CN116132103A - A network security situation monitoring method, device, electronic equipment and storage medium - Google Patents
A network security situation monitoring method, device, electronic equipment and storage mediumDownload PDFInfo
- Publication number
- CN116132103A CN116132103ACN202211555223.5ACN202211555223ACN116132103ACN 116132103 ACN116132103 ACN 116132103ACN 202211555223 ACN202211555223 ACN 202211555223ACN 116132103 ACN116132103 ACN 116132103A
- Authority
- CN
- China
- Prior art keywords
- network
- network element
- abnormal
- situation
- abnormality detection
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Pending
Links
Images
Classifications
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/14—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic
- H04L63/1408—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic by monitoring network traffic
- H04L63/1425—Traffic logging, e.g. anomaly detection
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06N—COMPUTING ARRANGEMENTS BASED ON SPECIFIC COMPUTATIONAL MODELS
- G06N3/00—Computing arrangements based on biological models
- G06N3/02—Neural networks
- G06N3/04—Architecture, e.g. interconnection topology
- G06N3/049—Temporal neural networks, e.g. delay elements, oscillating neurons or pulsed inputs
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/14—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic
- H04L63/1408—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic by monitoring network traffic
- H04L63/1416—Event detection, e.g. attack signature detection
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/14—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic
- H04L63/1433—Vulnerability analysis
Landscapes
- Engineering & Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- Computing Systems (AREA)
- General Engineering & Computer Science (AREA)
- Computer Hardware Design (AREA)
- Computer Networks & Wireless Communication (AREA)
- Signal Processing (AREA)
- Physics & Mathematics (AREA)
- Theoretical Computer Science (AREA)
- Artificial Intelligence (AREA)
- General Health & Medical Sciences (AREA)
- Biomedical Technology (AREA)
- Biophysics (AREA)
- Computational Linguistics (AREA)
- Data Mining & Analysis (AREA)
- Evolutionary Computation (AREA)
- Life Sciences & Earth Sciences (AREA)
- Molecular Biology (AREA)
- General Physics & Mathematics (AREA)
- Mathematical Physics (AREA)
- Software Systems (AREA)
- Health & Medical Sciences (AREA)
- Data Exchanges In Wide-Area Networks (AREA)
Abstract
Description
Translated fromChinese技术领域technical field
本发明涉及智能运维技术领域,特别是涉及一种网络安全态势监测方法、一种网络安全态势监测装置、一种电子设备和一种存储介质。The invention relates to the technical field of intelligent operation and maintenance, in particular to a network security situation monitoring method, a network security situation monitoring device, an electronic device and a storage medium.
背景技术Background technique
网络安全事件预测主要是指对网络系统中发现的重大安全事件运用科学的理论、方法和已有的经验去判断和预测其发展趋势和危害情况,是网络安全态势感知的重要阶段,也是网络安全态势感知的主要目标为进行网络安全事件预测,需要分析潜在的和可能的攻击路径,基于对我方网络和系统的漏洞情况对攻击路径进行预测,对新攻击模式进行持续学习,以及揭示并通晓攻击者所进行的混淆和欺骗行为。Network security incident prediction mainly refers to the use of scientific theories, methods and existing experience to judge and predict the development trend and hazard situation of major security incidents found in the network system. The main goal of situational awareness is to predict network security incidents. It is necessary to analyze potential and possible attack paths, predict attack paths based on the vulnerabilities of our network and systems, continue to learn new attack patterns, and reveal and be familiar with them. Obfuscation and deception by attackers.
智能运维的必要条件是建设好数据能力,即以数据中台、大数据平台、数据湖等形式存在的数据底座,提供数据采集、数据存储、数据治理、数据服务4项核心能力。在实施智能运维之前,必须对数据底座传输过来的数据进行预处理、将其适配于各类机器学习模型的训练中。The necessary condition for intelligent operation and maintenance is to build a good data capability, that is, a data base that exists in the form of a data center, a big data platform, and a data lake, and provides four core capabilities of data collection, data storage, data governance, and data services. Before implementing intelligent operation and maintenance, the data transmitted from the data base must be preprocessed and adapted to the training of various machine learning models.
在智能运维领域中的数据,多以结构化和半结构化数据为主,在特定场景中也会渉及一些图片、语音、视频等非结构化数据。由于在进行人工智能分析前,基本都需要输入结构化数据,因此需要对半结构化和非结构化数据进行结构化转换,对结构化数据也要进行一定的规范化处理。The data in the field of intelligent operation and maintenance is mostly structured and semi-structured data, and some unstructured data such as pictures, voice, and video will also be involved in specific scenarios. Since structured data is basically required to be input before artificial intelligence analysis, semi-structured and unstructured data need to be structured, and structured data must also be standardized.
传统的网络安全数据质量评估停留在数据质量完整性、有效性、及时性等指标的评价上,缺乏数据关联性。可见性能数据与源数据关联后的数据缺于管理运维,且传统的运维分析过程多用SQL(Structured Query Language,结构化查询语言)查询,效率低,无法及发现数据缺失。Traditional network security data quality assessment stays on the evaluation of data quality integrity, validity, timeliness and other indicators, lacking data relevance. It can be seen that the data associated with the performance data and the source data is lacking in management operation and maintenance, and the traditional operation and maintenance analysis process mostly uses SQL (Structured Query Language, Structured Query Language) query, which is inefficient and unable to find missing data in a timely manner.
发明内容Contents of the invention
鉴于上述问题,提出了本发明实施例以便提供一种克服上述问题或者至少部分地解决上述问题的一种网络安全态势监测方法、一种网络安全态势监测装置、一种电子设备和一种存储介质。In view of the above problems, embodiments of the present invention are proposed to provide a network security situation monitoring method, a network security situation monitoring device, an electronic device, and a storage medium that overcome the above problems or at least partially solve the above problems .
在本发明的第一个方面,本发明实施例公开了一种网络安全态势监测方法,应用于智能运维终端,所述智能运维终端运行有变分自编码器VAE网络和长短期记忆LSTM循环网络,所述方法包括:In the first aspect of the present invention, the embodiment of the present invention discloses a network security situation monitoring method, which is applied to an intelligent operation and maintenance terminal, and the intelligent operation and maintenance terminal runs a variational autoencoder VAE network and a long short-term memory LSTM A recurrent network, the method comprising:
在网络运行期间,获取网元异常检测数据;Obtain network element abnormality detection data during network operation;
依据所述网元异常检测数据确定目标异常网元;determining a target abnormal network element according to the network element abnormality detection data;
采用所述VAE网络和所述LSTM循环网络对所述网元异常检测数据进行分析,确定异常共性特征数据集合;Analyzing the network element abnormality detection data by using the VAE network and the LSTM loop network to determine the abnormal common feature data set;
依据所述目标异常网元和所述异常共性特征数据集合确定网络态势参数;determining network situation parameters according to the target abnormal network element and the abnormal common feature data set;
依据所述网络态势参数确定网络安全态势。The network security situation is determined according to the network situation parameters.
可选地,所述智能运维终端存储有全量网元标识,所述网元异常检测数据包括异常网元标识;所述依据所述网元异常检测数据确定目标异常网元的步骤包括:Optionally, the intelligent operation and maintenance terminal stores a full amount of network element identifiers, and the network element abnormality detection data includes abnormal network element identifiers; the step of determining the target abnormal network element according to the network element abnormality detection data includes:
对比所述异常网元标识与所述全量网元标识;comparing the abnormal network element identifier with the full network element identifier;
当所述全量网元标识包含所述异常网元标识时,确定所述异常网元标识对应的网元为目标异常网元。When the full number of network element identifiers includes the abnormal network element identifier, determine that the network element corresponding to the abnormal network element identifier is the target abnormal network element.
可选地,所述采用所述VAE网络和所述LSTM循环网络对所述网元异常检测数据进行分析,确定异常共性特征数据集合的步骤包括:Optionally, the step of using the VAE network and the LSTM loop network to analyze the network element abnormality detection data, and determining the abnormal common feature data set includes:
采用所述VAE网络对所述网元异常检测数据进行分析,确定第一异常特征数据;Using the VAE network to analyze the network element abnormality detection data, and determine the first abnormal characteristic data;
采用所述LSTM循环网络对所述网元异常检测数据进行分析,确定第二异常特征数据;Analyzing the network element abnormality detection data by using the LSTM loop network to determine second abnormality characteristic data;
确定所述第一异常特征数据和所述第二异常特征数据的交集,并将所述交集确定为所述异常共性特征数据集合。An intersection of the first abnormal feature data and the second abnormal feature data is determined, and the intersection is determined as the abnormal common feature data set.
可选地,所述异常共性特征数据集合包括:漏洞类型、攻击风险等级和任务量;所述依据所述目标异常网元和所述异常共性特征数据集合确定网络态势参数的步骤包括:Optionally, the abnormal common feature data set includes: vulnerability type, attack risk level, and task volume; the step of determining network situation parameters according to the target abnormal network element and the abnormal common feature data set includes:
确定所述目标异常网元对应的网元类型;determining a network element type corresponding to the target abnormal network element;
按照预设漏洞评分规则,确定所述漏洞类型对应的第一危险评分;According to preset vulnerability scoring rules, determine the first risk score corresponding to the vulnerability type;
按照预设攻击风险评分规则,确定所述攻击风险等级对应的第二危险评分;determining a second risk score corresponding to the attack risk level according to preset attack risk scoring rules;
结合所述第一危险评分、所述第二危险评分和所述任务量,得到网络安全总指数;Combining the first risk score, the second risk score and the task load to obtain a total network security index;
结合所述网络安全总指数和所述网元类型,确定网络态势参数。Combining the overall network security index and the network element type, a network situation parameter is determined.
可选地,所述第一危险评分对应有第一权重值,所述第二危险评分对应有第二权重值,所述任务量对应有第三权重值;所述结合所述第一危险评分、所述第二危险评分和所述任务量,得到网络安全总指数的步骤包括:Optionally, the first risk score corresponds to a first weight value, the second risk score corresponds to a second weight value, and the task amount corresponds to a third weight value; the combination of the first risk score , the second risk score and the task load, the steps of obtaining the total network security index include:
计算所述第一危险评分与所述第一权重值的第一乘积值;calculating a first product value of the first risk score and the first weight value;
计算所述第二危险评分与所述第二权重值的第二乘积值;calculating a second product value of the second risk score and the second weight value;
计算所述任务量与所述第三权重值的第三乘积值;calculating a third product value of the task amount and the third weight value;
确定所述第一乘积值、所述第二乘积值和所述第三乘积值的和值为网络安全总指数。It is determined that the sum of the first product value, the second product value and the third product value is a total network security index.
可选地,所述依据所述网络态势参数确定网络安全态势的步骤包括:Optionally, the step of determining the network security situation according to the network situation parameters includes:
当所述网元类型为预设目标网元类型,或所述网络安全总指数低于预设安全阈值时,确定所述网络安全态势处于待修复状态;When the network element type is a preset target network element type, or the total network security index is lower than a preset security threshold, determine that the network security situation is in a state to be repaired;
当所述网元类型不为所述预设目标网元类型,且所述网络安全总指数不低于预设安全阈值时,确定所述网络安全态势处于健康状态。When the network element type is not the preset target network element type and the total network security index is not lower than a preset security threshold, it is determined that the network security situation is in a healthy state.
可选地,所述智能运维终端设置有修复数据库,所述方法该包括:Optionally, the intelligent operation and maintenance terminal is provided with a repair database, and the method includes:
当所述网络安全态势处于所述待修复状态时,调用所述数据库;calling the database when the network security situation is in the state to be repaired;
从所述数据库中获取修复指令,并将所述修复指令发送至所述目标异常网元,所述目标异常网元用于运行所述修复指令进行修复。Obtain a repair instruction from the database, and send the repair instruction to the target abnormal network element, and the target abnormal network element is used to run the repair instruction to perform repair.
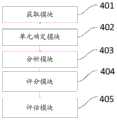
在本发明的第二个方面,本发明实施例公开了一种网络安全态势监测装置,应用于智能运维终端,所述智能运维终端运行有变分自编码器VAE网络和长短期记忆LSTM循环网络,所述装置包括:In the second aspect of the present invention, the embodiment of the present invention discloses a network security situation monitoring device, which is applied to an intelligent operation and maintenance terminal, and the intelligent operation and maintenance terminal runs a variational autoencoder VAE network and a long short-term memory LSTM A loop network, said means comprising:
获取模块,用于在网络运行期间,获取网元异常检测数据;An acquisition module, configured to acquire network element abnormality detection data during network operation;
单元确定模块,用于依据所述网元异常检测数据确定目标异常网元;A unit determination module, configured to determine a target abnormal network element according to the network element abnormality detection data;
分析模块,用于采用所述VAE网络和所述LSTM循环网络对所述网元异常检测数据进行分析,确定异常共性特征数据集合;An analysis module, configured to use the VAE network and the LSTM loop network to analyze the network element anomaly detection data, and determine an abnormal common feature data set;
评分模块,用于依据所述目标异常网元和所述异常共性特征数据集合确定网络态势参数;A scoring module, configured to determine network situation parameters according to the target abnormal network element and the abnormal common feature data set;
评估模块,用于依据所述网络态势参数确定网络安全态势。An assessment module, configured to determine the network security situation according to the network situation parameters.
在本发明的第三个方面,本发明实施例公开了一种电子设备,包括处理器、存储器及存储在所述存储器上并能够在所述处理器上运行的计算机程序,所述计算机程序被所述处理器执行时实现如上所述的网络安全态势监测方法的步骤。In the third aspect of the present invention, the embodiment of the present invention discloses an electronic device, including a processor, a memory, and a computer program stored on the memory and capable of running on the processor. The computer program is controlled by The processor implements the steps of the above-mentioned network security situation monitoring method when executed.
在本发明的第四个方面,本发明实施例公开了一种计算机可读存储介质,所述计算机可读存储介质上存储计算机程序,所述计算机程序被处理器执行时实现如上所述的网络安全态势监测方法的步骤。In the fourth aspect of the present invention, the embodiment of the present invention discloses a computer-readable storage medium, on which a computer program is stored, and when the computer program is executed by a processor, the above-mentioned network Steps of a security posture monitoring method.
本发明实施例包括以下优点:Embodiments of the present invention include the following advantages:
本发明实施例通过在网络运行期间,获取网元异常检测数据;依据所述网元异常检测数据确定目标异常网元;采用所述VAE网络和所述LSTM循环网络对所述网元异常检测数据进行分析,确定异常共性特征数据集合;依据所述目标异常网元和所述异常共性特征数据集合确定网络态势参数;依据所述网络态势参数确定网络安全态势。通过VAE网络和LSTM循环网络确定异常共性特征数据集合,及时发现网络安全态势的缺失,减少网络安全态势的监测盲点;通过目标异常网元和所常共性特征数据集合确定网络态势参数,可以直接确定网络安全态势提升监测网络安全态势的效率。In the embodiment of the present invention, network element abnormality detection data is obtained during network operation; target abnormal network elements are determined according to the network element abnormality detection data; the network element abnormality detection data is detected by using the VAE network and the LSTM loop network Performing analysis to determine an abnormal common characteristic data set; determining network situation parameters according to the target abnormal network element and the abnormal common characteristic data set; determining network security situation according to the network situation parameters. Through VAE network and LSTM cycle network to determine the abnormal common feature data set, timely discover the lack of network security situation, reduce the monitoring blind spots of network security situation; determine the network situation parameters through the target abnormal network element and the normal common feature data set, which can be directly determined Network security situation improves the efficiency of monitoring network security situation.
附图说明Description of drawings
图1是本发明的一种网络安全态势监测方法实施例的步骤流程图;Fig. 1 is a flow chart of the steps of an embodiment of a network security situation monitoring method of the present invention;
图2是本发明的另一种网络安全态势监测方法实施例的步骤流程图;Fig. 2 is a flow chart of steps of another embodiment of a network security situation monitoring method of the present invention;
图3是本发明的一种网络安全态势监测方法示例的执行示意图;Fig. 3 is a schematic diagram of execution of a network security situation monitoring method example of the present invention;
图4是本发明的一种网络安全态势监测装置实施例的结构框图。Fig. 4 is a structural block diagram of an embodiment of a network security situation monitoring device of the present invention.
具体实施方式Detailed ways
为使本发明的上述目的、特征和优点能够更加明显易懂,下面结合附图和具体实施方式对本发明作进一步详细的说明。In order to make the above objects, features and advantages of the present invention more comprehensible, the present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
参照图1,示出了本发明的一种网络安全态势监测方法实施例的步骤流程图,所述网络安全态势监测方法应用于智能运维终端,所述智能运维终端运行有变分自编码器VAE网络和长短期记忆LSTM循环网络。Referring to FIG. 1 , it shows a flow chart of the steps of an embodiment of a network security situation monitoring method of the present invention, the network security situation monitoring method is applied to an intelligent operation and maintenance terminal, and the intelligent operation and maintenance terminal runs a variational self-encoding VAE network and long short-term memory LSTM recurrent network.
智能运维终端即采用AIOps(自动化运维)技术进行运维管理的终端。该终端可以是电子设备,与可以是终端服务器。Intelligent operation and maintenance terminals are terminals that adopt AIOps (automated operation and maintenance) technology for operation and maintenance management. The terminal may be an electronic device, and may be a terminal server.
