CN115037452A - Data protection method and system and electronic equipment - Google Patents
Data protection method and system and electronic equipmentDownload PDFInfo
- Publication number
- CN115037452A CN115037452ACN202111400446.XACN202111400446ACN115037452ACN 115037452 ACN115037452 ACN 115037452ACN 202111400446 ACN202111400446 ACN 202111400446ACN 115037452 ACN115037452 ACN 115037452A
- Authority
- CN
- China
- Prior art keywords
- master key
- electronic device
- trust ring
- account
- ring
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Granted
Links
Images
Classifications
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
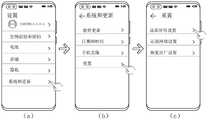
- H04L9/08—Key distribution or management, e.g. generation, sharing or updating, of cryptographic keys or passwords
- H04L9/0816—Key establishment, i.e. cryptographic processes or cryptographic protocols whereby a shared secret becomes available to two or more parties, for subsequent use
- H04L9/0819—Key transport or distribution, i.e. key establishment techniques where one party creates or otherwise obtains a secret value, and securely transfers it to the other(s)
- H04L9/0822—Key transport or distribution, i.e. key establishment techniques where one party creates or otherwise obtains a secret value, and securely transfers it to the other(s) using key encryption key
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/30—Authentication, i.e. establishing the identity or authorisation of security principals
- G06F21/45—Structures or tools for the administration of authentication
- G06F21/46—Structures or tools for the administration of authentication by designing passwords or checking the strength of passwords
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/60—Protecting data
- G06F21/602—Providing cryptographic facilities or services
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/10—Network architectures or network communication protocols for network security for controlling access to devices or network resources
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L67/00—Network arrangements or protocols for supporting network services or applications
- H04L67/01—Protocols
- H04L67/10—Protocols in which an application is distributed across nodes in the network
- H04L67/1095—Replication or mirroring of data, e.g. scheduling or transport for data synchronisation between network nodes
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L67/00—Network arrangements or protocols for supporting network services or applications
- H04L67/50—Network services
- H04L67/55—Push-based network services
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/32—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials
- H04L9/3226—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials using a predetermined code, e.g. password, passphrase or PIN
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W12/00—Security arrangements; Authentication; Protecting privacy or anonymity
- H04W12/30—Security of mobile devices; Security of mobile applications
Landscapes
- Engineering & Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- Signal Processing (AREA)
- Computer Networks & Wireless Communication (AREA)
- Theoretical Computer Science (AREA)
- Computer Hardware Design (AREA)
- General Engineering & Computer Science (AREA)
- Software Systems (AREA)
- General Physics & Mathematics (AREA)
- Physics & Mathematics (AREA)
- Computing Systems (AREA)
- Health & Medical Sciences (AREA)
- Bioethics (AREA)
- General Health & Medical Sciences (AREA)
- Storage Device Security (AREA)
Abstract
Translated fromChineseDescription
Translated fromChinese技术领域technical field
本申请实施例涉及终端设备领域,尤其涉及一种数据保护方法、系统及电子设备。The embodiments of the present application relate to the field of terminal devices, and in particular, to a data protection method, system, and electronic device.
背景技术Background technique
目前,终端设备可以将用户的数据保存在云端以便用户实时上传和下载该数据。用户的数据通常对应着某个特定的用户账号。然而,用户数据的安全完全依赖于账号安全,只要设备能够通过账号验证,就可以从云侧获得该数据。如果账号和云侧服务器中的任一个被攻击,用户数据就会发生泄露。并且,云侧服务器也存在解密用户数据的可能,云侧无法自证清白。因而,已知的方案安全性较低,无法为具有更高安全性要求的用户数据保护提供支撑。Currently, terminal devices can save user data in the cloud so that users can upload and download the data in real time. User data usually corresponds to a specific user account. However, the security of user data completely depends on account security. As long as the device can pass account verification, the data can be obtained from the cloud side. If either the account or the cloud server is attacked, user data will be leaked. In addition, the cloud-side server may also decrypt user data, and the cloud-side server cannot prove its innocence. Therefore, the known solutions have low security and cannot provide support for user data protection with higher security requirements.
发明内容SUMMARY OF THE INVENTION
本申请提供一种数据保护方法、系统及电子设备,电子设备成功入环后,在使用过程中,当检测到电子设备恢复出厂设置、关闭锁屏密码或还原所有设置时,主动触发下线流程删除电子设备的可信执行环境中的主密钥,或者被同账号设备被动下线。该数据保护方法,在电子设备入环后,当用户想要将电子设备从信任环中退出时,通过便捷地操作触发设备下线,能够提升用户的使用体验。再一方面,在恢复出厂设置、关闭锁屏密码或还原所有设置时,自动触发下线,可对同步至云端的业务数据进行保护。The present application provides a data protection method, system, and electronic device. After the electronic device successfully enters the loop, during use, when it is detected that the electronic device is restored to factory settings, the lock screen password is turned off, or all settings are restored, the offline process is actively triggered. Delete the master key in the trusted execution environment of the electronic device, or be passively offlined by the device with the same account. In the data protection method, after the electronic device enters the loop, when the user wants to withdraw the electronic device from the trust ring, the device can be offline through a convenient operation, which can improve the user experience. On the other hand, when restoring the factory settings, closing the lock screen password or restoring all settings, the offline is automatically triggered, which can protect the business data synchronized to the cloud.
第一方面,本申请实施例提供一种数据保护方法,应用于电子设备,该方法包括:依据用户输入的电子设备的锁屏码和获取的主密钥,生成电子设备的主密钥密文和认证参数;其中,所述电子设备已登录第一账号;基于主密钥密文和认证参数,在第一服务器中创建第一账号对应的第一信任环或者加入第一信任环;检测到电子设备恢复出厂设置、关闭锁屏密码或还原所有设置时,删除电子设备的可信执行环境中的主密钥。In a first aspect, an embodiment of the present application provides a data protection method, which is applied to an electronic device. The method includes: generating a master key ciphertext of the electronic device according to a screen lock code of the electronic device input by a user and an acquired master key and authentication parameters; wherein, the electronic device has logged into the first account; based on the master key ciphertext and authentication parameters, create a first trust ring corresponding to the first account in the first server or join the first trust ring; detect When the electronic device is restored to factory settings, the screen lock password is turned off, or all settings are restored, the master key in the trusted execution environment of the electronic device is deleted.
其中,本申请中的锁屏码也可以替换为其他用户信息,例如,用户信息可以是用户生日、用户姓名、父母或朋友的生日、姓名等等。这些信息是用户独有的信息,仅该用户自己知道,且该信息因用户的不同而不同。这些用户信息是用户容易记忆的,并且是云侧所不知道的。当基于用户信息对主密钥加密时,云侧无法解密,因此云侧可自证清白。除了用户自己,别人很难知道用户使用哪一个用户信息来加密主密钥,这样大大增加了主密钥密文的破解难度,提高了主密钥的安全性,进而能够提高使用主密钥的派生密钥保护的用户数据的安全性。同时,在信任环中的第2个设备及第2个以后的设备注册时,可以基于用户信息对已注册设备的身份进行验证,不需要与已注册设备进行交互,为用户提供了便利。The screen lock code in this application may also be replaced with other user information, for example, the user information may be the user's birthday, the user's name, the birthdays and names of parents or friends, and so on. This information is unique to the user, known only to the user, and varies from user to user. These user information is easy for users to remember and unknown to the cloud side. When the master key is encrypted based on user information, the cloud side cannot decrypt it, so the cloud side can prove its innocence. In addition to the user himself, it is difficult for others to know which user information the user uses to encrypt the master key, which greatly increases the difficulty of cracking the master key ciphertext and improves the security of the master key, which in turn can improve the use of the master key. Security of user data protected by derived keys. At the same time, when the second device in the trust ring and the second and subsequent devices are registered, the identity of the registered device can be verified based on the user information, and there is no need to interact with the registered device, which provides convenience for the user.
该种电子设备主动下线的方式,操作方式灵活、便捷。在恢复出厂设置、关闭锁屏密码或还原所有设置时,自动下线,可对同步至云端的业务数据进行保护。The electronic device takes the initiative to go offline, and the operation mode is flexible and convenient. When restoring the factory settings, closing the lock screen password or restoring all settings, it will automatically log off, which can protect the business data synchronized to the cloud.
根据第一方面,在删除电子设备的可信执行环境中的主密钥之后,该方法还包括:将电子设备的注册状态修改为未注册。及时的对电子设备的注册状态进行修改,便于后续加环、或创环时设备本地准确地进行注册状态确认。According to the first aspect, after deleting the master key in the trusted execution environment of the electronic device, the method further includes: modifying the registration status of the electronic device to unregistered. The registration status of the electronic device is modified in a timely manner, so that the device can confirm the registration status locally and accurately when adding a ring or creating a ring.
根据第一方面,或者以上第一方面的任意一种实现方式,依据用户输入的电子设备的锁屏码和获取的主密钥,生成所述电子设备的主密钥密文和认证参数;基于主密钥密文和认证参数,在第一服务器中创建第一账号对应的第一信任环或者加入第一信任环包括:电子设备作为第一电子设备,接收用户输入的第一电子设备的第一锁屏码,其中,第一电子设备已登录第一账号;在第一电子设备的可信执行环境中生成主密钥;基于第一锁屏码对所述主密钥进行加密,生成第一电子设备的第一主密钥密文;基于第一锁屏码生成第一认证参数;向第一服务器发送创环请求,以使第一服务器创建第一账号对应的第一信任环,并将第一主密钥密文和第一认证参数添加至第一信任环的信任环数据中,其中,创环请求中携带第一主密钥密文和第一认证参数。该种电子设备入环方法,基于用户秘密如锁屏码对账号级主密钥MK进行保护,由于用户秘密对于云侧来说是未知的,因此云侧不能对托管的主密钥密文进行解密,这样,降低了主密钥泄露的风险,提高了主密钥MK的安全性,同时使云侧能够自证清白,能够为具有高安全性要求的业务数据的数据同步提供支撑。需要说明的是,用户秘密并不局限于锁屏码,还可以为生日、问题答案等。According to the first aspect, or any implementation manner of the above first aspect, the ciphertext of the master key of the electronic device and the authentication parameters are generated according to the screen lock code of the electronic device input by the user and the obtained master key; The master key ciphertext and authentication parameters, creating the first trust ring corresponding to the first account in the first server or joining the first trust ring includes: the electronic device is used as the first electronic device, and the first electronic device of the first electronic device received by the user is input. A screen lock code, wherein the first electronic device has logged into the first account; a master key is generated in the trusted execution environment of the first electronic device; the master key is encrypted based on the first screen lock code, and the first electronic device is generated. A first master key ciphertext of an electronic device; generating a first authentication parameter based on the first screen lock code; sending a ring creation request to the first server, so that the first server creates a first trust ring corresponding to the first account, and The ciphertext of the first master key and the first authentication parameter are added to the trust ring data of the first trust ring, wherein the ring creation request carries the ciphertext of the first master key and the first authentication parameter. This method of entering the loop of an electronic device protects the account-level master key MK based on user secrets such as screen lock codes. Since the user secret is unknown to the cloud side, the cloud side cannot perform any encryption on the ciphertext of the escrowed master key. Decryption, in this way, reduces the risk of master key leakage, improves the security of the master key MK, and at the same time enables the cloud side to prove its innocence, which can provide support for data synchronization of business data with high security requirements. It should be noted that the user secret is not limited to the lock screen code, but can also be a birthday, an answer to a question, etc.
根据第一方面,或者以上第一方面的任意一种实现方式,依据用户输入的电子设备的锁屏码和获取的主密钥,生成电子设备的主密钥密文和认证参数;基于主密钥密文和认证参数,在第一服务器中创建第一账号对应的第一信任环或者加入第一信任环,包括:电子设备作为第二电子设备,接收用户输入的第二电子设备的第二锁屏码,其中,第二电子设备已登录第一账号;当第二锁屏码验证通过,接收用户输入的第一电子设备的第一锁屏码,其中第一电子设备是从第一服务器获取的第一账号对应的第一信任环的在环设备信息中的设备;当基于第一锁屏码对所述第一电子设备的身份验证通过,接收第一服务器发送的第一电子设备的第一主密钥密文;基于第一锁屏码对第一主密钥密文进行解密,得到主密钥;基于第二锁屏码对主密钥进行加密,生成第二电子设备的第二主密钥密文,以及基于第二锁屏码生成第二认证参数;向第一服务器发送加环请求,以使第一服务器将第二主密钥密文和第二认证参数添加至第一信任环的信任环数据中。According to the first aspect, or any implementation manner of the above first aspect, the master key ciphertext and authentication parameters of the electronic device are generated according to the screen lock code of the electronic device input by the user and the obtained master key; key ciphertext and authentication parameters, creating a first trust ring corresponding to the first account in the first server or joining the first trust ring, including: the electronic device is used as the second electronic device, and the second electronic device of the second electronic device received by the user is input. The screen lock code, where the second electronic device has logged into the first account; when the second screen lock code is verified, the first screen lock code of the first electronic device input by the user is received, wherein the first electronic device is obtained from the first server The device in the loop device information of the first trust ring corresponding to the obtained first account; when the identity verification of the first electronic device based on the first lock screen code is passed, receive the first electronic device sent by the first server. The first master key ciphertext; the first master key ciphertext is decrypted based on the first screen lock code to obtain the master key; the master key is encrypted based on the second screen lock code to generate the first master key of the second electronic device. The second master key ciphertext, and generating the second authentication parameter based on the second screen lock code; sending a ring-adding request to the first server, so that the first server adds the second master key ciphertext and the second authentication parameter to the first server In the trust ring data of a trust ring.
该种电子设备入环方法,基于用户秘密如锁屏码对账号级主密钥MK进行保护,由于用户秘密对于云侧来说是未知的,因此云侧不能对托管的主密钥密文进行解密,这样,降低了主密钥泄露的风险,提高了主密钥MK的安全性,同时使云侧能够自证清白,能够为具有高安全性要求的业务数据的数据同步提供支撑。This method of entering the loop of an electronic device protects the account-level master key MK based on user secrets such as screen lock codes. Since the user secret is unknown to the cloud side, the cloud side cannot perform any encryption on the ciphertext of the escrowed master key. Decryption, in this way, reduces the risk of master key leakage, improves the security of the master key MK, and at the same time enables the cloud side to prove its innocence, which can provide support for data synchronization of business data with high security requirements.
根据第一方面,或者以上第一方面的任意一种实现方式,该方法还包括:基于主密钥派生第一业务密钥,使用第一业务密钥对第一业务数据进行加密,得到第一业务数据密文;将第一业务数据密文发送给第二服务器,以使第二服务器保存第一业务数据密文。该种基于主密钥派生的业务密钥加密业务数据密文后同步上云的方式,由于主密钥云端不可知,因此上云的业务数据密文云端也不可知,能够确保业务数据的安全性,并且云端可自证清白。According to the first aspect, or any implementation manner of the above first aspect, the method further includes: deriving a first service key based on the master key, and using the first service key to encrypt the first service data to obtain the first service key. Service data ciphertext; sending the first service data ciphertext to the second server, so that the second server saves the first service data ciphertext. This method of encrypting the ciphertext of the business data based on the business key derived from the master key and then synchronizing the ciphertext to the cloud, since the master key is unknown to the cloud, the ciphertext of the business data that is uploaded to the cloud is also unknown to the cloud, which can ensure the security of the business data. sex, and the cloud can prove its innocence.
根据第一方面,或者以上第一方面的任意一种实现方式,该方法还包括:从第二服务器获取第二业务数据密文;基于主密钥派生第一业务密钥;使用第一业务密钥对第二业务数据密文进行解密,得到第二业务数据。该种从云端获取业务数据密文后在电子设备本地解密的方式,云端与电子设备间传输的业务数据密文即便被截获,由于截获仿无法获知主密钥以及主密钥派生第一业务密钥的规则,因此也无法解密得到的业务数据,能够提升业务数据的安全性。According to the first aspect, or any implementation manner of the above first aspect, the method further includes: obtaining the second service data ciphertext from the second server; deriving the first service key based on the master key; using the first service ciphertext Decrypt the ciphertext of the second service data with the key to obtain the second service data. In this method of obtaining the business data ciphertext from the cloud and decrypting it locally on the electronic device, even if the business data ciphertext transmitted between the cloud and the electronic device is intercepted, the master key and the master key to derive the first business secret cannot be obtained due to the interception. Therefore, the obtained business data cannot be decrypted, which can improve the security of business data.
第二方面,本申请实施例提供了一种数据保护方法,应用于第二电子设备,该方法包括:依据用户输入的所述第二电子设备的锁屏码和获取的主密钥,生成第二电子设备的主密钥密文和认证参数;其中,第二电子设备已登录第一账号;In a second aspect, an embodiment of the present application provides a data protection method, which is applied to a second electronic device. The method includes: generating a second electronic device according to a screen lock code of the second electronic device input by a user and an acquired master key. The master key ciphertext and authentication parameters of the second electronic device; wherein, the second electronic device has logged into the first account;
基于主密钥密文和认证参数,在第一服务器中创建第一账号对应的第一信任环或者加入第一信任环;接收到第一服务器发送的主密钥删除消息,其中,主密钥删除消息,是由第一服务器在第二电子设备被第一电子设备从第一账号中移除的情况下生成的;删除第二电子设备的可信执行环境中的主密钥。Create a first trust ring corresponding to the first account in the first server or join the first trust ring based on the master key ciphertext and authentication parameters; receive a master key deletion message sent by the first server, wherein the master key The deletion message is generated by the first server when the second electronic device is removed from the first account by the first electronic device; the master key in the trusted execution environment of the second electronic device is deleted.
该种电子设备被动下线的方式,用户跨设备远程操作电子设备下线,操作方式灵活、便捷。In the passive offline mode of the electronic device, the user remotely operates the electronic device offline across the devices, and the operation mode is flexible and convenient.
根据第二方面,该方法在删除电子设备的可信执行环境中的主密钥之后,还包括:将第二电子设备的注册状态修改为未注册。及时的对电子设备的注册状态进行修改,便于后续加环、或创环时设备本地准确地进行注册状态确认。According to the second aspect, after deleting the master key in the trusted execution environment of the electronic device, the method further includes: modifying the registration status of the second electronic device to unregistered. The registration status of the electronic device is modified in a timely manner, so that the device can confirm the registration status locally and accurately when adding a ring or creating a ring.
第三方面,本申请实施例提供一种电子设备,包括信任环服务模块和信任环模块,其中:信任环服务模块,用于:依据用户输入的电子设备的锁屏码和获取的主密钥,生成认证参数;其中,电子设备已登录第一账号;信任环模块,用于:依据锁屏码和主密钥,生成电子设备的主密钥密文;信任环服务模块,还用于:基于主密钥密文和认证参数,在第一服务器中创建第一账号对应的第一信任环或者加入第一信任环;信任环服务模块,用于:检测到电子设备恢复出厂设置、关闭锁屏密码或还原所有设置时,向信任环模块发送主密钥删除指令;信任环模块,用于:响应于主密钥删除指令,删除电子设备的可信执行环境中的主密钥。In a third aspect, an embodiment of the present application provides an electronic device, including a trust ring service module and a trust ring module, wherein: the trust ring service module is used for: a screen lock code of the electronic device input by a user and an acquired master key , to generate authentication parameters; wherein, the electronic device has logged into the first account; the trust ring module is used to: generate the master key ciphertext of the electronic device according to the screen lock code and the master key; the trust ring service module is also used to: Based on the ciphertext of the master key and the authentication parameters, a first trust ring corresponding to the first account is created in the first server or added to the first trust ring; the trust ring service module is used for: detecting that the electronic device is restored to factory settings and closing the lock When the screen password is displayed or all settings are restored, a master key deletion instruction is sent to the trust ring module; the trust ring module is used for: in response to the master key deletion instruction, delete the master key in the trusted execution environment of the electronic device.
根据第三方面,信任环服务模块,还用于:在删除电子设备的可信执行环境中的主密钥之后,将电子设备的注册状态修改为未注册。According to the third aspect, the trust ring service module is further configured to: after deleting the master key in the trusted execution environment of the electronic device, modify the registration state of the electronic device to unregistered.
根据第三方面,或者以上第三方面的任意一种实现方式,电子设备作为第一电子设备,信任环服务模块,用于:接收用户输入的第一电子设备的第一锁屏码,根据第一锁屏码生成第一派生密钥,并将第一派生密钥发送至信任环模块,其中,第一电子设备已登录第一账号;信任环模块,用于:在可信执行环境中生成主密钥,基于第一派生密钥对主密钥进行加密,生成第一电子设备的第一主密钥密文,并将第一主密钥密文发送至信任环服务模块;信任环服务模块,还用于:基于第一派生密钥生成第一认证参数,向第一服务器发送创环请求,以使第一服务器创建第一账号对应的第一信任环,并将第一主密钥密文和第一认证参数添加至第一信任环的信任环数据中,其中,创环请求中携带第一主密钥密文和第一认证参数。According to the third aspect, or any implementation manner of the above third aspect, the electronic device is used as the first electronic device, and the trust ring service module is configured to: receive the first screen lock code of the first electronic device input by the user, and according to the first electronic device A screen lock code generates a first derived key, and sends the first derived key to the trust ring module, wherein the first electronic device has logged in to the first account; the trust ring module is used for: generating in a trusted execution environment master key, encrypts the master key based on the first derived key, generates the first master key ciphertext of the first electronic device, and sends the first master key ciphertext to the trust ring service module; trust ring service The module is further configured to: generate a first authentication parameter based on the first derived key, and send a ring-creation request to the first server, so that the first server creates a first trust ring corresponding to the first account, and the first master key The ciphertext and the first authentication parameter are added to the trust ring data of the first trust ring, wherein the ring creation request carries the ciphertext of the first master key and the first authentication parameter.
根据第三方面,或者以上第三方面的任意一种实现方式,电子设备作为第二电子设备;信任环服务模块,用于:接收用户输入的第二电子设备的第二锁屏码,其中,第二电子设备已登录第一账号;当第二锁屏码验证通过,接收用户输入的第一电子设备的第一锁屏码,其中,第一电子设备是从第一服务器获取的第一账号对应的第一信任环的在环设备信息;当基于第一锁屏码对第一电子设备的身份验证通过,接收第一服务器发送的第一电子设备的第一主密钥密文;将第一主密钥密文发送给信任环模块;信任环模块,用于:基于第一锁屏码对第一主密钥密文进行解密,得到主密钥;基于第二锁屏码对主密钥进行加密,生成第二电子设备的第二主密钥密文;将第二主密钥密文发送给信任环服务模块;信任环服务模块,还用于:基于第二锁屏码生成第二认证参数;向第一服务器发送加环请求,以使第一服务器第二主密钥密文和第二认证参数添加至第一信任环的信任环数据中。According to the third aspect, or any implementation manner of the above third aspect, the electronic device is used as the second electronic device; the trust ring service module is configured to: receive the second screen lock code of the second electronic device input by the user, wherein, The second electronic device has logged into the first account; when the verification of the second screen lock code is passed, the first screen lock code of the first electronic device input by the user is received, wherein the first electronic device is the first account obtained from the first server Corresponding in-loop device information of the first trust ring; when the identity verification of the first electronic device based on the first screen lock code is passed, receive the first master key ciphertext of the first electronic device sent by the first server; A master key ciphertext is sent to the trust ring module; the trust ring module is used for: decrypting the first master key ciphertext based on the first screen lock code to obtain the master key; based on the second screen lock code to decrypt the master key encryption key to generate the second master key ciphertext of the second electronic device; sending the second master key ciphertext to the trust ring service module; the trust ring service module is also used for: generating the first key based on the second screen lock code Two authentication parameters; sending a ring adding request to the first server, so that the first server's second master key ciphertext and the second authentication parameter are added to the trust ring data of the first trust ring.
根据第三方面,或者以上第三方面的任意一种实现方式,电子设备还包括:业务数据同步服务模块、业务数据存储服务模块以及密钥管理模块;信任环服务模块,还用于:基于主密钥派生第一业务密钥,业务数据存储服务模块,用于:将第一业务数据发送至密钥管理模块;密钥管理模块,用于:从信任环模块读取第一业务密钥,使用第一业务密钥对第一业务数据进行加密,得到第一业务数据密文;将第一业务数据密文发送至业务数据存储服务模块;业务数据存储服务模块,还用于:通过业务数据同步服务模块,将第一业务数据密文发送至第二服务器,以使第二服务器保存第一业务数据密文。According to the third aspect, or any implementation manner of the above third aspect, the electronic device further includes: a business data synchronization service module, a business data storage service module, and a key management module; a trust ring service module, which is further configured to: The key derives the first service key, and the service data storage service module is used for: sending the first service data to the key management module; the key management module is used for: reading the first service key from the trust ring module, Encrypting the first service data by using the first service key to obtain the ciphertext of the first service data; sending the ciphertext of the first service data to the service data storage service module; the service data storage service module is also used to: pass the service data The synchronization service module sends the ciphertext of the first service data to the second server, so that the second server stores the ciphertext of the first service data.
根据第三方面,或者以上第三方面的任意一种实现方式,业务数据同步服务模块,还用于:从第二服务器获取第二业务数据密文,将第二业务数据密文存储至业务数据存储服务模块;业务数据存储服务模块,还用于:将第二业务数据发送至密钥管理模块;密钥管理模块,还用于:从信任环模块读取第一业务密钥,使用第一业务密钥对第二业务数据进行解密得到第二业务数据,将第二业务数据存储至业务数据存储服务模块中。According to the third aspect, or any implementation manner of the above third aspect, the business data synchronization service module is further configured to: obtain the ciphertext of the second business data from the second server, and store the ciphertext of the second business data in the business data A storage service module; a service data storage service module, further used for: sending the second service data to the key management module; the key management module, further used for: reading the first service key from the trust ring module, and using the first service key The service key decrypts the second service data to obtain the second service data, and stores the second service data in the service data storage service module.
第四方面,本申请实施例提供了一种电子设备,作为第二电子设备,包括:信任环服务模块和信任环模块,其中:信任环服务模块,用于:依据用户输入的第二电子设备的锁屏码和获取的主密钥,生成认证参数;其中电子设备已登录第一账号;信任环模块,用于:依据锁屏码和主密钥,生成电子设备的主密钥密文;信任环服务模块,还用于:基于主密钥密文和认证参数,在第一服务器中创建第一账号对应的第一信任环或者加入第一信任环;信任环服务模块,用于:接收到第一服务器发送的主密钥删除消息,其中,主密钥删除消息,是由第一服务器在第二电子设备被第一电子设备从第一账号中移除的情况下生成的;向信任环模块发送主密钥删除指令;信任环模块,用于:响应于主密钥删除指令,删除第二电子设备的可信执行环境中的主密钥。In a fourth aspect, an embodiment of the present application provides an electronic device, as a second electronic device, including: a trust ring service module and a trust ring module, wherein: the trust ring service module is used for: according to the second electronic device input by the user The screen lock code and the obtained master key are generated to generate authentication parameters; wherein the electronic device has logged into the first account; the trust ring module is used to: generate the master key ciphertext of the electronic device according to the screen lock code and the master key; The trust ring service module is further configured to: create a first trust ring corresponding to the first account in the first server or join the first trust ring based on the master key ciphertext and authentication parameters; the trust ring service module is used for: receiving The master key deletion message sent to the first server, wherein the master key deletion message is generated by the first server when the second electronic device is removed from the first account by the first electronic device; The ring module sends a master key deletion instruction; the trust ring module is used for: in response to the master key deletion instruction, delete the master key in the trusted execution environment of the second electronic device.
根据第四方面,信任环服务模块,还用于:在删除电子设备的可信执行环境中的主密钥之后,将第二电子设备的注册状态修改为未注册。According to the fourth aspect, the trust ring service module is further configured to: after deleting the master key in the trusted execution environment of the electronic device, modify the registration status of the second electronic device to unregistered.
第五方面,本申请实施例提供了一种数据保护系统,其特征在于,包括第一电子设备、第二电子设备和第一服务器、第二服务器,其中:第一电子设备,用于:响应于将第二电子设备从第一账号中移除的操作,向第二服务器发送从第一账号中移除第二电子设备的通知;第二服务器,用于:响应于从第一账号中移除第二电子设备的通知,向第一服务器发送将第二电子设备从第一账号的第一信任环删除的通知;第一服务器,用于:响应于将第二电子设备从第一账号的第一信任环删除的通知,向第二电子设备发送主密钥删除消息;第二电子设备,用于:响应于主密钥删除消息,删除第二电子设备的可信执行环境中的主密钥。In a fifth aspect, an embodiment of the present application provides a data protection system, characterized in that it includes a first electronic device, a second electronic device, a first server, and a second server, wherein: the first electronic device is used for: responding to In the operation of removing the second electronic device from the first account, send a notification to the second server to remove the second electronic device from the first account; the second server is used for: in response to removing the second electronic device from the first account In addition to the notification of the second electronic device, send a notification to the first server to delete the second electronic device from the first trust ring of the first account; the first server is configured to: in response to removing the second electronic device from the first account of the first account The notification of deletion of the first trust ring, sending a master key deletion message to the second electronic device; the second electronic device is configured to: in response to the master key deletion message, delete the master key in the trusted execution environment of the second electronic device key.
第三方面以及第三方面的任意一种实现方式分别与第一方面以及第一方面的任意一种实现方式相对应。第三方面以及第三方面的任意一种实现方式所对应的技术效果可参见上述第一方面以及第一方面的任意一种实现方式所对应的技术效果,此处不再赘述。The third aspect and any implementation manner of the third aspect correspond to the first aspect and any implementation manner of the first aspect, respectively. For the technical effects corresponding to the third aspect and any implementation manner of the third aspect, reference may be made to the technical effects corresponding to the first aspect and any implementation manner of the first aspect, which will not be repeated here.
第四方面以及第四方面的任意一种实现方式分别与第一方面以及第一方面的任意一种实现方式相对应。第二方面以及第二方面的任意一种实现方式所对应的技术效果可参见上述第一方面以及第一方面的任意一种实现方式所对应的技术效果,此处不再赘述。The fourth aspect and any implementation manner of the fourth aspect correspond to the first aspect and any implementation manner of the first aspect, respectively. For the technical effects corresponding to the second aspect and any implementation manner of the second aspect, reference may be made to the technical effects corresponding to the first aspect and any implementation manner of the first aspect, which will not be repeated here.
第六方面,本申请提供了一种计算机可读介质,用于存储计算机程序,该计算机程序包括用于执行第一方面或第一方面的任意可能的实现方式中的方法的指令,或者用于执行第二方面或第二方面的任意可能的实现方式中的方法的指令。In a sixth aspect, the present application provides a computer-readable medium for storing a computer program, the computer program comprising instructions for executing the method in the first aspect or any possible implementation manner of the first aspect, or for Instructions for performing the method of the second aspect or any possible implementation of the second aspect.
第七方面,本申请提供了一种计算机程序,该计算机程序包括用于执行第一方面或第一方面的任意可能的实现方式中的方法的指令,或者用于执行第二方面或第二方面的任意可能的实现方式中的方法的指令。In a seventh aspect, the present application provides a computer program comprising instructions for performing the first aspect or the method in any possible implementation of the first aspect, or for performing the second aspect or the second aspect A directive for a method in any possible implementation of .
附图说明Description of drawings
图1为示例性示出的电子设备100的结构示意图;FIG. 1 is a schematic structural diagram of an exemplary electronic device 100;
图2为示例性示出的本申请实施例的电子设备100的软件结构框图;FIG. 2 is a block diagram illustrating the software structure of the electronic device 100 according to the embodiment of the present application;
图3为示例性示出的创建信任环过程中的信息交互示意图;3 is an exemplary schematic diagram of information interaction in the process of creating a trust ring;
图4为示例性示出的创建信任环过程中设备与云侧的交互示意图;4 is a schematic diagram of the interaction between a device and a cloud side in an exemplary process of creating a trust ring;
图5A为示例性示出的已登录账号情况下进入“我的设备”应用的界面示意图;FIG. 5A is a schematic diagram of the interface of entering the “My Device” application in the case of an exemplary logged-in account;
图5B为示例性示出的未登录账号情况下进入“我的设备”应用的界面示意图;5B is an exemplary interface diagram of entering the "My Device" application without logging in to an account;
图6为示例性示出的从设备A中“我的设备”应用进入到“密码保险箱同步”应用的界面示意图;Fig. 6 is the interface schematic diagram exemplarily shown entering from the "My Device" application in the device A to the "Password Safe Sync" application;
图7A是示例性示出的设备A已设置锁屏码情况下进入“密码保险箱”界面的过程示意图;7A is a schematic diagram illustrating the process of entering a “password safe” interface when device A has set a screen lock code;
图7B是示例性示出的设备A未设置锁屏码情况下进入“密码保险箱”界面的过程示意图;Fig. 7B is the schematic diagram of the process of entering the "password safe" interface when the device A is exemplarily shown without setting the lock screen code;
图8为示例性示出的创建信任环的场景下开启“密码保险箱同步”开关的过程示意图;8 is a schematic diagram of the process of turning on the "password safe synchronization" switch under the scenario of creating a trust ring exemplarily shown;
图9为示例性示出的创建信任环的场景下开启“同步到荣耀账号”开关的过程示意图;9 is a schematic diagram of the process of turning on the "synchronize to Honor account" switch under the scenario of creating a trust ring exemplarily shown;
图10为示例性示出的创建信任环的流程示意图;FIG. 10 is an exemplary schematic flowchart of creating a trust ring;
图11为示例性示出的创建信任环后设备A同步业务数据密文到账号管理服务器的示意图;11 is an exemplary schematic diagram of device A synchronizing service data ciphertext to an account management server after a trust ring is created;
图12为示例性示出的同步业务数据密文的模块交互示意图;12 is an exemplary schematic diagram of module interaction for synchronizing service data ciphertext;
图13为示例性示出的同步业务数据密文到账号管理服务器的界面示意图;13 is an exemplary interface schematic diagram of synchronizing service data ciphertext to an account management server;
图14为示例性示出的设备B加入信任环过程中的信息交互示意图;FIG. 14 is an exemplary schematic diagram of information exchange in the process of device B joining the trust ring;
图15为示例性示出的从设备B中“我的设备”应用进入到“密码保险箱同步”应用的界面示意图;FIG. 15 is a schematic diagram of an interface for entering the “Password Safe Sync” application from the “My Device” application in the device B exemplarily shown;
图16A是示例性示出的设备B已设置锁屏码情况下进入“密码保险箱”界面并开启“密码保险箱同步”开关的过程示意图;16A is a schematic diagram illustrating the process of entering the “Password Safe” interface and turning on the “Password Safe Synchronization” switch when the device B has set a lock screen code;
图16B是示例性示出的设备B未设置锁屏码情况下进入“密码保险箱”界面并开启“密码保险箱同步”开关的过程示意图;16B is a schematic diagram illustrating the process of entering the “Password Safe” interface and turning on the “Password Safe Synchronization” switch when Device B does not set a lock screen code;
图17为示例性示出的设备B加入信任环的场景下开启“同步到荣耀账号”开关的过程示意图;17 is a schematic diagram of the process of turning on the switch of "synchronize to the Honor account" under the scenario that the device B joins the trust ring shown in an exemplary manner;
图18为示例性示出的设备B加入信任环的流程示意图;FIG. 18 is a schematic flowchart of an exemplary process of adding a trust ring to a device B;
图19为示例性示出的设备B加入信任环后从账号管理服务器同步业务数据密文的示意图;19 is an exemplary schematic diagram of synchronizing service data ciphertext from an account management server after device B joins the trust ring;
图20为示例性示出的从账号管理服务器同步业务数据密文的界面示意图;20 is an exemplary interface schematic diagram of synchronizing business data ciphertext from an account management server;
图21为示例性示出的设备C加入信任环过程中的信息交互示意图;FIG. 21 is an exemplary schematic diagram of information exchange in the process of device C joining the trust ring;
图22为示例性示出的设备C加入信任环的场景下开启“同步到荣耀账号”开关的过程中输入在环设备锁屏码的流程示意图;22 is a schematic flowchart of inputting the lock screen code of the device in the ring in the process of turning on the “sync to glory account” switch under the scenario that the device C is exemplarily added to the trust ring;
图23为示例性示出的关闭锁屏密码过程的界面示意图;Fig. 23 is the interface schematic diagram of the process of closing the lock screen password exemplarily shown;
图24为示例性示出的恢复出厂设置过程的界面示意图;FIG. 24 is a schematic interface diagram of an exemplary process of restoring factory settings;
图25为示例性示出的还原所有设置过程的界面示意图;FIG. 25 is a schematic interface diagram of an exemplary process of restoring all settings;
图26为示例性示出的设备A的下线流程示意图;Figure 26 is a schematic diagram of the offline process of the exemplary shown device A;
图27为示例性示出的设备B下线过程中的信息交互示意图;FIG. 27 is an exemplary schematic diagram of information interaction during the offline process of device B;
图28为示例性示出的从账号中移除设备过程的界面示意图;FIG. 28 is a schematic interface diagram of a process of removing a device from an account;
图29为示例性示出的设备B的下线流程示意图。FIG. 29 is a schematic diagram of the offline process of the device B shown by way of example.
具体实施方式Detailed ways
下面将结合本申请实施例中的附图,对本申请实施例中的技术方案进行清楚、完整地描述,显然,所描述的实施例是本申请一部分实施例,而不是全部的实施例。基于本申请中的实施例,本领域普通技术人员在没有作出创造性劳动前提下所获得的所有其他实施例,都属于本申请保护的范围。The technical solutions in the embodiments of the present application will be clearly and completely described below with reference to the accompanying drawings in the embodiments of the present application. Obviously, the described embodiments are part of the embodiments of the present application, not all of the embodiments. Based on the embodiments in the present application, all other embodiments obtained by those of ordinary skill in the art without creative work fall within the protection scope of the present application.
本文中术语“和/或”,仅仅是一种描述关联对象的关联关系,表示可以存在三种关系,例如,A和/或B,可以表示:单独存在A,同时存在A和B,单独存在B这三种情况。The term "and/or" in this article is only an association relationship to describe the associated objects, indicating that there can be three kinds of relationships, for example, A and/or B, it can mean that A exists alone, A and B exist at the same time, and A and B exist independently B these three cases.
本申请实施例的说明书和权利要求书中的术语“第一”和“第二”等是用于区别不同的对象,而不是用于描述对象的特定顺序。例如,第一目标对象和第二目标对象等是用于区别不同的目标对象,而不是用于描述目标对象的特定顺序。The terms "first" and "second" in the description and claims of the embodiments of the present application are used to distinguish different objects, rather than to describe a specific order of the objects. For example, the first target object, the second target object, etc. are used to distinguish different target objects, rather than to describe a specific order of the target objects.
在本申请实施例中,“示例性的”或者“例如”等词用于表示作例子、例证或说明。本申请实施例中被描述为“示例性的”或者“例如”的任何实施例或设计方案不应被解释为比其它实施例或设计方案更优选或更具优势。确切而言,使用“示例性的”或者“例如”等词旨在以具体方式呈现相关概念。In the embodiments of the present application, words such as "exemplary" or "for example" are used to represent examples, illustrations or illustrations. Any embodiments or designs described in the embodiments of the present application as "exemplary" or "such as" should not be construed as preferred or advantageous over other embodiments or designs. Rather, the use of words such as "exemplary" or "such as" is intended to present the related concepts in a specific manner.
在本申请实施例的描述中,除非另有说明,“多个”的含义是指两个或两个以上。例如,多个处理单元是指两个或两个以上的处理单元;多个系统是指两个或两个以上的系统。In the description of the embodiments of the present application, unless otherwise specified, the meaning of "plurality" refers to two or more. For example, multiple processing units refers to two or more processing units; multiple systems refers to two or more systems.
图1为示例性示出的电子设备100的结构示意图。应该理解的是,图1所示电子设备100仅是电子设备的一个范例,并且电子设备100可以具有比图中所示的更多的或者更少的部件,可以组合两个或多个的部件,或者可以具有不同的部件配置。图1中所示出的各种部件可以在包括一个或多个信号处理和/或专用集成电路在内的硬件、软件、或硬件和软件的组合中实现。FIG. 1 is a schematic structural diagram of an exemplary electronic device 100 . It should be understood that the electronic device 100 shown in FIG. 1 is only an example of an electronic device, and the electronic device 100 may have more or less components than those shown in the figure, and two or more components may be combined , or can have a different component configuration. The various components shown in FIG. 1 may be implemented in hardware, software, or a combination of hardware and software, including one or more signal processing and/or application specific integrated circuits.
其中,电子设备100可以为手机、平板等。The electronic device 100 may be a mobile phone, a tablet, or the like.
电子设备100可以包括:处理器110,外部存储器接口120,内部存储器121,通用串行总线(universal serial bus,USB)接口130,充电管理模块140,电源管理模块141,电池142,天线1,天线2,移动通信模块150,无线通信模块160,音频模块170,扬声器 170A,受话器170B,麦克风170C,耳机接口170D,传感器模块180,按键190,马达 191,指示器192,摄像头193,显示屏194,以及用户标识模块(subscriber identification module,SIM)卡接口195等。其中传感器模块180可以包括压力传感器180A,陀螺仪传感器180B,气压传感器180C,磁传感器180D,加速度传感器180E,距离传感器180F,接近光传感器180G,指纹传感器180H,温度传感器180J,触摸传感器180K,环境光传感器180L,骨传导传感器180M等。The electronic device 100 may include: a
电子设备100的软件系统可以采用分层架构、事件驱动架构、微核架构、微服务架构,或云架构。本申请实施例以分层架构的Android系统为例,示例性说明电子设备100 的软件结构。The software system of the electronic device 100 may adopt a layered architecture, an event-driven architecture, a microkernel architecture, a microservice architecture, or a cloud architecture. The embodiments of the present application take an Android system with a layered architecture as an example to exemplarily describe the software structure of the electronic device 100 .
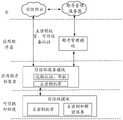
电子设备100的分层架构将软件分成若干个层,每一层都有清晰的角色和分工。层与层之间通过软件接口通信。在一些实施例中,将Android系统分为三层,从上至下分别为应用程序层,应用程序框架层,以及内核层。The layered architecture of the electronic device 100 divides the software into several layers, and each layer has a clear role and division of labor. Layers communicate with each other through software interfaces. In some embodiments, the Android system is divided into three layers, which are an application layer, an application framework layer, and a kernel layer from top to bottom.
应用程序层可以包括一系列应用程序包。The application layer can include a series of application packages.
如图2所示,应用程序包可以包括传感器(也可以称为桌面和壁纸)、HMS core、信任环、密码保险箱等应用程序。示例性的,传感器可以监测用户对屏幕的滑动、按压等操作,HMS core提供电子设备端、云开放能力的合集。信任环应用用于为账号创建、管理信任环,其中,对信任环的管理包括但不限于:向信任环中添加设备、从信任环中删除设备、删除信任环、冻结信任环、更新信任环下的主密钥密文等。密码保险箱用于管理用户同步至账号管理服务器的业务数据,例如:某业务的登录账号和密码。As shown in Figure 2, the application package can include applications such as sensors (also called desktop and wallpaper), HMS core, trust ring, password safe, etc. Exemplarily, the sensor can monitor the user's sliding, pressing and other operations on the screen, and the HMS core provides a collection of electronic device-side and cloud open capabilities. The trust ring application is used to create and manage a trust ring for an account. The management of the trust ring includes but is not limited to: adding a device to the trust ring, deleting a device from the trust ring, deleting the trust ring, freezing the trust ring, and updating the trust ring ciphertext of the master key, etc. The password safe is used to manage the business data synchronized by the user to the account management server, such as the login account and password of a business.
应用程序框架层为应用程序层的应用程序提供应用编程接口(applicationprogramming interface,API)和编程框架。应用程序框架层包括一些预先定义的函数。The application framework layer provides an application programming interface (application programming interface, API) and a programming framework for the applications of the application layer. The application framework layer includes some predefined functions.
如图2所示,应用程序框架层可以包括窗口管理器、视图系统、F接口以及资源管理器等。As shown in Figure 2, the application framework layer may include a window manager, a view system, an F interface, a resource manager, and the like.
窗口管理器用于管理窗口程序。窗口管理器可以获取显示屏大小,判断是否有状态栏,锁定屏幕,截取屏幕,向视图系统发送界面信息显示指令等。A window manager is used to manage window programs. The window manager can obtain the size of the display screen, determine whether there is a status bar, lock the screen, take screenshots, and send interface information display instructions to the view system.
视图系统包括可视控件,例如显示文字的控件,显示图片的控件等。视图系统可用于构建应用程序。显示界面可以由一个或多个视图组成的。例如,包括短信通知图标的显示界面,可以包括显示文字的视图以及显示图片的视图。The view system includes visual controls, such as controls for displaying text, controls for displaying pictures, and so on. View systems can be used to build applications. A display interface can consist of one or more views. For example, the display interface including the short message notification icon may include a view for displaying text and a view for displaying pictures.
资源管理器为应用程序提供各种资源,比如本地化字符串,图标,图片,布局文件,视频文件等等。The resource manager provides various resources for the application, such as localization strings, icons, pictures, layout files, video files and so on.
F接口为信任环的对外服务接口。The F interface is the external service interface of the trust ring.
应用程序层和应用程序框架层运行在虚拟机中。虚拟机将应用程序层和应用程序框架层的java文件执行为二进制文件。虚拟机用于执行对象生命周期的管理,堆栈管理,线程管理,安全和异常的管理,以及垃圾回收等功能。The application layer and the application framework layer run in virtual machines. The virtual machine executes the java files of the application layer and the application framework layer as binary files. The virtual machine is used to perform functions such as object lifecycle management, stack management, thread management, safety and exception management, and garbage collection.
系统库可以包括多个功能模块。例如:二维图形引擎(例如:SGL)、关键资产信任环CA、表面管理器等。A system library can include multiple functional modules. For example: 2D graphics engine (eg: SGL), key asset trust ring CA, surface manager, etc.
表面管理器用于对显示子系统进行管理,并且为多个应用程序提供了2D和3D图层的融合。二维图形引擎是二维图像的绘图引擎。The Surface Manager is used to manage the display subsystem and provides a fusion of 2D and 3D layers for multiple applications. A 2D graphics engine is a drawing engine for 2D images.
关键资产信任环CA又可称为信任环服务模块,主要用于上层信任环应用与下层关键资产信任环TA之间的消息透传。The key asset trust ring CA can also be called the trust ring service module, which is mainly used for the transparent transmission of messages between the upper-layer trust ring application and the lower-layer key asset trust ring TA.
内核层是硬件和软件之间的层。内核层至少包含显示驱动,传感器驱动,W-iFi驱动以及关键资产信任环TA。显示驱动用于驱动显示屏194,Wi-Fi驱动用于驱动无线通信模块160,传感器驱动用于驱动传感器模块180。The kernel layer is the layer between hardware and software. The kernel layer contains at least display driver, sensor driver, W-iFi driver and key asset trust ring TA. The display driver is used to drive the display screen 194 , the Wi-Fi driver is used to drive the
关键资产信任环TA又可称为信任环模块,用于实现核心安全逻辑,提供可信任执行环境,在可信任执行环境中生成主密钥、对主密钥进行加密生成主密钥密文等。对于关键资产信任环CA、关键资产信任环TA的具体功能,参照下文中创环、加环、删环、防暴、信任环中设备下线、更新主密钥、更新主密钥密文等流程说明中的相关介绍即可。The key asset trust ring TA can also be called the trust ring module, which is used to implement the core security logic, provide a trusted execution environment, generate the master key in the trusted execution environment, encrypt the master key to generate the master key ciphertext, etc. . For the specific functions of the key asset trust ring CA and key asset trust ring TA, please refer to the following procedures for creating a ring, adding a ring, deleting a ring, anti-riot, device offline in the trust ring, updating the master key, and updating the ciphertext of the master key. The relevant introduction in the description is enough.
可以理解的是,图2示出的系统框架层与运行时层包含的部件,并不构成对电子设备100的具体限定。在本申请另一些实施例中,电子设备100可以包括比图示更多或更少的部件,或者组合某些部件,或者拆分某些部件,或者不同的部件布置。It can be understood that the components included in the system framework layer and the runtime layer shown in FIG. 2 do not constitute a specific limitation on the electronic device 100 . In other embodiments of the present application, the electronic device 100 may include more or less components than shown, or combine some components, or separate some components, or arrange different components.
