CN114745154A - Safety control method for cable-controlled separate injection well - Google Patents
Safety control method for cable-controlled separate injection wellDownload PDFInfo
- Publication number
- CN114745154A CN114745154ACN202210246050.2ACN202210246050ACN114745154ACN 114745154 ACN114745154 ACN 114745154ACN 202210246050 ACN202210246050 ACN 202210246050ACN 114745154 ACN114745154 ACN 114745154A
- Authority
- CN
- China
- Prior art keywords
- safety
- protection
- control
- instruction
- cable
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Pending
Links
- 238000000034methodMethods0.000titleclaimsabstractdescription30
- 238000002347injectionMethods0.000titleclaimsabstractdescription27
- 239000007924injectionSubstances0.000titleclaimsabstractdescription27
- 238000012544monitoring processMethods0.000claimsabstractdescription21
- 230000005540biological transmissionEffects0.000claimsabstractdescription18
- XLYOFNOQVPJJNP-UHFFFAOYSA-NwaterSubstancesOXLYOFNOQVPJJNP-UHFFFAOYSA-N0.000claimsabstractdescription13
- 238000004458analytical methodMethods0.000claimsabstractdescription7
- 238000012502risk assessmentMethods0.000claimsabstractdescription4
- 230000007246mechanismEffects0.000claimsdescription8
- 238000013461designMethods0.000claimsdescription5
- 230000002159abnormal effectEffects0.000claimsdescription4
- 206010000117Abnormal behaviourDiseases0.000claimsdescription3
- 230000000903blocking effectEffects0.000claims1
- 239000000243solutionSubstances0.000abstractdescription4
- 238000010921in-depth analysisMethods0.000description5
- 238000009434installationMethods0.000description2
- 238000012795verificationMethods0.000description2
- 230000006399behaviorEffects0.000description1
- 230000009286beneficial effectEffects0.000description1
- 230000007812deficiencyEffects0.000description1
- 230000007774longtermEffects0.000description1
- 238000012986modificationMethods0.000description1
- 230000004048modificationEffects0.000description1
- 239000003208petroleumSubstances0.000description1
Images
Classifications
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/04—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks
- H04L63/0428—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks wherein the data content is protected, e.g. by encrypting or encapsulating the payload
- E—FIXED CONSTRUCTIONS
- E21—EARTH OR ROCK DRILLING; MINING
- E21B—EARTH OR ROCK DRILLING; OBTAINING OIL, GAS, WATER, SOLUBLE OR MELTABLE MATERIALS OR A SLURRY OF MINERALS FROM WELLS
- E21B43/00—Methods or apparatus for obtaining oil, gas, water, soluble or meltable materials or a slurry of minerals from wells
- E21B43/16—Enhanced recovery methods for obtaining hydrocarbons
- E21B43/20—Displacing by water
- G—PHYSICS
- G08—SIGNALLING
- G08B—SIGNALLING OR CALLING SYSTEMS; ORDER TELEGRAPHS; ALARM SYSTEMS
- G08B21/00—Alarms responsive to a single specified undesired or abnormal condition and not otherwise provided for
- G08B21/18—Status alarms
- G08B21/185—Electrical failure alarms
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/02—Network architectures or network communication protocols for network security for separating internal from external traffic, e.g. firewalls
- H04L63/0209—Architectural arrangements, e.g. perimeter networks or demilitarized zones
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/08—Network architectures or network communication protocols for network security for authentication of entities
- H04L63/0861—Network architectures or network communication protocols for network security for authentication of entities using biometrical features, e.g. fingerprint, retina-scan
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/10—Network architectures or network communication protocols for network security for controlling access to devices or network resources
- H04L63/101—Access control lists [ACL]
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/18—Network architectures or network communication protocols for network security using different networks or channels, e.g. using out of band channels
Landscapes
- Engineering & Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- Computer Hardware Design (AREA)
- Computing Systems (AREA)
- General Engineering & Computer Science (AREA)
- Computer Networks & Wireless Communication (AREA)
- Signal Processing (AREA)
- Physics & Mathematics (AREA)
- Geology (AREA)
- Mining & Mineral Resources (AREA)
- Life Sciences & Earth Sciences (AREA)
- Health & Medical Sciences (AREA)
- Environmental & Geological Engineering (AREA)
- Fluid Mechanics (AREA)
- Biomedical Technology (AREA)
- General Health & Medical Sciences (AREA)
- General Life Sciences & Earth Sciences (AREA)
- Geochemistry & Mineralogy (AREA)
- Business, Economics & Management (AREA)
- Emergency Management (AREA)
- General Physics & Mathematics (AREA)
- Testing And Monitoring For Control Systems (AREA)
Abstract
Description
Translated fromChinese技术领域technical field
本发明涉及海洋石油工程技术领域,更具体地说涉及一种缆控分注井安全控制方法。The invention relates to the technical field of offshore petroleum engineering, and more particularly to a safety control method for a cable-controlled injection well.
背景技术Background technique
缆控分注系统实现注水井对井下流量、压力、温度等参数的在线监测及控制;可以解决影响分注井分层注入数据及时、长期、全面获取及在线高效调控的难题,远程控制过程中安全问题十分重要,会直接导致不能有效注水、设备损坏、财务损失等影响。The cable-controlled dispensing system realizes the online monitoring and control of the downhole flow, pressure, temperature and other parameters of the water injection well; it can solve the problems affecting the timely, long-term and comprehensive acquisition of the layered injection data of the dispensing well and the efficient online control. During the remote control process Safety issues are very important and will directly lead to ineffective water injection, equipment damage, financial losses and other impacts.
目前,针对缆控分注系统更多通过口令、防火墙进行安全控制,执行装置缺乏安全监测,整体监测和安全控制方法还不够完善。At present, for the cable-controlled dispensing system, more security control is carried out through passwords and firewalls, the execution device lacks security monitoring, and the overall monitoring and security control methods are not perfect.
发明内容SUMMARY OF THE INVENTION
本发明克服了现有技术中的不足,现有的针对缆控分注系统的安全控制多是采用口令、防火墙进行,执行装置缺乏安全监测,整体监测和安全控制的方法还不够完善,提供了一种缆控分注井安全控制方法,本发明能够保障缆控分注系统远程控制安全,实现安全注水。The invention overcomes the deficiencies in the prior art. The existing security control for the cable-controlled dispensing system is mostly performed by using passwords and firewalls, the execution device lacks security monitoring, and the overall monitoring and security control methods are not perfect. A cable-controlled dispensing well safety control method, the invention can ensure the remote control safety of the cable-controlled dispensing system and realize safe water injection.
本发明的目的通过下述技术方案予以实现。The purpose of the present invention is achieved through the following technical solutions.
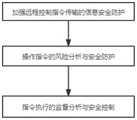
一种缆控分注井安全控制方法,按照下述步骤进行:A cable-controlled injection well safety control method is carried out according to the following steps:
步骤一:加强远程控制指令传输的信息安全防护:通过添加白名单、传输加密、多因素认证,建立工业防火墙的方式,确保指令的可信度;Step 1: Strengthen the information security protection of remote control command transmission: by adding whitelist, transmission encryption, multi-factor authentication, and establishing an industrial firewall to ensure the credibility of the command;
具体来说,采用TLS加密数据通道进行传输,与办公网络隔离,为数据传输网络设置独立网段,保障数据传输安全;Specifically, the TLS encrypted data channel is used for transmission, which is isolated from the office network, and an independent network segment is set up for the data transmission network to ensure the security of data transmission;
通过建立工业防火墙来对协议指令进行解析、实时事件监控和保护,其中,工业防火墙的防护特征,包括工业协议深度解析、黑白名单机制、实时事件监控和保护以及灵活布署、工业级设计,具体如下:By establishing an industrial firewall to parse protocol instructions, monitor and protect real-time events, the protection features of industrial firewalls include in-depth analysis of industrial protocols, black and white list mechanism, real-time event monitoring and protection, flexible deployment, and industrial-grade design. as follows:
工业协议深度解析:深度剖析工业控制网络专有协议数据包,确保数据内容合法性,实现工业控制网络的深度安全防护;In-depth analysis of industrial protocols: In-depth analysis of industrial control network proprietary protocol data packets to ensure the legality of data content and achieve in-depth security protection of industrial control networks;
黑白名单机制:内置可更新专业工控系统安全漏洞库,覆盖主流厂商,采用智能学习引擎自动收集数据,生成适应当前工控环境的白名单规则;Black and white list mechanism: built-in updateable professional industrial control system security vulnerability library, covering mainstream manufacturers, using intelligent learning engine to automatically collect data, and generate white list rules that adapt to the current industrial control environment;
实时事件监控和保护:提供综合事件监控和安全防护机制,对网络安全事件、设备管理操作以及平台系统事件进行实时监控和记录,对APT攻击和异常行为进行告警和阻断;Real-time event monitoring and protection: Provide comprehensive event monitoring and security protection mechanisms, monitor and record network security events, device management operations and platform system events in real time, and alert and block APT attacks and abnormal behaviors;
灵活布署、工业级设计:根据系统保护要求实现边界防护、区域防护、终端防护等不同配置方案;Flexible deployment and industrial-grade design: According to system protection requirements, different configuration schemes such as boundary protection, area protection, and terminal protection are realized;
加强远程指令传输的信息安全防护,对操作人员通过采取短信+人体生物特征识别的多因素认证方式,确保认证安全;Strengthen the information security protection of remote command transmission, and ensure the security of authentication by adopting the multi-factor authentication method of SMS + human biometric identification for operators;
步骤二:操作指令的风险分析与安全防护:系统根据控制指令限制条件分析当前控制指令的可执行性;Step 2: Risk analysis and security protection of operation instructions: The system analyzes the executability of the current control instructions according to the restriction conditions of the control instructions;
具体来说,基于缆控注水井操作指令建立知识库、风险指令库;通过远程控制系统进行配置限制规则;Specifically, the knowledge base and risk instruction base are established based on the operation instructions of the cable-controlled water injection well; the configuration restriction rules are carried out through the remote control system;
对边缘一体机下达远程控制指令前,系统自动根据控制指令限制条件分析当前控制指令的可执行性,如果当前指令不满足执行条件,系统不允许执行该操作并报警;Before the remote control command is issued to the edge integrated machine, the system automatically analyzes the executable of the current control command according to the restriction conditions of the control command. If the current command does not meet the execution conditions, the system does not allow the operation and alarms;
步骤三:指令执行的监督分析与安全控制:通过建立风险识别模型和知识库,对远程操作指令的执行风险进行识别;Step 3: Supervision analysis and security control of instruction execution: Identify the execution risk of remote operation instructions by establishing a risk identification model and knowledge base;
具体来说,建立风险识别模型和知识库,对接收到云端分层注水远程控制指令,执行智能分注设备的水嘴开度调整等操作过程中,对于操作中设备故障、非正常动作等进行报警,从而控制风险;Specifically, a risk identification model and a knowledge base are established, and during operations such as receiving remote control instructions for layered water injection in the cloud, and adjusting the opening of the nozzle of the intelligent dispensing equipment, the equipment failures and abnormal actions during operation are carried out. alarm to control risks;
通过知识库不断完善风险类型,通过模型自定义报警级别和方式,不断完善对执行装装置故障分析的识别和防护。Continuously improve the risk types through the knowledge base, customize the alarm level and method through the model, and continuously improve the identification and protection of the fault analysis of the installation equipment.
本发明的有益效果为:本发明方法从信息安全、指令执行的行为监测两方面入手构建安全注水的防护方法;针对目前缆控分注系统在执行装置缺乏安全监测,整体监测和安全控制方法不够完善的问题提供了一套有效解决方案。The beneficial effects of the invention are as follows: the method of the invention constructs a protection method for safe water injection from the aspects of information security and behavior monitoring of instruction execution; for the current cable-controlled dispensing system lacks safety monitoring in the execution device, the overall monitoring and safety control methods are insufficient A well-rounded problem provides a set of effective solutions.
附图说明Description of drawings
图1是本发明的流程示意图;Fig. 1 is the schematic flow sheet of the present invention;
图2是本发明分注井注水安全控制运行流程。Fig. 2 is the running flow of the water injection safety control of the injection well according to the present invention.
具体实施方式Detailed ways
下面通过具体的实施例对本发明的技术方案作进一步的说明。The technical solutions of the present invention will be further described below through specific embodiments.
一种缆控分注井安全控制方法,按照下述步骤进行:A cable-controlled injection well safety control method is carried out according to the following steps:
步骤一:加强远程控制指令传输的信息安全防护,通过添加白名单、传输加密、多因素认证等方式,确保指令的可信度。Step 1: Strengthen the information security protection of remote control command transmission, and ensure the credibility of the command by adding whitelist, transmission encryption, multi-factor authentication, etc.
本步骤中:In this step:
数据传输采用TLS加密数据通道传输,与办公网络隔离,为数据传输网络设置独立网段,保障数据传输安全。Data transmission adopts TLS encrypted data channel transmission, which is isolated from the office network, and an independent network segment is set up for the data transmission network to ensure the security of data transmission.
通过建立工业防火墙来对协议指令进行解析、实时事件监控和保护等。工业防火墙的防护包含且不限于以下几种:By establishing an industrial firewall, it can parse protocol instructions, monitor and protect real-time events, etc. The protection of industrial firewalls includes but is not limited to the following:
工业协议深度解析In-depth analysis of industrial protocols
深度剖析工业控制网络专有协议数据包,确保数据内容合法性,实现工业控制网络的深度安全防护;In-depth analysis of industrial control network proprietary protocol data packets to ensure the legality of data content and achieve in-depth security protection of industrial control networks;
黑白名单机制Black and white list mechanism
内置可更新专业工控系统安全漏洞库,覆盖主流厂商,采用智能学习引擎自动收集数据,生成适应当前工控环境的白名单规则。Built-in updateable professional industrial control system security vulnerability library, covering mainstream manufacturers, using an intelligent learning engine to automatically collect data and generate whitelist rules that adapt to the current industrial control environment.
实时事件监控和保护Real-time event monitoring and protection
提供综合事件监控和安全防护机制,对网络安全事件、设备管理操作以及平台系统事件进行实时监控和记录,对APT攻击和异常行为进行告警和阻断。Provide comprehensive event monitoring and security protection mechanisms, monitor and record network security events, device management operations and platform system events in real time, and alert and block APT attacks and abnormal behaviors.
灵活布署、工业级设计Flexible deployment, industrial-grade design
根据系统保护要求实现边界防护、区域防护、终端防护等不同配置方案。Different configuration schemes such as boundary protection, area protection, and terminal protection are implemented according to system protection requirements.
对使用人员加强认证,采取短信+人体生物特征识别双因素认证,确保认证安全。Strengthen the authentication of users, and adopt two-factor authentication of SMS + human biometric identification to ensure the security of authentication.
边缘端存储具有远程操控权限的人的生物特征(人脸或指纹),所有远程操控指令都需要在短信验证后,进行生物特征识别验证,验证通过后才能执行操控指令。The edge terminal stores the biometrics (face or fingerprint) of the person with remote control authority. All remote control instructions need to be verified by SMS verification, and the control instructions can only be executed after the verification is passed.
步骤二:操作指令的风险分析与安全防护,识别操作指令中的非正常操作。Step 2: Risk analysis and security protection of operation instructions, and identify abnormal operations in operation instructions.
本步骤中:In this step:
基于缆控注水井操作指令建立知识库、风险指令库;通过远程控制系统进行配置限制规则;Establish knowledge base and risk instruction base based on cable-controlled water injection well operation instructions; configure restriction rules through remote control system;
对边缘一体机下达远程控制指令前,系统自动根据控制指令限制条件分析当前控制指令的可执行性,如果当前指令不满足执行条件,系统不允许执行该操作并报警。Before issuing a remote control command to the edge integrated machine, the system automatically analyzes the executable of the current control command according to the restriction conditions of the control command. If the current command does not meet the execution conditions, the system does not allow the operation and alarms.
步骤三:指令执行的监督分析与安全控制Step 3: Supervision Analysis and Security Control of Instruction Execution
本步骤中:In this step:
建立风险识别模型和知识库,对接收到云端分层注水远程控制指令,执行智能分注设备的水嘴开度调整等操作过程中,对于操作中设备故障、非正常动作等进行报警,从而控制风险。Establish a risk identification model and knowledge base, and in the process of receiving remote control instructions for layered water injection in the cloud, and performing the adjustment of the opening of the nozzle of the intelligent dispensing equipment, it will alarm for equipment failures and abnormal actions during operation, so as to control risk.
通过知识库不断完善风险类型,通过模型自定义报警级别和方式,不断完善对执行装装置故障分析的识别和防护。Continuously improve the risk types through the knowledge base, customize the alarm level and method through the model, and continuously improve the identification and protection of the fault analysis of the installation equipment.
以上对本发明做了示例性的描述,应该说明的是,在不脱离本发明的核心的情况下,任何简单的变形、修改或者其他本领域技术人员能够不花费创造性劳动的等同替换均落入本发明的保护范围。The present invention has been exemplarily described above. It should be noted that, without departing from the core of the present invention, any simple deformations, modifications or other equivalent replacements that those skilled in the art can do without creative effort fall into the scope of the present invention. the scope of protection of the invention.
Claims (5)
Priority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202210246050.2ACN114745154A (en) | 2022-03-14 | 2022-03-14 | Safety control method for cable-controlled separate injection well |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202210246050.2ACN114745154A (en) | 2022-03-14 | 2022-03-14 | Safety control method for cable-controlled separate injection well |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| CN114745154Atrue CN114745154A (en) | 2022-07-12 |
Family
ID=82274489
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN202210246050.2APendingCN114745154A (en) | 2022-03-14 | 2022-03-14 | Safety control method for cable-controlled separate injection well |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN114745154A (en) |
Citations (3)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN103491108A (en)* | 2013-10-15 | 2014-01-01 | 浙江中控研究院有限公司 | Method and system for security protection of industrial control network |
| CN105208018A (en)* | 2015-09-09 | 2015-12-30 | 上海三零卫士信息安全有限公司 | Industrial control network information security monitoring method based on funnel type white list |
| CN112799358A (en)* | 2020-12-30 | 2021-05-14 | 上海磐御网络科技有限公司 | Industrial control safety defense system |
- 2022
- 2022-03-14CNCN202210246050.2Apatent/CN114745154A/enactivePending
Patent Citations (3)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN103491108A (en)* | 2013-10-15 | 2014-01-01 | 浙江中控研究院有限公司 | Method and system for security protection of industrial control network |
| CN105208018A (en)* | 2015-09-09 | 2015-12-30 | 上海三零卫士信息安全有限公司 | Industrial control network information security monitoring method based on funnel type white list |
| CN112799358A (en)* | 2020-12-30 | 2021-05-14 | 上海磐御网络科技有限公司 | Industrial control safety defense system |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| Zolanvari et al. | Machine learning-based network vulnerability analysis of industrial Internet of Things | |
| Irmak et al. | An overview of cyber-attack vectors on SCADA systems | |
| US9197652B2 (en) | Method for detecting anomalies in a control network | |
| CN109739203B (en) | Industrial network boundary protection system | |
| CN112306019A (en) | Industrial control safety audit system based on protocol deep analysis and application thereof | |
| CN119276602B (en) | An artificial intelligence-based substation network security defense system | |
| CN118018277A (en) | A computer information security intelligent monitoring method and system | |
| CN118632242B (en) | Building wireless intercom system based on Internet of things | |
| CN214306527U (en) | Gas pipe network scheduling monitoring network safety system | |
| Flå et al. | Tool-assisted threat modeling for smart grid cyber security | |
| CN110365709B (en) | Device for sensing unknown network attack behavior based on upstream probe | |
| CN118138362A (en) | LLM-driven self-adaptive industrial network safety protection method and firewall device | |
| CN119995996A (en) | Digital information security transmission system and method based on network protocol analysis | |
| CN107493187A (en) | A kind of Security Countermeasure for Information Network of Electric Power Enterprise management system with safe early warning | |
| CN117425149A (en) | Wireless network data security management system | |
| CN117763525A (en) | Mobile terminal information safety protection system and method | |
| CN116684202A (en) | Internet of things information security transmission method | |
| CN116668166A (en) | Software and hardware cooperated data security monitoring system | |
| CN112769709A (en) | Thing networking terminal equipment safety protection system | |
| CN112261041A (en) | A multi-level distributed monitoring and anti-penetration system for power terminals | |
| CN115694931A (en) | Relay protection remote operation and maintenance intrusion prevention and detection method and system | |
| CN114745154A (en) | Safety control method for cable-controlled separate injection well | |
| CN112565279A (en) | Sensor signal processing system based on safety network | |
| Calvo et al. | Key Vulnerabilities of Industrial Automation and Control Systems and Recommendations to Prevent Cyber-Attacks. | |
| CN212084141U (en) | A security reinforcement management device for industrial control terminals |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| RJ01 | Rejection of invention patent application after publication | Application publication date:20220712 | |
| RJ01 | Rejection of invention patent application after publication |