CN112134885A - A method and system for encryption of Internet terminal access - Google Patents
A method and system for encryption of Internet terminal accessDownload PDFInfo
- Publication number
- CN112134885A CN112134885ACN202011007005.9ACN202011007005ACN112134885ACN 112134885 ACN112134885 ACN 112134885ACN 202011007005 ACN202011007005 ACN 202011007005ACN 112134885 ACN112134885 ACN 112134885A
- Authority
- CN
- China
- Prior art keywords
- unit
- algorithm
- server
- data
- time
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Pending
Links
Images
Classifications
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/04—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks
- H04L63/0428—Network architectures or network communication protocols for network security for providing a confidential data exchange among entities communicating through data packet networks wherein the data content is protected, e.g. by encrypting or encapsulating the payload
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/08—Network architectures or network communication protocols for network security for authentication of entities
Landscapes
- Engineering & Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- Computer Hardware Design (AREA)
- Computing Systems (AREA)
- General Engineering & Computer Science (AREA)
- Computer Networks & Wireless Communication (AREA)
- Signal Processing (AREA)
- Information Transfer Between Computers (AREA)
Abstract
Translated fromChineseDescription
Translated fromChinese技术领域technical field
本发明涉及互联网安全技术领域,更具体地说,本发明涉及一种互联网终端访问加密的方法和系统。The present invention relates to the technical field of Internet security, and more particularly, the present invention relates to a method and system for encryption of Internet terminal access.
背景技术Background technique
网络软件一般是指系统的网络操作系统、网络通信协议和应用级的提供网络服务功能的专用软件。在计算机网络环境中,用于支持数据通信和各种网络活动的软件。连入计算机网络的系统,通常根据系统本身的特点、能力和服务对象,配置不同的网络应用系统。其目的是为了本机用户共享网中其他系统的资源,或是为了把本机系统的功能和资源提供给网中其他用户使用。为此,每个计算机网络都制订一套全网共同遵守的网络协议,并要求网中每个主机系统配置相应的协议软件,以确保网中不同系统之间能够可靠、有效地相互通信和合作。网络操作系统是用于管理网络软、硬资源,提供简单网络管理的系统软件。常见的网络操作系统有UNIX、Netware、Windows NT、Linux等。UNIX是一种强大的分时操作系统,以前在大型机和小型机上使用,已经向PC过渡。UNIX支持TCP/IP协议,安全性、可靠性强,缺点是操作使用复杂。Network software generally refers to the system's network operating system, network communication protocols, and application-level special software that provides network service functions. In a computer network environment, software used to support data communications and various network activities. A system connected to a computer network usually configures different network application systems according to the characteristics, capabilities and service objects of the system itself. Its purpose is to share the resources of other systems in the network for the local user, or to provide the functions and resources of the local system to other users in the network. To this end, each computer network formulates a set of network protocols that the entire network abides by, and requires each host system in the network to configure corresponding protocol software to ensure that different systems in the network can communicate and cooperate with each other reliably and effectively. . A network operating system is a system software used to manage network soft and hard resources and provide simple network management. Common network operating systems include UNIX, Netware, Windows NT, and Linux. UNIX, a powerful time-sharing operating system formerly used on mainframes and minicomputers, has transitioned to PCs. UNIX supports the TCP/IP protocol, with strong security and reliability. The disadvantage is that the operation and use are complicated.
网络软件的通讯基于广域网或者局域网,客户端在与服务器1或者系统内其他模块通讯时的安全是一个很重要的问题,没有有效的加密措施,就会发生虚假客户端、虚假控制台连接到服务器1或者数据库,传输错误数据甚至病毒木马等危害整体的系统安全。The communication of the network software is based on the wide area network or local area network. The security of the client when it communicates with the server 1 or other modules in the system is a very important issue. Without effective encryption measures, false clients and false consoles will connect to the server. 1 or database, transmission of wrong data or even virus Trojan horses, etc. endanger the overall system security.
发明内容SUMMARY OF THE INVENTION
为了克服现有技术的上述缺陷,本发明的实施例提供一种互联网终端访问加密的方法和系统,本发明所要解决的技术问题是:现有网络软件登录造成网络安全问题。In order to overcome the above-mentioned defects of the prior art, the embodiments of the present invention provide a method and system for encryption of Internet terminal access, and the technical problem to be solved by the present invention is: the existing network software login causes network security problems.
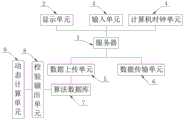
为实现上述目的,本发明提供如下技术方案:一种互联网终端访问加密系统,包括服务器,所述服务器的连接端设有显示单元、输入单元和计算机时钟单元,所述服务器连接端还设有数据上传单元和数据传输单元,所述数据上传单元连接端设有算法数据库,所述算法数据库连接端设有校验输出单元,所述校验输出单元连接端设有动态计算单元;In order to achieve the above purpose, the present invention provides the following technical solutions: an Internet terminal access encryption system, including a server, the connection end of the server is provided with a display unit, an input unit and a computer clock unit, and the server connection end is also provided with data an uploading unit and a data transmission unit, the connection end of the data uploading unit is provided with an algorithm database, the connection end of the algorithm database is provided with a check output unit, and the connection end of the check output unit is provided with a dynamic calculation unit;
所述服务器设置为用户PC端主机,用于PC的下载内容的处理和正常运行;The server is set as the user's PC end host, which is used for the processing and normal operation of the downloaded content of the PC;
所述显示单元设置为PC显示屏,用于显示操作步骤的进行及直接读取来自服务器的通知信息及常规的访问信息浏览;The display unit is set as a PC display screen, which is used to display the progress of the operation steps and directly read the notification information from the server and the conventional browsing of access information;
所述输入单元设置为与PC显示屏和PC端主机配套的鼠标和键盘,用于信息的输入及确定控制信息;The input unit is set as a mouse and a keyboard matched with the PC display screen and the PC end host, for inputting information and determining control information;
所述计算机时钟单元设置为服务器联网后的计算机时钟,设置为实时时间;The computer clock unit is set to the computer clock after the server is networked, and set to real-time time;
所述数据上传单元用于将校验输出单元输出的校验信息上传至服务器;The data uploading unit is used for uploading the verification information output by the verification output unit to the server;
所述数据传输单元用于数据的传输,对校验成功的客户端允许正常的访问及与服务器的连接;The data transmission unit is used for data transmission, and allows normal access and connection with the server to the client that has been successfully verified;
所述算法数据库用于存储各类的数据效验算法;The algorithm database is used to store various data validation algorithms;
所述校验输出单元用于将动态计算单元生成的数据和PC端主机的系统时间同时传输至数据上传单元;The verification output unit is used to simultaneously transmit the data generated by the dynamic calculation unit and the system time of the PC end host to the data upload unit;
所述动态计算单元用于采集输入信号,经算法数据库内的实时算法生成数据信息。The dynamic computing unit is used to collect input signals, and generate data information through real-time algorithms in the algorithm database.
在一个优选地实施方式中,所述计算机时钟单元的时间值与接入互联网的实时数据同步,无时间差。In a preferred embodiment, the time value of the computer clock unit is synchronized with the real-time data connected to the Internet without time difference.
在一个优选地实施方式中,所述算法数据库内算法数量设置为多个,且单个算法使用后摒弃,且算法数据库内算法由服务器进行不定时更新。In a preferred embodiment, the number of algorithms in the algorithm database is set to multiple, and a single algorithm is discarded after being used, and the algorithms in the algorithm database are updated from time to time by the server.
在一个优选地实施方式中,所述动态计算单元输出信息为算法数据库内随机算法生成数据,该数据信息设置为字符串。In a preferred embodiment, the output information of the dynamic computing unit is data generated by a random algorithm in the algorithm database, and the data information is set as a character string.
