CN112115205A - Cross-chain trust method, device, equipment and medium based on digital certificate authentication - Google Patents
Cross-chain trust method, device, equipment and medium based on digital certificate authenticationDownload PDFInfo
- Publication number
- CN112115205A CN112115205ACN202011316751.6ACN202011316751ACN112115205ACN 112115205 ACN112115205 ACN 112115205ACN 202011316751 ACN202011316751 ACN 202011316751ACN 112115205 ACN112115205 ACN 112115205A
- Authority
- CN
- China
- Prior art keywords
- node
- authorized
- asset
- certificate
- user
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Granted
Links
Images
Classifications
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/60—Protecting data
- G06F21/602—Providing cryptographic facilities or services
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F16/00—Information retrieval; Database structures therefor; File system structures therefor
- G06F16/20—Information retrieval; Database structures therefor; File system structures therefor of structured data, e.g. relational data
- G06F16/27—Replication, distribution or synchronisation of data between databases or within a distributed database system; Distributed database system architectures therefor
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/30—Authentication, i.e. establishing the identity or authorisation of security principals
- G06F21/31—User authentication
- G06F21/33—User authentication using certificates
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/30—Authentication, i.e. establishing the identity or authorisation of security principals
- G06F21/45—Structures or tools for the administration of authentication
- G06F21/46—Structures or tools for the administration of authentication by designing passwords or checking the strength of passwords
- G—PHYSICS
- G06—COMPUTING OR CALCULATING; COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/60—Protecting data
- G06F21/64—Protecting data integrity, e.g. using checksums, certificates or signatures
Landscapes
- Engineering & Computer Science (AREA)
- Theoretical Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- General Physics & Mathematics (AREA)
- General Engineering & Computer Science (AREA)
- Physics & Mathematics (AREA)
- Software Systems (AREA)
- Computer Hardware Design (AREA)
- General Health & Medical Sciences (AREA)
- Bioethics (AREA)
- Health & Medical Sciences (AREA)
- Databases & Information Systems (AREA)
- Computing Systems (AREA)
- Data Mining & Analysis (AREA)
- Management, Administration, Business Operations System, And Electronic Commerce (AREA)
Abstract
Description
Translated fromChinese技术领域technical field
本申请涉及区块链技术领域,尤其涉及一种基于数字证书认证的跨链信任方法、装置、设备以及介质。The present application relates to the field of blockchain technology, and in particular, to a cross-chain trust method, device, device and medium based on digital certificate authentication.
背景技术Background technique
目前的区块链系统都是各成一体的,不同的区块链之间无法直接进行信息之间的交换,而在面对多应用的综合系统中,通常需要在不同区块链中进行信息交互,实现区块链与区块链之间数据的互联互通是急需解决的重点问题。The current blockchain systems are all integrated, and information cannot be exchanged directly between different blockchains. In a comprehensive system with multiple applications, it is usually necessary to conduct information in different blockchains. Interaction and realizing the interconnection and intercommunication of data between blockchains are the key issues that need to be solved urgently.
现有技术中,若应用方需要从多条区块链中获取与用户A相关联的数据,则应用方需要获取用户A的授权(即对应用方开放查看用户A的相关数据的权限),由于应用方所在的区块链1与存储用户A相关数据的区块链2之间相互独立,因此可以在区块链1与区块链2之间通过第三方“连接器”(如公证人机制中由一组可行节点构成的公证人)进行数据传输;然而,在不同区块链的数据传输中,可能需要执行一系列的操作(如需要支持多重签名,并对多重签名进行验证),造成数据传输中的授权验证效率过低。In the prior art, if the application side needs to obtain the data associated with user A from multiple blockchains, the application side needs to obtain the authorization of user A (that is, the application side opens the permission to view the relevant data of user A), Since the blockchain 1 where the application party is located is independent from the
发明内容SUMMARY OF THE INVENTION
本申请实施例提供一种基于数字证书认证的跨链信任方法、装置、设备以及介质,可以提高跨链信任传输中的授权验证效率。The embodiments of the present application provide a cross-chain trust method, device, device, and medium based on digital certificate authentication, which can improve the efficiency of authorization verification in cross-chain trust transmission.
本申请实施例一方面提供了一种基于数字证书认证的跨链信任方法,包括:On the one hand, the embodiments of the present application provide a cross-chain trust method based on digital certificate authentication, including:
当资产授权用户的身份验证成功时,获取资产授权用户对应的证书签名,向证书授权节点发送包含证书签名的证书颁发请求,以使证书授权节点根据证书颁发请求,为被授权节点颁发包含证书签名的被授权节点证书;When the identity verification of the asset authorization user is successful, the certificate signature corresponding to the asset authorization user is obtained, and a certificate issuance request containing the certificate signature is sent to the certificate authority node, so that the certificate authority node can issue a certificate containing the certificate signature to the authorized node according to the certificate issuance request. the authorized node certificate;
接收证书授权节点返回的被授权节点证书,获取资产授权用户为被授权节点签署的授权合同;授权合同包含资产授权用户对应的用户签名和被授权节点对应的第一节点签名;Receive the authorized node certificate returned by the certificate authorization node, and obtain the authorization contract signed by the asset authorization user for the authorized node; the authorization contract includes the user signature corresponding to the asset authorization user and the first node signature corresponding to the authorized node;
将被授权节点证书和授权合同添加至被授权核心链,获取与被授权核心链相关联的跨链网关,将被授权节点证书和授权合同分配至跨链网关;Add the authorized node certificate and authorization contract to the authorized core chain, obtain the cross-chain gateway associated with the authorized core chain, and assign the authorized node certificate and authorization contract to the cross-chain gateway;
向跨链网关中的资产轻量节点发送针对资产授权用户的数据获取请求,以使资产轻量节点根据被授权节点证书和授权合同的数据验证结果,在资产轻量节点对应的资产核心链中,获取资产授权用户对应的目标资产数据;Send the data acquisition request for the asset authorized user to the asset lightweight node in the cross-chain gateway, so that the asset lightweight node can be stored in the asset core chain corresponding to the asset lightweight node according to the authorized node certificate and the data verification result of the authorization contract. , to obtain the target asset data corresponding to the asset authorized user;
通过跨链网关接收资产轻量节点返回的目标资产数据。Receive the target asset data returned by the asset lightweight node through the cross-chain gateway.
本申请实施例一方面提供了一种基于数字证书认证的跨链信任方法,包括:On the one hand, the embodiments of the present application provide a cross-chain trust method based on digital certificate authentication, including:
接收被授权节点发送的针对资产授权用户的数据获取请求,根据数据获取请求获取被授权节点对应的被授权节点证书,以及资产授权用户为被授权节点签署的授权合同;被授权节点证书是指证书授权节点为被授权节点颁发的数字证书,被授权节点证书包含资产授权用户对应的证书签名,授权合同包含资产授权用户对应的用户签名和证书授权节点对应的第一节点签名;Receive the data acquisition request sent by the authorized node for the asset authorized user, obtain the authorized node certificate corresponding to the authorized node according to the data acquisition request, and the authorization contract signed by the asset authorized user for the authorized node; the authorized node certificate refers to the certificate The authorization node is a digital certificate issued by the authorized node, the authorized node certificate contains the certificate signature corresponding to the asset authorization user, and the authorization contract contains the user signature corresponding to the asset authorization user and the first node signature corresponding to the certificate authorization node;
根据证书签名、用户签名以及第一节点签名,获取被授权节点证书和授权合同对应的数据验证结果;Obtain the data verification result corresponding to the authorized node certificate and the authorization contract according to the certificate signature, the user signature and the first node signature;
当数据验证结果为数据验证通过结果时,在资产轻量节点对应的资产核心链中,获取资产授权用户对应的目标资产数据;When the data verification result is the data verification pass result, obtain the target asset data corresponding to the asset authorized user in the asset core chain corresponding to the asset lightweight node;
通过资产轻量节点所属的跨链网关,向被授权节点返回目标资产数据。The target asset data is returned to the authorized node through the cross-chain gateway to which the asset lightweight node belongs.
本申请实施例一方面提供了一种基于数字证书认证的跨链信任装置,包括:On the one hand, the embodiments of the present application provide a cross-chain trust device based on digital certificate authentication, including:
证书申请模块,用于当资产授权用户的身份验证成功时,获取资产授权用户对应的证书签名,向证书授权节点发送包含证书签名的证书颁发请求,以使证书授权节点根据证书颁发请求,为被授权节点颁发包含证书签名的被授权节点证书;The certificate application module is used to obtain the certificate signature corresponding to the asset authorization user when the identity verification of the asset authorization user is successful, and send the certificate issuance request including the certificate signature to the certificate authority node, so that the certificate authority node can issue a certificate for the recipient according to the certificate issuance request. The authorized node issues the authorized node certificate containing the certificate signature;
第一获取模块,用于接收证书授权节点返回的被授权节点证书,获取资产授权用户为被授权节点签署的授权合同;授权合同包含资产授权用户对应的用户签名和被授权节点对应的第一节点签名;The first acquisition module is used to receive the authorized node certificate returned by the certificate authorization node, and obtain the authorization contract signed by the asset authorization user for the authorized node; the authorization contract includes the user signature corresponding to the asset authorization user and the first node corresponding to the authorized node. sign;
添加模块,用于将被授权节点证书和授权合同添加至被授权核心链,获取与被授权核心链相关联的跨链网关,将被授权节点证书和授权合同分配至跨链网关;Add a module for adding the authorized node certificate and authorization contract to the authorized core chain, obtaining the cross-chain gateway associated with the authorized core chain, and assigning the authorized node certificate and authorization contract to the cross-chain gateway;
第一发送模块,用于向跨链网关中的资产轻量节点发送针对资产授权用户的数据获取请求,以使资产轻量节点根据被授权节点证书和授权合同的数据验证结果,在资产轻量节点对应的资产核心链中,获取资产授权用户对应的目标资产数据;The first sending module is used to send the data acquisition request for the asset authorized user to the asset lightweight node in the cross-chain gateway, so that the asset lightweight node can verify the data in the asset lightweight node according to the authorized node certificate and the data verification result of the authorization contract. In the asset core chain corresponding to the node, obtain the target asset data corresponding to the asset authorized user;
第一接收模块,用于通过跨链网关接收资产轻量节点返回的目标资产数据。The first receiving module is used to receive the target asset data returned by the asset lightweight node through the cross-chain gateway.
其中,该装置包括:Wherein, the device includes:
身份验证模块,用于接收资产授权用户的资产授权请求,根据资产授权请求获取与资产授权用户相关联的用户身份数据,对用户身份数据进行验证得到资产授权用户的身份验证结果;The identity verification module is used to receive the asset authorization request of the asset authorized user, obtain the user identity data associated with the asset authorized user according to the asset authorization request, and verify the user identity data to obtain the identity verification result of the asset authorized user;
身份确定模块,用于当身份验证结果为身份验证通过结果时,确定资产授权用户的身份验证成功;The identity determination module is used to determine that the authentication of the asset authorized user is successful when the authentication result is the authentication passed result;
上述身份确定模块,还用于当身份验证结果为身份验证未通过结果时,确定资产授权用户的身份验证失败。The above-mentioned identity determination module is further configured to determine that the authentication of the asset authorization user fails when the authentication result is an authentication failure result.
其中,证书申请模块包括:Among them, the certificate application module includes:
验证结果发送单元,用于当资产授权用户的身份验证成功时,向资产授权用户返回身份验证通过结果;The verification result sending unit is used to return the authentication result to the asset authorization user when the authentication of the asset authorization user succeeds;
颁发请求生成单元,用于接收基于用户私钥所生成的证书签名,根据被授权节点对应的节点身份数据和证书签名生成证书颁发请求;用户私钥是指资产授权用户对应的私钥;The issuance request generation unit is used to receive the certificate signature generated based on the user's private key, and generate a certificate issuance request according to the node identity data and the certificate signature corresponding to the authorized node; the user's private key refers to the private key corresponding to the asset authorized user;
颁发请求发送单元,用于向证书授权节点发送证书颁发请求,以使证书授权节点根据节点身份信息和证书签名的验证结果,为被授权节点颁发包含证书签名的被授权节点证书。The issuance request sending unit is used to send a certificate issuance request to the certificate authority node, so that the certificate authority node can issue the authorized node certificate including the certificate signature to the authorized node according to the node identity information and the verification result of the certificate signature.
其中,第一获取模块包括:Wherein, the first acquisition module includes:
初始合同获取单元,用于获取资产授权用户为被授权节点签署的初始授权合同;初始授权合同包括授权数据类型和根据资产授权用户对应的用户私钥所生成的用户签名;The initial contract acquisition unit is used to obtain the initial authorization contract signed by the asset authorization user for the authorized node; the initial authorization contract includes the authorization data type and the user signature generated according to the user private key corresponding to the asset authorization user;
授权合同确定单元,用于根据被授权节点对应的第一节点私钥,生成初始授权合同对应的第一节点签名,将包含第一节点签名的初始授权合同确定为授权合同。The authorization contract determination unit is configured to generate the first node signature corresponding to the initial authorization contract according to the first node private key corresponding to the authorized node, and determine the initial authorization contract including the first node signature as the authorization contract.
其中,添加模块包括:Among them, the added modules include:
共识处理单元,用于将被授权节点证书和授权合同封装为授权区块,将授权区块进行共识处理;The consensus processing unit is used to encapsulate the authorized node certificate and authorization contract into authorized blocks, and perform consensus processing on the authorized blocks;
第一记账单元,用于当授权区块满足共识合法性条件时,将授权区块添加至被授权核心链;The first accounting unit is used to add the authorized block to the authorized core chain when the authorized block satisfies the consensus legality condition;
分配单元,用于获取与被授权核心链相关联的跨链网关,将授权区块的区块头数据分配至跨链网关;区块头数据用于指示被授权节点证书和授权合同在被授权核心链中的存储位置。The allocation unit is used to obtain the cross-chain gateway associated with the authorized core chain, and distribute the block header data of the authorized block to the cross-chain gateway; the block header data is used to indicate that the authorized node certificate and authorization contract are in the authorized core chain. storage location in .
其中,跨链网关的数量为至少两个;Among them, the number of cross-chain gateways is at least two;
分配单元具体用于:Allocation units are specifically used to:
获取与被授权核心链相关联的至少两个跨链网关,分别在至少两个跨链网关中确定被授权核心链对应的被授权轻量节点,将授权区块的区块头数据分配给被授权轻量节点。Obtain at least two cross-chain gateways associated with the authorized core chain, determine the authorized lightweight nodes corresponding to the authorized core chain in the at least two cross-chain gateways respectively, and assign the block header data of the authorized block to the authorized light-weight nodes. Lightweight Node.
本申请实施例一方面提供了一种基于数字证书认证的跨链信任装置,包括:On the one hand, the embodiments of the present application provide a cross-chain trust device based on digital certificate authentication, including:
第二接收模块,用于接收被授权节点发送的针对资产授权用户的数据获取请求,根据数据获取请求获取被授权节点对应的被授权节点证书,以及资产授权用户为被授权节点签署的授权合同;被授权节点证书是指证书授权节点为被授权节点颁发的数字证书,被授权节点证书包含资产授权用户对应的证书签名,授权合同包含资产授权用户对应的用户签名和被授权节点对应的第一节点签名;The second receiving module is configured to receive the data acquisition request sent by the authorized node for the asset authorized user, and obtain the authorized node certificate corresponding to the authorized node according to the data acquisition request, and the authorization contract signed by the asset authorized user for the authorized node; The authorized node certificate refers to the digital certificate issued by the certificate authority node for the authorized node. The authorized node certificate contains the certificate signature corresponding to the asset authorized user, and the authorization contract contains the user signature corresponding to the asset authorized user and the first node corresponding to the authorized node. sign;
验证模块,用于根据证书签名、用户签名以及第一节点签名,获取被授权节点证书和授权合同对应的数据验证结果;The verification module is used to obtain the data verification result corresponding to the authorized node certificate and the authorization contract according to the certificate signature, the user signature and the first node signature;
第二获取模块,用于当数据验证结果为数据验证通过结果时,在资产轻量节点对应的资产核心链中,获取资产授权用户对应的目标资产数据;The second obtaining module is used to obtain the target asset data corresponding to the asset authorized user in the asset core chain corresponding to the asset lightweight node when the data verification result is the data verification pass result;
第二发送模块,用于通过资产轻量节点所属的跨链网关,向被授权节点返回目标资产数据。The second sending module is used to return the target asset data to the authorized node through the cross-chain gateway to which the asset lightweight node belongs.
其中,第二接收模块包括:Wherein, the second receiving module includes:
获取请求接收单元,用于接收被授权节点发送的针对资产授权用户的数据获取请求,根据数据获取请求,在资产轻量节点所在的跨链网关中确定被授权节点对应的被授权轻量节点;The acquisition request receiving unit is used to receive the data acquisition request sent by the authorized node for the asset authorized user, and according to the data acquisition request, determine the authorized lightweight node corresponding to the authorized node in the cross-chain gateway where the asset lightweight node is located;
授权合同获取单元,用于通过被授权轻量节点,在被授权节点对应的被授权核心链中获取被授权节点对应的被授权节点证书,以及资产授权用户为被授权节点签署的授权合同。The authorization contract obtaining unit is used to obtain the authorized node certificate corresponding to the authorized node and the authorization contract signed by the asset authorization user for the authorized node in the authorized core chain corresponding to the authorized node through the authorized lightweight node.
其中,验证模块包括:Among them, the verification module includes:
证书获取单元,用于获取资产授权用户对应的授权用户证书,以及证书授权节点对应的根证书,在被授权节点证书中获取被授权节点对应的第一节点公钥,在根证书中获取证书授权节点的第二节点公钥;The certificate obtaining unit is used to obtain the authorized user certificate corresponding to the asset authorization user and the root certificate corresponding to the certificate authority node, obtain the first node public key corresponding to the authorized node in the authorized node certificate, and obtain the certificate authority in the root certificate The second node public key of the node;
用户公钥获取单元,用于若根据第二节点公钥检测到授权用户证书满足合法性条件,则在授权用户证书中获取资产授权用户的用户公钥;a user public key obtaining unit, configured to obtain the user public key of the asset authorized user in the authorized user certificate if it is detected that the authorized user certificate satisfies the legality condition according to the public key of the second node;
第一合法性验证单元,用于根据用户公钥对证书签名进行合法性验证,生成证书签名对应的第一签名验证结果,根据第二节点公钥对被授权节点证书中所包含的第二节点签名进行合法性验证,生成第二节点签名对应的第二签名验证结果;第二节点签名为根据证书授权节点的第二节点私钥所生成的数字签名;The first legitimacy verification unit is configured to perform legitimacy verification on the certificate signature according to the user's public key, generate a first signature verification result corresponding to the certificate signature, and verify the second node included in the authorized node certificate according to the second node's public key. The signature is verified for validity, and a second signature verification result corresponding to the signature of the second node is generated; the signature of the second node is a digital signature generated according to the private key of the second node of the certificate authority node;
证书验证结果生成单元,用于根据第一签名验证结果和第二签名验证结果,生成被授权节点证书对应的数据验证结果;a certificate verification result generating unit, configured to generate a data verification result corresponding to the authorized node certificate according to the first signature verification result and the second signature verification result;
第二合法性验证单元,用于根据第一节点公钥对第一节点签名进行合法性验证,生成第一节点签名对应的第三签名验证结果,根据用户公钥对用户签名进行合法性验证,生成用户签名对应的第四签名验证结果;The second legality verification unit is configured to perform legality verification on the signature of the first node according to the public key of the first node, generate a third signature verification result corresponding to the signature of the first node, and perform legality verification on the signature of the user according to the public key of the user, generating a fourth signature verification result corresponding to the user's signature;
合同验证结果生成单元,用于根据第三签名验证结果和第四签名验证结果,生成授权合同对应的数据验证结果。The contract verification result generating unit is configured to generate a data verification result corresponding to the authorization contract according to the third signature verification result and the fourth signature verification result.
其中,第二获取模块包括:Wherein, the second acquisition module includes:
第二记账单元,用于当数据验证结果为数据验证通过结果时,将被授权节点证书和授权合同添加至资产轻量节点对应的资产核心链;The second accounting unit is used to add the authorized node certificate and the authorization contract to the asset core chain corresponding to the asset lightweight node when the data verification result is the data verification pass result;
数据查询单元,用于获取资产授权用户对应的用户标识,在资产核心链中查询与用户标识相匹配的候选资产数据;The data query unit is used to obtain the user ID corresponding to the authorized user of the asset, and query the candidate asset data matching the user ID in the asset core chain;
数据选取单元,用于在授权合同中获取资产授权用户对应的授权数据类型,将属于授权资产类型的候选资产数据,确定为资产授权用户对应的目标资产数据。The data selection unit is used to obtain the authorization data type corresponding to the asset authorization user in the authorization contract, and determine the candidate asset data belonging to the authorized asset type as the target asset data corresponding to the asset authorization user.
本申请实施例一方面提供了一种计算机设备,包括存储器和处理器,存储器存储有计算机程序,计算机程序被处理器执行时,使得处理器执行本申请实施例中一方面中方法的步骤。An aspect of the embodiments of the present application provides a computer device, including a memory and a processor, the memory stores a computer program, and when the computer program is executed by the processor, the processor executes the steps of the method in one aspect of the embodiments of the present application.
本申请实施例一方面提供了一种计算机可读存储介质,计算机可读存储介质存储有计算机程序,计算机程序包括程序指令,程序指令当被处理器执行时,执行如本申请实施例中一方面中方法的步骤。An aspect of the embodiments of the present application provides a computer-readable storage medium, where the computer-readable storage medium stores a computer program, and the computer program includes program instructions. steps in the method.
根据本申请的一个方面,提供了一种计算机程序产品或计算机程序,该计算机程序产品或计算机程序包括计算机指令,该计算机指令存储在计算机可读存储介质中。计算机设备的处理器从计算机可读存储介质读取该计算机指令,处理器执行该计算机指令,使得该计算机设备执行上述一方面的各种可选方式中提供的方法。According to one aspect of the present application, there is provided a computer program product or computer program comprising computer instructions stored in a computer readable storage medium. The processor of the computer device reads the computer instructions from the computer-readable storage medium, and the processor executes the computer instructions to cause the computer device to perform the methods provided in various optional manners of the above aspect.
本申请实施例可以向证书授权节点申请包含该证书签名的被授权节点证书,并获取资产授权用户为被授权节点签署的授权合同,该授权合同包含资产授权用户对应的用户签名以及被授权节点对应的第一节点签名,进而可以将被授权节点证书和授权合同添加至被授权核心链,将被授权节点证书和授权合同分配至与被授权核心链相关联的跨链网关;此时的被授权节点可以向跨链网关中的资产轻量节点发送针对资产授权用户的数据获取请求,以使资产轻量节点可以根据被授权节点证书和授权合同的数据验证结果,在资产轻量节点对应的资产数据链中获取资产授权用户的目标资产数据,通过跨链网关将该目标资产数据返回至被授权节点。可见,通过证书授权节点对被授权节点和授权合同进行权威认证,实现资产授权用户对被授权节点的资产授权,根据被授权节点和授权合同,被授权核心链和资产核心链之间可以通过跨链网关进行信任数据传输,可以提高跨链信任传输中的授权验证效率。This embodiment of the application may apply to a certificate authority node for an authorized node certificate including the certificate signature, and obtain an authorization contract signed by an asset authorization user for the authorized node, where the authorization contract includes the user signature corresponding to the asset authorization user and the corresponding authorization node. Then the authorized node certificate and authorization contract can be added to the authorized core chain, and the authorized node certificate and authorization contract can be assigned to the cross-chain gateway associated with the authorized core chain; The node can send the data acquisition request for the asset authorized user to the asset lightweight node in the cross-chain gateway, so that the asset lightweight node can use the authorized node certificate and the data verification result of the authorization contract. The target asset data of the asset authorized user is obtained from the data chain, and the target asset data is returned to the authorized node through the cross-chain gateway. It can be seen that the authorized node and the authorization contract are authoritatively authenticated by the certificate authorization node, so as to realize the asset authorization of the authorized node by the asset authorization user. According to the authorized node and the authorization contract, the authorized core chain and the asset core chain can pass through the The chain gateway performs trust data transmission, which can improve the efficiency of authorization verification in cross-chain trust transmission.
附图说明Description of drawings
为了更清楚地说明本申请实施例或现有技术中的技术方案,下面将对实施例或现有技术描述中所需要使用的附图作简单地介绍,显而易见地,下面描述中的附图仅仅是本申请的一些实施例,对于本领域普通技术人员来讲,在不付出创造性劳动的前提下,还可以根据这些附图获得其他的附图。In order to more clearly illustrate the embodiments of the present application or the technical solutions in the prior art, the following briefly introduces the accompanying drawings required for the description of the embodiments or the prior art. Obviously, the drawings in the following description are only These are some embodiments of the present application. For those of ordinary skill in the art, other drawings can also be obtained based on these drawings without any creative effort.
图1是本申请实施例提供的一种网络架构的结构示意图;1 is a schematic structural diagram of a network architecture provided by an embodiment of the present application;
图2是本申请实施例提供的一种基于数字证书认证的跨链信任示意图;2 is a schematic diagram of a cross-chain trust based on digital certificate authentication provided by an embodiment of the present application;
图3是本申请实施例提供的一种基于数字证书认证的跨链信任方法的时序示意图;3 is a schematic time sequence diagram of a cross-chain trust method based on digital certificate authentication provided by an embodiment of the present application;
图4是本申请实施例提供的一种用户授权用户的身份验证示意图;FIG. 4 is a schematic diagram of the identity verification of a user authorized user provided by an embodiment of the present application;
图5是本申请实施例提供的一种授权区块上链过程的示意图;5 is a schematic diagram of an authorization block on-chain process provided by an embodiment of the present application;
图6是本申请实施例提供的一种授权合同的验证示意图;6 is a schematic diagram of verification of an authorization contract provided by an embodiment of the present application;
图7是本申请实施例提供的一种获取目标资产数据的示意图;7 is a schematic diagram of acquiring target asset data provided by an embodiment of the present application;
图8是本申请实施例提供的一种基于数字证书认证的跨链信任装置的结构示意图;8 is a schematic structural diagram of a cross-chain trust device based on digital certificate authentication provided by an embodiment of the present application;
图9是本申请实施例提供的一种基于数字证书认证的跨链信任装置的结构示意图;9 is a schematic structural diagram of a cross-chain trust device based on digital certificate authentication provided by an embodiment of the present application;
图10是本申请实施例提供的一种计算机设备的结构示意图;10 is a schematic structural diagram of a computer device provided by an embodiment of the present application;
图11是本申请实施例提供的一种计算机设备的结构示意图。FIG. 11 is a schematic structural diagram of a computer device provided by an embodiment of the present application.
具体实施方式Detailed ways
下面将结合本申请实施例中的附图,对本申请实施例中的技术方案进行清楚、完整地描述,显然,所描述的实施例仅仅是本申请一部分实施例,而不是全部的实施例。基于本申请中的实施例,本领域普通技术人员在没有作出创造性劳动前提下所获得的所有其他实施例,都属于本申请保护的范围。The technical solutions in the embodiments of the present application will be clearly and completely described below with reference to the drawings in the embodiments of the present application. Obviously, the described embodiments are only a part of the embodiments of the present application, but not all of the embodiments. Based on the embodiments in the present application, all other embodiments obtained by those of ordinary skill in the art without creative work fall within the protection scope of the present application.
本申请实施例涉及区块链技术和云安全,区块链(block chain)是借由密码学串接并保护内容的串连文字记录(又称区块)。每一个区块包含了前一个区块的加密散列、相应时间戳记以及交易数据(通常用默克尔树(Merkle tree)算法计算的散列值表示),这样的设计使得区块内容具有难以篡改的特性。用区块链技术所串接的分布式账本能让两方有效纪录交易,且可永久查验此交易。不同的区块链系统都是互相独立的,不同区块链之间不能直接进行信息交换。The embodiments of the present application relate to blockchain technology and cloud security. A blockchain (block chain) is a concatenated text record (also known as a block) that connects and protects content through cryptography. Each block contains the encrypted hash of the previous block, the corresponding timestamp and transaction data (usually represented by a hash value calculated by the Merkle tree algorithm), which makes the block content difficult to Tampered features. The distributed ledger connected by blockchain technology allows two parties to effectively record the transaction, and the transaction can be checked permanently. Different blockchain systems are independent of each other, and information cannot be exchanged directly between different blockchains.
云安全(Cloud Security) 是指基于云计算商业模式应用的安全软件、硬件、用户、机构、安全云平台的总称。云安全融合了并行处理、网格计算、未知病毒行为判断等新兴技术和概念,通过网状的大量客户端对网络中软件行为的异常监测,获取互联网中木马、恶意程序的最新信息,并发送到服务端进行自动分析和处理,再把病毒和木马的解决方案分发到每一个客户端。Cloud Security refers to the general term for security software, hardware, users, institutions, and security cloud platforms based on cloud computing business model applications. Cloud security integrates emerging technologies and concepts such as parallel processing, grid computing, and unknown virus behavior judgment. Through the abnormal monitoring of software behavior in the network by a large number of mesh clients, the latest information on Trojans and malicious programs in the Internet is obtained and sent. To the server for automatic analysis and processing, and then distribute the virus and Trojan solutions to each client.
