CN115987771A - Link abnormal location method, device, computer equipment and storage medium - Google Patents
Link abnormal location method, device, computer equipment and storage mediumDownload PDFInfo
- Publication number
- CN115987771A CN115987771ACN202211684395.2ACN202211684395ACN115987771ACN 115987771 ACN115987771 ACN 115987771ACN 202211684395 ACN202211684395 ACN 202211684395ACN 115987771 ACN115987771 ACN 115987771A
- Authority
- CN
- China
- Prior art keywords
- link
- target
- abnormal
- identifier
- service
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Granted
Links
- 230000002159abnormal effectEffects0.000titleclaimsabstractdescription263
- 238000000034methodMethods0.000titleclaimsabstractdescription63
- 238000013507mappingMethods0.000claimsabstractdescription70
- 238000012545processingMethods0.000claimsabstractdescription38
- 230000008569processEffects0.000claimsabstractdescription19
- 238000004590computer programMethods0.000claimsdescription48
- 238000001514detection methodMethods0.000claimsdescription29
- 238000009472formulationMethods0.000claimsdescription8
- 239000000203mixtureSubstances0.000claimsdescription8
- 238000005516engineering processMethods0.000abstractdescription3
- 230000005856abnormalityEffects0.000description46
- 238000010586diagramMethods0.000description11
- 230000008439repair processEffects0.000description4
- 238000004891communicationMethods0.000description3
- 238000004364calculation methodMethods0.000description2
- 230000008859changeEffects0.000description2
- 238000011161developmentMethods0.000description2
- 239000000463materialSubstances0.000description2
- OKTJSMMVPCPJKN-UHFFFAOYSA-NCarbonChemical compound[C]OKTJSMMVPCPJKN-UHFFFAOYSA-N0.000description1
- 238000004458analytical methodMethods0.000description1
- 230000001413cellular effectEffects0.000description1
- 238000001914filtrationMethods0.000description1
- 229910021389grapheneInorganic materials0.000description1
- 239000004973liquid crystal related substanceSubstances0.000description1
- 238000012986modificationMethods0.000description1
- 230000004048modificationEffects0.000description1
- 230000003287optical effectEffects0.000description1
- 230000003068static effectEffects0.000description1
Images
Landscapes
- Computer And Data Communications (AREA)
- Retry When Errors Occur (AREA)
- Debugging And Monitoring (AREA)
Abstract
Description
Translated fromChinese技术领域technical field
本申请涉及计算机技术领域,特别是涉及一种链路异常定位方法、装置、计算机设备以及存储介质。The present application relates to the field of computer technology, and in particular to a link abnormality location method, device, computer equipment and storage medium.
背景技术Background technique
随着各个企业规模的不断发展,越来越多的企业开始构建和使用符合本企业实际情况的微服务架构;伴随着微服务架构的出现,极大的降低了企业对于基础设施的管理难度。With the continuous development of various enterprise scales, more and more enterprises have begun to build and use microservice architectures that meet their actual conditions; with the emergence of microservice architectures, it has greatly reduced the difficulty of enterprise infrastructure management.
由于微服务架构中包含多个服务节点,每个服务节点又都具备多个实例,因此,当微服务架构执行业务请求的过程中出现异常时,难以及时准确的定位出现异常的服务节点,以及该业务请求对应的用户信息。Since the microservice architecture contains multiple service nodes, and each service node has multiple instances, when an exception occurs in the process of executing a business request in the microservice architecture, it is difficult to locate the abnormal service node in a timely and accurate manner, and User information corresponding to the service request.
发明内容Contents of the invention
基于此,有必要针对上述技术问题,提供一种能够在微服务架构执行业务请求的过程中出现异常时,准确的定位出现异常的服务节点,以及该业务请求对应的用户信息的链路异常定位方法、装置、计算机设备以及存储介质。Based on this, it is necessary to address the above technical problems and provide a service node that can accurately locate the abnormal service node when an exception occurs in the process of executing a business request in the microservice architecture, as well as link abnormal location of the user information corresponding to the business request Method, device, computer equipment and storage medium.
第一方面,本申请提供了一种链路异常定位方法。该方法包括:In a first aspect, the present application provides a link abnormality location method. The method includes:
基于用户发送的业务请求,确定业务请求对应的目标链路;Determine the target link corresponding to the service request based on the service request sent by the user;
确定业务请求对应的目标业务标识,以及目标链路中每一服务节点对应的目标链路标识,并构建目标业务标识和目标链路标识之间的标识映射关系;Determine the target service identifier corresponding to the service request, and the target link identifier corresponding to each service node in the target link, and construct an identifier mapping relationship between the target service identifier and the target link identifier;
在基于目标链路处理业务请求的过程中,若检测到目标链路出现异常,则基于标识映射关系,对目标链路进行异常定位,得到异常定位结果。In the process of processing service requests based on the target link, if an abnormality is detected in the target link, the abnormality location of the target link is performed based on the identification mapping relationship, and an abnormality location result is obtained.
在其中一个实施例中,基于标识映射关系,对目标链路进行异常定位,得到异常定位结果,包括:In one of the embodiments, based on the identification mapping relationship, abnormal location is performed on the target link, and the abnormal location result is obtained, including:
基于目标链路对应的异常定位需求,确定定位目标;Determine the positioning target based on the abnormal positioning requirements corresponding to the target link;
基于定位目标和标识映射关系,对目标链路进行异常定位,得到定位目标对应的异常定位结果。Based on the mapping relationship between the positioning target and the identification, the abnormal positioning of the target link is performed, and the abnormal positioning result corresponding to the positioning target is obtained.
在其中一个实施例中,基于定位目标和标识映射关系,对目标链路进行异常定位,得到定位目标对应的异常定位结果,包括:In one of the embodiments, based on the mapping relationship between the positioning target and the identification, abnormal positioning is performed on the target link, and an abnormal positioning result corresponding to the positioning target is obtained, including:
若定位目标为目标链路对应的用户,则确定目标链路对应的第一异常链路标识;If the positioning target is the user corresponding to the target link, then determine the first abnormal link identifier corresponding to the target link;
基于标识映射关系,确定第一异常链路标识对应的第一异常业务标识;Determine a first abnormal service identifier corresponding to the first abnormal link identifier based on the identifier mapping relationship;
基于第一异常业务标识,确定定位目标对应的异常定位结果。Based on the first abnormal service identifier, an abnormal positioning result corresponding to the positioning target is determined.
在其中一个实施例中,基于定位目标和标识映射关系,对目标链路进行异常定位,得到定位目标对应的异常定位结果,包括:In one of the embodiments, based on the mapping relationship between the positioning target and the identification, abnormal positioning is performed on the target link, and an abnormal positioning result corresponding to the positioning target is obtained, including:
若定位目标为目标链路中出现异常的服务节点,则确定业务请求对应的第二异常业务标识;If the positioning target is an abnormal service node in the target link, then determine the second abnormal service identifier corresponding to the service request;
基于标识映射关系,确定第二异常业务标识对应的第二异常链路标识;Determine a second abnormal link identifier corresponding to the second abnormal service identifier based on the identifier mapping relationship;
基于第二异常链路标识,确定定位目标对应的异常定位结果。Based on the second abnormal link identifier, an abnormal positioning result corresponding to the positioning target is determined.
在其中一个实施例中,基于用户发送的业务请求,确定业务请求对应的目标链路,包括:In one of the embodiments, based on the service request sent by the user, determining the target link corresponding to the service request includes:
基于用户发送的业务请求,确定业务请求对应的标准链路和待检测链路;Based on the service request sent by the user, determine the standard link and the link to be detected corresponding to the service request;
基于标准链路,对待检测链路进行结构检测,确定待检测链路中的目标链路。Based on the standard link, the structure detection of the link to be detected is carried out, and the target link in the link to be detected is determined.
在其中一个实施例中,基于标准链路,对待检测链路进行结构检测,确定待检测链路中的目标链路,包括:In one of the embodiments, based on the standard link, the structure detection of the link to be detected is carried out, and the target link in the link to be detected is determined, including:
将标准链路和待检测链路进行叠加处理;Superimpose the standard link and the link to be detected;
基于叠加处理结果,对待检测链路进行结构检测,确定待检测链路中的目标链路。Based on the superposition processing results, the structure detection of the link to be detected is carried out, and the target link in the link to be detected is determined.
在其中一个实施例中,基于用户发送的业务请求,确定业务请求对应的标准链路和待检测链路,包括:In one of the embodiments, based on the service request sent by the user, determining the standard link and the link to be detected corresponding to the service request includes:
基于用户发送的业务请求的类型,确定业务请求对应的标准链路;Based on the type of service request sent by the user, determine the standard link corresponding to the service request;
基于用户发送的业务请求的语义信息,确定是否符合语义制定规则;Based on the semantic information of the business request sent by the user, determine whether it complies with the semantic formulation rules;
若符合,则基于语义信息和标准链路,确定业务请求对应的待检测链路。If so, the link to be detected corresponding to the service request is determined based on the semantic information and the standard link.
第二方面,本申请还提供了一种链路异常定位装置。该装置包括:In a second aspect, the present application also provides a link abnormality locating device. The unit includes:
第一确定模块,用于基于用户发送的业务请求,确定业务请求对应的目标链路;The first determining module is configured to determine the target link corresponding to the service request based on the service request sent by the user;
第二确定模块,用于确定业务请求对应的目标业务标识,以及目标链路中每一服务节点对应的目标链路标识,并构建目标业务标识和目标链路标识之间的标识映射关系;The second determination module is configured to determine the target service identifier corresponding to the service request, and the target link identifier corresponding to each service node in the target link, and construct an identifier mapping relationship between the target service identifier and the target link identifier;
定位模块,用于在基于目标链路处理业务请求的过程中,若检测到目标链路出现异常,则基于标识映射关系,对目标链路进行异常定位,得到异常定位结果。The positioning module is configured to locate the abnormality of the target link based on the identification mapping relationship if an abnormality is detected in the target link during the process of processing the service request based on the target link, and obtain an abnormality positioning result.
