CN114329486A - Asset vulnerability management method and device, electronic equipment and storage medium - Google Patents
Asset vulnerability management method and device, electronic equipment and storage mediumDownload PDFInfo
- Publication number
- CN114329486A CN114329486ACN202111601386.8ACN202111601386ACN114329486ACN 114329486 ACN114329486 ACN 114329486ACN 202111601386 ACN202111601386 ACN 202111601386ACN 114329486 ACN114329486 ACN 114329486A
- Authority
- CN
- China
- Prior art keywords
- vulnerability
- asset
- information
- repair
- existing
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Pending
Links
- 238000007726management methodMethods0.000titleclaimsabstractdescription37
- 230000008439repair processEffects0.000claimsabstractdescription87
- 238000000034methodMethods0.000claimsabstractdescription69
- 238000012545processingMethods0.000claimsdescription18
- 230000011218segmentationEffects0.000claimsdescription18
- 238000004590computer programMethods0.000claimsdescription5
- 238000010586diagramMethods0.000description7
- 238000013102re-testMethods0.000description5
- 238000013515scriptMethods0.000description5
- 230000006870functionEffects0.000description4
- 238000012552reviewMethods0.000description2
- 238000004891communicationMethods0.000description1
- 238000001514detection methodMethods0.000description1
- 238000003062neural network modelMethods0.000description1
- 230000003287optical effectEffects0.000description1
Images
Landscapes
- Management, Administration, Business Operations System, And Electronic Commerce (AREA)
Abstract
Description
Translated fromChinese技术领域technical field
本申请涉及网络安全领域,具体地,涉及一种资产漏洞管理方法、一种资产漏洞管理装置、一种电子设备及一种计算机可读存储介质。The present application relates to the field of network security, and in particular, to an asset vulnerability management method, an asset vulnerability management device, an electronic device, and a computer-readable storage medium.
背景技术Background technique
现有技术中,在资产设备出现安全漏洞时,通常需要专业人员对安全漏洞进行修复,然而,由于没有对漏洞进行统一管理,在漏洞重复发生时,需要频繁调用人员对漏洞进行修复,从而导致相关人员的工作量大,修复漏洞耗时长,导致漏洞修复的效率低。漏洞频发与修复效率低都容易导致资产设备出现安全问题,从而出现财产损失。In the prior art, when a security loophole occurs in an asset device, a professional is usually required to repair the security loophole. However, since there is no unified management of the loophole, when the loophole occurs repeatedly, it is necessary to frequently call personnel to repair the loophole, which leads to The workload of relevant personnel is large, and it takes a long time to repair the vulnerability, resulting in low efficiency of vulnerability repair. Frequent vulnerabilities and low repair efficiency can easily lead to security problems in assets and equipment, resulting in property losses.
发明内容SUMMARY OF THE INVENTION
有鉴于此,本发明旨在提供一种资产漏洞管理方法、资产漏洞管理装置、一种电子设备及一种计算机可读存储介质,以减少漏洞修复人员的工作量,提高漏洞的修复效率以及减少资产设备安全问题的发生。In view of this, the present invention aims to provide an asset vulnerability management method, an asset vulnerability management device, an electronic device and a computer-readable storage medium, so as to reduce the workload of vulnerability repair personnel, improve the repair efficiency of vulnerabilities and reduce Occurrence of asset equipment security issues.
第一方面,本申请实施例中提供了一种资产漏洞管理方法,包括:对目标资产进行扫描,获取所述目标资产所存在的漏洞,所述目标资产基于用户的选择确定;将所述漏洞与漏洞库中的已修复的既有漏洞进行对比;在确定所述漏洞不在所述漏洞库内时,向技术人员反馈漏洞信息以使技术人员对所述漏洞进行修复,并将所述漏洞及对应的修复方法存入所述漏洞库中,以使在扫描出与所述漏洞相同的重复漏洞时,调用所述漏洞对应的修复方法对所述重复漏洞进行修复。In a first aspect, an asset vulnerability management method is provided in an embodiment of the present application, including: scanning a target asset to obtain vulnerabilities existing in the target asset, the target asset being determined based on a user's selection; Compare with the existing vulnerabilities that have been fixed in the vulnerability database; when it is determined that the vulnerability is not in the vulnerability database, feedback the vulnerability information to the technical personnel so that the technical personnel can repair the vulnerability, and the vulnerability and The corresponding repairing method is stored in the vulnerability library, so that when a repeated vulnerability that is the same as the vulnerability is scanned, the repairing method corresponding to the vulnerability is invoked to repair the repeated vulnerability.
本申请实施例中,通过获取目标资产所存在的漏洞,并将漏洞与漏洞库中的既有漏洞进行对比,可以快速判断目标资产所存在的漏洞是否与已经被修复过的既有漏洞相同,在确定漏洞不在漏洞库内时,向技术人员反馈并使技术人员对漏洞进行修复,同时将漏洞及技术人员对漏洞的修复方法进行保存,以便于后续资产中出现相同的漏洞时,可以快速调用对应的修复方法对重复漏洞进行修复,从而减少技术人员对漏洞修复的工作量,也可以简化修复过程,从而提高对漏洞的修复效率,通过将漏洞存入漏洞库进行统一管理,有助于提高对漏洞的管理效率,进而提高资产安全性,减少因漏洞导致的财产损失。In the embodiment of the present application, by obtaining the vulnerabilities existing in the target asset and comparing the vulnerabilities with the existing vulnerabilities in the vulnerability database, it can be quickly determined whether the existing vulnerabilities in the target assets are the same as the existing vulnerabilities that have been repaired, When it is determined that the vulnerability is not in the vulnerability library, feedback is given to the technicians and the technicians can repair the vulnerability. At the same time, the vulnerability and the repair method of the technician to the vulnerability are saved, so that when the same vulnerability appears in the subsequent assets, it can be quickly called. The corresponding repair method repairs repeated vulnerabilities, thereby reducing the workload of technicians for vulnerability repair, and also simplifies the repair process, thereby improving the repair efficiency of vulnerabilities. The management efficiency of loopholes can improve asset security and reduce property losses caused by loopholes.
一实施例中,所述将所述漏洞与漏洞库中的已修复的既有漏洞进行对比,包括:获取所述漏洞的漏洞信息;将所述漏洞信息与所述既有漏洞的既有漏洞信息对比;在所述漏洞信息与所述既有漏洞信息的相似度小于预设阈值时,确定所述漏洞不在所述漏洞库内。In an embodiment, the comparing the vulnerability with the existing vulnerabilities that have been fixed in the vulnerability database includes: acquiring vulnerability information of the vulnerability; comparing the vulnerability information with the existing vulnerabilities of the existing vulnerability Information comparison; when the similarity between the vulnerability information and the existing vulnerability information is less than a preset threshold, it is determined that the vulnerability is not in the vulnerability database.
本申请实施例中,通过将漏洞信息与漏洞库中既有漏洞的漏洞信息进行对比,在两者之间的相似度小于预设阈值时,确定漏洞不在漏洞库内,由此,可以快速判断出未修复过与该漏洞相同/相似的漏洞,以便于后续及时通知技术人员对该漏洞进行修复,进而提高漏洞修复的效率与减少漏洞存在的时间,提高资产安全性。In the embodiment of the present application, by comparing the vulnerability information with the vulnerability information of existing vulnerabilities in the vulnerability database, when the similarity between the two is less than a preset threshold, it is determined that the vulnerability is not in the vulnerability database, so that it can be quickly determined The same/similar vulnerabilities as the vulnerability have not been fixed, so that the technical personnel can be notified in time to repair the vulnerability, thereby improving the efficiency of vulnerability repair, reducing the time that the vulnerability exists, and improving asset security.