云安全主要研究方向包括:1、云计算安全,主要研究如何保障云自身及云上各种应用的安全,包括云计算机系统安全、用户数据的安全存储与隔离、用户接入认证、信息传输安全、网络攻击防护、合规审计等;2、安全基础设施的云化,主要研究如何采用云计算新建与整合安全基础设施资源,优化安全防护机制,包括通过云计算技术构建超大规模安全事件、信息采集与处理平台,实现对海量信息的采集与关联分析,提升全网安全事件把控能力及风险控制能力/3、云安全服务,主要研究各种基于云计算平台为用户提供的安全服务,如防病毒服务等。本申请实施例具体涉及云安全中的用户接入认证和信息传输安全,通过证书授权机构对数据获取方进行权威认证,以实现数据的安全传输。The main research directions of cloud security include: 1. Cloud computing security, which mainly studies how to ensure the security of the cloud itself and various applications on the cloud, including cloud computer system security, secure storage and isolation of user data, user access authentication, and information transmission security , network attack protection, compliance audit, etc.; 2. Cloudization of security infrastructure, mainly to study how to use cloud computing to build and integrate security infrastructure resources, and optimize security protection mechanisms, including building ultra-large-scale security events and information through cloud computing technology. The collection and processing platform realizes the collection and correlation analysis of massive information, and improves the ability to control security events and risk control of the entire network. Antivirus service, etc. The embodiments of the present application specifically relate to user access authentication and information transmission security in cloud security, and authoritative authentication is performed on the data acquirer through a certificate authority to realize secure data transmission.
本申请实施例还涉及以下几个概念:The embodiments of the present application also involve the following concepts:
证书授权节点:证书授权节点也称为证书授权机构,或者CA认证中心(CertifacateAuthority)。证书授权节点是数字证书颁发和管理的权威机构,可以承担公钥体系中公钥的发行检验的责任。数字证书的颁发过程一般为:用户(可以理解为个人或企业终端设备、客户端等)可以在本地产生自己的密钥对,将密钥对中的公钥及部分个人身份信息传送给CA认证中心;CA认证中心在核实身份后,并确定请求确实由该用户所发送后,可以发给用户一个数字证书,该证书内包含用户的个人信息和公钥信息,同时还附有认证中心的签名信息。当该用户需要在区块链网络中与其余用户进行通信时,其余用户可以通过该用户的数字证书验证该用户的身份。Certificate authority node: The certificate authority node is also called a certificate authority, or a CA certification authority (CertifacateAuthority). The certificate authority node is the authoritative organization for issuing and managing digital certificates, and can undertake the responsibility of issuing and verifying the public key in the public key system. The issuance process of digital certificates is generally as follows: users (which can be understood as personal or enterprise terminal devices, clients, etc.) can generate their own key pairs locally, and transmit the public key and some personal identity information in the key pair to CA certification. Center; after the CA certification center verifies the identity and confirms that the request is indeed sent by the user, it can issue a digital certificate to the user, which contains the user's personal information and public key information, as well as the signature of the certification center. information. When the user needs to communicate with other users in the blockchain network, the remaining users can verify the user's identity through the user's digital certificate.
轻量节点(Simplified Payment Verification,SPV):spv节点属于区块链当中支付验证体系中的一种,是为了适应简便、快速支付的验证手段,它不需要下载新区块所有数据,只需要保存区块头部数据,这些数据保存在默克尔树当中。spv节点可以将属于自己的数据保存在本地,方便读取。Lightweight node (Simplified Payment Verification, SPV): SPV node is one of the payment verification systems in the blockchain. It is a simple and fast payment verification method. It does not need to download all the data of the new block, but only needs to save the area. Block header data, which is stored in the Merkle tree. The spv node can save its own data locally for easy reading.
跨链网关:跨链网关是一种网关装置,可以用于集成不同区块链的spv节点。通过跨链网关,可以实现不同链的数据资产的交换转移,本申请实施例中的跨链可以理解为至少两个独立的区块链系统进行互操作。Cross-chain gateway: Cross-chain gateway is a gateway device that can be used to integrate spv nodes of different blockchains. Through the cross-chain gateway, the exchange and transfer of data assets of different chains can be realized, and the cross-chain in the embodiment of this application can be understood as the interoperation of at least two independent blockchain systems.
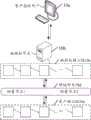
请参见图1,图1是本申请实施例提供的一种网络架构的结构示意图。如图1所示,该网络架构可以包括用户终端10a、服务器10b以及跨链网关10d。其中,用户终端10a可以为资产授权用户所使用的终端设备,服务器10b可以是资产授权用户所授权的被授权节点(可以理解为数据使用方),该服务器10b所存储的区块链为被授权核心链10c;跨链网关10d可以包括轻量节点1和轻量节点2,该轻量节点1可以是指被授权核心链部署在跨链网关10d中的轻量节点,轻量节点2可以是指资产核心链10e部署在跨链网关10d中的轻量节点,该资产核心链10e存储有资产授权用户对应的资产数据,通过该跨链网关10d可以实现被授权核心链10c与资产核心链10e之间的数据传输。Please refer to FIG. 1. FIG. 1 is a schematic structural diagram of a network architecture provided by an embodiment of the present application. As shown in FIG. 1, the network architecture may include a
其中,用户终端10a可以包括智能手机、平板电脑、笔记本电脑、台式计算机、掌上电脑、移动互联网设备(mobile internet device,MID)、可穿戴设备(例如智能手表、智能手环等)等,但并不局限于此。服务器10b可以是独立的物理服务器,也可以是多个物理服务器构成的服务器集群或者分布式系统,还可以是提供云服务、云数据库、云计算、云函数、云存储、网络服务、云通信、中间件服务、域名服务、安全服务、CDN、以及大数据和人工智能平台等基础云计算服务的云服务器。Wherein, the
在图1所示的网络架构中,资产授权用户对被授权节点进行数据授权时,需要证书授权节点对被授权节点进行身份鉴定,在鉴定无误后可以在资产授权用户为被授权节点签署的授权合同中进行签名,该证书授权节点的签名可以作为被授权节点鉴定通过的凭证。当被授权节点获得资产授权用户的数据授权之后,可以通过跨链网关10d向资产核心链10e发送数据获取请求,资产核心链10e在接收到数据获取请求后,可以对被授权节点的身份进行验证,即确认被授权节点是否真的具备获取资产授权用户相关数据的权限,如验证授权合同的合法性,验证通过后方可在资产核心链10e中获取数据,并通过跨链网关10d向被授权节点返回数据。In the network architecture shown in Figure 1, when the asset authorization user authorizes the data of the authorized node, the certificate authorization node is required to authenticate the authorized node. After the authentication is correct, the asset authorization user can sign the authorization for the authorized node. The contract is signed, and the signature of the certificate-authorized node can be used as the certificate for the authentication of the authorized node. After the authorized node obtains the data authorization of the asset authorization user, it can send a data acquisition request to the asset core chain 10e through the cross-chain gateway 10d. After receiving the data acquisition request, the asset core chain 10e can verify the identity of the authorized node. , that is, to confirm whether the authorized node really has the authority to obtain the relevant data of the asset authorized user, such as verifying the legality of the authorization contract, after the verification is passed, the data can be obtained in the asset core chain 10e and sent to the authorized node through the cross-chain gateway 10d. Return data.
请一并参见图2,图2是本申请实施例提供的一种基于数字证书认证的跨链信任示意图。如图2所示,资产授权用户20a对被授权节点进行资产授权的过程中,资产授权用户20a可以向被授权节点发送资产授权请求,被授权节点在接收到资产授权用户20a发送的资产授权请求后,可以对资产授权用户20a进行身份验证,身份验证的手段包括但不限于:人脸核实身份,密码验证。与此同时,被授权节点还需要验证资产授权用户的私钥签名的合法性,若资产授权用户20a的身份没有问题,且私钥签名符合合法性条件,则可以向资产授权用户20a返回身份验证通过结果。Please refer to FIG. 2 together. FIG. 2 is a schematic diagram of a cross-chain trust based on digital certificate authentication provided by an embodiment of the present application. As shown in FIG. 2 , in the process of asset authorization by the asset authorization user 20a to the authorized node, the asset authorization user 20a can send an asset authorization request to the authorized node, and the authorized node receives the asset authorization request sent by the asset authorization user 20a. After that, the asset authorized user 20a can be authenticated, and the means of authentication include but are not limited to: face verification, password verification. At the same time, the authorized node also needs to verify the legitimacy of the private key signature of the asset authorized user. If the identity of the asset authorized user 20a is correct and the private key signature meets the legality conditions, it can return the identity verification to the asset authorized user 20a through the results.
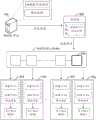
资产授权用户20a接收到被授权节点发送的身份验证通过结果后,可以为被授权节点生成证书签名以及授权合同,并将证书签名和授权合同发送至被授权节点,该授权合同可以包括资产授权用户20a使用自己的私钥所签署的用户签名,以及资产授权用户20a为被授权节点所授权的内容。被授权节点可以向证书授权机构20b发送携带上述证书签名的证书颁发请求,证书授权机构20b可以对被授权节点的身份信息、节点公钥以及证书签名进行核实,核实无误后可以为被授权节点颁发数字证书,被授权节点的数字证书可以称为被授权节点证书。可选的,被授权节点还可以将授权合同传输至证书权威机构20b,让证书权威机构20b作为第三方权威机构,为资产授权用户20a和被授权节点签订的授权合同进行认证,即最终有效的授权合同需要包括资产授权用户20a对应的用户签名以及证书授权机构20b对应的机构签名(也可以称为第一节点签名)。被授权节点可以将被授权节点证书和授权合同打包成授权区块添加至被授权核心链20c,该被授权核心链20c可以是指被授权节点所存储的区块链。After receiving the identity verification pass result sent by the authorized node, the asset authorization user 20a can generate a certificate signature and an authorization contract for the authorized node, and send the certificate signature and authorization contract to the authorized node, and the authorization contract can include the asset authorization user. 20a uses the user signature signed by its own private key, and the asset authorizes the content authorized by the user 20a for the authorized node. The authorized node can send a certificate issuance request carrying the above-mentioned certificate signature to the
被授权核心链20c中添加了被授权节点证书和授权合同后,可以将被授权节点证书和授权合同分配至被授权核心链20c在各个跨链网关中的被授权轻量节点。如图2所示,与被授权核心链20c相关联的跨链网关可以包括:跨链网关20d、跨链网关20e以及跨链网关20f。其中,跨链网关20d中包括被授权核心链20c对应的轻量节点1和资产核心链1对应的轻量节点2,该跨链网关20d可以实现被授权核心链20c和资产核心链1之间的数据传输;跨链网关20e中包括被授权核心链20c对应的轻量节点3和资产核心链2对应的轻量节点4,该跨链网关20e可以实现被授权核心链20c和资产核心链2之间的数据传输;跨链网关20f中包括被授权核心链20c对应的轻量节点5和资产核心链3对应的轻量节点6,该跨链网关20f可以实现被授权核心链20c和资产核心链3之间的数据传输。换言之,资产授权用户20a的资产数据可以存储在不同的资产区块链中,如资产授权用户20a的社保数据存储在社保数据核心链中,资产授权用户20a的税务数据存储在税务数据核心链中;资产授权用户20a对被授权节点进行一次授权后,可以实现从多个资产核心链中获取资产授权用户20a对应的资产数据,可以减少授权次数。After the authorized node certificate and the authorization contract are added to the authorized
当被授权节点需要从资产核心链1中获取资产授权用户20a的资产数据时,可以向资产核心链1对应的轻量节点2发送数据获取请求。轻量节点2在接收到被授权节点的数据获取请求后,可以通过跨链网关20d中的轻量节点1获取被授权节点对应的被授权节点证书和资产授权用户为被授权节点签署的授权合同。另外,轻量节点2可以从证书授权机构20b中获取根证书,以及资产授权用户20a对应的用户证书,该轻量节点2可以将根证书存储在本地,表明自己对证书权威机构20b是信任的。可以理解的是,用户证书是证书授权机构20b为资产授权用户20a颁发的数字证书,该用户证书可以包括证书授权机构20b的统一标识(ID)、资产授权用户的用户公钥以及证书授权机构的第一节点签名等信息;根证书可以是指证书授权机构使用自己的节点私钥对自己签署的数字证书。When the authorized node needs to acquire the asset data of the asset authorized user 20a from the asset core chain 1, it can send a data acquisition request to the
轻量节点2可以从根证书中获取证书授权机构20b的机构公钥,通过该机构公钥对用户证书中所携带机构签名进行正确性验证,若用户证书中所携带的机构签名是正确的,则轻量节点2可以确定用户证书没有问题,并从用户证书中获取资产授权用户20a的用户公钥,使用该用户公钥对授权合同中所携带的用户签名进行正确性验证;同时,轻量节点2还可以使用证书授权机构20b的机构公钥对授权合同中所携带的机构签名进行正确性验证,若授权合同中的用户签名和机构签名均正确,则可以确定该授权合同通过验证。同理,轻量节点2可以使用资产授权用户20a的用户公钥,对被授权节点对应的被授权节点证书中所携带的证书签名进行正确性验证,使用证书授权机构20b的机构公钥,对被授权节点证书中的机构签名进行正确性验证,若被授权节点证书中所包含的证书签名和机构签名均正确,则可以确定该被授权节点证书通过验证。The
当被授权节点证书和授权合同通过验证后,轻量节点2可以将被授权节点证书和授权合同打包成区块添加至资产核心链1,并在资产核心链1中查询与资产授权用户20a相关联的资产数据,并通过跨链网关20d将资产授权用户20a对应的资产数据返回至被授权节点。After the authorized node certificate and the authorization contract are verified, the
基于上述相同的方式,被授权节点可以分别从资产核心链2和资产核心链3中获取资产授权用户20a对应的资产数据,进而实现被授权核心链20c与多条资产核心链之间的跨链信任传输,可以提高跨链信任传输中的授权验证效率。Based on the same method as above, the authorized node can obtain the asset data corresponding to the asset authorized user 20a from the
请参见图3,图3是本申请实施例提供的一种基于数字证书认证的跨链信任方法的时序示意图。可以理解的是,该方法可以由被授权节点、证书授权节点以及资产轻量节点进行交互执行,被授权节点和资产轻量节点可以是不同区块链网络中的节点服务器,或者是不同区块链网络中的其他节点设备,证书授权节点可以负责数字证书的创建和颁发。如图3所示,该基于数字证书认证的跨链信任方法可以包括以下步骤:Please refer to FIG. 3 . FIG. 3 is a schematic time sequence diagram of a cross-chain trust method based on digital certificate authentication provided by an embodiment of the present application. It can be understood that this method can be executed interactively by authorized nodes, certificate authorization nodes and asset lightweight nodes. The authorized nodes and asset lightweight nodes can be node servers in different blockchain networks, or different blocks. For other node devices in the chain network, the certificate authority node can be responsible for the creation and issuance of digital certificates. As shown in Figure 3, the cross-chain trust method based on digital certificate authentication may include the following steps:
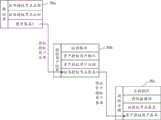
步骤S101,当资产授权用户的身份验证成功时,获取资产授权用户对应的证书签名。In step S101, when the identity verification of the asset authorization user is successful, a certificate signature corresponding to the asset authorization user is obtained.