在使用电子设备时,用户通常需要记忆很多密码数据,例如邮箱账号的密码、网盘账号的密码、智能家居控制权的密码等等。当这类密码数据较多时,如果让用户独立记录每种业务的密码数据,会给用户记忆造成较大的困难。因此,用户希望通过数据同步功能,将这类密码数据上传到云侧进行存储,使用时直接从云侧获取,而不必用户自己记忆。When using electronic devices, users usually need to memorize a lot of password data, such as email account passwords, network disk account passwords, and smart home control passwords. When there is a lot of such password data, if the user is allowed to independently record the password data of each service, it will cause great difficulty for the user to remember. Therefore, the user hopes to upload such password data to the cloud side for storage through the data synchronization function, and obtain it directly from the cloud side when using it, without the need for the user to memorize it.
然而,对于这类密码数据,用户具有与一般的待同步数据,例如,对于图片、通讯录、短信息等数据,不同的安全性要求。这类密码数据一旦泄露,将会给用户造成巨大损失。因此,用户对这类密码数据具有较高的安全性要求。此时,云侧不可自证清白的缺点使得同步到云侧的数据的安全性降低,无法满足这类密码数据的高安全性要求。However, for this type of password data, users have different security requirements from general data to be synchronized, for example, data such as pictures, address books, and short messages. Once such password data is leaked, it will cause huge losses to users. Therefore, users have higher security requirements for such password data. At this time, the cloud side cannot prove its innocence by itself, which reduces the security of the data synchronized to the cloud side, and cannot meet the high security requirements of such password data.
本申请提供一种使云侧能够自证清白的数据保护方法,能够为密码数据这类高安全性要求的业务数据的数据同步提供支撑。The present application provides a data protection method that enables the cloud side to self-certify innocence, and can provide support for data synchronization of business data with high security requirements such as password data.
下面结合附图,对本申请的数据保护方法进行详细说明。The data protection method of the present application will be described in detail below with reference to the accompanying drawings.
创建信任环Create a trust ring
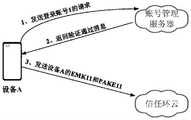
图3为示例性示出的创建信任环过程中的信息交互示意图。图4为示例性示出的创建信任环过程中设备与云侧的交互示意图。图10为示例性示出的创建信任环的流程示意图。FIG. 3 is an exemplary schematic diagram of information interaction in the process of creating a trust ring. FIG. 4 is an exemplary schematic diagram of interaction between a device and a cloud side in the process of creating a trust ring. FIG. 10 is an exemplary schematic flowchart of creating a trust ring.
下面结合图3、图4和图10,对本申请实施例的创建信任环过程进行详细说明。The following describes the process of creating a trust ring in this embodiment of the present application in detail with reference to FIG. 3 , FIG. 4 , and FIG. 10 .
本申请实施例中,假设设备A的荣耀账号为账号1,并以设备A向信任环云首次发起注册,创建账号1的信任环1为例对创建信任环的过程进行说明。其中,可以触发创建信任环流程的应用可以是荣耀账号下的任一个应用,本文中,以通过荣耀账号下的“密码保险箱同步”应用触发创建信任环流程为例进行说明。In the embodiment of this application, it is assumed that the glory account of device A is
其中,本文中的“注册”是指将设备添加到信任环中的过程。其中,首个设备注册时由于账号下还没有信任环,因此需要先创建信任环再将设备添加到信任环中,本文中将首个设备注册的过程称为创建信任环。非首设备注册时只需要将设备添加到已有的信任环,本文中将非首设备注册的过程称为加入信任环。Among them, "registration" in this article refers to the process of adding a device to the trust ring. Among them, since there is no trust ring under the account when the first device is registered, it is necessary to create a trust ring before adding the device to the trust ring. In this article, the process of registering the first device is called creating a trust ring. When the non-first device is registered, it only needs to add the device to the existing trust ring. In this article, the process of registering the non-first device is called joining the trust ring.
本文中假设账号1下包括3个设备,分别为荣耀V40(即设备A)、荣耀V30(记为设备B)、荣耀V50(记为设备C)。In this article, it is assumed that
需要说明的是,本文中各种云所执行的动作应当理解为相应云中的服务器所执行的动作。例如,信任环云所执行的动作是由信任环云服务器执行的。It should be noted that the actions performed by various clouds herein should be understood as actions performed by servers in the corresponding cloud. For example, the actions performed by the trust ring cloud are performed by the trust ring cloud server.
请参见图3,在创建信任环过程中,设备A向账号管理服务器发送登录账号1的请求,账号管理服务器对登录账号1的请求验证通过后,向设备A返回验证通过消息;设备A在接收到验证通过消息后,生成设备A的主密钥密文EMK11和设备A的认证参数 PAKE11,并将EMK11和PAKE11发送至信任环云,信任环云接收到设备A发送的EMK11 和PAKE11后,为账号1创建信任环1,并将设备A添加到信任环1中。Referring to Figure 3, in the process of creating a trust ring, device A sends a request for logging in to account 1 to the account management server. After the account management server verifies the request for logging in to
请参见图10,本申请实施例中,设备A创建信任环的过程可以包括如下步骤:Referring to FIG. 10 , in this embodiment of the present application, the process of creating a trust ring by device A may include the following steps:
步骤S1:设备A登录账号1。Step S1: Device A logs in to
本文中以设备A为荣耀V40手机为例进行说明。应当理解的是,设备A可以是已安装本申请中创建信任环功能的任意电子设备,本申请不做限制。In this article, the device A is the Honor V40 mobile phone as an example for illustration. It should be understood that the device A may be any electronic device that has installed the function of creating a trust ring in this application, which is not limited in this application.
设备A需要在已登录账号的情况下,才能向信任环云发起注册,以创建信任环。如果设备A还没有登录账号,需要先登录账号。Device A needs to have a logged-in account before registering with the trust ring cloud to create a trust ring. If device A has not yet logged in to the account, you need to log in to the account first.
图5A为示例性示出的已登录账号情况下进入“我的设备”应用的界面示意图。图5B为示例性示出的未登录账号情况下进入“我的设备”应用的界面示意图。图6为示例性示出的从设备A中“我的设备”应用进入到“密码保险箱同步”应用的界面示意图。FIG. 5A is an exemplary interface diagram of entering the "My Device" application in the case of a logged-in account. FIG. 5B is an exemplarily shown interface diagram of entering the "My Device" application without logging in an account. FIG. 6 is a schematic diagram of an interface for entering from the "My Device" application in the device A to the "Password Safe Synchronization" application exemplarily shown.
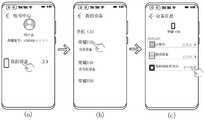
请参见图5A和图6,在设备A已登录账号1(假设账号1为1581991××××)的情况下,用户可以点击设备A主界面中的“设置”应用图标(如图5A的(a)图所示),进入到图5A的(b)图所示的“设置”界面。在“设置”界面,用户点击账号1(即1581991××××),进入到图5A的(b)图所示的“账号中心”界面。在“账号中心”界面,用户点击“我的设备”,进入到图6的(b)图所示的“我的设备”界面。在“我的设备”界面中找到当前设备,即荣耀V40,点击荣耀V40进入图6的(c)图所示的“设备信息”界面。在“设备信息”界面,用户继续点击该界面中的“密码保险箱同步”应用,可以进入“密码保险箱”界面。在“密码保险箱”界面,开启“密码保险箱同步”开关后,点击“同步到荣耀账号”开关,即触发创建信任环的流程。其中,进入“密码保险箱”界面、开启“密码保险箱同步”开关和开启“同步到荣耀账号”开关的过程在后文进行说明。Please refer to Figure 5A and Figure 6 , when device A has logged into account 1 (assuming
需要说明的是,如果账号1下已有信任环,在“我的设备”界面上已加入到信任环中的设备下面会显示“受信任设备”。被标识为“受信任设备”的设备是已经加入到信任环中的设备,即已注册设备,请参见后续图15的(b)图所示界面。如果账号1下无信任环,例如在图6的(b)图所示的设备A的“我的设备”界面上,3个荣耀设备均不是受信任设备,表示当前的账号1下没有信任环。It should be noted that if
请参见图5A、图5B和图6,在设备A未登录账号1的情况下,用户点击设备A主界面中的“设置”应用图标(如图5A的(a)图所示)后,进入到图5B的(a)图所示的“设置”界面。在“设置”界面,用户点击“登录荣耀账号”,进入到图5B的(b) 图所示的荣耀账号登录界面。在荣耀账号登录界面,用户输入账号1(1581991××××)和登录密码(假设为key1),设备A向账号管理服务器发送登录账号1的请求,请求中携带账号1(1581991××××)和登录密码key1。Please refer to Fig. 5A, Fig. 5B and Fig. 6. When device A is not logged into
请参见图4,用户可以通过设备A的应用程序层的账号管理模块,向账号管理服务器发送登录账号1的请求,以登录账号1。Referring to FIG. 4 , the user can log in to the
设备A成功登录账号1后,按照前述已登录账号情况下的流程触发创建信任环的流程,请参见图5A的(c)图、(d)图和图6所示,此处不再赘述。After the device A successfully logs in to
步骤S2:账号管理服务器返回验证通过消息。Step S2: The account management server returns a verification pass message.
账号管理服务器中预先保存账号1的信息,该信息包括账号1对应的登录密码,此处假设账号管理服务器保存的账号1的登录密码为key0。账号管理服务器接收到设备A 发送的登录账号1的请求后,根据账号管理服务器本地保存的账号1的信息对登录账号 1的请求进行验证。如果登录账号1的请求中携带的登录账号1的密码key1,与账号管理服务器本地保存的账号1的登录密码key0一致,账号管理服务器确定账号1的登录验证通过。此时,账号管理服务器向设备A返回验证通过消息。The account management server stores information of
如果登录账号1的请求中携带的登录账号1的密码key1,与账号管理服务器本地保存的账号1的登录密码key0不一致,账号管理服务器确定账号1的登录验证失败。此时,账号管理服务器向设备A返回验证失败消息。此时,用户需要通过图5B的(b)图重新输入账号和登录密码。If the password key1 of the
请参见图4和图10,设备A通过账号管理模块接收验证通过消息或验证失败消息。Referring to FIG. 4 and FIG. 10 , the device A receives the verification pass message or the verification failure message through the account management module.
S3:发送注册开启通知。S3: Send a registration opening notification.
请参见图4和图10,在设备A的账号管理模块接收到账号管理服务器返回的验证通过消息的情况下,设备A中的账号管理模块向应用程序框架层的信任环服务模块发送注册开启通知。注册开启通知用于指示信任环服务模块开启注册流程。Please refer to FIG. 4 and FIG. 10 , when the account management module of device A receives the verification pass message returned by the account management server, the account management module of device A sends a registration opening notification to the trust ring service module of the application framework layer . The registration opening notification is used to instruct the trust ring service module to start the registration process.
此处,对设备A在创建信任环过程中进入“密码保险箱”界面、开启“密码保险箱同步”开关的过程进行说明。Here, the process of entering the "Password Safe" interface and turning on the "Password Safe Synchronization" switch of Device A during the process of creating the trust ring will be described.
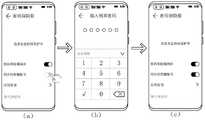
图7A是示例性示出的设备A已设置锁屏码情况下进入“密码保险箱”界面的过程示意图。请参见图7A,在设备A的用户已设置设备A的锁屏码(也可称为锁屏密码) 情况下,当用户在“设备信息”界面点击该界面中的“密码保险箱同步”应用(请参见图 7A的(a)图),设备A弹出“输入锁屏密码”界面(请参见图7A的(b)图)。如果用户在“输入锁屏密码”界面输入锁屏码且锁屏密码正确,设备A的屏幕就进入到“密码保险箱”界面(请参见图7A的(c)图)。此时,“密码保险箱”界面上的“密码保险箱同步”开关和“同步到荣耀账号”开关均处于关闭状态。FIG. 7A is a schematic diagram illustrating a process of entering a “password safe” interface when device A has set a screen lock code. Referring to FIG. 7A , in the case where the user of device A has set the screen lock code (also called screen lock password) of device A, when the user clicks the "Password Safe Sync" application in the "Device Information" interface ( Please refer to (a) of FIG. 7A ), the device A pops up an “enter screen lock password” interface (please refer to (b) of FIG. 7A ). If the user enters the screen lock code on the "Enter screen lock password" interface and the screen lock password is correct, the screen of Device A enters the "Password Safe" interface (see (c) of FIG. 7A ). At this point, the "Password Safe Synchronization" switch and the "Sync to Honor Account" switch on the "Password Safe" interface are both off.
图7B是示例性示出的设备A未设置锁屏码情况下进入“密码保险箱”界面的过程示意图。请参见图7B,在设备A的用户未设置设备A的锁屏码情况下,当用户在“设备信息”界面点击该界面中的“密码保险箱同步”应用(请参见图7B的(a)图),设备A 弹出“设置数字锁屏密码”界面(请参见图7B的(b)图)。用户在图7B的(b)图所示的“设置数字锁屏密码”界面输入锁屏码后,设备A弹出“设置数字锁屏密码”的确认密码的界面(请参见图7B的(c)图)。用户在图7B的(c)图所示的界面上再次输入锁屏码,如果该再次输入的锁屏码与用户在图7B的(b)图所示的界面输入的锁屏码一致,设备A的屏幕就进入到图7B的(d)图所示的“密码保险箱”界面,该界面与图7A的 (c)图所示界面相同。FIG. 7B is an exemplary schematic diagram of a process of entering a “password safe” interface when device A does not set a screen lock code. Please refer to FIG. 7B , in the case where the user of device A has not set the lock screen code of device A, when the user clicks the “password safe sync” application in the interface of “device information” (see (a) of FIG. 7B ), the device A pops up the "set digital lock screen password" interface (see (b) of FIG. 7B ). After the user enters the screen lock code on the "Set digital screen lock password" interface shown in (b) of FIG. 7B , the device A pops up a password confirmation interface of "Set digital screen lock password" (see (c) of FIG. 7B . picture). The user enters the screen lock code again on the interface shown in (c) of FIG. 7B , and if the screen lock code input again is consistent with the screen lock code entered by the user on the interface shown in (b) of FIG. 7B , the device The screen of A enters the "password safe" interface shown in (d) of FIG. 7B , which is the same as the interface shown in (c) of FIG. 7A .
图8为示例性示出的创建信任环的场景下开启“密码保险箱同步”开关的过程示意图。请参见图8,当用户点击“密码保险箱”界面上的“密码保险箱同步”开关(请参见图8的(a)图),设备A屏幕上弹出图8的(b)图所示的提醒界面,该提醒界面用于提醒用户是否同意开启密码保险箱同步服务。当用户点击提醒界面上的“同意”按钮(请参见图8的(b)图),“密码保险箱”界面上的“密码保险箱同步”开关开启(请参见图8的 (c)图)。FIG. 8 is a schematic diagram of a process of turning on a "password safe synchronization" switch in an exemplary scenario of creating a trust ring. Please refer to Figure 8, when the user clicks the "Password Safe Synchronization" switch on the "Password Safe" interface (refer to Figure 8 (a)), a reminder interface as shown in Figure 8 (b) will pop up on the screen of Device A , the reminder interface is used to remind the user whether to agree to enable the password vault synchronization service. When the user clicks the "Agree" button on the reminder interface (see Figure 8(b)), the "Password Safe Synchronization" switch on the "Password Safe" interface is turned on (see Figure 8 (c)).
信任环服务模块在接收到注册开启通知时,并不能确定是开启创建信任环的流程,还是加入信任环的流程,需要通过检测注册状态来确定。When the trust ring service module receives the registration opening notification, it cannot determine whether to start the process of creating the trust ring or the process of joining the trust ring, which needs to be determined by detecting the registration status.
S4:设备A中的信任环服务模块检测设备A的注册状态。S4: The trust ring service module in the device A detects the registration state of the device A.
注册状态包括未注册和已注册两种状态。其中,未注册状态用于指示设备当前未注册到信任环,已注册状态用于指示设备当前已注册到信任环。The registration status includes unregistered and registered status. The unregistered state is used to indicate that the device is not currently registered to the trust ring, and the registered state is used to indicate that the device is currently registered to the trust ring.