在该智能运维终端上运行有变分自编码器VAE网络和长短期记忆LSTM循环网络。VAE(Variational Auto-incoder E,变分自编码器)网络是一种将神经网络和统计分布结合的、用于无监督学习的生成神经网络。VAE网络由变分网络和生成网络组成。变分网络通过各种自定义结构的网络层来达到从样本数据中学习后,以分布Q(z|x)以模拟隐变量z的分布P(z)的目的,其中P(z)服从N(0,1)分布。用两个独立的网络层分别生成log(var(z))和mean(z)来表示Q(z|x)。生成网络则通过从隐变量Q(z|x)中进行采样重新得到后,利用网络层从隐变量中解码出P(x|z)。最后得到的P(x|z)是VAE通过编码和解码网络结构重组得到的重构输出。在此所使用的VAE网络结构,由于输入的正常网元数据很少出现大幅度变动,局部变动通常较小,所以选用激活函数来学习隐变量的log标准差:log(var(z)),同时加上一个随机数来防止神经元输出无限接近于0的数值时所导致的梯度消失。VAE网络采用特殊的ELBO(函数名)损失函数进行梯度下降优化。ELBO训练损失函数具体公式如下:There are variational autoencoder VAE network and long short-term memory LSTM cyclic network running on the intelligent operation and maintenance terminal. VAE (Variational Auto-incoder E, Variational Auto-encoder) network is a generative neural network for unsupervised learning that combines neural networks and statistical distributions. The VAE network consists of a variational network and a generative network. The variational network achieves the purpose of simulating the distribution P(z) of the latent variable z with the distribution Q(z|x) after learning from the sample data through various self-defined network layers, where P(z) obeys N (0,1) distribution. Q(z|x) is represented by two independent network layers generating log(var(z)) and mean(z) respectively. The generation network is re-obtained by sampling from the hidden variable Q(z|x), and then uses the network layer to decode P(x|z) from the hidden variable. The final P(x|z) is the reconstructed output of VAE obtained by reorganizing the encoding and decoding network structure. The VAE network structure used here, because the input normal network element data rarely changes greatly, and the local changes are usually small, so the activation function is selected to learn the log standard deviation of the hidden variable: log(var(z)), At the same time, a random number is added to prevent the gradient from disappearing when the neuron outputs a value infinitely close to 0. The VAE network uses a special ELBO (function name) loss function for gradient descent optimization. The specific formula of ELBO training loss function is as follows:
P(x|z)Lul=KL(p(z)||N(0,1))P(x|z)Lul =KL(p(z)||N(0,1))
L=re+ulL =re +ul
其中,交叉熵L反映生成网络的拟合效果,KL散度L反映变分网络合的程度。Among them, the cross entropy L reflects the fitting effect of the generated network, and the KL divergence L reflects the degree of variational network fit.
LSTM(Long short-term memory,长短期记忆)循环网络是一种特殊的RNN(Recurrent Neural Network,循环神经网络),适合序列数据中间较长期的历史信息。使用LSTM循环网络相于VAE网络,参数量更小,可以进一步压缩数据处理量;通过输入门,控制信息进入神经元中,遗忘门(Frt)决定处理信息是否保留,而输出门决定信息的输出程度。LSTM (Long short-term memory, long short-term memory) cyclic network is a special RNN (Recurrent Neural Network, cyclic neural network), which is suitable for long-term historical information in the middle of sequence data. Compared with the VAE network, the LSTM cyclic network has smaller parameters and can further compress the amount of data processing; through the input gate, the control information enters the neuron, the forget gate (Frt) determines whether the processed information is retained, and the output gate determines the output of the information degree.
所述网络安全态势监测方法具体可以包括如下步骤:The network security situation monitoring method may specifically include the following steps:
步骤101,在网络运行期间,获取网元异常检测数据;
在网络运行期间,网元(设备)会产生大量的运行日志,运行日志会记载有各网元自身的异常数据,即异常检测数据。During network operation, network elements (equipment) will generate a large number of operation logs, and the operation logs will record abnormal data of each network element itself, that is, abnormality detection data.
可以从存储运行日志的存储地址中,获取网元异常检测数据。The network element abnormality detection data can be obtained from the storage address where the operation log is stored.
步骤102,依据所述网元异常检测数据确定目标异常网元;
依据网元异常检测数据,从与智能运维终端连接的全部的网元中确定出至少一个目标异常网元,对目标异常网元进行进一步地分析其风险。According to the network element abnormality detection data, at least one target abnormal network element is determined from all the network elements connected to the intelligent operation and maintenance terminal, and the risk of the target abnormal network element is further analyzed.
步骤103,采用所述VAE网络和所述LSTM循环网络对所述网元异常检测数据进行分析,确定异常共性特征数据集合;
可以采用VAE网络和LSTM循环网络分别对网元异常检测数据进行分析,通过VAE网络和LSTM循环网络确定出不同目标异常网元之间存在共性异常,确定出异常共性特征数据集合。以此及时发现网络安全态势的缺失,减少网络安全态势的监测盲点The VAE network and LSTM cyclic network can be used to analyze the network element anomaly detection data respectively. Through the VAE network and LSTM cyclic network, it can be determined that there are common anomalies among different target abnormal network elements, and the abnormal common feature data set can be determined. In this way, the lack of network security situation can be discovered in time, and the blind spots of network security situation monitoring can be reduced.
步骤104,依据所述目标异常网元和所述异常共性特征数据集合确定网络态势参数;
在得到异常共性特征数据集合后,可以将异常共性特征数据集合与目标异常网元进行关联,共同确定反映当前网络态势的网络态势参数。可以直接确定网络安全态势,提升监测网络安全态势的效率。After obtaining the abnormal common feature data set, the abnormal common feature data set can be associated with the target abnormal network element to jointly determine the network situation parameters reflecting the current network situation. It can directly determine the network security situation and improve the efficiency of monitoring the network security situation.
步骤105,依据所述网络态势参数确定网络安全态势。
在本发明实施例中,依据网络态势参数的数值确定网络安全态势是否处于安全状态,In the embodiment of the present invention, it is determined whether the network security situation is in a safe state according to the value of the network situation parameter,
本发明实施例通过在网络运行期间,获取网元异常检测数据;依据所述网元异常检测数据确定目标异常网元;采用所述VAE网络和所述LSTM循环网络对所述网元异常检测数据进行分析,确定异常共性特征数据集合;依据所述目标异常网元和所述异常共性特征数据集合确定网络态势参数;依据所述网络态势参数确定网络安全态势。通过VAE网络和LSTM循环网络确定异常共性特征数据集合,及时发现网络安全态势的缺失,减少网络安全态势的监测盲点;通过目标异常网元和所常共性特征数据集合确定网络态势参数,可以直接确定网络安全态势,提升监测网络安全态势的效率。In the embodiment of the present invention, network element abnormality detection data is obtained during network operation; target abnormal network elements are determined according to the network element abnormality detection data; the network element abnormality detection data is detected by using the VAE network and the LSTM loop network Performing analysis to determine an abnormal common characteristic data set; determining network situation parameters according to the target abnormal network element and the abnormal common characteristic data set; determining network security situation according to the network situation parameters. Through VAE network and LSTM cycle network to determine the abnormal common feature data set, timely discover the lack of network security situation, reduce the monitoring blind spots of network security situation; determine the network situation parameters through the target abnormal network element and the normal common feature data set, which can be directly determined Network security situation, improve the efficiency of monitoring network security situation.
参照图2,示出了本发明的另一种网络安全态势监测方法实施例的步骤流程图,所述网络安全态势监测方法应用于智能运维终端,所述智能运维终端设置有修复数据库。其中,所述智能运维终端运行有变分自编码器VAE网络和长短期记忆LSTM循环网络。对于VAE网络和LSTM循环网络可以参照上述实施例,在本发明实施例不在赘述。对于修复数据库,内置有针对网络进行修复的指令集和数据。该修复数据库可以定时更新,以使修复数据库可以满足使用要求。Referring to FIG. 2 , it shows a flow chart of steps of another embodiment of a network security situation monitoring method of the present invention. The network security situation monitoring method is applied to an intelligent operation and maintenance terminal, and the intelligent operation and maintenance terminal is provided with a repair database. Wherein, the intelligent operation and maintenance terminal runs a variational autoencoder VAE network and a long short-term memory LSTM cycle network. For the VAE network and the LSTM cycle network, reference may be made to the foregoing embodiments, and details are not repeated in the embodiments of the present invention. For the repair database, there are built-in instruction sets and data for repairing the network. The repair database can be regularly updated so that the repair database can meet the use requirements.
所述网络安全态势监测方法具体可以包括如下步骤:The network security situation monitoring method may specifically include the following steps:
步骤201,在网络运行期间,获取网元异常检测数据;
在网络运行期间,可以从各个网元存储运行日志的存储地址中,该网元的运行期间的异常数据,从而获取到全部网元的网元异常检测数据。During the operation of the network, the abnormal data during the operation of the network element can be obtained from the storage address of the operation log of each network element, so as to obtain the network element abnormality detection data of all network elements.
步骤202,依据所述网元异常检测数据确定目标异常网元;
依据获取到的网元异常检测数据,确定出发生异常的网元,即目标异常网元。According to the obtained network element abnormality detection data, the abnormal network element is determined, that is, the target abnormal network element.
在本发明的一可选实施例中,所述智能运维终端存储有全量网元标识,所述网元异常检测数据包括异常网元标识;所述依据所述网元异常检测数据确定目标异常网元的步骤具体可以包括如下子步骤:In an optional embodiment of the present invention, the intelligent operation and maintenance terminal stores a full amount of network element identifiers, and the network element abnormality detection data includes abnormal network element identifiers; the determination of target abnormality according to the network element abnormality detection data The steps of the network element may specifically include the following sub-steps:
子步骤S2021,对比所述异常网元标识与所述全量网元标识;Sub-step S2021, comparing the abnormal network element identification with the full network element identification;
在实际应用中,智能运维终端存储有与其连接的全部网元对应的全量网元标识,而网元异常检测数据中包括有在运行期间存在异常现象的网元对应的异常网元标识。In practical applications, the intelligent operation and maintenance terminal stores the full number of network element identifications corresponding to all network elements connected to it, and the network element abnormality detection data includes abnormal network element identifications corresponding to network elements with abnormal phenomena during operation.
为此,可以将异常网元标识与全量网元标识中的每一个网元标识进行对比,当异常网元标识与全量网元标识中的其中一个网元标识相同,即可确定全量网元标识包含异常网元标识。当异常网元标识与全量网元标识中的网元标识都不相同,即可确定全量网元标识不包含异常网元标识。To this end, the abnormal NE ID can be compared with each NE ID in the full NE ID. When the abnormal NE ID is the same as one of the full NE IDs, the full NE ID can be determined. Contains the abnormal NE ID. When the abnormal network element identifier is different from the network element identifier in the full network element identifier, it can be determined that the full network element identifier does not include the abnormal network element identifier.
子步骤S2022,当所述全量网元标识包含所述异常网元标识时,确定所述异常网元标识对应的网元为目标异常网元。Sub-step S2022, when the full number of network element identifiers includes the abnormal network element identifier, determine that the network element corresponding to the abnormal network element identifier is the target abnormal network element.
当全量网元标识包含异常网元异常网元标识时,即该异常网元标识对应的网元为智能运维终端连接的网元之一,后续该网元的风险会影响网络安全态势;确定该异常网元标识对应的网元为目标异常网元。When the full amount of network element identification includes the abnormal network element identification, that is, the network element corresponding to the abnormal network element identification is one of the network elements connected to the intelligent operation and maintenance terminal, and the subsequent risk of the network element will affect the network security situation; determine The network element corresponding to the abnormal network element identifier is the target abnormal network element.
步骤203,采用所述VAE网络和所述LSTM循环网络对所述网元异常检测数据进行分析,确定异常共性特征数据集合;
采用VAE网络和LSTM循环网络中的一个为分析网络,另一个为对照网络,通过特征筛选排除噪声特征的干扰,对网元异常检测数据进行分析,找出的异常值,进一步提高检测性能,找出一些潜在的、未被专家规则、发现的异常网元的异常值,将VAE网络和LSTM循环网络得到的异常值汇集得到异常共性特征数据集合。其中,对于分析网络和对照网络的具体网络类型并不限定,即可以是对照网络为VAE网络、分析网络为LSTM循环网络;也可以是对照网络为LSTM循环网络、分析网络为VAE网络。One of the VAE network and the LSTM cyclic network is used as the analysis network, and the other is the control network. The interference of noise features is eliminated through feature screening, and the abnormal detection data of network elements is analyzed to find out the abnormal values, further improve the detection performance, and find The outliers of some potential abnormal network elements that have not been discovered by expert rules are collected, and the abnormal values obtained by the VAE network and the LSTM loop network are collected to obtain an abnormal common feature data set. Wherein, the specific network types of the analysis network and the comparison network are not limited, that is, the comparison network may be a VAE network, and the analysis network may be an LSTM cycle network; or the comparison network may be an LSTM cycle network, and the analysis network may be a VAE network.
在本发明的一可选实施例中,所述采用所述VAE网络和所述LSTM循环网络对所述网元异常检测数据进行分析,确定异常共性特征数据集合的步骤具体可以包括如下子步骤:In an optional embodiment of the present invention, the step of using the VAE network and the LSTM loop network to analyze the abnormality detection data of the network element, and determine the abnormal common feature data set may specifically include the following substeps:
子步骤S2031,采用所述VAE网络对所述网元异常检测数据进行分析,确定第一异常特征数据;Sub-step S2031, using the VAE network to analyze the network element abnormality detection data, and determine the first abnormal characteristic data;
在本发明实施例中,可以采用VAE网络对网元异常检测数据进行分析,通过VAE网络将异常检测数据中具有共性特征的异常进行分析,确定出网元的第一异常特征数据。即第一异常特征数据为通过VAE网络对网元异常检测数据进行分析得到的异常特征数据。In the embodiment of the present invention, the VAE network can be used to analyze the abnormality detection data of the network element, and the abnormality with common characteristics in the abnormality detection data can be analyzed through the VAE network to determine the first abnormality characteristic data of the network element. That is, the first abnormal feature data is abnormal feature data obtained by analyzing the network element abnormality detection data through the VAE network.
子步骤S2032,采用所述LSTM循环网络对所述网元异常检测数据进行分析,确定第二异常特征数据;Sub-step S2032, using the LSTM loop network to analyze the abnormality detection data of the network element, and determine the second abnormality characteristic data;
在本发明实施例中,还可以采用LSTM循环网络对网元异常检测数据进行分析,通过LSTM循环网络将异常检测数据中具有共性特征的异常进行分析,确定出网元的第二异常特征数据。即第二异常特征数据为通过LSTM循环网络对网元异常检测数据进行分析得到的异常特征数据。In the embodiment of the present invention, the LSTM loop network can also be used to analyze the abnormality detection data of the network element, and the abnormality with common characteristics in the abnormality detection data can be analyzed through the LSTM loop network to determine the second abnormality characteristic data of the network element. That is, the second abnormal feature data is abnormal feature data obtained by analyzing the network element abnormal detection data through the LSTM loop network.
需要说明的是,子步骤S2031和子步骤S2031的执行顺序不限定,可以先执行子步骤S2031再执行子步骤S2032;也可以先执行子步骤S2032再执行子步骤S2031;还可以同时执行步骤S2031和子步骤S2031。It should be noted that the execution order of sub-step S2031 and sub-step S2031 is not limited, sub-step S2031 can be executed first and then sub-step S2032 can be executed; sub-step S2032 can also be executed first and then sub-step S2031 can be executed; step S2031 and sub-step can also be executed simultaneously S2031.
子步骤S2033,确定所述第一异常特征数据和所述第二异常特征数据的交集,并将所述交集确定为所述异常共性特征数据集合。Sub-step S2033, determining the intersection of the first abnormal characteristic data and the second abnormal characteristic data, and determining the intersection as the abnormal common characteristic data set.
在得到第一异常特征数据和第二异常特征数据后,可以确定第一异常特征数据和第二异常特征数据的交集,将第一异常特征数据和第二异常特征数据中共同确定得到的异常值进行筛选,将共同确定的异常值即该交集确定为异常共性特征数据集合。After obtaining the first abnormal characteristic data and the second abnormal characteristic data, the intersection of the first abnormal characteristic data and the second abnormal characteristic data can be determined, and the abnormal value obtained by jointly determining the first abnormal characteristic data and the second abnormal characteristic data Screening is carried out, and the commonly determined outliers, ie, the intersection, are determined as an abnormal common feature data set.
步骤204,依据所述目标异常网元和所述异常共性特征数据集合确定网络态势参数;
在本发明实施例中,依据目标异常网元的所处的位置和异常共性特征数据集合计算出危险指数,确定出网络态势参数。In the embodiment of the present invention, the danger index is calculated according to the location of the target abnormal network element and the abnormal common feature data set, and the network situation parameters are determined.
在本发明的一可选实施例中,所述异常共性特征数据集合包括:漏洞类型、攻击风险等级和任务量;所述依据所述目标异常网元和所述异常共性特征数据集合确定网络态势参数的步骤具体可以包括如下子步骤:In an optional embodiment of the present invention, the abnormal common feature data set includes: vulnerability type, attack risk level and task volume; the network situation is determined based on the target abnormal network element and the abnormal common feature data set The steps of parameters may specifically include the following sub-steps:
子步骤S2041,确定所述目标异常网元对应的网元类型;Sub-step S2041, determining the network element type corresponding to the target abnormal network element;
在本发明实施例中,异常共性特征数据集合中可以包括漏洞类型、攻击风险等级和任务量。其中,漏洞类型为影响网络完全的漏洞类型,攻击风险等级,即为该异常现象导致被攻击的风险情况,可以采用若干级别进行表征。任务量则是网元处理的任务数量。该任务量可以为日任务量、周任务量或其他时间周期下的任务量,本领域技术人员可以根据实际需求进行确定,本发明实施例对此不作限定。In the embodiment of the present invention, the abnormal common characteristic data set may include vulnerability type, attack risk level and task amount. Among them, the vulnerability type is the type of vulnerability that affects the integrity of the network, and the attack risk level is the risk of being attacked by the abnormal phenomenon, which can be represented by several levels. The task volume is the number of tasks processed by the network element. The task amount may be a daily task amount, a weekly task amount, or a task amount in other time periods, which can be determined by those skilled in the art according to actual needs, which is not limited in this embodiment of the present invention.
