CN115243268A - Method, system and readable storage medium for identifying group fraud relationship - Google Patents
Method, system and readable storage medium for identifying group fraud relationshipDownload PDFInfo
- Publication number
- CN115243268A CN115243268ACN202210862406.5ACN202210862406ACN115243268ACN 115243268 ACN115243268 ACN 115243268ACN 202210862406 ACN202210862406 ACN 202210862406ACN 115243268 ACN115243268 ACN 115243268A
- Authority
- CN
- China
- Prior art keywords
- relationship
- mobile phone
- fraud
- phone number
- target mobile
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Granted
Links
- 238000000034methodMethods0.000titleclaimsabstractdescription41
- 238000004458analytical methodMethods0.000claimsabstractdescription19
- 239000011159matrix materialSubstances0.000claimsdescription56
- 230000006399behaviorEffects0.000claimsdescription30
- 238000011176poolingMethods0.000claimsdescription27
- 230000015654memoryEffects0.000claimsdescription18
- 239000013598vectorSubstances0.000claimsdescription17
- 230000002159abnormal effectEffects0.000claimsdescription11
- 238000004590computer programMethods0.000claimsdescription11
- 230000006870functionEffects0.000claimsdescription8
- 230000008859changeEffects0.000claimsdescription5
- 238000013507mappingMethods0.000claimsdescription3
- 238000010183spectrum analysisMethods0.000claims2
- 238000001228spectrumMethods0.000claims1
- 238000012805post-processingMethods0.000abstractdescription5
- 238000004519manufacturing processMethods0.000description29
- 238000010586diagramMethods0.000description11
- 230000011664signalingEffects0.000description8
- 230000008569processEffects0.000description5
- 238000012545processingMethods0.000description5
- 230000001105regulatory effectEffects0.000description5
- 238000007781pre-processingMethods0.000description4
- 238000004364calculation methodMethods0.000description2
- 238000006243chemical reactionMethods0.000description2
- 238000004891communicationMethods0.000description2
- 238000005516engineering processMethods0.000description2
- 238000012986modificationMethods0.000description2
- 230000004048modificationEffects0.000description2
- 238000013528artificial neural networkMethods0.000description1
- 238000013075data extractionMethods0.000description1
- 230000007812deficiencyEffects0.000description1
- 238000000605extractionMethods0.000description1
- 238000010295mobile communicationMethods0.000description1
- 230000003287optical effectEffects0.000description1
- 238000012216screeningMethods0.000description1
Images
Classifications
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W12/00—Security arrangements; Authentication; Protecting privacy or anonymity
- H04W12/12—Detection or prevention of fraud
- H04W12/128—Anti-malware arrangements, e.g. protection against SMS fraud or mobile malware
Landscapes
- Engineering & Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- Computer Networks & Wireless Communication (AREA)
- Signal Processing (AREA)
- Mobile Radio Communication Systems (AREA)
Abstract
Translated fromChineseDescription
Translated fromChinese技术领域technical field
本发明涉及网络技术领域,尤其涉及一种团体诈骗关系识别方法、系统及可读存储介质。The present invention relates to the field of network technology, and in particular, to a method, a system and a readable storage medium for identifying a group fraud relationship.
背景技术Background technique
目前,团体诈骗关系识别主要依托情报收集、作恶信息收集、用户业务层数据行为分析、异常信息(IP和手机号)库等技术手段,容易产生事后处理、诈骗关系判断准确度低、诈骗关系判断覆盖率低等问题。At present, the identification of group fraud relationship mainly relies on technical means such as intelligence collection, malicious information collection, user business layer data behavior analysis, abnormal information (IP and mobile phone number) database, etc., which is prone to post-processing, low accuracy of fraud relationship judgment, and fraud relationship judgment. problems such as low coverage.
发明内容SUMMARY OF THE INVENTION
本发明所要解决的技术问题是针对现有技术的上述不足,提供一种团体诈骗关系识别方法、系统及可读存储介质,能够实现事前处理且诈骗关系判断准确度高。The technical problem to be solved by the present invention is to aim at the above-mentioned deficiencies of the prior art, and provide a method, system and readable storage medium for group fraud relationship identification, which can realize pre-processing and have high accuracy of fraud relationship judgment.
第一方面,本发明提供一种团体诈骗关系识别方法,包括:In a first aspect, the present invention provides a method for identifying a group fraud relationship, including:
获取终端发送的团体诈骗关系识别请求,所述团体诈骗关系识别请求携带目标手机号;Obtain the group fraud relationship identification request sent by the terminal, where the group fraud relationship identification request carries the target mobile phone number;
判断所述目标手机号是否为黑产;Determine whether the target mobile phone number is a black product;
若是,则获取所述目标手机号对应的多条关联信息;If so, obtain multiple pieces of associated information corresponding to the target mobile phone number;
将所述多条关联信息输入预置的团体诈骗关系识别模型进行团体诈骗关系图谱分析,得到所述目标手机号对应的团体诈骗关系图谱;Inputting the multiple pieces of associated information into a preset group fraud relationship identification model to perform group fraud relationship graph analysis to obtain a group fraud relationship graph corresponding to the target mobile phone number;
将所述团体诈骗关系图谱发送给所述终端。Sending the group fraud relationship graph to the terminal.
进一步地,所述判断所述目标手机号是否为黑产,具体包括:Further, the judging whether the target mobile phone number is a black product specifically includes:
获取所述目标手机号对应的目标IP地址以及目标国际移动用户识别码IMSI号;Obtain the target IP address corresponding to the target mobile phone number and the target International Mobile Subscriber Identity Code IMSI number;
根据预置的黑产账户库、所述目标IP地址、目标IMSI号对所述目标手机号进行黑产识别,并获得黑产识别结果。The target mobile phone number is identified according to the preset account database, the target IP address, and the target IMSI number, and the identification result of the malicious product is obtained.
进一步地,所述根据预置的黑产账户库、所述目标IP地址、目标IMSI号对所述目标手机号进行黑产识别,并获得黑产识别结果,具体包括:Further, performing the black production identification on the target mobile phone number according to the preset black production account database, the target IP address, and the target IMSI number, and obtaining the black production identification result, specifically including:
根据以下公式计算所述目标手机号与所述黑产账户库中每个第一黑产手机号之间的精准匹配距离:Calculate the exact matching distance between the target mobile phone number and each first black-produced mobile phone number in the black-produced account database according to the following formula:
x=1,2,3,…,Cx=1,2,3,...,C
式中,C为黑产账户库中第一黑产手机号的数量,为的转置,为目标手机号对应的目标IP地址与目标IMSI号转换后的数值,为黑产账户库中的第x个第一黑产手机号对应的第一IP地址与第一IMSI号转换后的数值,η为调整系数,M为自主调整时刻范围,为第x个第一黑产手机号对应的黑产行为开始时间,为第x个第一黑产手机号对应的黑产行为结束时间,dx为目标手机号与第x个第一黑产手机号之间的精准匹配距离;In the formula, C is the number of the first black product mobile phone number in the black product account database, for transpose of , is the converted value between the target IP address corresponding to the target mobile phone number and the target IMSI number, is the converted value between the first IP address and the first IMSI number corresponding to the xth first black product mobile phone number in the black product account database, η is the adjustment coefficient, M is the self-adjusting time range, is the start time of the black product behavior corresponding to the xth first black product mobile phone number, is the end time of the black production behavior corresponding to the x-th first black-produced mobile phone number, and dx is the exact matching distance between the target mobile phone number and the x-th first black-produced mobile phone number;
获取所有所述精准匹配距离中的最小值,并判断所述精准匹配距离中的最小值是否小于等于预设的距离阀值;Obtain the minimum value of all the precise matching distances, and determine whether the minimum value of the precise matching distances is less than or equal to a preset distance threshold;
若是,则确定所述目标手机号为黑产,否则,不为黑产。If so, it is determined that the target mobile phone number is a black product, otherwise, it is not a black product.
进一步地,所述团体诈骗关系识别模型包括卷积部分、池化部分和全连接部分,所述将所述多条关联信息输入预置的团体诈骗关系识别模型进行团体诈骗关系图谱分析,得到所述目标手机号对应的团体诈骗关系图谱,具体包括:Further, the group fraud relationship identification model includes a convolution part, a pooling part and a fully connected part, and the multiple pieces of associated information are input into the preset group fraud relationship identification model to perform group fraud relationship graph analysis, and obtain the result. The group fraud relationship map corresponding to the target mobile phone number, including:
通过所述卷积部分获取所述多条关联信息对应的归一化后的图拉普拉斯矩阵的特征向量组成的矩阵U;Obtain the matrix U composed of the eigenvectors of the normalized graph Laplacian matrix corresponding to the multiple pieces of associated information through the convolution part;
通过所述池化部分对所述U进行平均池化处理,得到池化结果;Average pooling is performed on the U by the pooling part to obtain a pooling result;
通过所述全连接部分将平均池化处理后的池化结果连接成一个一维向量,得到所述团体诈骗关系图谱。The pooling results after the average pooling process are connected into a one-dimensional vector through the full connection part, so as to obtain the group fraud relationship graph.
进一步地,所述通过所述卷积部分获取所述多条关联信息对应的归一化后的图拉普拉斯矩阵的特征向量组成的矩阵U,具体包括:Further, the matrix U formed by the eigenvectors of the normalized graph Laplacian matrices corresponding to the multiple pieces of associated information obtained by the convolution part specifically includes:
通过所述卷积部分获取每条关联信息对应的异常关系判断准确度W和异常关系判断覆盖率C,并根据所述W和C组成向量得到所述U,其中,U=[W,C]。Obtain the abnormal relationship judgment accuracy W and abnormal relationship judgment coverage C corresponding to each piece of associated information through the convolution part, and obtain the U according to the W and C to form a vector, where U=[W, C] .
进一步地,所述图拉普拉斯矩阵L满足以下公式:Further, the graph Laplacian matrix L satisfies the following formula:
式中,IN为单位矩阵、D为图的度矩阵、A是图的邻接矩阵、∧是L的特征组成的对角矩阵,UT是归一化后的图拉普拉斯矩阵的特征向量组成的矩阵转置。In the formula, IN is the identity matrix, D is the degree matrix of the graph, A is the adjacency matrix of the graph, ∧ is the diagonal matrix composed of the features of L, and UT is the feature of the normalized graph Laplacian matrix. Matrix transpose of vectors.
进一步地,每条所述关联信息均包括以下属性:用户唯一标识、黑产行为开始时间、黑产行为结束时间、呼叫类型、计费方IMSI号、目标手机号、本端归属地区号、规整后的对方号码、对端归属地区号以及通话时长;Further, each piece of the associated information includes the following attributes: user unique identifier, start time of black production behavior, end time of black production behavior, call type, IMSI number of the billing party, target mobile phone number, home area code of the local end, regular After that, the number of the other party, the area code of the other party, and the duration of the call;
所述L的特征值函数gθ(∧)满足以下公式:The eigenvalue function gθ (∧) of the L satisfies the following formula:
其中,in,
Tk(∧)=2∧Tk-1(∧)-Tk-2(^),T0(^)=1,T1(^)=∧Tk (∧)=2∧Tk-1 (∧)-Tk-2 (^), T0 (^)=1, T1 (^)=∧
式中,θ1、θ2、θ3、θ4、θ5、θ6、θ7、θ8、θ9、θ10分别对映用户唯一标识、黑产行为开始时间、黑产行为结束时间、呼叫类型、计费方IMSI号、目标手机号、本端归属地区号、规整后的对方号码、对端归属地区号以及通话时长,θk∈Rk为切比雪夫系数向量,Λ为Λ的契比雪夫最大特征值矩阵变化,Tk(∧)为切比雪夫多项式,λmax是L的最大特征值,Tk-1(∧)、Tk-2(^)为递归式的切比雪夫多项式;In the formula, θ1 , θ2 , θ3 , θ4 , θ5 , θ6 , θ7 , θ8 , θ9 , θ10 correspond to the user's unique ID, the start time of black production behavior, and the end time of black production behavior, respectively , call type, IMSI number of the billing party, target mobile phone number, home area code of the local end, the regularized number of the other party, home area code of the opposite end, and call duration, θk ∈ Rk is the Chebyshev coefficient vector, and Λ is Λ The Chebyshev maximum eigenvalue matrix change of , Tk (∧) is the Chebyshev polynomial, λmax is the maximum eigenvalue of L, Tk-1 (∧), Tk-2 (^) are the recursive tangent Byshev polynomial;
所述L的契比雪夫最大特征值矩阵变化L满足以下公式:The Chebyshev maximum eigenvalue matrix variation L of L satisfies the following formula:
L=2L/λmax-IN=UΛUT。L=2L/λmax -IN =UΛUT.
第二方面,本发明提供一种团体诈骗关系识别系统,包括:In a second aspect, the present invention provides a system for identifying a group fraud relationship, including:
识别请求获取模块,用于获取终端发送的团体诈骗关系识别请求,所述团体诈骗关系识别请求携带目标手机号;an identification request acquisition module, used for acquiring a group fraud relationship identification request sent by the terminal, where the group fraud relationship identification request carries the target mobile phone number;
黑产判断模块,与所述识别请求获取模块连接,用于判断所述目标手机号是否为黑产;The black product judgment module is connected with the identification request acquisition module, and is used for judging whether the target mobile phone number is a black product;
关联信息获取模块,与所述黑产判断模块连接,用于若是,则获取所述目标手机号对应的多条关联信息;an associated information acquisition module, connected to the black product judgment module, and configured to acquire multiple pieces of associated information corresponding to the target mobile phone number if so;
图谱分析模块,与所述关联信息获取模块连接,用于将所述多条关联信息输入预置的团体诈骗关系识别模型进行团体诈骗关系图谱分析,得到所述目标手机号对应的团体诈骗关系图谱;a graph analysis module, connected with the associated information acquisition module, for inputting the multiple pieces of associated information into a preset group fraud relationship identification model to perform group fraud relationship graph analysis to obtain a group fraud relationship graph corresponding to the target mobile phone number ;
识别结果发送模块,与所述图谱分析模块连接,用于将所述团体诈骗关系图谱发送给所述终端。The identification result sending module is connected with the graph analysis module, and is used for sending the group fraud relationship graph to the terminal.
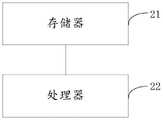
第三方面,本发明提供一种团体诈骗关系识别系统,包括存储器和处理器,所述存储器中存储有计算机程序,所述处理器被设置为运行所述计算机程序以实现上述第一方面所述的团体诈骗关系识别方法。In a third aspect, the present invention provides a system for identifying a group fraud relationship, comprising a memory and a processor, wherein a computer program is stored in the memory, and the processor is configured to run the computer program to implement the above-mentioned first aspect. method for identifying group fraud relationships.
第四方面,本发明提供一种计算机可读存储介质,所述计算机可读存储介质上存储有计算机程序,所述计算机程序被处理器执行时实现上述第一方面所述的团体诈骗关系识别方法。In a fourth aspect, the present invention provides a computer-readable storage medium, where a computer program is stored on the computer-readable storage medium, and when the computer program is executed by a processor, the method for identifying a group fraud relationship described in the first aspect above is implemented .
本发明提供的团体诈骗关系识别方法、系统及可读存储介质,首先获取终端发送的团体诈骗关系识别请求,所述团体诈骗关系识别请求携带目标手机号,然后判断所述目标手机号是否为黑产,若是,则获取所述目标手机号对应的多条关联信息,再将所述多条关联信息输入预置的团体诈骗关系识别模型进行团体诈骗关系图谱分析,能够得到所述目标手机号对应的团体诈骗关系图谱,最后将所述团体诈骗关系图谱发送给所述终端。本发明能够实现事前处理、且具有诈骗关系判断准确度高、诈骗关系判断覆盖率高等优势,解决了现有的团体诈骗关系识别方法容易产生事后处理、诈骗关系判断准确度低、诈骗关系判断覆盖率低等问题。The method, system and readable storage medium for group fraud relationship identification provided by the present invention first obtain a group fraud relationship identification request sent by a terminal, and the group fraud relationship identification request carries a target mobile phone number, and then judges whether the target mobile phone number is hacked If yes, then obtain multiple pieces of associated information corresponding to the target mobile phone number, and then input the multiple pieces of associated information into the preset group fraud relationship identification model to perform group fraud relationship graph analysis, and the corresponding target phone number can be obtained. and finally send the group fraud relationship map to the terminal. The invention can realize pre-processing, and has the advantages of high fraud relationship judgment accuracy and fraud relationship judgment coverage, and solves the problem that the existing group fraud relationship identification method is prone to post-processing, fraud relationship judgment accuracy, and fraud relationship judgment coverage. problems such as low rates.
附图说明Description of drawings
图1为本发明实施例的一种团体诈骗关系识别方法的场景图;1 is a scene diagram of a method for identifying a group fraud relationship according to an embodiment of the present invention;
图2为本发明实施例1的一种团体诈骗关系识别方法的流程图;2 is a flowchart of a method for identifying a group fraud relationship according to Embodiment 1 of the present invention;
图3为本发明实施例2的一种团体诈骗关系识别系统的结构示意图;3 is a schematic structural diagram of a system for identifying a group fraud relationship according to Embodiment 2 of the present invention;
图4为本发明实施例3的一种团体诈骗关系识别系统的结构示意图。FIG. 4 is a schematic structural diagram of a system for identifying a group fraud relationship according to Embodiment 3 of the present invention.
具体实施方式Detailed ways
为使本领域技术人员更好地理解本发明的技术方案,下面将结合附图对本发明实施方式作进一步地详细描述。In order for those skilled in the art to better understand the technical solutions of the present invention, the embodiments of the present invention will be further described in detail below with reference to the accompanying drawings.
可以理解的是,此处描述的具体实施例和附图仅仅用于解释本发明,而非对本发明的限定。It should be understood that the specific embodiments and accompanying drawings described herein are only used to explain the present invention, but not to limit the present invention.
可以理解的是,在不冲突的情况下,本发明中的各实施例及实施例中的各特征可相互组合。It will be understood that the various embodiments of the present invention and the various features of the embodiments may be combined with each other without conflict.
可以理解的是,为便于描述,本发明的附图中仅示出了与本发明相关的部分,而与本发明无关的部分未在附图中示出。It can be understood that, for the convenience of description, only the parts related to the present invention are shown in the drawings of the present invention, and the parts unrelated to the present invention are not shown in the drawings.
可以理解的是,本发明的实施例中所涉及的每个单元、模块可仅对应一个实体结构,也可由多个实体结构组成,或者,多个单元、模块也可集成为一个实体结构。It can be understood that each unit and module involved in the embodiments of the present invention may correspond to only one entity structure, or may be composed of multiple entity structures, or multiple units and modules may also be integrated into one entity structure.
可以理解的是,在不冲突的情况下,本发明的流程图和框图中所标注的功能、步骤可按照不同于附图中所标注的顺序发生。It should be understood that the functions and steps noted in the flowcharts and block diagrams of the present invention may occur out of the order noted in the drawings unless there is conflict.
可以理解的是,本发明的流程图和框图中,示出了按照本发明各实施例的系统、装置、设备、方法的可能实现的体系架构、功能和操作。其中,流程图或框图中的每个方框可代表一个单元、模块、程序段、代码,其包含用于实现规定的功能的可执行指令。而且,框图和流程图中的每个方框或方框的组合,可用实现规定的功能的基于硬件的系统实现,也可用硬件与计算机指令的组合来实现。It can be understood that the flowcharts and block diagrams of the present invention show possible implementation architectures, functions, and operations of the systems, apparatuses, devices, and methods according to various embodiments of the present invention. Wherein, each block in the flowchart or block diagram may represent a unit, module, program segment, or code, which contains executable instructions for implementing the specified function. Furthermore, each block or combination of blocks in the block diagrams and flowchart illustrations can be implemented by hardware-based systems that perform the specified functions, or by combinations of hardware and computer instructions.
可以理解的是,本发明实施例中所涉及的单元、模块可通过软件的方式实现,也可通过硬件的方式来实现,例如单元、模块可位于处理器中。It can be understood that, the units and modules involved in the embodiments of the present invention may be implemented in a software manner, and may also be implemented in a hardware manner, for example, the units and modules may be located in a processor.
如图1所示,为本申请实施例提供的一种团体诈骗关系识别方法的场景图,其中,各部分说明如下:As shown in FIG. 1 , a scene diagram of a method for identifying a group fraud relationship provided in an embodiment of the present application, wherein each part is described as follows:
(1)移网信令、3A日志:移网信令是运营商独有的底层信令数据,信令是在无线通信系统中,除了传输用户信息之外,为使全网有轶序地工作,用来保证正常通信所需要的控制信号。3A日志是运营商所独有的原始数据信息。(1) Mobile network signaling, 3A log: Mobile network signaling is the carrier's unique underlying signaling data. Signaling is in the wireless communication system. It is used to ensure the control signals required for normal communication. 3A logs are raw data information unique to operators.
(2)信令和3A数据抽取、转换服务器:用于不间断的筛选移网信令和/或3A日志中的黑产数据并添加至黑产账户库中,具体地,信令和3A数据抽取、转换服务器不间断的对用户唯一标识、黑产行为开始时间、黑产行为结束时间、呼叫类型(主叫1,被叫2)、计费方IMSI(International Mobile Subscriber Identity,国际移动用户识别码)号、手机号码、本端归属地区号、规整后的对方号码、对端归属地区号、通话时长、IP(Internet Protocol,互联网协议)地址、IP登录时间(年月日、时分秒)等数据进行分类、抽取、转换,并发送给黑产账户库。(2) Signaling and 3A data extraction and conversion server: used for uninterrupted screening of mobile network signaling and/or black production data in 3A logs and adding them to the black production account database, specifically, signaling and 3A data The extraction and conversion server continuously identifies the user's unique identifier, the start time of the black production behavior, the end time of the black production behavior, the call type (caller 1, callee 2), the billing party IMSI (International Mobile Subscriber Identity, International Mobile Subscriber Identity, International Mobile Subscriber Identity, International Mobile Subscriber Identity) code) number, mobile phone number, home area code of the local end, the regulated number of the other party, the home area code of the opposite end, call duration, IP (Internet Protocol, Internet Protocol) address, IP login time (year, month, day, hour, minute, second), etc. The data is classified, extracted, converted, and sent to the black production account library.
(3)黑产账户库:用于存储黑产数据,可以包括用户唯一标识、黑产行为开始时间、黑产行为结束时间、呼叫类型(主叫1,被叫2)、计费方IMSI号、手机号码、本端归属地区号、规整后的对方号码、对端归属地区号、通话时长、IP地址、IP登录时间(年月日、时分秒)等数据。(3) Black production account database: used to store black production data, which can include user unique identifier, black production behavior start time, black production behavior end time, call type (caller 1, called party 2), billing party IMSI number , mobile phone number, home area code of the local end, the regulated number of the other party, the home area code of the opposite end, call duration, IP address, IP login time (year, month, day, hour, minute, second) and other data.
(4)网站/APP:用于提供与团体诈骗关系识别系统交互的接口,用户可以通过终端设备上的网站/APP向团体诈骗关系识别系统发送团体欺诈关系识别请求。(4) Website/APP: It is used to provide an interface for interacting with the group fraud relationship identification system. Users can send a group fraud relationship identification request to the group fraud relationship identification system through the website/APP on the terminal device.
(5)团体诈骗关系识别系统:用于根据用户的团体欺诈关系识别请求进行团体诈骗关系图谱分析,并反馈相应的团体诈骗关系图谱给终端。(5) Group fraud relationship identification system: It is used to analyze the group fraud relationship graph according to the user's group fraud relationship identification request, and feed back the corresponding group fraud relationship graph to the terminal.
基于图1所示的场景图,下面介绍本申请涉及的团体诈骗关系识别方法的相关实施例。Based on the scene diagram shown in FIG. 1 , relevant embodiments of the method for identifying a group fraud relationship involved in the present application are described below.
实施例1:Example 1:
本实施例提供一种团体诈骗关系识别方法,如图2所示,该方法包括:This embodiment provides a method for identifying a group fraud relationship, as shown in FIG. 2 , the method includes:
步骤S101:获取终端发送的团体诈骗关系识别请求,所述团体诈骗关系识别请求携带目标手机号。Step S101: Obtain a group fraud relationship identification request sent by a terminal, where the group fraud relationship identification request carries a target mobile phone number.
在本实施例中,用户可以通过终端设备上的网站/APP向团体诈骗关系识别系统发送团体欺诈关系识别请求,终端设备如手机、平板等,该团体诈骗关系识别请求携带目标手机号,还可以携带IP地址或IP登录时间(年月日、时分秒),IP地址为目标手机号通过电信接入网分配的IP地址,可以是IPV4地址或IPV6地址,终端通过向团体诈骗关系识别系统发送团体诈骗关系识别请求以提出识别申请。In this embodiment, the user can send a group fraud relationship identification request to the group fraud relationship identification system through the website/APP on the terminal device. The terminal device is a mobile phone, tablet, etc., the group fraud relationship identification request carries the target mobile phone number, and can also Carry the IP address or IP login time (year, month, day, hour, minute, second). The IP address is the IP address assigned by the target mobile phone number through the telecom access network. It can be an IPV4 address or an IPV6 address. Fraudulent Relationship Identification Request to make an identification request.
步骤S102:判断所述目标手机号是否为黑产。Step S102: Determine whether the target mobile phone number is a black product.
在本实施例中,团体诈骗关系识别系统接收到团体诈骗关系识别请求后,先判断目标手机号是否为黑产,具体地,团体诈骗关系识别系统先获取所述目标手机号对应的目标IP地址以及目标IMSI号,再根据预置的黑产账户库、所述目标IP地址、目标IMSI号对所述目标手机号进行黑产识别,并获得黑产识别结果。其中,IMSI号用于在全球的移动通信网中唯一识别一个移动用户,为国际辨认码,运营商数据库中预先存储有所有手机号关联的IMSI号以及IP地址;黑产账户库是基于运营商独有的底层信令数据生成的,其中存储了目前已获取到的黑产数据。In this embodiment, after receiving the group fraud relationship identification request, the group fraud relationship identification system first determines whether the target mobile phone number is a fraudulent product. Specifically, the group fraud relationship identification system first obtains the target IP address corresponding to the target mobile phone number. and the target IMSI number, and then according to the preset black product account database, the target IP address, and the target IMSI number, carry out black product identification on the target mobile phone number, and obtain a black product identification result. Among them, the IMSI number is used to uniquely identify a mobile user in the global mobile communication network, and is an international identification code. The operator database pre-stores the IMSI numbers and IP addresses associated with all mobile phone numbers; It is generated from the unique underlying signaling data, which stores the black production data that has been obtained so far.
可选地,所述根据预置的黑产账户库、所述目标IP地址、目标IMSI号对所述目标手机号进行黑产识别,并获得黑产识别结果,具体包括:Optionally, the black product identification is performed on the target mobile phone number according to the preset black product account database, the target IP address, and the target IMSI number, and the black product identification result is obtained, specifically including:
根据以下公式计算所述目标手机号与所述黑产账户库中每个第一黑产手机号之间的精准匹配距离:Calculate the exact matching distance between the target mobile phone number and each first black-produced mobile phone number in the black-produced account database according to the following formula:
x=1,2,3,…,Cx=1,2,3,...,C
式中,C为黑产账户库中第一黑产手机号的数量,为的转置,为目标手机号对应的目标IP地址与目标IMSI号转换后的数值,为黑产账户库中的第x个第一黑产手机号对应的第一IP地址与第一IMSI号转换后的数值,η为调整系数,M为自主调整时刻范围,为第x个第一黑产手机号对应的黑产行为开始时间,为第x个第一黑产手机号对应的黑产行为结束时间,dx为目标手机号与第x个第一黑产手机号之间的精准匹配距离;In the formula, C is the number of the first black product mobile phone number in the black product account database, for transpose of , is the converted value between the target IP address corresponding to the target mobile phone number and the target IMSI number, is the converted value between the first IP address and the first IMSI number corresponding to the xth first black product mobile phone number in the black product account database, η is the adjustment coefficient, M is the self-adjusting time range, is the start time of the black product behavior corresponding to the xth first black product mobile phone number, is the end time of the black production behavior corresponding to the x-th first black-produced mobile phone number, and dx is the exact matching distance between the target mobile phone number and the x-th first black-produced mobile phone number;
获取所有所述精准匹配距离中的最小值,并判断所述精准匹配距离中的最小值是否小于等于预设的距离阀值;Obtain the minimum value of all the precise matching distances, and determine whether the minimum value of the precise matching distances is less than or equal to a preset distance threshold;
若是,则确定所述目标手机号为黑产,否则,不为黑产。If so, it is determined that the target mobile phone number is a black product, otherwise, it is not a black product.
在本实施例中,为了实现黑产用户的精准识别,采用上述精准匹配距离公式进行判断,需要说明的是,上述精准匹配距离公式仅是一种示例,本实施例也可以使用其他计算距离的公式来计算目标手机号与黑产账户库中每个第一黑产手机号之间的精准匹配距离。In this embodiment, in order to realize the accurate identification of black-produced users, the above-mentioned precise matching distance formula is used for judgment. It should be noted that the above precise matching distance formula is only an example, and this embodiment can also use other calculation distances. Formula to calculate the exact matching distance between the target mobile phone number and each first black-produced mobile phone number in the black-produced account database.
步骤S103:若是,则获取所述目标手机号对应的多条关联信息。Step S103: If yes, acquire multiple pieces of associated information corresponding to the target mobile phone number.
在本实施例中,每条所述关联信息均包括以下属性:用户唯一标识、黑产行为开始时间、黑产行为结束时间、呼叫类型(主叫1,被叫2)、计费方IMSI号、目标手机号、本端归属地区号、规整后的对方号码、对端归属地区号以及通话时长,还可以包括IP地址和IP登录时间(年月日、时分秒),各个属性信息可以从黑产账户库或其他帐户库中获取,其中,规整后的对方号码指满足预设格式的号码,比如有的号码位数不全可以相应补充,或者有的号码位数超出(比如前面多出个0)可以相应去除。计费方IMSI号可以是主叫的IMSI号,也可以是被叫的IMSI号,具体依据运营商规定获取。In this embodiment, each piece of the associated information includes the following attributes: user unique identifier, start time of hacking behavior, end time of hacking behavior, call type (caller 1, called party 2), billing party IMSI number , target mobile phone number, home area code of the local end, the adjusted number of the other party, the home area code of the opposite end, and call duration, and can also include the IP address and IP login time (year, month, day, hour, minute, and second). Obtained from the production account library or other account libraries, where the regularized counterparty number refers to the number that meets the preset format. For example, some numbers can be supplemented accordingly if the number of digits is incomplete, or the number of digits in some numbers exceeds (for example, there is an extra 0 in the front). ) can be removed accordingly. The IMSI number of the charging party may be the IMSI number of the calling party or the IMSI number of the called party, which is specifically obtained according to the operator's regulations.
步骤S104:将所述多条关联信息输入预置的团体诈骗关系识别模型进行团体诈骗关系图谱分析,得到所述目标手机号对应的团体诈骗关系图谱。Step S104: Input the pieces of associated information into a preset group fraud relationship identification model to perform group fraud relationship graph analysis, and obtain a group fraud relationship graph corresponding to the target mobile phone number.
在本实施例中,预置的团体诈骗关系识别模型为基于图神经网络的模型,该团体诈骗关系识别模型包括卷积部分、池化部分和全连接部分。In this embodiment, the preset group fraud relationship identification model is a model based on a graph neural network, and the group fraud relationship identification model includes a convolution part, a pooling part and a fully connected part.
可选地,所述将所述多条关联信息输入预置的团体诈骗关系识别模型进行团体诈骗关系图谱分析,得到所述目标手机号对应的团体诈骗关系图谱,具体可以包括:Optionally, inputting the multiple pieces of associated information into a preset group fraud relationship identification model to perform group fraud relationship graph analysis to obtain a group fraud relationship graph corresponding to the target mobile phone number, which may specifically include:
通过所述卷积部分获取所述多条关联信息对应的归一化后的图拉普拉斯矩阵的特征向量组成的矩阵U;Obtain the matrix U composed of the eigenvectors of the normalized graph Laplacian matrix corresponding to the multiple pieces of associated information through the convolution part;
通过所述池化部分对所述U进行平均池化处理,得到池化结果;Average pooling is performed on the U by the pooling part to obtain a pooling result;
通过所述全连接部分将平均池化处理后的池化结果连接成一个一维向量,得到所述团体诈骗关系图谱。The pooling results after the average pooling process are connected into a one-dimensional vector through the full connection part, so as to obtain the group fraud relationship graph.
在本实施例中,将每条关联信息作为一条记录输入团体诈骗关系识别模型,记录即为节点,记录的列值即为属性,每条关联信息的属性如表1所示,其中,手机号码具体为所述目标手机号。In this embodiment, each piece of associated information is entered as a record into the group fraud relationship identification model, the record is the node, and the column value of the record is the attribute, and the attributes of each piece of associated information are shown in Table 1. Specifically, the target mobile phone number.
表1:关联信息的属性Table 1: Attributes of associated information
可选地,所述通过所述卷积部分获取所述多条关联信息对应的归一化后的图拉普拉斯矩阵的特征向量组成的矩阵U,具体可以包括:Optionally, the matrix U composed of the eigenvectors of the normalized graph Laplacian matrices corresponding to the multiple pieces of association information obtained by the convolution part may specifically include:
通过所述卷积部分获取每条关联信息对应的异常关系判断准确度W和异常关系判断覆盖率C,并根据所述W和C组成向量得到所述U,其中,U=[W,C]。Obtain the abnormal relationship judgment accuracy W and abnormal relationship judgment coverage C corresponding to each piece of associated information through the convolution part, and obtain the U according to the W and C to form a vector, where U=[W, C] .
在本实施例中,卷积部分将目标手机号关联的用户唯一标识、黑产行为开始时间、黑产行为结束时间、呼叫类型(主叫1,被叫2)、计费方IMSI号、所述目标手机号、本端归属地区号、规整后的对方号码、对端归属地区号、通话时长对映θ1,θ2,θ3,θ4,θ5,θ6,θ7,θ8,θ9,θ10,将每条记录的异常关系判断准确度W、异常关系判断覆盖率C两者组成向量对映U,即U=[W,C],U是归一化图拉普拉斯矩阵的特征向量组成的矩阵。In this embodiment, the convolution part associates the user unique identifier associated with the target mobile phone number, the start time of the black production behavior, the end time of the black production behavior, the call type (caller 1, callee 2), the IMSI number of the billing party, the Describe the target mobile phone number, the home area code of the local end, the regular number of the other party, the home area code of the opposite end, and the call duration mapping θ1 , θ2 , θ3 , θ4 , θ5 , θ6 , θ7 , θ8 , θ9 , θ10 , the abnormal relationship judgment accuracy W and the abnormal relationship judgment coverage C of each record are composed of a vector map U, that is, U=[W, C], U is the normalized graph Lapp A matrix consisting of the eigenvectors of the Lass matrix.
具体地,所述图拉普拉斯矩阵L满足以下公式:Specifically, the graph Laplacian matrix L satisfies the following formula:
式中,IN为单位矩阵、D为图的度矩阵(拉普拉斯矩阵被定义为L=D-A,度矩阵表示原图中每个点的度数,即由该点发出的边之数量)、N为图中节点的个数,A是图的邻接矩阵、^是L的特征组成的对角矩阵,UT是归一化后的图拉普拉斯矩阵的特征向量组成的矩阵转置。In the formula, IN is the identity matrix, and D is the degree matrix of the graph (the Laplace matrix is defined as L=DA, and the degree matrix represents the degree of each point in the original graph, that is, the number of edges from the point) , N is the number of nodes in the graph, A is the adjacency matrix of the graph, ^ is the diagonal matrix composed of the features of L, UT is the matrix transpose composed of the eigenvectors of the normalized graph Laplacian matrix .
具体地,所述L的特征值函数gθ(^)满足以下公式:Specifically, the eigenvalue function gθ (^) of the L satisfies the following formula:
其中,in,
Tk(∧)=2∧Tk-1(∧)-Tk-2(∧),T0(∧)=1,T1(∧)=∧Tk (∧)=2∧Tk-1 (∧)-Tk-2 (∧), T0 (∧)=1, T1 (∧)=∧
式中,θk指关联信息的第k个属性,其中,θ1、θ2、θ3、θ4、θ5、θ6、θ7、θ8、θ9、θ10分别对映用户唯一标识、黑产行为开始时间、黑产行为结束时间、呼叫类型、计费方IMSI号、目标手机号、本端归属地区号、规整后的对方号码、对端归属地区号以及通话时长,θk∈Rk为切比雪夫系数向量,Λ为Λ的契比雪夫最大特征值矩阵变化,Tk(∧)为切比雪夫多项式,λmax是L的最大特征值,Tk-1(∧)、Tk-2(∧)为递归式的切比雪夫多项式;In the formula, θk refers to the k-th attribute of the associated information, wherein θ1 , θ2 , θ3 , θ4 , θ5 , θ6 , θ7 , θ8 , θ9 , θ10 correspond to the unique user Identification, start time of black production behavior, end time of illegal production behavior, call type, IMSI number of the billing party, target mobile phone number, local area code of the local end, the regulated number of the other party, the local area code of the opposite end, and call duration, θk ∈Rk is the Chebyshev coefficient vector, Λ is the maximum Chebyshev eigenvalue matrix change of Λ, Tk (∧) is the Chebyshev polynomial, λmax is the maximum eigenvalue of L, Tk-1 (∧) , Tk-2 (∧) is a recursive Chebyshev polynomial;
所述L的契比雪夫最大特征值矩阵变化L满足以下公式:The Chebyshev maximum eigenvalue matrix variation L of L satisfies the following formula:
L=2L/λmax-IN=UΛUT。L=2L/λmax -IN =UΛUT.
可选地,对图拉普拉斯矩阵的特征向量组成的矩阵进行归一化的公式为:Optionally, the formula for normalizing the matrix composed of the eigenvectors of the graph Laplacian matrix is:
在本实施例中,为了减少冗余参数,通过池化部分对卷积部分输出的归一化后的图拉普拉斯矩阵的特征向量组成的矩阵进行平均池化处理,得到池化结果,再通过全连接部分将平均池化处理后的池化结果连接成一个一维向量,即所述团体诈骗关系图谱。In this embodiment, in order to reduce redundant parameters, the pooling part performs average pooling on the matrix composed of the eigenvectors of the normalized graph Laplacian matrix output by the convolution part to obtain the pooling result, Then, the pooled results after the average pooling process are connected into a one-dimensional vector through the fully connected part, that is, the group fraud relationship graph.
步骤S105:将所述团体诈骗关系图谱发送给所述终端。Step S105: Send the group fraud relationship graph to the terminal.
在本实施例中,团体诈骗关系图谱具体根据关联信息中的呼叫类型(主叫1,被叫2)、手机号码以及规整后的对方号码生成,该团体诈骗关系图谱可以是包括手机号码以及与该手机号码有关联关系的其他黑产手机号码的关系图,也可以是包括手机号码对应的用户唯一标识以及与该手机号码有关联关系的其他黑产手机号码对应的用户唯一标识的关系图。该团体诈骗关系图谱可以采用稀疏矩阵存储。In this embodiment, the group fraud relationship graph is specifically generated according to the call type (caller 1, called party 2), the mobile phone number and the regulated number of the counterparty in the associated information, and the group fraud relationship graph may include the mobile phone number and The relationship diagram of other black-produced mobile phone numbers associated with the mobile phone number may also be a relationship diagram including the user unique identifier corresponding to the mobile phone number and the user unique identifier corresponding to other illegal mobile phone numbers associated with the mobile phone number. The group fraud relation graph can be stored in a sparse matrix.
本发明实施例提供的团体诈骗关系识别方法,首先获取终端发送的团体诈骗关系识别请求,所述团体诈骗关系识别请求携带目标手机号,然后判断所述目标手机号是否为黑产,若是,则获取所述目标手机号对应的多条关联信息,再将所述多条关联信息输入预置的团体诈骗关系识别模型进行团体诈骗关系图谱分析,能够得到所述目标手机号对应的团体诈骗关系图谱,最后将所述团体诈骗关系图谱发送给所述终端。本发明能够实现事前处理、且具有诈骗关系判断准确度高、诈骗关系判断覆盖率高等优势,解决了现有的团体诈骗关系识别方法容易产生事后处理、诈骗关系判断准确度低、诈骗关系判断覆盖率低等问题。The method for identifying a group fraud relationship provided by the embodiment of the present invention first obtains a group fraud relationship identification request sent by a terminal, and the group fraud relationship identification request carries a target mobile phone number, and then judges whether the target mobile phone number is a fraudulent product, and if so, then Obtain multiple pieces of associated information corresponding to the target mobile phone number, and then input the multiple pieces of associated information into a preset group fraud relationship identification model to perform group fraud relationship graph analysis, so as to obtain a group fraud relationship graph corresponding to the target mobile phone number , and finally send the group fraud relationship graph to the terminal. The invention can realize pre-processing, and has the advantages of high fraud relationship judgment accuracy and fraud relationship judgment coverage, and solves the problem that the existing group fraud relationship identification method is prone to post-processing, fraud relationship judgment accuracy, and fraud relationship judgment coverage. problems such as low rates.
实施例2:Example 2:
如图3所示,本实施例提供一种团体诈骗关系识别系统,用于执行上述团体诈骗关系识别方法,包括:As shown in FIG. 3 , this embodiment provides a system for identifying a group fraud relationship, which is used to implement the above-mentioned method for identifying a group fraud relationship, including:
识别请求获取模块11,用于获取终端发送的团体诈骗关系识别请求,所述团体诈骗关系识别请求携带目标手机号;The identification
黑产判断模块12,与所述识别请求获取模块11连接,用于判断所述目标手机号是否为黑产;The black
关联信息获取模块13,与所述黑产判断模块12连接,用于若是,则获取所述目标手机号对应的多条关联信息;The associated
图谱分析模块14,与所述关联信息获取模块13连接,用于将所述多条关联信息输入预置的团体诈骗关系识别模型进行团体诈骗关系图谱分析,得到所述目标手机号对应的团体诈骗关系图谱;The
识别结果发送模块15,与所述图谱分析模块14连接,用于将所述团体诈骗关系图谱发送给所述终端。The identification
可选地,所述黑产判断模块12具体包括:Optionally, the black
第一获取单元,用于获取所述目标手机号对应的目标IP地址以及目标国际移动用户识别码IMSI号;A first obtaining unit, for obtaining the target IP address corresponding to the target mobile phone number and the target International Mobile Subscriber Identity Code IMSI number;
黑产识别单元,用于根据预置的黑产账户库、所述目标IP地址、目标IMSI号对所述目标手机号进行黑产识别,并获得黑产识别结果。The black product identification unit is configured to perform black product identification on the target mobile phone number according to the preset black product account database, the target IP address, and the target IMSI number, and obtain a black product identification result.
可选地,所述黑产识别单元具体包括:Optionally, the black product identification unit specifically includes:
计算单元,用于根据以下公式计算所述目标手机号与所述黑产账户库中每个第一黑产手机号之间的精准匹配距离:A calculation unit, configured to calculate the exact matching distance between the target mobile phone number and each first black-produced mobile phone number in the black-produced account database according to the following formula:
x=1,2,3,…,Cx=1,2,3,...,C
式中,C为黑产账户库中第一黑产手机号的数量,为的转置,为目标手机号对应的目标IP地址与目标IMSI号转换后的数值,为黑产账户库中的第x个第一黑产手机号对应的第一IP地址与第一IMSI号转换后的数值,η为调整系数,M为自主调整时刻范围,为第x个第一黑产手机号对应的黑产行为开始时间,为第x个第一黑产手机号对应的黑产行为结束时间,dx为目标手机号与第x个第一黑产手机号之间的精准匹配距离;In the formula, C is the number of the first black product mobile phone number in the black product account database, for transpose of , is the converted value between the target IP address corresponding to the target mobile phone number and the target IMSI number, is the converted value between the first IP address and the first IMSI number corresponding to the xth first black product mobile phone number in the black product account database, η is the adjustment coefficient, M is the self-adjusting time range, is the start time of the black product behavior corresponding to the xth first black product mobile phone number, is the end time of the black production behavior corresponding to the x-th first black-produced mobile phone number, and dx is the exact matching distance between the target mobile phone number and the x-th first black-produced mobile phone number;
判断单元,用于获取所有所述精准匹配距离中的最小值,并判断所述精准匹配距离中的最小值是否小于等于预设的距离阀值;a judgment unit, configured to obtain the minimum value among all the precise matching distances, and judge whether the minimum value among the precise matching distances is less than or equal to a preset distance threshold;
确定单元,用于若是,则确定所述目标手机号为黑产,否则,不为黑产。The determining unit is used to determine if the target mobile phone number is a black product, otherwise, it is not a black product.
可选地,所述团体诈骗关系识别模型包括卷积部分、池化部分和全连接部分,所述图谱分析模块14具体包括:Optionally, the group fraud relationship identification model includes a convolution part, a pooling part and a fully connected part, and the
卷积处理单元,用于通过所述卷积部分获取所述多条关联信息对应的归一化后的图拉普拉斯矩阵的特征向量组成的矩阵U;A convolution processing unit, used for obtaining the matrix U formed by the eigenvectors of the normalized graph Laplacian matrices corresponding to the multiple pieces of associated information through the convolution part;
池化处理单元,用于通过所述池化部分对所述U进行平均池化处理,得到池化结果;a pooling processing unit, configured to perform an average pooling process on the U through the pooling part to obtain a pooling result;
全连接处理单元,用于通过所述全连接部分将平均池化处理后的池化结果连接成一个一维向量,得到所述团体诈骗关系图谱。The full-connection processing unit is used for connecting the pooled results after the average pooling process into a one-dimensional vector through the full-connection part to obtain the group fraud relationship graph.
可选地,所述卷积处理单元具体用于:Optionally, the convolution processing unit is specifically used for:
通过所述卷积部分获取每条关联信息对应的异常关系判断准确度W和异常关系判断覆盖率C,并根据所述W和C组成向量得到所述U,其中,U=[W,C]。Obtain the abnormal relationship judgment accuracy W and abnormal relationship judgment coverage C corresponding to each piece of associated information through the convolution part, and obtain the U according to the W and C to form a vector, where U=[W, C] .
可选地,所述图拉普拉斯矩阵L满足以下公式:Optionally, the graph Laplacian matrix L satisfies the following formula:
式中,IN为单位矩阵、D为图的度矩阵、A是图的邻接矩阵、∧是L的特征组成的对角矩阵,UT是归一化后的图拉普拉斯矩阵的特征向量组成的矩阵转置。In the formula, IN is the identity matrix, D is the degree matrix of the graph, A is the adjacency matrix of the graph, ∧ is the diagonal matrix composed of the features of L, and UT is the feature of the normalized graph Laplacian matrix. Matrix transpose of vectors.
可选地,每条所述关联信息均包括以下属性:用户唯一标识、黑产行为开始时间、黑产行为结束时间、呼叫类型、计费方IMSI号、目标手机号、本端归属地区号、规整后的对方号码、对端归属地区号以及通话时长;Optionally, each piece of associated information includes the following attributes: user unique identifier, start time of black production behavior, end time of black production behavior, call type, IMSI number of the billing party, target mobile phone number, home area code of the local end, The regulated number of the counterparty, the area code of the destination of the counterparty, and the duration of the call;
所述L的特征值函数gθ(∧)满足以下公式:The eigenvalue function gθ (∧) of the L satisfies the following formula:
其中,in,
Tk(∧)=2∧Tk-1(∧)-Tk-2(∧),T0(∧)=1,T1(∧)=∧Tk (∧)=2∧Tk-1 (∧)-Tk-2 (∧), T0 (∧)=1, T1 (∧)=∧
式中,θ1、θ2、θ3、θ4、θ5、θ6、θ7、θ8、θ9、θ10分别对映用户唯一标识、黑产行为开始时间、黑产行为结束时间、呼叫类型、计费方IMSI号、目标手机号、本端归属地区号、规整后的对方号码、对端归属地区号以及通话时长,θk∈Rk为切比雪夫系数向量,Λ为Λ的契比雪夫最大特征值矩阵变化,Tk(∧)为切比雪夫多项式,λmax是L的最大特征值,Tk-1(∧)、Tk-2(^)为递归式的切比雪夫多项式;In the formula, θ1 , θ2 , θ3 , θ4 , θ5 , θ6 , θ7 , θ8 , θ9 , θ10 correspond to the user's unique ID, the start time of black production behavior, and the end time of black production behavior, respectively , call type, IMSI number of the billing party, target mobile phone number, home area code of the local end, the regularized number of the other party, home area code of the opposite end, and call duration, θk ∈ Rk is the Chebyshev coefficient vector, and Λ is Λ The Chebyshev maximum eigenvalue matrix change of , Tk (∧) is the Chebyshev polynomial, λmax is the maximum eigenvalue of L, Tk-1 (∧), Tk-2 (^) are the recursive tangent Byshev polynomial;
所述L的契比雪夫最大特征值矩阵变化L满足以下公式:The Chebyshev maximum eigenvalue matrix variation L of L satisfies the following formula:
L=2L/λmax-IN=UΛUT。L=2L/λmax -IN =UΛUT.
实施例3:Example 3:
参考图4,本实施例提供一种团体诈骗关系识别系统,包括存储器21和处理器22,存储器21中存储有计算机程序,处理器22被设置为运行所述计算机程序以执行实施例1中的团体诈骗关系识别方法。Referring to FIG. 4 , the present embodiment provides a system for identifying a group fraud relationship, including a
其中,存储器21与处理器22连接,存储器21可采用闪存或只读存储器或其他存储器,处理器22可采用中央处理器或单片机。Wherein, the
实施例4:Example 4:
本实施例提供一种计算机可读存储介质,所述计算机可读存储介质上存储有计算机程序,所述计算机程序被处理器执行时实现上述实施例1中的团体诈骗关系识别方法。This embodiment provides a computer-readable storage medium, where a computer program is stored on the computer-readable storage medium, and when the computer program is executed by a processor, the method for identifying a group fraud relationship in the foregoing embodiment 1 is implemented.
该计算机可读存储介质包括在用于存储信息(诸如计算机可读指令、数据结构、计算机程序模块或其他数据)的任何方法或技术中实施的易失性或非易失性、可移除或不可移除的介质。计算机可读存储介质包括但不限于RAM(Random Access Memory,随机存取存储器),ROM(Read-Only Memory,只读存储器),EEPROM(Electrically ErasableProgrammable read only memory,带电可擦可编程只读存储器)、闪存或其他存储器技术、CD-ROM(Compact Disc Read-Only Memory,光盘只读存储器),数字多功能盘(DVD)或其他光盘存储、磁盒、磁带、磁盘存储或其他磁存储装置、或者可以用于存储期望的信息并且可以被计算机访问的任何其他的介质。The computer-readable storage medium includes volatile or nonvolatile, removable or Non-removable media. Computer-readable storage media include but are not limited to RAM (Random Access Memory, random access memory), ROM (Read-Only Memory, read only memory), EEPROM (Electrically Erasable Programmable read only memory, electrified erasable programmable read only memory) , Flash memory or other memory technology, CD-ROM (Compact Disc Read-Only Memory), Digital Versatile Disc (DVD) or other optical disk storage, magnetic cartridge, magnetic tape, magnetic disk storage or other magnetic storage device, or Any other medium that can be used to store the desired information and that can be accessed by a computer.
实施例2至实施例4提供的团体诈骗关系识别系统及可读存储介质,首先获取终端发送的团体诈骗关系识别请求,所述团体诈骗关系识别请求携带目标手机号,然后判断所述目标手机号是否为黑产,若是,则获取所述目标手机号对应的多条关联信息,再将所述多条关联信息输入预置的团体诈骗关系识别模型进行团体诈骗关系图谱分析,能够得到所述目标手机号对应的团体诈骗关系图谱,最后将所述团体诈骗关系图谱发送给所述终端。本发明能够实现事前处理、且具有诈骗关系判断准确度高、诈骗关系判断覆盖率高等优势,解决了现有的团体诈骗关系识别方法容易产生事后处理、诈骗关系判断准确度低、诈骗关系判断覆盖率低等问题。The group fraud relationship identification system and the readable storage medium provided by Embodiments 2 to 4 first obtain a group fraud relationship identification request sent by a terminal, and the group fraud relationship identification request carries a target mobile phone number, and then determine the target mobile phone number. Whether it is a fraudulent product, if so, obtain multiple pieces of related information corresponding to the target mobile phone number, and then input the multiple pieces of related information into the preset group fraud relationship identification model to perform group fraud relationship graph analysis, and the target can be obtained. The group fraud relationship map corresponding to the mobile phone number is sent to the terminal finally. The invention can realize pre-processing, and has the advantages of high fraud relationship judgment accuracy and fraud relationship judgment coverage, and solves the problem that the existing group fraud relationship identification method is prone to post-processing, fraud relationship judgment accuracy, and fraud relationship judgment coverage. problems such as low rates.
可以理解的是,以上实施方式仅仅是为了说明本发明的原理而采用的示例性实施方式,然而本发明并不局限于此。对于本领域内的普通技术人员而言,在不脱离本发明的精神和实质的情况下,可以做出各种变型和改进,这些变型和改进也视为本发明的保护范围。It can be understood that the above embodiments are only exemplary embodiments adopted to illustrate the principle of the present invention, but the present invention is not limited thereto. For those skilled in the art, without departing from the spirit and essence of the present invention, various modifications and improvements can be made, and these modifications and improvements are also regarded as the protection scope of the present invention.
Claims (10)
Priority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202210862406.5ACN115243268B (en) | 2022-07-20 | 2022-07-20 | A method, system and readable storage medium for identifying group fraud relationships |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202210862406.5ACN115243268B (en) | 2022-07-20 | 2022-07-20 | A method, system and readable storage medium for identifying group fraud relationships |
Publications (2)
| Publication Number | Publication Date |
|---|---|
| CN115243268Atrue CN115243268A (en) | 2022-10-25 |
| CN115243268B CN115243268B (en) | 2025-01-24 |
Family
ID=83675227
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN202210862406.5AActiveCN115243268B (en) | 2022-07-20 | 2022-07-20 | A method, system and readable storage medium for identifying group fraud relationships |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN115243268B (en) |
Cited By (1)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN115858946A (en)* | 2023-02-22 | 2023-03-28 | 昆明理工大学 | Graph theory-based clue reasoning and intelligence prediction method |
Citations (6)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN111428217A (en)* | 2020-04-12 | 2020-07-17 | 中信银行股份有限公司 | Method and device for identifying cheat group, electronic equipment and computer readable storage medium |
| CN112053222A (en)* | 2020-08-14 | 2020-12-08 | 百维金科(上海)信息科技有限公司 | Knowledge graph-based internet financial group fraud detection method |
| CN112533209A (en)* | 2020-12-10 | 2021-03-19 | 中国联合网络通信集团有限公司 | Black product identification method and black product identification device |
| CN113065943A (en)* | 2021-03-02 | 2021-07-02 | 苏宁金融科技(南京)有限公司 | Anti-fraud black product entity identification method and system |
| CN113962712A (en)* | 2021-10-29 | 2022-01-21 | 深圳市珍爱捷云信息技术有限公司 | Method for predicting fraud gangs and related equipment |
| CN114387005A (en)* | 2021-12-02 | 2022-04-22 | 天翼电子商务有限公司 | An Arbitrage Group Identification Method Based on Graph Classification |
- 2022
- 2022-07-20CNCN202210862406.5Apatent/CN115243268B/enactiveActive
Patent Citations (6)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN111428217A (en)* | 2020-04-12 | 2020-07-17 | 中信银行股份有限公司 | Method and device for identifying cheat group, electronic equipment and computer readable storage medium |
| CN112053222A (en)* | 2020-08-14 | 2020-12-08 | 百维金科(上海)信息科技有限公司 | Knowledge graph-based internet financial group fraud detection method |
| CN112533209A (en)* | 2020-12-10 | 2021-03-19 | 中国联合网络通信集团有限公司 | Black product identification method and black product identification device |
| CN113065943A (en)* | 2021-03-02 | 2021-07-02 | 苏宁金融科技(南京)有限公司 | Anti-fraud black product entity identification method and system |
| CN113962712A (en)* | 2021-10-29 | 2022-01-21 | 深圳市珍爱捷云信息技术有限公司 | Method for predicting fraud gangs and related equipment |
| CN114387005A (en)* | 2021-12-02 | 2022-04-22 | 天翼电子商务有限公司 | An Arbitrage Group Identification Method Based on Graph Classification |
Non-Patent Citations (2)
| Title |
|---|
| WANG, J.等: "Fraud Network Identification Model for Insurance Industry", 《BUSINESS INTELLIGENCE AND INFORMATION TECHNOLOGY》, 16 December 2021 (2021-12-16)* |
| 杨博雄: "深度学习理论与实践", 《北京邮电大学出版社》, 30 September 2020 (2020-09-30), pages 107 - 130* |
Cited By (1)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN115858946A (en)* | 2023-02-22 | 2023-03-28 | 昆明理工大学 | Graph theory-based clue reasoning and intelligence prediction method |
Also Published As
| Publication number | Publication date |
|---|---|
| CN115243268B (en) | 2025-01-24 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| CN107563757B (en) | Data risk identification method and device | |
| CN108154367B (en) | Block chain service checking method and device | |
| CN111372242A (en) | Fraud identification method, device, server and storage medium | |
| CN105740667A (en) | A method and device for information identification based on user behavior | |
| CN113515612B (en) | A method and device for identifying illegal mobile phone numbers | |
| CN109982257B (en) | Method, device and system for determining mobile user home region | |
| CN115243268A (en) | Method, system and readable storage medium for identifying group fraud relationship | |
| CN111542043A (en) | Method and device for identifying service request for changing mobile phone number | |
| CN111404835B (en) | Flow control method, device, equipment and storage medium | |
| US11412063B2 (en) | Method and apparatus for setting mobile device identifier | |
| CN111259007A (en) | Electric vehicle information monitoring method and device, server and electric vehicle management system | |
| CN114491106B (en) | Face recognition method, priority determination method, device and storage medium | |
| CN115935775A (en) | Neural network model training method, device, equipment and storage medium | |
| CN112148724A (en) | Equipment identification processing method and system, computer equipment and readable storage medium | |
| CN115623583B (en) | Method, device and equipment for identifying dual-card users on a single terminal | |
| CN115955528A (en) | Number identification method, device and readable storage medium | |
| CN109547921A (en) | A kind of method for positioning user, computer readable storage medium and terminal device | |
| CN115130605A (en) | Method, system and computer-readable storage medium for identifying fraudulent relationship | |
| CN112232970A (en) | Data relationship identification method and device, storage medium and electronic equipment | |
| CN115426167B (en) | Black product identification method and device and computer readable storage medium | |
| CN113556748B (en) | Signaling tracing identification method, device and system | |
| CN112822022A (en) | Multi-signature address updating method and related device | |
| CN110636451B (en) | Information management method and related device | |
| CN115062032B (en) | A method and device for updating graph data | |
| CN120030459A (en) | Multimedia object detection method, device, storage medium and electronic device |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| GR01 | Patent grant | ||
| GR01 | Patent grant |