CN112152968A - Network threat detection method and device - Google Patents
Network threat detection method and deviceDownload PDFInfo
- Publication number
- CN112152968A CN112152968ACN201910569503.3ACN201910569503ACN112152968ACN 112152968 ACN112152968 ACN 112152968ACN 201910569503 ACN201910569503 ACN 201910569503ACN 112152968 ACN112152968 ACN 112152968A
- Authority
- CN
- China
- Prior art keywords
- threat
- event
- score
- rule
- threat event
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Granted
Links
Images
Classifications
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/14—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic
- H04L63/1441—Countermeasures against malicious traffic
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06N—COMPUTING ARRANGEMENTS BASED ON SPECIFIC COMPUTATIONAL MODELS
- G06N3/00—Computing arrangements based on biological models
- G06N3/02—Neural networks
- G06N3/08—Learning methods
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/14—Network architectures or network communication protocols for network security for detecting or protecting against malicious traffic
Landscapes
- Engineering & Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- Computing Systems (AREA)
- General Engineering & Computer Science (AREA)
- Computer Hardware Design (AREA)
- Computer Networks & Wireless Communication (AREA)
- Signal Processing (AREA)
- Physics & Mathematics (AREA)
- Theoretical Computer Science (AREA)
- Artificial Intelligence (AREA)
- General Health & Medical Sciences (AREA)
- Biomedical Technology (AREA)
- Biophysics (AREA)
- Computational Linguistics (AREA)
- Data Mining & Analysis (AREA)
- Evolutionary Computation (AREA)
- Life Sciences & Earth Sciences (AREA)
- Molecular Biology (AREA)
- General Physics & Mathematics (AREA)
- Mathematical Physics (AREA)
- Software Systems (AREA)
- Health & Medical Sciences (AREA)
- Management, Administration, Business Operations System, And Electronic Commerce (AREA)
Abstract
Translated fromChineseDescription
Translated fromChinese技术领域technical field
本文涉及网络安全领域,尤其涉及一种网络威胁检测方法和装置。This paper relates to the field of network security, in particular to a method and device for detecting network threats.
背景技术Background technique
网络威胁识别产品的组成一般包括两部分:行为特征计算算法和基于特征数据的威胁判断规则库。出于对通用性和适用性等因素的考虑,预置的威胁判断规则库的召回率和准确率都不高,故在产品上线后需要对威胁判断规则库进行后续的维护调整。一般情况是乙方派技术员在甲方处驻场,了解业务后进行威胁判断规则库的定制修改,并在服务周期内持续提供威胁判断规则库的维护服务,维护成本高,效率很低,反应滞后。The composition of network threat identification products generally includes two parts: behavior characteristic calculation algorithm and threat judgment rule base based on characteristic data. Considering factors such as versatility and applicability, the recall rate and accuracy of the preset threat judgment rule base are not high. Therefore, the threat judgment rule base needs to be maintained and adjusted after the product is launched. Generally speaking, Party B sends technicians to stay at Party A's site to customize and modify the threat judgment rule base after understanding the business, and continue to provide maintenance services for the threat judgment rule base during the service period. The maintenance cost is high, the efficiency is very low, and the response is lagging. .
发明内容SUMMARY OF THE INVENTION
为克服相关技术中存在的问题,本文提供一种网络威胁检测方法和装置。In order to overcome the problems existing in the related art, this paper provides a network threat detection method and device.
根据本文的第一方面,提供一种网络威胁检测方法,包括根据预置的威胁规则库,检测得到威胁事件;According to the first aspect of this article, a network threat detection method is provided, including detecting and obtaining a threat event according to a preset threat rule base;
将所述威胁事件输入智能修正神经网络,获取所述威胁事件的修正分数;Inputting the threat event into an intelligent correction neural network to obtain a correction score of the threat event;
根据所述修正分数,对所述威胁事件进行修正,得到最终的威胁检测结果。According to the correction score, the threat event is corrected to obtain a final threat detection result.
优选的,所述预置的威胁规则库中包含多种攻击原因对应的规则,每个攻击原因对应至少一个规则,Preferably, the preset threat rule base includes rules corresponding to multiple attack causes, and each attack cause corresponds to at least one rule,
根据预置的威胁规则库,检测得到威胁事件的步骤包括:According to the preset threat rule base, the steps of detecting a threat event include:
在发生符合所述威胁规则库中的规则的事件时,判定发生与所述规则对应的攻击原因相关联的威胁事件。When an event that conforms to the rule in the threat rule base occurs, it is determined that a threat event associated with the attack cause corresponding to the rule occurs.
优选的,所述威胁规则库中的各个规则还具有威胁分数,Preferably, each rule in the threat rule base also has a threat score,
根据预置的威胁规则库,检测得到威胁事件的步骤还包括:According to the preset threat rule base, the steps of detecting a threat event further include:
获取判定发生所述威胁事件所依据的规则的威胁分数,作为所述威胁事件的威胁分数。Obtain the threat score of the rule based on which the threat event is determined to occur, as the threat score of the threat event.
优选的,根据预置的威胁规则库,检测得到威胁事件的步骤之前,还包括:Preferably, according to the preset threat rule base, before the step of detecting the threat event, the method further includes:
收集多个根据所述威胁规则库检测得到的威胁事件;Collect multiple threat events detected according to the threat rule base;
获取针对收集得到的所述威胁事件的反馈标注,反馈标注指示所述威胁事件正确或错误;Obtaining feedback annotations for the collected threat events, where the feedback annotations indicate that the threat events are correct or wrong;
根据所述反馈标注,生成训练样本;generating training samples according to the feedback annotation;
使用所述训练样本训练得到所述智能修正神经网络。The intelligent correction neural network is obtained by training using the training samples.
优选的,根据所述反馈标注,生成训练样本的步骤包括:Preferably, according to the feedback annotation, the step of generating training samples includes:
为所述反馈标注指示正确的威胁事件添加第一预测分数,为所述反馈标注指示错误的威胁事件添加第二预测分数,所述第一预测分数大于所述第二预测分数;adding a first prediction score for the threat event indicated by the feedback annotation as correct, and adding a second prediction score for the threat event in which the feedback annotation indicates an error, the first prediction score being greater than the second prediction score;
对所述威胁事件的各项行为特征进行特征工程转化得到特征数据;Perform feature engineering transformation on each behavioral feature of the threat event to obtain feature data;
将针对同一域名下同一攻击原因的多个威胁事件的各项行为特征的特征数据、威胁事件对应的第一预测分数或第二预测分数构成作为训练样本的输入矩阵。The feature data of each behavioral feature of multiple threat events with the same attack cause under the same domain name, the first prediction score or the second prediction score corresponding to the threat event constitute an input matrix as a training sample.
优选的,收集多个根据所述威胁规则库检测得到的威胁事件的步骤包括:Preferably, the step of collecting a plurality of threat events obtained according to the threat rule base detection includes:
收集威胁分数较低的威胁事件。Collect threat events with low threat scores.
优选的,将所述威胁事件输入智能修正神经网络,获取所述威胁事件的修正分数的步骤包括:Preferably, the threat event is input into an intelligent correction neural network, and the step of obtaining the correction score of the threat event includes:
将所述威胁事件的各项行为特征输入所述智能修正神经网络,获取所述威胁事件的修正分数,所述修正分数大于等于所述第二预测分数且小于等于所述第一预测分数。The behavioral features of the threat event are input into the intelligent correction neural network to obtain a correction score of the threat event, where the correction score is greater than or equal to the second prediction score and less than or equal to the first prediction score.
优选的,根据所述修正分数,对所述威胁事件进行修正,得到最终的威胁检测结果的步骤包括:Preferably, according to the correction score, the threat event is corrected, and the step of obtaining the final threat detection result includes:
取所述修正分数与所述威胁分数的平均值;taking the average of the correction score and the threat score;
在所述平均值低于预置的事件成立阈值时,判定所述威胁事件属于检测错误,最终的威胁检测结果为无威胁事件,When the average value is lower than the preset event establishment threshold, it is determined that the threat event is a detection error, and the final threat detection result is no threat event,
在所述平均值达到所述预置的事件成立阈值时,判定所述威胁事件属于检测正确,最终的威胁检测结果为发生所述威胁事件。When the average value reaches the preset event establishment threshold, it is determined that the threat event is correctly detected, and the final threat detection result is that the threat event occurs.
优选的,该方法还包括:Preferably, the method further includes:
使用所述智能修正神经网络预测所述训练样本中各威胁事件的修正分数;using the intelligent correction neural network to predict the correction score of each threat event in the training sample;
取各威胁事件的预测误差值的平均值,所述预测误差值为一威胁事件的第一预测分数或第二预测分数与修正分数差值的绝对值;Taking the average value of the prediction error values of each threat event, the prediction error value is the absolute value of the difference between the first prediction score or the second prediction score and the corrected score of a threat event;
以基准分数减去所述平均值的计算结果作为所述智能修正神经网络的成熟度。The calculation result of subtracting the average value from the benchmark score is used as the maturity of the intelligent correction neural network.
根据本文的另一方面,提供了一种网络威胁检测装置,包括:According to another aspect of this document, a network threat detection apparatus is provided, comprising:
威胁事件检测模块,用于根据预置的威胁规则库,检测得到威胁事件;The threat event detection module is used to detect threat events according to the preset threat rule base;
神经网络修正模块,用于将所述威胁事件输入智能修正神经网络,获取所述威胁事件的修正分数;A neural network correction module, configured to input the threat event into an intelligent correction neural network to obtain a correction score of the threat event;
结果判断模块,用于根据所述修正分数,对所述威胁事件进行修正,得到最终的威胁检测结果。The result judgment module is used to correct the threat event according to the correction score to obtain a final threat detection result.
优选的,所述预置的威胁规则库中包含多种攻击原因对应的规则,每个攻击原因对应至少一个规则,各个规则还具有威胁分数,Preferably, the preset threat rule base includes rules corresponding to multiple attack causes, each attack cause corresponds to at least one rule, and each rule also has a threat score,
所述威胁事件检测模块包括:The threat event detection module includes:
威胁事件确定单元,用于在发生符合所述威胁规则库中的规则的事件时,判定发生与所述规则对应的攻击原因相关联的威胁事件;a threat event determination unit, configured to determine that a threat event associated with the attack cause corresponding to the rule occurs when an event conforming to the rule in the threat rule base occurs;
威胁分数确定单元,用于获取判定发生所述威胁事件所依据的规则的威胁分数,作为所述威胁事件的威胁分数。A threat score determination unit, configured to obtain a threat score of the rule based on which the threat event is determined to occur, as the threat score of the threat event.
优选的,该装置还包括:Preferably, the device further includes:
事件收集模块,用于收集多个根据所述威胁规则库检测得到的威胁事件;an event collection module for collecting a plurality of threat events detected according to the threat rule base;
标注获取模块,用于获取针对收集得到的所述威胁事件的反馈标注,根据所述反馈标注生成训练样本,反馈标注指示所述威胁事件正确或错误;An annotation acquisition module, configured to acquire feedback annotations for the collected threat events, generate training samples according to the feedback annotations, and the feedback annotations indicate that the threat events are correct or wrong;
样本生成模块,用于根据所述反馈标注,生成训练样本;a sample generation module, configured to generate training samples according to the feedback annotation;
神经网络训练模块,用于使用所述训练样本训练得到所述智能修正神经网络。The neural network training module is used for obtaining the intelligent correction neural network by training the training samples.
优选的,所述结果判断模块包括:Preferably, the result judgment module includes:
平均值计算单元,用于取所述修正分数与所述威胁分数的平均值;an average value calculation unit, used for taking the average value of the correction score and the threat score;
结果评价单元,用于在所述平均值低于预置的事件成立阈值时,判定所述威胁事件属于检测错误,最终的威胁检测结果为无威胁事件,The result evaluation unit is used to determine that the threat event belongs to a detection error when the average value is lower than the preset event establishment threshold, and the final threat detection result is no threat event,
在所述平均值达到所述预置的事件成立阈值时,判定所述威胁事件属于检测正确,最终的威胁检测结果为发生所述威胁事件。When the average value reaches the preset event establishment threshold, it is determined that the threat event is correctly detected, and the final threat detection result is that the threat event occurs.
根据本文的另一方面,提供了一种计算机可读存储介质,其上存储有计算机程序,所述计算机程序被执行时实现如上述网络威胁检测方法的步骤。According to another aspect of this document, there is provided a computer-readable storage medium on which a computer program is stored, and when the computer program is executed, implements the steps of the above-mentioned network threat detection method.
根据本文的另一方面,提供了一种计算机设备,包括处理器、存储器和存储于所述存储器上的计算机程序,所述处理器执行所述计算机程序时实现如上述网络威胁检测方法的步骤。According to another aspect of this document, a computer device is provided, comprising a processor, a memory, and a computer program stored on the memory, the processor implementing the steps of the network threat detection method described above when the processor executes the computer program.
本文提供了一种网络威胁检测方法和装置,根据预置的威胁规则库,检测得到威胁事件,再将所述威胁事件输入智能修正神经网络,获取所述威胁事件的修正分数,然后根据所述修正分数,对所述威胁事件进行修正,得到最终的威胁检测结果。利用智能网络,在不对原始的威胁规则库进行修改的情况下,对威胁事件的检测判定系统进行维护更新,解决了派驻人员进行现场人工维护带来的成本高、效率低、反应滞后的问题,实现了灵活准确的威胁识别规则更新机制。This paper provides a network threat detection method and device. According to a preset threat rule base, a threat event is detected, and then the threat event is input into an intelligent correction neural network to obtain the correction score of the threat event, and then according to the The score is corrected, and the threat event is corrected to obtain the final threat detection result. Using the intelligent network, without modifying the original threat rule base, the detection and determination system of threat events is maintained and updated, which solves the problems of high cost, low efficiency and delayed response caused by dispatched personnel to perform on-site manual maintenance. A flexible and accurate threat identification rule update mechanism is implemented.
应当理解的是,以上的一般描述和后文的细节描述仅是示例性和解释性的,并不能限制本文。It is to be understood that both the foregoing general description and the following detailed description are exemplary and explanatory only and are not limiting.
附图说明Description of drawings
构成本文的一部分的附图用来提供对本文的进一步理解,本文的示意性实施例及其说明用于解释本文,并不构成对本文的不当限定。在附图中:The accompanying drawings, which form a part hereof, are used to provide a further understanding of this document, and the illustrative embodiments and their descriptions herein are used to explain this document and do not constitute an undue limitation to this document. In the attached image:
图1示例性地示出了本文的一实施例提供的一种网络威胁检测方法的实现原理逻辑。FIG. 1 exemplarily shows the implementation principle logic of a network threat detection method provided by an embodiment of this document.
图2示例性地示出了本文的一实施例提供的一种网络威胁检测方法的流程。FIG. 2 exemplarily shows a flow of a network threat detection method provided by an embodiment of this document.
图3示例性地示出了本文的一实施例提供的一种网络威胁检测方法的流程。FIG. 3 exemplarily shows a flow of a network threat detection method provided by an embodiment of this document.
图4示例性地示出了本文的一实施例提供的一种网络威胁检测装置的结构。FIG. 4 exemplarily shows the structure of a network threat detection apparatus provided by an embodiment of this document.
图5示例性地示出了图4中威胁事件检测模块401的结构。FIG. 5 exemplarily shows the structure of the threat
图6示例性地示出了本文的一实施例提供的一种网络威胁检测装置的结构。FIG. 6 exemplarily shows the structure of a network threat detection apparatus provided by an embodiment of this document.
图7示例性地示出了图4中结果判断模块403的结构。FIG. 7 exemplarily shows the structure of the
图8示例性地示出了本文的一实施例提供的一种计算机设备的框图(服务器的一般结构)。FIG. 8 exemplarily shows a block diagram of a computer device (general structure of a server) provided by an embodiment of this document.
具体实施方式Detailed ways
为使本文实施例的目的、技术方案和优点更加清楚,下面将结合本文实施例中的附图,对本文实施例中的技术方案进行清楚、完整地描述,显然,所描述的实施例是本文的一部分实施例,而不是全部的实施例。基于本文中的实施例,本领域普通技术人员在没有做出创造性劳动前提下所获得的所有其他实施例,都属于本文保护的范围。需要说明的是,在不冲突的情况下,本申请中的实施例及实施例中的特征可以相互任意组合。In order to make the purposes, technical solutions and advantages of the embodiments herein more clear, the technical solutions in the embodiments herein will be clearly and completely described below with reference to the accompanying drawings in the embodiments herein. some examples, but not all examples. Based on the embodiments herein, all other embodiments obtained by persons of ordinary skill in the art without creative efforts shall fall within the scope of protection herein. It should be noted that, the embodiments in the present application and the features in the embodiments may be arbitrarily combined with each other if there is no conflict.
威胁识别规则库调整方式具有如下缺点:The adjustment method of threat identification rule base has the following disadvantages:
1、定制威胁判定规则需要对产品的算法、逻辑、工作原理、行为特征、规则语法等诸多细节原理有充分的了解,导致甲方没有对威胁判断规则库自行维护的能力。1. Customizing threat judgment rules requires a full understanding of the product's algorithm, logic, working principle, behavioral characteristics, rule syntax, and many other detailed principles, resulting in Party A's inability to maintain the threat judgment rule base by itself.
2、乙方需要对甲方业务充分了解才能准确修改定制威胁判定规则,并长期持续提供维护服务,人力投入较大,成本高。2. Party B needs to fully understand the business of Party A in order to accurately modify the customized threat determination rules and provide maintenance services for a long time.
3、业务有变更时或有问题时,涉及双方的沟通协调,导致对问题的反应滞后,周期长。3. When there is a change in the business or there is a problem, the communication and coordination between the two parties are involved, resulting in a lag in the response to the problem and a long cycle.
为了解决以上的问题,本文的实施例提出了一种网络威胁检测方法和装置,基于通用的规则调整方式,使甲方不用了解产品的算法、后台逻辑、规则语法等技术细节,简单的通过对已经识别的事件做标注即可对规则的识别效果进行定向调整。In order to solve the above problems, the embodiments of this paper propose a network threat detection method and device, based on a general rule adjustment method, so that Party A does not need to know the technical details of the product's algorithm, background logic, rule syntax, etc. By labeling the identified events, you can make directional adjustments to the recognition effect of the rules.
本文的一实施例提供了一种网络威胁检测方法,其实现逻辑如图1所示,由推荐标注、反馈标注、训练、应用,四部分组成。其中,An embodiment of this paper provides a network threat detection method, the implementation logic of which is shown in Figure 1, and consists of four parts: recommendation labeling, feedback labeling, training, and application. in,
推荐标注用于:从历史威胁事件中选择最有标注价值的事件,推荐给用户标注。Recommended annotations are used to select the most valuable events from historical threat events and recommend them to users.
一个威胁原因/攻击原因对应多个检测规则,符合任一规则就认为检测到一个由该威胁原因/攻击原因导致的威胁事件。每个规则包含多个特征,在满足多个特征中的一个或多个或全部时,即判定发生了符合该规则的威胁事件。A threat cause/attack cause corresponds to multiple detection rules, and if any rule is met, a threat event caused by the threat cause/attack cause is considered to be detected. Each rule contains multiple features, and when one or more or all of the multiple features are satisfied, it is determined that a threat event that meets the rule has occurred.
一条规则是一个逻辑表达式,一个威胁原因包含多个规则,每个规则对应多种不同的特征。规则包含参数值和运算逻辑,而且要保证规则及其识别结果的可解释性,所以无法自动实现修改调整。以下为一条规则的示例:A rule is a logical expression, a threat cause contains multiple rules, each rule corresponds to a variety of different characteristics. The rules contain parameter values and operation logic, and the interpretability of the rules and their identification results must be guaranteed, so modification and adjustment cannot be implemented automatically. The following is an example of a rule:
clientIP.pv>16andclientIP.pv>16and
clientIP.4xxHttpCodeCount>domain.4xxHttpCodeCount*2andclientIP.4xxHttpCodeCount>domain.4xxHttpCodeCount*2and
clientIP.4xxHttpCodeCount/clientIP.pv>0.6andclientIP.4xxHttpCodeCount/clientIP.pv>0.6and
clientIP.requestPath.uniq/clientIP.pv>0.4clientIP.requestPath.uniq/clientIP.pv>0.4
反馈标注用于:收集用户添加的反馈标注。Feedback annotations are used to: collect feedback annotations added by users.
训练用于:使用标注样本训练修正威胁判定规则的智能修正神经网络。Training is used for: using labeled samples to train an intelligent correction neural network that corrects threat determination rules.
应用于:使用修正判定规则的智能修正神经网络得到的大概率预测结果修正威胁规则库。Application: Use the high-probability prediction result obtained by the intelligent correction neural network to correct the judgment rule to correct the threat rule base.
使用该方法完成威胁事件检测的流程如图2所示,包括:The process of using this method to complete threat event detection is shown in Figure 2, including:
步骤201、收集多个根据威胁规则库检测得到的威胁事件。Step 201: Collect multiple threat events detected according to the threat rule base.
本步骤中,具体的,收集威胁分数较低的威胁事件,以收集得到的威胁事件作为备选事件供后续反馈给用户标注使用。所述预置的威胁规则库中包含多种攻击原因对应的规则,每个攻击原因对应至少一个规则;所述威胁规则库中的各个规则还具有威胁分数,该威胁分数可根据规则中的具体特征进行计算,优选的,所述威胁分数为[1,100]区间内的值,即识别到的一定认为是威胁,同一种攻击原因威胁分数越高表明攻击行为与群体行为差异越大。In this step, specifically, a threat event with a low threat score is collected, and the collected threat event is used as an alternative event for subsequent feedback to the user for marking. The preset threat rule base includes rules corresponding to a variety of attack causes, and each attack cause corresponds to at least one rule; each rule in the threat rule base also has a threat score, and the threat score can be based on the specific rules in the rule. The characteristics are calculated. Preferably, the threat score is a value in the range of [1, 100], that is, the identified threat must be considered as a threat. The higher the threat score for the same attack reason, the greater the difference between the attack behavior and the group behavior.
例如,每5分钟就搜索前5分钟内的威胁事件,在每个域名的每个威胁原因下取威胁分数最低的一条威胁事件。将收集的威胁事件及其行为特征保存到推荐备选库用于标注推荐。For example, every 5 minutes, the threat events in the previous 5 minutes are searched, and the threat event with the lowest threat score is selected under each threat cause of each domain name. Save the collected threat events and their behavioral characteristics to the recommendation candidate library for labeling and recommendation.
优选的,还可删除推荐备选库中24小时以前收集的且尚未被标注的威胁事件。因为原始日志保存时间有限,过早的威胁事件没有原始日志不方便回溯和判断,因此将一段时间之前的威胁事件删除不用。Preferably, the threat events collected before 24 hours and not yet marked in the recommended candidate database can also be deleted. Because the original log is stored for a limited time, it is not convenient to trace back and judge the premature threat events without the original log, so delete the threat events before a certain period of time.
步骤202、获取针对收集得到的所述威胁事件的反馈标注,根据所述反馈标注生成训练样本。Step 202: Obtain feedback annotations for the collected threat events, and generate training samples according to the feedback annotations.
本步骤中,将收集得到的威胁事件以推荐等形式提供给用户标注,并获取用户的反馈标注,所述反馈标注指示所述威胁事件正确或错误。In this step, the collected threat events are provided to the user for annotations in the form of recommendations, etc., and the user's feedback annotations are obtained, and the feedback annotations indicate that the threat events are correct or wrong.
当需要推荐标注时,从推荐备选库中选取按分数倒序和时间倒序排序后的前若干条威胁事件作为推荐。可在用户主动对一威胁事件添加反馈标注时推荐更多收集得到的威胁事件。When it is necessary to recommend annotations, select the first several threat events sorted in reverse order of score and time from the recommended candidate library as recommendations. More collected threat events may be recommended when a user actively adds feedback annotations to a threat event.
当用户认为某项威胁事件识别有错误或需要强化正确的识别时,可添加指示威胁事件错误的反馈标注。当用户认为威胁事件的检测结果正确时,可添加指示威胁事件正确的反馈标注。可以通过界面点击进行标注,标注的详情确认页面同时会展示推荐标注的威胁事件。添加反馈标注后的威胁事件及其行为特征会存入样本库供训练神经网络使用。When the user believes that a threat event has been identified incorrectly or needs to be reinforced for correct identification, a feedback callout indicating that the threat event is wrong can be added. When the user believes that the detection result of a threat event is correct, a feedback callout indicating that the threat event is correct can be added. You can click to mark on the interface, and the marked details confirmation page will also display the threat events that are recommended to be marked. The threat events and their behavioral characteristics after adding feedback annotations will be stored in the sample library for training the neural network.
一般情况下,在对威胁事件添加反馈标注时,对一个威胁事件只添加一个反馈标注,但该反馈标注的内容可修改。Generally, when adding a feedback annotation to a threat event, only one feedback annotation is added to a threat event, but the content of the feedback annotation can be modified.
步骤203、根据所述反馈标注,生成训练样本。Step 203: Generate training samples according to the feedback annotations.
本步骤中,为反馈标注添加样本期望预测分数。具体的,为所述反馈标注指示正确的威胁事件添加第一预测分数,为所述反馈标注指示错误的威胁事件添加第二预测分数,所述第一预测分数大于所述第二预测分数。例如,设置第一预测分数为100分,设置第二预测分数为-100分。In this step, the sample expected prediction score is added to the feedback annotation. Specifically, a first prediction score is added to a threat event for which the feedback annotation indicates correctness, and a second prediction score is added to a threat event for which the feedback annotation indicates an error, where the first prediction score is greater than the second prediction score. For example, the first prediction score is set to 100 points, and the second prediction score is set to -100 points.
对威胁事件的各行为特征可进行特征工程后获取可应用于输入矩阵的特征数据,将特征值转换成相应的数字表示,具体转换方式可根据实际应用需求配置。Feature engineering can be performed on each behavioral feature of the threat event to obtain feature data that can be applied to the input matrix, and the feature value can be converted into a corresponding digital representation. The specific conversion method can be configured according to actual application requirements.
一个威胁事件的全部行为特征的特征数据和对应的第一/第二预测分数,即构成一条训练样本数据。The feature data of all behavioral features of a threat event and the corresponding first/second prediction scores constitute a piece of training sample data.
将针对同一域名下同一攻击原因的多个威胁事件训练样本数据集合在一起,构成作为训练样本的输入矩阵,每条训练样本数据即为该输入矩阵的一行。The training sample data of multiple threat events for the same attack reason under the same domain name are collected together to form an input matrix as a training sample, and each training sample data is a row of the input matrix.
智能修正神经网络可与一个域名下的一个攻击原因对应生成,即,每个域名下的每个攻击原因在存在足够的训练样本数据时,都可训练得到相应的智能修正神经网络。The intelligent correction neural network can be generated corresponding to an attack cause under a domain name, that is, each attack cause under each domain name can be trained to obtain a corresponding intelligent correction neural network when there is enough training sample data.
例如,当某一域名的某一攻击原因下的训练样本数据集合有更新、训练样本数据数量达到20条以上,且5分钟内没有新增反馈标注时,即可以生成训练样本,开始执行训练过程。取此域名下此攻击原因的所有训练样本数据,转换为统一格式的输入矩阵(每条训练样本数据为一行,每个特征一列,就可得到输入矩阵)。For example, when the training sample data set under a certain attack cause of a domain name is updated, the number of training sample data reaches more than 20, and no feedback label is added within 5 minutes, the training sample can be generated and the training process can be started. . Take all the training sample data of this attack cause under this domain name and convert it into an input matrix in a unified format (each training sample data is a row, and each feature has a column, the input matrix can be obtained).
特征/行为特征至少包含以下信息中的任一或任意多个:A characteristic/behavioral characteristic contains at least any one or more of the following information:
窗口内的pv,访问了多少不同的uri,访问uri是否有循环,各种状态码统计,平均请求时间,平均请求内容长度,等等。PV in the window, how many different URIs have been accessed, whether there are loops in accessing URIs, various status code statistics, average request time, average request content length, and so on.
步骤204、使用所述训练样本训练得到所述智能修正神经网络。
本步骤中,运行训练算法,不断迭代。In this step, run the training algorithm and iterate continuously.
当连续多次(优选的,5000次)迭代没有得到更小的损失值时,结束训练,得到智能修正神经网络。When a smaller loss value is not obtained after multiple (preferably, 5000) iterations in a row, the training is ended, and an intelligent correction neural network is obtained.
优选的,还可计算训练得到的智能修正神经网络的成熟度,具体包括:Preferably, the maturity of the intelligent correction neural network obtained by training can also be calculated, which specifically includes:
1、使用所述智能修正神经网络预测所述训练样本中各威胁事件的修正分数。1. Use the intelligent correction neural network to predict the correction score of each threat event in the training sample.
2、取各威胁事件的预测误差值的平均值,所述预测误差值为一威胁事件的第一预测分数或第二预测分数与修正分数差值的绝对值。2. Take the average value of the prediction error values of each threat event, where the prediction error value is the absolute value of the difference between the first prediction score or the second prediction score and the corrected score of a threat event.
3、以基准分数减去所述平均值的计算结果作为所述智能修正神经网络的成熟度。该基准分数可为100分。3. Taking the calculation result of subtracting the average value from the benchmark score as the maturity of the intelligent correction neural network. The benchmark score may be 100 points.
不同威胁事件可能有同样的行为特征,如果被添加了不同的反馈标注,就会使成熟度降低。成熟度越高证明符合标签判断的特征越明显,使用该智能修正神经网络得到的修正分数就更可靠。Different threat events may have the same behavioral characteristics, and if different feedback annotations are added, the maturity will be reduced. The higher the maturity, the more obvious the features that conform to the label judgment, and the more reliable the correction score obtained by using the intelligent correction neural network.
在完成神经网络训练后,即可使用训练得到的智能修正神经网络对威胁事件的检测结果进行修正,具体如图3所示,包括:After completing the neural network training, the intelligent correction neural network obtained by training can be used to correct the detection results of the threat event, as shown in Figure 3, including:
步骤301、根据预置的威胁规则库,检测得到威胁事件。Step 301: Detect a threat event according to a preset threat rule base.
本步骤中,在发生符合所述威胁规则库中的规则的事件时,判定发生与所述规则对应的攻击原因相关联的威胁事件,并获取判定发生所述威胁事件所依据的规则的威胁分数,作为所述威胁事件的威胁分数。In this step, when an event conforming to the rules in the threat rule base occurs, it is determined that a threat event associated with the attack cause corresponding to the rule occurs, and a threat score of the rule based on which the threat event is determined to occur is obtained. , as the threat score of the threat event.
步骤302、将所述威胁事件输入智能修正神经网络,获取所述威胁事件的修正分数。Step 302: Input the threat event into an intelligent correction neural network to obtain a correction score of the threat event.
本步骤中,在后续识别过程中,将所述威胁事件的各项行为特征输入所述智能修正神经网络,获取所述威胁事件的修正分数,所述修正分数大于等于所述第二预测分数且小于等于所述第一预测分数。优选的,所述修正分数为In this step, in the subsequent identification process, the behavioral characteristics of the threat event are input into the intelligent correction neural network to obtain a correction score of the threat event, where the correction score is greater than or equal to the second prediction score and less than or equal to the first prediction score. Preferably, the correction score is
[-100,100]区间内的值。修正分数距离第二预测分数越近,则表明与原威胁规则库中的判断结果越不符合,修正分数距离第一预测分数越近表明与标注内容为正确的反馈标注越符合,修正分数距离第二预测分数越近则表明与标注内容为错误的反馈标注越符合。A value in the interval [-100, 100]. The closer the corrected score is to the second prediction score, the more inconsistent it is with the judgment result in the original threat rule base. The closer the prediction score is, the more consistent it is with the feedback annotation with wrong annotation content.
步骤303、根据所述修正分数,对所述威胁事件进行修正,得到最终的威胁检测结果。Step 303: Correct the threat event according to the correction score to obtain a final threat detection result.
本步骤中,首先按照一定规则计算得到最终威胁分数。例如,取所述修正分数与所述威胁分数的平均值。然后,在所述平均值低于预置的事件成立阈值时,判定所述威胁事件属于检测错误,最终的威胁检测结果为无威胁事件;在所述平均值达到所述预置的事件成立阈值时,判定所述威胁事件属于检测正确,最终的威胁检测结果为发生所述威胁事件。In this step, the final threat score is first calculated according to certain rules. For example, take the average of the correction score and the threat score. Then, when the average value is lower than the preset event establishment threshold, it is determined that the threat event is a detection error, and the final threat detection result is no threat event; when the average value reaches the preset event establishment threshold , it is determined that the threat event is detected correctly, and the final threat detection result is that the threat event occurs.
威胁分数是对威胁行为的一个降维描述特征,通过设置事件成立阈值,在提高准确率和提高召回率两个需求之间进行平衡。Threat score is a dimensionality-reduced description feature of threat behavior. By setting the threshold of event establishment, it balances the two requirements of improving the accuracy rate and improving the recall rate.
例如,将预测修正分数(处于[-100,100]区间内的值)与威胁分数(处于[1,100]区间内的值)按一定规则运算(例如简单取平均)取得最终威胁分数,设置事件成立阈值为0。在最终威胁分数大于0时判定所述威胁事件属于检测正确,记录威胁事件。For example, the prediction correction score (value in the range of [-100, 100]) and the threat score (value in the range of [1, 100]) are calculated according to certain rules (such as simple averaging) to obtain the final threat score, and set The event establishment threshold is 0. When the final threat score is greater than 0, it is determined that the threat event is correctly detected, and the threat event is recorded.
本文的一实施例还提供了一种网络威胁检测装置,其结构如图4所示,包括:An embodiment of this document also provides a network threat detection device, the structure of which is shown in Figure 4, including:
威胁事件检测模块401,用于根据预置的威胁规则库,检测得到威胁事件;A threat
神经网络修正模块402,用于将所述威胁事件输入智能修正神经网络,获取所述威胁事件的修正分数;A neural
结果判断模块403,用于根据所述修正分数,对所述威胁事件进行修正,得到最终的威胁检测结果。The
优选的,所述预置的威胁规则库中包含多种攻击原因对应的规则,每个攻击原因对应至少一个规则,各个规则还具有威胁分数,Preferably, the preset threat rule base includes rules corresponding to multiple attack causes, each attack cause corresponds to at least one rule, and each rule also has a threat score,
所述威胁事件检测模块401的结构如图5所示,包括:The structure of the threat
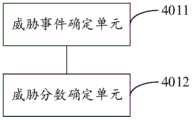
威胁事件确定单元4011,用于在发生符合所述威胁规则库中的规则的事件时,判定发生与所述规则对应的攻击原因相关联的威胁事件;a threat
威胁分数确定单元4012,用于获取判定发生所述威胁事件所依据的规则的威胁分数,作为所述威胁事件的威胁分数。The threat
优选的,该装置的结构如图6所示,还包括:Preferably, the structure of the device is shown in Figure 6, and further includes:
事件收集模块404,用于收集多个根据所述威胁规则库检测得到的威胁事件;An event collection module 404, configured to collect a plurality of threat events detected according to the threat rule base;
标注获取模块405,用于获取针对收集得到的所述威胁事件的反馈标注,根据所述反馈标注生成训练样本,反馈标注指示所述威胁事件正确或错误;An annotation acquisition module 405, configured to acquire feedback annotations for the collected threat events, generate training samples according to the feedback annotations, and the feedback annotations indicate that the threat events are correct or wrong;
样本生成模块406,用于根据所述反馈标注,生成训练样本;A sample generation module 406, configured to generate training samples according to the feedback annotation;
神经网络训练模块407,用于使用所述训练样本训练得到所述智能修正神经网络。The neural network training module 407 is configured to use the training samples to train to obtain the intelligent correction neural network.
优选的,所述结果判断模块403的结构如图7所示,包括:Preferably, the structure of the
平均值计算单元4031,用于取所述修正分数与所述威胁分数的平均值;an average
结果评价单元4032,用于在所述平均值低于预置的事件成立阈值时,判定所述威胁事件属于检测错误,最终的威胁检测结果为无威胁事件,The
在所述平均值达到所述预置的事件成立阈值时,判定所述威胁事件属于检测正确,最终的威胁检测结果为发生所述威胁事件。When the average value reaches the preset event establishment threshold, it is determined that the threat event is correctly detected, and the final threat detection result is that the threat event occurs.
如图4至7所述的网络威胁检测装置,可集成于云平台等远程服务平台中,也可集成于本地服务器设备中,由远程服务平台或本地服务器设备实现相应功能。The network threat detection device as shown in Figures 4 to 7 can be integrated into a remote service platform such as a cloud platform, or can be integrated into a local server device, and the remote service platform or the local server device can implement corresponding functions.
本文的一实施例还提供了一种计算机可读存储介质,其上存储有计算机程序,所述计算机程序被执行时实现本文的实施例提供的网络威胁检测方法的步骤。An embodiment of this document also provides a computer-readable storage medium, on which a computer program is stored, and when the computer program is executed, implements the steps of the network threat detection method provided by the embodiment of this document.
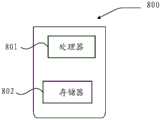
本文的一实施例还提供了一种用于网络威胁检测的计算机设备,如图所示,是该计算机设备800的框图。例如,计算机设备800可以被提供为一服务器。参照图8,计算机设备800包括处理器801,处理器的个数可以根据需要设置为一个或者多个。计算机设备800还包括存储器802,用于存储可由处理器801的执行的指令,例如应用程序。存储器的个数可以根据需要设置一个或者多个。其存储的应用程序可以为一个或者多个。处理器801被配置为执行指令,以执行上述方法。An embodiment of this document also provides a computer device for network threat detection, as shown in the figure, which is a block diagram of the
本文的实施例提供了一种网络威胁检测方法和装置,根据预置的威胁规则库,检测得到威胁事件,再将所述威胁事件输入智能修正神经网络,获取所述威胁事件的修正分数,然后根据所述修正分数,对所述威胁事件进行修正,得到最终的威胁检测结果。利用智能网络,在不对原始的威胁规则库进行修改的情况下,对威胁事件的检测判定系统进行维护更新,解决了派驻人员进行现场人工维护带来的成本高、效率低、反应滞后的问题,实现了灵活准确的威胁识别规则更新机制。The embodiments of this document provide a network threat detection method and device, which detects a threat event according to a preset threat rule base, and then inputs the threat event into an intelligent correction neural network to obtain a correction score of the threat event, and then According to the correction score, the threat event is corrected to obtain a final threat detection result. Using the intelligent network, without modifying the original threat rule base, the detection and determination system of threat events is maintained and updated, which solves the problems of high cost, low efficiency and delayed response caused by dispatched personnel to perform on-site manual maintenance. A flexible and accurate threat identification rule update mechanism is implemented.
使用本文的实施例提供的技术方案,用户不用了解算法、现有规则、规则语法等产品实现即可对判定规则识别效果进行定向调整,进而降识别规则低定制调整门槛,使得甲方可以自己对识别效果进行调整,节省了乙方技术支持投入及沟通协调成本。智能修正神经网络通过反馈标注样本学习用户判断逻辑,预测用户对威胁事件的判断,随着收集得到的反馈标注量增加,智能修正神经网络输出的判断结果与用户和业务的真正情况更贴合。本文实施例提供的技术方案中,对规则的修正不是修改规则,而是对规则的识别结果进行调整。在规则保证基本识别功能、保证识别结果的可解释性的前提下,模拟用户判断逻辑,对识别结果进行调整,例如:剔除用户很可能认为不正确的威胁事件,或降低其威胁分数,提高用户很可能认为识别正确的威胁事件和疑似威胁事件的威胁分数,避免标注不足或少量错误或样本覆盖不足时出现过多误判、漏判。简化了定制门槛、节省了用户支持成本,在提升用户体验的同时提高了准确率与召回率。Using the technical solutions provided by the embodiments of this paper, users can make targeted adjustments to the recognition effect of judgment rules without knowing the product implementation of algorithms, existing rules, and rule grammars, thereby lowering the threshold for customization and adjustment of recognition rules, so that Party A can make adjustments on its own. The identification effect is adjusted, which saves Party B's technical support investment and communication and coordination costs. The intelligent correction neural network learns the user's judgment logic through the feedback and annotation samples, and predicts the user's judgment on the threat event. As the amount of collected feedback annotation increases, the judgment result output by the intelligent correction neural network is more suitable for the real situation of the user and the business. In the technical solutions provided by the embodiments herein, the amendment to the rule is not to modify the rule, but to adjust the recognition result of the rule. On the premise that the rules ensure the basic recognition function and the interpretability of the recognition results, simulate the user's judgment logic and adjust the recognition results, for example: remove the threat events that the user is likely to think is incorrect, or reduce the threat score and improve the user It is likely to identify the correct threat events and the threat scores of suspected threat events, and avoid too many misjudgments and missed judgments when there is insufficient labeling or a small number of errors or insufficient sample coverage. It simplifies the customization threshold, saves user support costs, and improves the accuracy and recall rate while improving the user experience.
本领域技术人员应明白,本文的实施例可提供为方法、装置(设备)、或计算机程序产品。因此,本文可采用完全硬件实施例、完全软件实施例、或结合软件和硬件方面的实施例的形式。而且,本文可采用在一个或多个其中包含有计算机可用程序代码的计算机可用存储介质上实施的计算机程序产品的形式。计算机存储介质包括在用于存储信息(诸如计算机可读指令、数据结构、程序模块或其他数据)的任何方法或技术中实施的易失性和非易失性、可移除和不可移除介质,包括但不限于RAM、ROM、EEPROM、闪存或其他存储器技术、CD-ROM、数字多功能盘(DVD)或其他光盘存储、磁盒、磁带、磁盘存储或其他磁存储装置、或者可以用于存储期望的信息并且可以被计算机访问的任何其他的介质等。此外,本领域普通技术人员公知的是,通信介质通常包含计算机可读指令、数据结构、程序模块或者诸如载波或其他传输机制之类的调制数据信号中的其他数据,并且可包括任何信息递送介质。As will be appreciated by those skilled in the art, the embodiments herein may be provided as a method, an apparatus (apparatus), or a computer program product. Accordingly, this document may take the form of an entirely hardware embodiment, an entirely software embodiment, or an embodiment combining software and hardware aspects. Furthermore, this document may take the form of a computer program product embodied on one or more computer-usable storage media having computer-usable program code embodied therein. Computer storage media includes volatile and nonvolatile, removable and non-removable media implemented in any method or technology for storage of information such as computer readable instructions, data structures, program modules or other data , including but not limited to RAM, ROM, EEPROM, flash memory or other memory technology, CD-ROM, digital versatile disk (DVD) or other optical disk storage, magnetic cartridges, magnetic tape, magnetic disk storage or other magnetic storage devices, or may be used for Any other medium that stores desired information and can be accessed by a computer, etc. In addition, communication media typically embodies computer readable instructions, data structures, program modules, or other data in a modulated data signal such as a carrier wave or other transport mechanism, and can include any information delivery media, as is well known to those of ordinary skill in the art .
本文是参照根据本文实施例的方法、装置(设备)和计算机程序产品的流程图和/或方框图来描述的。应理解可由计算机程序指令实现流程图和/或方框图中的每一流程和/或方框、以及流程图和/或方框图中的流程和/或方框的结合。可提供这些计算机程序指令到通用计算机、专用计算机、嵌入式处理机或其他可编程数据处理设备的处理器以产生一个机器,使得通过计算机或其他可编程数据处理设备的处理器执行的指令产生用于实现在流程图一个流程或多个流程和/或方框图一个方框或多个方框中指定的功能的装置。Described herein with reference to flowchart illustrations and/or block diagrams of methods, apparatus (apparatus) and computer program products according to embodiments herein. It will be understood that each flow and/or block in the flowchart illustrations and/or block diagrams, and combinations of flows and/or blocks in the flowchart illustrations and/or block diagrams, can be implemented by computer program instructions. These computer program instructions may be provided to the processor of a general purpose computer, special purpose computer, embedded processor or other programmable data processing device to produce a machine such that the instructions executed by the processor of the computer or other programmable data processing device produce Means for implementing the functions specified in a flow or flow of a flowchart and/or a block or blocks of a block diagram.
这些计算机程序指令也可存储在能引导计算机或其他可编程数据处理设备以特定方式工作的计算机可读存储器中,使得存储在该计算机可读存储器中的指令产生包括指令装置的制造品,该指令装置实现在流程图一个流程或多个流程和/或方框图一个方框或多个方框中指定的功能。These computer program instructions may also be stored in a computer-readable memory capable of directing a computer or other programmable data processing apparatus to function in a particular manner, such that the instructions stored in the computer-readable memory result in an article of manufacture comprising instruction means, the instructions The apparatus implements the functions specified in the flow or flow of the flowcharts and/or the block or blocks of the block diagrams.
这些计算机程序指令也可装载到计算机或其他可编程数据处理设备上,使得在计算机或其他可编程设备上执行一系列操作步骤以产生计算机实现的处理,从而在计算机或其他可编程设备上执行的指令提供用于实现在流程图一个流程或多个流程和/或方框图一个方框或多个方框中指定的功能的步骤。These computer program instructions can also be loaded on a computer or other programmable data processing device to cause a series of operational steps to be performed on the computer or other programmable device to produce a computer-implemented process such that The instructions provide steps for implementing the functions specified in the flow or blocks of the flowcharts and/or the block or blocks of the block diagrams.
在本文中,术语“包括”、“包含”或者其任何其他变体意在涵盖非排他性的包含,从而使得包括一系列要素的物品或者设备不仅包括那些要素,而且还包括没有明确列出的其他要素,或者是还包括为这种物品或者设备所固有的要素。在没有更多限制的情况下,由语句“包括……”限定的要素,并不排除在包括所述要素的物品或者设备中还存在另外的相同要素。As used herein, the terms "comprising", "comprising" or any other variation thereof are intended to encompass a non-exclusive inclusion such that an article or device comprising a list of elements includes not only those elements, but also others not expressly listed elements, or elements inherent to the article or equipment. Without further limitation, an element defined by the phrase "comprising" does not preclude the presence of additional identical elements in the article or device comprising said element.
尽管已描述了本文的优选实施例,但本领域内的技术人员一旦得知了基本创造性概念,则可对这些实施例作出另外的变更和修改。所以,所附权利要求意欲解释为包括优选实施例以及落入本文范围的所有变更和修改。While the preferred embodiments have been described herein, additional changes and modifications to these embodiments may occur to those skilled in the art once the basic inventive concepts are known. Therefore, the appended claims are intended to be construed to include the preferred embodiment and all changes and modifications that fall within the scope of this document.
显然,本领域的技术人员可以对本文进行各种改动和变型而不脱离本文的精神和范围。这样,倘若本文的这些修改和变型属于本文权利要求及其等同技术的范围之内,则本文的意图也包含这些改动和变型在内。It will be apparent to those skilled in the art that various modifications and variations can be made in this document without departing from the spirit and scope of this document. Thus, provided that such modifications and variations herein come within the scope of the claims herein and their equivalents, it is intended that such modifications and variations are also included herein.
Claims (15)
Priority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN201910569503.3ACN112152968B (en) | 2019-06-27 | 2019-06-27 | Network threat detection method and device |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN201910569503.3ACN112152968B (en) | 2019-06-27 | 2019-06-27 | Network threat detection method and device |
Publications (2)
| Publication Number | Publication Date |
|---|---|
| CN112152968Atrue CN112152968A (en) | 2020-12-29 |
| CN112152968B CN112152968B (en) | 2022-07-22 |
Family
ID=73868807
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN201910569503.3AActiveCN112152968B (en) | 2019-06-27 | 2019-06-27 | Network threat detection method and device |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN112152968B (en) |
Cited By (1)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN113422785A (en)* | 2021-08-20 | 2021-09-21 | 北京生泰尔科技股份有限公司 | Malicious attack detection method and system based on network traffic and readable storage medium |
Citations (5)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN104486141A (en)* | 2014-11-26 | 2015-04-01 | 国家电网公司 | Misdeclaration self-adapting network safety situation predication method |
| CN106790292A (en)* | 2017-03-13 | 2017-05-31 | 摩贝(上海)生物科技有限公司 | The web application layer attacks detection and defence method of Behavior-based control characteristic matching and analysis |
| US20170235960A1 (en)* | 2016-02-16 | 2017-08-17 | James Andrew Austin | Intelligent system for forecasting threats in a virtual attack domain |
| US20180083988A1 (en)* | 2016-09-19 | 2018-03-22 | Ntt Innovation Institute, Inc. | Threat scoring system and method |
| CN109688105A (en)* | 2018-11-19 | 2019-04-26 | 中国科学院信息工程研究所 | A method and system for generating threat alarm information |
- 2019
- 2019-06-27CNCN201910569503.3Apatent/CN112152968B/enactiveActive
Patent Citations (5)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN104486141A (en)* | 2014-11-26 | 2015-04-01 | 国家电网公司 | Misdeclaration self-adapting network safety situation predication method |
| US20170235960A1 (en)* | 2016-02-16 | 2017-08-17 | James Andrew Austin | Intelligent system for forecasting threats in a virtual attack domain |
| US20180083988A1 (en)* | 2016-09-19 | 2018-03-22 | Ntt Innovation Institute, Inc. | Threat scoring system and method |
| CN106790292A (en)* | 2017-03-13 | 2017-05-31 | 摩贝(上海)生物科技有限公司 | The web application layer attacks detection and defence method of Behavior-based control characteristic matching and analysis |
| CN109688105A (en)* | 2018-11-19 | 2019-04-26 | 中国科学院信息工程研究所 | A method and system for generating threat alarm information |
Cited By (1)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN113422785A (en)* | 2021-08-20 | 2021-09-21 | 北京生泰尔科技股份有限公司 | Malicious attack detection method and system based on network traffic and readable storage medium |
Also Published As
| Publication number | Publication date |
|---|---|
| CN112152968B (en) | 2022-07-22 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| US8762180B2 (en) | Claims analytics engine | |
| CN111797629B (en) | Method and device for processing medical text data, computer equipment and storage medium | |
| US20180268258A1 (en) | Automated decision making using staged machine learning | |
| CN105718490A (en) | Method and device for updating classifying model | |
| CN109087667B (en) | Voice fluency recognition method and device, computer equipment and readable storage medium | |
| CN112906375A (en) | Text data labeling method, device, equipment and storage medium | |
| CN117275644B (en) | Detection result mutual recognition method, system and storage medium based on deep learning | |
| CN116932523A (en) | Platform for integrating and supervising third party environment detection mechanism | |
| CN116737580A (en) | Regression testing range determining method, device, equipment and storage medium | |
| CN116109007B (en) | Power generation power determination method, server and storage medium | |
| CN112152968B (en) | Network threat detection method and device | |
| CN119107194B (en) | Income and expenditure declaration data processing method and system based on multi-heterogeneous models | |
| CN112699887B (en) | Method and device for obtaining mathematical object annotation model and mathematical object annotation | |
| CN112149818B (en) | Threat identification result evaluation method and device | |
| US12073606B1 (en) | Machine learning model inference using user-created machine learning models while maintaining user privacy | |
| CN118395452A (en) | XGBoost-based implementation method for dynamically detecting intelligent contract loopholes | |
| CN114722025B (en) | Data prediction method, device, equipment and storage medium based on prediction model | |
| CN116681970A (en) | A model training method, device, equipment and storage medium | |
| CN116306909A (en) | Method for realizing model training, computer storage medium and terminal | |
| CN105824871B (en) | A kind of picture detection method and equipment | |
| CN112016607B (en) | A deep learning-based fault analysis method | |
| CN115310544A (en) | Model processing method and device, storage medium and equipment | |
| CN111160583B (en) | Data processing method and device | |
| CN115758389A (en) | Vulnerability processing result checking method and device, electronic equipment and storage medium | |
| CN119228367B (en) | Ship checking method and device based on artificial intelligence |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| GR01 | Patent grant | ||
| GR01 | Patent grant | ||
| TR01 | Transfer of patent right | ||
| TR01 | Transfer of patent right | Effective date of registration:20250805 Address after:100015 Beijing City Chaoyang District Dongsanhuan Middle Road 20 Building 17th Floor 1709 Unit Patentee after:BEIJING SHUJU XINYUN INFORMATION TECHNOLOGY Co.,Ltd. Country or region after:China Address before:100015 Beijing Chaoyang District Jiuxianqiao North Road 10 hospital 201 Building 5 floor 505 inside 02 Patentee before:BEIJING SHUAN XINYUN INFORMATION TECHNOLOGY Co.,Ltd. Country or region before:China |