CN115883510A - Data identification naming method in information center network - Google Patents
Data identification naming method in information center networkDownload PDFInfo
- Publication number
- CN115883510A CN115883510ACN202111135928.7ACN202111135928ACN115883510ACN 115883510 ACN115883510 ACN 115883510ACN 202111135928 ACN202111135928 ACN 202111135928ACN 115883510 ACN115883510 ACN 115883510A
- Authority
- CN
- China
- Prior art keywords
- data
- field
- identification
- basic structure
- network
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Pending
Links
- 238000000034methodMethods0.000titleclaimsabstractdescription60
- 238000004458analytical methodMethods0.000claimsabstractdescription19
- 238000013507mappingMethods0.000claimsabstractdescription16
- 238000013500data storageMethods0.000claimsabstractdescription3
- 238000004364calculation methodMethods0.000claimsdescription4
- 238000012545processingMethods0.000claimsdescription2
- 238000012795verificationMethods0.000abstractdescription7
- 238000003032molecular dockingMethods0.000abstractdescription2
- 230000008569processEffects0.000description10
- 238000010586diagramMethods0.000description8
- 230000006872improvementEffects0.000description6
- 238000005516engineering processMethods0.000description5
- 238000011161developmentMethods0.000description3
- WLNBMPZUVDTASE-HXIISURNSA-N(2r,3r,4s,5r)-2-amino-3,4,5,6-tetrahydroxyhexanal;sulfuric acidChemical compound[O-]S([O-])(=O)=O.O=C[C@H]([NH3+])[C@@H](O)[C@H](O)[C@H](O)CO.O=C[C@H]([NH3+])[C@@H](O)[C@H](O)[C@H](O)COWLNBMPZUVDTASE-HXIISURNSA-N0.000description2
- 239000000284extractSubstances0.000description2
- 230000007246mechanismEffects0.000description2
- 230000002776aggregationEffects0.000description1
- 238000004220aggregationMethods0.000description1
- 238000006243chemical reactionMethods0.000description1
- 238000004891communicationMethods0.000description1
- 230000007547defectEffects0.000description1
- 230000009977dual effectEffects0.000description1
- 230000010365information processingEffects0.000description1
- 239000000203mixtureSubstances0.000description1
- 238000012986modificationMethods0.000description1
- 230000004048modificationEffects0.000description1
- 230000006855networkingEffects0.000description1
- 238000011160researchMethods0.000description1
- 230000004044responseEffects0.000description1
- 238000000926separation methodMethods0.000description1
- 238000002910structure generationMethods0.000description1
Images
Landscapes
- Data Exchanges In Wide-Area Networks (AREA)
Abstract
Translated fromChineseDescription
Translated fromChinese技术领域technical field
本发明涉及网络技术和通信技术领域,尤其涉及一种信息中心网络中的数据标识命名方法。The invention relates to the fields of network technology and communication technology, in particular to a data identification and naming method in an information center network.
背景技术Background technique
随着物联网、移动接入、分布式信息处理、海量流媒体等新技术和应用的发展,当前基于TCP/IP架构的计算机网络性能已经逐渐趋于极限,信息内容服务的海量需求与网络带宽瓶颈的矛盾日益加剧。因IP网络结构而出现的网络细腰问题,已经成为阻碍当前网络应用层发展的重要因素。现有互联网TCP/IP体系结构在可扩展性、移动性、多宿主和流量工程等方面存在诸多问题。互联网现在使用的IP地址具备位置信息和身份信息双重含义,混淆了位置(locator)与标识(identifier)的功能界限,存在IP地址语义过载问题。这种命名机制也是制约网络技术发展的症结所在。With the development of new technologies and applications such as the Internet of Things, mobile access, distributed information processing, and massive streaming media, the performance of the current computer network based on the TCP/IP architecture has gradually reached its limit. The massive demand for information content services and the bottleneck of network bandwidth contradictions are intensifying. The thin waist of the network due to the IP network structure has become an important factor hindering the development of the current network application layer. There are many problems in the existing Internet TCP/IP architecture in terms of scalability, mobility, multi-homing and traffic engineering. The IP address currently used on the Internet has dual meanings of location information and identity information, which confuses the functional boundaries of location (locator) and identifier (identifier), and there is a problem of IP address semantic overload. This naming mechanism is also the crux of restricting the development of network technology.
