US10642968B2 - Controlling a device - Google Patents
Controlling a deviceDownload PDFInfo
- Publication number
- US10642968B2 US10642968B2US15/512,277US201415512277AUS10642968B2US 10642968 B2US10642968 B2US 10642968B2US 201415512277 AUS201415512277 AUS 201415512277AUS 10642968 B2US10642968 B2US 10642968B2
- Authority
- US
- United States
- Prior art keywords
- node
- channel
- value
- message
- local node
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Active, expires
Links
Images
Classifications
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/30—Authentication, i.e. establishing the identity or authorisation of security principals
- G06F21/31—User authentication
- G06F21/42—User authentication using separate channels for security data
- G06F21/43—User authentication using separate channels for security data wireless channels
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L12/00—Data switching networks
- H04L12/28—Data switching networks characterised by path configuration, e.g. LAN [Local Area Networks] or WAN [Wide Area Networks]
- H04L29/06—
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/04—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks
- H04L63/0428—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks wherein the data content is protected, e.g. by encrypting or encapsulating the payload
- H04L63/0492—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks wherein the data content is protected, e.g. by encrypting or encapsulating the payload by using a location-limited connection, e.g. near-field communication or limited proximity of entities
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/12—Applying verification of the received information
- H04L63/123—Applying verification of the received information received data contents, e.g. message integrity
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/18—Network architectures or network communication protocols for network security using different networks or channels, e.g. using out of band channels
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/06—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols the encryption apparatus using shift registers or memories for block-wise or stream coding, e.g. DES systems or RC4; Hash functions; Pseudorandom sequence generators
- H04L9/0643—Hash functions, e.g. MD5, SHA, HMAC or f9 MAC
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/32—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials
- H04L9/3215—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials using a plurality of channels
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/32—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials
- H04L9/3236—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials using cryptographic hash functions
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/32—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials
- H04L9/3236—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials using cryptographic hash functions
- H04L9/3242—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials using cryptographic hash functions involving keyed hash functions, e.g. message authentication codes [MACs], CBC-MAC or HMAC
- H04W12/003—
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W12/00—Security arrangements; Authentication; Protecting privacy or anonymity
- H04W12/50—Secure pairing of devices
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W4/00—Services specially adapted for wireless communication networks; Facilities therefor
- H04W4/70—Services for machine-to-machine communication [M2M] or machine type communication [MTC]
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W4/00—Services specially adapted for wireless communication networks; Facilities therefor
- H04W4/80—Services using short range communication, e.g. near-field communication [NFC], radio-frequency identification [RFID] or low energy communication
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W84/00—Network topologies
- H04W84/18—Self-organising networks, e.g. ad-hoc networks or sensor networks
Definitions
- the present inventionrelates to the field of signalling between electrically operated devices, to control them.
- Interacting with distributed systemsmay take place in a variety of ways.
- devicesare interconnected by the network and accessible to each other in a straightforward way.
- messaging between devicesmay take place using internet protocol, IP, addressing and domain names.
- IPinternet protocol
- a nodemay inquire for an IP address of a desired correspondent node based on a known domain name. Such an inquiry may be addressed to the domain name system, DNS.
- DNSdomain name system
- Sensor networksmay comprise sensor nodes interconnected with each other. Sensor nodes may be configured to communicate with each other and to provide sensor information to further nodes not comprised in the sensor network.
- a sensor networkmay have an internal addressing system distinct from an external IP network. At least one node in the sensor network may be either addressable from outside the sensor network, or be configured to provide information to a node external to the sensor network.
- IoTIn the Internet of Things, IoT, scheme it is envisioned that a large number of identifiable devices, or nodes, can be communicated with based on an addressing scheme that may depend on the situation and application in question.
- addressing in accordance with internet protocol version 6, IPv6is envisioned instead of the more limited IPv4 as IP addresses might otherwise run out.
- IPv4 addressingmay be extended and the scarcity of IPv4 addresses alleviated, with an impact on usability that may vary depending on what kind of communication is desired.
- IoT nodesare foreseen to have limitations in hardware and energy resources. For example, such nodes may be furnished with only limited memory capacity, they may operate on small batteries and/or they may have only modest processor capability.
- protocolssuch as the constrained application protocol, CoAP, have been designed. CoAP has been standardized by the Internet Engineering Task Force.
- an apparatuscomprising at least one receiver configured to receive, via a first channel, a secret value and an identifier of a local node and, via a second channel, a random value, and at least one processing core configured to cause transmission to the local node of a first message comprising a hash value, the hash value being derived based on a set comprising the secret value, the random value, and an instruction.
- the at least one processing coreis configured to derive the hash value
- the at least one receiveris further configured to receive, over the first channel, a pin code, and to derive the hash value based further on the pin code
- the first channelcomprises a Bluetooth channel, a Bluetooth low-energy channel, a near field communication channel, an infra-red channel or a visual pattern recognition channel
- the second channelcomprises a websocket channel, a hypertext transport protocol channel, a constrained application protocol channel, extensible messaging and presence protocol, message queue telemetry transport, alljoyn or hypertext transport protocol channel 2.0 channel
- the at least one processing coreis configured to cause the first message to be transmitted via the second channel
- the at least one processing coreis further configured to cause transmission of a second message to the local node, the second message comprising a second hash value, the second hash value being derived based on a set comprising the secret value, a second random value, and a second instruction, the second random value being received in the apparatus from the local node at least in part as a response to the first message
- the at least one receiveris further configured to receive, via the first channel, an identifier of a network node and the at least one processing core is configured to request, from the network node, control software configured to cause controlling of the local node, wherein the request comprises the identifier of the local node
- the identifier of the local nodecomprises an internet protocol address of the local node, a fully qualified domain name of the local node or a pointer to a websocket proxy
- the at least one processing coreis configured to process, in the apparatus, an indication concerning whether it is necessary to include the instruction in the message.
- an apparatuscomprising at least one processing core and at least one memory including computer program code, the at least one memory and the computer program code being configured to, with the at least one processing core, cause the apparatus at least to store a secret value associated with the apparatus, transmit to a node a random value, receive a message from the node, the message comprising a first hash value, verify the hash value by deriving a comparative hash value based on a set comprising the secret value, an instruction, and the random value, responsive to the comparative hash value matching the first hash value, cause the apparatus to act on the instruction, and transmit to the node a second random value.
- the messagecomprises, in addition to the first hash value, the instruction
- the at least one memory and the computer program codeare configured to, with the at least one processing core, cause the apparatus to provide the secret value to the node over a first channel, and to receive the message from the node over a second channel
- the at least one memory and the computer program codeare configured to, with the at least one processing core, cause the apparatus to derive the comparative hash value based at least in part on a pin code provided to the node from the apparatus via the first channel
- the at least one memory and the computer program codeare configured to, with the at least one processing core, cause the apparatus to periodically change the secret value
- the at least one memory and the computer program codeare configured to, with the at least one processing core, cause the apparatus to derive, after transmitting the random value to the node, at least two comparative hash values using at least two possible values for the instruction
- the at least one memory and the computer program codeare configured to, with the at least one processing core, cause the apparatus to transmit to the node a second random value responsive to receipt of the message.
- a methodcomprising receiving, via a first channel, a secret value and an identifier of a local node and, via a second channel, a random value, and causing transmission to the local node of a first message comprising a hash value, the hash value being derived based on a set comprising the secret value, the random value, and an instruction.
- Various embodiments of the third aspectmay comprise at least one feature corresponding to a feature from the preceding bulleted list laid out in connection with the first aspect.
- a methodcomprising storing a secret value associated with an apparatus, transmitting to a node a random value, receiving a message from the node, the message comprising a first hash value, verifying the first hash value by deriving a comparative hash value based on a set comprising the secret value, an instruction, and the random value, responsive to the comparative hash value matching the first hash value, causing the apparatus to act on the instruction, and transmitting to the node a second random value.
- Various embodiments of the fourth aspectmay comprise at least one feature corresponding to a feature from the preceding bulleted list laid out in connection with the second aspect.
- an apparatuscomprising means for receiving, via a first channel, a secret value and an identifier of a local node and, via a second channel, a random value, and means for causing transmission to the local node of a first message comprising a hash value, the hash value being derived based on a set comprising the secret value, the random value, and an instruction.
- an apparatuscomprising means for storing a secret value associated with the apparatus, means for transmitting to a node a random value, means for receiving a message from the node, the message comprising a first hash value, means for verifying the hash value by deriving a comparative hash value based on a set comprising the secret value, an instruction, and the random value, means for causing the apparatus to act on the instruction responsive to the comparative hash value matching the first hash value, and means for transmitting to the node a second random value.
- a non-transitory computer readable mediumhaving stored thereon a set of computer readable instructions that, when executed by at least one processor, cause an apparatus to at least receive, via a first channel, a secret value and an identifier of a local node and, via a second channel, a random value, and cause transmission to the local node of a first message comprising a hash value, the hash value being derived based on a set comprising the secret value, the random value, and an instruction.
- a non-transitory computer readable mediumhaving stored thereon a set of computer readable instructions that, when executed by at least one processor, cause an apparatus to at least store a secret value associated with the apparatus, transmit to a node a random value, receive a message from the node, the message comprising a first hash value, verify the hash value by deriving a comparative hash value based on a set comprising the secret value, an instruction, and the random value, responsive to the comparative hash value matching the first hash value, cause the apparatus to act on the instruction, and transmit to the node a second random value.
- At least some embodiments of the present inventionfind industrial application in secured control of local devices.
- FIG. 1illustrates an example system capable of supporting at least some embodiments of the present invention
- FIG. 2illustrates an example use case in accordance with at least some embodiments of the present invention
- FIG. 3illustrates an example apparatus capable of supporting at least some embodiments of the present invention
- FIG. 4illustrates signalling in accordance with at least some embodiments of the present invention
- FIG. 5is a first flow chart of a first method in accordance with at least some embodiments of the present invention.
- FIG. 6is a second flow chart of a second method in accordance with at least some embodiments of the present invention.
- a nodemay be built with low memory and/or processing requirements using embodiments of the invention described herein.
- a secret valueover a first channel to be used over communications over a second channel, access may be restricted to units having physical access to the node.
- a distinct random valuemay be employed for each message to prevent replay attacks.
- Instructionsmay be hashed together with the secret and random values to enable the node to verify them in a resource-efficient way, so that a cryptographic communication protocol such as transport layer security, TLS, needn't be implemented, for example.
- FIG. 1illustrates an example system capable of supporting at least some embodiments of the present invention.
- the system of FIG. 1comprises device 110 , which may comprise a smartphone, cellular phone, tablet device, phablet device, laptop or desktop computer, or other suitable electronic device, for example.
- Device 110may comprise a user interface, which may comprise a touchscreen user interface or a keypad plus display user interface, for example.
- Local node 120may comprise, for example, a sensor, a light control, a home automation control device or other suitable electronic device. Local node 120 is in the example of FIG. 1 connected to gateway 170 via connection 127 . Connection 127 may comprise a wire-line connection or at least in part a wireless connection. Gateway 170 is connected to network 160 via connection 176 . Network 160 may comprise the Internet or another suitable network, such as for example a corporate network. In some embodiments, local node 120 is directly connected to network 160 via connection 127 , and gateway 170 is absent.
- device 110is communicatively coupled to base station 130 via link 113 .
- Base station 130may be configured to operate in accordance with at least one wireless technology, such as wideband code division multiple access, WCDMA, long term evolution, LTE, IS-95 or wireless local area network WLAN, which is also known as Wi-Fi.
- Link 113conforms to a technology that base station 130 and device 110 are configured to support.
- Link 113may be two-way in that it may comprise a downlink for transferring information from base station 130 to device 110 , and an uplink for transferring information from device 110 to base station 130 .
- link 113comprises a wire-line link with a communication node that is communicatively coupled with network 160 .
- base station 130is communicatively coupled, via connection 134 , to network node 140 .
- Network node 140may comprise a radio network controller, switch or other network node.
- Network node 140is communicatively coupled, via connection 145 , to gateway 150 .
- Gateway 150in turn is connected to network 160 via connection 156 .
- Each of connections 134 , 145 and 156may be wire-line or at least in part wireless. Not all of connections 134 , 145 and 156 need to be of the same type.
- network node 140 and/or gateway 150are absent, leaving base station 130 in more direct contact with network 160 .
- Local link 112may comprise a near-field communication, NFC, Bluetooth, Bluetooth LE or optical link, for example.
- An optical linkmay comprise an infrared link, or an optical link may comprise that device 110 uses a camera comprised in device 110 to algorithmically recognize information that local node 120 displays, either permanently printed thereon on displayed on a display 122 comprised in local node 120 .
- Display 122may be a monochrome liquid-crystal display or an organic light emitting diode, OLED, display, for example.
- local link 112enables device 110 to obtain information from local node 120 when device 110 is physically near local node 120 .
- Nearmay comprise within a radius of 5 or 10 meters, for example.
- Display 122is absent in some embodiments.
- local link 112comprises a first channel and link 113 comprises a second channel.
- the first channelis therefore a local-range channel.
- the first and second channelsmay be based on different technologies.
- Device 110is capable of receiving information from local node 120 via both channels, in the case of local link 112 directly and in the case of link 113 via gateway 170 , network 160 , gateway 150 , network node 140 and base station 130 .
- local link 112comprising the first channel, is two-way whereas in other embodiments it is one-way in the sense that device 110 can receive information over it, but not transmit information over it to local node 120 .
- device 110may be configured to obtain information from local node 120 over local link 112 .
- Such informationmay comprise, for example, a secret value.
- the secret valuemay be expressed in binary, hexadecimal or decimal format, for example.
- the informationmay further comprise an identifier of local node 120 .
- the informationmay further comprise a pin code.
- the informationmay further comprise an identifier of a network node.
- An identifiermay comprise a uniform resource locator, URL, or uniform resource identifier, URI, for example.
- the network node the identifier of the network node relates tomay comprise network node 140 or another network node, such as for example a server.
- the identifier of local node 120may comprise, for example, a URL or URI of local node 120 .
- Device 110may fetch from the network node identified by the identifier of the network node control software configured to control, at least in part, local node 120 .
- Device 110may fetch this software by requesting, over link 113 , the software from the identified network node.
- Such a requestmay comprise, or be at least in part based on, the identifier of the network node obtained in device 110 from local node 120 .
- Such a requestmay comprise the identifier of local node 120 .
- Device 110may responsively receive the control software.
- the control softwaremay comprise, for example, a control panel.
- the control softwaremay comprise, for example, JavaScript software.
- the fetching and obtaining of the control softwaremay be based on secure hypertext transfer protocol, HTTPS, for example.
- the fetching of the control softwaremay be absent, or may comprise only updating the control software to a newer version. In some embodiments, device 110 does not need specific control software to control, at least in part, local node 120 so fetching such software is not done.
- Device 110is configured to open a connection to local node 120 .
- the connectionmay traverse base station 130 , network node 140 , gateway 150 , network 160 and gateway 170 , for example. In general the connection may be opened over the second channel.
