CN115051941A - Enterprise big data analysis platform - Google Patents
Enterprise big data analysis platformDownload PDFInfo
- Publication number
- CN115051941A CN115051941ACN202210591308.2ACN202210591308ACN115051941ACN 115051941 ACN115051941 ACN 115051941ACN 202210591308 ACN202210591308 ACN 202210591308ACN 115051941 ACN115051941 ACN 115051941A
- Authority
- CN
- China
- Prior art keywords
- module
- flow
- data
- time
- big data
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Pending
Links
Images
Classifications
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L43/00—Arrangements for monitoring or testing data switching networks
- H04L43/08—Monitoring or testing based on specific metrics, e.g. QoS, energy consumption or environmental parameters
- H04L43/0876—Network utilisation, e.g. volume of load or congestion level
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L41/00—Arrangements for maintenance, administration or management of data switching networks, e.g. of packet switching networks
- H04L41/06—Management of faults, events, alarms or notifications
- H04L41/0631—Management of faults, events, alarms or notifications using root cause analysis; using analysis of correlation between notifications, alarms or events based on decision criteria, e.g. hierarchy, tree or time analysis
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L43/00—Arrangements for monitoring or testing data switching networks
- H04L43/04—Processing captured monitoring data, e.g. for logfile generation
- H04L43/045—Processing captured monitoring data, e.g. for logfile generation for graphical visualisation of monitoring data
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/04—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks
- H04L63/0428—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks wherein the data content is protected, e.g. by encrypting or encapsulating the payload
- H04L63/0442—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks wherein the data content is protected, e.g. by encrypting or encapsulating the payload wherein the sending and receiving network entities apply asymmetric encryption, i.e. different keys for encryption and decryption
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L67/00—Network arrangements or protocols for supporting network services or applications
- H04L67/01—Protocols
- H04L67/02—Protocols based on web technology, e.g. hypertext transfer protocol [HTTP]
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/32—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials
- H04L9/3263—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials involving certificates, e.g. public key certificate [PKC] or attribute certificate [AC]; Public key infrastructure [PKI] arrangements
- H04L9/3268—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials involving certificates, e.g. public key certificate [PKC] or attribute certificate [AC]; Public key infrastructure [PKI] arrangements using certificate validation, registration, distribution or revocation, e.g. certificate revocation list [CRL]
Landscapes
- Engineering & Computer Science (AREA)
- Computer Networks & Wireless Communication (AREA)
- Signal Processing (AREA)
- Computer Security & Cryptography (AREA)
- Data Mining & Analysis (AREA)
- Computer Hardware Design (AREA)
- Computing Systems (AREA)
- General Engineering & Computer Science (AREA)
- Environmental & Geological Engineering (AREA)
- Data Exchanges In Wide-Area Networks (AREA)
Abstract
Description
Translated fromChinese技术领域technical field
本发明属于企业大数据技术领域,尤其是一种企业大数据分析平台。The invention belongs to the technical field of enterprise big data, in particular to an enterprise big data analysis platform.
背景技术Background technique
在ERP数据信息应用领域,由于企业数据量日益庞大和烦杂,往住会导致企业对自身数据无法全面快速进行管控,更无法通过数据对日常经营状况进行合理分析和提出管理上的建议,因此就需要一种企业大数据分析平台。In the field of ERP data information application, due to the increasingly large and complicated amount of enterprise data, it often leads to the inability of enterprises to comprehensively and quickly control their own data, and it is also impossible to reasonably analyze the daily operating conditions and put forward management suggestions through the data. An enterprise big data analytics platform is needed.
例如申请号为CN201621345179.5的一种基于大数据的企业隐患信息采集处理系统。该系统包括隐患信息采集系统,传输系统,大数据处理中心和Smart Safety Map企业隐患地图;主要是利用自动监测传感器、人工监测上报设备监测企业的隐患信息并上传;通过传输系统传输至企业大数据处理中心;利用大数据方法对隐患信息进行分级预警;由监控中心发出隐患预警,并在企业智慧安全地图上实时显示各系统隐患信息;实时通知整改主管部门下达到责任人员进行整改;现场安监人员或者主管负责人检查并确认整改效果,并上传整改信息。形成信息获取、隐患分级、整改任务下达、效果确认的闭环控制。通过使用上述系统,可对企业隐患信息进行全时空的监测,预防事故发生。For example, an application number CN201621345179.5 is a big data-based enterprise hidden danger information collection and processing system. The system includes a hidden danger information collection system, a transmission system, a big data processing center and a Smart Safety Map enterprise hidden danger map; it mainly uses automatic monitoring sensors, manual monitoring and reporting equipment to monitor the hidden danger information of the enterprise and upload it; it is transmitted to the enterprise big data through the transmission system. Processing center; use big data method to give early warning of hidden danger information; the monitoring center will issue early warning of hidden dangers, and display the hidden danger information of each system in real time on the enterprise smart safety map; notify the rectification department in real time and send it to the responsible personnel for rectification; on-site safety supervision Personnel or supervisors check and confirm the rectification effect, and upload the rectification information. Form a closed-loop control of information acquisition, hidden danger classification, rectification task assignment, and effect confirmation. Through the use of the above system, the full-time monitoring of enterprise hidden danger information can be carried out to prevent accidents.
但值得注意的是,现有的平台无法做到便捷的对发生风险的部门及发生时间进行定位查看。However, it is worth noting that the existing platform cannot easily locate and view the department where the risk occurs and the time of occurrence.
发明内容SUMMARY OF THE INVENTION
本发明的目的在于提供一种企业大数据分析平台,以解决背景技术中提出的问题。The purpose of the present invention is to provide an enterprise big data analysis platform to solve the problems raised in the background art.
技术方案:一种企业大数据分析平台,包括:Technical solution: an enterprise big data analysis platform, including:
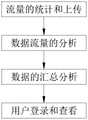
前端查看模块:通过多种方式实时对大数据分析结果进行查看;Front-end viewing module: real-time viewing of big data analysis results in various ways;
流量统计模块:对数据流量按照不同时间和不同部门的维度进行定量统计和分类;Traffic statistics module: Quantitative statistics and classification of data traffic according to the dimensions of different time and different departments;
流量上传模块:对统计的数据流量按照部门和时间的分类逐层进行打包,并在打包的过程中对数据包的前缀添加部门和时间标签,然后将打包好的数据进行加密,加密完成后即可上传数据;Traffic upload module: Pack the statistics data traffic layer by layer according to the classification of department and time, and add department and time labels to the prefix of the data packet during the packaging process, and then encrypt the packaged data. data can be uploaded;
流量分析模块:对获得的数据包进行解密,并按照部门和时间的顺序查看有无异常流量,若有则定位到该部门的对应时间段,然后对该数据流量标记异常信息并发送警报到前端查看模块;Traffic analysis module: Decrypt the obtained data packets, and check whether there is abnormal traffic in the order of department and time. If there is, locate the corresponding time period of the department, and then mark the abnormal information on the data traffic and send an alarm to the front end view module;
汇总分析模块:将数据流量按照部门和时间为轴实时绘制曲线图,并按照时间段将每个部门的曲线图分类保存到服务器。Summary analysis module: draw data flow graphs in real time according to the department and time axis, and save the graphs of each department to the server according to the time period.
在进一步的实施例中,所述前端查看模块包括:In a further embodiment, the front-end viewing module includes:
浏览器网页模块:用户通过浏览器进行登录认证,认证完毕后即可在网页端进行操作和查看;Browser web page module: users log in through the browser for authentication, and after authentication, they can operate and view on the web page;
手机应用模块:用户通过应用市场下载专属应用后即可登录认证,认证完毕后即可在应用端进行操作和查看;Mobile application module: After downloading the exclusive application through the application market, users can log in for authentication, and after the authentication is completed, they can operate and view on the application side;
小程序模块:用户在支持小程序的应用里搜索对应的小程序名称,打开小程序后进行登录认证,然后便可以在小程序端进行操作和查看。Mini Program Module: The user searches for the corresponding Mini Program name in an application that supports Mini Programs, opens the Mini Program and performs login authentication, and then can operate and view it on the Mini Program side.
在进一步的实施例中,所述浏览器在进行登录认证前需要下载对应的数字证书以确保安全。In a further embodiment, the browser needs to download a corresponding digital certificate to ensure security before performing login authentication.
在进一步的实施例中,所述流量统计模块包括:In a further embodiment, the traffic statistics module includes:
上传流量统计模块:专门对上传的流量进行统计;Upload traffic statistics module: specifically for statistics on uploaded traffic;
下载流量统计模块:专门对下载的流量进行统计。Download traffic statistics module: It is dedicated to statistics of downloaded traffic.
在进一步的实施例中,所述流量上传模块包括:In a further embodiment, the traffic uploading module includes:
数据封包模块:对统计的数据流量按照部门和时间的分类逐层进行打包;Data Packing Module: Pack the statistics data traffic layer by layer according to the classification of departments and time;
标签打印模块:在打包的过程中对数据包的前缀添加部门和时间标签;Label printing module: add department and time labels to the prefix of data packets during the packaging process;
加密模块:对完成打包的数据随后进行加密,加密完成后即进行上传。Encryption module: Encrypt the packaged data and upload it after encryption.
在进一步的实施例中,所述加密模块采用RSA算法进行加密。In a further embodiment, the encryption module uses RSA algorithm for encryption.
在进一步的实施例中,所述流量分析模块包括:In a further embodiment, the flow analysis module includes:
解密模块:对获得的数据包进行解密;Decryption module: decrypt the obtained data packets;
专属通道:通过专属网络通道将异常信息和警报发送到前端查看模块。Dedicated channel: Send abnormal information and alarms to the front-end viewing module through a dedicated network channel.
在进一步的实施例中,所述汇总分析模块包括:In a further embodiment, the summary analysis module includes:
多线程绘图模块:通过多线程处理器根据获得的多组数据流量同时进行绘图;Multi-threaded drawing module: draws simultaneously according to the multiple sets of data traffic obtained by the multi-threaded processor;
接口模块:管理人员可以通过接口模块实时接入并对绘图优先级进行调整。Interface module: Managers can access and adjust the drawing priority in real time through the interface module.
本发明的技术效果和优点:该企业大数据分析平台,流量分析模块按照部门和时间顺序查看并定位异常流量信息,发送警报时可以附带部门和时间信息,方便及时进行危险的定位,且发送警报通过专属通道,避免通信阻塞造成发送的延迟,能够能够便捷的对发生风险的部门及发生时间进行定位查看;The technical effects and advantages of the present invention: in the enterprise big data analysis platform, the traffic analysis module checks and locates abnormal traffic information in the order of departments and time, and the department and time information can be attached when sending an alarm, which is convenient for locating danger in a timely manner and sending an alarm. Through the dedicated channel, the delay in sending caused by communication congestion can be avoided, and the department and the time of occurrence of the risk can be conveniently located and checked;
汇总分析模块会按照部门和时间为轴实时绘制曲线图并保存到服务器,用户可以通过浏览器网页和手机应用等多种方式从服务器调取对应的曲线图进行查看,可以便捷的对各部门任意时间的流量信息进行直观的查看;The summary analysis module will draw the curve graph in real time according to the department and the time axis and save it to the server. Users can retrieve the corresponding curve graph from the server through various methods such as browser web pages and mobile applications for viewing, which can be convenient for each department. The flow information of time can be viewed intuitively;
该企业大数据分析平台,能够便捷的对发生风险的部门及发生时间进行定位查看,且可以便捷的对各部门任意时间的流量信息进行直观的查看。The enterprise big data analysis platform can conveniently locate and view the departments where risks occur and the time of occurrence, and can conveniently and intuitively view the traffic information of each department at any time.
附图说明Description of drawings
图1为本发明的步骤流程图。FIG. 1 is a flow chart of the steps of the present invention.
具体实施方式Detailed ways
在下文的描述中,给出了大量具体的细节以便提供对本发明更为彻底的理解。然而,对于本领域技术人员而言显而易见的是,本发明可以无需一个或多个这些细节而得以实施。在其他的例子中,为了避免与本发明发生混淆,对于本领域公知的一些技术特征未进行描述。In the following description, numerous specific details are set forth in order to provide a more thorough understanding of the present invention. It will be apparent, however, to one skilled in the art that the present invention may be practiced without one or more of these details. In other instances, some technical features known in the art have not been described in order to avoid obscuring the present invention.
为了解决提出的问题,本发明提供了如图1所示的一种企业大数据分析平台,包括:In order to solve the proposed problem, the present invention provides an enterprise big data analysis platform as shown in Figure 1, including:
前端查看模块:通过多种方式实时对大数据分析结果进行查看,包括:Front-end viewing module: View big data analysis results in real time in various ways, including:
浏览器网页模块:用户通过浏览器进行登录认证,认证完毕后即可在网页端进行操作和查看,浏览器在进行登录认证前需要下载对应的数字证书,数字证书可以显著提高浏览器访问的安全性,避免用户登录信息和企业数据被窃取;Browser web page module: The user performs login authentication through the browser. After the authentication is completed, they can operate and view on the web page. The browser needs to download the corresponding digital certificate before login authentication. The digital certificate can significantly improve the security of browser access. to avoid the theft of user login information and corporate data;
手机应用模块:用户通过应用市场下载专属应用后即可登录认证,认证完毕后即可在应用端进行操作和查看,操作相对网页更为顺畅;Mobile application module: Users can log in and authenticate after downloading the exclusive application through the application market. After the authentication is completed, they can operate and view on the application side, and the operation is smoother than that of the web page;
小程序模块:用户在支持小程序的应用里搜索对应的小程序名称,打开小程序后进行登录认证,然后便可以在小程序端进行操作和查看,相对手机应用更为轻量,可以实现大部分手机应用的操作;Mini Program Module: The user searches for the corresponding Mini Program name in the application that supports Mini Programs, opens the Mini Program and performs login authentication, and then can operate and view on the Mini Program side. Compared with mobile phone applications, it is lighter and can achieve large Operation of some mobile applications;
流量统计模块:对数据流量按照不同时间和不同部门的维度进行定量统计和分类,包括:Traffic statistics module: Quantitative statistics and classification of data traffic according to the dimensions of different time and different departments, including:
上传流量统计模块:专门对上传的流量进行统计;Upload traffic statistics module: specifically for statistics on uploaded traffic;
下载流量统计模块:专门对下载的流量进行统计,分开上传和下载流量的统计,使得统计结果不易互相影响;Download traffic statistics module: It is dedicated to the statistics of download traffic, and separates the statistics of upload and download traffic, so that the statistical results are not easy to affect each other;
流量上传模块:包括:Traffic upload module: including:
数据封包模块:对统计的数据流量按照部门和时间的分类逐层进行打包;Data Packing Module: Pack the statistics data traffic layer by layer according to the classification of departments and time;
标签打印模块:在打包的过程中对数据包的前缀添加部门和时间标签;Label printing module: add department and time labels to the prefix of data packets during the packaging process;
加密模块:对完成打包的数据随后进行加密,加密完成后即进行上传,加密模块采用RSA算法进行加密,RSA算法的安全性更高,可以避免上传的数据被不法分子获得;Encryption module: The packaged data is then encrypted, and uploaded after the encryption is completed. The encryption module uses RSA algorithm for encryption. The RSA algorithm is more secure and can prevent the uploaded data from being obtained by criminals;
流量分析模块:对获得的数据包进行解密,并按照部门和时间的顺序查看有无异常流量(所谓异常流量即某个短时间段内突发的爆发性流量上传/下载),若有则定位到该部门的对应时间段,然后对该数据流量标记异常信息并发送警报到前端查看模块,包括:Traffic analysis module: Decrypt the obtained data packets, and check whether there is abnormal traffic in the order of department and time (the so-called abnormal traffic refers to the sudden burst traffic upload/download in a short period of time), if there is, locate it to the corresponding time period of the department, and then mark abnormal information on the data traffic and send an alarm to the front-end viewing module, including:
解密模块:内建私钥,可以对获得的数据包进行解密;Decryption module: built-in private key, which can decrypt the obtained data packets;
专属通道:通过专属网络通道将异常信息和警报发送到前端查看模块,防止网络拥堵导致信息发送不及时;Exclusive channel: Send abnormal information and alarms to the front-end viewing module through the exclusive network channel to prevent network congestion from causing untimely information sending;
汇总分析模块:将数据流量按照部门和时间为轴实时绘制曲线图,并按照时间段将每个部门的曲线图分类保存到服务器,包括:Summary analysis module: draw data flow graphs in real time according to the department and time axis, and save the graphs of each department to the server according to the time period, including:
多线程绘图模块:通过多线程处理器根据获得的多组数据流量同时进行绘图,提高绘图效率;Multi-threaded drawing module: The multi-threaded processor performs drawing at the same time according to the obtained multiple sets of data traffic to improve drawing efficiency;
接口模块:管理人员可以通过接口模块实时接入并对绘图优先级进行调整,可以更快的对指定部门和时间段的曲线图进行查看。Interface module: Managers can access and adjust the drawing priority in real time through the interface module, and can view the graphs of the specified department and time period more quickly.
该企业大数据分析平台的分析步骤如下:The analysis steps of the enterprise big data analysis platform are as follows:
S1:流量的统计和上传:通过上传流量统计模块和下载流量统计模块配合来对数据流量按照不同时间和不同部门的维度进行定量统计和分类,然后通过数据封包模块对统计的数据流量按照部门和时间的分类逐层进行打包,同时通过标签打印模块打包的过程中对数据包的前缀添加部门和时间标签,接着通过加密模块对完成打包的数据随后进行加密,加密完成后即进行上传;S1: Traffic statistics and uploading: Through the cooperation of the upload traffic statistics module and the download traffic statistics module, the data traffic is quantitatively counted and classified according to the dimensions of different time and different departments, and then the statistics data traffic is classified by department and department through the data packet module. The classification of time is packaged layer by layer. At the same time, the prefix of the data packet is added with a department and time label during the packaging process by the label printing module, and then the packaged data is encrypted by the encryption module, and uploaded after the encryption is completed;
S2:数据流量的分析:通过解密模块对获得的数据包进行解密,并按照部门和时间的顺序查看有无异常流量,若有则定位到该部门的对应时间段,然后对该数据流量标记异常信息并通过专属通道发送警报到前端查看模块;S2: Analysis of data traffic: decrypt the obtained data packets through the decryption module, and check whether there is abnormal traffic in the order of department and time. If there is, locate the corresponding time period of the department, and then mark the data traffic as abnormal information and send alerts to the front-end viewing module through a dedicated channel;
S3:数据的汇总分析:通过多线程绘图模块根据获得的多组数据流量同时进行绘图,然后按照时间段将每个部门的曲线图分类保存到服务器;S3: Data summary analysis: The multi-threaded drawing module draws simultaneously according to the multiple sets of data flows obtained, and then the graphs of each department are classified and saved to the server according to the time period;
S4:用户登录和查看:用户通过浏览器网页模块、手机应用模块或小程序模块进行登录认证,然后便可以从服务器调取对应部门和时间段的曲线图进行查看。S4: User login and viewing: The user performs login authentication through the browser web page module, mobile phone application module or applet module, and then can retrieve the graph of the corresponding department and time period from the server for viewing.
需要说明的是,在本文中,诸如一和二之类的关系术语仅仅用来将一个实体或者操作与另一个实体或操作区分开来,而不一定要求或者暗示这些实体或操作之间存在任何这种实际的关系或者顺序。而且,术语“包括”、“包含”或者其任何其他变体意在涵盖非排他性的包含,从而使得包括一系列要素的过程、方法、物品或者设备不仅包括那些要素,而且还包括没有明确列出的其他要素,或者是还包括为这种过程、方法、物品或者设备所固有的要素。在没有更多限制的情况下。由语句“包括一个......限定的要素,并不排除在包括所述要素的过程、方法、物品或者设备中还存在另外的相同要素”。It should be noted that, in this document, relational terms such as one and two are used only to distinguish one entity or operation from another entity or operation, and do not necessarily require or imply any existence between these entities or operations. This actual relationship or sequence. Moreover, the terms "comprising", "comprising" or any other variation thereof are intended to encompass a non-exclusive inclusion such that a process, method, article or device that includes a list of elements includes not only those elements, but also includes not explicitly listed or other elements inherent to such a process, method, article or apparatus. without more restrictions. An element defined by the phrase "comprising an... does not preclude the presence of additional identical elements in a process, method, article or apparatus comprising said element".
尽管已经示出和描述了本发明的实施例,对于本领域的普通技术人员而言,可以理解在不脱离本发明的原理和精神的情况下可以对这些实施例进行多种变化、修改、替换和变型,本发明的范围由所附权利要求及其等同物限定。Although embodiments of the present invention have been shown and described, it will be understood by those skilled in the art that various changes, modifications, and substitutions can be made in these embodiments without departing from the principle and spirit of the invention and modifications, the scope of the present invention is defined by the appended claims and their equivalents.
Claims (8)
Priority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202210591308.2ACN115051941A (en) | 2022-05-27 | 2022-05-27 | Enterprise big data analysis platform |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202210591308.2ACN115051941A (en) | 2022-05-27 | 2022-05-27 | Enterprise big data analysis platform |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| CN115051941Atrue CN115051941A (en) | 2022-09-13 |
Family
ID=83160400
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN202210591308.2APendingCN115051941A (en) | 2022-05-27 | 2022-05-27 | Enterprise big data analysis platform |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN115051941A (en) |
Cited By (1)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN118798822A (en)* | 2024-09-10 | 2024-10-18 | 成都高新愿景数字科技有限公司 | An enterprise digital information security integrated management system |
Citations (10)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN104796290A (en)* | 2015-04-24 | 2015-07-22 | 广东电网有限责任公司信息中心 | Data security control method and data security control platform |
| EP3171568A1 (en)* | 2015-11-17 | 2017-05-24 | Zscaler, Inc. | Multi-tenant cloud-based firewall systems and methods |
| CN107683597A (en)* | 2015-06-04 | 2018-02-09 | 思科技术公司 | Network behavior data collection and analysis for abnormality detection |
| CN108337290A (en)* | 2017-12-26 | 2018-07-27 | 努比亚技术有限公司 | A kind of method and apparatus of enterprise staff user's behaviors analysis |
| CN109299044A (en)* | 2018-07-20 | 2019-02-01 | 浙江工业大学 | A security visual analysis system based on company internal logs |
| CN111915331A (en)* | 2020-08-08 | 2020-11-10 | 上海胭黛氪丝投资咨询有限公司 | Enterprise credit investigation data management method and system based on block chain |
| CN112150122A (en)* | 2020-10-16 | 2020-12-29 | 贵州电网有限责任公司 | Agile network resource positioning and decision-making system |
| CN113098892A (en)* | 2021-04-19 | 2021-07-09 | 恒安嘉新(北京)科技股份公司 | Data leakage prevention system and method based on industrial Internet |
| CN113364792A (en)* | 2021-06-11 | 2021-09-07 | 奇安信科技集团股份有限公司 | Training method of flow detection model, flow detection method, device and equipment |
| CN113872939A (en)* | 2021-08-30 | 2021-12-31 | 济南浪潮数据技术有限公司 | A flow detection method, device and storage medium |
- 2022
- 2022-05-27CNCN202210591308.2Apatent/CN115051941A/enactivePending
Patent Citations (10)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN104796290A (en)* | 2015-04-24 | 2015-07-22 | 广东电网有限责任公司信息中心 | Data security control method and data security control platform |
| CN107683597A (en)* | 2015-06-04 | 2018-02-09 | 思科技术公司 | Network behavior data collection and analysis for abnormality detection |
| EP3171568A1 (en)* | 2015-11-17 | 2017-05-24 | Zscaler, Inc. | Multi-tenant cloud-based firewall systems and methods |
| CN108337290A (en)* | 2017-12-26 | 2018-07-27 | 努比亚技术有限公司 | A kind of method and apparatus of enterprise staff user's behaviors analysis |
| CN109299044A (en)* | 2018-07-20 | 2019-02-01 | 浙江工业大学 | A security visual analysis system based on company internal logs |
| CN111915331A (en)* | 2020-08-08 | 2020-11-10 | 上海胭黛氪丝投资咨询有限公司 | Enterprise credit investigation data management method and system based on block chain |
| CN112150122A (en)* | 2020-10-16 | 2020-12-29 | 贵州电网有限责任公司 | Agile network resource positioning and decision-making system |
| CN113098892A (en)* | 2021-04-19 | 2021-07-09 | 恒安嘉新(北京)科技股份公司 | Data leakage prevention system and method based on industrial Internet |
| CN113364792A (en)* | 2021-06-11 | 2021-09-07 | 奇安信科技集团股份有限公司 | Training method of flow detection model, flow detection method, device and equipment |
| CN113872939A (en)* | 2021-08-30 | 2021-12-31 | 济南浪潮数据技术有限公司 | A flow detection method, device and storage medium |
Cited By (1)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN118798822A (en)* | 2024-09-10 | 2024-10-18 | 成都高新愿景数字科技有限公司 | An enterprise digital information security integrated management system |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| US8819807B2 (en) | Apparatus and method for analyzing and monitoring sap application traffic, and information protection system using the same | |
| US9875374B2 (en) | System and method for collecting, storing, and securing data | |
| CN112217835B (en) | Message data processing method and device, server and terminal equipment | |
| KR101504330B1 (en) | System and method for monitoring privacy information | |
| US20190098027A1 (en) | Joint defence method and apparatus for network security, and server and storage medium | |
| US9692759B1 (en) | Control of cloud application access for enterprise customers | |
| US8544100B2 (en) | Detecting secure or encrypted tunneling in a computer network | |
| CN109409045A (en) | Browser automated log on account number safety guard method and device | |
| CN111597173A (en) | Data warehouse system | |
| CN103475664A (en) | Credible extraction method for digital evidence of Android | |
| CN109639676A (en) | The method, apparatus, equipment and system of tampering detection when log transmission | |
| CN103095693A (en) | Method for positioning and accessing database user host information | |
| CN101931947A (en) | WSN data security processing method based on searchable ciphertext | |
| CN112149120A (en) | Transparent transmission type double-channel electric power Internet of things safety detection system | |
| CN115051941A (en) | Enterprise big data analysis platform | |
| CN118505235B (en) | A management method and system for e-commerce users | |
| CN111915331A (en) | Enterprise credit investigation data management method and system based on block chain | |
| CN103856443B (en) | Methods of judging and blocking outlets | |
| CN109684863B (en) | Data leakage prevention method, device, equipment and storage medium | |
| CN108833383A (en) | Linkage defense system based on deep learning and agent | |
| CN106612283A (en) | Method and device for identifying source of downloaded file | |
| CN111949476A (en) | A lightweight method and system for real-time monitoring of business health in APP | |
| CN101674191A (en) | Method for examining and monitoring internet content | |
| CN115766148A (en) | An encryption and desensitization system and method for personal biometric sensitive data | |
| Lee et al. | Web monitoring based encryption web traffic attack detection system |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| RJ01 | Rejection of invention patent application after publication | Application publication date:20220913 | |
| RJ01 | Rejection of invention patent application after publication |