具体的,不同的区块链之间通常是不能直接进行信息交换的,需要在不同的区块链之间建立跨链网关,在该跨链网关中可以集成不同区块链的轻量节点,通过该跨链网关可以实现不同区块链的信息交换转移。本申请实施例对同一个跨链网关所集成的区块链的数量不做限定,下面以两个区块链为例,对不同区块链之间的信息交换转移(也可以理解为两个独立的区块链系统之间的信息交换转移)进行描述。区块链系统中的区块链节点想要通过跨链网关从另一个区块链系统的区块链中获取数字资产数据时,需要数字资产持有用户对其进行数据授权,授权成功的区块链节点才能跨链获取数字资产持有用户对应的资产数据,此时授权成功的区块链节点可以称为被授权节点,为区块链节点进行数据授权的数字资产持有用户可以称为资产授权用户(如上述图2所对应实施例中的资产授权用户20a),资产授权用户可以是指个人用户,也可以是指法人用户(如企业用户)。Specifically, it is usually impossible to directly exchange information between different blockchains. It is necessary to establish a cross-chain gateway between different blockchains. In this cross-chain gateway, lightweight nodes of different blockchains can be integrated. Through this cross-chain gateway, information exchange and transfer of different blockchains can be realized. The embodiment of this application does not limit the number of blockchains integrated by the same cross-chain gateway. The following takes two blockchains as an example to describe the information exchange and transfer between different blockchains (which can also be understood as two Information exchange transfer between independent blockchain systems) is described. When a blockchain node in a blockchain system wants to obtain digital asset data from the blockchain of another blockchain system through a cross-chain gateway, it needs the digital asset holder to authorize its data. Only the blockchain node can obtain the asset data corresponding to the digital asset holding user across the chain. At this time, the blockchain node that is successfully authorized can be called the authorized node, and the digital asset holding user who authorizes the data for the blockchain node can be called as the authorized node. The asset authorized user (such as the asset authorized user 20a in the embodiment corresponding to FIG. 2 above), the asset authorized user may refer to an individual user or a legal person user (such as an enterprise user).
其中,资产授权用户向被授权节点进行数据授权时,可以向被授权节点发送资产授权请求,即被授权节点可以接收资产授权用户的资产授权请求,根据资产授权请求获取与资产授权用户相关联的用户身份数据,对用户身份数据进行验证以得到该资产授权用户的身份验证结果。被授权节点对资产授权用户的身份验证方式可以包括但不限于:人脸核身、支付验证;人脸核身可以是指被授权节点通过人脸识别来验证资产授权用户的身份,以确保资产授权用户为持有资产的用户,此时的人脸可以看成是资产授权用户的用户身份数据;支付验证可以是指被授权节点通过资产授权用户输入的支付密码来验证资产授权用户的身份,以确保资产授权用户为持有资产的用户,此时的支付密码可以看成是资产授权用户的用户身份数据;当然,被授权节点可以根据人脸核身和支付验证两种验证方式,对资产授权用户进行身份验证。当资产授权用户通过身份验证后,可以确定该资产授权用户的身份验证结果为身份验证通过结果,即资产授权用户身份验证成功,进而可以将身份验证通过结果返回给资产授权用户;当用户身份数据存在问题时,表示资产授权用户的身份验证结果为身份验证未通过结果,即资产授权用户的身份验证失败,可以将身份验证未通过结果返回给资产授权用户。Among them, when the asset authorization user authorizes data to the authorized node, it can send an asset authorization request to the authorized node, that is, the authorized node can receive the asset authorization request of the asset authorization user, and obtain the asset authorization user according to the asset authorization request. User identity data, verify the user identity data to obtain the authentication result of the authorized user of the asset. The identity verification methods of authorized nodes to authorized users of assets may include but are not limited to: face verification, payment verification; face verification may refer to authorized nodes verifying the identity of asset authorized users through face recognition to ensure assets The authorized user is the user who holds the asset, and the face at this time can be regarded as the user identity data of the asset authorized user; payment verification can refer to the authorized node verifying the identity of the asset authorized user through the payment password entered by the asset authorized user. In order to ensure that the asset authorized user is the user who holds the asset, the payment password at this time can be regarded as the user identity data of the asset authorized user; of course, the authorized node can verify the asset according to the two verification methods of face verification and payment verification. Authorize users to authenticate. After the asset authorized user passes the identity verification, it can be determined that the identity verification result of the asset authorized user is the identity verification result, that is, the identity verification of the asset authorized user is successful, and then the identity verification result can be returned to the asset authorized user; when the user identity data When there is a problem, it means that the authentication result of the asset authorization user is the authentication failure result, that is, the authentication failure of the asset authorization user fails, and the authentication failure result can be returned to the asset authorization user.
请一并参见图4,图4是本申请实施例提供的一种用户授权用户的身份验证示意图。如图4所示,资产授权用户可以通过用户终端30a向被授权节点30d发送资产授权请求,被授权节点30d在接收到用户终端30a发送的资产授权请求之后,可以获取针对资产授权用户的身份验证方式(例如,人脸核身验证方式),并将该人脸核身验证方式返回至用户终端30a,在该用户终端30a的终端屏幕中可以显示人脸验证框30b。资产授权用户可以将人脸对准用户终端30a中的人脸验证框30b,并跟随指示执行相应的动作(例如,摇头、点头、眨眼等动作),用户终端30a可以实时采集人脸验证框30b中的待验证人脸图像30c,并将实时采集到的待验证人脸图像30c发送至被授权节点30d。Please refer to FIG. 4 together. FIG. 4 is a schematic diagram of an identity verification of a user authorized by a user according to an embodiment of the present application. As shown in FIG. 4 , the asset authorization user can send an asset authorization request to the authorized
被授权节点30d可以获取用户终端30a发送的待验证人脸图像30c,并获取资产授权用户的证件人脸图像30d,该证件人脸图像30d可以是指资产授权用户预先上传的用于表征真实身份的证件中的图像。被授权节点30d可以将待验证人脸图像30c与证件人脸图像30d进行相似度比较,当待验证人脸图像30c与证件人脸图像30d之间的相似度大于或等于相似度阈值(例如,相似度阈值可以设置为90%)时,可以确定资产授权用户的人脸核身合法;当待验证人脸图像30c与证件人脸图像30d之间的相似度小于相似度阈值时,可以确定资产授权用户的人脸核身非法,进而可以确定资产授权用户的身份验证结果为身份验证未通过结果,并向用户终端30a发送身份有误的提示信息。可选的,被授权节点30d还可以预先设置资产授权用户的有效验证时长,若资产授权用户的实际验证时长大于有效验证时长,则可以确定资产授权用户的身份验证结果为身份验证未通过结果,向用户终端30a发送身份有误的提示信息,此时的资产授权用户需要重新进行人脸核身验证,直至通过身份验证;若资产授权用户的实际验证时长小于或等于有效验证时长,且人脸核身合法,则可以确定资产授权用户的身份验证结果为身份验证通过结果,进而可以向用户终端30a返回身份无误的提示信息。The authorized
进一步地,当资产授权用户接收到被授权节点返回的身份验证结果为身份验证未通过结果时,可以向被授权节点重新上传用户身份信息进行身份验证;当资产授权用户接收到被授权节点返回的身份验证结果为身份验证通过结果时,可以使用自己的用户私钥生成证书签名,并将证书签名发送至被授权节点。Further, when the asset authorization user receives that the identity verification result returned by the authorized node is the identity verification failure result, the user identity information can be re-uploaded to the authorized node for identity verification; When the authentication result is a successful authentication result, you can use your own user private key to generate a certificate signature and send the certificate signature to the authorized node.
步骤S102,发送包含证书签名的证书颁发请求。Step S102, sending a certificate issuance request including a certificate signature.
具体的,被授权节点在接收到资产授权用户发送的证书签名后,可以在本地生成一个密钥对(包括被授权节点对应的第一节点公钥和第一节点私钥);被授权节点可以将第一节点公钥分配给其余节点(例如,被授权节点所属区块链中的区块链节点),第一节点私钥可以由自己保管。被授权节点可以使用第一节点私钥对自己的节点身份数据进行签名,并将签名后的节点身份数据、证书签名以及第一节点公钥发送至证书授权节点,同时向证书节点证书发送证书颁发请求,以请求该证书授权节点为其创建并颁发数字证书,其中,该节点身份信息可以包括被授权节点的名称、编号等信息。Specifically, after receiving the certificate signature sent by the asset authorization user, the authorized node can locally generate a key pair (including the first node public key and the first node private key corresponding to the authorized node); the authorized node can The public key of the first node is distributed to other nodes (for example, the blockchain nodes in the blockchain to which the authorized node belongs), and the private key of the first node can be kept by itself. The authorized node can use the private key of the first node to sign its own node identity data, and send the signed node identity data, certificate signature and public key of the first node to the certificate authority node, and at the same time send the certificate issuance to the certificate node certificate request to request the certificate authority node to create and issue a digital certificate for it, wherein the node identity information may include information such as the name and number of the authorized node.
步骤S103,根据证书颁发请求,为被授权节点颁发包含证书签名的被授权节点证书。Step S103, issue an authorized node certificate including a certificate signature to the authorized node according to the certificate issuance request.
具体的,证书授权节点在接收到被授权节点发送的证书颁发请求后,可以根据第一节点公钥对签名后的节点身份数据进行解密,并核实被授权节点的节点身份数据的有效性,同时,证书授权节点还可以获取资产授权用户的用户公钥,根据用户公钥对证书签名进行正确性验证,当证书授权节点检测到节点身份数据、第一节点公钥以及证书签名均没有问题时,可以为被授权节点颁发数字证书(即被授权节点证书)。换言之,证书授权节点为被授权节点颁发被授权节点证书的前提条件是:资产授权用户和被授权节点均通过证书授权节点的鉴定,资产授权用户对应的证书签名、被授权节点的节点身份信息以及被授权节点的第一节点公钥均没有问题时,表示资产授权用户和被授权节点都获得了证书授权节点的信任。Specifically, after receiving the certificate issuance request sent by the authorized node, the certificate authority node can decrypt the signed node identity data according to the public key of the first node, and verify the validity of the node identity data of the authorized node. , the certificate authority node can also obtain the user public key of the asset authorization user, and verify the correctness of the certificate signature according to the user public key. When the certificate authority node detects that the node identity data, the first node public key and the certificate signature are all correct, Digital certificates (ie, authorized node certificates) can be issued to authorized nodes. In other words, the prerequisites for the certificate authority node to issue the authorized node certificate to the authorized node are: both the asset authorized user and the authorized node have passed the authentication of the certificate authorized node, the certificate signature corresponding to the asset authorized user, the node identity information of the authorized node, and When there is no problem with the first node public key of the authorized node, it means that both the asset authorization user and the authorized node have obtained the trust of the certificate authorization node.
需要说明的是,证书授权节点所颁发的数字证书中的证书内容可以包括但不限于:对象名称(Subject Name)、证书颁发者(Issuer Name)、签名算法(SignatureAlgorithm)、序列号(Serial Number)、生效期(Not Valid Before)、失效期(Not ValidAfter)、公钥(Public Key)、签名(Signature)。其中,对象名称可以用于识别数字证书的信息;证书颁发者为发布并签署该数字证书的实体的信息;签名算法可以是指数字证书中的签名所使用的算法;序列号可以是指证书授权节点分配给数字证书的唯一标识,一个数字证书对应一个序列号;公钥可以是指数字证书持有者可公开的密钥;签名是指通过签名算法计算证书内容后得到的数据,可以用于验证数字证书是否被篡改。对于上述被授权节点证书而言,对象名称可以是指被授权节点的名称或编号(ID),证书颁发者可以为证书授权节点的名称或者编号,公钥可以是指被授权节点对应的第一节点公钥,签名可以包括证书授权节点使用自己的私钥(可以称为第二节点私钥)为证书内容所生成的签名,以及资产授权用户使用自己的用户私钥为证书内容生成的证书签名。It should be noted that the certificate content in the digital certificate issued by the certificate authority node may include but is not limited to: subject name (Subject Name), certificate issuer (Issuer Name), signature algorithm (SignatureAlgorithm), serial number (Serial Number) , Not Valid Before, Not ValidAfter, Public Key, Signature. Among them, the object name can be used to identify the information of the digital certificate; the certificate issuer is the information of the entity that issued and signed the digital certificate; the signature algorithm can refer to the algorithm used for the signature in the digital certificate; the serial number can refer to the certificate authority The unique identifier assigned by the node to the digital certificate, a digital certificate corresponds to a serial number; the public key can refer to the public key of the digital certificate holder; the signature refers to the data obtained by calculating the content of the certificate through the signature algorithm, which can be used for Verify that the digital certificate has not been tampered with. For the above-mentioned authorized node certificate, the object name may refer to the name or number (ID) of the authorized node, the certificate issuer may be the name or number of the certificate authorization node, and the public key may refer to the first corresponding to the authorized node. The public key of the node, the signature can include the signature generated by the certificate authority node using its own private key (which can be called the second node private key) for the content of the certificate, and the signature of the certificate generated by the asset authorization user using its own private key for the content of the certificate .
可选的,资产授权用户在收到身份验证通过结果后,可以向被授权节点申请为被授权节点证书进行签名,资产授权用户可以首先对被授权用户进行签名以生成证书签名,随后由被授权节点向证书授权节点发送携带证书签名的证书颁发请求,以获取包含证书签名和证书授权节点签名的被授权节点证书;或者被授权节点可以先从证书授权节点处获取被授权节点证书,进而获取资产授权用户根据用户私钥为被授权节点证书所生成的证书签名,使得最终得到的被授权节点证书包括上述证书签名和证书授权节点的数字签名。Optionally, after receiving the authentication result, the asset authorization user can apply to the authorized node to sign the certificate of the authorized node. The asset authorization user can first sign the authorized user to generate a certificate signature, and then the authorized user The node sends a certificate issuance request with the certificate signature to the certificate authority node to obtain the authorized node certificate containing the certificate signature and the certificate authority node signature; or the authorized node can obtain the authorized node certificate from the certificate authority node first, and then obtain the asset The authorized user signs the certificate generated by the authorized node certificate according to the user's private key, so that the finally obtained authorized node certificate includes the above-mentioned certificate signature and the digital signature of the certificate authority node.
步骤S104,返回被授权节点证书。Step S104, the authorized node certificate is returned.
具体的,证书授权节点可以将被授权节点证书返回给被授权节点,被授权节点在接收到被授权节点证书后,可以使用被授权节点证书来证明自己身份的合法性。Specifically, the certificate authority node can return the authorized node certificate to the authorized node, and after receiving the authorized node certificate, the authorized node can use the authorized node certificate to prove the legitimacy of its identity.
步骤S105,获取资产授权用户为被授权节点签署的授权合同;授权合同包含资产授权用户对应的用户签名和被授权节点对应的第一节点签名。Step S105, obtaining an authorization contract signed by the asset authorization user for the authorized node; the authorization contract includes the user signature corresponding to the asset authorization user and the first node signature corresponding to the authorized node.
具体的,在资产授权用户通过身份验证,且该资产授权用户为被授权节点证书生成证书签名之后,表明资产授权用户和被授权节点双方均认可了对方的身份,此时的资产授权用户可以为被授权节点签署初始授权合同,即被授权节点可以从资产授权用户处获取初始授权合同,该初始授权合同可以包括授权数据类型(也可以称为授权数据项,如税务数据类型、证券数据类型等)和资产授权用户根据用户私钥所生成的用户签名。被授权节点可以对接收到的初始授权合同进行验证(包括初始授权合同的验签和授权数据项的合法性等),当初始授权合同在传输过程中没有发生篡改,且该初始授权合同中的授权数据类型合法时,被授权节点可以使用第一节点私钥对初始授权合同进行签名以生成第一节点签名,将包含第一节点签名的初始授权合同确定为最终的授权合同。可以理解的是,授权合同还可以包括合同ID,该合同ID可以用于唯一标识授权合同。Specifically, after the asset-authorized user passes the identity verification and the asset-authorized user generates a certificate signature for the authorized node certificate, it indicates that both the asset-authorized user and the authorized node have recognized the identity of the other party. At this time, the asset-authorized user can be The authorized node signs the initial authorization contract, that is, the authorized node can obtain the initial authorization contract from the asset authorized user, and the initial authorization contract can include authorization data types (also called authorization data items, such as tax data types, securities data types, etc. ) and the user signature generated by the asset authorized user based on the user's private key. The authorized node can verify the received initial authorization contract (including the verification of the initial authorization contract and the validity of the authorization data items, etc.), when the initial authorization contract has not been tampered with during the transmission process, and the When the authorization data type is legal, the authorized node can use the first node private key to sign the initial authorization contract to generate the first node signature, and determine the initial authorization contract including the first node signature as the final authorization contract. It can be understood that the authorization contract may further include a contract ID, and the contract ID may be used to uniquely identify the authorization contract.
可选的,以企业征信领域为例,企业A可以作为数字资产持有者,即是资产授权用户,企业征信应用作为企业数字资产的使用者,即是被授权节点。企业征信应用可以对企业A进行身份验证,以确保该企业A为真实持有数字资产且具有授权权限的企业,在企业A通过身份验证后,企业A可以为企业征信应用的数字证书进行证书签名,并为企业征信应用签署初始授权合同,该初始授权合同可以包括授权数据类型(例如,企业开户账号、资产负债表、损益表、税务数据、社保数据等)和企业签名;企业征信应用在获取到初始授权合同,并对该初始授权合同进行核实后,可以为初始授权合同进行签名,作为企业和企业征信应用双方的最终授权合同。Optionally, taking the enterprise credit reporting field as an example, enterprise A can act as a holder of digital assets, that is, an authorized user of assets, and an enterprise credit reporting application, as a user of enterprise digital assets, is an authorized node. The enterprise credit application can authenticate enterprise A to ensure that enterprise A is an enterprise that actually holds digital assets and has authorization rights. Certificate signature, and sign the initial authorization contract for the enterprise credit reporting application. The initial authorization contract can include the authorization data type (for example, the enterprise account number, balance sheet, profit and loss statement, tax data, social security data, etc.) and enterprise signature; After the credit application obtains the initial authorization contract and verifies the initial authorization contract, it can sign the initial authorization contract as the final authorization contract for both the enterprise and the enterprise credit application.
步骤S106,将被授权节点证书和授权合同添加至被授权核心链,获取与被授权核心链相关联的跨链网关,将被授权节点证书和授权合同分配至跨链网关。Step S106, adding the authorized node certificate and authorization contract to the authorized core chain, obtaining the cross-chain gateway associated with the authorized core chain, and assigning the authorized node certificate and authorization contract to the cross-chain gateway.
具体的,被授权节点可以将被授权节点证书和授权合同封装为授权区块,将授权区块进行共识处理,当该授权区块满足共识合法性条件时,将该授权区块添加至被授权核心链,获取与该被授权核心链相关联的跨链网关,将授权区块的区块头数据分配至该跨链网关,其中,区块头数据用于指示被授权节点证书和授权合同在被授权核心链中的存储位置。被授权节点将被授权节点证书和授权合同封装为授权区块后,将在被授权节点所属的区块链系统中对该授权区块进行广播,当授权区块在被授权节点所属的区块链系统中达成共识时(如被授权节点所属的区块链系统中存在超过2/3的区块链节点通过了授权区块的验证),可以将该授权区块写入被授权核心链中,此处的被授权核心链可以理解为被授权节点所属的区块链系统共同维护的区块链。Specifically, the authorized node can encapsulate the authorized node certificate and the authorization contract into an authorized block, and perform consensus processing on the authorized block. When the authorized block satisfies the consensus legality conditions, the authorized block is added to the authorized block. The core chain, obtains the cross-chain gateway associated with the authorized core chain, and assigns the block header data of the authorized block to the cross-chain gateway, wherein the block header data is used to indicate that the authorized node certificate and authorization contract are authorized. The storage location in the core chain. After the authorized node encapsulates the authorized node certificate and authorization contract into an authorized block, it will broadcast the authorized block in the blockchain system to which the authorized node belongs. When the authorized block is in the block to which the authorized node belongs When a consensus is reached in the chain system (for example, more than 2/3 of the blockchain nodes in the blockchain system to which the authorized node belongs have passed the verification of the authorized block), the authorized block can be written into the authorized core chain , the authorized core chain here can be understood as the blockchain jointly maintained by the blockchain system to which the authorized nodes belong.
可选的,被授权节点证书和授权合同可以是被授权节点在不同时间获得的,因此被授权节点证书和授权合同可以分别封装成区块,并写入被授权核心链中。换言之,被授权节点证书和授权合同可以封装进同一个区块写入被授权核心链中,也可以封装进不同的区块写入被授权核心链中。Optionally, the authorized node certificate and the authorization contract can be obtained by the authorized node at different times, so the authorized node certificate and the authorization contract can be encapsulated into blocks respectively and written into the authorized core chain. In other words, the authorized node certificate and authorization contract can be encapsulated into the same block and written into the authorized core chain, or can be encapsulated into different blocks and written into the authorized core chain.
可选的,与被授权核心链相关联的跨链网关可以为一个或者多个,每个跨链网关均可以包括被授权核心链与其余区块链所对应的轻量节点,即可以获取与被授权核心链相关联的至少两个跨链网关,分别在至少两个跨链网关中确定被授权核心链对应的被授权轻量节点,并将授权区块的区块头数据分配给被授权轻量节点。换言之,将被授权节点证书和授权合同写入被授权核心链后,该授权核心链部署在各个跨链网关中的被授权轻量节点均可以获取被授权节点证书和授权合同。Optionally, there may be one or more cross-chain gateways associated with the authorized core chain, and each cross-chain gateway may include lightweight nodes corresponding to the authorized core chain and other At least two cross-chain gateways associated with the authorized core chain, determine the authorized lightweight nodes corresponding to the authorized core chain in the at least two cross-chain gateways respectively, and assign the block header data of the authorized block to the authorized lightweight nodes. quantity node. In other words, after writing the authorized node certificate and authorization contract into the authorized core chain, the authorized lightweight nodes deployed in each cross-chain gateway of the authorized core chain can obtain the authorized node certificate and authorization contract.
请一并参见图5,图5是本申请实施例提供的一种授权区块上链过程的示意图。如图5所示,被授权节点40a在获得被授权节点证书和授权合同后,可以将被授权节点证书和授权合同分别作为交易封装进授权区块40b中,被授权节点40a可以在自身所在的区块链系统中,对授权区块40b进行广播,以使该区块链系统中的共识节点对该授权节点40b进行共识处理。当授权区块40b在该区块链系统中达成共识后,可以将授权区块40b添加至被授权核心链40c。Please refer to FIG. 5 together. FIG. 5 is a schematic diagram of an authorization block on-chain process provided by an embodiment of the present application. As shown in FIG. 5 , after obtaining the authorized node certificate and the authorization contract, the authorized
在授权区块40b添加至被授权核心链40c后,可以将授权区块40b中所存储的被授权节点证书和授权合同,清分至被授权核心链40c部署在各跨链网关中的轻量节点。如图5所示,被授权核心链40c可以分别与资产核心链1、资产核心链2、资产核心链3以及资产核心链4建立跨链网关,被授权核心链40c可以在跨链网关40d中部署轻量节点1,资产核心链1可以在跨链网关40d中部署轻量节点2,被授权核心链40c和资产核心链1可以通过跨链网关40d进行数据传输;被授权核心链40c可以在跨链网关40e中部署轻量节点3,资产核心链2可以在跨链网关40e中部署轻量节点4,被授权核心链40c和资产核心链2可以通过跨链网关40e进行数据传输;被授权核心链40c可以在跨链网关40f中部署轻量节点5,资产核心链3可以在跨链网关40f中部署轻量节点6,被授权核心链40c和资产核心链3可以通过跨链网关40f进行数据传输;被授权核心链40c可以在跨链网关40g中部署轻量节点7,资产核心链4可以在跨链网关40g中部署轻量节点8,被授权核心链40c和资产核心链4可以通过跨链网关40g进行数据传输。其中,轻量节点1、轻量节点3、轻量节点5以及轻量节点7可以称为被授权轻量节点,轻量节点2、轻量节点4、轻量节点6以及轻量节点8可以称为资产轻量节点。After the
步骤S107,发送针对资产授权用户的数据获取请求。Step S107, sending a data acquisition request for the asset authorized user.
具体的,被授权节点将被授权节点证书和授权合同添加至被授权核心链后,可以通过跨链网关向资产核心链获取与资产授权用户相关联的目标资产数据。当被授权节点想要从资产核心链中获取目标资产数据时,被授权节点可以向资产核心链部署在跨链网关中的资产轻量节点发送针对资产授权用户的数据获取请求,该数据获取请求用于指示在资产核心链中获取与资产授权用户相关联的目标资产数据。Specifically, after the authorized node adds the authorized node certificate and the authorization contract to the authorized core chain, it can obtain the target asset data associated with the asset authorized user from the asset core chain through the cross-chain gateway. When the authorized node wants to obtain the target asset data from the asset core chain, the authorized node can send a data acquisition request for the asset authorized user to the asset lightweight node deployed in the asset core chain in the cross-chain gateway, the data acquisition request. It is used to instruct to obtain the target asset data associated with the asset authorized user in the asset core chain.
步骤S108,获取被授权节点证书和授权合同,根据证书签名、用户签名以及第一节点签名,获取被授权节点证书和授权合同对应的数据验证结果。Step S108: Obtain the authorized node certificate and the authorization contract, and obtain the data verification result corresponding to the authorized node certificate and the authorization contract according to the certificate signature, the user signature and the first node signature.
具体的,资产轻量节点在接收到被授权节点发送的数据获取请求后,可以根据数据获取请求,在资产轻量节点所在的跨链网关中确定被授权节点对应的被授权轻量节点;通过被授权轻量节点在被授权节点对应的被授权核心链中获取被授权节点对应的被授权节点证书,以及资产授权用户为被授权节点签署的授权合同。换言之,资产轻量节点可以通过被授权核心链对应的被授权轻量节点,获取被授权节点对应的被授权节点证书和资产授权用户为被授权节点签署的授权合同。Specifically, after receiving the data acquisition request sent by the authorized node, the asset lightweight node can determine the authorized lightweight node corresponding to the authorized node in the cross-chain gateway where the asset lightweight node is located according to the data acquisition request; The authorized lightweight node obtains the authorized node certificate corresponding to the authorized node and the authorization contract signed by the asset authorization user for the authorized node in the authorized core chain corresponding to the authorized node. In other words, the asset lightweight node can obtain the authorized node certificate corresponding to the authorized node and the authorization contract signed by the asset authorization user for the authorized node through the authorized lightweight node corresponding to the authorized core chain.
进一步地,资产轻量节点可以获取资产授权用户对应的授权用户证书,以及证书授权节点对应的根证书,在被授权节点证书中获取被授权节点对应的第一节点公钥,在根证书中获取证书授权节点的第二节点公钥;若根据第二节点公钥检测到授权用户证书满足合法性条件,则在授权用户证书中获取资产授权用户的用户公钥;根据用户公钥对证书签名进行合法性验证,生成证书签名对应的第一签名验证结果,根据第二节点公钥对被授权节点证书中所携带的第二节点签名进行合法性验证,生成第二节点签名对应的第二签名验证结果;第二节点签名为根据证书授权节点的第二节点私钥所生成的数字签名;根据第一签名验证结果和第二签名验证结果,生成被授权节点证书对应的数据验证结果;根据第一节点公钥对第一节点签名进行合法性验证,生成第一节点签名对应的第三签名验证结果,根据用户公钥对用户签名进行合法性验证,生成用户签名对应的第四签名验证结果;根据第三签名验证结果和第四签名验证结果,生成授权合同对应的数据验证结果。Further, the asset lightweight node can obtain the authorized user certificate corresponding to the asset authorized user, and the root certificate corresponding to the certificate authorization node, obtain the public key of the first node corresponding to the authorized node in the authorized node certificate, and obtain in the root certificate. The second node public key of the certificate authority node; if it is detected that the authorized user certificate meets the validity conditions according to the second node public key, the user public key of the asset authorized user is obtained from the authorized user certificate; the certificate signature is performed according to the user public key. Legality verification, generating a first signature verification result corresponding to the certificate signature, verifying the legality of the second node signature carried in the authorized node certificate according to the second node public key, and generating a second signature verification corresponding to the second node signature Result; the second node signature is a digital signature generated according to the private key of the second node of the certificate authority node; according to the first signature verification result and the second signature verification result, the data verification result corresponding to the authorized node certificate is generated; The node public key verifies the validity of the signature of the first node, generates a third signature verification result corresponding to the signature of the first node, and verifies the validity of the user's signature according to the user's public key, and generates a fourth signature verification result corresponding to the user's signature; The third signature verification result and the fourth signature verification result generate the data verification result corresponding to the authorization contract.
可以理解地,被授权节点证书可以携带资产授权用户签署的证书签名和证书授权节点的签名(可以称为第二节点签名),授权合同可以携带资产授权用户的用户签名和被授权节点的第一节点签名,在对被授权节点证书和授权合同的验证过程中,需要对证书签名、第二节点签名、用户签名以及第一节点签名进行正确性验证,当然,还可以对被授权节点证书的证书序列号、有效期限等证书内容进行验证。若被授权节点证书中所携带的证书签名和第二节点签名均正确,且被授权节点证书中的证书内容均无误,则可以确定被授权节点证书的数据验证结果为数据验证通过结果;若被授权节点证书中所携带的证书签名和第二节点签名任一个存在问题,则可以确定被授权节点证书的数据验证结果为数据验证未通过结果。若授权合同中所携带的用户签名和第一节点签名均正确,则可以确定授权合同的数据验证结果为数据验证通过结果;若授权合同中所携带的用户签名和第一节点签名任一个存在错误,则可以确定授权合同的数据验证结果为数据验证未通过结果。Understandably, the authorized node certificate can carry the certificate signature signed by the asset authorized user and the signature of the certificate authorized node (which can be called the second node signature), and the authorization contract can carry the user signature of the asset authorized user and the first authorized node. Node signature. During the verification process of the authorized node certificate and the authorization contract, it is necessary to verify the correctness of the certificate signature, the second node signature, the user signature and the first node signature. Of course, the certificate of the authorized node certificate can also be verified. The content of the certificate such as serial number and expiration date is verified. If the certificate signature carried in the authorized node certificate and the signature of the second node are correct, and the content of the certificate in the authorized node certificate is correct, it can be determined that the data verification result of the authorized node certificate is the data verification result; If there is a problem with either the certificate signature carried in the certificate of the authorized node or the signature of the second node, it can be determined that the data verification result of the authorized node certificate is a data verification failure result. If both the user signature and the first node signature carried in the authorization contract are correct, it can be determined that the data verification result of the authorization contract is the data verification pass result; if there is an error in either the user signature or the first node signature carried in the authorization contract , it can be determined that the data verification result of the authorization contract is the data verification failure result.
请一并参见图6,图6是本申请实施例提供的一种授权合同的验证示意图。如图6所示,资产轻量节点可以从证书授权节点获取根证书50a,并获取资产授权用户对应的授权用户证书,该根证书50a可以包括证书授权节点名称、证书授权节点公钥(可以称为第二公钥)以及数字签名1等信息,该数字签名1为证书授权节点的自签名;授权用户证书50b可以包括证书编号、资产授权用户标识、资产授权用户公钥(可以称为用户公钥)以及证书授权节点签名(可以称为第二节点签名)等信息,资产授权用户标识可以是指证书授权节点为资产授权用户统一分配的编号;授权合同50c可以包括合同标识、授权数据项、被授权节点签名(可以称为第一节点签名)以及资产授权用户签名(可以称为用户签名)等信息,授权数据项可以是指资产授权用户为被授权节点所授权的数据类型。Please refer to FIG. 6 together. FIG. 6 is a schematic diagram of verification of an authorization contract provided by an embodiment of the present application. As shown in FIG. 6, the asset lightweight node can obtain the
资产轻量节点可以使用根证书50a中的证书授权节点公钥,对授权用户证书50b中的证书授权节点签名进行合法性验证,证书授权节点签名验证通过后,可以使用授权用户证书50b中的资产授权用户公钥,对授权合同50c中的资产授权用户签名进行合法性验证,资产授权用户签名验证通过后,资产轻量节点可以使用被授权节点的第一节点公钥,对授权合同50c中的被授权节点签名进行合法性验证。当被授权节点签名和资产授权用户签名均通过验证时,可以确定授权合同50c的数据验证结果为数据验证通过结果。The asset lightweight node can use the certificate authority node public key in the
步骤S109,当数据验证结果为数据验证通过结果时,在资产轻量节点对应的资产核心链中,获取资产授权用户对应的目标资产数据。Step S109, when the data verification result is the data verification pass result, acquire the target asset data corresponding to the asset authorized user in the asset core chain corresponding to the asset lightweight node.
具体的,当数据验证结果为数据验证通过结果时,资产轻量节点可以将被授权节点证书和授权合同添加至资产轻量节点对应的资产核心链;与此同时,资产轻量节点可以获取资产授权用户对应的用户标识(也可以称为资产授权用户标识),在资产核心链中查询与用户标识相匹配的候选资产数据,进而在授权合同中获取资产授权用户对应的授权数据类型,将属于授权资产类型的候选资产数据,确定为资产授权用户对应的目标资产数据。例如,在企业征信领域中,用户标识可以是指企业(资产授权用户)的纳税识别号,也可以为其余编号,通过纳税识别号在资产核心链中查询与企业相关联的税务数据。Specifically, when the data verification result is the data verification pass result, the asset lightweight node can add the authorized node certificate and the authorization contract to the asset core chain corresponding to the asset lightweight node; at the same time, the asset lightweight node can obtain the asset The user ID corresponding to the authorized user (also known as the asset authorization user ID), query the candidate asset data matching the user ID in the asset core chain, and then obtain the authorization data type corresponding to the asset authorization user in the authorization contract, which will belong to The candidate asset data of the authorized asset type is determined as the target asset data corresponding to the asset authorized user. For example, in the field of enterprise credit reporting, the user ID can refer to the tax identification number of the enterprise (asset authorized user), or it can be other numbers. The tax identification number can be used to query the tax data associated with the enterprise in the asset core chain.
步骤S110,通过资产轻量节点所属的跨链网关返回目标资产数据。In step S110, the target asset data is returned through the cross-chain gateway to which the asset lightweight node belongs.
具体的,资产轻量节点可以通过跨链网关,向被授权节点返回资产授权用户对应的目标资产数据。可以理解地,被授权节点可以从多个资产核心链中获取与资产授权用户相关联的不同类型的目标资产数据。Specifically, the asset lightweight node can return the target asset data corresponding to the asset authorized user to the authorized node through the cross-chain gateway. Understandably, an authorized node can acquire different types of target asset data associated with asset authorized users from multiple asset core chains.
举例来说,以企业征信领域为例,企业A可以作为数字资产持有者,即是资产授权用户,企业征信应用作为企业数字资产的使用者,即是被授权节点。企业征信应用可以通过跨链网关从社保数据核心链、税务数据核心链以及金融数据核心链等区块链中,获取企业A对应的不同类型的数据;根据不同类型的数据,可以评估企业A的征信情况。For example, taking the enterprise credit reporting field as an example, enterprise A can act as a digital asset holder, that is, an authorized user of assets, and an enterprise credit reporting application, as a user of enterprise digital assets, is an authorized node. The enterprise credit application can obtain different types of data corresponding to enterprise A from the social security data core chain, tax data core chain, financial data core chain and other blockchains through the cross-chain gateway; according to different types of data, enterprise A can be evaluated of credit information.
请一并参见图7,图7是本申请实施例提供的一种获取目标资产数据的示意图。如图7所示,被授权节点60a可以通过跨链网关60b向资产轻量节点发送数据获取请求,资产轻量节点在接收到数据获取请求之后,可以从跨链网关60b中的被授权轻量节点处获取被授权节点证书和授权合同,进而可以对被授权节点证书和授权合同进行验证,若被授权节点证书和授权合同验证通过,则可以将授权节点证书和授权合同打包成授权区块进行上链,并从资产轻量节点对应的资产核心链60c中查询与资产授权用户相关联的目标资产数据,通过跨链网关60b将目标资产数据返回至被授权节点60a;若被授权节点证书和授权合同验证未通过,则向被授权节点返回数据获取失败的提示信息。Please refer to FIG. 7 together. FIG. 7 is a schematic diagram of acquiring target asset data according to an embodiment of the present application. As shown in FIG. 7 , the authorized
本申请实施例中,可以通过证书授权节点对被授权节点和授权合同进行权威认证,实现资产授权用户对被授权节点的资产授权,根据被授权节点和授权合同,被授权核心链和资产核心链之间可以通过跨链网关进行信任数据传输,可以提高跨链信任传输中的授权验证效率;资产授权用户对被授权节点进行数据授权,达到一次授权,多个资产核心链使用的目的,可以提高授权效率。In the embodiment of the present application, the authorized node and the authorization contract can be authoritatively authenticated by the certificate authorization node, so as to realize the asset authorization of the authorized node by the asset authorization user. According to the authorized node and the authorization contract, the authorized core chain and the asset core chain The trust data transmission can be carried out through the cross-chain gateway, which can improve the authorization verification efficiency in the cross-chain trust transmission; the asset authorization user authorizes the data of the authorized node to achieve the purpose of one authorization and the use of multiple asset core chains, which can improve the Authorization Efficiency.
请参见图8,图8是本申请实施例提供的一种基于数字证书认证的跨链信任装置的结构示意图。该基于数字证书认证的跨链信任装置可以是运行于被授权节点中的一个计算机程序(包括程序代码),该装置可以用于执行图3所对应实施例提供的方法中的相应步骤。如图8所示,基于数字证书认证的跨链信任装置1可以包括:证书申请模块11,第一获取模块12,添加模块13,第一发送模块14,第一接收模块15;Please refer to FIG. 8. FIG. 8 is a schematic structural diagram of a cross-chain trust device based on digital certificate authentication provided by an embodiment of the present application. The cross-chain trust device based on digital certificate authentication may be a computer program (including program code) running in an authorized node, and the device may be used to execute corresponding steps in the method provided by the embodiment corresponding to FIG. 3 . As shown in FIG. 8 , the cross-chain trust device 1 based on digital certificate authentication may include: a
证书申请模块11,用于当资产授权用户的身份验证成功时,获取资产授权用户对应的证书签名,向证书授权节点发送包含证书签名的证书颁发请求,以使证书授权节点根据证书颁发请求,为被授权节点颁发包含证书签名的被授权节点证书;The
第一获取模块12,用于接收证书授权节点返回的被授权节点证书,获取资产授权用户为被授权节点签署的授权合同;授权合同包含资产授权用户对应的用户签名和被授权节点对应的第一节点签名;The first obtaining
添加模块13,用于将被授权节点证书和授权合同添加至被授权核心链,获取与被授权核心链相关联的跨链网关,将被授权节点证书和授权合同分配至跨链网关;The adding
第一发送模块14,用于向跨链网关中的资产轻量节点发送针对资产授权用户的数据获取请求,以使资产轻量节点根据被授权节点证书和授权合同的数据验证结果,在资产轻量节点对应的资产核心链中,获取资产授权用户对应的目标资产数据;The
第一接收模块15,用于通过跨链网关接收资产轻量节点返回的目标资产数据。The
其中,证书申请模块11,第一获取模块12,添加模块13,第一发送模块14,第一接收模块15的具体功能实现方式可以参见上述图3所对应实施例中的步骤S101-步骤S107以及步骤S110,这里不再进行赘述。Among them, for the specific function implementation of the
请一并参见图8,基于数字证书认证的跨链信任装置1还可以包括:用户身份验证模块16,身份确定模块17;Please refer to FIG. 8 together, the cross-chain trust device 1 based on digital certificate authentication may further include: a user
用户身份验证模块16,用于接收资产授权用户的资产授权请求,根据资产授权请求获取与资产授权用户相关联的用户身份数据,对用户身份数据进行验证得到资产授权用户的身份验证结果;The user
身份确定模块17,用于当身份验证结果为身份验证通过结果时,确定资产授权用户的身份验证成功;The
上述身份确定模块17,还用于当身份验证结果为身份验证未通过结果时,确定资产授权用户的身份验证失败。The above-mentioned
其中,用户身份验证模块16,身份确定模块17的具体功能实现方式可以参见上述图3所对应实施例中的步骤S101,这里不再进行赘述。The specific function implementation manner of the user
请一并参见图8,证书申请模块11可以包括:验证结果发送单元111,颁发请求生成单元112,颁发请求发送单元113;Please refer to FIG. 8 together, the
验证结果发送单元111,用于当资产授权用户的身份验证成功时,向资产授权用户返回身份验证通过结果;The verification
颁发请求生成子单元112,用于接收基于用户私钥所生成的证书签名,根据被授权节点对应的节点身份数据和证书签名生成证书颁发请求;用户私钥是指资产授权用户对应的私钥;The issuance
颁发请求发送单元113,用于向证书授权节点发送证书颁发请求,以使证书授权节点根据节点身份信息和证书签名的验证结果,为被授权节点颁发包含证书签名的被授权节点证书。The issuance
其中,验证结果发送单元111,颁发请求生成单元112,颁发请求发送单元113的具体功能实现方式可以参见上述图3所对应实施例中的步骤S102-步骤S104,这里不再进行赘述。The specific function implementation of the verification
请一并参见图8,第一获取模块12可以包括:初始合同获取单元121,授权合同确定单元122;Please refer to FIG. 8 together, the
初始合同获取单元121,用于获取资产授权用户为被授权节点签署的初始授权合同;初始授权合同包括授权数据类型和资产授权用户根据用户私钥生成的用户签名;The initial
授权合同确定单元122,用于根据被授权节点对应的第一节点私钥,生成初始授权合同对应的第一节点签名,将包含第一节点签名的初始授权合同确定为授权合同。The authorization
其中,初始合同获取单元121,授权合同确定单元122的具体功能实现方式可以参见上述图3所对应实施例中的步骤S105,这里不再进行赘述。The specific function implementation manner of the initial
请一并参见图8,添加模块13可以包括:共识处理单元131,第一记账单元132,分配单元133;Please refer to FIG. 8 together, the adding
共识处理单元131,用于将被授权节点证书和授权合同封装为授权区块,将授权区块进行共识处理;The
第一记账单元132,用于当授权区块满足共识合法性条件时,将授权区块添加至被授权核心链;The
分配单元133,用于获取与被授权核心链相关联的跨链网关,将授权区块的区块头数据分配至跨链网关;区块头数据用于指示被授权节点证书和授权合同在被授权核心链中的存储位置。The
其中,跨链网关的数量为至少两个;Among them, the number of cross-chain gateways is at least two;
分配单元133可以具体用于:The
获取与被授权核心链相关联的至少两个跨链网关,分别在至少两个跨链网关中确定被授权核心链对应的被授权轻量节点,将授权区块的区块头数据分配给被授权轻量节点。Obtain at least two cross-chain gateways associated with the authorized core chain, determine the authorized lightweight nodes corresponding to the authorized core chain in the at least two cross-chain gateways respectively, and assign the block header data of the authorized block to the authorized light-weight nodes. Lightweight Node.
其中,共识处理单元131,第一记账单元132,分配单元133的具体功能实现方式可以参见上述图3所对应实施例中的步骤S106,这里不再进行赘述。The specific functions of the
本申请实施例中,可以通过证书授权节点对被授权节点和授权合同进行权威认证,实现资产授权用户对被授权节点的资产授权,根据被授权节点和授权合同,被授权核心链和资产核心链之间可以通过跨链网关进行信任数据传输,可以提高跨链信任传输中的授权验证效率;资产授权用户对被授权节点进行数据授权,达到一次授权,多个资产核心链使用的目的,可以提高授权效率。In the embodiment of the present application, the authorized node and the authorization contract can be authoritatively authenticated by the certificate authorization node, so as to realize the asset authorization of the authorized node by the asset authorization user. According to the authorized node and the authorization contract, the authorized core chain and the asset core chain The trust data transmission can be carried out through the cross-chain gateway, which can improve the authorization verification efficiency in the cross-chain trust transmission; the asset authorization user authorizes the data of the authorized node to achieve the purpose of one authorization and the use of multiple asset core chains, which can improve the Authorization Efficiency.
请参见图9,图9是本申请实施例提供的一种基于数字证书认证的跨链信任装置的结构示意图。该基于数字证书认证的跨链信任装置可以是运行于资产轻量节点中的一个计算机程序(包括程序代码),该装置可以用于执行图3所对应实施例提供的方法中的相应步骤。如图9所示,基于数字证书认证的跨链信任装置2可以包括:第二接收模块21,验证模块22,第二获取模块23,第二发送模块24;Please refer to FIG. 9. FIG. 9 is a schematic structural diagram of a cross-chain trust device based on digital certificate authentication provided by an embodiment of the present application. The cross-chain trust device based on digital certificate authentication may be a computer program (including program code) running in the asset lightweight node, and the device may be used to execute the corresponding steps in the method provided by the embodiment corresponding to FIG. 3 . As shown in FIG. 9 , the
第二接收模块21,用于接收被授权节点发送的针对资产授权用户的数据获取请求,根据数据获取请求获取被授权节点对应的被授权节点证书,以及资产授权用户为被授权节点签署的授权合同;被授权节点证书是指证书授权节点为被授权节点颁发的数字证书,被授权节点证书包含资产授权用户对应的证书签名,授权合同包含资产授权用户对应的用户签名和被授权节点对应的第一节点签名;The
验证模块22,用于根据证书签名、用户签名以及第一节点签名,获取被授权节点证书和授权合同对应的数据验证结果;The
第二获取模块23,用于当数据验证结果为数据验证通过结果时,在资产轻量节点对应的资产核心链中,获取资产授权用户对应的目标资产数据;The second obtaining
第二发送模块24,用于通过资产轻量节点所属的跨链网关,向被授权节点返回目标资产数据。The
其中,第二接收模块21,验证模块22,第二获取模块23,第二发送模块24的具体功能实现方式可以参见上述图3所对应实施例中的步骤S107-步骤S110,这里不再进行赘述。Wherein, for the specific function implementation manner of the
请一并参见图9,第二接收模块21可以包括:获取请求接收单元211,授权合同获取单元212;Please refer to FIG. 9 together, the
获取请求接收单元211,用于接收被授权节点发送的针对资产授权用户的数据获取请求,根据数据获取请求,在资产轻量节点所在的跨链网关中确定被授权节点对应的被授权轻量节点;The acquisition
授权合同获取单元212,用于通过被授权轻量节点,在被授权节点对应的被授权核心链中获取被授权节点对应的被授权节点证书,以及资产授权用户为被授权节点签署的授权合同。The authorization
其中,获取请求接收单元211,授权合同获取单元212的具体功能实现方式可以参见上述图3所对应实施例中的步骤S108,这里不再进行赘述。The specific function implementation manner of the acquisition
请一并参见图9,验证模块22可以包括:证书获取单元221,用户公钥获取单元222,第一合法性验证单元223,证书验证结果生成单元224,第二合法性验证单元225,合同验证结果生成单元226;Please refer to FIG. 9 together, the
证书获取单元221,用于获取资产授权用户对应的授权用户证书,以及证书授权节点对应的根证书,在被授权节点证书中获取被授权节点对应的第一节点公钥,在根证书中获取证书授权节点的第二节点公钥;The
用户公钥获取单元222,用于若根据第二节点公钥检测到授权用户证书满足合法性条件,则在授权用户证书中获取资产授权用户的用户公钥;The user public
第一合法性验证单元223,用于根据用户公钥对证书签名进行合法性验证,生成证书签名对应的第一签名验证结果,根据第二节点公钥对被授权节点证书中所包含的第二节点签名进行合法性验证,生成第二节点签名对应的第二签名验证结果;第二节点签名为根据证书授权节点的第二节点私钥所生成的数字签名;The first
证书验证结果生成单元224,用于根据第一签名验证结果和第二签名验证结果,生成被授权节点证书对应的数据验证结果;The certificate verification
第二合法性验证单元225,用于根据第一节点公钥对第一节点签名进行合法性验证,生成第一节点签名对应的第三签名验证结果,根据用户公钥对用户签名进行合法性验证,生成用户签名对应的第四签名验证结果;The second
合同验证结果生成单元226,用于根据第三签名验证结果和第四签名验证结果,生成授权合同对应的数据验证结果。The contract verification
其中,证书获取单元221,用户公钥获取单元222,第一合法性验证单元223,证书验证结果生成单元224,第二合法性验证单元225,合同验证结果生成单元226的具体功能实现方式可以参见上述图3所对应实施例中的步骤S108,这里不再进行赘述。Among them, the
请一并参见图9,第二获取模块23可以包括:第二记账单元231,数据查询单元232,数据选取单元233;Please refer to FIG. 9 together, the
第二记账单元231,用于当数据验证结果为数据验证通过结果时,将被授权节点证书和授权合同添加至资产轻量节点对应的资产核心链;The
数据查询单元232,用于获取资产授权用户对应的用户标识,在资产核心链中查询与用户标识相匹配的候选资产数据;The data query
数据选取单元233,用于在授权合同中获取资产授权用户对应的授权数据类型,将属于授权资产类型的候选资产数据,确定为资产授权用户对应的目标资产数据。The
其中,第二记账单元231,数据查询单元232,数据选取单元233的具体功能实现方式可以参见上述图3所对应实施例中的步骤S109,这里不再进行赘述。The specific function implementation manner of the
本申请实施例中,可以通过证书授权节点对被授权节点和授权合同进行权威认证,实现资产授权用户对被授权节点的资产授权,根据被授权节点和授权合同,被授权核心链和资产核心链之间可以通过跨链网关进行信任数据传输,可以提高跨链信任传输中的授权验证效率;资产授权用户对被授权节点进行数据授权,达到一次授权,多个资产核心链使用的目的,可以提高授权效率。In the embodiment of the present application, the authorized node and the authorization contract can be authoritatively authenticated by the certificate authorization node, so as to realize the asset authorization of the authorized node by the asset authorization user. According to the authorized node and the authorization contract, the authorized core chain and the asset core chain The trust data transmission can be carried out through the cross-chain gateway, which can improve the authorization verification efficiency in the cross-chain trust transmission; the asset authorization user authorizes the data of the authorized node to achieve the purpose of one authorization and the use of multiple asset core chains, which can improve the Authorization Efficiency.
请参见图10,图10是本申请实施例提供的一种计算机设备的结构示意图。如图10所示,该计算机设备1000可以包括:处理器1001,网络接口1004和存储器1005,此外,上述计算机设备1000还可以包括:用户接口1003,和至少一个通信总线1002。其中,通信总线1002用于实现这些组件之间的连接通信。其中,用户接口1003可以包括显示屏(Display)、键盘(Keyboard),可选用户接口1003还可以包括标准的有线接口、无线接口。可选的,网络接口1004可以包括标准的有线接口、无线接口(如WI-FI接口)。存储器1005可以是高速RAM存储器,也可以是非不稳定的存储器(non-volatile memory),例如至少一个磁盘存储器。可选的,存储器1005还可以是至少一个位于远离前述处理器1001的存储装置。如图10所示,作为一种计算机可读存储介质的存储器1005中可以包括操作系统、网络通信模块、用户接口模块以及设备控制应用程序。Please refer to FIG. 10. FIG. 10 is a schematic structural diagram of a computer device provided by an embodiment of the present application. As shown in FIG. 10 , the
在如图10所示的计算机设备1000中,网络接口1004可提供网络通讯功能;而用户接口1003主要用于为用户提供输入的接口;而处理器1001可以用于调用存储器1005中存储的设备控制应用程序,以实现:In the
当资产授权用户的身份验证成功时,获取资产授权用户对应的证书签名,向证书授权节点发送包含证书签名的证书颁发请求,以使证书授权节点根据证书颁发请求,为被授权节点颁发包含证书签名的被授权节点证书;When the identity verification of the asset authorization user is successful, the certificate signature corresponding to the asset authorization user is obtained, and a certificate issuance request containing the certificate signature is sent to the certificate authority node, so that the certificate authority node can issue a certificate containing the certificate signature to the authorized node according to the certificate issuance request. the authorized node certificate;
接收证书授权节点返回的被授权节点证书,获取资产授权用户为被授权节点签署的授权合同;授权合同包含资产授权用户对应的用户签名和被授权节点对应的第一节点签名;Receive the authorized node certificate returned by the certificate authorization node, and obtain the authorization contract signed by the asset authorization user for the authorized node; the authorization contract includes the user signature corresponding to the asset authorization user and the first node signature corresponding to the authorized node;
将被授权节点证书和授权合同添加至被授权核心链,获取与被授权核心链相关联的跨链网关,将被授权节点证书和授权合同分配至跨链网关;Add the authorized node certificate and authorization contract to the authorized core chain, obtain the cross-chain gateway associated with the authorized core chain, and assign the authorized node certificate and authorization contract to the cross-chain gateway;
向跨链网关中的资产轻量节点发送针对资产授权用户的数据获取请求,以使资产轻量节点根据被授权节点证书和授权合同的数据验证结果,在资产轻量节点对应的资产核心链中,获取资产授权用户对应的目标资产数据;Send the data acquisition request for the asset authorized user to the asset lightweight node in the cross-chain gateway, so that the asset lightweight node can be stored in the asset core chain corresponding to the asset lightweight node according to the authorized node certificate and the data verification result of the authorization contract. , to obtain the target asset data corresponding to the asset authorized user;
通过跨链网关接收资产轻量节点返回的目标资产数据。Receive the target asset data returned by the asset lightweight node through the cross-chain gateway.
应当理解,本申请实施例中所描述的计算机设备1000可执行前文图3所对应实施例中对基于数字证书认证的跨链信任方法的描述,也可执行前文图8所对应实施例中对基于数字证书认证的跨链信任装置1的描述,在此不再赘述。另外,对采用相同方法的有益效果描述,也不再进行赘述。It should be understood that the
请参见图11,图11是本申请实施例提供的一种计算机设备的结构示意图。如图11所示,该计算机设备2000可以包括:处理器2001,网络接口2004和存储器2005,此外,上述计算机设备2000还可以包括:用户接口2003,和至少一个通信总线2002。其中,通信总线2002用于实现这些组件之间的连接通信。其中,用户接口2003可以包括显示屏(Display)、键盘(Keyboard),可选用户接口2003还可以包括标准的有线接口、无线接口。网络接口2004可选的可以包括标准的有线接口、无线接口(如WI-FI接口)。存储器2005可以是高速RAM存储器,也可以是非不稳定的存储器(non-volatile memory),例如至少一个磁盘存储器。存储器2005可选的还可以是至少一个位于远离前述处理器2001的存储装置。如图11所示,作为一种计算机可读存储介质的存储器2005中可以包括操作系统、网络通信模块、用户接口模块以及设备控制应用程序。Referring to FIG. 11 , FIG. 11 is a schematic structural diagram of a computer device provided by an embodiment of the present application. As shown in FIG. 11 , the
在如图11所示的计算机设备2000中,网络接口2004可提供网络通讯功能;而用户接口2003主要用于为用户提供输入的接口;而处理器2001可以用于调用存储器2005中存储的设备控制应用程序,以实现:In the
接收被授权节点发送的针对资产授权用户的数据获取请求,根据数据获取请求获取被授权节点对应的被授权节点证书,以及资产授权用户为被授权节点签署的授权合同;被授权节点证书是指证书授权节点为被授权节点颁发的数字证书,被授权节点证书包含资产授权用户对应的证书签名,授权合同包含资产授权用户对应的用户签名和被授权节点对应的第一节点签名;Receive the data acquisition request sent by the authorized node for the asset authorized user, obtain the authorized node certificate corresponding to the authorized node according to the data acquisition request, and the authorization contract signed by the asset authorized user for the authorized node; the authorized node certificate refers to the certificate The authorized node is a digital certificate issued by the authorized node, the authorized node certificate contains the certificate signature corresponding to the asset authorized user, and the authorization contract contains the user signature corresponding to the asset authorized user and the first node signature corresponding to the authorized node;
根据证书签名、用户签名以及第一节点签名,获取被授权节点证书和授权合同对应的数据验证结果;Obtain the data verification result corresponding to the authorized node certificate and the authorization contract according to the certificate signature, the user signature and the first node signature;
当数据验证结果为数据验证通过结果时,在资产轻量节点对应的资产核心链中,获取资产授权用户对应的目标资产数据;When the data verification result is the data verification pass result, obtain the target asset data corresponding to the asset authorized user in the asset core chain corresponding to the asset lightweight node;
通过资产轻量节点所属的跨链网关,向被授权节点返回目标资产数据。The target asset data is returned to the authorized node through the cross-chain gateway to which the asset lightweight node belongs.
应当理解,本申请实施例中所描述的计算机设备2000可执行前文图3所对应实施例中对基于数字证书认证的跨链信任方法的描述,也可执行前文图9所对应实施例中对基于数字证书认证的跨链信任装置2的描述,在此不再赘述。另外,对采用相同方法的有益效果描述,也不再进行赘述。It should be understood that the
此外,这里需要指出的是:本申请实施例还提供了一种计算机可读存储介质,且计算机可读存储介质中存储有前文提及的基于数字证书认证的跨链信任装置1和基于数字证书认证的跨链信任装置2所执行的计算机程序,且计算机程序包括程序指令,当处理器执行程序指令时,能够执行前文图3所对应实施例中对基于数字证书认证的跨链信任方法的描述,因此,这里将不再进行赘述。另外,对采用相同方法的有益效果描述,也不再进行赘述。对于本申请所涉及的计算机可读存储介质实施例中未披露的技术细节,请参照本申请方法实施例的描述。作为示例,程序指令可被部署在一个计算设备上执行,或者在位于一个地点的多个计算设备上执行,又或者,在分布在多个地点且通过通信网络互连的多个计算设备上执行,分布在多个地点且通过通信网络互连的多个计算设备可以组成区块链系统。In addition, it should be pointed out here that the embodiment of the present application also provides a computer-readable storage medium, and the computer-readable storage medium stores the aforementioned cross-chain trust device 1 based on digital certificate authentication and digital certificate-based cross-chain trust device 1 The computer program executed by the certified
此外,需要说明的是:本申请实施例还提供了一种计算机程序产品或计算机程序,该计算机程序产品或者计算机程序可以包括计算机指令,该计算机指令可以存储在计算机可读存储介质中。计算机设备的处理器从计算机可读存储介质读取该计算机指令,处理器可以执行该计算机指令,使得该计算机设备执行前文图3所对应实施例中对基于数字证书认证的跨链信任方法的描述,因此,这里将不再进行赘述。另外,对采用相同方法的有益效果描述,也不再进行赘述。对于本申请所涉及的计算机程序产品或者计算机程序实施例中未披露的技术细节,请参照本申请方法实施例的描述。In addition, it should be noted that the embodiments of the present application further provide a computer program product or computer program, and the computer program product or computer program may include computer instructions, and the computer instructions may be stored in a computer-readable storage medium. The processor of the computer device reads the computer instruction from the computer-readable storage medium, and the processor can execute the computer instruction, so that the computer device executes the description of the cross-chain trust method based on digital certificate authentication in the embodiment corresponding to FIG. 3 above. , therefore, it will not be repeated here. In addition, the description of the beneficial effects of using the same method will not be repeated. For the technical details not disclosed in the computer program products or computer program embodiments involved in the present application, please refer to the description of the method embodiments of the present application.
需要说明的是,对于前述的各个方法实施例,为了简单描述,故将其都表述为一系列的动作组合,但是本领域技术人员应该知悉,本申请并不受所描述的动作顺序的限制,因为依据本申请,某一些步骤可以采用其他顺序或者同时进行。其次,本领域技术人员也应该知悉,说明书中所描述的实施例均属于优选实施例,所涉及的动作和模块并不一定是本申请所必须的。It should be noted that, for the sake of simple description, the foregoing method embodiments are all expressed as a series of action combinations, but those skilled in the art should know that the present application is not limited by the described action sequence. Because in accordance with the present application, certain steps may be performed in other orders or simultaneously. Secondly, those skilled in the art should also know that the embodiments described in the specification are all preferred embodiments, and the actions and modules involved are not necessarily required by the present application.
本申请实施例方法中的步骤可以根据实际需要进行顺序调整、合并和删减。The steps in the method of the embodiment of the present application may be adjusted, combined and deleted in sequence according to actual needs.
本申请实施例装置中的模块可以根据实际需要进行合并、划分和删减。The modules in the apparatus of the embodiment of the present application may be combined, divided and deleted according to actual needs.
本领域普通技术人员可以理解实现上述实施例方法中的全部或部分流程,是可以通过计算机程序来指令相关的硬件来完成,计算机程序可存储于一计算机可读取存储介质中,该程序在执行时,可包括如上述各方法的实施例的流程。其中,存储介质可为磁碟、光盘、只读存储器(Read-Only Memory,ROM)或随机存储器(Random Access Memory,RAM)等。Those of ordinary skill in the art can understand that all or part of the processes in the methods of the above embodiments can be implemented by instructing the relevant hardware through a computer program, and the computer program can be stored in a computer-readable storage medium, and the program can be executed , may include the flow of the above-mentioned method embodiments. The storage medium may be a magnetic disk, an optical disk, a read-only memory (Read-Only Memory, ROM), or a random access memory (Random Access Memory, RAM), or the like.
以上所揭露的仅为本申请较佳实施例而已,当然不能以此来限定本申请之权利范围,因此依本申请权利要求所作的等同变化,仍属本申请所涵盖的范围。The above disclosures are only the preferred embodiments of the present application, and of course, the scope of the rights of the present application cannot be limited by this. Therefore, equivalent changes made according to the claims of the present application are still within the scope of the present application.
Claims (14)
Translated fromChinesePriority Applications (2)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202011316751.6ACN112115205B (en) | 2020-11-23 | 2020-11-23 | Cross-chain trust method, device, device and medium based on digital certificate authentication |
| CN202110114957.9ACN112733178B (en) | 2020-11-23 | 2020-11-23 | Cross-chain trust method, device, equipment and medium based on digital certificate authentication |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202011316751.6ACN112115205B (en) | 2020-11-23 | 2020-11-23 | Cross-chain trust method, device, device and medium based on digital certificate authentication |
Related Child Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN202110114957.9ADivisionCN112733178B (en) | 2020-11-23 | 2020-11-23 | Cross-chain trust method, device, equipment and medium based on digital certificate authentication |
Publications (2)
| Publication Number | Publication Date |
|---|---|
| CN112115205Atrue CN112115205A (en) | 2020-12-22 |
| CN112115205B CN112115205B (en) | 2021-02-02 |
Family
ID=73794402
Family Applications (2)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN202110114957.9AActiveCN112733178B (en) | 2020-11-23 | 2020-11-23 | Cross-chain trust method, device, equipment and medium based on digital certificate authentication |
| CN202011316751.6AActiveCN112115205B (en) | 2020-11-23 | 2020-11-23 | Cross-chain trust method, device, device and medium based on digital certificate authentication |
Family Applications Before (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN202110114957.9AActiveCN112733178B (en) | 2020-11-23 | 2020-11-23 | Cross-chain trust method, device, equipment and medium based on digital certificate authentication |
Country Status (1)
| Country | Link |
|---|---|
| CN (2) | CN112733178B (en) |
Cited By (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN112785318A (en)* | 2021-01-16 | 2021-05-11 | 苏州浪潮智能科技有限公司 | Block chain-based transparent supply chain authentication method, device, equipment and medium |
| CN113779637A (en)* | 2021-11-10 | 2021-12-10 | 腾讯科技(深圳)有限公司 | Attribute data processing method, attribute data processing device, attribute data processing equipment and attribute data processing medium |
| CN114189830A (en)* | 2021-11-24 | 2022-03-15 | 中汽数据(天津)有限公司 | Subject authority control method, device and storage medium based on Internet of Vehicles |
| CN115001801A (en)* | 2022-05-30 | 2022-09-02 | 北京沸铜科技有限公司 | Block chain-based digital content heterogeneous chain cross-chain authorization method |
Families Citing this family (2)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN113850599B (en)* | 2021-12-01 | 2022-02-15 | 南京金宁汇科技有限公司 | Cross-link transaction method and system applied to alliance link |
| CN114780932B (en)* | 2022-06-21 | 2022-09-02 | 中铁电气化局集团有限公司 | Cross-block chain data interaction verification method, system and equipment for management three-mode platform |
Citations (8)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20170243213A1 (en)* | 2016-02-22 | 2017-08-24 | Bank Of America Corporation | System to enable contactless access to a transaction terminal using a process data network |
| CN108305072A (en)* | 2018-01-04 | 2018-07-20 | 上海点融信息科技有限责任公司 | Dispose method, equipment and the computer storage media of block chain network |
| CN109033788A (en)* | 2018-06-15 | 2018-12-18 | 北京文创园投资管理有限公司 | A kind of certificate management method and device based on block chain technology |
| CN109992953A (en)* | 2019-02-18 | 2019-07-09 | 深圳壹账通智能科技有限公司 | Digital certificate issuance, verification methods, equipment, systems and media on the blockchain |
| CN110335147A (en)* | 2019-05-29 | 2019-10-15 | 西安电子科技大学 | A blockchain-based digital asset information exchange system and method |
| CN111080295A (en)* | 2019-12-04 | 2020-04-28 | 腾讯科技(深圳)有限公司 | Block chain-based electronic contract processing method and equipment |
| US10726346B2 (en)* | 2016-11-09 | 2020-07-28 | Cognitive Scale, Inc. | System for performing compliance operations using cognitive blockchains |
| CN111884815A (en)* | 2020-08-07 | 2020-11-03 | 上海格尔安全科技有限公司 | Block chain-based distributed digital certificate authentication system |
Family Cites Families (5)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN107301536B (en)* | 2017-06-12 | 2019-07-12 | 腾讯科技(深圳)有限公司 | Resource transfers method and device |
| CN108154366B (en)* | 2017-12-25 | 2021-09-14 | 丁江 | Cross-chain digital asset transfer method and terminal equipment |
| CN110020860B (en)* | 2019-04-09 | 2023-09-05 | 湖南天河国云科技有限公司 | Cross-chain asset transfer method, system and computer readable storage medium |
| CN111681003B (en)* | 2020-07-07 | 2021-06-25 | 腾讯科技(深圳)有限公司 | Resource cross-chain transfer method and device, computer equipment and storage medium |
| CN111970129B (en)* | 2020-10-21 | 2021-01-01 | 腾讯科技(深圳)有限公司 | Data processing method and device based on block chain and readable storage medium |
- 2020
- 2020-11-23CNCN202110114957.9Apatent/CN112733178B/enactiveActive
- 2020-11-23CNCN202011316751.6Apatent/CN112115205B/enactiveActive
Patent Citations (8)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20170243213A1 (en)* | 2016-02-22 | 2017-08-24 | Bank Of America Corporation | System to enable contactless access to a transaction terminal using a process data network |
| US10726346B2 (en)* | 2016-11-09 | 2020-07-28 | Cognitive Scale, Inc. | System for performing compliance operations using cognitive blockchains |
| CN108305072A (en)* | 2018-01-04 | 2018-07-20 | 上海点融信息科技有限责任公司 | Dispose method, equipment and the computer storage media of block chain network |
| CN109033788A (en)* | 2018-06-15 | 2018-12-18 | 北京文创园投资管理有限公司 | A kind of certificate management method and device based on block chain technology |
| CN109992953A (en)* | 2019-02-18 | 2019-07-09 | 深圳壹账通智能科技有限公司 | Digital certificate issuance, verification methods, equipment, systems and media on the blockchain |
| CN110335147A (en)* | 2019-05-29 | 2019-10-15 | 西安电子科技大学 | A blockchain-based digital asset information exchange system and method |
| CN111080295A (en)* | 2019-12-04 | 2020-04-28 | 腾讯科技(深圳)有限公司 | Block chain-based electronic contract processing method and equipment |
| CN111884815A (en)* | 2020-08-07 | 2020-11-03 | 上海格尔安全科技有限公司 | Block chain-based distributed digital certificate authentication system |
Cited By (6)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN112785318A (en)* | 2021-01-16 | 2021-05-11 | 苏州浪潮智能科技有限公司 | Block chain-based transparent supply chain authentication method, device, equipment and medium |
| CN112785318B (en)* | 2021-01-16 | 2022-05-17 | 苏州浪潮智能科技有限公司 | Block chain-based transparent supply chain authentication method, device, equipment and medium |
| CN113779637A (en)* | 2021-11-10 | 2021-12-10 | 腾讯科技(深圳)有限公司 | Attribute data processing method, attribute data processing device, attribute data processing equipment and attribute data processing medium |
| CN114189830A (en)* | 2021-11-24 | 2022-03-15 | 中汽数据(天津)有限公司 | Subject authority control method, device and storage medium based on Internet of Vehicles |
| CN115001801A (en)* | 2022-05-30 | 2022-09-02 | 北京沸铜科技有限公司 | Block chain-based digital content heterogeneous chain cross-chain authorization method |
| CN115001801B (en)* | 2022-05-30 | 2023-05-30 | 北京沸铜科技有限公司 | Digital content heterogeneous chain cross-chain authorization method based on blockchain |
Also Published As
| Publication number | Publication date |
|---|---|
| CN112733178A (en) | 2021-04-30 |
| CN112115205B (en) | 2021-02-02 |
| CN112733178B (en) | 2022-05-13 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| EP3788523B1 (en) | System and method for blockchain-based cross-entity authentication | |
| EP3814948B1 (en) | System and method for blockchain-based cross-entity authentication | |
| US11533164B2 (en) | System and method for blockchain-based cross-entity authentication | |
| US11025435B2 (en) | System and method for blockchain-based cross-entity authentication | |
| EP4120114A1 (en) | Data processing method and apparatus, smart device and storage medium | |
| CN112115205B (en) | Cross-chain trust method, device, device and medium based on digital certificate authentication | |
| US20160127355A1 (en) | Embedded extrinsic source for digital certificate validation | |
| WO2022166637A1 (en) | Blockchain network-based method and apparatus for data processing, and computer device | |
| CN111769956B (en) | Service processing method, device, equipment and medium | |
| CN115967508A (en) | Data access control method and device, equipment, storage medium and program product | |
| CN113869901B (en) | Key generation method, key generation device, computer-readable storage medium and computer equipment | |
| CN115409511A (en) | Personal information protection system based on block chain | |
| CN116980136A (en) | Interface processing method, device, equipment, storage medium and product of intelligent contract | |
| CN111275461A (en) | Data processing method and device and computer readable storage medium | |
| HK40042046B (en) | Digital certificate authentication-based cross-chain trust method and apparatus, device, and medium | |
| HK40042046A (en) | Digital certificate authentication-based cross-chain trust method and apparatus, device, and medium | |
| HK40024743A (en) | Method and device for processing data and computer readable storage medium | |
| HK40040359A (en) | Key management method and apparatus based on blockchain, medium, and device | |
| HK40040359B (en) | Key management method and apparatus based on blockchain, medium, and device | |
| CN119027120A (en) | Virtual resource transaction method, device, electronic device and readable medium | |
| CN120219079A (en) | Asset protection method, device, computer, medium and program product | |
| CN118981767A (en) | Identity authentication method, device, equipment, readable storage medium and program product | |
| CN118278932A (en) | Block chain-based transaction method, device, equipment and medium | |
| HK40030105B (en) | Data processing method and apparatus, intelligent device and storage medium | |
| HK40030105A (en) | Data processing method and apparatus, intelligent device and storage medium |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| GR01 | Patent grant | ||
| GR01 | Patent grant |