CN112131588A - Application access method, apparatus, electronic device and storage medium - Google Patents
Application access method, apparatus, electronic device and storage mediumDownload PDFInfo
- Publication number
- CN112131588A CN112131588ACN202011025733.2ACN202011025733ACN112131588ACN 112131588 ACN112131588 ACN 112131588ACN 202011025733 ACN202011025733 ACN 202011025733ACN 112131588 ACN112131588 ACN 112131588A
- Authority
- CN
- China
- Prior art keywords
- client
- application
- access
- target application
- page data
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Granted
Links
Images
Classifications
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/60—Protecting data
- G06F21/604—Tools and structures for managing or administering access control systems
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/30—Authentication, i.e. establishing the identity or authorisation of security principals
- G06F21/31—User authentication
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F2221/00—Indexing scheme relating to security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F2221/21—Indexing scheme relating to G06F21/00 and subgroups addressing additional information or applications relating to security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F2221/2141—Access rights, e.g. capability lists, access control lists, access tables, access matrices
Landscapes
- Engineering & Computer Science (AREA)
- Theoretical Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- General Physics & Mathematics (AREA)
- Physics & Mathematics (AREA)
- General Engineering & Computer Science (AREA)
- Software Systems (AREA)
- Computer Hardware Design (AREA)
- Automation & Control Theory (AREA)
- Health & Medical Sciences (AREA)
- Bioethics (AREA)
- General Health & Medical Sciences (AREA)
- Storage Device Security (AREA)
Abstract
Description
Translated fromChinese技术领域technical field
本发明实施例涉及信息安全技术,尤其涉及一种应用访问方法、装置、电子设备和存储介质。Embodiments of the present invention relate to information security technologies, and in particular, to an application access method, apparatus, electronic device, and storage medium.
背景技术Background technique
随着互联网技术的发展,网站提供的越来越有价值。各种服务器或网站在接收客户端的访问应用的访问请求时,可能会受到黑客或恶意客户端的攻击,导致服务器或网站被黑或无法使用,造成很大的经济损失。With the development of Internet technology, the website provides more and more valuable. When various servers or websites receive access requests from clients to access applications, they may be attacked by hackers or malicious clients, causing the servers or websites to be hacked or unavailable, resulting in great economic losses.
现有技术中,客户端访问服务器中的应用,当服务器接收到访问请求时,此时访问请求已进入到应用程序内部,如果客户端利用大量的恶意请求来攻击服务器,则会导致服务器宕机。In the prior art, when a client accesses an application in a server, when the server receives an access request, the access request has entered the application program. If the client uses a large number of malicious requests to attack the server, the server will be down. .
发明内容SUMMARY OF THE INVENTION
本发明实施例提供一种应用访问方法、装置、电子设备和存储介质,以实现安全访问应用的效果。Embodiments of the present invention provide an application access method, apparatus, electronic device, and storage medium, so as to achieve the effect of securely accessing applications.
第一方面,本发明实施例提供了一种应用访问方法,该方法包括:In a first aspect, an embodiment of the present invention provides an application access method, which includes:
接收客户端发送的访问应用的访问请求;Receive the access request sent by the client to access the application;
基于所述访问请求,对所述客户端进行认证,若认证成功,则接收所述客户端的访问权限信息;Based on the access request, the client is authenticated, and if the authentication is successful, the access authority information of the client is received;
基于所述访问权限信息,确定所述客户端具有访问权限的应用列表;Based on the access permission information, determine a list of applications to which the client has access permission;
接收所述客户端对所述应用列表中的目标应用的触发操作,将所述目标应用的页面数据发送至所述客户端。Receive the triggering operation of the target application in the application list by the client, and send the page data of the target application to the client.
第二方面,本发明实施例还提供了一种应用访问装置,该装置包括:In a second aspect, an embodiment of the present invention further provides an application access device, the device comprising:
访问请求接收模块,用于接收客户端发送的访问应用的访问请求;The access request receiving module is used to receive the access request sent by the client to access the application;
访问权限信息获取模块,用于基于所述访问请求,对所述客户端进行认证,若认证成功,则接收所述客户端的访问权限信息;an access authority information acquisition module, configured to authenticate the client based on the access request, and if the authentication is successful, receive the access authority information of the client;
应用列表确定模块,用于基于所述访问权限信息,确定所述客户端具有访问权限的应用列表;an application list determination module, configured to determine, based on the access permission information, an application list for which the client has access permission;
页面数据发送模块,用于接收所述客户端对所述应用列表中的目标应用的触发操作,将所述目标应用的页面数据发送至所述客户端。The page data sending module is configured to receive the trigger operation of the target application in the application list by the client, and send the page data of the target application to the client.
第三方面,本发明实施例还提供了一种电子设备,该电子设备包括:In a third aspect, an embodiment of the present invention further provides an electronic device, the electronic device comprising:
一个或多个处理器;one or more processors;
存储装置,用于存储一个或多个程序;a storage device for storing one or more programs;
当所述一个或多个程序被所述一个或多个处理器执行,使得所述一个或多个处理器实现本发明实施例中任一所述的应用访问方法。When the one or more programs are executed by the one or more processors, the one or more processors implement the application access method described in any of the embodiments of the present invention.
第四方面,本发明实施例还提供了一种包含计算机可执行指令的存储介质,所述计算机可执行指令在由计算机处理器执行时用于执行本发明实施例中任一所述的应用访问方法。In a fourth aspect, an embodiment of the present invention further provides a storage medium containing computer-executable instructions, where the computer-executable instructions are used to execute the application access described in any of the embodiments of the present invention when executed by a computer processor method.
本发明实施例的技术方案,通过接收客户端发送的访问应用的访问请求,基于访问请求,对客户端进行认证,若认证成功,则接收客户端的访问权限信息,基于访问权限信息,确定客户端具有访问权限的应用列表,接收客户端对应用列表中的目标应用的触发操作,将目标应用的页面数据发送至客户端,这样确保客户端访问的应用是认证成功的,且是客户端就有访问权限的应用,保证了应用访问的安全性。The technical solution of the embodiment of the present invention is to authenticate the client based on the access request by receiving the access request sent by the client to access the application. If the authentication is successful, the access authority information of the client is received, and the client is determined based on the access authority information. List of applications with access rights, receive the trigger operation of the target application in the application list from the client, and send the page data of the target application to the client, so as to ensure that the application accessed by the client is authenticated successfully, and the client has The application with access rights ensures the security of application access.
附图说明Description of drawings
图1是本发明实施例一中的应用访问方法的流程图;1 is a flowchart of an application access method in Embodiment 1 of the present invention;
图2是本发明实施例一中的Nginx反向代理服务器的实现方式示意图;2 is a schematic diagram of an implementation manner of an Nginx reverse proxy server in Embodiment 1 of the present invention;
图3是本发明实施例一中的Nginx反向代理服务器实现负载均衡配置的示意图;3 is a schematic diagram of the Nginx reverse proxy server in Embodiment 1 of the present invention implementing load balancing configuration;
图4是本发明实施例三中的应用访问方法的流程图;4 is a flowchart of an application access method in Embodiment 3 of the present invention;
图5是本发明实施例四中的应用访问装置的结构示意图;5 is a schematic structural diagram of an application access device in Embodiment 4 of the present invention;
图6是本发明实施例五中的一种电子设备的结构示意图。FIG. 6 is a schematic structural diagram of an electronic device in Embodiment 5 of the present invention.
具体实施方式Detailed ways
下面结合附图和实施例对本发明作进一步的详细说明。可以理解的是,此处所描述的具体实施例仅仅用于解释本发明,而非对本发明的限定。另外还需要说明的是,为了便于描述,附图中仅示出了与本发明相关的部分而非全部结构。The present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments. It should be understood that the specific embodiments described herein are only used to explain the present invention, but not to limit the present invention. In addition, it should be noted that, for the convenience of description, the drawings only show some but not all structures related to the present invention.
实施例一Example 1
图1为本发明实施例一提供的应用访问方法的流程图,本实施例可适用于安全的对应用进行访问的情况,该方法可以由应用访问装置来执行,该应用访问装置可以由软件和/或硬件来实现,该应用访问装置可以配置在电子计算设备上,具体包括如下步骤:FIG. 1 is a flowchart of an application access method provided by Embodiment 1 of the present invention. This embodiment is applicable to the case of securely accessing an application, and the method can be executed by an application access device, and the application access device can be implemented by software and / or hardware, the application access device can be configured on an electronic computing device, and specifically includes the following steps:
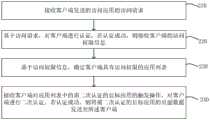
S110、接收客户端发送的访问应用的访问请求。S110. Receive an access request for accessing the application sent by the client.
示例性的,访问请求可以是客户端访问任一应用的请求。Exemplarily, the access request may be a request by the client to access any application.
这里的客户端可以是任一可发送访问请求的设备,例如,可以是手机、平板或电脑等其中的任意一种。The client here can be any device that can send an access request, for example, it can be any one of a mobile phone, a tablet, or a computer.
需要说明的是,本发明实施例的执行主体是代理服务器。It should be noted that the execution body of the embodiment of the present invention is a proxy server.
需要说明的是,本发明实施例是基于Nginx来实现的。Nginx是一款高性能的、轻量级的HTTP服务器、反向代理服务器和电子邮件(IMAP/POP3)代理服务器,在BSD-like协议下发行。其特点是占有内存少,并发能力强。It should be noted that the embodiments of the present invention are implemented based on Nginx. Nginx is a high-performance, lightweight HTTP server, reverse proxy server and email (IMAP/POP3) proxy server, released under a BSD-like protocol. Its characteristics are that it occupies less memory and has strong concurrency capabilities.
S120、基于访问请求,对客户端进行认证,若认证成功,则接收客户端的访问权限信息。S120. Authenticate the client based on the access request, and if the authentication succeeds, receive the access authority information of the client.
示例性的,客户端的访问权限信息可以是客户端具有访问权限的应用信息。例如,客户端具有访问应用A、应用B和应用C的权限,则接收客户端可访问应用A、应用B和应用C的信息,比如,可以是接收一个客户端可访问的应用的列表。Exemplarily, the access permission information of the client may be application information to which the client has access permission. For example, if the client has permission to access application A, application B, and application C, receiving information that the client can access application A, application B, and application C may be, for example, receiving a list of applications that the client can access.
可选的,在客户端发送访问请求时,在访问请求中包括:该客户端的IP地址、用户名和密码等信息。Optionally, when the client sends an access request, the access request includes: the client's IP address, user name, password and other information.
需要说明的是,这里的代理服务器可基于访问请求,对客户端进行认证,具体的可以是根据客户端的用户名和密码对客户端进行认证。若认证成功,代理服务器可将认证结果即时发送给客户端,以使客户端将其访问权限信息发送给代理服务器。It should be noted that the proxy server here may authenticate the client based on the access request, and specifically may authenticate the client according to the user name and password of the client. If the authentication is successful, the proxy server can immediately send the authentication result to the client, so that the client can send its access authority information to the proxy server.
需要说明的是,上述实现方式除了可利用代理服务器这一个设备来实现外,还可以利用多个设备来协同作用完成,示例性的可以是:It should be noted that, in addition to using the proxy server as one device, the above-mentioned implementation mode can also be implemented by using multiple devices to cooperate with each other. An example can be:
代理服务器接收访问请求后,将该访问请求导向访问控制引擎中的认证模块,由认证模块进行多维度用户交互认证操作,具体的可以是用户输入用户名和密码,认证模块根据用户输入的用户名和密码,与接收的访问请求中的用户名和密码进行比对,若比对成功,则认证成功。After the proxy server receives the access request, it directs the access request to the authentication module in the access control engine, and the authentication module performs the multi-dimensional user interactive authentication operation. , and compare with the username and password in the received access request. If the comparison is successful, the authentication is successful.
当认证成功后,访问控制引擎将认证结果即时发送给代理服务器,代理服务器将认证结果发送给客户端。此时,访问控制引擎同时通过其内部联动将客户端的访问权限信息发送给代理服务器。When the authentication is successful, the access control engine immediately sends the authentication result to the proxy server, and the proxy server sends the authentication result to the client. At this time, the access control engine also sends the client's access authority information to the proxy server through its internal linkage.
上述两种实现方式,用户可根据自己需求自行选取,这里不做限定。The above two implementation methods can be selected by users according to their own needs, which are not limited here.
需要说明的是,当基于访问请求,对客户端认证不成功时,则拦截该访问请求,不让该客户端访问其要访问的应用。这样保证了应用访问的安全。It should be noted that when the client authentication is unsuccessful based on the access request, the access request is intercepted, and the client is not allowed to access the application to be accessed. This ensures the security of application access.
S130、基于访问权限信息,确定客户端具有访问权限的应用列表。S130. Based on the access permission information, determine a list of applications to which the client has access permission.
示例性的,根据接收的访问权限信息,确定客户端具有访问权限的应用列表,并将该应用列表发送给客户端。Exemplarily, according to the received access permission information, a list of applications to which the client has access permissions is determined, and the list of applications is sent to the client.
这里的用于列表中具有客户端想要访问的,且其具有权项访问的应用的列表。例如,客户端想要访问应用A、应用B、应用C和应用D,但其具有访问权项的是应用A、应用B和应用D,则确定客户端具有访问权项的应用列表中具有应用A、应用B和应用D,并没有应用C。Here is a list of applications that the client wants to access and which have the right to access in the list. For example, if the client wants to access application A, application B, application C, and application D, but it has access right items are application A, application B, and application D, it is determined that the client has applications in the list of applications that have access right items. A, application B and application D, and no application C.
这样确保返回给客户端的是其具有访问权限的应用,避免其访问其不具有访问权限的应用,保证了应用访问的安全。In this way, it is ensured that the application that has access rights is returned to the client, and the application to which it does not have access rights is prevented from being accessed, thereby ensuring the security of application access.
S140、接收客户端对应用列表中的目标应用的触发操作,将目标应用的页面数据发送至客户端。S140. Receive a trigger operation of the client on the target application in the application list, and send page data of the target application to the client.
示例性的,目标应用可以是用户当前进行访问的应用。例如,当客户端接收到应用列表后,确定其要当前要访问应用A,则应用A为目标应用。Exemplarily, the target application may be an application currently accessed by the user. For example, after the client receives the application list and determines that it wants to access application A currently, application A is the target application.
当客户端接收到应用列表后,若用户确定其当前要访问应用A,则用户在客户端中对应用列表中的应用A进行操作,例如,可以是用户点击应用列表中的应用A的区域或点击应用列表中的应用A的选择控件等,客户端响应于用户的触发操作,将该触发操作发送至代理服务器,代理服务器接收到该触发操作后,将应用A的页面数据发送至客户端。After the client receives the application list, if the user determines that he currently wants to access application A, the user operates the application A in the application list in the client, for example, the user can click on the area of application A in the application list or Click the selection control of application A in the application list, and the client sends the trigger operation to the proxy server in response to the user's trigger operation. After receiving the trigger operation, the proxy server sends the page data of application A to the client.
需要说明的是,用户可访问多个应用,代理服务器基于接收的对应用列表中的目标应用的触发操作,将目标应用的页面数据发送给客户端。例如,当用户访问完应用A后,或者当用户在访问应用A的同时,还要访问应用B(此时,应用B为目标应用),则此时,用户可点击应用列表中的应用B的区域或点击应用列表中的应用B的选择控件等,客户端响应于用户的触发操作,将该触发操作发送至代理服务器,代理服务器接收到该触发操作后,将应用B的页面数据发送至客户端。以实现代理服务器与客户端间的交互。It should be noted that the user can access multiple applications, and the proxy server sends the page data of the target application to the client based on the received trigger operation on the target application in the application list. For example, when the user finishes accessing application A, or when the user accesses application A while also accessing application B (in this case, application B is the target application), at this time, the user can click the button of application B in the application list. area or click the selection control of application B in the application list, etc., the client sends the trigger operation to the proxy server in response to the user's trigger operation. After the proxy server receives the trigger operation, it sends the page data of application B to the client. end. In order to realize the interaction between the proxy server and the client.
需要说明的是,由于本发明实施例的技术方案,是基于Nginx来实现的,因此,本发明实施例的技术方案,在网络部署方面具有很好的网络安全。这是由于基于Nginx的反向代理将防火墙后的业务服务提供给Internet用户访问,用户并不知道自己访问的是一个代理服务器,真正的服务部署在内网中,从而有效地提高了网络安全性。It should be noted that, since the technical solutions of the embodiments of the present invention are implemented based on Nginx, the technical solutions of the embodiments of the present invention have good network security in terms of network deployment. This is because the Nginx-based reverse proxy provides business services behind the firewall to Internet users. Users do not know that they are accessing a proxy server, and the real service is deployed in the intranet, thereby effectively improving network security. .
本发明实施例的技术方案,在系统性能方面也具有很高的系统性能,这是由于利用基于Nginx反向代理的负载均衡配置功能,可以对后端业务服务进行多种策略负载分配的集群部署,能够有效提高系统的性能。The technical solutions of the embodiments of the present invention also have high system performance in terms of system performance. This is because using the Nginx reverse proxy-based load balancing configuration function, the back-end business services can be deployed in clusters with multiple policy load distributions , which can effectively improve the performance of the system.
下面通过图2所述的Nginx反向代理服务器的实现方式示意图,来详细介绍一下Nginx反向代理服务器的负载均衡配置功能:The following describes the load balancing configuration function of the Nginx reverse proxy server in detail through the schematic diagram of the implementation of the Nginx reverse proxy server described in Figure 2:
访问代理服务器通过两块网卡同时连接互联网和内网,然后配置访问代理服务器的端口应用,具体的可以是将不同的端口请求转发到不同的业务应用,例如,10001端口对应业务应用1、10002端口对应业务应用2、10003端口对应业务应用3;客户端用户A经互联网向访问代理服务器请求访问10001端口,访问代理服务器将其转发到业务应用1;客户端用户B经互联网向访问代理服务器请求访问10002端口,访问代理服务器将其转发到业务应用2;最后访问代理服务器将被代理业务应用处理后的响应结果(页面数据)作为自己的响应结果返回给用户。The access proxy server connects to the Internet and the intranet at the same time through two network cards, and then configures the port application of the access proxy server. Specifically, it can forward different port requests to different business applications. For example, port 10001 corresponds to business application 1 and 10002 ports. Corresponding to business application 2, port 10003 corresponds to business application 3; client user A requests access to port 10001 from the access proxy server via the Internet, and the access proxy server forwards it to business application 1; client user B requests access to the access proxy server via the Internet 10002 port, the access proxy server forwards it to service application 2; finally, the access proxy server returns the response result (page data) processed by the proxy service application to the user as its own response result.
在另一具体实施例中,若某业务应用X需要集群部署,可以方便的利用Nginx访问代理服务器实现,参考图3所述Nginx反向代理服务器实现负载均衡配置的示意图:假设业务应用X需要三台服务器实现,三台服务器名为X-1、X-2、X-3。在Nginx访问代理服务器上为业务应用X的三个服务器地址配置不同的访问代理端口即可,如:10001端口对应业务应用X-1、10002端口对应X-2、10003端口对应X-3。这样即实现了负载均衡配置的功能。In another specific embodiment, if a business application X needs to be deployed in a cluster, it can be easily implemented by using Nginx to access the proxy server. Referring to the schematic diagram of the Nginx reverse proxy server implementing the load balancing configuration shown in FIG. 3: Assume that the business application X needs three The three servers are named X-1, X-2, and X-3. On the Nginx access proxy server, you can configure different access proxy ports for the three server addresses of service application X. For example, port 10001 corresponds to service application X-1, port 10002 corresponds to X-2, and port 10003 corresponds to X-3. In this way, the function of load balancing configuration is realized.
在实际应用中,Nginx访问代理服务器有4种典型的负载均衡配置方式,分别为轮询方式、权重方式、ip_hash方式和利用第三方模块的方式。不同方式适用于不同业务场景,具体场景可根据具体方式来实现,这部分属于现有技术,在此不做详述。In practical applications, there are four typical load balancing configuration methods for Nginx access proxy server, namely polling method, weighting method, ip_hash method and the method of using third-party modules. Different methods are suitable for different business scenarios, and specific scenarios can be implemented according to specific methods. This part belongs to the prior art and will not be described in detail here.
本发明实施例的技术方案,通过接收客户端发送的访问应用的访问请求,基于访问请求,对客户端进行认证,若认证成功,则接收客户端的访问权限信息,基于访问权限信息,确定客户端具有访问权限的应用列表,接收客户端对应用列表中的目标应用的触发操作,将目标应用的页面数据发送至客户端,这样确保客户端访问的应用是认证成功的,且是客户端就有访问权限的应用,保证了应用访问的安全性。The technical solution of the embodiment of the present invention is to authenticate the client based on the access request by receiving the access request sent by the client to access the application. If the authentication is successful, the access authority information of the client is received, and the client is determined based on the access authority information. List of applications with access rights, receive the trigger operation of the target application in the application list from the client, and send the page data of the target application to the client, so as to ensure that the application accessed by the client is authenticated successfully, and the client has The application with access rights ensures the security of application access.
实施例二Embodiment 2
本发明实施例与上述实施例中各个可选方案可以结合。在上述实施例的基础上,本发明实施例还包括如下方法:The embodiments of the present invention may be combined with various optional solutions in the foregoing embodiments. On the basis of the foregoing embodiments, the embodiments of the present invention further include the following methods:
可选的,在所述将目标应用的页面数据发送至客户端的过程中,还包括:当检测到客户端的IP地址变更时,则对客户端停止提供目标应用的页面数据。Optionally, in the process of sending the page data of the target application to the client, the method further includes: when it is detected that the IP address of the client is changed, stopping providing the page data of the target application to the client.
示例性的,当代理服务器检测到客户端更换的IP地址,例如客户端更换了登录设备,这代理服务器终止与客户端之间的交互,即不向客户端提供目标应用的页面数据,使客户端无法继续访问目标应用。Exemplarily, when the proxy server detects that the client has changed the IP address, for example, the client has changed the login device, the proxy server terminates the interaction with the client, that is, does not provide the client with the page data of the target application, so that the client The client cannot continue to access the target application.
可选的,在所述将目标应用的页面数据发送至客户端的过程中,还包括:每隔预设时间,对客户端进行一次认证,若认证成功,则将目标应用的页面数据发送至客户端。Optionally, in the process of sending the page data of the target application to the client, it also includes: performing authentication on the client every preset time, and if the authentication is successful, sending the page data of the target application to the client. end.
示例性的,预设时间可以是预先设置的时间,例如可以是5分钟。Exemplarily, the preset time may be a preset time, such as 5 minutes.
当代理服务器与客户端进行交互的过程中,可每隔5分钟,对客户端进行一次认证,具体的可以是每隔5分钟,让客户端输入一次用户名和密码,若认证成功,则继续与客户端进行交互,这样以确保应用的安全访问。During the interaction between the proxy server and the client, the client can be authenticated every 5 minutes. Specifically, the client can be asked to enter the user name and password once every 5 minutes. If the authentication is successful, it will continue to communicate with the client. The client interacts in this way to ensure secure access to the application.
可选的,在所述将目标应用的页面数据发送至客户端的过程中,还包括:当检测到客户端在第一预设时间段内未与目标应用进行交互,若在第一预设时间段至第二预设时间段内,检测到客户端与目标应用进行交互的触发操作时,将客户端与目标应用进行交互的触发操作所对应的目标应用的页面数据发送至所述客户端。Optionally, in the process of sending the page data of the target application to the client, it also includes: when it is detected that the client does not interact with the target application within the first preset time period, if the first preset time Within the second preset time period, when a triggering operation of the interaction between the client and the target application is detected, the page data of the target application corresponding to the triggering operation of the interaction between the client and the target application is sent to the client.
示例性的,第一预设时间段可以是预先设置的时间段,例如可以是15分钟。Exemplarily, the first preset time period may be a preset time period, such as 15 minutes.
第二预设时间段可以是预先设置的另一时间段,例如可以是30分钟。The second preset time period may be another preset time period, for example, may be 30 minutes.
当客户端访问目标应用A的过程中,用户可能临时有事,或者此时没有对应用A进行任何的触发操作,当用户15分钟内没有对应用A进行任何的操作,则若用户在第15-30分钟内,又重新对应用A进行了操作,例如应用A是淘宝,用户打开淘宝15分钟之内并没有做任何操作,在15-30分钟内,点击了某一个物品的图标,则代理服务器将与用户点击某个物品的图标的操作对应的页面数据(该物品的图片、详情等信息)发送给客户端。When the client accesses the target application A, the user may be temporarily busy, or the user may not perform any trigger operation on application A at this time. Within 30 minutes, the application A is re-operated. For example, application A is Taobao. The user does not do anything within 15 minutes of opening Taobao. Within 15-30 minutes, if he clicks the icon of an item, the proxy server Send the page data corresponding to the user's operation of clicking the icon of an item (the image, details and other information of the item) to the client.
可选的,在所述将目标应用的页面数据发送至客户端的过程中,还包括:当检测到客户端在第二预设时间段内未与目标应用进行交互,若检测到客户端与目标应用进行交互的触发操作时,将停止将目标应用的页面数据发送至客户端。Optionally, in the process of sending the page data of the target application to the client, it also includes: when it is detected that the client does not interact with the target application within the second preset time period, if it is detected that the client interacts with the target When the application interacts with the trigger operation, it will stop sending the page data of the target application to the client.
示例性的,当客户端访问目标应用A的过程中,用户可能临时有事,或者此时没有对应用A进行任何的触发操作,当用户30分钟内没有对应用A进行任何的操作,则代理服务器停止将目标应用的页面数据发送给客户端,即代理服务器停止客户端对应用A的访问。例如,应用A是淘宝,用户打开淘宝30分钟之内并没有做任何操作,在30分钟后,点击了某一个物品的图标,则代理服务器不会将与用户点击某个物品的图标的操作对应的页面数据(该物品的图片、详情等信息)发送给客户端。即代理服务器强制客户端退出对淘宝的访问。Exemplarily, when the client accesses the target application A, the user may be temporarily busy, or does not perform any trigger operation on application A at this time. When the user does not perform any operation on application A within 30 minutes, the proxy server Stop sending the page data of the target application to the client, that is, the proxy server stops the client's access to application A. For example, application A is Taobao, and the user does not do anything within 30 minutes after opening Taobao. After 30 minutes, if the icon of an item is clicked, the proxy server will not correspond to the operation of the user clicking the icon of an item. The page data (image, details and other information of the item) are sent to the client. That is, the proxy server forces the client to withdraw from accessing Taobao.
上述发明实施例的实施方式,确保了应用的安全访问。The implementation of the above embodiments of the invention ensures secure access of applications.
实施例三Embodiment 3
图4为本发明实施例三提供的应用访问方法的流程图,本发明实施例与上述实施例中各个可选方案可以结合。在本发明实施例中,可选的,当目标应用为需二次认证的目标应用时,所述接收客户端对应用列表中的目标应用的触发操作,将目标应用的页面数据发送至客户端,包括:接收客户端对应用列表中的需二次认证的目标应用的触发操作,对客户端进行二次认证,若认证成功,则将需二次认证的目标应用的页面数据发送至所述客户端。FIG. 4 is a flowchart of an application access method provided in Embodiment 3 of the present invention, and the embodiment of the present invention may be combined with each optional solution in the foregoing embodiment. In this embodiment of the present invention, optionally, when the target application is a target application requiring secondary authentication, the receiving client's trigger operation on the target application in the application list, and sending the page data of the target application to the client , including: receiving the trigger operation of the client on the target application requiring secondary authentication in the application list, performing secondary authentication on the client, and if the authentication is successful, sending the page data of the target application requiring secondary authentication to the client.
如图4所示,本发明实施例的方法具体包括如下步骤:As shown in FIG. 4 , the method of the embodiment of the present invention specifically includes the following steps:
S210、接收客户端发送的访问应用的访问请求。S210. Receive an access request for accessing the application sent by the client.
S220、基于访问请求,对客户端进行认证,若认证成功,则接收客户端的访问权限信息。S220: Authenticate the client based on the access request, and if the authentication succeeds, receive the access authority information of the client.
S230、基于访问权限信息,确定客户端具有访问权限的应用列表。S230. Based on the access permission information, determine a list of applications to which the client has access permission.
S240、接收客户端对应用列表中的需二次认证的目标应用的触发操作,对客户端进行二次认证,若认证成功,则将需二次认证的目标应用的页面数据发送至所述客户端。S240. Receive the trigger operation of the client on the target application that requires secondary authentication in the application list, perform secondary authentication on the client, and if the authentication is successful, send the page data of the target application that requires secondary authentication to the client end.
示例性的,需二次认证的目标应用可以是安全性能比较高的或者较敏感的应用。Exemplarily, the target application requiring secondary authentication may be an application with relatively high security performance or relatively sensitive.
当客户端接收到代理服务器返回的应用列表后,若用户想要访问应用C,而应用C是安全性能较高的敏感应用,需要用户二次认证,则当用户点击该应用C后,用户需重新输入自己的用户名和密码,当代理服务器接收到用户输入的用户和密码,与访问请求中的一致时,则二次认证成功,则代理服务器将该应用C的页面数据反馈至客户端。After the client receives the application list returned by the proxy server, if the user wants to access application C, which is a sensitive application with high security performance and requires user secondary authentication, after the user clicks the application C, the user needs to Re-enter your user name and password. When the proxy server receives the user and password entered by the user and is consistent with the access request, the secondary authentication is successful, and the proxy server feeds back the page data of the application C to the client.
这样确保了需二次认证的应用的安全。This ensures the security of applications requiring secondary authentication.
本发明实施例的技术方案,当用户需访问需二次认证的目标应用时,通过接收客户端对应用列表中的需二次认证的目标应用的触发操作,对客户端进行二次认证,若认证成功,则将需二次认证的目标应用的页面数据发送至所述客户端,确保了需二次认证的应用的安全性。According to the technical solution of the embodiment of the present invention, when a user needs to access a target application requiring secondary authentication, the client is subjected to secondary authentication by receiving a trigger operation of the client on the target application requiring secondary authentication in the application list. If the authentication is successful, the page data of the target application requiring secondary authentication is sent to the client to ensure the security of the application requiring secondary authentication.
实施例四Embodiment 4
图5为本发明实施例四提供的应用访问装置的结构示意图,如图5所示,该装置包括:访问请求接收模块31、访问权限信息获取模块32、应用列表确定模块33和页面数据发送模块34。FIG. 5 is a schematic structural diagram of an application access device provided in Embodiment 4 of the present invention. As shown in FIG. 5 , the device includes: an access
其中,访问请求接收模块31,用于接收客户端发送的访问应用的访问请求;Wherein, the access
访问权限信息获取模块32,用于基于所述访问请求,对所述客户端进行认证,若认证成功,则接收所述客户端的访问权限信息;an access authority
应用列表确定模块33,用于基于所述访问权限信息,确定所述客户端具有访问权限的应用列表;an application
页面数据发送模块34,用于接收所述客户端对所述应用列表中的目标应用的触发操作,将所述目标应用的页面数据发送至所述客户端。The page
在上述实施例的技术方案的基础上,该装置还包括:On the basis of the technical solutions of the foregoing embodiments, the device further includes:
信息变更模块,用于当检测到所述客户端的IP地址变更时,则对所述客户端停止提供目标应用的页面数据。The information change module is configured to stop providing page data of the target application to the client when it is detected that the IP address of the client is changed.
在上述实施例的技术方案的基础上,该装置还包括:On the basis of the technical solutions of the foregoing embodiments, the device further includes:
持续认证模块,用于每隔预设时间,对所述客户端进行一次认证,若认证成功,则将所述目标应用的页面数据发送至所述客户端。The continuous authentication module is configured to authenticate the client once every preset time, and if the authentication is successful, send the page data of the target application to the client.
在上述实施例的技术方案的基础上,该装置还包括:On the basis of the technical solutions of the foregoing embodiments, the device further includes:
第一交互模块,用于当检测到所述客户端在第一预设时间段内未与所述目标应用进行交互,若在第一预设时间段至第二预设时间段内,检测到所述客户端与所述目标应用进行交互的触发操作时,将所述客户端与所述目标应用进行交互的触发操作所对应的目标应用的页面数据发送至所述客户端。The first interaction module is used to detect that the client does not interact with the target application within the first preset time period, if it is detected within the first preset time period to the second preset time period, During the trigger operation of the interaction between the client and the target application, the page data of the target application corresponding to the trigger operation of the interaction between the client and the target application is sent to the client.
在上述实施例的技术方案的基础上,该装置还包括:On the basis of the technical solutions of the foregoing embodiments, the device further includes:
第二交互模块,用于当检测到所述客户端在所述第二预设时间段内未与所述目标应用进行交互,若检测到所述客户端与所述目标应用进行交互的触发操作时,将停止将所述目标应用的页面数据发送至所述客户端。The second interaction module is configured to, when it is detected that the client does not interact with the target application within the second preset time period, if a triggering operation is detected that the client interacts with the target application , it will stop sending the page data of the target application to the client.
可选的,当所述目标应用为需二次认证的目标应用时,页面数据发送模块34具体用于:Optionally, when the target application is a target application requiring secondary authentication, the page
接收所述客户端对所述应用列表中的需二次认证的目标应用的触发操作,对所述客户端进行二次认证,若认证成功,则将所述需二次认证的目标应用的页面数据发送至所述客户端。Receive the triggering operation of the client on the target application that requires secondary authentication in the application list, perform secondary authentication on the client, and if the authentication is successful, change the page of the target application that requires secondary authentication Data is sent to the client.
本发明实施例所提供的应用访问装置可执行本发明任意实施例所提供的应用访问方法,具备执行方法相应的功能模块和有益效果。The application access device provided by the embodiment of the present invention can execute the application access method provided by any embodiment of the present invention, and has functional modules and beneficial effects corresponding to the execution method.
实施例五Embodiment 5
图6本发明实施例五提供的一种电子设备的结构示意图,如图6所示,该电子设备包括处理器70、存储器71、输入装置72和输出装置73;电子设备中处理器70的数量可以是一个或多个,图6中以一个处理器70为例;电子设备中的处理器70、存储器71、输入装置72和输出装置73可以通过总线或其他方式连接,图6中以通过总线连接为例。FIG. 6 is a schematic structural diagram of an electronic device provided in Embodiment 5 of the present invention. As shown in FIG. 6 , the electronic device includes a
存储器71作为一种计算机可读存储介质,可用于存储软件程序、计算机可执行程序以及模块,如本发明实施例中的应用访问方法对应的程序指令/模块(例如,访问请求接收模块31、访问权限信息获取模块32、应用列表确定模块33和页面数据发送模块34)。处理器70通过运行存储在存储器71中的软件程序、指令以及模块,从而执行电子设备的各种功能应用以及数据处理,即实现上述的应用访问方法。As a computer-readable storage medium, the
存储器71可主要包括存储程序区和存储数据区,其中,存储程序区可存储操作系统、至少一个功能所需的应用程序;存储数据区可存储根据终端的使用所创建的数据等。此外,存储器71可以包括高速随机存取存储器,还可以包括非易失性存储器,例如至少一个磁盘存储器件、闪存器件、或其他非易失性固态存储器件。在一些实例中,存储器71可进一步包括相对于处理器70远程设置的存储器,这些远程存储器可以通过网络连接至电子设备。上述网络的实例包括但不限于互联网、企业内部网、局域网、移动通信网及其组合。The
输入装置72可用于接收输入的数字或字符信息,以及产生与电子设备的用户设置以及功能控制有关的键信号输入。输出装置73可包括显示屏等显示设备。The
实施例六Embodiment 6
本发明实施例六还提供一种包含计算机可执行指令的存储介质,所述计算机可执行指令在由计算机处理器执行时用于执行一种应用访问方法。Embodiment 6 of the present invention further provides a storage medium containing computer-executable instructions, where the computer-executable instructions are used to execute an application access method when executed by a computer processor.
当然,本发明实施例所提供的一种包含计算机可执行指令的存储介质,其计算机可执行指令不限于如上所述的方法操作,还可以执行本发明任意实施例所提供的应用访问方法中的相关操作。Of course, a storage medium containing computer-executable instructions provided by an embodiment of the present invention, the computer-executable instructions of which are not limited to the above-mentioned method operations, and can also execute any of the application access methods provided by any embodiment of the present invention. related operations.
通过以上关于实施方式的描述,所属领域的技术人员可以清楚地了解到,本发明可借助软件及必需的通用硬件来实现,当然也可以通过硬件实现,但很多情况下前者是更佳的实施方式。基于这样的理解,本发明的技术方案本质上或者说对现有技术做出贡献的部分可以以软件产品的形式体现出来,该计算机软件产品可以存储在计算机可读存储介质中,如计算机的软盘、只读存储器(Read-Only Memory,ROM)、随机存取存储器(RandomAccess Memory,RAM)、闪存(FLASH)、硬盘或光盘等,包括若干指令用以使得一台计算机电子设备(可以是个人计算机,服务器,或者网络设备等)执行本发明各个实施例所述的方法。From the above description of the embodiments, those skilled in the art can clearly understand that the present invention can be realized by software and necessary general-purpose hardware, and of course can also be realized by hardware, but in many cases the former is a better embodiment . Based on such understanding, the technical solutions of the present invention can be embodied in the form of software products in essence or the parts that make contributions to the prior art, and the computer software products can be stored in a computer-readable storage medium, such as a floppy disk of a computer , read-only memory (Read-Only Memory, ROM), random access memory (Random Access Memory, RAM), flash memory (FLASH), hard disk or optical disk, etc., including several instructions to make a computer electronic device (which can be a personal computer , server, or network device, etc.) to execute the methods described in the various embodiments of the present invention.
值得注意的是,上述应用访问装置的实施例中,所包括的各个单元和模块只是按照功能逻辑进行划分的,但并不局限于上述的划分,只要能够实现相应的功能即可;另外,各功能单元的具体名称也只是为了便于相互区分,并不用于限制本发明的保护范围。It is worth noting that, in the above-mentioned embodiments of the application access device, the included units and modules are only divided according to functional logic, but are not limited to the above-mentioned division, as long as the corresponding functions can be realized; The specific names of the functional units are only for the convenience of distinguishing from each other, and are not used to limit the protection scope of the present invention.
注意,上述仅为本发明的较佳实施例及所运用技术原理。本领域技术人员会理解,本发明不限于这里所述的特定实施例,对本领域技术人员来说能够进行各种明显的变化、重新调整和替代而不会脱离本发明的保护范围。因此,虽然通过以上实施例对本发明进行了较为详细的说明,但是本发明不仅仅限于以上实施例,在不脱离本发明构思的情况下,还可以包括更多其他等效实施例,而本发明的范围由所附的权利要求范围决定。Note that the above are only preferred embodiments of the present invention and applied technical principles. Those skilled in the art will understand that the present invention is not limited to the specific embodiments described herein, and various obvious changes, readjustments and substitutions can be made by those skilled in the art without departing from the protection scope of the present invention. Therefore, although the present invention has been described in detail through the above embodiments, the present invention is not limited to the above embodiments, and can also include more other equivalent embodiments without departing from the concept of the present invention. The scope is determined by the scope of the appended claims.
Claims (10)
Translated fromChinesePriority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202011025733.2ACN112131588B (en) | 2020-09-25 | 2020-09-25 | Application access method, device, electronic equipment and storage medium |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202011025733.2ACN112131588B (en) | 2020-09-25 | 2020-09-25 | Application access method, device, electronic equipment and storage medium |
Publications (2)
| Publication Number | Publication Date |
|---|---|
| CN112131588Atrue CN112131588A (en) | 2020-12-25 |
| CN112131588B CN112131588B (en) | 2024-07-26 |
Family
ID=73840246
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN202011025733.2AActiveCN112131588B (en) | 2020-09-25 | 2020-09-25 | Application access method, device, electronic equipment and storage medium |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN112131588B (en) |
Cited By (1)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN118473814A (en)* | 2024-06-07 | 2024-08-09 | 北京火山引擎科技有限公司 | Access control method, device, equipment, medium and program product of application gateway |
Citations (11)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN101764742A (en)* | 2009-12-30 | 2010-06-30 | 福建星网锐捷网络有限公司 | Network resource visit control system and method |
| CN103927474A (en)* | 2014-04-01 | 2014-07-16 | 可牛网络技术(北京)有限公司 | Method and device for monitoring application programs |
| CN104683320A (en)* | 2013-12-03 | 2015-06-03 | 中兴通讯股份有限公司 | Home network multimedia content sharing access control method and device |
| CN106487774A (en)* | 2015-09-01 | 2017-03-08 | 阿里巴巴集团控股有限公司 | A kind of cloud host services authority control method, device and system |
| CN108964885A (en)* | 2017-05-27 | 2018-12-07 | 华为技术有限公司 | Method for authenticating, device, system and storage medium |
| US20190057386A1 (en)* | 2017-08-15 | 2019-02-21 | Mani Fazeli | Application server for automated data transfers and associated methods |
| CN110232292A (en)* | 2019-05-06 | 2019-09-13 | 平安科技(深圳)有限公司 | Data access authority authentication method, server and storage medium |
| CN110287682A (en)* | 2019-07-01 | 2019-09-27 | 北京芯盾时代科技有限公司 | A kind of login method, apparatus and system |
| CN110636057A (en)* | 2019-09-10 | 2019-12-31 | 腾讯科技(深圳)有限公司 | Application access method and device and computer readable storage medium |
| CN110781468A (en)* | 2019-10-24 | 2020-02-11 | 腾讯科技(深圳)有限公司 | An identity authentication processing method, device, electronic device and storage medium |
| CN111131202A (en)* | 2019-12-12 | 2020-05-08 | 厦门市美亚柏科信息股份有限公司 | Identity authentication method and system based on multiple information authentication |
- 2020
- 2020-09-25CNCN202011025733.2Apatent/CN112131588B/enactiveActive
Patent Citations (11)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN101764742A (en)* | 2009-12-30 | 2010-06-30 | 福建星网锐捷网络有限公司 | Network resource visit control system and method |
| CN104683320A (en)* | 2013-12-03 | 2015-06-03 | 中兴通讯股份有限公司 | Home network multimedia content sharing access control method and device |
| CN103927474A (en)* | 2014-04-01 | 2014-07-16 | 可牛网络技术(北京)有限公司 | Method and device for monitoring application programs |
| CN106487774A (en)* | 2015-09-01 | 2017-03-08 | 阿里巴巴集团控股有限公司 | A kind of cloud host services authority control method, device and system |
| CN108964885A (en)* | 2017-05-27 | 2018-12-07 | 华为技术有限公司 | Method for authenticating, device, system and storage medium |
| US20190057386A1 (en)* | 2017-08-15 | 2019-02-21 | Mani Fazeli | Application server for automated data transfers and associated methods |
| CN110232292A (en)* | 2019-05-06 | 2019-09-13 | 平安科技(深圳)有限公司 | Data access authority authentication method, server and storage medium |
| CN110287682A (en)* | 2019-07-01 | 2019-09-27 | 北京芯盾时代科技有限公司 | A kind of login method, apparatus and system |
| CN110636057A (en)* | 2019-09-10 | 2019-12-31 | 腾讯科技(深圳)有限公司 | Application access method and device and computer readable storage medium |
| CN110781468A (en)* | 2019-10-24 | 2020-02-11 | 腾讯科技(深圳)有限公司 | An identity authentication processing method, device, electronic device and storage medium |
| CN111131202A (en)* | 2019-12-12 | 2020-05-08 | 厦门市美亚柏科信息股份有限公司 | Identity authentication method and system based on multiple information authentication |
Cited By (1)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN118473814A (en)* | 2024-06-07 | 2024-08-09 | 北京火山引擎科技有限公司 | Access control method, device, equipment, medium and program product of application gateway |
Also Published As
| Publication number | Publication date |
|---|---|
| CN112131588B (en) | 2024-07-26 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| US10608821B2 (en) | Providing cross site request forgery protection at an edge server | |
| US9942251B1 (en) | Malware detection based on traffic analysis | |
| US10728245B2 (en) | HTTP proxy authentication using custom headers | |
| US8875220B2 (en) | Proxy-based network access protection | |
| US9338165B2 (en) | Common internet file system proxy authentication of multiple servers | |
| US8407324B2 (en) | Dynamic modification of the address of a proxy | |
| US11770385B2 (en) | Systems and methods for malicious client detection through property analysis | |
| US9973490B2 (en) | Single login authentication for users with multiple IPV4/IPV6 addresses | |
| JP6875482B2 (en) | Computer-readable storage media for legacy integration and methods and systems for using it | |
| US10911485B2 (en) | Providing cross site request forgery protection at an edge server | |
| US11620354B2 (en) | System and method for protected proxy design for dynamic API scanning service | |
| EP3982614B1 (en) | Resource security integration platform | |
| US11336692B1 (en) | Employing SNI hostname extraction to populate a reverse DNS listing to protect against potentially malicious domains | |
| US11736528B2 (en) | Low latency cloud-assisted network security with local cache | |
| US11252143B2 (en) | Authentication system, authentication server and authentication method | |
| US9032490B1 (en) | Techniques for authenticating a user with heightened security | |
| US11128638B2 (en) | Location assurance using location indicators modified by shared secrets | |
| US10032027B2 (en) | Information processing apparatus and program for executing an electronic data in an execution environment | |
| US10924505B2 (en) | Passcode based access-control with randomized limits | |
| CN112395020B (en) | Safety protection method of intranet, client, target server and storage medium | |
| CN118829983A (en) | Systems and methods for providing multi-factor authentication to RDP services via a zero-trust cloud environment | |
| CN114301872B (en) | Domain name based access method and device, electronic equipment and storage medium | |
| CN112131588B (en) | Application access method, device, electronic equipment and storage medium | |
| CN114938288A (en) | Data access method, device, equipment and storage medium | |
| US11550902B2 (en) | Using security event correlation to describe an authentication process |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| GR01 | Patent grant | ||
| GR01 | Patent grant | ||
| PE01 | Entry into force of the registration of the contract for pledge of patent right | Denomination of invention:Application access methods, devices, electronic devices, and storage media Granted publication date:20240726 Pledgee:China Co. truction Bank Corp Beijing Zhongguancun branch Pledgor:RUN TECHNOLOGIES Co.,Ltd. BEIJING Registration number:Y2025110000082 | |
| PE01 | Entry into force of the registration of the contract for pledge of patent right |