CN116438532A - Device authentication method, device, electronic device, server and storage medium - Google Patents
Device authentication method, device, electronic device, server and storage mediumDownload PDFInfo
- Publication number
- CN116438532A CN116438532ACN202080106970.3ACN202080106970ACN116438532ACN 116438532 ACN116438532 ACN 116438532ACN 202080106970 ACN202080106970 ACN 202080106970ACN 116438532 ACN116438532 ACN 116438532A
- Authority
- CN
- China
- Prior art keywords
- electronic device
- request
- server
- information
- certificate
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Pending
Links
Images
Classifications
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/30—Authentication, i.e. establishing the identity or authorisation of security principals
- G06F21/31—User authentication
- G06F21/32—User authentication using biometric data, e.g. fingerprints, iris scans or voiceprints
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/30—Authentication, i.e. establishing the identity or authorisation of security principals
- G06F21/31—User authentication
- G06F21/33—User authentication using certificates
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/30—Authentication, i.e. establishing the identity or authorisation of security principals
- G06F21/44—Program or device authentication
Landscapes
- Engineering & Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- Theoretical Computer Science (AREA)
- Computer Hardware Design (AREA)
- Software Systems (AREA)
- Physics & Mathematics (AREA)
- General Engineering & Computer Science (AREA)
- General Physics & Mathematics (AREA)
- Management, Administration, Business Operations System, And Electronic Commerce (AREA)
Abstract
Translated fromChineseDescription
Translated fromChinese本申请涉及物联网领域,尤其涉及一种设备认证方法、装置、电子设备、服务器及存储介质。The present application relates to the field of the Internet of Things, and in particular to a device authentication method, device, electronic device, server and storage medium.
设备在加入物联网(IoT,The Internet of Things)时,需要由网络侧对设备进行设备认证,相关技术中,设备认证过程会导致网络资源开销增加。When a device joins the Internet of Things (IoT, The Internet of Things), the device needs to be authenticated by the network side. In related technologies, the device authentication process will lead to an increase in network resource overhead.
发明内容Contents of the invention
有鉴于此,本申请实施例提供一种设备认证方法,以至少解决相关技术出现的网络资源需求量增大的问题。In view of this, an embodiment of the present application provides a device authentication method, so as to at least solve the problem of increased demand for network resources in related technologies.
本申请实施例的技术方案是这样实现的:The technical scheme of the embodiment of the application is realized in this way:
本申请实施例提供了一种设备认证方法,应用于电子设备,所述方法包括:An embodiment of the present application provides a method for device authentication, which is applied to electronic devices, and the method includes:
与第一服务器建立基于安全传输层(TLS,Transport Layer Security)协议的第一连接;Establishing a first connection based on a Transport Layer Security (TLS, Transport Layer Security) protocol with the first server;
基于所述第一连接,向所述第一服务器发送第一请求;所述第一请求用于请求对所述电子设备进行身份认证;所述第一请求基于第一信息生成;所述第一信息表征所述电子设备的数字证书;Based on the first connection, send a first request to the first server; the first request is used to request identity authentication of the electronic device; the first request is generated based on first information; the first information characterizing a digital certificate of said electronic device;
基于所述第一连接,接收所述第一服务器下发的关于所述第一请求的第一响应信息;所述第一响应信息中携带所述第一服务器对所述电子设备的身份认证结果。Based on the first connection, receiving first response information about the first request issued by the first server; the first response information carries an identity authentication result of the electronic device by the first server .
上述方案中,所述第一信息包括所述电子设备的设备证书。In the above solution, the first information includes the device certificate of the electronic device.
上述方案中,所述第一信息包括所述电子设备的产品证书;所述基于所述第一连接,向所述第一服务器发送第一请求,包括:In the above solution, the first information includes the product certificate of the electronic device; the sending a first request to the first server based on the first connection includes:
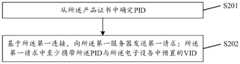
从所述产品证书中确定产品识别码(PID,Product id);Determining a product identification code (PID, Product id) from said product certificate;
基于所述第一连接,向所述第一服务器发送第一请求;所述第一请求中至少携带所述PID与所述电子设备中预置的供应商标识(VID,Vendor Device id)。Based on the first connection, send a first request to the first server; the first request carries at least the PID and a vendor identification (VID, Vendor Device id) preset in the electronic device.
上述方案中,所述第一请求中还携带第一密钥;所述第一密钥在所述电子设备首次上电时随机生成。In the above solution, the first request also carries a first key; the first key is randomly generated when the electronic device is powered on for the first time.
上述方案中,所述方法还包括:In the above scheme, the method also includes:
从所述电子设备的存储介质中读取所述第一信息;或,reading the first information from a storage medium of the electronic device; or,
从第二服务器中下载所述第一信息;所述第二服务器上存储有至少一个电子设备中的每个电子设备对应的第一信息。downloading the first information from a second server; the first information corresponding to each of the at least one electronic device is stored on the second server.
本申请实施例还提供了另一种设备认证方法,应用于第一服务器,所述方法包括:The embodiment of the present application also provides another device authentication method, which is applied to the first server, and the method includes:
与电子设备建立基于TLS协议的第一连接;establishing a first connection with the electronic device based on the TLS protocol;
基于所述第一连接,接收所述电子设备发送的第一请求;所述第一请求用于请求对所述电子设备进行身份认证;所述第一请求基于第一信息生成;所述第一信息表征所述电子设备的数字证书;Based on the first connection, receive a first request sent by the electronic device; the first request is used to request identity authentication for the electronic device; the first request is generated based on first information; the first information characterizing a digital certificate of said electronic device;
基于所述第一请求,对所述电子设备进行身份认证,得到身份认证结果;performing identity authentication on the electronic device based on the first request, and obtaining an identity authentication result;
基于所述第一连接,向所述电子设备下发的关于所述第一请求的第一响应信息;所述第一响应信息中携带所述身份认证结果。First response information about the first request sent to the electronic device based on the first connection; the first response information carries the identity authentication result.
上述方案中,所述第一信息包括所述电子设备的产品证书;所述第一请求中至少携带PID和VID;所述向所述电子设备下发的关于所述第一请求的第一响应信息,包括:In the above solution, the first information includes the product certificate of the electronic device; the first request carries at least PID and VID; the first response to the first request issued to the electronic device information, including:
在对所述电子设备的身份认证成功的情况下,基于所述PID和所述VID确定所述电子设备的设备证书;If the identity authentication of the electronic device is successful, determine the device certificate of the electronic device based on the PID and the VID;
向所述电子设备下发所述第一响应信息;所述第一响应信息中携带所述设备证书。Sending the first response information to the electronic device; the first response information carries the device certificate.
上述方案中,所述第一请求还携带第一密钥;所述第一密钥在所述电子设备首次上电时随机生成,所述对所述电子设备进行身份认证,得到身份认证结果,包括:In the above solution, the first request also carries a first key; the first key is randomly generated when the electronic device is powered on for the first time, and the identity authentication is performed on the electronic device to obtain an identity authentication result, include:
在所述电子设备未激活过的情况下,对应保存所述VID和所述第一密钥;或,If the electronic device has not been activated, store the VID and the first key correspondingly; or,
在所述电子设备曾经激活过的情况下,确认所述第一请求中的第一密钥与第二密钥是否相同;所述第二密钥为所述第一服务器保存的所述VID对应的密钥;当所述第一密钥与所述第二密钥相同时,得到对所述电子设备的身份认证成功的身份认证结果;当所述第一密钥与所述第二密钥不同时,对所述电子设备的身份认证失败的身份认证结果。In the case that the electronic device has been activated, confirm whether the first key in the first request is the same as the second key; the second key corresponds to the VID saved by the first server key; when the first key is the same as the second key, obtain an identity authentication result that the identity authentication of the electronic device is successful; when the first key is the same as the second key At the same time, an identity authentication result indicating that the identity authentication of the electronic device fails.
上述方案中,在对所述电子设备的身份认证失败的情况下,所述方法还包括:In the above solution, in the case that the identity authentication of the electronic device fails, the method further includes:
终止所述第一连接。Terminate the first connection.
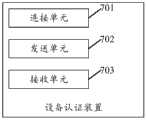
本申请实施例还提供了一种设备认证装置,其特征在于,包括:The embodiment of the present application also provides a device authentication device, which is characterized in that it includes:
连接单元,用于与第一服务器建立基于安全传输层TLS协议的第一连接;A connection unit, configured to establish a first connection with the first server based on the TLS protocol;
发送单元,用于基于所述第一连接,向所述第一服务器发送第一请求;所述第一请求用于请求对所述电子设备进行身份认证;所述第一请求基于第一信息生成;所述第一信息表征所述电子设备的数字证书;A sending unit, configured to send a first request to the first server based on the first connection; the first request is used to request identity authentication of the electronic device; the first request is generated based on first information ; The first information represents a digital certificate of the electronic device;
接收单元,用于基于所述第一连接,接收所述第一服务器下发的关于所述第一请求的第一响应信息;所述第一响应信息中携带所述第一服务器对所述电子设备的身份认证结果。A receiving unit, configured to receive, based on the first connection, first response information about the first request issued by the first server; The authentication result of the device.
本申请实施例还提供了另一种设备认证装置,其特征在于,包括:The embodiment of this application also provides another device authentication device, which is characterized in that it includes:
连接单元,用于与电子设备建立基于TLS协议的第一连接;A connection unit, configured to establish a first connection with the electronic device based on the TLS protocol;
接收单元,用于基于所述第一连接,接收所述电子设备发送的第一请求;所述第一请求用于请求对所述电子设备进行身份认证;所述第一请求基于第一信息生成;所述第一信息表征所述电子设备的数字证书;A receiving unit, configured to receive a first request sent by the electronic device based on the first connection; the first request is used to request identity authentication of the electronic device; the first request is generated based on first information ; The first information represents a digital certificate of the electronic device;
认证单元,用于基于所述第一请求,对所述电子设备进行身份认证,得到身份认证结果;An authentication unit, configured to perform identity authentication on the electronic device based on the first request, and obtain an identity authentication result;
发送单元,用于基于所述第一连接,向所述电子设备下发的关于所述第一请求的第一响应信息;所述第一响应信息中携带所述身份认证结果。A sending unit, configured to send first response information about the first request to the electronic device based on the first connection; the first response information carries the identity authentication result.
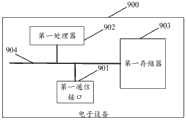
本申请实施例还提供了一种电子设备,包括:处理器和用于存储能够在处理器上运行的计算机程序的存储器,The embodiment of the present application also provides an electronic device, including: a processor and a memory for storing a computer program that can run on the processor,
其中,所述处理器用于运行所述计算机程序时,执行上述电子设备侧任一方法的步骤。Wherein, when the processor is configured to run the computer program, it executes the steps of any one of the above methods on the electronic device side.
本申请实施例还提供了一种第一服务器,包括:处理器和用于存储能够在处理器上运行的计算机程序的存储器,The embodiment of the present application also provides a first server, including: a processor and a memory for storing a computer program that can run on the processor,
其中,所述处理器用于运行所述计算机程序时,执行上述第一服务器侧任一方法的步骤。Wherein, when the processor is configured to run the computer program, it executes the steps of any method on the first server side above.
本申请实施例还提供了一种存储介质,其上存储有计算机程序,所述计算机程序被处理器执行时实现上述任一方法的步骤。The embodiment of the present application also provides a storage medium on which a computer program is stored, and when the computer program is executed by a processor, the steps of any one of the above methods are implemented.
在本申请实施例中,与第一服务器建立基于安全传输层TLS协议的第一连接,基于第一连接向第一服务器发送第一请求,第一请求用于请求对电子设备进行身份认证,第一请求基于第一信息生成,第一信息表征电子设备的数字证书,基于第一连接,接收第一服务器下发的关于第一请求的第一响应信息,第一响应信息中携带第一服务器对电子设备的身份认证结果,从而能够通过安全传输层TLS协议建立的连接进行设备认证,并不需要在设备认证的过程中提供额外的网络资源,减少网络资源的需求量的同时,还能提高了设备认证的安全性。In this embodiment of the present application, a first connection based on the TLS protocol is established with the first server, and a first request is sent to the first server based on the first connection. The first request is used to request identity authentication for the electronic device. A request is generated based on the first information, the first information represents the digital certificate of the electronic device, based on the first connection, the first response information about the first request sent by the first server is received, and the first response information carries the first server pair The result of the identity authentication of the electronic device, so that the device can be authenticated through the connection established by the secure transport layer TLS protocol. It does not need to provide additional network resources in the process of device authentication, which reduces the demand for network resources and improves the efficiency. Security for device authentication.
图1为本申请一实施例提供的设备认证方法的实现流程示意图;FIG. 1 is a schematic diagram of an implementation flow of a device authentication method provided by an embodiment of the present application;
图2为本申请又一实施例提供的设备认证方法的实现流程示意图;FIG. 2 is a schematic diagram of an implementation flow of a device authentication method provided in another embodiment of the present application;
图3为本申请又一实施例提供的设备认证方法的实现流程示意图;FIG. 3 is a schematic diagram of an implementation flow of a device authentication method provided in another embodiment of the present application;
图4为本申请又一实施例提供的设备认证方法的实现流程示意图;FIG. 4 is a schematic diagram of an implementation flow of a device authentication method provided in another embodiment of the present application;
图5为本申请一应用实施例提供的电子设备身份认证的交互示意图;FIG. 5 is an interactive schematic diagram of electronic device identity authentication provided by an application embodiment of the present application;
图6为本申请又一应用实施例提供的电子设备身份认证的交互示意图;FIG. 6 is an interactive schematic diagram of electronic device identity authentication provided by another application embodiment of the present application;
图7为本申请又一应用实施例提供的电子设备身份认证的交互示意图;FIG. 7 is an interactive schematic diagram of electronic device identity authentication provided by another application embodiment of the present application;
图8为本申请一实施例提供的设备认证装置的结构示意图;FIG. 8 is a schematic structural diagram of an equipment authentication device provided by an embodiment of the present application;
图9为本申请又一实施例提供的设备认证装置的结构示意图;FIG. 9 is a schematic structural diagram of a device authentication device provided in another embodiment of the present application;
图10为本申请一实施例提供电子设备的结构示意图;FIG. 10 is a schematic structural diagram of an electronic device provided by an embodiment of the present application;
图11为本申请一实施例提供第一服务器的结构示意图。FIG. 11 is a schematic structural diagram of a first server provided by an embodiment of the present application.
