CN114884662A - Chip key programming method and device, display equipment and storage medium - Google Patents
Chip key programming method and device, display equipment and storage mediumDownload PDFInfo
- Publication number
- CN114884662A CN114884662ACN202210485682.4ACN202210485682ACN114884662ACN 114884662 ACN114884662 ACN 114884662ACN 202210485682 ACN202210485682 ACN 202210485682ACN 114884662 ACN114884662 ACN 114884662A
- Authority
- CN
- China
- Prior art keywords
- key
- chip
- spliced
- receiving chip
- data
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Granted
Links
Images
Classifications
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/14—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols using a plurality of keys or algorithms
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/08—Key distribution or management, e.g. generation, sharing or updating, of cryptographic keys or passwords
- H04L9/0816—Key establishment, i.e. cryptographic processes or cryptographic protocols whereby a shared secret becomes available to two or more parties, for subsequent use
- H04L9/085—Secret sharing or secret splitting, e.g. threshold schemes
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04N—PICTORIAL COMMUNICATION, e.g. TELEVISION
- H04N21/00—Selective content distribution, e.g. interactive television or video on demand [VOD]
- H04N21/40—Client devices specifically adapted for the reception of or interaction with content, e.g. set-top-box [STB]; Operations thereof
- H04N21/41—Structure of client; Structure of client peripherals
- H04N21/426—Internal components of the client ; Characteristics thereof
Landscapes
- Engineering & Computer Science (AREA)
- Signal Processing (AREA)
- Computer Security & Cryptography (AREA)
- Computer Networks & Wireless Communication (AREA)
- Multimedia (AREA)
- Storage Device Security (AREA)
Abstract
Description
Translated fromChinese技术领域technical field
本发明涉及芯片烧写技术领域,尤其涉及一种芯片秘钥烧写方法、装置、显示设备及存储介质。The invention relates to the technical field of chip programming, and in particular, to a chip secret key programming method, device, display device and storage medium.
背景技术Background technique
从目前电视行业的情况来看,分体电视是未来电视行业发展的新趋势,传统的一体机电视虽说能够给带来画质的享受,但是在音质方面还是存在一定的缺失。由于音响腔体的体积大小,厚度限制,喇叭朝向都会影响声音的效果,正因如此,一体电视由于喇叭布局的限制因素,无法达到最佳的音画体验。所以说用户如果想到体验最佳的音画效果,除了电视搭配一套家庭影院外,只有分体电视可以做到,分体电视的出现就可以让电视呈现天籁之音。由于分体电视背部架构的调整,内部硬件单元已经完全脱离电视屏幕,这样可以让为用户呈现更薄更时尚的产品。分体电视主要由主机盒子,电子线,屏体端三部分组成。由于电子线外漏,电子线传输的信号容易被非法录制,需要对信号发送端和接收端进行HDCPkey加密保护处理。Judging from the current situation of the TV industry, split TV is a new trend in the development of the TV industry in the future. Although the traditional all-in-one TV can bring enjoyment of picture quality, there is still a certain lack of sound quality. Due to the volume and thickness of the audio cavity, the orientation of the speakers will affect the sound effect. Because of this, the integrated TV cannot achieve the best audio and video experience due to the limitations of the speaker layout. Therefore, if users want to experience the best audio and video effects, in addition to a TV with a home theater, only a split TV can do it. The emergence of a split TV can make the TV present the sound of nature. Due to the adjustment of the back structure of the split TV, the internal hardware unit has been completely separated from the TV screen, which allows users to present thinner and more fashionable products. The split TV is mainly composed of three parts: the host box, the electronic wire and the screen body. Due to the leakage of the electronic wire, the signal transmitted by the electronic wire is easy to be illegally recorded. It is necessary to perform HDCPkey encryption protection processing on the signal transmitter and receiver.
上述内容仅用于辅助理解本发明的技术方案,并不代表承认上述内容是现有技术。The above content is only used to assist the understanding of the technical solutions of the present invention, and does not mean that the above content is the prior art.
发明内容SUMMARY OF THE INVENTION
本发明的主要目的在于提供一种芯片秘钥烧写方法、装置、显示设备及存储介质,旨在解决现有技术显示终端的接收端芯片烧写需要外接端口,操作不方便的技术问题。The main purpose of the present invention is to provide a chip secret key programming method, device, display device and storage medium, aiming to solve the technical problem that the receiving end chip programming of the display terminal in the prior art requires an external port and is inconvenient to operate.
为实现上述目的,本发明提供了一种芯片秘钥烧写方法,应用于显示设备,所述显示设备包括分体的屏体端以及主机端,所述主机端通过I2C与接收芯片连接,所述芯片秘钥烧写方法包括:In order to achieve the above purpose, the present invention provides a method for burning and writing a chip secret key, which is applied to a display device. The display device includes a separate screen end and a host end. The host end is connected to the receiving chip through I2C, so The chip key programming method includes:
在所述接收芯片进行芯片秘钥烧写时,将所述主机端以及所述接收芯片的待处理秘钥按照预设切割方式进行切割,得到第一待拼接秘钥和第二待拼接秘钥;When the receiving chip performs chip key programming, the host and the receiving chip's unprocessed secret keys are cut according to a preset cutting method to obtain a first unspliced secret key and a second unspliced secret key ;
将所述第一待拼接秘钥与第二待拼接秘钥进行拼接,得到接收芯片秘钥;Splicing the first secret key to be spliced with the second secret key to be spliced to obtain a receiving chip secret key;
将所述接收芯片秘钥通过所述I2C传输到所述接收芯片,以使所述接收芯片通过所述接收芯片秘钥进行芯片烧写。The receiving chip secret key is transmitted to the receiving chip through the I2C, so that the receiving chip performs chip programming through the receiving chip secret key.
可选地,所述在所述接收芯片进行芯片秘钥烧写时,将所述主机端以及所述接收芯片的待处理秘钥按照预设切割方式进行切割,得到第一待拼接秘钥和第二待拼接秘钥之前,还包括:Optionally, when the receiving chip performs chip key programming, the host terminal and the to-be-processed key of the receiving chip are cut according to a preset cutting method to obtain the first to-be-spliced key and Before the second key to be spliced, it also includes:
当所述显示设备开机时,获取标准秘钥数据;When the display device is powered on, obtain standard key data;
将所述标准秘钥数据与存储中的已烧写秘钥数据进行比较,得到比较结果;Comparing the standard key data with the programmed key data in the storage to obtain a comparison result;
在所述比较结果为所述标准秘钥数据与所述已烧写秘钥数据不同,且所述标准秘钥数据符合标准格式规范时,判断需要进行芯片秘钥烧写。When the comparison result is that the standard key data is different from the programmed key data, and the standard key data conforms to the standard format specification, it is determined that chip key programming is required.
可选地,所述在所述接收芯片进行芯片秘钥烧写时,将所述主机端以及所述接收芯片的待处理秘钥按照预设切割方式进行切割,得到第一待拼接秘钥和第二待拼接秘钥,包括:Optionally, when the receiving chip performs chip key programming, the host terminal and the to-be-processed key of the receiving chip are cut according to a preset cutting method to obtain the first to-be-spliced key and The second secret key to be spliced, including:
获取所述主机端的主芯片标准秘钥和所述接收芯片的接收芯片标准秘钥;Obtain the master chip standard key of the host side and the receiving chip standard key of the receiving chip;
将所述主芯片标准秘钥和所述接收芯片标准秘钥作为待处理秘钥;Using the master chip standard key and the receiving chip standard key as the key to be processed;
将所述主芯片标准秘钥使用切割工具按照预设切割规范进行切割,得到第一待拼接秘钥;The main chip standard key is cut according to the preset cutting specification using a cutting tool to obtain the first key to be spliced;
将所述接收芯片标准秘钥使用所述切割工具按照所述预设切割规范进行切割,得到第二待拼接秘钥。The receiving chip standard key is cut according to the preset cutting specification by using the cutting tool to obtain a second key to be spliced.
可选地,所述将所述第一待拼接秘钥与第二待拼接秘钥进行拼接,得到接收芯片秘钥,包括:Optionally, splicing the first secret key to be spliced with the second secret key to be spliced to obtain a receiving chip secret key, including:
获取所述第一待拼接秘钥的第一数据结构信息;obtaining the first data structure information of the first secret key to be spliced;
获取所述第二待拼接秘钥的第二数据结构信息;Obtain the second data structure information of the second key to be spliced;
根据所述第一数据结构信息和所述第二数据结构信息将所述第一待拼接秘钥和第二待拼接秘钥通过预设拼接工具进行拼接,得到接收芯片秘钥。According to the first data structure information and the second data structure information, the first key to be spliced and the second key to be spliced are spliced by a preset splicing tool to obtain a receiving chip key.
