CN112149105A - Data processing system, method, related equipment and storage medium - Google Patents
Data processing system, method, related equipment and storage mediumDownload PDFInfo
- Publication number
- CN112149105A CN112149105ACN202011137091.5ACN202011137091ACN112149105ACN 112149105 ACN112149105 ACN 112149105ACN 202011137091 ACN202011137091 ACN 202011137091ACN 112149105 ACN112149105 ACN 112149105A
- Authority
- CN
- China
- Prior art keywords
- access
- control server
- credential
- data
- target
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Pending
Links
Images
Classifications
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/30—Authentication, i.e. establishing the identity or authorisation of security principals
- G06F21/44—Program or device authentication
- G06F21/445—Program or device authentication by mutual authentication, e.g. between devices or programs
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/60—Protecting data
- G06F21/602—Providing cryptographic facilities or services
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/60—Protecting data
- G06F21/62—Protecting access to data via a platform, e.g. using keys or access control rules
- G06F21/6218—Protecting access to data via a platform, e.g. using keys or access control rules to a system of files or objects, e.g. local or distributed file system or database
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/60—Protecting data
- G06F21/64—Protecting data integrity, e.g. using checksums, certificates or signatures
Landscapes
- Engineering & Computer Science (AREA)
- Theoretical Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- Software Systems (AREA)
- General Physics & Mathematics (AREA)
- Computer Hardware Design (AREA)
- Physics & Mathematics (AREA)
- General Engineering & Computer Science (AREA)
- General Health & Medical Sciences (AREA)
- Bioethics (AREA)
- Health & Medical Sciences (AREA)
- Databases & Information Systems (AREA)
- Storage Device Security (AREA)
Abstract
Translated fromChineseDescription
Translated fromChinese技术领域technical field
本申请涉及计算机技术领域,尤其涉及一种数据处理系统、方法、相关设备及存储介质。The present application relates to the field of computer technology, and in particular, to a data processing system, method, related device and storage medium.
背景技术Background technique
为了保证对限制访问设备进行数据访问时的安全性,在对限制访问设备进行数据访问的时候,需要对数据访问请求中的访问凭证进行校验,为了实现对访问凭证的校验,对该访问凭证进行校验的则需要存储所有的访问凭证的票据信息,而由于当前针对限制访问设备的数据访问请求的数量较多,所以,需要校验服务器存储的票据信息也就越来越多,由此可见,采用当前的对访问凭证进行校验的方法,对校验服务器的内存要求较高,所以如何降低服务器在对访问凭证进行校验时对服务器的内存要求,并保证对访问凭证的校验准确度成为了当前的研究热点。In order to ensure the security of data access to restricted access devices, the access credentials in the data access request need to be verified when accessing restricted access devices. To verify the credentials, it is necessary to store the ticket information of all the access credentials. Since there are currently a large number of data access requests for restricted access devices, more and more ticket information needs to be stored by the verification server. It can be seen that using the current method of verifying access credentials, the memory requirements of the verification server are relatively high, so how to reduce the memory requirements of the server when verifying the access credentials, and ensure the verification of the access credentials. The test accuracy has become a current research hotspot.
发明内容SUMMARY OF THE INVENTION
本发明实施例提供了一种数据处理系统、方法、相关设备及存储介质,可降低对访问凭证校验时的服务器的内存要求,并可提升对访问凭证的校验精准度。The embodiments of the present invention provide a data processing system, method, related equipment and storage medium, which can reduce the memory requirements of the server when verifying access credentials, and can improve the verification accuracy of access credentials.
一方面,本发明实施例提供了一种数据处理系统,所述数据处理系统至少总控服务器和目标分控服务器,所述总控服务器与所述目标分控服务器进行级联;所述总控服务器中存储有针对限制访问设备的访问凭证,以及生成所述访问凭证时使用的凭证数据;其中,On the one hand, an embodiment of the present invention provides a data processing system, the data processing system at least a master control server and a target sub-control server, the master control server and the target sub-control server are cascaded; the master control server and the target sub-control server are cascaded; The server stores the access credential for the restricted access device, and credential data used when generating the access credential; wherein,
所述目标分控服务器,用于响应目标客户端针对限制访问设备进行数据访问时的鉴权请求,并从所述鉴权请求中获取所述访问凭证,以及从所述目标分控服务器的缓存空间中获取所述凭证数据,若从所述缓存空间中获取失败,则向所述总控服务器发送所述凭证数据的获取请求;The target sub-control server is used to respond to the authentication request when the target client carries out data access to the restricted access device, and obtains the access credential from the authentication request, and from the cache of the target sub-control server Acquire the credential data in the space, and if the acquisition from the cache space fails, send an acquisition request for the credential data to the master control server;
所述总控服务器,用于响应所述目标分控服务器发送的获取请求,并向所述目标分控服务器返回所述凭证数据;The master control server is used to respond to the acquisition request sent by the target sub-control server, and return the voucher data to the target sub-control server;
所述目标分控服务器,还用于根据所述凭证数据生成参考访问凭证,并采用所述参考访问凭证对所述访问凭证进行校验。The target sub-control server is further configured to generate a reference access credential according to the credential data, and use the reference access credential to verify the access credential.
再一方面,本发明实施例提供了一种数据处理方法,所述数据处理方法由第一方面所述目标分控服务器执行,包括:In another aspect, an embodiment of the present invention provides a data processing method, where the data processing method is executed by the target sub-control server of the first aspect, including:
响应于目标客户端针对限制访问设备进行数据访问时的鉴权请求,从所述鉴权请求中获取所述访问凭证;Acquiring the access credential from the authentication request in response to an authentication request made by the target client for data access to the restricted access device;
从缓存空间中获取所述凭证数据,若从所述缓存空间中获取失败,则请求总控服务器返回生成所述访问凭证时使用的凭证数据;其中,所述总控服务器中存储有针对限制访问设备的访问凭证,以及生成所述访问凭证时使用的凭证数据;Acquire the credential data from the cache space, and if the acquisition from the cache space fails, request the general control server to return the credential data used in generating the access credential; wherein, the general control server stores information for restricting access. Access credentials for the device, and the credential data used in generating said access credentials;
根据所述凭证数据生成参考访问凭证,并采用所述参考访问凭证对所述访问凭证进行校验。A reference access credential is generated according to the credential data, and the access credential is verified by using the reference access credential.
再一方面,本发明实施例提供了一种数据处理装置,包括:In another aspect, an embodiment of the present invention provides a data processing apparatus, including:
获取单元,用于响应于目标客户端针对限制访问设备进行数据访问时的鉴权请求,从所述鉴权请求中获取所述访问凭证;an obtaining unit, configured to obtain the access credential from the authentication request in response to an authentication request when the target client performs data access to the restricted access device;
所述获取单元,还用于从缓存空间中获取所述凭证数据;The obtaining unit is further configured to obtain the credential data from the cache space;
请求单元,用于若从所述缓存空间中获取失败,则请求总控服务器返回生成所述访问凭证时使用的凭证数据;其中,所述总控服务器中存储有针对限制访问设备的访问凭证,以及生成所述访问凭证时使用的凭证数据;a requesting unit, configured to request the general control server to return the credential data used when generating the access credential if the acquisition from the cache space fails; wherein, the general control server stores the access credential for the restricted access device, and the credential data used in generating said access credential;
生成单元,用于根据所述凭证数据生成参考访问凭证;a generating unit, configured to generate a reference access credential according to the credential data;
校验单元,用于采用所述参考访问凭证对所述访问凭证进行校验。A verification unit, configured to verify the access credential by using the reference access credential.
再一方面,本发明实施例提供了一种服务器,包括处理器、输入设备、输出设备和存储器,所述处理器、输入设备、输出设备和存储器相互连接,其中,所述存储器用于存储支持终端执行上述方法的计算机程序,所述计算机程序包括程序指令,所述处理器被配置用于调用所述程序指令,执行如下步骤:In another aspect, an embodiment of the present invention provides a server, including a processor, an input device, an output device, and a memory, wherein the processor, the input device, the output device, and the memory are connected to each other, wherein the memory is used to store support The terminal executes the computer program of the above method, the computer program includes program instructions, the processor is configured to call the program instructions, and performs the following steps:
响应于目标客户端针对限制访问设备进行数据访问时的鉴权请求,从所述鉴权请求中获取所述访问凭证;Acquiring the access credential from the authentication request in response to an authentication request made by the target client for data access to the restricted access device;
从缓存空间中获取所述凭证数据,若从所述缓存空间中获取失败,则请求总控服务器返回生成所述访问凭证时使用的凭证数据;其中,所述总控服务器中存储有针对限制访问设备的访问凭证,以及生成所述访问凭证时使用的凭证数据;Acquire the credential data from the cache space, and if the acquisition from the cache space fails, request the general control server to return the credential data used in generating the access credential; wherein, the general control server stores information for restricting access. Access credentials for the device, and the credential data used in generating said access credentials;
根据所述凭证数据生成参考访问凭证,并采用所述参考访问凭证对所述访问凭证进行校验。A reference access credential is generated according to the credential data, and the access credential is verified by using the reference access credential.
再一方面,本发明实施例提供了一种计算机可读存储介质,所述计算机可读存储介质中存储有程序指令,所述程序指令被处理器执行时,用于执行如第一方面所述的数据处理方法。In another aspect, an embodiment of the present invention provides a computer-readable storage medium, where program instructions are stored in the computer-readable storage medium, and when the program instructions are executed by a processor, the program instructions are used to execute the method described in the first aspect. data processing method.
在本发明实施例中,数据处理系统中的总控服务器和目标分控服务器可级联部署,目标分控服务器检测到目标客户端对限制访问设备进行数据访问的鉴权请求时,可从该鉴权请求中确定出访问凭证,并在从总控访问中请求得到生成该访问凭证所使用的凭证数据后,按照生成该访问凭证时使用的凭证数据和生成该访问凭证时所使用的生成方法实时生成参考访问凭证,由于该参考访问凭证是基于凭证数据和生成方法实时生成的,所以该参考访问凭证被篡改的概率较低,也就使得目标分控服务器可获取到较高可信度的参考访问凭证,那么目标分控服务器则可基于该实时生成的参考访问凭证,对获取得到的访问凭证进行校验,以确定对该访问凭证的校验是否通过。由于参考访问凭证的可信度较高,且被篡改的可能性较低,那么基于参考访问凭证对获取得到的访问凭证的校验,得到的针对该访问凭证的校验结果的精准度也就比较高。In the embodiment of the present invention, the master control server and the target sub-control server in the data processing system can be deployed in cascade, and when the target sub-control server detects the authentication request of the target client for data access to the restricted access device, it can download the data from the The access credential is determined in the authentication request, and after requesting the credential data used to generate the access credential from the master control access, follow the credential data used in generating the access credential and the generation method used in generating the access credential The reference access credential is generated in real time. Since the reference access credential is generated in real time based on the credential data and the generation method, the probability of the reference access credential being tampered with is low, which also enables the target sub-control server to obtain high-credibility information. With reference to the access credential, the target sub-control server can verify the obtained access credential based on the reference access credential generated in real time to determine whether the verification of the access credential is passed. Since the reference access credential has high reliability and is less likely to be tampered with, the accuracy of the verification result for the access credential obtained by verifying the obtained access credential based on the reference access credential is also relatively high.
附图说明Description of drawings
为了更清楚地说明本发明实施例技术方案,下面将对实施例描述中所需要使用的附图作简单地介绍,显而易见地,下面描述中的附图是本发明的一些实施例,对于本领域普通技术人员来讲,在不付出创造性劳动的前提下,还可以根据这些附图获得其他的附图。In order to explain the technical solutions of the embodiments of the present invention more clearly, the following briefly introduces the accompanying drawings used in the description of the embodiments. Obviously, the drawings in the following description are some embodiments of the present invention, which are of great significance to the art For those of ordinary skill, other drawings can also be obtained from these drawings without any creative effort.
图1a是本发明实施例提供的一种数据处理系统的示意图;1a is a schematic diagram of a data processing system provided by an embodiment of the present invention;
图1b是本发明实施例提供的一种访问权限配置策略的示意图;1b is a schematic diagram of an access rights configuration policy provided by an embodiment of the present invention;
图1c是本发明实施例提供的一种对可信应用的配置示意图;1c is a schematic diagram of a configuration of a trusted application provided by an embodiment of the present invention;
图1d是本发明实施例提供的一种目标客户端的登录界面的示意图;1d is a schematic diagram of a login interface of a target client provided by an embodiment of the present invention;
图1e是本发明实施例提供的一种下发的可信应用的详情信息的示意图;1e is a schematic diagram of detailed information of a trusted application delivered according to an embodiment of the present invention;
图1f是本发明实施例提供的一种对限制访问设备具备访问权限的应用的示意图;1f is a schematic diagram of an application having access rights to a restricted access device according to an embodiment of the present invention;
图2a是本发明实施例提供的一种访问限制设备的示意图;2a is a schematic diagram of an access restriction device provided by an embodiment of the present invention;
图2b是本发明实施例提供的一种访问限制设备的示意图;2b is a schematic diagram of an access restriction device provided by an embodiment of the present invention;
图2c是本发明实施例提供的一种基于零信任进行数据访问的示意图;2c is a schematic diagram of data access based on zero trust provided by an embodiment of the present invention;
图2d是本发明实施例提供的一种分布式部署服务器的示意图;2d is a schematic diagram of a distributed deployment server provided by an embodiment of the present invention;
图2e是本发明实施例提供的一种分布式部署服务器的示意图;2e is a schematic diagram of a distributed deployment server provided by an embodiment of the present invention;
图3是本发明实施例提供的一种生成访问凭证的示意图;3 is a schematic diagram of generating an access credential provided by an embodiment of the present invention;
图4是本发明实施例提供的一种校验访问凭证的示意图;4 is a schematic diagram of verifying an access credential provided by an embodiment of the present invention;
图5是本发明实施例提供的一种数据处理方法的示意流程图;5 is a schematic flowchart of a data processing method provided by an embodiment of the present invention;
图6是本发明实施例提供的一种数据处理装置的示意流程图;6 is a schematic flowchart of a data processing apparatus provided by an embodiment of the present invention;
图7是本发明实施例提供的一种服务器的示意流程图。FIG. 7 is a schematic flowchart of a server provided by an embodiment of the present invention.
具体实施方式Detailed ways
本发明实施例提出了一种数据处理系统,该数据处理系统包括总控服务器和目标分控服务器,所述总控服务器与所述目标分控服务器进行级联;其中,该总控服务器用于存储该分控服务器生成的访问凭证,以及生成所述访问凭证时使用的凭证数据。基于本发明实施例提出的分层部署(级联部署)的数据处理系统,可实现对零信任的访问凭证的生成和校验,其中,该数据处理系统为该访问凭证的生成和校验提供相关服务,该数据处理系统的每个服务器可当做一个零信任节点,该零信任节点可独立地为每个数据访问请求颁发单独的访问凭证(或网络请求凭证)。进而,智能网关在转发该数据访问请求之前,可向该数据处理系统请求对携带的访问凭证进行校验,并在校验通过时才对该数据访问请求进行转发,通过引入级联部署的数据处理系统对访问凭证进行生成和校验,可解决在分布式部署的场景中,服务端单纯通过总控节点来生成访问凭证,并将生成的访问凭证全量同步给子节点来实现验证访问凭证的导致服务端存储压力过大的问题,通过本发明实施例提出的数据处理系统对访问凭证的处理,各个零信任节点之间相对独立,方便平行扩容,同时某个节点的故障也不会影响使用,能够做到对服务器的高效访问,实现数据处理系统的高可用、高并发以及链路安全。An embodiment of the present invention provides a data processing system, the data processing system includes a master control server and a target sub-control server, the master control server and the target sub-control server are cascaded; wherein, the master control server is used for The access credential generated by the sub-control server and credential data used in generating the access credential are stored. The data processing system based on the layered deployment (cascading deployment) proposed in the embodiment of the present invention can realize the generation and verification of zero-trust access credentials, wherein the data processing system provides the generation and verification of the access credentials. For related services, each server of the data processing system can be regarded as a zero-trust node, and the zero-trust node can independently issue a separate access credential (or network request credential) for each data access request. Furthermore, before forwarding the data access request, the intelligent gateway may request the data processing system to verify the carried access credentials, and only forward the data access request when the verification is passed. The processing system generates and verifies the access credentials, which can be solved in the distributed deployment scenario. The server simply generates the access credentials through the master control node, and synchronizes all the generated access credentials to the child nodes to verify the access credentials. Due to the problem of excessive storage pressure on the server, through the processing of access credentials by the data processing system proposed in the embodiment of the present invention, each zero-trust node is relatively independent, which is convenient for parallel expansion, and the failure of a node will not affect the use of , can achieve efficient access to the server, and achieve high availability, high concurrency and link security of the data processing system.
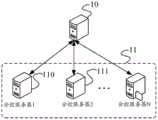
本发明实施例通过构建总控节点(总控服务器)和二级节点(二级服务器,或分控服务器),其中零信任网络访问服务(即对访问凭证进行生成和校验的服务)可以在二级节点部署,那么请求进行数据访问时的访问凭证可以在任意一个二级零信任节点生成,而在对该访问凭证进行校验时,也可以在任意一个二级零信任节点验证。在一个实施例中,该数据处理系统可以包括多个与总控服务器级联的分控服务器,如图1a所示,其中,级联结构中的总控服务器可以是如图1a中由10标记的服务器,与该总控服务器级联的分控服务器可以是如图1a中由11标记的任意一个或多个分控服务器,该数据处理系统中包括的总控服务器10和至少一个分控服务器11可以是相同类型的服务器,也可以是不同类型的服务器,本发明实施例对总控服务器和分控服务器的服务器类型不做限定。其中,目标分控服务器为与该总控服务器级联的多个分控服务器中的任一个;该目标分控服务器用于响应目标客户端针对限制访问设备进行数据访问时的鉴权请求,并从所述鉴权请求中获取所述访问凭证,以及从所述目标分控服务器的缓存空间中获取所述凭证数据,若从所述缓存空间中获取失败,则向所述总控服务器发送所述凭证数据的获取请求。In this embodiment of the present invention, by constructing a master control node (master control server) and a secondary node (secondary server, or sub-control server), the zero-trust network access service (that is, the service for generating and verifying access credentials) can be If the second-level node is deployed, the access credentials for requesting data access can be generated at any second-level zero-trust node, and when the access credentials are verified, they can also be verified at any second-level zero-trust node. In one embodiment, the data processing system may include a plurality of sub-control servers cascaded with the master control server, as shown in FIG. 1a, wherein the master control server in the cascade structure may be marked by 10 in FIG. 1a The server, the sub-control server cascaded with the main control server can be any one or more sub-control servers marked by 11 in Fig. 1a, the
在一个实施例中,该目标分控服务器可以是图1a中由11标记的至少一个分控服务器中的任意一个,该目标分控服务器例如可以是如图1a中由110标记的服务器,或者是图1a中由111标记的服务器。所述总控服务器10,用于响应所述获取请求,并向所述目标分控服务器返回生成所述访问凭证时使用的凭证数据;所述目标分控服务器,还用于根据所述总控服务器返回的凭证数据生成参考访问凭证,并采用所述参考访问凭证对所述访问凭证进行校验。在一个实施例中,所述所述数据处理系统还包括智能网关,该智能网关用于从所述目标客户端针对所述限制访问设备的数据访问请求中获取所述访问凭证,并将携带所述访问凭证的鉴权请求发送给所述目标分控服务器,此外,该智能网关还用于从所述目标分控服务器获取针对所述访问凭证的校验结果,并在所述校验结果指示所述访问凭证通过校验时,允许所述目标客户端访问所述限制访问设备;在校验结果指示所述访问凭证未通过校验,所述智能网关则禁止所述目标客户端访问所述限制访问设备。在一个实施例中,该智能网关也可以是所述数据处理系统的外接设备,该智能网关和目标分控服务器建立有通信连接。In one embodiment, the target sub-control server may be any one of the at least one sub-control server marked by 11 in FIG. 1a, and the target sub-control server may be, for example, the server marked by 110 in FIG. 1a, or The server marked by 111 in Figure 1a. The
在一个实施例中,所述访问凭证是由与总控服务器级联的任一分控服务器生成的;若所述访问凭证是由所述目标分控服务器生成的,则所述目标分控服务器的本地缓存中存储有生成该访问凭证时所使用的凭证数据,在生成参考访问凭证时,该目标分控服务器则可从本地缓存中获取生成所述访问凭证时使用的凭证数据。或者,若所述访问凭证是由所述至少一个分控服务器中除所述目标分控服务器之外的任一个生成的,则所述目标分控服务器的本地缓存中未存储生成该访问凭证时所需的凭证数据,但生成该访问凭证的分控服务器将生成该访问凭证时使用的凭证数据上传到总控服务器中进行了存储,所以,目标分控服务器可在生成参考访问凭证时,请求所述总控服务器返回生成所述访问凭证时使用的凭证数据。其中,若生成该访问凭证的分控服务器为参考分控服务器,则总控服务器与所述参考分控服务器进行级联;那么,也就是说,所述总控服务器中存储的所述访问凭证,以及生成所述访问凭证时使用的凭证数据是由所述目标分控服务器生成并上报的;或者,所述总控服务器中存储的所述访问凭证,以及生成所述访问凭证时使用的凭证数据是由所述参考分控服务器生成并上报的。In one embodiment, the access credential is generated by any sub-control server cascaded with the master control server; if the access credential is generated by the target sub-control server, the target sub-control server The credential data used when generating the access credential is stored in the local cache of the target sub-control server. When generating the reference access credential, the target sub-control server can obtain the credential data used in generating the access credential from the local cache. Or, if the access credential is generated by any one of the at least one sub-control server except the target sub-control server, then the local cache of the target sub-control server does not store the time when the access credential is generated. The required credential data, but the sub-control server that generates the access credential uploads the credential data used in generating the access credential to the master control server for storage, so the target sub-control server can request the access credential when generating the reference access credential. The master control server returns the credential data used in generating the access credential. Wherein, if the sub-control server that generates the access credential is a reference sub-control server, the main control server is cascaded with the reference sub-control server; then, that is, the access credential stored in the main control server , and the credential data used when generating the access credential is generated and reported by the target sub-control server; or, the access credential stored in the master control server, and the credential used when generating the access credential The data is generated and reported by the reference sub-control server.
在一个实施例中,目标客户端在需要对限制访问设备进行访问时,向数据处理系统中的分控服务器请求访问凭证,若该目标客户端从参考分控服务器中获取到访问凭证,该目标客户端在对限制访问设备进行访问时,需要先将获取到的访问凭证添加到数据访问请求中,并将该数据访问请求发送到智能网关;该智能网关用于接收目标客户端请求针对限制访问设备的数据访问请求后,从该数据访问请求中获取得到访问凭证,并将携带该访问凭证的鉴权请求发送给目标分控服务器,目标分控服务器则可在接收到该鉴权请求后,对该鉴权请求中携带的访问凭证进行校验。在一个实施例中,对访问凭证进行校验的目标分控服务器和生成访问凭证的参考分控服务器可以是同一分控服务器,也可以是不同分控服务器,如该目标分控服务器和该参考分控服务器可以都是如图1a中由110标记的服务器,或者该目标分控服务器可以是由110标记的服务器,而参考分控服务器是由111标记的服务器。In one embodiment, when the target client needs to access the restricted access device, it requests the access credential from the sub-control server in the data processing system. If the target client obtains the access credential from the reference sub-control server, the target When the client accesses the restricted access device, it needs to add the obtained access credential to the data access request first, and send the data access request to the intelligent gateway; the intelligent gateway is used to receive the target client's request for restricted access. After the data access request of the device, the access credential is obtained from the data access request, and the authentication request carrying the access credential is sent to the target sub-control server. After receiving the authentication request, the target sub-control server can Verify the access credential carried in the authentication request. In one embodiment, the target sub-control server that verifies the access credential and the reference sub-control server that generates the access credential may be the same sub-control server or different sub-control servers, such as the target sub-control server and the reference sub-control server. The sub-control servers may all be servers denoted by 110 in FIG. 1a, or the target sub-control server may be a server denoted by 110 and the reference sub-control server is a server denoted by 111.
在一个实施例中,限制访问设备的管理人员将预先配置并下发零信任策略到目标客户端,该零信任策略用于确定终端设备中各应用对限制访问设备(或限制访问设备中的部分或全部功能)的访问权限,如图1b所示,零信任策略由组织架构里的用户(或用户组),可信应用(即上述的目标应用)和业务系统这三方面配置。其中,可信应用是指目标客户端授信的,对应终端设备可访问内部业务系统的应用载体,具体包括应用名,应用MD5(一种消息摘要算法),签名信息等。如图1b中所示的用户或用户组为零信任策略的粒度为单个用户,如果为某个用户组下发零信任策略,则该用户组的所有用户共享同一个零信任策略,可信应用为管理端(管理人员)授信的,终端设备可访问内部业务系统的应用载体,包括应用名,应用MD5,签名信息等,业务系统包括至少一个限制访问设备,业务系统一般由企业内部OA站点,开发测试环境,运维和正式生产环境等组成,是访问主体(人/设备/应用)需要访问的对象,其中,访问主体对访问客体进行访问,访问主体是数据访问请求中发起该数据访问请求的一方,对业务资源进行访问的人/设备/应用,访问客体是数据访问请求中被访问的一方,例如可以是限制访问设备中的业务资源,数据,开发测试环境,运维环境等等。In one embodiment, the administrator of the restricted access device will pre-configure and deliver a zero-trust policy to the target client, where the zero-trust policy is used to determine whether each application in the terminal device has any effect on the restricted access device (or part of the restricted access device). As shown in Figure 1b, the zero trust policy is configured by users (or user groups) in the organizational structure, trusted applications (that is, the above-mentioned target applications) and business systems. The trusted application refers to the application carrier trusted by the target client and the corresponding terminal device can access the internal business system, specifically including the application name, application MD5 (a message digest algorithm), signature information, and the like. As shown in Figure 1b, the granularity of the zero-trust policy for a user or user group is a single user. If a zero-trust policy is issued for a user group, all users of the user group share the same zero-trust policy, and the trusted application For the management terminal (manager), the terminal device can access the application carrier of the internal business system, including the application name, application MD5, signature information, etc. The business system includes at least one restricted access device. The development and test environment, operation and maintenance, and formal production environment are the objects that the access subject (person/device/application) needs to access. The access subject accesses the access object, and the access subject is the data access request initiated in the data access request. The person/device/application that accesses business resources, and the object of access is the party accessed in the data access request, for example, it can be restricted access to business resources, data, development and testing environments, operation and maintenance environments, etc. in the device.
在一个实施例中,用户组是企业组织架构里的一个节点,同父节点和子节点具有上下级的关系,如图1b中的A用户属于测试用户组,测试用户组又属于全网账户。其中,针对可信应用的配置可如图1c所示,具体包括包括进程名、签名信息、版本,进程MD5和sha256(一种加密哈希算法)的配置。在管理人员配置好业务系统和可信应用后,只需要选定需要下发零信任策略(包括记录有可信应用的访问权限的访问权限信息),即可完成对零信任策略的下发。对应的,终端用户则可通过登录目标客户端实现零信任办公功能,其中,对目标客户端的登录界面如图1d所示,在登录完成后,登录用户即可看到管理用户下发的可信应用的详情信息,如图1e所示,根据管理人员下发的用户级策略,登录用户具有对指定的限制访问设备的访问权限,如图1f所示。其中,该目标客户端例如可以是iOA客户端,iOA客户端是一种基于零信任策略的客户端,该零信任策略记录了iOA客户端的登陆用户可使用的进程以及可访问的业务站点(或业务服务器,或限制访问设备等),该零信任策略的粒度为登录用户。In one embodiment, the user group is a node in the enterprise organizational structure, and has a superior-subordinate relationship with the parent node and child node. As shown in Figure 1b, user A belongs to the test user group, which in turn belongs to the entire network account. The configuration for the trusted application may be as shown in Figure 1c, and specifically includes the configuration including the process name, signature information, version, process MD5 and sha256 (an encryption hash algorithm). After the administrator has configured the business system and trusted applications, he only needs to select the zero-trust policy to be issued (including the access authority information that records the access authority of the trusted application), and then the zero-trust policy can be issued. Correspondingly, the terminal user can realize the zero-trust office function by logging in to the target client. The login interface of the target client is shown in Figure 1d. After the login is completed, the logged-in user can see the trusted information issued by the management user The detailed information of the application is shown in Figure 1e. According to the user-level policy issued by the administrator, the logged-in user has access rights to the specified restricted access device, as shown in Figure 1f. Wherein, the target client may be, for example, an iOA client, which is a client based on a zero-trust policy, and the zero-trust policy records the processes that can be used by the logged-in user of the iOA client and the accessible business sites (or business servers, or restrict access to devices, etc.), the granularity of this zero-trust policy is the logged-in user.
终端设备在登录用户登录目标客户端对限制访问设备请求访问时,对登录用户对该限制访问设备的网络请求进行劫持,其中,对网络请求的劫持可以是由该终端设备包括的目标客户端劫持的,或者,也可以是由终端设备包括的代理客户端劫持的。可以理解的是,在零信任策略保护下的任何业务设备(如上述的限制访问设备)在被访问时,均需要先对访问请求进行校验(即对该访问请求中携带的访问凭证进行校验),并在校验通过后再执行访问,以保障被访问的业务设备的安全性。其中,基于对网络请求的劫持,劫持该网络请求的目标客户端(或代理客户端)可获取得到源网际互连协议(Internet Protocol,IP),源端口,目的IP,目的端口,目标应用的进程标识(Process Identification,PID)等参数,其中,IP也可称作域名,源IP即是目标应用的IP,目的IP即是限制访问设备的IP。When the login user logs in to the target client and requests access to the restricted access device, the terminal device hijacks the network request of the login user to the restricted access device, wherein the hijacking of the network request may be hijacked by the target client included in the terminal device Alternatively, it can also be hijacked by the proxy client included in the terminal device. It can be understood that when any business device (such as the above-mentioned restricted access device) under the protection of the zero trust policy is accessed, the access request needs to be verified first (that is, the access credential carried in the access request is verified. verification), and perform the access after the verification is passed to ensure the security of the accessed service equipment. Among them, based on the hijacking of the network request, the target client (or proxy client) that hijacks the network request can obtain the source Internet Protocol (Internet Protocol, IP), source port, destination IP, destination port, target application Process identification (Process Identification, PID) and other parameters, where IP can also be called a domain name, the source IP is the IP of the target application, and the destination IP is the IP that restricts access to the device.
在一个实施例中,如果对网络请求的劫持是由代理客户端劫执行的,且生成并发放对限制访问设备进行访问时所需的访问凭证,以及对该访问凭证进行校验的分控服务器均为目标分控服务器,如图2a所示,代理客户端(如图2a中由20标记的客户端)在劫持到该网络请求后,则可将源IP,源端口,目的IP,目的端口,应用进程PID等参数发送给目标客户端(iOA客户端,如图2a中由21标记的客户端),目标客户端21通过代理客户端20发送的进程PID可采集得到进程的MD5(一种消息摘要算法),进程路径,进程的最近修改时间,版权信息,签名信息等,并可连同代理客户端传递过来的网络请求的源IP(或源域名),源端口,目的IP(或目的域名),目的端口,向目标分控服务器(如图2a中由21标记的控服务器,可以理解,该目标分控服务器可以是如图1a中由11标记的任一分控服务器)发送申请访问凭证的请求,其中,如果申请成功,目标分控服务器21则将访问凭证,访问凭证的最大使用次数,该访问凭证的有效时间作为响应发送给目标客户端21,该目标客户端21则转发访问凭证,访问凭证的最大使用次数,该访问凭证的有效时间给该代理客户端20。In one embodiment, if the hijacking of the network request is performed by the proxy client, the access credentials required for accessing the restricted access device are generated and issued, and the sub-control server that verifies the access credentials Both are target sub-control servers. As shown in Figure 2a, after the proxy client (the client marked by 20 in Figure 2a) hijacks the network request, it can send the source IP, source port, destination IP, destination port , the application process PID and other parameters are sent to the target client (iOA client, the client marked by 21 in Figure 2a), the target client 21 can collect the MD5 of the process through the process PID sent by the proxy client 20 (a kind of message digest algorithm), process path, the last modification time of the process, copyright information, signature information, etc., and can be combined with the source IP (or source domain name), source port, destination IP (or destination domain name) of the network request passed by the proxy client ), the destination port, to the target sub-control server (the control server marked by 21 in Figure 2a, it can be understood that the target sub-control server can be any sub-control server marked by 11 in Figure 1a) to send the application for access credentials If the application is successful, the target sub-control server 21 sends the access credential, the maximum number of times the access credential is used, and the valid time of the access credential to the target client 21 as a response, and the target client 21 forwards the access credential , the maximum number of times the access credential is used, and the valid time of the access credential is given to the proxy client 20 .
访问凭证也可称之为网络请求凭证(小票),该访问凭证是目标分控服务器22为单个网络请求(或访问请求)发放的授权信息,用于标识该网络请求的授权状态。代理客户端20用于接收访问凭证,向智能网关(如图2a中由13标记的网关)发送数据访问请求,该数据访问请求可以是基于超文本传输安全协议(Hyper Text Transfer Protocol overSecureSocket Layer,Https)的请求(或http请求),其中,在代理客户端20向智能网关23发送该Https请求时,可在该Https请求的授权(Authorization)首部字段中带上该访问凭证,智能网关23收到该数据访问请求,可从该数据访问请求中解析得到访问凭证,并将该访问平针添加到校验请求后发送给目标分控服务器22,目标分控服务器22则可对访问凭证进行校验,如果目标分控服务器22对访问凭证的校验成功,则该智能网关23跟代理客户端20成功建立连接,之后代理客户端20则可代理目标应用(如图2a中由24标记的任一应用)对限制访问设备(如图2a中由25标记的业务服务器中的任一业务服务器)进行访问。The access credential may also be referred to as a network request credential (small ticket), the access credential is the authorization information issued by the
在目标客户端21向目标分控服务器22申请获取访问凭证时,为了充分检验对限制访问设备25的访问进程是否为恶意进程,目标客户端21会向服务端22发起进程送检请求,请求的参数包括请求访问的限制访问设备25的目的统一资源定位系统(uniform resourcelocator,url)的标识,进程MD5,哈希编码,进程路径,证书链详细信息等。其中证书链详细信息包括:摘要算法、根证书名称、根证书序列号、根证书到期时间、中级证书名称、中级证书序列号、中级证书到期时间、签名证书名称、签名证书序列号、签名证书到期时间、签名状态、签名用户的姓名、时间戳、签名验证错误信息。目标分控服务器22接收到这些信息后,可定期向威胁情报云查服务安知、tav(一种杀毒引擎)(如图2a中由26的标记所示)等发起文件送检请求,如果是恶意进程文件,则目标分控服务器22会通知目标客户端21,中断目标应用24对限制访问设备25的访问请求,以禁止目标应用24对限制访问设备25的访问。When the
在一个实施例中,智能网关23部署在限制访问设备(或限制访问设备的应用程序)和数据资源的入口,负责每一个访问限制访问设备的会话请求的验证,授权和转发;目标客户端21是安装在该终端设备(如图2a中由200标记的设备所示)上的安全代理(Agent),负责验证终端设备上登陆用户的可信身份,验证该终端设备是否可信以及目标应用是否可信,并将未知的进程(如对业务目标分控服务器的访问请求或访问进程等)向目标分控服务器申请送检;代理客户端20通过TUN/TAP(一种操作系统内核中的虚拟网络设备)虚拟网卡劫持网络请求,通过目标客户端21鉴权后负责将访问请求转发给智能网关,如果没有通过鉴权则直接中断连接。目标分控服务器22包括策略中心,送检服务和凭证(或票据)中心,该策略中心通过策略控制引擎对业务流量进行安全调度,按照人-设备-软件-应用颗粒度授权;目标分控服务器基于送检服务定期向威胁情报云查服务安知或tav定期发起文件送检,并在识别出恶意进程后通知目标客户端执行异步阻断操作;凭证中心用于生成和下发访问凭证,此外,该目标分控服务器还包括各种模块,身份验证模块对用户身份进行验证,设备可信模块验证设备硬件信息和设备安全状态,应用检测模块检测应用进程是否安全,如是否有漏洞,是否有病毒木马等。In one embodiment, the intelligent gateway 23 is deployed at the entrance of the restricted access device (or the application program of the restricted access device) and the data resource, and is responsible for the verification, authorization and forwarding of each session request of the restricted access device; the
在一个实施例中,如果对网络请求的劫持是由目标客户端劫持的,生成并发放对限制访问设备进行访问时所需的访问凭证,以及对该访问凭证进行校验的分控服务器均为目标分控服务器,如图2b所示,目标客户端21在劫持到目标应用24发起的网络请求后,则可直接向目标分控服务器22(即目标分控服务器的凭证中心)发送申请访问凭证的请求,如果申请成功,目标分控服务器22则将访问凭证,访问凭证的最大使用次数,该访问凭证的有效时间作为响应发送给目标客户端21,并由目标客户端21向智能网关23发送https请求,在智能网关23从目标分控服务器22获取到对该请求中携带的访问凭证校验成功后,与该目标客户端21建立通信连接,以使该目标客户端21代理目标应用24对限制访问设备25的数据访问。在具体实现中,目标分控服务器22在获取到该访问凭证的获取请求后,则可基于获取到的各参数生成访问凭证,并将生成的访问凭证发送给目标客户端21,其中,在该目标客户端21接收到该访问凭证后,则该目标客户端21可代理该目标应用发起对限制访问设备的数据访问。In one embodiment, if the hijacking of the network request is hijacked by the target client, the access credential required for accessing the restricted access device is generated and issued, and the sub-control server that verifies the access credential is both The target sub-control server, as shown in Figure 2b, after the
在一个实施例中,目标客户端21在代理对限制访问设备25的数据访问时,该目标客户端21可先将携带访问凭证的数据访问请求发送给目标分控服务器22,目标分控服务器22在接收到该数据访问请求后,则可从该数据访问请求中确定出针对限制访问设备的访问凭证(即的访问凭证),并对该访问凭证进行校验,其中,在目标分控服务器22对访问凭证的校验通过后,才允许目标客户端对限制访问设备的代理访问,可有效保障目标客户端对限制访问设备的访问安全性问题。在一个实施例中,目标分控服务器22在从接收到的数据访问请求中确定出访问凭证后,可先确定该目标分控服务器22在生成该访问凭证时采用的凭证数据,该凭证数据包括上述的各参数等,进而目标分控服务器22可按照生成该访问凭证时所采取的算法对该凭证数据进行处理,从而重新生成参考访问凭证,其中,生成的参考访问凭证是可信的访问凭证。目标分控服务器在对目标客户端发送过来的访问凭证进行校验时,则可采用该参考访问凭证对该目标客户端发送的访问凭证进行校验,如可将该参考访问凭证和目标客户端发送的访问凭证进行对比,从而根据对比结果确定目标客户端发送的访问凭证是否验证通过,其中,如果对比结果指示参考访问凭证和目标客户端发送的访问凭证一致,或者对比结果指示参考访问凭证和目标客户端发送的访问凭证的相似程度满足预设相似度阈值(如98%等),则可认为对目标客户端发送的访问凭证的校验通过。In one embodiment, when the
在目标分控服务器确定对该目标客户端发送的针对限制访问设备的访问凭证的校验通过后,则可允许目标客户端发起的代理目标应用对限制访问设备进行访问的数据访问请求。其中,通过本发明实施例提出的在目标客户端基于访问凭证对限制访问设备进行访问时,目标分控服务器采用实时生成参考访问凭证以实现对该目标客户端的访问凭证进行校验的方法,可有效提升对访问凭证的校验的精准度,基于对访问凭证的校验精准度的提升,可保证对限制访问设备时的安全性。After the target sub-control server determines that the verification of the access credential sent by the target client for the restricted access device is passed, the proxy target application initiated by the target client can be allowed to access the data access request to the restricted access device. Wherein, when the target client accesses the restricted access device based on the access credential proposed in the embodiment of the present invention, the target sub-control server adopts the method of generating the reference access credential in real time to realize the verification of the access credential of the target client. Effectively improve the accuracy of the verification of the access credentials, based on the improvement of the verification accuracy of the access credentials, it can ensure the security when restricting access to the device.
在一个实施例中,上述的数据处理系统充当零信任网络安全服务的提供方,并基于零信任代理(如上述的目标客户端或代理客户端)和智能网关,为访问主体(如上述的目标应用)通过网络请求访问客体(如上述的限制访问设备)的资源提供统一入口,其中,该数据处理系统(具体为该数据处理系统中的目标分控服务器)也为统一入口提供鉴权操作,只有通过鉴权的网络请求才能由零信任代理转发给智能网关,通过访问网关代理实际业务系统的访问,如图2c所示。其中,该数据处理系统既能够通过单一部署方式适应中型企事业单位和政府,也能够通过分布式级联部署方式适应大型企业集团和多级垂直政府电子政务系统。为了保障零信任网络访问核心业务(即限制访问设备所提供的全部或部分业务)的稳定运行,可采取零信任核心服务异地多活的方案,其中,核心业务和基础业务部署在总控服务器(或总控节点),各个不同的业务部署在不同的分控服务器(或分控节点,或二级节点)中。该总控服务器通过集群部署实现自身的可用性,并定期与各分控服务器之间实现配置和数据同步。如图2d所示,其中,总控服务器可提供并分发到各分控服务器的配置可包括:短连接服务配置,日志上报服务配置,长连接服务配置,控制中心服务配置,以及下载服务配置等。该总控服务器通过集群部署实现对分控服务器,以及分控服务器提供的业务和网关节点进行控制,如对业务2对应的分控服务器和对应的网关节点进行控制,对业务3的分控控服务器和对应的网关节点进行控制,其中,该总控服务器和分控服务器可建立在不同的机房中,如可将总控服务器建立在机房1,而将分控服务器分别建立在机房2和机房3中。In one embodiment, the above-mentioned data processing system acts as a provider of zero-trust network security services, and based on a zero-trust proxy (such as the above-mentioned target client or proxy client) and an intelligent gateway, provides access to the subject (such as the above-mentioned target application) through the network request to access the resources of the object (such as the above-mentioned restricted access device) to provide a unified entry, wherein, the data processing system (specifically, the target sub-control server in the data processing system) also provides an authentication operation for the unified entry, Only the authenticated network request can be forwarded to the intelligent gateway by the zero-trust proxy, and the access to the actual business system is represented by the access gateway, as shown in Figure 2c. Among them, the data processing system can adapt to medium-sized enterprises, institutions and governments through a single deployment method, and can also adapt to large enterprise groups and multi-level vertical government e-government systems through distributed cascade deployment. In order to ensure the stable operation of zero-trust network access to core services (that is, to restrict access to all or part of the services provided by devices), a zero-trust core service remote multi-active solution can be adopted, in which the core services and basic services are deployed on the master control server ( or master control node), and different services are deployed in different sub-control servers (or sub-control nodes, or secondary nodes). The master control server realizes its own availability through cluster deployment, and periodically realizes configuration and data synchronization with each sub-control server. As shown in Figure 2d, the configuration that the master control server can provide and distribute to each sub-control server can include: short connection service configuration, log reporting service configuration, long connection service configuration, control center service configuration, and download service configuration, etc. . The master control server can control the sub-control server, the services provided by the sub-control server, and the gateway nodes through cluster deployment. The server and the corresponding gateway node are controlled, wherein the master control server and the sub-control server can be established in different computer rooms, for example, the master control server can be established in
在一个实施例中,总控服务器,分控服务器,目标客户端,代理客户端和智能网关的数据交换关系可如图2e所示。总控服务器部署的核心基础服务例如可以是心跳服务,策略同步服务,设备管控服务等,总控服务器可定期将相关配置和数据同步给各分控服务器,各分控服务器中的数据或配置需要修改时,可通过总控服务器进行修改,并将修改完成的配置和数据同步给各分控服务器。在一个实施例中,目标客户端(iOA客户端)可通过心跳服务(心跳服务的频率可以设置)从总控服务器(或分控服务器)定期拉取系统全局配置和当前登录用户的零信任策略,并加密存储在目标客户端本地。其中,系统全局配置包括当前总控服务器的连接地址,各分控服务器的连接地址,和各业务对应的分控服务器,以及网关集群的所有服务连接地址等,以使客户端可基于上述地址进行访问凭证的获取和转发。下面对访问凭证的生成和校验过程进行详细说明。In one embodiment, the data exchange relationship between the master control server, the sub-control server, the target client, the proxy client and the intelligent gateway may be as shown in FIG. 2e. The core basic services deployed by the master control server can be, for example, heartbeat service, policy synchronization service, equipment management and control service, etc. The master control server can periodically synchronize relevant configuration and data to each sub-control server, and the data or configuration in each sub-control server needs to be When modifying, it can be modified through the master control server, and the modified configuration and data can be synchronized to each sub-control server. In one embodiment, the target client (iOA client) can periodically pull the system global configuration and the zero-trust policy of the currently logged-in user from the master control server (or sub-control server) through the heartbeat service (the frequency of the heartbeat service can be set). , and encrypted and stored locally on the target client. Among them, the global configuration of the system includes the connection address of the current master control server, the connection address of each sub-control server, the sub-control server corresponding to each business, and the connection addresses of all services of the gateway cluster, etc. Acquisition and forwarding of access credentials. The generation and verification process of the access credential is described in detail below.
在一个实施例中,目标分控服务器从目标客户端获取到的针对限制访问设备的数据访问请求,是目标应用请求对限制访问设备进行业务访问(或数据访问)时生成的,其中,为了保证限制访问设备被访问时的安全性,以避免该限制访问设备被恶意的数据访问请求攻击,并造成限制访问设备的设备故障,或重要数据丢失的问题,在目标应用请求访问该限制访问设备时,该目标应用所在的终端设备可对该目标应用请求访问该限制访问设备的流量(或网络请求)进行劫持,其中,该终端设备在对该目标应用请求对限制访问设备进行访问的流量进行劫持时,可以由该终端设备中的目标客户端执行,或者,也可以由该终端设备中的代理客户端执行。在本发明实施例中,以该网络请求被代理客户端进行劫持的情况进行详细说明,在该网络请求被目标客户端劫持时,可以理解,由目标客户端执行该代理客户端的相关步骤,那么在该网络请求是由目标客户端劫持时的实施方式可参见本发明实施例。In one embodiment, the data access request for the restricted access device obtained by the target sub-control server from the target client is generated when the target application requests service access (or data access) to the restricted access device. The security of the restricted access device when it is accessed, to avoid the restricted access device being attacked by malicious data access requests, and cause the device failure of the restricted access device, or the loss of important data, when the target application requests access to the restricted access device. , the terminal device where the target application is located can hijack the traffic (or network request) that the target application requests to access the restricted access device, wherein the terminal device requests the target application to hijack the traffic of the restricted access device to access , it can be executed by the target client in the terminal device, or it can also be executed by the proxy client in the terminal device. In the embodiment of the present invention, the case where the network request is hijacked by the proxy client is described in detail. When the network request is hijacked by the target client, it can be understood that if the target client executes the relevant steps of the proxy client, then For the implementation when the network request is hijacked by the target client, reference may be made to the embodiments of the present invention.
在代理客户端在劫持到网络请求后,则可向目标客户端发起访问凭证(即小票)的申请,目标客户端则可尝试申请访问凭证。其中,若该目标客户端申请向参考分控服务器申请访问凭证,参考分控服务器可从目标客户端获取得到登陆用户登陆该目标客户端的登陆用户id,目标应用id,终端设备id和请求访问的限制访问设备的设备标识(如目的uzl和端口)等参数;此外,参考分控服务器还可在获取到目标客户端对访问凭证的申请时,从本地缓存中获取登陆凭证,从而可基于登陆凭证,和前述获取到的登陆用户id,目标应用id,终端设备id和限制访问设备的设备标识(如目的uzl和端口)等访问参数进行票据置换(即大票换取小票),从而得到访问凭证(小票)。其中,该登陆凭证是登陆用户登陆目标客户端时生成的。在一个实施例中,如果参考分控服务器从本地缓存中获取登陆凭证失败,则该参考分控服务器可基于终端设备id从总控服务器中获取到该登陆用户登陆目标客户端时的登陆凭证。其中,需要说明的是,目标客户端每次进行票据置换之前均会先从本地缓存中查找所需的访问凭证,如果在本地缓存中未查找到该所需的访问凭证,该目标客户端在可采集网络请求的进程可移植的执行体(Portable Execute,PE)文件信息,如进程文件全路径、MD5、签名信息、进程修改时间等信息,以及操作系统信息,url访问信息,设备信息,和登陆用户的登录信息代理、登录票据等相关信息,同步给参考分控服务器发起小票申请。After the proxy client hijacks the network request, it can initiate an application for an access credential (ie, a small ticket) to the target client, and the target client can try to apply for the access credential. Wherein, if the target client applies for an access credential from the reference sub-control server, the reference sub-control server can obtain from the target client the login user id, target application id, terminal device id and the requesting access Parameters such as device identification (such as destination uzl and port) of the access device are restricted; in addition, the reference sub-control server can also obtain the login credentials from the local cache when it obtains the target client's application for access credentials, so that it can be based on the login credentials. , and perform ticket replacement (that is, exchange a large ticket for a small ticket) with the access parameters such as the login user id, target application id, terminal device id and device identification (such as destination uzl and port) that restrict access to the device obtained above, so as to obtain the access credential (receipt). The login credentials are generated when the login user logs in to the target client. In one embodiment, if the reference sub-control server fails to obtain the login credentials from the local cache, the reference sub-control server can obtain the login credentials of the login user when logging in to the target client from the master control server based on the terminal device id. Among them, it should be noted that the target client will look up the required access credential from the local cache before each ticket replacement. If the required access credential is not found in the local cache, the target client will It can collect the Portable Execute (PE) file information of the process requested by the network, such as the full path of the process file, MD5, signature information, process modification time and other information, as well as operating system information, url access information, device information, and The log-in information agent, log-in ticket and other related information of the logged-in user are synchronized to the reference sub-control server to initiate a small ticket application.
登陆凭证为登陆用户登陆iOA客户端时,为该登陆用户分配的登陆凭证,不同用户登陆目标客户端后,基于登陆用户的身份不同可确定登陆用户对应允许访问的业务设备(或站点),也就是说,基于登陆用户的身份的不同,该参考分控服务器为不同登陆用户所生成的登陆凭证也不相同,其中,该登录凭证是登陆用户成功登录目标客户端(如上述的iOA客户端)后,参考分控服务器为登陆用户指定的一个加密串,该加密串(即该登陆凭证)表示该登陆用户的登录授权信息,包括用户信息和授权有效期,其中,参考分控服务器在生成该登陆凭证后,可将该登陆凭证可加密存储在目标客户端中,或进行本地存储。参考分控服务器获取到访问参数和登陆凭证后,则可基于该登陆凭证和该访问参数生成对限制访问设备进行访问时所需的访问凭证。可以理解的是,该参考分控服务器即是该目标客户端的后台服务器。The login credential is the login credential assigned to the login user when the login user logs in to the iOA client. After different users log in to the target client, the business device (or site) that the login user is allowed to access can be determined based on the identity of the login user. That is to say, based on the different identities of the login users, the login credentials generated by the reference sub-control server for different login users are also different, wherein the login credentials are the login users successfully log in to the target client (such as the above iOA client) Then, refer to an encrypted string specified by the sub-control server for the login user, and the encrypted string (that is, the login credential) represents the login authorization information of the login user, including user information and authorization validity period, wherein, the reference sub-control server generates the login After the credentials, the login credentials can be encrypted and stored in the target client, or stored locally. After the access parameter and the login credential are obtained with reference to the sub-control server, the access credential required for accessing the restricted access device can be generated based on the login credential and the access parameter. It can be understood that the reference sub-control server is the background server of the target client.
在参考分控服务器基于登陆凭证和访问参数生成访问凭证时,该参考分控服务器可先从数据库中加载一个盐值(salt,一种加密随机数),并由该盐值和登陆凭证共同组成加密密钥,并采用加密密钥对访问参数进行加密处理,从而生成访问凭证。其中,生成访问凭证的分控服务器对访问凭证的生成方式为:响应于所述目标客户端针对所述访问凭证的获取请求,从所述目标客户端获取凭证数据;对从所述目标客户端获取的凭证数据进行数据校验,并根据数据校验完成的凭证数据生成访问凭证;其中,所述数据校验包括以下一项或多项:格式校验,有效期校验以及合法性校验。When the reference sub-control server generates the access credential based on the login credentials and the access parameters, the reference sub-control server can first load a salt value (salt, an encrypted random number) from the database, which is composed of the salt value and the login credential. Encryption key, and use the encryption key to encrypt access parameters to generate access credentials. Wherein, the way of generating the access credential by the sub-control server that generates the access credential is: in response to the acquisition request of the target client for the access credential, acquiring credential data from the target client; The obtained credential data is subjected to data verification, and an access credential is generated according to the verified credential data; wherein, the data verification includes one or more of the following: format verification, validity period verification, and legality verification.
在一个实施例中,所述获取请求是所述目标客户端劫持到用于申请访问所述限制访问设备的网络请求后,根据所述网络请求生成的,进一步地,所述获取请求是所述目标客户端劫持到用于申请访问所述限制访问设备的网络请求后,并在所述目标客户端对所述网络请求的目标应用访问所述限制访问设备的访问权限进行校验,且在校验通过后,根据所述网络请求生成的。其中,所述目标客户端对所述目标应用访问所述限制访问设备时的访问权限的校验,是所述目标客户端根据管理人员为所述目标客户端配置并下发的零信任策略确定的;其中,所述零信任策略用于指示对所述限制访问设备具备访问权限的应用。也即,目标客户端生成限制访问设备的数据访问请求的时机在于,目标客户端所在的终端设备劫持到目标应用对限制访问设备的网络请求时生成的,其中,该限制访问设备为某些企事业单位的机密设备,为了保证该限制访问设备被访问时的安全性,终端设备在检测到目标应用对限制访问设备的访问请求流量时,则可对该目标应用的网络请求进行劫持,并通过终端设备中的其他客户端代理该目标应用对限制访问设备的访问。在一个实施例中,生成访问凭证的分控服务器对访问凭证的生成过程如图3所示,具体执行步骤s21~s28:In one embodiment, the acquisition request is generated according to the network request after the target client hijacks a network request for applying to access the restricted access device. Further, the acquisition request is the After the target client hijacks the network request for applying to access the restricted access device, the target client verifies the access authority of the target application of the network request to access the restricted access device, and is in school. After the verification is passed, it is generated according to the network request. The verification of the access authority of the target client when the target application accesses the restricted access device is determined by the target client according to the zero-trust policy configured and issued by the administrator for the target client. ; wherein the zero trust policy is used to indicate an application that has access rights to the restricted access device. That is, the time when the target client generates the data access request of the restricted access device is generated when the terminal device where the target client is located hijacks the network request of the target application to the restricted access device, wherein the restricted access device is some enterprise. The confidential equipment of the institution, in order to ensure the security of the restricted access device when it is accessed, when the terminal device detects the access request traffic of the target application to the restricted access device, it can hijack the network request of the target application and pass Other clients in the terminal device proxy the target application's access to the restricted access device. In one embodiment, the generation process of the access credential by the sub-control server that generates the access credential is shown in FIG. 3 , and steps s21 to s28 are specifically performed:
s21、根据目标客户端发送的票据置换请求,确定请求中携带的凭证数据,并对该凭证数据的数据格式进行校验,如果格式校验失败,则返回数据格式错误的提示信息,如果格式校验成功,则执行步骤s22;s21. According to the ticket replacement request sent by the target client, determine the voucher data carried in the request, and verify the data format of the voucher data. If the format verification fails, return a prompt message that the data format is incorrect. If the test is successful, execute step s22;
s22、从本地缓存中获取设备黑名单的目录信息,检查当前的终端设备是否在黑名单中,如果在,则给目标客户端返回错误提示信息,如果不在,则检查终端设备的安全性,如果终端设备未达到预设的安全级别,则确定该终端设备为不安全设备,则向目标客户端返回终端设备不安全的提示信息;而如果确定该终端设备为安全设备,则可执行步骤s23;s22. Obtain the directory information of the device blacklist from the local cache, check whether the current terminal device is in the blacklist, if so, return an error message to the target client, if not, check the security of the terminal device, if If the terminal device does not reach the preset security level, it is determined that the terminal device is an unsafe device, and a prompt message that the terminal device is unsafe is returned to the target client; and if it is determined that the terminal device is a secure device, step s23 can be executed;
s23、检查凭证数据的数据特征信息,如检查该凭证数据中接入进程的版本、MD5等特征信息,如果检查不通过,则给目标客户端返回特征信息不合格的提示信息,如果检查通过,则执行步骤s24;s23. Check the data feature information of the credential data, such as checking the version of the access process, MD5 and other feature information in the credential data, if the check fails, return a prompt message that the feature information is unqualified to the target client, if the check passes, Then execute step s24;
s24、先从本地缓存中获取登录用户登录目标客户端后生成的登录凭证(大票),如果在本地成功找到该登录凭证,则基于查找到登录凭证生成访问凭证;而如果未找到登录凭证,则根据终端设备id从总控服务器中获取登录凭证。此外,在获取登录凭证成功后,对该登录凭证进行有效性检测,以确定该登录凭证是否在有效期内,如果该登录凭证不在有效期内,则返回登录凭证过期的通知消息,而如果该登录凭证在有效期内,则执行步骤s25;s24. First obtain the login credentials (large ticket) generated by the login user after logging in to the target client from the local cache. If the login credentials are successfully found locally, the access credentials are generated based on the login credentials found; and if the login credentials are not found, Then, the login credentials are obtained from the master control server according to the terminal device id. In addition, after the login credential is successfully obtained, the validity of the login credential is checked to determine whether the login credential is within the validity period. Within the validity period, execute step s25;
s25、基于零信任控制策略检查当前的登录用户是否具有对该限制访问设备的访问权限,如果没有,则返回当前的登录用户无指定限制访问设备的通知信息,否则执行步骤s26;s25, based on the zero-trust control policy, check whether the current logged-in user has access to the restricted access device, if not, return notification information that the current logged-in user has no specified restricted access to the device, otherwise, perform step s26;
s26、根据预设的生成的访问凭证的有效时间,最大使用次数,登录凭证,进行信息(包括PID,进程全路径,md5),访问的目的站点信息(即限制访问设备的设备信息,具体包括url信息和端口信息等),以及登录用户的用户信息(如登录用户id等)生成加密数据,该加密数据即是生成的访问凭证;s26. According to the preset valid time of the generated access credential, the maximum number of times of use, the login credential, the process information (including the PID, the full path of the process, and md5), the destination site information of the visit (that is, the device information that restricts access to the device, specifically including url information and port information, etc.), and the user information of the logged-in user (such as the logged-in user id, etc.) to generate encrypted data, which is the generated access credential;
s27、成功生成访问凭证后,在本地存储访问凭证与登录凭证的对应关系。其中,可采用键值对进行存储,Key存储访问凭证,Value存储登录凭证,设备信息以及用户信息。s27. After the access credential is successfully generated, the corresponding relationship between the access credential and the login credential is stored locally. Among them, key-value pairs can be used for storage, Key stores access credentials, and Value stores login credentials, device information, and user information.
s28、将生成的访问凭证返回给目标客户端。s28. Return the generated access credential to the target client.
在一个实施例中,生成的访问凭证的数据格式可以如式1.1所示:In one embodiment, the data format of the generated access credential may be as shown in Equation 1.1:
访问凭证=A|B式1.1Access Credentials = A|B Formula 1.1
其中,访问凭证包括的A部分数据是一个Base64(一种加密算法)值,该A部分数据是参考分控服务器对登陆用户id,访问凭证的有效时间和该访问凭证的生成时间,采用Base64算法进行加密处理后得到的。该访问凭证包括的B部分数据是一个哈希(Hash)值,B部分数据的明文数据由登录凭证(大票)、目标应用id,终端设备id,登录用户id,访问凭证的有效时间,该访问凭证的生成时间构成,分控服务器(参考分控服务器或目标分控服务器)在生成B部分数据时,先采用前述的加密密钥对该部分的明文数据进行加密运算,生成对应的密文数据,进而可采用加密算法对该密文数据再次加密,得到该B部分数据,在一个实施例中,该加密算法可以死活哈希算法,如SHA256(一种哈希加密算法)算法等。在一个实施例中,分控服务器生成的访问凭证也可只包含上述B部分数据,在将生成的访问凭证(只包含B部分数据)发送给目标客户端时,可同时将该访问凭证的有效水时间和生成时间一并发送给目标客户端。Among them, the A part of the data included in the access credential is a Base64 (an encryption algorithm) value, and the A part of the data refers to the sub-control server for the login user id, the valid time of the access credential and the generation time of the access credential, using the Base64 algorithm obtained after encryption. The B part of the data included in the access credential is a Hash value. The plaintext data of the B part of the data consists of the login credential (large ticket), the target application id, the terminal device id, the login user id, the valid time of the access credential, the The generation time of the access voucher is composed. When the sub-control server (refer to the sub-control server or the target sub-control server) generates the data of part B, it first uses the aforementioned encryption key to encrypt the plaintext data of this part, and generates the corresponding ciphertext. Then, the ciphertext data can be encrypted again by using an encryption algorithm to obtain the B part of the data. In one embodiment, the encryption algorithm can be a dead-alive hash algorithm, such as SHA256 (a hash encryption algorithm) algorithm. In one embodiment, the access credential generated by the sub-control server may also only contain the above-mentioned data of part B. When sending the generated access credential (including only the data of part B) to the target client, the validity of the access credential can be simultaneously The water time is sent to the target client along with the spawn time.
分控服务器在生成对限制访问设备进行访问时所需的访问凭证后,该参考分控服务器可在本地存储该访问凭证,并将该访问凭证和登陆凭证进行关联存储,其中,在参考分控服务器将该访问凭证和登陆凭证进行关联存储时,可采用键值对(key-value)的形式进行关联存储,其中,可在键(key)存储访问凭证(即小票),在值(value)存储登陆凭证(即大票),以及终端设备信息(如终端设备id)和登陆用户信息(如登陆用户id)。此外,该参考分控服务器在生成访问凭证后,还需要将该访问凭证和登陆凭证的关联关系上传到总控服务器中,以在总控服务器中关联存储该访问凭证和登陆凭证。After the sub-control server generates the access credential required for accessing the restricted access device, the reference sub-control server can store the access credential locally, and store the access credential and the login credential in an associated manner. When the server associates and stores the access credential and the login credential, it can associate the storage in the form of a key-value pair (key-value). ) to store the login credentials (ie large tickets), as well as terminal device information (such as terminal device id) and login user information (such as login user id). In addition, after generating the access credential, the reference sub-control server also needs to upload the association relationship between the access credential and the login credential to the master control server, so as to associate and store the access credential and the login credential in the master control server.
在一个实施例中,分控服务器在生成该访问凭证后,可通过目标客户端将生成的访问凭证发送给代理客户端,代理客户端则可将该访问凭证添加到针对限制访问设备的数据访问请求中,并将该数据访问请求发送给智能网关,该智能网关在接收到该代理客户端发送过来的数据访问请求后,则可从该数据访问请求中获取到访问凭证,并向目标分控服务器发送携带该访问凭证的鉴权请求。目标分控服务器在获取到访问凭证后,为了对该访问凭证进行校验,可重新基于该访问凭证的生成方法生成新的访问凭证(或参考访问凭证),从而基于新生成的参考访问凭证对获取得到的的访问凭证进行校验。在具体实现中,如果目标分控服务器获取的访问凭证的数据格式如上述式1.1所示,那么,目标分控服务器新生成参考访问凭证时,该目标分控服务器可先获取加密随机数,并根据加密随机数生成加密密钥;进而,所述目标分控服务器可采用所述加密密钥对所述总控服务器返回的凭证数据进行加密处理,并根据加密处理得到的密文数据确定所述参考访问凭证。在一个实施例中,该目标分控服务器在根据加密处理得到的密文数据确定参考访问凭证时,该目标分控服务器可先确定对所述密文数据进行加密处理的加密算法,并采用所述加密算法对所述密文数据进行加密处理;从而该目标分控服务器可将加密后的密文数据作为所述参考访问凭证。In one embodiment, after generating the access credential, the sub-control server can send the generated access credential to the proxy client through the target client, and the proxy client can add the access credential to the data access for the restricted access device request, and send the data access request to the intelligent gateway. After receiving the data access request sent by the proxy client, the intelligent gateway can obtain the access credential from the data access request and send it to the target sub-controller The server sends an authentication request carrying the access credential. After the target sub-control server obtains the access credential, in order to verify the access credential, a new access credential (or reference access credential) can be regenerated based on the generation method of the access credential, so that a pair of Obtain the obtained access credentials for verification. In the specific implementation, if the data format of the access credential obtained by the target sub-control server is as shown in the above formula 1.1, then when the target sub-control server newly generates the reference access credential, the target sub-control server can first obtain the encrypted random number, and Generate an encryption key according to the encrypted random number; furthermore, the target sub-control server can use the encryption key to encrypt the voucher data returned by the master control server, and determine the See Access Credentials. In one embodiment, when the target sub-control server determines the reference access credential according to the ciphertext data obtained by the encryption process, the target sub-control server may first determine an encryption algorithm for encrypting the ciphertext data, and use the The encryption algorithm is used to encrypt the ciphertext data; thus, the target sub-control server can use the encrypted ciphertext data as the reference access credential.
目标分控服务器新生成参考访问凭证时,具体执行如下步骤:When the target sub-control server newly generates a reference access credential, perform the following steps:
s11、确定发起该数据访问请求的目标应用的应用id,以及对应终端设备的设备id,其中,该应用id是指代理客户端的进程PID,设备id是终端设备的唯一标识符;s11. Determine the application id of the target application that initiates the data access request, and the device id of the corresponding terminal device, wherein the application id refers to the process PID of the proxy client, and the device id is the unique identifier of the terminal device;
s12、确定的访问凭证(小票),并确定生成所述访问凭证时使用的凭证数据,其中,目标分控设备在生成所述访问凭证时使用的凭证数据时,可先从本地缓存中查找生成所述访问凭证时使用的凭证数据;所述目标分控服务器若未从本地缓存找查找到所述凭证数据,则请求总控服务器返回生成所述访问凭证时使用的凭证数据。其中,目标分控服务器是根据设备id从总控服务器中获取与该访问凭证对应的登陆凭证的。s12. Determine the access credential (small ticket), and determine the credential data used when generating the access credential, wherein, when the target sub-control device generates the credential data used in the access credential, it can first look up the credential data from the local cache credential data used when generating the access credential; if the target sub-control server does not find the credential data from the local cache, requesting the general control server to return the credential data used in generating the access credential. The target sub-control server obtains the login credential corresponding to the access credential from the master control server according to the device id.
由于目标分控服务器和支持目标客户端登陆,并为目标客户端的登陆下发登陆凭证的参考分控服务器为不同的服务器,由于该参考分控服务器在为目标客户端生成登陆凭证后,将生成的登陆凭证和该目标客户端所在终端设备的设备id上传到总控设备,所以在目标分控服务器需要获取该登陆凭证时,则可基于该设备id从总控服务器中进行获取。或者,如果该目标分控服务器和参考分控服务器为同一分控服务器,则该目标分控服务器则可从本地缓存中获取到登陆凭证。Since the target sub-control server and the reference sub-control server that supports the target client's login and issues the login credentials for the target client's login are different servers, after the reference sub-control server generates the login credentials for the target client, it will generate The login credentials of the target client and the device id of the terminal device where the target client is located are uploaded to the master control device, so when the target sub-control server needs to obtain the login credentials, it can be obtained from the master control server based on the device id. Alternatively, if the target sub-control server and the reference sub-control server are the same sub-control server, the target sub-control server can obtain the login credentials from the local cache.
s13、从的访问凭证中分离得到A部分数据和B部分数据,针对分离得到的A部分数据,目标分控服务器可执行base64解码得到登录用户id,访问凭证的有效时间和生成时间。s13. Separate the data of part A and the data of part B from the access credential. For the separated data of part A, the target sub-control server can perform base64 decoding to obtain the login user id, the valid time and generation time of the access credential.
s14、从数据库中读取出指定的盐值(salt),加上步骤s12中获取得到的登录凭证组合生成加密密钥。其中,目标分控服务器从数据库中读取出的指定的盐值就是生成访问凭证过程中的盐值。s14. Read out the specified salt value (salt) from the database, and combine the login credentials obtained in step s12 to generate an encryption key. The specified salt value read from the database by the target sub-control server is the salt value in the process of generating the access credential.
s15、根据步骤s11获取的应用id和设备id,以及步骤s12获取的登录凭证,目标分控服务器可根据步骤s13获取的登陆用户id,访问凭证的有效时间和生成时间作为所需的凭证数据,即该凭证数据包括:登录凭证+应用id+设备id+登陆用户id+有效时间+生成时间。s15, according to the application id and device id obtained in step s11, and the login credential obtained in step s12, the target sub-control server can use the login user id obtained in step s13, the valid time and generation time of the access credential as the required credential data, That is, the credential data includes: login credential + application id + device id + login user id + valid time + generation time.
s16、采用步骤s14生成的加密密钥,对步骤s15得到的凭证数据进行加密处理,得到密文数据。s16. Using the encryption key generated in step s14, perform encryption processing on the credential data obtained in step s15 to obtain ciphertext data.
s17、对步骤s16生成的密文数据执行哈希运算,如采用SHA256算法对该密文数据进行哈希运算,得到密文数据的哈希值。其中,该密文数据的哈希值即是生成的参考访问凭证。s17. Perform a hash operation on the ciphertext data generated in step s16, for example, using the SHA256 algorithm to perform a hash operation on the ciphertext data to obtain a hash value of the ciphertext data. The hash value of the ciphertext data is the generated reference access credential.
在一个实施例中,如果目标分控服务器获取的访问凭证只包括上述式1.1中的B部分数据,那么目标分控服务器在新生成参考访问凭证时,和上述步骤s11~s17存在的区别在于步骤s13,其中,如果目标分控服务器获取的访问凭证只包括B部分数据,那么目标分控服务器将不会对获取到的访问凭证进行分离以得到该B部分数据,但目标分控服务器需要基于终端设备id查找到登录用户id和访问凭证的有效时间和生成时间信息。在目标分控服务器采用生成访问凭证时所需的凭证数据,以及生成该凭证数据的方法生成具有较高可信度的参考访问凭证后,则可基于该参考访问凭证对获取到的访问凭证进行校验。In one embodiment, if the access credential obtained by the target sub-control server only includes the data in part B in the above formula 1.1, then when the target sub-control server newly generates the reference access credential, the difference from the above steps s11 to s17 lies in the steps s13, wherein, if the access credential obtained by the target sub-control server only includes data of part B, then the target sub-control server will not separate the obtained access credentials to obtain the data of part B, but the target sub-control server needs to be based on the terminal. The device id finds the valid time and generation time of the login user id and access credential. After the target sub-control server uses the credential data required for generating the access credential and the method for generating the credential data to generate the reference access credential with high reliability, the obtained access credential can be processed based on the reference access credential. check.
在目标分控服务器确定出参考访问凭证(即上述步骤s17生成的密文数据的哈希值),并获取得到的访问凭证后,则可将该参考访问凭证和的访问凭证(即步骤s13中的B部分数据)进行比较,如果对比结果指示该参考访问凭证和该的访问凭证一致,则认为对访问凭证的验证通过,或者,如果对比结果指示参考访问凭证和的访问凭证不一致,则认为对访问凭证的验证未通过。在一个实施例中,目标分控服务器也可在参考访问凭证和的访问凭证的相似度达到预设相似度阈值(如98%或者95%等)时,则认为该参考访问凭证和的访问凭证一致,并通过对该访问凭证的校验。采用实时生成可信度较高的参考访问凭证,以实现对获取的访问凭证的校验,可有效提升对访问凭证的校验精度。After the target sub-control server determines the reference access credential (that is, the hash value of the ciphertext data generated in the above step s17), and obtains the obtained access credential, the reference access credential and the access credential (that is, in step s13) can be obtained. If the comparison result indicates that the reference access credential is consistent with the access credential, it is considered that the verification of the access credential has passed, or, if the comparison result indicates that the reference access credential is inconsistent with the access credential, it is considered that the access credential is inconsistent. Validation of access credentials failed. In one embodiment, the target sub-control server may also consider the reference access credential and the access credential when the similarity between the reference access credential and the access credential reaches a preset similarity threshold (such as 98% or 95%, etc.) Consistent, and pass the verification of the access credential. The reference access credential with high reliability is generated in real time to realize the verification of the obtained access credential, which can effectively improve the verification accuracy of the access credential.
下面以数据处理系统级联部署为例,介绍对访问凭证的校验流程,其中,如图4所示,该数据处理系统包括图4所示的存储集群、长链集群、总控集群和零信任节点,其中,存储节点通过部署集群实现主备切换,用来存储总控节点和零信任节点的数据;长链节点主要用于iOA客户端和该数据处理系统中,该iOA客户端的后台服务器(如参考分控服务器)通过长链接周期性发送心跳和策略服务,通过集群实现主备切换。总控服务器包括管理服务,计算服务,短链服务(拉取策略,处理上报数据等)和登录服务,通过几圈实现主备切换。零信任节点(即分控服务器)即负责处理零信任网络访问的服务节点,包括登录服务,网关服务(上图所示的智能网关),策略服务(负责零信任访问控制策略)和票据服务(负责处理客户端的票据置换请求)The following takes the cascading deployment of the data processing system as an example to introduce the verification process for access credentials. As shown in Figure 4, the data processing system includes the storage cluster, long-chain cluster, master control cluster and zero-chain cluster shown in Figure 4. Trust nodes, among which, storage nodes realize active/standby switching by deploying clusters to store data of master control nodes and zero-trust nodes; long-chain nodes are mainly used for iOA clients and the data processing system, the backend server of the iOA client (For example, refer to the sub-control server) periodically send heartbeats and policy services through long links, and realize active-standby switchover through clusters. The master control server includes management services, computing services, short-chain services (pulling policies, processing and reporting data, etc.) and login services, and realizes active/standby switchover through several laps. The zero-trust node (ie the sub-control server) is the service node responsible for handling zero-trust network access, including the login service, the gateway service (the smart gateway shown in the figure above), the policy service (responsible for the zero-trust access control policy) and the ticket service ( Responsible for handling the client's ticket replacement request)
在一个实施例中,如果登陆用户通过iOA客户端在A分控服务器登录,并将访问凭证提交到A分控服务器进行校验,A分控服务器则可以在本地缓存中找到生成该访问凭证时的登陆凭证,并在A分控服务器实现对该访问凭证的校验。那么,A分控服务器则即为上述的目标分控服务器,又是上述的参考分控服务器。In one embodiment, if the login user logs in to the sub-control server A through the iOA client, and submits the access credential to the sub-control server A for verification, the sub-control server A can find the time when the access credential is generated in the local cache. and verify the access credentials on the sub-control server A. Then, the sub-control server A is the above-mentioned target sub-control server and the above-mentioned reference sub-control server.
在一个实施例中,如果登陆用户通过iOA客户端在B分控服务器执行登录,登录成功后B分控服务器会把凭证数据(包括用户信息和登陆凭证)上报到总控服务器,如果通过目标应用访问C分控服务器业务(用户配置此业务优先走C分控服务器或者其他零信任节点的分控服务异常),此时C分控服务器无法获取到生成该登陆凭证的访问凭证的凭证数据,于是去总控服务器进行凭证数据的获取,请求总控数据返回该凭证数据,总控服务器如果有该用户的登录记录,则会返回凭证数据(包括凭证数据),C分控服务器拿到凭证数据后,则生成访问凭证,与数据访问请求中的访问凭证进行比对,校验通过后返回业务信息,并将访问凭证缓存到本地,下次就可直接在本地校验。通过此种访问凭证的校验逻辑,各个零信任节点(即分控服务器)之间相对独立,方便平行扩容,同时某个分控服务器的故障也不会影响访问系统的使用,可以做到系统的高可用、高并发以及链路安全。那么,可以理解,B是上述的参考分控服务器,而C是上述的目标分控服务器。In one embodiment, if the logged-in user performs login on the sub-control server B through the iOA client, the sub-control server B will report the credential data (including user information and login credentials) to the master control server after the login is successful. Access to the C sub-control server service (the user configures this service to give priority to the C sub-control server or the sub-control service of other zero-trust nodes), at this time, the C sub-control server cannot obtain the credential data of the access credential that generates the login credential, so Go to the master control server to obtain the voucher data, request the master control data to return the voucher data, if the master control server has the user's login record, it will return the voucher data (including the voucher data). After the C sub-control server gets the voucher data , the access credentials are generated and compared with the access credentials in the data access request. After the verification is passed, the business information is returned, and the access credentials are cached locally, and can be verified locally next time. Through this access credential verification logic, each zero-trust node (ie sub-control server) is relatively independent, which is convenient for parallel expansion. At the same time, the failure of a sub-control server will not affect the use of the access system, and the system can be high availability, high concurrency and link security. Then, it can be understood that B is the above-mentioned reference sub-control server, and C is the above-mentioned target sub-control server.
在本发明实施例中,数据处理系统中的总控服务器和目标分控服务器可级联部署,目标分控服务器检测到目标客户端对限制访问设备进行数据访问的鉴权请求时,可从该鉴权请求中确定出访问凭证,并在从总控访问中请求得到生成该访问凭证所使用的凭证数据后,按照生成该访问凭证时使用的凭证数据和生成该访问凭证时所使用的生成方法实时生成参考访问凭证,由于该参考访问凭证是基于凭证数据和生成方法实时生成的,所以该参考访问凭证被篡改的概率较低,也就使得目标分控服务器可获取到较高可信度的参考访问凭证,那么目标分控服务器则可基于该实时生成的参考访问凭证,对获取得到的访问凭证进行校验,以确定对该访问凭证的校验是否通过。由于参考访问凭证的可信度较高,且被篡改的可能性较低,那么基于参考访问凭证对获取得到的访问凭证的校验,得到的针对该访问凭证的校验结果的精准度也就比较高。In the embodiment of the present invention, the master control server and the target sub-control server in the data processing system can be deployed in cascade, and when the target sub-control server detects the authentication request of the target client for data access to the restricted access device, it can download the data from the The access credential is determined in the authentication request, and after requesting the credential data used to generate the access credential from the master control access, follow the credential data used in generating the access credential and the generation method used in generating the access credential The reference access credential is generated in real time. Since the reference access credential is generated in real time based on the credential data and the generation method, the probability of the reference access credential being tampered with is low, which also enables the target sub-control server to obtain high-credibility information. With reference to the access credential, the target sub-control server can verify the obtained access credential based on the reference access credential generated in real time to determine whether the verification of the access credential is passed. Since the reference access credential has high reliability and is less likely to be tampered with, the accuracy of the verification result for the access credential obtained by verifying the obtained access credential based on the reference access credential is also relatively high.
请参见图5,是本发明实施例提出的一种数据处理方法,该方法可由上述数据处理系统中的目标分控服务器执行,如图5所示,该方法可包括:Please refer to FIG. 5, which is a data processing method proposed by an embodiment of the present invention. The method can be executed by the target sub-control server in the above-mentioned data processing system. As shown in FIG. 5, the method may include:
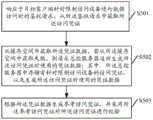
S501,响应于目标客户端针对限制访问设备进行数据访问时的鉴权请求,从所述鉴权请求中获取所述访问凭证。S501: Acquire the access credential from the authentication request in response to an authentication request made by the target client when the access device is restricted to access data.
S502,从缓存空间中获取所述凭证数据,若从所述缓存空间中获取失败,则请求总控服务器返回生成所述访问凭证时使用的凭证数据;其中,所述总控服务器中存储有针对限制访问设备的访问凭证,以及生成所述访问凭证时使用的凭证数据。S502: Acquire the credential data from the cache space, and if the acquisition from the cache space fails, request the general control server to return the credential data used in generating the access credential; wherein, the general control server stores data for Access credentials that restrict access to the device, and credential data used in generating said access credentials.
S503,根据所述凭证数据生成参考访问凭证,并采用所述参考访问凭证对所述访问凭证进行校验。S503. Generate a reference access credential according to the credential data, and use the reference access credential to verify the access credential.
步骤S501~S503可参见上述实施例中的描述,在此不再进行赘述。For steps S501 to S503, reference may be made to the descriptions in the foregoing embodiments, and details are not repeated here.
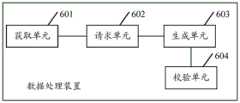
基于上述数据处理方法实施例的描述,本发明实施例还提出了一种数据处理装置,该数据处理装置可以是运行于上述目标分控服务器中的一个计算机程序(包括程序代码)。该数据处理装置可用于执行如图5所述的数据处理方法,请参见图6,该数据处理装置包括:获取单元601,请求单元602,生成单元603和校验单元604。Based on the description of the above data processing method embodiments, the embodiments of the present invention further provide a data processing apparatus, which may be a computer program (including program code) running in the above target sub-control server. The data processing apparatus can be used to execute the data processing method as described in FIG. 5 , please refer to FIG.
获取单元601,用于响应于目标客户端针对限制访问设备进行数据访问时的鉴权请求,从所述鉴权请求中获取所述访问凭证;an obtaining
所述获取单元601,还用于从缓存空间中获取所述凭证数据;The obtaining
请求单元602,用于若从所述缓存空间中获取失败,则请求总控服务器返回生成所述访问凭证时使用的凭证数据;其中,所述总控服务器中存储有针对限制访问设备的访问凭证,以及生成所述访问凭证时使用的凭证数据;The requesting
生成单元603,用于根据所述凭证数据生成参考访问凭证;a
校验单元604,用于采用所述参考访问凭证对所述访问凭证进行校验。The
请参见图7,是本发明实施例提供的一种服务器的结构示意性框图,该服务器可以是独立的物理服务器,也可以是多个物理服务器构成的服务器集群或者分布式系统,还可以是提供云服务、云数据库、云计算、云函数、云存储、网络服务、云通信、中间件服务、域名服务、安全服务、CDN、以及大数据和人工智能平台等基础云计算服务的云服务器。终端可以是智能手机、平板电脑、笔记本电脑、台式计算机、智能音箱、智能手表等,但并不局限于此。如图7所示的本实施例中的服务器可包括:一个或多个处理器701;一个或多个输入设备702,一个或多个输出设备703和存储器704。上述处理器701、输入设备702、输出设备703和存储器704通过总线705连接。存储器704用于存储计算机程序,所述计算机程序包括程序指令,处理器701用于执行所述存储器704存储的程序指令。Please refer to FIG. 7 , which is a schematic block diagram of the structure of a server provided by an embodiment of the present invention. The server may be an independent physical server, a server cluster or a distributed system composed of multiple physical servers, or a server that provides Cloud servers for basic cloud computing services such as cloud services, cloud databases, cloud computing, cloud functions, cloud storage, network services, cloud communications, middleware services, domain name services, security services, CDN, and big data and artificial intelligence platforms. The terminal may be a smart phone, a tablet computer, a notebook computer, a desktop computer, a smart speaker, a smart watch, etc., but is not limited thereto. The server in this embodiment as shown in FIG. 7 may include: one or
所述存储器704可以包括易失性存储器(volatile memory),如随机存取存储器(random-access memory,RAM);存储器704也可以包括非易失性存储器(non-volatilememory),如快闪存储器(flash memory),固态硬盘(solid-state drive,SSD)等;存储器704还可以包括上述种类的存储器的组合。The
所述处理器701可以是中央处理器(central processing unit,CPU)。所述处理器701还可以进一步包括硬件芯片。上述硬件芯片可以是专用集成电路(application-specific integrated circuit,ASIC),可编程逻辑器件(programmablelogic device,PLD)等。该PLD可以是现场可编程逻辑门阵列(field-programmablegate array,FPGA),通用阵列逻辑(generic array logic,GAL)等。所述处理器701也可以为上述结构的组合。The
本发明实施例中,所述存储器704用于存储计算机程序,所述计算机程序包括程序指令,处理器701用于执行存储器704存储的程序指令,用来实现上述如图5中相应方法的步骤。In this embodiment of the present invention, the
在一个实施例中,所述处理器701被配置调用所述程序指令,用于执行:In one embodiment, the
响应于目标客户端针对限制访问设备进行数据访问时的鉴权请求,从所述鉴权请求中获取所述访问凭证;Acquiring the access credential from the authentication request in response to an authentication request made by the target client for data access to the restricted access device;
从缓存空间中获取所述凭证数据,若从所述缓存空间中获取失败,则请求总控服务器返回生成所述访问凭证时使用的凭证数据;其中,所述总控服务器中存储有针对限制访问设备的访问凭证,以及生成所述访问凭证时使用的凭证数据;Acquire the credential data from the cache space, and if the acquisition from the cache space fails, request the general control server to return the credential data used in generating the access credential; wherein, the general control server stores information for restricting access. Access credentials for the device, and the credential data used in generating said access credentials;
根据所述凭证数据生成参考访问凭证,并采用所述参考访问凭证对所述访问凭证进行校验。A reference access credential is generated according to the credential data, and the access credential is verified by using the reference access credential.
本发明实施例提供了一种计算机程序产品或计算机程序,该计算机程序产品或计算机程序包括计算机指令,该计算机指令存储在计算机可读存储介质中。计算机设备的处理器从计算机可读存储介质读取该计算机指令,处理器执行该计算机指令,使得该计算机设备执行上述如图5所示的方法实施例。其中,所述的计算机可读存储介质可为磁碟、光盘、只读存储记忆体(Read-Only Memory,ROM)或随机存储记忆体(Random Access Memory,RAM)等。Embodiments of the present invention provide a computer program product or computer program, where the computer program product or computer program includes computer instructions, and the computer instructions are stored in a computer-readable storage medium. The processor of the computer device reads the computer instructions from the computer-readable storage medium, and the processor executes the computer instructions, so that the computer device executes the method embodiment shown in FIG. 5 above. The computer-readable storage medium may be a magnetic disk, an optical disk, a read-only memory (Read-Only Memory, ROM), or a random access memory (Random Access Memory, RAM) or the like.
以上所揭露的仅为本发明的局部实施例而已,当然不能以此来限定本发明之权利范围,本领域普通技术人员可以理解实现上述实施例的全部或局部流程,并依本发明权利要求所作的等同变化,仍属于发明所涵盖的范围。The above disclosure is only a partial embodiment of the present invention, and of course, it cannot limit the scope of the right of the present invention. Those of ordinary skill in the art can understand the whole or part of the process of realizing the above embodiment, and make according to the claims of the present invention. The equivalent changes of the invention still belong to the scope covered by the invention.
Claims (15)
Priority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202011137091.5ACN112149105A (en) | 2020-10-21 | 2020-10-21 | Data processing system, method, related equipment and storage medium |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202011137091.5ACN112149105A (en) | 2020-10-21 | 2020-10-21 | Data processing system, method, related equipment and storage medium |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| CN112149105Atrue CN112149105A (en) | 2020-12-29 |
Family
ID=73954511
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN202011137091.5APendingCN112149105A (en) | 2020-10-21 | 2020-10-21 | Data processing system, method, related equipment and storage medium |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN112149105A (en) |
Cited By (15)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN111352740A (en)* | 2018-12-21 | 2020-06-30 | 腾讯科技(深圳)有限公司 | Application interaction processing method and device |
| CN112788019A (en)* | 2020-12-30 | 2021-05-11 | 杭州天谷信息科技有限公司 | Application fusion scheme under zero trust concept |
| CN113014565A (en)* | 2021-02-19 | 2021-06-22 | 北京天维信通科技有限公司 | Zero trust architecture for realizing port scanning prevention and service port access method and equipment |
| CN113422757A (en)* | 2021-06-04 | 2021-09-21 | 广西电网有限责任公司 | Document management system based on encryption application |
| CN113486060A (en)* | 2021-06-25 | 2021-10-08 | 青岛海尔科技有限公司 | Data access processing method and device, storage medium and electronic equipment |
| CN113779603A (en)* | 2021-09-13 | 2021-12-10 | 成都高新愿景数字科技有限公司 | Asset authority control system and method based on 4A unified security management platform |
| CN113806710A (en)* | 2021-09-26 | 2021-12-17 | 北京沃东天骏信息技术有限公司 | A data processing method, device, equipment and storage medium |
| CN114398659A (en)* | 2021-10-28 | 2022-04-26 | 上海哔哩哔哩科技有限公司 | A resource verification method, device, device and storage medium |
| CN114745145A (en)* | 2021-01-07 | 2022-07-12 | 腾讯科技(深圳)有限公司 | Business data access method, device and equipment and computer storage medium |
| CN114785465A (en)* | 2022-04-26 | 2022-07-22 | 上海识装信息科技有限公司 | Method, server and storage medium for realizing remote multi-activity |
| CN115296847A (en)* | 2022-07-06 | 2022-11-04 | 杭州涂鸦信息技术有限公司 | Flow control method and device, computer equipment and storage medium |
| CN116032500A (en)* | 2021-10-25 | 2023-04-28 | 腾讯科技(深圳)有限公司 | Service access flow control method, device, equipment and medium |
| WO2023071819A1 (en)* | 2021-10-29 | 2023-05-04 | 支付宝(杭州)信息技术有限公司 | Data management and control method for zero-trust security container |
| CN116723238A (en)* | 2023-06-27 | 2023-09-08 | 电子科技大学 | API encrypted flow collection and labeling method based on man-in-the-middle agent |
| CN117318969A (en)* | 2022-06-23 | 2023-12-29 | 华为云计算技术有限公司 | Business communication methods, devices and systems for realizing disaster recovery |
Citations (5)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20030088648A1 (en)* | 2001-11-02 | 2003-05-08 | Gilles Bellaton | Supporting access control checks in a directory server using a chaining backend method |
| US20120151565A1 (en)* | 2010-12-10 | 2012-06-14 | Eric Fiterman | System, apparatus and method for identifying and blocking anomalous or improper use of identity information on computer networks |
| CN107241293A (en)* | 2016-03-28 | 2017-10-10 | 杭州萤石网络有限公司 | A kind of resource access method, apparatus and system |
| CN109194673A (en)* | 2018-09-20 | 2019-01-11 | 江苏满运软件科技有限公司 | Authentication method, system, equipment and storage medium based on authorized user message |
| CN111416822A (en)* | 2020-03-20 | 2020-07-14 | 数篷科技(深圳)有限公司 | Method for access control, electronic device and storage medium |
- 2020
- 2020-10-21CNCN202011137091.5Apatent/CN112149105A/enactivePending
Patent Citations (5)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20030088648A1 (en)* | 2001-11-02 | 2003-05-08 | Gilles Bellaton | Supporting access control checks in a directory server using a chaining backend method |
| US20120151565A1 (en)* | 2010-12-10 | 2012-06-14 | Eric Fiterman | System, apparatus and method for identifying and blocking anomalous or improper use of identity information on computer networks |
| CN107241293A (en)* | 2016-03-28 | 2017-10-10 | 杭州萤石网络有限公司 | A kind of resource access method, apparatus and system |
| CN109194673A (en)* | 2018-09-20 | 2019-01-11 | 江苏满运软件科技有限公司 | Authentication method, system, equipment and storage medium based on authorized user message |
| CN111416822A (en)* | 2020-03-20 | 2020-07-14 | 数篷科技(深圳)有限公司 | Method for access control, electronic device and storage medium |
Cited By (20)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN111352740A (en)* | 2018-12-21 | 2020-06-30 | 腾讯科技(深圳)有限公司 | Application interaction processing method and device |
| CN111352740B (en)* | 2018-12-21 | 2023-04-18 | 腾讯科技(深圳)有限公司 | Application interaction processing method and device |
| CN112788019A (en)* | 2020-12-30 | 2021-05-11 | 杭州天谷信息科技有限公司 | Application fusion scheme under zero trust concept |
| CN114745145A (en)* | 2021-01-07 | 2022-07-12 | 腾讯科技(深圳)有限公司 | Business data access method, device and equipment and computer storage medium |
| CN113014565A (en)* | 2021-02-19 | 2021-06-22 | 北京天维信通科技有限公司 | Zero trust architecture for realizing port scanning prevention and service port access method and equipment |
| CN113422757B (en)* | 2021-06-04 | 2023-04-07 | 广西电网有限责任公司 | Document management system based on encryption application |
| CN113422757A (en)* | 2021-06-04 | 2021-09-21 | 广西电网有限责任公司 | Document management system based on encryption application |
| CN113486060A (en)* | 2021-06-25 | 2021-10-08 | 青岛海尔科技有限公司 | Data access processing method and device, storage medium and electronic equipment |
| CN113486060B (en)* | 2021-06-25 | 2023-06-16 | 青岛海尔科技有限公司 | Data access processing method and device, storage medium and electronic equipment |
| CN113779603A (en)* | 2021-09-13 | 2021-12-10 | 成都高新愿景数字科技有限公司 | Asset authority control system and method based on 4A unified security management platform |
| CN113806710A (en)* | 2021-09-26 | 2021-12-17 | 北京沃东天骏信息技术有限公司 | A data processing method, device, equipment and storage medium |
| CN116032500A (en)* | 2021-10-25 | 2023-04-28 | 腾讯科技(深圳)有限公司 | Service access flow control method, device, equipment and medium |
| CN114398659A (en)* | 2021-10-28 | 2022-04-26 | 上海哔哩哔哩科技有限公司 | A resource verification method, device, device and storage medium |
| WO2023071819A1 (en)* | 2021-10-29 | 2023-05-04 | 支付宝(杭州)信息技术有限公司 | Data management and control method for zero-trust security container |
| CN114785465A (en)* | 2022-04-26 | 2022-07-22 | 上海识装信息科技有限公司 | Method, server and storage medium for realizing remote multi-activity |
| CN114785465B (en)* | 2022-04-26 | 2024-04-12 | 上海识装信息科技有限公司 | Implementation method, server and storage medium for multiple activities in different places |
| CN117318969A (en)* | 2022-06-23 | 2023-12-29 | 华为云计算技术有限公司 | Business communication methods, devices and systems for realizing disaster recovery |
| CN115296847A (en)* | 2022-07-06 | 2022-11-04 | 杭州涂鸦信息技术有限公司 | Flow control method and device, computer equipment and storage medium |
| CN115296847B (en)* | 2022-07-06 | 2024-02-13 | 杭州涂鸦信息技术有限公司 | Flow control method, flow control device, computer equipment and storage medium |
| CN116723238A (en)* | 2023-06-27 | 2023-09-08 | 电子科技大学 | API encrypted flow collection and labeling method based on man-in-the-middle agent |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| CN112149105A (en) | Data processing system, method, related equipment and storage medium | |
| CN112422532B (en) | Service communication method, system and device and electronic equipment | |
| US11394703B2 (en) | Methods for facilitating federated single sign-on (SSO) for internal web applications and devices thereof | |
| US11184336B2 (en) | Public key pinning for private networks | |
| US9237021B2 (en) | Certificate grant list at network device | |
| JP6446032B2 (en) | Synchronizing credential hashes across directory services | |
| US9325697B2 (en) | Provisioning and managing certificates for accessing secure services in network | |
| US20180020008A1 (en) | Secure asynchronous communications | |
| CN111651739B (en) | Login authentication service system and method, authentication service node and electronic equipment | |
| US11658812B1 (en) | Distributed key management system | |
| CN114745145B (en) | Business data access method, device and equipment and computer storage medium | |
| US20220123950A1 (en) | Multi-party cloud authenticator | |
| US11784993B2 (en) | Cross site request forgery (CSRF) protection for web browsers | |
| US10931662B1 (en) | Methods for ephemeral authentication screening and devices thereof | |
| US12348614B2 (en) | Distributed key management system with a key lookup service | |
| US10791119B1 (en) | Methods for temporal password injection and devices thereof | |
| CN115001707A (en) | Blockchain-based device authentication method and related devices | |
| CN118802149A (en) | Access processing method and device based on zero-trust network, electronic device, and medium | |
| Huang et al. | Pruning Blockchain Protocols for Efficient Access Control in IoT Systems | |
| CN115130116A (en) | Business resource access method, device, equipment, readable storage medium and system | |
| HK40035767A (en) | Data processing system and method, related appartus and storage medium | |
| US10812266B1 (en) | Methods for managing security tokens based on security violations and devices thereof | |
| US12445299B2 (en) | Service communication method, system, apparatus, electronic device, and storage medium | |
| Kuzminykh et al. | Mechanisms of ensuring security in Keystone service | |
| US12445438B2 (en) | Techniques for managing cookies through a secure web gateway |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| REG | Reference to a national code | Ref country code:HK Ref legal event code:DE Ref document number:40035767 Country of ref document:HK | |
| TA01 | Transfer of patent application right | Effective date of registration:20210924 Address after:100190 Beijing Haidian District Zhichun Road 49 No. 3 West 309 Applicant after:TENCENT CLOUD COMPUTING (BEIJING) Co.,Ltd. Address before:518057 Tencent Building, No. 1 High-tech Zone, Nanshan District, Shenzhen City, Guangdong Province, 35 floors Applicant before:TENCENT TECHNOLOGY (SHENZHEN) Co.,Ltd. | |
| TA01 | Transfer of patent application right | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination |