CN115883140A - A data security model architecture and a data security system - Google Patents
A data security model architecture and a data security systemDownload PDFInfo
- Publication number
- CN115883140A CN115883140ACN202211412591.4ACN202211412591ACN115883140ACN 115883140 ACN115883140 ACN 115883140ACN 202211412591 ACN202211412591 ACN 202211412591ACN 115883140 ACN115883140 ACN 115883140A
- Authority
- CN
- China
- Prior art keywords
- data
- user
- access
- information
- security
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Withdrawn
Links
Images
Landscapes
- Storage Device Security (AREA)
Abstract
Translated fromChineseDescription
Translated fromChinese技术领域technical field
本申请涉及网络安全领域,特别是涉及一种数据安全模型架构、数据安全系统。The present application relates to the field of network security, in particular to a data security model architecture and a data security system.
背景技术Background technique
随着用户对网络数据请求的增加,互联网技术(Internet Technology,IT)架构变得越来越复杂,远程办公、多分支机构办公、私有云、混合云等多种形式的不断演进,加速了企业变革,同时,也带来新的安全风险。传统的网络安全架构是基于边界的访问控制,即认为所有授权的人和设备是可以无限制地访问所属的权限,但是一旦攻击者突破边界,则内网的横向攻击将不再受阻碍,由此导致内网全部失陷。With the increase of users' requests for network data, the Internet Technology (IT) architecture has become more and more complex, and the continuous evolution of various forms such as remote office, multi-branch office, private cloud, and hybrid cloud has accelerated the development of enterprises. Change, at the same time, also brings new security risks. The traditional network security architecture is based on boundary access control, which means that all authorized people and devices can have unlimited access to their permissions, but once the attacker breaks through the boundary, the horizontal attack on the intranet will no longer be hindered, by This caused the entire intranet to fall.
由于可见,如何提高数据的安全性是本领域人员亟需解决的技术问题。As can be seen, how to improve data security is a technical problem urgently needed to be solved by those skilled in the art.
发明内容Contents of the invention
本申请的目的是提供一种数据安全模型架构、数据安全系统,用于提高数据的安全性。The purpose of this application is to provide a data security model architecture and a data security system for improving data security.
为解决上述技术问题,本申请提供一种数据安全模型架构,包括:控制平台、数据平台、安全评估系统;In order to solve the above technical problems, this application provides a data security model architecture, including: a control platform, a data platform, and a security assessment system;
所述控制平台分别与所述数据平台、所述安全策略系统连接;The control platform is respectively connected with the data platform and the security policy system;
所述数据平台与所述安全策略系统连接;The data platform is connected to the security policy system;
所述安全策略系统用于提供对用户访问信息、用户的请求信息、所述用户访问所述数据时的信息进行安全性评估的参考数据,并将所述参考数据传输至所述控制平台、所述数据平台;The security policy system is used to provide reference data for security evaluation of user access information, user request information, and information when the user accesses the data, and transmit the reference data to the control platform, the data platform;
所述控制平台至少包括策略引擎组件,所述策略引擎组件用于根据所述参考数据确定所述用户访问所述数据的初步权限;The control platform includes at least a policy engine component, and the policy engine component is used to determine the preliminary authority of the user to access the data according to the reference data;
所述数据平台由决策执行组件组成;其中,所述决策执行组件用于在所述用户访问所述数据的情况下,根据所述参考数据分别对所述用户访问信息、所述用户的请求信息、所述用户访问所述数据时的信息进行安全性评估,并获取评估结果;根据所述评估结果和所述初步权限确定所述用户访问所述数据的最终权限。The data platform is composed of decision-making execution components; wherein, the decision-making execution component is used to separately analyze the user's access information and the user's request information according to the reference data when the user accesses the data. , performing a security assessment on the information when the user accesses the data, and obtaining an assessment result; determining the final authority of the user to access the data according to the assessment result and the preliminary authority.
优选地,所述策略引擎组件用于根据所述参考数据确定所述用户访问所述数据的初步权限包括:Preferably, the policy engine component is used to determine the preliminary permission of the user to access the data according to the reference data comprising:
所述策略引擎组件用于获取目标数据;其中,所述目标数据至少包括所述用户访问信息、所述用户的请求信息、资产状态、资源访问要求、风险威胁;The policy engine component is used to obtain target data; wherein, the target data includes at least the user access information, the user request information, asset status, resource access requirements, and risk threats;
将所述目标数据和所述参考数据作为信任算法的输入;using said target data and said reference data as input to a trust algorithm;
通过所述信任算法输出用于评估所述用户的综合信任分数;outputting a composite trust score for evaluating the user through the trust algorithm;
在所述综合信任分数大于或等于第一阈值的情况下,确定所述用户访问所述数据的所述初步权限为授权。In a case where the comprehensive trust score is greater than or equal to a first threshold, it is determined that the preliminary permission for the user to access the data is authorized.
优选地,所述控制平台用于在确定所述用户访问所述数据的所述初步权限为授权之后,根据所述用户的请求信息为确定所述初步权限为授权的所述用户分配与所述请求信息对应的企业资源。Preferably, the control platform is configured to, after determining that the user's preliminary permission to access the data is authorized, assign the user who is determined to have the preliminary permission to be authorized according to the user's request information with the The enterprise resource corresponding to the requested information.
优选地,所述用户访问信息至少包括所述用户的信息、所述用户使用的设备的信息、所述用户使用的包含所述数据的应用的信息、所述用户使用所述应用时所在的环境的信息。Preferably, the user access information includes at least information about the user, information about the device used by the user, information about the application containing the data used by the user, and the environment in which the user uses the application Information.
优选地,所述安全策略系统至少包括连续诊断系统、行业合规系统、威胁情报系统、关键行为日志、数据访问系统、公钥基础设施、身份管理系统、安全信息管理系统。Preferably, the security policy system includes at least a continuous diagnosis system, an industry compliance system, a threat intelligence system, a key behavior log, a data access system, a public key infrastructure, an identity management system, and a security information management system.
优选地,所述控制平台包括:策略管理器;Preferably, the control platform includes: a policy manager;
所述策略管理器分别与所述策略引擎组件、所述策略执行组件连接,用于在所述策略引擎组件确定的所述初步权限为授权的情况下,第一预设时间内控制所述策略执行组件建立所述用户访问所述数据时的应用与所述数据所在的数据库之间的数据传输链路;The policy manager is respectively connected to the policy engine component and the policy execution component, and is used to control the policy within a first preset time when the preliminary authority determined by the policy engine component is authorization. The execution component establishes a data transmission link between the application when the user accesses the data and the database where the data is located;
在所述策略引擎组件确定的所述初步权限为拒绝的情况下,第二预设时间内控制所述策略执行组件断开所述用户访问所述数据时的应用与所述数据所在的所述数据库之间的所述数据传输链路。If the preliminary permission determined by the policy engine component is denial, control the policy enforcement component to disconnect the application when the user accesses the data from the application where the data is located within a second preset time. The data transmission link between databases.
优选地,所述决策执行组件用于在所述根据所述评估结果和所述初步权限确定所述用户访问所述数据的最终权限之后,获取所述用户访问所述数据时的应用与所述数据所在的所述数据库之间的所述数据传输链路的状态;Preferably, the decision execution component is configured to obtain the application and the user's access to the data when the user accesses the data after determining the final authority of the user to access the data according to the evaluation result and the preliminary authority. the state of the data transmission link between the databases where the data is located;
在所述数据传输链路处于断开状态的情况下,自确定出所述最终权限为授权开始,第三预设时间内建立所述数据传输链路,以便于所述用户通过所述数据传输链路访问所述数据。When the data transmission link is disconnected, the data transmission link is established within a third preset time period since it is determined that the final authority is authorization, so that the user can pass the data transmission link to access the data.
优选地,所述控制平台用于获取所述决策执行组件确定出的所述最终权限;在所述最终权限为拒绝的情况下,输出用于表征访问所述数据失败的提示信息。Preferably, the control platform is configured to acquire the final permission determined by the decision execution component; and output prompt information indicating failure to access the data when the final permission is denied.
优选地,所述控制平台用于获取访问所述数据失败的所述用户,并记录所述用户访问所述数据失败的次数;在所述次数大于或等于第二阈值的情况下,标记所述用户的信息以及更新所述安全策略系统。Preferably, the control platform is used to obtain the user who failed to access the data, and record the number of times the user failed to access the data; when the number of times is greater than or equal to a second threshold, mark the User information and update the security policy system.
为了解决上述技术问题,本申请还提供一种数据安全系统,包括上述的数据安全模型架构。In order to solve the above-mentioned technical problems, the present application further provides a data security system, including the above-mentioned data security model architecture.
本申请所提供的数据安全模型架构,包括:控制平台、数据平台、安全评估系统;控制平台分别与数据平台、安全策略系统连接;数据平台与安全策略系统连接;安全策略系统用于提供对用户访问信息、用户的请求信息、用户访问数据时的信息进行安全性评估的参考数据,并将参考数据传输至控制平台、数据平台;控制平台至少包括策略引擎组件,策略引擎组件用于根据参考数据确定用户访问数据的初步权限;数据平台由决策执行组件组成;其中,决策执行组件用于在用户访问数据的情况下,根据参考数据分别对用户访问信息、用户的请求信息、用户访问数据时的信息进行安全性评估,并获取评估结果;根据评估结果和初步权限确定用户访问数据的最终权限。相比于之前的在访问数据时,所有授权的人和设备是可以无限制地访问所属的权限,本申请提供的安全模型架构中,数据平台中的策略执行组件对用户的信息、用户的请求信息、以及用户在访问数据时的信息进行安全性评估。用户的请求信息即代表用户待访问数据时的信息,通过对用户待访问数据时的信息、用户在访问数据时的信息进行安全性评估,实现了持续性的动态评估与数据安全管控,使得权限动态变化;此外,控制平台中的策略引擎组件初步确定了用户访问数据的权限,然后结合数据平台中的策略执行组件最终确定出用户访问数据的权限,即实现了多次判断最终确定用户的访问权限,尽可能地保证了数据的安全性。The data security model architecture provided by this application includes: control platform, data platform, and security assessment system; the control platform is connected to the data platform and the security policy system respectively; the data platform is connected to the security policy system; the security policy system is used to provide user Reference data for security assessment of access information, user request information, and information when users access data, and transmit the reference data to the control platform and data platform; the control platform includes at least a policy engine component, and the policy engine component is used for reference data. Determine the preliminary authority of users to access data; the data platform is composed of decision-making execution components; among them, the decision-making execution components are used to separately analyze user access information, user request information, and user access data according to reference data when users access data. The security assessment of the information is carried out, and the assessment result is obtained; the final authority of the user to access the data is determined according to the assessment result and preliminary authority. Compared with the previous access to data, all authorized people and devices can access their rights without restriction. In the security model architecture provided by this application, the policy execution component in the data platform is responsible for user information and user requests. information, as well as the information of users when accessing data for security assessment. The user's request information represents the information when the user is about to access the data. Through the security assessment of the information when the user is about to access the data and the information when the user is accessing the data, continuous dynamic evaluation and data security control are realized, making the authority Dynamic changes; in addition, the policy engine component in the control platform preliminarily determines the user's access to data, and then combines the policy execution component in the data platform to finally determine the user's access to data, that is, it realizes multiple judgments and finally determines the user's access Permissions ensure data security as much as possible.
此外,本申请还提供一种数据安全系统,与上述提到的数据安全模型架构具有相同或相对应的技术特征,效果同上。In addition, the present application also provides a data security system, which has the same or corresponding technical features as the aforementioned data security model architecture, and has the same effect as above.
附图说明Description of drawings
为了更清楚地说明本申请实施例,下面将对实施例中所需要使用的附图做简单的介绍,显而易见地,下面描述中的附图仅仅是本申请的一些实施例,对于本领域普通技术人员来讲,在不付出创造性劳动的前提下,还可以根据这些附图获得其他的附图。In order to illustrate the embodiments of the present application more clearly, the following will briefly introduce the accompanying drawings used in the embodiments. Obviously, the accompanying drawings in the following description are only some embodiments of the present application. As far as people are concerned, other drawings can also be obtained based on these drawings on the premise of not paying creative work.
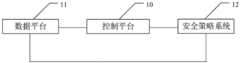
图1为本申请实施例提供的一种数据安全模型架构的示意图;FIG. 1 is a schematic diagram of a data security model architecture provided by an embodiment of the present application;
图2为本申请实施例提供的一种零信任数据安全访问动态管理组件的示意图;FIG. 2 is a schematic diagram of a zero-trust data security access dynamic management component provided by an embodiment of the present application;
图3为本申请实施例提供的一种用户通过数据安全模型架构访问业务应用数据资源的示意图。FIG. 3 is a schematic diagram of a user accessing a business application data resource through a data security model architecture provided by an embodiment of the present application.
具体实施方式Detailed ways
下面将结合本申请实施例中的附图,对本申请实施例中的技术方案进行清楚、完整地描述,显然,所描述的实施例仅仅是本申请一部分实施例,而不是全部实施例。基于本申请中的实施例,本领域普通技术人员在没有做出创造性劳动前提下,所获得的所有其他实施例,都属于本申请保护范围。The following will clearly and completely describe the technical solutions in the embodiments of the present application with reference to the drawings in the embodiments of the present application. Obviously, the described embodiments are only some of the embodiments of the present application, not all of them. Based on the embodiments in this application, all other embodiments obtained by persons of ordinary skill in the art without making creative efforts belong to the protection scope of this application.
本申请的核心是提供一种数据安全模型架构、数据安全系统,用于提高数据的安全性。当前,典型的IT架构变得越来越复杂,远程办公、多分支机构办公、私有云、混合云等多种形式的不断演进,加速了企业变革,同时,也带来新的安全风险,传统的网络安全架构是基于边界的访问控制,即认为所有授权的人和设备是可以无限制的访问所属的权限,但是一旦攻击者突破边界,则内网的横向攻击将不再受阻碍,由此导致内网全部失陷;此外,传统的基于静态策略授予访问权限的控制模型难以适应当前敏感数据泄露和各种网络攻击的难题,系统无法防止新的主体访问请求对资源产生的安全威胁,传统的访问控制方式中,而并未考虑多源属性以及由于授权后的属性变化可能导致的安全问题,因此需要实现更细粒度的主体属性访问控制。本申请中利用控制平台中的策略引擎组件以及数据平台中的策略执行组件对用户待访问数据时的信息、用户在访问数据时的信息进行安全性评估,实现持续性的动态评估与数据安全管控,使得权限动态变化,提高数据的安全性。The core of the present application is to provide a data security model architecture and a data security system for improving data security. At present, the typical IT architecture is becoming more and more complex, and the continuous evolution of various forms such as remote office, multi-branch office, private cloud, and hybrid cloud has accelerated enterprise transformation, and at the same time, it has also brought new security risks. The network security architecture is based on boundary access control, that is, all authorized people and devices are considered to have unlimited access to their rights, but once the attacker breaks through the boundary, the horizontal attack on the intranet will no longer be hindered, thus In addition, the traditional access control model based on static policies is difficult to adapt to the current problems of sensitive data leakage and various network attacks, and the system cannot prevent new subject access requests from posing security threats to resources. Traditional In the access control method, it does not consider multi-source attributes and security issues that may be caused by attribute changes after authorization, so it is necessary to implement more fine-grained subject attribute access control. In this application, the policy engine component in the control platform and the policy execution component in the data platform are used to evaluate the security of the information of the user when accessing data and the information of the user when accessing data, so as to realize continuous dynamic evaluation and data security control , making the permissions change dynamically and improving data security.
为了使本技术领域的人员更好地理解本申请方案,下面结合附图和具体实施方式对本申请作进一步的详细说明。图1为本申请实施例提供的一种数据安全模型架构的示意图,如图1所示,该模型架构包括:控制平台10、数据平台11、安全评估系统12;In order to enable those skilled in the art to better understand the solution of the present application, the present application will be further described in detail below in conjunction with the drawings and specific implementation methods. FIG. 1 is a schematic diagram of a data security model architecture provided by an embodiment of the present application. As shown in FIG. 1 , the model architecture includes: a
控制平台10分别与数据平台11、安全策略系统12连接;The
数据平台11与安全策略系统12连接;The data platform 11 is connected with the
安全策略系统12用于提供对用户访问信息、用户的请求信息、用户访问数据时的信息进行安全性评估的参考数据,并将参考数据传输至控制平台10、数据平台11;The
控制平台10至少包括策略引擎组件,策略引擎组件用于根据参考数据确定用户访问数据的初步权限;The
数据平台11由决策执行组件组成;其中,决策执行组件用于在用户访问数据的情况下,根据参考数据分别对用户访问信息、用户的请求信息、用户访问数据时的信息进行安全性评估,并获取评估结果;根据评估结果和初步权限确定用户访问数据的最终权限。The data platform 11 is composed of decision-making execution components; wherein, the decision-making execution component is used to perform security assessment on user access information, user request information, and information when the user accesses data according to the reference data when the user accesses data, and Obtain the evaluation result; determine the final permission of the user to access the data according to the evaluation result and the preliminary permission.
为了提高数据的安全性,在模型架构中设置安全策略系统。安全策略系统提供对用户访问数据时的信息进行安全性评估的参考数据。用户访问数据时的信息包含用户访问信息、用户的请求信息以及用户访问数据时的信息,具体地,用户访问信息可以包含用户的身份信息、用户的访问数据时所用的网络信息、用户访问数据时所用的应用等;用户的请求可以包括针对数据的请求、针对关键敏感数据库的请求等;用户访问数据时的信息可以包含数据的加密情况、访问的频率等。如在安全策略系统中建立身份管理系统,在身份管理系统中记录一些异常身份信息,当用户待访问数据时,可以参考身份管理系统中记录的身份信息确定用户身份是否异常。In order to improve data security, a security policy system is set in the model architecture. The security policy system provides reference data for security assessment of information when users access data. Information when users access data includes user access information, user request information, and information when users access data. Specifically, user access information may include user identity information, network information used when users access data, and information when users access data. The applications used, etc.; user requests may include requests for data, requests for key sensitive databases, etc.; information when users access data may include data encryption, access frequency, etc. For example, an identity management system is established in the security policy system, and some abnormal identity information is recorded in the identity management system. When users want to access data, they can refer to the identity information recorded in the identity management system to determine whether the user identity is abnormal.
控制平台分别与数据平台和安全策略系统连接,控制平台中的策略引擎组件可以根据安全策略系统提供的参数确定用户访问数据的初步权限。如根据安全策略系统中的身份管理系统确定出用户身份异常,控制平台可以拒绝用户访问数据;反之,则可以授权用户访问数据。The control platform is respectively connected with the data platform and the security policy system, and the policy engine component in the control platform can determine the initial authority of the user to access the data according to the parameters provided by the security policy system. If the identity management system in the security policy system determines that the identity of the user is abnormal, the control platform can deny the user access to the data; otherwise, the user can be authorized to access the data.
在控制平台确定出用户访问数据的初步权限之后,决策执行组件根据参考数据分别对用户访问信息、用户的请求信息、用户访问数据时的信息进行安全性评估,这三种信息可以分别对应用户访问阶段、应用访问阶段以及访问控制阶段产生的信息,即在这三个阶段分别进行安全性评估,并获取评估结果,根据评估结果和初步权限确定用户访问数据的最终权限。策略执行组件负责建立访问主体和被访问对象之间的安全通道,根据策略决策点的判断结果执行最终授权策略,同时负责激活、监视和终止主体与对象之间的连接。After the control platform determines the preliminary authority of the user to access the data, the decision-making execution component performs security assessment on the user access information, user request information, and information when the user accesses the data according to the reference data. These three types of information can correspond to user access respectively. The information generated in the stage, application access stage, and access control stage, that is, security assessments are performed in these three stages, and the assessment results are obtained, and the final permissions of users to access data are determined based on the assessment results and preliminary permissions. The policy execution component is responsible for establishing a secure channel between the access subject and the accessed object, executing the final authorization policy according to the judgment result of the policy decision point, and responsible for activating, monitoring and terminating the connection between the subject and the object.
确定用户访问数据的最终权限是由策略决策组件和策略执行组件共同决定的。如策略决策组件确定出用户访问数据的初步权限为拒绝,但是策略决策组件的评估结果为用户可信,则确定用户访问数据的最终权限为授权;策略决策组件确定出用户访问数据的初步权限为授权,但是策略决策组件的评估结果为用户不可信,则确定用户访问数据的最终权限为拒绝;或者策略决策组件确定出用户访问数据的初步权限为授权,但是策略决策组件的评估结果为用户不可信,则策略决策组件对用户信息进行再次识别分析,假设确定出用户可信,则确定用户访问数据的最终权限为授权。Determining the final authority of users to access data is determined jointly by the policy decision-making component and the policy execution component. If the policy decision-making component determines that the initial permission of the user to access data is denial, but the evaluation result of the policy decision-making component is that the user is credible, then it is determined that the final permission of the user to access data is authorization; the policy decision-making component determines that the preliminary permission of the user to access data is Authorization, but the evaluation result of the policy decision component is that the user is untrustworthy, then determine that the final permission of the user to access data is denied; or the policy decision component determines that the preliminary permission of the user to access data is authorization, but the evaluation result of the policy decision component is that the user cannot If the user is trusted, the policy decision-making component will re-identify and analyze the user information. Assuming that the user is determined to be credible, it will determine that the user's final authority to access data is authorization.
本实施例所提供的数据安全模型架构,包括:控制平台、数据平台、安全评估系统;控制平台分别与数据平台、安全策略系统连接;数据平台与安全策略系统连接;安全策略系统用于提供对用户访问信息、用户的请求信息、用户访问数据时的信息进行安全性评估的参考数据,并将参考数据传输至控制平台、数据平台;控制平台至少包括策略引擎组件,策略引擎组件用于根据参考数据确定用户访问数据的初步权限;数据平台由决策执行组件组成;其中,决策执行组件用于在用户访问数据的情况下,根据参考数据分别对用户访问信息、用户的请求信息、用户访问数据时的信息进行安全性评估,并获取评估结果;根据评估结果和初步权限确定用户访问数据的最终权限。相比于之前的在访问数据时,所有授权的人和设备是可以无限制地访问所属的权限,本实施例提供的安全模型架构中,数据平台中的策略执行组件对用户的信息、用户的请求信息、以及用户在访问数据时的信息进行安全性评估。用户的请求信息即代表用户待访问数据时的信息,通过对用户待访问数据时的信息、用户在访问数据时的信息进行安全性评估,实现了持续性的动态评估与数据安全管控,使得权限动态变化;此外,控制平台中的策略引擎组件初步确定了用户访问数据的权限,然后结合数据平台中的策略执行组件最终确定出用户访问数据的权限,即实现了多次判断最终确定用户的访问权限,尽可能地保证了数据的安全性。The data security model architecture provided in this embodiment includes: a control platform, a data platform, and a security assessment system; the control platform is connected to the data platform and the security policy system respectively; the data platform is connected to the security policy system; the security policy system is used to provide Reference data for security assessment of user access information, user request information, and information when users access data, and transmit the reference data to the control platform and data platform; the control platform includes at least a policy engine component, which is used to The data determines the initial authority of the user to access the data; the data platform is composed of decision-making execution components; among them, the decision-making execution component is used to separately analyze the user access information, user request information, and user access data according to the reference data when the user accesses the data. Conduct security assessments on the information and obtain the assessment results; determine the final permissions for users to access data based on the assessment results and preliminary permissions. Compared with the previous access to data, all authorized people and devices can access their rights without restriction. In the security model architecture provided by this embodiment, the policy execution component in the data platform has strict control over user information and user information. Request information, as well as user information when accessing data, is evaluated for security. The user's request information represents the information when the user is about to access the data. Through the security assessment of the information when the user is about to access the data and the information when the user is accessing the data, continuous dynamic evaluation and data security control are realized, making the authority Dynamic changes; in addition, the policy engine component in the control platform preliminarily determines the user's access to data, and then combines the policy execution component in the data platform to finally determine the user's access to data, that is, it realizes multiple judgments and finally determines the user's access Permissions ensure data security as much as possible.
为了使策略引擎组件确定出的初步权限较为准确,优选的实施方式是,策略引擎组件用于根据参考数据确定用户访问数据的初步权限包括:In order to make the preliminary permission determined by the policy engine component more accurate, in a preferred embodiment, the policy engine component is used to determine the preliminary permission of the user to access data according to the reference data including:
策略引擎组件用于获取目标数据;其中,目标数据至少包括用户访问信息、用户的请求信息、资产状态、资源访问要求、风险威胁;The policy engine component is used to obtain target data; wherein, the target data includes at least user access information, user request information, asset status, resource access requirements, and risk threats;
将目标数据和参考数据作为信任算法的输入;Use target data and reference data as input to the trust algorithm;
通过信任算法输出用于评估用户的综合信任分数;Output a comprehensive trust score for evaluating users through a trust algorithm;
在综合信任分数大于或等于第一阈值的情况下,确定用户访问数据的初步权限为授权。In the case that the comprehensive trust score is greater than or equal to the first threshold, it is determined that the user's preliminary right to access data is authorized.
策略引擎组件确定是否授予主体访问对象权限。该组件使用安全工具收集和分析参与对象、访问行为等多源信息,并结合安全策略作为信任算法的输入,计算得到代表主体综合可信度的综合信任分数。对于综合信任分数大于或等于第一阈值的用户授予访问数据的权限。The Policy Engine component determines whether to grant a principal access to an object. This component uses security tools to collect and analyze multi-source information such as participating objects and access behaviors, and combines security policies as the input of the trust algorithm to calculate a comprehensive trust score representing the comprehensive credibility of the subject. Authorization to access data is granted to users whose composite trust scores are greater than or equal to the first threshold.
策略引擎接受来自多个内部或外部数据源的数据输入,主要有以下5个方面的数据。The strategy engine accepts data input from multiple internal or external data sources, mainly including the following five aspects of data.
1)主体信息:表明谁在请求访问资源。包括用户的基本信息、活动信息、权限、历史用户行为等,以及常用位置、登录失败次数等设备使用信息。1) Subject information: indicates who is requesting access to resources. Including the user's basic information, activity information, permissions, historical user behavior, etc., as well as device usage information such as frequently used locations and failed login times.
2)访问请求:访问主体发起的实际请求。包含有关请求主体的信息和要请求的信息。2) Access request: the actual request initiated by the access subject. Contains information about the body of the request and the information to be requested.
3)资产状态:该记录将现有资产的位置和状态(请求的位置、补丁级别等)与数据库的资产状态进行比较,以确定对资源的访问是通过还是拒绝。3) Asset Status: This record compares the location and status of existing assets (requested location, patch level, etc.) with the database's asset status to determine whether access to the resource was passed or denied.
4)资源访问要求:定义策略的最低要求,包括资源敏感级别、访问者级别、网络之间互连的协议(Internet Protocol,IP)黑白名单等,快速排除完全不符合要求的访问者。4) Resource access requirements: Define the minimum requirements for policies, including resource sensitivity levels, visitor levels, Internet Protocol (IP) black and white lists, etc., to quickly exclude visitors who do not meet the requirements.
5)风险威胁:指当前系统中可能存在的威胁和恶意软件的信息,如恶意信息源或恶意软件命令。5) Risk threat: refers to the threat and malware information that may exist in the current system, such as malicious information sources or malware commands.
本实施例所提供的策略引擎组件,通过接受多个来自内部或外部数据源的数据输入,使得能够综合分析出用户的可信度,从而确定是否为用户授予访问数据的权限,从而提高数据安全性。The policy engine component provided by this embodiment can comprehensively analyze the credibility of the user by accepting multiple data inputs from internal or external data sources, so as to determine whether to grant the user access to data, thereby improving data security sex.
在上述实施例的基础上,当确定初步权限为授权之后,为了尽可能地保证数据的安全性,优选的实施方式是,控制平台用于在确定用户访问数据的初步权限为授权之后,根据用户的请求信息为确定初步权限为授权的用户分配与请求信息对应的企业资源。On the basis of the above-mentioned embodiments, after determining that the preliminary permission is authorization, in order to ensure data security as much as possible, a preferred implementation is that the control platform is used to The request information is to determine the preliminary authorization and assign the enterprise resource corresponding to the request information to the authorized user.
在实施中,可以按照最低权限原则,策略引擎组件对任何一个主体的身份认证和授权结果都是持续变化的,因此,为了提高数据的安全性,本实施例中仅授予主体合理的最小资源权限。如当前请求访问的是目标数据,则只向该用户分配访问目标数据的权限,而不是将访问整个数据库的权限分配给该用户。In implementation, according to the principle of least authority, the identity authentication and authorization results of any subject by the policy engine component are constantly changing. Therefore, in order to improve data security, in this embodiment, only reasonable minimum resource authority is granted to the subject . If the current request to access is the target data, only assign the user the authority to access the target data, instead of assigning the user the authority to access the entire database.
本实施例所提供的控制平台,对于初步权限为授权的用户,只分配访问预设大小的资源的访问权限,从而提高数据的安全性。The control platform provided by this embodiment only assigns access rights to resources of a preset size to users whose preliminary rights are authorized, thereby improving data security.
为了能够较准确地确定出访问数据的用户身份的安全性,优选的实施方式是,用户访问信息至少包括用户的信息、用户使用的设备的信息、用户使用的包含数据的应用的信息、用户使用应用时所在的环境的信息。In order to more accurately determine the security of the identity of the user accessing the data, a preferred embodiment is that the user access information includes at least the information of the user, the information of the device used by the user, the information of the application containing the data used by the user, the Information about the environment in which the application is made.
用户访问信息即代表的用户访问阶段的信息。访问主体包括用户、设备、应用和所处的环境。用户层面包括用户身份识别码、岗位、职务、账户状态、历史访问行为等;设备层面包括操作系统、地址服务等;应用层面包括应用软件等;环境层面包括地理位置、网络环境、计算环境等,在访问阶段,会将非法用户和非法终端拦截在用户访问阶段之外,直接阻断恶意用户和非法终端的访问。The user access information refers to the information of the user access stage represented. Access subjects include users, devices, applications, and environments. The user level includes user identification codes, positions, positions, account status, historical access behavior, etc.; the device level includes operating systems, address services, etc.; the application level includes application software, etc.; the environment level includes geographic location, network environment, computing environment, etc. In the access phase, illegal users and illegal terminals will be blocked outside the user access phase, and the access of malicious users and illegal terminals will be blocked directly.
本实施例所提供的确定用户访问信息的安全性的方式,从多个层面综合分析用户的访问信息,较准确地识别出用户访问的安全性,从而提高数据的安全性。The method for determining the security of user access information provided in this embodiment comprehensively analyzes the user access information from multiple levels, and more accurately identifies the security of user access, thereby improving data security.
同样地,为了提高数据的安全性,优选的实施方式是,安全策略系统至少包括连续诊断系统、行业合规系统、威胁情报系统、关键行为日志、数据访问系统、公钥基础设施、身份管理系统、安全信息管理系统。Similarly, in order to improve data security, the preferred embodiment is that the security policy system includes at least continuous diagnosis system, industry compliance system, threat intelligence system, key behavior log, data access system, public key infrastructure, identity management system , Safety information management system.
本实施例所提供的安全策略系统,包含多个方面的参考数据,使得能够根据该安全策略系统较准确地确定出用户访问数据时的安全性。The security policy system provided in this embodiment includes reference data in various aspects, so that the security of users accessing data can be determined more accurately according to the security policy system.
为了能够及时地将策略引擎组件确定的初步权限的结果传输给策略决策组件,优选的实施方式是,控制平台包括:策略管理器;In order to transmit the result of the preliminary authority determined by the policy engine component to the policy decision-making component in a timely manner, the preferred embodiment is that the control platform includes: a policy manager;
策略管理器分别与策略引擎组件、策略执行组件连接,用于在策略引擎组件确定的初步权限为授权的情况下,第一预设时间内控制策略执行组件建立用户访问数据时的应用与数据所在的数据库之间的数据传输链路;The policy manager is respectively connected with the policy engine component and the policy execution component, and is used to control the policy execution component to establish the application and data location when the user accesses the data within the first preset time under the condition that the preliminary authority determined by the policy engine component is authorization. The data transmission link between the databases;
在策略引擎组件确定的初步权限为拒绝的情况下,第二预设时间内控制策略执行组件断开用户访问数据时的应用与数据所在的数据库之间的数据传输链路。In the case that the preliminary permission determined by the policy engine component is denial, the control policy execution component disconnects the data transmission link between the application when the user accesses the data and the database where the data is located within the second preset time.
策略管理器组件依据策略引擎的信任评估结果,持续判断访问主体的授权策略是允许还是拒绝。访问请求已获得许可,并且请求认证通过,该组件将配置策略执行点以启动会话;如果拒绝访问请求,则通知策略执行点断开主体和对象的数据传输链路。对于第一预设时间和第二预设时间不作限定,根据实际情况。The policy manager component continuously judges whether the authorization policy of the access subject is allowed or denied according to the trust evaluation result of the policy engine. If the access request has been approved and the request is authenticated, the component will configure the policy enforcement point to start the session; if the access request is denied, the policy enforcement point will be notified to disconnect the data transmission link between the subject and the object. There is no limitation on the first preset time and the second preset time, according to the actual situation.
本实施例所提供的在控制平台中设置策略管理组件,通过策略管理组件通知策略执行组件建立或断开主体与对象的数据传输链路。由于通常情况下,控制平台中通常需要执行多种业务,因此,本实施例中通过控制平台中的策略管理器的控制管理作用,使得能够及时通知到策略执行组件。The policy management component provided in this embodiment is set in the control platform, and the policy management component notifies the policy execution component to establish or disconnect the data transmission link between the subject and the object. Usually, the control platform usually needs to execute multiple services, therefore, in this embodiment, the control and management function of the policy manager in the control platform enables timely notification to the policy execution component.
在确定了最终权限之后,需要主体与对象之间进行数据传输。为了能尽快传输数据,优选的实施方式是,决策执行组件用于在根据评估结果和初步权限确定用户访问数据的最终权限之后,获取用户访问数据时的应用与数据所在的数据库之间的数据传输链路的状态;After determining the final authority, data transmission between the subject and the object is required. In order to transmit data as soon as possible, the preferred implementation mode is that the decision execution component is used to obtain the data transmission between the application when the user accesses the data and the database where the data is located after determining the final authority of the user to access the data according to the evaluation result and the preliminary authority the state of the link;
在数据传输链路处于断开状态的情况下,自确定出最终权限为授权开始,第三预设时间内建立数据传输链路,以便于用户通过数据传输链路访问数据。When the data transmission link is disconnected, the data transmission link is established within a third preset time period since the final authority is determined to be authorization, so that the user can access data through the data transmission link.
在上文中描述的实施例中,策略引擎组件确定出初步权限为授权的情况下,可以为用户分配较小的资源,因此,此时主体与对象之间的数据传输链路是连接;反之,主体与对象之间的数据传输链路是断开的。故而,在确定出最终权限之后,可以先进行输出传输链路的连接状态的判断。当数据传输链路是连接状态,便可以直接进行数据传输;当数据传输链路是断开状态,则在第三预设时间内建立数据传输链路,以便进行主体与对象之间的数据传输。对于第三预设时间不作限定,优选地,为了能够及时地进行数据传输,在确定出最终权限为授权开始,立即建立数据传输链路。In the embodiment described above, when the policy engine component determines that the preliminary authority is authorization, it can allocate relatively small resources to the user. Therefore, at this time, the data transmission link between the subject and the object is a connection; otherwise, The data transmission link between the subject and the object is broken. Therefore, after the final authority is determined, the connection state of the output transmission link can be judged first. When the data transmission link is connected, data transmission can be performed directly; when the data transmission link is disconnected, the data transmission link is established within the third preset time for data transmission between the subject and the object . The third preset time is not limited. Preferably, in order to perform data transmission in a timely manner, the data transmission link is established immediately after it is determined that the final authority is authorization.
本实施例所提供的方法中,通过对数据传输链路的判断,使得能够及时了解数据传输链路的情况,从而及时地对断开的数据传输链路进行建立,进而进行数据的传输。In the method provided in this embodiment, by judging the data transmission link, the situation of the data transmission link can be known in time, so that the disconnected data transmission link can be established in time, and then data transmission can be performed.
为了方便用户及时了解到访问数据的权限,优选的实施方式是,控制平台用于获取决策执行组件确定出的最终权限;在最终权限为拒绝的情况下,输出用于表征访问数据失败的提示信息。In order to facilitate users to know the authority to access data in a timely manner, the preferred embodiment is that the control platform is used to obtain the final authority determined by the decision-making execution component; when the final authority is denied, output prompt information for indicating failure to access data .
本实施例所提供的方法中,通过提示信息,使得用户能够及时了解到是否可以访问数据。In the method provided in this embodiment, the user can know in time whether the data can be accessed through the prompt information.
为了提高数据的安全性,需要将安全策略系统中的参考数据进行更新,从而根据参考数据对用户的异常行为进行较准确地识别。优选的实施方式是,控制平台用于获取访问数据失败的用户,并记录用户访问数据失败的次数;在次数大于或等于第二阈值的情况下,标记用户的信息以及更新安全策略系统。In order to improve data security, it is necessary to update the reference data in the security policy system, so as to accurately identify the abnormal behavior of users according to the reference data. A preferred embodiment is that the control platform is used to obtain users who fail to access data, and record the number of times users fail to access data; when the number of times is greater than or equal to the second threshold, mark the user's information and update the security policy system.
对于第二阈值不作限定,根据实际情况确定。由于安全策略系统中包含多个方面,因此,可以定期对安全策略系统进行更新,使得能够根据安全策略系统较准确地识别出用户访问数据时的异常情况。There is no limitation on the second threshold, which is determined according to actual conditions. Since the security policy system includes multiple aspects, the security policy system can be updated regularly, so that abnormal situations when users access data can be more accurately identified according to the security policy system.
上文中描述了一种数据安全模型架构,本实施例还提供一种数据安全系统,包括上述的数据安全模型架构。A data security model architecture is described above, and this embodiment also provides a data security system, including the above-mentioned data security model architecture.
本实施例所提供的数据安全系统与上述提到的数据安全模型架构具有相对应的技术特征,上文中已对数据安全模型架构的实施例进行了详细的描述,此处对于数据安全系统的实施例不再赘述,并且具有与上述提到的数据安全模型架构相同的有益效果。The data security system provided by this embodiment has corresponding technical features with the data security model architecture mentioned above. The embodiment of the data security model architecture has been described in detail above. Here, the implementation of the data security system The example will not be described in detail, and it has the same beneficial effect as the data security model architecture mentioned above.
为了使本技术领域的人员更好地理解本申请方案,下面结合附图2和附图3和具体实施方式对本申请作进一步的详细说明。图2为本申请实施例提供的一种零信任数据安全访问动态管理组件的示意图。如图2所示,安全管理系统包括连续诊断系统、行业合规系统、威胁情报系统、关键行为日志、数据访问系统、公钥基础设施、身份管理系统、安全信息管理系统;控制平台中包含策略决策组件,策略决策组件具体包括策略引擎组件和策略管理器;数据平台中包含策略执行组件,在数据平台中,在主体不可信的情况下,通过策略执行组件再次对主体的可信性进行确认,在主体可信的情况下,允许主体访问企业资源;主体可信的情况下,可以直接访问企业资源。In order to enable those skilled in the art to better understand the solution of the present application, the present application will be further described in detail below in conjunction with accompanying drawings 2 and 3 and specific implementation methods. FIG. 2 is a schematic diagram of a zero-trust data security access dynamic management component provided by an embodiment of the present application. As shown in Figure 2, the security management system includes continuous diagnosis system, industry compliance system, threat intelligence system, key behavior log, data access system, public key infrastructure, identity management system, and security information management system; the control platform contains policy Decision-making component, the policy decision-making component specifically includes the policy engine component and the policy manager; the data platform includes the policy execution component, in the data platform, when the subject is untrustworthy, the credibility of the subject is confirmed again through the policy execution component , if the subject is credible, the subject is allowed to access enterprise resources; if the subject is credible, it can directly access enterprise resources.
图3为本申请实施例提供的一种用户通过数据安全模型架构访问业务应用数据资源的示意图。整个过程主要分为三个部分,用户访问阶段、应用访问阶段、访问控制阶段。当主体发起访问时,主体区的每个访问行为都要接受动态信任评估,经过数据安全信任评估授权后,访问相应的客体资源如业务应用和数据资源等。FIG. 3 is a schematic diagram of a user accessing a business application data resource through a data security model architecture provided by an embodiment of the present application. The whole process is mainly divided into three parts, user access phase, application access phase, and access control phase. When the subject initiates access, each access behavior in the subject area must undergo a dynamic trust assessment, and after being authorized by the data security trust assessment, access to the corresponding object resources such as business applications and data resources.
1、用户访问阶段1. User access stage
访问主体包括用户、设备、应用和所处的环境。用户层面包括用户身份识别码、岗位、职务、账户状态、历史访问行为等;设备层面包括操作系统、地址服务等;应用层面包括应用软件等;环境层面包括地理位置、网络环境、计算环境等,在访问阶段,会将非法用户和非法终端拦截在用户访问阶段之外,直接阻断恶意用户和非法终端的访问。Access subjects include users, devices, applications, and environments. The user level includes user identification codes, positions, positions, account status, historical access behavior, etc.; the device level includes operating systems, address services, etc.; the application level includes application software, etc.; the environment level includes geographic location, network environment, computing environment, etc. In the access phase, illegal users and illegal terminals will be blocked outside the user access phase, and the access of malicious users and illegal terminals will be blocked directly.
2、应用访问阶段2. Application access stage
应用访问阶段,主要是针对合法主体的请求进行判别,包括针对数据的请求、针对关键敏感数据库的请求、针对服务器的请求等,并识别出异常行为和中间人攻击行为。In the application access stage, it mainly judges the requests of legal subjects, including requests for data, requests for key sensitive databases, requests for servers, etc., and identifies abnormal behaviors and man-in-the-middle attacks.
3、访问控制阶段3. Access control stage
访问阶段,访问控制包含动态访问控制、信任评估、网络隐身、访问代理、传输加密等功能。应用访问延时趋势展示可帮助管理人员直观地了解整个监控周期内发生的访问行为是否存在安全威胁,利用动态访问控制能力,以评估信任能力,将访问客体中包含的数据资源、应用资源和服务资源等按照资源属性进行细粒度的划分。In the access phase, access control includes functions such as dynamic access control, trust evaluation, network stealth, access proxy, and transmission encryption. The display of application access delay trends can help managers intuitively understand whether there are security threats in the access behaviors that occur during the entire monitoring cycle, and use dynamic access control capabilities to assess trust capabilities, and access data resources, application resources, and services included in the object Resources are divided into fine-grained divisions according to resource attributes.
其中,在访问控制阶段,对于动态权限的安全访问模型架构设计是重中之重,通过图2中所示的零信任数据安全访问动态管理组件,实现监控行为,由策略决策组件和相应的策略执行组件共同决定主体的访问权限。Among them, in the access control stage, the security access model architecture design for dynamic permissions is the most important. Through the zero trust data security access dynamic management component shown in Figure 2, the monitoring behavior is realized, and the policy decision component and the corresponding strategy The executive components collectively determine the access rights of the principals.
由此可见,本申请提出一种基于零信任的企业数据安全模型架构,将企业数据安全访问的全生命周期分成三个阶段,即:用户访问请求阶段、应用访问请求阶段、访问控制判断阶段,通过持续性的动态评估与数据安全管控,来实现安全访问的目的;采取动态的信任评估与安全管控架构,在访问控制判断阶段,通过控制平台的策略引擎组件和策略管理器、以及数据平台的策略执行点来实现数据访问策略、公钥基础设施、身份管理系统、安全信息与数据管理系统的“全域数据信任”,提高了数据的安全性。It can be seen that this application proposes a zero-trust-based enterprise data security model architecture, which divides the entire life cycle of enterprise data security access into three stages, namely: user access request stage, application access request stage, and access control judgment stage. Through continuous dynamic evaluation and data security control, the purpose of secure access is realized; a dynamic trust assessment and security control framework is adopted, and in the access control judgment stage, the policy engine component and policy manager of the control platform, as well as the data platform Policy enforcement points are used to realize the "global data trust" of data access policy, public key infrastructure, identity management system, security information and data management system, which improves data security.
以上对本申请所提供的一种数据安全模型架构、数据安全系统进行了详细介绍。说明书中各个实施例采用递进的方式描述,每个实施例重点说明的都是与其他实施例的不同之处,各个实施例之间相同相似部分互相参见即可。对于实施例公开的装置而言,由于其与实施例公开的方法相对应,所以描述的比较简单,相关之处参见方法部分说明即可。应当指出,对于本技术领域的普通技术人员来说,在不脱离本申请原理的前提下,还可以对本申请进行若干改进和修饰,这些改进和修饰也落入本申请权利要求的保护范围内。A data security model framework and a data security system provided by the present application have been introduced in detail above. Each embodiment in the description is described in a progressive manner, each embodiment focuses on the difference from other embodiments, and the same and similar parts of each embodiment can be referred to each other. As for the device disclosed in the embodiment, since it corresponds to the method disclosed in the embodiment, the description is relatively simple, and for the related information, please refer to the description of the method part. It should be pointed out that those skilled in the art can make some improvements and modifications to the application without departing from the principles of the application, and these improvements and modifications also fall within the protection scope of the claims of the application.
还需要说明的是,在本说明书中,诸如第一和第二等之类的关系术语仅仅用来将一个实体或者操作与另一个实体或操作区分开来,而不一定要求或者暗示这些实体或操作之间存在任何这种实际的关系或者顺序。而且,术语“包括”、“包含”或者其任何其他变体意在涵盖非排他性的包含,从而使得包括一系列要素的过程、方法、物品或者设备不仅包括那些要素,而且还包括没有明确列出的其他要素,或者是还包括为这种过程、方法、物品或者设备所固有的要素。在没有更多限制的情况下,由语句“包括一个……”限定的要素,并不排除在包括所述要素的过程、方法、物品或者设备中还存在另外的相同要素。It should also be noted that in this specification, relative terms such as first and second are only used to distinguish one entity or operation from another entity or operation, and do not necessarily require or imply that these entities or operations There is no such actual relationship or order between the operations. Furthermore, the term "comprises", "comprises" or any other variation thereof is intended to cover a non-exclusive inclusion such that a process, method, article, or apparatus comprising a set of elements includes not only those elements, but also includes elements not expressly listed. other elements of or also include elements inherent in such a process, method, article, or device. Without further limitations, an element defined by the phrase "comprising a ..." does not exclude the presence of additional identical elements in the process, method, article or apparatus comprising said element.
Claims (10)
Translated fromChinesePriority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202211412591.4ACN115883140A (en) | 2022-11-11 | 2022-11-11 | A data security model architecture and a data security system |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202211412591.4ACN115883140A (en) | 2022-11-11 | 2022-11-11 | A data security model architecture and a data security system |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| CN115883140Atrue CN115883140A (en) | 2023-03-31 |
Family
ID=85759729
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN202211412591.4AWithdrawnCN115883140A (en) | 2022-11-11 | 2022-11-11 | A data security model architecture and a data security system |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN115883140A (en) |
Cited By (1)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN118677648A (en)* | 2024-05-24 | 2024-09-20 | 中国电子科技集团公司第三十研究所 | Zero trust safety protection system of integrated platform |
Citations (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN113901499A (en)* | 2021-10-18 | 2022-01-07 | 北京八分量信息科技有限公司 | A zero-trust access authority control system and method based on trusted computing |
| CN114205116A (en)* | 2021-11-16 | 2022-03-18 | 广西中科曙光云计算有限公司 | Zero-trust borderless security access system |
| CN114268494A (en)* | 2021-12-22 | 2022-04-01 | 赛尔网络有限公司 | Secure access method, system, device and medium |
| CN114499922A (en)* | 2021-11-30 | 2022-05-13 | 中国大唐集团科学技术研究总院有限公司 | Intelligent zero-trust dynamic authorization method |
- 2022
- 2022-11-11CNCN202211412591.4Apatent/CN115883140A/ennot_activeWithdrawn
Patent Citations (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN113901499A (en)* | 2021-10-18 | 2022-01-07 | 北京八分量信息科技有限公司 | A zero-trust access authority control system and method based on trusted computing |
| CN114205116A (en)* | 2021-11-16 | 2022-03-18 | 广西中科曙光云计算有限公司 | Zero-trust borderless security access system |
| CN114499922A (en)* | 2021-11-30 | 2022-05-13 | 中国大唐集团科学技术研究总院有限公司 | Intelligent zero-trust dynamic authorization method |
| CN114268494A (en)* | 2021-12-22 | 2022-04-01 | 赛尔网络有限公司 | Secure access method, system, device and medium |
Cited By (2)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN118677648A (en)* | 2024-05-24 | 2024-09-20 | 中国电子科技集团公司第三十研究所 | Zero trust safety protection system of integrated platform |
| CN118677648B (en)* | 2024-05-24 | 2025-09-23 | 中国电子科技集团公司第三十研究所 | An integrated platform zero-trust security protection system |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| Stafford | Zero trust architecture | |
| CN116545731A (en) | Zero-trust network access control method and system based on time window dynamic switching | |
| US9635029B2 (en) | Role-based access control permissions | |
| CN116708037B (en) | Cloud platform access permission control method and system | |
| CN116418568B (en) | A data security access control method, system and storage medium based on dynamic trust evaluation | |
| CN111917714B (en) | Zero trust architecture system and use method thereof | |
| CN112765639A (en) | Security micro-service architecture based on zero trust access strategy and implementation method | |
| CN111131176A (en) | Resource access control method, device, device and storage medium | |
| CN115296916B (en) | A zero-trust security system based on decision tree model | |
| US10320829B1 (en) | Comprehensive modeling and mitigation of security risk vulnerabilities in an enterprise network | |
| CN117729057A (en) | Method for accessing zero trust based on identity security | |
| CN115987644A (en) | Intelligent power distribution internet of things safety authentication system | |
| Salman et al. | Multi-level security for the 5G/IoT ubiquitous network | |
| Kim et al. | A study on the security requirements analysis to build a zero trust-based remote work environment | |
| Nawaz et al. | A Survey on Latest Trends and Technologies of Computer Systems Network | |
| CN115883140A (en) | A data security model architecture and a data security system | |
| Almarhabi | An improved smart contract-based bring your own device (BYOD) security control framework | |
| US11805418B2 (en) | System and method for location-based endpoint security | |
| KR20210026710A (en) | Trust-Aware Role-based System in Public Internet-of-Things | |
| CN117938502A (en) | Processing system and method for network security event | |
| CN115766067B (en) | A method and device for managing function services | |
| CN117650920A (en) | Zero trust safety protection method and system for evolution of power monitoring system | |
| CN116566691A (en) | General access control method and system based on PBAC and risk assessment | |
| Seefeldt | what’s new in nist zero trust architecture | |
| CN119652678B (en) | A microservice security control method in a container cloud environment |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| WW01 | Invention patent application withdrawn after publication | ||
| WW01 | Invention patent application withdrawn after publication | Application publication date:20230331 |