本发明还包括一种互联网终端访问加密的方法,其具体加密步骤如下:The present invention also includes a method for Internet terminal access encryption, and its specific encryption steps are as follows:
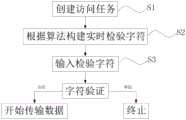
S1、创建访问任务:使用输入单元由服务器进行客户端的登录,客户端与服务器通讯前会先做一次握手操作;S1. Create an access task: use the input unit to log in to the client by the server, and the client will do a handshake operation before communicating with the server;
S2、生成实时字符:根据步骤S1的握手操作,以计算机时钟单元的时间点为基准由动态计算单元根据算法数据库预埋的算法实时计算出一个字符串;S2, generate real-time characters: according to the handshake operation of step S1, take the time point of the computer clock unit as a benchmark and calculate a character string in real time by the dynamic calculation unit according to the algorithm embedded in the algorithm database;
S3、字符检验:同时将步骤S2中计算出的字符串和系统时间上传至校验输出单元,校验输出单元通过收到的数据对算法数据库内实时算法进行效验算法;S3, character inspection: the character string calculated in step S2 and the system time are uploaded to the verification output unit simultaneously, and the verification output unit carries out the verification algorithm to the real-time algorithm in the algorithm database by the data received;
若得到的是合法的算法,数据上传单元将校验结果上传至服务器,服务器控制显示单元显示握手成功的通知,然后服务器控制数据传输单元开始传输数据;If the obtained algorithm is legal, the data uploading unit uploads the verification result to the server, the server controls the display unit to display a notification that the handshake is successful, and then the server controls the data transmission unit to start transmitting data;
若得到的是非法的算法,则访问终止。If an illegal algorithm is obtained, the access is terminated.
本发明的技术效果和优点:Technical effects and advantages of the present invention:
本发明通过服务器会不定时更新算法,发送给客户端,并不止一个算法,每次握手都会抛弃掉一个算法,这种状态下计算机使用者或者恶意程序无法通过穷举、截获、反运算等方式来破解效验的密钥以及算法;所有的关键值都是动态的,这样将获得一个更加安全的加密结果。In the present invention, the server will update the algorithm from time to time and send it to the client. There are not more than one algorithm, and one algorithm will be discarded each time a handshake is performed. In this state, computer users or malicious programs cannot use methods such as exhaustive, interception, and inverse operation. The key and algorithm to crack the verification; all key values are dynamic, so that a more secure encryption result will be obtained.
附图说明Description of drawings
图1为本发明的整体模块示意图。FIG. 1 is a schematic diagram of an overall module of the present invention.
图2为本发明的整体流程示意图。FIG. 2 is a schematic diagram of the overall flow of the present invention.
附图标记为:1服务器、2显示单元、3输入单元、4计算机时钟单元、5数据上传单元、6数据传输单元、7算法数据库、8校验输出单元、9动态计算单元。Reference numerals are: 1 server, 2 display unit, 3 input unit, 4 computer clock unit, 5 data upload unit, 6 data transmission unit, 7 algorithm database, 8 check output unit, 9 dynamic calculation unit.
具体实施方式Detailed ways
下面将结合本发明实施例中的附图,对本发明实施例中的技术方案进行清楚、完整地描述,显然,所描述的实施例仅仅是本发明一部分实施例,而不是全部的实施例。基于本发明中的实施例,本领域普通技术人员在没有做出创造性劳动前提下所获得的所有其他实施例,都属于本发明保护的范围。The technical solutions in the embodiments of the present invention will be clearly and completely described below with reference to the accompanying drawings in the embodiments of the present invention. Obviously, the described embodiments are only a part of the embodiments of the present invention, but not all of the embodiments. Based on the embodiments of the present invention, all other embodiments obtained by those of ordinary skill in the art without creative efforts shall fall within the protection scope of the present invention.
实施例1:Example 1:
本发明提供了一种互联网终端访问加密系统,包括服务器1,所述服务器1的连接端设有显示单元2、输入单元3和计算机时钟单元4,所述服务器1连接端还设有数据上传单元5和数据传输单元6,所述数据上传单元5连接端设有算法数据库7,所述算法数据库7连接端设有校验输出单元8,所述校验输出单元8连接端设有动态计算单元9;The present invention provides an Internet terminal access encryption system, including a server 1, the connection end of the server 1 is provided with a
所述服务器1设置为用户PC端主机,用于PC的下载内容的处理和正常运行;The server 1 is set as the user's PC end host, which is used for the processing and normal operation of the downloaded content of the PC;
所述显示单元2设置为PC显示屏,用于显示操作步骤的进行及直接读取来自服务器1的通知信息及常规的访问信息浏览;The
所述输入单元3设置为与PC显示屏和PC端主机配套的鼠标和键盘,用于信息的输入及确定控制信息;The
所述计算机时钟单元4设置为服务器1联网后的计算机时钟,设置为实时时间,所述计算机时钟单元4的时间值与接入互联网的实时数据同步,无时间差;Described
所述数据上传单元5用于将校验输出单元8输出的校验信息上传至服务器1;The
所述数据传输单元6用于数据的传输,对校验成功的客户端允许正常的访问及与服务器1的连接;The
所述算法数据库7用于存储各类的数据效验算法,所述算法数据库7内算法数量设置为多个,且单个算法使用后摒弃,且算法数据库7内算法由服务器1进行不定时更新;The
所述校验输出单元8用于将动态计算单元9生成的数据和PC端主机的系统时间同时传输至数据上传单元5;The verification output unit 8 is used to simultaneously transmit the data generated by the dynamic calculation unit 9 and the system time of the PC end host to the
所述动态计算单元9用于采集输入信号,经算法数据库7内的实时算法生成数据信息,所述动态计算单元9输出信息为算法数据库7内随机算法生成数据,该数据信息设置为字符串。The dynamic calculation unit 9 is used to collect input signals and generate data information through the real-time algorithm in the
本发明还包括一种互联网终端访问加密的方法,其具体加密步骤如下:The present invention also includes a method for Internet terminal access encryption, and its specific encryption steps are as follows:
S1、创建访问任务:使用输入单元3由服务器1进行客户端的登录,客户端与服务器1通讯前会先做一次握手操作;S1, create an access task: use the
S2、生成实时字符:根据步骤S1的握手操作,以计算机时钟单元4的时间点为基准由动态计算单元9根据算法数据库7预埋的算法实时计算出一个字符串;S2, generate real-time characters: according to the handshake operation of step S1, take the time point of the
S3、字符检验:同时将步骤S2中计算出的字符串和系统时间上传至校验输出单元8,校验输出单元8通过收到的数据对算法数据库7内实时算法进行效验算法;若得到的是合法的算法,数据上传单元5将校验结果上传至服务器1,服务器1控制显示单元2显示握手成功的通知,然后服务器1控制数据传输单元6开始传输数据。S3, character inspection: the character string calculated in step S2 and the system time are uploaded to the verification output unit 8 simultaneously, and the verification output unit 8 carries out the verification algorithm to the real-time algorithm in the
实施例2:Example 2:
本发明提供了一种互联网终端访问加密系统,包括服务器1,所述服务器1的连接端设有显示单元2、输入单元3和计算机时钟单元4,所述服务器1连接端还设有数据上传单元5和数据传输单元6,所述数据上传单元5连接端设有算法数据库7,所述算法数据库7连接端设有校验输出单元8,所述校验输出单元8连接端设有动态计算单元9;The present invention provides an Internet terminal access encryption system, including a server 1, the connection end of the server 1 is provided with a
所述服务器1设置为用户PC端主机,用于PC的下载内容的处理和正常运行;The server 1 is set as the user's PC end host, which is used for the processing and normal operation of the downloaded content of the PC;
所述显示单元2设置为PC显示屏,用于显示操作步骤的进行及直接读取来自服务器1的通知信息及常规的访问信息浏览;The
所述输入单元3设置为与PC显示屏和PC端主机配套的鼠标和键盘,用于信息的输入及确定控制信息;The
所述计算机时钟单元4设置为服务器1联网后的计算机时钟,设置为实时时间,所述计算机时钟单元4的时间值与接入互联网的实时数据同步,无时间差;Described
所述数据上传单元5用于将校验输出单元8输出的校验信息上传至服务器1;The
所述数据传输单元6用于数据的传输,对校验成功的客户端允许正常的访问及与服务器1的连接;The
所述算法数据库7用于存储各类的数据效验算法,所述算法数据库7内算法数量设置为多个,且单个算法使用后摒弃,且算法数据库7内算法由服务器1进行不定时更新;The
所述校验输出单元8用于将动态计算单元9生成的数据和PC端主机的系统时间同时传输至数据上传单元5;The verification output unit 8 is used to simultaneously transmit the data generated by the dynamic calculation unit 9 and the system time of the PC end host to the data upload
所述动态计算单元9用于采集输入信号,经算法数据库7内的实时算法生成数据信息,所述动态计算单元9输出信息为算法数据库7内随机算法生成数据,该数据信息设置为字符串。The dynamic calculation unit 9 is used to collect input signals and generate data information through the real-time algorithm in the
本发明还包括一种互联网终端访问加密的方法,其具体加密步骤如下:The present invention also includes a method for Internet terminal access encryption, and its specific encryption steps are as follows:
S1、创建访问任务:使用输入单元3由服务器1进行客户端的登录,客户端与服务器1通讯前会先做一次握手操作;S1, create an access task: use the
S2、生成实时字符:根据步骤S1的握手操作,以计算机时钟单元4的时间点为基准由动态计算单元9根据算法数据库7预埋的算法实时计算出一个字符串;S2, generate real-time characters: according to the handshake operation of step S1, take the time point of the
S3、字符检验:同时将步骤S2中计算出的字符串和系统时间上传至校验输出单元8,校验输出单元8通过收到的数据对算法数据库7内实时算法进行效验算法;若得到的是非法的算法,则访问终止。S3, character inspection: the character string calculated in step S2 and the system time are uploaded to the verification output unit 8 simultaneously, and the verification output unit 8 carries out the verification algorithm to the real-time algorithm in the
本发明工作原理:The working principle of the present invention:
参照说明书附图1-2,客户端与服务器1通讯前会先做一次握手操作,以双方的一台特殊字符串来相互效验,以输出握手成功或者握手失败的结果,握手效验双方都是用动态计算方式,以计算机时钟单元4的计算机时钟为基准,根据算法数据库7内的预埋算法实时计算出一个字符串,然后动态计算单元9和数据上传单元5同时上传字符串和系统时间,然后后台服务器1会通过收到的数据效验算法,是合法的算法才会做握手成功的通知,然后开始传输数据。Referring to Figure 1-2 in the description, before the client communicates with the server 1, a handshake operation will be performed first, and a special string of both parties will be used to verify each other to output the result of a successful handshake or a failed handshake. Both sides of the handshake verification use The dynamic calculation method, based on the computer clock of the
最后应说明的几点是:首先,在本申请的描述中,需要说明的是,除非另有规定和限定,术语“安装”、“相连”、“连接”应做广义理解,可以是机械连接或电连接,也可以是两个元件内部的连通,可以是直接相连,“上”、“下”、“左”、“右”等仅用于表示相对位置关系,当被描述对象的绝对位置改变,则相对位置关系可能发生改变;The last points to be noted are: First of all, in the description of this application, it should be noted that, unless otherwise specified and limited, the terms "installation", "connection" and "connection" should be understood in a broad sense, and may be mechanical connection. or electrical connection, or internal communication between two components, or direct connection, "up", "down", "left", "right", etc. are only used to indicate relative positional relationship, when the absolute position of the object being described changes, the relative positional relationship may change;
其次:本发明公开实施例附图中,只涉及到与本公开实施例涉及到的结构,其他结构可参考通常设计,在不冲突情况下,本发明同一实施例及不同实施例可以相互组合;Secondly: in the drawings of the disclosed embodiments of the present invention, only the structures involved in the embodiments of the present disclosure are involved, other structures may refer to the general design, and the same embodiment and different embodiments of the present invention can be combined with each other under the condition of no conflict;
最后:以上所述仅为本发明的优选实施例而已,并不用于限制本发明,凡在本发明的精神和原则之内,所作的任何修改、等同替换、改进等,均应包含在本发明的保护范围之内。Finally: the above is only the preferred embodiment of the present invention, and is not intended to limit the present invention. Any modification, equivalent replacement, improvement, etc. made within the spirit and principle of the present invention should be included in the present invention. within the scope of protection.
Claims (5)
Translated fromChinesePriority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202011007005.9ACN112134885A (en) | 2020-09-23 | 2020-09-23 | A method and system for encryption of Internet terminal access |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202011007005.9ACN112134885A (en) | 2020-09-23 | 2020-09-23 | A method and system for encryption of Internet terminal access |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| CN112134885Atrue CN112134885A (en) | 2020-12-25 |
Family
ID=73842672
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN202011007005.9APendingCN112134885A (en) | 2020-09-23 | 2020-09-23 | A method and system for encryption of Internet terminal access |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN112134885A (en) |
Citations (15)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN1808975A (en)* | 2006-01-26 | 2006-07-26 | 黄涛 | System and method of preventing network account from stolen |
| CN101163014A (en)* | 2007-11-30 | 2008-04-16 | 中国电信股份有限公司 | Dynamic password identification authenticating system and method |
| CN101291228A (en)* | 2008-06-18 | 2008-10-22 | 华为技术有限公司 | A method, system, and device for generating and authenticating a super password |
| CN101325483A (en)* | 2008-07-28 | 2008-12-17 | 中国电信股份有限公司 | Method and apparatus for updating symmetrical cryptographic key, symmetrical ciphering method and symmetrical deciphering method |
| US20100257372A1 (en)* | 2009-03-26 | 2010-10-07 | Ryan Seifert | Integrated file level cryptographical access control |
| CN104052742A (en)* | 2014-06-11 | 2014-09-17 | 上海康煦智能科技有限公司 | Internet of things communication protocol capable of being encrypted dynamically |
| CN105450397A (en)* | 2015-12-29 | 2016-03-30 | 深圳市瑞铭无限科技有限公司 | Data encryption method and client based on sending encryption algorithm |
| CN106789054A (en)* | 2016-12-23 | 2017-05-31 | 携程旅游网络技术(上海)有限公司 | The update method and system of dynamic encryption and decryption algorithm |
| CN106936573A (en)* | 2014-04-21 | 2017-07-07 | 岳文伟 | Dynamic password formation method based on integrated mode |
| CN107566112A (en)* | 2016-06-30 | 2018-01-09 | 中国电信股份有限公司 | Dynamic encryption and decryption method and server |
| CN108306881A (en)* | 2018-01-31 | 2018-07-20 | 苏州锦佰安信息技术有限公司 | A kind of auth method and device |
| CN108777615A (en)* | 2018-09-17 | 2018-11-09 | 上海并擎软件科技有限公司 | Dynamic password authentication method and device |
| CN109587180A (en)* | 2019-01-28 | 2019-04-05 | 杭州涂鸦信息技术有限公司 | A kind of method that establishing connection, client and server |
| CN110351230A (en)* | 2018-04-08 | 2019-10-18 | 湖南青普科技有限公司 | A kind of online controller with identity identifying and authenticating function |
| CN111327629A (en)* | 2020-03-04 | 2020-06-23 | 广州柏视医疗科技有限公司 | Identity verification method, client and server |
- 2020
- 2020-09-23CNCN202011007005.9Apatent/CN112134885A/enactivePending
Patent Citations (15)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN1808975A (en)* | 2006-01-26 | 2006-07-26 | 黄涛 | System and method of preventing network account from stolen |
| CN101163014A (en)* | 2007-11-30 | 2008-04-16 | 中国电信股份有限公司 | Dynamic password identification authenticating system and method |
| CN101291228A (en)* | 2008-06-18 | 2008-10-22 | 华为技术有限公司 | A method, system, and device for generating and authenticating a super password |
| CN101325483A (en)* | 2008-07-28 | 2008-12-17 | 中国电信股份有限公司 | Method and apparatus for updating symmetrical cryptographic key, symmetrical ciphering method and symmetrical deciphering method |
| US20100257372A1 (en)* | 2009-03-26 | 2010-10-07 | Ryan Seifert | Integrated file level cryptographical access control |
| CN106936573A (en)* | 2014-04-21 | 2017-07-07 | 岳文伟 | Dynamic password formation method based on integrated mode |
| CN104052742A (en)* | 2014-06-11 | 2014-09-17 | 上海康煦智能科技有限公司 | Internet of things communication protocol capable of being encrypted dynamically |
| CN105450397A (en)* | 2015-12-29 | 2016-03-30 | 深圳市瑞铭无限科技有限公司 | Data encryption method and client based on sending encryption algorithm |
| CN107566112A (en)* | 2016-06-30 | 2018-01-09 | 中国电信股份有限公司 | Dynamic encryption and decryption method and server |
| CN106789054A (en)* | 2016-12-23 | 2017-05-31 | 携程旅游网络技术(上海)有限公司 | The update method and system of dynamic encryption and decryption algorithm |
| CN108306881A (en)* | 2018-01-31 | 2018-07-20 | 苏州锦佰安信息技术有限公司 | A kind of auth method and device |
| CN110351230A (en)* | 2018-04-08 | 2019-10-18 | 湖南青普科技有限公司 | A kind of online controller with identity identifying and authenticating function |
| CN108777615A (en)* | 2018-09-17 | 2018-11-09 | 上海并擎软件科技有限公司 | Dynamic password authentication method and device |
| CN109587180A (en)* | 2019-01-28 | 2019-04-05 | 杭州涂鸦信息技术有限公司 | A kind of method that establishing connection, client and server |
| CN111327629A (en)* | 2020-03-04 | 2020-06-23 | 广州柏视医疗科技有限公司 | Identity verification method, client and server |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| US10187400B1 (en) | Packet filters in security appliances with modes and intervals | |
| JP5396051B2 (en) | Method and system for creating and updating a database of authorized files and trusted domains | |
| CN111651757A (en) | Monitoring method, device, device and storage medium for attack behavior | |
| JP4733885B2 (en) | Vulnerability assessment program, method and system | |
| WO2016186975A1 (en) | Detection of sql injection attacks | |
| CN103607385A (en) | Method and apparatus for security detection based on browser | |
| CN115412547A (en) | File uploading method and file uploading system | |
| CN114745145A (en) | Business data access method, device and equipment and computer storage medium | |
| CN114675567A (en) | Access processing method, device and storage medium for remotely controlling terminal | |
| CN116074029A (en) | Risk prediction information determining method and device, electronic equipment and storage medium | |
| CN106357727A (en) | Method and system to upload files to multiple servers simultaneously | |
| CN114491582A (en) | Authentication method, device and terminal device | |
| JP2008015733A (en) | Log management computer | |
| CN118886014B (en) | Operating system safety control method and system based on risk detection | |
| CN110602134A (en) | Method, device and system for identifying illegal terminal access based on session label | |
| CN110750290A (en) | Software version upgrading method and device based on DNS query | |
| CN111324872A (en) | Method and system for redirected centralized audit of login records and operation records | |
| JP2020038438A (en) | Management device, management system and program | |
| CN118316688A (en) | Gateway authentication method, device and system | |
| CN112134885A (en) | A method and system for encryption of Internet terminal access | |
| WO2021026937A1 (en) | Method and apparatus for checking login behavior, and system, storage medium and electronic apparatus | |
| CN118055157A (en) | Service calling method, device, equipment and storage medium | |
| CN103701595A (en) | System, method and device for log-in authentication | |
| CN115130116A (en) | Business resource access method, device, equipment, readable storage medium and system | |
| CN115514531B (en) | Data hijacking alarm method, system, electronic device and storage medium |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| CB03 | Change of inventor or designer information | Inventor after:Liao Xiaoyun Inventor after:Tang Haitao Inventor after:Sun Lili Inventor after:Yu Jin Inventor after:Wang Wanyong Inventor after:Wang Zhihua Inventor after:Chen Haitao Inventor after:Ni Gege Inventor after:Han Yi Inventor after:Wu Bo Inventor after:Cai Ming Inventor after:Yao Jun Inventor after:Liu Li Inventor after:Other inventor requests not to publish the name Inventor after:Zhu Yisong Inventor after:Weng Beibei Inventor after:OuYang Lijian Inventor after:Chen Ya Inventor after:Shi Aijun Inventor after:Yang Junzhong Inventor after:Ju Ling Inventor before:Liao Xiaoyun Inventor before:Wang Wanyong Inventor before:Wang Zhihua Inventor before:Chen Haitao Inventor before:Ni Gege Inventor before:Han Yi Inventor before:Wu Bo Inventor before:Xu Jun Inventor before:Cai Ming Inventor before:Ju Ling Inventor before:Liu Li Inventor before:Zhu Yisong Inventor before:OuYang Lijian Inventor before:Chen Ya Inventor before:Shi Aijun Inventor before:Yang Junzhong Inventor before:Tang Haitao Inventor before:Sun Lili Inventor before:Yu Jin | |
| CB03 | Change of inventor or designer information | ||
| TA01 | Transfer of patent application right | Effective date of registration:20210827 Address after:No.2, Fenghuang West Road, Taizhou City, Jiangsu Province Applicant after:STATE GRID JIANGSU ELECTRIC POWER Co.,Ltd. TAIZHOU POWER SUPPLY BRANCH Address before:No.2, Fenghuang West Road, Taizhou City, Jiangsu Province Applicant before:STATE GRID JIANGSU ELECTRIC POWER Co.,Ltd. TAIZHOU POWER SUPPLY BRANCH Applicant before:STATE GRID JIANGSU ELECTRIC POWER Co.,Ltd. Applicant before:NANJING YISHU INFORMATION SCIENCE & TECHNOLOGY CO.,LTD. | |
| TA01 | Transfer of patent application right | ||
| RJ01 | Rejection of invention patent application after publication | Application publication date:20201225 | |
| RJ01 | Rejection of invention patent application after publication |