CN112836232B - Dynamic web page privacy protection method based on k-anonymity under the background of web page fingerprinting - Google Patents
Dynamic web page privacy protection method based on k-anonymity under the background of web page fingerprintingDownload PDFInfo
- Publication number
- CN112836232B CN112836232BCN201911159839.9ACN201911159839ACN112836232BCN 112836232 BCN112836232 BCN 112836232BCN 201911159839 ACN201911159839 ACN 201911159839ACN 112836232 BCN112836232 BCN 112836232B
- Authority
- CN
- China
- Prior art keywords
- webpage
- false
- anonymous
- web page
- select
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Active
Links
Images
Classifications
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/60—Protecting data
- G06F21/62—Protecting access to data via a platform, e.g. using keys or access control rules
- G06F21/6218—Protecting access to data via a platform, e.g. using keys or access control rules to a system of files or objects, e.g. local or distributed file system or database
- G06F21/6245—Protecting personal data, e.g. for financial or medical purposes
- G06F21/6254—Protecting personal data, e.g. for financial or medical purposes by anonymising data, e.g. decorrelating personal data from the owner's identification
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/60—Protecting data
- G06F21/62—Protecting access to data via a platform, e.g. using keys or access control rules
- G06F21/6218—Protecting access to data via a platform, e.g. using keys or access control rules to a system of files or objects, e.g. local or distributed file system or database
- G06F21/6245—Protecting personal data, e.g. for financial or medical purposes
- G06F21/6263—Protecting personal data, e.g. for financial or medical purposes during internet communication, e.g. revealing personal data from cookies
Landscapes
- Engineering & Computer Science (AREA)
- Health & Medical Sciences (AREA)
- Bioethics (AREA)
- General Health & Medical Sciences (AREA)
- Theoretical Computer Science (AREA)
- Computer Hardware Design (AREA)
- Databases & Information Systems (AREA)
- Computer Security & Cryptography (AREA)
- Software Systems (AREA)
- Physics & Mathematics (AREA)
- General Engineering & Computer Science (AREA)
- General Physics & Mathematics (AREA)
- Medical Informatics (AREA)
- Computer And Data Communications (AREA)
- Information Transfer Between Computers (AREA)
Abstract
Translated fromChineseDescription
Translated fromChinese技术领域technical field
本发明涉及计算机网络安全通信技术领域,特别是一种网页指纹识别背景下基于k匿名的动态网页隐私保护方法。The invention relates to the technical field of computer network security communication, in particular to a dynamic webpage privacy protection method based on k-anonymity under the background of webpage fingerprint identification.
背景技术Background technique
动态网页隐私安全是网络安全的重要的一个环节,如今Web技术的不断革新推动了当前互联网的高速发展,极大地改变了人们获取信息以及沟通的方式。在当前技术背景下,人们依附于匿名通信网络来保护个人的隐私和信息。随着隐私保护技术的不断深入发展,如VPN、SOCKS代理和Tor匿名网络等多种匿名通信技术也得到了较快速度的发展。匿名技术要求通信内容和通信双方都被隐藏,通过将匿名网络和k-匿名技术结合,可以有效地保护用户的个人隐私信息。Dynamic web page privacy security is an important part of network security. The continuous innovation of Web technology has promoted the rapid development of the current Internet, which has greatly changed the way people obtain information and communicate. In the current technological context, people rely on anonymous communication networks to protect their privacy and information. With the continuous and in-depth development of privacy protection technology, various anonymous communication technologies such as VPN, SOCKS proxy and Tor anonymous network have also developed at a relatively rapid speed. Anonymity technology requires that both the content of communication and the communication parties be hidden. By combining the anonymous network and k-anonymity technology, the personal privacy information of users can be effectively protected.
在通信过程中,从源到目的地的信息流称为一个连接,一个连接由连接的开始和结束时间、生存时间、流量的有效负载、带宽以及信息包之间的时间间隔等特征来表示,称为流量模式。流量分析攻击就是通过分析网络上传送的数据包来推断出一些重要信息。为了解决网页浏览过程中用户的个人信息和隐私可能泄漏的问题,同时避免浏览器对用户网页信息进行记录,减少网站对特定用户进行锁定和追踪,要求用户在网页浏览时,先用某种算法对网页流量以及负载包进行加密处理,经过处理之后的网页的流量可能是经过负载包填充或者经过丢包的情况。In the communication process, the information flow from the source to the destination is called a connection, and a connection is represented by characteristics such as the start and end time of the connection, the time to live, the payload of the flow, the bandwidth, and the time interval between packets. called the traffic pattern. Traffic analysis attack is to infer some important information by analyzing the data packets transmitted on the network. In order to solve the problem of possible leakage of users’ personal information and privacy during web browsing, avoid browsers from recording user web page information, and reduce websites’ locking and tracking of specific users, users are required to use a certain algorithm when browsing web pages The webpage traffic and payload packets are encrypted, and the webpage traffic after processing may be filled with payload packets or lost packets.
在当前技术背景下也产生了许多攻击窃取个人信息的方法,在众多攻击方法中,流量分析方法(website fingerprinting attack)是比较常见的方法,因此,在有效预防攻击者进行流量分析的同时,基于信息论方法,采用信息熵作为隐私度量的标准,可以有效增加攻击难度。攻击者的目的是对用户进行辨识,通过对用户流量模式进行分析,因此可以进一步将第一阶段的有效负载流映射为一个预定义模式,根据Shannon的完全保密理论,熵值越大体系越混乱,攻击者越难识别。In the current technical background, there are also many methods of attacking and stealing personal information. Among the many attack methods, the traffic analysis method (website fingerprinting attack) is a relatively common method. Therefore, while effectively preventing attackers from performing traffic analysis, based on The information theory method uses information entropy as the standard of privacy measurement, which can effectively increase the difficulty of attack. The purpose of the attacker is to identify the user. By analyzing the user traffic pattern, the payload flow of the first stage can be further mapped to a predefined pattern. According to Shannon's theory of complete secrecy, the larger the entropy value, the more chaotic the system , the attacker is harder to identify.
由于真实场景是用户在访问网站时经常会连续地访问关联链接页面,而当前的技术一般仅仅考虑的是对于单个网页的加密过程,忽略了网页之间动态跳转的特性,根据这种访问模式,攻击者可以根据拥有的知识背景对当前网页发起攻击,进而降低网页的匿名度。Since the real scenario is that users often visit the associated link pages continuously when visiting the website, and the current technology generally only considers the encryption process for a single webpage, ignoring the characteristics of dynamic jumps between webpages, according to this access mode , the attacker can launch an attack on the current webpage according to the knowledge background he has, thereby reducing the anonymity of the webpage.
发明内容Contents of the invention
本发明的目的在于提供一种可靠性高、能够对用户的隐私进行有效保护的网页指纹识别背景下基于k匿名的动态网页隐私保护方法。The purpose of the present invention is to provide a dynamic webpage privacy protection method based on k-anonymity under the background of webpage fingerprint recognition with high reliability and capable of effectively protecting user privacy.
实现本发明目的的技术解决方案为:一种网页指纹识别背景下基于k匿名的动态网页隐私保护方法,包括以下步骤:The technical solution for realizing the object of the present invention is: a dynamic webpage privacy protection method based on k-anonymity under the background of webpage fingerprint identification, comprising the following steps:
步骤1,从网络中截取数据流量包,按照数据包的格式读取TCP协议下数据流负载的有效荷载部分;Step 1, intercept the data flow packet from the network, and read the payload part of the data flow load under the TCP protocol according to the format of the data packet;
步骤2,通过流量填补技术,将网络中有效数据长度不同的数据包规范为等长的数据包;Step 2, normalize data packets with different effective data lengths in the network into equal-length data packets through flow filling technology;
步骤3,依据网页流行度先选择4*k个虚假网页,k为匿名网页集中设定的虚假网页的个数,并将该4*k个虚假网页加入网页备胎池;Step 3, first select 4*k false webpages according to the webpage popularity, k is the number of false webpages set in the anonymous webpage set, and add the 4*k false webpages to the webpage spare tire pool;
步骤4,从网页备胎池中选择虚假网页和当前真实网页,计算路径熵值,根据路径熵值选择k-1个虚假网页组成匿名网页集,发送至服务器;Step 4, select the false webpage and the current real webpage from the webpage spare tire pool, calculate the path entropy value, select k-1 false webpages according to the path entropy value to form an anonymous webpage set, and send it to the server;
步骤5,判断是否存在下一次跳转:若存在则跳转到步骤2继续进行流量填充并计算路径熵值;否则结束匿名过程。Step 5, judge whether there is a next jump: if there is, jump to step 2 to continue traffic filling and calculate path entropy; otherwise end the anonymous process.
进一步地,步骤2所述将网络中有效数据长度不同的数据包规范为等长的数据包,具体如下:Further, as described in step 2, the data packets with different valid data lengths in the network are standardized into equal-length data packets, specifically as follows:
步骤2.1,通过流量填补技术,将网络中有效数据长度不同的数据包规范为等长的数据包,长度为网络允许传送的最大的数据包的大小;Step 2.1, through the flow filling technology, the data packets with different effective data lengths in the network are standardized into equal-length data packets, and the length is the largest data packet size allowed to be transmitted by the network;
步骤2.2,如果数据包长度超过允许传送的最大的数据包的大小,则将数据包进行分片处理后再进行流量填充;Step 2.2, if the length of the data packet exceeds the size of the largest data packet allowed to be transmitted, the data packet is fragmented and then filled with traffic;
步骤2.3,以相同的时间间隔发送数据包。Step 2.3, send data packets at the same time interval.
进一步地,步骤3所述的依据网页流行度先选择4*k个虚假网页,k为匿名网页集中设定的虚假网页的个数,并将该4*k个虚假网页加入网页备胎池,具体如下:Further, first select 4*k false webpages according to the popularity of webpages described in step 3, k is the number of false webpages set in the anonymous webpage set, and add these 4*k false webpages to the webpage spare tire pool, details as follows:
步骤3.1,根据网页排名算法迭代计算网页的流行度;Step 3.1, iteratively calculating the popularity of the webpage according to the webpage ranking algorithm;
步骤3.2,根据网页流行度计算网页被访问的可能性,选择网页流行度最相近的4*k个虚假网页加入网页备胎池。Step 3.2, calculate the possibility of the webpage being accessed according to the popularity of the webpage, and select 4*k false webpages with the closest webpage popularity to join the webpage spare tire pool.
进一步地,步骤4中所述的从网页备胎池中选择虚假网页和当前真实网页,计算路径熵值,根据路径熵值选择k-1个虚假网页组成匿名网页集,发送至服务器,具体如下:Further, select the false webpage and the current real webpage from the webpage spare tire pool described in step 4, calculate the path entropy value, select k-1 false webpages according to the path entropy value to form an anonymous webpage set, and send it to the server, as follows :
步骤4.1,从网页备胎池中选择虚假网页和当前真实网页,计算路径熵值,选择使得路径熵值最大的k-1个虚假网页组成匿名网页集;路径熵值的计算方法如下:Step 4.1, select the false web page and the current real web page from the web page spare tire pool, calculate the path entropy value, and select k-1 false web pages with the largest path entropy value to form an anonymous web page set; the calculation method of the path entropy value is as follows:
其中,Ht是所求得的路径熵;Pr[]表示求概率;s表示当前选择的正确的动态网页跳转路径,m表示路径长度;k是匿名网页集的大小,即匿名网页集中网页的个数,i表示的当前选择的正确的网页;是求得的路径概率;Among them, Ht is the obtained path entropy; Pr[] represents the probability; s represents the correct dynamic webpage jump path currently selected, and m represents the path length; k is the size of the anonymous webpage set, that is, the webpage in the anonymous webpage set The number of , i represents the currently selected correct web page; is the obtained path probability;
步骤4.2,将匿名网页集发送给服务器。Step 4.2, sending the anonymous webpage set to the server.
本发明与现有技术相比,其显著优点在于:(1)用户在访问网站时经常会连续地访问关联链接页面,根据这种访问模式,引入隐马尔可夫模型,同时进一步采用K-匿名的方法,采用路径熵值来对隐私保护程度进行衡量,满足安全机制的需求;(2)通过分析网页指纹的特性,在此基础上对动态网页隐私进行保护,提高了动态网页隐私信息的安全性和可靠性。Compared with the prior art, the present invention has significant advantages in that: (1) when users visit the website, they often visit the associated link pages continuously. According to this access pattern, a hidden Markov model is introduced, and K-anonymity The method uses the path entropy value to measure the degree of privacy protection to meet the needs of the security mechanism; (2) By analyzing the characteristics of webpage fingerprints, the privacy of dynamic webpages is protected on this basis, and the security of private information on dynamic webpages is improved. sex and reliability.
附图说明Description of drawings
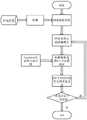
图1为本发明网页指纹识别背景下基于k匿名的动态网页隐私保护方法的流程图。Fig. 1 is a flow chart of a dynamic webpage privacy protection method based on k-anonymity under the background of webpage fingerprint identification of the present invention.
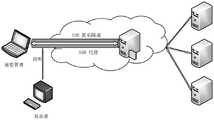
图2为本发明实施例中网站指纹攻击模型的结构示意图。FIG. 2 is a schematic structural diagram of a website fingerprint attack model in an embodiment of the present invention.
具体实施方式detailed description
本发明网页指纹识别背景下基于k匿名的动态网页隐私保护方法,包括以下步骤:Under the web page fingerprint identification background of the present invention, the dynamic web page privacy protection method based on k anonymity comprises the following steps:
步骤1,从网络中截取数据流量包,按照数据包的格式读取TCP协议下数据流负载的有效荷载部分;Step 1, intercept the data flow packet from the network, and read the payload part of the data flow load under the TCP protocol according to the format of the data packet;
步骤2,通过流量填补技术,将网络中有效数据长度不同的数据包规范为等长的数据包;Step 2, normalize data packets with different effective data lengths in the network into equal-length data packets through flow filling technology;
步骤3,依据网页流行度先选择4*k个虚假网页,k为匿名网页集中设定的虚假网页的个数,并将该4*k个虚假网页加入网页备胎池;Step 3, first select 4*k false webpages according to the webpage popularity, k is the number of false webpages set in the anonymous webpage set, and add the 4*k false webpages to the webpage spare tire pool;
步骤4,从网页备胎池中选择虚假网页和当前真实网页,计算路径熵值,根据路径熵值选择k-1个虚假网页组成匿名网页集,发送至服务器;Step 4, select the false webpage and the current real webpage from the webpage spare tire pool, calculate the path entropy value, select k-1 false webpages according to the path entropy value to form an anonymous webpage set, and send it to the server;
步骤5,判断是否存在下一次跳转:若存在则跳转到步骤2继续进行流量填充并计算路径熵值;否则结束匿名过程。Step 5, judge whether there is a next jump: if there is, jump to step 2 to continue traffic filling and calculate path entropy; otherwise end the anonymous process.
进一步地,进一步地,步骤2所述将网络中有效数据长度不同的数据包规范为等长的数据包,具体如下:Further, further, as described in step 2, the data packets with different effective data lengths in the network are standardized into equal-length data packets, as follows:
步骤2.1,通过流量填补技术,将网络中有效数据长度不同的数据包规范为等长的数据包,长度为网络允许传送的最大的数据包的大小;Step 2.1, through the flow filling technology, the data packets with different effective data lengths in the network are standardized into equal-length data packets, and the length is the largest data packet size allowed to be transmitted by the network;
步骤2.2,如果数据包长度超过允许传送的最大的数据包的大小,则将数据包进行分片处理后再进行流量填充;Step 2.2, if the length of the data packet exceeds the size of the largest data packet allowed to be transmitted, the data packet is fragmented and then filled with traffic;
步骤2.3,以相同的时间间隔发送数据包。Step 2.3, send data packets at the same time interval.
进一步地,步骤3所述的依据网页流行度先选择4*k个虚假网页,k为匿名网页集中设定的虚假网页的个数,并将该4*k个虚假网页加入网页备胎池,具体如下:Further, first select 4*k false webpages according to the popularity of webpages described in step 3, k is the number of false webpages set in the anonymous webpage set, and add these 4*k false webpages to the webpage spare tire pool, details as follows:
步骤3.1,根据网页排名算法迭代计算网页的流行度;Step 3.1, iteratively calculating the popularity of the webpage according to the webpage ranking algorithm;
步骤3.2,根据网页流行度计算网页被访问的可能性,选择网页流行度最相近的4*k个虚假网页加入网页备胎池。Step 3.2, calculate the possibility of the webpage being accessed according to the popularity of the webpage, and select 4*k false webpages with the closest webpage popularity to join the webpage spare tire pool.
进一步地,步骤4中所述的从网页备胎池中选择虚假网页和当前真实网页,计算路径熵值,根据路径熵值选择k-1个虚假网页组成匿名网页集,发送至服务器,具体如下:Further, select the false webpage and the current real webpage from the webpage spare tire pool described in step 4, calculate the path entropy value, select k-1 false webpages according to the path entropy value to form an anonymous webpage set, and send it to the server, as follows :
步骤4.1,从网页备胎池中选择虚假网页和当前真实网页,计算路径熵值,选择使得路径熵值最大的k-1个虚假网页组成匿名网页集;路径熵值的计算方法如下:Step 4.1, select the false web page and the current real web page from the web page spare tire pool, calculate the path entropy value, and select k-1 false web pages with the largest path entropy value to form an anonymous web page set; the calculation method of the path entropy value is as follows:
其中,Ht是所求得的路径熵;Pr[]表示求概率;s表示当前选择的正确的动态网页跳转路径,m表示路径长度;k是匿名网页集的大小,即匿名网页集中网页的个数,i表示的当前选择的正确的网页;是求得的路径概率;Among them, Ht is the obtained path entropy; Pr[] represents the probability; s represents the correct dynamic webpage jump path currently selected, and m represents the path length; k is the size of the anonymous webpage set, that is, the webpage in the anonymous webpage set The number of , i represents the currently selected correct web page; is the obtained path probability;
步骤4.2,将匿名网页集发送给服务器。Step 4.2, sending the anonymous webpage set to the server.
下面结合附图和具体实施方式对本发明作进一步的详细说明。The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
实施例Example
结合图1~2,本发明网页指纹识别背景下基于k匿名的动态网页隐私保护方法,分为四个阶段:In conjunction with Figures 1 to 2, the dynamic webpage privacy protection method based on k-anonymity under the background of webpage fingerprint identification of the present invention is divided into four stages:
第一阶段:在网页连接过程中,首先对网络流量进行流量填充,这样攻击者就无法从中获得与流量负载流有关的信息,从而降低了隐私泄露的可能性。The first stage: During the web page connection process, the network traffic is first filled with traffic, so that the attacker cannot obtain information related to the traffic load flow, thereby reducing the possibility of privacy leakage.
第二阶段:根据网页排名算法迭代计算网页的流行度,并根据网页流行度计算网页被访问的可能性,选择可能性相近的网页加入网页备胎池,容量大小为4*k,k为匿名网页集中设定的虚假网页的个数大小。The second stage: Iteratively calculate the popularity of the webpage according to the ranking algorithm of the webpage, and calculate the possibility of the webpage being visited according to the popularity of the webpage, and select the webpage with similar possibility to join the webpage spare tire pool, the capacity is 4*k, and k is anonymous The number of fake web pages set in the web page set.
第三阶段:根据网页备胎池中挑选k-1个虚假网页和真实网页组成匿名网页集,并计算路径熵值,选择使得路径熵值最大的匿名网页集,并将匿名网页集发送给服务器。The third stage: select k-1 fake webpages and real webpages to form an anonymous webpage set from the webpage spare tire pool, calculate the path entropy value, select the anonymous webpage set with the largest path entropy value, and send the anonymous webpage set to the server .
第四阶段:判断是否存在下一时刻的网页跳转,是则根据对下一时刻跳转的网页进行网页流量填充,k-匿名化操作,否则结束匿名化过程。The fourth stage: judging whether there is a webpage jump at the next moment, if yes, fill the webpage traffic according to the webpage to be jumped at the next moment, k-anonymization operation, otherwise end the anonymization process.
具体包括以下步骤:Specifically include the following steps:
步骤1、网络数据采集,具体如下:Step 1, network data collection, as follows:
步骤1.1、从网络中截取部分数据流量包;Step 1.1, intercepting some data traffic packets from the network;
步骤1.2、按照数据包的格式读取TCP协议下数据流负载的有效荷载部分。Step 1.2, read the payload part of the data flow load under the TCP protocol according to the format of the data packet.
步骤2、网络有效负载流量填充,具体如下:Step 2. Network payload traffic filling, as follows:
步骤2.1,通过流量填补技术,将网络中有效数据长度不同的数据包规范为等长的数据包,长度为网络允许传送的最大的数据包的大小;Step 2.1, through the flow filling technology, the data packets with different effective data lengths in the network are standardized into equal-length data packets, and the length is the largest data packet size allowed to be transmitted by the network;
步骤2.2,如果数据包长度超过允许传送的最大的数据包的大小,则将数据包进行分片处理后再进行流量填充;Step 2.2, if the length of the data packet exceeds the size of the largest data packet allowed to be transmitted, the data packet is fragmented and then filled with traffic;
步骤2.3,以相同的时间间隔发送数据包。Step 2.3, send data packets at the same time interval.
步骤3、所述的依据网页流行度先选择4*k个虚假网页,k为匿名网页集中设定的虚假网页的个数,并将该4*k个虚假网页加入网页备胎池,具体如下:Step 3, first select 4*k false webpages based on webpage popularity, k is the number of false webpages set in the anonymous webpage set, and add the 4*k false webpages to the webpage spare tire pool, as follows :
步骤3.1,根据网页排名算法迭代计算网页的流行度;Step 3.1, iteratively calculating the popularity of the webpage according to the webpage ranking algorithm;
步骤3.2,根据网页流行度计算网页被访问的可能性,选择网页流行度最相近的4*k个虚假网页加入网页备胎池。Step 3.2, calculate the possibility of the webpage being accessed according to the popularity of the webpage, and select 4*k false webpages with the closest webpage popularity to join the webpage spare tire pool.
步骤4、从网页备胎池中选择虚假网页和当前真实网页,计算路径熵值,根据路径熵值选择k-1个虚假网页组成匿名网页集,发送至服务器,具体如下:Step 4. Select the false webpage and the current real webpage from the webpage spare tire pool, calculate the path entropy value, select k-1 false webpages according to the path entropy value to form an anonymous webpage set, and send it to the server, as follows:
步骤4.1,从网页备胎池中选择虚假网页和当前真实网页,计算路径熵值,选择使得路径熵值最大的k-1个虚假网页组成匿名网页集;路径熵值的计算方法如下:Step 4.1, select the false web page and the current real web page from the web page spare tire pool, calculate the path entropy value, and select k-1 false web pages with the largest path entropy value to form an anonymous web page set; the calculation method of the path entropy value is as follows:
其中,Ht是所求得的路径熵;Pr[]表示求概率;s表示当前选择的正确的动态网页跳转路径,m表示路径长度;k是匿名网页集的大小,即匿名网页集中网页的个数,i表示的当前选择的正确的网页;是求得的路径概率;Among them, Ht is the obtained path entropy; Pr[] represents the probability; s represents the correct dynamic webpage jump path currently selected, and m represents the path length; k is the size of the anonymous webpage set, that is, the webpage in the anonymous webpage set The number of , i represents the currently selected correct web page; is the obtained path probability;
步骤4.2,将匿名网页集发送给服务器。Step 4.2, sending the anonymous webpage set to the server.
步骤5、判断是否存在下一次跳转,是则跳转到步骤2继续进行流量填充并计算路径熵值;否则结束匿名过程。Step 5. Judging whether there is a next jump, if yes, jump to step 2 to continue filling traffic and calculating path entropy; otherwise, end the anonymous process.
步骤5.1、判断是否存在下一时刻的跳转,是则执行步骤5.2,否则执行步骤5.3;Step 5.1, judge whether there is a jump at the next moment, if yes, execute step 5.2, otherwise execute step 5.3;
步骤5.2、跳转到步骤2,对当前时刻的网页继续进行匿名化;然后计算路径熵值,根据最大路径熵值选择虚假网页组成匿名网页集。Step 5.2, jump to step 2, continue to anonymize the webpage at the current moment; then calculate the path entropy value, and select false webpages according to the maximum path entropy value to form an anonymous webpage set.
本发明通过分析网页指纹的特性对动态网页隐私进行保护,提高了动态网页隐私信息的安全性和可靠性。The invention protects the privacy of dynamic webpages by analyzing the characteristics of webpage fingerprints, and improves the security and reliability of dynamic webpage privacy information.
Claims (3)
Translated fromChinesePriority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN201911159839.9ACN112836232B (en) | 2019-11-22 | 2019-11-22 | Dynamic web page privacy protection method based on k-anonymity under the background of web page fingerprinting |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN201911159839.9ACN112836232B (en) | 2019-11-22 | 2019-11-22 | Dynamic web page privacy protection method based on k-anonymity under the background of web page fingerprinting |
Publications (2)
| Publication Number | Publication Date |
|---|---|
| CN112836232A CN112836232A (en) | 2021-05-25 |
| CN112836232Btrue CN112836232B (en) | 2022-12-13 |
Family
ID=75921759
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN201911159839.9AActiveCN112836232B (en) | 2019-11-22 | 2019-11-22 | Dynamic web page privacy protection method based on k-anonymity under the background of web page fingerprinting |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN112836232B (en) |
Families Citing this family (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN113434801B (en)* | 2021-07-07 | 2022-01-28 | 中国人民解放军国防科技大学 | Website fingerprint identification method based on topic probability model |
| CN113783859A (en)* | 2021-08-31 | 2021-12-10 | 广东君略科技咨询有限公司 | Web page construction method and processing terminal supporting trace k-anonymity |
| CN115086030A (en)* | 2022-06-14 | 2022-09-20 | 中国电信股份有限公司 | Fingerprint attack protection method and device for HTTPS encrypted traffic, electronic equipment and medium |
| CN116015969A (en)* | 2023-01-07 | 2023-04-25 | 江苏大学 | A website fingerprinting defense method based on anti-obfuscation of traffic front domain |
Citations (2)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN109067750A (en)* | 2018-08-14 | 2018-12-21 | 中国科学院信息工程研究所 | A kind of location privacy protection method and device based on anonymity |
| CN109831448A (en)* | 2019-03-05 | 2019-05-31 | 南京理工大学 | For the detection method of particular encryption web page access behavior |
Family Cites Families (1)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CA2715024C (en)* | 2008-03-14 | 2017-05-02 | Cardinal Commerce Corporation | System and method for tracking user identity and/or activity across multiple websites |
- 2019
- 2019-11-22CNCN201911159839.9Apatent/CN112836232B/enactiveActive
Patent Citations (2)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN109067750A (en)* | 2018-08-14 | 2018-12-21 | 中国科学院信息工程研究所 | A kind of location privacy protection method and device based on anonymity |
| CN109831448A (en)* | 2019-03-05 | 2019-05-31 | 南京理工大学 | For the detection method of particular encryption web page access behavior |
Also Published As
| Publication number | Publication date |
|---|---|
| CN112836232A (en) | 2021-05-25 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| CN112836232B (en) | Dynamic web page privacy protection method based on k-anonymity under the background of web page fingerprinting | |
| US11128621B2 (en) | Method and apparatus for accessing website | |
| US10270792B1 (en) | Methods for detecting malicious smart bots to improve network security and devices thereof | |
| CN103780622B (en) | A kind of data classification encryption method of facing cloud storage | |
| US9152820B1 (en) | Method and apparatus for cookie anonymization and rejection | |
| CN107209830B (en) | Method for identifying and resisting network attack | |
| CN104322001B (en) | TLS flow control using service name identification | |
| US8893278B1 (en) | Detecting malware communication on an infected computing device | |
| JP6188832B2 (en) | Method, computer program product, data processing system, and database system for processing database client requests | |
| US8495358B2 (en) | Software based multi-channel polymorphic data obfuscation | |
| CN102158493B (en) | A kind of Cookie analytic method, device and a kind of client | |
| Zeng et al. | Flow context and host behavior based shadowsocks’s traffic identification | |
| US8161538B2 (en) | Stateful application firewall | |
| CN106576051B (en) | A method, network device, and non-transitory machine-readable medium for detecting zero-day threats | |
| Vanhoef et al. | HEIST: HTTP Encrypted Information can be Stolen through TCP-windows | |
| WO2017020585A1 (en) | Cdn-based access control method and relevant device | |
| CN115622757A (en) | A network abnormal behavior detection method based on data multidimensional entropy fingerprint | |
| WO2018076697A1 (en) | Method and apparatus for detecting zombie feature | |
| US12401681B2 (en) | Method and apparatus for finding hidden IP address in malicious site using DNS service | |
| CN116938507A (en) | A power Internet of Things security defense terminal and its control system | |
| US12034731B2 (en) | Evaluating access requests using assigned common actor identifiers | |
| CN112073418B (en) | Encrypted flow detection method and device and computer readable storage medium | |
| CN113904810A (en) | An Efficient Privacy-Preserving Safe Browsing Method | |
| CN108701195B (en) | Data security protection method and device | |
| CN106295366A (en) | Sensitive data recognition methods and device |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| CB03 | Change of inventor or designer information | Inventor after:Qian Yuwen Inventor after:Zhang Li Inventor after:Li Jun Inventor after:Ma Chuan Inventor before:Zhang Li Inventor before:Qian Yuwen Inventor before:Li Jun Inventor before:Ma Chuan | |
| CB03 | Change of inventor or designer information | ||
| GR01 | Patent grant | ||
| GR01 | Patent grant |