一实施例中,在所述漏洞信息与所述既有漏洞信息的相似度大于所述预设阈值时,确定所述漏洞为重复漏洞。In one embodiment, when the similarity between the vulnerability information and the existing vulnerability information is greater than the preset threshold, it is determined that the vulnerability is a duplicate vulnerability.
本申请实施例中,通过将漏洞信息与漏洞库中既有漏洞的漏洞信息进行对比,在两者之间的相似度大于预设阈值时,确定该漏洞为重复漏洞,即漏洞库中存在与该漏洞相同/相似的漏洞,由此,可以快速判断是否有该漏洞对应的修复方法,以便于后续调用修复方法及时对漏洞进行修复,进而提高漏洞修复的效率与减少漏洞存在的时间,提高资产安全性。In the embodiment of the present application, by comparing the vulnerability information with the vulnerability information of existing vulnerabilities in the vulnerability database, when the similarity between the two is greater than a preset threshold, it is determined that the vulnerability is a duplicate vulnerability, that is, there is a similar vulnerability in the vulnerability database. The vulnerability is the same/similar vulnerability, thus, it can be quickly judged whether there is a repair method corresponding to the vulnerability, so as to facilitate the subsequent invocation of the repair method to repair the vulnerability in time, thereby improving the efficiency of vulnerability repair and reducing the time that the vulnerability exists, and improving assets. safety.
一实施例中,所述将所述漏洞与漏洞库中的已修复的既有漏洞进行对比之前,所述方法还包括:对所述漏洞信息进行ik分词,获取分词结果;所述将所述漏洞信息与所述既有漏洞的既有漏洞信息对比,包括:将所述分词结果与所述既有漏洞的既有漏洞信息进行对比。In an embodiment, before comparing the vulnerability with the existing vulnerabilities that have been fixed in the vulnerability database, the method further includes: performing ik word segmentation on the vulnerability information to obtain a word segmentation result; Comparing the vulnerability information with the existing vulnerability information of the existing vulnerability includes: comparing the word segmentation result with the existing vulnerability information of the existing vulnerability.
本申请实施例中,通过ik分词,可以提取漏洞信息的关键词,获取分词结果,以便于判断该漏洞的重要程度、紧急程度等信息,进而及时对该漏洞进行修复,减少因漏洞导致的损失,提高资产的安全性。In the embodiment of the present application, through ik word segmentation, keywords of vulnerability information can be extracted, and word segmentation results can be obtained, so as to judge the importance, urgency and other information of the vulnerability, and then repair the vulnerability in time to reduce losses caused by the vulnerability. , improve the security of assets.
一实施例中,所述对目标资产进行扫描之前,所述方法还包括:基于用户的操作录入资产及对应的资产信息;对所述资产信息进行加密,生成所述资产对应的资产主键并存入资产数据库中,所述资产主键为用于表征资产信息的标识字符串。In one embodiment, before the scanning of the target asset, the method further includes: inputting the asset and corresponding asset information based on the user's operation; encrypting the asset information, and generating the asset primary key corresponding to the asset and co-existing into the asset database, and the asset primary key is an identification string used to characterize asset information.
本申请实施例中,通过基于用户的操作录入资产信息,以使用户能够选择目标资产并进行扫描。通过对资产信息进行加密,提高资产信息的安全性。In this embodiment of the present application, asset information is entered based on the user's operation, so that the user can select and scan the target asset. By encrypting asset information, the security of asset information is improved.
一实施例中,所述对目标资产进行扫描,获取所述目标资产所存在的漏洞,包括:基于用户所选择的所述目标资产创建扫描任务;基于所述扫描任务的数量从预先创建的多线程中获取相同数量的线程执行所述扫描任务,分别对所述扫描任务对应的所述目标资产进行扫描,其中,所述线程与漏洞扫描引擎数量相同且一对一绑定。In an embodiment, the scanning the target asset to obtain the vulnerabilities existing in the target asset includes: creating a scanning task based on the target asset selected by the user; The same number of threads are obtained from the threads to execute the scanning task, and the target assets corresponding to the scanning task are respectively scanned, wherein the threads and the vulnerability scanning engine have the same number and are bound one-to-one.
本申请实施例中,一个线程绑定一个漏洞扫描引擎,通过使用多线程分别对不同扫描任务对应的目标资产进行扫描,可以同时进行多个扫描任务,同时对多个资产进行扫描,有助于提高扫描效率,对一个扫描任务仅使用一个线程及对应的漏洞扫描引擎,可以避免因多个漏洞扫描引擎同时扫描一个目标资产导致的漏洞扫描结果重复的问题。In the embodiment of the present application, one thread is bound to one vulnerability scanning engine, and by using multiple threads to scan target assets corresponding to different scanning tasks, multiple scanning tasks can be performed simultaneously, and multiple assets can be scanned at the same time, which is helpful for Improve scanning efficiency, use only one thread and corresponding vulnerability scanning engine for a scanning task, which can avoid the problem of duplicate vulnerability scanning results caused by multiple vulnerability scanning engines scanning a target asset at the same time.
一实施例中,在对所述漏洞进行修复,并将所述漏洞及对应的修复方法存入所述漏洞库中之后,所述方法还包括:对所述目标资产进行复测,以确定所述目标资产的漏洞修复完成。In one embodiment, after the vulnerability is repaired and the vulnerability and the corresponding repair method are stored in the vulnerability database, the method further includes: re-testing the target asset to determine the The vulnerability repair of the target asset described above is completed.
本申请实施例中,通过对目标资产进行复测,确保漏洞已经修复完成,可以减少因漏洞未修复完成导致的安全隐患,同时复测还可以避免新漏洞发生未及时被发现的问题。In the embodiment of the present application, by re-testing the target asset to ensure that the vulnerability has been repaired, security risks caused by unrepaired vulnerabilities can be reduced, and the re-test can also avoid the problem that new vulnerabilities are not discovered in time.
第二方面,本申请实施例中提供了一种资产漏洞管理装置,包括:扫描模块,用于基于用户创建的扫描任务对目标资产进行扫描,获取所述目标资产所存在的漏洞;处理模块,将所述漏洞与漏洞库中的已修复的既有漏洞进行对比;所述处理模块,还用于在确定所述漏洞为不在所述漏洞库时,向技术人员反馈漏洞信息,以使技术人员对所述漏洞进行修复,并将所述漏洞及对应的修复方法存入所述漏洞库中,以使发生与所述漏洞相同的重复漏洞时,调用所述修复方法对所述重复漏洞进行修复。In a second aspect, an embodiment of the present application provides an asset vulnerability management device, including: a scanning module, configured to scan a target asset based on a scanning task created by a user, and acquire the vulnerabilities existing in the target asset; a processing module, Comparing the vulnerability with the existing vulnerabilities that have been fixed in the vulnerability library; the processing module is also used to feed back the vulnerability information to the technician when it is determined that the vulnerability is not in the vulnerability library, so that the technician can Repair the vulnerability, and store the vulnerability and the corresponding repair method in the vulnerability library, so that when the same repeated vulnerability as the vulnerability occurs, the repair method is invoked to repair the repeated vulnerability .
第三方面,本申请实施例提供了一种电子设备,包括存储器和处理器,所述存储器中存储有计算机可读指令,所述计算机可读指令被所述处理器执行时,使得所述处理器执行如第一方面所述的一种资产漏洞管理方法或实现如第二方面所述的资产漏洞管理装置的功能。In a third aspect, an embodiment of the present application provides an electronic device, including a memory and a processor, where computer-readable instructions are stored in the memory, and when the computer-readable instructions are executed by the processor, the processing The device executes the asset vulnerability management method according to the first aspect or implements the function of the asset vulnerability management device according to the second aspect.
第四方面,本申请实施例提供了一种计算机可读存储介质,所述可读存储介质中存储有计算机程序,当所述计算机程序在计算机上运行时,使得所述计算机执行如第一方面所述的一种资产漏洞管理方法或实现如第二方面所述的资产漏洞管理装置的功能。In a fourth aspect, an embodiment of the present application provides a computer-readable storage medium, where a computer program is stored in the readable storage medium, and when the computer program runs on a computer, the computer is made to execute the first aspect The asset vulnerability management method or the function of the asset vulnerability management device described in the second aspect is realized.
本公开的其他特征和优点将在随后的说明书中阐述,或者,部分特征和优点可以从说明书推知或毫无疑义地确定,或者通过实施本公开的上述技术即可得知。Additional features and advantages of the present disclosure will be set forth in the description that follows, or some may be inferred or unambiguously determined from the description, or may be learned by practicing the above-described techniques of the present disclosure.
为使本发明的上述目的、特征和优点能更明显易懂,下文特举本发明较佳实施例,并配合所附附图,作详细说明如下。In order to make the above-mentioned objects, features and advantages of the present invention more clearly understood, preferred embodiments of the present invention are exemplified below, and are described in detail as follows in conjunction with the accompanying drawings.
附图说明Description of drawings
为了更清楚地说明本申请实施例的技术方案,下面将对本申请实施例中所需要使用的附图作简单地介绍,应当理解,以下附图仅示出了本申请的某些实施例,因此不应被看作是对范围的限定,对于本领域普通技术人员来讲,在不付出创造性劳动的前提下,还可以根据这些附图获得其他相关的附图。In order to explain the technical solutions of the embodiments of the present application more clearly, the following briefly introduces the accompanying drawings that need to be used in the embodiments of the present application. It should be understood that the following drawings only show some embodiments of the present application, therefore It should not be regarded as a limitation of the scope. For those of ordinary skill in the art, other related drawings can also be obtained from these drawings without any creative effort.
图1为本申请实施例提供的一种资产漏洞管理方法的流程图;1 is a flowchart of a method for asset vulnerability management provided by an embodiment of the present application;
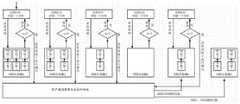
图2为本申请实施例提供的多线程处理任务的示意图;2 is a schematic diagram of a multi-threaded processing task provided by an embodiment of the present application;
图3为本申请实施例提供的一种资产漏洞管理装置的结构框图;FIG. 3 is a structural block diagram of an asset vulnerability management device according to an embodiment of the present application;
图4为本申请实施例提供的一种电子设备的结构框图。FIG. 4 is a structural block diagram of an electronic device provided by an embodiment of the present application.
图标:资产漏洞管理装置200;扫描模块220;处理模块210。Icons: asset vulnerability management device 200 ; scanning module 220 ; processing module 210 .
具体实施方式Detailed ways
为了使本申请的目的、技术方案及优点更加清楚明白,以下结合附图及实施例,对本申请进行进一步详细说明。应当理解,此处所描述的具体实施例仅仅用以解释本申请,并不用于限定本申请。In order to make the purpose, technical solutions and advantages of the present application more clearly understood, the present application will be described in further detail below with reference to the accompanying drawings and embodiments. It should be understood that the specific embodiments described herein are only used to explain the present application, but not to limit the present application.
资产是指公司所拥有的各种形式的设备、系统、软件等,如电脑、服务器、操作系统、数据库等,各种资产中通常存储有公司的各种资料、文件等,而当资产中出现安全漏洞时,就可能遭受入侵,从而导致公司的资料数据泄露,给公司带来财产上的损失,因此需定期对资产进行扫描,并对所存在的漏洞进行修复。Assets refer to the various forms of equipment, systems, software, etc. owned by the company, such as computers, servers, operating systems, databases, etc. Various assets usually store various company data, documents, etc., and when the assets appear When there is a security breach, it may be invaded, which will lead to the leakage of the company's data and data, and bring property losses to the company. Therefore, it is necessary to regularly scan the assets and repair the existing vulnerabilities.
漏洞的扫描可以利用一些脚本检测开放端口及服务,如利用各安全工具进行人工操作,下发扫描、检测的任务,对所需扫描的资产进行检测,确定出资产设备中所存在的漏洞。在扫描出漏洞之后,通常需要专门的技术人员对漏洞进行修复,以使资产恢复正常,避免被入侵造成的资料泄露与财产损失。然而,现有技术中,由于未对漏洞进行统一的管理,因此,在漏洞发生时,需要技术人员对每一个漏洞都进行修复,导致工作量大,且人工进行修复的效率低。Vulnerability scanning can use some scripts to detect open ports and services, such as using various security tools to perform manual operations, issue scanning and detection tasks, detect the assets to be scanned, and determine the vulnerabilities existing in the asset equipment. After the vulnerabilities are scanned, specialized technicians are usually required to repair the vulnerabilities to restore the assets to normal and avoid data leakage and property losses caused by the intrusion. However, in the prior art, since there is no unified management of vulnerabilities, when a vulnerability occurs, a technician is required to repair each vulnerability, resulting in a large workload and low efficiency of manual repair.
请参照图1,图1为本申请一实施例提供的一种资产漏洞管理方法的流程图,该方法可以包括如下步骤:Please refer to FIG. 1. FIG. 1 is a flowchart of an asset vulnerability management method provided by an embodiment of the present application. The method may include the following steps:
S110,对目标资产进行扫描,获取目标资产所存在的漏洞,目标资产基于用户的选择确定。S110: Scan the target asset to obtain loopholes existing in the target asset, and the target asset is determined based on the user's selection.
一实施例中,对目标资产进行扫描的过程包括:基于用户所选择的目标资产创建扫描任务;基于扫描任务的数量从预先创建的多线程中获取相同数量的线程执行所述扫描任务,分别对扫描任务对应的目标资产进行扫描,其中,线程与漏洞扫描引擎数量相同且一对一绑定。In one embodiment, the process of scanning the target asset includes: creating a scanning task based on the target asset selected by the user; obtaining the same number of threads from pre-created multi-threads based on the number of scanning tasks to execute the scanning task, respectively The target assets corresponding to the scanning task are scanned, and the number of threads and vulnerability scanning engines are the same and bound one-to-one.
本实施例中,在用户选择所需要扫描的目标资产后,可以生成对目标资产进行扫描的扫描任务。例如,用户在需对会议室的电脑进行扫描时,可以选择会议室的电脑,根据用户的选择,生成对会议室电脑的扫描任务。在一些实施例中,还可以接收用户终端所创建的扫描任务,从扫描任务中确定用户所选择的目标资产。In this embodiment, after the user selects the target asset to be scanned, a scanning task for scanning the target asset may be generated. For example, when the user needs to scan the computer in the conference room, he can select the computer in the conference room, and according to the user's selection, a scanning task for the computer in the conference room is generated. In some embodiments, the scanning task created by the user terminal may also be received, and the target asset selected by the user may be determined from the scanning task.
本实施例中,在生成对目标资产的扫描任务后,还可以将扫描任务发送至相关负责人的终端设备进行审核,在扫描任务通过负责人的审核之后,将扫描任务下发至任务队列中等待扫描。In this embodiment, after the scanning task for the target asset is generated, the scanning task can also be sent to the terminal device of the relevant person in charge for review, and after the scanning task passes the review of the person in charge, the scanning task is sent to the task queue Waiting for scan.
本实施例中,通过调用多线程中的线程执行扫描任务,对目标资产进行扫描,在利用多线程执行扫描任务之前,需先创建能够扫描漏洞的多线程。In this embodiment, the target asset is scanned by invoking a thread in the multi-thread to perform the scanning task. Before using the multi-thread to perform the scanning task, a multi-thread capable of scanning vulnerabilities needs to be created.
请参阅图2,图2为本申请一实施例提供的多线程处理任务的示意图。Please refer to FIG. 2 , which is a schematic diagram of a multi-thread processing task provided by an embodiment of the present application.
本实施例中,创建多线程的方式包括:根据扫描引擎的数量创建相同数量的线程,在创建线程之后,将线程与引擎绑定,一个线程与一个引擎绑定。如图2所示,线程1与引擎1绑定,线程2与引擎2绑定,线程3与引擎3绑定。在将线程与引擎绑定之后,将线程与引擎放入线程池中,由此,在执行扫描任务时,可以调用线程,进而调用线程所绑定的引擎对扫描任务所对应的目标资产进行扫描。In this embodiment, the method of creating multiple threads includes: creating the same number of threads according to the number of scanning engines, and after the threads are created, binding the threads to the engines, and binding one thread to one engine. As shown in Figure 2, thread 1 is bound to engine 1, thread 2 is bound to engine 2, and thread 3 is bound to engine 3. After the thread and the engine are bound, the thread and the engine are put into the thread pool, so that when the scan task is executed, the thread can be called, and then the engine bound to the thread can be called to scan the target asset corresponding to the scan task .
本实施例中,一个线程可以执行一个扫描任务,多线程可以同时执行多个扫描任务。具体地,在线程池存在未处于使用状态的线程时,可以从线程池中调用线程执行扫描任务,且一个线程执行一个扫描任务,例如,线程1-3可以分别执行三个扫描任务,由此,同时执行多个任务可以有效提高对漏洞扫描的效率,还可以避免出现扫描结果重复的问题。其中,扫描任务可以仅为一个目标资产,也可以包括多个目标资产,在包括多个目标资产时,扫描引擎逐个对目标资产进行扫描,以确定目标资产中所存在的漏洞。在线程池中没有可执行扫描任务的线程时,即线程池中的线程为0时,扫描任务在扫描队列中等待,在有线程完成扫描任务重新回到线程池中时,再从线程池中调用该线程执行扫描任务。In this embodiment, one thread may execute one scanning task, and multiple threads may execute multiple scanning tasks at the same time. Specifically, when there are threads in the thread pool that are not in use, a thread can be called from the thread pool to execute a scan task, and one thread executes one scan task. For example, threads 1-3 can execute three scan tasks respectively, thereby , executing multiple tasks at the same time can effectively improve the efficiency of vulnerability scanning, and can also avoid the problem of duplication of scanning results. The scanning task may be only one target asset, or may include multiple target assets. When multiple target assets are included, the scanning engine scans the target assets one by one to determine the vulnerabilities existing in the target asset. When there is no thread in the thread pool that can execute the scanning task, that is, when the thread in the thread pool is 0, the scanning task waits in the scanning queue. Call this thread to perform the scan task.
一实施例中,在用于选择目标资产进行扫描之前,需对资产的信息进行录入,录入过程包括:基于用户的操作录入资产及对应的资产信息;对资产信息进行加密,生成资产对应的资产主键并存入资产数据库中,资产主键为用于表征资产信息的标识字符串。In one embodiment, before being used to select a target asset for scanning, the information of the asset needs to be entered, and the entry process includes: entering the asset and the corresponding asset information based on the user's operation; encrypting the asset information to generate the asset corresponding to the asset The primary key is stored in the asset database, and the asset primary key is an identification string used to represent asset information.
本实施例中,需先将资产的信息录入到资产数据库中,以使用户能够从资产数据库中选择所需扫描的目标资产。具体地,所需录入的信息可以包括:资产的IP地址、设备类型、业务系统、端口号、所属部门、操作系统、登录用户名及密码等信息,用户可以根据资产本身的信息进行相应的录入,可以理解的是,不同的场景可以录入不同类型的信息,不同的资产所录入的信息也不同,所需录入的信息可以根据需求进行合理地选择与设定。其中,资产数据库可以是MySQL数据库、SQLServer数据库等。In this embodiment, the asset information needs to be entered into the asset database first, so that the user can select the target asset to be scanned from the asset database. Specifically, the information to be entered may include: the asset's IP address, device type, business system, port number, department to which it belongs, operating system, login user name and password, etc. The user can enter the information according to the asset itself. It can be understood that different types of information can be entered in different scenarios, and the information entered by different assets is also different. The information to be entered can be reasonably selected and set according to needs. The asset database may be a MySQL database, a SQL Server database, or the like.
本实施例中,还可以是在对资产的信息进行加密之后录入资产数据库,具体地,可以使用MD5的加密方式对资产的信息进行加密,生成资产对应的资产主键,资产主键为表征资产信息的标识字符串,将资产主键保存进数据库中,由此,可以提高资产信息的安全性。In this embodiment, the asset information can also be entered into the asset database after the asset information is encrypted. Specifically, the MD5 encryption method can be used to encrypt the asset information to generate an asset primary key corresponding to the asset. The identification string is used to save the asset primary key into the database, thereby improving the security of asset information.
S120,将漏洞与漏洞库中的已修复的既有漏洞进行对比。S120, compare the vulnerability with the existing vulnerabilities that have been fixed in the vulnerability library.
本实施例中,还设置有漏洞库,漏洞库中存储有已经被修复修复的漏洞及漏洞对应的漏洞信息,即已经修复的漏洞为既有漏洞。In this embodiment, a vulnerability database is further provided, and the vulnerability database stores the vulnerabilities that have been repaired and the vulnerability information corresponding to the vulnerabilities, that is, the vulnerabilities that have been repaired are existing vulnerabilities.
一实施例中,将漏洞与漏洞库中的已修复的既有漏洞进行对比包括:获取漏洞的漏洞信息;将漏洞信息与既有漏洞的既有漏洞信息对比;在漏洞信息与所述既有漏洞信息的相似度小于预设阈值时,确定漏洞不在所述漏洞库内。In one embodiment, comparing the vulnerability with the existing vulnerabilities that have been fixed in the vulnerability database includes: obtaining vulnerability information of the vulnerability; comparing the vulnerability information with the existing vulnerability information of the existing vulnerability; comparing the vulnerability information with the existing vulnerability information When the similarity of the vulnerability information is less than the preset threshold, it is determined that the vulnerability is not in the vulnerability database.
本实施例中,在将漏洞与既有漏洞进行对比之前,可以对漏洞进行解析,获取描述该漏洞的漏洞信息,例如,漏洞类别、漏洞的问题描述、漏洞的关键词等。在获取到漏洞信息之后,可以向用户展示该漏洞的信息,如漏洞的状态、漏洞的名称、存在时间、所在位置等。In this embodiment, before comparing the vulnerability with the existing vulnerability, the vulnerability may be analyzed to obtain vulnerability information describing the vulnerability, for example, the vulnerability category, the problem description of the vulnerability, and the keyword of the vulnerability. After obtaining the vulnerability information, the user can display the information of the vulnerability, such as the status of the vulnerability, the name of the vulnerability, the existence time, the location, and so on.
本实施例中,在获取到漏洞信息之后,将漏洞信息与漏洞库的既有漏洞的既有漏洞信息进行对比,可以是计算漏洞信息与既有漏洞信息的相似度,在相似度大于预设阈值时,将该漏洞确定为重复漏洞,也即该漏洞在漏洞库内,在相似度小于预设阈值时,确定该漏洞不在漏洞库内,例如,在目标资产的第一漏洞与漏洞库中的其中一个或多个漏洞之间的相似度大于85%时,确定第一漏洞为重复漏洞,目标资产的第二漏洞与漏洞库中的既有漏洞之间的相似度均低于85%时,确定第二漏洞不在漏洞库内。其中,相似度可以采取神经网络模型计算。In this embodiment, after the vulnerability information is obtained, the vulnerability information is compared with the existing vulnerability information of the existing vulnerabilities in the vulnerability database, which can be calculated by calculating the similarity between the vulnerability information and the existing vulnerability information. When the threshold is set, the vulnerability is determined as a duplicate vulnerability, that is, the vulnerability is in the vulnerability database, and when the similarity is less than the preset threshold, it is determined that the vulnerability is not in the vulnerability database, for example, in the first vulnerability and vulnerability database of the target asset When the similarity between one or more of the vulnerabilities is greater than 85%, the first vulnerability is determined to be a duplicate vulnerability, and the similarity between the second vulnerability of the target asset and the existing vulnerabilities in the vulnerability library is lower than 85% , determine that the second vulnerability is not in the vulnerability library. Among them, the similarity can be calculated by the neural network model.
本实施例中,在确定漏洞不在漏洞库内时,可以对漏洞的信息进行加密,生成漏洞主键,其中,加密方式可以使用MD5,则漏洞主键为标识字符串,在加密后,建立漏洞主键与资产主键及扫描任务的信息存入数据库中,便于后续查阅。In this embodiment, when it is determined that the vulnerability is not in the vulnerability database, the information of the vulnerability can be encrypted to generate the vulnerability primary key, wherein the encryption method can use MD5, and the vulnerability primary key is an identification string. After encryption, the vulnerability primary key and the vulnerability primary key are established. The asset primary key and scan task information are stored in the database for easy follow-up.
一实施例中,在将漏洞信息与既有漏洞信息进行对比之前,还可以对漏洞信息进行ik分词,获取分词结果,具体地,分词结果可以包括预先设置关键字词及漏洞的其他信息,在利用ik分词对漏洞信息进行分词时,提取漏洞信息中所包括的预先设置的关键词,在实际情况中,可以根据实际情况对关键词进行设置,例如,设置涉及漏洞紧急状态的关键词,漏洞所发生的位置等,在分词之后,还可以将分词结果与既有漏洞的既有漏洞信息进行对比,进而确认漏洞是否在漏洞库内。由此,用户可通过ik分词,可以获取漏洞的紧急情况、严重程度等漏洞信息,进而合理安排对该漏洞的修复顺序、修复的技术人员调用等。In one embodiment, before comparing the vulnerability information with the existing vulnerability information, ik word segmentation may also be performed on the vulnerability information to obtain a word segmentation result. Specifically, the word segmentation result may include preset key words and other information of vulnerabilities. When using ik word segmentation to segment the vulnerability information, the preset keywords included in the vulnerability information are extracted. In actual situations, the keywords can be set according to the actual situation. The location of the occurrence, etc., after the word segmentation, the word segmentation result can also be compared with the existing vulnerability information of the existing vulnerability, and then confirm whether the vulnerability is in the vulnerability database. As a result, users can obtain vulnerability information such as the emergency situation and severity of the vulnerability through ik segmentation, and then reasonably arrange the repair sequence of the vulnerability and the call of the repaired technicians.
S130,在确定漏洞不在漏洞库内时,向技术人员反馈漏洞信息以使技术人员对漏洞进行修复,并将漏洞及对应的修复方法存入漏洞库中,以使在扫描出与漏洞相同的重复漏洞时,调用漏洞对应的修复方法对重复漏洞进行修复。S130, when it is determined that the vulnerability is not in the vulnerability database, feedback the vulnerability information to the technician so that the technician can repair the vulnerability, and store the vulnerability and the corresponding repair method in the vulnerability database, so that the same duplicates as the vulnerability are scanned out. When there is a vulnerability, the repair method corresponding to the vulnerability is called to repair the repeated vulnerability.
本实施例中,漏洞库还存储有已修复的漏洞对应的修复方法,其中,修复方法可以是修复脚本,补丁等,对于目标资产中所出现的漏洞中存在重复漏洞时,可以从漏洞库中调用该漏洞对应的修复方法,对漏洞进行修复。In this embodiment, the vulnerability library also stores a repair method corresponding to the repaired vulnerability, wherein the repair method can be a repair script, a patch, etc. When there are repeated vulnerabilities among the vulnerabilities in the target asset, the repair method can be retrieved from the vulnerability library. Call the repair method corresponding to the vulnerability to repair the vulnerability.
本实施例中,在确定漏洞不在漏洞库内时,需通知相关的技术人员对漏洞进行修复,在技术人员对漏洞进行修复后,将技术人员的修复过程及使用到的脚本、补丁生成为修复脚本包,及生成为对应的修复方法。同时,将漏洞及对应的修复方法存入漏洞库中,具体地,可以是将漏洞主键及对应的修复脚本包存入漏洞库中。在将漏洞及对应的修复方法存入漏洞库后,后续再遇到重复漏洞时,可以直接调用对应的修复方法对该漏洞进行修复。In this embodiment, when it is determined that the vulnerability is not in the vulnerability database, relevant technical personnel need to be notified to repair the vulnerability. After the technical personnel repairs the vulnerability, the repair process of the technician and the scripts and patches used are generated as the repairing process. Script package, and generate the corresponding fix method. At the same time, the vulnerability and the corresponding repair method are stored in the vulnerability database, specifically, the vulnerability primary key and the corresponding repair script package may be stored in the vulnerability database. After the vulnerability and the corresponding repair method are stored in the vulnerability library, when a repeated vulnerability is encountered later, the corresponding repair method can be directly called to repair the vulnerability.
一实施例中,在对漏洞进行修复,并将漏洞及对应的修复方法存入漏洞库中之后,对目标资产进行复测,以确定目标资产的漏洞修复完成。In one embodiment, after the vulnerability is repaired and the vulnerability and the corresponding repair method are stored in the vulnerability database, the target asset is re-tested to determine that the vulnerability repair of the target asset is completed.
本实施例中,在一个扫描任务中的所有目标资产中所扫描出的漏洞全修复完成之后,可以将扫描任务、目标资产的资产主键及漏洞主键存入查询数据库中,以供用户或技术人员从查询数据库中查询资产、漏洞及任务的相关信息,以便于及时了解资产的安全状态,进而提高资产的安全性。其中,查询数据库可以是elasticsearch数据库。In this embodiment, after all the vulnerabilities scanned in all target assets in a scanning task are fully repaired, the scanning task, the asset primary key of the target asset and the vulnerability primary key can be stored in the query database for users or technicians Query the relevant information of assets, vulnerabilities and tasks from the query database, so as to know the security status of the assets in time and improve the security of the assets. The query database may be an elasticsearch database.
本实施例中,在通过调用修复方法或安排技术人员对目标资产的所有漏洞进行修复之后,可以将目标资产的状态修改为已修复。同时,定期生成对目标资产的复测任务,以确定目标资产中的漏洞已经修复完成,同时也检查目标资产是否存在新的漏洞。In this embodiment, after invoking the repair method or arranging for technicians to repair all the vulnerabilities of the target asset, the state of the target asset can be modified to be repaired. At the same time, a retest task for the target asset is periodically generated to determine that the vulnerabilities in the target asset have been repaired, and at the same time, the target asset is also checked for new vulnerabilities.
本申请实施例中,通过对漏洞从生成,扫描,修复及管理的全生命周期进行管理,有效提高对漏洞修复效率及管理效率,进而提高资产安全性。其中,通过获取目标资产所存在的漏洞,并与漏洞库中的既有漏洞进行对比,可以快速判断目标资产所存在的漏洞是否与已修复过的既有漏洞相同,在不相同时,即确定漏洞不在漏洞库内时,向技术人员反馈并修复,将漏洞及技术人员对漏洞的修复方法保存,可以便于后续资产中出现相同的漏洞时,可以快速调用对应的修复方法对重复漏洞进行修复,从而减少技术人员对漏洞修复的工作量,调用修复方法对漏洞直接简化修复过程,提高对漏洞的修复效率,提高资产安全性,及时对漏洞进行修复,减少因漏洞导致的财产损失。In the embodiments of the present application, by managing the full life cycle of vulnerabilities from generation, scanning, repairing and management, the efficiency of repairing and managing vulnerabilities is effectively improved, thereby improving asset security. Among them, by obtaining the vulnerabilities existing in the target asset and comparing them with the existing vulnerabilities in the vulnerability database, it is possible to quickly determine whether the existing vulnerabilities in the target assets are the same as the existing vulnerabilities that have been fixed. When the vulnerability is not in the vulnerability library, feedback and repair it to the technicians, and save the vulnerability and the repair method of the technician to the vulnerability, so that when the same vulnerability appears in the subsequent assets, the corresponding repair method can be quickly called to repair the repeated vulnerability. In this way, the workload of technicians for vulnerability repair is reduced, and the repair method is used to directly simplify the repair process of the vulnerability, improve the repair efficiency of the vulnerability, improve the security of assets, repair the vulnerability in time, and reduce the property loss caused by the vulnerability.
请参阅图3,图3为本申请实施例提供的一种资产漏洞管理装置的结构框图,资产漏洞管理装置200包括:处理模块210和扫描模块220。Please refer to FIG. 3 , which is a structural block diagram of an asset vulnerability management apparatus according to an embodiment of the present application. The asset vulnerability management apparatus 200 includes a processing module 210 and a scanning module 220 .
扫描模块220,用于对目标资产进行扫描,获取目标资产所存在的漏洞;The scanning module 220 is used for scanning the target asset to obtain the loopholes existing in the target asset;
处理模块210,与扫描模块连接,可以调用资产数据库和漏洞库,用于将漏洞与漏洞库中的已修复的既有漏洞进行对比;The processing module 210, connected with the scanning module, can call the asset database and the vulnerability library to compare the vulnerability with the existing vulnerabilities that have been fixed in the vulnerability library;
处理模块210,还用于在确定漏洞为不在漏洞库时,向技术人员反馈漏洞信息,以使技术人员对漏洞进行修复,并将漏洞及对应的修复方法存入漏洞库中,以使发生与漏洞相同的重复漏洞时,调用修复方法对重复漏洞进行修复。The processing module 210 is further configured to feed back the vulnerability information to the technician when it is determined that the vulnerability is not in the vulnerability library, so that the technician can repair the vulnerability, and store the vulnerability and the corresponding repair method in the vulnerability library, so that the occurrence of the vulnerability and the corresponding repair method are stored in the vulnerability library. When there are duplicate vulnerabilities with the same vulnerability, the repair method is called to repair the duplicate vulnerabilities.
处理模块210,还用于获取漏洞的漏洞信息;将漏洞信息与既有漏洞的既有漏洞信息对比;在漏洞信息与所述既有漏洞信息的相似度小于预设阈值时,确定该漏洞不在漏洞库内;在漏洞信息与既有漏洞信息的相似度大于预设阈值时,确定漏洞为重复漏洞。The processing module 210 is further configured to obtain the vulnerability information of the vulnerability; compare the vulnerability information with the existing vulnerability information of the existing vulnerability; when the similarity between the vulnerability information and the existing vulnerability information is less than a preset threshold, determine that the vulnerability is not present In the vulnerability database; when the similarity between the vulnerability information and the existing vulnerability information is greater than the preset threshold, the vulnerability is determined to be a duplicate vulnerability.
处理模块210,还用于对漏洞信息进行ik分词,获取分词结果,并将分词结果与既有漏洞的既有漏洞信息进行对比。The processing module 210 is further configured to perform ik word segmentation on the vulnerability information, obtain a word segmentation result, and compare the word segmentation result with the existing vulnerability information of existing vulnerabilities.
处理模块210,还用于基于用户的操作录入资产及对应的资产信息;对资产信息进行加密,生成资产对应的资产主键并存入资产数据库中,资产主键为用于表征资产信息的标识字符串。The processing module 210 is further configured to input assets and corresponding asset information based on user operations; encrypt the asset information, generate an asset primary key corresponding to the asset and store it in the asset database, where the asset primary key is an identification string used to characterize asset information .
处理模块210,还用于基于用户所选择的目标资产创建扫描任务;基于扫描任务的数量从预先创建的多线程中获取相同数量的线程执行扫描任务,分别对扫描任务对应的所述目标资产进行扫描,其中,线程与漏洞扫描引擎数量相同且一对一绑定。The processing module 210 is further configured to create a scanning task based on the target asset selected by the user; obtain the same number of threads from the pre-created multi-threads to execute the scanning task based on the number of scanning tasks, and perform the scanning task respectively on the target asset corresponding to the scanning task. Scanning, where threads are bound one-to-one with the same number of threads as vulnerability scanning engines.
处理模块210,还与用户所使用的终端远程连接,用于接收用户使用的终端录入的资产信息,并对资产信息加密后,存入资产数据库中。处理模块还可以接收用户在所使用的终端创建的资产扫描任务,以完成对目标资产的扫描与漏洞修复。The processing module 210 is also remotely connected to the terminal used by the user, for receiving the asset information entered by the terminal used by the user, encrypting the asset information and storing it in the asset database. The processing module can also receive the asset scanning task created by the user on the terminal used, so as to complete the scanning and vulnerability repair of the target asset.
扫描模块220,还用于对目标资产进行复测,以确定目标资产的漏洞修复完成。The scanning module 220 is further configured to re-test the target asset to determine that the vulnerability repair of the target asset is completed.
可以理解,本申请提供的资产漏洞管理装置200与本申请提供的资产漏洞管理方法对应,为使说明书简洁,相同或相似部分可以参照资产漏洞管理方法部分的内容,在此不再赘述。It can be understood that the asset vulnerability management apparatus 200 provided by the present application corresponds to the asset vulnerability management method provided by the present application. In order to make the description concise, the same or similar parts may refer to the content of the asset vulnerability management method, which will not be repeated here.
上述资产漏洞管理装置中的各个模块可全部或部分通过软件、硬件及其组合来实现。上述各模块可以硬件形式内嵌于或独立于服务器中的处理器中,也可以以软件形式存储于服务器中的存储器中,以便于处理器调用执行以上各个模块对应的操作。该处理器可以为中央处理单元(CPU)、微处理器、单片机等。Each module in the above asset vulnerability management device may be implemented in whole or in part by software, hardware and combinations thereof. The above modules may be embedded in or independent of the processor in the server in the form of hardware, or may be stored in the memory in the server in the form of software, so that the processor can call and execute operations corresponding to the above modules. The processor may be a central processing unit (CPU), a microprocessor, a single-chip microcomputer, or the like.
上述资产漏洞管理方法或存储装置可以实现为一种计算机可读指令的形式,计算机可读指令可以在如图4所示的电子设备上运行。The above asset vulnerability management method or storage device may be implemented in the form of computer-readable instructions, and the computer-readable instructions may be executed on the electronic device as shown in FIG. 4 .
本申请实施例还提供的一种电子设备,包括存储器、处理器及存储在存储器上并可在处理器上运行的计算机可读指令,该处理器执行该程序时实现上述的资产漏洞管理方法。An embodiment of the present application further provides an electronic device, including a memory, a processor, and computer-readable instructions stored in the memory and executable on the processor, and the processor implements the above-mentioned asset vulnerability management method when the program is executed.
图4为根据本申请的一个实施例的电子设备的内部结构示意图,电子设备可以为服务器。请参阅图4,该电子设备包括通过系统总线连接的处理器、非易失性存储介质、内存储器、输入装置、显示屏和网络接口。其中,该电子设备的非易失性存储介质可存储操作系统和计算机可读指令,该计算机可读指令被执行时,可使得处理器执行本申请各实施例的一种资产漏洞管理方法,该方法的具体实现过程可参考图1、图3的具体内容,在此不再赘述。该电子设备的处理器用于提供计算和控制能力,支撑整个电子设备的运行。该内存储器中可储存有计算机可读指令,该计算机可读指令被处理器执行时,可使得处理器执行一种资产漏洞管理方法。电子设备的输入装置用于各个参数的输入,电子设备的显示屏用于进行显示,电子设备的网络接口用于进行网络通信。本领域技术人员可以理解,图4中示出的结构,仅仅是与本申请方案相关的部分结构的框图,并不构成对本申请方案所应用于其上的电子设备的限定,具体的电子设备可以包括比图中所示更多或更少的部件,或者组合某些部件,或者具有不同的部件布置。FIG. 4 is a schematic diagram of an internal structure of an electronic device according to an embodiment of the present application, and the electronic device may be a server. Referring to FIG. 4 , the electronic device includes a processor, a non-volatile storage medium, an internal memory, an input device, a display screen and a network interface connected through a system bus. The non-volatile storage medium of the electronic device can store an operating system and computer-readable instructions. When the computer-readable instructions are executed, the processor can execute an asset vulnerability management method according to the embodiments of the present application. For the specific implementation process of the method, reference may be made to the specific content of FIG. 1 and FIG. 3 , which will not be repeated here. The processor of the electronic device is used to provide computing and control capabilities to support the operation of the entire electronic device. Computer-readable instructions may be stored in the internal memory, and when executed by the processor, the computer-readable instructions may cause the processor to execute an asset vulnerability management method. The input device of the electronic device is used for inputting various parameters, the display screen of the electronic device is used for display, and the network interface of the electronic device is used for network communication. Those skilled in the art can understand that the structure shown in FIG. 4 is only a block diagram of a part of the structure related to the solution of the present application, and does not constitute a limitation on the electronic device to which the solution of the present application is applied. The specific electronic device may be Include more or fewer components than shown in the figures, or combine certain components, or have a different arrangement of components.
基于同一发明构思,本申请实施例还提供一种计算机可读存储介质,可读存储介质中存储有计算机程序,当计算机程序在计算机上运行时,使得计算机执行资产漏洞管理方法。Based on the same inventive concept, embodiments of the present application also provide a computer-readable storage medium, where a computer program is stored in the readable storage medium, and when the computer program runs on a computer, the computer executes the asset vulnerability management method.
在本申请所提供的实施例中,应该理解到,所揭露的方法和装置,也可以通过其它的方式实现。以上所描述的装置实施例仅仅是示意性的。在本申请各个实施例中的各功能模块可以集成在一起形成一个独立的部分,也可以是各个模块单独存在,也可以两个或两个以上模块集成形成一个独立的部分。In the embodiments provided in this application, it should be understood that the disclosed method and apparatus may also be implemented in other manners. The apparatus embodiments described above are merely illustrative. Each functional module in each embodiment of the present application may be integrated together to form an independent part, or each module may exist independently, or two or more modules may be integrated to form an independent part.
所述功能如果以软件功能模块的形式实现并作为独立的产品销售或使用时,可以存储在一个计算机可读取存储介质中。基于这样的理解,本申请的技术方案本质上或者说对现有技术做出贡献的部分或者该技术方案的部分可以以软件产品的形式体现出来,该计算机软件产品存储在一个存储介质中,包括若干指令用以使得一台计算机设备(可以是个人计算机,服务器,或者网络设备等)执行本申请各个实施例所述方法的全部或部分步骤。而前述的存储介质包括:U盘、移动硬盘、只读存储器(ROM,Read-Only Memory)、随机存取存储器(RAM,Random Access Memory)、磁碟或者光盘等各种可以存储程序代码的介质。If the functions are implemented in the form of software function modules and sold or used as independent products, they can be stored in a computer-readable storage medium. Based on this understanding, the technical solution of the present application can be embodied in the form of a software product in essence, or the part that contributes to the prior art or the part of the technical solution. The computer software product is stored in a storage medium, including Several instructions are used to cause a computer device (which may be a personal computer, a server, or a network device, etc.) to execute all or part of the steps of the methods described in the various embodiments of the present application. The aforementioned storage medium includes: U disk, mobile hard disk, Read-Only Memory (ROM, Read-Only Memory), Random Access Memory (RAM, Random Access Memory), magnetic disk or optical disk and other media that can store program codes .
以上所述,仅为本申请的具体实施方式,但本申请的保护范围并不局限于此,任何熟悉本技术领域的技术人员在本申请揭露的技术范围内,可轻易想到变化或替换,都应涵盖在本申请的保护范围之内。因此,本申请的保护范围应所述以权利要求的保护范围为准。The above are only specific embodiments of the present application, but the protection scope of the present application is not limited to this. should be covered within the scope of protection of this application. Therefore, the protection scope of the present application should be based on the protection scope of the claims.
需要说明的是,在本文中,诸如第一和第二等之类的关系术语仅仅用来将一个实体或者操作与另一个实体或操作区分开来,而不一定要求或者暗示这些实体或操作之间存在任何这种实际的关系或者顺序。而且,术语“包括”、“包含”或者其任何其他变体意在涵盖非排他性的包含,从而使得包括一系列要素的过程、方法、物品或者设备不仅包括那些要素,而且还包括没有明确列出的其他要素,或者是还包括为这种过程、方法、物品或者设备所固有的要素。在没有更多限制的情况下,由语句“包括一个……”限定的要素,并不排除在包括所述要素的过程、方法、物品或者设备中还存在另外的相同要素。It should be noted that, in this document, relational terms such as first and second are only used to distinguish one entity or operation from another entity or operation, and do not necessarily require or imply any relationship between these entities or operations. any such actual relationship or sequence exists. Moreover, the terms "comprising", "comprising" or any other variation thereof are intended to encompass a non-exclusive inclusion such that a process, method, article or device that includes a list of elements includes not only those elements, but also includes not explicitly listed or other elements inherent to such a process, method, article or apparatus. Without further limitation, an element qualified by the phrase "comprising a..." does not preclude the presence of additional identical elements in a process, method, article or apparatus that includes the element.
Claims (10)
Priority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202111601386.8ACN114329486A (en) | 2021-12-24 | 2021-12-24 | Asset vulnerability management method and device, electronic equipment and storage medium |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202111601386.8ACN114329486A (en) | 2021-12-24 | 2021-12-24 | Asset vulnerability management method and device, electronic equipment and storage medium |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| CN114329486Atrue CN114329486A (en) | 2022-04-12 |
Family
ID=81013488
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN202111601386.8APendingCN114329486A (en) | 2021-12-24 | 2021-12-24 | Asset vulnerability management method and device, electronic equipment and storage medium |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN114329486A (en) |
Cited By (3)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN115314276A (en)* | 2022-08-03 | 2022-11-08 | 厦门国际银行股份有限公司 | Security check management system, method and terminal equipment |
| CN116010940A (en)* | 2022-09-19 | 2023-04-25 | 康键信息技术(深圳)有限公司 | Method, device, equipment and storage medium for monitoring system security |
| CN116208386A (en)* | 2023-01-18 | 2023-06-02 | 重庆长安汽车股份有限公司 | Vulnerability management method, system, electronic equipment and medium for automobile network security |
Citations (8)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN110933083A (en)* | 2019-11-29 | 2020-03-27 | 中电福富信息科技有限公司 | Vulnerability grade evaluation device and method based on word segmentation and attack matching |
| CN111240994A (en)* | 2020-01-20 | 2020-06-05 | 北京国舜科技股份有限公司 | Vulnerability processing method and device, electronic equipment and readable storage medium |
| CN112035843A (en)* | 2020-08-20 | 2020-12-04 | 深信服科技股份有限公司 | Vulnerability processing method and device, electronic equipment and storage medium |
| CN112395616A (en)* | 2019-08-15 | 2021-02-23 | 奇安信安全技术(珠海)有限公司 | Vulnerability processing method and device and computer equipment |
| CN112528294A (en)* | 2020-12-21 | 2021-03-19 | 网神信息技术(北京)股份有限公司 | Vulnerability matching method and device, computer equipment and readable storage medium |
| US20210124830A1 (en)* | 2019-10-29 | 2021-04-29 | Dell Products L.P. | Code vulnerability remediation |
| CN113642004A (en)* | 2021-08-11 | 2021-11-12 | 杭州安恒信息技术股份有限公司 | A method, device and device for security scanning and repairing of container images |
| CN113709174A (en)* | 2021-09-03 | 2021-11-26 | 国网山东省电力公司电力科学研究院 | Network vulnerability heat reappearance and repair method for power monitoring system |
- 2021
- 2021-12-24CNCN202111601386.8Apatent/CN114329486A/enactivePending
Patent Citations (8)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN112395616A (en)* | 2019-08-15 | 2021-02-23 | 奇安信安全技术(珠海)有限公司 | Vulnerability processing method and device and computer equipment |
| US20210124830A1 (en)* | 2019-10-29 | 2021-04-29 | Dell Products L.P. | Code vulnerability remediation |
| CN110933083A (en)* | 2019-11-29 | 2020-03-27 | 中电福富信息科技有限公司 | Vulnerability grade evaluation device and method based on word segmentation and attack matching |
| CN111240994A (en)* | 2020-01-20 | 2020-06-05 | 北京国舜科技股份有限公司 | Vulnerability processing method and device, electronic equipment and readable storage medium |
| CN112035843A (en)* | 2020-08-20 | 2020-12-04 | 深信服科技股份有限公司 | Vulnerability processing method and device, electronic equipment and storage medium |
| CN112528294A (en)* | 2020-12-21 | 2021-03-19 | 网神信息技术(北京)股份有限公司 | Vulnerability matching method and device, computer equipment and readable storage medium |
| CN113642004A (en)* | 2021-08-11 | 2021-11-12 | 杭州安恒信息技术股份有限公司 | A method, device and device for security scanning and repairing of container images |
| CN113709174A (en)* | 2021-09-03 | 2021-11-26 | 国网山东省电力公司电力科学研究院 | Network vulnerability heat reappearance and repair method for power monitoring system |
Cited By (3)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN115314276A (en)* | 2022-08-03 | 2022-11-08 | 厦门国际银行股份有限公司 | Security check management system, method and terminal equipment |
| CN116010940A (en)* | 2022-09-19 | 2023-04-25 | 康键信息技术(深圳)有限公司 | Method, device, equipment and storage medium for monitoring system security |
| CN116208386A (en)* | 2023-01-18 | 2023-06-02 | 重庆长安汽车股份有限公司 | Vulnerability management method, system, electronic equipment and medium for automobile network security |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| US11716349B2 (en) | Machine learning detection of database injection attacks | |
| US12120134B2 (en) | System for automatically discovering, enriching and remediating entities interacting in a computer network | |
| Chen et al. | Understanding and discovering software configuration dependencies in cloud and datacenter systems | |
| US11263071B2 (en) | Enabling symptom verification | |
| US11748487B2 (en) | Detecting a potential security leak by a microservice | |
| CN114329486A (en) | Asset vulnerability management method and device, electronic equipment and storage medium | |
| US9122804B2 (en) | Logic validation and deployment | |
| WO2023177442A1 (en) | Data traffic characterization prioritization | |
| CN112422484B (en) | Method, apparatus, and storage medium for determining scenario for processing security event | |
| CN109062965B (en) | Big data analysis system, server, data processing method and storage medium | |
| WO2019104891A1 (en) | Method and device for importing and exporting report, storage medium, and terminal | |
| US12248455B1 (en) | Systems and methods for generic data parsing applications | |
| CN107003931B (en) | Decoupling test validation from test execution | |
| US20240054225A1 (en) | Intelligent service security enforcement system | |
| CN114817038A (en) | Blockchain system testing method, system, computer equipment and storage medium | |
| WO2025020918A1 (en) | Data providing method and apparatus, device, and storage medium | |
| CN112015715A (en) | Industrial Internet data management service testing method and system | |
| US12282719B1 (en) | Building and simulating execution of managed artificial intelligence pipelines | |
| CN112583890B (en) | Message pushing method and device based on enterprise office system and computer equipment | |
| CN107229977A (en) | A kind of automatic reinforcement means of Host Security baseline and system | |
| US20250272422A1 (en) | Deduplicating role-based access control policies using symbolic abstraction models and satisfiability solver models | |
| CN114386047A (en) | Application vulnerability detection method, device, electronic device and storage medium | |
| CN115774581A (en) | Method and related device for executing robot script | |
| WO2017167015A1 (en) | Method and device for server device security management and computer storage medium | |
| CN108132866A (en) | A kind of method and system of monitor operating system data integrity |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| RJ01 | Rejection of invention patent application after publication | Application publication date:20220412 | |
| RJ01 | Rejection of invention patent application after publication |