CN113271309A - Hierarchical file encryption method and system - Google Patents
Hierarchical file encryption method and systemDownload PDFInfo
- Publication number
- CN113271309A CN113271309ACN202110566884.7ACN202110566884ACN113271309ACN 113271309 ACN113271309 ACN 113271309ACN 202110566884 ACN202110566884 ACN 202110566884ACN 113271309 ACN113271309 ACN 113271309A
- Authority
- CN
- China
- Prior art keywords
- node
- data consumer
- sub
- ciphertext
- public key
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Granted
Links
Images
Classifications
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/04—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks
- H04L63/0428—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks wherein the data content is protected, e.g. by encrypting or encapsulating the payload
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/60—Protecting data
- G06F21/602—Providing cryptographic facilities or services
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/04—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks
- H04L63/0428—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks wherein the data content is protected, e.g. by encrypting or encapsulating the payload
- H04L63/0435—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks wherein the data content is protected, e.g. by encrypting or encapsulating the payload wherein the sending and receiving network entities apply symmetric encryption, i.e. same key used for encryption and decryption
Landscapes
- Engineering & Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- General Engineering & Computer Science (AREA)
- Computer Hardware Design (AREA)
- Signal Processing (AREA)
- Computer Networks & Wireless Communication (AREA)
- Computing Systems (AREA)
- Theoretical Computer Science (AREA)
- Software Systems (AREA)
- General Physics & Mathematics (AREA)
- Physics & Mathematics (AREA)
- Health & Medical Sciences (AREA)
- General Health & Medical Sciences (AREA)
- Bioethics (AREA)
- Storage Device Security (AREA)
Abstract
Translated fromChineseDescription
Translated fromChinese技术领域technical field
本发明涉及共享数据加密技术领域,具体涉及一种分层文件加密方法及系统。The invention relates to the technical field of shared data encryption, in particular to a layered file encryption method and system.
背景技术Background technique
近年来,随着互联网的飞速发展,数据的规模变得越来越大。云环境因其既可以提供计算服务,也可以提供存储服务,已成为解决数据共享问题最有前景的应用平台之一。在云环境中,为确保数据不被其他用户或恶意服务器获取和破坏,用户需在共享数据前需要对数据进行加密。基于属性加密(ABE)由于能够保护数据隐私,实现细粒度、一对多和非交互的访问控制而受到广泛的关注。基于密文策略的属性加密(CP-ABE)方案具有较大的灵活性和适用性,因此是一种更为可行的方案。In recent years, with the rapid development of the Internet, the scale of data has become larger and larger. The cloud environment has become one of the most promising application platforms to solve the data sharing problem because it can provide both computing services and storage services. In a cloud environment, in order to ensure that data is not obtained and destroyed by other users or malicious servers, users need to encrypt data before sharing it. Attribute-based encryption (ABE) has received extensive attention due to its ability to protect data privacy and enable fine-grained, one-to-many, and non-interactive access control. Ciphertext Policy Based Attribute Encryption (CP-ABE) scheme has greater flexibility and applicability, so it is a more feasible scheme.
然而在实际应用中,多个共享的数据文件通常具有层次结构关系,尤其是在政府、高校和医疗等领域体现尤为明显。传统的CP-ABE方案只能实现在一个访问策略中加密一个文件,要实现层次结构关系中多个文件的加密则需要构造多个访问策略逐一进行加密,造成加解密效率极低且缺乏灵活性。针对此问题,高效的基于文件分层的CP-ABE(FH-CP-ABE)方案被提出,此方案使用一个集成的访问策略对多个层次文件进行加密,提高了加解密效率。但是此方案无法实现同一层次加密多个文件,同时在解密时,与层次节点相对应的用户可相互解密导致同一层次的加密文件存在泄密风险。针对此问题,拓展的基于文件分层的CP-ABE(EFH-CP-ABE)方案被提出,此方案实现了同一层次加密多个文件,同时解决了层次节点相对应的用户可相互解密的问题,提高了方案的安全性,但是这两个方案在加密过程中分别存在用户越权访问,用户协作攻击的安全问题,影响文件加密的安全性。However, in practical applications, multiple shared data files usually have a hierarchical relationship, especially in the fields of government, universities, and medical care. The traditional CP-ABE scheme can only encrypt one file in one access policy. To realize the encryption of multiple files in a hierarchical relationship, it is necessary to construct multiple access policies to encrypt one by one, resulting in extremely low encryption and decryption efficiency and lack of flexibility. . To solve this problem, an efficient file-hierarchical-based CP-ABE (FH-CP-ABE) scheme is proposed. This scheme uses an integrated access policy to encrypt multiple levels of files, improving the encryption and decryption efficiency. However, this scheme cannot encrypt multiple files at the same level. At the same time, during decryption, users corresponding to the level nodes can decrypt each other, resulting in the risk of leakage of encrypted files at the same level. In response to this problem, an extended CP-ABE (EFH-CP-ABE) scheme based on file hierarchy is proposed. This scheme realizes the encryption of multiple files at the same level and solves the problem that users corresponding to hierarchical nodes can decrypt each other. , which improves the security of the scheme, but the two schemes have security problems of unauthorized user access and user cooperative attack in the encryption process, which affect the security of file encryption.
发明内容SUMMARY OF THE INVENTION
本发明要解决的技术问题是现有的文件分层的CP-ABE方案存在用户越权访问及协作攻击的安全性问题。因此,本发明提供一种分层文件加密方法及系统,通过构造新的与传输节点相关的密文子项消除用户越权访问和协作攻击的可能性,提高文件加密的安全性。The technical problem to be solved by the present invention is that the existing file layered CP-ABE scheme has security problems of unauthorized access by users and cooperative attacks. Therefore, the present invention provides a layered file encryption method and system, which eliminates the possibility of user unauthorized access and cooperative attacks by constructing a new ciphertext sub-item related to the transmission node, and improves the security of file encryption.
本发明通过下述技术方案实现:The present invention is achieved through the following technical solutions:
一种分层文件加密方法,包括:A layered file encryption method comprising:
根据待加密分层文件和各待加密分层文件的层次关系构造单向门访问树;基于所述单向门访问树,通过系统公钥对待加密分层文件进行加密,获得加密密文并发送给云服务提供商进行存储;A one-way gate access tree is constructed according to the hierarchical relationship between the layered file to be encrypted and each layered file to be encrypted; based on the one-way gate access tree, the layered file to be encrypted is encrypted by the system public key, and the encrypted ciphertext is obtained and sent. storage for cloud service providers;
当数据消费者属性集的所有属性满足部分或全部的单向门访问树,则通过系统公钥和数据消费者私钥对所述加密密文进行解密,获得解密后的明文,否则解密失败。When all attributes of the data consumer attribute set satisfy part or all of the one-way gate access tree, the encrypted ciphertext is decrypted through the system public key and the data consumer private key to obtain the decrypted plaintext, otherwise the decryption fails.
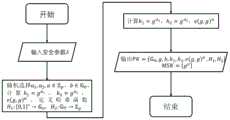
进一步地,所述分层文件加密方法还包括系统初始化参数λ,所述分层文件加密方法包括阶为p的群和的生成元g,双线性映射e,即e:Further, the layered file encryption method also includes a system initialization parameter λ, and the layered file encryption method includes a group whose order is p. and The generator g of , the bilinear map e, that is, e:
所述系统公钥PK的计算过程具体为:基于所述系统初始化参数λ,从中随机选择a1,a2,α,为p阶整数域;从随机选择b,系统公钥子项的计算为:e(g,g)α,并定义两个哈希函数所述系统公钥The calculation process of the system public key PK is specifically: based on the system initialization parameter λ, from randomly select a1 , a2 , α in is the p-order integer field; from Randomly select b, and the calculation of the system public key sub-item is: e(g,g)α , and define two hash functions the system public key
所述系统主密钥MSK的计算过程具体为:基于所述系统初始化参数λ,计算系统主密钥子项gα,得到系统主密钥,所述系统主密钥MSK={gα}。The calculation process of the system master key MSK is specifically: based on the system initialization parameter λ, calculate the system master key sub-item gα to obtain the system master key, where the system master key MSK={gα }.
进一步地,所述分层文件加密方法还包括数据消费者身份信息,所述数据消费者身份信息包括数据消费者标识;所述数据消费者属性集S中包括控制属性Ac,即Ac∈S);Further, the layered file encryption method further includes data consumer identity information, where the data consumer identity information includes a data consumer identifier; the data consumer attribute set S includes a control attributeAc , that is, A c∈ S);
所述基于所述系统公钥PK、系统主秘钥MSK和数据消费者属性集S计算数据消费者私钥SK,包括:The calculation of the data consumer private key SK based on the system public key PK, the system master key MSK and the data consumer attribute set S includes:
从中为每个数据消费者选择随机数r表示作为数据消费者标识,根据所述系统公钥PK计算消费者私钥SK的私钥子项K=gαh1r,L=gr,数据消费者属性集S中除控制属性Ac之外的属性对应的私钥子项,即控制属性Ac的私钥子项from Select a random number r for each data consumer to represent the data consumer identification, and calculate the private key sub-item of the consumer's private key SK according to the system public key PK K=gα h1r , L=gr , The private key sub-items corresponding to attributes other than the control attribute Ac in the data consumer attribute set S, namely Control the private key subkey of attribute Ac
所述数据消费者私钥the data consumer private key
进一步地,所述单向门访问树携带有控制属性和单向门,其中,所述数据消费者属性集中包含控制属性,单向门支持用户由高层次向低层次进行解密,阻止用户由低层次向高层次进行解密;Further, the one-way gate access tree carries a control attribute and a one-way gate, wherein the data consumer attribute set includes a control attribute, and the one-way gate supports the user to decrypt from a high level to a low level, and prevents the user from changing from a low level to a low level. Decryption from level to high level;
所述单向门访问树的具体构造过程具体为:The specific construction process of the one-way gate access tree is as follows:
存储文件的层次节点数量与其父节点的门限值(除根节点R)有以下两种关系:The number of hierarchical nodes storing files and the threshold value of their parent nodes (except the root node R) have the following two relationships:
当存储文件的层次节点数量小于其父节点的门限值时,即使用户进行协作也无法满足相关的访问结构,因此无需考虑协作问题。当存储文件的层次节点数量大于或等于其父节点的门限值时,用户可通过协作的方式满足相关的访问结构,因此需要考虑协作问题。When the number of hierarchical nodes storing files is less than the threshold value of their parent nodes, even if users cooperate, the relevant access structure cannot be satisfied, so there is no need to consider the cooperation problem. When the number of hierarchical nodes of the stored file is greater than or equal to the threshold value of its parent node, users can satisfy the relevant access structure through cooperation, so the problem of cooperation needs to be considered.
在构造单向门访问树时,首先根据待加密分层文件cki定义分层访问树,当待加密分层文件cki的层次节点数量大于或等于其父节点的门限值时,使用“AND”门作为单向门替代分层访问树中的传输节点,以传输节点为根节点的子树作为所述单向门的子树,由控制属性生成的节点作为所述单向门的另外一个子节点,生成单向门访问树;其中,所述传输节点为其子节点至少包含一个门限值的节点;若所述传输节点存储有文件,则文件转存在单向门中。When constructing a one-way gate access tree, first define a hierarchical access tree according to the hierarchical file cki to be encrypted, when the number of hierarchical nodes in the hierarchical file cki to be encrypted is greater than or equal to the threshold value of its parent node, use " The AND" gate is used as a one-way gate to replace the transmission node in the hierarchical access tree, the subtree with the transmission node as the root node is used as the subtree of the one-way gate, and the node generated by the control attribute is used as the other side of the one-way gate. A child node, generating a one-way gate access tree; wherein, the transfer node is a node whose child node contains at least one threshold value; if the transfer node stores a file, the file is transferred to the one-way gate.
将分层访问树拓展为单向门访问树使用“AND”门A′作为单向门替换分层访问树中的传输节点A,子树与控制属性则作为单向门A′的子树,构成单向门访问子树,文件m2则存储在单向门A′中。此时在单向门访问树中,即使满足和的不同用户通过协作向上层进行访问,其仍解密不出上层文件m2。反之,满足子树的用户则可通过控制节点解密出上层文件m2。需要说明的是,拓展后的单向门访问树的访问层次不变,即为3个访问层次,仍为3个访问层次。will access the tree hierarchically Extended to a one-way gate access tree Replacing a hierarchical access tree with an "AND" gate A' as a one-way gate Transit node A in the subtree The AND control attribute is used as a subtree of the one-way gate A' to form a one-way gate access subtree, and the file m2 is stored in the one-way gate A'. At this point in the one-way gate access tree , even if satisfied and Different users of
进一步地,所述基于所述单向门访问树,通过系统公钥对待加密分层文件进行加密,包括:Further, based on the one-way gate access tree, encrypt the layered file to be encrypted by the system public key, including:
在所述单向门访问树中从上到下从左到右设置k个层次节点ck1,…,ckk,其中,cki表示使用对称加密算法得到的第i个待加密分层文件;从中随机选择随机数s1,s2,…,sk对应各层次节点;access tree at the one-way gate Set k hierarchical nodes ck1 ,...,ckk from top to bottom and from left to right, where cki represents the i-th layered file to be encrypted obtained by using the symmetric encryption algorithm; Randomly select random numbers s1 , s2 ,..., sk corresponding to each level node;
基于所述待加密分层文件、单向门访问树和系统公钥,计算层次节点的密文子项和C′i;Based on the layered file to be encrypted, one-way gate access tree and the system public key, calculate the ciphertext sub-item of the hierarchical node and C′i ;
基于所述单向门访问树非控制属性叶子节点y和系统公钥,计算非控制属性叶子节点的密文子项Cy和Dy;其中,非控制属性叶子节点y∈Y,Y表示单向门访问树中叶子节点的集合;Access the tree based on the one-way gate The non-control attribute leaf node y and the system public key, calculate the ciphertext sub-items Cy and Dy of the non-control attribute leaf node; wherein, the non-control attribute leaf node y∈Y, Y represents the one-way gate access tree A collection of leaf nodes in the middle;
基于所述单向门访问树控制属性叶子节点Ac和系统公钥,计算控制属性叶子节点的密文子项和Access the tree based on the one-way gate Control attribute leaf node Ac and system public key, calculate the ciphertext sub-item of the control attribute leaf node and
基于所述单向门访问树传输节点x和系统公钥,计算传输节点的密文子项Cx,k和Ex,k;其中,传输节点x∈X,X为传输节点x的集合,TN-CT(x)={chx,1,…,chx,k}为传输节点x的子节点的门限集合。Access the tree based on the one-way gate The transmission node x and the system public key, calculate the ciphertext sub-items Cx,k and Ex,k of the transmission node; wherein, the transmission node x∈X, X is the set of the transmission node x, TN-CT(x)={chx,1 ,...,chx,k } is the threshold set of the child nodes of the transmission node x.
