CN116305273A - Verifiable joint keyword efficient search method, device, client and server - Google Patents
Verifiable joint keyword efficient search method, device, client and serverDownload PDFInfo
- Publication number
- CN116305273A CN116305273ACN202310259730.2ACN202310259730ACN116305273ACN 116305273 ACN116305273 ACN 116305273ACN 202310259730 ACN202310259730 ACN 202310259730ACN 116305273 ACN116305273 ACN 116305273A
- Authority
- CN
- China
- Prior art keywords
- search
- joint
- ciphertext
- verification
- result
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Pending
Links
Images
Classifications
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/60—Protecting data
- G06F21/62—Protecting access to data via a platform, e.g. using keys or access control rules
- G06F21/6218—Protecting access to data via a platform, e.g. using keys or access control rules to a system of files or objects, e.g. local or distributed file system or database
- G06F21/6227—Protecting access to data via a platform, e.g. using keys or access control rules to a system of files or objects, e.g. local or distributed file system or database where protection concerns the structure of data, e.g. records, types, queries
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F16/00—Information retrieval; Database structures therefor; File system structures therefor
- G06F16/90—Details of database functions independent of the retrieved data types
- G06F16/95—Retrieval from the web
- G06F16/951—Indexing; Web crawling techniques
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/60—Protecting data
- G06F21/604—Tools and structures for managing or administering access control systems
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/60—Protecting data
- G06F21/64—Protecting data integrity, e.g. using checksums, certificates or signatures
- Y—GENERAL TAGGING OF NEW TECHNOLOGICAL DEVELOPMENTS; GENERAL TAGGING OF CROSS-SECTIONAL TECHNOLOGIES SPANNING OVER SEVERAL SECTIONS OF THE IPC; TECHNICAL SUBJECTS COVERED BY FORMER USPC CROSS-REFERENCE ART COLLECTIONS [XRACs] AND DIGESTS
- Y02—TECHNOLOGIES OR APPLICATIONS FOR MITIGATION OR ADAPTATION AGAINST CLIMATE CHANGE
- Y02D—CLIMATE CHANGE MITIGATION TECHNOLOGIES IN INFORMATION AND COMMUNICATION TECHNOLOGIES [ICT], I.E. INFORMATION AND COMMUNICATION TECHNOLOGIES AIMING AT THE REDUCTION OF THEIR OWN ENERGY USE
- Y02D10/00—Energy efficient computing, e.g. low power processors, power management or thermal management
Landscapes
- Engineering & Computer Science (AREA)
- Theoretical Computer Science (AREA)
- General Engineering & Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- Physics & Mathematics (AREA)
- General Physics & Mathematics (AREA)
- Bioethics (AREA)
- General Health & Medical Sciences (AREA)
- Computer Hardware Design (AREA)
- Software Systems (AREA)
- Health & Medical Sciences (AREA)
- Databases & Information Systems (AREA)
- Automation & Control Theory (AREA)
- Data Mining & Analysis (AREA)
- Information Retrieval, Db Structures And Fs Structures Therefor (AREA)
Abstract
Description
Translated fromChinese技术领域technical field
本申请涉及动态对称可搜索加密技术领域,特别涉及一种可验证联合关键词高效搜索方法、装置、客户端及服务器。The present application relates to the technical field of dynamic symmetric searchable encryption, in particular to a method, device, client and server for efficient search of verifiable joint keywords.
背景技术Background technique
随着大数据时代的到来,云计算得到广泛应用。越来越多的用户将数据和计算外包到云服务器以节约存储和计算成本。然而云服务器可能面临着外部敌手的攻击和云服务提供商内部管理者的人为泄露和破坏,直接将明文数据存储在云服务器中将导致用户隐私信息泄露。With the advent of the era of big data, cloud computing has been widely used. More and more users outsource data and computing to cloud servers to save storage and computing costs. However, cloud servers may face attacks from external adversaries and artificial disclosure and destruction by internal managers of cloud service providers. Directly storing plaintext data in cloud servers will lead to leakage of user privacy information.
相关技术中,可搜索加密可以使得密文数据具有可搜索性,即可保障用户安全方便地使用云存储服务,又能解决服务器处理密文数据的难题。但是其仅适用于静态环境;因此,为了支持云端数据动态更新产生了DSSE(Dynamic Symmetric SearchableEncryption,动态对称可搜索加密)方案,但是仍存在以下缺陷:(1)就其表达能力而言,大部分动态对称可搜索加密方案只能进行简单的单关键词叠加搜索,增加了计算负担且产生的结果过于粗糙,适用性和实用性不高,降低了用户体验感;(2)就其功能性而言,容易遭受恶意敌手的攻击,导致了云服务器可能为节省自身资源或者隐瞒计算错误有意返回不正确或不完整的搜索结果,用户隐私泄露等,安全性较低,从而降低了用户体验感。In related technologies, searchable encryption can make ciphertext data searchable, which can ensure users to use cloud storage services safely and conveniently, and can also solve the problem of servers processing ciphertext data. But it is only applicable to the static environment; therefore, in order to support the dynamic update of cloud data, a DSSE (Dynamic Symmetric Searchable Encryption, dynamic symmetric searchable encryption) scheme is produced, but there are still the following defects: (1) in terms of its expressive ability, most The dynamic symmetric searchable encryption scheme can only perform simple single-keyword superposition search, which increases the computational burden and produces too rough results, which is not high in applicability and practicability, and reduces the sense of user experience; (2) in terms of its functionality In other words, it is easy to be attacked by malicious opponents, causing the cloud server to return incorrect or incomplete search results intentionally in order to save its own resources or conceal calculation errors, leaking user privacy, etc., and the security is low, thereby reducing the sense of user experience.
发明内容Contents of the invention
本申请提供一种可验证联合关键词高效搜索方法、装置、客户端及服务器,以解决相关技术中动态对称可搜索加密方案搜索效率低下及结果不完整和准确导致了成本较高、容易遭受恶意攻击导致安全性较低、降低了用户体验感等问题。This application provides a method, device, client and server for efficient search of verifiable joint keywords to solve the problem of low search efficiency and incomplete and accurate results of dynamic symmetric searchable encryption schemes in related technologies, which lead to high cost and vulnerability to malicious Attacks lead to problems such as low security and reduced user experience.
本申请第一方面实施例提供一种可验证联合关键词高效搜索方法,所述方法应用于客户端,其中,所述方法包括以下步骤:获取关键词集和联合搜索标签;根据所述关键词集和联合搜索标签生成联合搜索令牌,发送所述联合搜索令牌至服务器,其中,所述服务器根据所述联合搜索令牌对密文索引进行搜索,获得密文搜索结果,并生成所述密文搜索结果对应的验证证据;接收所述服务器发送的密文搜索结果和对应的验证证据,解密所述密文搜索结果得到明文结果,利用所述验证证据验证对应的明文结果的正确性和/或完整性,输出验证通过的明文结果。The embodiment of the first aspect of the present application provides a verifiable joint keyword efficient search method, the method is applied to the client, wherein the method includes the following steps: obtaining a keyword set and a joint search tag; according to the keyword set and the joint search tag to generate a joint search token, and send the joint search token to the server, wherein the server searches the ciphertext index according to the joint search token, obtains the ciphertext search result, and generates the Verification evidence corresponding to the ciphertext search result; receiving the ciphertext search result and corresponding verification evidence sent by the server, decrypting the ciphertext search result to obtain a plaintext result, and using the verification evidence to verify the correctness and accuracy of the corresponding plaintext result /or integrity, output the plaintext result of the verification.
可选地,在服务器根据所述联合搜索令牌对密文索引进行搜索之前,还包括:根据安全参数初始化数据结构,得到对称密钥集合,其中,所述数据结构包括第一键值型数据库、第二键值型数据库、文件个数计数器和搜索标签;利用文档标识符关键词对更新关键词对应的文件个数计数器,并计算所述文档标识符关键词对的密文值和存储地址,利用更新后的文件个数计数器和对称密钥集合计算动态盲元素,将所述动态盲元素和所述密文值存入所述存储地址对应的第一键值型数据库;根据所述对称密钥集合、更新操作和伪随机函数计算动态交叉标签,并将所述动态交叉标签放入搜索标签对应的第二键值型数据库,将所述第二键值型数据库的搜索标签存入使用头插法构建的链表结点中,并保存最新结点值;计算所述第一键值型数据库中密文值的累加值,利用所述动态盲元素、所述动态交叉标签和所述最新结点值更新所述累加值,并在所述累加值更新时同步更新所述搜索标签和密文索引,否则不进行更新。Optionally, before the server searches the ciphertext index according to the joint search token, it further includes: initializing a data structure according to a security parameter to obtain a symmetric key set, wherein the data structure includes a first key-value database , a second key-value database, a file number counter and a search label; use the document identifier keyword pair to update the file number counter corresponding to the keyword, and calculate the ciphertext value and storage address of the document identifier keyword pair , using the updated file number counter and symmetric key set to calculate the dynamic blind element, storing the dynamic blind element and the ciphertext value into the first key-value database corresponding to the storage address; according to the symmetric The key set, the update operation and the pseudo-random function calculate the dynamic cross label, and put the dynamic cross label into the second key-value database corresponding to the search label, and store the search label of the second key-value database in the use In the linked list node constructed by the head interpolation method, and save the latest node value; calculate the accumulated value of the ciphertext value in the first key-value database, use the dynamic blind element, the dynamic cross label and the latest The node value updates the accumulated value, and when the accumulated value is updated, the search tag and the ciphertext index are updated synchronously, otherwise no update is performed.
可选地,所述服务器根据所述联合搜索令牌对密文索引进行搜索,获得密文搜索结果,并根据所述联合搜索标签集生成所述密文搜索结果对应的验证证据,包括:解析所述服务器的安全索引区中密文索引,得到第一键值型数据库、第二键值型数据库和所述累加值;根据所述联合搜索令牌的当前值遍历所述链表得到所述联合搜索令牌的历史值,根据所述联合搜索令牌的当前值和历史值对所述第一键值型数据库和第二键值型数据库进行关键词搜索和联合搜索;根据关键词和联合搜索的搜索结果分别生成第一验证证据和第二验证证据,发送所述关键词和联合搜索的搜索结果、所述第一验证证据和所述第二验证证据至客户端。Optionally, the server searches the ciphertext index according to the joint search token, obtains the ciphertext search result, and generates the verification evidence corresponding to the ciphertext search result according to the joint search tag set, including: parsing The ciphertext index in the security index area of the server obtains the first key-value database, the second key-value database and the accumulated value; traverses the linked list according to the current value of the joint search token to obtain the joint Searching for the historical value of the token, performing a keyword search and a joint search on the first key-value database and the second key-value database according to the current value and historical value of the joint search token; according to the keyword and the joint search Generate first verification evidence and second verification proof for the search results respectively, and send the keyword and the search result of joint search, the first verification proof and the second verification proof to the client.
可选地,所述利用所述验证证据验证对应的明文结果的正确性和/或完整性,包括:若所述关键词和联合搜索的搜索结果均为空集,且若文件个数计数器为空集时,验证通过,否则验证不通过;若所述关键词的搜索结果为非空集,所述联合搜索的搜索结果为空集时,检查所述关键词的搜索结果是否满足完整性要求,若满足,则从所述关键词的搜索结果中随机抽取一个或多个元素,按照样本检测验证法检查元素之间的非成员关系,以确定搜索结果的正确性,若正确,则验证通过,否则验证不通过;若所述关键词和联合搜索的搜索结果均为非空集,分别对所述关键词和联合搜索的搜索结果进行完整性和正确性的验证,若正确,则验证通过,否则验证不通过。Optionally, using the verification evidence to verify the correctness and/or completeness of the corresponding plaintext results includes: if the keywords and the search results of the joint search are both empty sets, and if the file number counter is When the set is empty, the verification passes, otherwise the verification fails; if the search result of the keyword is a non-empty set, when the search result of the joint search is an empty set, check whether the search result of the keyword meets the integrity requirement , if satisfied, one or more elements are randomly selected from the search results of the keyword, and the non-member relationship between elements is checked according to the sample detection and verification method to determine the correctness of the search results. If it is correct, the verification is passed , otherwise the verification fails; if the keywords and the search results of the joint search are both non-empty sets, verify the completeness and correctness of the keywords and the search results of the joint search respectively, and if they are correct, the verification passes , otherwise the verification fails.
本申请第二方面实施例提供一种可验证联合关键词高效搜索方法,所述方法应用于服务器,其中,所述方法包括以下步骤:接收客户端发送的联合搜索令牌;根据所述联合搜索令牌对密文索引进行搜索,获得密文搜索结果,并生成所述密文搜索结果对应的验证证据;发送所述密文搜索结果和对应的验证证据至客户端,其中,所述客户端解密所述密文搜索结果得到明文结果,利用所述验证证据验证对应的明文结果的正确性和/或完整性,输出验证通过的明文结果。The embodiment of the second aspect of the present application provides a verifiable joint keyword efficient search method, the method is applied to the server, wherein the method includes the following steps: receiving the joint search token sent by the client; according to the joint search The token searches the ciphertext index, obtains the ciphertext search result, and generates the verification evidence corresponding to the ciphertext search result; sends the ciphertext search result and the corresponding verification proof to the client, wherein the client Decrypt the ciphertext search result to obtain a plaintext result, use the verification evidence to verify the correctness and/or integrity of the corresponding plaintext result, and output the verified plaintext result.
本申请第三方面实施例提供一种可验证联合关键词高效搜索装置,所述装置应用于客户端,其中,所述装置包括:获取模块,用于获取关键词集和联合搜索标签;第一发送模块,用于根据所述关键词集和联合搜索标签生成联合搜索令牌,发送所述联合搜索令牌至服务器,其中,所述服务器根据所述联合搜索令牌对密文索引进行搜索,获得密文搜索结果,并根据所述密文搜索结果对应的验证证据;第一接收模块,用于接收所述服务器发送的密文搜索结果和对应的验证证据,解密所述密文搜索结果得到明文结果,利用所述验证证据验证对应的明文结果的正确性和/或完整性,输出验证通过的明文结果。The embodiment of the third aspect of the present application provides a verifiable joint keyword efficient search device, the device is applied to the client, wherein the device includes: an acquisition module, used to acquire the keyword set and the joint search tag; the first A sending module, configured to generate a joint search token according to the keyword set and the joint search tag, and send the joint search token to a server, wherein the server searches the ciphertext index according to the joint search token, Obtain the ciphertext search result, and according to the verification evidence corresponding to the ciphertext search result; the first receiving module is configured to receive the ciphertext search result and the corresponding verification evidence sent by the server, and decrypt the ciphertext search result to obtain The plaintext result uses the verification evidence to verify the correctness and/or integrity of the corresponding plaintext result, and outputs the verified plaintext result.
本申请第四方面实施例提供一种可验证联合关键词高效搜索装置,所述装置应用于服务器,其中,所述装置包括:第二接收模块,用于接收客户端发送的联合搜索令牌;搜索模块,用于根据所述联合搜索令牌对密文索引进行搜索,获得密文搜索结果,并生成所述密文搜索结果对应的验证证据;第二发送模块,用于发送所述密文搜索结果和对应的验证证据至客户端,其中,所述客户端解密所述密文搜索结果得到明文结果,利用所述验证证据验证对应的明文结果的正确性和/或完整性,输出验证通过的明文结果。The embodiment of the fourth aspect of the present application provides a verifiable joint keyword efficient search device, the device is applied to a server, wherein the device includes: a second receiving module, configured to receive the joint search token sent by the client; The search module is used to search the ciphertext index according to the joint search token, obtain the ciphertext search result, and generate the verification evidence corresponding to the ciphertext search result; the second sending module is used to send the ciphertext The search result and the corresponding verification evidence are sent to the client, wherein the client decrypts the ciphertext search result to obtain a plaintext result, uses the verification evidence to verify the correctness and/or integrity of the corresponding plaintext result, and the output verification passes The plaintext result of .
本申请第五方面实施例提供一种客户端,包括:存储器、处理器及存储在所述存储器上并可在所述处理器上运行的计算机程序,所述处理器执行所述程序,以实现如上述实施例所述的可验证联合关键词高效搜索方法。The embodiment of the fifth aspect of the present application provides a client, including: a memory, a processor, and a computer program stored on the memory and operable on the processor, and the processor executes the program to realize As described in the above-mentioned embodiments, the method for efficient search of verifiable joint keywords.
本申请第六方面实施例提供一种服务器,包括:存储器、处理器及存储在所述存储器上并可在所述处理器上运行的计算机程序,所述处理器执行所述程序,以实现如上述实施例所述的可验证联合关键词高效搜索方法。The embodiment of the sixth aspect of the present application provides a server, including: a memory, a processor, and a computer program stored on the memory and operable on the processor, and the processor executes the program to implement the following: The verifiable joint keyword efficient search method described in the above-mentioned embodiments.
本申请第七方面实施例提供一种计算机可读存储介质,其上存储有计算机程序,该程序被处理器执行,以用于实现如上述实施例所述的可验证联合关键词高效搜索方法。The embodiment of the seventh aspect of the present application provides a computer-readable storage medium, on which a computer program is stored, and the program is executed by a processor, so as to realize the efficient search method for verifiable joint keywords as described in the above-mentioned embodiments.
由此,本申请至少具有如下有益效果:Thus, the application at least has the following beneficial effects:
(1)本申请实施例满足前向安全和后向安全的可验证联合搜索方案,使得在恶意服务器环境下可确保搜索结果的正确性和完整性,在搜索结果为空时,也可进行高效验证;此外,在实现可验证功能和高安全性的基础上,仍可确保联合关键词搜索的高效率。(1) The embodiment of this application satisfies the verifiable joint search scheme of forward security and backward security, so that the correctness and integrity of the search results can be ensured in a malicious server environment, and efficient search results can also be performed when the search results are empty. Verification; In addition, on the basis of realizing verifiable functions and high security, it can still ensure the high efficiency of joint keyword search.
(2)本申请实施例在更新阶段时,实现了轻量级数据更新,动态盲元素和交叉标签实时计算,验证证据进行常数级更新,设计搜索标签引入安全索引之中,确保旧搜索令牌无法搜索到新添加的文件和验证信息,保证前向安全;且安全索引中的验证信息与数据同步更新,验证信息只是常数大小的累加值,通信负载低,且不会泄露更新关键词的任何信息。(2) In the update stage, the embodiment of this application realizes lightweight data update, real-time calculation of dynamic blind elements and cross-labels, constant-level update of verification evidence, design of search tags into security indexes, and guarantee of old search tokens Newly added files and verification information cannot be searched to ensure forward security; and the verification information in the security index is updated synchronously with the data, the verification information is only a constant-sized cumulative value, the communication load is low, and no information about the updated keywords will be leaked. information.
(3)本申请实施例利用不经意共享计算确保搜索开销独立于数据库,仅与更新频率最低的关键词有关,单轮通信即可实现联合关键词搜索和证据匹配,同时保证后向安全。(3) The embodiment of this application uses inadvertently shared computing to ensure that the search overhead is independent of the database and only related to keywords with the lowest update frequency. A single round of communication can realize joint keyword search and evidence matching, while ensuring backward security.
(4)本申请实施例在搜索阶段时,客户端和服务器端时间花销均较小,仅与更新频率最低的关键词有关;同时,验证效率较高且索引存储花销较低。(4) In the search phase of the embodiment of the present application, the time spent on both the client and the server is small, and it is only related to keywords with the lowest update frequency; meanwhile, the verification efficiency is high and the index storage cost is low.
本申请附加的方面和优点将在下面的描述中部分给出,部分将从下面的描述中变得明显,或通过本申请的实践了解到。Additional aspects and advantages of the application will be set forth in part in the description which follows, and in part will be obvious from the description, or may be learned by practice of the application.
附图说明Description of drawings
本申请上述的和/或附加的方面和优点从下面结合附图对实施例的描述中将变得明显和容易理解,其中:The above and/or additional aspects and advantages of the present application will become apparent and easy to understand from the following description of the embodiments in conjunction with the accompanying drawings, wherein:
图1为根据本申请一个实施例提供的一种可验证联合关键词高效搜索方法的流程图;Fig. 1 is a flow chart of a method for efficiently searching verifiable combined keywords according to an embodiment of the present application;
图2为根据本申请另一个实施例的一种可验证联合关键词高效搜索方法的示例图;FIG. 2 is an example diagram of a verifiable joint keyword efficient search method according to another embodiment of the present application;
图3为根据本申请实施例的系统流程示意图;FIG. 3 is a schematic diagram of a system flow according to an embodiment of the present application;
图4为根据本申请实施例的更新过程示意图;FIG. 4 is a schematic diagram of an update process according to an embodiment of the present application;
图5为根据本申请实施例的联合搜索令牌生成过程示意图;FIG. 5 is a schematic diagram of a joint search token generation process according to an embodiment of the present application;
图6为根据本申请实施例的搜索阶段的不经意共享计算过程示意图;FIG. 6 is a schematic diagram of an inadvertently shared calculation process in the search phase according to an embodiment of the present application;
图7为根据本申请一个实施例提供的一种可验证联合关键词高效搜索装置的示意图;FIG. 7 is a schematic diagram of an efficient search device for verifiable joint keywords provided according to an embodiment of the present application;
图8为根据本申请另一个实施例提供的一种可验证联合关键词高效搜索装置的示意图;Fig. 8 is a schematic diagram of a verifiable joint keyword efficient search device provided according to another embodiment of the present application;
图9为根据本申请实施例的客户端结构示意图;FIG. 9 is a schematic structural diagram of a client according to an embodiment of the present application;
图10为根据本申请实施例的服务器的结构示意图。FIG. 10 is a schematic structural diagram of a server according to an embodiment of the present application.
