CN112257054B - A software application unauthorized risk detection method, electronic equipment and storage medium - Google Patents
A software application unauthorized risk detection method, electronic equipment and storage mediumDownload PDFInfo
- Publication number
- CN112257054B CN112257054BCN202011140562.8ACN202011140562ACN112257054BCN 112257054 BCN112257054 BCN 112257054BCN 202011140562 ACN202011140562 ACN 202011140562ACN 112257054 BCN112257054 BCN 112257054B
- Authority
- CN
- China
- Prior art keywords
- code
- authority
- unauthorized
- scope
- source code
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Active
Links
Images
Classifications
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/30—Authentication, i.e. establishing the identity or authorisation of security principals
- G06F21/44—Program or device authentication
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/50—Monitoring users, programs or devices to maintain the integrity of platforms, e.g. of processors, firmware or operating systems
- G06F21/57—Certifying or maintaining trusted computer platforms, e.g. secure boots or power-downs, version controls, system software checks, secure updates or assessing vulnerabilities
- G06F21/577—Assessing vulnerabilities and evaluating computer system security
Landscapes
- Engineering & Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- Computer Hardware Design (AREA)
- General Engineering & Computer Science (AREA)
- Theoretical Computer Science (AREA)
- Software Systems (AREA)
- Physics & Mathematics (AREA)
- General Physics & Mathematics (AREA)
- Computing Systems (AREA)
- Stored Programmes (AREA)
Abstract
Description
Translated fromChinese技术领域technical field
本说明书一个或多个实施例涉及计算机软件安全技术领域,尤其涉及一种软件应用越权风险检测方法、电子设备及存储介质。One or more embodiments of this specification relate to the technical field of computer software security, and in particular to a software application unauthorized risk detection method, an electronic device, and a storage medium.
背景技术Background technique
随着信息系统和互联网技术的不断发展,应用程序功能随之增大,其程序源代码的规模也越来越大,而容易被利用的安全漏洞、代码后门以及代码中的逻辑错误也不再局限于以往形式,使得用传统软件测试方法来检测源代码中的安全漏洞变得非常困难,信息安全和软件安全面临着前所未有的巨大挑战。With the continuous development of information systems and Internet technologies, the functions of applications have increased, and the scale of their program source codes has also increased, while security holes, code backdoors, and logic errors in codes that are easy to be exploited are no longer It is limited to the previous form, which makes it very difficult to detect security holes in the source code with traditional software testing methods, and information security and software security are facing unprecedented challenges.
静态分析技术是目前常见的源代码缺陷检测技术之一,该方法的主要特点是在检测代码漏洞和逻辑错误的时候并不需要实际运行程序代码,并且检测过程中无需人工干预,只需由检测程序扫描待测项目的全部或者部分源代码即可发现潜在的软件缺陷和安全漏洞。相比于动态分析技术,静态分析技术具有更高的覆盖率和较低的漏报率等优点。Static analysis technology is one of the common source code defect detection technologies at present. The main feature of this method is that it does not need to actually run the program code when detecting code vulnerabilities and logic errors, and does not require manual intervention during the detection process. The program scans all or part of the source code of the project to be tested to find potential software defects and security holes. Compared with dynamic analysis technology, static analysis technology has the advantages of higher coverage and lower false negative rate.
现有的针对程序源代码的静态分析工具对于已知漏洞依赖较大,更多关注于常规代码缺陷,例如信息数据泄露、危险API接口、密码管理等漏洞,而对于越权行为这类逻辑漏洞不能进行很好的检测;规模较大的程序源代码往往会用到第三方开源框架来实现某些业务功能,在使用这些框架时会采用面向切面编程(AOP)的方式,现有的静态分析方法无法在业务逻辑中有效找到切入业务逻辑中的代码,因此对于相应代码中存在的逻辑漏洞不能及时发现或检测结果漏报率较高。Existing static analysis tools for program source code rely heavily on known vulnerabilities, and pay more attention to conventional code defects, such as information data leakage, dangerous API interfaces, password management and other vulnerabilities, while logic vulnerabilities such as unauthorized behavior cannot Perform good detection; large-scale program source codes often use third-party open source frameworks to achieve certain business functions, and use aspect-oriented programming (AOP) when using these frameworks. Existing static analysis methods The code that cuts into the business logic cannot be effectively found in the business logic, so the logical loopholes in the corresponding code cannot be found in time or the detection result has a high rate of false positives.
发明内容Contents of the invention
有鉴于此,本说明书一个或多个实施例的目的在于提出一种软件应用越权风险检测方法、电子设备及存储介质,能够对软件应用程序中可能存在的越权行为类的逻辑漏洞进行全面准确检测。In view of this, the purpose of one or more embodiments of this specification is to propose a software application unauthorized risk detection method, electronic equipment and storage media, which can comprehensively and accurately detect logical vulnerabilities that may exist in software applications. .
基于上述目的,本说明书一个或多个实施例提供了一种软件应用越权风险检测方法,包括:Based on the above purpose, one or more embodiments of this specification provide a software application unauthorized risk detection method, including:
获取待检测软件程序的源代码,对所述源代码进行解析,确定权限验证相关代码与作用范围,对应生成权限-范围映射表;Obtaining the source code of the software program to be detected, analyzing the source code, determining the relevant code and scope of authority verification, and generating a corresponding authority-scope mapping table;
根据所述权限-范围映射表,对所述源代码进行权限验证逻辑插桩,生成插桩中间表示代码;According to the authority-range mapping table, perform authority verification logic instrumentation on the source code, and generate an instrumentation intermediate representation code;
根据所述插桩中间表示代码,确定所述源代码的信息流图;Determine the information flow graph of the source code according to the intermediate representation code of the instrumentation;
在所述信息流图中选取敏感行为节点,以所述敏感行为节点为起点进行越权风险路径检测,确定越权风险路径。Select sensitive behavior nodes in the information flow graph, and use the sensitive behavior nodes as a starting point to perform unauthorized risk path detection to determine the unauthorized risk path.
可选的,所述对所述源代码进行解析,确定权限验证相关代码与作用范围,对应生成权限-范围映射表,包括:Optionally, the source code is analyzed to determine the authority verification related code and the scope of action, and a corresponding authority-scope mapping table is generated, including:
确定所述源代码所使用的安全框架;determine the security framework used by said source code;
根据所述安全框架的语义规则,利用解析器对所述源代码的配置文件与注解信息进行解析;According to the semantic rules of the security framework, a parser is used to parse the configuration file and annotation information of the source code;
根据解析结果,获取所述权限验证相关代码与相应所述作用范围,所述权限验证相关代码包括权限验证代码所在的包名、类名、方法函数名、参数列表和返回值类型,所述作用范围是指与所述权限验证相关代码相对应的具体的包、具体的类、具体方法函数与具体语句;According to the parsing result, obtain the relevant code of the authority verification and the corresponding scope of action, the relevant code of the authority verification includes the package name, class name, method function name, parameter list and return value type where the authority verification code is located, and the function The scope refers to the specific package, specific class, specific method function and specific statement corresponding to the code related to the authorization verification;
根据所述权限验证相关代码与所述作用范围生成所述权限-范围映射表。The authority-scope mapping table is generated according to the authority verification related code and the scope of action.
可选的,所述根据所述权限-范围映射表,对所述源代码进行权限验证逻辑插桩,生成插桩中间表示代码,包括:Optionally, according to the authority-range mapping table, the authority verification logic instrumentation is performed on the source code, and the instrumentation intermediate representation code is generated, including:
读取所述权限-范围映射表,根据所述权限-范围映射表中范围字段对应的所述作用范围,在所述源代码中确定对应代码位置并进行代码标定;Read the authority-scope mapping table, determine the corresponding code position in the source code according to the scope of action corresponding to the scope field in the authority-scope mapping table, and perform code calibration;
根据所述权限-范围映射表确定与所述范围字段对应的权限字段,根据所述权限字段确定相应的权限验证代码;determining a permission field corresponding to the scope field according to the permission-range mapping table, and determining a corresponding permission verification code according to the permission field;
根据所述权限验证代码,在所标定的代码位置处进行权限验证逻辑代码插桩,生成所述插桩中间表示代码。According to the authorization verification code, the authorization verification logic code is inserted at the marked code position, and the intermediate representation code of the insertion is generated.
可选的,所述在所述源代码中确定对应代码位置进行代码标定,包括:Optionally, the determining the corresponding code position in the source code for code calibration includes:
根据所述作用范围在所述源代码中查找到相匹配的代码对象;Finding a matching code object in the source code according to the scope of action;
若所述代码对象为具体的包,则对所述包中每一个类的每一个方法的方法体中的第一条语句进行标定;If the code object is a specific package, then mark the first statement in the method body of each method of each class in the package;
若所述代码对象为具体的方法函数,则对所述方法函数的方法体重第一条语句进行标定;If the code object is a specific method function, then calibrate the first statement of the method weight of the method function;
若所述代码对象为具体的语句,则对所述语句进行标定。If the code object is a specific statement, then mark the statement.
可选的,所述根据所述权限验证代码,在所标定的代码位置处进行权限验证逻辑代码插桩,生成所述插桩中间表示代码,包括:Optionally, according to the authority verification code, performing authority verification logic code insertion at the marked code position to generate the insertion intermediate representation code, including:
根据所述权限验证代码确定相应的权限验证逻辑代码;determining a corresponding authority verification logic code according to the authority verification code;
遍历所述源代码中所有标定代码位置,以所述标定代码位置相对应的所述作用范围为键、以所述标定代码位置相应的所述权限验证逻辑代码为值,构造Map对象;Traversing all calibration code positions in the source code, using the scope of action corresponding to the calibration code position as a key, and using the authority verification logic code corresponding to the calibration code position as a value, construct a Map object;
在将所述源代码转化为中间代码的过程中,根据所述Map对象在所述中间代码中插入所述权限验证逻辑代码,生成所述插桩中间表示代码。In the process of converting the source code into the intermediate code, insert the authority verification logic code into the intermediate code according to the Map object, and generate the intermediate representation code of the insertion.
可选的,所述信息流图包括函数调用关系图、控制流图与数据流图。Optionally, the information flow graph includes a function call graph, a control flow graph, and a data flow graph.
可选的,所述在所述信息流图中选取敏感行为节点,以所述敏感行为节点为起点进行越权风险路径检测,包括:Optionally, selecting a sensitive behavior node in the information flow graph, and starting from the sensitive behavior node to detect an unauthorized risk path, including:
获取越权敏感操作列表,所述越权敏感操作列表包括需验证权限以及与所述需验证权限相关的越权敏感操作;Obtaining a list of unauthorized sensitive operations, where the list of unauthorized sensitive operations includes permissions to be verified and sensitive operations related to the permissions to be verified;
将所述敏感操作与所述信息流图进行对比,从所述信息流图中筛选出与所述敏感操作相对应的函数或语句进行节点标记;Comparing the sensitive operation with the information flow graph, and selecting functions or statements corresponding to the sensitive operation from the information flow graph to mark nodes;
在所述信息流图中,从标记节点处开始进行反向遍历,判断反向遍历路径中是否存在权限验证逻辑代码;In the information flow diagram, reverse traversal is performed from the marked node, and it is judged whether there is authority verification logic code in the reverse traversal path;
若直到终点仍未检测到所述权限验证逻辑代码,则所述反向遍历路径中存在越权风险;If the authority verification logic code is not detected until the end point, there is a risk of exceeding authority in the reverse traversal path;
若存在所述权限验证逻辑代码,则判断所述权限验证逻辑代码与所述标记节点所对应的所述需验证权限是否匹配,若不匹配则从所述标记节点至所述权限验证逻辑代码的反向遍历路径中存在越权风险。If there is the authority verification logic code, it is judged whether the authority verification logic code matches the authority to be verified corresponding to the marked node, and if it does not match, from the marked node to the authority verification logic code There is a risk of unauthorized access in the reverse traversal path.
可选的,所述确定越权风险路径,包括:Optionally, the determination of the ultra vires risk path includes:
将存在越权风险的所述反向遍历路径提取,根据所述信息流图与所述插桩中间表示代码的对应关系,确定风险中间代码路径;Extracting the reverse traversal path that has the risk of exceeding authority, and determining the risk intermediate code path according to the correspondence between the information flow graph and the intermediate representation code of the instrumentation;
将所述风险中间代码路径还原转化为所述源代码中的对应路径得到所述越权风险路径,输出所述越权风险路径。Restoring and transforming the risky intermediate code path into a corresponding path in the source code to obtain the unauthorized risk path, and outputting the unauthorized risk path.
基于上述目的,本说明书一个或多个实施例提供了一种软件应用越权风险检测电子设备,包括存储器、处理器及存储在存储器上并可在处理器上运行的计算机程序,所述处理器执行所述程序时实现如下方法:Based on the above purpose, one or more embodiments of this specification provide an electronic device for software application unauthorized risk detection, including a memory, a processor, and a computer program stored on the memory and operable on the processor, and the processor executes The following methods are implemented during the program:
获取待检测软件程序的源代码,对所述源代码进行解析,确定权限验证相关代码与作用范围,对应生成权限-范围映射表;Obtaining the source code of the software program to be detected, analyzing the source code, determining the relevant code and scope of authority verification, and generating a corresponding authority-scope mapping table;
根据所述权限-范围映射表,对所述源代码进行权限验证逻辑插桩,生成插桩中间表示代码;According to the authority-range mapping table, perform authority verification logic instrumentation on the source code, and generate an instrumentation intermediate representation code;
根据所述插桩中间表示代码,确定所述源代码的信息流图;Determine the information flow graph of the source code according to the intermediate representation code of the instrumentation;
在所述信息流图中选取敏感行为节点,以所述敏感行为节点为起点进行越权风险路径检测,确定越权风险路径。Select sensitive behavior nodes in the information flow graph, and use the sensitive behavior nodes as a starting point to perform unauthorized risk path detection to determine the unauthorized risk path.
基于上述目的,本说明书一个或多个实施例提供了一种软件应用越权风险检测非暂态计算机可读存储介质,所述非暂态计算机可读存储介质存储计算机指令,所述计算机指令用于使所述计算机执行如下方法:Based on the above purpose, one or more embodiments of this specification provide a software application unauthorized risk detection non-transitory computer-readable storage medium, the non-transitory computer-readable storage medium stores computer instructions, and the computer instructions are used to Make described computer carry out following method:
获取待检测软件程序的源代码,对所述源代码进行解析,确定权限验证相关代码与作用范围,对应生成权限-范围映射表;Obtaining the source code of the software program to be detected, analyzing the source code, determining the relevant code and scope of authority verification, and generating a corresponding authority-scope mapping table;
根据所述权限-范围映射表,对所述源代码进行权限验证逻辑插桩,生成插桩中间表示代码;According to the authority-range mapping table, perform authority verification logic instrumentation on the source code, and generate an instrumentation intermediate representation code;
根据所述插桩中间表示代码,确定所述源代码的信息流图;Determine the information flow graph of the source code according to the intermediate representation code of the instrumentation;
在所述信息流图中选取敏感行为节点,以所述敏感行为节点为起点进行越权风险路径检测,确定越权风险路径。Select sensitive behavior nodes in the information flow graph, and use the sensitive behavior nodes as a starting point to perform unauthorized risk path detection to determine the unauthorized risk path.
从上面所述可以看出,本说明书一个或多个实施例提供的一种软件应用越权风险检测方法、电子设备及存储介质,将软件应用所涉及安全框架考虑在内,通过对软件应用的源代码进行解析确定权限验证相关代码和其作用范围,并生成相对应的权限-范围映射表;根据所述权限-范围映射表,在解析源码生成中间表示形式时,在源代码业务逻辑中进行权限验证逻辑插桩,并在插桩后的生成中间表示形式;在中间表示形式的基础上,获取相关的信息流图;将中间表示的信息流图结合越权行为检测策略,对系统代码逻辑进行越权行为检测;获取越权行为高风险路径及检测结果。由于在对源码解析时将使用的第三方框架考虑在内,避免了使用第三方框架的方法时对于一些潜在的越权行为的漏报,同时采用了基于中间代码的插桩方式将权限验证逻辑与业务逻辑相结合的方法,在不破坏原有源代码的基础上实现了对越权行为风险的检测,从而在源头和根本上保障了应用软件和信息系统的安全,能够实现对可能存在的越权行为类的逻辑漏洞进行全面准确检测。It can be seen from the above that one or more embodiments of this specification provide a software application unauthorized risk detection method, electronic equipment, and storage medium, taking into account the security framework involved in the software application, and by analyzing the source of the software application The code is analyzed to determine the relevant code and its scope of authority verification, and the corresponding authority-scope mapping table is generated; according to the authority-scope mapping table, when parsing the source code to generate an intermediate representation, the authority is performed in the source code business logic Verify the logic insertion, and generate an intermediate representation after the insertion; obtain the relevant information flow graph on the basis of the intermediate representation; combine the information flow graph of the intermediate representation with the unauthorized behavior detection strategy, and perform unauthorized authorization on the system code logic Behavior detection; obtain high-risk paths and detection results of ultra vires behaviors. Since the third-party framework used is taken into account when parsing the source code, the underreporting of some potential unauthorized behaviors when using the third-party framework method is avoided. The method of combining business logic realizes the detection of the risk of unauthorized behavior on the basis of not destroying the original source code, thereby guaranteeing the security of application software and information system at the source and fundamentally, and realizing the detection of possible unauthorized behavior Comprehensive and accurate detection of class logic vulnerabilities.
附图说明Description of drawings
为了更清楚地说明本说明书一个或多个实施例或现有技术中的技术方案,下面将对实施例或现有技术描述中所需要使用的附图作简单地介绍,显而易见地,下面描述中的附图仅仅是本说明书一个或多个实施例,对于本领域普通技术人员来讲,在不付出创造性劳动的前提下,还可以根据这些附图获得其他的附图。In order to more clearly illustrate one or more embodiments of this specification or the technical solutions in the prior art, the following will briefly introduce the drawings that need to be used in the description of the embodiments or prior art. Obviously, in the following description The accompanying drawings are only one or more embodiments of this specification, and those of ordinary skill in the art can also obtain other drawings according to these drawings without creative work.
图1为本说明书一个或多个实施例所提供的软件应用越权风险检测方法示意图;FIG. 1 is a schematic diagram of a software application unauthorized risk detection method provided by one or more embodiments of this specification;
图2为本说明书一个或多个实施例所提供的软件应用越权风险检测方法中生成权限-范围映射表方法示意图;FIG. 2 is a schematic diagram of a method for generating a rights-range mapping table in the software application unauthorized risk detection method provided by one or more embodiments of this specification;
图3为本说明书一个或多个实施例所提供的软件应用越权风险检测方法中生成插桩中间表示代码示方法意图;Fig. 3 is a schematic diagram of a method for generating intermediary representation codes for instrumentation in the software application unauthorized risk detection method provided by one or more embodiments of this specification;
图4为本说明书一个或多个实施例所提供的软件应用越权风险检测电子设备结构示意图。Fig. 4 is a schematic structural diagram of an electronic device for software application unauthorized risk detection provided by one or more embodiments of this specification.
具体实施方式Detailed ways
为使本公开的目的、技术方案和优点更加清楚明白,以下结合具体实施例,并参照附图,对本公开进一步详细说明。In order to make the purpose, technical solutions and advantages of the present disclosure clearer, the present disclosure will be further described in detail below in conjunction with specific embodiments and with reference to the accompanying drawings.
需要说明的是,除非另外定义,本说明书一个或多个实施例使用的技术术语或者科学术语应当为本公开所属领域内具有一般技能的人士所理解的通常意义。本说明书一个或多个实施例中使用的“第一”、“第二”以及类似的词语并不表示任何顺序、数量或者重要性,而只是用来区分不同的组成部分。“包括”或者“包含”等类似的词语意指出现该词前面的元件或者物件涵盖出现在该词后面列举的元件或者物件及其等同,而不排除其他元件或者物件。“连接”或者“相连”等类似的词语并非限定于物理的或者机械的连接,而是可以包括电性的连接,不管是直接的还是间接的。“上”、“下”、“左”、“右”等仅用于表示相对位置关系,当被描述对象的绝对位置改变后,则该相对位置关系也可能相应地改变。It should be noted that, unless otherwise defined, the technical terms or scientific terms used in one or more embodiments of the present specification shall have ordinary meanings understood by those skilled in the art to which the present disclosure belongs. "First", "second" and similar words used in one or more embodiments of the present specification do not indicate any order, quantity or importance, but are only used to distinguish different components. "Comprising" or "comprising" and similar words mean that the elements or items appearing before the word include the elements or items listed after the word and their equivalents, without excluding other elements or items. Words such as "connected" or "connected" are not limited to physical or mechanical connections, but may include electrical connections, whether direct or indirect. "Up", "Down", "Left", "Right" and so on are only used to indicate the relative positional relationship. When the absolute position of the described object changes, the relative positional relationship may also change accordingly.
在一方面,本说明书实施例提供了一种软件应用越权风险检测方法。In one aspect, the embodiment of this specification provides a software application unauthorized risk detection method.
如图1所示,本说明书的一个或多个可选实施例提供了一种软件应用越权风险检测方法,包括:As shown in Figure 1, one or more optional embodiments of this specification provide a software application unauthorized risk detection method, including:
S1:获取待检测软件程序的源代码,对所述源代码进行解析,确定权限验证相关代码与作用范围,对应生成权限-范围映射表;S1: Obtain the source code of the software program to be detected, analyze the source code, determine the relevant code and scope of authority verification, and generate a corresponding authority-scope mapping table;
一些可选的获取所述待测软件程序的源代码的方法,由用户上传待检测的软件项目源代码压缩包,也可以由用户指定代码存放位置,如Github、Gitlab地址等,自动拉取项目的源代码。Some optional methods for obtaining the source code of the software program to be tested are uploaded by the user to the source code compressed package of the software project to be tested, or the user can specify the code storage location, such as Github, Gitlab address, etc., to automatically pull the project source code.
S2:根据所述权限-范围映射表,对所述源代码进行权限验证逻辑插桩,生成插桩中间表示代码;S2: According to the authority-scope mapping table, perform authority verification logic instrumentation on the source code, and generate an instrumentation intermediate representation code;
S3:根据所述插桩中间表示代码,确定所述源代码的信息流图;S3: Determine the information flow graph of the source code according to the intermediate representation code of the instrumentation;
S4:在所述信息流图中选取敏感行为节点,以所述敏感行为节点为起点进行越权风险路径检测,确定越权风险路径。S4: Select a sensitive behavior node in the information flow graph, and use the sensitive behavior node as a starting point to detect an unauthorized risk path to determine an unauthorized risk path.
所述软件应用越权风险检测方法,通过对软件应用的源代码进行解析确定权限验证相关代码和其作用范围,并生成相对应的权限-范围映射表;根据所述权限-范围映射表,在解析源码生成中间表示形式时,在源代码业务逻辑中进行权限验证逻辑插桩,并在插桩后生成中间表示形式;在中间表示形式的基础上,获取相关的信息流图;将中间表示的信息流图结合越权行为检测策略,对系统代码逻辑进行越权行为检测;获取越权行为高风险路径及检测结果。由于在对源码解析时将使用的第三方框架考虑在内,避免了使用第三方框架的方法时对于一些潜在的越权行为的漏报,同时采用了基于中间代码的插桩方式将权限验证逻辑与业务逻辑相结合的方法,在不破坏原有源代码的基础上实现了对越权行为风险的检测,从而在源头和根本上保障了应用软件和信息系统的安全,能够实现对可能存在的越权行为类的逻辑漏洞进行全面准确检测。The software application unauthorized risk detection method, by analyzing the source code of the software application, determines the authority verification related code and its scope of action, and generates a corresponding authority-scope mapping table; according to the authority-scope mapping table, in the analysis When the source code generates an intermediate representation, the authority verification logic is inserted in the source code business logic, and the intermediate representation is generated after the insertion; on the basis of the intermediate representation, the relevant information flow diagram is obtained; the information of the intermediate representation is The flow graph combines the ultra-authority behavior detection strategy to detect the system code logic for ultra-authority behavior; obtain the high-risk path and detection results of the ultra-authority behavior. Since the third-party framework used is taken into account when parsing the source code, the underreporting of some potential unauthorized behaviors when using the third-party framework method is avoided. The method of combining business logic realizes the detection of the risk of unauthorized behavior on the basis of not destroying the original source code, thereby guaranteeing the security of application software and information system at the source and fundamentally, and realizing the detection of possible unauthorized behavior Comprehensive and accurate detection of class logic vulnerabilities.
如图2所示,在本说明书的一个或多个可选实施例所提供的一种软件应用越权风险检测方法中,所述对所述源代码进行解析,确定权限验证相关代码与作用范围,对应生成权限-范围映射表,包括:As shown in FIG. 2, in a software application unauthorized risk detection method provided by one or more optional embodiments of this specification, the source code is analyzed to determine the relevant code and scope of authority verification, Correspondingly generate a permission-scope mapping table, including:
S201:确定所述源代码所使用的安全框架;S201: Determine the security framework used by the source code;
S202:根据所述安全框架的语义规则,利用解析器对所述源代码的配置文件与注解信息进行解析;S202: According to the semantic rules of the security framework, use a parser to parse the configuration file and annotation information of the source code;
S203:根据解析结果,获取所述权限验证相关代码与相应所述作用范围,所述权限验证相关代码包括权限验证代码所在的包名、类名、方法函数名、参数列表和返回值类型,所述作用范围是指与所述权限验证相关代码相对应的具体的包、具体的类、具体方法函数与具体语句;S203: Obtain the authority verification related code and the corresponding scope of action according to the analysis result. The authority verification related code includes the package name, class name, method function name, parameter list and return value type where the authority verification code is located. The scope of action refers to the specific package, specific class, specific method function and specific statement corresponding to the code related to the authorization verification;
S204:根据所述权限验证相关代码与所述作用范围生成所述权限-范围映射表。S204: Generate the authority-scope mapping table according to the authority verification related code and the scope of action.
在所述软件应用越权风险检测方法中,可以根据所述源代码的配置文件确定所用到的安全框架。例如,Java语言被广泛应用在Web应用系统和手机移动应用Android平台,以Java语言编程应用软件为例,根据待测的Java软件项目的上述源代码的配置文件能够自动识别出所使用的安全框架,如Springsecurity、Shiro等第三方开源框架。可以根据检测系统内置的解析器或用户自定义的解析器根据对应的安全检测框架的语法对其XML等配置文件和相关注解进行解析,并提取出相关信息,从而确定所述权限验证相关代码与相应所述作用范围。之后将权限验证的相关代码和所作用的范围结合生成权限-范围映射表,其中权限验证的相关代码包括权限验证代码所在的包名、类名、方法函数、参数列表和返回值类型,而所作用的范围包括具体的包、具体的类、具体方法函数和具体语句。In the software application unauthorized risk detection method, the used security framework can be determined according to the configuration file of the source code. For example, the Java language is widely used in web application systems and mobile phone mobile application Android platforms. Taking the Java language programming application software as an example, the security framework used can be automatically identified according to the configuration file of the above source code of the Java software project to be tested. Third-party open source frameworks such as Springsecurity and Shiro. According to the built-in parser of the detection system or user-defined parser according to the syntax of the corresponding security detection framework, it can parse its XML and other configuration files and related annotations, and extract relevant information, so as to determine the relevant code of the authorization verification and corresponding to the scope of action described. Then combine the relevant codes of permission verification and the scope of action to generate a permission-scope mapping table, where the relevant codes of permission verification include the package name, class name, method function, parameter list and return value type of the permission verification code, and all The scope of action includes specific packages, specific classes, specific method functions, and specific statements.
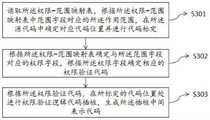
如图3所示,在本说明书的一个或多个可选实施例所提供的一种软件应用越权风险检测方法中,所述根据所述权限-范围映射表,对所述源代码进行权限验证逻辑插桩,生成插桩中间表示代码,包括:As shown in FIG. 3 , in a software application unauthorized risk detection method provided in one or more optional embodiments of this specification, the authority verification is performed on the source code according to the authority-range mapping table Logical instrumentation, generating instrumentation intermediate representation code, including:
S301:读取所述权限-范围映射表,根据所述权限-范围映射表中范围字段对应的所述作用范围,在所述源代码中确定对应代码位置并进行代码标定;S301: Read the authority-scope mapping table, determine the corresponding code position in the source code according to the scope corresponding to the scope field in the authority-scope mapping table, and perform code calibration;
在一些可选实施例方式中,先读取权限-范围映射表,其中权限字段代表权限验证的相关代码,范围字段代表权限代码所作用的范围,根据所述范围字段的值,获取权限代码对应的上述作用范围,而所述权限代码所作用的范围包括具体的包、具体的类、具体方法函数和具体语句,可以将所确定的所述作用范围并保存在List类型中。之后扫描与权限代码作用的范围相匹配的Java项目源码位置,并进行代码标定。In some optional embodiments, the permission-range mapping table is first read, wherein the permission field represents the relevant code of permission verification, and the scope field represents the scope of the permission code. According to the value of the scope field, the corresponding The above scope of action, and the scope of action of the permission code includes specific packages, specific classes, specific method functions, and specific statements, and the determined scope of action can be stored in the List type. Then scan the source code location of the Java project that matches the scope of the permission code, and perform code calibration.
S302:根据所述权限-范围映射表确定与所述范围字段对应的权限字段,根据所述权限字段确定相应的权限验证代码;S302: Determine an authority field corresponding to the scope field according to the authority-range mapping table, and determine a corresponding authority verification code according to the authority field;
S303:根据所述权限验证代码,在所标定的代码位置处进行权限验证逻辑代码插桩,生成所述插桩中间表示代码。S303: According to the authorization verification code, perform authorization verification logic code insertion at the marked code position, and generate the insertion intermediate representation code.
根据标定的代码具体位置所对应的范围值,获取在权限-映射表中对应的权限验证代码,通过编写程序在待测项目程序的标定代码位置处进行权限验证代码的插桩操作,将与所述权限验证代码对应的权限验证逻辑代码插入,生成所述插桩中间表示代码。According to the range value corresponding to the specific position of the calibrated code, obtain the corresponding authority verification code in the authority-mapping table, and perform the instrumentation operation of the authority verification code at the calibrated code position of the project program to be tested by writing a program, which will be consistent with all The authority verification logic code corresponding to the authority verification code is inserted to generate the intermediate representation code of the insertion.
在本说明书的一个或多个可选实施例所提供的一种软件应用越权风险检测方法中,所述在所述源代码中确定对应代码位置进行代码标定,包括:In a software application unauthorized risk detection method provided in one or more optional embodiments of this specification, the determining the corresponding code position in the source code for code calibration includes:
根据所述作用范围在所述源代码中查找到相匹配的代码对象;Finding a matching code object in the source code according to the scope of action;
若所述代码对象为具体的包,则对所述包中每一个类的每一个方法的方法体中的第一条语句进行标定;If the code object is a specific package, then mark the first statement in the method body of each method of each class in the package;
若所述代码对象为具体的方法函数,则对所述方法函数的方法体重第一条语句进行标定;If the code object is a specific method function, then calibrate the first statement of the method weight of the method function;
若所述代码对象为具体的语句,则对所述语句进行标定。If the code object is a specific statement, then mark the statement.
在所标定的代码位置处进行权限验证逻辑代码插桩,是指在所标定的语句之前进行所述权限验证逻辑代码插桩操作。Performing the authority verification logic code insertion at the marked code position refers to performing the authority verification logic code insertion operation before the marked statement.
在本说明书的一个或多个可选实施例所提供的一种软件应用越权风险检测方法中,所述根据所述权限验证代码,在所标定的代码位置处进行权限验证逻辑代码插桩,生成所述插桩中间表示代码,包括:In a software application unauthorized risk detection method provided in one or more optional embodiments of this specification, the authorization verification logic code is inserted at the marked code position according to the authorization verification code to generate The instrumentation intermediate representation code includes:
根据所述权限验证代码确定相应的权限验证逻辑代码;determining a corresponding authority verification logic code according to the authority verification code;
遍历所述源代码中所有标定代码位置,以所述标定代码位置相对应的所述作用范围为键、以所述标定代码位置相应的所述权限验证逻辑代码为值,构造Map对象;Traversing all calibration code positions in the source code, using the scope of action corresponding to the calibration code position as a key, and using the authority verification logic code corresponding to the calibration code position as a value, construct a Map object;
在将所述源代码转化为中间代码的过程中,根据所述Map对象在所述中间代码中插入所述权限验证逻辑代码,生成所述插桩中间表示代码。In the process of converting the source code into the intermediate code, insert the authority verification logic code into the intermediate code according to the Map object, and generate the intermediate representation code of the insertion.
在所述软件应用越权风险检测方法中,在所述源代码的标定代码位置处进行权限验证逻辑代码插桩,不改变所述源代码的整体性和原始性,从而能够保证之后根据所述插桩中间表示代码生成信息流图时不会出现因整体性和原始性方面的原因所造成的误差。In the software application unauthorized risk detection method, the authority verification logic code insertion is performed at the marked code position of the source code, without changing the integrity and originality of the source code, so that it can be ensured according to the insertion The middle of the pile means that there will be no errors caused by integrity and originality when the code generates the information flow graph.
在本说明书的一个或多个可选实施例所提供的一种软件应用越权风险检测方法中,所述信息流图包括函数调用关系图、控制流图与数据流图。所述函数调用图、所述数据流图和所述控制流图等信息流图,均包含了插桩后植入的权限验证逻辑,并且基于中间表示生成的,其优点在于屏蔽了不同软件应用所采用不同版本各自的特性,统一为同一种表现形式,避免了不同软件应用因为采用不同版本或编程方式所造成的逻辑顺序差异的影响,并且简化了信息流图的生成步骤。In a software application unauthorized risk detection method provided in one or more optional embodiments of this specification, the information flow graph includes a function call relationship graph, a control flow graph, and a data flow graph. Information flow graphs such as the function call graph, the data flow graph, and the control flow graph all include authorization verification logic implanted after stubbing, and are generated based on an intermediate representation, which has the advantage of shielding different software applications The respective characteristics of the different versions adopted are unified into the same form of expression, which avoids the influence of differences in logical order caused by different versions or programming methods of different software applications, and simplifies the generation steps of the information flow diagram.
在本说明书的一个或多个可选实施例所提供的一种软件应用越权风险检测方法中,所述在所述信息流图中选取敏感行为节点,以所述敏感行为节点为起点进行越权风险路径检测,包括:In a software application unauthorized risk detection method provided in one or more optional embodiments of this specification, the sensitive behavior nodes are selected in the information flow graph, and the unauthorized risk Path detection, including:
获取越权敏感操作列表,所述越权敏感操作列表包括需验证权限以及与所述需验证权限相关的越权敏感操作;Obtaining a list of unauthorized sensitive operations, where the list of unauthorized sensitive operations includes permissions to be verified and sensitive operations related to the permissions to be verified;
所述越权敏感操作列表可以通过预先提取进行设置,也可以通过人工设定,其主要用于体现不同可能存在的越权行为以及与所述越权行为对应的敏感性操作信息。The unauthorized sensitive operation list can be set by pre-extraction, or can be set manually, which is mainly used to reflect different possible unauthorized behaviors and sensitive operation information corresponding to the unauthorized behaviors.
将所述敏感操作与所述信息流图进行对比,从所述信息流图中筛选出与所述敏感操作相对应的函数或语句进行节点标记;Comparing the sensitive operation with the information flow graph, and selecting functions or statements corresponding to the sensitive operation from the information flow graph to mark nodes;
这里,可以使用正则匹配的方式判断所述越权敏感操作的相关函数或语句在信息流图中是否存在以及存在的位置,如果存在,会获取相关的节点位置并进行标记;之后,再重新读取所述越权敏感操作列表的下一项目需验证权限以及与所述需验证权限相关的越权敏感操作,再次进行匹配。Here, regular matching can be used to determine whether the relevant function or statement of the unauthorized sensitive operation exists in the information flow diagram and where it exists. If it exists, the relevant node position will be obtained and marked; after that, read again The verification permission of the next item in the unauthorized sensitive operation list and the unauthorized sensitive operation related to the verification required permission are matched again.
对于筛选出的标记节点,在所述信息流图中,从标记节点处开始进行反向遍历,判断反向遍历路径中是否存在权限验证逻辑代码;For the filtered marked nodes, in the information flow diagram, reverse traversal is performed from the marked nodes, and it is judged whether there is an authority verification logic code in the reverse traverse path;
越权行为主要包扩了未被认证的用户能够访问需要被认证的方法和未被授权的用户能够访问需要授权的方法,对于所关注的越权行为风险,正常获得认证的运行逻辑为首先进行权限认证,认证通过之后执行相对应的敏感操作,即越权敏感行为与权限验证之间应当存在对应关系,因此所述软件应用越权风险检测方法中先确定与敏感操作对应的函数或语句,然后往前追溯,对越权敏感行为与权限验证之间所应当存在一一对应关系进行判断,具体的,从标记节点处开始进行反向遍历,判断反向遍历路径中是否存在权限验证逻辑代码;The unauthorized behavior mainly includes that unauthenticated users can access the methods that need to be authenticated and the unauthorized users can access the methods that need to be authorized. For the risk of unauthorized behavior that is concerned, the normal operation logic of obtaining authentication is to first perform authorization authentication , after the authentication is passed, the corresponding sensitive operation is executed, that is, there should be a corresponding relationship between the unauthorized sensitive behavior and the authorization verification, so in the software application unauthorized risk detection method, first determine the function or statement corresponding to the sensitive operation, and then trace back , judging the one-to-one correspondence between the sensitive behavior of ultra vires and the authority verification, specifically, starting from the marked node to perform reverse traversal, and judging whether there is authority verification logic code in the reverse traversal path;
若直到终点仍未检测到所述权限验证逻辑代码,则所述反向遍历路径中存在越权风险;If the authority verification logic code is not detected until the end point, there is a risk of exceeding authority in the reverse traversal path;
直到终点仍未检测到所述权限验证逻辑代码的情况下,说明执行敏感操作前没有进行权限认证,因此是存在越权风险的;If the authorization verification logic code is not detected until the end point, it means that the authorization verification has not been performed before performing the sensitive operation, so there is a risk of exceeding the authorization;
若存在所述权限验证逻辑代码,则判断所述权限验证逻辑代码与所述标记节点所对应的所述需验证权限是否匹配;If the authority verification logic code exists, it is judged whether the authority verification logic code matches the authority to be verified corresponding to the marked node;
若不匹配则从所述标记节点至所述权限验证逻辑代码的反向遍历路径中存在越权风险。If they do not match, there is a risk of overreach in the reverse traversal path from the marked node to the authority verification logic code.
即使检测到所述权限验证逻辑代码,仍需要判断所检测到的权限验证逻辑代码与所述越权敏感操作之间的对应关系,对于二者不匹配的情况,仍是存在越权风险的。在一些可选的实施方式中,判断二者是否匹配可采用的方法为:将所获取得到所述权限验证逻辑信息与所述越权敏感操作列表中该路径上标记节点对应的权限进行具体的比较,包括操作的权限,获取权限的传递的用户参数,权限验证逻辑的顺序等,若这些信息对比和验证均相同,则说明这一路径中权限验证逻辑正确,所检测到的权限验证逻辑代码与所述越权敏感操作之间是相互匹配的,不存在越权行为的风险。Even if the authority verification logic code is detected, it is still necessary to judge the corresponding relationship between the detected authority verification logic code and the unauthorized sensitive operation. If the two do not match, there is still a risk of exceeding authority. In some optional implementation manners, the method that can be used to determine whether the two match is: specifically compare the obtained authority verification logic information with the authority corresponding to the marked node on the path in the unauthorized sensitive operation list , including the permission of the operation, the user parameters passed to obtain the permission, the order of the permission verification logic, etc. If the comparison and verification of these information are the same, it means that the permission verification logic in this path is correct, and the detected permission verification logic code is the same as The unauthorized sensitive operations are compatible with each other, and there is no risk of unauthorized behavior.
在本说明书的一个或多个可选实施例所提供的一种软件应用越权风险检测方法中,所述确定越权风险路径,包括:In a software application unauthorized risk detection method provided in one or more optional embodiments of this specification, the determination of the unauthorized risk path includes:
将存在越权风险的所述反向遍历路径提取,根据所述信息流图与所述插桩中间表示代码的对应关系,确定风险中间代码路径;Extracting the reverse traversal path that has the risk of exceeding authority, and determining the risk intermediate code path according to the correspondence between the information flow graph and the intermediate representation code of the instrumentation;
将所述风险中间代码路径还原转化为所述源代码中的对应路径得到所述越权风险路径,输出所述越权风险路径。Restoring and transforming the risky intermediate code path into a corresponding path in the source code to obtain the unauthorized risk path, and outputting the unauthorized risk path.
在一些可选实施例中,在还原转化所述越权风险路径时,根据所述中间代码路径相应的函数名、变量和函数调用对应源代码的函数、变量和函数调用以及对应的位置和类别,在输出所述越权风险路径时还输出越权操作相应的位置和类别信息,以及所述源代码的函数、变量和函数调用信息。In some optional embodiments, when restoring and transforming the unauthorized risk path, according to the corresponding function name, variable, and function call of the intermediate code path, the function, variable, and function call corresponding to the source code and the corresponding location and category, When outputting the unauthorized risk path, the location and category information corresponding to the unauthorized operation, as well as the function, variable and function call information of the source code are also output.
上述对本说明书特定实施例进行了描述。其它实施例在所附权利要求书的范围内。在一些情况下,在权利要求书中记载的动作或步骤可以按照不同于实施例中的顺序来执行并且仍然可以实现期望的结果。另外,在附图中描绘的过程不一定要求示出的特定顺序或者连续顺序才能实现期望的结果。在某些实施方式中,多任务处理和并行处理也是可以的或者可能是有利的。The foregoing describes specific embodiments of the present specification. Other implementations are within the scope of the following claims. In some cases, the actions or steps recited in the claims can be performed in an order different from that in the embodiments and still achieve desirable results. In addition, the processes depicted in the accompanying figures do not necessarily require the particular order shown, or sequential order, to achieve desirable results. Multitasking and parallel processing are also possible or may be advantageous in certain embodiments.
在另一方面,本说明书实施例提供了一种软件应用越权风险检测电子设备。In another aspect, the embodiment of this specification provides an electronic device for software application unauthorized risk detection.
所述电子设备,包括存储器、处理器及存储在存储器上并可在处理器上运行的计算机程序,所述处理器执行所述程序时实现所述软件应用越权风险检测方法:The electronic device includes a memory, a processor, and a computer program stored on the memory and operable on the processor. When the processor executes the program, the software application unauthorized risk detection method is implemented:
获取待检测软件程序的源代码,对所述源代码进行解析,确定权限验证相关代码与作用范围,对应生成权限-范围映射表;Obtaining the source code of the software program to be detected, analyzing the source code, determining the relevant code and scope of authority verification, and generating a corresponding authority-scope mapping table;
根据所述权限-范围映射表,对所述源代码进行权限验证逻辑插桩,生成插桩中间表示代码;According to the authority-range mapping table, perform authority verification logic instrumentation on the source code, and generate an instrumentation intermediate representation code;
根据所述插桩中间表示代码,确定所述源代码的信息流图;Determine the information flow graph of the source code according to the intermediate representation code of the instrumentation;
在所述信息流图中选取敏感行为节点,以所述敏感行为节点为起点进行越权风险路径检测,确定越权风险路径。Select sensitive behavior nodes in the information flow graph, and use the sensitive behavior nodes as a starting point to perform unauthorized risk path detection to determine the unauthorized risk path.
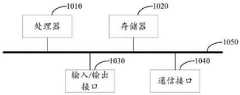
图4示出了本实施例所提供的一种更为具体的电子设备硬件结构示意图,该设备可以包括:处理器1010、存储器1020、输入/输出接口1030、通信接口1040和总线1050。其中处理器1010、存储器1020、输入/输出接口1030和通信接口1040通过总线1050实现彼此之间在设备内部的通信连接。FIG. 4 shows a schematic diagram of a more specific hardware structure of an electronic device provided by this embodiment. The device may include: a
处理器1010可以采用通用的CPU(CentralProcessingUnit,中央处理器)、微处理器、应用专用集成电路(ApplicationSpecificIntegratedCircuit,ASIC)、或者一个或多个集成电路等方式实现,用于执行相关程序,以实现本说明书实施例所提供的所述软件应用越权风险检测方法。The
存储器1020可以采用ROM(ReadOnlyMemory,只读存储器)、RAM(RandomAccessMemory,随机存取存储器)、静态存储设备,动态存储设备等形式实现。存储器1020可以存储操作系统和其他应用程序,在通过软件或者固件来实现本说明书实施例所提供的所述软件应用越权风险检测方法时,相关的程序代码保存在存储器1020中,并由处理器1010来调用执行。The
输入/输出接口1030用于连接输入/输出模块,以实现信息输入及输出。输入输出/模块可以作为组件配置在设备中(图中未示出),也可以外接于设备以提供相应功能。其中输入设备可以包括键盘、鼠标、触摸屏、麦克风、各类传感器等,输出设备可以包括显示器、扬声器、振动器、指示灯等。The input/
通信接口1040用于连接通信模块(图中未示出),以实现本设备与其他设备的通信交互。其中通信模块可以通过有线方式(例如USB、网线等)实现通信,也可以通过无线方式(例如移动网络、WIFI、蓝牙等)实现通信。The
总线1050包括一通路,在设备的各个组件(例如处理器1010、存储器1020、输入/输出接口1030和通信接口1040)之间传输信息。
需要说明的是,尽管上述设备仅示出了处理器1010、存储器1020、输入/输出接口1030、通信接口1040以及总线1050,但是在具体实施过程中,该设备还可以包括实现正常运行所必需的其他组件。此外,本领域的技术人员可以理解的是,上述设备中也可以仅包含实现本说明书实施例所述软件应用越权风险检测方法所必需的组件,而不必包含图中所示的全部组件。It should be noted that although the above device only shows the
在另一方面,本说明书实施例提供了一种软件应用越权风险检测存储介质。In another aspect, the embodiment of this specification provides a software application unauthorized risk detection storage medium.
本说明书一个或多个实施例提供的所述软件应用越权风险检测非暂态计算机可读存储介质存储计算机指令,所述计算机指令用于使所述计算机执行所述软件应用越权风险检测方法:The software application unauthorized risk detection non-transitory computer-readable storage medium provided by one or more embodiments of this specification stores computer instructions, and the computer instructions are used to make the computer execute the software application unauthorized risk detection method:
获取待检测软件程序的源代码,对所述源代码进行解析,确定权限验证相关代码与作用范围,对应生成权限-范围映射表;Obtaining the source code of the software program to be detected, analyzing the source code, determining the relevant code and scope of authority verification, and generating a corresponding authority-scope mapping table;
根据所述权限-范围映射表,对所述源代码进行权限验证逻辑插桩,生成插桩中间表示代码;According to the authority-range mapping table, perform authority verification logic instrumentation on the source code, and generate an instrumentation intermediate representation code;
根据所述插桩中间表示代码,确定所述源代码的信息流图;Determine the information flow graph of the source code according to the intermediate representation code of the instrumentation;
在所述信息流图中选取敏感行为节点,以所述敏感行为节点为起点进行越权风险路径检测,确定越权风险路径。Select sensitive behavior nodes in the information flow graph, and use the sensitive behavior nodes as a starting point to perform unauthorized risk path detection to determine the unauthorized risk path.
本实施例的计算机可读介质包括永久性和非永久性、可移动和非可移动媒体可以由任何方法或技术来实现信息存储。信息可以是计算机可读指令、数据结构、程序的模块或其他数据。计算机的存储介质的例子包括,但不限于相变内存(PRAM)、静态随机存取存储器(SRAM)、动态随机存取存储器(DRAM)、其他类型的随机存取存储器(RAM)、只读存储器(ROM)、电可擦除可编程只读存储器(EEPROM)、快闪记忆体或其他内存技术、只读光盘只读存储器(CD-ROM)、数字多功能光盘(DVD)或其他光学存储、磁盒式磁带,磁带磁磁盘存储或其他磁性存储设备或任何其他非传输介质,可用于存储可以被计算设备访问的信息。The computer-readable medium in this embodiment includes permanent and non-permanent, removable and non-removable media, and information storage can be realized by any method or technology. Information may be computer readable instructions, data structures, modules of a program, or other data. Examples of computer storage media include, but are not limited to, phase change memory (PRAM), static random access memory (SRAM), dynamic random access memory (DRAM), other types of random access memory (RAM), read only memory (ROM), Electrically Erasable Programmable Read-Only Memory (EEPROM), Flash memory or other memory technology, Compact Disc Read-Only Memory (CD-ROM), Digital Versatile Disc (DVD) or other optical storage, Magnetic tape cartridge, tape magnetic disk storage or other magnetic storage device or any other non-transmission medium that can be used to store information that can be accessed by a computing device.
所属领域的普通技术人员应当理解:以上任何实施例的讨论仅为示例性的,并非旨在暗示本公开的范围(包括权利要求)被限于这些例子;在本公开的思路下,以上实施例或者不同实施例中的技术特征之间也可以进行组合,步骤可以以任意顺序实现,并存在如上所述的本说明书一个或多个实施例的不同方面的许多其它变化,为了简明它们没有在细节中提供。Those of ordinary skill in the art should understand that: the discussion of any of the above embodiments is exemplary only, and is not intended to imply that the scope of the present disclosure (including claims) is limited to these examples; under the idea of the present disclosure, the above embodiments or Combinations can also be made between technical features in different embodiments, steps can be implemented in any order, and there are many other variations of the different aspects of one or more embodiments of this specification as described above, which are not included in the details for the sake of brevity. supply.
另外,为简化说明和讨论,并且为了不会使本说明书一个或多个实施例难以理解,在所提供的附图中可以示出或可以不示出与集成电路(IC)芯片和其它部件的公知的电源/接地连接。此外,可以以框图的形式示出装置,以便避免使本说明书一个或多个实施例难以理解,并且这也考虑了以下事实,即关于这些框图装置的实施方式的细节是高度取决于将要实施本说明书一个或多个实施例的平台的(即,这些细节应当完全处于本领域技术人员的理解范围内)。在阐述了具体细节(例如,电路)以描述本公开的示例性实施例的情况下,对本领域技术人员来说显而易见的是,可以在没有这些具体细节的情况下或者这些具体细节有变化的情况下实施本说明书一个或多个实施例。因此,这些描述应被认为是说明性的而不是限制性的。In addition, for simplicity of illustration and discussion, and so as not to obscure one or more embodiments of the present description, connections to integrated circuit (IC) chips and other components may or may not be shown in the provided figures. Well known power/ground connections. Furthermore, devices may be shown in block diagram form in order to avoid obscuring one or more embodiments of the description, and this also takes into account the fact that details regarding the implementation of these block diagram devices are highly dependent on the implementation of the invention to be implemented. The platform of one or more embodiments is described (ie, the details should be well within the purview of those skilled in the art). Where specific details (eg, circuits) have been set forth to describe example embodiments of the present disclosure, it will be apparent to those skilled in the art that other applications may be made without or with variations from these specific details. One or more embodiments of this specification are implemented below. Accordingly, these descriptions should be regarded as illustrative rather than restrictive.
尽管已经结合了本公开的具体实施例对本公开进行了描述,但是根据前面的描述,这些实施例的很多替换、修改和变型对本领域普通技术人员来说将是显而易见的。例如,其它存储器架构(例如,动态RAM(DRAM))可以使用所讨论的实施例。Although the disclosure has been described in conjunction with specific embodiments thereof, many alternatives, modifications and variations of those embodiments will be apparent to those of ordinary skill in the art from the foregoing description. For example, other memory architectures such as dynamic RAM (DRAM) may use the discussed embodiments.
本说明书一个或多个实施例旨在涵盖落入所附权利要求的宽泛范围之内的所有这样的替换、修改和变型。因此,凡在本说明书一个或多个实施例的精神和原则之内,所做的任何省略、修改、等同替换、改进等,均应包含在本公开的保护范围之内。The description of one or more embodiments is intended to embrace all such alterations, modifications and variations that fall within the broad scope of the appended claims. Therefore, any omission, modification, equivalent replacement, improvement, etc. made within the spirit and principles of one or more embodiments of this specification shall fall within the protection scope of the present disclosure.
Claims (10)
Translated fromChinesePriority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202011140562.8ACN112257054B (en) | 2020-10-22 | 2020-10-22 | A software application unauthorized risk detection method, electronic equipment and storage medium |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202011140562.8ACN112257054B (en) | 2020-10-22 | 2020-10-22 | A software application unauthorized risk detection method, electronic equipment and storage medium |
Publications (2)
| Publication Number | Publication Date |
|---|---|
| CN112257054A CN112257054A (en) | 2021-01-22 |
| CN112257054Btrue CN112257054B (en) | 2022-11-15 |
Family
ID=74264026
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN202011140562.8AActiveCN112257054B (en) | 2020-10-22 | 2020-10-22 | A software application unauthorized risk detection method, electronic equipment and storage medium |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN112257054B (en) |
Families Citing this family (7)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN112783513B (en)* | 2021-03-18 | 2024-02-27 | 中国工商银行股份有限公司 | Code risk checking method, device and equipment |
| CN112948835B (en)* | 2021-03-26 | 2022-07-19 | 支付宝(杭州)信息技术有限公司 | Small program risk detection method and device |
| CN113609487B (en)* | 2021-07-16 | 2023-05-12 | 深圳开源互联网安全技术有限公司 | Method for detecting backdoor code through static analysis |
| CN115529171B (en)* | 2022-09-16 | 2024-07-23 | 浙江网商银行股份有限公司 | Behavior detection method and device |
| CN115982724B (en)* | 2023-03-20 | 2023-05-30 | 北京万道数智科技有限公司 | Code-level security protection method, storage medium and electronic equipment |
| CN116796318B (en)* | 2023-03-24 | 2024-11-15 | 成都海葫沿科技有限公司 | Method and system for protecting computer software |
| CN119918059A (en)* | 2024-12-26 | 2025-05-02 | 中国科学院信息工程研究所 | A method and system for detecting unauthorized vulnerabilities in Java Web systems |
Family Cites Families (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| KR101886203B1 (en)* | 2016-07-19 | 2018-09-06 | 주식회사 스패로우 | Apparatus and method for analyzing programs |
| CN107133518B (en)* | 2017-04-10 | 2019-09-24 | 中国民生银行股份有限公司 | Source code based on parameter and information flow is gone beyond one's commission detection method and device |
| CN108846282A (en)* | 2018-06-04 | 2018-11-20 | 西安电子科技大学 | Android application program permission based on the analysis of static stain reveals leak detection method |
| CN110688659B (en)* | 2019-09-10 | 2020-10-16 | 深圳开源互联网安全技术有限公司 | Method and system for dynamically detecting horizontal override based on IAST test tool |
- 2020
- 2020-10-22CNCN202011140562.8Apatent/CN112257054B/enactiveActive
Also Published As
| Publication number | Publication date |
|---|---|
| CN112257054A (en) | 2021-01-22 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| CN112257054B (en) | A software application unauthorized risk detection method, electronic equipment and storage medium | |
| CN109426723B (en) | Detection method, system, equipment and storage medium using released memory | |
| TWI575397B (en) | Point-wise protection of application using runtime agent and dynamic security analysis | |
| CN102737190B (en) | Based on the detection method of leakage of information hidden danger in the Android application daily record of static analysis | |
| CN112733158B (en) | Android system vulnerability detection method, electronic equipment and storage medium | |
| CN108595597A (en) | Data lead-in method, device, computer equipment and storage medium | |
| US20120254839A1 (en) | Simulating black box test results using information from white box testing | |
| CN108846282A (en) | Android application program permission based on the analysis of static stain reveals leak detection method | |
| US20240121261A1 (en) | Automated Security Analysis of Software Libraries | |
| CN104408366A (en) | Android application permission usage behavior tracking method based on plug-in technology | |
| US20140372988A1 (en) | Using a Static Analysis for Configuring a Follow-On Dynamic Analysis for the Evaluation of Program Code | |
| US11474795B2 (en) | Static enforcement of provable assertions at compile | |
| WO2022095410A1 (en) | Component development method, apparatus, storage medium, and electronic device | |
| US9158923B2 (en) | Mitigating security risks via code movement | |
| CN117807595B (en) | Rebound shell detection method and device, electronic equipment and storage medium | |
| Wang et al. | Detecting SQL vulnerability attack based on the dynamic and static analysis technology | |
| CN114065222A (en) | Source code risk analysis method, device, electronic device and storage medium | |
| CN112861134B (en) | Vulnerability detection method, device, equipment and medium based on optimization variation strategy | |
| US9171168B2 (en) | Determine anomalies in web application code based on authorization checks | |
| CN111143858B (en) | Data checking method and device | |
| Xiao et al. | WakeMint: Detecting Sleepminting Vulnerabilities in NFT Smart Contracts | |
| CN115357894A (en) | Application program bug detection method and system with custom verification function | |
| CN111027073B (en) | Vulnerability detection method, device, equipment and storage medium | |
| KR101476536B1 (en) | The method and system for inspecting program | |
| Zhou et al. | LogPruner: detect, analyze and prune logging calls in Android apps |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| GR01 | Patent grant | ||
| GR01 | Patent grant |