CN116318719A - Setting value document verification method, device, equipment and medium - Google Patents
Setting value document verification method, device, equipment and mediumDownload PDFInfo
- Publication number
- CN116318719A CN116318719ACN202310179844.6ACN202310179844ACN116318719ACN 116318719 ACN116318719 ACN 116318719ACN 202310179844 ACN202310179844 ACN 202310179844ACN 116318719 ACN116318719 ACN 116318719A
- Authority
- CN
- China
- Prior art keywords
- digital
- verified
- electronic document
- document
- signature
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Pending
Links
Images
Classifications
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/32—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials
- H04L9/3247—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials involving digital signatures
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/04—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks
- H04L63/0428—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks wherein the data content is protected, e.g. by encrypting or encapsulating the payload
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/12—Applying verification of the received information
- H04L63/123—Applying verification of the received information received data contents, e.g. message integrity
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/32—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials
- H04L9/3236—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials using cryptographic hash functions
- H04L9/3239—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials using cryptographic hash functions involving non-keyed hash functions, e.g. modification detection codes [MDCs], MD5, SHA or RIPEMD
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/32—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials
- H04L9/3297—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials involving time stamps, e.g. generation of time stamps
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L2463/00—Additional details relating to network architectures or network communication protocols for network security covered by H04L63/00
- H04L2463/121—Timestamp
- Y—GENERAL TAGGING OF NEW TECHNOLOGICAL DEVELOPMENTS; GENERAL TAGGING OF CROSS-SECTIONAL TECHNOLOGIES SPANNING OVER SEVERAL SECTIONS OF THE IPC; TECHNICAL SUBJECTS COVERED BY FORMER USPC CROSS-REFERENCE ART COLLECTIONS [XRACs] AND DIGESTS
- Y04—INFORMATION OR COMMUNICATION TECHNOLOGIES HAVING AN IMPACT ON OTHER TECHNOLOGY AREAS
- Y04S—SYSTEMS INTEGRATING TECHNOLOGIES RELATED TO POWER NETWORK OPERATION, COMMUNICATION OR INFORMATION TECHNOLOGIES FOR IMPROVING THE ELECTRICAL POWER GENERATION, TRANSMISSION, DISTRIBUTION, MANAGEMENT OR USAGE, i.e. SMART GRIDS
- Y04S40/00—Systems for electrical power generation, transmission, distribution or end-user application management characterised by the use of communication or information technologies, or communication or information technology specific aspects supporting them
- Y04S40/20—Information technology specific aspects, e.g. CAD, simulation, modelling, system security
Landscapes
- Engineering & Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- Computer Networks & Wireless Communication (AREA)
- Signal Processing (AREA)
- Computer Hardware Design (AREA)
- Computing Systems (AREA)
- General Engineering & Computer Science (AREA)
- Storage Device Security (AREA)
Abstract
Description
Translated fromChinese技术领域technical field
本发明涉及文档加密传输技术领域,尤其涉及一种整定值文档验证方法、装置、设备和介质。The invention relates to the technical field of document encryption transmission, in particular to a method, device, device and medium for verifying a set value document.
背景技术Background technique
继电保护系统是电力系统安全稳定运行的第一道防线,而整定值的准确是继电保护及安全自动装置正确动作的重要保证。随着电力系统对调度、管理、运维等各专业自动化水平的要求不断提高,装置整定值的管理也应实现全程可控的闭环管理。The relay protection system is the first line of defense for the safe and stable operation of the power system, and the accuracy of the setting value is an important guarantee for the correct operation of the relay protection and safety automatic devices. With the continuous improvement of the power system's requirements for the automation level of dispatching, management, operation and maintenance, etc., the management of device setting values should also achieve a fully controllable closed-loop management.
目前电力自动装置整定值文档在完成编制、校核、审核、批准等流程环节后,一般采用手工签名或者在电子文档中嵌入签名图片表示签字确认。At present, after completing the preparation, verification, review, approval and other process links of the setting value documents of electric power automatic devices, manual signatures are generally used or signature pictures are embedded in electronic documents to indicate signature confirmation.
但上述整定值文档的签名认证方法不便于使用信息化手段对文档及签名的关联性、真实性、完整性等进行验证,从而导致电力系统的安全性降低。However, the signature authentication method of the above-mentioned setting value document is not convenient to use information technology to verify the relevance, authenticity, and integrity of the document and the signature, which leads to a decrease in the security of the power system.
发明内容Contents of the invention
本发明提供了一种整定值文档验证方法、装置、设备和介质,解决了现有技术中整定值文档的签名认证方法不便于使用信息化手段对文档及签名的关联性、真实性、完整性等进行验证,从而导致电力系统的安全性降低的技术问题。The present invention provides a set value document verification method, device, equipment and medium, which solves the problem that the signature verification method of the set value document in the prior art is inconvenient to use information means to verify the relevance, authenticity and integrity of the document and the signature And so on to verify, which leads to the technical problem of reducing the security of the power system.
本发明第一方面提供的一种整定值文档验证方法,包括:A setting value document verification method provided by the first aspect of the present invention includes:
当接收到电力系统整定值文档时,计算所述电力系统整定值文档内的原文对应的第一数字摘要;When receiving the power system setting value document, calculate the first digital abstract corresponding to the original text in the power system setting value document;
采用第一私钥对所述第一数字摘要进行加密,得到第一数字签名并获取对应的签名时间戳;Encrypting the first digital digest with a first private key to obtain a first digital signature and a corresponding signature timestamp;
组合所述第一数字摘要与所述签名时间戳并采用第二私钥进行加密,得到第二数字签名;combining the first digital digest and the signature timestamp and encrypting with a second private key to obtain a second digital signature;
采用所述原文、所述第一数字签名、所述签名时间戳和所述第二数字签名,生成电子文档并传输至目标电力系统;Using the original text, the first digital signature, the signature timestamp and the second digital signature to generate an electronic document and transmit it to the target power system;
当所述目标电力系统接收到所述电子文档时,对所述电子文档进行解密,判断所述电子文档是否被篡改;When the target power system receives the electronic document, decrypt the electronic document to determine whether the electronic document has been tampered with;
若所述电子文档未被篡改,则采用所述电子文档配置所述目标电力系统内的整定值。If the electronic file has not been tampered with, the electronic file is used to configure the setting value in the target power system.
