CN115002775A - Device network access method and device, electronic device and storage medium - Google Patents
Device network access method and device, electronic device and storage mediumDownload PDFInfo
- Publication number
- CN115002775A CN115002775ACN202210583588.2ACN202210583588ACN115002775ACN 115002775 ACN115002775 ACN 115002775ACN 202210583588 ACN202210583588 ACN 202210583588ACN 115002775 ACN115002775 ACN 115002775A
- Authority
- CN
- China
- Prior art keywords
- fingerprint
- network
- information
- access
- devices
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Granted
Links
Images
Classifications
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W12/00—Security arrangements; Authentication; Protecting privacy or anonymity
- H04W12/08—Access security
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/08—Network architectures or network communication protocols for network security for authentication of entities
- H04L63/0876—Network architectures or network communication protocols for network security for authentication of entities based on the identity of the terminal or configuration, e.g. MAC address, hardware or software configuration or device fingerprint
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/30—Public key, i.e. encryption algorithm being computationally infeasible to invert or user's encryption keys not requiring secrecy
- H04L9/3066—Public key, i.e. encryption algorithm being computationally infeasible to invert or user's encryption keys not requiring secrecy involving algebraic varieties, e.g. elliptic or hyper-elliptic curves
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/32—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials
- H04L9/3236—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials using cryptographic hash functions
- H04L9/3242—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials using cryptographic hash functions involving keyed hash functions, e.g. message authentication codes [MACs], CBC-MAC or HMAC
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/32—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials
- H04L9/3271—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials using challenge-response
- H04L9/3273—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials using challenge-response for mutual authentication
- Y—GENERAL TAGGING OF NEW TECHNOLOGICAL DEVELOPMENTS; GENERAL TAGGING OF CROSS-SECTIONAL TECHNOLOGIES SPANNING OVER SEVERAL SECTIONS OF THE IPC; TECHNICAL SUBJECTS COVERED BY FORMER USPC CROSS-REFERENCE ART COLLECTIONS [XRACs] AND DIGESTS
- Y02—TECHNOLOGIES OR APPLICATIONS FOR MITIGATION OR ADAPTATION AGAINST CLIMATE CHANGE
- Y02E—REDUCTION OF GREENHOUSE GAS [GHG] EMISSIONS, RELATED TO ENERGY GENERATION, TRANSMISSION OR DISTRIBUTION
- Y02E10/00—Energy generation through renewable energy sources
- Y02E10/70—Wind energy
- Y02E10/72—Wind turbines with rotation axis in wind direction
Landscapes
- Engineering & Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- Computer Networks & Wireless Communication (AREA)
- Signal Processing (AREA)
- Power Engineering (AREA)
- Theoretical Computer Science (AREA)
- Computing Systems (AREA)
- Physics & Mathematics (AREA)
- General Engineering & Computer Science (AREA)
- Algebra (AREA)
- General Physics & Mathematics (AREA)
- Mathematical Analysis (AREA)
- Mathematical Optimization (AREA)
- Mathematical Physics (AREA)
- Pure & Applied Mathematics (AREA)
- Computer Hardware Design (AREA)
- Telephonic Communication Services (AREA)
- Data Exchanges In Wide-Area Networks (AREA)
Abstract
Description
Translated fromChinese技术领域technical field
本公开涉及组网技术领域,具体地,涉及一种设备入网方法、装置、电子设备以及存储介质。The present disclosure relates to the technical field of networking, and in particular, to a method, an apparatus, an electronic device, and a storage medium for device network access.
背景技术Background technique
现如今国家大力发展清洁能源,其中,风力发电是我国主要清洁能源来源之一。基于风力发电的特点,风机部署通常分布较广,部署地点较为偏僻,且部署风机数量较多,通常通过物联网设备对风机的安全进行监察、防护。但由于物联网的组网特点,以及物联网设备本身的特性,给物联网安全防护带来一定的安全隐患。Nowadays, the country is vigorously developing clean energy, among which wind power is one of the main sources of clean energy in my country. Based on the characteristics of wind power generation, the deployment of wind turbines is usually widely distributed, the deployment locations are relatively remote, and the number of deployed wind turbines is large. The safety of wind turbines is usually monitored and protected through IoT devices. However, due to the networking characteristics of the Internet of Things and the characteristics of the Internet of Things devices themselves, it brings certain security risks to the security protection of the Internet of Things.
发明内容SUMMARY OF THE INVENTION
本公开的目的是提供一种设备入网方法、装置、电子设备以及存储介质,旨在解决上述技术问题。The purpose of the present disclosure is to provide a method, apparatus, electronic device, and storage medium for device network access, aiming to solve the above technical problems.
为了实现上述目的,本公开第一方面提供一种设备入网方法,包括:采集待入网的第一设备的设备信息,其中,所述设备信息的种类为多种;根据所述设备信息生成所述第一设备的设备指纹作为第一设备指纹;若对所述第一设备指纹校验成功,则控制所述第一设备入网。In order to achieve the above object, a first aspect of the present disclosure provides a method for device network access, including: collecting device information of a first device to be connected to the network, wherein the device information is of multiple types; generating the device information according to the device information The device fingerprint of the first device is used as the first device fingerprint; if the fingerprint verification of the first device is successful, the first device is controlled to access the network.
可选地,所述根据所述设备信息生成所述第一设备的设备指纹作为第一设备指纹,包括:利用贝叶斯算法对多个设备信息进行特征融合,获得融合后的多个设备信息;采用哈希算法对所述融合后的多个设备信息进行哈希计算,获得哈希值;将所述哈希值确定为所述第一设备的设备指纹并作为所述第一设备指纹。Optionally, the generating the device fingerprint of the first device as the first device fingerprint according to the device information includes: using a Bayesian algorithm to perform feature fusion on a plurality of device information to obtain the fused multiple device information. ; Use a hash algorithm to perform hash calculation on the fused pieces of device information to obtain a hash value; determine the hash value as the device fingerprint of the first device and use it as the first device fingerprint.
可选地,所述将所述哈希值确定为所述第一设备的设备指纹作为第一设备指纹,包括:根据多种设备信息获得碰撞率,其中,所述碰撞率用于表征所述哈希值的重复概率;若所述碰撞率低于预设概率,则将所述哈希值确定为所述第一设备的设备指纹;将所述第一设备的设备指纹作为第一设备指纹。Optionally, the determining the hash value as the device fingerprint of the first device as the first device fingerprint includes: obtaining a collision rate according to a variety of device information, where the collision rate is used to characterize the The repetition probability of the hash value; if the collision rate is lower than the preset probability, the hash value is determined as the device fingerprint of the first device; the device fingerprint of the first device is used as the first device fingerprint .
可选地,所述若对所述第一设备指纹校验成功,则控制所述第一设备入网,包括:若所述第一设备指纹与指纹库中的多个第二设备指纹均不相同,则确定所述第一设备指纹校验成功,控制所述第一设备入网。Optionally, if the fingerprint verification of the first device is successful, controlling the first device to access the network includes: if the fingerprint of the first device is different from the fingerprints of multiple second devices in the fingerprint database. , then it is determined that the fingerprint verification of the first device is successful, and the first device is controlled to access the network.
可选地,所述若所述第一设备指纹与指纹库中的多个第二设备指纹均不相同,则确定所述第一设备指纹校验成功,控制所述第一设备入网之前,还包括:获取已入网的多个第二设备中每个第二设备的设备指纹作为第二设备指纹;根据多个第二设备指纹构建所述指纹库。Optionally, if the fingerprint of the first device is different from multiple second device fingerprints in the fingerprint database, it is determined that the fingerprint verification of the first device is successful, and before the first device is controlled to access the network, the The method includes: acquiring the device fingerprint of each second device among the plurality of second devices that have entered the network as the second device fingerprint; and constructing the fingerprint database according to the plurality of second device fingerprints.
可选地,所述若对所述第一设备指纹校验成功,则控制所述第一设备入网之后,还包括:将所述第一设备的设备标识和所述第一设备指纹发送至多个第二设备,其中,所述多个第二设备与所述第一设备处于同一网络中;当接收到第二设备发送的通信请求时,从所述多个第二设备中确定发送所述通信请求的第二设备作为目标设备,其中,所述通信请求用于请求与所述第一设备通信;若所述多个第二设备中满足预设数量的第二设备对所述第一设备的身份校验成功,则建立所述第一设备和所述目标设备之间的通信连接。Optionally, if the fingerprint verification of the first device is successful, after controlling the first device to access the network, the method further includes: sending the device identification of the first device and the fingerprint of the first device to multiple A second device, wherein the plurality of second devices and the first device are in the same network; when receiving a communication request sent by the second device, determine from the plurality of second devices to send the communication The requested second device is used as the target device, wherein the communication request is used to request communication with the first device; If the identity verification is successful, the communication connection between the first device and the target device is established.
可选地,所述第一设备的设备信息包括SDK、IP地址、MAC地址、设备型号、设备所在地点坐标中的至少两个。Optionally, the device information of the first device includes at least two of SDK, IP address, MAC address, device model, and coordinates of the location where the device is located.
本公开第二方面提供一种设备入网装置,所述装置包括:采集模块,用于采集待入网的第一设备的设备信息,其中,所述设备信息的种类为多种;生成模块,用于根据所述设备信息生成所述第一设备的设备指纹作为第一设备指纹;入网模块,用于若对所述第一设备指纹校验成功,则控制所述第一设备入网。A second aspect of the present disclosure provides a device network access device, the device includes: a collection module for collecting device information of a first device to be connected to the network, wherein the types of the device information are multiple; a generation module for The device fingerprint of the first device is generated according to the device information as the first device fingerprint; the network access module is configured to control the first device to access the network if the fingerprint verification of the first device is successful.
本公开第三方面提供一种电子设备,包括:存储器,其上存储有计算机程序;处理器,用于执行所述存储器中的所述计算机程序,以实现上述方法的步骤。A third aspect of the present disclosure provides an electronic device, comprising: a memory on which a computer program is stored; and a processor for executing the computer program in the memory to implement the steps of the above method.
本公开第四方面提供一种非临时性计算机可读存储介质,其上存储有计算机程序,该程序被处理器执行时实现上述方法的步骤。A fourth aspect of the present disclosure provides a non-transitory computer-readable storage medium on which a computer program is stored, and when the program is executed by a processor, implements the steps of the above method.
本申请提供的一种设备入网方法、装置、电子设备以及存储介质,采集待入网的第一设备的设备信息,其中,设备信息的种类为多种;根据设备信息生成第一设备的设备指纹作为第一设备指纹;若对第一设备指纹校验成功,则控制第一设备入网,第一设备经过验证后入网,保证了网络中信息的安全性。A method, device, electronic device and storage medium for device network access provided by the present application collect device information of a first device to be connected to the network, wherein the types of device information are multiple; the device fingerprint of the first device is generated according to the device information as The fingerprint of the first device; if the fingerprint verification of the first device is successful, the first device is controlled to enter the network, and the first device enters the network after verification, which ensures the security of information in the network.
本公开的其他特征和优点将在随后的具体实施方式部分予以详细说明。Other features and advantages of the present disclosure will be described in detail in the detailed description that follows.
附图说明Description of drawings
附图是用来提供对本公开的进一步理解,并且构成说明书的一部分,与下面的具体实施方式一起用于解释本公开,但并不构成对本公开的限制。在附图中:The accompanying drawings are used to provide a further understanding of the present disclosure, and constitute a part of the specification, and together with the following detailed description, are used to explain the present disclosure, but not to limit the present disclosure. In the attached image:
图1是本公开实施例提供的一种物网联网系统拓扑图;1 is a topology diagram of an Internet of Things system provided by an embodiment of the present disclosure;
图2是根据一示例性实施例示出的一种设备入网方法的流程图;FIG. 2 is a flow chart of a method for device network access according to an exemplary embodiment;
图3是根据图2中实施例示出的一种设备入网方法的步骤S120的流程图;FIG. 3 is a flowchart of step S120 of a method for accessing a device network according to the embodiment in FIG. 2;
图4是本公开实施例提供的一种物网联网系统拓扑图;4 is a topology diagram of an Internet of Things system provided by an embodiment of the present disclosure;
图5是根据另一示例性实施例示出的一种设备入网方法的流程图;FIG. 5 is a flowchart of a method for device network access according to another exemplary embodiment;
图6是根据一示例性实施例示出的一种设备入网装置的示意图;6 is a schematic diagram of a device network access device according to an exemplary embodiment;
图7是根据一示例性实施例示出的一种电子设备的框图。Fig. 7 is a block diagram of an electronic device according to an exemplary embodiment.
附图标记说明Description of reference numerals
1-物联网系统、700-电子设备、200-第二设备、300-第一设备。1-Internet of things system, 700-electronic device, 200-second device, 300-first device.
具体实施方式Detailed ways
以下结合附图对本公开的具体实施方式进行详细说明。应当理解的是,此处所描述的具体实施方式仅用于说明和解释本公开,并不用于限制本公开。The specific embodiments of the present disclosure will be described in detail below with reference to the accompanying drawings. It should be understood that the specific embodiments described herein are only used to illustrate and explain the present disclosure, but not to limit the present disclosure.
需要说明的是,本公开中所有获取信号、信息或数据的动作都是在遵照所在地国家相应的数据保护法规政策的前提下,并获得由相应装置所有者给予授权的情况下进行的。It should be noted that all the actions of obtaining signals, information or data in the present disclosure are carried out under the premise of complying with the corresponding data protection laws and policies of the local country, and under the condition of obtaining authorization from the corresponding device owner.
现如今国家大力发展清洁能源,其中,风力发电是我国主要清洁能源来源之一。基于风力发电的特点,风机部署通常分布较广,部署地点较为偏僻,且部署风机数量较多,通常通过物联网设备对风机的安全进行监察、防护。但由于物联网的组网特点,以及物联网设备本身的特性,给物联网安全防护带来一定的安全隐患,例如,存在如下隐患:Nowadays, the country is vigorously developing clean energy, among which wind power is one of the main sources of clean energy in my country. Based on the characteristics of wind power generation, the deployment of wind turbines is usually widely distributed, the deployment locations are relatively remote, and the number of deployed wind turbines is large. The safety of wind turbines is usually monitored and protected through IoT devices. However, due to the networking characteristics of the Internet of Things and the characteristics of the Internet of Things devices themselves, certain security risks are brought to the security protection of the Internet of Things. For example, there are the following hidden dangers:
(1)感知节点问题(1) Perception node problem
物联网应用方面有许多人类无法取代的优势,例如,能够在高温、低温等恶劣环境中代替人类工作。因此,物联网系统的感知节点可以安装在一些无人监管的环境当中。如果攻击者对感知节点进行破坏,导致无法监测到风机的工作情况,更严重的是,如果攻击者更换感知节点相应的配件,并且通过更换的配件读取检测数据,导致检测数据的泄露。There are many advantages that humans cannot replace in the application of the Internet of Things, for example, it can replace human work in harsh environments such as high temperature and low temperature. Therefore, the sensing nodes of the IoT system can be installed in some unsupervised environments. If the attacker destroys the sensing node, the working condition of the wind turbine cannot be monitored. More seriously, if the attacker replaces the corresponding accessories of the sensing node and reads the detection data through the replaced accessories, the detection data will be leaked.
(2)安全标签问题(2) Safety label problem
攻击者可能会窃取物联网设备上射频识别标签实体,通过将标签内部的实体芯片拆除以达到获取其上信息的目的。同时,阅读器通过无线视频信号读取标签中的信息,无线射频信号无法区分阅读器的合法性。并且无线射频信号还具备穿透力强的特点,可以直接穿过建筑进行传播,可能因为物联网设备发出的无线射频信号的频率与攻击者的阅读器发出的信号的频率吻合,攻击者的阅读器可以通过无线射频信号对标签进行读取,导致标签上携带的信息个人身份认证、密码等的泄露。且标签的嵌入对象被随身携带,攻击者就可以随时掌握携带者的地理位置。Attackers may steal the entity of the RFID tag on the IoT device, and obtain the information on it by removing the entity chip inside the tag. At the same time, the reader reads the information in the tag through the wireless video signal, and the wireless radio frequency signal cannot distinguish the legitimacy of the reader. Moreover, the radio frequency signal also has the characteristics of strong penetrating power and can be transmitted directly through the building. It may be because the frequency of the radio frequency signal sent by the IoT device matches the frequency of the signal sent by the attacker's reader. The device can read the tag through the radio frequency signal, resulting in the disclosure of the information carried on the tag, personal identity authentication, password, etc. And the embedded object of the tag is carried around, and the attacker can grasp the geographical location of the carrier at any time.
(3)通信安全(3) Communication security
由于物联网的感知节点容易被破坏,并且物联网使用的无线信道为开放信道,导致无线信号在传输过程中容易被窃听和破坏。物联网处于无线网络和传感网络的工作环境中时,攻击者可以将恶意程序通过若干个入口实施入侵。介于物联网安全防护的特点,对其设备的准入安全性可以进行深入研究。区块链技术作为一种分布式共享数据库,在数据共识上、溯源、不可篡改的基础上可进行安全防护应用。区块链通过生成公钥以及私钥的方式保证了数据的安全性和不可篡改性。设备指纹是根据设备的特点生成的唯一的身份标识。通常设备的指纹生成会考虑到设备的名称、型号、功能等相关特点。但是传统的软件开发工具包(Software Development Kit,简称SDK)容易暴露,攻击者可以购买相同的设备通过逆向破解设备信息。通过结合区块链的形式度设备指纹进行管理共识,同时使用零知识证明应用区块链方面加强数据保密性。Since the sensing nodes of the Internet of Things are easily destroyed, and the wireless channels used by the Internet of Things are open channels, the wireless signals are easily eavesdropped and destroyed during the transmission process. When the Internet of Things is in the working environment of wireless networks and sensor networks, attackers can intrude malicious programs through several entrances. Due to the characteristics of IoT security protection, the access security of its equipment can be studied in depth. As a distributed shared database, blockchain technology can be used for security protection on the basis of data consensus, traceability, and immutability. The blockchain ensures the security and immutability of data by generating public and private keys. Device fingerprints are unique identifications generated according to the characteristics of the device. Usually, the fingerprint generation of the device will take into account the name, model, function and other related characteristics of the device. However, the traditional software development kit (Software Development Kit, SDK for short) is easy to be exposed, and attackers can purchase the same device and decrypt the device information through reverse. The management consensus is carried out by combining the formal device fingerprint of the blockchain, and the data confidentiality is enhanced by applying the blockchain using zero-knowledge proof.
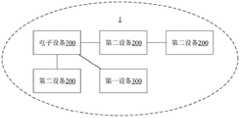
请参阅图1,物联网系统1包括电子设备700和多个第二设备200,第二设备200可以直接与电子设备700连接,可以通过其他第二设备与电子设备连接,共同组成物联网系统1,物联网系统1中的设备可以相互通信。当有待入网的第一设备300想要加入物联网系统1时,为了保证物联网系统中数据的安全性,因此,需要对第一设备进行校验。Referring to FIG. 1 , the
针对上述技术问题,发明人经过长期的研究发现并提出了一种设备入网方法,该方法的执行主体可以为电子设备,其中,电子设备可以是云端、网关、电脑、或者网络中的物联网设备等。请参阅图2,所述设备入网方法具体可以包括以下步骤:In response to the above technical problems, the inventor has found and proposed a method for device network access after long-term research. The execution subject of the method can be an electronic device, wherein the electronic device can be a cloud, a gateway, a computer, or an Internet of Things device in the network. Wait. Referring to FIG. 2, the method for accessing a network by a device may specifically include the following steps:
步骤S110、采集待入网的第一设备的设备信息,其中,所述设备信息的种类为多种。Step S110: Collect device information of the first device to be connected to the network, where the device information is of various types.
在第一设备向电子设备发送入网请求时,电子设备采集第一设备的设备信息,其中,所述第一设备的设备信息包括SDK、网络之间互连的协议(Internet Protocol,简称IP)地址、以太网(Media Access Control,简称MAC)地址、设备型号、设备所在地点坐标中的至少两个。When the first device sends a network access request to the electronic device, the electronic device collects device information of the first device, wherein the device information of the first device includes the SDK and the Internet Protocol (IP) address for interconnection between networks , Ethernet (Media Access Control, MAC for short) address, device model, and at least two of the coordinates of the location where the device is located.
可选地,第一设备信息还可以包括第一设备向电子设备注册时的注册信息。Optionally, the first device information may further include registration information when the first device registers with the electronic device.
步骤S120、根据所述设备信息生成所述第一设备的设备指纹作为第一设备指纹。Step S120: Generate a device fingerprint of the first device as a first device fingerprint according to the device information.
根据多种设备信息相互融合生成第一设备的设备指纹,并将该设备指纹作为第一设备指纹,可以理解的是,第一设备指纹具有唯一性,可以唯一表征第一设备。The device fingerprint of the first device is generated by mutual fusion of various device information, and the device fingerprint is used as the first device fingerprint. It can be understood that the first device fingerprint is unique and can uniquely characterize the first device.
在一种实施方式中,如图3所示,步骤S120可以包括如下子步骤:In one embodiment, as shown in FIG. 3 , step S120 may include the following sub-steps:
子步骤S121、利用贝叶斯算法对多种设备信息进行特征融合,获得融合后的多种设备信息。Sub-step S121 , using a Bayesian algorithm to perform feature fusion on a variety of equipment information to obtain the fused multiple equipment information.
通过贝叶斯算法融合多种设备信息的特征,获得融合后的多种设备信息。The features of various equipment information are fused by Bayesian algorithm, and the fused various equipment information is obtained.
子步骤S122、采用哈希算法对所述融合后的多个设备信息进行哈希计算,获得哈希值。Sub-step S122: Use a hash algorithm to perform hash calculation on the fused pieces of device information to obtain a hash value.
子步骤S123、将所述哈希值确定为所述第一设备的设备指纹并作为所述第一设备指纹。Sub-step S123: Determine the hash value as the device fingerprint of the first device and use it as the first device fingerprint.
作为一种方式,根据多种设备信息获得碰撞率,其中,所述碰撞率用于表征所述哈希值的重复概率。若所述碰撞率低于预设概率,则说明计算出的哈希值不容易被复制,泄漏的可能性低,将所述哈希值确定为所述第一设备的设备指纹;将所述第一设备的设备指纹作为第一设备指纹。In one way, the collision rate is obtained according to a variety of device information, wherein the collision rate is used to represent the repetition probability of the hash value. If the collision rate is lower than the preset probability, it means that the calculated hash value is not easy to be copied, and the possibility of leakage is low, and the hash value is determined as the device fingerprint of the first device; The device fingerprint of the first device is used as the first device fingerprint.
步骤S130、若对所述第一设备指纹校验成功,则控制所述第一设备入网。Step S130: If the fingerprint verification of the first device is successful, control the first device to access the network.
在一种实施方式中,可以根据指纹库对第一设备指纹进行校验,可选地,获取已入网的多个第二设备中每个第二设备的设备指纹作为第二设备指纹;根据多个第二设备指纹构建所述指纹库。根据预先建立的指纹库中存储的第二设备指纹对第一设备指纹进行校验,例如,判断第一设备指纹与指纹库中的多个第二设备指纹是否相同,若第一设备指纹与多个第二设备指纹中任意一项相同,说明指纹库中的第二设备指纹可能被泄露或者被攻击者重新生成,为保证网络中信息的安全性,第一设备入网失败;若所述第一设备指纹与指纹库中的多个第二设备指纹均不相同,则确定所述第一设备指纹校验成功,控制所述第一设备入网。In one embodiment, the fingerprint of the first device can be verified according to the fingerprint database, and optionally, the device fingerprint of each second device in the multiple second devices that have entered the network is obtained as the second device fingerprint; A second device fingerprint is used to construct the fingerprint database. Verify the first device fingerprint according to the second device fingerprint stored in the pre-established fingerprint database, for example, determine whether the first device fingerprint is the same as multiple second device fingerprints in the fingerprint database, if the first device fingerprint is the same as the multiple second device fingerprints in the fingerprint database Any one of the second device fingerprints is the same, indicating that the second device fingerprint in the fingerprint database may be leaked or regenerated by an attacker. In order to ensure the security of information in the network, the first device fails to access the network; if the first device fails to access the network; If the device fingerprint is different from the multiple second device fingerprints in the fingerprint database, it is determined that the fingerprint verification of the first device is successful, and the first device is controlled to access the network.
示例性地,如图4所示,第一设备300通过与电子设备连接实现入网,或者是,第一设备300通过与多个第二设备中的至少一个连接实现入网。Exemplarily, as shown in FIG. 4 , the first device 300 implements network access by connecting with an electronic device, or the first device 300 implements network access by connecting with at least one of a plurality of second devices.
在本实施例提供的设备入网方法,采集待入网的第一设备的设备信息,其中,设备信息的种类为多种;根据设备信息生成第一设备的设备指纹作为第一设备指纹;若对第一设备指纹校验成功,则控制第一设备入网,第一设备经过验证后入网,保证了网络中信息的安全性。In the device network access method provided in this embodiment, the device information of the first device to be connected to the network is collected, wherein the types of device information are multiple; the device fingerprint of the first device is generated according to the device information as the first device fingerprint; Once the fingerprint verification of the device is successful, the first device is controlled to access the network, and the first device is connected to the network after verification, which ensures the security of information in the network.
可选地,在第一设备入网后,可以参与网络中的通信,请参阅图5,所述设备入网方法具体可以包括以下步骤:Optionally, after the first device is connected to the network, it can participate in the communication in the network, please refer to FIG. 5 , and the method for the device network access may specifically include the following steps:
步骤S210、采集待入网的第一设备的设备信息,其中,所述设备信息的种类为多种。Step S210: Collect device information of the first device to be connected to the network, where the device information is of various types.
步骤S220、根据所述设备信息生成所述第一设备的设备指纹作为第一设备指纹。Step S220: Generate a device fingerprint of the first device as a first device fingerprint according to the device information.
步骤S230、若对所述第一设备指纹校验成功,则控制所述第一设备入网。Step S230: If the fingerprint verification of the first device is successful, control the first device to access the network.
本实施例中,步骤S210-步骤S230的具体描述可以参考上述实施例中步骤S110-步骤S130,在此不再赘述。In this embodiment, for the specific description of step S210-step S230, reference may be made to step S110-step S130 in the foregoing embodiment, and details are not repeated here.
步骤S240、将所述第一设备的设备标识和所述第一设备指纹发送至多个第二设备,其中,所述多个第二设备与所述第一设备处于同一网络中。Step S240: Send the device identification of the first device and the fingerprint of the first device to multiple second devices, where the multiple second devices and the first device are in the same network.
网络中的所有设备均存储有其他设备的设备标识和设备指纹,便于通过设备标识和设备指纹校验设备身份,因此,电子设备可以通过自身的通信模块,将第一设备的设备标识以及第一设备指纹发送至网络中的多个第二设备。同样,将网络中的多个第二设备的设备标识和对应的第二设备指纹发送至第一设备。All devices in the network store the device identifiers and device fingerprints of other devices, so that the device identity can be verified through the device identifiers and device fingerprints. Therefore, the electronic device can use its own communication module. The device fingerprint is sent to multiple second devices in the network. Likewise, the device identifiers and corresponding fingerprints of the second devices of the plurality of second devices in the network are sent to the first device.
可以理解的是,网络中的每个第二设备均存储有其他第二设备的设备标识和第二设备指纹。It can be understood that each second device in the network stores the device identifiers and second device fingerprints of other second devices.
步骤S250、当接收到第二设备发送的通信请求时,从所述多个第二设备中确定发送所述通信请求的第二设备作为目标设备,其中,所述通信请求用于请求与所述第一设备通信。Step S250: When receiving the communication request sent by the second device, determine the second device that sends the communication request as the target device from the plurality of second devices, wherein the communication request is used to request communication with the The first device communicates.
步骤S260、若所述多个第二设备中满足预设数量的第二设备对所述第一设备的身份校验成功,则建立所述第一设备和所述目标设备之间的通信连接。Step S260: If the identity verification of the first device by the second devices satisfying the preset number among the plurality of second devices is successful, establish a communication connection between the first device and the target device.
为保证信息的安全,需要对第一设备的身份进行校验,多个第二设备中的每个第二设备根据自身存储的第一设备的设备标识和第一设备指纹,与第一设备发送的第一设备指纹比较,如果两者一致,说明该第二设备对第一设备的身份校验成功,在多个第二设备中存在预设个数(例如2个)或者预设比例(例如51%)的第二设备校验成功,则确定第一身份的身份校验成功,建立第一设备与目标设备之间的通信连接,第一设备可以与目标设备可以根据该连接关系进行通信。In order to ensure the security of information, the identity of the first device needs to be verified, and each second device in the plurality of second devices sends a message to the first device according to the device identification and the first device fingerprint of the first device stored by itself. If the fingerprints of the first device are compared, if the two are consistent, it means that the identity verification of the second device on the first device is successful, and there are preset numbers (for example, 2) or preset ratios (for example, 2) in the plurality of second devices. 51%) of the second device verification is successful, then it is determined that the identity verification of the first identity is successful, and a communication connection between the first device and the target device is established, and the first device and the target device can communicate according to the connection relationship.
可选地,可以采用同样的方法对目标设备的身份进行验证,基于设备相互认证(Mutual Authentication)机制,保证了通信数据的安全性。Optionally, the same method can be used to verify the identity of the target device, and the security of the communication data is ensured based on the device mutual authentication (Mutual Authentication) mechanism.
可选地,在设备进行通信前,还可以生成密钥,用于对通信消息进行加密,多个设备通过各自的密钥生成模块生成公钥和私钥,具体包括:基于椭圆曲线离散对数问题构建公钥-私钥种子矩阵,对设备指纹进行哈希运算,获取设备指纹的哈希值,通过计算线映射算法设备指纹的散列值得到对应的线坐标序列,并根据行坐标序列提取出种子中的公钥-私钥矩阵关键因子,对关键因子进行组合运算,获取物联网设备的公钥和私钥。获得的公钥和私钥用于对通信数据的加密,进一步提高了通信数据的安全性。Optionally, before the device communicates, a key can also be generated for encrypting the communication message, and multiple devices generate public keys and private keys through their respective key generation modules, specifically including: based on elliptic curve discrete logarithm; The problem is to construct a public-private key seed matrix, perform a hash operation on the device fingerprint, obtain the hash value of the device fingerprint, obtain the corresponding line coordinate sequence by calculating the hash value of the device fingerprint of the line mapping algorithm, and extract the corresponding line coordinate sequence according to the row coordinate sequence. The key factors of the public key-private key matrix in the seed are obtained, and the key factors are combined to obtain the public key and private key of the IoT device. The obtained public key and private key are used to encrypt the communication data, which further improves the security of the communication data.
在本实施例中,在校验了设备身份后,再建立至少两个需要通信的设备的通信连接,保证了通信数据的安全性。In this embodiment, after the device identity is verified, a communication connection of at least two devices that need to communicate is established, so as to ensure the security of the communication data.
可选地,还可以基于区块链技术,每个设备依据自身的设备指纹生成区块,用于存储带有时间戳的工作数据。Optionally, based on the blockchain technology, each device can generate a block according to its own device fingerprint, which is used to store the work data with time stamps.
识别能力可通过主动探测和流量学习两种方式对物联网终端进行学习、识别,获取指纹信息实现对终端设备的唯一标识,为终端认证、准入控制等安全能力提供依据。准入管控白名单根据指纹学习结果形成终端接入控制白名单,有效阻断非业务终端访问网络,对终端提供有效的身份识别及准入控制。智能建立行为基线可自动化的学习业务终端的日常行为,并智能化生成每个终端的行为基线作为判断终端正常是否正常提供长时间样本参考模型。终端行为控制,根据行为基线可自动或手动生成行为管控策略,并根据策略规范终端行为,达到屏蔽终端异常动作、指令、行为等访问的目的,有效防止被感染终端实施违法操作。The identification capability can learn and identify IoT terminals through active detection and traffic learning, and obtain fingerprint information to uniquely identify terminal devices, providing a basis for security capabilities such as terminal authentication and access control. The access control whitelist forms a terminal access control whitelist based on the fingerprint learning results, effectively blocking non-service terminals from accessing the network, and providing effective identification and access control for terminals. The intelligent establishment of behavioral baseline can automatically learn the daily behavior of business terminals, and intelligently generate the behavioral baseline of each terminal as a reference model for judging whether the terminal is normal or not. Terminal behavior control, based on behavior baselines, behavior management and control policies can be automatically or manually generated, and terminal behaviors can be regulated according to policies to achieve the purpose of shielding access to abnormal terminal actions, instructions, and behaviors, and effectively prevent infected terminals from performing illegal operations.
(1)区块链设备指纹白名单管控机制,通常终端访问有效区分为2类,即业务终端数据和非业务终端数据,并在允许业务类数据通过的同时,有效阻断非业务数据访问用户网络。相比黑名单机制,白名单具备明显的安全优势。非业务数据具备范围大、不能准确预测的特点。白名单仅允许合法业务通过,可以有效阻断非法业务请求;而黑名单机制准确率依托于特征库是,一般均具有不完善、滞后的特点,无法有效覆盖安全威胁,也就无法全面阻断非业务类数据访问。(1) The fingerprint whitelist management and control mechanism of blockchain devices. Usually, terminal access is effectively divided into two categories, namely business terminal data and non-business terminal data. While allowing business data to pass through, it effectively blocks users who access non-business data. network. Compared with the blacklist mechanism, the whitelist has obvious security advantages. Non-business data has the characteristics of large scope and cannot be accurately predicted. The whitelist only allows legitimate business to pass through, which can effectively block illegal business requests; while the accuracy of the blacklist mechanism relies on the signature database, which generally has the characteristics of imperfection and lag, and cannot effectively cover security threats, so it cannot be fully blocked. Non-business data access.
(2)终端行为基线自学习,能够通过终端流经设备的日常流量内容的分析,自动形成终行为基线,当终端遭遇攻击侵入、病毒感染、非法控制、指纹冒用等情况,无法通过指纹准入进行防范时形成第二道安全防线,仅允许终端发起的符合行为基线的操作通过设备,阻断非法操作行为,在入侵者控制了终端设备的情况下也无法进行非法的入侵操作。(2) Self-learning of the terminal behavior baseline, which can automatically form the final behavior baseline through the analysis of the daily traffic content of the terminal flowing through the device. When the terminal encounters attacks, virus infection, illegal control, fingerprint fraud, etc. It forms a second security line of defense when preventing intrusions. Only operations initiated by the terminal that conform to the behavior baseline are allowed to pass through the device to block illegal operations. Even if the intruder controls the terminal device, illegal intrusion operations cannot be performed.
(3)物联网设备准入控制,基于设备在构建区块链网络的认证机制,基于二级网络入网需要认证,再开始构建的时候对设备的操作写入联盟链,可以得知设备的操作,设备运行状态的监测,以及发现异常。对操作可以进行溯源,由此保证设备操作信息的溯源,对设备进行溯源管理。(3) Internet of Things device access control, based on the authentication mechanism of the device in the construction of the blockchain network, based on the secondary network access to the network requires authentication, and the operation of the device is written into the alliance chain when the construction starts, and the operation of the device can be known. , monitoring of equipment running status, and abnormal detection. The operation can be traced to the source, thus ensuring the traceability of the equipment operation information and the traceability management of the equipment.
(4)具备深度状态展示能力,通过集中收集进一步整合终端安全状态数据,分层次、分区域、从整体到每一终端详细分析、展示终端安全状态,并进行有效展示;具备完善数据接口,与多种集控平台、态势感知系统具备无缝对接整合能。其方法主要在于在生成的每个区块之间查看设备状态信息,对其日志进行审查,对每个区块节点新生成区块查看投票情况,以此查看出状态异常的区块,以此帮助准入功能实现。(4) Have the ability to display in-depth status, further integrate terminal security status data through centralized collection, analyze and display terminal security status in detail from the whole to each terminal at different levels, subregions, and from the whole to each terminal; Various centralized control platforms and situational awareness systems have seamless integration capabilities. The method is mainly to check the device status information between each generated block, review its log, and check the voting status of the newly generated block of each block node, so as to check the block with abnormal status. Help access function implementation.
为实现上述触控方法的实施例,本实施例提供一种设备入网装置,请参阅图6,设备入网装置400包括:采集模块410、生成模块420以及入网模块430。In order to implement the above embodiments of the touch control method, this embodiment provides a device network access device. Please refer to FIG. 6 . The device network access device 400 includes a collection module 410 , a generation module 420 and a network access module 430 .
采集模块410,用于采集待入网的第一设备的设备信息,其中,所述设备信息的种类为多种;The collection module 410 is configured to collect the device information of the first device to be connected to the network, wherein the types of the device information are multiple;
生成模块420,用于根据所述设备信息生成所述第一设备的设备指纹作为第一设备指纹;A generating module 420, configured to generate the device fingerprint of the first device as the first device fingerprint according to the device information;
入网模块430,用于若对所述第一设备指纹校验成功,则控制所述第一设备入网。The network access module 430 is configured to control the first device to access the network if the fingerprint verification of the first device is successful.
可选地,生成模块420包括:融合模块、计算模块以及确定模块。Optionally, the generating module 420 includes: a fusion module, a calculation module and a determination module.
融合模块,用于利用贝叶斯算法对多种设备信息进行特征融合,获得融合后的多种设备信息;The fusion module is used to perform feature fusion of various equipment information by using Bayesian algorithm, and obtain the fused various equipment information;
计算模块,用于采用哈希算法对所述融合后的多个设备信息进行哈希计算,获得哈希值;a calculation module, configured to perform hash calculation on the fused pieces of device information by using a hash algorithm to obtain a hash value;
确定模块,用于将所述哈希值确定为所述第一设备的设备指纹并作为所述第一设备指纹。A determination module, configured to determine the hash value as the device fingerprint of the first device and use it as the first device fingerprint.
可选地,确定模块包括:碰撞率获得模块、比较模块以及第一设备指纹获取模块。Optionally, the determining module includes: a collision rate obtaining module, a comparing module, and a first device fingerprint obtaining module.
碰撞率获得模块,用于根据多种设备信息获得碰撞率,其中,所述碰撞率用于表征所述哈希值的重复概率;a collision rate obtaining module, configured to obtain a collision rate according to a variety of device information, wherein the collision rate is used to represent the repetition probability of the hash value;
比较模块,用于若所述碰撞率低于预设概率,则将所述哈希值确定为所述第一设备的设备指纹;a comparison module, configured to determine the hash value as the device fingerprint of the first device if the collision rate is lower than a preset probability;
第一设备指纹获取模块,用于将所述第一设备的设备指纹作为第一设备指纹。A first device fingerprint acquisition module, configured to use the device fingerprint of the first device as the first device fingerprint.
可选地,入网模块430包括:校验模块。Optionally, the network access module 430 includes: a verification module.
校验模块,用于若所述第一设备指纹与指纹库中的多个第二设备指纹均不相同,则确定所述第一设备指纹校验成功,控制所述第一设备入网。A verification module, configured to determine that the fingerprint verification of the first device is successful if the fingerprint of the first device is different from the fingerprints of multiple second devices in the fingerprint database, and control the first device to access the network.
可选地,设备入网装置400还包括:第二设备指纹获取模块以及构建模块。Optionally, the device network access apparatus 400 further includes: a second device fingerprint acquisition module and a building module.
第二设备指纹获取模块,用于获取已入网的多个第二设备中每个第二设备的设备指纹作为第二设备指纹;The second device fingerprint obtaining module is used to obtain the device fingerprint of each second device in the plurality of second devices that have entered the network as the second device fingerprint;
构建模块,用于根据多个第二设备指纹构建所述指纹库。a building module for building the fingerprint library according to the plurality of second device fingerprints.
可选地,设备入网装置400还包括:发送模块、目标设备获取模块以及通信建立模块。Optionally, the device network access apparatus 400 further includes: a sending module, a target device acquiring module, and a communication establishing module.
发送模块,用于将所述第一设备的设备标识和所述第一设备指纹发送至多个第二设备,其中,所述多个第二设备与所述第一设备处于同一网络中;a sending module, configured to send the device identification of the first device and the fingerprint of the first device to a plurality of second devices, wherein the plurality of second devices and the first device are in the same network;
目标设备获取模块,用于当接收到第二设备发送的通信请求时,从所述多个第二设备中确定发送所述通信请求的第二设备作为目标设备,其中,所述通信请求用于请求与所述第一设备通信;A target device acquiring module, configured to, when receiving a communication request sent by a second device, determine from the plurality of second devices the second device that sent the communication request as a target device, wherein the communication request is used for requesting communication with the first device;
通信建立模块,用于若所述多个第二设备中满足预设数量的第二设备对所述第一设备的身份校验成功,则建立所述第一设备和所述目标设备之间的通信连接。A communication establishment module is configured to establish a communication between the first device and the target device if the identity verification of the first device is successful by the second devices that satisfy the preset number among the plurality of second devices. communication connection.
可选地,所述第一设备的设备信息包括SDK、IP地址、MAC地址、设备型号、设备所在地点坐标中的至少两个。Optionally, the device information of the first device includes at least two of SDK, IP address, MAC address, device model, and coordinates of the location where the device is located.
关于上述实施例中的装置,其中各个模块执行操作的具体方式已经在有关该方法的实施例中进行了详细描述,此处将不做详细阐述说明。Regarding the apparatus in the above-mentioned embodiment, the specific manner in which each module performs operations has been described in detail in the embodiment of the method, and will not be described in detail here.
图7是根据一示例性实施例示出的一种电子设备的框图。如图7所示,该电子设备700可以包括:处理器701,存储器702。该电子设备700还可以包括多媒体组件703,输入/输出(I/O)接口704,以及通信组件705中的一者或多者。Fig. 7 is a block diagram of an electronic device according to an exemplary embodiment. As shown in FIG. 7 , the
其中,处理器701用于控制该电子设备700的整体操作,以完成上述的设备入网方法中的全部或部分步骤。存储器702用于存储各种类型的数据以支持在该电子设备700的操作,这些数据例如可以包括用于在该电子设备700上操作的任何应用程序或方法的指令,以及应用程序相关的数据,例如联系人数据、收发的消息、图片、音频、视频等等。该存储器702可以由任何类型的易失性或非易失性存储设备或者它们的组合实现,例如静态随机存取存储器(Static Random Access Memory,简称SRAM),电可擦除可编程只读存储器(Electrically Erasable Programmable Read-Only Memory,简称EEPROM),可擦除可编程只读存储器(Erasable Programmable Read-Only Memory,简称EPROM),可编程只读存储器(Programmable Read-Only Memory,简称PROM),只读存储器(Read-Only Memory,简称ROM),磁存储器,快闪存储器,磁盘或光盘。多媒体组件703可以包括屏幕和音频组件。其中屏幕例如可以是触摸屏,音频组件用于输出和/或输入音频信号。例如,音频组件可以包括一个麦克风,麦克风用于接收外部音频信号。所接收的音频信号可以被进一步存储在存储器702或通过通信组件705发送。音频组件还包括至少一个扬声器,用于输出音频信号。I/O接口704为处理器701和其他接口模块之间提供接口,上述其他接口模块可以是键盘,鼠标,按钮等。这些按钮可以是虚拟按钮或者实体按钮。通信组件705用于该电子设备700与其他设备之间进行有线或无线通信。无线通信,例如Wi-Fi,蓝牙,近场通信(Near FieldCommunication,简称NFC),2G、3G、4G、NB-IOT、eMTC、或其他5G等等,或它们中的一种或几种的组合,在此不做限定。因此相应的该通信组件705可以包括:Wi-Fi模块,蓝牙模块,NFC模块等等。Wherein, the
在一示例性实施例中,电子设备700可以被一个或多个应用专用集成电路(Application Specific Integrated Circuit,简称ASIC)、数字信号处理器(DigitalSignal Processor,简称DSP)、数字信号处理设备(Digital Signal Processing Device,简称DSPD)、可编程逻辑器件(Programmable Logic Device,简称PLD)、现场可编程门阵列(Field Programmable Gate Array,简称FPGA)、控制器、微控制器、微处理器或其他电子元件实现,用于执行上述的设备入网方法。In an exemplary embodiment, the
在另一示例性实施例中,还提供了一种包括程序指令的计算机可读存储介质,该程序指令被处理器执行时实现上述的设备入网方法的步骤。例如,该计算机可读存储介质可以为上述包括程序指令的存储器702,上述程序指令可由电子设备700的处理器701执行以完成上述的设备入网方法。In another exemplary embodiment, a computer-readable storage medium including program instructions is also provided, and when the program instructions are executed by a processor, the steps of the above-mentioned method for device network access are implemented. For example, the computer-readable storage medium can be the above-mentioned
以上结合附图详细描述了本公开的优选实施方式,但是,本公开并不限于上述实施方式中的具体细节,在本公开的技术构思范围内,可以对本公开的技术方案进行多种简单变型,这些简单变型均属于本公开的保护范围。The preferred embodiments of the present disclosure have been described above in detail with reference to the accompanying drawings. However, the present disclosure is not limited to the specific details of the above-mentioned embodiments. Various simple modifications can be made to the technical solutions of the present disclosure within the scope of the technical concept of the present disclosure. These simple modifications all fall within the protection scope of the present disclosure.
另外需要说明的是,在上述具体实施方式中所描述的各个具体技术特征,在不矛盾的情况下,可以通过任何合适的方式进行组合,为了避免不必要的重复,本公开对各种可能的组合方式不再另行说明。In addition, it should be noted that the various specific technical features described in the above-mentioned specific embodiments can be combined in any suitable manner unless they are inconsistent. In order to avoid unnecessary repetition, the present disclosure provides The combination method will not be specified otherwise.
此外,本公开的各种不同的实施方式之间也可以进行任意组合,只要其不违背本公开的思想,其同样应当视为本公开所公开的内容。In addition, the various embodiments of the present disclosure can also be arbitrarily combined, as long as they do not violate the spirit of the present disclosure, they should also be regarded as the contents disclosed in the present disclosure.
Claims (10)
Translated fromChinesePriority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202210583588.2ACN115002775B (en) | 2022-05-25 | 2022-05-25 | Device network access method, device, electronic device and storage medium |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202210583588.2ACN115002775B (en) | 2022-05-25 | 2022-05-25 | Device network access method, device, electronic device and storage medium |
Publications (2)
| Publication Number | Publication Date |
|---|---|
| CN115002775Atrue CN115002775A (en) | 2022-09-02 |
| CN115002775B CN115002775B (en) | 2024-11-26 |
Family
ID=83028459
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN202210583588.2AActiveCN115002775B (en) | 2022-05-25 | 2022-05-25 | Device network access method, device, electronic device and storage medium |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN115002775B (en) |
Cited By (1)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN117675755A (en)* | 2024-01-31 | 2024-03-08 | 浙江省电子信息产品检验研究院(浙江省信息化和工业化融合促进中心) | Intelligent networking equipment management method and device |
Citations (18)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20060242423A1 (en)* | 2005-04-22 | 2006-10-26 | Kussmaul John W | Isolated authentication device and associated methods |
| CN107426235A (en)* | 2017-08-08 | 2017-12-01 | 北京洋浦伟业科技发展有限公司 | Purview certification method, apparatus and system based on device-fingerprint |
| CN107667515A (en)* | 2015-05-31 | 2018-02-06 | 苹果公司 | Synchronization group and validation group in relevant device |
| WO2018119587A1 (en)* | 2016-12-26 | 2018-07-05 | 深圳前海达闼云端智能科技有限公司 | Data processing method, device, and system, and information acquisition apparatus |
| US20190068566A1 (en)* | 2017-06-27 | 2019-02-28 | Uniken, Inc. | Network-based key distribution system, method, and apparatus |
| CN110311785A (en)* | 2019-06-10 | 2019-10-08 | 平安科技(深圳)有限公司 | A kind of Intranet access method and relevant apparatus |
| CN110798307A (en)* | 2019-10-30 | 2020-02-14 | 武汉极意网络科技有限公司 | Method, device and equipment for marking distributed anti-crawler user equipment and storage medium |
| WO2020164272A1 (en)* | 2019-02-13 | 2020-08-20 | 平安科技(深圳)有限公司 | Network access device identifying method and apparatus, storage medium and computer device |
| CN111698255A (en)* | 2020-06-15 | 2020-09-22 | 南京领行科技股份有限公司 | Service data transmission method, device and system |
| WO2020206899A1 (en)* | 2019-04-12 | 2020-10-15 | 平安科技(深圳)有限公司 | Timestamp-based identity verification method, apparatus and device, and storage medium |
| CN111935021A (en)* | 2020-09-27 | 2020-11-13 | 翱捷智能科技(上海)有限公司 | Method and system for quickly matching network data packets |
| CN112469034A (en)* | 2020-11-25 | 2021-03-09 | 中国科学技术大学 | Internet of things gateway device capable of safely authenticating physical sensing equipment and access method thereof |
| CN112953928A (en)* | 2020-12-30 | 2021-06-11 | 山东鲁能软件技术有限公司 | Network security protection system and method for video monitoring front-end equipment |
| CN112968770A (en)* | 2021-03-15 | 2021-06-15 | 北京智芯微电子科技有限公司 | Fingerprint extraction method and device for Internet of things intelligent terminal equipment and electronic equipment |
| CN114218554A (en)* | 2021-12-07 | 2022-03-22 | 中信银行股份有限公司 | Equipment fingerprint generation method, device, equipment and readable storage medium |
| CN114268508A (en)* | 2021-12-30 | 2022-04-01 | 天翼物联科技有限公司 | Internet of things equipment secure access method, device, equipment and medium |
| US20220131854A1 (en)* | 2020-10-26 | 2022-04-28 | Stripe, Inc. | Systems and methods for identity verification reuse |
| CN114499895A (en)* | 2022-04-06 | 2022-05-13 | 国网浙江省电力有限公司电力科学研究院 | A data trusted processing method and system integrating trusted computing and blockchain |
- 2022
- 2022-05-25CNCN202210583588.2Apatent/CN115002775B/enactiveActive
Patent Citations (18)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20060242423A1 (en)* | 2005-04-22 | 2006-10-26 | Kussmaul John W | Isolated authentication device and associated methods |
| CN107667515A (en)* | 2015-05-31 | 2018-02-06 | 苹果公司 | Synchronization group and validation group in relevant device |
| WO2018119587A1 (en)* | 2016-12-26 | 2018-07-05 | 深圳前海达闼云端智能科技有限公司 | Data processing method, device, and system, and information acquisition apparatus |
| US20190068566A1 (en)* | 2017-06-27 | 2019-02-28 | Uniken, Inc. | Network-based key distribution system, method, and apparatus |
| CN107426235A (en)* | 2017-08-08 | 2017-12-01 | 北京洋浦伟业科技发展有限公司 | Purview certification method, apparatus and system based on device-fingerprint |
| WO2020164272A1 (en)* | 2019-02-13 | 2020-08-20 | 平安科技(深圳)有限公司 | Network access device identifying method and apparatus, storage medium and computer device |
| WO2020206899A1 (en)* | 2019-04-12 | 2020-10-15 | 平安科技(深圳)有限公司 | Timestamp-based identity verification method, apparatus and device, and storage medium |
| CN110311785A (en)* | 2019-06-10 | 2019-10-08 | 平安科技(深圳)有限公司 | A kind of Intranet access method and relevant apparatus |
| CN110798307A (en)* | 2019-10-30 | 2020-02-14 | 武汉极意网络科技有限公司 | Method, device and equipment for marking distributed anti-crawler user equipment and storage medium |
| CN111698255A (en)* | 2020-06-15 | 2020-09-22 | 南京领行科技股份有限公司 | Service data transmission method, device and system |
| CN111935021A (en)* | 2020-09-27 | 2020-11-13 | 翱捷智能科技(上海)有限公司 | Method and system for quickly matching network data packets |
| US20220131854A1 (en)* | 2020-10-26 | 2022-04-28 | Stripe, Inc. | Systems and methods for identity verification reuse |
| CN112469034A (en)* | 2020-11-25 | 2021-03-09 | 中国科学技术大学 | Internet of things gateway device capable of safely authenticating physical sensing equipment and access method thereof |
| CN112953928A (en)* | 2020-12-30 | 2021-06-11 | 山东鲁能软件技术有限公司 | Network security protection system and method for video monitoring front-end equipment |
| CN112968770A (en)* | 2021-03-15 | 2021-06-15 | 北京智芯微电子科技有限公司 | Fingerprint extraction method and device for Internet of things intelligent terminal equipment and electronic equipment |
| CN114218554A (en)* | 2021-12-07 | 2022-03-22 | 中信银行股份有限公司 | Equipment fingerprint generation method, device, equipment and readable storage medium |
| CN114268508A (en)* | 2021-12-30 | 2022-04-01 | 天翼物联科技有限公司 | Internet of things equipment secure access method, device, equipment and medium |
| CN114499895A (en)* | 2022-04-06 | 2022-05-13 | 国网浙江省电力有限公司电力科学研究院 | A data trusted processing method and system integrating trusted computing and blockchain |
Non-Patent Citations (4)
| Title |
|---|
| 尹心明;胡正梁;陈国梁;黄海晔;: "基于设备指纹决策树分类的IP视频专网入网检测方案研究", 信息网络安全, no. 12, 10 December 2016 (2016-12-10)* |
| 李古月;俞佳宝;胡爱群;: "基于设备与信道特征的物理层安全方法", 密码学报, no. 02, 15 April 2020 (2020-04-15)* |
| 郑瑞环;潘亚雄;胡勇;: "基于无线设备指纹的伪AP检测技术研究", 信息安全研究, no. 05, 5 May 2020 (2020-05-05)* |
| 陈洁;文红;陈松林;刘文洁;张金玲;: "物联网中移动终端的协同身份检测机制研究", 通信技术, no. 12, 10 December 2017 (2017-12-10)* |
Cited By (2)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN117675755A (en)* | 2024-01-31 | 2024-03-08 | 浙江省电子信息产品检验研究院(浙江省信息化和工业化融合促进中心) | Intelligent networking equipment management method and device |
| CN117675755B (en)* | 2024-01-31 | 2024-04-19 | 浙江省电子信息产品检验研究院(浙江省信息化和工业化融合促进中心) | Intelligent networking equipment management method and device |
Also Published As
| Publication number | Publication date |
|---|---|
| CN115002775B (en) | 2024-11-26 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| Al‐Turjman et al. | An overview of security and privacy in smart cities' IoT communications | |
| Hassija et al. | A survey on IoT security: application areas, security threats, and solution architectures | |
| Nandy et al. | Review on security of internet of things authentication mechanism | |
| Srivastava et al. | Future IoT‐enabled threats and vulnerabilities: State of the art, challenges, and future prospects | |
| Neshenko et al. | Demystifying IoT security: An exhaustive survey on IoT vulnerabilities and a first empirical look on internet-scale IoT exploitations | |
| Wang et al. | IoT-praetor: Undesired behaviors detection for IoT devices | |
| Yang et al. | A comprehensive survey of security issues of smart home system:“Spear” and “Shields,” theory and practice | |
| US11895144B2 (en) | Systems and methods for network security | |
| CN107148019B (en) | It is a kind of for connecting the method and apparatus of wireless access point | |
| JP2019531567A (en) | Device authentication system and method | |
| Fan et al. | Understanding security in smart city domains from the ant-centric perspective | |
| Chen et al. | A survey on security issues of m2m communications in cyber-physical systems. | |
| Chen et al. | A full lifecycle authentication scheme for large-scale smart IoT applications | |
| Puthal et al. | Decision tree based user-centric security solution for critical IoT infrastructure | |
| CN108337219A (en) | A kind of method and storage medium of Internet of Things anti-intrusion | |
| Jeyavel et al. | Security vulnerabilities and intelligent solutions for iomt systems | |
| Bou-Harb et al. | Cyber threat intelligence for the internet of things | |
| Li et al. | ZPA: A smart home privacy analysis system based on ZigBee encrypted traffic | |
| Paliokas et al. | A blockchain platform in connected medical-device environments: Trustworthy technology to guard against cyberthreats | |
| Sisodia | On the state of internet of things security: Vulnerabilities, attacks, and recent countermeasures | |
| Kondeti et al. | Mapping cyber attacks on the internet of medical things: A taxonomic review | |
| Patel et al. | Safeguarding the IoT: Taxonomy, security solutions, and future research opportunities | |
| CN115002775A (en) | Device network access method and device, electronic device and storage medium | |
| Varma et al. | User privacy in smart systems: recent findings and countermeasures | |
| Gautam et al. | Challenges, attacks, QoS, and other security issues for an IoT environment |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| GR01 | Patent grant | ||
| GR01 | Patent grant |