第三方面,本申请还提供了一种计算机设备。计算机设备包括存储器和处理器,存储器存储有计算机程序,处理器执行计算机程序时实现如上述第一方面任一实施例的链路异常定位方法。In a third aspect, the present application also provides a computer device. The computer device includes a memory and a processor, the memory stores a computer program, and when the processor executes the computer program, the link anomaly location method according to any embodiment of the first aspect above is realized.
第四方面,本申请还提供了一种计算机可读存储介质。计算机可读存储介质,其上存储有计算机程序,计算机程序被处理器执行时实现如上述第一方面任一实施例的链路异常定位方法。In a fourth aspect, the present application also provides a computer-readable storage medium. A computer-readable storage medium, on which a computer program is stored, and when the computer program is executed by a processor, implements the link anomaly locating method according to any embodiment of the first aspect above.
第五方面,本申请还提供了一种计算机程序产品。计算机程序产品,包括计算机程序,该计算机程序被处理器执行时实现如上述第一方面任一实施例的链路异常定位方法。In a fifth aspect, the present application also provides a computer program product. A computer program product includes a computer program, and when the computer program is executed by a processor, implements the link anomaly locating method according to any embodiment of the first aspect above.
根据本申请的技术方案,通过确定业务请求对应的目标链路,保证了后续能够根据目标链路,确定目标链路标识,进而根据目标链路标识对目标链路进行异常定位,得到异常定位结果,保证了异常定位结果的准确性;通过确定目标业务标识、目标链路标识和标识映射关系,保证了后续当目标链路出现异常时,能够根据目标业务标识、目标链路标识和标识映射关系,确定异常定位结果,进而实现在微服务架构执行业务请求的过程中出现异常时,准确的定位出现异常的服务节点,以及该业务请求对应的用户信息,进一步保证了针对出现异常的服务节点的快速修复,以及异常业务请求对应的用户的快速通知,降低了当目标链路出现异常时造成的异常影响,提高了针对异常的处理效率。According to the technical solution of this application, by determining the target link corresponding to the service request, it is ensured that the target link identifier can be determined according to the target link, and then the abnormal location of the target link can be performed according to the target link identifier, and the abnormal location result can be obtained , to ensure the accuracy of abnormal location results; by determining the target service ID, target link ID, and ID mapping relationship, it is ensured that when an abnormality occurs in the target link, the target service ID, target link ID, and ID mapping relationship can be determined. , to determine the abnormal location result, and then to realize the accurate positioning of the abnormal service node and the user information corresponding to the business request when an abnormality occurs in the process of executing the business request of the microservice architecture, which further ensures the service node for the abnormal service node Quick repair and quick notification of users corresponding to abnormal business requests reduce the impact of abnormalities when the target link is abnormal and improve the efficiency of abnormal processing.
附图说明Description of drawings
图1为本申请实施例提供的一种链路异常定位方法的应用环境图;FIG. 1 is an application environment diagram of a link anomaly location method provided in an embodiment of the present application;
图2为本申请实施例提供的一种链路异常定位方法的流程图;FIG. 2 is a flow chart of a link abnormality location method provided in an embodiment of the present application;
图3为本申请实施例提供的一种确定异常定位结果的步骤流程图;FIG. 3 is a flow chart of steps for determining an abnormal location result provided by an embodiment of the present application;
图4为本申请实施例提供的一种确定目标链路的步骤流程图;FIG. 4 is a flow chart of steps for determining a target link provided in an embodiment of the present application;
图5为本申请实施例提供的一种标准链路和待检测链路的叠加图;FIG. 5 is an overlay diagram of a standard link and a link to be detected provided in an embodiment of the present application;
图6为本申请实施例提供的另一种链路异常定位方法的流程图;FIG. 6 is a flow chart of another link abnormality location method provided in the embodiment of the present application;
图7为本申请实施例提供的第一种链路异常定位装置的结构框图;FIG. 7 is a structural block diagram of the first link anomaly locating device provided by the embodiment of the present application;
图8为本申请实施例提供的第二种链路异常定位装置的结构框图;FIG. 8 is a structural block diagram of a second link anomaly locating device provided by an embodiment of the present application;
图9为本申请实施例提供的第三种链路异常定位装置的结构框图;FIG. 9 is a structural block diagram of a third link anomaly locating device provided in an embodiment of the present application;
图10为一个实施例中计算机设备的内部结构图。Figure 10 is a diagram of the internal structure of a computer device in one embodiment.
具体实施方式Detailed ways
为了使本申请的目的、技术方案及优点更加清楚明白,以下结合附图及实施例,对本申请进行进一步详细说明。应当理解,此处描述的具体实施例仅仅用以解释本申请,并不用于限定本申请。In order to make the purpose, technical solution and advantages of the present application clearer, the present application will be further described in detail below in conjunction with the accompanying drawings and embodiments. It should be understood that the specific embodiments described here are only used to explain the present application, and are not intended to limit the present application.
应当理解,此处描述的具体实施例仅仅用以解释本申请,并不用于限定本申请。在本申请的描述中,参考术语“一个实施例”、“一些实施例”、“示例”、“具体示例”、或“一些示例”等的描述意指结合该实施例或示例描述的具体特征、结构、材料或者特点包含于本申请的至少一个实施例或示例中。在本说明书中,对上述术语的示意性表述不必须针对的是相同的实施例或示例。而且,描述的具体特征、结构、材料或者特点可以在任一个或多个实施例或示例中以合适的方式结合。此外,在不相互矛盾的情况下,本领域的技术人员可以将本说明书中描述的不同实施例或示例以及不同实施例或示例的特征进行结合和组合。It should be understood that the specific embodiments described here are only used to explain the present application, and are not intended to limit the present application. In the description of this application, reference to the terms "one embodiment," "some embodiments," "example," "specific examples," or "some examples" means that specific features described in connection with that embodiment or example , structure, material or characteristic is included in at least one embodiment or example of the present application. In this specification, the schematic representations of the above terms are not necessarily directed to the same embodiment or example. Furthermore, the described specific features, structures, materials or characteristics may be combined in any suitable manner in any one or more embodiments or examples. In addition, those skilled in the art can combine and combine different embodiments or examples and features of different embodiments or examples described in this specification without conflicting with each other.
随着各个企业规模的不断发展,越来越多的企业开始构建和使用符合本企业实际情况的微服务架构;伴随着微服务架构的出现,极大的降低了企业对于基础设施的管理难度。With the continuous development of various enterprise scales, more and more enterprises have begun to build and use microservice architectures that meet their actual conditions; with the emergence of microservice architectures, it has greatly reduced the difficulty of enterprise infrastructure management.
由于微服务架构中包含多个服务节点,每个服务节点又都具备多个实例,因此,当微服务架构执行业务请求的过程中出现异常时,难以及时准确的定位出现异常的服务节点,以及该业务请求对应的用户信息。Since the microservice architecture contains multiple service nodes, and each service node has multiple instances, when an exception occurs in the process of executing a business request in the microservice architecture, it is difficult to locate the abnormal service node in a timely and accurate manner, and User information corresponding to the service request.
本申请实施例提供的链路异常定位方法,可以应用于如图1所示的应用环境中。在一个实施例中,提供了一种计算机设备,该计算机设备可以是服务器,其内部结构图可以如图1所示。该计算机设备包括通过系统总线连接的处理器、存储器和网络接口。其中,该计算机设备的处理器用于提供计算和控制能力。该计算机设备的存储器包括非易失性存储介质和内存储器。该非易失性存储介质存储有操作系统、计算机程序和数据库。该内存储器为非易失性存储介质中的操作系统和计算机程序的运行提供环境。该计算机设备的数据库用于存储链路异常定位的获取数据。该计算机设备的网络接口用于与外部的终端通过网络连接通信。该计算机程序被处理器执行时以实现一种链路异常定位方法。The link anomaly location method provided in the embodiment of the present application can be applied to the application environment shown in FIG. 1 . In one embodiment, a computer device is provided. The computer device may be a server, and its internal structure may be as shown in FIG. 1 . The computer device includes a processor, memory and a network interface connected by a system bus. Wherein, the processor of the computer device is used to provide calculation and control capabilities. The memory of the computer device includes a non-volatile storage medium and an internal memory. The non-volatile storage medium stores an operating system, computer programs and databases. The internal memory provides an environment for the operation of the operating system and computer programs in the non-volatile storage medium. The database of the computer device is used to store the acquired data of link abnormal location. The network interface of the computer device is used to communicate with an external terminal via a network connection. When the computer program is executed by the processor, a link abnormality location method is realized.
本申请公开了一种链路异常定位方法、装置、计算机设备以及存储介质。工作人员的计算机设备通过确定业务请求对应的目标链路,并基于目标链路,确定目标业务标识和目标链路标识;确定目标业务标识和目标链路标识之间的标识映射关系,当检测到目标链路出现异常时,根据目标业务标识、目标链路标识和标识映射关系,对目标链路进行异常定位,得到异常定位结果。The application discloses a link abnormality location method, device, computer equipment and storage medium. The staff's computer equipment determines the target link corresponding to the service request, and based on the target link, determines the target service identifier and the target link identifier; determines the identifier mapping relationship between the target service identifier and the target link identifier, and when detected When the target link is abnormal, according to the target service identifier, the target link identifier and the mapping relationship of the identifier, the abnormal location of the target link is performed to obtain the abnormal location result.
在一个实施例中,如图2所示,图2为本申请实施例提供的一种链路异常定位方法的流程图,提供了一种链路异常定位方法,图1中的计算机设备执行的链路异常定位方法可以包括以下步骤:In one embodiment, as shown in FIG. 2, FIG. 2 is a flow chart of a link anomaly locating method provided in an embodiment of the present application, and provides a link anomaly locating method. The computer device in FIG. 1 executes the The link abnormal location method may include the following steps:
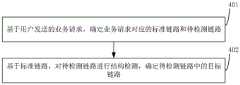
步骤201,基于用户发送的业务请求,确定业务请求对应的目标链路。
需要说明的是,目标链路中包含业务请求中包含的各个处理流程,以及各个处理流程分别对应的处理顺序;因此,当需要确定业务请求对应的目标链路时,需要根据用户发送的业务请求,确定该业务请求对应的各个处理流程,以及各个处理流程对应的处理顺序;进而,根据该业务请求对应的各个处理流程,以及各个处理流程对应的处理顺序,确定业务请求对应的目标链路。It should be noted that the target link includes each processing flow included in the service request, and the processing sequence corresponding to each processing flow; therefore, when it is necessary to determine the target link corresponding to the service request, it is necessary to , determine each processing flow corresponding to the service request, and the processing order corresponding to each processing flow; furthermore, determine the target link corresponding to the service request according to each processing flow corresponding to the service request, and the processing sequence corresponding to each processing flow.
进一步说明,当确定业务请求对应的目标链路之前,需要对用户发送的业务请求进行合法性验证;确定业务请求对应的语义信息是否合法,若业务请求对应的语义信息合法,则可基于用户发送的业务请求,确定业务请求对应的目标链路,并向用户进行信息反馈,以表明该业务请求对应的目标链路确定完成;若业务请求对应的语义信息不合法,则向用户进行信息反馈,以表明该业务请求对应的语义信息不合法,无法确定目标链路。To further explain, before determining the target link corresponding to the service request, it is necessary to verify the validity of the service request sent by the user; determine whether the semantic information corresponding to the service request is legal, and if the semantic information corresponding to the service request is legal, it can be sent based on the user business request, determine the target link corresponding to the business request, and provide information feedback to the user to indicate that the target link corresponding to the business request has been determined; if the semantic information corresponding to the business request is illegal, then feedback information to the user, To indicate that the semantic information corresponding to the service request is illegal, and the target link cannot be determined.
步骤202,确定业务请求对应的目标业务标识,以及目标链路中每一服务节点对应的目标链路标识,并构建目标业务标识和目标链路标识之间的标识映射关系。
需要说明的是,目标业务标识用于对用户发送的业务请求进行标记,以保证了能够根据目标业务标识,实现发送业务请求的目标的确定,进一步的,目标业务标识中可包括发送业务请求的用户的相关信息;根据该发送业务请求的用户的相关信息,可实现针对用户的快速定位。It should be noted that the target service identifier is used to mark the service request sent by the user, so as to ensure that the target of sending the service request can be determined according to the target service identifier. Further, the target service identifier may include the Relevant information of the user: According to the relevant information of the user who sends the service request, rapid positioning for the user can be realized.
其中,发送业务请求的用户的相关信息可以包括但不限于:业务请求对应的业务流水号、用户对应的身份标识和业务请求对应的发送时间等。Wherein, the relevant information of the user who sends the service request may include but not limited to: the service serial number corresponding to the service request, the identity corresponding to the user, and the sending time corresponding to the service request.
在本申请的一种实施例中,当需要确定业务请求对应的目标业务标识时,可预先确定业务请求对应的标识行李(Baggage,其由若干<key,value>键值对组成),进而将确定的业务请求对应的目标业务标识,存入标识行李中。In one embodiment of the present application, when it is necessary to determine the target service identifier corresponding to the service request, the identification baggage (Baggage, which is composed of several <key, value> key-value pairs) corresponding to the service request can be determined in advance, and then the The target service identifier corresponding to the determined service request is stored in the identifier luggage.
需要说明的是,目标链路标识用于表示目标链路中各个服务节点的运行状态,进一步的,根据目标链路标识中各个服务节点的运行状态,可用于判断目标链路中是否出现异常的服务节点,以及当目标链路中出现异常的服务节点的异常位置。It should be noted that the target link identifier is used to indicate the running status of each service node in the target link. Further, according to the running status of each service node in the target link ID, it can be used to determine whether there is an abnormality in the target link. The service node, and the abnormal position of the service node when an exception occurs in the target link.
进一步说明,为保证能够根据目标业务标识和目标链路标识,对目标链路进行异常定位,需要能够在目标链路出现异常时,基于异常的目标链路标识,确定该异常目标链路标识对应的目标业务标识;以及,在目标链路出现异常时,基于异常的目标业务标识,确定该异常目标业务标识对应的目标链路标识;因此,需要创建目标业务标识和目标链路标识之间的标识映射关系,以保证根据标识映射关系,实现基于异常的目标链路标识,确定该异常目标链路标识对应的目标业务标识,以及,基于异常的目标业务标识,确定该异常目标业务标识对应的目标链路标识。Further explanation, in order to ensure that the abnormal location of the target link can be performed according to the target service ID and the target link ID, it is necessary to be able to determine the corresponding and, when the target link is abnormal, based on the abnormal target service identifier, determine the target link identifier corresponding to the abnormal target service identifier; therefore, it is necessary to create a link between the target service identifier and the target link identifier An identification mapping relationship, so as to ensure that according to the identification mapping relationship, the target link identification based on the abnormality is realized, the target service identification corresponding to the abnormal target link identification is determined, and, based on the abnormal target service identification, the abnormal target service identification is determined. Target link ID.
步骤203,在基于目标链路处理业务请求的过程中,若检测到目标链路出现异常,则基于标识映射关系,对目标链路进行异常定位,得到异常定位结果。
在本申请的一种实施例中,当需要对目标链路进行针对用户的异常定位,得到异常定位结果时,可基于标识映射关系,确定异常的目标链路标识,确定该异常目标链路标识对应的目标业务标识;进而根据该目标业务标识,确定异常定位结果。In one embodiment of the present application, when it is necessary to perform abnormal location on the target link for users and obtain the abnormal location result, the abnormal target link identifier can be determined based on the identifier mapping relationship, and the abnormal target link identifier can be determined The corresponding target service identifier; and then according to the target service identifier, determine the abnormal location result.
在本申请的一种实施例中,当需要对目标链路进行针对目标链路中服务节点的异常定位,得到异常定位结果时,可基于标识映射关系,异常的目标业务标识,确定该异常目标业务标识对应的目标链路标识;进而根据该目标链路标识,确定异常定位结果。In one embodiment of the present application, when it is necessary to perform abnormal location on the target link for the service node in the target link and obtain the abnormal location result, the abnormal target can be determined based on the identification mapping relationship and the abnormal target service ID A target link identifier corresponding to the service identifier; and then according to the target link identifier, an abnormal location result is determined.
根据本申请的链路异常定位方法,通过确定业务请求对应的目标链路,保证了后续能够根据目标链路,确定目标链路标识,进而根据目标链路标识对目标链路进行异常定位,得到异常定位结果,保证了异常定位结果的准确性;通过确定目标业务标识、目标链路标识和标识映射关系,保证了后续当目标链路出现异常时,能够根据目标业务标识、目标链路标识和标识映射关系,确定异常定位结果,进而实现在微服务架构执行业务请求的过程中出现异常时,准确的定位出现异常的服务节点,以及该业务请求对应的用户信息,进一步保证了针对出现异常的服务节点的快速修复,以及异常业务请求对应的用户的快速通知,降低了当目标链路出现异常时造成的异常影响,提高了针对异常的处理效率。According to the link abnormal location method of the present application, by determining the target link corresponding to the service request, it is ensured that the target link identifier can be determined according to the target link, and then the abnormal location of the target link is performed according to the target link identifier, and the obtained The abnormal location results ensure the accuracy of the abnormal location results; by determining the target business identifier, target link identifier and identifier mapping relationship, it is ensured that when the target link is abnormal, the target service identifier, target link identifier and Identify the mapping relationship, determine the abnormal location result, and then realize the accurate location of the abnormal service node and the user information corresponding to the business request when an exception occurs in the process of executing the business request of the microservice architecture, which further ensures the abnormality of the exception. The rapid repair of service nodes and the rapid notification of users corresponding to abnormal business requests reduce the impact of abnormalities when the target link is abnormal and improve the processing efficiency for abnormalities.
需要说明的是,可通过确定定位目标,进而根据定位目标和标识映射关系,确定异常定位结果。可选地,如图3所示,图3为本申请实施例提供的一种确定异常定位结果的步骤流程图。具体的,确定异常定位结果可以包括以下步骤:It should be noted that the abnormal location result can be determined by determining the location target, and then according to the mapping relationship between the location target and the identifier. Optionally, as shown in FIG. 3 , FIG. 3 is a flow chart of steps for determining an abnormal location result provided in an embodiment of the present application. Specifically, determining the abnormal location result may include the following steps:
步骤301,基于目标链路对应的异常定位需求,确定定位目标。Step 301: Determine the location target based on the abnormal location requirement corresponding to the target link.
需要说明的是,异常定位需求中至少包含需要进行定位的定位目标,其中,定位目标可以为:目标链路对应的用户或者目标链路中出现异常的服务节点。由于,不同的定位目标,对应的标识也不相同,因此,在确定异常定位结果之前,需要根据目标链路对应的异常定位需求,确定定位目标。It should be noted that the anomaly location requirements include at least a location target to be located, where the location target may be: a user corresponding to the target link or a service node where an exception occurs in the target link. Since different positioning targets have different corresponding identifiers, it is necessary to determine the positioning target according to the abnormal positioning requirements corresponding to the target link before determining the abnormal positioning result.
进一步说明,若已知出现异常的目标链路,而异常目标链路对应的用户未知时,则定位目标即为目标链路对应的用户;若已知出现异常的业务请求对应的用户,而出现异常的服务节点未知时,则定位目标即为目标链路中出现异常的服务节点。Further explanation, if the abnormal target link is known, but the user corresponding to the abnormal target link is unknown, then the location target is the user corresponding to the target link; if the user corresponding to the abnormal service request is known, and the abnormal When the abnormal service node is unknown, the positioning target is the abnormal service node in the target link.
步骤302,基于定位目标和标识映射关系,对目标链路进行异常定位,得到定位目标对应的异常定位结果。
需要说明的是,确定异常定位结果具体可包括以下步骤:若定位目标为目标链路对应的用户,则确定目标链路对应的第一异常链路标识;基于标识映射关系,确定第一异常链路标识对应的第一异常业务标识;基于第一异常业务标识,确定定位目标对应的异常定位结果。It should be noted that determining the abnormal location result may specifically include the following steps: if the location target is the user corresponding to the target link, then determine the first abnormal link identifier corresponding to the target link; determine the first abnormal link identifier based on the identifier mapping relationship The first abnormal service identifier corresponding to the road identifier; based on the first abnormal service identifier, determine the abnormal location result corresponding to the location target.
在本申请的一种实施例中,当目标链路发生异常,则确定目标链路对应的第一异常链路标识;由于定位目标为目标链路对应的用户,因此,需要确定该用户对应的第一异常业务标识;进而,可根据标识映射关系,确定第一异常链路标识对应的第一异常业务标识,根据该第一异常业务标识,即可确定目标链路对应的用户,该目标链路对应的用户即为异常定位结果。In one embodiment of the present application, when the target link is abnormal, the first abnormal link identifier corresponding to the target link is determined; since the positioning target is the user corresponding to the target link, it is necessary to determine the corresponding The first abnormal service identifier; furthermore, according to the identifier mapping relationship, the first abnormal service identifier corresponding to the first abnormal link identifier can be determined, and according to the first abnormal service identifier, the user corresponding to the target link can be determined, and the target link The user corresponding to the path is the abnormal location result.
需要说明的是,确定异常定位结果具体可包括以下步骤:若定位目标为目标链路中出现异常的服务节点,则确定业务请求对应的第二异常业务标识;基于标识映射关系,确定第二异常业务标识对应的第二异常链路标识;基于第二异常链路标识,确定定位目标对应的异常定位结果。It should be noted that determining the abnormality location result may specifically include the following steps: if the location target is an abnormal service node in the target link, then determine the second abnormal service identifier corresponding to the service request; determine the second abnormal service identifier based on the identifier mapping relationship A second abnormal link identifier corresponding to the service identifier; based on the second abnormal link identifier, determine an abnormal location result corresponding to the location target.
在本申请的一种实施例中,当业务请求发生异常,确定业务请求对应的第二异常业务标识;由于定位目标为目标链路中出现异常的服务节点,因此,需要确定该目标链路对应的第二异常链路标识;进而,可根据标识映射关系,确定第二异常业务标识对应的第二异常链路标识;根据该第二异常链路标识,即可确定目标链路中出现异常的服务节点,该目标链路中出现异常的服务节点即为异常定位结果。In one embodiment of the present application, when the service request is abnormal, the second abnormal service identifier corresponding to the service request is determined; since the positioning target is the abnormal service node in the target link, it is necessary to determine the corresponding service node of the target link. The second abnormal link identifier; furthermore, according to the identifier mapping relationship, the second abnormal link identifier corresponding to the second abnormal service identifier can be determined; according to the second abnormal link identifier, the abnormal link in the target link can be determined Service node, the abnormal service node in the target link is the abnormal location result.
根据本申请的链路异常定位方法,通过异常定位需求,确定定位目标,保证能够根据不同的定位目标和标识映射关系,实现目标业务标识或者目标链路标识的确定,进而根据目标业务标识或者目标链路标识,确定异常定位结果;保证了确定异常定位结果的准确性,使得异常定位结果能够符合异常定位需求中的定位目标;进一步说明,通过确定第一异常链路标识,为后续确定第一异常业务标识提供了数据基础,保证了能够准确获取目标链路对应的用户,保证了当定位目标为目标链路对应的用户时,异常定位结果的快速确定;并且,通过确定第二异常业务标识,为后续确定第二异常链路标识提供了数据基础,保证了能够准确定位目标链路中出现异常的服务节点,保证了当定位目标为目标链路中出现异常的服务节点时,异常定位结果的快速确定。According to the link abnormality positioning method of the present application, the positioning target is determined through the abnormal positioning requirements, so as to ensure that the target service ID or target link ID can be determined according to different positioning targets and identification mapping relationships, and then according to the target service identification or target The link identification determines the abnormal location result; it ensures the accuracy of determining the abnormal location result, so that the abnormal location result can meet the location target in the abnormal location requirements; The abnormal service identification provides a data basis, which ensures that the user corresponding to the target link can be accurately obtained, and ensures that when the positioning target is the user corresponding to the target link, the abnormal location result can be quickly determined; and, by determining the second abnormal service identification , provides a data basis for the subsequent identification of the second abnormal link, ensures that the abnormal service node in the target link can be accurately located, and ensures that when the positioning target is the abnormal service node in the target link, the abnormal positioning result quick determination.
需要说明的是,可通过确定标准链路和待检测链路,进而确定待检测链路中的目标链路。可选地,如图4所示,图4为本申请实施例提供的一种确定目标链路的步骤流程图。具体的,确定目标链路可以包括以下步骤:It should be noted that, by determining the standard link and the link to be detected, the target link among the links to be detected can be determined. Optionally, as shown in FIG. 4 , FIG. 4 is a flow chart of steps for determining a target link provided in an embodiment of the present application. Specifically, determining the target link may include the following steps:
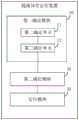
步骤401,基于用户发送的业务请求,确定业务请求对应的标准链路和待检测链路。
其中,标准链路,指的是该业务请求的业务类别对应的模板链路;待检测链路指的是根据该用户发送的业务请求,确定的未完成结构检测的链路。Wherein, the standard link refers to the template link corresponding to the service category of the service request; the link to be detected refers to the link determined according to the service request sent by the user and has not completed the structure detection.
需要说明的是,同一业务类别的业务请求对应的待检测链路均与该业务类别的标准链路具有相同的结构;因此,可通过对待检测链路与标准链路进行结构检测,以实现对待检测链路的筛选。It should be noted that the link to be detected corresponding to the service request of the same service category has the same structure as the standard link of the service category; Filtering for detection links.
需要说明的是,当需要确定标准链路和待检测链路时,具体可包括以下步骤:基于用户发送的业务请求的类型,确定业务请求对应的标准链路;基于用户发送的业务请求的语义信息,确定是否符合语义制定规则;若符合,则基于语义信息和标准链路,确定业务请求对应的待检测链路。It should be noted that when it is necessary to determine the standard link and the link to be detected, it may specifically include the following steps: based on the type of service request sent by the user, determine the standard link corresponding to the service request; based on the semantics of the service request sent by the user information to determine whether it complies with the semantic formulation rules; if so, determine the link to be detected corresponding to the service request based on the semantic information and the standard link.
进一步说明,当需要确定待检测链路时,需要保证待检测链路符合业务请求的语义信息,并且待检测链路需要包含标准链路中的服务节点,因此,需要根据语义信息和标准链路,确定待检测链路。Further explanation, when it is necessary to determine the link to be detected, it is necessary to ensure that the link to be detected conforms to the semantic information of the service request, and the link to be detected needs to contain service nodes in the standard link. Therefore, it is necessary to , to determine the link to be detected.
步骤402,基于标准链路,对待检测链路进行结构检测,确定待检测链路中的目标链路。Step 402: Based on the standard link, perform structural detection on the link to be detected, and determine a target link in the link to be detected.
需要说明的是,在对待检测链路进行结构检测时,具体可包括以下步骤,将标准链路和待检测链路进行叠加处理;基于叠加处理结果,对待检测链路进行结构检测,确定待检测链路中的目标链路。It should be noted that, when the structure detection of the link to be detected is carried out, the following steps may be specifically included: performing superimposition processing on the standard link and the link to be detected; The target link in the link.
进一步说明,当基于叠加处理结果,对待检测链路进行结构检测时,需要确定叠加处理结果中的待检测链路与标准链路的结构完全相同,若叠加处理结果中的待检测链路与标准链路的结构完全相同,则表示待检测链路的结构检测通过;若叠加处理结果中的待检测链路与标准链路的结构不完全相同,则表示待检测链路的结构检测未通过。It is further explained that when the structure detection of the link to be detected is performed based on the superposition processing result, it is necessary to determine that the structure of the link to be detected in the superposition processing result is exactly the same as that of the standard link. If the structures of the links are exactly the same, it means that the structure detection of the link to be detected passes; if the structure of the link to be detected in the superposition processing result is not exactly the same as that of the standard link, it means that the structure detection of the link to be detected fails.
在本申请的一种实施例中,当将标准链路和待检测链路进行叠加处理后,叠加处理后的标准链路和待检测链路可如图5所示,图5为本申请实施例提供的一种标准链路和待检测链路的叠加图,其中,step01至step08指的是不同的服务节点,并且,图5中的实线部分即为标准链路,图5中的虚线部分即为待检测链路,当需要对待检测链路进行结构检测时,可确定待检测链路仅包括step01、step02、step04;而标准链路中还包含step05、step06和step08,因此,可确定叠加处理结果中的待检测链路与标准链路的结构不完全相同,则表示待检测链路的结构检测未通过。In one embodiment of the present application, after superimposing the standard link and the link to be detected, the superimposed standard link and the link to be detected can be shown in Figure 5, and Figure 5 is an implementation of the present application. An overlay diagram of a standard link and a link to be detected is provided as an example, wherein step01 to step08 refer to different service nodes, and the solid line in Figure 5 is the standard link, and the dotted line in Figure 5 Part of it is the link to be detected. When the structure detection of the link to be detected is required, it can be determined that the link to be detected only includes step01, step02, and step04; while the standard link also includes step05, step06, and step08. Therefore, it can be determined If the structure of the link to be detected in the superposition processing result is not exactly the same as that of the standard link, it means that the structure detection of the link to be detected has failed.
根据本申请的链路异常定位方法,通过确定标准链路和待检测链路,保证后续能够标准链路对待检测链路进行结构检测,进而实现目标链路的确定,保证了目标链路均与标准链路具有相同的结构,保证了目标链路的准确性,保证了用户业务请求的顺利执行,防止由于目标链路的结构错误而导致用户业务请求无法顺利执行。进一步说明,通过对标准链路和待检测链路进行叠加处理,保证了能够更加准确的对待检测链路进行结构检测,提高了对待检测链路进行结构检测的效率,实现了快速判断待检测链路与标准链路是否存在结构差异。According to the link anomaly location method of the present application, by determining the standard link and the link to be detected, it is ensured that the structure detection of the standard link and the link to be detected can be carried out subsequently, and then the determination of the target link is realized, ensuring that the target link is consistent with the The standard link has the same structure, which ensures the accuracy of the target link, ensures the smooth execution of user service requests, and prevents the smooth execution of user service requests due to the wrong structure of the target link. It is further explained that by superimposing the standard link and the link to be detected, it is ensured that the structure detection of the link to be detected can be performed more accurately, the efficiency of structural detection of the link to be detected is improved, and the rapid judgment of the link to be detected is realized. Whether there are structural differences between the road and the standard link.
在本申请的一种实施例中,如图6所示,图6为本申请实施例提供的另一种链路异常定位方法的流程图,当对目标链路进行异常定位时,具体可包括以下步骤:In one embodiment of the present application, as shown in FIG. 6, FIG. 6 is a flow chart of another link abnormal location method provided in the embodiment of the present application. When performing abnormal location on the target link, it may specifically include The following steps:
步骤601,基于用户发送的业务请求的类型,确定业务请求对应的标准链路。
步骤602,基于用户发送的业务请求的语义信息,确定是否符合语义制定规则。
步骤603,若符合,则基于语义信息和标准链路,确定业务请求对应的待检测链路。
步骤604,将标准链路和待检测链路进行叠加处理。
步骤605,基于叠加处理结果,对待检测链路进行结构检测,确定待检测链路中的目标链路。Step 605: Based on the superposition processing result, perform structure detection on the links to be detected, and determine a target link in the links to be detected.
步骤606,确定业务请求对应的目标业务标识,以及目标链路中每一服务节点对应的目标链路标识,并构建目标业务标识和目标链路标识之间的标识映射关系。Step 606: Determine the target service ID corresponding to the service request and the target link ID corresponding to each service node in the target link, and construct an ID mapping relationship between the target service ID and the target link ID.
步骤607,在基于目标链路处理业务请求的过程中,若检测到目标链路出现异常,基于目标链路对应的异常定位需求,确定定位目标。Step 607: In the process of processing the service request based on the target link, if an abnormality is detected in the target link, determine the positioning target based on the abnormal location requirements corresponding to the target link.
步骤608,基于定位目标和标识映射关系,对目标链路进行异常定位,得到定位目标对应的异常定位结果。
在本申请的一种实施例中,若定位目标为目标链路对应的用户,则确定目标链路对应的第一异常链路标识;基于标识映射关系,确定第一异常链路标识对应的第一异常业务标识;基于第一异常业务标识,确定定位目标对应的异常定位结果。In one embodiment of the present application, if the positioning target is the user corresponding to the target link, then determine the first abnormal link identifier corresponding to the target link; based on the identifier mapping relationship, determine the first abnormal link identifier corresponding to the first abnormal link identifier. An abnormal service identifier; based on the first abnormal service identifier, determine an abnormal location result corresponding to the location target.
在本申请的另一种实施例中,若定位目标为目标链路中出现异常的服务节点,则确定业务请求对应的第二异常业务标识;基于标识映射关系,确定第二异常业务标识对应的第二异常链路标识;基于第二异常链路标识,确定定位目标对应的异常定位结果。In another embodiment of the present application, if the positioning target is an abnormal service node in the target link, then determine the second abnormal service identifier corresponding to the service request; based on the identifier mapping relationship, determine the corresponding second abnormal service identifier A second abnormal link identifier; based on the second abnormal link identifier, determine an abnormal location result corresponding to the location target.
根据本申请的链路异常定位方法,通过确定业务请求对应的目标链路,保证了后续能够根据目标链路,确定目标链路标识,进而根据目标链路标识对目标链路进行异常定位,得到异常定位结果,保证了异常定位结果的准确性;通过确定目标业务标识、目标链路标识和标识映射关系,保证了后续当目标链路出现异常时,能够根据目标业务标识、目标链路标识和标识映射关系,确定异常定位结果,进而实现在微服务架构执行业务请求的过程中出现异常时,准确的定位出现异常的服务节点,以及该业务请求对应的用户信息,进一步保证了针对出现异常的服务节点的快速修复,以及异常业务请求对应的用户的快速通知,降低了当目标链路出现异常时造成的异常影响,提高了针对异常的处理效率。According to the link abnormal location method of the present application, by determining the target link corresponding to the service request, it is ensured that the target link identifier can be determined according to the target link, and then the abnormal location of the target link is performed according to the target link identifier, and the obtained The abnormal location results ensure the accuracy of the abnormal location results; by determining the target business identifier, target link identifier and identifier mapping relationship, it is ensured that when the target link is abnormal, the target service identifier, target link identifier and Identify the mapping relationship, determine the abnormal location result, and then realize the accurate location of the abnormal service node and the user information corresponding to the business request when an exception occurs in the process of executing the business request of the microservice architecture, which further ensures the abnormality of the exception. The rapid repair of service nodes and the rapid notification of users corresponding to abnormal business requests reduce the impact of abnormalities when the target link is abnormal and improve the processing efficiency for abnormalities.
应该理解的是,虽然如上的各实施例所涉及的流程图中的各个步骤按照箭头的指示依次显示,但是这些步骤并不是必然按照箭头指示的顺序依次执行。除非本文中有明确的说明,这些步骤的执行并没有严格的顺序限制,这些步骤可以以其它的顺序执行。而且,如上的各实施例所涉及的流程图中的至少一部分步骤可以包括多个步骤或者多个阶段,这些步骤或者阶段并不必然是在同一时刻执行完成,而是可以在不同的时刻执行,这些步骤或者阶段的执行顺序也不必然是依次进行,而是可以与其它步骤或者其它步骤中的步骤或者阶段的至少一部分轮流或者交替地执行。It should be understood that although the steps in the flow charts involved in the above embodiments are shown sequentially as indicated by the arrows, these steps are not necessarily executed sequentially in the order indicated by the arrows. Unless otherwise specified herein, there is no strict order restriction on the execution of these steps, and these steps can be executed in other orders. Moreover, at least some of the steps in the flow charts involved in the above embodiments may include multiple steps or stages, and these steps or stages are not necessarily executed at the same time, but may be executed at different times, The execution order of these steps or stages is not necessarily performed sequentially, but may be performed in turn or alternately with other steps or at least a part of steps or stages in other steps.
基于同样的发明构思,本申请实施例还提供了一种用于实现上述所涉及的链路异常定位方法的链路异常定位装置。该装置所提供的解决问题的实现方案与上述方法中所记载的实现方案相似,故下面所提供的一个或多个链路异常定位装置实施例中的具体限定可以参见上文中对于链路异常定位方法的限定,在此不再赘述。Based on the same inventive concept, an embodiment of the present application further provides a link anomaly locating device for implementing the above-mentioned link anomaly locating method. The solution to the problem provided by the device is similar to the implementation described in the above method, so for the specific limitations in one or more embodiments of the link abnormal location device provided below, please refer to the link abnormal location above The limitation of the method will not be repeated here.
在一个实施例中,如图7所示,图7为本申请实施例提供的第一种链路异常定位装置的结构框图,提供了一种链路异常定位装置,包括:第一确定模块10、第二确定模块20和定位模块30,其中:In one embodiment, as shown in FIG. 7, FIG. 7 is a structural block diagram of the first link anomaly locating device provided in the embodiment of the present application, which provides a link anomaly locating device, including: a
第一确定模块10,用于基于用户发送的业务请求,确定业务请求对应的目标链路。The first determining
第二确定模块20,用于确定业务请求对应的目标业务标识,以及目标链路中每一服务节点对应的目标链路标识,并构建目标业务标识和目标链路标识之间的标识映射关系。The
定位模块30,用于在基于目标链路处理业务请求的过程中,若检测到目标链路出现异常,则基于标识映射关系,对目标链路进行异常定位,得到异常定位结果。The
根据本申请的链路异常定位装置,通过确定业务请求对应的目标链路,保证了后续能够根据目标链路,确定目标链路标识,进而根据目标链路标识对目标链路进行异常定位,得到异常定位结果,保证了异常定位结果的准确性;通过确定目标业务标识、目标链路标识和标识映射关系,保证了后续当目标链路出现异常时,能够根据目标业务标识、目标链路标识和标识映射关系,确定异常定位结果,进而实现在微服务架构执行业务请求的过程中出现异常时,准确的定位出现异常的服务节点,以及该业务请求对应的用户信息,进一步保证了针对出现异常的服务节点的快速修复,以及异常业务请求对应的用户的快速通知,降低了当目标链路出现异常时造成的异常影响,提高了针对异常的处理效率。According to the link abnormality locating device of the present application, by determining the target link corresponding to the service request, it is ensured that the target link identifier can be determined subsequently according to the target link, and then the abnormal location of the target link is performed according to the target link identifier, and the obtained The abnormal location results ensure the accuracy of the abnormal location results; by determining the target business identifier, target link identifier and identifier mapping relationship, it is ensured that when the target link is abnormal, the target service identifier, target link identifier and Identify the mapping relationship, determine the abnormal location result, and then realize the accurate location of the abnormal service node and the user information corresponding to the business request when an exception occurs in the process of executing the business request of the microservice architecture, which further ensures the abnormality of the exception. The rapid repair of service nodes and the rapid notification of users corresponding to abnormal business requests reduce the impact of abnormalities when the target link is abnormal and improve the processing efficiency for abnormalities.
在一个实施例中,如图8所示,图8为本申请实施例提供的第二种链路异常定位装置的结构框图,提供了一种链路异常定位装置,该链路异常定位装置中定位模块30包括:第一确定单元31和定位单元32,其中:In one embodiment, as shown in FIG. 8, FIG. 8 is a structural block diagram of a second link anomaly locating device provided in an embodiment of the present application, which provides a link anomaly locating device, in which the link anomaly locating device The
第一确定单元31,用于基于目标链路对应的异常定位需求,确定定位目标。The first determining
定位单元32,用于基于定位目标和标识映射关系,对目标链路进行异常定位,得到定位目标对应的异常定位结果。The
在本申请的一种实施例中,若定位目标为目标链路对应的用户,则确定目标链路对应的第一异常链路标识;基于标识映射关系,确定第一异常链路标识对应的第一异常业务标识;基于第一异常业务标识,确定定位目标对应的异常定位结果。In one embodiment of the present application, if the positioning target is the user corresponding to the target link, then determine the first abnormal link identifier corresponding to the target link; based on the identifier mapping relationship, determine the first abnormal link identifier corresponding to the first abnormal link identifier. An abnormal service identifier; based on the first abnormal service identifier, determine an abnormal location result corresponding to the location target.