在确定网络态势参数时,首先确定该目标异常网元对应的网元类型,即确定目标异常网元在网络中的位置,当其位置越靠近末端,对网络安全态势的影响越小。When determining network situation parameters, first determine the network element type corresponding to the target abnormal network element, that is, determine the position of the target abnormal network element in the network. When its position is closer to the end, the impact on the network security situation is smaller.
子步骤S2042,按照预设漏洞评分规则,确定所述漏洞类型对应的第一危险评分;Sub-step S2042, according to the preset vulnerability scoring rules, determine the first risk score corresponding to the vulnerability type;
企业级网络中的漏洞评估是在没有攻击的情况下,网络自身的脆弱情况,包括网络自身能够承受多大的攻击、多少攻击以及攻击会给网络带来多大的危害和损失等要素。可以预先根据这些确定出预设漏洞评分规则。然后按照预设漏洞评分规则,对漏洞类型进行评分,确定每个漏洞类型对应的第一危险评分,即第一危险评分为针对漏洞类型进行评分后的评分值。Vulnerability assessment in an enterprise-level network refers to the vulnerability of the network itself in the absence of an attack, including how many attacks the network itself can withstand, how many attacks, and how much damage and loss the attack will bring to the network. Preset vulnerability scoring rules may be determined in advance based on these. Then, score the vulnerability types according to the preset vulnerability scoring rules, and determine the first risk score corresponding to each vulnerability type, that is, the first risk score is the score value after scoring the vulnerability types.
子步骤S2043,按照预设攻击风险评分规则,确定所述攻击风险等级对应的第二危险评分;Sub-step S2043, according to the preset attack risk scoring rules, determine the second risk score corresponding to the attack risk level;
在企业级网络中主要考虑网络攻击对网络的影响,网络攻击以网络告警的形式存在,并且是由多个安全设备采集的事件关联分析产生,对应诸多网络攻击的攻击风险评估要素的层次结构。可以针对网络攻击对网络因素的因素制定不同攻击风险等级对应的危险系数的预设攻击风险评分规则。按照预设攻击风险评分规则,去顶出该攻击风险等级对应的第二危险评分。即二危险评分为针对攻击风险等级进行评分后的评分值。In an enterprise-level network, the impact of network attacks on the network is mainly considered. Network attacks exist in the form of network alarms, and are generated by correlation analysis of events collected by multiple security devices, corresponding to the hierarchical structure of attack risk assessment elements of many network attacks. A preset attack risk scoring rule with risk coefficients corresponding to different attack risk levels can be formulated according to the factors of network attack on network factors. According to the preset attack risk scoring rules, the second risk score corresponding to the attack risk level is ejected. That is, the second risk score is a score value after scoring according to the attack risk level.
子步骤S2044,结合所述第一危险评分、所述第二危险评分和所述任务量,得到网络安全总指数;Sub-step S2044, combining the first risk score, the second risk score and the task amount to obtain a total network security index;
确定了网络安全态势中各部分的评分值以后,需要对各评估要素进行汇总确定网络安全总指数。After determining the scoring value of each part of the network security situation, it is necessary to summarize each assessment element to determine the total network security index.
在本发明的一可选实施例中,所述第一危险评分对应有第一权重值,所述第二危险评分对应有第二权重值,所述任务量对应有第三权重值;所述结合所述第一危险评分、所述第二危险评分和所述任务量,得到网络安全总指数的步骤具体可以包括如下子步骤:In an optional embodiment of the present invention, the first risk score corresponds to a first weight value, the second risk score corresponds to a second weight value, and the task amount corresponds to a third weight value; the Combining the first risk score, the second risk score and the task amount, the step of obtaining the overall network security index may specifically include the following sub-steps:
子步骤S20441,计算所述第一危险评分与所述第一权重值的第一乘积值;Sub-step S20441, calculating a first product value of the first risk score and the first weight value;
在实际应用中,确定了各个评估要素的评分以后,采用层次分析法确定各指标权重。由网络安全指标体系的构建过程可知,整个网络安全是各安全指标综合作用的结果,而且,各指标及子指标对系统安全影响的权重各不相同。为此,第一危险评分对应有第一权重值,第二危险评分对应有第二权重值,任务量对应有第三权重值;为不同的评估部分确定对应的权重值。In practical application, after determining the scores of each evaluation element, the weight of each index is determined by the AHP. It can be seen from the construction process of the network security index system that the entire network security is the result of the comprehensive effect of various security indicators, and the weight of each indicator and sub-indicator on the system security is different. Therefore, the first risk score corresponds to a first weight value, the second risk score corresponds to a second weight value, and the task volume corresponds to a third weight value; corresponding weight values are determined for different evaluation parts.
首先,计算第一危险评分与第一权重值的乘积值,确定该乘积值为第一乘积值。Firstly, the product value of the first risk score and the first weight value is calculated, and the product value is determined as the first product value.
子步骤S20442,计算所述第二危险评分与所述第二权重值的第二乘积值;Sub-step S20442, calculating a second product value of the second risk score and the second weight value;
计算第二危险评分与第二权重值的乘积值,确定该乘积值为第二乘积值。A product value of the second risk score and the second weight value is calculated, and the product value is determined as a second product value.
子步骤S20443,计算所述任务量与所述第三权重值的第三乘积值;Sub-step S20443, calculating a third product value of the task amount and the third weight value;
计算任务量与第三权重值的乘积值,并确定该乘积值为第三乘积值。其中,对于子步骤S20441至子步骤S20443的顺序不作限定。Calculate the product value of the task amount and the third weight value, and determine the product value as the third product value. Wherein, the order of the sub-steps S20441 to S20443 is not limited.
子步骤S20444,确定所述第一乘积值、所述第二乘积值和所述第三乘积值的和值为网络安全总指数。Sub-step S20444, determining that the sum of the first product value, the second product value and the third product value is a total network security index.
将第一乘积值、第二乘积值和第三乘积值相加,确定出第一乘积值、第二乘积值和第三乘积值的和值,并该和值确定为网络安全总指数。The first product value, the second product value and the third product value are added together to determine the sum of the first product value, the second product value and the third product value, and the sum value is determined as the overall network security index.
结合步骤S20441至子步骤S20444,可得如下公式:Combining step S20441 to sub-step S20444, the following formula can be obtained:
IC=F*F+Wv*V+WR*RIC=F *F+Wv *V+WR *R
其中,IC为网络安全总指数;Among them, IC is the total network security index;
IF为第一危险评分;IF is the first risk score;
IV为第二危险评分;IV is the second risk score;
IR为任务量;IR is the task volume;
WF为第一权重值;WF is the first weight value;
WV为第二权重值;WV is the second weight value;
WR为第三权重值。WR is the third weight value.
子步骤S2045,结合所述网络安全总指数和所述网元类型,确定网络态势参数。Sub-step S2045, combining the total network security index and the network element type to determine network situation parameters.
将网络安全总指数与目标异常网元的网元类型关联结合,确定网络态势参数。The overall network security index is associated with the network element type of the target abnormal network element to determine the network situation parameters.
步骤205,依据所述网络态势参数确定网络安全态势;
根据网络态势参数的大小确定网络安全态势,使得网络安全态势可以量化,直接确定网络安全态势的实际情况,提高对网络安全态势判断的效率。Determine the network security situation according to the size of the network situation parameters, so that the network security situation can be quantified, directly determine the actual situation of the network security situation, and improve the efficiency of judging the network security situation.
在本发明的一可选实施例中,所述依据所述网络态势参数确定网络安全态势的步骤具体可以包括如下子步骤:In an optional embodiment of the present invention, the step of determining the network security situation according to the network situation parameters may specifically include the following sub-steps:
子步骤S2051,当所述网元类型为预设目标网元类型,或所述网络安全总指数低于预设安全阈值时,确定所述网络安全态势处于待修复状态;Sub-step S2051, when the network element type is a preset target network element type, or the total network security index is lower than a preset safety threshold, determine that the network security situation is in a state to be repaired;
预设目标网元类型为网络中对网络安全影响较大的网元类型,预设目标网元类型的具体类型可以根据实际情况进行确定,本发明实施例不作限定。预设安全阈值则可以根据网络的安全程度确定,具体数值本发明实施例也不作限定。The preset target network element type is a network element type that has a greater impact on network security in the network, and the specific type of the preset target network element type can be determined according to actual conditions, and is not limited in this embodiment of the present invention. The preset security threshold can be determined according to the security level of the network, and the specific value is not limited in this embodiment of the present invention.
当目标异常网元对应的网元类型为预设目标网元类型,即目标异常网元处于重要位置,其异常会对网络存在较大的影响;或网络安全总指数低于预设安全阈值,网络的安全性较差,可以确定网络安全态势处于待修复状态,需要对目标异常网元进行修复,以提升网络安全性。When the network element type corresponding to the target abnormal network element is the preset target network element type, that is, the target abnormal network element is in an important position, and its abnormality will have a greater impact on the network; or the total network security index is lower than the preset security threshold, If the security of the network is poor, it can be determined that the network security situation is in a state to be repaired, and the target abnormal network element needs to be repaired to improve network security.
子步骤S2052,当所述网元类型不为所述预设目标网元类型,且所述网络安全总指数不低于预设安全阈值时,确定所述网络安全态势处于健康状态。Sub-step S2052, when the network element type is not the preset target network element type, and the total network security index is not lower than a preset security threshold, determine that the network security situation is in a healthy state.
当目标异常网元对应的网元类型不为预设目标网元类型,即目标异常网元对网络安全的影响较小;且网络安全总指数不低于预设安全阈值,网络的安全性良好,可以确定网络安全态势处于健康状态,继续监控网络完全的态势。When the network element type corresponding to the target abnormal network element is not the preset target network element type, that is, the impact of the target abnormal network element on network security is small; and the total network security index is not lower than the preset safety threshold, the network security is good , you can determine that the network security situation is in a healthy state, and continue to monitor the network's complete situation.
步骤206,当所述网络安全态势处于所述待修复状态时,调用所述数据库;
当网络安全态势处于待修复状态时,为了可以对网络中的目标异常网元进行修复,可调用数据库,利用数据库对其进行修复。When the network security situation is in the state to be repaired, in order to repair the target abnormal network element in the network, the database can be invoked, and the database can be used to repair it.
步骤207,从所述数据库中获取修复指令,并将所述修复指令发送至所述目标异常网元,所述目标异常网元用于运行所述修复指令进行修复。In
可以从数据库中的指令集中,获取修复指令,该修复指令携带有修复数据。并且将修复指令发送至目标异常网元,目标异常网元接收到修复指令后,运行该修复指令进行修复,以消除异常现象。The repair instruction can be obtained from the instruction set in the database, and the repair instruction carries repair data. And the repair instruction is sent to the target abnormal network element, and after receiving the repair instruction, the target abnormal network element executes the repair instruction to repair, so as to eliminate the abnormal phenomenon.
本发明实施例通过在网络运行期间,获取网元异常检测数据;依据所述网元异常检测数据确定目标异常网元;采用所述VAE网络和所述LSTM循环网络对所述网元异常检测数据进行分析,确定异常共性特征数据集合;依据所述目标异常网元和所述异常共性特征数据集合确定网络态势参数;依据所述网络态势参数确定网络安全态势;当所述网络安全态势处于所述待修复状态时,调用所述数据库;从所述数据库中获取修复指令,并将所述修复指令发送至所述目标异常网元,所述目标异常网元用于运行所述修复指令进行修复。通过VAE网络和LSTM循环网络确定异常共性特征数据集合,及时发现网络安全态势的缺失,减少网络安全态势的监测盲点;通过目标异常网元和所常共性特征数据集合确定网络态势参数,可以直接确定网络安全态势,提升监测网络安全态势的效率;并且在网络安全态势处于待修复状态时,对目标异常网元进行修复,提升网络安全性。In the embodiment of the present invention, network element abnormality detection data is obtained during network operation; target abnormal network elements are determined according to the network element abnormality detection data; the network element abnormality detection data is detected by using the VAE network and the LSTM loop network Perform analysis to determine the abnormal common feature data set; determine the network situation parameters according to the target abnormal network element and the abnormal common characteristic data set; determine the network security situation according to the network situation parameters; when the network security situation is in the When the state is to be repaired, the database is invoked; a repair instruction is obtained from the database, and the repair instruction is sent to the target abnormal network element, and the target abnormal network element is used to execute the repair instruction for repair. Through VAE network and LSTM cycle network to determine the abnormal common feature data set, timely discover the lack of network security situation, reduce the monitoring blind spots of network security situation; determine the network situation parameters through the target abnormal network element and the normal common feature data set, which can be directly determined The network security situation improves the efficiency of monitoring the network security situation; and when the network security situation is in a state to be repaired, the target abnormal network element is repaired to improve network security.
为了使本领域技术人员能够更好地理解本发明实施例,下面通过一个例子对本发明实施例加以说明:In order to enable those skilled in the art to better understand the embodiment of the present invention, the following uses an example to illustrate the embodiment of the present invention:
参照图3,示出了本发明的一种网络安全态势监测方法示例的示意图。Referring to FIG. 3 , it shows a schematic diagram of an example of a network security situation monitoring method of the present invention.
在网络运行期间,获取到网元异常检测数据;During the operation of the network, the network element abnormality detection data is obtained;
网元异常检测数据分别输入到VAE网络和LSTM循环网络;VAE网络和LSTM循环网络确定出异常共性特征数据集合;Network element anomaly detection data are input to VAE network and LSTM cyclic network respectively; VAE network and LSTM cyclic network determine abnormal common characteristic data set;
确定网元异常检测数据对应的目标异常网元;determining a target abnormal network element corresponding to the network element abnormality detection data;
将目标异常网元和异常共性特征数据集合确定网络态势参数,以对网络安全态势进行评估。The target abnormal network element and abnormal common feature data are collected to determine the network situation parameters to evaluate the network security situation.
需要说明的是,对于方法实施例,为了简单描述,故将其都表述为一系列的动作组合,但是本领域技术人员应该知悉,本发明实施例并不受所描述的动作顺序的限制,因为依据本发明实施例,某些步骤可以采用其他顺序或者同时进行。其次,本领域技术人员也应该知悉,说明书中所描述的实施例均属于优选实施例,所涉及的动作并不一定是本发明实施例所必须的。It should be noted that, for the method embodiment, for the sake of simple description, it is expressed as a series of action combinations, but those skilled in the art should know that the embodiment of the present invention is not limited by the described action sequence, because According to the embodiment of the present invention, certain steps may be performed in other orders or simultaneously. Secondly, those skilled in the art should also know that the embodiments described in the specification belong to preferred embodiments, and the actions involved are not necessarily required by the embodiments of the present invention.
参照图4,示出了本发明的一种网络安全态势监测装置实施例的结构框图,所述网络安全态势监测装置用于智能运维终端,所述智能运维终端运行有变分自编码器VAE网络和长短期记忆LSTM循环网络。Referring to FIG. 4 , it shows a structural block diagram of an embodiment of a network security situation monitoring device of the present invention, the network security situation monitoring device is used for an intelligent operation and maintenance terminal, and the intelligent operation and maintenance terminal runs a variational autoencoder VAE network and long short-term memory LSTM recurrent network.
所述具体网络安全态势监测装置可以包括如下模块:The specific network security situation monitoring device may include the following modules:
获取模块401,用于在网络运行期间,获取网元异常检测数据;An
单元确定模块402,用于依据所述网元异常检测数据确定目标异常网元;A
分析模块403,用于采用所述VAE网络和所述LSTM循环网络对所述网元异常检测数据进行分析,确定异常共性特征数据集合;An
评分模块404,用于依据所述目标异常网元和所述异常共性特征数据集合确定网络态势参数;A
评估模块405,用于依据所述网络态势参数确定网络安全态势。An
在本发明的一可选实施例中,所述智能运维终端存储有全量网元标识,所述网元异常检测数据包括异常网元标识;所述单元确定模块402包括:In an optional embodiment of the present invention, the intelligent operation and maintenance terminal stores a full amount of network element identifiers, and the network element abnormality detection data includes abnormal network element identifiers; the
对比子模块,用于对比所述异常网元标识与所述全量网元标识;A comparison submodule, configured to compare the abnormal network element identifier with the full network element identifier;
单元确定子模块,用于当所述全量网元标识包含所述异常网元标识时,确定所述异常网元标识对应的网元为目标异常网元。A unit determining submodule, configured to determine that the network element corresponding to the abnormal network element identifier is a target abnormal network element when the total number of network element identifiers includes the abnormal network element identifier.
在本发明的一可选实施例中,所述分析模块403包括:In an optional embodiment of the present invention, the
第一分析子模块,用于采用所述VAE网络对所述网元异常检测数据进行分析,确定第一异常特征数据;The first analysis submodule is used to analyze the network element abnormality detection data by using the VAE network, and determine the first abnormal characteristic data;
第二分析子模块,用于采用所述LSTM循环网络对所述网元异常检测数据进行分析,确定第二异常特征数据;The second analysis submodule is used to analyze the network element abnormality detection data by using the LSTM loop network, and determine the second abnormality characteristic data;
交集子模块,用于确定所述第一异常特征数据和所述第二异常特征数据的交集,并将所述交集确定为所述异常共性特征数据集合。The intersection submodule is configured to determine the intersection of the first abnormal characteristic data and the second abnormal characteristic data, and determine the intersection as the abnormal common characteristic data set.
在本发明的一可选实施例中,所述异常共性特征数据集合包括:漏洞类型、攻击风险等级和任务量;所述评分模块404包括:In an optional embodiment of the present invention, the abnormal common feature data set includes: vulnerability type, attack risk level and task amount; the
网元类型确定子模块,用于确定所述目标异常网元对应的网元类型;A network element type determining submodule, configured to determine the network element type corresponding to the target abnormal network element;
第一评分子模块,用于按照预设漏洞评分规则,确定所述漏洞类型对应的第一危险评分;The first scoring submodule is configured to determine a first risk score corresponding to the vulnerability type according to preset vulnerability scoring rules;
第二评分子模块,用于按照预设攻击风险评分规则,确定所述攻击风险等级对应的第二危险评分;The second scoring submodule is configured to determine a second risk score corresponding to the attack risk level according to preset attack risk scoring rules;
结合子模块,用于结合所述第一危险评分、所述第二危险评分和所述任务量,得到网络安全总指数;A combining submodule, configured to combine the first risk score, the second risk score and the task volume to obtain a total network security index;
评分子模块,用于结合所述网络安全总指数和所述网元类型,确定网络态势参数。The scoring sub-module is used to combine the total network security index and the network element type to determine network situation parameters.
在本发明的一可选实施例中,所述第一危险评分对应有第一权重值,所述第二危险评分对应有第二权重值,所述任务量对应有第三权重值;所述结合子模块包括:In an optional embodiment of the present invention, the first risk score corresponds to a first weight value, the second risk score corresponds to a second weight value, and the task amount corresponds to a third weight value; the Binding submodules include:
第一计算单元,用于计算所述第一危险评分与所述第一权重值的第一乘积值;a first calculation unit, configured to calculate a first product value of the first risk score and the first weight value;
第二计算单元,用于计算所述第二危险评分与所述第二权重值的第二乘积值;a second calculation unit, configured to calculate a second product value of the second risk score and the second weight value;
第三计算单元,用于计算所述任务量与所述第三权重值的第三乘积值;a third calculation unit, configured to calculate a third product value of the task amount and the third weight value;
结合单元,用于确定所述第一乘积值、所述第二乘积值和所述第三乘积值的和值为网络安全总指数。A combining unit, configured to determine that the sum of the first product value, the second product value and the third product value is a total network security index.
在本发明的一可选实施例中,所述评估模块405包括:In an optional embodiment of the present invention, the
第一评估子模块,用于当所述网元类型为预设目标网元类型,或所述网络安全总指数低于预设安全阈值时,确定所述网络安全态势处于待修复状态;A first evaluation submodule, configured to determine that the network security situation is in a state to be repaired when the network element type is a preset target network element type, or the total network security index is lower than a preset security threshold;
第二评估子模块,用于当所述网元类型不为所述预设目标网元类型,且所述网络安全总指数不低于预设安全阈值时,确定所述网络安全态势处于健康状态。A second evaluation submodule, configured to determine that the network security situation is in a healthy state when the network element type is not the preset target network element type and the total network security index is not lower than a preset security threshold .
在本发明的一可选实施例中,所述智能运维终端设置有修复数据库,所述装置还包括:In an optional embodiment of the present invention, the intelligent operation and maintenance terminal is provided with a repair database, and the device also includes:
调用模块,用于当所述网络安全态势处于所述待修复状态时,调用所述数据库;A calling module, used to call the database when the network security situation is in the state to be repaired;
修复模块,用于从所述数据库中获取修复指令,并将所述修复指令发送至所述目标异常网元,所述目标异常网元用于运行所述修复指令进行修复。A repairing module, configured to obtain a repairing instruction from the database, and send the repairing instruction to the target abnormal network element, and the target abnormal network element is used to execute the repairing instruction to perform repairing.
对于装置实施例而言,由于其与方法实施例基本相似,所以描述的比较简单,相关之处参见方法实施例的部分说明即可。As for the device embodiment, since it is basically similar to the method embodiment, the description is relatively simple, and for related parts, please refer to the part of the description of the method embodiment.
本发明实施例还提供了一种电子设备,包括:The embodiment of the present invention also provides an electronic device, including:
处理器和存储介质,所述存储介质存储有所述处理器可执行的计算机程序,当电子设备运行时,所述处理器执行所述计算机程序,以执行如本发明实施例任一项所述的方法。具体实现方式和技术效果与方法实施例部分类似,这里不再赘述。A processor and a storage medium, the storage medium stores a computer program executable by the processor, and when the electronic device is running, the processor executes the computer program to perform the operation described in any one of the embodiments of the present invention. Methods. The specific implementation and technical effects are similar to those in the method embodiments, and will not be repeated here.
存储介质可以包括随机存取存储器(Random Access Memory,简称RAM),也可以包括非易失性存储器(non-volatile memory),例如至少一个磁盘存储器。可选的,存储介质还可以是至少一个位于远离前述处理器的存储装置。The storage medium may include a random access memory (Random Access Memory, RAM for short), and may also include a non-volatile memory (non-volatile memory), such as at least one disk memory. Optionally, the storage medium may also be at least one storage device located far away from the aforementioned processor.
上述的处理器可以是通用处理器,包括中央处理器(Central Processing Unit,简称CPU)、网络处理器(Network Processor,简称NP)等;还可以是数字信号处理器(Digital Signal Processing,简称DSP)、专用集成电路(Application SpecificIntegrated Circuit,简称ASIC)、现场可编程门阵列(Field-Programmable Gate Array,简称FPGA)或者其他可编程逻辑器件、分立门或者晶体管逻辑器件、分立硬件组件。The above-mentioned processor can be a general-purpose processor, including a central processing unit (Central Processing Unit, referred to as CPU), a network processor (Network Processor, referred to as NP), etc.; it can also be a digital signal processor (Digital Signal Processing, referred to as DSP) , Application Specific Integrated Circuit (ASIC for short), Field Programmable Gate Array (Field-Programmable Gate Array, FPGA for short) or other programmable logic devices, discrete gate or transistor logic devices, discrete hardware components.
本发明实施例还提供了一种计算机可读存储介质,所述存储介质上存储有计算机程序,所述计算机程序被处理器运行时执行如本发明实施例任一项所述的方法。具体实现方式和技术效果与方法实施例部分类似,这里不再赘述。An embodiment of the present invention also provides a computer-readable storage medium, on which a computer program is stored, and when the computer program is executed by a processor, the method described in any one of the embodiments of the present invention is executed. The specific implementation and technical effects are similar to those in the method embodiments, and will not be repeated here.
本说明书中的各个实施例均采用递进的方式描述,每个实施例重点说明的都是与其他实施例的不同之处,各个实施例之间相同相似的部分互相参见即可。Each embodiment in this specification is described in a progressive manner, each embodiment focuses on the difference from other embodiments, and the same and similar parts of each embodiment can be referred to each other.
本领域内的技术人员应明白,本发明实施例的实施例可提供为方法、装置、或计算机程序产品。因此,本发明实施例可采用完全硬件实施例、完全软件实施例、或结合软件和硬件方面的实施例的形式。而且,本发明实施例可采用在一个或多个其中包含有计算机可用程序代码的计算机可用存储介质(包括但不限于磁盘存储器、CD-ROM、光学存储器等)上实施的计算机程序产品的形式。Those skilled in the art should understand that the embodiments of the present invention may be provided as methods, devices, or computer program products. Accordingly, embodiments of the invention may take the form of an entirely hardware embodiment, an entirely software embodiment, or an embodiment combining software and hardware aspects. Furthermore, embodiments of the invention may take the form of a computer program product embodied on one or more computer-usable storage media (including but not limited to disk storage, CD-ROM, optical storage, etc.) having computer-usable program code embodied therein.
本发明实施例是参照根据本发明实施例的方法、终端设备(系统)、和计算机程序产品的流程图和/或方框图来描述的。应理解可由计算机程序指令实现流程图和/或方框图中的每一流程和/或方框、以及流程图和/或方框图中的流程和/或方框的结合。可提供这些计算机程序指令到通用计算机、专用计算机、嵌入式处理机或其他可编程数据处理终端设备的处理器以产生一个机器,使得通过计算机或其他可编程数据处理终端设备的处理器执行的指令产生用于实现在流程图一个流程或多个流程和/或方框图一个方框或多个方框中指定的功能的装置。Embodiments of the present invention are described with reference to flowcharts and/or block diagrams of methods, terminal devices (systems), and computer program products according to embodiments of the present invention. It should be understood that each procedure and/or block in the flowchart and/or block diagram, and a combination of procedures and/or blocks in the flowchart and/or block diagram can be realized by computer program instructions. These computer program instructions may be provided to a general purpose computer, special purpose computer, embedded processor or processor of other programmable data processing terminal equipment to produce a machine such that instructions executed by the computer or processor of other programmable data processing terminal equipment Produce means for realizing the functions specified in one or more procedures of the flowchart and/or one or more blocks of the block diagram.
这些计算机程序指令也可存储在能引导计算机或其他可编程数据处理终端设备以特定方式工作的计算机可读存储器中,使得存储在该计算机可读存储器中的指令产生包括指令装置的制造品,该指令装置实现在流程图一个流程或多个流程和/或方框图一个方框或多个方框中指定的功能。These computer program instructions may also be stored in a computer-readable memory capable of directing a computer or other programmable data processing terminal to operate in a specific manner, such that the instructions stored in the computer-readable memory produce an article of manufacture comprising instruction means, the The instruction means implements the functions specified in one or more procedures of the flowchart and/or one or more blocks of the block diagram.
这些计算机程序指令也可装载到计算机或其他可编程数据处理终端设备上,使得在计算机或其他可编程终端设备上执行一系列操作步骤以产生计算机实现的处理,从而在计算机或其他可编程终端设备上执行的指令提供用于实现在流程图一个流程或多个流程和/或方框图一个方框或多个方框中指定的功能的步骤。These computer program instructions can also be loaded into a computer or other programmable data processing terminal equipment, so that a series of operational steps are performed on the computer or other programmable terminal equipment to produce computer-implemented processing, thereby The instructions executed above provide steps for implementing the functions specified in one or more procedures of the flowchart and/or one or more blocks of the block diagram.
尽管已描述了本发明实施例的优选实施例,但本领域内的技术人员一旦得知了基本创造性概念,则可对这些实施例做出另外的变更和修改。所以,所附权利要求意欲解释为包括优选实施例以及落入本发明实施例范围的所有变更和修改。Having described preferred embodiments of embodiments of the present invention, additional changes and modifications to these embodiments can be made by those skilled in the art once the basic inventive concept is appreciated. Therefore, the appended claims are intended to be interpreted to cover the preferred embodiment and all changes and modifications which fall within the scope of the embodiments of the present invention.
最后,还需要说明的是,在本文中,诸如第一和第二等之类的关系术语仅仅用来将一个实体或者操作与另一个实体或操作区分开来,而不一定要求或者暗示这些实体或操作之间存在任何这种实际的关系或者顺序。而且,术语“包括”、“包含”或者其任何其他变体意在涵盖非排他性的包含,从而使得包括一系列要素的过程、方法、物品或者终端设备不仅包括那些要素,而且还包括没有明确列出的其他要素,或者是还包括为这种过程、方法、物品或者终端设备所固有的要素。在没有更多限制的情况下,由语句“包括一个……”限定的要素,并不排除在包括所述要素的过程、方法、物品或者终端设备中还存在另外的相同要素。Finally, it should also be noted that in this text, relational terms such as first and second etc. are only used to distinguish one entity or operation from another, and do not necessarily require or imply that these entities or operations, any such actual relationship or order exists. Furthermore, the term "comprises", "comprises" or any other variation thereof is intended to cover a non-exclusive inclusion such that a process, method, article, or terminal equipment comprising a set of elements includes not only those elements, but also includes elements not expressly listed. other elements identified, or also include elements inherent in such a process, method, article, or terminal equipment. Without further limitations, an element defined by the phrase "comprising a ..." does not exclude the presence of additional identical elements in the process, method, article or terminal device comprising said element.
以上对本发明所提供的一种网络安全态势监测方法、装置、电子设备和存储介质,进行了详细介绍,本文中应用了具体个例对本发明的原理及实施方式进行了阐述,以上实施例的说明只是用于帮助理解本发明的方法及其核心思想;同时,对于本领域的一般技术人员,依据本发明的思想,在具体实施方式及应用范围上均会有改变之处,综上所述,本说明书内容不应理解为对本发明的限制。A network security situation monitoring method, device, electronic equipment, and storage medium provided by the present invention have been introduced in detail above. In this paper, specific examples have been used to illustrate the principle and implementation of the present invention. The description of the above embodiments It is only used to help understand the method of the present invention and its core idea; at the same time, for those of ordinary skill in the art, according to the idea of the present invention, there will be changes in the specific implementation and scope of application. In summary, The contents of this description should not be construed as limiting the present invention.
Claims (10)
Translated fromChinesePriority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202211555223.5ACN116132103A (en) | 2022-12-06 | 2022-12-06 | A network security situation monitoring method, device, electronic equipment and storage medium |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202211555223.5ACN116132103A (en) | 2022-12-06 | 2022-12-06 | A network security situation monitoring method, device, electronic equipment and storage medium |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| CN116132103Atrue CN116132103A (en) | 2023-05-16 |
Family
ID=86294698
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN202211555223.5APendingCN116132103A (en) | 2022-12-06 | 2022-12-06 | A network security situation monitoring method, device, electronic equipment and storage medium |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN116132103A (en) |
Cited By (1)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN116915511A (en)* | 2023-09-13 | 2023-10-20 | 中移(苏州)软件技术有限公司 | Information processing method, device, equipment and storage medium |
Citations (5)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| WO2018080957A1 (en)* | 2016-10-27 | 2018-05-03 | Src, Inc. | Method for the continuous calculation of a cyber security risk index |
| CN110381013A (en)* | 2019-05-28 | 2019-10-25 | 三明学院 | A kind of network safety situation sensing control method, apparatus, equipment and storage medium |
| CN111726350A (en)* | 2020-06-16 | 2020-09-29 | 桂林电子科技大学 | An Insider Threat Detection Method Based on VAE and BPNN |
| CN112580788A (en)* | 2020-12-25 | 2021-03-30 | 中国电子科技集团公司信息科学研究院 | Situation cognition method, device, equipment and medium based on long-time and short-time memory network |
| CN115237880A (en)* | 2022-07-13 | 2022-10-25 | 中国农业银行股份有限公司 | Method, device and equipment for detecting abnormity of time sequence data and storage medium |
- 2022
- 2022-12-06CNCN202211555223.5Apatent/CN116132103A/enactivePending
Patent Citations (5)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| WO2018080957A1 (en)* | 2016-10-27 | 2018-05-03 | Src, Inc. | Method for the continuous calculation of a cyber security risk index |
| CN110381013A (en)* | 2019-05-28 | 2019-10-25 | 三明学院 | A kind of network safety situation sensing control method, apparatus, equipment and storage medium |
| CN111726350A (en)* | 2020-06-16 | 2020-09-29 | 桂林电子科技大学 | An Insider Threat Detection Method Based on VAE and BPNN |
| CN112580788A (en)* | 2020-12-25 | 2021-03-30 | 中国电子科技集团公司信息科学研究院 | Situation cognition method, device, equipment and medium based on long-time and short-time memory network |
| CN115237880A (en)* | 2022-07-13 | 2022-10-25 | 中国农业银行股份有限公司 | Method, device and equipment for detecting abnormity of time sequence data and storage medium |
Cited By (2)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN116915511A (en)* | 2023-09-13 | 2023-10-20 | 中移(苏州)软件技术有限公司 | Information processing method, device, equipment and storage medium |
| CN116915511B (en)* | 2023-09-13 | 2023-12-08 | 中移(苏州)软件技术有限公司 | Information processing method, device, equipment and storage medium |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| WO2024148880A1 (en) | System detection method and apparatus based on multi-source heterogeneous data | |
| CN111309539A (en) | Abnormity monitoring method and device and electronic equipment | |
| CN115987544A (en) | Network security threat prediction method and system based on threat intelligence | |
| CN117349102B (en) | Digital twin operation and maintenance data quality inspection method, system and medium | |
| CN117436073B (en) | Security log alarming method, medium and equipment based on intelligent label | |
| CN110109888A (en) | A kind of document handling method and device | |
| CN111597550A (en) | A kind of log information analysis method and related device | |
| CN117407800A (en) | A social media robot detection method and system based on random forest and XGBoost model | |
| CN117395072A (en) | Method and device for generating network killing chain and electronic equipment | |
| CN113052509B (en) | Model evaluation method, model evaluation device, electronic apparatus, and storage medium | |
| CN119383573A (en) | A 5G message, SMS and voice integrated information access method and system | |
| CN118710224A (en) | Enterprise platform security management method and system based on artificial intelligence | |
| CN116132103A (en) | A network security situation monitoring method, device, electronic equipment and storage medium | |
| CN116227916A (en) | Real-time wind control system and method based on rule engine | |
| CN119341888A (en) | Security early warning methods, devices, equipment, media and program products | |
| CN114862372A (en) | Intelligent education data tamper-proof processing method and system based on block chain | |
| CN118295842A (en) | Data processing method, device and server for transaction system abnormal event | |
| CN115328786B (en) | Automatic testing method and device based on blockchain and storage medium | |
| CN117076244A (en) | Method, device, equipment and storage medium for generating host running state information | |
| CN116384370A (en) | A big data security analysis method and system for online business session interaction | |
| CN118211183B (en) | Cross-space-time data continuous fusion method, device and medium based on large model | |
| CN118350011B (en) | DNS query text data analysis method and system based on machine learning | |
| CN118733704B (en) | Public opinion data analysis method, device, electronic device and readable storage medium | |
| CN120017414B (en) | A data access risk early warning method based on artificial intelligence | |
| CN120729556A (en) | SecGPT-based network security alarm method, system, equipment and storage medium |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| RJ01 | Rejection of invention patent application after publication | Application publication date:20230516 |