CN1150718C - Method for Ensuring Internet Protocol Security on Tunnel Virtual Interface of Virtual Private Network - Google Patents
Method for Ensuring Internet Protocol Security on Tunnel Virtual Interface of Virtual Private NetworkDownload PDFInfo
- Publication number
- CN1150718C CN1150718CCNB011198303ACN01119830ACN1150718CCN 1150718 CCN1150718 CCN 1150718CCN B011198303 ACNB011198303 ACN B011198303ACN 01119830 ACN01119830 ACN 01119830ACN 1150718 CCN1150718 CCN 1150718C
- Authority
- CN
- China
- Prior art keywords
- private network
- tunnel
- ipsec
- virtual interface
- interface
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Expired - Fee Related
Links
Images
Landscapes
- Data Exchanges In Wide-Area Networks (AREA)
Abstract
Translated fromChineseDescription
Translated fromChinese技术领域technical field
本发明涉及一种保证互联网协议IP报文安全传输的方法,确切地说,涉及一种在虚拟私有网的隧道虚接口上保证互联网协议安全的实现方法,属于数字信息的传输中保证通信安全的技术领域。The present invention relates to a method for ensuring the safe transmission of Internet Protocol IP messages, to be precise, it relates to a method for realizing the safety of Internet Protocol on the tunnel virtual interface of a virtual private network, which belongs to the method of ensuring communication safety in the transmission of digital information technology field.
背景技术Background technique
互联网协议安全IPSec(IP Security)是IETF制定的IP层报文安全传输的标准。在IP报文封装的方式上,互联网协议安全IPSec是提供隧道方式的封装,利用这个特性可以实现虚拟私有网VPN功能。在设置IPSec的安全保护技术手段的过程中,如果和访问控制列表ACL(Access Control Lists)相结合,可以实现对不同的数据流执行不同的安全保护措施。目前,传统技术是把设置好的安全保护技术措施应用到实际的物理接口上,完成对进出该物理接口的IP报文进行数据加密(解密)、验证、防重放攻击等保证通信安全的各项技术保障手段。如果IPSec的保证通信安全的各项技术方法只能应用在实际的物理接口上,那它就只能为进出这个实际物理接口上的IP报文实施安全保护。然而,在虚拟私有网VPN的隧道虚接口上,尚不能应用上述IPSec的保证通信安全的各项技术方法。如果在虚拟私有网VPN的隧道虚接口上也能够应用上述IPSec的安全技术保障手段的话,那将能够给进出该VPN的隧道虚接口的IP报文也提供安全保护的技术。这样,无疑将会受到虚拟私有网VPN的众多用户的衷心欢迎。Internet Protocol Security IPSec (IP Security) is a standard for the secure transmission of IP layer packets formulated by the IETF. In the way of IP packet encapsulation, Internet Protocol Security IPSec provides tunnel encapsulation, and this feature can be used to realize the virtual private network VPN function. In the process of setting IPSec security protection technical means, if combined with access control list ACL (Access Control Lists), different security protection measures can be implemented for different data streams. At present, the traditional technology is to apply the set security protection technical measures to the actual physical interface, and complete the data encryption (decryption), verification, and anti-replay attack of the IP packets entering and leaving the physical interface to ensure communication security. technical support means. If the various technical methods of IPSec to ensure communication security can only be applied on the actual physical interface, then it can only implement security protection for the IP packets entering and leaving the actual physical interface. However, on the tunnel virtual interface of the virtual private network VPN, the various technical methods for ensuring communication security of the above-mentioned IPSec cannot yet be applied. If the above-mentioned IPSec security technology guarantee means can also be applied on the tunnel virtual interface of the virtual private network VPN, it will also be able to provide security protection technology for the IP packets entering and leaving the tunnel virtual interface of the VPN. In this way, it will undoubtedly be welcomed by many users of the virtual private network VPN.
例如,参见图1所示,一个有着私有IP地址的私有网B中的用户A访问另外一个私有网C中的某一台服务器D,这两个私有网B、C之间则是通过Internet相连的(这是一个典型的虚拟私有网VPN的应用实例)。私有网B通过一台路由器R1和Internet连接。在路由器R1和Internet直接相连的物理接口上通常都是设置有应用IPSec的安全技术保障方法。该安全技术保障方法规定所有进出该物理接口、并且应用协议是传输控制协议TCP(Transmission ControlProtocol)的IP报文都应该使用IPSec的隧道加密功能。但是,该项安全技术保障方法是不想让其他应用协议(例如用户数据报协议UDP和普通路由封装GRE)的IP报文也能够应用IPSec的加密措施。然而,为了所有拥护不同应用层协议的IP报文都能实现虚拟私有网VPN功能,在路由器R1上创建了一个VPN的隧道虚接口,在这个虚接口上封装了普通路由封装GRE(GenericRouting Encapsulation)协议,其指定隧道的对端地址是私有网C和Internet相连的路由器R2上的Internet网公有地址,并且由路由模块确定所有到私有网C的IP报文都要先经过这个VPN隧道虚接口。申请人出版的《Quidway系列路由器用户手册配置指导分册V1.3》中的第11-37页“路由器配置举例”部分(资料版本:T1-080139-20010615-C-1.3)对如何应用访问控制列表ACL(Access Control Lists)和隧道方式的封装特性相结合,对不同的数据流实现不同的安全保护措施的方法作了详细又具体的说明,即采用下列两个操作步骤:首先设置至少一项访问控制列表ACL,然后定义如何应用上述步骤设置的访问控制列表ACL的IPSec安全技术保障方法。其中第一步骤和第二步骤分别与上述资料文档配置举例部分的第1、2条命令和第3~17条命令相对应(有关参考资料中路由器A配置举例的全部指令内容因为是过于具体的程序指令,故在此不再赘述)。这样,通常用户A就会以为所有通过Internet的TCP报文是可以经过IPSec加密而保证通信安全的,而实际的事实却是:在目前的状况下所有访问私有网C的TCP报文在Internet上传输时是不受IPSec保护的。For example, as shown in Figure 1, a user A in a private network B with a private IP address accesses a server D in another private network C, and the two private networks B and C are connected through the Internet (This is a typical application example of a virtual private network VPN). Private network B is connected to the Internet through a router R1. The physical interface directly connected to the Internet on the router R1 is usually equipped with a security technology guarantee method using IPSec. The security technology guarantee method stipulates that all IP packets entering and exiting the physical interface and whose application protocol is Transmission Control Protocol (TCP) should use the tunnel encryption function of IPSec. However, this security technology guarantee method is not to allow IP packets of other application protocols (such as User Datagram Protocol UDP and common routing encapsulation GRE) to also apply the encryption measures of IPSec. However, in order to realize the virtual private network VPN function for all IP packets supporting different application layer protocols, a VPN tunnel virtual interface is created on the router R1, and the general routing encapsulation GRE (Generic Routing Encapsulation) is encapsulated on this virtual interface. Protocol, the peer address of the specified tunnel is the public address of the Internet network on the router R2 connected to the private network C and the Internet, and the routing module determines that all IP packets to the private network C must first pass through this VPN tunnel virtual interface. In the "Quidway Series Router User Manual Configuration Guide Volume V1.3" published by the applicant, the "Router Configuration Example" section on pages 11-37 (data version: T1-080139-20010615-C-1.3) has a detailed explanation on how to apply the access control list Combining ACL (Access Control Lists) with the encapsulation characteristics of the tunnel method, the method of implementing different security protection measures for different data streams is described in detail, that is, the following two steps are adopted: first, set at least one access Control list ACL, and then define how to apply the IPSec security technology guarantee method of the access control list ACL set in the above steps. Among them, the first step and the second step correspond to the 1st and 2nd commands and the 3rd to 17th commands in the configuration example part of the above-mentioned information document respectively (the content of all the instructions in the configuration example of router A in the reference material is too specific. program instructions, so it will not be repeated here). In this way, user A usually thinks that all TCP packets passing through the Internet can be encrypted by IPSec to ensure communication security, but the actual fact is that in the current situation, all TCP packets accessing the private network C are encrypted on the Internet. Transmission is not protected by IPSec.
发明内容Contents of the invention
本发明的目的是提供一种在虚拟私有网的隧道虚接口上保证互联网协议安全的实现方法,也就是说,将一种在实际物理接口上已经普遍使用的IPSec安全技术保障方法提供给虚拟私有网VPN的隧道虚接口上应用,以使所有访问私有网的各类报文,不管其属于哪类协议,都能够得到IPSec的安全技术保障,以保证通信安全。The purpose of the present invention is to provide a method for realizing the security of the Internet protocol on the tunnel virtual interface of the virtual private network, that is to say, to provide a virtual private network with an IPSec security technology guarantee method generally used on the actual physical interface It is applied on the tunnel virtual interface of the network VPN, so that all kinds of messages accessing the private network, no matter what type of protocol they belong to, can be guaranteed by IPSec security technology to ensure communication security.
本发明的目的是这样实现的:一种在虚拟私有网的隧道虚接口上保证互联网协议安全的实现方法,是将在实际物理接口上应用的IPSec安全技术保障方法,移植应用到虚拟私有网VPN的隧道虚接口上;包括有下列操作步骤:The purpose of the present invention is achieved like this: a kind of realization method that guarantees Internet Protocol security on the tunnel virtual interface of virtual private network, is the IPSec security technology guarantee method that will be applied on actual physical interface, transplants and applies to virtual private network VPN on the virtual interface of the tunnel; including the following steps:
(1)设置至少一项访问控制列表ACL;(1) Set at least one access control list ACL;
(2)定义如何应用第(1)步骤设置的访问控制列表ACL的IPSec安全技术保障方法;(2) define how to apply the IPSec security technology guarantee method of the access control list ACL that (1) step is set;
其特征在于:该方法进一步包括有以下操作步骤:It is characterized in that: the method further includes the following steps:
(3)设置隧道虚接口;(3) Set the tunnel virtual interface;
(4)在隧道虚接口上应用第(2)步骤生成的IPSec安全技术保障方法。(4) Apply the IPSec security technology guarantee method generated in step (2) on the tunnel virtual interface.
本发明的特点是将在在物理接口上应用的IPSec安全技术保障方法,移植到虚拟私有网VPN的隧道虚接口上应用,这样,所有IPSec安全技术保障方法应用在物理接口上所获得的好处,在VPN隧道虚接口上应用时同样可以获得,例如数据加密、报文验证、防重放攻击等。所以,如果应用本发明,图1中的用户A发出的通过Internet传输的TCP报文也可以得到IPSec安全技术保护了。The feature of the present invention is that the IPSec security technology guarantee method applied on the physical interface is transplanted to the tunnel virtual interface of the virtual private network VPN for application, like this, all IPSec security technology guarantee methods are applied to the benefits obtained on the physical interface, It can also be obtained when it is applied on the virtual interface of the VPN tunnel, such as data encryption, message verification, anti-replay attack, etc. Therefore, if the present invention is applied, the TCP message sent by user A in Fig. 1 and transmitted through the Internet can also be protected by IPSec security technology.
附图说明Description of drawings
图1是应用本发明方法的第一实施例-用户A通过VPN访问服务器D-的系统组成示意图。Fig. 1 is a schematic diagram of the system composition of the first embodiment of the application of the method of the present invention - user A accessing server D through VPN.
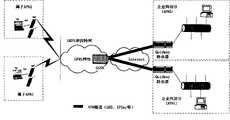
图2是应用本发明方法的第二实施例-GPRS/WCDMA中手机用户非透明方式通过Internet访问企业网-的系统组成示意图。Fig. 2 is a schematic diagram of the system composition of the second embodiment of the application of the method of the present invention-the mobile phone user accesses the enterprise network through the Internet in a non-transparent mode in GPRS/WCDMA.
具体实施方式Detailed ways
下面结合附图详细介绍本发明的方法步骤、特点和功效:Introduce method steps, characteristics and effect of the present invention in detail below in conjunction with accompanying drawing:
参见图1所示的一典型虚拟私有网VPN的应用实例:一个有着私有IP地址的私有网B中的用户A访问另外一个私有网C中的某一台服务器D,这两个私有网B、C之间则通过Internet相连。其中私有网B通过一台路由器R1和Internet连接。在路由器R1和Internet直接相连的物理接口上通常都设置有应用IPSec的安全技术保障方法。本发明则是将在实际物理接口上应用的IPSec安全技术保障方法,再移植到虚拟私有网VPN的隧道虚接口上应用。其具体包括有下列步骤:1、设置至少一项访问控制列表ACL(Access Control Lists),2、定义如何应用第1步设置的访问控制列表ACL的IPSec安全技术保障方法,3、设置隧道虚接口,4、在隧道虚接口上应用第2步生成的IPSec安全技术保障方法。Referring to the application example of a typical virtual private network VPN shown in Figure 1: a user A in a private network B with a private IP address accesses a certain server D in another private network C, the two private networks B, C is connected through the Internet. The private network B is connected to the Internet through a router R1. The physical interface directly connected to the Internet on the router R1 is usually equipped with a security technology guarantee method using IPSec. The present invention transplants the IPSec security technology guarantee method applied on the actual physical interface to the tunnel virtual interface of the virtual private network VPN for application. It specifically includes the following steps: 1, setting at least one access control list ACL (Access Control Lists), 2, defining how to apply the IPSec security technology guarantee method of the access control list ACL set in the first step, 3, setting the tunnel virtual interface 4. Apply the IPSec security technology guarantee method generated in step 2 on the tunnel virtual interface.
原来在路由器R1和Internet相连的物理接口上应用的IPSec安全技术保障方法是不想让应用层协议是普通路由封装GRE的报文也使用IPSec的加密功能,而且采用GRE+IPSec的方法实现虚拟私有网VPN的效率与直接使用IPSec的隧道方式实现VPN的效率相比较明显要低。但是,利用本发明的方法可以在路由器R1封装GRE协议的VPN隧道虚接口上直接应用IPSec的安全技术保障方法。此时,只要条件符合(即符合IPSec的安全技术保障方法中匹配的访问控制列表ACL的规定),就可以直接应用IPSec的安全技术保障方法了。Originally, the IPSec security technology guarantee method applied on the physical interface connecting router R1 to the Internet does not want the application layer protocol to be a common route. Packets encapsulated with GRE also use the encryption function of IPSec, and the method of GRE+IPSec is used to realize the virtual private network. The efficiency of VPN is obviously lower than the efficiency of directly using IPSec tunnel to realize VPN. However, the method of the present invention can directly apply the security technology guarantee method of IPSec on the virtual interface of the VPN tunnel encapsulating the GRE protocol of the router R1. At this point, as long as the conditions are met (that is, comply with the provisions of the matching access control list ACL in the IPSec security technology guarantee method), the IPSec security technology guarantee method can be directly applied.
本发明的方法已经在通用分组无线业务GPRS/宽带码分多址WCDMA系统中进行实施试验,即在不同的手机用户拥有不同的访问点名APN(AccessPoint Name)所分配的相同的私有IP地址的环境下,通过使用本发明的方法,即在VPN的隧道虚接口上应用IPSec的安全技术保障方法,就可以实现各手机用户通过IPSec隧道访问不同APN的应用目的。实施试验的结果是成功的,达到了预期的效果。The method of the present invention has carried out implementation experiment in general packet radio service GPRS/wideband code division multiple access WCDMA system, promptly has the environment of the same private IP address that different access point name APN (AccessPoint Name) distributes in different mobile phone users Next, by using the method of the present invention, that is, applying the IPSec security technology guarantee method on the tunnel virtual interface of the VPN, the application purpose of each mobile phone user accessing different APNs through the IPSec tunnel can be realized. The result of the implementation test was successful and the expected effect was achieved.
为了能够让拥有相同私有IP地址的不同手机用户访问不同的APN,在GGSN上必须将相同IP地址的报文根据其所属的不同APN送入不同的VPN隧道虚接口,以便封装进不同的VPN隧道。图2所示的即为分属于APN1和APN2的两个手机用户的手机MT的IP私有地址是相同的情况,此时,如果只能在实际物理接口上应用IPSec的安全技术保障方法,为了能够应用IPSec的方式安全地传输IP报文,就只能采取某种VPN协议(例如普通路由封装GRE)+IPSec这种低效率的传输方式(因为IPSec协议本身就直接支持VPN功能),而且不能根据实际的不同数据流应用不同的安全技术保障方法。因为经过VPN封装后的IP报文,它们的源和目的IP地址都是相同的,应用层协议也是相同的(VPN协议),即在IP层看来它们两者已经没有差异,无法区分开。然而,使用本发明的方法,在VPN隧道虚接口上直接应用IPSec的安全技术保障方法,那么,上述的所有缺点就都能够克服和解决了。图2中分属于不同访问点名APN1和APN2、且拥有相同IP私有地址的两个手机用户就可以通过手机MT或者通过便携式电脑TE(此时需要藉助起到类似MODEM功能的手机MT),根据其所属的不同的APN(Access Point Name)送入不同的VPN隧道虚接口直接应用IPSec的安全技术保障方法,即通过不同的IPSec隧道访问不同的APN(例如图2中所示的两个企业网APN1和APN2)。In order to allow different mobile phone users with the same private IP address to access different APNs, the GGSN must send packets with the same IP address to different VPN tunnel virtual interfaces according to the different APNs they belong to, so as to be encapsulated into different VPN tunnels . Shown in Fig. 2 is the situation that the IP private addresses of the mobile phone MTs of two mobile phone users belonging to APN1 and APN2 are the same. Applying IPSec to securely transmit IP packets can only adopt a certain VPN protocol (such as ordinary routing encapsulation GRE) + IPSec, which is an inefficient transmission method (because the IPSec protocol itself directly supports the VPN function), and cannot be based on Different security technology protection methods are applied to different actual data streams. Because the IP packets after VPN encapsulation have the same source and destination IP addresses, and the application layer protocol is also the same (VPN protocol), that is, from the perspective of the IP layer, there is no difference between them and they cannot be distinguished. However, by using the method of the present invention and directly applying the security technology guarantee method of IPSec on the virtual interface of the VPN tunnel, then all the above-mentioned shortcomings can be overcome and resolved. In Fig. 2, two mobile phone users who belong to different access point names APN1 and APN2 and have the same IP private address can pass through the mobile phone MT or the portable computer TE (the mobile phone MT with a similar MODEM function needs to be used at this time), according to its The different APNs (Access Point Name) that belong to are sent to different VPN tunnel virtual interfaces and directly apply the IPSec security technology guarantee method, that is, access different APNs through different IPSec tunnels (for example, the two enterprise network APN1 shown in Figure 2 and APN2).
Claims (1)
Translated fromChinesePriority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CNB011198303ACN1150718C (en) | 2001-06-29 | 2001-06-29 | Method for Ensuring Internet Protocol Security on Tunnel Virtual Interface of Virtual Private Network |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CNB011198303ACN1150718C (en) | 2001-06-29 | 2001-06-29 | Method for Ensuring Internet Protocol Security on Tunnel Virtual Interface of Virtual Private Network |
Publications (2)
| Publication Number | Publication Date |
|---|---|
| CN1394042A CN1394042A (en) | 2003-01-29 |
| CN1150718Ctrue CN1150718C (en) | 2004-05-19 |
Family
ID=4663745
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CNB011198303AExpired - Fee RelatedCN1150718C (en) | 2001-06-29 | 2001-06-29 | Method for Ensuring Internet Protocol Security on Tunnel Virtual Interface of Virtual Private Network |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN1150718C (en) |
Families Citing this family (21)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| DE602004010519T2 (en)* | 2003-07-04 | 2008-11-13 | Nippon Telegraph And Telephone Corp. | REMOTE ACCESS VPN TREATMENT PROCESS AND TREATMENT DEVICE |
| US7978716B2 (en) | 2003-11-24 | 2011-07-12 | Citrix Systems, Inc. | Systems and methods for providing a VPN solution |
| US8146148B2 (en)* | 2003-11-19 | 2012-03-27 | Cisco Technology, Inc. | Tunneled security groups |
| US8495305B2 (en) | 2004-06-30 | 2013-07-23 | Citrix Systems, Inc. | Method and device for performing caching of dynamically generated objects in a data communication network |
| US8739274B2 (en) | 2004-06-30 | 2014-05-27 | Citrix Systems, Inc. | Method and device for performing integrated caching in a data communication network |
| US7757074B2 (en) | 2004-06-30 | 2010-07-13 | Citrix Application Networking, Llc | System and method for establishing a virtual private network |
| CN100385885C (en)* | 2004-07-09 | 2008-04-30 | 威达电股份有限公司 | Security gateway with SSL protection function and method |
| EP1771998B1 (en) | 2004-07-23 | 2015-04-15 | Citrix Systems, Inc. | Systems and methods for optimizing communications between network nodes |
| EP2264956B1 (en) | 2004-07-23 | 2017-06-14 | Citrix Systems, Inc. | Method for securing remote access to private networks |
| CN101076992A (en) | 2004-08-13 | 2007-11-21 | 塞特里克斯系统公司 | A method and systems for securing remote access to private networks |
| US7810089B2 (en) | 2004-12-30 | 2010-10-05 | Citrix Systems, Inc. | Systems and methods for automatic installation and execution of a client-side acceleration program |
| US8700695B2 (en) | 2004-12-30 | 2014-04-15 | Citrix Systems, Inc. | Systems and methods for providing client-side accelerated access to remote applications via TCP pooling |
| US8706877B2 (en) | 2004-12-30 | 2014-04-22 | Citrix Systems, Inc. | Systems and methods for providing client-side dynamic redirection to bypass an intermediary |
| US8549149B2 (en) | 2004-12-30 | 2013-10-01 | Citrix Systems, Inc. | Systems and methods for providing client-side accelerated access to remote applications via TCP multiplexing |
| US8954595B2 (en) | 2004-12-30 | 2015-02-10 | Citrix Systems, Inc. | Systems and methods for providing client-side accelerated access to remote applications via TCP buffering |
| US8255456B2 (en) | 2005-12-30 | 2012-08-28 | Citrix Systems, Inc. | System and method for performing flash caching of dynamically generated objects in a data communication network |
| CN102123178B (en) | 2005-01-24 | 2014-04-09 | 茨特里克斯系统公司 | Systems and methods for performing caching of dynamically generated objects in network |
| US8301839B2 (en) | 2005-12-30 | 2012-10-30 | Citrix Systems, Inc. | System and method for performing granular invalidation of cached dynamically generated objects in a data communication network |
| US7921184B2 (en) | 2005-12-30 | 2011-04-05 | Citrix Systems, Inc. | System and method for performing flash crowd caching of dynamically generated objects in a data communication network |
| CN100440846C (en)* | 2007-01-26 | 2008-12-03 | 成都迈普产业集团有限公司 | Dynamic connection method for virtual private network |
| CN101499972B (en)* | 2009-03-16 | 2012-01-11 | 杭州华三通信技术有限公司 | IP security packet forwarding method and apparatus |
- 2001
- 2001-06-29CNCNB011198303Apatent/CN1150718C/ennot_activeExpired - Fee Related
Also Published As
| Publication number | Publication date |
|---|---|
| CN1394042A (en) | 2003-01-29 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| CN1150718C (en) | Method for Ensuring Internet Protocol Security on Tunnel Virtual Interface of Virtual Private Network | |
| US7616597B2 (en) | System and method for integrating mobile networking with security-based VPNs | |
| KR100758733B1 (en) | System and method for managing a proxy request over a secure network using inherited security attributes | |
| US8910272B2 (en) | Computer communication system for communication via public networks | |
| KR101680955B1 (en) | Multi-tunnel virtual private network | |
| EP1771979B1 (en) | A method and systems for securing remote access to private networks | |
| US20160080328A1 (en) | Proxy ssl handoff via mid-stream renegotiation | |
| US20030014626A1 (en) | Data handling in IPSec enabled network stack | |
| EP1463239A3 (en) | Protection of network infrastructure and secure communication of control information thereto | |
| CN1762140A (en) | Communication between private network and roaming mobile terminal | |
| CN1643947A (en) | Method to provide dynamic internet protocol security policy service | |
| US20150288651A1 (en) | Ip packet processing method and apparatus, and network system | |
| CN101753531A (en) | Method utilizing https/http protocol to realize encapsulation of IPsec protocol | |
| CN101222412B (en) | Network address translation traversal method and system | |
| CN103051535A (en) | Data access method, data access device and data access system | |
| US7680102B2 (en) | Method and system for connecting manipulation equipment between operator's premises and the internet | |
| Ahmed et al. | Security threats for IPv6 transition strategies: A review | |
| CN109167774B (en) | A data message and a data flow security mutual access method on a firewall | |
| CN1949705A (en) | Dynamic tunnel construction method for safety access special LAN and apparatus therefor | |
| CN104618323B (en) | Operation system transmission safety encryption based on networks filter driver | |
| CN1118171C (en) | On-demand system and method for access repeater applied to virtual private network | |
| CN1770761A (en) | An Address Update Method Based on Network Key Exchange Protocol | |
| CN103905302A (en) | Method for binding source IP on Windows host adopting virtual network interface card | |
| Gaynor et al. | Firewall Enhancement Protocol (FEP) | |
| CN100362809C (en) | A control method for data transmission of BT client |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| C10 | Entry into substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| C06 | Publication | ||
| PB01 | Publication | ||
| C10 | Entry into substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| C14 | Grant of patent or utility model | ||
| GR01 | Patent grant | ||
| CF01 | Termination of patent right due to non-payment of annual fee | Granted publication date:20040519 Termination date:20170629 | |
| CF01 | Termination of patent right due to non-payment of annual fee |