CN1767495A - Method for Ensuring Data Security of Layer 2 Ethernet Switches in Metropolitan Area Transmission Equipment - Google Patents
Method for Ensuring Data Security of Layer 2 Ethernet Switches in Metropolitan Area Transmission EquipmentDownload PDFInfo
- Publication number
- CN1767495A CN1767495ACNA2004100868275ACN200410086827ACN1767495ACN 1767495 ACN1767495 ACN 1767495ACN A2004100868275 ACNA2004100868275 ACN A2004100868275ACN 200410086827 ACN200410086827 ACN 200410086827ACN 1767495 ACN1767495 ACN 1767495A
- Authority
- CN
- China
- Prior art keywords
- message
- routing table
- port
- switch
- mac address
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Granted
Links
Images
Landscapes
- Data Exchanges In Wide-Area Networks (AREA)
- Small-Scale Networks (AREA)
Abstract
Description
Translated fromChinese技术领域technical field
本发明涉及网络通信技术领域,具体涉及一种保证城域传输设备中二层以太网交换机数据安全的方法。The invention relates to the technical field of network communication, in particular to a method for ensuring the data security of a Layer 2 Ethernet switch in metro transmission equipment.
背景技术Background technique
随着城域网技术的发展,传统的以太网透传技术已无法满足城域传输网应用的需求,因此出现了多种基于城域传输的二层以太网交换机,二层交换机属数据链路层设备,可以识别数据包中的MAC(媒体接入控制)地址信息,根据MAC地址进行转发,并将这些MAC地址与对应的端口记录在路由表中,该路由表标明了MAC地址和交换机端口的对应关系。当交换机从某个端口收到一个数据包,它先读取包头中的源MAC地址,这样它就知道源MAC地址的机器是连在哪个端口上的;再去读取包头中的目的MAC地址,并在路由表中查找相应的端口;如表中有与这目的MAC地址对应的端口,把数据包直接复制到这端口上;如表中找不到相应的端口则把数据包广播到所有端口上,当目的机器对源机器回应时,交换机又可以学习一目的MAC地址与哪个端口对应,在下次传送数据时就不再需要对所有端口进行广播了。With the development of metropolitan area network technology, the traditional Ethernet transparent transmission technology can no longer meet the needs of metropolitan area transmission network applications. Therefore, there have been a variety of Layer 2 Ethernet switches based on metropolitan area transmission. The Layer 2 switch is a data link Layer device, which can identify the MAC (Media Access Control) address information in the data packet, forward according to the MAC address, and record these MAC addresses and corresponding ports in the routing table, which indicates the MAC address and switch port corresponding relationship. When the switch receives a data packet from a certain port, it first reads the source MAC address in the packet header, so that it knows which port the machine with the source MAC address is connected to; then reads the destination MAC address in the packet header , and look up the corresponding port in the routing table; if there is a port corresponding to the destination MAC address in the table, copy the data packet directly to this port; if the corresponding port cannot be found in the table, broadcast the data packet to all On the port, when the destination machine responds to the source machine, the switch can learn which port a destination MAC address corresponds to, and it is no longer necessary to broadcast to all ports when transmitting data next time.
不断循环上述过程,对于全网的MAC地址信息都可以学习到,二层交换机即可建立并维护它自己的地址表。Continuously repeating the above process, the MAC address information of the whole network can be learned, and the layer 2 switch can establish and maintain its own address table.
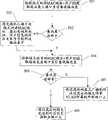
传统的二层以太网交换机对报文的转发流程如图1所示:The packet forwarding process of a traditional Layer 2 Ethernet switch is shown in Figure 1:
路由表可以静态配置,也可以动态建立,即通过交换机根据接收报文中的MAC地址不断学习而建立的。The routing table can be statically configured or dynamically established, that is, established by the switch based on the MAC address in the received message.
交换机收到报文后,如果没有相应的路由,则根据报文的源MAC地址+端口学习,建立源MAC地址和交换机端口的对应关系;该对应关系建立后,还要根据报文的目的MAC地址进行出端口的查找。After the switch receives the message, if there is no corresponding route, it will establish the corresponding relationship between the source MAC address and the switch port according to the source MAC address of the message + port learning; Address for outbound port lookup.
可能有以下几种情况:There are several possible situations:
(1)报文中的目的MAC地址为单播地址,且路由表中没有相应的路由;(1) The destination MAC address in the message is a unicast address, and there is no corresponding route in the routing table;
(2)报文中的目的MAC地址为组播地址,且路由表中没有相应的路由;(2) The destination MAC address in the message is a multicast address, and there is no corresponding route in the routing table;
(3)报文中的目的MAC地址为广播地址。(3) The destination MAC address in the message is a broadcast address.
在上述三种情况下,都需要对报文进行广播处理,将报文复制到所有端口上。根据回应报文学习到对应的出端口,从而在路由表中建立起相应的路由。In the above three cases, it is necessary to broadcast the message and copy the message to all ports. The corresponding outbound port is learned according to the response message, so as to establish the corresponding route in the routing table.
可见,二层以太网交换机只单纯地利用MAC地址查找路由,由此会存在以下安全隐患:It can be seen that the Layer 2 Ethernet switch only uses the MAC address to find the route, so there will be the following security risks:
a、端口攻击,即网络黑客利用交换机广播到本端口的另一个用户的报文获取MAC地址,通过一个或多个端口向这个用户的某端口发送大量垃圾报文,致使被攻击用户带宽资源被大量占用甚至被耗尽,网络处于瘫痪状态。a. Port attack, that is, a network hacker obtains the MAC address by using the message broadcast by the switch to another user on this port, and sends a large number of junk messages to a certain port of this user through one or more ports, causing the bandwidth resources of the attacked user to be blocked. It is heavily used or even exhausted, and the network is in a state of paralysis.
b、黑客可利用MAC地址假冒窃取被攻击方报文信息。b. Hackers can use the MAC address to fake and steal the packet information of the attacked party.
如图2所示:端口A和端口C属于VLAN1,端口B和端口D属于VLAN2,端口A和端口C之间存在路由,在端口B发送源MAC地址与端口A所连接设备MAC地址相同的报文,则端口C的报文就会发往端口B,这样网络黑客便利用端口B窃取了端口C的信息。As shown in Figure 2: port A and port C belong to VLAN1, port B and port D belong to VLAN2, there is a route between port A and port C, and port B sends a packet with the same source MAC address as the MAC address of the device connected to port A. In this way, the network hacker uses port B to steal the information of port C.
c、当MAC地址共享不同的VLAN(虚拟局域网)和用户/VB(虚拟网桥)/Stack VLAN(嵌套虚拟局域网)/QinQ(多层802.1Q标签封装报文格式)时,由于表项的链接过多,导致查找效率降低,从而报文的转发效率也会随着降低。c. When MAC addresses share different VLANs (virtual local area network) and user/VB (virtual network bridge)/Stack VLAN (nested virtual local area network)/QinQ (multi-layer 802.1Q label encapsulation message format), due to the Too many links will reduce the search efficiency, and thus the packet forwarding efficiency will also decrease.
而且,二层以太网交换机的广播机制也存在潜在的隐患:当交换机在路由表项中找不到相应的端口则把数据包广播到所有端口上,攻击者就可以在某一个端口上接收到其它端口广播过来的报文,这样也会出现信息安全隐患。Moreover, the broadcast mechanism of the Layer 2 Ethernet switch also has potential hidden dangers: when the switch cannot find the corresponding port in the routing table entry, it broadcasts the data packet to all ports, and the attacker can receive the packet on a certain port. Packets broadcast from other ports will also cause potential information security risks.
发明内容Contents of the invention
本发明的目的是提供一种保证城域传输设备中二层以太网交换机数据安全的方法,以克服现有技术中单纯利用MAC地址查找路由及查找路由时采用广播机制存在的安全隐患,提高城域传输设备中数据的安全性。The purpose of the present invention is to provide a method for ensuring the data security of the two-layer Ethernet switch in the metropolitan area transmission equipment, so as to overcome the potential safety hazards in the prior art that simply use the MAC address to find the route and use the broadcast mechanism to improve the urban security. Security of data in domain transfer devices.
本发明的目的是通过以下技术方案实现的:The purpose of the present invention is achieved through the following technical solutions:
一种保证城域传输设备中二层以太网交换机数据安全的方法,包括:A method for ensuring the data security of a Layer 2 Ethernet switch in a metropolitan area transmission device, comprising:
A、建立报文过滤表;A. Establish a message filtering table;
B、根据所述报文过滤表对所述交换机接收的报文进行过滤;B. Filtering the messages received by the switch according to the message filtering table;
C、建立路由表,所述路由表包括:MAC地址及与其对应的交换机端口、用户信息、虚拟局域网标识;C, establish routing table, described routing table includes: MAC address and switch port corresponding thereto, user information, virtual local area network mark;
D、根据所述路由表对过滤后的报文进行转发。D. Forwarding the filtered message according to the routing table.
所述步骤A具体为:根据所述交换机的配置信息建立所述报文过滤表,所述报文过滤表包括:交换机入端口、所述交换机入端口所属的虚拟局域网标识和用户信息。The step A specifically includes: establishing the message filtering table according to the configuration information of the switch, and the message filtering table includes: a switch ingress port, a virtual local area network identifier to which the switch ingress port belongs, and user information.
所述步骤B包括:Described step B comprises:
B1、获取所述交换机接收的报文相关信息,所述报文相关信息包括:报文中的虚拟局域网标识、接收报文的入端口、所述报文的入端口对应的用户信息。B1. Obtain information related to the message received by the switch, where the message related information includes: a virtual local area network identifier in the message, an inbound port for receiving the message, and user information corresponding to the inbound port of the message.
B2、根据所述获取的报文相关信息查找所述报文过滤表;B2. Searching the message filtering table according to the obtained message-related information;
B3、当所述报文相关信息与所述过滤表中交换机入端口所属的虚拟局域网标识和用户信息不同时,丢弃所述报文。B3. When the message-related information is different from the virtual local area network identifier and user information to which the ingress port of the switch belongs in the filter table, discard the message.
所述步骤D包括:Said step D comprises:
D1、获取路由表入端口索引;D1. Obtain the ingress port index of the routing table;
D2、根据所述路由表入端口索引查找所述路由表;D2. Searching the routing table according to the in-port index of the routing table;
D3、当所述路由表中没有与所述路由表入端口索引对应的表项时,将所述交换机入端口与所述报文的源MAC地址、虚拟局域网标识、用户信息的对应关系学习到所述路由表中;D3. When there is no entry corresponding to the entry port index of the routing table in the routing table, learn the corresponding relationship between the entry port of the switch and the source MAC address, virtual local area network identifier, and user information of the message in said routing table;
D4、当所述路由表有与所述路由表入端口索引对应的表项时,获取路由表出端口索引;D4. When the routing table has an entry corresponding to the routing table ingress port index, obtain the routing table egress port index;
D5、根据所述路由表出端口索引查找所述路由表;D5. Searching the routing table according to the outgoing port index of the routing table;
D6、根据查找结果对所述过滤后的报文进行转发。D6. Forward the filtered message according to the search result.
可选地,所述步骤D1具体为:根据所述获取的报文中的源MAC地址获取路由表入端口索引。与此对应,所述步骤D4具体为:根据所述获取的报文中的目的MAC地址获取路由表出端口索引。Optionally, the step D1 specifically includes: obtaining an ingress port index of a routing table according to the source MAC address in the obtained message. Correspondingly, the step D4 specifically includes: obtaining the routing table egress port index according to the destination MAC address in the obtained message.
可选地,所述步骤D1具体为:根据二元组“源MAC地址+虚拟局域网标识或用户信息”获取路由表入端口索引。与此对应,所述步骤D4具体为:根据二元组“目的MAC地址+虚拟局域网标识或用户信息”获取路由表出端口索引。Optionally, the step D1 specifically includes: obtaining the ingress port index of the routing table according to the two-tuple "source MAC address + virtual local area network identifier or user information". Correspondingly, the step D4 specifically includes: obtaining the routing table egress port index according to the two-tuple "destination MAC address+VLAN identifier or user information".
可选地,所述步骤D1具体为:根据三元组“源MAC地址+虚拟局域网标识+用户信息”获取路由表入端口索引。与此对应,所述步骤D4具体为:根据三元组“目的MAC地址+虚拟局域网标识+用户信息”获取路由表出端口索引。Optionally, the step D1 specifically includes: obtaining the ingress port index of the routing table according to the triplet "source MAC address + virtual local area network identifier + user information". Correspondingly, the step D4 specifically includes: obtaining the routing table egress port index according to the triplet "destination MAC address+VLAN identifier+user information".
所述步骤D6包括:Described step D6 comprises:
D61、当所述路由表中有与所述路由表出端口索引对应的表项时,则将所述过滤后的报文发送到对应的交换机出端口上;D61. When there is an entry corresponding to the outgoing port index of the routing table in the routing table, sending the filtered message to the corresponding outgoing port of the switch;
D62、当所述路由表中没有与所述路由表出端口索引对应的表项时,则将所述过滤后的报文广播到所述过滤后的报文所带虚拟局域网标识所属的所有端口上。D62. When there is no entry corresponding to the outgoing port index of the routing table in the routing table, broadcast the filtered message to all ports to which the virtual local area network identifier carried in the filtered message belongs superior.
所述用户信息具体为:用户标识或虚拟网桥标识或嵌套虚拟局域网或多层802.1Q标签封装报文格式。The user information is specifically: a user identifier or a virtual bridge identifier or a nested virtual local area network or a multi-layer 802.1Q label encapsulation message format.
由以上本发明提供的技术方案可以看出,本发明利用过滤机制来隔离不同的VLAN和用户/VB/Stack VLAN/QinQ,有效地避免了假冒MAC地址的端口攻击,保障了交换机中数据的安全;利用不同的查找方式:只通过MAC地址、通过MAC地址与VLAN和/或用户ID/VBID/Stack VLAN/QinQ构成二元组或三元组来查找路由,从而使查找路由支持区分同一VLAN内的不同用户ID/VBID/Stack VLAN/QinQ具有相同的MAC地址的应用,进一步增强了对报文的过滤功能,提高了网络的安全性。利用优选的方式:用户ID/VBID/StackVLAN/QinQ+VLAN+MAC三元组查找路由还可以缩短路由表表项查找深度,提高MAC地址共享VLAN、用户/VB/Stack VLAN/QinQ时的表项查找效率。As can be seen from the technical solutions provided by the present invention above, the present invention utilizes filtering mechanisms to isolate different VLANs and users/VB/Stack VLAN/QinQ, effectively avoiding the port attack of counterfeit MAC addresses, and ensuring the security of data in the switch ;Use different lookup methods: look up routes only through MAC address, through MAC address and VLAN and/or user ID/VBID/Stack VLAN/QinQ to form a tuple or triplet, so that the lookup route supports distinguishing the same VLAN Different user ID/VBID/Stack VLAN/QinQ have the same MAC address, which further enhances the filtering function of the message and improves the security of the network. Using the preferred method: User ID/VBID/StackVLAN/QinQ+VLAN+MAC triplet to search for routes can also shorten the search depth of routing table entries and improve the table entries when MAC addresses share VLAN, user/VB/Stack VLAN/QinQ Find efficiency.
附图说明Description of drawings
图1是现有技术中二层以太网交换机对报文的转发流程图;Fig. 1 is the flow chart of the forwarding of message by Layer 2 Ethernet switch in the prior art;
图2是现有技术中利用MAC地址假冒进行网络攻击的示意图;FIG. 2 is a schematic diagram of a network attack using MAC address counterfeiting in the prior art;
图3是本发明方法的实现流程图;Fig. 3 is the realization flowchart of the inventive method;
图4是本发明方法中报文过滤转发的第一实施例的实现流程图;Fig. 4 is the realization flowchart of the first embodiment of message filtering and forwarding in the method of the present invention;
图5是本发明方法中报文过滤转发的第二实施例的实现流程图;Fig. 5 is the implementation flowchart of the second embodiment of message filtering and forwarding in the method of the present invention;
图6是本发明方法中报文过滤转发的第三实施例的实现流程图。Fig. 6 is an implementation flowchart of the third embodiment of packet filtering and forwarding in the method of the present invention.
具体实施方式Detailed ways
本发明的核心在于根据交换机的配置信息预先建立表示交换机入端口与其所属VLAN(虚拟局域网)和用户ID/VBID/Stack VLAN/QinQ对应关系的报文过滤表,交换机接收报文后,首先对收到的报文进行端口过滤,将不属于本交换机入端口接收的报文丢弃,以防止端口攻击并保证端口数据安全;同时,利用MAC地址与用户ID/VBID/Stack VLAN/QinQ、VLAN组成二元组或三元组来查找路由,以提高查找效率。The core of the present invention is to set up in advance according to the configuration information of the switch the message filter table that represents the corresponding relationship between the switch input port and its VLAN (virtual local area network) and user ID/VBID/Stack VLAN/QinQ. Port filtering is performed on incoming packets, and packets that do not belong to the incoming ports of the switch are discarded to prevent port attacks and ensure port data security; at the same time, use MAC addresses and user ID/VBID/Stack VLAN/QinQ, Tuples or triples to look up routes to improve lookup efficiency.
为了使本技术领域的人员更好地理解本发明方案,下面结合附图和实施方式对本发明作进一步的详细说明。In order to enable those skilled in the art to better understand the solution of the present invention, the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
参照图3,图3示出了本发明方法的实现流程,包括以下步骤:With reference to Fig. 3, Fig. 3 has shown the implementation process of the method of the present invention, comprises the following steps:
步骤301:根据交换机的配置信息建立报文过滤表,所述报文过滤表包括:交换机入端口、所述交换机入端口所属的虚拟局域网标识和用户信息。所述用户信息具体为:用户标识或虚拟网桥标识或嵌套虚拟局域网或多层802.1Q标签封装报文格式。Step 301: Establish a message filtering table according to the configuration information of the switch. The message filtering table includes: an inbound port of the switch, a virtual local area network identifier to which the inbound port of the switch belongs, and user information. The user information is specifically: a user identifier or a virtual bridge identifier or a nested virtual local area network or a multi-layer 802.1Q label encapsulation message format.
本技术领域人员知道,用户是二层交换机中报文的所属域,一般是根据端口划分的,即每个端口只能属于一个用户,每个用户拥有一个完整的VLAN(虚拟局域网)域。用户ID(标识码)就是二层交换机中用来标识用户的,从原理上来讲,VBID(虚拟网桥标识)、Stack VLAN(嵌套VLAN)在二层交换机所起的作用与用户ID是相同的,VB(虚拟网桥)就是在二层交换机中划分出多个不同的虚拟域,这些虚拟域在对报文处理时是完全隔离的,VBID就是标识这些VB的,Stack VLAN实际上就是对VLAN(虚拟局域网)的扩充,在二层交换时可以起到与VB相同的隔离作用,而QinQ(多层802.1Q标签封装报文格式)标签在报文中可能存在多层,只有一层时就相当于StackVLAN,当存在两层以上时,就相当于对Stack VLAN的扩充,在二层交换时也起着信息隔离的作用。Those skilled in the art know that users are the domains of messages in the Layer 2 switch, which are generally divided according to ports, that is, each port can only belong to one user, and each user has a complete VLAN (Virtual Local Area Network) domain. User ID (identification code) is used to identify users in Layer 2 switches. In principle, VBID (Virtual Bridge ID) and Stack VLAN (nested VLAN) play the same role as User ID in Layer 2 switches. Yes, VB (Virtual Network Bridge) is to divide multiple different virtual domains in the layer 2 switch. These virtual domains are completely isolated when processing packets. VBID is to identify these VBs. Stack VLAN is actually for The expansion of VLAN (Virtual Local Area Network) can play the same isolation role as VB in Layer 2 switching, and QinQ (multi-layer 802.1Q label encapsulation message format) labels may have multiple layers in the message. It is equivalent to StackVLAN. When there are more than two layers, it is equivalent to the expansion of Stack VLAN, and it also plays the role of information isolation during Layer 2 switching.
这四个概念一般不会在同一个二层交换机中同时存在。因此,为了描述方便,下面仅以用户来说明。These four concepts generally do not exist in the same Layer 2 switch. Therefore, for the convenience of description, only users are used for description below.
步骤302:根据报文过滤表对交换机接收的报文进行过滤。具体过滤过程为:Step 302: Filter the packets received by the switch according to the packet filtering table. The specific filtering process is:
首先,交换机接收报文并获取报文的相关信息,即:报文中的虚拟局域网标识、接收报文的入端口、所述报文的入端口对应的用户信息。其中,虚拟局域网标识是报文本身所带的;接收报文的入端口是交换机自己可以知道的;有了接收报文的入端口信息,则根据交换机的配置信息就可获知该入端口对应的用户信息。First, the switch receives the message and obtains relevant information of the message, namely: the virtual local area network identifier in the message, the ingress port of the received message, and the user information corresponding to the ingress port of the message. Among them, the virtual local area network identification is carried by the message itself; the ingress port of the received message can be known by the switch itself; with the ingress port information of the received message, the corresponding ingress port can be known according to the configuration information of the switch User Info.
然后,根据获取的报文中的虚拟局域网标识、入端口信息查找报文过滤表。Then, search the message filtering table according to the virtual local area network identifier and inbound port information in the obtained message.
如果报文中的虚拟局域网标识与交换机入端口所属的虚拟局域网标识和用户信息不相同,则丢掉该报文;否则,将该报文作为合法报文,即过滤后的报文。If the VLAN ID in the message is different from the VLAN ID and user information to which the ingress port of the switch belongs, the message is discarded; otherwise, the message is regarded as a legal message, that is, a filtered message.
这样,即可排除交换机接收的非法报文。In this way, illegal packets received by the switch can be eliminated.
步骤303:建立路由表,所述路由表包括:MAC地址及与其对应的交换机端口、用户信息、虚拟局域网标识。Step 303: Establish a routing table, the routing table includes: MAC addresses and corresponding switch ports, user information, and virtual local area network identifiers.
步骤304:根据路由表对过滤后的报文进行转发。Step 304: forward the filtered message according to the routing table.
由上述流程可见,根据网络实际需要及交换机的配置信息,可以首先使交换机对接收的报文进行过滤,利用过滤表来隔离不同的VLAN和用户,可有效地避免网络中的端口攻击。然后,再根据路由表对过滤后的报文进行转发。It can be seen from the above process that according to the actual needs of the network and the configuration information of the switch, the switch can first filter the received packets, and use the filter table to isolate different VLANs and users, which can effectively avoid port attacks in the network. Then, forward the filtered message according to the routing table.
在本发明中,可以采用多种不同的路由检索方式,来支持区分同一VLAN内的不同用户具有相同的MAC地址的应用。In the present invention, a variety of different route retrieval methods can be used to support different applications that have the same MAC address among different users in the same VLAN.
下面分别对不同的检索转发流程作详细描述。The different retrieval and forwarding processes are described in detail below.
参照图4所示报文过滤转发的第一实施例的实现流程,在该实施例中,只通过MAC地址来查找路由,具体包括以下步骤:With reference to the implementation process of the first embodiment of message filtering and forwarding shown in Figure 4, in this embodiment, only by MAC address to search route, specifically comprise the following steps:
首先,在步骤401:根据报文的源MAC地址获取路由表入端口索引查找路由表,比如利用常用的Hash算法,但不限于这种算法。First, in step 401: Obtain the routing table according to the source MAC address of the message and enter the port index to search the routing table, such as using a commonly used Hash algorithm, but not limited to this algorithm.
步骤402:判断查找是否命中,也就是说,路由表中是否有对应该路由表入端口索引的表项。Step 402: Determine whether the search hits, that is, whether there is an entry corresponding to the in-port index of the routing table in the routing table.
如果没有,则进到步骤403:将交换机入端口与报文的源MAC地址、VLAN标识、用户ID的对应关系学习到所述路由表中,也就是说在路由表中增加交换机入端口与报文的源MAC地址、VLAN标识、用户ID的对应关系的表项,因为该报文是过滤后的报文,说明交换机的入端口已划分给对应于报文中的VLAN和相应的用户,只是还未建立对应于该报文的转发路由,因此可以将交换机入端口与报文的源MAC地址、VLAN、用户ID的路由学习到路由表中,建立起入端口的路由。然后,再通过后面将描述的广播方式,将报文发送到出端口,在出端口有报文回应后通过与上面相同的步骤建立起出端口的路由,使路由表不仅可以通过静态配置的方式建立,还可通过动态学习的方式进行维护。If not, then go to step 403: learn the corresponding relationship between the switch inlet port and the source MAC address, VLAN identification, and user ID of the message in the routing table, that is to say, increase the switch inlet port and the message in the routing table. The source MAC address, VLAN ID, and user ID correspondence table entry of the message, because the message is a filtered message, indicating that the ingress port of the switch has been assigned to the VLAN corresponding to the message and the corresponding user. The forwarding route corresponding to the message has not been set up yet, so the routes of the ingress port of the switch and the source MAC address, VLAN, and user ID of the message can be learned into the routing table to set up the route of the ingress port. Then, through the broadcast method described later, the message is sent to the egress port, and the route of the egress port is established through the same steps as above after the egress port responds with a message, so that the routing table can not only be statically configured It can be established and maintained through dynamic learning.
如果查找命中,则直接进到步骤404:根据报文的目的MAC地址获取路由表出端口索引查找路由表,使用与步骤401相同的算法。If the search hits, then go directly to step 404: obtain the routing table output port index according to the destination MAC address of the message to search the routing table, and use the same algorithm as
然后,进到步骤405:判断查找是否命中,也就是说,路由表中是否有对应该路由表出端口索引的表项。Then, go to step 405: determine whether the search hits, that is, whether there is an entry corresponding to the outgoing port index of the routing table in the routing table.
如果有,则进到步骤406:将过滤后的报文发送到对应的交换机出端口上,根据报文的目的MAC地址的不同,可能有两种情况:单播或组播。If so, proceed to step 406: send the filtered message to the corresponding switch egress port. According to the difference of the destination MAC address of the message, there may be two situations: unicast or multicast.
如果是单播,则将报文发送到对应的出端口上;如果是组播,则将报文复制到该组播组内所有的出端口上。If it is unicast, send the message to the corresponding outbound port; if it is multicast, copy the message to all the outbound ports in the multicast group.
如果没有,则进到步骤407:将过滤后的报文广播到所述过滤后的报文所带VLAN所属的所有端口上。If not, proceed to step 407: broadcast the filtered message to all ports to which the VLAN carried by the filtered message belongs.
参照图5所示报文转发的第二实施例的实现流程,在该实施例中,通过“MAC地址+用户ID”二元组来查找路由,具体包括以下步骤:With reference to the implementation process of the second embodiment of message forwarding shown in Figure 5, in this embodiment, the route is searched by the two-tuple of "MAC address+user ID", specifically comprising the following steps:
首先,在步骤501:根据报文的“源MAC地址+用户ID”获取路由表入端口索引查找路由表,比如利用常用的Hash算法,但不限于这种算法。Firstly, in step 501: according to the "source MAC address + user ID" of the message, the routing table is obtained and the port index is used to search the routing table, such as using a commonly used Hash algorithm, but not limited to this algorithm.
步骤502:判断查找是否命中,也就是说,路由表中是否有对应该路由表入端口索引的表项。Step 502: Determine whether the search hits, that is, whether there is an entry corresponding to the in-port index of the routing table in the routing table.
如果没有,则进到步骤503:将交换机入端口与报文的源MAC地址、VLAN标识、用户ID的对应关系学习到路由表中,也就是说在路由表中增加交换机入端口与报文的源MAC地址、VLAN标识、用户ID的对应关系的表项,因为该报文是过滤后的报文,说明交换机的入端口已划分给对应于报文中的VLAN和相应的用户,只是还未建立对应于该报文的转发路由,因此可以将交换机入端口与报文的源MAC地址、VLAN、用户ID的对应关系学习到路由表中,建立起入端口的路由。然后,再通过后面将描述的广播方式将报文发送到出端口,在出端口有报文回应后通过与上面相同的步骤建立起出端口的路由,使路由表不仅可以通过静态配置的方式建立,还可通过动态学习的方式进行维护。If not, then proceed to step 503: learn the corresponding relationship between the switch inlet port and the source MAC address, VLAN identification, and user ID of the message in the routing table, that is to say, increase the connection between the switch inlet port and the message in the routing table Source MAC address, VLAN ID, and user ID correspondence table entry, because this message is a filtered message, indicating that the ingress port of the switch has been assigned to the VLAN corresponding to the message and the corresponding user, but it has not yet been The forwarding route corresponding to the message is established, so the corresponding relationship between the ingress port of the switch and the source MAC address, VLAN, and user ID of the message can be learned into the routing table, and the route of the ingress port is established. Then, send the message to the egress port through the broadcast method described later, and establish the route of the egress port through the same steps as above after the egress port responds with a message, so that the routing table can not only be established through static configuration , and can also be maintained through dynamic learning.
如果查找命中,则直接进到步骤504:根据报文的“目的MAC地址+用户ID”获取路由表出端口索引查找路由表,使用与步骤501相同的算法。If the search hits, then go directly to step 504: obtain the routing table output port index according to the "destination MAC address+user ID" of the message to search the routing table, and use the same algorithm as
然后,进到步骤505:判断查找是否命中,也就是说,路由表中是否有对应该路由表出端口索引的表项。Then, go to step 505: determine whether the search hits, that is, whether there is an entry corresponding to the outgoing port index of the routing table in the routing table.
如果有,则进到步骤506:将过滤后的报文发送到对应的交换机出端口上,根据报文的目的MAC地址的不同,可能有两种情况:单播或组播。If so, proceed to step 506: send the filtered message to the corresponding switch egress port. According to the difference of the destination MAC address of the message, there may be two situations: unicast or multicast.
如果是单播,则将报文发送到对应的出端口上;如果是组播,则将报文复制到该组播组内所有的出端口上。If it is unicast, send the message to the corresponding outbound port; if it is multicast, copy the message to all the outbound ports in the multicast group.
如果没有,则进到步骤507:将过滤后的报文广播到所述过滤后的报文所带VLAN所属的所有端口上。If not, proceed to step 507: broadcast the filtered message to all ports to which the VLAN carried by the filtered message belongs.
同样,还可以通过“MAC地址+VLAN”二元组来查找路由,实现过程同图5所示流程类似,在此不再赘述。Similarly, the route can also be searched through the two-tuple of "MAC address+VLAN". The implementation process is similar to that shown in Figure 5, and will not be repeated here.
在上述路由查找过程中,利用了Hash算法或其他类似算法来计算路由查找索引。本技术领域人员知道,根据Hash算法,在MAC地址共享VLAN、用户时,表项可能会产生冲突,这时就需要通过链表等方式加大表项深度,也就是一个MAC地址会对应多个查找结果。为了在这多个查找结果中找到正确的结果,就要对这多个结果进行遍历,当表项冲突较多时查找效率会降低。In the above route lookup process, a Hash algorithm or other similar algorithms are used to calculate the route lookup index. Those skilled in the art know that according to the Hash algorithm, when MAC addresses share VLANs and users, table entries may conflict. At this time, it is necessary to increase the depth of table entries through linked lists, that is, one MAC address will correspond to multiple lookups. result. In order to find the correct result among the multiple search results, it is necessary to traverse the multiple results, and the search efficiency will decrease when there are many table item conflicts.
因此,为了缩短这种表项的查找深度,提高路由查找效率,从而进一步提高报文的转发效率,本发明还提供了更优化的路由查找方式,即利用“MAC地址+VLAN+用户ID”三元组查找路由。Therefore, in order to shorten the search depth of such table entries, improve the efficiency of routing search, and further improve the forwarding efficiency of messages, the present invention also provides a more optimized routing search method, that is, using the "MAC address+VLAN+user ID" ternary Group lookup routes.
图6示出了这种方式的详细流程,包括以下步骤:Figure 6 shows the detailed process of this method, including the following steps:
首先,在步骤601:根据报文的“源MAC地址+VLAN+用户ID”获取路由表入端口索引查找路由表,同样,可以利用Hash算法,但不限于这种算法。First, in step 601: according to the "source MAC address+VLAN+user ID" of the message, the routing table is obtained and the port index is entered to search the routing table. Similarly, the Hash algorithm can be used, but not limited to this algorithm.
步骤602:判断查找是否命中。Step 602: Determine whether the search hits.
如果没有,则进到步骤603:将交换机入端口与报文的源MAC地址、VLAN标识、用户ID的对应关系学习到路由表中,也就是说在路由表中增加交换机入端口与报文的源MAC地址、VLAN标识、用户ID的对应关系的表项,因为该报文是过滤后的报文,说明交换机的入端口已划分给对应于报文中的VLAN和相应的用户,只是还未建立对应于该报文的转发路由,因此可以将交换机入端口与报文的源MAC地址、VLAN、用户ID的路由学习到路由表中,建立起入端口的路由。然后,再通过后面将描述的广播方式将报文发送到出端口,在出端口有报文回应后通过与上面相同的步骤建立起出端口的路由,使路由表不仅可以通过静态配置的方式建立,还可通过动态配置的方式进行维护。If not, then proceed to step 603: learn the correspondence between the switch inlet port and the source MAC address, VLAN ID, and user ID of the message in the routing table, that is to say, increase the connection between the switch inlet port and the message in the routing table. Source MAC address, VLAN ID, and user ID correspondence table entry, because this message is a filtered message, indicating that the ingress port of the switch has been assigned to the VLAN corresponding to the message and the corresponding user, but it has not yet been The forwarding route corresponding to the message is established, so the routes of the switch ingress port and the source MAC address, VLAN, and user ID of the message can be learned into the routing table, and the route of the ingress port is established. Then, send the message to the egress port through the broadcast method described later, and establish the route of the egress port through the same steps as above after the egress port responds with a message, so that the routing table can not only be established through static configuration , and can also be maintained through dynamic configuration.
如果查找命中,则直接进到步骤604:根据报文的“目的MAC地址+VLAN+用户ID”获取路由表出端口索引查找路由表。If the search is successful, go directly to step 604: obtain the routing table output port index according to the "destination MAC address+VLAN+user ID" of the message to search the routing table.
然后,进到步骤605:判断查找是否命中,也就是说,路由表中是否有对应该路由表出端口索引的表项。Then, go to step 605: determine whether the search hits, that is, whether there is an entry corresponding to the outgoing port index of the routing table in the routing table.
如果有,则进到步骤606:将过滤后的报文发送到对应的交换机出端口上,根据报文的目的MAC地址的不同,可能有两种情况:单播或组播。If so, proceed to step 606: send the filtered message to the corresponding switch egress port. According to the difference of the destination MAC address of the message, there may be two situations: unicast or multicast.
如果是单播,则将报文发送到对应的出端口上;如果是组播,则将报文复制到该组播组内所有的出端口上。If it is unicast, send the message to the corresponding outbound port; if it is multicast, copy the message to all the outbound ports in the multicast group.
如果没有,则进到步骤607:将过滤后的报文广播到所述过滤后的报文所带VLAN所属的所有端口上。If not, proceed to step 607: broadcast the filtered message to all ports to which the VLAN carried by the filtered message belongs.
通过上述对不同的实施例的描述可见,与现有技术中二层以太网交换机大都根据MAC地址查找路由相比,本发明利用MAC地址和用户ID/VBID/StackVLAN/QinQ、VLAN组成二、三元组查找路由,这样网络便可支持区分同一VLAN内的不同用户/VB/Stack VLAN/QinQ具有相同的MAC地址的应用,同时主要可通过不同用户/VB/Stack VLAN/QiniQ之间的隔离来加强城域传输设备中的二层以太网交换机的安全性能,进行端口过滤防止恶意MAC地址攻击,同时还通过缩短表项查找深度解决MAC地址共享VLAN、用户ⅣB/StackVLAN/QinQ导致的效率过低问题。Visible by above-mentioned description to different embodiment, compared with the two-layer Ethernet switch in the prior art mostly according to MAC address search route, the present invention utilizes MAC address and user ID/VBID/StackVLAN/QinQ, VLAN to form two, three Tuple lookup routes, so that the network can support different users/VB/Stack VLAN/QinQ applications with the same MAC address in the same VLAN, and at the same time, it can be separated mainly through the isolation between different users/VB/Stack VLAN/QinQ Strengthen the security performance of the Layer 2 Ethernet switch in the metro transmission equipment, perform port filtering to prevent malicious MAC address attacks, and at the same time shorten the lookup depth of table entries to solve the low efficiency caused by MAC address shared VLAN and user IVB/StackVLAN/QinQ question.
虽然通过实施例描绘了本发明,本领域普通技术人员知道,本发明有许多变形和变化而不脱离本发明的精神,希望所附的权利要求包括这些变形和变化而不脱离本发明的精神。While the invention has been described by way of example, those skilled in the art will appreciate that there are many variations and changes to the invention without departing from the spirit of the invention, and it is intended that the appended claims cover such variations and changes without departing from the spirit of the invention.
Claims (12)
Translated fromChinesePriority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CNB2004100868275ACN100496017C (en) | 2004-10-28 | 2004-10-28 | Method for Ensuring Data Security of Layer 2 Ethernet Switches in Metropolitan Area Transmission Equipment |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CNB2004100868275ACN100496017C (en) | 2004-10-28 | 2004-10-28 | Method for Ensuring Data Security of Layer 2 Ethernet Switches in Metropolitan Area Transmission Equipment |
Publications (2)
| Publication Number | Publication Date |
|---|---|
| CN1767495Atrue CN1767495A (en) | 2006-05-03 |
| CN100496017C CN100496017C (en) | 2009-06-03 |
Family
ID=36743111
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CNB2004100868275AExpired - Fee RelatedCN100496017C (en) | 2004-10-28 | 2004-10-28 | Method for Ensuring Data Security of Layer 2 Ethernet Switches in Metropolitan Area Transmission Equipment |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN100496017C (en) |
Cited By (12)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| WO2008006313A1 (en)* | 2006-07-03 | 2008-01-17 | Huawei Technologies Co., Ltd. | A routing method and system based on packet network |
| WO2009079933A1 (en)* | 2007-12-20 | 2009-07-02 | Hangzhou H3C Technologies Co., Ltd. | Message processing method and device |
| WO2009121253A1 (en)* | 2008-03-31 | 2009-10-08 | 华为技术有限公司 | Network configuring method for preventing attack, method and device for preventing attack |
| CN102025521A (en)* | 2010-12-20 | 2011-04-20 | 中兴通讯股份有限公司 | Message broadcasting method and device |
| CN101383772B (en)* | 2008-09-26 | 2011-08-10 | 中兴通讯股份有限公司 | Method and device for automatically discovering and establishing MAC route information table |
| CN102427429A (en)* | 2012-01-12 | 2012-04-25 | 神州数码网络(北京)有限公司 | Method and system for realizing safety protection of message inside switch and switch |
| CN102780627A (en)* | 2012-07-31 | 2012-11-14 | 深圳市共进电子股份有限公司 | Method for forwarding Linux kernel protocol stack network bridge data |
| CN103812746A (en)* | 2012-11-14 | 2014-05-21 | 深圳市共进电子股份有限公司 | Bridging device based on linux operation system and communication method thereof |
| CN106230684A (en)* | 2016-08-05 | 2016-12-14 | 锐捷网络股份有限公司 | Message forwarding method, switch and system |
| CN107968749A (en)* | 2017-11-21 | 2018-04-27 | 锐捷网络股份有限公司 | Realize method, exchange chip and the interchanger of QinQ route terminations |
| CN112688846A (en)* | 2020-12-31 | 2021-04-20 | 北京物芯科技有限责任公司 | Routing method, device, equipment and storage medium of CAN message |
| CN114448740A (en)* | 2022-01-14 | 2022-05-06 | 绿盟科技集团股份有限公司 | Multicast method, device, medium, product and equipment |
- 2004
- 2004-10-28CNCNB2004100868275Apatent/CN100496017C/ennot_activeExpired - Fee Related
Cited By (20)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| WO2008006313A1 (en)* | 2006-07-03 | 2008-01-17 | Huawei Technologies Co., Ltd. | A routing method and system based on packet network |
| CN101102266B (en)* | 2006-07-03 | 2010-05-19 | 华为技术有限公司 | Routing method and system based on packet network |
| WO2009079933A1 (en)* | 2007-12-20 | 2009-07-02 | Hangzhou H3C Technologies Co., Ltd. | Message processing method and device |
| US8259740B2 (en) | 2007-12-20 | 2012-09-04 | Hangzhou H3C Technologies Co., Ltd. | Method and an apparatus for processing packets |
| WO2009121253A1 (en)* | 2008-03-31 | 2009-10-08 | 华为技术有限公司 | Network configuring method for preventing attack, method and device for preventing attack |
| CN101383772B (en)* | 2008-09-26 | 2011-08-10 | 中兴通讯股份有限公司 | Method and device for automatically discovering and establishing MAC route information table |
| CN102025521A (en)* | 2010-12-20 | 2011-04-20 | 中兴通讯股份有限公司 | Message broadcasting method and device |
| CN102427429A (en)* | 2012-01-12 | 2012-04-25 | 神州数码网络(北京)有限公司 | Method and system for realizing safety protection of message inside switch and switch |
| CN102427429B (en)* | 2012-01-12 | 2016-12-14 | 神州数码网络(北京)有限公司 | A kind of realize the method for switch built-in message security protection, system and switch |
| CN102780627B (en)* | 2012-07-31 | 2015-11-18 | 深圳市共进电子股份有限公司 | A kind of Linux kernel protocol stack network bridge data forwarding method |
| CN102780627A (en)* | 2012-07-31 | 2012-11-14 | 深圳市共进电子股份有限公司 | Method for forwarding Linux kernel protocol stack network bridge data |
| CN103812746A (en)* | 2012-11-14 | 2014-05-21 | 深圳市共进电子股份有限公司 | Bridging device based on linux operation system and communication method thereof |
| CN103812746B (en)* | 2012-11-14 | 2018-08-28 | 深圳市共进电子股份有限公司 | Bridging device based on linux operating systems and its communication means |
| CN106230684A (en)* | 2016-08-05 | 2016-12-14 | 锐捷网络股份有限公司 | Message forwarding method, switch and system |
| CN107968749A (en)* | 2017-11-21 | 2018-04-27 | 锐捷网络股份有限公司 | Realize method, exchange chip and the interchanger of QinQ route terminations |
| CN107968749B (en)* | 2017-11-21 | 2021-04-20 | 锐捷网络股份有限公司 | Method for realizing QinQ route termination, switching chip and switch |
| CN112688846A (en)* | 2020-12-31 | 2021-04-20 | 北京物芯科技有限责任公司 | Routing method, device, equipment and storage medium of CAN message |
| CN112688846B (en)* | 2020-12-31 | 2022-06-28 | 北京物芯科技有限责任公司 | Routing method, device, equipment and storage medium of CAN message |
| CN114448740A (en)* | 2022-01-14 | 2022-05-06 | 绿盟科技集团股份有限公司 | Multicast method, device, medium, product and equipment |
| CN114448740B (en)* | 2022-01-14 | 2023-11-07 | 绿盟科技集团股份有限公司 | Multicast method, device, medium, product and equipment |
Also Published As
| Publication number | Publication date |
|---|---|
| CN100496017C (en) | 2009-06-03 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| CN1310467C (en) | Port based network access control method | |
| CN100442772C (en) | A bridge forwarding method | |
| CN1414749A (en) | A three-layer virtual private network and its construction method | |
| CN1708029A (en) | How to create a forwarding flow table | |
| CN1581818A (en) | Method for supporting multi-port virtual LAN by multi-protocol label swtich | |
| CN1722698A (en) | Multi-protocol label switching virtual private network and its control and forwarding method | |
| CN101043355A (en) | Method for preventing MAC address cheat | |
| CN1809032A (en) | Method of dynamically learning address on MAC layer | |
| CN101052022A (en) | System and method for virtual special net user to access public net | |
| CN1767495A (en) | Method for Ensuring Data Security of Layer 2 Ethernet Switches in Metropolitan Area Transmission Equipment | |
| CN1925452A (en) | Data transferring system, method and network transferring apparatus | |
| CN1716904A (en) | A multicast implementation method based on multi-service transmission platform | |
| CN1929444A (en) | Operator's boundary notes, virtual special LAN service communication method and system | |
| CN1630268A (en) | A method of egress routing in multi-ISP LAN | |
| CN1691629A (en) | Method for Realizing Layer 2 Device Interconnection in Network Based on Resilient Packet Ring | |
| CN1297105C (en) | Method for implementing multirole main machine based on virtual local network | |
| CN1558615A (en) | A physical network topology discovery system and method thereof | |
| CN101043356A (en) | Method for preventing MAC address cheat | |
| CN101035088A (en) | Method, system and access device for realizing the intercommunication of two layers of local specific service | |
| CN101043462A (en) | Method for processing link condition announcement and router | |
| CN1677950A (en) | Data Exchange Method Based on Virtual Local Area Network | |
| CN1185831C (en) | Method for managing users in wide hand city network | |
| CN1917474A (en) | Method and network equipment for implementing inspection of reversal path of unicast | |
| CN1866904A (en) | Method and apparatus for astringing two layer MAC address | |
| CN1235368C (en) | Address conversion method for simultaneously supporting one-to-one and many-to-many under the PAT mode |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| C06 | Publication | ||
| PB01 | Publication | ||
| C10 | Entry into substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| C14 | Grant of patent or utility model | ||
| GR01 | Patent grant | ||
| TR01 | Transfer of patent right | ||
| TR01 | Transfer of patent right | Effective date of registration:20201214 Address after:No.88 Liaohe West Road, Pizhou Economic Development Zone, Xuzhou City, Jiangsu Province Patentee after:SU Normal University Semiconductor Materials and Equipment Research Institute (Pizhou) Co.,Ltd. Address before:Unit 2414-2416, main building, no.371, Wushan Road, Tianhe District, Guangzhou City, Guangdong Province Patentee before:GUANGDONG GAOHANG INTELLECTUAL PROPERTY OPERATION Co.,Ltd. Effective date of registration:20201214 Address after:Unit 2414-2416, main building, no.371, Wushan Road, Tianhe District, Guangzhou City, Guangdong Province Patentee after:GUANGDONG GAOHANG INTELLECTUAL PROPERTY OPERATION Co.,Ltd. Address before:518129 Bantian HUAWEI headquarters office building, Longgang District, Guangdong, Shenzhen Patentee before:HUAWEI TECHNOLOGIES Co.,Ltd. | |
| CF01 | Termination of patent right due to non-payment of annual fee | ||
| CF01 | Termination of patent right due to non-payment of annual fee | Granted publication date:20090603 Termination date:20201028 |