S5:当检测到设备A的注册状态为未注册,设备A向信任环云发送注册状态对比请求。S5: When it is detected that the registration status of device A is unregistered, device A sends a registration status comparison request to the trust ring cloud.
其中,注册状态对比请求用于指示获取信任环服务模块检测到的设备A的注册状态与信任环云中存储的设备A的注册状态的比对结果。The registration state comparison request is used to instruct to obtain the comparison result of the registration state of the device A detected by the trust ring service module and the registration state of the device A stored in the trust ring cloud.
注册状态对比请求中包括设备A的UID(设备标识)和设备A所属的账号的UDID (账号标识)。The registration status comparison request includes the UID (device identification) of the device A and the UDID (account identification) of the account to which the device A belongs.
S6:信任环云向设备A中的信任环服务模块返回第一注册状态确认消息。S6: The trust ring cloud returns a first registration state confirmation message to the trust ring service module in the device A.
其中,第一注册状态确认消息用于指示账号1下不存在信任环。The first registration status confirmation message is used to indicate that there is no trust ring under
信任环云在接收到设备A的注册状态对比请求后,首先比对账号1下是否存在信任环,在账号1下存在信任环的情况下,再比对设备A是否在信任环中。当账号1下不存在信任环,信任环云生成第一注册状态确认消息,并发送给设备A。After receiving the registration status comparison request of device A, the trust ring cloud first checks whether there is a trust ring under
基于信任环云返回的第一注册状态确认消息,设备A确定本次注册执行创建信任环流程。Based on the first registration status confirmation message returned by the trust ring cloud, device A determines that the current registration is performed to create a trust ring process.
S7:设备A中的信任环服务模块接收用户输入的设备A的锁屏码pw11。S7: The trust ring service module in the device A receives the screen lock code pw11 of the device A input by the user.
此处,对创建信任环过程中开启“同步到荣耀账号”开关的过程进行说明。Here, the process of turning on the "Sync to Honor Account" switch during the creation of the trust ring is described.
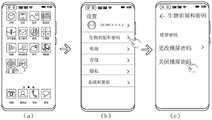
图9为示例性示出的创建信任环的场景下开启“同步到荣耀账号”开关的过程示意图。请参见图9,当用户在“密码保险箱同步”开关已开启的“密码保险箱”界面上点击“同步到荣耀账号”开关(请参见图9的(a)图),设备A屏幕上弹出“输入锁屏密码”界面(请参见图9的(b)图)。如果用户在“输入锁屏密码”界面输入设备A的锁屏码,设备A中的信任环服务模块就会接收到用户输入的设备A的锁屏码。如果用户输入的设备A的锁屏密码正确,设备A执行完创建信任环流程后就进入到“密码保险箱同步”开关和“同步到荣耀账号”开关均处于开启状态的“密码保险箱”界面(请参见图9的(c) 图)。FIG. 9 is a schematic diagram of a process of turning on the switch of "synchronize to glory account" in the scenario of creating a trust ring. Please refer to Figure 9. When the user clicks the "Sync to Honor Account" switch on the "Password Safe" interface where the "Password Safe Synchronization" switch is turned on (see (a) of Figure 9), a pop-up "Input "Lock screen password" interface (see (b) of Figure 9). If the user inputs the screen lock code of device A on the "Enter screen lock password" interface, the trust ring service module in device A will receive the screen lock code of device A entered by the user. If the lock screen password of device A entered by the user is correct, device A will enter the "Password Safe" interface with both "Password Safe Sync" and "Sync to Honor Account" switches turned on after completing the process of creating a trust ring (please See Fig. 9(c) panel).
需要说明的是,用户在图9的(a)图所示的界面上点击“同步到荣耀账号”开关的操作(请参见图9的(a)图)触发设备A执行图10中的步骤S3以及步骤S3之后的创建信任环流程步骤。It should be noted that the operation of the user clicking the "Sync to Honor Account" switch on the interface shown in (a) of FIG. 9 (see (a) of FIG. 9 ) triggers the device A to execute step S3 in FIG. 10 and the steps in the process of creating a trust ring after step S3.
设备A的锁屏码属于设备A的用户秘密,对于云侧来说,设备A的锁屏码是未知的。The screen lock code of device A belongs to the user secret of device A. For the cloud side, the screen lock code of device A is unknown.
S8:设备A的信任环服务模块验证设备A的锁屏码pw11。S8: The trust ring service module of device A verifies the screen lock code pw11 of device A.
验证设备A的锁屏码的过程可以为:设备A将用户输入的锁屏码与设备A中预先存储的锁屏码进行比对,如果二者一致,验证通过,否则验证失败。The process of verifying the screen lock code of device A may be as follows: device A compares the screen lock code input by the user with the screen lock code pre-stored in device A, and if the two are consistent, the verification passes, otherwise the verification fails.
此处,信任环服务模块对用户在图9的(b)图所示的界面上输入的设备A的锁屏码进行再次验证,验证通过后才能继续执行后续的步骤S9。如果验证失败,设备A将退回到图9的(b)图所示的界面,并在该界面提示输入的锁屏码错误。Here, the trust ring service module verifies again the screen lock code of device A input by the user on the interface shown in (b) of FIG. If the verification fails, the device A will return to the interface shown in (b) of FIG. 9 , and the interface will prompt that the entered lock screen code is incorrect.
S9:信任环服务模块基于设备A的锁屏码派生PWUATH11。S9: The trust ring service module derives PWUATH11 based on the screen lock code of device A.
假设用户本次输入的锁屏码为pw11,信任环服务模块基于pw11派生PWUATH11。Assuming that the screen lock code entered by the user this time is pw11, the trust ring service module derives PWUATH11 based on pw11.
由于pw11属于设备A的用户秘密,云侧无法获得pw11,从而云侧无法获得基于pw11派生的PWUATH11。Since pw11 belongs to the user secret of device A, the cloud side cannot obtain pw11, so the cloud side cannot obtain PWUATH11 derived from pw11.
由于PWUATH11是基于云侧未知的用户秘密pw11生成的,因此对云侧来说PWUATH11是未知的。Since PWUATH11 is generated based on the unknown user secret pw11 on the cloud side, PWUATH11 is unknown to the cloud side.
S10:设备A的信任环服务模块向设备A的可信执行环境中的信任环模块发送PWAUTH11。S10: The trust ring service module of the device A sends PWAUTH11 to the trust ring module in the trusted execution environment of the device A.
后续,信任环模块基于PWAUTH11生成主密钥密文EMK11和参数PAKE11,EMK11 和PAKE11的生成方式详见图10的步骤S11至S14。Subsequently, the trust ring module generates the master key ciphertext EMK11 and the parameters PAKE11 based on the PWAUTH11. For details of the generation methods of EMK11 and PAKE11, please refer to steps S11 to S14 in FIG. 10 .
S11:信任环模块生成MK。S11: The trust ring module generates MK.
设备A通过信任环模块生成MK即主密钥,MK保存在设备A的可信执行环境中,即便设备A受攻击MK也不会被窃取,因此安全性很高。Device A generates MK, the master key, through the trust ring module. MK is stored in the trusted execution environment of device A. Even if device A is attacked, MK will not be stolen, so the security is very high.
S12:信任环模块基于PWAUTH11对MK进行加密,生成EMK11。S12: The trust ring module encrypts MK based on PWAUTH11 to generate EMK11.
EMK11即第一主密钥密文。信任环模块基于PWAUTH11派生一个秘钥KEK11,再基于该KEK11加密MK,生成EMK11。EMK11 is the ciphertext of the first master key. The trust ring module derives a secret key KEK11 based on PWAUTH11, and then encrypts MK based on the KEK11 to generate EMK11.
S13:设备A的信任环模块向设备A的信任环服务模块发送EMK11。S13: The trust ring module of device A sends EMK11 to the trust ring service module of device A.
信任环模块生成EMK11后,将EMK11发送至信任环服务模块,在发送EMK11的同时也将salt_enc11发送至信任环服务模块。After the trust ring module generates EMK11, it sends EMK11 to the trust ring service module, and also sends salt_enc11 to the trust ring service module when sending EMK11.
S14:设备A中的信任环服务模块基于PWAUTH11生成参数PAKE11。S14: The trust ring service module in device A generates parameter PAKE11 based on PWAUTH11.
S15:设备A通过信任环服务模块向信任环云发送携带EMK11、参数PAKE11的创环请求。S15: Device A sends a ring creation request carrying EMK11 and parameter PAKE11 to the trust ring cloud through the trust ring service module.
设备A通过信任环服务模块向信任环云发送创环请求,通过该请求即可完成PAKE11 参数注册以及EMK11托管。Device A sends a ring creation request to the trust ring cloud through the trust ring service module, and the PAKE11 parameter registration and EMK11 hosting can be completed through the request.
为提升EMK11的安全性,信任环服务模块在发送EMK11前,可以基于登录时获得的信任环云HSM的公钥对EMK11进行二次加密,得到主密钥的二层密文。In order to improve the security of EMK11, before sending EMK11, the trust ring service module can perform secondary encryption on EMK11 based on the public key of the trust ring cloud HSM obtained during login to obtain the second-layer ciphertext of the master key.
S16:信任环云响应于创环请求,创建账号1的信任环1,并将设备A添加到信任环 1中。S16: The trust ring cloud creates a
信任环云响应于设备A发送的创环请求,为账号1创建信任环1,当账号1下的其他设备如设备B、设备C向信任环云发送注册状态比对请求时,信任环云将返回存在信任环1但设备B、设备C不在信任环中的确认消息,设备B、设备C执行加入信任环的流程,加入信任环的具体流程参照后续相关说明即可。In response to the ring creation request sent by device A, the trust ring cloud creates a
信任环1创建完成后,信任环云中管理的信任环1数据如表1中所示:After the
表1Table 1
S17:信任环云向设备A的信任环服务模块返回创环成功消息。S17: The trust ring cloud returns a ring creation success message to the trust ring service module of device A.
信任环云为账号1创建信任环1,并将设备A添加到信任环1中后,向设备A返回创环成功消息,设备A接收到创环成功消息后,开启密码保险箱界面中的“同步到荣耀账号”开关,如图9的(c)图所示。“同步到荣耀账号”开关开启后用户可感知设备A已成功加入信任环,密码保险箱中的业务数据可同步至账号管理服务器,以使账号1下的其他在信任环1中的设备能够共享该业务数据。Trust Ring Cloud creates
至此,创建信任环过程结束,设备A完成注册。So far, the process of creating the trust ring is over, and the device A completes the registration.
设备A完成注册后,设备A的信任环服务模块将设备A的注册状态修改为已注册。After device A completes the registration, the trust ring service module of device A modifies the registration status of device A to registered.
设备A完成注册后,设备A的信任环服务模块将设备A的注册状态修改为已注册。After device A completes the registration, the trust ring service module of device A modifies the registration status of device A to registered.
通过创建信任环过程可见,本申请实施例基于用户秘密对账号级主密钥MK进行保护,由于用户秘密对于云侧来说是未知的,因此云侧不能对托管的主密钥密文进行解密,这样,降低了主密钥泄露的风险,提高了主密钥MK的安全性,同时使云侧能够自证清白,能够为具有高安全性要求的业务数据的数据同步提供支撑。It can be seen from the process of creating a trust ring that the embodiment of the present application protects the account-level master key MK based on the user secret. Since the user secret is unknown to the cloud side, the cloud side cannot decrypt the escrowed master key ciphertext In this way, the risk of master key leakage is reduced, the security of the master key MK is improved, and at the same time, the cloud side can prove its innocence, which can provide support for data synchronization of business data with high security requirements.
需要说明的是,上述过程应当理解为本申请中创建信任环过程的示意性举例,并不用于对本申请进行限制。It should be noted that the above process should be understood as a schematic example of the process of creating a trust ring in the present application, and is not used to limit the present application.
图11为示例性示出的创建信任环后设备A同步业务数据密文到账号管理服务器的示意图。图12为示例性示出的同步业务数据密文的模块交互示意图。图13为示例性示出的同步业务数据密文到账号管理服务器的界面示意图。请参考图11、图12和图13,在已创建账号1的信任环1,并且设备A已添加到信任环1的情况下,设备A可以用MK 对敏感业务数据进行加密,得到业务数据密文,并将业务数据密文上传到账号管理服务器。FIG. 11 is an exemplary schematic diagram of device A synchronizing the ciphertext of service data to the account management server after the trust ring is created. FIG. 12 is an exemplary schematic diagram of module interaction for synchronizing service data ciphertext. FIG. 13 is an exemplary schematic diagram of an interface for synchronizing ciphertext of service data to an account management server. Please refer to Figure 11, Figure 12 and Figure 13, in the case that the
其中,创建信任环后设备A同步业务数据密文到账号管理服务器的过程如下:The process for device A to synchronize service data ciphertext to the account management server after the trust ring is created is as follows:
请参见图12,设备A中应用程序层的密码保险箱读取业务数据明文,然后将业务数据明文存储到应用程序框架层的业务数据存储服务模块中,业务数据存储服务模块将业务数据明文发送给可信执行环境中的密钥管理模块。信任环模块根据MK生成业务密钥 dkey,密钥管理模块从信任环模块读取dkey,使用dkey对业务数据data进行加密,得到业务数据密文Edata。密钥管理模块将业务数据密文Edata返回给业务数据存储服务模块,业务数据存储服务模块通过业务数据同步服务模块和应用程序层的账号管理服务器同步框架,将业务数据密文Edata上传至账号管理服务器。Referring to Figure 12, the password safe of the application layer in device A reads the plaintext of the business data, and then stores the plaintext of the business data in the business data storage service module of the application framework layer, and the business data storage service module sends the plaintext of the business data to Key management module in Trusted Execution Environment. The trust ring module generates the service key dkey according to the MK, and the key management module reads the dkey from the trust ring module, uses the dkey to encrypt the service data data, and obtains the service data ciphertext Edata. The key management module returns the business data ciphertext Edata to the business data storage service module, and the business data storage service module uploads the business data ciphertext Edata to the account management through the business data synchronization service module and the account management server synchronization framework of the application layer. server.
需要说明的是,不同的业务对应的业务密钥dkey不同,设备A可以根据MK生成不同业务的业务密钥。It should be noted that the service keys dkey corresponding to different services are different, and the device A can generate the service keys of different services according to the MK.
例如,请参见图13,用户在设备A上使用业务1时,需要输入业务1的账号和密码,如图13的(a)图所示。在输入完业务1的账号和密码后,设备A弹出提示是否将业务 1的账号和密码同步到密码保险箱的信息,如图13的(b)图所示。如果用户同意,设备 A将业务1的账号和密码作为业务1的业务数据data1,按照上述与业务数据data相同的同步过程,将data1的密文Edata1上传至账号管理服务器。For example, referring to FIG. 13 , when the user uses
由上可见,本申请实施例中,账号管理服务器中的业务数据密文不完全依赖账号安全,还依赖MK的安全,即使账号失窃,不影响云上数据的安全。It can be seen from the above that in the embodiment of the present application, the ciphertext of the business data in the account management server does not completely depend on the security of the account, but also on the security of the MK. Even if the account is stolen, the security of the data on the cloud will not be affected.
基于高安全性的主密钥对用户的业务数据进行加密,然后同步业务数据密文到账号管理服务器,降低了业务数据密文泄露的风险,提高了数据同步备份的安全性。The user's business data is encrypted based on the high-security master key, and then the business data ciphertext is synchronized to the account management server, which reduces the risk of business data ciphertext leakage and improves the security of data synchronization and backup.
加入信任环Join the trust ring
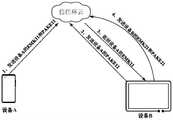
在设备A已经创建了账号1的信任环1的基础上,账号1下的设备B可以根据如下实施例中的加入信任环流程加入到信任环1中。在设备B加入信任环1之前,信任环1 中只有设备A这一个在环设备。On the basis that the device A has created the
图14为示例性示出的设备B加入信任环过程中的信息交互示意图。图18为示例性示出的设备B加入信任环的流程示意图。FIG. 14 is an exemplary schematic diagram of information exchange in the process of device B joining the trust ring. FIG. 18 is a schematic flowchart of an exemplary process of adding device B to a trust ring.
下面结合图14和图18,对本申请实施例的加入信任环过程进行详细说明。The following describes the process of joining a trust ring in this embodiment of the present application in detail with reference to FIG. 14 and FIG. 18 .
请参见图14,在设备A作为首设备注册后,创建信任环过程完成,设备A已将设备 A的主密钥密文EMK11,即第一主密钥密文,和设备A的认证参数PAKE11上传至信任环云,此后,其他设备,例如设备B通过加入信任环流程进行注册。在设备B加入信任环1的过程中,设备B向信任环云发送已在信任环1中的设备A的认证参数PAKE12,信任环云在确认PAKE12与信任环1中已存储的设备A的认证参数PAKE11一致后,将设备A的主密钥密文EMK11返回给设备B。然后,设备B从EMK11中解密出MK,并基于设备B的锁屏码加密MK,生成设备B的主密钥密文EMK21,即第二主密钥密文,和设备B的认证参数PAKE21,并将EMK21和PAKE21发送至信任环云。Referring to Figure 14, after device A is registered as the first device, the process of creating the trust ring is completed, and device A has the master key ciphertext EMK11 of device A, that is, the first master key ciphertext, and device A's authentication parameter PAKE11 After uploading to the trust ring cloud, other devices, such as device B, register by joining the trust ring process. During the process of device B joining
请参见图18,本申请实施例中,设备B加入信任环过程可以包括如下步骤:Referring to FIG. 18 , in this embodiment of the present application, the process of device B joining the trust ring may include the following steps:
S1:设备B登录账号1。S1: Device B logs in to
同设备A一样,设备B通过向账号管理服务器发送登录账号1的请求来登录账号1。设备B登录账号1的详细过程请参见前述设备A登录账号1的过程说明,此处不再赘述。Like device A, device B logs in to
S2:账号管理服务器向设备B返回验证通过消息。S2: The account management server returns a verification pass message to the device B.
账号管理服务器对设备B登录账号1的请求的处理过程请参见前述账号管理服务器对设备A登录账号1的请求的处理过程,此处不再赘述。For the processing process of the request by the account management server for the device B to log in to the
设备B成功登录账号1后,用户可以通过图5A的(b)图和(c)图所指示的流程进入“账号中心”界面,找到“我的设备”应用。After device B successfully logs into
S3:发送注册开启通知。S3: Send a registration opening notification.
请参见图4和图18,在设备B的账号管理模块接收到账号管理服务器返回的验证通过消息的情况下,设备B中的账号管理模块向应用程序框架层的信任环服务模块发送注册开启通知。注册开启通知用于指示设备B的信任环服务模块开启注册流程。Please refer to FIG. 4 and FIG. 18 , when the account management module of device B receives the verification pass message returned by the account management server, the account management module of device B sends a registration opening notification to the trust ring service module of the application framework layer . The registration start notification is used to instruct the trust ring service module of device B to start the registration process.
此处,对设备B在加入信任环过程中进入“密码保险箱”界面、开启“密码保险箱同步”开关的过程进行说明。Here, the process of entering the "Password Safe" interface and turning on the "Password Safe Synchronization" switch of Device B during the process of joining the trust ring will be described.
图15为示例性示出的从设备B中“我的设备”应用进入到“密码保险箱同步”应用的界面示意图。对比图6可见,在加入信任环过程中,设备B的“我的设备”界面上,有一个受信任设备荣耀V40,即设备A。这说明账号1下已存在信任环。FIG. 15 is a schematic diagram of an exemplarily shown interface from the "My Device" application in the device B to the "Password Safe Sync" application. Comparing Figure 6, it can be seen that during the process of joining the trust ring, there is a trusted device Honor V40, that is, device A, on the "My Device" interface of device B. This indicates that a trust ring already exists under
图16A是示例性示出的设备B已设置锁屏码情况下进入“密码保险箱”界面并开启“密码保险箱同步”开关的过程示意图。请参见图16A,在设备B的用户已设置设备B 的锁屏码情况下,当用户在“设备信息”界面点击该界面中的“密码保险箱同步”应用 (请参见图16A的(a)图),设备B弹出“输入锁屏密码”界面(请参见图16A的(b) 图)。如果用户在“输入锁屏密码”界面输入锁屏码且锁屏密码正确,设备B的屏幕就进入到“密码保险箱”界面(请参见图16A的(c)图)。此时,“密码保险箱”界面上的“密码保险箱同步”开关和“同步到荣耀账号”开关均处于关闭状态。与设备A在创建信任环过程中不同的是,设备B在加入信任环过程中,当用户点击图16A的(c)图所示“密码保险箱”界面上的“密码保险箱同步”开关,设备B的屏幕直接切换到图16A的(d) 图所示的界面,即“密码保险箱同步”开关已开启、而“同步到荣耀账号”未开启的界面。FIG. 16A is an exemplary schematic diagram showing the process of entering the “Password Safe” interface and turning on the “Password Safe Synchronization” switch when the device B has set a lock screen code. Please refer to FIG. 16A , in the case that the user of device B has set the screen lock code of device B, when the user clicks on the “Password Safe Sync” application in the “Device Information” interface (see FIG. 16A (a) ), the device B pops up the “Enter screen lock password” interface (see (b) of FIG. 16A ). If the user enters the screen lock code on the "Enter screen lock password" interface and the screen lock password is correct, the screen of device B enters the "Password Safe" interface (see (c) of FIG. 16A ). At this point, the "Password Safe Synchronization" switch and the "Sync to Honor Account" switch on the "Password Safe" interface are both off. The difference from the process of creating a trust ring of device A is that when device B joins the trust ring, when the user clicks the "Password Safe Sync" switch on the "Password Safe" interface shown in (c) of FIG. The screen of 16A is directly switched to the interface shown in (d) of FIG. 16A , that is, the interface in which the “password safe synchronization” switch is turned on, but the “sync to glory account” is not turned on.
图16B是示例性示出的设备B未设置锁屏码情况下进入“密码保险箱”界面并开启“密码保险箱同步”开关的过程示意图。请参见图16B,设备B未设置锁屏码情况下进入“密码保险箱”界面并开启“密码保险箱同步”开关的过程,与图16A所示的设备B 已设置锁屏码情况下进入“密码保险箱”界面并开启“密码保险箱同步”开关的过程相比,所不同的是设备B未设置锁屏码情况下需要设置锁屏密码(请参见图16B的(b) 图)和确认锁屏密码(请参见图16B的(c)图),其余过程与已设置锁屏码情况下的过程相同,此处不再赘述。FIG. 16B is a schematic diagram illustrating the process of entering the "Password Safe" interface and turning on the "Password Safe Synchronization" switch when the device B does not set a lock screen code. Please refer to Figure 16B, the process of entering the "Password Safe" interface and turning on the "Password Safe Synchronization" switch when device B has not set a screen lock code, which is the same as the process of entering the "Password Safe" when device B has set a screen lock code as shown in Figure 16A. ” interface and turn on the “Password Safe Synchronization” switch, the difference is that if device B does not set a lock screen code, it needs to set a lock screen password (see (b) of Figure 16B ) and confirm the lock screen password ( Please refer to (c) of FIG. 16B , the rest of the process is the same as the process in the case where the screen lock code has been set, and will not be repeated here.
S4:设备B中的信任环服务模块检测设备B的注册状态。S4: The trust ring service module in the device B detects the registration state of the device B.
关于此步骤的说明请参见前述对图10的步骤S4的描述,此处不再赘述。For the description of this step, please refer to the foregoing description of step S4 in FIG. 10 , which will not be repeated here.
S5:当检测到设备B的注册状态为未注册,发送注册状态对比请求。S5: When it is detected that the registration status of the device B is unregistered, a registration status comparison request is sent.
关于此步骤的说明请参见前述对图10的步骤S5的描述,此处不再赘述。For the description of this step, please refer to the foregoing description of step S5 in FIG. 10 , which will not be repeated here.
S6:返回第二注册状态确认消息,第二注册状态确认消息。S6: Return the second registration state confirmation message, the second registration state confirmation message.
其中,第二注册状态确认消息用于指示账号1下存在信任环1、但设备B不在信任环1上。The second registration status confirmation message is used to indicate that the
信任环云在接收到设备B的注册状态对比请求后,首先比对账号1下是否存在信任环。此时,由于在设备A注册时信任环已经创建了账号1的信任环1,因此确认账号1 下存在信任环。然后,信任环云根据表1所示的账号1的信任环数据,确认设备B不在信任环中,此时,信任环云生成第二注册状态确认消息,并发送给设备B。After receiving the registration status comparison request of device B, the trust ring cloud first compares whether there is a trust ring under
基于信任环云返回的第二注册状态确认消息,设备B确定本次注册执行加入信任环流程。Based on the second registration status confirmation message returned by the trust ring cloud, device B determines that this registration is performed to join the trust ring process.
S7:设备B中的信任环服务模块接收用户输入的设备B的锁屏码pw21。S7: The trust ring service module in the device B receives the screen lock code pw21 of the device B input by the user.
图17为示例性示出的设备B加入信任环的场景下开启“同步到荣耀账号”开关的过程示意图。请参见图17,当用户在“密码保险箱同步”开关已开启的“密码保险箱”界面上点击“同步到荣耀账号”开关(请参见图17的(a)图),设备B屏幕上弹出“输入锁屏密码”界面(请参见图17的(b)图)。如果用户在“输入锁屏密码”界面输入设备 B的锁屏码,设备B中的信任环服务模块就会接收到用户输入的设备B的锁屏码。FIG. 17 is a schematic diagram illustrating the process of turning on the switch of "sync to the Honor account" in the scenario where the device B joins the trust ring. Please refer to Figure 17. When the user clicks the "Sync to Honor Account" switch on the "Password Safe" interface where the "Password Safe Synchronization" switch is turned on (see (a) of Figure 17), a pop-up "Input "Lock screen password" interface (see (b) of Figure 17). If the user enters the screen lock code of device B on the "Enter screen lock password" interface, the trust ring service module in device B will receive the screen lock code of device B entered by the user.
S8:设备B的信任环服务模块验证设备B的锁屏码pw21,基于设备B的锁屏码 pw21派生PWAUTH21。S8: The trust ring service module of device B verifies the screen lock code pw21 of device B, and derives PWAUTH21 based on the screen lock code pw21 of device B.
其中,验证设备B的锁屏码pw21的过程请参见前述验证设备A的锁屏码pw11的过程,此处不再赘述。For the process of verifying the screen lock code pw21 of the device B, please refer to the aforementioned process of verifying the screen lock code pw11 of the device A, which will not be repeated here.
S9:设备B的信任环服务模块获取信任环1中的设备列表。S9: The trust ring service module of the device B obtains the device list in the
设备B的信任环服务模块可以向信任环云发送信任环1中的设备列表的获取请求,信任环云接收到该请求后,向设备B的信任环服务模块返回信任环1中的设备列表。The trust ring service module of device B can send a request for obtaining the device list in
S10:信任环云向设备B的信任环服务模块返回信任环1中的设备列表。S10: The trust ring cloud returns the device list in the
信任环1中的设备列表中包括当前已加入到信任环1中的所有设备。本申请实施例中,由于设备A是创建信任环1的设备,而设备B是首个加入信任环1的设备,因此,在设备B加入信任环1的过程中,信任环云返回的信任环1中的设备列表只包括设备A 一个设备。The list of devices in the
S11:设备B的信任环服务模块显示设备A锁屏码输入界面,接收用户输入的设备 A的锁屏码pw12,并基于锁屏码pw12生成参数PAKE12。S11: The trust ring service module of the device B displays the screen lock code input interface of the device A, receives the screen lock code pw12 of the device A input by the user, and generates a parameter PAKE12 based on the screen lock code pw12.
请继续参见图17,如果用户在图17的(b)图所示界面输入的设备B的锁屏密码正确,设备B屏幕上弹出“输入其他荣耀设备锁屏密码”界面(请参见图17的(c)图),图17的(c)图中的“其他荣耀设备”为荣耀V40,即设备A。用户在“输入其他荣耀设备锁屏密码”界面输入设备A的锁屏码pw12,如果用户输入的设备A的锁屏码pw12正确,设备B执行完加入信任环流程后就进入到“密码保险箱同步”开关和“同步到荣耀账号”开关均处于开启状态的“密码保险箱”界面(请参见图17的(d)图)。Please continue to refer to Fig. 17, if the screen lock password of device B entered by the user on the interface shown in (b) of (c) Figure), "Other Honor devices" in Figure 17 (c) is Honor V40, that is, device A. The user enters the lock screen code pw12 of device A on the "Enter other Honor device lock screen password" interface. If the lock screen code pw12 of device A entered by the user is correct, device B will enter the "Password Safe Sync" after completing the process of joining the trust ring. "Password Safe" interface with both the "Sync to Honor Account" switch and the "Sync to Honor Account" switch turned on (please refer to (d) of Figure 17).
需要说明的是,用户在图17的(a)图所示的界面上点击“同步到荣耀账号”开关的操作(请参见图17的(a)图)触发设备A执行图18中的步骤S3以及步骤S3之后的加入信任环流程步骤。It should be noted that the operation of the user clicking the "Sync to Honor Account" switch on the interface shown in (a) of FIG. 17 (see (a) of FIG. 17 ) triggers the device A to execute step S3 in FIG. 18 And the steps of joining the trust ring after step S3.
设备B的锁屏码属于设备B的用户秘密,对于云侧来说,设备B的锁屏码是未知的。The screen lock code of device B belongs to the user secret of device B. For the cloud side, the screen lock code of device B is unknown.
其中,参数PAKE12与前述的参数PAKE11的生成原理相同,此处不再赘述。The generation principle of the parameter PAKE12 is the same as that of the aforementioned parameter PAKE11, which will not be repeated here.
S12:设备B的信任环服务模块向信任环云发送参数PAKE12。S12: The trust ring service module of the device B sends the parameter PAKE12 to the trust ring cloud.
在设备B加入信任环1过程中,信任环云需要对已在信任环1中的设备的身份进行验证,当验证通过,才允许加入到信任环1,否则信任环云禁止设备B加入到信任环1 中。During the process of device B joining the
S13:信任环云基于参数PAKE12对设备A的身份验证通过后,向设备B的信任环服务模块返回设备A的EMK11。S13: After passing the authentication of the device A based on the parameter PAKE12, the trust ring cloud returns the EMK11 of the device A to the trust ring service module of the device B.
S14:设备B的信任环服务模块向设备B的信任环模块发送EMK11和PWAUTH21。S14: The trust ring service module of device B sends EMK11 and PWAUTH21 to the trust ring module of device B.
信任环模块位于设备B的可信执行环境中,设备B需要在可信执行环境中对EMK11进行解密,以取出MK,并且在可信执行环境中基于PWAUTH21对MK进行加密,得到 EMK21。The trust ring module is located in the trusted execution environment of device B. Device B needs to decrypt EMK11 in the trusted execution environment to extract the MK, and encrypt the MK based on PWAUTH21 in the trusted execution environment to obtain EMK21.
S15:设备B的信任环模块对EMK11进行解密得到MK,并基于PWAUTH21对MK 进行加密,得到EMK21。S15: The trust ring module of device B decrypts EMK11 to obtain MK, and encrypts MK based on PWAUTH21 to obtain EMK21.
S16:设备B的信任环模块向设备B的信任环服务模块发送EMK21。S16: The trust ring module of device B sends EMK21 to the trust ring service module of device B.
S17:设备B基于PWAUTH21生成参数PAKE21。S17: Device B generates parameter PAKE21 based on PWAUTH21.
此过程请参见前述S15中的说明,此处不再赘述。For this process, please refer to the description in the foregoing S15, which will not be repeated here.
S18:设备B的信任环服务模块向信任环云发送携带EMK21和参数PAKE21的加环请求。S18: The trust ring service module of device B sends a ring adding request carrying EMK21 and parameter PAKE21 to the trust ring cloud.
S19:信任环云响应于加环请求,将设备B加入信任环1中。S19: The trust ring cloud adds the device B to the
设备B加入信任环1后,信任环云中管理的信任环1数据如表2中所示:After device B joins
表2Table 2
S20:信任环云向设备B的信任环服务模块返回加环成功消息。S20: The trust ring cloud returns a ring addition success message to the trust ring service module of the device B.
信任环云将设备B添加到信任环1中后,向设备B返回加环成功消息,设备B接收到加环成功消息后,开启密码保险箱界面中的“同步到荣耀账号”开关,如图17的(d) 图所示。“同步到荣耀账号”开关开启后用户可感知设备B已成功加入信任环,密码保险箱中的业务数据可同步至账号管理服务器,以使账号1下的其他在信任环1中的设备能够共享该业务数据。After the trust ring cloud adds device B to trust
至此,设备B加入信任环1的过程完成,设备B完成注册。So far, the process of device B joining the
设备B完成注册后,设备B的信任环服务模块将设备B的注册状态修改为已注册。After the device B completes the registration, the trust ring service module of the device B modifies the registration status of the device B to registered.
通过加入信任环过程可见,本申请实施例中,云侧将已注册设备的托管主密钥密文发送给加环设备,加环设备基于已注册设备的用户秘密对已注册设备的主密钥密文进行解密,得到主密钥MK,由于已注册设备的用户秘密对于云侧来说是未知的,并且已注册设备的用户秘密不需要经过云侧的转发,因此,云侧不可解密主密钥密文,可自证清白。It can be seen from the process of joining the trust ring that in the embodiment of this application, the cloud side sends the ciphertext of the escrow master key of the registered device to the ring-enhancing device, and the ring-enhancing device determines the master key of the registered device based on the user secret of the registered device. Decrypt the ciphertext to obtain the master key MK. Since the user secret of the registered device is unknown to the cloud side, and the user secret of the registered device does not need to be forwarded by the cloud side, the cloud side cannot decrypt the master secret The key ciphertext can be self-certified.
需要说明的是,上述过程应当理解为本申请中加入信任环过程的示意性举例,并不用于对本申请进行限制。It should be noted that the above process should be understood as a schematic example of the process of adding a trust ring in this application, and is not used to limit this application.
图19为示例性示出的设备B加入信任环后从账号管理服务器同步业务数据密文的示意图。图20为示例性示出的从账号管理服务器同步业务数据密文的界面示意图。请参考图19、图12和图20,在已创建账号1的信任环1、设备A已添加到信任环1、设备A 已将业务数据密文Edata上传到账号管理服务器的情况下,设备B可以从账号管理服务器同步业务数据密文Edata到设备B,并在设备B本地用MK解密,得到业务数据明文 data。FIG. 19 is an exemplary schematic diagram of synchronizing service data ciphertext from the account management server after device B joins the trust ring. FIG. 20 is a schematic diagram of an interface for synchronizing ciphertext of service data from an account management server. Referring to Figure 19, Figure 12 and Figure 20, when the
其中,加入信任环后设备B从账号管理服务器中同步业务数据密文的过程如下:The process for device B to synchronize service data ciphertext from the account management server after joining the trust ring is as follows:
请参见图12,设备B中的业务数据同步服务模块通过应用程序层的账号管理服务器同步框架,从账号管理服务器获取到业务数据密文Edata。然后,设备B中的业务数据同步服务模块将业务数据密文Edata发送给设备B中的业务数据存储服务模块,业务数据存储服务模块将业务数据密文Edata发送给可设备B中的信执行环境中的密钥管理模块。信任环模块根据MK生成业务密钥dkey,密钥管理模块从信任环模块读取dkey,密钥管理模块从信任环模块读取dkey,使用dkey对业务数据密文Edata进行解密,得到业务数据明文data。接着,密钥管理模块将业务数据明文data返回给业务数据存储服务模块,业务数据存储服务模块存储业务数据明文data。Referring to FIG. 12 , the business data synchronization service module in the device B obtains the business data ciphertext Edata from the account management server through the account management server synchronization framework of the application layer. Then, the business data synchronization service module in device B sends the business data ciphertext Edata to the business data storage service module in device B, and the business data storage service module sends the business data ciphertext Edata to the information execution environment in device B The key management module in . The trust ring module generates the service key dkey according to the MK, the key management module reads the dkey from the trust ring module, the key management module reads the dkey from the trust ring module, and uses the dkey to decrypt the service data ciphertext Edata to obtain the service data plaintext data. Next, the key management module returns the business data plaintext data to the business data storage service module, and the business data storage service module stores the business data plaintext data.
例如,请参见图20,用户在设备B上使用业务1时,需要输入业务1的账号和密码。在业务1的账号和密码的输入界面,如图20的(a)图所示,设备B弹出提示是否使用密码保险箱已同步的业务1的账号和密码的信息。如果用户同意,设备B将密码保险箱已同步的业务1的账号和密码自动填充到图20的(a)图所示的界面,填充后如图20的 (b)图所示。这样就不需要用户为每种业务独立记录密码,提升了用户体验。For example, referring to FIG. 20 , when the user uses
需要说明的是,设备B加入到信任环1后,也可以将设备B中的业务数据用主密钥MK加密后同步到账号管理服务器中,此同步过程请参见前述对设备A同步业务数据到账号管理服务器的说明,此处不再赘述。It should be noted that after device B is added to trust
在设备A已经创建了账号1的信任环1、设备B已通过图18的加入信任环流程加入信任环1的基础上,账号1下的设备C也可以根据图18所示的加入信任环流程加入到信任环1中。设备C加入信任环1中的详细过程请参见前述对设备B加入信任环1中的过程的说明,此处不再赘述。On the basis that device A has created
与设备B所不同的是,在设备C加入信任环1之前,信任环1中有设备A、设备B 这两个在环设备。因此,在验证旧设备(本文中旧设备指在环设备,即已经注册到信任环的设备)锁屏码时,设备C可以从设备A、设备B这两个在环设备中选择任一个作为旧设备。即,在设备C加入信任环1的过程中,图18所示的步骤S10中信任环云向设备C 返回的设备列表中包括2个受信任设备—设备A(请参见图22的(b)图的荣耀V40) 和设备B(请参见图22的(b)图的荣耀V30)。在设备C弹出的“输入其他荣耀设备锁屏密码”界面中,默认输入第一个注册设备(本申请实施例中为设备A)的锁屏密码,如图17的(c)图所示,即此界面中的“其他设备”为荣耀V40(设备A)。此时,设备C可以通过图17的(c)图所示界面上的“选择验证设备”操作选项,选择输入其他旧设备,例如设备B的锁屏码。下面结合图22对设备C更改验证设备的过程进行说明。The difference from device B is that before device C joins
图22为示例性示出的设备C加入信任环的场景下开启“同步到荣耀账号”开关的过程中输入在环设备锁屏码的流程示意图。请参见图22,设备C加入信任环的过程中,当进入到图17的(c)图所示的界面后,用户在该界面上点击“选择验证设备”,如图22的 (a)图所示。这样,设备C就进入到“选择验证设备”的界面,如图22的(b)图所示。由于此时信任环1中已经有2个在环设备(设备A和设备B),因此,“选择验证设备”界面有2个设备,即荣耀V40(设备A)和荣耀V30(设备B)。用户点击“荣耀V30”,即表示用户选择设备B作为验证的旧设备。点击后,设备C弹出“输入其他荣耀设备锁屏密码”界面,该界面中的“其他设备”更改为荣耀V30,如图22的(c)图所示。用户在图22的(c)图所示界面上输入的设备B的锁屏码正确时,“同步到荣耀账号”开关开启。FIG. 22 is a schematic flowchart of inputting the lock screen code of the device in the ring during the process of turning on the switch of “synchronize to the Honor account” in the scenario that the device C joins the trust ring. Please refer to Fig. 22. During the process of adding device C to the trust ring, after entering the interface shown in (c) of Fig. 17, the user clicks "select verification device" on the interface, as shown in (a) of Fig. 22 shown. In this way, the device C enters into the interface of "select verification device", as shown in (b) of FIG. 22 . Since there are already 2 in-ring devices (device A and device B) in
图21为示例性示出的设备C加入信任环过程中的信息交互示意图。请参见图21,在设备C加入信任环1中的过程中,设备C选择设备B作为旧设备,在输入旧设备锁屏码时设备C输入设备B的锁屏码pw22,并基于锁屏码pw22生成设备B的认证参数 PAKE22,然后设备C向信任环云发送设备B的认证参数PAKE22。信任环云在确认 PAKE22与信任环1中已存储的设备B的认证参数PAKE21一致后,将设备B的主密钥密文EMK21返回给设备C。然后,设备C从EMK21中解密出MK,并基于设备C的锁屏码pw31加密MK,生成设备C的主密钥密文EMK31,即第三主密钥密文,以及基于设备C的锁屏码pw31生成设备C的认证参数PAKE31,然后设备C将EMK31和PAKE31 发送至信任环云,信任环云将设备C添加到信任环1中。至此,设备C加入信任环1的过程完成,设备C完成注册。FIG. 21 is an exemplary schematic diagram of information exchange in the process of device C joining the trust ring. Referring to Figure 21, during the process of adding device C to trust
设备C加入信任环1后,信任环云中管理的信任环1数据如表3中所示:After device C joins
表3table 3
设备C加入到信任环1后,可以将设备C中的业务数据用主密钥MK加密后同步到账号管理服务器中,也可以将账号管理服务器中其他在环设备已同步的数据同步到设备 C中。其中,同步业务数据到账号管理服务器的过程请参见前述对设备A同步业务数据到账号管理服务器过程的说明,从账号管理服务器同步业务数据到设备C的过程请参见前述对设备B从账号管理服务器同步业务数据到设备B本地的过程的说明,此处不再赘述。After device C is added to trust
设备下线equipment offline
在本文中,下线是指已注册设备从信任环中退出、成为未注册设备的过程。下线分为两种情况,一种是设备自身引起的下线,称为主动下线,另一种是由其他设备引起的本设备下线,称为被动下线。下面分别对这两种下线过程进行说明。In this context, decommissioning refers to the process by which a registered device is withdrawn from the trust ring and becomes an unregistered device. There are two kinds of offline situations, one is the offline caused by the device itself, which is called active offline, and the other is the offline caused by other devices, which is called passive offline. The two offline processes are described below.
主动下线Take the initiative to go offline
当设备基于本设备上的操作而满足下线条件时,触发设备的主动下线。这里以设备 A为例,说明设备主动下线的过程。When the device satisfies the offline condition based on the operation on the device, the active offline of the device is triggered. Here, device A is used as an example to illustrate the process of the device taking the initiative to go offline.
图23~25示出了满足下线条件的三种场景。图23为示例性示出的关闭锁屏密码过程的界面示意图。请参见图23,当用户想要注销账号时,用户在设备A主界面上点击“设置”应用图标,如图23的(a)图所示,点击后,进入图23的(b)图所示的“设置”界面。在“设置”界面,用户点击“生物识别和密码”选项,进入图23的(c)图所示的“生物识别和密码”界面。在“生物识别和密码”界面,用户点击“关闭锁屏密码”选项,设备A即可执行关闭锁屏密码的处理。Figures 23 to 25 show three scenarios that satisfy the offline condition. FIG. 23 is a schematic diagram of an interface of an exemplary process of turning off the lock screen password. Please refer to Fig. 23, when the user wants to cancel the account, the user clicks the "Settings" application icon on the main interface of the device A, as shown in (a) of Fig. 23, after clicking, the user enters the one shown in (b) of Fig. 23 the "Settings" interface shown. On the “Settings” interface, the user clicks the “Biometrics and Password” option to enter the “Biometrics and Password” interface shown in (c) of FIG. 23 . On the "Biometrics and Password" interface, the user clicks the "Close screen lock password" option, and Device A can perform the process of closing the screen lock password.
图24为示例性示出的恢复出厂设置过程的界面示意图。请参见图24,当用户想要将设备A恢复出厂设置时,首先通过在设备A主界面上点击“设置”应用图标(请参见如图23的(a)图),进入图24的(a)图所示的“设置”界面。在“设置”界面,用户点击“系统和更新”选项,进入图24的(b)图所示的“系统和更新”界面。在“系统和更新”界面,用户点击“重置”选项,进入图24的(c)图所示的“重置”界面。在“重置”界面,用户点击“恢复出厂设置”选项,设备A即可执行恢复出厂设置的处理。FIG. 24 is a schematic interface diagram of an exemplary process of restoring factory settings. Please refer to Fig. 24. When the user wants to restore the factory settings of device A, he first clicks the "Settings" application icon on the main interface of device A (see (a) of Fig. 23), and enters (a) of Fig. 24. ) as shown in the "Settings" interface. On the “Settings” interface, the user clicks the “System and Update” option to enter the “System and Update” interface shown in (b) of FIG. 24 . On the “System and Update” interface, the user clicks the “Reset” option to enter the “Reset” interface shown in (c) of FIG. 24 . On the "Reset" interface, the user clicks the "Restore to Factory Settings" option, and Device A can perform the process of restoring the factory settings.
图25为示例性示出的还原所有设置过程的界面示意图。请参见图25,当用户想要将设备A还原所有设置时,首先根据图25的(a)图和(b)图所示进入图25的(c)图所示的“重置”界面,此过程请参见对图24的(a)图和(b)图的说明,此处不再赘述。然后,在“重置”界面,用户点击“还原所有设置”选项,设备A即可执行还原所有设置的处理。FIG. 25 is a schematic diagram of an interface for restoring all settings in an exemplary manner. Please refer to Figure 25, when the user wants to restore all settings of device A, first enter the "reset" interface shown in (c) of Figure 25 according to Figures (a) and (b) of Figure 25, For this process, please refer to the description of (a) and (b) of FIG. 24 , which will not be repeated here. Then, on the "Reset" interface, the user clicks the "Restore All Settings" option, and Device A can perform the process of restoring all settings.
当满足任一下线条件,设备A就可以通过图26所示的流程完成下线。图26为示例性示出的设备A的下线流程示意图。请参见图26,设备A主动下线的流程可以包括如下步骤:When any of the offline conditions are met, device A can complete the offline process through the process shown in FIG. 26 . FIG. 26 is a schematic diagram of the offline process of the device A shown by way of example. Referring to Figure 26, the process of actively going offline of device A may include the following steps:
S1,设备A的信任环服务模块检测到设备A恢复出厂设置、关闭锁屏密码或还原所有设置时,确定满足下线条件。S1, when the trust ring service module of the device A detects that the device A restores the factory settings, closes the screen lock password, or restores all settings, it determines that the offline condition is satisfied.
S2,设备A的信任环服务模块向信任环模块发送MK删除指令。S2, the trust ring service module of device A sends an MK deletion instruction to the trust ring module.
S3,设备A的信任环模块接收到MK删除指令,删除信任环模块中的主密钥MK。S3, the trust ring module of device A receives the MK deletion instruction, and deletes the master key MK in the trust ring module.
删除主密钥MK后,设备A的信任环服务模块将设备A的注册状态修改为未注册。After the master key MK is deleted, the trust ring service module of device A modifies the registration status of device A to unregistered.
被动下线Passive offline
当设备基于本设备以外的其他设备上的操作而满足下线条件时,触发设备的被动下线。假设信任环1上有两个设备,即设备A和设备B。这里以设备B为例,说明设备被动下线的过程。When the device meets the offline condition based on the operation on other devices other than this device, the passive offline of the device is triggered. Suppose there are two devices on
图27为示例性示出的设备B下线过程中的信息交互示意图。请参见图27,当用户在设备A中执行从账号1中移除设备B的操作,设备A向账号管理服务器发送从账号1 中移除设备B的通知。账号管理服务器接收到从账号1中移除设备B的通知,向信任环云发送将设备B从信任环1中删除的通知。信任环云接收到将设备B从信任环1中删除的通知,向设备B发送push(推送)消息。设备B接收到push消息,将设备B中的MK 删除。FIG. 27 is an exemplary schematic diagram of information interaction in the process of going offline of device B. Referring to FIG. 27 , when the user performs an operation of removing device B from
图28为示例性示出的从账号中移除设备过程的界面示意图。请参见图28,用户进入到“账号安全”界面,如图28的(a)图所示。在“账号安全”界面,用户点击“登录设备管理”选项,进入图28的(b)图所示的“登录设备管理”界面。在“登录设备管理”界面,用户点击“荣耀V30”(即设备B),进入图28的(c)图所示的“荣耀V30”的设备信息界面。在“荣耀V30”的设备信息界面,用户点击“从账号中移除”操作选项,即可将设备B从账号1中移除。之后,设备A执行图29所示的将设备B下线的流程。FIG. 28 is an interface diagram exemplarily shown in the process of removing a device from an account. Referring to Figure 28, the user enters the "Account Security" interface, as shown in (a) of Figure 28. On the “Account Security” interface, the user clicks the “Login Device Management” option to enter the “Login Device Management” interface shown in (b) of FIG. 28 . On the "Login Device Management" interface, the user clicks "Honor V30" (ie device B) to enter the device information interface of "Honor V30" shown in (c) of Figure 28. On the device information interface of "Honor V30", the user can click the "Remove from account" option to remove device B from
图29为示例性示出的设备B的下线流程示意图。请参见图29,设备B被动下线的流程可以包括如下步骤:FIG. 29 is a schematic diagram of the offline process of the device B shown by way of example. Referring to Figure 29, the process of passively going offline of device B may include the following steps:
S1,设备A的账号管理模块接收将设备B从账号1中移除的操作。S1, the account management module of the device A receives the operation of removing the device B from the
S2,设备A的账号管理模块向账号管理服务器发送从账号1中移除设备B的通知。S2, the account management module of the device A sends a notification to the account management server to remove the device B from the
S3,账号管理服务器向信任环云发送将设备B从账号1的信任环1删除的通知。S3 , the account management server sends a notification of deleting the device B from the
S4,信任环云将设备B的EMK21和PAKE21从信任环1删除。S4, the trust ring cloud deletes EMK21 and PAKE21 of device B from
S5,信任环云向设备B发送MK删除消息。S5, the trust ring cloud sends the MK deletion message to device B.
MK删除消息即图27中的push消息。The MK delete message is the push message in FIG. 27 .
S6,设备B删除设备B中存储的MK。S6, device B deletes the MK stored in device B.
至此,设备B下线完成。So far, device B is offline.
通过被动下线流程,在设备丢失的情况下,为了保证账号管理服务器中账号对应的业务数据的安全,可以在其他设备上将丢失设备下线。这样,丢失设备就无法从账号管理服务器中同步业务数据,防止重要业务数据的泄露,提高业务数据的安全性。Through the passive offline process, if the device is lost, in order to ensure the security of the business data corresponding to the account in the account management server, the lost device can be offlined on other devices. In this way, the lost device cannot synchronize business data from the account management server, preventing leakage of important business data and improving the security of business data.
设备下线后,可以通过前述的加入信任环的流程再次添加到信任环中。After the device goes offline, it can be added to the trust ring again through the aforementioned process of adding a trust ring.
其中,本实施例提供的电子设备、计算机存储介质、计算机程序产品或芯片均用于执行上文所提供的对应的方法,因此,其所能达到的有益效果可参考上文所提供的对应的方法中的有益效果,此处不再赘述。Wherein, the electronic device, computer storage medium, computer program product or chip provided in this embodiment are all used to execute the corresponding method provided above. Therefore, for the beneficial effects that can be achieved, reference can be made to the corresponding provided above. The beneficial effects in the method will not be repeated here.
通过以上实施方式的描述,所属领域的技术人员可以了解到,为描述的方便和简洁,仅以上述各功能模块的划分进行举例说明,实际应用中,可以根据需要而将上述功能分配由不同的功能模块完成,即将装置的内部结构划分成不同的功能模块,以完成以上描述的全部或者部分功能。From the description of the above embodiments, those skilled in the art can understand that for the convenience and brevity of the description, only the division of the above functional modules is used as an example for illustration. In practical applications, the above functions can be allocated by different The function module is completed, that is, the internal structure of the device is divided into different function modules, so as to complete all or part of the functions described above.
在本申请所提供的几个实施例中,应该理解到,所揭露的装置和方法,可以通过其它的方式实现。例如,以上所描述的装置实施例仅仅是示意性的,例如,模块或单元的划分,仅仅为一种逻辑功能划分,实际实现时可以有另外的划分方式,例如多个单元或组件可以结合或者可以集成到另一个装置,或一些特征可以忽略,或不执行。另一点,所显示或讨论的相互之间的耦合或直接耦合或通信连接可以是通过一些接口,装置或单元的间接耦合或通信连接,可以是电性,机械或其它的形式。In the several embodiments provided in this application, it should be understood that the disclosed apparatus and method may be implemented in other manners. For example, the apparatus embodiments described above are only illustrative. For example, the division of modules or units is only a logical function division. In actual implementation, there may be other division methods. For example, multiple units or components may be combined or May be integrated into another device, or some features may be omitted, or not implemented. On the other hand, the shown or discussed mutual coupling or direct coupling or communication connection may be through some interfaces, indirect coupling or communication connection of devices or units, and may be in electrical, mechanical or other forms.
作为分离部件说明的单元可以是或者也可以不是物理上分开的,作为单元显示的部件可以是一个物理单元或多个物理单元,即可以位于一个地方,或者也可以分布到多个不同地方。可以根据实际的需要选择其中的部分或者全部单元来实现本实施例方案的目的。Units described as separate components may or may not be physically separated, and components shown as units may be one physical unit or multiple physical units, that is, may be located in one place, or may be distributed in multiple different places. Some or all of the units may be selected according to actual needs to achieve the purpose of the solution in this embodiment.
另外,在本申请各个实施例中的各功能单元可以集成在一个处理单元中,也可以是各个单元单独物理存在,也可以两个或两个以上单元集成在一个单元中。上述集成的单元既可以采用硬件的形式实现,也可以采用软件功能单元的形式实现。In addition, each functional unit in each embodiment of the present application may be integrated into one processing unit, or each unit may exist physically alone, or two or more units may be integrated into one unit. The above-mentioned integrated units may be implemented in the form of hardware, or may be implemented in the form of software functional units.
本申请各个实施例的任意内容,以及同一实施例的任意内容,均可以自由组合。对上述内容的任意组合均在本申请的范围之内。Any content of each embodiment of the present application and any content of the same embodiment can be freely combined. Any combination of the above is within the scope of this application.
集成的单元如果以软件功能单元的形式实现并作为独立的产品销售或使用时,可以存储在一个可读取存储介质中。基于这样的理解,本申请实施例的技术方案本质上或者说对现有技术做出贡献的部分或者该技术方案的全部或部分可以以软件产品的形式体现出来,该软件产品存储在一个存储介质中,包括若干指令用以使得一个设备(可以是单片机,芯片等)或处理器(processor)执行本申请各个实施例方法的全部或部分步骤。而前述的存储介质包括:U盘、移动硬盘、只读存储器(read only memory,ROM)、随机存取存储器(random access memory,RAM)、磁碟或者光盘等各种可以存储程序代码的介质。The integrated unit, if implemented in the form of a software functional unit and sold or used as a stand-alone product, may be stored in a readable storage medium. Based on such understanding, the technical solutions of the embodiments of the present application can be embodied in the form of software products in essence, or the parts that contribute to the prior art, or all or part of the technical solutions, which are stored in a storage medium , including several instructions to make a device (which may be a single chip microcomputer, a chip, etc.) or a processor (processor) to execute all or part of the steps of the methods in the various embodiments of the present application. The aforementioned storage medium includes: a U disk, a removable hard disk, a read only memory (ROM), a random access memory (RAM), a magnetic disk or an optical disk and other media that can store program codes.
上面结合附图对本申请的实施例进行了描述,但是本申请并不局限于上述的具体实施方式,上述的具体实施方式仅仅是示意性的,而不是限制性的,本领域的普通技术人员在本申请的启示下,在不脱离本申请宗旨和权利要求所保护的范围情况下,还可做出很多形式,均属于本申请的保护之内。The embodiments of the present application have been described above in conjunction with the accompanying drawings, but the present application is not limited to the above-mentioned specific embodiments, which are merely illustrative rather than restrictive. Under the inspiration of this application, without departing from the scope of protection of the purpose of this application and the claims, many forms can be made, which all fall within the protection of this application.
Claims (18)
Priority Applications (2)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202311095819.6ACN117278204B (en) | 2021-11-19 | 2021-11-19 | Data protection method and storage medium |
| CN202111400446.XACN115037452B (en) | 2021-11-19 | 2021-11-19 | Data protection methods, systems and electronic devices |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202111400446.XACN115037452B (en) | 2021-11-19 | 2021-11-19 | Data protection methods, systems and electronic devices |
Related Child Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN202311095819.6ADivisionCN117278204B (en) | 2021-11-19 | 2021-11-19 | Data protection method and storage medium |
Publications (2)
| Publication Number | Publication Date |
|---|---|
| CN115037452Atrue CN115037452A (en) | 2022-09-09 |
| CN115037452B CN115037452B (en) | 2023-09-12 |
Family
ID=83117723
Family Applications (2)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN202111400446.XAActiveCN115037452B (en) | 2021-11-19 | 2021-11-19 | Data protection methods, systems and electronic devices |
| CN202311095819.6AActiveCN117278204B (en) | 2021-11-19 | 2021-11-19 | Data protection method and storage medium |
Family Applications After (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN202311095819.6AActiveCN117278204B (en) | 2021-11-19 | 2021-11-19 | Data protection method and storage medium |
Country Status (1)
| Country | Link |
|---|---|
| CN (2) | CN115037452B (en) |
Citations (10)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20130145447A1 (en)* | 2011-12-01 | 2013-06-06 | Dashlane SAS | Cloud-based data backup and sync with secure local storage of access keys |
| US8489889B1 (en)* | 2010-09-17 | 2013-07-16 | Symantec Corporation | Method and apparatus for restricting access to encrypted data |
| CN105210073A (en)* | 2012-11-28 | 2015-12-30 | 豪沃克有限公司 | A method and system of providing authentication of user access to a computer resource via a mobile device using multiple separate security factors |
| CN108134789A (en)* | 2017-12-21 | 2018-06-08 | 北京深思数盾科技股份有限公司 | The method and Cloud Server of data synchronization between devices are carried out by cloud |
| US20180199205A1 (en)* | 2016-01-29 | 2018-07-12 | Tencent Technology (Shenzhen) Company Limited | Wireless network connection method and apparatus, and storage medium |
| US20180337914A1 (en)* | 2017-05-18 | 2018-11-22 | Oracle International Corporation | User authentication using kerberos with identity cloud service |
| US20190028273A1 (en)* | 2016-01-18 | 2019-01-24 | Roland Harras | Method for saving data with multi-layer protection, in particular log-on data and passwords |
| US20200280559A1 (en)* | 2017-09-27 | 2020-09-03 | Huawei Technologies Co., Ltd. | Security enhanced technique of authentication protocol based on trusted execution environment |
| US20210334356A1 (en)* | 2019-07-31 | 2021-10-28 | Huawei Technologies Co., Ltd. | Authentication credential protection method and system |
| CN113609498A (en)* | 2021-07-15 | 2021-11-05 | 荣耀终端有限公司 | Data protection method and electronic equipment |
Family Cites Families (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US7853992B2 (en)* | 2007-05-31 | 2010-12-14 | Microsoft Corporation | Configuring security mechanisms utilizing a trust system |
| US20160041879A1 (en)* | 2014-08-06 | 2016-02-11 | Motorola Mobility Llc | Data backup to and restore from trusted devices |
| US20180254898A1 (en)* | 2017-03-06 | 2018-09-06 | Rivetz Corp. | Device enrollment protocol |
| US10693641B2 (en)* | 2018-01-12 | 2020-06-23 | Blackberry Limited | Secure container based protection of password accessible master encryption keys |
- 2021
- 2021-11-19CNCN202111400446.XApatent/CN115037452B/enactiveActive
- 2021-11-19CNCN202311095819.6Apatent/CN117278204B/enactiveActive
Patent Citations (10)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US8489889B1 (en)* | 2010-09-17 | 2013-07-16 | Symantec Corporation | Method and apparatus for restricting access to encrypted data |
| US20130145447A1 (en)* | 2011-12-01 | 2013-06-06 | Dashlane SAS | Cloud-based data backup and sync with secure local storage of access keys |
| CN105210073A (en)* | 2012-11-28 | 2015-12-30 | 豪沃克有限公司 | A method and system of providing authentication of user access to a computer resource via a mobile device using multiple separate security factors |
| US20190028273A1 (en)* | 2016-01-18 | 2019-01-24 | Roland Harras | Method for saving data with multi-layer protection, in particular log-on data and passwords |
| US20180199205A1 (en)* | 2016-01-29 | 2018-07-12 | Tencent Technology (Shenzhen) Company Limited | Wireless network connection method and apparatus, and storage medium |
| US20180337914A1 (en)* | 2017-05-18 | 2018-11-22 | Oracle International Corporation | User authentication using kerberos with identity cloud service |
| US20200280559A1 (en)* | 2017-09-27 | 2020-09-03 | Huawei Technologies Co., Ltd. | Security enhanced technique of authentication protocol based on trusted execution environment |
| CN108134789A (en)* | 2017-12-21 | 2018-06-08 | 北京深思数盾科技股份有限公司 | The method and Cloud Server of data synchronization between devices are carried out by cloud |
| US20210334356A1 (en)* | 2019-07-31 | 2021-10-28 | Huawei Technologies Co., Ltd. | Authentication credential protection method and system |
| CN113609498A (en)* | 2021-07-15 | 2021-11-05 | 荣耀终端有限公司 | Data protection method and electronic equipment |
Non-Patent Citations (4)
| Title |
|---|
| ZHEN MO ET AL.: ""On Deletion of Outsourced Data in Cloud Computing"", 《2014 IEEE 7TH INTERNATIONAL CONFERENCE ON CLOUD COMPUTING》* |
| ZHEN MO ET AL.: ""On Deletion of Outsourced Data in Cloud Computing"", 《2014 IEEE 7TH INTERNATIONAL CONFERENCE ON CLOUD COMPUTING》, 4 December 2014 (2014-12-04)* |
| ZHINING LV ET AL.: ""Research on Trusted Terminal System Based on Trust Chain"", 《2020 IEEE 3RD INTERNATIONAL CONFERENCE ON INFORMATION SYSTEMS AND COMPUTER AIDED EDUCATION (ICISCAE)》* |
| ZHINING LV ET AL.: ""Research on Trusted Terminal System Based on Trust Chain"", 《2020 IEEE 3RD INTERNATIONAL CONFERENCE ON INFORMATION SYSTEMS AND COMPUTER AIDED EDUCATION (ICISCAE)》, 2 November 2020 (2020-11-02)* |
Also Published As
| Publication number | Publication date |
|---|---|
| CN117278204B (en) | 2024-10-25 |
| CN117278204A (en) | 2023-12-22 |
| CN115037452B (en) | 2023-09-12 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| KR102399582B1 (en) | System access using mobile devices | |
| EP3195555B1 (en) | Secure key management for roaming protected content | |
| TWI673990B (en) | User terminals, and methods and computer-readable recording mediums storing computer programs for transmitting and receiving messages | |
| US10659226B2 (en) | Data encryption method, decryption method, apparatus, and system | |
| US11456872B2 (en) | Offline protection of secrets | |
| JP2017535896A (en) | Roaming content wipe actions across devices | |
| EP2974123B1 (en) | Systems and methods for account recovery using a platform attestation credential | |
| CN115021894B (en) | Data protection method, system and electronic device | |
| CN116346339B (en) | Data protection methods, systems and electronic devices | |
| CN115037451B (en) | Data protection method and electronic device | |
| US20240305450A1 (en) | Authentication system for a multiuser device | |
| CN115037452B (en) | Data protection methods, systems and electronic devices | |
| WO2024088145A1 (en) | Data processing method and apparatus, and program product, computer device and storage medium | |
| CN115037456B (en) | Data protection method, system and electronic device | |
| CN115037455B (en) | Data protection method, system and electronic device | |
| CN115037450B (en) | Data protection method and electronic device | |
| CN115037454B (en) | Data protection method and electronic equipment | |
| CN115021895B (en) | Data protection method, system and electronic device | |
| US11831759B1 (en) | Optimized authentication system for a multiuser device |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| GR01 | Patent grant | ||
| GR01 | Patent grant | ||
| CP03 | Change of name, title or address | Address after:Unit 3401, unit a, building 6, Shenye Zhongcheng, No. 8089, Hongli West Road, Donghai community, Xiangmihu street, Futian District, Shenzhen, Guangdong 518040 Patentee after:Honor Terminal Co.,Ltd. Country or region after:China Address before:3401, unit a, building 6, Shenye Zhongcheng, No. 8089, Hongli West Road, Donghai community, Xiangmihu street, Futian District, Shenzhen, Guangdong Patentee before:Honor Device Co.,Ltd. Country or region before:China | |
| CP03 | Change of name, title or address |