针对于上述问题,学术界和各标准组织加强了针对未来新型互联网架构的研究。本世纪初,以互联网的主要需求为导向,提出了以信息/内容为中心构建网络体系架构,解耦信息与位置关系的信息中心网络技术(Information-Centric Networking,ICN),增加网络存储信息能力,从网络层面提升内容获取、移动性支持和面向内容的安全机制能力。ICN系列的典型项目包括:NDN、DONA、NetInf、PURSUIT等。In response to the above problems, the academic community and various standards organizations have strengthened research on the future new Internet architecture. At the beginning of this century, guided by the main needs of the Internet, the information-centric network technology (Information-Centric Networking, ICN) was proposed to build a network architecture centered on information/content, decouple the relationship between information and location, and increase the ability of the network to store information , from the network level to enhance content acquisition, mobility support and content-oriented security mechanism capabilities. Typical projects of the ICN series include: NDN, DONA, NetInf, PURSUIT, etc.
目前ICN体系中的命名方法主要分为层次命名和扁平化命名方法两大类,除此之外还有基于属性命名和其他混合命名方法。CCN和TRIAD等使用层次化命名方法,具备聚合性和人类可读性等优点,与现有URL等命名方式匹配。DONA、PSIRP和NetInf等使用扁平命名方法,采用没有语义的哈希串标识数据,标识中包含标签和作为内容发布者公钥的哈希,使得内容与发布者之前存在天然安全绑定关系,具有较好的稳定性和唯一性;且由于标识长度固定,路由查找效率更高,但不便于记忆和理解。At present, the naming methods in the ICN system are mainly divided into two categories: hierarchical naming and flat naming methods. In addition, there are attribute-based naming and other hybrid naming methods. CCN and TRIAD use a hierarchical naming method, which has the advantages of aggregation and human readability, and matches the existing URL and other naming methods. DONA, PSIRP, and NetInf use flat naming methods, and use semantically-less hash strings to identify data. The identification includes tags and hashes that serve as the public key of the content publisher, so that there is a natural security binding relationship between the content and the publisher. Good stability and uniqueness; and because the identification length is fixed, the routing search efficiency is higher, but it is not easy to remember and understand.
发明内容Contents of the invention
本发明的目的在于克服现有ICN命名方法存在的技术缺陷,提出了一种信息中心网络中的数据标识命名方法,是兼具路由效率、安全保证和可读性的数据标识命名方法。The purpose of the present invention is to overcome the technical defects in the existing ICN naming method, and propose a data identification naming method in the information center network, which is a data identification naming method with routing efficiency, security guarantee and readability.
为了实现上述目的,本发明提出了一种信息中心网络中的数据标识命名方法,基于解析系统实现,所述方法包括:In order to achieve the above object, the present invention proposes a data identification and naming method in the information center network, which is realized based on the analysis system, and the method includes:
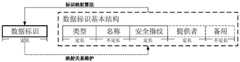
根据数据提供者提供的数据,生成数据标识基本结构;According to the data provided by the data provider, generate the basic structure of the data identification;
采用标识映射算法将数据标识基本结构映射为唯一的数据标识,所述数据标识用于提供给信息中心网络进行路由寻址和安全认证;Using the identification mapping algorithm to map the basic structure of the data identification into a unique data identification, the data identification is used to provide the information center network for routing addressing and security authentication;
向解析系统注册数据标识与存储数据的实体网络地址的映射关系,并同时注册数据标识基本结构。Register the mapping relationship between the data identifier and the network address of the entity storing the data with the parsing system, and register the basic structure of the data identifier at the same time.
作为上述方法的一种改进,所述根据数据提供者提供的数据,生成数据标识基本结构;具体包括:As an improvement of the above method, the basic structure of data identification is generated according to the data provided by the data provider; specifically includes:
根据数据内容、数据提供者和数据的URI信息,生成数据标识基本结构,所述数据标识基本结构包括:类型字段、名称字段、安全指纹字段、提供者字段以及备用字段;其中,According to the URI information of data content, data provider and data, generate the data identification basic structure, described data identification basic structure includes: type field, name field, security fingerprint field, provider field and spare field; Wherein,
所述类型字段,用于标明数据标识的类型,包括数据、设备、服务和用户,字段为固定长度;The type field is used to indicate the type of data identifier, including data, equipment, service and user, and the field is of fixed length;
所述名称字段,用于标明数据的名称,名称命名方式包括:自定义方式、URI方式、继承应用层命名方式和兼容其它网络或系统标识的命名方式,字段长度为不定长;The name field is used to indicate the name of the data, and the naming methods include: custom method, URI method, inheritance application layer naming method and naming method compatible with other network or system identifiers, and the length of the field is variable;
所述安全指纹字段,用于对数据的完整性进行验证,通过对数据进行哈希或编码计算生成,字段为固定长度;The security fingerprint field is used to verify the integrity of the data, and is generated by performing hash or encoding calculations on the data, and the field is a fixed length;
所述提供者字段,用于标明数据的原始提供者,提供者字段的命名方式包括:数据提供者的标识和数据提供者持有公钥;字段为可选字段,固定长度;The provider field is used to identify the original provider of the data. The naming method of the provider field includes: the identification of the data provider and the public key held by the data provider; the field is an optional field with a fixed length;
所述备用字段,用于扩展数据标识的其它属性,包括数据的类型,字段为可选字段,字段长度为不定长。The spare field is used to extend other attributes of the data identifier, including the type of data, the field is an optional field, and the length of the field is indefinite.
作为上述方法的一种改进,所述标识映射算法包括:使用全部或部分数据标识基本结构的字段,进行哈希算法和编码算法的处理。As an improvement of the above method, the identification mapping algorithm includes: using all or part of the fields of the data identification basic structure, and performing hash algorithm and encoding algorithm processing.
作为上述方法的一种改进,所述数据标识为固定长度。As an improvement of the above method, the data identifier is of fixed length.
作为上述方法的一种改进,所述解析系统,用于维护数据标识与数据存储实体网络地址的映射关系,配合信息中心网络完成基于数据标识的路由寻址;还用于以数据标识属性字段的方式维护数据标识基本结构,支持通过数据标识解析地址的同时携带数据标识基本结构,以进行安全认证。As an improvement of the above method, the parsing system is used to maintain the mapping relationship between the data identifier and the network address of the data storage entity, cooperate with the information center network to complete the routing addressing based on the data identifier; it is also used to use the data identifier attribute field The method maintains the basic structure of the data identification, and supports carrying the basic structure of the data identification while resolving the address through the data identification for security authentication.
作为上述方法的一种改进,所述路由寻址具体包括:As an improvement of the above method, the routing addressing specifically includes:
网络内部路由寻址时,基于数据标识向解析系统查询获得数据标识对应的存储实体的网络地址和数据标识基本结构,并基于网络地址进行路由转发;When routing within the network, query the parsing system based on the data identifier to obtain the network address of the storage entity corresponding to the data identifier and the basic structure of the data identifier, and perform routing and forwarding based on the network address;
与其他网络体制混合路由时,基于数据标识基本结构中的名称字段获得其他网络体制中数据的标识,进而在其他网络中进行路由寻址。When routing with other network systems, based on the name field in the data identification basic structure, the data identification in other network systems is obtained, and then routing addressing is performed in other networks.
作为上述方法的一种改进,所述安全认证具体包括:As an improvement of the above method, the security authentication specifically includes:
基于数据标识向解析系统查询获得数据标识对应的存储实体的网络地址和数据标识基本结构,基于数据标识基本结构中的安全指纹字段验证数据的完整性,基于数据标识基本结构中的提供者字段对数据提供者进行认证Query the parsing system based on the data identifier to obtain the network address of the storage entity corresponding to the data identifier and the basic structure of the data identifier, verify the integrity of the data based on the security fingerprint field in the basic structure of the data identifier, and verify the integrity of the data based on the provider field in the basic structure of the data identifier. The data provider is authenticated
与现有技术相比,本发明的优势在于:Compared with the prior art, the present invention has the advantages of:
本发明的方法在标识基本结构中引入数据原有名称、安全指纹、提供者等信息,基于标识基本结构生成固定长度的数据标识,并借助解析系统维护标识与基本结构的映射关系,使得数据标识在具备ICN网络中路由寻址功能的同时,兼具了对数据完整性和提供者身份验证等安全功能,同时,由于标识基本结构中保留了数据在其他网络、系统或应用中的标识或名称,为多种网络体制混合路由和与其他系统应用的对接提供了基础支撑。The method of the present invention introduces the original data name, security fingerprint, provider and other information into the basic structure of the identification, generates a fixed-length data identification based on the basic structure of the identification, and maintains the mapping relationship between the identification and the basic structure by means of the analysis system, so that the data identification While having the routing addressing function in the ICN network, it also has security functions such as data integrity and provider identity verification. At the same time, because the identification basic structure retains the identification or name of the data in other networks, systems or applications , providing basic support for the mixed routing of various network systems and the docking with other system applications.
附图说明Description of drawings
图1是本发明实施例1的示例场景图;FIG. 1 is an example scene diagram of
图2是本发明的数据标识基本结构示意图;Fig. 2 is a schematic diagram of the basic structure of the data identification of the present invention;
图3是本发明的数据标识与基本结构生成示意图,其中图3(a)是图1的ID1数据标识基本结构,图3(b)是图1的ID2数据标识基本结构;Fig. 3 is a schematic diagram of data identification and basic structure generation of the present invention, wherein Fig. 3 (a) is the ID1 data identification basic structure of Fig. 1, and Fig. 3 (b) is the ID2 data identification basic structure of Fig. 1;
图4是本发明的基于数据标识的路由寻址示意图,其中图4(a)是图1的用户A基于数据标识ID1获取数据demo1的流程,图4(b)是图1的用户A基于数据标识ID2获取数据demo2.mpg的流程;Fig. 4 is a schematic diagram of routing addressing based on data identification in the present invention, wherein Fig. 4(a) is the flow of user A in Fig. 1 acquiring data demo1 based on data identification ID1 , and Fig. 4(b) is user A in Fig. 1 based on Process for data identification ID2 to obtain data demo2.mpg;
图5是本发明的基于数据标识的完整性认证示意图;Fig. 5 is a schematic diagram of integrity authentication based on data identification in the present invention;
图6是本发明的基于数据标识的用户权限认证示意图。Fig. 6 is a schematic diagram of user authority authentication based on data identification in the present invention.
具体实施方式Detailed ways
下面结合附图和实施例对本发明的技术方案进行详细的说明。The technical solutions of the present invention will be described in detail below in conjunction with the drawings and embodiments.
实施例1Example 1
如图1所示,本发明的实施例1提供了一种信息中心网络中的数据标识命名方法。As shown in FIG. 1 ,
标识符,是指与网络地址无关的全局唯一的能够代表一个网络实体的标识符,包括但不限于数据标识符等;网络地址,是指该网络实体所在位置的网络可路由的地址信息,包括但不限于使用IP地址等信息。所描述的实施例中,左侧ICN网络实例为一种基于标识与地址分离的网络架构,使用解析系统完成标识与地址的映射后,再基于地址进行路由,其数据标识的生成使用本发明所述方法。NDN网络为一种直接使用标识进行路由寻址的ICN网络。实施例中ICN网络实例与NDN网络混合路由,通过网关E进行协议转换,实施例中所描述的示例场景如图1所示。其中:数据提供者D提供图像数据demo2.mpg,在NDN网络中的标识为NDN/videos/demo2.mpg,在ICN网络实例中的标识为ID2。数据提供者C提供数据为百度应用数据demo1,应用内名称为:baidu.com/data/demo1,在ICN网络实例中的标识为ID1。Identifier refers to a globally unique identifier that can represent a network entity regardless of the network address, including but not limited to data identifiers, etc.; network address refers to the network routable address information where the network entity is located, including But not limited to the use of information such as IP addresses. In the described embodiment, the ICN network example on the left is a network architecture based on the separation of identifiers and addresses. After using the resolution system to complete the mapping between identifiers and addresses, routing is performed based on addresses. The data identifiers are generated using the described method. The NDN network is an ICN network that directly uses identifiers for routing addressing. In the embodiment, the ICN network instance and the NDN network mix routing, and the protocol conversion is performed through the gateway E. The example scene described in the embodiment is shown in FIG. 1 . Among them: data provider D provides image data demo2.mpg, which is identified as NDN/videos/demo2.mpg in the NDN network, and ID2 in the ICN network instance. The data provided by data provider C is Baidu application data demo1, the name in the application is: baidu.com/data/demo1, and the identifier in the ICN network instance is ID1.
实施例中数据安全指纹的计算方法采用SHA-1算法生成160bit哈希值,提供者的身份使用提供者的公钥表示。结合所描述的实施例,对标识生成、标识发布、基于标识的路由寻址、基于标识的安全认证的详细过程进行描述。如图2所示为数据标识基本结构示意图。根据数据内容、数据提供者和数据的URI信息,生成数据标识基本结构,所述数据标识基本结构包括:类型、名称、安全指纹、提供者以及备用字段;其中,The calculation method of the data security fingerprint in the embodiment uses the SHA-1 algorithm to generate a 160-bit hash value, and the provider's identity is represented by the provider's public key. In conjunction with the described embodiments, the detailed processes of ID generation, ID issuance, ID-based routing addressing, and ID-based security authentication are described. Figure 2 is a schematic diagram of the basic structure of data identification. According to the URI information of data content, data provider and data, generate the basic structure of data identification, the basic structure of data identification includes: type, name, security fingerprint, provider and spare field; wherein,
所述类型字段,用于标明标识的类型,为固定长度,包括但不限于:数据、设备、服务和用户等;The type field is used to indicate the type of identification, which is a fixed length, including but not limited to: data, equipment, service and user, etc.;
所述名称字段,用于标明数据的名称,长度为不定长,名称命名方式包括但不限于:自定义方式、URI方式、继承应用层命名方式和兼容其它网络或系统标识的命名方式等;The name field is used to indicate the name of the data, and the length is variable. The naming methods include but are not limited to: custom methods, URI methods, inherited application layer naming methods, and naming methods compatible with other network or system identifiers;
所述安全指纹字段,用于对数据的完整性进行验证,长度为定长,通过对数据进行哈希、编码计算生成,使用的哈希算法包括但不限于:SHA-1、SHA256或SM3等;优选的算法为SHA-1、SHA256或SM3。The security fingerprint field is used to verify the integrity of the data, the length is fixed, and is generated by hashing and encoding calculations on the data. The hash algorithm used includes but is not limited to: SHA-1, SHA256 or SM3, etc. ; the preferred algorithm is SHA-1, SHA256 or SM3.
所述提供者字段,用于标明数据的原始提供者,长度为定长,为可选字段;提供者字段的命名方式包括但不限于:数据提供者的标识和数据提供者持有公钥等;The provider field is used to indicate the original provider of the data, the length is fixed, and it is an optional field; the naming method of the provider field includes but is not limited to: the identification of the data provider and the public key held by the data provider, etc. ;
所述备用字段,用于扩展数据标识的其它属性,为可选字段,长度为不定长,包括但不限于:数据的类型等。The spare field is used to expand other attributes of the data identifier, and is an optional field with an indefinite length, including but not limited to: the type of data, etc.
(1)标识生成过程(1) Logo generation process
对于数据提供者C提供的数据demo1的类型、名称、安全指纹和提供者公钥相关字段信息如下所示。For the data demo1 provided by data provider C, the type, name, security fingerprint and related field information of the provider public key are as follows.
类型:0X01Type: 0X01
名称:baidu.com/data/demo1Name: baidu.com/data/demo1
安全指纹:SHA-1(demo1)Security fingerprint: SHA-1 (demo1)
提供者公钥:PKx:PKyProvider public key: PKx :PKy
基于以上原始信息,生成数据标识ID1和标识基本结构Struc1,如图3(a)所示。ID1作为该数据在ICN网络实例中的唯一标识,配合解析系统和Struc1,用于后面的路由寻址和安全认证。Based on the above original information, a data identifier ID1 and an identifier basic structure Struc1 are generated, as shown in Fig. 3(a). ID1 is used as the unique identifier of the data in the ICN network instance, and it is used for subsequent routing addressing and security authentication in conjunction with the analysis system and Struc1 .
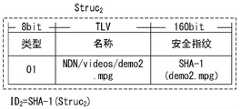
对于数据提供者D提供的数据demo.jpg的类型、名称、安全指纹相关字段信息如下所示。The type, name, and security fingerprint related field information of the data demo.jpg provided by data provider D are as follows.
类型:0X01Type: 0X01
名称:NDN/videos/demo2.mpgName: NDN/videos/demo2.mpg
安全指纹:SHA-1(demo2.mpg)Security fingerprint: SHA-1 (demo2.mpg)
基于以上原始信息,生成数据标识ID2和标识基本结构Struc2,如图3(b)所示。ID2作为该数据在ICN网络实例中的唯一标识,配合解析系统和Struc2,用于后面的混合路由寻址过程。Based on the above original information, a data identifier ID2 and a basic identifier structure Struc2 are generated, as shown in Fig. 3(b). ID2 is used as the unique identifier of the data in the ICN network instance, and is used in the subsequent hybrid routing addressing process in conjunction with the analysis system and Struc2 .
(2)标识发布过程(2) Logo release process
数据提供者C需要向解析系统注册和发布数据标识ID1和网络地址IP3的映射关系,并以属性(tag)方式携带ID1的标识基本结构Struc1信息,数据标识ID1在解析系统中注册结构的示意如表1所示。其中标识基本结构Struc1的各个字段使用tag1~tag5保存在解析系统中,标识解析时可携带相关信息。当网络节点缓存数据时,需要向解析系统注册数据标识ID1和缓存节点网络地址IP2的映射关系。Data provider C needs to register and publish the mapping relationship between data identifier ID1 and network address IP3 with the analysis system, and carry the identification basic structure Struc1 information of ID1 in the form of attribute (tag), and the data identifier ID1 is in the analysis system The schematic diagram of the registration structure is shown in Table 1. Each field of the identification basic structure Struc1 is stored in the analysis system using tag1-tag5, and relevant information can be carried during identification analysis. When the network node caches data, it needs to register the mapping relationship between the data identifier ID1 and the cache node network address IP2 with the parsing system.
表1 ID1在解析系统中的注册结构Table 1 Registration structure of ID1 in the analysis system
数据提供者D为NDN网络内的实体,要使得提供的数据在ICN网络实例中可见,需要通过网关B向解析系统注册和发布数据标识ID2和网关网络地址IP4的映射关系,并以属性(tag)方式携带ID2的标识基本结构Struc2信息,数据标识ID2在解析系统中注册结构的示意如表2所示。其中标识基本结构Struc2的各个字段使用tag1~tag5保存在解析系统中,标识解析时可携带相关信息。The data provider D is an entity in the NDN network. To make the provided data visible in the ICN network instance, it needs to register and release the mapping relationship between the data identification ID2 and the gateway network address IP4 to the analysis system through the gateway B, and use the attribute The (tag) method carries the Struc2 information of the identification basic structure of ID2 , and the registration structure of the data identification ID2 in the parsing system is shown in Table 2. Among them, each field of the identification basic structure Struc2 is stored in the analysis system using tag1~tag5, and relevant information can be carried during identification analysis.
表2 ID2在解析系统中注册结构Table 2 ID2 registration structure in the analysis system
(3)基于数据标识的路由寻址(3) Routing addressing based on data identification
用户A基于数据标识ID1获取数据demo1的流程如图4(a)所示,具体步骤如下:The process for user A to obtain data demo1 based on data ID1 is shown in Figure 4(a), and the specific steps are as follows:
步骤1)用户A基于ID1向解析系统发起解析请求;Step 1) User A initiates a resolution request to the resolution system based on ID1 ;
步骤2)解析系统返回ID1对应的网络地址IP3,以及标识基本结构信息Struc1;Step 2) the parsing system returns the network address IP3 corresponding to ID1 , and identifies the basic structural information Struc1 ;
步骤3)用户A基于IP3进行路由寻址,获取图像数据demo1。Step 3) User A performs routing addressing based on IP3 to obtain image data demo1.
(4)基于数据标识的异构网络混合路由寻址(4) Hybrid routing addressing for heterogeneous networks based on data identification
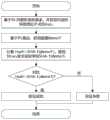
用户A基于数据标识ID2获取数据demo2.mpg的流程如图4(b)所示,具体步骤如下:The process for user A to obtain data demo2.mpg based on the data identifier ID2 is shown in Figure 4(b), and the specific steps are as follows:
步骤1)用户A基于ID2向解析系统发起解析请求;Step 1) User A initiates a resolution request to the resolution system based on ID2 ;
步骤2)解析系统返回ID2对应的网络地址IP4,以及标识基本结构信息Struc2;Step 2) the parsing system returns the network address IP4 corresponding to ID2 , and identifies the basic structural information Struc2 ;
步骤3)用户A基于IP4进行路由寻址,到达网关E;Step 3) User A performs routing addressing based on IP4 and reaches gateway E;
步骤4)在网关E处,提取Struc2中的名称字段NDN/videos/demo2.mpg,基于此字段对应标识在NDN网络中进行路由寻址,获取图像数据demo2.mpg。Step 4) At the gateway E, extract the name field NDN/videos/demo2.mpg in Struc2 , and perform routing addressing in the NDN network based on the corresponding identifier of this field to obtain the image data demo2.mpg.
(5)基于数据标识的安全认证(5) Security authentication based on data identification
用户A基于数据标识ID1请求获取数据demo1过程中,进行安全认证的流程分为:完整性验证和数据提供者验证。用户A对数据的完整性进行验证的过程如图5所示,具体步骤如下:In the process of user A requesting to obtain data demo1 based on data identification ID1 , the security authentication process is divided into: integrity verification and data provider verification. The process of user A verifying the integrity of the data is shown in Figure 5, and the specific steps are as follows:
步骤1)用户A基于ID1向解析系统获取对应的地址IP2和Struc2;Step 1) User A obtains corresponding address IP2 and Struc2 from the resolution system based on ID1 ;
步骤2)用户A基于IP2进行路由寻址,获取数据demo1’;Step 2) User A performs routing addressing based on IP2 to obtain data demo1';
步骤3)用户A计算Hash’=SHA-1(demo1’);Step 3) User A calculates Hash'=SHA-1(demo1');
步骤4)将Hash’与Struc2安全指纹字段SHA-1(demo1’)对比,若Hash’=SHA-1(demo1),则完整性验证通过;否则,验证失败。Step 4) Compare Hash' with Struc2 security fingerprint field SHA-1(demo1'), if Hash'=SHA-1(demo1), the integrity verification is passed; otherwise, the verification fails.
网络设备B为存储数据demo1的实体,数据提供者C为原始数据的提供者,用户A基于数据标识ID1请求获取数据demo1时,网络设备B要验证用户A是否具备权限获取相应数据,在此实施例中规定数据请求者为数据提供者或提供者授权用户时有权限获取相应数据。基于以上场景,需要基于数据的提供者对用户权限进行验证,如图6所示,具体步骤如下:Network device B is the entity that stores data demo1, and data provider C is the provider of the original data. When user A requests to obtain data demo1 based on data identification ID1 , network device B needs to verify whether user A has the authority to obtain the corresponding data. Here It is stipulated in the embodiment that the data requester has the right to obtain the corresponding data when he is a data provider or a user authorized by the provider. Based on the above scenarios, the data provider needs to verify user permissions, as shown in Figure 6, and the specific steps are as follows:
步骤1)用户A向网络实体B请求ID1对应的数据;Step 1) User A requests data corresponding to ID1 from network entity B;
步骤2)网络实体B基于ID1向解析系统发起解析请求获取标识ID1基本结构信息Struc1,提取提供者字段PKx:PKy;Step 2) Network entity B initiates a parsing request to the parsing system based on ID1 to obtain the basic structural information Struc1 of ID1 , and extracts the provider field PKx :PKy ;
步骤3)网络实体B通过数据提供者C的公钥,验证用户A提供的认证证书是否为提供者C签名的证书,若验证通过,则用户A为授权用户,提供数据给用户A;若验证不通过,则为非授权用户,不提供相关数据最后所应说明的是,以上实施例仅用以说明本发明的技术方案而非限制。尽管参照实施例对本发明进行了详细说明,本领域的普通技术人员应当理解,对本发明的技术方案进行修改或者等同替换,都不脱离本发明技术方案的精神和范围,其均应涵盖在本发明的权利要求范围当中。Step 3) Network entity B uses the public key of data provider C to verify whether the authentication certificate provided by user A is a certificate signed by provider C. If the verification is passed, user A is an authorized user and provides data to user A; if verified If it fails, it is an unauthorized user, and relevant data will not be provided. Finally, it should be noted that the above embodiments are only used to illustrate the technical solution of the present invention rather than limit it. Although the present invention has been described in detail with reference to the embodiments, those skilled in the art should understand that modifications or equivalent replacements to the technical solutions of the present invention do not depart from the spirit and scope of the technical solutions of the present invention, and all of them should be included in the scope of the present invention. within the scope of the claims.
Claims (7)
Priority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202111135928.7ACN115883510A (en) | 2021-09-27 | 2021-09-27 | Data identification naming method in information center network |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202111135928.7ACN115883510A (en) | 2021-09-27 | 2021-09-27 | Data identification naming method in information center network |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| CN115883510Atrue CN115883510A (en) | 2023-03-31 |
Family
ID=85762939
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN202111135928.7APendingCN115883510A (en) | 2021-09-27 | 2021-09-27 | Data identification naming method in information center network |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN115883510A (en) |
Citations (5)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN105812261A (en)* | 2016-03-07 | 2016-07-27 | 北京交通大学 | Message forwarding method and system in information center network |
| US20170359254A1 (en)* | 2016-06-14 | 2017-12-14 | Cisco Technology, Inc. | Flow classification for information centric network protocols |
| US20180227390A1 (en)* | 2014-08-29 | 2018-08-09 | Idac Holdings, Inc. | Apparatus for interfacing between information centric networks (icns) and internet protocol (ip) networks |
| CN110099135A (en)* | 2018-01-29 | 2019-08-06 | 中国科学院声学研究所 | A kind of data open service system and method based on ICN name |
| US20190297014A1 (en)* | 2018-03-22 | 2019-09-26 | Futurewei Technologies, Inc. | System and method for supporting icn-within-ip networking |
- 2021
- 2021-09-27CNCN202111135928.7Apatent/CN115883510A/enactivePending
Patent Citations (5)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20180227390A1 (en)* | 2014-08-29 | 2018-08-09 | Idac Holdings, Inc. | Apparatus for interfacing between information centric networks (icns) and internet protocol (ip) networks |
| CN105812261A (en)* | 2016-03-07 | 2016-07-27 | 北京交通大学 | Message forwarding method and system in information center network |
| US20170359254A1 (en)* | 2016-06-14 | 2017-12-14 | Cisco Technology, Inc. | Flow classification for information centric network protocols |
| CN110099135A (en)* | 2018-01-29 | 2019-08-06 | 中国科学院声学研究所 | A kind of data open service system and method based on ICN name |
| US20190297014A1 (en)* | 2018-03-22 | 2019-09-26 | Futurewei Technologies, Inc. | System and method for supporting icn-within-ip networking |
Non-Patent Citations (1)
| Title |
|---|
| 廖怡;盛益强;王劲林;: "ICN名字解析技术研究综述", 网络新媒体技术, no. 04, 15 July 2020 (2020-07-15)* |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| CN112311530B (en) | Block chain-based alliance trust distributed identity certificate management authentication method | |
| JP5215476B2 (en) | System and method for data authorization in a distributed storage network | |
| Ren et al. | Potential identity resolution systems for the industrial Internet of Things: A survey | |
| US11140177B2 (en) | Distributed data authentication and validation using blockchain | |
| US7613812B2 (en) | Peer-to-peer identity management interfaces and methods | |
| US11533161B1 (en) | DNS-based public key infrastructure for digital object architectures | |
| CN102045413B (en) | DHT expanded DNS mapping system and method for realizing DNS security | |
| CN102427427B (en) | Method for querying resolution server in Hash network and index server | |
| CN115021989B (en) | Mutual trust and mutual recognition method and system for industrial internet heterogeneous identification analysis system | |
| CN101471777B (en) | Access control system and method between domains based on domain name | |
| CN114629631B (en) | Data trusted interaction method and system based on alliance chain and electronic equipment | |
| CN101771537A (en) | Processing method and certificating method for distribution type certificating system and certificates of certification thereof | |
| WO2010127619A1 (en) | Mapping method, system and domain name server of hierarchical routing architecture | |
| Xiong et al. | Bdim: A blockchain-based decentralized identity management scheme for large scale internet of things | |
| CN115996122A (en) | Access control method, device and system | |
| Wang et al. | Scalable identifier system for industrial internet based on multi-identifier network architecture | |
| CN114448936A (en) | IPv 6-based encoding traceable network transmission rule verification method | |
| CN114449363A (en) | IPv 6-based encodable and traceable digital object control method | |
| CN110190948A (en) | A social network location sharing method that does not rely on third-party servers | |
| CN111835755B (en) | Mutual authentication method and device for IoT device and IoT business system | |
| CN114006724B (en) | A method and system for discovering and authenticating an encrypted DNS resolver | |
| CN108243190A (en) | A trusted management method and system for network identification | |
| CN115883510A (en) | Data identification naming method in information center network | |
| CN116684869A (en) | A trusted access method, system and medium for campus wireless network based on IPv6 | |
| Ashraf et al. | Dynamic naming scheme and lookup method based on trie for vehicular named data network |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| TA01 | Transfer of patent application right | ||
| TA01 | Transfer of patent application right | Effective date of registration:20230809 Address after:Room 1601, 16th Floor, East Tower, Ximei Building, No. 6 Changchun Road, High-tech Industrial Development Zone, Zhengzhou City, Henan Province, 450000 Applicant after:Zhengzhou xinrand Network Technology Co.,Ltd. Address before:100190, No. 21 West Fourth Ring Road, Beijing, Haidian District Applicant before:INSTITUTE OF ACOUSTICS, CHINESE ACADEMY OF SCIENCES Applicant before:Zhengzhou xinrand Network Technology Co.,Ltd. |