可选地,所述根据所述第一数据结构信息和所述第二数据结构信息将所述第一待拼接秘钥和第二待拼接秘钥通过预设拼接工具进行拼接,得到接收芯片秘钥,包括:Optionally, according to the first data structure information and the second data structure information, the first secret key to be spliced and the second secret key to be spliced are spliced by a preset splicing tool to obtain the receiving chip secret key. keys, including:
根据所述第一数据结构信息确定待拼接数据头和第一其它数据;Determine the data header to be spliced and the first other data according to the first data structure information;
将所述待拼接数据头附加预设字节,得到接收芯片秘钥数据头;adding a preset byte to the data header to be spliced to obtain a receiving chip secret key data header;
根据所述第二数据结构信息确定待拼接数据尾和第二其它数据;Determine the tail of the data to be spliced and the second other data according to the second data structure information;
将所述待拼接数据尾附加预设序列码,得到接收芯片秘钥数据尾;adding a preset sequence code to the tail of the data to be spliced to obtain the data tail of the receiving chip secret key;
将所述接收芯片秘钥数据头、所述接收芯片秘钥数据尾、所述第一其它数据以及所述第二其它数据进行拼接,得到接收芯片秘钥。The receiving chip secret key is obtained by splicing the receiving chip key data header, the receiving chip secret key data tail, the first other data and the second other data.
可选地,所述将所述接收芯片秘钥通过I2C传输到所述接收芯片,包括:Optionally, the transmitting the receiving chip secret key to the receiving chip through I2C includes:
将所述接收芯片秘钥烧录到主机端存储器中,并通过中间件解析所述接收芯片秘钥,得到解析文件;Burning the receiving chip secret key into the host-side memory, and parsing the receiving chip secret key through middleware to obtain a parsing file;
根据所述解析文件确定目标秘钥;Determine the target key according to the analysis file;
将所述目标秘钥通过预设函数传输至目标硬件层,以使所述目标硬件层通过I2C将所述目标秘钥传输至所述接收芯片。The target key is transmitted to the target hardware layer through a preset function, so that the target hardware layer transmits the target key to the receiving chip through I2C.
可选地,所述根据所述解析文件确定目标秘钥,包括:Optionally, the determining the target secret key according to the parsing file includes:
根据所述解析文件确定所述接收芯片秘钥的配置信息;Determine the configuration information of the received chip key according to the analysis file;
根据所述配置信息确定数据长度和数据偏移地址;Determine the data length and the data offset address according to the configuration information;
根据所述数据长度和所述数据偏移地址确定目标秘钥。The target key is determined according to the data length and the data offset address.
此外,为实现上述目的,本发明还提出一种芯片秘钥烧写装置,所述芯片秘钥烧写装置包括分体的屏体端以及主机端,所述主机端通过I2C与接收芯片连接,所述芯片秘钥烧写装置还包括:In addition, in order to achieve the above purpose, the present invention also proposes a chip secret key burning device, the chip secret key burning device includes a separate screen body end and a host end, the host end is connected to the receiving chip through I2C, The chip secret key programming device also includes:
切割模块,用于在所述接收芯片进行芯片秘钥烧写时,将所述主机端以及所述接收芯片的待处理秘钥按照预设切割方式进行切割,得到第一待拼接秘钥和第二待拼接秘钥;The cutting module is used to cut the to-be-processed keys of the host end and the receiving chip according to a preset cutting method when the receiving chip performs chip key programming, to obtain a first key to be spliced and a second key to be spliced. Second, the secret key to be spliced;
拼接模块,用于将所述第一待拼接秘钥与第二待拼接秘钥进行拼接,得到接收芯片秘钥;a splicing module for splicing the first secret key to be spliced with the second secret key to be spliced to obtain a receiving chip secret key;
烧写模块,用于将所述接收芯片秘钥通过I2C传输到接收芯片,以使所述接收芯片通过所述接收芯片秘钥进行芯片烧写。The programming module is used to transmit the receiving chip secret key to the receiving chip through I2C, so that the receiving chip can perform chip programming through the receiving chip secret key.
此外,为实现上述目的,本发明还提出一种显示设备,所述显示设备包括:存储器、处理器及存储在所述存储器上并可在所述处理器上运行的芯片秘钥烧写程序,所述芯片秘钥烧写程序配置为实现如上文所述的芯片秘钥烧写方法的步骤。In addition, in order to achieve the above object, the present invention also proposes a display device, the display device includes: a memory, a processor, and a chip key programming program stored on the memory and running on the processor, The chip key programming program is configured to implement the steps of the chip key programming method as described above.
此外,为实现上述目的,本发明还提出一种存储介质,所述存储介质上存储有芯片秘钥烧写程序,所述芯片秘钥烧写程序被处理器执行时实现如上文所述的芯片秘钥烧写方法的步骤。In addition, in order to achieve the above purpose, the present invention also proposes a storage medium on which a chip secret key programming program is stored, and when the chip secret key programming program is executed by a processor, the chip as described above is implemented. The steps of the key burning method.
本发明在所述接收芯片进行芯片秘钥烧写时,将所述主机端以及所述接收芯片的待处理秘钥按照预设切割方式进行切割,得到第一待拼接秘钥和第二待拼接秘钥;将所述第一待拼接秘钥与第二待拼接秘钥进行拼接,得到接收芯片秘钥;将所述接收芯片秘钥通过所述I2C传输到所述接收芯片,以使所述接收芯片通过所述接收芯片秘钥进行芯片烧写。通过这种方式,实现了通过主机端完成接收芯片的秘钥的烧写,而不需要通过外接串口的方式实现接收芯片的秘钥烧写,在保证了信号通过电子线传输时的安全性的前提下,也更加方便和快捷。并且本发明通用性、扩展性强,可以移植推广到其它平台实施,也便于标准化设计,节约了开发时间,提升了开发效率。In the present invention, when the receiving chip performs chip key programming, the to-be-processed keys of the host and the receiving chip are cut according to a preset cutting method to obtain a first key to be spliced and a second key to be spliced secret key; splicing the first secret key to be spliced with the second secret key to be spliced to obtain a receiving chip secret key; transmitting the receiving chip secret key to the receiving chip through the I2C, so that the The receiving chip performs chip programming through the receiving chip secret key. In this way, the secret key programming of the receiving chip is realized through the host side, without the need to implement the secret key programming of the receiving chip through an external serial port, which ensures the security of the signal when the signal is transmitted through the electronic line. On the premise, it is also more convenient and faster. Moreover, the present invention has strong versatility and expansibility, can be transplanted and extended to other platforms for implementation, is also convenient for standardized design, saves development time and improves development efficiency.
附图说明Description of drawings
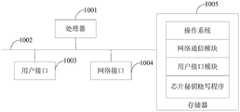
图1是本发明实施例方案涉及的硬件运行环境的显示设备的结构示意图;1 is a schematic structural diagram of a display device of a hardware operating environment involved in an embodiment of the present invention;
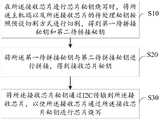
图2为本发明芯片秘钥烧写方法第一实施例的流程示意图;2 is a schematic flowchart of a first embodiment of a method for writing a chip secret key according to the present invention;
图3为本发明芯片秘钥烧写方法一实施例中显示设备开机秘钥检查的流程示意图;FIG. 3 is a schematic flowchart of a display device power-on key check in an embodiment of a chip key programming method according to the present invention;
图4为本发明芯片秘钥烧写方法第二实施例的流程示意图;FIG. 4 is a schematic flowchart of a second embodiment of a chip secret key programming method according to the present invention;
图5为本发明芯片秘钥烧写装置第一实施例的结构框图。FIG. 5 is a structural block diagram of the first embodiment of the device for writing a chip secret key according to the present invention.
本发明目的的实现、功能特点及优点将结合实施例,参照附图做进一步说明。The realization, functional characteristics and advantages of the present invention will be further described with reference to the accompanying drawings in conjunction with the embodiments.
具体实施方式Detailed ways
应当理解,此处所描述的具体实施例仅用以解释本发明,并不用于限定本发明。It should be understood that the specific embodiments described herein are only used to explain the present invention, but not to limit the present invention.
参照图1,图1为本发明实施例方案涉及的硬件运行环境的显示设备结构示意图。Referring to FIG. 1 , FIG. 1 is a schematic structural diagram of a display device of a hardware operating environment involved in an embodiment of the present invention.
如图1所示,该显示设备可以包括:处理器1001,例如中央处理器(CentralProcessing Unit,CPU),通信总线1002、用户接口1003,网络接口1004,存储器1005。其中,通信总线1002用于实现这些组件之间的连接通信。用户接口1003可以包括显示屏(Display)、输入单元比如键盘(Keyboard),可选用户接口1003还可以包括标准的有线接口、无线接口。网络接口1004可选的可以包括标准的有线接口、无线接口(如无线保真(Wireless-Fidelity,Wi-Fi)接口)。存储器1005可以是高速的随机存取存储器(RandomAccess Memory,RAM)存储器,也可以是稳定的非易失性存储器(Non-Volatile Memory,NVM),例如磁盘存储器。存储器1005可选的还可以是独立于前述处理器1001的存储装置。As shown in FIG. 1 , the display device may include: a
本领域技术人员可以理解,图1中示出的结构并不构成对显示设备的限定,可以包括比图示更多或更少的部件,或者组合某些部件,或者不同的部件布置。Those skilled in the art can understand that the structure shown in FIG. 1 does not constitute a limitation on the display device, and may include more or less components than the one shown, or combine some components, or arrange different components.
如图1所示,作为一种存储介质的存储器1005中可以包括操作系统、网络通信模块、用户接口模块以及芯片秘钥烧写程序。As shown in FIG. 1 , the
在图1所示的显示设备中,网络接口1004主要用于与网络服务器进行数据通信;用户接口1003主要用于与用户进行数据交互;本发明显示设备中的处理器1001、存储器1005可以设置在显示设备中,所述显示设备通过处理器1001调用存储器1005中存储的芯片秘钥烧写程序,并执行本发明实施例提供的芯片秘钥烧写方法。In the display device shown in FIG. 1, the
本发明实施例提供了一种芯片秘钥烧写方法,参照图2,图2为本发明一种芯片秘钥烧写方法第一实施例的流程示意图。An embodiment of the present invention provides a method for writing a chip secret key. Referring to FIG. 2 , FIG. 2 is a schematic flowchart of a first embodiment of a method for writing a chip secret key according to the present invention.
本实施例中,所述芯片秘钥烧写方法应用于显示设备,所述显示设备包括分体的屏体端以及主机端,所述主机端通过I2C与接收芯片连接,所述芯片秘钥烧写方法包括以下步骤:In this embodiment, the method for burning a chip key is applied to a display device, and the display device includes a separate screen end and a host end, the host end is connected to the receiving chip through I2C, and the chip secret key burns The writing method includes the following steps:
步骤S10:在所述接收芯片进行芯片秘钥烧写时,将所述主机端以及所述接收芯片的待处理秘钥按照预设切割方式进行切割,得到第一待拼接秘钥和第二待拼接秘钥。Step S10: When the receiving chip performs chip key programming, the host and the receiving chip's unprocessed secret keys are cut according to a preset cutting method to obtain a first unspliced secret key and a second unprocessed secret key. Splicing key.
需要说明的是,本实施例所实施的芯片秘钥烧写方法应用的显示设备,为主机端与屏体、显示端分离的结构,可以为例如分体电视等将主处理模块与显示模块分离的显示设备,本实施例对此不加以限制。It should be noted that the display device to which the chip secret key programming method implemented in this embodiment is applied is a structure in which the host side is separated from the screen body and the display side. The display device is not limited in this embodiment.
应理解的是,本实施例中显示设备的显示模式为:处于主机端的电视主芯片输出VBO信号给外挂输出芯片,也就是RTK2800TX芯片,RTK2800TX将VBO信号转换成HDMI信号通过电子线给到外挂的接收芯片,也就是RTK2800RX芯片,RTK2800RX将接收到的HDMI信号转换成VBO信号给到屏体端。而在这个过程中由于电子线外漏,需要将RTK2800TX送出来的HDMI信号通过HDCP TX Key也就是输出芯片秘钥加密后给到RTK2800RX,使用HDCP2.2 Key的方式进行加密,RTK2800RX再用HDCP RX Key接收芯片秘钥解密后,再把VBO信号给到屏体端,其中RTK2800TX所需的HDCP TX Key可以所有的RTK2800TX芯片共用一个,但RTK2800RX所需的HDCP RX Key需要每一颗RTK2800RX芯片有独立的Key,这就涉及到RTK2800RX HDCPKey烧写,而在目前的情况下,接收芯片秘钥的烧写需要借助外接的串口进行烧写,例如:U盘等设备将已经烧写好的接收芯片秘钥烧写到接收芯片中,但是这样并不方便,本实施例提出的芯片秘钥烧写方法实现了不需要将接收芯片外接串口,通过主机端的主电视芯片进行接收芯片秘钥的烧写。It should be understood that the display mode of the display device in this embodiment is: the main TV chip on the host side outputs the VBO signal to the plug-in output chip, that is, the RTK2800TX chip, and the RTK2800TX converts the VBO signal into an HDMI signal and sends it to the plug-in via an electronic wire. The receiving chip, that is, RTK2800RX chip, RTK2800RX converts the received HDMI signal into VBO signal and sends it to the screen body. In this process, due to the leakage of the electronic line, the HDMI signal sent by RTK2800TX needs to be encrypted by HDCP TX Key, that is, the output chip key, and then sent to RTK2800RX, using HDCP2.2 Key for encryption, RTK2800RX and then HDCP RX Key receives the chip key and decrypts it, and then sends the VBO signal to the screen. The HDCP TX Key required by RTK2800TX can be shared by all RTK2800TX chips, but the HDCP RX Key required by RTK2800RX requires that each RTK2800RX chip has an independent This involves RTK2800RX HDCPKey programming. In the current situation, the programming of the receiving chip key needs to be done with the help of an external serial port. The key is programmed into the receiving chip, but this is inconvenient. The chip key programming method proposed in this embodiment realizes that the receiving chip does not need to be externally connected to a serial port, and the receiving chip key is programmed through the main TV chip on the host side.
在具体实施中,本实施例的执行主体为显示设备的主机端上的控制器,可以是控制芯片秘钥烧写方法的控制器,可以为显示设备的主机端上的系统处理器,或者其它能实现此功能的设备,本实施例对此不加以限制。In specific implementation, the execution body of this embodiment is the controller on the host side of the display device, which may be the controller that controls the method for writing the chip secret key, the system processor on the host side of the display device, or other A device capable of implementing this function is not limited in this embodiment.
需要说明的是,在所述接收芯片进行芯片秘钥烧写时,将所述主机端以及所述接收芯片的待处理秘钥按照预设切割方式进行切割,得到第一待拼接秘钥和第二待拼接秘钥指的是:在判断到接收芯片需要重新进行芯片秘钥烧写时,将主机端的主芯片标准秘钥和接收芯片的接收芯片标准秘钥作为待处理秘钥进行切割,然后切割得到了第一待拼接秘钥和第二待拼接秘钥。It should be noted that, when the receiving chip performs the chip key programming, the unprocessed secret keys of the host side and the receiving chip are cut according to a preset cutting method to obtain the first secret key to be spliced and the second secret key to be spliced. The second key to be spliced refers to: when it is judged that the receiving chip needs to be re-programmed with the chip key, the standard key of the main chip on the host side and the standard key of the receiving chip of the receiving chip are cut as the key to be processed, and then The first key to be spliced and the second key to be spliced are obtained by cutting.
进一步地,为了能够准确的判断是否需要进行接收芯片的秘要烧写,步骤S10之前,还包括:当所述显示设备开机时,获取标准秘钥数据;将所述标准秘钥数据与存储中的已烧写秘钥数据进行比较,得到比较结果;在所述比较结果为所述标准秘钥数据与所述已烧写秘钥数据不同,且所述标准秘钥数据符合标准格式规范时,判断需要进行芯片秘钥烧写。Further, in order to accurately judge whether it is necessary to program the secret key of the receiving chip, before step S10, it also includes: when the display device is turned on, obtaining standard secret key data; The programmed secret key data is compared to obtain a comparison result; when the comparison result is that the standard secret key data is different from the programmed secret key data, and the standard secret key data conforms to the standard format specification, It is judged that the chip key programming needs to be performed.
应理解的是,标准秘钥数据指的是:开机启动时获取的skyhal层也就是指定的硬件抽象层中传递过来的RTK2800RX HDCP2.2 key的896数据里面的SHA256的32个数据。It should be understood that the standard key data refers to the 32 SHA256 data in the 896 data of the RTK2800RX HDCP2.2 key passed in the skyhal layer obtained at startup, that is, the specified hardware abstraction layer.
在具体实施中,存储中的已烧写秘钥数据指的是:通过I2C协议读取RTK2800RX存入到Flash里面的SHA256的32个数据。In the specific implementation, the programmed secret key data in the storage refers to reading 32 data of SHA256 stored in the Flash by RTK2800RX through the I2C protocol.
需要说明的是,如图3所示为显示设备开机时是否需要进行芯片秘钥烧写的判断流程示意图,在所述比较结果为所述标准秘钥数据与所述已烧写秘钥数据不同,且所述标准秘钥数据符合标准格式规范时,判断需要进行芯片秘钥烧写指的是:当比较结果为标准秘钥数据和已烧写秘钥数据出现任意一个数据不同时,则判定比较结果为标准秘钥数据与已烧写秘钥数据不同,然后判定标准秘钥数据是否符合标准格式规范,即RTK2800RXHDCP2.2 key的896个数据格式否符合规范,只有符合规范才会通过I2C烧写秘钥。It should be noted that, as shown in FIG. 3, it is a schematic diagram of the judgment flow of whether the chip key programming needs to be performed when the device is turned on. In the comparison result, the standard key data is different from the programmed key data. , and when the standard key data conforms to the standard format specification, judging that the chip key programming is required refers to: when the comparison result is that the standard key data and the programmed key data appear any data is different, then it is determined that The comparison result is that the standard key data is different from the programmed key data, and then it is determined whether the standard key data conforms to the standard format specification, that is, whether the 896 data formats of the RTK2800RXHDCP2.2 key conform to the specification, and only if it conforms to the specification will it pass the I2C burning. Write the secret key.
应理解的是,SHA256是安全散列算法SHA系列算法之一,其摘要长度为256bits,即32个字节,故称SHA256。对于任意长度(按bit计算)的消息,SHA256都会产生一个32个字节长度数据,称作消息摘要。当接收到消息的时候,这个消息摘要可以用来验证数据是否发生改变,即验证其完整性。在这里是对RTK2800RX HDCP2.2 key 816个字节的数据进行SHA256校验,生成校验码。只要RTK2800RX HDCP2.2 key有一个数据不一样,通过SHA256生成的校验码就会不一样。It should be understood that SHA256 is one of the SHA series of secure hash algorithms, and its digest length is 256 bits, that is, 32 bytes, so it is called SHA256. For messages of any length (calculated in bits), SHA256 will generate a 32-byte length data, called a message digest. When a message is received, this message digest can be used to verify whether the data has changed, ie, verify its integrity. Here is to perform SHA256 verification on the RTK2800RX HDCP2.2 key 816-byte data to generate a verification code. As long as the RTK2800RX HDCP2.2 key has a different data, the check code generated by SHA256 will be different.
通过这种方式,实现了在显示设备开机时自动判断是否需要重新烧写芯片秘钥,不需要每一次开机时都重新烧写,可以有效减少设备的开机时间,减少开机时系统执行的程序步骤。In this way, when the display device is powered on, it is automatically determined whether the chip key needs to be re-programmed, and it is not necessary to re-program the chip key every time it is powered on, which can effectively reduce the boot time of the device and the program steps executed by the system when booting. .
进一步地,为了能够精确地切割得到第一待拼接秘钥和第二待拼接秘钥,步骤S10包括:获取所述主机端的主芯片标准秘钥和所述接收芯片的接收芯片标准秘钥;将所述主芯片标准秘钥和所述接收芯片标准秘钥作为待处理秘钥;将所述主芯片标准秘钥使用切割工具按照预设切割规范进行切割,得到第一待拼接秘钥;将所述接收芯片标准秘钥使用所述切割工具按照所述预设切割规范进行切割,得到第二待拼接秘钥。Further, in order to accurately obtain the first key to be spliced and the second key to be spliced, step S10 includes: obtaining the master chip standard key of the host end and the receiving chip standard key of the receiving chip; The standard key of the main chip and the standard key of the receiving chip are regarded as the keys to be processed; the standard key of the main chip is cut according to the preset cutting specification by using a cutting tool to obtain the first key to be spliced; The receiving chip standard key is cut using the cutting tool according to the preset cutting specification to obtain a second key to be spliced.
需要说明的是,获取所述主机端的主芯片标准秘钥和所述接收芯片的接收芯片标准秘钥指的是:获取存储在主机端的主芯片的主芯片标准秘钥,也就是主芯片上存储的HDCP格式的标准秘钥。然后获取接收芯片对应的HDCP格式的标准秘钥,并作为待处理秘钥。It should be noted that obtaining the standard key of the main chip of the host side and the standard key of the receiving chip of the receiving chip refers to: obtaining the standard key of the main chip of the main chip stored on the host side, that is, the storage on the main chip. standard key in HDCP format. Then, the standard key in HDCP format corresponding to the receiving chip is obtained and used as the key to be processed.
应理解的是,将所述主芯片标准秘钥使用切割工具按照预设切割规范进行切割,得到第一待拼接秘钥,以及将所述接收芯片标准秘钥使用所述切割工具按照所述预设切割规范进行切割,得到第二待拼接秘钥指的是:将待处理秘钥中的主芯片标准秘钥和接收芯片标准秘钥分别使用切割工具将数据结构进行切割,得到第一待拼接秘钥和第二待拼接秘钥。具体的,工具切割出来的第一待拼接秘钥和第二待拼接秘钥的数据结构为:a)、第1个KEY码的起始地址统一在0x20单元(空出前32个Bytes用于记录本批KEY的外围基本信息);b)、本次提供KEY码的总数值用压缩型Hex格式放在0x11(高位)和0x12(低位)地址单元,如本批提供1500台机器的KEY,则0x11单元内为05,0x12单元内为DC;c)、用压缩型的HEX格式在0x13(高位)和0x14(低位)地址内放入本批数据单个HDCP1.4的KEY的有效字节数(即实际写入机器EEPROM内的字节数),如某方案固定为289个,则0x13单元内为01,0x14单元内为21;在0x17(高位)和0x18(低位)地址内存放本批数据单个HDCP2.0KEY的有效字节数,如某方案固定为862个,则0x17为03,0x18为5E;在0x1B(高位)和0x1C(低位)地址内存放本批数据单个HDCP2.2 KEY的有效字节数,如某方案的HDCP2.2有效字节数为1024个,则0x1B为0x04,0x1C为0x00;d)、各种KEY码排列顺序分别为HDCP1.4,HDCP2.0,HDCP2.2;如果在c)中定义的相关地址位上的数值为00则表示不烧录此种KEY码;如在0X17与0X18地址上的值均为00,则表示此机型只需烧录HDCP1.4和HDCP2.2,如果0x17,0X18,0X1B,0X1C四个地址上的值均为00,则表示只需烧录HDCP1.4;(兼容目前只需烧录HDCP1.4的机型);e)、用压缩型的HEX格式在0x15(高位)和0x16(低位)地址内存放本批数据单个HDCP 1.4KEY的字节总数(包括c中HDCP1.4 KEY的有效字节数和f中HDCP1.4 KEY的附加字节数);在0x19(高位)和0x1A(低位)地址内存放本批数据单个HDCP2.0KEY的字节总数(包括c中HDCP2.0 KEY的有效字节数和f中HDCP2.0 KEY的附加字节数);在0x1D(高位)和0X1E(低位)地址存放本批数据单个HDCP2.2 KEY的字节总数(包括c中HDCP2.2 KEY的有效字节数和f中HDCP2.2 KEY的附加字节数);f)、在每种KEY(HDCP1.4/HDCP2.0/HDCP2.2)的每个KEY的末尾允许有附加字节用于对数据管理或者数据分割等;g)、要求每个总KEY的最后4个字节(由高到低)附加有压缩型的Hex序列码,为递增+1序列,起始序列码值不作要求。(如某方案的各KEY码的总长度(e中的总长度)为2022字节则KEY的第2019字节(最高位)到第2022字节(最低位)附加有序列码)。为了满足g),则要求单个总KEY的最后一个组成KEY(如果需要烧录3种KEY则最后一个组成KEY为HDCP2.2,如果需要烧录2种KEY则最后一个组成KEY为HDCP2.0或HDCP2.2)至少有四个附加字节用来存放有序序列码。先用MTK9950切割key的工具切割出对应的hdcp key,再用RTK2800RX切割Key的工具切割出对应的hdcp key。It should be understood that the standard key of the main chip is cut according to the preset cutting specification using a cutting tool to obtain the first key to be spliced, and the standard key of the receiving chip is cut according to the preset cutting tool using the cutting tool. Setting the cutting specification to cut, and obtaining the second key to be spliced refers to: using the cutting tool to cut the data structure of the master chip standard key and the receiving chip standard key in the key to be processed, respectively, to obtain the first key to be spliced secret key and the second secret key to be spliced. Specifically, the data structures of the first key to be spliced and the second key to be spliced cut out by the tool are: a), the start address of the first KEY code is unified in unit 0x20 (the first 32 Bytes are vacated for recording The peripheral basic information of this batch of KEYs); b), the total value of the KEY code provided this time is placed in the 0x11 (high-order) and 0x12 (low-order) address units in compressed Hex format. If the KEY of 1500 machines is provided in this batch, then Unit 0x11 is 05, and unit 0x12 is DC; c) Use compressed HEX format to put the effective number of bytes of the KEY of a single HDCP1. That is, the number of bytes actually written into the machine EEPROM), if a certain scheme is fixed to 289, then the 0x13 unit is 01, and the 0x14 unit is 21; this batch of data is stored in the 0x17 (high) and 0x18 (low) addresses. The number of valid bytes of a single HDCP2.0KEY, if a certain scheme is fixed to 862, then 0x17 is 03, 0x18 is 5E; store this batch of data in the addresses of 0x1B (high order) and 0x1C (low order) The validity of a single HDCP2.2 KEY The number of bytes, such as the number of valid HDCP2.2 bytes of a scheme is 1024, then 0x1B is 0x04, 0x1C is 0x00; d), the order of various KEY codes are HDCP1.4, HDCP2.0, HDCP2.2 ; If the value of the relevant address bit defined in c) is 00, it means that this KEY code is not to be burned; if the value of the 0X17 and 0X18 addresses are both 00, it means that this model only needs to burn HDCP1. 4 and HDCP2.2, if the values at the four addresses of 0x17, 0X18, 0X1B, 0X1C are all 00, it means that only HDCP1.4 needs to be burned; (compatible with current models that only need to burn HDCP1.4); e ), use the compressed HEX format to store the total number of bytes of a single HDCP 1.4KEY of this batch of data (including the effective number of bytes of HDCP1.4 KEY in c and HDCP1 in f. 4 The number of additional bytes of KEY); the total number of bytes of a single HDCP2.0KEY of this batch of data is stored in the addresses of 0x19 (high order) and 0x1A (low order) (including the effective number of bytes of HDCP2.0 KEY in c and HDCP2 in f .0 The number of additional bytes of KEY); the total number of bytes of a single HDCP2.2 KEY of this batch of data is stored at 0x1D (high order) and 0X1E (low order) addresses (including the effective number of bytes of HDCP2.2 KEY in c and in f Additional bytes of HDCP2.2 KEY); f), additional bytes are allowed at the end of each KEY of each KEY (HDCP1.4/HDCP2.0/HDCP2.2) for data management or data segmentation etc.; g), require each total KE The last 4 bytes of Y (from high to low) are attached with a compressed Hex sequence code, which is an incrementing +1 sequence, and the value of the initial sequence code is not required. (If the total length of each KEY code in a certain scheme (the total length in e) is 2022 bytes, then the 2019th byte (highest bit) to the 2022nd byte (lowest bit) of the KEY is appended with a sequence code). In order to satisfy g), the last composition KEY of a single total KEY is required (if 3 kinds of KEYs need to be burned, the last composition KEY is HDCP2.2; if 2 kinds of KEYs need to be burned, the last composition KEY is HDCP2.0 or HDCP2.2) at least four additional bytes are used to store the ordered sequence code. First use the MTK9950 key cutting tool to cut the corresponding hdcp key, and then use the RTK2800RX key cutting tool to cut the corresponding hdcp key.
通过这种方式,实现了通过预设切割方式,即使用切割工具按照预设切割规范进行切割,得到第一待拼接秘钥和第二待拼接秘钥,进而使得接收芯片秘钥的拼接更加准确。In this way, the preset cutting method is realized, that is, the cutting tool is used to cut according to the preset cutting specification, so as to obtain the first key to be spliced and the second key to be spliced, thereby making the splicing of the receiving chip key more accurate .
步骤S20:将所述第一待拼接秘钥与第二待拼接秘钥进行拼接,得到接收芯片秘钥。Step S20: splicing the first key to be spliced and the second key to be spliced to obtain a receiving chip key.
需要说明的是,将所述第一待拼接秘钥与第二待拼接秘钥进行拼接,得到接收芯片秘钥指的是:将第一待拼接秘钥与第二待拼接秘钥进行数据结构的处理,然后结合接收芯片秘钥数据头、所述接收芯片秘钥数据尾、所述第一其它数据以及所述第二其它数据进行拼接,最终得到了接收芯片需要的接收芯片秘钥。It should be noted that splicing the first secret key to be spliced and the second secret key to be spliced to obtain the receiving chip secret key refers to: performing a data structure on the first secret key to be spliced and the second secret key to be spliced Then, combine the receiving chip secret key data header, the receiving chip secret key data tail, the first other data and the second other data for splicing, and finally obtain the receiving chip secret key required by the receiving chip.
步骤S30:将所述接收芯片秘钥通过所述I2C传输到所述接收芯片,以使所述接收芯片通过所述接收芯片秘钥进行芯片烧写。Step S30: Transmit the receiving chip secret key to the receiving chip through the I2C, so that the receiving chip performs chip programming through the receiving chip secret key.
应理解的是,此处的I2C指的是两线式串行总线,只需要两根线即可在连接于总线上的器件之间传送信息。It should be understood that I2C here refers to a two-wire serial bus, and only two wires are needed to transmit information between devices connected to the bus.
在具体实施中,将所述接收芯片秘钥通过I2C传输到所述接收芯片指的是:当接收芯片秘钥拼接完成之后,进行解析得到目标秘钥,然后将目标秘钥通过I2C和I2C传输到接收芯片,使得最终完成芯片的烧写。In a specific implementation, transmitting the receiving chip secret key to the receiving chip through I2C means: after the receiving chip secret key splicing is completed, parsing to obtain the target secret key, and then transmitting the target secret key through I2C and I2C to the receiving chip, so that the programming of the chip is finally completed.
进一步地,为了能够根据接收芯片秘钥完成接收芯片的秘钥烧写,步骤S30包括:将所述接收芯片秘钥烧录到主机端存储器中,并通过中间件解析所述接收芯片秘钥,得到解析文件;根据所述解析文件确定目标秘钥;将所述目标秘钥通过预设函数传输至目标硬件层,以使所述目标硬件层通过I2C将所述目标秘钥传输至所述接收芯片。Further, in order to be able to complete the secret key programming of the receiving chip according to the receiving chip secret key, step S30 includes: burning the receiving chip secret key into the host-side memory, and parsing the receiving chip secret key through middleware, Obtain a parsing file; determine a target key according to the parsing file; transmit the target secret key to the target hardware layer through a preset function, so that the target hardware layer transmits the target secret key to the receiver through I2C chip.
需要说明的是,将所述接收芯片秘钥烧录到主机端存储器中,并通过中间件解析所述接收芯片秘钥,得到解析文件指的是:最终拼接完成接收芯片秘钥之后,得到一个包含10个HDCP Key的文件,按照工厂生产的串口/网口烧写指令,把合成的接收芯片秘钥烧录到FlashEeprom中,然后中间件对文件进行解析,得到的ini文件即为解析文件。It should be noted that burning the receiving chip secret key into the host-side memory, and parsing the receiving chip secret key through middleware to obtain a parsing file means: after the receiving chip secret key is finally spliced, a A file containing 10 HDCP Keys, according to the serial/network port programming instructions produced by the factory, burn the synthesized receiving chip secret key into FlashEeprom, and then the middleware parses the file, and the obtained ini file is the parsing file.
应理解的是,根据所述解析文件确定目标秘钥指的是:根据解析文件确定接收芯片秘钥的数据长度和数据偏移地址,最后基于数据长度和数据偏移地址确定目标秘钥。It should be understood that determining the target key according to the analysis file refers to: determining the data length and data offset address of the receiving chip key according to the analysis file, and finally determining the target key based on the data length and the data offset address.
在具体实施中,将所述目标秘钥通过预设函数传输至目标硬件层,以使所述目标硬件层通过I2C将所述目标秘钥传输至所述接收芯片指的是:将得到的RTK2800RX Key通过函数传给skyhal层,skyhal层通过I2C协议将key发给RTK2800RX,RTK2800RX收到key后写入到Flash芯片进行保存。In a specific implementation, transmitting the target secret key to the target hardware layer through a preset function, so that the target hardware layer transmits the target secret key to the receiving chip through I2C refers to: transferring the obtained RTK2800RX The key is passed to the skyhal layer through the function, and the skyhal layer sends the key to the RTK2800RX through the I2C protocol, and the RTK2800RX writes the key to the Flash chip for saving after receiving the key.
通过这种方式,实现了根据接收芯片秘钥确定目标秘钥,然后将目标秘钥传输到接收芯片,完成接收芯片的秘钥烧写。In this way, the target key is determined according to the key of the receiving chip, and then the target key is transmitted to the receiving chip to complete the key programming of the receiving chip.
进一步地,为了准确的得到目标秘钥,根据所述解析文件确定目标秘钥的步骤包括:根据所述解析文件确定所述接收芯片秘钥的配置信息;根据所述配置信息确定数据长度和数据偏移地址;根据所述数据长度和所述数据偏移地址确定目标秘钥。Further, in order to obtain the target key accurately, the step of determining the target key according to the analysis file includes: determining the configuration information of the receiving chip key according to the analysis file; determining the data length and data according to the configuration information. Offset address; determine the target key according to the data length and the data offset address.
需要说明的是,接收芯片秘钥的配置信息中包括但不限于接收芯片秘钥的数据长度和数据偏移地址,也可以包括其它接收芯片秘钥的数据结构的相关信息。It should be noted that the configuration information of the receiving chip key includes, but is not limited to, the data length and data offset address of the receiving chip key, and may also include other information related to the data structure of the receiving chip key.
应理解的是,根据所述配置信息确定数据长度和数据偏移地址指的是:从配置信息中确定接收芯片秘钥的数据的总长度,以及数据偏移的地址。It should be understood that determining the data length and the data offset address according to the configuration information refers to: determining the total length of the data of the received chip key and the address of the data offset from the configuration information.
通过这种方式,实现了根据接收芯片秘钥的数据长度和数据偏移地址确定目标秘钥,即最终需要烧录到接收芯片的秘钥,使得接收芯片的秘钥烧录更加便捷和准确。In this way, the target secret key is determined according to the data length and data offset address of the secret key of the receiving chip, that is, the secret key that needs to be burned into the receiving chip finally, which makes burning the secret key of the receiving chip more convenient and accurate.
本实施例通过在所述接收芯片进行芯片秘钥烧写时,将所述主机端以及所述接收芯片的待处理秘钥按照预设切割方式进行切割,得到第一待拼接秘钥和第二待拼接秘钥;将所述第一待拼接秘钥与第二待拼接秘钥进行拼接,得到接收芯片秘钥;将所述接收芯片秘钥通过所述I2C传输到所述接收芯片,以使所述接收芯片通过所述接收芯片秘钥进行芯片烧写。通过这种方式,实现了通过主机端完成接收芯片的秘钥的烧写,而不需要通过外接串口的方式实现接收芯片的秘钥烧写,在保证了信号通过电子线传输时的安全性的前提下,也更加方便和快捷。并且本发明通用性、扩展性强,可以移植推广到其它平台实施,也便于标准化设计,节约了开发时间,提升了开发效率。In this embodiment, when the receiving chip performs the chip key programming, the to-be-processed keys of the host side and the receiving chip are cut according to a preset cutting method to obtain a first key to be spliced and a second key to be spliced. The secret key to be spliced; the first secret key to be spliced and the second secret key to be spliced are spliced to obtain a receiving chip secret key; the receiving chip secret key is transmitted to the receiving chip through the I2C, so that The receiving chip performs chip programming through the receiving chip secret key. In this way, the secret key programming of the receiving chip is realized through the host side, without the need to implement the secret key programming of the receiving chip through an external serial port, which ensures the security of the signal when the signal is transmitted through the electronic line. On the premise, it is also more convenient and faster. Moreover, the present invention has strong versatility and expansibility, can be transplanted and extended to other platforms for implementation, is also convenient for standardized design, saves development time and improves development efficiency.
参考图4,图4为本发明一种芯片秘钥烧写方法第二实施例的流程示意图。Referring to FIG. 4 , FIG. 4 is a schematic flowchart of a second embodiment of a method for programming a chip key according to the present invention.
基于上述第一实施例,本实施例芯片秘钥烧写方法在所述步骤S20包括:Based on the above-mentioned first embodiment, the method for writing a chip key in the present embodiment includes in step S20:
步骤S201:获取所述第一待拼接秘钥的第一数据结构信息。Step S201: Obtain first data structure information of the first key to be spliced.
需要说明的是,第一数据结构信息指的是第一待拼接秘钥的数据结构相关信息,包括但不限于:第一待拼接秘钥的数据结构中的数据长度、各个字节所在位置等。It should be noted that the first data structure information refers to information related to the data structure of the first secret key to be spliced, including but not limited to: the data length in the data structure of the first secret key to be spliced, the location of each byte, etc. .
步骤S202:获取所述第二待拼接秘钥的第二数据结构信息。Step S202: Obtain second data structure information of the second key to be spliced.
应理解的是,第二数据结构信息指的是第二待拼接秘钥的数据结构相关信息,包括但不限于:第二待拼接秘钥的数据结构中的数据长度、各个字节所在位置等。It should be understood that the second data structure information refers to the data structure related information of the second secret key to be spliced, including but not limited to: the data length in the data structure of the second secret key to be spliced, the location of each byte, etc. .
步骤S203:根据所述第一数据结构信息和所述第二数据结构信息将所述第一待拼接秘钥和第二待拼接秘钥通过预设拼接工具进行拼接,得到接收芯片秘钥。Step S203: According to the first data structure information and the second data structure information, the first key to be spliced and the second key to be spliced are spliced by a preset splicing tool to obtain a receiving chip key.
在具体实施中,根据所述第一数据结构信息和所述第二数据结构信息将所述第一待拼接秘钥和第二待拼接秘钥通过预设拼接工具进行拼接,得到接收芯片秘钥指的是:根据第一数据结构信息将第一待拼接秘钥分解成待拼接数据头和第一其它数据,然后根据第二数据结构信息将第二待拼接秘钥分解成待拼接数据尾和第二其它数据,最后结合待拼接数据头、第一其它数据、待拼接数据尾和第二其它数据拼接得到接收芯片秘钥。In a specific implementation, the first secret key to be spliced and the second secret key to be spliced are spliced by a preset splicing tool according to the first data structure information and the second data structure information to obtain the receiving chip secret key Refers to: the first key to be spliced is decomposed into the data header to be spliced and the first other data according to the first data structure information, and then the second key to be spliced is decomposed into the tail of the data to be spliced and the second data to be spliced according to the second data structure information. The second other data is finally combined with the data header to be spliced, the first other data, the tail of the data to be spliced, and the second other data to obtain the receiving chip secret key.
进一步地,为了能够准确的进行拼接,步骤S203包括:根据所述第一数据结构信息确定待拼接数据头和第一其它数据;将所述待拼接数据头附加预设字节,得到接收芯片秘钥数据头;根据所述第二数据结构信息确定待拼接数据尾和第二其它数据;将所述待拼接数据尾附加预设序列码,得到接收芯片秘钥数据尾;将所述接收芯片秘钥数据头、所述接收芯片秘钥数据尾、所述第一其它数据以及所述第二其它数据进行拼接,得到接收芯片秘钥。Further, in order to be able to splicing accurately, step S203 includes: determining the data header to be spliced and the first other data according to the first data structure information; adding a preset byte to the data header to be spliced to obtain the receiving chip secret. key data header; determine the tail of the data to be spliced and the second other data according to the second data structure information; add a preset sequence code to the tail of the data to be spliced to obtain the data tail of the receiving chip secret key; The key data header, the receiving chip key data tail, the first other data and the second other data are spliced to obtain the receiving chip key.
需要说明的是,待拼接数据头指的是第一待拼接秘钥的数据头,而第一其它数据指的是第一待拼接秘钥的数据包中除去数据头之外的剩余数据;同理,待拼接数据尾指的是第二待拼接秘钥的数据尾,而第二其它数据指的是第二待拼接秘钥的数据包中除去数据尾的剩余数据。It should be noted that the data header to be spliced refers to the data header of the first key to be spliced, and the first other data refers to the remaining data except the data header in the data packet of the first key to be spliced; the same In principle, the tail of the data to be spliced refers to the data tail of the second key to be spliced, and the second other data refers to the remaining data excluding the data tail in the data packet of the second key to be spliced.
应理解的是,将所述待拼接数据头附加预设字节,得到接收芯片秘钥数据头指的是:将待拼接数据头加上预设字节的附加字节,得到接收芯片秘钥数据头。其中,预设字节指的是用户自行设定的指定长度的字节,本实施例对此不加以限制,一般预设字节为4个字节。It should be understood that adding preset bytes to the data header to be spliced to obtain the receiving chip key data header refers to: adding the additional bytes of the preset bytes to the data header to be spliced to obtain the receiving chip secret key. data header. The preset byte refers to a byte with a specified length set by the user, which is not limited in this embodiment, and generally the preset byte is 4 bytes.
在具体实施中,将所述待拼接数据尾附加预设序列码,得到接收芯片秘钥数据尾指的是:将待拼接数据尾附加预设序列码,得到接收芯片秘钥数据尾。其中,预设序列码指的是用户自行设定的指定长度的序列码,本实施例对此不加以限制,一般预设序列码为4个字节长度。In a specific implementation, adding a preset sequence code to the tail of the data to be spliced to obtain the data tail of the receiving chip key refers to: adding a preset sequence code to the tail of the data to be spliced to obtain the data tail of the receiving chip key. The preset sequence code refers to a sequence code with a specified length set by the user, which is not limited in this embodiment. Generally, the preset sequence code has a length of 4 bytes.
需要说明的是,将所述接收芯片秘钥数据头、所述接收芯片秘钥数据尾、所述第一其它数据以及所述第二其它数据进行拼接,得到接收芯片秘钥指的是:按照接收芯片秘钥数据头++第一其它数据+第二其它数据接收芯片秘钥数据尾的顺序通过TOOL工具合成为一个新的秘钥,即为接收芯片秘钥。It should be noted that splicing the receiving chip secret key data header, the receiving chip secret key data tail, the first other data and the second other data to obtain the receiving chip secret key refers to: The sequence of receiving chip key data header + first other data + second other data receiving chip key data tail is synthesized into a new key by the TOOL tool, which is the receiving chip key.
通过这种方式,实现了对第一待拼接秘钥和第二待拼接秘钥的数据结构进行处理,得到了合成和拼接后的用于烧写到接收芯片的秘钥,即接收芯片秘钥。使得接收芯片秘钥的合成更加准确和快捷,不需要外界串口进行编写。In this way, the data structures of the first secret key to be spliced and the second secret key to be spliced are processed, and the synthesized and spliced secret key for programming to the receiving chip is obtained, that is, the secret key of the receiving chip . It makes the synthesis of the receiving chip secret key more accurate and fast, and does not require an external serial port to write.
本实施例获取所述第一待拼接秘钥的第一数据结构信息;获取所述第二待拼接秘钥的第二数据结构信息;根据所述第一数据结构信息和所述第二数据结构信息将所述第一待拼接秘钥和第二待拼接秘钥通过预设拼接工具进行拼接,得到接收芯片秘钥。通过这种方式,实现了根据第一待拼接秘钥和第二待拼接秘钥的数据结构确定接收芯片秘钥的各个组成部分然后进行拼接,使得接收芯片秘钥的拼接和处理更准确而快速。This embodiment obtains first data structure information of the first key to be spliced; obtains second data structure information of the second key to be spliced; according to the first data structure information and the second data structure The information splices the first secret key to be spliced and the second secret key to be spliced through a preset splicing tool to obtain the receiving chip secret key. In this way, according to the data structures of the first key to be spliced and the second key to be spliced, each component of the receiving chip key is determined and then spliced, so that the splicing and processing of the receiving chip key is more accurate and fast. .
此外,本发明实施例还提出一种存储介质,所述存储介质上存储有芯片秘钥烧写程序,所述芯片秘钥烧写程序被处理器执行时实现如上文所述的芯片秘钥烧写方法的步骤。In addition, an embodiment of the present invention also provides a storage medium, where a chip key burning program is stored on the storage medium, and when the chip key burning program is executed by a processor, the chip key burning as described above is implemented Write the steps of the method.
由于本存储介质采用了上述所有实施例的全部技术方案,因此至少具有上述实施例的技术方案所带来的所有有益效果,在此不一一赘述。Since the storage medium adopts all the technical solutions of the above-mentioned embodiments, it has at least all the beneficial effects brought about by the technical solutions of the above-mentioned embodiments, which will not be repeated here.
参照图5,图5为本发明芯片秘钥烧写装置第一实施例的结构框图。Referring to FIG. 5 , FIG. 5 is a structural block diagram of a first embodiment of a device for writing a chip secret key according to the present invention.
如图5所示,本发明实施例提出的芯片秘钥烧写装置包括:As shown in FIG. 5 , the device for writing a chip secret key proposed by an embodiment of the present invention includes:
切割模块10,用于在所述接收芯片进行芯片秘钥烧写时,将所述主机端以及所述接收芯片的待处理秘钥按照预设切割方式进行切割,得到第一待拼接秘钥和第二待拼接秘钥。The cutting
拼接模块20,用于将所述第一待拼接秘钥与第二待拼接秘钥进行拼接,得到接收芯片秘钥。The
烧写模块30,用于将所述接收芯片秘钥通过I2C传输到接收芯片,以使所述接收芯片通过所述接收芯片秘钥进行芯片烧写。The
本实施例通过在所述接收芯片进行芯片秘钥烧写时,将所述主机端以及所述接收芯片的待处理秘钥按照预设切割方式进行切割,得到第一待拼接秘钥和第二待拼接秘钥;将所述第一待拼接秘钥与第二待拼接秘钥进行拼接,得到接收芯片秘钥;将所述接收芯片秘钥通过所述I2C传输到所述接收芯片,以使所述接收芯片通过所述接收芯片秘钥进行芯片烧写。通过这种方式,实现了通过主机端完成接收芯片的秘钥的烧写,而不需要通过外接串口的方式实现接收芯片的秘钥烧写,在保证了信号通过电子线传输时的安全性的前提下,也更加方便和快捷。并且本发明通用性、扩展性强,可以移植推广到其它平台实施,也便于标准化设计,节约了开发时间,提升了开发效率。In this embodiment, when the receiving chip performs the chip key programming, the to-be-processed keys of the host side and the receiving chip are cut according to a preset cutting method to obtain a first key to be spliced and a second key to be spliced. The secret key to be spliced; the first secret key to be spliced and the second secret key to be spliced are spliced to obtain a receiving chip secret key; the receiving chip secret key is transmitted to the receiving chip through the I2C, so that The receiving chip performs chip programming through the receiving chip secret key. In this way, the secret key programming of the receiving chip is realized through the host side, without the need to implement the secret key programming of the receiving chip through an external serial port, which ensures the security of the signal when the signal is transmitted through the electronic line. On the premise, it is also more convenient and faster. Moreover, the present invention has strong versatility and expansibility, can be transplanted and extended to other platforms for implementation, is also convenient for standardized design, saves development time and improves development efficiency.
在一实施例中,所述切割模块10,还用于当所述显示设备开机时,获取标准秘钥数据;将所述标准秘钥数据与存储中的已烧写秘钥数据进行比较,得到比较结果;在所述比较结果为所述标准秘钥数据与所述已烧写秘钥数据不同,且所述标准秘钥数据符合标准格式规范时,判断需要进行芯片秘钥烧写。In one embodiment, the cutting
在一实施例中,所述切割模块10,还用于获取所述主机端的主芯片标准秘钥和所述接收芯片的接收芯片标准秘钥;将所述主芯片标准秘钥和所述接收芯片标准秘钥作为待处理秘钥;将所述主芯片标准秘钥使用切割工具按照预设切割规范进行切割,得到第一待拼接秘钥;将所述接收芯片标准秘钥使用所述切割工具按照所述预设切割规范进行切割,得到第二待拼接秘钥。In one embodiment, the cutting
在一实施例中,所述拼接模块20,还用于获取所述第一待拼接秘钥的第一数据结构信息;获取所述第二待拼接秘钥的第二数据结构信息;根据所述第一数据结构信息和所述第二数据结构信息将所述第一待拼接秘钥和第二待拼接秘钥通过预设拼接工具进行拼接,得到接收芯片秘钥。In one embodiment, the
在一实施例中,所述拼接模块20,还用于根据所述第一数据结构信息确定待拼接数据头和第一其它数据;将所述待拼接数据头附加预设字节,得到接收芯片秘钥数据头;根据所述第二数据结构信息确定待拼接数据尾和第二其它数据;将所述待拼接数据尾附加预设序列码,得到接收芯片秘钥数据尾;将所述接收芯片秘钥数据头、所述接收芯片秘钥数据尾、所述第一其它数据以及所述第二其它数据进行拼接,得到接收芯片秘钥。In one embodiment, the
在一实施例中,所述烧写模块30,还用于将所述接收芯片秘钥烧录到主机端存储器中,并通过中间件解析所述接收芯片秘钥,得到解析文件;根据所述解析文件确定目标秘钥;将所述目标秘钥通过预设函数传输至目标硬件层,以使所述目标硬件层通过I2C将所述目标秘钥传输至所述接收芯片。In one embodiment, the
在一实施例中,所述烧写模块30,还用于根据所述解析文件确定所述接收芯片秘钥的配置信息;根据所述配置信息确定数据长度和数据偏移地址;根据所述数据长度和所述数据偏移地址确定目标秘钥。In one embodiment, the
应当理解的是,以上仅为举例说明,对本发明的技术方案并不构成任何限定,在具体应用中,本领域的技术人员可以根据需要进行设置,本发明对此不做限制。It should be understood that the above are only examples, and do not constitute any limitation to the technical solutions of the present invention. In specific applications, those skilled in the art can make settings as required, which is not limited by the present invention.
由于本装置采用了上述所有实施例的全部技术方案,因此至少具有上述实施例的技术方案所带来的所有有益效果,在此不一一赘述。Since this device adopts all the technical solutions of all the above-mentioned embodiments, it has at least all the beneficial effects brought about by the technical solutions of the above-mentioned embodiments, which will not be repeated here.
需要说明的是,以上所描述的工作流程仅仅是示意性的,并不对本发明的保护范围构成限定,在实际应用中,本领域的技术人员可以根据实际的需要选择其中的部分或者全部来实现本实施例方案的目的,此处不做限制。It should be noted that the above-described workflow is only illustrative, and does not limit the protection scope of the present invention. In practical applications, those skilled in the art can select some or all of them to implement according to actual needs. The purpose of the solution in this embodiment is not limited here.
另外,未在本实施例中详尽描述的技术细节,可参见本发明任意实施例所提供的芯片秘钥烧写方法,此处不再赘述。In addition, for technical details that are not described in detail in this embodiment, reference may be made to the method for writing a chip key provided by any embodiment of the present invention, which will not be repeated here.
此外,需要说明的是,在本文中,术语“包括”、“包含”或者其任何其它变体意在涵盖非排他性的包含,从而使得包括一系列要素的过程、方法、物品或者系统不仅包括那些要素,而且还包括没有明确列出的其它要素,或者是还包括为这种过程、方法、物品或者系统所固有的要素。在没有更多限制的情况下,由语句“包括一个……”限定的要素,并不排除在包括该要素的过程、方法、物品或者系统中还存在另外的相同要素。Furthermore, it should be noted that, herein, the terms "comprising", "comprising" or any other variation thereof are intended to encompass non-exclusive inclusion, such that a process, method, article or system comprising a series of elements includes not only those elements, but also other elements not expressly listed or inherent to such a process, method, article or system. Without further limitation, an element qualified by the phrase "comprising a..." does not preclude the presence of additional identical elements in the process, method, article or system that includes the element.
上述本发明实施例序号仅仅为了描述,不代表实施例的优劣。The above-mentioned serial numbers of the embodiments of the present invention are only for description, and do not represent the advantages or disadvantages of the embodiments.
通过以上的实施方式的描述,本领域的技术人员可以清楚地了解到上述实施例方法可借助软件加必需的通用硬件平台的方式来实现,当然也可以通过硬件,但很多情况下前者是更佳的实施方式。基于这样的理解,本发明的技术方案本质上或者说对现有技术做出贡献的部分可以以软件产品的形式体现出来,该计算机软件产品存储在一个存储介质(如只读存储器(Read Only Memory,ROM)/RAM、磁碟、光盘)中,包括若干指令用以使得一台终端设备(可以是手机,计算机,服务器,或者网络设备等)执行本发明各个实施例所述的方法。From the description of the above embodiments, those skilled in the art can clearly understand that the method of the above embodiment can be implemented by means of software plus a necessary general hardware platform, and of course can also be implemented by hardware, but in many cases the former is better implementation. Based on such understanding, the technical solutions of the present invention can be embodied in the form of software products in essence or the parts that make contributions to the prior art, and the computer software products are stored in a storage medium (such as a read-only memory). , ROM)/RAM, magnetic disk, optical disk), including several instructions to make a terminal device (which may be a mobile phone, a computer, a server, or a network device, etc.) execute the methods described in the various embodiments of the present invention.
以上仅为本发明的优选实施例,并非因此限制本发明的专利范围,凡是利用本发明说明书及附图内容所作的等效结构或等效流程变换,或直接或间接运用在其它相关的技术领域,均同理包括在本发明的专利保护范围内。The above are only preferred embodiments of the present invention, and are not intended to limit the scope of the present invention. Any equivalent structure or equivalent process transformation made by using the contents of the description and drawings of the present invention, or directly or indirectly applied in other related technical fields , are similarly included in the scope of patent protection of the present invention.
Claims (10)
Translated fromChinesePriority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202210485682.4ACN114884662B (en) | 2022-05-06 | 2022-05-06 | Chip key burning method, device, display device and storage medium |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202210485682.4ACN114884662B (en) | 2022-05-06 | 2022-05-06 | Chip key burning method, device, display device and storage medium |
Publications (2)
| Publication Number | Publication Date |
|---|---|
| CN114884662Atrue CN114884662A (en) | 2022-08-09 |
| CN114884662B CN114884662B (en) | 2025-01-24 |
Family
ID=82673650
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN202210485682.4AActiveCN114884662B (en) | 2022-05-06 | 2022-05-06 | Chip key burning method, device, display device and storage medium |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN114884662B (en) |
Citations (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20070005512A1 (en)* | 2005-06-30 | 2007-01-04 | Fujitsu Limited | IC chip, board, information processing equipment and storage medium |
| US20070098179A1 (en)* | 2005-10-31 | 2007-05-03 | Texas Instruments Incorporated | Wave torque retract of disk drive actuator |
| CN106506149A (en)* | 2016-11-07 | 2017-03-15 | 福建星海通信科技有限公司 | Key generation method and system between a kind of TBOX terminals and TSP platforms |
| CN113691884A (en)* | 2021-08-11 | 2021-11-23 | 康佳集团股份有限公司 | Television-based KEY burning processing method and device, intelligent terminal and medium |
- 2022
- 2022-05-06CNCN202210485682.4Apatent/CN114884662B/enactiveActive
Patent Citations (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20070005512A1 (en)* | 2005-06-30 | 2007-01-04 | Fujitsu Limited | IC chip, board, information processing equipment and storage medium |
| US20070098179A1 (en)* | 2005-10-31 | 2007-05-03 | Texas Instruments Incorporated | Wave torque retract of disk drive actuator |
| CN106506149A (en)* | 2016-11-07 | 2017-03-15 | 福建星海通信科技有限公司 | Key generation method and system between a kind of TBOX terminals and TSP platforms |
| CN113691884A (en)* | 2021-08-11 | 2021-11-23 | 康佳集团股份有限公司 | Television-based KEY burning processing method and device, intelligent terminal and medium |
Non-Patent Citations (2)
| Title |
|---|
| SANU K. MATHEW等: "16.2 A 0.19pJ/b PVT-variation-tolerant hybrid physically unclonable function circuit for 100% stable secure key generation in 22nm CMOS", 2014 IEEE INTERNATIONAL SOLID-STATE CIRCUITS CONFERENCE DIGEST OF TECHNICAL PAPERS (ISSCC), 6 March 2014 (2014-03-06)* |
| 徐元哲等: "Fs88x6系列加密芯片烧录器的设计与实现", 中国优秀硕士学位论文全文数据库, 15 January 2011 (2011-01-15)* |
Also Published As
| Publication number | Publication date |
|---|---|
| CN114884662B (en) | 2025-01-24 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| CN105183675B (en) | To the access method of USB device, device, terminal, server and system | |
| CN110442366B (en) | A screen transmission processing method, device, device and storage medium | |
| TW201830240A (en) | Electronic apparatus and operation method thereof | |
| US20230198760A1 (en) | Verified presentation of non-fungible tokens | |
| CN108156152B (en) | Method, apparatus, storage medium and the terminal device Streaming Media downloading and played | |
| CN115066877B (en) | Electronic device and method for identifying an audio output device connected to a USB Type-C connector | |
| WO2021159864A1 (en) | Method for transmitting video and audio data, cloud server and system | |
| CN111338673B (en) | Equipment debugging method and device, electronic equipment and storage medium | |
| WO2020124920A1 (en) | Voice interaction method and bluetooth device | |
| KR20200131035A (en) | Electronic device and method for receiving push message stored in blockchain | |
| CN110545542B (en) | Main control key downloading method and device based on asymmetric encryption algorithm and computer equipment | |
| CN104714760B (en) | Method and device for reading and writing storage devices | |
| CN112905464B (en) | Application running environment data processing method and device | |
| CN114884662A (en) | Chip key programming method and device, display equipment and storage medium | |
| WO2022062980A1 (en) | Communication method and apparatus, and electronic device and storage medium | |
| CN112306553B (en) | Processing method and device for extension information in installation package file and electronic equipment | |
| CN107992760A (en) | Secret key wiring method, device, equipment and storage medium | |
| US20120005485A1 (en) | Storage device and information processing apparatus | |
| CN110764806A (en) | TWS earphone and upgrading method and device thereof | |
| CN105975624B (en) | A kind of data transmission method, equipment and system | |
| CN116185450A (en) | A method, system, device and storage medium for updating CPLD firmware | |
| CN117201026A (en) | Charging safety verification method and device, electronic equipment and storage medium | |
| US20080071950A1 (en) | Thin client implementation based on redirection of virtual i/o devices | |
| CN115348494A (en) | Method and device for configuring earphones in earphone storage box and computer equipment | |
| WO2021102753A1 (en) | Flash packet encryption method and apparatus, electronic device, and computer storage medium |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| GR01 | Patent grant | ||
| GR01 | Patent grant |