothy W. Barnett | Systems and methods for securely transferring personal identifiers |
| US20130106690A1 (en) | 2011-11-01 | 2013-05-02 | Pepsico, Inc. | Dispensing System and User Interface |
| US20130117573A1 (en) | 2011-11-03 | 2013-05-09 | Proxama Limited | Method for verifying a password |
| US20140201831A1 (en) | 2011-11-10 | 2014-07-17 | Soongsil University Research Consortium Techno-Park | Method and apparatus for authenticating password of user terminal |
| US20130148044A1 (en) | 2011-12-13 | 2013-06-13 | Japan Display West, Inc. | Liquid crystal display device and electronic apparatus |
| US20140096201A1 (en) | 2011-12-15 | 2014-04-03 | Arupratan Gupta | Systems and methods for secured entry of user authentication data |
| US20130154981A1 (en) | 2011-12-20 | 2013-06-20 | Samsung Electronics Co., Ltd. | Method and apparatus for providing a shortcut number in a user device |
| US20130159196A1 (en) | 2011-12-20 | 2013-06-20 | Ebay, Inc. | Secure PIN Verification for Mobile Payment Systems |
| US20130154937A1 (en) | 2011-12-20 | 2013-06-20 | Electronics And Telecommunications Research Institute | Apparatus and method for providing customized keyboard user interface |
| US20170235926A1 (en) | 2012-01-26 | 2017-08-17 | Blackberry Limited | Methods and devices for distributing content to an electronic device |
| US20130198459A1 (en) | 2012-01-27 | 2013-08-01 | Fusion-Io, Inc. | Systems and methods for a de-duplication cache |
| US20130207902A1 (en) | 2012-02-10 | 2013-08-15 | Hand Held Products, Inc. | Apparatus having random ordered keypad |
| US20140324698A1 (en) | 2012-02-29 | 2014-10-30 | Mobeewave, Inc. | Method, device, add-on and secure element for conducting a secured financial transaction on a device |
| WO2013148044A1 (en) | 2012-03-26 | 2013-10-03 | Symbol Technologies, Inc. | Mobile computer with integrated near field communication antenna |
| US20130265136A1 (en) | 2012-04-05 | 2013-10-10 | Bank Of America | Dynamic keypad and fingerprinting sequence authentication |
| US20130298246A1 (en) | 2012-05-07 | 2013-11-07 | International Business Machines Corporation | Obfuscating entry of sensitive information |
| US20130301830A1 (en) | 2012-05-08 | 2013-11-14 | Hagai Bar-El | Device, system, and method of secure entry and handling of passwords |
| US20140324708A1 (en) | 2012-06-12 | 2014-10-30 | Square, Inc. | Raw sensor input encryption for passcode entry security |
| US8762876B2 (en) | 2012-06-21 | 2014-06-24 | Google Inc. | Secure data entry via a virtual keyboard |
| US20140002558A1 (en) | 2012-06-29 | 2014-01-02 | Xerox Corporation | Method and apparatus for determining a degree of cure in an ultraviolet printing system |
| US20150116225A1 (en) | 2012-07-05 | 2015-04-30 | Tencent Technology (Shenzhen) Company Limited | Character Input Method And Apparatus |
| US20140013252A1 (en) | 2012-07-06 | 2014-01-09 | Sap Ag | Organizer for Managing Employee Time and Attendance |
| US20140283022A1 (en) | 2012-07-11 | 2014-09-18 | Jason Chris BELONCIK | Methods and sysems for improving the security of secret authentication data during authentication transactions |
| US8453207B1 (en)* | 2012-07-11 | 2013-05-28 | Daon Holdings Limited | Methods and systems for improving the security of secret authentication data during authentication transactions |
| US20140168083A1 (en) | 2012-07-18 | 2014-06-19 | Sap Ag | Virtual touchscreen keyboards |
| US10366215B2 (en) | 2012-07-20 | 2019-07-30 | Licentia Group Limited | Authentication method and system |
| US20160314293A1 (en) | 2012-07-20 | 2016-10-27 | Licentia Group Limited | Authentication Method and System |
| US20200226235A1 (en) | 2012-07-20 | 2020-07-16 | Licentia Group Limited | Authentication method and system |
| GB2520207A (en) | 2012-07-20 | 2015-05-13 | Licentia Group Ltd | Authentication method and system |
| US20200210557A1 (en) | 2012-07-20 | 2020-07-02 | Licentia Group Limited | Authentication method and system |
| US20200201960A1 (en) | 2012-07-20 | 2020-06-25 | Licentia Group Limited | Authentication method and system |
| US20150154414A1 (en) | 2012-07-20 | 2015-06-04 | Licentia Group Limited | Authentication Method and System |
| US20160224771A1 (en) | 2012-07-20 | 2016-08-04 | Licentia Group Limited | Authentication method and system |
| US9552465B2 (en) | 2012-07-20 | 2017-01-24 | Licentia Group Limited | Authentication method and system |
| WO2014013252A2 (en) | 2012-07-20 | 2014-01-23 | Licentia Group Limited | Authentication method and system |
| US10108796B2 (en) | 2012-12-12 | 2018-10-23 | BBPOS Limited | System and method for PIN entry on mobile devices |
| US20140173492A1 (en) | 2012-12-14 | 2014-06-19 | Samsung Electronics Co., Ltd. | Method and apparatus for virtual keypad control |
| US20140195429A1 (en) | 2013-01-08 | 2014-07-10 | Cirque Corporation | Method for protecting cardholder data in a mobile device that performs secure payment transactions and which enables the mobile device to function as a secure payment terminal |
| US20150371213A1 (en) | 2013-01-18 | 2015-12-24 | Mypinpad Limited | Authentication Device & Related Methods |
| US20200005273A1 (en) | 2013-01-18 | 2020-01-02 | Licentia Group Limited | Authentication Device & Related Methods |
| WO2014111689A1 (en) | 2013-01-18 | 2014-07-24 | Licentia Group Limited | Authentication device & related methods |
| US20160006718A1 (en) | 2013-02-26 | 2016-01-07 | Visa International Service Association | Systems, methods and devices for performing passcode authentication |
| WO2014132193A2 (en) | 2013-02-26 | 2014-09-04 | Visa International Service Association | Systems, methods and devices for performing passcode authentication |
| EP2775421A1 (en) | 2013-03-05 | 2014-09-10 | Wincor Nixdorf International GmbH | Trusted terminal platform |
| US20140310531A1 (en) | 2013-04-15 | 2014-10-16 | International Business Machines Corporation | Method and system for securing the entry of data to a device |
| US20160154980A1 (en) | 2013-07-12 | 2016-06-02 | ADUCID s.r.o | Method of secret information entering into electronic digital devices |
| US8965066B1 (en) | 2013-09-16 | 2015-02-24 | Eye Verify LLC | Biometric template security and key generation |
| US20150095241A1 (en) | 2013-09-30 | 2015-04-02 | Square, Inc. | Scrambling passcode entry interface |
| US20160034718A1 (en) | 2013-10-02 | 2016-02-04 | Criptext, Inc. | Method and apparatus for communicating private messages with partially obscured content to limit or prevent unauthorized use of data to impede privacy violations |
| WO2015055973A1 (en) | 2013-10-16 | 2015-04-23 | Mads Landrok | Trusted user interface and touchscreen |
| US9576411B2 (en) | 2013-10-18 | 2017-02-21 | Electronics And Telecommunications Research Institute | Apparatus and method for providing security keypad through shift of keypad |
| WO2015063474A1 (en) | 2013-10-29 | 2015-05-07 | Cryptomathic Ltd | Secure mobile user interface and mobile device case |
| US20150154598A1 (en) | 2013-12-02 | 2015-06-04 | At&T Intellectual Property I, L.P. | Secure Interaction with Input Devices |
| US20160314468A1 (en) | 2013-12-26 | 2016-10-27 | Ned M. Smith | Secure transactions using a personal device |
| US20160337857A1 (en) | 2014-01-10 | 2016-11-17 | Telsy Elettronica E Telecomunicazioni Spa | Secure voice and data method and system |
| US20150261968A1 (en) | 2014-03-12 | 2015-09-17 | Ebay Inc. | Visualizing random characters for keyboard-less devices |
| US20170270764A1 (en) | 2014-05-09 | 2017-09-21 | Smiths Heimann Gmbh | The method and device for monitoring the attentiveness of an operating person |
| US20150332038A1 (en) | 2014-05-17 | 2015-11-19 | Adriana Lyons | Secure entry of secrets |
| US20150347774A1 (en) | 2014-05-30 | 2015-12-03 | Apple Inc. | Restricted resource classes of an operating system |
| US20150350163A1 (en) | 2014-06-02 | 2015-12-03 | Blackberry Limited | System and method for initiating protected instant messaging conversations |
| US20150379288A1 (en) | 2014-06-25 | 2015-12-31 | International Business Machines Corporation | Secure access to running client application features from a browser application |
| EP3163926A1 (en) | 2014-06-26 | 2017-05-03 | Harexinfotech Inc. | User authentication method and system using variable keypad and biometric identification |
| US20160042190A1 (en) | 2014-08-11 | 2016-02-11 | International Business Machines Corporation | Providing access control of applications on computing device by establishing screen passcodes that allow access to designated screens with designated applications |
| US20160065546A1 (en) | 2014-08-27 | 2016-03-03 | Microsoft Technology Licensing, Llc | Sharing content with permission control using near field communication |
| US20160063230A1 (en) | 2014-08-29 | 2016-03-03 | Dropbox, Inc. | Fingerprint gestures |
| WO2016046458A1 (en) | 2014-09-22 | 2016-03-31 | Prove & Run | Smartphone or tablet having a secure display |
| WO2016048236A1 (en) | 2014-09-23 | 2016-03-31 | Singapore Management University | Leakage resilient password system and method |
| US20160125193A1 (en) | 2014-10-29 | 2016-05-05 | Square, Inc. | Secure Display Element |
| KR101520803B1 (en) | 2014-12-01 | 2015-05-15 | 금오공과대학교 산학협력단 | Apparatus and method for inputting personal identification number with enhanced security |
| US20160246955A1 (en) | 2015-02-24 | 2016-08-25 | Image Match Design Inc. | Fingerprint encoding method and system, and fingerprint authenticating method and system |
| US20160253508A1 (en) | 2015-02-26 | 2016-09-01 | Kairos Social Solutions, Inc. | Device, System, and Method of Preventing Unauthorized Recording of Visual Content Displayed on an Electronic Device |
| US20160283013A1 (en) | 2015-03-25 | 2016-09-29 | Sony Mobile Communications Inc. | Device display control for protecting sensitive data |
| GB2542512A (en) | 2015-05-27 | 2017-03-22 | Licentia Group Ltd | Authentication methods and systems |
| US20180150630A1 (en) | 2015-05-27 | 2018-05-31 | Licentia Group Limited | Authentication Methods and Systems |
| WO2016189325A1 (en) | 2015-05-27 | 2016-12-01 | Licentia Group Limited | Authentication methods and systems |
| US20180150623A1 (en) | 2015-05-27 | 2018-05-31 | Licentia Group Limited | Authentication Methods and Systems |
| GB2556474A (en) | 2015-05-27 | 2018-05-30 | Licentia Group Ltd | Authentication methods and systems |
| US20180150628A1 (en) | 2015-05-27 | 2018-05-31 | Licentia Group Limited | Authentication Methods and Systems |
| US20180150629A1 (en) | 2015-05-27 | 2018-05-31 | Licentia Group Limited | Encoding Methods and Systems |
| EP3176722A1 (en) | 2015-05-28 | 2017-06-07 | Smart Electronic Industrial (Dong Guan) Co., Ltd. | Password setting method and equipment therefor |
| US20170006140A1 (en) | 2015-07-01 | 2017-01-05 | Lg Electronics Inc. | Method of transmitting and receiving data using new layer in wireless communication system |
| US20170061408A1 (en) | 2015-08-31 | 2017-03-02 | Seungshin CHOI | Security key input system and method using one-time keypad |
| EP3355512A1 (en) | 2015-09-23 | 2018-08-01 | Harex Infotech Inc. | Method and system for authenticating identity using variable keypad |
| WO2017065576A1 (en) | 2015-10-14 | 2017-04-20 | 주식회사 하렉스인포텍 | User authentication method and system, which use variable keypad |
| US20180374392A1 (en) | 2015-12-28 | 2018-12-27 | Mobeewave, Inc. | System for and method of authenticating a user on a device |
| WO2017190561A1 (en) | 2016-05-06 | 2017-11-09 | 平安科技(深圳)有限公司 | Method for realizing password inputting by means of virtual keyboard, terminal, server, system and storage medium |
| CN105956857A (en) | 2016-05-06 | 2016-09-21 | 上海动联信息技术股份有限公司 | System and method for generating security virtual password keyboard |
| CN106022172A (en) | 2016-05-24 | 2016-10-12 | 中国银行股份有限公司 | Password input method and system protecting password keyboard button input operation |
| KR20180056116A (en) | 2016-11-18 | 2018-05-28 | 조선대학교산학협력단 | Method and apparatus for authentication using circulation secure keypad and overlapping image |
Non-Patent Citations (35)
| Title |
|---|
| Anonymous, "Fujitsu Develops World's First Authentication Technology to Extract and Match 2,048-bit Feature Codes from Palm Vein Images", Fujitsu Global, Kawasaki, Japan, (Aug. 5, 2013), URL: http://www.fujitsu.com/global/about/resources/news/press-releases/2013/0805-01.h tml, (Aug. 1, 2016), XP055292505, 4 pages. |
| Australian Office Action dated Jan. 18, 2021 of application No. 2016269268. |
| Chinese Office Action dated Dec. 3, 2020 of Application No. 201680039203.9. |
| Ciphercard: A Token-Based Approach Against Camera-Based Shoulder Surfing Attacks on Common Touchscreen Devices Authors: Teddy Seyed; Xing-Dong Yang; Anthony Tang; Saul Greenberg; Jiawei Gubin; Zhuxiang Cao. |
| Decision to Grant for related GB2520207 dated Dec. 8, 2015. 2 pages. |
| Examination Report of Application No. GB1619853.3 dated Mar. 8, 2017. 3 pages. |
| Examination Report of Indian Application No. 2301/KOLNP/2015 dated Oct. 18, 2019. 5 pages. |
| EyeDecrypt—Private Interactions in plain Sight, Forte et al., Proc. 9th Conference on Security and Cryptography for Networks (SCN 2014). |
| GlobalPlatform Device Technology Trusted User Interface API, Version 1.0, Jun. 2013, Document Reference: GPD_SPE_020. |
| https://patentscope.wipo.int/search/en/detail.jsf?docId=WO2011116570&tab=PCTBIBLIO&maxRec=1000 (Year: 2010), 4 pages. |
| https://patentscope.wipo.int/search/en/detail.jsf?docId=WO2016188127&tab=PCTBIBLIO&maxRec=1000 (Year: 2015), 6 pages. |
| Indian Office Action dated Feb. 1, 2021 of application No. 20173704209. |
| Indian Office Action dated Jan. 21, 2021 of application No. 201737042169. |
| International Search Report and Written Opinion of International Application No. PCT/GB2016/051548 dated Aug. 8, 2016, 10 pages. |
| International Search Report and Written Opinion of International Application No. PCT/GB2016/051549 dated Aug. 10, 2016, 11 pages. |
| International Search Report and Written Opinion of International Application No. PCT/GB2016/051550 dated Aug. 8, 2016, 10 pages. |
| International Search Report and Written Opinion of International Application No. PCT/GB2016/051553 dated Aug. 4, 2016, 9 pages. |
| International Search Report in related PCT Application No. PCT/GB2013/051913 dated Feb. 6, 2014. 6 pages. |
| Japanese Office Action dated Sep. 8, 2020 of application No. 2017-561754. |
| PCI Mobile Payment Acceptance Security Guidelines for Developers, Version 1.0, Emerging Technologies, PCI Security Standards Council, Sep. 2012. |
| PCI Mobile Payment Acceptance Security Guidelines for Merchants as End-Users, Version 1.0, Emerging Technologies, PCI Security Standards Council, Feb. 2013. |
| Roos, "Automatically Downloading My ING Direct Transactions-Chris Roos", Jun. 23, 2007, XP055085833. 7 pages. |
| Scramblepad, Scrambleprox, Scramblesmart, Scramblesmartprox Author: Hirsch Electronics Date: Jul. 27, 2013. |
| Search and Examination Report of Application No. GB1906165.4 dated Aug. 23, 2019, 5 pages. |
| Search Report cited in Office Action dated Nov. 26, 2019 of Russian Application No. 2017141194/08, 2 pages. |
| Search Report dated Jul. 22, 2020 of GB application No. GB1916441.7, 2 pages. |
| Search Report in related GB Application No. GB1212878.1 dated Dec. 3, 2012. 4 pages. |
| Search Report issued by United Kingdom Intellectual Property Office dated Oct. 6, 2017 for Application No. GB1321505.8, 3 pages. |
| Secure Mobile Payment on NFC-Enabled Mobile Phones Formally Analysed Using CasperFDR, S. Abughazalah et al, 2014 IEEE 13th International Conference on Trust, Security and Privacy in Computing and Communications, pp. 422-431. |
| Thales e-Security mPOS Secure Mobile Card Acceptance White Paper, Nov. 2013. |
| The Usability of Picture Passwords, Fraser, Jul. 23, 2014, 11 pages. |
| Touch Screen Remote Arming Station (RAS) Author: Tecom Date: Mar. 18, 2015. |
| Translation of Office Action dated Nov. 26, 2019 of Russian Application No. 2017141194/08, 6 pages. |
| Using Biometrics to Generate Public and Private Keys, Satrugna Pakala, (May 31, 2006) Retrieved from internet; URL: http://www.sci.tamucc.edu/˜cams/GraduateProjects/view. php? view=266, 50 pages. |
| Written Opinion of the Intl Searching Authority in related PCT Application No. PCT/GB2013/051913, 201 , dated Jan. 20, 2015, 11 pages. |
Also Published As
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| US11048783B2 (en) | Authentication method and system | |
| US20170228525A1 (en) | Accessing a secured software application | |
| CA2987184A1 (en) | Encoding methods and systems |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| FEPP | Fee payment procedure | Free format text:ENTITY STATUS SET TO UNDISCOUNTED (ORIGINAL EVENT CODE: BIG.); ENTITY STATUS OF PATENT OWNER: LARGE ENTITY | |
| AS | Assignment | Owner name:MYPINPAD LIMITED, GREAT BRITAIN Free format text:ASSIGNMENT OF ASSIGNORS INTEREST;ASSIGNOR:PIKE, JUSTIN;REEL/FRAME:052159/0818 Effective date:20120720 Owner name:LICENTIA GROUP LIMITED, GREAT BRITAIN Free format text:ASSIGNMENT OF ASSIGNORS INTEREST;ASSIGNOR:PIKE, JUSTIN;REEL/FRAME:052159/0818 Effective date:20120720 | |
| STPP | Information on status: patent application and granting procedure in general | Free format text:DOCKETED NEW CASE - READY FOR EXAMINATION | |
| STPP | Information on status: patent application and granting procedure in general | Free format text:NOTICE OF ALLOWANCE MAILED -- APPLICATION RECEIVED IN OFFICE OF PUBLICATIONS | |
| STPP | Information on status: patent application and granting procedure in general | Free format text:PUBLICATIONS -- ISSUE FEE PAYMENT RECEIVED | |
| STPP | Information on status: patent application and granting procedure in general | Free format text:PUBLICATIONS -- ISSUE FEE PAYMENT VERIFIED | |
| STCF | Information on status: patent grant | Free format text:PATENTED CASE | |
| STPP | Information on status: patent application and granting procedure in general | Free format text:WITHDRAW FROM ISSUE AWAITING ACTION | |
| STPP | Information on status: patent application and granting procedure in general | Free format text:AWAITING TC RESP., ISSUE FEE NOT PAID | |
| STPP | Information on status: patent application and granting procedure in general | Free format text:NOTICE OF ALLOWANCE MAILED -- APPLICATION RECEIVED IN OFFICE OF PUBLICATIONS | |
| STPP | Information on status: patent application and granting procedure in general | Free format text:PUBLICATIONS -- ISSUE FEE PAYMENT VERIFIED | |
| STCF | Information on status: patent grant | Free format text:PATENTED CASE | |
| FEPP | Fee payment procedure | Free format text:MAINTENANCE FEE REMINDER MAILED (ORIGINAL EVENT CODE: REM.); ENTITY STATUS OF PATENT OWNER: LARGE ENTITY | |
| LAPS | Lapse for failure to pay maintenance fees | Free format text:PATENT EXPIRED FOR FAILURE TO PAY MAINTENANCE FEES (ORIGINAL EVENT CODE: EXP.); ENTITY STATUS OF PATENT OWNER: LARGE ENTITY | |
| STCH | Information on status: patent discontinuation | Free format text:PATENT EXPIRED DUE TO NONPAYMENT OF MAINTENANCE FEES UNDER 37 CFR 1.362 | |
| FP | Lapsed due to failure to pay maintenance fee | Effective date:20250629 |