CN114372801A - A kind of identification method of biometric information and related device - Google Patents
A kind of identification method of biometric information and related deviceDownload PDFInfo
- Publication number
- CN114372801A CN114372801ACN202011102334.1ACN202011102334ACN114372801ACN 114372801 ACN114372801 ACN 114372801ACN 202011102334 ACN202011102334 ACN 202011102334ACN 114372801 ACN114372801 ACN 114372801A
- Authority
- CN
- China
- Prior art keywords
- target
- information
- key
- end service
- module
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Pending
Links
Images
Classifications
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06Q—INFORMATION AND COMMUNICATION TECHNOLOGY [ICT] SPECIALLY ADAPTED FOR ADMINISTRATIVE, COMMERCIAL, FINANCIAL, MANAGERIAL OR SUPERVISORY PURPOSES; SYSTEMS OR METHODS SPECIALLY ADAPTED FOR ADMINISTRATIVE, COMMERCIAL, FINANCIAL, MANAGERIAL OR SUPERVISORY PURPOSES, NOT OTHERWISE PROVIDED FOR
- G06Q20/00—Payment architectures, schemes or protocols
- G06Q20/38—Payment protocols; Details thereof
- G06Q20/40—Authorisation, e.g. identification of payer or payee, verification of customer or shop credentials; Review and approval of payers, e.g. check credit lines or negative lists
- G06Q20/401—Transaction verification
- G06Q20/4014—Identity check for transactions
- G06Q20/40145—Biometric identity checks
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06Q—INFORMATION AND COMMUNICATION TECHNOLOGY [ICT] SPECIALLY ADAPTED FOR ADMINISTRATIVE, COMMERCIAL, FINANCIAL, MANAGERIAL OR SUPERVISORY PURPOSES; SYSTEMS OR METHODS SPECIALLY ADAPTED FOR ADMINISTRATIVE, COMMERCIAL, FINANCIAL, MANAGERIAL OR SUPERVISORY PURPOSES, NOT OTHERWISE PROVIDED FOR
- G06Q20/00—Payment architectures, schemes or protocols
- G06Q20/38—Payment protocols; Details thereof
- G06Q20/382—Payment protocols; Details thereof insuring higher security of transaction
- G06Q20/3829—Payment protocols; Details thereof insuring higher security of transaction involving key management
Landscapes
- Business, Economics & Management (AREA)
- Engineering & Computer Science (AREA)
- Accounting & Taxation (AREA)
- Computer Security & Cryptography (AREA)
- Finance (AREA)
- Strategic Management (AREA)
- Physics & Mathematics (AREA)
- General Business, Economics & Management (AREA)
- General Physics & Mathematics (AREA)
- Theoretical Computer Science (AREA)
- Collating Specific Patterns (AREA)
Abstract
Translated fromChineseDescription
Translated fromChinese技术领域technical field
本申请涉及计算机技术领域,尤其涉及一种生物特征信息的识别方法以及相关装置。The present application relates to the field of computer technology, and in particular, to a method for identifying biometric information and a related device.
背景技术Background technique
随着互联网技术的迅速发展,生物特征信息的利用出现在越来越多的场景中。例如在人脸识别的支付过程中,通过人脸识别进行用户的判定,从而指示对应的支付过程的正常进行。With the rapid development of Internet technology, the utilization of biometric information appears in more and more scenarios. For example, in the payment process of face recognition, the user is judged through face recognition, so as to indicate the normal progress of the corresponding payment process.
一般,在通过人脸识别进行用户的判定的过程中,可以对摄像头采集的人脸信息进行加密,进而保证识别过程的安全性。Generally, in the process of determining the user through face recognition, the face information collected by the camera may be encrypted, thereby ensuring the security of the recognition process.
但是,对人脸信息进行加密的过程一般在普通执行环境中进行,该执行环境容易被攻击并植入恶意视频流或被窍取密钥后进行伪造请求,影响识别过程的安全性。However, the process of encrypting face information is generally carried out in a common execution environment, which is easily attacked and implanted with malicious video streams or tricked to obtain a key to make a forged request, which affects the security of the identification process.
发明内容SUMMARY OF THE INVENTION
有鉴于此,本申请提供一种生物特征信息的识别方法,可以有效提高识别过程的安全性。In view of this, the present application provides a method for identifying biometric information, which can effectively improve the security of the identification process.
本申请第一方面提供一种生物特征信息的识别方法,可以应用于终端设备中包含生物特征信息的识别功能的系统或程序中,具体包括:A first aspect of the present application provides a method for identifying biometric information, which can be applied to a system or program that includes an identification function of biometric information in a terminal device, specifically including:
获取采集模块采集的生物特征信息;Obtain the biometric information collected by the collection module;
基于所述目标密钥对所述生物特征信息进行签名,以得到签名加密信息;Sign the biometric information based on the target key to obtain signed encrypted information;
将所述采集模块对应的目标标识与所述签名加密信息输入后端服务模块中,以使得所述后端服务模块对所述签名加密信息进行验证得到验证结果,所述验证结果基于所述目标密钥与验证密钥的对应关系确定,所述验证密钥为所述后端服务模块基于所述模块标识调用所得;Input the target identifier corresponding to the collection module and the signature encryption information into the back-end service module, so that the back-end service module verifies the signature and encryption information to obtain a verification result, and the verification result is based on the target The corresponding relationship between the key and the verification key is determined, and the verification key is obtained by calling the back-end service module based on the module identifier;
若所述验证结果指示所述目标密钥与所述验证密钥相对应,则所述后端服务模块基于所述验证密钥对所述签名加密信息进行解密,以进行识别得到目标识别信息。If the verification result indicates that the target key corresponds to the verification key, the back-end service module decrypts the signed encrypted information based on the verification key to perform identification to obtain target identification information.
本申请第二方面提供一种生物特征信息的识别装置,包括:获取单元,用于获取采集模块采集的生物特征信息;A second aspect of the present application provides a device for identifying biometric information, comprising: an acquisition unit configured to acquire biometric information collected by an acquisition module;
签名单元,用于基于所述目标密钥对所述生物特征信息进行签名,以得到签名加密信息;a signature unit for signing the biometric information based on the target key to obtain signature encryption information;
输入单元,用于将所述采集模块对应的目标标识与所述签名加密信息输入后端服务模块中,以使得所述后端服务模块对所述签名加密信息进行验证得到验证结果,所述验证结果基于所述目标密钥与验证密钥的对应关系确定,所述验证密钥为所述后端服务模块基于所述模块标识调用所得;an input unit, configured to input the target identifier corresponding to the acquisition module and the signature encryption information into the back-end service module, so that the back-end service module verifies the signature and encryption information to obtain a verification result, and the verification The result is determined based on the corresponding relationship between the target key and the verification key, and the verification key is obtained by calling the back-end service module based on the module identifier;
识别单元,用于若所述验证结果指示所述目标密钥与所述验证密钥相对应,则所述后端服务模块基于所述验证密钥对所述签名加密信息进行解密,以进行识别得到目标识别信息。an identification unit, configured to decrypt the signature encrypted information based on the verification key by the back-end service module to identify the target key if the verification result indicates that the target key corresponds to the verification key Get target identification information.
可选的,在本申请一些可能的实现方式中,所述输入单元,具体用于基于网络密钥对所述采集模块对应的目标标识与所述签名加密信息进行处理,以得到网络加密包;Optionally, in some possible implementations of the present application, the input unit is specifically configured to process the target identifier corresponding to the acquisition module and the signature encryption information based on a network key to obtain a network encryption package;
所述输入单元,具体用于将所述网络加密包输入所述后端服务模块中,以使得所述后端服务模块根据所述网络密钥对所述网络加密包解密得到所述模块标识与所述签名加密信息;The input unit is specifically configured to input the network encryption packet into the back-end service module, so that the back-end service module decrypts the network encryption packet according to the network key to obtain the module identifier and the module identifier. the signature encrypted information;
所述输入单元,具体用于对所述签名加密信息进行验证得到验证结果。The input unit is specifically configured to verify the signed encrypted information to obtain a verification result.
可选的,在本申请一些可能的实现方式中,所述输入单元,具体用于将所述网络加密包输入所述后端服务模块中,以使得所述后端服务模块根据所述网络密钥确定身份信息;Optionally, in some possible implementation manners of the present application, the input unit is specifically configured to input the network encryption packet into the back-end service module, so that the back-end service module can perform the encryption according to the network encryption. key to determine identity information;
所述输入单元,具体用于若所述身份信息通过验证,则所述后端服务模块根据所述网络密钥对所述网络加密包解密得到所述模块标识与所述签名加密信息。The input unit is specifically configured to, if the identity information passes the verification, the back-end service module decrypts the network encryption packet according to the network key to obtain the module identifier and the signature encryption information.
可选的,在本申请一些可能的实现方式中,所述识别单元,具体用于所述后端服务模块基于所述验证密钥对所述签名加密信息进行解密,以得到目标数据流;Optionally, in some possible implementations of the present application, the identifying unit is specifically configured for the back-end service module to decrypt the signature encryption information based on the verification key to obtain the target data stream;
所述识别单元,具体用于基于目标特征对所述目标数据流中的图像序列进行筛选,以得到至少一张目标图像,所述目标特征与所述生物特征信息相关联;The identifying unit is specifically configured to screen the image sequence in the target data stream based on the target feature to obtain at least one target image, and the target feature is associated with the biometric information;
所述识别单元,具体用于对所述目标图像进行识别,以得到目标识别信息。The identifying unit is specifically configured to identify the target image to obtain target identification information.
可选的,在本申请一些可能的实现方式中,所述识别单元,具体用于获取所述目标数据流对应的深度信息和红外信息;Optionally, in some possible implementation manners of the present application, the identifying unit is specifically configured to acquire depth information and infrared information corresponding to the target data stream;
所述识别单元,具体用于提取所述目标图像在所述深度信息中对应的深度图像;The identifying unit is specifically configured to extract the depth image corresponding to the target image in the depth information;
所述识别单元,具体用于提取所述目标图像在所述红外信息中对应的红外图像;The identifying unit is specifically configured to extract the infrared image corresponding to the target image in the infrared information;
所述识别单元,具体用于根据所述目标图像、所述深度图像和所述红外图像进行图像识别,以得到目标识别信息。The recognition unit is specifically configured to perform image recognition according to the target image, the depth image and the infrared image to obtain target recognition information.
可选的,在本申请一些可能的实现方式中,所述识别单元,具体用于若所述验证结果指示所述目标密钥与所述验证密钥不对应,则所述后端服务模块反馈异常标识;Optionally, in some possible implementations of the present application, the identifying unit is specifically configured to, if the verification result indicates that the target key does not correspond to the verification key, the back-end service module feedback abnormal identification;
所述识别单元,具体用于基于所述异常标识触发对所述目标标识进行查验,以对所述目标标识进行更新。The identifying unit is specifically configured to trigger checking the target identifier based on the abnormal identifier, so as to update the target identifier.
可选的,在本申请一些可能的实现方式中,所述获取单元,具体用于确定目标采集任务;Optionally, in some possible implementations of the present application, the acquisition unit is specifically configured to determine a target acquisition task;
所述获取单元,具体用于基于所述目标采集任务确定采集参数,所述采集参数包括采集区域与采集时长;The acquisition unit is specifically configured to determine a collection parameter based on the target collection task, where the collection parameter includes a collection area and a collection duration;
所述获取单元,具体用于根据所述采集参数对所述采集模块进行设置,以使得所述采集模块采集所述生物特征信息。The acquisition unit is specifically configured to set the acquisition module according to the acquisition parameter, so that the acquisition module acquires the biological feature information.
可选的,在本申请一些可能的实现方式中,所述识别单元,具体用于基于目标工具获取所述采集模块对应的模块信息;Optionally, in some possible implementation manners of the present application, the identifying unit is specifically configured to acquire module information corresponding to the acquisition module based on a target tool;
所述识别单元,具体用于根据所述模块信息确定所述目标标识;The identifying unit is specifically configured to determine the target identifier according to the module information;
所述识别单元,具体用于将所述目标标识传输至所述后端服务模块,以使得所述后端服务模块根据所述目标标识生成所述目标密钥和所述验证密钥,所述目标密钥和所述验证密钥相对应;The identifying unit is specifically configured to transmit the target identifier to the back-end service module, so that the back-end service module generates the target key and the verification key according to the target identifier, and the The target key corresponds to the verification key;
所述识别单元,具体用于将所述目标密钥反馈至所述采集模块对应的存储模块中存储。The identifying unit is specifically configured to feed back the target key to the storage module corresponding to the collection module for storage.
可选的,在本申请一些可能的实现方式中,所述识别单元,具体用于将所述验证密钥上传至云端服务器进行存储,存储在所述云端服务器中的所述验证密钥响应于所述目标标识的输入进行下发。Optionally, in some possible implementations of the present application, the identification unit is specifically configured to upload the verification key to a cloud server for storage, and the verification key stored in the cloud server responds to The input of the target identifier is issued.
本申请第三方面提供一种基于生物特征信息识别的交易方法,包括:A third aspect of the present application provides a transaction method based on biometric information identification, including:
响应于目标交易指令,触发采集模块采集生物特征信息;In response to the target transaction instruction, trigger the acquisition module to collect biometric information;
基于所述目标密钥对所述生物特征信息进行签名,以得到签名加密信息;Sign the biometric information based on the target key to obtain signed encrypted information;
将所述采集模块对应的目标标识与所述签名加密信息输入后端服务模块中,以使得所述后端服务模块对所述签名加密信息进行验证得到验证结果,所述验证结果基于所述目标密钥与验证密钥的对应关系确定,所述验证密钥为所述后端服务模块基于所述模块标识调用所得;Input the target identifier corresponding to the collection module and the signature encryption information into the back-end service module, so that the back-end service module verifies the signature and encryption information to obtain a verification result, and the verification result is based on the target The corresponding relationship between the key and the verification key is determined, and the verification key is obtained by calling the back-end service module based on the module identifier;
若所述验证结果指示所述目标密钥与所述验证密钥相对应,则所述后端服务模块基于所述验证密钥对所述签名加密信息进行解密,以进行识别得到目标识别信息;If the verification result indicates that the target key corresponds to the verification key, the back-end service module decrypts the signature encryption information based on the verification key to identify and obtain target identification information;
若所述目标识别信息满足预设条件,则执行所述目标交易指令对应的交易操作。If the target identification information satisfies the preset condition, the transaction operation corresponding to the target transaction instruction is executed.
本申请第四方面提供一种基于生物特征信息识别的交易装置,包括:A fourth aspect of the present application provides a transaction device based on biometric information identification, including:
采集单元,用于响应于目标交易指令,触发采集模块采集生物特征信息;a collection unit, used for triggering the collection module to collect biometric information in response to the target transaction instruction;
签名单元,用于基于所述目标密钥对所述生物特征信息进行签名,以得到签名加密信息;a signature unit for signing the biometric information based on the target key to obtain signature encryption information;
验证单元,用于将所述采集模块对应的目标标识与所述签名加密信息输入后端服务模块中,以使得所述后端服务模块对所述签名加密信息进行验证得到验证结果,所述验证结果基于所述目标密钥与验证密钥的对应关系确定,所述验证密钥为所述后端服务模块基于所述模块标识调用所得;A verification unit, configured to input the target identifier corresponding to the acquisition module and the signature encryption information into the back-end service module, so that the back-end service module verifies the signature and encryption information to obtain a verification result, and the verification The result is determined based on the corresponding relationship between the target key and the verification key, and the verification key is obtained by calling the back-end service module based on the module identifier;
识别单元,用于若所述验证结果指示所述目标密钥与所述验证密钥相对应,则所述后端服务模块基于所述验证密钥对所述签名加密信息进行解密,以进行识别得到目标识别信息;an identification unit, configured to decrypt the signature encrypted information based on the verification key by the back-end service module to identify the target key if the verification result indicates that the target key corresponds to the verification key Obtain target identification information;
交易单元,用于若所述目标识别信息满足预设条件,则执行所述目标交易指令对应的交易操作。A transaction unit, configured to execute a transaction operation corresponding to the target transaction instruction if the target identification information satisfies a preset condition.
本申请第五方面提供一种生物特征信息的采集装置,包括:A fifth aspect of the present application provides a device for collecting biometric information, including:
确定单元,用于确定模块信息中的目标标识;a determining unit, used to determine the target identifier in the module information;
传输单元,用于将所述目标标识传输至后端服务模块,以使得所述后端服务模块根据所述目标标识生成目标密钥和验证密钥,所述目标密钥和所述验证密钥相对应;A transmission unit, configured to transmit the target identification to the back-end service module, so that the back-end service module generates a target key and a verification key according to the target identification, the target key and the verification key Corresponding;
存储单元,用于存储所述后端服务模块反馈的所述目标密钥;a storage unit, configured to store the target key fed back by the back-end service module;
采集单元,用于采集生物特征信息;a collection unit for collecting biometric information;
签名单元,用于基于所述目标密钥对所述生物特征信息进行签名,以得到签名加密信息,所述签名加密信息用于指示所述生物特征信息的识别过程。A signature unit, configured to sign the biometric information based on the target key to obtain signature encryption information, where the signature encryption information is used to indicate the identification process of the biometric information.
本申请第六方面提供一种计算机设备,包括:存储器、处理器以及总线系统;所述存储器用于存储程序代码;所述处理器用于根据所述程序代码中的指令执行上述任一项所述的生物特征信息的识别方法。A sixth aspect of the present application provides a computer device, including: a memory, a processor, and a bus system; the memory is used for storing program codes; the processor is used for executing any one of the above according to instructions in the program codes identification method of biometric information.
本申请第七方面提供一种计算机可读存储介质,所述计算机可读存储介质中存储有指令,当其在计算机上运行时,使得计算机执行上述任一项所述的生物特征信息的识别方法。A seventh aspect of the present application provides a computer-readable storage medium, where instructions are stored in the computer-readable storage medium, and when the computer-readable storage medium runs on a computer, the computer executes the method for identifying biometric information described in any one of the above .
根据本申请的一个方面,提供了一种计算机程序产品或计算机程序,该计算机程序产品或计算机程序包括计算机指令,该计算机指令存储在计算机可读存储介质中。计算机设备的处理器从计算机可读存储介质读取该计算机指令,处理器执行该计算机指令,使得该计算机设备执行上述各种可选实现方式中提供的生物特征信息的识别方法。According to one aspect of the present application, there is provided a computer program product or computer program comprising computer instructions stored in a computer readable storage medium. The processor of the computer device reads the computer instructions from the computer-readable storage medium, and the processor executes the computer instructions, so that the computer device executes the methods for identifying biometric information provided in the various optional implementation manners described above.
从以上技术方案可以看出,本申请实施例具有以下优点:As can be seen from the above technical solutions, the embodiments of the present application have the following advantages:
通过获取采集模块采集的生物特征信息,该采集模块烧录有唯一的目标密钥;然后基于目标密钥对生物特征信息进行签名,以得到签名加密信息;并将采集模块对应的目标标识与签名加密信息输入后端服务模块中,以使得后端服务模块对签名加密信息进行验证得到验证结果,验证结果基于目标密钥与验证密钥的对应关系确定,验证密钥为后端服务模块基于模块标识调用所得;当验证结果指示目标密钥与验证密钥相对应时,则后端服务模块基于验证密钥对签名加密信息进行解密,以进行识别得到目标识别信息。从而实现安全的生物特征信息的识别过程,由于采用唯一的目标密钥对采集模块进行信息源的可信度验证,保证了信息的安全性,且解密过程在后端服务模块中执行,对生物特征信息进行了隔离,使得恶意攻击无法执行,提高了识别过程的安全性。By acquiring the biometric information collected by the acquisition module, the acquisition module is programmed with a unique target key; then the biometric information is signed based on the target key to obtain the signature encryption information; the target identification and signature corresponding to the acquisition module are The encrypted information is input into the back-end service module, so that the back-end service module verifies the signed encrypted information to obtain the verification result. The verification result is determined based on the corresponding relationship between the target key and the verification key. The verification key is the back-end service module based on the module. Identifies the result obtained from the call; when the verification result indicates that the target key corresponds to the verification key, the back-end service module decrypts the signed encrypted information based on the verification key to identify and obtain the target identification information. In this way, the identification process of secure biometric information is realized. Because the unique target key is used to verify the credibility of the information source for the acquisition module, the security of the information is ensured, and the decryption process is performed in the back-end service module. The feature information is isolated, so that malicious attacks cannot be executed, and the security of the identification process is improved.
附图说明Description of drawings
为了更清楚地说明本申请实施例或现有技术中的技术方案,下面将对实施例或现有技术描述中所需要使用的附图作简单地介绍,显而易见地,下面描述中的附图仅仅是本申请的实施例,对于本领域普通技术人员来讲,在不付出创造性劳动的前提下,还可以根据提供的附图获得其他的附图。In order to more clearly illustrate the embodiments of the present application or the technical solutions in the prior art, the following briefly introduces the accompanying drawings required for the description of the embodiments or the prior art. Obviously, the drawings in the following description are only It is an embodiment of the present application. For those of ordinary skill in the art, other drawings can also be obtained according to the provided drawings without any creative effort.
图1为生物特征信息的识别系统运行的网络架构图;Fig. 1 is the network architecture diagram of the operation of the identification system of biometric information;
图2为本申请实施例提供的一种生物特征信息的识别的流程架构图;FIG. 2 is a flowchart structure diagram of identification of biometric information provided by an embodiment of the present application;
图3为本申请实施例提供的一种生物特征信息的识别方法的流程图;3 is a flowchart of a method for identifying biometric information provided by an embodiment of the present application;
图4为本申请实施例提供的一种生物特征信息的识别方法的场景示意图;FIG. 4 is a schematic scene diagram of a method for identifying biometric information provided by an embodiment of the present application;
图5为本申请实施例提供的另一种生物特征信息的识别方法的场景示意图;FIG. 5 is a schematic scene diagram of another method for identifying biometric information provided by an embodiment of the present application;
图6为本申请实施例提供的另一种生物特征信息的识别方法的流程图;6 is a flowchart of another method for identifying biometric information provided by an embodiment of the present application;
图7为本申请实施例提供的一种生物特征信息的识别装置的结构示意图;7 is a schematic structural diagram of a device for identifying biometric information provided by an embodiment of the present application;
图8为本申请实施例提供的一种生物特征信息的交易装置的结构示意图;FIG. 8 is a schematic structural diagram of a transaction apparatus for biometric information provided by an embodiment of the present application;
图9为本申请实施例提供的一种生物特征信息的采集装置的结构示意图;9 is a schematic structural diagram of a device for collecting biometric information provided by an embodiment of the present application;
图10为本申请实施例提供的一种终端设备的结构示意图;FIG. 10 is a schematic structural diagram of a terminal device according to an embodiment of the present application;
图11为本申请实施例提供的一种服务器的结构示意图。FIG. 11 is a schematic structural diagram of a server according to an embodiment of the present application.
具体实施方式Detailed ways
本申请实施例提供了一种生物特征信息的识别方法以及相关装置,可以应用于终端设备中包含生物特征信息的识别功能的系统或程序中,通过获取采集模块采集的生物特征信息,该采集模块烧录有唯一的目标密钥;然后基于目标密钥对生物特征信息进行签名,以得到签名加密信息;并将采集模块对应的目标标识与签名加密信息输入后端服务模块中,以使得后端服务模块对签名加密信息进行验证得到验证结果,验证结果基于目标密钥与验证密钥的对应关系确定,验证密钥为后端服务模块基于模块标识调用所得;当验证结果指示目标密钥与验证密钥相对应时,则后端服务模块基于验证密钥对签名加密信息进行解密,以进行识别得到目标识别信息。从而实现安全的生物特征信息的识别过程,由于采用唯一的目标密钥对采集模块进行信息源的可信度验证,保证了信息的安全性,且解密过程在后端服务模块中执行,对生物特征信息进行了隔离,使得恶意攻击无法执行,提高了识别过程的安全性。The embodiments of the present application provide a method and a related device for identifying biometric information, which can be applied to a system or program that includes a biometric information identification function in a terminal device. By acquiring the biometric information collected by a collection module, the collection module Burn a unique target key; then sign the biometric information based on the target key to obtain the signature encryption information; input the target identification and signature encryption information corresponding to the acquisition module into the back-end service module, so that the back-end The service module verifies the signature and encrypted information to obtain the verification result. The verification result is determined based on the corresponding relationship between the target key and the verification key. The verification key is obtained by the back-end service module based on the module identification. When the verification result indicates that the target key and the verification key When the keys correspond, the back-end service module decrypts the signed encrypted information based on the verification key to identify and obtain the target identification information. In this way, the identification process of secure biometric information is realized. Because the unique target key is used to verify the credibility of the information source for the acquisition module, the security of the information is ensured, and the decryption process is performed in the back-end service module. The feature information is isolated, so that malicious attacks cannot be executed, and the security of the identification process is improved.
本申请的说明书和权利要求书及上述附图中的术语“第一”、“第二”、“第三”、“第四”等(如果存在)是用于区别类似的对象,而不必用于描述特定的顺序或先后次序。应该理解这样使用的数据在适当情况下可以互换,以便这里描述的本申请的实施例例如能够以除了在这里图示或描述的那些以外的顺序实施。此外,术语“包括”和“对应于”以及他们的任何变形,意图在于覆盖不排他的包含,例如,包含了一系列步骤或单元的过程、方法、系统、产品或设备不必限于清楚地列出的那些步骤或单元,而是可包括没有清楚地列出的或对于这些过程、方法、产品或设备固有的其它步骤或单元。The terms "first", "second", "third", "fourth", etc. (if any) in the description and claims of this application and the above-mentioned drawings are used to distinguish similar objects and are not necessarily used to describe a specific order or sequence. It is to be understood that the data so used may be interchanged under appropriate circumstances such that the embodiments of the application described herein can, for example, be practiced in sequences other than those illustrated or described herein. Furthermore, the terms "comprising" and "corresponding to", and any variations thereof, are intended to cover non-exclusive inclusion, eg, a process, method, system, product or device comprising a series of steps or units not necessarily limited to those expressly listed but may include other steps or units not expressly listed or inherent to these processes, methods, products or devices.
首先,对本申请实施例中可能出现的一些名词进行解释。First, some terms that may appear in the embodiments of the present application are explained.
人脸识别:通过人脸多媒体信息换取人身份信息的技术。Face recognition: a technology that exchanges human identity information through face multimedia information.
三维摄像头:类比传统摄像头,添加了活体相关软硬件,包括深度相机,和红外相机,保证信息安全。3D camera: Similar to traditional cameras, it adds living-related software and hardware, including depth cameras and infrared cameras, to ensure information security.
可信执行环境(Trusted Execution Environment,TEE):在设备中提供一个安全区域,确保敏感数据在隔离、可信的环境中存储、处理和保护。Trusted Execution Environment (TEE): Provides a secure enclave within the device to ensure sensitive data is stored, processed and protected in an isolated, trusted environment.
普通执行环境(Rich Execution Environment,REE):包括运行在通用的处理器上的普通操作系统及其上的客户端应用程序。Common Execution Environment (Rich Execution Environment, REE): includes a common operating system running on a general-purpose processor and client applications on it.
密钥烧录工具:运行在个人电脑(PC)端的软件,用于将PC侧的数据写入到摄像头内部的安全元件芯片中。Key burning tool: software running on the personal computer (PC) side to write the data on the PC side to the secure element chip inside the camera.
应理解,本申请提供的生物特征信息的识别方法可以应用于终端设备中包含生物特征信息的识别功能的系统或程序中,例如互动剧,具体的,生物特征信息的识别系统可以运行于如图1所示的网络架构中,如图1所示,是生物特征信息的识别系统运行的网络架构图,如图可知,生物特征信息的识别系统可以提供与多个信息源的生物特征信息的识别过程,即通过终端进行生物特征信息的采集,然后发送至服务器进行识别以进行身份验证;或在终端本地进行生物特征信息的识别,并将识别得到的信息发送至服务器进行身份验证;可以理解的是,图1中示出了多种终端设备,终端设备可以为计算机设备,在实际场景中可以有更多或更少种类的终端设备参与到生物特征信息的识别的过程中,具体数量和种类因实际场景而定,此处不做限定,另外,图1中示出了一个服务器,但在实际场景中,也可以有多个服务器的参与,具体服务器数量因实际场景而定。It should be understood that the identification method of biometric information provided by this application can be applied to a system or program that includes the identification function of biometric information in the terminal device, such as an interactive drama. Specifically, the identification system of biometric information can run as shown in Fig. In the network architecture shown in Figure 1, as shown in Figure 1, it is the network architecture diagram of the operation of the biometric information identification system. As can be seen from the figure, the biometric information identification system can provide identification of biometric information with multiple information sources. process, that is, collecting biometric information through the terminal, and then sending it to the server for identification for identity verification; or identifying the biometric information locally on the terminal, and sending the identified information to the server for identity verification; understandable Yes, Figure 1 shows a variety of terminal devices, and the terminal devices can be computer devices. In actual scenarios, there may be more or less types of terminal devices participating in the process of identifying It depends on the actual scene, which is not limited here. In addition, one server is shown in FIG. 1, but in the actual scene, multiple servers may also participate, and the specific number of servers depends on the actual scene.
本实施例中,服务器可以是独立的物理服务器,也可以是多个物理服务器构成的服务器集群或者分布式系统,还可以是提供云服务、云数据库、云计算、云函数、云存储、网络服务、云通信、中间件服务、域名服务、安全服务、CDN、以及大数据和人工智能平台等基础云计算服务的云服务器。终端可以是智能手机、平板电脑、笔记本电脑、台式计算机、智能音箱、智能手表等,但并不局限于此。终端以及服务器可以通过有线或无线通信方式进行直接或间接地连接,终端以及服务器可以连接组成区块链网络,本申请在此不做限制。In this embodiment, the server may be an independent physical server, or a server cluster or a distributed system composed of multiple physical servers, or may provide cloud services, cloud databases, cloud computing, cloud functions, cloud storage, and network services , cloud communications, middleware services, domain name services, security services, CDN, and cloud servers for basic cloud computing services such as big data and artificial intelligence platforms. The terminal may be a smart phone, a tablet computer, a notebook computer, a desktop computer, a smart speaker, a smart watch, etc., but is not limited thereto. The terminal and the server can be connected directly or indirectly through wired or wireless communication, and the terminal and the server can be connected to form a blockchain network, which is not limited in this application.
可以理解的是,上述生物特征信息的识别系统可以运行于个人移动终端,例如:作为互动剧这样的应用,也可以运行于服务器,还可以作为运行于第三方设备以提供生物特征信息的识别,以得到信息源的生物特征信息的识别处理结果;具体的生物特征信息的识别系统可以是以一种程序的形式在上述设备中运行,也可以作为上述设备中的系统部件进行运行,还可以作为云端服务程序的一种,具体运作模式因实际场景而定,此处不做限定。It can be understood that the identification system for the above-mentioned biometric information can be run on a personal mobile terminal, for example: as an application such as an interactive drama, it can also run on a server, and it can also run on a third-party device to provide identification of biometric information, In order to obtain the identification processing result of the biometric information of the information source; the identification system of the specific biometric information can be run in the above-mentioned equipment in the form of a program, or can be run as a system component in the above-mentioned equipment, or can be used as a program. A type of cloud service program. The specific operation mode depends on the actual scene and is not limited here.
随着互联网技术的迅速发展,生物特征信息的利用出现在越来越多的场景中。例如在人脸识别的支付过程中,通过人脸识别进行用户的判定,从而指示对应的支付过程的正常进行。With the rapid development of Internet technology, the utilization of biometric information appears in more and more scenarios. For example, in the payment process of face recognition, the user is judged through face recognition, so as to indicate the normal progress of the corresponding payment process.
一般,在通过人脸识别进行用户的判定的过程中,可以对摄像头采集的人脸信息进行加密,进而保证识别过程的安全性。Generally, in the process of determining the user through face recognition, the face information collected by the camera may be encrypted, thereby ensuring the security of the recognition process.
但是,对人脸信息进行加密的过程一般在普通执行环境中进行,该执行环境容易被攻击并植入恶意视频流或被窍取密钥后进行伪造请求,影响识别过程的安全性。However, the process of encrypting face information is generally carried out in a common execution environment, which is easily attacked and implanted with malicious video streams or tricked to obtain a key to make a forged request, which affects the security of the identification process.
为了解决上述问题,本申请提出了一种生物特征信息的识别方法,该方法应用于图2所示的生物特征信息的识别的流程框架中,如图2所示,为本申请实施例提供的一种生物特征信息的识别的流程架构图,用户通过界面层中的目标操作触发生物特征信息的获取,从而得到对应的数据流;进而在应用层中对数据流进行基于目标密钥的签名加密,以得到签名加密数据,进一步的根据目标标识调用对应的验证密钥在后端服务中进行解密,从而保证生物特征信息的安全识别过程。In order to solve the above problems, the present application proposes a method for identifying biometric information, which is applied to the process framework of identifying biometric information shown in FIG. 2 , as shown in FIG. A process architecture diagram of identification of biometric information, the user triggers the acquisition of biometric information through the target operation in the interface layer, so as to obtain the corresponding data stream; and then performs signature encryption based on the target key on the data stream in the application layer , to obtain the signed encrypted data, and then call the corresponding verification key according to the target identification to decrypt it in the back-end service, thereby ensuring the safe identification process of the biometric information.
可以理解的是,本申请所提供的方法可以为一种程序的写入,以作为硬件系统中的一种处理逻辑,也可以作为一种生物特征信息的识别装置,采用集成或外接的方式实现上述处理逻辑。作为一种实现方式,该生物特征信息的识别装置通过获取采集模块采集的生物特征信息,该采集模块烧录有唯一的目标密钥;然后基于目标密钥对生物特征信息进行签名,以得到签名加密信息;并将采集模块对应的目标标识与签名加密信息输入后端服务模块中,以使得后端服务模块对签名加密信息进行验证得到验证结果,验证结果基于目标密钥与验证密钥的对应关系确定,验证密钥为后端服务模块基于模块标识调用所得;当验证结果指示目标密钥与验证密钥相对应时,则后端服务模块基于验证密钥对签名加密信息进行解密,以进行识别得到目标识别信息。从而实现安全的生物特征信息的识别过程,由于采用唯一的目标密钥对采集模块进行信息源的可信度验证,保证了信息的安全性,且解密过程在后端服务模块中执行,对生物特征信息进行了隔离,使得恶意攻击无法执行,提高了识别过程的安全性。It can be understood that the method provided by this application can be written as a program, as a processing logic in a hardware system, or as a biometric information identification device, implemented in an integrated or external manner. The above processing logic. As an implementation manner, the biometric information identification device obtains the biometric information collected by the acquisition module, which is programmed with a unique target key; and then signs the biometric information based on the target key to obtain the signature Encrypted information; input the target identification and signature encryption information corresponding to the acquisition module into the back-end service module, so that the back-end service module verifies the signature and encryption information to obtain a verification result, and the verification result is based on the correspondence between the target key and the verification key The relationship is determined, and the verification key is obtained by the back-end service module based on the module identification call; when the verification result indicates that the target key corresponds to the verification key, the back-end service module decrypts the signed encrypted information based on the verification key to perform Identify the target identification information. In this way, the identification process of secure biometric information is realized. Because the unique target key is used to verify the credibility of the information source for the acquisition module, the security of the information is ensured, and the decryption process is performed in the back-end service module. The feature information is isolated, so that malicious attacks cannot be executed, and the security of the identification process is improved.
结合上述流程架构,下面将对本申请中生物特征信息的识别方法进行介绍,请参阅图3,图3为本申请实施例提供的一种生物特征信息的识别方法的流程图,该管理方法可以是由终端设备执行的,本申请实施例至少包括以下步骤:In combination with the above process architecture, the following will introduce the identification method of biometric information in the present application, please refer to FIG. 3, FIG. 3 is a flowchart of a biometric information identification method provided by an embodiment of the present application, and the management method may be: Executed by the terminal device, this embodiment of the present application includes at least the following steps:
301、获取采集模块采集的生物特征信息。301. Obtain the biological feature information collected by the collection module.
本实施例中,采集模块可以是具有生物特征采集功能的设备,例如摄像机;另外,生物特征信息可以包括人脸识别、瞳孔识别、虹膜识别等。具体的,生物特征信息为人脸识别的场景中,采集模块可以为移动终端上的摄像头。In this embodiment, the collection module may be a device with a biometric feature collection function, such as a camera; in addition, the biometric information may include face recognition, pupil recognition, iris recognition, and the like. Specifically, in a scenario where the biometric information is face recognition, the collection module may be a camera on a mobile terminal.
应当注意的是,采集模块烧录有唯一的目标密钥,例如采集模块为摄像头,则在该摄像头量产前,针对摄像头烧录唯一目标密钥,即该目标密钥只对应于该摄像头;具体的目标密钥可以是基于设备标识设定的,也可以是基于特定的加密算法设定的,此处不做限定。It should be noted that the acquisition module is programmed with a unique target key. For example, if the acquisition module is a camera, before mass production of the camera, a unique target key is programmed for the camera, that is, the target key only corresponds to the camera; The specific target key may be set based on the device identification, or may be set based on a specific encryption algorithm, which is not limited here.
在一种可能的场景中,采集生物特征信息的过程是基于任务的设定进行的,例如对于人脸识别,需要录制一定时长的视频流进行识别;具体的,即首先确定目标采集任务;然后基于目标采集任务确定采集参数,采集参数包括采集区域与采集时长;进而根据采集参数对采集模块进行设置,以使得采集模块采集生物特征信息,从而保证了生物特征信息采集的准确性,使得对应的生物特征识别过程可以正常进行。In a possible scenario, the process of collecting biometric information is based on task settings. For example, for face recognition, a video stream of a certain length needs to be recorded for recognition; specifically, the target acquisition task is first determined; then The acquisition parameters are determined based on the target acquisition task, and the acquisition parameters include the acquisition area and the acquisition duration; and then the acquisition module is set according to the acquisition parameters, so that the acquisition module collects biometric information, thereby ensuring the accuracy of biometric information collection, so that the corresponding The biometric identification process can proceed normally.
302、基于目标密钥对生物特征信息进行签名,以得到签名加密信息。302. Sign the biometric information based on the target key to obtain signed encrypted information.
本实施例中,采集模块对应的目标密钥可以是采集模块与后端服务模块事先约定的唯一私钥,即通过在采集模块和后端服务模块设定唯一私钥,可以保证采集模块获取的信息在后端服务模块才能被解析,保证了信息的安全性。In this embodiment, the target key corresponding to the collection module may be the unique private key agreed upon by the collection module and the back-end service module in advance, that is, by setting the unique private key in the collection module and the back-end service module, it is possible to ensure that the data obtained by the collection module can be guaranteed. The information can only be parsed in the back-end service module, which ensures the security of the information.
具体的,目标密钥可以是基于高级加密标准(Advanced Encryption Standard,AES)算法所得,也可以是采用其他的加密算法,具体的密钥生成算法因实际场景而定。Specifically, the target key may be obtained based on an Advanced Encryption Standard (Advanced Encryption Standard, AES) algorithm, or other encryption algorithms may be used, and the specific key generation algorithm depends on the actual scenario.
303、将采集模块对应的目标标识与签名加密信息输入后端服务模块中,以使得后端服务模块对签名加密信息进行验证得到验证结果。303. Input the target identifier and the signature encryption information corresponding to the collection module into the back-end service module, so that the back-end service module verifies the signature and encryption information to obtain a verification result.
本实施例中,验证结果基于目标密钥与验证密钥的对应关系确定,即判断目标密钥与验证密钥是否对应;而对于验证密钥,为后端服务模块基于模块标识调用所得,即在采集模块与后端服务模块进行唯一私钥(目标密钥)的配置过程中,后端服务模块会将根据采集模块对应的目标标识配置好的唯一私钥发送至采集模块进行存储,并将唯一私钥保存在本地或云端作为验证密钥,当目标密钥与验证密钥对应时,即说明采集模块为可信的设备,安全性有保障。In this embodiment, the verification result is determined based on the corresponding relationship between the target key and the verification key, that is, it is determined whether the target key corresponds to the verification key; and the verification key is obtained by calling the back-end service module based on the module identifier, that is, During the configuration process of the unique private key (target key) between the acquisition module and the back-end service module, the back-end service module will send the unique private key configured according to the target identifier corresponding to the acquisition module to the acquisition module for storage, and store the The unique private key is stored locally or in the cloud as the verification key. When the target key corresponds to the verification key, it means that the acquisition module is a trusted device and the security is guaranteed.
具体的,采集模块对应的目标标识可以是中央处理器序列(CPUID),也可以是其他能唯一标识摄像头的文本序列号,具体标识形式因实际场景而定。Specifically, the target identifier corresponding to the acquisition module may be a central processing unit sequence (CPUID), or other text serial numbers that can uniquely identify the camera, and the specific identification form depends on the actual scene.
可选的,考虑到将采集模块对应的目标标识与签名加密信息输入后端服务模块涉及网络传输的过程,为了避免网络传输造成的安全隐患,可以首先基于网络密钥对采集模块对应的目标标识与签名加密信息进行处理,以得到网络加密包,其中,网路密钥可以是通用的网络AES密钥;将网络加密包输入后端服务模块中,以使得后端服务模块根据网络密钥对网络加密包解密得到模块标识与签名加密信息;进而后端服务模块对签名加密信息进行验证得到验证结果。从而提高了数据传输过程的安全性。Optionally, considering that the process of inputting the target identifier and signature encryption information corresponding to the acquisition module into the back-end service module involves network transmission, in order to avoid potential security risks caused by network transmission, the target identifier corresponding to the acquisition module can be first paired based on the network key. Process with the signature encryption information to obtain a network encryption package, wherein the network key can be a general network AES key; input the network encryption package into the back-end service module, so that the back-end service module can pair the network key according to the network key. The network encryption packet is decrypted to obtain the module identification and signature encryption information; then the back-end service module verifies the signature encryption information to obtain the verification result. Thus, the security of the data transmission process is improved.
进一步的,由于本步骤应用于应用程序中,例如移动支付软件;故在网络数据传输的过程中,还可以对身份信息进行验证,即发送端的可信度。具体的,首先将网络加密包输入后端服务模块中,以使得后端服务模块根据网络密钥确定身份信息;若身份信息通过验证,则后端服务模块根据网络密钥对网络加密包解密得到模块标识与签名加密信息。从而进一步提高了数据传输过程的安全性。Further, since this step is applied to application programs, such as mobile payment software; therefore, in the process of network data transmission, identity information can also be verified, that is, the credibility of the sender. Specifically, the network encryption package is firstly input into the back-end service module, so that the back-end service module determines the identity information according to the network key; if the identity information passes the verification, the back-end service module decrypts the network encryption package according to the network key to obtain Module identification and signature encryption information. Thus, the security of the data transmission process is further improved.
304、若验证结果指示目标密钥与验证密钥相对应,则后端服务模块基于验证密钥对签名加密信息进行解密,以进行识别得到目标识别信息。304. If the verification result indicates that the target key corresponds to the verification key, the back-end service module decrypts the signed encrypted information based on the verification key to perform identification to obtain the target identification information.
本实施例中,目标密钥与验证密钥相对应即说明采集设备为可信的设备,对应的数据流来源于可信的数据源,故可以根据采集模块与后端服务模块事先配置的唯一密钥(验证密钥)对签名加密信息进行解密,从而得到生物特征信息,进而执行信息识别的过程。In this embodiment, the correspondence between the target key and the verification key means that the collection device is a trusted device, and the corresponding data stream originates from a trusted data source. The key (verification key) decrypts the signed encrypted information to obtain biometric information, and then performs the process of information identification.
可以理解的是,后端服务模块可以是终端设备中与应用程序所在REE不同的可信执行环境,TEE是CPU内的一个安全区域。它运行在一个独立的环境中且与操作系统并行运行。CPU确保TEE中代码和数据的机密性和完整性都得到保护。通过同时使用硬件和软件来保护数据和代码,TEE比操作系统更加安全。在TEE中运行的受信任应用程序可以访问设备主处理器和内存的全部功能,而硬件隔离保护这些组件不受主操作系统中运行的用户安装应用程序的影响。故运行在TEE中的代码和数据,是保密且不可篡改的。It can be understood that the back-end service module may be a trusted execution environment in the terminal device that is different from the REE where the application is located, and the TEE is a security area in the CPU. It runs in a separate environment and runs in parallel with the operating system. The CPU ensures that both the confidentiality and integrity of the code and data in the TEE are protected. By using both hardware and software to protect data and code, TEEs are more secure than operating systems. Trusted applications running in the TEE have access to the full capabilities of the device's main processor and memory, while hardware isolation protects these components from user-installed applications running in the main operating system. Therefore, the code and data running in the TEE are confidential and cannot be tampered with.
具体的,TEE在不同CPU上有不同的实现方案,例如在ARM芯片,也就是一般移动终端CPU上实现TEE的技术为TrustZone,且由于ARM由不同厂商定制,实际方案有很多,例如Kinibi、QSEE、TEE OS、Knox等;而在Intel的CPU上实现TEE的技术为软件保护扩展(Software Guard Extensions,SGX),为硬件级的隐私保护计算技术,使应用程序能够在信任的执行环境中执行代码和保护秘密,让开发者直接控制他们的应用程序安全,具体的可信执行环境下的隐私保护计算技术由实际场景而定,本实施例中以TrustZone为例进行说明,并不做限定。Specifically, TEE has different implementation schemes on different CPUs. For example, the technology for implementing TEE on ARM chips, that is, general mobile terminal CPUs, is TrustZone, and since ARM is customized by different manufacturers, there are many actual schemes, such as Kinibi, QSEE , TEE OS, Knox, etc.; and the technology to implement TEE on Intel's CPU is Software Guard Extensions (SGX), a hardware-level privacy-preserving computing technology that enables applications to execute code in a trusted execution environment and protection of secrets, allowing developers to directly control the security of their application programs. The specific privacy protection computing technology in a trusted execution environment depends on the actual scenario. In this embodiment, TrustZone is used as an example for description, which is not limited.
另外,后端服务模块也可以是云端服务器中的可信执行环境,具体的设备分布因实际场景而定。In addition, the back-end service module can also be a trusted execution environment in the cloud server, and the specific device distribution depends on the actual scenario.
在一种可能的场景中,对于识别得到目标识别信息的过程,可以是首先后端服务模块基于验证密钥对签名加密信息进行解密,以得到目标数据流;然后基于目标特征对目标数据流中的图像序列进行筛选,以得到至少一张目标图像,目标特征与生物特征信息相关联;对目标图像进行识别,以得到目标识别信息。例如筛选得到图像质量分最高的图像进行识别,从而保证目标识别信息的准确性。In a possible scenario, for the process of identifying and obtaining the target identification information, the back-end service module can first decrypt the signed encrypted information based on the verification key to obtain the target data stream; The image sequence is screened to obtain at least one target image, and the target feature is associated with the biometric information; the target image is identified to obtain the target identification information. For example, the image with the highest image quality score is obtained by screening for identification, so as to ensure the accuracy of the target identification information.
可选的,在人脸识别中,采集模块可以采用3D摄像头,从而可以获得多个维度的图像信息,具体的,首先获取目标数据流对应的深度信息和红外信息;然后提取目标图像在深度信息中对应的深度图像;并提取目标图像在红外信息中对应的红外图像;进而根据目标图像、深度图像和红外图像进行图像识别,以得到目标识别信息。从而从不同的维度进行图像识别,保证了识别结果的准确性。Optionally, in face recognition, the acquisition module can use a 3D camera, so that image information in multiple dimensions can be obtained. Specifically, the depth information and infrared information corresponding to the target data stream are first obtained; then the depth information of the target image is extracted. and extract the infrared image corresponding to the target image in the infrared information; and then perform image recognition according to the target image, the depth image and the infrared image to obtain the target identification information. Thus, image recognition is performed from different dimensions, which ensures the accuracy of the recognition results.
上述实施例介绍了验证通过的场景,而对于验证不通过的场景,即目标密钥与验证密钥不对应时,则反馈验证不通过,停止识别进程。另外,还可以触发对目标标识进行查验的过程,即若验证结果指示目标密钥与验证密钥不对应,则后端服务模块反馈异常标识;并基于异常标识触发对目标标识进行查验,以对目标标识进行更新。即确定当前获取的目标标识是否准确,进而二次获取,从而提高识别过程的容错率。The above-mentioned embodiment introduces a scenario in which the verification passes, and for a scenario in which the verification fails, that is, when the target key does not correspond to the verification key, the verification is rejected and the identification process is stopped. In addition, the process of checking the target identification can also be triggered, that is, if the verification result indicates that the target key does not correspond to the verification key, the back-end service module feeds back the abnormal identification; The target ID is updated. That is, it is determined whether the currently acquired target identifier is accurate, and then secondary acquisition is performed, thereby improving the fault tolerance rate of the identification process.
下面,结合一种具体的硬件场景对上述识别过程进行说明,如图4所示,图4为本申请实施例提供的一种生物特征信息的识别方法的场景示意图,图中示出了终端设备包括采集模块和普通执行环境中运行的应用程序,以及应用程序与后端服务模块的交互场景。其中,采集模块包括传感器(SENSOR)和微处理器(digital signal processor,DSP),该微处理器是以数字信号来处理大量信息的器件,其中包含了用于为数据流签名加密的签名模块以及存储目标密钥的安全元件(Secure Element,SE)。The above identification process will be described below in conjunction with a specific hardware scenario. As shown in FIG. 4 , FIG. 4 is a scene schematic diagram of a method for identifying biometric information provided by an embodiment of the present application. The figure shows a terminal device. Including the acquisition module and the application running in the common execution environment, as well as the interaction scene between the application and the back-end service module. Among them, the acquisition module includes a sensor (SENSOR) and a microprocessor (digital signal processor, DSP), the microprocessor is a device that processes a large amount of information with digital signals, which includes a signature module for signing and encrypting data streams and The Secure Element (SE) where the target key is stored.
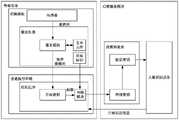
具体的,采集模块(摄像头)内部,具备SE模块,用于存储摄像头唯一性标识的CPUID,以及前期通过密钥烧录工具烧录的唯一密钥。另外,摄像头内部,具备签名模块,用于将读SE中的密钥,以及用该密钥对数据流进行签名。另外,REE为非安全的android OS运行环境,其中运行用户操作的业务APP。APP中包括了用于网络通信认证的密钥,由于是在APP中,容易被破解或泄漏。故需要将数据流输入后端服务模块进行识别。而对于后端服务模块,其中的流媒体服务用于将来自摄像头的数据流进行验证以及优选,选出最优的人脸图片。验证分为通用AES私钥验证网络通信认证身份,以及针对该CPUID对应唯一私钥验证数据源合法性;人脸识别服务则用于将来自流媒体服务的人脸图片进行人脸识别,换取该人脸图片对应的用户身份信息,并且将信息返回给摄像头。Specifically, inside the acquisition module (camera), there is an SE module, which is used to store the CPUID of the unique identification of the camera, and the unique key burned by the key burning tool in the early stage. In addition, inside the camera, there is a signature module, which is used to read the key in the SE and use the key to sign the data stream. In addition, REE is a non-secure android OS operating environment, in which a business APP operated by a user is run. The APP includes the key used for network communication authentication, because it is in the APP, it is easy to be cracked or leaked. Therefore, it is necessary to input the data stream into the back-end service module for identification. As for the back-end service module, the streaming media service is used to verify and optimize the data stream from the camera, and select the best face picture. Verification is divided into general AES private key verification of network communication authentication identity, and verification of the legality of the data source against the unique private key corresponding to the CPUID; face recognition service is used to perform face recognition on face pictures from streaming media services, in exchange for the person The user identity information corresponding to the face picture, and the information is returned to the camera.
结合图4所示的模块关联关系,在摄像头进行人脸识别的场景中,可以基于如下步骤进行信息识别。即摄像头采集生成未签名的裸数据流,通过DSP中的签名模块,读取SE中的唯一AES密钥进行签名。然后将签名数据流传递到REE中的APP,APP通过APK中预置的通用AES网络通信认证密钥进行签名,同时读取摄像头的CPUID,通过网络模块一并将数据传送给后端服务。在后端流媒体服务在收到终端的请求后,通过通用的AES私验证网络请求的身份,验证通过后,拆解网络包,得到CPUID和签名数据流。再通过唯的AES私钥对签名数据流进行解密。过程中认证不通过则返回终端认证失败,终止流程。而对于数据识别的过程,流媒体服务将解密后视频流数据进行人脸优选,选出最优图,即人脸图片质量分最高的图,并获取与该图对应的深度图和红外图。进而在获取三张图片后,传递给人脸识别服务进行人脸识别,并且最终人脸识别结果返回给APP。Combined with the module association shown in FIG. 4 , in the scene where the camera performs face recognition, information recognition can be performed based on the following steps. That is, the camera collects and generates an unsigned raw data stream, and reads the unique AES key in the SE for signature through the signature module in the DSP. Then the signed data stream is transmitted to the APP in the REE, and the APP is signed by the general AES network communication authentication key preset in the APK, and at the same time reads the CPUID of the camera, and transmits the data to the back-end service through the network module. After receiving the request from the terminal, the back-end streaming media service uses the common AES to privately verify the identity of the network request. After the verification is passed, the network packet is disassembled to obtain the CPUID and the signed data stream. Then decrypt the signed data stream through the unique AES private key. If the authentication fails during the process, the terminal authentication failure will be returned, and the process will be terminated. For the data identification process, the streaming media service performs face selection on the decrypted video stream data, selects the optimal image, that is, the image with the highest quality score of the face image, and obtains the depth map and infrared image corresponding to the image. Then, after obtaining three pictures, it is passed to the face recognition service for face recognition, and the final face recognition result is returned to the APP.
上述实施例中指出采集模块与后端服务模块之间存在事先配置的过程,下面对该事先配置的过程进行说明,即首先基于目标工具(例如烧录工具)获取采集模块对应的模块信息(例如CPU信息);然后根据模块信息确定目标标识(例如CPUID);进而将目标标识传输至后端服务模块,以使得后端服务模块根据目标标识生成目标密钥和验证密钥(例如采用AES算法生成唯一密钥),且目标密钥和验证密钥相对应;并使得后端服务模块将目标密钥反馈至采集模块对应的存储模块中存储。In the above-mentioned embodiment, it is pointed out that there is a pre-configured process between the acquisition module and the back-end service module. The pre-configured process will be described below, that is, first obtain the module information ( For example, CPU information); then determine the target identification (for example, CPUID) according to the module information; and then transmit the target identification to the back-end service module, so that the back-end service module generates a target key and a verification key (for example, using AES algorithm) according to the target identification Generate a unique key), and the target key corresponds to the verification key; and make the back-end service module feed back the target key to the storage module corresponding to the acquisition module for storage.
在一种可能的场景中,后端服务模块还可以将验证密钥上传至云端服务器进行存储,存储在云端服务器中的验证密钥响应于目标标识的输入进行下发,从而不会受到本地硬件的限制。In a possible scenario, the back-end service module can also upload the verification key to the cloud server for storage, and the verification key stored in the cloud server is issued in response to the input of the target identifier, so that it will not be affected by the local hardware limits.
下面结合一种具体的硬件场景对实现配置目标密钥的过程进行说明,如图5所示,图5为本申请实施例提供的一种生物特征信息的识别方法的场景示意图,图中示出了首先运行在PC端的烧录工具(目标工具),并读取当前摄像头的CPUID(目标标识)。进而烧录工具将该CPUID上传到后端服务模块,后端服务模块针对该CPUID分配唯一的AES密钥(目标密钥),存储在云端数据库中,并同时将该密钥返回给烧录工具。进一步额,烧录工具在获取到该密钥后,写入摄像头的SE芯片内,以在数据流获取时进行加密签名,从而保证采集模块的可信度。The following describes the process of implementing the configuration target key with reference to a specific hardware scenario. As shown in FIG. 5 , FIG. 5 is a scene schematic diagram of a method for identifying biometric information provided by an embodiment of the present application. First, run the burning tool (target tool) on the PC side, and read the CPUID (target identification) of the current camera. Then the burning tool uploads the CPUID to the back-end service module, and the back-end service module allocates a unique AES key (target key) for the CPUID, stores it in the cloud database, and returns the key to the burning tool at the same time . Furthermore, after obtaining the key, the burning tool writes it into the SE chip of the camera to encrypt and sign when the data stream is obtained, thereby ensuring the credibility of the acquisition module.
结合上述实施例可知,通过获取采集模块采集的生物特征信息,该采集模块烧录有唯一的目标密钥;然后基于目标密钥对生物特征信息进行签名,以得到签名加密信息;并将采集模块对应的目标标识与签名加密信息输入后端服务模块中,以使得后端服务模块对签名加密信息进行验证得到验证结果,验证结果基于目标密钥与验证密钥的对应关系确定,验证密钥为后端服务模块基于模块标识调用所得;当验证结果指示目标密钥与验证密钥相对应时,则后端服务模块基于验证密钥对签名加密信息进行解密,以进行识别得到目标识别信息。从而实现安全的生物特征信息的识别过程,由于采用唯一的目标密钥对采集模块进行信息源的可信度验证,保证了信息的安全性,且解密过程在后端服务模块中执行,对生物特征信息进行了隔离,使得恶意攻击无法执行,提高了识别过程的安全性。Combining the above embodiments, it can be known that by acquiring the biometric information collected by the acquisition module, the acquisition module is programmed with a unique target key; then the biometric information is signed based on the target key to obtain signature encryption information; and the acquisition module The corresponding target identifier and signature encryption information are input into the back-end service module, so that the back-end service module verifies the signature and encryption information to obtain the verification result. The verification result is determined based on the correspondence between the target key and the verification key. The verification key is The back-end service module is obtained by calling based on the module identifier; when the verification result indicates that the target key corresponds to the verification key, the back-end service module decrypts the signed encrypted information based on the verification key to identify and obtain the target identification information. In this way, the identification process of secure biometric information is realized. Because the unique target key is used to verify the credibility of the information source for the acquisition module, the security of the information is ensured, and the decryption process is performed in the back-end service module. The feature information is isolated, so that malicious attacks cannot be executed, and the security of the identification process is improved.
上述生物特征信息的识别方法可以应用于移动终端的移动支付场景中,下面对该场景进行说明。请参阅图6,图6为本申请实施例提供的另一种生物特征信息的识别方法的流程图,本申请实施例至少包括以下步骤:The above identification method of biometric information can be applied to a mobile payment scenario of a mobile terminal, and the scenario will be described below. Please refer to FIG. 6. FIG. 6 is a flowchart of another method for identifying biometric information provided by an embodiment of the present application. The embodiment of the present application includes at least the following steps:
601、采集模块和后端服务模块之间进行目标密钥的配置。601. The target key is configured between the collection module and the back-end service module.
本实施例中,配置目标密钥的过程可以参考图5所示实施例的过程,此处不做赘述。In this embodiment, for the process of configuring the target key, reference may be made to the process of the embodiment shown in FIG. 5 , which will not be repeated here.
602、采集模块响应于目标交易指令,获取数据流。602. The acquisition module acquires the data stream in response to the target transaction instruction.
本实施例中,目标交易指令可以是用户在移动终端进行支付操作时,需要输入密码进行身份验证,而身份验证是采用人脸识别的方式进行,此时进行人脸识别的过程即产生了目标交易指令,从而获取对应的数据流,即人脸数据(生物特征信息)。In this embodiment, the target transaction instruction may be that the user needs to enter a password for identity verification when performing a payment operation on the mobile terminal, and the identity verification is performed by means of face recognition. At this time, the process of face recognition generates the target. Transaction instructions to obtain the corresponding data stream, that is, face data (biometric information).
603、采集模块基于目标密钥进行签名,得到加密数据流。603. The acquisition module performs a signature based on the target key to obtain an encrypted data stream.
本实施例中,加密数据流即为签名加密信息,在REE中不会被破解或篡改,从而保证了数据的安全性。In this embodiment, the encrypted data stream is the signed encrypted information, which will not be cracked or tampered with in the REE, thereby ensuring data security.
604、采集模块向应用程序发送加密数据流。604. The collection module sends the encrypted data stream to the application.
本实施例中,应用程序可以是移动支付软件,或其他需要进行支付验证的软件,具体程序形式因实际场景而定。In this embodiment, the application program may be mobile payment software, or other software requiring payment verification, and the specific program form depends on the actual scene.
605、应用程序确定目标标识。605. The application program determines the target identifier.
本实施例中,应用程序确定目标标识的过程即调用摄像头(采集模块)存储的目标标识,或历史缓存中的标识信息以作为目标标识。In this embodiment, the process of determining the target identifier by the application program is to call the target identifier stored by the camera (acquisition module) or the identifier information in the history cache as the target identifier.
606、应用程序进行网络密钥加密,以得到网络数据包。606. The application program performs network key encryption to obtain network data packets.
本实施例中,为了避免网络劫持的情况发生,可以进行通用网络的AES算法的加密过程,从而保证网络传输的安全性。In this embodiment, in order to avoid the occurrence of network hijacking, the encryption process of the AES algorithm of the general network can be performed, so as to ensure the security of network transmission.
607、应用程序向后端服务模块发送网络数据包。607. The application sends a network data packet to the back-end service module.
608、后端服务模块进行网络数据包拆解。608. The back-end service module disassembles the network data packet.
本实施例中,进行网络数据包拆解的过程即采用通用网络的AES算法的解密过程,从而进行数据流来源的验证,即对采集模块进行验证。In this embodiment, the process of disassembling the network data packet is the decryption process using the AES algorithm of the general network, so as to verify the source of the data stream, that is, to verify the acquisition module.
609、后端服务模块验证加密数据流。609. The back-end service module verifies the encrypted data stream.
本实施例中,验证加密数据流的过程即后端服务模块根据目标标识调用对应的验证密钥,若验证密钥与目标密钥对应,则可以进行解密得到数据流。In this embodiment, the process of verifying the encrypted data stream is that the back-end service module invokes the corresponding verification key according to the target identifier. If the verification key corresponds to the target key, the data stream can be obtained by decryption.
610、后端服务模块进行数据流的生物特征识别。610. The back-end service module performs biometric identification of the data stream.
本实施例中,生物特征识别的过程可以采用多维度的识别,即彩色图、深度图、红外图的结合识别,从而保证识别的准确性。In this embodiment, the process of biometric identification can adopt multi-dimensional identification, that is, the combined identification of color image, depth image and infrared image, so as to ensure the accuracy of identification.
611、后端服务模块进行身份验证。611. The back-end service module performs authentication.
本实施例中,身份验证的过程即确定识别得到的用户信息与应用程序中登录的用户是否对应,若对应,则说明身份验证通过。In this embodiment, the process of identity verification is to determine whether the identified user information corresponds to the user logged in in the application program, and if so, the identity verification is passed.
612、后端服务模块向应用程序发送身份验证结果。612. The back-end service module sends an authentication result to the application.
613、应用程序执行目标交易指令对应的交易操作。613. The application executes a transaction operation corresponding to the target transaction instruction.
本实施例中,若身份验证结果指示身份验证通过,则应用程序执行目标交易指令对应的交易操作,例如执行付款操作,或执行授信操作等。In this embodiment, if the identity verification result indicates that the identity verification is passed, the application program executes the transaction operation corresponding to the target transaction instruction, such as executing a payment operation, or executing a credit granting operation.
本实施例通过摄像头内置唯一密钥,对数据进行签名及后端验证,有效解决APP内密钥被窍取或在REE环境中,应用被攻破导致的数据不可信问题,保证数据可信,杜绝恶意攻击导致的数据安全问题,从而提高了基于生物特征信息进行交易过程中的安全性。In this embodiment, the unique key built into the camera is used to sign the data and verify the back-end data, which effectively solves the problem of untrustworthy data caused by the key in the APP being acquired or the application being breached in the REE environment, ensuring the credibility of the data and eliminating the need for Data security problems caused by malicious attacks, thereby improving the security of transactions based on biometric information.
为了更好的实施本申请实施例的上述方案,下面还提供用于实施上述方案的相关装置。请参阅图7,图7为本申请实施例提供的一种生物特征信息的识别装置的结构示意图,识别装置700包括:In order to better implement the above solutions of the embodiments of the present application, related devices for implementing the above solutions are also provided below. Please refer to FIG. 7. FIG. 7 is a schematic structural diagram of an apparatus for identifying biometric information provided by an embodiment of the present application. The identifying
获取单元701,用于获取采集模块采集的生物特征信息;an obtaining
签名单元702,用于基于所述目标密钥对所述生物特征信息进行签名,以得到签名加密信息;a
输入单元703,用于将所述采集模块对应的目标标识与所述签名加密信息输入后端服务模块中,以使得所述后端服务模块对所述签名加密信息进行验证得到验证结果,所述验证结果基于所述目标密钥与验证密钥的对应关系确定,所述验证密钥为所述后端服务模块基于所述模块标识调用所得;The
识别单元704,用于若所述验证结果指示所述目标密钥与所述验证密钥相对应,则所述后端服务模块基于所述验证密钥对所述签名加密信息进行解密,以进行识别得到目标识别信息。The
可选的,在本申请一些可能的实现方式中,所述输入单元703,具体用于基于网络密钥对所述采集模块对应的目标标识与所述签名加密信息进行处理,以得到网络加密包;Optionally, in some possible implementations of the present application, the
所述输入单元703,具体用于将所述网络加密包输入所述后端服务模块中,以使得所述后端服务模块根据所述网络密钥对所述网络加密包解密得到所述模块标识与所述签名加密信息;The
所述输入单元703,具体用于对所述签名加密信息进行验证得到验证结果。The
可选的,在本申请一些可能的实现方式中,所述输入单元703,具体用于将所述网络加密包输入所述后端服务模块中,以使得所述后端服务模块根据所述网络密钥确定身份信息;Optionally, in some possible implementations of the present application, the
所述输入单元703,具体用于若所述身份信息通过验证,则所述后端服务模块根据所述网络密钥对所述网络加密包解密得到所述模块标识与所述签名加密信息。The
可选的,在本申请一些可能的实现方式中,所述识别单元704,具体用于所述后端服务模块基于所述验证密钥对所述签名加密信息进行解密,以得到目标数据流;Optionally, in some possible implementations of the present application, the identifying
所述识别单元704,具体用于基于目标特征对所述目标数据流中的图像序列进行筛选,以得到至少一张目标图像,所述目标特征与所述生物特征信息相关联;The identifying
所述识别单元704,具体用于对所述目标图像进行识别,以得到目标识别信息。The identifying
可选的,在本申请一些可能的实现方式中,所述识别单元704,具体用于获取所述目标数据流对应的深度信息和红外信息;Optionally, in some possible implementations of the present application, the identifying
所述识别单元704,具体用于提取所述目标图像在所述深度信息中对应的深度图像;The identifying
所述识别单元704,具体用于提取所述目标图像在所述红外信息中对应的红外图像;The identifying
所述识别单元704,具体用于根据所述目标图像、所述深度图像和所述红外图像进行图像识别,以得到目标识别信息。The
可选的,在本申请一些可能的实现方式中,所述识别单元704,具体用于若所述验证结果指示所述目标密钥与所述验证密钥不对应,则所述后端服务模块反馈异常标识;Optionally, in some possible implementations of the present application, the identifying
所述识别单元704,具体用于基于所述异常标识触发对所述目标标识进行查验,以对所述目标标识进行更新。The identifying
可选的,在本申请一些可能的实现方式中,所述获取单元701,具体用于确定目标采集任务;Optionally, in some possible implementation manners of the present application, the acquiring
所述获取单元701,具体用于基于所述目标采集任务确定采集参数,所述采集参数包括采集区域与采集时长;The obtaining
所述获取单元701,具体用于根据所述采集参数对所述采集模块进行设置,以使得所述采集模块采集所述生物特征信息。The
可选的,在本申请一些可能的实现方式中,所述识别单元704,具体用于基于目标工具获取所述采集模块对应的模块信息;Optionally, in some possible implementation manners of the present application, the identifying
所述识别单元704,具体用于根据所述模块信息确定所述目标标识;The identifying
所述识别单元704,具体用于将所述目标标识传输至所述后端服务模块,以使得所述后端服务模块根据所述目标标识生成所述目标密钥和所述验证密钥,所述目标密钥和所述验证密钥相对应;The identifying
所述识别单元704,具体用于将所述目标密钥反馈至所述采集模块对应的存储模块中存储。The identifying
可选的,在本申请一些可能的实现方式中,所述识别单元704,具体用于将所述验证密钥上传至云端服务器进行存储,存储在所述云端服务器中的所述验证密钥响应于所述目标标识的输入进行下发。Optionally, in some possible implementations of the present application, the identifying
通过获取采集模块采集的生物特征信息,该采集模块烧录有唯一的目标密钥;然后基于目标密钥对生物特征信息进行签名,以得到签名加密信息;并将采集模块对应的目标标识与签名加密信息输入后端服务模块中,以使得后端服务模块对签名加密信息进行验证得到验证结果,验证结果基于目标密钥与验证密钥的对应关系确定,验证密钥为后端服务模块基于模块标识调用所得;当验证结果指示目标密钥与验证密钥相对应时,则后端服务模块基于验证密钥对签名加密信息进行解密,以进行识别得到目标识别信息。从而实现安全的生物特征信息的识别过程,由于采用唯一的目标密钥对采集模块进行信息源的可信度验证,保证了信息的安全性,且解密过程在后端服务模块中执行,对生物特征信息进行了隔离,使得恶意攻击无法执行,提高了识别过程的安全性。By acquiring the biometric information collected by the acquisition module, the acquisition module is programmed with a unique target key; then the biometric information is signed based on the target key to obtain the signature encryption information; the target identification and signature corresponding to the acquisition module are The encrypted information is input into the back-end service module, so that the back-end service module verifies the signed encrypted information to obtain the verification result. The verification result is determined based on the corresponding relationship between the target key and the verification key. The verification key is the back-end service module based on the module. Identifies the result obtained from the call; when the verification result indicates that the target key corresponds to the verification key, the back-end service module decrypts the signed encrypted information based on the verification key to identify and obtain the target identification information. In this way, the identification process of secure biometric information is realized. Because the unique target key is used to verify the credibility of the information source for the acquisition module, the security of the information is ensured, and the decryption process is performed in the back-end service module. The feature information is isolated, so that malicious attacks cannot be executed, and the security of the identification process is improved.
本申请实施例还提供了一种基于生物特征信息识别的交易装置,如图8所示,图8为本申请实施例提供的一种基于生物特征信息识别的交易装置,交易装置800包括:The embodiment of the present application also provides a transaction device based on identification of biometric information, as shown in FIG. 8 , which is a transaction device based on identification of biometric information provided by the embodiment of the present application. The
采集单元801,用于响应于目标交易指令,触发采集模块采集生物特征信息;A
签名单元802,用于基于所述目标密钥对所述生物特征信息进行签名,以得到签名加密信息;a
验证单元803,用于将所述采集模块对应的目标标识与所述签名加密信息输入后端服务模块中,以使得所述后端服务模块对所述签名加密信息进行验证得到验证结果,所述验证结果基于所述目标密钥与验证密钥的对应关系确定,所述验证密钥为所述后端服务模块基于所述模块标识调用所得;A
识别单元804,用于若所述验证结果指示所述目标密钥与所述验证密钥相对应,则所述后端服务模块基于所述验证密钥对所述签名加密信息进行解密,以进行识别得到目标识别信息;The
交易单元805,用于若所述目标识别信息满足预设条件,则执行所述目标交易指令对应的交易操作。The
本申请实施例还提供了一种生物特征信息的采集装置,如图9所示,图9为本申请实施例提供的一种生物特征信息的采集装置,采集装置900包括:An embodiment of the present application also provides a device for collecting biometric information, as shown in FIG. 9 , which is a device for collecting biometric information provided by an embodiment of the present application. The collecting
确定单元901,用于确定模块信息中的目标标识;Determining
传输单元902,用于将所述目标标识传输至后端服务模块,以使得所述后端服务模块根据所述目标标识生成目标密钥和验证密钥,所述目标密钥和所述验证密钥相对应;The
存储单元903,相当于图4中的安全元件,用于存储所述后端服务模块反馈的所述目标密钥;The
采集单元904,相当于图4中的传感器,用于采集生物特征信息;The
签名单元905,相当于图4中的签名模块,用于基于所述目标密钥对所述生物特征信息进行签名,以得到签名加密信息,所述签名加密信息用于指示所述生物特征信息的识别过程。The
可以理解的是,该采集装置可以作为摄像头应用于终端设备中,下面对该终端设备进行说明。It can be understood that the collection device can be used as a camera in a terminal device, and the terminal device will be described below.
本申请实施例还提供了一种终端设备,如图10所示,是本申请实施例提供的另一种终端设备的结构示意图,为了便于说明,仅示出了与本申请实施例相关的部分,具体技术细节未揭示的,请参照本申请实施例方法部分。该终端可以为包括手机、平板电脑、个人数字助理(personal digital assistant,PDA)、销售终端(point of sales,POS)、车载电脑等任意终端设备,以终端为手机为例:An embodiment of the present application further provides a terminal device. As shown in FIG. 10 , it is a schematic structural diagram of another terminal device provided by an embodiment of the present application. For the convenience of description, only the part related to the embodiment of the present application is shown. , if the specific technical details are not disclosed, please refer to the method part of the embodiments of the present application. The terminal may be any terminal device including a mobile phone, a tablet computer, a personal digital assistant (PDA), a point of sales (POS), a vehicle-mounted computer, etc. The terminal is a mobile phone as an example:
图10示出的是与本申请实施例提供的终端相关的手机的部分结构的框图。参考图10,手机包括:射频(radio frequency,RF)电路1010、存储器1020、输入单元1030、显示单元1040、传感器1050、音频电路1060、无线保真(wireless fidelity,WiFi)模块1070、处理器1080、以及电源1090等部件。本领域技术人员可以理解,图10中示出的手机结构并不构成对手机的限定,可以包括比图示更多或更少的部件,或者组合某些部件,或者不同的部件布置。FIG. 10 is a block diagram showing a partial structure of a mobile phone related to a terminal provided by an embodiment of the present application. 10 , the mobile phone includes: a radio frequency (RF)
下面结合图10对手机的各个构成部件进行具体的介绍:The following describes the various components of the mobile phone in detail with reference to Figure 10:
RF电路1010可用于收发信息或通话过程中,信号的接收和发送,特别地,将基站的下行信息接收后,给处理器1080处理;另外,将设计上行的数据发送给基站。通常,RF电路1010包括但不限于天线、至少一个放大器、收发信机、耦合器、低噪声放大器(low noiseamplifier,LNA)、双工器等。此外,RF电路1010还可以通过无线通信与网络和其他设备通信。上述无线通信可以使用任一通信标准或协议,包括但不限于全球移动通讯系统(globalsystem of mobile communication,GSM)、通用分组无线服务(general packet radioservice,GPRS)、码分多址(code division multiple access,CDMA)、宽带码分多址(wideband code division multiple access,WCDMA)、长期演进(long term evolution,LTE)、电子邮件、短消息服务(short messaging service,SMS)等。The
存储器1020可用于存储软件程序以及模块,处理器1080通过运行存储在存储器1020的软件程序以及模块,从而执行手机的各种功能应用以及数据处理。存储器1020可主要包括存储程序区和存储数据区,其中,存储程序区可存储操作系统、至少一个功能所需的应用程序(比如声音播放功能、图像播放功能等)等;存储数据区可存储根据手机的使用所创建的数据(比如音频数据、电话本等)等。此外,存储器1020可以包括高速随机存取存储器,还可以包括非易失性存储器,例如至少一个磁盘存储器件、闪存器件、或其他易失性固态存储器件。The
输入单元1030可用于接收输入的数字或字符信息,以及产生与手机的用户设置以及功能控制有关的键信号输入。具体地,输入单元1030可包括触控面板1031以及其他输入设备1032。触控面板1031,也称为触摸屏,可收集用户在其上或附近的触摸操作(比如用户使用手指、触笔等任何适合的物体或附件在触控面板1031上或在触控面板1031附近的操作,以及在触控面板1031上一定范围内的隔空触控操作),并根据预先设定的程式驱动相应的连接装置。可选的,触控面板1031可包括触摸检测装置和触摸控制器两个部分。其中,触摸检测装置检测用户的触摸方位,并检测触摸操作带来的信号,将信号传送给触摸控制器;触摸控制器从触摸检测装置上接收触摸信息,并将它转换成触点坐标,再送给处理器1080,并能接收处理器1080发来的命令并加以执行。此外,可以采用电阻式、电容式、红外线以及表面声波等多种类型实现触控面板1031。除了触控面板1031,输入单元1030还可以包括其他输入设备1032。具体地,其他输入设备1032可以包括但不限于物理键盘、功能键(比如音量控制按键、开关按键等)、轨迹球、鼠标、操作杆等中的一种或多种。The
显示单元1040可用于显示由用户输入的信息或提供给用户的信息以及手机的各种菜单。显示单元1040可包括显示面板1041,可选的,可以采用液晶显示器(liquidcrystal display,LCD)、有机发光二极管(organic light-emitting diode,OLED)等形式来配置显示面板1041。进一步的,触控面板1031可覆盖显示面板1041,当触控面板1031检测到在其上或附近的触摸操作后,传送给处理器1080以确定触摸事件的类型,随后处理器1080根据触摸事件的类型在显示面板1041上提供相应的视觉输出。虽然在图10中,触控面板1031与显示面板1041是作为两个独立的部件来实现手机的输入和输入功能,但是在某些实施例中,可以将触控面板1031与显示面板1041集成而实现手机的输入和输出功能。The
手机还可包括至少一种传感器1050,比如光传感器、运动传感器以及其他传感器。具体地,光传感器可包括环境光传感器及接近传感器,其中,环境光传感器可根据环境光线的明暗来调节显示面板1041的亮度,接近传感器可在手机移动到耳边时,关闭显示面板1041和/或背光。作为运动传感器的一种,加速计传感器可检测各个方向上(一般为三轴)加速度的大小,静止时可检测出重力的大小及方向,可用于识别手机姿态的应用(比如横竖屏切换、相关游戏、磁力计姿态校准)、振动识别相关功能(比如计步器、敲击)等;至于手机还可配置的陀螺仪、气压计、湿度计、温度计、红外线传感器等其他传感器,在此不再赘述。The cell phone may also include at least one
音频电路1060、扬声器1061,传声器1062可提供用户与手机之间的音频接口。音频电路1060可将接收到的音频数据转换后的电信号,传输到扬声器1061,由扬声器1061转换为声音信号输出;另一方面,传声器1062将收集的声音信号转换为电信号,由音频电路1060接收后转换为音频数据,再将音频数据输出处理器1080处理后,经RF电路1010以发送给比如另一手机,或者将音频数据输出至存储器1020以便进一步处理。The
WiFi属于短距离无线传输技术,手机通过WiFi模块1070可以帮助用户收发电子邮件、浏览网页和访问流式媒体等,它为用户提供了无线的宽带互联网访问。虽然图10示出了WiFi模块1070,但是可以理解的是,其并不属于手机的必须构成,完全可以根据需要在不改变发明的本质的范围内而省略。WiFi is a short-distance wireless transmission technology. The mobile phone can help users to send and receive emails, browse web pages, and access streaming media through the
处理器1080是手机的控制中心,利用各种接口和线路连接整个手机的各个部分,通过运行或执行存储在存储器1020内的软件程序和/或模块,以及调用存储在存储器1020内的数据,执行手机的各种功能和处理数据,从而对手机进行整体监控。可选的,处理器1080可包括一个或多个处理单元;可选的,处理器1080可集成应用处理器和调制解调处理器,其中,应用处理器主要处理操作系统、用户界面和应用程序等,调制解调处理器主要处理无线通信。可以理解的是,上述调制解调处理器也可以不集成到处理器1080中。The
手机还包括给各个部件供电的电源1090(比如电池),可选的,电源可以通过电源管理系统与处理器1080逻辑相连,从而通过电源管理系统实现管理充电、放电、以及功耗管理等功能。The mobile phone also includes a power supply 1090 (such as a battery) for supplying power to various components. Optionally, the power supply can be logically connected to the
尽管未示出,手机还可以包括摄像头、蓝牙模块等,在此不再赘述。Although not shown, the mobile phone may also include a camera, a Bluetooth module, and the like, which will not be repeated here.
在本申请实施例中,该终端所包括的处理器1080还具有执行如上述页面处理方法的各个步骤的功能。In this embodiment of the present application, the
本申请实施例还提供了一种服务器,请参阅图11,图11是本申请实施例提供的一种服务器的结构示意图,该服务器1100可因配置或性能不同而产生比较大的差异,可以包括一个或一个以上中央处理器(central processing units,CPU)1122(例如,一个或一个以上处理器)和存储器1132,一个或一个以上存储应用程序1142或数据1144的存储介质1130(例如一个或一个以上海量存储设备)。其中,存储器1132和存储介质1130可以是短暂存储或持久存储。存储在存储介质1130的程序可以包括一个或一个以上模块(图示没标出),每个模块可以包括对服务器中的一系列指令操作。更进一步地,中央处理器1122可以设置为与存储介质1130通信,在服务器1100上执行存储介质1130中的一系列指令操作。An embodiment of the present application also provides a server. Please refer to FIG. 11. FIG. 11 is a schematic structural diagram of a server provided by an embodiment of the present application. The
服务器1100还可以包括一个或一个以上电源1126,一个或一个以上有线或无线网络接口1150,一个或一个以上输入输出接口1158,和/或,一个或一个以上操作系统1141,例如Windows ServerTM,Mac OS XTM,UnixTM,LinuxTM,FreeBSDTM等等。
上述实施例中由管理装置所执行的步骤可以基于该图11所示的服务器结构。The steps performed by the management apparatus in the above-described embodiment may be based on the server structure shown in FIG. 11 .
本申请实施例中还提供一种计算机可读存储介质,该计算机可读存储介质中存储有生物特征信息的识别指令,当其在计算机上运行时,使得计算机执行如前述图2至图6所示实施例描述的方法中生物特征信息的识别装置所执行的步骤。Embodiments of the present application further provide a computer-readable storage medium, where an identification instruction of biometric information is stored in the computer-readable storage medium, and when the computer-readable storage medium runs on a computer, causes the computer to execute the instructions shown in FIGS. 2 to 6 above. The steps performed by the apparatus for identifying biometric information in the method described in the exemplary embodiment.
本申请实施例中还提供一种包括生物特征信息的识别指令的计算机程序产品,当其在计算机上运行时,使得计算机执行如前述图2至图6所示实施例描述的方法中生物特征信息的识别装置所执行的步骤。The embodiments of the present application also provide a computer program product including identification instructions for biometric information, which, when running on a computer, enables the computer to execute the biometric information in the methods described in the embodiments shown in the foregoing FIG. 2 to FIG. 6 . The steps performed by the identification device.
本申请实施例还提供了一种生物特征信息的识别系统,所述生物特征信息的识别系统可以包含图7所描述实施例中的生物特征信息的识别装置,或图10所描述实施例中的终端设备,或者图11所描述的服务器。An embodiment of the present application also provides a biometric information identification system, and the biometric information identification system may include the biometric information identification device in the embodiment depicted in FIG. 7 , or the biometric information identification device in the embodiment depicted in FIG. Terminal equipment, or the server described in Figure 11.
所属领域的技术人员可以清楚地了解到,为描述的方便和简洁,上述描述的系统,装置和单元的具体工作过程,可以参考前述方法实施例中的对应过程,在此不再赘述。Those skilled in the art can clearly understand that, for the convenience and brevity of description, the specific working process of the system, device and unit described above may refer to the corresponding process in the foregoing method embodiments, which will not be repeated here.
在本申请所提供的几个实施例中,应该理解到,所揭露的系统,装置和方法,可以通过其它的方式实现。例如,以上所描述的装置实施例仅仅是示意性的,例如,所述单元的划分,仅仅为一种逻辑功能划分,实际实现时可以有另外的划分方式,例如多个单元或组件可以结合或者可以集成到另一个系统,或一些特征可以忽略,或不执行。另一点,所显示或讨论的相互之间的耦合或直接耦合或通信连接可以是通过一些接口,装置或单元的间接耦合或通信连接,可以是电性,机械或其它的形式。In the several embodiments provided in this application, it should be understood that the disclosed system, apparatus and method may be implemented in other manners. For example, the apparatus embodiments described above are only illustrative. For example, the division of the units is only a logical function division. In actual implementation, there may be other division methods. For example, multiple units or components may be combined or Can be integrated into another system, or some features can be ignored, or not implemented. On the other hand, the shown or discussed mutual coupling or direct coupling or communication connection may be through some interfaces, indirect coupling or communication connection of devices or units, and may be in electrical, mechanical or other forms.
所述作为分离部件说明的单元可以是或者也可以不是物理上分开的,作为单元显示的部件可以是或者也可以不是物理单元,即可以位于一个地方,或者也可以分布到多个网络单元上。可以根据实际的需要选择其中的部分或者全部单元来实现本实施例方案的目的。The units described as separate components may or may not be physically separated, and components displayed as units may or may not be physical units, that is, may be located in one place, or may be distributed to multiple network units. Some or all of the units may be selected according to actual needs to achieve the purpose of the solution in this embodiment.
另外,在本申请各个实施例中的各功能单元可以集成在一个处理单元中,也可以是各个单元单独物理存在,也可以两个或两个以上单元集成在一个单元中。上述集成的单元既可以采用硬件的形式实现,也可以采用软件功能单元的形式实现。In addition, each functional unit in each embodiment of the present application may be integrated into one processing unit, or each unit may exist physically alone, or two or more units may be integrated into one unit. The above-mentioned integrated units may be implemented in the form of hardware, or may be implemented in the form of software functional units.
所述集成的单元如果以软件功能单元的形式实现并作为独立的产品销售或使用时,可以存储在一个计算机可读取存储介质中。基于这样的理解,本申请的技术方案本质上或者说对现有技术做出贡献的部分或者该技术方案的全部或部分可以以软件产品的形式体现出来,该计算机软件产品存储在一个存储介质中,包括若干指令用以使得一台计算机设备(可以是个人计算机,生物特征信息的识别装置,或者网络设备等)执行本申请各个实施例所述方法的全部或部分步骤。而前述的存储介质包括:U盘、移动硬盘、只读存储器(read-only memory,ROM)、随机存取存储器(random access memory,RAM)、磁碟或者光盘等各种可以存储程序代码的介质。The integrated unit, if implemented in the form of a software functional unit and sold or used as an independent product, may be stored in a computer-readable storage medium. Based on this understanding, the technical solutions of the present application can be embodied in the form of software products in essence, or the parts that contribute to the prior art, or all or part of the technical solutions, and the computer software products are stored in a storage medium , including several instructions to make a computer device (which may be a personal computer, a device for identifying biometric information, or a network device, etc.) to execute all or part of the steps of the methods described in the various embodiments of the present application. The aforementioned storage medium includes: U disk, removable hard disk, read-only memory (ROM), random access memory (RAM), magnetic disk or optical disk and other media that can store program codes .
以上所述,以上实施例仅用以说明本申请的技术方案,而非对其限制;尽管参照前述实施例对本申请进行了详细的说明,本领域的普通技术人员应当理解:其依然可以对前述各实施例所记载的技术方案进行修改,或者对其中部分技术特征进行等同替换;而这些修改或者替换,并不使相应技术方案的本质脱离本申请各实施例技术方案的精神和范围。As mentioned above, the above embodiments are only used to illustrate the technical solutions of the present application, but not to limit them; although the present application has been described in detail with reference to the foregoing embodiments, those of ordinary skill in the art should understand: The technical solutions described in the embodiments are modified, or some technical features thereof are equivalently replaced; and these modifications or replacements do not make the essence of the corresponding technical solutions deviate from the spirit and scope of the technical solutions in the embodiments of the present application.
Claims (15)
Translated fromChinesePriority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202011102334.1ACN114372801A (en) | 2020-10-15 | 2020-10-15 | A kind of identification method of biometric information and related device |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202011102334.1ACN114372801A (en) | 2020-10-15 | 2020-10-15 | A kind of identification method of biometric information and related device |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| CN114372801Atrue CN114372801A (en) | 2022-04-19 |
Family
ID=81138662
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN202011102334.1APendingCN114372801A (en) | 2020-10-15 | 2020-10-15 | A kind of identification method of biometric information and related device |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN114372801A (en) |
Cited By (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN115527556A (en)* | 2022-05-09 | 2022-12-27 | 青岛海尔智能家电科技有限公司 | Speech continuous recognition method, device and intelligent switch panel |
| CN115941183A (en)* | 2023-02-27 | 2023-04-07 | 紫光同芯微电子有限公司 | Biological information processing method and related device |
| CN116112174A (en)* | 2022-12-09 | 2023-05-12 | 中信银行股份有限公司 | Face recognition authentication processing method and device |
| CN117494092A (en)* | 2023-11-14 | 2024-02-02 | 深圳市策城软件有限公司 | Scenic spot ticket non-inductive verification method, system and medium based on living organism identification |
Citations (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN107733635A (en)* | 2017-11-29 | 2018-02-23 | 四川长虹电器股份有限公司 | Data safe transmission method based on gateway |
| CN110414200A (en)* | 2019-04-08 | 2019-11-05 | 广州腾讯科技有限公司 | Auth method, device, storage medium and computer equipment |
| CN110555706A (en)* | 2019-08-30 | 2019-12-10 | 北京银联金卡科技有限公司 | Face payment security method and platform based on security unit and trusted execution environment |
| CN111598573A (en)* | 2020-04-10 | 2020-08-28 | 维沃移动通信有限公司 | Device fingerprint verification method and device |
- 2020
- 2020-10-15CNCN202011102334.1Apatent/CN114372801A/enactivePending
Patent Citations (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN107733635A (en)* | 2017-11-29 | 2018-02-23 | 四川长虹电器股份有限公司 | Data safe transmission method based on gateway |
| CN110414200A (en)* | 2019-04-08 | 2019-11-05 | 广州腾讯科技有限公司 | Auth method, device, storage medium and computer equipment |
| CN110555706A (en)* | 2019-08-30 | 2019-12-10 | 北京银联金卡科技有限公司 | Face payment security method and platform based on security unit and trusted execution environment |
| CN111598573A (en)* | 2020-04-10 | 2020-08-28 | 维沃移动通信有限公司 | Device fingerprint verification method and device |
Cited By (8)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN115527556A (en)* | 2022-05-09 | 2022-12-27 | 青岛海尔智能家电科技有限公司 | Speech continuous recognition method, device and intelligent switch panel |
| CN115527556B (en)* | 2022-05-09 | 2025-09-30 | 青岛海尔智能家电科技有限公司 | Continuous voice recognition method, device and intelligent switch panel |
| CN116112174A (en)* | 2022-12-09 | 2023-05-12 | 中信银行股份有限公司 | Face recognition authentication processing method and device |
| CN116112174B (en)* | 2022-12-09 | 2024-12-24 | 中信银行股份有限公司 | A face recognition authentication processing method and device |
| CN115941183A (en)* | 2023-02-27 | 2023-04-07 | 紫光同芯微电子有限公司 | Biological information processing method and related device |
| CN115941183B (en)* | 2023-02-27 | 2023-10-13 | 紫光同芯微电子有限公司 | Biological information processing method and related device |
| CN117494092A (en)* | 2023-11-14 | 2024-02-02 | 深圳市策城软件有限公司 | Scenic spot ticket non-inductive verification method, system and medium based on living organism identification |
| CN117494092B (en)* | 2023-11-14 | 2024-06-04 | 深圳市策城软件有限公司 | Scenic spot ticket non-inductive verification method, system and medium based on living organism identification |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| CN112733107B (en) | Information verification method, related device, equipment and storage medium | |
| US20210336780A1 (en) | Key updating method, apparatus, and system | |
| US11669465B1 (en) | Secure storage of data through a multifaceted security scheme | |
| CN109600223B (en) | Verification method, activation method, device, equipment and storage medium | |
| CN107592964B (en) | System, apparatus and method for multi-owner transfer of ownership of a device | |
| US11943256B2 (en) | Link detection method and apparatus, electronic device, and storage medium | |
| CN107211025B (en) | Secure Communication with Wearables | |
| CN114372801A (en) | A kind of identification method of biometric information and related device | |
| WO2021120793A1 (en) | Face image transmission method and apparatus, numerical value transfer method and apparatus, and electronic device | |
| CN113395159A (en) | Data processing method based on trusted execution environment and related device | |
| US11431684B2 (en) | Data response method, terminal device, and server | |
| WO2017041599A1 (en) | Service processing method and electronic device | |
| US11017066B2 (en) | Method for associating application program with biometric feature, apparatus, and mobile terminal | |
| CN111181909B (en) | Identity information acquisition method and related device | |
| CN111475832B (en) | Data management method and related device | |
| WO2017028711A1 (en) | Method for processing data, wearable electronic equipment and system | |
| CN113821821B (en) | Security architecture system, cryptographic operation method of security architecture system and computing device | |
| CN111598573A (en) | Device fingerprint verification method and device | |
| CN108763876A (en) | A resource copyright verification method, device and equipment | |
| CN108460251B (en) | Method, device and system for running application program | |
| CN113923005B (en) | Method and system for writing data | |
| CN108737341B (en) | Service processing method, terminal and server | |
| CN114697007B (en) | Key management method, corresponding device and system | |
| EP3896592B1 (en) | Electronic device for selecting key to be used for encryption on basis of amount of information of data to be encrypted, and operation method of electronic device | |
| WO2017000237A1 (en) | Algorithm update method, device to be updated, and server |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination |