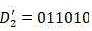CN115760126A - Financial transaction information encryption method - Google Patents
Financial transaction information encryption methodDownload PDFInfo
- Publication number
- CN115760126A CN115760126ACN202310036270.7ACN202310036270ACN115760126ACN 115760126 ACN115760126 ACN 115760126ACN 202310036270 ACN202310036270 ACN 202310036270ACN 115760126 ACN115760126 ACN 115760126A
- Authority
- CN
- China
- Prior art keywords
- node
- edge
- coding sequence
- shortest path
- encryption
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Granted
Links
- 238000000034methodMethods0.000titleclaimsabstractdescription40
- 108091026890Coding regionProteins0.000claimsabstractdescription139
- 238000010586diagramMethods0.000claimsabstractdescription16
- 230000011218segmentationEffects0.000claimsdescription12
- 230000002776aggregationEffects0.000claimsdescription9
- 238000004220aggregationMethods0.000claimsdescription9
- 238000010845search algorithmMethods0.000claimsdescription3
- 230000008569processEffects0.000description13
- 230000000694effectsEffects0.000description9
- 230000000903blocking effectEffects0.000description4
- 238000001179sorption measurementMethods0.000description4
- 230000008859changeEffects0.000description3
- 230000009286beneficial effectEffects0.000description1
- 230000018109developmental processEffects0.000description1
- 238000012986modificationMethods0.000description1
- 230000004048modificationEffects0.000description1
- 230000000750progressive effectEffects0.000description1
Images
Landscapes
- Storage Device Security (AREA)
Abstract
Description
Technical Field
The invention relates to the technical field of data encryption, in particular to a financial transaction information encryption method.
Background
In the field of financial transactions, with the development of mobile payment, the types of card swiping are gradually increased, and are not only limited to card swiping by using a physical card, but also card swiping by using a two-dimensional code, such as a common public transportation two-dimensional code card swiping device, and the like.
Data encryption is generally based on original data and the relationship between the data to replace or scramble the data, but transaction time and transaction users repeatedly exist for transaction data of a card reader, and the relationship between the transaction data of different times is obvious, but the existing encryption method does not utilize the relationship between the transaction data, but directly utilizes the existing encryption algorithm to encrypt the transaction data based on the original transaction data, at the moment, the chaos degree of the encrypted transaction data is not enough, the encryption effect is not good, and the relationship between the data is less, so that the key required by encryption is too large, and the storage of an encrypted ciphertext and the safety of financial transaction are not facilitated.
Disclosure of Invention
In order to solve the above technical problems, an object of the present invention is to provide a financial transaction information encryption method, which adopts the following technical solutions:
one embodiment of the invention provides a financial transaction information encryption method, which comprises the following steps: acquiring transaction information of a card reader, including a transaction user, transaction time and transaction amount; constructing a graph structure based on transaction information, wherein nodes in the graph structure are used for representing transaction users and transaction time respectively, and the length of edges connected between the nodes is used for representing transaction amount; obtaining a node coding sequence of each node and an edge coding sequence of edges between the nodes;
the product of the number of edges connected with one node and the number of edges between the nodes connected with the node is the complexity of the node, and the node with the maximum complexity is a reference node; obtaining the shortest path from the reference node to other nodes in the structure chart; numbering the shortest path according to the moving sequence of the reference node along the shortest path to obtain a path number; numbering edges and nodes respectively according to the sequence of the edges and the nodes in each shortest path to obtain edge labels and node labels;
setting the number of encryption rounds, the first round of encryption of the graph structure is as follows: and when the reference node moves on each shortest path, encrypting the edge coding sequence of the edge and the node coding sequence of the node in each shortest path according to the node coding sequence of the reference node, the path number of the shortest path, the edge label of the edge and the node label of the node to finish one round of encryption of the graph structure, and so on, sequentially selecting the node as the reference node according to the complexity of the node to perform each round of encryption of the graph structure until the set number of encryption rounds is finished to obtain encrypted transaction information.
Preferably, the transaction graph structure is constructed based on transaction information, including: respectively taking the transaction user and the transaction time as nodes in a graph structure; and connecting the node representing the trading user with the node representing the trading time according to the trading time of one trading user to form a graph structure.
Preferably, obtaining the node encoding sequence of each node and the edge encoding sequence of edges between the nodes comprises: the method comprises the steps that transaction user data of nodes representing transaction users are converted into binary codes to obtain node coding sequences; converting the transaction time data of the node representing the transaction time into a binary code to obtain a node coding sequence; and converting the transaction amount represented by the length of the edge in the structural diagram into a binary code to obtain an edge coding sequence of the edge.
Preferably, obtaining the shortest path from the reference node to each of the other nodes in the structure diagram includes: obtaining the shortest path from the reference node to each node in the structure chart by using a breadth-first search algorithm; when the shortest path from the reference node to one node in the structure diagram is more than one, the aggregation coefficient of each node on each shortest path corresponding to the node is obtained, and the shortest path with the maximum aggregation coefficient is the shortest path of the node.
Preferably, when the reference node moves on each shortest path, the edge coding sequence of the edge and the node coding sequence of the node in each shortest path are encrypted according to the node coding sequence of the reference node, the path number of the shortest path, the edge label of the edge, and the node label of the node, and the method includes:
when a reference node moves on the shortest path with the path number of 1 and passes through the edge with the edge number of 1, extracting a first code in the node code sequence of the reference node to obtain a new node code sequence of the reference node and the mobile code, and moving the mobile code to a first position in the edge code sequence of the edge with the edge number of 1 to obtain an encrypted code sequence of the edge with the edge number of 1; when a reference node moves to a node with the node number of 1, connecting the new node coding sequence of the reference node and the node coding sequence of the node with the node number of 1 end to end and moving one bit backwards to obtain a segmentation coding sequence, segmenting the segmentation coding sequence according to the number of codes in the new node coding sequence and the node coding sequence of the node with the node number of 1, and respectively obtaining a first new node coding sequence and an encryption coding sequence of the reference node and the node with the node number of 1;
when the reference node moves to the edge with the edge label of 2, extracting a first code in the first new node code sequence of the reference node to obtain a mobile code and a second new node code sequence of the reference node, and moving the mobile code to a second position in the edge code sequence of the edge with the edge label of 2 to obtain an encrypted code sequence of the edge with the edge label of 2; when the reference node moves to the node with the node number of 2, connecting the second new node coding sequence of the reference node with the node coding sequence of the node with the node number of 2 end to end and moving backward for two bits to obtain a first segmentation coding sequence, segmenting the first segmentation coding sequence according to the second new node coding sequence and the number of codes in the node coding sequence of the node with the node number of 2, and respectively obtaining a third new node coding sequence and an encryption coding sequence of the reference node and the node with the node number of 2; by analogy, the encryption of the node coding sequence of the node on the shortest path with the path number of 1 and the edge coding sequence of the edge is completed, and the encryption coding sequence of the last node on the shortest path with the path number of 1 is used as the replacement coding sequence of the reference node; and encrypting the edge coding sequence of the edge on the path number 2 and the node coding sequence of the node by using the replacement coding sequence of the reference node, and by analogy, encrypting the edge coding sequences of the edges and the node coding sequences of the nodes on all shortest paths in the structure diagram to complete the first round of encryption of the structure diagram.
Preferably, before extracting the first code in the node code sequence of the reference node, the method further comprises: and comparing the number of codes in the node code sequence of the reference node with the number of edges in the shortest path with the path number of 1, and if the number of codes in the node code sequence of the reference node is smaller than the number of edges in the shortest path with the path number of 1, adding a binary code from the end of the node code sequence of the reference node to ensure that the number of codes in the node code sequence of the reference node is equal to the number of edges in the shortest path with the path number of 1.
The embodiment of the invention at least has the following beneficial effects: according to the method and the device, a graph structure is constructed by utilizing the user data, the time data and the transaction amount in the transaction information of the card reader, and the transaction information of the card reader is encrypted based on the graph structure, so that the security of the encrypted data is improved, and meanwhile, the relationship among the transaction data is also revealed; the node with the maximum complexity in the graph structure is obtained to be used as a reference node, and the comprehensiveness of encrypting the edge coding sequence of the edge and the node coding sequence of the node in the graph structure by using the node coding sequence of the reference node in the follow-up process can be ensured; furthermore, the shortest path from the reference node to other nodes is obtained, so that the calculated amount of data transaction can be reduced; finally, the edge coding sequence of the edge and the node coding sequence of the node in each shortest path are encrypted according to the node coding sequence of the reference node, the path number of the shortest path, the edge label of the edge and the node label of the node to complete one round of encryption of the graph structure, the relationship between transaction data is combined, the original transaction information represented by the node and the edge in each shortest path is changed, the complexity of the encrypted transaction information of the card reader is improved, the security of the transaction information is ensured, the graph structure is also encrypted in multiple rounds, and the security of the encrypted transaction information is further ensured; and because the relation among the transaction data is combined in each round of encryption process of the graph structure, the encryption which is carried out by using the original transaction information, namely the encryption which is carried out by using the node coding sequence of the reference node, so that the key is smaller, the storage of the encrypted data is facilitated, and the security of financial transaction is ensured.
Drawings
In order to more clearly illustrate the embodiments of the present invention or the technical solutions and advantages of the prior art, the drawings used in the description of the embodiments or the prior art will be briefly described below, it is obvious that the drawings in the following description are only some embodiments of the present invention, and other drawings can be obtained by those skilled in the art without creative efforts.
FIG. 1 is a flowchart of a method for encrypting financial transaction information according to an embodiment of the present invention;
fig. 2 is a partial schematic diagram of a structural diagram provided in an embodiment of the present invention.
Detailed Description
To further illustrate the technical means and effects of the present invention for achieving the predetermined objects, the following detailed description of the financial transaction information encryption method according to the present invention, its specific implementation, structure, features and effects will be given in conjunction with the accompanying drawings and the preferred embodiments. In the following description, different "one embodiment" or "another embodiment" refers to not necessarily the same embodiment. Furthermore, the particular features, structures, or characteristics may be combined in any suitable manner in one or more embodiments.
Unless defined otherwise, all technical and scientific terms used herein have the same meaning as commonly understood by one of ordinary skill in the art to which this invention belongs.
The following describes a specific scheme of the financial transaction information encryption method provided by the present invention in detail with reference to the accompanying drawings.
Example (b):
the main application scenarios of the invention are as follows: in the field of financial transactions, transaction information of a card reader generally needs to be encrypted because the transaction information includes user privacy information. The general data encryption mainly aims at the relationship between data, and in the transaction information of the card reader, the corresponding relationship which is not unique between a user and the transaction time exists, so the invention establishes a graph structure aiming at the corresponding relationship between the user and the transaction time, represents the corresponding relationship between all the users and the transaction time by using the connection of graph nodes, and encrypts the original transaction information of the card reader by using the movement of the nodes in the graph structure.
Referring to fig. 1, a flowchart of a method for encrypting financial transaction information according to an embodiment of the present invention is shown, where the method includes the following steps:
step S1, acquiring transaction information of a card reader, wherein the transaction information comprises user data, time data and transaction amount; constructing a graph structure based on transaction information, wherein nodes in the graph structure are used for representing user data and time data respectively, and the length of edges connected between the nodes is used for representing transaction amount; a node encoding sequence for each node and an edge encoding sequence for edges between the nodes are obtained.
When each card swiping transaction is completed, the storage unit in the card swiping device directly records the information of the transaction user, the transaction time, the transaction amount and the like contained in each transaction. Therefore, the transaction information of the card reader is obtained from the storage unit of the card reader, and comprises transaction users, transaction time and transaction amount, the same transaction user can carry out transactions at multiple times, and multiple users can also carry out transactions at the same transaction time, so that the transaction information of card reading can be repeated with the previous information every time, at the moment, aiming at the characteristics that one transaction user corresponds to multiple transaction times and one transaction time corresponds to multiple user transactions, one node represents the transaction time or the user through constructing a graph structure, the corresponding relation of the transaction information is represented through the connection relation among the nodes, one node in the graph structure represents the transaction user or the transaction time, the time when one transaction user carries out transactions is determined, namely the transaction time of the transaction user, the node representing the transaction user is connected with the node representing the transaction time of the transaction user, and the node representing the transaction time in the graph structure is connected with the two nodes representing the transaction times, and the node representing the transaction time in the graph structure is connected with the two nodesThe length of the edge between the points represents the transaction amount of the transaction, as shown in FIG. 2, FIG. 2 is a partial schematic diagram of a block diagram, FIG. 2For nodes representing users of transactions, wherein a node representing a user of a transaction contains data of a user of a transaction, FIG. 2In order to represent the nodes of the transaction time, one node representing the transaction time contains transaction time data, and the length of the edge in the graph structure represents the transaction amount.
In the complete graph structure, the node representing the transaction user isIn whichThe node representing the number of transaction users and the transaction time isIn whichRepresenting the amount of time a transaction takes place, each linked in the block diagramAndi.e. representing a card-swipe transaction,andrespectively representing the time of the transaction and the user, oneConnect a plurality ofIndicating that there are multiple users performing card transactions at the same transaction time, oneConnect a plurality ofIndicating that the same user has performed card transactions at multiple times.
The graph structure representing the transaction information is obtained, the transaction user and the transaction time are taken as nodes, the original transaction information is converted into the graph structure, the transaction time and the transaction user which repeatedly appear in the original transaction information are taken as one node, the original data redundancy is greatly reduced, the data encryption and storage are facilitated, the security of the encrypted data is increased, the relationship among the transaction data is revealed, and the graph structure is conveniently encrypted based on the relationship among the transaction data.
In the encryption process, data is generally required to be converted into binary codes, so that transaction user data of nodes representing transaction users in a graph structure is converted into the binary codes to obtain node coding sequences, transaction time data of the nodes representing transaction time is converted into the binary codes to obtain the node coding sequences, transaction money represented by the length of edges in a structure graph is converted into the binary codes to obtain edge coding sequences of the edges, subsequent encryption is facilitated, it needs to be noted that the data is converted into the binary codes to form a known technology, and detailed description is not given here.
S2, the product of the number of edges connected with one node and the number of edges between the nodes connected with the node is the complexity of the node, and the node with the maximum complexity is a reference node; obtaining the shortest path from the reference node to other nodes in the structure chart; numbering the shortest path according to the moving sequence of the reference node along the shortest path to obtain a path number; and numbering the edges and the nodes respectively according to the sequence of the edges and the nodes in each shortest path to obtain edge labels and node labels.
In step S1, the transaction information is obtained, and at this time, the transaction information of the card reader is encrypted by using the relationship of the edge connection nodes in the graph structure. In the invention, the graph structure information is replaced and scrambled by using the relationship of edges between nodes, so that the encryption of the original transaction information is realized.
In order to unify the relationship representation between the nodes, the node representing the trading user and the node representing the trading time in the step S1 are not distinguished, and are uniformly represented asAnd N represents the number of nodes in the current graph structure. Firstly, according to a currently constructed graph structure and the complexity of an edge relation corresponding to a node, selecting a node as a reference node for encrypting the current graph structure, wherein the complexity of each node is as follows:
wherein,indicating the complexity of the v-th node,indicating the number of edges connected by the vth node,indicating the number of edges between nodes connected to the vth node.A larger represents a greater complexity of the vth node,the larger the local concentration of the edge of the v-th node, i.e. the more complex the edge relationship of the node,i.e. the complexity of representing the edge relation corresponding to the vth node,the larger the graph structure is, the more complicated the edge relation of the v-th node is, and the higher the relevance between the v-th node and other nodes is, so that when the graph structure is encrypted by using the relationship between the nodes, the node corresponding to the highest complexity is selected as the reference node, namely, the reference node expressed as。
The reference node with the most complex edge relation is obtained, the reference node is started, the most nodes can be covered, more nodes are involved in the encryption process, the graph structure is encrypted more comprehensively, the comprehensiveness of graph structure encryption is guaranteed, and the encryption effect is improved.
Furthermore, a graph structure constructed by the transaction information of the original card reader is obtained, the expression forms of the transaction information in the current graph structure are different, all the information represented by the nodes and the information represented by the edges in the graph structure are coded in step S1 in order to facilitate the expression forms of the graph structure and the hiding of the graph structure information, the node coding sequences of the nodes and the edge coding sequences of the edges are obtained, and at the moment, the node coding sequences of the nodes and the edge coding sequences of the edges are replaced and scrambled according to the connection relation of the nodes, so that the encryption of the original transaction information is realized.
Because the node coding sequence of other nodes and the edge coding sequence of the edge on the graph structure are encrypted based on the node coding sequence of the reference node, the reference node is required to move on the structure graph, so that the shortest path from the reference node to other nodes on the structure graph is required to be acquired, and the specific process is as follows:
node of reference nodeThe coding sequence is represented asIn the graph structure, when a connection edge moves to another node, the shortest path between the reference node and the other node, that is, the movement path, is first determined. Outputting the shortest paths between the reference node and other nodes by using the existing breadth-first search algorithm after the graph structure is input, namely obtaining the moving path of the reference node; when a plurality of shortest paths exist between the reference node and one node, the aggregation coefficient of each node on each shortest path corresponding to the node is obtained at the moment, and the shortest path with the maximum sum of the aggregation coefficients of all the nodes is selected as the shortest path of the node. The aggregation coefficient is a characteristic quantity of a graph structure, and is input into a node and all nodes connected with the node, and the aggregation coefficient of the corresponding node is output, and the acquisition of the aggregation coefficient of one node is the prior art.
In the process of moving the reference node to other nodes, the information represented by each node and each edge on the shortest path is changed, and the change of the information represented by each node and each edge on the shortest path has a corresponding relationship with the movement of the reference node, so in order to record the corresponding relationship between the change of the information represented by each node and each edge on the shortest path and the movement of the reference node, the moving sequence of the reference node to different nodes needs to be set before moving, and the moving sequence is stored as a key. That is, each shortest path needs to be numbered, specifically, when a reference node moves for the first time along a first shortest path corresponding to a first node to reach the first node, the path number corresponding to the node is 1, when the reference node moves for the second time along a second shortest path corresponding to a second node to reach the second node, the path number corresponding to the node is 2, and so on, the shortest paths are numbered according to the sequence of movement of the reference node along the shortest paths to obtain the path number of each shortest path, so far, it needs to be noted that when the shortest paths are numbered, an implementer can set rules to number according to specific situations.
Therefore, the moving path and the moving sequence of the reference node in the graph structure are obtained, the unique corresponding relation between the change of the information represented by each node and each edge and the movement of the reference node is ensured, and data decryption is ensured.
Finally, the edges and the nodes are respectively numbered according to the order of the edges and the nodes in each shortest path to obtain edge labels and node labels, specifically, the edge label of the first edge on one shortest path is 1, the node label of the first node is also 1, the edge label of the second edge is 2, the node label of the second node is also 2, and the edge label of each edge on one shortest path and the node label of each node are obtained by the same method. The preparation work before the graph structure is encrypted by using the reference node is completed, and the encryption process can be determined by using the path number of the shortest path, the edge label of the edge and the node label of the node.
Step S3, setting the number of encryption rounds, and then the first round of encryption of the graph structure is as follows: and when the reference node moves on each shortest path, encrypting the edge coding sequence of the edge and the node coding sequence of the node in each shortest path according to the node coding sequence of the reference node, the path number of the shortest path, the edge label of the edge and the node label of the node to finish one round of encryption of the graph structure, and so on, sequentially selecting the node as the reference node according to the complexity of the node to perform each round of encryption of the graph structure until the set number of encryption rounds is finished to obtain encrypted transaction information.
If only one round of encryption is performed on the graph structure, the situation that the graph structure is incompletely encrypted may occur, so that multiple rounds of encryption are required to be performed on the graph structure, each round of encryption uses different reference nodes, the first round of encryption uses the node with the highest complexity as the reference node, and the first round of encryption is described below, wherein each round of encryption only uses different reference nodes and the encryption process is the same.
In each round of encryption process, when the reference node moves on a shortest path, the code sequence of the edge of the shortest path has adsorption and blocking effects on the codes in the node code sequence of the reference node, and particularlyIn the first round of encryption, the "adsorption" effect is represented as: when a reference node moves on the shortest path with the path number of 1 and passes through the edge with the edge number of 1, a first code in the node coding sequence of the reference node is extracted to obtain a new node coding sequence of the mobile code and the reference node, the mobile code is moved to a first position in the edge coding sequence of the edge with the edge number of 1 to obtain an encrypted coding sequence of the edge with the edge number of 1, at the moment, the edge with the edge number of 1 adsorbs the code in the node coding sequence of the reference node to the edge coding sequence of the edge with the edge number of 1, for example, the node coding sequence of the reference node is the edge coding sequence of the edge with the edge number of 1The edge code sequence with the edge label 1 on the shortest path with the path number 1 isIf the edge with the edge label of 1 is absorbed, the mobile code is 1, and the new node code sequence of the reference node is 1Encrypted code sequence for edges with edge number 1At this time, the reference node completes the encryption of the edge encoding sequence of the first edge with the path number 1.
Further, when the reference node moves to the node with node number 1, the node with node number 1 has a blocking effect on the new node coding sequence of the reference node, and the "blocking" effect is represented as: connecting the new node code sequence of the reference node and the node code sequence of the node with the node number 1 end to end and moving one bit backwards to obtain a segmentation code sequence, segmenting the segmentation code sequence according to the number of codes in the new node code sequence and the node code sequence of the node with the node number 1 to respectively obtain a first new node code sequence and an addition code sequence of the reference node and the node with the node number 1A secret coding sequence; the new node coding sequence, e.g. the reference node, isNode code sequence of node with node number 1 isThen the code sequence generated end to end isMoving the code sequence generated by head-to-tail connection backward by one bit to obtain a segmented code sequenceThen the first new node code sequence of the reference node obtained after the division isThe node with node number 1 has the encryption coding sequence asAnd completing the encryption of the node coding sequence of the first node.
Then, the reference node continues to move, when the reference node moves to the edge with the edge label of 2, the first code in the first new node code sequence of the reference node is extracted to obtain the mobile code and the second new node code sequence of the reference node, the mobile code is moved to the second position in the edge code sequence of the edge with the edge label of 2, and at the moment, the first new node code sequence is the second position in the edge code sequence of the edge label of 2If the mobile code is 0, the second new node code sequence of the reference node isThe edge coding sequence of the edge with edge number 2 isThe encrypted code sequence of the side marked 2 by the "adsorption" effect。
When the reference node moves to the node with the node number of 2, connecting the second new node coding sequence of the reference node with the node coding sequence of the node with the node number of 2 end to end and moving backward for two bits to obtain a first segmentation coding sequence, segmenting the first segmentation coding sequence according to the second new node coding sequence and the number of codes in the node coding sequence of the node with the node number of 2, and respectively obtaining a third new node coding sequence and an encryption coding sequence of the reference node and the node with the node number of 2; for example, when the second new node encoding sequence of the reference node isNode code sequence of node with node number 2Then the code sequence generated end to end isThe code sequence is shifted backward by two bits to obtain the first divided code sequenceThe first division coding sequence is divided to obtain a third new node coding sequence of the reference nodeThe node marked with the number 2 has the encryption coding sequence of. By analogy, the reference node can be used for completing the edge coding sequence of the edge on the shortest path with the path number of 1And encrypting a node coding sequence of the node, further, using an encrypted coding sequence of the last node on the shortest path with the path number of 1 as a replacement coding sequence of the reference node, and encrypting an edge coding sequence of an edge on the path number of 2 and a node coding sequence of the node by using the replacement coding sequence of the reference node in the same manner as the shortest path with the path number of 1, wherein the obtained replacement coding sequence of the reference node is because the length of the node coding sequence of the reference node is continuously reduced in the moving process, so that the length of the node coding sequence of the reference node passing through one movement may not be enough to continue the movement of the reference node next time, so that the replacement coding sequence of the reference node is obtained to ensure that the next movement on the shortest path is performed by using the replacement coding sequence of the reference node when the reference node moves on the shortest path with the path number of 1, and when moving and encrypting on other shortest paths, the replacement coding sequence of the reference node obtained by replacement when each piece of shortest path is encrypted.
It should be noted that, when the edge coding sequence of an edge is encrypted, the edge label of the edge may be greater than the length of the edge coding sequence of the edge, and at this time, when finding where the moving code is added to the edge coding sequence, it is necessary to return to the first bit from the last bit of the edge coding sequence to continue finding, for example, if the moving code is 1, the edge label of an edge is 10, the edge coding sequence is 00110110, and the encryption coding sequence of the edge is 010110110. Meanwhile, when an edge coding sequence of an edge on a moving path and a node coding sequence of a node are encrypted, whether the length of the node coding sequence of a reference node supports the encryption of a shortest path is determined, taking the shortest path with the path number of 1 as an example, the number of codes in the node coding sequence of the reference node is compared with the number of edges in the shortest path with the path number of 1, if the number of codes in the node coding sequence of the reference node is smaller than the number of edges in the shortest path with the path number of 1, a binary code is added from the end of the node coding sequence of the reference node, so that the number of codes in the node coding sequence of the reference node is equal to the number of edges in the shortest path with the path number of 1. It should be noted that, when the permutation code sequence of the reference node is used to encrypt the edge code sequence of the edge in the shortest path with the path number 2 and the node code sequence of the node, the number of codes in the permutation code sequence of the reference node is compared with the number of edges in the shortest path with the path number 2, so as to determine whether the permutation code sequence needs to be subjected to bit padding. And by parity of reasoning, completing the first round of encryption of the graph structure to obtain a first round of encrypted graph structure.
Finally, the number of encryption rounds is set, preferably, the number of decryption rounds is set to 5 in this embodiment, and it should be noted that the implementer can set the number of encryption rounds according to specific situations. In the second round of encryption, the encryption is carried out on the first round of encryption graph structure, because the connection relation of the graph structure is not changed, at this time, the node with the second highest complexity is selected as the reference node to carry out mobile encryption, similarly, when the third round of encryption is carried out, the node with the third highest complexity is selected as the reference node to carry out mobile encryption, and when the fifth round of encryption is carried out, the node with the fifth highest complexity is selected as the reference node to carry out mobile encryption, so that all encryption rounds of the graph structure are completed, and the encrypted transaction information is obtained.
In each round of encryption process, the node coding sequence of the reference node and the edge coding sequence of the edge are changed simultaneously through the adsorption of the edge to the code of the reference node, and similarly, the coding information of the reference node and the coding information of the node are also changed through the blocking of the node to the code of the reference node, so that the chaos degree of an encryption result is improved, no additional parameter needs to be set in the changing process, the encryption of original data is carried out by utilizing the attribute of a graph structure, a key needing to be stored is small, and the storage of the encrypted data is facilitated. The multi-round encryption also further ensures the encryption effect, and the more complex the connection relationship of the graph structure, the better the encryption effect.
Therefore, the encryption of the transaction information of the card reader is completed, the encrypted transaction information is obtained, and the security of the transaction information in financial transactions can be guaranteed, so that the transaction information is not easy to crack.
It should be noted that: the sequence of the above embodiments of the present invention is only for description, and does not represent the advantages or disadvantages of the embodiments. And specific embodiments thereof have been described above. In addition, the processes depicted in the accompanying figures do not necessarily require the particular order shown, or sequential order, to achieve desirable results. In some embodiments, multitasking and parallel processing may also be possible or may be advantageous.
The embodiments in the present specification are described in a progressive manner, and the same and similar parts among the embodiments are referred to each other, and each embodiment focuses on the differences from the other embodiments.
The above description is only for the purpose of illustrating the preferred embodiments of the present invention and is not to be construed as limiting the present invention, and any modifications, equivalents, improvements and the like made within the scope of the present invention are intended to be included therein.
Claims (6)
1. A method for encrypting financial transaction information, the method comprising:
acquiring transaction information of a card reader, wherein the transaction information comprises a transaction user, transaction time and transaction amount; constructing a graph structure based on transaction information, wherein nodes in the graph structure are used for representing transaction users and transaction time respectively, and the length of edges connected between the nodes is used for representing transaction amount; obtaining a node coding sequence of each node and an edge coding sequence of edges between the nodes;
the product of the number of edges connected with one node and the number of edges between the nodes connected with the node is the complexity of the node, and the node with the maximum complexity is a reference node; obtaining the shortest path from the reference node to other nodes in the structure chart; numbering the shortest path according to the sequence of the movement of the reference node along the shortest path to obtain a path number; numbering edges and nodes respectively according to the sequence of the edges and the nodes in each shortest path to obtain edge labels and node labels;
setting the number of encryption rounds, the first round of encryption of the graph structure is as follows: and when the reference node moves on each shortest path, encrypting the edge coding sequence of the edge and the node coding sequence of the node in each shortest path according to the node coding sequence of the reference node, the path number of the shortest path, the edge label of the edge and the node label of the node to finish one round of encryption of the graph structure, and so on, sequentially selecting the node as the reference node according to the complexity of the node to perform each round of encryption of the graph structure until the set number of encryption rounds is finished to obtain encrypted transaction information.
2. The financial transaction information encryption method according to claim 1, wherein the constructing of the transaction graph structure based on the transaction information includes: respectively taking the transaction user and the transaction time as nodes in a graph structure; and connecting the node representing the trading user with the node representing the trading time according to the trading time of one trading user to form a graph structure.
3. The financial transaction information encryption method according to claim 1, wherein the obtaining of the node encoding sequence of each node and the edge encoding sequence of the edges between the nodes comprises: the method comprises the steps that transaction user data of nodes representing transaction users are converted into binary codes to obtain node coding sequences; converting the transaction time data of the node representing the transaction time into a binary code to obtain a node coding sequence; and converting the transaction amount represented by the length of the edge in the structural diagram into a binary code to obtain an edge coding sequence of the edge.
4. The method as claimed in claim 1, wherein the obtaining the shortest path from the reference node to each of the other nodes in the structure diagram comprises: obtaining the shortest path from the reference node to each node in the structure chart by using a breadth-first search algorithm; when the shortest path from the reference node to one node in the structure diagram is not more than one, the aggregation coefficient of each node on each shortest path corresponding to the node is obtained, and the shortest path with the largest sum of the aggregation coefficients is the shortest path of the node.
5. The financial transaction information encryption method of claim 1, wherein the encrypting the edge code sequence of the edge and the node code sequence of the node in each shortest path according to the node code sequence of the reference node, the path number of the shortest path, the edge label of the edge and the node label of the node when the reference node moves on each shortest path comprises:
when a reference node moves on the shortest path with the path number of 1 and passes through the edge with the edge number of 1, extracting a first code in the node code sequence of the reference node to obtain a new node code sequence of the mobile code and the reference node, and moving the mobile code to a first position in the edge code sequence of the edge with the edge number of 1 to obtain an encrypted code sequence of the edge with the edge number of 1; when a reference node moves to a node with the node number of 1, connecting the new node coding sequence of the reference node and the node coding sequence of the node with the node number of 1 end to end and moving one bit backwards to obtain a segmentation coding sequence, segmenting the segmentation coding sequence according to the number of codes in the new node coding sequence and the node coding sequence of the node with the node number of 1, and respectively obtaining a first new node coding sequence and an encryption coding sequence of the reference node and the node with the node number of 1;
when the reference node moves to the edge with the edge label of 2, extracting a first code in the first new node code sequence of the reference node to obtain a mobile code and a second new node code sequence of the reference node, and moving the mobile code to a second position in the edge code sequence of the edge with the edge label of 2 to obtain an encrypted code sequence of the edge with the edge label of 2; when the reference node moves to the node with the node number of 2, connecting the second new node coding sequence of the reference node with the node coding sequence of the node with the node number of 2 end to end and moving backward for two bits to obtain a first segmentation coding sequence, segmenting the first segmentation coding sequence according to the second new node coding sequence and the number of codes in the node coding sequence of the node with the node number of 2, and respectively obtaining a third new node coding sequence and an encryption coding sequence of the reference node and the node with the node number of 2; by analogy, the node coding sequence of the node on the shortest path with the path number of 1 and the edge coding sequence of the edge are encrypted, and the encrypted coding sequence of the last node on the shortest path with the path number of 1 is used as the replacement coding sequence of the reference node; and encrypting the edge coding sequence of the edge on the path number 2 and the node coding sequence of the node by using the replacement coding sequence of the reference node, and by analogy, encrypting the edge coding sequences of the edges and the node coding sequences of the nodes on all shortest paths in the structure diagram to complete the first round of encryption of the structure diagram.
6. The method of claim 5, wherein before extracting the first one of the node code sequences of the reference node, the method further comprises: and comparing the number of codes in the node coding sequence of the reference node with the number of edges in the shortest path with the path number of 1, and if the number of codes in the node coding sequence of the reference node is less than the number of edges in the shortest path with the path number of 1, adding a binary code from the tail of the node coding sequence of the reference node to ensure that the number of codes in the node coding sequence of the reference node is equal to the number of edges in the shortest path with the path number of 1.
Priority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202310036270.7ACN115760126B (en) | 2023-01-10 | 2023-01-10 | Financial transaction information encryption method |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202310036270.7ACN115760126B (en) | 2023-01-10 | 2023-01-10 | Financial transaction information encryption method |
Publications (2)
| Publication Number | Publication Date |
|---|---|
| CN115760126Atrue CN115760126A (en) | 2023-03-07 |
| CN115760126B CN115760126B (en) | 2023-05-02 |
Family
ID=85348966
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN202310036270.7AActiveCN115760126B (en) | 2023-01-10 | 2023-01-10 | Financial transaction information encryption method |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN115760126B (en) |
Cited By (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN116150714A (en)* | 2023-04-20 | 2023-05-23 | 无锡弘鼎软件科技有限公司 | Security management method for software development data |
| CN118350025A (en)* | 2024-05-07 | 2024-07-16 | 罗普特科技集团股份有限公司 | A graph data secure caching method, terminal device and storage medium |
| CN120011370A (en)* | 2025-04-18 | 2025-05-16 | 北京天耀宏图科技有限公司 | A multi-source heterogeneous spatial data retrieval method and system based on R-tree improvement |
| CN118350025B (en)* | 2024-05-07 | 2025-10-14 | 罗普特科技集团股份有限公司 | A graph data secure caching method, terminal device and storage medium |
Citations (6)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20200084027A1 (en)* | 2018-09-06 | 2020-03-12 | Bank Of Montreal | Systems and methods for encryption of data on a blockchain |
| CN113240420A (en)* | 2021-05-23 | 2021-08-10 | 上海瞳越科技有限公司 | Financial encryption payment method and system based on big data |
| CN114513297A (en)* | 2022-01-26 | 2022-05-17 | 湖南管章科技有限公司 | A POS machine data encryption method and device |
| CN114884968A (en)* | 2022-04-29 | 2022-08-09 | 深圳市迅雷网络技术有限公司 | Situation awareness method based on block chain privacy transaction and related device |
| CN115270165A (en)* | 2022-09-28 | 2022-11-01 | 南通佳茂霖智能科技有限公司 | Information management method for engineering survey |
| CN115470508A (en)* | 2022-11-02 | 2022-12-13 | 北京点聚信息技术有限公司 | Format file vectorization encryption method |
- 2023
- 2023-01-10CNCN202310036270.7Apatent/CN115760126B/enactiveActive
Patent Citations (6)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20200084027A1 (en)* | 2018-09-06 | 2020-03-12 | Bank Of Montreal | Systems and methods for encryption of data on a blockchain |
| CN113240420A (en)* | 2021-05-23 | 2021-08-10 | 上海瞳越科技有限公司 | Financial encryption payment method and system based on big data |
| CN114513297A (en)* | 2022-01-26 | 2022-05-17 | 湖南管章科技有限公司 | A POS machine data encryption method and device |
| CN114884968A (en)* | 2022-04-29 | 2022-08-09 | 深圳市迅雷网络技术有限公司 | Situation awareness method based on block chain privacy transaction and related device |
| CN115270165A (en)* | 2022-09-28 | 2022-11-01 | 南通佳茂霖智能科技有限公司 | Information management method for engineering survey |
| CN115470508A (en)* | 2022-11-02 | 2022-12-13 | 北京点聚信息技术有限公司 | Format file vectorization encryption method |
Cited By (5)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN116150714A (en)* | 2023-04-20 | 2023-05-23 | 无锡弘鼎软件科技有限公司 | Security management method for software development data |
| CN118350025A (en)* | 2024-05-07 | 2024-07-16 | 罗普特科技集团股份有限公司 | A graph data secure caching method, terminal device and storage medium |
| CN118350025B (en)* | 2024-05-07 | 2025-10-14 | 罗普特科技集团股份有限公司 | A graph data secure caching method, terminal device and storage medium |
| CN120011370A (en)* | 2025-04-18 | 2025-05-16 | 北京天耀宏图科技有限公司 | A multi-source heterogeneous spatial data retrieval method and system based on R-tree improvement |
| CN120011370B (en)* | 2025-04-18 | 2025-06-27 | 北京天耀宏图科技有限公司 | A multi-source heterogeneous spatial data retrieval method and system based on R-tree improvement |
Also Published As
| Publication number | Publication date |
|---|---|
| CN115760126B (en) | 2023-05-02 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| CN115760126A (en) | Financial transaction information encryption method | |
| US6411223B1 (en) | Generating high weight encoding symbols using a basis | |
| CN107276744B (en) | File storage encryption method and system | |
| Chee et al. | Query-efficient locally decodable codes of subexponential length | |
| CN115865953B (en) | Distributed storage system based on cross-border payment | |
| EP0851627A1 (en) | Method and device for compressing and ciphering data | |
| CN109359276B (en) | Anti-counterfeiting code generation method, device, equipment and storage medium | |
| CN115659409A (en) | Financial asset transaction data safe storage method | |
| EP4181456A1 (en) | Secure integer comparison using binary trees | |
| CN117955629A (en) | Encryption encoding method and device in DNA storage, electronic equipment and storage medium | |
| Hayashi et al. | Unified approach to secret sharing and symmetric private information retrieval with colluding servers in quantum systems | |
| US11038738B2 (en) | Encoding method and encoder for (n,n(n-1),n-1) permutation group code in communication modulation system | |
| US6411714B1 (en) | Data decompression/decryption method and system | |
| Lu et al. | Efficient 2PC for constant round secure equality testing and comparison | |
| CN108804933A (en) | A kind of system conversion method for big data | |
| CN116318867B (en) | Resource platform data transmission method based on out-of-order encryption and decryption | |
| CN105279728A (en) | Intelligent mobile terminal image steganography method based on secret information encryption pretreatment | |
| CN106712957A (en) | Two-factor authentication method based on convolutional coding | |
| Pham et al. | Sequence reconstruction problem for deletion channels: A complete asymptotic solution | |
| CN117811720A (en) | Ciphertext processing method, ciphertext processing unit, electronic device, and storage medium | |
| CN113240429B (en) | Method and system for payment verification based on picture coding | |
| CN116506105A (en) | Data theft and tampering prevention encryption method based on block chain | |
| CN115952526A (en) | Ciphertext sorting method, device and storage medium | |
| CN113965312A (en) | Space encryption method based on three-dimensional CAP constellation | |
| Rongali et al. | Investigating Applications of Run Length Encoding in Data Compression & Source Coding |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| GR01 | Patent grant | ||
| GR01 | Patent grant | ||
| TR01 | Transfer of patent right | Effective date of registration:20230630 Address after:518000 Room 201, building A, No. 1, Qian Wan Road, Qianhai Shenzhen Hong Kong cooperation zone, Shenzhen, Guangdong (Shenzhen Qianhai business secretary Co., Ltd.) Patentee after:Shenzhen aotongping Technology Co.,Ltd. Address before:No. J4, 17/F, No. 1, Zhongguancun Street, Haidian District, Beijing, 100000 Patentee before:Beijing Houfang Technology Co.,Ltd. | |
| TR01 | Transfer of patent right |