可选地,所述组合所述第一数字摘要与所述签名时间戳并采用第二私钥进行加密,得到第二数字签名的步骤,包括:Optionally, the step of combining the first digital digest and the signature timestamp and encrypting with a second private key to obtain a second digital signature includes:
组合所述第一数字摘要和所述签名时间戳,生成更新文档;combining the first digital digest and the signature timestamp to generate an update document;
计算所述更新文档对应的第二数字摘要;calculating a second digital digest corresponding to the updated document;
采用所述第二私钥对所述第二数字摘要进行加密,得到第二数字签名。Encrypting the second digital digest with the second private key to obtain a second digital signature.
可选地,所述当所述目标电力系统接收到所述电子文档时,对所述电子文档进行解密,判断所述电子文档是否被篡改的步骤,包括:Optionally, when the target power system receives the electronic document, the step of decrypting the electronic document and determining whether the electronic document has been tampered with includes:
当所述目标电力系统接收到所述电子文档时,解析所述电子文档,得到待验证原文、第一待验证数字签名、待验证时间戳和第二待验证数字签名;When the target power system receives the electronic document, parse the electronic document to obtain the original text to be verified, the first digital signature to be verified, the time stamp to be verified, and the second digital signature to be verified;
根据所述待验证原文与所述第一待验证数字签名,判断所述待验证原文是否被篡改;judging whether the original text to be verified has been tampered with according to the original text to be verified and the first digital signature to be verified;
若判定所述待验证原文未被篡改,则根据所述待验证时间戳与所述第二待验证数字签名,判断所述电子文档是否被篡改。If it is determined that the original text to be verified has not been tampered with, it is determined whether the electronic document has been tampered with according to the time stamp to be verified and the second digital signature to be verified.
可选地,所述根据所述待验证原文与所述第一待验证数字签名,判断所述待验证原文是否被篡改的步骤,包括:Optionally, the step of judging whether the original text to be verified has been tampered with according to the original text to be verified and the first digital signature to be verified includes:
计算所述待验证原文对应的第三数字摘要;Calculating the third digital abstract corresponding to the original text to be verified;
采用第一公钥对所述第一待验证数字签名进行解密,得到第四数字摘要;Decrypting the first digital signature to be verified by using the first public key to obtain a fourth digital digest;
比对所述第三数字摘要与所述第四数字摘要;comparing the third digital digest with the fourth digital digest;
若所述第三数字摘要与所述第四数字摘要相同,则判定所述待验证原文未被篡改;If the third digital abstract is the same as the fourth digital abstract, it is determined that the original text to be verified has not been tampered with;
若所述第三数字摘要与所述第四数字摘要不相同,则判定所述待验证原文被篡改。If the third digital digest is different from the fourth digital digest, it is determined that the original text to be verified has been tampered with.
可选地,所述若判定所述待验证原文未被篡改,则根据所述待验证时间戳与所述第二待验证数字签名,判断所述电子文档是否被篡改的步骤,包括:Optionally, if it is determined that the original text to be verified has not been tampered with, the step of judging whether the electronic document has been tampered with according to the time stamp to be verified and the second digital signature to be verified includes:
若判定所述待验证原文未被篡改,则组合所述待验证时间戳与所述第三数字摘要,得到待验证文档;If it is determined that the original text to be verified has not been tampered with, combining the time stamp to be verified and the third digital abstract to obtain the document to be verified;
计算所述待验证文档对应的第五数字摘要;calculating a fifth digital digest corresponding to the document to be verified;
采用第二公钥对所述第二待验证数字签名进行解密,得到第六数字摘要;Decrypting the second digital signature to be verified by using the second public key to obtain a sixth digital digest;
比对所述第五数字摘要与所述第六数字摘要;comparing said fifth digital digest with said sixth digital digest;
若所述第五数字摘要与所述第六数字摘要相同,则判定所述电子文档未被篡改;If the fifth digital abstract is the same as the sixth digital abstract, it is determined that the electronic document has not been tampered with;
若所述第五数字摘要与所述第六数字摘要不相同,则判定所述电子文档被篡改。If the fifth digital abstract is different from the sixth digital abstract, it is determined that the electronic document has been tampered with.
可选地,所述若所述电子文档未被篡改,则采用所述电子文档配置所述目标电力系统内的整定值的步骤,包括:Optionally, if the electronic document has not been tampered with, the step of using the electronic document to configure the setting value in the target power system includes:
若所述电子文档未被篡改,则通过所述目标电力系统从所述电子文档中获取待验证原文;If the electronic document has not been tampered with, the original text to be verified is obtained from the electronic document through the target power system;
按照配置项目检索所述待验证原文,匹配各个所述配置项目分别对应的整定值;Retrieve the original text to be verified according to the configuration items, and match the setting values corresponding to each of the configuration items;
将各所述整定值按照所述配置项目分别加载至所述目标电力系统。Each of the setting values is respectively loaded to the target power system according to the configuration items.
可选地,所述签名时间戳由所述目标电力系统认可的时间戳机构提供。Optionally, the signature time stamp is provided by a time stamp mechanism recognized by the target power system.
本发明第二方面提供了一种整定值文档验证装置,包括:The second aspect of the present invention provides a setting value document verification device, including:
第一数字摘要生成模块,用于当接收到电力系统整定值文档时,计算所述电力系统整定值文档内的原文对应的第一数字摘要;The first digital summary generation module is used to calculate the first digital summary corresponding to the original text in the power system setting value document when receiving the power system setting value document;
一次加密模块,用于采用第一私钥对所述第一数字摘要进行加密,得到第一数字签名并获取对应的签名时间戳;A primary encryption module, configured to encrypt the first digital digest with a first private key, obtain a first digital signature and obtain a corresponding signature timestamp;
二次加密模块,用于组合所述第一数字摘要与所述签名时间戳并采用第二私钥进行加密,得到第二数字签名;A secondary encryption module, configured to combine the first digital digest and the signature timestamp and encrypt with a second private key to obtain a second digital signature;
电子文档生成模块,用于采用所述原文、所述第一数字签名、所述签名时间戳和所述第二数字签名,生成电子文档并传输至目标电力系统;An electronic document generating module, configured to use the original text, the first digital signature, the signature timestamp and the second digital signature to generate an electronic document and transmit it to the target power system;
篡改判断模块,用于当所述目标电力系统接收到所述电子文档时,对所述电子文档进行解密,判断所述电子文档是否被篡改;A tampering judging module, configured to decrypt the electronic document when the target power system receives the electronic document, and judge whether the electronic document has been tampered with;
整定值配置模块,用于若所述电子文档未被篡改,则采用所述电子文档配置所述目标电力系统内的整定值。A setting value configuration module, configured to use the electronic file to configure the setting value in the target power system if the electronic file has not been tampered with.
本发明第三方面提供了一种电子设备,包括存储器及处理器,所述存储器中储存有计算机程序,所述计算机程序被所述处理器执行时,使得所述处理器执行如本发明第一方面任一项所述的整定值文档验证方法的步骤。The third aspect of the present invention provides an electronic device, including a memory and a processor, wherein a computer program is stored in the memory, and when the computer program is executed by the processor, the processor executes the first method according to the present invention. The steps of the setting value document verification method described in any one of the aspects.
本发明第四方面提供了一种计算机可读存储介质,其上存储有计算机程序,所述计算机程序被执行时实现如本发明第一方面任一项所述的整定值文档验证方法。A fourth aspect of the present invention provides a computer-readable storage medium, on which a computer program is stored, and when the computer program is executed, the setting value document verification method according to any one of the first aspect of the present invention is implemented.
从以上技术方案可以看出,本发明具有以下优点:As can be seen from the above technical solutions, the present invention has the following advantages:
当接收到电力系统整定值文档时,计算电力系统整定值文档内的原文对应的第一数字摘要;采用第一私钥对第一数字摘要进行加密,得到第一数字签名并获取对应的签名时间戳;组合第一数字摘要与签名时间戳并采用第二私钥进行加密,得到第二数字签名;采用原文、第一数字签名、签名时间戳和第二数字签名,生成电子文档并传输至目标电力系统;当目标电力系统接收到电子文档时,对电子文档进行解密,判断电子文档是否被篡改;若电子文档未被篡改,则采用电子文档配置目标电力系统内的整定值,从而解决现有技术中整定值文档的签名认证方法不便于使用信息化手段对文档及签名的关联性、真实性、完整性等进行验证,从而导致电力系统的安全性降低的技术问题,提高电力系统安全性。When receiving the power system setting value document, calculate the first digital digest corresponding to the original text in the power system setting value document; use the first private key to encrypt the first digital digest, obtain the first digital signature and obtain the corresponding signature time stamp; combine the first digital abstract and signature timestamp and encrypt with the second private key to obtain the second digital signature; use the original text, the first digital signature, the signature timestamp and the second digital signature to generate an electronic document and transmit it to the target Power system; when the target power system receives the electronic document, it decrypts the electronic document to determine whether the electronic document has been tampered with; if the electronic document has not been tampered with, then use the electronic document to configure the setting value in the target power system, thereby solving the existing The signature authentication method of the setting value document in the technology is not convenient to use information technology to verify the relevance, authenticity and integrity of the document and the signature, which leads to the technical problem of reducing the security of the power system and improving the security of the power system.
附图说明Description of drawings
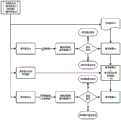
为了更清楚地说明本发明实施例或现有技术中的技术方案,下面将对实施例或现有技术描述中所需要使用的附图作简单地介绍,显而易见地,下面描述中的附图仅仅是本发明的一些实施例,对于本领域普通技术人员来讲,在不付出创造性劳动性的前提下,还可以根据这些附图获得其它的附图。In order to more clearly illustrate the technical solutions in the embodiments of the present invention or the prior art, the following will briefly introduce the drawings that need to be used in the description of the embodiments or the prior art. Obviously, the accompanying drawings in the following description are only These are some embodiments of the present invention. For those skilled in the art, other drawings can also be obtained according to these drawings on the premise of not paying creative efforts.
图1为本发明实施例提供的一种整定值文档验证方法的步骤流程图;Fig. 1 is a flow chart of the steps of a method for verifying a setting value document provided by an embodiment of the present invention;
图2为本发明实施例提供的电子文档的生成过程的流程图;FIG. 2 is a flow chart of an electronic document generation process provided by an embodiment of the present invention;
图3为本发明实施例提供的电子文档的验证过程的流程图;FIG. 3 is a flow chart of the electronic document verification process provided by the embodiment of the present invention;
图4为本发明实施例提供的一种整定值文档验证装置的结构框图。Fig. 4 is a structural block diagram of a setting value document verification device provided by an embodiment of the present invention.
具体实施方式Detailed ways
本发明实施例提供了一种整定值文档验证方法、装置、设备和介质,用于解决现有技术中整定值文档的签名认证方法不便于使用信息化手段对文档及签名的关联性、真实性、完整性等进行验证,从而导致电力系统的安全性降低的技术问题。The embodiment of the present invention provides a set value document verification method, device, equipment and medium, which are used to solve the problem of the inconvenient use of informatization means to verify the relevance and authenticity of the document and the signature in the signature verification method of the set value document in the prior art , Integrity, etc. are verified, which leads to the technical problem of reducing the security of the power system.
为使得本发明的发明目的、特征、优点能够更加的明显和易懂,下面将结合本发明实施例中的附图,对本发明实施例中的技术方案进行清楚、完整地描述,显然,下面所描述的实施例仅仅是本发明一部分实施例,而非全部的实施例。基于本发明中的实施例,本领域普通技术人员在没有做出创造性劳动前提下所获得的所有其它实施例,都属于本发明保护的范围。In order to make the purpose, features and advantages of the present invention more obvious and understandable, the technical solutions in the embodiments of the present invention will be clearly and completely described below in conjunction with the accompanying drawings in the embodiments of the present invention. Obviously, the following The described embodiments are only some, not all, embodiments of the present invention. Based on the embodiments of the present invention, all other embodiments obtained by persons of ordinary skill in the art without making creative efforts belong to the protection scope of the present invention.
请参阅图1,图1为本发明实施例提供的一种整定值文档验证方法的步骤流程图。Please refer to FIG. 1 . FIG. 1 is a flowchart of steps of a method for verifying a setting value document provided by an embodiment of the present invention.
本发明提供的一种整定值文档验证方法,包括:A method for verifying a setting value document provided by the present invention includes:
步骤101,当接收到电力系统整定值文档时,计算电力系统整定值文档内的原文对应的第一数字摘要;
电力系统整定值文档指的是记载例如继电保护装置、安全自动装置、安全稳定控制装置、测控装置等电力自动装置内的各个项目与组件的整定值的文档。其中,整定值也叫设定值,就是在自动控制系统里,当某一物理量,达到某一数值时,将发生某一动作。另一种情况,如某一电动机,速度是自动控制的,把速度控制装置设置为1000转/分,那么这个1000转/分就是电动机速度的整定值。The power system setting value document refers to a document that records the setting values of various items and components in power automatic devices such as relay protection devices, safety automatic devices, safety and stability control devices, and measurement and control devices. Among them, the set value is also called the set value, that is, in the automatic control system, when a certain physical quantity reaches a certain value, a certain action will occur. In another case, such as a certain motor, the speed is automatically controlled, and the speed control device is set to 1000 rpm, then this 1000 rpm is the set value of the motor speed.
在本申请实施例中,当接收到电力系统整定值文档时,可以通过摘要算法计算电力系统整定值文档内原文对应的第一数字摘要。其中,摘要算法可以为哈希算法等,本申请实施例对此不做限制。In the embodiment of the present application, when the power system setting value document is received, the first digital abstract corresponding to the original text in the power system setting value document may be calculated through a summary algorithm. Wherein, the digest algorithm may be a hash algorithm, etc., which is not limited in this embodiment of the present application.
步骤102,采用第一私钥对第一数字摘要进行加密,得到第一数字签名并获取对应的签名时间戳;
在得到第一数字摘要后,可以采用本地存储的第一私钥对第一数字摘要进行加密,得到第一数字签名,与此同时获取该第一数字签名生成时的签名时间戳。After obtaining the first digital abstract, the locally stored first private key may be used to encrypt the first digital abstract to obtain the first digital signature, and at the same time obtain the signature time stamp when the first digital signature is generated.
其中,签名时间戳可以从本装置认可的时间戳机构获取,私钥与使用第一数字签名方认可的签名机构的数字证书相对应。Wherein, the signature time stamp can be obtained from a time stamp organization approved by the device, and the private key corresponds to the digital certificate of the signature organization approved by the first digital signatory.
可选地,签名时间戳由目标电力系统认可的时间戳机构提供。Optionally, the signature timestamp is provided by a timestamp institution recognized by the target power system.
步骤103,组合第一数字摘要与签名时间戳并采用第二私钥进行加密,得到第二数字签名;
可选地,步骤103可以包括以下子步骤:Optionally,
组合第一数字摘要和签名时间戳,生成更新文档;Combine the first digital digest and the signature timestamp to generate an updated document;
计算更新文档对应的第二数字摘要;calculating a second digital digest corresponding to the updated document;
采用第二私钥对第二数字摘要进行加密,得到第二数字签名。The second digital abstract is encrypted by using the second private key to obtain the second digital signature.
在本申请实施例中,可以通过组合第一数字摘要和签名时间戳生成更新文档,再采用摘要算法计算更新文档对应的第二数字摘要后,可以再次获取本地存储的第二私钥对第二数字摘要进行加密,得到第二数字签名。In the embodiment of this application, the update document can be generated by combining the first digital digest and the signature timestamp, and then the digest algorithm is used to calculate the second digital digest corresponding to the update document, and the locally stored second private key pair can be obtained again. The digital digest is encrypted to obtain a second digital signature.
其中,第二数字签名包含签名时间戳。Wherein, the second digital signature includes a signature timestamp.
步骤104,采用原文、第一数字签名、签名时间戳和第二数字签名,生成电子文档并传输至目标电力系统;
在得到第二数字签名后,为发送电子文档至目标电力系统,可以采用原文、第一数字签名、签名时间戳和第二数字签名进行组合,生成新的电子文档并传输至目标电力系统。After obtaining the second digital signature, in order to send the electronic document to the target power system, the original text, the first digital signature, the signature time stamp and the second digital signature can be combined to generate a new electronic document and transmit it to the target power system.
如图2所示,电子文档的生成过程可以包括如下步骤:As shown in Figure 2, the generation process of electronic documents may include the following steps:
[步骤A1]将文档的原文C1使用摘要算法计算得到数字摘要D1。[Step A1] Calculate the original text C1 of the document using a digest algorithm to obtain a digital digest D1.
[步骤A2]使用私钥P1对[步骤A1]得到的数字摘要D1进行加密(私钥P1与使用数字签名方认可的签名机构的数字证书相对应),得到数字签名S1。[Step A2] Use the private key P1 to encrypt the digital digest D1 obtained in [Step A1] (the private key P1 corresponds to the digital certificate of the signing authority recognized by the digital signing party), and obtain the digital signature S1.
[步骤A3]将[步骤A2]得到的数字签名S1,通过认证方认可的时间戳机构获得执行数字签名的时间戳T。[Step A3] Use the digital signature S1 obtained in [Step A2] to obtain the time stamp T for executing the digital signature through the time stamp organization approved by the authenticator.
[步骤A4]将[步骤A1]得到的数字摘要D1与[步骤A3]得到的T组合在一起作为内容C2,使用摘要算法计算得到数字摘要D2。[Step A4] Combining the digital digest D1 obtained in [Step A1] and T obtained in [Step A3] as content C2, and calculating the digital digest D2 using a digest algorithm.
[步骤A5]使用时间戳服务私钥P2对[步骤A4]得到的D2进行加密,得到包含时间戳信息的数字签名S2。[Step A5] Use the timestamp service private key P2 to encrypt the D2 obtained in [Step A4] to obtain the digital signature S2 including the timestamp information.
[步骤A6]将文档原文C1和[步骤A2、A3、A5]得到的S1、T、S2组合在一起,形成可信的电子文档。[Step A6] Combine the original text C1 of the document with S1, T, and S2 obtained in [Steps A2, A3, A5] to form a credible electronic document.
步骤105,当目标电力系统接收到电子文档时,对电子文档进行解密,判断电子文档是否被篡改;
可选地,步骤105可以包括以下子步骤S11-S13:Optionally,
S11、当目标电力系统接收到电子文档时,解析电子文档,得到待验证原文、第一待验证数字签名、待验证时间戳和第二待验证数字签名;S11. When the target power system receives the electronic document, analyze the electronic document to obtain the original text to be verified, the first digital signature to be verified, the time stamp to be verified, and the second digital signature to be verified;
S12、根据待验证原文与第一待验证数字签名,判断待验证原文是否被篡改;S12. According to the original text to be verified and the first digital signature to be verified, determine whether the original text to be verified has been tampered with;
进一步地,S12可以包括以下子步骤:Further, S12 may include the following substeps:
计算待验证原文对应的第三数字摘要;Calculate the third digital abstract corresponding to the original text to be verified;
采用第一公钥对第一待验证数字签名进行解密,得到第四数字摘要;Decrypting the first digital signature to be verified by using the first public key to obtain a fourth digital digest;
比对第三数字摘要与第四数字摘要;comparing the third digital digest with the fourth digital digest;
若第三数字摘要与第四数字摘要相同,则判定待验证原文未被篡改;If the third digital abstract is the same as the fourth digital abstract, it is determined that the original text to be verified has not been tampered with;
若第三数字摘要与第四数字摘要不相同,则判定待验证原文被篡改。If the third digital abstract is different from the fourth digital abstract, it is determined that the original text to be verified has been tampered with.
S13、若判定待验证原文未被篡改,则根据待验证时间戳与第二待验证数字签名,判断电子文档是否被篡改。S13. If it is determined that the original text to be verified has not been tampered with, then determine whether the electronic document has been tampered with according to the time stamp to be verified and the second digital signature to be verified.
进一步地,S13可以包括以下子步骤:Further, S13 may include the following substeps:
若判定待验证原文未被篡改,则组合待验证时间戳与第三数字摘要,得到待验证文档;If it is determined that the original text to be verified has not been tampered with, the time stamp to be verified and the third digital abstract are combined to obtain the document to be verified;
计算待验证文档对应的第五数字摘要;Calculate the fifth digital digest corresponding to the document to be verified;
采用第二公钥对第二待验证数字签名进行解密,得到第六数字摘要;Decrypting the second digital signature to be verified by using the second public key to obtain a sixth digital digest;
比对第五数字摘要与第六数字摘要;Comparing the abstract of the fifth digit and the abstract of the sixth digit;
若第五数字摘要与第六数字摘要相同,则判定电子文档未被篡改;If the fifth digital abstract is the same as the sixth digital abstract, it is determined that the electronic document has not been tampered with;
若第五数字摘要与第六数字摘要不相同,则判定电子文档被篡改。If the fifth digital abstract is different from the sixth digital abstract, it is determined that the electronic document has been tampered with.
如图3所示,判断电子文档是否被篡改的过程可以如下所示:As shown in Figure 3, the process of judging whether an electronic document has been tampered with can be as follows:
[步骤B1]将待签名验证的文档分解得到文档的原文C1、对应原文信息C1的数字签名S1、S1的时间戳T和包含原文和时间戳信息的数字签名S2。[Step B1] Decompose the document to be signed and verified to obtain the original text C1 of the document, the digital signature S1 corresponding to the original text information C1, the time stamp T of S1, and the digital signature S2 including the original text and time stamp information.
[步骤B2]将[步骤B1]得到的原文C1使用摘要算法计算得到数字摘要D1。[Step B2] Calculate the original text C1 obtained in [Step B1] using a digest algorithm to obtain a digital digest D1.
[步骤B3]使用公钥对[步骤B1]得到的数字签名S1进行解密,得到数字摘要D1*。[Step B3] Use the public key to decrypt the digital signature S1 obtained in [Step B1] to obtain a digital digest D1*.
[步骤B4]比较[步骤B2]得到的D1和[步骤B3]得到的D1*,如果相同,则可以认为该文档的原文C1在经过电子签名后没有发生过变化。[Step B4] Compare the D1 obtained in [Step B2] with the D1* obtained in [Step B3]. If they are the same, it can be considered that the original text C1 of the document has not changed after the electronic signature.
[步骤B5]将[步骤B2]得到的数字摘要D1与[步骤B1]得到的时间戳T组合在一起作为内容C2,使用摘要算法计算得到数字摘要D2。[Step B5] Combine the digital digest D1 obtained in [Step B2] and the time stamp T obtained in [Step B1] as content C2, and use the digest algorithm to calculate the digital digest D2.
[步骤B6]使用时间戳服务公钥对[步骤B1]得到的数字签名S2进行解密,得到数字摘要D2*。[Step B6] Use the time stamp service public key to decrypt the digital signature S2 obtained in [Step B1] to obtain a digital digest D2*.
[步骤B7]比较[步骤B5]得到的D2和[步骤B6]得到的D2*,如果相同,则可以认为该文档的原文C1对应的数字摘要D1和时间戳T的组合在经过电子签名后没有发生过变化。[Step B7] Compare the D2 obtained in [Step B5] with the D2* obtained in [Step B6]. If they are the same, it can be considered that the combination of the digital abstract D1 corresponding to the original text C1 of the document and the time stamp T has not been electronically signed. There have been changes.
[步骤B8]如果[步骤B4]和[步骤B7]判断的结果同时成立,则可以认为[步骤B1]得到的时间戳T在经过电子签名后没有发生过变化。[Step B8] If the judgment results of [Step B4] and [Step B7] are both true, it can be considered that the time stamp T obtained in [Step B1] has not changed after the electronic signature.
步骤106,若电子文档未被篡改,则采用电子文档配置目标电力系统内的整定值。
可选地,步骤106可以包括以下子步骤:Optionally,
若电子文档未被篡改,则通过目标电力系统从电子文档中获取待验证原文;If the electronic document has not been tampered with, obtain the original text to be verified from the electronic document through the target power system;
按照配置项目检索待验证原文,匹配各个配置项目分别对应的整定值;Retrieve the original text to be verified according to the configuration items, and match the setting values corresponding to each configuration item;
将各整定值按照配置项目分别加载至目标电力系统。Load each setting value to the target power system according to the configuration items.
在本申请实施例中,当接收到电力系统整定值文档时,计算电力系统整定值文档内的原文对应的第一数字摘要;采用第一私钥对第一数字摘要进行加密,得到第一数字签名并获取对应的签名时间戳;组合第一数字摘要与签名时间戳并采用第二私钥进行加密,得到第二数字签名;采用原文、第一数字签名、签名时间戳和第二数字签名,生成电子文档并传输至目标电力系统;当目标电力系统接收到电子文档时,对电子文档进行解密,判断电子文档是否被篡改;若电子文档未被篡改,则采用电子文档配置目标电力系统内的整定值,从而解决现有技术中整定值文档的签名认证方法不便于使用信息化手段对文档及签名的关联性、真实性、完整性等进行验证,从而导致电力系统的安全性降低的技术问题,提高电力系统安全性。In the embodiment of the present application, when the power system setting value file is received, the first digital abstract corresponding to the original text in the power system setting value file is calculated; the first digital abstract is encrypted with the first private key to obtain the first digital Sign and obtain the corresponding signature time stamp; combine the first digital abstract and signature time stamp and encrypt with the second private key to obtain the second digital signature; use the original text, the first digital signature, the signature time stamp and the second digital signature, Generate an electronic document and transmit it to the target power system; when the target power system receives the electronic document, it decrypts the electronic document to determine whether the electronic document has been tampered with; if the electronic document has not been tampered with, use the electronic document to configure the target power system. setting value, so as to solve the technical problem that the signature authentication method of the setting value document in the prior art is not convenient to use information technology to verify the relevance, authenticity and integrity of the document and the signature, which leads to the reduction of the security of the power system , to improve the security of the power system.
请参见图4,图4示出了本申请实施例的一种整定值文档验证装置的结构框图。Please refer to FIG. 4 , which shows a structural block diagram of an apparatus for verifying a setting value document according to an embodiment of the present application.
本发明实施例提供了一种整定值文档验证装置,包括:An embodiment of the present invention provides a setting value document verification device, including:
第一数字摘要生成模块401,用于当接收到电力系统整定值文档时,计算电力系统整定值文档内的原文对应的第一数字摘要;The first digital summary generation module 401 is used to calculate the first digital summary corresponding to the original text in the power system setting value document when receiving the power system setting value document;
一次加密模块402,用于采用第一私钥对第一数字摘要进行加密,得到第一数字签名并获取对应的签名时间戳;A one-time encryption module 402, configured to encrypt the first digital digest with the first private key, obtain the first digital signature and obtain the corresponding signature timestamp;
二次加密模块403,用于组合第一数字摘要与签名时间戳并采用第二私钥进行加密,得到第二数字签名;The secondary encryption module 403 is used to combine the first digital abstract and the signature timestamp and encrypt it with the second private key to obtain the second digital signature;
电子文档生成模块404,用于采用原文、第一数字签名、签名时间戳和第二数字签名,生成电子文档并传输至目标电力系统;An electronic document generation module 404, configured to generate an electronic document using the original text, the first digital signature, the signature time stamp and the second digital signature, and transmit it to the target power system;
篡改判断模块405,用于当目标电力系统接收到电子文档时,对电子文档进行解密,判断电子文档是否被篡改;A tampering judging module 405, configured to decrypt the electronic document when the target power system receives the electronic document, and determine whether the electronic document has been tampered with;
整定值配置模块406,用于若电子文档未被篡改,则采用电子文档配置目标电力系统内的整定值。The setting value configuration module 406 is configured to use the electronic file to configure the setting value in the target power system if the electronic file has not been tampered with.
可选地,二次加密模块403,具体用于:Optionally, the secondary encryption module 403 is specifically used for:
组合第一数字摘要和签名时间戳,生成更新文档;Combine the first digital digest and the signature timestamp to generate an updated document;
计算更新文档对应的第二数字摘要;calculating a second digital digest corresponding to the updated document;
采用第二私钥对第二数字摘要进行加密,得到第二数字签名。The second digital abstract is encrypted by using the second private key to obtain the second digital signature.
可选地,篡改判断模块405包括:Optionally, the tampering judging module 405 includes:
电子文档解析子模块,用于当目标电力系统接收到电子文档时,解析电子文档,得到待验证原文、第一待验证数字签名、待验证时间戳和第二待验证数字签名;The electronic document analysis sub-module is used to analyze the electronic document when the target power system receives the electronic document, and obtain the original text to be verified, the first digital signature to be verified, the time stamp to be verified and the second digital signature to be verified;
第一篡改判断子模块,用于根据待验证原文与第一待验证数字签名,判断待验证原文是否被篡改;The first tampering judging submodule is used to judge whether the original text to be verified has been tampered with according to the original text to be verified and the first digital signature to be verified;
第二篡改判断子模块,用于若判定待验证原文未被篡改,则根据待验证时间戳与第二待验证数字签名,判断电子文档是否被篡改。The second tampering judging sub-module is used to judge whether the electronic document has been tampered with according to the time stamp to be verified and the second digital signature to be verified if it is determined that the original text to be verified has not been tampered with.
可选地,第一篡改判断子模块具体用于:Optionally, the first tampering judgment submodule is specifically used for:
计算待验证原文对应的第三数字摘要;Calculate the third digital abstract corresponding to the original text to be verified;
采用第一公钥对第一待验证数字签名进行解密,得到第四数字摘要;Decrypting the first digital signature to be verified by using the first public key to obtain a fourth digital digest;
比对第三数字摘要与第四数字摘要;comparing the third digital digest with the fourth digital digest;
若第三数字摘要与第四数字摘要相同,则判定待验证原文未被篡改;If the third digital abstract is the same as the fourth digital abstract, it is determined that the original text to be verified has not been tampered with;
若第三数字摘要与第四数字摘要不相同,则判定待验证原文被篡改。If the third digital abstract is different from the fourth digital abstract, it is determined that the original text to be verified has been tampered with.
可选地,第二篡改判断子模块具体用于:Optionally, the second tampering judgment submodule is specifically used for:
若判定待验证原文未被篡改,则组合待验证时间戳与第三数字摘要,得到待验证文档;If it is determined that the original text to be verified has not been tampered with, the time stamp to be verified and the third digital abstract are combined to obtain the document to be verified;
计算待验证文档对应的第五数字摘要;Calculate the fifth digital digest corresponding to the document to be verified;
采用第二公钥对第二待验证数字签名进行解密,得到第六数字摘要;Decrypting the second digital signature to be verified by using the second public key to obtain a sixth digital digest;
比对第五数字摘要与第六数字摘要;Comparing the abstract of the fifth digit and the abstract of the sixth digit;
若第五数字摘要与第六数字摘要相同,则判定电子文档未被篡改;If the fifth digital abstract is the same as the sixth digital abstract, it is determined that the electronic document has not been tampered with;
若第五数字摘要与第六数字摘要不相同,则判定电子文档被篡改。If the fifth digital abstract is different from the sixth digital abstract, it is determined that the electronic document has been tampered with.
可选地,整定值配置模块406具体用于:Optionally, the setting value configuration module 406 is specifically used for:
若电子文档未被篡改,则通过目标电力系统从电子文档中获取待验证原文;If the electronic document has not been tampered with, obtain the original text to be verified from the electronic document through the target power system;
按照配置项目检索待验证原文,匹配各个配置项目分别对应的整定值;Retrieve the original text to be verified according to the configuration items, and match the setting values corresponding to each configuration item;
将各整定值按照配置项目分别加载至目标电力系统。Load each setting value to the target power system according to the configuration items.
可选地,签名时间戳由目标电力系统认可的时间戳机构提供。Optionally, the signature timestamp is provided by a timestamp institution recognized by the target power system.
本发明实施例还提供了一种电子设备,包括存储器及处理器,所述存储器中储存有计算机程序,所述计算机程序被所述处理器执行时,使得所述处理器执行如本发明任一实施例所述的整定值文档验证方法的步骤。The embodiment of the present invention also provides an electronic device, including a memory and a processor, wherein a computer program is stored in the memory, and when the computer program is executed by the processor, the processor executes any one of the present invention. Steps of the setting value document verification method described in the embodiment.
本发明实施例提供了一种计算机可读存储介质,其上存储有计算机程序,所述计算机程序被执行时实现如本发明任一实施例所述的整定值文档验证方法。An embodiment of the present invention provides a computer-readable storage medium, on which a computer program is stored. When the computer program is executed, the method for verifying a setting value document according to any embodiment of the present invention is implemented.
所属领域的技术人员可以清楚地了解到,为描述的方便和简洁,上述描述的装置、模块和子模块的具体工作过程,可以参考前述方法实施例中的对应过程,在此不再赘述。Those skilled in the art can clearly understand that for the convenience and brevity of description, the specific working process of the above-described devices, modules and sub-modules can refer to the corresponding process in the foregoing method embodiments, which will not be repeated here.
在本申请所提供的几个实施例中,应该理解到,所揭露的装置和方法,可以通过其它的方式实现。例如,以上所描述的装置实施例仅仅是示意性的,例如,所述单元的划分,仅仅为一种逻辑功能划分,实际实现时可以有另外的划分方式,例如多个单元或组件可以结合或者可以集成到另一个系统,或一些特征可以忽略,或不执行。另一点,所显示或讨论的相互之间的耦合或直接耦合或通信连接可以是通过一些接口,装置或单元的间接耦合或通信连接,可以是电性,机械或其它的形式。In the several embodiments provided in this application, it should be understood that the disclosed devices and methods may be implemented in other ways. For example, the device embodiments described above are only illustrative. For example, the division of the units is only a logical function division. In actual implementation, there may be other division methods. For example, multiple units or components can be combined or May be integrated into another system, or some features may be ignored, or not implemented. In another point, the mutual coupling or direct coupling or communication connection shown or discussed may be through some interfaces, and the indirect coupling or communication connection of devices or units may be in electrical, mechanical or other forms.
所述作为分离部件说明的单元可以是或者也可以不是物理上分开的,作为单元显示的部件可以是或者也可以不是物理单元,即可以位于一个地方,或者也可以分布到多个网络单元上。可以根据实际的需要选择其中的部分或者全部单元来实现本实施例方案的目的。The units described as separate components may or may not be physically separated, and the components shown as units may or may not be physical units, that is, they may be located in one place, or may be distributed to multiple network units. Part or all of the units can be selected according to actual needs to achieve the purpose of the solution of this embodiment.
另外,在本发明各个实施例中的各功能单元可以集成在一个处理单元中,也可以是各个单元单独物理存在,也可以两个或两个以上单元集成在一个单元中。上述集成的单元既可以采用硬件的形式实现,也可以采用软件功能单元的形式实现。In addition, each functional unit in each embodiment of the present invention may be integrated into one processing unit, each unit may exist separately physically, or two or more units may be integrated into one unit. The above-mentioned integrated units can be implemented in the form of hardware or in the form of software functional units.
所述集成的单元如果以软件功能单元的形式实现并作为独立的产品销售或使用时,可以存储在一个计算机可读取存储介质中。基于这样的理解,本发明的技术方案本质上或者说对现有技术做出贡献的部分或者该技术方案的全部或部分可以以软件产品的形式体现出来,该计算机软件产品存储在一个存储介质中,包括若干指令用以使得一台计算机设备(可以是个人计算机,服务器,或者网络设备等)执行本发明各个实施例所述方法的全部或部分步骤。而前述的存储介质包括:U盘、移动硬盘、只读存储器(ROM,Read-OnlyMemory)、随机存取存储器(RAM,Random Access Memory)、磁碟或者光盘等各种可以存储程序代码的介质。If the integrated unit is realized in the form of a software function unit and sold or used as an independent product, it can be stored in a computer-readable storage medium. Based on such an understanding, the essence of the technical solution of the present invention or the part that contributes to the prior art or all or part of the technical solution can be embodied in the form of a software product, and the computer software product is stored in a storage medium , including several instructions to make a computer device (which may be a personal computer, a server, or a network device, etc.) execute all or part of the steps of the method described in each embodiment of the present invention. The aforementioned storage medium includes: U disk, mobile hard disk, read-only memory (ROM, Read-Only Memory), random access memory (RAM, Random Access Memory), magnetic disk or optical disk, and other media that can store program codes.
以上所述,以上实施例仅用以说明本发明的技术方案,而非对其限制;尽管参照前述实施例对本发明进行了详细的说明,本领域的普通技术人员应当理解:其依然可以对前述各实施例所记载的技术方案进行修改,或者对其中部分技术特征进行等同替换;而这些修改或者替换,并不使相应技术方案的本质脱离本发明各实施例技术方案的精神和范围。As mentioned above, the above embodiments are only used to illustrate the technical solutions of the present invention, rather than to limit them; although the present invention has been described in detail with reference to the foregoing embodiments, those of ordinary skill in the art should understand that: it can still understand the foregoing The technical solutions recorded in each embodiment are modified, or some of the technical features are replaced equivalently; and these modifications or replacements do not make the essence of the corresponding technical solutions deviate from the spirit and scope of the technical solutions of the various embodiments of the present invention.
Claims (10)
Priority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202310179844.6ACN116318719A (en) | 2023-02-27 | 2023-02-27 | Setting value document verification method, device, equipment and medium |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202310179844.6ACN116318719A (en) | 2023-02-27 | 2023-02-27 | Setting value document verification method, device, equipment and medium |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| CN116318719Atrue CN116318719A (en) | 2023-06-23 |
Family
ID=86837241
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN202310179844.6APendingCN116318719A (en) | 2023-02-27 | 2023-02-27 | Setting value document verification method, device, equipment and medium |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN116318719A (en) |
Citations (8)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20030159048A1 (en)* | 2002-02-20 | 2003-08-21 | Tsutomu Matsumoto | Time stamping system for electronic documents and program medium for the same |
| CN101364869A (en)* | 2007-08-09 | 2009-02-11 | 鸿富锦精密工业(深圳)有限公司 | Electronic document digital sign-off system and method |
| CN105591750A (en)* | 2015-10-30 | 2016-05-18 | 中国银联股份有限公司 | Electronic signature generation method and system |
| CN109818747A (en)* | 2018-12-28 | 2019-05-28 | 苏州科达科技股份有限公司 | Digital signature method and device |
| CN112637836A (en)* | 2020-12-18 | 2021-04-09 | 珠海格力电器股份有限公司 | Data processing method and device, electronic equipment and storage medium |
| CN114329622A (en)* | 2021-12-20 | 2022-04-12 | 北京信安世纪科技股份有限公司 | A file protection method, verification method, apparatus, device and medium |
| CN114386053A (en)* | 2021-12-08 | 2022-04-22 | 深圳市梦网物联科技发展有限公司 | Medical data encryption storage method and storage medium |
| CN115277093A (en)* | 2022-06-24 | 2022-11-01 | 北京奕斯伟计算技术股份有限公司 | Tamper verification method, system and device thereof and electronic equipment |
- 2023
- 2023-02-27CNCN202310179844.6Apatent/CN116318719A/enactivePending
Patent Citations (8)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20030159048A1 (en)* | 2002-02-20 | 2003-08-21 | Tsutomu Matsumoto | Time stamping system for electronic documents and program medium for the same |
| CN101364869A (en)* | 2007-08-09 | 2009-02-11 | 鸿富锦精密工业(深圳)有限公司 | Electronic document digital sign-off system and method |
| CN105591750A (en)* | 2015-10-30 | 2016-05-18 | 中国银联股份有限公司 | Electronic signature generation method and system |
| CN109818747A (en)* | 2018-12-28 | 2019-05-28 | 苏州科达科技股份有限公司 | Digital signature method and device |
| CN112637836A (en)* | 2020-12-18 | 2021-04-09 | 珠海格力电器股份有限公司 | Data processing method and device, electronic equipment and storage medium |
| CN114386053A (en)* | 2021-12-08 | 2022-04-22 | 深圳市梦网物联科技发展有限公司 | Medical data encryption storage method and storage medium |
| CN114329622A (en)* | 2021-12-20 | 2022-04-12 | 北京信安世纪科技股份有限公司 | A file protection method, verification method, apparatus, device and medium |
| CN115277093A (en)* | 2022-06-24 | 2022-11-01 | 北京奕斯伟计算技术股份有限公司 | Tamper verification method, system and device thereof and electronic equipment |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| TWI454111B (en) | Techniques for ensuring authentication and integrity of communications | |
| EP2956852B1 (en) | Data security service | |
| CN110493197A (en) | A kind of login process method and relevant device | |
| CN106571951B (en) | Audit log obtaining method, system and device | |
| CN102024127A (en) | Control platform, user terminal, distribution system and method of application software | |
| US20070050626A1 (en) | Document management system, document processing computer, signature generating computer, storage medium storing program for document management, and document management method | |
| CN113452526B (en) | Electronic file certification method, verification method and corresponding devices | |
| CN115952560B (en) | Method, system, equipment and medium for verifying authenticity of electronic archive file based on original handwriting signature | |
| EP2465246A1 (en) | Layered protection and validation of identity data delivered online via multiple intermediate clients | |
| CN112699353B (en) | Financial information transmission method and financial information transmission system | |
| CN114697040B (en) | Electronic signature method and system based on symmetric key | |
| CN109309645A (en) | A kind of software distribution security guard method | |
| CN105721508A (en) | Information security protection monitoring method of LED asynchronous control card | |
| WO2020042508A1 (en) | Method, system and electronic device for processing claim incident based on blockchain | |
| CN112804217A (en) | Block chain technology-based evidence storing method and device | |
| CN110826107A (en) | File signature method and device, electronic equipment and readable storage medium | |
| CN115203749A (en) | Data transaction method and system based on block chain | |
| CN116318717A (en) | Electronic file certification method, system, terminal and medium based on trusted timestamp | |
| CN115801281A (en) | Authorization method, electronic device, and computer-readable storage medium | |
| CN113194090B (en) | Authentication method, authentication device, terminal device and computer readable storage medium | |
| CN119520073A (en) | Data transmission method, device and computer equipment | |
| CN115549930B (en) | Verification method for logging in operating system | |
| CN118114222A (en) | Authentication method, device, system, equipment and medium for data product | |
| CN111382451A (en) | Security level identification method and device, electronic equipment and storage medium | |
| CN116318719A (en) | Setting value document verification method, device, equipment and medium |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination |