CN115603950A - Decryption outsourcing attribute encryption access method and system based on same sub-strategy - Google Patents
Decryption outsourcing attribute encryption access method and system based on same sub-strategyDownload PDFInfo
- Publication number
- CN115603950A CN115603950ACN202211147664.1ACN202211147664ACN115603950ACN 115603950 ACN115603950 ACN 115603950ACN 202211147664 ACN202211147664 ACN 202211147664ACN 115603950 ACN115603950 ACN 115603950A
- Authority
- CN
- China
- Prior art keywords
- key
- strategy
- decryption
- same sub
- ciphertext
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Pending
Links
Images
Classifications
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/06—Network architectures or network communication protocols for network security for supporting key management in a packet data network
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/04—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks
- H04L63/0428—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks wherein the data content is protected, e.g. by encrypting or encapsulating the payload
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/20—Network architectures or network communication protocols for network security for managing network security; network security policies in general
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L67/00—Network arrangements or protocols for supporting network services or applications
- H04L67/01—Protocols
- H04L67/10—Protocols in which an application is distributed across nodes in the network
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/08—Key distribution or management, e.g. generation, sharing or updating, of cryptographic keys or passwords
- H04L9/0816—Key establishment, i.e. cryptographic processes or cryptographic protocols whereby a shared secret becomes available to two or more parties, for subsequent use
- H04L9/0819—Key transport or distribution, i.e. key establishment techniques where one party creates or otherwise obtains a secret value, and securely transfers it to the other(s)
- H04L9/0825—Key transport or distribution, i.e. key establishment techniques where one party creates or otherwise obtains a secret value, and securely transfers it to the other(s) using asymmetric-key encryption or public key infrastructure [PKI], e.g. key signature or public key certificates
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/08—Key distribution or management, e.g. generation, sharing or updating, of cryptographic keys or passwords
- H04L9/0861—Generation of secret information including derivation or calculation of cryptographic keys or passwords
Landscapes
- Engineering & Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- Computer Networks & Wireless Communication (AREA)
- Signal Processing (AREA)
- Computer Hardware Design (AREA)
- Computing Systems (AREA)
- General Engineering & Computer Science (AREA)
- Storage Device Security (AREA)
Abstract
Description
Translated fromChinese技术领域technical field
本发明属于数据访问控制技术领域,特别涉及一种基于相同子策略的解密外包属性加密访问方法及系统。The invention belongs to the technical field of data access control, in particular to a decryption outsourcing attribute encryption access method and system based on the same sub-strategy.
背景技术Background technique
随着云计算的不断发展,云存储已经成为重要的研究课题。为减小本地数据存储负担,越来越多的用户选择将数据存储到云端。然而,云服务商(Cloud Service Provider,CSP)并非完全可信的。为了防止CSP窥探或泄露用户隐私数据,将数据加密后再存储成为一种必然的趋势。传统的对称和非对称密码技术虽然能够加密数据,但只能实现一对一的数据共享及粗粒度的访问控制。因此,如何实现云端数据一对多的数据共享及细粒度的访问控制成为亟需解决的问题。属性基加密(Attribute-Based Encryption,ABE)算法作为一种新型的公钥密码机制,通过制定不同的访问策略令属性集合满足相应访问策略的用户即可解密密文,能够实现一对多的数据共享和细粒度的访问控制。根据密文和密钥嵌入位置的不同,可以进一步将ABE机制细分为密钥策略的属性基加密(Key-Policy Attribute-BasedEncryption,KP-ABE)方案和密文策略的属性基加密(Ciphertext-Policy Attribute-Based Encryption,CP-ABE)方案。基于CP-ABE访问策略能够由数据拥有者按需制定的特点,云环境下的CP-ABE机制得到了广泛的研究。With the continuous development of cloud computing, cloud storage has become an important research topic. In order to reduce the burden of local data storage, more and more users choose to store data in the cloud. However, a cloud service provider (Cloud Service Provider, CSP) is not completely trustworthy. In order to prevent CSPs from snooping or leaking user privacy data, it is an inevitable trend to encrypt data before storing it. Although traditional symmetric and asymmetric cryptographic techniques can encrypt data, they can only achieve one-to-one data sharing and coarse-grained access control. Therefore, how to realize one-to-many data sharing and fine-grained access control of cloud data has become an urgent problem to be solved. Attribute-Based Encryption (ABE) algorithm is a new type of public key encryption mechanism. By formulating different access policies, users whose attribute sets meet the corresponding access policies can decrypt the ciphertext, which can realize one-to-many data encryption. Sharing and fine-grained access control. According to the embedding positions of ciphertext and key, the ABE mechanism can be further subdivided into Key-Policy Attribute-Based Encryption (Key-Policy Attribute-BasedEncryption, KP-ABE) scheme and ciphertext-policy attribute-based encryption (Ciphertext- Policy Attribute-Based Encryption, CP-ABE) scheme. Based on the feature that CP-ABE access policies can be formulated by data owners on demand, the CP-ABE mechanism in the cloud environment has been extensively studied.
CP-ABE机制有效地解决了云端数据的机密性保护以及访问控制问题。但目前大部分CP-ABE方案基于椭圆曲线双线性群构建,在加解密阶段需要大量的指数运算和双线性对运算,给用户带来了沉重的计算负担,而效率是决定一个方案从理论走向实际应用的关键指标之一。因此,研究更高效的CP-ABE密码方案具有重要的现实意义。现有的一些提升加解密效率ABE方案通过预处理、减少双线性对计算量、外包给第三方等技术手段来解决ABE方案加解密效率低的问题,但这些方案并没有考虑到不同访问策略中存在的相同子策略时,带来的重复计算问题对加密计算开销的影响。The CP-ABE mechanism effectively solves the confidentiality protection and access control problems of cloud data. However, most of the current CP-ABE schemes are based on the construction of elliptic curve bilinear groups. In the encryption and decryption stage, a large number of exponential operations and bilinear pairing operations are required, which brings a heavy computational burden to users. The efficiency is determined by a scheme from It is one of the key indicators of theory moving towards practical application. Therefore, it is of great practical significance to study more efficient CP-ABE encryption schemes. Some existing ABE schemes to improve encryption and decryption efficiency solve the problem of low encryption and decryption efficiency of ABE schemes through preprocessing, reducing the amount of bilinear pairing calculations, outsourcing to third parties, etc., but these schemes do not take into account different access strategies When the same sub-strategy exists in , the impact of the double calculation problem on the encryption calculation overhead.
发明内容Contents of the invention
为此,本发明提供一种基于相同子策略的解密外包属性加密访问方法及系统,降低计算量和计算成本,有效提升数据访问控制的安全性和效率。Therefore, the present invention provides a decryption outsourcing attribute encryption access method and system based on the same sub-strategy, which reduces calculation amount and cost and effectively improves the security and efficiency of data access control.
按照本发明所提供的设计方案,提供一种基于相同子策略的解密外包属性加密访问方法,包含如下内容:According to the design scheme provided by the present invention, a decryption outsourcing attribute encryption access method based on the same sub-strategy is provided, which includes the following content:
初始阶段,可信授权机构依据设置的安全参数生成公钥和主密钥,并依据公钥、主密钥和用户属性集合生成用户对应的属性密钥,利用随机参数在属性密钥基础上生成云端密文所需的转换密钥,并将转换密钥上传至云端,将随机参数作为用户解密密钥并通过安全信道传递给数据访问者;In the initial stage, the trusted authority generates the public key and master key according to the set security parameters, and generates the attribute key corresponding to the user according to the public key, master key and user attribute set, and uses random parameters to generate on the basis of the attribute key The conversion key required by the cloud ciphertext, and the conversion key is uploaded to the cloud, and the random parameter is used as the user decryption key and passed to the data visitor through a secure channel;
加密阶段,将不同访问策略存在的重复部分作为该不同访问策略的相同子策略,数据拥有者将包含相同子策略的不同访问策略进行合并处理,将重复部分的交叉节点作为相同子策略的根节点,以相同子策略的根节点作为起点构造访问树结构的多项式,将具有相同子策略的明文进行统一加密处理,并将密文上传至云端;In the encryption stage, the repeated part of different access policies is regarded as the same sub-policy of the different access policy, and the data owner merges the different access policies containing the same sub-policy, and uses the intersection node of the repeated part as the root node of the same sub-policy , using the root node of the same sub-strategy as the starting point to construct a polynomial of the access tree structure, perform unified encryption processing on the plaintext with the same sub-strategy, and upload the ciphertext to the cloud;
解密阶段,云端的云服务提供商利用转换密钥对密文执行预解密操作,以将密文转换成中间密文;数据访问者利用自身保存的解密密钥对中间密文进行解密,获取对应明文。In the decryption phase, the cloud service provider on the cloud uses the conversion key to perform pre-decryption operations on the ciphertext to convert the ciphertext into an intermediate ciphertext; the data visitor uses the decryption key saved by itself to decrypt the intermediate ciphertext to obtain the corresponding clear text.
作为本发明中基于相同子策略的解密外包属性加密访问方法,进一步地,可信授权机构生成公钥和主密钥时,从有限域中随机选择两个参数,并利用两个p阶循环群、群生成元及群生成元的双线性映射来获取公钥,利用群生成元及随机选择的两个参数来获取主密钥,并将主密钥秘密保存。As the decryption outsourcing attribute encryption access method based on the same sub-strategy in the present invention, further, when the trusted authority generates the public key and the master key, two parameters are randomly selected from the finite field, and two p-order cyclic groups are used to , group generator and the bilinear mapping of the group generator to obtain the public key, use the group generator and two randomly selected parameters to obtain the master key, and keep the master key secret.
作为本发明中基于相同子策略的解密外包属性加密访问方法,进一步地,可信授权机构生成用户属性密钥及转换密钥时,对于公钥、主密钥和用户属性集合中的每个属性,分别从有限域中选择一个随机参数,通过密钥生成算法来计算得到属性密钥;然后,再从有限域中选择一个额随机参数,通过密钥生成算法来计算获取转换密钥和用户解密密钥。As the decryption outsourcing attribute encryption access method based on the same sub-strategy in the present invention, further, when the trusted authority generates the user attribute key and converts the key, for each attribute in the public key, master key and user attribute set , respectively select a random parameter from the finite field, and calculate the attribute key through the key generation algorithm; then, select a random parameter from the finite field, and use the key generation algorithm to calculate the conversion key and user decryption key.
作为本发明中基于相同子策略的解密外包属性加密访问方法,进一步地,以相同子策略的根节点作为起点构造访问树结构的多项式时,访问树结构中的叶子节点表示不同节点用户属性,非叶子节点由当前节点的孩子节点数量和该数量门限阈值组成,并在访问数构造中从有限域中选取一个随机参数,将该随机参数嵌入到相同子策略的根节点,通过计算来获取相同子策略根节点的父亲节点以及其他孩子节点的常数。As the decryption outsourcing attribute encryption access method based on the same sub-strategy in the present invention, further, when the root node of the same sub-strategy is used as the starting point to construct the polynomial of the access tree structure, the leaf nodes in the access tree structure represent different node user attributes, not The leaf node is composed of the number of child nodes of the current node and the threshold of the number, and a random parameter is selected from the finite field in the construction of the access number, and the random parameter is embedded into the root node of the same sub-strategy, and the same sub-strategy is obtained by calculation. Constants for the parent node of the strategy root node and other child nodes.
作为本发明基于相同子策略的解密外包属性加密访问方法,进一步地,预解密操作中,针对转换密钥,云服务提供商首先验证转换密钥对应的属性是否满足密文中嵌入的访问策略,若不满足,则输出异常,若满足,则云服务提供商通过转换密钥对密文进行预解密操作,将密文转换为中间密文。As the decryption outsourcing attribute encryption access method based on the same sub-strategy of the present invention, further, in the pre-decryption operation, for the conversion key, the cloud service provider first verifies whether the attribute corresponding to the conversion key satisfies the access policy embedded in the ciphertext, if If it is not satisfied, the output will be abnormal. If it is satisfied, the cloud service provider will pre-decrypt the ciphertext by converting the key, and convert the ciphertext into an intermediate ciphertext.
作为本发明基于相同子策略的解密外包属性加密访问方法,进一步地,针对转换密钥中属性集合满足密文对应的访问策略时,云服务提供商通过执行递归算法来对密文进行预解密操作。As the decryption outsourcing attribute encryption access method based on the same sub-strategy of the present invention, further, when the attribute set in the conversion key satisfies the access strategy corresponding to the ciphertext, the cloud service provider performs a pre-decryption operation on the ciphertext by executing a recursive algorithm .
作为本发明基于相同子策略的解密外包属性加密访问方法,进一步地,执行递归算法来进行预解密操作中,如果当前节点是访问策略中的叶子节点,则将密文、转换密钥和当前节点作为解密函数输入,通过节点用户属性来访问树结构,以进行解密操作;若当前节点不是访问策略中的叶子节点,则将密文、转换密钥和当前节点中的所有孩子节点作为解密函数输入,并通过当前节点的父节点及在其父节点分支下的序号来访问树结构,以进行解密操作。As the decryption outsourcing attribute encryption access method based on the same sub-strategy of the present invention, further, in executing the recursive algorithm to perform the pre-decryption operation, if the current node is a leaf node in the access strategy, the ciphertext, the conversion key and the current node As the input of the decryption function, the tree structure is accessed through the node user attribute to perform the decryption operation; if the current node is not a leaf node in the access strategy, the ciphertext, conversion key and all child nodes in the current node are used as the input of the decryption function , and access the tree structure through the parent node of the current node and the sequence number under its parent node branch to perform decryption operations.
作为本发明基于相同子策略的解密外包属性加密访问方法,进一步地,数据访问者对中间密文进行解密时,利用解密密钥对中间密文进行指数运算来获取对应的数据明文。As the decryption outsourcing attribute encryption access method based on the same sub-strategy of the present invention, further, when the data visitor decrypts the intermediate ciphertext, the decryption key is used to perform exponential operation on the intermediate ciphertext to obtain the corresponding data plaintext.
进一步地,本发明还提供一种基于相同子策略的解密外包属性加密访问系统,包含:云端、可信授权机构、数据拥有者和数据访问者,其中,Further, the present invention also provides a decryption outsourcing attribute encryption access system based on the same sub-strategy, including: cloud, trusted authority, data owner and data visitor, wherein,
可信授权机构,依据设置的安全参数生成公钥和主密钥,并依据公钥、主密钥和用户属性集合生成用户对应的属性密钥,利用随机参数在属性密钥基础上生成云端密文所需的转换密钥,并将转换密钥上传至云端,将随机参数作为用户解密密钥并通过安全信道传递给数据访问者;The trusted authority generates the public key and master key according to the set security parameters, and generates the attribute key corresponding to the user according to the public key, master key and user attribute set, and uses random parameters to generate the cloud key based on the attribute key. The conversion key required by the document, and the conversion key is uploaded to the cloud, and the random parameter is used as the user's decryption key and passed to the data visitor through a secure channel;
数据拥有者,将不同访问策略存在的重复部分作为该不同访问策略的相同子策略,数据拥有者将包含相同子策略的不同访问策略进行合并处理,将重复部分的交叉节点作为相同子策略的根节点,以相同子策略的根节点作为起点构造访问树结构的多项式,将具有相同子策略的明文进行统一加密处理,并将密文上传至云端;The data owner takes the repeated part of different access strategies as the same sub-strategy of the different access strategy, and the data owner merges the different access strategies containing the same sub-strategy, and uses the intersection node of the repeated part as the root of the same sub-strategy Node, using the root node of the same sub-strategy as the starting point to construct a polynomial of the access tree structure, perform unified encryption processing on the plaintext with the same sub-strategy, and upload the ciphertext to the cloud;
云端,云服务提供商利用转换密钥对密文执行预解密操作,以将密文转换成中间密文;On the cloud, the cloud service provider performs a pre-decryption operation on the ciphertext using the conversion key to convert the ciphertext into an intermediate ciphertext;
数据访问者,利用自身保存的解密密钥对中间密文进行解密,获取对应明文。The data visitor uses the decryption key saved by itself to decrypt the intermediate ciphertext to obtain the corresponding plaintext.
本发明的有益效果:Beneficial effects of the present invention:
本发明通过将不同访问策略的相同子策略合并,构造基于相同子策略的访问树结构,对数据进行统一加密,使原先需要重复计算的相同子策略部分只需要计算一次即可,消除了具有相同子策略的不同文件加密时重复的计算量,减轻了数据拥有者加密阶段的计算成本,提高了加密效率;通过引入转换密钥,可将大部分的解密操作外包到CSP(云服务提供商)执行的外包解密算法,使数据访问者在本地仅需要很小的计算开销即可获得明文数据。此外,本方案中的转换密钥生成过程由授权中心执行,避免给数据访问者造成额外的计算负担。并进一步通过严格的安全性证明,验证本案方案在标准模型下的安全性,并从存储开销、计算开销、模拟实验三个不同的角度与其他方案进行对比分析,说明本案方案在安全性、效率方面都达到了较好的效果,便于实际数据访问控制场景中的应用。The present invention merges the same sub-strategies of different access strategies, constructs an access tree structure based on the same sub-strategies, and performs unified encryption on the data, so that the same sub-strategies that originally required repeated calculations only need to be calculated once, eliminating the need to The amount of repeated calculations during the encryption of different files of the sub-strategy reduces the calculation cost of the data owner's encryption stage and improves the encryption efficiency; by introducing the conversion key, most of the decryption operations can be outsourced to the CSP (cloud service provider) The executed outsourced decryption algorithm enables data visitors to obtain plaintext data locally with only a small computational overhead. In addition, the conversion key generation process in this scheme is performed by the authorization center, which avoids extra computational burden for data accessors. And further pass the strict security proof to verify the security of the scheme in this case under the standard model, and compare and analyze it with other schemes from three different angles of storage overhead, computing overhead, and simulation experiments, to illustrate the security and efficiency of the scheme in this case. All aspects have achieved good results, which is convenient for application in actual data access control scenarios.
附图说明:Description of drawings:
图1为实施例中属性加密访问控制流程示意图;Fig. 1 is a schematic diagram of an attribute encryption access control flow in an embodiment;
图2为实施例中访问树结构示意图;Fig. 2 is a schematic diagram of an access tree structure in an embodiment;
图3为实施例中相同子策略合并示意;Fig. 3 is the same sub-strategy merging diagram in the embodiment;
图4为实施例中相同子策略属性数目对加密时间的影响示意;FIG. 4 is a schematic diagram of the influence of the number of attributes of the same sub-strategy on the encryption time in an embodiment;
图5为实施例中用户本地解密时间开销示意。Fig. 5 is a schematic diagram of the user's local decryption time overhead in the embodiment.
具体实施方式:detailed description:
为使本发明的目的、技术方案和优点更加清楚、明白,下面结合附图和技术方案对本发明作进一步详细的说明。In order to make the purpose, technical solution and advantages of the present invention more clear and understandable, the present invention will be further described in detail below in conjunction with the accompanying drawings and technical solutions.
现有提升加解密效率CP-ABE方案通过预处理、减少双线性对计算量、外包给第三方等技术手段来解决CP-ABE方案加解密效率低的问题,但这些方案并没有考虑到不同访问策略中存在的相同子策略时,带来的重复计算问题对加密计算开销的影响。以某医院的病历管理为例:医院病历库规定心脏病患者甲某的病历只有属性集合满足访问策略T1=(心内科and(医生or护士))的用户才能访问,皮肤病患者的乙某的病历只有属性集合满足访问策略T2=(皮肤科and(医生or护士))的用户才能访问。显而易见,这两个策略均包含一个相同的子策略T=(医生or护士)。在这种场景下使用传统ABE的访问控制方案时,需要分别加密甲某和乙某的病历,而相同子策略T对应的部分则要被计算两次,所以当数据拥有者需要共享的多个数据都存在相同的子策略时,将产生不容忽视的重复计算量,会给数据拥有者的带来了沉重的计算负担。由于每个用户都不可避免的属于某个团体或机构(如:学校、公司、社团等),所以这些用户往往有一个共同的属性集,可以用一个访问子策略来表示。因此,上述场景会发生在相当多的组织、企业中,进而考虑一种可避免重复计算子策略的高效的属性加密方案算法是有必要的。为此,本发明实施例,提供一种基于相同子策略的解密外包属性加密访问方法,包含:The existing CP-ABE schemes to improve encryption and decryption efficiency solve the problem of low encryption and decryption efficiency of CP-ABE schemes through preprocessing, reducing the amount of bilinear pairing calculations, outsourcing to third parties, etc., but these schemes do not take into account different When accessing the same sub-policy that exists in the policy, the impact of the double calculation problem on the encryption calculation overhead. Take the medical record management of a certain hospital as an example: the hospital medical record database stipulates that only users whose attribute set satisfies the access strategy T1 = (cardiology and (doctor or nurse)) can access the medical records of heart disease patient A, and B of skin disease patients Only users whose attribute set satisfies the access policy T2 = (dermatology and (doctor or nurse)) can access the medical records of . Obviously, both of these two strategies contain a same sub-strategy T=(doctor or nurse). When using the traditional ABE access control scheme in this scenario, the medical records of A and B need to be encrypted separately, and the part corresponding to the same sub-strategy T needs to be calculated twice, so when the data owner needs to share multiple When the same sub-strategy exists in the data, it will generate a non-negligible amount of repeated calculation, which will bring a heavy calculation burden to the data owner. Since each user inevitably belongs to a certain group or organization (such as: school, company, community, etc.), these users often have a common attribute set, which can be represented by an access sub-policy. Therefore, the above scenario will occur in quite a few organizations and enterprises, and it is necessary to consider an efficient attribute encryption scheme algorithm that can avoid double-computing sub-strategies. To this end, an embodiment of the present invention provides a decryption outsourcing attribute encryption access method based on the same sub-strategy, including:
初始阶段,可信授权机构依据设置的安全参数生成公钥和主密钥,并依据公钥、主密钥和用户属性集合生成用户对应的属性密钥,利用随机参数在属性密钥基础上生成云端密文所需的转换密钥,并将转换密钥上传至云端,将随机参数作为用户解密密钥并通过安全信道传递给数据访问者;In the initial stage, the trusted authority generates the public key and master key according to the set security parameters, and generates the attribute key corresponding to the user according to the public key, master key and user attribute set, and uses random parameters to generate on the basis of the attribute key The conversion key required by the cloud ciphertext, and the conversion key is uploaded to the cloud, and the random parameter is used as the user decryption key and passed to the data visitor through a secure channel;
加密阶段,将不同访问策略存在的重复部分作为该不同访问策略的相同子策略,数据拥有者将包含相同子策略的不同访问策略进行合并处理,将重复部分的交叉节点作为相同子策略的根节点,以相同子策略的根节点作为起点构造访问树结构的多项式,将具有相同子策略的明文进行统一加密处理,并将密文上传至云端;In the encryption stage, the repeated part of different access policies is regarded as the same sub-policy of the different access policy, and the data owner merges the different access policies containing the same sub-policy, and uses the intersection node of the repeated part as the root node of the same sub-policy , using the root node of the same sub-strategy as the starting point to construct a polynomial of the access tree structure, perform unified encryption processing on the plaintext with the same sub-strategy, and upload the ciphertext to the cloud;
解密阶段,云端的云服务提供商利用转换密钥对密文执行预解密操作,以将密文转换成中间密文;数据访问者利用自身保存的解密密钥对中间密文进行解密,获取对应明文。In the decryption phase, the cloud service provider on the cloud uses the conversion key to perform pre-decryption operations on the ciphertext to convert the ciphertext into an intermediate ciphertext; the data visitor uses the decryption key saved by itself to decrypt the intermediate ciphertext to obtain the corresponding clear text.
假设G0,G1为两个p阶循环群,双线性映射e:G0×G0→G1满足:1.双线性(Bilinearity):使e(ga,g1b)=e(g,g1)ab。2.非退化性(Non-degeneracy):使得e(g,g1)≠1。3.可计算性(Computability):在有效的时间内能够计算出e(g,g1)。Assuming that G0 and G1 are two cyclic groups of order p, the bilinear map e:G0 ×G0 →G1 satisfies: 1. Bilinearity: Let e(ga , g1b )=e(g, g1 )ab . 2. Non-degeneracy: Make e(g,g1 )≠1. 3. Computability: e(g,g1 ) can be calculated in an efficient time.
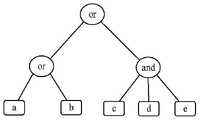
访问树结构作为访问策略一种表现方式,树中的节点由叶子节点和非叶子节点两部分组成。其中,叶子节点表示不同的属性,非叶子节点x可以用(kx,numx)表示。numx表示节点x的孩子节点的数量,kx为其阈值(1≤kx≤numx),规定当kx=1时表示“或”门,当kx=numx表示“与”门,当1<kx<numx表示门限。通过定义att(x)、parent(x)、index(x)来描述访问树。其中,att(x)表示节点x的属性,parent(x)表示节点x的父节点,index(x)表示节点x在其父节点分支下的序号。如果用户A的属性集合满足访问树结构,那么用户A为授权用户,用户A对应的属性集合称为授权集,用户A可以获得秘密值。否则,用户A为非授权用户,用户A对应的属性集合称为非授权集,用户A不能获得秘密消息值。访问树结构如图2所示,对应的逻辑表达式可以记为T=(a orb)or(candd ande)。其中,属性全集可以表示为S=(a,b,c,d,e),如果用户A的属性集合可以被表示为SA=(a,c,d),由于SA包含属性a即可满足访问树结构,所以用户A为授权用户,属性集合SA被称为授权集。如果用户B的属性集合为SB=(c,d),由于SB仅包含属性c,d不能满足访问树结构的任何一个分支,所以用户B为非授权用户,属性集合SB则是非授权集。The access tree structure is a way of expressing the access strategy. The nodes in the tree are composed of leaf nodes and non-leaf nodes. Among them, the leaf nodes represent different attributes, and the non-leaf node x can be represented by (kx , numx ). numx represents the number of child nodes of node x, and kx is its threshold value (1≤kx ≤numx ), it is stipulated that when kx =1, it represents an "or" gate, and when kx = numx represents an "and" gate , when 1<kx <numx represents the threshold. The access tree is described by defining att(x), parent(x), index(x). Among them,att (x) represents the attribute of node x, parent(x) represents the parent node of node x, and index(x) represents the sequence number of node x under its parent node branch. If the attribute set of user A satisfies the access tree structure, then user A is an authorized user, and the attribute set corresponding to user A is called an authorized set, and user A can obtain the secret value. Otherwise, user A is an unauthorized user, and the attribute set corresponding to user A is called an unauthorized set, and user A cannot obtain the secret message value. The access tree structure is shown in Figure 2, and the corresponding logic expression can be recorded as T=(a orb)or(candd ande). Among them, the complete set of attributes can be expressed as S=(a,b,c,d,e), if the attribute set of user A can be expressed as SA =(a,c,d), since SA contains attribute a The access tree structure is satisfied, so user A is an authorized user, and the attribute set SA is called an authorized set. If the attribute set of user B is SB = (c, d), since SB only contains attributes c and d, which cannot satisfy any branch of the access tree structure, user B is an unauthorized user, and the attribute set SB is an unauthorized user. set.
参加图1所示,可信授权机构在完成初始化后,紧接着按照数据访问者所拥有的属性集合为其生成对应的属性密钥,然后通过一个随机参数在属性密钥的基础上生成转换云端密文所需要的转换密钥上传并至云端,并将随机参数作为用户解密密钥通过安全信道传递给数据访问者。在执行加密操作前,数据拥有者先将包含相同子策略的不同的访问策略合并处理,基于相同子策略的根节点开始构造多项式。传统基于访问树结构的CP-ABE方案往往从每棵访问树的根节点开始构造树结构,那么当存在多棵包含相同子策略的访问结构时,每棵访问树都计算了相同子策略所对应的多项式。本案实施例中,以相同子策略的根节点为起点开始构造访问树的方式,通过相同子策略的根节点可以计算出其上层父亲节点的值,从而可以计算出这个父亲节点的所有孩子节点的值,而相同子策略树的孩子节点则可通过根节点计算得出,那么相同的子策略部分则只计算了一次。至此,每棵访问树中的节点多项式均构造完毕。然后,数据拥有者将具有相同子策略的明文进行统一的加密处理得到密文。对于不同访问策略中相同子策略的密文只需要计算一次,减小了密文的重复计算量。用户解密前首先由CSP执行解密预处理操作,在这一步中本方案引入转换密钥用来将密文转换成中间密文,当CSP获取到转换密钥时先验证转换密钥对应的属性是否能够满足密文中嵌入的访问策略,如果不满足,则直接输出⊥。否则CSP则通过转换密钥对密文进行执行预解密操作,将密文转换为中间解密密文,而这个预解密阶段则由CSP承担了解密所需要计算的绝大部分双线性对、指数运算操作。数据访问者获取到中间密文后,利用自己保存的解密密钥对中间密文进行一次简单的指数运算即可得到对应的数据明文。与传统的CP-ABE方案需要由数据访问者承担全部的解密工作而言,由于本案方案将大部分解密计算都转移到了CSP,所以在很大程度上减轻了数据访问者本地解密的计算开销。对应算法可设计如下:As shown in Figure 1, after the trusted authority completes the initialization, it generates the corresponding attribute key according to the attribute set owned by the data visitor, and then generates the conversion cloud based on the attribute key through a random parameter. The conversion key required for the ciphertext is uploaded to the cloud, and the random parameter is passed to the data visitor through a secure channel as the user decryption key. Before performing the encryption operation, the data owner first merges different access policies containing the same sub-policy, and starts to construct a polynomial based on the root node of the same sub-policy. The traditional CP-ABE scheme based on the access tree structure usually constructs a tree structure from the root node of each access tree, so when there are multiple access structures containing the same sub-strategy, each access tree calculates the corresponding of polynomials. In the embodiment of this case, starting from the root node of the same sub-strategy to construct the access tree, the value of the upper parent node can be calculated through the root node of the same sub-strategy, so that the value of all child nodes of the parent node can be calculated value, and the child nodes of the same sub-strategy tree can be calculated through the root node, then the same sub-strategy part is only calculated once. So far, the node polynomials in each access tree have been constructed. Then, the data owner performs uniform encryption on the plaintext with the same sub-policy to obtain the ciphertext. The ciphertext of the same sub-policy in different access policies only needs to be calculated once, which reduces the amount of repeated calculation of the ciphertext. Before the user decrypts, the CSP first performs the decryption preprocessing operation. In this step, the scheme introduces a conversion key to convert the ciphertext into an intermediate ciphertext. When the CSP obtains the conversion key, it first verifies whether the attribute corresponding to the conversion key is It can satisfy the access strategy embedded in the ciphertext, if not, it will directly output ⊥. Otherwise, the CSP performs a pre-decryption operation on the ciphertext by converting the key, and converts the ciphertext into an intermediate decryption ciphertext. In this pre-decryption stage, the CSP undertakes most of the bilinear pairings and exponents required for decryption. arithmetic operation. After the data visitor obtains the intermediate ciphertext, he can perform a simple exponent operation on the intermediate ciphertext with the decryption key saved by himself to obtain the corresponding data plaintext. Compared with the traditional CP-ABE scheme that requires the data visitor to undertake all the decryption work, since the scheme in this case transfers most of the decryption calculations to the CSP, it greatly reduces the computational overhead of the data visitor's local decryption. The corresponding algorithm can be designed as follows:
(1)Setup(λ)→(PK,MK):系统初始化算法由可信授权机构执行,输入安全参数λ,输出系统公钥PK和必须秘密保存的主密钥MK。(1) Setup(λ)→(PK,MK): The system initialization algorithm is executed by a trusted authority, which inputs the security parameter λ, and outputs the system public key PK and the master key MK that must be kept secret.
(2)Keygen(PK,MK,S)→(SK,TK,UK):生成用户属性密钥算法由可信授权机构执行,输入系统公钥PK和主密钥MK以及用户属性集合S,输出用户属性私钥SK,转换密钥TK和用户解密密钥UK。(2) Keygen(PK,MK,S)→(SK,TK,UK): The user attribute key generation algorithm is executed by a trusted authority, input the system public key PK, master key MK and user attribute set S, and output User attribute private key SK, conversion key TK and user decryption key UK.
(3)Enc(PK,m1,T1,m2,T2)→(CT1,CT2):加密算法由数据拥有者执行,输入公开的系统公钥PK,明文m1,m2和访问结构T1,T2,输出明文m1,m2对应的密文CT1,CT2。(3) Enc(PK,m1 ,T1 ,m2 ,T2 )→(CT1 ,CT2 ): the encryption algorithm is executed by the data owner, and the public system public key PK is input, and the plaintext m1 ,m2 And access structure T1 , T2 , output ciphertext CT1 , CT2 corresponding to plaintext m1 , m2 .
(4)Cloud-Dec(PK,SK,CT1)→(IC):外包解密算法由云服务商执行,以解密CT1为例,输入公开的系统公钥PK,转换密钥TK以及密文CT1,输出中间密文IC。(4) Cloud-Dec(PK,SK,CT1 )→(IC): The outsourced decryption algorithm is executed by the cloud service provider. Taking the decryption of CT1 as an example, input the public system public key PK, conversion key TK and ciphertext CT1 , output the intermediate ciphertext IC.
(5)User-Dec(UK,IC)→(m1):用户解密算法由数据访问者执行,输入用户密钥UK以及中间密文IC,输出明文m1。(5) User-Dec(UK,IC)→(m1 ): The user decryption algorithm is executed by the data visitor, who inputs the user key UK and intermediate ciphertext IC, and outputs plaintext m1 .
其中,所涉及的变量符号及其所代表的具体含义如表1所示。Among them, the variable symbols involved and their specific meanings are shown in Table 1.
表1符号表示Table 1 symbol representation
进一步地,可信授权机构生成公钥和主密钥时,从有限域中随机选择两个参数,并利用两个p阶循环群、群生成元及群生成元的双线性映射来获取公钥,利用群生成元及随机选择的两个参数来获取主密钥,并将主密钥秘密保存。Furthermore, when the trusted authority generates the public key and the master key, two parameters are randomly selected from the finite field, and two p-order cyclic groups, group generators and bilinear mappings of group generators are used to obtain key, use the group generator and two randomly selected parameters to obtain the master key, and keep the master key secret.
令G0,G1是两个p阶循环群,g为群的生成元。e:G0×G0→G1为双线性映射,H1:{0,1}*→G0为哈希函数。随机选择两个参数α,β∈Zp(有限域).输出系统公钥PK和主密钥MK。Let G0 , G1 be two cyclic groups of order p, and g be the generator of the group. e: G0 ×G0 →G1 is a bilinear map, H1 :{0,1}* →G0 is a hash function. Randomly select two parameters α, β∈Zp (finite field). Output system public key PK and master key MK.
PK=(G0,g,gβ,e(g,g)α)PK=(G0 ,g,gβ ,e(g,g)α )
MK=(β,gα)MK=(β,gα )
可信授权机构生成用户属性密钥及转换密钥时,对于公钥、主密钥和用户属性集合中的每个属性,分别从有限域中选择一个随机参数,通过密钥生成算法来计算得到属性密钥;然后,再从有限域中选择一个额随机参数,通过密钥生成算法来计算获取转换密钥和用户解密密钥。When the trusted authority generates the user attribute key and converts the key, for each attribute in the public key, master key and user attribute set, a random parameter is selected from the finite field and calculated by the key generation algorithm attribute key; then, select a random parameter from the finite field, and calculate and obtain the conversion key and user decryption key through the key generation algorithm.
首先,输入用户属性集合S,系统公钥PK和主密钥MK选择一个随机参数对于每个属性j都有j∈S,然后对于属性集合S中的每个属性j随机选择通过计算可得出属性密钥SK。First, input user attribute set S, system public key PK and master key MK to select a random parameter For each attribute j there is j ∈ S, and then for each attribute j in the attribute set S a random selection The attribute key SK can be obtained through calculation.
接着,选择一个随机参数计算得到转换密钥TK和用户解密密钥UK。Next, choose a random parameter The conversion key TK and the user decryption key UK are obtained through calculation.
然后,将转换密钥TK发送给云服务商,将用户解密密钥UK通过安全信道发送给数据访问者。Then, the conversion key TK is sent to the cloud service provider, and the user decryption key UK is sent to the data visitor through a secure channel.
作为优选实施例,进一步地,以相同子策略的根节点作为起点构造访问树结构的多项式时,访问树结构中的叶子节点表示不同节点用户属性,非叶子节点由当前节点的孩子节点数量和该数量门限阈值组成,并在访问数构造中从有限域中选取一个随机参数,将该随机参数嵌入到相同子策略的根节点,通过计算来获取相同子策略根节点的父亲节点以及其他孩子节点的常数。As a preferred embodiment, further, when the root node of the same sub-strategy is used as the starting point to construct the polynomial of the access tree structure, the leaf nodes in the access tree structure represent different node user attributes, and the non-leaf nodes are determined by the number of child nodes of the current node and the In the access number construction, select a random parameter from the finite field, embed the random parameter into the root node of the same sub-strategy, and obtain the parent node and other child nodes of the same sub-strategy root node through calculation constant.
如图3所示,访问策略T1,T2存在重复部分,本文将重复存在的部分称为相同子策略T,其中重复部分的交叉节点为o,称o为相同子策略T的根节点。首先,数据拥有者将具有相同的子策略的访问策略进行合并操作,然后执行加密算法加密数据生成密文并上传到云端保存。与传统的CP-ABE方案以访问树的根节点为起点从上至下的构造访问树结构不同,本文方案以相同子策略的根节点为起点开始构造访问树,将一个随机参数嵌入到相同子策略的根节点,通过计算可得到相同子策略根节点的父亲节点以及其它孩子节点的常数项,从而,可以得到所有节点的多项式构造。As shown in Figure 3, access strategies T1 and T2 have repeated parts. In this paper, the repeated part is called the same sub-strategy T, and the intersection node of the repeated part is o, which is called the root node of the same sub-strategy T. First, the data owner merges the access policies with the same sub-policy, and then executes the encryption algorithm to encrypt the data to generate ciphertext and upload it to the cloud for storage. Different from the traditional CP-ABE scheme, which starts from the root node of the access tree and constructs the access tree structure from top to bottom, the scheme in this paper starts from the root node of the same sub-strategy to construct the access tree, and embeds a random parameter into the same sub-strategy. For the root node of the strategy, the parent node of the root node of the same sub-strategy and the constant items of other child nodes can be obtained through calculation, so that the polynomial construction of all nodes can be obtained.
为访问策略T1,T2中的每个节点x选择一个多项式qx,其中多项式qx的阶dx为节点x的门限值kx-1即dx=kx-1。选择一个随机参数s∈Zp,并令qo(0)=s。由于p,q为o的父亲节点所以可以得出qo(0)=qp(index(o))=qq(index(o)),可进一步计算出等式令节点o在访问策略T1,T2中的索引值均为1,于是s=qp(1)=qq(1)即通过计算可得出p0和q0最终可确定多项式qp(x)和qq(x),对于访问策略T1,T2中的其他节点t令qt(0)=qparent(t)(index(t)),通过选择其他dt个点来确定qt(x),从而访问策略T1,T2中除共享子策略节点外的每一个节点均可以被确定。令Y(T1)为访问策略T1叶子节点的集合,令Y(T2)为访问策略T2叶子节点的集合。经计算可分别得出明文m1,m2对应的密文CT1,CT2如下:Select a polynomial qx for each node x in the access strategy T1 , T2 , where the order dx of the polynomial qx is the threshold value kx -1 of the node x, ie dx =kx -1. Choose a random parameter s∈Zp , and let qo (0)=s. Since p and q are the parent nodes of o, it can be concluded that qo (0)=qp (index(o))=qq (index(o)), and the equation can be further calculated Let the index value of node o in access strategy T1 and T2 be 1, then s=qp (1)=qq (1) that is Through calculation, it can be obtained that p0 and q0 can finally determine the polynomials qp (x) and qq (x). For the access strategy T1 , other nodes t in T2 set qt (0)=qparent(t ) (index(t)), determine qt (x) by selecting other dt points, so that every node in the access strategy T1 , T2 except the shared sub-strategy node can be determined. Let Y(T1 ) be the set of leaf nodes of access policy T1 , and let Y(T2 ) be the set of leaf nodes of access policy T2 . After calculation, the ciphertext CT1 and CT2 corresponding to the plaintext m1 and m2 can be obtained as follows:
其中,令Y(T)为相同子策略T叶子节点的集合,对于集合Y(T)在计算密文CT1,CT2时只需要计算一次即可。Among them, let Y(T) be the set of leaf nodes of the same sub-strategy T, and the set Y(T) only needs to be calculated once when calculating the ciphertext CT1 and CT2 .
表2基于相同子策略的加密算法Table 2 Encryption algorithms based on the same sub-strategy
作为优选实施例,进一步地,预解密操作中,针对转换密钥,云服务提供商首先验证转换密钥对应的属性是否满足密文中嵌入的访问策略,若不满足,则输出异常,若满足,则云服务提供商通过转换密钥对密文进行预解密操作,将密文转换为中间密文。针对转换密钥中属性集合满足密文对应的访问策略时,云服务提供商通过执行递归算法来对密文进行预解密操作。进一步,执行递归算法来进行预解密操作中,如果当前节点是访问策略中的叶子节点,则将密文、转换密钥和当前节点作为解密函数输入,通过节点用户属性来访问树结构,以进行解密操作;若当前节点不是访问策略中的叶子节点,则将密文、转换密钥和当前节点中的所有孩子节点作为解密函数输入,并通过当前节点的父节点及在其父节点分支下的序号来访问树结构,以进行解密操作。As a preferred embodiment, further, in the pre-decryption operation, for the conversion key, the cloud service provider first verifies whether the attribute corresponding to the conversion key satisfies the access policy embedded in the ciphertext, if not, an exception is output, and if it is satisfied, Then the cloud service provider pre-decrypts the ciphertext by converting the key, and converts the ciphertext into an intermediate ciphertext. When the attribute set in the conversion key satisfies the access policy corresponding to the ciphertext, the cloud service provider performs a pre-decryption operation on the ciphertext by executing a recursive algorithm. Further, in performing the recursive algorithm to perform the pre-decryption operation, if the current node is a leaf node in the access strategy, the ciphertext, the conversion key and the current node are input as the decryption function, and the tree structure is accessed through the node user attribute to perform Decryption operation; if the current node is not a leaf node in the access strategy, the ciphertext, conversion key and all child nodes in the current node will be input as the decryption function, and the parent node of the current node and the branches under its parent node The sequence number is used to access the tree structure for decryption operations.
假设需要解密的密文为CT1,如果转换密钥TK中的属性集合满足密文CT1对应的访问策略T1,云服务商执行解密操作计算出中间解密密文。该解密算法可以表示为一个递归算法,如果x为访问策略T1中的一个叶子节点,那么令i=att(x)并计算Assuming that the ciphertext to be decrypted is CT1 , if the attribute set in the conversion key TK satisfies the access policy T1 corresponding to the ciphertext CT1 , the cloud service provider performs the decryption operation to calculate the intermediate decrypted ciphertext. The decryption algorithm can be expressed as a recursive algorithm, if x is a leaf node in the access strategy T1 , then let i=att(x) and calculate
如果x并非叶子节点,对x中的所有孩子节点z,调用函数DecryptNode(CT1,TK,z)并将结果保存为Fz。令Sx为孩子节点z的集合,并且每个节点z都满足Fz≠⊥。If x is not a leaf node, call the function DecryptNode(CT1 ,TK,z) for all child nodes z in x and save the result as Fz . Let Sx be the set of child nodes z, and each node z satisfies Fz ≠ ⊥.
其中,i=index(z),Sx′={index(z):z∈Sx}。因此,若转换密钥TK对应的属性集合满足密文CT1对应的访问策略T1则根节点root解密为Wherein, i=index(z), Sx ′={index(z):z∈Sx }. Therefore, if the attribute set corresponding to the conversion key TK satisfies the access policy T1 corresponding to the ciphertext CT1 , then the root node root is decrypted as
表3外包解密算法Table 3 Outsourced decryption algorithm
进一步地,数据访问者对中间密文进行解密时,利用解密密钥对中间密文进行指数运算来获取对应的数据明文。Further, when the data visitor decrypts the intermediate ciphertext, the decryption key is used to perform exponential operation on the intermediate ciphertext to obtain the corresponding data plaintext.
输入用户解密密钥UK以及中间密文IC计算可得到明文m1。Enter the user decryption key UK and the intermediate ciphertext IC to calculate and obtain the plaintext m1 .
进一步地,基于上述的方法,本发明实施例还提供一种基于相同子策略的解密外包属性加密访问系统,包含:云端、可信授权机构、数据拥有者和数据访问者,其中,Further, based on the above method, the embodiment of the present invention also provides a decryption outsourcing attribute encryption access system based on the same sub-strategy, including: cloud, trusted authority, data owner and data visitor, wherein,
可信授权机构,依据设置的安全参数生成公钥和主密钥,并依据公钥、主密钥和用户属性集合生成用户对应的属性密钥,利用随机参数在属性密钥基础上生成云端密文所需的转换密钥,并将转换密钥上传至云端,将随机参数作为用户解密密钥并通过安全信道传递给数据访问者;The trusted authority generates the public key and master key according to the set security parameters, and generates the attribute key corresponding to the user according to the public key, master key and user attribute set, and uses random parameters to generate the cloud key based on the attribute key. The conversion key required by the document, and the conversion key is uploaded to the cloud, and the random parameter is used as the user's decryption key and passed to the data visitor through a secure channel;
数据拥有者,将不同访问策略存在的重复部分作为该不同访问策略的相同子策略,数据拥有者将包含相同子策略的不同访问策略进行合并处理,将重复部分的交叉节点作为相同子策略的根节点,以相同子策略的根节点作为起点构造访问树结构的多项式,将具有相同子策略的明文进行统一加密处理,并将密文上传至云端;The data owner takes the repeated part of different access strategies as the same sub-strategy of the different access strategy, and the data owner merges the different access strategies containing the same sub-strategy, and uses the intersection node of the repeated part as the root of the same sub-strategy Node, using the root node of the same sub-strategy as the starting point to construct a polynomial of the access tree structure, perform unified encryption processing on the plaintext with the same sub-strategy, and upload the ciphertext to the cloud;
云端,云服务提供商利用转换密钥对密文执行预解密操作,以将密文转换成中间密文;On the cloud, the cloud service provider performs a pre-decryption operation on the ciphertext using the conversion key to convert the ciphertext into an intermediate ciphertext;
数据访问者,利用自身保存的解密密钥对中间密文进行解密,获取对应明文。The data visitor uses the decryption key saved by itself to decrypt the intermediate ciphertext to obtain the corresponding plaintext.
为验证本案方案有效性,下面结合理论推理和实验数据做进一步解释说明:In order to verify the effectiveness of the scheme in this case, the following is a further explanation combined with theoretical reasoning and experimental data:
1、安全性证明1. Safety certificate
设定:如果在一定的时间范围内,不存在能够以一定的优势破解本案方案的攻击者则可证明方案是安全的。Setting: If within a certain time range, there is no attacker who can crack the scheme with a certain advantage Then it can be proved that the scheme is safe.
证明:基于已知安全的BSW方案证明本案方案的安全性,如果攻击者能够在可计算的时间内以一定的优势攻破本章方案,那么就存在一个挑战者能够以同样的优势攻破BSW方案。Proof: Prove the security of the scheme based on the known security BSW scheme, if the attacker If it is possible to break through the scheme of this chapter with a certain advantage within a calculable time, then there is a challenger The BSW scheme can be broken with the same advantage.
初始化阶段:挑战者给攻击者提交公钥PK=(G0,g,gβ,e(g,g)α)。Initialization Phase: Challenger to the attacker Submit the public key PK=(G0 ,g,gβ ,e(g,g)α ).
密钥查询阶段1:攻击者向挑战者查询属性集合S的私钥,挑战者选择两个随机变量通过计算后可获得对应的私钥为挑战者再次选择一个随机变量利用SK计算出转换密钥TK,将SK*=(n,TK)返回给攻击者可以向挑战者查询多次,挑战者会一直回答攻击者的查询。Key query phase 1: Attacker challenger Query the private key of the attribute set S, the challenger Choose two random variables After calculation, the corresponding private key can be obtained as challenger choose a random variable again Use SK to calculate the conversion key TK, and return SK* = (n, TK) to the attacker challenger Queries multiple times, challenger will always answer the attacker query.
挑战阶段:攻击者向挑战者提交两个等长的明文消息对{m1,m1′},{m2,m′2},一对存在相同子策略的挑战访问策略T*和T。其中,在查询阶段1询问过的任意属性集合都不能够满足T*和T。挑战者随机选择b∈{0,1},并用访问策略T*加密mb,访问策略T加密mb′。随后,攻击者获取加密后产生的密文。Challenge Phase: Attacker challenger Submit two equal-length plaintext message pairs {m1 ,m1 ′}, {m2 ,m′2 }, a pair of challenge access policies T* and T with the same sub-strategy. Among them, any attribute set queried in query phase 1 cannot satisfy T* and T. challenger Randomly choose b ∈ {0,1}, and encrypt mb with access strategy T* , and access strategy T encrypts mb′ . Subsequently, the attacker Get the encrypted ciphertext.
密钥查询阶段2:攻击者向挑战者发起查询,若S不满足T*和T则继续以查询阶段1的模式查询更多属性集合。否则,挑战者选择随机参数Key query phase 2: Attacker challenger Initiate a query, if S does not satisfy T* and T, continue to query more attribute sets in the mode of query phase 1. Otherwise, the challenger choose random parameters
猜测阶段:攻击者输出关于b′∈{0,1}的猜测。如果b=b′那么攻击者赢得游戏的优势可以定义为AdvA=|Pr[b=b′]-1/2|。Guessing Phase: Attacker Output a guess about b′ ∈ {0,1}. If b = b' then the attacker The advantage of winning the game can be defined as AdvA =|Pr[b=b']-1/2|.
综上所述,在多项式时间内攻击者能够以不可忽略的优势赢得安全游戏,那么可以得出存在挑战者以同样的优势攻破BSW方案,与已知事实相互矛盾,故可证本文方案是安全的。In summary, in polynomial time the attacker can win the security game by a non-negligible margin, then it follows that there exists a challenger Breaking the BSW scheme with the same advantage is contradictory to the known facts, so it can be proved that the scheme in this paper is safe.
2、分析与模拟2. Analysis and Simulation
表4存储开销对比Table 4 Storage overhead comparison
表5计算开销对比Table 5 Computational overhead comparison
为了评估本案方案的性能,将其与一些提升方案性能的代表性方案Li方案、Herranz方案、Susilo方案以及Zhang方案分别从存储开销和计算开销两个不同的方面进行了分析对比。其中,Li方案为支持属性撤销的外包CP-ABE方案;Herranz方案和Susilo方案中,通过限制属性的个数或者密文的长度来降低加解密开销,但是只能支持门限访问结构或者与门访问策略,导致这些方案访问策略表达能力较弱难以满足实际应用中复杂的访问控制需求;Zhang方案中,支持快速解密的CP-ABE方案,在一定程度上减少了方案的解密开销,但该方案并未解决加密成本较高的问题。为了使对比结果更加显而易见,用n表示需要共享的文件的个数,nU表示系统中全体属性的数量,nS表示用户属性集的大小,nA表示访问策略中属性的数目,nC表示访问策略中相同子策略属性的个数,G0,G1分别用来表示循环群G0和G1中元素的大小,用pair、exp表示双线性对和指数运算的计算开销。In order to evaluate the performance of the scheme in this case, it is analyzed and compared with some representative schemes Li scheme, Herranz scheme, Susilo scheme and Zhang scheme to improve the performance of the scheme from two different aspects of storage cost and computing cost. Among them, the Li scheme is an outsourced CP-ABE scheme that supports attribute revocation; in the Herranz scheme and Susilo scheme, the overhead of encryption and decryption is reduced by limiting the number of attributes or the length of ciphertext, but only supports threshold access structure or AND gate access As a result, these schemes have weak ability to express access policies and are difficult to meet the complex access control requirements in practical applications; in Zhang's scheme, the CP-ABE scheme that supports fast decryption reduces the decryption overhead of the scheme to a certain extent, but the scheme does not The high cost of encryption is not addressed. In order to make the comparison result more obvious, use n to represent the number of files to be shared, nU to represent the number of all attributes in the system, nS to represent the size of user attribute sets, nA to represent the number of attributes in access policies, and nC to represent The number of the same sub-strategy attributes in the access strategy, G0 and G1 are used to represent the size of elements in the cyclic group G0 and G1 respectively, and pair and exp are used to represent the calculation overhead of bilinear pairing and exponential operation.
不同方案的密钥、密文存储开销对比如表4所示,Li方案、Herranz方案、Susilo方案中的公钥的存储开销随着关联属性的数量线性增长,而Zhang方案与本方案公钥存储开销与涉及的属性数量无关,但Zhang方案的公钥大小却是本案方案公钥大小的两倍。此外,通过观察私钥存储开销与密文存储开销对比,由于Herranz方案、Susilo方案通过恒定的属性的个数与密文大小来减小加解密运算的次数,这两个方案中的密文大小是常量,所以本方案的属性私钥与密文略大于Herranz方案、Susilo方案。The key and ciphertext storage overhead comparison of different schemes is shown in Table 4. The public key storage overhead in the Li scheme, Herranz scheme, and Susilo scheme increases linearly with the number of associated attributes, while the public key storage overhead of the Zhang scheme and this scheme The overhead is independent of the number of attributes involved, but the public key size of Zhang's scheme is twice the size of the public key of the scheme in this case. In addition, by observing the comparison between the private key storage cost and the ciphertext storage cost, since the Herranz scheme and the Susilo scheme reduce the number of encryption and decryption operations through a constant number of attributes and ciphertext size, the ciphertext size in these two schemes is a constant, so the attribute private key and ciphertext of this scheme are slightly larger than Herranz scheme and Susilo scheme.
计算开销对比如表5所示,在表4中给出了这些方案在资源受限设备上加密、外包解密和用户解密过程中计算开销对比。从表中不难看出当加密n个文件时,在总属性数目一定的情况下,Li方案、Herranz方案、Susilo方案以及Zhang方案的通信成本会随着相关属性的数量而增长,而本案方案的计算成本会随着相同子策略个数的增加而减少。Herranz方案、Susilo方案以及Zhang方案的解密开销会随着访问策略复杂度或属性的个数增加而增加,但是在Li方案与本案方案中无论属性的数量如何变化,用户解密开销均保持不变。除此之外,Li方案的用户解密开销是本案方案的两倍。在外包解密开销方面,由于外包解密由第三方执行并不影响用户的计算效率,故在此不再考虑外包解密所需要的计算成本。The calculation overhead comparison is shown in Table 5, and the calculation overhead comparison of these schemes in the process of encryption on resource-constrained devices, outsourced decryption, and user decryption is given in Table 4. It is not difficult to see from the table that when encrypting n files, the communication cost of the Li scheme, Herranz scheme, Susilo scheme and Zhang scheme will increase with the number of related attributes when the total number of attributes is fixed, while the scheme of this case Computational cost decreases as the number of identical sub-strategies increases. The decryption cost of Herranz scheme, Susilo scheme and Zhang scheme will increase with the increase of access policy complexity or the number of attributes, but in Li scheme and this case scheme no matter how the number of attributes changes, the user decryption cost remains unchanged. In addition, the user decryption cost of the Li scheme is twice that of the scheme in this case. In terms of outsourced decryption costs, since outsourced decryption is performed by a third party and does not affect the user's computing efficiency, the computational cost required for outsourced decryption is no longer considered here.
基于Java语言的密码库JPBC(Java Pairing Based Cryptography Library)。在实验设备为Intel(R)Core(TM)i9—9880H CPU@2.30GHZ,2.30GHz,内存32GB的环境下对本案方案与Li方案进行了模拟实验。在模拟实验中,主要通过方案中的双线性对运算与指数运算的计算时间,测量本案方案与Li方案加密、解密运算过程中的计算成本开销,并非算法实际的计算时间。为使结果更加准确在所有的测试数据均取50次模拟实验的平均值作为对比项。Java language-based cryptographic library JPBC (Java Pairing Based Cryptography Library). In the environment where the experimental equipment is Intel(R) Core(TM) i9-9880H CPU@2.30GHZ, 2.30GHz, and memory 32GB, the simulation experiment of the scheme of this case and the scheme of Li was carried out. In the simulation experiment, the calculation cost of the encryption and decryption process of the scheme and the Li scheme is mainly measured through the calculation time of bilinear pairing operation and exponential operation in the scheme, not the actual calculation time of the algorithm. In order to make the results more accurate, the average value of 50 simulation experiments is taken as a comparison item for all test data.
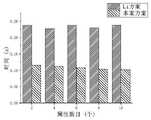
在模拟实验中,设加密明文数据的个数为2,访问策略中的属性数目固定为30,当相同子策略中的属性数目发生变化时,本案方案与Li方案中的加密时间开销如图4所示。当加密明文的数目与访问策略中属性总数目固定不变时,由于本案方案相同子策略进行了合并处理,所以随着相同子策略中的属性数目的增加本章方案总的加密时间成本逐渐减小,而LZZ方案中的加密时间开销基本保持不变。故可以推测当系统内相同子策略中的属性数目达到一定的数量时,本案方案的加密优势将会更显著。如图5所示,随着属性数目的增加本案方案中用户解密开销基本保持不变,由于本案方案将大部分解密计算外包到云端,所以无论属性数目如何变化,用户在本地解密阶段的运算量恒定。In the simulation experiment, the number of encrypted plaintext data is set to 2, and the number of attributes in the access strategy is fixed at 30. When the number of attributes in the same sub-strategy changes, the encryption time overhead of this scheme and the Li scheme is shown in Figure 4 shown. When the number of encrypted plaintext and the total number of attributes in the access policy are fixed, since the same sub-strategy of the scheme in this case is merged, the total encryption time cost of the scheme in this chapter decreases gradually with the increase of the number of attributes in the same sub-policy , while the encryption time overhead in the LZZ scheme basically remains unchanged. Therefore, it can be speculated that when the number of attributes in the same sub-strategy in the system reaches a certain number, the encryption advantages of the scheme in this case will be more significant. As shown in Figure 5, with the increase of the number of attributes, the user’s decryption cost remains basically unchanged in this case. Since most of the decryption calculations are outsourced to the cloud in this case, no matter how the number of attributes changes, the calculation amount of the user in the local decryption stage constant.
综上所述,本案方案中通过对加密、解密过程的优化,不仅减轻了数据拥有者的加密负担也降低了数据访问者的本地计算开销,使方案的总体计算效率得到显著的提升。除此之外,本案方案可扩展应用到智能手机、手环等轻量级设备共享社交数据和健康数据,使其在未来的工作中更加实用。To sum up, the optimization of the encryption and decryption process in this case scheme not only reduces the encryption burden of the data owner but also reduces the local computing overhead of the data visitor, so that the overall computing efficiency of the scheme is significantly improved. In addition, the solution in this case can be extended to share social data and health data with lightweight devices such as smartphones and bracelets, making it more practical in future work.
除非另外具体说明,否则在这些实施例中阐述的部件和步骤的相对步骤、数字表达式和数值并不限制本发明的范围。Relative steps, numerical expressions and numerical values of components and steps set forth in these embodiments do not limit the scope of the present invention unless specifically stated otherwise.
本说明书中各个实施例采用递进的方式描述,每个实施例重点说明的都是与其他实施例的不同之处,各个实施例之间相同相似部分互相参见即可。对于实施例公开的系统而言,由于其与实施例公开的方法相对应,所以描述的比较简单,相关之处参见方法部分说明即可。Each embodiment in this specification is described in a progressive manner, each embodiment focuses on the difference from other embodiments, and the same and similar parts of each embodiment can be referred to each other. As for the system disclosed in the embodiment, since it corresponds to the method disclosed in the embodiment, the description is relatively simple, and for the related information, please refer to the description of the method part.
结合本文中所公开的实施例描述的各实例的单元及方法步骤,能够以电子硬件、计算机软件或者二者的结合来实现,为了清楚地说明硬件和软件的可互换性,在上述说明中已按照功能一般性地描述了各示例的组成及步骤。这些功能是以硬件还是软件方式来执行,取决于技术方案的特定应用和设计约束条件。本领域普通技术人员可以对每个特定的应用来使用不同方法来实现所描述的功能,但是这种实现不认为超出本发明的范围。The units and method steps of the examples described in conjunction with the embodiments disclosed herein can be implemented by electronic hardware, computer software, or a combination of the two. In order to clearly illustrate the interchangeability of hardware and software, in the above description The composition and steps of each example have been generally described in terms of functions. Whether these functions are performed by hardware or software depends on the specific application and design constraints of the technical solution. Those of ordinary skill in the art may use different methods to implement the described functions for each particular application, but such implementation is not considered to exceed the scope of the present invention.
本领域普通技术人员可以理解上述方法中的全部或部分步骤可通过程序来指令相关硬件完成,所述程序可以存储于计算机可读存储介质中,如:只读存储器、磁盘或光盘等。可选地,上述实施例的全部或部分步骤也可以使用一个或多个集成电路来实现,相应地,上述实施例中的各模块/单元可以采用硬件的形式实现,也可以采用软件功能模块的形式实现。本发明不限制于任何特定形式的硬件和软件的结合。Those of ordinary skill in the art can understand that all or part of the steps in the above method can be completed by instructing relevant hardware through a program, and the program can be stored in a computer-readable storage medium, such as: a read-only memory, a magnetic disk or an optical disk, and the like. Optionally, all or part of the steps in the above embodiments can also be implemented using one or more integrated circuits. Correspondingly, each module/unit in the above embodiments can be implemented in the form of hardware, or can be implemented in the form of software function modules. The form is realized. The present invention is not limited to any specific combination of hardware and software.
最后应说明的是:以上所述实施例,仅为本发明的具体实施方式,用以说明本发明的技术方案,而非对其限制,本发明的保护范围并不局限于此,尽管参照前述实施例对本发明进行了详细的说明,本领域的普通技术人员应当理解:任何熟悉本技术领域的技术人员在本发明揭露的技术范围内,其依然可以对前述实施例所记载的技术方案进行修改或可轻易想到变化,或者对其中部分技术特征进行等同替换;而这些修改、变化或者替换,并不使相应技术方案的本质脱离本发明实施例技术方案的精神和范围,都应涵盖在本发明的保护范围之内。因此,本发明的保护范围应所述以权利要求的保护范围为准。Finally, it should be noted that: the above-described embodiments are only specific implementations of the present invention, used to illustrate the technical solutions of the present invention, rather than limiting them, and the scope of protection of the present invention is not limited thereto, although referring to the foregoing The embodiment has described the present invention in detail, and those skilled in the art should understand that any person familiar with the technical field can still modify the technical solutions described in the foregoing embodiments within the technical scope disclosed in the present invention Changes can be easily thought of, or equivalent replacements are made to some of the technical features; and these modifications, changes or replacements do not make the essence of the corresponding technical solutions deviate from the spirit and scope of the technical solutions of the embodiments of the present invention, and should be included in the scope of the present invention within the scope of protection. Therefore, the protection scope of the present invention should be based on the protection scope of the claims.
Claims (10)
Translated fromChinesePriority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202211147664.1ACN115603950A (en) | 2022-09-19 | 2022-09-19 | Decryption outsourcing attribute encryption access method and system based on same sub-strategy |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202211147664.1ACN115603950A (en) | 2022-09-19 | 2022-09-19 | Decryption outsourcing attribute encryption access method and system based on same sub-strategy |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| CN115603950Atrue CN115603950A (en) | 2023-01-13 |
Family
ID=84845661
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN202211147664.1APendingCN115603950A (en) | 2022-09-19 | 2022-09-19 | Decryption outsourcing attribute encryption access method and system based on same sub-strategy |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN115603950A (en) |
Cited By (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN116305208A (en)* | 2023-03-02 | 2023-06-23 | 深圳市领存技术有限公司 | A behavioral data collection method, device and medium based on attribute encryption |
| CN116527358A (en)* | 2023-04-28 | 2023-08-01 | 国网山西省电力公司信息通信分公司 | A time-sensitive access control method and device based on CP-ABE edge computing |
| CN118041622A (en)* | 2024-02-06 | 2024-05-14 | 北京邮电大学 | Attribute-based hierarchical data encryption and decryption method, device and storage medium |
| CN118413325A (en)* | 2024-07-03 | 2024-07-30 | 贵州大学 | A cross-chain data sharing method, device, medium and product |
Citations (2)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN112260829A (en)* | 2020-10-19 | 2021-01-22 | 浙江工商大学 | Multi-authorization-based CP-ABE method for supporting mobile devices under hybrid cloud |
| WO2021255845A1 (en)* | 2020-06-17 | 2021-12-23 | 三菱電機株式会社 | Re-encryption device, cryptosystem, re-encryption method, and re-encryption program |
- 2022
- 2022-09-19CNCN202211147664.1Apatent/CN115603950A/enactivePending
Patent Citations (2)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| WO2021255845A1 (en)* | 2020-06-17 | 2021-12-23 | 三菱電機株式会社 | Re-encryption device, cryptosystem, re-encryption method, and re-encryption program |
| CN112260829A (en)* | 2020-10-19 | 2021-01-22 | 浙江工商大学 | Multi-authorization-based CP-ABE method for supporting mobile devices under hybrid cloud |
Non-Patent Citations (2)
| Title |
|---|
| 晋云霞等: "一种支持解密外包的KP-ABE方案", 电子学报, vol. 48, no. 3, 31 March 2020 (2020-03-31), pages 2 - 3* |
| 李伟: "云计算中基于共享子策略的属性密码体制研究", 中国博士学位论文全文数据库,信息科技辑, 15 August 2019 (2019-08-15), pages 3* |
Cited By (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN116305208A (en)* | 2023-03-02 | 2023-06-23 | 深圳市领存技术有限公司 | A behavioral data collection method, device and medium based on attribute encryption |
| CN116527358A (en)* | 2023-04-28 | 2023-08-01 | 国网山西省电力公司信息通信分公司 | A time-sensitive access control method and device based on CP-ABE edge computing |
| CN118041622A (en)* | 2024-02-06 | 2024-05-14 | 北京邮电大学 | Attribute-based hierarchical data encryption and decryption method, device and storage medium |
| CN118413325A (en)* | 2024-07-03 | 2024-07-30 | 贵州大学 | A cross-chain data sharing method, device, medium and product |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| Li et al. | An efficient ciphertext-policy weighted attribute-based encryption for the internet of health things | |
| Chen et al. | A blockchain‐based medical data sharing mechanism with attribute‐based access control and privacy protection | |
| Sun et al. | Lightweight and privacy-aware fine-grained access control for IoT-oriented smart health | |
| Miao et al. | Secure online/offline data sharing framework for cloud-assisted industrial Internet of Things | |
| CN115603950A (en) | Decryption outsourcing attribute encryption access method and system based on same sub-strategy | |
| CN111986755A (en) | Data sharing system based on block chain and attribute-based encryption | |
| Annane et al. | Blockchain based context-aware CP-ABE schema for Internet of Medical Things security | |
| CN104135473B (en) | A kind of method that identity base broadcast enciphering is realized by the attribute base encryption of Ciphertext policy | |
| Huang et al. | FSSR: Fine-grained EHRs sharing via similarity-based recommendation in cloud-assisted eHealthcare system | |
| CN113411323B (en) | Medical record data access control system and method based on attribute encryption | |
| Barua et al. | SPS: Secure personal health information sharing with patient-centric access control in cloud computing | |
| CN113660278B (en) | Quantum attack resistant non-interactive attribute proxy re-encryption method and system | |
| CN106209354A (en) | A kind of support attribute hide can verify that attribute base encrypt outsourcing scheme | |
| Wang et al. | Data verifiable personalized access control electronic healthcare record sharing based on blockchain in IoT environment | |
| Roy et al. | Mh-abe: multi-authority and hierarchical attribute based encryption scheme for secure electronic health record sharing | |
| Shynu et al. | An Enhanced ABE based Secure Access Control Scheme for E-health Clouds. | |
| KR101468379B1 (en) | Access method for decrypting encryption data | |
| CN118312997A (en) | A data security decision analysis system and method for attribute encryption and blockchain | |
| Waghe et al. | Blockchain-Enabled Cybersecurity Framework for Safeguarding Patient Data in Medical Informatics. | |
| Sun et al. | Fine-grained ranked multi-keyword search over hierarchical data for IoT-oriented health system | |
| Li et al. | A hybrid encryption algorithm based approach for secure privacy protection of big data in hospitals | |
| Guo et al. | Privacy-Preserving and Revocable Redactable Blockchains With Expressive Policies in IoT | |
| Zhao et al. | Revocable Attribute-Base Scheme with Enhanced Security and Privacy for Healthcare Data Sharing | |
| Pandit et al. | Secure fine grained access control for telecare medical communication system | |
| Zheng et al. | A privacy-aware electronic medical record sharing scheme based on blockchain and identity-based cryptography |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| CB02 | Change of applicant information | Country or region after:China Address after:450000 Science Avenue 62, Zhengzhou High-tech Zone, Henan Province Applicant after:Information Engineering University of the Chinese People's Liberation Army Cyberspace Force Address before:No. 62 Science Avenue, High tech Zone, Zhengzhou City, Henan Province Applicant before:Information Engineering University of Strategic Support Force,PLA Country or region before:China | |
| CB02 | Change of applicant information | ||
| RJ01 | Rejection of invention patent application after publication | Application publication date:20230113 |