CN112135295A - Method and device for carrying out safety monitoring on user - Google Patents
Method and device for carrying out safety monitoring on userDownload PDFInfo
- Publication number
- CN112135295A CN112135295ACN202011008155.1ACN202011008155ACN112135295ACN 112135295 ACN112135295 ACN 112135295ACN 202011008155 ACN202011008155 ACN 202011008155ACN 112135295 ACN112135295 ACN 112135295A
- Authority
- CN
- China
- Prior art keywords
- user
- terminal
- security
- monitored
- monitoring
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Pending
Links
Images
Classifications
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04W—WIRELESS COMMUNICATION NETWORKS
- H04W4/00—Services specially adapted for wireless communication networks; Facilities therefor
- H04W4/90—Services for handling of emergency or hazardous situations, e.g. earthquake and tsunami warning systems [ETWS]
Landscapes
- Engineering & Computer Science (AREA)
- Business, Economics & Management (AREA)
- Health & Medical Sciences (AREA)
- Emergency Management (AREA)
- Environmental & Geological Engineering (AREA)
- Public Health (AREA)
- Computer Networks & Wireless Communication (AREA)
- Signal Processing (AREA)
- Mobile Radio Communication Systems (AREA)
Abstract
Translated fromChineseDescription
Translated fromChinese技术领域technical field
本发明实施例涉及物联网技术领域,特别涉及一种保护儿童安全的方法、装置。The embodiments of the present invention relate to the technical field of the Internet of Things, and in particular, to a method and device for protecting children's safety.
背景技术Background technique
随着现代通信技术的不断发展,借助于互联网、物联网,各种类型、用途的设备,如智能家电、可穿戴设备、智能监控设备等数以万计的设备接入网络,通过网络的连接设备之间可以随时进行信息交互,为用户提供便利。With the continuous development of modern communication technology, with the help of the Internet and the Internet of Things, tens of thousands of devices of various types and uses, such as smart home appliances, wearable devices, and smart monitoring devices, are connected to the network. Information exchange between devices can be carried out at any time to provide convenience for users.
物联网在保护儿童安全方面发挥着重要的作用,在例如车联网、智慧家居等各个应用场景中都离不开物联网。如在智慧家居中,现代家庭中各种电器越来越多,儿童接触电器的概率也相对较高,此外,家庭中也存在一些对儿童而言危险的区域,如厨房,为了防止儿童接触这些危险源,市场上对插线板做了很多改进,如智能插座,当判断儿童接近插座时,直接进行断电保护或者进行报警;或者通过摄像头监控儿童的位置或行为,从而进行安全防护。The Internet of Things plays an important role in protecting children's safety, and the Internet of Things is inseparable from various application scenarios such as the Internet of Vehicles and smart homes. For example, in the smart home, there are more and more electrical appliances in modern homes, and the probability of children coming into contact with electrical appliances is relatively high. In addition, there are also some dangerous areas for children in the family, such as the kitchen, in order to prevent children from contacting these Dangerous sources, many improvements have been made to the power strip in the market, such as smart sockets, when it is judged that children are approaching the socket, it will directly perform power-off protection or alarm; or monitor the position or behavior of children through cameras for safety protection.
然而上述方式存在很多不足,对儿童进行安全防护前需要复杂的设置,如需要预先建立儿童携带的智能设备的标识与安全策略的关联关系,当设备更新时,需要重新设置,不够灵活,尤其在公共场所,这种方式几乎不可实现。However, the above methods have many shortcomings, and complex settings are required before children are protected. For example, it is necessary to pre-establish the association between the identification of the smart device carried by children and the security policy. When the device is updated, it needs to be reset, which is not flexible enough, especially in In public places, this approach is almost impossible.
此外,对于例如智能插座,存在频繁对插座断电的缺陷,智能控制策略也不能根据儿童的认知水平进行自适应调整;对于摄像头监控方式,存在监控盲区的缺陷。In addition, for example, for smart sockets, there is a defect that the socket is frequently powered off, and the intelligent control strategy cannot be adaptively adjusted according to the cognitive level of children; for the camera monitoring method, there is a defect of monitoring blind spots.
因此,如何提高在家庭,尤其公共场所对儿童以及老人的安全监控以及追踪,以及提高安全监控的智能性、灵活性是目前急需解决的问题。Therefore, how to improve the safety monitoring and tracking of children and the elderly in families, especially public places, and how to improve the intelligence and flexibility of safety monitoring are urgent problems to be solved at present.
发明内容SUMMARY OF THE INVENTION
针对现有技术中的上述问题,本发明提供了一种安全监控的方法、装置。In view of the above problems in the prior art, the present invention provides a method and device for security monitoring.
本发明实施例提供了一种信标帧的发送方法,所述方法包括:An embodiment of the present invention provides a method for sending a beacon frame, and the method includes:
在信标帧中增加新的字段Security Flag,用于指示设备是否具有识别接入网络的终端的用户为需要被安全监控的用户的能力;A new field Security Flag is added to the beacon frame to indicate whether the device has the ability to identify the user of the terminal accessing the network as the user who needs to be monitored safely;
发送信标帧。Send a beacon frame.
优选的,在信标帧的Frame Body的保留字段中增加所述新的字段Security Flag。Preferably, the new field Security Flag is added to the reserved field of the Frame Body of the beacon frame.
优选的,该信标帧具有三种格式,分别为:Preferably, the beacon frame has three formats, which are:
格式1——Security Flag字段为必选字段;Format 1 - The Security Flag field is a required field;
格式2——Security Flag字段为可选字段,当设备具有该能力时,在信标帧中携带该字段,不具有该能力时,不携带该字段;Format 2 - The Security Flag field is an optional field. When the device has this capability, it carries this field in the beacon frame, and when it does not have this capability, it does not carry this field;
格式3——现有技术的信标帧格式,信标帧中不指示网络是否具有该能力。Format 3 - the prior art beacon frame format, the beacon frame does not indicate whether the network has the capability.
优选的,在信标帧中增加一个新的字段beacon format,用于指示信标帧的格式类型。Preferably, a new field beacon format is added to the beacon frame to indicate the format type of the beacon frame.
本发明实施例提供了一种信标发送装置,其特征在于,该装置包括An embodiment of the present invention provides a device for sending a beacon, which is characterized in that the device includes
生成单元,用于在信标帧中增加新的字段Security Flag,用于指示设备是否具有识别接入网络的终端的用户为需要被安全监控的用户的能力;A generating unit, for adding a new field Security Flag in the beacon frame, for indicating whether the device has the ability to identify the user of the terminal accessing the network as the user who needs to be monitored safely;
发送单元,用于发送信标帧。The sending unit is used to send the beacon frame.
优选的,生成单元,用于在信标帧的Frame Body的保留字段中增加所述新的字段Security Flag。Preferably, the generating unit is configured to add the new field Security Flag to the reserved field of the Frame Body of the beacon frame.
优选的,该信标帧具有三种格式,分别为:Preferably, the beacon frame has three formats, which are:
格式1——Security Flag字段为必选字段;Format 1 - The Security Flag field is a required field;
格式2——Security Flag字段为可选字段,当设备具有该能力时,在信标帧中携带该字段,不具有该能力时,不携带该字段;Format 2 - The Security Flag field is an optional field. When the device has this capability, it carries this field in the beacon frame, and when it does not have this capability, it does not carry this field;
格式3——现有技术的信标帧格式,信标帧中不指示网络是否具有该能力。Format 3 - the prior art beacon frame format, the beacon frame does not indicate whether the network has the capability.
优选的,生成单元,用于在信标帧中增加一个新的字段beacon format,用于指示信标帧的格式类型。Preferably, the generating unit is configured to add a new field beacon format to the beacon frame, which is used to indicate the format type of the beacon frame.
本发明实施例提供了一种接入设备AP,其特征在于,包括如上所述的装置。An embodiment of the present invention provides an access device AP, which is characterized in that it includes the above-mentioned apparatus.
本发明实施例提供了一种接入网络的方法,其特征在于,所述方法包括:An embodiment of the present invention provides a method for accessing a network, characterized in that the method includes:
步骤300,判断终端的用户是否需要被安全监控,若是,发送携带Security Flag字段的探测请求帧,若否,发送不携带Security Flag字段的探测请求帧; Security Flag字段用于指示终端的用户需要被安全监控;Step 300, determine whether the user of the terminal needs to be monitored by security, if so, send a probe request frame carrying the Security Flag field, if not, send a probe request frame that does not carry the Security Flag field; the Security Flag field is used to indicate that the user of the terminal needs to be monitored. Security Monitoring;
步骤301,AP接收该探测请求帧,判断探测请求帧中是否携带Security Flag 字段,若是,则发送携带Security Flag字段的探测响应消息,以提示用户可以被安全监控。Step 301, the AP receives the probe request frame, determines whether the probe request frame carries a Security Flag field, and if so, sends a probe response message carrying the Security Flag field to prompt the user that the security flag can be monitored.
优选的,若网络具有识别接入网络的终端的用户为需要被安全监控的用户的能力,则执行所述判断步骤;Preferably, if the network has the ability to identify the user of the terminal accessing the network as the user who needs to be monitored safely, the judging step is performed;
若网络不具有该能力,则不对Security Flag字段解析,发送不携带SecurityFlag字段的探测响应帧。If the network does not have this capability, the Security Flag field is not parsed, and a probe response frame without the SecurityFlag field is sent.
优选的,在步骤300前,终端接收到信标帧,解析信标帧中携带的Security Flag字段,该字段指示AP是否具有识别接入网络的终端的用户为需要被安全监控的用户的能力;Preferably, before step 300, the terminal receives the beacon frame and parses the Security Flag field carried in the beacon frame, which indicates whether the AP has the ability to identify the user of the terminal accessing the network as the user who needs to be monitored securely;
在确定网络具有该能力时,执行步骤300。When it is determined that the network has the capability, step 300 is performed.
优选的,判断终端的用户是否需要被安全监控,具体包括获取携带终端的用户的特征信息,根据该特征信息判断用户是否需要被安全监控。Preferably, judging whether the user of the terminal needs to be monitored safely includes acquiring characteristic information of the user carrying the terminal, and determining whether the user needs to be monitored safely according to the characteristic information.
本发明实施例提供了一种接入网络的系统,其特征在于,所述系统包括终端和AP,An embodiment of the present invention provides a system for accessing a network, wherein the system includes a terminal and an AP,
终端执行步骤300,判断用户是否需要被安全监控,若是,发送携带Security Flag字段的探测请求帧,若否,发送不携带Security Flag字段的探测请求帧; Security Flag字段用于指示终端的用户需要被安全监控;The terminal performs step 300 to determine whether the user needs to be monitored by security, and if so, sends a probe request frame carrying the Security Flag field, and if not, sends a probe request frame that does not carry the Security Flag field; the Security Flag field is used to indicate that the user of the terminal needs to be monitored. Security Monitoring;
AP执行步骤301,接收该探测请求帧,判断探测请求帧中是否携带Security Flag字段,若是,则发送携带Security Flag字段的探测响应消息,以提示用户可以被安全监控。The AP executes step 301, receives the probe request frame, determines whether the probe request frame carries the Security Flag field, and if so, sends a probe response message carrying the Security Flag field to prompt the user that the security flag can be monitored.
优选的,若AP具有识别接入网络的终端的用户为需要被安全监控的用户的能力,则执行所述判断步骤;Preferably, if the AP has the ability to identify the user of the terminal accessing the network as the user who needs to be safely monitored, the judging step is performed;
若AP不具有该能力,则不对Security Flag字段解析,发送不携带Security Flag字段的探测响应帧。If the AP does not have this capability, it does not parse the Security Flag field and sends a probe response frame without the Security Flag field.
优选的,在步骤300前,终端接收到信标帧,解析信标帧中携带的Security Flag字段,该字段指示AP是否具有识别接入网络的终端的用户为需要被安全监控的用户的能力;Preferably, before step 300, the terminal receives the beacon frame and parses the Security Flag field carried in the beacon frame, which indicates whether the AP has the ability to identify the user of the terminal accessing the network as the user who needs to be monitored securely;
在确定AP具有该能力时,执行步骤300。When it is determined that the AP has the capability, step 300 is performed.
优选的,终端判断用户是否需要被安全监控,具体包括获取携带终端的用户的特征信息,根据该特征信息判断用户是否需要被安全监控。Preferably, the terminal determines whether the user needs to be monitored safely, which specifically includes acquiring characteristic information of the user carrying the terminal, and determining whether the user needs to be monitored safely according to the characteristic information.
本发明实施例提供了一种安全监控方法,其特征在于,所述方法包括:An embodiment of the present invention provides a security monitoring method, characterized in that the method includes:
判断终端成功接入到该AP时,触发AP向终端发送该安全监控列表,该安全监控列表为预先设置的用于对用户进行安全监控的列表;When judging that the terminal successfully accesses the AP, triggering the AP to send the security monitoring list to the terminal, where the security monitoring list is a preset list for performing security monitoring on the user;
所述安全监控列表以用户界面的方式在终端显示,作为安全监控界面;The security monitoring list is displayed on the terminal in the form of a user interface as a security monitoring interface;
该界面包括:区域1,设置有搜索区,用于搜索安全监控策略的条目;区域 2,用于显示安全监控策略的条目。The interface includes:
优选的,区域2中,与安全监控策略条目对应的位置设置有按钮,用于将终端添加至对应的监控条目中,或者从对应的监控条目中删除终端。Preferably, in
优选的,安全监控界面还包括区域3,在区域3中包括紧急联系人按钮,该按钮用于添加终端的紧急联系人,当发生需要提醒的事件时,向添加的紧急联系人提示。Preferably, the security monitoring interface further includes an
优选的,当终端对应的监控条目添加紧急联系人后,其中被添加紧急联系人的条目前面具有一个特定的符号,该符号表示为该条目添加了紧急联系人。Preferably, when an emergency contact is added to the monitoring item corresponding to the terminal, the item to which the emergency contact is added has a specific symbol in front, and the symbol indicates that an emergency contact is added to the item.
本发明实施例提供了一种安全监控系统,其特征在于,所述系统包括AP和终端,An embodiment of the present invention provides a security monitoring system, characterized in that the system includes an AP and a terminal,
AP判断终端成功接入到该AP时,向终端发送该安全监控列表,该安全监控列表为预先设置的用于对用户进行安全监控的列表;When the AP determines that the terminal successfully accesses the AP, it sends the security monitoring list to the terminal, where the security monitoring list is a preset list for performing security monitoring on the user;
所述安全监控列表以用户界面的方式在终端显示,作为安全监控界面;The security monitoring list is displayed on the terminal in the form of a user interface as a security monitoring interface;
该界面包括:区域1,设置有搜索区,用于搜索安全监控策略的条目;区域 2,用于显示安全监控策略的条目。The interface includes:
优选的,区域2中,与安全监控策略条目对应的位置设置有按钮,用于将终端添加至对应的监控条目中,或者从对应的监控条目中删除终端。Preferably, in
优选的,安全监控界面还包括区域3,在区域3中包括紧急联系人按钮,该按钮用于添加终端的紧急联系人,当发生需要提醒的事件时,向添加的紧急联系人提示。Preferably, the security monitoring interface further includes an
优选的,当终端对应的监控条目添加紧急联系人后,其中被添加紧急联系人的条目前面具有一个特定的符号,该符号表示为该条目添加了紧急联系人。Preferably, when an emergency contact is added to the monitoring item corresponding to the terminal, the item to which the emergency contact is added has a specific symbol in front, and the symbol indicates that an emergency contact is added to the item.
本发明实施例提供了一种对用户进行安全监控的方法,其特征在于,该方法包括以下步骤:An embodiment of the present invention provides a method for security monitoring of a user, characterized in that the method includes the following steps:
获取用户的位置信息;Obtain the user's location information;
获取的一个或多个终端的位置信息;Obtained location information of one or more terminals;
确定用户携带的终端;Determine the terminal carried by the user;
获取用于识别终端的信息;Obtain information used to identify the terminal;
将该终端的信息添加到用户对应的安全监控策略条目中;Add the information of the terminal to the security monitoring policy entry corresponding to the user;
其中安全监控策略是设置的用于对用户进行监控的列表。The security monitoring policy is a set list for monitoring users.
优选的,判断终端是否在用户对应的安全监控策略条目以外的其他安全监控策略条目中,如果在,则进行删除。Preferably, it is judged whether the terminal is in other security monitoring policy entries other than the security monitoring policy entry corresponding to the user, and if so, it is deleted.
优选的,发送用户的特征信息至具有安全监控策略的监控设备;Preferably, the feature information of the user is sent to a monitoring device with a security monitoring policy;
监控设备根据接收的用户的特征信息确定用户对应于哪条安全监控条目,将用户携带的终端添加到该对应的条目中。The monitoring device determines which security monitoring entry the user corresponds to according to the received feature information of the user, and adds the terminal carried by the user to the corresponding entry.
优选的,终端定期获取携带该终端的用户的特征信息,基于获取的用户的特征信息判断携带终端的用户是否改变,若发生改变,则向监控设备发送被监控用户改变的消息。Preferably, the terminal periodically acquires the characteristic information of the user carrying the terminal, determines whether the user carrying the terminal changes based on the acquired characteristic information of the user, and if there is a change, sends a message that the monitored user changes to the monitoring device.
本发明实施例提供了一种对用户进行安全监控的系统,其特征在于,该系统包括终端和监控设备,An embodiment of the present invention provides a system for security monitoring of users, characterized in that the system includes a terminal and a monitoring device,
监控设备获取用户的位置信息;The monitoring device obtains the user's location information;
监控设备获取的一个或多个终端的位置信息;The location information of one or more terminals obtained by the monitoring device;
监控设备确定用户携带的终端;The monitoring device determines the terminal carried by the user;
监控设备获取用于识别终端的信息;The monitoring device obtains information used to identify the terminal;
监控设备将该终端的信息添加到用户对应的安全监控策略条目中;The monitoring device adds the information of the terminal to the security monitoring policy entry corresponding to the user;
其中安全监控策略是设置的用于对用户进行监控的列表。The security monitoring policy is a set list for monitoring users.
优选的,监控设备判断终端是否在用户对应的安全监控策略条目以外的其他安全监控策略条目中,如果在,则进行删除。Preferably, the monitoring device determines whether the terminal is in other security monitoring policy entries other than the security monitoring policy entry corresponding to the user, and if so, deletes it.
优选的,终端发送用户的特征信息至具有安全监控策略的监控设备;Preferably, the terminal sends the feature information of the user to a monitoring device with a security monitoring policy;
监控设备根据接收的用户的特征信息确定用户对应于哪条安全监控条目,将用户携带的终端添加到该对应的条目中。The monitoring device determines which security monitoring entry the user corresponds to according to the received feature information of the user, and adds the terminal carried by the user to the corresponding entry.
优选的,终端定期获取携带该终端的用户的特征信息,基于获取的用户的特征信息判断携带终端的用户是否改变,若发生改变,则向监控设备发送被监控用户改变的消息。Preferably, the terminal periodically acquires the characteristic information of the user carrying the terminal, determines whether the user carrying the terminal changes based on the acquired characteristic information of the user, and if there is a change, sends a message that the monitored user changes to the monitoring device.
本发明实施例提供了一种安全监控的方法,其特征在于:An embodiment of the present invention provides a method for security monitoring, characterized in that:
AP发送携带具有识别接入网络的终端的用户为需要被安全监控的用户的能力的信标帧;The AP sends a beacon frame that carries the ability to identify a user of a terminal accessing the network as a user that needs to be securely monitored;
终端监听并接收信标帧;The terminal monitors and receives beacon frames;
判断终端的用户是否需要被安全监控;Determine whether the user of the terminal needs to be monitored safely;
若是,则解析信标帧,判断AP是否具有识别接入网络的终端的用户为需要被安全监控的用户的能力;If so, parse the beacon frame to determine whether the AP has the ability to identify the user of the terminal accessing the network as the user who needs to be monitored safely;
若具有该能力,则向AP发送请求对终端的用户进行安全监控的探测请求帧;If it has this capability, send a probe request frame requesting security monitoring of the user of the terminal to the AP;
AP接收并解析探测请求帧,根据终端的所述请求将终端添加到安全监控策略列表。The AP receives and parses the probe request frame, and adds the terminal to the security monitoring policy list according to the request of the terminal.
优选的,获取终端的位置信息,将终端添加到在终端预设范围内的被监控对象对应的安全监控策略列表。Preferably, the location information of the terminal is acquired, and the terminal is added to the security monitoring policy list corresponding to the monitored objects within the preset range of the terminal.
优选的,AP根据认证过程中终端是否发送接入密码向终端提供不同的访问权限;当认证过程中接收到终端发送的接入密码,且密码正确,则向终端提供网络的访问权;若未接收到终端发送的接入密码,则仅支持请求对终端的用户进行安全监控的终端接入网络。Preferably, the AP provides the terminal with different access rights according to whether the terminal sends an access password during the authentication process; when it receives the access password sent by the terminal during the authentication process, and the password is correct, it provides the terminal with access rights to the network; if not After receiving the access password sent by the terminal, only the terminal that requests the security monitoring of the user of the terminal is supported to access the network.
优选的,若未接收到终端发送的接入密码,限制所述终端使用网络的服务。Preferably, if the access password sent by the terminal is not received, the terminal is restricted from using the services of the network.
本发明实施例提供了一种安全监控的系统,其特征在于:该系统包括AP和终端,An embodiment of the present invention provides a security monitoring system, characterized in that: the system includes an AP and a terminal,
AP发送携带具有识别接入网络的终端的用户为需要被安全监控的用户的能力的信标帧;The AP sends a beacon frame that carries the ability to identify a user of a terminal accessing the network as a user that needs to be securely monitored;
终端监听并接收信标帧;The terminal monitors and receives beacon frames;
判断终端的用户是否需要被安全监控;Determine whether the user of the terminal needs to be monitored safely;
若是,则解析信标帧,判断AP是否具有识别接入网络的终端的用户为需要被安全监控的用户的能力;If so, parse the beacon frame to determine whether the AP has the ability to identify the user of the terminal accessing the network as the user who needs to be monitored safely;
若具有该能力,则向AP发送请求对终端的用户进行安全监控的探测请求帧;If it has this capability, send a probe request frame requesting security monitoring of the user of the terminal to the AP;
AP接收并解析探测请求帧,根据终端的所述请求将终端添加到安全监控策略列表。The AP receives and parses the probe request frame, and adds the terminal to the security monitoring policy list according to the request of the terminal.
6、根据权利要求5所述的系统,其特征在于6. The system of claim 5, wherein
AP获取终端的位置信息,将终端添加到在终端预设范围内的被监控对象对应的安全监控策略列表。The AP acquires the location information of the terminal, and adds the terminal to the security monitoring policy list corresponding to the monitored object within the preset range of the terminal.
优选的,AP根据认证过程中终端是否发送接入密码向终端提供不同的访问权限;当认证过程中接收到终端发送的接入密码,且密码正确,则向终端提供网络的访问权;若未接收到终端发送的接入密码,则仅支持请求对终端的用户进行安全监控的终端接入网络。Preferably, the AP provides the terminal with different access rights according to whether the terminal sends an access password during the authentication process; when it receives the access password sent by the terminal during the authentication process, and the password is correct, it provides the terminal with access rights to the network; if not After receiving the access password sent by the terminal, only the terminal that requests the security monitoring of the user of the terminal is supported to access the network.
优选的,AP若未接收到终端发送的接入密码,限制所述终端使用网络的服务。Preferably, if the AP does not receive the access password sent by the terminal, the terminal is restricted from using the network service.
本发明实施例提供了一种提醒用户的方法,其特征在于,该方法包括An embodiment of the present invention provides a method for reminding a user, characterized in that the method includes:
步骤730,判断被监控终端是否满足对其采取其对应的安全监控策略条目中的安全措施的条件,若是,向被监控终端发送提示信息,执行步骤740;若否,重复执行步骤730;Step 730, determine whether the monitored terminal satisfies the conditions for taking the security measures in its corresponding security monitoring policy entry, if so, send a prompt message to the monitored terminal, and execute step 740; if not, repeat step 730;
步骤740,判断是否接收到被监控终端的反馈信息;若是,则执行步骤750,若否,执行步骤760;Step 740, judge whether the feedback information of the monitored terminal is received; if yes, go to step 750, if not, go to step 760;
步骤750,不采取安全措施中的安全措施,继续对终端进行监控,判断终端是否更接近被监控对象或更接近被监控对象会造成的危险事件,若是,判断终端与被监控对象的距离是否大于第一阈值小于第二阈值,若距离满足该要求,则再次向终端发送提示信息,并执行步骤740;若终端与被监控对象的距离小于等于第一阈值,则按安全措施执行相应的操作;若终端远离被监控对象或远离被监控对象会造成的危险事件,则不执行安全措施的相应操作;Step 750, do not take the security measures in the security measures, continue to monitor the terminal, determine whether the terminal is closer to the monitored object or a dangerous event that will be caused by the monitored object, if so, determine whether the distance between the terminal and the monitored object is greater than The first threshold is less than the second threshold, and if the distance meets the requirement, the prompt information is sent to the terminal again, and step 740 is performed; if the distance between the terminal and the monitored object is less than or equal to the first threshold, corresponding operations are performed according to safety measures; If the terminal is far away from the monitored object or the dangerous event caused by the monitored object, the corresponding operation of the security measures will not be performed;
步骤760,判断该提示信息发送的次数是否满足阈值,若是,执行步骤770,若否,再次向用户发送提示信息,执行步骤740;Step 760, determine whether the number of times the prompt information is sent meets the threshold, if yes, go to step 770, if not, send prompt information to the user again, go to step 740;
步骤770,根据安全措施执行相应的操作。Step 770, perform corresponding operations according to the security measures.
优选的,所述提示信息还包括向终端推送的内容。Preferably, the prompt information further includes content pushed to the terminal.
优选的,在步骤730中判断为是时,向被监控用户的紧急联系人发送消息,查询被安全监控的用户是否学习过针对该被监控对象的安全知识,若否,则向被监控用户的终端推送相关安全知识。Preferably, in step 730, when it is determined to be yes, send a message to the emergency contact of the monitored user to inquire whether the monitored user has learned the security knowledge for the monitored object; if not, send a message to the monitored user's emergency contact. Terminal pushes relevant security knowledge.
优选的,该安全知识是视频或音频的形式。Preferably, the safety knowledge is in the form of video or audio.
本发明实施例提供了一种提醒用户的装置,其特征在于,An embodiment of the present invention provides a device for reminding a user, which is characterized in that:
设置单元执行步骤730,判断被监控终端是否满足对其采取其对应的安全监控策略条目中的安全措施的条件,若是,发送单元向被监控终端发送提示信息,执行步骤740;若否,重复执行步骤730;The setting unit executes step 730 to determine whether the monitored terminal satisfies the conditions for taking the security measures in its corresponding security monitoring policy entry. If so, the sending unit sends prompt information to the monitored terminal, and executes step 740; if not, repeats the execution Step 730;
设置单元执行步骤740,判断是否接收到被监控终端的反馈信息;若是,则执行步骤750,若否,执行步骤760;The setting unit executes step 740 to determine whether the feedback information of the monitored terminal is received; if yes, executes step 750, if not, executes step 760;
步骤750,不采取安全措施中的安全措施,继续对终端进行监控,判断终端是否更接近被监控对象,若是,判断终端与被监控对象的距离是否大于第一阈值小于第二阈值,若距离满足该要求,则发送单元再次向终端发送提示信息,并执行步骤740;若终端与被监控对象的距离小于等于第一阈值,则设置单元按安全措施执行相应的操作;若终端远离被监控对象,则不执行安全措施的相应操作;Step 750, do not take the security measures in the security measures, continue to monitor the terminal, determine whether the terminal is closer to the monitored object, if so, determine whether the distance between the terminal and the monitored object is greater than the first threshold and less than the second threshold, if the distance satisfies If the request is requested, the sending unit sends the prompt information to the terminal again, and executes step 740; if the distance between the terminal and the monitored object is less than or equal to the first threshold, the setting unit performs corresponding operations according to safety measures; if the terminal is far away from the monitored object, The corresponding operation of the safety measures is not carried out;
设置单元执行步骤760,判断该提示信息发送的次数是否满足阈值,若是,执行步骤770,若否,发送单元再次向用户发送提示信息,执行步骤740;The setting unit executes step 760 to determine whether the number of times the prompt information is sent meets the threshold, if yes, executes step 770, if not, the sending unit sends the prompt information to the user again, executes step 740;
设置单元执行步骤770,根据安全措施执行相应的操作。The setting unit executes step 770, and performs corresponding operations according to the safety measures.
优选的,所述提示信息还包括向终端推送的内容。Preferably, the prompt information further includes content pushed to the terminal.
优选的,在步骤730中判断为是时,发送单元向被监控用户的紧急联系人发送消息,查询被安全监控的用户是否学习过针对该被监控对象的安全知识,若否,则向被监控用户的终端推送相关安全知识。Preferably, when it is determined in step 730 as yes, the sending unit sends a message to the emergency contact of the monitored user to inquire whether the monitored user has learned the security knowledge for the monitored object, if not, send a message to the monitored user. The user's terminal pushes relevant security knowledge.
优选的,该安全知识是视频或音频的形式。Preferably, the safety knowledge is in the form of video or audio.
本发明实施例提供了一种信标发送装置,其特征在于,包括上所述的装置。An embodiment of the present invention provides a device for sending a beacon, which is characterized in that it includes the device described above.
本发明实施例还提供了一种计算机设备,所述计算机设备包括处理器和存储器,所述存储器存储可被处理器执行的计算机指令,当处理器执行上述计算机指令时,实现如上所述的方法。An embodiment of the present invention further provides a computer device, the computer device includes a processor and a memory, the memory stores computer instructions that can be executed by the processor, and when the processor executes the computer instructions, the above method is implemented .
本发明实施例还提供了一种计算机可读存储介质,用于存储计算机指令,所述计算机指令用于实现如上所述的方法。Embodiments of the present invention also provide a computer-readable storage medium for storing computer instructions, where the computer instructions are used to implement the above method.
通过本发明的方法,可以提高在家庭,尤其公共场所对儿童以及老人的安全监控的便利性、无需增加额外的基础设施基础上扩大监控范围以及提高安全监控的智能性、灵活性。Through the method of the present invention, the convenience of safety monitoring for children and the elderly in families, especially public places, can be improved, the scope of monitoring can be expanded without adding additional infrastructure, and the intelligence and flexibility of safety monitoring can be improved.
附图说明Description of drawings
图1是管理帧的帧格式;Fig. 1 is the frame format of the management frame;
图2是本发明实施例的终端接入网络的示意图;2 is a schematic diagram of a terminal accessing a network according to an embodiment of the present invention;
图3是本发明实施例的一种信标发送方法;3 is a beacon sending method according to an embodiment of the present invention;
图4a-图4n是本发明实施例的终端的用户界面示意图;4a-4n are schematic diagrams of user interfaces of a terminal according to an embodiment of the present invention;
图5是本发明实施例的一种安全监控方法;5 is a security monitoring method according to an embodiment of the present invention;
图6是本发明实施例的另一种安全监控方法;6 is another security monitoring method according to an embodiment of the present invention;
图7是本发明实施例的信标发送装置。FIG. 7 is a beacon sending apparatus according to an embodiment of the present invention.
图8是本发明实施例的终端。FIG. 8 is a terminal according to an embodiment of the present invention.
具体实施方式Detailed ways
为了使本发明的目的、技术方案及优点更加清楚明白,以下结合附图及实施例,对本发明进行进一步详细说明。应当理解,此处所描述的具体实施例仅仅用以解释本发明,并不用于限定本发明。In order to make the objectives, technical solutions and advantages of the present invention clearer, the present invention will be further described in detail below with reference to the accompanying drawings and embodiments. It should be understood that the specific embodiments described herein are only used to explain the present invention, but not to limit the present invention.
下文以终端接入WiFi网络为例进行描述。The following description takes a terminal accessing a WiFi network as an example for description.
终端接入局域网主要包括以下几个步骤,首先通过主动或被动扫描发现周围的无线服务,再通过认证和关联两个过程后,才能和AP建立连接,最终接入无线局域网。终端有两种方式可以获取到周围的无线网络信息:Accessing a terminal to a local area network mainly includes the following steps. First, the surrounding wireless services are discovered through active or passive scanning, and then the connection with the AP can be established after passing through the two processes of authentication and association, and finally access to the wireless local area network. The terminal can obtain the surrounding wireless network information in two ways:
被动扫描(passive scanning):监听周围AP发送的信标帧Beacon;Passive scanning: monitor the beacon frames sent by surrounding APs;
主动扫描(active scanning):主动发送一个探测请求帧(Probe Request帧),接收AP返回的探测响应帧(Probe Response)。Active scanning: Actively send a probe request frame (Probe Request frame) and receive a probe response frame (Probe Response) returned by the AP.
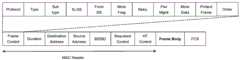
IEEE 802.11包括三种类型的帧结构:管理帧、数据帧和控制帧。其中管理帧的帧格式如图1所示,管理帧使用信息元素(information element)来与终端进行信息交换。其中,管理帧的帧控制(Frame Control)字段中的Sub Type字段用于进一步判断帧的子类型,如信标帧、探测请求帧、探测响应帧等,将其设置信标帧的值,则该帧为信标帧。信标帧的Frame Body字段是可变长度字段,携带信标相关的参数,如时间戳、信标间隔、能力、SSID等信息。IEEE 802.11 includes three types of frame structures: management frames, data frames, and control frames. The frame format of the management frame is shown in FIG. 1 , and the management frame uses an information element (information element) to exchange information with the terminal. Among them, the Sub Type field in the frame control (Frame Control) field of the management frame is used to further determine the subtype of the frame, such as beacon frame, probe request frame, probe response frame, etc., and set the value of the beacon frame, then This frame is a beacon frame. The Frame Body field of the beacon frame is a variable-length field, carrying beacon-related parameters, such as timestamp, beacon interval, capability, SSID and other information.
在本发明中,对信标帧、探测请求帧以及探测响应帧进行改进,其中在Frame Body的保留字段中增加新的字段Security Flag,在信标帧和探测响应帧中, Security Flag字段用于指示AP是否具有识别接入网络的终端的用户为需要被安全监控的用户的能力;在探测请求帧中Security Flag字段指示终端的用户是否需要被安全监控。优选的,该用户为老人和/或儿童。In the present invention, the beacon frame, the probe request frame and the probe response frame are improved, wherein a new field Security Flag is added to the reserved field of the Frame Body. In the beacon frame and the probe response frame, the Security Flag field is used for Indicates whether the AP has the ability to identify the user of the terminal accessing the network as the user who needs to be monitored by security; the Security Flag field in the probe request frame indicates whether the user of the terminal needs to be monitored by security. Preferably, the user is an elderly person and/or a child.
通过该方法,使得终端能够根据信标帧或探测响应帧识别网络是否具有安全监控的能力,而且当终端需要网络对其进行安全监控时,可以直接通过 Security Flag字段向网络指示其被监控的需求,便于网络侧识别终端的需求以及解析接收的探测请求帧,而且可以同现有的IEEE802.11协议兼容。Through this method, the terminal can identify whether the network has the capability of security monitoring according to the beacon frame or the detection response frame, and when the terminal needs the network to perform security monitoring on it, it can directly indicate its monitoring requirement to the network through the Security Flag field. , which is convenient for the network side to identify the needs of the terminal and parse the received probe request frame, and is compatible with the existing IEEE802.11 protocol.
优选的,管理帧的信息元素通常包含一个元素标识符(Element ID)字段、一个长度(Length)字段以及一个长度不定的字段,在本发明中利用未使用的保留信息元素对信标帧、探测请求帧、探测响应帧进行扩展,选择一个未使用的保留信息元素作为本发明中要添加的信息元素,其中选择未使用的保留元素中的一个元素标识符的值作为在信标帧、探测请求帧、探测响应帧中增加的信息元素的元素标识符的值,在长度不定的字段中设置Security Flag字段,优选的,设置该字段长度为1bit。Preferably, the information element of the management frame usually includes an element identifier (Element ID) field, a length (Length) field and a field of indeterminate length. The request frame and the probe response frame are extended, and an unused reserved information element is selected as the information element to be added in the present invention, and the value of an element identifier in the unused reserved element is selected as the value of the element identifier in the beacon frame, the probe request The value of the element identifier of the information element added in the frame and the probe response frame, the Security Flag field is set in the field of variable length, preferably, the length of this field is set to 1 bit.
具体的,终端接收到信标帧时,可以通过以下方式确定网络是否具有该能力:Specifically, when the terminal receives the beacon frame, it can determine whether the network has the capability in the following ways:
方式一:当信标帧中携带该字段时,确定网络具有该能力,不携带该字段时,网络不具有该能力。可选的,当信标帧中携带该字段时,将该字段的值设置为1或0。Manner 1: When the field is carried in the beacon frame, it is determined that the network has the capability, and when the field is not carried, the network does not have the capability. Optionally, when this field is carried in the beacon frame, the value of this field is set to 1 or 0.
方式二:当信标帧中携带该字段时,确定网络具有该能力,当信标帧中不携带该字段时,无法直接根据信标帧确定网络是否具有该能力,需进一步判断,具体判断方式在下文中详细描述。Method 2: When this field is carried in the beacon frame, it is determined that the network has this capability. When this field is not carried in the beacon frame, it is impossible to directly determine whether the network has this capability according to the beacon frame, and further judgment is required. The specific judgment method Described in detail below.
方式三:设置信标帧中携带该字段,根据该字段的值判断网络是否具有该能力,假设Security Flag值为1时,表示网络具有该能力,Security Flag值为0 时,网络不具有该能力;同样的,也可以设置Security Flag值为0时,表示网络具有该能力,Security Flag值为1时,网络不具有该能力。该值的设置可以为任意设置方式。Method 3: Set the field to be carried in the beacon frame, and judge whether the network has the capability according to the value of the field. Suppose that the value of the Security Flag is 1, indicating that the network has the capability, and when the value of the Security Flag is 0, the network does not have the capability ; Similarly, when the Security Flag value is 0, it means that the network has this capability, and when the Security Flag value is 1, the network does not have this capability. This value can be set in any way.
由此可见,在本发明中,具有三种信标帧格式:It can be seen that, in the present invention, there are three beacon frame formats:
格式1——Security Flag字段为必选字段,即如方式三的设置方式;Format 1 - The Security Flag field is a mandatory field, that is, the setting method as in
格式2——Security Flag字段为可选字段,当AP具有该能力时,在信标帧中携带该字段,不具有该能力时,不携带该字段,即如方式一的设置方式;Format 2 - The Security Flag field is an optional field. When the AP has this capability, it carries this field in the beacon frame.
格式3——即现有技术的信标帧格式,在信标中不指示网络是否具有该能力。
同样的,终端向网络发送探测请求帧时,当探测请求帧中携带了Security Flag字段,指示终端的用户需要被安全监控,当不携带该字段时,指示该终端的用户无需被安全监控。Similarly, when the terminal sends a probe request frame to the network, when the probe request frame carries the Security Flag field, it indicates that the user of the terminal needs to be monitored by security, and when this field is not carried, it indicates that the user of the terminal does not need to be monitored by security.
AP基于接收到的终端发送的探测请求帧,向终端设备发送探测响应帧,当接收的探测请求帧中携带了Security Flag字段,则在探测响应帧中携带Security Flag字段,其中,当网络具有识别接入网络的终端的用户为需要被安全监控的用户的能力时,则将该字段的值设置为指示网络具有该能力的值,否则,设置为网络不具有该能力的值。或者当接收的探测请求帧中携带了Security Flag字段,当网络具有该能力时,探测响应帧中携带该字段,采用如上的方式指示网络是否具有该能力,当网络不具有该能力,或者网络无法识别该Security Flag 字段时,探测响应帧中不携带关于对该字段的任何应答字段。Based on the received probe request frame sent by the terminal, the AP sends a probe response frame to the terminal device. When the received probe request frame carries the Security Flag field, it carries the Security Flag field in the probe response frame. When the user of the terminal accessing the network has the capability of the user that needs to be monitored safely, the value of this field is set to a value indicating that the network has the capability; otherwise, it is set to the value that the network does not have the capability. Or when the received probe request frame carries the Security Flag field, when the network has this capability, the probe response frame carries this field, and uses the above method to indicate whether the network has the capability, when the network does not have the capability, or the network cannot When identifying this Security Flag field, the probe response frame does not carry any response field for this field.
当接收的探测请求帧中未携带Security Flag字段,则按现有技术的方式向终端发送探测响应帧,即网络是否具有该能力,都不在探测响应帧中携带该字段。When the received probe request frame does not carry the Security Flag field, the probe response frame is sent to the terminal according to the prior art, that is, whether the network has the capability, does not carry this field in the probe response frame.
下面实例性的给出了几种终端接入网络的过程。优选的,各个实施方式之间可以组合。The following exemplarily provides several processes for the terminal to access the network. Preferably, various embodiments can be combined.
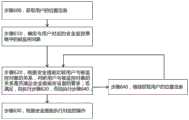
实施方式一:Embodiment 1:
在该实施方式中,信标帧格式为格式1或格式2。具体流程如图2所示。In this embodiment, the beacon frame format is either
步骤100,AP判断网络是否具有识别接入网络的终端的用户为需要被安全监控的用户的能力,若具有,则设置信标帧中Security Flag字段的值,指示网络具有该能力;否则,设置信标帧中Security Flag字段的值,指示网络不具有该能力,或者,在信标帧中不携带Security Flag字段。Step 100, the AP judges whether the network has the ability to identify the user of the terminal accessing the network as the user who needs to be monitored by security, and if so, sets the value of the Security Flag field in the beacon frame to indicate that the network has the ability; otherwise, set The value of the Security Flag field in the beacon frame indicates that the network does not have this capability, or the beacon frame does not carry the Security Flag field.
在该步骤中,Security Flag字段的值的设置方式同上文所述方式相同。In this step, the value of the Security Flag field is set in the same way as described above.
步骤101,终端进行主动扫描,监听周围AP发送的信标帧,接收并解析 AP发送的信标帧,判断信标帧中是否携带Security Flag字段,若信标帧中携带 Security Flag字段,则根据该字段的值判断网络是否具有识别接入网络的终端的用户为需要被安全监控的用户的能力,若网络具有该能力,判断终端的用户是否需要被安全监控,若用户需要被安全监控,则向AP发送携带Security Flag字段的探测请求帧,若用户不需要被安全监控,则向AP发送不携带Security Flag 字段的探测请求帧;若Security Flag字段指示网络不具有该能力,或者信标帧未携带Security Flag字段,则终端接入网络的方式与现有技术相同,即发送不携带Security Flag字段的探测请求帧。Step 101, the terminal actively scans, monitors the beacon frames sent by the surrounding APs, receives and parses the beacon frames sent by the AP, and determines whether the beacon frame carries the Security Flag field. The value of this field determines whether the network has the ability to identify the user of the terminal accessing the network as the user who needs to be monitored safely. If the network has this capability, it is determined whether the user of the terminal needs to be monitored safely. Send a probe request frame with the Security Flag field to the AP. If the user does not need to be monitored by security, send a probe request frame without the Security Flag field to the AP; if the Security Flag field indicates that the network does not have this capability, or the beacon frame does not If the Security Flag field is carried, the terminal accesses the network in the same manner as in the prior art, that is, sending a probe request frame without the Security Flag field.
优选的,上述判断用户是否需要被安全监控与判断信标帧是否携带SecurityFlag字段的步骤的顺序可以调换,在判断用户需要被安全监控时,判断信标帧中是否携带Security Flag字段,若信标帧中携带Security Flag字段,则根据该字段的值判断网络是否具有识别接入网络的终端的用户为需要被安全监控的用户的能力,若网络具有该能力,则向AP发送携带Security Flag字段的探测请求帧,若用户不需要被安全监控,则不执行解析Security Flag字段以及判断信标帧中是否携带Security Flag字段的步骤。Preferably, the order of the above steps of judging whether the user needs to be security monitored and judging whether the beacon frame carries the SecurityFlag field can be reversed. When judging that the user needs to be security monitored, it is determined whether the beacon frame carries the Security Flag field. The frame carries the Security Flag field, and according to the value of this field, it is judged whether the network has the ability to identify the user of the terminal accessing the network as the user who needs to be monitored for security. In the detection request frame, if the user does not need to be monitored by security, the steps of parsing the Security Flag field and judging whether the beacon frame carries the Security Flag field are not performed.
优选的,当终端接收到多个AP发送的信标帧,若终端的用户不需要被安全监控,则按现有技术方式,如选择信号强度最强的AP或按其他设置的选择策略选择要连接的AP;若终端的用户需要被安全监控,则解析多个AP发送的信标帧,根据信标帧选择具有识别接入网络的终端的用户为需要被安全监控的用户的能力的AP作为候选AP,从候选AP中选择要连接的AP的方法同现有技术,如选择信号强度最强的AP或按其他设置的选择策略选择要连接的AP。Preferably, when the terminal receives beacon frames sent by multiple APs, if the user of the terminal does not need to be monitored safely, select the AP with the strongest signal strength according to the prior art method, or select the AP with the strongest signal strength according to other set selection strategies. Connected AP; if the user of the terminal needs to be monitored safely, it parses the beacon frames sent by multiple APs, and selects the AP with the ability to identify the user of the terminal accessing the network as the user who needs to be monitored according to the beacon frame as the user who needs to be monitored safely. Candidate AP, the method of selecting the AP to be connected from the candidate APs is the same as the prior art, such as selecting the AP with the strongest signal strength or selecting the AP to be connected according to other set selection strategies.
步骤102,接收终端发送的探测请求帧,根据探测请求帧中是否携带SecurityFlag字段判断终端的用户是否需要被安全监控,若是,则将终端添加到被安全监控终端列表,并发送携带Security Flag字段的探测响应帧,以提示用户已被安全监控;若否,则发送不携带Security Flag字段的探测响应帧。Step 102: Receive the detection request frame sent by the terminal, and determine whether the user of the terminal needs to be monitored according to whether the SecurityFlag field is carried in the detection request frame. A probe response frame to remind the user that the user has been monitored by security; if not, a probe response frame without the Security Flag field is sent.
优选的,为了降低发送信令的开销,无论探测请求帧中是否携带Security Flag字段,探测响应帧均不携带Security Flag字段,其响应方式同现有技术,其中若AP具有该能力,且允许需要被安全监控的用户的终端接入网络时,发送的允许终端接入网络的探测响应消息也默认网络已将该终端添加到被安全监控终端列表。Preferably, in order to reduce the overhead of sending signaling, no matter whether the probe request frame carries the Security Flag field, the probe response frame does not carry the Security Flag field, and the response method is the same as that of the prior art. When the terminal of the user under security monitoring accesses the network, the sent probe response message allowing the terminal to access the network also defaults that the network has added the terminal to the list of security monitored terminals.
实施方式二:Embodiment 2:
在该实施方式中,信标帧格式为格式3。In this embodiment, the beacon frame format is
步骤200,AP发送信标帧;Step 200, the AP sends a beacon frame;
步骤201,终端进行主动扫描,监听周围AP发送的信标帧,判断终端的用户是否需要被安全监控,若用户需要被安全监控,向AP发送携带Security Flag 字段的探测请求帧,否则,发送不携带Security Flag字段的探测请求帧。Step 201, the terminal actively scans, monitors the beacon frames sent by the surrounding APs, and determines whether the user of the terminal needs to be monitored safely. A probe request frame carrying the Security Flag field.
优选的,当终端接收到多个AP发送的信标帧,若终端的用户不需要被安全监控,则按现有技术方式,如选择信号强度最强的AP或按其他设置的选择策略选择要连接的AP;若终端的用户需要被安全监控,则首先根据设定的策略选择候选AP,该策略同现有技术相同,如选择信号强度高于阈值的AP、或者允许接入的AP等,或者是根据用户设定的策略选择候选AP,确定候选AP后,向候选AP发送携带Security Flag字段的探测请求帧,根据接收的探测响应帧优先接入具有识别接入网络的终端的用户为需要被安全监控的用户的能力的网络。Preferably, when the terminal receives beacon frames sent by multiple APs, if the user of the terminal does not need to be monitored safely, select the AP with the strongest signal strength according to the prior art method, or select the AP with the strongest signal strength according to other set selection strategies. Connected AP; if the user of the terminal needs to be monitored safely, first select the candidate AP according to the set strategy, which is the same as the existing technology, such as selecting the AP whose signal strength is higher than the threshold, or the AP that is allowed to access, etc. Or select a candidate AP according to the policy set by the user, after determining the candidate AP, send a probe request frame carrying the Security Flag field to the candidate AP, and preferentially access users with terminals that identify the access network according to the received probe response frame. The ability of the user to be securely monitored over the network.
步骤202,接收终端发送的探测请求帧,根据探测请求帧中是否携带SecurityFlag字段判断终端的用户是否需要被安全监控,若是,判断网络是否具有识别接入网络的终端的用户为需要进行安全监控的用户的能力,若具有该能力,则将终端添加到被安全监控终端列表,并发送携带Security Flag字段的探测响应帧,以提示用户可以被监控;若不具有该能力,则发送不携带Security Flag字段的探测响应帧。若探测请求帧中未携带Security Flag字段,则发送的探测响应帧中不携带该字段,响应方式同现有技术相同。Step 202: Receive the detection request frame sent by the terminal, and judge whether the user of the terminal needs to be monitored according to whether the SecurityFlag field is carried in the detection request frame. The capability of the user. If the capability is available, the terminal will be added to the list of security monitored terminals, and a probe response frame with the Security Flag field will be sent to remind the user that it can be monitored; field of the probe response frame. If the Security Flag field is not carried in the probe request frame, the sent probe response frame does not carry this field, and the response method is the same as that in the prior art.
为了与现有的WiFi接入方式兼容,当AP不能解析探测请求帧中携带的 SecurityFlag字段时,也不影响终端正常接入网络。In order to be compatible with the existing WiFi access mode, when the AP cannot parse the SecurityFlag field carried in the probe request frame, it does not affect the normal access of the terminal to the network.
优选的,AP接收到携带Security Flag字段的探测请求帧,当AP不能解析该字段时,则直接忽略该字段,其余操作与现有技术相同。Preferably, when the AP receives the probe request frame carrying the Security Flag field, when the AP cannot parse the field, it directly ignores the field, and other operations are the same as in the prior art.
实施方式三:Embodiment three:
对于终端的主动扫描加入网络情况,主要包括以下步骤:For the active scanning of the terminal to join the network, it mainly includes the following steps:
步骤300,判断终端的用户是否需要被安全监控,若是,发送携带Security Flag字段的探测请求帧,若否,发送不携带Security Flag字段的探测请求帧;Step 300, determine whether the user of the terminal needs to be monitored by security, if so, send a probe request frame carrying the Security Flag field, if not, send a probe request frame that does not carry the Security Flag field;
步骤301,AP接收该探测请求帧,若网络具有识别接入网络的终端的用户为需要被安全监控的用户的能力,判断探测请求帧中是否携带Security Flag字段,若是,则发送携带Security Flag字段的探测响应消息,以提示用户可以被监控。若网络不具有该能力,则不对该字段解析,则发送不携带Security Flag字段的探测响应帧。Step 301, the AP receives the probe request frame, and if the network has the ability to identify the user of the terminal accessing the network as the user that needs to be monitored by security, it determines whether the probe request frame carries the Security Flag field, and if so, sends the device carrying the Security Flag field. The probe response message to prompt the user that it can be monitored. If the network does not have this capability, the field will not be parsed, and a probe response frame without the Security Flag field will be sent.
通过上述方法,无论终端是主动扫描接入网络还是被动扫描接入网络,均可以在终端的用户需要被安全监控时,向网络发送该请求。同时当AP不具有识别该字段的能力时,不影响终端的正常接入,实现了与现有协议的兼容性。Through the above method, regardless of whether the terminal is actively scanning the access network or passively scanning the access network, the request can be sent to the network when the user of the terminal needs to be monitored safely. At the same time, when the AP does not have the ability to identify this field, the normal access of the terminal is not affected, and the compatibility with the existing protocol is realized.
实施方式四:Embodiment four:
为了便于终端正确解析接收的信标帧,对于上述不同格式的信标帧,可以在终端和网络侧预先约定采用的信标帧格式,或者为了便于不同厂商设置自己的信标帧格式,在信标帧中增加一个新的字段beacon format,用于指示信标帧的格式类型,其中在本发明的增加的信息元素中增加beacon format字段,设置为2bit,具体定义如下表1:In order to facilitate the terminal to correctly parse the received beacon frame, for the beacon frames of different formats, the beacon frame format used by the terminal and the network side can be pre-agreed, or in order to facilitate different manufacturers to set their own beacon frame formats, in the beacon frame format. A new field beacon format is added in the mark frame, which is used to indicate the format type of the beacon frame, wherein the beacon format field is added in the added information element of the present invention, and is set to 2bit, and the specific definition is as follows in Table 1:
表1 beacon format字段值Table 1 beacon format field values
优选的,在另一实施方式中,当采用格式3时,也就是现有技术的信标帧格式,不对信标帧进行改进,即不设置beacon format字段,在这种情况下,beacon format字段可以设置为1bit,设置为0时,指示格式1,设置为1时,指示格式 2,或者,设置为1时,指示格式1,设置为0时,指示格式2。Preferably, in another embodiment, when using
终端接收到信标帧时,通过该字段识别信标帧采用的格式,基于识别的信标帧的格式,判断发送信标帧的AP是否具有识别接入网络的终端的用户为需要被安全监控的用户的能力。When the terminal receives the beacon frame, it uses this field to identify the format of the beacon frame, and based on the identified format of the beacon frame, it is judged whether the AP sending the beacon frame has a user that identifies the terminal accessing the network and needs to be monitored safely. capabilities of users.
实施方式五:Embodiment five:
下面分别从AP侧和终端侧说明接入网络的方法。The methods for accessing the network are described below from the AP side and the terminal side respectively.
AP侧:AP side:
AP发送信标帧:AP sends beacon frame:
其中,若AP为未采用本发明的方法的AP时,直接发送现有技术的信标帧,并且其接收到探测请求帧时也不去判断或识别探测请求帧中是否携带Security Flag字段,根据接收的探测请求帧确定是否允许终端接入,处理方式同现有技术相同。Wherein, if the AP is an AP that does not adopt the method of the present invention, it directly sends the beacon frame of the prior art, and when it receives the probe request frame, it does not judge or identify whether the probe request frame carries the Security Flag field. The received probe request frame determines whether the terminal is allowed to access, and the processing method is the same as that in the prior art.
若AP为采用本发明方法的AP时,其判断自身是否具有识别接入网络的终端的用户为需要被安全监控的用户的能力,根据自身能力情况确定发送的信标帧的方式,如采用上述实施方式一或实施方式二的方式发送,具体选择哪种方式可以根据用户或厂家的设置,发送的信标帧的格式采用本发明所述的信标帧格式之一。If the AP adopts the method of the present invention, it judges whether it has the ability to identify the user of the terminal accessing the network as the user who needs to be monitored safely, and determines the way of sending the beacon frame according to its own ability. The way of sending in
AP解析探测请求帧以及对探测请求帧的应答:The AP parses the probe request frame and the response to the probe request frame:
同样的,若AP为未采用本发明的方法的AP时,其接收到探测请求帧时按现有技术方式解析探测请求帧,忽略本发明引入的新字段,若AP为采用本发明的方法的AP时,其接收到探测请求帧并解析时,判断探测请求帧中是否携带本发明提出的字段,若携带则解析该字段,根据解析结果以及AP的所述能力以及其他本发明所提的因素发送对应的探测响应消息或本发明提及的其他消息。若未携带该字段,则按现有技术方式解析探测请求帧。Similarly, if the AP is an AP that does not adopt the method of the present invention, when it receives the probe request frame, it parses the probe request frame according to the prior art method, ignoring the new fields introduced by the present invention, and if the AP adopts the method of the present invention When the AP receives the probe request frame and parses it, it determines whether the probe request frame carries the field proposed by the present invention, and if it does, it parses the field. Send a corresponding probe response message or other messages mentioned in the present invention. If this field is not carried, the probe request frame is parsed according to the prior art.
终端侧:Terminal side:
对于被动扫描接入网络的方式,终端接收到信标帧,若为未采用本发明的方法的终端时,不去解析信标帧中本发明所引入的字段,按照现有技术方式解析信标帧;若为采用本发明的方法的终端时,判断终端的用户是否需要被安全监控,若无需安全监控,不去解析信标帧中本发明所引入的字段,按现有技术方式解析信标帧,以及选择要接入的AP;若需要被安全监控,解析并判断信标帧中是否携带Security Flag字段,若携带,根据SecurityFlag字段的值,按本发明中提及的方法执行对应操作,若未携带Security Flag字段,可以按以下方式之一执行:For the mode of passive scanning access network, when the terminal receives the beacon frame, if it is a terminal that does not adopt the method of the present invention, it does not parse the fields introduced by the present invention in the beacon frame, and parses the beacon according to the prior art. frame; if it is a terminal using the method of the present invention, it is judged whether the user of the terminal needs to be monitored safely. If no security monitoring is required, the fields introduced by the present invention in the beacon frame are not analyzed, and the beacon is analyzed according to the prior art. frame, and select the AP to be accessed; if it needs to be monitored by security, parse and judge whether the beacon frame carries the Security Flag field, if so, according to the value of the SecurityFlag field, perform the corresponding operation according to the method mentioned in the present invention, If the Security Flag field is not included, you can perform one of the following methods:
判断信标帧中是否携带beacon format字段,若携带,则根据该字段判断信标帧的格式,基于信标帧的格式以及Security Flag字段的值确定网络是否具有识别接入网络的终端的用户为需要被安全监控的用户的能力,若能够确定网络具有该能力,则按照本发明的方法执行后续的步骤,如接入该网络,若确定网络不具有该能力,则按照现有技术方式接入网络或者选择其他网络进行接入,优先的选择具有该能力的网络接入,其中判断其他网络是否具有该能力的方法同上述步骤。当信标帧中不携带beacon format字段时,则无法确定网络是否具有识别接入网络的终端的用户为需要被安全监控的用户的能力,需终端向网络发送携带Security Flag字段的探测请求帧,具体方式如本发明其他实施方式中所描述。Determine whether the beacon format field is carried in the beacon frame. If it is, the format of the beacon frame is determined according to this field. Based on the format of the beacon frame and the value of the Security Flag field, it is determined whether the network has a user that identifies the terminal accessing the network. The capability of the user that needs to be monitored safely, if it can be determined that the network has the capability, then follow the method of the present invention to perform the subsequent steps, such as accessing the network, if it is determined that the network does not have the capability, then access according to the prior art The network or other networks are selected for access, and the network with the capability is preferentially selected for access, wherein the method for judging whether other networks have the capability is the same as the above steps. When the beacon frame does not carry the beacon format field, it cannot be determined whether the network has the ability to identify the user of the terminal accessing the network as the user who needs to be monitored securely. The terminal needs to send a probe request frame carrying the Security Flag field to the network. The specific mode is as described in other embodiments of the present invention.
相应的,终端接收到探测响应帧时,若为未采用本发明的方法的终端时,不去解析探测响应帧中本发明所引入的字段,按照现有技术方式解析探测响应帧;若为采用本发明的方法的终端时,当该终端需要被安全监控,则判断探测响应帧是否携带Security Flag字段或者按照本发明其他实施方式的方法执行后续步骤,当该终端不需要被安全监控,不解析以及判断Security Flag字段的值,按照现有技术方式执行相应的操作。Correspondingly, when the terminal receives the probe response frame, if it is a terminal that does not adopt the method of the present invention, it does not parse the fields introduced by the present invention in the probe response frame, and parses the probe response frame according to the prior art; For the terminal of the method of the present invention, when the terminal needs to be monitored by security, it is judged whether the detection response frame carries the Security Flag field or the subsequent steps are performed according to the methods of other embodiments of the present invention. When the terminal does not need to be monitored by security, no analysis And determine the value of the Security Flag field, and perform corresponding operations according to the prior art.
实施方式六:Embodiment six:
为了节省网络中信令开销,本申请提出了一种发送信标帧的方法,该方法尤其适合在公共场所,如商场等环境中。在该方法中,网络周期性发送不同格式的信标,或者根据特定条件选择发送信标的格式,如图3所示,本发明中AP 根据发送信标帧的条件发送不同格式的信标帧,并且发送不同类型的信标帧的周期也可以不同。具体包括以下步骤:In order to save signaling overhead in the network, the present application proposes a method for sending beacon frames, which is especially suitable for environments such as public places, such as shopping malls. In this method, the network periodically sends beacons in different formats, or selects the format for sending beacons according to specific conditions. As shown in FIG. 3, in the present invention, the AP sends beacon frames in different formats according to the conditions for sending beacon frames. And the period of sending different types of beacon frames can also be different. Specifically include the following steps:
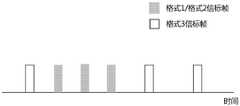
步骤400,AP获取发送信标帧的条件;Step 400, the AP obtains the conditions for sending the beacon frame;
在该步骤中,AP实时,或者周期性,或者在事件触发时获取发送信标帧的条件。In this step, the AP acquires the conditions for sending the beacon frame in real time, or periodically, or when an event is triggered.
步骤401,判断该条件是否满足发送格式1或格式2信标帧的条件一;若满足该条件一,则将AP发送的信标帧格式设置为格式1或格式2进行发送;若不满足该条件一,则将AP发送的信标帧格式设置为格式3进行发送,即信标帧中不包括本发明增加的信息元素。Step 401, determine whether the condition satisfies the first condition of sending the
具体的,条件一包括以下一种或多种的组合:Specifically, condition one includes a combination of one or more of the following:
1)满足发送格式1或格式2的信标帧的时间段。1) The time period for sending the beacon frame of
具体的,获取当前时刻,判断是否属于发送格式1或格式2信标帧的时间段内的时间,若是,则将信标帧格式设置为格式1或格式2,同时启动计时器,并在到达发送信标帧的时刻时,发送信标帧。当计时器时长达到发送格式1或格式2的信标帧的时间段的结束时间时,则执行步骤400。Specifically, the current time is obtained, and it is judged whether it belongs to the time period in which the
其中,根据当前时刻与发送格式1或格式2的信标帧的时间段的时刻之间的时间差设置计时器的计时时长,在计时器达到计时时长时触发AP执行步骤 400,使AP再次获取发送信标帧的条件。The timing duration of the timer is set according to the time difference between the current moment and the moment at which the beacon frame of
优选的,当AP实时,或者周期性获取发送信标帧的条件时,在满足发送格式1或格式2的信标帧的时间段结束前停止执行获取发送信标帧条件的步骤,直到接收到上述触发。Preferably, when the AP obtains the conditions for sending beacon frames in real time or periodically, it stops executing the step of obtaining the conditions for sending beacon frames before the end of the time period for sending beacon frames of
该方式尤其适合在公共场所,如存在教育机构、儿童娱乐场所的场景中,在该场景中,儿童大量出现的时间段较为固定,将儿童大量出现的时间段设为发送格式1或格式2信标帧的时间段,便于对儿童的安全监控。This method is especially suitable for public places, such as educational institutions and children's entertainment venues. In this scenario, the time period during which children appear in large numbers is relatively fixed, and the time period during which children appear in large numbers is set to send
优选的,发送格式1或格式2信标帧的时间段由用户根据需要设置,或者 AP周期性的根据统计周期内得到的时间段设置。Preferably, the time period for sending the
具体的,AP获取统计周期内终端接入网络的日志,在与该统计周期具有相同属性的时间按该统计周期内统计得到的发送格式1或格式2信标帧的时间段发送格式1或格式2信标帧,其余时间发送格式3信标帧,如该统计周期为1 周,从周一到周日,则在周一到周日按该得到的时间段发送格式1或格式2信标帧。Specifically, the AP obtains the log of the terminal accessing the network during the statistical period, and sends the
上述相同的属性如都是对应于工作日,或者都对应于周末,或为每月的同一日,或者以周为对应。For example, the same attributes above all correspond to working days, or all correspond to weekends, or the same day of each month, or correspond to weeks.
设置统计周期包括一天或多天;优选的,该统计周期为1周。其中,将一天的时间分为N个时间段,统计各时间段增加的接入网络的被安全监控的终端的数量,当连续M个时间段内所述增加的接入网络的被安全监控的终端的数量大于等于第一预设数量的时间段大于等于预设时间段数时,则在M个时间段发送格式1或格式2信标帧;发送格式1或格式2信标帧的开始时间为M个连续时间段的开始时间,结束时间为M个连续时间段的结束时间;其中M≤N。The set statistical period includes one or more days; preferably, the statistical period is one week. Among them, the time of a day is divided into N time periods, and the number of security-monitored terminals of the access network increased in each time period is counted. When the number of terminals is greater than or equal to the first preset number of time periods greater than or equal to the preset number of time periods, the
2)当前时间段增加的接入网络的被安全监控的终端的数量大于等于第二预设数量。2) The number of security-monitored terminals accessing the network increased in the current time period is greater than or equal to the second preset number.
具体的,选择最近的一段时间段,获取增加的接入网络的被安全监控的终端的数量,当该数据大于等于第二预设数量时,预测在最近的一段时间将有较多的需要被监控的终端接入,设置发送格式1或格式2的信标帧的时间长度为第二时间长度,同时启动计时器,并在到达发送信标帧的时刻时,发送格式1 或格式2信标帧。当计时器时长达到第二时间长度时,则执行步骤400。Specifically, a recent period of time is selected to obtain the increased number of terminals that are connected to the network under security monitoring. When the data is greater than or equal to the second preset number, it is predicted that there will be more terminals that need to be monitored in the recent period of time. The monitored terminal accesses, sets the time length for sending the beacon frame of
同样的,当AP实时,或者周期性获取发送信标帧的条件时,在满足发送格式1或格式2的信标帧的时间段结束前停止执行获取发送信标帧条件的步骤,直到接收到上述触发。Similarly, when the AP obtains the conditions for sending beacon frames in real time or periodically, it stops executing the step of obtaining the conditions for sending beacon frames before the end of the time period for sending beacon frames of
优选的,AP判断网络是否具有所述能力,若具有,则执行该实施方式的方法,若不具有,则仅发送格式3的信标帧。从而可以降低发送的数据量。Preferably, the AP judges whether the network has the capability, and if so, executes the method of this embodiment, and if not, only sends the beacon frame of
优选的,发送不同格式信标帧的周期可以是相同或不同的,而且发送相同格式的信标帧的周期满足不同条件时也可以是自适应改变的。Preferably, the periods for sending beacon frames in different formats may be the same or different, and the periods for transmitting beacon frames in the same format may also be adaptively changed when different conditions are met.
具体的,考虑到当需要被安全监控的终端接入网络后可以提高对终端用户的安全监控性,判断网络具有该能力时,设置发送格式1或格式2的信标帧的周期小于发送格式3信标帧的周期。优选的,判断接入网络的被安全监控的终端的增长速率大于速率阈值时,发送格式1或格式2的信标帧的周期是预设周期与增长因子的乘机,该增长因子为大于0小于1的数。Specifically, considering that the security monitoring of terminal users can be improved after the terminal that needs to be securely monitored is connected to the network, when it is judged that the network has this capability, the period for sending the beacon frame of
优选的,发送格式3信标帧的周期设置为固定周期,在另一实施方式中,判断接入网络的终端的增长速率大于速率阈值时,发送格式3的信标帧的周期是预设周期与所述增长因子的乘机。Preferably, the period for sending the
通过该方式,可以选择性的发送不同格式的信标帧,既可以节省信令开销,也可以使需要被监控的终端及时获知网络的能力,根据网络能力接入网络。In this way, beacon frames in different formats can be selectively sent, which not only saves signaling overhead, but also enables the terminal that needs to be monitored to know the capabilities of the network in time, and access the network according to the capabilities of the network.
实施方式七:Embodiment 7:
在各种环境中部署的AP,有的接入密码不公开,用户无法获取,属于私人 AP,有的为用户可以获取密码的AP,或者无需密码即可接入使用的AP。为了提高用户被安全监控的覆盖范围,并且合理利用用户无法获取密码的AP,本发明的方法进一步进一步提出了以下方法。Some APs deployed in various environments are private APs whose access passwords are not disclosed and cannot be obtained by users. In order to improve the coverage of the user being monitored by security, and to reasonably utilize the AP whose password cannot be obtained by the user, the method of the present invention further proposes the following method.
在该实施方式中,假设该AP设置有接入密码。In this embodiment, it is assumed that the AP is set with an access password.
步骤500,终端发送携带Security Flag字段的探测请求帧;Step 500, the terminal sends a probe request frame carrying the Security Flag field;
步骤501,AP接收到携带Security Flag字段的探测请求帧;Step 501, the AP receives the probe request frame carrying the Security Flag field;
步骤502,若AP具有识别接入网络的终端的用户为需要被安全监控的用户的能力,判断探测请求帧中是否携带Security Flag字段,若是,则发送携带 Security Flag字段的探测响应消息;若网络不具有该能力,则不对该字段解析,则发送不携带Security Flag字段的探测响应帧;Step 502, if the AP has the ability to identify the user of the terminal accessing the network as the user that needs to be monitored by security, judge whether the probe request frame carries the Security Flag field, if so, send a probe response message carrying the Security Flag field; if the network If this capability is not available, the field will not be parsed, and a probe response frame without the Security Flag field will be sent;
步骤503,终端接收探测响应消息;判断探测响应消息是否携带Security Flag 字段,若携带则执行步骤504;若不携带,判断是否继续执行步骤504,若是,执行步骤504,若否,结束;Step 503, the terminal receives the probe response message; judges whether the probe response message carries the Security Flag field, and if so, executes step 504;
在该步骤中,若探测响应消息不携带Security Flag字段,可以向用户界面发送提示消息,如提示网络是否具有识别接入网络的终端的用户为需要被安全监控的用户的能力,进一步的询问用户是否继续接入网络,由用户在界面确定是否继续执行接入网络的过程,若是,则通过点击界面的确认按钮继续接入过程,若否,则点击取消按钮放弃本次网络接入。In this step, if the detection response message does not carry the Security Flag field, a prompt message may be sent to the user interface, such as prompting the network whether the user of the terminal accessing the network has the ability to identify the user who needs to be monitored for security, and further ask the user Whether to continue to access the network, the user determines whether to continue the process of accessing the network on the interface. If so, click the OK button on the interface to continue the access process. If not, click the Cancel button to abandon this network access.
步骤504,终端判断是否具有该AP的接入密码,若具有,则在认证过程中向AP发送接入密码进行认证;若不具有该AP的密码,则当判断探测响应消息中携带Security Flag字段时,在认证过程中不向AP发送接入密码;Step 504, the terminal determines whether it has the access password of the AP, and if so, sends the access password to the AP for authentication during the authentication process; if it does not have the password of the AP, it determines that the detection response message carries the Security Flag field. , the access password is not sent to the AP during the authentication process;
步骤505,AP根据认证过程中终端是否发送接入密码向终端提供不同的访问权限;当认证过程中接收到终端发送的接入密码,且密码正确,则向终端提供网络的访问权;若未接收到终端发送的接入密码,则仅支持发送携带Security Flag字段的探测请求帧的终端接入网络,对终端进行安全监控,限制终端使用网络的服务。Step 505, the AP provides different access rights to the terminal according to whether the terminal sends an access password during the authentication process; when it receives the access password sent by the terminal during the authentication process, and the password is correct, it provides the terminal with access rights to the network; After receiving the access password sent by the terminal, only the terminal that sends the probe request frame carrying the Security Flag field is supported to access the network, to monitor the security of the terminal, and to restrict the terminal from using the services of the network.
优选的,终端接入AP提供的网络后,对其应用AP中的安全监控策略。Preferably, after the terminal accesses the network provided by the AP, the security monitoring policy in the AP is applied to it.
在该实施方式中,对于终端无法获取密码的AP,当终端请求连接该AP执行安全监控时,该AP允许终端接入,但是限制终端的访问权限,一方面可以使 AP发挥安全监控的作用,另一方面不会因为大量终端的接入,不影响AP向其服务的终端提供服务的性能。进一步的,通过该方法,使得一些私有AP发挥安全监控的功能,提高对于被监控用户监控的范围和能力,可以有效降低安全事故。In this embodiment, for an AP whose terminal cannot obtain a password, when the terminal requests to connect to the AP to perform security monitoring, the AP allows the terminal to access, but restricts the access authority of the terminal. On the one hand, the AP can play the role of security monitoring. On the other hand, the access of a large number of terminals will not affect the performance of the AP providing services to the terminals it serves. Further, through this method, some private APs are enabled to play the function of security monitoring, the scope and capability of monitoring for monitored users are improved, and security incidents can be effectively reduced.
实施方式八:Embodiment eight:
在对终端进行安全监控时,当需要对终端进行安全预警时,通常会采取一定安全措施,例如在家庭中,当儿童接近插座时,将插座断电等,或者向终端发送提示信息,然而这些处理方式存在一些缺陷,例如对于需要儿童的紧急联系人采取一定干预措施的场景,其紧急联系人无法及时获知该提示信息,因此本发明对该方法提出了进一步的改进措施。During security monitoring of the terminal, certain security measures are usually taken when a security warning is required for the terminal. For example, in the family, when children approach the socket, the socket is powered off, etc., or a prompt message is sent to the terminal. However, these There are some defects in the processing method. For example, in the scenario that the emergency contact of the child needs to take certain intervention measures, the emergency contact cannot obtain the prompt information in time. Therefore, the present invention proposes further improvement measures for the method.
当被安全监控的用户需要在安全预警时提示紧急联系人时,在终端发送探测请求帧时还携带紧急联系人的信息,如紧急联系人的手机号,终端标识等信息,该信息用于网络根据该信息向紧急联系人发送提示信息。When the user under security monitoring needs to prompt the emergency contact during the security warning, the terminal also carries the information of the emergency contact when sending the detection request frame, such as the mobile phone number of the emergency contact, the terminal identification and other information. This information is used by the network Based on this information, prompt information is sent to emergency contacts.
优选的,在探测请求帧的上述新增的信息元素中增加一个Care Info字段,用于携带紧急联系人的信息;该字段为可选字段,根据用户需要确定是否携带该字段。Preferably, a Care Info field is added to the above-mentioned newly added information element of the probe request frame, which is used to carry emergency contact information; this field is an optional field, and whether to carry this field is determined according to user needs.
发送的探测请求帧中携带了Care Info字段时,当网络侧需要向终端进行预警时,同时向Care Info字段指示的紧急联系人发送提醒消息。When the sent probe request frame carries the Care Info field, when the network side needs to give an early warning to the terminal, it simultaneously sends an alert message to the emergency contact indicated by the Care Info field.
通过该方法,使得网络可以有针对性的向紧急联系人提供提示。Through this method, the network can provide prompts to emergency contacts in a targeted manner.
实施方式九:Embodiment nine:
通过网络对终端的用户进行安全监控时,通常需要预先设置各种安全预警策略,当被安全监控的终端满足被预警的条件时,则采取相应的措施。然而,在大型公共区域,或者在家庭中,不同的被安全监控人员有不同的监控需求,若针对每个被监控人员都单独设置一次监控策略,则用户需要执行的操作太繁琐,若针对不同的被监控人员采用相同的监控策略,则存在过度监控的缺陷,因此,本发明对该监控策略的设置提出了改进。When performing security monitoring on users of terminals through a network, various security warning policies need to be set in advance, and corresponding measures are taken when the terminals to be security monitored meet the conditions for being warned. However, in large public areas or in homes, different security monitoring personnel have different monitoring requirements. If a monitoring strategy is set separately for each monitored person, the operations that users need to perform are too cumbersome. If the monitored personnel adopt the same monitoring strategy, there is a defect of excessive monitoring. Therefore, the present invention proposes an improvement in the setting of the monitoring strategy.
在本发明中,可以在AP中预先设置安全监控策略列表,或者根据接入AP 的终端的用户的输入动态生成安全监控策略。优选的,安全监控策略列表中包括一个或多个安全监控条目,示例性的,该列表包括以下条目:In the present invention, the security monitoring policy list may be preset in the AP, or the security monitoring policy may be dynamically generated according to the input of the user of the terminal accessing the AP. Preferably, the security monitoring policy list includes one or more security monitoring entries. Exemplarily, the list includes the following entries:
表2安全监控策略Table 2 Security monitoring strategy
在该列表中,索引用于标识各个监控策略条目,监控对象为对被安全监控用户而言需要关注的对象,如属于存在危险或者需要被安全监控的用户远离的对象,或者其他需要向被安全监控的人员进行预警的对象,如在家庭中的带电插座、洗衣机、打开窗户的阳台,厨房,商场中的扶梯附近、儿童娱乐场所的出口等对象;安全措施为针对不同的监控对象,满足预警条件时采取的安全措施,例如,当被监控对象为插座时,安全措施为当儿童距离插座1m时对插座断电;被监控对象为电梯时,安全措施为当儿童距离电梯1.5m时,提醒被监控用户;优选的,针对同一个监控对象,满足不同条件时,对应不同的安全措施。被监控终端,用于记录请求对相应监控对象执行监控的终端,也就是需要被安全监控的用户的终端,该项目也可以根据终端的请求添加到对应条目或者根据使用终端的用户的特点添加到对应条目。In this list, the index is used to identify each monitoring policy entry, and the monitoring object is the object that needs attention for the security monitoring user, such as the object that is dangerous or needs to be kept away from the security monitoring user, or other objects that need to be sent to the security monitoring user. The objects that the monitoring personnel will warn against, such as the live sockets, washing machines, balconies with open windows in the home, kitchens, near the escalators in shopping malls, exits of children's entertainment places, etc. For example, when the monitored object is a socket, the safety measure is to power off the socket when the child is 1m away from the socket; when the monitored object is an elevator, the safety measure is to remind the child when the child is 1.5m away from the elevator. The monitored user; preferably, for the same monitoring object, when different conditions are met, different security measures are corresponding. The monitored terminal is used to record the terminal that requests to perform monitoring on the corresponding monitoring object, that is, the terminal of the user who needs to be monitored safely. This item can also be added to the corresponding entry according to the request of the terminal or added to the user according to the characteristics of the user using the terminal. corresponding entry.
在一个实施方式中,安全监控策略还包括被监控对象的位置信息。In one embodiment, the security monitoring policy further includes location information of the monitored object.
在一个实施方式中,当被安全监控的终端接入网络后,可以将终端添加到所有安全监控策略条目中。In one embodiment, after the terminal to be monitored for security accesses the network, the terminal may be added to all security monitoring policy entries.
在另一个实施方式中,网络侧,如AP存储有各个被监控对象的位置信息,当被安全监控的终端接入网络后,AP获取终端的位置信息,将终端添加到在终端预设范围内的被监控对象对应的被监控终端项中。例如终端在商场中,该预设范围为终端所在楼层,则只将终端添加到其所在楼层的被监控对象对应的被监控终端项中。由此可以减少对终端的不必要监控。优选的,AP周期性的或实时监控终端的位置,根据终端的位置将终端更新至终端预设范围内的被监控对象对应的被监控终端项中,从而根据终端的位置自适应的调整所需要关注的被监控对象。In another embodiment, the network side, such as the AP, stores the location information of each monitored object. After the terminal to be safely monitored accesses the network, the AP obtains the location information of the terminal, and adds the terminal to the preset range of the terminal. in the monitored terminal item corresponding to the monitored object. For example, if the terminal is in a shopping mall, and the preset range is the floor where the terminal is located, only the terminal is added to the monitored terminal item corresponding to the monitored object on the floor where the terminal is located. Thereby, unnecessary monitoring of the terminal can be reduced. Preferably, the AP monitors the position of the terminal periodically or in real time, and updates the terminal to the monitored terminal item corresponding to the monitored object within the preset range of the terminal according to the position of the terminal, so as to adapt to the needs of the adjustment according to the position of the terminal The monitored object of interest.
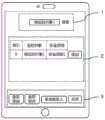
在另一个实施方式中,根据接入AP的终端的用户的操作生成对应该终端的安全监控策略。具体为:判断被安全监控的用户的终端成功接入到该AP时,触发AP向终端发送该安全监控列表,其可以以用户界面的方式在终端显示,如图 4a所示,为了便于表述,称该界面为安全监控界面,该界面包括三个区域,区域1设置有搜索区,区域2用于显示安全监控策略,图中示例性的显示了安全监控策略所包括的部分内容,优选的,其显示的内容可以根据需要显示,除了显示索引、监控对象、安全措施外,优选的还显示被监控对象的位置,以便用户根据需要将自身添加至对应的监控策略条目。优选的,显示的安全监控策略中不包括被监控终端项,尤其在公共场所中,不显示被监控终端项可以防止其他用户获取被监控终端的信息,提高安全性;在每个安全监控策略条目后具有一个按钮;区域3用于显示全部添加按钮和全部取消等按钮。In another embodiment, the security monitoring policy corresponding to the terminal is generated according to the operation of the user of the terminal accessing the AP. Specifically: when it is judged that the terminal of the user under security monitoring successfully accesses the AP, the AP is triggered to send the security monitoring list to the terminal, which can be displayed on the terminal in the form of a user interface, as shown in Figure 4a, for the convenience of expression, This interface is called a security monitoring interface, and the interface includes three areas. The
具体的,区域1的搜索区,用于用户输入例如与安全监控策略相关的信息,如被监控对象相关的关键词,或者安全措施有关的关键词等,从而搜索所需的监控条目,当用户输入搜索内容后,在区域2显示搜索结果。例如用户在搜索区输入被监控对象1,则在区域2显示搜索结果,如图4b所示。Specifically, the search area in
在区域2中,与安全监控策略条目对应的按钮用于将终端添加至对应的监控条目的被监控终端项中,由此实现对终端针对该安全监控策略条目的安全监控,或者将终端从对应的监控条目的被监控终端项中移除,则取消对终端针对该条目的监控。具体的,当未将终端添加到安全监控策略条目对应的被监控终端项目中时,该按钮显示添加,当将终端添加到安全监控策略条目对应的被监控终端项目中后,该按钮显示取消,如图4a所示,索引0、1对应的按钮显示“添加”,则表示还未将终端添加到该条目的被监控终端项中,索引2对应的按钮显示“取消”,则表示已经将终端添加至该条目的被监控终端项中。点击“添加”按钮,可实现将终端添加到对应的安全监控策略条目的被监控终端项中,点击“取消”按钮,可实现将终端从对应的监控条目的被监控终端项中移除。此外,当终端被添加到该条目后,该按钮显示“取消”,以用于终端通过点击该按钮将自身从该条目删除,当终端未被添加到该条目时,该按钮显示“添加”,以用于终端通过点击该按钮将自身添加到该条目,以被安全监控In
区域3中还包括其他按钮,其中全部添加按钮用于将终端添加到所有安全监控策略条目对应的被监控终端项中,同样的,全部取消按钮用于将终端从包括该终端的所有的安全监控条目中移除。
优选的,区域3还包括紧急联系人按钮,该按钮用于添加终端的紧急联系人,当发生需要提醒的事件时,不仅向终端进行提示,还可以向添加的紧急联系人提示。Preferably, the
优选的,区域3还包括关闭按钮,用于关闭该页面,在另一实施方式中,该关闭按钮可以为一个符号,点击该符号则关闭页面。Preferably, the
具体的,获取用户点击紧急联系人按钮的操作,进入输入紧急联系人界面,如图4c所示,用户输入紧急联系人信息后,当获取到用户点击确认时,获取用户输入的信息,将其作为终端的紧急联系人,与终端的安全监控策略条目对应存储;当用户点击取消按钮时,返回上一次显示的界面。Specifically, the operation of the user clicking the emergency contact button is obtained, and the emergency contact input interface is entered. As shown in Figure 4c, after the user enters the emergency contact information, when the user clicks confirmation is obtained, the information input by the user is obtained, and it is As the emergency contact of the terminal, it is stored corresponding to the security monitoring policy entry of the terminal; when the user clicks the cancel button, the interface that was displayed last time is returned.
进一步的,为了使得设置更加灵活方便,满足用户对某些安全监控条目无提醒需要的场景,获取用户点击紧急联系人按钮的操作,进入输入紧急联系人界面,如图4d所示,该界面包括用于用户输入紧急联系人的输入区域,用户已添加的安全监控策略条目,在每个安全监控策略条目前面有一个可选中的符号,用户通过选中该符号使得选中其中的条目,如图中所示,条目0对应的符号被选中,用户选中条目对应的符号,以及输入紧急联系人信息后,当获取到用户点击确认按钮时,获取用户选中的条目,以及获取用户输入的紧急联系人信息,针对选中的条目为终端添加紧急联系人,未选中的条目不添加紧急联系人。通过该方式,可以使用户根据需要为部分条目添加紧急联系人。Further, in order to make the setting more flexible and convenient, and to meet the scenario where the user does not need to remind some security monitoring items, obtain the operation of the user clicking the emergency contact button, and enter the emergency contact input interface, as shown in Figure 4d, the interface includes: The input area for the user to input the emergency contact, the security monitoring policy entry that the user has added, there is an optional symbol in front of each security monitoring policy entry, the user can select the entry by selecting the symbol, as shown in the figure. shows that the symbol corresponding to
为了便于用户确认执行的操作是否成功,当成功时,AP向用户反馈成功的提示,若失败,则向用户反馈失败的提示,进一步的,若能够确定失败的原因,则向用户提示失败的原因。In order to facilitate the user to confirm whether the executed operation is successful, when successful, the AP feeds back a prompt of success to the user. If it fails, it feeds back a prompt of failure to the user. Further, if the cause of the failure can be determined, the AP will prompt the user of the cause of the failure. .
优选的,在该界面中,当添加紧急联系人后,其中被添加紧急联系人的条目前面具有一个特定的符号,该符号可以是圆形、方形、三角形等任意形状的符号,该符号表示为该条目添加了紧急联系人,如图4e所示,◆表示该监控条目已添加紧急联系人信息。在一个实施方式中,点击该符号,则在该符号旁边悬浮出现该符号对应的解释,即紧急联系人信息,如图4f所示,点击索引0对应的◆,则在其旁边悬浮显示对应的紧急联系人信息13512314568。显示设定时间后,不再显示该解释,在另一实施方式中,点击该符号时,在该页面下方显示与该符号对应的紧急联系人信息,如图4g所示。优选的,不同的符号对应不同的联系人,或者以符号的不同颜色区分不同的紧急联系人。其中还可以在该页面直接显示不同颜色的符号对应的紧急联系人信息,如图4h所示。当对应的监控条目具有多个紧急联系人,则在该条目前具有多个表示对应紧急联系人的符号。Preferably, in this interface, after the emergency contact is added, the item to which the emergency contact is added has a specific symbol in front of it, and the symbol can be a symbol in any shape such as a circle, a square, a triangle, etc. The symbol is expressed as An emergency contact is added to this entry, as shown in Figure 4e, ◆ indicates that emergency contact information has been added to the monitoring entry. In one embodiment, clicking on the symbol will display the corresponding explanation of the symbol, namely emergency contact information. As shown in Figure 4f, click on the ◆ corresponding to
优选的,该界面中仅对与终端相关的监控条目添加了紧急联系人时显示该关于添加紧急联系人的符号,从而便于用户查看与自身相关的信息。Preferably, in the interface, the symbol about adding an emergency contact is displayed only when an emergency contact is added to a monitoring item related to the terminal, so that the user can view information related to himself.
优选的,可以对已添加紧急联系人的条目或未添加紧急联系人的条目再次添加紧急联系人,该联系人可以为用户设置的任意联系人。同样的,选中需要添加紧急联系人的条目,该条目包括已添加紧急联系人的条目和/或未添加紧急联系人的条目,在紧急联系人输入区域输入紧急联系人信息,点击确认按钮,如前述添加紧急联系人方法相同,即可添加紧急联系人。对于已经添加过紧急联系人的条目,通过该方法则将之前添加的紧急联系人替换为当前添加的紧急联系人。优选的,对于已经添加过紧急联系人的条目,当再次被选中添加紧急联系人时,判断输入的紧急联系人信息与之前添加的紧急联系人信息是否相同,若相同则不对该条目执行任何操作,若不相同,则在操作界面上向用户显示提示消息,提示用户是否替换已有的紧急联系人信息,还是对该条目额外增加紧急联系人信息,或者忽视该操作,即保持不变。Preferably, an emergency contact can be added again to an entry to which an emergency contact has been added or an entry to which no emergency contact has been added, and the contact can be any contact set by the user. Similarly, select the entry to be added with emergency contact, the entry includes the entry with emergency contact added and/or the entry without emergency contact, enter emergency contact information in the emergency contact input area, and click the confirm button, such as The method for adding an emergency contact is the same as described above, and you can add an emergency contact. For an entry that has already added an emergency contact, this method replaces the previously added emergency contact with the currently added emergency contact. Preferably, for an entry that has already added an emergency contact, when it is selected to add an emergency contact again, it is determined whether the input emergency contact information is the same as the previously added emergency contact information, and if it is the same, no operation is performed on the entry. , if not, a prompt message is displayed to the user on the operation interface, prompting the user whether to replace the existing emergency contact information, or to add additional emergency contact information to the entry, or ignore the operation, that is, keep it unchanged.
具体的,假设用户当前紧急联系人设置如图4h所示,用户选中索引1、2 添加紧急联系人,用户输入的紧急联系人信息与◆对应的紧急联系人信息相同,获取用户输入确认操作后,判断索引1对应的紧急联系人信息与用户新输入的紧急联系人信息相同,则不对该索引执行任何操作,判断索引0对应的紧急联系人信息与新输入的紧急联系人信息不同,则在当前界面弹出提示界面,提示用户选择对紧急联系人信息改变的索引执行的操作,如图4i所示,该界面显示存在该不同的条目,进一步的,在该界面显示已添加的紧急联系人信息,便于用户判断执行哪种操作。Specifically, it is assumed that the user's current emergency contact settings are shown in Figure 4h, the user selects
接着,检测用户的选择,基于用户的选择执行对应操作,即若用户选择替换,则将紧急联系人更新为新输入的信息,若用户选择增加,则增加新的紧急联系人信息,若用户选择保持,则不对该条目执行操作。优选的,为了便于用户获知已添加的紧急联系人信息,在提示界面显示该条目已添加的紧急联系人信息。进一步的,当多个条目存在上述情况,可以按顺序每次向用户提示一条监控条目的相关信息,当检测到用户对该条目选择确认后,显示下一需提醒的监控条目,直到所有需提醒的监控条目全部处理完成。在另一实施方式中,将各个监控条目按紧急联系人分组显示,方便用户批量处理,例如如图4j所示,页面显示了设置了两个不同紧急联系人的分组,当一个页面无法全部显示时,页面具有翻页的按钮,如图所示的“→”,通过向左的箭头、或向右的箭头实现翻页的功能。用户可以根据需要选择每个监控条目前的选择按钮,如图中的○,确定要执行的操作,当多个监控条目执行相同的操作,可以同时选中多个条目后再执行对应的操作,及替换、增加或保持。Next, the user's selection is detected, and a corresponding operation is performed based on the user's selection, that is, if the user chooses to replace, the emergency contact will be updated to the newly input information; if the user chooses to add, the new emergency contact information will be added. Hold, no action is performed on the entry. Preferably, in order to facilitate the user to know the emergency contact information that has been added, the emergency contact information that has been added to the entry is displayed on the prompt interface. Further, when the above situation exists in multiple items, the relevant information of one monitoring item can be prompted to the user in sequence each time. When it is detected that the user selects and confirms the item, the next monitoring item that needs to be reminded is displayed until all the items that need to be reminded are displayed. The monitoring entries of all have been processed. In another embodiment, each monitoring item is displayed in groups of emergency contacts, which is convenient for users to process in batches. For example, as shown in Figure 4j, the page displays the grouping of two different emergency contacts. When one page cannot display all of them , the page has a page turning button, as shown in the figure "→", and the page turning function is realized by the left arrow or the right arrow. The user can select the selection button in front of each monitoring item as required, such as ○ in the figure, to determine the operation to be performed. When multiple monitoring items perform the same operation, they can select multiple items at the same time and then perform the corresponding operation, and Replace, add or keep.
优选的,添加紧急联系人信息时,可以一次输入多个紧急联系人信息,即在紧急联系人输入区域同时输入多个紧急联系人信息;优选的,可以在多个联系人中间通过标点符号或者空格隔开,AP接收到该消息时,以标点符号或者空格为分界区分多个紧急联系人信息,在本发明中,不限定标点符号的具体要求,只要用户输入了标点符号或者空格则按不同联系人对待;或者可以当用户输入时,在输入窗口旁边以悬浮窗口的方式提示用户对于多个紧急联系人信息如何输入。Preferably, when adding emergency contact information, multiple emergency contact information can be input at one time, that is, multiple emergency contact information can be input simultaneously in the emergency contact input area; Spaces are separated. When the AP receives the message, it uses punctuation marks or spaces as the boundary to distinguish multiple emergency contact information. In the present invention, the specific requirements for punctuation marks are not limited, as long as the user inputs punctuation marks or spaces Contact treatment; or when the user inputs, the user can be prompted how to input multiple emergency contact information in the form of a floating window next to the input window.
优选的,该界面还包括全部选中和全部取消按钮,方便用户选中全部需要选择的条目或者取消全部选中的条目。Preferably, the interface further includes select all and cancel all buttons, which is convenient for the user to select all the items to be selected or cancel all the selected items.
优选的,将安全监控界面作为主页,如图4a所示的界面,在每个界面中都显示可以切换到主页的按钮,通过点击该按钮,切换到安全监控界面;或者设置切换到主页的触摸方式、手势等交互方式,检测到相应操作时,切换到主页。Preferably, the security monitoring interface is used as the home page, such as the interface shown in Figure 4a, a button that can be switched to the home page is displayed in each interface, and by clicking the button, the security monitoring interface is switched; or a touch switch to the home page is set. mode, gestures and other interaction methods, when the corresponding operation is detected, switch to the home page.
在一个实施方式中,在主页设置“个人设置”按钮,点击该按钮,可以显示针对该终端已添加的安全监控条目以及紧急联系人信息。In one embodiment, a "personal settings" button is set on the home page, and by clicking the button, the added security monitoring items and emergency contact information for the terminal can be displayed.
优选的,在主页还包括个性化设置按钮。当已有的安全监控策略条目都不符合用户的要求时,用户点击该个性化设置按钮,进入个性化设置监控需求的界面,如图所示,包括安全措施输入窗口,用户根据个人监控需求输入监控要求,点击确定按钮则发送至AP,AP接收到该监控要求后,解析监控要求,生成对应的安全监控条目,将生成的安全监控条目发送至终端的界面,请求终端进行确认,若生成的安全监控条目符合用户的要求,用户点击确认按钮,检测到用户点击确认操作时,发送至AP最终生成对应的安全监控条目,若生成的安全监控条目不符合用户的要求,用户可以对该安全监控条目修改,修改后点击确认按钮,发送至AP最终生成修改后的安全监控条目。Preferably, a personalized setting button is also included on the home page. When the existing security monitoring policy items do not meet the user's requirements, the user clicks the personalized setting button to enter the interface of personalized monitoring requirements, as shown in the figure, including the security measure input window, the user can input according to the personal monitoring requirements Monitoring requirements, click the OK button to send them to the AP. After receiving the monitoring requirements, the AP parses the monitoring requirements, generates the corresponding security monitoring entries, sends the generated security monitoring entries to the interface of the terminal, and requests the terminal to confirm. The security monitoring entry meets the user's requirements. The user clicks the confirm button, and when the user clicks the confirmation operation is detected, it is sent to the AP to finally generate the corresponding security monitoring entry. If the generated security monitoring entry does not meet the user's requirements, the user can monitor the security. After modifying the entry, click the Confirm button to send it to the AP to finally generate the modified security monitoring entry.
具体的,如图4k所示,用户在终端A的输入区域输入安全监控要求,如输入“当终端靠近电梯时进行提醒”,点击确定按钮发送至AP,AP解析该要求,根据解析结果生成对应的安全监控条目,如下表所示:Specifically, as shown in Figure 4k, the user enters the safety monitoring requirement in the input area of terminal A, such as inputting "remind when the terminal is close to the elevator", clicks the OK button to send it to the AP, the AP parses the requirement, and generates a corresponding request according to the analysis result. security monitoring entries, as shown in the following table:
表3个性化安全监控策略Table 3 Personalized security monitoring strategy
AP将该个性化安全监控条目发送至终端,终端的显示界面如图4l所示,若终端确定当前安全监控条目无误,则点击确认,发送确认消息至AP,生成的安全监控条目与上文中提及的安全监控条目相同,用户可以按上述方式进一步添加紧急联系人或执行其他操作。The AP sends the personalized security monitoring entry to the terminal. The display interface of the terminal is shown in Figure 41. If the terminal determines that the current security monitoring entry is correct, click Confirm to send a confirmation message to the AP. The generated security monitoring entry is the same as the one mentioned above. and the security monitoring entries are the same, and users can further add emergency contacts or perform other operations as described above.
若终端确定当前安全监控条目与用户期望的不同,则可以直接在对应的表项中修改,例如将小于1.5m时提醒修改为小于1m时提醒,终端侧修改后的界面显示如图4m所示,优选的,对于修改的项目以不同的颜色显示,以进行区分,用户修改完成后,点击确认按钮发送AP生成对应的安全监控条目。If the terminal determines that the current security monitoring entry is different from what the user expects, it can be directly modified in the corresponding entry. For example, change the reminder when it is less than 1.5m to a reminder when it is less than 1m. The modified interface on the terminal side is displayed as shown in Figure 4m , Preferably, the modified items are displayed in different colors to distinguish them. After the modification is completed, the user clicks the confirm button to send the AP to generate the corresponding security monitoring items.
优选的,该界面还包括输入区域,如图4n,用户一方面可以修改AP发送的安全监控条目的信息,另一方面可以继续输入,添加新的安全监控条目,或者为当前的安全监控条目添加新的内容,如用户修改相应项目同时,在输入区域输入“添加紧急联系人13810000012”,终端检测到用户点击确认按钮后,向 AP发送消息,AP接收到终端发送的消息后,根据用户的修改生成对应的安全监控条目。Preferably, the interface also includes an input area, as shown in Figure 4n. On the one hand, the user can modify the information of the security monitoring item sent by the AP, and on the other hand, he can continue to input, add a new security monitoring item, or add a new security monitoring item to the current security monitoring item. For new content, such as when the user modifies the corresponding item, enter "Add emergency contact 13810000012" in the input area. After the terminal detects that the user clicks the confirm button, it sends a message to the AP. After the AP receives the message sent by the terminal, it changes according to the user's modification. Generate corresponding security monitoring entries.
在另一实施方式中,个性化设置界面显示安全监控条目,其中包括索引,监控对象,安全措施项目,优选的,还包括紧急联系人项目。用户在监控对象项目中,通过点击该项目的输入区域,以下拉菜单的方式查看并选择可选的监控对象,如下拉菜单包括电梯、楼梯等,用户可以选择其中的项目,对于安全策略条目,用户通过输入的方式设置个性化需求,如输入“终端与电梯距离小于1m时提醒”,优选的,对于用户不关注的项目,可以保持空白,如紧急联系人,用户未输入任何信息。终端检测到用户点击确认按钮后,向AP发送消息, AP根据该消息生成对应的安全监控条目。In another embodiment, the personalized setting interface displays security monitoring items, including indexes, monitoring objects, security measures items, and preferably, emergency contact items. In the monitoring object item, the user clicks the input area of the item to view and select the optional monitoring object in the form of a drop-down menu. The drop-down menu includes elevators, stairs, etc., and the user can select the items. For the security policy entry, The user sets individualized requirements by input, such as "remind when the distance between the terminal and the elevator is less than 1m", preferably, for items that the user does not pay attention to, it can be left blank, such as emergency contacts, the user has not input any information. After detecting that the user clicks the confirmation button, the terminal sends a message to the AP, and the AP generates a corresponding security monitoring entry according to the message.
优选的,对于限制终端使用网络的服务的场景,AP设置是否在终端接入网络后弹出该主页界面,此外,AP还可以设置对于限制使用服务的终端在主页可以使用的功能,如仅部分安全监控条目对该终端是可用的,基于其许可的功能在终端的界面显示相应的内容。Preferably, for the scenario of restricting the terminal to use the service of the network, the AP sets whether to pop up the homepage interface after the terminal accesses the network. In addition, the AP can also set the functions that can be used on the homepage for the terminal that restricts the use of the service, such as only partial security. The monitoring item is available to the terminal, and the corresponding content is displayed on the interface of the terminal based on its permitted functions.
在该实施方式中,通过界面直观的向用户显示安全监控策略,可以使用户灵活方便的选择被安全监控用户的监控项目,无需用户预先在AP中进行设置,尤其适合需要接入公共场所的AP对终端进行安全监控的场景,因为在该场景中,AP无法预先获知需要进行安全监控的终端以及对其监控的条目,通过该方式可以便利的添加被监控终端以及便于终端基于界面获知的信息添加适合自身的安全监控条目。In this embodiment, the security monitoring policy is intuitively displayed to the user through the interface, so that the user can flexibly and conveniently select the monitoring items of the security-monitored user without the need for the user to set the AP in advance, which is especially suitable for the AP that needs to access public places. In the scenario of security monitoring of terminals, because in this scenario, the AP cannot know in advance the terminals that need to be monitored for security and the items to be monitored. In this way, the monitored terminals can be easily added and the terminals can be easily added based on the information obtained from the interface. A security monitoring entry that suits you.
实施方式十:Embodiment ten:
在日常生活中,用户携带的终端存在不固定的情况,在进行安全监控时,若对终端设定相应的监控策略,容易使得针对该终端的监控策略不适合携带该终端的用户,如基于前次携带终端的用户为3岁儿童设置了对应的安全监控策略,而当前携带该终端的用户为6岁儿童,之前针对3岁儿童设置的安全监控策略则不再适合当前6岁儿童。基于上述场景,本发明提出另一种设置安全监控策略的方法。In daily life, the terminal carried by the user is not fixed. During security monitoring, if a corresponding monitoring strategy is set for the terminal, it is easy to make the monitoring strategy for the terminal unsuitable for the user who carries the terminal. The user carrying the terminal for the second time has set a corresponding security monitoring policy for a 3-year-old child, and the user currently carrying the terminal is a 6-year-old child. The security monitoring policy previously set for a 3-year-old child is no longer suitable for the current 6-year-old child. Based on the above scenario, the present invention proposes another method for setting a security monitoring policy.
优选的,安全监控策略条目还包括被监控用户项目,该项目包括携带终端的用户的特征信息,如年龄,身高,指纹,照片等表明用户特征的信息。如下表所示。Preferably, the security monitoring policy entry further includes a monitored user item, and the item includes characteristic information of the user who carries the terminal, such as age, height, fingerprint, photo and other information indicating user characteristics. as shown in the table below.
表4安全监控策略Table 4 Security monitoring strategy
在一个实施方式中,AP预先配置安全监控策略的所有项目,或者,AP可以不对被监控终端进行设置,其中,对于同一被监控对象,具有不同特征的被监控用户对应于相同或不同的安全措施。从而使得该监控策略可以结合用户的特征信息生成针对具有该特征信息的用户的安全措施。例如在家庭中,被监控的用户通常是固定的,则用户在对AP的安全监控策略设置时,在被监控用户项目中输入用户的特征信息,以及对其他需要设置的项目进行设置,AP获取用户的输入,设置对应的安全监控策略。In one embodiment, the AP configures all items of the security monitoring policy in advance, or the AP may not set the monitored terminal, wherein, for the same monitored object, monitored users with different characteristics correspond to the same or different security measures . Therefore, the monitoring strategy can combine the characteristic information of the user to generate security measures for the user with the characteristic information. For example, in a family, the monitored user is usually fixed. When the user sets the security monitoring policy of the AP, the user enters the user's characteristic information in the monitored user item, and sets other items that need to be set. The AP obtains User input to set the corresponding security monitoring policy.
在另一实施方式中,通过用户输入的方式设置安全监控策略,同上述方法,终端接入AP后,显示上述主页,采用上述相同的方法根据用户选择或输入生成安全监控策略。In another embodiment, the security monitoring policy is set by user input, which is the same as the above method. After the terminal accesses the AP, the home page is displayed, and the security monitoring policy is generated according to the user selection or input using the same method described above.
在另一实施方式中,终端在发送探测请求帧前,获取用户的特征信息,将获取的用户的特征信息发送至AP,AP根据用户的特征信息与安全监控策略进行比较,当符合安全监控条目中的特征信息时,将终端对应添加到该条目的被监控终端项中。In another embodiment, before sending the probe request frame, the terminal obtains the user's feature information, and sends the obtained user's feature information to the AP. The AP compares the user's feature information with the security monitoring policy, and when the security monitoring entry is met When the feature information in the entry is added, the terminal is correspondingly added to the monitored terminal item of the entry.
优选的,终端周期性获取用户特征信息,判断获取的用户特征信息与发送探测请求帧前获取的用户的特征信息是否相同,若相同则等下一获取用户特征信息时间到来时再一次获取用户特征信息,如此重复,若不相同,则将该不同的特征信息发送至AP,AP接收到终端发送的特征信息后,与安全监控策略的条目进行比较,将终端更新至符合该特征信息的被监控终端项目中。Preferably, the terminal periodically obtains the user feature information, and determines whether the obtained user feature information is the same as the user feature information obtained before sending the probe request frame, and if it is the same, the user feature is obtained again when the next time to obtain the user feature information arrives. If it is not the same, then send the different feature information to the AP. After receiving the feature information sent by the terminal, the AP compares it with the items of the security monitoring policy, and updates the terminal to the monitored one that conforms to the feature information. in the terminal project.
通过该方法,当用户携带的终端发生改变时,可以及时对该用户的状况继续跟踪监控,而且可以结合被监控用户的特点为其配置合适的监控策略。With this method, when the terminal carried by the user changes, the status of the user can be continuously tracked and monitored in time, and an appropriate monitoring strategy can be configured for the monitored user in combination with the characteristics of the monitored user.
实施方式十一:Embodiment eleven:
在判断终端的用户是否需要被安全监控时,可以通过终端获取携带终端的用户的特征信息,根据该特征信息判断用户是否需要被安全监控,如可以在终端中提前设置需要被安全监控的用户的特征信息,将获取的特征信息与提前设置的特征信息进行比较,符合被安全监控的特征时,终端向AP发送携带Security Flag字段的探测请求帧,优选的,该特征信息与上述特征信息相同。When judging whether the user of the terminal needs to be monitored safely, the characteristic information of the user carrying the terminal can be obtained through the terminal, and whether the user needs to be monitored safely can be determined according to the characteristic information. Feature information, the acquired feature information is compared with the feature information set in advance, and when it matches the features to be monitored by security, the terminal sends a probe request frame carrying a Security Flag field to the AP. Preferably, the feature information is the same as the above feature information.
此外,在本发明的方法中,用户通过终端输入信息时,可以通过语音的方式输入信息,终端获取用户语音信息,对其解析,将相应内容填写到对应的输入区,或者终端根据用户的语音指令向AP发送对应的消息,该方法可以便利于用户,提高用户体验。In addition, in the method of the present invention, when the user inputs information through the terminal, the information can be input by voice, and the terminal obtains the user's voice information, parses it, and fills in the corresponding content in the corresponding input area, or the terminal according to the user's voice The instruction sends a corresponding message to the AP, and the method can facilitate the user and improve the user experience.
此外,当AP对终端进行安全监控时,终端的接入网络的图标旁边显示一符号,该符号表明终端处于被安全监控的状态。此外,用户点击该符号,还可以在终端的界面显示上述主页界面,从而使得用户可以随时更改或者查看其对应的安全监控条目。In addition, when the AP performs security monitoring on the terminal, a symbol is displayed next to the icon of the terminal's access network, and the symbol indicates that the terminal is in a security monitoring state. In addition, when the user clicks the symbol, the above-mentioned home page interface can also be displayed on the interface of the terminal, so that the user can change or view the corresponding security monitoring entry at any time.
在另一实施方式中,发挥安全监控的终端通常包括可穿戴设备等便携式设备,为了便于对屏幕较小或者无屏幕的终端进行设置,本发明还提出了以下方法:In another embodiment, the terminal that performs security monitoring usually includes a portable device such as a wearable device. In order to facilitate the setting of a terminal with a small screen or no screen, the present invention also proposes the following method:
将终端与另一终端建立连接,通过连接的建立使得终端共享另一终端的屏幕,从而可以通过在另一终端上执行相应的操作对终端进行相关设置。A connection is established between the terminal and another terminal, and through the establishment of the connection, the terminal can share the screen of the other terminal, so that relevant settings can be performed on the terminal by performing corresponding operations on the other terminal.
实施方式十二:Embodiment 12:
具有安全监控需求的用户接入到具有识别接入网络的终端的用户为需要被安全监控的用户的能力的AP后,对该用户进行安全监控,主要包括以下步骤,如图5:After a user with security monitoring requirements accesses an AP that has the ability to identify a user of a terminal accessing the network as a user who needs to be securely monitored, security monitoring for the user mainly includes the following steps, as shown in Figure 5:
步骤600,获取用户的位置信息;Step 600, obtaining the location information of the user;
在该步骤中,用户的终端获取用户的位置信息,发送至AP,或者AP获取用户的位置信息,如基于信号强度、其他设备提供的信息获取用户的位置信息;In this step, the user's terminal acquires the user's location information and sends it to the AP, or the AP acquires the user's location information, such as acquiring the user's location information based on signal strength and information provided by other devices;
步骤610,确定与用户对应的安全监控策略中的被监控对象;Step 610, determine the monitored object in the security monitoring policy corresponding to the user;
在该步骤中,通过查找安全监控策略,获取与用户对应的安全监控条目,从而得到与用户对应的被监控对象。In this step, by searching for the security monitoring policy, the security monitoring entry corresponding to the user is obtained, so as to obtain the monitored object corresponding to the user.
步骤620,根据安全措施比较用户与被监控对象的关系,判断用户与被监控对象的关系是否满足安全措施所设置的要求;若满足,则执行步骤630,否则执行步骤640;Step 620, compare the relationship between the user and the monitored object according to the security measures, and determine whether the relationship between the user and the monitored object meets the requirements set by the security measures; if so, go to step 630, otherwise go to step 640;
在该步骤中,即判断用户是否满足预警条件或者需要采取一定措施的条件,比如用户对应的被监控对象为电梯,当前用户与电梯的距离小于1m,则满足了安全策略的预警条件。又例如用户对应的被监控对象为插座,安全措施为控制插座断电。In this step, it is judged whether the user meets the warning condition or the condition that certain measures need to be taken. For example, the monitored object corresponding to the user is an elevator, and the current distance between the user and the elevator is less than 1m, then the warning condition of the safety policy is met. Another example is that the monitored object corresponding to the user is an outlet, and the safety measure is to control the outlet to be powered off.
步骤630,根据安全措施执行对应的操作。In step 630, a corresponding operation is performed according to the security measure.
在该步骤中,基于安全措施,例如对终端进行提醒,或者向紧急联系人发送提醒消息。In this step, based on safety measures, for example, the terminal is reminded, or a reminder message is sent to the emergency contact.
在另一实施方式中,安全措施包括对被监控对象的控制,如向被监控对象或者与其关联的设备发送控制命令,接收控制命令的设备执行该命令,从而消除被监控对象对用户可能造成的危险。In another embodiment, the security measures include the control of the monitored object, such as sending a control command to the monitored object or a device associated with it, and the device receiving the control command executes the command, so as to eliminate the possible effects of the monitored object on the user. Danger.
步骤640,继续获取用户的位置信息,并执行步骤620。Step 640, continue to acquire the location information of the user, and perform step 620.
在该步骤中,继续获取用户的位置信息,可以为周期性的获取,或者实时的获取。In this step, the location information of the user is continuously acquired, which may be acquired periodically or acquired in real time.
优选的,基于用户当前的位置以及被监控对象的位置,预测用户最快到达安全措施中设置的用户与被监控对象达到预警关系的时间长度,设置计时器,当计时器时间达到该预测的时间长度时,执行该步骤。Preferably, based on the current position of the user and the position of the monitored object, predict the length of time for the user to reach the early warning relationship between the user and the monitored object set in the security measures as soon as possible, and set a timer, when the timer reaches the predicted time length, perform this step.
其中预测该时间长度的步骤包括:获取用户的特征信息,基于用户的特征信息确定具有该特征信息的用户的最快速度,基于该速度预测该时间长度。The step of predicting the time length includes: acquiring characteristic information of the user, determining the fastest speed of the user with the characteristic information based on the characteristic information of the user, and predicting the time length based on the speed.
例如获取用户的身高,基于用户的身高预测用户的速度;或者获取用户的年龄,基于用户的年龄预测用户的速度。其中用户身高与速度的关系以及用户年龄与速度的关系为基于大数据统计分析得到。For example, the user's height is obtained, and the user's speed is predicted based on the user's height; or the user's age is obtained, and the user's speed is predicted based on the user's age. The relationship between user height and speed and the relationship between user age and speed are obtained based on statistical analysis of big data.
实施方式十三:Thirteenth implementation:
在上述实施方式中提到在AP中存储对应特定用户的安全监控策略,终端获取用户的特征信息,如指纹、图像、年龄、身高等信息,将上述信息发送至AP 从而可以使得AP识别携带该终端的用户,进一步针对该终端应用该用户对应的安全监控策略。在另一个实施方式中,获取用户特征信息的设备可以是其他设备,上述设备识别并获取用户特征信息以及识别用户携带的终端,将识别的用户特征信息以及识别的终端的信息发送至AP,AP基于其他设备发送的信息将终端添加到对应该用户的安全监控条目中,或者其他设备将用户特征信息发送至识别出的用户携带的终端,由终端将用户特征信息发送至AP。In the above embodiment, it is mentioned that the security monitoring policy corresponding to a specific user is stored in the AP, and the terminal obtains the user's characteristic information, such as fingerprint, image, age, height and other information, and sends the above information to the AP, so that the AP can identify and carry the information. For the user of the terminal, the security monitoring policy corresponding to the user is further applied to the terminal. In another embodiment, the device that obtains the user feature information may be other devices. The above-mentioned device identifies and obtains the user feature information and identifies the terminal carried by the user, and sends the identified user feature information and information of the identified terminal to the AP. The AP The terminal is added to the security monitoring entry corresponding to the user based on the information sent by other devices, or other devices send user feature information to the terminal carried by the identified user, and the terminal sends the user feature information to the AP.
在一个实施方式中,安全措施不仅是向被监控用户以及紧急联系人发出提醒预警,还可以是采取必要的安全措施,以消除或避免可能发生的危险事件,如当被监控用户靠近插座时,将插座进行断电处理。然而频繁的断电对电器会造成一定的伤害,而且儿童可能在家长的教育下意识到插座的危险,不会总是去触碰插座。为了解决该问题,本发明还提出了以下方法,如图6所示。In one embodiment, the safety measure is not only to issue an alert to the monitored user and emergency contacts, but also to take necessary safety measures to eliminate or avoid possible dangerous events, such as when the monitored user approaches the socket, Power off the socket. However, frequent power outages will cause certain damage to electrical appliances, and children may be aware of the dangers of sockets under the education of their parents and will not always touch the sockets. In order to solve this problem, the present invention also proposes the following method, as shown in FIG. 6 .
步骤700,获取用户的特征信息;Step 700, obtaining the characteristic information of the user;
如前面所述,可以是用户携带的终端获取用户的特征信息,也可以是其他设备获取用户的特征信息,其中特征信息可以是用户的指纹、声纹、具有用户的图像、视频等可以用于识别用户身份的信息。As mentioned above, the terminal carried by the user may obtain the user's characteristic information, or other devices may obtain the user's characteristic information, wherein the characteristic information may be the user's fingerprint, voiceprint, images with the user, videos, etc. Information that identifies the user.
优选的,还可以获取用户携带的终端的信息,如可以为用于识别终端的信息,或者为终端的位置信息。Preferably, information of the terminal carried by the user may also be acquired, such as information for identifying the terminal, or location information of the terminal.
优选的,该步骤可以在终端被添加到安全监控策略条目以后执行,也可以在未将终端添加到安全监控策略条目时执行。Preferably, this step may be performed after the terminal is added to the security monitoring policy entry, or may be performed when the terminal is not added to the security monitoring policy entry.
步骤710,发送用户的特征信息至具有安全监控策略的监控设备;Step 710, sending the feature information of the user to a monitoring device with a security monitoring policy;
在本步骤中,具有安全监控策略的监控设备可以为网络的AP,也可以为其他具有安全监控策略的监控设备,如智能插座等设备。In this step, the monitoring device with a security monitoring policy may be an AP of the network, or may be other monitoring devices with a security monitoring policy, such as a smart socket and other devices.
优选的,将用户携带的终端的信息也发送至监控设备。Preferably, the information of the terminal carried by the user is also sent to the monitoring device.
步骤720,监控设备根据接收的用户的特征信息确定用户对应于哪条安全监控条目,将用户携带的终端添加到该对应的条目中;Step 720, the monitoring device determines which security monitoring entry the user corresponds to according to the received feature information of the user, and adds the terminal carried by the user to the corresponding entry;
在一个实施方式中,监控设备接收的用户特征信息,根据接收的用户特征信息与安全监控策略中的被监控用户项比较,若存在比较一致的条目,则将用户携带的终端添加到该用户对应的条目的被监控终端项中,若不存在具有该特征的被安全监控的用户,优选的,则进一步根据用户的特征确定其是否属于需要被安全监控的用户类型,该需要被安全监控的用户类型可以根据已存储的安全监控策略学习得出,优选的,是根据被安全监控用户的特征学习得出,比如根据已存储的安全监控策略学习得到被监控用户类型为儿童、老人、残疾人等;具体的,比如判断用户是否属于上述类型中的一种,若属于,则其应当属于被安全监控的用户,若不属于上述类型,则无需对该用户进行安全监控,不将其添加到安全监控策略的条目中,结束。In one embodiment, the user feature information received by the monitoring device is compared with the monitored user item in the security monitoring policy according to the received user feature information, and if there is a relatively consistent entry, the terminal carried by the user is added to the corresponding user item. In the monitored terminal item of the entry, if there is no user to be monitored by security with this characteristic, preferably, it is further determined according to the characteristics of the user whether it belongs to the type of user that needs to be monitored by security. The type can be learned according to the stored security monitoring strategy, preferably, it is learned according to the characteristics of the user to be monitored safely, for example, the type of the monitored user can be learned according to the stored security monitoring strategy: children, the elderly, the disabled, etc. ; Specifically, for example, to determine whether the user belongs to one of the above types, if so, it should belong to the user under security monitoring; In the entry of the monitoring policy, end.
对于属于上述类型的用户,向用户发送提示消息,提示是否将其添加到安全监控策略中,若用户反馈是,则如前所述,向用户发送上述主页界面,由用户自行设置其对应的安全监控条目,或者向用户发送提示,询问是否由AP为其自动生成安全监控策略条目,若是,则根据其所述用户类型,AP参照安全监控策略中与该用户属于同类型用户的安全监控条目自动为其生成对应的安全监控条目。若用户反馈否,则结束。也可以不向用户发送询问消息,直接自动生成安全监控条目。例如家里来了客人,该客人的5岁孩子携带一终端,获取该孩子的用户特征,判断安全监控策略中不存在与该孩子匹配的条目,进一步判断用户属于哪种类型,确定其属于儿童,则向其携带的终端发送提示消息,使用户确定是否要对其进行安全监控,该提示消息可以是以界面的方式显示,或者同时语音提示,若用户确认需要对其进行安全监控,则按上述方式生成安全监控条目。For users belonging to the above types, a prompt message is sent to the user, prompting whether to add it to the security monitoring policy. If the user feedback is yes, the above home page interface is sent to the user as described above, and the user can set the corresponding security. Monitoring entry, or send a prompt to the user to ask whether the AP automatically generates a security monitoring policy entry for it, if so, according to the user type, the AP automatically refers to the security monitoring entry of the same type of user as the user in the security monitoring policy. Generate corresponding security monitoring entries for them. If the user feedback no, end. It is also possible to automatically generate security monitoring entries directly without sending an inquiry message to the user. For example, there is a guest at home, the 5-year-old child of the guest carries a terminal, obtains the user characteristics of the child, judges that there is no entry matching the child in the security monitoring policy, further judges the type of the user, and determines that he belongs to the child, Then send a prompt message to the terminal carried by it, so that the user can determine whether to monitor it safely. The prompt message can be displayed in the form of an interface, or a voice prompt can be displayed at the same time. If the user confirms that it needs to be monitored safely, press the above way to generate security monitoring entries.
优选的,向用户发送提示前,先向对AP具有控制能力的终端发送提示消息,询问是否允许为该用户生成安全监控条目,若是,则执行向用户发送提示的步骤,若否,则结束。Preferably, before sending the prompt to the user, a prompt message is sent to the terminal having the control ability to the AP, asking whether to allow the user to generate a security monitoring entry.
进一步的,具有控制能力的终端向AP发送删除指示,该删除指示用于指示 AP,当其未检测到该用户时间达到预设时间长度时,删除该用户对应的安全监控条目,从而节省AP的存储空间。Further, the terminal with control capability sends a deletion instruction to the AP, and the deletion instruction is used to instruct the AP to delete the security monitoring entry corresponding to the user when it does not detect that the user's time reaches the preset time length, thereby saving the AP's storage.
优选的,监控设备获取用户的位置信息,例如该位置信息为其他设备发送给监控设备,或者监控设备基于获取的用户的视频识别用户所处的位置,基于用户的位置信息以及监控设备获取的一个或多个终端的位置信息确定用户携带的终端。在该步骤中,终端可以是与监控设备建立连接的终端,监控设备基于与终端之间的无线信号确定终端的位置,或者终端周期性的或满足一定条件时将自身位置信息发送至监控设备,或者监控设备基于检测到的终端的信号确定终端的位置信息,监控设备基于终端的位置信息确定哪个终端是用户携带的终端。监控设备确定了哪个终端是用户携带的终端后,获取用于识别终端的信息,将该终端添加到用户对应的安全监控策略条目的被监控终端项中。Preferably, the monitoring device acquires the location information of the user, for example, the location information is sent to the monitoring device by other devices, or the monitoring device recognizes the location of the user based on the acquired video of the user, based on the location information of the user and the one obtained by the monitoring device. The location information of one or more terminals determines the terminal carried by the user. In this step, the terminal may be a terminal that establishes a connection with the monitoring device, and the monitoring device determines the location of the terminal based on the wireless signal with the terminal, or the terminal periodically or when certain conditions are met, sends its own location information to the monitoring device, Or the monitoring device determines the location information of the terminal based on the detected signal of the terminal, and the monitoring device determines which terminal is the terminal carried by the user based on the location information of the terminal. After determining which terminal is carried by the user, the monitoring device obtains information for identifying the terminal, and adds the terminal to the monitored terminal item of the security monitoring policy entry corresponding to the user.
优选的,还包括以下步骤,判断终端是否在用户对应的安全监控策略条目的被监控终端项以外的其他被监控终端项中,如果在,则进行删除,如果不在,不执行任何操作。通过该步骤,可以防止对用户应用不必要的安全措施。Preferably, it also includes the following steps: judging whether the terminal is in other monitored terminal items other than the monitored terminal item of the security monitoring policy entry corresponding to the user, if so, delete it, if not, do nothing. By this step, unnecessary security measures can be prevented from being applied to the user.
优选的,终端设备具备获取用户特征信息的能力时,定期获取携带终端的用户的特征信息,基于获取的用户的特征信息判断携带终端的用户是否改变,若发生改变,则向监控设备发送被监控用户改变的消息,并携带改变后的用户的特征信息,监控设备接收该信息,基于该信息判断用户是否保存在安全监控策略条目的被监控用户中,即比较接收的信息与安全监控条目中的被监控用户的特征信息,比较一致则说明该用户有被监控的需求,否则用户不具有安全监控需求,或者进一步执行上述用户类型的判断的相关步骤,以确定是否生成新的安全监控条目,在此不再详细描述。相应的,比较一致时则将终端添加到该被监控用户对应的被监控终端项中,删除其他被监控终端项中记录的该终端的信息。Preferably, when the terminal device has the ability to acquire user feature information, it periodically acquires the feature information of the user who carries the terminal, and judges whether the user who carries the terminal changes based on the acquired feature information of the user. The message that the user has changed, and carries the feature information of the changed user. The monitoring device receives the information and judges whether the user is saved in the monitored user of the security monitoring policy entry based on the information, that is, compares the received information with the security monitoring entry. If the characteristic information of the monitored user is consistent, it indicates that the user needs to be monitored, otherwise the user does not have the security monitoring requirement, or further perform the relevant steps of the judgment of the above user type to determine whether to generate a new security monitoring entry. This will not be described in detail. Correspondingly, if they are consistent, the terminal is added to the monitored terminal item corresponding to the monitored user, and the information of the terminal recorded in other monitored terminal items is deleted.
在另一实施方式中,监控设备周期性获取用户的位置以及在监控策略表中记录的被监控用户对应的终端的位置,判断二者位置是否一致,一致则不做处理,若不一致,则执行上述获取一个或多个终端的位置,基于终端的位置信息确定哪个终端是用户携带的终端以及后续的步骤,从而更新安全监控策略的条目。In another embodiment, the monitoring device periodically obtains the location of the user and the location of the terminal corresponding to the monitored user recorded in the monitoring strategy table, and determines whether the two locations are consistent. The above-mentioned acquiring the location of one or more terminals, determining which terminal is the terminal carried by the user based on the location information of the terminals, and subsequent steps, so as to update the entry of the security monitoring policy.
通过上述步骤,可以使得携带终端的用户变更时,及时根据携带终端的用户的特征更新终端在安全监控策略中被监控终端项的内容,从而使得对终端的安全监控与携带该终端的用户匹配。克服了针对同一终端采用固定的监控策略的缺陷。Through the above steps, when the user carrying the terminal changes, the content of the terminal item to be monitored in the security monitoring policy of the terminal can be updated in time according to the characteristics of the user carrying the terminal, so that the security monitoring of the terminal matches the user carrying the terminal. It overcomes the defect of adopting a fixed monitoring strategy for the same terminal.
进一步的,该方法还包括以下步骤:Further, the method also includes the following steps:
步骤730,判断被监控终端是否满足对其采取其对应的安全监控策略条目中的安全措施的条件,若是,向被监控终端发送提示信息,执行步骤740;若否,重复执行步骤730;Step 730, determine whether the monitored terminal satisfies the conditions for taking the security measures in its corresponding security monitoring policy entry, if so, send a prompt message to the monitored terminal, and execute step 740; if not, repeat step 730;
在该步骤中,安全措施中明确了需要对被监控用户防范的安全事件,和/或满足特定条件时执行的操作。如安全措施为当用户离插座1m时,对插座断电。In this step, the security measures specify security events that need to be guarded against the monitored user, and/or operations to be performed when certain conditions are met. For example, the safety measure is to cut off the power to the socket when the user is 1m away from the socket.
步骤740,判断是否接收到被监控终端的反馈信息;若是,则执行步骤750,若否,执行步骤760;Step 740, judge whether the feedback information of the monitored terminal is received; if yes, go to step 750, if not, go to step 760;
优选的,该反馈信息用于表示被监控终端的用户已接收到该提示信息,并且明白其中的安全隐患或者危险性。例如被安全监控的用户离插座1m时,向用户发送提示信息,该提示可以是语音提示或者文字提示,提示前方的插座有电,不能触摸。若用户理解了该含义,则发送反馈消息,该反馈消息可以是语音确认或者通过其他方式发送的反馈消息。Preferably, the feedback information is used to indicate that the user of the monitored terminal has received the prompt information and understands the potential safety hazards or dangers therein. For example, when the user under security monitoring is 1m away from the socket, a prompt message is sent to the user, and the prompt can be a voice prompt or a text prompt, indicating that the socket in front is powered and cannot be touched. If the user understands the meaning, a feedback message is sent, and the feedback message may be a voice confirmation or a feedback message sent by other means.
步骤750,不采取安全措施条目中的安全措施,继续对终端进行监控,判断终端是否更接近被监控对象或更远离被监控对象会造成的危险事件,若是,判断终端与被监控对象的距离是否大于第一阈值小于第二阈值,若距离满足该要求,则再次向终端发送提示信息,并执行步骤740;若终端与被监控对象的距离小于等于第一阈值,则按安全措施项执行相应的操作;若终端远离被监控对象,则不执行安全措施项的相应操作;Step 750, do not take the security measures in the security measure item, continue to monitor the terminal, determine whether the terminal is closer to the monitored object or is farther away from the dangerous event that will be caused by the monitored object, and if so, determine whether the distance between the terminal and the monitored object is not. It is greater than the first threshold and less than the second threshold. If the distance meets the requirement, the prompt information is sent to the terminal again, and step 740 is executed; if the distance between the terminal and the monitored object is less than or equal to the first threshold, the corresponding security measures are executed Operation; if the terminal is far away from the monitored object, the corresponding operation of the security measure item will not be performed;
进一步的,当未执行安全措施项的相应操作时,调整安全监控策略中的安全措施中判断满足对其采取其对应的安全措施的条件,使其比当前条件要求降低。例如当前的条件是儿童与插座距离为1.5m,则对插座断电,调整后为1m。Further, when the corresponding operation of the security measure item is not performed, it is judged that the security measures in the security monitoring policy are adjusted to satisfy the conditions for taking the corresponding security measures, so that the requirements are lower than the current conditions. For example, if the current condition is that the distance between the child and the socket is 1.5m, then the socket is powered off and adjusted to 1m.
进一步的,当该条件要求降低的次数超过门限时,向被监控用户的紧急联系人发送问询消息,确认是否还需要保留该安全监控条目,若接收到无需保留,则删除对应的安全监控条目,若接收到需要保留,则保留该项目,并且当预定时间段内未提醒过被监控用户,则再次向被监控用户的紧急联系人发送问询消息,如上所述。Further, when the number of times the condition requires reduction exceeds the threshold, an inquiry message is sent to the emergency contact of the monitored user to confirm whether the security monitoring entry still needs to be retained, and if no need to be retained is received, the corresponding security monitoring entry is deleted. , if it is received that the item needs to be retained, the item is retained, and when the monitored user is not reminded within a predetermined time period, an inquiry message is sent to the emergency contact of the monitored user again, as described above.
步骤760,判断该提示信息发送的次数是否满足阈值,若是,执行步骤770,若否,再次向用户发送提示信息,执行步骤740;Step 760, determine whether the number of times the prompt information is sent meets the threshold, if yes, go to step 770, if not, send prompt information to the user again, go to step 740;
步骤770,根据安全措施执行对应的操作。In step 770, a corresponding operation is performed according to the security measure.
在另一个实施方式中,在步骤730判断为是时,向被监控用户的紧急联系人发送消息,查询被安全监控的用户是否学习过针对该被监控对象的安全知识,若接收到是,不采取安全措施条目中的安全措施,继续对终端进行监控,判断终端是否更接近被监控对象或接近被监控对象会造成的危险事件,若更接近被监控对象或接近被监控对象会造成的危险事件,则向被监控用户的终端推送相关安全知识;进一步的,判断被监控用户是否进行学习,若是,则监测被监控用户学习安全知识后的行为,若被监控用户远离被监控对象或远离被监控对象会造成的危险事件,则调整安全监控策略中的安全措施中判断满足对其采取其对应的安全措施的条件,使其比当前条件要求降低;若被监控用户未进行学习,则向被监控用户携带的终端推送其感兴趣的内容,该内容为视频或音频,若通过视频或音频的播放阻止被监控用户靠近被监控对象或远离被监控对象会造成的危险事件,则不执行安全措施的相应安全措施,否则执行安全措施的操作。In another embodiment, when it is determined to be yes in step 730, a message is sent to the emergency contact of the monitored user to inquire whether the monitored user has learned the security knowledge for the monitored object, and if yes, no Take the security measures in the security measures item, continue to monitor the terminal, determine whether the terminal is closer to the monitored object or the dangerous event that will be caused by the monitored object, and the dangerous event that will be caused if it is closer to the monitored object or close to the monitored object , then push relevant security knowledge to the terminal of the monitored user; further, determine whether the monitored user is learning, if so, monitor the behavior of the monitored user after learning the security knowledge, if the monitored user is far away from the monitored object or away from the monitored user If the dangerous events caused by the object, adjust the security measures in the security monitoring strategy to determine that the conditions for taking the corresponding security measures are met, so that the requirements are lower than the current conditions; if the monitored user does not learn, it will be sent to the monitored The terminal carried by the user pushes the content they are interested in, which is video or audio. If the monitored user is prevented from approaching the monitored object or staying away from the monitored object through the playback of video or audio, it will cause dangerous events, and no security measures will be implemented. Appropriate security measures, otherwise perform the operation of security measures.
若接收到被监控用户未学习过针对该被监控对象的安全知识的消息,则向终端推送针对该被监控对象的安全知识,优选的,该安全知识为视频或音频。优选的,继续执行上述判断被监控用户是否进行学习及之后的步骤。If a message is received that the monitored user has not learned the security knowledge for the monitored object, the security knowledge for the monitored object is pushed to the terminal. Preferably, the security knowledge is video or audio. Preferably, the above steps of judging whether the monitored user is learning and the following steps are continued.
进一步的,若未接收到紧急联系人的确认消息,则重传所述消息,若满足重传最大次数,则不再向其紧急联系人发送所述消息,直接向被监控用户推送安全知识。Further, if the confirmation message of the emergency contact is not received, the message is retransmitted, and if the maximum number of retransmissions is satisfied, the message is not sent to the emergency contact, and the security knowledge is directly pushed to the monitored user.
上述步骤和前述步骤730的步骤可以是替换的方式,也可以都执行。The above steps and the steps of the aforementioned step 730 may be alternative manners, or both may be performed.
通过该方法,一方面可以根据被监控用户行为调整安全措施,另一方面可以有效的避免频繁的执行安全措施,同时还可以通过学习的方式提供被监控用户的安全意识。Through this method, on the one hand, the security measures can be adjusted according to the behavior of the monitored user, on the other hand, frequent execution of the security measures can be effectively avoided, and the security awareness of the monitored user can also be provided by means of learning.
通过本发明的方法,对信标帧进行改进,直接基于接收到的信标帧确定网络是否可以监控儿童的安全,为其提供安全警示作用,无需专门布设监控设备,可以利用已有基础设施,使不具有接入密码的终端接入网络,提高安全监控的覆盖范围,降低安全监控成本。此外,该方法无需预先建立被监控终端的列表或者建立被监控终端与安全策略的关联关系,可以根据用户的需求灵活设置,尤其适合于公共场所。Through the method of the present invention, the beacon frame is improved, whether the network can monitor the safety of children is directly determined based on the received beacon frame, and a safety warning function is provided for it, no special monitoring equipment is required, and the existing infrastructure can be used, Make the terminal without access password access the network, improve the coverage of security monitoring, and reduce the cost of security monitoring. In addition, the method does not need to establish a list of monitored terminals in advance or establish an association relationship between monitored terminals and security policies, and can be flexibly set according to user requirements, especially suitable for public places.
本发明实施例还提供了一种安全监控系统,包括信标发送装置(如图7所示),终端(如图8所示);优选的,AP或其他监控设备包括该信标发送装置。An embodiment of the present invention also provides a security monitoring system, including a beacon sending device (as shown in FIG. 7 ) and a terminal (as shown in FIG. 8 ); preferably, an AP or other monitoring equipment includes the beacon sending device.
本发明实施例还提供了信标发送装置,用于执行上述方法,具体包括:The embodiment of the present invention also provides a beacon sending device, which is used for executing the above method, and specifically includes:
生成单元,用于生成信标帧;a generating unit for generating a beacon frame;
发送单位,用于发送信标帧;Sending unit, used to send beacon frames;
生成单元还用于根据探测请求帧生成探测响应帧;The generating unit is further configured to generate a probe response frame according to the probe request frame;
具体的,生成单元按前述方式执行相应的判断等操作,根据要求生成相应的信标帧,探测响应帧。Specifically, the generating unit performs operations such as corresponding judgments in the aforementioned manner, and generates corresponding beacon frames and detection response frames according to requirements.
具体的,生成单元在Frame Body的保留字段中增加新的字段Security Flag。Specifically, the generating unit adds a new field Security Flag to the reserved field of Frame Body.
终端的接收模块接收到信标帧时,终端的生成模块可以通过以下方式确定网络是否具有该能力:When the receiving module of the terminal receives the beacon frame, the generating module of the terminal can determine whether the network has the capability in the following ways:
方式一:当信标帧中携带该字段时,确定网络具有该能力,不携带该字段时,网络不具有该能力。Manner 1: When the field is carried in the beacon frame, it is determined that the network has the capability, and when the field is not carried, the network does not have the capability.
方式二:当信标帧中携带该字段时,确定网络具有该能力,当信标帧中不携带该字段时,无法直接根据信标帧确定网络是否具有该能力,需进一步判断。Method 2: When the beacon frame carries this field, it is determined that the network has the capability; when the beacon frame does not carry this field, it is impossible to directly determine whether the network has the capability according to the beacon frame, and further judgment is required.
方式三:设置信标帧中携带该字段,根据该字段的值判断网络是否具有该能力,假设Security Flag值为1时,表示网络具有该能力,Security Flag值为0 时,网络不具有该能力;同样的,也可以设置Security Flag值为0时,表示网络具有该能力,Security Flag值为1时,网络不具有该能力。Method 3: Set the field to be carried in the beacon frame, and judge whether the network has the capability according to the value of the field. Suppose the value of the Security Flag is 1, indicating that the network has the capability, and when the value of the Security Flag is 0, the network does not have the capability ; Similarly, when the Security Flag value is 0, it means that the network has this capability, and when the Security Flag value is 1, the network does not have this capability.
终端的生成模块还用于生成探测请求帧,其生成方式按本发明前述方式生成;The generation module of the terminal is also used to generate the detection request frame, and the generation method is generated according to the foregoing method of the present invention;
终端的发送模块向网络发送探测请求帧时,当探测请求帧中携带了SecurityFlag字段,指示终端的用户需要被安全监控,当不携带该字段时,指示该终端的用户无需被安全监控。When the sending module of the terminal sends the probe request frame to the network, when the probe request frame carries the SecurityFlag field, it indicates that the user of the terminal needs to be monitored by security, and when this field is not carried, it indicates that the user of the terminal does not need to be monitored.
信标发送装置还包括接收单元,用于接收各种消息,信标发送装置的生成单元基于接收到的终端发送的探测请求帧生成探测响应帧,当接收的探测请求帧中携带了Security Flag字段,则在探测响应帧中携带Security Flag字段,其中,当网络具有识别接入网络的终端的用户为需要被安全监控的用户的能力时,则将该字段的值设置为指示网络具有该能力的值,否则,设置为网络不具有该能力的值。或者当接收的探测请求帧中携带了Security Flag字段,当网络具有该能力时,探测响应帧中携带该字段,采用如上的方式指示网络是否具有该能力,当网络不具有该能力,或者网络无法识别该Security Flag字段时,探测响应帧中不携带关于对该字段的任何应答字段。The beacon sending device also includes a receiving unit for receiving various messages. The generating unit of the beacon sending device generates a probe response frame based on the probe request frame sent by the received terminal. When the received probe request frame carries the Security Flag field , the Security Flag field is carried in the probe response frame, wherein, when the network has the ability to identify the user of the terminal accessing the network as the user who needs to be monitored by security, the value of this field is set to indicate that the network has the ability. value, otherwise, set to a value that the network does not have the capability to. Or when the received probe request frame carries the Security Flag field, when the network has this capability, the probe response frame carries this field, and uses the above method to indicate whether the network has the capability, when the network does not have the capability, or the network cannot When identifying this Security Flag field, the probe response frame does not carry any response field for this field.
当接收的探测请求帧中未携带Security Flag字段,则按现有技术的方式向终端发送探测响应帧,即网络是否具有该能力,都不在探测响应帧中携带该字段。When the received probe request frame does not carry the Security Flag field, the probe response frame is sent to the terminal according to the prior art, that is, whether the network has the capability, does not carry this field in the probe response frame.
信标发送装置的发送单元,还用于向终端设备发送探测响应帧。The sending unit of the beacon sending apparatus is further configured to send a probe response frame to the terminal equipment.
具体的,在该实施方式中,信标帧格式为格式1或格式2。Specifically, in this embodiment, the beacon frame format is
生成单元,判断网络是否具有识别接入网络的终端的用户为需要被安全监控的用户的能力,若具有,则设置信标帧中Security Flag字段的值,指示网络具有该能力;否则,设置信标帧中Security Flag字段的值,指示网络不具有该能力,或者,在信标帧中不携带Security Flag字段。The generating unit judges whether the network has the ability to identify the user of the terminal accessing the network as the user that needs to be monitored safely, and if so, set the value of the Security Flag field in the beacon frame to indicate that the network has the ability; otherwise, set the The value of the Security Flag field in the beacon frame indicates that the network does not have this capability, or the beacon frame does not carry the Security Flag field.
终端的接收模块,进行主动扫描,监听并接收信标帧,The receiving module of the terminal performs active scanning, monitors and receives beacon frames,
生成模块,解析信标帧,判断信标帧中是否携带Security Flag字段,若信标帧中携带Security Flag字段,则根据该字段的值判断网络是否具有识别接入网络的终端的用户为需要被安全监控的用户的能力,若网络具有该能力,判断终端的用户是否需要被安全监控,若用户需要被安全监控,则生成携带Security Flag 字段的探测请求帧,若用户不需要被安全监控,则生成不携带Security Flag字段的探测请求帧;若Security Flag字段指示网络不具有该能力,或者信标帧未携带 Security Flag字段,则终端接入网络的方式与现有技术相同,即生成不携带 Security Flag字段的探测请求帧。The generation module parses the beacon frame and determines whether the beacon frame carries the Security Flag field. If the beacon frame carries the Security Flag field, it is judged according to the value of the field whether the network has a user that identifies the terminal accessing the network. The capability of the user for security monitoring. If the network has this capability, determine whether the user of the terminal needs to be monitored by security. If the user needs to be monitored by security, a detection request frame with the Security Flag field will be generated. If the user does not need to be monitored by security, then Generate a probe request frame that does not carry the Security Flag field; if the Security Flag field indicates that the network does not have the capability, or the beacon frame does not carry the Security Flag field, the terminal accesses the network in the same way as the prior art, that is, the generation does not carry the Security Flag field. The probe request frame of the Flag field.
发送模块,发送探测请求帧。The sending module sends a probe request frame.
优选的,上述判断用户是否需要被安全监控与判断信标帧是否携带SecurityFlag字段的步骤的顺序可以调换,在判断用户需要被安全监控时,判断信标帧中是否携带Security Flag字段,若信标帧中携带Security Flag字段,则根据该字段的值判断网络是否具有识别接入网络的终端的用户为需要被安全监控的用户的能力,若网络具有该能力,则发送携带Security Flag字段的探测请求帧,若用户不需要被安全监控,则不执行解析Security Flag字段以及判断信标帧中是否携带Security Flag字段的步骤。Preferably, the order of the above steps of judging whether the user needs to be security monitored and judging whether the beacon frame carries the SecurityFlag field can be reversed. When judging that the user needs to be security monitored, it is determined whether the beacon frame carries the Security Flag field. The frame carries the Security Flag field, and according to the value of this field, it is judged whether the network has the ability to identify the user of the terminal accessing the network as the user who needs to be monitored for security. If the network has this ability, a detection request carrying the Security Flag field is sent. If the user does not need to be monitored by security, the steps of parsing the Security Flag field and judging whether the beacon frame carries the Security Flag field are not performed.
优选的,当终端的接收模块接收到多个不同装置发送的信标帧,终端的选择模块若判断终端的用户不需要被安全监控,则按现有技术方式,如选择信号强度最强的装置或按其他设置的选择策略选择要连接的装置;若判断终端的用户需要被安全监控,则解析多个装置发送的信标帧,根据信标帧选择具有识别接入网络的终端的用户为需要被安全监控的用户的能力的装置作为候选装置,从候选装置中选择要连接的装置的方法同现有技术,如选择信号强度最强的装置或按其他设置的选择策略选择要连接的装置。Preferably, when the receiving module of the terminal receives the beacon frames sent by a plurality of different devices, if the selection module of the terminal determines that the user of the terminal does not need to be monitored safely, it selects the device with the strongest signal strength according to the prior art method. Or select the device to be connected according to the selection strategy set by other settings; if it is determined that the user of the terminal needs to be monitored safely, then analyze the beacon frames sent by multiple devices, and select the user with the terminal that identifies the access network according to the beacon frame. The device with the capability of the user under security monitoring is used as a candidate device, and the method of selecting the device to be connected from the candidate devices is the same as that in the prior art, such as selecting the device with the strongest signal strength or selecting the device to be connected according to other set selection strategies.
信标发送装置的接收单元接收终端发送的探测请求帧,生成单元根据探测请求帧中是否携带Security Flag字段判断终端的用户是否需要被安全监控,若是,则将终端添加到被安全监控终端列表,并生成携带Security Flag字段的探测响应帧,以提示用户已被安全监控;若否,则生成不携带Security Flag字段的探测响应帧。发送单元,用于发送该探测请求帧。The receiving unit of the beacon sending device receives the detection request frame sent by the terminal, and the generating unit judges whether the user of the terminal needs to be security monitored according to whether the security flag field is carried in the detection request frame, and if so, then adds the terminal to the security monitoring terminal list, And generate a detection response frame carrying the Security Flag field to remind the user that the security has been monitored; if not, generate a detection response frame without the Security Flag field. A sending unit, configured to send the probe request frame.
优选的,为了降低发送信令的开销,无论探测请求帧中是否携带Security Flag字段,探测响应帧均不携带Security Flag字段,其响应方式同现有技术,其中若AP具有该能力,且允许需要被安全监控的用户的终端接入网络时,发送的允许终端接入网络的探测响应消息也默认网络已将该终端添加到被安全监控终端列表。Preferably, in order to reduce the overhead of sending signaling, no matter whether the probe request frame carries the Security Flag field, the probe response frame does not carry the Security Flag field, and the response method is the same as that of the prior art. When the terminal of the user under security monitoring accesses the network, the sent probe response message allowing the terminal to access the network also defaults that the network has added the terminal to the list of security monitored terminals.
在该实施方式中,信标帧格式为格式3。In this embodiment, the beacon frame format is
信标发送装置的发送单元发送信标帧;The sending unit of the beacon sending device sends a beacon frame;
终端的接收模块进行主动扫描,监听周围装置发送的信标帧,生成模块判断终端的用户是否需要被安全监控,若用户需要被安全监控,生成携带 Security Flag字段的探测请求帧,否则,生成不携带Security Flag字段的探测请求帧。发送模块,用于发送该探测请求帧。The receiving module of the terminal actively scans, monitors the beacon frames sent by the surrounding devices, and the generating module determines whether the user of the terminal needs to be monitored by security. If the user needs to be monitored by security, a detection request frame carrying the Security Flag field is generated. A probe request frame carrying the Security Flag field. The sending module is used for sending the probe request frame.
优选的,当终端的接收模块接收到多个装置发送的信标帧,选择模块判断终端的用户不需要被安全监控,则按现有技术方式,如选择信号强度最强的AP 或按其他设置的选择策略选择要连接的装置;若判断终端的用户需要被安全监控,则首先根据设定的策略选择候选装置,该策略同现有技术相同,如选择信号强度高于阈值的装置、或者允许接入的装置等,或者是根据用户设定的策略选择候选装置,确定候选装置后,生成模块生成携带Security Flag字段的探测请求帧,发送模块向候选装置发送该探测请求帧,选择模块根据接收的探测响应帧优先接入具有识别接入网络的终端的用户为需要被安全监控的用户的能力的网络。Preferably, when the receiving module of the terminal receives the beacon frames sent by multiple devices, the selection module determines that the user of the terminal does not need to be monitored safely, and then selects the AP with the strongest signal strength according to the prior art, such as selecting the AP with the strongest signal strength or other settings. The selection strategy selects the device to be connected; if it is determined that the user of the terminal needs to be monitored safely, first select the candidate device according to the set strategy, which is the same as the prior art, such as selecting a device with a signal strength higher than a threshold, or allowing The connected device, etc., or the candidate device is selected according to the policy set by the user. After the candidate device is determined, the generation module generates a detection request frame carrying the Security Flag field, the transmission module sends the detection request frame to the candidate device, and the selection module receives the detection request frame. The probe response frame of the network preferentially accesses the network with the ability to identify the user of the terminal accessing the network as the user that needs to be monitored safely.
信标发送装置的接收单元接收终端发送的探测请求帧,生成单元根据探测请求帧中是否携带Security Flag字段判断终端的用户是否需要被安全监控,若是,判断网络是否具有识别接入网络的终端的用户为需要进行安全监控的用户的能力,若具有该能力,则将终端添加到被安全监控终端列表,并生成携带 Security Flag字段的探测响应帧,以提示用户可以被监控;若不具有该能力,则生成不携带Security Flag字段的探测响应帧。若探测请求帧中未携带Security Flag字段,则发送的探测响应帧中不携带该字段,响应方式同现有技术相同。发送单元,用于发送探测响应帧。The receiving unit of the beacon sending device receives the detection request frame sent by the terminal, and the generating unit judges whether the user of the terminal needs to be safely monitored according to whether the Security Flag field is carried in the detection request frame, and if so, judges whether the network has the ability to identify the terminal accessing the network. The user is the capability of the user who needs to perform security monitoring. If the capability is available, the terminal will be added to the list of security monitored terminals, and a probe response frame with the Security Flag field will be generated to prompt the user that it can be monitored; if the capability is not available , a probe response frame without the Security Flag field is generated. If the Security Flag field is not carried in the probe request frame, the sent probe response frame does not carry this field, and the response method is the same as that in the prior art. The sending unit is used to send the probe response frame.
优选的,信标发送装置的接收单元接收到携带Security Flag字段的探测请求帧,当生成单元不能解析该字段时,则直接忽略该字段,其余操作与现有技术相同。Preferably, the receiving unit of the beacon sending device receives the probe request frame carrying the Security Flag field, and when the generating unit cannot parse the field, it directly ignores the field, and other operations are the same as in the prior art.
优选的,还包括以下实施方式Preferably, the following embodiments are also included
终端的生成模块判断终端的用户是否需要被安全监控,若是,生成携带 SecurityFlag字段的探测请求帧,若否,生成不携带Security Flag字段的探测请求帧;发送模块发送探测请求帧。The generation module of the terminal determines whether the user of the terminal needs to be monitored by security, and if so, generates a detection request frame with the SecurityFlag field, if not, generates a detection request frame without the Security Flag field; the sending module sends the detection request frame.
接收单元接收该探测请求帧,若网络具有识别接入网络的终端的用户为需要被安全监控的用户的能力,所述生成单元判断探测请求帧中是否携带Security Flag字段,若是,则生成携带Security Flag字段的探测响应消息,以提示用户可以被监控。若网络不具有该能力,则不对该字段解析,则生成不携带Security Flag 字段的探测响应帧。发送单元发送探测响应帧。The receiving unit receives the detection request frame, and if the network has the ability to identify the user of the terminal accessing the network as the user who needs to be monitored by security, the generating unit determines whether the detection request frame carries the Security Flag field, and if so, generates a security flag carrying the Security Flag field. The probe response message of the Flag field to prompt the user that it can be monitored. If the network does not have this capability, the field will not be parsed, and a probe response frame without the Security Flag field will be generated. The transmitting unit transmits the probe response frame.
优选的,为了便于终端正确解析接收的信标帧,对于上述不同格式的信标帧,可以在终端和网络侧预先约定采用的信标帧格式,或者为了便于不同厂商设置自己的信标帧格式,所述生成单元还在信标帧中增加一个新的字段beacon format,用于指示信标帧的格式类型。Preferably, in order to facilitate the terminal to correctly parse the received beacon frame, for the beacon frames of different formats, the beacon frame format used by the terminal and the network side can be pre-agreed, or in order to facilitate different manufacturers to set their own beacon frame formats , the generating unit also adds a new field beacon format to the beacon frame, which is used to indicate the format type of the beacon frame.
在另一实施方式中,当采用格式3时,也就是现有技术的信标帧格式,不对信标帧进行改进,即不设置beacon format字段,在这种情况下,beacon format 字段可以设置为1bit,设置为0时,指示格式1,设置为1时,指示格式2,或者,设置为1时,指示格式1,设置为0时,指示格式2。In another embodiment, when
终端的接收模块接收到信标帧,生成模块通过该字段识别信标帧采用的格式,基于识别的信标帧的格式,判断发送信标帧的AP是否具有识别接入网络的终端的用户为需要被安全监控的用户的能力。The receiving module of the terminal receives the beacon frame, and the generating module identifies the format used by the beacon frame through this field, and based on the format of the identified beacon frame, determines whether the AP sending the beacon frame has a user that identifies the terminal accessing the network: The capabilities of users who need to be securely monitored.
在另一实施方式中,In another embodiment,
信标发送装置的发送单元发送信标帧:The sending unit of the beacon sending device sends the beacon frame:
其中,若为未采用本发明的方法的信标发送装置时,直接发送现有技术的信标帧,并且生成单元在接收单元接收到探测请求帧时也不去判断或识别探测请求帧中是否携带Security Flag字段,根据接收的探测请求帧确定是否允许终端接入,处理方式同现有技术相同。Wherein, if it is a beacon sending device that does not adopt the method of the present invention, the beacon frame of the prior art is directly sent, and the generating unit does not judge or identify whether the detection request frame is received by the receiving unit. The Security Flag field is carried, and whether the terminal is allowed to access is determined according to the received probe request frame, and the processing method is the same as that in the prior art.
为采用本发明的方法的信标发送装置时,生成单元判断自身是否具有识别接入网络的终端的用户为需要被安全监控的用户的能力,根据自身能力情况确定发送的信标帧的方式,如采用上述实施方式一或实施方式二的方式发送,具体选择哪种方式可以根据用户或厂家的设置,发送的信标帧的格式采用本发明所述的信标帧格式之一,生成单元根据所确定的结果生成相应的信标帧。When using the beacon sending device of the method of the present invention, the generating unit judges whether it has the ability to identify the user of the terminal accessing the network as the user who needs to be safely monitored, and determines the way of sending the beacon frame according to its own ability, If the mode of the above-mentioned
生成单元解析探测请求帧以及对探测请求帧的应答:The generation unit parses the probe request frame and the response to the probe request frame:
同样的,若为未采用本发明的方法的信标发送装置时,生成单元在接收单元接收到探测请求帧时按现有技术方式解析探测请求帧,忽略本发明引入的新字段,若为采用本发明的方法的信标发送装置时,生成单元在接收单元接收到探测请求帧时进行解析,判断探测请求帧中是否携带本发明提出的字段,若携带则解析该字段,根据解析结果以及信标发送装置的所述能力以及其他本发明所提的因素生成对应的探测响应消息或本发明提及的其他消息。若未携带该字段,则按现有技术方式解析探测请求帧。Similarly, if it is a beacon sending device that does not adopt the method of the present invention, the generating unit parses the probe request frame according to the prior art method when the receiving unit receives the probe request frame, and ignores the new fields introduced by the present invention. In the beacon sending device of the method of the present invention, the generating unit parses when the receiving unit receives the probe request frame, determines whether the probe request frame carries the field proposed by the present invention, and parses the field if it does, and parses the field according to the parsing result and the information. The capabilities of the target sending device and other factors mentioned in the present invention generate corresponding probe response messages or other messages mentioned in the present invention. If this field is not carried, the probe request frame is parsed according to the prior art.
对于被动扫描接入网络的方式,终端的生成模块在接收模块接收到信标帧,若为未采用本发明的方法的终端时,不去解析信标帧中本发明所引入的字段,按照现有技术方式解析信标帧;若为采用本发明的方法的终端时,判断终端的用户是否需要被安全监控,若无需安全监控,不去解析信标帧中本发明所引入的字段,按现有技术方式解析信标帧,选择模块按现有技术方式选择要接入的装置;生成模块判断需要被安全监控,解析并判断信标帧中是否携带Security Flag字段,若携带,根据Security Flag字段的值,按本发明中提及的方法执行对应操作,若未携带Security Flag字段,可以按以下方式之一执行:For the passive scanning access network mode, when the receiving module receives the beacon frame, the generation module of the terminal does not parse the fields introduced by the present invention in the beacon frame if it is a terminal that does not adopt the method of the present invention. There are technical ways to parse the beacon frame; if it is a terminal using the method of the present invention, determine whether the user of the terminal needs to be monitored safely, if no security monitoring is required, do not parse the fields introduced by the present invention in the beacon frame, press There are technical ways to parse the beacon frame, and the selection module selects the device to be accessed according to the prior art; the generation module judges that it needs to be monitored by security, parses and judges whether the beacon frame carries the Security Flag field, and if so, according to the Security Flag field The value of , perform the corresponding operation according to the method mentioned in the present invention, if it does not carry the Security Flag field, it can be performed in one of the following ways:
判断信标帧中是否携带beacon format字段,若携带,则根据该字段判断信标帧的格式,基于信标帧的格式以及Security Flag字段的值确定网络是否具有识别接入网络的终端的用户为需要被安全监控的用户的能力,若能够确定网络具有该能力,则按照本发明的方法执行后续的步骤,如选择模块选择接入该网络,若确定网络不具有该能力,则按照现有技术方式接入网络或者选择其他网络进行接入,优先的选择具有该能力的网络接入,其中判断其他网络是否具有该能力的方法同上述步骤。当信标帧中不携带beacon format字段时,则无法确定网络是否具有识别接入网络的终端的用户为需要被安全监控的用户的能力,需终端的发送模块向网络发送携带Security Flag字段的探测请求帧。Determine whether the beacon format field is carried in the beacon frame. If it is, the format of the beacon frame is determined according to this field. Based on the format of the beacon frame and the value of the Security Flag field, it is determined whether the network has a user that identifies the terminal accessing the network. The ability of the user who needs to be monitored safely, if it can be determined that the network has the ability, then follow the method of the present invention to perform the subsequent steps, such as selecting the module to choose to access the network, if it is determined that the network does not have the ability, then according to the prior art access to the network or select other networks for access, preferentially select the network with this capability to access, wherein the method for judging whether other networks have this capability is the same as the above steps. When the beacon frame does not carry the beacon format field, it cannot be determined whether the network has the ability to identify the user of the terminal accessing the network as the user who needs to be monitored for security. request frame.
相应的,终端的接收模块接收到探测响应帧时,若为未采用本发明的方法的终端时,生成模块不去解析探测响应帧中本发明所引入的字段,按照现有技术方式解析探测响应帧;若为采用本发明的方法的终端时,生成模块判断该终端需要被安全监控,则判断探测响应帧是否携带Security Flag字段或者按照本发明其他实施方式的方法执行后续步骤,当该终端不需要被安全监控,不解析以及判断Security Flag字段的值,按照现有技术方式执行相应的操作。Correspondingly, when the receiving module of the terminal receives the probe response frame, if it is a terminal that does not adopt the method of the present invention, the generating module does not parse the fields introduced by the present invention in the probe response frame, and parses the probe response according to the prior art. frame; if it is a terminal that adopts the method of the present invention, the generation module judges that the terminal needs to be monitored by security, then judges whether the detection response frame carries the Security Flag field or performs subsequent steps according to the methods of other embodiments of the present invention, when the terminal does not It needs to be monitored by security, and the value of the Security Flag field is not parsed and judged, and corresponding operations are performed according to the prior art.
在另一个实施方式中,In another embodiment,
生成单元,用于执行以下方法:Build cells that execute the following methods:
步骤400,获取发送信标帧的条件;Step 400, obtaining conditions for sending beacon frames;
其中,实时,或者周期性,或者在事件触发时获取发送信标帧的条件。The conditions for sending the beacon frame are acquired in real time, or periodically, or when an event is triggered.
步骤401,判断该条件是否满足发送格式1或格式2信标帧的条件一;若满足该条件一,则将信标帧格式设置为格式1或格式2进行发送;若不满足该条件一,则将信标帧格式设置为格式3进行发送,即信标帧中不包括本发明增加的信息元素。Step 401, determine whether the condition satisfies the first condition for sending the
具体的,条件一包括以下一种或多种的组合:Specifically, condition one includes a combination of one or more of the following:
1)满足发送格式1或格式2的信标帧的时间段。1) The time period for sending the beacon frame of
具体的,获取当前时刻,判断是否属于发送格式1或格式2信标帧的时间段内的时间,若是,则将信标帧格式设置为格式1或格式2,同时启动计时器,并在到达发送信标帧的时刻时,发送信标帧。当计时器时长达到发送格式1或格式2的信标帧的时间段的结束时间时,则执行步骤400。Specifically, the current time is obtained, and it is judged whether it belongs to the time period in which the
其中,根据当前时刻与发送格式1或格式2的信标帧的时间段的时刻之间的时间差设置计时器的计时时长,在计时器达到计时时长时触发生成单元执行步骤400,使该装置再次获取发送信标帧的条件。Wherein, the timing duration of the timer is set according to the time difference between the current moment and the moment at which the beacon frame of
优选的,当该装置实时,或者周期性获取发送信标帧的条件时,在满足发送格式1或格式2的信标帧的时间段结束前停止执行获取发送信标帧条件的步骤,直到接收到上述触发。Preferably, when the device obtains the conditions for sending beacon frames in real time or periodically, it stops executing the step of obtaining the conditions for sending beacon frames before the end of the time period for sending beacon frames of
优选的,生成单元判断网络是否具有所述能力,若具有,则执行该实施方式的方法,若不具有,则仅生成格式3的信标帧。Preferably, the generating unit judges whether the network has the capability, and if so, executes the method of this embodiment, and if not, generates only the beacon frame of
优选的,发送不同格式信标帧的周期可以是相同或不同的,而且发送相同格式的信标帧的周期满足不同条件时也可以是自适应改变的。Preferably, the periods for sending beacon frames in different formats may be the same or different, and the periods for transmitting beacon frames in the same format may also be adaptively changed when different conditions are met.
发送单元判断网络具有该能力时,设置发送格式1或格式2的信标帧的周期小于发送格式3信标帧的周期。优选的,判断接入网络的被安全监控的终端的增长速率大于速率阈值时,发送格式1或格式2的信标帧的周期是预设周期与增长因子的乘机,该增长因子为大于0小于1的数。When the sending unit judges that the network has this capability, the period for sending beacon frames of
优选的,发送格式3信标帧的周期设置为固定周期,在另一实施方式中,发送单元判断接入网络的终端的增长速率大于速率阈值时,发送格式3的信标帧的周期是预设周期与所述增长因子的乘机。Preferably, the period for sending the
优选的,发送格式1或格式2信标帧的时间段由用户通过该装置的设置单元根据需要设置,或者生成单元周期性的根据统计周期内得到的时间段设置。Preferably, the time period for sending the
具体的,生成单元获取统计周期内终端接入网络的日志,在与该统计周期具有相同属性的时间按该统计周期内统计得到的发送格式1或格式2信标帧的时间段发送格式1或格式2信标帧,其余时间发送格式3信标帧,如该统计周期为1周,从周一到周日,则在周一到周日按该得到的时间段发送格式1或格式2信标帧。Specifically, the generating unit acquires the log of the terminal accessing the network within the statistical period, and sends the
上述相同的属性如都是对应于工作日,或者都对应于周末,或为每月的同一日,或者以周为对应。For example, the same attributes above all correspond to working days, or all correspond to weekends, or the same day of each month, or correspond to weeks.
设置统计周期包括一天或多天;优选的,该统计周期为1周。其中,将一天的时间分为N个时间段,统计各时间段增加的接入网络的被安全监控的终端的数量,当连续M个时间段内所述增加的接入网络的被安全监控的终端的数量大于等于第一预设数量的时间段大于等于预设时间段数时,则在M个时间段发送格式1或格式2信标帧;发送格式1或格式2信标帧的开始时间为M个连续时间段的开始时间,结束时间为M个连续时间段的结束时间;其中M≤N。The set statistical period includes one or more days; preferably, the statistical period is one week. Among them, the time of a day is divided into N time periods, and the number of security-monitored terminals of the access network increased in each time period is counted. When the number of terminals is greater than or equal to the first preset number of time periods greater than or equal to the preset number of time periods, the
2)当前时间段增加的接入网络的被安全监控的终端的数量大于等于第二预设数量。2) The number of security-monitored terminals accessing the network increased in the current time period is greater than or equal to the second preset number.
具体的,选择最近的一段时间段,获取增加的接入网络的被安全监控的终端的数量,当该数据大于等于第二预设数量时,预测在最近的一段时间将有较多的需要被监控的终端接入,设置发送格式1或格式2的信标帧的时间长度为第二时间长度,同时启动计时器,并在到达发送信标帧的时刻时,发送格式1 或格式2信标帧。当计时器时长达到第二时间长度时,则执行步骤400。Specifically, a recent period of time is selected to obtain the increased number of terminals that are connected to the network under security monitoring. When the data is greater than or equal to the second preset number, it is predicted that there will be more terminals that need to be monitored in the recent period of time. The monitored terminal accesses, sets the time length for sending the beacon frame of
同样的,当生成单元实时,或者周期性获取发送信标帧的条件时,在满足发送格式1或格式2的信标帧的时间段结束前停止执行获取发送信标帧条件的步骤,直到接收到上述触发。Similarly, when the generating unit obtains the conditions for sending beacon frames in real time or periodically, it stops executing the step of obtaining the conditions for sending beacon frames before the end of the time period that satisfies the sending of beacon frames of
在另一实施方式中,在各种环境中部署的该装置,有的接入密码不公开,用户无法获取,属于私人物品,有的为用户可以获取密码的装置,或者无需密码即可接入使用的装置。为了提高用户被安全监控的覆盖范围,并且合理利用用户无法获取密码的装置,本发明的方法进一步进一步提出了以下方法。In another embodiment, some of the devices deployed in various environments have access passwords that are not public and cannot be obtained by users, and are personal items, and some are devices that users can obtain passwords for, or can be accessed without a password. device used. In order to improve the coverage of the user being monitored by security, and to reasonably utilize the device where the user cannot obtain the password, the method of the present invention further proposes the following method.
在该实施方式中,假设该装置设置有接入密码。In this embodiment, it is assumed that the device is provided with an access code.
终端的发送模块发送携带Security Flag字段的探测请求帧;The sending module of the terminal sends a probe request frame carrying the Security Flag field;
信标生成模块的接收单元接收到携带Security Flag字段的探测请求帧;The receiving unit of the beacon generation module receives the probe request frame carrying the Security Flag field;
生成单元判断该装置具有识别接入网络的终端的用户为需要被安全监控的用户的能力,判断探测请求帧中是否携带Security Flag字段,若是,则生成单元生成并由发送单元发送携带Security Flag字段的探测响应消息;生成单元判断网络不具有该能力,则不对该字段解析,则发送不携带Security Flag字段的探测响应帧;The generating unit judges that the device has the ability to identify the user of the terminal accessing the network as a user who needs to be monitored safely, and judges whether the probe request frame carries the Security Flag field, if so, the generating unit generates and is sent by the sending unit to carry the Security Flag field. The detection response message; the generation unit judges that the network does not have this capability, then does not parse the field, then sends a detection response frame that does not carry the Security Flag field;
终端的接收模块接收探测响应消息;生成模块判断探测响应消息是否携带Security Flag字段,若携带则执行步骤504;若不携带,判断是否继续执行步骤 504,若是,执行步骤504,若否,结束;The receiving module of the terminal receives the detection response message; the generation module judges whether the detection response message carries the Security Flag field, and if it does, executes step 504;
步骤504,终端的生成模块判断是否具有该装置的接入密码,若具有,则发送模块在认证过程中向该信标发送装置发送接入密码进行认证;若不具有该信标发送装置的密码,则当判断探测响应消息中携带Security Flag字段时,在认证过程中不向信标发送装置发送接入密码;Step 504, the generation module of the terminal judges whether it has the access password of the device, if so, the sending module sends the access password to the beacon sending device for authentication during the authentication process; if it does not have the password of the beacon sending device , then when it is judged that the Security Flag field is carried in the probe response message, the access password is not sent to the beacon sending device during the authentication process;
信标发送装置的设置单元根据认证过程中终端是否发送接入密码向终端提供不同的访问权限;当认证过程中接收到终端发送的接入密码,且密码正确,则向终端提供网络的访问权;若未接收到终端发送的接入密码,则仅支持发送携带Security Flag字段的探测请求帧的终端接入网络,对终端进行安全监控,限制终端使用网络的服务。The setting unit of the beacon sending device provides different access rights to the terminal according to whether the terminal sends the access password during the authentication process; when the access password sent by the terminal is received during the authentication process, and the password is correct, then the access right to the network is provided to the terminal. ; If the access password sent by the terminal is not received, only the terminal that sends the probe request frame carrying the Security Flag field is supported to access the network, to monitor the security of the terminal and limit the terminal to use the services of the network.
优选的,终端接入信标发送装置提供的网络后,对其应用信标发送装置中的安全监控策略。Preferably, after the terminal accesses the network provided by the beacon sending apparatus, the security monitoring policy in the beacon sending apparatus is applied to it.
优选的,当限制终端使用网络的服务时,发送单元向终端发送提示其接入网络仅可以执行安全监控,无法使用网络的其他服务的消息。Preferably, when the terminal is restricted from using the services of the network, the sending unit sends to the terminal a message prompting the terminal that it can access the network only to perform security monitoring and cannot use other services of the network.
在另一实施方式中,当被安全监控的用户需要在安全预警时提示紧急联系人时,终端的生成模块生成,发送模块发送探测请求帧,并且携带紧急联系人的信息,如紧急联系人的手机号,终端标识等信息,该信息用于网络根据该信息向紧急联系人发送提示信息。In another embodiment, when the user under security monitoring needs to prompt the emergency contact during the security warning, the generation module of the terminal generates, and the transmission module sends a detection request frame, which carries the information of the emergency contact, such as the emergency contact's information. Information such as mobile phone number, terminal identification, etc., which is used by the network to send prompt information to emergency contacts according to the information.
优选的,生成模块在探测请求帧的上述新增的信息元素中增加一个Care Info字段,用于携带紧急联系人的信息;该字段为可选字段,根据用户需要确定是否携带该字段。Preferably, the generating module adds a Care Info field to the above-mentioned newly added information element of the probe request frame, which is used to carry the information of the emergency contact; this field is an optional field, and whether to carry the field is determined according to the user's needs.
发送的探测请求帧中携带了Care Info字段时,当信标发送装置需要向终端进行预警时,同时向Care Info字段指示的紧急联系人发送提醒消息。When the sent probe request frame carries the Care Info field, when the beacon sending apparatus needs to give an early warning to the terminal, it simultaneously sends an alert message to the emergency contact indicated by the Care Info field.
在本发明中,可以在信标发送装置中通过设置单元预先设置安全监控策略列表,或者根据接入AP的终端的用户的输入动态生成安全监控策略。优选的,安全监控策略列表中包括一个或多个安全监控条目。In the present invention, the security monitoring policy list can be preset in the beacon sending device through the setting unit, or the security monitoring policy can be dynamically generated according to the input of the user of the terminal accessing the AP. Preferably, the security monitoring policy list includes one or more security monitoring entries.
在一个实施方式中,当被安全监控的终端接入网络后,设置单元可以将终端添加到所有安全监控策略条目中。In one embodiment, after the terminal to be monitored for security accesses the network, the setting unit may add the terminal to all security monitoring policy entries.
在另一个实施方式中,网络侧,如信标发送装置的存储单元存储有各个被监控对象的位置信息,当被安全监控的终端接入网络后,设置单元获取终端的位置信息,将终端添加到在终端预设范围内的被监控对象对应的被监控终端项中。例如终端在商场中,该预设范围为终端所在楼层,则只将终端添加到其所在楼层的被监控对象对应的被监控终端项中。优选的,设置单元周期性的或实时监控终端的位置,根据终端的位置将终端更新至终端预设范围内的被监控对象对应的被监控终端项中,从而根据终端的位置自适应的调整所需要关注的被监控对象。In another embodiment, the network side, such as the storage unit of the beacon sending device, stores the location information of each monitored object. After the terminal to be safely monitored accesses the network, the setting unit acquires the location information of the terminal, and adds the terminal to the network. to the monitored terminal item corresponding to the monitored object within the preset range of the terminal. For example, if the terminal is in a shopping mall, and the preset range is the floor where the terminal is located, only the terminal is added to the monitored terminal item corresponding to the monitored object on the floor where the terminal is located. Preferably, the setting unit monitors the position of the terminal periodically or in real time, and updates the terminal to the monitored terminal item corresponding to the monitored object within the preset range of the terminal according to the position of the terminal, so as to adaptively adjust the position of the terminal according to the position of the terminal. The monitored object that needs attention.
在另一个实施方式中,设置单元根据接入信标发送装置的终端的用户的操作生成对应该终端的安全监控策略。具体为:判断被安全监控的用户的终端成功接入到该信标发送装置时,触发设置单元向终端发送该安全监控列表,其可以以用户界面的方式在终端的显示模块显示,如图4a所示,为了便于表述,称该界面为安全监控界面,该界面包括三个区域,区域1设置有搜索区,区域2 用于显示安全监控策略,图中实例性的显示了安全监控策略所包括的部分内容,优选的,其显示的内容可以根据需要显示,除了显示索引、监控对象、安全措施外,优选的还显示被监控对象的位置,以便用户根据需要将自身添加至对应的监控策略条目。优选的,显示的安全监控策略中不包括被监控终端项,尤其在公共场所中,不显示被监控终端项可以防止其他用户获取被监控终端的信息,提高安全性;在每个安全监控策略条目后具有一个按钮;区域3用于显示全部添加按钮和全部取消等按钮。In another embodiment, the setting unit generates the security monitoring policy corresponding to the terminal according to the operation of the user of the terminal accessing the beacon sending apparatus. Specifically: when it is judged that the terminal of the user under security monitoring successfully accesses the beacon sending device, the setting unit is triggered to send the security monitoring list to the terminal, which can be displayed on the display module of the terminal in the form of a user interface, as shown in Figure 4a For the convenience of description, the interface is called the security monitoring interface. The interface includes three areas. The
具体的,区域1的搜索区,用于用户输入例如与安全监控策略相关的信息,如被监控对象相关的关键词,或者安全措施有关的关键词等,从而搜索所需的监控条目,当终端的输入模块检测到用户输入搜索内容后,通过显示模块在区域2显示搜索结果。例如用户在搜索区输入被监控对象1,则在区域2显示搜索结果,如图4b所示。其中,输入模块用户检测用户的输入,包括文字输入、对显示模块的触摸、语音输入等,基于检测到大输入,通过显示模块显示对应的结果。Specifically, the search area in
在区域2中,与安全监控策略条目对应的按钮用于将终端添加至对应的监控条目的被监控终端项中,由此实现对终端针对该安全监控策略条目的安全监控,或者将终端从对应的监控条目的被监控终端项中移除,则取消对终端针对该条目的监控。具体的,当未将终端添加到安全监控策略条目对应的被监控终端项目中时,该按钮显示添加,当将终端添加到安全监控策略条目对应的被监控终端项目中后,该按钮显示取消,如图4a所示,索引0、1对应的按钮显示“添加”,则表示还未将终端添加到该条目的被监控终端项中,索引2对应的按钮显示“取消”,则表示已经将终端添加至该条目的被监控终端项中。点击“添加”按钮,可实现将终端添加到对应的安全监控策略条目的被监控终端项中,点击“取消”按钮,可实现将终端从对应的监控条目的被监控终端项中移除。此外,当终端被添加到该条目后,该按钮显示“取消”,以用于终端通过点击该按钮将自身从该条目删除,当终端未被添加到该条目时,该按钮显示“添加”,以用于终端通过点击该按钮将自身添加到该条目,以被安全监控In
区域3中还包括其他按钮,其中全部添加按钮用于将终端添加到所有安全监控策略条目对应的被监控终端项中,同样的,全部取消按钮用于将终端从包括该终端的所有的安全监控条目中移除。
优选的,区域3还包括紧急联系人按钮,该按钮用于添加终端的紧急联系人,当发生需要提醒的事件时,不仅向终端进行提示,还可以向添加的紧急联系人提示。Preferably, the
优选的,区域3还包括关闭按钮,用于关闭该页面,在另一实施方式中,该关闭按钮可以为一个符号,点击该符号则关闭页面。Preferably, the
具体的,输入模块获取用户点击紧急联系人按钮的操作,显示模块显示输入紧急联系人界面,如图4c所示,用户输入紧急联系人信息后,输入模块获取到用户点击确认时,获取用户输入的信息,将其作为终端的紧急联系人,发送模块将该信息发送至信标发送装置,设置单元将其与终端的安全监控策略条目对应存储;输入模块检测到用户点击取消按钮时,显示模块显示上一次显示的界面。Specifically, the input module obtains the operation of the user clicking the emergency contact button, and the display module displays an interface for inputting the emergency contact, as shown in Figure 4c, after the user enters the emergency contact information, the input module obtains the user input when the user clicks to confirm The information of the terminal is taken as the emergency contact of the terminal, the sending module sends the information to the beacon sending device, and the setting unit stores it corresponding to the security monitoring policy entry of the terminal; when the input module detects that the user clicks the cancel button, the display module Displays the last displayed interface.
进一步的,为了使得设置更加灵活方便,满足用户对某些安全监控条目无提醒需要的场景,输入模块获取用户点击紧急联系人按钮的操作,显示模块显示输入紧急联系人界面,如图4d所示,该界面包括用于用户输入紧急联系人的输入区域,用户已添加的安全监控策略条目,在每个安全监控策略条目前面有一个可选中的符号,用户通过选中该符号使得选中其中的条目,如图中所示,条目0对应的符号被选中,用户选中条目对应的符号,以及输入紧急联系人信息后,当输入模块获取到用户点击确认按钮时,获取用户选中的条目,以及获取用户输入的紧急联系人信息,发送模块将该信息发送至信标发送装置,设置单元针对选中的条目为终端添加紧急联系人,未选中的条目不添加紧急联系人。为了便于用户确认执行的操作是否成功,当成功时,信标发送装置的发送单元向用户反馈成功的提示,若失败,则向用户反馈失败的提示,进一步的,若能够确定失败的原因,则向用户提示失败的原因。Further, in order to make the setting more flexible and convenient, and to meet the scenario where the user has no need to remind some security monitoring items, the input module obtains the operation of the user clicking the emergency contact button, and the display module displays the emergency contact input interface, as shown in Figure 4d. , the interface includes an input area for the user to input emergency contacts, security monitoring policy entries that the user has added, and an optional symbol in front of each security monitoring policy entry, the user selects the entry by selecting the symbol. As shown in the figure, the symbol corresponding to
优选的,在该界面中,当添加紧急联系人后,其中被添加紧急联系人的条目前面具有一个特定的符号,该符号可以是圆形、方形、三角形等任意形状的符号,该符号表示为该条目添加了紧急联系人,如图4e所示,◆表示该监控条目已添加紧急联系人信息。在一个实施方式中,输入模块获取到用户点击该符号,显示模块在该符号旁边悬浮显示出现该符号对应的解释,即紧急联系人信息,如图4f所示,输入模块获取到用户点击索引0对应的◆,显示模块在其旁边悬浮显示对应的紧急联系人信息13512314568。显示设定时间后,不再显示该解释,在另一实施方式中,输入模块获取到用户点击该符号时,显示模块在该页面下方显示与该符号对应的紧急联系人信息,如图4g所示。优选的,不同的符号对应不同的联系人,或者以符号的不同颜色区分不同的紧急联系人。其中还可以在该页面直接显示不同颜色的符号对应的紧急联系人信息,如图4h所示。当对应的监控条目具有多个紧急联系人,则在该条目前具有多个表示对应紧急联系人的符号。Preferably, in this interface, after the emergency contact is added, the item to which the emergency contact is added has a specific symbol in front of it, and the symbol can be a symbol in any shape such as a circle, a square, a triangle, etc. The symbol is expressed as An emergency contact is added to this entry, as shown in Figure 4e, ◆ indicates that emergency contact information has been added to the monitoring entry. In one embodiment, the input module acquires that the user clicks on the symbol, and the display module displays the explanation corresponding to the symbol in a floating display next to the symbol, that is, emergency contact information. As shown in Figure 4f, the input module acquires the
优选的,显示模块在该界面中仅对与终端相关的监控条目添加了紧急联系人时显示该关于添加紧急联系人的符号,从而便于用户查看与自身相关的信息。Preferably, the display module displays the symbol about adding an emergency contact only when an emergency contact is added to the monitoring item related to the terminal in the interface, so as to facilitate the user to view information related to himself.
优选的,可以对已添加紧急联系人的条目或未添加紧急联系人的条目再次添加紧急联系人,该联系人可以为用户设置的任意联系人。同样的,输入模块获取到用户选中需要添加紧急联系人的条目,该条目包括已添加紧急联系人的条目和/或未添加紧急联系人的条目,并获取到用户在紧急联系人输入区域输入紧急联系人信息,以及点击确认按钮,如前述添加紧急联系人方法相同,发送模块将相关信息发送至信标发送装置,由设置单元为其添加紧急联系人。对于已经添加过紧急联系人的条目,通过该方法则将之前添加的紧急联系人替换为当前添加的紧急联系人。优选的,对于已经添加过紧急联系人的条目,当再次被选中添加紧急联系人时,设置单元判断输入的紧急联系人信息与之前添加的紧急联系人信息是否相同,若相同则不对该条目执行任何操作,若不相同,发送单元向终端发送提示消息,显示模块在操作界面上向用户显示提示消息,提示用户是否替换已有的紧急联系人信息,还是对该条目额外增加紧急联系人信息,或者忽视该操作,即保持不变。Preferably, an emergency contact can be added again to an entry to which an emergency contact has been added or an entry to which no emergency contact has been added, and the contact can be any contact set by the user. Similarly, the input module obtains that the user selects an item that needs to be added with an emergency contact, the item includes an item that has been added an emergency contact and/or an item that has not been added an emergency contact, and obtains that the user enters an emergency contact in the emergency contact input area Contact information, and click the confirmation button, the method for adding emergency contacts is the same as the above-mentioned method, the sending module sends the relevant information to the beacon sending device, and the setting unit adds emergency contacts to it. For an entry that has already added an emergency contact, this method replaces the previously added emergency contact with the currently added emergency contact. Preferably, for an item that has already added an emergency contact, when it is selected to add an emergency contact again, the setting unit determines whether the input emergency contact information is the same as the previously added emergency contact information, and if it is the same, the entry is not executed. If any operation is different, the sending unit sends a prompt message to the terminal, and the display module displays a prompt message to the user on the operation interface, prompting the user whether to replace the existing emergency contact information, or to add additional emergency contact information to the entry, Or ignore the operation, i.e. leave it unchanged.
接着,输入模块检测用户的选择,由发送模块发送至信标发送装置,设置单元基于用户的选择执行对应操作,即若用户选择替换,则将紧急联系人更新为新输入的信息,若用户选择增加,则增加新的紧急联系人信息,若用户选择保持,则不对该条目执行操作。优选的,为了便于用户获知已添加的紧急联系人信息,向用户发送提示信息,显示模块在提示界面显示该条目已添加的紧急联系人信息。进一步的,当多个条目存在上述情况,可以按顺序每次向用户提示一条监控条目的相关信息,当检测到用户对该条目选择确认后,显示下一需提醒的监控条目,直到所有需提醒的监控条目全部处理完成,根据用户的选择发送模块将用户的所有处理在一条消息中发送至设置单元,设置单元根据用户的选择进行设置。在另一实施方式中,显示模块将各个监控条目按紧急联系人分组显示,方便用户批量处理,例如如图4j所示,页面显示了设置了两个不同紧急联系人的分组,当一个页面无法全部显示时,页面具有翻页的按钮,如图所示的“→”,通过向左的箭头、或向右的箭头实现翻页的功能。用户可以根据需要选择每个监控条目前的选择按钮,如图中的○,确定要执行的操作,当多个监控条目执行相同的操作,可以同时选中多个条目后再执行对应的操作,及替换、增加或保持。Next, the input module detects the user's selection, and the sending module sends it to the beacon sending device, and the setting unit performs the corresponding operation based on the user's selection. If added, new emergency contact information is added, and if the user chooses to keep, no operation is performed on the entry. Preferably, in order for the user to know the added emergency contact information, prompt information is sent to the user, and the display module displays the added emergency contact information of the entry on the prompt interface. Further, when the above situation exists in multiple items, the relevant information of one monitoring item can be prompted to the user in sequence each time. When it is detected that the user selects and confirms the item, the next monitoring item that needs to be reminded is displayed until all the items that need to be reminded are displayed. The monitoring items are all processed, and according to the user's selection, the sending module sends all the processing of the user to the setting unit in a message, and the setting unit performs the setting according to the user's selection. In another embodiment, the display module displays each monitoring item in groups of emergency contacts, which is convenient for users to process in batches. For example, as shown in Figure 4j, the page displays the grouping of two different emergency contacts. When all are displayed, the page has a page turning button, as shown in the figure "→", and the page turning function is realized by the left arrow or the right arrow. The user can select the selection button in front of each monitoring item as required, such as ○ in the figure, to determine the operation to be performed. When multiple monitoring items perform the same operation, they can select multiple items at the same time and then perform the corresponding operation, and Replace, add or keep.
优选的,添加紧急联系人信息时,可以一次输入多个紧急联系人信息,即在紧急联系人输入区域同时输入多个紧急联系人信息;优选的,可以在多个联系人中间通过标点符号或者空格隔开,AP接收到该消息时,以标点符号或者空格为分界区分多个紧急联系人信息,在本发明中,不限定标点符号的具体要求,只要用户输入了标点符号或者空格则按不同联系人对待;或者可以当用户输入时,在输入窗口旁边以悬浮窗口的方式提示用户对于多个紧急联系人信息如何输入。Preferably, when adding emergency contact information, multiple emergency contact information can be input at one time, that is, multiple emergency contact information can be input simultaneously in the emergency contact input area; Spaces are separated. When the AP receives the message, it uses punctuation marks or spaces as the boundary to distinguish multiple emergency contact information. In the present invention, the specific requirements for punctuation marks are not limited, as long as the user inputs punctuation marks or spaces Contact treatment; or when the user inputs, the user can be prompted how to input multiple emergency contact information in the form of a floating window next to the input window.
输入模块获取用户的输入,发送模块将其发送给信标发送装置,其设置单元解析消息,进行设置。The input module obtains the user's input, the sending module sends it to the beacon sending device, and the setting unit parses the message and sets it.
优选的,该界面还包括全部选中和全部取消按钮,方便用户选中全部需要选择的条目或者取消全部选中的条目。Preferably, the interface further includes select all and cancel all buttons, which is convenient for the user to select all the items to be selected or cancel all the selected items.
优选的,将安全监控界面作为主页,如图4a所示的界面,在每个界面中都显示可以切换到主页的按钮,输入模块获取到用户点击该按钮,显示单元将界面切换到安全监控界面;或者终端设置切换到主页的触摸方式、手势等交互方式,检测到相应操作时,切换到主页。Preferably, the security monitoring interface is used as the home page, as shown in FIG. 4a, a button that can be switched to the home page is displayed in each interface, the input module obtains that the user clicks the button, and the display unit switches the interface to the security monitoring interface ; Or the terminal sets the touch mode, gesture and other interaction modes for switching to the home page, and switches to the home page when a corresponding operation is detected.
在一个实施方式中,在主页设置“个人设置”按钮,输入模块获取到用户点击该按钮,显示单元显示针对该终端已添加的安全监控条目以及紧急联系人信息。In one embodiment, a "personal settings" button is set on the home page, the input module acquires that the user clicks the button, and the display unit displays the added security monitoring items and emergency contact information for the terminal.
优选的,在主页还包括个性化设置按钮。当已有的安全监控策略条目都不符合用户的要求时,输入模块获取用户点击该个性化设置按钮,进入个性化设置监控需求的界面,如图所示,包括安全措施输入窗口,输入模块获取用户根据个人监控需求输入监控要求,以及点击确定按钮,发送模块将用户输入发送至信标发送装置,接收单元接收该监控要求,设置单元解析监控要求,生成对应的安全监控条目,发送模块将生成的安全监控条目发送至终端,由显示模块显示,以请求终端进行确认,若生成的安全监控条目符合用户的要求,用户点击确认按钮,检测到用户点击确认操作时,发送至信标发送装置,设置单元最终生成对应的安全监控条目,若生成的安全监控条目不符合用户的要求,用户可以对该安全监控条目修改,修改后点击确认按钮,发送至信标发送装置,设置单元最终生成修改后的安全监控条目。Preferably, a personalized setting button is also included on the home page. When the existing security monitoring policy entries do not meet the user's requirements, the input module obtains the user's click on the personalized setting button to enter the interface for personalized monitoring requirements, as shown in the figure, including the security measure input window, the input module obtains The user inputs the monitoring requirements according to the personal monitoring requirements, and clicks the OK button, the sending module sends the user input to the beacon sending device, the receiving unit receives the monitoring requirements, the setting unit parses the monitoring requirements, and generates corresponding security monitoring entries, and the sending module will generate The generated security monitoring entry is sent to the terminal, and displayed by the display module to request the terminal to confirm. If the generated security monitoring entry meets the user's requirements, the user clicks the confirmation button, and when the user clicks confirmation operation is detected, it is sent to the beacon sending device. The setting unit finally generates the corresponding security monitoring entry. If the generated security monitoring entry does not meet the user's requirements, the user can modify the security monitoring entry, click the confirmation button after modification, and send it to the beacon sending device. The setting unit finally generates the modified security monitoring entry.
优选的,该界面还包括输入区域,用户一方面可以修改AP发送的安全监控条目的信息,另一方面可以继续输入,添加新的安全监控条目,或者为当前的安全监控条目添加新的内容,如用户修改相应项目同时,在输入区域输入“添加紧急联系人13810000012”,输入模块检测到用户点击确认按钮后,向信标发送装置发送消息,设置单元接收到终端发送的消息后,根据用户的修改生成对应的安全监控条目。Preferably, the interface further includes an input area. On the one hand, the user can modify the information of the security monitoring entry sent by the AP, and on the other hand, the user can continue to input, add a new security monitoring entry, or add new content to the current security monitoring entry, For example, when the user modifies the corresponding item, input "add emergency contact 13810000012" in the input area, the input module detects that the user clicks the confirmation button, and sends a message to the beacon sending device. After the setting unit receives the message sent by the terminal, according to the user's Modify and generate corresponding security monitoring entries.
在另一实施方式中,个性化设置界面显示安全监控条目,其中包括索引,监控对象,安全措施项目,优选的,还包括紧急联系人项目。用户在监控对象项目中,通过点击该项目的输入区域,以下拉菜单的方式查看并选择可选的监控对象,如下拉菜单包括电梯、楼梯等,用户可以选择其中的项目,对于安全策略条目,用户通过输入的方式设置个性化需求,如输入“终端与电梯距离小于1m时提醒”,优选的,对于用户不关注的项目,可以保持空白,如紧急联系人,用户未输入任何信息。输入模块检测到用户点击确认按钮后,向信标发送装置发送消息,设置单元根据该消息生成对应的安全监控条目。In another embodiment, the personalized setting interface displays security monitoring items, including indexes, monitoring objects, security measures items, and preferably, emergency contact items. In the monitoring object item, the user clicks the input area of the item to view and select the optional monitoring object in the form of a drop-down menu. The drop-down menu includes elevators, stairs, etc., and the user can select the items. For the security policy entry, The user sets individualized requirements by input, such as "remind when the distance between the terminal and the elevator is less than 1m", preferably, for items that the user does not pay attention to, it can be left blank, such as emergency contacts, the user has not input any information. After the input module detects that the user clicks the confirmation button, it sends a message to the beacon sending device, and the setting unit generates a corresponding security monitoring entry according to the message.
优选的,对于限制终端使用网络的服务的场景,设置单元设置是否在终端接入网络后弹出该主页界面,此外,设置单元还可以设置对于限制使用服务的终端在主页可以使用的功能,如仅部分安全监控条目对该终端是可用的,基于其许可的功能在终端的界面显示相应的内容。Preferably, for the scenario of restricting the terminal to use the service of the network, the setting unit sets whether to pop up the homepage interface after the terminal accesses the network. In addition, the setting unit can also set the functions that can be used on the homepage for the terminal that restricts the use of the service, such as only Some security monitoring items are available to the terminal, and the corresponding content is displayed on the interface of the terminal based on the permitted functions.
优选的,安全监控策略条目还包括被监控用户项目,该项目包括携带终端的用户的特征信息,如年龄,身高,指纹,照片等表明用户特征的信息。在一个实施方式中,设置单元预先配置安全监控策略的所有项目,或者,设置单元可以不对被监控终端进行设置,其中,对于同一被监控对象,具有不同特征的被监控用户对应于相同或不同的安全措施。从而使得设置单元可以结合用户的特征信息生成针对具有该特征信息的用户的安全措施。Preferably, the security monitoring policy entry further includes a monitored user item, and the item includes characteristic information of the user who carries the terminal, such as age, height, fingerprint, photo and other information indicating user characteristics. In one embodiment, the setting unit preconfigures all items of the security monitoring policy, or the setting unit may not set the monitored terminal, wherein, for the same monitored object, monitored users with different characteristics correspond to the same or different safety measures. Therefore, the setting unit can generate security measures for the user with the characteristic information in combination with the characteristic information of the user.
通过用户输入的方式设置安全监控策略,同上述方法,终端接入信标发送装置后,显示模块显示上述主页,采用上述相同的方法根据用户选择或输入生成安全监控策略。The security monitoring policy is set by user input, the same as the above method. After the terminal accesses the beacon sending device, the display module displays the above home page, and the security monitoring policy is generated according to user selection or input using the same method as above.
在另一实施方式中,终端的发送模块在发送探测请求帧前,终端的检测模块获取用户的特征信息,发送模块将获取的用户的特征信息发送至信标发送装置,发送模块根据用户的特征信息与安全监控策略进行比较,当符合安全监控条目中的特征信息时,将终端对应添加到该条目的被监控终端项中。In another embodiment, before the sending module of the terminal sends the probe request frame, the detection module of the terminal obtains the feature information of the user, the sending module sends the obtained feature information of the user to the beacon sending device, and the sending module according to the feature of the user The information is compared with the security monitoring policy, and when the feature information in the security monitoring entry is met, the terminal is correspondingly added to the monitored terminal item of the entry.
优选的,检测模块周期性获取用户特征信息,判断获取的用户特征信息与发送探测请求帧前获取的用户的特征信息是否相同,若相同则等下一获取用户特征信息时间到来时再一次获取用户特征信息,如此重复,若不相同,则将该不同的特征信息发送至信标发送装置,信标发送装置接收到终端发送的特征信息后,设置单元与安全监控策略的条目进行比较,将终端更新至符合该特征信息的被监控终端项目中。Preferably, the detection module periodically obtains user feature information, and determines whether the obtained user feature information is the same as the user feature information obtained before sending the detection request frame, and if it is the same, the user will be obtained again when the next time to obtain user feature information arrives. The feature information is repeated in this way. If it is not the same, the different feature information is sent to the beacon sending device. After the beacon sending device receives the feature information sent by the terminal, the setting unit compares it with the entry of the security monitoring policy, and the terminal Update to the monitored terminal item that matches the characteristic information.
在判断终端的用户是否需要被安全监控时,可以通过终的检测模块端获取携带终端的用户的特征信息,根据该特征信息判断用户是否需要被安全监控,如可以在终端中提前设置需要被安全监控的用户的特征信息,将获取的特征信息与提前设置的特征信息进行比较,符合被安全监控的特征时,终端的发送模块向AP发送携带Security Flag字段的探测请求帧,优选的,该特征信息与上述特征信息相同。When judging whether the user of the terminal needs to be monitored safely, the characteristic information of the user carrying the terminal can be obtained through the terminal detection module, and whether the user needs to be monitored safely can be determined according to the characteristic information. The feature information of the monitored user is compared with the feature information set in advance, and when it matches the features to be monitored safely, the sending module of the terminal sends a detection request frame carrying the Security Flag field to the AP. Preferably, this feature The information is the same as the above-mentioned characteristic information.
此外,在本发明的方法中,用户通过终端输入信息时,可以通过语音的方式输入信息,终端的输入模块获取用户语音信息,对其解析,将相应内容填写到对应的输入区,或者终端的发送模块根据用户的语音指令向AP发送对应的消息。In addition, in the method of the present invention, when the user inputs information through the terminal, the information can be input by voice, and the input module of the terminal obtains the user's voice information, parses it, and fills in the corresponding content in the corresponding input area, or the terminal's input module The sending module sends a corresponding message to the AP according to the user's voice command.
此外,当信标发送装置对终端进行安全监控时,终端的接入网络的图标旁边显示一符号,该符号表明终端处于被安全监控的状态。此外,输入模块获取到用户点击该符号,显示模块在终端的界面显示上述主页界面,从而使得用户可以随时更改或者查看其对应的安全监控条目。In addition, when the beacon sending apparatus monitors the security of the terminal, a symbol is displayed next to the icon of the access network of the terminal, and the symbol indicates that the terminal is in a state of security monitoring. In addition, the input module obtains that the user clicks the symbol, and the display module displays the above-mentioned home page interface on the interface of the terminal, so that the user can change or view the corresponding security monitoring item at any time.
在另一实施方式中,发挥安全监控的终端通常包括可穿戴设备等便携式设备,为了便于对屏幕较小或者无屏幕的终端进行设置,本发明还提出了以下方法:In another embodiment, the terminal that performs security monitoring usually includes a portable device such as a wearable device. In order to facilitate the setting of a terminal with a small screen or no screen, the present invention also proposes the following method:
将终端的通信单元与另一终端建立连接,通过连接的建立使得终端共享另一终端的屏幕,通信单元将需要显示的信息发送至另一终端,以及接收另一终端发送的用户在其上执行的操作的消息,对于需要发送至其他设备的消息将其发送至其他设备,如信标发送装置,从而可以通过在另一终端上执行相应的操作对终端进行相关设置。A connection is established between the communication unit of the terminal and another terminal, the terminal shares the screen of the other terminal through the establishment of the connection, the communication unit sends the information that needs to be displayed to the other terminal, and receives the information sent by the other terminal and executes the operation on it. For messages that need to be sent to other devices, send them to other devices, such as a beacon sending device, so that relevant settings can be performed on the terminal by performing corresponding operations on another terminal.
在另一实施方式中,具有安全监控需求的用户接入到具有识别接入网络的终端的用户为需要被安全监控的用户的能力的信标发送装置后,对该用户进行安全监控,主要包括以下步骤:In another embodiment, after a user with security monitoring requirements accesses a beacon sending device capable of identifying a user of a terminal accessing the network as a user who needs to be monitored for security, security monitoring for the user is performed, which mainly includes the following steps: The following steps:
终端的检测模块执行步骤600,获取用户的位置信息;The detection module of the terminal executes step 600 to obtain the location information of the user;
在该步骤中,检测模块获取用户的位置信息,发送模块发送至信标发送装置,或者信标发送装置的设置单元获取用户的位置信息,如基于信号强度、其他设备提供的信息获取用户的位置信息;In this step, the detection module obtains the user's location information, the sending module sends it to the beacon sending device, or the setting unit of the beacon sending device obtains the user's location information, such as obtaining the user's location based on signal strength and information provided by other devices information;
信标发送装置的设置单元执行步骤610,确定与用户对应的安全监控策略中的被监控对象;The setting unit of the beacon sending device executes step 610 to determine the monitored object in the security monitoring policy corresponding to the user;
在该步骤中,通过查找安全监控策略,获取与用户对应的安全监控条目,从而得到与用户对应的被监控对象。In this step, by searching for the security monitoring policy, the security monitoring entry corresponding to the user is obtained, so as to obtain the monitored object corresponding to the user.
设置单元执行步骤620,根据安全措施比较用户与被监控对象的关系,判断用户与被监控对象的关系是否满足安全措施所设置的要求;若满足,则执行步骤630,否则执行步骤640;The setting unit executes step 620, compares the relationship between the user and the monitored object according to the security measures, and determines whether the relationship between the user and the monitored object meets the requirements set by the security measures; if it is satisfied, then executes step 630, otherwise executes step 640;
在该步骤中,即判断用户是否满足预警条件或者需要采取一定措施的条件,比如用户对应的被监控对象为电梯,当前用户与电梯的距离小于1m,则满足了安全策略的预警条件。又例如用户对应的被监控对象为插座,安全措施为控制插座断电。In this step, it is judged whether the user meets the warning condition or the condition that certain measures need to be taken. For example, the monitored object corresponding to the user is an elevator, and the current distance between the user and the elevator is less than 1m, then the warning condition of the safety policy is met. Another example is that the monitored object corresponding to the user is an outlet, and the safety measure is to control the outlet to be powered off.
步骤630,根据安全措施执行对应的操作。In step 630, a corresponding operation is performed according to the security measure.
在该步骤中,基于安全措施,例如设置单元通过发送单元发送消息,对终端进行提醒,或者向紧急联系人发送提醒消息。In this step, based on security measures, for example, the setting unit sends a message through the sending unit to remind the terminal, or send a reminder message to the emergency contact.
在另一实施方式中,安全措施包括对被监控对象的控制,如向被监控对象或者与其关联的设备发送控制命令,接收控制命令的设备执行该命令,从而消除被监控对象对用户可能造成的危险。In another embodiment, the security measures include the control of the monitored object, such as sending a control command to the monitored object or a device associated with it, and the device receiving the control command executes the command, so as to eliminate the possible effects of the monitored object on the user. Danger.
设置单元执行步骤640,继续获取用户的位置信息,并执行步骤620。The setting unit executes step 640 , continues to acquire the user's location information, and executes step 620 .
或者检测模块获取用户的位置信息,发送模块发送至信标发送装置。Or the detection module obtains the user's location information, and the sending module sends the information to the beacon sending device.
在该步骤中,继续获取用户的位置信息,可以为周期性的获取,或者实时的获取。In this step, the location information of the user is continuously acquired, which may be acquired periodically or acquired in real time.
优选的,基于用户当前的位置以及被监控对象的位置,预测用户最快到达安全措施中设置的用户与被监控对象达到预警关系的时间长度,设置计时器,当计时器时间达到该预测的时间长度时,执行该步骤。Preferably, based on the current position of the user and the position of the monitored object, predict the length of time for the user to reach the early warning relationship between the user and the monitored object set in the security measures as soon as possible, and set a timer, when the timer reaches the predicted time length, perform this step.
其中预测该时间长度的步骤包括:设置单元或检测模块获取用户的特征信息,基于用户的特征信息确定具有该特征信息的用户的最快速度,基于该速度预测该时间长度。The step of predicting the time length includes: the setting unit or the detection module obtains the characteristic information of the user, determines the fastest speed of the user with the characteristic information based on the characteristic information of the user, and predicts the time length based on the speed.
例如获取用户的身高,基于用户的身高预测用户的速度;或者获取用户的年龄,基于用户的年龄预测用户的速度。其中用户身高与速度的关系以及用户年龄与速度的关系为基于大数据统计分析得到。For example, the user's height is obtained, and the user's speed is predicted based on the user's height; or the user's age is obtained, and the user's speed is predicted based on the user's age. The relationship between user height and speed and the relationship between user age and speed are obtained based on statistical analysis of big data.
在上述实施方式中提到在信标发送装置中存储对应特定用户的安全监控策略,终端的检测模块获取用户的特征信息,如指纹、图像、年龄、身高等信息,发送模块将上述信息发送至信标发送装置从而可以使得信标发送装置的设置单元识别携带该终端的用户,进一步针对该终端应用该用户对应的安全监控策略。在另一个实施方式中,获取用户特征信息的设备可以是其他设备,上述设备识别并获取用户特征信息以及识别用户携带的终端,将识别的用户特征信息以及识别的终端的信息发送至信标发送装置,信标发送装置的设置单元基于其他设备发送的信息将终端添加到对应该用户的安全监控条目中,或者其他设备将用户特征信息发送至识别出的用户携带的终端,由终端的发送模块将用户特征信息发送至信标发送装置。In the above embodiment, it is mentioned that the security monitoring policy corresponding to a specific user is stored in the beacon sending device, the detection module of the terminal obtains the user's characteristic information, such as fingerprint, image, age, height and other information, and the sending module sends the above information to The beacon sending device can thus enable the setting unit of the beacon sending device to identify the user who carries the terminal, and further apply the security monitoring policy corresponding to the user to the terminal. In another embodiment, the device that obtains the user feature information may be other devices, and the above-mentioned device identifies and obtains the user feature information and identifies the terminal carried by the user, and sends the identified user feature information and information of the identified terminal to the beacon for sending device, the setting unit of the beacon sending device adds the terminal to the security monitoring entry corresponding to the user based on the information sent by other devices, or other devices send user feature information to the terminal carried by the identified user, and the sending module of the terminal is sent by the terminal. The user characteristic information is sent to the beacon sending device.
在一个实施方式中,本发明的装置还执行以下方法。In one embodiment, the apparatus of the present invention also performs the following method.
检测模块或其他设备执行步骤700,获取用户的特征信息;The detection module or other equipment executes step 700 to obtain the feature information of the user;
优选的,还可以获取用户携带的终端的信息,如可以为用于识别终端的信息,或者为终端的位置信息。Preferably, information of the terminal carried by the user may also be acquired, such as information for identifying the terminal, or location information of the terminal.
优选的,该步骤可以在终端被添加到安全监控策略条目以后执行,也可以在未将终端添加到安全监控策略条目时执行。Preferably, this step may be performed after the terminal is added to the security monitoring policy entry, or may be performed when the terminal is not added to the security monitoring policy entry.
发送模块执行步骤710,发送用户的特征信息至具有安全监控策略的信标发送装置;The sending module executes step 710, and sends the user's characteristic information to the beacon sending device with the security monitoring policy;
优选的,将用户携带的终端的信息也发送至信标发送装置。Preferably, the information of the terminal carried by the user is also sent to the beacon sending device.
设置单元执行步骤720,根据接收的用户的特征信息确定用户对应于哪条安全监控条目,将用户携带的终端添加到该对应的条目中;The setting unit executes step 720, determines which security monitoring entry the user corresponds to according to the received feature information of the user, and adds the terminal carried by the user to the corresponding entry;
在一个实施方式中,设置单元根据接收的用户特征信息与安全监控策略中的被监控用户项比较,若存在比较一致的条目,则将用户携带的终端添加到该用户对应的条目的被监控终端项中;若不存在具有该特征的被安全监控的用户,优选的,则进一步根据用户的特征确定其是否属于需要被安全监控的用户类型,该需要被安全监控的用户类型可以根据已存储的安全监控策略学习得出,优选的,是根据被安全监控用户的特征学习得出;具体的,判断用户是否属于上述类型中的一种,若属于,则其应当属于被安全监控的用户,若不属于上述类型,则无需对该用户进行安全监控,不将其添加到安全监控策略的条目中,结束。In one embodiment, the setting unit compares the received user feature information with the monitored user item in the security monitoring policy, and if there is a relatively consistent item, adds the terminal carried by the user to the monitored terminal of the item corresponding to the user Item; if there is no user with this feature to be monitored safely, preferably, then further determine whether it belongs to the user type that needs to be monitored safely according to the user's feature, and the type of user that needs to be safely monitored can be based on the stored data. The security monitoring strategy is learned, and preferably, it is learned based on the characteristics of the security monitored user; specifically, it is judged whether the user belongs to one of the above types, and if so, it should belong to the security monitored user. If it does not belong to the above types, it is not necessary to perform security monitoring on the user, and it will not be added to the entry of the security monitoring policy, and the end.
对于属于上述类型的用户,发送单元向用户发送提示消息,提示是否将其添加到安全监控策略中,若用户反馈是,则如前所述,发送单元向用户发送上述主页界面,由用户自行设置其对应的安全监控条目,或者向用户发送提示,询问是否由AP为其自动生成安全监控策略条目,若接收单元接收到用户反馈的为其自动生成的应答消息,设置单元则根据其所属用户类型,参照安全监控策略中与该用户属于同类型用户的安全监控条目自动为其生成对应的安全监控条目。若接收单元接收到用户反馈否,则结束。也可以不向用户发送询问消息,设置单元直接自动生成安全监控条目。For users belonging to the above types, the sending unit sends a prompt message to the user, prompting whether to add it to the security monitoring policy. If the user feedback is yes, as described above, the sending unit sends the above home page interface to the user, which is set by the user. Its corresponding security monitoring entry, or send a prompt to the user to ask whether the AP will automatically generate a security monitoring policy entry for it, if the receiving unit receives a response message fed back by the user and automatically generated for it, the setting unit will be based on the user type to which it belongs. , the corresponding security monitoring entry is automatically generated for the user with reference to the security monitoring entry of the same type of user as the user in the security monitoring policy. If the receiving unit receives no feedback from the user, the process ends. It is also possible not to send an inquiry message to the user, and the setting unit may directly and automatically generate security monitoring items.
优选的,向用户发送提示前,发送单元先向对AP具有控制能力的终端发送提示消息,询问是否允许为该用户生成安全监控条目,若接收单元接收到是,则执行向用户发送提示的步骤,若否,则结束。Preferably, before sending the prompt to the user, the sending unit first sends a prompt message to the terminal that has the ability to control the AP, asking whether it is allowed to generate a security monitoring entry for the user, and if the receiving unit receives yes, execute the step of sending the prompt to the user , if not, end.
进一步的,具有控制能力的终端向AP发送删除指示,该删除指示用于指示 AP,设置单元未检测到该用户时间达到预设时间长度时,删除该用户对应的安全监控条目。Further, the terminal with control capability sends a deletion instruction to the AP, the deletion instruction is used to instruct the AP, and the setting unit does not detect that the user's time reaches a preset time length, and deletes the security monitoring entry corresponding to the user.
优选的,设置单元获取用户的位置信息,例如该位置信息为其他设备发送给设置单元,或者设置单元基于获取的用户的视频识别用户所处的位置,基于用户的位置信息以及设置单元获取的一个或多个终端的位置信息确定用户携带的终端。在该步骤中,终端可以是与信标发送装置建立连接的终端,设置单元基于与终端之间的无线信号确定终端的位置,或者终端周期性的或满足一定条件时将自身位置信息发送至信标发送装置,或者设置单元基于检测到的终端的信号确定终端的位置信息,设置单元基于终端的位置信息确定哪个终端是用户携带的终端。设置单元确定了哪个终端是用户携带的终端后,获取用于识别终端的信息,将该终端添加到用户对应的安全监控策略条目的被监控终端项中。Preferably, the setting unit acquires the location information of the user, for example, the location information is sent to the setting unit by other devices, or the setting unit recognizes the location of the user based on the acquired video of the user, based on the location information of the user and the one obtained by the setting unit The location information of one or more terminals determines the terminal carried by the user. In this step, the terminal may be a terminal that establishes a connection with the beacon sending device, and the setting unit determines the location of the terminal based on the wireless signal between the terminal and the terminal, or the terminal sends its own location information to the beacon periodically or when certain conditions are met The sending device, or the setting unit determines the location information of the terminal based on the detected signal of the terminal, and the setting unit determines which terminal is the terminal carried by the user based on the location information of the terminal. After determining which terminal is the terminal carried by the user, the setting unit acquires information for identifying the terminal, and adds the terminal to the monitored terminal item of the security monitoring policy entry corresponding to the user.
优选的,还包括以下步骤,设置单元判断终端是否在用户对应的安全监控策略条目的被监控终端项以外的其他被监控终端项中,如果在,则进行删除,如果不在,不执行任何操作。通过该步骤,可以防止对用户应用不必要的安全措施。Preferably, it also includes the following steps: the setting unit determines whether the terminal is in other monitored terminal items other than the monitored terminal item of the security monitoring policy entry corresponding to the user, and if so, deletes it, and if not, performs no operation. By this step, unnecessary security measures can be prevented from being applied to the user.
优选的,终端设备具备获取用户特征信息的能力时,检测模块定期获取携带终端的用户的特征信息,基于获取的用户的特征信息判断携带终端的用户是否改变,若发生改变,发送模块向信标发送装置发送被监控用户改变的消息,并携带改变后的用户的特征信息,设置单元接收该信息,基于该信息判断用户是否保存在安全监控策略条目的被监控用户中,即比较接收的信息与安全监控条目中的被监控用户的特征信息,比较一致则说明该用户有被监控的需求,否则用户不具有安全监控需求,或者进一步执行上述用户类型的判断的相关步骤,以确定是否生成新的安全监控条目,在此不再详细描述。相应的,比较一致时则将终端添加到该被监控用户对应的被监控终端项中,删除其他被监控终端项中记录的该终端的信息。Preferably, when the terminal device has the ability to obtain user feature information, the detection module periodically obtains the feature information of the user carrying the terminal, and determines whether the user carrying the terminal changes based on the obtained feature information of the user, and if there is a change, the sending module sends a beacon to the The sending device sends a message that the monitored user has changed, and carries the feature information of the changed user. The setting unit receives the information, and based on the information, judges whether the user is saved in the monitored user of the security monitoring policy entry, that is, compares the received information with that of the monitored user. If the characteristic information of the monitored user in the security monitoring entry is consistent, it means that the user needs to be monitored, otherwise the user does not have the security monitoring requirement, or further perform the above steps related to the judgment of the user type to determine whether to generate a new one. Security monitoring items, which will not be described in detail here. Correspondingly, if they are consistent, the terminal is added to the monitored terminal item corresponding to the monitored user, and the information of the terminal recorded in other monitored terminal items is deleted.
在另一实施方式中,设置单元周期性获取用户的位置以及在监控策略表中记录的被监控用户对应的终端的位置,判断二者位置是否一致,一致则不做处理,若不一致,则执行上述获取一个或多个终端的位置,基于终端的位置信息确定哪个终端是用户携带的终端以及后续的步骤,从而更新安全监控策略的条目。In another embodiment, the setting unit periodically obtains the location of the user and the location of the terminal corresponding to the monitored user recorded in the monitoring strategy table, and judges whether the two locations are consistent. The above-mentioned acquiring the location of one or more terminals, determining which terminal is the terminal carried by the user based on the location information of the terminals, and subsequent steps, so as to update the entry of the security monitoring policy.
进一步的,该方法还包括以下步骤:Further, the method also includes the following steps:
设置单元执行步骤730,判断被监控终端是否满足对其采取其对应的安全监控策略条目中的安全措施的条件,若是,发送单元向被监控终端发送提示信息,执行步骤740;若否,重复执行步骤730;The setting unit executes step 730 to determine whether the monitored terminal satisfies the conditions for taking the security measures in its corresponding security monitoring policy entry. If so, the sending unit sends prompt information to the monitored terminal, and executes step 740; if not, repeats the execution Step 730;
在该步骤中,安全措施中明确了需要对被监控用户防范的安全事件,和/或满足特定条件时执行的操作。如安全措施为当用户离插座1m时,对插座断电。In this step, the security measures specify security events that need to be guarded against the monitored user, and/or operations to be performed when certain conditions are met. For example, the safety measure is to cut off the power to the socket when the user is 1m away from the socket.
设置单元执行步骤740,判断是否接收到被监控终端的反馈信息;若是,则执行步骤750,若否,执行步骤760;The setting unit executes step 740 to determine whether the feedback information of the monitored terminal is received; if yes, executes step 750, if not, executes step 760;
步骤750,不采取安全措施条目中的安全措施,继续对终端进行监控,判断终端是否更接近被监控对象或更接近被监控对象会造成的危险事件,若是,判断终端与被监控对象的距离是否大于第一阈值小于第二阈值,若距离满足该要求,发送单元再次向终端发送提示信息,并执行步骤740;若终端与被监控对象的距离小于等于第一阈值,则设置单元按安全措施项执行相应的操作;若终端远离被监控对象,则不执行安全措施项的相应操作;Step 750, do not take the security measures in the security measure item, continue to monitor the terminal, determine whether the terminal is closer to the monitored object or a dangerous event that will be caused by the monitored object, and if so, determine whether the distance between the terminal and the monitored object is not. Greater than the first threshold and less than the second threshold, if the distance meets the requirement, the sending unit sends the prompt information to the terminal again, and executes step 740; if the distance between the terminal and the monitored object is less than or equal to the first threshold, the setting unit presses the safety measure item Perform the corresponding operation; if the terminal is far away from the monitored object, the corresponding operation of the security measure item will not be performed;
进一步的,当未执行安全措施项的相应操作时,设置单元调整安全监控策略中的安全措施中判断满足对其采取其对应的安全措施的条件,使其比当前条件要求降低。Further, when the corresponding operation of the security measure item is not performed, the setting unit adjusts the security measures in the security monitoring policy to determine that the conditions for taking the corresponding security measures are satisfied, so that the requirements are lower than the current conditions.
进一步的,当该条件要求降低的次数超过门限时,发送单元向被监控用户的紧急联系人发送问询消息,确认是否还需要保留该安全监控条目,若设置单元接收到无需保留,则删除对应的安全监控条目,若接收到需要保留,则保留该项目,并且当预定时间段内未提醒过被监控用户,则再次向被监控用户的紧急联系人发送问询消息,如上所述。Further, when the number of times that this condition requires reduction exceeds the threshold, the sending unit sends an inquiry message to the emergency contact of the monitored user to confirm whether it is necessary to retain the security monitoring entry, and if the setting unit receives that it is not necessary to retain, then delete the corresponding If the security monitoring item is received and needs to be retained, the item is retained, and when the monitored user is not reminded within a predetermined period of time, an inquiry message is sent to the emergency contact of the monitored user again, as described above.
设置单元执行步骤760,判断该提示信息发送的次数是否满足阈值,若是,执行步骤770,若否,发送单元再次向用户发送提示信息,执行步骤740;The setting unit executes step 760 to determine whether the number of times the prompt information is sent meets the threshold, if yes, executes step 770, if not, the sending unit sends the prompt information to the user again, executes step 740;
设置单元执行步骤770,根据安全措施执行对应的操作。The setting unit executes step 770, and executes corresponding operations according to the safety measures.
在另一个实施方式中,在步骤730判断为是时,发送单元向被监控用户的紧急联系人发送消息,查询被安全监控的用户是否学习过针对该被监控对象的安全知识,若设置单元接收到是,不采取安全措施条目中的安全措施,继续对终端进行监控,判断终端是否更接近被监控对象或接近被监控对象会造成的危险事件,若是,则向被监控用户的终端推送相关安全知识;In another embodiment, when the determination in step 730 is yes, the sending unit sends a message to the emergency contact of the monitored user to inquire whether the monitored user has learned the security knowledge for the monitored object, if the setting unit receives If yes, do not take the security measures in the security measures item, continue to monitor the terminal, determine whether the terminal is closer to the monitored object or the dangerous event that will be caused by the monitored object, if so, push relevant security measures to the terminal of the monitored user Knowledge;
进一步的,设置单元判断被监控用户是否进行学习,若是,则监测被监控用户学习安全知识后的行为,若被监控用户远离被监控对象或远离被监控对象会造成的危险事件,则调整安全监控策略中的安全措施中判断满足对其采取其对应的安全措施的条件,使其比当前条件要求降低;若被监控用户未进行学习,则发送单元向被监控用户携带的终端推送其感兴趣的内容,该内容为视频或音频,若设置单元检测到通过视频或音频的播放阻止被监控用户靠近被监控对象或远离被监控对象会造成的危险事件,则不执行安全措施的相应安全措施,否则执行安全措施的操作。Further, the setting unit judges whether the monitored user is learning, if yes, then monitors the behavior of the monitored user after learning the safety knowledge, if the monitored user is far away from the monitored object or the dangerous event that will be caused by the monitored object, then adjust the safety monitoring In the security measures in the policy, it is judged that the conditions for taking the corresponding security measures are met, so that the requirements are lower than the current conditions; Content, the content is video or audio, if the setting unit detects a dangerous event that prevents the monitored user from approaching the monitored object or away from the monitored object through the playback of video or audio, the corresponding security measures of the security measures will not be implemented, otherwise Action to perform safety measures.
设置单元若接收到被监控用户未学习过针对该被监控对象的安全知识的消息,发送单元则向终端推送针对该被监控对象的安全知识,优选的,该安全知识为视频或音频。优选的,继续执行上述判断被监控用户是否进行学习及之后的步骤。If the setting unit receives the message that the monitored user has not learned the security knowledge for the monitored object, the sending unit pushes the security knowledge for the monitored object to the terminal. Preferably, the security knowledge is video or audio. Preferably, the above steps of judging whether the monitored user is learning and the following steps are continued.
进一步的,接收单元若未接收到紧急联系人的确认消息,则重传所述消息,若满足重传最大次数,则不再向其紧急联系人发送所述消息,直接向被监控用户推送安全知识。Further, if the receiving unit does not receive the confirmation message of the emergency contact, it will retransmit the message, and if the maximum number of retransmissions is satisfied, it will not send the message to the emergency contact, and directly push the safety message to the monitored user. Knowledge.
上述步骤和前述步骤730的步骤可以是替换的方式,也可以都执行。The above steps and the steps of the aforementioned step 730 may be alternative manners, or both may be performed.
优选的,本发明的方法可以由设置有执行上述方法的部件的设备实现,上述方法步骤可以由一个或多个部件实现,而且本发明的AP可以是具有AP功能的监控设备等类型设备。Preferably, the method of the present invention can be implemented by a device provided with components for executing the above method, the above method steps can be implemented by one or more components, and the AP of the present invention can be a type of equipment such as a monitoring device with AP function.
本发明实施例提供了一种计算机设备,所述计算机设备包括处理器和存储器,所述存储器存储可被处理器执行的计算机指令,当处理器执行上述计算机指令时,实现如上所述的方法。An embodiment of the present invention provides a computer device, the computer device includes a processor and a memory, the memory stores computer instructions executable by the processor, and when the processor executes the computer instructions, the above method is implemented.
本发明实施例提供了一种计算机可读存储介质,用于存储计算机指令,所述计算机指令用于实现如上所述的方法。Embodiments of the present invention provide a computer-readable storage medium for storing computer instructions, where the computer instructions are used to implement the above method.
可以采用一个或多个计算机可读的介质的任意组合。计算机可读介质可以是计算机可读信号介质或者计算机可读存储介质。计算机可读存储介质例如可以是但不限于电、磁、光、电磁、红外线、或半导体的系统、装置或器件,或者任意以上的组合。计算机可读存储介质可以包括:具有一个或多个导线的电连接、便携式计算机磁盘、硬盘、随机存取存储器(RAM)、只读存储器(ROM)、闪存、可擦式可编程只读存储器(EPROM)、光纤、便携式紧凑磁盘只读存储器 (CD-ROM)、光存储器件、磁存储器件、或者上述的任意合适的组合。在本文件中,计算机可读存储介质可以是任何包含或存储程序的有形介质,该程序可以被指令执行系统、装置或者器件使用或者与其结合使用。Any combination of one or more computer-readable media may be employed. The computer-readable medium may be a computer-readable signal medium or a computer-readable storage medium. The computer-readable storage medium may be, for example, but not limited to, an electrical, magnetic, optical, electromagnetic, infrared, or semiconductor system, apparatus or device, or a combination of any of the above. Computer readable storage media may include: electrical connections with one or more wires, portable computer magnetic disks, hard disks, random access memory (RAM), read only memory (ROM), flash memory, erasable programmable read only memory ( EPROM), optical fiber, portable compact disk read only memory (CD-ROM), optical storage devices, magnetic storage devices, or any suitable combination of the foregoing. In this document, a computer-readable storage medium can be any tangible medium that contains or stores a program that can be used by or in conjunction with an instruction execution system, apparatus, or device.
可以以一种或多种程序设计语言或其组合来编写用于执行本发明操作的计算机程序代码Computer program code for carrying out operations of the present invention may be written in one or more programming languages or combinations thereof
以上说明只是为了方便理解本发明而举出的例子,不用于限定本发明的范围。在具体实现时,本领域技术人员可以根据实际情况对装置的部件进行变更、增加、减少,在不影响方法所实现的功能的基础上可以根据实际情况对方法的步骤进行变更、增加、减少或改变顺序。The above descriptions are merely examples for facilitating understanding of the present invention, and are not intended to limit the scope of the present invention. During the specific implementation, those skilled in the art can change, increase, or decrease the components of the device according to the actual situation, and can change, increase, decrease or decrease the steps of the method according to the actual situation without affecting the functions realized by the method. Change the order.
尽管已经示出和描述了本发明的实施例,本领域技术人员应当理解:在不脱离本发明的原理和宗旨的情况下可以对这些实施例进行多种变化、修改、替换和变型,本发明的范围由权利要求及其等同替换所限定,在未经创造性劳动所作的改进等,均应包含在本发明的保护范围之内。Although embodiments of the present invention have been shown and described, it should be understood by those skilled in the art that various changes, modifications, substitutions and alterations can be made in these The scope of the invention is defined by the claims and their equivalents, and any improvements made without creative work, etc., shall be included within the protection scope of the present invention.
Claims (10)
Translated fromChinesePriority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202011008155.1ACN112135295A (en) | 2020-09-23 | 2020-09-23 | Method and device for carrying out safety monitoring on user |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202011008155.1ACN112135295A (en) | 2020-09-23 | 2020-09-23 | Method and device for carrying out safety monitoring on user |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| CN112135295Atrue CN112135295A (en) | 2020-12-25 |
Family
ID=73842774
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN202011008155.1APendingCN112135295A (en) | 2020-09-23 | 2020-09-23 | Method and device for carrying out safety monitoring on user |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN112135295A (en) |
Cited By (1)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN115016882A (en)* | 2022-06-28 | 2022-09-06 | 上海浦东发展银行股份有限公司 | Monitoring interface generation method, device, equipment and storage medium |
Citations (9)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| JP2007193506A (en)* | 2006-01-18 | 2007-08-02 | Sogo Keibi Hosho Co Ltd | Monitoring system and monitoring method |
| US20120124637A1 (en)* | 2010-11-11 | 2012-05-17 | International Business Machines Corporation | Secure access to healthcare information |
| CN102917115A (en)* | 2011-08-04 | 2013-02-06 | 国际商业机器公司 | System and method for preventing and/or limiting use of a mobile device |
| CN105094009A (en)* | 2015-06-09 | 2015-11-25 | 小米科技有限责任公司 | Method and apparatus for disconnecting power source |
| CN105409265A (en)* | 2013-08-29 | 2016-03-16 | 诺基亚技术有限公司 | Adaptive security indicator for wireless devices |
| CN105701967A (en)* | 2016-03-29 | 2016-06-22 | 北京小米移动软件有限公司 | Position prompting method and position prompting device |
| CN107832615A (en)* | 2012-10-19 | 2018-03-23 | 迈克菲公司 | Place perceives safety |
| US20180159899A1 (en)* | 2016-12-07 | 2018-06-07 | Cisco Technology, Inc. | User interface for low-touch security policy provisioning |
| CN111083446A (en)* | 2019-12-27 | 2020-04-28 | 中科劲点(北京)科技有限公司 | Tracking and positioning method, system and equipment combining visual signal and wireless signal |
- 2020
- 2020-09-23CNCN202011008155.1Apatent/CN112135295A/enactivePending
Patent Citations (9)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| JP2007193506A (en)* | 2006-01-18 | 2007-08-02 | Sogo Keibi Hosho Co Ltd | Monitoring system and monitoring method |
| US20120124637A1 (en)* | 2010-11-11 | 2012-05-17 | International Business Machines Corporation | Secure access to healthcare information |
| CN102917115A (en)* | 2011-08-04 | 2013-02-06 | 国际商业机器公司 | System and method for preventing and/or limiting use of a mobile device |
| CN107832615A (en)* | 2012-10-19 | 2018-03-23 | 迈克菲公司 | Place perceives safety |
| CN105409265A (en)* | 2013-08-29 | 2016-03-16 | 诺基亚技术有限公司 | Adaptive security indicator for wireless devices |
| CN105094009A (en)* | 2015-06-09 | 2015-11-25 | 小米科技有限责任公司 | Method and apparatus for disconnecting power source |
| CN105701967A (en)* | 2016-03-29 | 2016-06-22 | 北京小米移动软件有限公司 | Position prompting method and position prompting device |
| US20180159899A1 (en)* | 2016-12-07 | 2018-06-07 | Cisco Technology, Inc. | User interface for low-touch security policy provisioning |
| CN111083446A (en)* | 2019-12-27 | 2020-04-28 | 中科劲点(北京)科技有限公司 | Tracking and positioning method, system and equipment combining visual signal and wireless signal |
Cited By (2)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN115016882A (en)* | 2022-06-28 | 2022-09-06 | 上海浦东发展银行股份有限公司 | Monitoring interface generation method, device, equipment and storage medium |
| CN115016882B (en)* | 2022-06-28 | 2024-06-07 | 上海浦东发展银行股份有限公司 | Monitoring interface generation method, device, equipment and storage medium |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| US10382729B2 (en) | Home automation system-initiated calls | |
| US10504346B2 (en) | Home automation communication system | |
| US11025863B2 (en) | Home automation system-initiated calls | |
| JP6130081B2 (en) | Signal transmission control method, apparatus, electronic device, program, and recording medium | |
| US20200053538A1 (en) | Emergency call-for-help method and system based on fingerprint identification for mobile terminal, and mobile terminal | |
| US10250702B2 (en) | Method and apparatus for pushing information | |
| EP4325946A2 (en) | Proximity communication method and apparatus | |
| US20150350820A1 (en) | Beacon additional service of electronic device and electronic device for same background arts | |
| US11412555B2 (en) | Mobile terminal | |
| CN105262652A (en) | Network configuration method for network household appliance | |
| CN113408006B (en) | Monitoring data access method and device, indoor monitoring system and storage medium | |
| CN104540091A (en) | Automatic pairing system and automatic pairing method based on bluetooth equipment | |
| CN112185059B (en) | Method and device for reminding user | |
| US20230121623A1 (en) | Method for notifying a message of a smart home based on a smart screen Apparatus and Smart screen | |
| CN112165518B (en) | Security monitoring strategy generation method and device | |
| US12034561B2 (en) | Processing method, device and storage medium | |
| US20150256962A1 (en) | M2m gateway device and applying method thereof | |
| CN106792694A (en) | A kind of access authentication method, and access device | |
| CN104616408B (en) | Doorbell control method and device | |
| CN110798444B (en) | Data synchronization method and device based on Internet of things | |
| KR102317051B1 (en) | Computer readable medium and electronic apparatus for performing wireless communication | |
| CN112135295A (en) | Method and device for carrying out safety monitoring on user | |
| CN112165707B (en) | A beacon sending method and device | |
| CN105094028A (en) | Abnormal state prompt method and server of sweeping robot | |
| CN116419197A (en) | Communication method, device and terminal |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| TA01 | Transfer of patent application right | Effective date of registration:20220110 Address after:310024 floor 5, zone 2, building 3, Hangzhou cloud computing Industrial Park, Zhuantang street, Xihu District, Hangzhou City, Zhejiang Province Applicant after:Hangzhou suddenly Cognitive Technology Co.,Ltd. Address before:100083 gate 3, block a, 768 Creative Industry Park, Zhongguancun, No.5 Xueyuan Road, Haidian District, Beijing Applicant before:BEIJING MORAN COGNITIVE TECHNOLOGY Co.,Ltd. | |
| TA01 | Transfer of patent application right | ||
| RJ01 | Rejection of invention patent application after publication | Application publication date:20201225 | |
| RJ01 | Rejection of invention patent application after publication |