具体实施方式Detailed ways
下面详细描述本申请的实施例,所述实施例的示例在附图中示出,其中自始至终相同或类似的标号表示相同或类似的元件或具有相同或类似功能的元件。下面通过参考附图描述的实施例是示例性的,旨在用于解释本申请,而不能理解为对本申请的限制。Embodiments of the present application are described in detail below, examples of which are shown in the drawings, wherein the same or similar reference numerals denote the same or similar elements or elements having the same or similar functions throughout. The embodiments described below by referring to the figures are exemplary, and are intended to explain the present application, and should not be construed as limiting the present application.
随着大数据时代的到来,云计算得到广泛应用,越来越多的用户将数据和计算外包到云服务器以节约存储和计算成本。然而,云服务器可能面临着外部敌手的攻击和云服务提供商内部管理者的人为泄露和破坏,直接将明文数据存储在云服务器中将导致用户隐私信息泄露。其中传统加密(如AES加密等)可以保护数据机密性,但又引发了数据可用性问题。With the advent of the big data era, cloud computing has been widely used, and more and more users outsource data and computing to cloud servers to save storage and computing costs. However, the cloud server may face attacks from external adversaries and artificial disclosure and destruction by the internal managers of the cloud service provider. Directly storing plaintext data in the cloud server will lead to leakage of user privacy information. Among them, traditional encryption (such as AES encryption, etc.) can protect data confidentiality, but it also causes data availability problems.
为了解决外包数据机密性和可用性之间的矛盾,一种使密文数据具有可搜索性的结构化加密技术,即可搜索加密被提出,其既可保障用户安全方便地使用云存储服务,又能解决服务器处理密文数据的难题。In order to solve the contradiction between the confidentiality and availability of outsourced data, a structured encryption technology that makes ciphertext data searchable, i.e. searchable encryption, is proposed, which can not only ensure users to use cloud storage services safely and conveniently, but also It can solve the problem of server processing ciphertext data.
早期的可搜索加密仅适用于静态环境,即密文数据上传至云服务器后就不可再进行更新与修改。随着用户的本地数据不断产生,支持云端数据动态更新的DSSE(DynamicSymmetric Searchable Encryption,动态对称可搜索加密)被提出,一个DSSE方案包括密钥生成、搜索令牌生成、搜索和更新四个阶段。数据更新功能的引入同时又带来了新的泄露隐患,例如,(1)向云服务器中添加文件f,可能会泄露f包含的以前搜索过的关键词;(2)搜索关键词w可能会显示出已删除的包含w的文件。其中,(1)对应的安全问题就是前向安全;2016年文件注入攻击被首次提出,文件注入攻击简单高效,敌手可以任意设定可能的关键字空间,如果敌手事先了解用户的使用背景就可以限定到一个更小的关键字空间使得攻击更为成功,使得具有前向安全特性的DSSE方案可抵御文件注入攻击,因而受到了广泛的关注和研究。(2)对应的安全问题即后向安全;后向安全可以隐藏在搜索w之前被删除的包含w的文件标识符,即已被删除的文件不会再被搜索到,后向安全也是DSSE的一个重要安全属性,目前相关的研究成果较少。Early searchable encryption was only applicable to static environments, that is, after the ciphertext data was uploaded to the cloud server, it could no longer be updated and modified. As the user's local data continues to be generated, DSSE (Dynamic Symmetric Searchable Encryption, Dynamic Symmetric Searchable Encryption) that supports cloud data dynamic update is proposed. A DSSE scheme includes four stages: key generation, search token generation, search and update. The introduction of the data update function also brings new hidden dangers of leakage. For example, (1) adding a file f to the cloud server may leak the previously searched keywords contained in f; (2) the search keyword w may reveal Show deleted files containing w. Among them, (1) the corresponding security problem is forward security; the file injection attack was proposed for the first time in 2016. The file injection attack is simple and efficient, and the adversary can arbitrarily set the possible keyword space. Restricting to a smaller keyword space makes the attack more successful, so that the DSSE scheme with forward security can resist the file injection attack, so it has received extensive attention and research. (2) The corresponding security problem is backward security; backward security can hide the file identifier containing w that was deleted before searching for w, that is, the deleted file will not be searched again, and backward security is also DSSE It is an important security attribute, and there are few relevant research results so far.
DSSE方案就表达能力而言,大部分都只支持单关键词搜索,当需要进行多个关键词联合搜索时,只能进行简单的单关键词叠加搜索,然后由服务器或者用户对搜索结果求交集,这往往会产生过于粗糙的结果并增加额外的计算负担,不足以满足实际应用需求。因此,设计新的联合关键词搜索方案可以提高搜索效率和用户体验,从而丰富DSSE的表达能力。In terms of expression ability, most of the DSSE solutions only support single-keyword search. When multiple keyword joint searches are required, only simple single-keyword superimposed search can be performed, and then the server or user can intersect the search results. , which often produces too rough results and adds additional computational burden, which is not enough to meet the needs of practical applications. Therefore, designing a new joint keyword search scheme can improve search efficiency and user experience, thereby enriching the expressive power of DSSE.
DSSE方案就功能性而言,常以服务器作为敌手,其中恶意敌手即不可信云服务器可能为了节省自身资源或者隐瞒计算错误有意返回不正确或不完整的搜索结果。由于云服务器的操作细节对用户并不完全公开透明,因此用户无法确定云服务器是否正确且诚实地执行了计算过程。In terms of functionality, DSSE schemes often use servers as opponents, in which malicious opponents, namely untrusted cloud servers, may intentionally return incorrect or incomplete search results in order to save their own resources or conceal calculation errors. Since the operation details of the cloud server are not completely open and transparent to the user, the user cannot be sure whether the cloud server has performed the computing process correctly and honestly.
因此,本申请设计了一个新的可以抵抗文件注入攻击,并满足前向安全和后向安全的高效联合搜索方法;并且本申请的可验证功能确保用户搜索结果的正确性和完整性,有效抵抗恶意敌手,解决了现实应用中对密文搜索方案的效率、安全性、表达能力以及可验证性的综合要求的瓶颈性问题。Therefore, this application designs a new efficient joint search method that can resist file injection attacks and satisfy forward security and backward security; and the verifiable function of this application ensures the correctness and integrity of user search results, effectively resisting Malicious adversary solves the bottleneck problem of comprehensive requirements for efficiency, security, expressiveness and verifiability of ciphertext search schemes in practical applications.
下面参考附图描述本申请实施例的可验证联合关键词高效搜索方法、装置、客户端及服务器。具体而言,图1为本申请一个实施例所提供的可验证联合关键词高效搜索方法的流程示意图。The method, device, client and server for efficiently searching verifiable joint keywords according to the embodiments of the present application are described below with reference to the accompanying drawings. Specifically, FIG. 1 is a schematic flowchart of an efficient search method for verifiable combined keywords provided by an embodiment of the present application.
如图1所示,该可验证联合关键词高效搜索方法应用于客户端,其中,包括以下步骤:As shown in Figure 1, the verifiable joint keyword efficient search method is applied to the client, which includes the following steps:
在步骤S101中,获取关键词集和联合搜索标签。In step S101, a keyword set and a joint search tag are obtained.
其中,关键词集可以是由数据库的多个关键词w组成,联合搜索标签stSrchCt由搜索标签SrchCt生成,在此不做具体限定。Wherein, the keyword set may be composed of multiple keywords w in the database, and the joint search labelstSrchCt is generated by the search label SrchCt, which is not specifically limited here.
可以理解的是,本申请实施例通过获取关键词集和联合搜索标签,以便于后续生成联合搜索令牌,并将联合搜索令牌发送至服务器。It can be understood that, in this embodiment of the present application, the keyword set and the joint search tag are acquired to facilitate subsequent generation of the joint search token and send the joint search token to the server.
在步骤S102中,根据关键词集和联合搜索标签生成联合搜索令牌,发送联合搜索令牌至服务器,其中,服务器根据联合搜索令牌对密文索引进行搜索,获得密文搜索结果,并生成密文搜索结果对应的验证证据。In step S102, generate a joint search token according to the keyword set and the joint search tag, and send the joint search token to the server, wherein, the server searches the ciphertext index according to the joint search token, obtains the ciphertext search result, and generates The verification evidence corresponding to the ciphertext search result.
其中,联合搜索令牌如下:Among them, the federated search token is as follows:
其中,stsrchCt=F(KS,SrchCt),stokenList,xtokenList1,…,/>为空列表。 Among them, stsrchCt = F(KS, SrchCt), tokenList, xtokenList1, ..., /> is an empty list.
其中,密文索引EDB={TSet,Xset},其中,TSet,XSet为键值型数据库。Wherein, the ciphertext index EDB={TSet, Xset}, where TSet and XSet are key-value databases.
可以理解的是,本申请实施例根据关键词和联合搜索标签生成联合搜索令牌发送至服务器,服务器根据联合搜索令牌对密文索引进行搜索,获得密文搜索结果,并生成密文搜索结果对应的验证证据,能够确保用户搜索结果的正确性和完整性,有效抵抗恶意敌手。It can be understood that, in this embodiment of the application, a joint search token is generated based on keywords and joint search tags and sent to the server, and the server searches the ciphertext index according to the joint search token, obtains ciphertext search results, and generates ciphertext search results The corresponding verification evidence can ensure the correctness and integrity of the user's search results and effectively resist malicious opponents.
在本申请实施例中,在服务器根据联合搜索令牌对密文索引进行搜索之前,还包括:根据安全参数初始化数据结构,得到对称密钥集合,其中,数据结构包括第一键值型数据库、第二键值型数据库、文件个数计数器和搜索标签;利用文档标识符关键词对更新关键词对应的文件个数计数器,并计算文档标识符关键词对的密文值和存储地址,利用更新后的文件个数计数器和对称密钥集合计算动态盲元素,将动态盲元素和密文值存入存储地址对应的第一键值型数据库;根据对称密钥集合、更新操作和伪随机函数计算动态交叉标签,并将动态交叉标签放入搜索标签对应的第二键值型数据库,将第二键值型数据库的搜索标签存入使用头插法构建的链表结点中,并保存最新结点值;计算第一键值型数据库中密文值的累加值,利用动态盲元素、动态交叉标签和最新结点值更新累加值,并在累加值更新时同步更新搜索标签和密文索引,否则不进行更新。In this embodiment of the application, before the server searches the ciphertext index according to the joint search token, it also includes: initializing the data structure according to the security parameters to obtain a symmetric key set, wherein the data structure includes the first key-value database, The second key-value database, the number of files counter and the search label; use the document identifier keyword to update the file number counter corresponding to the keyword, and calculate the ciphertext value and storage address of the document identifier keyword pair, and use the update The final file number counter and symmetric key set calculate the dynamic blind element, and store the dynamic blind element and ciphertext value in the first key-value database corresponding to the storage address; calculate according to the symmetric key set, update operation and pseudo-random function Dynamic cross tags, and put the dynamic cross tags into the second key-value database corresponding to the search tag, store the search tag of the second key-value database in the linked list node constructed by using the head insertion method, and save the latest node value; calculate the accumulated value of the ciphertext value in the first key-value database, update the accumulated value by using the dynamic blind element, the dynamic cross label and the latest node value, and update the search label and the ciphertext index synchronously when the accumulated value is updated, otherwise No updates are made.
其中,初始化数据结构DS={TSet,XSet,UpdCnt,SrchCt};其中,第一键值型数据库为TSet,第二键值型数据库为XSet,文件个数计数器为UpdCnt,且关键词w对应的文件个数计数器为UpdCnt[w],搜索标签为SrchCt。Wherein, the initialization data structure DS={TSet, XSet, UpdCnt, SrchCt}; wherein, the first key-value database is TSet, the second key-value database is XSet, the number of files counter is UpdCnt, and the keyword w corresponds The file number counter is UpdCnt[w], and the search tag is SrchCt.
其中,对称密钥集合MK={KT,KX,KY,KZ};密文值存储地址addr=F(KT,w||UpdCnt[w]||0);Among them, the symmetric key set MK={KT , KX , KY , KZ }; the ciphertext value Storage address addr=F(KT ,w||UpdCnt[w]||0);
其中,盲元素α=Fp(KY,id)·Fp(Kz,UpdCnt[w]))-1,存储地址对应的第一键值型数据库为Tset[addr]=(val,α)。Among them, the blind element α=Fp (KY ,id)·Fp (Kz ,UpdCnt[w]))-1 , the first key-value database corresponding to the storage address is Tset[addr]=(val,α ).
其中,动态交叉标签为搜索标签对应的第二键值型数据库为/>where the dynamic cross label is The second key-value database corresponding to the search tag is />
其中,伪随机函数可以是F:{0,1}λ×{0,1}λ→{0,1}λ或是Fp:可根据实际情况进行选取,在此不做具体限定。Among them, the pseudo-random function can be F: {0, 1}λ × {0, 1}λ → {0, 1}λ or Fp : It can be selected according to the actual situation, and no specific limitation is made here.
其中,动态交叉标签Among them, the dynamic cross label
其中,头插法可以是从一个空表开始,重复读入数据,生成新节点,将读入数据存放到新节点的数据域中,然后将新节点插入到当前链表的表头节点之后,直至读入结束标志为止。Among them, the head insertion method can start from an empty table, read in data repeatedly, generate new nodes, store the read data in the data field of the new node, and then insert the new node after the head node of the current linked list until until the end flag is read.
其中,第二键值型数据库根据SrchCt的不同,被区分为不同的其中,stSrchCt=F(KS,SrchCt)。Among them, the second key-value database is divided into different Wherein, stSrchCt = F(KS , SrchCt).
其中,密文值的累加值为Acc(VALw),若是首次计算Acc(VALw),则若非首次计算则利用双线性映射累加器的动态更新性计算Acc(VALw)←Acc(VALw)val+s。Among them, the cumulative value of the ciphertext value is Acc(VALw ), if Acc(VALw ) is calculated for the first time, then If it is not the first calculation, Acc(VALw )←Acc(VALw )val+s is calculated using the dynamic update property of the bilinear mapping accumulator.
可以理解的是,本申请实施例通过初始化阶段为整个系统生成所需要的密钥和数据结构,通过更新阶段将客户端的数据生成相应的密文索引上传至服务器,使得安全索引中的验证信息与数据同步更新,验证信息只是常数大小的累加值,通信负载低,不会泄露更新关键词的任何信息,并且计算效率较高、验证效率较高且索引存储花销较低。It can be understood that the embodiment of the present application generates the required keys and data structures for the entire system through the initialization phase, and generates the corresponding ciphertext index for the client data and uploads it to the server through the update phase, so that the verification information in the security index is consistent with the The data is updated synchronously, the verification information is only a constant-sized cumulative value, the communication load is low, and any information about the updated keywords will not be leaked, and the calculation efficiency is high, the verification efficiency is high, and the index storage cost is low.
在本申请实施例中,服务器根据联合搜索令牌对密文索引进行搜索,获得密文搜索结果,并根据联合搜索标签集生成密文搜索结果对应的验证证据,包括:解析服务器的安全索引区中密文索引,得到第一键值型数据库、第二键值型数据库和累加值;根据联合搜索令牌的当前值遍历链表得到联合搜索令牌的历史值,根据联合搜索令牌的当前值和历史值对第一键值型数据库和第二键值型数据库进行关键词搜索和联合搜索;根据关键词和联合搜索的搜索结果分别生成第一验证证据和第二验证证据,发送关键词和联合搜索的搜索结果、第一验证证据和第二验证证据至客户端。In this embodiment of the application, the server searches the ciphertext index according to the joint search token, obtains the ciphertext search result, and generates the verification evidence corresponding to the ciphertext search result according to the joint search tag set, including: parsing the security index area of the server In the ciphertext index, the first key-value database, the second key-value database and the accumulated value are obtained; according to the current value of the joint search token, the linked list is traversed to obtain the historical value of the joint search token, and according to the current value of the joint search token Perform keyword search and joint search on the first key-value database and the second key-value database with historical values; generate first verification evidence and second verification evidence according to the search results of keywords and joint search, and send keywords and The search results of the federated search, the first verification proof and the second verification proof are sent to the client.
其中,联合搜索令牌的当前值可以是stSrchCt,联合搜索令牌的历史值可以是stSrchCt-1,…,st1,在此不做具体限定。Wherein, the current value of the joint search token may be stSrchCt , and the historical value of the joint search token may be stSrchCt-1 , . . . , st1 , which are not specifically limited here.
可以理解的是,本申请实施例服务器根据客户端发来的联合搜索令牌对密文索引进行搜索,获得密文搜索结果并发给客户端,客户端对加密的文档标识符进行解密获得最终的明文结果,既可以确保联合关键词搜索的高效率,也可以实现可验证功能和高安全性。It can be understood that in this embodiment of the application, the server searches the ciphertext index according to the joint search token sent by the client, obtains the ciphertext search result and sends it to the client, and the client decrypts the encrypted document identifier to obtain the final Clear text results can not only ensure the high efficiency of joint keyword search, but also realize verifiable functions and high security.
在步骤S103中,接收服务器发送的密文搜索结果和对应的验证证据,解密密文搜索结果得到明文结果,利用验证证据验证对应的明文结果的正确性和/或完整性,输出验证通过的明文结果。In step S103, receive the ciphertext search result and the corresponding verification evidence sent by the server, decrypt the ciphertext search result to obtain the plaintext result, use the verification evidence to verify the correctness and/or integrity of the corresponding plaintext result, and output the verified plaintext result.
其中,验证证据可以是proof1=⊥。Wherein, the verification proof may be proof1 =⊥.
可以理解的是,本申请实施例客户端根据服务器发来的验证证据和明文搜索结果,并对其进行解密密文搜索结果得到明文结果,利用验证证据验证对应的明文结果的正确性和/或完整性,输出验证通过的明文结果,从而抵抗恶意服务器,通过测试部分搜索结果降低客户端计算开销并实现低假阳率。It can be understood that, according to the embodiment of the present application, the client decrypts the ciphertext search results to obtain the plaintext results according to the verification evidence and plaintext search results sent by the server, and uses the verification evidence to verify the correctness and/or Integrity, output the plaintext results that pass the verification, so as to resist malicious servers, reduce client computing overhead and achieve low false positive rate by testing part of the search results.
在本申请实施例中,利用验证证据验证对应的明文结果的正确性和/或完整性,包括:若关键词和联合搜索的搜索结果均为空集,且若文件个数计数器为空集时,验证通过,否则验证不通过;若关键词的搜索结果为非空集,联合搜索的搜索结果为空集时,检查关键词的搜索结果是否满足完整性要求,若满足,则从关键词的搜索结果中随机抽取一个或多个元素,按照样本检测验证法检查元素之间的非成员关系,以确定搜索结果的正确性,若正确,则验证通过,否则验证不通过;若关键词和联合搜索的搜索结果均为非空集,分别对关键词和联合搜索的搜索结果进行完整性和正确性的验证,若正确,则验证通过,否则验证不通过。In this embodiment of the application, verification evidence is used to verify the correctness and/or completeness of the corresponding plaintext results, including: if the keywords and the search results of the joint search are both empty sets, and if the file number counter is an empty set , the verification is passed, otherwise the verification is not passed; if the search result of the keyword is a non-empty set, and the search result of the joint search is an empty set, check whether the search result of the keyword meets the integrity requirement, and if so, then from the keyword One or more elements are randomly selected from the search results, and the non-member relationship between elements is checked according to the sample detection and verification method to determine the correctness of the search results. If it is correct, the verification is passed, otherwise the verification is not passed; The search results of the search are all non-empty sets, and the completeness and correctness of the keywords and the search results of the joint search are verified respectively. If they are correct, the verification passes, otherwise the verification fails.
其中,样本检测验证法是以高准确度低样本数进行验证计算。Among them, the sample detection verification method is to carry out verification calculation with high accuracy and low number of samples.
可以理解的是,本申请实施例客户端通过验证服务器发来的成员元素证明确保搜索结果的正确性,引入样本检测验证法确保搜索结果的完整性,能够有效抵抗恶意敌手。It can be understood that in the embodiment of the present application, the client ensures the correctness of the search results by verifying the member element certification sent by the server, and introduces a sample detection and verification method to ensure the integrity of the search results, which can effectively resist malicious opponents.
根据本申请实施例提出的可验证联合关键词高效搜索方法,通过获取的关键词集和联合搜索标签生成联合搜索令牌,并将其发送至服务器,服务器根据联合搜索令牌对密文索引进行搜索,获得密文搜索结果,并生成密文搜搜结果对应的验证证据,客户端接收服务器发送的密文搜索结果和对应的验证证据,并解析密文搜索结果得到明文结果,利用验证证据验证对应的明文结果的正确性和/或完整性,输出验证通过的明文结果,主要通过初始化阶段、更新阶段、搜索阶段和验证阶段确保了用户搜索结果的正确性、完整性和安全性,实现了高效的联合关键词搜索,节省了开销,提升用户体验感。由此,解决了相关技术中动态对称可搜索加密方案搜索效率低下及结果不完整和准确导致的成本较高、容易遭受恶意攻击导致安全性较低、降低了用户体验感等问题。According to the verifiable joint keyword efficient search method proposed in the embodiment of the present application, a joint search token is generated through the obtained keyword set and joint search tags, and sent to the server, and the server searches the ciphertext index according to the joint search token Search, obtain the ciphertext search results, and generate verification evidence corresponding to the ciphertext search results, the client receives the ciphertext search results and corresponding verification evidence sent by the server, and parses the ciphertext search results to obtain plaintext results, and uses the verification evidence to verify The correctness and/or integrity of the corresponding plaintext results, and the output of plaintext results that pass the verification, mainly through the initialization phase, update phase, search phase, and verification phase to ensure the correctness, integrity, and security of user search results, and realize Efficient joint keyword search saves expenses and improves user experience. As a result, the problems of low search efficiency, incomplete and accurate results caused by high cost caused by dynamic symmetric searchable encryption schemes in related technologies, low security due to vulnerability to malicious attacks, and reduced user experience are solved.
其次参照附图描述根据本申请另一个实施例所提供的可验证联合关键词高效搜索方法。Next, a method for efficiently searching verifiable joint keywords according to another embodiment of the present application will be described with reference to the accompanying drawings.
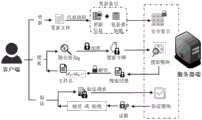
图2是本申请实施例的可验证联合关键词高效搜索方法的流程示意图。FIG. 2 is a schematic flowchart of a method for efficiently searching verifiable joint keywords according to an embodiment of the present application.
如图2所示,该可验证联合关键词高效搜索方法应用于服务器,其中,包括以下步骤:As shown in Figure 2, the efficient search method for verifiable joint keywords is applied to the server, which includes the following steps:
在步骤S201中,接收客户端发送的联合搜索令牌。In step S201, a federated search token sent by a client is received.
可以理解的是,本申请实施例中服务器接收来自客户端发送的联合搜索令牌,以便于后续利用联合搜索令牌对密文索引进行搜索,并生成密文搜索结果对应的验证证据。It can be understood that, in the embodiment of the present application, the server receives the joint search token sent from the client, so as to use the joint search token to search the ciphertext index and generate verification evidence corresponding to the ciphertext search result.
在步骤S202中,根据联合搜索令牌对密文索引进行搜索,获得密文搜索结果,并生成密文搜索结果对应的验证证据。In step S202, the ciphertext index is searched according to the joint search token, the ciphertext search result is obtained, and the verification evidence corresponding to the ciphertext search result is generated.
可以理解的是,本申请实施例服务器根据联合搜索令牌对密文索引进行搜索,获得密文搜索结果,并生成密文搜索结果对应的验证证据,以便于将其发送至客户端,解密密文搜索结果并验证明文结果的正确性和/或完整性。It can be understood that, in this embodiment of the application, the server searches the ciphertext index according to the joint search token, obtains the ciphertext search result, and generates the verification evidence corresponding to the ciphertext search result, so that it can be sent to the client to decrypt the encrypted text search results and verify the correctness and/or completeness of the plain text results.
在步骤S203中,发送密文搜索结果和对应的验证证据至客户端,其中,客户端解密密文搜索结果得到明文结果,利用验证证据验证对应的明文结果的正确性和/或完整性,输出验证通过的明文结果。In step S203, send the ciphertext search result and the corresponding verification evidence to the client, where the client decrypts the ciphertext search result to obtain the plaintext result, uses the verification evidence to verify the correctness and/or integrity of the corresponding plaintext result, and outputs The plaintext result of the verification.
可以理解的是,本申请实施例通过将密文搜索结果和对应的验证证据发送至客户端,客户端解密密文搜索结果得到明文结果,利用验证证据验证对应的明文结果的正确性和/或完整性,输出验证通过的明文结果,确保了用户搜索结果的正确性、完整性和安全性。It can be understood that, in this embodiment of the present application, by sending the ciphertext search results and the corresponding verification evidence to the client, the client decrypts the ciphertext search results to obtain the plaintext results, and uses the verification evidence to verify the correctness and/or Integrity, outputting plaintext results that pass verification, ensuring the correctness, integrity and security of user search results.
根据本申请实施例提出的可验证联合关键词高效搜索方法,接收来自客户端发送的联合搜索令牌,服务器根据联合搜索令牌对密文索引进行搜索,获得密文搜索结果,并生成密文搜索结果对应的验证证据,将密文搜索结果和对应的验证证据发送至客户端,客户端解密密文搜索结果得到明文结果,利用验证证据验证对应的明文结果的正确性和/或完整性,输出验证通过的明文结果,确保了用户搜索结果的正确性、完整性和安全性,实现了高效的联合关键词搜索,节省了开销,提升用户体验感。由此,解决了相关技术中动态对称可搜索加密方案搜索效率低下及结果不完整和准确导致了成本较高、容易遭受恶意攻击导致安全性较低、降低了用户体验感等问题。According to the verifiable joint keyword efficient search method proposed in the embodiment of this application, the joint search token sent from the client is received, the server searches the ciphertext index according to the joint search token, obtains the ciphertext search result, and generates the ciphertext The verification evidence corresponding to the search result, the ciphertext search result and the corresponding verification evidence are sent to the client, the client decrypts the ciphertext search result to obtain the plaintext result, and uses the verification evidence to verify the correctness and/or integrity of the corresponding plaintext result, The plaintext results that pass the verification are output, which ensures the correctness, integrity and security of the user's search results, realizes efficient joint keyword search, saves overhead, and improves user experience. As a result, the problems of low search efficiency, incomplete and accurate results resulting in high cost, low security due to vulnerability to malicious attacks, and reduced user experience in related technologies are solved.
下面将结合图3对可验证联合关键词高效搜索方法进行详细阐述,分为5个阶段,具体阶段如下:The following is a detailed description of the verifiable joint keyword efficient search method in conjunction with Figure 3, which is divided into five stages. The specific stages are as follows:
1、初始化阶段1. Initialization phase
客户端输入安全参数λ,λ取值256;输出相应密钥及初始化后的数据结构,具体步骤如下:The client inputs the security parameter λ, and the value of λ is 256; outputs the corresponding key and the initialized data structure, the specific steps are as follows:
(1)使用PRF F均匀随机采样密钥KT。选择大素数p,使用PRFFp均匀随机采样密钥KX,KY,KZ。设置密钥集合MK={KT,KX,KY,KZ}表示客户端拥有的所有对称密钥;其中,伪随机函数F:{0,1}λ×{0,1}λ→{0,1}λ,伪随机函数Fp:(1) Use PRFF to uniformly randomly sample the key KT . Choose a large prime number p, and use PRFFp to uniformly randomly sample keys KX , KY , KZ . Set the key set MK={KT , KX , KY , KZ } to represent all the symmetric keys owned by the client; among them, the pseudo-random function F: {0, 1}λ × {0, 1}λ → {0, 1}λ , pseudorandom function Fp :
(2)计算累加器公钥t是成员元素上界,t的值即为数据库中关键词-文件标识符对的个数;私钥/>(2) Calculate the accumulator public key t is the upper bound of member elements, and the value of t is the number of keyword-file identifier pairs in the database; private key/>
(3)将键值型数据库TSet,XSet,关键词更新计数器UpdCnt,链表L初始化为空,初始化搜索标签SrchCt值为1。(3) Initialize key-value database TSet, XSet, keyword update counter UpdCnt, linked list L as empty, and initialize search label SrchCt as 1.
2、更新阶段2. Update stage
如图4所示,客户端输入相关密钥及更新数据,调用Update算法,输出更新索引EDB。As shown in Figure 4, the client inputs relevant keys and update data, calls the Update algorithm, and outputs the update index EDB.
(1)对于关键词-文件标识符对(w,id),更新关键词w对应的文件个数计数器UpdCnt[w]←UpdCnt[w]+1,计算(w,id)的密文值和val的存储地址addr=F(Kp,w||UpdCnt[w]||0)。(1) For the keyword-file identifier pair (w, id), update the file number counter UpdCnt[w]←UpdCnt[w]+1 corresponding to the keyword w, and calculate the ciphertext value of (w, id) and the storage address of val addr=F(Kp ,w||UpdCnt[w]||0).
(2)计算动态盲元素α=Fp(KY,id)·Fp(KZ,UpdCnt[w]))-1,将val和α存入TSet中Tset[addr]=(val,α)。(2) Calculate the dynamic blind element α=Fp (KY ,id)·Fp (KZ ,UpdCnt[w]))-1 , store val and α in TSet Tset[addr]=(val,α ).
(3)计算动态交叉标签将xtag放入/>中。动态交叉标签xtag分为两部分,一部分与w和op相关,另一部分与id相关,xtag是实现不经意计算的关键。(3) Calculate dynamic cross-label put xtag in /> middle. The dynamic cross tag xtag is divided into two parts, one part is related to w and op, and the other part is related to id, xtag is the key to realize inadvertent calculation.
(4)使用头插法构建链表L,将stSrchCt=F(KS,SrchCt)存入链表L的结点中。同一批次更新,只需要构建结点一次,即SrchCt的值未更新,则不需要重复进行此步骤;若SrchCt的值更新,假设SrchCt值为SrchCt+1,则构建新结点stSrchCt+1=F(KS,SrchCt+1)。其中客户端只保存当前最新结点st值。(4) Construct the linked list L by using the header insertion method, and store stSrchCt =F(KS , SrchCt) in the nodes of the linked list L. For the same batch update, you only need to build the node once, that is, if the value of SrchCt is not updated, you do not need to repeat this step; if the value of SrchCt is updated, assuming that the value of SrchCt is SrchCt+1, then build a new node stSrchCt+1 =F(KS ,SrchCt+1). Among them, the client only saves the current latest node st value.
(5)计算关键词w对应的密文值的累加值Acc(VALw)。若首次计算Acc(VALw),则计算否则,利用双线性映射累加器的动态更新性计算Acc(VALw)←Acc(VALw)val+s。由客户端保存Acc(VALw),且只保存最新计算值。(5) Calculate the cumulative value Acc(VALw ) of the ciphertext value corresponding to the keyword w. If Acc(VALw ) is calculated for the first time, then calculate Otherwise, Acc(VALw )←Acc(VALw )val+s is calculated using the dynamic update property of the bilinear mapping accumulator. Acc(VALw ) is saved by the client, and only the latest calculated value is saved.
(6)若XSet=⊥,计算XSet的累加值Acc(Xset)←gxtag+s;否则,Acc(Xset)←Acc(Xset)xtag+s。XSet是所有的的集合,其中,SrchCt的值为1,2,……。由客户端保存Acc(Xset),且只保存最新计算值。(6) If XSet=⊥, calculate the accumulated value of XSet Acc(Xset)←gxtag+s ; otherwise, Acc(Xset)←Acc(Xset)xtag+s . XSet is all A collection of , where the value of SrchCt is 1, 2, .... Acc(Xset) is saved by the client, and only the latest calculated value is saved.
(7)将更新索引EDB={TSet,Xset}发送给服务器,存入服务器的安全索引EDB区域。(7) Send the update index EDB={TSet, Xset} to the server, and store it in the security index EDB area of the server.
本申请中,客户端可多次执行步骤(1)至(6)进行批量更新,并将相应的动态交叉标签xtag存储在中,客户端发起搜索之后,再次更新的数据则存储在中且令SrchCt=SrchCt+1。值得注意的是,若未进行下一轮数据更新,无论执行多少次搜索,搜索标签SrchCt只会增加一次。In this application, the client can perform steps (1) to (6) multiple times to perform batch updates, and store the corresponding dynamic cross tag xtag in In , after the client initiates a search, the updated data is stored in and let SrchCt=
3、联合搜索令牌生成阶段3. Joint search token generation stage
如图5所示,客户端输入关键词更新计数器UpdCnt,搜索标签SrchCt,联合查询q=(w1,...,wd),进行搜索令牌生成,输出联合搜索令牌SToken。具体步骤如下:As shown in FIG. 5 , the client inputs the keyword update counter UpdCnt, search label SrchCt, joint query q=(w1 ,...,wd ), generates a search token, and outputs a joint search token SToken. Specific steps are as follows:
(1)假设使用UpdCnt确定更新次数最低的关键词为w1,即最低频关键词。初始化stokenList,xtokenList1,…,为空列表。(1) Assuming that UpdCnt is used to determine that the keyword with the lowest number of updates is w1 , that is, the keyword with the lowest frequency. Initialize tokenList, xtokenList1, ..., is an empty list.
(2)当1≤j≤UpdCnt[w1],生成关键词w1的密文存储地址addrj=F(KT,w1||j||0),并将addrj并入列表stokenList中。(2) When 1≤j≤UpdCnt[w1 ], generate the ciphertext storage address addrj =F(KT ,w1 ||j||0) of keyword w1 , and incorporate addrj into the list tokenList middle.
当1≤i≤d,计算联合搜索的交叉令牌,并放入列表xtokenListj中。When 1 ≤ i ≤ d, compute the cross tokens for the joint search, And put into the list xtokenListj .
(3)由客户端执行,将生成包含关键词的联合搜索令牌发送给服务器。(3) Executed by the client, a joint search token containing keywords will be generated sent to the server.
4、搜索阶段4. Search stage
如图6所示,服务器输入主密钥MK,公钥pk,联合查询q=(w1,...,wd),搜索令牌SToken,安全索引EDB,进行搜索,输出联合搜索结果列表sIdList。As shown in Figure 6, the server inputs master key MK, public key pk, joint query q=(w1 ,...,wd ), search token SToken, security index EDB, searches, and outputs a list of joint search results sIdList.
(1)将安全索引EDB的内容解析成TSet,XSet,Acc(Xset)。将集合XT,R和初始化为空。(1) Parse the content of the security index EDB into TSet, XSet, Acc (Xset). will set XT, R and Initialize to empty.
(2)根据stSrchCt值遍历链表获得stSrchCt-1,…,st1。(2) Traverse the linked list according to the value of stSrchCt to obtain stSrchCt-1 ,...,st1 .
(3)j初始值为1,当1≤j≤stokenList.size时,(3) The initial value of j is 1, when 1≤j≤stokenList.size,
1)设置计数器值cntj为0。1) Set the counter value cntj to 0.
2)将TSet[stokenList[j]]值解析为(svalj,αj),将svalj并入2) Parse the value of TSet[stokenList[j]] into (svalj ,αj ), and incorporate svalj into
i初始值为1,当1≤i≤d时,计算The initial value of i is 1, when 1≤i≤d, calculate
若对任意i=1,2,…,d,均有且/>将/>放入XT集合中。此时联合查询q=(w1,...,wd)对应的条目(j,svalj)存在且未被删除,将(j,svalj)并入R。本步骤是不经意共享计算的关键步骤。If for any i=1,2,...,d, there are and/> will /> into the XT collection. At this time, the entry (j, svalj ) corresponding to the joint query q=(w1 , . . . , wd ) exists and has not been deleted, and (j, svalj ) is incorporated into R. This step is a critical step in inadvertently sharing computation.
(4)如果关键词w1的搜索结果为空,那么生成证据proof1←⊥,否则/>证据的具体计算过程见文末。(4) If the search result of keyword w1 is empty, then generate evidence proof1 ←⊥, otherwise /> See the end of the paper for the specific calculation process of the evidence.
(5)如果联合搜索结果R为空,那么生成证据proof2←⊥,否则根据集合XT中的值生成证据proof2←WXT,Xset。(5) If the joint search result R is empty, then generate proof2 ←⊥, otherwise generate proof2 ←WXT,Xset according to the value in the set XT.
(6)将发送给客户端。(6) Will sent to the client.
客户端根据服务器发来的搜索结果R做最终计算,得出相应明文搜索结果,步骤如下:The client makes the final calculation based on the search result R sent by the server, and obtains the corresponding plaintext search result. The steps are as follows:
(1)初始化sIdList为空列表,len=1。(1) Initialize sIdList as an empty list, len=1.
(2)当1≤len≤R.size时,解析R为(j,svalj),将svalj与F(KT,w1||j||1)进行异或得到(idj||add),将idj放入sIdList列表中。(2) When 1≤len≤R.size, analyze R as (j,svalj ), and perform XOR between svalj and F(KT ,w1 ||j||1) to get (idj || add), put idj into the sIdList list.
(3)客户端输出sIdList,即为明文搜索结果。(3) The client outputs sIdList, which is the plaintext search result.
5、验证阶段5. Verification stage
客户端进行验证,输出接受验证结果Accept或者拒绝Reject。The client performs verification, and outputs Accept or rejects the verification result.
验证算法分为以下三种类型。Authentication algorithms are classified into the following three types.
类型1:是空集时,表明关键词w1没有匹配的搜索结果,则联合搜索结果也为空。这种情况下,服务器发送给客户端相应验证证据proof1=⊥。客户端检查UpdCnt[w1]是否为空,若空,客户端输出Accept,否则返回Reject。Type 1: When is an empty set, it indicates that there is no matching search result for keyword w1 , and the joint search result is also empty. In this case, the server sends the corresponding verification proof proof1 =⊥ to the client. The client checks whether UpdCnt[w1 ] is empty, if it is empty, the client outputs Accept, otherwise it returns Reject.
类型2:不是空集,R是空集,关键词w1有匹配的搜索结果,但联合搜索结果为空。具体分为以下两步:Type 2: is not an empty set, R is an empty set, keyword w1 has a matching search result, but the joint search result is empty. Specifically divided into the following two steps:
(1)用户通过公式(1)检查的完整性。若成立,继续进行(2),否则,返回Reject。(1) The user checks through the formula (1) integrity. If true, proceed to (2), otherwise, return Reject.
(2)引入样本检测思想,以高准确度低样本数进行验证计算。从中随机抽取k个元素,按照样本检测验证法检查相应非成员关系。(2) Introduce the idea of sample detection, and perform verification calculation with high accuracy and low sample number. from Randomly select k elements in , and check the corresponding non-membership relationship according to the sample detection and verification method.
类型3:和R都不是空集。验证方法类似情况2,唯一差别是从/>中随机抽取k个元素。Type 3: and R are not empty sets. The verification method is similar to
其中,样本检测验证法,具体介绍如下:Among them, the sample detection verification method is described in detail as follows:
首先,由客户端随机生成k个xtag值,其次由服务器响应生成证据,最后由客户端进行验证。具体内容如下所示:Firstly, k xtag values are randomly generated by the client, secondly, evidence is generated by the server response, and finally verified by the client. The specific content is as follows:
客户端执行:Client executes:
(1)客户端从中随机选择{ind1,…,indk},初始化i为1,j为2。(1) Client from randomly select {ind1 ,…,indk }, initialize i to 1, and j to 2.
(2)当1≤i≤k时,将xtag[i]初始化为空。(2) When 1≤i≤k, initialize xtag[i] to empty.
当j=2,…,d时,计算和/>并将xtag[i,j]add和xtag[i,j]del放入xtag[i]。When j=2,...,d, calculate and /> And put xtag[i,j]add and xtag[i,j]del into xtag[i].
(3)客户端把xtag←{xtag[1],...,xtag[k]}发给云服务器。(3) The client sends xtag←{xtag[1],...,xtag[k]} to the cloud server.
服务器执行:The server executes:
初始化j为2,对所有xtag[i]∈xtag进行以下操作:Initialize j as 2, do the following for all xtag[i]∈xtag:
(1)当j=2,…,d时(1) When j=2,...,d
若那么生成非成员证据/>结束(1)操作。like Then generate non-member evidence /> End (1) operation.
若那么生成成员证据proof[i]←Wxtag[i,j],XSet,结束(2)操作。like Then generate membership evidence proof[i]←Wxtag[i,j],XSet and end (2) operation.
(2)将proof[i]放入proof中。(2) Put proof[i] into proof.
客户端执行:对于proof中的所有proof[i],若验证成功返回Accept,否则返回Reject。Client execution: For all proof[i] in the proof, if the verification is successful, it returns Accept, otherwise it returns Reject.
k的具体计算方法如下:The specific calculation method of k is as follows:
使用样本检测法,即随机选择联合搜索结果的一部分来验证搜索结果的完整性。具体地说,即从中随机选择k个元素进行完整性检测。令PX表示用户检测到服务器错误行为的概率。/>n是/>的元素个数,t是搜索结果的错误文档个数。因为/>确定了错误文档的百分比,就可以通过检查与数据集大小无关的一定数量的文档,高概率检测到错误行为。例如,为了达到99%的概率,分别在t=10%·n,t=20%·n和t=50%·n时检查65、21和7个文档。Verify the integrity of the search results using sample testing, which randomly selects a portion of the federated search results. Specifically, from Randomly select k elements for integrity check. Let PX denote the probability that a user detects a server misbehavior. /> n is /> The number of elements, t is the number of wrong documents in the search results. because /> Once the percentage of erroneous documents is determined, erroneous behavior can be detected with high probability by examining a certain number of documents independent of the size of the dataset. For example, to achieve a probability of 99%, 65, 21 and 7 documents are examined at t=10%·n, t=20%·n and t=50%·n, respectively.
双线性映射累加器的使用方法,以及成员证据和非成员证据具体计算方法如下:The usage method of the bilinear mapping accumulator, and the specific calculation methods of membership evidence and non-member evidence are as follows:
基于双线性映射的累加器是一种密码认证原语,用于验证集合成员关系,它可以为(不)属于给定集合的任何子集提供(非)成员身份的简短证明。给定大素数p,双线性映射e:G1×G1→G2,|G1|=|G2|=p。累加器管理员随机选取累加器的私钥g是G1的一个生成元,计算对应的公钥/>t是成员元素上界。对于包含N个成员元素的集合/>计算其累加器值:Bilinear map-based accumulators are a cryptographic authentication primitive for verifying set membership that can provide short proofs of (non-)membership for any subset that (does not) belong to a given set. Given a large prime number p, bilinear mapping e: G1 ×G1 →G2 , |G1 |=|G2 |=p. The accumulator administrator randomly picks the private key of the accumulator g is a generator of G1 , calculate the corresponding public key /> t is the upper bound of the member elements. For a set containing N member elements /> Calculate its accumulator value:
服务器为创建成员证据时,计算/>验证者可验证等式(3)是否成立,若等式成立,则/>The server is When creating membership proofs, compute the /> The verifier can verify whether the equation (3) is true, if the equation is true, then />
证明元素则创建非成员证据/>proof element then create a non-member evidence />
令fS(s)为Acc(S)的指数,即fS(s)=∏x∈S(x+s),对于任意非成员证据为其中,Let fS (s) be the index of Acc(S), that is, fS (s)=∏x∈S (x+s), for any Evidence for non-membership is in,
且(y+s)|[f(s)+uy] And (y+s)|[f(s)+uy ]
验证者检查等式是否成立,若等式成立,则Verifier Check Equation Whether it is established, if the equation is established, then
此外,添加元素x至累加器,即更新累加器Acc(S∪{x})=Acc(S)x+s。从累加器中删除值x时,更新累加器Acc(S\{x})=Acc(S)1/(x+s)。In addition, add element x to the accumulator, that is, update the accumulator Acc(S∪{x})=Acc(S)x+s . When the value x is deleted from the accumulator, the accumulator Acc(S\{x})=Acc(S)1/(x+s) is updated.
综上,本申请是具有前向和后向安全的可验证联合关键词高效搜索方案,解决了当前最优的基于OXT算法的动态联合搜索方案无法满足前向安全和删除功能失效的问题,利用双线性映射累加器实现可验证功能,可抵抗服务器作恶,在综合考虑安全性、表达能力以及可验证性的基础上,仍可确保高搜索效率,以及比同类方案更高效的更新和验证方法。To sum up, this application is a verifiable joint keyword efficient search scheme with forward and backward security, which solves the problem that the current optimal dynamic joint search scheme based on OXT algorithm cannot meet the forward security and invalidation of deletion functions. The bilinear map accumulator realizes the verifiable function, which can resist the server from being malicious. On the basis of comprehensive consideration of security, expressiveness and verifiability, it can still ensure high search efficiency and a more efficient update and verification method than similar solutions .
其次参照附图描述根据本申请一个实施例提出的可验证联合关键词高效搜索装置。Next, a device for efficient search for verifiable joint keywords proposed according to an embodiment of the present application will be described with reference to the accompanying drawings.
图7是本申请实施例的可验证联合关键词高效搜索装置的方框示意图。Fig. 7 is a schematic block diagram of an efficient search device for verifiable joint keywords according to an embodiment of the present application.
如图7所示,该可验证联合关键词高效搜索装置10应用于客户端,包括:获取模块110、第一发送模块120和第一接收模块130。As shown in FIG. 7 , the
其中,获取模块,用于获取关键词集和联合搜索标签;第一发送模块,用于根据关键词集和联合搜索标签生成联合搜索令牌,发送联合搜索令牌至服务器,其中,服务器根据联合搜索令牌对密文索引进行搜索,获得密文搜索结果,并生成密文搜索结果对应的验证证据;第一接收模块,用于接收服务器发送的密文搜索结果和对应的验证证据,解密密文搜索结果得到明文结果,利用验证证据验证对应的明文结果的正确性和/或完整性,输出验证通过的明文结果。Among them, the obtaining module is used to obtain the keyword set and the joint search tag; the first sending module is used to generate a joint search token according to the keyword set and the joint search tag, and send the joint search token to the server, wherein the server according to the joint The search token searches the ciphertext index, obtains the ciphertext search results, and generates verification evidence corresponding to the ciphertext search results; the first receiving module is used to receive the ciphertext search results and corresponding verification evidence sent by the server, and decrypt the encrypted The plaintext result is obtained from the text search result, the correctness and/or completeness of the corresponding plaintext result is verified by using the verification evidence, and the verified plaintext result is output.
需要说明的是,前述对可验证联合关键词高效搜索方法实施例的解释说明也适用于该实施例的可验证联合关键词高效搜索装置,此处不再赘述。It should be noted that the foregoing explanations on the embodiment of the method for efficiently searching for verifiable joint keywords are also applicable to the device for efficiently searching for verifiable joint keywords in this embodiment, and details are not repeated here.
根据本申请实施例提出的可验证联合关键词高效搜索装置,通过获取的关键词集和联合搜索标签生成联合搜索令牌,并将其发送至服务器,服务器根据联合搜索令牌对密文索引进行搜索,获得密文搜索结果,并生成密文搜搜结果对应的验证证据,客户端接收服务器发送的密文搜索结果和对应的验证证据,并解析密文搜索结果得到明文结果,利用验证证据验证对应的明文结果的正确性和/或完整性,输出验证通过的明文结果,主要通过初始化阶段、更新阶段、搜索阶段和验证阶段确保了用户搜索结果的正确性、完整性和安全性,实现了高效的联合关键词搜索,节省了开销,提升用户体验感。由此,解决了相关技术中动态对称可搜索加密方案搜索效率低下及结果不完整和准确导致了成本较高、容易遭受恶意攻击导致安全性较低、降低了用户体验感等问题。According to the verifiable joint keyword efficient search device proposed in the embodiment of this application, a joint search token is generated through the obtained keyword set and joint search tags, and sent to the server, and the server performs ciphertext indexing based on the joint search token Search, obtain the ciphertext search results, and generate verification evidence corresponding to the ciphertext search results, the client receives the ciphertext search results and corresponding verification evidence sent by the server, and parses the ciphertext search results to obtain plaintext results, and uses the verification evidence to verify The correctness and/or integrity of the corresponding plaintext results, and the output of plaintext results that pass the verification, mainly through the initialization phase, update phase, search phase, and verification phase to ensure the correctness, integrity, and security of user search results, and realize Efficient joint keyword search saves expenses and improves user experience. As a result, the problems of low search efficiency, incomplete and accurate results resulting in high cost, low security due to vulnerability to malicious attacks, and reduced user experience in related technologies are solved.
其次参照附图描述根据本申请另一个实施例提出的可验证联合关键词高效搜索装置。Next, a device for efficient search for verifiable combined keywords according to another embodiment of the present application is described with reference to the accompanying drawings.
图8是本申请实施例的可验证联合关键词高效搜索装置的方框示意图。Fig. 8 is a schematic block diagram of an efficient search device for verifiable joint keywords according to an embodiment of the present application.
如图8所示,该可验证联合关键词高效搜索装置10应用于服务器,包括:第二接收模块210、搜索模块220和第二发送模块230。As shown in FIG. 8 , the
其中,第二接收模块210用于接收客户端发送的联合搜索令牌;搜索模块220用于根据联合搜索令牌对密文索引进行搜索,获得密文搜索结果,并生成密文搜索结果对应的验证证据;第二发送模块230用于发送密文搜索结果和对应的验证证据至客户端,其中,客户端解密密文搜索结果得到明文结果,利用验证证据验证对应的明文结果的正确性和/或完整性,输出验证通过的明文结果。Wherein, the
需要说明的是,前述对可验证联合关键词高效搜索方法实施例的解释说明也适用于该实施例的可验证联合关键词高效搜索装置,此处不再赘述。It should be noted that the foregoing explanations on the embodiment of the method for efficiently searching for verifiable joint keywords are also applicable to the device for efficiently searching for verifiable joint keywords in this embodiment, and details are not repeated here.
根据本申请实施例提出的可验证联合关键词高效搜索装置,接收来自客户端发送的联合搜索令牌,服务器根据联合搜索令牌对密文索引进行搜索,获得密文搜索结果,并生成密文搜索结果对应的验证证据,将密文搜索结果和对应的验证证据发送至客户端,客户端解密密文搜索结果得到明文结果,利用验证证据验证对应的明文结果的正确性和/或完整性,输出验证通过的明文结果,确保了用户搜索结果的正确性、完整性和安全性,实现了高效的联合关键词搜索,节省了开销,提升用户体验感。由此,解决了相关技术中动态对称可搜索加密方案搜索效率低下及结果不完整和准确导致了成本较高、容易遭受恶意攻击导致安全性较低、降低了用户体验感等问题。According to the verifiable joint keyword efficient search device proposed in the embodiment of this application, the joint search token sent from the client is received, and the server searches the ciphertext index according to the joint search token, obtains the ciphertext search result, and generates the ciphertext The verification evidence corresponding to the search result, the ciphertext search result and the corresponding verification evidence are sent to the client, the client decrypts the ciphertext search result to obtain the plaintext result, and uses the verification evidence to verify the correctness and/or integrity of the corresponding plaintext result, The plaintext results that pass the verification are output, which ensures the correctness, integrity and security of the user's search results, realizes efficient joint keyword search, saves overhead, and improves user experience. As a result, the problems of low search efficiency, incomplete and accurate results resulting in high cost, low security due to vulnerability to malicious attacks, and reduced user experience in related technologies are solved.
图9为本申请实施例提供的客户端的结构示意图。该客户端可以包括:FIG. 9 is a schematic structural diagram of a client provided by an embodiment of the present application. This client can include:
存储器901、处理器902及存储在存储器901上并可在处理器902上运行的计算机程序。A
处理器902执行程序时实现上述实施例中提供的可验证联合关键词高效搜索方法。When the
进一步地,客户端还包括:Further, the client also includes:
通信接口903,用于存储器901和处理器902之间的通信。The
存储器901,用于存放可在处理器902上运行的计算机程序。The
存储器901可能包含高速RAM(Random Access Memory,随机存取存储器)存储器,也可能还包括非易失性存储器,例如至少一个磁盘存储器。The
如果存储器901、处理器902和通信接口903独立实现,则通信接口903、存储器901和处理器902可以通过总线相互连接并完成相互间的通信。总线可以是ISA(IndustryStandard Architecture,工业标准体系结构)总线、PCI(Peripheral Component,外部设备互连)总线或EISA(Extended Industry Standard Architecture,扩展工业标准体系结构)总线等。总线可以分为地址总线、数据总线、控制总线等。为便于表示,图9中仅用一条粗线表示,但并不表示仅有一根总线或一种类型的总线。If the
可选的,在具体实现上,如果存储器901、处理器902及通信接口903,集成在一块芯片上实现,则存储器901、处理器902及通信接口903可以通过内部接口完成相互间的通信。Optionally, in terms of specific implementation, if the
处理器902可能是一个CPU(Central Processing Unit,中央处理器),或者是ASIC(Application Specific Integrated Circuit,特定集成电路),或者是被配置成实施本申请实施例的一个或多个集成电路。The
图10为本申请实施例提供的服务器的结构示意图。该服务器可以包括:FIG. 10 is a schematic structural diagram of a server provided by an embodiment of the present application. This server can include:
存储器1001、处理器1002及存储在存储器1001上并可在处理器1002上运行的计算机程序。A
处理器1002执行程序时实现上述实施例中提供的可验证联合关键词高效搜索方法。When the
进一步地,服务器还包括:Further, the server also includes:
通信接口1003,用于存储器1001和处理器1002之间的通信。The
存储器1001,用于存放可在处理器1002上运行的计算机程序。The
存储器1001可能包含高速RAM(Random Access Memory,随机存取存储器)存储器,也可能还包括非易失性存储器,例如至少一个磁盘存储器。The
如果存储器1001、处理器1002和通信接口1003独立实现,则通信接口1003、存储器1001和处理器1002可以通过总线相互连接并完成相互间的通信。总线可以是ISA(IndustryStandard Architecture,工业标准体系结构)总线、PCI(Peripheral Component,外部设备互连)总线或EISA(Extended Industry Standard Architecture,扩展工业标准体系结构)总线等。总线可以分为地址总线、数据总线、控制总线等。为便于表示,图10中仅用一条粗线表示,但并不表示仅有一根总线或一种类型的总线。If the
可选的,在具体实现上,如果存储器1001、处理器1002及通信接口1003,集成在一块芯片上实现,则存储器1001、处理器1002及通信接口1003可以通过内部接口完成相互间的通信。Optionally, in specific implementation, if the
处理器1002可能是一个CPU(Central Processing Unit,中央处理器),或者是ASIC(Application Specific Integrated Circuit,特定集成电路),或者是被配置成实施本申请实施例的一个或多个集成电路。The
本申请实施例还提供一种计算机可读存储介质,其上存储有计算机程序,该程序被处理器执行时实现如上的可验证联合关键词高效搜索方法。The embodiment of the present application also provides a computer-readable storage medium, on which a computer program is stored, and when the program is executed by a processor, the above efficient search method for verifiable joint keywords is realized.
在本说明书的描述中,参考术语“一个实施例”、“一些实施例”、“示例”、“具体示例”、或“一些示例”等的描述意指结合该实施例或示例描述的具体特征、结构、材料或者特点包含于本申请的至少一个实施例或示例中。在本说明书中,对上述术语的示意性表述不是必须针对的是相同的实施例或示例。而且,描述的具体特征、结构、材料或者特点可以在任一个或N个实施例或示例中以合适的方式结合。此外,在不相互矛盾的情况下,本领域的技术人员可以将本说明书中描述的不同实施例或示例以及不同实施例或示例的特征进行结合和组合。In the description of this specification, descriptions referring to the terms "one embodiment", "some embodiments", "example", "specific examples", or "some examples" mean that specific features described in connection with the embodiment or example , structure, material or characteristic is included in at least one embodiment or example of the present application. In this specification, the schematic representations of the above terms are not necessarily directed to the same embodiment or example. Moreover, the described specific features, structures, materials or characteristics may be combined in any one or N embodiments or examples in an appropriate manner. In addition, those skilled in the art can combine and combine different embodiments or examples and features of different embodiments or examples described in this specification without conflicting with each other.
此外,术语“第一”、“第二”仅用于描述目的,而不能理解为指示或暗示相对重要性或者隐含指明所指示的技术特征的数量。由此,限定有“第一”、“第二”的特征可以明示或者隐含地包括至少一个该特征。在本申请的描述中,“N个”的含义是至少两个,例如两个,三个等,除非另有明确具体的限定。In addition, the terms "first" and "second" are used for descriptive purposes only, and cannot be interpreted as indicating or implying relative importance or implicitly specifying the quantity of indicated technical features. Thus, the features defined as "first" and "second" may explicitly or implicitly include at least one of these features. In the description of the present application, "N" means at least two, such as two, three, etc., unless otherwise specifically defined.
流程图中或在此以其他方式描述的任何过程或方法描述可以被理解为,表示包括一个或更N个用于实现定制逻辑功能或过程的步骤的可执行指令的代码的模块、片段或部分,并且本申请的优选实施方式的范围包括另外的实现,其中可以不按所示出或讨论的顺序,包括根据所涉及的功能按基本同时的方式或按相反的顺序,来执行功能,这应被本申请的实施例所属技术领域的技术人员所理解。Any process or method description in a flowchart or otherwise described herein may be understood to represent a module, segment or portion of code comprising one or more executable instructions for implementing a custom logical function or step of a process , and the scope of preferred embodiments of the present application includes additional implementations in which functions may be performed out of the order shown or discussed, including in substantially simultaneous fashion or in reverse order depending on the functions involved, which shall It should be understood by those skilled in the art to which the embodiments of the present application belong.
应当理解,本申请的各部分可以用硬件、软件、固件或它们的组合来实现。在上述实施方式中,N个步骤或方法可以用存储在存储器中且由合适的指令执行系统执行的软件或固件来实现。如,如果用硬件来实现和在另一实施方式中一样,可用本领域公知的下列技术中的任一项或他们的组合来实现:具有用于对数据信号实现逻辑功能的逻辑门电路的离散逻辑电路,具有合适的组合逻辑门电路的专用集成电路,可编程门阵列,现场可编程门阵列等。It should be understood that each part of the present application may be realized by hardware, software, firmware or a combination thereof. In the above embodiments, the N steps or methods may be implemented by software or firmware stored in memory and executed by a suitable instruction execution system. For example, if implemented in hardware as in another embodiment, it can be implemented by any one or a combination of the following techniques known in the art: a discrete Logic circuits, ASICs with suitable combinational logic gates, programmable gate arrays, field programmable gate arrays, etc.
本技术领域的普通技术人员可以理解实现上述实施例方法携带的全部或部分步骤是可以通过程序来指令相关的硬件完成,所述的程序可以存储于一种计算机可读存储介质中,该程序在执行时,包括方法实施例的步骤之一或其组合。Those of ordinary skill in the art can understand that all or part of the steps carried by the methods of the above embodiments can be completed by instructing related hardware through a program, and the program can be stored in a computer-readable storage medium. During execution, one or a combination of the steps of the method embodiments is included.
尽管上面已经示出和描述了本申请的实施例,可以理解的是,上述实施例是示例性的,不能理解为对本申请的限制,本领域的普通技术人员在本申请的范围内可以对上述实施例进行变化、修改、替换和变型。Although the embodiments of the present application have been shown and described above, it can be understood that the above embodiments are exemplary and should not be construed as limitations on the present application, and those skilled in the art can make the above-mentioned The embodiments are subject to changes, modifications, substitutions and variations.
Claims (10)
Translated fromChinesePriority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202310259730.2ACN116305273A (en) | 2023-03-13 | 2023-03-13 | Verifiable joint keyword efficient search method, device, client and server |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202310259730.2ACN116305273A (en) | 2023-03-13 | 2023-03-13 | Verifiable joint keyword efficient search method, device, client and server |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| CN116305273Atrue CN116305273A (en) | 2023-06-23 |
Family
ID=86782989
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN202310259730.2APendingCN116305273A (en) | 2023-03-13 | 2023-03-13 | Verifiable joint keyword efficient search method, device, client and server |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN116305273A (en) |
Cited By (3)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN118673518A (en)* | 2024-06-19 | 2024-09-20 | 南京邮电大学 | Static connection keyword ciphertext retrieval method and system based on exclusive or filter and OXT protocol |
| CN118820322A (en)* | 2024-06-25 | 2024-10-22 | 南京邮电大学 | A connection keyword search method and system based on distributed key-value storage |
| CN119203220A (en)* | 2024-09-05 | 2024-12-27 | 中国传媒大学 | An oblivious dynamically searchable encryption method |
- 2023
- 2023-03-13CNCN202310259730.2Apatent/CN116305273A/enactivePending
Cited By (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN118673518A (en)* | 2024-06-19 | 2024-09-20 | 南京邮电大学 | Static connection keyword ciphertext retrieval method and system based on exclusive or filter and OXT protocol |
| CN118673518B (en)* | 2024-06-19 | 2025-01-10 | 南京邮电大学 | Static connection keyword ciphertext retrieval method and system based on exclusive or filter and OXT protocol |
| CN118820322A (en)* | 2024-06-25 | 2024-10-22 | 南京邮电大学 | A connection keyword search method and system based on distributed key-value storage |
| CN119203220A (en)* | 2024-09-05 | 2024-12-27 | 中国传媒大学 | An oblivious dynamically searchable encryption method |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| Ge et al. | Towards achieving keyword search over dynamic encrypted cloud data with symmetric-key based verification | |
| Zhang et al. | GEM^ 2-tree: A gas-efficient structure for authenticated range queries in blockchain | |
| Meng et al. | Grecs: Graph encryption for approximate shortest distance queries | |
| KR102805317B1 (en) | Script based blockchain interaction | |
| Chen et al. | BPVSE: Publicly verifiable searchable encryption for cloud-assisted electronic health records | |
| Basin et al. | Automated symbolic proofs of observational equivalence | |
| Chase et al. | Substring-searchable symmetric encryption | |
| Ge et al. | Enabling efficient verifiable fuzzy keyword search over encrypted data in cloud computing | |
| Boldyreva et al. | Efficient fuzzy search on encrypted data | |
| CN116305273A (en) | Verifiable joint keyword efficient search method, device, client and server | |
| Li et al. | A searchable symmetric encryption scheme using blockchain | |
| CN114048448A (en) | Blockchain-based dynamic searchable encryption method and device | |
| CN110110163A (en) | Safe substring search is with filtering enciphered data | |
| Li et al. | Integrity-verifiable conjunctive keyword searchable encryption in cloud storage | |
| Papamanthou et al. | Time and space efficient algorithms for two-party authenticated data structures | |
| Shi et al. | ESVSSE: Enabling efficient, secure, verifiable searchable symmetric encryption | |
| Miao et al. | VKSE-MO: Verifiable keyword search over encrypted data in multi-owner settings | |
| Li et al. | Towards efficient verifiable boolean search over encrypted cloud data | |
| CN111587452A (en) | Registration device, retrieval operation device, data management device, registration program, retrieval operation program and data management program | |
| Chen et al. | Verifiable dynamic ranked search with forward privacy over encrypted cloud data | |
| Ge et al. | Toward verifiable phrase search over encrypted cloud-based IoT data | |
| Kundu et al. | How to authenticate graphs without leaking | |
| Zhu et al. | A Verifiable and Efficient Symmetric Searchable Encryption Scheme for Dynamic Dataset With Forward and Backward Privacy | |
| Tamassia et al. | Certification and Authentication of Data Structures. | |
| Tang et al. | Reputation audit in multi-cloud storage through integrity verification and data dynamics |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination |