CN115706994A - Access control method and electronic equipment - Google Patents
Access control method and electronic equipmentDownload PDFInfo
- Publication number
- CN115706994A CN115706994ACN202110897966.XACN202110897966ACN115706994ACN 115706994 ACN115706994 ACN 115706994ACN 202110897966 ACN202110897966 ACN 202110897966ACN 115706994 ACN115706994 ACN 115706994A
- Authority
- CN
- China
- Prior art keywords
- application
- security policy
- target service
- request
- calling
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Pending
Links
Images
Landscapes
- Storage Device Security (AREA)
Abstract
Description
Translated fromChinese【技术领域】【Technical field】
本发明涉及遥控技术领域,尤其涉及一种访问控制方法和电子设备。The invention relates to the technical field of remote control, in particular to an access control method and electronic equipment.
【背景技术】【Background technique】
传统移动操作系统(Operating System,OS)中,三方应用程序(Application,APP)通过访问多个敏感服务的方式可以造成用户隐私泄露的风险。例如,先通过位置服务获取用户位置,然后通过网络服务将用户位置信息泄露出去。这种作恶方式可以通过基于单APP的服务或管控接口调用来进行阻断,如通过管控APP调用不同敏感接口的时机,防止单APP泄露用户实时位置。但是,多设备组成的分布式系统中,APP通过多应用协同的方式,可以很容易的绕过上述管控手段。In a traditional mobile operating system (Operating System, OS), a third-party application (Application, APP) may cause a risk of user privacy leakage by accessing multiple sensitive services. For example, the location of the user is first obtained through the location service, and then the location information of the user is leaked through the network service. This kind of evil method can be blocked by calling a single APP-based service or control interface, such as controlling the timing of APP calling different sensitive interfaces to prevent a single APP from leaking the user's real-time location. However, in a distributed system composed of multiple devices, APP can easily bypass the above-mentioned control methods through multi-application collaboration.
因此,目前移动OS无法在多设备组成的分布式系统下,有效的发现和阻断用户隐私泄露问题。Therefore, the current mobile OS cannot effectively discover and block user privacy leakage problems in a distributed system composed of multiple devices.
【发明内容】【Content of invention】
有鉴于此,本发明实施例提供了一种访问控制方法和电子设备,使得目前移动OS在多设备组成的分布式系统下,能够有效的发现并阻断用户隐私泄露问题。In view of this, the embodiments of the present invention provide an access control method and an electronic device, so that the current mobile OS can effectively discover and block user privacy leakage problems under a distributed system composed of multiple devices.
第一方面,本发明实施例提供了一种访问控制方法,所述方法包括:In a first aspect, an embodiment of the present invention provides an access control method, the method comprising:
通过调用第一应用生成调用请求,所述调用请求用于请求第二应用对目标服务的调用;generating a call request by calling the first application, where the call request is used to request the second application to call the target service;
根据用户预先配置的安全策略、所述目标服务、所述第一应用和所述第二应用,判断是否允许所述调用请求;judging whether to allow the invocation request according to the security policy preconfigured by the user, the target service, the first application, and the second application;
若判断出不允许所述调用请求,拒绝所述调用请求并生成用于提示所述第一应用异常操作的提醒信息。If it is determined that the call request is not allowed, reject the call request and generate reminder information for prompting abnormal operation of the first application.
结合第一方面,在第一方面的某些实现方式中,所述根据用户预先配置的安全策略、所述目标服务、所述第一应用和所述第二应用,判断是否允许所述调用请求,具体包括:With reference to the first aspect, in some implementations of the first aspect, the determining whether to allow the invocation request is based on the security policy preconfigured by the user, the target service, the first application, and the second application , including:
判断是否存在于所述第一应用和所述第二应用对应的所述安全策略,或者是否存在与所述目标服务对应的所述安全策略;judging whether the security policy corresponding to the first application and the second application exists, or whether the security policy corresponding to the target service exists;
若判断出存在于所述第一应用和所述第二应用对应的所述安全策略,或者存在与所述目标服务对应的所述安全策略,则判断出不允许所述调用请求;If it is determined that the security policy corresponding to the first application and the second application exists, or the security policy corresponding to the target service exists, then it is determined that the calling request is not allowed;
若判断出不存在于所述第一应用和所述第二应用对应的所述安全策略,并且不存在与所述目标服务对应的所述安全策略,则判断出允许所述调用请求。If it is determined that the security policy corresponding to the first application and the second application does not exist, and the security policy corresponding to the target service does not exist, it is determined that the calling request is allowed.
结合第一方面,在第一方面的某些实现方式中,所述根据用户预先配置的安全策略、所述目标服务、所述第一应用和所述第二应用,判断是否允许所述调用请求之前,还包括:With reference to the first aspect, in some implementations of the first aspect, the determining whether to allow the invocation request is based on the security policy preconfigured by the user, the target service, the first application, and the second application Previously, also included:
拦截所述调用请求。Intercept the calling request.
结合第一方面,在第一方面的某些实现方式中,所述根据用户预先配置的安全策略、所述目标服务、所述第一应用和所述第二应用,判断是否允许所述调用请求之后,还包括:With reference to the first aspect, in some implementations of the first aspect, the determining whether to allow the invocation request is based on the security policy preconfigured by the user, the target service, the first application, and the second application After that, also include:
若判断出允许所述调用请求,通过调用所述第二应用调用所述目标服务。If it is determined that the calling request is allowed, calling the target service by calling the second application.
第二方面,本发明实施例提供了一种访问控制方法,所述方法包括:In a second aspect, an embodiment of the present invention provides an access control method, the method comprising:
接收第一电子设备通过调用第一应用发送的调用请求,所述调用请求用于请求第二应用对目标服务的调用;receiving a call request sent by the first electronic device by calling the first application, where the call request is used to request the second application to call the target service;
根据用户预先配置的安全策略、所述目标服务、所述第一应用和所述第二应用,判断是否允许所述调用请求;judging whether to allow the invocation request according to the security policy preconfigured by the user, the target service, the first application, and the second application;
若判断出不允许所述调用请求,拒绝所述调用请求并生成用于提示所述第一应用异常操作的提醒信息。If it is determined that the call request is not allowed, reject the call request and generate reminder information for prompting abnormal operation of the first application.
结合第二方面,在第二方面的某些实现方式中,所述根据用户预先配置的安全策略、所述目标服务、所述第一应用和所述第二应用,判断是否允许所述调用请求,具体包括:With reference to the second aspect, in some implementations of the second aspect, the determining whether to allow the invocation request is based on the security policy preconfigured by the user, the target service, the first application, and the second application , including:
判断是否存在于所述第一应用和所述第二应用对应的所述安全策略,或者是否存在与所述目标服务对应的所述安全策略;judging whether the security policy corresponding to the first application and the second application exists, or whether the security policy corresponding to the target service exists;
若判断出存在于所述第一应用和所述第二应用对应的所述安全策略,或者存在与所述目标服务对应的所述安全策略,则判断出不允许所述调用请求;If it is determined that the security policy corresponding to the first application and the second application exists, or the security policy corresponding to the target service exists, then it is determined that the calling request is not allowed;
若判断出不存在于所述第一应用和所述第二应用对应的所述安全策略,并且不存在与所述目标服务对应的所述安全策略,则判断出允许所述调用请求。If it is determined that the security policy corresponding to the first application and the second application does not exist, and the security policy corresponding to the target service does not exist, it is determined that the calling request is allowed.
结合第二方面,在第二方面的某些实现方式中,所述根据用户预先配置的安全策略、所述目标服务、所述第一应用和所述第二应用,判断是否允许所述调用请求之前,还包括:With reference to the second aspect, in some implementations of the second aspect, the determining whether to allow the invocation request is based on the security policy preconfigured by the user, the target service, the first application, and the second application Previously, also included:
拦截所述调用请求。Intercept the calling request.
结合第二方面,在第二方面的某些实现方式中,所述根据用户预先配置的安全策略、所述目标服务、所述第一应用和所述第二应用,判断是否允许所述调用请求之后,还包括:With reference to the second aspect, in some implementations of the second aspect, the determining whether to allow the invocation request is based on the security policy preconfigured by the user, the target service, the first application, and the second application After that, also include:
若判断出允许所述调用请求,通过调用所述第二应用调用所述目标服务。If it is determined that the calling request is allowed, calling the target service by calling the second application.
第三方面,本发明实施例提供了一种电子设备,包括处理器和存储器,其中,所述存储器用于存储计算机程序,所述计算机程序包括程序指令,当所述处理器运行所述程序指令时,使所述电子设备执行以下步骤:In a third aspect, an embodiment of the present invention provides an electronic device, including a processor and a memory, wherein the memory is used to store a computer program, the computer program includes program instructions, and when the processor runs the program instructions , causing the electronic device to perform the following steps:
通过调用第一应用生成调用请求,所述调用请求用于请求第二应用对目标服务的调用;generating a call request by calling the first application, where the call request is used to request the second application to call the target service;
根据用户预先配置的安全策略、所述目标服务、所述第一应用和所述第二应用,判断是否允许所述调用请求;judging whether to allow the invocation request according to the security policy preconfigured by the user, the target service, the first application, and the second application;
若判断出不允许所述调用请求,拒绝所述调用请求并生成用于提示所述第一应用异常操作的提醒信息。If it is determined that the call request is not allowed, reject the call request and generate reminder information for prompting abnormal operation of the first application.
结合第三方面,在第三方面的某些实现方式中,当所述处理器运行所述程序指令时,使所述电子设备执行以下步骤:With reference to the third aspect, in some implementation manners of the third aspect, when the processor runs the program instruction, the electronic device is caused to perform the following steps:
所述根据用户预先配置的安全策略、所述目标服务、所述第一应用和所述第二应用,判断是否允许所述调用请求,具体包括:The judging whether to allow the invocation request according to the security policy preconfigured by the user, the target service, the first application, and the second application specifically includes:
判断是否存在于所述第一应用和所述第二应用对应的所述安全策略,或者是否存在与所述目标服务对应的所述安全策略;judging whether the security policy corresponding to the first application and the second application exists, or whether the security policy corresponding to the target service exists;
若判断出存在于所述第一应用和所述第二应用对应的所述安全策略,或者存在与所述目标服务对应的所述安全策略,则判断出不允许所述调用请求;If it is determined that the security policy corresponding to the first application and the second application exists, or the security policy corresponding to the target service exists, then it is determined that the calling request is not allowed;
若判断出不存在于所述第一应用和所述第二应用对应的所述安全策略,并且不存在与所述目标服务对应的所述安全策略,则判断出允许所述调用请求。If it is determined that the security policy corresponding to the first application and the second application does not exist, and the security policy corresponding to the target service does not exist, it is determined that the calling request is allowed.
结合第三方面,在第三方面的某些实现方式中,当所述处理器运行所述程序指令时,使所述电子设备执行以下步骤:With reference to the third aspect, in some implementation manners of the third aspect, when the processor runs the program instruction, the electronic device is caused to perform the following steps:
所述根据用户预先配置的安全策略、所述目标服务、所述第一应用和所述第二应用,判断是否允许所述调用请求之前,还包括:Before the judging whether to allow the call request according to the security policy pre-configured by the user, the target service, the first application, and the second application, the method further includes:
拦截所述调用请求。Intercept the calling request.
结合第三方面,在第三方面的某些实现方式中,当所述处理器运行所述程序指令时,使所述电子设备执行以下步骤:With reference to the third aspect, in some implementation manners of the third aspect, when the processor runs the program instruction, the electronic device is caused to perform the following steps:
所述根据用户预先配置的安全策略、所述目标服务、所述第一应用和所述第二应用,判断是否允许所述调用请求之后,还包括:After the judging whether to allow the call request according to the security policy pre-configured by the user, the target service, the first application, and the second application, the method further includes:
若判断出允许所述调用请求,通过调用所述第二应用调用所述目标服务。If it is determined that the calling request is allowed, calling the target service by calling the second application.
