CN115426183A - Identity authentication method, device, device and computer readable medium - Google Patents
Identity authentication method, device, device and computer readable mediumDownload PDFInfo
- Publication number
- CN115426183A CN115426183ACN202211064943.1ACN202211064943ACN115426183ACN 115426183 ACN115426183 ACN 115426183ACN 202211064943 ACN202211064943 ACN 202211064943ACN 115426183 ACN115426183 ACN 115426183A
- Authority
- CN
- China
- Prior art keywords
- node
- virtual node
- data interface
- terminal node
- virtual
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Granted
Links
- 238000000034methodMethods0.000titleclaimsabstractdescription70
- 230000005540biological transmissionEffects0.000claimsabstractdescription36
- 230000004044responseEffects0.000claimsabstractdescription35
- 238000004891communicationMethods0.000claimsdescription10
- 239000012634fragmentSubstances0.000claimsdescription4
- 238000004590computer programMethods0.000claimsdescription3
- 230000003993interactionEffects0.000claimsdescription3
- 238000012546transferMethods0.000abstractdescription29
- 238000005516engineering processMethods0.000description21
- 230000008569processEffects0.000description11
- 238000011161developmentMethods0.000description9
- 238000004088simulationMethods0.000description6
- 238000010586diagramMethods0.000description5
- 241000700605VirusesSpecies0.000description4
- 238000010295mobile communicationMethods0.000description4
- 238000012545processingMethods0.000description4
- 238000012790confirmationMethods0.000description3
- 238000004519manufacturing processMethods0.000description3
- 239000000463materialSubstances0.000description3
- 238000012986modificationMethods0.000description3
- 230000004048modificationEffects0.000description3
- 230000001360synchronised effectEffects0.000description3
- 230000003190augmentative effectEffects0.000description2
- 238000013461designMethods0.000description2
- 230000006870functionEffects0.000description2
- 238000013473artificial intelligenceMethods0.000description1
- 238000013500data storageMethods0.000description1
- 230000000694effectsEffects0.000description1
- 230000010354integrationEffects0.000description1
- 230000002452interceptive effectEffects0.000description1
- 230000003287optical effectEffects0.000description1
- 238000011160researchMethods0.000description1
- 238000013468resource allocationMethods0.000description1
- 230000009466transformationEffects0.000description1
- 230000007723transport mechanismEffects0.000description1
- 238000012795verificationMethods0.000description1
Images
Classifications
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/08—Network architectures or network communication protocols for network security for authentication of entities
- H04L63/0876—Network architectures or network communication protocols for network security for authentication of entities based on the identity of the terminal or configuration, e.g. MAC address, hardware or software configuration or device fingerprint
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/04—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks
- H04L63/0428—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks wherein the data content is protected, e.g. by encrypting or encapsulating the payload
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L67/00—Network arrangements or protocols for supporting network services or applications
- H04L67/01—Protocols
- H04L67/06—Protocols specially adapted for file transfer, e.g. file transfer protocol [FTP]
Landscapes
- Engineering & Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- Computer Networks & Wireless Communication (AREA)
- Signal Processing (AREA)
- Computer Hardware Design (AREA)
- Computing Systems (AREA)
- General Engineering & Computer Science (AREA)
- Power Engineering (AREA)
- Telephonic Communication Services (AREA)
Abstract
Translated fromChineseDescription
Translated fromChinese技术领域technical field
本发明涉及元宇宙和区块链技术领域,具体涉及一种身份认证方法、装置、设备和计算机可读介质。The present invention relates to the technical fields of Metaverse and blockchain, and in particular to an identity authentication method, device, equipment and computer-readable medium.
背景技术Background technique
元宇宙(Metaverse)是利用科技手段进行链接与创造的,与现实世界映射与交互的虚拟世界,具备新型社会体系的数字生活空间。Metaverse (Metaverse) is a virtual world that is linked and created by means of technology, mapped and interacted with the real world, and a digital living space with a new social system.
在元宇宙这个虚拟世界中,若交互对象例如用户之间或者节点之间需要传输数据,则需要验证对方身份的可靠性,才敢接受对方传输的数据包,以避免不法黑客传输的文件带有病毒,给用户的终端带来安全隐患。In the virtual world of the metaverse, if interactive objects such as users or nodes need to transmit data, they need to verify the reliability of the identity of the other party before they dare to accept the data packets transmitted by the other party, so as to avoid files transmitted by illegal hackers with Viruses bring security risks to user terminals.
发明内容Contents of the invention
为此,本发明提供一种身份认证方法、装置、设备和计算机可读介质,以解决相关技术中在元宇宙虚拟系统中进行数据传输的安全隐患问题。To this end, the present invention provides an identity authentication method, device, device and computer-readable medium, so as to solve the security risk of data transmission in the metaverse virtual system in the related art.
为了实现上述目的,本发明第一方面提供一种身份认证方法,应用于区块链系统中的第一终端节点,所述第一终端节点与元宇宙系统中的第一虚拟节点相对应;所述区块链系统中还包括第二终端节点,所述第二终端节点与元宇宙系统中的第二虚拟节点相对应;In order to achieve the above purpose, the first aspect of the present invention provides an identity authentication method, which is applied to the first terminal node in the blockchain system, and the first terminal node corresponds to the first virtual node in the Metaverse system; The blockchain system also includes a second terminal node, which corresponds to the second virtual node in the Metaverse system;
该方法包括:在通过所述第一虚拟节点的数据接口接收到所述第二虚拟节点的文件传输请求的情况下,使用预定传输路径向所述第二虚拟节点的数据接口发送认证信息获取请求;通过所述第一虚拟节点的数据接口,接收所述第二虚拟节点的数据接口响应于所述认证信息获取请求而通过相同传输路径返回的预定类型的认证信息;若通过所述第一虚拟节点确定所述第二终端节点的认证信息符合信息类型要求,则通过所述第一虚拟节点的数据接口发送所述第一终端节点的呼叫号码的加密信息至所述第二虚拟节点的数据接口;响应于所述第二终端节点对所述呼叫号码发起的呼叫请求,接通所述第二终端节点的呼叫,以用于基于接通后的通话内容对所述第二虚拟节点进行身份认证,并根据身份认证结果确定对所述文件传输请求的响应结果。The method includes: when the file transfer request of the second virtual node is received through the data interface of the first virtual node, using a predetermined transmission path to send an authentication information acquisition request to the data interface of the second virtual node ; Through the data interface of the first virtual node, receiving the predetermined type of authentication information returned by the data interface of the second virtual node through the same transmission path in response to the authentication information acquisition request; if through the first virtual node The node determines that the authentication information of the second terminal node meets the information type requirements, and sends the encrypted information of the call number of the first terminal node to the data interface of the second virtual node through the data interface of the first virtual node ; In response to the call request initiated by the second terminal node for the call number, connect the call of the second terminal node, so as to authenticate the identity of the second virtual node based on the connected call content , and determine the response result to the file transfer request according to the identity authentication result.
其中,所述认证信息包括运营商标识;所述若通过所述第一虚拟节点确定所述第二终端节点的认证信息符合信息类型要求,则通过所述第一虚拟节点的数据接口发送所述第一终端节点的呼叫号码的加密信息至所述第二虚拟节点的数据接口,包括:Wherein, the authentication information includes an operator identifier; if it is determined by the first virtual node that the authentication information of the second terminal node meets the information type requirements, then the data interface of the first virtual node is used to send the The data interface from the encrypted information of the call number of the first terminal node to the second virtual node includes:
根据所述运营商标识,确定所述第二终端节点的呼叫号码对应的运营商的类别;若根据所述类别确定所述运营商为预定运营商,则基于与所述运营商的类别对应的编码规则,对所述第一终端节点在真实世界中的号码片段进行编码,得到所述第一终端节点的呼叫号码;发送所述第一终端节点的呼叫号码至所述第二虚拟节点的数据接口。According to the operator identification, determine the category of the operator corresponding to the call number of the second terminal node; if it is determined according to the category that the operator is a predetermined operator, then based on the category corresponding to the operator Encoding rules, encoding the number segment of the first terminal node in the real world to obtain the call number of the first terminal node; sending the call number of the first terminal node to the data of the second virtual node interface.
其中,所述预定运营商的类别与所述第一终端节点的呼叫号码对应的运营商的类别相同;所述编码规则,是预先根据所述运营商的类别设置的短号码编码规则。Wherein, the type of the predetermined operator is the same as the type of the operator corresponding to the call number of the first terminal node; the coding rule is a short number coding rule set in advance according to the type of the operator.
其中,所述通话内容包括:通话双方在元宇宙系统中分别对应的虚拟节点的身份标识的相关内容;所述根据身份认证结果确定对所述文件传输请求的响应结果,包括:若身份认证成功,则确定所述响应结果包括:用于同意接收来自所述第一虚拟节点的数据接口所传输的文件的消息;若身份认证失败,则确定所述响应结果包括:用于拒绝接收来自所述第一虚拟节点的数据接口所传输的文件的消息。Wherein, the call content includes: related content of the identities of virtual nodes corresponding to the two parties in the Metaverse system; the determination of the response result to the file transfer request according to the identity authentication result includes: if the identity authentication is successful , then determining the response result includes: for agreeing to receive the message of the file transmitted from the data interface of the first virtual node; if the identity authentication fails, then determining the response result includes: for refusing to receive the message from the The message of the file transmitted by the data interface of the first virtual node.
本发明第二方面提供一种身份认证方法,应用于区块链系统中的第二终端节点,所述第二终端节点与元宇宙系统中的第二虚拟节点相对应,所述区块链系统中还包括第一终端节点,所述第一终端节点与元宇宙系统中的第一虚拟节点相对应;The second aspect of the present invention provides an identity authentication method, which is applied to the second terminal node in the blockchain system, and the second terminal node corresponds to the second virtual node in the Metaverse system. The blockchain system also includes a first terminal node, the first terminal node corresponds to the first virtual node in the Metaverse system;
该方法包括:在通过所述第二虚拟节点的数据接口发送文件传输请求至所述第一虚拟节点之后,继续通过所述第二虚拟节点的数据接口,接收所述第一虚拟节点的数据接口响应于所述文件传输请求而通过预定传输路径发送的认证信息获取请求;通过所述第二虚拟节点的数据接口响应于所述认证信息获取请求,通过相同传输路径向所述第一虚拟节点的数据接口返回预定类型的认证信息;通过所述第二虚拟节点的数据接口接收所述第一终端节点的呼叫号码;其中,所述第一终端节点的呼叫号码是所述第一虚拟节点在确定所述认证信息符合信息类型要求的情况下,通过所述第一虚拟节点的数据接口发送的呼叫号码;向所述第一终端节点的呼叫号码发送呼叫请求,以使所述第一终端节点根据呼叫接通后的通话内容对所述第二虚拟节点进行身份认证。The method includes: after sending a file transfer request to the first virtual node through the data interface of the second virtual node, continuing to receive the data interface of the first virtual node through the data interface of the second virtual node an authentication information acquisition request sent through a predetermined transmission path in response to the file transmission request; through the data interface of the second virtual node in response to the authentication information acquisition request, to the first virtual node through the same transmission path The data interface returns a predetermined type of authentication information; the call number of the first terminal node is received through the data interface of the second virtual node; wherein, the call number of the first terminal node is determined by the first virtual node When the authentication information meets the information type requirements, the calling number sent through the data interface of the first virtual node; sending a call request to the calling number of the first terminal node, so that the first terminal node according to The call content after the call is connected performs identity authentication on the second virtual node.
其中,所述第一终端节点的呼叫号码,是基于与指定运营商的类别对应的编码规则,对所述第一终端节点在真实世界中的号码片段进行编码得到的呼叫号码;所述预定运营商的类别与所述第一终端节点的呼叫号码对应的运营商的类别相同;所述编码规则,是预先根据所述运营商的类别设置的短号码编码规则。Wherein, the calling number of the first terminal node is a calling number obtained by encoding the number segment of the first terminal node in the real world based on a coding rule corresponding to the category of the designated operator; The category of the operator is the same as the category of the operator corresponding to the call number of the first terminal node; the coding rule is a short number coding rule set in advance according to the category of the operator.
其中,所述向所述第一终端节点的呼叫号码发送呼叫请求,包括:根据相同的编码规则,对所述第二终端节点在真实世界中的号码片段进行编码,得到所述第二终端节点的呼叫号码;通过移动交换网的语音呼叫方式,向所述第一终端节点发起的呼叫请求;其中,在呼叫请求中,所述第二终端节点的呼叫号码为主叫号码,所述第一终端节点的呼叫号码为被叫号码。Wherein, the sending a call request to the call number of the first terminal node includes: encoding the number segment of the second terminal node in the real world according to the same encoding rule to obtain the second terminal node the calling number; the call request initiated to the first terminal node through the voice call mode of the mobile switching network; wherein, in the call request, the calling number of the second terminal node is the calling number, and the first The calling number of the terminal node is the called number.
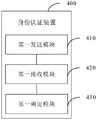
本发明第三方面提供一种身份认证装置,应用于区块链系统中的第一终端节点,所述第一终端节点与元宇宙系统中的第一虚拟节点相对应;所述区块链系统中还包括第二终端节点,所述第二终端节点与元宇宙系统中的第二虚拟节点相对应;The third aspect of the present invention provides an identity authentication device, which is applied to the first terminal node in the blockchain system, and the first terminal node corresponds to the first virtual node in the Metaverse system; the blockchain system also includes a second terminal node, the second terminal node corresponds to the second virtual node in the Metaverse system;
该装置包括:第一发送模块,用于在通过所述第一虚拟节点的数据接口接收到所述第二虚拟节点的文件传输请求的情况下,使用预定传输路径向所述第二虚拟节点的数据接口发送认证信息获取请求;第一接收模块,用于通过所述第一虚拟节点的数据接口,接收所述第二虚拟节点的数据接口响应于所述认证信息获取请求而通过相同传输路径返回的预定类型的认证信息;所述第一发送模块,还用于若通过所述第一虚拟节点确定所述第二终端节点的认证信息符合信息类型要求,则通过所述第一虚拟节点的数据接口发送所述第一终端节点的呼叫号码的加密信息至所述第二虚拟节点的数据接口;第一确定模块,用于响应于所述第二终端节点对所述呼叫号码发起的呼叫请求,接通所述第二终端节点的呼叫,以用于基于接通后的通话内容对所述第二虚拟节点进行身份认证,并根据身份认证结果确定对所述文件传输请求的响应结果。The device includes: a first sending module, configured to send a file transfer request of the second virtual node to the second virtual node using a predetermined transmission path when the file transfer request of the second virtual node is received through the data interface of the first virtual node The data interface sends an authentication information acquisition request; the first receiving module is configured to receive, through the data interface of the first virtual node, the data interface of the second virtual node to return through the same transmission path in response to the authentication information acquisition request The predetermined type of authentication information; the first sending module is further configured to: if the first virtual node determines that the authentication information of the second terminal node meets the information type requirements, the data of the first virtual node The interface sends the encrypted information of the calling number of the first terminal node to the data interface of the second virtual node; the first determination module is configured to respond to the call request initiated by the second terminal node for the calling number, Connecting the call of the second terminal node, so as to perform identity authentication on the second virtual node based on the connected call content, and determine a response result to the file transfer request according to the identity authentication result.
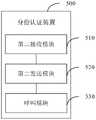
本发明第四方面提供一种身份认证装置,应用于区块链系统中的第二终端节点,所述第二终端节点与元宇宙系统中的第二虚拟节点相对应,所述区块链系统中还包括第一终端节点,所述第一终端节点与元宇宙系统中的第一虚拟节点相对应;The fourth aspect of the present invention provides an identity authentication device, which is applied to the second terminal node in the blockchain system, the second terminal node corresponds to the second virtual node in the Metaverse system, and the blockchain system also includes a first terminal node, the first terminal node corresponds to the first virtual node in the Metaverse system;
该装置包括:第二接收模块,用于在通过所述第二虚拟节点的数据接口发送文件传输请求至所述第一虚拟节点之后,继续通过所述第二虚拟节点的数据接口,接收所述第一虚拟节点的数据接口响应于所述文件传输请求而通过预定传输路径发送的认证信息获取请求;第二发送模块,用于通过所述第二虚拟节点的数据接口响应于所述认证信息获取请求,通过相同传输路径向所述第一虚拟节点的数据接口返回预定类型的认证信息;所述第二接收模块,还用于通过所述第二虚拟节点的数据接口接收所述第一终端节点的呼叫号码;其中,所述第一终端节点的呼叫号码是所述第一虚拟节点在确定所述认证信息符合信息类型要求的情况下,通过所述第一虚拟节点的数据接口发送的呼叫号码;呼叫模块,用于向所述第一终端节点的呼叫号码发送呼叫请求,以使所述第一终端节点根据呼叫接通后的通话内容对所述第二虚拟节点进行身份认证。The device includes: a second receiving module, configured to continue to receive the file transfer request through the data interface of the second virtual node after sending the file transfer request to the first virtual node through the data interface of the second virtual node An authentication information acquisition request sent by the data interface of the first virtual node through a predetermined transmission path in response to the file transfer request; a second sending module, configured to respond to the authentication information acquisition through the data interface of the second virtual node Request, return predetermined type of authentication information to the data interface of the first virtual node through the same transmission path; the second receiving module is further configured to receive the first terminal node through the data interface of the second virtual node The call number of the first terminal node; wherein, the call number of the first terminal node is the call number sent by the first virtual node through the data interface of the first virtual node when it is determined that the authentication information meets the information type requirements a calling module, configured to send a call request to the calling number of the first terminal node, so that the first terminal node authenticates the identity of the second virtual node according to the call content after the call is connected.
本发明第五方面提供一种电子设备,包括:一个或多个处理器;存储器,其上存储有一个或多个程序,当所述一个或多个程序被所述一个或多个处理器执行,使得所述一个或多个处理器实现本发明的身份认证方法;一个或多个I/O接口,连接在所述处理器与存储器之间,配置为实现所述处理器与存储器的信息交互。The fifth aspect of the present invention provides an electronic device, including: one or more processors; memory, on which one or more programs are stored, when the one or more programs are executed by the one or more processors , so that the one or more processors implement the identity authentication method of the present invention; one or more I/O interfaces, connected between the processor and the memory, configured to realize information interaction between the processor and the memory .
本发明第六方面提供一种计算机可读介质,其上存储有计算机程序,所述程序被处理器执行时实现根据本发明上述一种身份认证方法。A sixth aspect of the present invention provides a computer-readable medium on which a computer program is stored, and when the program is executed by a processor, the above-mentioned identity authentication method according to the present invention is implemented.
本发明具有如下优点:本发明提出一种基于运营商数据库对元宇宙中的虚拟节点的身份可靠性的认证方法,根据该方法,可以在元宇宙系统中根据对方虚拟节点返回的认证信息和与对方节点对应的现实社会中的终端的通信呼叫内容,进行节点身份认证,实现元宇宙内的节点的安全身份认证,以便于认可通过后才可以接收对方传输的数据。随着元宇宙系统对整个现实社会的模拟程度加强,在虚拟世界里形成可信任的认证体系,促进了元宇宙技术的应用和发展。The present invention has the following advantages: the present invention proposes a method for authenticating the identity reliability of virtual nodes in the Metaverse based on the operator database. The communication and call content of the terminal in the real world corresponding to the other node is used for node identity authentication to realize the secure identity authentication of the node in the Metaverse, so that the data transmitted by the other party can only be received after the approval is passed. As the metaverse system strengthens the simulation of the entire real society, a trustworthy authentication system is formed in the virtual world, which promotes the application and development of metaverse technology.
附图说明Description of drawings
附图是用来提供对本发明的进一步理解,并且构成说明书的一部分,与下面的具体实施方式一起用于解释本发明,但并不构成对本发明的限制。The accompanying drawings are used to provide a further understanding of the present invention, and constitute a part of the description, together with the following specific embodiments, are used to explain the present invention, but do not constitute a limitation to the present invention.
图1为本发明实施例提供的一种认证方法的流程图;Fig. 1 is a flow chart of an authentication method provided by an embodiment of the present invention;
图2为本发明实施例提供的一种认证方法的流程图;FIG. 2 is a flowchart of an authentication method provided by an embodiment of the present invention;
图3为本发明示例性实施例的认证方法的流程图;Fig. 3 is the flowchart of the authentication method of exemplary embodiment of the present invention;
图4为本发明实施例提供的一种认证装置的结构图;FIG. 4 is a structural diagram of an authentication device provided by an embodiment of the present invention;
图5为本发明实施例提供的一种认证装置的结构图;FIG. 5 is a structural diagram of an authentication device provided by an embodiment of the present invention;
图6为本发明实施例提供的一种电子设备的结构图。FIG. 6 is a structural diagram of an electronic device provided by an embodiment of the present invention.
具体实施方式detailed description
以下结合附图对本发明的具体实施方式进行详细说明。应当理解的是,此处所描述的具体实施方式仅用于说明和解释本发明,并不用于限制本发明。Specific embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings. It should be understood that the specific embodiments described here are only used to illustrate and explain the present invention, not to limit the present invention.
如本发明所使用的,术语“和/或”包括一个或多个相关列举条目的任何和全部组合。As used in the present invention, the term "and/or" includes any and all combinations of one or more related listed items.
本发明所使用的术语仅用于描述特定实施例,且不意欲限制本发明。如本发明所使用的,单数形式“一个”和“该”也意欲包括复数形式,除非上下文另外清楚指出。The terms used in the present invention are for describing specific embodiments only, and are not intended to limit the present invention. As used herein, the singular forms "a" and "the" are intended to include the plural unless the context clearly dictates otherwise.
当本发明中使用术语“包括”和/或“由……制成”时,指定存在特征、整体、步骤、操作、元件和/或组件,但不排除存在或添加一个或多个其它特征、整体、步骤、操作、元件、组件和/或其群组。When the terms "comprising" and/or "consisting of" are used in the present invention, it specifies the presence of features, integers, steps, operations, elements and/or components, but does not preclude the presence or addition of one or more other features, Integrals, steps, operations, elements, components and/or groups thereof.
本发明实施例可借助本发明的理想示意图而参考平面图和/或截面图进行描述。因此,可根据制造技术和/或容限来修改示例图示。Embodiments of the invention may be described with reference to plan views and/or cross-sectional views by way of idealized schematic illustrations of the invention. Accordingly, the example illustrations may be modified according to manufacturing techniques and/or tolerances.
除非另外限定,否则本发明所用的全部术语(包括技术和科学术语)的含义与本领域普通技术人员通常理解的含义相同。还将理解,诸如那些在常用字典中限定的那些术语应当被解释为具有与其在相关技术以及本发明的背景下的含义一致的含义,且将不解释为具有理想化或过度形式上的含义,除非本发明明确如此限定。Unless otherwise defined, all terms (including technical and scientific terms) used in this invention have the same meaning as commonly understood by one of ordinary skill in the art. It will also be understood that terms such as those defined in commonly used dictionaries should be interpreted as having meanings consistent with their meanings in the context of the related art and the present invention, and will not be interpreted as having idealized or excessive formal meanings, unless the invention is expressly so limited.
在本发明实施例中,元宇宙本质上是对现实世界的虚拟化、数字化过程,需要对内容生产、经济系统、用户体验以及实体世界内容等进行大量改造。元宇宙可以基于扩展现实技术提供沉浸式体验,基于数字孪生技术生成现实世界的镜像,基于区块链技术搭建经济体系,将虚拟世界与现实世界在经济系统、社交系统、身份系统上密切融合,并且允许每个用户进行内容生产和世界编辑。In the embodiment of the present invention, the metaverse is essentially a process of virtualization and digitization of the real world, which requires extensive transformation of content production, economic system, user experience, and physical world content. Metaverse can provide immersive experience based on extended reality technology, generate a mirror image of the real world based on digital twin technology, build an economic system based on blockchain technology, and closely integrate the virtual world with the real world in terms of economic system, social system, and identity system. And each user is allowed to perform content production and world editing.
根据相关学者的研究和技术资料的记载,元宇宙本身不是一种技术,而是一个理念和概念,它需要整合不同的新技术,如第五代移动通信技术(5th Generation MobileCommunication Technology,5G)、第六代移动通信技术(6th Generation MobileCommunication Technology,6G)、人工智能、大数据等,强调虚实相融。According to the research of relevant scholars and the records of technical materials, the metaverse itself is not a technology, but an idea and concept, which needs to integrate different new technologies, such as the fifth generation mobile communication technology (5th Generation Mobile Communication Technology, 5G), The sixth generation of mobile communication technology (6th Generation Mobile Communication Technology, 6G), artificial intelligence, big data, etc., emphasizes the integration of virtual and real.
元宇宙主要有以下几项核心技术:一是扩展现实技术,包括虚拟现实(VirtualReality,VR)和增强现实(Augmented Reality,AR)。扩展现实技术可以提供沉浸式的体验;二是数字孪生,能够把现实世界镜像到虚拟世界里面去。三是用区块链来搭建经济体系。随着元宇宙进一步发展,对整个现实社会的模拟程度加强,在元宇宙中还可以进行资源交换处理,例如资源获取和资源分配,再例如进行经济活动例如费用支出、费用进账(例如花钱、赚钱)等,从而在虚拟世界里同样形成资源体系、经济体系。Metaverse mainly has the following core technologies: First, extended reality technology, including virtual reality (Virtual Reality, VR) and augmented reality (Augmented Reality, AR). Extended reality technology can provide an immersive experience; the second is digital twins, which can mirror the real world into the virtual world. The third is to use blockchain to build an economic system. With the further development of the metaverse, the degree of simulation of the entire real society is strengthened. In the metaverse, resource exchange processing, such as resource acquisition and resource allocation, can also be performed, such as economic activities such as expense expenditure and expense receipt (such as spending money, making money), etc., thus forming a resource system and an economic system in the virtual world.
在元宇宙虚拟世界中,交互双方例如用户和用户之间或者节点和节点之间需要传输数据,那么就需要先验证对方身份的可靠性,再接受对方传输的数据包,避免不法黑客传输的文件带有病毒给用户的终端带来安全隐患。基于此,本发明可以提供一种认证方法、设备和计算机可读介质,解决如何验证元宇宙中节点的身份的安全可靠性的问题。In the virtual world of the metaverse, if the two sides of the interaction, such as between users or between nodes, need to transmit data, they need to verify the reliability of the other party's identity first, and then accept the data packets transmitted by the other party to avoid files transmitted by illegal hackers. Viruses bring security risks to users' terminals. Based on this, the present invention can provide an authentication method, device, and computer-readable medium to solve the problem of how to verify the security and reliability of the identity of nodes in the Metaverse.
下面结合附图,详细描述本发明实施例的认证方法、设备和计算机可读介质。下面各实施例均可以应用于本实施例的系统架构。为了描述简洁,下面各个实施例可以相互参考和引用。The authentication method, device, and computer-readable medium of the embodiments of the present invention will be described in detail below with reference to the accompanying drawings. Each of the following embodiments can be applied to the system architecture of this embodiment. For brevity of description, the following embodiments may refer to and quote each other.
本发明实施例涉及到两个时间和空间平行的世界,一个是真实世界(也称真实场景、现实世界,可以对应区块链系统),一个是元宇宙的虚拟世界(可以对应元宇宙系统)。The embodiment of the present invention involves two parallel worlds in time and space, one is the real world (also called real scene, real world, which can correspond to the blockchain system), and the other is the virtual world of the metaverse (which can correspond to the metaverse system) .
为了便于理解,在下述实施例的描述中,可以将区块链系统中的第一终端节点称为是节点B,将区块链系统中的第二终端节点称为是节点A;将元宇宙系统中的第一虚拟节点称为是节点D,将第二虚拟节点称为是节点C;其中,区块链系统中的节点B与元宇宙系统中节点D相对应,区块链系统中的节点A与元宇宙系统中节点C相对应。即:节点A和节点B,在元宇宙中分别对应节点C和节点D。For ease of understanding, in the description of the following embodiments, the first terminal node in the blockchain system can be referred to as node B, and the second terminal node in the blockchain system can be referred to as node A; The first virtual node in the system is called node D, and the second virtual node is called node C; among them, node B in the blockchain system corresponds to node D in the Metaverse system, and node B in the blockchain system corresponds to node D in the metaverse system. Node A corresponds to node C in the Metaverse system. That is: node A and node B correspond to node C and node D in the Metaverse.
因为元宇宙中的节点标识或者人,都是与现实生活中可以一一对应的,需要保障互相传输数据的双方的安全性。Because the node identifiers or people in the Metaverse can correspond one-to-one with real life, it is necessary to ensure the security of both parties transmitting data to each other.
第一方面,本发明实施例提供一种认证方法;该认证方法可以应用于区块链系统中的第一终端节点,第一终端节点与元宇宙系统中的第一虚拟节点相对应;区块链系统中还包括第二终端节点,第二终端节点与元宇宙系统中的第二虚拟节点相对应。In the first aspect, the embodiment of the present invention provides an authentication method; the authentication method can be applied to the first terminal node in the blockchain system, and the first terminal node corresponds to the first virtual node in the Metaverse system; the block The chain system also includes a second terminal node, which corresponds to the second virtual node in the Metaverse system.
图1是示出根据本发明实施例的身份认证方法的流程图,如图1所示,本发明实施例中的身份认证方法包括以下步骤。Fig. 1 is a flowchart illustrating an identity authentication method according to an embodiment of the present invention. As shown in Fig. 1 , the identity authentication method in the embodiment of the present invention includes the following steps.
S110,在通过第一虚拟节点的数据接口接收到第二虚拟节点的文件传输请求的情况下,使用预定传输路径向第二虚拟节点的数据接口发送认证信息获取请求。S110. In a case where the file transfer request of the second virtual node is received through the data interface of the first virtual node, send an authentication information acquisition request to the data interface of the second virtual node using a predetermined transmission path.
示例性地,元宇宙中的第一虚拟节点(例如节点D)接收到第二虚拟节点(例如节点C)的文件传输请求,说明元宇宙中的节点C中要向元宇宙中的节点D传输文件材料;在没有对节点C进行身份认证的情况下,节点D若直接接受元宇宙里的陌生节点传输的文件,则会存在文件中包含病毒的安全隐患;因此,节点D向节点C发起认证信息获取请求,认证信息获取请求中可以包含挑战信息,通过该挑战信息询问:节点C所属的现实社会中的对应节点(例如节点A)所对应的运营商的标识。Exemplarily, the first virtual node (such as node D) in the metaverse receives a file transfer request from the second virtual node (such as node C), indicating that node C in the metaverse wants to transfer files to node D in the metaverse File materials; without identity authentication for node C, if node D directly accepts files transmitted by unfamiliar nodes in the metaverse, there will be a security risk that the files contain viruses; therefore, node D initiates authentication to node C In the information acquisition request, the authentication information acquisition request may include challenge information, and the challenge information is used to inquire about the identity of the operator corresponding to the corresponding node (eg, node A) in the real world to which node C belongs.
S120,通过第一虚拟节点的数据接口,接收第二虚拟节点的数据接口响应于认证信息获取请求而通过相同传输路径返回的预定类型的认证信息。S120. Through the data interface of the first virtual node, receive the predetermined type of authentication information returned by the data interface of the second virtual node through the same transmission path in response to the authentication information acquisition request.
S130,若通过第一虚拟节点确定第二终端节点的认证信息符合信息类型要求,则通过第一虚拟节点的数据接口发送第一终端节点的呼叫号码的加密信息至第二虚拟节点的数据接口。S130, if the first virtual node determines that the authentication information of the second terminal node meets the information type requirements, send the encrypted information of the call number of the first terminal node to the data interface of the second virtual node through the data interface of the first virtual node.
S140,响应于第二终端节点对呼叫号码发起的呼叫请求,接通第二终端节点的呼叫,以用于基于接通后的通话内容对第二虚拟节点进行身份认证,并根据身份认证结果确定对文件传输请求的响应结果。S140. In response to the call request initiated by the second terminal node for the call number, connect the call of the second terminal node, so as to perform identity authentication on the second virtual node based on the call content after connection, and determine according to the identity authentication result The result of the response to the file transfer request.
根据本发明实施例的身份认证方法,可以在元宇宙系统中根据对方虚拟节点返回的认证信息和与对方节点对应的现实社会中的终端的通信呼叫内容,进行节点身份认证,实现元宇宙内的节点的安全身份认证,以便于认可通过后才可以接收对方传输的数据。随着元宇宙进一步发展,对整个现实社会的模拟程度加强,在虚拟世界里形成可信任的认证体系,促进了元宇宙技术的应用和发展。According to the identity authentication method of the embodiment of the present invention, node identity authentication can be performed in the Metaverse system according to the authentication information returned by the other party's virtual node and the communication call content of the terminal corresponding to the other party's node in the real world, so as to realize the identity authentication in the Metaverse. The security identity authentication of the node, so that the data transmitted by the other party can only be received after the approval is passed. With the further development of the metaverse, the degree of simulation of the entire real society is strengthened, and a trusted authentication system is formed in the virtual world, which promotes the application and development of the metaverse technology.
在一些实施例中,认证信息包括运营商标识;步骤S130具体可以包括如下步骤:S11,根据运营商标识,确定第二终端节点的呼叫号码对应的运营商的类别;S12,若根据类别确定运营商为预定运营商,则基于与运营商的类别对应的编码规则,对第一终端节点在真实世界中的号码片段进行编码,得到第一终端节点的呼叫号码;S13,发送第一终端节点的呼叫号码至第二虚拟节点的数据接口。In some embodiments, the authentication information includes the operator identification; step S130 may specifically include the following steps: S11, according to the operator identification, determine the category of the operator corresponding to the call number of the second terminal node; S12, if the operator is determined according to the category If the provider is a predetermined operator, then based on the encoding rule corresponding to the category of the operator, encode the number segment of the first terminal node in the real world to obtain the calling number of the first terminal node; S13, send the first terminal node’s Call the number to the data interface of the second virtual node.
在步骤S12,预定运营商的类别与第一终端节点的呼叫号码对应的运营商的类别不同,该运营商的类别预先已经被认证通过,例如可以包括:如下运营商中的至少一种:联通、移动、电信。In step S12, the category of the scheduled operator is different from the category of the operator corresponding to the call number of the first terminal node, and the category of the operator has been authenticated in advance, for example, it may include: at least one of the following operators: China Unicom , mobile, telecommunications.
在一些实施例中,预定运营商的类别与第一终端节点的呼叫号码对应的运营商的类别相同;编码规则,是预先根据运营商的类别设置的短号码编码规则。In some embodiments, the type of the predetermined operator is the same as the type of the operator corresponding to the calling number of the first terminal node; the coding rule is a short number coding rule set in advance according to the type of the operator.
在该实施例中,若第二终端节点的呼叫号码对应的运营商的类别与第一终端节点的呼叫号码对应的运营商的类别相同,则说明第一终端节点的手机号码和第二终端节点的手机号码属于同一公司下属的集团用户号码,在现实世界是可以通过拨打短号码电话在该运营商提供的移动交换网中通过语音进行通过呼叫。In this embodiment, if the category of the operator corresponding to the call number of the second terminal node is the same as the category of the operator corresponding to the call number of the first terminal node, then the mobile phone number of the first terminal node and the second terminal node The mobile phone number belongs to the group user number of the same company. In the real world, it is possible to make a voice call on the mobile switching network provided by the operator by dialing a short number.
应理解,与不同类别的运营商对应的短号码编码规则可以根据实际需要进行预先设置,本发明实施例不做具体限定。It should be understood that the short number encoding rules corresponding to different types of operators may be preset according to actual needs, which is not specifically limited in this embodiment of the present invention.
在一些实施例中,通话内容包括:通话双方在元宇宙系统中分别对应的虚拟节点的身份标识的相关内容;上述步骤S140中,根据身份认证结果确定对文件传输请求的响应结果的步骤,具体可以包括:若身份认证成功,则确定响应结果包括:用于同意接收来自第一虚拟节点的数据接口所传输的文件的消息;若身份认证失败,则确定响应结果包括:用于拒绝接收来自第一虚拟节点的数据接口所传输的文件的消息。In some embodiments, the content of the call includes: the content related to the identities of virtual nodes corresponding to the two parties in the Metaverse system; in the above step S140, the step of determining the response result to the file transfer request according to the identity authentication result, specifically It may include: if the identity authentication is successful, determining the response result includes: a message for agreeing to receive the file transmitted from the data interface of the first virtual node; A file message transmitted by the data interface of a virtual node.
在该实施例中,如果电话接通,双方互相沟通在元宇宙中第一虚拟节点和第二虚拟节点的身份标识,以此确认了互相是可信任的。则元宇宙中的第一虚拟节点同意接受第二虚拟节点传输的文件。In this embodiment, if the phone is connected, the two parties communicate with each other about the identities of the first virtual node and the second virtual node in the Metaverse, thereby confirming that they are trustworthy to each other. Then the first virtual node in the Metaverse agrees to accept the file transmitted by the second virtual node.
本发明实施例的身份认证方法,涉及元宇宙系统中的通信双方的两个虚拟节点的互相身份认证可靠性的过程,使用本发明实施例的方法来实现对元宇宙中的虚拟节点之间的身份的可靠性的确认,实现元宇宙内的两个节点之间的安全身份的互相认可,认可通过后才可以接收对方传输的数据,从而可以保障互相传输数据的双方的安全性;The identity authentication method of the embodiment of the present invention involves the process of mutual identity authentication reliability of two virtual nodes of the communicating parties in the Metaverse system, using the method of the embodiment of the present invention to realize the authentication between the virtual nodes in the Metaverse The confirmation of the reliability of the identity realizes the mutual recognition of the security identity between the two nodes in the metaverse, and the data transmitted by the other party can only be received after the recognition is passed, so as to ensure the security of the two parties that transmit data to each other;
第二方面,本发明实施例提供一种身份认证方法;该认证方法可以应用于区块链系统中的第二终端节点,第二终端节点与元宇宙系统中的第二虚拟节点相对应;区块链系统中还包括第一终端节点,第一终端节点与元宇宙系统中的第一虚拟节点相对应;图2是示出根据本发明实施例的身份认证方法的流程图。In the second aspect, the embodiment of the present invention provides an identity authentication method; the authentication method can be applied to the second terminal node in the blockchain system, and the second terminal node corresponds to the second virtual node in the Metaverse system; the area The block chain system also includes a first terminal node, which corresponds to the first virtual node in the Metaverse system; FIG. 2 is a flow chart showing an identity authentication method according to an embodiment of the present invention.
如图2所示,该身份认证方法包括如下步骤。As shown in Figure 2, the identity authentication method includes the following steps.
S210,在通过第二虚拟节点的数据接口发送文件传输请求至第一虚拟节点之后,继续通过第二虚拟节点的数据接口,接收第一虚拟节点的数据接口响应于文件传输请求而通过预定传输路径发送的认证信息获取请求。S210, after sending the file transfer request to the first virtual node through the data interface of the second virtual node, continue to pass through the data interface of the second virtual node, and receive the data interface of the first virtual node through a predetermined transmission path in response to the file transfer request Sent authentication information acquisition request.
S220,通过第二虚拟节点的数据接口响应于认证信息获取请求,通过相同传输路径向第一虚拟节点的数据接口返回预定类型的认证信息。S220. Respond to the authentication information acquisition request through the data interface of the second virtual node, and return the predetermined type of authentication information to the data interface of the first virtual node through the same transmission path.
S230,通过第二虚拟节点的数据接口接收第一终端节点的呼叫号码;其中,第一终端节点的呼叫号码是第一虚拟节点在确定认证信息符合信息类型要求的情况下,通过第一虚拟节点的数据接口发送的呼叫号码。S230. Receive the call number of the first terminal node through the data interface of the second virtual node; wherein, the call number of the first terminal node is that the first virtual node passes through the first virtual node when it is determined that the authentication information meets the information type requirements. The calling number sent by the data interface.
S240,向第一终端节点的呼叫号码发送呼叫请求,以使第一终端节点根据呼叫接通后的通话内容对第二虚拟节点进行身份认证。S240. Send a call request to the calling number of the first terminal node, so that the first terminal node performs identity authentication on the second virtual node according to the call content after the call is connected.
在一些实施例中,该身份认证方法还可以包括:S250,通过第二虚拟节点的数据接口,接收来自第一虚拟节点的数据接口的身份认证结果,以根据身份认证结果确定相应的文件传输结果。In some embodiments, the identity authentication method may further include: S250, receiving the identity authentication result from the data interface of the first virtual node through the data interface of the second virtual node, so as to determine the corresponding file transfer result according to the identity authentication result .
在本发明实施例中,可以在元宇宙系统中根据对方虚拟节点返回的认证信息和与对方节点对应的现实社会中的终端的通信呼叫内容,进行节点身份认证,实现元宇宙内的节点的安全身份认证,以便于认可通过后才可以接收对方传输的数据。随着元宇宙系统对整个现实社会的模拟程度加强,在虚拟世界里形成可信任的认证体系,促进了元宇宙技术的应用和发展。In the embodiment of the present invention, node identity authentication can be performed in the Metaverse system according to the authentication information returned by the counterparty virtual node and the communication call content of the terminal corresponding to the counterparty node in the real world, so as to realize the security of the nodes in the Metaverse Identity authentication, so that the data transmitted by the other party can only be received after the approval is passed. As the metaverse system strengthens the simulation of the entire real society, a trustworthy authentication system is formed in the virtual world, which promotes the application and development of metaverse technology.
在一些实施例中,第一终端节点的呼叫号码,是基于与指定运营商的类别对应的编码规则,对第一终端节点在真实世界中的号码片段进行编码得到的呼叫号码。In some embodiments, the calling number of the first terminal node is the calling number obtained by encoding the number segment of the first terminal node in the real world based on the encoding rule corresponding to the category of the specified operator.
在一些实施例中,预定运营商的类别与第一终端节点的呼叫号码对应的运营商的类别相同;编码规则,是预先根据运营商的类别设置的短号码编码规则。In some embodiments, the type of the predetermined operator is the same as the type of the operator corresponding to the calling number of the first terminal node; the coding rule is a short number coding rule set in advance according to the type of the operator.
在该实施例中,若第二终端节点的呼叫号码对应的运营商的类别与第一终端节点的呼叫号码对应的运营商的类别相同,则说明第一终端节点的手机号码和第二终端节点的手机号码属于同一公司下属的集团用户号码,在现实世界是可以通过拨打短号码电话在该运营商提供的移动交换网中通过语音进行通过呼叫。In this embodiment, if the category of the operator corresponding to the call number of the second terminal node is the same as the category of the operator corresponding to the call number of the first terminal node, then the mobile phone number of the first terminal node and the second terminal node The mobile phone number belongs to the group user number of the same company. In the real world, it is possible to make a voice call on the mobile switching network provided by the operator by dialing a short number.
应理解,运营商的类别也可以采用运营商的名称来进行区分,不同类别的运营商所对应的短号码编码规则可以根据实际需要进行预先设置,本发明实施例不做具体限定。It should be understood that the types of operators can also be distinguished by their names, and the short number encoding rules corresponding to different types of operators can be preset according to actual needs, which is not specifically limited in this embodiment of the present invention.
在一些实施例中,S240中的向第一终端节点的呼叫号码发送呼叫请求的步骤,具体可以包括如下步骤。In some embodiments, the step of sending the call request to the calling number of the first terminal node in S240 may specifically include the following steps.
S21,根据相同的编码规则,对第二终端节点在真实世界中的号码片段进行编码,得到第二终端节点的呼叫号码;S22,通过移动交换网的语音呼叫方式,向第一终端节点发起的呼叫请求;其中,在呼叫请求中,第二终端节点的呼叫号码为主叫号码,第一终端节点的呼叫号码为被叫号码。S21, according to the same encoding rule, code the number segment of the second terminal node in the real world to obtain the calling number of the second terminal node; A call request; wherein, in the call request, the calling number of the second terminal node is the calling number, and the calling number of the first terminal node is the called number.
根据上述步骤S21-S22,若电话接通,双方可以互相沟通在元宇宙中第一虚拟节点和第二虚拟节点的身份标识,以此确认了互相是可信任的节点,则元宇宙中的第一虚拟节点同意接受第二虚拟节点传输的文件。According to the above steps S21-S22, if the phone is connected, the two parties can communicate with each other about the identities of the first virtual node and the second virtual node in the metaverse, thereby confirming that they are trustworthy nodes, then the first virtual node in the metaverse A virtual node agrees to accept the file transmitted by the second virtual node.
根据本发明实施例的身份认证方法,涉及元宇宙系统中的通信双方的两个虚拟节点的互相身份认证可靠性的过程,使用本发明实施例的方法来实现对元宇宙中的虚拟节点之间的身份的可靠性的确认,实现元宇宙内的两个节点之间的安全身份的互相认可,认可通过后才可以接收对方传输的数据,从而保障互相传输数据的双方的安全性。According to the identity authentication method of the embodiment of the present invention, it involves the process of mutual identity authentication reliability of two virtual nodes of the communicating parties in the Metaverse system. The confirmation of the reliability of the identities realizes the mutual recognition of security identities between two nodes in the metaverse, and the data transmitted by the other party can only be received after the recognition is passed, thereby ensuring the security of both parties transmitting data to each other.
下面通过具体实施例,描述本发明实施例的身份认证方法的具体流程;在该实施例中,涉及到两个时间和空间平行的世界,一个是现实世界,一个是元宇宙的虚拟世界,节点A和节点B分别在现实世界和元宇宙中都有自己对应的身份和标识以及现实社会的手机号码分别是1861xxxxxxx,1862xxxxxxx,这两个手机号码为同一运营商(例如联通运营商)的用户号码。The specific flow of the identity authentication method of the embodiment of the present invention is described below through a specific embodiment; in this embodiment, two parallel worlds of time and space are involved, one is the real world, and the other is the virtual world of the Metaverse. A and node B have their own corresponding identities and logos in the real world and the metaverse respectively, and the mobile phone numbers in the real world are 1861xxxxxxx and 1862xxxxxxx respectively. These two mobile phone numbers are the user numbers of the same operator (such as China Unicom operator). .
在一些实施例中,该两个号码可以是属于同一个公司下属的集团用户号码,在现实世界可以通过拨打小号的短号码电话在该同一运营商提供的移动交换网中语音呼叫对方。In some embodiments, the two numbers may be group user numbers belonging to the same company, and in the real world, a voice call can be made to the other party in the mobile switching network provided by the same operator by dialing a short number of a small number.
例如1861xxxxxxx使用集团用户的编码规则尾号的N(N大于或等于1)个数字固定的前缀(例如+66等数字前缀),来拨打与自己同属一个集团内的用户号码。假设节点A用户和节点B的用户属于一个单位,所以由单位给该单元的用户都办理了同一类别的运营商的用户业务,方便于本公司内部的用户之间互相拨打电话是免费的,增强了员工之间的交流,并且节约了企业的通信费的报销成本。For example, 1861xxxxxxx uses a fixed prefix of N (N is greater than or equal to 1) digits (such as +66 and other digit prefixes) at the end of the code rule of the group user to dial the user number in the same group as itself. Assuming that the users of Node A and the users of Node B belong to the same unit, so the unit handles the user services of the same type of operator for the users of the unit, so that it is convenient for users within the company to make calls to each other for free. Enhanced It improves the communication between employees and saves the reimbursement cost of communication expenses of the enterprise.
在该实施例中,现实社会中的区块链系统中节点包括:节点A和节点B,具体地,区块链系统中的第一终端节点为节点B,区块链系统中的第二终端节点为节点A;元宇宙系统中的第一虚拟节点为节点D,元宇宙系统中的第二虚拟节点为节点C;其中,区块链系统中的节点B与元宇宙系统中节点D相对应,区块链系统中的节点A与元宇宙系统中节点C相对应。即现实世界的区块链系统中的节点A和节点B,在元宇宙系统中分别对应节点C和节点D。In this embodiment, the nodes in the block chain system in the real society include: node A and node B, specifically, the first terminal node in the block chain system is node B, and the second terminal node in the block chain system The node is node A; the first virtual node in the metaverse system is node D, and the second virtual node in the metaverse system is node C; among them, node B in the blockchain system corresponds to node D in the metaverse system , node A in the blockchain system corresponds to node C in the Metaverse system. That is, node A and node B in the blockchain system of the real world correspond to node C and node D in the metaverse system respectively.
图3示出本发明示例性实施例的认证方法的流程图。如图3所示,该认证方法包括如下步骤。Fig. 3 shows a flowchart of an authentication method in an exemplary embodiment of the present invention. As shown in Figure 3, the authentication method includes the following steps.
S301,通过第二虚拟节点向第一虚拟节点发送文件传输请求。S301. Send a file transfer request to the first virtual node through the second virtual node.
在该步骤中,节点C在元宇宙中向元宇宙里面的节点D传输文件材料。In this step, node C transmits file materials in the metaverse to node D in the metaverse.
S302,通过第一虚拟节点响应于该文件传输请求,向第二虚拟节点发送信息获取请求。S302. The first virtual node sends an information acquisition request to the second virtual node in response to the file transfer request.
示例性地,由于节点D不敢接受元宇宙里的陌生节点传输的文件,怕里面有病毒;所以节点D通过信息获取请求向节点C发起身份认证的挑战信息,以用于询问节点C所属的现实社会中的对应节点所对应的运营商的标识;若根据该运营商的标识,节点D认为如果节点C和自己在现实世界对应的终端节点分别对应的用户,是一个单位的同事的概率较大,那么就可以接收对方的传输文件。For example, because node D dare not accept files transmitted by unfamiliar nodes in the Metaverse, for fear of viruses in them; so node D initiates an identity authentication challenge message to node C through an information acquisition request to ask node C to belong to The identity of the operator corresponding to the corresponding node in the real world; if according to the identity of the operator, node D believes that if the user corresponding to node C and its corresponding terminal node in the real world are colleagues of the same unit, the probability is relatively low Large, then you can receive the transfer file from the other party.
S303,通过第二虚拟节点响应于信息获取请求,向第一虚拟节点回复认证信息。S303. The second virtual node responds to the information acquisition request by replying the authentication information to the first virtual node.
其中,该认证信息中包括与第二虚拟节点对应的现实社会中的终端节点所对应的运营商的运营商标识。Wherein, the authentication information includes the operator identifier of the operator corresponding to the terminal node in the real society corresponding to the second virtual node.
示例性地,节点C在元宇宙中通过IP网络收到该询问自己的所属运营商的询问,则通过原路径将节点C所属的现实社会中的对应节点所对应的运营商的标识回复至节点D。Exemplarily, when node C receives the inquiry about its own operator through the IP network in the Metaverse, it will reply to the node through the original route the identity of the operator corresponding to the corresponding node in the real society to which node C belongs d.
S304,通过第一虚拟节点发送呼叫号码至第二虚拟节点。S304. Send the calling number to the second virtual node through the first virtual node.
示例性地,节点D收到该标识以后,发现节点C和自己所对应的现实社会中的节点的号码属于同一运营商,则节点D为了保证自己所对应的现实世界的节点B的手机号码的安全性,节点D不会将自己的手机号码直接发送给节点C,而是节点D将自己所对应的现实世界的节点B的手机号码的后四位(例如7777)发送给节点C。For example, after node D receives the identification, it finds that the number of node C and its corresponding node in the real world belong to the same operator. In order to ensure that the mobile phone number of its corresponding node B in the real world For security, node D will not directly send its mobile phone number to node C, but node D will send the last four digits (for example, 7777) of its corresponding real-world node B's mobile phone number to node C.
S305,第二终端节点呼叫第一终端节点,以用于对元宇宙中第一虚拟节点和第二虚拟节点的身份信息进行沟通。S305. The second terminal node calls the first terminal node, so as to communicate the identity information of the first virtual node and the second virtual node in the Metaverse.
示例性地,节点C收到了该呼叫号码(例如四位手机尾号7777),节点C对应的现实世界的节点A使用自己的手机,根据预先根据运营商的类别设置的短号码编码规则(预定前缀加上接收到的号码片段)将7777编辑为集团用户号码667777,然后移动交换网的语音呼叫方式来呼叫对方。Exemplarily, node C receives the call number (for example, the four-digit mobile phone suffix number 7777), and node A corresponding to node C in the real world uses its own mobile phone, according to the short number encoding rule set in advance according to the type of operator (predetermined prefix plus the received number fragment) to edit 7777 into a group user number 667777, and then call the other party in the voice call mode of the mobile switching network.
S306,第一终端节点接听第二终端节点的呼叫,以根据通话内容进行身份认证。S306, the first terminal node answers the call of the second terminal node, so as to perform identity authentication according to the content of the call.
示例性地,元宇宙中的节点D所对应的现实世界的节点B的手机收到了集团号码662222的呼叫,显示出来的是自己所属的运营商的集团号码,因此节点B可以接听该电话。Exemplarily, the mobile phone of Node B in the real world corresponding to Node D in the Metaverse receives a call from group number 662222, which displays the group number of the operator to which it belongs, so Node B can answer the call.
如果电话接通,双方互相沟通了在元宇宙中节点C和节点D的身份标识,以此确认了互相是可信任的;则元宇宙中的节点D同意接受节点C传输的文件。If the phone is connected, the two parties have communicated with each other about the identities of node C and node D in the metaverse, thereby confirming that they are trustworthy; then node D in the metaverse agrees to accept the file transmitted by node C.
本文利用了现实世界的同一个单位的员工的手机号码是同一个运营商的集团用户的情况,来确认元宇宙中两个不认识的节点是否可以接受对方传输的资料的情况,以此来保障了节点身份的真实性和可靠性。并且本次互相确认身份后,节点A更新自己本地保存的白名单列表,可以将元宇宙中的节点D的标识加入到列表中。同样的,节点B也可以更新自己本地保存的白名单列表,可以将元宇宙中的节点C的标识加入到列表中。This article uses the fact that the mobile phone numbers of employees of the same unit in the real world are group users of the same operator to confirm whether two unknown nodes in the Metaverse can accept the data transmitted by each other, so as to ensure The authenticity and reliability of the node identity are ensured. And after confirming each other's identities this time, node A updates its locally saved whitelist, and can add the identity of node D in the Metaverse to the list. Similarly, node B can also update its locally saved whitelist, and can add the identity of node C in the Metaverse to the list.
根据本发明实施例的认证方法,可以将元宇宙中的虚拟节点之间身份的可靠性的确认和现实世界的运营商的数据相结合,实现元宇宙内的节点的安全身份认证,以便于认可通过后才可以接收对方传输的数据,从而在虚拟世界里形成可信任的认证体系,促进元宇宙技术的应用和发展。According to the authentication method of the embodiment of the present invention, the confirmation of the reliability of identities between the virtual nodes in the metaverse can be combined with the data of the operators in the real world to realize the secure identity authentication of the nodes in the metaverse, so as to facilitate the recognition Only after passing can the data transmitted by the other party be received, so as to form a trusted authentication system in the virtual world and promote the application and development of Metaverse technology.
上面各种方法的步骤划分,只是为了描述清楚,实现时可以合并为一个步骤或者对某些步骤进行拆分,分解为多个步骤,只要包括相同的逻辑关系,都在本专利的保护范围内;对算法中或者流程中添加无关紧要的修改或者引入无关紧要的设计,但不改变其算法和流程的核心设计都在该专利的保护范围内。The step division of the above various methods is only for the sake of clarity of description. During implementation, it can be combined into one step or some steps can be split and decomposed into multiple steps. As long as they include the same logical relationship, they are all within the scope of protection of this patent. ; Adding insignificant modifications or introducing insignificant designs to the algorithm or process, but not changing the core design of the algorithm and process are all within the scope of protection of this patent.
第三方面,本发明实施例提供一种身份认证装置。In a third aspect, an embodiment of the present invention provides an identity authentication device.
图4示出了根据本发明一实施例提供的身份认证装置的结构示意图。在一些实施例中,该装置应用于区块链系统中的第一终端节点,第一终端节点与元宇宙系统中的第一虚拟节点相对应;区块链系统中还包括至少一个运营商节点和第二终端节点,第二终端节点与元宇宙系统中的第二虚拟节点相对应;如图4所示,身份认证装置400包括如下模块。Fig. 4 shows a schematic structural diagram of an identity authentication device provided according to an embodiment of the present invention. In some embodiments, the device is applied to the first terminal node in the blockchain system, and the first terminal node corresponds to the first virtual node in the Metaverse system; the blockchain system also includes at least one operator node and the second terminal node, the second terminal node corresponds to the second virtual node in the Metaverse system; as shown in FIG. 4 , the
第一发送模块410,用于在通过第一虚拟节点的数据接口接收到第二虚拟节点的文件传输请求的情况下,使用预定传输路径向第二虚拟节点的数据接口发送认证信息获取请求;The
第一接收模块420,用于通过第一虚拟节点的数据接口,接收第二虚拟节点的数据接口响应于认证信息获取请求而通过相同传输路径返回的预定类型的认证信息;The
第一发送模块410,还用于若通过第一虚拟节点确定第二终端节点的认证信息符合信息类型要求,则通过第一虚拟节点的数据接口发送第一终端节点的呼叫号码的加密信息至第二虚拟节点的数据接口;The
第一确定模块430,用于响应于第二终端节点对呼叫号码发起的呼叫请求,接通第二终端节点的呼叫,以用于基于接通后的通话内容对第二虚拟节点进行身份认证,并根据身份认证结果确定对文件传输请求的响应结果。The
在一些实施例中,认证信息包括运营商标识;第一发送模块410,包括:类别确定单元,用于根据运营商标识,确定第二终端节点的呼叫号码对应的运营商的类别;编码单元,用于若根据类别确定运营商为预定运营商,则基于与运营商的类别对应的编码规则,对第一终端节点在真实世界中的号码片段进行编码,得到第一终端节点的呼叫号码;第一发送模块410,还用于发送第一终端节点的呼叫号码至第二虚拟节点的数据接口。In some embodiments, the authentication information includes an operator identifier; the
在一些实施例中,预定运营商的类别与第一终端节点的呼叫号码对应的运营商的类别相同;编码规则,是预先根据运营商的类别设置的短号码编码规则。In some embodiments, the type of the predetermined operator is the same as the type of the operator corresponding to the calling number of the first terminal node; the coding rule is a short number coding rule set in advance according to the type of the operator.
在一些实施例中,通话内容包括:通话双方在元宇宙系统中分别对应的虚拟节点的身份标识的相关内容;第一确定模块430,在用于根据身份认证结果确定对文件传输请求的响应结果时,具体用于:若身份认证成功,则确定响应结果包括:用于同意接收来自第一虚拟节点的数据接口所传输的文件的消息;若身份认证失败,则确定响应结果包括:用于拒绝接收来自第一虚拟节点的数据接口所传输的文件的消息。In some embodiments, the content of the call includes: related content of the identities of virtual nodes corresponding to the two parties in the Metaverse system; the
根据本发明实施例的身份认证装置,可以在元宇宙系统中根据对方虚拟节点返回的认证信息和与对方节点对应的现实社会中的终端的通信呼叫内容,进行节点身份认证,实现元宇宙内的节点的安全身份认证,以便于认可通过后才可以接收对方传输的数据。随着元宇宙进一步发展,对整个现实社会的模拟程度加强,在虚拟世界里形成可信任的认证体系,促进了元宇宙技术的应用和发展。The identity authentication device according to the embodiment of the present invention can perform node identity authentication in the Metaverse system according to the authentication information returned by the other party's virtual node and the communication call content of the terminal corresponding to the other party's node in the real world, and realize the identity authentication in the Metaverse. The security identity authentication of the node, so that the data transmitted by the other party can only be received after the approval is passed. With the further development of the metaverse, the degree of simulation of the entire real society is strengthened, and a trusted authentication system is formed in the virtual world, which promotes the application and development of the metaverse technology.
第四方面,本发明实施例提供一种身份认证装置。In a fourth aspect, an embodiment of the present invention provides an identity authentication device.
在一些实施例中,该装置应用于区块链系统中的第二终端节点,第二终端节点与元宇宙系统中的第二虚拟节点相对应,区块链系统中还包括第一终端节点,第一终端节点与元宇宙系统中的第一虚拟节点相对应。In some embodiments, the device is applied to the second terminal node in the blockchain system, the second terminal node corresponds to the second virtual node in the Metaverse system, and the blockchain system also includes the first terminal node, The first terminal node corresponds to the first virtual node in the metaverse system.
图5示出了根据本发明一实施例提供的身份认证装置的结构示意图。如图5所示,身份认证装置500包括如下模块。Fig. 5 shows a schematic structural diagram of an identity authentication device provided according to an embodiment of the present invention. As shown in FIG. 5 , the
第二接收模块510,用于在通过第二虚拟节点的数据接口发送文件传输请求至第一虚拟节点之后,继续通过第二虚拟节点的数据接口,接收第一虚拟节点的数据接口响应于文件传输请求而通过预定传输路径发送的认证信息获取请求;The
第二发送模块520,用于通过第二虚拟节点的数据接口响应于认证信息获取请求,通过相同传输路径向第一虚拟节点的数据接口返回预定类型的认证信息;The
第二接收模块510,还用于通过第二虚拟节点的数据接口接收第一终端节点的呼叫号码;其中,第一终端节点的呼叫号码是第一虚拟节点在确定认证信息符合信息类型要求的情况下,通过第一虚拟节点的数据接口发送的呼叫号码;The
呼叫模块530,用于向第一终端节点的呼叫号码发送呼叫请求,以使第一终端节点根据呼叫接通后的通话内容对第二虚拟节点进行身份认证。The calling
在一些实施例中,身份认证装置500还可以包括:第二确定模块,用于通过第二虚拟节点的数据接口,接收来自第一虚拟节点的数据接口的身份认证结果,以根据身份认证结果确定相应的文件传输结果。In some embodiments, the
在一些实施例中,第一终端节点的呼叫号码,是基于与指定运营商的类别对应的编码规则,对第一终端节点在真实世界中的号码片段进行编码得到的呼叫号码;预定运营商的类别与第一终端节点的呼叫号码对应的运营商的类别相同;编码规则,是预先根据运营商的类别设置的短号码编码规则。In some embodiments, the calling number of the first terminal node is the calling number obtained by encoding the number segment of the first terminal node in the real world based on the encoding rule corresponding to the category of the designated operator; The category is the same as the category of the operator corresponding to the call number of the first terminal node; the coding rule is a short number coding rule set in advance according to the category of the operator.
在一些实施例中,呼叫模块530,在用于向第一终端节点的呼叫号码发送呼叫请求时,具体用于:根据相同的编码规则,对第二终端节点在真实世界中的号码片段进行编码,得到第二终端节点的呼叫号码;通过移动交换网的语音呼叫方式,向第一终端节点发起的呼叫请求;其中,在呼叫请求中,第二终端节点的呼叫号码为主叫号码,第一终端节点的呼叫号码为被叫号码。In some embodiments, when the
根据本发明实施例的是身份认证装置,可以在元宇宙系统中根据对方虚拟节点返回的认证信息和与对方节点对应的现实社会中的终端的通信呼叫内容,进行节点身份认证,实现元宇宙内的节点的安全身份认证,以便于认可通过后才可以接收对方传输的数据。随着元宇宙系统对整个现实社会的模拟程度加强,在虚拟世界里形成可信任的认证体系,促进了元宇宙技术的应用和发展。According to the embodiment of the present invention, the identity authentication device can perform node identity authentication in the Metaverse system according to the authentication information returned by the other party's virtual node and the communication call content of the terminal corresponding to the other party's node in the real world, so as to realize the identity verification within the Metaverse. The security identity authentication of the node, so that the data transmitted by the other party can only be received after the approval is passed. As the metaverse system strengthens the simulation of the entire real society, a trustworthy authentication system is formed in the virtual world, which promotes the application and development of metaverse technology.
需要明确的是,本发明并不局限于上文实施例中所描述并在图中示出的特定配置和处理。为了描述的方便和简洁,这里省略了对已知方法的详细描述,并且上述描述的系统、模块和单元的具体工作过程,可以参考前述方法实施例中的对应过程,在此不再赘述。It should be clear that the present invention is not limited to the specific configurations and processes described in the above embodiments and shown in the drawings. For the convenience and brevity of description, detailed descriptions of known methods are omitted here, and the specific working processes of the above-described systems, modules, and units can refer to the corresponding processes in the foregoing method embodiments, and are not repeated here.
参照图6,本发明实施例提供一种电子设备,其包括:Referring to FIG. 6, an embodiment of the present invention provides an electronic device, which includes:
一个或多个处理器601;one or
存储器602,其上存储有一个或多个程序,当一个或多个程序被一个或多个处理器执行,使得一个或多个处理器实现上述任意一项的身份认证方法;
一个或多个读写接口(Input/Output,I/O)接口603,连接在处理器601与存储器602之间,配置为实现处理器601与存储器602的信息交互。One or more read/write interface (Input/Output, I/O) interfaces 603 are connected between the
其中,处理器601为具有数据处理能力的器件,其包括但不限于中央处理器(CPU)等;存储器602为具有数据存储能力的器件,其包括但不限于随机存取存储器(RandomAccess Memory,RAM,更具体如同步动态随机存取记忆体(Synchronous Dynamic RandomAccess Memory,SDRAM)、双倍速率(Double Data Rate,DDR)同步动态随机存储器等)、只读存储器(Read-Only Memory,ROM)、带电可擦可编程只读存储器(Electrically ErasableProgrammable read only memory,EEPROM)、闪存(FLASH);I/O接口603连接在处理器601与存储器602间,能实现处理器601与存储器602的信息交互,其包括但不限于数据总线(Bus)等。Wherein,
在一些实施例中,处理器601、存储器602和I/O接口603通过总线相互连接,进而与计算设备的其它组件连接。In some embodiments, the
本实施例还提供一种计算机可读介质,其上存储有计算机程序,程序被处理器执行时实现本实施例提供的身份认证方法,为避免重复描述,在此不再赘述本实施例的身份认证方法的具体步骤。This embodiment also provides a computer-readable medium on which a computer program is stored. When the program is executed by a processor, the identity authentication method provided by this embodiment is implemented. To avoid repeated descriptions, the identity of this embodiment will not be repeated here. The specific steps of the authentication method.
本领域普通技术人员可以理解,上文中所发明方法中的全部或某些步骤、系统、装置中的功能模块/单元可以被实施为软件、固件、硬件及其适当的组合。在硬件实施方式中,在以上描述中提及的功能模块/单元之间的划分不一定对应于物理组件的划分;例如,一个物理组件可以具有多个功能,或者一个功能或步骤可以由若干物理组件合作执行。某些物理组件或所有物理组件可以被实施为由处理器,如中央处理器、数字信号处理器或微处理器执行的软件,或者被实施为硬件,或者被实施为集成电路,如专用集成电路。这样的软件可以分布在计算机可读介质上,计算机可读介质可以包括计算机存储介质(或非暂时性介质)和通信介质(或暂时性介质)。如本领域普通技术人员公知的,术语计算机存储介质包括在用于存储信息(诸如计算机可读指令、数据结构、程序模块或其它数据)的任何方法或技术中实施的易失性和非易失性、可移除和不可移除介质。计算机存储介质包括但不限于RAM、ROM、EEPROM、闪存或其它存储器技术、CD-ROM、数字多功能盘(DVD)或其它光盘存储、磁盒、磁带、磁盘存储或其它磁存储装置、或者可以用于存储期望的信息并且可以被计算机访问的任何其它的介质。此外,本领域普通技术人员公知的是,通信介质通常包含计算机可读指令、数据结构、程序模块或者诸如载波或其它传输机制之类的调制数据信号中的其它数据,并且可包括任何信息递送介质。Those of ordinary skill in the art can understand that all or some of the steps in the methods, systems, and functional modules/units in the devices disclosed above can be implemented as software, firmware, hardware, and an appropriate combination thereof. In a hardware implementation, the division between functional modules/units mentioned in the above description does not necessarily correspond to the division of physical components; for example, one physical component may have multiple functions, or one function or step may be composed of several physical components. Components cooperate to execute. Some or all of the physical components may be implemented as software executed by a processor, such as a central processing unit, digital signal processor, or microprocessor, or as hardware, or as an integrated circuit, such as an application-specific integrated circuit . Such software may be distributed on computer readable media, which may include computer storage media (or non-transitory media) and communication media (or transitory media). As known to those of ordinary skill in the art, the term computer storage media includes both volatile and nonvolatile media implemented in any method or technology for storage of information, such as computer readable instructions, data structures, program modules, or other data. permanent, removable and non-removable media. Computer storage media include, but are not limited to, RAM, ROM, EEPROM, flash memory or other memory technology, CD-ROM, digital versatile disk (DVD) or other optical disk storage, magnetic cartridges, magnetic tape, magnetic disk storage or other magnetic storage devices, or can Any other medium used to store desired information and which can be accessed by a computer. In addition, as is well known to those of ordinary skill in the art, communication media typically embodies computer readable instructions, data structures, program modules, or other data in a modulated data signal such as a carrier wave or other transport mechanism, and may include any information delivery media .
需要说明的是,在本文中,术语“包括”、“包含”或者其任何其他变体意在涵盖非排他性的包含,从而使得包括一系列要素的过程、方法、物品或者装置不仅包括那些要素,而且还包括没有明确列出的其他要素,或者是还包括为这种过程、方法、物品或者装置所固有的要素。在没有更多限制的情况下,由语句“包括一个……”限定的要素,并不排除在包括该要素的过程、方法、物品或者装置中还存在另外的相同要素。It should be noted that, in this document, the term "comprising", "comprising" or any other variation thereof is intended to cover a non-exclusive inclusion such that a process, method, article or apparatus comprising a set of elements includes not only those elements, It also includes other elements not expressly listed, or elements inherent in the process, method, article, or device. Without further limitations, an element defined by the phrase "comprising a ..." does not preclude the presence of additional identical elements in the process, method, article, or apparatus comprising that element.
本领域的技术人员能够理解,尽管在此所述的一些实施例包括其它实施例中所包括的某些特征而不是其它特征,但是不同实施例的特征的组合意味着处于本实施例的范围之内并且形成不同的实施例。Those skilled in the art will understand that although some embodiments described herein include some features included in other embodiments but not others, combinations of features from different embodiments are meant to be within the scope of the embodiments. and form different embodiments.
可以理解的是,以上实施方式仅仅是为了说明本发明的原理而采用的示例性实施方式,然而本发明并不局限于此。对于本领域内的普通技术人员而言,在不脱离本发明的精神和实质的情况下,可以做出各种变型和改进,这些变型和改进也视为本发明的保护范围。It can be understood that, the above embodiments are only exemplary embodiments adopted for illustrating the principle of the present invention, but the present invention is not limited thereto. For those skilled in the art, various modifications and improvements can be made without departing from the spirit and essence of the present invention, and these modifications and improvements are also regarded as the protection scope of the present invention.
Claims (11)
Priority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202211064943.1ACN115426183B (en) | 2022-09-01 | 2022-09-01 | Identity authentication method, device, equipment and computer readable medium |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202211064943.1ACN115426183B (en) | 2022-09-01 | 2022-09-01 | Identity authentication method, device, equipment and computer readable medium |
Publications (2)
| Publication Number | Publication Date |
|---|---|
| CN115426183Atrue CN115426183A (en) | 2022-12-02 |
| CN115426183B CN115426183B (en) | 2024-04-12 |
Family
ID=84201351
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN202211064943.1AActiveCN115426183B (en) | 2022-09-01 | 2022-09-01 | Identity authentication method, device, equipment and computer readable medium |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN115426183B (en) |
Citations (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20090210483A1 (en)* | 2008-02-15 | 2009-08-20 | Sony Ericsson Mobile Communications Ab | Systems Methods and Computer Program Products for Remotely Controlling Actions of a Virtual World Identity |
| CN111491064A (en)* | 2020-04-01 | 2020-08-04 | 支付宝(杭州)信息技术有限公司 | Voice service identity authentication method and system |
| CN114285674A (en)* | 2022-03-07 | 2022-04-05 | 湖南兆物信链科技集团有限公司 | A digital authentication system for metaverse super-entrance |
| CN114780868A (en)* | 2022-06-17 | 2022-07-22 | 深圳市标签数据有限公司 | Method and system for generating virtual avatar by user tag of metauniverse |
- 2022
- 2022-09-01CNCN202211064943.1Apatent/CN115426183B/enactiveActive
Patent Citations (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20090210483A1 (en)* | 2008-02-15 | 2009-08-20 | Sony Ericsson Mobile Communications Ab | Systems Methods and Computer Program Products for Remotely Controlling Actions of a Virtual World Identity |
| CN111491064A (en)* | 2020-04-01 | 2020-08-04 | 支付宝(杭州)信息技术有限公司 | Voice service identity authentication method and system |
| CN114285674A (en)* | 2022-03-07 | 2022-04-05 | 湖南兆物信链科技集团有限公司 | A digital authentication system for metaverse super-entrance |
| CN114780868A (en)* | 2022-06-17 | 2022-07-22 | 深圳市标签数据有限公司 | Method and system for generating virtual avatar by user tag of metauniverse |
Non-Patent Citations (2)
| Title |
|---|
| 孙小华;江慧;戴百克;袁淑娟;: "一种新的移动应用身份验证系统设计研究", 无线互联科技, no. 01, 10 January 2018 (2018-01-10)* |
| 韩民青: "宇宙的结构、演化与人类的作用新探――元宇宙、本宇宙、超宇宙与人类", 东岳论丛, no. 01, 28 February 2002 (2002-02-28)* |
Also Published As
| Publication number | Publication date |
|---|---|
| CN115426183B (en) | 2024-04-12 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| CN102761549B (en) | Processing method and system of resource sharing and service platforms | |
| CN106162574A (en) | Group system is applied universal retrieval method, server and terminal | |
| CN113255014B (en) | Data processing method based on block chain and related equipment | |
| WO2008008014A1 (en) | Method and arrangement for authentication procedures in a communication network | |
| CN116743377B (en) | Data processing method, device, equipment and storage medium based on blockchain key | |
| CN104754009A (en) | Service acquisition and invocation method, device, client-side and server | |
| CN113556234A (en) | Block chain cross-chain communication method and system | |
| CN112202564B (en) | Transaction transfer method and device, electronic equipment and readable storage medium | |
| WO2019056971A1 (en) | Authentication method and device | |
| CN112822678B (en) | A method for service-based architecture authorization | |
| CN111985000A (en) | Model service output method, device, equipment and storage medium | |
| CN113992406A (en) | A permission access control method for consortium chain cross-chain | |
| CN111741468A (en) | MEC-based AMF (advanced metering library) and identity authentication method, construction method and device thereof | |
| CN116980148A (en) | Data management method, system and equipment | |
| CN115426178B (en) | Calling method, calling device, electronic equipment and computer readable medium | |
| CN115426183B (en) | Identity authentication method, device, equipment and computer readable medium | |
| CN114786170B (en) | Uplink data security processing entity switching method, terminal, USIM and system | |
| CN116582338A (en) | Face authentication method and device | |
| CN109429226B (en) | A method for generating temporary user credentials, user card, terminal and network device | |
| CN115442804B (en) | Authentication method, apparatus, and computer-readable medium | |
| WO2021073447A1 (en) | Management and control method, terminal, system and computer-readable storage medium | |
| CN117040934B (en) | A secure re-verification method for university VPN user identities based on proportional mapping | |
| CN108012255B (en) | Mobile terminal number binding method and device | |
| CN114528579B (en) | Block chain strengthening method | |
| CN115409506B (en) | Block chain-based data processing method, related equipment and storage medium |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| GR01 | Patent grant | ||
| GR01 | Patent grant |