进一步地,计算所述层次节点的密文子项的公式具体为其中,cki表示第i个层次节点对应的待加密分层文件,e(g,g)α为系统公钥的子项,si表示第i个层次节点对应的随机数;Further, calculate the ciphertext sub-item of the hierarchical node The formula is specifically Among them, cki represents the layered file to be encrypted corresponding to the ith level node, e(g, g)α is the sub-item of the system public key, andsi represents the random number corresponding to the ith level node;
计算层次节点的密文子项Ci′的公式具体为其中,g为系统公钥的子项,si表示第i个层次节点对应的随机数;The formula for calculating the ciphertext sub-item Ci ' of the hierarchical node is specifically: Among them, g is the sub-item of the system public key, and si represents the random number corresponding to the i-th level node;
计算非控制属性叶子节点的密文子项Cy的公式具体为其中,ry表示为非控制属性叶子节点y选择的随机值,g为系统公钥的子项,qy(0)表示非控制属性叶子节点y的秘密值,表示对非控制属性叶子节点y的随机值ry取负后进行哈希计算得到的值;The formula for calculating the ciphertext sub-item Cy of the non-control attribute leaf node is as follows: Among them, ry represents the random value selected by the non-control attribute leaf nodey , g is the sub-item of the system public key, qy (0) represents the secret value of the non-control attribute leaf node y, Represents the value obtained by hashing the random value ry of the non-control attribute leaf node y after negation;
计算非控制属性叶子节点的密文子项Dy的公式具体为其中,ry表示为非控制属性叶子节点y选择的随机值,g为系统公钥的子项;The formula for calculating the ciphertext sub-itemDy of the non-control attribute leaf node is as follows: Among them, ry represents the random value selected by the non-control attribute leaf nodey , and g is the sub-item of the system public key;
计算控制属性叶子节点的密文子项的公式具体为其中,h1为系统公钥的子项,表示控制属性叶子节点Ac的秘密值,rAc表示为控制属性叶子节点Ac选择的随机值,g,b为系统公钥子项,表示对控制属性叶子节点Ac的随机值rAc取负后进行哈希计算得到的值;Calculate the ciphertext children of the leaf node of the control attribute The formula is specifically Among them, h1 is the sub-item of the system public key, represents the secret value of the control attribute leaf node Ac , rAc represents the random value selected for the control attribute leaf node Ac , g, b are the system public key sub-items, Represents the value obtained by hash calculation after the random value rAc of the control attribute leaf node Ac is negative;
计算控制属性叶子节点的密文子项DAc的公式具体为其中,表示为控制属性叶子节点Ac选择的随机值,g为系统公钥子项;The formula for calculating the ciphertext sub-item DAc of the leaf node of the control attribute is specifically: in, Represents the random value selected for the control attribute leaf node Ac , and g is the sub-key of the system public key;
计算传输节点的密文子项Cx,k的公式具体为其中,e(g,g)表示双线性映射,τx,k表示为TN-CT(x)中的节点选择的随机值,qx(0)为传输节点x对应的秘密值,表示传输节点x的子节点chx,k对应的秘密值,e(g,g)α系统公钥的子项,表示对进行哈希计算得到的值;The formula for calculating the ciphertext sub-item Cx,k of the transmission node is as follows: Among them, e(g, g) represents the bilinear mapping, τx, k represents the random value selected by the nodes in TN-CT(x), qx (0) is the secret value corresponding to the transmission node x, represents the secret value corresponding to the child node chx, k of the transmission node x, the child of the public key of e(g, g)α system, express right The value obtained by the hash calculation;
计算传输节点的密文子项Ex,k的公式具体为其中,g为系统公钥子项,τx,k表示为TN-CT(x)中的节点选择的随机值The formula for calculating the ciphertext sub-itemEx,k of the transmission node is as follows Among them, g is the sub-item of the system public key, τx, k is the random value selected by the node in TN-CT(x)
进一步地,所述通过系统公钥和数据消费者私钥对所述加密密文进行解密,获得解密后的明文,包括:Further, the encrypted ciphertext is decrypted by the system public key and the private key of the data consumer to obtain the decrypted plaintext, including:
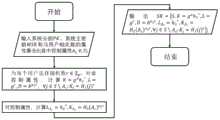
对单向门访问树和数据消费者属性集S执行访问树匹配函数其中,表示以x节点为根节点的子访问树,所述访问树匹配函数执行的过程具体为:Access tree for one-way gates Execute the access tree matching function with the data consumer attribute set S in, Represents the child access tree with the x node as the root node, and the process performed by the access tree matching function is specifically:
I.对单向门访问树中每个节点x执行对应的访问树匹配函数表示数据消费者属性集合S满足单向门访问树中的子树I. Access tree to one-way gates Each node x in the implementation of the corresponding access tree matching function Indicates that the data consumer attribute set S satisfies the one-way gate access tree subtree in
II.若数据消费者属性集S合满足子树基于所述系统公钥,待加密分层文件和数据消费者私钥,执行节点解密函数DecryptNode(CT,SK,x),得到解密后的明文cki。II. If the data consumer attribute set S satisfies the subtree Based on the public key of the system, the layered file to be encrypted and the private key of the data consumer, the node decryption function DecryptNode(CT, SK, x) is executed to obtain the decrypted plaintext cki .
进一步地,所述对单向门访问树中每个节点x执行对应的访问树匹配函数包括:Further, the pair of one-way gate access tree Each node x in the implementation of the corresponding access tree matching function include:
若x为非叶子节点,计算节点x的所有孩子节点x′的访问树匹配函数当且仅当至少kx个孩子节点返回1时,If x is a non-leaf node, calculate the access tree matching function of all child nodes x' of node x if and only if at least kx child nodes return 1,
若x为叶子节点,当x∈S时,If x is a leaf node, when x∈S,
进一步地,所述基于所述系统公钥,待加密分层文件和数据消费者私钥,执行节点解密函数DecryptNode(CT,SK,x),具体为:Further, based on the system public key, the layered file to be encrypted and the private key of the data consumer, execute the node decryption function DecryptNode(CT,SK,x), specifically:
若x为叶子节点,且数据消费者属性集S不满足单向门访问树则DecryptNode(CT,SK,x)=⊥,即解密终止;If x is a leaf node, and the data consumer attribute set S does not satisfy the one-way gate access tree Then DecryptNode(CT,SK,x)=⊥, that is, the decryption is terminated;
对于叶子节点x为数据消费者属性集S中非控制属性叶子节点,即叶子节点x∈S\Ac,则令i=attr(x),计算其中Ci,Di为密文CT中叶子节点密文子项,L,Ki为数据消费者私钥SK中的私钥子项;If the leaf node x is a non-control attribute leaf node in the data consumer attribute set S, that is, the leaf node x∈S\Ac , then let i=attr(x), calculate Wherein Ci , Di are the leaf node ciphertext sub-items in the ciphertext CT, L, Ki are the private key sub-items in the data consumer's private key SK;
对于叶子节点x为数据消费者属性集S中控制属性叶子节点Ac,计算其中,为加密密文CT中叶子节点的密文子项,D及和为数据消费者私钥SK中的私钥子项;For the leaf node x is the control attribute leaf node Ac in the data consumer attribute set S, calculate in, is the ciphertext sub-item of the leaf node in the encrypted ciphertext CT, D and is the private key sub-item in the data consumer's private key SK;
若x为非叶子节点,计算其中,i=index(z),s′x={index(z):z∈Sx},表示拉格朗日系数,Sx为x的任意kx个孩子节点z的集合;If x is a non-leaf node, compute where, i=index(z), s′x ={index(z):z∈Sx }, Represents the Lagrangian coefficient, Sx is the set of any kx child nodes z of x;
若数据消费者属性集S满足全部或部分单向门访问树即满足全部或部分层次节点,对应层次节点计算其中,C′i为密文CT中层次节点的密文子项,K为数据消费者私钥SK中的私钥子项,DecryptNode(CT,SK,xi)为解密层次节点xi的值;If the data consumer attribute set S satisfies all or part of the one-way gate access tree That is, all or part of the hierarchical nodes are satisfied, and the corresponding hierarchical nodes are calculated Wherein, C′i is the ciphertext sub-item of the hierarchical node in the ciphertext CT, K is the private key sub-item in the private key SK of the data consumer, and DecryptNode(CT, SK, xi ) is the value of the decrypted hierarchical nodexi ;
基于层次节点,若数据消费者属性集S包含层级较低的授权节点,计算获得所有授权的层次节点的值,其中,Cx,k,Ex,k为密文CT中传输节点的密文子项;Based on hierarchical nodes, if the data consumer attribute set S contains lower-level authorization nodes, calculate Obtain the values of all authorized hierarchical nodes, where Cx,k and Ex,k are the ciphertext sub-items of the transmission node in the ciphertext CT;
基于层次节点对应的内容密钥{cki,…,ckk}计算其中密文CT中层次节点的密文子项,并使用对称解密算法对相应的加密密文进行解密。Calculated based on the content keys {cki ,...,ckk } corresponding to the hierarchical nodes in The ciphertext sub-items of the hierarchical nodes in the ciphertext CT, and use the symmetric decryption algorithm to decrypt the corresponding encrypted ciphertext.
一种分层文件加密系统,包括授权机构、数据所有者、云服务提供商和数据消费者;A layered file encryption system including authorities, data owners, cloud service providers and data consumers;
所述授权机构,用于通过系统初始化参数λ,计算获得系统公钥PK和系统主密钥MSK,并从数据消费者获得数据消费者身份信息和对应的数据消费者属性集S;基于所述系统公钥PK、系统主秘钥MSK和数据消费者属性集S计算数据消费者私钥SK;将所述系统公钥PK发送给数据所有者,并根据数据消费者的身份信息将对应的数据消费者私钥SK发送给对应的数据消费者;The authorization agency is used to obtain the system public key PK and the system master key MSK through the system initialization parameter λ, and obtain the data consumer identity information and the corresponding data consumer attribute set S from the data consumer; The system public key PK, the system master secret key MSK and the data consumer attribute set S calculate the data consumer private key SK; send the system public key PK to the data owner, and convert the corresponding data according to the identity information of the data consumer The consumer private key SK is sent to the corresponding data consumer;
所述数据所有者,用于从所述授权机构获得系统公钥PK,并根据待加密分层文件cki和各待加密分层文件的层次关系构造单向门访问树基于所述待加密分层文件cki、所述单向门访问树和所述系统公钥PK对待加密分层文件进行加密,获得加密密文CT并发送给云服务提供商进行存储;The data owner is used to obtain the system public key PK from the authorized organization, and construct a one-way gate access tree according to the hierarchical file cki to be encrypted and the hierarchical relationship of each hierarchical file to be encrypted Based on the to-be-encrypted hierarchical file cki , the one-way gate access tree Encrypt the layered file to be encrypted with the system public key PK, obtain the encrypted ciphertext CT and send it to the cloud service provider for storage;
所述云服务提供商,用于存储所述数据所有者上传的加密密文CT,并进行数据传输;the cloud service provider, for storing the encrypted ciphertext CT uploaded by the data owner, and performing data transmission;
所述数据消费者,用于从所述云服务提供商中下载加密密文CT,当所述数据消费者属性集S的所有属性满足部分或全部的单向门访问树,则通过获取的系统公钥PK和数据消费者私钥MSK对下载的所述加密密文CT进行解密,获得解密后的明文cki,否则解密失败。The data consumer is used to download the encrypted ciphertext CT from the cloud service provider. When all the attributes of the attribute set S of the data consumer satisfy part or all of the one-way gate access tree, the obtained system The public key PK and the private key MSK of the data consumer decrypt the downloaded encrypted ciphertext CT to obtain the decrypted plaintext cki , otherwise the decryption fails.
本发明提供的一种分层文件加密方法及系统,通过引入控制属性和单向门相结合构造单向门访问树,在此基础上构造控制属性的密钥子项和密文子项,并重新构造传输节点的密文子项,从而解决了越权访问及协作攻击的问题,实现了多层次文件的安全加密。The invention provides a layered file encryption method and system. The one-way gate access tree is constructed by introducing the control attribute and the one-way gate, and on this basis, the key sub-item and the ciphertext sub-item of the control attribute are constructed, and the The ciphertext sub-item of the transmission node is constructed, so as to solve the problem of unauthorized access and cooperative attack, and realize the secure encryption of multi-level files.
附图说明Description of drawings
此处所说明的附图用来提供对本发明实施例的进一步理解,构成本申请的一部分,并不构成对本发明实施例的限定。在附图中:The accompanying drawings described herein are used to provide further understanding of the embodiments of the present invention, and constitute a part of the present application, and do not constitute limitations to the embodiments of the present invention. In the attached image:
图1为本发明一种分层文件加密系统的原理框图。FIG. 1 is a schematic block diagram of a layered file encryption system according to the present invention.
图2为本发明一实施例中系统公钥和系统主密钥的流程图。FIG. 2 is a flowchart of a system public key and a system master key in an embodiment of the present invention.
图3为本发明一实施例中数据消费者私钥的流程图。FIG. 3 is a flowchart of a private key of a data consumer in an embodiment of the present invention.
图4为本发明一实施例中对待加密分层文件进行加密处理的流程图。FIG. 4 is a flow chart of encrypting a layered file to be encrypted in an embodiment of the present invention.
图5为本发明一实施例中对加密密文进行解密的流程图。FIG. 5 is a flowchart of decrypting encrypted ciphertext in an embodiment of the present invention.
图6为本发明一实施例中的单向门访问树的示意图。FIG. 6 is a schematic diagram of a one-way gate access tree in an embodiment of the present invention.
具体实施方式Detailed ways
为使本发明的目的、技术方案和优点更加清楚明白,下面结合实施例和附图,对本发明作进一步的详细说明,本发明的示意性实施方式及其说明仅用于解释本发明,并不作为对本发明的限定。In order to make the purpose, technical solutions and advantages of the present invention clearer, the present invention will be further described in detail below with reference to the embodiments and the accompanying drawings. as a limitation of the present invention.
实施例1Example 1
本发明提供的一种分层文件加密方法,应用在如图1所示的加密系统中。该分层文件加密方法包括:A layered file encryption method provided by the present invention is applied in the encryption system as shown in FIG. 1 . The layered file encryption method includes:
根据待加密分层文件和各待加密分层文件的层次关系构造单向门访问树;基于所述单向门访问树通过系统公钥PK对待加密分层文件cki进行加密,获得加密密文并发送给云服务提供商进行存储。Construct a one-way gate access tree according to the layered file to be encrypted and the hierarchical relationship of each layered file to be encrypted; based on the one-way gate access tree The layered file cki to be encrypted is encrypted by the system public key PK, and the encrypted ciphertext is obtained and sent to the cloud service provider for storage.
当数据消费者属性集的所有属性满足部分或全部的单向门访问树,则通过系统公钥和数据消费者私钥对加密密文进行解密,获得解密后的明文,否则解密失败。When all the attributes of the data consumer attribute set satisfy part or all of the one-way gate access tree, the encrypted ciphertext is decrypted by the system public key and the data consumer private key to obtain the decrypted plaintext, otherwise the decryption fails.
其中,数据消费者属性集S包括但不限于用户的职业,职称及所属单位。Wherein, the data consumer attribute set S includes but is not limited to the user's occupation, professional title and affiliated unit.
进一步地,如图2所示,该分层文件加密方法还包括系统初始化参数λ,系统初始化参数λ包括阶为p的群和的生成元g,双线性映射e,即e:Further, as shown in Figure 2, the layered file encryption method also includes a system initialization parameter λ, and the system initialization parameter λ includes a group whose order is p. and The generator g of , the bilinear map e, that is, e:
系统公钥PK的计算过程具体为:基于系统初始化参数λ,从中随机选择a1,a2,α,为p阶整数域;从随机选择b,系统公钥子项的计算为:e(g,g)α,并定义两个哈希函数系统公钥The calculation process of the system public key PK is as follows: based on the system initialization parameter λ, from randomly select a1 , a2 , α in is the p-order integer field; from Randomly select b, and the calculation of the system public key sub-item is: e(g,g)α , and define two hash functions system public key
系统主密钥MSK的计算过程具体为:基于系统初始化参数λ,计算系统主密钥子项gα,得到系统主密钥,系统主密钥MSK={gα}。The calculation process of the system master key MSK is specifically: based on the system initialization parameter λ, calculating the sub-item gα of the system master key to obtain the system master key, where the system master key MSK={gα }.
进一步地,如图3所示,该分层文件加密方法还包括数据消费者身份信息,数据消费者身份信息包括数据消费者标识;数据消费者属性集S中包括控制属性Ac,即Ac∈S)。Further, as shown in Figure 3, the layered file encryption method also includes data consumer identity information, and the data consumer identity information includes a data consumer identification; the data consumer attribute set S includes a control attribute Ac , that is, Ac ∈S).
基于系统公钥PK、系统主秘钥MSK和数据消费者属性集S计算数据消费者私钥SK,包括:Calculate the data consumer private key SK based on the system public key PK, the system master key MSK and the data consumer attribute set S, including:
从中为每个数据消费者选择随机数r表示作为数据消费者标识,根据系统公钥PK计算消费者私钥SK的私钥子项K=gαh1r,L=gr,数据消费者属性集S中除控制属性Ac之外的属性对应的私钥子项,即控制属性Ac的私钥子项from Select a random number r for each data consumer to represent the data consumer identifier, and calculate the private key sub-item of the consumer's private key SK according to the system public key PK K=gα h1r , L=gr , The private key sub-items corresponding to attributes other than the control attribute Ac in the data consumer attribute set S, namely Control the private key subkey of attribute Ac
数据消费者私钥Data consumer private key
进一步地,单向门访问树携带有控制属性和单向门,其中,数据消费者属性集中包含控制属性,单向门支持用户由高层次向低层次进行解密,阻止用户由低层次向高层次进行解密。Further, the one-way gate access tree carries control attributes and one-way gates, wherein, the data consumer attributes collectively include control attributes, and the one-way gate supports users to decrypt from high-level to low-level, preventing users from low-level to high-level. to decrypt.
如图6所示,单向门访问树的具体构造过程具体为:As shown in Figure 6, the specific construction process of the one-way gate access tree is as follows:
存储文件的层次节点数量与其父节点的门限值(除根节点R)有以下两种关系:The number of hierarchical nodes storing files and the threshold value of their parent nodes (except the root node R) have the following two relationships:
当存储文件的层次节点数量小于其父节点的门限值时,即使用户进行协作也无法满足相关的访问结构,因此无需考虑协作问题。当存储文件的层次节点数量大于或等于其父节点的门限值时,用户可通过协作的方式满足相关的访问结构,因此需要考虑协作问题。When the number of hierarchical nodes storing files is less than the threshold value of their parent nodes, even if users cooperate, the relevant access structure cannot be satisfied, so there is no need to consider the cooperation problem. When the number of hierarchical nodes of the stored file is greater than or equal to the threshold value of its parent node, users can satisfy the relevant access structure through cooperation, so the problem of cooperation needs to be considered.
在构造单向门访问树时,首先根据待加密分层文件cki定义分层访问树,当待加密分层文件cki的层次节点数量大于或等于其父节点的门限值时,使用“AND”门作为单向门替代分层访问树中的传输节点,以传输节点为根节点的子树作为单向门的子树,由控制属性生成的节点作为单向门的另外一个子节点,生成单向门访问树;其中,传输节点为其子节点至少包含一个门限值的节点;若传输节点存储有文件,则文件转存在单向门中。When constructing a one-way gate access tree, first define a hierarchical access tree according to the hierarchical file cki to be encrypted, when the number of hierarchical nodes in the hierarchical file cki to be encrypted is greater than or equal to the threshold value of its parent node, use " The AND" gate is used as a one-way gate to replace the transmission node in the hierarchical access tree, the subtree with the transmission node as the root node is used as the subtree of the one-way gate, and the node generated by the control attribute is used as another child node of the one-way gate. A one-way gate access tree is generated; wherein, the transmission node is a node whose child node contains at least one threshold value; if the transmission node stores a file, the file is transferred to the one-way gate.
将分层访问树拓展为单向门访问树使用“AND”门A′作为单向门替换分层访问树中的传输节点A,子树与控制属性则作为单向门A′的子树,构成单向门访问子树,文件m2则存储在单向门A′中。此时在单向门访问树中,即使满足和的不同用户通过协作向上层进行访问,其仍解密不出上层文件m2。反之,满足子树的用户则可通过控制节点解密出上层文件m2。需要说明的是,拓展后的单向门访问树的访问层次不变,即为3个访问层次,仍为3个访问层次。will access the tree hierarchically Extended to a one-way gate access tree Replacing a hierarchical access tree with an "AND" gate A' as a one-way gate Transit node A in the subtree The AND control attribute is used as a subtree of the one-way gate A' to form a one-way gate access subtree, and the file m2 is stored in the one-way gate A'. At this point in the one-way gate access tree , even if satisfied and Different users of
进一步地,如图4所示,基于所述单向门访问树通过系统公钥PK对待加密分层文件cki进行加密,包括:Further, as shown in FIG. 4, the tree is accessed based on the one-way gate The layered file cki to be encrypted is encrypted by the system public key PK, including:
在单向门访问树中从上到下从左到右设置k个层次节点ck1,…,ckk,其中,cki表示使用对称加密算法得到的第i个待加密分层文件;从中随机选择随机数s1,s2,…,sk对应各层次节点。Access tree at one-way gate Set k hierarchical nodes ck1 ,...,ckk from top to bottom and from left to right, where cki represents the i-th layered file to be encrypted obtained by using the symmetric encryption algorithm; Randomly select random numbers s1 , s2 ,...,sk corresponding to each level node.
基于待加密分层文件、单向门访问树和系统公钥,计算层次节点的密文子项和C′i。Access tree based on hierarchical file to be encrypted and one-way gate and the system public key, calculate the ciphertext sub-item of the hierarchical node and C′i .
基于单向门访问树非控制属性叶子节点y和系统公钥,计算非控制属性叶子节点的密文子项Cy和Dy;其中,非控制属性叶子节点y∈Y,Y表示单向门访问树中叶子节点的集合。Access tree based on one-way gate The non-control attribute leaf node y and the system public key, calculate the ciphertext sub-items Cy and Dy of the non-control attribute leaf node; wherein, the non-control attribute leaf node y∈Y, Y represents the one-way gate access tree A collection of leaf nodes in .
基于单向门访问树控制属性叶子节点Ac和系统公钥,计算控制属性叶子节点的密文子项和Access tree based on one-way gate Control attribute leaf node Ac and system public key, calculate the ciphertext sub-item of the control attribute leaf node and
基于单向门访问树传输节点x和系统公钥,计算传输节点的密文子项Cx,k和Ex,k;其中,传输节点x∈X,X为传输节点x的集合,TN-CT(x)={chx,1,…,chx,k}为传输节点x的子节点的门限集合。Access tree based on one-way gate The transmission node x and the system public key, calculate the ciphertext sub-items Cx,k and Ex,k of the transmission node; wherein, the transmission node x∈X, X is the set of the transmission node x, TN-CT(x)={chx,1 ,...,chx,k } is the threshold set of the child nodes of the transmission node x.
进一步地,计算层次节点的密文子项的公式具体为其中,cki表示第i个层次节点对应的待加密分层文件,e(g,g)α为系统公钥的子项,si表示第i个层次节点对应的随机数。Further, calculate the ciphertext sub-items of the hierarchical nodes The formula is specifically Among them, cki represents the layered file to be encrypted corresponding to the ith level node, e(g, g)α is the sub-item of the system public key, andsi represents the random number corresponding to the ith level node.
计算层次节点的密文子项C′i的公式具体为其中,g为系统公钥的子项,si表示第i个层次节点对应的随机数。The formula for calculating the ciphertext sub-itemC'i of the hierarchical node is as follows Among them, g is the sub-item of the system public key, andsi represents the random number corresponding to the i-th level node.
计算非控制属性叶子节点的密文子项Cy的公式具体为其中,ry表示为非控制属性叶子节点y选择的随机值,g为系统公钥的子项,qy(0)表示非控制属性叶子节点y的秘密值,表示对非控制属性叶子节点y的随机值ry取负后进行哈希计算得到的值。The formula for calculating the ciphertext sub-item Cy of the non-control attribute leaf node is as follows: Among them, ry represents the random value selected by the non-control attribute leaf nodey , g is the sub-item of the system public key, qy (0) represents the secret value of the non-control attribute leaf node y, Indicates the value obtained by hashing the random value ry of the non-control attribute leaf node y after negative.
计算非控制属性叶子节点的密文子项Dy的公式具体为其中,ry表示为非控制属性叶子节点y选择的随机值,g为系统公钥的子项。The formula for calculating the ciphertext sub-itemDy of the non-control attribute leaf node is as follows: Among them, ry represents the random value selected by the non-control attribute leaf nodey , and g is the sub-item of the system public key.
计算控制属性叶子节点的密文子项的公式具体为其中,h1为系统公钥的子项,表示控制属性叶子节点Ac的秘密值,rAc表示为控制属性叶子节点Ac选择的随机值,g,b为系统公钥子项,表示对控制属性叶子节点Ac的随机值rAc取负后进行哈希计算得到的值。Calculate the ciphertext children of the leaf node of the control attribute The formula is specifically Among them, h1 is the sub-item of the system public key, represents the secret value of the control attribute leaf node Ac , rAc represents the random value selected for the control attribute leaf node Ac , g, b are the system public key sub-items, Indicates the value obtained by hashing the random value rAc of the leaf node Ac of the control attribute negative.
计算控制属性叶子节点的密文子项DAc的公式具体为其中,表示为控制属性叶子节点Ac选择的随机值,g为系统公钥子项。The formula for calculating the ciphertext sub-item DAc of the leaf node of the control attribute is specifically: in, Indicates the random value selected for the control attribute leaf node Ac , and g is the sub-key of the system public key.
计算传输节点的密文子项Cx,k的公式具体为其中,e(g,g)表示双线性映射,τx,k表示为TN-CT(x)中的节点选择的随机值,qx(0)为传输节点x对应的秘密值,表示传输节点x的子节点chx,k对应的秘密值,e(g,g)α系统公钥的子项,表示对进行哈希计算得到的值。The formula for calculating the ciphertext sub-item Cx,k of the transmission node is as follows: Among them, e(g,g) represents the bilinear mapping, τx,k represents the random value selected by the nodes in TN-CT(x), qx (0) is the secret value corresponding to the transmission node x, represents the secret value corresponding to the child node chx,k of the transmission node x, e(g,g) is the child of the public key of theα system, express right The value obtained from the hash calculation.
计算传输节点的密文子项Ex,k的公式具体为其中,g为系统公钥子项,τx,k表示为TN-CT(x)中的节点选择的随机值The formula for calculating the ciphertext sub-itemEx,k of the transmission node is as follows: Among them, g is the sub-item of the system public key, τx,k is the random value selected by the node in TN-CT(x)
进一步地,如图5所示,通过系统公钥和数据消费者私钥对加密密文进行解密,获得解密后的明文cki,包括:Further, as shown in Figure 5, the encrypted ciphertext is decrypted by the system public key and the private key of the data consumer, and the decrypted plaintext cki is obtained, including:
对单向门访问树和数据消费者属性集S执行访问树匹配函数其中,表示以x节点为根节点的子访问树,访问树匹配函数执行的过程具体为:Access tree for one-way gates Execute the access tree matching function with the data consumer attribute set S in, Indicates the child access tree with the x node as the root node. The process of the access tree matching function execution is as follows:
I.对单向门访问树中每个节点x执行对应的访问树匹配函数表示数据消费者属性集合S满足单向门访问树中的子树I. Access tree to one-way gates Each node x in the implementation of the corresponding access tree matching function Indicates that the data consumer attribute set S satisfies the one-way gate access tree subtree in
II.若数据消费者属性集S满足子树基于系统公钥,待加密分层文件和数据消费者私钥,执行节点解密函数DecryptNode(CT,SK,x),得到解密后的明文cki。可以理解地,解密后的明文即就是待加密分层文件。II. If the data consumer attribute set S satisfies the subtree Based on the system public key, the layered file to be encrypted and the private key of the data consumer, the node decryption function DecryptNode(CT,SK,x) is executed to obtain the decrypted plaintext cki . Understandably, the decrypted plaintext is the layered file to be encrypted.
进一步地,对单向门访问树中每个节点x执行对应的访问树匹配函数包括:Further, access the tree for one-way gates Each node x in the implementation of the corresponding access tree matching function include:
若x为非叶子节点,计算节点x的所有孩子节点x′的访问树匹配函数当且仅当至少kx个孩子节点返回1时,If x is a non-leaf node, calculate the access tree matching function of all child nodes x' of node x if and only if at least kx child nodes return 1,
若x为叶子节点,当x∈S时,If x is a leaf node, when x∈S,
进一步地,基于系统公钥,待加密分层文件和数据消费者私钥,执行节点解密函数DecryptNode(CT,SK,x),具体为:Further, based on the system public key, the layered file to be encrypted and the private key of the data consumer, execute the node decryption function DecryptNode(CT,SK,x), specifically:
若x为叶子节点,且数据消费者属性集S不满足单向门访问树则DecryptNode(CT,SK,x)=⊥,即解密终止。If x is a leaf node, and the data consumer attribute set S does not satisfy the one-way gate access tree Then DecryptNode(CT,SK,x)=⊥, that is, the decryption is terminated.
对于叶子节点x为数据消费者属性集S中非控制属性叶子节点,即叶子节点x∈S\Ac,则令i=attr(x),计算其中Ci,Di为密文CT中叶子节点密文子项,L,Ki为数据消费者私钥SK中的私钥子项。If the leaf node x is a non-control attribute leaf node in the data consumer attribute set S, that is, the leaf node x∈S\Ac , then let i=attr(x), calculate Among them, Ci and Di are the ciphertext sub-items of the leaf node in the ciphertext CT, and L and Ki are the private key sub-items in the private key SK of the data consumer.
对于叶子节点x为数据消费者属性集S中控制属性叶子节点Ac,计算其中,为加密密文CT中叶子节点的密文子项,D和为数据消费者私钥SK中的私钥子项。For the leaf node x is the control attribute leaf node Ac in the data consumer attribute set S, calculate in, is the ciphertext sub-item of the leaf node in the encrypted ciphertext CT, D and It is the private key subkey in the data consumer's private key SK.
若x为非叶子节点,计算其中,i=index(z),s′x={index(z):z∈Sx},表示拉格朗日系数,Sx为x的任意kx个孩子节点z的集合。If x is a non-leaf node, compute where, i=index(z), s′x ={index(z):z∈Sx }, Denotes the Lagrangian coefficient, and Sx is the set of any kx child nodes z of x.
若数据消费者属性集S满足全部或部分单向门访问树即满足全部或部分层次节点,对应层次节点计算其中,C′i为密文CT中层次节点的密文子项,K为数据消费者私钥SK中的私钥子项,DecryptNode(CT,SK,xi)为解密层次节点xi的值。If the data consumer attribute set S satisfies all or part of the one-way gate access tree That is, all or part of the hierarchical nodes are satisfied, and the corresponding hierarchical nodes are calculated Among them, C'i is the ciphertext sub-item of the hierarchical node in the ciphertext CT, K is the private key sub-item in the data consumer's private key SK, and DecryptNode(CT, SK,xi ) is the value of the decrypted hierarchical nodexi .
基于层次节点,若数据消费者属性集S包含层级较低的授权节点,计算获得所有授权的层次节点的值,其中,Cx,k,Ex,k为密文CT中传输节点的密文子项。Based on hierarchical nodes, if the data consumer attribute set S contains lower-level authorization nodes, calculate Obtain the values of all authorized hierarchical nodes, where Cx,k and Ex,k are the ciphertext sub-items of the transmission node in the ciphertext CT.
基于层次节点对应的内容密钥{cki,…,ckk}计算其中密文CT中层次节点的密文子项,并使用对称解密算法对相应的加密密文进行解密,得到解密后的明文cki。Calculated based on the content keys {cki ,...,ckk } corresponding to the hierarchical nodes in The ciphertext sub-items of the hierarchical nodes in the ciphertext CT, and the corresponding encrypted ciphertext is decrypted using a symmetric decryption algorithm to obtain the decrypted plaintext cki .
实施例2Example 2
如图1所示,本发明提供一种分层文件加密系统,包括授权机构、数据所有者、云服务提供商和数据消费者。As shown in FIG. 1, the present invention provides a layered file encryption system, including an authority, a data owner, a cloud service provider and a data consumer.
授权机构(CA),用于通过系统初始化参数λ,计算获得系统公钥PK和系统主密钥MSK,并从数据消费者获得数据消费者身份信息和对应的数据消费者属性集S;基于系统公钥PK、系统主秘钥MSK和数据消费者属性集S计算数据消费者私钥SK;将系统公钥PK发送给数据所有者,并根据数据消费者的身份信息将对应的数据消费者私钥SK发送给对应的数据消费者。Authorization Authority (CA), which is used to obtain the system public key PK and the system master key MSK through the system initialization parameter λ, and obtain the data consumer identity information and the corresponding data consumer attribute set S from the data consumer; based on the system The public key PK, the system master key MSK and the data consumer attribute set S calculate the data consumer private key SK; send the system public key PK to the data owner, and send the corresponding data consumer private key according to the data consumer's identity information. The key SK is sent to the corresponding data consumer.
数据所有者(CSP),用于从授权机构获得系统公钥PK,并根据待加密分层文件cki和各待加密分层文件的层次关系构造单向门访问树基于所述单向门访问树通过系统公钥PK对待加密分层文件cki进行加密,获得加密密文CT并发送给云服务提供商进行存储。The data owner (CSP) is used to obtain the system public key PK from the authorized institution, and construct a one-way gate access tree according to the hierarchical relationship of the hierarchical file cki to be encrypted and each hierarchical file to be encrypted Access the tree based on the one-way gate The layered file cki to be encrypted is encrypted by the system public key PK, and the encrypted ciphertext CT is obtained and sent to the cloud service provider for storage.
云服务提供商(DO),用于存储数据所有者上传的加密密文CT,并进行数据传输。The cloud service provider (DO) is used to store the encrypted ciphertext CT uploaded by the data owner and perform data transmission.
数据消费者(DU),用于从云服务提供商中下载加密密文CT,当数据消费者属性集S的所有属性满足部分或全部的单向门访问树,则通过获取的系统公钥PK和数据消费者私钥MSK对下载的加密密文CT进行解密,获得解密后的明文,否则解密失败。The data consumer (DU) is used to download the encrypted ciphertext CT from the cloud service provider. When all the attributes of the data consumer attribute set S satisfy part or all of the one-way gate access tree, the obtained system public key PK Decrypt the downloaded encrypted ciphertext CT with the private key MSK of the data consumer to obtain the decrypted plaintext, otherwise the decryption fails.
所属领域的技术人员可以清楚地了解到,为了描述的方便和简洁,仅以上述各功能单元、模块的划分进行举例说明,实际应用中,可以根据需要而将上述功能分配由不同的功能单元、模块完成,即将装置的内部结构划分成不同的功能单元或模块,以完成以上描述的全部或者部分功能。Those skilled in the art can clearly understand that, for the convenience and simplicity of description, only the division of the above-mentioned functional units and modules is used as an example. Module completion means dividing the internal structure of the device into different functional units or modules to complete all or part of the functions described above.
以上所述的具体实施方式,对本发明的目的、技术方案和有益效果进行了进一步详细说明,所应理解的是,以上所述仅为本发明的具体实施方式而已,并不用于限定本发明的保护范围,凡在本发明的精神和原则之内,所做的任何修改、等同替换、改进等,均应包含在本发明的保护范围之内。The specific embodiments described above further describe the objectives, technical solutions and beneficial effects of the present invention in detail. It should be understood that the above descriptions are only specific embodiments of the present invention, and are not intended to limit the scope of the present invention. Any modification, equivalent replacement, improvement, etc. made within the spirit and principle of the present invention shall be included within the protection scope of the present invention.
Claims (10)
Translated fromChinesePriority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202110566884.7ACN113271309B (en) | 2021-05-24 | 2021-05-24 | A kind of layered file encryption method and system |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202110566884.7ACN113271309B (en) | 2021-05-24 | 2021-05-24 | A kind of layered file encryption method and system |
Publications (2)
| Publication Number | Publication Date |
|---|---|
| CN113271309Atrue CN113271309A (en) | 2021-08-17 |
| CN113271309B CN113271309B (en) | 2022-04-08 |
Family
ID=77232515
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN202110566884.7AActiveCN113271309B (en) | 2021-05-24 | 2021-05-24 | A kind of layered file encryption method and system |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN113271309B (en) |
Cited By (1)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN119520078A (en)* | 2024-11-18 | 2025-02-25 | 华南农业大学 | Traceable encryption method, device, equipment and medium based on file hierarchical attribute-based encryption and key delegation |
Citations (12)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20130173929A1 (en)* | 2010-12-22 | 2013-07-04 | Nippon Telegraph And Telephone Corporation | Cryptographic processing system, key generation device, encryption device, decryption device, cryptographic processing method, and cryptographic processing program |
| CN103891195A (en)* | 2011-09-28 | 2014-06-25 | 皇家飞利浦有限公司 | Encryption and Decryption Based on Hierarchical Attributes |
| US20160055347A1 (en)* | 2014-08-19 | 2016-02-25 | Electronics And Telecommunications Research Institute | Data access control method in cloud |
| CN105991278A (en)* | 2016-07-11 | 2016-10-05 | 河北省科学院应用数学研究所 | Ciphertext access control method based on CP-ABE (Ciphertext-Policy Attribute-Based Encryption) |
| CN108540280A (en)* | 2018-02-09 | 2018-09-14 | 上海交通大学 | A kind of the secure data sharing method and system of resource high-efficiency |
| CN108881291A (en)* | 2018-07-19 | 2018-11-23 | 上海海事大学 | A kind of weight properties base encryption method based on layered authorization mechanism |
| CN109617855A (en)* | 2018-10-25 | 2019-04-12 | 深圳技术大学(筹) | File sharing method, device, device and medium based on CP-ABE hierarchical access control |
| CN109740363A (en)* | 2019-01-04 | 2019-05-10 | 贵州大学 | Document classification desensitization encryption method |
| WO2019148335A1 (en)* | 2018-01-30 | 2019-08-08 | Nokia Technologies Oy | Secure data processing |
| CN110611662A (en)* | 2019-08-30 | 2019-12-24 | 徐州工业职业技术学院 | Attribute-based encryption-based fog collaborative cloud data sharing method |
| CN111614680A (en)* | 2020-05-25 | 2020-09-01 | 华中科技大学 | A traceable cloud storage access control method and system based on CP-ABE |
| CN111970296A (en)* | 2020-08-25 | 2020-11-20 | 福建师范大学 | Efficient file hierarchical attribute-based encryption method and system |
- 2021
- 2021-05-24CNCN202110566884.7Apatent/CN113271309B/enactiveActive
Patent Citations (12)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20130173929A1 (en)* | 2010-12-22 | 2013-07-04 | Nippon Telegraph And Telephone Corporation | Cryptographic processing system, key generation device, encryption device, decryption device, cryptographic processing method, and cryptographic processing program |
| CN103891195A (en)* | 2011-09-28 | 2014-06-25 | 皇家飞利浦有限公司 | Encryption and Decryption Based on Hierarchical Attributes |
| US20160055347A1 (en)* | 2014-08-19 | 2016-02-25 | Electronics And Telecommunications Research Institute | Data access control method in cloud |
| CN105991278A (en)* | 2016-07-11 | 2016-10-05 | 河北省科学院应用数学研究所 | Ciphertext access control method based on CP-ABE (Ciphertext-Policy Attribute-Based Encryption) |
| WO2019148335A1 (en)* | 2018-01-30 | 2019-08-08 | Nokia Technologies Oy | Secure data processing |
| CN108540280A (en)* | 2018-02-09 | 2018-09-14 | 上海交通大学 | A kind of the secure data sharing method and system of resource high-efficiency |
| CN108881291A (en)* | 2018-07-19 | 2018-11-23 | 上海海事大学 | A kind of weight properties base encryption method based on layered authorization mechanism |
| CN109617855A (en)* | 2018-10-25 | 2019-04-12 | 深圳技术大学(筹) | File sharing method, device, device and medium based on CP-ABE hierarchical access control |
| CN109740363A (en)* | 2019-01-04 | 2019-05-10 | 贵州大学 | Document classification desensitization encryption method |
| CN110611662A (en)* | 2019-08-30 | 2019-12-24 | 徐州工业职业技术学院 | Attribute-based encryption-based fog collaborative cloud data sharing method |
| CN111614680A (en)* | 2020-05-25 | 2020-09-01 | 华中科技大学 | A traceable cloud storage access control method and system based on CP-ABE |
| CN111970296A (en)* | 2020-08-25 | 2020-11-20 | 福建师范大学 | Efficient file hierarchical attribute-based encryption method and system |
Non-Patent Citations (4)
| Title |
|---|
| SHENGLI ZHOU,GUANGXUAN CHEN,GUANGJIE HUANG,JIN SHI,TING KONG: "Research on multi-authority CP-ABE access control model in multicloud", 《IEEE》* |
| 李媛媛: "基于云存储的大数据安全处理机制研究", 《中国优秀硕士学位论文全文数据库信息科技辑》* |
| 李航,冯朝胜,刘帅南,刘彬,赵开强: "支持离线/在线加密及可验证外包解密的CP-WABE方案", 《电子学报》* |
| 林曦等: "基于属性加密的共享文件分级访问控制方案", 《燕山大学学报》* |
Cited By (2)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN119520078A (en)* | 2024-11-18 | 2025-02-25 | 华南农业大学 | Traceable encryption method, device, equipment and medium based on file hierarchical attribute-based encryption and key delegation |
| CN119520078B (en)* | 2024-11-18 | 2025-09-12 | 华南农业大学 | Traceable encryption method, device, equipment and medium based on file hierarchical attribute-based encryption and key delegation |
Also Published As
| Publication number | Publication date |
|---|---|
| CN113271309B (en) | 2022-04-08 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| CN107864139B (en) | Cryptographic attribute base access control method and system based on dynamic rules | |
| CN114039790B (en) | A fine-grained cloud storage security access control method based on blockchain | |
| Maffei et al. | Privacy and access control for outsourced personal records | |
| CN108600171B (en) | A Deterministic Deletion Method for Cloud Data Supporting Fine-Grained Access | |
| CN105959111B (en) | Information security big data resource access control system based on cloud computing and trust computing | |
| CN103701833B (en) | A kind of ciphertext access control method and system based on cloud computing platform | |
| CN106059763B (en) | Attribute-based multi-organization hierarchical ciphertext policy weight encryption method in cloud environment | |
| CN110933033B (en) | Cross-domain access control method for multiple IoT domains in smart city environment | |
| CN108111540B (en) | Hierarchical access control system and method supporting data sharing in cloud storage | |
| CN109327448B (en) | Cloud file sharing method, device, equipment and storage medium | |
| CN109617855B (en) | File sharing method, device, device and medium based on CP-ABE hierarchical access control | |
| Zhao et al. | A verifiable hidden policy CP‐ABE with decryption testing scheme and its application in VANET | |
| Xu et al. | Enabling authorized encrypted search for multi-authority medical databases | |
| CN117240452A (en) | A blockchain-based secure sharing method for plateau data | |
| CN117763592A (en) | Ciphertext retrieval method and system supporting hierarchical access control and user revocation | |
| Tian et al. | An efficient scheme of cloud data assured deletion | |
| Guo et al. | CD‐ABSE: Attribute‐Based Searchable Encryption Scheme Supporting Cross‐Domain Sharing on Blockchain | |
| Merdassi et al. | A new LTMA-ABE location and time access security control scheme for mobile cloud. | |
| CN113271309B (en) | A kind of layered file encryption method and system | |
| CN111343273A (en) | Attribute-based strategy hiding outsourcing signcryption method in Internet of vehicles environment | |
| CN117896160A (en) | A data searchable encryption method based on on-chain and off-chain collaboration | |
| CN117648706A (en) | Access control method based on block chain and attribute encryption | |
| CN117395048A (en) | Encryption method based on file hierarchy attribute for preventing user key collusion | |
| Kumar et al. | Secure Cloud Data Access: Unifying Quantum Key Distribution and Attribute-Based Encryption for Enhanced Data Protection | |
| CN114244567B (en) | A CP-ABE method supporting circuit structure in cloud environment |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| GR01 | Patent grant | ||
| GR01 | Patent grant |