第四方面,本发明实施例提供了一种电子设备,包括处理器和存储器,其中,所述存储器用于存储计算机程序,所述计算机程序包括程序指令,当所述处理器运行所述程序指令时,使所述电子设备执行以下步骤:In a fourth aspect, an embodiment of the present invention provides an electronic device, including a processor and a memory, wherein the memory is used to store a computer program, the computer program includes program instructions, and when the processor runs the program instructions , causing the electronic device to perform the following steps:
接收第一电子设备通过调用第一应用发送的调用请求,所述调用请求用于请求第二应用对目标服务的调用;receiving a call request sent by the first electronic device by calling the first application, where the call request is used to request the second application to call the target service;
根据用户预先配置的安全策略、所述目标服务、所述第一应用和所述第二应用,判断是否允许所述调用请求;judging whether to allow the invocation request according to the security policy preconfigured by the user, the target service, the first application, and the second application;
若判断出不允许所述调用请求,拒绝所述调用请求并生成用于提示所述第一应用异常操作的提醒信息。If it is determined that the call request is not allowed, reject the call request and generate reminder information for prompting abnormal operation of the first application.
结合第四方面,在第四方面的某些实现方式中,当所述处理器运行所述程序指令时,使所述电子设备执行以下步骤:With reference to the fourth aspect, in some implementation manners of the fourth aspect, when the processor runs the program instructions, the electronic device is caused to perform the following steps:
所述根据用户预先配置的安全策略、所述目标服务、所述第一应用和所述第二应用,判断是否允许所述调用请求,具体包括:The judging whether to allow the invocation request according to the security policy preconfigured by the user, the target service, the first application, and the second application specifically includes:
判断是否存在于所述第一应用和所述第二应用对应的所述安全策略,或者是否存在与所述目标服务对应的所述安全策略;judging whether the security policy corresponding to the first application and the second application exists, or whether the security policy corresponding to the target service exists;
若判断出存在于所述第一应用和所述第二应用对应的所述安全策略,或者存在与所述目标服务对应的所述安全策略,则判断出不允许所述调用请求;If it is determined that the security policy corresponding to the first application and the second application exists, or the security policy corresponding to the target service exists, then it is determined that the calling request is not allowed;
若判断出不存在于所述第一应用和所述第二应用对应的所述安全策略,并且不存在与所述目标服务对应的所述安全策略,则判断出允许所述调用请求。If it is determined that the security policy corresponding to the first application and the second application does not exist, and the security policy corresponding to the target service does not exist, it is determined that the calling request is allowed.
结合第四方面,在第四方面的某些实现方式中,当所述处理器运行所述程序指令时,使所述电子设备执行以下步骤:With reference to the fourth aspect, in some implementation manners of the fourth aspect, when the processor runs the program instructions, the electronic device is caused to perform the following steps:
所述根据用户预先配置的安全策略、所述目标服务、所述第一应用和所述第二应用,判断是否允许所述调用请求之前,还包括:Before the judging whether to allow the call request according to the security policy pre-configured by the user, the target service, the first application, and the second application, the method further includes:
拦截所述调用请求。Intercept the calling request.
结合第四方面,在第四方面的某些实现方式中,当所述处理器运行所述程序指令时,使所述电子设备执行以下步骤:With reference to the fourth aspect, in some implementation manners of the fourth aspect, when the processor runs the program instructions, the electronic device is caused to perform the following steps:
所述根据用户预先配置的安全策略、所述目标服务、所述第一应用和所述第二应用,判断是否允许所述调用请求之后,还包括:After the judging whether to allow the call request according to the security policy pre-configured by the user, the target service, the first application, and the second application, the method further includes:
若判断出允许所述调用请求,通过调用所述第二应用调用所述目标服务。If it is determined that the calling request is allowed, calling the target service by calling the second application.
第五方面,本发明实施例提供了一种计算机可读存储介质,所述计算机可读存储介质存储有计算机程序,所述计算机程序包括程序指令,当所述程序指令被计算机运行时使所述计算机执行如上述所述的方法。In a fifth aspect, an embodiment of the present invention provides a computer-readable storage medium, the computer-readable storage medium stores a computer program, the computer program includes program instructions, and when the program instructions are executed by a computer, the A computer executes the method as described above.
本发明实施例提供的访问控制方法和电子设备的技术方案中,通过调用第一应用生成调用请求,或者,接收第一电子设备通过调用第一应用发送的调用请求,所述调用请求用于请求第二应用对目标服务的调用;根据用户预先配置的安全策略、所述目标服务、所述第一应用和所述第二应用,判断是否允许所述调用请求;若判断出不允许所述调用请求,拒绝所述调用请求并生成用于提示所述第一应用异常操作的提醒信息。本发明实施例使得目前移动OS在多设备组成的分布式系统下,能够有效的发现并阻断用户隐私泄露问题。In the access control method and the technical solution of the electronic device provided by the embodiments of the present invention, a call request is generated by calling the first application, or a call request sent by the first electronic device by calling the first application is received, and the call request is used to request The second application calls the target service; according to the security policy preconfigured by the user, the target service, the first application and the second application, determine whether to allow the call request; if it is determined that the call is not allowed request, rejecting the call request and generating reminder information for prompting abnormal operation of the first application. The embodiments of the present invention enable the current mobile OS to effectively discover and block user privacy leakage problems under a distributed system composed of multiple devices.
【附图说明】【Description of drawings】
为了更清楚地说明本发明实施例的技术方案,下面将对实施例中所需要使用的附图作简单地介绍,显而易见地,下面描述中的附图仅仅是本发明的一些实施例,对于本领域普通技术人员来讲,在不付出创造性劳动性的前提下,还可以根据这些附图获得其它的附图。In order to illustrate the technical solutions of the embodiments of the present invention more clearly, the accompanying drawings used in the embodiments will be briefly introduced below. Obviously, the accompanying drawings in the following description are only some embodiments of the present invention. Those of ordinary skill in the art can also obtain other drawings based on these drawings without paying creative labor.
图1为传统单机系统的示意图;Fig. 1 is the schematic diagram of traditional stand-alone system;
图2为分布式系统的示意图;Fig. 2 is the schematic diagram of distributed system;
图3为分布式系统中设备间通信的示意图;3 is a schematic diagram of communication between devices in a distributed system;
图4为分布式系统中多应用协同作恶的示意图;Fig. 4 is a schematic diagram of multi-application cooperative evil in a distributed system;
图5本发明实施例提供的一种访问控制系统的架构图;FIG. 5 is a structural diagram of an access control system provided by an embodiment of the present invention;
图6为本发明实施例提供的又一种访问控制系统的架构图;FIG. 6 is an architecture diagram of another access control system provided by an embodiment of the present invention;
图7本发明一实施例提供的一种访问控制方法的流程图;FIG. 7 is a flowchart of an access control method provided by an embodiment of the present invention;
图8为本发明实施例提供的一种访问控制的示意图;FIG. 8 is a schematic diagram of an access control provided by an embodiment of the present invention;
图9为本发明又一实施例提供的一种访问控制方法的流程图;FIG. 9 is a flow chart of an access control method provided by another embodiment of the present invention;
图10为本发明实施例提供的又一种访问控制的示意图;FIG. 10 is a schematic diagram of another access control provided by an embodiment of the present invention;
图11为本发明实施例提供的一种电子设备的结构示意图。FIG. 11 is a schematic structural diagram of an electronic device provided by an embodiment of the present invention.
【具体实施方式】【Detailed ways】
为了更好的理解本发明的技术方案,下面结合附图对本发明实施例进行详细描述。In order to better understand the technical solutions of the present invention, the embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings.
应当明确,所描述的实施例仅仅是本发明一部分实施例,而不是全部的实施例。基于本发明中的实施例,本领域普通技术人员在没有作出创造性劳动前提下所获得的所有其它实施例,都属于本发明保护的范围。It should be clear that the described embodiments are only some of the embodiments of the present invention, not all of them. Based on the embodiments of the present invention, all other embodiments obtained by persons of ordinary skill in the art without creative efforts fall within the protection scope of the present invention.
在本发明实施例中使用的术语是仅仅出于描述特定实施例的目的,而非旨在限制本发明。在本发明实施例和所附权利要求书中所使用的单数形式的“一种”、“所述”和“该”也旨在包括多数形式,除非上下文清楚地表示其他含义。Terms used in the embodiments of the present invention are only for the purpose of describing specific embodiments, and are not intended to limit the present invention. As used in the embodiments of the present invention and the appended claims, the singular forms "a", "said" and "the" are also intended to include the plural forms unless the context clearly indicates otherwise.
应当理解,本文中使用的术语“和/或”仅仅是一种描述关联对象的关联关系,表示可以存在三种关系,例如,甲和/或乙,可以表示:单独存在甲,同时存在甲和乙,单独存在乙这三种情况。另外,本文中字符“/”,一般表示前后关联对象是一种“或”的关系。It should be understood that the term "and/or" used herein is only an association relationship describing associated objects, which means that there may be three relationships, for example, A and/or B, which may mean that A exists alone, and A and B exist simultaneously. B, there are three situations of B alone. In addition, the character "/" in this article generally indicates that the contextual objects are an "or" relationship.
传统单机系统下,如图1所示,移动OS中的应用程序以独立主体的形式存在,通过访问服务获取系统中的敏感资源向用户提供各类功能,比如基于移动位置服务(LocationBased Service,LBS)。多设备组成的分布式系统下,如图2所示,APP的工作模式发生了很大变化,APP通过访问本设备或其他设备中的服务的方式,协同的为用户提供一项功能,充分利用各设备的能力为用户带来全新的体验。Under the traditional stand-alone system, as shown in Figure 1, the application program in the mobile OS exists in the form of an independent subject, and provides users with various functions by accessing the service to obtain sensitive resources in the system, such as location-based service (Location Based Service, LBS ). Under the distributed system composed of multiple devices, as shown in Figure 2, the working mode of the APP has undergone great changes. The APP provides users with a function cooperatively by accessing services in this device or other devices, making full use of The capabilities of each device bring a new experience to the user.
传统移动OS中,三方APP通过访问多个服务的方式可以造成用户隐私泄露的风险。例如,先通过位置服务获取用户位置,然后通过网络服务将用户位置信息泄露出去。这种作恶方式可以通过基于单APP的服务或管控接口调用来进行阻断,如通过管控APP调用不同敏感接口的时机,防止单APP泄露用户实时位置。In the traditional mobile OS, three-party APPs may cause the risk of user privacy leakage by accessing multiple services. For example, the location of the user is first obtained through the location service, and then the location information of the user is leaked through the network service. This kind of evil method can be blocked by calling a single APP-based service or control interface, such as controlling the timing of APP calling different sensitive interfaces to prevent a single APP from leaking the user's real-time location.
多设备组成的分布式系统,比如iOS的智能家居系统下,如图3所示,各设备主要通过设备连接模块来建立设备间的通信通道。对于设备间的应用互调,由分布式服务发现模块完成,各设备无法感知调用双方的应用信息。A distributed system composed of multiple devices, such as the iOS smart home system, as shown in Figure 3, each device mainly establishes a communication channel between devices through a device connection module. The application intermodulation between devices is completed by the distributed service discovery module, and each device cannot perceive the application information of the calling parties.
进一步的,多设备组成的分布式系统中,APP通过多应用协同的方式,可以很容易的绕过上述管控手段。如图4所示,APP1首先通过服务A获取用户的位置,然后调用设备B中的APP2,将个人信息发送给APP2,并通过APP2调用网络服务的方式,间接的将用户的实时位置信息进行泄露。Furthermore, in a distributed system composed of multiple devices, the APP can easily bypass the above-mentioned control methods through multi-application collaboration. As shown in Figure 4, APP1 first obtains the user's location through service A, then calls APP2 in device B, sends personal information to APP2, and indirectly leaks the user's real-time location information by calling the network service through APP2 .
综上,目前移动OS无法在多设备组成的分布式系统下,有效的发现和阻断该类信息泄露问题。To sum up, the current mobile OS cannot effectively discover and block such information leakage problems in a distributed system composed of multiple devices.
为了解决上述技术问题,本发明实施例提供一种访问控制方法和电子设备。In order to solve the above technical problems, embodiments of the present invention provide an access control method and an electronic device.
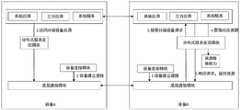
参见图5,图5为本发明实施例提供的一种访问控制系统的架构图。如图5所示,访问控制系统包括第一电子设备100。其中,第一电子设备100包括第一系统应用、第一应用、第二应用、第一系统服务、应用调用链管理、调用信息库、服务信息管理、分布式服务发现模块、分布式服务访问控制管理、服务访问策略模块、安全策略库、异常提醒服务、服务调用管理、调用记录库、第一设备连接模块和第一底层通信模块。Referring to FIG. 5 , FIG. 5 is a structural diagram of an access control system provided by an embodiment of the present invention. As shown in FIG. 5 , the access control system includes a first
图5中,第一系统应用包括第一电子设备100中所有的系统应用。第一应用和第二应用均为第一电子设备100中的三方APP,其中,第一应用和第二应用不同。第一系统服务,用于处理第一电子设备100中的系统任务。第一设备连接模块,用于第一电子设备100与分布式系统建立连接;第一底层通信模块,用于第一电子设备100的底层通信。In FIG. 5 , the first system application includes all system applications in the first
参见图6,图6为本发明实施例提供的又一种访问控制系统的架构图。本发明实施例的访问控制系统包括两个电子设备,其中,两个电子设备可包括第一电子设备和第二电子设备,第一电子设备和第二电子设备均位于分布式系统。如图6所示,访问控制系统包括第一电子设备100和第二电子设备200。其中,第一电子设备100包括第一系统应用、第一应用、第一系统服务、应用调用链管理、调用信息库、第一设备连接模块和第一底层通信模块。第二电子设备200包括第二系统应用、第二应用、第二系统服务、服务信息管理、分布式服务发现模块、分布式服务访问控制管理、服务访问策略模块、安全策略库、异常提醒服务、服务调用管理、调用记录库、第二设备连接模块和第二底层通信模块。Referring to FIG. 6, FIG. 6 is a structural diagram of another access control system provided by an embodiment of the present invention. The access control system in this embodiment of the present invention includes two electronic devices, where the two electronic devices may include a first electronic device and a second electronic device, and both the first electronic device and the second electronic device are located in a distributed system. As shown in FIG. 6 , the access control system includes a first
图6中,第一系统应用包括第一电子设备100中所有的系统应用。第一应用为第一电子设备100中的三方APP。第一系统服务,用于处理第一电子设备100中的系统任务。第一设备连接模块,用于第一电子设备100与分布式系统建立连接;第一底层通信模块,用于第一电子设备100的底层通信。In FIG. 6 , the first system application includes all system applications in the first
第二系统应用包括第二电子设备200中所有的系统应用。第二应用为第二电子设备200中的三方APP。第二系统服务,用于处理第二电子设备200中的系统任务。第二设备连接模块,用于第二电子设备200与分布式系统建立连接;第二底层通信模块,用于第二电子设备200的底层通信。The second system application includes all system applications in the second
在图5和图6中,第一应用,用于生成调用请求,并向应用调用链管理发送该调用请求;其中,调用请求用于请求第二应用对目标服务的调用。应用调用链管理,用于根据调用请求查询第二应用,并向第二应用发送调用请求,同时将此次调用关系,即调用链记录至调用信息库中。调用信息库,用于存储调用链。第二应用,用于根据调用请求向服务信息管理发送调用请求。分布式服务发现模块,用于在第二电子设备200通过第二设备连接模块与分布式系统建立连接后,发现分布式系统中各个电子设备中提供的服务,并将所有服务的服务信息同步至服务信息管理中。服务信息管理,用于根据调用请求查找与调用请求对应的目标服务。分布式服务访问控制管理,用于拦截第二应用向服务信息管理发送调用请求,并根据用户预先配置的安全策略、目标服务、第一应用和第二应用,判断是否允许调用请求;若判断出不允许调用请求,拒绝调用请求;若判断出允许调用请求,允许第二应用调用目标服务。异常提醒服务,用于若分布式服务访问控制管理判断出不允许调用请求,生成用于提示第一应用异常操作的提醒信息。服务调用管理,用于从分布式服务访问控制管理获取调用请求的判断结果,并将判断结果记录至调用记录库中。其中,服务访问策略模块,用于获取用户配置应用的安全策略,并将安全策略记录至安全策略库中;安全策略库,用于存储应用的安全策略。例如,第一应用包括APP1,目标服务包括用户实时位置,APP1的安全策略包括:允许APP1获取用户实时位置,但禁止APP1将用户实时位置发送出去。In FIG. 5 and FIG. 6, the first application is used to generate a call request and send the call request to the application call chain management; wherein, the call request is used to request the second application to call the target service. The application call chain management is used to query the second application according to the call request, send the call request to the second application, and record the call relationship, that is, the call chain, into the call information base. The call information base is used to store the call chain. The second application is configured to send a call request to the service information management according to the call request. The distributed service discovery module is used to discover the services provided by each electronic device in the distributed system after the second
例如,提醒信息包括:调用第一应用调用第二应用,并访问目标服务,存在泄露个人隐私风险。For example, the reminder information includes: calling the first application to call the second application, and accessing the target service, there is a risk of leaking personal privacy.
本发明实施例中,提醒信息的提醒方式不限于弹框、语音提醒或者设置项中单独页面呈现。In the embodiment of the present invention, the reminder mode of the reminder information is not limited to pop-up box, voice reminder or individual page presentation in the setting item.
本发明实施例针对多设备组成的分布式系统中,应用程序访问自身设备中的应用程序或者服务,或者跨设备访问其他设备中的应用程序或者服务时,依据应用程序的身份、应用程序所调用服务的信息、被调用应用程序的身份、被调用应用程序所访问的服务信息,来阻止APP通过协同作恶的方式泄露用户个人隐私。即当被调用的APP发起服务访问请求时,根据调用者的信息、调用者所访问的服务以及对应的安全策略,来决定是否允许被调用的APP访问当前服务。本发明实施例支持基于调用,即调用链的服务访问控制,也支持根据用户或系统默认配置的服务访问的安全策略控制多APP协同的服务访问,以实现系统级的服务访问调用管控,防止用户敏感信息泄露。The embodiment of the present invention is aimed at a distributed system composed of multiple devices. When an application program accesses an application program or service in its own device, or cross-device accesses an application program or service in other devices, the The information of the service, the identity of the called application, and the service information accessed by the called application are used to prevent the APP from leaking the user's personal privacy through collaborative evil. That is, when the called APP initiates a service access request, it determines whether to allow the called APP to access the current service according to the information of the caller, the service accessed by the caller, and the corresponding security policy. The embodiment of the present invention supports service access control based on calls, that is, call chains, and also supports multi-APP collaborative service access control according to the security policy of service access configured by the user or the system by default, so as to realize system-level service access call management and control, and prevent users from Sensitive information disclosure.
基于上述图5提供的架构图,本发明实施例提供一种访问控制方法,应用于第一电子设备100。图7为本发明一实施例提供的一种访问控制方法的流程图。如图7所示,该方法包括:Based on the architecture diagram provided in FIG. 5 above, an embodiment of the present invention provides an access control method, which is applied to the first
步骤102、通过调用第一应用生成调用请求,调用请求用于请求第二应用对目标服务的调用。Step 102: Generate a call request by calling the first application, where the call request is used to request the second application to call the target service.
其中,第一应用和第二应用均为第三方应用,且均位于第一电子设备。第一应用和第二应不相同。Wherein, both the first application and the second application are third-party applications, and both are located in the first electronic device. The first application and the second should be different.
本发明实施例中,如图5所示,第一电子设备100通过调用第一应用生成调用请求,应用调用链管理根据调用请求查询第二应用,并向第二应用发送调用请求,同时将此次调用关系,即调用链记录至调用信息库中。In the embodiment of the present invention, as shown in FIG. 5 , the first
步骤104、根据用户预先配置的安全策略、目标服务、第一应用和第二应用,判断是否允许调用请求,若是,执行步骤106;若否,执行步骤108。
本发明实施例中,如图5所示,用户通过第一电子设备100的服务访问策略模块配置应用的安全策略,服务访问策略模块将安全策略存储至调用记录库。In the embodiment of the present invention, as shown in FIG. 5 , the user configures the security policy of the application through the service access policy module of the first
如图5所示,第二应用接收到调用请求后,分布式服务访问控制管理根据用户预先配置的安全策略、目标服务、第一应用和第二应用,判断是否允许调用请求。As shown in FIG. 5 , after the second application receives the invocation request, the distributed service access control management judges whether to allow the invocation request according to the user's pre-configured security policy, target service, first application, and second application.
本发明实施例中,步骤104,具体包括:判断是否存在于第一应用和第二应用对应的安全策略,或者是否存在与目标服务对应的安全策略,若是,则判断出不允许调用请求,执行步骤108;若否,则判断出允许调用请求,执行步骤106。In the embodiment of the present invention, step 104 specifically includes: judging whether there is a security policy corresponding to the first application and the second application, or whether there is a security policy corresponding to the target service, if so, judging that the call request is not allowed, and executing
本发明实施例中,在步骤104之前,还包括:In the embodiment of the present invention, before
步骤102’、拦截调用请求。Step 102', intercepting the calling request.
本发明实施例中,如图5所示,分布式服务访问控制管理在判断是否允许调用请求之前,需要拦截第二应用向服务信息管理发送调用请求。因为,第二应用在接收到调用请求后,会向服务信息管理发送调用请求,服务信息管理根据调用请求查找与调用请求对应的目标服务后,会直接调用目标服务。因此,为了防止用户隐私泄露,分布式服务访问控制管理需要先拦截第二应用向服务信息管理发送调用请求,再判断是否允许调用请求。In the embodiment of the present invention, as shown in FIG. 5 , before the distributed service access control management judges whether to allow the call request, it needs to intercept the call request sent by the second application to the service information management. Because, after receiving the invocation request, the second application will send the invocation request to the service information management, and the service information management will directly invoke the target service after finding the target service corresponding to the invocation request according to the invocation request. Therefore, in order to prevent leakage of user privacy, the distributed service access control management needs to first intercept the call request sent by the second application to the service information management, and then determine whether to allow the call request.
步骤106、通过调用第二应用调用目标服务;流程结束。
本发明实施例中,如图5所示,分布式服务访问控制管理若判断出允许调用请求,允许第二应用调用目标服务,即第二应用向服务信息管理发送调用请求,服务信息管理根据调用请求查找与调用请求对应的目标服务后,调用目标服务。同时,服务调用管理从分布式服务访问控制管理获取调用请求的判断结果,并将判断结果记录至调用记录库中。In the embodiment of the present invention, as shown in Figure 5, if the distributed service access control management judges that the call request is allowed, the second application is allowed to call the target service, that is, the second application sends a call request to the service information management, and the service information management After the request finds the target service corresponding to the call request, the target service is invoked. At the same time, the service call management obtains the judgment result of the call request from the distributed service access control management, and records the judgment result in the call record library.
步骤108、拒绝调用请求并生成用于提示第一应用异常操作的提醒信息;流程结束。
本发明实施例中,如图5所示,分布式服务访问控制管理若判断出不允许调用请求,拒绝调用请求,即拒绝第二应用向服务信息管理发送调用请求。同时,异常提醒服务生成用于提示第一应用异常操作的提醒信息。同时,服务调用管理从分布式服务访问控制管理获取调用请求的判断结果,并将判断结果记录至调用记录库中。In the embodiment of the present invention, as shown in FIG. 5 , if the distributed service access control management determines that the invocation request is not allowed, the invocation request is rejected, that is, the second application is refused to send the invocation request to the service information management. At the same time, the abnormal reminder service generates reminder information for prompting the abnormal operation of the first application. At the same time, the service call management obtains the judgment result of the call request from the distributed service access control management, and records the judgment result in the call record library.
例如,提醒信息包括:调用第一应用调用第二应用,并访问目标服务,存在泄露个人隐私风险。For example, the reminder information includes: calling the first application to call the second application, and accessing the target service, there is a risk of leaking personal privacy.
本发明实施例中,提醒信息的提醒方式不限于弹框、语音提醒或者设置项中单独页面呈现。In the embodiment of the present invention, the reminder mode of the reminder information is not limited to pop-up box, voice reminder or individual page presentation in the setting item.
本发明实施例针对多设备组成的分布式系统中,应用程序访问自身设备中的应用程序或者服务,依据应用程序的身份、应用程序所调用服务的信息、被调用应用程序的身份、被调用应用程序所访问的服务信息,来阻止APP通过协同作恶的方式泄露用户个人隐私。即当被调用的APP发起服务访问请求时,根据调用者的信息、调用者所访问的服务以及对应的安全策略,来决定是否允许被调用的APP访问当前服务。如图8所示,本发明实施例支持基于调用,即调用链的服务访问控制,也支持根据用户或系统默认配置的服务访问的安全策略控制多APP协同的服务访问,以实现系统级的服务访问调用管控,防止用户敏感信息泄露。The embodiment of the present invention is aimed at the distributed system composed of multiple devices, the application program accesses the application program or service in its own device, according to the identity of the application program, the information of the service called by the application program, the identity of the called application program, the called application program The service information accessed by the program is used to prevent the APP from leaking the user's personal privacy through collaborative evil. That is, when the called APP initiates a service access request, it determines whether to allow the called APP to access the current service according to the information of the caller, the service accessed by the caller, and the corresponding security policy. As shown in Figure 8, the embodiment of the present invention supports service access control based on calls, that is, call chains, and also supports multi-APP coordinated service access control based on the security policy of service access configured by the user or the system by default, so as to realize system-level services. Access and call control to prevent leakage of user sensitive information.
本发明实施例提供的访问控制方法的技术方案中,通过调用第一应用生成调用请求,调用请求用于请求第二应用对目标服务的调用;根据用户预先配置的安全策略、目标服务、第一应用和第二应用,判断是否允许调用请求;若判断出不允许调用请求,拒调用请求并生成用于提示第一应用异常操作的提醒信息。本发明实施例使得目前移动OS在多设备组成的分布式系统下,能够有效的发现并阻断用户隐私泄露问题。In the technical solution of the access control method provided by the embodiment of the present invention, a call request is generated by calling the first application, and the call request is used to request the second application to call the target service; according to the user's pre-configured security policy, target service, first The application and the second application judge whether to allow the calling request; if it is judged that the calling request is not allowed, reject the calling request and generate a reminder message for prompting the abnormal operation of the first application. The embodiments of the present invention enable the current mobile OS to effectively discover and block user privacy leakage problems under a distributed system composed of multiple devices.
基于上述图6提供的架构图,本发明实施例提供一种访问控制方法,应用于第二电子设备200。图9为本发明又一实施例提供的一种访问控制方法的流程图。如图9所示,该方法包括:Based on the architecture diagram provided in FIG. 6 above, an embodiment of the present invention provides an access control method, which is applied to the second
步骤202、接收第一电子设备通过调用第一应用发送的调用请求,调用请求用于请求第二应用对目标服务的调用。Step 202: Receive a call request sent by the first electronic device by calling the first application, where the call request is used to request the second application to call the target service.
其中,第一应用和第二应用均为第三方应用,第一应用位于第一电子设备,第二应用位于第二电子设备。Wherein, both the first application and the second application are third-party applications, the first application is located on the first electronic device, and the second application is located on the second electronic device.
本发明实施例中,如图6所示,第一电子设备100通过调用第一应用生成调用请求,应用调用链管理根据调用请求查询第二应用所在的电子设备,在查询到第二应用所在的电子设备为第二电子设备200后,向第二电子设备200的第二应用发送调用请求,同时将此次调用关系,即调用链记录至调用信息库中。In the embodiment of the present invention, as shown in FIG. 6 , the first
步骤204、根据用户预先配置的安全策略、目标服务、第一应用和第二应用,判断是否允许调用请求,若是,执行步骤206;若否,执行步骤208。
本发明实施例中,如图6所示,用户通过第二电子设备200的服务访问策略模块配置应用的安全策略,服务访问策略模块将安全策略存储至调用记录库。In the embodiment of the present invention, as shown in FIG. 6 , the user configures the security policy of the application through the service access policy module of the second
如图6所示,第二应用接收到调用请求后,分布式服务访问控制管理根据用户预先配置的安全策略、目标服务、第一应用和第二应用,判断是否允许调用请求。As shown in FIG. 6 , after the second application receives the invocation request, the distributed service access control management judges whether to allow the invocation request according to the user's pre-configured security policy, target service, first application, and second application.
本发明实施例中,步骤204,具体包括:判断是否存在于第一应用和第二应用对应的安全策略,或者是否存在与目标服务对应的安全策略,若是,则判断出不允许调用请求,执行步骤208;若否,则判断出允许调用请求,执行步骤206。In the embodiment of the present invention, step 204 specifically includes: judging whether there is a security policy corresponding to the first application and the second application, or whether there is a security policy corresponding to the target service, if so, judging that the call request is not allowed, and executing
本发明实施例中,在步骤204之前,还包括:In the embodiment of the present invention, before
步骤202’、拦截调用请求。Step 202', intercepting the calling request.
本发明实施例中,如图6所示,分布式服务访问控制管理在判断是否允许调用请求之前,需要拦截第二应用向服务信息管理发送调用请求。因为,第二应用在接收到调用请求后,会向服务信息管理发送调用请求,服务信息管理根据调用请求查找与调用请求对应的目标服务后,会直接调用目标服务。因此,为了防止用户隐私泄露,分布式服务访问控制管理需要先拦截第二应用向服务信息管理发送调用请求,再判断是否允许调用请求。In the embodiment of the present invention, as shown in FIG. 6 , before the distributed service access control management judges whether to allow the call request, it needs to intercept the call request sent by the second application to the service information management. Because, after receiving the calling request, the second application will send the calling request to the service information management, and the service information management will directly call the target service after finding the target service corresponding to the calling request according to the calling request. Therefore, in order to prevent leakage of user privacy, the distributed service access control management needs to first intercept the call request sent by the second application to the service information management, and then determine whether to allow the call request.
步骤206、通过调用第二应用调用目标服务;流程结束。
本发明实施例中,如图6所示,分布式服务访问控制管理若判断出允许调用请求,允许第二应用调用目标服务,即第二应用向服务信息管理发送调用请求,服务信息管理根据调用请求查找与调用请求对应的目标服务后,调用目标服务。同时,服务调用管理从分布式服务访问控制管理获取调用请求的判断结果,并将判断结果记录至调用记录库中。In the embodiment of the present invention, as shown in Figure 6, if the distributed service access control management judges that the call request is allowed, the second application is allowed to call the target service, that is, the second application sends a call request to the service information management, and the service information management After the request finds the target service corresponding to the call request, the target service is invoked. At the same time, the service call management obtains the judgment result of the call request from the distributed service access control management, and records the judgment result in the call record library.
步骤208、拒绝调用请求并生成用于提示第一应用异常操作的提醒信息;流程结束。
本发明实施例中,如图6所示,分布式服务访问控制管理若判断出不允许调用请求,拒绝调用请求,即拒绝第二应用向服务信息管理发送调用请求。同时,异常提醒服务生成用于提示第一应用异常操作的提醒信息。同时,服务调用管理从分布式服务访问控制管理获取调用请求的判断结果,并将判断结果记录至调用记录库中。In the embodiment of the present invention, as shown in FIG. 6 , if the distributed service access control management determines that the invocation request is not allowed, the invocation request is rejected, that is, the second application is refused to send the invocation request to the service information management. At the same time, the abnormal reminder service generates reminder information for prompting the abnormal operation of the first application. At the same time, the service call management obtains the judgment result of the call request from the distributed service access control management, and records the judgment result in the call record library.
例如,提醒信息包括:调用第一应用调用第二应用,并访问目标服务,存在泄露个人隐私风险。For example, the reminder information includes: calling the first application to call the second application, and accessing the target service, there is a risk of leaking personal privacy.
本发明实施例中,提醒信息的提醒方式不限于弹框、语音提醒或者设置项中单独页面呈现。In the embodiment of the present invention, the reminder mode of the reminder information is not limited to pop-up box, voice reminder or individual page presentation in the setting item.
本发明实施例针对多设备组成的分布式系统中,应用程序跨设备访问其他设备中的应用程序或者服务,依据应用程序的身份、应用程序所调用服务的信息、被调用应用程序的身份、被调用应用程序所访问的服务信息,来阻止APP通过协同作恶的方式泄露用户个人隐私。即当被调用的APP发起服务访问请求时,根据调用者的信息、调用者所访问的服务以及对应的安全策略,来决定是否允许被调用的APP访问当前服务。如图10所示,本发明实施例支持基于调用,即调用链的服务访问控制,也支持根据用户或系统默认配置的服务访问的安全策略控制多APP协同的服务访问,以实现系统级的服务访问调用管控,防止用户敏感信息泄露。The embodiment of the present invention is aimed at the distributed system composed of multiple devices, the application program accesses the application program or service in other devices across devices, according to the identity of the application program, the information of the service called by the application program, the identity of the called application program, the called Call the service information accessed by the application to prevent the APP from leaking the user's personal privacy through collaborative evil. That is, when the called APP initiates a service access request, it determines whether to allow the called APP to access the current service according to the information of the caller, the service accessed by the caller, and the corresponding security policy. As shown in Figure 10, the embodiment of the present invention supports service access control based on calls, that is, call chains, and also supports multi-APP collaborative service access control based on the security policy of service access configured by the user or the system by default, so as to realize system-level services. Access and call control to prevent leakage of user sensitive information.
本发明实施例提供的访问控制方法的技术方案中,接收第一电子设备通过调用第一应用发送的调用请求,调用请求用于请求第二应用对目标服务的调用;根据用户预先配置的安全策略、目标服务、第一应用和第二应用,判断是否允许调用请求;若判断出不允许调用请求,拒绝调用请求并生成用于提示第一应用异常操作的提醒信息。本发明实施例使得目前移动OS在多设备组成的分布式系统下,能够有效的发现并阻断用户隐私泄露问题。In the technical solution of the access control method provided by the embodiment of the present invention, the call request sent by the first electronic device by calling the first application is received, and the call request is used to request the second application to call the target service; according to the security policy preconfigured by the user , the target service, the first application, and the second application, and determine whether the call request is allowed; if it is judged that the call request is not allowed, reject the call request and generate a reminder message for prompting the abnormal operation of the first application. The embodiments of the present invention enable the current mobile OS to effectively discover and block user privacy leakage problems under a distributed system composed of multiple devices.
上文结合图1至图10,详细描述了本发明实施例提供的访问控制方法,下面将结合图11,详细描述本发明的装置实施例。应理解,本发明实施例中的电子设备可以执行前述本发明实施例的各种方法,即以下各种产品的具体工作过程,可以参考前述方法实施例中的对应过程。The access control method provided by the embodiment of the present invention is described in detail above with reference to FIG. 1 to FIG. 10 , and the device embodiment of the present invention will be described in detail below in conjunction with FIG. 11 . It should be understood that the electronic device in the embodiment of the present invention can execute various methods in the foregoing embodiments of the present invention, that is, for specific working processes of the following various products, reference may be made to the corresponding processes in the foregoing method embodiments.
本发明实施例提供一种电子设备,该电子设备可以是终端设备也可以是内置于所述终端设备的电路设备。该电子设备可以用于执行上述方法实施例中的功能/步骤。An embodiment of the present invention provides an electronic device, which may be a terminal device or a circuit device built in the terminal device. The electronic device may be used to execute the functions/steps in the foregoing method embodiments.
图11为本发明实施例提供的一种电子设备300的结构示意图。电子设备300可以包括处理器310,外部存储器接口320,内部存储器321,通用串行总线(universal serialbus,USB)接口330,充电管理模块340,电源管理模块341,电池342,天线1,天线2,移动通信模块350,无线通信模块360,音频模块370,扬声器370A,受话器370B,麦克风370C,耳机接口370D,传感器模块380,按键390,马达391,指示器392,摄像头393,显示屏394,以及用户标识模块(subscriber identification module,SIM)卡接口395等。其中传感器模块380可以包括压力传感器380A,陀螺仪传感器380B,气压传感器380C,磁传感器380D,加速度传感器380E,距离传感器380F,接近光传感器380G,指纹传感器380H,温度传感器380J,触摸传感器380K,环境光传感器380L,骨传导传感器380M等。FIG. 11 is a schematic structural diagram of an electronic device 300 provided by an embodiment of the present invention. The electronic device 300 may include a
可以理解的是,本发明实施例示意的结构并不构成对电子设备300的具体限定。在本发明另一些实施例中,电子设备300可以包括比图示更多或更少的部件,或者组合某些部件,或者拆分某些部件,或者不同的部件布置。图示的部件可以以硬件,软件或软件和硬件的组合实现。It can be understood that, the structure shown in the embodiment of the present invention does not constitute a specific limitation on the electronic device 300 . In other embodiments of the present invention, the electronic device 300 may include more or fewer components than shown, or combine certain components, or separate certain components, or arrange different components. The illustrated components can be realized in hardware, software or a combination of software and hardware.
处理器310可以包括一个或多个处理单元,例如:处理器310可以包括应用处理器(application processor,AP),调制解调处理器,图形处理器(graphics processingunit,GPU),图像信号处理器(image signal processor,ISP),控制器,视频编解码器,数字信号处理器(digital signal processor,DSP),基带处理器,和/或神经网络处理器(neural-network processing unit,NPU)等。其中,不同的处理单元可以是独立的器件,也可以集成在一个或多个处理器中。The
控制器可以根据指令操作码和时序信号,产生操作控制信号,完成取指令和执行指令的控制。The controller can generate an operation control signal according to the instruction opcode and timing signal, and complete the control of fetching and executing the instruction.
处理器310中还可以设置存储器,用于存储指令和数据。在一些实施例中,处理器310中的存储器为高速缓冲存储器。该存储器可以保存处理器310刚用过或循环使用的指令或数据。如果处理器310需要再次使用该指令或数据,可从所述存储器中直接调用。避免了重复存取,减少了处理器310的等待时间,因而提高了系统的效率。A memory may also be provided in the
在一些实施例中,处理器310可以包括一个或多个接口。接口可以包括集成电路(inter-integrated circuit,I2C)接口,集成电路内置音频(inter-integrated circuitsound,I2S)接口,脉冲编码调制(pulse code modulation,PCM)接口,通用异步收发传输器(universal asynchronous receiver/transmitter,UART)接口,移动产业处理器接口(mobile industry processor interface,MIPI),通用输入输出(general-purposeinput/output,GPIO)接口,用户标识模块(subscriber identity module,SIM)接口,和/或通用串行总线(universal serial bus,USB)接口等。In some embodiments,
I2C接口是一种双向同步串行总线,包括一根串行数据线(serial data line,SDA)和一根串行时钟线(derail clock line,SCL)。在一些实施例中,处理器310可以包含多组I2C总线。处理器310可以通过不同的I2C总线接口分别耦合触摸传感器380K,充电器,闪光灯,摄像头393等。例如:处理器310可以通过I2C接口耦合触摸传感器380K,使处理器310与触摸传感器380K通过I2C总线接口通信,实现电子设备300的触摸功能。The I2C interface is a bidirectional synchronous serial bus, including a serial data line (serial data line, SDA) and a serial clock line (derail clock line, SCL). In some embodiments,
I2S接口可以用于音频通信。在一些实施例中,处理器310可以包含多组I2S总线。处理器310可以通过I2S总线与音频模块370耦合,实现处理器310与音频模块370之间的通信。在一些实施例中,音频模块370可以通过I2S接口向无线通信模块360传递音频信号,实现通过蓝牙耳机接听电话的功能。The I2S interface can be used for audio communication. In some embodiments,
PCM接口也可以用于音频通信,将模拟信号抽样,量化和编码。在一些实施例中,音频模块370与无线通信模块360可以通过PCM总线接口耦合。在一些实施例中,音频模块370也可以通过PCM接口向无线通信模块360传递音频信号,实现通过蓝牙耳机接听电话的功能。所述I2S接口和所述PCM接口都可以用于音频通信。The PCM interface can also be used for audio communication, sampling, quantizing and encoding the analog signal. In some embodiments, the
UART接口是一种通用串行数据总线,用于异步通信。该总线可以为双向通信总线。它将要传输的数据在串行通信与并行通信之间转换。在一些实施例中,UART接口通常被用于连接处理器310与无线通信模块360。例如:处理器310通过UART接口与无线通信模块360中的蓝牙模块通信,实现蓝牙功能。在一些实施例中,音频模块370可以通过UART接口向无线通信模块360传递音频信号,实现通过蓝牙耳机播放音乐的功能。The UART interface is a universal serial data bus used for asynchronous communication. The bus can be a bidirectional communication bus. It converts the data to be transmitted between serial communication and parallel communication. In some embodiments, a UART interface is generally used to connect the
MIPI接口可以被用于连接处理器310与显示屏394,摄像头393等外围器件。MIPI接口包括摄像头串行接口(camera serial interface,CSI),显示屏串行接口(displayserial interface,DSI)等。在一些实施例中,处理器310和摄像头393通过CSI接口通信,实现电子设备300的拍摄功能。处理器310和显示屏394通过DSI接口通信,实现电子设备300的显示功能。The MIPI interface can be used to connect the
GPIO接口可以通过软件配置。GPIO接口可以被配置为控制信号,也可被配置为数据信号。在一些实施例中,GPIO接口可以用于连接处理器310与摄像头393,显示屏394,无线通信模块360,音频模块370,传感器模块380等。GPIO接口还可以被配置为I2C接口,I2S接口,UART接口,MIPI接口等。The GPIO interface can be configured by software. The GPIO interface can be configured as a control signal or as a data signal. In some embodiments, the GPIO interface can be used to connect the
USB接口330是符合USB标准规范的接口,具体可以是Mini USB接口,Micro USB接口,USB Type C接口等。USB接口330可以用于连接充电器为电子设备300充电,也可以用于电子设备300与外围设备之间传输数据。也可以用于连接耳机,通过耳机播放音频。该接口还可以用于连接其他电子设备,例如AR设备等。The USB interface 330 is an interface conforming to the USB standard specification, specifically, it may be a Mini USB interface, a Micro USB interface, a USB Type C interface, and the like. The USB interface 330 can be used to connect a charger to charge the electronic device 300 , and can also be used to transmit data between the electronic device 300 and peripheral devices. It can also be used to connect headphones and play audio through them. This interface can also be used to connect other electronic devices, such as AR devices.
可以理解的是,本发明实施例示意的各模块间的接口连接关系,只是示意性说明,并不构成对电子设备300的结构限定。在本发明另一些实施例中,电子设备300也可以采用上述实施例中不同的接口连接方式,或多种接口连接方式的组合。It can be understood that the interface connection relationship between the modules shown in the embodiment of the present invention is only a schematic illustration, and does not constitute a structural limitation of the electronic device 300 . In other embodiments of the present invention, the electronic device 300 may also adopt different interface connection manners in the foregoing embodiments, or a combination of multiple interface connection manners.
充电管理模块340用于从充电器接收充电输入。其中,充电器可以是无线充电器,也可以是有线充电器。在一些有线充电的实施例中,充电管理模块340可以通过USB接口330接收有线充电器的充电输入。在一些无线充电的实施例中,充电管理模块340可以通过电子设备300的无线充电线圈接收无线充电输入。充电管理模块340为电池342充电的同时,还可以通过电源管理模块341为电子设备供电。The
电源管理模块341用于连接电池342,充电管理模块340与处理器310。电源管理模块341接收电池342和/或充电管理模块340的输入,为处理器310,内部存储器321,显示屏394,摄像头393,和无线通信模块360等供电。电源管理模块341还可以用于监测电池容量,电池循环次数,电池健康状态(漏电,阻抗)等参数。在其他一些实施例中,电源管理模块341也可以设置于处理器310中。在另一些实施例中,电源管理模块341和充电管理模块340也可以设置于同一个器件中。The
电子设备300的无线通信功能可以通过天线1,天线2,移动通信模块350,无线通信模块360,调制解调处理器以及基带处理器等实现。The wireless communication function of the electronic device 300 can be realized by the antenna 1 , the antenna 2 , the
天线1和天线2用于发射和接收电磁波信号。电子设备300中的每个天线可用于覆盖单个或多个通信频带。不同的天线还可以复用,以提高天线的利用率。例如:可以将天线1复用为无线局域网的分集天线。在另外一些实施例中,天线可以和调谐开关结合使用。Antenna 1 and Antenna 2 are used to transmit and receive electromagnetic wave signals. Each antenna in electronic device 300 may be used to cover single or multiple communication frequency bands. Different antennas can also be multiplexed to improve the utilization of the antennas. For example: Antenna 1 can be multiplexed as a diversity antenna of a wireless local area network. In other embodiments, the antenna may be used in conjunction with a tuning switch.
移动通信模块350可以提供应用在电子设备300上的包括2G/3G/4G/5G等无线通信的解决方案。移动通信模块350可以包括至少一个滤波器,开关,功率放大器,低噪声放大器(low noise amplifier,LNA)等。移动通信模块350可以由天线1接收电磁波,并对接收的电磁波进行滤波,放大等处理,传送至调制解调处理器进行解调。移动通信模块350还可以对经调制解调处理器调制后的信号放大,经天线1转为电磁波辐射出去。在一些实施例中,移动通信模块350的至少部分功能模块可以被设置于处理器310中。在一些实施例中,移动通信模块350的至少部分功能模块可以与处理器310的至少部分模块被设置在同一个器件中。The
调制解调处理器可以包括调制器和解调器。其中,调制器用于将待发送的低频基带信号调制成中高频信号。解调器用于将接收的电磁波信号解调为低频基带信号。随后解调器将解调得到的低频基带信号传送至基带处理器处理。低频基带信号经基带处理器处理后,被传递给应用处理器。应用处理器通过音频设备(不限于扬声器370A,受话器370B等)输出声音信号,或通过显示屏394显示图像或视频。在一些实施例中,调制解调处理器可以是独立的器件。在另一些实施例中,调制解调处理器可以独立于处理器310,与移动通信模块350或其他功能模块设置在同一个器件中。A modem processor may include a modulator and a demodulator. Wherein, the modulator is used for modulating the low-frequency baseband signal to be transmitted into a medium-high frequency signal. The demodulator is used to demodulate the received electromagnetic wave signal into a low frequency baseband signal. Then the demodulator sends the demodulated low-frequency baseband signal to the baseband processor for processing. The low-frequency baseband signal is passed to the application processor after being processed by the baseband processor. The application processor outputs sound signals through audio equipment (not limited to
无线通信模块360可以提供应用在电子设备300上的包括无线局域网(wirelesslocal area networks,WLAN)(如无线保真(wireless fidelity,Wi-Fi)网络),蓝牙(bluetooth,BT),全球导航卫星系统(global navigation satellite system,GNSS),调频(frequency modulation,FM),近距离无线通信技术(near field communication,NFC),红外技术(infrared,IR)等无线通信的解决方案。无线通信模块360可以是集成至少一个通信处理模块的一个或多个器件。无线通信模块360经由天线2接收电磁波,将电磁波信号调频以及滤波处理,将处理后的信号发送到处理器310。无线通信模块360还可以从处理器310接收待发送的信号,对其进行调频,放大,经天线2转为电磁波辐射出去。The wireless communication module 360 can provide applications on the electronic device 300 including wireless local area networks (wireless local area networks, WLAN) (such as wireless fidelity (wireless fidelity, Wi-Fi) network), bluetooth (bluetooth, BT), global navigation satellite system (global navigation satellite system, GNSS), frequency modulation (frequency modulation, FM), near field communication technology (near field communication, NFC), infrared technology (infrared, IR) and other wireless communication solutions. The wireless communication module 360 may be one or more devices integrating at least one communication processing module. The wireless communication module 360 receives electromagnetic waves via the antenna 2 , frequency-modulates and filters the electromagnetic wave signals, and sends the processed signals to the
在一些实施例中,电子设备300的天线1和移动通信模块350耦合,天线2和无线通信模块360耦合,使得电子设备300可以通过无线通信技术与网络以及其他设备通信。所述无线通信技术可以包括全球移动通讯系统(global system for mobile communications,GSM),通用分组无线服务(general packet radio service,GPRS),码分多址接入(codedivision multiple access,CDMA),宽带码分多址(wideband code division multipleaccess,WCDMA),时分码分多址(time-division code division multiple access,TD-SCDMA),长期演进(long term evolution,LTE),BT,GNSS,WLAN,NFC,FM,和/或IR技术等。所述GNSS可以包括全球卫星定位系统(global positioning system,GPS),全球导航卫星系统(global navigation satellite system,GLONASS),北斗卫星导航系统(beidounavigation satellite system,BDS),准天顶卫星系统(quasi-zenith satellitesystem,QZSS)和/或星基增强系统(satellite based augmentation systems,SBAS)。In some embodiments, the antenna 1 of the electronic device 300 is coupled to the
电子设备300通过GPU,显示屏394,以及应用处理器等实现显示功能。GPU为图像处理的微处理器,连接显示屏394和应用处理器。GPU用于执行数学和几何计算,用于图形渲染。处理器310可包括一个或多个GPU,其执行程序指令以生成或改变显示信息。The electronic device 300 implements a display function through a GPU, a display screen 394, and an application processor. The GPU is a microprocessor for image processing, connected to the display screen 394 and the application processor. GPUs are used to perform mathematical and geometric calculations for graphics rendering.
显示屏394用于显示图像,视频等。显示屏394包括显示面板。显示面板可以采用液晶显示屏(liquid crystal display,LCD),有机发光二极管(organic light-emittingdiode,OLED),有源矩阵有机发光二极体或主动矩阵有机发光二极体(active-matrixorganic light emitting diode的,AMOLED),柔性发光二极管(flex light-emittingdiode,FLED),Miniled,MicroLed,Micro-oLed,量子点发光二极管(quantum dot lightemitting diodes,QLED)等。在一些实施例中,电子设备300可以包括1个或N个显示屏394,N为大于1的正整数。The display screen 394 is used to display images, videos and the like. Display 394 includes a display panel. The display panel may be a liquid crystal display (LCD), an organic light-emitting diode (OLED), an active-matrix organic light-emitting diode or an active-matrix organic light-emitting diode (active-matrix organic light emitting diode). AMOLED), flexible light-emitting diode (flex light-emitting diode, FLED), Miniled, MicroLed, Micro-oLed, quantum dot light-emitting diodes (quantum dot light emitting diodes, QLED), etc. In some embodiments, the electronic device 300 may include 1 or N display screens 394, where N is a positive integer greater than 1.
电子设备300可以通过ISP,摄像头393,视频编解码器,GPU,显示屏394以及应用处理器等实现拍摄功能。The electronic device 300 can realize the shooting function through an ISP, a camera 393 , a video codec, a GPU, a display screen 394 , and an application processor.
ISP用于处理摄像头393反馈的数据。例如,拍照时,打开快门,光线通过镜头被传递到摄像头感光元件上,光信号转换为电信号,摄像头感光元件将所述电信号传递给ISP处理,转化为肉眼可见的图像。ISP还可以对图像的噪点,亮度,肤色进行算法优化。ISP还可以对拍摄场景的曝光,色温等参数优化。在一些实施例中,ISP可以设置在摄像头393中。The ISP is used for processing the data fed back by the camera 393 . For example, when taking a picture, open the shutter, the light is transmitted to the photosensitive element of the camera through the lens, and the light signal is converted into an electrical signal, and the photosensitive element of the camera transmits the electrical signal to the ISP for processing, and converts it into an image visible to the naked eye. ISP can also perform algorithm optimization on image noise, brightness, and skin color. ISP can also optimize the exposure, color temperature and other parameters of the shooting scene. In some embodiments, the ISP may be located in the camera 393 .
摄像头393用于捕获静态图像或视频。物体通过镜头生成光学图像投射到感光元件。感光元件可以是电荷耦合器件(charge coupled device,CCD)或互补金属氧化物半导体(complementary metal-oxide-semiconductor,CMOS)光电晶体管。感光元件把光信号转换成电信号,之后将电信号传递给ISP转换成数字图像信号。ISP将数字图像信号输出到DSP加工处理。DSP将数字图像信号转换成标准的RGB,YUV等格式的图像信号。在一些实施例中,电子设备300可以包括1个或N个摄像头393,N为大于1的正整数。Camera 393 is used to capture still images or video. The object generates an optical image through the lens and projects it to the photosensitive element. The photosensitive element may be a charge coupled device (charge coupled device, CCD) or a complementary metal-oxide-semiconductor (complementary metal-oxide-semiconductor, CMOS) phototransistor. The photosensitive element converts the light signal into an electrical signal, and then transmits the electrical signal to the ISP to convert it into a digital image signal. The ISP outputs the digital image signal to the DSP for processing. DSP converts digital image signals into standard RGB, YUV and other image signals. In some embodiments, the electronic device 300 may include 1 or N cameras 393, where N is a positive integer greater than 1.
数字信号处理器用于处理数字信号,除了可以处理数字图像信号,还可以处理其他数字信号。例如,当电子设备300在频点选择时,数字信号处理器用于对频点能量进行傅里叶变换等。Digital signal processors are used to process digital signals. In addition to digital image signals, they can also process other digital signals. For example, when the electronic device 300 selects a frequency point, the digital signal processor is used to perform Fourier transform on the energy of the frequency point.
视频编解码器用于对数字视频压缩或解压缩。电子设备300可以支持一种或多种视频编解码器。这样,电子设备300可以播放或录制多种编码格式的视频,例如:动态图像专家组(moving picture experts group,MPEG)1,MPEG2,MPEG3,MPEG4等。Video codecs are used to compress or decompress digital video. The electronic device 300 may support one or more video codecs. In this way, the electronic device 300 can play or record videos in various encoding formats, for example: moving picture experts group (moving picture experts group, MPEG) 1, MPEG2, MPEG3, MPEG4 and so on.
NPU为神经网络(neural-network,NN)计算处理器,通过借鉴生物神经网络结构,例如借鉴人脑神经元之间传递模式,对输入信息快速处理,还可以不断的自学习。通过NPU可以实现电子设备300的智能认知等应用,例如:图像识别,人脸识别,语音识别,文本理解等。The NPU is a neural-network (NN) computing processor. By referring to the structure of biological neural networks, such as the transfer mode between neurons in the human brain, it can quickly process input information and continuously learn by itself. Applications such as intelligent cognition of the electronic device 300 can be realized through the NPU, such as image recognition, face recognition, speech recognition, text understanding, and the like.
外部存储器接口320可以用于连接外部存储卡,例如Micro SD卡,实现扩展电子设备300的存储能力。外部存储卡通过外部存储器接口320与处理器310通信,实现数据存储功能。例如将音乐,视频等文件保存在外部存储卡中。The
内部存储器321可以用于存储计算机可执行程序代码,所述可执行程序代码包括指令。内部存储器321可以包括存储程序区和存储数据区。其中,存储程序区可存储操作系统,至少一个功能所需的应用程序(比如声音播放功能,图像播放功能等)等。存储数据区可存储电子设备300使用过程中所创建的数据(比如音频数据,电话本等)等。此外,内部存储器321可以包括高速随机存取存储器,还可以包括非易失性存储器,例如至少一个磁盘存储器件,闪存器件,通用闪存存储器(universal flash storage,UFS)等。处理器310通过运行存储在内部存储器321的指令,和/或存储在设置于处理器中的存储器的指令,执行电子设备300的各种功能应用以及数据处理。The internal memory 321 may be used to store computer-executable program code, which includes instructions. The internal memory 321 may include an area for storing programs and an area for storing data. Wherein, the stored program area can store an operating system, at least one application program required by a function (such as a sound playing function, an image playing function, etc.) and the like. The storage data area can store data (such as audio data, phone book, etc.) created during the use of the electronic device 300 . In addition, the internal memory 321 may include a high-speed random access memory, and may also include a non-volatile memory, such as at least one magnetic disk storage device, flash memory device, universal flash storage (universal flash storage, UFS) and the like. The
电子设备300可以通过音频模块370,扬声器370A,受话器370B,麦克风370C,耳机接口370D,以及应用处理器等实现音频功能。例如音乐播放,录音等。The electronic device 300 can implement audio functions through an
音频模块370用于将数字音频信息转换成模拟音频信号输出,也用于将模拟音频输入转换为数字音频信号。音频模块370还可以用于对音频信号编码和解码。在一些实施例中,音频模块370可以设置于处理器310中,或将音频模块370的部分功能模块设置于处理器310中。The
扬声器370A,也称“喇叭”,用于将音频电信号转换为声音信号。电子设备300可以通过扬声器370A收听音乐,或收听免提通话。
受话器370B,也称“听筒”,用于将音频电信号转换成声音信号。当电子设备300接听电话或语音信息时,可以通过将受话器370B靠近人耳接听语音。
麦克风370C,也称“话筒”,“传声器”,用于将声音信号转换为电信号。当拨打电话或发送语音信息时,用户可以通过人嘴靠近麦克风370C发声,将声音信号输入到麦克风370C。电子设备300可以设置至少一个麦克风370C。在另一些实施例中,电子设备300可以设置两个麦克风370C,除了采集声音信号,还可以实现降噪功能。在另一些实施例中,电子设备300还可以设置三个,四个或更多麦克风370C,实现采集声音信号,降噪,还可以识别声音来源,实现定向录音功能等。The
耳机接口370D用于连接有线耳机。耳机接口370D可以是USB接口330,也可以是3.5mm的开放移动电子设备平台(open mobile terminal platform,OMTP)标准接口,美国蜂窝电信工业协会(cellular telecommunications industry association of the USA,CTIA)标准接口。The
压力传感器380A用于感受压力信号,可以将压力信号转换成电信号。在一些实施例中,压力传感器380A可以设置于显示屏394。The pressure sensor 380A is used to sense the pressure signal and convert the pressure signal into an electrical signal. In some embodiments, pressure sensor 380A may be located on display screen 394 .
压力传感器380A的种类很多,如电阻式压力传感器,电感式压力传感器,电容式压力传感器等。电容式压力传感器可以是包括至少两个具有导电材料的平行板。当有力作用于压力传感器380A,电极之间的电容改变。电子设备300根据电容的变化确定压力的强度。当有触摸操作作用于显示屏394,电子设备300根据压力传感器380A检测所述触摸操作强度。电子设备300也可以根据压力传感器380A的检测信号计算触摸的位置。在一些实施例中,作用于相同触摸位置,但不同触摸操作强度的触摸操作,可以对应不同的操作指令。例如:当有触摸操作强度小于第一压力阈值的触摸操作作用于短消息应用图标时,执行查看短消息的指令。当有触摸操作强度大于或等于第一压力阈值的触摸操作作用于短消息应用图标时,执行新建短消息的指令。There are many types of pressure sensors 380A, such as resistive pressure sensors, inductive pressure sensors, and capacitive pressure sensors. A capacitive pressure sensor may be comprised of at least two parallel plates with conductive material. When a force is applied to pressure sensor 380A, the capacitance between the electrodes changes. The electronic device 300 determines the intensity of pressure according to the change in capacitance. When a touch operation acts on the display screen 394, the electronic device 300 detects the intensity of the touch operation according to the pressure sensor 380A. The electronic device 300 may also calculate the touched position according to the detection signal of the pressure sensor 380A. In some embodiments, touch operations acting on the same touch position but with different touch operation intensities may correspond to different operation instructions. For example: when a touch operation with a touch operation intensity less than the first pressure threshold acts on the short message application icon, an instruction to view short messages is executed. When a touch operation whose intensity is greater than or equal to the first pressure threshold acts on the icon of the short message application, the instruction of creating a new short message is executed.
陀螺仪传感器380B可以用于确定电子设备300的运动姿态。在一些实施例中,可以通过陀螺仪传感器380B确定电子设备300围绕三个轴(即,x,y和z轴)的角速度。陀螺仪传感器380B可以用于拍摄防抖。示例性的,当按下快门,陀螺仪传感器380B检测电子设备300抖动的角度,根据角度计算出镜头模组需要补偿的距离,让镜头通过反向运动抵消电子设备300的抖动,实现防抖。陀螺仪传感器380B还可以用于导航,体感游戏场景。The gyro sensor 380B can be used to determine the motion posture of the electronic device 300 . In some embodiments, the angular velocity of the electronic device 300 about three axes (ie, x, y and z axes) may be determined by the gyro sensor 380B. The gyro sensor 380B can be used for image stabilization. Exemplarily, when the shutter is pressed, the gyro sensor 380B detects the shaking angle of the electronic device 300, calculates the distance that the lens module needs to compensate according to the angle, and allows the lens to counteract the shaking of the electronic device 300 through reverse movement to achieve anti-shake. The gyroscope sensor 380B can also be used for navigation and somatosensory game scenes.
气压传感器380C用于测量气压。在一些实施例中,电子设备300通过气压传感器380C测得的气压值计算海拔高度,辅助定位和导航。The air pressure sensor 380C is used to measure air pressure. In some embodiments, the electronic device 300 calculates the altitude based on the air pressure value measured by the air pressure sensor 380C to assist positioning and navigation.
磁传感器380D包括霍尔传感器。电子设备300可以利用磁传感器380D检测翻盖皮套的开合。在一些实施例中,当电子设备300是翻盖机时,电子设备300可以根据磁传感器380D检测翻盖的开合。进而根据检测到的皮套的开合状态或翻盖的开合状态,设置翻盖自动解锁等特性。The magnetic sensor 380D includes a Hall sensor. The electronic device 300 may use the magnetic sensor 380D to detect the opening and closing of the flip leather case. In some embodiments, when the electronic device 300 is a flip machine, the electronic device 300 can detect opening and closing of the flip according to the magnetic sensor 380D. Furthermore, according to the detected opening and closing state of the leather case or the opening and closing state of the flip cover, features such as automatic unlocking of the flip cover are set.
加速度传感器380E可检测电子设备300在各个方向上(一般为三轴)加速度的大小。当电子设备300静止时可检测出重力的大小及方向。还可以用于识别电子设备姿态,应用于横竖屏切换,计步器等应用。The acceleration sensor 380E can detect the acceleration of the electronic device 300 in various directions (generally three axes). The magnitude and direction of gravity can be detected when the electronic device 300 is stationary. It can also be used to identify the posture of electronic devices, and can be used in applications such as horizontal and vertical screen switching, pedometers, etc.
距离传感器380F,用于测量距离。电子设备300可以通过红外或激光测量距离。在一些实施例中,拍摄场景,电子设备300可以利用距离传感器380F测距以实现快速对焦。The distance sensor 380F is used to measure the distance. The electronic device 300 can measure the distance by infrared or laser. In some embodiments, when shooting a scene, the electronic device 300 can use the distance sensor 380F to measure distance to achieve fast focusing.
接近光传感器380G可以包括例如发光二极管(LED)和光检测器,例如光电二极管。发光二极管可以是红外发光二极管。电子设备300通过发光二极管向外发射红外光。电子设备300使用光电二极管检测来自附近物体的红外反射光。当检测到充分的反射光时,可以确定电子设备300附近有物体。当检测到不充分的反射光时,电子设备300可以确定电子设备300附近没有物体。电子设备300可以利用接近光传感器380G检测用户手持电子设备300贴近耳朵通话,以便自动熄灭屏幕达到省电的目的。接近光传感器380G也可用于皮套模式,口袋模式自动解锁与锁屏。Proximity light sensor 380G may include, for example, light emitting diodes (LEDs) and light detectors, such as photodiodes. The light emitting diodes may be infrared light emitting diodes. The electronic device 300 emits infrared light through the light emitting diode. Electronic device 300 uses photodiodes to detect infrared reflected light from nearby objects. When sufficient reflected light is detected, it may be determined that there is an object near the electronic device 300 . When insufficient reflected light is detected, the electronic device 300 may determine that there is no object near the electronic device 300 . The electronic device 300 can use the proximity light sensor 380G to detect that the user holds the electronic device 300 close to the ear to make a call, so as to automatically turn off the screen to save power. The proximity light sensor 380G can also be used in leather case mode, automatic unlock and lock screen in pocket mode.
环境光传感器380L用于感知环境光亮度。电子设备300可以根据感知的环境光亮度自适应调节显示屏394亮度。环境光传感器380L也可用于拍照时自动调节白平衡。环境光传感器380L还可以与接近光传感器380G配合,检测电子设备300是否在口袋里,以防误触。The ambient light sensor 380L is used for sensing ambient light brightness. The electronic device 300 can adaptively adjust the brightness of the display screen 394 according to the perceived ambient light brightness. The ambient light sensor 380L can also be used to automatically adjust the white balance when taking pictures. The ambient light sensor 380L can also cooperate with the proximity light sensor 380G to detect whether the electronic device 300 is in the pocket to prevent accidental touch.
指纹传感器380H用于采集指纹。电子设备300可以利用采集的指纹特性实现指纹解锁,访问应用锁,指纹拍照,指纹接听来电等。The fingerprint sensor 380H is used to collect fingerprints. The electronic device 300 can use the collected fingerprint characteristics to implement fingerprint unlocking, access to the application lock, take pictures with the fingerprint, answer calls with the fingerprint, and the like.
温度传感器380J用于检测温度。在一些实施例中,电子设备300利用温度传感器380J检测的温度,执行温度处理策略。例如,当温度传感器380J上报的温度超过阈值,电子设备300执行降低位于温度传感器380J附近的处理器的性能,以便降低功耗实施热保护。在另一些实施例中,当温度低于另一阈值时,电子设备300对电池342加热,以避免低温导致电子设备300异常关机。在其他一些实施例中,当温度低于又一阈值时,电子设备300对电池342的输出电压执行升压,以避免低温导致的异常关机。The temperature sensor 380J is used to detect temperature. In some embodiments, the electronic device 300 uses the temperature detected by the temperature sensor 380J to implement a temperature treatment strategy. For example, when the temperature reported by the temperature sensor 380J exceeds the threshold, the electronic device 300 may reduce the performance of the processor located near the temperature sensor 380J, so as to reduce power consumption and implement thermal protection. In some other embodiments, when the temperature is lower than another threshold, the electronic device 300 heats the battery 342 to avoid abnormal shutdown of the electronic device 300 caused by the low temperature. In some other embodiments, when the temperature is lower than another threshold, the electronic device 300 boosts the output voltage of the battery 342 to avoid abnormal shutdown caused by low temperature.
触摸传感器380K,也称“触控器件”。触摸传感器380K可以设置于显示屏394,由触摸传感器380K与显示屏394组成触摸屏,也称“触控屏”。触摸传感器380K用于检测作用于其上或附近的触摸操作。触摸传感器可以将检测到的触摸操作传递给应用处理器,以确定触摸事件类型。可以通过显示屏394提供与触摸操作相关的视觉输出。在另一些实施例中,触摸传感器380K也可以设置于电子设备300的表面,与显示屏394所处的位置不同。Touch sensor 380K, also known as "touch device". The touch sensor 380K can be arranged on the display screen 394, and the touch sensor 380K and the display screen 394 form a touch screen, also called “touch screen”. The touch sensor 380K is used to detect a touch operation on or near it. The touch sensor can pass the detected touch operation to the application processor to determine the type of touch event. Visual output related to touch operations can be provided through the display screen 394 . In other embodiments, the touch sensor 380K may also be disposed on the surface of the electronic device 300 , which is different from the position of the display screen 394 .
骨传导传感器380M可以获取振动信号。在一些实施例中,骨传导传感器380M可以获取人体声部振动骨块的振动信号。骨传导传感器380M也可以接触人体脉搏,接收血压跳动信号。在一些实施例中,骨传导传感器380M也可以设置于耳机中,结合成骨传导耳机。音频模块370可以基于所述骨传导传感器380M获取的声部振动骨块的振动信号,解析出语音信号,实现语音功能。应用处理器可以基于所述骨传导传感器380M获取的血压跳动信号解析心率信息,实现心率检测功能。The bone conduction sensor 380M can acquire vibration signals. In some embodiments, the bone conduction sensor 380M can acquire the vibration signal of the vibrating bone mass of the human voice. The bone conduction sensor 380M can also contact the human pulse and receive the blood pressure beating signal. In some embodiments, the bone conduction sensor 380M can also be disposed in the earphone, combined into a bone conduction earphone. The
按键390包括开机键,音量键等。按键390可以是机械按键。也可以是触摸式按键。电子设备300可以接收按键输入,产生与电子设备300的用户设置以及功能控制有关的键信号输入。The keys 390 include a power key, a volume key and the like. The key 390 may be a mechanical key. It can also be a touch button. The electronic device 300 may receive key input and generate key signal input related to user settings and function control of the electronic device 300 .
马达391可以产生振动提示。马达391可以用于来电振动提示,也可以用于触摸振动反馈。例如,作用于不同应用(例如拍照,音频播放等)的触摸操作,可以对应不同的振动反馈效果。作用于显示屏394不同区域的触摸操作,马达391也可对应不同的振动反馈效果。不同的应用场景(例如:时间提醒,接收信息,闹钟,游戏等)也可以对应不同的振动反馈效果。触摸振动反馈效果还可以支持自定义。The motor 391 can generate a vibrating prompt. The motor 391 can be used for incoming call vibration prompts, and can also be used for touch vibration feedback. For example, touch operations applied to different applications (such as taking pictures, playing audio, etc.) may correspond to different vibration feedback effects. The motor 391 can also correspond to different vibration feedback effects for touch operations acting on different areas of the display screen 394 . Different application scenarios (for example: time reminder, receiving information, alarm clock, games, etc.) can also correspond to different vibration feedback effects. The touch vibration feedback effect can also support customization.
指示器392可以是指示灯,可以用于指示充电状态,电量变化,也可以用于指示消息,未接来电,通知等。The indicator 392 can be an indicator light, which can be used to indicate the charging status, the change of the battery capacity, and can also be used to indicate messages, missed calls, notifications and the like.
SIM卡接口395用于连接SIM卡。SIM卡可以通过插入SIM卡接口395,或从SIM卡接口395拔出,实现和电子设备300的接触和分离。电子设备300可以支持1个或N个SIM卡接口,N为大于1的正整数。SIM卡接口395可以支持Nano SIM卡,Micro SIM卡,SIM卡等。同一个SIM卡接口395可以同时插入多张卡。所述多张卡的类型可以相同,也可以不同。SIM卡接口395也可以兼容不同类型的SIM卡。SIM卡接口395也可以兼容外部存储卡。电子设备300通过SIM卡和网络交互,实现通话以及数据通信等功能。在一些实施例中,电子设备300采用eSIM,即:嵌入式SIM卡。eSIM卡可以嵌在电子设备300中,不能和电子设备300分离。The
本发明实施例提供一种计算机可读存储介质,该计算机可读存储介质中存储有指令,当该指令在终端设备上运行时,使得终端设备执行如上述方法实施例中的功能/步骤。An embodiment of the present invention provides a computer-readable storage medium, where instructions are stored in the computer-readable storage medium, and when the instructions are run on a terminal device, the terminal device is made to perform the functions/steps in the foregoing method embodiments.
本发明实施例还提供了一种包含指令的计算机程序产品,当该计算机程序产品在计算机或任一至少一种处理器上运行时,使得计算机执行如上述方法实施例中的功能/步骤。The embodiment of the present invention also provides a computer program product containing instructions, and when the computer program product is run on a computer or any at least one processor, it causes the computer to execute the functions/steps in the above method embodiments.
本发明实施例中,“至少一个”是指一个或者多个,“多个”是指两个或两个以上。“和/或”,描述关联对象的关联关系,表示可以存在三种关系,例如,A和/或B,可以表示单独存在A、同时存在A和B、单独存在B的情况。其中A,B可以是单数或者复数。字符“/”一般表示前后关联对象是一种“或”的关系。“以下至少一项”及其类似表达,是指的这些项中的任意组合,包括单项或复数项的任意组合。例如,a,b和c中的至少一项可以表示:a,b,c,a-b,a-c,b-c,或a-b-c,其中a,b,c可以是单个,也可以是多个。In the embodiments of the present invention, "at least one" means one or more, and "multiple" means two or more. "And/or" describes the association relationship of associated objects, indicating that there may be three kinds of relationships, for example, A and/or B may indicate that A exists alone, A and B exist simultaneously, or B exists alone. Among them, A and B can be singular or plural. The character "/" generally indicates that the contextual objects are an "or" relationship. "At least one of the following" and similar expressions refer to any combination of these items, including any combination of single items or plural items. For example, at least one of a, b, and c may represent: a, b, c, a-b, a-c, b-c, or a-b-c, wherein a, b, and c may be single or multiple.
本领域普通技术人员可以意识到,本文中公开的实施例中描述的各单元及算法步骤,能够以电子硬件、计算机软件和电子硬件的结合来实现。这些功能究竟以硬件还是软件方式来执行,取决于技术方案的特定应用和设计约束条件。专业技术人员可以对每个特定的应用来使用不同方法来实现所描述的功能,但是这种实现不应认为超出本发明的范围。Those of ordinary skill in the art can appreciate that each unit and algorithm steps described in the embodiments disclosed herein can be realized by a combination of electronic hardware, computer software and electronic hardware. Whether these functions are executed by hardware or software depends on the specific application and design constraints of the technical solution. Those skilled in the art may use different methods to implement the described functions for each specific application, but such implementation should not be regarded as exceeding the scope of the present invention.
所属领域的技术人员可以清楚地了解到,为描述的方便和简洁,上述描述的系统、装置和单元的具体工作过程,可以参考前述方法实施例中的对应过程,在此不再赘述。Those skilled in the art can clearly understand that for the convenience and brevity of the description, the specific working process of the above-described system, device and unit can refer to the corresponding process in the foregoing method embodiment, which will not be repeated here.
在本发明所提供的几个实施例中,任一功能如果以软件功能单元的形式实现并作为独立的产品销售或使用时,可以存储在一个计算机可读取存储介质中。基于这样的理解,本发明的技术方案本质上或者说对现有技术做出贡献的部分或者该技术方案的部分可以以软件产品的形式体现出来,该计算机软件产品存储在一个存储介质中,包括若干指令用以使得一台电子设备(可以是个人计算机,服务器,或者网络设备等)执行本发明各个实施例所述方法的全部或部分步骤。而前述的存储介质包括:U盘、移动硬盘、只读存储器(read-only memory,ROM)、随机存取存储器(random access memory,RAM)、磁碟或者光盘等各种可以存储程序代码的介质。In the several embodiments provided by the present invention, if any function is realized in the form of a software function unit and sold or used as an independent product, it can be stored in a computer-readable storage medium. Based on this understanding, the essence of the technical solution of the present invention or the part that contributes to the prior art or the part of the technical solution can be embodied in the form of a software product, and the computer software product is stored in a storage medium, including Several instructions are used to make an electronic device (which may be a personal computer, a server, or a network device, etc.) execute all or part of the steps of the methods described in various embodiments of the present invention. The aforementioned storage medium includes: U disk, mobile hard disk, read-only memory (read-only memory, ROM), random access memory (random access memory, RAM), magnetic disk or optical disk and other various media that can store program codes. .
以上所述,仅为本发明的具体实施方式,任何熟悉本技术领域的技术人员在本发明揭露的技术范围内,可轻易想到变化或替换,都应涵盖在本发明的保护范围之内。本发明的保护范围应以所述权利要求的保护范围为准。The above is only a specific implementation of the present invention, and any person skilled in the art can easily think of changes or substitutions within the technical scope disclosed in the present invention, which should be covered by the protection scope of the present invention. The protection scope of the present invention shall be determined by the protection scope of the claims.
Claims (17)
Translated fromChinesePriority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202110897966.XACN115706994A (en) | 2021-08-05 | 2021-08-05 | Access control method and electronic equipment |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202110897966.XACN115706994A (en) | 2021-08-05 | 2021-08-05 | Access control method and electronic equipment |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| CN115706994Atrue CN115706994A (en) | 2023-02-17 |
Family
ID=85178880
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN202110897966.XAPendingCN115706994A (en) | 2021-08-05 | 2021-08-05 | Access control method and electronic equipment |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN115706994A (en) |
Cited By (1)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| WO2025025782A1 (en)* | 2023-07-31 | 2025-02-06 | 华为技术有限公司 | Application management and control method and electronic device |
Citations (5)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20180123971A1 (en)* | 2015-06-29 | 2018-05-03 | Huawei Technologies Co., Ltd. | Application Implementation Method and Service Controller |
| CN109933960A (en)* | 2019-03-15 | 2019-06-25 | Oppo广东移动通信有限公司 | Service calling control method, service calling method, device and terminal |
| US20190303219A1 (en)* | 2016-10-13 | 2019-10-03 | Alibaba Group Holding Limited | Embedding an interface of one application into an interface of another application |
| US20200099738A1 (en)* | 2018-09-24 | 2020-03-26 | Citrix Systems, Inc. | Systems and methods for bridge protocol between diverse applications |
| CN111523136A (en)* | 2020-07-06 | 2020-08-11 | 腾讯科技(深圳)有限公司 | Authority management method, device and equipment of application program and storage medium |
- 2021
- 2021-08-05CNCN202110897966.XApatent/CN115706994A/enactivePending
Patent Citations (5)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20180123971A1 (en)* | 2015-06-29 | 2018-05-03 | Huawei Technologies Co., Ltd. | Application Implementation Method and Service Controller |
| US20190303219A1 (en)* | 2016-10-13 | 2019-10-03 | Alibaba Group Holding Limited | Embedding an interface of one application into an interface of another application |
| US20200099738A1 (en)* | 2018-09-24 | 2020-03-26 | Citrix Systems, Inc. | Systems and methods for bridge protocol between diverse applications |
| CN109933960A (en)* | 2019-03-15 | 2019-06-25 | Oppo广东移动通信有限公司 | Service calling control method, service calling method, device and terminal |
| CN111523136A (en)* | 2020-07-06 | 2020-08-11 | 腾讯科技(深圳)有限公司 | Authority management method, device and equipment of application program and storage medium |
Cited By (1)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| WO2025025782A1 (en)* | 2023-07-31 | 2025-02-06 | 华为技术有限公司 | Application management and control method and electronic device |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| US20230189366A1 (en) | Bluetooth Communication Method, Terminal Device, and Computer-Readable Storage Medium | |
| US12135692B2 (en) | File sharing method of mobile terminal and device | |
| CN111182140B (en) | Motor control method and device, computer readable medium and terminal device | |
| CN114125130B (en) | Method for controlling communication service state, terminal device and readable storage medium | |
| US20230125956A1 (en) | Wireless Communication System and Method | |
| WO2022100610A1 (en) | Screen projection method and apparatus, and electronic device and computer-readable storage medium | |
| CN111835907A (en) | A method, device and system for transferring services across electronic devices | |
| CN114554012B (en) | Methods for answering incoming calls, electronic equipment and storage media | |
| WO2020088633A1 (en) | Payment method, device, and user equipment unit | |
| CN113973398B (en) | Wireless network connection method, electronic device and chip system | |
| WO2021052204A1 (en) | Address book-based device discovery method, audio and video communication method, and electronic device | |
| CN114466107A (en) | Sound effect control method, device, electronic device, and computer-readable storage medium | |
| CN110673889A (en) | Application opening method in folding screen equipment and related device | |
| US20240098354A1 (en) | Connection establishment method and electronic device | |
| CN114095599B (en) | Message display method and electronic device | |
| CN113343193B (en) | Identity verification method and device and electronic equipment | |
| CN112527220B (en) | Electronic equipment display method and electronic equipment | |
| CN114489876A (en) | Text input method, electronic equipment and system | |
| CN114765768B (en) | Network selection method and device | |
| CN111339513B (en) | Method and device for data sharing | |
| CN113590884A (en) | Distributed data searching method and index file sharing method | |
| CN115706994A (en) | Access control method and electronic equipment | |
| CN110737916A (en) | Communication terminal and processing method | |
| CN114500725B (en) | Target content transfer method, master device, slave device and storage medium | |
| CN116437194A (en) | Method, device and readable storage medium for displaying preview images |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination |