CN114491520A - Application program protection method and related equipment - Google Patents
Application program protection method and related equipmentDownload PDFInfo
- Publication number
- CN114491520A CN114491520ACN202011158204.XACN202011158204ACN114491520ACN 114491520 ACN114491520 ACN 114491520ACN 202011158204 ACN202011158204 ACN 202011158204ACN 114491520 ACN114491520 ACN 114491520A
- Authority
- CN
- China
- Prior art keywords
- program
- execution environment
- protected
- monitoring
- interface
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Pending
Links
Images
Classifications
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/50—Monitoring users, programs or devices to maintain the integrity of platforms, e.g. of processors, firmware or operating systems
- G06F21/55—Detecting local intrusion or implementing counter-measures
- G06F21/56—Computer malware detection or handling, e.g. anti-virus arrangements
- G06F21/566—Dynamic detection, i.e. detection performed at run-time, e.g. emulation, suspicious activities
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F11/00—Error detection; Error correction; Monitoring
- G06F11/36—Prevention of errors by analysis, debugging or testing of software
- G06F11/3698—Environments for analysis, debugging or testing of software
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/10—Protecting distributed programs or content, e.g. vending or licensing of copyrighted material ; Digital rights management [DRM]
- G06F21/12—Protecting executable software
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F9/00—Arrangements for program control, e.g. control units
- G06F9/06—Arrangements for program control, e.g. control units using stored programs, i.e. using an internal store of processing equipment to receive or retain programs
- G06F9/46—Multiprogramming arrangements
- G06F9/48—Program initiating; Program switching, e.g. by interrupt
- G06F9/4806—Task transfer initiation or dispatching
- G06F9/4843—Task transfer initiation or dispatching by program, e.g. task dispatcher, supervisor, operating system
- G06F9/4881—Scheduling strategies for dispatcher, e.g. round robin, multi-level priority queues
Landscapes
- Engineering & Computer Science (AREA)
- Theoretical Computer Science (AREA)
- Software Systems (AREA)
- General Engineering & Computer Science (AREA)
- Physics & Mathematics (AREA)
- Computer Security & Cryptography (AREA)
- Computer Hardware Design (AREA)
- General Physics & Mathematics (AREA)
- Technology Law (AREA)
- Multimedia (AREA)
- Health & Medical Sciences (AREA)
- General Health & Medical Sciences (AREA)
- Virology (AREA)
- Quality & Reliability (AREA)
- Debugging And Monitoring (AREA)
Abstract
Description
Translated fromChinese技术领域technical field
本申请涉及程序安全技术领域,尤其涉及一种应用程序保护方法及相关设备。The present application relates to the technical field of program security, and in particular, to an application program protection method and related equipment.
背景技术Background technique
应用程序安全是指使用软件、硬件和程序方法来防止应用程序受外部威胁。Application security refers to the use of software, hardware, and procedural methods to protect applications from external threats.
在软件设计之后,在开发过程中,安全性变得越来越重要,因为应用程序一旦在网络上可以广泛获得,就很容易受到各种威胁。应用程序内置的安全措施能尽量避免黑客操纵、访问、窃取、修改或删除敏感数据。After software design, during development, security becomes more and more important, as applications are vulnerable to various threats once they are widely available on the web. The security measures built into the application minimize the manipulation, access, theft, modification or deletion of sensitive data by hackers.
现有的应用程序保护方法,黑客仍然能通过一些调试工具或其他手段获得应用程序的核心逻辑,给应用程序开发者带来巨大损失。With the existing application protection methods, hackers can still obtain the core logic of the application through some debugging tools or other means, which brings huge losses to the application developers.
发明内容SUMMARY OF THE INVENTION
本申请实施例提供了一种应用程序保护方法及相关设备,可以更有效的保护应用程序的核心逻辑。The embodiments of the present application provide an application protection method and related equipment, which can more effectively protect the core logic of the application.
本申请实施例的第一方面提供了一种应用程序保护方法,包括:A first aspect of the embodiments of the present application provides an application protection method, including:
创建待保护程序的执行环境监测模拟接口和执行环境监测真实接口;Create the execution environment monitoring simulation interface and the execution environment monitoring real interface of the program to be protected;
创建所述待保护程序的模拟接口和真实接口;Create the simulated interface and the real interface of the program to be protected;
判断接口调用指示,当所述待保护程序的执行环境监测真实接口被调用时,运行执行环境监测真实逻辑,以监测所述待保护程序的执行环境,当所述待保护程序的执行环境监测模拟接口被调用时,不运行执行环境监测真实逻辑;Judging the interface calling instruction, when the execution environment monitoring real interface of the program to be protected is called, run the execution environment monitoring real logic to monitor the execution environment of the program to be protected, when the execution environment monitoring simulation of the program to be protected is simulated When the interface is called, the real logic of the execution environment monitoring is not run;
根据所述待保护程序的执行环境监测真实接口获得的结果数据,执行程序保护逻辑,其中,所述程序保护逻辑包括:若通过所述待保护程序的执行环境监测真实接口获得的结果数据指示监测到所述执行环境存在风险,则不调用所述待保护程序的真实接口和/或调用所述待保护程序的模拟接口,若通过所述待保护程序的执行环境监测真实接口获得的结果数据指示未监测到所述执行环境存在风险,则调用所述待保护程序的真实接口。Execute program protection logic according to the result data obtained by the execution environment monitoring real interface of the program to be protected, wherein the program protection logic includes: if the result data obtained through the execution environment monitoring real interface of the program to be protected indicates monitoring If there is a risk to the execution environment, do not call the real interface of the program to be protected and/or call the simulated interface of the program to be protected, if the result data obtained by monitoring the real interface through the execution environment of the program to be protected indicates that If no risk is detected in the execution environment, the real interface of the program to be protected is called.
可选地,所述判断接口调用指示之前,所述应用程序保护方法还包括:Optionally, before the judging the interface invocation indication, the application protection method further includes:
获取所述待保护程序的执行设备的唯一标识信息,其中,所述唯一标识信息包括:所述执行设备的CPU序列号或磁盘序列号;Obtain the unique identification information of the execution device of the program to be protected, wherein the unique identification information includes: the CPU serial number or disk serial number of the executing device;
若所述唯一标识信息指示所述执行设备的运行环境曾存在风险,则执行程序保护逻辑。If the unique identification information indicates that the operating environment of the execution device has been at risk, program protection logic is executed.
可选地,运行执行环境监测真实逻辑,以监测所述待保护程序的执行环境的步骤之前,所述方法还包括:Optionally, before running the execution environment monitoring real logic to monitor the execution environment of the program to be protected, the method further includes:
接收服务器发来的所述待保护程序的执行设备的身份信息;receiving the identity information of the execution device of the program to be protected from the server;
若所述身份信息指示所述执行设备为If the identity information indicates that the execution device is
高权限用户,则不对所述待保护程序的执行环境进行监测;For high-privileged users, the execution environment of the program to be protected is not monitored;
若所述身份信息指示所述执行设备为非高权限用户,则监测所述待保护程序的执行环境。If the identity information indicates that the execution device is a non-high-authority user, the execution environment of the program to be protected is monitored.
可选地,所述运行执行环境监测真实逻辑,以监测所述待保护程序的执行环境,具体包括:Optionally, the running execution environment monitoring real logic to monitor the execution environment of the to-be-protected program specifically includes:
每间隔预定时间,遍历当前运行的所有进程;Traverse all currently running processes at predetermined time intervals;
根据预设监测规则对所述进程进行监测,以判断所述进程中是否存在调试工具,若存在调试工具,则表示所述待保护程序的执行环境存在风险。The process is monitored according to a preset monitoring rule to determine whether a debugging tool exists in the process. If there is a debugging tool, it means that the execution environment of the program to be protected is at risk.
可选地,所述根据预设监测规则对所述进程进行监测,具体包括:Optionally, the monitoring of the process according to a preset monitoring rule specifically includes:
监测所述进程的名称是否与预设调试工具名称相同,若监测到所述进程的名称与预设教师工具名称相同,则判定执行环境中存在调试工具;和/或Monitor whether the name of the process is the same as the name of the preset debugging tool, and if the name of the monitored process is the same as the name of the preset teacher tool, it is determined that a debugging tool exists in the execution environment; and/or
监测所述进程是否有特征代码与预设调试工具的特征代码相同,若监测到所述进程有特征代码与预设调试工具的特征代码相同,则判定执行环境中存在调试工具;和/或Monitoring whether the process has a feature code that is the same as the feature code of the preset debugging tool, and if it is detected that the process has the feature code that is the same as the feature code of the preset debugging tool, it is determined that there is a debugging tool in the execution environment; and/or
监测所述进程加载的程序模块是否与预设程序模块相同,若监测所述进程加载的程序模块与预设程序模块相同,则判定执行环境中存在调试工具;和/或Monitoring whether the program module loaded by the process is the same as the preset program module, and if the program module loaded by the monitoring process is the same as the preset program module, it is determined that a debugging tool exists in the execution environment; and/or
监测所述进程创建的窗口名称是否与预设窗口名称相同,若监测所述进程创建的窗口名称与预设窗口名称相同,则判定执行环境中存在调试工具;和/或Monitoring whether the name of the window created by the process is the same as the name of the preset window, and if the name of the window created by the monitoring process is the same as the name of the preset window, it is determined that a debugging tool exists in the execution environment; and/or
监测所述进程是否附加有其他进程,若监测所述进程附加有其他进程,则判定执行环境中存在调试工具;和/或Monitoring whether the process is attached to other processes, and if monitoring the process is attached to other processes, it is determined that a debugging tool exists in the execution environment; and/or
监测所述进程的执行时间是否超过预设执行时间,若监测所述进程的执行时间超过预设执行时间,则判定执行环境中存在调试工具。Whether the execution time of the process exceeds the preset execution time is monitored, and if the execution time of the monitored process exceeds the preset execution time, it is determined that a debugging tool exists in the execution environment.
可选的,所述监测所述待保护程序的执行环境的步骤之前,所述方法还包括:Optionally, before the step of monitoring the execution environment of the program to be protected, the method further includes:
更新监测所述待保护程序的执行环境待使用的实例变量。An instance variable to be used for monitoring the execution environment of the program to be protected is updated.
可选的,所述通过所述待保护程序的执行环境监测真实接口获得的结果数据模板参数为且使用智能指针Optionally, the result data template parameter obtained by monitoring the real interface of the execution environment of the program to be protected is and uses a smart pointer.
unique_ptr通过函数unique_ptr pass function
unique_ptr<MockCheckData>mockcheck=make_unique<MockCheckData>()限定其不可复制,unique_ptr<MockCheckData>mockcheck=make_unique<MockCheckData>() restricts it to not be copied,
其中,MockCheckData为上述待保护程序的执行环境监测真实接口获得的结果数据。Wherein, MockCheckData is the result data obtained by the execution environment monitoring real interface of the program to be protected.
本申请实施例第二方面提供了一种应用程序保护装置,包括:A second aspect of the embodiments of the present application provides an application protection device, including:
第一虚拟模块集成单元,用于创建待保护程序的执行环境监测模拟接口和执行环境监测真实接口;a first virtual module integration unit, used to create an execution environment monitoring simulation interface and an execution environment monitoring real interface of the program to be protected;
第二虚拟模块集成单元,用于创建所述待保护程序的模拟接口和真实接口;a second virtual module integration unit, used to create a simulated interface and a real interface of the program to be protected;
监测单元,用于判断接口调用指示,当所述待保护程序的执行环境监测真实接口被调用时,运行执行环境监测真实逻辑,以监测所述待保护程序的执行环境,当所述待保护程序的执行环境监测模拟接口被调用时,不运行执行环境监测真实逻辑;The monitoring unit is used for judging the interface calling instruction, when the execution environment monitoring real interface of the program to be protected is called, run the execution environment monitoring real logic to monitor the execution environment of the program to be protected, when the program to be protected is called When the execution environment monitoring simulation interface is called, the real logic of execution environment monitoring is not executed;
处理单元,用于根据所述待保护程序的执行环境监测真实接口获得的结果数据,执行程序保护逻辑,其中,所述程序保护逻辑包括:若通过所述待保护程序的执行环境监测真实接口获得的结果数据指示监测到所述执行环境存在风险,则不调用所述待保护程序的真实接口和/或调用所述待保护程序的模拟接口,若通过所述待保护程序的执行环境监测真实接口获得的结果数据指示未监测到所述执行环境存在风险,则调用所述待保护程序的真实接口。a processing unit, configured to execute program protection logic according to the result data obtained by monitoring the real interface of the execution environment of the program to be protected, wherein the program protection logic includes: if the execution environment of the program to be protected is obtained by monitoring the real interface The result data indicates that there is a risk in monitoring the execution environment, the real interface of the program to be protected is not called and/or the simulated interface of the program to be protected is called, if the real interface is monitored through the execution environment of the program to be protected If the obtained result data indicates that the execution environment is not at risk, the real interface of the program to be protected is called.
本申请实施例第三方面提供了一种电子设备,包括存储器、处理器,所述处理器用于执行存储器中存储的计算机程序时实现上述的应用程序保护方法的步骤。A third aspect of an embodiment of the present application provides an electronic device, including a memory and a processor, where the processor is configured to implement the steps of the foregoing application program protection method when executing a computer program stored in the memory.
本申请实施例第四方面提供了一种计算机可读存储介质,其上存储有计算机程序,所述计算机程序被处理器执行时实现上述的应用程序保护方法的步骤。A fourth aspect of the embodiments of the present application provides a computer-readable storage medium on which a computer program is stored, and when the computer program is executed by a processor, implements the steps of the foregoing application program protection method.
综上,本申请实施例提供的应用程序保护方法,通过创建待保护程序的执行环境监测模拟接口、待保护程序的执行环境监测真实接口、待保护程序的模拟接口和待保护程序的真实接口,从而将虚拟模块集成到待保护程序中;另外通过监测上述待保护程序的执行环境,并在上述待保护程序的执行环境监测真实接口获得的结果数据指示该执行环境存在风险时,执行程序保护逻辑,其中,上述程序保护逻辑包括:不执行上述待保护程序和/或调用上述待保护程序的模拟接口,用以在监测到执行环境存在风险时,避免执行应用程序的核心逻辑,这样既模拟了执行环境监测逻辑又模拟了应用程序中核心逻辑的执行,从而对应用程序进行双重保护,提高了应用程序的安全性。To sum up, the application program protection method provided by the embodiments of the present application, by creating an execution environment monitoring simulation interface of the program to be protected, a real interface of the execution environment monitoring of the program to be protected, a simulation interface of the program to be protected, and a real interface of the program to be protected, Thus, the virtual module is integrated into the program to be protected; in addition, by monitoring the execution environment of the program to be protected, and when the result data obtained from the execution environment of the program to be protected is monitored by the real interface and indicates that the execution environment is at risk, the program protection logic is executed. , wherein the program protection logic includes: not executing the program to be protected and/or calling the simulation interface of the program to be protected, so as to avoid executing the core logic of the application program when the execution environment is monitored to be at risk, thus simulating both The execution environment monitoring logic simulates the execution of the core logic in the application program, so as to double-protect the application program and improve the security of the application program.
相应地,本发明实施例提供的电子设备和计算机可读存储介质,也同样具有上述技术效果。Correspondingly, the electronic device and the computer-readable storage medium provided by the embodiments of the present invention also have the above technical effects.
附图说明Description of drawings
图1为本申请实施例提供的一种可能的应用程序保护方法的流程示意图;1 is a schematic flowchart of a possible application protection method provided by an embodiment of the present application;
图2为本申请实施例提供的一种可能的应用程序保护装置的示意性结构框图;FIG. 2 is a schematic structural block diagram of a possible application protection device provided by an embodiment of the present application;
图3为本申请实施例提供的一种可能的应用程序保护装置的硬件结构示意图;3 is a schematic diagram of the hardware structure of a possible application protection device provided by an embodiment of the present application;
图4为本申请实施例提供的一种可能的电子设备的示意性结构框图;FIG. 4 is a schematic structural block diagram of a possible electronic device provided by an embodiment of the present application;
图5为本申请实施例提供的一种可能的计算机可读存储介质的示意性结构框图。FIG. 5 is a schematic structural block diagram of a possible computer-readable storage medium provided by an embodiment of the present application.
具体实施方式Detailed ways
本申请实施例提供了一种应用程序保护方法及相关设备,可以更有效的保护应用程序的核心逻辑。The embodiments of the present application provide an application protection method and related equipment, which can more effectively protect the core logic of the application.
本申请的说明书和权利要求书及上述附图中的术语“第一”、“第二”、“第三”、“第四”等(如果存在)是用于区别类似的对象,而不必用于描述特定的顺序或先后次序。应该理解这样使用的数据在适当情况下可以互换,以便这里描述的实施例能够以除了在这里图示或描述的内容以外的顺序实施。此外,术语“包括”和“具有”以及他们的任何变形,意图在于覆盖不排他的包含,例如,包含了一系列步骤或单元的过程、方法、系统、产品或设备不必限于清楚地列出的那些步骤或单元,而是可包括没有清楚地列出的或对于这些过程、方法、产品或设备固有的其它步骤或单元。下面将结合本申请实施例中的附图,对本申请实施例中的技术方案进行清楚、完整地描述,显然,所描述的实施例仅仅是本申请一部分实施例,而不是全部的实施例。The terms "first", "second", "third", "fourth", etc. (if any) in the description and claims of this application and the above-mentioned drawings are used to distinguish similar objects and are not necessarily used to describe a specific order or sequence. It is to be understood that data so used may be interchanged under appropriate circumstances so that the embodiments described herein can be practiced in sequences other than those illustrated or described herein. Furthermore, the terms "comprising" and "having" and any variations thereof, are intended to cover non-exclusive inclusion, for example, a process, method, system, product or device comprising a series of steps or units is not necessarily limited to those expressly listed Rather, those steps or units may include other steps or units not expressly listed or inherent to these processes, methods, products or devices. The technical solutions in the embodiments of the present application will be clearly and completely described below with reference to the drawings in the embodiments of the present application. Obviously, the described embodiments are only a part of the embodiments of the present application, but not all of the embodiments.
请参阅图1,为本申请实施例提供的一种应用程序保护方法的流程图,具体可以包括:S110-S140。Please refer to FIG. 1 , which is a flowchart of an application program protection method provided by an embodiment of the present application, which may specifically include: S110-S140.
S110,创建待保护程序的执行环境监测模拟接口和执行环境监测真实接口。S110: Create an execution environment monitoring simulation interface and an execution environment monitoring real interface of the program to be protected.
具体地,上述待保护程序可以是在互联网中发布的用户端程序。例如,直播软件的电脑客户端程序或直播软件的手机客户端程序。在对应用程序进行保护时,需要对应用程序的执行环境进行检测,执行环境的检测目的是识别当前是在正常环境执行还是异常环境执行。例如,应用程序可能在黑客的电脑上执行,或者是当前程序处于被调试等异常环境。Specifically, the above program to be protected may be a client program published on the Internet. For example, the computer client program of the live broadcast software or the mobile phone client program of the live broadcast software. When protecting an application, it is necessary to detect the execution environment of the application. The purpose of detecting the execution environment is to identify whether it is currently executing in a normal environment or an abnormal environment. For example, the application may be executed on the hacker's computer, or the current program is in an abnormal environment such as being debugged.
上述模拟接口可以基于mock模拟获得,而mock模拟测试通常用于对开发后的代码进行测试,用于模拟程序中的接口,从而便于测试代码。因此,mock功能一般是在开发阶段用于测试代码的正确性,而在应用程序发布时则不随程序一起发布。The above simulation interface can be obtained based on mock simulation, and the mock simulation test is usually used to test the developed code, and is used to simulate the interface in the program, so as to facilitate the testing of the code. Therefore, the mock function is generally used to test the correctness of the code in the development phase, and is not released with the program when the application is released.
由于mock具有可以动态的修改执行逻辑的特性,使得可以通过创建待保护程序的执行环境监测模拟接口,降低执行环境监测程序被破解的风险,提高应用程序的安全性。Since the mock has the characteristic of dynamically modifying the execution logic, the execution environment monitoring simulation interface of the program to be protected can be created, the risk of the execution environment monitoring program being cracked is reduced, and the security of the application program is improved.
上述应用程序保护方法,除了可以对外提供经mock的待保护程序的执行环境监测模拟接口,也可以提供待保护程序的执行环境监测真实接口,以便调用待保护程序的执行环境监测的真实程序。具体地,可以通过getDevice_base来定义执行环境监测真实接口,保证应用程序自身能够调用真实的环境监测程序来进行执行环境的监测。The above application protection method can not only provide the mocked execution environment monitoring simulation interface of the program to be protected, but also provide the execution environment monitoring real interface of the to-be-protected program, so as to call the real program of the execution environment monitoring of the to-be-protected program. Specifically, the real interface of execution environment monitoring can be defined through getDevice_base, so as to ensure that the application program itself can call the real environment monitoring program to monitor the execution environment.
S120,创建上述待保护程序的模拟接口和真实接口。S120, creating the above simulation interface and real interface of the program to be protected.
相应的,由于mock具有可以动态的修改执行逻辑的特性,使得可以通过创建待保护程序的模拟接口,可以极大的提高真实逻辑执行的复杂度,进一步降低应用程序被破解的风险,提高应用程序的安全性。Correspondingly, since the mock has the characteristics of dynamically modifying the execution logic, it is possible to create a mock interface of the program to be protected, which can greatly improve the complexity of the real logic execution, further reduce the risk of application program being cracked, and improve the application program. security.
具体地,可以通过Class Core和Specifically, through Class Core and
Virtual void CoreLogic(Check*check)=0语句来定义应用程序核心逻辑的真实接口,其中,核心逻辑真实接口有个模板参数,需要传入一个参数,参数类型则是Check的基类指针,便于后续扩展执行环境监测的不同具体逻辑,并也可以此来将应用程序核心逻辑的执行与Check环境监测逻辑进行关联。具体实现如下:The virtual void CoreLogic(Check*check)=0 statement defines the real interface of the core logic of the application. The real interface of the core logic has a template parameter, which needs to be passed in. The parameter type is the base class pointer of Check, which is convenient for subsequent The different specific logics of the execution environment monitoring are expanded, and the execution of the core logic of the application program can also be associated with the Check environment monitoring logic. The specific implementation is as follows:
class MockCore:public Coreclass MockCore: public Core
MOCK_METHOD(void,CoreLogic,(Check*check))MOCK_METHOD(void,CoreLogic,(Check*check))
其中,可以将核心逻辑的mock类取名为MockCore,并通过Void CoreLogic_base()定义调用真实核心逻辑的功能接口。Among them, the mock class of the core logic can be named MockCore, and the function interface for calling the real core logic can be defined through Void CoreLogic_base().
另外,可以通过Core*pCoreInstance=new MockCore(),创建mock功能的MockCore实例,从而提供了对核心逻辑执行的保护功能。In addition, a MockCore instance of the mock function can be created through Core*pCoreInstance=new MockCore(), thereby providing a protection function for the execution of the core logic.
S130,判断接口调用指示,当上述待保护程序的执行环境监测真实接口被调用时,运行执行环境监测真实逻辑,以监测上述待保护程序的执行环境,当上述待保护程序的执行环境监测模拟接口被调用时,不运行执行环境监测真实逻辑。S130, judging the interface calling instruction, when the execution environment monitoring real interface of the program to be protected is called, run the execution environment monitoring real logic to monitor the execution environment of the program to be protected, and when the execution environment monitoring simulation interface of the program to be protected is called When called, the execution environment monitoring real logic is not run.
具体地,可以通过调用上述待保护程序的执行环境监测接口,来对待保护程序的执行环境进行监测。由于通过mock功能设置了待保护程序的执行环境监测虚拟端口,极大增加了黑客取待保护程序的执行环境监测真实接口的复杂度,从而提高了破解待保护程序的执行环境监测逻辑的难度。Specifically, the execution environment of the program to be protected can be monitored by calling the execution environment monitoring interface of the program to be protected. Since the virtual port for monitoring the execution environment of the program to be protected is set through the mock function, it greatly increases the complexity for hackers to obtain the real interface for monitoring the execution environment of the program to be protected, thereby increasing the difficulty of cracking the execution environment monitoring logic of the program to be protected.
S140,根据上述待保护程序的执行环境监测真实接口获得的结果数据,执行程序保护逻辑,其中,上述程序保护逻辑包括:若通过上述待保护程序的执行环境监测真实接口获得的结果数据指示监测到上述执行环境存在风险,则不调用上述待保护程序的真实接口和/或调用上述待保护程序的模拟接口,若通过上述待保护程序的执行环境监测真实接口获得的结果数据指示未监测到上述执行环境存在风险,则调用上述待保护程序的真实接口。在一些示例中,若通过上述待保护程序的执行环境监测真实接口获得的结果数据指示上述执行环境存在风险,则需要对待保护程序进行保护操作,可以是不执行上述待保护程序,也可以是调用上述待保护程序的模拟接口,避免黑客所感知到应用程序核心逻辑的执行,因为应用程序的核心逻辑不执行,所以黑客也无法调试分析应用程序的核心逻辑代码,从而保护对应代码的安全性。上述实施例提供的应用程序保护方法巧妙的利用了mock的特性来进行一系列的程序保护动作,从而将真实核心逻辑的执行安全的保护起来。S140: Execute program protection logic according to the result data obtained by the execution environment monitoring real interface of the program to be protected, wherein the program protection logic includes: if the result data obtained through the execution environment monitoring real interface of the program to be protected indicates that monitoring There is a risk in the above-mentioned execution environment, then the real interface of the above-mentioned program to be protected is not called and/or the simulated interface of the above-mentioned program to be protected is not called, if the result data obtained by monitoring the real interface of the above-mentioned program to be protected by the execution environment of the above-mentioned program to be protected indicates that the above-mentioned execution is not monitored. If the environment is at risk, call the real interface of the program to be protected above. In some examples, if the result data obtained through the execution environment monitoring real interface of the program to be protected indicates that the execution environment is at risk, it is necessary to perform a protection operation on the program to be protected, either by not executing the program to be protected, or by calling the program to be protected. The above simulation interface of the program to be protected prevents the hacker from perceiving the execution of the core logic of the application program. Because the core logic of the application program is not executed, the hacker cannot debug and analyze the core logic code of the application program, thereby protecting the security of the corresponding code. The application program protection method provided by the above-mentioned embodiment skillfully utilizes the characteristics of mock to perform a series of program protection actions, thereby safely protecting the execution of the real core logic.
可以通过以下语句来实现,通过执行环境监测逻辑来判断执行环境是否存在风险,进而确定是否执行应用程序的真实核心逻辑的功能:It can be achieved by the following statement, and the execution environment monitoring logic is used to judge whether there is a risk in the execution environment, and then determine whether to execute the function of the real core logic of the application:
EXPECT_CALL(*pCoreInstance,CoreLogic()).WillRepeatedly(Invoke([&](Check*check){EXPECT_CALL(*pCoreInstance,CoreLogic()).WillRepeatedly(Invoke([&](Check*check){
If(check->EnvironmentCheck(mockcheck)){If(check->EnvironmentCheck(mockcheck)){
}else{}else{
CoreLogic_base();CoreLogic_base();
}}
其中,可以基于参数check来查看当前环境是否存在问题,如果执行环境存在风险,即check->EnvironmentCheck(mockcheck),可以不调用待保护程序的真实接口,也就是不执行待保护程序,那么这里可以什么也不做,如果执行环境不存在风险,则可以调用CoreLogic_base()执行待保护程序。综上,本申请实施例提供的应用程序保护方法,通过创建待保护程序的执行环境监测模拟接口、待保护程序的执行环境监测真实接口、待保护程序的模拟接口和待保护程序的真实接口,从而将虚拟模块集成到待保护程序中;另外通过监测上述待保护程序的执行环境,并在上述待保护程序的执行环境监测真实接口获得的结果数据指示该执行环境存在风险时,执行程序保护逻辑,其中,上述程序保护逻辑包括:不执行上述待保护程序和/或调用上述待保护程序的模拟接口,用以在监测到执行环境存在风险时,避免执行应用程序的核心逻辑,这样既模拟了执行环境监测逻辑又模拟了应用程序中核心逻辑的执行,从而对应用程序进行双重保护,提高了应用程序的安全性。Among them, you can check whether there is a problem in the current environment based on the parameter check. If there is a risk in the execution environment, that is, check->EnvironmentCheck(mockcheck), you can not call the real interface of the program to be protected, that is, not execute the program to be protected, then you can Do nothing, if the execution environment is not at risk, you can call CoreLogic_base() to execute the program to be protected. To sum up, the application program protection method provided by the embodiments of the present application, by creating an execution environment monitoring simulation interface of the program to be protected, a real interface of the execution environment monitoring of the program to be protected, a simulation interface of the program to be protected, and a real interface of the program to be protected, Thus, the virtual module is integrated into the program to be protected; in addition, by monitoring the execution environment of the program to be protected, and when the result data obtained from the execution environment of the program to be protected is monitored by the real interface and indicates that the execution environment is at risk, the program protection logic is executed. , wherein the program protection logic includes: not executing the program to be protected and/or calling the simulation interface of the program to be protected, so as to avoid executing the core logic of the application program when the execution environment is monitored to be at risk, thus simulating both The execution environment monitoring logic simulates the execution of the core logic in the application program, so as to double-protect the application program and improve the security of the application program.
为了能够快速识别曾经已经认定存在风险的硬件执行环境,从而不经执行环境监测而直接执行程序保护逻辑,进而提高应用程序保护的效率,因此在上述判断接口调用指示之前,上述应用程序保护方法还可以包括:In order to quickly identify the hardware execution environment that has been identified as having a risk, so as to directly execute the program protection logic without monitoring the execution environment, thereby improving the efficiency of application program protection, before the above-mentioned judgment of the interface calling instruction, the above-mentioned application program protection method also Can include:
获取上述待保护程序的执行设备的唯一标识信息;Obtain the unique identification information of the execution device of the above-mentioned program to be protected;
若上述唯一标识信息指示上述执行设备的运行环境曾存在风险,则执行程序保护逻辑。If the above-mentioned unique identification information indicates that the operating environment of the above-mentioned execution device has been at risk, the program protection logic is executed.
其中,上述执行设备的唯一标识信息可以执行设备无法变更的信息,例如,执行设备的CPU序列号、磁盘序列号等,以用于唯一标识这台设备。示例性的,在发现黑客的设备后,可以通过该唯一标识信息对黑客设备总是指向异常逻辑,而不执行应用程序的核心逻辑代码。The above-mentioned unique identification information of the executing device may be information that cannot be changed by the executing device, such as the CPU serial number and disk serial number of the executing device, so as to uniquely identify the device. Exemplarily, after the hacker's device is discovered, the unique identification information can always point to the abnormal logic to the hacker's device without executing the core logic code of the application.
上述指示上述执行设备的运行环境曾存在风险的信息可以通过服务器主动获取,服务器在接收到上述唯一标识信息后下发到相应客户端应用程序。具体地,可以通过创建一个gmock类来mock每个接口,从而接口的调用可以依据与服务器动态下发数据来表明该客户端是否需要进行环境监测的功能。class MockCheckData:public CheckData;用于表示mock类取名为MockCheckData。MOCK_METHOD(string,getDevice,();用于表示mock获取设备接口,从而获得执行设备的唯一标识信息。The above-mentioned information indicating that the operating environment of the above-mentioned execution device has a risk may be actively acquired by the server, and the server will deliver the above-mentioned unique identification information to the corresponding client application program after receiving the above-mentioned unique identification information. Specifically, each interface can be mocked by creating a gmock class, so that the invocation of the interface can indicate whether the client needs to perform the function of environment monitoring according to the data dynamically delivered to the server. class MockCheckData: public CheckData; used to indicate that the mock class is named MockCheckData. MOCK_METHOD(string, getDevice, (); is used to indicate that the mock obtains the device interface, thereby obtaining the unique identification information of the executing device.
根据一些实施例,监测上述待保护程序的执行环境的步骤之前,上述方法还可以包括:According to some embodiments, before the step of monitoring the execution environment of the program to be protected, the above method may further include:
接收服务器发来的上述待保护程序的执行设备的身份信息;Receive the identity information of the execution device of the above-mentioned program to be protected from the server;
若上述身份信息指示上述执行设备为非高权限用户,则监测上述待保护程序的执行环境。If the above-mentioned identity information indicates that the above-mentioned execution device is a non-high-authority user, the execution environment of the above-mentioned program to be protected is monitored.
在一些示例中,上述身份信息可以是客户端用户的等级,若用户被标记为VIP,则代表该用户拥有较高权限,可以不监测上述待保护程序的执行环境。相反,如果用户被标记为低权限用户,就需要监测上述待保护程序的执行环境。In some examples, the above-mentioned identity information may be the level of the client user. If the user is marked as a VIP, it means that the user has higher authority, and the execution environment of the above-mentioned program to be protected may not be monitored. On the contrary, if the user is marked as a low-privileged user, it is necessary to monitor the execution environment of the above-mentioned program to be protected.
具体地,服务器认为该用户属于高级VIP用户,不存在风险,可以不去执行环境监测相关的功能,而对于有风险的用户再可以开启环境监测。上述身份信息可以是服务器主动下发,或客户端程序自动向服务器获取得到,在此不做限定。Specifically, the server considers that the user is an advanced VIP user, and there is no risk, and may not perform functions related to environmental monitoring, but can turn on environmental monitoring for users at risk. The above-mentioned identity information may be actively issued by the server, or automatically obtained by the client program from the server, which is not limited herein.
在一些示例中,可以通过以下语句来实现,通过接收到服务器信息确定用户是否为VIP,来确定是否调用执行环境监测的功能:In some examples, the following statement can be used to determine whether to invoke the function of performing environment monitoring by determining whether the user is a VIP by receiving server information:
EXPECT_CALL(*mockcheck.get(),getDevice()).WillRepeatedly(Invoke([&](){EXPECT_CALL(*mockcheck.get(),getDevice()).WillRepeatedly(Invoke([&](){
If(isvip){If(isvip){
return string()return string()
}else{}else{
Return getDevice_base()Return getDevice_base()
}))}))
其中,isvip标记是服务器对该用户是判断数据,isvip为true表示是一个vip用户,那么此时则直接返回一个空的字符串表明执行环境不存在风险,不执行环境监测,否则需要执行环境监测。在一些示例中,可以通过以下语句来实现,通过接收到服务器信息确定用户是否为VIP,来确定是否调用用来判断是否存在调试工具名称的执行环境监测的功能:Among them, the isvip flag is the server's judgment data for the user, and isvip is true to indicate that it is a vip user, then an empty string is directly returned to indicate that there is no risk in the execution environment, and environmental monitoring is not performed. Otherwise, environmental monitoring needs to be performed. . In some examples, the following statement can be used to determine whether the user is a VIP by receiving server information to determine whether to invoke the execution environment monitoring function for judging whether the name of the debugging tool exists:
EXPECT_CALL(*mockcheck.get(),CheckDebugTool()).WillRepeatedly(Invoke([&](){EXPECT_CALL(*mockcheck.get(),CheckDebugTool()).WillRepeatedly(Invoke([&](){
If(isvip){If(isvip){
return falsereturn false
}else{}else{
Return CheckDebugTool_base()Return CheckDebugTool_base()
}))}))
其中,isvip标记是服务器对该用户是判断数据,isvip为true表示是一个vip用户,那么此时则直接返回false执行环境中表明没有调试工具,则不需要执行判断调试工具名称的执行环境监测的逻辑。Among them, the isvip flag means that the server is the judgment data for the user, and isvip is true to indicate that it is a vip user, then it will directly return false in the execution environment to indicate that there is no debugging tool, and there is no need to execute the execution environment monitoring for judging the name of the debugging tool. logic.
具体地,可以通过以下语句来实现,通过接收到服务器信息确定用户是否为VIP,来确定是否调用用来判断是否存在附加进程的执行环境监测的功能:Specifically, it can be implemented by the following statement, by receiving server information to determine whether the user is a VIP, to determine whether to invoke the execution environment monitoring function used to determine whether there is an additional process:
EXPECT_CALL(*mockcheck.get(),CheckAttach()).WillRepeatedly(Invoke([&](){EXPECT_CALL(*mockcheck.get(),CheckAttach()).WillRepeatedly(Invoke([&](){
If(isvip){If(isvip){
return falsereturn false
}else{}else{
Return CheckAttach_base()Return CheckAttach_base()
}))}))
其中,isvip标记是服务器对该用户是判断数据,isvip为true表示是一个vip用户,那么此时则直接返回false执行环境中表明没有调试工具,则不需要执行判断附加进程的执行环境监测的逻辑。Among them, the isvip flag means that the server is the judgment data for the user, and isvip is true to indicate that it is a vip user, then it will directly return false in the execution environment to indicate that there is no debugging tool, and there is no need to execute the execution environment monitoring logic for judging the attached process. .
具体地,为了避免长时间没有监测硬件的执行环境而存在漏检现象,上述监测上述待保护程序的执行环境,具体可以包括:Specifically, in order to avoid the phenomenon of missing detection without monitoring the execution environment of the hardware for a long time, the above-mentioned monitoring of the execution environment of the program to be protected may specifically include:
每间隔预定时间,遍历当前运行的所有进程;Traverse all currently running processes at predetermined time intervals;
根据预设监测规则对上述进程进行监测,以判断上述进程中是否存在调试工具,若存在调试工具,则表示上述待保护程序的执行环境存在风险。The above process is monitored according to the preset monitoring rules to determine whether there is a debugging tool in the above process. If there is a debugging tool, it means that the execution environment of the above-mentioned program to be protected is at risk.
具体地,可以每间隔一定的时间检测一次应用程序的执行环境,例如,可以是5分钟检测一次,或者每隔更短的时间检测一次,从而保障不会存在漏检情况。Specifically, the execution environment of the application program may be detected at a certain interval, for example, the detection may be performed once every 5 minutes, or the detection may be performed at a shorter time interval, so as to ensure that there is no missed detection.
在一些示例中,上述根据预设监测规则对上述进程进行监测,具体可以包括:In some examples, the above process is monitored according to preset monitoring rules, which may specifically include:
可以监测上述进程的名称是否与预设调试工具名称相同,若监测到上述进程的名称与预设教师工具名称相同,则判定执行环境中存在调试工具;在一些示例中,可以设计一个类Class CheckData表示依据执行环境的信息来监测的类。其中,可以采用接口Virtualstring getDevice()获取设备信息,具体则是获取执行设备相关的数据,并返回对应的数据。在一些示例中,可以通过监测上述进程的名称,检测上述运行环境是否存在常用的调试工具,存在则说明当前有打开调试工具。例如,进程是否有打开静态代码调试工具如ida.exe,动态代码调试工具如windbg或ollydbg。可以通过函数Virtual boolCheckDebugTool(),定义此接口是用于获取调试工具的接口,包含上述监测调试工具的功能,返回结果则是用于返回是否具有调试工具。并且,具体地,可以通过以下语句mock获取监测调试工具的接口:You can monitor whether the name of the above process is the same as the name of the default debugging tool. If the name of the monitored process is the same as the name of the default teacher tool, it is determined that there is a debugging tool in the execution environment; in some examples, you can design a class Class CheckData Represents a class to monitor based on information about the execution environment. Among them, the interface Virtualstring getDevice() can be used to obtain the device information, and specifically, the data related to the execution device is obtained, and the corresponding data is returned. In some examples, it can be detected by monitoring the name of the above-mentioned process whether there is a commonly used debugging tool in the above-mentioned running environment, and the existence of the above-mentioned debugging tool indicates that a debugging tool is currently opened. For example, whether the process has open static code debugging tools such as ida.exe, dynamic code debugging tools such as windbg or ollydbg. The function Virtual boolCheckDebugTool() can be used to define this interface as an interface for obtaining debugging tools, including the functions of the above monitoring and debugging tools, and the returned result is used to return whether there is a debugging tool. And, specifically, the interface of the monitoring and debugging tool can be obtained through the following statement mock:
MOCK_METHOD(bool,CheckDebugTool,())MOCK_METHOD(bool,CheckDebugTool,())
和/或and / or
可以监测上述进程是否有特征代码与预设调试工具的特征代码相同,若监测到上述进程有特征代码与预设调试工具的特征代码相同,则判定执行环境中存在调试工具;在一些示例中,可以事先收集上述调试工具的特征代码,通过遍历所有进程,在每个进程中搜索是否存在收集到的特征代码,如果存在则说明有调试工具。可以进一步防止黑客修改了调试工具的名称而无法查找的情况。例如,收集ida.exe的代码特征,从而通过对比进程的代码特征就可以查找到是否存在对应的进程。It is possible to monitor whether the above-mentioned process has the same feature code as that of the preset debugging tool, and if it is detected that the above-mentioned process has the same feature code as that of the preset debugging tool, it is determined that a debugging tool exists in the execution environment; in some examples, The feature codes of the above debugging tools can be collected in advance, and by traversing all processes, each process is searched for whether the collected feature codes exist. If there is, it means that there is a debugging tool. This can further prevent hackers from changing the name of the debugging tool and not being able to find it. For example, the code features of ida.exe are collected, so that whether there is a corresponding process can be found by comparing the code features of the process.
和/或and / or
可以监测上述进程加载的程序模块是否与预设程序模块相同,若监测上述进程加载的程序模块与预设程序模块相同,则判定执行环境中存在调试工具;在一些示例中,可以通过收集调试工具的核心模块的名称,然后对比进程加载的所有模块是否都包含收集的核心模块名称,如果包含则可以识别该进程是调试工具。It is possible to monitor whether the program module loaded by the above-mentioned process is the same as the preset program module. If the program module loaded by the above-mentioned process is the same as the preset program module, it is determined that a debugging tool exists in the execution environment; in some examples, debugging tools can be collected by collecting debugging tools. The name of the core module, and then compare whether all the modules loaded by the process contain the collected core module name, if so, it can identify the process as a debugging tool.
和/或and / or
可以监测上述进程创建的窗口名称是否与预设窗口名称相同,若监测上述进程创建的窗口名称与预设窗口名称相同,则判定执行环境中存在调试工具;在一些示例中,可以通过遍历当前的窗口名称,因为调试工具会创建窗口,并且每个窗口都有对应的名称,因此,通过收集调试工具的名称,可以通过遍历系统的所有窗口来查找是否有打开调试工具。可以通过函数Virtual book CheckWindows(),定义此接口是用于监测当前程序是否有调试窗口,其返回结果则表明是否有。并且,具体地,可以通过以下语句mock获取监测进程调试窗口:It can be monitored whether the name of the window created by the above process is the same as the name of the preset window. If the name of the window created by the monitoring process is the same as the name of the preset window, it is determined that a debugging tool exists in the execution environment; Window name, because the debugging tool will create a window, and each window has a corresponding name, so by collecting the name of the debugging tool, you can find whether there is a debugging tool open by traversing all the windows of the system. The function Virtual book CheckWindows() can be used to define this interface to monitor whether the current program has a debug window, and the returned result indicates whether there is. And, specifically, you can obtain the monitoring process debugging window through the following statement mock:
MOCK_METHOD(bool,CheckWindows,())MOCK_METHOD(bool,CheckWindows,())
和/或and / or
可以监测上述进程是否附加有其他进程,若监测上述进程附加有其他进程,则判定执行环境中存在调试工具;在一些示例中,可以通过检测当前进程是否有被附加其他的进程,如果有被附加则说明程序被调试。可以通过函数Virtual book CheckAttach(),定义此接口是用于监测当前程序是否被附加调试了,其返回结果则表明是否被附加。并且,具体地,可以通过以下语句mock获取监测进程被附加的接口:It is possible to monitor whether the above process is attached to other processes. If the above process is monitored to be attached to other processes, it is determined that there is a debugging tool in the execution environment; in some examples, it can be detected by detecting whether the current process is attached to other processes, if any are attached. The program is debugged. The function Virtual book CheckAttach() can be used to define this interface to monitor whether the current program is attached and debugged, and the return result indicates whether it is attached. And, specifically, the interface to which the monitoring process is attached can be obtained through the following statement mock:
MOCK_METHOD(bool,CheckAttach,())MOCK_METHOD(bool,CheckAttach,())
和/或and / or
可以监测上述进程的执行时间是否超过预设执行时间,若监测上述进程的执行时间超过预设执行时间,则判定执行环境中存在调试工具。Whether the execution time of the above process exceeds the preset execution time can be monitored, and if the execution time of the monitored process exceeds the preset execution time, it is determined that a debugging tool exists in the execution environment.
需要说明的是,上述的所有方法只要有一种满足监测规则,就可以识别到调试程序,并且上述的调试工具查找方法可以并行进行,并且每个监测规则需要开启一个独立的线程。String getDevice_base();这里由于程序执行中会存在调用真实检测的情况,因此需要提供调用真实监测接口的接口。可以采用上述getDevice_base接口实际调用了基类的getDevice方法来获取执行设备的信息。It should be noted that as long as one of the above methods satisfies the monitoring rules, the debugger can be identified, and the above methods for finding debugging tools can be performed in parallel, and each monitoring rule needs to open an independent thread. String getDevice_base(); Here, since the real detection may be called in the program execution, it is necessary to provide an interface for calling the real monitoring interface. The above-mentioned getDevice_base interface can be used to actually call the getDevice method of the base class to obtain the information of the executing device.
Return CheckData::getDevice();Return CheckData::getDevice();
bool CheckDebugTool_base();其中,CheckDebugTool也一样实现一个基类的调用方法。bool CheckDebugTool_base(); Among them, CheckDebugTool also implements a base class calling method.
Return CheckData::CheckDebugTool();Return CheckData::CheckDebugTool();
bool CheckAttach_base();其中,CheckAttach也一样实现一个基类的调用方法。bool CheckAttach_base(); Among them, CheckAttach also implements a base class calling method.
Return CheckData::CheckAttach();Return CheckData::CheckAttach();
bool CheckWindows_base();其中,CheckWindows也一样实现一个基类的调用方法。bool CheckWindows_base(); Among them, CheckWindows also implements the calling method of a base class.
Return CheckData::CheckWindows();这样环境监测程序对外提供了mock的接口,也提供了真实调用环境监测程序的接口。Return CheckData::CheckWindows(); In this way, the environment monitoring program provides a mock interface to the outside world, and also provides an interface for actually calling the environment monitoring program.
为了进一步确执行保环境监测逻辑的安全,根据一些实施例,上述监测上述待保护程序的执行环境的步骤之前,上述方法还包括:In order to further ensure the security of the execution environment monitoring logic, according to some embodiments, before the above step of monitoring the execution environment of the program to be protected, the above method further includes:
更新监测上述待保护程序的执行环境待使用的实例变量。Update the instance variables to be used for monitoring the execution environment of the program to be protected.
示例性的,为了保障对环境监测结果数据的安全性,每次监测都会创建一个新的实例,并且使用完成后会自动销毁,这样数据都是新创建的,从而其内存是新分配的,不易于被黑客所hook和查找到。Exemplarily, in order to ensure the security of the data of environmental monitoring results, a new instance will be created for each monitoring, and will be automatically destroyed after use, so that the data is newly created, and its memory is newly allocated, not Easy to be hooked and found by hackers.
根据一些实施例,通过上述待保护程序的执行环境监测真实接口获得的结果数据模板参数为且使用智能指针限定其不可复制。According to some embodiments, the result data template parameter obtained through the above-mentioned execution environment monitoring real interface of the program to be protected is , and a smart pointer is used to limit that it cannot be copied.
示例性的,上述智能指针可以是unique_ptr指针,表明整个程序中只有一份,不能进行拷贝。Exemplarily, the above smart pointer may be a unique_ptr pointer, indicating that there is only one copy in the entire program and cannot be copied.
考虑到后续可能会存在不同类型的环境监测结果数据,为了能够适应后续不同类型环境监测结果数据的扩展,以及接口的变更。在一些示例中,上述待保护程序的执行环境监测真实接口获得的结果数据在使用了unique_ptr指针的同时也可以是一个模板参数。具体地,在定义执行环境监测逻辑时可以通过以下代码实现:Considering that there may be different types of environmental monitoring result data in the future, in order to be able to adapt to the subsequent expansion of different types of environmental monitoring result data, as well as the change of the interface. In some examples, the result data obtained by the execution environment monitoring real interface of the program to be protected may also be a template parameter while using the unique_ptr pointer. Specifically, when defining the execution environment monitoring logic, it can be implemented by the following code:
Class Check{Class Check{
Public:Public:
Template<typename T>Template<typename T>
Virtual bool EnvironmentCheck(unique_ptr<T>data)=0;Virtual bool EnvironmentCheck(unique_ptr<T>data) = 0;
其中,可以特例化具体的模板参数类型T来实现不同的环境监测结果数据,从而能够支持多种环境监测接口EnvironmentCheck。在EnvironmentCheck中会调用检测类的所有接口,只要有一个检测是有风险的,则认为程序执行环境是具有风险的。并且,在一些示例中,可以通过以下语句创建一个唯一实例化对象mockcheck用以保障环境监测过程的安全:Among them, a specific template parameter type T can be specialized to realize different environmental monitoring result data, so that various environmental monitoring interfaces EnvironmentCheck can be supported. All interfaces of the detection class will be called in EnvironmentCheck. As long as one detection is risky, the program execution environment is considered to be risky. And, in some examples, a uniquely instantiated object mockcheck can be created to secure the environment monitoring process with the following statement:
unique_ptr<MockCheckData>mockcheck=make_unique<MockCheckData>()unique_ptr<MockCheckData>mockcheck=make_unique<MockCheckData>()
上面对本申请实施例中应用程序保护方法进行了描述,下面对本申请实施例中的应用程序保护装置进行描述。The application protection method in the embodiment of the present application is described above, and the application protection device in the embodiment of the present application is described below.
请参阅图2,本申请实施例中应用程序保护装置的一个实施例,可以包括:Referring to FIG. 2, an embodiment of the application protection device in the embodiment of the present application may include:
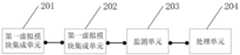
第一虚拟模块集成单元201,用于创建待保护程序的执行环境监测模拟接口和真实接口;The first virtual
第二虚拟模块集成单元202,用于创建上述待保护程序的模拟接口和真实接口;The second virtual
监测单元203,用于判断接口调用指示,当上述待保护程序的执行环境监测真实接口被调用时,运行执行环境监测真实逻辑,以监测上述待保护程序的执行环境,当上述待保护程序的执行环境监测模拟接口被调用时,不运行执行环境监测真实逻辑;The
处理单元204,用于根据上述待保护程序的执行环境监测真实接口获得的结果数据,执行程序保护逻辑,其中,上述程序保护逻辑包括:若通过上述待保护程序的执行环境监测真实接口获得的结果数据指示监测到上述执行环境存在风险,则不调用上述待保护程序的真实接口和/或调用上述待保护程序的模拟接口,若通过上述待保护程序的执行环境监测真实接口获得的结果数据指示未监测到上述执行环境存在风险,则调用上述待保护程序的真实接口。The
综上,上述实施例提供的应用程序保护装置,通过创建待保护程序的执行环境监测模拟接口、待保护程序的执行环境监测真实接口、待保护程序的模拟接口和待保护程序的真实接口,从而将虚拟模块集成到待保护程序中;另外通过监测上述待保护程序的执行环境,并在上述待保护程序的执行环境监测真实接口获得的结果数据指示该执行环境存在风险时,执行程序保护逻辑,其中,上述程序保护逻辑包括:不执行上述待保护程序和/或调用上述待保护程序的模拟接口,用以在监测到执行环境存在风险时,避免执行应用程序的核心逻辑,这样既模拟了执行环境监测逻辑又模拟了应用程序中核心逻辑的执行,从而对应用程序进行双重保护,提高了应用程序的安全性。To sum up, the application protection device provided by the above-mentioned embodiment, by creating the execution environment monitoring simulation interface of the program to be protected, the execution environment monitoring real interface of the program to be protected, the simulation interface of the program to be protected, and the real interface of the program to be protected, thereby Integrate the virtual module into the program to be protected; in addition, by monitoring the execution environment of the program to be protected, and when the result data obtained by the execution environment of the program to be protected monitoring the real interface indicates that the execution environment is at risk, the program protection logic is executed, The above-mentioned program protection logic includes: not executing the above-mentioned program to be protected and/or calling the simulation interface of the above-mentioned program to be protected, so as to avoid executing the core logic of the application program when a risk in the execution environment is detected, which not only simulates execution The environment monitoring logic simulates the execution of the core logic in the application program, so as to double-protect the application program and improve the security of the application program.
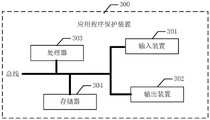
上面图2从模块化功能实体的角度对本申请实施例中的应用程序保护装置进行了描述,下面从硬件处理的角度对本申请实施例中的应用程序保护装置进行详细描述,请参阅图3,本申请实施例中的应用程序保护装置300一个实施例,包括:FIG. 2 above describes the application protection device in the embodiment of the present application from the perspective of modular functional entities. The following describes the application protection device in the embodiment of the present application in detail from the perspective of hardware processing. An embodiment of the
输入装置301、输出装置302、处理器303和存储器304,其中,处理器303的数量可以一个或多个,图3中以一个处理器303为例。在本申请的一些实施例中,输入装置301、输出装置502、处理器303和存储器304可通过总线或其它方式连接,其中,图3中以通过总线连接为例。The
其中,通过调用存储器304存储的操作指令,处理器303,用于执行如下步骤:Wherein, by calling the operation instructions stored in the
创建待保护程序的执行环境监测模拟接口和真实接口;Create the execution environment monitoring simulation interface and real interface of the program to be protected;
创建上述待保护程序的模拟接口和真实接口;Create the simulated interface and real interface of the above program to be protected;
监测上述待保护程序的执行环境;Monitor the execution environment of the above programs to be protected;
若通过上述待保护程序的执行环境监测真实接口获得的结果数据指示上述执行环境存在风险,则执行程序保护逻辑,其中,上述程序保护逻辑包括:不执行上述待保护程序和/或调用上述待保护程序的模拟接口。If the result data obtained through the execution environment monitoring real interface of the program to be protected indicates that the execution environment is at risk, program protection logic is executed, wherein the program protection logic includes: not executing the program to be protected and/or calling the program to be protected The program's mock interface.
通过调用存储器304存储的操作指令,处理器303,还用于执行图1对应的实施例中的任一方式。By calling the operation instructions stored in the
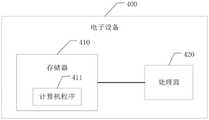
请参阅图4,图4为本申请实施例提供的电子设备的实施例示意图。Please refer to FIG. 4 , which is a schematic diagram of an embodiment of an electronic device provided by an embodiment of the present application.
如图4所示,本申请实施例提供了一种电子设备,包括存储器410、处理器420及存储在存储器420上并可在处理器420上运行的计算机程序411,处理器420执行计算机程序411时实现以下步骤:As shown in FIG. 4 , an embodiment of the present application provides an electronic device, including a
创建待保护程序的执行环境监测模拟接口和真实接口;Create the execution environment monitoring simulation interface and real interface of the program to be protected;
创建上述待保护程序的模拟接口和真实接口;Create the simulated interface and real interface of the above program to be protected;
监测上述待保护程序的执行环境;Monitor the execution environment of the above programs to be protected;
若通过上述待保护程序的执行环境监测真实接口获得的结果数据指示上述执行环境存在风险,则执行程序保护逻辑,其中,上述程序保护逻辑包括:不执行上述待保护程序和/或调用上述待保护程序的模拟接口。If the result data obtained through the execution environment monitoring real interface of the program to be protected indicates that the execution environment is at risk, program protection logic is executed, wherein the program protection logic includes: not executing the program to be protected and/or calling the program to be protected The program's mock interface.
在具体实施过程中,处理器420执行计算机程序411时,可以实现图1对应的实施例中任一实施方式。In a specific implementation process, when the
由于本实施例所介绍的电子设备为实施本申请实施例中一种应用程序保护装置所采用的设备,故而基于本申请实施例中所介绍的方法,本领域所属技术人员能够了解本实施例的电子设备的具体实施方式以及其各种变化形式,所以在此对于该电子设备如何实现本申请实施例中的方法不再详细介绍,只要本领域所属技术人员实施本申请实施例中的方法所采用的设备,都属于本申请所欲保护的范围。Since the electronic device introduced in this embodiment is a device used for implementing an application program protection device in this embodiment, based on the method introduced in this embodiment, those skilled in the art can understand the The specific implementation of the electronic device and its various variations, so how the electronic device implements the methods in the embodiments of the present application will not be described in detail here, as long as those skilled in the art implement the methods in the embodiments of the present application. equipment, all belong to the scope of protection of this application.
请参阅图5,图5为本申请实施例提供的一种计算机可读存储介质的实施例示意图。Please refer to FIG. 5, which is a schematic diagram of an embodiment of a computer-readable storage medium provided by an embodiment of the present application.
如图5所示,本实施例提供了一种计算机可读存储介质500,其上存储有计算机程序511,该计算机程序511被处理器执行时实现如下步骤:As shown in FIG. 5 , this embodiment provides a computer-
创建待保护程序的执行环境监测模拟接口和真实接口;Create the execution environment monitoring simulation interface and real interface of the program to be protected;
创建上述待保护程序的模拟接口和真实接口;Create the simulated interface and real interface of the above program to be protected;
监测上述待保护程序的执行环境;Monitor the execution environment of the above programs to be protected;
若通过上述待保护程序的执行环境监测真实接口获得的结果数据指示上述执行环境存在风险,则执行程序保护逻辑,其中,上述程序保护逻辑包括:不执行上述待保护程序和/或调用上述待保护程序的模拟接口。If the result data obtained through the execution environment monitoring real interface of the program to be protected indicates that the execution environment is at risk, program protection logic is executed, wherein the program protection logic includes: not executing the program to be protected and/or calling the program to be protected The program's mock interface.
在具体实施过程中,该计算机程序511被处理器执行时可以实现图1对应的实施例中任一实施方式。In a specific implementation process, when the
需要说明的是,在上述实施例中,对各个实施例的描述都各有侧重,某个实施例中没有详细描述的部分,可以参见其它实施例的相关描述。It should be noted that, in the foregoing embodiments, the description of each embodiment has its own emphasis, and for parts that are not described in detail in a certain embodiment, reference may be made to the relevant descriptions of other embodiments.
本领域内的技术人员应明白,本申请的实施例可提供为方法、系统、或计算机程序产品。因此,本申请可采用完全硬件实施例、完全软件实施例、或结合软件和硬件方面的实施例的形式。而且,本申请可采用在一个或多个其中包含有计算机可用程序代码的计算机可用存储介质(包括但不限于磁盘存储器、CD-ROM、光学存储器等)上实施的计算机程序产品的形式。As will be appreciated by those skilled in the art, the embodiments of the present application may be provided as a method, a system, or a computer program product. Accordingly, the present application may take the form of an entirely hardware embodiment, an entirely software embodiment, or an embodiment combining software and hardware aspects. Furthermore, the present application may take the form of a computer program product embodied on one or more computer-usable storage media (including, but not limited to, disk storage, CD-ROM, optical storage, etc.) having computer-usable program code embodied therein.
本申请是参照根据本申请实施例的方法、设备(系统)、和计算机程序产品的流程图和/或方框图来描述。应理解可由计算机程序指令实现流程图和/或方框图中的每一流程和/或方框、以及流程图和/或方框图中的流程和/或方框的结合。可提供这些计算机程序指令到通用计算机、专用计算机、嵌入式计算机或者其他可编程数据处理设备的处理器以产生一个机器,使得通过计算机或其他可编程数据处理设备的处理器执行的指令产生用于实现在流程图一个流程或多个流程和/或方框图一个方框或多个方框中指定的功能的装置。The present application is described with reference to flowchart illustrations and/or block diagrams of methods, apparatus (systems), and computer program products according to embodiments of the present application. It will be understood that each flow and/or block in the flowchart illustrations and/or block diagrams, and combinations of flows and/or blocks in the flowchart illustrations and/or block diagrams, can be implemented by computer program instructions. These computer program instructions may be provided to the processor of a general purpose computer, special purpose computer, embedded computer or other programmable data processing device to produce a machine such that the instructions executed by the processor of the computer or other programmable data processing device produce Means implementing the functions specified in one or more of the flowcharts and/or one or more blocks of the block diagrams.
这些计算机程序指令也可存储在能引导计算机或其他可编程数据处理设备以特定方式工作的计算机可读存储器中,使得存储在该计算机可读存储器中的指令产生包括指令装置的制造品,该指令装置实现在流程图一个流程或多个流程和/或方框图一个方框或多个方框中指定的功能。These computer program instructions may also be stored in a computer-readable memory capable of directing a computer or other programmable data processing apparatus to function in a particular manner, such that the instructions stored in the computer-readable memory result in an article of manufacture comprising instruction means, the instructions The apparatus implements the functions specified in the flow or flow of the flowcharts and/or the block or blocks of the block diagrams.
这些计算机程序指令也可装载到计算机或其他可编程数据处理设备上,使得在计算机或其他可编程设备上执行一系列操作步骤以产生计算机实现的处理,从而在计算机或其他可编程设备上执行的指令提供用于实现在流程图一个流程或多个流程和/或方框图一个方框或多个方框中指定的功能的步骤。These computer program instructions can also be loaded on a computer or other programmable data processing device to cause a series of operational steps to be performed on the computer or other programmable device to produce a computer-implemented process such that The instructions provide steps for implementing the functions specified in the flow or blocks of the flowcharts and/or the block or blocks of the block diagrams.
本申请实施例还提供了一种计算机程序产品,该计算机程序产品包括计算机软件指令,当计算机软件指令在处理设备上运行时,使得处理设备执行如图1对应实施例中的应用程序保护方法中的流程。The embodiment of the present application also provides a computer program product, the computer program product includes computer software instructions, when the computer software instructions are executed on the processing device, the processing device is made to execute the application protection method in the embodiment corresponding to FIG. 1 . process.
所述计算机程序产品包括一个或多个计算机指令。在计算机上加载和执行所述计算机程序指令时,全部或部分地产生按照本申请实施例所述的流程或功能。所述计算机可以是通用计算机、专用计算机、计算机网络、或者其他可编程装置。所述计算机指令可以存储在计算机可读存储介质中,或者从一个计算机可读存储介质向另一计算机可读存储介质传输,例如,所述计算机指令可以从一个网站站点、计算机、服务器或数据中心通过有线(例如同轴电缆、光纤、数字用户线(digital subscriber line,DSL))或无线(例如红外、无线、微波等)方式向另一个网站站点、计算机、服务器或数据中心进行传输。所述计算机可读存储介质可以是计算机能够存储的任何可用介质或者是包含一个或多个可用介质集成的服务器、数据中心等数据存储设备。所述可用介质可以是磁性介质,(例如,软盘、硬盘、磁带)、光介质(例如,DVD)、或者半导体介质(例如固态硬盘(solid state disk,SSD))等。The computer program product includes one or more computer instructions. When the computer program instructions are loaded and executed on a computer, all or part of the processes or functions described in the embodiments of the present application are generated. The computer may be a general purpose computer, special purpose computer, computer network, or other programmable device. The computer instructions may be stored in or transmitted from one computer-readable storage medium to another computer-readable storage medium, for example, the computer instructions may be downloaded from a website site, computer, server, or data center Transmission to another website site, computer, server, or data center by wire (eg, coaxial cable, optical fiber, digital subscriber line (DSL)) or wireless (eg, infrared, wireless, microwave, etc.). The computer-readable storage medium may be any available medium that can be stored by a computer, or a data storage device such as a server, data center, etc., which includes one or more available media integrated. The usable media may be magnetic media (eg, floppy disks, hard disks, magnetic tapes), optical media (eg, DVDs), or semiconductor media (eg, solid state disks (SSDs)), and the like.
所属领域的技术人员可以清楚地了解到,为描述的方便和简洁,上述描述的系统,装置和单元的具体工作过程,可以参考前述方法实施例中的对应过程,在此不再赘述。Those skilled in the art can clearly understand that, for the convenience and brevity of description, the specific working process of the system, device and unit described above may refer to the corresponding process in the foregoing method embodiments, which will not be repeated here.
在本申请所提供的几个实施例中,应该理解到,所揭露的系统,装置和方法,可以通过其它的方式实现。例如,以上所描述的装置实施例仅仅是示意性的,例如,所述单元的划分,仅仅为一种逻辑功能划分,实际实现时可以有另外的划分方式,例如多个单元或组件可以结合或者可以集成到另一个系统,或一些特征可以忽略,或不执行。另一点,所显示或讨论的相互之间的耦合或直接耦合或通信连接可以是通过一些接口,装置或单元的间接耦合或通信连接,可以是电性,机械或其它的形式。In the several embodiments provided in this application, it should be understood that the disclosed system, apparatus and method may be implemented in other manners. For example, the apparatus embodiments described above are only illustrative. For example, the division of the units is only a logical function division. In actual implementation, there may be other division methods. For example, multiple units or components may be combined or Can be integrated into another system, or some features can be ignored, or not implemented. On the other hand, the shown or discussed mutual coupling or direct coupling or communication connection may be through some interfaces, indirect coupling or communication connection of devices or units, and may be in electrical, mechanical or other forms.
所述作为分离部件说明的单元可以是或者也可以不是物理上分开的,作为单元显示的部件可以是或者也可以不是物理单元,即可以位于一个地方,或者也可以分布到多个网络单元上。可以根据实际的需要选择其中的部分或者全部单元来实现本实施例方案的目的。The units described as separate components may or may not be physically separated, and components displayed as units may or may not be physical units, that is, may be located in one place, or may be distributed to multiple network units. Some or all of the units may be selected according to actual needs to achieve the purpose of the solution in this embodiment.
另外,在本申请各个实施例中的各功能单元可以集成在一个处理单元中,也可以是各个单元单独物理存在,也可以两个或两个以上单元集成在一个单元中。上述集成的单元既可以采用硬件的形式实现,也可以采用软件功能单元的形式实现。In addition, each functional unit in each embodiment of the present application may be integrated into one processing unit, or each unit may exist physically alone, or two or more units may be integrated into one unit. The above-mentioned integrated units may be implemented in the form of hardware, or may be implemented in the form of software functional units.
所述集成的单元如果以软件功能单元的形式实现并作为独立的产品销售或使用时,可以存储在一个计算机可读取存储介质中。基于这样的理解,本申请的技术方案本质上或者说对现有技术做出贡献的部分或者该技术方案的全部或部分可以以软件产品的形式体现出来,该计算机软件产品存储在一个存储介质中,包括若干指令用以使得一台计算机设备(可以是个人计算机,服务器,或者网络设备等)执行本申请各个实施例所述方法的全部或部分步骤。而前述的存储介质包括:U盘、移动硬盘、只读存储器(Read-Only Memory,ROM)、随机存取存储器(Random Access Memory,RAM)、磁碟或者光盘等各种可以存储程序代码的介质。The integrated unit, if implemented in the form of a software functional unit and sold or used as an independent product, may be stored in a computer-readable storage medium. Based on this understanding, the technical solutions of the present application can be embodied in the form of software products in essence, or the parts that contribute to the prior art, or all or part of the technical solutions, and the computer software products are stored in a storage medium , including several instructions for causing a computer device (which may be a personal computer, a server, or a network device, etc.) to execute all or part of the steps of the methods described in the various embodiments of the present application. The aforementioned storage medium includes: U disk, mobile hard disk, read-only memory (Read-Only Memory, ROM), random access memory (Random Access Memory, RAM), magnetic disk or optical disk and other media that can store program codes .
以上所述,以上实施例仅用以说明本申请的技术方案,而非对其限制;尽管参照前述实施例对本申请进行了详细的说明,本领域的普通技术人员应当理解:其依然可以对前述各实施例所记载的技术方案进行修该,或者对其中部分技术特征进行等同替换;而这些修该或者替换,并不使相应技术方案的本质脱离本申请各实施例技术方案的精神和范围。As mentioned above, the above embodiments are only used to illustrate the technical solutions of the present application, but not to limit them; although the present application has been described in detail with reference to the foregoing embodiments, those of ordinary skill in the art should understand: The technical solutions recorded in the embodiments are modified, or some technical features thereof are equivalently replaced; and these modifications or replacements do not make the essence of the corresponding technical solutions deviate from the spirit and scope of the technical solutions in the embodiments of the present application.
Claims (10)
Translated fromChinesePriority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202011158204.XACN114491520A (en) | 2020-10-26 | 2020-10-26 | Application program protection method and related equipment |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202011158204.XACN114491520A (en) | 2020-10-26 | 2020-10-26 | Application program protection method and related equipment |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| CN114491520Atrue CN114491520A (en) | 2022-05-13 |
Family
ID=81470235
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN202011158204.XAPendingCN114491520A (en) | 2020-10-26 | 2020-10-26 | Application program protection method and related equipment |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN114491520A (en) |
Citations (7)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN103164643A (en)* | 2011-12-08 | 2013-06-19 | 北京深思洛克软件技术股份有限公司 | Method and device using hardware to debug |
| CN104267994A (en)* | 2014-09-30 | 2015-01-07 | 北京奇虎科技有限公司 | Application running device and terminal device |
| CN104866734A (en)* | 2014-02-25 | 2015-08-26 | 北京娜迦信息科技发展有限公司 | DEX (Dalvik VM executes) file protecting method and device |
| CN106126981A (en)* | 2016-08-30 | 2016-11-16 | 电子科技大学 | The software security means of defence replaced based on virtual function table |
| CN106650341A (en)* | 2016-11-18 | 2017-05-10 | 湖南鼎源蓝剑信息科技有限公司 | Android application reinforcement method based on the process confusion technology |
| CN106778104A (en)* | 2017-01-20 | 2017-05-31 | 武汉斗鱼网络科技有限公司 | A kind of anti-debug method and system of application program |
| CN107463810A (en)* | 2017-08-15 | 2017-12-12 | 合肥爱吾宠科技有限公司 | The method that protecting computer software is realized based on network communication |
- 2020
- 2020-10-26CNCN202011158204.XApatent/CN114491520A/enactivePending
Patent Citations (7)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN103164643A (en)* | 2011-12-08 | 2013-06-19 | 北京深思洛克软件技术股份有限公司 | Method and device using hardware to debug |
| CN104866734A (en)* | 2014-02-25 | 2015-08-26 | 北京娜迦信息科技发展有限公司 | DEX (Dalvik VM executes) file protecting method and device |
| CN104267994A (en)* | 2014-09-30 | 2015-01-07 | 北京奇虎科技有限公司 | Application running device and terminal device |
| CN106126981A (en)* | 2016-08-30 | 2016-11-16 | 电子科技大学 | The software security means of defence replaced based on virtual function table |
| CN106650341A (en)* | 2016-11-18 | 2017-05-10 | 湖南鼎源蓝剑信息科技有限公司 | Android application reinforcement method based on the process confusion technology |
| CN106778104A (en)* | 2017-01-20 | 2017-05-31 | 武汉斗鱼网络科技有限公司 | A kind of anti-debug method and system of application program |
| CN107463810A (en)* | 2017-08-15 | 2017-12-12 | 合肥爱吾宠科技有限公司 | The method that protecting computer software is realized based on network communication |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| JP7531816B2 (en) | Image-based malicious code detection method and device and artificial intelligence-based endpoint threat detection and response system using the same | |
| KR102017756B1 (en) | Apparatus and method for detecting abnormal behavior | |
| US8762948B1 (en) | System and method for establishing rules for filtering insignificant events for analysis of software program | |
| CN107609396B (en) | An escape detection method based on sandbox virtual machine | |
| RU2757597C1 (en) | Systems and methods for reporting computer security incidents | |
| CN111683084B (en) | A smart contract intrusion detection method, device, terminal device and storage medium | |
| CN106874763A (en) | The Android software malicious act triggering system and method for modelling customer behavior | |
| CN105069354A (en) | Attack tree model based Android software hybrid detection method | |
| CN105718793A (en) | Method and system for preventing malicious code from identifying sandbox on the basis of sandbox environment modification | |
| Tang et al. | Towards dynamically monitoring android applications on non-rooted devices in the wild | |
| CN108073499A (en) | The test method and device of application program | |
| JP5613000B2 (en) | Application characteristic analysis apparatus and program | |
| CN113572719A (en) | Domain name detection method, apparatus, device and readable storage medium | |
| US20240419810A1 (en) | Non-Intrusive Method of Detecting Security Flaws of a Computer Program | |
| CN114546857A (en) | Interface test case generation method and device, electronic device, and storage medium | |
| CN111274585B (en) | Method, device, equipment and medium for detecting unauthorized vulnerability of Web application | |
| CN109190376A (en) | A kind of Web page wooden horse detecting method, system and electronic equipment and storage medium | |
| CN114491520A (en) | Application program protection method and related equipment | |
| CN112632547A (en) | Data processing method and related device | |
| CN107798244A (en) | A kind of method and device for detecting Remote Code Execution Vulnerability | |
| CN117609995A (en) | Industrial control system security protection methods, devices, terminal equipment and storage media | |
| CN114070580B (en) | Anti-serialization attack detection method, device, electronic equipment, medium and program | |
| Ali et al. | Source code analysis for mobile applications for privacy leaks | |
| TW202319944A (en) | Verification method and verification system for information and communication security protection mechanism | |
| CN115470479A (en) | Authority control method of application program, electronic device and storage medium |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination |