CN116318637A - Method and system for secure network access communication of equipment - Google Patents
Method and system for secure network access communication of equipmentDownload PDFInfo
- Publication number
- CN116318637A CN116318637ACN202111572609.2ACN202111572609ACN116318637ACN 116318637 ACN116318637 ACN 116318637ACN 202111572609 ACN202111572609 ACN 202111572609ACN 116318637 ACN116318637 ACN 116318637A
- Authority
- CN
- China
- Prior art keywords
- key
- data
- authentication
- equipment
- serial number
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Pending
Links
Images
Classifications
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/08—Key distribution or management, e.g. generation, sharing or updating, of cryptographic keys or passwords
- H04L9/0861—Generation of secret information including derivation or calculation of cryptographic keys or passwords
- H04L9/0866—Generation of secret information including derivation or calculation of cryptographic keys or passwords involving user or device identifiers, e.g. serial number, physical or biometrical information, DNA, hand-signature or measurable physical characteristics
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/04—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks
- H04L63/0428—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks wherein the data content is protected, e.g. by encrypting or encapsulating the payload
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/08—Network architectures or network communication protocols for network security for authentication of entities
- H04L63/0869—Network architectures or network communication protocols for network security for authentication of entities for achieving mutual authentication
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/06—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols the encryption apparatus using shift registers or memories for block-wise or stream coding, e.g. DES systems or RC4; Hash functions; Pseudorandom sequence generators
- H04L9/0643—Hash functions, e.g. MD5, SHA, HMAC or f9 MAC
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/08—Key distribution or management, e.g. generation, sharing or updating, of cryptographic keys or passwords
- H04L9/0816—Key establishment, i.e. cryptographic processes or cryptographic protocols whereby a shared secret becomes available to two or more parties, for subsequent use
- H04L9/0838—Key agreement, i.e. key establishment technique in which a shared key is derived by parties as a function of information contributed by, or associated with, each of these
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/08—Key distribution or management, e.g. generation, sharing or updating, of cryptographic keys or passwords
- H04L9/0861—Generation of secret information including derivation or calculation of cryptographic keys or passwords
- H04L9/0869—Generation of secret information including derivation or calculation of cryptographic keys or passwords involving random numbers or seeds
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/08—Key distribution or management, e.g. generation, sharing or updating, of cryptographic keys or passwords
- H04L9/0894—Escrow, recovery or storing of secret information, e.g. secret key escrow or cryptographic key storage
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/14—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols using a plurality of keys or algorithms
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/32—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials
- H04L9/3236—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials using cryptographic hash functions
- H04L9/3242—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials using cryptographic hash functions involving keyed hash functions, e.g. message authentication codes [MACs], CBC-MAC or HMAC
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/32—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials
- H04L9/3247—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials involving digital signatures
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/32—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials
- H04L9/3263—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials involving certificates, e.g. public key certificate [PKC] or attribute certificate [AC]; Public key infrastructure [PKI] arrangements
- H04L9/3268—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials involving certificates, e.g. public key certificate [PKC] or attribute certificate [AC]; Public key infrastructure [PKI] arrangements using certificate validation, registration, distribution or revocation, e.g. certificate revocation list [CRL]
Landscapes
- Engineering & Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- Computer Networks & Wireless Communication (AREA)
- Signal Processing (AREA)
- Power Engineering (AREA)
- Computer Hardware Design (AREA)
- Computing Systems (AREA)
- General Engineering & Computer Science (AREA)
- Storage Device Security (AREA)
Abstract
Translated fromChineseDescription
Translated fromChinese技术领域technical field
本申请涉及信息安全领域,尤其涉及设备安全入网通信的方法和系统。The present application relates to the field of information security, in particular to a method and system for secure network access communication of equipment.
背景技术Background technique
现代社会已经入万物互联时代,智能家居、终端已逐步进入普通家庭,同时步入家居联网,接受服务商联网管理。网络社会生存至今一直面临着被非法仿冒身份、偷窃、和篡改数据,甚至受到病毒入清破坏数据;如果智能家居、终端进入互联网后,受到这些攻击,将造成不可估量的后果。Modern society has entered the era of the Internet of Everything, and smart homes and terminals have gradually entered ordinary families, and at the same time entered the home network and accepted the network management of service providers. The survival of the network society has been faced with illegal identity counterfeiting, theft, and data tampering, and even the destruction of data by viruses; if smart homes and terminals are connected to the Internet, they are attacked by these attacks, which will cause immeasurable consequences.
智能家居系统将住宅中各种设备(如智能照明、空调、窗帘、电视、音频设备、门锁等)通过联网方式进行集中管理,可以提升家居的安全性、便利性、舒适性及艺术性等,改善生活质量。当有外部威胁进入智能家居系统,轻则破坏家居正常运行,重则仿冒个人身份、窃取个人隐私信息,因此对于智能家居系统的设备管理,甚至设备间通信都需要安全防护及管理。The smart home system centrally manages various devices in the house (such as smart lighting, air conditioners, curtains, TVs, audio equipment, door locks, etc.) through networking, which can improve the safety, convenience, comfort and artistry of the home. Improve quality of life. When an external threat enters the smart home system, it can destroy the normal operation of the home, or counterfeit personal identity and steal personal privacy information. Therefore, the device management of the smart home system, and even the communication between devices requires security protection and management.
在智能家居之外,其它智能终端使用范围更广泛、网络通信更复杂,如用于汽车电子、能源、城市、公共服务等方向的智能终端,也需要对接入网络的行为进行管理,如果没有安全防护,那么网络通信极易被人入侵,造成数据窃取及设备故障。In addition to smart homes, other smart terminals are used in a wider range and have more complex network communications. For example, smart terminals used in automotive electronics, energy, cities, public services, etc. also need to manage the behavior of accessing the network. If there is no If there is no security protection, the network communication is very easy to be invaded, resulting in data theft and equipment failure.
因此,所述智能家居系统、智能终端系统需要保证通信对象的身份可信、传输的通信数据不会被窃取、破坏、篡改。Therefore, the smart home system and the smart terminal system need to ensure that the identity of the communication object is credible and that the transmitted communication data will not be stolen, destroyed or tampered with.
当前网络通信要实现安全、可靠地完成数据通信,往往先进行身份认证,确保对方身份可信。现有的身份认证系统一般使用一种认证因素和两种认证因素的身份认证,其中两种认证因素认证方式又称强身份认证。一种认证因素的身份认证方式一般使用对称密钥算法实现,强身份认证方式一般非对称算法实现。强身份认证方式往往使用CA证书、私钥授权及私钥签名,如“私钥授权密码+CA证书+私钥签名”、“私钥授权指纹+CA证书+私钥签名”等,保证通信双方身份是可信的,虽然强身份认证方式安全可靠,但是智能设备、智能终端往往通信频繁导致无法为每一次通信进行私钥授权。单一类型身份认证方式实现简单,但是需要通信双方有对方的认证密钥,而如何确保通信一方拥有另一方认证密钥而不泄露其认证密钥是一个难题。In order to achieve safe and reliable data communication in current network communication, identity authentication is often performed first to ensure that the identity of the other party is credible. Existing identity authentication systems generally use identity authentication of one authentication factor and two authentication factors, and the authentication method of two authentication factors is also called strong identity authentication. The identity authentication method of an authentication factor is generally realized by using a symmetric key algorithm, and the strong identity authentication method is generally realized by an asymmetric algorithm. Strong identity authentication methods often use CA certificates, private key authorization and private key signatures, such as "private key authorization password + CA certificate + private key signature", "private key authorization fingerprint + CA certificate + private key signature", etc., to ensure that both parties in communication Identity is trustworthy. Although strong identity authentication is safe and reliable, smart devices and smart terminals often communicate frequently, making it impossible to authorize private keys for each communication. The implementation of the single-type identity authentication method is simple, but both communication parties need to have the other party's authentication key, and how to ensure that the communication party has the other party's authentication key without revealing its authentication key is a difficult problem.
当智能设备、智能终端与业务服务器通信时,现有的系统一般对数据先加密再传输,保证通信数据的保密性。在加密数据之前,需要通信双方能安全可靠地协商出对数据加密的密钥。当使用非对称算法协商密钥时,协商需要的数据长度往往远远大于目标密钥长度,而且获得一个密钥需要多次协商通信过程;当使用对称算法协商密钥时,如何保证密钥的安全性、保密性仍然是其首要难题。When smart devices and smart terminals communicate with business servers, the existing systems generally encrypt the data before transmitting it to ensure the confidentiality of the communication data. Before encrypting data, it is necessary for both communicating parties to negotiate a key for data encryption safely and reliably. When an asymmetric algorithm is used to negotiate a key, the length of the data required for negotiation is often far greater than the target key length, and obtaining a key requires multiple negotiation communication processes; when a symmetric algorithm is used to negotiate a key, how to ensure the integrity of the key? Safety and confidentiality are still its primary problems.
阿里ID2产品提供身份认证、安全连接、业务数据保护和密钥管理,其产品架构如图1所示。身份认证方式是基于ID2提供双向身份认证服务,防止设备被篡改和仿冒;安全连接提供兼容TLS和DTLS的iTLS/iDTLS轻量级安全协议,保障安全性的同时减少设备的资源消耗;业务数据保护是基于设备可信根派生的密钥,可支持多种算法,为设备固件、业务数据及应用授权等敏感数据提供保护;密钥管理对IOT设备、应用和业务使用的密钥提供集中管理,包括密钥生成、密钥销毁和端到端的密钥安全分发。目前阿里ID2关联系统适用于芯片/模组商,并且芯片/模组商在线申请可将阿里ID2烧录如芯片/模组中。阿里ID2特点有三大特点,如下:The Ali ID2 product provides identity authentication, secure connection, business data protection, and key management. Its product architecture is shown in Figure 1. The identity authentication method is based on ID2 to provide two-way identity authentication services to prevent devices from being tampered with and counterfeited; the secure connection provides iTLS/iDTLS lightweight security protocols compatible with TLS and DTLS, ensuring security while reducing device resource consumption; business data Protection is based on the key derived from the root of trust of the device, which supports multiple algorithms and provides protection for sensitive data such as device firmware, business data, and application authorization; key management provides centralized management of keys used by IOT devices, applications, and services , including key generation, key destruction, and end-to-end secure key distribution. At present, the Ali ID2 association system is applicable to chip/module manufacturers, and chip/module manufacturers can apply online to burn Ali ID2 into the chip/module. Ali ID2 features three major features, as follows:
1、轻量化,使用ID2代替CA证书,节省存储空间、网络资源;1. Lightweight, use ID2 instead of CA certificate to save storage space and network resources;
2、高安全,为设备提供云端可信根,基于可信根为上层服务提供可信服务,从源头确保设备的合法性和数据的安全性;2. High security, providing cloud root of trust for devices, providing trusted services for upper-layer services based on root of trust, ensuring the legitimacy of devices and data security from the source;
3、适用范围广,适用于多种安全等级的设备应用场景,支持不同安全等级的载体。3. It has a wide range of applications and is suitable for equipment application scenarios with various security levels, and supports carriers with different security levels.
阿里ID2现有技术虽然实现了密钥管理、身份认证及数据加解密服务技术,但从ID2基础开始,该技术方案存在不足,首先不适用于使用CA证书的应用场景;其次ID2数据从申请开始到烧录入芯片模组中,只能在线分发,传输方式单一,严重依赖网络安全及烧录桌面环境安全,当网络和烧录桌面存在安全隐患时,会威胁到使用ID2的设备。Although the existing technology of Ali ID2 has realized key management, identity authentication and data encryption and decryption service technologies, starting from the basis of ID2 , this technical solution has shortcomings. First, it is not suitable for application scenarios using CA certificates; secondly, ID2 data From the beginning of application to burning into the chip module, it can only be distributed online, and the transmission method is single. It relies heavily on network security and the security of the burning desktop environment. When there are security risks in the network and burning desktop, it will threaten the use of ID2 . equipment.
发明内容Contents of the invention
针对现有技术中存在的问题,本申请提供了一种设备安全入网通信的方法和系统,解决智能设备、智能终端与业务服务通信时身份可信、数据免受破坏及窃取,实现了智能设备、智能终端身份的认证,保证入网设备的身份可信、设备所访问的服务的身份可信,及保证设备与服务之间通信数据的安全性、保密性。Aiming at the problems existing in the prior art, this application provides a method and system for secure network access communication of devices, which solves the problem of trusted identities and data protection from damage and theft when smart devices, smart terminals communicate with business services, and realizes smart devices , The authentication of the identity of the smart terminal ensures that the identity of the network-connected device is credible, the identity of the service accessed by the device is credible, and the security and confidentiality of the communication data between the device and the service are guaranteed.
根据本申请的第一个方面,提供一种智能设备安全入网通信的方法,包括:According to the first aspect of the present application, a method for secure network access communication of a smart device is provided, including:
响应于智能设备的出厂信息申请,产生出厂信息,所述出厂信息包括设备序列号、设备密钥、设备证书和服务器的公钥;In response to the application for the delivery information of the smart device, the delivery information is generated, and the delivery information includes the device serial number, the device key, the device certificate and the public key of the server;
通过根文件保护密钥离散出文件传输密钥,所述文件传输密钥用于加密所述出厂信息,形成密文出厂信息;discretizing the file transfer key through the root file protection key, and the file transfer key is used to encrypt the delivery information to form ciphertext delivery information;
将所述密文出厂信息和所述文件传输密钥发送至所述智能设备,其中,所述密文出厂信息用于灌入所述智能设备的安全芯片。Sending the ciphertext delivery information and the file transfer key to the smart device, wherein the ciphertext delivery information is used to fill the security chip of the smart device.
根据本申请的第二个方面,提供一种智能设备安全入网通信的系统,其包括智能设备、业务服务平台和安全云设备,其中所述智能设备内设有安全芯片,所述业务服务平台包括认证密钥分发业务平台、身份认证业务平台和数据密文通信业务平台,所述安全云设备执行如第一方面所述的方法。According to the second aspect of the present application, a system for secure network access communication of smart devices is provided, which includes smart devices, a business service platform and a secure cloud device, wherein the smart device is provided with a security chip, and the business service platform includes Authenticating the key distribution service platform, the identity authentication service platform, and the data ciphertext communication service platform, the secure cloud device executes the method as described in the first aspect.
根据本申请提供的设备安全入网通信的方法和系统,能够带来如下好处:According to the method and system for secure network access communication of equipment provided in this application, the following benefits can be brought:
1、安全地为智能设备/智能终端提供出厂信息,并以安全芯片存储,并使用专用工具将出厂信息灌入到安全芯片中。其中,出厂信息包括设备序列号、设备密钥、设备证书、服务器的公钥,在认证密钥分发、身份认证和数据加解密的过程中都会用到出厂信息;1. Safely provide factory information for smart devices/smart terminals, store it in a security chip, and use special tools to fill the factory information into the security chip. Among them, the factory information includes the device serial number, device key, device certificate, and server public key, which are used in the process of authentication key distribution, identity authentication, and data encryption and decryption;
2、在不存储出厂信息中主控密钥的情况下,安全云设备能根据设备序列号重新计算出出厂信息中主控密钥;2. Without storing the master key in the factory information, the security cloud device can recalculate the master key in the factory information according to the serial number of the device;
3、安全地为智能设备/智能终端在线分发一个密文认证密钥;当分发认证密钥时,网络无需传输保护认证密钥的密钥;3. Securely distribute a ciphertext authentication key online for smart devices/smart terminals; when distributing the authentication key, the network does not need to transmit the key that protects the authentication key;
4、提供支持多种密钥算法、多种身份认证方式的身份认证。支持使用认证密钥或非对称密钥进行单向确认智能设备/智能终端身份,实现身份认证;支持使用认证密钥或非对称密钥在安全云与智能设备/智能终端之间互相确认对方身份,实现身份认证;身份认证过程只需传递少量的随机数(例如,16字节),不传输身份认证明文内容,加强身份认证的安全性。4. Provide identity authentication that supports multiple key algorithms and multiple identity authentication methods. Support the use of authentication keys or asymmetric keys for one-way confirmation of the identity of smart devices/smart terminals to achieve identity authentication; support the use of authentication keys or asymmetric keys to mutually confirm the identity of each other between the security cloud and smart devices/smart terminals , to achieve identity authentication; the identity authentication process only needs to transmit a small amount of random numbers (for example, 16 bytes), and does not transmit identity authentication plaintext content, thereby strengthening the security of identity authentication.
5、安全地、快速地提供加密数据、解密数据的密钥。当智能设备/智能终端与安全云完成身份认证后,智能设备/智能终端和安全云可使用身份认证过程中传输的数据在本地协商计算出对方保护数据的密钥,其中加密数据的密钥用来加密发送给对方的数据,解密数据的密钥是解密对方加密后的数据。5. Safely and quickly provide the key for encrypting data and decrypting data. After the smart device/smart terminal and the security cloud complete the identity authentication, the smart device/smart terminal and the security cloud can use the data transmitted during the identity authentication process to negotiate locally to calculate the key for the other party's protected data, where the key for encrypting the data is used To encrypt the data sent to the other party, the key to decrypt the data is to decrypt the encrypted data of the other party.
附图说明Description of drawings
为了更清楚地说明本申请实施例中的技术方案,下面将对实施例描述中所需要使用的附图作简单地介绍,显而易见地,下面描述中的附图仅仅是本申请的一些实施例,对于本领域普通技术人员来讲,还可以根据这些附图获得其他的附图,而并不超出本申请要求保护的范围。In order to more clearly illustrate the technical solutions in the embodiments of the present application, the drawings that need to be used in the description of the embodiments will be briefly introduced below. Obviously, the drawings in the following description are only some embodiments of the present application. Those skilled in the art can also obtain other drawings based on these drawings without going beyond the protection scope of the present application.
图1是阿里ID2产品架构图。Figure 1 is a product architecture diagram of Ali ID2 .
图2是根据本申请实施例的实现设备安全入网通信系统的逻辑图。Fig. 2 is a logic diagram of a communication system for realizing secure network access of devices according to an embodiment of the present application.
图3是根据本申请实施例的生成出厂信息的方法流程图。Fig. 3 is a flowchart of a method for generating delivery information according to an embodiment of the present application.
图4是根据本申请实施例的安全云设备分发对称认证密钥到智能设备的方法流程图。Fig. 4 is a flowchart of a method for a secure cloud device to distribute a symmetric authentication key to a smart device according to an embodiment of the present application.
图5是根据本申请实施例的安全云设备使用对称认证密钥认证智能设备身份的方法流程图。Fig. 5 is a flow chart of a method for a secure cloud device to authenticate an identity of a smart device using a symmetric authentication key according to an embodiment of the present application.
图6是根据本申请实施例的安全云设备使用对称认证密钥与智能设备相互鉴别对方身份的方法流程图。Fig. 6 is a flow chart of a method for a secure cloud device to use a symmetric authentication key to authenticate each other's identity with a smart device according to an embodiment of the present application.
图7为根据本申请实施例的安全云设备使用RSA密钥算法认证智能设备身份的方法流程图。FIG. 7 is a flow chart of a method for a secure cloud device to authenticate an identity of a smart device using an RSA key algorithm according to an embodiment of the present application.
图8为根据本申请实施例的安全云设备使用RSA密钥算法与智能设备相互鉴别对方身份的方法流程图。FIG. 8 is a flow chart of a method for a security cloud device to use an RSA key algorithm to authenticate each other's identity with a smart device according to an embodiment of the present application.
图9为根据本申请实施例的安全云设备使用SM2密钥算法认证智能设备身份的方法流程图。FIG. 9 is a flow chart of a method for a secure cloud device to authenticate the identity of a smart device using the SM2 key algorithm according to an embodiment of the present application.
图10为根据本申请实施例的安全云设备使用SM2密钥算法与智能设备相互鉴别对方身份的方法流程图。FIG. 10 is a flow chart of a method for a secure cloud device to authenticate each other with a smart device using the SM2 key algorithm according to an embodiment of the present application.
图11为根据本申请实施例的安全云设备使用SM9密钥算法认证智能设备身份的方法流程图。FIG. 11 is a flowchart of a method for a secure cloud device to authenticate a smart device identity using an SM9 key algorithm according to an embodiment of the present application.
图12为根据本申请实施例的安全云设备使用SM9密钥算法与智能设备相互鉴别对方身份的方法流程图。FIG. 12 is a flow chart of a method for a secure cloud device to use the SM9 key algorithm to authenticate each other's identity with a smart device according to an embodiment of the present application.
图13是根据本申请实施例的安全云设备使用对称认证密钥协商数据加密密钥和解密密钥的方法的一个流程图。Fig. 13 is a flow chart of a method for negotiating a data encryption key and a decryption key by a secure cloud device using a symmetric authentication key according to an embodiment of the present application.
图14是根据本申请实施例的安全云设备使用非对称密钥协商数据加密密钥和解密密钥的方法的另一个流程图。Fig. 14 is another flow chart of a method for negotiating a data encryption key and a decryption key by a secure cloud device using an asymmetric key according to an embodiment of the present application.
具体实施方式Detailed ways
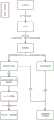
下面将结合本申请实施例中的附图,对本申请实施例中的技术方案进行清楚、完整地描述,显然,所描述的实施例是本申请一部分实施例,而不是全部的实施例。基于本申请中的实施例,本领域技术人员在没有做出创造性劳动前提下所获得的所有其他实施例,都属于本申请保护的范围。The following will clearly and completely describe the technical solutions in the embodiments of the present application with reference to the drawings in the embodiments of the present application. Obviously, the described embodiments are part of the embodiments of the present application, not all of them. Based on the embodiments in this application, all other embodiments obtained by those skilled in the art without making creative efforts belong to the scope of protection of this application.
图2是根据本申请实施例的实现设备安全入网通信系统的逻辑图。如图2所示,该系统包括安全云设备、智能设备/智能终端、智能设备/智能终端的安全芯片以及三种业务服务平台,其中,安全云设备包括安全云和密码装置,三种业务服务平台分别为对称认证密钥业务分发平台、身份认证业务平台和数据密文通信业务平台,其中身份认证业务平台包括对称身份认证业务平台和非对称身份认证业务平台,而非对称身份认证业务平台包括RSA身份认证业务平台、SM2身份认证业务平台和SM9身份认证业务平台。Fig. 2 is a logic diagram of a communication system for realizing secure network access of devices according to an embodiment of the present application. As shown in Figure 2, the system includes security cloud devices, smart devices/smart terminals, security chips of smart devices/smart terminals, and three business service platforms. The platforms are the symmetric authentication key service distribution platform, the identity authentication service platform and the data ciphertext communication service platform, among which the identity authentication service platform includes the symmetric identity authentication service platform and the asymmetric identity authentication service platform, and the asymmetric identity authentication service platform includes RSA identity authentication service platform, SM2 identity authentication service platform and SM9 identity authentication service platform.
在图2所示的系统中,安全云设备中的密码装置可以采用具有PKI算法的密码装置,提供密钥管理、身份认证和数据加解密功能,在智能设备或终端联网与具体业务通信时,保证通信双方身份可信、数据安全传递;同时使用四种密文根密钥安全地管理安全芯片所需的各种密钥,其中,四种根密钥分别为根主控密钥、根应用密钥、根数据保护密钥、根文件保护密钥,依次用于离散出安全芯片的主控密钥、认证密钥、保护安全芯片主控密钥的数据保护密钥、保护生产数据的文件保护密钥。这四种密文根密钥均由密码装置加密(例如通过SM2公钥加密)存储在安全载体中,例如专门的服务器。密码装置负责本系统中所有使用的密钥运算,运算中密钥不出密码装置并且使用完后立即销毁,是本系统实现安全功能的基础设备。In the system shown in Figure 2, the cryptographic device in the security cloud device can use a cryptographic device with a PKI algorithm to provide key management, identity authentication, and data encryption and decryption functions. When smart devices or terminals are connected to the Internet and communicate with specific services, To ensure the credible identity of both communication parties and secure data transmission; at the same time, four kinds of ciphertext root keys are used to securely manage various keys required by the security chip. Among them, the four root keys are the root master control key, key, root data protection key, and root file protection key, which are used in turn to separate the master key of the security chip, the authentication key, the data protection key of the master control key of the security chip, and the file protection of the production data. key. These four ciphertext root keys are all encrypted by cryptographic means (for example, encrypted by SM2 public key) and stored in a secure carrier, such as a dedicated server. The cryptographic device is responsible for all the key calculations used in the system. During the operation, the key does not come out of the cryptographic device and is destroyed immediately after use. It is the basic equipment for the system to realize the security function.
在图2所示的系统中,智能设备具有安全芯片例如,采用PKI算法的安全芯片,联网连接业务服务时,可识别业务服务的身份,同时向业务服务证明身份,并具有传递加密数据给业务服务、解密来自业务的密文数据,实现安全可靠的通信。In the system shown in Figure 2, the smart device has a security chip, for example, a security chip using the PKI algorithm. When connecting to a business service on the Internet, it can identify the identity of the business service, at the same time prove its identity to the business service, and has the ability to transmit encrypted data to the business Serving and decrypting ciphertext data from business to achieve safe and reliable communication.
在图2所示的系统中,业务服务平台采用本系统功能,可识别接入智能设备或终端的身份,同时证明自身身份,并实现加密、解密传输的数据,达到接入设备或终端可信、业务数据传递保密。业务服务平台从逻辑上分为对称认证密钥业务分发平台、身份认证业务平台和数据密文通信业务平台三种业务服务平台,需要注意的是,这三种业务服务平台可以分别分布在一个或多个设备或服务器中,也可以共同分别在同一个设备或服务器中,本申请对此不做任何限制。In the system shown in Figure 2, the business service platform adopts the functions of this system, which can identify the identity of the connected smart device or terminal, at the same time prove its identity, and realize the encryption and decryption of the transmitted data, so as to achieve the trustworthiness of the connected device or terminal. , Business data transfer confidentiality. The business service platform is logically divided into three business service platforms: the symmetric authentication key business distribution platform, the identity authentication business platform, and the data ciphertext communication business platform. It should be noted that these three business service platforms can be distributed in one or Multiple devices or servers may also be in the same device or server respectively, and this application does not impose any limitation on this.
图3是根据本申请实施例的生成出厂信息的方法流程图。申请人经过智能设备向安全云设备为安全芯片申请出厂信息(可以一次性为多个安全芯片申请出厂信息),安全云设备的密码装置生成出厂信息和加密出厂信息的密钥,并加密出厂信息,将密文出厂信息、密钥送达申请人;申请人通过专用工具用密钥解密出厂信息,并用工具将出厂信息灌入安全芯片中。具体来说,图3所示的方法包括如下步骤。Fig. 3 is a flowchart of a method for generating delivery information according to an embodiment of the present application. The applicant applies for the factory information for the security chip from the security cloud device through the smart device (the factory information can be applied for multiple security chips at one time), and the encryption device of the security cloud device generates the factory information and the key for encrypting the factory information, and encrypts the factory information , deliver the ciphertext factory information and key to the applicant; the applicant uses a special tool to decrypt the factory information with the key, and uses the tool to pour the factory information into the security chip. Specifically, the method shown in FIG. 3 includes the following steps.
1、智能设备的安全芯片向安全云设备申请出厂信息。1. The security chip of the smart device applies to the security cloud device for factory information.
2、安全云设备在收到出厂信息申请后,产生出厂信息。2. After receiving the application for ex-factory information, the security cloud device generates ex-factory information.
在一个实施例中,出厂信息包括设备序列号、设备密钥、服务器的公钥;当出厂信息包含了RSA密钥或SM2密钥时,还包括设备证书,其中服务器的公钥为服务器证书的公钥;当出厂信息包含了SM9密钥时,其中服务器的公钥为服务器SM9签名和加密主公钥。设备密钥包括主控密钥。为安全芯片分配设备序列号,主控密钥是以设备序列号为离散因子,使用根主控密钥生成的。In one embodiment, the factory information includes the device serial number, device key, and server public key; when the factory information includes an RSA key or SM2 key, it also includes a device certificate, wherein the server's public key is the server certificate's Public key; when the factory information contains the SM9 key, the server's public key is the server's SM9 signature and encryption master public key. Device keys include master keys. The device serial number is assigned to the security chip, and the master control key is generated using the root master control key based on the device serial number as the discrete factor.
3、安全云设备通过根文件保护密钥离散出文件传输密钥,所述文件传输密钥用于加密出厂信息,形成密文出厂信息。3. The security cloud device discretizes the file transfer key through the root file protection key, and the file transfer key is used to encrypt the delivery information to form ciphertext delivery information.
4、安全云设备通过根数据保护密钥离散出第一数据保护密钥,所述第一数据保护密钥用于加密所述主控密钥。4. The security cloud device discretizes the first data protection key through the root data protection key, and the first data protection key is used to encrypt the master control key.
5、将密文出厂信息、第一数据保护密钥和文件传输密钥发送至所述智能设备。5. Send the ciphertext factory information, the first data protection key and the file transfer key to the smart device.
在一个实施例中,将密文出厂信息和文件传输密钥分开递交给安全生产人员,其中,将密文出厂信息通过加密电子邮件递交给安全生产人员;将文件传输密钥装入带安全芯片的安全卡片中,并将安全卡片安全递交给安全生产人员。在安全芯片生产时,由生产人员在安全环境下通过插有安全卡片的专用生产工具,将密文出厂信息灌入智能设备的安全芯片。In one embodiment, the ciphertext delivery information and the file transfer key are delivered to the safety production personnel separately, wherein, the ciphertext delivery information is submitted to the safety production personnel through encrypted email; the file transfer key is loaded into the security chip in the safety card, and safely hand over the safety card to the safety production personnel. During the production of the security chip, the production personnel will pour the ciphertext factory information into the security chip of the smart device through a special production tool with a security card inserted in a safe environment.
在一个实施例中,图3所示的方法还可以包括:对密文出厂信息进行数据完整性计算,得到MD5值;以及将MD5值发送至所述智能设备。MD5值用于保证密文出厂信息的数据完整性。In one embodiment, the method shown in FIG. 3 may further include: performing data integrity calculation on the ciphertext factory information to obtain an MD5 value; and sending the MD5 value to the smart device. The MD5 value is used to ensure the data integrity of the ciphertext factory information.
在一个实施例中,安全云设备使用密码装置为安全芯片产生需要的非对称密钥,如RSA或SM2,并为该密钥生成一个证书,即设备证书;其中公钥为设备公钥,私钥为设备私钥。这样,设备密钥还包括设备公钥和设备私钥,所述设备公钥和所述设备私钥是安全云设备为所述智能设备的安全芯片产生的非对称密钥。对于该非对称密钥,图3所示的方法还可以包括:通过根数据保护密钥离散出第二数据保护密钥,所述第二数据保护密钥用于加密所述设备私钥;以及将所述第二数据保护密钥发送至所述智能设备。In one embodiment, the security cloud device uses a cryptographic device to generate a required asymmetric key for the security chip, such as RSA or SM2, and generates a certificate for the key, that is, a device certificate; wherein the public key is the device public key, and the private key is The key is the device private key. In this way, the device key also includes a device public key and a device private key, and the device public key and the device private key are asymmetric keys generated by the security cloud device for the security chip of the smart device. For the asymmetric key, the method shown in FIG. 3 may further include: discretizing a second data protection key through the root data protection key, and the second data protection key is used to encrypt the device private key; and sending the second data protection key to the smart device.
智能设备使用专用工具将密文出厂信息灌入安全芯片。在专用工具内部,使用所接收的文件传输密钥和数据保护密钥对密文出厂信息进行解密,将解密后的出厂信息存储在安全芯片的安全区域。The smart device uses a special tool to pour the ciphertext factory information into the security chip. Inside the special tool, use the received file transfer key and data protection key to decrypt the ciphertext delivery information, and store the decrypted delivery information in the security area of the security chip.
通过图3所述的方法,安全地为智能设备提供出厂信息,并以安全芯片存储,并使用专用工具将出厂信息灌入到芯片中。安全芯片在出厂过程中就预置了用于产生后续所要加解密密钥和认证密钥所需信息,无需在线分发,这样不会严重依赖密钥分发过程中的网络安全或烧录桌面环境安全。Through the method described in Figure 3, the factory information is safely provided for the smart device, stored in a secure chip, and the factory information is poured into the chip using a special tool. The security chip is preset with the information required to generate subsequent encryption and decryption keys and authentication keys during the factory process, without online distribution, so that it will not rely heavily on network security or burning desktop environment security during the key distribution process .
图4是根据本申请实施例的安全云设备分发对称认证密钥到智能设备的方法流程图。当智能设备使用对称密钥算法进行身份认证时,需要通过业务服务平台向安全云设备申请认证密钥,安全云设备中的密码装置为安全芯片分配一个唯一的认证密钥,并以密文形式传递给智能设备;最后智能设备在安全芯片内部解密密文认证密钥,并存储到安全芯片的安全区域。具体来说,图4所示的方法包括如下步骤。Fig. 4 is a flowchart of a method for a secure cloud device to distribute a symmetric authentication key to a smart device according to an embodiment of the present application. When a smart device uses a symmetric key algorithm for identity authentication, it needs to apply for an authentication key from the security cloud device through the business service platform. Pass it to the smart device; finally, the smart device decrypts the ciphertext authentication key inside the security chip and stores it in the secure area of the security chip. Specifically, the method shown in FIG. 4 includes the following steps.
1、安全芯片生成随机数,智能设备从安全芯片中获取随机数和设备序列号,形成认证密钥申请信息,并传输给认证密钥分发业务平台,申请认证密钥;1. The security chip generates a random number, and the smart device obtains the random number and device serial number from the security chip, forms the authentication key application information, and transmits it to the authentication key distribution service platform to apply for the authentication key;
2、认证密钥分发业务平台根据认证密钥申请信息获取随机数、设备序列号,并传输给安全云设备,请求安全云设备分发认证密钥;2. The authentication key distribution service platform obtains random numbers and device serial numbers according to the authentication key application information, and transmits them to the security cloud device, requesting the security cloud device to distribute the authentication key;
3、安全云设备使用设备序列号查询是否存在此安全芯片的生产数据,如果不存在,通知认证密钥分发业务平台终止本次申请;如果存在执行步骤4;3. The security cloud device uses the device serial number to check whether there is production data of this security chip. If it does not exist, notify the authentication key distribution service platform to terminate this application; if it exists, go to step 4;
4、安全云设备使用根主控密钥以设备序列号为离散因子,重新在密码装置内计算出安全芯片的主控密钥;4. The security cloud device uses the root master key to recalculate the master key of the security chip in the cryptographic device with the serial number of the device as the discrete factor;
5、安全云设备的密码装置使用主控密钥对随机数进行加密,获得保护认证密钥的保护密钥;5. The cryptographic device of the secure cloud device uses the master key to encrypt the random number to obtain the protection key for protecting the authentication key;
6、安全云设备使用根应用密钥在密码装置内生成认证密钥,并以保护密钥加密,同时对密文认证密钥计算MAC值,将密文认证密钥和MAC值封装成认证密钥数据,返回给认证密钥分发业务平台;6. The secure cloud device uses the root application key to generate an authentication key in the cryptographic device, encrypts it with the protection key, and calculates the MAC value for the ciphertext authentication key, and encapsulates the ciphertext authentication key and MAC value into an authentication key. The key data is returned to the authentication key distribution business platform;
7、认证密钥分发业务平台将认证密钥数据传给智能设备;7. The authentication key distribution service platform transmits the authentication key data to the smart device;
8、智能设备使用安全芯片验证认证密钥数据中的MAC值,如果正确后,将密文认证密钥写入安全芯片;8. The smart device uses the security chip to verify the MAC value in the authentication key data, and if it is correct, write the ciphertext authentication key into the security chip;
9、安全芯片内部解密密文认证密钥,将解密后的认证密钥存储到安全芯片的安全区。9. The security chip internally decrypts the ciphertext authentication key, and stores the decrypted authentication key in the security area of the security chip.
通过图4所示的方法,安全地为智能设备在线分发一个认证密钥;当分发认证密钥时,网络无需传输保护认证密钥的密钥。Through the method shown in Figure 4, an authentication key is safely distributed online for smart devices; when the authentication key is distributed, the network does not need to transmit the key that protects the authentication key.
图5是根据本申请实施例的安全云设备使用对称认证密钥认证智能设备身份的方法流程图。图6是根据本申请实施例的安全云设备使用对称认证密钥与智能设备相互鉴别对方身份的方法流程图。当智能设备通过业务服务平台,与安全云设备进行身份认证时,使用安全芯片生成认证信息(认证码和其它信息),并递交给安全云设备;安全云设备收到智能设备的认证信息时,使用密码装置检验认证信息是否有效,并将结果返回给业务服务;如果身份认证是双向的且智能设备的认证信息有效时,安全云设备会生成认证信息,并将认证信息返回给智能设备,最后智能设备使用安全芯片验证安全云设备的认证信息,如果检测到认证信息无效,终止通信。Fig. 5 is a flow chart of a method for a secure cloud device to authenticate an identity of a smart device using a symmetric authentication key according to an embodiment of the present application. Fig. 6 is a flow chart of a method for a secure cloud device to use a symmetric authentication key to authenticate each other's identity with a smart device according to an embodiment of the present application. When the smart device authenticates with the security cloud device through the business service platform, use the security chip to generate authentication information (authentication code and other information) and submit it to the security cloud device; when the security cloud device receives the authentication information of the smart device, Use a cryptographic device to check whether the authentication information is valid, and return the result to the business service; if the identity authentication is two-way and the authentication information of the smart device is valid, the security cloud device will generate the authentication information, and return the authentication information to the smart device, and finally The smart device uses the security chip to verify the authentication information of the security cloud device, and if it detects that the authentication information is invalid, the communication is terminated.
具体来说,图5所示的方法包括如下步骤。Specifically, the method shown in FIG. 5 includes the following steps.
1、智能设备向对称身份认证业务平台发起身份验证申请;1. The smart device initiates an identity verification application to the symmetric identity authentication business platform;
2、对称身份认证业务平台收到所述身份验证申请后,向安全云设备请求为该申请生成随机数,参与智能设备产生身份认证信息;2. After receiving the identity verification application, the symmetrical identity authentication service platform requests the secure cloud device to generate a random number for the application, and participates in the smart device to generate identity authentication information;
3、安全云设备的密码装置生成随机数,记为随机数A,并递交给对称身份认证业务平台;3. The cryptographic device of the secure cloud device generates a random number, which is recorded as the random number A, and submitted to the symmetric identity authentication service platform;
4、对称身份认证业务平台将随机数A送达智能设备;4. The symmetric identity authentication service platform delivers the random number A to the smart device;
5、智能设备收到随机数A后,向安全芯片申请产生能验证安全芯片的身份信息;5. After receiving the random number A, the smart device applies to the security chip to generate identity information that can verify the security chip;
6、安全芯片产生随机数B,以随机数A和B为认证信息元数据,使用对称认证密钥将该元数据生成第一认证码,将包含第一认证码和设备序列号的身份认证信息返回给智能设备;6. The security chip generates a random number B, uses the random numbers A and B as the authentication information metadata, uses the symmetric authentication key to generate the first authentication code from the metadata, and will include the identity authentication information of the first authentication code and the device serial number return to the smart device;
7、智能设备向对称身份认证业务平台递交身份认证信息;7. The smart device submits identity authentication information to the symmetric identity authentication service platform;
8、对称身份认证业务平台将身份认证信息送达安全云设备,请求验证该信息的有效性;8. The symmetric identity authentication business platform sends the identity authentication information to the security cloud device, requesting to verify the validity of the information;
9、安全云设备从身份认证信息中取出安全芯片的设备序列号、随机数B、第一认证码,使用根应用密钥在密码装置内重新计算出安全芯片的认证密钥,并使用该认证密钥将随机数A和B重新计算出第二认证码,将两个认证码进行比较,如果相同,说明安全芯片的身份合法,通知对称身份认证业务平台身份认证成功,否则,通知对称身份认证业务平台身份认证失败。9. The security cloud device takes out the device serial number of the security chip, random number B, and the first authentication code from the identity authentication information, uses the root application key to recalculate the authentication key of the security chip in the cryptographic device, and uses the authentication key The key recalculates the second authentication code from the random numbers A and B, and compares the two authentication codes. If they are the same, it means that the identity of the security chip is legal, and the symmetric identity authentication service platform is notified that the identity authentication is successful. Otherwise, the symmetric identity authentication is notified. The service platform identity authentication failed.
图6是安全云设备使用对称认证密钥与智能设备相互鉴别对方身份的方法流程图。与图5相比,区别在于,对称身份认证业务平台接收到安全云认证结果后,如果不成功,终止身份认证业务,如果成功,则进一步执行如下步骤:Fig. 6 is a flow chart of a method for a secure cloud device to use a symmetric authentication key to authenticate each other's identity with a smart device. Compared with Figure 5, the difference is that after the symmetric identity authentication service platform receives the security cloud authentication result, if it is unsuccessful, the identity authentication service is terminated, and if it succeeds, the following steps are further performed:
1、安全云设备返回安全云身份认证信息,安全云身份认证信息包括第三认证码,其中,该第三认证码为使用该认证密钥按照组合规则基于随机数A和B计算得到的,对称身份认证业务平台将安全云身份认证信息返回给智能终端;1. The secure cloud device returns the secure cloud identity authentication information, which includes the third authentication code, where the third authentication code is calculated based on the random numbers A and B using the authentication key according to the combination rules, and is symmetrical The identity authentication business platform returns the security cloud identity authentication information to the smart terminal;
2、智能终端收到安全云身份认证信息后,将第三认证码送达安全芯片,认证安全云设备身份是否可信;2. After receiving the security cloud identity authentication information, the smart terminal sends the third authentication code to the security chip to verify whether the security cloud device identity is credible;
3、安全芯片根据安全云设备计算认证码的规则,以随机数A和随机数B为元数据按照组合规则,重新计算出第四认证码,将第三和第四认证码进行比较,如果相同,通知智能设备安全云设备身份可信,否则通知智能设备安全云设备身份不可信。3. The security chip recalculates the fourth authentication code according to the rules for computing authentication codes of security cloud devices, using random number A and random number B as metadata according to the combination rules, and compares the third and fourth authentication codes. If they are the same , notify the smart device security cloud that the device identity is credible, otherwise notify the smart device security cloud that the device identity is untrustworthy.
在双向身份认证成功后,可以进入其它业务或密文通信业务。After the two-way identity authentication is successful, other services or ciphertext communication services can be entered.
通过图5和图6所示的方法,提供支持多种密钥算法、多种身份认证方式的身份认证。支持使用认证密钥进行单向确认智能设备/智能终端身份,实现身份认证;支持使用认证密钥在安全云与智能设备/智能终端之间互相确认对方身份,实现身份认证;身份认证过程只需传递少量的随机数(例如,16字节),不传输身份认证明文内容,加强身份认证的安全性。Through the methods shown in Fig. 5 and Fig. 6, identity authentication supporting multiple key algorithms and multiple identity authentication methods is provided. Supports the use of authentication keys for one-way confirmation of the identity of smart devices/smart terminals to achieve identity authentication; supports the use of authentication keys to mutually confirm the identity of each other between the security cloud and smart devices/smart terminals to achieve identity authentication; the identity authentication process only needs Pass a small amount of random numbers (for example, 16 bytes), and do not transmit the identity authentication plaintext content, so as to strengthen the security of identity authentication.
图7为根据本申请实施例的安全云设备使用RSA密钥算法认证智能设备身份的方法流程图。如图7所示,安全云设备使用RSA密钥对密钥算法,单向认证设备或终端身份信息的过程,具体步骤如下:FIG. 7 is a flow chart of a method for a secure cloud device to authenticate an identity of a smart device using an RSA key algorithm according to an embodiment of the present application. As shown in Figure 7, the security cloud device uses the RSA key-to-key algorithm to unidirectionally authenticate the identity information of the device or terminal. The specific steps are as follows:
1、智能设备获取安全芯片的设备证书、设备序列号,使用安全芯片生成随机数A,并以随机数A和设备序列号为元数据,在安全芯片内用设备私钥对该元数据签名生成签名数据,向RSA身份认证业务平台递交包含设备证书、设备序列号、随机数A和签名数据的设备认证信息,发起身份验证申请;1. The smart device obtains the device certificate and device serial number of the security chip, uses the security chip to generate a random number A, and uses the random number A and the device serial number as metadata, and uses the device private key to sign the metadata in the security chip to generate Signature data, submit device authentication information including device certificate, device serial number, random number A and signature data to the RSA identity authentication business platform, and initiate an identity verification application;
2、RSA身份认证业务平台收到所述身份验证申请后,将设备认证信息送达安全云设备,请求安全云设备验证该信息的有效性;2. After receiving the identity verification application, the RSA identity authentication service platform sends the device authentication information to the security cloud device, and requests the security cloud device to verify the validity of the information;
3、安全云设备检查认证信息中设备序列号是否有效,如果无效,通知RSA身份认证业务平台认证失败;通过密码装置,使用根证书验证认证信息中的设备证书是否有效,如果无效,通知RSA身份认证业务平台认证失败;使用设备证书中的公钥、认证信息中的元数据在密码装置内验证签名是否有效,如果签名无效,通知RSA身份认证业务平台认证失败;所有验证有效后,发送验证成功信息,例如使用密码装置产生随机数B,将随机数B返会RSA身份认证业务平台表示认证成功;3. The security cloud device checks whether the device serial number in the authentication information is valid. If it is invalid, it notifies the RSA identity authentication business platform that the authentication fails; through the password device, it uses the root certificate to verify whether the device certificate in the authentication information is valid. If it is invalid, it notifies the RSA identity The authentication service platform authentication fails; use the public key in the device certificate and the metadata in the authentication information to verify whether the signature is valid in the cryptographic device, if the signature is invalid, notify the RSA identity authentication service platform of the authentication failure; after all the verifications are valid, send the verification success Information, such as using a cryptographic device to generate a random number B, returning the random number B to the RSA identity authentication service platform to indicate that the authentication is successful;
4、RSA身份认证业务平台将随机数B送达智能设备;4. The RSA identity authentication service platform delivers the random number B to the smart device;
5、智能设备收到随机数B后,身份认证结束。5. After the smart device receives the random number B, the identity authentication ends.
图8为根据本申请实施例的安全云设备使用RSA密钥算法与智能设备相互鉴别对方身份的方法流程图。如图8所示,安全云设备使用RSA密钥对密钥算法,与智能设备进行相互认证身份信息的过程,具体步骤如下:FIG. 8 is a flow chart of a method for a security cloud device to use an RSA key algorithm to authenticate each other's identity with a smart device according to an embodiment of the present application. As shown in Figure 8, the security cloud device uses the RSA key-to-key algorithm to perform mutual authentication of identity information with the smart device. The specific steps are as follows:
1、智能设备获取安全芯片的设备证书、设备序列号,使用安全芯片生成随机数A,并以随机数A和设备序列号为元数据,在安全芯片内用设备私钥对该元数据签名生成签名数据,向RSA身份认证业务平台递交包含设备证书、设备序列号、随机数A和签名数据的设备认证信息,发起身份验证申请;1. The smart device obtains the device certificate and device serial number of the security chip, uses the security chip to generate a random number A, and uses the random number A and the device serial number as metadata, and uses the device private key to sign the metadata in the security chip to generate Signature data, submit device authentication information including device certificate, device serial number, random number A and signature data to the RSA identity authentication business platform, and initiate an identity verification application;
2、RSA身份认证业务平台收到所述身份验证申请后,将设备认证信息送达安全云设备,请求安全云设备验证该信息的有效性;2. After receiving the identity verification application, the RSA identity authentication service platform sends the device authentication information to the security cloud device, and requests the security cloud device to verify the validity of the information;
3、安全云设备检查认证信息中设备序列号是否有效,如果无效,通知RSA身份认证业务平台认证失败;通过密码装置,使用根证书验证认证信息中的设备证书是否有效,如果无效,通知RSA身份认证业务平台认证失败;使用设备证书中的公钥、认证信息中的元数据在密码装置内验证签名是否有效,如果签名无效,通知RSA身份认证业务平台认证失败;所有验证有效后,使用密码装置产生随机数B,并以随机数B和设备序列号为元数据,在密码装置内用安全云根私钥对元数据签名,将包含随机数B和签名数据的安全云认证信息B返会RSA身份认证业务平台表示认证成功;3. The security cloud device checks whether the device serial number in the authentication information is valid. If it is invalid, it notifies the RSA identity authentication business platform that the authentication fails; through the password device, it uses the root certificate to verify whether the device certificate in the authentication information is valid. If it is invalid, it notifies the RSA identity The authentication service platform authentication fails; use the public key in the device certificate and the metadata in the authentication information to verify whether the signature is valid in the cryptographic device, if the signature is invalid, notify the RSA identity authentication service platform of the authentication failure; after all verifications are valid, use the cryptographic device Generate a random number B, use the random number B and the device serial number as metadata, sign the metadata with the secure cloud root private key in the cryptographic device, and return the secure cloud authentication information B containing the random number B and signature data to RSA The identity authentication business platform indicates that the authentication is successful;
4、RSA身份认证业务平台将安全云认证信息B送达智能设备;4. The RSA identity authentication business platform delivers the security cloud authentication information B to the smart device;
5、智能设备收到安全云认证信息B后,在安全芯片内用安全云公钥对认证信息B中的签名数据验证签名,如果验证失败,说明安全云不可信,结束通信。5. After receiving the security cloud authentication information B, the smart device uses the security cloud public key to verify the signature of the signature data in the authentication information B in the security chip. If the verification fails, it means that the security cloud is not trustworthy and the communication ends.
图9为根据本申请实施例的安全云设备使用SM2密钥算法认证智能设备身份的方法流程图。如图9所示,安全云设备使用SM2密钥对密钥算法,单向认证设备或终端身份信息的过程,具体步骤如下:FIG. 9 is a flow chart of a method for a secure cloud device to authenticate the identity of a smart device using the SM2 key algorithm according to an embodiment of the present application. As shown in Figure 9, the security cloud device uses the SM2 key-to-key algorithm to unidirectionally authenticate the identity information of the device or terminal. The specific steps are as follows:
1、智能设备获取安全芯片的设备证书、设备序列号,使用安全芯片生成随机数A,并以随机数A、设备序列号和默认用户ID为元数据,在安全芯片内用设备私钥对该元数据签名生成签名数据,向SM2身份认证业务平台递交包含设备证书、设备序列号、随机数A和签名数据的设备认证信息,发起身份验证申请;1. The smart device obtains the device certificate and device serial number of the security chip, uses the security chip to generate a random number A, and uses the random number A, device serial number and default user ID as metadata, and uses the device private key in the security chip to Metadata signature generates signature data, submits device authentication information including device certificate, device serial number, random number A and signature data to SM2 identity authentication business platform, and initiates an identity verification application;
2、SM2身份认证业务平台收到所述身份验证申请后,将设备认证信息送达安全云设备,请求安全云设备验证该信息的有效性;2. After receiving the identity verification application, the SM2 identity authentication service platform sends the device authentication information to the security cloud device, and requests the security cloud device to verify the validity of the information;
3、安全云设备检查认证信息中设备序列号是否有效,如果无效,通知SM2身份认证业务平台认证失败;通过密码装置,使用根证书验证认证信息中的设备证书是否有效,如果无效,通知SM2身份认证业务平台认证失败;使用设备证书中的公钥、认证信息中的元数据及默认用户ID在密码装置内验证签名是否有效,如果签名无效,通知SM2身份认证业务平台认证失败;所有验证有效后,使用密码装置产生SM2密钥协商公钥和私钥,将包含密钥协商公钥和安全云标识数据的安全云认证信息B返回SM2身份认证业务平台表示认证成功;3. The security cloud device checks whether the device serial number in the authentication information is valid. If it is invalid, notify the SM2 identity authentication business platform of authentication failure; use the root certificate to verify whether the device certificate in the authentication information is valid through the password device, and notify SM2 if it is invalid. The authentication service platform authentication fails; use the public key in the device certificate, the metadata in the authentication information and the default user ID to verify whether the signature is valid in the cryptographic device, if the signature is invalid, notify the SM2 identity authentication service platform of the authentication failure; after all verifications are valid , using a cryptographic device to generate the SM2 key negotiation public key and private key, returning the security cloud authentication information B including the key negotiation public key and the security cloud identification data to the SM2 identity authentication service platform to indicate that the authentication is successful;
4、SM2身份认证业务平台将安全云认证信息B送达智能设备;4. The SM2 identity authentication business platform delivers the security cloud authentication information B to the smart device;
5、智能设备收到安全云认证信息B后,身份认证结束。5. After the smart device receives the security cloud authentication information B, the identity authentication ends.
图10为根据本申请实施例的安全云设备使用SM2密钥算法与智能设备相互鉴别对方身份的方法流程图。如图10所示,安全云设备使用SM2密钥对密钥算法,与智能设备进行相互认证身份信息的过程,具体步骤如下:FIG. 10 is a flow chart of a method for a secure cloud device to authenticate each other with a smart device using the SM2 key algorithm according to an embodiment of the present application. As shown in Figure 10, the security cloud device uses the SM2 key pair key algorithm to perform mutual authentication of identity information with the smart device. The specific steps are as follows:
1、智能设备获取安全芯片的设备证书、设备序列号,使用安全芯片生成随机数A,并以随机数A、设备序列号和默认用户ID为元数据,在安全芯片内用设备私钥对该元数据签名生成签名数据,向SM2身份认证业务平台递交包含设备证书、设备序列号、随机数A和签名数据的设备认证信息,发起身份验证申请;1. The smart device obtains the device certificate and device serial number of the security chip, uses the security chip to generate a random number A, and uses the random number A, device serial number and default user ID as metadata, and uses the device private key in the security chip to Metadata signature generates signature data, submits device authentication information including device certificate, device serial number, random number A and signature data to SM2 identity authentication business platform, and initiates an identity verification application;
2、SM2身份认证业务平台收到所述身份验证申请后,将设备认证信息送达安全云设备,请求安全云设备验证该信息的有效性;2. After receiving the identity verification application, the SM2 identity authentication service platform sends the device authentication information to the security cloud device, and requests the security cloud device to verify the validity of the information;
3、安全云设备检查认证信息中设备序列号是否有效,如果无效,通知SM2身份认证业务平台认证失败;通过密码装置,使用根证书验证认证信息中的设备证书是否有效,如果无效,通知SM2身份认证业务平台认证失败;使用设备证书中的公钥、认证信息中的元数据及默认用户ID在密码装置内验证签名是否有效,如果签名无效,通知SM2身份认证业务平台认证失败;所有验证有效后,使用密码装置产生随机数B,并以随机数B、设备序列号和默认用户ID为元数据,在密码装置内用安全云根私钥对元数据签名,同时产生SM2密钥协商公钥和私钥,将包含随机数B、安全云标识数据、签名数据和密钥协商公钥的认证信息B返会SM2身份认证业务平台表示认证成功;3. The security cloud device checks whether the device serial number in the authentication information is valid. If it is invalid, notify the SM2 identity authentication business platform of authentication failure; use the root certificate to verify whether the device certificate in the authentication information is valid through the password device, and notify SM2 if it is invalid. The authentication service platform authentication fails; use the public key in the device certificate, the metadata in the authentication information and the default user ID to verify whether the signature is valid in the cryptographic device, if the signature is invalid, notify the SM2 identity authentication service platform of the authentication failure; after all verifications are valid , use a cryptographic device to generate a random number B, and use the random number B, device serial number and default user ID as metadata, use the secure cloud root private key to sign the metadata in the cryptographic device, and generate the SM2 key negotiation public key and Private key, return authentication information B including random number B, secure cloud identification data, signature data, and key negotiation public key to the SM2 identity authentication service platform to indicate that the authentication is successful;
4、SM2身份认证业务平台将认证信息B送达智能设备;4. The SM2 identity authentication business platform delivers the authentication information B to the smart device;
5、智能设备收到安全云认证信息B后,在安全芯片内用安全云公钥对认证信息B中的签名数据验证签名,如果验证失败,说明安全云不可信,结束通信。5. After receiving the security cloud authentication information B, the smart device uses the security cloud public key to verify the signature of the signature data in the authentication information B in the security chip. If the verification fails, it means that the security cloud is not trustworthy and the communication ends.
图11为根据本申请实施例的安全云设备使用SM9密钥算法认证智能设备身份的方法流程图。如图11所示,安全云设备使用SM9密钥对密钥算法,单向认证设备或终端身份信息的过程,具体步骤如下:FIG. 11 is a flowchart of a method for a secure cloud device to authenticate a smart device identity using an SM9 key algorithm according to an embodiment of the present application. As shown in Figure 11, the security cloud device uses the SM9 key-to-key algorithm to unidirectionally authenticate the identity information of the device or terminal. The specific steps are as follows:
1、智能设备获取设备序列号,使用安全芯片生成随机数A,并以随机数A和设备序列号为元数据,在安全芯片内用设备私钥对该元数据签名生成签名数据,向SM9身份认证业务平台递交包含设备序列号、随机数A和签名数据的设备认证信息,发起身份验证申请;1. The smart device obtains the device serial number, uses the security chip to generate a random number A, and takes the random number A and the device serial number as metadata, uses the device private key to sign the metadata in the security chip to generate signature data, and submits the signature data to the SM9 identity The authentication business platform submits the device authentication information including the device serial number, random number A and signature data, and initiates an identity verification application;
2、SM9身份认证业务平台收到所述身份验证申请后,将设备认证信息送达安全云设备,请求安全云设备验证该信息的有效性;2. After receiving the identity verification application, the SM9 identity authentication service platform sends the device authentication information to the security cloud device, and requests the security cloud device to verify the validity of the information;
3、安全云设备检查认证信息中设备序列号是否有效,如果无效,通知SM9身份认证业务平台认证失败;通过设备序列号获取设备的用户ID,使用签名主公钥、认证信息中的元数据及用户ID在密码装置内验证签名是否有效,如果签名无效,通知SM9身份认证业务平台认证失败;所有验证有效后,使用密码装置产生SM9密钥协商公钥和私钥,将包含密钥协商公钥和安全云标识数据的安全云信息B返会SM9身份认证业务平台表示认证成功;3. The security cloud device checks whether the device serial number in the authentication information is valid. If it is invalid, it notifies the SM9 identity authentication service platform of authentication failure; obtains the user ID of the device through the device serial number, and uses the signature master public key, metadata in the authentication information and The user ID verifies whether the signature is valid in the cryptographic device. If the signature is invalid, notify the SM9 identity authentication service platform that the authentication fails; after all verifications are valid, use the cryptographic device to generate the SM9 key negotiation public key and private key, which will contain the key negotiation public key The security cloud information B of the security cloud identification data will return to the SM9 identity authentication service platform to indicate that the authentication is successful;
4、SM9身份认证业务平台将安全云信息B送达智能设备;4. The SM9 identity authentication business platform delivers the security cloud information B to the smart device;
5、智能设备收到安全云信息B后,身份认证结束。5. After the smart device receives the security cloud information B, the identity authentication ends.
图12为根据本申请实施例的安全云设备使用SM9密钥算法与智能设备相互鉴别对方身份的方法流程图。如图12所示,安全云设备使用SM9密钥对密钥算法,与智能设备进行相互认证身份信息的过程,具体步骤如下:FIG. 12 is a flow chart of a method for a secure cloud device to use the SM9 key algorithm to authenticate each other's identity with a smart device according to an embodiment of the present application. As shown in Figure 12, the security cloud device uses the SM9 key pair key algorithm to perform mutual authentication of identity information with the smart device. The specific steps are as follows:
1、智能设备获取安全芯片的设备序列号,使用安全芯片生成随机数A,并以随机数A和设备序列号为元数据,在安全芯片内用设备私钥对该元数据签名生成签名数据,向SM9身份认证业务平台递交包含设备序列号、随机数A和签名数据的设备认证信息,发起身份验证申请;1. The smart device obtains the device serial number of the security chip, uses the security chip to generate a random number A, and uses the random number A and the device serial number as metadata, and uses the device private key to sign the metadata in the security chip to generate signature data. Submit the device authentication information including the device serial number, random number A and signature data to the SM9 identity authentication service platform, and initiate an identity verification application;
2、SM9身份认证业务平台收到所述身份验证申请后,将设备认证信息送达安全云设备,请求安全云设备验证该信息的有效性;2. After receiving the identity verification application, the SM9 identity authentication service platform sends the device authentication information to the security cloud device, and requests the security cloud device to verify the validity of the information;
3、安全云设备检查认证信息中设备序列号是否有效,如果无效,通知SM9身份认证业务平台认证失败;通过设备序列号获取设备的用户ID,使用签名主公钥、认证信息中的元数据及用户ID在密码装置内验证签名是否有效,如果签名无效,通知SM9身份认证业务平台认证失败;所有验证有效后,使用密码装置产生随机数B,并以随机数B和安全云标识数据为元数据,在密码装置内用安全云根私钥对元数据签名,同时产生SM9密钥协商公钥和私钥,将包含随机数B、安全云标识数据、签名数据和密钥协商公钥的认证信息B返会SM9身份认证业务平台表示认证成功;3. The security cloud device checks whether the device serial number in the authentication information is valid. If it is invalid, it notifies the SM9 identity authentication service platform of authentication failure; obtains the user ID of the device through the device serial number, and uses the signature master public key, metadata in the authentication information and The user ID verifies whether the signature is valid in the cryptographic device, and if the signature is invalid, notify the SM9 identity authentication service platform of authentication failure; after all verifications are valid, use the cryptographic device to generate a random number B, and use the random number B and the security cloud identification data as metadata , use the security cloud root private key to sign the metadata in the cryptographic device, and generate the SM9 key negotiation public key and private key at the same time, which will include random number B, security cloud identification data, signature data and key negotiation public key authentication information B will return to the SM9 identity authentication business platform to indicate that the authentication is successful;
4、SM9身份认证业务平台将认证信息B送达智能设备;4. The SM9 identity authentication business platform delivers the authentication information B to the smart device;
5、智能设备收到安全云认证信息B后,在安全芯片内用安全云签名主公钥和安全云标识数据对认证信息B中的签名数据验证签名,如果验证失败,说明安全云不可信,结束通信。5. After the smart device receives the security cloud authentication information B, it uses the security cloud signature master public key and the security cloud identification data to verify the signature of the signature data in the authentication information B in the security chip. If the verification fails, it means that the security cloud is not trustworthy. End communication.
当智能设备与业务平台进行密文通信时,必须使用身份认证信息中的数据产生加密或解密数据的密钥,统称为会话密钥,根据身份认证方式不同,加密或解密的密钥产生方式也不同。其中使用对称认证密钥和RSA密钥进行身份认证的认证方式,产生会话密钥流程完全相同,均使用对称认证密钥产生,称为对称认证密钥生成方式;而使用SM 2和SM 9密钥进行身份认证的认证方式,产生会话密钥流程相似,都是按照国密标准文档中对应的密钥协商原理产生,称为密钥协商生成方式。下面为它们的详细介绍。When the smart device communicates with the service platform in ciphertext, the data in the identity authentication information must be used to generate the key for encrypting or decrypting the data, collectively referred to as the session key. Depending on the identity authentication method, the encryption or decryption key generation method is different different. Among them, the authentication method using symmetric authentication key and RSA key for identity authentication has exactly the same process of generating session key, both of which are generated using symmetric authentication key, which is called symmetric authentication key generation method; while using SM 2 and SM 9 encryption The authentication method for identity authentication using a key is similar to the process of generating a session key, which is generated according to the corresponding key negotiation principle in the national secret standard document, which is called the key negotiation generation method. The following are their detailed introductions.
图13是根据本申请实施例的安全云设备使用对称认证密钥协商数据加密密钥和解密密钥的方法的一个流程图。图14是根据本申请实施例的安全云设备使用非对称密钥协商数据加密密钥和解密密钥的方法的另一个流程图。当智能设备与安全云设备之间通过身份认证后,智能设备计算出自身的加密数据的加密密钥和安全云设备的加密数据的加密密钥。当智能设备与业务服务平台之间传输带敏感的数据时,通信流程如下:Fig. 13 is a flow chart of a method for negotiating a data encryption key and a decryption key by a secure cloud device using a symmetric authentication key according to an embodiment of the present application. Fig. 14 is another flow chart of a method for negotiating a data encryption key and a decryption key by a secure cloud device using an asymmetric key according to an embodiment of the present application. After identity authentication is passed between the smart device and the security cloud device, the smart device calculates the encryption key of its own encrypted data and the encryption key of the encrypted data of the security cloud device. When sensitive data is transmitted between the smart device and the business service platform, the communication process is as follows:
密文上发:智能设备与业务服务平台进行敏感信息通信时,使用自身的加密密钥对数据加密,并发送给业务服务平台。业务服务平台将密文数据传给安全云设备,请求解密;安全云设备使用密码装置计算出智能设备的加密数据的密钥,对密文解密返回明文数据给业务服务平台;Cipher text upload: When the smart device communicates sensitive information with the business service platform, it uses its own encryption key to encrypt the data and sends it to the business service platform. The business service platform transmits the ciphertext data to the security cloud device and requests decryption; the security cloud device uses the cryptographic device to calculate the key of the encrypted data of the smart device, decrypts the ciphertext and returns the plaintext data to the business service platform;
密文下发:当业务服务平台需要传输密文给智能设备时,将明文数据传给安全云设备;安全云设备使用密码装置计算出安全云设备的加密数据的密钥、加密明文数据,并返回给业务服务平台;最后业服务平台将密文结果返回给智能设备;智能设备收到密文数据后,使用安全芯片计算出安全云设备的加密数据的密钥,解密密文。Ciphertext delivery: When the business service platform needs to transmit ciphertext to the smart device, it transmits the plaintext data to the security cloud device; the security cloud device uses the cryptographic device to calculate the key of the encrypted data of the security cloud device, encrypts the plaintext data, and Return to the business service platform; finally, the business service platform returns the ciphertext result to the smart device; after the smart device receives the ciphertext data, it uses the security chip to calculate the key of the encrypted data of the security cloud device, and decrypts the ciphertext.
图13是关于采用认证密钥生成会话密钥的方法。在身份认证成功后,安全云设备根据加密或解密申请,分别在密码装置内生成对应的加密密钥或解密密钥,完成申请请求。具体来说,图13包括如下步骤。Fig. 13 is about the method of generating session key using authentication key. After successful identity authentication, the security cloud device generates a corresponding encryption key or decryption key in the cryptographic device according to the encryption or decryption application, and completes the application request. Specifically, Fig. 13 includes the following steps.
1、智能设备向数据密文通信业务平台传输密文数据时,将身份认证过程中随机数A传给安全芯片,并要求安全芯片加密待传输的数据;1. When the smart device transmits ciphertext data to the data ciphertext communication service platform, it transmits the random number A in the identity authentication process to the security chip, and requires the security chip to encrypt the data to be transmitted;
2、安全芯片按照指定协议将随机数A和B重新封装为一组数据,以该数据为离散因子,使用认证密钥离散出加密会话密钥,记为会话密钥A,使用会话密钥A将待传输的数据加密,并返回给智能设备;2. The security chip repackages the random numbers A and B into a set of data according to the specified protocol, uses the data as the discretization factor, and uses the authentication key to discretize the encrypted session key, which is recorded as the session key A, and uses the session key A Encrypt the data to be transmitted and return it to the smart device;
3、智能设备将密文数据、设备序列号封装成业务数据传输给数据密文通信业务平台,进行业务通信;3. The smart device encapsulates the ciphertext data and the device serial number into business data and transmits it to the data ciphertext communication business platform for business communication;
4、数据密文通信业务平台接收到来自智能设备的业务数据后,从业务数据中获取密文数据和设备序列号,并将密文数据和设备序列号传给安全云设备,请求安全云设备解密密文数据;4. After the data ciphertext communication service platform receives the business data from the smart device, it obtains the ciphertext data and the device serial number from the business data, and transmits the ciphertext data and the device serial number to the security cloud device, and requests the security cloud device Decrypt the ciphertext data;
5、安全云设备使用设备序列号在密码装置内重新计算出认证密钥,并以缓存的身份认证信息中随机数A和B为离散因子,离散出解密会话密钥(与会话密钥A相同),将密文数据解密,然后安全地返回给数据密文通信业务平台;5. The security cloud device uses the device serial number to recalculate the authentication key in the cryptographic device, and uses the random numbers A and B in the cached identity authentication information as the discrete factors to discretely generate the decryption session key (same as the session key A ), decrypt the ciphertext data, and then safely return it to the data ciphertext communication service platform;
6、数据密文通信业务平台收到解密后的数据后,进行业务处理,如果需要以密文方式返回数据给智能设备时,数据密文通信业务平台将待加密的数据和设备序列号安全地传给安全云设备,请求加密该数据;6. After receiving the decrypted data, the data ciphertext communication service platform performs business processing. If it is necessary to return the data to the smart device in ciphertext, the data ciphertext communication service platform will securely store the data to be encrypted and the serial number of the device. Send it to the security cloud device and request to encrypt the data;
7、安全云设备收到待加密的数据后,使用设备序列号重新在密码装置内计算出认证密钥,并以缓存的身份认证信息中随机数A和B为离散因子,离散出加密会话密钥,记为会话密钥B,用该密钥加密待加密数据,并安全地传给数据密文通信业务平台;7. After the security cloud device receives the data to be encrypted, it uses the device serial number to recalculate the authentication key in the cryptographic device, and uses the random numbers A and B in the cached identity authentication information as discrete factors to discretely generate the encrypted session key. Key, recorded as session key B, encrypts the data to be encrypted with this key, and securely transmits it to the data ciphertext communication service platform;
8、数据密文通信业务平台将密文数据封装成业务数据,返回给智能设备;8. The data ciphertext communication business platform encapsulates the ciphertext data into business data and returns it to the smart device;
9、智能设备收到包含密文的业务数据后,取出密文数据,并传给安全芯片,要求解密该密文数据;9. After the smart device receives the business data containing ciphertext, it takes out the ciphertext data and transmits it to the security chip, requesting to decrypt the ciphertext data;
10、安全芯片以随机数A和B为离散因子,使用认证密钥计算出解密会话密钥(与会话密钥B相同),将密文数据解密,并返回给智能设备;10. The security chip uses random numbers A and B as discrete factors, uses the authentication key to calculate the decryption session key (same as session key B), decrypts the ciphertext data, and returns it to the smart device;
11、智能设备获取到明文数据后,一次密文通信结束。11. After the smart device obtains the plaintext data, a ciphertext communication ends.
图14是关于采用密钥协商生成会话密钥的方法。在身份认证成功后,安全云设备根据加密、解密申请,分别在密码装置内生成唯一的会话密钥,完成申请请求。具体来说,图14包括如下步骤。Fig. 14 is about the method of generating session key by key agreement. After the identity authentication is successful, the security cloud device generates a unique session key in the cryptographic device according to the encryption and decryption application, and completes the application request. Specifically, Fig. 14 includes the following steps.
1、智能设备将身份认证过程中密钥协商数据传给安全芯片,要求安全芯片产生会话密钥;所述密钥协商数据为密钥协商参数、安全云密钥协商公钥和安全芯片响应公钥组成;当身份认证为SM2密钥身份认证时,所述密钥协商参数为安全云标识数据、安全云公钥、设备公钥和用户ID;当身份认证为SM9密钥身份认证时,所述密钥协商参数为包含安全云加密主公钥、安全云标识数据和用户ID,其中所述用户ID为设备SM9私钥对应的公钥标识数据;1. The smart device transmits the key negotiation data during the identity authentication process to the security chip, and requires the security chip to generate a session key; the key negotiation data is the key negotiation parameters, the security cloud key negotiation public key, and the security chip response public key. Key components; when identity authentication is SM2 key identity authentication, the key negotiation parameters are security cloud identification data, security cloud public key, device public key and user ID; when identity authentication is SM9 key identity authentication, the key negotiation parameters are The key negotiation parameters include the secure cloud encryption master public key, secure cloud identification data and user ID, wherein the user ID is the public key identification data corresponding to the device SM9 private key;
2、安全芯片根据所述密钥协商数据,按照密钥协商原理(例如,国密SM2或SM9),正确地产生会话密钥,并将会话密钥产生过程中生成的响应公钥返回给智能设备,所述响应公钥是安全芯片根据密钥协商数据基于密钥协商原理产生会话密钥时生成的所述安全芯片的临时公钥;2. According to the key negotiation data, the security chip correctly generates the session key according to the key negotiation principle (for example, SM2 or SM9), and returns the response public key generated during the generation of the session key to the smart phone. For the device, the response public key is the temporary public key of the security chip generated when the security chip generates a session key based on the key negotiation data based on the key negotiation principle;
3、智能设备将响应公钥、用户ID和设备序列号封装成密钥响应数据,传给密钥协商业务平台(例如,SM2或SM9密钥协商业务平台),申请密钥协商;3. The smart device encapsulates the response public key, user ID and device serial number into key response data, and transmits it to the key agreement service platform (for example, SM2 or SM9 key agreement service platform), and applies for key agreement;
4、密钥协商业务平台将密钥响应数据传给安全云设备,请求完成密钥协商;4. The key negotiation service platform transmits the key response data to the security cloud device, requesting to complete the key negotiation;
5、安全云设备从密钥响应数据中取出用户ID、响应公钥、设备序列号,根据密钥协商类型进行密钥协商。如果是SM2密钥协商,通过设备序列号获取设备公钥,使用密钥协商数据,即设备公钥、响应公钥、用户ID、安全云标识数据和安全云公钥,按照国密SM2密钥协商原理生成会话密钥;如果是SM9密钥协商,使用密钥协商数据,即用户ID、响应公钥、安全云标识数据、安全云加密主公钥和安全云密钥协商公钥,按照国密SM9密钥协商原理生成会话密钥;将会话密钥与设备序列号绑定安全地缓存存储,并通知密钥协商业务平台密钥协商已完成;5. The security cloud device extracts the user ID, response public key, and device serial number from the key response data, and performs key negotiation according to the key negotiation type. If it is SM2 key negotiation, obtain the device public key through the device serial number, and use the key negotiation data, that is, the device public key, response public key, user ID, security cloud identification data and security cloud public key, according to the national secret SM2 key The negotiation principle generates the session key; if it is SM9 key negotiation, use the key negotiation data, that is, user ID, response public key, security cloud identification data, security cloud encryption master public key and security cloud key negotiation public key, according to the national The secret SM9 key negotiation principle generates the session key; binds the session key and the device serial number to cache and store it securely, and notifies the key negotiation service platform that the key negotiation has been completed;
6、密钥协商业务平台通知智能设备密钥协商已成功;6. The key negotiation service platform notifies the smart device that the key negotiation has been successful;
7、智能设备将需要加密的数据传给安全芯片,要求安全芯片加密数据;7. The smart device transmits the data that needs to be encrypted to the security chip, and requires the security chip to encrypt the data;
8、安全芯片使用会话密钥加数据加密,并返回给智能设备;8. The security chip uses the session key to add data encryption and returns it to the smart device;
9、智能设备将包含设备序列号和加密后的通信数据传给数据密文通信业务平台,进行通信;9. The smart device transmits the communication data including the device serial number and encrypted data to the data ciphertext communication service platform for communication;
10、数据密文通信业务平台接收到来自智能设备或终端业务数据后,从业务数据中获取密文数据和设备序列号,并将密文数据传给安全云设备,请求智能设备云解密密文数据;10. After the data ciphertext communication service platform receives business data from smart devices or terminals, it obtains the ciphertext data and device serial number from the business data, and transmits the ciphertext data to the security cloud device, requesting the smart device cloud to decrypt the ciphertext data;
11、安全云设备使用设备序列号从缓存的找出会话密钥,通过密码装置用会话密钥将密文数据解密,然后安全地返回给数据密文通信业务平台;11. The security cloud device uses the device serial number to find the session key from the cache, decrypts the ciphertext data with the session key through the cryptographic device, and then safely returns it to the data ciphertext communication service platform;
12、数据密文通信业务平台收到解密后的数据后,进行业务处理,如果需要以密文方式返回数据给智能设备时,数据密文通信业务平台将待加密的数据和设备序列号安全地传给安全云设备,请求加密该数据;12. After the data ciphertext communication service platform receives the decrypted data, it performs business processing. If it is necessary to return the data to the smart device in ciphertext, the data ciphertext communication service platform will securely store the data to be encrypted and the serial number of the device. Send it to the security cloud device and request to encrypt the data;
13、安全云设备收到待加密的数据后,使用设备序列号从缓存里找出会话密钥,通过密码装置用会话密钥将待加密的数据加密,然后安全地返回给数据密文通信业务平台;13. After receiving the data to be encrypted, the security cloud device uses the device serial number to find the session key from the cache, encrypts the data to be encrypted with the session key through the cryptographic device, and then safely returns it to the data ciphertext communication service platform;
14、数据密文通信业务平台将密文数据封装成业务数据,返回给智能设备;14. The data ciphertext communication business platform encapsulates the ciphertext data into business data and returns it to the smart device;
15、智能设备收到包含密文的业务数据后,取出密文数据,并传给安全芯片,要求解密该密文数据;15. After the smart device receives the business data containing ciphertext, it takes out the ciphertext data and transmits it to the security chip, requesting to decrypt the ciphertext data;
16、安全芯片用会话密钥将密文数据解密,并返回给智能设备;16. The security chip uses the session key to decrypt the ciphertext data and returns it to the smart device;
17、智能设备获取到明文数据后,一次密文通信结束。17. After the smart device obtains the plaintext data, a ciphertext communication ends.
通过图13和图14所示的方法,安全地、快速地提供加密数据、解密数据的密钥。当智能设备/智能终端与安全云完成身份认证后,智能设备/智能终端和安全云可使用身份认证过程中传输的数据在本地协计算出对方加密数据的密钥,其中加密数据的密钥用来加密发送给对方的数据,解密数据的密钥是解密对方加密后的数据。Through the methods shown in Fig. 13 and Fig. 14, keys for encrypting data and decrypting data are provided safely and quickly. After the smart device/smart terminal and the security cloud complete the identity authentication, the smart device/smart terminal and the security cloud can use the data transmitted during the identity authentication process to jointly calculate the key of the encrypted data of the other party locally, where the key of the encrypted data is used To encrypt the data sent to the other party, the key to decrypt the data is to decrypt the encrypted data of the other party.
以上对本申请实施例进行了详细介绍,本文中应用了具体个例对本申请的原理及实施方式进行了阐述,以上实施例的说明仅用于帮助理解本申请的方法及其核心思想。同时,本领域技术人员依据本申请的思想,基于本申请的具体实施方式及应用范围上做出的改变或变形之处,都属于本申请保护的范围。综上所述,本说明书内容不应理解为对本申请的限制。The above is a detailed introduction to the embodiments of the present application. In this paper, specific examples are used to illustrate the principles and implementation methods of the present application. The descriptions of the above embodiments are only used to help understand the methods and core ideas of the present application. At the same time, changes or deformations made by those skilled in the art based on the ideas of the application, specific implementation methods and application scopes of the application all belong to the scope of protection of the application. To sum up, the contents of this specification should not be understood as limiting the application.
Claims (21)
Priority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202111572609.2ACN116318637A (en) | 2021-12-21 | 2021-12-21 | Method and system for secure network access communication of equipment |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202111572609.2ACN116318637A (en) | 2021-12-21 | 2021-12-21 | Method and system for secure network access communication of equipment |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| CN116318637Atrue CN116318637A (en) | 2023-06-23 |
Family
ID=86798297
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN202111572609.2APendingCN116318637A (en) | 2021-12-21 | 2021-12-21 | Method and system for secure network access communication of equipment |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN116318637A (en) |
Cited By (2)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN117955740A (en)* | 2024-03-26 | 2024-04-30 | 长城信息股份有限公司 | Equipment security authentication method and system |
| CN119826326A (en)* | 2023-10-12 | 2025-04-15 | 青岛海信日立空调系统有限公司 | Operation terminal, air conditioner and air conditioning system |
Citations (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| KR20120108599A (en)* | 2011-03-25 | 2012-10-05 | 주식회사 스마트솔루션 | Credit card payment service using online credit card payment device |
| CN106227503A (en)* | 2016-07-29 | 2016-12-14 | 苏州国芯科技有限公司 | Safety chip COS firmware update, service end, terminal and system |
| CN108833101A (en)* | 2018-09-28 | 2018-11-16 | 腾讯科技(深圳)有限公司 | Data transmission method, internet of things equipment and the authentication platform of internet of things equipment |
| CN111211906A (en)* | 2019-12-20 | 2020-05-29 | 福建魔方电子科技有限公司 | Method, system, device, equipment and medium for realizing one-machine-one-secret of terminal equipment |
- 2021
- 2021-12-21CNCN202111572609.2Apatent/CN116318637A/enactivePending
Patent Citations (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| KR20120108599A (en)* | 2011-03-25 | 2012-10-05 | 주식회사 스마트솔루션 | Credit card payment service using online credit card payment device |
| CN106227503A (en)* | 2016-07-29 | 2016-12-14 | 苏州国芯科技有限公司 | Safety chip COS firmware update, service end, terminal and system |
| CN108833101A (en)* | 2018-09-28 | 2018-11-16 | 腾讯科技(深圳)有限公司 | Data transmission method, internet of things equipment and the authentication platform of internet of things equipment |
| CN111211906A (en)* | 2019-12-20 | 2020-05-29 | 福建魔方电子科技有限公司 | Method, system, device, equipment and medium for realizing one-machine-one-secret of terminal equipment |
Cited By (2)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN119826326A (en)* | 2023-10-12 | 2025-04-15 | 青岛海信日立空调系统有限公司 | Operation terminal, air conditioner and air conditioning system |
| CN117955740A (en)* | 2024-03-26 | 2024-04-30 | 长城信息股份有限公司 | Equipment security authentication method and system |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| US9847882B2 (en) | Multiple factor authentication in an identity certificate service | |
| JP6976949B2 (en) | Methods and systems for key distribution between servers and medical devices | |
| US12353519B2 (en) | Digital rights management authorization token pairing | |
| US9137017B2 (en) | Key recovery mechanism | |
| US7688975B2 (en) | Method and apparatus for dynamic generation of symmetric encryption keys and exchange of dynamic symmetric key infrastructure | |
| EP1697818B1 (en) | Authentication system for networked computer applications | |
| CN103780618B (en) | A Cross-Heterogeneous Domain Identity Authentication and Session Key Agreement Method Based on Access Authorization Ticket | |
| US7334255B2 (en) | System and method for controlling access to multiple public networks and for controlling access to multiple private networks | |
| CN111756529B (en) | Quantum session key distribution method and system | |
| EP1376976A1 (en) | Methods for authenticating potential members invited to join a group | |
| KR102177794B1 (en) | Distributed device authentication protocol in internet of things blockchain environment | |
| CN105791272A (en) | A method and device for secure communication in the Internet of Things | |
| US8806206B2 (en) | Cooperation method and system of hardware secure units, and application device | |
| CN108809633B (en) | Identity authentication method, device and system | |
| CN101605137A (en) | Safe distribution file system | |
| CN118659922B (en) | Quantum security enhancement method for open authorization protocol | |
| US20240113885A1 (en) | Hub-based token generation and endpoint selection for secure channel establishment | |
| CN113918971A (en) | Block chain based message transmission method, device, equipment and readable storage medium | |
| CN115801232A (en) | Private key protection method, device, equipment and storage medium | |
| CN114091009A (en) | Method for establishing secure link by using distributed identity | |
| WO2021082222A1 (en) | Communication method and apparatus, storage method and apparatus, and operation method and apparatus | |
| CN116318637A (en) | Method and system for secure network access communication of equipment | |
| CN120474752A (en) | Access security verification method for Internet of things equipment | |
| CN118713833B (en) | Quantum security enhancement method for open identity connection protocol | |
| CN102882882B (en) | A kind of user resources authorization method |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination |