CN115941512A - Network device management method, network device and electronic device - Google Patents
Network device management method, network device and electronic deviceDownload PDFInfo
- Publication number
- CN115941512A CN115941512ACN202211385941.2ACN202211385941ACN115941512ACN 115941512 ACN115941512 ACN 115941512ACN 202211385941 ACN202211385941 ACN 202211385941ACN 115941512 ACN115941512 ACN 115941512A
- Authority
- CN
- China
- Prior art keywords
- agent program
- authority
- information
- equipment
- network device
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Granted
Links
Images
Classifications
- Y—GENERAL TAGGING OF NEW TECHNOLOGICAL DEVELOPMENTS; GENERAL TAGGING OF CROSS-SECTIONAL TECHNOLOGIES SPANNING OVER SEVERAL SECTIONS OF THE IPC; TECHNICAL SUBJECTS COVERED BY FORMER USPC CROSS-REFERENCE ART COLLECTIONS [XRACs] AND DIGESTS
- Y04—INFORMATION OR COMMUNICATION TECHNOLOGIES HAVING AN IMPACT ON OTHER TECHNOLOGY AREAS
- Y04S—SYSTEMS INTEGRATING TECHNOLOGIES RELATED TO POWER NETWORK OPERATION, COMMUNICATION OR INFORMATION TECHNOLOGIES FOR IMPROVING THE ELECTRICAL POWER GENERATION, TRANSMISSION, DISTRIBUTION, MANAGEMENT OR USAGE, i.e. SMART GRIDS
- Y04S40/00—Systems for electrical power generation, transmission, distribution or end-user application management characterised by the use of communication or information technologies, or communication or information technology specific aspects supporting them
- Y04S40/20—Information technology specific aspects, e.g. CAD, simulation, modelling, system security
Landscapes
- Computer And Data Communications (AREA)
Abstract
Translated fromChineseDescription
Translated fromChinese技术领域technical field
本申请涉及针对网络设备的管理领域,特别涉及一种网络设备的管理方法、网络设备及电子设备。The present application relates to the field of management of network equipment, in particular to a management method of network equipment, network equipment and electronic equipment.
背景技术Background technique
目前,网络安全厂商的产品线涵盖各种类型的网络设备,如网络安全设备:边界防火墙、Web应用防火墙、云计算虚拟防火墙、网络审计系统(堡垒机)等。尽管单个网络设备具备图形化的管理界面,但是许多组织或企业希望可通过集中管理平台对多个网络安全产品进行集中管理。但在使用时需要集中管理平台获取网络设备的账号信息,并基于账号信息与网络设备进行交互,增加了集中管理平台与网络设备之间频繁交互造成的性能消耗,以及增加了用于对相应的管理操作进行验证的认证信息的泄露风险。At present, the product line of network security manufacturers covers various types of network equipment, such as network security equipment: border firewall, web application firewall, cloud computing virtual firewall, network audit system (bastion host), etc. Although a single network device has a graphical management interface, many organizations or enterprises hope to centrally manage multiple network security products through a centralized management platform. However, when using it, the centralized management platform needs to obtain the account information of the network device, and interact with the network device based on the account information, which increases the performance consumption caused by the frequent interaction between the centralized management platform and the network device, and increases the corresponding Manage the risk of leakage of authentication information for verification of operations.
发明内容Contents of the invention
本申请实施例的目的在于提供一种网络设备的管理方法、网络设备及电子设备,该方法能够降低网络设备的性能消耗,并降低相关认证信息的泄露风险。The purpose of the embodiments of the present application is to provide a network device management method, network device and electronic device, the method can reduce the performance consumption of the network device and reduce the risk of leakage of relevant authentication information.
为了实现上述目的,本申请实施例提供了一种网络设备的管理方法,该方法应用于网络设备,所述方法包括:In order to achieve the above purpose, an embodiment of the present application provides a method for managing a network device, the method is applied to a network device, and the method includes:
利用安装在所述网络设备中的代理程序,获取集中管理平台发送的登陆信息,其中所述网络设备在所述集中管理平台注册;Using the agent program installed in the network device to obtain the login information sent by the centralized management platform, wherein the network device is registered on the centralized management platform;
基于所述登陆信息,利用所述代理程序生成请求操作所述网络设备的访问信息,其中所述访问信息包括请求操作所述网络设备的设备权限;Based on the login information, using the proxy program to generate access information requesting to operate the network device, wherein the access information includes a device authority requesting to operate the network device;
利用所述代理程序,将所述访问信息发送给所述网络设备的设备本体,以使所述设备本体基于所述访问信息,生成用于认证登陆所述设备本体并进行操作的认证标识,并将所述认证标识反馈给所述代理程序;Using the agent program, sending the access information to the device body of the network device, so that the device body generates an authentication identifier for authenticating login and operation of the device body based on the access information, and feeding back the authentication identifier to the agent program;
在所述代理程序获取配置请求的情况下,通过所述代理程序将所述配置请求和所述认证标识发送给所述设备本体,以请求对所述设备本体进行管理;When the agent program obtains the configuration request, the agent program sends the configuration request and the authentication identifier to the device body to request management of the device body;
在所述认证标识通过验证的情况下,控制所述设备本体响应所述配置请求,以对所述设备本体进行管理。When the authentication identification is verified, the device body is controlled to respond to the configuration request, so as to manage the device body.
作为可选,所述基于所述登陆信息,利用所述代理程序生成请求操作所述网络设备的访问信息,包括:Optionally, using the agent program to generate access information requesting to operate the network device based on the login information includes:
在所述登陆信息为具有第一操作权限的管理员信息的情况下,基于所述管理员信息,利用所述代理程序生成所述访问信息;When the login information is administrator information with the first operation authority, using the agent program to generate the access information based on the administrator information;
将所述访问信息中的设备权限与所述访问信息中的账号信息相关联。Associating the device authority in the access information with the account information in the access information.
作为可选,所述利用所述代理程序,将所述访问信息发送给所述网络设备的设备本体,以使所述设备本体基于所述访问信息,生成用于认证登陆所述设备本体并进行操作的认证标识,并将所述认证标识反馈给所述代理程序,包括:Optionally, the agent program is used to send the access information to the device body of the network device, so that the device body generates an authentication log on the device body based on the access information and performs The authentication identification of the operation, and feeding back the authentication identification to the agent program, including:
通过所述代理程序将所述设备权限和所述账号信息发送给所述设备本体,以使所述设备本体生成与所述代理程序唯一对应的所述认证标识;sending the device authority and the account information to the device body through the agent program, so that the device body generates the authentication identifier uniquely corresponding to the agent program;
通过所述代理程序获取所述认证标识,其中所述认证标识能够表征所述代理程序的身份信息以及相关联的所述设备权限。The authentication ID is acquired through the agent program, where the authentication ID can represent the identity information of the agent program and the associated device authority.
作为可选,所述在所述代理程序获取配置请求的情况下,通过所述代理程序将所述配置请求和所述认证标识发送给所述设备本体,包括:Optionally, when the agent program obtains the configuration request, sending the configuration request and the authentication identifier to the device body through the agent program includes:
通过所述代理程序,从所述集中管理平台获取所述配置请求;Obtain the configuration request from the centralized management platform through the agent program;
将所述配置请求和所述认证标识发送给所述设备本体,以请求所述设备本体对所述代理程序进行鉴权。Send the configuration request and the authentication identifier to the device body, so as to request the device body to authenticate the agent program.
作为可选,所述在所述认证标识通过验证的情况下,控制所述设备本体响应所述配置请求,以对所述设备本体进行管理,包括:Optionally, the controlling the device body to respond to the configuration request to manage the device body when the authentication identifier is verified includes:
利用与所述网络设备关联的授权单元,对所述认证标识进行鉴权,其中包括对所述代理程序的身份信息进行验证,以及确定所述代理程序管理所述设备本体的权限;Using an authorization unit associated with the network device to authenticate the authentication identifier, including verifying the identity information of the agent program and determining the authority of the agent program to manage the device itself;
在所述代理程序通过身份验证的情况下,基于确定的管理所述设备本体的权限,对所述设备本体进行管理。When the agent program passes the authentication, the device body is managed based on the determined right to manage the device body.
作为可选,所述方法还包括:Optionally, the method also includes:
基于所述设备本体中建立的代理程序列表,对所述代理程序颁发可信凭证;issuing a trusted credential to the agent program based on the agent program list established in the device body;
基于所述可信凭证,将所述网络设备在所述集中管理平台进行注册。Registering the network device on the centralized management platform based on the trusted credential.
作为可选,所述方法还包括:Optionally, the method also includes:
将所述网络设备预先构建的权限模板发送给所述集中管理平台,以使所述集中管理平台基于所述权限模板确定所述第一操作权限,其中所述权限模板包括所述设备权限与设备功能之间的对应关系。sending the pre-built authority template of the network device to the centralized management platform, so that the centralized management platform determines the first operation authority based on the authority template, wherein the authority template includes the device authority and the device Correspondence between functions.
本申请实施例还提供了一种网络设备,包括:The embodiment of the present application also provides a network device, including:
获取模块,其配置为利用安装在所述网络设备中的代理程序,获取集中管理平台发送的登陆信息,其中所述网络设备在所述集中管理平台注册;An acquisition module configured to use an agent program installed in the network device to obtain login information sent by a centralized management platform, where the network device is registered on the centralized management platform;
生成模块,其配置为基于所述登陆信息,利用所述代理程序生成请求操作所述网络设备的访问信息,其中所述访问信息包括请求操作所述网络设备的设备权限;A generating module configured to use the proxy program to generate access information requesting to operate the network device based on the login information, wherein the access information includes a device authority requesting to operate the network device;
发送模块,其配置为利用所述代理程序,将所述访问信息发送给所述网络设备的设备本体,以使所述设备本体基于所述访问信息,生成用于认证登陆所述设备本体并进行操作的认证标识,并将所述认证标识反馈给所述代理程序;A sending module, configured to use the agent program to send the access information to the device body of the network device, so that the device body generates an authentication log on the device body based on the access information and performs An authentication identifier of the operation, and feeding the authentication identifier back to the agent program;
管理模块,其配置为在所述代理程序获取配置请求的情况下,通过所述代理程序将所述配置请求和所述认证标识发送给所述设备本体,以请求对所述设备本体进行管理;A management module configured to send the configuration request and the authentication identifier to the device body through the agent program to request management of the device body when the agent program obtains the configuration request;
在所述认证标识通过验证的情况下,控制所述设备本体响应所述配置请求,以对所述设备本体进行管理。When the authentication identification is verified, the device body is controlled to respond to the configuration request, so as to manage the device body.
本申请实施例还提供了一种电子设备,包括处理器和存储器,所述存储器中存储有可执行程序,所述处理器执行所述可执行程序以进行如上所述的方法的步骤。An embodiment of the present application also provides an electronic device, including a processor and a memory, where an executable program is stored in the memory, and the processor executes the executable program to perform the steps of the above method.
本申请实施例还提供了一种存储介质,所述存储介质承载有一个或者多个计算机程序,其特征在于,所述一个或者多个计算机程序被处理器执行以实现如上所述方法的步骤。The embodiment of the present application also provides a storage medium, the storage medium carries one or more computer programs, wherein the one or more computer programs are executed by a processor to implement the steps of the method described above.
本申请的该管理方法通过在网络设备中设置代理程序,利用代理程序与网络设备的设备本体进行交互,降低了集中管理平台与网络设备之间频繁交互造成的性能消耗,并降低了相关的认证信息的泄露风险。The management method of this application reduces the performance consumption caused by the frequent interaction between the centralized management platform and the network device by setting the agent program in the network device, and using the agent program to interact with the device body of the network device, and reduces the related authentication. Information disclosure risk.
此外,设备本体还可以在认证标识中所表征的设备权限下,响应配置信息,从而灵活实现对网络设备的配置权限管理。In addition, the device body can also respond to configuration information under the device authority represented in the authentication identifier, so as to flexibly realize the configuration authority management of network devices.
附图说明Description of drawings
图1为本申请实施例的网络设备的管理方法的流程图;FIG. 1 is a flowchart of a method for managing a network device according to an embodiment of the present application;
图2为本申请实施例的图1中步骤S200的一个实施例的流程图;FIG. 2 is a flowchart of an embodiment of step S200 in FIG. 1 of the embodiment of the present application;
图3为本申请实施例的图1中步骤S300的一个实施例的流程图;FIG. 3 is a flowchart of an embodiment of step S300 in FIG. 1 of the embodiment of the present application;
图4为本申请实施例的图1中步骤S400的一个实施例的流程图;FIG. 4 is a flowchart of an embodiment of step S400 in FIG. 1 of the embodiment of the present application;
图5为本申请实施例的图1中步骤S500的一个实施例的流程图;FIG. 5 is a flowchart of an embodiment of step S500 in FIG. 1 of the embodiment of the present application;
图6为本申请实施例的管理方法的一个实施例的流程图;FIG. 6 is a flowchart of an embodiment of the management method of the embodiment of the present application;
图7为本申请实施例的管理方法的另一个具体实施例的流程图;FIG. 7 is a flowchart of another specific embodiment of the management method of the embodiment of the present application;
图8为本申请实施例的网络设备的结构框图;FIG. 8 is a structural block diagram of a network device according to an embodiment of the present application;
图9为本申请实施例的电子设备的结构框图。FIG. 9 is a structural block diagram of an electronic device according to an embodiment of the present application.
具体实施方式Detailed ways
此处参考附图描述本申请的各种方案以及特征。Various aspects and features of the present application are described herein with reference to the accompanying drawings.
应理解的是,可以对此处申请的实施例做出各种修改。因此,上述说明书不应该视为限制,而仅是作为实施例的范例。本领域的技术人员将想到在本申请的范围和精神内的其他修改。It should be understood that various modifications may be made to the embodiments applied for herein. Accordingly, the above description should not be viewed as limiting, but only as exemplifications of embodiments. Those skilled in the art will envision other modifications within the scope and spirit of the application.
包含在说明书中并构成说明书的一部分的附图示出了本申请的实施例,并且与上面给出的对本申请的大致描述以及下面给出的对实施例的详细描述一起用于解释本申请的原理。The accompanying drawings, which are incorporated in and constitute a part of this specification, illustrate embodiments of the application and, together with the general description of the application given above and the detailed description of the embodiments given below, serve to explain the embodiments of the application. principle.
通过下面参照附图对给定为非限制性实例的实施例的优选形式的描述,本申请的这些和其它特性将会变得显而易见。These and other characteristics of the present application will become apparent from the following description of preferred forms of embodiment given as non-limiting examples with reference to the accompanying drawings.
还应当理解,尽管已经参照一些具体实例对本申请进行了描述,但本领域技术人员能够确定地实现本申请的很多其它等效形式。It should also be understood that, while the application has been described with reference to a few specific examples, those skilled in the art will be able to implement certain other equivalents of the application.
当结合附图时,鉴于以下详细说明,本申请的上述和其他方面、特征和优势将变得更为显而易见。The above and other aspects, features and advantages of the present application will become more apparent in view of the following detailed description when taken in conjunction with the accompanying drawings.
此后参照附图描述本申请的具体实施例;然而,应当理解,所申请的实施例仅仅是本申请的实例,其可采用多种方式实施。熟知和/或重复的功能和结构并未详细描述以避免不必要或多余的细节使得本申请模糊不清。因此,本文所申请的具体的结构性和功能性细节并非意在限定,而是仅仅作为权利要求的基础和代表性基础用于教导本领域技术人员以实质上任意合适的详细结构多样地使用本申请。Specific embodiments of the present application are hereinafter described with reference to the accompanying drawings; however, it should be understood that the applied embodiments are merely examples of the present application, which can be implemented in various ways. Well-known and/or repetitive functions and constructions are not described in detail to avoid obscuring the application with unnecessary or redundant detail. Therefore, specific structural and functional details disclosed herein are not intended to be limiting, but merely as a basis for the claims and as a representative basis for teaching one skilled in the art to variously employ the present invention in virtually any suitable detailed structure. Apply.
本说明书可使用词组“在一种实施例中”、“在另一个实施例中”、“在又一实施例中”或“在其他实施例中”,其均可指代根据本申请的相同或不同实施例中的一个或多个。This specification may use the phrases "in one embodiment," "in another embodiment," "in yet another embodiment," or "in other embodiments," which may refer to the same or one or more of the different embodiments.
本申请实施例的一种网络设备的管理方法,应用于网络设备,网络设备可以是应用于网络的设备,包括网络安全设备,如边界防火墙、Web应用防火墙、云计算虚拟防火墙、网络审计系统等。该方法能够对网络设备进行安全有效的管理,且提高管理效率。该方法包括在网络设备中预先设置代理程序,代理程序分别与集中管理平台和设备本体连接,代理程序可以从设备本体处获取到用于认证登陆设备本体并进行操作的认证标识。在集中管理平台向代理程序发送配置请求以请求配置设备本体,代理程序可以将配置请求和认证标识发送给设备本体。设备本体需要对该认证标识进行认证,在认证标识通过验证后,用户可以通过集中管理平台经由代理程序对设备本体进行管理。而该认证过程并不需要设备本体频繁的与集中管理平台进行数据交互,仅仅是与代理程序进行交互即可实现认证,降低了网络设备的性能消耗。同时也降低了对集中管理平台进行认证的认证信息的泄露风险。A network device management method according to an embodiment of the present application is applied to a network device, and the network device may be a device applied to a network, including a network security device, such as a border firewall, a web application firewall, a cloud computing virtual firewall, a network audit system, etc. . The method can safely and effectively manage network equipment and improve management efficiency. The method includes presetting an agent program in the network device, the agent program is respectively connected with the centralized management platform and the device body, and the agent program can obtain an authentication identification for authenticating and logging in to the device body and performing operations from the device body. The centralized management platform sends a configuration request to the agent program to request configuration of the device body, and the agent program can send the configuration request and the authentication identifier to the device body. The device body needs to authenticate the authentication logo. After the authentication logo is verified, the user can manage the device body through the agent program through the centralized management platform. However, the authentication process does not require frequent data interaction between the device itself and the centralized management platform, but only through interaction with the agent program to achieve authentication, which reduces the performance consumption of network devices. At the same time, it also reduces the leakage risk of authentication information for authentication of the centralized management platform.
下面结合附图对该管理方法进行详细说明,图1为本申请实施例的网络设备的管理方法的流程图,如图1所示并结合图7,所述方法包括以下步骤:The management method will be described in detail below in conjunction with the accompanying drawings. FIG. 1 is a flow chart of a management method for a network device according to an embodiment of the present application. As shown in FIG. 1 and in combination with FIG. 7, the method includes the following steps:
S100,利用安装在所述网络设备中的代理程序,获取集中管理平台发送的登陆信息,其中所述网络设备在所述集中管理平台注册。S100. Use an agent program installed in the network device to obtain login information sent by a centralized management platform, where the network device is registered on the centralized management platform.
示例性的,代理程序可以预先安装在网络设备中,如在网络设备出厂前可以预先安装,或者在用户使用网络设备的过程中安装等,可以根据实际使用场景而灵活操作。Exemplarily, the agent program can be pre-installed in the network device, for example, it can be pre-installed before the network device leaves the factory, or it can be installed during the user's use of the network device, etc., and can be flexibly operated according to actual usage scenarios.
代理程序分别与集中管理平台和网络设备的设备本体连接,集中管理平台可以通过代理程序向设备本体请求认证,而代理程序安装在网络设备上,从而避免了将相关的认证信息频繁在集中管理平台和设备本体之间流转,也避免了整体系统资源的过度消耗。The agent program is respectively connected to the centralized management platform and the device body of the network device. The centralized management platform can request authentication from the device body through the agent program, and the agent program is installed on the network device, thus avoiding the frequent transfer of relevant authentication information to the centralized management platform. It also avoids excessive consumption of overall system resources.
集中管理平台可以设置在不同于网络设备的其他设备上,集中管理平台可以与用户进行交互,接收用户输入信息,生成相应的指令。如基于用户的操作信息而生成相应的配置信息,用于对网络设备进行配置。网络设备可以在集中管理平台注册,从而建立集中管理平台与网络设备之间的关系。The centralized management platform can be installed on other devices different from network devices, and the centralized management platform can interact with users, receive user input information, and generate corresponding instructions. For example, corresponding configuration information is generated based on the user's operation information to configure the network device. Network devices can be registered on the centralized management platform, thereby establishing a relationship between the centralized management platform and network devices.
在需要对网络设备进行操作前,用户可以登录集中管理平台,通过集中管理平台向代理程序发送登陆信息。登陆信息是用于认证集中管理平台,以及设置管理网络设备权限的相关信息,如可以包括用户名、密码。代理程序对登陆信息进行认证,从而确定集中管理平台的合法性。Before operating the network equipment, the user can log in to the centralized management platform, and send login information to the agent program through the centralized management platform. The login information is used for authenticating the centralized management platform and setting the authority to manage network devices, such as user name and password. The agent program authenticates the login information to determine the legitimacy of the centralized management platform.
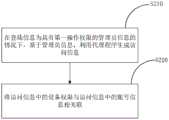
S200,基于所述登陆信息,利用所述代理程序生成请求操作所述网络设备的访问信息,其中所述访问信息包括请求操作所述网络设备的设备权限。S200. Based on the login information, use the proxy program to generate access information requesting to operate the network device, where the access information includes a device authority requesting to operate the network device.
示例性的,登陆信息可以是用于认证集中管理平台,以及设置管理网络设备权限的相关信息。代理程序可以根据登陆信息中的内容对集中管理平台进行认证,如通过认证,则代理程序可以基于登陆信息生成请求操作所述网络设备的访问信息。该访问信息用于申请访问网络设备,包括账号信息以及设备权限,其中设备权限为请求操作所述网络设备的权限。通过该账号信息登陆后可以使用该设备权限对网络设备进行管理。Exemplarily, the login information may be relevant information for authenticating the centralized management platform and setting permissions for managing network devices. The agent program can authenticate the centralized management platform according to the content in the login information. If the authentication is passed, the agent program can generate access information requesting to operate the network device based on the login information. The access information is used to apply for access to the network device, including account information and device authority, wherein the device authority is the authority to request to operate the network device. After logging in with this account information, you can use this device authority to manage network devices.
在一个实施例中,代理程序可以根据登陆信息生成访问信息,该访问信息包括一个或多个账号信息及其对应的设备权限。例如,第一账号对应了第一设备权限,以第一账号请求使用第一设备权限访问网络设备;第二账号对应了第二设备权限,以第二账号请求使用第二设备权限访问网络设备等。In an embodiment, the agent program can generate access information according to the login information, where the access information includes one or more account information and corresponding device permissions. For example, the first account corresponds to the first device authority, and the first account is used to request to use the first device authority to access the network device; the second account corresponds to the second device authority, and the second account is used to request to use the second device authority to access the network device, etc. .
在另一个实施例中,设备权限可以是设备本体与集中管理平台进行约定的权限,该设备权限可以与设备本体的功能相关联,各个设备权限可以关联与其相对应的功能。In another embodiment, the device permission may be a permission agreed between the device body and the centralized management platform, the device permission may be associated with the function of the device body, and each device permission may be associated with its corresponding function.
S300,利用所述代理程序,将所述访问信息发送给所述网络设备的设备本体,以使所述设备本体基于所述访问信息,生成用于认证登陆所述设备本体并进行操作的认证标识,并将所述认证标识反馈给所述代理程序。S300, using the agent program to send the access information to the device body of the network device, so that the device body generates an authentication identifier for authenticating the device body to log in and operate based on the access information , and feed back the authentication identifier to the agent program.
示例性的,代理程序将访问信息发送给设备本体,使得设备本体可以基于访问信息对代理程序进行认证,而代理程序安装在网络设备上,从而在认证过程中可以有效提高认证效率节省系统资源。Exemplarily, the agent program sends the access information to the device body, so that the device body can authenticate the agent program based on the access information, and the agent program is installed on the network device, thereby effectively improving authentication efficiency and saving system resources during the authentication process.
访问信息可以包括设备权限和账号信息,设备权限可以是针对管理网络设备的权限,如管理员权限、普通人员权限等。而账号信息可以包括用户名、密码等信息。设备本体可以基于访问信息,生成用于认证登陆设备本体并进行操作的认证标识。该认证标识可以用于验证代理程序的身份信息,进而验证从代理程序接收到的相应的配置请求是否合法。The access information may include device permissions and account information, and the device permissions may be permissions for managing network devices, such as administrator permissions, ordinary personnel permissions, and the like. The account information may include user name, password and other information. Based on the access information, the device body can generate an authentication ID for authenticating the login and operation of the device body. The authentication ID can be used to verify the identity information of the agent, and then verify whether the corresponding configuration request received from the agent is legal.
设备本体可以将该认证标识反馈给代理程序,代理程序可以将该认证标识存储。在一个实施例中,该认证标识与代理程序唯一对应,可以表征代理程序的合法身份。The device body can feed back the authentication identifier to the agent program, and the agent program can store the authentication identifier. In one embodiment, the authentication identifier uniquely corresponds to the agent program, and can represent the legal identity of the agent program.
S400,在所述代理程序获取配置请求的情况下,通过所述代理程序将所述配置请求和所述认证标识发送给所述设备本体,以请求对所述设备本体进行管理。S400. When the agent program obtains the configuration request, send the configuration request and the authentication identifier to the device body through the agent program, so as to request management of the device body.
示例性的,配置请求可以是集中管理平台向网络设备发送的请求,用于请求对网络设备进行管理,包括参数的配置、功能的配置等。Exemplarily, the configuration request may be a request sent by the centralized management platform to the network device, for requesting management of the network device, including configuration of parameters, configuration of functions, and the like.
集中管理平台将该配置请求发送给代理程序。在一个实施例中,代理程序在接收到该配置请求的情况下,可以先对集中管理平台进行身份确认,确认合法后可以将配置请求以及自身存储的认证标识发送给设备本体,以请求对所述设备本体进行管理。The centralized management platform sends the configuration request to the agent program. In one embodiment, when the agent program receives the configuration request, it can first confirm the identity of the centralized management platform, and after confirming that it is legal, it can send the configuration request and the authentication ID stored by itself to the device body, so as to request for all The above-mentioned device body is managed.
S500,在所述认证标识通过验证的情况下,控制所述设备本体响应所述配置请求,以对所述设备本体进行管理。S500. Control the device body to respond to the configuration request, so as to manage the device body if the authentication identifier passes the verification.
示例性的,设备本体可以通过对认证标识的验证而对代理程序进行身份认证,具体的验证过程可以根据预先约定方式进行。Exemplarily, the device body may authenticate the agent program by verifying the authentication identifier, and the specific verification process may be performed in a pre-agreed manner.
例如,设备本体可以基于约定方式对认证标识进行加密,再将加密后的认证标识发送给代理程序进行存储。当随后接收到代理程序发送的加密后的认证标识后,可以通过相应的解密方式对认证标识进行解密,如果解密通过则可以确认证标识通过验证,确定代理程序的身份合法。当然对认证标识进行验证的方式还可以是其他多种形式。再例如,将认证标识与预存的标准标识进行对比,如相同则可以确定认证标识通过验证。For example, the device body can encrypt the authentication identifier based on the agreed method, and then send the encrypted authentication identifier to the agent program for storage. After receiving the encrypted authentication ID sent by the agent program, the authentication ID can be decrypted through the corresponding decryption method. If the decryption is successful, the authentication ID can be confirmed and the identity of the agent program is determined to be legal. Of course, the manner of verifying the certification mark may also be in other forms. For another example, the certification mark is compared with the pre-stored standard mark, and if they are the same, it can be determined that the certification mark has passed the verification.
在认证标识通过验证的情况下,设备本体可以基于配置请求进行配置操作,如对参数进行配置、对功能进行配置等。在一个实施例中可以基于认证标识中所表征的设备权限,控制设备本体响应配置请求。从而在该设备权限下实现对网络设备的管理。When the authentication mark is verified, the device body can perform configuration operations based on the configuration request, such as configuring parameters, configuring functions, and so on. In one embodiment, the device body can be controlled to respond to the configuration request based on the device authority represented in the authentication identifier. In this way, the management of network devices is realized under the authority of the device.
本申请的该管理方法通过在网络设备中设置代理程序,利用代理程序与网络设备的设备本体进行交互,降低了集中管理平台与网络设备之间频繁交互造成的性能消耗,并降低了相关的认证信息的泄露风险。The management method of this application reduces the performance consumption caused by the frequent interaction between the centralized management platform and the network device by setting the agent program in the network device, and using the agent program to interact with the device body of the network device, and reduces the related authentication. Information disclosure risk.
此外,设备本体还可以在认证标识中所表征的设备权限下,响应配置信息,从而灵活实现对网络设备的配置权限管理。In addition, the device body can also respond to configuration information under the device authority represented in the authentication identifier, so as to flexibly realize the configuration authority management of network devices.
在本申请的一个实施中,所述登陆信息包括具有第一操作权限的管理员信息,所述基于所述登陆信息,利用所述代理程序生成请求操作所述网络设备的访问信息,如图2所示,包括:In an implementation of the present application, the login information includes administrator information with the first operation authority, and based on the login information, the agent program is used to generate access information requesting to operate the network device, as shown in Figure 2 shown, including:
S210,在所述登陆信息为具有第一操作权限的管理员信息的情况下,基于所述管理员信息,利用所述代理程序生成所述访问信息。S210, if the login information is administrator information with the first operation authority, use the agent program to generate the access information based on the administrator information.
示例性的,登陆信息可以是具有第一操作权限的管理员信息,第一操作权限可以是使用集中管理平台的管理员权限,通过管理员信息操作集中管理平台时可以拥有第一操作权限,第一操作权限可以对应有设备权限。Exemplarily, the login information may be administrator information with the first operation authority, the first operation authority may be the administrator authority to use the centralized management platform, and the administrator may have the first operation authority when operating the centralized management platform through the administrator information. An operation authority may correspond to a device authority.
在一个实施例中,可以预先将管理员信息与网络设备的设备权限相关联,如可以在网络设备在集中管理平台注册过程中进行关联,从而使得使用管理员信息进行登陆并管理网络设备时可以具有相应的设备权限。当然登陆信息还可以是其他用户信息,该其他用户信息具有不同于第一操作权限的第二操作权限,第二操作权限也可以对应有设备权限。In one embodiment, the administrator information can be associated with the device authority of the network device in advance, for example, it can be associated during the registration process of the network device on the centralized management platform, so that the administrator information can be used to log in and manage the network device. have the appropriate device permissions. Of course, the login information may also be other user information, and the other user information has a second operation authority different from the first operation authority, and the second operation authority may also correspond to a device authority.
代理程序可以基于管理员信息,生成访问信息。该访问信息表征了管理员使用集中管理平台来管理网络设备,该管理员信息对应了相应的设备权限。Agents can generate access information based on administrator information. The access information indicates that the administrator uses the centralized management platform to manage network devices, and the administrator information corresponds to corresponding device permissions.
S220,将所述访问信息中的设备权限与所述访问信息中的账号信息相关联。S220. Associate the device authority in the access information with the account information in the access information.
在一个实施例中,访问信息包括设备权限以及账号信息,代理程序可以将该账号信息和设备权限发送给设备本体。不同的账号信息具有各自对应的设备权限。In one embodiment, the access information includes device authority and account information, and the agent program can send the account information and device authority to the device body. Different account information has its own corresponding device permissions.
在本申请的一个实施中,所述利用所述代理程序,将所述访问信息发送给所述网络设备的设备本体,以使所述设备本体基于所述访问信息,生成用于认证登陆所述设备本体并进行操作的认证标识,并将所述认证标识反馈给所述代理程序,如图3所示,包括:In one implementation of the present application, the agent program is used to send the access information to the device body of the network device, so that the device body generates the authentication log-in device based on the access information. The authentication mark of the device body and operation, and the authentication mark is fed back to the agent program, as shown in Figure 3, including:
S310,通过所述代理程序将所述设备权限和所述账号信息发送给所述设备本体,以使所述设备本体生成与所述代理程序唯一对应的所述认证标识;S310. Send the device authority and the account information to the device body through the agent program, so that the device body generates the authentication identifier uniquely corresponding to the agent program;
S320,通过所述代理程序获取所述认证标识,其中所述认证标识能够表征所述代理程序的身份信息以及相关联的所述设备权限。S320. Acquire the authentication ID through the agent program, where the authentication ID can represent the identity information of the agent program and the associated device authority.
具体来说,代理程序可以将该账号信息和设备权限发送给设备本体后,设备本体可以基于该账号信息和/或设备权限生成相应的认证标识。认证标识能够表征代理程序的身份信息以及相关联的设备权限,进而确定了集中管理平台管理网络设备的权限。Specifically, after the agent program can send the account information and device authority to the device body, the device body can generate a corresponding authentication identifier based on the account information and/or device authority. The authentication ID can represent the identity information of the agent program and the associated device authority, and then determine the authority of the centralized management platform to manage network equipment.
在本申请的一个实施中,所述在所述代理程序获取配置请求的情况下,通过所述代理程序将所述配置请求和所述认证标识发送给所述设备本体,如图4所示,包括:In an implementation of the present application, when the agent program obtains the configuration request, the agent program sends the configuration request and the authentication identifier to the device body, as shown in FIG. 4 , include:
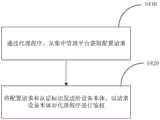
S410,通过所述代理程序,从所述集中管理平台获取所述配置请求。S410. Obtain the configuration request from the centralized management platform through the agent program.
示例性的,配置请求可以是用户通过集中管理平台向代理程序发送的请求,用于请求对网络设备进行配置,如参数的配置、功能的配置等。Exemplarily, the configuration request may be a request sent by the user to the agent program through the centralized management platform, for requesting configuration of the network device, such as configuration of parameters, configuration of functions, and the like.
在一个实施例中,集中管理平台向代理程序发送的登陆信息时,可以在登陆过程中将配置请求也发送给代理程序。In one embodiment, when the centralized management platform sends the login information to the agent program, a configuration request may also be sent to the agent program during the login process.
在另一个实施例中,集中管理平台也可以在向其他阶段向代理程序发送该配置请求,代理程序从集中管理平台获取到该配置请求的同时也可以确定与该配置请求相关联的账户信息,如果确定该账户信息合法,则可以确定该配置请求合法。In another embodiment, the centralized management platform may also send the configuration request to the agent program at other stages, and the agent program may also determine the account information associated with the configuration request while obtaining the configuration request from the centralized management platform, If it is determined that the account information is legal, it can be determined that the configuration request is legal.
S420,将所述配置请求和所述认证标识发送给所述设备本体,以请求所述设备本体对所述代理程序进行鉴权。S420. Send the configuration request and the authentication identifier to the device body, so as to request the device body to authenticate the agent program.
示例性的,设备本体基于认证标识对代理程序进行身份的鉴权,进而可以对配置请求进行合法性认证。Exemplarily, the device body authenticates the identity of the agent program based on the authentication identifier, and then can authenticate the validity of the configuration request.
如确定该认证标识合法,则可以确定代理成程序合法,进而确定配置请求合法。从而可以正常的响应该配置请求。If it is determined that the authentication identifier is legal, it can be determined that the proxy program is legal, and then the configuration request is determined to be legal. Therefore, the configuration request can be responded normally.
在本申请的一个实施中,所述在所述认证标识通过验证的情况下,控制所述设备本体响应所述配置请求,以对所述设备本体进行管理,如图5所示,包括如下步骤:In one implementation of the present application, the controlling the device body to respond to the configuration request to manage the device body when the authentication identifier is verified, as shown in FIG. 5 , includes the following steps :
S510,利用与所述网络设备关联的授权单元,对所述认证标识进行鉴权,其中包括对所述代理程序的身份信息进行验证,以及确定所述代理程序管理所述设备本体的权限。S510. Use an authorization unit associated with the network device to authenticate the authentication identifier, including verifying the identity information of the agent program and determining the authority of the agent program to manage the device body.
示例性的,授权单元与网络设备关联,可以设置在网络设备中,也可以设置于相对独立的其他位置。设备本体接收到该认证标识后,授权单元可以对其进行鉴权,从而验证当前请求配置设备本体的操作的合法性。Exemplarily, the authorization unit is associated with the network device, and may be set in the network device, or may be set in a relatively independent location. After the device body receives the authentication identifier, the authorization unit can authenticate it, so as to verify the legitimacy of the current request to configure the device body.
该鉴权的过程包括对代理程序的身份信息进行验证,以及确定代理程序管理设备本体的权限。The authentication process includes verifying the identity information of the agent program and determining the authority of the agent program to manage the device body.
S520,在所述代理程序通过身份验证的情况下,基于确定的管理所述设备本体的权限,对所述设备本体进行管理。S520. When the agent program passes the identity verification, manage the device body based on the determined right to manage the device body.
示例性的,认证标识能够表征代理程序的身份信息以及相关联的设备权限,进而确定了集中管理平台管理网络设备的权限。Exemplarily, the authentication identifier can represent the identity information of the agent program and the associated device authority, thereby determining the authority of the centralized management platform to manage network devices.
代理程序通过身份验证,则设备本体可以确定当前与其交互的代理程序合法。进而可以基于认证标识确定管理设备本体的设备权限。从而设备本体允许响应由集中管理平台发出的配置请求,代理程序基于该设备权限来对设备本体进行管理。Once the agent is authenticated, the device ontology can determine that the agent currently interacting with it is legitimate. Furthermore, the device right to manage the device body can be determined based on the authentication identifier. Therefore, the device body is allowed to respond to the configuration request issued by the centralized management platform, and the agent program manages the device body based on the device authority.
在本申请的一个实施中,如图6所示,所述方法还包括以下步骤:In one implementation of the present application, as shown in Figure 6, the method further includes the following steps:
S600,基于所述设备本体中建立的代理程序列表,对所述代理程序颁发可信凭证;S600. Based on the list of agent programs established in the device body, issue a trusted certificate to the agent program;
S700,基于所述可信凭证,将所述网络设备在所述集中管理平台进行注册。S700. Register the network device on the centralized management platform based on the trusted credential.
示例性的,设备本体中可以预先建立代理程序列表,代理程序列表中对一个或多个代理程序进行合法性的标识。如,在代理程序列表中显示的代理程序均为合法程序。设备本体可以对代理程序列表中记录的代理程序颁发可信凭证。该可信凭证中包括对代理程序以及相关的网络设备的合法性认证内容。Exemplarily, an agent program list may be pre-established in the device body, and the legality of one or more agent programs is identified in the agent program list. For example, the agents displayed in the agent list are legitimate programs. The device ontology can issue trusted credentials to the agents recorded in the agent list. The trusted credential includes legality authentication content for the agent program and related network equipment.
代理程序获取到该可信凭证后,可以基于该可信凭证,将网络设备在集中管理平台进行注册,从而建立了网络设备与集中管理平台的关联关系。After the agent program obtains the credible credential, it can register the network device on the centralized management platform based on the credible credential, thereby establishing an association relationship between the network device and the centralized management platform.
在一个实施例中,网络设备在集中管理平台注册一次后便可以建立两者的长期安全信任关系,从而可以减少集中管理平台与网络设备因频繁建立安全信任关系而导致系统资源消耗。In one embodiment, after the network device registers once with the centralized management platform, a long-term security trust relationship between the two can be established, thereby reducing the consumption of system resources caused by the frequent establishment of security trust relationships between the centralized management platform and the network device.
在本申请的一个实施中,结合图7,所述方法还包括以下步骤:In one implementation of the present application, with reference to FIG. 7, the method further includes the following steps:
将所述网络设备预先构建的权限模板发送给所述集中管理平台,以使所述集中管理平台基于所述权限模板确定所述第一操作权限,其中所述权限模板包括所述设备权限与设备功能之间的对应关系。sending the pre-built authority template of the network device to the centralized management platform, so that the centralized management platform determines the first operation authority based on the authority template, wherein the authority template includes the device authority and the device Correspondence between functions.
示例性的,权限模板包括设备权限与设备功能之间的对应关系。例如,具有第一设备权限的管理操作可以对第一设备功能(其中可以包括多项子功能)进行管理;具有第二设备权限的管理操作可以对第二设备功能(其中可以包括多项子功能)进行管理等。Exemplarily, the permission template includes a correspondence between device permissions and device functions. For example, the management operation with the first device authority can manage the first device function (which can include multiple sub-functions); the management operation with the second device authority can manage the second device function (which can include multiple sub-functions) ) for management, etc.
集中管理平台可以根据该权限模板来构建第一操作权限的具体内容,如设置管理员权限操作网络设备的哪些具体功能,从而实现了对网络设备细粒度的权限控制。The centralized management platform can construct the specific content of the first operation authority according to the authority template, such as setting which specific functions of the network equipment the administrator authority can operate, thereby realizing fine-grained authority control on the network equipment.
基于同样的发明构思,本申请实施例还提供了一种网络设备,该网络设备可以是应用于网络的设备,包括网络安全设备,如边界防火墙、Web应用防火墙、云计算虚拟防火墙、网络审计系统等。如图8所示,该网络设备包括:Based on the same inventive concept, the embodiment of this application also provides a network device, which can be a device applied to the network, including network security devices, such as border firewalls, web application firewalls, cloud computing virtual firewalls, and network audit systems wait. As shown in Figure 8, the network equipment includes:
获取模块,其配置为利用安装在所述网络设备中的代理程序,获取集中管理平台发送的登陆信息,其中所述网络设备在所述集中管理平台注册。An acquisition module configured to acquire login information sent by a centralized management platform by using an agent program installed in the network device, where the network device is registered on the centralized management platform.
示例性的,代理程序可以预先安装在网络设备中,如在网络设备出厂前可以预先安装,或者在用户使用网络设备的过程中安装等,可以根据实际使用场景而灵活操作。Exemplarily, the agent program can be pre-installed in the network device, for example, it can be pre-installed before the network device leaves the factory, or it can be installed during the user's use of the network device, etc., and can be flexibly operated according to actual usage scenarios.
代理程序分别与集中管理平台和网络设备的设备本体连接,集中管理平台可以通过代理程序向设备本体请求认证,而代理程序安装在网络设备上,从而避免了将相关的认证信息频繁在集中管理平台和设备本体之间流转,也避免了整体系统资源的过度消耗。The agent program is respectively connected to the centralized management platform and the device body of the network device. The centralized management platform can request authentication from the device body through the agent program, and the agent program is installed on the network device, thus avoiding the frequent transfer of relevant authentication information to the centralized management platform. It also avoids excessive consumption of overall system resources.
集中管理平台可以设置在不同于网络设备的其他设备上,集中管理平台可以与用户进行交互,接收用户输入信息,生成相应的指令。如基于用户的操作信息而生成相应的配置信息,用于对网络设备进行配置。网络设备可以在集中管理平台注册,从而建立集中管理平台与网络设备之间的关系。The centralized management platform can be installed on other devices different from network devices, and the centralized management platform can interact with users, receive user input information, and generate corresponding instructions. For example, corresponding configuration information is generated based on the user's operation information to configure the network device. Network devices can be registered on the centralized management platform, thereby establishing a relationship between the centralized management platform and network devices.
在需要对网络设备进行操作前,用户可以登录集中管理平台,通过集中管理平台向代理程序发送登陆信息。登陆信息是用于认证集中管理平台,以及设置管理网络设备权限的相关信息,如可以包括用户名、密码。获取模块可以利用代理程序对登陆信息进行认证,从而确定集中管理平台的合法性。Before operating the network equipment, the user can log in to the centralized management platform, and send login information to the agent program through the centralized management platform. The login information is used for authenticating the centralized management platform and setting the authority to manage network devices, such as user name and password. The acquisition module can use the agent program to authenticate the login information, so as to determine the legitimacy of the centralized management platform.
生成模块,其配置为基于所述登陆信息,利用所述代理程序生成请求操作所述网络设备的访问信息,其中所述访问信息包括请求操作所述网络设备的设备权限。A generating module configured to use the agent program to generate access information requesting to operate the network device based on the login information, wherein the access information includes a device authority requesting to operate the network device.
示例性的,登陆信息可以是用于认证集中管理平台,以及设置管理网络设备权限的相关信息。代理程序可以根据登陆信息中的内容对集中管理平台进行认证,如通过认证,则生成模块可以利用代理程序基于登陆信息生成请求操作所述网络设备的访问信息。该访问信息用于申请访问网络设备,包括账号信息以及设备权限,其中设备权限为请求操作所述网络设备的权限。通过该账号信息登陆后可以使用该设备权限对网络设备进行管理。Exemplarily, the login information may be relevant information for authenticating the centralized management platform and setting permissions for managing network devices. The agent program can authenticate the centralized management platform according to the content in the login information. If the authentication is passed, the generation module can use the agent program to generate access information requesting to operate the network device based on the login information. The access information is used to apply for access to the network device, including account information and device authority, wherein the device authority is the authority to request to operate the network device. After logging in with this account information, you can use this device authority to manage network devices.
在一个实施例中,生成模块可以利用代理程序根据登陆信息生成访问信息,该访问信息包括一个或多个账号信息及其对应的设备权限。例如,第一账号对应了第一设备权限,以第一账号请求使用第一设备权限访问网络设备;第二账号对应了第二设备权限,以第二账号请求使用第二设备权限访问网络设备等。In one embodiment, the generation module may use an agent program to generate access information according to the login information, where the access information includes one or more account information and corresponding device permissions. For example, the first account corresponds to the first device authority, and the first account is used to request to use the first device authority to access the network device; the second account corresponds to the second device authority, and the second account is used to request to use the second device authority to access the network device, etc. .
在另一个实施例中,设备权限可以是设备本体与集中管理平台进行约定的权限,该设备权限可以与设备本体的功能相关联,各个设备权限可以关联与其相对应的功能。In another embodiment, the device permission may be a permission agreed between the device body and the centralized management platform, the device permission may be associated with the function of the device body, and each device permission may be associated with its corresponding function.
发送模块,其配置为利用所述代理程序,将所述访问信息发送给所述网络设备的设备本体,以使所述设备本体基于所述访问信息,生成用于认证登陆所述设备本体并进行操作的认证标识,并将所述认证标识反馈给所述代理程序。A sending module, configured to use the agent program to send the access information to the device body of the network device, so that the device body generates an authentication log on the device body based on the access information and performs The authentication ID of the operation, and feeds back the authentication ID to the agent program.
示例性的,发送模块通过代理程序将访问信息发送给设备本体,使得设备本体可以基于访问信息对代理程序进行认证,而代理程序安装在网络设备上,从而在认证过程中可以有效提高认证效率节省系统资源。Exemplarily, the sending module sends the access information to the device body through the agent program, so that the device body can authenticate the agent program based on the access information, and the agent program is installed on the network device, so that the authentication process can effectively improve the authentication efficiency and save system resource.
访问信息可以包括设备权限和账号信息,设备权限可以是针对管理网络设备的权限,如管理员权限、普通人员权限等。而账号信息可以包括用户名、密码等信息。设备本体可以基于访问信息,生成用于认证登陆设备本体并进行操作的认证标识。该认证标识可以用于验证代理程序的身份信息,进而验证从代理程序接收到的相应的配置请求是否合法。The access information may include device permissions and account information, and the device permissions may be permissions for managing network devices, such as administrator permissions, ordinary personnel permissions, and the like. The account information may include user name, password and other information. Based on the access information, the device body can generate an authentication ID for authenticating the login and operation of the device body. The authentication ID can be used to verify the identity information of the agent, and then verify whether the corresponding configuration request received from the agent is legal.
设备本体可以将该认证标识反馈给代理程序,代理程序可以将该认证标识存储。在一个实施例中,该认证标识与代理程序唯一对应,可以表征代理程序的合法身份。The device body can feed back the authentication identifier to the agent program, and the agent program can store the authentication identifier. In one embodiment, the authentication identifier uniquely corresponds to the agent program, and can represent the legal identity of the agent program.
管理模块,其配置为在所述代理程序获取配置请求的情况下,通过所述代理程序将所述配置请求和所述认证标识发送给所述设备本体,以请求对所述设备本体进行管理;A management module configured to send the configuration request and the authentication identifier to the device body through the agent program to request management of the device body when the agent program obtains the configuration request;
在所述认证标识通过验证的情况下,控制所述设备本体响应所述配置请求,以对所述设备本体进行管理。When the authentication identification is verified, the device body is controlled to respond to the configuration request, so as to manage the device body.
示例性的,配置请求可以是集中管理平台向网络设备发送的请求,用于请求对网络设备进行管理,包括参数的配置、功能的配置等。Exemplarily, the configuration request may be a request sent by the centralized management platform to the network device, for requesting management of the network device, including configuration of parameters, configuration of functions, and the like.
集中管理平台将该配置请求发送给代理程序。在一个实施例中,代理程序在接收到该配置请求的情况下,管理模块可以先对集中管理平台进行身份确认,确认合法后再利用代理程序将配置请求以及代理程序存储的认证标识发送给设备本体,以请求对所述设备本体进行管理。The centralized management platform sends the configuration request to the agent program. In one embodiment, when the agent program receives the configuration request, the management module can first confirm the identity of the centralized management platform, and then use the agent program to send the configuration request and the authentication identifier stored by the agent program to the device after confirming that it is legal ontology, to request management of the device ontology.
设备本体可以通过对认证标识的验证而对代理程序进行身份认证,具体的验证过程可以根据预先约定方式进行。The device body can authenticate the identity of the agent program by verifying the authentication mark, and the specific verification process can be carried out according to a pre-agreed manner.
例如,设备本体可以基于约定方式对认证标识进行加密,再将加密后的认证标识发送给代理程序进行存储。当随后接收到代理程序发送的加密后的认证标识后,可以通过相应的解密方式对认证标识进行解密,如果解密通过则可以确认证标识通过验证,确定代理程序的身份合法。当然对认证标识进行验证的方式还可以是其他多种形式。再例如,将认证标识与预存的标准标识进行对比,如相同则可以确定认证标识通过验证。For example, the device body can encrypt the authentication identifier based on the agreed method, and then send the encrypted authentication identifier to the agent program for storage. After receiving the encrypted authentication ID sent by the agent program, the authentication ID can be decrypted through the corresponding decryption method. If the decryption is successful, the authentication ID can be confirmed and the identity of the agent program is determined to be legal. Of course, the manner of verifying the certification mark may also be in other forms. For another example, the certification mark is compared with the pre-stored standard mark, and if they are the same, it can be determined that the certification mark has passed the verification.
在认证标识通过验证的情况下,设备本体可以基于配置请求进行配置操作,如对参数进行配置、对功能进行配置等。在一个实施例中,管理模块可以基于认证标识中所表征的设备权限,控制设备本体响应配置请求。从而在该设备权限下实现对网络设备的管理。When the authentication mark is verified, the device body can perform configuration operations based on the configuration request, such as configuring parameters, configuring functions, and so on. In an embodiment, the management module can control the device body to respond to the configuration request based on the device authority represented in the authentication identifier. In this way, the management of network devices is realized under the authority of the device.
在本申请的一个实施例中,生成模块进一步配置为:In one embodiment of the present application, the generation module is further configured to:
在所述登陆信息为具有第一操作权限的管理员信息的情况下,基于所述管理员信息,利用所述代理程序生成所述访问信息;When the login information is administrator information with the first operation authority, using the agent program to generate the access information based on the administrator information;
将所述访问信息中的设备权限与所述访问信息中的账号信息相关联。Associating the device authority in the access information with the account information in the access information.
在本申请的一个实施例中,发送成模块进一步配置为:In one embodiment of the present application, the sending module is further configured as:
通过所述代理程序将所述设备权限和所述账号信息发送给所述设备本体,以使所述设备本体生成与所述代理程序唯一对应的所述认证标识;sending the device authority and the account information to the device body through the agent program, so that the device body generates the authentication identifier uniquely corresponding to the agent program;
通过所述代理程序获取所述认证标识,其中所述认证标识能够表征所述代理程序的身份信息以及相关联的所述设备权限。The authentication ID is acquired through the agent program, where the authentication ID can represent the identity information of the agent program and the associated device authority.
在本申请的一个实施例中,管理模块进一步配置为:In one embodiment of the present application, the management module is further configured as:
通过所述代理程序,从所述集中管理平台获取所述配置请求;Obtain the configuration request from the centralized management platform through the agent program;
将所述配置请求和所述认证标识发送给所述设备本体,以请求所述设备本体对所述代理程序进行鉴权。Send the configuration request and the authentication identifier to the device body, so as to request the device body to authenticate the agent program.
在本申请的一个实施例中,管理模块进一步配置为:In one embodiment of the present application, the management module is further configured as:
利用与所述网络设备关联的授权单元,对所述认证标识进行鉴权,其中包括对所述代理程序的身份信息进行验证,以及确定所述代理程序管理所述设备本体的权限;Using an authorization unit associated with the network device to authenticate the authentication identifier, including verifying the identity information of the agent program and determining the authority of the agent program to manage the device itself;
在所述代理程序通过身份验证的情况下,基于确定的管理所述设备本体的权限,对所述设备本体进行管理。When the agent program passes the authentication, the device body is managed based on the determined right to manage the device body.
在本申请的一个实施例中,管理模块进一步配置为:In one embodiment of the present application, the management module is further configured as:
基于所述设备本体中建立的代理程序列表,对所述代理程序颁发可信凭证;issuing a trusted credential to the agent program based on the agent program list established in the device body;
基于所述可信凭证,将所述网络设备在所述集中管理平台进行注册。Registering the network device on the centralized management platform based on the trusted credential.
在本申请的一个实施例中,管理模块进一步配置为:In one embodiment of the present application, the management module is further configured as:
将所述网络设备预先构建的权限模板发送给所述集中管理平台,以使所述集中管理平台基于所述权限模板确定所述第一操作权限,其中所述权限模板包括所述设备权限与设备功能之间的对应关系。sending the pre-built authority template of the network device to the centralized management platform, so that the centralized management platform determines the first operation authority based on the authority template, wherein the authority template includes the device authority and the device Correspondence between functions.
基于同样的发明构思,本申请实施例还提供了一种电子设备,如图9所示,包括处理器和存储器,所述存储器中存储有可执行程序,所述处理器执行所述可执行程序以进行如上所述的方法的步骤。Based on the same inventive concept, an embodiment of the present application also provides an electronic device, as shown in FIG. 9 , including a processor and a memory, an executable program is stored in the memory, and the processor executes the executable program. to carry out the steps of the method as described above.
基于同样的发明构思,本申请实施例还提供了一种存储介质,其特征在于,所述存储介质承载有一个或者多个计算机程序,所述一个或者多个计算机程序被处理器执行以实现如上所述方法的步骤。Based on the same inventive concept, an embodiment of the present application also provides a storage medium, which is characterized in that the storage medium carries one or more computer programs, and the one or more computer programs are executed by a processor to implement the above The steps of the method.
本领域技术人员应明白,本申请的实施例可提供为方法、电子设备、计算机可读存储介质或计算机程序产品。因此,本申请可采用完全硬件实施例、完全软件实施例、或结合软件和硬件的实施例的形式。而且,本申请可采用在一个或多个其中包含有计算机可用程序代码的计算机可用存储介质上实施的计算机程序产品的形式。当通过软件实现时,可以将这些功能存储在计算机可读介质中或者作为计算机可读介质上的一个或多个指令或代码进行传输。Those skilled in the art should understand that the embodiments of the present application may be provided as a method, an electronic device, a computer-readable storage medium, or a computer program product. Accordingly, the present application may take the form of an entirely hardware embodiment, an entirely software embodiment, or an embodiment combining software and hardware. Furthermore, the present application may take the form of a computer program product embodied on one or more computer-usable storage media having computer-usable program code embodied therein. When implemented in software, the functions may be stored on or transmitted over as one or more instructions or code on a computer-readable medium.
上述处理器可以是通用处理器、数字信号处理器、专用集成电路(application-specific integrated circuit,ASIC),可编程逻辑器件(programmable logic device,PLD)或其组合。上述PLD可以是复杂可编程逻辑器件(complex programmable logicdevice,CPLD),现场可编程逻辑门阵列(field-programmable gate array,FPGA),通用阵列逻辑(generic array logic,简称GAL)或其任意组合。通用处理器可以是微处理器或者任何常规的处理器等。The aforementioned processor may be a general processor, a digital signal processor, an application-specific integrated circuit (ASIC), a programmable logic device (PLD) or a combination thereof. The above-mentioned PLD may be a complex programmable logic device (complex programmable logic device, CPLD), a field-programmable gate array (field-programmable gate array, FPGA), a general array logic (generic array logic, referred to as GAL) or any combination thereof. A general purpose processor may be a microprocessor or any conventional processor or the like.
上述存储器可能包括计算机可读介质中的非永久性存储器,随机存取存储器(RAM)和/或非易失性内存等形式,如只读存储器(ROM)或闪存(flash RAM)。存储器是计算机可读介质的示例。The above-mentioned memory may include non-permanent memory in computer-readable media, random access memory (RAM) and/or non-volatile memory, such as read-only memory (ROM) or flash memory (flash RAM). The memory is an example of a computer readable medium.
上述可读存储介质可为磁碟、光盘、DVD、USB、只读存储记忆体(ROM)或随机存储记忆体(RAM)等,本申请对具体的存储介质形式不作限定。The above-mentioned readable storage medium may be a magnetic disk, an optical disk, a DVD, a USB, a read-only memory (ROM) or a random access memory (RAM), etc. The present application does not limit the specific form of the storage medium.
以上实施例仅为本申请的示例性实施例,不用于限制本申请,本申请的保护范围由权利要求书限定。本领域技术人员可以在本申请的实质和保护范围内,对本申请做出各种修改或等同替换,这种修改或等同替换也应视为落在本申请的保护范围内。The above embodiments are only exemplary embodiments of the present application, and are not intended to limit the present application, and the protection scope of the present application is defined by the claims. Those skilled in the art may make various modifications or equivalent replacements to the present application within the spirit and protection scope of the present application, and such modifications or equivalent replacements shall also be deemed to fall within the protection scope of the present application.
Claims (10)
Priority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202211385941.2ACN115941512B (en) | 2022-11-07 | 2022-11-07 | Network device management method, network device and electronic device |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202211385941.2ACN115941512B (en) | 2022-11-07 | 2022-11-07 | Network device management method, network device and electronic device |
Publications (2)
| Publication Number | Publication Date |
|---|---|
| CN115941512Atrue CN115941512A (en) | 2023-04-07 |
| CN115941512B CN115941512B (en) | 2025-05-09 |
Family
ID=86653117
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN202211385941.2AActiveCN115941512B (en) | 2022-11-07 | 2022-11-07 | Network device management method, network device and electronic device |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN115941512B (en) |
Cited By (1)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN118734276A (en)* | 2024-07-31 | 2024-10-01 | 江苏财经职业技术学院 | Financial data management method and system |
Citations (5)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US10678906B1 (en)* | 2016-12-22 | 2020-06-09 | Amazon Technologies, Inc. | Multi-service and multi-protocol credential provider |
| CN112492597A (en)* | 2020-12-14 | 2021-03-12 | 中国联合网络通信集团有限公司 | Authentication method and device |
| CN113051545A (en)* | 2020-12-11 | 2021-06-29 | 北京芯盾时代科技有限公司 | User authentication method and device |
| CN113190828A (en)* | 2021-05-25 | 2021-07-30 | 网宿科技股份有限公司 | Request proxy method, client device and proxy service device |
| CN115145973A (en)* | 2022-07-20 | 2022-10-04 | 墨奇科技(北京)有限公司 | Data operation method, program product, storage medium and electronic device |
- 2022
- 2022-11-07CNCN202211385941.2Apatent/CN115941512B/enactiveActive
Patent Citations (5)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US10678906B1 (en)* | 2016-12-22 | 2020-06-09 | Amazon Technologies, Inc. | Multi-service and multi-protocol credential provider |
| CN113051545A (en)* | 2020-12-11 | 2021-06-29 | 北京芯盾时代科技有限公司 | User authentication method and device |
| CN112492597A (en)* | 2020-12-14 | 2021-03-12 | 中国联合网络通信集团有限公司 | Authentication method and device |
| CN113190828A (en)* | 2021-05-25 | 2021-07-30 | 网宿科技股份有限公司 | Request proxy method, client device and proxy service device |
| CN115145973A (en)* | 2022-07-20 | 2022-10-04 | 墨奇科技(北京)有限公司 | Data operation method, program product, storage medium and electronic device |
Cited By (1)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN118734276A (en)* | 2024-07-31 | 2024-10-01 | 江苏财经职业技术学院 | Financial data management method and system |
Also Published As
| Publication number | Publication date |
|---|---|
| CN115941512B (en) | 2025-05-09 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| CN109936569B (en) | Decentralized digital identity login management system based on Ether house block chain | |
| US8532620B2 (en) | Trusted mobile device based security | |
| US9038138B2 (en) | Device token protocol for authorization and persistent authentication shared across applications | |
| JP5745690B2 (en) | Dynamic platform reconfiguration with multi-tenant service providers | |
| US20190052626A1 (en) | Generation and distribution of secure or cryptographic material | |
| CN108964885B (en) | Authentication method, device, system and storage medium | |
| CN100580610C (en) | Method for managing safety link in dynamic network | |
| EP1914658B1 (en) | Identity controlled data center | |
| CN101605137B (en) | Safe distribution file system | |
| WO2020143470A1 (en) | Method for issuing digital certificate, digital certificate issuing center, and medium | |
| CN105187362A (en) | Method and device for connection authentication between desktop cloud client and server-side | |
| JP2005085102A (en) | Warranty system | |
| CN109492358A (en) | A kind of open interface uniform authentication method | |
| US9059962B2 (en) | Secure access to applications behind firewall | |
| US20160285843A1 (en) | System and method for scoping a user identity assertion to collaborative devices | |
| CN116707849A (en) | Method for setting cloud service access rights and cloud management platform for enclave instances | |
| Zwattendorfer et al. | A federated cloud identity broker-model for enhanced privacy via proxy re-encryption | |
| CN119227051B (en) | Equipment access method, product, equipment and medium | |
| CN114598463B (en) | Data authentication system | |
| WO2023160632A1 (en) | Method for setting cloud service access permissions of enclave instance, and cloud management platform | |
| CN115941512B (en) | Network device management method, network device and electronic device | |
| US20090327704A1 (en) | Strong authentication to a network | |
| WO2023116239A1 (en) | Permission determination method and apparatus, and computer device and computer-readable storage medium | |
| JP2008287359A (en) | Authentication apparatus and program | |
| CN114124362B (en) | Key distribution method, device and computer readable medium |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| GR01 | Patent grant | ||
| GR01 | Patent grant |