CN114640451A - Method, system and consensus node for realizing distributed key generation on block chain - Google Patents
Method, system and consensus node for realizing distributed key generation on block chainDownload PDFInfo
- Publication number
- CN114640451A CN114640451ACN202210325828.9ACN202210325828ACN114640451ACN 114640451 ACN114640451 ACN 114640451ACN 202210325828 ACN202210325828 ACN 202210325828ACN 114640451 ACN114640451 ACN 114640451A
- Authority
- CN
- China
- Prior art keywords
- node
- consensus
- share
- signature
- contract
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Pending
Links
Images
Classifications
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/08—Key distribution or management, e.g. generation, sharing or updating, of cryptographic keys or passwords
- H04L9/0861—Generation of secret information including derivation or calculation of cryptographic keys or passwords
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L67/00—Network arrangements or protocols for supporting network services or applications
- H04L67/01—Protocols
- H04L67/10—Protocols in which an application is distributed across nodes in the network
- H04L67/104—Peer-to-peer [P2P] networks
- H04L67/1059—Inter-group management mechanisms, e.g. splitting, merging or interconnection of groups
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/08—Key distribution or management, e.g. generation, sharing or updating, of cryptographic keys or passwords
- H04L9/0861—Generation of secret information including derivation or calculation of cryptographic keys or passwords
- H04L9/0869—Generation of secret information including derivation or calculation of cryptographic keys or passwords involving random numbers or seeds
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/30—Public key, i.e. encryption algorithm being computationally infeasible to invert or user's encryption keys not requiring secrecy
- H04L9/3066—Public key, i.e. encryption algorithm being computationally infeasible to invert or user's encryption keys not requiring secrecy involving algebraic varieties, e.g. elliptic or hyper-elliptic curves
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/32—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials
- H04L9/3247—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials involving digital signatures
- H04L9/3249—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols including means for verifying the identity or authority of a user of the system or for message authentication, e.g. authorization, entity authentication, data integrity or data verification, non-repudiation, key authentication or verification of credentials involving digital signatures using RSA or related signature schemes, e.g. Rabin scheme
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/50—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols using hash chains, e.g. blockchains or hash trees
Landscapes
- Engineering & Computer Science (AREA)
- Computer Networks & Wireless Communication (AREA)
- Signal Processing (AREA)
- Computer Security & Cryptography (AREA)
- Theoretical Computer Science (AREA)
- Mathematical Analysis (AREA)
- General Physics & Mathematics (AREA)
- Mathematical Optimization (AREA)
- Mathematical Physics (AREA)
- Pure & Applied Mathematics (AREA)
- Algebra (AREA)
- Computing Systems (AREA)
- Physics & Mathematics (AREA)
- Information Retrieval, Db Structures And Fs Structures Therefor (AREA)
Abstract
Translated fromChineseDescription
Translated fromChinese技术领域technical field
本说明书实施例属于区块链技术领域,尤其涉及一种区块链上实现分布式密钥生成的方法、系统和共识节点。The embodiments of this specification belong to the technical field of blockchain, and in particular, relate to a method, system and consensus node for realizing distributed key generation on a blockchain.
背景技术Background technique
区块链(Blockchain)是分布式数据存储、点对点传输、共识机制、加密算法等计算机技术的新型应用模式。区块链系统中按照时间顺序将数据区块以顺序相连的方式组合成链式数据结构,并以密码学方式保证的不可篡改和不可伪造的分布式账本。由于区块链具有去中心化、信息不可篡改、自治性等特性,区块链也受到人们越来越多的重视和应用。Blockchain is a new application mode of computer technology such as distributed data storage, point-to-point transmission, consensus mechanism, and encryption algorithm. In the blockchain system, the data blocks are sequentially connected to form a chain data structure according to the time sequence, and a distributed ledger that cannot be tampered with and cannot be forged by cryptography. Due to the characteristics of decentralization, non-tampering of information, and autonomy, blockchain has also received more and more attention and applications.
发明内容SUMMARY OF THE INVENTION
本说明书的目的在于提供一种区块链上实现分布式密钥生成的方法、系统和共识节点,包括:The purpose of this specification is to provide a method, system and consensus node for realizing distributed key generation on the blockchain, including:
一种区块链上实现分布式密钥生成的方法,包括:A method for implementing distributed key generation on a blockchain, comprising:
每一共识节点生成n个秘密份额,自身保留一份,并将其中n-1个秘密份额分别加密发送至其它n-1个节点;Each consensus node generates n secret shares, keeps one for itself, and encrypts the n-1 secret shares and sends them to other n-1 nodes;
每一共识节点生成自身秘密份额对应的公共验证参数并通过链上合约广播;Each consensus node generates public verification parameters corresponding to its own secret share and broadcasts it through the on-chain contract;
每一共识节点对接收到的每一秘密份额和对应的公共验证参数进行验证;Each consensus node verifies each received secret share and the corresponding public verification parameters;
每一共识节点对每一验证通过后,将通过验证的节点编号发送至所述链上合约;After each consensus node passes each verification, it sends the verified node number to the on-chain contract;
所述链上G合约根据各共识节点发来的交易确定节点集合;The G contract on the chain determines the node set according to the transactions sent by each consensus node;
每一共识节点各自基于验证参数及节点集合计算公钥份额,并基于本地的秘密份额和节点集合计算自身对应的私钥份额。Each consensus node calculates the public key share based on the verification parameters and the node set, and calculates its corresponding private key share based on the local secret share and the node set.
一种在上述方法基础上实现区块链上产生随机数种子的方法,包括:A method for generating random number seeds on the blockchain based on the above method, comprising:
在PBFT的commit阶段,每一共识节点基于门限签名算法,采用自身私钥份额对包含本次共识中原始交易列表特有值的原始报文进行签名,生成签名份额,并将该签名份额加入到广播的commit消息中;In the commit stage of PBFT, each consensus node uses its own private key share to sign the original message containing the unique value of the original transaction list in this consensus based on the threshold signature algorithm, generates a signature share, and adds the signature share to the broadcast in the commit message;
每一共识节点收集齐至少quorum数量的commit消息后,采用公钥份额对所述接收到的commit消息中的签名份额进行验证;After each consensus node collects at least quorum commit messages, the public key share is used to verify the signature share in the received commit message;
每一共识节点将通过验证的至少quorum数量的签名份额经过所述门限签名算法产生的私钥份额所对应的恢复函数得到完整签名;Each consensus node will obtain a complete signature through the recovery function corresponding to the private key share generated by the threshold signature algorithm through the verified signature shares of at least quorum;
每一共识节点基于所述完整签名得到随机数种子。Each consensus node obtains a random number seed based on the full signature.
一种区块链上实现分布式密钥生成的方法,包括:A method for implementing distributed key generation on a blockchain, comprising:
第一节点接收其它节点生成的秘密份额,并通过链上合约广播接收对应的公共验证参数;The first node receives the secret shares generated by other nodes, and receives the corresponding public verification parameters through the contract broadcast on the chain;
第一节点对接收到的每一秘密份额和对应的公共验证参数进行验证;The first node verifies each received secret share and the corresponding public verification parameters;
第一节点对每一验证通过后,将通过验证的节点编号发送至所述链上合约;After passing each verification, the first node sends the verified node number to the on-chain contract;
第一节点接收所述链上合约确定的节点集合;The first node receives the set of nodes determined by the on-chain contract;
第一节点基于验证参数及节点集合计算公钥份额,并基于所述秘密份额和节点集合计算自身对应的私钥份额。The first node calculates the public key share based on the verification parameter and the node set, and calculates its corresponding private key share based on the secret share and the node set.
一种在上述方法基础上实现区块链上产生随机数种子的方法,包括:A method for generating random number seeds on the blockchain based on the above method, comprising:
在PBFT的commit阶段,第一节点基于门限签名算法,采用自身私钥份额对包含本次共识中原始交易列表特有值的原始报文进行签名,生成签名份额,并将该签名份额加入到广播的commit消息中;In the commit stage of PBFT, the first node uses its own private key share to sign the original message containing the unique value of the original transaction list in this consensus based on the threshold signature algorithm, generates a signature share, and adds the signature share to the broadcast In the commit message;
第一节点收集齐至少quorum数量的commit消息后,采用公钥份额对所述接收到的commit消息中的签名份额进行验证;After the first node has collected at least the quorum number of commit messages, the public key share is used to verify the signature share in the received commit message;
第一节点将通过验证的至少quorum数量的签名份额经过所述门限签名算法产生的私钥份额所对应的回复方法得到完整签名;The first node will obtain a complete signature through the reply method corresponding to the private key share generated by the threshold signature algorithm through the verified signature shares of at least quorum;
第一节点基于所述完整签名得到随机数种子。The first node obtains a random number seed based on the complete signature.
一种区块链系统,包括若干个共识节点,其中:A blockchain system including several consensus nodes, wherein:
每一共识节点生成n个秘密份额,自身保留一份,并将其中n-1个秘密份额分别加密发送至其它n-1个节点;Each consensus node generates n secret shares, keeps one for itself, and encrypts the n-1 secret shares and sends them to other n-1 nodes;
每一节点生成自身秘密份额对应的公共验证参数并通过链上合约广播;Each node generates the public verification parameters corresponding to its own secret share and broadcasts it through the on-chain contract;
每一共识节点对接收到的每一秘密份额和对应的公共验证参数进行验证;Each consensus node verifies each received secret share and the corresponding public verification parameters;
每一共识节点对每一验证通过后,将通过验证的节点编号发送至所述链上合约;After each consensus node passes each verification, it sends the verified node number to the on-chain contract;
所述链上合约根据各共识节点发来的交易确定节点集合;The on-chain contract determines the node set according to the transactions sent by each consensus node;
每一共识节点各自在本地基于验证参数及节点集合计算公钥份额,并基于本地的秘密份额和节点集合计算自身对应的私钥份额。Each consensus node calculates the public key share locally based on the verification parameters and the node set, and calculates its corresponding private key share based on the local secret share and the node set.
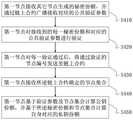
一种区块链系统中的第一共识节点,包括:A first consensus node in a blockchain system, comprising:
第一共识节点接收其它节点生成的秘密份额,并通过链上合约广播接收对应的公共验证参数;The first consensus node receives the secret shares generated by other nodes, and broadcasts the corresponding public verification parameters through the on-chain contract;
第一共识节点对接收到的每一秘密份额和对应的公共验证参数进行验证;The first consensus node verifies each received secret share and the corresponding public verification parameters;
第一共识节点对每一验证通过后,将通过验证的节点编号发送至链上合约;After the first consensus node passes each verification, it sends the verified node number to the contract on the chain;
第一共识节点接收所述链上合约确定的节点集合;The first consensus node receives the node set determined by the on-chain contract;
第一共识节点基于验证参数及节点集合计算公钥份额,并基于所述秘密份额和节点集合计算自身对应的私钥份额。The first consensus node calculates the public key share based on the verification parameter and the node set, and calculates its corresponding private key share based on the secret share and the node set.
本说明书提供的上述方案,在共识机制保障区块链网络整体一致性和同步的基础上,结合区块链智能合约实现分布式密钥生成,保障了分布式密钥的生成一方面是由各个参与方通过协作来生成的,另一方面生成的结果是一致和可靠的,从而摆脱了原有的区块链之外实现分布式密钥生成对网络同步的强依赖,并解决了该情况下生成结果的不可靠性问题。The above solutions provided in this specification, on the basis of the consensus mechanism to ensure the overall consistency and synchronization of the blockchain network, combined with blockchain smart contracts to achieve distributed key generation, ensure that the generation of distributed keys is performed by each It is generated by the participating parties through cooperation, and on the other hand, the generated results are consistent and reliable, thus getting rid of the strong dependence on network synchronization for distributed key generation outside the original blockchain, and solving the problem of Unreliability of generated results.
附图说明Description of drawings
图1是一实施例中实用拜占庭容错算法常规阶段的示意图;1 is a schematic diagram of a conventional stage of a practical Byzantine fault-tolerant algorithm in one embodiment;
图2是一实施例中实用拜占庭容错算法视图切换阶段的示意图;2 is a schematic diagram of a view switching stage of a practical Byzantine fault-tolerant algorithm in an embodiment;
图3是一实施例中共识节点都没有宕机情况下实用拜占庭容错算法常规阶段的示意图;FIG. 3 is a schematic diagram of a conventional stage of a practical Byzantine fault-tolerant algorithm under the condition that none of the consensus nodes are down in an embodiment;
图4是本说明书一实施例中区块链上产生随机数种子的流程图;FIG. 4 is a flow chart of generating random number seeds on the blockchain according to an embodiment of this specification;
图5是本说明书一实施例中区块头结构的示意图;5 is a schematic diagram of a block header structure in an embodiment of the present specification;
图6是本说明书一实施例中区块链上产生随机数种子的流程图;FIG. 6 is a flow chart of generating random number seeds on the blockchain according to an embodiment of this specification;
图7是本说明书一实施例中区块链上实现分布式密钥生成的方法;7 is a method for realizing distributed key generation on a blockchain in an embodiment of this specification;
图8是本说明书一实施例中区块链上实现分布式密钥生成的方法。FIG. 8 is a method for realizing distributed key generation on a blockchain according to an embodiment of this specification.
具体实施方式Detailed ways
为了使本技术领域的人员更好地理解本说明书中的技术方案,下面将结合本说明书实施例中的附图,对本说明书实施例中的技术方案进行清楚、完整地描述,显然,所描述的实施例仅仅是本说明书一部分实施例,而不是全部的实施例。基于本说明书中的实施例,本领域普通技术人员在没有作出创造性劳动前提下所获得的所有其他实施例,都应当属于本说明书保护的范围。In order to make those skilled in the art better understand the technical solutions in this specification, the technical solutions in the embodiments of this specification will be clearly and completely described below with reference to the accompanying drawings in the embodiments of this specification. Obviously, the described The embodiments are only some of the embodiments of the present specification, but not all of the embodiments. Based on the embodiments in this specification, all other embodiments obtained by persons of ordinary skill in the art without creative efforts shall fall within the protection scope of this specification.
区块链1.0时代通常是指在2009年到2014年之间,区块链应用发展阶段,它们主要致力于解决货币和支付手段的去中心化问题。从2014年开始,开发者们越来越注重于解决前述方案在技术和扩展性方面的不足。2013年底,Vitalik Buterin将智能合约引入区块链,打开了区块链在货币领域以外的应用,从而开启了区块链2.0时代。The era of blockchain 1.0 usually refers to the development stage of blockchain applications between 2009 and 2014, and they mainly focus on solving the decentralization of currency and payment methods. Since 2014, developers have increasingly focused on solving the technical and scalability deficiencies of the aforementioned solutions. At the end of 2013, Vitalik Buterin introduced smart contracts into the blockchain, opening up the application of blockchain outside the currency field, thus ushering in the era of blockchain 2.0.
区块链系统中,不同参与方通过部署的节点(Node)可以建立一个分布式的区块链网络。利用链式区块结构构造的去中心化(或称为多中心化)的分布式账本,保存于分布式的区块链网络中的每个节点(或大多节点上,如共识节点)上。这样的区块链系统需要解决去中心化(或多中心化)的多个节点上各自的账本数据的一致性和正确性的问题。每个节点(或多个节点)上都运行着区块链程序,在一定容错需求的设计下,通过共识(consensus)机制保证所有忠诚节点具有相同的交易,从而保证所有忠诚节点对相同交易的执行结果一致,并将交易及执行结果打包生成区块。In the blockchain system, different participants can establish a distributed blockchain network through deployed nodes (Node). The decentralized (or multi-centralized) distributed ledger constructed using the chain block structure is stored on each node (or most nodes, such as consensus nodes) in the distributed blockchain network. Such a blockchain system needs to solve the problems of consistency and correctness of the respective ledger data on the decentralized (or multi-centralized) nodes. Each node (or multiple nodes) runs a blockchain program. Under the design of certain fault tolerance requirements, the consensus mechanism is used to ensure that all loyal nodes have the same transaction, thereby ensuring that all loyal nodes have the same transaction. The execution results are consistent, and the transaction and execution results are packaged to generate blocks.
智能合约是一种基于规定触发规则的,可自动执行的计算机合约,也可以看作是传统合约的数字版本。智能合约这一概念最早由跨领域法律学者、密码学研究工作者尼克·萨博(Nick Szabo)在1994年提出。这项技术曾一度因为缺乏可编程数字系统和相关技术而没有被用于实际产业中,直到区块链技术的出现为其提供了可靠的执行环境。由于区块链技术采用块链式账本,产生的数据不可篡改或者删除,且整个账本将不断新增账本数据,从而保证了历史数据的可追溯;同时,去中心化的运行机制避免了中心化因素的影响。基于区块链技术的智能合约不仅可以发挥智能合约在成本、效率方面的优势,而且可以避免恶意行为对合约正常执行的干扰。将智能合约以数字化的形式写入区块链中,由区块链技术的特性保障存储、读取、执行整个过程透明可跟踪、不可篡改。A smart contract is a computer contract that can be executed automatically based on prescribed triggering rules, and can also be regarded as a digital version of a traditional contract. The concept of smart contracts was first proposed by Nick Szabo, a cross-disciplinary legal scholar and cryptography researcher, in 1994. This technology was not used in actual industry for a time due to the lack of programmable digital systems and related technologies, until the emergence of blockchain technology provided it with a reliable execution environment. Since the blockchain technology adopts a blockchain ledger, the generated data cannot be tampered with or deleted, and the entire ledger will continue to add ledger data, thus ensuring the traceability of historical data; at the same time, the decentralized operating mechanism avoids centralization influence of factors. Smart contracts based on blockchain technology can not only give play to the advantages of smart contracts in terms of cost and efficiency, but also avoid the interference of malicious behaviors on the normal execution of contracts. The smart contract is written into the blockchain in a digital form, and the entire process of storage, reading, and execution is guaranteed by the characteristics of blockchain technology to be transparent, traceable, and non-tamperable.
区块链发展及应用多样化。一些业务逻辑被编辑为智能合约并在区块链平台上执行。具体的,这些包含业务逻辑的智能合约可以运行于区块链网络中的每个节点(或大多节点上,如共识节点)上。相对于中心化的业务逻辑执行环境所带来的单点故障导致整个中心化系统不可用的问题,区块链环境中执行智能合约也被称为“世界计算机”,这是因为分布式的区块链网络中有较多节点各自独立执行智能合约。如前所述,这些不同节点上执行相同逻辑的智能合约,需要获得相同的执行结果,从而保证这些节点中的多数保存的账本是一致的。Blockchain development and application diversification. Some business logic is compiled into smart contracts and executed on the blockchain platform. Specifically, these smart contracts containing business logic can run on each node (or most nodes, such as consensus nodes) in the blockchain network. Compared with the problem of unavailability of the entire centralized system due to the single point of failure brought about by the centralized business logic execution environment, the execution of smart contracts in the blockchain environment is also called "world computer", because the distributed area There are many nodes in the blockchain network that independently execute smart contracts. As mentioned above, smart contracts that execute the same logic on these different nodes need to obtain the same execution results, so as to ensure that the ledgers saved by most of these nodes are consistent.
一些业务逻辑中,可能需要基于随机数产生一个结果,例如实现抽奖的业务逻辑,实现摇号的业务逻辑,或者实现一定范围内随机金额发红包或盲盒等的业务逻辑,这一般需要在智能合约中包含产生随机数的程序。再例如,一些系统合约中,可能需要实现对主节点的投票或对小规模委员会的投票,这个投票逻辑中可能采用随机的方式或者是用到随机数。如前所述,分布式的区块链网络中有一个显著特点,是为了保证分布式的区块链网络整体可用而需要多数节点中的账本是一致的,这也就需要多数节点中的智能合约产生的随机数是一致的。In some business logic, it may be necessary to generate a result based on random numbers, such as the business logic of implementing lottery draws, the business logic of lottery, or the business logic of sending red envelopes or blind boxes with random amounts within a certain range, which generally requires smart contracts. Contains programs that generate random numbers. For another example, in some system contracts, it may be necessary to implement voting on the master node or voting on the small-scale committee. The voting logic may adopt a random method or use random numbers. As mentioned above, a distinctive feature of distributed blockchain network is that in order to ensure the overall availability of the distributed blockchain network, the ledger in most nodes needs to be consistent, which also requires the intelligence in most nodes. The random numbers generated by the contract are consistent.
前述提到,每个节点(或多个节点)上都运行着区块链程序,在一定容错需求的设计下,通过共识机制保证所有忠诚节点具有相同的交易,从而保证所有忠诚节点对相同交易的执行结果一致,并将交易及执行结果打包生成区块。当前主流的共识机制包括:工作量证明(Proof of Work,POW)、股权证明(Proof of Stake,POS)、委任权益证明(DelegatedProof of Stake,DPOS)、实用拜占庭容错(Practical Byzantine Fault Tolerance,PBFT)算法,蜜獾拜占庭容错(HoneyBadgerBFT)算法等。As mentioned above, each node (or multiple nodes) runs a blockchain program. Under the design of certain fault tolerance requirements, the consensus mechanism ensures that all loyal nodes have the same transaction, thereby ensuring that all loyal nodes have the same transaction. The execution results are consistent, and the transaction and execution results are packaged to generate blocks. The current mainstream consensus mechanisms include: Proof of Work (POW), Proof of Stake (POS), Delegated Proof of Stake (DPOS), Practical Byzantine Fault Tolerance (PBFT) Algorithm, Honey Badger Byzantine Fault Tolerance (HoneyBadgerBFT) algorithm, etc.
以PBFT为例,该算法是Miguel Castro(卡斯特罗)和Barbara Liskov(利斯科夫)在1999年提出来的,解决了原始拜占庭容错算法效率不高的问题,将算法复杂度由指数级降低到多项式级,使得拜占庭容错算法在实际系统应用中变得可行。该论文发表在1999年的操作系统设计与实现国际会议上(OSDI99)。PBFT算法中,所有的副本(replica)在一个被称为视图(View)的轮换过程(succession of configuration)中运行。在某个视图中,一个副本作为主节点(primary),其他的副本作为备份节点(backups)。视图是连续编号的整数。主节点可以由公式p=v mod|R|计算得到,这里v是视图编号,p是副本编号,|R|是副本集合的个数。该算法中假设,当最多存在f个副本(即节点)失效时,如果存在总数为至少3f+1个副本,就能保证在异步系统中提供安全性和活性。为了能够确保所有副本的数据一致性要求和容错要求而需要的一定数量副本的集合,一般是分布式系统中的大多数节点构成的集合,构成大多数(Quorum)。例如在总节点数n为3f+1(n=3f+2或n=3f的情况一般不会对容错效果带来提升)的情况下,Quorum为2f+1。这样,对于包含四个节点的分布式系统,任意三个节点可以构成一个Quorum。Taking PBFT as an example, this algorithm was proposed by Miguel Castro (Castro) and Barbara Liskov (Liskov) in 1999, which solved the problem of low efficiency of the original Byzantine fault-tolerant algorithm, and changed the algorithm complexity from exponential The level is reduced to the polynomial level, making the Byzantine fault-tolerant algorithm feasible in practical system applications. The paper was published at the 1999 International Conference on Operating System Design and Implementation (OSDI99). In the PBFT algorithm, all replicas operate in a succession of configuration called a view. In a view, one replica acts as the primary node (primary) and the other replicas act as backup nodes (backups). Views are consecutively numbered integers. The master node can be calculated by the formula p=v mod|R|, where v is the view number, p is the replica number, and |R| is the number of replica sets. It is assumed in the algorithm that when there are at most f replicas (ie nodes) failures, if there are at least 3f+1 replicas in total, security and liveness can be guaranteed in an asynchronous system. The set of a certain number of replicas required to ensure the data consistency requirements and fault tolerance requirements of all replicas is generally a set composed of most nodes in a distributed system, constituting a majority (Quorum). For example, when the total number of nodes n is 3f+1 (the case of n=3f+2 or n=3f generally does not improve the fault tolerance effect), the Quorum is 2f+1. In this way, for a distributed system containing four nodes, any three nodes can form a Quorum.
PBFT包括Normal Case Phase和View Change Phase两个过程,图1为Normal CasePhase(常规阶段)过程的流程图。Normal Case Phase中主要包括PRE-PREPARE(预准备)、PREPARE(准备)和COMMIT(提交)三个阶段,其中3号节点例如可以表示宕机的节点(图1中以×表示)。当主节点失效的时候(图2中以×表示,如更换视图前主节点Primary也就是Replica 0(副本0)失效)就需要启动视图更换(view change)过程,从而在系统存在故障时进行调整,更换新的主节点(如更换视图后Replica 1为主节点Primary)。图2为ViewChange Phase(视图切换)的示意图。如果主节点掉线或者作恶而不广播客户端的请求等,客户端可以设置超时机制。如果超时的话,客户端可以向所有副本节点广播请求消息。副本节点检测出主节点作恶或者下线后,也可以发起View Change协议阶段,以更换主节点(经常简称为“换主”)。此外,也可能由于主节点发起错误的提议导致PRE-PREPARE、PREPARE和COMMIT三阶段共识过程失败,或者,PREPARE、COMMIT阶段可能达不成Quorum数量(如3f+1个节点中的2f+1个,也称为法定数量)的一致,也都无法完成共识。这些情况下也可能发起View Change协议阶段,以更换主节点。PBFT includes two processes, Normal Case Phase and View Change Phase. Figure 1 is a flowchart of the Normal Case Phase (regular phase) process. The Normal Case Phase mainly includes three phases: PRE-PREPARE (pre-preparation), PREPARE (preparation) and COMMIT (commit), in which
在正常情况下,即共识节点都没有宕机,共识消息也能在一定时间内到达对方,即不会发生换主的情况下,PBFT中的Normal Case Phase过程可以如图3所示,该图仍然以4个共识节点为例。Under normal circumstances, that is, the consensus nodes are not down, and the consensus messages can reach the other party within a certain period of time, that is, under the condition that no master change occurs, the Normal Case Phase process in PBFT can be shown in Figure 3. Still take 4 consensus nodes as an example.
在第r-1轮的Normal Case Phase过程,0号节点作为主节点收集一定数量的待共识交易(或读写集之类,后续以交易为例作说明)后,发起预准备过程(即前述的PRE-PREPARE,也简称为PP阶段),进而节点1、2、3进入准备过程(即前述的PREPARE,也简称为P阶段),之后节点0、1、2、3进入提交过程(即前述的COMMIT,也简称为C阶段)。PP阶段、P阶段、C阶段一般也合称为PBFT的三阶段。这样,在正常情况下就完成了第r-1轮PBFT的三阶段过程,也就完成了第m-1个区块对应的交易数据的共识,同时也产生了这个区块的区块号等信息。从而,各个共识节点可以各自以共识的交易数据为基础,按照共识的交易数据的顺序和内容,顺序执行这些交易,进而生成世界状态和收据。具体的,各个节点各自在本地基于共识的交易数据可以构建Merkle树(包括MPT树等树形结构,MPT全称为Merkle PatriciaTree,是结合了Merkle Tree(默克尔树)和Patricia Tree(压缩前缀树,一种更节省空间的Trie树,字典树)的一种树形结构)并生成这颗Merkle树的树根的hash(也称为交易根hash),类似的,可以基于世界状态数据构建Merkle树并生成这颗Merkle树的树根的hash(也称为状态根hash),可以基于收据数据构建Merkle树并生成这颗Merkle树的树根的hash(也称为收据根hash)。各个节点各自在本地生成这三个根hash后,可以在本地生成第m-1个区块。该第m-1个区块的区块头中可以包括前述区块号、交易根hash、状态根hash、收据根hash等信息,区块体可以包括交易数据集合、世界状态集合和收据集合。这样,就生成了第m-1个区块。In the Normal Case Phase process of the r-1 round,
在第m个区块的生成过程中,将重复PBFT中的三阶段过程。如图3中,对于第m个区块,0号节点作为主节点收集一定数量的待共识交易后,发起PP过程,进而节点1、2、3进入P过程,之后节点0、1、2、3进入C过程。这样,在正常情况下就完成了第r轮PBFT的三阶段过程,也就完成了第m个区块对应的交易数据的共识,同时也产生了这个区块的区块号等信息。各个节点可以各自以共识的交易数据为基础,按照共识的交易数据的顺序和内容,顺序执行这些交易,进而生成世界状态和收据。各个节点各自在本地生成如前所述的三个根hash后,可以在本地生成第m个区块。该第m个区块的区块头中可以包括前述区块号、交易根hash、状态根hash、收据根hash等信息,区块体可以包括交易数据集合、世界状态集合和收据集合。这样,就生成了第m个区块。类似的,生成第m+1个区块,在这个过程中包含如图3中所示的第r+1轮PBFT的三阶段过程。During the generation of the mth block, the three-stage process in PBFT will be repeated. As shown in Figure 3, for the mth block,
可见,常规产生区块的情况下,每个共识节点在每个区块的产生过程中包含一次PBFT的Normal Case Phase过程。随着区块的不断产生,每个共识节点将会重复这个共识过程,图3中仅示例性的示出了第r-1、r和r+1轮共识过程。其中,有的共识节点作为PBFT中的主节点的角色,有的共识节点作为PBFT中的备份节点的角色。It can be seen that in the case of conventional block generation, each consensus node includes a Normal Case Phase process of PBFT in the process of generating each block. With the continuous generation of blocks, each consensus node will repeat this consensus process, and Fig. 3 only exemplarily shows the r-1, r and r+1 rounds of consensus process. Among them, some consensus nodes play the role of master nodes in PBFT, and some consensus nodes play the role of backup nodes in PBFT.
在一次共识过程中,即一次PBFT的三阶段过程中,可以包括:In a consensus process, that is, a three-stage process of a PBFT, it can include:
a110:(PRE-PREPARE预准备阶段)主节点0收集一定数量的待共识交易后,将待共识交易排序并打包为消息m(也称为原始交易列表),发送pre-prepare请求至备份节点1、2、3,pre-prepare请求中包括原始交易列表;a110: (PRE-PREPARE preparation stage) After the
a120:(PREPARE准备阶段)节点1、2、3收到pre-prepare请求后,如果检查原始交易列表合法,则分别通过prepare消息广播其收到的消息m的hash值(广播的内容一般不包括消息m本身,因为消息m包括了若干个原始交易请求,体积一般比较大)。具体的,节点1将prepare消息扩散至节点0、2、3,节点2将prepare消息扩散至节点0、1、3,节点3将prepare消息扩散至节点0、1、2。相应的,每一节点还接收其他节点广播的prepare消息。每一节点将自己发送的prepare消息(其中包含消息m的hash值,代表自己的认可)和收到的prepare消息(其中包含消息m的hash值,代表其它节点的认可)都添加到本地日志(Log)中。如果某一节点收集齐来自不同节点的至少Quorum个数量的合法的pp消息/p消息后(包括自身发出的pre-prepare、prepare消息,和收到的prepare消息),转变成prepared状态。a120: (PREPARE preparation stage) After
a130:(COMMIT提交阶段)参与共识的节点中的每一个在进入prepared状态后,发送commit消息给其他的共识节点,并将自己发送的commit消息添加到本地Log中(代表自己的认可),而且,每一节点还接收其他节点广播的commit消息。某一节点如果收集齐来自不同节点的至少Quorum数量的合法的commit消息后,添加到本地Log中(这时加上自己添加到本地Log中的共有Quorum个),转变成committed状态。a130: (COMMIT submission stage) After each node participating in the consensus enters the prepared state, it sends a commit message to other consensus nodes, and adds the commit message sent by itself to the local Log (representing its own approval), and , each node also receives commit messages broadcast by other nodes. If a node collects at least the number of valid commit messages from different nodes and adds it to the local log (in this case, plus the total number of quorums that it has added to the local log), it changes to the committed state.
a140:转变为committed状态的节点将消息m输出为本轮的共识结果。a140: The node that transitions to the committed state outputs the message m as the consensus result of this round.
消息m中包含哪些交易,以及所包含的交易的前后顺序,一般是由主节点在a110中决定的。确定包含哪些交易,包含的交易的前后顺序,这两个是共识机制的重要内容。区块链网络中可能接收到很多交易请求,a110中主节点打包哪些交易,决定了哪些交易会被区块链网络处理,交易的执行结果会上链。即使一组相同的交易,前后执行顺序不同会导致最终结果不同,而这影响到各个节点上的账本是否一致。Which transactions are included in the message m and the sequence of the included transactions are generally determined by the master node in a110. Determining which transactions are included and the sequence of included transactions are two important parts of the consensus mechanism. There may be many transaction requests received in the blockchain network. Which transactions are packaged by the master node in a110 determines which transactions will be processed by the blockchain network, and the execution results of the transactions will be uploaded to the chain. Even if a group of the same transactions are executed in different order, the final result will be different, which affects whether the ledgers on each node are consistent.
本说明书提供一种区块链上产生随机数种子的方法,可以结合上述PBFT三阶段的过程实现。如图4所示,包括:This specification provides a method for generating random number seeds on the blockchain, which can be implemented in combination with the above three-stage process of PBFT. As shown in Figure 4, including:
S110:在PBFT的commit阶段,每一共识节点基于门限签名算法,采用自身私钥份额对包含本次共识中原始交易列表特有值的原始报文进行签名,生成签名份额,并将该签名份额加入到广播的commit消息中。S110: In the commit stage of PBFT, each consensus node uses its own private key share to sign the original message containing the unique value of the original transaction list in this consensus based on the threshold signature algorithm, generate a signature share, and add the signature share to the into the broadcast commit message.
门限签名是普通数字签名的一个重要分支,是门限秘密共享技术和数字签名的一种结合。传统的签名方案,可以采用RSA算法实现。RSA算法是一种非对称加密算法,由罗纳德·李维斯特(Ron Rivest)、阿迪·萨莫尔(Adi Shamir)和伦纳德·阿德曼(LeonardAdleman)于1977年一起提出。RSA算法可以在不直接传递密钥的情况下完成解密,这能够确保信息的安全性的同时,避免直接传递密钥所造成的信息被破解的风险。RSA中包括私钥和公钥,这个私钥和公钥是成对。一个信息由公钥加密后,只能由对应的私钥解密;类似的,一个信息由私钥加密后,只能由对应的公钥解密。之所以具有这样的性质,是因为成对的私钥和公钥之间在数学原理上具有相关性,例如一种底层原理是根据数论,寻求两个大素数比较简单,而将它们的乘积进行因式分解却极其困难,因此可以将乘积公开作为加密密钥,从而可以保证安全性。私钥通常要严格保密,不能泄露,而公钥是公开的(且可以由多人持有)。由于私钥是由持有者严格保密的,其他人在无法获得私钥的前提下,就无法伪造私钥持有者的签名。Threshold signature is an important branch of ordinary digital signature, which is a combination of threshold secret sharing technology and digital signature. The traditional signature scheme can be implemented using the RSA algorithm. The RSA algorithm is an asymmetric encryption algorithm proposed by Ron Rivest, Adi Shamir and Leonard Adleman in 1977. The RSA algorithm can complete decryption without directly passing the key, which can ensure the security of information and avoid the risk of information being cracked caused by directly passing the key. RSA includes a private key and a public key, and the private key and public key are paired. After a message is encrypted by the public key, it can only be decrypted by the corresponding private key; similarly, after a message is encrypted by the private key, it can only be decrypted by the corresponding public key. The reason for this property is that there is a mathematical correlation between pairs of private keys and public keys. For example, an underlying principle is that according to number theory, it is relatively simple to find two large prime numbers, and the product of them is calculated. Factoring is extremely difficult, so the product can be made public as an encryption key, which guarantees security. The private key is usually kept strictly secret and cannot be leaked, while the public key is public (and can be held by multiple people). Since the private key is strictly kept secret by the holder, others cannot forge the signature of the holder of the private key without obtaining the private key.
RSA签名机制,可以保证报文传递过程中的完整性。例如节点A需要将报文传送至节点B,且中间可能经过若干个节点的中转。则A可以采用RSA签名机制,将报文连同签名一并经由若干个中间节点传送至B,而B对签名的验证可以确信收到的报文是A发出的,且在传送过程中没有经过篡改。一种RSA签名的过程如下:The RSA signature mechanism can ensure the integrity of the message transmission process. For example, node A needs to transmit the message to node B, and may pass through several nodes in the middle. Then A can use the RSA signature mechanism to transmit the message together with the signature to B through several intermediate nodes, and B can verify the signature that the received message is sent by A and has not been tampered with during the transmission process. . An RSA signature process is as follows:
b1:A生成一对密钥(公钥和私钥),私钥不公开,自己保留。公钥为公开的,任何人可以获取。b1: A generates a pair of keys (public key and private key), and the private key is not disclosed and kept by itself. The public key is public and can be obtained by anyone.
b2:A用自己的私钥对原始报文的hash值进行签名,并将原始报文和签名结果一并传递给B。如前所述,这个传递过程可能经过若干个中间节点的转发。b2: A signs the hash value of the original message with its own private key, and passes the original message and the signature result to B. As mentioned above, this transfer process may be forwarded by several intermediate nodes.
hash算法也称为散列算法,可以将原始内容映射为一个固定长度的序列,这个序列即为hash值。一般有sha256,sha384,sha512等hash算法。sha256的结果是256个bits,可以表示2的256次方个原始内容。类似的,sha384的结果是384bits,sha512的结果是512bits。这些hash算法,可以针对内容较多体积较大的原始内容,因而hash值相对来说可以比原始内容小很多。好的hash算法可以确保不同原始内容有极大概率映射为不同的hash值,同时这种映射是杂乱无章的,即无法预测不同的原始内容得到的hash值的关联性;而且也是抗逆运算的,即无法由hash值倒推得到原始内容。The hash algorithm, also known as the hash algorithm, can map the original content into a fixed-length sequence, which is the hash value. Generally, there are hash algorithms such as sha256, sha384, and sha512. The result of sha256 is 256 bits, which can represent the original content of 2 to the power of 256. Similarly, the result of sha384 is 384bits, and the result of sha512 is 512bits. These hash algorithms can target the original content with more content and larger volume, so the hash value can be relatively much smaller than the original content. A good hash algorithm can ensure that different original content has a great probability to map to different hash values. At the same time, this mapping is messy, that is, it is impossible to predict the correlation of hash values obtained from different original content; and it is also resistant to inverse operations. That is, the original content cannot be derived from the hash value.
原始报文可能内容较多,体积较大,采用私钥直接对原始报文进行签名计算可能比较费时和耗费算力。因此,可以将原始报文采用一种hash算法计算到一个hash值,这样这个hash值长度较小,又可以完全代表原始报文。进而,采用私钥对这个hash值进行加密计算,得到的结果即为签名。The original message may have a lot of content and a large volume. It may be time-consuming and computationally expensive to use the private key to directly sign the original message. Therefore, the original message can be calculated to a hash value using a hash algorithm, so that the hash value has a small length and can fully represent the original message. Furthermore, the hash value is encrypted and calculated with the private key, and the result obtained is the signature.
b3:B收到消息后,采用A的公钥进行验签。b3: After B receives the message, it uses A's public key to verify the signature.
一方面,B可以采用与A相同的hash算法来计算原始报文的hash值,计为hash1;另一方面,B采用A的公钥对签名结果进行解密计算,得到hash2。如果hash1与hash2相同,则可以确定收到的原始报文是A发出的,且在传送过程中没有被篡改过。On the one hand, B can use the same hash algorithm as A to calculate the hash value of the original message, which is calculated as hash1; on the other hand, B uses A's public key to decrypt the signature result to obtain hash2. If hash1 and hash2 are the same, it can be determined that the original message received is sent by A and has not been tampered with during transmission.
门限签名方案,首先是包括1个总公钥和n个公私钥对。每个公私钥对中的1个公钥称为公钥份额,每个公私钥对中的1个私钥称为私钥份额。其次,存在与这个总公钥和n个公私钥对对应的恢复函数,该恢复函数可以将至少门限数量个不同私钥份额签名的签名份额恢复成一个完整签名,这个生成的完整签名也可以由所述的那1个总公钥来验证正确性。而任意少于门限数量的签名份额则无法恢复生成该完整签名。The threshold signature scheme firstly includes 1 total public key and n public-private key pairs. One public key in each public-private key pair is called the public key share, and one private key in each public-private key pair is called the private key share. Secondly, there is a recovery function corresponding to this total public key and n public-private key pairs. The recovery function can recover the signature shares of at least a threshold number of different private key share signatures into a complete signature. The generated complete signature can also be generated by The said 1 total public key is used to verify the correctness. Any less than the threshold number of signature shares cannot resume generating the full signature.
除了可以采用基于RSA的门限签名机制外,还可以采用基于ECDSA((EllipticCurve Digital Signature Algorithm,椭圆曲线数字签名算法)的门限签名机制、基于Schnorr(一种基于离散对数难题的知识证明机制)的门限签名机制、基于BLS(Boneh-Lynn-Shacham Signature)的门限签名机制等。In addition to the threshold signature mechanism based on RSA, the threshold signature mechanism based on ECDSA ((EllipticCurve Digital Signature Algorithm, elliptic curve digital signature algorithm), the threshold signature mechanism based on Schnorr (a knowledge proof mechanism based on discrete logarithm problem) can also be used Threshold signature mechanism, threshold signature mechanism based on BLS (Boneh-Lynn-Shacham Signature), etc.
需要说明的是,在区块链中所采用的门限签名,私钥份额的个数可以等于共识节点的个数,恢复函数产生完整签名的最少签名份额的个数(即门限数量)可以等于PBFT算法中的quorum。当然,私钥的个数也可以不等于共识节点的个数,恢复函数产生完整签名的最少签名份额的个数可以不等于PBFT算法中的quorum。以下以前者为例说明。It should be noted that, for the threshold signature used in the blockchain, the number of private key shares can be equal to the number of consensus nodes, and the number of minimum signature shares (that is, the threshold number) for the recovery function to generate a complete signature can be equal to PBFT quorum in algorithms. Of course, the number of private keys may not be equal to the number of consensus nodes, and the number of minimum signature shares for the recovery function to generate a complete signature may not be equal to the quorum in the PBFT algorithm. The former is described below as an example.
所述1个总公钥和n个公私钥对,可以由一个中心化的dealer生成,并分发给n个区块链共识节点,这种属于中心化的密钥分配方式。这样,结合共识算法,n个私钥份额可以是每个区块链共识节点持有其中一个。同时,每个区块链共识节点可以持有相同的1个总公钥。此外,还存在去中心化的密钥分配方式,即取消dealer,而是由n个共识节点通过密钥协商过程协商得到成对的n个公私钥对和1个总公钥,仍然是每个共识节点单独持有n个私钥份额中的一个,且各共识节点持有同一个总公钥。The one total public key and n public-private key pairs can be generated by a centralized dealer and distributed to n blockchain consensus nodes, which is a centralized key distribution method. In this way, combined with the consensus algorithm, n private key shares can be one of which each blockchain consensus node holds. At the same time, each blockchain consensus node can hold the same 1 total public key. In addition, there is also a decentralized key distribution method, that is, cancel the dealer, and negotiate with n consensus nodes through the key negotiation process to obtain a pair of n public-private key pairs and a total public key, which is still each Consensus nodes individually hold one of n private key shares, and each consensus node holds the same total public key.
采用门限签名算法,每一共识节点都可以采用自身特有的那一份私钥(例如包含4个节点且采用PBFT作为共识算法的区块链网络中,节点0、节点1、节点2、节点3采用门限签名算法所持有的私钥份额分别是sk0,sk1,sk2,sk3,下标数字可以表示节点的编号)对包含本次共识中原始交易列表特有值的原始报文进行签名,得到签名结果。这里,原始交易列表的特有值可以作为签名所针对的原始报文。Using the threshold signature algorithm, each consensus node can use its own unique private key (for example, in a blockchain network containing 4 nodes and using PBFT as the consensus algorithm,
原始交易列表的特有值,可以包括原始交易列表本身或者原始交易列表的hash值。一般来说,不同的交易,交易内容是不同的,这样,不同的原始交易列表或其hash值一般都不相同。因此,原始报文中可以至少包括原始交易列表或其hash值,这样由hash函数的性质,足以区分不同区块对应的共识过程完毕后所生成的随机数种子。The unique value of the original transaction list, which can include the original transaction list itself or the hash value of the original transaction list. Generally speaking, different transactions have different transaction contents, so that different original transaction lists or their hash values are generally different. Therefore, the original message can at least include the original transaction list or its hash value, so that the nature of the hash function is enough to distinguish the random number seeds generated after the consensus process corresponding to different blocks is completed.
考虑到共识过程中会为本次共识的内容生成一个编号,如果共识完成,生成的编号可以作为本次共识所对应的区块的区块号,因此,区块号(也就是编号)也可以作为原始报文中的内容。不论第N+1个区块中所包含的原始交易列表与第N个区块中所包含的原始交易表是否相同,区块生成是顺序的,可以体现为后一区块的区块号是前一区块的区块号+1。因此,区块号作为原始报文中的内容,即使第N+1个区块中所包含的原始交易列表与第N个区块中所包含的原始交易表相同,仍然由各个节点采用自身私钥基于(原始交易列表+区块号)得到不同的签名,主节点仍然无法获知其它节点的签名,从而无法预测第N+1号区块的完整签名,因此主节点无法使用第N号块已公开的随机数种子来预测第N+1号块的随机数种子,达到了不可预测的目的。与编号类似的,时间戳也是一个区块特有的,且后一区块的时间戳在前一区块之后。因此,时间戳也可以作为原始报文中的内容。Considering that a number will be generated for the content of this consensus during the consensus process, if the consensus is completed, the generated number can be used as the block number of the block corresponding to this consensus. Therefore, the block number (that is, the number) can also be used. as the content in the original message. Regardless of whether the original transaction list contained in the N+1th block is the same as the original transaction list contained in the Nth block, the block generation is sequential, which can be reflected as the block number of the next block is The block number of the
除了原始交易列表的特有值之外,签名的对象还可以加入其它内容,例如上一区块中产生的随机数种子,即原始报文中还可以包括上一区块中产生的随机数种子。前述a140执行之后,如前所述,各个节点可以各自以共识的交易数据为基础,生成第m个区块。由于第m个区块是各个节点在本地各自独立生成的,因此,如果区块链节点之间没有相互广播自身生成的上一区块的hash值并比对,各个节点可能都无法确定区块链网络中生成的第m个区块是否相同,或者从区块链系统整体可用的角度来说是否有至少quorum数量的共识节点上生成的第m个区块是相同的。经过本说明书中随机数种子的生成过程,相同区块的随机数种子应当是相同的,不同区块中的随机数种子应当是不同的,因此可以将随机数种子加入到原始报文中。这样,如果各个节点各自生成的第m个区块对应的随机数种子有所不同,根据门限签名算法的性质,可能无法在第m+1号区块的产生随机数种子的过程中通过恢复函数得出完整签名,从而可以根据本说明书的方案帮助共识节点确认上一区块是否一致。也可采用上一区块的hash值来代替上一区块的随机数种子,由于一个区块的hash值一般是唯一的,因此也可以帮助共识节点确认上一区块是否一致。In addition to the unique value of the original transaction list, the signed object can also add other content, such as the random number seed generated in the previous block, that is, the original message can also include the random number seed generated in the previous block. After the execution of the aforementioned a140, as described above, each node may generate the mth block based on the consensus transaction data. Since the mth block is independently generated by each node locally, if the blockchain nodes do not broadcast and compare the hash value of the previous block generated by themselves, each node may not be able to determine the block. Whether the mth block generated in the chain network is the same, or from the perspective of the overall availability of the blockchain system, whether the mth block generated on at least a quorum number of consensus nodes is the same. After the random number seed generation process in this specification, the random number seeds of the same block should be the same, and the random number seeds in different blocks should be different, so the random number seeds can be added to the original message. In this way, if the random number seeds corresponding to the mth block generated by each node are different, depending on the nature of the threshold signature algorithm, it may not be possible to pass the recovery function in the process of generating the random number seed for the m+1th block. A complete signature is obtained, which can help the consensus node to confirm whether the previous block is consistent according to the scheme of this specification. The hash value of the previous block can also be used to replace the random number seed of the previous block. Since the hash value of a block is generally unique, it can also help the consensus node to confirm whether the previous block is consistent.
采用自身私钥份额对包含本次共识中原始交易列表特有值的原始报文进行签名,这个原始报文里可以包括的原始交易列表的特有值,可以是原始交易列表。一般在PBFT的PP阶段已经广播过原始交易列表,且C阶段广播的commit消息较小的话更利于传播及节省带宽,因此原始交易列表特有值可以是原始交易列表的hash值。Use its own private key share to sign the original message containing the unique value of the original transaction list in this consensus. The unique value of the original transaction list that can be included in this original message can be the original transaction list. Generally, the original transaction list has been broadcast in the PP stage of PBFT, and the smaller commit message broadcast in the C stage is more conducive to spreading and saving bandwidth. Therefore, the unique value of the original transaction list can be the hash value of the original transaction list.
对于原始报文包括多个内容,例如包括原始交易列表hash值、区块号、上一区块中产生的随机数种子的情况下,可以先计算原始报文的hash值,进而采用私钥份额对该原始报文hash值进行签名,得到签名结果。If the original message includes multiple contents, such as the hash value of the original transaction list, the block number, and the random number seed generated in the previous block, the hash value of the original message can be calculated first, and then the private key share can be used. Sign the hash value of the original message to obtain the signature result.
对原始报文进行签名,生成的签名结果和原始报文可以一并加入到广播的commit消息中。这样,在commit阶段,参与共识的节点中的每一个都发送commit消息给其他的共识节点,并将自己发送的commit消息添加到本地Log中(代表自己的认可),而且,每一节点还接收其他节点广播的commit消息。The original message is signed, and the generated signature result and the original message can be added to the broadcast commit message. In this way, in the commit phase, each of the nodes participating in the consensus sends a commit message to other consensus nodes, and adds the commit message sent by itself to the local Log (representing its own approval), and each node also receives Commit messages broadcast by other nodes.
S120:每一共识节点收集齐至少门限数量的commit消息后,将通过验证的至少门限数量的签名份额经过所述门限签名算法产生的私钥份额所对应的恢复函数得到完整签名。S120: After collecting at least a threshold number of commit messages, each consensus node obtains a complete signature by passing at least a threshold number of signature shares that have passed the verification through the recovery function corresponding to the private key shares generated by the threshold signature algorithm.
如前所述,门限签名算法在应用中,可以产生成对的1个总公钥和n个公私钥对,并可以产生该n个公私钥对所对应的恢复函数。前述提到,该恢复函数可以将验证正确的至少门限个签名恢复生成一个完整签名,门限签名算法的门限值即门限数量可以设为w。当然,正确的签名多于w个时也可以通过该恢复函数生成一个完整签名。也就是说,正确的签名大于等于门限数量w时,都可以通过该恢复函数生成一个完整签名,且生成的这个完整签名是确定的,不会因为输入的正确签名的个数而发生变化(只要大于等于w)。As mentioned above, in the application of the threshold signature algorithm, a pair of a total public key and n public-private key pairs can be generated, and a recovery function corresponding to the n public-private key pairs can be generated. As mentioned above, the restoration function can restore at least a threshold number of signatures that have been verified to be correct to generate a complete signature, and the threshold value of the threshold signature algorithm, that is, the threshold number, can be set to w. Of course, when there are more than w correct signatures, a complete signature can also be generated through this recovery function. That is to say, when the correct signature is greater than or equal to the threshold number w, a complete signature can be generated through the restoration function, and the generated complete signature is deterministic and will not change due to the number of input correct signatures (as long as greater than or equal to w).
这个生成的完整签名可以由所述的那1个总公钥来验证正确性。这样,任何持有这个总公钥的节点都可以采用该总公钥来验证这个完整签名的正确性。例如,节点1生成完整签名后,可以采用总公钥验证该完整签名的完整性,例如采用总公钥对完整签名进行密码学运算得到第一hash,并对原始报文进行hash运算得到第二hash,如果第一hash与第二hash一致则可以确定该完整签名的完整性。所述完整性包括该完整签名是针对所述原始报文的,且该原始报文没有经过篡改。再例如,节点1生成完整签名后,可以将该完整签名、总公钥和原始报文发送至区块链以外的一个设备,该设备可以采用所述总公钥和原始报文验证这个完整签名的正确性,原理同上不再赘述。这里的报文原文仍然是前述的包含本次共识中原始交易列表特有值的内容,或还包括当前区块的区块号和/或时间戳和/或上一区块中产生的随机数种子。This generated full signature can be verified for correctness by the said 1 total public key. In this way, any node holding the total public key can use the total public key to verify the correctness of the complete signature. For example, after
此外,也可以是每一共识节点收集每一commit消息后,采用对应的公钥份额对所述接收到的commit消息中的签名份额进行验证,然后再将所述至少门限数量的签名份额经过所述门限签名算法产生的私钥份额所对应的恢复函数得到完整签名。相对于采用总公钥对生成的完整签名进行验证的方式,采用公钥份额对每一签名份额进行验证,验证通过后再经恢复函数恢复为完整签名的方式,能够确定哪个签名是错误的,从而能够确定哪个节点可能是作恶节点。In addition, after collecting each commit message, each consensus node may use the corresponding public key share to verify the signature share in the received commit message, and then pass the at least threshold number of signature shares through all the The recovery function corresponding to the private key share generated by the threshold signature algorithm is used to obtain a complete signature. Compared with the method of using the total public key to verify the generated complete signature, the public key share is used to verify each signature share, and after the verification is passed, the recovery function restores the complete signature to determine which signature is wrong. Thus, it can be determined which node may be the malicious node.
门限签名算法中,每个共识节点都具有1个总公钥和n个公私钥对中的1个私钥份额和对应的1个公钥份额,如前所述,可以是由dealer生成并分发的,也可以是各共识节点协商得到的。In the threshold signature algorithm, each consensus node has 1 total public key, 1 private key share in n public-private key pairs, and 1 corresponding public key share. As mentioned above, it can be generated and distributed by the dealer. It can also be negotiated by each consensus node.
每个共识节点可以采用对应的公钥份额对接收到的commit消息中的签名份额进行验证。具体的,例如在包含4个共识节点的采用PBFT共识算法的联盟链中,节点0在S110中向节点1、2、3广播自身生成的签名份额σ3,0,其中σ3,0的下标3可以表示区块号,0可以表示这是节点0的签名份额;在S120中,节点0也接收到节点1、2分别广播的签名份额σ3,1、σ3,2。这样,节点0已经收齐至少3个签名份额,其中包括自身广播的签名份额σ3,0和节点1、2广播的签名份额σ3,1、σ3,2。当然,节点0也可以收集齐所有的签名份额σ3,0、σ3,1、σ3,2和σ3,3,这样也当然满足至少quorum数量。Each consensus node can use the corresponding public key share to verify the signature share in the received commit message. Specifically, for example, in a consortium chain that includes 4 consensus nodes and adopts the PBFT consensus algorithm,
进而,节点0可以用对应的公钥份额来验证收集的σ3,0、σ3,1、σ3,2或还包括σ3,3(或者是σ3,0、σ3,1、σ3,3或还包括σ3,2,或者是σ3,1、σ3,2、σ3,3或还包括σ3,0,或者是σ3,0、σ3,2、σ3,3或还包括σ3,1)的正确性。具体的,例如,节点0可以采用对应的公钥份额来对签名份额σ3,1进行计算,得到一个hash值,记为hash3,1;节点0还可以对原始报文进行同样的hash计算得到hash′3,1。如果hash3,1与hash′3,1相等,可以证明原始报文是节点1发出的,且在传送过程中没有被篡改过。这样,σ3,1的正确性得到验证。类似的,节点0可以对σ3,2等进行验证,不再赘述。Further,
同样的,节点1可以用对应的公钥份额来验证收集的σ3,0、σ3,1、σ3,2或还包括σ3,3(或者是σ3,0、σ3,1、σ3,3或还包括σ3,2,或者是σ3,1、σ3,2、σ3,3或还包括σ3,0,或者是σ3,0、σ3,2、σ3,3或还包括σ3,1)的正确性。Likewise,
同样的,节点2可以用对应的公钥份额来验证收集的σ3,0、σ3,1、σ3,2或还包括σ3,3(或者是σ3,0、σ3,1、σ3,3或还包括σ3,2,或者是σ3,1、σ3,2、σ3,3或还包括σ3,0,或者是σ3,0、σ3,2、σ3,3或还包括σ3,1)的正确性。Likewise,
同样的,节点3可以用对应的公钥份额来验证收集的σ3,0、σ3,1、σ3,2或还包括σ3,3(或者是σ3,0、σ3,1、σ3,3或还包括σ3,2,或者是σ3,1、σ3,2、σ3,3或还包括σ3,0,或者是σ3,0、σ3,2、σ3,3或还包括σ3,1)的正确性。Likewise,
S130:每一共识节点基于所述完整签名得到随机数种子。S130: Each consensus node obtains a random number seed based on the complete signature.
随机数种子(random seed),是指在伪随机数生成器中用于生成伪随机数的初始数值。对于一个伪随机数生成器,从相同的随机数种子出发,可以得到相同的随机数序列。对于单机来说,随机数种子可以由当前计算机的状态确定,如当前的时间。而对于分布式系统来说,要在各个节点上产生相同的随机数种子,以在系统合约/业务合约/区块链平台功能等中基于相同的随机数种子产生相同的随机数,且不应由任一节点以其可操控的、可预测的、可撤销的方式产生随机数。这就需要由参与共识的节点共同确定。而且,考虑到分布式网络往往是异步网络或半同步网络,从即时性出发,还需要在当前区块中的交易执行时即可以产生随机数并采用。The random seed refers to the initial value used in the pseudo-random number generator to generate pseudo-random numbers. For a pseudo-random number generator, starting from the same random number seed, the same random number sequence can be obtained. For a single computer, the random number seed can be determined by the current state of the computer, such as the current time. For distributed systems, the same random number seed should be generated on each node to generate the same random number based on the same random number seed in system contracts/business contracts/blockchain platform functions, etc., and should not Random numbers are generated by any node in a manipulable, predictable, and revocable manner. This needs to be jointly determined by the nodes participating in the consensus. Moreover, considering that distributed networks are often asynchronous networks or semi-synchronous networks, from the point of view of immediacy, it is also necessary to generate random numbers and use them when the transactions in the current block are executed.
经过上述S110-S120的步骤,正常情况下每个共识节点都可以得到相同的完整签名。当然,考虑到分布式系统的容错特性,在采用PBFT共识算法的区块链网络中至少应当有quorum数量的共识节点各自都可以分别得到相同的完整签名。After the above steps S110-S120, under normal circumstances, each consensus node can obtain the same complete signature. Of course, considering the fault-tolerant characteristics of distributed systems, there should be at least a quorum number of consensus nodes in a blockchain network using the PBFT consensus algorithm, each of which can obtain the same complete signature.
这样,基于完整签名,各共识节点可以采用相同的随机数种子生成算法生成随机数种子。一种较为简单的随机数种子生成算法例如是sha256算法。当然,也可以直接将完整签名作为随机数种子。In this way, based on the complete signature, each consensus node can use the same random number seed generation algorithm to generate random number seeds. A relatively simple random number seed generation algorithm is, for example, the sha256 algorithm. Of course, the full signature can also be directly used as the random number seed.
经过上述过程,即可在区块链上产生随机数种子。After the above process, the random number seed can be generated on the blockchain.
这样,区块链节点在执行当前共识完毕后输出共识结果的过程中,即执行确定了内容和顺序的一系列交易的过程中,如果其中包含需要使用随机数的智能合约/系统合约/区块链平台代码,可以基于S130的随机数种子来执行。例如,在C++语言编写的智能合约中,可以采用C++标准库或boost库提供的mt19937(r)方法来构造一个跨平台一致的随机数引擎,其中的参数r即为随机数种子。类似的,python中的random库,java中的random库,也都提供了类似的随机数生成方法。基于相同的随机数种子,在相同的随机数生成算法下可以生成相同的随机数。这样,例如各个区块链节点各自分别执行相同区块中的相同交易时,对于其中相同的随机数生成过程,可以基于相同随机数种子产生相同的随机数,从而完成诸如摇号、发红包、盲盒之类的业务逻辑,或完成系统合约/区块链平台功能,并在各个节点上得到一致的执行结果。In this way, in the process of outputting the consensus result after executing the current consensus, that is, in the process of executing a series of transactions whose content and order are determined, if a smart contract/system contract/block that needs to use random numbers is included in it The chain platform code can be executed based on the random number seed of S130. For example, in a smart contract written in C++ language, the mt19937(r) method provided by the C++ standard library or the boost library can be used to construct a cross-platform consistent random number engine, where the parameter r is the random number seed. Similarly, the random library in python and the random library in java also provide similar random number generation methods. Based on the same random number seed, the same random number can be generated under the same random number generation algorithm. In this way, for example, when each blockchain node executes the same transaction in the same block, for the same random number generation process, the same random number can be generated based on the same random number seed, so as to complete operations such as lottery, red envelope, blind business logic such as boxes, or complete system contract/blockchain platform functions, and get consistent execution results on each node.
此外,在上述方案基础上,还可以包括如下步骤:In addition, on the basis of the above scheme, the following steps may also be included:
S140:每一共识节点将得到的随机数种子放至在生成的当前区块的区块头中。S140: Each consensus node puts the obtained random number seed in the block header of the generated current block.
图4是一个区块的区块头的结构示意图。由图5所示的结构中,每一区块的区块头包括若干字段,例如上一区块哈希previous_Hash(图中的Prev Hash),Nonce(这是工作量证明涉及的随机数,与本说明书中的随机数种子不同,且在一些联盟链中并不启用这个nonce),时间戳Timestamp,上一区块号Block Num,状态根哈希State Root,交易根哈希Transaction Root,收据根哈希Receipt Root等。其中,下一区块(如区块N+1)的区块头中的Prev Hash指向上一区块(如区块N),即为上一区块的hash值,也就是上一区块的区块头的hash值。区块头的hash值,可以是区块头中所包含的各个字段顺序拼接后经某种hash算法计算得到的hash值。通过这种方式,区块链上通过区块头实现了下一区块对上一区块的锁定。特别的,如前所述,state root是当前区块中所有账户的状态组成的MPT树的根的哈希值,指向state_root的为一颗MPT形式的状态树state trie。Transaction Root一般是本区块包含的原始交易列表的组织成一种树形结构后的树根节点的hash值,Receipt Root一般是本区块包含的交易经过执行后生成的所有收据组织成一种树形结构后的树根节点的hash值。FIG. 4 is a schematic structural diagram of a block header of a block. In the structure shown in Figure 5, the block header of each block includes several fields, such as the previous block hash previous_Hash (Prev Hash in the figure), Nonce (this is the random number involved in the proof of work, and this The random number seed in the manual is different, and this nonce is not enabled in some alliance chains), timestamp Timestamp, last block number Block Num, state root hash State Root, transaction root hash Transaction Root, receipt root hash Xi Receipt Root et al. Among them, the Prev Hash in the block header of the next block (such as block N+1) points to the previous block (such as block N), which is the hash value of the previous block, that is, the hash value of the previous block. The hash value of the block header. The hash value of the block header can be the hash value calculated by a certain hash algorithm after the fields contained in the block header are sequentially spliced. In this way, the block header locks the next block to the previous block on the blockchain. In particular, as mentioned above, the state root is the hash value of the root of the MPT tree composed of the states of all accounts in the current block, and the one pointing to the state_root is a state trie in the form of MPT. Transaction Root is generally the hash value of the tree root node after the original transaction list contained in this block is organized into a tree structure, and Receipt Root is generally all receipts generated after the transactions contained in this block are executed into a tree structure The hash value of the root node of the tree after the structure.
这里需要注意的是,本说明书可以在区块头中增加一个字段——“随机数种子”,即S130中的随机数种子。这样,本区块产生的随机数种子,可以记录在区块链账本上,此外,对于回放区块来说,可以按照区块头中的随机数种子来回放区块中涉及随机数的交易。It should be noted here that this specification can add a field to the block header - "random number seed", that is, the random number seed in S130. In this way, the random number seed generated by this block can be recorded on the blockchain ledger. In addition, for the playback block, transactions involving random numbers in the block can be played back according to the random number seed in the block header.
本说明书提供的上述方案,将门限签名算法与PBFT共识算法相结合,使得对应每个区块的原始交易列表在通过PBFT算法达成共识后,即可通过采用的门限签名算法得到完整签名,从而得到随机数种子,在执行本区块对应的原始交易列表中的交易的过程中,即可以采用随机数,这样,执行本区块的交易不需要额外的等待。The above solution provided in this specification combines the threshold signature algorithm with the PBFT consensus algorithm, so that after the original transaction list corresponding to each block reaches a consensus through the PBFT algorithm, a complete signature can be obtained through the adopted threshold signature algorithm, thereby obtaining The random number seed can be used in the process of executing the transaction in the original transaction list corresponding to this block, so that no additional waiting is required to execute the transaction in this block.
本说明书提供的上述方案,基于门限签名算法的性质,各共识节点各自分别基于至少门限数量的签名份额通过恢复函数可以恢复出相同的完整签名,进而生成相同的随机数种子,从而,各个区块链节点各自分别执行相同区块中的相同交易时,对于其中相同的随机数生成过程可以基于相同随机数种子产生相同的随机数,从而完成诸如摇号、发红包、盲盒之类的业务逻辑,或完成系统合约/区块链平台功能,并在各个节点上得到一致的执行结果。The above solutions provided in this specification, based on the properties of the threshold signature algorithm, each consensus node can recover the same complete signature through the recovery function based on at least a threshold number of signature shares, and then generate the same random number seed, thus, each block When each chain node executes the same transaction in the same block, the same random number generation process can generate the same random number based on the same random number seed, so as to complete the business logic such as lottery, red envelope, blind box, etc. Or complete system contract/blockchain platform functions, and get consistent execution results on each node.
本说明书提供的上述方案,将门限签名算法与PBFT共识算法相结合,使得任一共识节点在共识完成前无法预测完整签名,即使是PBFT的主节点也无法预测完整签名,也就无法预测随机数种子和随机数。特别是当门限=quorum时,一旦完成共识,由于quorum数量的节点对交易列表的内容和顺序已达成一致,即生成新区块的基础内容已经确定,这时至少quorum数量的节点根据恢复函数得到的完整签名是相同的,这quorum数量的节点生成的随机数种子也必然相同,即使有不超过f个节点作恶而想要控制或撤销得到的随机数种子,这f个节点也不会影响系统的一致性,即这f个节点不可操控或撤销生成的完整签名、随机数种子和随机数。The above solution provided in this manual combines the threshold signature algorithm with the PBFT consensus algorithm, so that any consensus node cannot predict the complete signature before the consensus is completed, and even the master node of PBFT cannot predict the complete signature, so it cannot predict the random number. seeds and random numbers. Especially when the threshold = quorum, once the consensus is completed, since the quorum number of nodes has reached an agreement on the content and order of the transaction list, that is, the basic content of generating a new block has been determined, then at least the quorum number of nodes obtained according to the recovery function The complete signature is the same, and the random number seeds generated by the quorum number of nodes must also be the same. Even if no more than f nodes do evil and want to control or revoke the random number seeds obtained, these f nodes will not affect the system. Consistency, that is, the complete signature, random number seed and random number generated by these f nodes cannot be manipulated or revoked.
本说明书中的方法,可以在每一区块生成的过程中实施,这样,每一区块的区块头中都可以包括随机数种子这一字段。即使某一区块的区块体中并不包含涉及随机数的交易,该区块的生成过程中仍然可以包含生成随机数种子的过程。The method in this specification can be implemented in the process of generating each block, so that the field of random number seed can be included in the block header of each block. Even if the block body of a block does not contain transactions involving random numbers, the generation process of the block can still include the process of generating random number seeds.
以下在先共识交易列表后执行共识的交易列表中的交易的区块链网络中,以区块链网络中一个共识节点的角度介绍本说明书一种区块链上产生随机数种子的方法,且采用的共识算法中通过最后一阶段中相互广播提交提议来输出共识结果,则共识节点执行如图6所示内容:The following describes a method for generating random number seeds on a blockchain in this specification from the perspective of a consensus node in the blockchain network in a blockchain network where the transactions in the transaction list are first agreed upon and then the consensus is executed, and In the adopted consensus algorithm, the consensus result is output by submitting proposals by mutual broadcast in the last stage, and the consensus node executes the content shown in Figure 6:
S210:在所述共识算法中最后一阶段中,所述共识节点基于门限签名算法,采用自身私钥份额对包含本次共识中原始交易列表特有值的原始报文进行签名,生成签名份额,并将该签名份额加入到广播的所述共识消息中。S210: In the last stage of the consensus algorithm, the consensus node uses its own private key share to sign the original message containing the unique value of the original transaction list in this consensus, based on the threshold signature algorithm, to generate a signature share, and This signed share is added to the broadcasted consensus message.
除了PBFT通过最后一阶段中相互广播提交提议来输出共识结果,还有一些共识算法也可以通过最后一阶段中相互广播提交提议来输出共识结果,后者例如为中国专利ZL202111175184.1、ZL202111178795.1、ZL202111178745.3、ZL202111178754.2、ZL202111175144.7、ZL202111175151.7以及中国专利申请CN202111178779.2。In addition to PBFT outputting consensus results by submitting proposals by mutual broadcast in the last stage, there are some consensus algorithms that can also output consensus results by submitting proposals by mutual broadcast in the last stage. , ZL202111178745.3, ZL202111178754.2, ZL202111175144.7, ZL202111175151.7 and Chinese patent application CN202111178779.2.
采用门限签名算法,共识节点可以采用自身特有的那一份私钥份额对包含本次共识中原始交易列表特有值的原始报文进行签名,得到签名结果。这里,原始交易列表的特有值可以作为签名所针对的原始报文。Using the threshold signature algorithm, the consensus node can use its own private key share to sign the original message containing the unique value of the original transaction list in this consensus, and obtain the signature result. Here, the unique value of the original transaction list can be used as the original message targeted for the signature.
原始交易列表的特有值,可以包括原始交易列表本身或者原始交易列表的hash值。区块号(也就是编号)和/或时间戳也可以作为原始报文中的内容。除了原始交易列表的特有值之外,签名的对象还可以加入其它内容,例如上一区块中产生的随机数种子,即原始列表中还可以包括上一区块中产生的随机数种子,这样可以根据本说明书的方案帮助共识节点确认上一区块是否一致。The unique value of the original transaction list, which can include the original transaction list itself or the hash value of the original transaction list. Block numbers (ie numbers) and/or timestamps can also be used as content in the original message. In addition to the unique value of the original transaction list, the signed object can also add other content, such as the random number seed generated in the previous block, that is, the original list can also include the random number seed generated in the previous block, so that It can help consensus nodes to confirm whether the previous block is consistent according to the scheme in this manual.
S220:所述共识节点收集齐至少门限数量的所述共识消息后,将所述至少门限数量的签名份额经过所述门限签名算法产生的私钥份额所对应的恢复函数得到完整签名。S220: After the consensus node has collected at least a threshold number of the consensus messages, the at least threshold number of signature shares are subjected to a recovery function corresponding to the private key share generated by the threshold signature algorithm to obtain a complete signature.
如前所述,门限签名算法在应用中,可以产生1个总公钥和n个公私钥对,并可以产生该n个公私钥对所对应的恢复函数。前述提到,该恢复函数可以将验证正确的至少门限数量个签名恢复生成一个完整签名,门限签名算法的门限值即门限数量可以设为w。当然,正确的签名多于w个时也可以通过该恢复函数生成一个完整签名。也就是说,正确的签名大于等于门限数量w时,都可以通过该恢复函数生成一个完整签名,且生成的这个完整签名是确定的,不会因为输入的正确签名的个数而发生变化(只要大于等于w)。As mentioned above, in the application of the threshold signature algorithm, one total public key and n public-private key pairs can be generated, and a recovery function corresponding to the n public-private key pairs can be generated. As mentioned above, the restoration function can restore at least a threshold number of signatures that have been verified to be correct to generate a complete signature, and the threshold value of the threshold signature algorithm, that is, the threshold number, can be set to w. Of course, when there are more than w correct signatures, a complete signature can also be generated through this recovery function. That is to say, when the correct signature is greater than or equal to the threshold number w, a complete signature can be generated through the restoration function, and the generated complete signature is deterministic and will not change due to the number of input correct signatures (as long as greater than or equal to w).
这个生成的完整签名可以由所述的那1个总公钥来验证正确性。这样,任何持有这个总公钥的节点或其它设备都可以采用该总公钥来验证这个完整签名的正确性。例如,节点1生成完整签名后,可以采用总公钥验证该完整签名的完整性,例如采用总公钥对完整签名进行密码学运算得到第一hash,并对原始报文进行hash运算得到第二hash,如果第一hash与第二hash一致则可以确定该完整签名的完整性。所述完整性包括该完整签名是针对所述原始报文的,且该原始报文没有经过篡改。再例如,节点1生成完整签名后,可以将该完整签名、总公钥和原始报文发送至区块链以外的一个设备,该设备可以采用所述总公钥和原始报文验证这个完整签名的正确性,原理同上不再赘述。这里的报文原文仍然是前述的包含本次共识中原始交易列表特有值的内容,或还包括当前区块的区块号和/或时间戳和/或上一区块中产生的随机数种子。This generated full signature can be verified for correctness by the said 1 total public key. In this way, any node or other device that holds the total public key can use the total public key to verify the correctness of the complete signature. For example, after
此外,也可以是每一共识节点收集每一commit消息后,采用对应的公钥份额对所述接收到的commit消息中的签名份额进行验证,然后再将所述至少门限数量的签名份额经过所述门限签名算法产生的私钥份额所对应的恢复函数得到完整签名。相对于采用总公钥对生成的完整签名进行验证的方式,采用公钥份额对每一签名份额进行验证,验证通过后再经恢复函数恢复为完整签名的方式,能够确定哪个签名是错误的,从而能够确定哪个节点可能是作恶节点。In addition, after collecting each commit message, each consensus node may use the corresponding public key share to verify the signature share in the received commit message, and then pass the at least threshold number of signature shares through all the The recovery function corresponding to the private key share generated by the threshold signature algorithm is used to obtain a complete signature. Compared with the method of using the total public key to verify the generated complete signature, the public key share is used to verify each signature share, and after the verification is passed, the recovery function restores the complete signature to determine which signature is wrong. Thus, it can be determined which node may be the malicious node.
门限签名算法中,每个共识节点都具有1个总公钥和n个公私钥对中的1个私钥份额和对应的1个公钥份额,如前所述,可以是由dealer生成并分发的,也可以是各共识节点协商得到的。In the threshold signature algorithm, each consensus node has 1 total public key, 1 private key share in n public-private key pairs, and 1 corresponding public key share. As mentioned above, it can be generated and distributed by the dealer. It can also be negotiated by each consensus node.
每个共识节点可以采用对应的公钥份额对接收到的commit消息中的签名份额进行验证。具体的,例如在包含4个共识节点的采用PBFT共识算法的联盟链中,节点0在S210中向节点1、2、3广播自身生成的签名份额σ3,0,其中σ3,0的下标3可以表示区块号,0可以表示这是节点0的签名份额;在S220中,节点0也接收到节点1、2分别广播的签名份额σ3,1、σ3,2。这样,节点0已经收齐至少3个签名份额,其中包括自身广播的签名份额σ3,0和节点1、2广播的签名份额σ3,1、σ3,2。当然,节点0也可以收集齐所有的签名份额σ3,0、σ3,1、σ3,2和σ3,3,这样也当然满足至少quorum数量。Each consensus node can use the corresponding public key share to verify the signature share in the received commit message. Specifically, for example, in a consortium chain that includes 4 consensus nodes and adopts the PBFT consensus algorithm,
进而,节点0可以用对应的公钥份额来验证收集的σ3,0、σ3,1、σ3,2或还包括σ3,3(或者是σ3,0、σ3,1、σ3,3或还包括σ3,2,或者是σ3,1、σ3,2、σ3,3或还包括σ3,0,或者是σ3,0、σ3,2、σ3,3或还包括σ3,1)的正确性。具体的,例如,节点0可以采用对应的公钥份额来对签名份额σ3,1进行计算,得到一个hash值,记为hash3,1;节点0还可以对原始报文进行同样的hash计算得到hash′3,1。如果hash3,1与hash′3,1相等,可以证明原始报文是节点1发出的,且在传送过程中没有被篡改过。这样,σ3,1的正确性得到验证。类似的,节点0可以对σ3,2等进行验证,不再赘述。Further,
同样的,节点1可以用对应的公钥份额来验证收集的σ3,0、σ3,1、σ3,2或还包括σ3,3(或者是σ3,0、σ3,1、σ3,3或还包括σ3,2,或者是σ3,1、σ3,2、σ3,3或还包括σ3,0,或者是σ3,0、σ3,2、σ3,3或还包括σ3,1)的正确性。Likewise,
同样的,节点2可以用对应的公钥份额来验证收集的σ3,0、σ3,1、σ3,2或还包括σ3,3(或者是σ3,0、σ3,1、σ3,3或还包括σ3,2,或者是σ3,1、σ3,2、σ3,3或还包括σ3,0,或者是σ3,0、σ3,2、σ3,3或还包括σ3,1)的正确性。Likewise,
同样的,节点3可以用对应的公钥份额来验证收集的σ3,0、σ3,1、σ3,2或还包括σ3,3(或者是σ3,0、σ3,1、σ3,3或还包括σ3,2,或者是σ3,1、σ3,2、σ3,3或还包括σ3,0,或者是σ3,0、σ3,2、σ3,3或还包括σ3,1)的正确性。Likewise,
S230:所述共识节点基于所述完整签名得到随机数种子。S230: The consensus node obtains a random number seed based on the complete signature.
经过上述S210-S220的步骤,正常情况下所述共识节点可以得到完整签名。这样,基于完整签名,所述共识节点可以采用随机数种子生成算法生成随机数种子。一种较为简单的随机数种子生成算法例如是sha256算法。当然,也可以直接将完整签名作为随机数种子。After the above steps S210-S220, the consensus node can obtain a complete signature under normal circumstances. In this way, based on the complete signature, the consensus node can generate a random number seed by using a random number seed generation algorithm. A relatively simple random number seed generation algorithm is, for example, the sha256 algorithm. Of course, the full signature can also be directly used as the random number seed.
经过上述过程,即可在所述共识节点本地的区块链上产生随机数种子。After the above process, a random number seed can be generated on the local blockchain of the consensus node.
本说明书还提供一种生成区块头的方法,在上述S210-S230方法基础上还可以包括:所述共识节点将得到的随机数种子放至在生成的当前区块的区块头中。This specification also provides a method for generating a block header, which may further include: the consensus node putting the obtained random number seed in the block header of the current block generated.
本说明书还提供一种区块链上产生随机数的方法,在上述S210-S230方法基础上还可以包括:所述共识节点基于产生的随机数种子产生随机数。This specification also provides a method for generating random numbers on a blockchain, which may further include: the consensus node generates random numbers based on the generated random number seeds based on the above-mentioned S210-S230 methods.
前面提到,门限签名算法可以采用基于RSA的门限签名机制,基于ECDSA的门限签名机制、基于Schnorr的门限签名机制或基于BLS的门限签名机制等。采用的门限签名算法中,一般都需要生成1个总公钥和n个公私钥对。一种典型且简洁的实现中,私钥份额的个数可以等于共识节点的个数,每个共识节点持有其中一个私钥,也即一个私钥份额。这样,每一共识节点基于门限签名算法,采用自身私钥份额对原始报文进行签名以生成签名份额。恢复函数产生完整签名的最少个数即门限数量w可以等于PBFT算法中的quorum,也就是至少w个签名份额可以由对应的恢复函数生成一个确定的完整签名,而不论是n个签名份额中的至少哪w个,只要这至少w个签名是采用各自正确的私钥份额对同一原始报文所做的签名。As mentioned above, the threshold signature algorithm may adopt a threshold signature mechanism based on RSA, a threshold signature mechanism based on ECDSA, a threshold signature mechanism based on Schnorr, or a threshold signature mechanism based on BLS. In the threshold signature algorithm used, it is generally necessary to generate 1 total public key and n public-private key pairs. In a typical and concise implementation, the number of private key shares can be equal to the number of consensus nodes, and each consensus node holds one of the private keys, that is, one private key share. In this way, each consensus node uses its own private key share to sign the original message based on the threshold signature algorithm to generate a signature share. The minimum number of complete signatures generated by the recovery function, that is, the threshold number w can be equal to the quorum in the PBFT algorithm, that is, at least w signature shares can generate a definite complete signature by the corresponding recovery function, regardless of the n signature shares. Which w at least as long as the at least w signatures are signatures made on the same original message with their respective correct private key shares.
为了在区块链的共识节点上实现门限签名算法,需要通过一种机制使得n个共识节点分别具有1个私钥份额和对应的1个公钥份额,且都具有同一个总公钥。前述提到,可以由一个中心化的dealer生成,并分发给n个区块链共识节点,这种属于中心化的密钥分配方式。这种中心化的密钥分配方式,需要借助第三方dealer,则要求这个dealer不会作恶。例如一种分布式密钥生成(Distributed Key Generation)协议的实现,原理上需要生成一个t次多项式,然后根据这个多项式形成的曲线,在上面取出n个点,通过这n个点生成n个私钥份额,并分给n个阈值签名的参与者。这个过程如果放在一个dealer上进行,那么如果这个dealer作恶,则这个dealer可以获取所有n个参与者的私钥份额,不符合区块链系统的安全要求。In order to implement the threshold signature algorithm on the consensus nodes of the blockchain, it is necessary to use a mechanism to make n consensus nodes have 1 private key share and 1 corresponding public key share, and all have the same total public key. As mentioned above, it can be generated by a centralized dealer and distributed to n blockchain consensus nodes. This is a centralized key distribution method. This centralized key distribution method requires the help of a third-party dealer, which requires that the dealer will not do evil. For example, the realization of a distributed key generation (Distributed Key Generation) protocol needs to generate a t-degree polynomial in principle, and then according to the curve formed by this polynomial, n points are taken out on it, and n private keys are generated through these n points. Key shares are distributed to n threshold signing participants. If this process is carried out on a dealer, then if the dealer does evil, the dealer can obtain the private key shares of all n participants, which does not meet the security requirements of the blockchain system.
此外,还存在去中心化的密钥生成和分配方式,即取消dealer,而是由n个共识节点通过密钥协商过程协商得到n个公私钥对和1个总公钥,仍然是每个共识节点单独持有n个私钥份额中的一个,且各共识节点持有同一个总公钥。上述这种方式,传统的是在区块链之外实现,并且依赖网络同步。区块链上的节点在构成分布式网络,而分布式网络一般是半同步或者异步的。因此,在区块链之外实现分布式网络各节点之间的密钥生成和分配,是不可靠的。而实现可靠的分布式密钥协议,又是区块链上生成随机数种子的重要前提。In addition, there is also a decentralized key generation and distribution method, that is, canceling the dealer, and negotiating n public-private key pairs and 1 total public key by n consensus nodes through the key negotiation process, which is still each consensus Nodes individually hold one of the n private key shares, and each consensus node holds the same total public key. The above method is traditionally implemented outside the blockchain and relies on network synchronization. The nodes on the blockchain form a distributed network, and the distributed network is generally semi-synchronous or asynchronous. Therefore, it is unreliable to realize the key generation and distribution among the nodes of the distributed network outside the blockchain. The realization of a reliable distributed key agreement is an important prerequisite for generating random number seeds on the blockchain.
前述提到的PBFT协议属于半同步(partial synchronous)协议,其特点是假设网络一开始是异步的,但是能够从某一时刻开始同步。要在网络中让不同节点对同一提议达成共识,最简便的方式是设置主节点,由主节点来统一各个节点的意见。通过设置定时器,可以防止主节点出错。PBFT中,如果在有限时间内没有完成Normal Case Phase,会触发Backups发起View Change Phase,以更换主节点。PBFT将主节点固定在一个位置,所有请求都可以先发送到主节点,再由主节点广播到其他共识节点。与此相对的,HoneyBadgerBFT(也常简称为HBBFT)算法属于一种异步(asynchronous)协议。异步协议适用于异步网络,也就是这个网络中节点间的消息可以被任意延迟,但最终会到达。HoneyBadgerBFT中去掉了定时器,而是通过消息来驱动协议的执行。同时,HoneyBadgerBFT算法中所有节点都是对等的,没有主节点和备份节点之分,也就没有换主的过程。HBBFT等异步网络共识协议无主节点的概念,各节点都可提议请求,尝试构造区块,因此异步网络协议在一定程度上缓解了公平性和单节点瓶颈的问题。The aforementioned PBFT protocol is a partial synchronous protocol, which is characterized by assuming that the network is asynchronous at the beginning, but can be synchronized from a certain moment. To allow different nodes to reach a consensus on the same proposal in the network, the easiest way is to set up a master node, and the master node unifies the opinions of each node. By setting a timer, the master node can be prevented from errors. In PBFT, if the Normal Case Phase is not completed within a limited time, Backups will be triggered to initiate a View Change Phase to replace the master node. PBFT fixes the master node in one location, and all requests can be sent to the master node first, and then broadcast by the master node to other consensus nodes. In contrast, the HoneyBadgerBFT (also often referred to as HBBFT) algorithm is an asynchronous protocol. Asynchronous protocols are suitable for asynchronous networks, that is, messages between nodes in this network can be arbitrarily delayed, but will eventually arrive. In HoneyBadgerBFT, the timer is removed, and the execution of the protocol is driven by messages. At the same time, all nodes in the HoneyBadgerBFT algorithm are equal, there is no distinction between the master node and the backup node, and there is no process of changing the master. Asynchronous network consensus protocols such as HBBFT do not have the concept of a master node. Each node can propose requests and try to construct blocks. Therefore, asynchronous network protocols alleviate the problems of fairness and single-node bottlenecks to a certain extent.
例如为中国专利ZL202111175184.1、ZL202111178795.1、ZL202111178745.3、ZL202111178754.2、ZL202111175144.7、ZL202111175151.7以及中国专利申请CN202111178779.2,都考虑了区块链网络的半同步或异步网络的特性的前提下提出了新的共识算法。For example, Chinese patents ZL202111175184.1, ZL202111178795.1, ZL202111178745.3, ZL202111178754.2, ZL202111175144.7, ZL202111175151.7 and Chinese patent application CN202111178745.3, all consider the characteristics of semi-synchronous or asynchronous network. On the premise of this, a new consensus algorithm is proposed.
通过区块链网络中的各种共识机制,可以保障区块链网络的整体一致性和同步。对于后者,只要区块链能够持续的出块,就能实现区块的同步。那么,结合区块链实现分布式密钥生成将是可靠的。Through various consensus mechanisms in the blockchain network, the overall consistency and synchronization of the blockchain network can be guaranteed. For the latter, as long as the blockchain can continuously generate blocks, the synchronization of blocks can be achieved. Then, it will be reliable to implement distributed key generation in combination with blockchain.
以下结合图7介绍本说明书一种区块链上实现分布式密钥生成的方法,包括:The following describes a method for implementing distributed key generation on a blockchain in this specification with reference to FIG. 7, including:
S310:每一共识节点生成一组特有的n个秘密份额,自身保留一个,并将其中n-1个秘密份额分别加密发送至其它n-1个节点。S310: Each consensus node generates a unique set of n secret shares, keeps one for itself, and encrypts the n-1 secret shares and sends them to other n-1 nodes respectively.
DKG算法中对节点重新进行了编号,从1开始。这里为了与DKG算法一致,也将共识节点从1开始编号。Nodes are renumbered in the DKG algorithm, starting from 1. Here, in order to be consistent with the DKG algorithm, the consensus nodes are also numbered from 1.
椭圆曲线(Elliptic Curve Cryptography,ECC)加密算法是一种公钥加密技术,以椭圆曲线理论为基础。利用有限域上椭圆曲线的点构成的阿贝尔(Abel)群离散对数难解性,实现加密、解密和数字签名。以下以椭圆曲线为例进行说明。每一个节点可以在群Zq上随机选择一个t度多项式。N次多项式函数由N+1个点唯一决定,因为最终需要区块链网络中quorum个共识节点能够恢复签名,则quorum=N+1,因此多项式的次数t为quorum-1。这样,可以实现由quorum(quorum=t+1)个签名份额经恢复函数恢复得到一个完整签名。当然,也可以将t设置为其它数值。用该多项式构建的椭圆曲线可以如下表示:Elliptic Curve Cryptography (ECC) encryption algorithm is a public key encryption technology based on elliptic curve theory. Encryption, decryption and digital signature are realized by using the discrete logarithm intractability of Abel group formed by points of elliptic curve on finite field. An elliptic curve is used as an example for description below. Each node can randomly choose a polynomial of degree t on the group Zq . The N-degree polynomial function is uniquely determined by N+1 points, because quorum consensus nodes in the blockchain network are ultimately required to restore the signature, then quorum=N+1, so the degree t of the polynomial is quorum-1. In this way, a complete signature can be obtained by restoring the quorum (quorum=t+1) signature shares through the restoration function. Of course, t can also be set to other values. The elliptic curve constructed with this polynomial can be represented as follows:
fi(z)=ai0+ai1z+ai2z2+…+aitzt 公式(1)fi (z)=ai0 +ai1 z+ai2 z2 +…+ait zt Formula (1)
公式(1)中,ai0,ai1,ai2,ai3,...,ait为多项式的系数,通过这一组系数可以确定一个多项式。In formula (1), ai0 , ai1 , ai2 , ai3 , . . . , ait are coefficients of a polynomial, and a polynomial can be determined by this set of coefficients.
当区块链网络的共识节点数量n设置为4时,采用PBFT、HBBFT之类算法的quorum为3的情况下,这时t=2。这时,这个多项式为:When the number of consensus nodes n of the blockchain network is set to 4, and the quorum of algorithms such as PBFT and HBBFT is 3, then t=2. At this time, this polynomial is:
fi(z)=ai0+ai1z+ai2z2 公式(2)fi (z)=ai0 +ai1 z+ai2 z2 Formula (2)
节点1可以从一个有限素数域中随机选择一组数作为系数,即作为a10,a11,a12,则生成的多项式为:f1(z)=a10+a11z+a12z2。
类似的,节点2可以从同一有限素数域中随机选择一组数作为系数,即作为a20,a21,a22,则生成的多项式为:f2(z)=a20+a21z+a22z2。Similarly,
类似的,节点3可以从同一有限素数域中随机选择一组数作为系数,即作为a30,a31,a32,则生成的多项式为:f3(z)=a30+a31z+a32z2。Similarly,
类似的,节点4可以从同一有限素数域中随机选择一组数作为系数,即作为a40,a41,a42,则生成的多项式为:f4(z)=a40+a41z+a42z2。Similarly, node 4 can randomly select a set of numbers from the same finite prime number field as coefficients, that is, as a40 , a41 , a42 , then the generated polynomial is: f4 (z)=a40 +a41 z+ a42 z2 .
每个节点基于确定的多项式,可以进一步确定一组秘密份额。可以根据如下公式由多项式系数确定秘密份额:Each node can further determine a set of secret shares based on a certain polynomial. The secret share can be determined from the polynomial coefficients according to the following formula:
sij=fi(j)mod q(j=1,…,n) 公式(3)sij =fi (j)mod q(j=1,...,n) Formula (3)
公式(3)中,q是每个节点采用的相同的一个大数,对fi(j)用q取模的目的是将fi(j)的值限定在[0,q-1]的范围内。例如:In formula (3), q is the same large number used by each node, and the purpose of taking modulo q for fi (j) is to limit the value of fi (j) to the value of [0,q-1]. within the range. E.g:
共识节点1生成4个秘密份额,分别为S11=f1(1)mod q,S12=f1(2)mod q,S13=f1(3)mod q,S14=f1(4)mod q。这里的4个秘密份额,4即是共识节点的总数。也就是说,如果要最终实现在从n个签名份额中取任意w个即可通过恢复函数生成一个完整签名,这里需要生成n个秘密份额。下同。
共识节点2生成4个秘密份额,分别为S21=f2(1)mod q,S22=f2(2)mod q,S23=f2(3)mod q,S24=f2(4)mod q。
共识节点3生成4个秘密份额,分别为S31=f3(1)mod q,S32=f3(2)mod q,S33=f3(3)mod q,S34=f3(4)mod q。
共识节点4生成4个秘密份额,分别为S41=f4(1)mod q,S42=f4(2)mod q,S43=f4(3)mod q,S44=f4(4)mod q。Consensus node 4 generates 4 secret shares, respectively S41 = f4 (1) mod q, S42 = f4 (2) mod q, S43 = f4 (3) mod q, S44 = f4 ( 4) mod q.
进而,每个节点除了保留一份秘密份额外,可以通过P2P网络与其它共识节点交换生成的其它秘密份额。具体可以如下:Furthermore, in addition to retaining a secret share, each node can exchange other generated secret shares with other consensus nodes through the P2P network. Specifically, it can be as follows:
共识节点1保留S11,将S12发送至节点2,将S13发送至节点3,将S14发送至节点4,可以通过区块链网络中底层的P2P(Peer to Peer,点对点)网络组件发送。发送出的秘密份额需要保密,共识节点1可以分别用接收方的公钥对待发送的秘密份额加密后再发送至接收方,或者通过TLS(Transport Layer Security,安全传输层协议)之类的安全连接发送至接收方。
共识节点2保留S22,将S21发送至节点1,将S23发送至节点3,将S24发送至节点4,可以通过区块链网络中底层的P2P网络组件发送。同样的,发送出的秘密份额需要保密,共识节点2可以分别用接收方的公钥对待发送的秘密份额加密后再发送至接收方,或者通过TLS之类的安全连接发送至接收方。
共识节点3保留S33,将S31发送至节点1,将S32发送至节点2,将S34发送至节点4,可以通过区块链网络中底层的P2P网络组件发送。同样的,发送出的秘密份额需要保密,共识节点3可以分别用接收方的公钥对待发送的秘密份额加密后再发送至接收方,或者通过TLS之类的安全连接发送至接收方。
共识节点4保留S44,将S41发送至节点1,将S42发送至节点2,将S43发送至节点3,可以通过区块链网络中底层的P2P网络组件发送。同样的,发送出的秘密份额需要保密,共识节点4可以分别用接收方的公钥对待发送的秘密份额加密后再发送至接收方,或者通过TLS之类的安全连接发送至接收方。Consensus node 4 retains S44 , sends S41 to
可见秘密份额的下标中的两个数字,左边的可以表示发出秘密份额的节点的编号,右边的可以表示接收秘密份额的节点。这样:The two numbers in the subscript of the secret share can be seen, the left one can represent the number of the node that issued the secret share, and the right one can represent the node that received the secret share. so:
共识节点1本地具有不同节点生成的秘密份额S11、S21、S31、S41;The
共识节点2本地具有不同节点生成的秘密份额S12、S22、S32、S42;The
共识节点3本地具有不同节点生成的秘密份额S13、S23、S33、S43;The
共识节点4本地具有不同节点生成的秘密份额S14、S24、S34、S44。The consensus node 4 locally has secret shares S14 , S24 , S34 , and S44 generated by different nodes.
其中,共识节点1本地具有的S11是自己生成的,共识节点2本地具有的S22是自己生成的,共识节点3本地具有的S33是自己生成的,共识节点4本地具有的S44是自己生成的。Among them, S11 locally owned by consensus node1 is generated by itself,S22 locally owned by
共识节点最好是对待发出的秘密份额进行签名,例如用自身私钥签名,或者采用MAC(Message Authentication Code,消息验证码),从而保证消息完整性,避免中间人攻击。相应的,接收到秘密份额的节点可以验证签名的正确性。It is best for the consensus node to sign the secret share to be sent, such as signing with its own private key, or using MAC (Message Authentication Code, message verification code), so as to ensure the integrity of the message and avoid man-in-the-middle attacks. Accordingly, the node receiving the secret share can verify the correctness of the signature.
S320:每一节点生成自身秘密份额对应的公共验证参数并通过DKG合约广播。S320: Each node generates a public verification parameter corresponding to its own secret share and broadcasts it through the DKG contract.
每一共识节点可以生成自身密钥份额对应的一组验证参数,生成方法可以采用下面公式:Each consensus node can generate a set of verification parameters corresponding to its own key share, and the generation method can use the following formula:
公式(4)中,g是椭圆曲线上的基点。根据椭圆曲线的运算性质,g的幂次方也是椭圆曲线上的一个点。t是多项式的次数,一般设置为(quorum-1)。如前所述,如果要最终实现在从n个签名份额中取任意w个即可通过恢复函数生成一个完整签名,这里需要设置多项式的次数是t,其中t=w-1。下同。In formula (4), g is the base point on the elliptic curve. According to the operational nature of elliptic curves, the power of g is also a point on the elliptic curve. t is the degree of the polynomial, generally set to (quorum-1). As mentioned above, if we want to finally realize that a complete signature can be generated by taking any w from n signature shares through the recovery function, the degree of polynomial needs to be set to t, where t=w-1. The same below.
基于上述公式(4),设t=2,共识节点1生成的一组验证参数为<A10,A11,A12>,通过链上合约广播这一组验证参数。类似的,基于上述公式,共识节点2生成的一组验证参数为<A20,A21,A22>,通过链上合约广播这一组验证参数。类似的,基于上述公式,共识节点3生成的一组验证参数为<A30,A31,A32>,通过链上合约广播这一组验证参数。类似的,基于上述公式,共识节点4生成的一组验证参数为<A40,A41,A42>,通过链上合约广播这一组验证参数。Based on the above formula (4), set t=2, a set of verification parameters generated by
基于密码学的性质,Aik公布出去,也不会倒推得到aik,因此即使从链上获得公布的Aik,也不能得到S310中的多项式。Based on the nature of cryptography, if Aik is published, aik will not be obtained by inversion, so even if the published Aik is obtained from the chain, the polynomial in S310 cannot be obtained.
通过链上合约广播,具体的,可以由各个节点以自身私钥签名一笔交易发到区块链上。每个节点可以内置区块链SDK(Software Development kit,软件开发工具包)。SDK是一系列程序接口、文档、范例、开发工具等的集合。通过内置SDK,区块链节点可以像区块链客户端一样向区块链网络发起交易。区块链节点用自身私钥签名发出的交易中,可以包含对区块链上的智能合约的调用。被调用的合约,例如是DKG合约。这个DKG合约可以是系统级的合约,即是预先部署在区块链上的合约,例如由具有系统管理员权限的账户创建的合约,起到系统级的控制功能,而非由用户自行开发并部署的实现某种具体的业务逻辑的合约。Through the contract broadcast on the chain, specifically, each node can sign a transaction with its own private key and send it to the blockchain. Each node can have a built-in blockchain SDK (Software Development kit). SDK is a collection of programming interfaces, documentation, examples, development tools, etc. With the built-in SDK, blockchain nodes can initiate transactions to the blockchain network just like blockchain clients. Transactions signed by blockchain nodes with their own private keys can include calls to smart contracts on the blockchain. The called contract, such as the DKG contract. This DKG contract can be a system-level contract, that is, a contract that is pre-deployed on the blockchain, such as a contract created by an account with system administrator privileges, which plays a system-level control function, rather than being developed and implemented by users themselves. A deployed contract that implements some specific business logic.
像其它合约一样,DKG合约可以在虚拟机(例如Ethereum Virtual Machine,EVM)中执行,当然也可以是在容器(例如docker)中执行,这里并不限定。外部账户向区块链发起一笔调用链上合约的交易,可以触发该合约的执行。交易的f内容例如包括from字段、to字段、value字段、data字段。from字段可以是交易发起方的账户地址,to字段可以代表被调用的智能合约的地址,value字段可以是区块链上原生的通证,data字段可以包含的调用智能合约的方法和参数。通过在to字段指明调用的智能合约的地址,可以表明是对区块链上某个智能合约的调用。智能合约中一般可以包括一个或多个函数,每个函数可以包括一些输入的参数。交易中通过data字段可以指明所要调用的智能合约中的某个函数,并在data字段中填入需要传入的参数。Like other contracts, DKG contracts can be executed in virtual machines (such as Ethereum Virtual Machine, EVM), and of course in containers (such as docker), which is not limited here. An external account initiates a transaction to the blockchain that calls a contract on the chain, which can trigger the execution of the contract. The f content of the transaction includes, for example, a from field, a to field, a value field, and a data field. The from field can be the account address of the transaction initiator, the to field can represent the address of the called smart contract, the value field can be the native token on the blockchain, and the data field can contain methods and parameters for calling the smart contract. By specifying the address of the called smart contract in the to field, it can indicate that it is a call to a smart contract on the blockchain. A smart contract can generally include one or more functions, and each function can include some input parameters. In the transaction, you can specify a function in the smart contract to be called through the data field, and fill in the parameters that need to be passed in in the data field.
合约执行的结果,一方面可以改变合约的存储,即合约的世界状态,另一方面,该交易的执行结果或相关信息可以记录在区块链的收据(receipt)中。具体的,合约执行结果/相关信息可以表现为收据中的事件(event)。事件的结构例如为如下格式:The result of contract execution can change the storage of the contract, that is, the world state of the contract, and on the other hand, the execution result or related information of the transaction can be recorded in the receipt of the blockchain. Specifically, the contract execution result/related information can be represented as an event in the receipt. The structure of the event is, for example, in the following format:
Event:Event:
[topic][msg][topic][msg]
[topic][msg][topic][msg]
............
在上述示例中,事件的数量可以为一个或多个。每个事件可以包括主题(topic)和数据(data)等字段。交易执行时输出的事件的格式,可以在合约中指定。通过内置的SDK,区块链客户端或区块链节点可以监听特定topic的事件,并在监听到特定topic事件的情况下,拉取相应的msg的内容,以及可以监听到特定topic或对应msg中的某些内容后执行预设的处理。In the above example, the number of events may be one or more. Each event can include fields such as topic and data. The format of the event output when the transaction is executed can be specified in the contract. Through the built-in SDK, the blockchain client or blockchain node can monitor the events of a specific topic, and when listening to a specific topic event, pull the content of the corresponding msg, and can monitor the specific topic or the corresponding msg After some content in the preset processing is executed.
通过这种事件机制,节点可以将执行结果存放到某个topic对应的msg中,从而监听该topic的监听方(即内置区块链SDK的客户端或区块链节点)可以获得相应的执行结果。S320中,可以是某一节点将生成的所述公共验证参数通过发起调用DKG合约中第一函数(例如名为Broadcast的函数,其中该函数可以包括参数,参数可以包括公共验证参数)的方式传入区块链网络,区块链网络执行该交易的一个结果是将所述公共验证参数置入收据中特定topic对应的msg中。从而监听该topic的节点可以获取msg字段中的内容,即获得所述公共验证参数。这样,即完成了链上合约广播。Through this event mechanism, the node can store the execution result in the msg corresponding to a topic, so that the listener listening to the topic (ie the client or blockchain node with the built-in blockchain SDK) can obtain the corresponding execution result . In S320, a certain node may transmit the generated public verification parameters by initiating a call to the first function in the DKG contract (for example, a function named Broadcast, where the function may include parameters, and the parameters may include public verification parameters). Enter the blockchain network, and one result of the blockchain network executing the transaction is to place the public verification parameters in the msg corresponding to the specific topic in the receipt. Therefore, the node monitoring the topic can obtain the content in the msg field, that is, obtain the public verification parameter. In this way, the on-chain contract broadcast is completed.
可以通过SDK向区块链节点注册要监听事件。具体的,区块链节点可以在运行的区块链平台代码中对生成的事件绑定一个钩子函数(钩子函数可以与平台代码一同在开发阶段编辑完成)。这个钩子函数属于一种回调函数,其可以在监听的事件发生时被调用,并可以执行一定的处理逻辑。监听代码例如可以包括监听区块链交易的交易内容,智能合约的合约状态,合约产生的收据等一种或多种。通过SDK向区块链节点注册监听事件后,区块链节点可以保存监听事件与监听者(例如置入SDK并发起事件监听的客户端/节点的网络连接,一般可以包括IP地址、端口号等信息)的映射关系,例如保存监听某个合约的某个事件与监听者的映射关系。当钩子函数监听到对应的事件主题(topic)发生时,可以调用钩子函数,进而钩子函数可以查询所述映射关系,将监听的事件推送至所述网络连接。这样,发起监听的SDK可以通过保持的网络连接获得监听的事件。合约的执行也是通过类似方式的实现链上合约广播。具体的,合约的执行结果和本区块其它交易的执行结果一并存入区块链节点的一个交易结果缓存区。当该区块链的所有交易都执行完毕并组织成块后,区块链平台代码可以监听交易结果中的收据,从中将被监听的事件广播至发起监听的SDK。这里,通过这种监听机制,节点可以监听注册的特定topic事件,并在这样的事件发生时,通过保持的连接获取这个topic对应的msg,从而获得msg中的内容,这里msg中的内容包括公共验证参数。总之,可以通过区块链的事件机制实现广播公共验证参数,并通过事件监听机制实现对广播内容的接收。You can register with the blockchain node to listen for events through the SDK. Specifically, the blockchain node can bind a hook function to the generated event in the running blockchain platform code (the hook function can be edited together with the platform code during the development phase). This hook function belongs to a callback function, which can be called when the monitored event occurs, and can execute certain processing logic. For example, the monitoring code may include monitoring the transaction content of the blockchain transaction, the contract status of the smart contract, the receipt generated by the contract, and so on. After registering the monitoring event with the blockchain node through the SDK, the blockchain node can save the monitoring event and the listener (for example, the network connection of the client/node that is placed in the SDK and initiates event monitoring, which can generally include IP address, port number, etc. Information) mapping relationship, such as saving the mapping relationship between a certain event monitoring a contract and the listener. When the hook function monitors the occurrence of a corresponding event topic (topic), the hook function can be called, and then the hook function can query the mapping relationship and push the monitored event to the network connection. In this way, the SDK that initiates the monitoring can obtain the monitored events through the maintained network connection. The execution of the contract is also implemented in a similar way through the on-chain contract broadcast. Specifically, the execution result of the contract and the execution results of other transactions in this block are stored in a transaction result buffer area of the blockchain node. When all transactions of the blockchain are executed and organized into blocks, the blockchain platform code can monitor the receipts in the transaction results, and broadcast the monitored events to the SDK that initiated the monitoring. Here, through this monitoring mechanism, the node can listen to the registered specific topic event, and when such an event occurs, obtain the msg corresponding to the topic through the maintained connection, so as to obtain the content in the msg, where the content in the msg includes the public Validate parameters. In short, the public verification parameters can be broadcast through the event mechanism of the blockchain, and the broadcast content can be received through the event monitoring mechanism.
这样,通过链上广播各节点生成的公共验证参数的结果可以如下:In this way, the results of the public verification parameters generated by each node by broadcasting on the chain can be as follows:
共识节点1本地具有不同节点生成的秘密份额S11、S21、S31、S41,以及验证参数<A10,A11,A12>,并可以从链上获得公共验证参数<A20,A21,A22>,<A30,A31,A32>,<A40,A41,A42>;
共识节点2本地具有不同节点生成的秘密份额S12、S22、S32、S42,以及验证参数<A20,A21,A22>,并可以从链上获得公共验证参数<A10,A11,A12>,<A30,A31,A32>,<A40,A41,A42>;
共识节点3本地具有不同节点生成的秘密份额S13、S23、S33、S43,以及验证参数<A30,A31,A32>,并可以从链上获得公共验证参数<A10,A11,A12>,<A20,A21,A22>,<A40,A41,A42>;
共识节点4本地具有不同节点生成的秘密份额S14、S24、S34、S44,以及验证参数<A40,A41,A42>,并可以从链上获得公共验证参数<A10,A11,A12>,<A20,A21,A22>,<A30,A31,A32>。The consensus node 4 locally has secret shares S14 , S24 , S34 , S44 generated by different nodes, and verification parameters <A40 , A41 , A42 >, and can obtain public verification parameters <A10 from the chain, A11 , A12 >, <A20 , A21 , A22 >, <A30 , A31 , A32 >.
S330:每一共识节点对接收到的每一秘密份额和对应的公共验证参数进行验证。S330: Each consensus node verifies each received secret share and corresponding public verification parameters.
每一共识节点可以接收其它任一节点发来的秘密份额,并接收链上合约广播的公共验证参数。Each consensus node can receive the secret share sent by any other node, and receive the public verification parameters broadcast by the contract on the chain.
前述S310中提到,每一共识节点生成n个秘密份额Sij,自己保留一份,并将其中n-1个秘密份额分别通过P2P网络组件并加密发送至其它n-1个节点。前述S320中提到,每一节点生成自身秘密份额对应的公共验证参数并通过链上合约广播。As mentioned in the aforementioned S310, each consensus node generates n secret shares Sij , keeps one for itself, and sends the n-1 secret shares to other n-1 nodes through the P2P network component and encrypted respectively. As mentioned in the aforementioned S320, each node generates public verification parameters corresponding to its own secret share and broadcasts it through the on-chain contract.
如果每一节点发出的秘密份额和对应的公共验证参数是归属于同一个多项式的,则下面等式应当成立:If the secret shares sent by each node and the corresponding public verification parameters belong to the same polynomial, the following equation should hold:
如前所述,t=quorum-1;n=4时,quorum=3,这时t=2。As mentioned above, t=quorum-1; when n=4, quorum=3, then t=2.
基于公式(5)这样的性质,可以用该公式对接收到的每一秘密份额和公共验证参数进行验证。如果验证等式成立,说明秘密份额和对应的公共验证参数是归属于同一多项式,否则不归属于同一多项式。这样也可以检验生成秘密份额和对应公共验证参数的节点是否存在作恶行为。典型的作恶行为例如为节点根据第一个多项式生成了Sij,但是又以不同的多项式生成了Aik(k=0,...,t)。Based on the properties of formula (5), each received secret share and public verification parameters can be verified with this formula. If the verification equation is established, it means that the secret share and the corresponding public verification parameters belong to the same polynomial, otherwise they do not belong to the same polynomial. In this way, it is also possible to check whether the nodes that generate the secret shares and the corresponding public verification parameters have malicious behavior. A typical malicious behavior is, for example, that the node generates Sij according to the first polynomial, but generates Aik (k=0, . . . , t) with a different polynomial.
上述验证,具体的:The above verification, specifically:
j=1时,即共识节点1可以验证以下内容:When j=1, that is,
i=1:(事实上,共识节点1可以不验证这个等式是否成立,因为秘密份额S11和验证参数<A11,A12,A13>都是自身生成的)i=1: (In fact, the
i=2:i=2:
i=3:i=3:
i=4:i=4:
j=2时,即共识节点2可以验证以下内容:When j=2, that is,
i=1:i=1:
i=2:(事实上,共识节点2可以不验证这个等式是否成立,因为秘密份额S22和验证参数<A20,A21,A22>都是自身生成的)i=2: (In fact, the
i=3:i=3:
i=4:i=4:
j=3时,即共识节点3可以验证以下内容:When j=3, that is,
i=1:i=1:
i=2:i=2:
i=3:(事实上,共识节点3可以不验证这个等式是否成立,因为秘密份额S33和验证参数<A30,A31,A32>都是自身生成的)i=3: (In fact, the
i=4:i=4:
j=4时,即共识节点4可以验证以下内容:When j=4, that is, consensus node 4 can verify the following:
i=1:i=1:
i=2:i=2:
i=3:i=3:
i=4:(事实上,共识节点4可以不验证这个等式是否成立,因为秘密份额S44和验证参数<A40,A41,A42>都是自身生成的)i=4: (In fact, the consensus node 4 may not verify whether this equation holds, because the secret share S44 and the verification parameters <A40 , A41 , A42 > are all generated by themselves)
S340:每一共识节点对每一验证通过后,将通过验证的节点编号发送至所述合约;所述合约根据各共识节点发来的节点编号确定节点集合。S340: After each consensus node passes the verification, it sends the verified node number to the contract; the contract determines the node set according to the node number sent by each consensus node.
共识节点2验证等式成立,则可以发起调用DKG合约的交易,该调用合约的交易中可以带有节点1的编号,以表明节点2对节点1发出的秘密份额及对应公共验证参数通过检验;例如可以是发起调用DKG的验证节点成功的函数(例如名称为confirm(v),其中的参数v例如为确认的节点的编号)。
共识节点3验证等式成立,则可以发起调用DKG合约的交易,该调用合约的交易中可以带有节点1的编号,以表明节点3对节点1发出的秘密份额及对应公共验证参数通过检验;类似的,可以发起调用DKG合约中的confirm(v)函数。
共识节点4验证等式成立,则可以发起调用DKG合约的交易,该调用合约的交易中可以带有节点1的编号,以表明节点4对节点1发出的秘密份额及对应公共验证参数通过检验;类似的,可以发起调用DKG合约中的confirm(v)函数。Consensus node 4 verifies the equation If established, a transaction to invoke the DKG contract can be initiated. The transaction of the invoking contract can carry the number of
这样,DKG合约可以收集齐除节点1之外的其它所有节点对节点1通过验证的确认,因此可以认为节点1发出的秘密份额及对应公共验证参数都是归属于同一多项式的。In this way, the DKG contract can collect all other nodes except
类似的:akin:
共识节点1验证等式成立,则可以发起调用DKG合约的交易,该调用合约的交易中可以带有节点2的编号,以表明节点1对节点2发出的秘密份额及对应公共验证参数通过检验;类似的,可以发起调用DKG合约中的confirm(v)函数。
共识节点3验证等式成立,则可以发起调用DKG合约的交易,该调用合约的交易中可以带有节点2的编号,以表明节点3对节点2发出的秘密份额及对应公共验证参数通过检验;类似的,可以发起调用DKG合约中的confirm(v)函数。
共识节点4验证等式成立,则可以发起调用DKG合约的交易,该调用合约的交易中可以带有节点2的编号,以表明节点4对节点2发出的秘密份额及对应公共验证参数通过检验;类似的,可以发起调用DKG合约中的confirm(v)函数。Consensus node 4 verifies the equation If established, a transaction to call the DKG contract can be initiated. The transaction of the call contract can have the number of
这样,DKG合约可以收集齐除节点2之外的其它所有节点对节点2通过验证的确认,因此可以认为节点2发出的秘密份额及对应公共验证参数都是归属于同一多项式的。In this way, the DKG contract can collect all other nodes except
类似的:akin:
共识节点1验证等式成立,则可以发起调用DKG合约的交易,该调用合约的交易中可以带有节点1的编号,以表明节点1对节点3发出的秘密份额及对应公共验证参数通过检验;类似的,可以发起调用DKG合约中的confirm(v)函数。
共识节点2验证等式成立,则可以发起调用DKG合约的交易,该调用合约的交易中可以带有节点3的编号,以表明节点2对节点3发出的秘密份额及对应公共验证参数通过检验;类似的,可以发起调用DKG合约中的confirm(v)函数。
共识节点4验证等式成立,则可以发起调用DKG合约的交易,该调用合约的交易中可以带有节点1的编号,以表明节点4对节点3发出的秘密份额及对应公共验证参数通过检验;类似的,可以发起调用DKG合约中的confirm(v)函数。Consensus node 4 verifies the equation If established, a transaction to invoke the DKG contract can be initiated. The transaction of the invoking contract can carry the number of
这样,DKG合约可以收集齐除节点3之外的其它所有节点对节点3通过验证的确认,因此可以认为节点3发出的秘密份额及对应公共验证参数都是归属于同一多项式的。In this way, the DKG contract can collect all other nodes except
类似的:akin:
共识节点1验证等式成立,则可以发起调用DKG合约的交易,该调用合约的交易中可以带有节点1的编号,以表明节点1对节点4发出的秘密份额及对应公共验证参数通过检验;类似的,可以发起调用DKG合约中的confirm(v)函数。
共识节点2验证等式成立,则可以发起调用DKG合约的交易,该调用合约的交易中可以带有节点3的编号,以表明节点2对节点4发出的秘密份额及对应公共验证参数通过检验;类似的,可以发起调用DKG合约中的confirm(v)函数。
共识节点4验证等式成立,则可以发起调用DKG合约的交易,该调用合约的交易中可以带有节点1的编号,以表明节点3对节点4发出的秘密份额及对应公共验证参数通过检验;类似的,可以发起调用DKG合约中的confirm(v)函数。Consensus node 4 verifies the equation If established, a transaction to invoke the DKG contract can be initiated. The transaction of the invoking contract can carry the number of
这样,DKG合约可以收集齐除节点4之外的其它所有节点对节点4通过验证的确认,因此可以认为节点4发出的秘密份额及对应公共验证参数都是归属于同一多项式的。In this way, the DKG contract can collect all other nodes except node 4's confirmation that node 4 has passed the verification, so it can be considered that the secret share sent by node 4 and the corresponding public verification parameters belong to the same polynomial.
进一步,所述合约可以根据各共识节点发来的节点编号确定节点集合。Further, the contract may determine the node set according to the node numbers sent by each consensus node.
例如所述DKG合约,可以根据各共识节点发来的交易校验确定节点集合,具体的,对于一个节点,如果DKG合约收到了所有其它节点对其的确认,则DKG合约将被确认的节点加入节点集合。这个集合例如是QUAL集合。For example, in the DKG contract, the set of nodes can be determined according to the transaction verification sent by each consensus node. Specifically, for a node, if the DKG contract has received confirmation from all other nodes, the DKG contract will add the confirmed node to the contract. collection of nodes. This set is, for example, the QUAL set.
例如,S340的例子中,DKG合约收到了节点2、节点3和节点4对节点1的确认,则DKG合约将节点1加入到QUAL集合中;类似的,DKG合约收到了节点1、节点3和节点4对节点2的确认,则DKG合约将节点2加入到QUAL集合中;类似的,DKG合约收到了节点1、节点2和节点4对节点3的确认,则DKG合约将节点3加入到QUAL集合中;类似的,DKG合约收到了节点1、节点2和节点3对节点4的确认,则DKG合约将节点4加入到QUAL集合中。For example, in the example of S340, the DKG contract has received the confirmation of
经过上述合约的执行,QUAL集合中包括节点集合为{1,2,3,4}。After the execution of the above contract, the node set included in the QUAL set is {1, 2, 3, 4}.
需要说明的是,在区块链网络中,由于半同步或异步的网络特性,合约的执行并不一定是在同一个区块中执行的,而是可能在不同的区块中分别执行一部分。这种情况,一般可以再合约中设置状态机,从而在执行完一部分的情况下转变状态机的状态,或直至状态机转变为某种最终状态。状态机执行的每一步,可以是在接收到一个交易后执行并触发的。因此,本步骤中DKG合约确定节点的集合,可能会延续多个区块。It should be noted that in the blockchain network, due to the semi-synchronous or asynchronous network characteristics, the execution of the contract is not necessarily executed in the same block, but may be executed separately in different blocks. In this case, the state machine can generally be set up in the contract, so that the state of the state machine can be changed after part of the execution, or until the state machine changes to a certain final state. Each step executed by the state machine can be executed and triggered after receiving a transaction. Therefore, in this step, the DKG contract determines the set of nodes, which may continue for multiple blocks.
S350:每一共识节点获得所述节点集合,并在基于验证参数及所述节点集合计算公钥份额,并基于本地的秘密份额和节点集合计算自身对应的私钥份额。S350: Each consensus node obtains the node set, calculates the public key share based on the verification parameters and the node set, and calculates its own corresponding private key share based on the local secret share and the node set.
一方面,每一共识节点各自可以在本地基于验证参数及合约中的节点集合计算公钥份额,可以按照下面公式计算该公钥份额:On the one hand, each consensus node can calculate the public key share locally based on the verification parameters and the node set in the contract, and the public key share can be calculated according to the following formula:
这样,例如共识节点1计算的公钥份额可以是:Thus, for example, the public key share calculated by
类似的,例如共识节点2计算的公钥份额可以是:Similarly, for example, the public key share calculated by
类似的,例如共识节点3计算的公钥份额可以是:Similarly, for example, the public key share calculated by
类似的,例如共识节点4计算的公钥份额可以是:Similarly, for example, the public key share calculated by consensus node 4 can be:
另一方面,每一共识节点各自基于本地的秘密份额和合约中的节点集合计算自身对应的私钥份额,可以按照下面公式计算:On the other hand, each consensus node calculates its corresponding private key share based on the local secret share and the node set in the contract, which can be calculated according to the following formula:
xj=∑i∈QUALsijmod q公式(7)xj =∑i∈QUAL sij mod q Formula (7)
例如,共识节点1在本地计算自身的私钥份额:For example,
共识节点2在本地计算自身的私钥份额:
共识节点3在本地计算自身的私钥份额:
共识节点4在本地计算自身的私钥份额:Consensus node 4 calculates its own private key share locally:
可见,节点1、节点2、节点3和节点4计算得到的私钥份额不相同。It can be seen that the private key shares calculated by
再一方面,每一共识节点各自可以在本地基于验证参数及合约中的节点集合计算总公钥,可以按照下面公式计算该总公钥:On the other hand, each consensus node can calculate the total public key locally based on the verification parameters and the node set in the contract, and the total public key can be calculated according to the following formula:
y=∏i∈QUALyi公式(8)y=∏i∈QUAL yi Formula (8)
其中,yi=Ai0。where yi =Ai0 .
这样,例如共识节点1计算总公钥可以是:In this way, for
y=y1*y2*y3*y4=A10*A20*A30*A40y=y1 *y2 *y3 *y4 =A10 *A20 *A30 *A40
类似的,例如共识节点2计算总公钥可以是:Similarly, for example, the total public key calculated by
y=y1*y2*y3*y4=A10*A20*A30*A40y=y1 *y2 *y3 *y4 =A10 *A20 *A30 *A40
类似的,例如共识节点3计算总公钥可以是:Similarly, for example, the total public key calculated by
y=y1*y2*y3*y4=A10*A20*A30*A40y=y1 *y2 *y3 *y4 =A10 *A20 *A30 *A40
类似的,例如共识节点4计算总公钥可以是:Similarly, for example, the total public key calculated by consensus node 4 can be:
y=y1*y2*y3*y4=A10*A20*A30*A40y=y1 *y2 *y3 *y4 =A10 *A20 *A30 *A40
可见,节点1、节点2、节点3和节点4计算得到的总公钥相同,即通过上述方法,各节点获得相同的总公钥。It can be seen that the total public keys calculated by
上述私钥份额x1与公钥份额pub1对应,私钥份额x2与公钥份额pub2对应,私钥份额x3与公钥份额pub3对应,私钥份额x4与公钥份额pub4对应。如前所述,每一公钥份额,可以对对应私钥份额所做的签名份额进行验证。而且,至少quorum个私钥份额产生的签名份额经恢复函数恢复出的一个完整签名,可以由对应的那1个总公钥进行验证。The private key share x1 corresponds to the public key share pub1 , the private key share x2 corresponds to the public key share pub2 , the private key share x3 corresponds to the public key share pub3 , and the private key share x4 corresponds to the public key share pub4 corresponds. As mentioned above, each public key share can verify the signature share made by the corresponding private key share. Moreover, a complete signature recovered by the recovery function for the signature shares generated by at least quorum private key shares can be verified by the corresponding total public key.
通过上述方法,在共识机制保障区块链网络整体一致性和同步的基础上,结合区块链智能合约实现分布式密钥生成,保障了分布式密钥密钥的生成一方面是由各个参与方通过协作来生成的,另一方面生成的结果是一致和可靠的,从而摆脱了原有的区块链之外实现分布式密钥生成对网络同步的强依赖,并解决了该情况下生成结果的不可靠性问题。Through the above method, on the basis of the consensus mechanism to ensure the overall consistency and synchronization of the blockchain network, the distributed key generation is realized in combination with the blockchain smart contract, which ensures that the generation of the distributed key key is performed by each participant. On the other hand, the generated results are consistent and reliable, thus getting rid of the strong dependence on network synchronization for distributed key generation outside the original blockchain, and solving the problem of generating Unreliability of results.
以下结合图8以一个共识节点的角度描述区块链上实现分布式密钥生成的方法,包括:The following describes the method for realizing distributed key generation on the blockchain from the perspective of a consensus node, including:
S410,第一节点接收其它节点生成的秘密份额,并通过链上合约广播接收对应的公共验证参数;S410, the first node receives the secret shares generated by other nodes, and receives the corresponding public verification parameters through the contract broadcast on the chain;
S420,第一共识节点对接收到的每一秘密份额和对应的公共验证参数进行验证;S420, the first consensus node verifies each received secret share and corresponding public verification parameters;
S430,第一共识节点对每一验证通过后,将通过验证的节点编号发送至链上合约;S430, after each verification is passed by the first consensus node, the node number that has passed the verification is sent to the contract on the chain;
S440,第一共识节点接收所述链上合约确定的节点集合;S440, the first consensus node receives the node set determined by the on-chain contract;
S450,第一共识节点基于验证参数及节点集合计算公钥份额,并基于所述秘密份额和节点集合计算自身对应的私钥份额。S450, the first consensus node calculates the public key share based on the verification parameter and the node set, and calculates its corresponding private key share based on the secret share and the node set.
第一共识节点还可以基于验证参数及节点集合计算总公钥。The first consensus node may also calculate the total public key based on the verification parameters and the node set.
其中,第一节点通过P2P网络组件接收所述其它节点生成的秘密份额。The first node receives the secret shares generated by the other nodes through the P2P network component.
其中,第一节点还对接收到的其它节点生成的秘密份额进行签名验证。The first node also performs signature verification on the received secret shares generated by other nodes.
其中,第一节点通过链上合约广播接收对应的公共验证参数,包括:Among them, the first node broadcasts and receives the corresponding public verification parameters through the contract on the chain, including:
第一节点通过区块链的事件监听机制接收公共验证参数。The first node receives public verification parameters through the event monitoring mechanism of the blockchain.
在上述方法基础上实现区块链上产生随机数种子的方法,包括:On the basis of the above method, the method for generating random number seeds on the blockchain includes:
在PBFT的commit阶段,第一共识节点基于门限签名算法,采用自身私钥份额对包含本次共识中原始交易列表特有值的原始报文进行签名,生成签名份额,并将该签名份额加入到广播的commit消息中;In the commit stage of PBFT, the first consensus node uses its own private key share to sign the original message containing the unique value of the original transaction list in this consensus based on the threshold signature algorithm, generates a signature share, and adds the signature share to the broadcast in the commit message;
第一共识节点收集齐至少quorum数量的commit消息后,采用公钥份额对所述接收到的commit消息中的签名份额进行验证;After the first consensus node collects at least quorum commit messages, the public key share is used to verify the signature share in the received commit message;
第一共识节点将通过验证的至少quorum数量的签名份额经过所述门限签名算法产生的私钥份额所对应的恢复函数得到完整签名;The first consensus node obtains a complete signature through the recovery function corresponding to the private key share generated by the threshold signature algorithm through the verified signature shares of at least quorum;
第一共识节点基于所述完整签名得到随机数种子。The first consensus node obtains a random number seed based on the complete signature.
其中,所述原始交易列表的特有值包括:Wherein, the unique values of the original transaction list include:
原始交易列表本身或者原始交易列表的hash值。The original transaction list itself or the hash value of the original transaction list.
其中,所述原始报文还包括区块号和/或时间戳。Wherein, the original message further includes a block number and/or a timestamp.
其中,所述原始报文还包括上一区块中产生的随机数种子或区块hash。Wherein, the original message also includes the random number seed or block hash generated in the previous block.
其中还包括:It also includes:
第一共识节点将得到的随机数种子放至在生成的当前区块的区块头中。The first consensus node puts the obtained random number seed in the block header of the generated current block.
以下介绍本说明书提供的一种区块链系统,包括若干个共识节点,其中:The following introduces a blockchain system provided in this specification, including several consensus nodes, among which:
每一共识节点生成n个秘密份额,自身保留一份,并将其中n-1个秘密份额分别加密发送至其它n-1个节点;Each consensus node generates n secret shares, keeps one for itself, and encrypts the n-1 secret shares and sends them to other n-1 nodes;
每一节点生成自身秘密份额对应的公共验证参数并通过链上合约广播;Each node generates the public verification parameters corresponding to its own secret share and broadcasts it through the on-chain contract;
每一共识节点对接收到的每一秘密份额和对应的公共验证参数进行验证;Each consensus node verifies each received secret share and the corresponding public verification parameters;
每一共识节点对每一验证通过后,将通过验证的节点编号发送至链上合约;After each consensus node passes each verification, it sends the verified node number to the contract on the chain;
所述链上合约根据各共识节点发来的交易确定节点集合;The on-chain contract determines the node set according to the transactions sent by each consensus node;
每一共识节点各自在本地基于验证参数及节点集合计算公钥份额,并基于本地的秘密份额和节点集合计算自身对应的私钥份额。Each consensus node calculates the public key share locally based on the verification parameters and the node set, and calculates its corresponding private key share based on the local secret share and the node set.
每一共识节点各自在本地还可以基于验证参数及节点集合计算总公钥。Each consensus node can also calculate the total public key locally based on the verification parameters and the node set.
以下介绍本说明书提供的一种区块链系统中的第一共识节点,包括The following introduces the first consensus node in a blockchain system provided by this specification, including
第一节点接收其它节点生成的秘密份额,并通过链上合约广播接收对应的公共验证参数;The first node receives the secret shares generated by other nodes, and receives the corresponding public verification parameters through the contract broadcast on the chain;
第一共识节点对接收到的每一秘密份额和对应的公共验证参数进行验证;The first consensus node verifies each received secret share and the corresponding public verification parameters;
第一共识节点对每一验证通过后,将通过验证的节点编号发送至所述链上合约;After passing each verification, the first consensus node sends the verified node number to the on-chain contract;
第一共识节点接收所述链上合约确定的节点集合;The first consensus node receives the node set determined by the on-chain contract;
第一共识节点基于验证参数及节点集合计算公钥份额,并基于所述秘密份额和节点集合计算自身对应的私钥份额。The first consensus node calculates the public key share based on the verification parameter and the node set, and calculates its corresponding private key share based on the secret share and the node set.
第一共识节点还可以基于验证参数及节点集合计算总公钥。The first consensus node may also calculate the total public key based on the verification parameters and the node set.
在20世纪90年代,对于一个技术的改进可以很明显地区分是硬件上的改进(例如,对二极管、晶体管、开关等电路结构的改进)还是软件上的改进(对于方法流程的改进)。然而,随着技术的发展,当今的很多方法流程的改进已经可以视为硬件电路结构的直接改进。设计人员几乎都通过将改进的方法流程编程到硬件电路中来得到相应的硬件电路结构。因此,不能说一个方法流程的改进就不能用硬件实体模块来实现。例如,可编程逻辑器件(Programmable Logic Device,PLD)(例如现场可编程门阵列(Field Programmable GateArray,FPGA))就是这样一种集成电路,其逻辑功能由用户对器件编程来确定。由设计人员自行编程来把一个数字系统“集成”在一片PLD上,而不需要请芯片制造厂商来设计和制作专用的集成电路芯片。而且,如今,取代手工地制作集成电路芯片,这种编程也多半改用“逻辑编译器(logic compiler)”软件来实现,它与程序开发撰写时所用的软件编译器相类似,而要编译之前的原始代码也得用特定的编程语言来撰写,此称之为硬件描述语言(Hardware Description Language,HDL),而HDL也并非仅有一种,而是有许多种,如ABEL(Advanced Boolean Expression Language)、AHDL(Altera Hardware DescriptionLanguage)、Confluence、CUPL(Cornell University Programming Language)、HDCal、JHDL(Java Hardware Description Language)、Lava、Lola、MyHDL、PALASM、RHDL(RubyHardware Description Language)等,目前最普遍使用的是VHDL(Very-High-SpeedIntegrated Circuit Hardware Description Language)与Verilog。本领域技术人员也应该清楚,只需要将方法流程用上述几种硬件描述语言稍作逻辑编程并编程到集成电路中,就可以很容易得到实现该逻辑方法流程的硬件电路。In the 1990s, improvements in a technology could be clearly differentiated between improvements in hardware (eg, improvements to circuit structures such as diodes, transistors, switches, etc.) or improvements in software (improvements in method flow). However, with the development of technology, the improvement of many methods and processes today can be regarded as a direct improvement of the hardware circuit structure. Designers almost get the corresponding hardware circuit structure by programming the improved method flow into the hardware circuit. Therefore, it cannot be said that the improvement of a method flow cannot be realized by hardware entity modules. For example, a Programmable Logic Device (PLD) (eg, Field Programmable Gate Array (FPGA)) is an integrated circuit whose logic function is determined by user programming of the device. It is programmed by the designer to "integrate" a digital system on a PLD without having to ask the chip manufacturer to design and manufacture a dedicated integrated circuit chip. And, instead of making integrated circuit chips by hand, these days, much of this programming is done using software called a "logic compiler", which is similar to the software compiler used in program development and writing, but before compiling The original code also has to be written in a specific programming language, which is called Hardware Description Language (HDL), and there is not only one HDL, but many kinds, such as ABEL (Advanced Boolean Expression Language) , AHDL (Altera Hardware Description Language), Confluence, CUPL (Cornell University Programming Language), HDCal, JHDL (Java Hardware Description Language), Lava, Lola, MyHDL, PALASM, RHDL (RubyHardware Description Language), etc. The most commonly used are VHDL (Very-High-Speed Integrated Circuit Hardware Description Language) and Verilog. It should also be clear to those skilled in the art that a hardware circuit for implementing the logic method process can be easily obtained by simply programming the method process in the above-mentioned several hardware description languages and programming it into the integrated circuit.
控制器可以按任何适当的方式实现,例如,控制器可以采取例如微处理器或处理器以及存储可由该(微)处理器执行的计算机可读程序代码(例如软件或固件)的计算机可读介质、逻辑门、开关、专用集成电路(Application Specific Integrated Circuit,ASIC)、可编程逻辑控制器和嵌入微控制器的形式,控制器的例子包括但不限于以下微控制器:ARC 625D、Atmel AT91SAM、Microchip PIC18F26K20以及Silicone Labs C8051F320,存储器控制器还可以被实现为存储器的控制逻辑的一部分。本领域技术人员也知道,除了以纯计算机可读程序代码方式实现控制器以外,完全可以通过将方法步骤进行逻辑编程来使得控制器以逻辑门、开关、专用集成电路、可编程逻辑控制器和嵌入微控制器等的形式来实现相同功能。因此这种控制器可以被认为是一种硬件部件,而对其内包括的用于实现各种功能的装置也可以视为硬件部件内的结构。或者甚至,可以将用于实现各种功能的装置视为既可以是实现方法的软件模块又可以是硬件部件内的结构。The controller may be implemented in any suitable manner, for example, the controller may take the form of eg a microprocessor or processor and a computer readable medium storing computer readable program code (eg software or firmware) executable by the (micro)processor , logic gates, switches, application specific integrated circuits (ASICs), programmable logic controllers and embedded microcontrollers, examples of controllers include but are not limited to the following microcontrollers: ARC 625D, Atmel AT91SAM, Microchip PIC18F26K20 and Silicon Labs C8051F320, the memory controller can also be implemented as part of the control logic of the memory. Those skilled in the art also know that, in addition to implementing the controller in the form of pure computer-readable program code, the controller can be implemented as logic gates, switches, application-specific integrated circuits, programmable logic controllers and embedded devices by logically programming the method steps. The same function can be realized in the form of a microcontroller, etc. Therefore, such a controller can be regarded as a hardware component, and the devices included therein for realizing various functions can also be regarded as a structure within the hardware component. Or even, the means for implementing various functions can be regarded as both a software module implementing a method and a structure within a hardware component.
上述实施例阐明的系统、装置、模块或单元,具体可以由计算机芯片或实体实现,或者由具有某种功能的产品来实现。一种典型的实现设备为服务器系统。当然,本说明书不排除随着未来计算机技术的发展,实现上述实施例功能的计算机例如可以为个人计算机、膝上型计算机、车载人机交互设备、蜂窝电话、相机电话、智能电话、个人数字助理、媒体播放器、导航设备、电子邮件设备、游戏控制台、平板计算机、可穿戴设备或者这些设备中的任何设备的组合。The systems, devices, modules or units described in the above embodiments may be specifically implemented by computer chips or entities, or by products with certain functions. A typical implementation device is a server system. Of course, this specification does not exclude that with the development of computer technology in the future, the computer that realizes the functions of the above embodiments may be, for example, a personal computer, a laptop computer, a vehicle-mounted human-computer interaction device, a cellular phone, a camera phone, a smart phone, or a personal digital assistant. , media players, navigation devices, email devices, game consoles, tablets, wearables, or a combination of any of these devices.
虽然本说明书一个或多个实施例提供了如实施例或流程图所述的方法操作步骤,但基于常规或者无创造性的手段可以包括更多或者更少的操作步骤。实施例中列举的步骤顺序仅仅为众多步骤执行顺序中的一种方式,不代表唯一的执行顺序。在实际中的装置或终端产品执行时,可以按照实施例或者附图所示的方法顺序执行或者并行执行(例如并行处理器或者多线程处理的环境,甚至为分布式数据处理环境)。术语“包括”、“包含”或者其任何其他变体意在涵盖非排他性的包含,从而使得包括一系列要素的过程、方法、产品或者设备不仅包括那些要素,而且还包括没有明确列出的其他要素,或者是还包括为这种过程、方法、产品或者设备所固有的要素。在没有更多限制的情况下,并不排除在包括所述要素的过程、方法、产品或者设备中还存在另外的相同或等同要素。例如若使用到第一,第二等词语用来表示名称,而并不表示任何特定的顺序。Although one or more embodiments of the present specification provide method operation steps as described in the embodiments or flow charts, more or less operation steps may be included based on conventional or non-inventive means. The sequence of steps enumerated in the embodiments is only one of the execution sequences of many steps, and does not represent the only execution sequence. When an actual device or terminal product is executed, it can be executed sequentially or in parallel according to the methods shown in the embodiments or the drawings (eg, a parallel processor or multi-threaded processing environment, or even a distributed data processing environment). The terms "comprising", "comprising" or any other variation thereof are intended to encompass a non-exclusive inclusion such that a process, method, product or device comprising a list of elements includes not only those elements, but also others not expressly listed elements, or also include elements inherent to such a process, method, product or device. Without further limitation, it does not preclude the presence of additional identical or equivalent elements in a process, method, product or apparatus comprising the stated elements. For example, words such as first, second, etc. are used to denote names and do not denote any particular order.
为了描述的方便,描述以上装置时以功能分为各种模块分别描述。当然,在实施本说明书一个或多个时可以把各模块的功能在同一个或多个软件和/或硬件中实现,也可以将实现同一功能的模块由多个子模块或子单元的组合实现等。以上所描述的装置实施例仅仅是示意性的,例如,所述单元的划分,仅仅为一种逻辑功能划分,实际实现时可以有另外的划分方式,例如多个单元或组件可以结合或者可以集成到另一个系统,或一些特征可以忽略,或不执行。另一点,所显示或讨论的相互之间的耦合或直接耦合或通信连接可以是通过一些接口,装置或单元的间接耦合或通信连接,可以是电性,机械或其它的形式。For the convenience of description, when describing the above device, the functions are divided into various modules and described respectively. Of course, when implementing one or more of this specification, the functions of each module can be implemented in the same one or more software and/or hardware, and the modules that implement the same function can also be implemented by a combination of multiple sub-modules or sub-units, etc. . The apparatus embodiments described above are only illustrative. For example, the division of the units is only a logical function division. In actual implementation, there may be other division methods. For example, multiple units or components may be combined or integrated. to another system, or some features can be ignored, or not implemented. On the other hand, the shown or discussed mutual coupling or direct coupling or communication connection may be through some interfaces, indirect coupling or communication connection of devices or units, and may be in electrical, mechanical or other forms.
本说明书是参照根据本说明书实施例的方法、装置(系统)、和计算机程序产品的流程图和/或方框图来描述的。应理解可由计算机程序指令实现流程图和/或方框图中的每一流程和/或方框、以及流程图和/或方框图中的流程和/或方框的结合。可提供这些计算机程序指令到通用计算机、专用计算机、嵌入式处理机或其他可编程数据处理设备的处理器以产生一个机器,使得通过计算机或其他可编程数据处理设备的处理器执行的指令产生用于实现在流程图一个流程或多个流程和/或方框图一个方框或多个方框中指定的功能的装置。The specification is described with reference to flowchart illustrations and/or block diagrams of methods, apparatus (systems), and computer program products according to embodiments of the specification. It will be understood that each flow and/or block in the flowchart illustrations and/or block diagrams, and combinations of flows and/or blocks in the flowchart illustrations and/or block diagrams, can be implemented by computer program instructions. These computer program instructions may be provided to the processor of a general purpose computer, special purpose computer, embedded processor or other programmable data processing device to produce a machine such that the instructions executed by the processor of the computer or other programmable data processing device produce Means for implementing the functions specified in a flow or flow of a flowchart and/or a block or blocks of a block diagram.
这些计算机程序指令也可存储在能引导计算机或其他可编程数据处理设备以特定方式工作的计算机可读存储器中,使得存储在该计算机可读存储器中的指令产生包括指令装置的制造品,该指令装置实现在流程图一个流程或多个流程和/或方框图一个方框或多个方框中指定的功能。These computer program instructions may also be stored in a computer-readable memory capable of directing a computer or other programmable data processing apparatus to function in a particular manner, such that the instructions stored in the computer-readable memory result in an article of manufacture comprising instruction means, the instructions The apparatus implements the functions specified in the flow or flow of the flowcharts and/or the block or blocks of the block diagrams.
这些计算机程序指令也可装载到计算机或其他可编程数据处理设备上,使得在计算机或其他可编程设备上执行一系列操作步骤以产生计算机实现的处理,从而在计算机或其他可编程设备上执行的指令提供用于实现在流程图一个流程或多个流程和/或方框图一个方框或多个方框中指定的功能的步骤。These computer program instructions can also be loaded on a computer or other programmable data processing device to cause a series of operational steps to be performed on the computer or other programmable device to produce a computer-implemented process such that The instructions provide steps for implementing the functions specified in the flow or blocks of the flowcharts and/or the block or blocks of the block diagrams.
在一个典型的配置中,计算设备包括一个或多个处理器(CPU)、输入/输出接口、网络接口和内存。In a typical configuration, a computing device includes one or more processors (CPUs), input/output interfaces, network interfaces, and memory.
内存可能包括计算机可读介质中的非永久性存储器,随机存取存储器(RAM)和/或非易失性内存等形式,如只读存储器(ROM)或闪存(flash RAM)。内存是计算机可读介质的示例。Memory may include non-persistent memory in computer readable media, random access memory (RAM) and/or non-volatile memory in the form of, for example, read only memory (ROM) or flash memory (flash RAM). Memory is an example of a computer-readable medium.
计算机可读介质包括永久性和非永久性、可移动和非可移动媒体可以由任何方法或技术来实现信息存储。信息可以是计算机可读指令、数据结构、程序的模块或其他数据。计算机的存储介质的例子包括,但不限于相变内存(PRAM)、静态随机存取存储器(SRAM)、动态随机存取存储器(DRAM)、其他类型的随机存取存储器(RAM)、只读存储器(ROM)、电可擦除可编程只读存储器(EEPROM)、快闪记忆体或其他内存技术、只读光盘只读存储器(CD-ROM)、数字多功能光盘(DVD)或其他光学存储、磁盒式磁带,磁带磁磁盘存储、石墨烯存储或其他磁性存储设备或任何其他非传输介质,可用于存储可以被计算设备访问的信息。按照本文中的界定,计算机可读介质不包括暂存电脑可读媒体(transitory media),如调制的数据信号和载波。Computer-readable media includes both persistent and non-permanent, removable and non-removable media, and storage of information may be implemented by any method or technology. Information may be computer readable instructions, data structures, modules of programs, or other data. Examples of computer storage media include, but are not limited to, phase-change memory (PRAM), static random access memory (SRAM), dynamic random access memory (DRAM), other types of random access memory (RAM), read only memory (ROM), Electrically Erasable Programmable Read Only Memory (EEPROM), Flash Memory or other memory technology, Compact Disc Read Only Memory (CD-ROM), Digital Versatile Disc (DVD) or other optical storage, Magnetic tape cassettes, magnetic tape magnetic disk storage, graphene storage or other magnetic storage devices or any other non-transmission medium that can be used to store information that can be accessed by computing devices. As defined herein, computer-readable media does not include transitory computer-readable media, such as modulated data signals and carrier waves.
本领域技术人员应明白,本说明书一个或多个实施例可提供为方法、系统或计算机程序产品。因此,本说明书一个或多个实施例可采用完全硬件实施例、完全软件实施例或结合软件和硬件方面的实施例的形式。而且,本说明书一个或多个实施例可采用在一个或多个其中包含有计算机可用程序代码的计算机可用存储介质(包括但不限于磁盘存储器、CD-ROM、光学存储器等)上实施的计算机程序产品的形式。As will be appreciated by one skilled in the art, one or more embodiments of this specification may be provided as a method, system or computer program product. Accordingly, one or more embodiments of this specification may take the form of an entirely hardware embodiment, an entirely software embodiment, or an embodiment combining software and hardware aspects. Furthermore, one or more embodiments of the present specification may employ a computer program implemented on one or more computer-usable storage media (including, but not limited to, disk storage, CD-ROM, optical storage, etc.) having computer-usable program code embodied therein form of the product.
本说明书一个或多个实施例可以在由计算机执行的计算机可执行指令的一般上下文中描述,例如程序模块。一般地,程序模块包括执行特定任务或实现特定抽象数据类型的例程、程序、对象、组件、数据结构等等。也可以在分布式计算环境中实践本本说明书一个或多个实施例,在这些分布式计算环境中,由通过通信网络而被连接的远程处理设备来执行任务。在分布式计算环境中,程序模块可以位于包括存储设备在内的本地和远程计算机存储介质中。One or more embodiments of this specification may be described in the general context of computer-executable instructions, such as program modules, being executed by a computer. Generally, program modules include routines, programs, objects, components, data structures, etc. that perform particular tasks or implement particular abstract data types. One or more embodiments of the present specification may also be practiced in distributed computing environments where tasks are performed by remote processing devices that are linked through a communications network. In a distributed computing environment, program modules may be located in both local and remote computer storage media including storage devices.
本说明书中的各个实施例均采用递进的方式描述,各个实施例之间相同相似的部分互相参见即可,每个实施例重点说明的都是与其他实施例的不同之处。尤其,对于系统实施例而言,由于其基本相似于方法实施例,所以描述的比较简单,相关之处参见方法实施例的部分说明即可。在本说明书的描述中,参考术语“一个实施例”、“一些实施例”、“示例”、“具体示例”、或“一些示例”等的描述意指结合该实施例或示例描述的具体特征、结构、材料或者特点包含于本说明书的至少一个实施例或示例中。在本说明书中,对上述术语的示意性表述不必须针对的是相同的实施例或示例。而且,描述的具体特征、结构、材料或者特点可以在任一个或多个实施例或示例中以合适的方式结合。此外,在不相互矛盾的情况下,本领域的技术人员可以将本说明书中描述的不同实施例或示例以及不同实施例或示例的特征进行结合和组合。Each embodiment in this specification is described in a progressive manner, and the same and similar parts between the various embodiments may be referred to each other, and each embodiment focuses on the differences from other embodiments. In particular, as for the system embodiments, since they are basically similar to the method embodiments, the description is relatively simple, and for related parts, please refer to the partial descriptions of the method embodiments. In the description of this specification, description with reference to the terms "one embodiment," "some embodiments," "example," "specific example," or "some examples", etc., mean specific features described in connection with the embodiment or example , structure, material or feature is included in at least one embodiment or example of this specification. In this specification, schematic representations of the above terms are not necessarily directed to the same embodiment or example. Furthermore, the particular features, structures, materials or characteristics described may be combined in any suitable manner in any one or more embodiments or examples. Furthermore, those skilled in the art may combine and combine the different embodiments or examples described in this specification, as well as the features of the different embodiments or examples, without conflicting each other.
以上所述仅为本说明书一个或多个实施例的实施例而已,并不用于限制本本说明书一个或多个实施例。对于本领域技术人员来说,本说明书一个或多个实施例可以有各种更改和变化。凡在本说明书的精神和原理之内所作的任何修改、等同替换、改进等,均应包含在权利要求范围之内。The above descriptions are merely examples of one or more embodiments of the present specification, and are not intended to limit the one or more embodiments of the present specification. Various modifications and variations of the one or more embodiments of this specification are possible for those skilled in the art. Any modification, equivalent replacement, improvement, etc. made within the spirit and principle of this specification shall be included within the scope of the claims.
Claims (23)
Priority Applications (2)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202210325828.9ACN114640451A (en) | 2022-03-29 | 2022-03-29 | Method, system and consensus node for realizing distributed key generation on block chain |
| CN202410688789.8ACN118473659A (en) | 2022-03-29 | 2022-03-29 | Method, system and consensus node for realizing distributed key generation on block chain |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202210325828.9ACN114640451A (en) | 2022-03-29 | 2022-03-29 | Method, system and consensus node for realizing distributed key generation on block chain |
Related Child Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN202410688789.8ADivisionCN118473659A (en) | 2022-03-29 | 2022-03-29 | Method, system and consensus node for realizing distributed key generation on block chain |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| CN114640451Atrue CN114640451A (en) | 2022-06-17 |
Family
ID=81950747
Family Applications (2)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN202210325828.9APendingCN114640451A (en) | 2022-03-29 | 2022-03-29 | Method, system and consensus node for realizing distributed key generation on block chain |
| CN202410688789.8APendingCN118473659A (en) | 2022-03-29 | 2022-03-29 | Method, system and consensus node for realizing distributed key generation on block chain |
Family Applications After (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN202410688789.8APendingCN118473659A (en) | 2022-03-29 | 2022-03-29 | Method, system and consensus node for realizing distributed key generation on block chain |
Country Status (1)
| Country | Link |
|---|---|
| CN (2) | CN114640451A (en) |
Cited By (6)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN115296843A (en)* | 2022-06-29 | 2022-11-04 | 蚂蚁区块链科技(上海)有限公司 | Transaction execution method in blockchain system, first node and second node |
| CN115865341A (en)* | 2022-11-30 | 2023-03-28 | 蚂蚁区块链科技(上海)有限公司 | Method, system and node for realizing distributed key generation on block chain |
| CN115941164A (en)* | 2022-10-31 | 2023-04-07 | 蚂蚁区块链科技(上海)有限公司 | Method, system and node for realizing distributed key generation on block chain |
| CN116015621A (en)* | 2022-11-30 | 2023-04-25 | 蚂蚁区块链科技(上海)有限公司 | Method, system and node for realizing distributed key generation on blockchain |
| CN117318940A (en)* | 2023-11-27 | 2023-12-29 | 山东师范大学 | Multi-party collaborative signature method and system based on authentication secret sharing |
| CN120090809A (en)* | 2025-04-30 | 2025-06-03 | 北京握奇智能科技有限公司 | Digital signature method, system, electronic device, storage medium and program product |
Citations (7)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN101711027A (en)* | 2009-12-22 | 2010-05-19 | 上海大学 | Method for managing dispersed keys based on identities in wireless sensor network |
| CN107395349A (en)* | 2017-08-16 | 2017-11-24 | 深圳国微技术有限公司 | A kind of block chain network cryptographic key distribution method based on self-certified public key system |
| CN110825349A (en)* | 2019-11-14 | 2020-02-21 | 深圳市网心科技有限公司 | Random number generation method, block chain node, system and medium |
| CN111371744A (en)* | 2020-02-21 | 2020-07-03 | 重庆邮电大学 | Byzantine fault-tolerant consensus method based on distributed key |
| CN111385098A (en)* | 2018-12-29 | 2020-07-07 | 华为技术有限公司 | Key generation method and device |
| US20200353167A1 (en)* | 2019-05-08 | 2020-11-12 | Icu Medical, Inc. | Threshold signature based medical device management |
| CN114157427A (en)* | 2021-12-02 | 2022-03-08 | 南京邮电大学 | Threshold signature method based on SM2 digital signature |
- 2022
- 2022-03-29CNCN202210325828.9Apatent/CN114640451A/enactivePending
- 2022-03-29CNCN202410688789.8Apatent/CN118473659A/enactivePending
Patent Citations (7)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN101711027A (en)* | 2009-12-22 | 2010-05-19 | 上海大学 | Method for managing dispersed keys based on identities in wireless sensor network |
| CN107395349A (en)* | 2017-08-16 | 2017-11-24 | 深圳国微技术有限公司 | A kind of block chain network cryptographic key distribution method based on self-certified public key system |
| CN111385098A (en)* | 2018-12-29 | 2020-07-07 | 华为技术有限公司 | Key generation method and device |
| US20200353167A1 (en)* | 2019-05-08 | 2020-11-12 | Icu Medical, Inc. | Threshold signature based medical device management |
| CN110825349A (en)* | 2019-11-14 | 2020-02-21 | 深圳市网心科技有限公司 | Random number generation method, block chain node, system and medium |
| CN111371744A (en)* | 2020-02-21 | 2020-07-03 | 重庆邮电大学 | Byzantine fault-tolerant consensus method based on distributed key |
| CN114157427A (en)* | 2021-12-02 | 2022-03-08 | 南京邮电大学 | Threshold signature method based on SM2 digital signature |
Cited By (9)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN115296843A (en)* | 2022-06-29 | 2022-11-04 | 蚂蚁区块链科技(上海)有限公司 | Transaction execution method in blockchain system, first node and second node |
| CN115296843B (en)* | 2022-06-29 | 2024-04-16 | 蚂蚁区块链科技(上海)有限公司 | Transaction execution method, first node and second node in blockchain system |
| CN115941164A (en)* | 2022-10-31 | 2023-04-07 | 蚂蚁区块链科技(上海)有限公司 | Method, system and node for realizing distributed key generation on block chain |
| WO2024092936A1 (en)* | 2022-10-31 | 2024-05-10 | 蚂蚁区块链科技(上海)有限公司 | Method for realizing distributed key generation on blockchain, system, and node |
| CN115865341A (en)* | 2022-11-30 | 2023-03-28 | 蚂蚁区块链科技(上海)有限公司 | Method, system and node for realizing distributed key generation on block chain |
| CN116015621A (en)* | 2022-11-30 | 2023-04-25 | 蚂蚁区块链科技(上海)有限公司 | Method, system and node for realizing distributed key generation on blockchain |
| CN117318940A (en)* | 2023-11-27 | 2023-12-29 | 山东师范大学 | Multi-party collaborative signature method and system based on authentication secret sharing |
| CN117318940B (en)* | 2023-11-27 | 2024-02-23 | 山东师范大学 | Multiparty collaborative signature method and system based on authentication secret sharing |
| CN120090809A (en)* | 2025-04-30 | 2025-06-03 | 北京握奇智能科技有限公司 | Digital signature method, system, electronic device, storage medium and program product |
Also Published As
| Publication number | Publication date |
|---|---|
| CN118473659A (en) | 2024-08-09 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| CN114650132A (en) | Method, system and consensus node for realizing distributed key generation on block chain | |
| WO2024092935A1 (en) | Method for realizing distributed key generation on blockchain, and system and node | |
| CN114640451A (en) | Method, system and consensus node for realizing distributed key generation on block chain | |
| WO2023185045A1 (en) | Method and system for generating random seed on blockchain, and consensus node | |
| CN114640452B (en) | Method and system for starting distributed key generation process on block chain | |
| CN110832825B (en) | Network method and node for increasing verification speed through tamper-proof data | |
| US20200143366A1 (en) | Methods for decentralized digital asset transfer and smart contract state transition | |
| WO2023185051A1 (en) | Method for generating random number seeds on blockchain, and system and consensus node | |
| CN114640450B (en) | Method and system for realizing retransmission of secret share and determining failure node on block chain | |
| KR20200074911A (en) | Perform recovery process for network nodes in distributed systems | |
| WO2024092936A1 (en) | Method for realizing distributed key generation on blockchain, system, and node | |
| US12008569B2 (en) | Transaction verification system and method of operation thereof | |
| CN113630257B (en) | A consensus method, blockchain system and consensus nodes | |
| CN113645044B (en) | A consensus method, blockchain system and consensus nodes | |
| WO2023056967A1 (en) | Consensus method, blockchain system and consensus nodes | |
| WO2023056976A1 (en) | Consensus method, blockchain system and consensus node | |
| WO2023056964A1 (en) | Consensus method, blockchain system, and consensus node | |
| CN116015621A (en) | Method, system and node for realizing distributed key generation on blockchain | |
| WO2023056966A1 (en) | Consensus method, blockchain system, and consensus node | |
| CN115174048B (en) | Consensus method, system and consensus node | |
| Liu et al. | Kronos: A secure and generic sharding blockchain consensus with optimized overhead | |
| Civit et al. | DARE to agree: Byzantine agreement with optimal resilience and adaptive communication | |
| WO2023185046A1 (en) | Method for rotating consensus nodes in blockchain system, and nodes and blockchain system | |
| CN115865341A (en) | Method, system and node for realizing distributed key generation on block chain | |
| WO2025139338A1 (en) | Certificate issuing method and system, and blockchain node |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| AD01 | Patent right deemed abandoned | ||
| AD01 | Patent right deemed abandoned | Effective date of abandoning:20241122 |