下面结合附图及具体实施例对本申请作进一步详细的说明。The present application will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
以下描述中,为了说明而不是为了限定,提出了诸如特定系统结构、技术之类的具体细节,以便透彻理解本申请实施例。然而,本领域的技术人员应当清楚,在没有这些具体细节的其它实施例中也可以实现本申请。在其它情况中,省略对众所周知的系统、装置以及方法的详细说明,以免不必要的细节妨碍本申请的描述。In the following description, specific details such as specific system structures and technologies are presented for the purpose of illustration rather than limitation, so as to thoroughly understand the embodiments of the present application. It will be apparent, however, to one skilled in the art that the present application may be practiced in other embodiments without these specific details. In other instances, detailed descriptions of well-known systems, devices, and methods are omitted so as not to obscure the description of the present application with unnecessary detail.
需要说明的是,本申请实施例所记载的技术方案之间,在不冲突的情况下,可以任意组合。It should be noted that the technical solutions described in the embodiments of the present application may be combined arbitrarily if there is no conflict.
另外,在本申请实施例中,“第一”、“第二”等是用于区别类似的对象,而不必用于描述特定的顺序或先后次序。In addition, in the embodiments of the present application, "first", "second", etc. are used to distinguish similar objects, and are not necessarily used to describe a specific sequence or sequence.
图1示出了本申请实施例提供的设备认证方法的实现流程,以使电子设备在注册绑定的时候,对电子设备身份进行认证以验证电子设备是否合法,从而能够保证数据在物联网中进行安全通信。如图1所示,所述方法应用于电子设备,所述方法包括:Figure 1 shows the implementation process of the device authentication method provided by the embodiment of the present application, so that when the electronic device is registered and bound, the identity of the electronic device is authenticated to verify whether the electronic device is legal, so as to ensure that the data in the Internet of Things Communicate securely. As shown in Figure 1, the method is applied to electronic equipment, and the method includes:
S101:与第一服务器建立基于安全传输层(Transport Layer Security,TLS)协议的第一连接。S101: Establish a first connection with a first server based on a transport layer security (Transport Layer Security, TLS) protocol.
这里,将电子设备与第一服务器建立基于TLS协议的第一连接,其中,电子设备是指物联网(Internet Of Things,IOT)设备,例如射频识别装置、红外感应器等设备,第一服务器是用于进行电子设备身份认证的平台,传输的数据在通过TLS协议时都会被加密,基于TLS协议建立的第一连接能够加密连接上的传输信息,能够保证信息传输的安全。在实际应用中,TLS协议是可选的,需要通过对电子设备与第一服务器进行配置之后才可以使用,当电子设备与第一服务器都同意使用TLS协议的情况下,通过一个握手过程协商出以一个有状态的连接进行数据传输。Here, the first connection based on the TLS protocol is established between the electronic device and the first server, wherein the electronic device refers to an Internet of Things (Internet Of Things, IOT) device, such as a radio frequency identification device, an infrared sensor, and the like, and the first server uses For the platform for electronic device identity authentication, the transmitted data will be encrypted when passing through the TLS protocol. The first connection established based on the TLS protocol can encrypt the transmission information on the connection, which can ensure the security of information transmission. In practical applications, the TLS protocol is optional and can only be used after configuring the electronic device and the first server. When both the electronic device and the first server agree to use the TLS protocol, a handshake process is negotiated Data transfer is performed on a stateful connection.
S102:基于所述第一连接,向所述第一服务器发送第一请求;所述第一请求用于请求对所述电子设备进行身份认证;所述第一请求基于第一信息生成;所述第一信息表征所述电子设备的数字证书。S102: Based on the first connection, send a first request to the first server; the first request is used to request identity authentication for the electronic device; the first request is generated based on first information; the The first information characterizes a digital certificate of the electronic device.
这里,基于TLS协议建立的第一连接,向第一服务器发送第一请求,第一请求用于请求对电子设备进行身份认证,第一请求是基于第一信息生成的,第一信息表征电子设备的数字证书,其中,数字证书是指身份信息的一个数字认证,电子设备的数字证书是能够将电子设备与电子设备的身份进行绑定,通过电子设备的数字证书可以识别电子设备的身份,需要说明的是,本申请涉及的数字证书可以是证书本身,也可以是用来组成、生成、构成证书的相关信息。Here, based on the first connection established by the TLS protocol, a first request is sent to the first server. The first request is used to request identity authentication for the electronic device. The first request is generated based on the first information, which represents the electronic device A digital certificate, where a digital certificate refers to a digital certification of identity information, a digital certificate of an electronic device can bind the identity of the electronic device and the electronic device, and the identity of the electronic device can be identified through the digital certificate of the electronic device. It should be noted that the digital certificate involved in this application may be the certificate itself, or the relevant information used to compose, generate and constitute the certificate.
例如,所述数字证书可包括一个公钥(public key,PKI)、名称以及证书授权中心的数字签名。For example, the digital certificate may include a public key (PKI), name and digital signature of the certificate authority.
通过包括公钥的一对密钥可实施对信息的加密和解密。其中,私钥主要用于签名和 解密,可由用户自定义,只有用户自己知道;公钥用于签名验证和加密,可被多个用户共享。发送方在发送信息前,需先与接收方联系,同时利用公钥加密信息,信息在进行传输的过程当中一直是处于密文状态,包括接收方接收后也是加密的,确保了信息传输的单一性,由此,即使信息被窃取或截取,也必须利用接收方的私钥才可解读数据,而无法更改数据,这也有利保障信息的完整性和安全性。Encryption and decryption of information may be performed by a pair of keys including a public key. Among them, the private key is mainly used for signature and decryption, which can be customized by the user, and only the user knows it; the public key is used for signature verification and encryption, and can be shared by multiple users. Before sending the information, the sender needs to contact the receiver first, and at the same time use the public key to encrypt the information. The information is always in the state of ciphertext during the transmission process, including the receiver is also encrypted after receiving, ensuring the single transmission of information Therefore, even if the information is stolen or intercepted, the receiver's private key must be used to interpret the data, and the data cannot be changed, which is also conducive to ensuring the integrity and security of the information.
此外,数字证书的数据签名过程中,可基于发送方的私钥进行签名,接收方可基于发送方的公钥对签名进行验证,由于发送方的私钥具唯一性和私密性,这也保证了签名的真实性和可靠性,进而保障信息的安全性。In addition, in the data signing process of the digital certificate, the signature can be based on the private key of the sender, and the receiver can verify the signature based on the public key of the sender. Since the private key of the sender is unique and private, this also guarantees This ensures the authenticity and reliability of the signature, thereby ensuring the security of the information.
需要说明的是,本申请实施例对数字证书的具体实现方式不作限定。It should be noted that, the embodiment of the present application does not limit the specific implementation manner of the digital certificate.
例如,本申请实施例对数字证书的格式版本不作限定。作为示例,所述数字证书的格式版本包括但不限于:X.509v3、X509v4、X.509v1以及TUTrec.x.509V3等。应当理解,不论是哪一个版本的数字证书,只要获得数字证书,用户就可以将其应用于网络安全中。For example, the embodiment of this application does not limit the format version of the digital certificate. As an example, the format version of the digital certificate includes, but is not limited to: X.509v3, X509v4, X.509v1, TUTrec.x.509V3 and so on. It should be understood that no matter which version of the digital certificate is, as long as the digital certificate is obtained, the user can apply it to network security.
再如,本申请实施例对数字证书包括的具体内容不作限定。作为示例,所述数字证书可包括证书序列号、证书有效期和公钥等信息。再如,本申请实施例对数字证书的类型不作限定。作为示例,所述数字证书可以是根证书。根证书可以理解为未被签名的公钥证书或自签名的证书。根证书可以是认证中心给自己颁发的证书,是信任链的起始点。根证书意味着对认证中心的信任。For another example, the embodiment of the present application does not limit the specific content included in the digital certificate. As an example, the digital certificate may include certificate serial number, certificate validity period, public key and other information. For another example, the embodiment of the present application does not limit the type of the digital certificate. As an example, the digital certificate may be a root certificate. The root certificate can be understood as an unsigned public key certificate or a self-signed certificate. The root certificate can be a certificate issued by the certification center to itself, and it is the starting point of the chain of trust. A root certificate implies trust in a certificate authority.
下面以根证书为例对数字证书进行说明。The following uses the root certificate as an example to describe digital certificates.
根证书可包括三部分,即用户的信息,用户的公钥,还有认证中心对该证书中的信息的签名。验证一份证书的真伪,为便于描述,下面将待验证的证书称为待验证证书,即验证认证中心对待验证证书的签名是否有效,需要用认证中心的公钥对待验证证书进行验证,而认证中心的公钥存在于对待验证证书进行签名的证书内,故需要下载签发待验证证书的证书,但使用该证书验证又需先验证该证书本身的真伪,故又要用签发该证书的证书来验证,这样一来就构成一条证书链的关系,用于终结这条证书链的证书即为根证书。根证书是一份特殊的证书,它的签发者是它本身。换言之,验证一份证书的真伪需要建立起一个验证证书的链条,而证书的验证追溯至根证书即为结束。换言之,用户在使用自己的数字证书之前必须先下载根证书,并基于根证书验证一份证书的真伪。The root certificate can include three parts, namely the user's information, the user's public key, and the signature of the information in the certificate by the certification authority. To verify the authenticity of a certificate, for the convenience of description, the certificate to be verified is called the certificate to be verified below, that is, to verify whether the signature of the certificate to be verified by the certification center is valid, the public key of the certification center needs to be used to verify the certificate to be verified, and The public key of the certification center exists in the certificate to be signed by the certificate to be verified, so it is necessary to download the certificate that issues the certificate to be verified, but to use the certificate to verify the authenticity of the certificate itself must be verified first, so the certificate that issued the certificate must be used Certificates are used to verify, so that a certificate chain relationship is formed, and the certificate used to terminate this certificate chain is the root certificate. A root certificate is a special certificate whose issuer is itself. In other words, to verify the authenticity of a certificate, a chain of verification certificates needs to be established, and the verification of the certificate can be traced back to the root certificate. In other words, users must download the root certificate before using their own digital certificate, and verify the authenticity of a certificate based on the root certificate.
下面结合具体的证书对本申请的数字证书进行说明。The digital certificate of this application will be described below in combination with specific certificates.
作为一个示例,本申请中的数字证书可以是根证书x509格式。As an example, the digital certificate in this application may be in root certificate x509 format.
例如,根证书x509格式可包括以下信息中的至少一项:For example, the root certificate x509 format may include at least one of the following information:
序列号(Serial Number);serial number (Serial Number);
签名算法(Signature Algorithm);例如,ecdsa-with-SHA256;Signature Algorithm; for example, ecdsa-with-SHA256;
发布者(Issuer);例如,联盟信息。Issuer; for example, affiliate information.
有效期(Validity);例如,Redacted for brevity;Validity; for example, Redacted for brevity;
主体(Subject);例如,联盟信息;Subject (Subject); for example, alliance information;
主体公钥信息(Subject Public Key Info);Subject Public Key Info;
公钥算法(Public Key Algorithm);例如,id-ecPublicKey;Public Key Algorithm; for example, id-ecPublicKey;
公钥(Public-Key);例如,公钥的位长为256bit;Public key (Public-Key); for example, the bit length of the public key is 256bit;
公钥的值(Value);The value of the public key (Value);
ASN注册的标识(ASN1 OID);例如,prime256v1;ASN registered identifier (ASN1 OID); for example, prime256v1;
NIST曲线(NIST CURVE);例如,P-256;NIST CURVE; for example, P-256;
X509v3扩展(X509v3 extensions);例如,可包括X509v3基本限制(X509v3 Basic Constraints:critical);X509v3 extensions (X509v3 extensions); for example, can include X509v3 basic constraints (X509v3 Basic Constraints: critical);
认证(CA);例如,CA可设置为真实(TRUE),即用于签发证书;Certification (CA); for example, CA can be set to true (TRUE), which is used to issue certificates;
私钥作用(X509v3 Key Usage);例如,私钥作用可包括数字签名(Digital Signature), 认证签名(Certificate Sign);该私钥和上述公钥可形成一对密钥,进而实现对信息的加密和解密;Private key function (X509v3 Key Usage); for example, the private key function can include digital signature (Digital Signature), certification signature (Certificate Sign); the private key and the above public key can form a pair of keys, and then realize the encryption of information and decrypt;
签名算法(Signature Algorithm);例如,ecdsa-with-SHA256。Signature Algorithm; for example, ecdsa-with-SHA256.
作为另一示例,本申请中的数字证书可以是中间认证证书x509格式。As another example, the digital certificate in this application may be in the format of intermediate authentication certificate x509.
例如,中间认证证书x509格式可包括以下信息中的至少一项:For example, the x509 format of the intermediate authentication certificate may include at least one of the following information:
序列号(Serial Number);serial number (Serial Number);
签名算法(Signature Algorithm);例如,ecdsa-with-SHA256;Signature Algorithm; for example, ecdsa-with-SHA256;
发布者(Issuer);例如,联盟信息。Issuer; for example, affiliate information.