- the connectionmay comprise a maintained state in at least one node enabling delivery of messages between device 110 and local node 120 .
- the connectionmay comprise a Websocket, CoAP or hypertext transfer protocol, HTTP, connection, for example.
- the connectionmay be a non-cryptographic connection in that data communicated over the connection is not encrypted by the connection protocol.
- Websocket connectionsmay be run with limited resources, making it a useful option where local node 120 is resource-constrained.
- the set-up of the connectioncomprises exchange of at least one message between device 110 and local node 120 .
- Local node 120may transmit, for example in a message comprised in the connection set-up process on in another message, to device 110 a random value local node 120 has generated.
- Local node 120may store a copy of the random value in a memory comprised in local node 120 .
- the random valuemay be expressed in binary, hexadecimal or decimal format, for example.
- Local node 120may use a software-based random number generator, or local node 120 may at least in part use a hardware-based random value generation process.
- An example of a hardware element usable for generating random valuesis a thermal noise random number generator.
- device 110may transmit an instruction to local node 120 .
- the instructionmay be comprised in a first message transmitted from device 110 to local node 120 , for example.
- the instructionmay comprise, for example, an instruction to turn off air conditioning in case local node 120 is a home automation control device.
- Another exampleis an instruction to provide to device 110 a measurement of atmospheric pressure in case local node 120 is a sensor node equipped with a barometer.
- Device 110may be configured to compute a hash, such as for example a rolling hash or a secure hash, of a set of data that comprises the secret value, the random value and the instruction.
- the hash function usedcan be a cryptographic hash function.
- the pin codemay be included in the input to the hash function as well.
- Device 110may provide the output of the hash function, known simply as the hash value or the hash, to local node 120 in a message. The message may further comprise the instruction separately from the hash.
- local node 120may verify the hash is correct by deriving a hash of the secret value, the random value, the instruction and in case a pin code is used, the pin code. In case the derived hash is the same as the hash received in the message, the hash is correctly verified. In case the hashes fail to match, local node 120 may be configured to discard the message, and/or provide over the connection an error signal to device 110 .
- the message comprising the hash from device 110 to local node 120needn't separately comprise the instruction.
- the number of possible instructionsis limited, and local node 120 may pre-calculate, after sending the random value to device 110 , hashes of the secret value, the random value and each of the possible instructions.
- the pin codeis also used in pre-calculating the hashes.
- pre-calculated hashesmay be stored in memory of local node 120 , and local node 120 may verify the hash it receives from device 110 by comparing it with the pre-calculated hashes until a match is found, in which case the received hash is thereby verified and the instruction may be acted on, since local node 120 will know which instruction was used in deriving the hash that matches the one received from device 110 .
- verificationfails and local node 120 may discard the message, and/or provide over the connection an error signal to device 110 .
- Pre-calculatingmay be done after transmission of the random value toward device 110 , for example responsive to transmission of the random value toward device 110 .
- local node 120is configured to begin pre-calculating hashes after transmitting the random value to device 110 , but may continue deriving hashes with possible instructions after receiving a message from device 110 comprising a hash. This may be the case, for example, where local node 120 doesn't have the time to completely pre-calculate the hashes by the time device 110 sends its message with the hash. Alternatively, the pre-calculation process in local node 120 may have low priority, which may cause it to proceed slowly. In some embodiments, post-calculation is performed instead of pre-calculation, wherein local node 120 begins deriving hashes with possible instructions, one by one, responsive to receiving from device 110 the message comprising the hash. This way, local node 120 may stop deriving the hashes responsive to a determination that one of the hashes derived in local node 120 matches the one received from device 110 .
- device 110may receive an indication that messages it sends to local node 120 to instruct local node 120 needn't comprise the instruction in addition to the hash. Such an indication may be received from local node 120 in connection with establishing the connection between device 110 and local node 120 , for example.
- control softwareconfigured to control local node 120 may know that including separately also the instruction is unnecessary, and that sending the hash suffices.
- Whether including the instruction is necessarymay depend on the number of possible instructions, in detail in case the number of possible different instructions device 110 may send to local node 120 is high, deriving the hashes on the local node side may be too arduous. Where pre-calculation is done, memory constraints in local node 120 may limit the possibility to pre-calculate and store hashes. In case of post-calculation, a large number of possible instructions may cause delay between receiving the message from device 110 and acting on the instruction, as local node 120 derives hashes one by one in search of one that matches the one received from device 110 .
- local node 120may be configured to responsively act on the instruction and to transmit, over the connection, a second message back to device 110 .
- the second messagemay comprise an acknowledgement and/or result relating to the instruction, and a second random value generated in local node 120 .
- the second random valuemay be sent from local node 120 to device 110 in an additional message. Should device 110 subsequently send a second instruction to local node 120 , a similar process is used as was used with the instruction of the first message, but the second random value is used when calculating the hash.
- the second messagesent from local node 120 to device 110 , may further comprise a hash derived using as input the secret value and the second random value.
- device 110is enabled to check that the second message originates from a node that is in possession of the secret value.
- the pin codemay also be used as input when deriving this hash.
- Local node 120may be configured to change the secret value periodically, for example by generating a random value to be used as the new secret value. This increases security as devices seeking control of local node 120 need to obtain the new secret value over the first channel, and cannot rely on a previously obtained secret value.
- the set of devices that can transmit instructions to local node 120is limited to those devices that are physically close enough to obtain the secret value from local node 120 , over the first channel. For example, in case local node is in a hotel room, an office or other access-controlled location, it may be useful to enable control of local node 120 by devices that are physically close. Thus no cryptographic protocol needs to be used for the connection between device 110 and local node 120 , which saves computational and memory resources in device 110 and local node 120 .
- the changing random valuerenders pin code guessing attacks significantly slower, as in addition to the pin code, an attacker would need to guess the prevailing random value.
- the hashesmay be transmitted between device 110 and local node 120 over a connection that in itself is not encrypted. For example, determining the secret value by eavesdropping on messages exchanged between device 110 and local node 120 would be very difficult owing to mathematical properties of hash functions.
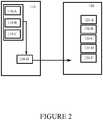
- FIG. 2illustrates an example use case in accordance with at least some embodiments of the present invention.
- device 110and local node 120 , which have been described above in connection with FIG. 1 .
- local node 120stores pre-calculated hash values 120 -A, 120 -B, 120 -C, 120 -D and 120 -E, each of which is derived using a possible instruction. In other words, there are five possible instructions in the example of FIG. 2 .
- device 110derives hash 110 -D from input data which comprises the secret value 110 -A, the random value 110 -B, and finally the instruction 110 -C that device 110 wants local device 120 to carry out.
- hash 110 -DOnce hash 110 -D has been derived, it is transmitted from device 110 to local node 120 .
- Local node 120determines whether the hash 110 -D matches any of the pre-calculated hash values, and if so which one, enabling local node 120 to determine which instruction device 110 is instructing local node 120 to carry out.
- FIG. 3illustrates an example apparatus capable of supporting at least some embodiments of the present invention. Illustrated is device 300 , which may comprise, for example, device 110 of FIG. 1 or FIG. 2 .
- processor 310which may comprise, for example, a single- or multi-core processor wherein a single-core processor comprises one processing core and a multi-core processor comprises more than one processing core.
- Processor 310may comprise a Qualcomm Snapdragon 800 processor, for example.
- Processor 310may comprise more than one processor.
- a processing coremay comprise, for example, a Cortex-A8 processing core manufactured by Intel Corporation or a Brisbane processing core produced by Advanced Micro Devices Corporation.
- Processor 310may comprise at least one application-specific integrated circuit, ASIC.
- Processor 310may comprise at least one field-programmable gate array, FPGA.
- Processor 310may be means for performing method steps in device 300 .
- Processor 310may be configured, at least in part by computer instructions, to perform actions.
- Device 300may comprise memory 320 .
- Memory 320may comprise random-access memory and/or permanent memory.
- Memory 320may comprise at least one RAM chip.
- Memory 320may comprise magnetic, optical and/or holographic memory, for example.
- Memory 320may be at least in part accessible to processor 310 .
- Memory 320may be means for storing information.
- Memory 320may comprise computer instructions that processor 310 is configured to execute. When computer instructions configured to cause processor 310 to perform certain actions are stored in memory 320 , and device 300 overall is configured to run under the direction of processor 310 using computer instructions from memory 320 , processor 310 and/or its at least one processing core may be considered to be configured to perform said certain actions.
- Device 300may comprise a transmitter 330 .
- Device 300may comprise a receiver 340 .
- Transmitter 330 and receiver 340may be configured to transmit and receive, respectively, information in accordance with at least one cellular or non-cellular standard.
- Transmitter 330may comprise more than one transmitter.
- Receiver 340may comprise more than one receiver.
- Transmitter 330 and/or receiver 340may be configured to operate in accordance with global system for mobile communication, GSM, wideband code division multiple access, WCDMA, long term evolution, LTE, IS-95, wireless local area network, WLAN, Ethernet and/or worldwide interoperability for microwave access, WiMAX, standards, for example.
- Device 300may comprise a near-field communication, NFC, transceiver 350 .
- NFC transceiver 350may support at least one NFC technology, such as NFC, Bluetooth, Wibree or similar technologies.
- Device 300may comprise user interface, UI, 360 .
- UI 360may comprise at least one of a display, a keyboard, a touchscreen, a vibrator arranged to signal to a user by causing device 300 to vibrate, a speaker and a microphone.
- a usermay be able to operate device 300 via UI 360 , for example to accept incoming telephone calls, to originate telephone calls or video calls, to browse the Internet, to manage digital files stored in memory 320 or on a cloud accessible via transmitter 330 and receiver 340 , or via NFC transceiver 350 , and/or to control a local node such as local node 120 of FIG. 1 or FIG. 2 .
- Device 300may comprise or be arranged to accept a user identity module 370 .
- User identity module 370may comprise, for example, a subscriber identity module, SIM, card installable in device 300 .
- a user identity module 370may comprise information identifying a subscription of a user of device 300 .
- a user identity module 370may comprise cryptographic information usable to verify the identity of a user of device 300 and/or to facilitate encryption of communicated information and billing of the user of device 300 for communication effected via device 300 .
- Processor 310may be furnished with a transmitter arranged to output information from processor 310 , via electrical leads internal to device 300 , to other devices comprised in device 300 .
- a transmittermay comprise a serial bus transmitter arranged to, for example, output information via at least one electrical lead to memory 320 for storage therein.
- the transmittermay comprise a parallel bus transmitter.
- processor 310may comprise a receiver arranged to receive information in processor 310 , via electrical leads internal to device 300 , from other devices comprised in device 300 .
- Such a receivermay comprise a serial bus receiver arranged to, for example, receive information via at least one electrical lead from receiver 340 for processing in processor 310 .
- the receivermay comprise a parallel bus receiver.
- Device 300may comprise further devices not illustrated in FIG. 3 .
- device 300may comprise at least one digital camera.
- Some devices 300may comprise a back-facing camera and a front-facing camera, wherein the back-facing camera may be intended for digital photography and the front-facing camera for video telephony.
- Device 300may comprise a fingerprint sensor arranged to authenticate, at least in part, a user of device 300 .
- device 300lacks at least one device described above.
- some devices 300may lack a NFC transceiver 350 and/or user identity module 370 .
- Processor 310 , memory 320 , transmitter 330 , receiver 340 , NFC transceiver 350 , UI 360 and/or user identity module 370may be interconnected by electrical leads internal to device 300 in a multitude of different ways.
- each of the aforementioned devicesmay be separately connected to a master bus internal to device 300 , to allow for the devices to exchange information.
- thisis only one example and depending on the embodiment various ways of interconnecting at least two of the aforementioned devices may be selected without departing from the scope of the present invention.
- FIG. 4illustrates signalling in accordance with at least some embodiments of the present invention.
- server SRVOn the vertical axes are disposed, from left to right, server SRV, device 110 and local node 120 .
- Device 110 and local node 120may correspond essentially to like elements discussed above in connection with FIG. 1 and FIG. 2 .
- Server SRVmay essentially correspond to the network node discussed above where device 110 may fetch the control software described above. Time advances from top toward the bottom of the figure.
- device 110obtains from local device 120 information over the first channel.
- This informationmay comprise the secret value and an identifier of local device 120 .
- the informationmay further comprise a pin code and/or an identifier of server SRV.
- device 110may request and receive, respectively, control software configured to enable control of local node 120 .
- the requesting of phase 420may be based at least in part on the identifier of the server SRV.
- phase 440device 110 and local node 120 form a connection, such as for example a protocol connection, such as for example a Websocket connection.
- a connectionsuch as for example a protocol connection, such as for example a Websocket connection.
- local node 120provides to device 110 a random value.
- local node 120transmits in connection with phase 440 an indication as to whether device 110 needs to transmit an instruction and a hash, or only a hash, when instructing local node 120 .
- device 110determines an instruction it desires to send to local node 120 .
- Device 110derives a hash value based at least in part on the secret value, the random value and the instruction.
- device 110transmits, over the connection, a message comprising the hash, and, optionally, the instruction, to local node 120 .
- device 110may omit the instruction from the message of phase 460 .
- Device 110may also omit the instruction in case it has received an indication to this effect in connection with phase 440 , as described above.
- phase 470local node 120 verifies the hash received in phase 460 .
- the message of phase 460comprises the instruction in addition to the hash
- local node 120may derive the hash itself, using at least the secret value, the random value and the instruction, and then compare the received hash to the hash derived in local node 120 . In case the received hash matches with the hash derived in local node 120 , the instruction used in the hash is verified, and acted upon.
- local node 120may compare the hash received in phase 460 to hashes derived in local node 120 with different possible instructions. In case the received hash matches with one of the hashes derived in local node 120 , the instruction used in the derived hash is verified, and acted upon.
- the hashes derived in local node 120may be pre-calculated between phase 440 and phase 460 , or they may at least in part be derived after receipt of the message of phase 460 .
- phase 480local node 120 may transmit a message to device 110 informing device 110 , explicitly or implicitly, that the instruction of phase 460 was carried out, or alternatively that verification of the hash in the message of phase 460 failed.
- the message of phase 480may comprise a second random value.
- device 110determines to send a second instruction to local node 120 , and derives a hash using the second random value, the secret, and the second instruction.
- the derived hashis transmitted to local node 120 in phase 4100 .
- the hashis verified in local node 120 in phase 4110 , and in phase 4120 local node 120 informs device 110 concerning acting on the second instruction.
- the message of phase 4120may comprise a third random value, for use in a subsequent instruction from device 110 to local node 120 .
- FIG. 5is a first flow chart of a first method in accordance with at least some embodiments of the present invention.
- the phases of the illustrated methodmay be performed in device 110 , or in a control device, such as processor or chipset, configured to at least in part control device 110 when implanted therein.
- Phase 510comprises receiving, via a first channel, a secret value and an identifier of a local node and, via a second channel, a random value.
- Phase 520comprises causing transmission to the local node of a first message comprising a hash value, the hash value being derived based on a set comprising the secret value, the random value, and an instruction.
- the first messagemay be conveyed to the local node via the second channel.
- FIG. 6is a second flow chart of a second method in accordance with at least some embodiments of the present invention.
- the phases of the second methodmay be performed in local node 120 , or in a control device, such as processor or chipset, configured to at least in part control local node 120 when implanted therein.
- Phase 610comprises storing a secret value associated with an apparatus.
- the apparatusmay comprise an apparatus performing the second method.
- Phase 620comprises transmitting to a node a random value.
- Phase 630comprises receiving a message from the node, the message comprising a first hash value.
- Phase 640comprises verifying the first hash value by deriving a comparative hash value based on a set comprising the secret value, an instruction, and the random value.
- Phase 650comprises, responsive to the comparative hash value matching the first hash value, causing the apparatus to act on the instruction.
- phase 660comprises transmitting to the node a second random value.
Landscapes
- Engineering & Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- Computer Networks & Wireless Communication (AREA)
- Signal Processing (AREA)
- Computer Hardware Design (AREA)
- General Engineering & Computer Science (AREA)
- Computing Systems (AREA)
- Theoretical Computer Science (AREA)
- Power Engineering (AREA)
- Software Systems (AREA)
- Physics & Mathematics (AREA)
- General Physics & Mathematics (AREA)
- Mobile Radio Communication Systems (AREA)
Abstract
Description
Claims (16)
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| PCT/FI2014/050724WO2016046446A1 (en) | 2014-09-24 | 2014-09-24 | Controlling a device |
Publications (2)
| Publication Number | Publication Date |
|---|---|
| US20170277882A1 US20170277882A1 (en) | 2017-09-28 |
| US10642968B2true US10642968B2 (en) | 2020-05-05 |
Family
ID=55580362
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US15/512,277Active2035-03-13US10642968B2 (en) | 2014-09-24 | 2014-09-24 | Controlling a device |
Country Status (4)
| Country | Link |
|---|---|
| US (1) | US10642968B2 (en) |
| EP (1) | EP3198785B1 (en) |
| CN (1) | CN106797315B (en) |
| WO (1) | WO2016046446A1 (en) |
Families Citing this family (3)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US11170094B2 (en)* | 2016-01-27 | 2021-11-09 | Secret Double Octopus Ltd. | System and method for securing a communication channel |
| US10437220B1 (en)* | 2017-11-29 | 2019-10-08 | Vivid Robotics, Inc. | Distributed machine cooperation in assembly |
| JP7210989B2 (en)* | 2018-10-04 | 2023-01-24 | 富士電機株式会社 | Management server, vending machine, and method for adding device identification information |
Citations (48)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN1321386A (en) | 1999-06-29 | 2001-11-07 | 索尼公司 | Communication device, communication method, and communication terminal device |
| WO2005083927A1 (en) | 2004-02-27 | 2005-09-09 | Canon Kabushiki Kaisha | Information processing apparatus, print control apparatus, print control system |
| US20050203582A1 (en)* | 2004-03-15 | 2005-09-15 | Healy Scott J. | Cryptographic authentication for telemetry with an implantable medical device |
| US20050253717A1 (en) | 2004-05-13 | 2005-11-17 | Cisco Technology, Inc. | Methods and devices for assigning RFID device personality |
| US20060112171A1 (en) | 2004-11-19 | 2006-05-25 | Rader Shawn T | System and method to control devices using a remote control device via hypertext transfer protocol (HTTP) |
| US20070156876A1 (en) | 2005-12-30 | 2007-07-05 | Prabakar Sundarrajan | System and method for performing flash caching of dynamically generated objects in a data communication network |
| US20080120439A1 (en) | 2006-11-16 | 2008-05-22 | International Business Machines Corporation | Automated solution to provide immediate requisite access to data and applications on an attached external device |
| CN101217563A (en) | 2008-01-10 | 2008-07-09 | 中山大学 | A method for remotely controlling file transfer with a smart phone |
| CN101267626A (en) | 2008-04-30 | 2008-09-17 | 金子光 | Automatic connection method between mobile phone and Internet computer |
| US20090112769A1 (en) | 2007-10-24 | 2009-04-30 | Kent Dicks | Systems and methods for remote patient monitoring |
| CN100531083C (en) | 2004-05-13 | 2009-08-19 | 思科技术公司 | Methods and devices for assigning RFID device personality |
| US7650509B1 (en) | 2004-01-28 | 2010-01-19 | Gordon & Howard Associates, Inc. | Encoding data in a password |
| CN101977543A (en) | 2008-03-19 | 2011-02-16 | 艾利森电话股份有限公司 | Nfc communications for implanted medical data acquisition devices |
| US20110126010A1 (en) | 2009-11-23 | 2011-05-26 | Electronics And Telecommunications Research Institute | Server, system and method for managing identity |
| CN102281251A (en) | 2010-06-09 | 2011-12-14 | 中兴通讯股份有限公司 | Device, system and method for realizing intelligent household application |
| CN102316606A (en) | 2010-06-29 | 2012-01-11 | 上海贝尔股份有限公司 | Method and device for realizing wireless fidelity (WiFi) service agency |
| US20120079582A1 (en) | 2010-09-27 | 2012-03-29 | Research In Motion Limited | Authenticating an auxiliary device from a portable electronic device |
| CN102404413A (en) | 2011-12-29 | 2012-04-04 | Tcl集团股份有限公司 | Method and system for realizing automatic matching of functional applications among digital home devices |
| CN102571702A (en) | 2010-12-22 | 2012-07-11 | 中兴通讯股份有限公司 | Key generation method, system and equipment in Internet of things |
| CN102652445A (en) | 2009-12-09 | 2012-08-29 | 皇家飞利浦电子股份有限公司 | Wireless communication method based on proxy redundancy |
| US20120280801A1 (en) | 2010-02-22 | 2012-11-08 | Nec Corporation | Controlled device, device control system, device control program and device control method |
| US8347370B2 (en) | 2008-05-13 | 2013-01-01 | Veritrix, Inc. | Multi-channel multi-factor authentication |
| US20130010954A1 (en) | 2010-03-11 | 2013-01-10 | Rainer Falk | Method for the secure unindirectional transmission of signals |
| US20130038425A1 (en) | 2011-08-12 | 2013-02-14 | Nobukazu Sugiyama | System and method for performing commands from a remote source |
| WO2013038230A1 (en) | 2011-09-12 | 2013-03-21 | Nokia Corporation | Methods and apparatus for launching an application identified by a sensor |
| US20130080898A1 (en) | 2011-09-26 | 2013-03-28 | Tal Lavian | Systems and methods for electronic communications |
| US20130090773A1 (en) | 2011-10-06 | 2013-04-11 | Samsung Electronics Co., Ltd. | Apparatus and method for preventing command conflicts in a smart grid network |
| US20130097274A1 (en) | 2011-10-13 | 2013-04-18 | People Power Company | Method and system for managing a slave device through a master device |
| WO2013057493A1 (en) | 2011-10-18 | 2013-04-25 | Limited Berg | System and method for providing services to devices via a common interface |
| WO2013063381A1 (en) | 2011-10-28 | 2013-05-02 | Tovbot | Smartphone and internet service enabled robot systems and methods |
| CN103200570A (en) | 2013-03-19 | 2013-07-10 | 成都秦川科技发展有限公司 | Internet of things smart water meter information security management module |
| WO2013119730A1 (en) | 2012-02-09 | 2013-08-15 | Cisco Technology, Inc. | Application context transfer for distributed computing resources |
| US20130211622A1 (en) | 2012-02-14 | 2013-08-15 | Verizon Patent And Licensing Inc. | Hashed Strings for Machine-to-Machine Communication Based on Time and Secret Strings |
| US20130238744A1 (en) | 2012-03-08 | 2013-09-12 | Research In Motion Limited | Object mediated data transfer between electronic devices |
| US20130241743A1 (en) | 2012-03-15 | 2013-09-19 | Mucha Loic | iKT Universal Electronic Monitoring Device and Method of Use for Smart Cooking |
| CN203219496U (en) | 2013-04-11 | 2013-09-25 | 成都秦川科技发展有限公司 | Internet of Things intelligent ammeter embedded with information security management module |
| US20130298642A1 (en) | 2012-05-08 | 2013-11-14 | Logimesh IP, LLC | Remote air monitoring array system |
| EP2683146A1 (en) | 2012-07-05 | 2014-01-08 | Martin Lambert | Smartphone and microcontroller based remote monitoring and control system |
| US8639391B1 (en) | 2012-11-08 | 2014-01-28 | Green Edge Technologies, Inc. | Systems, devices, and methods for automation and energy management |
| WO2014024078A1 (en) | 2012-08-07 | 2014-02-13 | Koninklijke Philips N.V. | Timed lighting control |
| US20140047322A1 (en) | 2012-08-09 | 2014-02-13 | Korea Advanced Institute Of Science And Technology | Method and system for browsing things of internet of things on ip using web platform |
| US8713701B2 (en) | 2000-09-05 | 2014-04-29 | Strikeforce Technologies, Inc. | Multichannel device utilizing a centralized out-of-band authentication system (COBAS) |
| WO2014072725A1 (en) | 2012-11-07 | 2014-05-15 | Crisp Telecom Limited | Mobile tag reader security system |
| WO2014076927A1 (en) | 2012-11-13 | 2014-05-22 | パナソニック株式会社 | Method used in system for remotely operating device |
| WO2014096505A1 (en) | 2012-12-20 | 2014-06-26 | Nokia Corporation | Method and apparatus for handling messages |
| US20140304381A1 (en) | 2013-04-05 | 2014-10-09 | Nokia Corporation | Method and apparatus for communicating with smart objects |
| US20150006695A1 (en)* | 2013-06-26 | 2015-01-01 | Qualcomm Incorporated | USER PRESENCE BASED CONTROL OF REMOTE COMMUNICATION WITH INTERNET OF THINGS (IoT) DEVICES |
| WO2015088481A1 (en) | 2013-12-09 | 2015-06-18 | Nokia Technologies Oy | Switching to advertising locator after connection establishment |
- 2014
- 2014-09-24CNCN201480082284.1Apatent/CN106797315B/enactiveActive
- 2014-09-24USUS15/512,277patent/US10642968B2/enactiveActive
- 2014-09-24WOPCT/FI2014/050724patent/WO2016046446A1/enactiveApplication Filing
- 2014-09-24EPEP14902683.3Apatent/EP3198785B1/enactiveActive
Patent Citations (51)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN1321386A (en) | 1999-06-29 | 2001-11-07 | 索尼公司 | Communication device, communication method, and communication terminal device |
| US8713701B2 (en) | 2000-09-05 | 2014-04-29 | Strikeforce Technologies, Inc. | Multichannel device utilizing a centralized out-of-band authentication system (COBAS) |
| US7650509B1 (en) | 2004-01-28 | 2010-01-19 | Gordon & Howard Associates, Inc. | Encoding data in a password |
| US20120278624A1 (en)* | 2004-02-27 | 2012-11-01 | Canon Kabushiki Kaisha | Information processing apparatus, print control apparatus, print control system, storage medium of storing computer-readable program, and program |
| WO2005083927A1 (en) | 2004-02-27 | 2005-09-09 | Canon Kabushiki Kaisha | Information processing apparatus, print control apparatus, print control system |
| US20050203582A1 (en)* | 2004-03-15 | 2005-09-15 | Healy Scott J. | Cryptographic authentication for telemetry with an implantable medical device |
| US20050253717A1 (en) | 2004-05-13 | 2005-11-17 | Cisco Technology, Inc. | Methods and devices for assigning RFID device personality |
| CN100531083C (en) | 2004-05-13 | 2009-08-19 | 思科技术公司 | Methods and devices for assigning RFID device personality |
| US20060112171A1 (en) | 2004-11-19 | 2006-05-25 | Rader Shawn T | System and method to control devices using a remote control device via hypertext transfer protocol (HTTP) |
| CN1829153A (en) | 2004-11-19 | 2006-09-06 | 英特尔公司 | System and method for controlling a device using a remote control device via hypertext transfer protocol |
| WO2006055484A1 (en) | 2004-11-19 | 2006-05-26 | Intel Corporation | System and method to control devices using a remote control device via hypertext transfer protocol (http) |
| US20070156876A1 (en) | 2005-12-30 | 2007-07-05 | Prabakar Sundarrajan | System and method for performing flash caching of dynamically generated objects in a data communication network |
| US20080120439A1 (en) | 2006-11-16 | 2008-05-22 | International Business Machines Corporation | Automated solution to provide immediate requisite access to data and applications on an attached external device |
| US20090112769A1 (en) | 2007-10-24 | 2009-04-30 | Kent Dicks | Systems and methods for remote patient monitoring |
| CN101217563A (en) | 2008-01-10 | 2008-07-09 | 中山大学 | A method for remotely controlling file transfer with a smart phone |
| CN101977543A (en) | 2008-03-19 | 2011-02-16 | 艾利森电话股份有限公司 | Nfc communications for implanted medical data acquisition devices |
| CN101267626A (en) | 2008-04-30 | 2008-09-17 | 金子光 | Automatic connection method between mobile phone and Internet computer |
| US8347370B2 (en) | 2008-05-13 | 2013-01-01 | Veritrix, Inc. | Multi-channel multi-factor authentication |
| US20110126010A1 (en) | 2009-11-23 | 2011-05-26 | Electronics And Telecommunications Research Institute | Server, system and method for managing identity |
| CN102652445A (en) | 2009-12-09 | 2012-08-29 | 皇家飞利浦电子股份有限公司 | Wireless communication method based on proxy redundancy |
| US20120280801A1 (en) | 2010-02-22 | 2012-11-08 | Nec Corporation | Controlled device, device control system, device control program and device control method |
| US20130010954A1 (en) | 2010-03-11 | 2013-01-10 | Rainer Falk | Method for the secure unindirectional transmission of signals |
| CN102281251A (en) | 2010-06-09 | 2011-12-14 | 中兴通讯股份有限公司 | Device, system and method for realizing intelligent household application |
| CN102316606A (en) | 2010-06-29 | 2012-01-11 | 上海贝尔股份有限公司 | Method and device for realizing wireless fidelity (WiFi) service agency |
| US20120079582A1 (en) | 2010-09-27 | 2012-03-29 | Research In Motion Limited | Authenticating an auxiliary device from a portable electronic device |
| CN102571702A (en) | 2010-12-22 | 2012-07-11 | 中兴通讯股份有限公司 | Key generation method, system and equipment in Internet of things |
| US20130038425A1 (en) | 2011-08-12 | 2013-02-14 | Nobukazu Sugiyama | System and method for performing commands from a remote source |
| WO2013038230A1 (en) | 2011-09-12 | 2013-03-21 | Nokia Corporation | Methods and apparatus for launching an application identified by a sensor |
| US20130080898A1 (en) | 2011-09-26 | 2013-03-28 | Tal Lavian | Systems and methods for electronic communications |
| US20130090773A1 (en) | 2011-10-06 | 2013-04-11 | Samsung Electronics Co., Ltd. | Apparatus and method for preventing command conflicts in a smart grid network |
| US20130097274A1 (en) | 2011-10-13 | 2013-04-18 | People Power Company | Method and system for managing a slave device through a master device |
| WO2013057493A1 (en) | 2011-10-18 | 2013-04-25 | Limited Berg | System and method for providing services to devices via a common interface |
| WO2013063381A1 (en) | 2011-10-28 | 2013-05-02 | Tovbot | Smartphone and internet service enabled robot systems and methods |
| CN102404413A (en) | 2011-12-29 | 2012-04-04 | Tcl集团股份有限公司 | Method and system for realizing automatic matching of functional applications among digital home devices |
| WO2013119730A1 (en) | 2012-02-09 | 2013-08-15 | Cisco Technology, Inc. | Application context transfer for distributed computing resources |
| US20130211622A1 (en) | 2012-02-14 | 2013-08-15 | Verizon Patent And Licensing Inc. | Hashed Strings for Machine-to-Machine Communication Based on Time and Secret Strings |
| US20130238744A1 (en) | 2012-03-08 | 2013-09-12 | Research In Motion Limited | Object mediated data transfer between electronic devices |
| US20130241743A1 (en) | 2012-03-15 | 2013-09-19 | Mucha Loic | iKT Universal Electronic Monitoring Device and Method of Use for Smart Cooking |
| US20130298642A1 (en) | 2012-05-08 | 2013-11-14 | Logimesh IP, LLC | Remote air monitoring array system |
| EP2683146A1 (en) | 2012-07-05 | 2014-01-08 | Martin Lambert | Smartphone and microcontroller based remote monitoring and control system |
| WO2014024078A1 (en) | 2012-08-07 | 2014-02-13 | Koninklijke Philips N.V. | Timed lighting control |
| US20140047322A1 (en) | 2012-08-09 | 2014-02-13 | Korea Advanced Institute Of Science And Technology | Method and system for browsing things of internet of things on ip using web platform |
| WO2014072725A1 (en) | 2012-11-07 | 2014-05-15 | Crisp Telecom Limited | Mobile tag reader security system |
| US8639391B1 (en) | 2012-11-08 | 2014-01-28 | Green Edge Technologies, Inc. | Systems, devices, and methods for automation and energy management |
| WO2014076927A1 (en) | 2012-11-13 | 2014-05-22 | パナソニック株式会社 | Method used in system for remotely operating device |
| WO2014096505A1 (en) | 2012-12-20 | 2014-06-26 | Nokia Corporation | Method and apparatus for handling messages |
| CN103200570A (en) | 2013-03-19 | 2013-07-10 | 成都秦川科技发展有限公司 | Internet of things smart water meter information security management module |
| US20140304381A1 (en) | 2013-04-05 | 2014-10-09 | Nokia Corporation | Method and apparatus for communicating with smart objects |
| CN203219496U (en) | 2013-04-11 | 2013-09-25 | 成都秦川科技发展有限公司 | Internet of Things intelligent ammeter embedded with information security management module |
| US20150006695A1 (en)* | 2013-06-26 | 2015-01-01 | Qualcomm Incorporated | USER PRESENCE BASED CONTROL OF REMOTE COMMUNICATION WITH INTERNET OF THINGS (IoT) DEVICES |
| WO2015088481A1 (en) | 2013-12-09 | 2015-06-18 | Nokia Technologies Oy | Switching to advertising locator after connection establishment |
Non-Patent Citations (50)
| Title |
|---|
| "About HTML5 WebSocket", Websocket.org, Retrieved on Apr. 7, 2017, Webpage available at : http://www.websocket.org/aboutwebsocket.html. |
| "CoAP Option for Authentication Token", IETF, Retrieved on Mar. 21, 2017, Webpage available at : https://www.ietf.org/mail-archive/web/core/current/msg05445.html. |
| "Copper (Cu): Add-ons for Firefox", Mozilla Add-Ons, Retrieved on Apr. 7, 2017, Webpage available at : https://addons.mozilla.org/en-us/firefox/addon/copper-270430/. |
| "CORS Access-Control-Allow-Origin despite correct headers", Stackoverflow, Retrieved on Apr. 7, 2017, Webpage available at : http://stackoverflow.com/questions/9613210/cors-access-control-allow-origin-despite-correct-headers. |
| "CORS Enabled", W3C, Retrieved on Apr. 7, 2017, Webpage available at : https://www.w3.org/wiki/CORS_Enabled. |
| "Cross-origin resource sharing", Wikipedia, Retrieved on Apr. 7, 2017, Webpage available at : https://en.wikipedia.org/wiki/Cross-origin_resource_sharing. |
| "Cross-site xmlhttprequest with CORS", Hacks, Retrieved on Apr. 7, 2017, Webpage available at :https://hacks.mozilla.org/2009/07/cross-site-xmlhttprequest-with-cors/. |
| "LazarSoft/jsqrcode", Github, Retrieved on Apr. 7, 2017, Webpage available at :https://github.com/LazarSoft/jsqcrode. |
| "Near field communications (NEC)", W3C, Retrieved on Apr. 7, 2017, Webpage available at :https://www.w3.org/wiki/Near_field_communications_(NFC). |
| "Network Service Discovery Api Support in Opera", Dev.Opera, Retrieved on Apr. 7, 2017, Webpage available at : https://dev.opera.com/articles/network-service-discovery-api/. |
| "Network Service Discovery", W3C, Retrieved on Apr. 7, 2017, Webpage available at : https://dvcs.w3.org/hg/dap/raw-file/tip/discovery-api/Overview.html#dfn-http-response. |
| "Re: [core] CoAP Option for Authentication Token", IETF, Retrieved on Mar. 21, 2017, Webpage available at :https://www.ietf.org/mail-archive/web/core/current/msg05447.html. |
| "Same-Origin policy", Wikipedia, Retrieved on Apr. 7, 2017, Webpage available at: https://en.wikipedia.org/wiki/Same-origin_policy. |
| "Security token", Wikipedia, Retrieved on Mar. 21, 2017, Webpage available at : https://en.wikipedia.org/wiki/Security_token. |
| "System Applications Working Group Charter", W3C, Retrieved on Apr. 7, 2017, Webpage available at: https://www.w3.org/2012/09/sysapps-wg-charter.html. |
| "Using CORS", HTML5 Rocks, Retrieved on Apr. 7, 2017, Webpage available at : https://www.html5rocks.com/en/tutorials/cors/. |
| "Web Intents", Wikipedia, Retrieved on Apr. 7, 2017, Webpage available at : https://en.wikipedia.org/wiki/Web_Intents. |
| "Webstorage", HTML, Retrieved on Apr. 7, 2017, Webpage available at : https://html.spec.whatwg.org/multipage/webstorage.html. |
| "XMLHttpRequest", Wikipedia, Retrieved on Apr. 7, 2017, Webpage available at : https://en.wikipedia.org/wiki/XMLHttpRequest. |
| Briseno et al., "Using RFID/NFC and QR-code in Mobile Phones to Link the Physical and the Digital World" Interactive Multimedia, Mar. 7, 2012, pp. 219-243. |
| Castellani et al., "Best Practices for HTTP-CoAP Mapping Implementation", draft-castellani-core-http-mapping-07, Core Working Group, Feb. 25, 2013, pp. 1-16. |
| Chinese Office Action corresponding to CN Appln. No. 201480082284.1, dated Dec. 12, 2019. |
| Communication pursuant to Article 94(3) EPC issued in corresponding European Patent Application No. 14902683.3, dated Jun. 21, 2019. |
| Dodson et al., "Micro-interactions with NFC-enabled Mobile Phones", MobiCase, 2011, pp. 1-20. |
| Extended European Search Report received for corresponding European Patent Application No. 14878737.7, dated Jun. 6, 2017, 12 pages. |
| Extended European Search Report received for corresponding European Patent Application No. 14902683.3, dated Feb. 6, 2018, 6 pages. |
| Final Office action received for corresponding U.S. Appl. No. 14/891,970, dated Aug. 27, 2018, 14 pages. |
| Final Office action received for corresponding U.S. Appl. No. 15/108,568, dated Jul. 28, 2017, 11 pages. |
| First Office Action issued in corresponding Chinese Patent Application No. 2014800822841, dated Jun. 5, 2019, with partial English translation. |
| Huang, "Web Technologies for the Internet of Things", Thesis, Jul. 7, 2013, pp. 1-66. |
| International Search Report and Written Opinion received for corresponding Patent Cooperation Treaty Application No. PCT/FI2013/050540, dated Sep. 12, 2013, 8 pages. |
| International Search Report and Written Opinion received for corresponding Patent Cooperation Treaty Application No. PCT/FI2014/050724 dated Apr. 27, 2015, 14 pages. |
| International Search Report and Written Opinion received for corresponding Patent Cooperation Treaty Application No. PCT/IB2014/058291, dated Nov. 7, 2014, 19 pages. |
| Kent et al., "Secure Communication via Shared Knowledge and a Salted Flash in Ad-hoc Environments", IEEE Annual Computer Software and Applications Conference Workshops, Jul. 18-22, 2011, pp. 122-127. |
| Keoh et al., "Securing the Internet of Things: A Standardization Perspective", IEEE Internet of Things Journal, vol. 1, No. 3, Jun. 2014, pp. 265-275. |
| Lee et al., "The Internet of Things-Concept and Problem Statement", draft-Iee-iot-problem-statement-05.txt, IRTF, Jul. 30, 2012, pp. 1-19. |
| Non-Final Office action received for corresponding U.S. Appl. No. 14/891,970, dated Feb. 22, 2018, 13 pages. |
| Non-Final Office action received for corresponding U.S. Appl. No. 15/108,568, dated Mar. 23, 2017, 10 pages. |
| Non-Final Office action received for corresponding U.S. Appl. No. 15/108,568, dated Nov. 7, 2017, 10 pages. |
| Office action received for corresponding Chinese Patent Application No. 201380078302.4, dated Apr. 28, 2018, 7 pages of office action and no page of translation available. |
| Office action received for corresponding Chinese Patent Application No. 201380078302.4, dated Jan. 11, 2019, 3 pages of office action and no page of translation available. |
| Office action received for corresponding Chinese Patent Application No. 201480073085.4, dated Sep. 25, 2018, 7 pages of office action and no page of translation available. |
| Office action received for corresponding European Patent Application No. 13728776.9, dated Jun. 21, 2018, 7 pages. |
| Office action received for corresponding European Patent Application No. 14878737.7, dated Mar. 21, 2018, 8 pages. |
| Office action received for corresponding European Patent Application No. 14902683.3, dated Feb. 8, 2019, 4 pages. |
| Savolainen et al., "CoAP over WebSockets", draft-savolainen-core-coap-websockets-01, Core Working Group, Oct. 18, 2013, pp. 1-18. |
| Savolainen et al., "CoAP over WebSockets", draft-savolainen-core-coap-websockets-02, Core Working Group, Apr. 10, 2014, pp. 1-15. |
| Shelby et al., "Constrained Application Protocol (COAP)", draft-ietf-core-coap-18, Core Working Group, Jun. 28, 2013, pp. 1-118. |
| Shelby et al., "The Constrained Application Protocol (CoAP)", RFC 7252, IETF, Jun. 2014, pp. 1-97. |
| Vial, "CoRE Mirror Server", draft-vial-core-mirror-proxy-01, Jul. 13, 2012, pp. 1-20. |
Also Published As
| Publication number | Publication date |
|---|---|
| EP3198785A4 (en) | 2018-03-07 |
| EP3198785B1 (en) | 2020-10-21 |
| EP3198785A1 (en) | 2017-08-02 |
| WO2016046446A1 (en) | 2016-03-31 |
| CN106797315B (en) | 2021-02-02 |
| CN106797315A (en) | 2017-05-31 |
| US20170277882A1 (en) | 2017-09-28 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| JP7421591B2 (en) | Network-assisted bootstrapping for machine-to-machine communication | |
| US9439069B2 (en) | Subscriber identity module provider apparatus for over-the-air provisioning of subscriber identity module containers and methods | |
| US10212140B2 (en) | Key management | |
| CN105191370A (en) | Identifier for Proximity Services | |
| EP3117576B1 (en) | Pairing of devices | |
| US20140304419A1 (en) | System and terminal for p2p connection in mobile environment and method for p2p connection using the same | |
| US10425812B2 (en) | Method and apparatus for establishment of private communication between devices | |
| US20180095500A1 (en) | Tap-to-dock | |
| CN108028755B (en) | Method and apparatus for authentication | |
| CN114286335A (en) | Server selection method and device | |
| EP3665921B1 (en) | Virtual profile for bluetooth | |
| US10642968B2 (en) | Controlling a device | |
| JP2014002716A (en) | Information processing apparatus, network system, data sharing method, and computer program allowing data sharing | |
| CN108235823A (en) | Proxy Free Cellular Roaming | |
| US12001853B2 (en) | Device bootstrapping | |
| EP3605992B1 (en) | Remotely configuring a customer premise equipment | |
| US20190087562A1 (en) | Sensor-based interaction |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| AS | Assignment | Owner name:NOKIA CORPORATION, FINLAND Free format text:ASSIGNMENT OF ASSIGNORS INTEREST;ASSIGNORS:SAVOLAINEN, TEEMU ILMARI;RANTAESKOLA, ANTTI VELI;SIGNING DATES FROM 20140930 TO 20141001;REEL/FRAME:041616/0030 Owner name:NOKIA TECHNOLOGIES OY, FINLAND Free format text:ASSIGNMENT OF ASSIGNORS INTEREST;ASSIGNOR:NOKIA CORPORATION;REEL/FRAME:041616/0055 Effective date:20150116 | |
| STPP | Information on status: patent application and granting procedure in general | Free format text:NON FINAL ACTION MAILED | |
| STPP | Information on status: patent application and granting procedure in general | Free format text:RESPONSE TO NON-FINAL OFFICE ACTION ENTERED AND FORWARDED TO EXAMINER | |
| STPP | Information on status: patent application and granting procedure in general | Free format text:FINAL REJECTION MAILED | |
| STPP | Information on status: patent application and granting procedure in general | Free format text:RESPONSE AFTER FINAL ACTION FORWARDED TO EXAMINER | |
| STPP | Information on status: patent application and granting procedure in general | Free format text:ADVISORY ACTION MAILED | |
| STPP | Information on status: patent application and granting procedure in general | Free format text:DOCKETED NEW CASE - READY FOR EXAMINATION | |
| STPP | Information on status: patent application and granting procedure in general | Free format text:NON FINAL ACTION MAILED | |
| STPP | Information on status: patent application and granting procedure in general | Free format text:RESPONSE TO NON-FINAL OFFICE ACTION ENTERED AND FORWARDED TO EXAMINER | |
| STCF | Information on status: patent grant | Free format text:PATENTED CASE | |
| MAFP | Maintenance fee payment | Free format text:PAYMENT OF MAINTENANCE FEE, 4TH YEAR, LARGE ENTITY (ORIGINAL EVENT CODE: M1551); ENTITY STATUS OF PATENT OWNER: LARGE ENTITY Year of fee payment:4 |