在本申请的一种实施例中,若定位目标为目标链路中出现异常的服务节点,则确定业务请求对应的第二异常业务标识;基于标识映射关系,确定第二异常业务标识对应的第二异常链路标识;基于第二异常链路标识,确定定位目标对应的异常定位结果。In an embodiment of the present application, if the positioning target is an abnormal service node in the target link, then determine the second abnormal service identifier corresponding to the service request; based on the identifier mapping relationship, determine the second abnormal service identifier corresponding to the second abnormal service identifier. 2. Abnormal link identification: Based on the second abnormal link identification, determine the abnormal positioning result corresponding to the positioning target.
根据本申请的链路异常定位装置,通过异常定位需求,确定定位目标,保证能够根据不同的定位目标和标识映射关系,实现目标业务标识或者目标链路标识的确定,进而根据目标业务标识或者目标链路标识,确定异常定位结果;保证了确定异常定位结果的准确性,使得异常定位结果能够符合异常定位需求中的定位目标;进一步说明,通过确定第一异常链路标识,为后续确定第一异常业务标识提供了数据基础,保证了能够准确获取目标链路对应的用户,保证了当定位目标为目标链路对应的用户时,异常定位结果的快速确定;并且,通过确定第二异常业务标识,为后续确定第二异常链路标识提供了数据基础,保证了能够准确定位目标链路中出现异常的服务节点,保证了当定位目标为目标链路中出现异常的服务节点时,异常定位结果的快速确定。According to the link abnormality positioning device of the present application, the positioning target is determined according to the abnormal positioning requirements, so as to ensure that the target service ID or the target link ID can be determined according to different positioning targets and identification mapping relationships, and then according to the target service identification or target The link identification determines the abnormal location result; it ensures the accuracy of determining the abnormal location result, so that the abnormal location result can meet the location target in the abnormal location requirements; The abnormal service identification provides a data basis, which ensures that the user corresponding to the target link can be accurately obtained, and ensures that when the positioning target is the user corresponding to the target link, the abnormal location result can be quickly determined; and, by determining the second abnormal service identification , provides a data basis for the subsequent identification of the second abnormal link, ensures that the abnormal service node in the target link can be accurately located, and ensures that when the positioning target is the abnormal service node in the target link, the abnormal positioning result quick determination.
在一个实施例中,如图9所示,图9为本申请实施例提供的第三种链路异常定位装置的结构框图,提供了一种链路异常定位装置,该链路异常定位装置中第一确定模块10包括:第二确定单元11和第三确定单元12,其中:In one embodiment, as shown in FIG. 9, FIG. 9 is a structural block diagram of a third link anomaly locating device provided in an embodiment of the present application, which provides a link anomaly locating device, in which the link anomaly locating device The first determining
第二确定单元11,用于基于用户发送的业务请求,确定业务请求对应的标准链路和待检测链路。The
需要说明的是,基于用户发送的业务请求的类型,确定业务请求对应的标准链路;基于用户发送的业务请求的语义信息,确定是否符合语义制定规则;若符合,则基于语义信息和标准链路,确定业务请求对应的待检测链路。It should be noted that, based on the type of business request sent by the user, the standard link corresponding to the business request is determined; based on the semantic information of the business request sent by the user, it is determined whether it complies with the semantic formulation rules; if so, based on the semantic information and the standard link Determine the link to be detected corresponding to the service request.
第三确定单元12,用于基于标准链路,对待检测链路进行结构检测,确定待检测链路中的目标链路。The third determining
需要说明的是,将标准链路和待检测链路进行叠加处理;基于叠加处理结果,对待检测链路进行结构检测,确定待检测链路中的目标链路。It should be noted that the standard link and the link to be detected are superimposed; based on the result of the superposition processing, the structure of the link to be detected is detected to determine the target link in the link to be detected.
根据本申请的链路异常定位装置,通过确定标准链路和待检测链路,保证后续能够标准链路对待检测链路进行结构检测,进而实现目标链路的确定,保证了目标链路均与标准链路具有相同的结构,保证了目标链路的准确性,保证了用户业务请求的顺利执行,防止由于目标链路的结构错误而导致用户业务请求无法顺利执行。进一步说明,通过对标准链路和待检测链路进行叠加处理,保证了能够更加准确的对待检测链路进行结构检测,提高了对待检测链路进行结构检测的效率,实现了快速判断待检测链路与标准链路是否存在结构差异。According to the link anomaly positioning device of the present application, by determining the standard link and the link to be detected, it is ensured that the follow-up structure detection of the standard link and the link to be detected can be carried out, and then the determination of the target link is realized, ensuring that the target link is consistent with the The standard link has the same structure, which ensures the accuracy of the target link, ensures the smooth execution of user service requests, and prevents the smooth execution of user service requests due to the wrong structure of the target link. It is further explained that by superimposing the standard link and the link to be detected, it is ensured that the structure detection of the link to be detected can be performed more accurately, the efficiency of structural detection of the link to be detected is improved, and the rapid judgment of the link to be detected is realized. Whether there are structural differences between the road and the standard link.
上述链路异常定位装置中的各个模块可全部或部分通过软件、硬件及其组合来实现。上述各模块可以硬件形式内嵌于或独立于计算机设备中的处理器中,也可以以软件形式存储于计算机设备中的存储器中,以便于处理器调用执行以上各个模块对应的操作。Each module in the above-mentioned link abnormality locating device can be fully or partially realized by software, hardware and a combination thereof. The above-mentioned modules can be embedded in or independent of the processor in the computer device in the form of hardware, and can also be stored in the memory of the computer device in the form of software, so that the processor can invoke and execute the corresponding operations of the above-mentioned modules.
在一个实施例中,提供了一种计算机设备,该计算机设备可以是终端,其内部结构图可以如图10所示。该计算机设备包括通过系统总线连接的处理器、存储器、通信接口、显示屏和输入装置。其中,该计算机设备的处理器用于提供计算和控制能力。该计算机设备的存储器包括非易失性存储介质、内存储器。该非易失性存储介质存储有操作系统和计算机程序。该内存储器为非易失性存储介质中的操作系统和计算机程序的运行提供环境。该计算机设备的通信接口用于与外部的终端进行有线或无线方式的通信,无线方式可通过WIFI、移动蜂窝网络、NFC(近场通信)或其他技术实现。该计算机程序被处理器执行时以实现一种链路异常定位方法。该计算机设备的显示屏可以是液晶显示屏或者电子墨水显示屏,该计算机设备的输入装置可以是显示屏上覆盖的触摸层,也可以是计算机设备外壳上设置的按键、轨迹球或触控板,还可以是外接的键盘、触控板或鼠标等。In one embodiment, a computer device is provided. The computer device may be a terminal, and its internal structure may be as shown in FIG. 10 . The computer device includes a processor, a memory, a communication interface, a display screen and an input device connected through a system bus. Wherein, the processor of the computer device is used to provide calculation and control capabilities. The memory of the computer device includes a non-volatile storage medium and an internal memory. The non-volatile storage medium stores an operating system and computer programs. The internal memory provides an environment for the operation of the operating system and computer programs in the non-volatile storage medium. The communication interface of the computer device is used to communicate with an external terminal in a wired or wireless manner, and the wireless manner can be realized through WIFI, mobile cellular network, NFC (Near Field Communication) or other technologies. When the computer program is executed by the processor, a link abnormality location method is realized. The display screen of the computer device may be a liquid crystal display screen or an electronic ink display screen, and the input device of the computer device may be a touch layer covered on the display screen, or a button, a trackball or a touch pad provided on the casing of the computer device , and can also be an external keyboard, touchpad, or mouse.
本领域技术人员可以理解,图10中示出的结构,仅仅是与本申请方案相关的部分结构的框图,并不构成对本申请方案所应用于其上的计算机设备的限定,具体的计算机设备可以包括比图中所示更多或更少的部件,或者组合某些部件,或者具有不同的部件布置。Those skilled in the art can understand that the structure shown in Figure 10 is only a block diagram of a part of the structure related to the solution of this application, and does not constitute a limitation to the computer equipment on which the solution of this application is applied. The specific computer equipment can be More or fewer components than shown in the figures may be included, or some components may be combined, or have a different arrangement of components.
在一个实施例中,提供了一种计算机设备,包括存储器和处理器,存储器中存储有计算机程序,该处理器执行计算机程序时实现以下步骤:In one embodiment, a computer device is provided, including a memory and a processor, a computer program is stored in the memory, and the processor implements the following steps when executing the computer program:
基于用户发送的业务请求,确定业务请求对应的目标链路;Determine the target link corresponding to the service request based on the service request sent by the user;
确定业务请求对应的目标业务标识,以及目标链路中每一服务节点对应的目标链路标识,并构建目标业务标识和目标链路标识之间的标识映射关系;Determine the target service identifier corresponding to the service request, and the target link identifier corresponding to each service node in the target link, and construct an identifier mapping relationship between the target service identifier and the target link identifier;
在基于目标链路处理业务请求的过程中,若检测到目标链路出现异常,则基于标识映射关系,对目标链路进行异常定位,得到异常定位结果。In the process of processing service requests based on the target link, if an abnormality is detected in the target link, the abnormality location of the target link is performed based on the identification mapping relationship, and an abnormality location result is obtained.
在一个实施例中,处理器执行计算机程序时还实现以下步骤:In one embodiment, the following steps are also implemented when the processor executes the computer program:
基于目标链路对应的异常定位需求,确定定位目标;Determine the positioning target based on the abnormal positioning requirements corresponding to the target link;
基于定位目标和标识映射关系,对目标链路进行异常定位,得到定位目标对应的异常定位结果。Based on the mapping relationship between the positioning target and the identification, the abnormal positioning of the target link is performed, and the abnormal positioning result corresponding to the positioning target is obtained.
在一个实施例中,处理器执行计算机程序时还实现以下步骤:In one embodiment, the following steps are also implemented when the processor executes the computer program:
若定位目标为目标链路对应的用户,则确定目标链路对应的第一异常链路标识;If the positioning target is the user corresponding to the target link, then determine the first abnormal link identifier corresponding to the target link;
基于标识映射关系,确定第一异常链路标识对应的第一异常业务标识;Determine a first abnormal service identifier corresponding to the first abnormal link identifier based on the identifier mapping relationship;
基于第一异常业务标识,确定定位目标对应的异常定位结果。Based on the first abnormal service identifier, an abnormal positioning result corresponding to the positioning target is determined.
在一个实施例中,处理器执行计算机程序时还实现以下步骤:In one embodiment, the following steps are also implemented when the processor executes the computer program:
若定位目标为目标链路中出现异常的服务节点,则确定业务请求对应的第二异常业务标识;If the positioning target is an abnormal service node in the target link, then determine the second abnormal service identifier corresponding to the service request;
基于标识映射关系,确定第二异常业务标识对应的第二异常链路标识;Determine a second abnormal link identifier corresponding to the second abnormal service identifier based on the identifier mapping relationship;
基于第二异常链路标识,确定定位目标对应的异常定位结果。Based on the second abnormal link identifier, an abnormal positioning result corresponding to the positioning target is determined.
在一个实施例中,处理器执行计算机程序时还实现以下步骤:In one embodiment, the following steps are also implemented when the processor executes the computer program:
基于用户发送的业务请求,确定业务请求对应的标准链路和待检测链路;Based on the service request sent by the user, determine the standard link and the link to be detected corresponding to the service request;
基于标准链路,对待检测链路进行结构检测,确定待检测链路中的目标链路。Based on the standard link, the structure detection of the link to be detected is carried out, and the target link in the link to be detected is determined.
在一个实施例中,处理器执行计算机程序时还实现以下步骤:In one embodiment, the following steps are also implemented when the processor executes the computer program:
将标准链路和待检测链路进行叠加处理;Superimpose the standard link and the link to be detected;
基于叠加处理结果,对待检测链路进行结构检测,确定待检测链路中的目标链路。Based on the superposition processing results, the structure detection of the link to be detected is carried out, and the target link in the link to be detected is determined.
在一个实施例中,处理器执行计算机程序时还实现以下步骤:In one embodiment, the following steps are also implemented when the processor executes the computer program:
基于用户发送的业务请求的类型,确定业务请求对应的标准链路;Based on the type of service request sent by the user, determine the standard link corresponding to the service request;
基于用户发送的业务请求的语义信息,确定是否符合语义制定规则;Based on the semantic information of the business request sent by the user, determine whether it complies with the semantic formulation rules;
若符合,则基于语义信息和标准链路,确定业务请求对应的待检测链路。If so, the link to be detected corresponding to the service request is determined based on the semantic information and the standard link.
在一个实施例中,提供了一种计算机可读存储介质,其上存储有计算机程序,计算机程序被处理器执行时实现以下步骤:In one embodiment, a computer-readable storage medium is provided, on which a computer program is stored, and when the computer program is executed by a processor, the following steps are implemented:
基于用户发送的业务请求,确定业务请求对应的目标链路;Determine the target link corresponding to the service request based on the service request sent by the user;
确定业务请求对应的目标业务标识,以及目标链路中每一服务节点对应的目标链路标识,并构建目标业务标识和目标链路标识之间的标识映射关系;Determine the target service identifier corresponding to the service request, and the target link identifier corresponding to each service node in the target link, and construct an identifier mapping relationship between the target service identifier and the target link identifier;
在基于目标链路处理业务请求的过程中,若检测到目标链路出现异常,则基于标识映射关系,对目标链路进行异常定位,得到异常定位结果。In the process of processing service requests based on the target link, if an abnormality is detected in the target link, the abnormality location of the target link is performed based on the identification mapping relationship, and an abnormality location result is obtained.
在一个实施例中,计算机程序被处理器执行时还实现以下步骤:In one embodiment, when the computer program is executed by the processor, the following steps are also implemented:
基于目标链路对应的异常定位需求,确定定位目标;Determine the positioning target based on the abnormal positioning requirements corresponding to the target link;
基于定位目标和标识映射关系,对目标链路进行异常定位,得到定位目标对应的异常定位结果。Based on the mapping relationship between the positioning target and the identification, the abnormal positioning of the target link is performed, and the abnormal positioning result corresponding to the positioning target is obtained.
在一个实施例中,计算机程序被处理器执行时还实现以下步骤:In one embodiment, when the computer program is executed by the processor, the following steps are also implemented:
若定位目标为目标链路对应的用户,则确定目标链路对应的第一异常链路标识;If the positioning target is the user corresponding to the target link, then determine the first abnormal link identifier corresponding to the target link;
基于标识映射关系,确定第一异常链路标识对应的第一异常业务标识;Determine a first abnormal service identifier corresponding to the first abnormal link identifier based on the identifier mapping relationship;
基于第一异常业务标识,确定定位目标对应的异常定位结果。Based on the first abnormal service identifier, an abnormal positioning result corresponding to the positioning target is determined.
在一个实施例中,计算机程序被处理器执行时还实现以下步骤:In one embodiment, when the computer program is executed by the processor, the following steps are also implemented:
若定位目标为目标链路中出现异常的服务节点,则确定业务请求对应的第二异常业务标识;If the positioning target is an abnormal service node in the target link, then determine the second abnormal service identifier corresponding to the service request;
基于标识映射关系,确定第二异常业务标识对应的第二异常链路标识;Determine a second abnormal link identifier corresponding to the second abnormal service identifier based on the identifier mapping relationship;
基于第二异常链路标识,确定定位目标对应的异常定位结果。Based on the second abnormal link identifier, an abnormal positioning result corresponding to the positioning target is determined.
在一个实施例中,计算机程序被处理器执行时还实现以下步骤:In one embodiment, when the computer program is executed by the processor, the following steps are also implemented:
基于用户发送的业务请求,确定业务请求对应的标准链路和待检测链路;Based on the service request sent by the user, determine the standard link and the link to be detected corresponding to the service request;
基于标准链路,对待检测链路进行结构检测,确定待检测链路中的目标链路。Based on the standard link, the structure detection of the link to be detected is carried out, and the target link in the link to be detected is determined.
在一个实施例中,计算机程序被处理器执行时还实现以下步骤:In one embodiment, when the computer program is executed by the processor, the following steps are also implemented:
将标准链路和待检测链路进行叠加处理;Superimpose the standard link and the link to be detected;
基于叠加处理结果,对待检测链路进行结构检测,确定待检测链路中的目标链路。Based on the superposition processing results, the structure detection of the link to be detected is carried out, and the target link in the link to be detected is determined.
在一个实施例中,计算机程序被处理器执行时还实现以下步骤:In one embodiment, when the computer program is executed by the processor, the following steps are also implemented:
基于用户发送的业务请求的类型,确定业务请求对应的标准链路;Based on the type of service request sent by the user, determine the standard link corresponding to the service request;
基于用户发送的业务请求的语义信息,确定是否符合语义制定规则;Based on the semantic information of the business request sent by the user, determine whether it complies with the semantic formulation rules;
若符合,则基于语义信息和标准链路,确定业务请求对应的待检测链路。If so, the link to be detected corresponding to the service request is determined based on the semantic information and the standard link.
在一个实施例中,提供了一种计算机程序产品,包括计算机程序,该计算机程序被处理器执行时实现以下步骤:In one embodiment, a computer program product is provided, comprising a computer program, which, when executed by a processor, implements the following steps:
基于用户发送的业务请求,确定业务请求对应的目标链路;Determine the target link corresponding to the service request based on the service request sent by the user;
确定业务请求对应的目标业务标识,以及目标链路中每一服务节点对应的目标链路标识,并构建目标业务标识和目标链路标识之间的标识映射关系;Determine the target service identifier corresponding to the service request, and the target link identifier corresponding to each service node in the target link, and construct an identifier mapping relationship between the target service identifier and the target link identifier;
在基于目标链路处理业务请求的过程中,若检测到目标链路出现异常,则基于标识映射关系,对目标链路进行异常定位,得到异常定位结果。In the process of processing service requests based on the target link, if an abnormality is detected in the target link, the abnormality location of the target link is performed based on the identification mapping relationship, and an abnormality location result is obtained.
在一个实施例中,计算机程序被处理器执行时还实现以下步骤:In one embodiment, when the computer program is executed by the processor, the following steps are also implemented:
基于目标链路对应的异常定位需求,确定定位目标;Determine the positioning target based on the abnormal positioning requirements corresponding to the target link;
基于定位目标和标识映射关系,对目标链路进行异常定位,得到定位目标对应的异常定位结果。Based on the mapping relationship between the positioning target and the identification, the abnormal positioning of the target link is performed, and the abnormal positioning result corresponding to the positioning target is obtained.
在一个实施例中,计算机程序被处理器执行时还实现以下步骤:In one embodiment, when the computer program is executed by the processor, the following steps are also implemented:
若定位目标为目标链路对应的用户,则确定目标链路对应的第一异常链路标识;If the positioning target is the user corresponding to the target link, then determine the first abnormal link identifier corresponding to the target link;
基于标识映射关系,确定第一异常链路标识对应的第一异常业务标识;Determine a first abnormal service identifier corresponding to the first abnormal link identifier based on the identifier mapping relationship;
基于第一异常业务标识,确定定位目标对应的异常定位结果。Based on the first abnormal service identifier, an abnormal positioning result corresponding to the positioning target is determined.
在一个实施例中,计算机程序被处理器执行时还实现以下步骤:In one embodiment, when the computer program is executed by the processor, the following steps are also implemented:
若定位目标为目标链路中出现异常的服务节点,则确定业务请求对应的第二异常业务标识;If the positioning target is an abnormal service node in the target link, then determine the second abnormal service identifier corresponding to the service request;
基于标识映射关系,确定第二异常业务标识对应的第二异常链路标识;Determine a second abnormal link identifier corresponding to the second abnormal service identifier based on the identifier mapping relationship;
基于第二异常链路标识,确定定位目标对应的异常定位结果。Based on the second abnormal link identifier, an abnormal positioning result corresponding to the positioning target is determined.
在一个实施例中,计算机程序被处理器执行时还实现以下步骤:In one embodiment, when the computer program is executed by the processor, the following steps are also implemented:
基于用户发送的业务请求,确定业务请求对应的标准链路和待检测链路;Based on the service request sent by the user, determine the standard link and the link to be detected corresponding to the service request;
基于标准链路,对待检测链路进行结构检测,确定待检测链路中的目标链路。Based on the standard link, the structure detection of the link to be detected is carried out, and the target link in the link to be detected is determined.
在一个实施例中,计算机程序被处理器执行时还实现以下步骤:In one embodiment, when the computer program is executed by the processor, the following steps are also implemented:
将标准链路和待检测链路进行叠加处理;Superimpose the standard link and the link to be detected;
基于叠加处理结果,对待检测链路进行结构检测,确定待检测链路中的目标链路。Based on the superposition processing results, the structure detection of the link to be detected is carried out, and the target link in the link to be detected is determined.
在一个实施例中,计算机程序被处理器执行时还实现以下步骤:In one embodiment, when the computer program is executed by the processor, the following steps are also implemented:
基于用户发送的业务请求的类型,确定业务请求对应的标准链路;Based on the type of service request sent by the user, determine the standard link corresponding to the service request;
基于用户发送的业务请求的语义信息,确定是否符合语义制定规则;Based on the semantic information of the business request sent by the user, determine whether it complies with the semantic formulation rules;
若符合,则基于语义信息和标准链路,确定业务请求对应的待检测链路。If so, the link to be detected corresponding to the service request is determined based on the semantic information and the standard link.
需要说明的是,本申请所涉及的用户信息(包括但不限于用户设备信息、用户个人信息等)和数据(包括但不限于用于分析的数据、存储的数据、展示的数据等),均为经用户授权或者经过各方充分授权的信息和数据。It should be noted that the user information (including but not limited to user equipment information, user personal information, etc.) and data (including but not limited to data used for analysis, stored data, displayed data, etc.) involved in this application are all Information and data authorized by the user or fully authorized by all parties.
本领域普通技术人员可以理解实现上述实施例方法中的全部或部分流程,是可以通过计算机程序来指令相关的硬件来完成,的计算机程序可存储于一非易失性计算机可读取存储介质中,该计算机程序在执行时,可包括如上述各方法的实施例的流程。其中,本申请所提供的各实施例中所使用的对存储器、数据库或其它介质的任何引用,均可包括非易失性和易失性存储器中的至少一种。非易失性存储器可包括只读存储器(Read-OnlyMemory,ROM)、磁带、软盘、闪存、光存储器、高密度嵌入式非易失性存储器、阻变存储器(ReRAM)、磁变存储器(Magnetoresistive Random Access Memory,MRAM)、铁电存储器(Ferroelectric Random Access Memory,FRAM)、相变存储器(Phase Change Memory,PCM)、石墨烯存储器等。易失性存储器可包括随机存取存储器(Random Access Memory,RAM)或外部高速缓冲存储器等。作为说明而非局限,RAM可以是多种形式,比如静态随机存取存储器(Static Random Access Memory,SRAM)或动态随机存取存储器(Dynamic RandomAccess Memory,DRAM)等。本申请所提供的各实施例中所涉及的数据库可包括关系型数据库和非关系型数据库中至少一种。非关系型数据库可包括基于区块链的分布式数据库等,不限于此。本申请所提供的各实施例中所涉及的处理器可为通用处理器、中央处理器、图形处理器、数字信号处理器、可编程逻辑器、基于量子计算的数据处理逻辑器等,不限于此。Those of ordinary skill in the art can understand that realizing all or part of the processes in the methods of the above embodiments can be completed by instructing related hardware through computer programs, and the computer programs can be stored in a non-volatile computer-readable storage medium , when the computer program is executed, it may include the procedures of the embodiments of the above-mentioned methods. Wherein, any reference to storage, database or other media used in the various embodiments provided in the present application may include at least one of non-volatile and volatile storage. Non-volatile memory can include read-only memory (Read-Only Memory, ROM), tape, floppy disk, flash memory, optical memory, high-density embedded non-volatile memory, resistive variable memory (ReRAM), magnetic variable memory (Magnetoresistive Random Access Memory, MRAM), Ferroelectric Random Access Memory (FRAM), Phase Change Memory (Phase Change Memory, PCM), graphene memory, etc. The volatile memory may include random access memory (Random Access Memory, RAM) or external cache memory, etc. By way of illustration and not limitation, RAM can be in various forms, such as Static Random Access Memory (SRAM) or Dynamic Random Access Memory (DRAM). The databases involved in the various embodiments provided in this application may include at least one of a relational database and a non-relational database. The non-relational database may include a blockchain-based distributed database, etc., but is not limited thereto. The processors involved in the various embodiments provided by this application can be general-purpose processors, central processing units, graphics processors, digital signal processors, programmable logic devices, data processing logic devices based on quantum computing, etc., and are not limited to this.
以上实施例的各技术特征可以进行任意的组合,为使描述简洁,未对上述实施例中的各个技术特征所有可能的组合都进行描述,然而,只要这些技术特征的组合不存在矛盾,都应当认为是本说明书记载的范围。The technical features of the above embodiments can be combined arbitrarily. To make the description concise, all possible combinations of the technical features in the above embodiments are not described. However, as long as there is no contradiction in the combination of these technical features, they should be It is considered to be within the range described in this specification.
以上实施例仅表达了本申请的几种实施方式,其描述较为具体和详细,但并不能因此而理解为对本申请专利范围的限制。应当指出的是,对于本领域的普通技术人员来说,在不脱离本申请构思的前提下,还可以做出若干变形和改进,这些都属于本申请的保护范围。因此,本申请的保护范围应以所附权利要求为准。The above examples only express several implementation modes of the present application, and the description thereof is relatively specific and detailed, but should not be construed as limiting the patent scope of the present application. It should be noted that those skilled in the art can make several modifications and improvements without departing from the concept of the present application, and these all belong to the protection scope of the present application. Therefore, the protection scope of the present application should be determined by the appended claims.
Claims (11)
Translated fromChinesePriority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202211684395.2ACN115987771B (en) | 2022-12-27 | 2022-12-27 | Link anomaly positioning method, device, computer equipment and storage medium |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202211684395.2ACN115987771B (en) | 2022-12-27 | 2022-12-27 | Link anomaly positioning method, device, computer equipment and storage medium |
Publications (2)
| Publication Number | Publication Date |
|---|---|
| CN115987771Atrue CN115987771A (en) | 2023-04-18 |
| CN115987771B CN115987771B (en) | 2025-04-08 |
Family
ID=85971859
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN202211684395.2AActiveCN115987771B (en) | 2022-12-27 | 2022-12-27 | Link anomaly positioning method, device, computer equipment and storage medium |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN115987771B (en) |
Cited By (2)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN116881245A (en)* | 2023-06-05 | 2023-10-13 | 中国银行股份有限公司 | Business data splicing method, device, computer equipment and storage medium |
| CN117041686A (en)* | 2023-06-27 | 2023-11-10 | 广州开得联智能科技有限公司 | Method, device, equipment and medium for constructing video processing link |
Citations (2)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN110245035A (en)* | 2019-05-20 | 2019-09-17 | 平安普惠企业管理有限公司 | A kind of link trace method and device |
| CN113169900A (en)* | 2018-11-29 | 2021-07-23 | 华为技术有限公司 | Method and device for tracking business execution process in distributed system |
- 2022
- 2022-12-27CNCN202211684395.2Apatent/CN115987771B/enactiveActive
Patent Citations (2)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN113169900A (en)* | 2018-11-29 | 2021-07-23 | 华为技术有限公司 | Method and device for tracking business execution process in distributed system |
| CN110245035A (en)* | 2019-05-20 | 2019-09-17 | 平安普惠企业管理有限公司 | A kind of link trace method and device |
Cited By (2)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN116881245A (en)* | 2023-06-05 | 2023-10-13 | 中国银行股份有限公司 | Business data splicing method, device, computer equipment and storage medium |
| CN117041686A (en)* | 2023-06-27 | 2023-11-10 | 广州开得联智能科技有限公司 | Method, device, equipment and medium for constructing video processing link |
Also Published As
| Publication number | Publication date |
|---|---|
| CN115987771B (en) | 2025-04-08 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| US12339822B2 (en) | Method and system for migrating content between enterprise content management systems | |
| CN115987771A (en) | Link abnormal location method, device, computer equipment and storage medium | |
| US20190372755A1 (en) | System and method for recording changing standards using blockchain | |
| CA3208255A1 (en) | Generation and execution of processing workflows for correcting data quality issues in data sets | |
| CN114756293A (en) | Service processing method, device, computer equipment and storage medium | |
| CN114866447B (en) | Automatic test method and device for message receiving and sending of vehicle controller | |
| CN117370051A (en) | System fault detection method, device, equipment, storage medium and program product | |
| CN114490415B (en) | Business testing method, computer device, storage medium and computer program product | |
| EP4453712A1 (en) | Automated developer governance system | |
| CN114756363A (en) | Resource allocation detection method and device | |
| CN112488862A (en) | Error reporting information processing method and device | |
| CN114141322B (en) | Clinical trial analysis report configuration method, device and computer equipment | |
| CN107851165B (en) | A key system, a key client, and a key management method | |
| CN114581109B (en) | Data consistency detection method, device, computer equipment and storage medium | |
| CN119311312B (en) | Code combining state detection method, apparatus, device, readable storage medium and program product | |
| CN114519062B (en) | Basic data updating method, device, computer equipment and storage medium | |
| CN117435478A (en) | Program logic function detection method, device, computer equipment and storage medium | |
| CN116910038A (en) | Information analysis methods, devices, computer equipment and computer program products | |
| CN116781786A (en) | Request execution method, request execution device, computer equipment and storage medium thereof | |
| CN116566720A (en) | Firewall policy translation method, device, computer equipment and storage medium | |
| CN119577029A (en) | Data synchronization method, device, computer equipment, storage medium and program product | |
| CN117331812A (en) | Service code verification method, device, computer equipment, storage medium and product | |
| CN118394650A (en) | Code testing method, device, computer equipment and storage medium | |
| CN116881116A (en) | Interface test method, apparatus, computer device, storage medium, and program product | |
| CN120255989A (en) | Resource interaction service processing method, device, computer equipment and storage medium |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| GR01 | Patent grant | ||
| GR01 | Patent grant |