有效期(Validity);例如,Redacted for brevity;Validity; for example, Redacted for brevity;
主体(Subject);例如,供应商的信息;Subject (Subject); for example, supplier information;
主体公钥信息(Subject Public Key Info);Subject Public Key Info;
公钥算法(Public Key Algorithm);例如,id-ecPublicKey;Public Key Algorithm; for example, id-ecPublicKey;
公钥(Public-Key);例如,公钥的位长为256bit;Public key (Public-Key); for example, the bit length of the public key is 256bit;
公钥的值(Value);The value of the public key (Value);
ASN注册的标识(ASN1 OID);例如,prime256v1;ASN registered identifier (ASN1 OID); for example, prime256v1;
NIST曲线(NIST CURVE);例如,P-256;NIST CURVE; for example, P-256;
X509v3扩展(X509v3 extensions);例如,可包括X509v3基本限制(X509v3 Basic Constraints:critical);X509v3 extensions (X509v3 extensions); for example, can include X509v3 basic constraints (X509v3 Basic Constraints: critical);
认证(CA);例如,CA可设置为真实(TRUE),即用于签发证书;Certification (CA); for example, CA can be set to true (TRUE), which is used to issue certificates;
私钥作用(X509v3 Key Usage);例如,私钥作用可包括数字签名(Digital Signature),认证签名(Certificate Sign);该私钥和上述公钥可形成一对密钥,进而实现对信息的加密和解密;Private key function (X509v3 Key Usage); for example, the private key function can include digital signature (Digital Signature), certification signature (Certificate Sign); the private key and the above public key can form a pair of keys, and then realize the encryption of information and decrypt;
签名算法(Signature Algorithm);例如,ecdsa-with-SHA256。Signature Algorithm; for example, ecdsa-with-SHA256.
作为另一示例,本申请中的数字证书可以是设备认证证书x509格式,也可以称为设备的证书链。As another example, the digital certificate in this application may be in a device authentication certificate x509 format, and may also be referred to as a certificate chain of the device.
例如,设备认证证书x509格式可包括以下信息中的至少一项:For example, the x509 format of the device authentication certificate may include at least one of the following information:
序列号(Serial Number);serial number (Serial Number);
签名算法(Signature Algorithm);例如,ecdsa-with-SHA256;Signature Algorithm; for example, ecdsa-with-SHA256;
发布者(Issuer);例如,供应商的信息。Issuer; for example, supplier information.
有效期(Validity);例如,Redacted for brevity;Validity; for example, Redacted for brevity;
主体(Subject);例如,供应商和产品信息(Vendor_Product);Subject (Subject); for example, vendor and product information (Vendor_Product);
主体公钥信息(Subject Public Key Info);Subject Public Key Info;
公钥算法(Public Key Algorithm);例如,id-ecPublicKey;Public Key Algorithm; for example, id-ecPublicKey;
公钥(Public-Key);例如,公钥的位长为256bit;Public key (Public-Key); for example, the bit length of the public key is 256bit;
公钥的值(Value);The value of the public key (Value);
ASN注册的标识(ASN1 OID);例如,prime256v1;ASN registered identifier (ASN1 OID); for example, prime256v1;
NIST曲线(NIST CURVE);例如,P-256;NIST CURVE; for example, P-256;
X509v3扩展(X509v3 extensions);例如,可包括X509v3基本限制(X509v3 Basic Constraints:critical);X509v3 extensions (X509v3 extensions); for example, can include X509v3 basic constraints (X509v3 Basic Constraints: critical);
认证(CA);例如,CA可设置为错误(FALSE),即不用于签发证书;Certification (CA); for example, CA can be set to false (FALSE), that is, not used to issue certificates;
私钥作用(X509v3 Key Usage);例如,私钥作用可包括数字签名(Digital Signature),私钥加密(Key Encipherment);例如,在协商对称密钥阶段进行私钥加密。该私钥和上述公钥可形成一对密钥,进而实现对信息的加密和解密;Private key usage (X509v3 Key Usage); for example, private key usage can include digital signature (Digital Signature), private key encryption (Key Encipherment); for example, private key encryption is performed during the phase of negotiating a symmetric key. The private key and the above-mentioned public key can form a pair of keys, and then realize the encryption and decryption of information;
证书的接入信息(Authority Information Access);例如,URL;Certificate Access Information (Authority Information Access); for example, URL;
签名算法(Signature Algorithm);例如,ecdsa-with-SHA256。Signature Algorithm; for example, ecdsa-with-SHA256.
作为另一示例,本申请中的数字证书可以是设备操作证书x509格式,也可以称为平 台认证中心颁发的证书。该证书可用于设备和平台建立连接。As another example, the digital certificate in this application may be in the form of a device operation certificate x509, and may also be called a certificate issued by a platform certification authority. This certificate can be used to establish a connection between the device and the platform.
例如,设备操作证书x509格式可包括以下信息中的至少一项:For example, the equipment operation certificate x509 format may include at least one of the following information:
序列号(Serial Number);serial number (Serial Number);
签名算法(Signature Algorithm);例如,ecdsa-with-SHA256;Signature Algorithm; for example, ecdsa-with-SHA256;
发布者(Issuer);例如,平台的信息。Issuer; for example, platform information.
有效期(Validity);例如,Redacted for brevity;Validity; for example, Redacted for brevity;
主体(Subject);例如,设备标识;Subject (Subject); for example, device identification;
主体公钥信息(Subject Public Key Info);Subject Public Key Info;
公钥算法(Public Key Algorithm);例如,id-ecPublicKey;Public Key Algorithm; for example, id-ecPublicKey;
公钥(Public-Key);例如,公钥的位长为256bit;Public key (Public-Key); for example, the bit length of the public key is 256bit;
公钥的值(Value);The value of the public key (Value);
ASN注册的标识(ASN1 OID);例如,prime256v1;ASN registered identifier (ASN1 OID); for example, prime256v1;
NIST曲线(NIST CURVE);例如,P-256;NIST CURVE; for example, P-256;
X509v3扩展(X509v3 extensions);例如,可包括X509v3基本限制(X509v3 Basic Constraints:critical);X509v3 extensions (X509v3 extensions); for example, may include X509v3 basic constraints (X509v3 Basic Constraints: critical);
认证(CA);例如,CA可设置为错误(FALSE),即不用于签发证书;Certification (CA); for example, CA can be set to false (FALSE), that is, not used to issue certificates;
私钥作用(X509v3 Key Usage);例如,私钥作用可包括数字签名(Digital Signature),密钥协商(Key Agreement);Private key function (X509v3 Key Usage); for example, the private key function can include digital signature (Digital Signature), key agreement (Key Agreement);
签名算法(Signature Algorithm);例如,ecdsa-with-SHA256。Signature Algorithm; for example, ecdsa-with-SHA256.
例如,电子设备的数字证书可以为设备证书,从而能够通过设备证书区分不同的电子设备的身份,电子设备的数字证书还可以为电子设备的产品证书,从而能够通过产品证书确定电子设备所在的产品型号。在实际应用中,在对电子设备进行认证的时候,需要根据电子设备的数字证书完成认证过程,第一请求中含有第一信息,从而能够使第一服务器根据接收的第一请求中的第一信息对电子设备进行认证。For example, the digital certificate of an electronic device can be a device certificate, so that the identities of different electronic devices can be distinguished through the device certificate. The digital certificate of the electronic device can also be a product certificate of the electronic device, so that the product certificate of the electronic device can be determined through the product certificate. model. In practical applications, when authenticating an electronic device, it is necessary to complete the authentication process according to the digital certificate of the electronic device. The first request contains the first information, so that the first server can The information authenticates the electronic device.
S103:基于所述第一连接,接收所述第一服务器下发的关于所述第一请求的第一响应信息;所述第一响应信息中携带所述第一服务器对所述电子设备的身份认证结果。S103: Based on the first connection, receive first response information about the first request sent by the first server; the first response information carries the identity of the first server to the electronic device Authentication result.
这里,基于第一连接,接收第一服务器下发的关于第一请求的第一响应信息,第一响应信息中携带有第一服务器对电子设备的身份认证结果,在实际应用中,第一服务器在对电子设备进行认证处理之后,电子设备能够通过第一连接,接收第一服务器下发的认证结果,其中,认证结果包括了认证成功和认证失败,当第一响应信息表征认证成功的时候,电子设备与第一服务器之间可以继续后续数据交互。在实际应用中,电子设备通过第一服务器进行设备认证的时候,第一服务器会通过第一连接向电子设备返回一个设备证书,电子设备并不需要通过其他连接通道才能接收第一服务器下发的设备证书,这个设备证书是第一服务器针对电子设备签发的合法身份凭证,通过第一连接接收第一服务器下发的设备证书,能够保证设备证书在传输过程中的安全性,从而避免设备证书的泄露。Here, based on the first connection, the first response information about the first request issued by the first server is received, and the first response information carries the identity authentication result of the first server for the electronic device. In practical applications, the first server After performing authentication processing on the electronic device, the electronic device can receive the authentication result sent by the first server through the first connection, wherein the authentication result includes authentication success and authentication failure, and when the first response information indicates that the authentication is successful, Subsequent data interaction may continue between the electronic device and the first server. In practical applications, when the electronic device is authenticated by the first server, the first server will return a device certificate to the electronic device through the first connection, and the electronic device does not need to pass through other connection channels to receive the certificate issued by the first server. Device certificate, this device certificate is the legal identity certificate issued by the first server for the electronic device, receiving the device certificate issued by the first server through the first connection can ensure the security of the device certificate during transmission, thereby avoiding the device certificate. Give way.
换言之,设备证书也可以作为第一服务器对电子设备的认证结果。In other words, the device certificate may also be used as an authentication result of the electronic device by the first server.
在上述实施例中,电子设备与第一服务器建立基于TLS协议的第一连接,基于第一连接,向第一服务器发送第一请求,第一请求用于请求对电子设备进行身份认证,第一请求基于第一信息生成,第一信息表征电子设备的数字证书,基于第一连接,接收第一服务器下发的关于第一请求的第一响应信息,第一响应信息中携带第一服务器对电子设备的身份认证结果,从而能够基于TLS协议的连接在第一服务器与设备之间完成设备的认证,并不需要其他的连接通道完成设备的认证,从而能够减少认证过程中网络资源的需求量,并且还能加强认证过程中的数据传输的安全性,以及避免设备的信息泄露。In the above embodiment, the electronic device establishes a first connection with the first server based on the TLS protocol, and based on the first connection, sends a first request to the first server, the first request is used to request identity authentication for the electronic device, and the first The request is generated based on the first information. The first information represents the digital certificate of the electronic device. Based on the first connection, the first response information about the first request sent by the first server is received. The identity authentication result of the device, so that the authentication of the device can be completed between the first server and the device based on the connection of the TLS protocol, and no other connection channels are required to complete the authentication of the device, thereby reducing the demand for network resources during the authentication process. And it can also strengthen the security of data transmission in the authentication process, and avoid device information leakage.
在一实施例中,所述第一信息包括电子设备的设备证书。In an embodiment, the first information includes a device certificate of the electronic device.
这里,第一信息包括电子设备的设备证书,设备证书是一种由可信组织签发的证明 设备唯一合法身份的凭证,设备证书的格式可以为X.509,电子设备能够根据第一信息生成第一请求,将第一请求发送到第一服务器后,使第一服务器可以根据第一信息中的电子设备的设备证书,对设备进行认证。Here, the first information includes the device certificate of the electronic device. The device certificate is a certificate issued by a trusted organization to prove the unique legal identity of the device. The format of the device certificate can be X.509. The electronic device can generate the second A request, after the first request is sent to the first server, the first server can authenticate the device according to the device certificate of the electronic device in the first information.
在上述实施例中,第一信息包括电子设备的设备证书,从而能够通过电子设备的设备证书,对电子设备进行身份认证,从而能够根据电子设备的不同信息完成认证,提高了电子设备认证的适用性。In the above embodiment, the first information includes the device certificate of the electronic device, so that the identity authentication of the electronic device can be performed through the device certificate of the electronic device, so that the authentication can be completed according to different information of the electronic device, and the application of electronic device authentication is improved. sex.
在一实施例中,如图2所示,所述第一信息包括所述电子设备的产品证书;所述基于所述第一连接,向所述第一服务器发送第一请求,包括:In one embodiment, as shown in FIG. 2, the first information includes the product certificate of the electronic device; the sending a first request to the first server based on the first connection includes:
S201:从所述产品证书中确定产品识别码(product ID,PID)。S201: Determine a product identification code (product ID, PID) from the product certificate.
S202:基于所述第一连接,向所述第一服务器发送第一请求;所述第一请求中至少携带所述PID与所述电子设备中预置的供应商标识(Vendor ID,VID)。S202: Based on the first connection, send a first request to the first server; the first request carries at least the PID and a vendor identification (Vendor ID, VID) preset in the electronic device.
这里,第一信息包括电子设备的产品证书,产品证书是针对同一型号的电子设备签发的合法身份凭证,产品证书的格式可以为X.509,在通过第一服务器进行电子设备认证时,需要从产品证书中确定PID,产品证书中含有电子设备对应的PID,通过查阅产品证书能够确定出电子设备对应的PID。Here, the first information includes the product certificate of the electronic device. The product certificate is a legal identity certificate issued for the same type of electronic device. The format of the product certificate can be X.509. The PID is determined in the product certificate, which contains the PID corresponding to the electronic device, and the PID corresponding to the electronic device can be determined by consulting the product certificate.
S202:基于所述第一连接,向所述第一服务器发送第一请求;所述第一请求中至少携带所述PID与所述电子设备中预置的VID。S202: Based on the first connection, send a first request to the first server; the first request carries at least the PID and the VID preset in the electronic device.
这里,通过第一连接,向第一服务器发送第一请求,第一请求中至少携带有电子设备的PID与VID,其中,VID是电子设备中预置的,是设备单独写入的,VID需要提前在第一服务器进行登记。在实际应用中,在进行电子设备认证的时候,通过携带有PID与VID的第一请求以使第一服务器能够根据PID与VID确定电子设备的合法性,当第一服务器认为电子设备合法的时候,电子设备能够通过第一连接接收到第一服务器下发的身份认证结果。在实际应用中,由于同一型号的电子设备对应的产品证书都是相同的,因此,需要第一服务器为同一型号的电子设备签发不同的设备证书,从而完成电子设备的认证。在实际应用中,同一型号的电子设备的产品证书都是相同的,但是同一型号中的每个电子设备对应的VID是不相同,因此可以将大量同一型号的电子设备对应的VID导入到第一服务器中,实现对电子设备进行批量身份认证。Here, the first request is sent to the first server through the first connection, and the first request carries at least the PID and VID of the electronic device, wherein, the VID is preset in the electronic device and written by the device separately, and the VID needs to be Register with the first server in advance. In practical applications, when performing electronic device authentication, the first server can determine the legitimacy of the electronic device based on the PID and VID through the first request carrying the PID and VID. When the first server considers the electronic device to be legal , the electronic device can receive the identity authentication result delivered by the first server through the first connection. In practical applications, since the product certificates corresponding to the same type of electronic device are the same, the first server needs to issue different device certificates for the same type of electronic device, so as to complete the authentication of the electronic device. In practical applications, the product certificates of electronic devices of the same model are the same, but the VIDs corresponding to each electronic device of the same model are different, so the VIDs corresponding to a large number of electronic devices of the same model can be imported into the first In the server, batch identity authentication for electronic devices is realized.
在上述实施例中,第一信息包括电子设备的产品证书,从产品证书中确定PID,基于第一连接,向第一服务器发送第一请求,第一请求中至少携带有PID与电子设备中预置的VID,从而能够在电子设备的数字证书为产品证书的情况下,通过电子设备的设备信息,完成对电子设备的认证,并对电子设备签发证书,从而能够根据电子设备的不同信息完成认证,提高了电子设备认证的适用性,另外,还可以将电子设备的设备信息批量导入到第一服务器中,实现批量电子设备的身份认证。In the above embodiment, the first information includes the product certificate of the electronic device, the PID is determined from the product certificate, and based on the first connection, the first request is sent to the first server, the first request carries at least the PID and the electronic device's preset The VID is set, so that when the digital certificate of the electronic device is a product certificate, the device information of the electronic device can be used to complete the authentication of the electronic device, and issue a certificate to the electronic device, so that the authentication can be completed according to different information of the electronic device , improving the applicability of the electronic device authentication, and in addition, the device information of the electronic devices can also be imported into the first server in batches, so as to realize the identity authentication of the electronic devices in batches.
在一实施例中,所述第一请求中还携带第一密钥;所述第一密钥在所述电子设备首次上电时随机生成。In an embodiment, the first request also carries a first key; the first key is randomly generated when the electronic device is powered on for the first time.
这里,第一请求中还携带有第一密钥,第一密钥在电子设备首次上电时随机生成的,生成第一密钥后可以将第一密钥进行存储,使每个电子设备对应一个第一密钥。在实际应用中,可以通过电子设备的第一密钥识别仿冒设备,具体地,当电子设备通过携带的数字证书进行身份认证的时候,可以检测电子设备的密钥是否发生变化,如果发生变化,说明电子设备已经被仿冒了,从而拒绝仿冒的电子设备的身份认证。Here, the first request also carries the first key. The first key is randomly generated when the electronic device is powered on for the first time. After the first key is generated, the first key can be stored so that each electronic device corresponds to A first key. In practical applications, counterfeit devices can be identified through the first key of the electronic device. Specifically, when the electronic device performs identity authentication through the digital certificate it carries, it can be detected whether the key of the electronic device has changed. If there is a change, It indicates that the electronic device has been counterfeited, so the identity authentication of the counterfeit electronic device is rejected.
在上述实施例中,第一请求中还携带有第一密钥,第一密钥在电子设备首次上电时随机生成的,从而能够通过电子设备携带的密钥判断电子设备是否被仿冒,从而能够提高电子设备的身份认证的安全性。In the above-mentioned embodiment, the first request also carries the first key, which is randomly generated when the electronic device is powered on for the first time, so that it can be judged whether the electronic device is counterfeited through the key carried by the electronic device, thereby The security of the identity authentication of the electronic device can be improved.
在一实施例中,所述方法还包括;In one embodiment, the method further includes;
从所述电子设备的存储介质中读取所述第一信息;或,reading the first information from a storage medium of the electronic device; or,
从第二服务器中下载所述第一信息;所述第二服务器上存储有至少一个电子设备中 的每个电子设备对应的第一信息。Downloading the first information from a second server; the first information corresponding to each electronic device in the at least one electronic device is stored on the second server.
这里,第一信息可以从电子设备的存储介质中读取,电子设备的生产商可以在生产设备的时候,将第一信息提前烧录到电子设备上,在电子设备需要进行身份认证的时候,基于电子设备的存储介质中读取的第一信息对电子设备进行认证。此外,除了将第一信息提前烧录到电子设备上,还可以从第二服务器中下载相应的第一信息,其中,第二服务器可以是电子设备生产厂商指定的服务器,第二服务器上存储有至少一个电子设备中的每个电子设备对应的第一信息,在电子设备上电联网后,向第二服务器发起请求,获取第一信息,从而能够通过不同的方式获取第一信息。Here, the first information can be read from the storage medium of the electronic device, and the manufacturer of the electronic device can burn the first information into the electronic device in advance when producing the device. When the electronic device needs to perform identity authentication, The electronic device is authenticated based on the first information read from the storage medium of the electronic device. In addition, in addition to burning the first information to the electronic device in advance, the corresponding first information can also be downloaded from the second server, wherein the second server can be a server designated by the electronic device manufacturer, and the second server stores the For the first information corresponding to each of the at least one electronic device, after the electronic device is connected to the Internet, a request is made to the second server to obtain the first information, so that the first information can be obtained in different ways.
在上述实施例中,通过从所述电子设备的存储介质中读取第一信息,或者从第二服务器中下载第一信息得到第一信息,第二服务器上存储有至少一个电子设备中的每个电子设备对应的第一信息,从而能够通过不同方式获取电子设备的第一信息,从而完成电子设备的身份认证,提高了电子设备认证的适用性。In the above embodiment, the first information is obtained by reading the first information from the storage medium of the electronic device, or downloading the first information from the second server, and the second server stores each The first information corresponding to each electronic device, so that the first information of the electronic device can be obtained in different ways, thereby completing the identity authentication of the electronic device, and improving the applicability of the electronic device authentication.
图3示出了本申请实施例提供的另一种设备认证方法,如图3所示,所示方法应用于第一服务器,所述方法包括:Figure 3 shows another device authentication method provided by the embodiment of the present application. As shown in Figure 3, the shown method is applied to the first server, and the method includes:
S301:与电子设备建立基于TLS协议的第一连接。S301: Establish a first connection based on the TLS protocol with the electronic device.
这里,第一服务器与电子设备建立基于TLS协议的第一连接,第一连接可以作为第一服务器与电子设备之间的数据传输的通道,第一服务器是负责对电子设备进行身份认证,并向电子设备返回相应的认证结果。在实际应用中,在通过基于TLS协议建立的第一连接进行数据传输的时候,能够对传输的数据进行加密,从而能够保证信息传输的安全。在实际应用中,需要第一服务器与电子设备都同意使用TLS协议的情况下,第一服务器与电子设备才能建立基于TLS协议的第一连接。Here, the first server and the electronic device establish a first connection based on the TLS protocol. The first connection can be used as a channel for data transmission between the first server and the electronic device. The first server is responsible for authenticating the electronic device and sending The electronic device returns a corresponding authentication result. In practical applications, when data is transmitted through the first connection established based on the TLS protocol, the transmitted data can be encrypted, thereby ensuring the security of information transmission. In practical applications, the first server and the electronic device can establish the first connection based on the TLS protocol only when both the first server and the electronic device agree to use the TLS protocol.
S302:基于所述第一连接,接收所述电子设备发送的第一请求;所述第一请求用于请求对所述电子设备进行身份认证;所述第一请求基于第一信息生成;所述第一信息表征所述电子设备的数字证书。S302: Based on the first connection, receive a first request sent by the electronic device; the first request is used to request identity authentication for the electronic device; the first request is generated based on first information; the The first information characterizes a digital certificate of the electronic device.
这里,第一服务器通过第一连接,能够接收到电子设备发送的第一请求,第一请求用于请求对电子设备进行身份认证,第一请求基于第一信息生成,第一信息表征电子设备的数字证书,其中,数字证书是指身份信息的一个数字认证,电子设备的数字证书是能够将电子设备与电子设备的身份进行绑定,通过电子设备的数字证书可以识别电子设备的身份,例如,电子设备的数字证书可以为设备证书,从而能够通过设备证书区分不同的电子设备的身份,电子设备的数字证书还可以为电子设备的产品证书,从而能够通过产品证书确定电子设备所在的产品型号。当第一服务器接收到第一请求的时候,第一服务器会开始准备对电子设备进行身份认证。在实际应用中,第一请求会携带有电子设备的设备信息,第一服务器通过第一连接接收第一请求,能够保证传输的信息的安全性。Here, the first server can receive the first request sent by the electronic device through the first connection. The first request is used to request identity authentication for the electronic device. The first request is generated based on the first information, and the first information represents the identity of the electronic device. Digital certificate, where the digital certificate refers to a digital certification of identity information, the digital certificate of the electronic device can bind the electronic device with the identity of the electronic device, and the identity of the electronic device can be identified through the digital certificate of the electronic device, for example, The digital certificate of the electronic device can be a device certificate, so that the identities of different electronic devices can be distinguished through the device certificate, and the digital certificate of the electronic device can also be a product certificate of the electronic device, so that the product model of the electronic device can be determined through the product certificate. When the first server receives the first request, the first server will start to prepare for identity authentication of the electronic device. In practical applications, the first request will carry device information of the electronic device, and the first server receives the first request through the first connection, which can ensure the security of the transmitted information.
S303:基于所述第一请求,对所述电子设备进行身份认证,得到身份认证结果。S303: Perform identity authentication on the electronic device based on the first request, and obtain an identity authentication result.
这里,第一服务器能够基于第一请求,对电子设备进行身份认证,得到身份认证结果。在实际应用中,第一服务器能够对电子设备的数字证书进行解析,根据对数字证书的解析结果得到相应的身份认证结果,示例地,当第一服务器能够对电子设备的数字证书进行合法解析,说明电子设备的数字证书是合法的,从而能够生成表征认证成功的身份认证结果,如果第一服务器不能对电子设备的数字证书进行合法解析,说明电子设备的证书不合法,从而生成表征认证失败的身份认证结果。Here, the first server can perform identity authentication on the electronic device based on the first request, and obtain an identity authentication result. In practical applications, the first server can analyze the digital certificate of the electronic device, and obtain the corresponding identity authentication result according to the result of the analysis of the digital certificate. For example, when the first server can legally analyze the digital certificate of the electronic device, It indicates that the digital certificate of the electronic device is legal, so that an identity authentication result indicating that the authentication is successful can be generated. If the first server cannot legally parse the digital certificate of the electronic device, it means that the certificate of the electronic device is illegal, thereby generating a result indicating that the authentication failed. Authentication result.
S304:基于所述第一连接,向所述电子设备下发的关于所述第一请求的第一响应信息;所述第一响应信息中携带所述身份认证结果。S304: Based on the first connection, send first response information about the first request to the electronic device; the first response information carries the identity authentication result.
这里,基于第一连接,向电子设备下发的关于第一请求的第一响应信息,第一响应信息中携带身份认证结果。在实际应用中,第一服务器可以通过第一连接接收电子设备发送的第一请求,还可以通过第一连接将第一响应信息返回到电子设备中,并不需要通过其他通道才能向电子设备返回第一响应信息。在实际应用中,第一服务器在对电子设 备进行身份认证的时候,会通过第一连接向电子设备返回对应的设备证书,从而能够保证设备证书在传输过程中的安全性。在实际应用中,第一信息可以为电子设备的设备证书,第一服务器能够根据第一请求中的第一信息对电子设备进行身份认证。设备证书是一种由可信组织签发的证明电子设备唯一合法身份的凭证,设备证书的格式可以为X.509。合法的设备证书是由可信组织签发的,当第一服务器能够完成设备证书的合法解析,表明电子设备的设备证书是合法,从而生成表征电子设备合法的身份认证结果。当第一服务器不能对设备证书进行合法解析的时候,表明电子设备的设备证书不合法,从而生成表征电子设备不合法的身份认证结果。Here, based on the first connection, the first response information about the first request is delivered to the electronic device, and the first response information carries an identity authentication result. In practical applications, the first server can receive the first request sent by the electronic device through the first connection, and can also return the first response information to the electronic device through the first connection, and does not need to pass through other channels to return to the electronic device First response message. In practical applications, when the first server authenticates the electronic device, it will return the corresponding device certificate to the electronic device through the first connection, so as to ensure the security of the device certificate during transmission. In practical applications, the first information may be a device certificate of the electronic device, and the first server can perform identity authentication on the electronic device according to the first information in the first request. A device certificate is a certificate issued by a trusted organization to prove the unique legal identity of an electronic device. The format of the device certificate can be X.509. A legal device certificate is issued by a trusted organization. When the first server can complete the legal analysis of the device certificate, it indicates that the device certificate of the electronic device is legal, thereby generating an identity authentication result representing the legality of the electronic device. When the first server cannot legally parse the device certificate, it indicates that the device certificate of the electronic device is invalid, thereby generating an identity authentication result indicating that the electronic device is illegal.
在上述实施例中,第一服务器与电子设备建立基于TLS协议的第一连接,基于第一连接,接收电子设备发送的第一请求,第一请求用于请求电子设备进行身份认证,第一请求基于第一信息生成,第一信息表征电子设备的数字证书,基于第一请求,对电子设备进行身份认证,得到身份认证结果,基于第一连接,向电子设备下发的关于第一请求的第一响应信息,第一响应信息中携带有身份认证结果,从而能够基于TLS协议的连接通道进行电子设备与第一服务器之间的数据传输以完成电子设备的认证,从而保证了设备认证过程中的数据传输的安全性,并且减少认证过程中网络资源的需求量。In the above embodiment, the first server and the electronic device establish a first connection based on the TLS protocol, and based on the first connection, receive the first request sent by the electronic device, the first request is used to request the electronic device to perform identity authentication, and the first request Based on the generation of the first information, the first information represents the digital certificate of the electronic device, based on the first request, the electronic device is authenticated, and the identity authentication result is obtained, based on the first connection, the electronic device is issued the first request related to the first request One response information, the first response information carries the identity authentication result, so that the data transmission between the electronic device and the first server can be performed based on the connection channel of the TLS protocol to complete the authentication of the electronic device, thus ensuring the security of the device during the authentication process. The security of data transmission, and reduce the demand of network resources in the authentication process.
在一实施例中,如图4所示,所述第一信息包括所述电子设备的产品证书;所述第一请求中至少携带PID和VID;所述向所述电子设备下发的关于所述第一请求的第一响应信息,包括:In one embodiment, as shown in FIG. 4 , the first information includes the product certificate of the electronic device; the first request carries at least PID and VID; The first response information of the first request includes:
S401:在对所述电子设备的身份认证成功的情况下,基于所述PID和所述VID生成所述电子设备的设备证书。S401: If the identity authentication of the electronic device is successful, generate a device certificate of the electronic device based on the PID and the VID.
这里,当第一信息为电子设备的产品证书的时候,第一服务器接收到的第一请求携带了PID和VID,其中,产品证书中含有PID,PID是从产品证书中确定出来的,VID是由电子设备预先配置得到的,产品证书是针对同一型号的电子设备签发的合法身份凭证,产品证书的格式可以为X.509。在实际应用中,同一型号的电子设备的产品证书是相同的,因此在通过产品证书对电子设备进行身份认证的时候,还需要通过VID和PID信息确定电子设备的设备证书。在实际应用中,第一服务器会根据第一请求携带的PID与VID确定电子的设备的合法性,通过第一信息中的产品证书,对电子设备的身份进行认证,当第一服务器对电子设备的身份认证成功的情况下,根据第一请求中携带的PID和VID确定电子设备的设备证书。在实际应用中,同一型号的电子设备的产品证书是相同的,因此在通过产品证书对电子设备进行身份认证的时候,还需要通过VID和PID信息确定电子设备的设备证书。在实际应用中,对于同一型号的电子设备的产品证书是相同的,并且是基于电子设备的PID与VID对电子设备进行身份认证,因此,第一服务器可以同时接受大量同一型号的电子设备发送的VID,从而能够对电子设备进行批量身份认证,提高了电子设备身份认证的效率。Here, when the first information is the product certificate of the electronic device, the first request received by the first server carries PID and VID, wherein the product certificate contains the PID, the PID is determined from the product certificate, and the VID is Obtained by pre-configuration of electronic equipment, the product certificate is a legal identity certificate issued for the same type of electronic equipment, and the format of the product certificate can be X.509. In practical applications, the product certificates of electronic devices of the same model are the same. Therefore, when the electronic device is authenticated through the product certificate, it is also necessary to determine the device certificate of the electronic device through VID and PID information. In practical applications, the first server will determine the legitimacy of the electronic device according to the PID and VID carried in the first request, and authenticate the identity of the electronic device through the product certificate in the first information. In the case of successful identity authentication, the device certificate of the electronic device is determined according to the PID and VID carried in the first request. In practical applications, the product certificates of electronic devices of the same model are the same. Therefore, when the electronic device is authenticated through the product certificate, it is also necessary to determine the device certificate of the electronic device through VID and PID information. In practical applications, the product certificates for the same type of electronic equipment are the same, and the electronic equipment is authenticated based on the PID and VID of the electronic equipment. Therefore, the first server can simultaneously accept a large number of electronic equipment of the same type. VID, so that batch identity authentication can be performed on the electronic equipment, and the efficiency of the identity authentication of the electronic equipment is improved.
S402:向所述电子设备下发所述第一响应信息;所述第一响应信息中携带所述设备证书。S402: Deliver the first response information to the electronic device; the first response information carries the device certificate.
这里,在确定了电子设备的设备证书的时候,向电子设备下发第一响应信息,其中,第一响应信息中携带有设备证书,从而能够根据产品证书对电子设备进行身份认证,并且为电子设备分配对应的设备证书。在实际应用中,第一服务器是通过第一连接将设备证书下发到电子设备中,并不需要额外的网络资源才能完成设备证书的下发,并且还能够保证设备证书在传输过程中的安全性,Here, when the device certificate of the electronic device is determined, the first response information is sent to the electronic device, wherein the first response information carries the device certificate, so that the identity of the electronic device can be authenticated according to the product certificate, and the electronic The device is assigned a corresponding device certificate. In practical applications, the first server issues the device certificate to the electronic device through the first connection, which does not require additional network resources to complete the issuance of the device certificate, and can also ensure the security of the device certificate during transmission sex,
在上述实施例中,第一信息包括电子设备的产品证书,第一请求中至少携带PID和VID,在电子设备的身份认证成功的情况下,基于PID和VID生成电子设备的设备证书,向电子设备下发第一响应信息,第一响应信息中携带设备证书,从而能够根据电子设备的产品证书对电子设备进行身份认证,并且通过批量导入VID能够实现对电子设备进行批量认证,并且为电子设备下发设备证书,此外,还可以保证设备证书在传输过程中的 安全性,降低了网络资源的需求量。In the above embodiment, the first information includes the product certificate of the electronic device, and at least the PID and VID are carried in the first request. The device sends the first response information, and the first response information carries the device certificate, so that the electronic device can be authenticated according to the product certificate of the electronic device, and the electronic device can be authenticated in batches by importing VIDs in batches, and for the electronic device Issuing device certificates, in addition, can also ensure the security of device certificates during transmission, reducing the demand for network resources.
在一实施例中,所述第一请求还携带第一密钥;所述第一密钥在所述电子设备首次上电时随机生成;所述对所述电子设备进行身份认证,得到身份认证结果,包括:In one embodiment, the first request also carries a first key; the first key is randomly generated when the electronic device is powered on for the first time; Results, including:
在所述电子设备未激活过的情况下,对应保存所述VID和所述第一密钥;或,If the electronic device has not been activated, store the VID and the first key correspondingly; or,
在所述电子设备曾经激活过的情况下,确认所述第一请求中的第一密钥与第二密钥是否相同;所述第二密钥为所述第一服务器保存的所述VID对应的密钥;当所述第一密钥与所述第二密钥相同时,得到对所述电子设备的身份认证成功的身份认证结果;当所述第一密钥与所述第二密钥不同时,得到对所述电子设备的身份认证失败的身份认证结果。In the case that the electronic device has been activated, confirm whether the first key in the first request is the same as the second key; the second key corresponds to the VID saved by the first server key; when the first key is the same as the second key, obtain an identity authentication result that the identity authentication of the electronic device is successful; when the first key is the same as the second key At the same time, an identity authentication result that the identity authentication of the electronic device fails is obtained.
这里,当电子设备具备的数字证书为产品证书的情况下,第一服务器接收的第一请求中还携带有第一密钥,第一密钥是电子设备首次上电时随机生成的,并且每个电子设备对应一个密钥。在对电子设备进行身份认证的时候,当电子设备处于未激活过的情况下,对应保存VID和第一密钥,其中,电子设备未激活过是指第一服务器没有为当前的电子设备下发设备证书,可以通过第一服务器是否存储电子设备对应的VID进行判断,示例地,当第一服务器中没有存储电子设备对应的VID,可以确定电子设备处于未激活过的状态,将电子设备第一信息中携带的VID与第一密钥关联保存。在电子设备曾经激活过的情况下,示例地,当第一服务器中存储有电子设备对应的VID,可以确定电子设备曾经激活过,说明了第一服务器已经为电子设备下发过设备证书,并且第一服务器记录了电子设备对应的VID与电子设备对应的密钥,通过确认第一请求中的第一密钥与第二密钥是否相同,第二密钥是第一服务器保存的VID对应的密钥,当第一密钥与第二密钥相同的时候,说明当前申请获取设备证书的电子设备与曾经激活过的电子设备为同一个电子设备,当前电子设备在之前通过第一服务器的身份认证并已经获得相应的设备证书,可以得到对电子设备的身份认证成功的身份认证结果。在实际应用中,由于同一电子设备只能申请一次设备证书,第一服务器还可以通过第一连接将电子设备曾经注册时的设备证书下发给电子设备,从而能够保证对同一电子设备下发一个设备证书,避免将多个设备证书下发到同一个电子设备。当第一密钥与第二密钥不相同的时候,说明申请获取设备证书的电子设备与曾经激活过的电子设备不是同一个电子设备,可能存在VID泄露而导致电子设备冒用VID以获取设备证书的风险,第一服务器向电子设备返回身份认证失败的身份认证结果。Here, when the digital certificate of the electronic device is a product certificate, the first request received by the first server also carries a first key, which is randomly generated when the electronic device is powered on for the first time, and every Each electronic device corresponds to a key. When performing identity authentication on an electronic device, when the electronic device has not been activated, the VID and the first key are stored correspondingly, where the electronic device has not been activated means that the first server has not issued The device certificate can be judged by whether the VID corresponding to the electronic device is stored in the first server. For example, when the VID corresponding to the electronic device is not stored in the first server, it can be determined that the electronic device is The VID carried in the information is stored in association with the first key. In the case that the electronic device has been activated, for example, when the VID corresponding to the electronic device is stored in the first server, it can be determined that the electronic device has been activated, indicating that the first server has issued a device certificate for the electronic device, and The first server records the VID corresponding to the electronic device and the key corresponding to the electronic device. By confirming whether the first key in the first request is the same as the second key, the second key is the key corresponding to the VID saved by the first server. Key, when the first key is the same as the second key, it means that the electronic device currently applying for obtaining the device certificate is the same electronic device as the electronic device that has been activated, and the current electronic device passed the identity of the first server before After the authentication and the corresponding device certificate has been obtained, the identity authentication result of the successful identity authentication of the electronic device can be obtained. In practical applications, since the same electronic device can only apply for a device certificate once, the first server can also issue the device certificate when the electronic device was registered to the electronic device through the first connection, so as to ensure that a certificate is issued to the same electronic device. Device certificates to avoid issuing multiple device certificates to the same electronic device. When the first key is not the same as the second key, it means that the electronic device applying for the device certificate is not the same electronic device as the electronic device that has been activated, and there may be a VID leak that may cause the electronic device to fraudulently use the VID to obtain the device. certificate risk, the first server returns to the electronic device an identity authentication result of identity authentication failure.
在上述实施例中,第一请求还携带第一密钥,第一密钥在电子设备首次上电时随机生成,在电子设备未激活过的情况下,对应保存VID和第一密钥,或,在电子设备曾经激活过的情况下,确认第一请求中的第一密钥与第二密钥是否相同,第二密钥为第一服务器保存的VID对应的密钥,当第一密钥与第二密钥相同时,得到对电子设备的身份认证成功的身份认证结果,当第一密钥与第二密钥不同时,得到对电子设备的身份认证失败的身份认证结果,从而能够避免同一电子设备申请多个设备证书,同时还能提高识别仿冒的电子设备的能力,保证了电子设备的安全。In the above embodiment, the first request also carries the first key, which is randomly generated when the electronic device is powered on for the first time, and if the electronic device has not been activated, the VID and the first key are stored correspondingly, or , in the case that the electronic device has been activated, confirm whether the first key in the first request is the same as the second key, the second key is the key corresponding to the VID saved by the first server, when the first key When it is the same as the second key, the identity authentication result of the electronic device’s identity authentication success is obtained, and when the first key is different from the second key, the identity authentication result of the electronic device’s identity authentication failure is obtained, thereby avoiding Applying for multiple device certificates for the same electronic device can also improve the ability to identify counterfeit electronic devices and ensure the safety of electronic devices.
在一实施例中,在对所述电子设备的身份认证失败的情况下,所述方法还包括:In an embodiment, when the identity authentication of the electronic device fails, the method further includes:
终止所述第一连接。Terminate the first connection.
这里,当第一服务器对电子设备的身份认证失败的情况下,终止第一服务器与电子设备的第一连接,从而避免未能成功认证的电子设备与第一服务器继续建立联系,获取第一服务器中的数据。Here, when the first server fails to authenticate the identity of the electronic device, the first connection between the first server and the electronic device is terminated, thereby preventing the electronic device that fails to authenticate from continuing to establish contact with the first server, and obtaining the data in .
在上述实施例中,在对电子设备的身份认证失败的情况下终止第一连接,从而能够保护电子设备相关数据的安全性,避免数据的泄露。In the above embodiment, the first connection is terminated when the identity authentication of the electronic device fails, so that the security of data related to the electronic device can be protected and data leakage can be avoided.
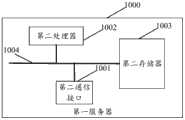
本发明还提供了一应用实施例,如图5所示,图5示出了电子设备身份认证的交互示意图。The present invention also provides an application embodiment, as shown in FIG. 5 , which shows an interactive schematic diagram of electronic device identity authentication.
S501:从电子设备的存储介质中读取设备证书。这里,生产厂商提前批量申请好电 子设备的设备证书,在生产电子设备的时候,将设备证书烧录到设备中。S501: Read a device certificate from a storage medium of an electronic device. Here, the manufacturer applies for the device certificates of electronic devices in batches in advance, and burns the device certificates into the devices when producing electronic devices.
S502:电子设备与第一服务器建立基于TLS协议的第一连接。这里,电子设备与第一服务器之间能够通过第一连接进行数据传输。S502: The electronic device establishes a first connection based on the TLS protocol with the first server. Here, data transmission can be performed between the electronic device and the first server through the first connection.
S503:向第一服务器发送第一请求。这里,根据电子设备的设备证书生成第一请求,第一请求用于向第一服务器请求对电子设备进行身份认证,。S503: Send a first request to the first server. Here, the first request is generated according to the device certificate of the electronic device, and the first request is used to request the first server to perform identity authentication on the electronic device.
S504:第一服务器根据第一请求中的设备证书对电子设备进行身份认证。S504: The first server performs identity authentication on the electronic device according to the device certificate in the first request.
S505:返回第一响应信息。这里,当第一服务器完成电子设备的身份认证的时候,向电子设备返回第一响应信息,第一响应信息中携带有第一服务器对电子设备的身份认证结果。S505: Return the first response information. Here, when the first server completes the identity authentication of the electronic device, it returns the first response information to the electronic device, and the first response information carries the result of the identity authentication of the electronic device by the first server.
S506:进行后续交互。这里,当设备身份认证成功时候,第一服务器与设备之间继续进行数据交互。S506: Perform subsequent interaction. Here, when the identity authentication of the device succeeds, the data exchange between the first server and the device continues.
本发明还提供了另一个应用实施例,如图6所示,图6示出了电子设备身份认证的交互示意图。The present invention also provides another application embodiment, as shown in FIG. 6 , which shows an interactive schematic diagram of electronic device identity authentication.
S601:从电子设备的存储介质中读取产品证书。这里,生产厂商提前批量申请好产品证书,在生产电子设备的时候,将产品证书写入到代码中。S601: Read the product certificate from the storage medium of the electronic device. Here, the manufacturer applies for product certificates in batches in advance, and writes the product certificates into the code when producing electronic devices.
S602:电子设备与第一服务器建立基于TLS协议的第一连接。这里,电子设备与第一服务器之间能够通过第一连接进行数据传输。S602: The electronic device establishes a first connection based on the TLS protocol with the first server. Here, data transmission can be performed between the electronic device and the first server through the first connection.
S603:向第一服务器发送第一请求。这里,根据电子设备的产品证书生成第一请求,并且,第一请求中携带有PID、VID、第一密钥,第一请求用于向第一服务器请求对电子设备进行身份认证,其中,PID是从产品证书中确定出,VID由电子设备写入的,第一密钥是电子设备首次上电时随机生成的。S603: Send a first request to the first server. Here, the first request is generated according to the product certificate of the electronic device, and the first request carries PID, VID, and a first key, and the first request is used to request the first server to authenticate the electronic device, wherein the PID It is determined from the product certificate, the VID is written by the electronic device, and the first key is randomly generated when the electronic device is powered on for the first time.
S604:第一服务器根据第一请求中的产品证书对电子设备进行身份认证,并根据PID与VID确定下发设备证书。S604: The first server performs identity authentication on the electronic device according to the product certificate in the first request, and determines to issue the device certificate according to the PID and VID.
S605:返回第一响应信息。这里,当第一服务器完成电子设备的身份认证的时候,向电子设备返回第一响应信息,第一响应信息中携带有第一服务器对电子设备的身份认证结果以及设备证书,从而电子设备能够获取对应的设备证书。S605: Return the first response information. Here, when the first server completes the identity authentication of the electronic device, it returns the first response information to the electronic device, and the first response information carries the identity authentication result of the first server for the electronic device and the device certificate, so that the electronic device can obtain The corresponding device certificate.
S606:进行后续交互。这里,当设备身份认证成功时候,第一服务器与设备之间继续进行数据交互。S606: Perform subsequent interaction. Here, when the identity authentication of the device succeeds, the data exchange between the first server and the device continues.
本发明还提供了另一个应用实施例,如图7所示,图7示出了电子设备身份认证的交互示意图。The present invention also provides another application embodiment, as shown in FIG. 7 , which shows an interactive schematic diagram of electronic device identity authentication.
应当理解,图7所示的电子设备可以是任意具有通信功能的设备。例如,电子设备可以是智能家电。图7所示的配置器可以任意一种具有用户界面的设备。例如,配置器可以是智能手机。图7所示的服务器可以是用于进行接入认证的设备或系统。例如,该服务器可以是部署在云上的系统,还可以是部署在其他系统的模块子系统。再如,该服务器还可以是物联网服务器。It should be understood that the electronic device shown in FIG. 7 may be any device with a communication function. For example, an electronic device may be a smart home appliance. The configurator shown in Figure 7 can be any device with a user interface. For example, the configurator can be a smartphone. The server shown in FIG. 7 may be a device or system for performing access authentication. For example, the server may be a system deployed on the cloud, or a module subsystem deployed in other systems. For another example, the server may also be an Internet of Things server.
S611,电子设备向配置器发送VID、PID、媒体接入控制(Media Access Control,MAC)、个人识别码(Personal Identification Number,PIN)。S611. The electronic device sends a VID, a PID, a media access control (Media Access Control, MAC), and a personal identification number (Personal Identification Number, PIN) to the configurator.
例如,电子设备向配置器发送配置信息,该配置信息包括VID、PID、MAC、PIN。再如,电子设备向配置器发送的MAC可以是MAC地址。For example, the electronic device sends configuration information to the configurator, and the configuration information includes VID, PID, MAC, and PIN. For another example, the MAC sent by the electronic device to the configurator may be a MAC address.
再如,PIN可以是电子设备出厂时预配置的信息,用于建立安全通道。For another example, the PIN may be information pre-configured when the electronic device leaves the factory, and is used to establish a secure channel.
再如,电子设备上电后可以获取该配置信息。For another example, the configuration information may be obtained after the electronic device is powered on.
S612,配置器向服务器发送请求,包括VID、PID、MAC。S612, the configurator sends a request to the server, including VID, PID, and MAC.
例如,配置器收到包括VID、PID、MAC、PIN的配置信息后,向服务器发送包括VID、PID、MAC的请求,以便服务器生成电子设备的设备标识和注册码。For example, after receiving the configuration information including VID, PID, MAC, and PIN, the configurator sends a request including VID, PID, and MAC to the server, so that the server can generate the device identification and registration code of the electronic device.
其中,VID、PID、MAC的请求可用于服务器定位电子设备,进而为电子设备分配设备标识。例如,该服务器为认证中心平台,该设备标识为该认证中心平台下的用于唯 一标识电子设备的标识。例如,该注册码可以该服务器为电子设备分配的,且关联至用户和/或该电子设备的信息。Wherein, the request of VID, PID, and MAC can be used by the server to locate the electronic device, and then assign a device identifier to the electronic device. For example, the server is an authentication center platform, and the device identifier is an identifier for uniquely identifying an electronic device under the authentication center platform. For example, the registration code may be assigned by the server to the electronic device and be associated with information on the user and/or the electronic device.
S613,服务器生成设备标识和注册码。S613. The server generates a device identification and a registration code.
S614,服务器向配置器发送响应,包括设备标识、注册码、证书撤销列表(Certificate Revocation List,CRL)。S614. The server sends a response to the configurator, including the device identifier, the registration code, and the certificate revocation list (Certificate Revocation List, CRL).
其中,CRL可用于验证证书链是否有效。Among them, CRL can be used to verify whether the certificate chain is valid.
当然,在S614中,该响应也可额外包括S629中涉及的挑战码。即,服务器向配置器发送包括挑战码的响应。Of course, in S614, the response may additionally include the challenge code involved in S629. That is, the server sends a response including a challenge code to the configurator.
S615,电子设备和配置器建立连接。S615. Establishing a connection between the electronic device and the configurator.
S616,配置器生成挑战码。S616. The configurator generates a challenge code.
例如,该挑战码可以是一个随机数。For example, the challenge code can be a random number.
当然,在S616中,配置器也可以直接使用S614服务器发送的挑战码。Of course, in S616, the configurator can also directly use the challenge code sent by the server in S614.
S617,配置器向电子设备发送认证请求,包括挑战码。S617. The configurator sends an authentication request, including a challenge code, to the electronic device.
S618,电子设备对证书链和挑战码进行签名。S618. The electronic device signs the certificate chain and the challenge code.
S619,电子设备向配置器发送认证响应,包括挑战码、证书链和签名。S619. The electronic device sends an authentication response to the configurator, including a challenge code, a certificate chain, and a signature.
S620,配置器认证电子设备。S620, the configurator authenticates the electronic device.
其中,挑战码用于基于挑战/响应方式的身份认证机制。Among them, the challenge code is used for the identity authentication mechanism based on the challenge/response method.
简言之,S616至620(即位于上方的虚线框中的流程)可理解为基于挑战/响应方式的身份认证过程。具体而言,配置器生成挑战码,并向电子设备发送认证请求,该认证请求中包括该挑战码。电子设备收到挑战码后,根据电子设备和配置器之间共享的密钥信息以及收到的挑战码做出相应的应答,即认证响应。配置器可以根据认证响应确定是否接受电子设备的身份声明。In short, S616 to 620 (that is, the process in the dotted box above) can be understood as an identity authentication process based on a challenge/response method. Specifically, the configurator generates a challenge code, and sends an authentication request to the electronic device, and the authentication request includes the challenge code. After receiving the challenge code, the electronic device makes a corresponding response according to the key information shared between the electronic device and the configurator and the received challenge code, that is, an authentication response. The configurator may determine whether to accept the identity statement of the electronic device according to the authentication response.
此外,S617至620也可以理解为电子设备进行配网前的认证过程。In addition, S617 to S620 can also be understood as an authentication process before the electronic equipment is distributed to the network.
S621,配置器向电子设备发送配网数据,包括云的URL,注册码、设备标识,服务集标识符(Service Set Identifier,SSID)、密码。S621. The configurator sends network configuration data to the electronic device, including cloud URL, registration code, device identifier, service set identifier (Service Set Identifier, SSID), and password.
其中,SSID和密码可用于接入网络。例如,SSID和密码可用于接入家庭网络。Among them, SSID and password can be used to access the network. For example, an SSID and password can be used to access a home network.
当然,在S621中,该配网数据也可额外包括S629中涉及的挑战码。即,配置器向电子设备发送包括挑战码的配网数据。Of course, in S621, the network configuration data may additionally include the challenge code involved in S629. That is, the configurator sends the network configuration data including the challenge code to the electronic device.
S622,电子设备向配置器发送配网响应。S622. The electronic device sends a network configuration response to the configurator.
S623,电子设备连接本地网络。S623. The electronic device connects to the local network.
S624,配置器连接本地网络。S624. The configurator connects to the local network.
S625,配置器向服务器发送认证通知,包括设备标识。S625. The configurator sends an authentication notification to the server, including the device identification.
其中,该认证通知可以用于指示电子设备在接入本地网络之前已通过配置器的身份认证。或者说,该认证通知可以用于指示电子设备已做过或已经过身份认证。Wherein, the authentication notification may be used to indicate that the electronic device has passed the identity authentication of the configurator before accessing the local network. In other words, the authentication notification may be used to indicate that the electronic device has done or passed identity authentication.
S626,电子设备和服务器之间建立单向TLS。S626. Establish a one-way TLS between the electronic device and the server.
其中,单项TLS可以理解为只需要电子设备对服务器的证书进行单向认证。简言之,单项TLS也可以理解为只需要进行单向认证的TLS。单向认证可以指只需要对一个端的证书合法性进行验证。Among them, the single-item TLS can be understood as only requiring the electronic device to perform one-way authentication on the server's certificate. In short, one-way TLS can also be understood as TLS that only requires one-way authentication. One-way authentication can mean that only one terminal needs to verify the validity of the certificate.
S627,电子设备向服务器发送注册请求,包括设备标识、注册码、设备信息、公钥和签名。S627. The electronic device sends a registration request to the server, including the device identification, registration code, device information, public key and signature.
S628,服务器确定电子设备是否已认证,若未认证,生成挑战码。S628. The server determines whether the electronic device has been authenticated, and if not, generates a challenge code.
例如,服务器可以基于S625确定电子设备是否已经经过身份认证。作为示例,若服务器接收到该认证通知,则说明该电子设备已经经过身份认证;若服务器没有收到该认证通知,则说明该电子设备没有经过身份认证。For example, the server may determine whether the electronic device has been authenticated based on S625. As an example, if the server receives the authentication notification, it means that the electronic device has passed identity authentication; if the server does not receive the authentication notification, it means that the electronic device has not passed identity authentication.
当然,若S621中的配网数据包括挑战码,S628中涉及的挑战码可以是S621中的挑战码。Of course, if the network configuration data in S621 includes a challenge code, the challenge code involved in S628 may be the challenge code in S621.
例如,该挑战码可以是一个随机数。For example, the challenge code can be a random number.
S629,服务器向电子设备发送认证请求,包括挑战码。S629. The server sends an authentication request, including a challenge code, to the electronic device.
需要说明的是,若S621中的配网数据包括挑战码,可省略S629。即,电子设备可直接基于S621中的挑战码向服务器发送认证响应。It should be noted that, if the network configuration data in S621 includes a challenge code, S629 may be omitted. That is, the electronic device may directly send an authentication response to the server based on the challenge code in S621.
S630,电子设备对证书链和挑战码进行签名。S630. The electronic device signs the certificate chain and the challenge code.
S631,电子设备向服务器发送认证响应,包括挑战码、证书链和签名。S631. The electronic device sends an authentication response to the server, including a challenge code, a certificate chain, and a signature.
S632,服务器对电子设备进行认证。S632. The server authenticates the electronic device.
简言之,S628至632(即位于下方的虚线框中的流程)可理解为基于挑战/响应方式的身份认证过程。具体而言,服务器在确定电子设备未进过认证的情况下,生成挑战码,并向电子设备发送认证请求,该认证请求中包括该挑战码。电子设备收到挑战码后,根据电子设备和服务器之间共享的密钥信息以及收到的挑战码做出相应的应答,即认证响应。服务器可以根据认证响应确定是否接受电子设备的身份声明。In short, S628 to 632 (that is, the process in the dotted box below) can be understood as an identity authentication process based on a challenge/response method. Specifically, when the server determines that the electronic device has not been authenticated, it generates a challenge code, and sends an authentication request to the electronic device, and the authentication request includes the challenge code. After receiving the challenge code, the electronic device makes a corresponding response according to the key information shared between the electronic device and the server and the received challenge code, that is, an authentication response. The server may determine whether to accept the identity statement of the electronic device according to the authentication response.
此外,S628至632也可以理解为服务器对电子设备的认证过程。In addition, S628 to S632 can also be understood as an authentication process of the server to the electronic device.
需要说明的是,S629至632为可选的。It should be noted that S629 to S632 are optional.
例如,在步骤S628中,若服务器确定电子设备已经过身份认证,可以忽略S629至632。For example, in step S628, if the server determines that the electronic device has been authenticated, steps S629 to S632 may be ignored.
S633,服务器基于公钥产生证书。S633. The server generates a certificate based on the public key.
S634,服务器项电子设备发送注册响应,包括设备标识和证书。S634, the server sends a registration response to the electronic device, including the device identification and the certificate.
S635,电子设备和服务器之间建立基于证书建立双向TLS。S635. Establish a mutual TLS based on the certificate between the electronic device and the server.
需要说明的是,S635是可选的。即可以在不建立双向TLS的情况下,电子设备直接向服务器发送登录请求。It should be noted that S635 is optional. That is, the electronic device can directly send a login request to the server without establishing a two-way TLS.
S636,电子设备向服务器发送登录请求,包括设备标识。S636. The electronic device sends a login request to the server, including the device identification.
S637,服务器向电子设备发送登录响应,包括访问令牌、刷新令牌以及有效期。S637. The server sends a login response to the electronic device, including the access token, the refresh token, and the validity period.
其中,访问令牌(access token)是用来描述进程或线程安全上下文的对象,令牌所包含的信息是与用户账户相关的进程或线程的身份和权限信息。当用户登录时,认证中心通过将用户输入的密码与储存在安全数据库中的密码进行对比。若密码正确,系统此时会为用户生成一个访问令牌。之后,该用户执行的每个进程都会拥有一个该访问令牌的拷贝。刷新令牌(refresh token)用来支持用户在得到资源拥有者的首次授权之后,在访问令牌失效之后,可以获取新的访问令牌,而不需要资源拥有者的再次授权。有效期(timeout)指访问令牌的时效。即,超出时效时,可以使用刷新令牌去重新获取访问令牌。Wherein, the access token (access token) is an object used to describe the process or thread security context, and the information contained in the token is the identity and permission information of the process or thread related to the user account. When a user logs in, the authentication center compares the password entered by the user with the password stored in the secure database. If the password is correct, an access token is now generated for the user. Afterwards, every process executed by that user will have a copy of that access token. The refresh token (refresh token) is used to support the user to obtain a new access token after the first authorization of the resource owner and after the access token expires, without re-authorization by the resource owner. The validity period (timeout) refers to the aging of the access token. That is, when the time limit expires, the refresh token can be used to reacquire the access token.
需要说明的是,在本申请实施例中,上述涉及的单项TLS可以理解为本申请中针对第一连接的具体实现。换言之,S627中涉及的注册请求,可以理解为本申请中针对第一请求的具体实现,注册请求中的设备标识、注册码、设备信息、公钥和签名可以理解为该第一请求中的第一信息,以便服务器基于注册请求对电子设备的身份进行认证。当然,也可以结合S625对电子设备的身份进行认证。It should be noted that, in this embodiment of the application, the above-mentioned single-item TLS can be understood as a specific implementation of the first connection in this application. In other words, the registration request involved in S627 can be understood as the specific implementation of the first request in this application, and the device identification, registration code, device information, public key and signature in the registration request can be understood as the first request in the first request. Information for the server to authenticate the identity of the electronic device based on the registration request. Of course, the identity of the electronic device may also be authenticated in conjunction with S625.
以上所述,仅为本申请的具体实施方式,但本申请的保护范围并不局限于此,任何熟悉本技术领域的技术人员在本申请揭露的技术范围内,可轻易想到变化或替换,都应涵盖在本申请的保护范围之内。因此,本申请的保护范围应以所述权利要求的保护范围为准。The above is only a specific implementation of the application, but the scope of protection of the application is not limited thereto. Anyone familiar with the technical field can easily think of changes or substitutions within the technical scope disclosed in the application. Should be covered within the protection scope of this application. Therefore, the protection scope of the present application should be determined by the protection scope of the claims.
为实现本申请实施例的方法,本申请实施例还提供了一种设备认证装置,如图8所示,该装置包括:In order to implement the method of the embodiment of the present application, the embodiment of the present application also provides a device authentication device, as shown in Figure 8, the device includes:
连接单元701,用于与第一服务器建立基于TLS协议的第一连接;A
发送单元702,用于基于所述第一连接,向所述第一服务器发送第一请求;所述第一请求用于请求对所述电子设备进行身份认证;所述第一请求基于第一信息生成;所述第一信息表征所述电子设备的数字证书;A sending
接收单元703,用于基于所述第一连接,接收所述第一服务器下发的关于所述第一请求的第一响应信息;所述第一响应信息中携带所述第一服务器对所述电子设备的身份认证结果。The receiving
在一实施例中,所述发送单元702基于所述第一连接,向所述第一服务器发送第一请求,所述第一请求包括所述电子设备的设备证书。In an embodiment, the sending
在一实施例中,所述发送单元702从所述产品证书中确定产品识别码PID;基于所述第一连接,向所述第一服务器发送第一请求;所述第一请求中至少携带所述PID与所述电子设备中预置的供应商标识VID;所述第一信息包括所述电子设备的产品证书。In one embodiment, the sending
在一实施例中,所述发送单元702基于所述第一连接,向所述第一服务器发送第一请求,所述第一请求中还携带第一密钥;所述第一密钥在所述电子设备首次上电时随机生成。In an embodiment, the sending
在一实施例中,所述发送单元702从所述电子设备的存储介质中读取所述第一信息;或,从网络中下载所述第一信息。In an embodiment, the sending
实际应用时,连接单元701、发送单元702、接收单元703可由设备认证装置中的处理器来实现。当然,处理器需要运行存储器中存储的程序来实现上述各程序模块的功能。In actual application, the
本申请实施例还提供了一种设备认证装置,如图9所示,该装置包括:The embodiment of this application also provides a device authentication device, as shown in Figure 9, the device includes:
连接单元801,用于与电子设备建立基于TLS协议的第一连接;A
接收单元802,用于基于所述第一连接,接收所述电子设备发送的第一请求;所述第一请求用于请求对所述电子设备进行身份认证;所述第一请求基于第一信息生成;所述第一信息表征所述电子设备的数字证书;The receiving
认证单元803,用于基于所述第一请求,对所述电子设备进行身份认证,得到身份认证结果;An
发送单元804,用于基于所述第一连接,向所述电子设备下发的关于所述第一请求的第一响应信息;所述第一响应信息中携带所述身份认证结果。The sending
在一实施例中,所述接收单元802基于所述第一连接,接收所述电子设备发送的第一请求,所述第一信息包括所述电子设备的设备证书;所述第一请求中至少携带PID和VID;所述发送单元804基于所述第一连接,向所述电子设备下发的关于所述第一请求的第一响应信息,包括:In an embodiment, the receiving
在对所述电子设备的身份认证成功的情况下,基于所述PID和所述VID生成所述电子设备的设备证书;If the identity authentication of the electronic device is successful, generating a device certificate of the electronic device based on the PID and the VID;
向所述电子设备下发所述第一响应信息;所述第一响应信息中携带所述设备证书。Sending the first response information to the electronic device; the first response information carries the device certificate.
在一实施例中,所述接收单元802基于所述第一连接,接收所述电子设备发送的第一请求,所述第一请求还携带第一密钥;所述第一密钥在所述电子设备首次上电时随机生成;所述认证单元803基于所述第一请求,对所述电子设备进行身份认证,得到身份认证结果,包括以下之一:In an embodiment, the receiving
在所述电子设备未激活过的情况下,对应保存所述VID和所述第一密钥;或,If the electronic device has not been activated, store the VID and the first key correspondingly; or,
在所述电子设备曾经激活过的情况下,确认所述第一请求中的第一密钥与第二密钥是否相同;所述第二密钥为所述第一服务器保存的所述VID对应的密钥;当所述第一密钥与所述第二密钥相同时,得到对所述电子设备的身份认证成功的身份认证结果;当所述第一密钥与所述第二密钥不同时,得到对所述电子设备的身份认证失败的身份认证结果。In the case that the electronic device has been activated, confirm whether the first key in the first request is the same as the second key; the second key corresponds to the VID saved by the first server key; when the first key is the same as the second key, obtain an identity authentication result that the identity authentication of the electronic device is successful; when the first key is the same as the second key At the same time, an identity authentication result that the identity authentication of the electronic device fails is obtained.
在一实施例中,在对所述电子设备的身份认证失败的情况下,连接单元801还包括:In an embodiment, when the identity authentication of the electronic device fails, the
终止所述第一连接。Terminate the first connection.
实际应用时,连接单元801、接收单元802、认证单元803、发送单元804可由设备认证装置中的处理器来实现。当然,处理器需要运行存储器中存储的程序来实现上述各程序模块的功能。In actual application, the
需要说明的是,上述图8和图9实施例提供的设备认证装置在进行设备认证时,仅以上述各程序模块的划分进行举例说明,实际应用中,可以根据需要而将上述处理分配由不同的程序模块完成,即将装置的内部结构划分成不同的程序模块,以完成以上描述的全部或者部分处理。另外,上述实施例提供的设备认证装置与设备认证方法实施例属于同一构思,其具体实现过程详见方法实施例,这里不再赘述。It should be noted that, when the device authentication device provided by the above-mentioned embodiments in FIG. 8 and FIG. The program modules are completed, that is, the internal structure of the device is divided into different program modules, so as to complete all or part of the processing described above. In addition, the device authentication device and the device authentication method embodiments provided in the above embodiments belong to the same idea, and the specific implementation process thereof is detailed in the method embodiments, and will not be repeated here.
基于上述程序模块的硬件实现,且为了实现本申请实施例电子设备侧的方法,本申请实施例还提供了一种电子设备,如图10所示,电子设备900包括:Based on the hardware implementation of the above program modules, and in order to implement the method on the electronic device side of the embodiment of the present application, the embodiment of the present application also provides an electronic device. As shown in FIG. 10 , the
第一通信接口901,能够与第一服务器进行信息交互;The
第一处理器902,与所述第一通信接口901连接,以实现与第一服务器进行信息交互,用于运行计算机程序时,执行上述电子设备侧一个或多个技术方案提供的方法。而所述计算机程序存储在第一存储器903上。The
具体地,所述第一通信接口901,用于与第一服务器建立基于安全传输层TLS协议的第一连接;基于所述第一连接,向所述第一服务器发送第一请求;所述第一请求用于请求对所述电子设备进行身份认证;所述第一请求基于第一信息生成;所述第一信息表征所述电子设备的数字证书;基于所述第一连接,接收所述第一服务器下发的关于所述第一请求的第一响应信息;所述第一响应信息中携带所述第一服务器对所述电子设备的身份认证结果。Specifically, the
在一实施例中,所述第一信息包括所述电子设备的设备证书。In an embodiment, the first information includes a device certificate of the electronic device.
在一实施例中,所述第一信息包括所述电子设备的产品证书;所述第一通信接口901基于所述第一连接,向所述第一服务器发送第一请求,包括:In an embodiment, the first information includes the product certificate of the electronic device; the
从所述产品证书中确定产品识别码PID;determining the product identification code PID from the product certificate;
基于所述第一连接,向所述第一服务器发送第一请求;所述第一请求中至少携带所述PID与所述电子设备中预置的供应商标识VID。Based on the first connection, a first request is sent to the first server; the first request carries at least the PID and the VID preset in the electronic device.
在一实施例中,所述第一请求中还携带第一密钥;所述第一密钥在所述电子设备首次上电时随机生成。In an embodiment, the first request also carries a first key; the first key is randomly generated when the electronic device is powered on for the first time.
在一实施例中,第一处理器902,还用于In one embodiment, the
从所述电子设备的存储介质中读取所述第一信息;或,reading the first information from a storage medium of the electronic device; or,
从第二服务器中下载所述第一信息;所述第二服务器上存储有至少一个电子设备中的每个电子设备对应的第一信息。downloading the first information from a second server; the first information corresponding to each of the at least one electronic device is stored on the second server.
需要说明的是:第一处理器902和第一通信接口901的具体处理过程可参照上述方法理解。It should be noted that the specific processing procedures of the
当然,实际应用时,电子设备900中的各个组件通过总线系统904耦合在一起。可理解,总线系统904用于实现这些组件之间的连接通信。总线系统904除包括数据总线之外,还包括电源总线、控制总线和状态信号总线。但是为了清楚说明起见,在图10中将各种总线都标为总线系统904。Of course, in practical applications, various components in the
本申请实施例中的第一存储器903用于存储各种类型的数据以支持电子设备900的操作。这些数据的示例包括:用于在电子设备900上操作的任何计算机程序。The
上述本申请实施例揭示的方法可以应用于所述第一处理器902中,或者由所述第一处理器902实现。所述第一处理器902可能是一种集成电路芯片,具有信号的处理能力。在实现过程中,上述方法的各步骤可以通过所述第一处理器902中的硬件的集成逻辑电路或者软件形式的指令完成。上述的所述第一处理器902可以是通用处理器、数字信号处理器(DSP,Digital Signal Processor),或者其他可编程逻辑器件、分立门或者晶体管逻辑器件、分立硬件组件等。所述第一处理器902可以实现或者执行本申请实施例中的公开的各方法、步骤及逻辑框图。通用处理器可以是微处理器或者任何常规的处理器等。结合本申请实施例所公开的方法的步骤,可以直接体现为硬件译码处理器执行完成,或者用译码处理器中的硬件及软件模块组合执行完成。软件模块可以位于存储介质中,该 存储介质位于第一存储器903,所述第一处理器902读取第一存储器903中的信息,结合其硬件完成前述方法的步骤。The methods disclosed in the foregoing embodiments of the present application may be applied to the
在示例性实施例中,电子设备900可以被一个或多个应用专用集成电路(ASIC,Application Specific Integrated Circuit)、DSP、可编程逻辑器件(PLD,Programmable Logic Device)、复杂可编程逻辑器件(CPLD,Complex Programmable Logic Device)、现场可编程门阵列(FPGA,Field-Programmable Gate Array)、通用处理器、控制器、微控制器(MCU,Micro Controller Unit)、微处理器(Microprocessor)、或者其他电子元件实现,用于执行前述方法。In an exemplary embodiment, the
基于上述程序模块的硬件实现,且为了实现本申请实施例第一服务器侧的方法,本申请实施例还提供了一种第一服务器,如图11所示,该第一服务器1000包括:Based on the hardware implementation of the above program modules, and in order to implement the method on the first server side of the embodiment of the present application, the embodiment of the present application further provides a first server, as shown in FIG. 11 , the first server 1000 includes:
第二通信接口1001,能够与电子设备进行信息交互;The
第二处理器1002,与所述第二通信接口1002连接,以实现与电子设备进行信息交互,用于运行计算机程序时,执行上述第一服务器侧一个或多个技术方案提供的方法。而所述计算机程序存储在第二存储器1003上。The
具体地,所述第二通信接口1001,用于与电子设备建立基于TLS协议的第一连接;基于所述第一连接,接收所述电子设备发送的第一请求;所述第一请求用于请求对所述电子设备进行身份认证;所述第一请求基于第一信息生成;所述第一信息表征所述电子设备的数字证书;Specifically, the
所述第二处理器1002,用于基于所述第一请求,对所述电子设备进行身份认证,得到身份认证结果;The
所述第二通信接口1001,用于基于所述第一连接,向所述电子设备下发的关于所述第一请求的第一响应信息;所述第一响应信息中携带所述身份认证结果。The
在一实施例中,所述第一信息包括所述电子设备的产品证书;所述第一请求中至少携带PID和VID;所述第二处理器1002,用于在对所述电子设备的身份认证成功的情况下,基于所述PID和所述VID确定所述电子设备的设备证书;In an embodiment, the first information includes the product certificate of the electronic device; the first request carries at least PID and VID; the
所述第二通信接口1001,用于向所述电子设备下发所述第一响应信息;所述第一响应信息中携带所述设备证书。The
在一实施例中,所述第一请求还携带第一密钥;所述第一密钥在所述电子设备首次上电时随机生成时,所述第二处理器1002对所述电子设备进行身份认证,得到身份认证结果,包括:In an embodiment, the first request also carries a first key; when the first key is randomly generated when the electronic device is powered on for the first time, the
在所述电子设备未激活过的情况下,对应保存所述VID和所述第一密钥;或,If the electronic device has not been activated, store the VID and the first key correspondingly; or,
在所述电子设备曾经激活过的情况下,确认所述第一请求中的第一密钥与第二密钥是否相同;所述第二密钥为所述第一服务器保存的所述VID对应的密钥;当所述第一密钥与所述第二密钥相同时,得到对所述电子设备的身份认证成功的身份认证结果;当所述第一密钥与所述第二密钥不同时,得到对所述电子设备的身份认证失败的身份认证结果。In the case that the electronic device has been activated, confirm whether the first key in the first request is the same as the second key; the second key corresponds to the VID saved by the first server key; when the first key is the same as the second key, obtain an identity authentication result that the identity authentication of the electronic device is successful; when the first key is the same as the second key At the same time, an identity authentication result that the identity authentication of the electronic device fails is obtained.
在一实施例中,在对所述电子设备的身份认证失败的情况下,所述第二通信接口1001还用于终止所述第一连接。In an embodiment, when the identity authentication of the electronic device fails, the
需要说明的是:第二处理器1002和第二通信接口1001的具体处理过程可参照上述方法理解。It should be noted that: the specific processing process of the
当然,实际应用时,第一服务器1000中的各个组件通过总线系统1004耦合在一起。可理解,总线系统1004用于实现这些组件之间的连接通信。总线系统1004除包括数据总线之外,还包括电源总线、控制总线和状态信号总线。但是为了清楚说明起见,在图11中将各种总线都标为总线系统1004。Of course, in actual application, various components in the first server 1000 are coupled together through the
本申请实施例中的第二存储器1003用于存储各种类型的数据以支持第一服务器1000操作。这些数据的示例包括:用于在第一服务器1000上操作的任何计算机程序。The
上述本申请实施例揭示的方法可以应用于所述第二处理器1002中,或者由所述第二处理器1002实现。所述第二处理器1002可能是一种集成电路芯片,具有信号的处理能力。在实现过程中,上述方法的各步骤可以通过所述第二处理器1002中的硬件的集成逻辑电路或者软件形式的指令完成。上述的所述第二处理器1002可以是通用处理器、DSP,或者其他可编程逻辑器件、分立门或者晶体管逻辑器件、分立硬件组件等。所述第二处理器1002可以实现或者执行本申请实施例中的公开的各方法、步骤及逻辑框图。通用处理器可以是微处理器或者任何常规的处理器等。结合本申请实施例所公开的方法的步骤,可以直接体现为硬件译码处理器执行完成,或者用译码处理器中的硬件及软件模块组合执行完成。软件模块可以位于存储介质中,该存储介质位于第二存储器1003,所述第二处理器1002读取第二存储器1003中的信息,结合其硬件完成前述方法的步骤。The methods disclosed in the foregoing embodiments of the present application may be applied to the
在示例性实施例中,第一服务器1000可以被一个或多个ASIC、DSP、PLD、CPLD、FPGA、通用处理器、控制器、MCU、Microprocessor、或其他电子元件实现,用于执行前述方法。In an exemplary embodiment, the first server 1000 may be implemented by one or more ASICs, DSPs, PLDs, CPLDs, FPGAs, general processors, controllers, MCUs, Microprocessors, or other electronic components for performing the aforementioned methods.
可以理解,本申请实施例的存储器(第一存储器903、第二存储器1003)可以是易失性存储器或者非易失性存储器,也可包括易失性和非易失性存储器两者。其中,非易失性存储器可以是只读存储器(ROM,Read Only Memory)、可编程只读存储器(PROM,Programmable Read-Only Memory)、可擦除可编程只读存储器(EPROM,Erasable Programmable Read-Only Memory)、电可擦除可编程只读存储器(EEPROM,Electrically Erasable Programmable Read-Only Memory)、磁性随机存取存储器(FRAM,ferromagnetic random access memory)、快闪存储器(Flash Memory)、磁表面存储器、光盘、或只读光盘(CD-ROM,Compact Disc Read-Only Memory);磁表面存储器可以是磁盘存储器或磁带存储器。易失性存储器可以是随机存取存储器(RAM,Random Access Memory),其用作外部高速缓存。通过示例性但不是限制性说明,许多形式的RAM可用,例如静态随机存取存储器(SRAM,Static Random Access Memory)、同步静态随机存取存储器(SSRAM,Synchronous Static Random Access Memory)、动态随机存取存储器(DRAM,Dynamic Random Access Memory)、同步动态随机存取存储器(SDRAM,Synchronous Dynamic Random Access Memory)、双倍数据速率同步动态随机存取存储器(DDRSDRAM,Double Data Rate Synchronous Dynamic Random Access Memory)、增强型同步动态随机存取存储器(ESDRAM,Enhanced Synchronous Dynamic Random Access Memory)、同步连接动态随机存取存储器(SLDRAM,SyncLink Dynamic Random Access Memory)、直接内存总线随机存取存储器(DRRAM,Direct Rambus Random Access Memory)。本申请实施例描述的存储器旨在包括但不限于这些和任意其它适合类型的存储器。It can be understood that the storage (the
在示例性实施例中,本申请实施例还提供了一种存储介质,即计算机存储介质,具体为计算机可读存储介质,例如包括存储计算机程序的第一存储器903,上述计算机程序可由电子设备900的第一处理器902执行,以完成前述电子设备侧方法所述步骤。再比如包括存储计算机程序的第二存储器1003,上述计算机程序可由第一服务器1000的第二处理器1002执行,以完成前述第一服务器侧方法所述步骤。计算机可读存储介质可以是FRAM、ROM、PROM、EPROM、EEPROM、Flash Memory、磁表面存储器、光盘、或CD-ROM等存储器。In an exemplary embodiment, the embodiment of the present application also provides a storage medium, that is, a computer storage medium, specifically a computer-readable storage medium, for example, including a
需要说明的是:“第一”、“第二”等是用于区别类似的对象,而不必用于描述特定的顺序或先后次序。It should be noted that: "first", "second", etc. are used to distinguish similar objects, and not necessarily used to describe a specific order or sequence.
另外,本申请实施例所记载的技术方案之间,在不冲突的情况下,可以任意组合。In addition, the technical solutions described in the embodiments of the present application may be combined arbitrarily if there is no conflict.
以上所述,仅为本申请的较佳实施例而已,并非用于限定本申请的保护范围。The above descriptions are only preferred embodiments of the present application, and are not intended to limit the protection scope of the present application.
Claims (14)
Translated fromChineseApplications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| PCT/CN2020/129523WO2022104556A1 (en) | 2020-11-17 | 2020-11-17 | Device authentication method and apparatus, and electronic device, server and storage medium |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| CN116438532Atrue CN116438532A (en) | 2023-07-14 |
Family
ID=81707986
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN202080106970.3APendingCN116438532A (en) | 2020-11-17 | 2020-11-17 | Device authentication method, device, electronic device, server and storage medium |
Country Status (2)
| Country | Link |
|---|---|
| CN (1) | CN116438532A (en) |
| WO (1) | WO2022104556A1 (en) |
Family Cites Families (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US10362021B2 (en)* | 2016-05-31 | 2019-07-23 | Airwatch Llc | Device authentication based upon tunnel client network requests |
| CN106534086B (en)* | 2016-10-31 | 2019-08-30 | 深圳数字电视国家工程实验室股份有限公司 | A kind of equipment authentication method, terminal device, server and system |
| CN111083102A (en)* | 2019-10-23 | 2020-04-28 | 全球能源互联网研究院有限公司 | Internet of things data processing method, device and equipment |
| CN111949967B (en)* | 2020-08-31 | 2024-06-18 | Oppo广东移动通信有限公司 | Device authentication method, device, electronic device, server and storage medium |
- 2020
- 2020-11-17CNCN202080106970.3Apatent/CN116438532A/enactivePending
- 2020-11-17WOPCT/CN2020/129523patent/WO2022104556A1/ennot_activeCeased
Also Published As
| Publication number | Publication date |
|---|---|
| WO2022104556A1 (en) | 2022-05-27 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| JP5745690B2 (en) | Dynamic platform reconfiguration with multi-tenant service providers | |
| JP2020523806A (en) | Internet of Things (IOT) device management | |
| CN111949967B (en) | Device authentication method, device, electronic device, server and storage medium | |
| CN109639427A (en) | A kind of method and apparatus that data are sent | |
| JP2012514255A (en) | Apparatus and method for granting access rights to apparatus | |
| CN115037480B (en) | Device authentication and verification method, device, equipment and storage medium | |
| JP6650513B2 (en) | Method and device for registering and authenticating information | |
| CN103999496A (en) | Method for transferring control of a security module from a first entity to a second entity | |
| US20240187262A1 (en) | Encrypted and authenticated firmware provisioning with root-of-trust based security | |
| CN114866251A (en) | A device interconnection security authentication system, method, device, server and medium | |
| WO2014183704A1 (en) | Software registration control method, authentication server and terminal | |
| CN115150831B (en) | Method, device, server and medium for processing network access request | |
| US20240380616A1 (en) | Secure root-of-trust enrolment and identity management of embedded devices | |
| KR20170111809A (en) | Bidirectional authentication method using security token based on symmetric key | |
| US20090327704A1 (en) | Strong authentication to a network | |
| WO2016165662A1 (en) | Mobile phone quasi-digital certificate subsystem, and system and method thereof | |
| CN117728958A (en) | A communication method, device and system | |
| US20240195641A1 (en) | Interim root-of-trust enrolment and device-bound public key registration | |
| CN116438532A (en) | Device authentication method, device, electronic device, server and storage medium | |
| WO2023116239A1 (en) | Permission determination method and apparatus, and computer device and computer-readable storage medium | |
| CN115941512A (en) | Network device management method, network device and electronic device | |
| WO2023240587A1 (en) | Device permission configuration method and apparatus, and terminal device | |
| TWI673621B (en) | Information registration, authentication method and device | |
| TW202139037A (en) | Method and apparatus for certifying an application-specific key and for requesting such certification | |
| KR20130125201A (en) | Apparatus and method for authenticating based on public key |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination |