CN114882427A - Risk identification method, device and system and computer equipment - Google Patents
Risk identification method, device and system and computer equipmentDownload PDFInfo
- Publication number
- CN114882427A CN114882427ACN202110078552.4ACN202110078552ACN114882427ACN 114882427 ACN114882427 ACN 114882427ACN 202110078552 ACN202110078552 ACN 202110078552ACN 114882427 ACN114882427 ACN 114882427A
- Authority
- CN
- China
- Prior art keywords
- behavior
- transaction
- area
- type
- image data
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Pending
Links
Images
Classifications
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/70—Protecting specific internal or peripheral components, in which the protection of a component leads to protection of the entire computer
- G06F21/82—Protecting input, output or interconnection devices
- G06F21/83—Protecting input, output or interconnection devices input devices, e.g. keyboards, mice or controllers thereof
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06Q—INFORMATION AND COMMUNICATION TECHNOLOGY [ICT] SPECIALLY ADAPTED FOR ADMINISTRATIVE, COMMERCIAL, FINANCIAL, MANAGERIAL OR SUPERVISORY PURPOSES; SYSTEMS OR METHODS SPECIALLY ADAPTED FOR ADMINISTRATIVE, COMMERCIAL, FINANCIAL, MANAGERIAL OR SUPERVISORY PURPOSES, NOT OTHERWISE PROVIDED FOR
- G06Q10/00—Administration; Management
- G06Q10/06—Resources, workflows, human or project management; Enterprise or organisation planning; Enterprise or organisation modelling
- G06Q10/063—Operations research, analysis or management
- G06Q10/0635—Risk analysis of enterprise or organisation activities
- G—PHYSICS
- G07—CHECKING-DEVICES
- G07F—COIN-FREED OR LIKE APPARATUS
- G07F19/00—Complete banking systems; Coded card-freed arrangements adapted for dispensing or receiving monies or the like and posting such transactions to existing accounts, e.g. automatic teller machines
- G07F19/20—Automatic teller machines [ATMs]
- G07F19/207—Surveillance aspects at ATMs
Landscapes
- Engineering & Computer Science (AREA)
- Business, Economics & Management (AREA)
- Human Resources & Organizations (AREA)
- Physics & Mathematics (AREA)
- General Physics & Mathematics (AREA)
- Theoretical Computer Science (AREA)
- Computer Hardware Design (AREA)
- Strategic Management (AREA)
- Entrepreneurship & Innovation (AREA)
- Economics (AREA)
- Development Economics (AREA)
- Computer Security & Cryptography (AREA)
- Accounting & Taxation (AREA)
- General Engineering & Computer Science (AREA)
- Educational Administration (AREA)
- Software Systems (AREA)
- Game Theory and Decision Science (AREA)
- Finance (AREA)
- Marketing (AREA)
- Operations Research (AREA)
- Quality & Reliability (AREA)
- Tourism & Hospitality (AREA)
- General Business, Economics & Management (AREA)
- Financial Or Insurance-Related Operations Such As Payment And Settlement (AREA)
Abstract
Description
Translated fromChinese技术领域technical field
本申请涉识别领域,尤其涉及一种风险识别的方法、装置、系统和计算机设备。The present application relates to the field of identification, and in particular, to a method, apparatus, system and computer equipment for risk identification.
背景技术Background technique
由于自助式交易设备不需要专门的工作人员进行管理,方便快捷,并且可以24小时随时使用,用户和商家都更倾向于使用无人交易设备完成交易活动,自助式交易设备的普及率也越来越高,因此也产生了很多利用这些设备盗取他人钱财以及使用者的身份信息的犯罪案件。传统的识别用户的交易行为是否具有风险的方法通过面部识别记录使用者的身份信息,这种方法只能在用户已经发生风险行为之后通过面部识别进行身份追踪,不具有实时性,并且不能有效识别到故意进行面部遮挡的违法人员的身份。因此,如何针对自助式交易设备上的交易行为提供一种实时有效的风险识别方法成为了亟待解决的技术问题。Since self-service transaction equipment does not require special staff to manage, is convenient and fast, and can be used 24 hours a day, users and merchants are more inclined to use unmanned transaction equipment to complete transaction activities, and the popularity of self-service transaction equipment is also increasing. The higher it is, there have also been many criminal cases of using these devices to steal other people's money and the user's identity information. The traditional method of identifying whether the user's transaction behavior is risky records the user's identity information through facial recognition. This method can only track the identity of the user through facial recognition after the user has taken a risky behavior, which is not real-time and cannot be effectively identified. to the identity of the offender who intentionally covered the face. Therefore, how to provide a real-time and effective risk identification method for the transaction behavior on the self-service transaction equipment has become an urgent technical problem to be solved.
发明内容SUMMARY OF THE INVENTION
本申请提供了一种风险识别的方法、装置和计算设备,以此实时并准确地评估用户在使用自主交易设备时交易行为的风险性,减少违法行为的发生。The present application provides a method, device and computing device for risk identification, so as to evaluate the risk of a user's transaction behavior when using an autonomous transaction device in real time and accurately, and reduce the occurrence of illegal behavior.
第一方面,提供一种风险识别的方法,包括:获取交易设备的图像数据,其中,交易设备包括交易区和键盘区,图像数据包括交易区的图像和键盘区的图像。根图像数据确定交易区的第一行为类型和键盘区的第二行为类型,并根据第一行为类型和第二行为类型确定交易行为的风险行为。通过上述方法,可以将交易设备划分为交易区和键盘区,通过图像数据自动判断两个区域的交易行为的类型,高效地识别交易行为的风险性。In a first aspect, a method for risk identification is provided, comprising: acquiring image data of a transaction device, wherein the transaction device includes a transaction area and a keyboard area, and the image data includes an image of the transaction area and an image of the keyboard area. The first behavior type of the transaction area and the second behavior type of the keyboard area are determined based on the image data, and the risk behavior of the transaction behavior is determined according to the first behavior type and the second behavior type. Through the above method, the transaction equipment can be divided into a transaction area and a keyboard area, and the types of transaction behaviors in the two areas can be automatically judged through image data, so as to efficiently identify the risk of transaction behaviors.
作为一种可能的实现方式,第一行为类型包括交易区正常行为和交易区风险行为;第二行为类型包括键盘区正常行为和键盘区风险行为。As a possible implementation manner, the first behavior type includes normal behavior in the transaction area and risk behavior in the transaction area; the second behavior type includes normal behavior in the keyboard area and risk behavior in the keyboard area.
作为另一种可能的实现方式,根据第一行为类型和第二行为类型确定交易行为的风险性,包括:当第一行为类型和第二行为类型中至少一种为风险行为时,确定交易行为是风险行为。通过上述方法,可以综合判断交易区和键盘区的交易行为的类型,能更加准确地识别交易行为的风险性。As another possible implementation manner, determining the riskiness of the transaction behavior according to the first behavior type and the second behavior type includes: when at least one of the first behavior type and the second behavior type is a risky behavior, determining the transaction behavior is risky behavior. Through the above method, the types of transaction behaviors in the transaction area and the keyboard area can be comprehensively judged, and the risk of the transaction behavior can be more accurately identified.
作为另一种可能的实现方式,根据图像数据确定交易区的第一行为类型和键盘区的第二行为类型,还包括:根据图像数据获取交易区的第一行为类型是风险行为的概率和键盘区的第二行为类型是风险行为的概率;则根据第一行为类型和第二行为类型确定交易行为的风险行为,包括:当第一行为类型是风险行为的概率和第二行为类型是风险行为的概率中至少一个大于或等于第一阈值时,确定交易行是为风险行为。通过上述方法,可以使用概率进一步提高风险识别的准确性。As another possible implementation manner, determining the first behavior type of the transaction area and the second behavior type of the keyboard area according to the image data, further comprising: acquiring the probability that the first behavior type of the transaction area is a risk behavior and the keyboard area according to the image data The second behavior type of the zone is the probability of risky behavior; then the risky behavior of trading behavior is determined according to the first behavior type and the second behavior type, including: when the first behavior type is the probability of risky behavior and the second behavior type is risky behavior When at least one of the probabilities of is greater than or equal to the first threshold, it is determined that the transaction behavior is a risky behavior. Through the above method, probability can be used to further improve the accuracy of risk identification.
作为另一种可能的实现方式,所述根据图像数据确定交易区的第一行为类型,包括:根据图像数据截取交易区的图像,以及使用交易区的图像数据作为分类网络的输入,得到第一行为类型。分类网络可以有效识别出交易区的行为的类型,提高风险识别的准确性。As another possible implementation manner, the determining the first behavior type of the transaction area according to the image data includes: intercepting the image of the transaction area according to the image data, and using the image data of the transaction area as the input of the classification network to obtain the first behavior type of the transaction area. type of behavior. The classification network can effectively identify the types of behaviors in the trading area and improve the accuracy of risk identification.
作为另一种可能的实现方式,所述根据图像数据确定键盘区的第二行为类型,包括:根据图像数据截取键盘区的图像,以及使用键盘区的图像数据作为对抗网络的输入,得到第二行为类型。对抗网络在使用的过程中学习出键盘区的所有的错误行为类型,避免因为键盘区手部正常动作的干扰而导致行为识别的失败。As another possible implementation manner, the determining the second behavior type of the keyboard area according to the image data includes: intercepting the image of the keyboard area according to the image data, and using the image data of the keyboard area as the input of the adversarial network to obtain the second behavior type of the keyboard area. type of behavior. In the process of using the adversarial network, it learns all types of wrong behaviors in the keyboard area, and avoids the failure of behavior recognition due to the interference of normal hand movements in the keyboard area.
作为另一种可能的实现方式,交易设备包括:自动取款机、存取款一体机、虚拟柜台系统、自动售卖机、自动售票机、自动充值机以及自动缴费机。As another possible implementation, the transaction equipment includes: an automatic teller machine, an integrated deposit and withdrawal machine, a virtual counter system, an automatic vending machine, an automatic ticket vending machine, an automatic recharge machine, and an automatic payment machine.
第二方面,本申请提供一种风险识别装置,包括用于执行第一方面或第一方面任一种可能实现方式中的感知方法的各个模块。In a second aspect, the present application provides a risk identification device, including various modules for executing the first aspect or the sensing method in any possible implementation manner of the first aspect.
第三方面,本申请提供了一种风险识别的系统,包括交易设备和计算设备。其中,交易设备包括摄像头、交易区和键盘区,摄像头用于获取交易设备的图像数据,图像数据包括交易区的图像和键盘区的图像。计算设备用于实现如上述第一方面及第一方面任意一种可能实现方式中相应主体所执行的方法的操作步骤。通过上述系统,计算设备可以远程识别交易设备的风险行为,并为交易设备提供统一的风险管理,减少了人工的工作量。In a third aspect, the present application provides a system for risk identification, including a transaction device and a computing device. Wherein, the transaction equipment includes a camera, a transaction area and a keyboard area, the camera is used to obtain image data of the transaction equipment, and the image data includes an image of the transaction area and an image of the keyboard area. The computing device is configured to implement the operation steps of the method performed by the corresponding subject in the above-mentioned first aspect and any possible implementation manner of the first aspect. Through the above system, the computing device can remotely identify the risk behavior of the transaction device, and provide unified risk management for the transaction device, reducing the manual workload.
第四方面,本申请提供了一种交易设备,包括摄像头、交易区、键盘区和处理器。其中,摄像头用于获取交易设备的图像数据,图像数据包括交易区的图像和键盘区的图像,处理器用于执行实现如上述第一方面及第一方面任意一种可能实现方式中相应主体所执行的方法的操作步骤。通过上述交易设备,可以实时监控用户在使用交易设备的交易行为的风险性,即时制止违法行为的发生。In a fourth aspect, the present application provides a transaction device including a camera, a transaction area, a keyboard area and a processor. Wherein, the camera is used to acquire image data of the transaction device, and the image data includes the image of the transaction area and the image of the keyboard area, and the processor is used to implement the first aspect and any one of the possible implementations of the first aspect. the operating steps of the method. Through the above-mentioned transaction equipment, the risk of the user's transaction behavior using the transaction equipment can be monitored in real time, and the occurrence of illegal acts can be stopped immediately.
第五方面,本申请提供一种计算机可读存储介质,所述计算机可读存储介质中存储有指令,当其在计算机上运行时,使得计算机执行上述第一方面或第一方面任一种可能实现方式中所述方法的操作步骤。In a fifth aspect, the present application provides a computer-readable storage medium, where instructions are stored in the computer-readable storage medium to enable the computer to execute the first aspect or any one of the first aspects when it runs on a computer. Operation steps of the method described in the implementation manner.
第六方面,本申请提供了一种包含指令的计算机程序产品,当其在计算机上运行时,使得计算机执行第一方面或第一方面任一种可能实现方式中所述方法的操作步骤。In a sixth aspect, the present application provides a computer program product comprising instructions that, when run on a computer, cause the computer to perform the operation steps of the method described in the first aspect or any possible implementation manner of the first aspect.
本申请在上述各方面提供的实现方式的基础上,还可以进行进一步组合以提供更多实现方式。On the basis of the implementation manners provided by the above aspects, the present application may further combine to provide more implementation manners.
附图说明Description of drawings
图1为本申请实施例提供的一种风险识别的系统的结构示意图;1 is a schematic structural diagram of a system for risk identification provided by an embodiment of the present application;
图2为本申请提供的一种风险识别的方法的流程示意图;2 is a schematic flowchart of a method for risk identification provided by the present application;
图3是本申请提供的一种获取交易区的行为类型的流程示意图;Fig. 3 is a kind of schematic flow chart of acquiring the behavior type of transaction area provided by this application;
图4为本申请实施例提供的一种交易区的行为的关键区域的示例图;FIG. 4 is an exemplary diagram of a key area of a transaction area behavior provided by an embodiment of the present application;
图5为本实施例提供的一种resNet的结构示例图;Fig. 5 is a structural example diagram of resNet provided by this embodiment;
图6为本申请实施例提供的一种3×3卷积核的计算流程图;FIG. 6 is a calculation flowchart of a 3×3 convolution kernel provided by an embodiment of the present application;
图7为本申请实施例提供的一种分类网络的结构图;7 is a structural diagram of a classification network provided by an embodiment of the present application;
图8是本申请实施例提供的一种获取键盘区的行为类型的方法的流程示意图;8 is a schematic flowchart of a method for obtaining a behavior type of a keyboard area provided by an embodiment of the present application;
图9是本申请实施例提供的一种GAN的结构示意图;9 is a schematic structural diagram of a GAN provided by an embodiment of the present application;
图10是本申请提供的一种用于显示交易行为风险性的界面的示意图;FIG. 10 is a schematic diagram of an interface for displaying the riskiness of trading behavior provided by the present application;
图11是本申请提供的一种用于显示交易行为风险性的界面的示意图;11 is a schematic diagram of an interface for displaying the riskiness of trading behavior provided by the present application;
图12是本申请提供的一种用于显示交易行为风险性的界面的示意图;FIG. 12 is a schematic diagram of an interface for displaying the riskiness of trading behavior provided by the present application;
图13是本申请提供的一种用于显示交易行为风险性的界面的示意图;FIG. 13 is a schematic diagram of an interface for displaying the riskiness of transaction behavior provided by the present application;
图14是本申请实施例提供的一种风险识别的装置的结构示意图;14 is a schematic structural diagram of a risk identification device provided by an embodiment of the present application;
图15为本申请实施例提供的一种计算机设备示意图。FIG. 15 is a schematic diagram of a computer device according to an embodiment of the present application.
具体实施方式Detailed ways
下面结合附图对本申请实施例中的技术方案进行描述。The technical solutions in the embodiments of the present application will be described below with reference to the accompanying drawings.
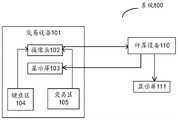
图1为本申请实施例提供的一种风险识别的系统100的结构示意图,如图所示,系统100包括数据交易设备101、计算设备110以及显示屏111。其中,交易设备101包括摄像头102、显示屏103、键盘区104以及交易区105。用户使用交易设备完成交易行为,包括支付操作、充值操作以及信息查询。交易设备可以是自动取款机(automated teller machine,ATM)、存取款一体机(cash recycling system,CRS)、虚拟柜台系统(virtualtellersystem,VTS)、自动售卖机、自动售票机、自动充值机或者自动缴费机。交易行为主要发生在键盘区104和交易区105。1 is a schematic structural diagram of a system 100 for risk identification provided by an embodiment of the present application. As shown in the figure, the system 100 includes a data transaction device 101 , a computing device 110 and a display screen 111 . The transaction device 101 includes a camera 102 , a display screen 103 , a
摄像头102可以采集键盘区104和交易区105的图像,采集后通过网络将图像发送给计算设备110,以便于监控用户在键盘区104和交易区105的交易行为。可选地,摄像头还可以部署于交易设备外,此时摄像头可以调整角度保证能完全看见用户在键盘区104和交易区105的交易行为。The camera 102 can capture images of the
键盘区104用于用户与交付设备进行互动,例如输入密码或者按照交易设备的指示输入命令。交易区105用于用户使用支付媒介完成交易,支付媒介包括:金融卡和手机。其中,金融卡又可以包括:银行卡、交通卡、储值卡、购物卡以及定制卡。使用支付媒介的方式包括插卡交易、刷卡交易以及使用二维码扫码。The
系统100包括两个显示屏,显示屏103部署于交易设备上,用于向用户显示交易行为的风险性;可选地,用户还可以通过键盘操作显示屏或者触摸显示屏完成与交易设备的互动。显示屏111部署于交易设备外,用于交易设备的管理人员获取当前交易设备的交易行为的风险性。The system 100 includes two display screens, and the display screen 103 is deployed on the trading device to display the risk of the trading behavior to the user; optionally, the user can also operate the display screen through the keyboard or touch the display screen to complete the interaction with the trading device . The display screen 111 is deployed outside the transaction equipment, and is used for the management personnel of the transaction equipment to obtain the risk of the transaction behavior of the current transaction equipment.
计算设备110可以获取摄像头采集的视频或图像,并可以使用人工智能算法识别视频或图像中的交易行为的类型,进一步判断用户的行为是否具有风险。交易设备的风险行为包括以下两类:The computing device 110 can acquire the video or image captured by the camera, and can use an artificial intelligence algorithm to identify the type of transaction behavior in the video or image, and further determine whether the user's behavior is risky. The risky behavior of trading equipment includes the following two categories:
键盘区风险行为:安装摄像头、破坏键盘、改造键盘保护盖。Keyboard area risky behavior: install cameras, destroy keyboards, modify keyboard covers.
交易区风险行为:安装违规的刷卡设备、破快读卡器、改装读卡器以及粘贴虚假二维码。Risky behavior in the trading area: installing illegal card swiping devices, breaking card readers, modifying card readers, and pasting fake QR codes.
计算设备110可以在识别出风险行为之后,通过显示屏103向用户发出警告以及通过显示屏111向交易设备的管理人员发出警告。The computing device 110 may issue a warning to the user through the display screen 103 and to the management of the transaction device through the display screen 111 after identifying the risky behavior.
可选地,计算设备还可以实时地获取当前交易行为的风险值,并显示在显示屏103和显示屏111上。可选地,交易设备的管理人员还可以通过计算设备控制交易设备,例如,当管理人员发现用户的交易行为被识别为风险行为时之后,可以锁定当前的交易设备,以阻止用户继续操作。Optionally, the computing device may also acquire the risk value of the current transaction behavior in real time, and display it on the display screen 103 and the display screen 111 . Optionally, the manager of the transaction device can also control the transaction device through the computing device. For example, when the manager finds that the user's transaction behavior is identified as a risky behavior, the current transaction device can be locked to prevent the user from continuing to operate.
具体实施中,计算设备可以是部署在服务器中的软件模块,也可以是一台服务器,还可以是由若干台服务器组成的服务器集群,或者是一个云计算服务中心,本申请实施例对此不做限定。其中,服务器也称伺服器,是提供计算服务的设备。在本申请实施例中,所述服务器可以是X86服务器,X86服务器又称复杂指令集(complex instruction setcomputer,CISC)架构服务器,即通常所讲的个人计算机(personal computer,PC)服务器,它是基于PC机体系结构,使用英特尔或其它兼容x86指令集的处理器芯片和操作系统的服务器。In specific implementation, the computing device may be a software module deployed in a server, or a server, or a server cluster composed of several servers, or a cloud computing service center, which is not the case in the embodiments of the present application. Do limit. Among them, a server, also called a server, is a device that provides computing services. In this embodiment of the present application, the server may be an X86 server, which is also called a complex instruction set computer (CISC) architecture server, which is commonly referred to as a personal computer (personal computer, PC) server, which is based on PC architecture, using Intel or other processor chips compatible with the x86 instruction set and operating system server.
需要说明的是,计算设备110可以连接至少一个交易设备,应当理解,系统100中计算设备连接的交易设备的数量并不构成对本申请的限定,图1仅以系统包括一台交易设备为例进行说明。It should be noted that the computing device 110 can be connected to at least one transaction device. It should be understood that the number of transaction devices connected to the computing device in the system 100 does not constitute a limitation on this application. FIG. 1 only takes the system including one transaction device as an example. illustrate.
可选地,计算设备110也可以是部署在交易设备中的软件模块。Optionally, the computing device 110 may also be a software module deployed in the transaction device.
值得说明的是,图1所示的系统架构仅仅是为了更好的说明本申请所提供的模型评估的方法所提供的系统架构的示例,并不构成对本申请实施例的限定。It should be noted that the system architecture shown in FIG. 1 is only an example of the system architecture provided by the model evaluation method provided in the present application, and does not constitute a limitation to the embodiments of the present application.
基于图1所示的系统,本申请实施例提供一种行为检测的方法,可以将交易设备分为键盘区和交易区两部分,分别监控用户两个区域的行为,实时获取用户交易行为的风险性,减少了人工监控的工作量。本申请的详细方案请参考下述实施例的描述。Based on the system shown in FIG. 1 , an embodiment of the present application provides a method for behavior detection, which can divide a transaction device into two parts: a keyboard area and a transaction area, monitor the behavior of the user in the two areas respectively, and obtain the risk of the user's transaction behavior in real time. This reduces the workload of manual monitoring. For the detailed solution of the present application, please refer to the description of the following examples.
接下来,进一步结合图2详细介绍本申请提供的模型评估的方法。图2为本申请提供的一种风险识别的方法的流程示意图,如图所示,具体方法包括:Next, the method for model evaluation provided by the present application will be described in detail with reference to FIG. 2 . 2 is a schematic flowchart of a method for risk identification provided by the application, as shown in the figure, the specific method includes:
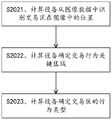
S201、计算设备获取交易区和键盘区的图像数据。S201. The computing device acquires image data of the transaction area and the keyboard area.
摄像头可以将采集到的视频数据按照设定的时间间隔抽样转化为图像数据,并将图像数据发送给计算设备以完成下一步的操作。摄像头采集到的视频数据应该包括完整的交易区以及键盘区图像。可选地,摄像头还可以直接将视频数据发送给计算设备,由计算设备自行按照设定的时间间隔将视频抽样转化为图像数据,之后再进行下一步的操作。The camera can convert the collected video data into image data by sampling according to the set time interval, and send the image data to the computing device to complete the next operation. The video data collected by the camera should include the complete transaction area and keyboard area images. Optionally, the camera may also directly send the video data to the computing device, and the computing device will convert the video samples into image data according to the set time interval, and then proceed to the next step.
S202、计算设备根据图像数据获取交易区的行为类型。图3是本申请提供的一种获取交易区的行为类型的流程示意图,如图所示,该步骤又可以具体包括:S202, the computing device acquires the behavior type of the transaction area according to the image data. Fig. 3 is a kind of schematic flow chart of obtaining the behavior type of transaction area provided by the present application. As shown in the figure, this step can specifically include:
S2021、计算设备从图像数据中识别交易区在图像中的位置。S2021. The computing device identifies the position of the transaction area in the image from the image data.
当摄像头与交易设备的相对位置保持不变时,例如摄像头部署于交易设备上,或者摄像头和交易设备均固定在同一空间中,此时摄像头相对于交易区的拍摄方向和拍摄距离固定,则交易区在每一帧图像数据中的位置都保持不变。可以计算一张图像中的交易区在图像数据中的坐标区域,之后对每一帧图像都选取相同的坐标区域。When the relative position of the camera and the trading device remains unchanged, for example, the camera is deployed on the trading device, or the camera and the trading device are both fixed in the same space, and the shooting direction and shooting distance of the camera relative to the trading area are fixed, then the trading The position of the region in each frame of image data remains unchanged. You can calculate the coordinate area of the transaction area in an image in the image data, and then select the same coordinate area for each frame of image.
可选地,还可以使用目标检测算法识别每一帧图像中交易区的坐标区域。目标检测算法包括基于传统图像处理的目标检测算法和基于深度学习的目标检测算法。对于基于传统图像处理的目标检测算法,可以首先提取图像的特征,将图像数据转换为标识交易区的属性的信息。特征提取的常用方法包括尺度不变特征变换(scale invariant featuretransform,SIFT)方法、方向梯度直方图(histogram of oriented gradient,HOG)方法和高斯函数差分(difference of guassian,DOG)方法。然后使用分类器对提取到的特征进行识别与分类,将提取到的交易区的图像特征与已知的交易区的图像特征进行匹配,最终得到交易区的坐标区域。常用的分类器包括支持向量机(support vector machine,SVM)和自适应增强机(adaptive boosting,AdaBoost)。对于基于深度学习目标检测算法,可以使用基于区域的卷积神经网络(region-based convolutional neural networks,RCNN)、空间金字塔池化网络(spatial pyramid pooling,SPP)网络、快速基于区域的卷积神经网络(fast-RCNN)、更快基于区域的卷积神经网络(faster-RCNN)等优化算法。他们的共同特点是首先找到图像中可能的物体的边界框,然后使用分类器确定框里的物体的类别,最终得到交易区的坐标区域。还可以使用只看一次(you only look once,YOLO)、单枪多箱检测器(single shot multiBox detector,SSD)等算法直接同时识别出交易区以及交易区的坐标区域。Optionally, an object detection algorithm can also be used to identify the coordinate area of the transaction area in each frame of image. Target detection algorithms include target detection algorithms based on traditional image processing and target detection algorithms based on deep learning. For the target detection algorithm based on traditional image processing, the features of the image can be extracted first, and the image data can be converted into information identifying the attributes of the trading area. Common methods of feature extraction include scale invariant feature transform (SIFT) method, histogram of oriented gradient (HOG) method and difference of guassian (DOG) method. Then use the classifier to identify and classify the extracted features, match the extracted image features of the transaction area with the known image features of the transaction area, and finally obtain the coordinate area of the transaction area. Commonly used classifiers include support vector machine (support vector machine, SVM) and adaptive boosting machine (adaptive boosting, AdaBoost). For deep learning-based target detection algorithms, region-based convolutional neural networks (RCNN), spatial pyramid pooling (SPP) networks, and fast region-based convolutional neural networks can be used. (fast-RCNN), faster region-based convolutional neural network (faster-RCNN) and other optimization algorithms. Their common feature is to first find the bounding box of possible objects in the image, then use the classifier to determine the category of the objects in the box, and finally get the coordinate area of the transaction area. Algorithms such as you only look once (YOLO) and single shot multiBox detector (SSD) can also be used to directly identify the transaction area and the coordinate area of the transaction area at the same time.
由于一些交易设备中交易区与交易区周围的设备环境相接近,直接使用目标检测算法不能准确地识别出交易区的坐标区域。此时可以首先利用上述目标检测算法识别出图像中包含的交易设备中具有明显特征的物体,例如交易设备上带有颜色的标签、反光的显示屏等。然后再根据设备上的交易区与已经识别出的物体之间的相对距离,计算出交易区的坐标区域。Since the transaction area in some transaction equipment is close to the equipment environment around the transaction area, the coordinate area of the transaction area cannot be accurately identified by using the target detection algorithm directly. At this time, the above-mentioned target detection algorithm can be used to identify objects with obvious features in the transaction equipment contained in the image, such as colored labels and reflective display screens on the transaction equipment. Then, according to the relative distance between the transaction area on the device and the recognized object, the coordinate area of the transaction area is calculated.
当使用目标检测算法识别交易区的坐标区域时,摄像头相对于交易设备的相对位置可以变动。When using the object detection algorithm to identify the coordinate area of the trading area, the relative position of the camera relative to the trading device can vary.
S2022、计算设备确定交易行为关键区域。S2022, the computing device determines the key area of the transaction behavior.
可以使用能完全覆盖步骤2021中得到的坐标区域的轮廓的矩形作为交易区的行为的关键区域,图4为本申请实施例提供的一种交易区的行为的关键区域的示例图。由于用户在交易区的行为幅度可能超出交易区的范围,因此矩形的区域以比原来的识别得到的交易区的坐标区域的更大,具体的值可以根据经验值指定,本方案在此不作限定。例如,如图所示,401为步骤2021中得到的坐标区域,则402为确定的交易区的行为类型的关键区域。A rectangle that can completely cover the outline of the coordinate area obtained in step 2021 can be used as the key area of the behavior of the transaction area. FIG. 4 is an example diagram of a key area of the behavior of the transaction area provided by the embodiment of the present application. Since the user's behavior in the transaction area may exceed the scope of the transaction area, the rectangular area is larger than the coordinate area of the transaction area obtained by the original identification. . For example, as shown in the figure, 401 is the coordinate area obtained in
S2023、计算设备确定交易区的行为类型。S2023, the computing device determines the behavior type of the transaction area.
计算设备从获取的图像数据中截取交易区的行为的关键区域,假设关键区域的图像P的大小为M×N,每一行有M个像素,每一列有N个像素。将截取的图像输入分类网络中,可以识别出经过分类后的行为类型,包括背景、正常交易区行为以及风险交易区行为三种类型。下面以残差网络(resNet)为例,阐述如何使用分类网络对交易区的行为进行识别。The computing device intercepts the key area of the behavior of the transaction area from the acquired image data, assuming that the size of the image P of the key area is M×N, each row has M pixels, and each column has N pixels. Input the intercepted image into the classification network, and the classified behavior types can be identified, including three types: background, normal transaction area behavior, and risky transaction area behavior. The following takes the residual network (resNet) as an example to illustrate how to use the classification network to identify the behavior of the trading area.
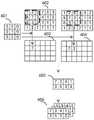
图5为本实施例提供的一种resNet的结构示例图,矩阵x输入resNet后首先经过64个3×3的卷积核。图6为本申请实施例提供的一种3×3卷积核的计算流程图,如图所示,601为一个3×3的卷积核,602为输入的6×4的矩阵x。需要说明的是,矩阵x的大小以及数值仅仅用来说明卷积核的计算流程,并不构成对本申请的限定。从矩阵的左上角开始,使用3×3计算区域中每个像素分别与卷积核的每个元素相乘,所有乘积之和作为计算区域中心像素的新值,例如经过第一次计算之后矩阵602变为矩阵603。将计算区域向左移动一个数据,经过同样的方法计算得到矩阵604。之后,继续向左以及向下移动计算区域最终可以得到4×2的矩阵605。当同时使用矩阵x经过多个3×3的卷积核时,分别使用每一个卷积核对矩阵进行计算,将计算后的4×2矩阵组合在一起,得到一个多维矩阵606。例如,当使用矩阵x经过4个3×3的卷积核是,最终得到一个4×3×3的矩阵。FIG. 5 is a schematic diagram of the structure of a resNet provided in this embodiment. After the matrix x is input to the resNet, it first goes through 64 3×3 convolution kernels. FIG. 6 is a flow chart of calculation of a 3×3 convolution kernel provided by an embodiment of the present application. As shown in the figure, 601 is a 3×3 convolution kernel, and 602 is an input 6×4 matrix x. It should be noted that the size and value of the matrix x are only used to illustrate the calculation process of the convolution kernel, and do not constitute a limitation on this application. Starting from the upper left corner of the matrix, each pixel in the 3×3 calculation area is multiplied by each element of the convolution kernel, and the sum of all products is used as the new value of the center pixel of the calculation area. For example, after the first calculation, the
接下来,经过卷积核的矩阵x输入修正线性单元(rectified linear unit,ReLU)进行计算,如公式一所示,ReLU函数是一个分段线性函数,当x为负值时,输出均为0;当x为正值时,输出保持不变。Next, the matrix x of the convolution kernel is input to the rectified linear unit (ReLU) for calculation. As shown in
之后,矩阵x再次经过64个3×3的卷积核,将输出与刚开始输入的矩阵x相加后再次经过ReLU后即可得到resNet的输出。After that, the matrix x passes through 64 3×3 convolution kernels again, and the output of resNet is obtained by adding the output to the matrix x that was input at the beginning and passing through ReLU again.
一个完整的分类网络可以将多个resNet叠加使用,图7为本实施例提供的一种分类网络的结构图,如图所示,包括64个7×7的卷积核、16个resNet以及1个全连接层。全连接层也是一个卷积核,其大小等于最后一个resNet输出的矩阵的大小乘以分类网络输出的类型数量,例如当最后一个resNet输出的矩阵大小为3×3×5,且整个分类网络的结果时三种类型时,全连接层的卷积核的大小为3×3×5×3。A complete classification network can be used by stacking multiple resNets. Figure 7 is a structural diagram of a classification network provided in this embodiment. As shown in the figure, it includes 64 7×7 convolution kernels, 16 resNets, and 1 a fully connected layer. The fully connected layer is also a convolution kernel whose size is equal to the size of the matrix output by the last resNet multiplied by the number of types output by the classification network. When there are three types of results, the size of the convolution kernel of the fully connected layer is 3×3×5×3.
使用分类网络识别交易区的行为类型之前,首先需要对分类网络中卷积核的参数进行训练,训练步骤可以在本申请的风险识别的方法开始之前完成。具体训练方法如下:Before using the classification network to identify the behavior type of the transaction area, the parameters of the convolution kernel in the classification network need to be trained first, and the training step can be completed before the risk identification method of the present application starts. The specific training methods are as follows:
1)使用摄像头采集多张用户在交易区的行为的图像并且人工识别出这些图像中的交易区的行为类型,打上标签,图像的大小与交易区的关键区域的图像的大小一致。1) Use the camera to collect multiple images of the user's behavior in the transaction area, manually identify the behavior type of the transaction area in these images, and label the image, and the size of the image is consistent with the size of the image in the key area of the transaction area.
2)设置分类网络中的卷积核的参数的初始值,初始值可以为任意值,本申请对此不做限定。2) Set the initial value of the parameters of the convolution kernel in the classification network, and the initial value can be any value, which is not limited in this application.
3)将一张摄像头采集的图像输入分类网络,计算该图像经过分类网络后输出的分类结果与标签的误差。3) Input an image collected by a camera into the classification network, and calculate the error between the classification result and the label output after the image passes through the classification network.
4)使用梯度下降法,根据误差与待训练参数的偏导数,从分类网络的最后一层的节点开始,反向更新每一个卷积核的每一个节点的参数。4) Using the gradient descent method, according to the partial derivative of the error and the parameter to be trained, starting from the node of the last layer of the classification network, the parameters of each node of each convolution kernel are reversely updated.
5)使用更新后的参数值返回执行步骤(3)和步骤(4)直到得到的误差的数值小于第一阈值。5) Using the updated parameter values, go back to performing steps (3) and (4) until the obtained error value is less than the first threshold.
6)重复步骤(3)、(4)和(5),直到摄像头采集的所有图像执行完毕,即得到最终的训练好的分类网络。6) Repeat steps (3), (4) and (5) until all images collected by the camera are executed, that is, the final trained classification network is obtained.
使用训练好的分类网络识别交易区的行为类型时,将交易区的关键区域的图像P输入分类网络,依次经过一个64个7×7的卷积核、16个相同的resNet以及最后经过一个全连接层后,最终可以识别出交易区的行为属于哪一种类型以及属于该类型的概率。When using the trained classification network to identify the behavior type of the trading area, the image P of the key area of After connecting the layers, it is finally possible to identify which type of behavior the trading area belongs to and the probability of belonging to that type.
可选地,分类网络中还可以使用大规模深度卷积(very deep convolutional,VGG)网络和深度卷积网络(dense convolutional network,DSNet),方法与使用resNet类似,在此不再赘述。Optionally, a large-scale deep convolutional (VGG) network and a deep convolutional network (DSNet) can also be used in the classification network. The method is similar to using resNet, and will not be repeated here.
可选地,还可以将交易区正常行为的具体类型以及交易区风险行为的具体类型作为输出,例如可以将交易区的行为类型分为6类:背景、插入卡片、拔出卡片、安装违规的刷卡设备、破坏读卡器和改装读卡器。此时,分类网络中的全连接层的卷积核的大小以及训练过程也需要进行相应的更改。Optionally, the specific types of normal behaviors in the trading area and the specific types of risky behaviors in the trading area can also be output. Swipe card devices, destroy card readers, and modify card readers. At this time, the size of the convolution kernel of the fully connected layer in the classification network and the training process also need to be changed accordingly.
识别出交易区的行为类型后,计算设备还需要结合键盘区的行为类型,综合判断交易行为的风险程度。After identifying the behavior type of the transaction area, the computing device also needs to combine the behavior type of the keyboard area to comprehensively judge the risk level of the transaction behavior.
S203、计算设备根据图像数据获取键盘区的行为类型。图8是本申请提供的一种获取键盘区的行为类型的方法的流程示意图,如图所示,该方法具体包括:S203, the computing device acquires the behavior type of the keyboard area according to the image data. 8 is a schematic flowchart of a method for obtaining a behavior type of a keyboard area provided by the present application. As shown in the figure, the method specifically includes:
S2031、计算设备从图像数据中识别键盘区在图像中的位置。S2031. The computing device identifies the position of the keyboard area in the image from the image data.
计算设备识别键盘区在图像中的位置的方法与S2021中计算设备识别交易区在图像中的位置的方法类似,不同的是,由于隐私保护,键盘区会被黑色遮挡物覆盖,而交易设备地其他区域通常不为黑色,因此使用目标检测算法识别图像中键盘区的坐标区域时,可以直接提取图像中的像素的颜色特征,将颜色为黑色的区域作为键盘区的坐标区域。The method for the computing device to identify the position of the keyboard area in the image is similar to the method for the computing device to identify the position of the transaction area in the image in S2021. Other areas are usually not black, so when using the target detection algorithm to identify the coordinate area of the keyboard area in the image, you can directly extract the color features of the pixels in the image, and use the black area as the coordinate area of the keyboard area.
S2032、计算设备确定键盘区的行为的关键区域。S2032. The computing device determines the key area of the behavior of the keyboard area.
与S2032类似,可以使用能完全覆盖步骤2031中得到的坐标区域的轮廓的矩形作为键盘区的行为的关键区域。Similar to S2032, a rectangle that can completely cover the outline of the coordinate area obtained in step 2031 can be used as a key area for the behavior of the keyboard area.
S2033、计算设备确定键盘区的行为类型。S2033, the computing device determines the behavior type of the keyboard area.
键盘区通常存在一个平台,用户可能会在等待的过程中添加多种手部动作,例如:把包、手机等物品放置在该位置,这些行为都可能对键盘区的行为类型的识别造成干扰,无法通过简单的分类网络解决。但是键盘区的具有风险的行为类型是有限的,例如安装摄像头、破坏键盘以及改造键盘保护盖,因此可以采用基于生成对抗网络(generativeadversarial network,GAN)的异常检测算法,只识别出键盘区的风险行为。There is usually a platform in the keyboard area, and users may add a variety of hand actions during the waiting process, such as placing bags, mobile phones and other items in this position. These behaviors may interfere with the recognition of the behavior type of the keyboard area. It cannot be solved by a simple classification network. However, the types of risky behaviors in the keyboard area are limited, such as installing cameras, destroying the keyboard, and changing the keyboard cover. Therefore, an anomaly detection algorithm based on a generative adversarial network (GAN) can be used to identify only the risks in the keyboard area. Behavior.
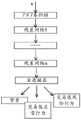
首先计算设备从获取的图像数据中截取键盘区的行为的关键区域,假设关键区域的图像P的大小为M×N,每一行有M个像素,每一列有N个像素。将截取的图像输入GAN中,即可以识别出键盘区风险行为的类型。图9是本申请提供的一种GAN的结构示意图。如图所示,GAN包括两个网络,分别为生成器G(generator)802和判别器D(discriminator)801。G用于根据输入图片的矩阵生成一张图片。D用于判别一张图片是否为真实图片,输入是代表图像的矩阵数据x,输出是x为真实图片的概率804,当输出的概率为1时,表示x百分百是真实的图片,当输出的概率为0时,代表x不可能为真实图片。在GAN中,生成器和判别器可以为梯度算子,也可以为神经网络模型。First, the computing device intercepts the key area of the behavior of the keyboard area from the acquired image data, assuming that the size of the image P of the key area is M×N, each row has M pixels, and each column has N pixels. Inputting the captured images into the GAN can identify the type of risky behavior in the keyboard area. FIG. 9 is a schematic structural diagram of a GAN provided by this application. As shown in the figure, the GAN includes two networks, namely a generator G (generator) 802 and a discriminator D (discriminator) 801. G is used to generate a picture from the matrix of the input picture. D is used to determine whether a picture is a real picture. The input is the matrix data x representing the image, and the output is the
使用GAN识别键盘区的行为类型之前,首先需要对GAN中生成器和判别器的参数进行训练,训练步骤可以在本申请的风险识别的方法开始之前完成。具体训练方法如下:Before using GAN to identify the behavior type of the keyboard area, the parameters of the generator and the discriminator in the GAN need to be trained first, and the training step can be completed before the risk identification method of this application starts. The specific training methods are as follows:
1)使用摄像头采集多张用户在见键盘区的风险行为的图像数据x803,图像的大小与键盘区的关键区域的图像的大小一致。1) Use a camera to collect multiple pieces of image data x803 of the user's risky behavior in the keyboard area, and the size of the image is consistent with the size of the image in the key area of the keyboard area.
2)使用随机生成的噪声数据z输入生成器,得到一张新的图片G(z),并将G(z)输入判别器进行判断。2) Input the randomly generated noise data z into the generator to get a new picture G(z), and input G(z) into the discriminator for judgment.
3)判别器计算G(x)为一张真实图片的概率D(G(z)),以及计算摄像头采集的风险行的图像数据x的概率D(x),根据两个概率之间的差值,更新判别器自身的参数,更新的公式二如下:3) The discriminator calculates the probability D(G(z)) that G(x) is a real picture, and calculates the probability D(x) of the image data x of the risk row collected by the camera, according to the difference between the two probabilities value, update the parameters of the discriminator itself, and the updated
4)使用公式三更新生成器的参数。4)
5)重复执行步骤3和步骤4,直到判别器的参数和生成器的参数不再改变。5) Repeat steps 3 and 4 until the parameters of the discriminator and the generator no longer change.
使用训练好的GAN识别键盘区的行为类型时,将键盘区的关键区域的图像数据P(803)输入生成器,得到一张新的生成的图片,将生成的图片输入判别器得到是否为真实图片的概率,当概率高于或等于第一阈值时,输入的图像数据为风险行为,其概率即为判别器生成的是否为真实图片的概率,当概率低于第一阈值时,输入的图像为正常行为。When using the trained GAN to identify the behavior type of the keyboard area, input the image data P(803) of the key area of the keyboard area into the generator, get a new generated image, and input the generated image into the discriminator to get whether it is real The probability of the picture, when the probability is higher than or equal to the first threshold, the input image data is a risk behavior, and its probability is the probability of whether the discriminator generates a real picture, when the probability is lower than the first threshold, the input image for normal behavior.
S204、计算设备根据交易区的行为类型和键盘区的行为类型确定交易行为的风险性。S204. The computing device determines the risk of the transaction behavior according to the behavior type of the transaction area and the behavior type of the keyboard area.
当交易区为与键盘区中的至少一种行为类型为风险行为时,将交易行为确定为风险行为。When at least one behavior type in the transaction area and the keyboard area is a risk behavior, the transaction behavior is determined as a risk behavior.
可选地,当交易区与键盘区中的至少一种行为类型为风险行为的概率大于第二阈值时,将交易行为确定为风险行为。Optionally, when the probability that at least one behavior type in the transaction area and the keyboard area is a risky behavior is greater than the second threshold, the transaction behavior is determined as a risky behavior.
当用户的交易行为被确定为风险行为之后,计算设备可以通过显示屏111向管理员发送警告,管理人员接收到警告之后,可以限制该用户的交易操作;或者计算设备通过交易设备的显示屏103向用户发送警告。When the user's transaction behavior is determined to be a risky behavior, the computing device can send a warning to the administrator through the display screen 111, and the administrator can restrict the user's transaction operation after receiving the warning; or the computing device can use the display screen 103 of the transaction device to send a warning. Send a warning to the user.
可选地,计算机还可以实时将交易区和键盘区的行为类型以及行为类型的概率,通过显示屏111向管理员发送展示,或者通过交易设备的显示屏103向用户展示。Optionally, the computer can also display the behavior types and the probability of the behavior types in the transaction area and the keyboard area in real time to the administrator through the display screen 111 , or to the user through the display screen 103 of the transaction device.
可选地,警告或者实时的风险信息还可以通过网络发送至管理人员的终端设备。Optionally, the warning or real-time risk information can also be sent to the terminal device of the manager through the network.
图10是本申请提供的一种用于显示交易行为风险性的界面1000,界面1000包括警告标志1003、具有风险行为的设备的型号1001,以及该设备的位置1002。例如,当某区某银行中的0001交易设备出现风险行为的时候,显示屏和显示屏中均可以呈现图10中所示的界面。FIG. 10 is an interface 1000 provided by the present application for displaying the riskiness of a transaction behavior. The interface 1000 includes a
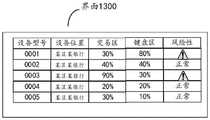
可选地,当计算设备连接多个交易设备时,图11是本申请提供的另一种用于显示交易行为风险性的界面1100,用于呈现在显示屏中向管理员展示所有发生风险行为的交易设备。1100界面可以包括计算设备所连接的每一个交易设备的设备型号、设备位置以及风险性,例如,图11中展示了计算设备所连接的5台设备的风险性,其中设备1和设备3处用户具有风险行为。Optionally, when the computing device is connected to multiple transaction devices, FIG. 11 is another interface 1100 provided by the present application for displaying the riskiness of transaction behaviors, which is used to display all occurrences of risky behaviors on the display screen to the administrator. trading equipment. The 1100 interface may include the device model, device location, and risk of each transaction device connected to the computing device. For example, Figure 11 shows the risk of 5 devices connected to the computing device, where the user at
图12是本申请提供的另一种用于显示交易行为风险性的界面1200,界面1200包括设备的型号1201,设备的位置1202、设备交易区行为是风险行为的概率1203和键盘区行为是风险行为的概率1204,用于向正在使用该交易设备的用户展示交易行为的风险性。当交易行为是风险行为时,可以在界面上使用警告标识1205提醒用户注意。例如,界面1200是某区某银行中的0001交易设备的显示界面,设备交易区行为是风险行为的概率为80%,设备交易区行为是风险行为的概率为50%,此时交易设备的出现风险行为,界面的中间显示警告标识。FIG. 12 is another interface 1200 provided by the present application for displaying the riskiness of transaction behavior. The interface 1200 includes the model 1201 of the device, the
可选地,当计算设备连接多个交易设备时,图13是本申请提供的另一种用于显示交易行为风险性的界面1300,用于呈现在显示屏中向管理员展示计算设备连接的所有交易设备的风险行。1100界面可以包括计算设备所连接的每一个交易设备的设备型号、设备位置、设备交易区行为是风险行为的概率、键盘区行为是风险行为的概率以及风险性,例如,图13中展示了计算设备所连接的5台设备的风险性,其中设备1和设备3处用户具有风险行为。Optionally, when the computing device is connected to multiple transaction devices, FIG. 13 is another interface 1300 provided by the present application for displaying the risk of transaction behavior, which is used to present an interface 1300 showing the connection of the computing device to the administrator in the display screen. Risk row for all trading equipment. The 1100 interface may include the device model of each transaction device connected to the computing device, the location of the device, the probability that the behavior of the device transaction area is a risky behavior, the probability that the behavior of the keyboard area is a risky behavior, and the risk. For example, Figure 13 shows the calculation The risk of the 5 devices connected to the device, in which users at
综上所述,本申请提供的一种风险识别的方法,可以基于摄像头的图像,远端识别交易行为的风险性,无需人工检测。并且本申请提供的风险识别方法采用不同的算法直接识别交易区和键盘区的行为类型,可以减少对于用户的徘徊、遮挡等间接行为导致的交易行为风险性的误判。To sum up, the method for risk identification provided by the present application can remotely identify the risk of transaction behavior based on the image of the camera, without manual detection. In addition, the risk identification method provided by the present application uses different algorithms to directly identify the behavior types of the transaction area and the keyboard area, which can reduce the misjudgment of the risk of transaction behavior caused by indirect behaviors such as wandering and blocking of users.
值得说明的是,对于上述方法实施例,为了简单描述,故将其都表述为一系列的动作组合,但是本领域技术人员应该知悉,本申请并不受所描述的动作顺序的限制。It is worth noting that, for the sake of simple description, the above method embodiments are expressed as a series of action combinations, but those skilled in the art should know that the present application is not limited by the described action sequence.
本领域的技术人员根据以上描述的内容,能够想到的其他合理的步骤组合,也属于本申请的保护范围内。其次,本领域技术人员也应该熟悉,说明书中所描述的实施例均属于优选实施例,所涉及的动作并不一定是本申请所必须的。Other reasonable step combinations that those skilled in the art can think of based on the above description also fall within the protection scope of the present application. Secondly, those skilled in the art should also be familiar with that, the embodiments described in the specification are all preferred embodiments, and the actions involved are not necessarily required by the present application.
上文中结合图2至图13,详细描述了本申请实施例所提供的风险识别的方法,下面将结合图14和图15,进一步介绍本申请实施例所提供的风险识别的装置和计算机设备。The risk identification method provided by the embodiments of the present application is described in detail above with reference to FIGS. 2 to 13 , and the apparatus and computer equipment for risk identification provided by the embodiments of the present application will be further described below with reference to FIGS. 14 and 15 .
图14是本申请提供的一种风险识别的装置1400,包括:获取单元1401、处理单元1402和确定单元1402。FIG. 14 is an apparatus 1400 for risk identification provided by the present application, including: an acquiring unit 1401 , a processing unit 1402 and a determining unit 1402 .
获取单元1401,用于获取交易设备的图像数据,其中交易设备包括交易区和键盘区,图像数据包括交易区的图像和键盘区的图像。The acquiring unit 1401 is configured to acquire image data of a transaction device, wherein the transaction device includes a transaction area and a keyboard area, and the image data includes an image of the transaction area and an image of the keyboard area.
处理单元1402,用于根据图像数据确定交易区的第一行为类型和键盘区的第二行为类型。The processing unit 1402 is configured to determine the first behavior type of the transaction area and the second behavior type of the keyboard area according to the image data.
确定单元1403,用于根据第一行为类型和第二行为类型确定交易行为的风险性。The determining unit 1403 is configured to determine the risk of the transaction behavior according to the first behavior type and the second behavior type.
应理解的是,本申请实施例的风险识别的装置1400可以通过通用处理器,例如,中央处理器Central processing unit,CPU),装置1400也可以通过专用集成电路(application-specific integrated circuit,ASIC)实现,或可编程逻辑器件(programmable logic device,PLD)实现,上述PLD可以是复杂程序逻辑器件(complexprogrammable logical device,CPLD),现场可编程门阵列(field-programmable gatearray,FPGA),通用阵列逻辑(generic array logic,GAL)或其任意组合。也可以通过软件实现图2至图5所示的感知方法时,感知装置600及其各个模块也可以为软件模块。It should be understood that the apparatus 1400 for risk identification in this embodiment of the present application may use a general-purpose processor, for example, a central processing unit (Central processing unit, CPU), and the apparatus 1400 may also use an application-specific integrated circuit (application-specific integrated circuit, ASIC) realization, or programmable logic device (programmable logic device, PLD) realization, the above-mentioned PLD can be complex program logic device (complex programmable logical device, CPLD), field-programmable gate array (field-programmable gate array, FPGA), general-purpose array logic ( generic array logic, GAL) or any combination thereof. When the sensing methods shown in FIGS. 2 to 5 can also be implemented by software, the sensing apparatus 600 and its respective modules can also be software modules.
可选地,确定单元1403还用于当第一行为类型和第二行为类型中至少一种为风险行为时,确定交易行为时风险行为。Optionally, the determining unit 1403 is further configured to determine that the transaction behavior is a risky behavior when at least one of the first behavior type and the second behavior type is a risky behavior.
可选地,处理单元1402根据图像数据获取交易区的第一行为类型是风险行为的概率和键盘区的第二行为类型是风险行为的概率;则确定单元1403用于当第一行为类型是风险行为的概率和第二行为类型是风险行为的概率中至少一个大于或等于第一阈值时,确定交易行为是风险行为。Optionally, the processing unit 1402 obtains the probability that the first behavior type in the transaction area is a risky behavior and the probability that the second behavior type in the keyboard area is a risky behavior according to the image data; then the determining unit 1403 is used when the first behavior type is a risky behavior. When at least one of the probability of the behavior and the probability that the second behavior type is a risky behavior is greater than or equal to the first threshold, it is determined that the transaction behavior is a risky behavior.
可选地,处理单元1402还用于根据图像数据截取交易区的图像,并使用交易区的图像数据作为分类网络的输入,得到第一行为类型。Optionally, the processing unit 1402 is further configured to intercept the image of the transaction area according to the image data, and use the image data of the transaction area as the input of the classification network to obtain the first behavior type.
可选地,处理单元1402还用于根据图像数据截取键盘区的图像,并使用键盘区的图像数据作为对抗网络的输入,得到第二行为类型。Optionally, the processing unit 1402 is further configured to intercept the image of the keyboard area according to the image data, and use the image data of the keyboard area as the input of the adversarial network to obtain the second behavior type.
根据本申请实施例的风险识别的装置1400可对应于执行本申请实施例中描述的方法,并且风险识别的装置1400中的各个单元的上述和其它操作和/或功能分别为了实现图2至图13中的各个方法的相应流程,为了简洁,在此不再赘述。The apparatus 1400 for risk identification according to the embodiments of the present application may correspond to executing the methods described in the embodiments of the present application, and the above and other operations and/or functions of the respective units in the apparatus 1400 for risk identification are for realizing FIGS. 2 to 2 , respectively. For the sake of brevity, the corresponding processes of each method in 13 will not be repeated here.
综上所述,本申请实施例提供的风险识别的装置1400,处理单元可以结合交易区和键盘区的行为类型,综合判断交易行为的风险性,降低了误判的概率。To sum up, in the risk identification device 1400 provided by the embodiment of the present application, the processing unit can comprehensively judge the risk of the transaction behavior in combination with the behavior types of the transaction area and the keyboard area, thereby reducing the probability of misjudgment.
图15为本申请实施例提供的一种计算机设备1500的示意图,如图所示,计算机设备1500包括处理器1501、存储器1502、通信接口1503总线1504和内存1505。其中,处理器1501、存储器1502、通信接口1503、内存1505通过总线1504进行通信,也可以通过无线传输等其他手段实现通信。内存1505用于存储计算机执行指令,处理器1501用于执行内存1505存储的计算机执行指令以实现下述操作步骤:15 is a schematic diagram of a
获取交易设备的图像数据,所述交易设备包括交易区和键盘区,所述图像数据包括交易区的图像和键盘区的图像;acquiring image data of a transaction device, the transaction device including a transaction area and a keyboard area, and the image data including an image of the transaction area and an image of the keyboard area;
根据所述图像数据确定所述交易区的第一行为类型和所述键盘区的第二行为类型;Determine the first behavior type of the transaction area and the second behavior type of the keyboard area according to the image data;
根据所述第一行为类型和所述第二行为类型确定交易行为的风险性。The riskiness of the transaction behavior is determined according to the first behavior type and the second behavior type.
应理解,在本申请实施例中,该处理器1501可以是CPU,该处理器1501还可以是其他通用处理器、数字信号处理器(digital signal processing,DSP)、专用集成电路(application specific integrated circuit,ASIC)、现场可编程门阵列(fieldprogrammable gate array,FPGA)或者其他可编程逻辑器件、分立门或者晶体管逻辑器件、分立硬件组件等。通用处理器可以是微处理器或者是任何常规的处理器等。It should be understood that, in this embodiment of the present application, the
该存储器1502可以包括只读存储器和随机存取存储器,并向处理器1501提供指令和数据。存储器1502还可以包括非易失性随机存取存储器。例如,存储器1502还可以存储设备类型的信息。The
该存储器1502可以是易失性存储器或非易失性存储器,或可包括易失性和非易失性存储器两者。其中,非易失性存储器可以是只读存储器(read-only memory,ROM)、可编程只读存储器(programmable ROM,PROM)、可擦除可编程只读存储器(erasable PROM,EPROM)、电可擦除可编程只读存储器(electrically EPROM,EEPROM)或闪存。易失性存储器可以是随机存取存储器(random access memory,RAM),其用作外部高速缓存。通过示例性但不是限制性说明,许多形式的RAM可用,例如静态随机存取存储器(static RAM,SRAM)、动态随机存取存储器(DRAM)、同步动态随机存取存储器(synchronous DRAM,SDRAM)、双倍数据速率同步动态随机存取存储器(double data date SDRAM,DDR SDRAM)、增强型同步动态随机存取存储器(enhanced SDRAM,ESDRAM)、同步连接动态随机存取存储器(synchlinkDRAM,SLDRAM)和直接内存总线随机存取存储器(direct rambus RAM,DR RAM)。The
该总线1504除包括数据总线之外,还可以包括电源总线、控制总线和状态信号总线等。但是为了清楚说明起见,在图中将各种总线都标为总线1504。In addition to the data bus, the
应理解,根据本申请实施例的计算机设备1500可对应于本申请实施例中的风险识别装置1400,并可以对应于执行根据本申请实施例中图2至图13所示的方法200中的计算设备,并且计算机设备1500中的各个模块的上述和其它操作和/或功能分别为了实现图中的各个方法的相应流程,为了简洁,在此不再赘述。It should be understood that the
综上所述,本申请实施例提供的计算机设备,能自动识别并实时监控交易设备的风险性,提高了交易行为的安全性。To sum up, the computer equipment provided by the embodiments of the present application can automatically identify and monitor the risk of transaction equipment in real time, thereby improving the security of transaction behavior.
本申请还提供一种风险识别的系统,包括交易设备和计算设备。其中,交易设备包括摄像头、交易区和键盘区,摄像头用于获取交易设备的图像数据,图像数据包括交易区的图像和键盘区的图像。计算设备用于实现如上述第一方面及第一方面任意一种可能实现方式中相应主体所执行的方法的操作步骤。通过上述系统,计算设备可以远程识别交易设备的风险行为,并为交易设备提供统一的风险管理,减少了人工的工作量。The present application also provides a system for risk identification, including a transaction device and a computing device. Wherein, the transaction equipment includes a camera, a transaction area and a keyboard area, the camera is used to obtain image data of the transaction equipment, and the image data includes an image of the transaction area and an image of the keyboard area. The computing device is configured to implement the operation steps of the method performed by the corresponding subject in the above-mentioned first aspect and any possible implementation manner of the first aspect. Through the above system, the computing device can remotely identify the risk behavior of the transaction device, and provide unified risk management for the transaction device, reducing the manual workload.
本申请还提供一种交易设备,包括摄像头、交易区、键盘区和处理器。其中,摄像头用于获取交易设备的图像数据,图像数据包括交易区的图像和键盘区的图像,处理器用于执行实现如上述第一方面及第一方面任意一种可能实现方式中相应主体所执行的方法的操作步骤。通过上述交易设备,可以实时监控用户在使用交易设备的交易行为的风险性,即时制止违法行为的发生。The present application also provides a transaction device including a camera, a transaction area, a keyboard area and a processor. Wherein, the camera is used to acquire image data of the transaction device, and the image data includes the image of the transaction area and the image of the keyboard area, and the processor is used to implement the first aspect and any one of the possible implementations of the first aspect. the operating steps of the method. Through the above-mentioned transaction equipment, the risk of the user's transaction behavior using the transaction equipment can be monitored in real time, and the occurrence of illegal acts can be stopped immediately.
上述实施例,可以全部或部分地通过软件、硬件、固件或其他任意组合来实现。当使用软件实现时,上述实施例可以全部或部分地以计算机程序产品的形式实现。所述计算机程序产品包括一个或多个计算机指令。在计算机上加载或执行所述计算机程序指令时,全部或部分地产生按照本申请实施例所述的流程或功能。所述计算机可以为通用计算机、专用计算机、计算机网络、或者其他可编程装置。所述计算机指令可以存储在计算机可读存储介质中,或者从一个计算机可读存储介质向另一个计算机可读存储介质传输,例如,所述计算机指令可以从一个网站站点、计算机、服务器或数据中心通过有线(例如同轴电缆、光纤、数字用户线(digital subscriber line,DSL))或无线(例如红外、无线、微波等)方式向另一个网站站点、计算机、服务器或数据中心进行传输。所述计算机可读存储介质可以是计算机能够存取的任何可用介质或者是包含一个或多个可用介质集合的服务器、数据中心等数据存储设备。所述可用介质可以是磁性介质(例如,软盘、硬盘、磁带)、光介质(例如,DVD)、或者半导体介质。半导体介质可以是固态硬盘(solid state drive,SSD)。The above embodiments may be implemented in whole or in part by software, hardware, firmware or any other combination. When implemented in software, the above-described embodiments may be implemented in whole or in part in the form of a computer program product. The computer program product includes one or more computer instructions. When the computer program instructions are loaded or executed on a computer, all or part of the processes or functions described in the embodiments of the present application are generated. The computer may be a general purpose computer, special purpose computer, computer network, or other programmable device. The computer instructions may be stored in or transmitted from one computer readable storage medium to another computer readable storage medium, for example, the computer instructions may be downloaded from a website site, computer, server or data center Transmission to another website site, computer, server or data center via wired (eg coaxial cable, optical fiber, digital subscriber line, DSL) or wireless (eg infrared, wireless, microwave, etc.) means. The computer-readable storage medium can be any available medium that can be accessed by a computer or a data storage device such as a server, a data center, or the like that contains one or more sets of available media. The usable media may be magnetic media (eg, floppy disks, hard disks, magnetic tapes), optical media (eg, DVDs), or semiconductor media. The semiconductor medium may be a solid state drive (SSD).
以上所述,仅为本申请的具体实施方式。熟悉本技术领域的技术人员根据本申请提供的具体实施方式,可想到变化或替换,都应涵盖在本申请的保护范围之内。The above descriptions are merely specific embodiments of the present application. Those skilled in the art can think of changes or substitutions based on the specific embodiments provided by the present application, which should all fall within the protection scope of the present application.
Claims (17)
Priority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202110078552.4ACN114882427A (en) | 2021-01-21 | 2021-01-21 | Risk identification method, device and system and computer equipment |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202110078552.4ACN114882427A (en) | 2021-01-21 | 2021-01-21 | Risk identification method, device and system and computer equipment |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| CN114882427Atrue CN114882427A (en) | 2022-08-09 |
Family
ID=82667683
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN202110078552.4APendingCN114882427A (en) | 2021-01-21 | 2021-01-21 | Risk identification method, device and system and computer equipment |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN114882427A (en) |
- 2021
- 2021-01-21CNCN202110078552.4Apatent/CN114882427A/enactivePending
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| JP6911154B2 (en) | Access control methods and devices, systems, electronic devices, programs and media | |
| US11837061B2 (en) | Techniques to provide and process video data of automatic teller machine video streams to perform suspicious activity detection | |
| Schreyer et al. | Adversarial learning of deepfakes in accounting | |
| CN106503703A (en) | System and method of the using terminal equipment to recognize credit card number and due date | |
| US12093379B2 (en) | Preventing unauthorized screen capture activity | |
| US12136093B2 (en) | Techniques to improve fraud detection at financial terminals | |
| US20210304571A1 (en) | Cognitive automation platform for providing enhanced automated teller machine (atm) security | |
| KR100715323B1 (en) | Apparatus and method for preventing electronic banking fraudulent transactions using face recognition technology | |
| WO2023129886A1 (en) | Fraud detection using aggregate fraud score for confidence of liveness/similarity decisions of live and identity document photos | |
| CN105868693A (en) | Identity authentication method and system | |
| Hu et al. | Anomaly detection based on local nearest neighbor distance descriptor in crowded scenes | |
| CA3146127A1 (en) | System for detecting associated records in a record log | |
| CN111798356B (en) | A method for identifying rail transit passenger flow abnormal patterns based on big data | |
| Panimalar et al. | ATM theft detection using artificial intelligence | |
| Devi et al. | Deep learn helmets-enhancing security at ATMs | |
| CN109993178A (en) | A feature data generation and feature matching method and device | |
| CN117010893B (en) | Transaction risk control method, device and computer equipment based on biometric identification | |
| CN114882427A (en) | Risk identification method, device and system and computer equipment | |
| Jaleel et al. | Towards Proactive Surveillance through CCTV Cameras under Edge‐Computing and Deep Learning | |
| CN114117467A (en) | Method, apparatus, computer equipment and storage medium for protecting user information security | |
| US12387571B2 (en) | Automated teller machine digital twin with an anti NFC/RFID skimming threat device through mist computation | |
| Sesha Talpa Sai et al. | Face Recognition for Secure ATM Using Haar Cascade Algorithm | |
| Bhalerao et al. | Block Crime: Criminal Incidence Detection Using Facial Recognition Based on Concepts of Blockchain | |
| Thakre et al. | Attenuation YOLOv5-based detection of anomalous behavior in ATM | |
| Juliano et al. | Automated Vehicle Access Control System Utilizing Computer Vision-Based License Plate Recognition |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination |